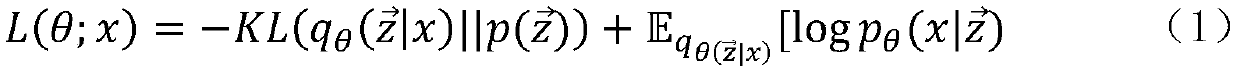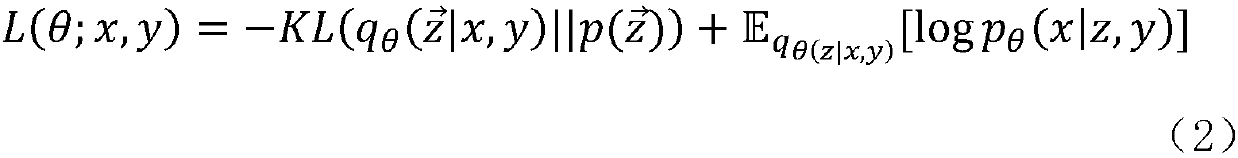Patents
Literature
150 results about "Password strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Password strength is a measure of the effectiveness of a password against guessing or brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.
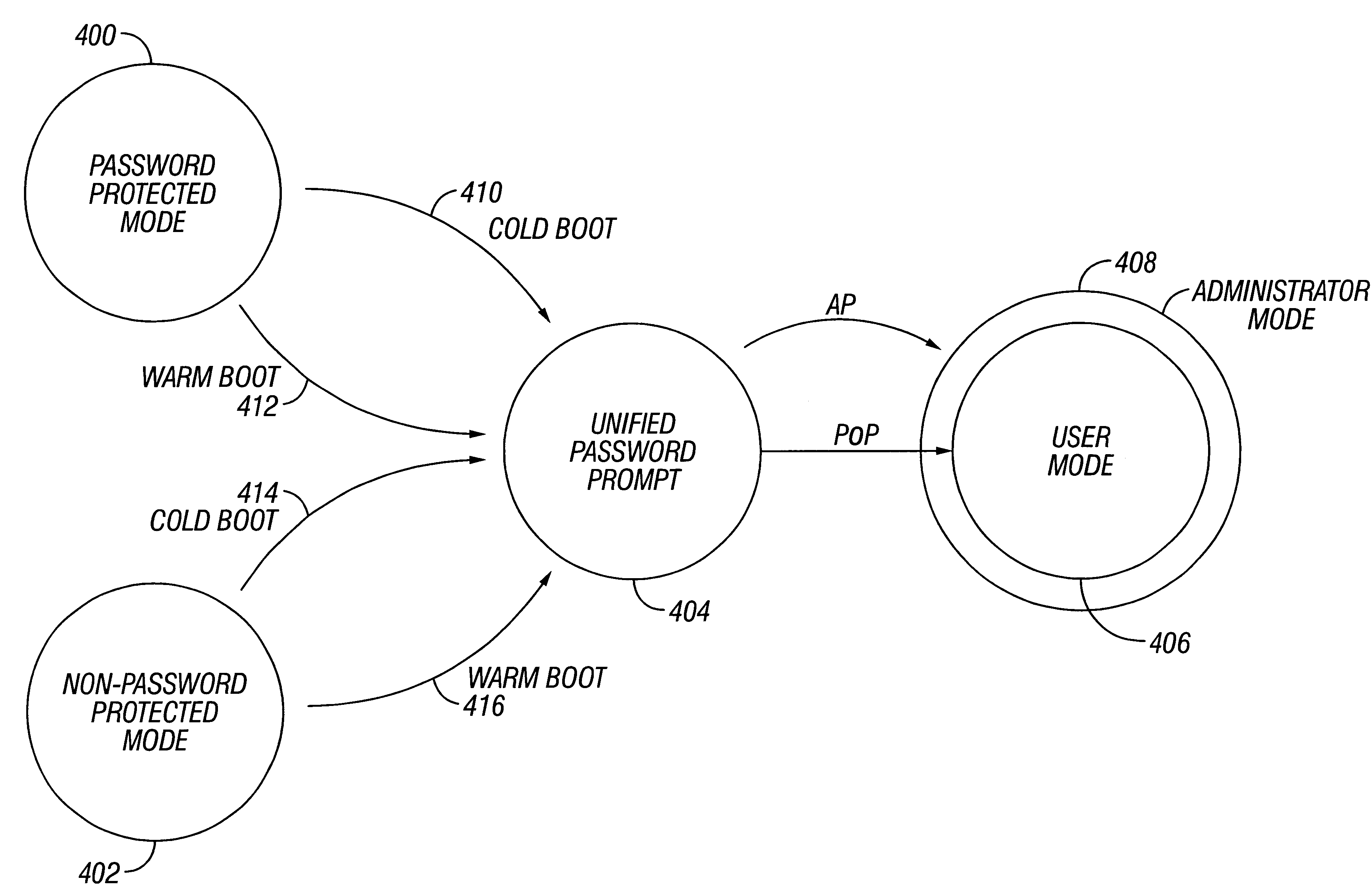
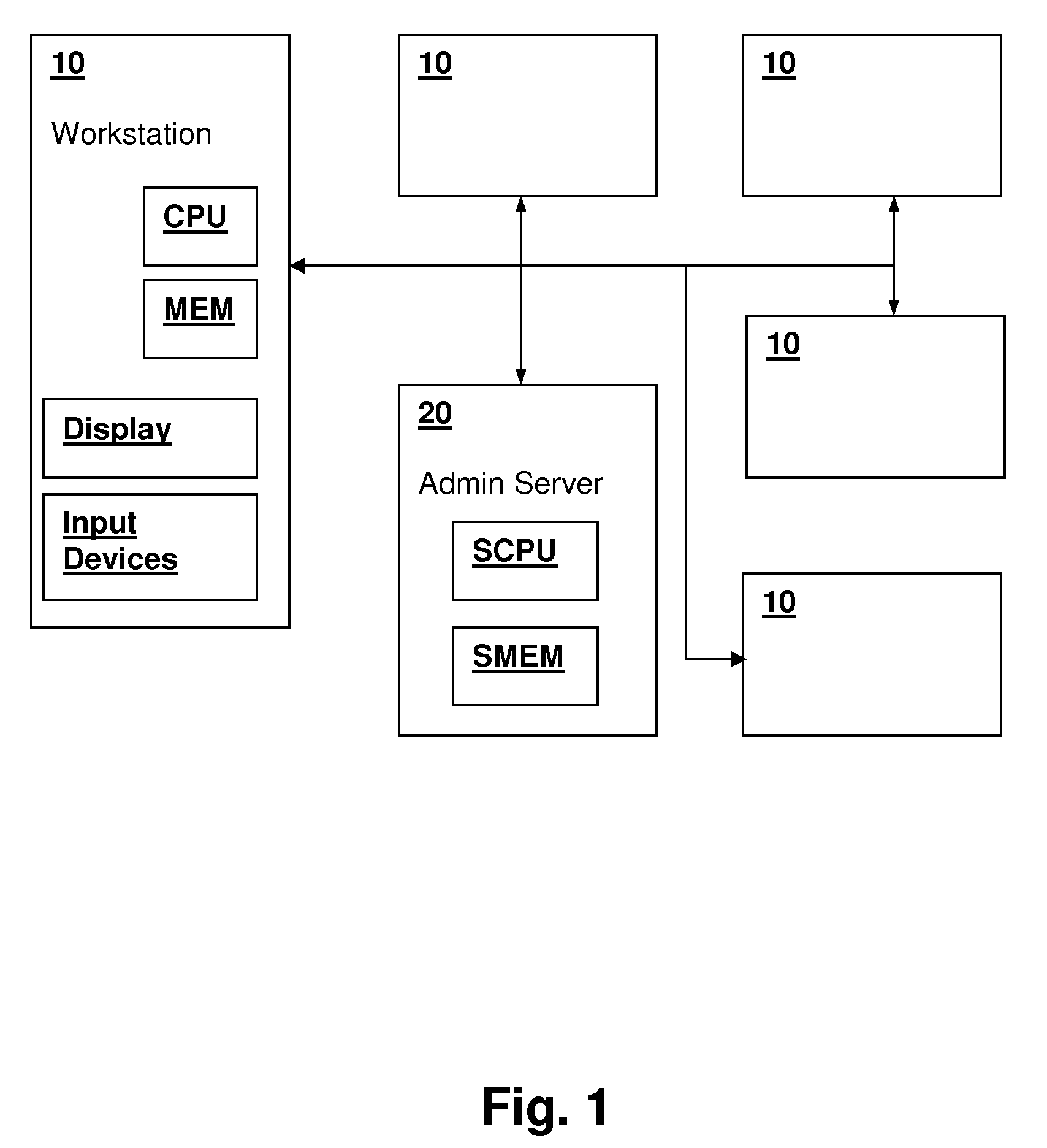
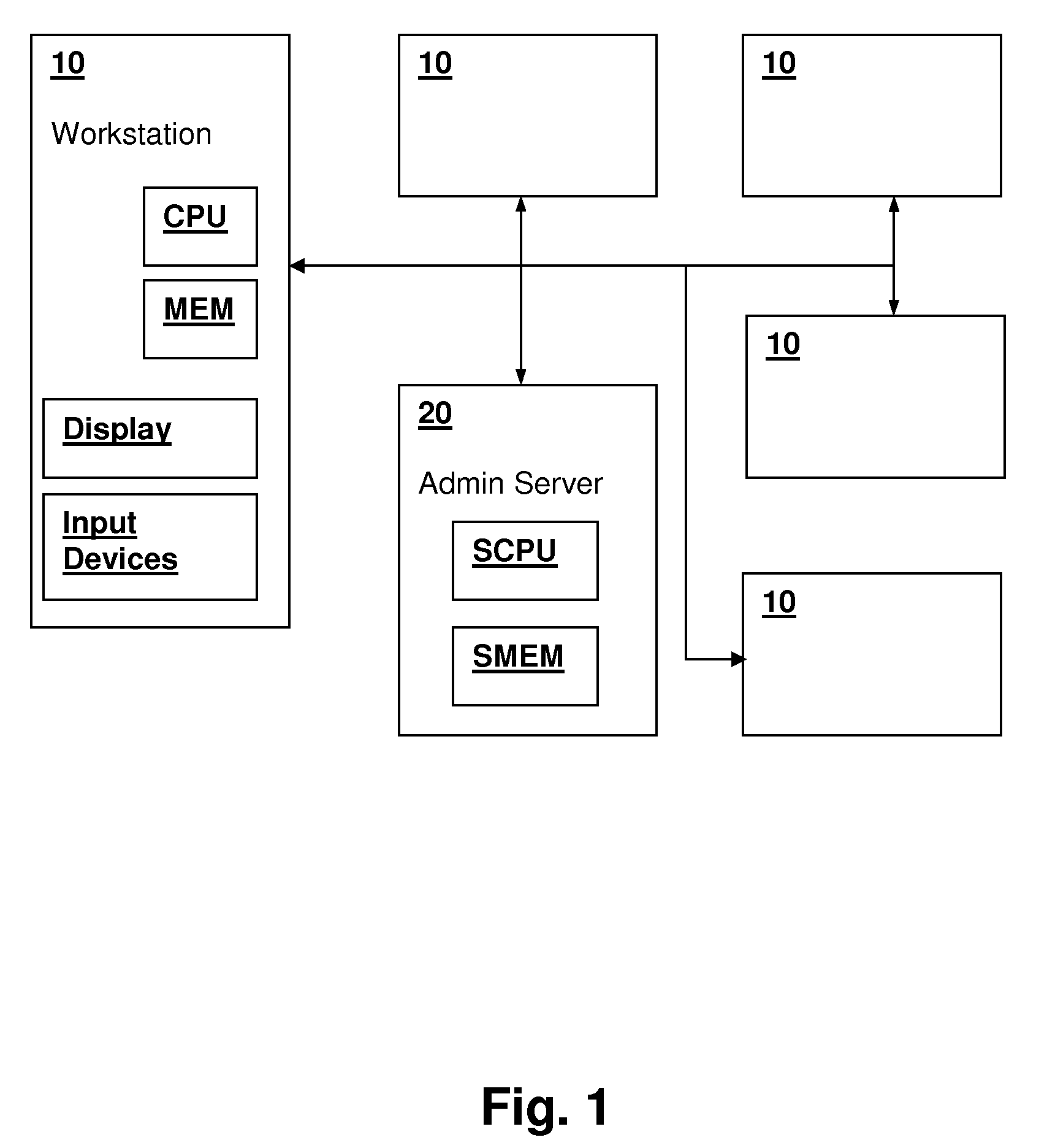
Unified password prompt of a computer system
InactiveUS6397337B1Digital data processing detailsDigital computer detailsComputerized systemPassword hashing
A computer system provides a unified password prompt for accepting a user power-on password or an administrator password. A password string entered by the system administrator at the unified password prompt is compared with a stored power-on password. If the user password string matches the stored power-on password, then access to system resources is granted. If the user password string does not match the stored power-on password, then the user password string is compared to a stored administrator password. If the user password string matches the stored administrative password, then access to system resources is granted. If the user password string does not match the stored administrative password, then the system administrator is given a predetermined number of times to enter a password string matching either the stored power-on password or the stored administrator password. If a password string matching either the stored power-on password or the stored administrator password is not provided in the predetermined number of times, access to system resources is denied. The unified password prompt does not require a system administrator to know a user's power-on password in order to access system resources. The unified password prompt also permits a system administrator to configure a plurality of computer systems by providing a single administrative password rather than a plurality of user power-on passwords.
Owner:HEWLETT PACKARD CO
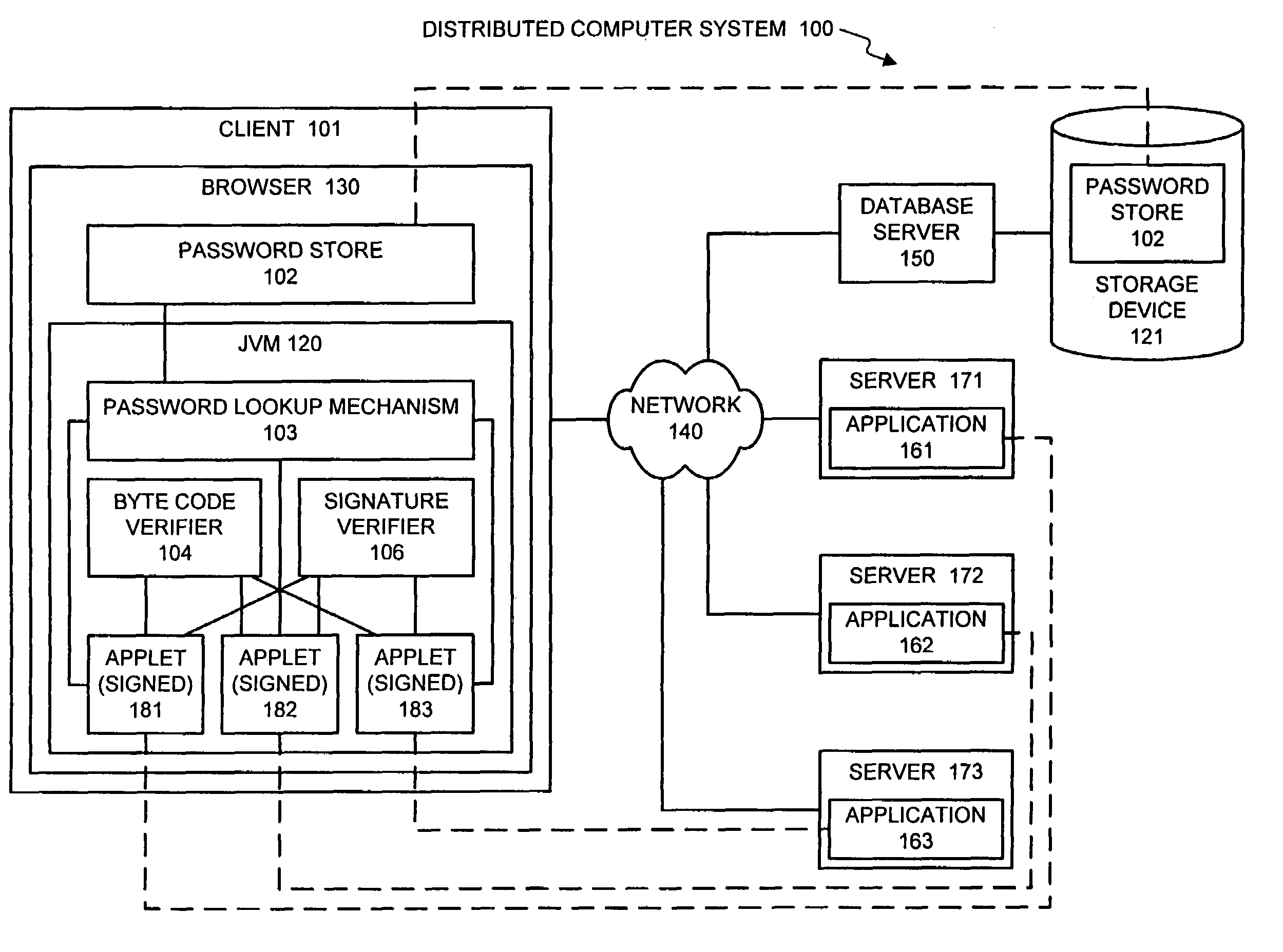
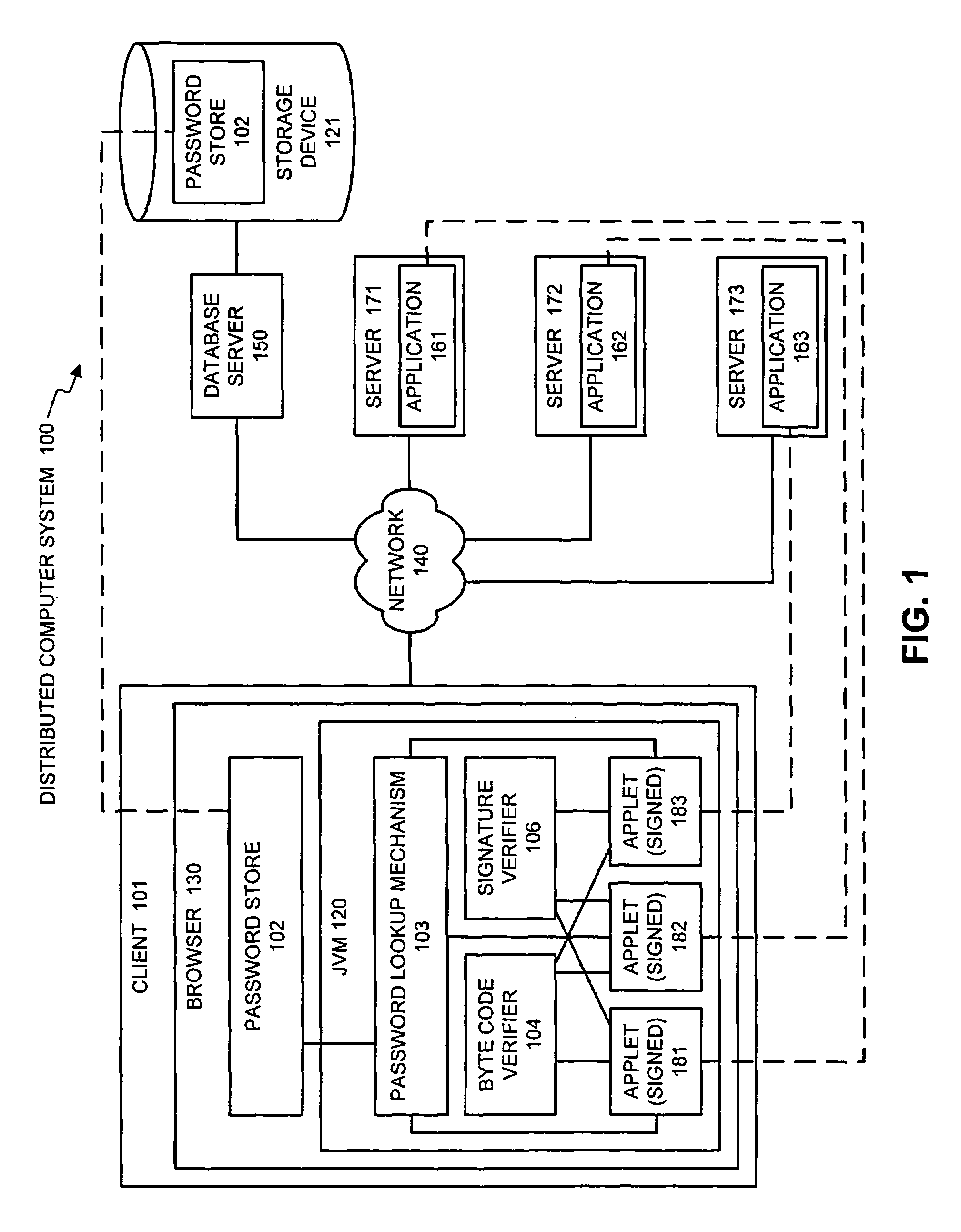
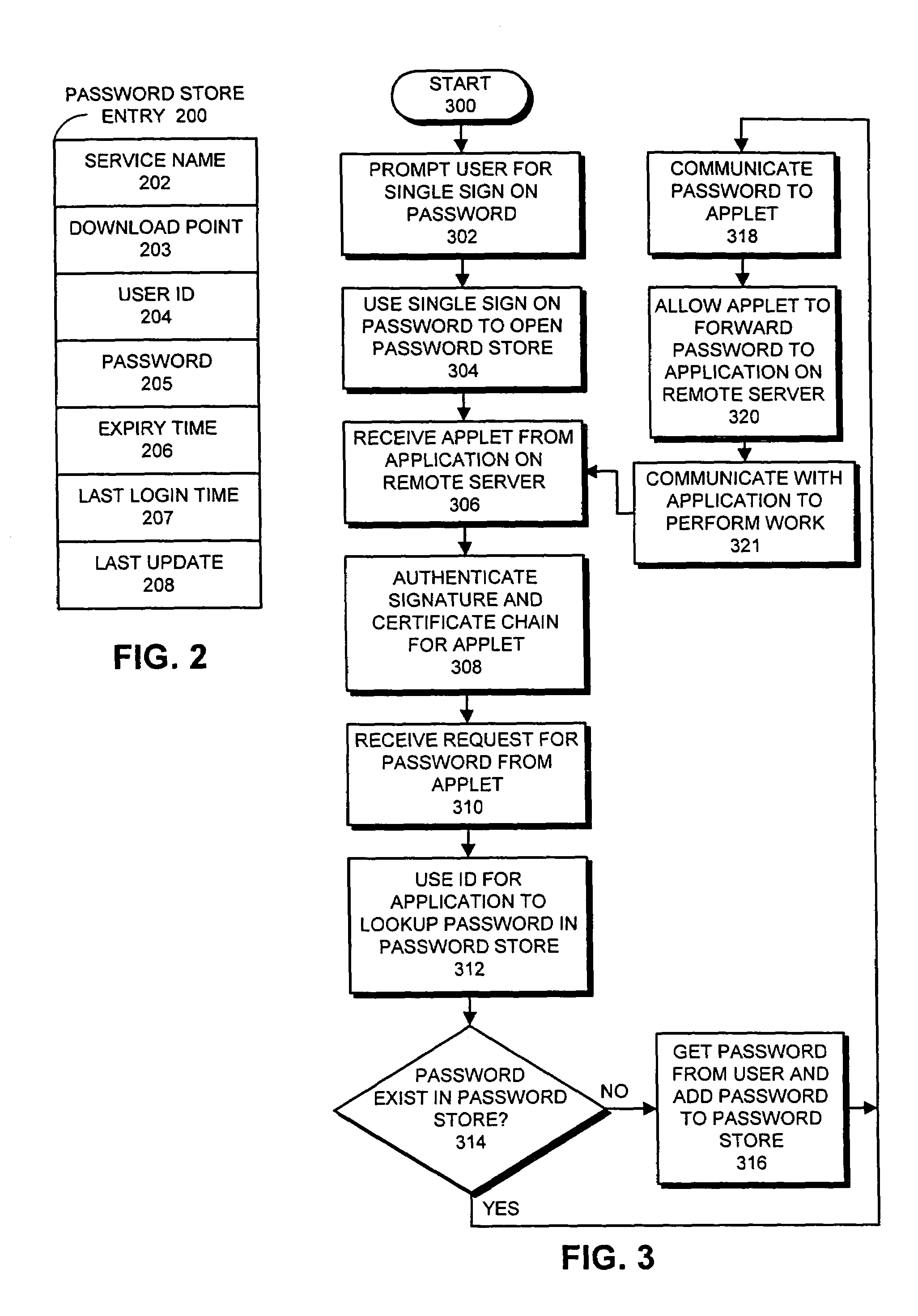
Facilitating single sign-on by using authenticated code to access a password store
InactiveUS7150038B1Easy accessDigital data processing detailsUser identity/authority verificationPasswordRemote computer
One embodiment of the present invention provides a system that facilitates accessing to a plurality of applications that require passwords. When the system receives a request for a password from an application running on a remote computer system, the system first authenticates the request to ensure that it originated from a trusted source. Next, the system uses an identifier for the application to look up the password for the application in a password store, which contains passwords associated with the plurality of applications. If the password exists in the password store, the system sends the password or a function of the password to the application on the remote computer system. Hence, the system creates the illusion that there is a single sign on to a large number of applications, whereas in reality the system automatically provides different passwords to the applications as they are requested. In one embodiment of the present invention, the request for the password includes computer code that when run on the local computer system requests the password on behalf of the application on the remote computer system. In a variation on this embodiment, the computer code is in the form of a JAVA™ applet that runs on a JAVA™ virtual machine on the local computer system. In one embodiment of the present invention, the JAVA™ applet is a signed JAVA™ applet, and authenticating the request involves authenticating the JAVA™ applet's certificate chain.
Owner:ORACLE INT CORP
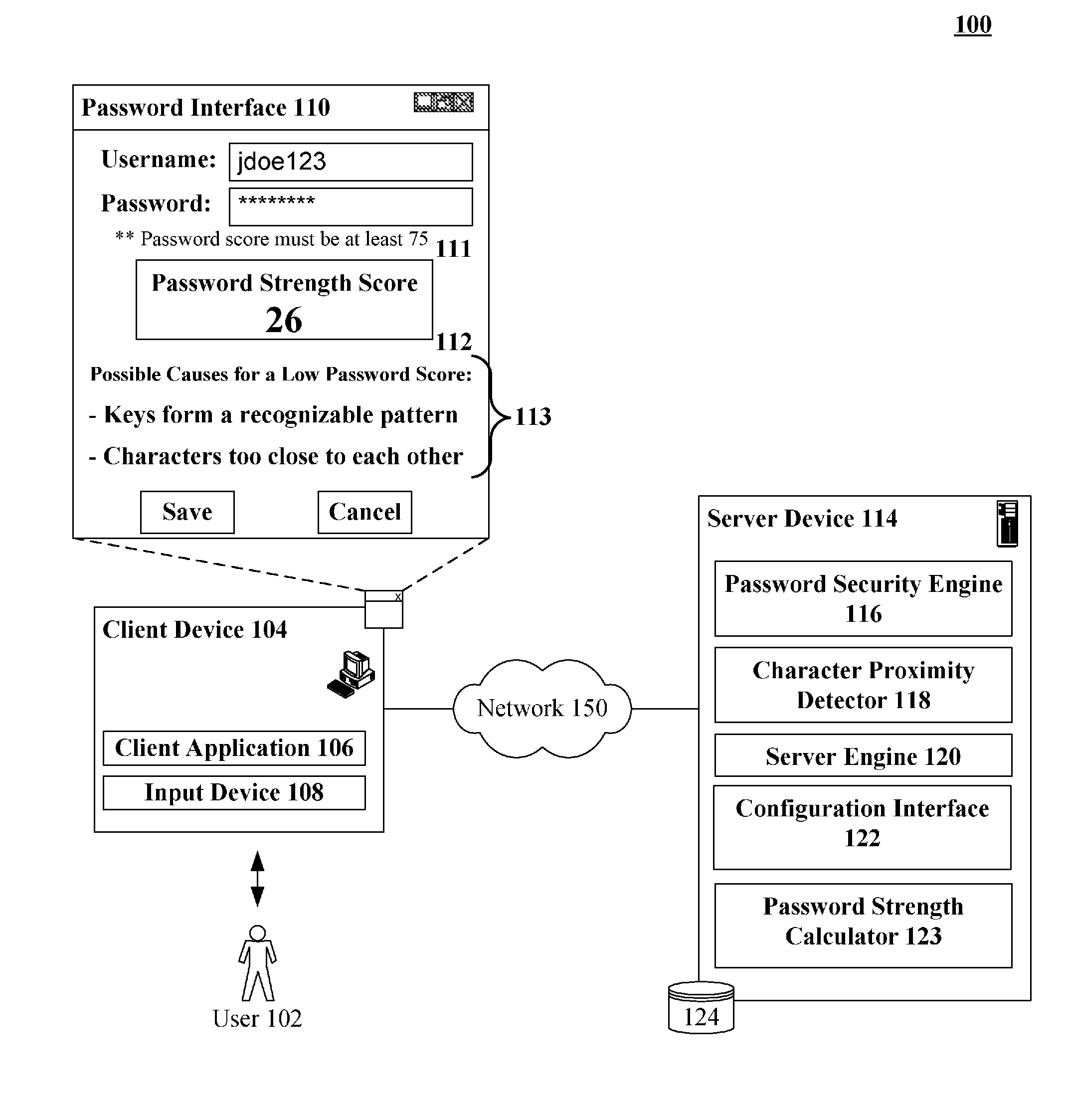
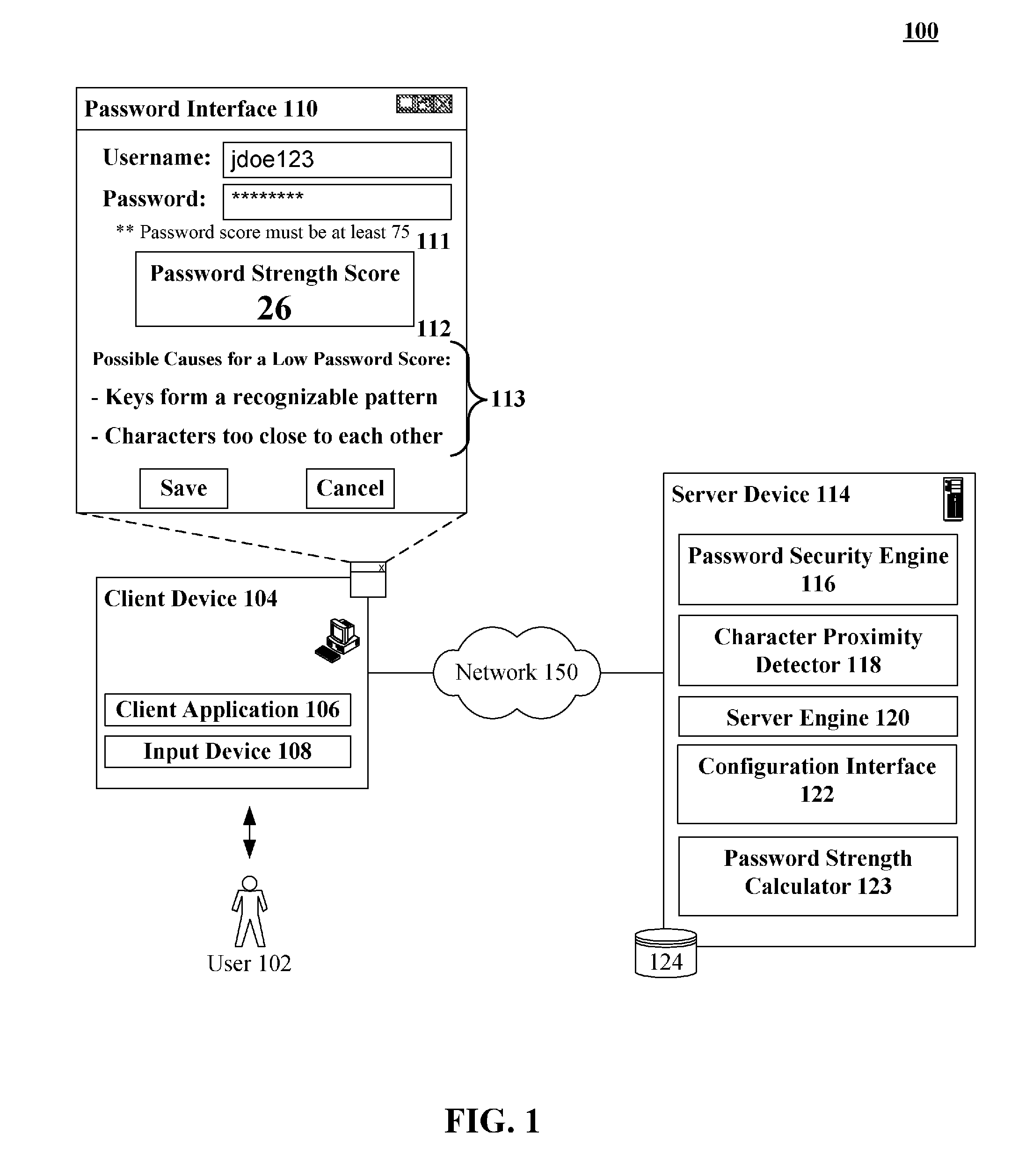
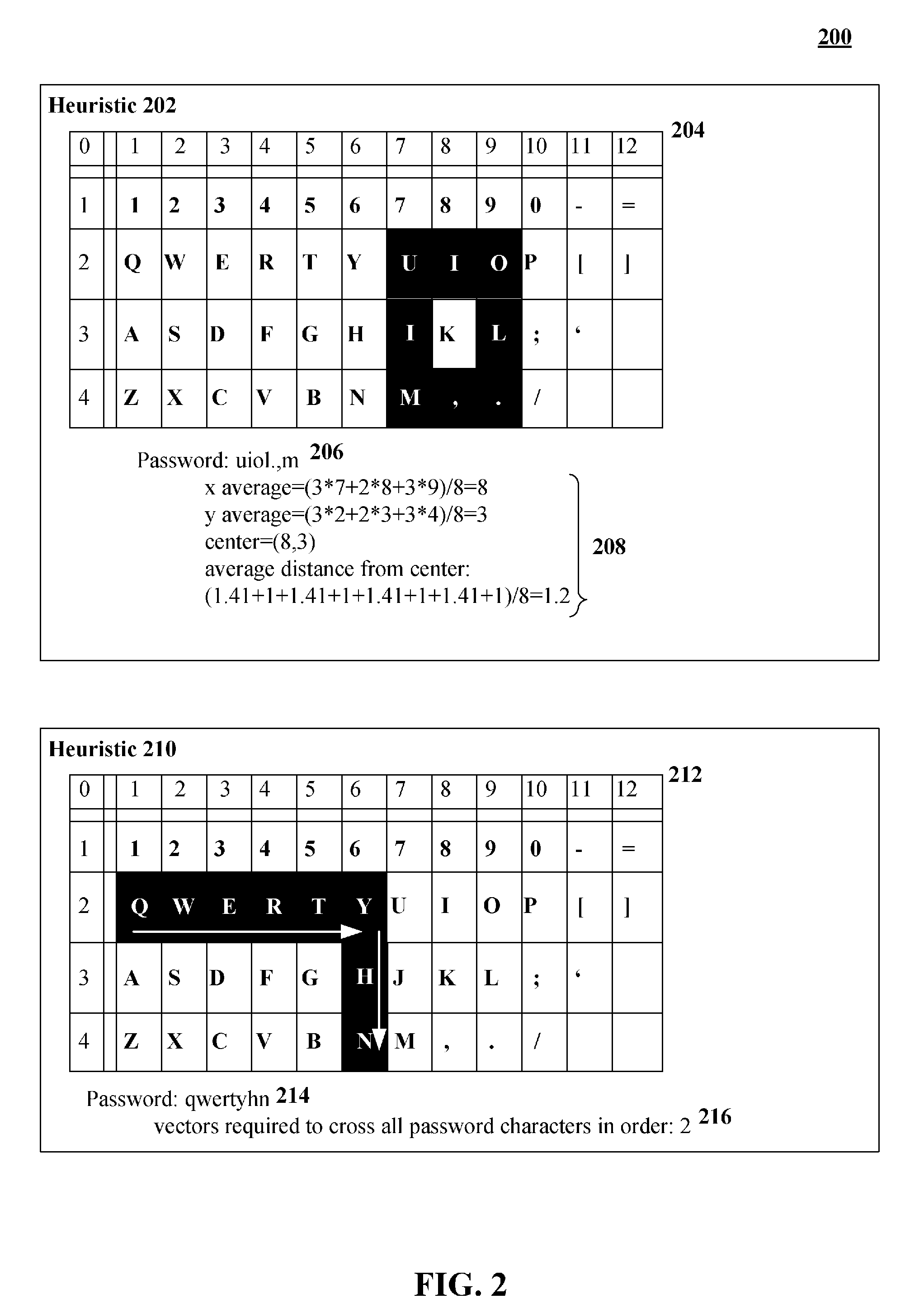
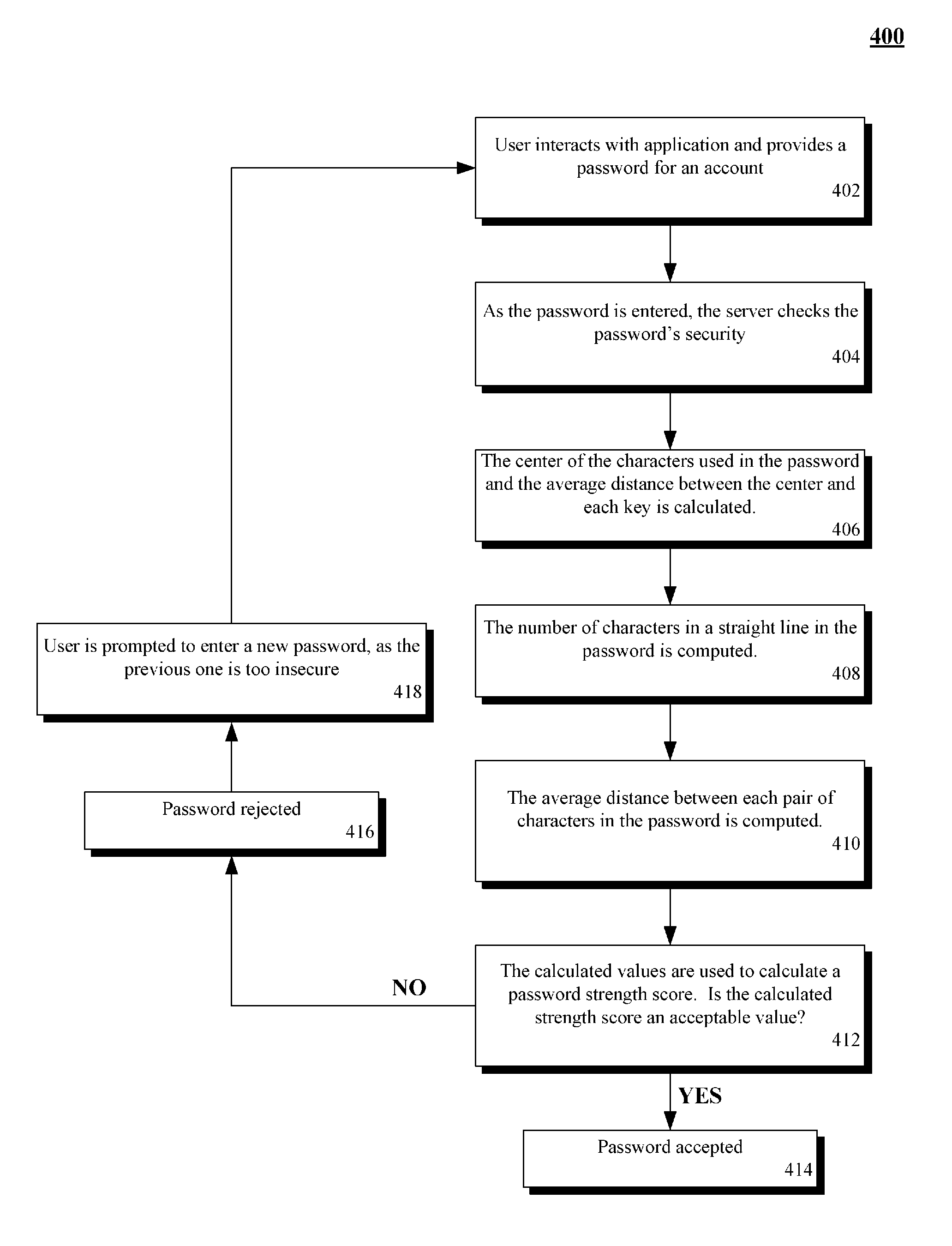
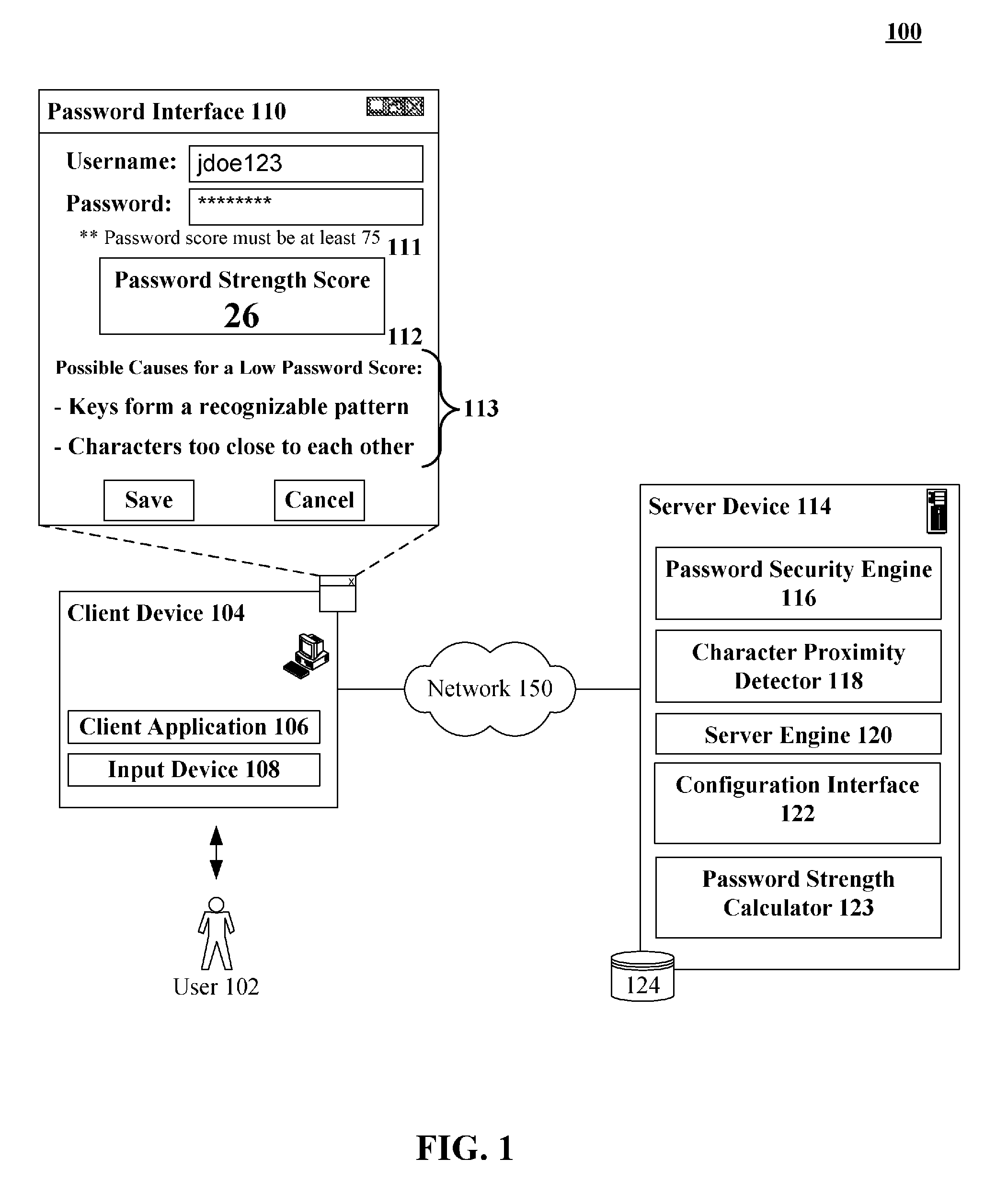
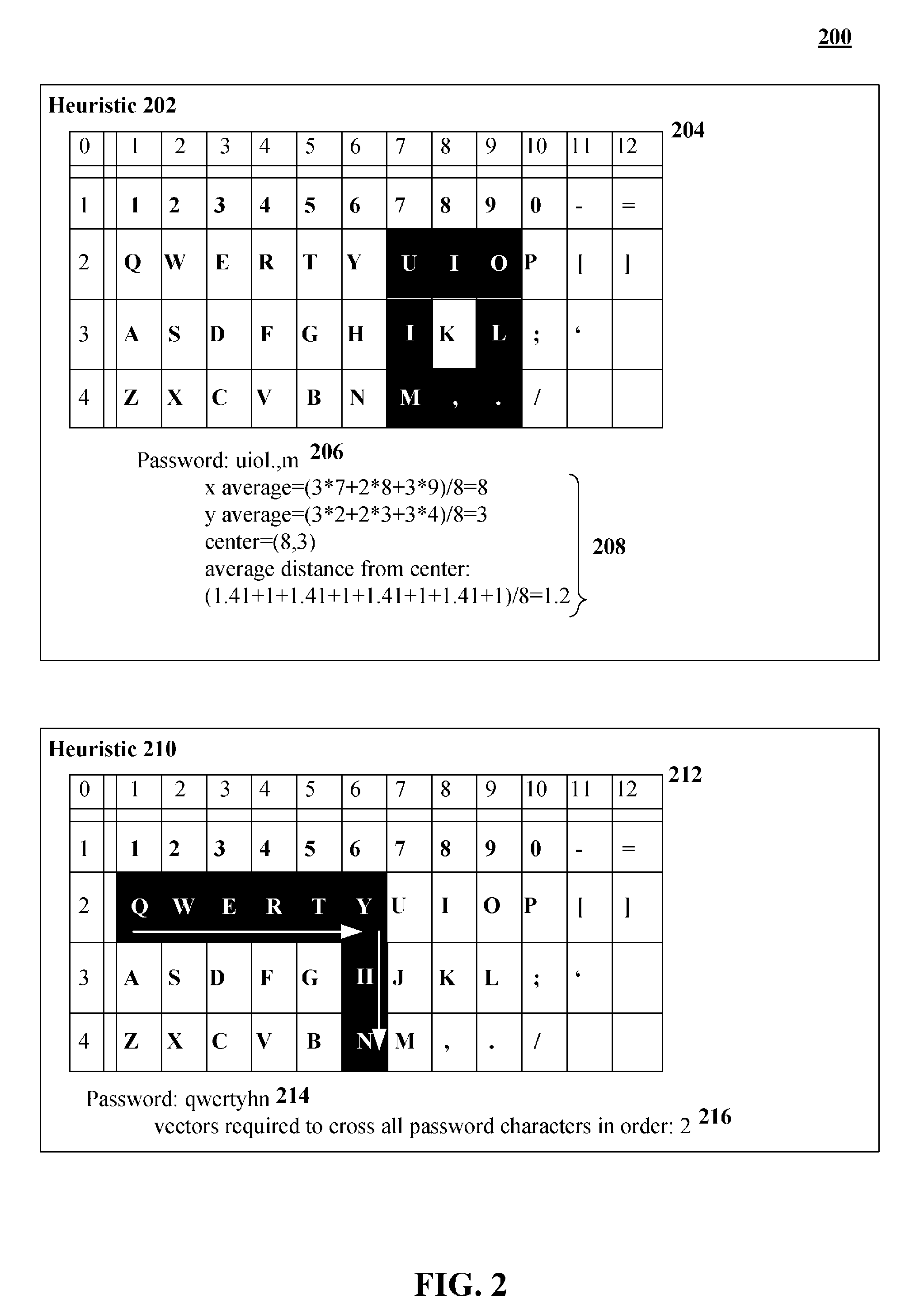
Calculating a password strength score based upon character proximity and relative position upon an input device
InactiveUS20090313696A1Memory loss protectionError detection/correctionPasswordHuman–computer interaction
A solution for computing password strength based upon layout positions of input mechanisms of an input device that entered a password. A password including an ordered sequence of at least two characters can be identified. A position of each of the characters of the sequence can be determined relative to a layout of an input device used for password entry. Each position can correspond to an input region (key) of the input device (keyboard). A proximity algorithm can generate a proximately score for the determined positions based upon a pattern produced by the positions given the layout of the input device. A password strength score can be computed based at least in part upon the proximity score.
Owner:IBM CORP
Managing password strength
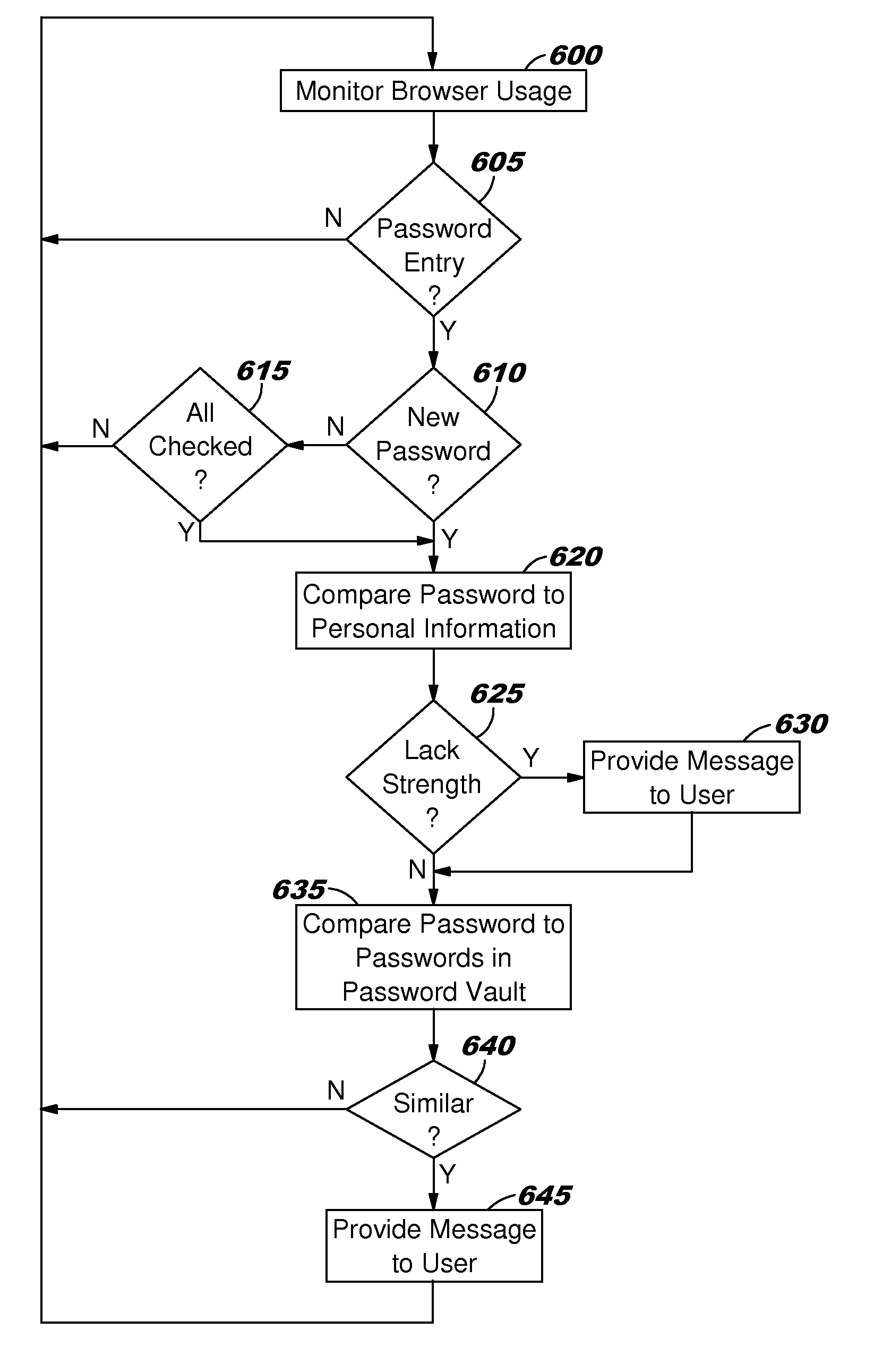
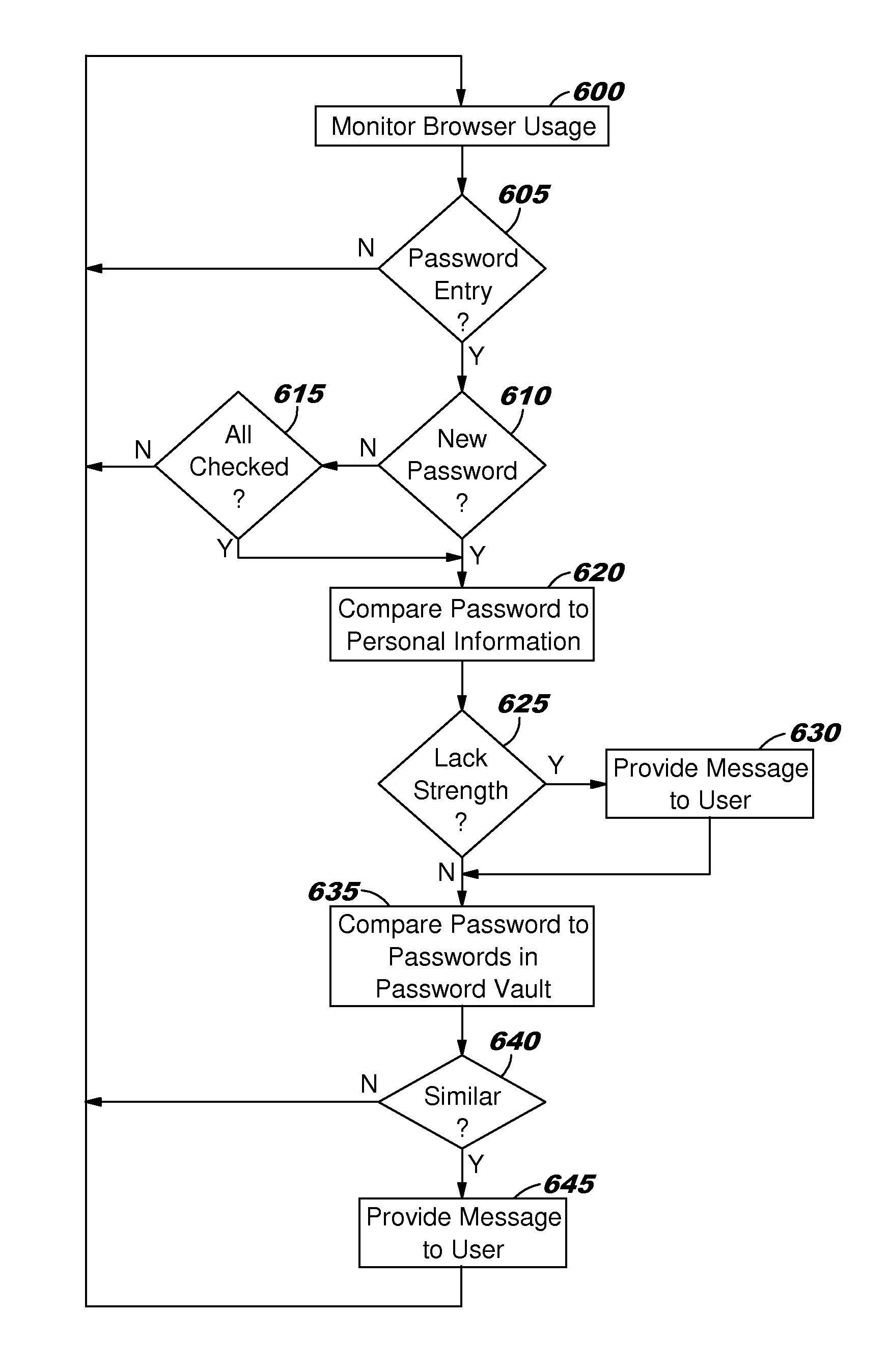
A system or computer usable program product for managing password strength including receiving a password on a data processing system for a user, filtering for personal information about the user from multiple independent data sources accessible across a computer network, computing the password strength by the data processing system using an algorithm which compares the password to the filtered personal information about the user, and presenting feedback to the user through a user interface on a data processing system display regarding the computed password strength.
Owner:INT BUSINESS MASCH CORP
Pattern entropy password strength estimator
ActiveUS20130269010A1Increase ratingsHigh strengthDigital data processing detailsMultiple digital computer combinationsPasswordEvaluation system
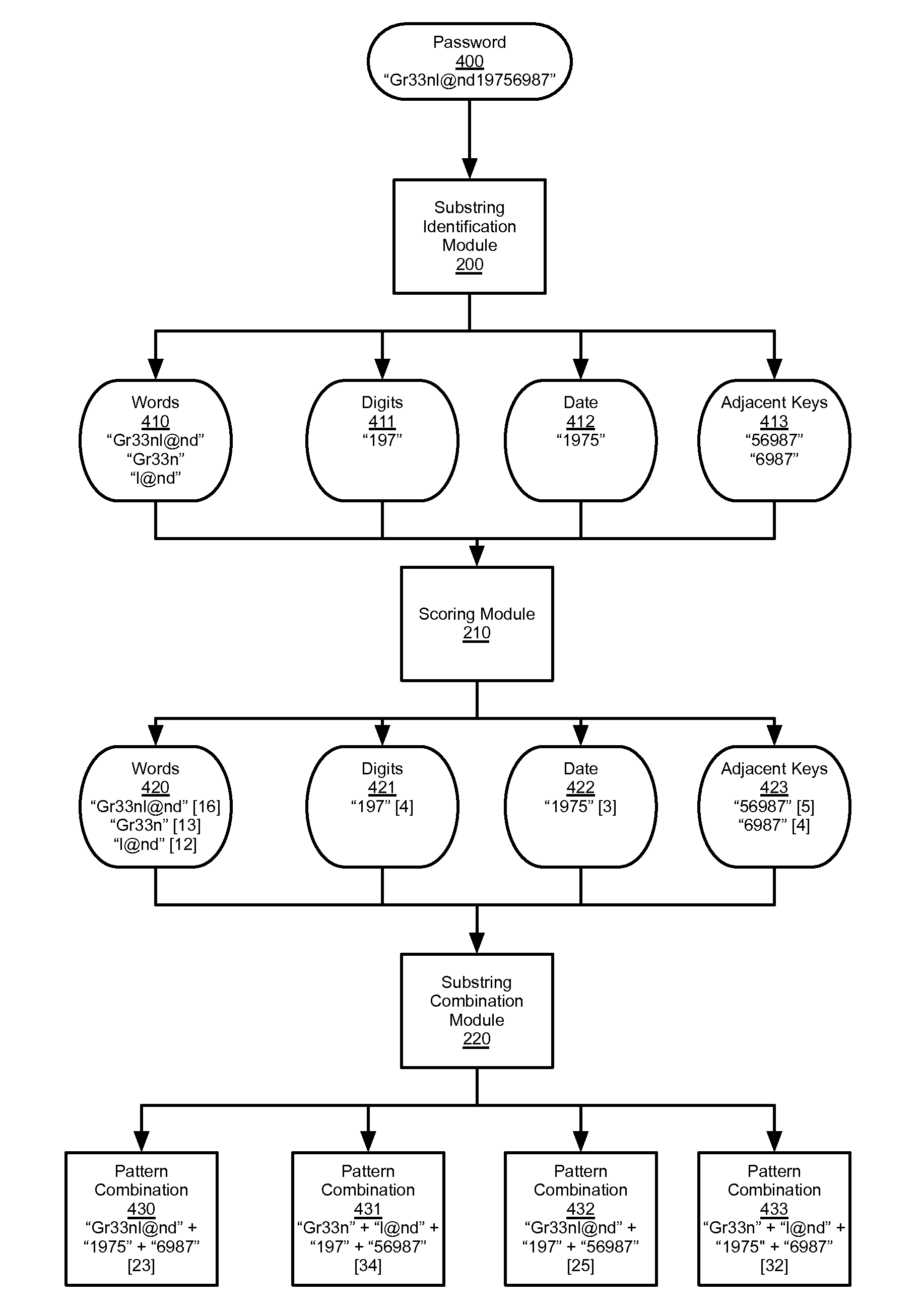
A password evaluation system is provided for determining the password strength of a password. A password is provided for evaluation. The password is parsed and substrings are identified from the password. Each substring is associated with a pattern that can generate the substring. The substrings are scored to determine a substring strength measure for the substring. The substrings are combined to identify non-overlapping substring combinations, which together make up the password. The combinations are assigned a combination strength score based in part on the substring strength of the substrings contained in the substring combinations. The substring combination with the lowest combination strength measure is identified and the associated combination strength measure is used as the password strength measure for the password.
Owner:DROPBOX
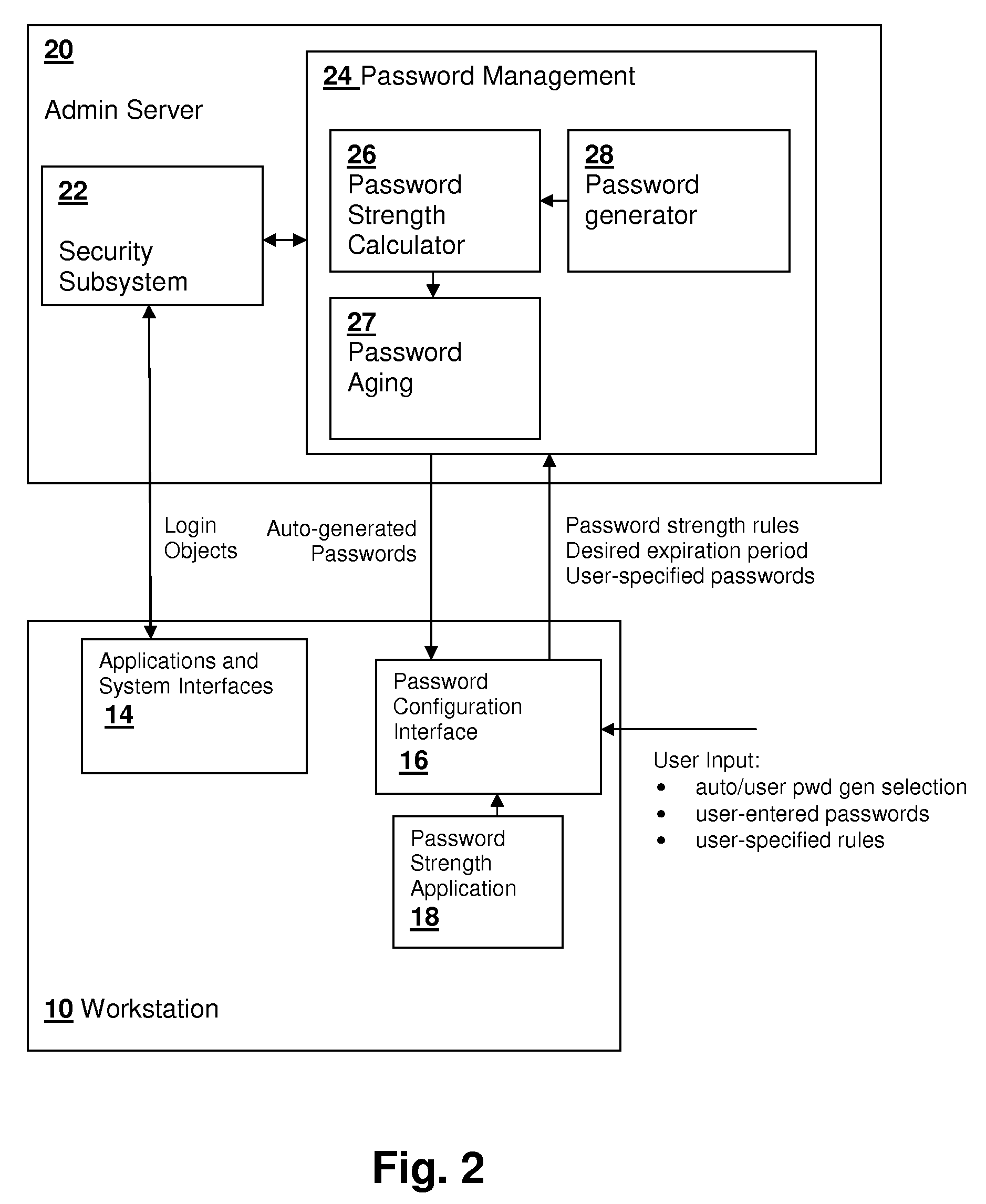
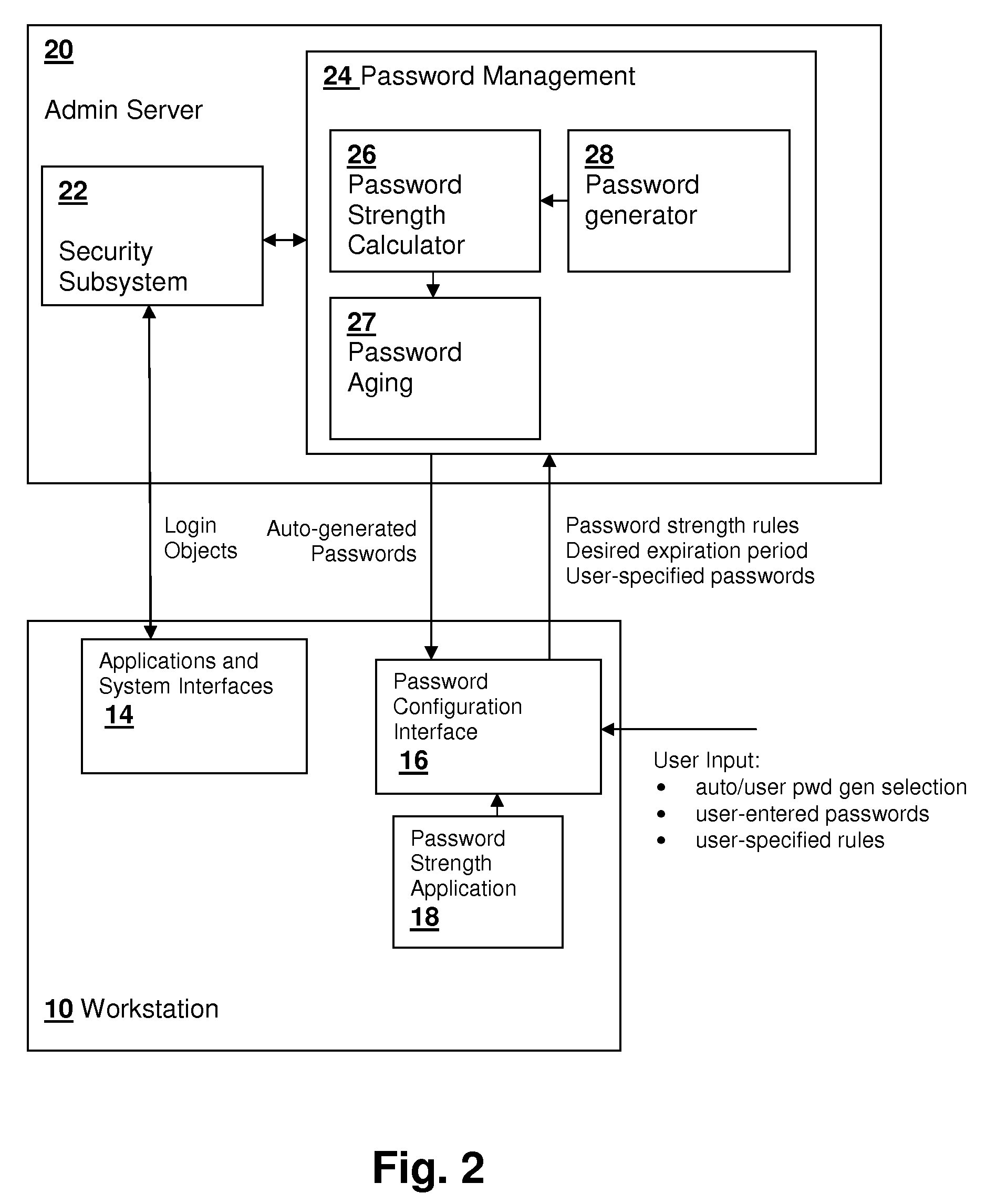
User policy manageable strength-based password aging
InactiveUS20100031343A1Digital data processing detailsUser identity/authority verificationPassword strengthPassword
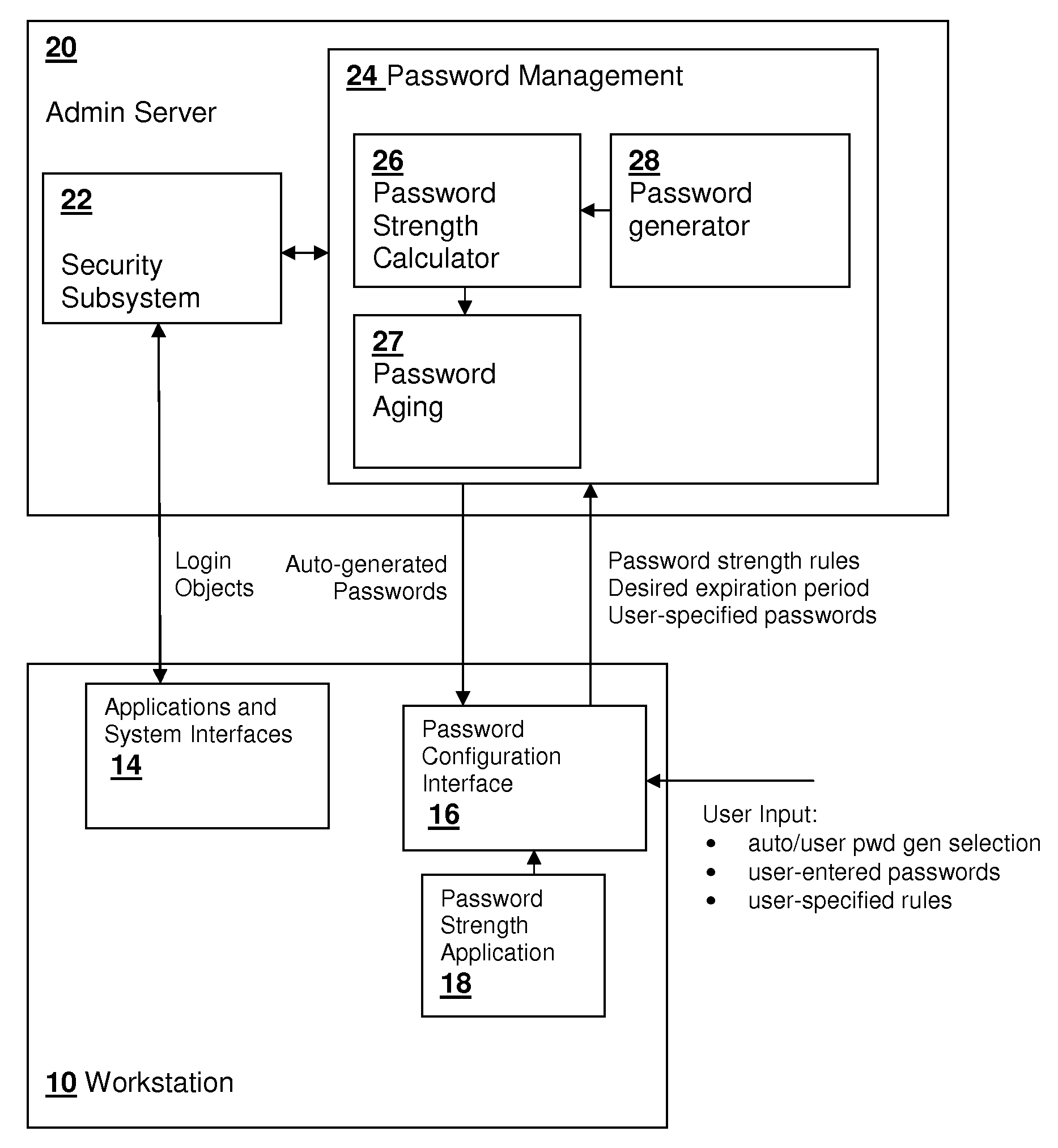
Password aging based on the strength of the password provides an incentive for users to generate and / or memorize more complex passwords. The strength of the password is computed from a formula that relates the length of the password and the types of characters contained in the password to a strength value, which can be performed using a lookup table having values for different characteristics of the password, determining partial strength values corresponding to the ranges in which the characteristics fall, and then adding the partial strength values. Alternatively, a separate password strength application may be used to provide the strength value, which is entered by the user or administrator generating a new password. Alternatively, the password may be generated based on a specified desired expiration period, with the strength computation performed to ensure that the strength is sufficient to merit the desired expiration period.
Owner:IBM CORP
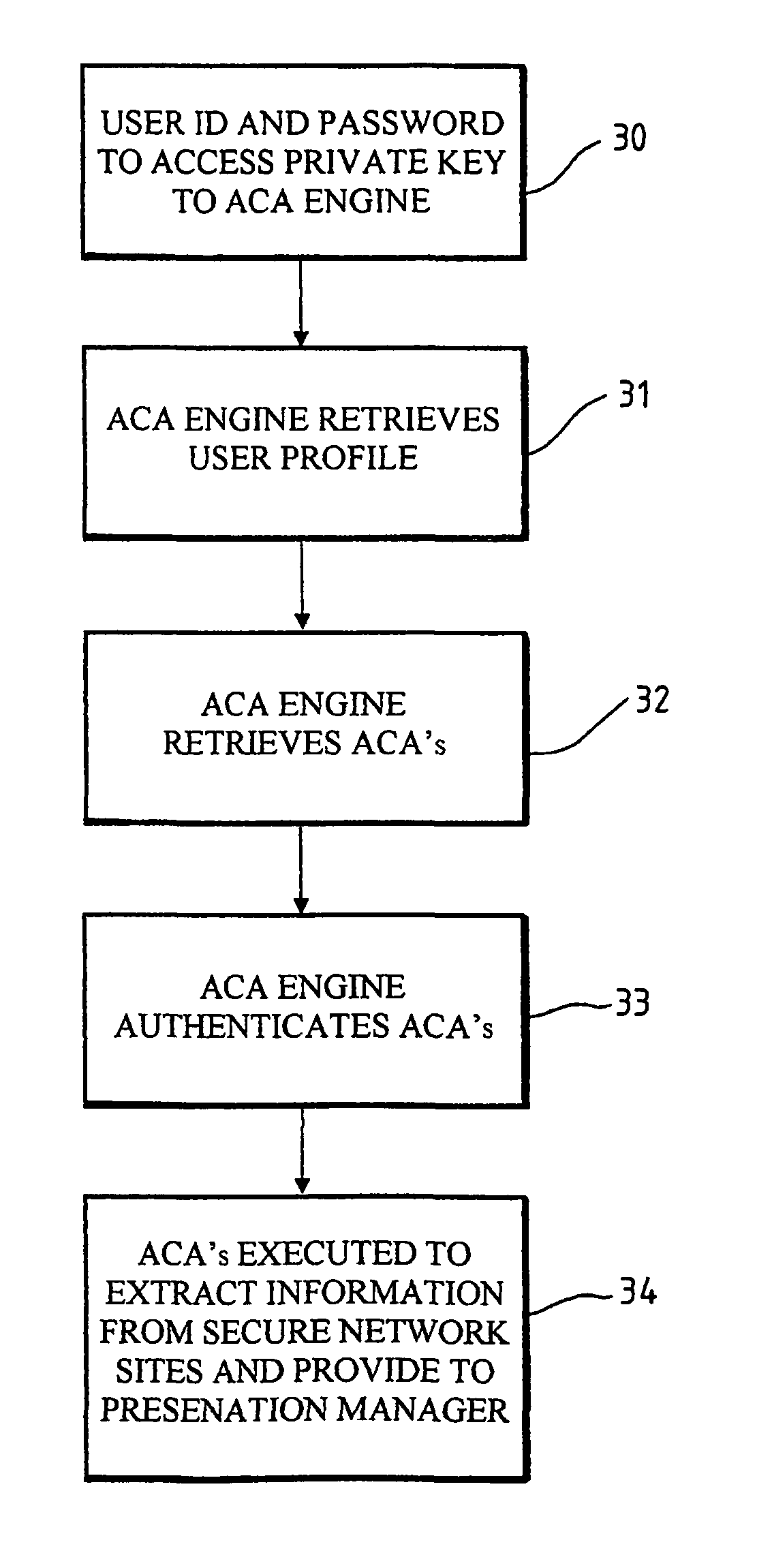
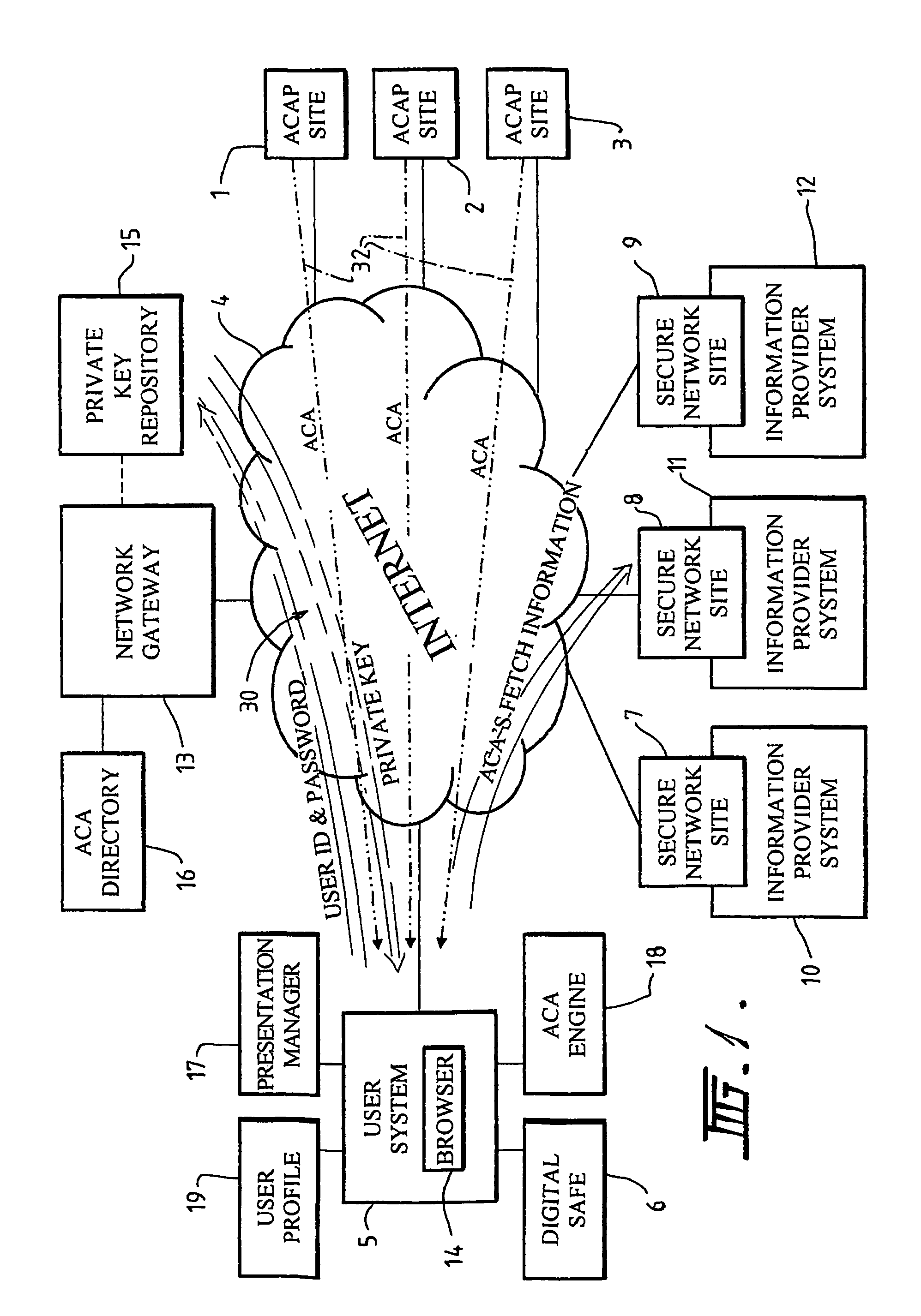
Secure network access
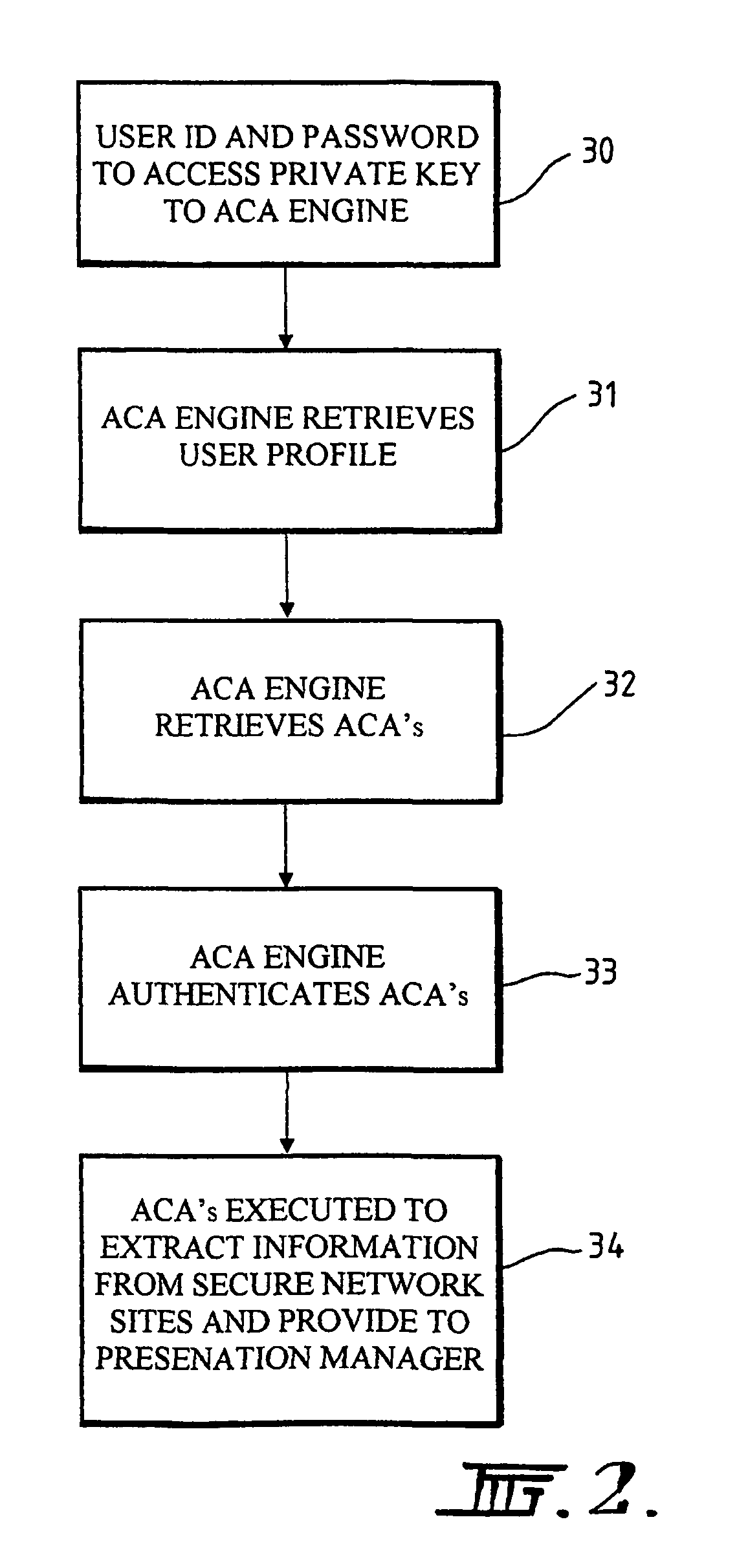
The present invention relates to a system and method for facilitating access to secure network sites, such as sites providing secure financial information. An active software agent is utilized to fetch passwords and user identifiers from a user computing system and to use the passwords and identifiers to extract required information from the secure site. The password sites and identifiers are encrypted and an encryption key is stored at a network mode remote from the user's computer and is fetched in order to enable the passwords and identifiers to be decrypted so that the active agent can use them to obtain the required information.
Owner:EWISE SYST
Managing password strength
InactiveUS20140068733A1Digital data processing detailsMultiple digital computer combinationsData processing systemPassword
A method for managing password strength including receiving a password on a data processing system for a user, filtering for personal information about the user from multiple independent data sources accessible across a computer network, computing the password strength by the data processing system using an algorithm which compares the password to the filtered personal information about the user, and presenting feedback to the user through a user interface on a data processing system display regarding the computed password strength.
Owner:IBM CORP
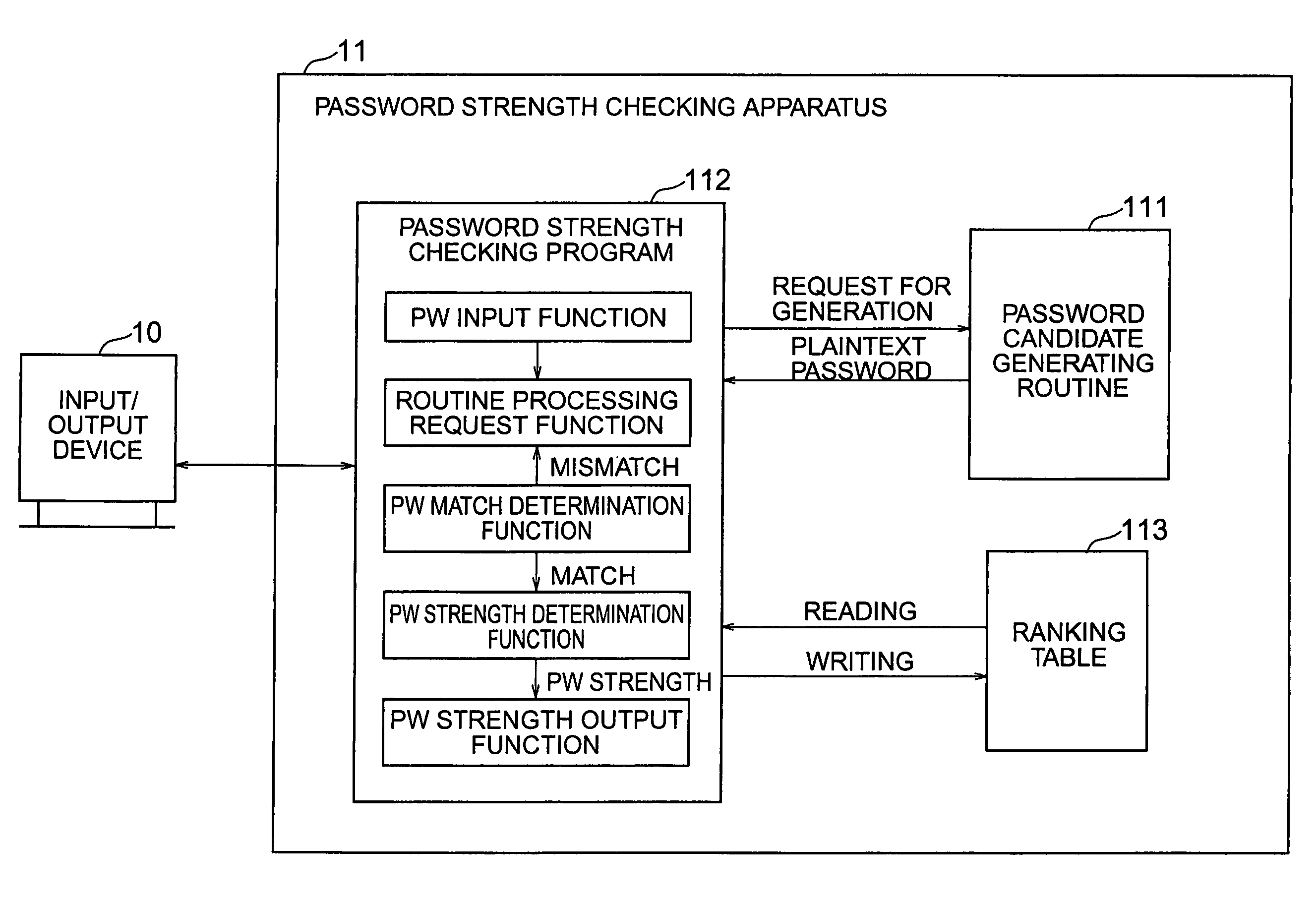
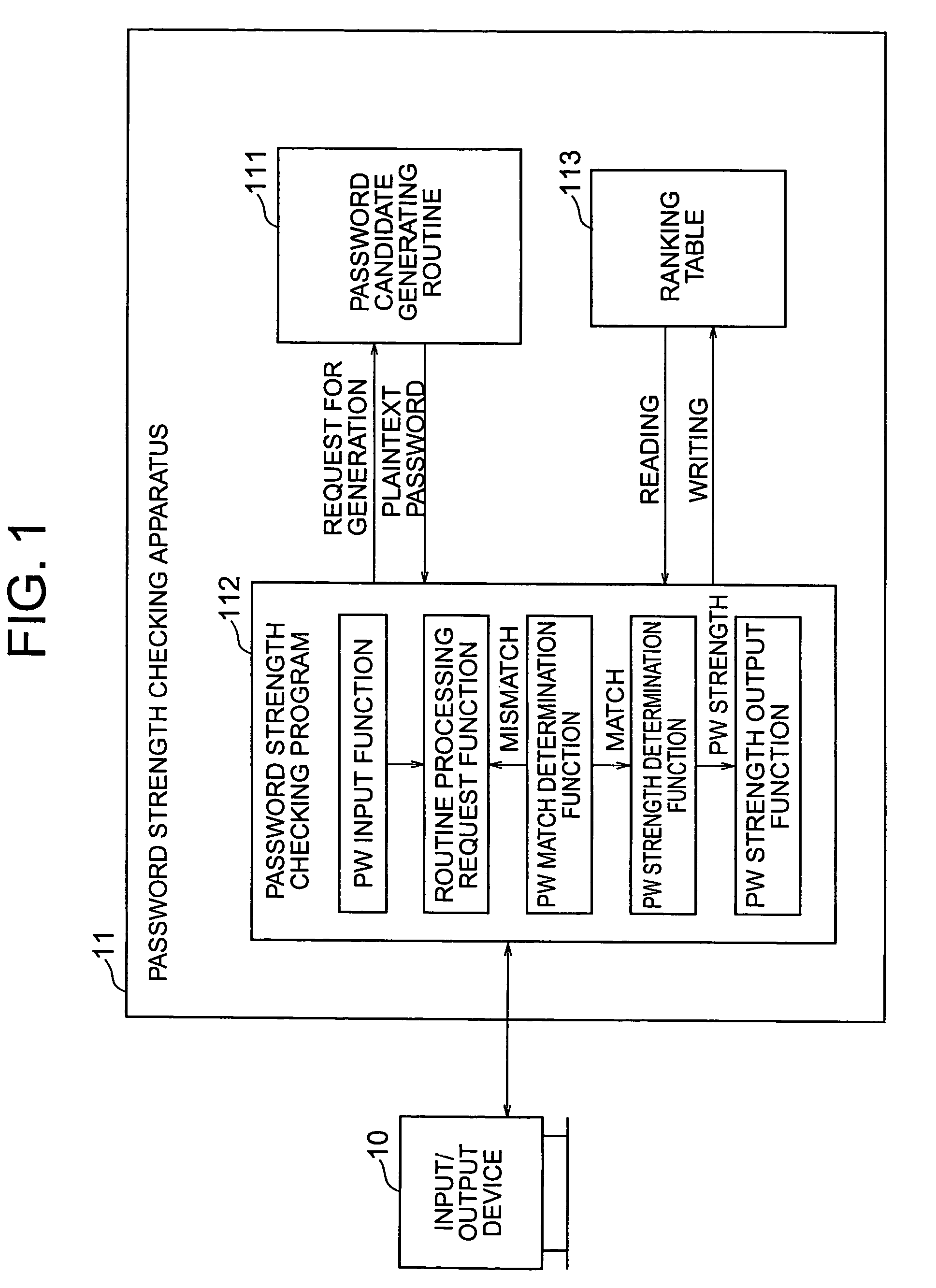
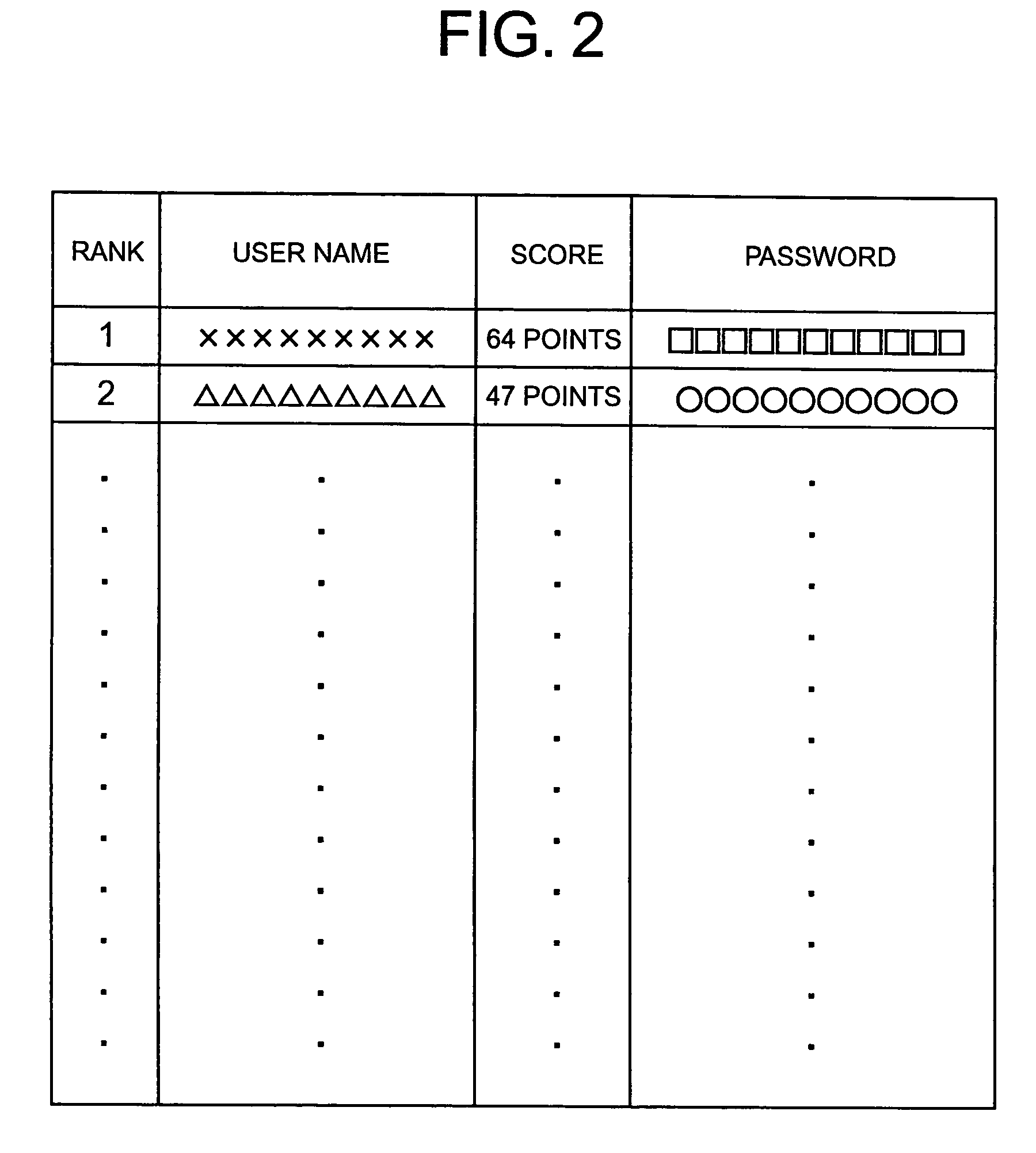
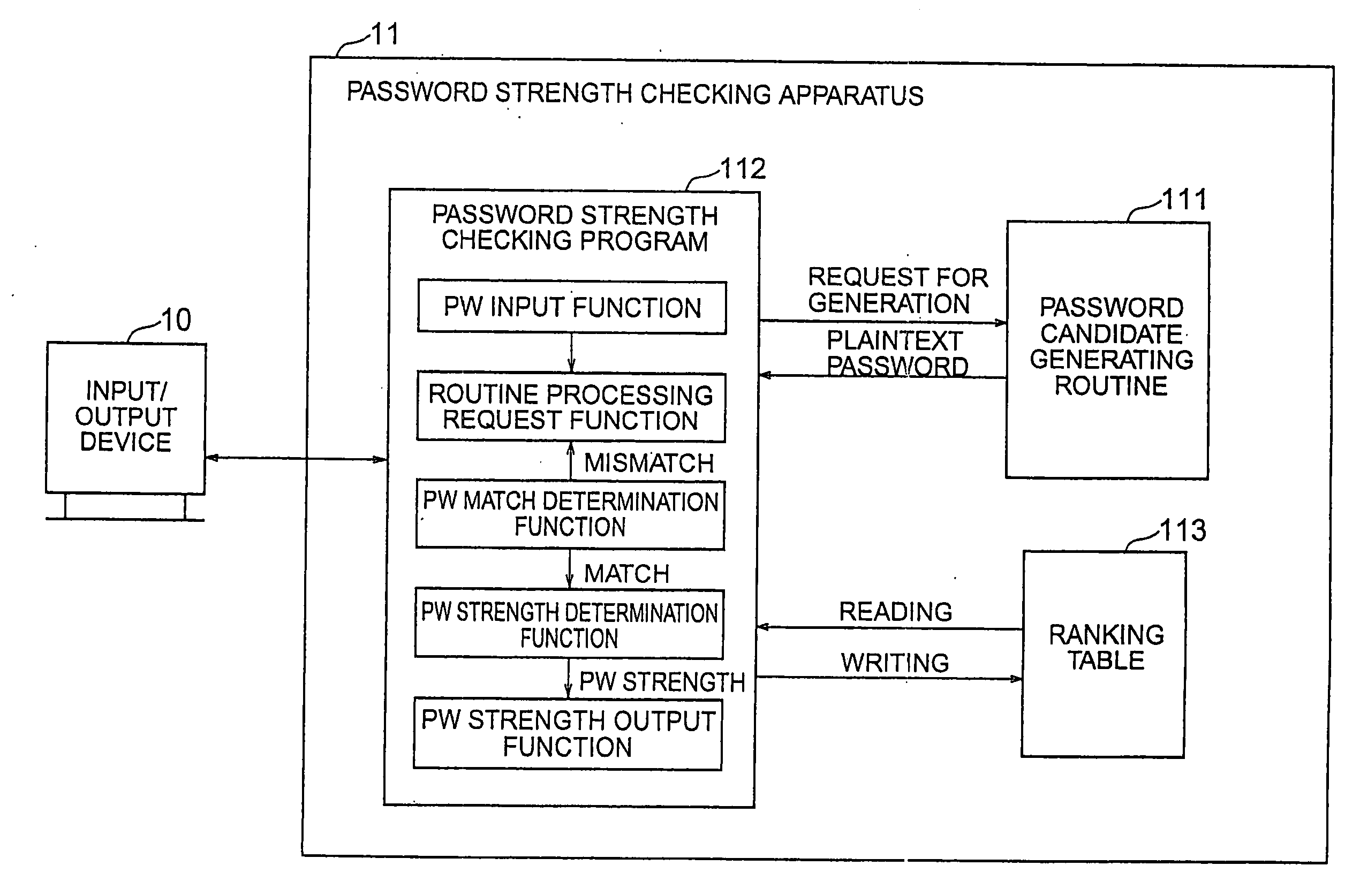
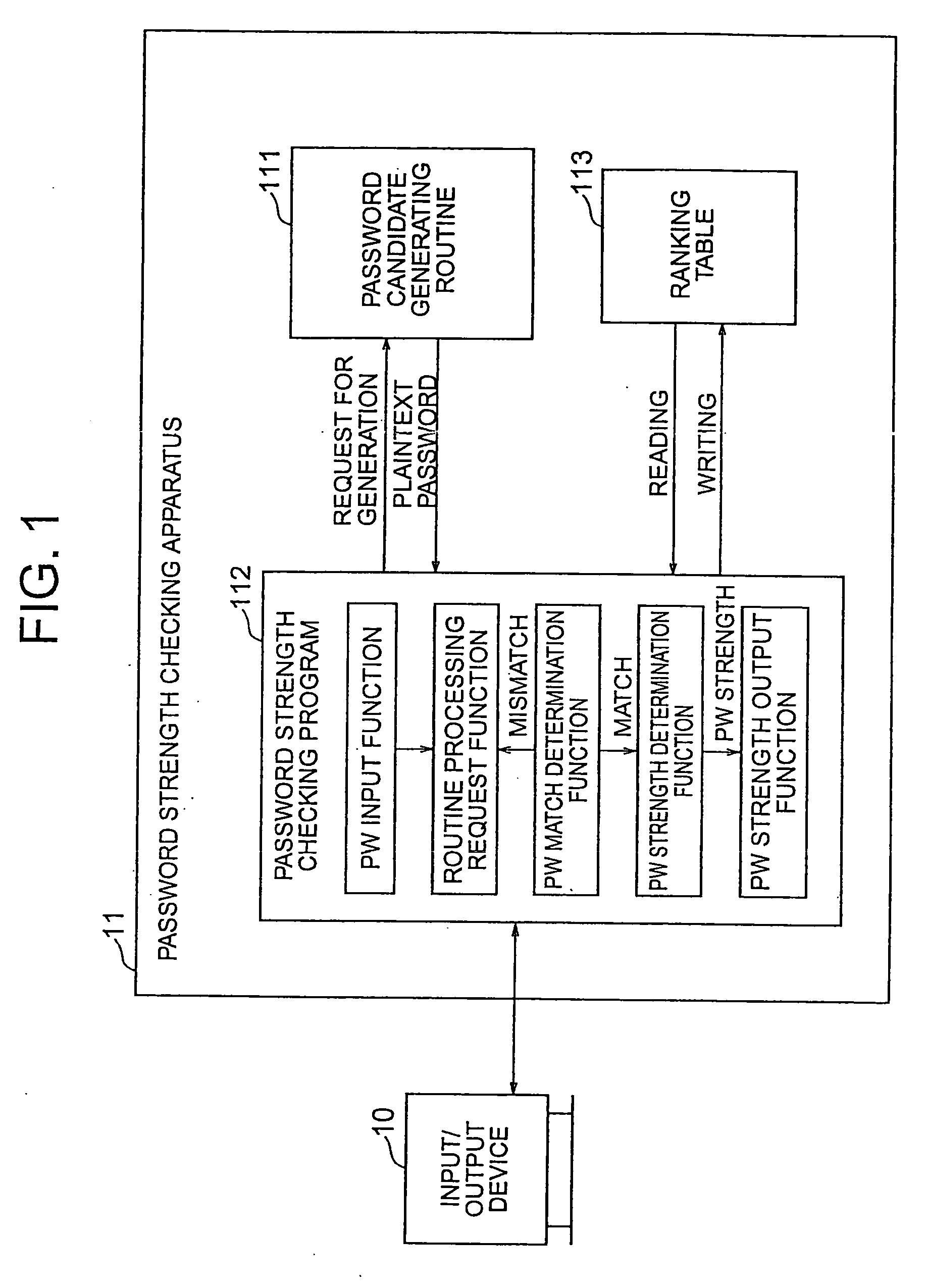
Password strength checking method and apparatus and program and recording medium thereof, password creation assisting method and program thereof, and password creating method and program thereof
ActiveUS7367053B2Digital data processing detailsUser identity/authority verificationPlaintextPassword
A password strength checking method has the steps of inputting a password to be checked, generating a plaintext password candidate according to the same generation procedure as that used by a password guessing tool, determining whether or not the inputted password and the generated password candidate match each other, directing generation of the next password candidate when the match is not determined, determining strength of the inputted password based on the number of the generated password candidates when the match is determined, and outputting information of the determined password strength.
Owner:YAMATAKE HONEYWELL CO LTD
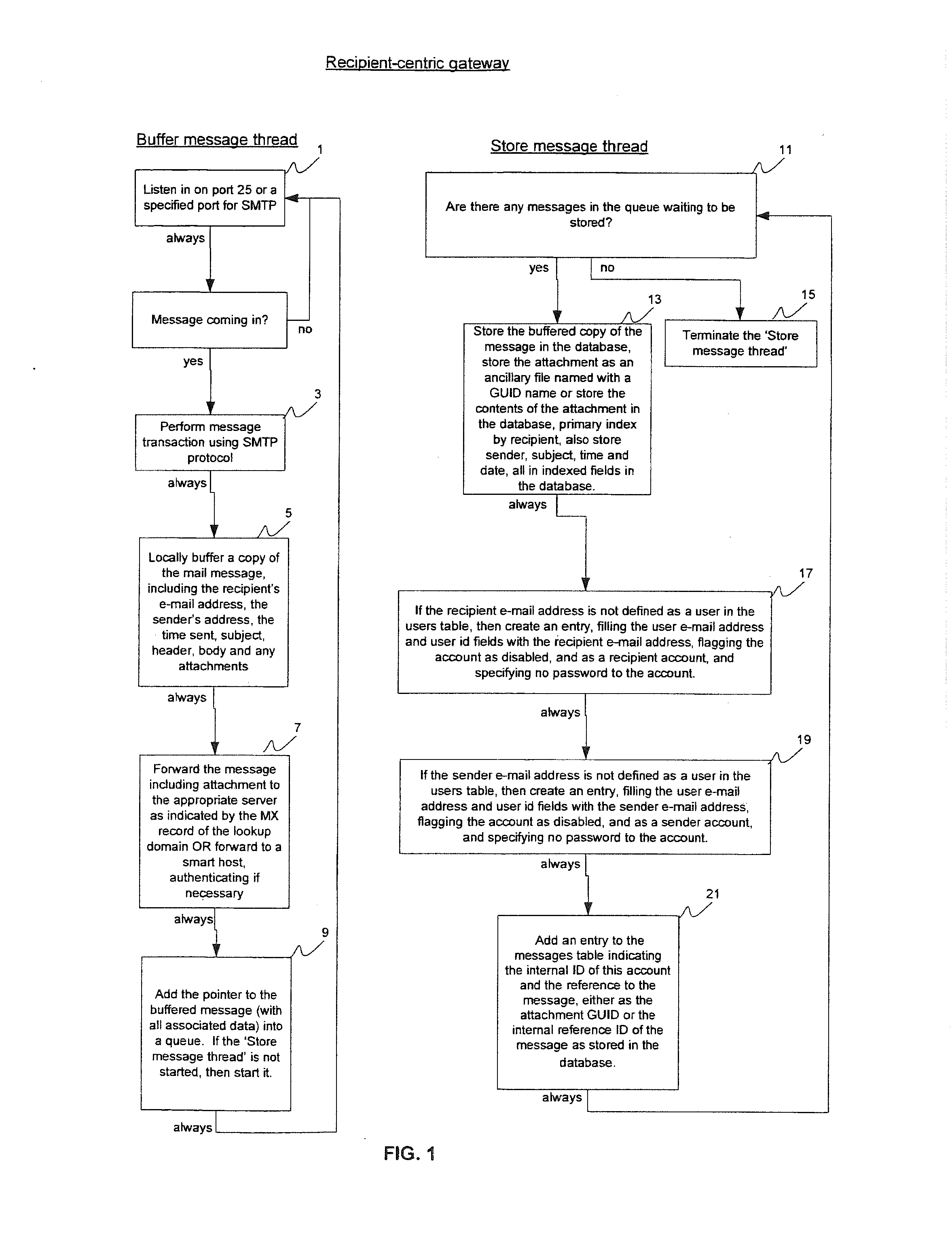
System and method for managing email and email security
InactiveUS20160269440A1Maximizing responsiveness of systemPassword reset costMultiple keys/algorithms usagePublic key for secure communicationThird partyDomain name
A recipient-centric gateway sits at the corporate network perimeter, retaining all outgoing e-mail, organizing the e-mail by recipient so that senders or other designated individuals can view the retained mail from the perspective of the recipient. A login retry limit is based on password strength. A system that guarantees the sender that the recipient is not phished with e-mail fraudulently purported to be from the sender's domain. A system that, without communicating certificates or publishing certificates to third parties and without requiring any workflow changes, enables the transparent two way sending of secure e-mail. A system that, based on feedback and usage, optimizes mailbox responsiveness across the network.
Owner:HARTMAN ROBERT
Password strength checking method and appartatus and program and recording medium thereof, password creation assisting method and program thereof, and password creating method and program thereof
InactiveUS20080216170A1Digital data processing detailsUser identity/authority verificationPlaintextPassword
A password strength checking method includes operations of inputting a password to be checked, generating a plaintext password candidate according to the same generation procedure as that used by a password guessing tool, determining whether or not the inputted password and the generated password candidate match each other, directing generation of the next password candidate when the match is not determined, determining strength of the inputted password based on the number of the generated password candidates when the match is determined, and outputting information of the determined password strength.
Owner:YAMATAKE HONEYWELL CO LTD
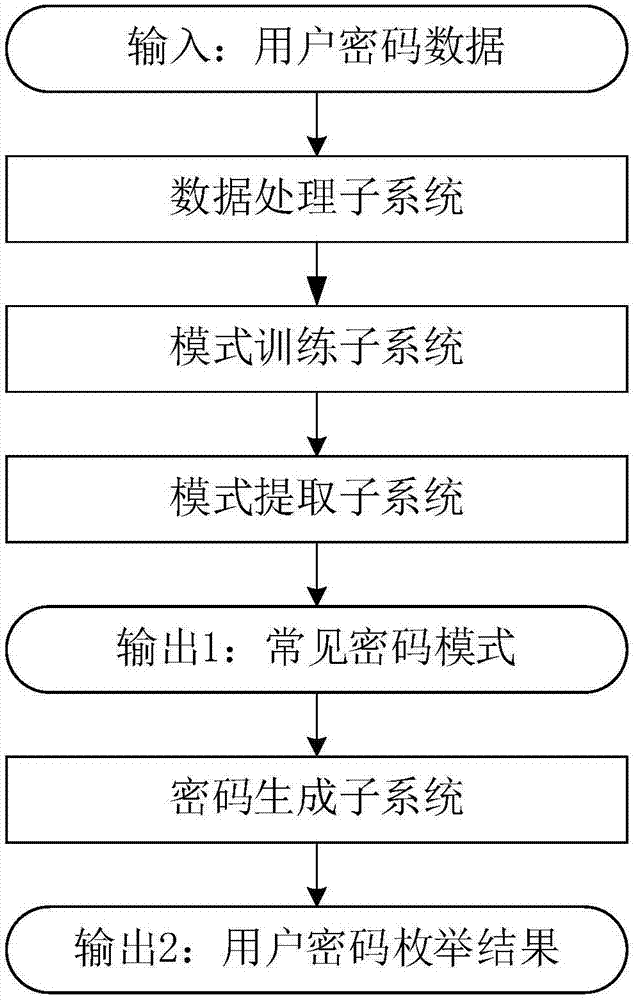
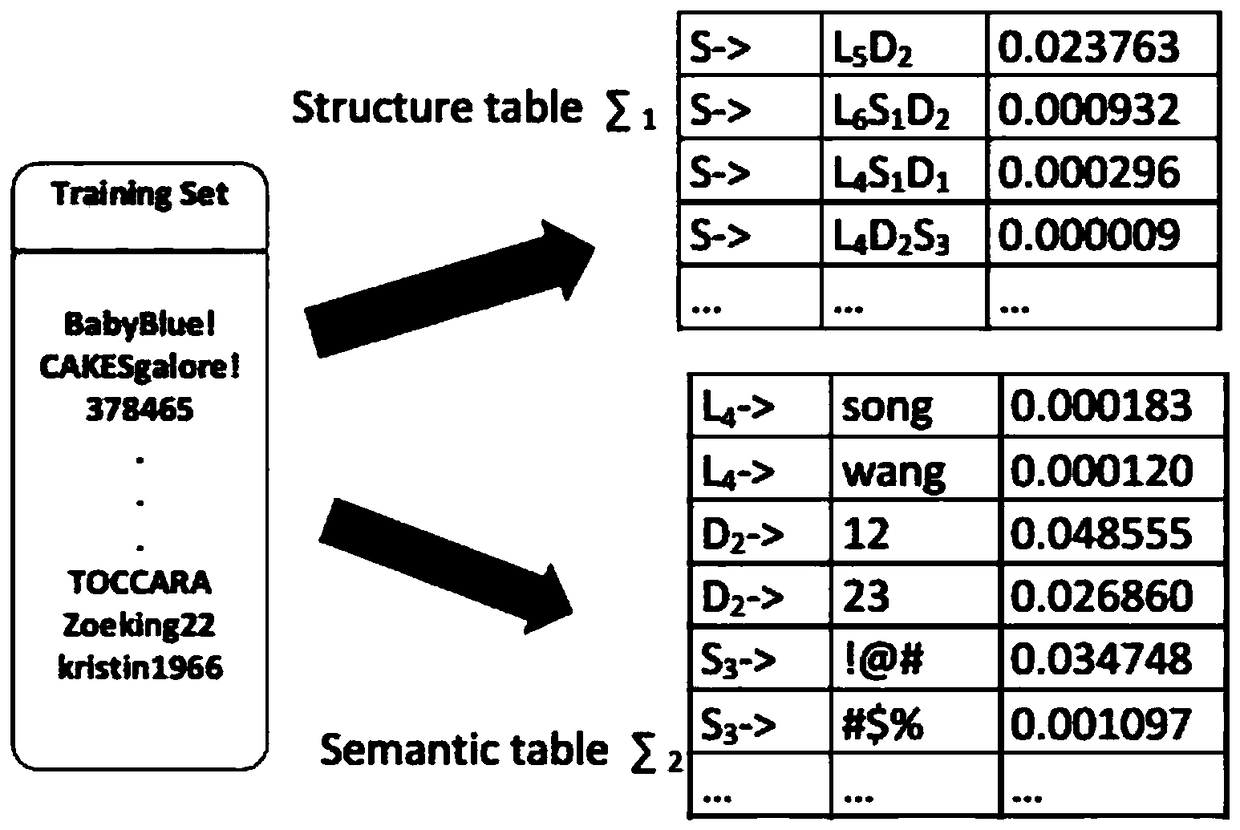
User password guessing system based on deep learning
ActiveCN107122479AEnhance expressive abilityReduce guessworkDigital data authenticationSpecial data processing applicationsLearning basedData set
The invention provides a user password guessing system based on deep learning. According to the system, a password common formation mode of a user can be mined by analyzing a leaked password data set; a password possibly used by the user can be generated based on user personal information according to the learned password common formation mode; the system comprises four subsystems, namely a data processing subsystem, a mode training subsystem, a common mode extraction subsystem and a password generation subsystem; user password data is analyzed; a method based on a recurrent neural network is proposed to establish a user password mode probability model according to the user password data; a most common user password mode is generated according to a Beam Search method based on the user password mode probability model obtained through learning; and the password possibly used by the user is generated based on the user personal information according to the generated common password mode. The system can be used for guessing the user password, assessing user password strength, providing as few as modification suggestions for the user, improving the user password strength and the like.
Owner:XI AN JIAOTONG UNIV
Increasing Chosen Password Strength
ActiveUS20140282939A1Increase password strengthDigital data processing detailsMultiple digital computer combinationsPasswordUltimate tensile strength
An approach is provided to increase password strength in a group of users. The approach detects a password event corresponding to one of the users. In response to the detected password event, the approach identifies a strength of the user's password and compares it to one or more password strength metrics that correspond to the group of users. The password strength comparison data is then transmitted as feedback back to the user.
Owner:IBM CORP
User policy manageable strength-based password aging
InactiveUS8370925B2Digital data processing detailsUnauthorized memory use protectionPasswordLookup table
Password aging based on the strength of the password provides an incentive for users to generate and / or memorize more complex passwords. The strength of the password is computed from a formula that relates the length of the password and the types of characters contained in the password to a strength value, which can be performed using a lookup table having values for different characteristics of the password, determining partial strength values corresponding to the ranges in which the characteristics fall, and then adding the partial strength values. Alternatively, a separate password strength application may be used to provide the strength value, which is entered by the user or administrator generating a new password. Alternatively, the password may be generated based on a specified desired expiration period, with the strength computation performed to ensure that the strength is sufficient to merit the desired expiration period.
Owner:IBM CORP
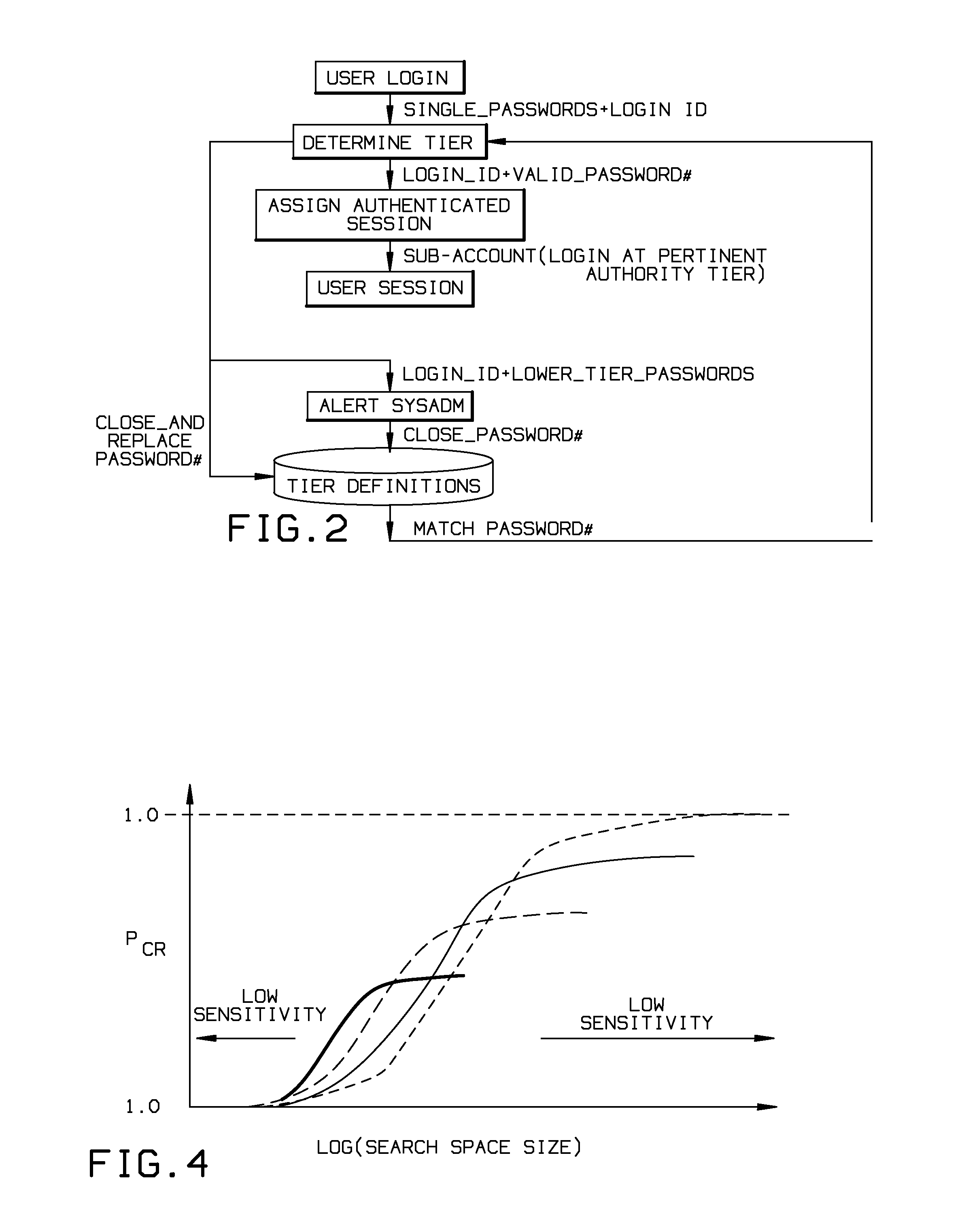
Graduated access multi-password authentication
InactiveUS20150040192A1Digital data processing detailsMultiple digital computer combinationsPasswordSecurity level
Methods and systems for accessing computer data and systems require different sequential and serial passwords to drive a user into a tiered set of sub-accounts of graduated access. At the same time, the tiered hierarchy of access acts as a honey pot system where remote intruders would statistically tend to break through the slightly less secure passwords first, triggering the notification system upon entry into the restricted or firewalled honey pot or virtual systems. With this system, the system administrator can manage multiple sessions for each user where the passwords are of a different level of security based on commercially available password strength tools. The system administrator creates the less secure passwords and lower access sub-accounts and optionally allows users to have such lower levels.
Owner:KOBOLD MICHAEL CHRISTOPHER
Calculating a password strength score based upon character proximity and relative position upon an input device
A solution for computing password strength based upon layout positions of input mechanisms of an input device that entered a password. A password including an ordered sequence of at least two characters can be identified. A position of each of the characters of the sequence can be determined relative to a layout of an input device used for password entry. Each position can correspond to an input region (key) of the input device (keyboard). A proximity algorithm can generate a proximately score for the determined positions based upon a pattern produced by the positions given the layout of the input device. A password strength score can be computed based at least in part upon the proximity score.
Owner:IBM CORP
System, device and method for authentication
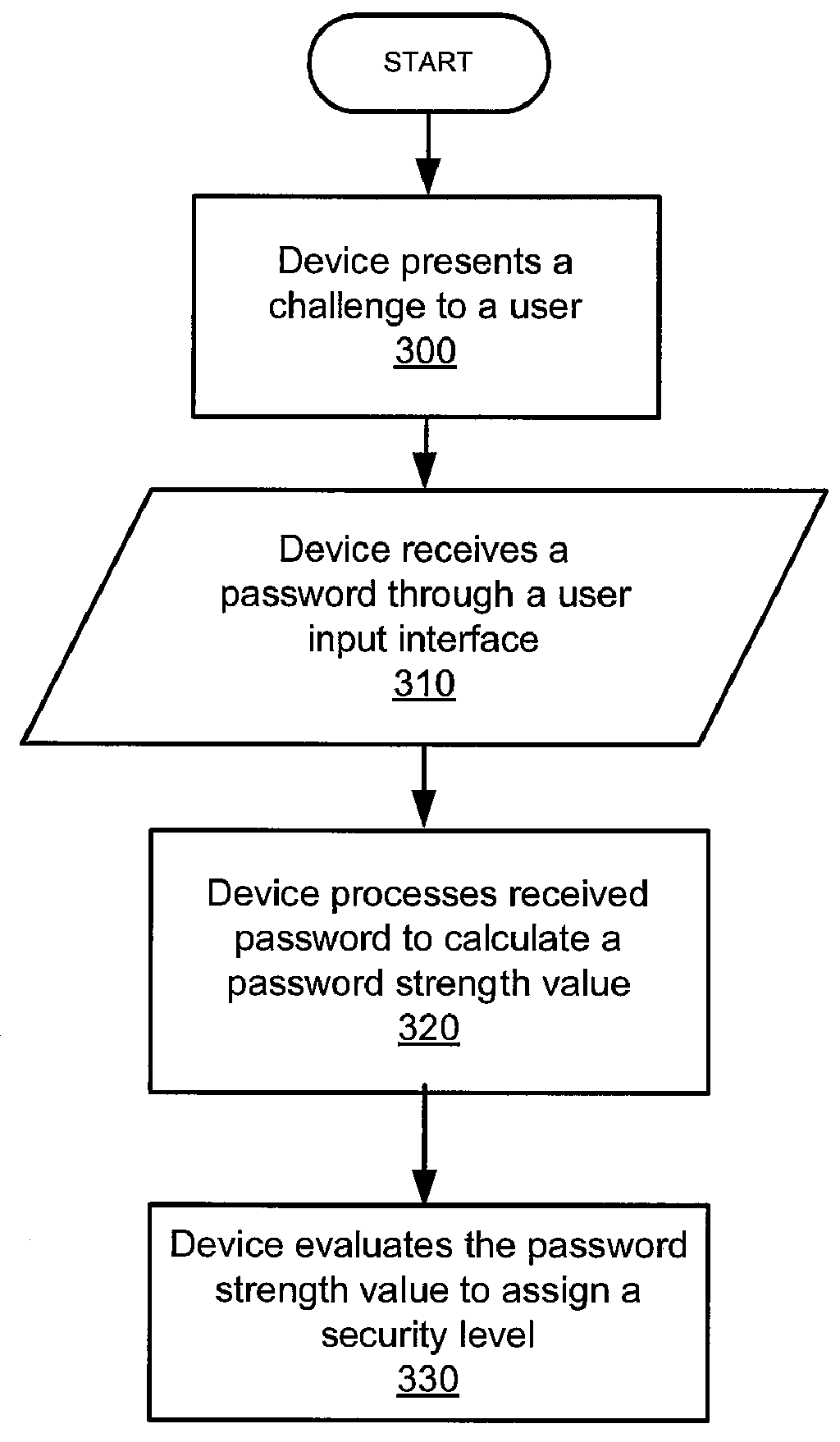
InactiveUS20130055379A1Digital data processing detailsUser identity/authority verificationPasswordUser input
A computing device and computing device implemented method for setting a security level of the computing device. The method may comprise the computing device presenting a challenge to a user of the computing device. The challenge requiring the user to register a password with the computing device. The computing device may receive the password through a user input interface of the computing device in response to the challenge. The computing device may process the received password to calculate a password strength value and evaluate the password strength value to assign the security level. In an aspect, the security level may assign a higher security level when the password strength value is relatively high. In an aspect, the security level may allow for an expanded range of user selectable security options when the password strength value is relatively high.
Owner:BLACKBERRY LTD
Bulk password grading priori check method
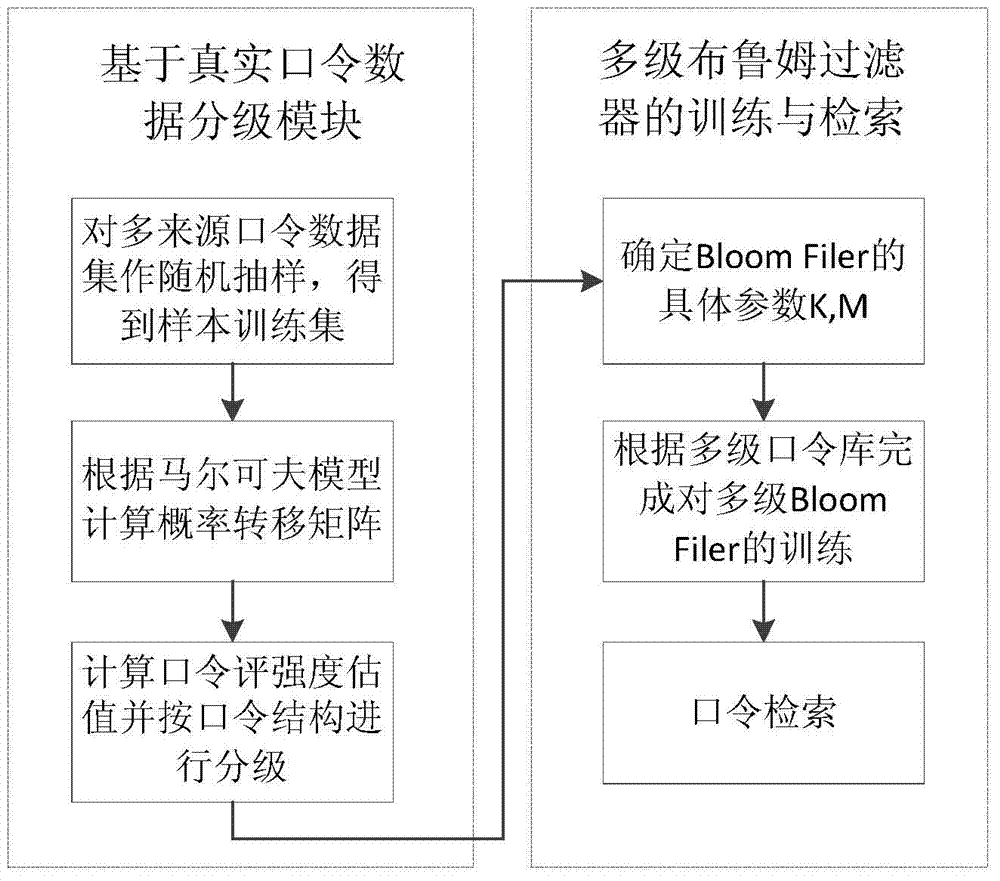
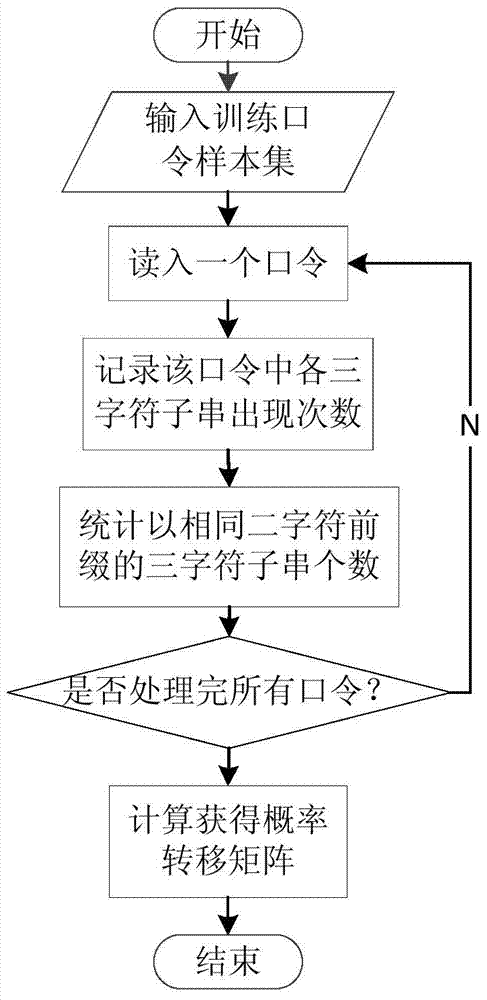
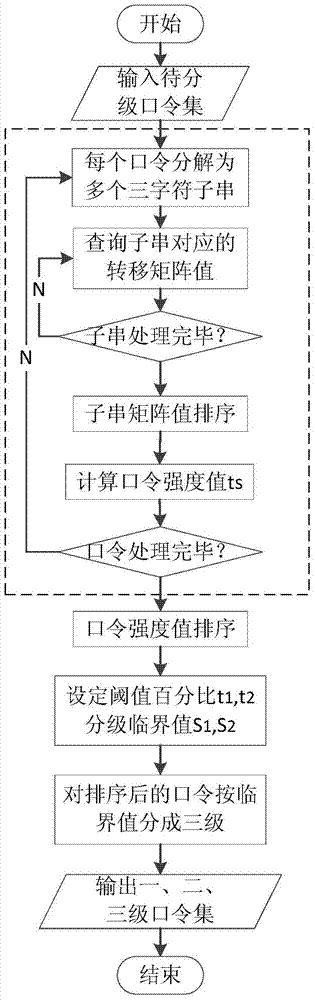
ActiveCN104268450AEasy to guessProtection securityCharacter and pattern recognitionDigital data authenticationHash functionTransition probability matrix
A bulk password grading priori check method includes two steps of grading based on actual password data as well as training and retrieval of a grading password model. The grading includes the steps of firstly sampling and extracting millions of Chinese user password data to obtain a sample training set, then obtaining password probability transfer matrix through a second-order Markov model according to the sample training set and calculating to obtain a strength assessed value of each password, and finally grading all password data according to the password assessed value and a password hierarchy. The training and retrieval of the grading password model includes the steps of storing grading results at a bit vector of a Bloom filter at each grade through hash functions by building a password Bloom filter of different strength for the password set of each grade so as to build a grading password model, and using the password Bloom filters of multiple grades for quickly and efficiently determining the strength of passwords to be checked during retrieval.
Owner:ZHEJIANG UNIV OF TECH
Managing password strength
InactiveUS20140068731A1Digital data processing detailsMultiple digital computer combinationsData processing systemPassword
A method, system or computer usable program product for managing password strength including receiving a password on a data processing system for a user, filtering for personal information about the user from multiple independent data sources accessible across a computer network, computing the password strength by the data processing system using an algorithm which compares the password to the filtered personal information about the user, and presenting feedback to the user through a user interface on a data processing system display regarding the computed password strength.
Owner:IBM CORP
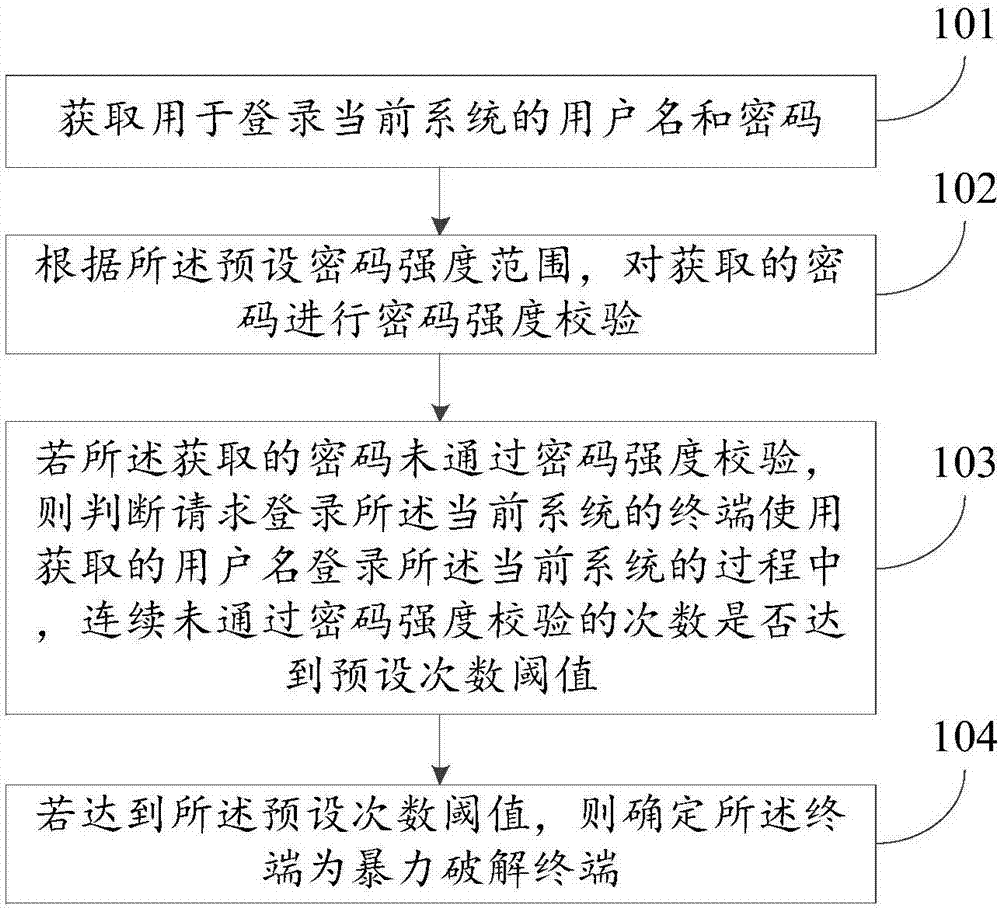
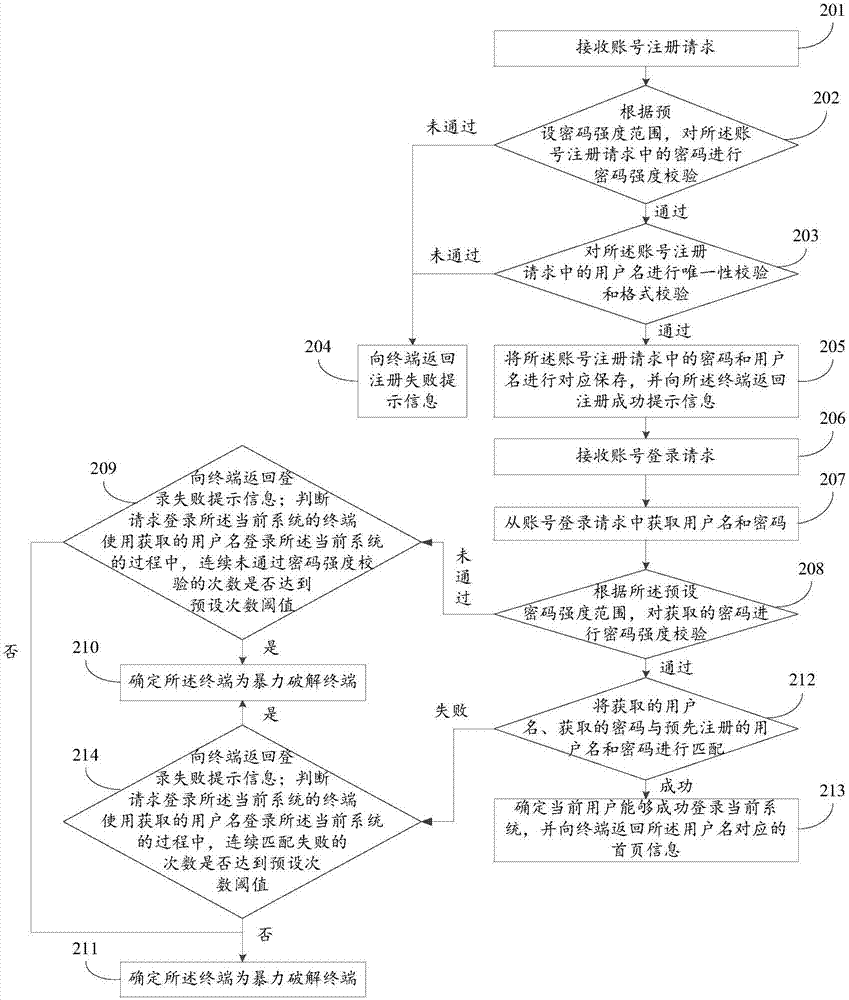
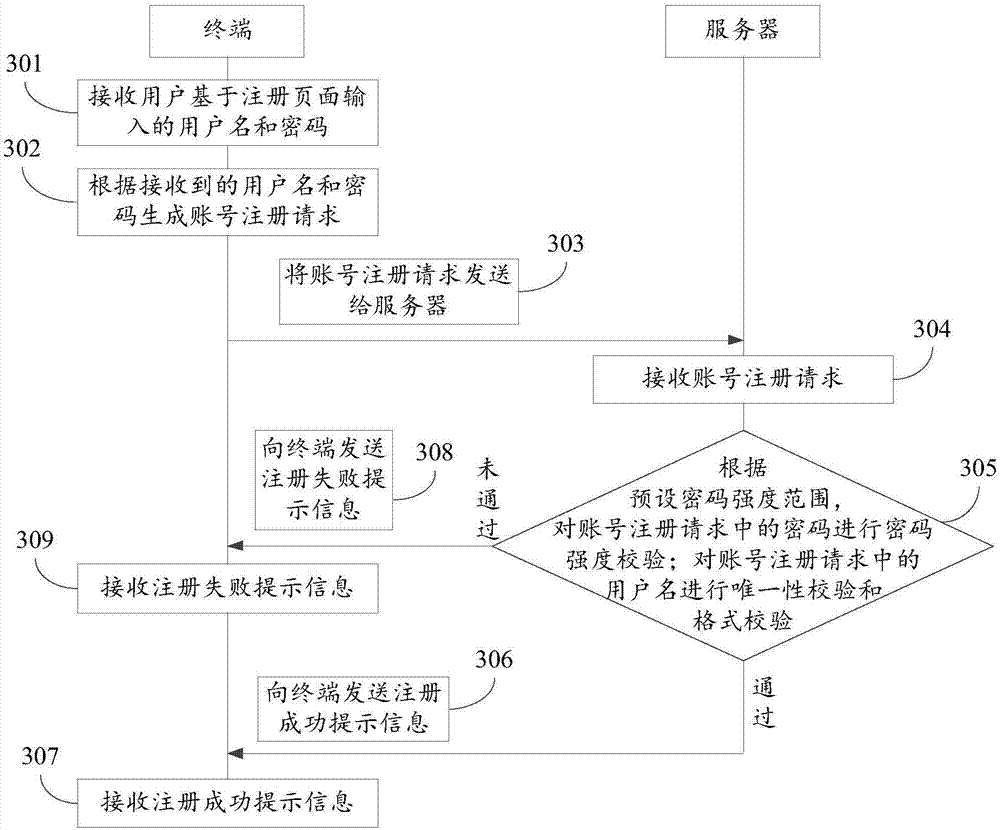
Method and device for identifying brute-force cracking
ActiveCN108011863AImprove the efficiency of identifying brute force attacksTransmissionBrute forceNumber times
The invention, which relates to the field of data security technology, discloses a method and device for identifying brute-force cracking so that a problem of low brute-force cracking identification efficiency in the prior art can be solved. The method comprises: a user name and a password that are used for logging in a current system are obtained, wherein a password meeting a preset password strength range and a corresponding user name are registered in advance in the current system; according to the preset password strength range, password strength checking is carried out on the obtained password; if the obtained password does not pass the password strength checking, whether the number of times of not passing the password strength checking reaches a preset number times threshold during the process of logging in the current system by the terminal making a request of logging in the current system by using the obtained user name is determined; and if so, the terminal is determined to bea brute-force cracking terminal. The method and device are mainly applied to the account login scene.
Owner:BEIJING CO WHEELS TECH CO LTD
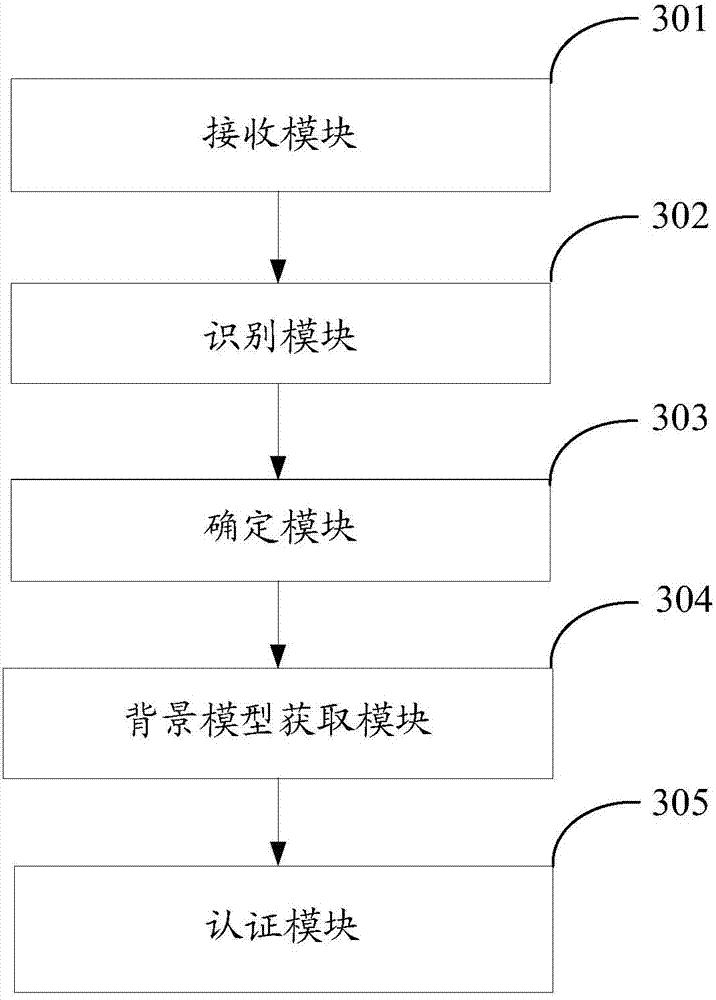
Voiceprint authentication method and system
ActiveCN104765996AMeet the needs of frequent changesReal-time online generationSpeech analysisDigital data authenticationPasswordUser input
The invention discloses a voiceprint authentication method and system, and belongs to the technical field of password authentication. The method comprises the steps of receiving a voice signal inputted by a user; recognizing voice of a voice signal to obtain a password text; determining whether a background model is corresponding to the password text; if so, acquiring the background model; if not so, expending a voice generating unit model which is obtained by pre-training according to the password text so as to obtain the background model corresponding the password text; authenticating the user according to the voiceprint feature sequence in the voice signal, the background model and the voiceprint password module of the user. With the adoption of the method and the system, the demand of user on customizing a password and frequently changing the password can be met.
Owner:ANHUI IFLYTEK INTELLIGENT SYST
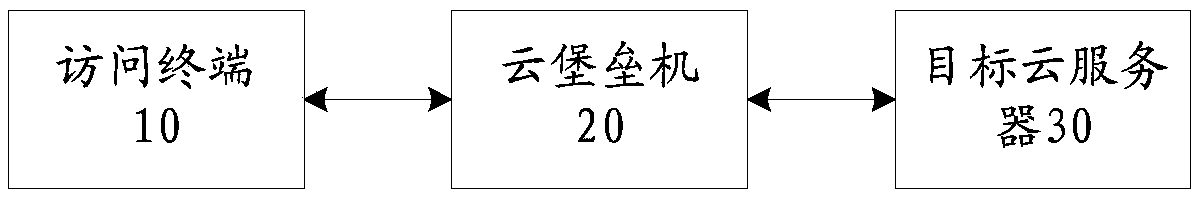
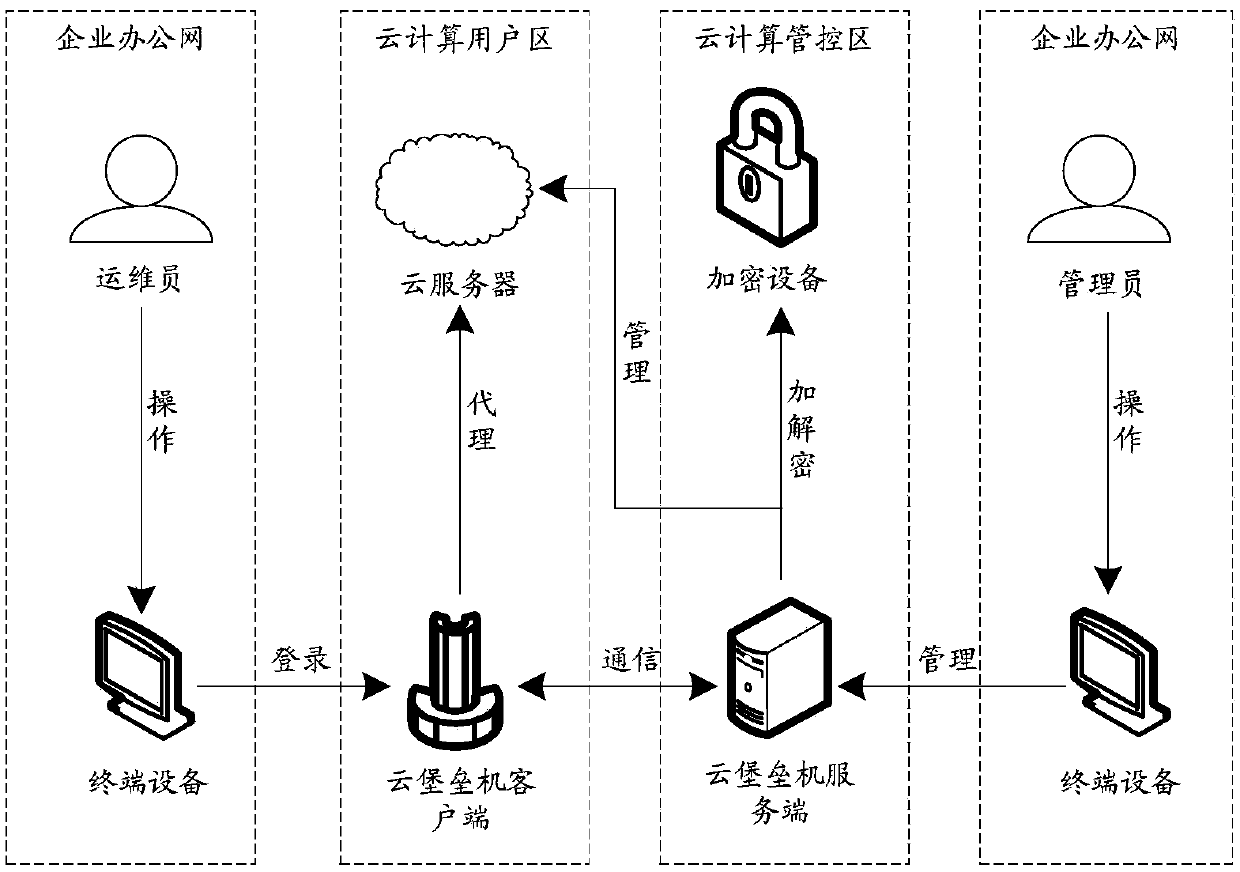
Remote login method, device and system
The invention discloses a remote login method, a device and a system. The system comprises an access terminal used for determining a target cloud server to be logged in; a cloud bastion host which isconnected with the access terminal, wherein a key pair of the target cloud server is stored in the cloud bastion host, the key pair comprises a public key and a private key corresponding to the publickey, and the cloud bastion host is used for performing signature by using the private key in the key pair; and the target cloud server which is connected with the cloud bastion host, stores a publickey of the key pair, and is used for performing signature verification on the signature by using the public key of the key pair, and establishes communication with the cloud bastion host under the condition that the signature verification is passed. The technical problem that in the prior art, the login credential of the cloud server is manually set by an administrator, and consequently the password strength is low is solved.
Owner:ALIBABA GRP HLDG LTD
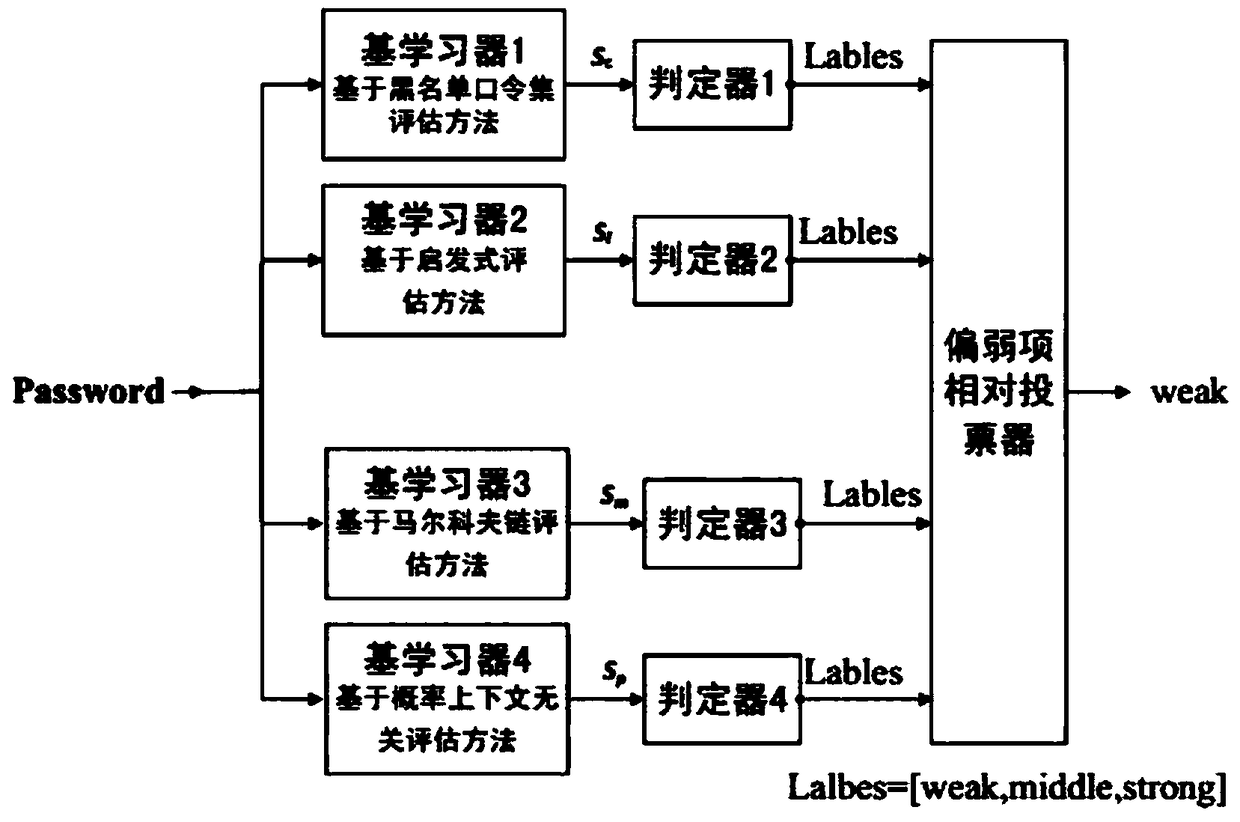
Password strength evaluation model based on ensemble learning
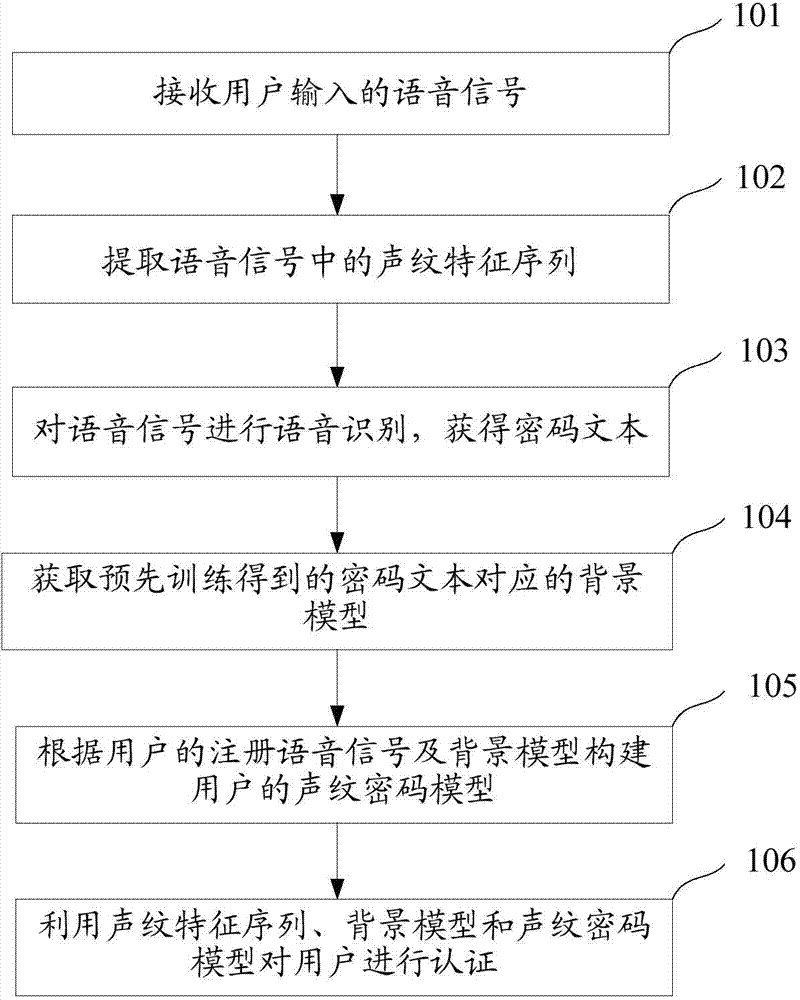
InactiveCN108763920AAvoid problems that affect the results of the assessmentImprove accuracyDigital data authenticationEvaluation resultPassword
The invention designs a password strength evaluation model based on multi-model ensemble learning. Firstly, a real password training set is used to train several existing password evaluation models assub-models. Secondly, several trained sub-models are used as base learners for ensemble learning, and the advantage integration of each sub-model is realized by the combination strategy of partial weak-term voting. Finally, a universal password evaluation model is implemented based on high accuracy. Password strength evaluation based on a multi-model ensemble learning model for passwords with different levels of complexity is performed, the evaluation results are high in accuracy and versatility, the multi-model ensemble learning has good applicability in password evaluation.
Owner:SICHUAN UNIV
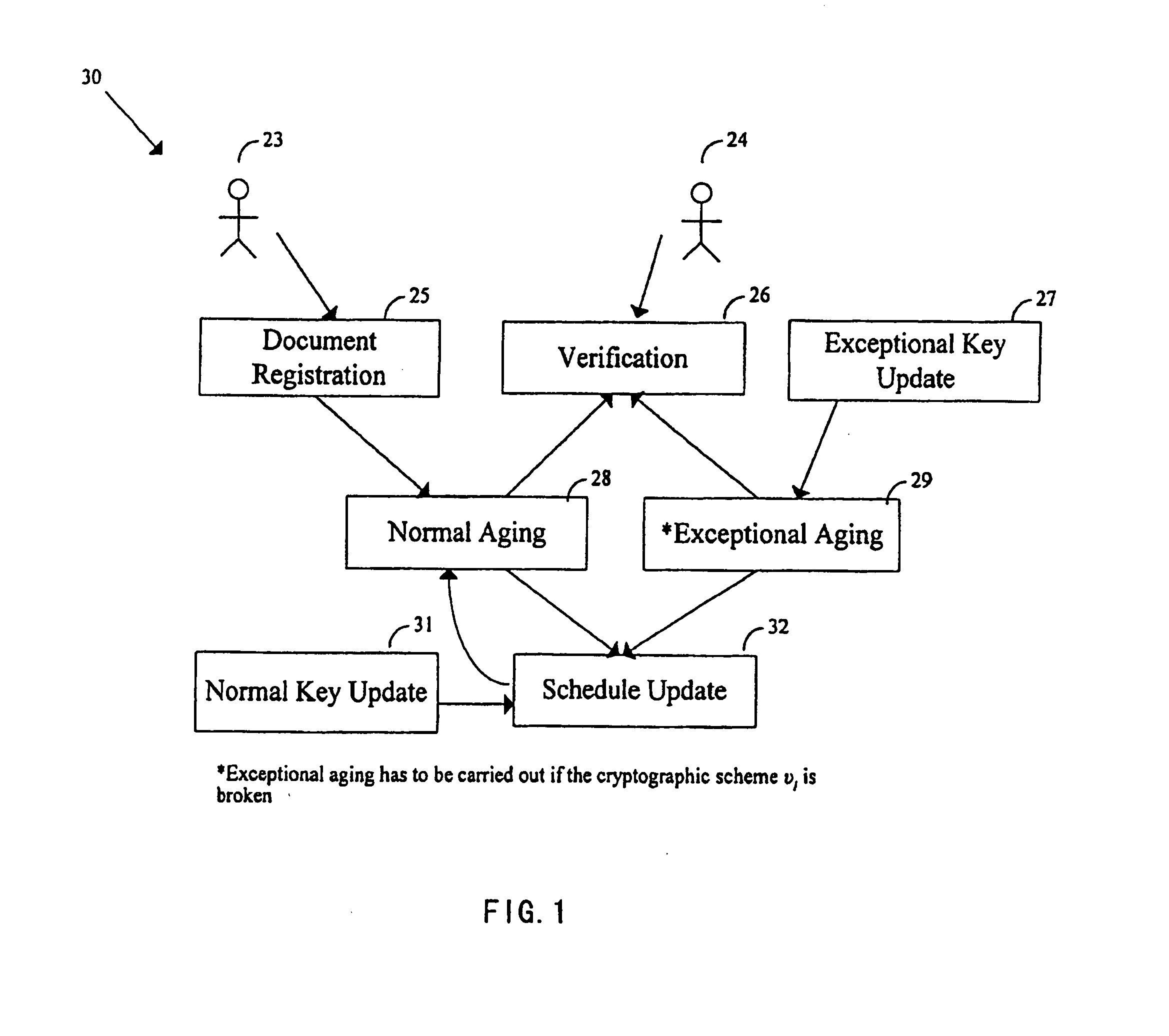
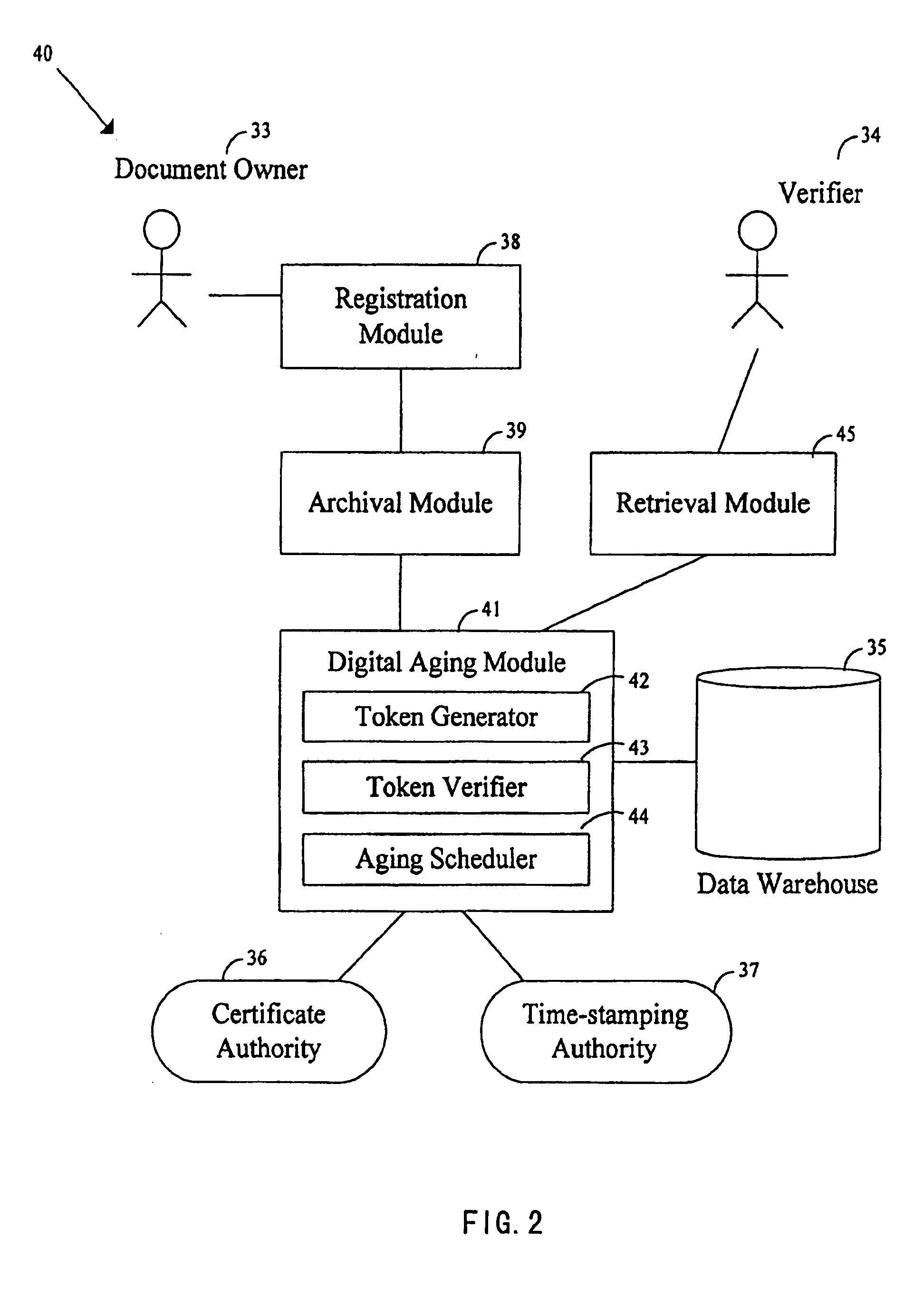
System and method for secure preservation and long term archival of electronic documents
InactiveUS20050235140A1The process is simple and effectiveUser identity/authority verificationElectronic documentTimestamp
A method and system for long term electronic document archiving. The system collects a certificate revocation information for a certificate from a certificate authority that indicates the validity of the certificate used in an electronic document. The certificates are collected from a certificate authority. The system then generates at least two layers of signature and timestamp from the electronic document, certificate revocation information collected, and the collected certificate. Cryptographic primitives of different strength are used, and the two layers of signature and timestamp generated have different cryptographic strengths. The signature is generated using a system signing key whereas the timestamp is generated by an external entity. A digital aging token is then formed by combining the original electronic document, certificate revocation information, and certificate collected to the layers generated.
Owner:HONG KONG THE UNIV OF
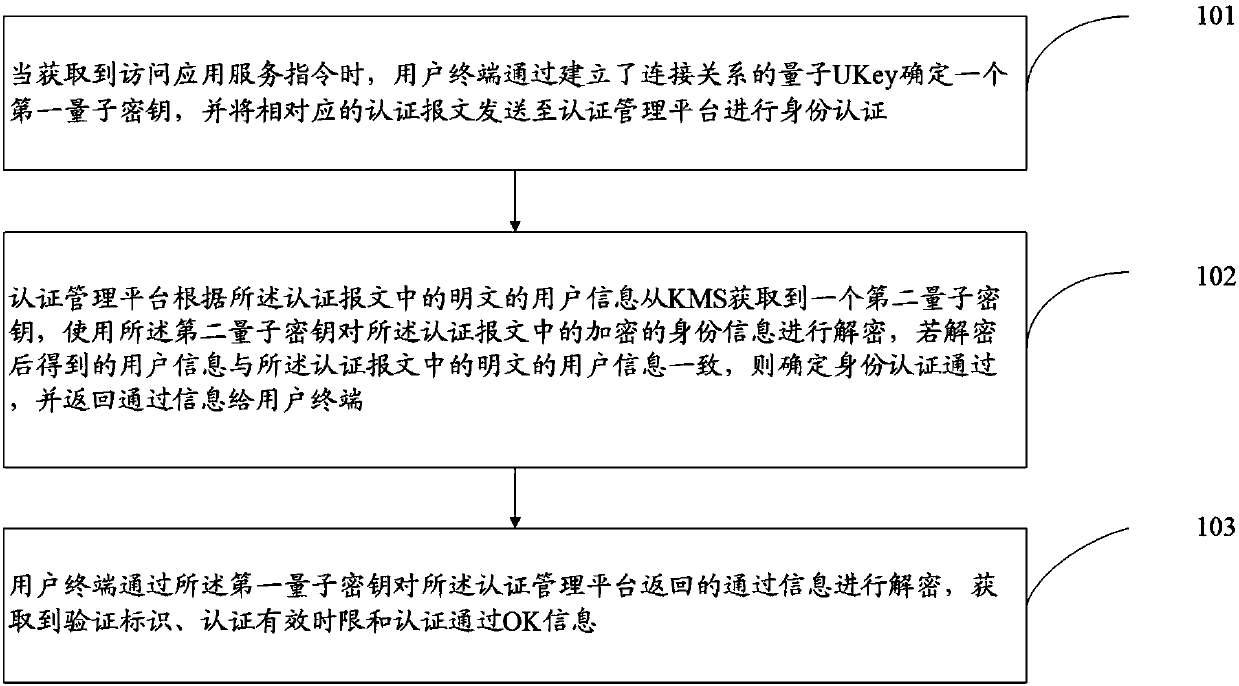
Communication method and system based on quantum Ukey
ActiveCN107769913ATo achieve an organic combinationImprove securityKey distribution for secure communicationPlaintextApplication server
The invention discloses a communication method and system based on the quantum Ukey, aiming to solve the potential safety hazards that the algorithm is not safe, the user password strength is not highenough, the user password plaintext input, secret key distribution and management are difficult, and the secret key cannot be automatically updated in the aspects of current identity authentication and security access cloud service application. The communication method based on the quantum Ukey comprises the following steps that when an access application service instruction is acquired, a user terminal determines a first quantum key by the quantum Ukey established the connection relation, and sending the corresponding authentication message to an authentication management platform for identity authentication; the authentication management platform obtains a second quantum key from the KMS according to the authentication message, and decrypting the encrypted information in the authentication message, if the decrypted information is consistent with the plaintext information in the authentication message, the identity authentication is determined to pass, and the passing information isreturned to the user terminal, so that the user terminal accesses the application server through the first quantum key.
Owner:QUANTUMCTEK GUANGDONG CO LTD
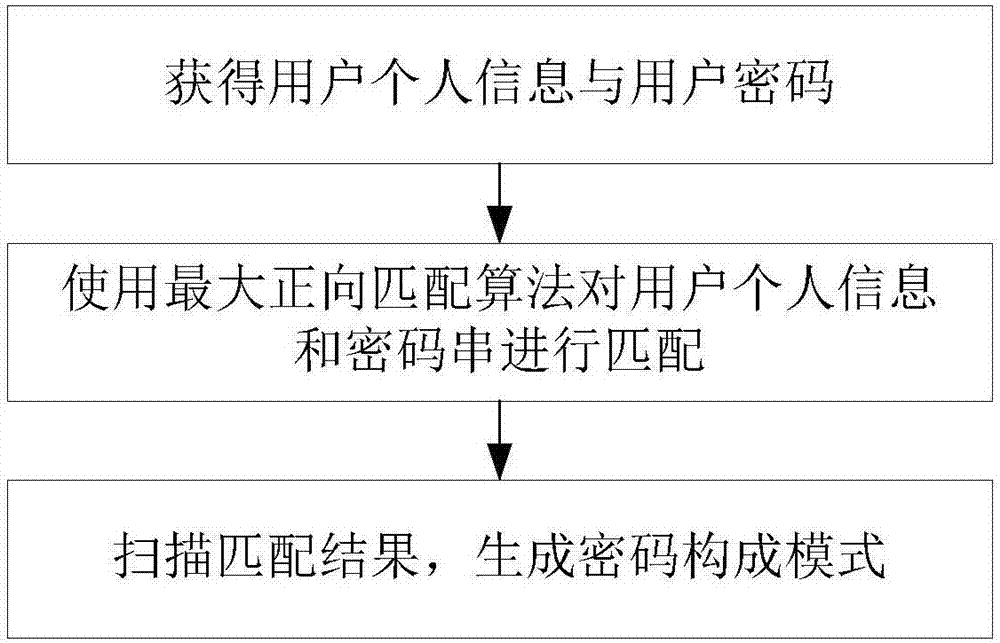
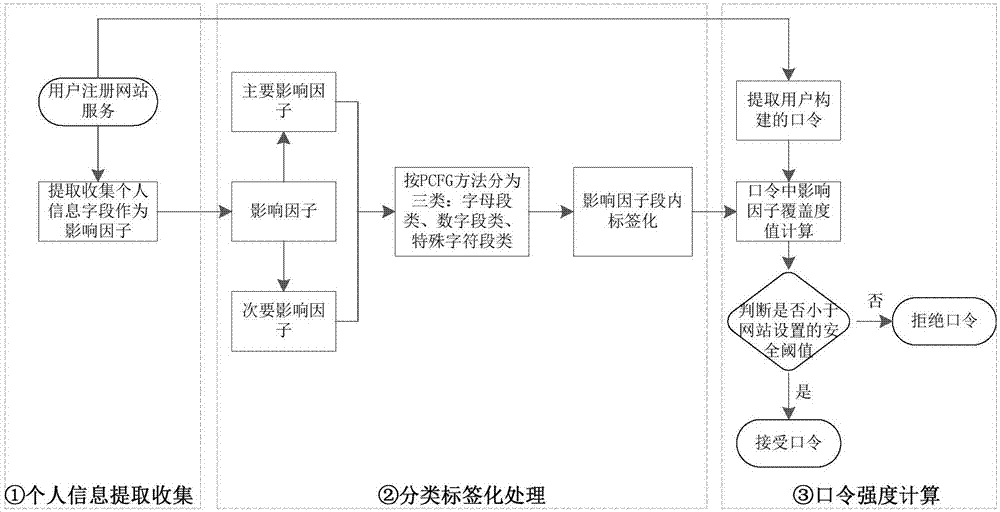
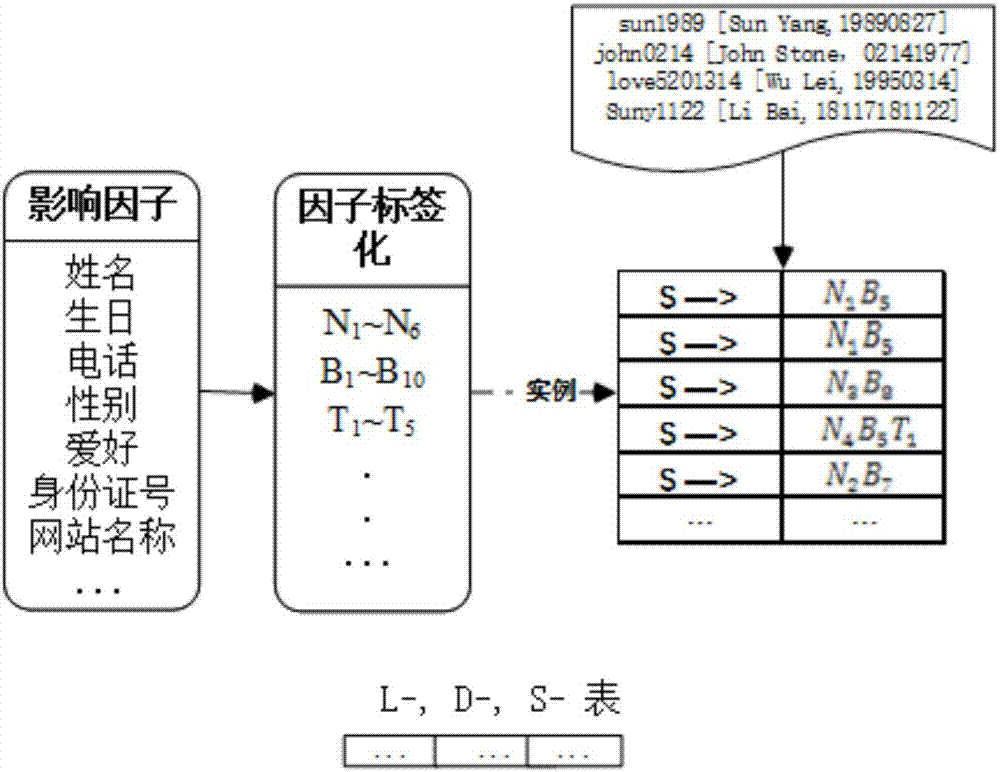
Password strength evaluation method based on personal information
ActiveCN106934275AAccurate judgmentImprove securityDigital data authenticationPattern detectionPassword
The invention discloses a password strength evaluation method based on personal information. The method comprises the following steps that: when a user registers website service, collecting the influence factor field of personal information used for user password construction; independently carrying out classification on the influence factor field, and carrying out tagging processing on the influence factor field according to a practical transformation form; when the user inputs the password, according to an extracted and collected user information influence factor, calculating a coverage degree value which contains the personal information in the influence factor field in the password constructed by a current user, and combining the coverage value with a traditional heuristic method and pattern detection method to calculate a password strength value; and selecting a maximum threshold value which permits to contain the personal identification information in an acceptance password by a target website as an acceptance measurement index of the password strength. The invention puts forward the password strength evaluation method in which a personal identification information measurement factor is added. The method has the characteristics that the password strength value is instantly and effectively fed back, and an influence factor is plug and play and can be easily selected, and a user is assisted in selecting the password with a higher safety degree.
Owner:EAST CHINA NORMAL UNIV
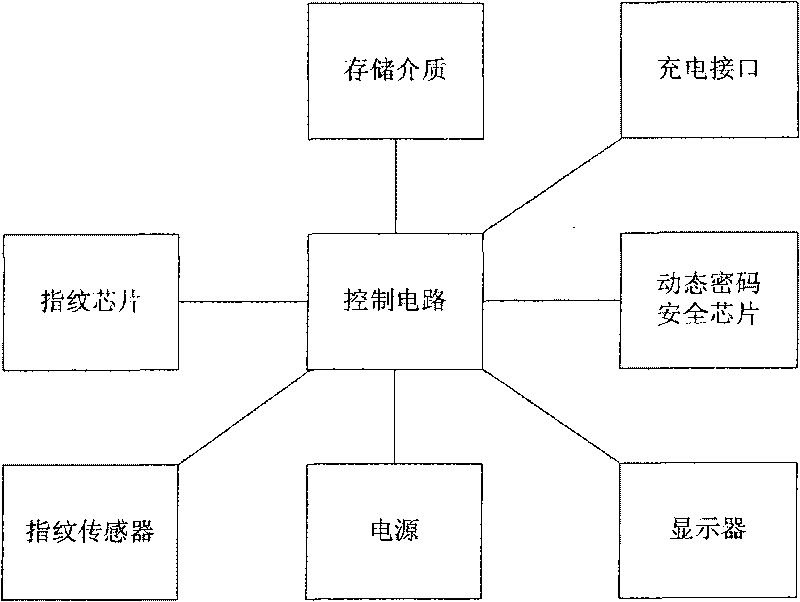
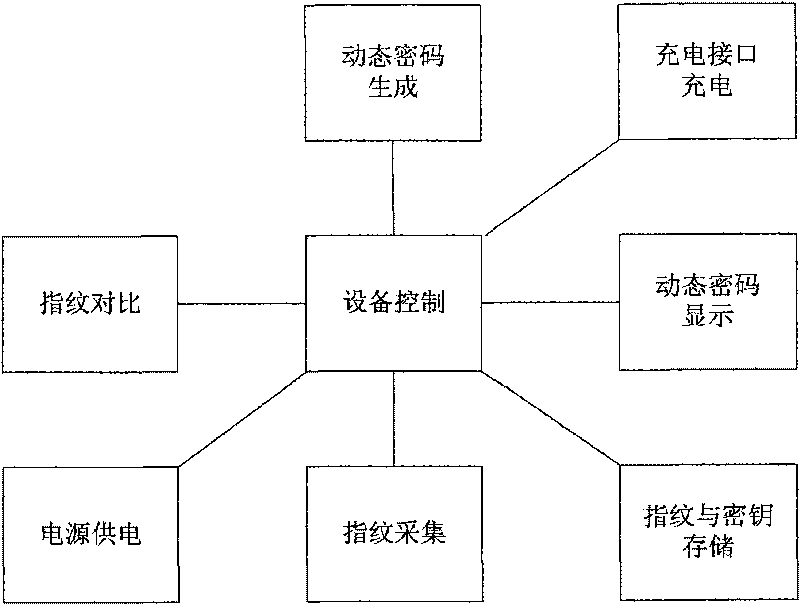
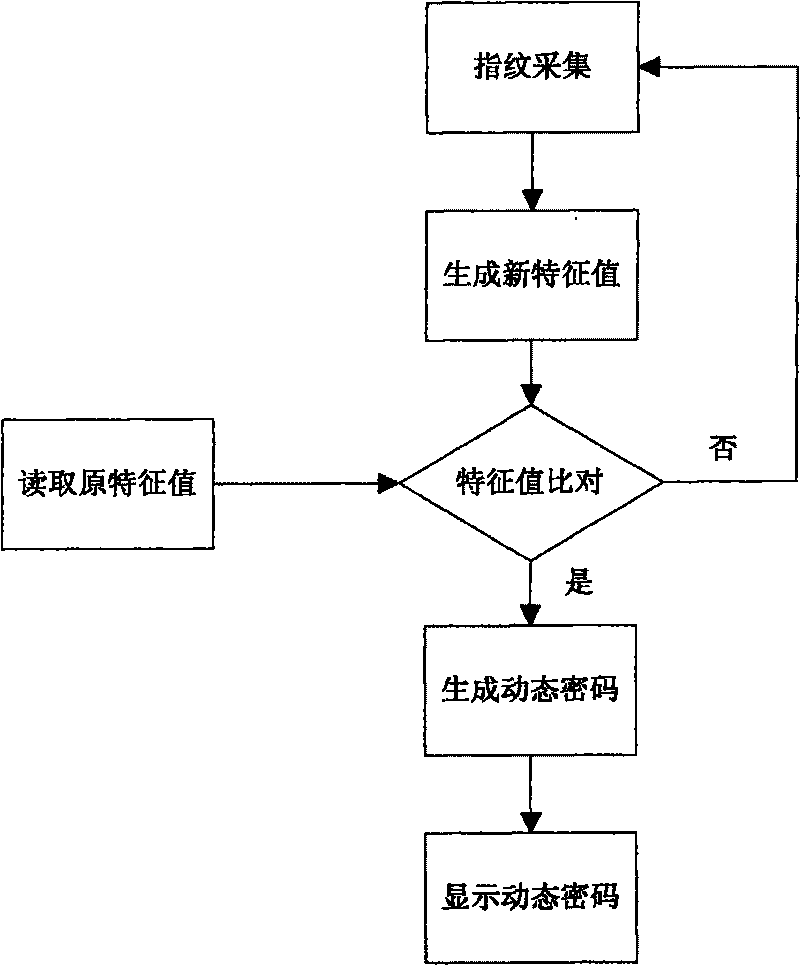
Fingerprint dynamic password ID authentication device and the implementation method thereof
InactiveCN101753301ANot easy to embezzleEnsure safetyUser identity/authority verificationCharacter and pattern recognitionPasswordDisplay device
The invention aims to provide a fingerprint dynamic password ID authentication device and the implementation method thereof, which can effectively address the problems of equipment steal, insufficient cryptographic strength, inreversible generated dynamic passwords, lower security, great system consumption and the like in the ID authentication field. The equipment related to by the invention comprises a fingerprint chip, a fingerprint sensor, a dynamic password chip, a display, a storage medium, a power supply, a recharging interface and a control circuit; wherein, the control circuit is respectively connected with the fingerprint chip, fingerprint sensor, dynamic password chip, display, storage medium, power supply and recharging interface. The fingerprint dynamic password ID authentication device has the advantages that the fingerprint dynamic password ID authentication device can employ double authentications, namely authenticating a user's right to use a device through the user fingerprint and then authenticating the user's right to perform operations on a terminal through a dynamic password generated by the device, to ensure the user authentication device can be only used by the user himself and the authentication information is not stolen, thus sufficiently ensuring the security of the user account and rights.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Safety communication method suitable for remote control with limited capability at controlled end
InactiveCN101931623AImprove confidentialityLimited number of solutionsError prevention/detection by using return channelSecure communicationTelecommunications link
The invention discloses a safety communication method suitable for remote control with a limited capability at a controlled end. The method comprises the following steps of: setting password sets at a control end and the controlled end and generating a password set according to an input initialization password by an irreversible method, wherein the password set comprises an index number and the password per se and encryption and decryption are performed by using the password corresponding to the recorded index number in a normal communication process; when the password is asynchronous, transmitting the index number by encrypting to perform password synchronization; and when a password set updating condition is met, negotiating about the update of the password set by transmitting a selected index number. A password set generating device for calculating the password set and communicating with the controlled end only when the password set is needed to be generated is arranged at the controlled end. Various attacks are resisted effectively by using a dynamic password and operation of real-time password calculation needed by the transmission of each data packet is avoided. Simultaneously, the password per se does not need to be transmitted on a communication link in password synchronizing and password set updating processes, so that simpleness and safety are realized.
Owner:SOUTH CHINA UNIV OF TECH
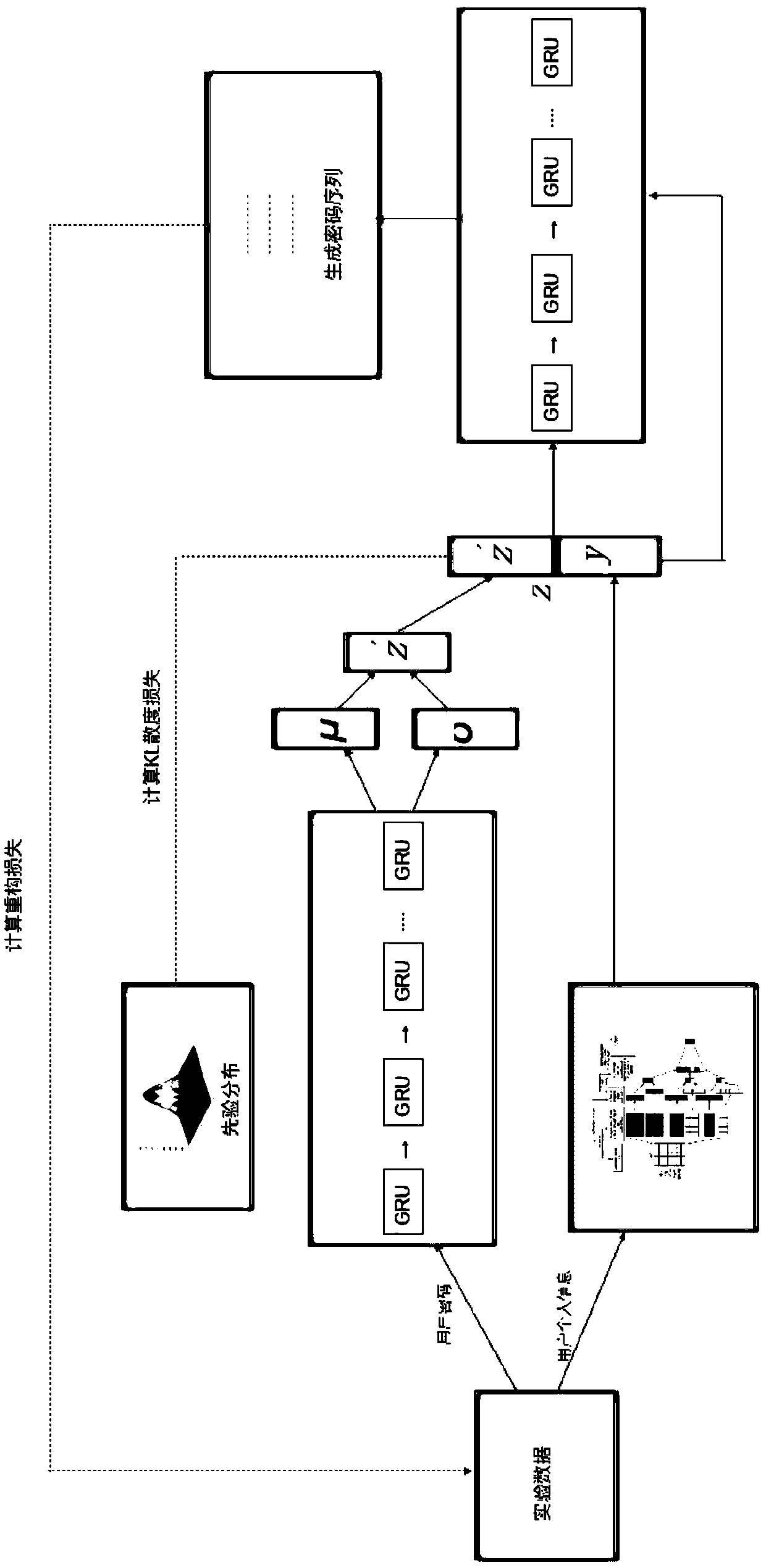
A password attack evaluation method based on conditional variational self-coding
ActiveCN109670303AHigh strengthImprove securityDigital data protectionPlatform integrity maintainanceAttack modelPassword
The invention provides a password attack evaluation method based on conditional variational self-coding. The method comprises the following steps of constructing a variational self-coding model, constructing a conditional variational self-coding model, constructing a password attack model, and comprehensively utilizing the conditional variational self-coding model and the password attack model. According to the invention, a conditional variational self-coding model, and the condition characteristics in the personal information of the user, such as the user name, the mailbox address, the telephone number, etc. are used to train the cryptographic attack model, a bidirectional GRU recurrent neural network and a CNN text convolutional neural network are respectively used at the encoder end, sothat the code of a password sequence and personal information of a user and abstract extraction of characteristics can be achieved, the distribution of password data and a character combination rulecan be effectively fitted, the high-quality guessing password data can be generated, and the method has a remarkable effect on improving the password strength and safety of the user.
Owner:BEIJING WISEWEB TECH
Cipher strength evaluation apparatus
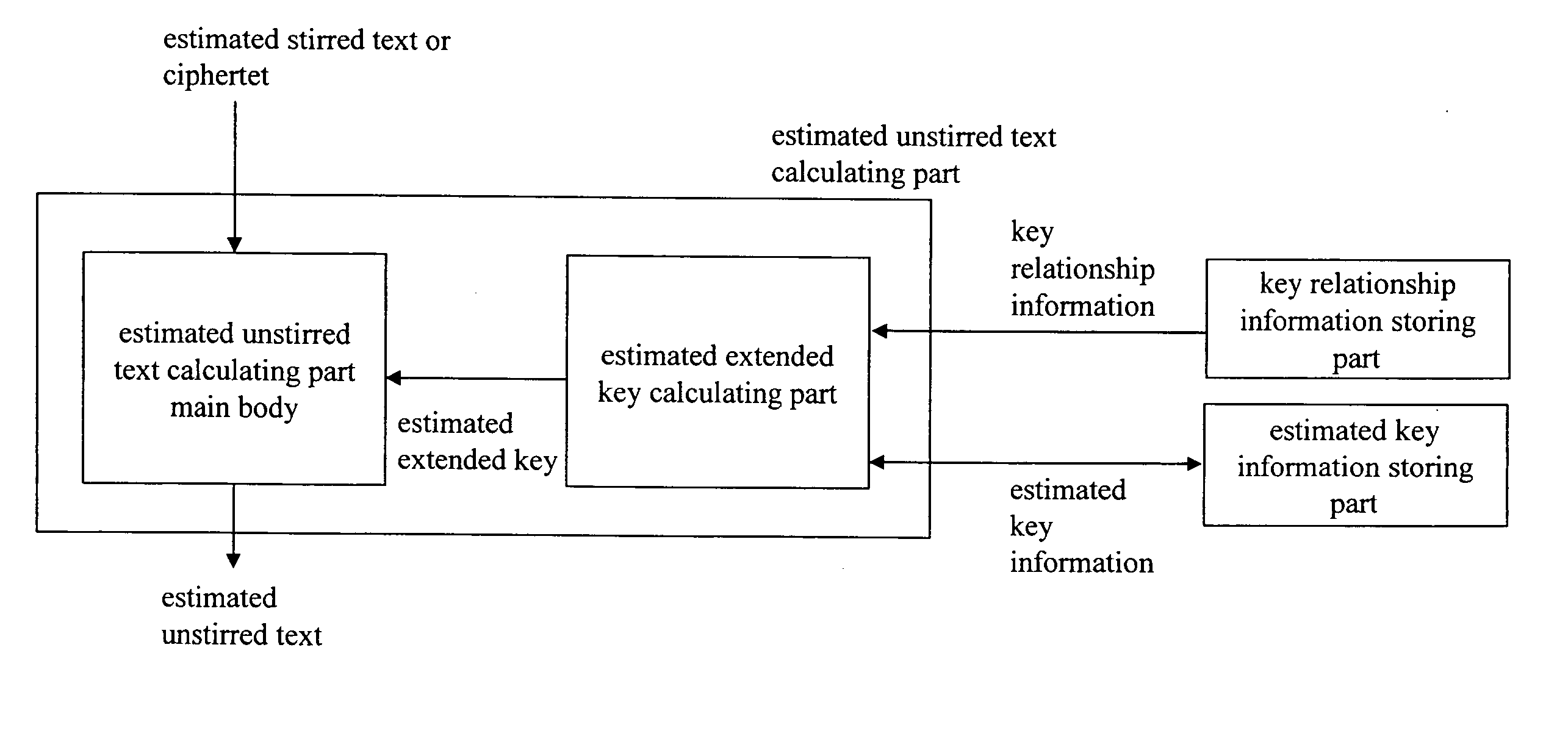
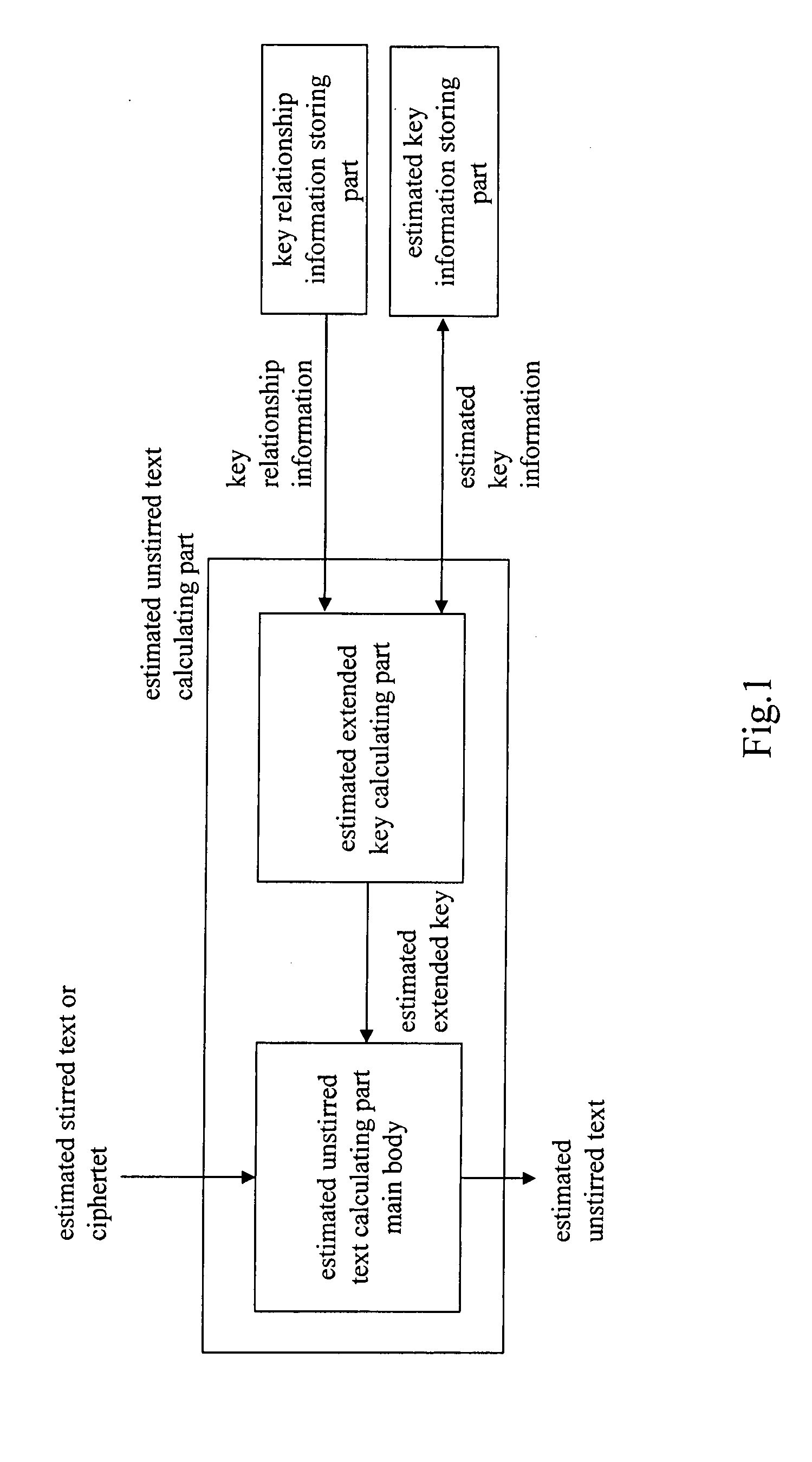
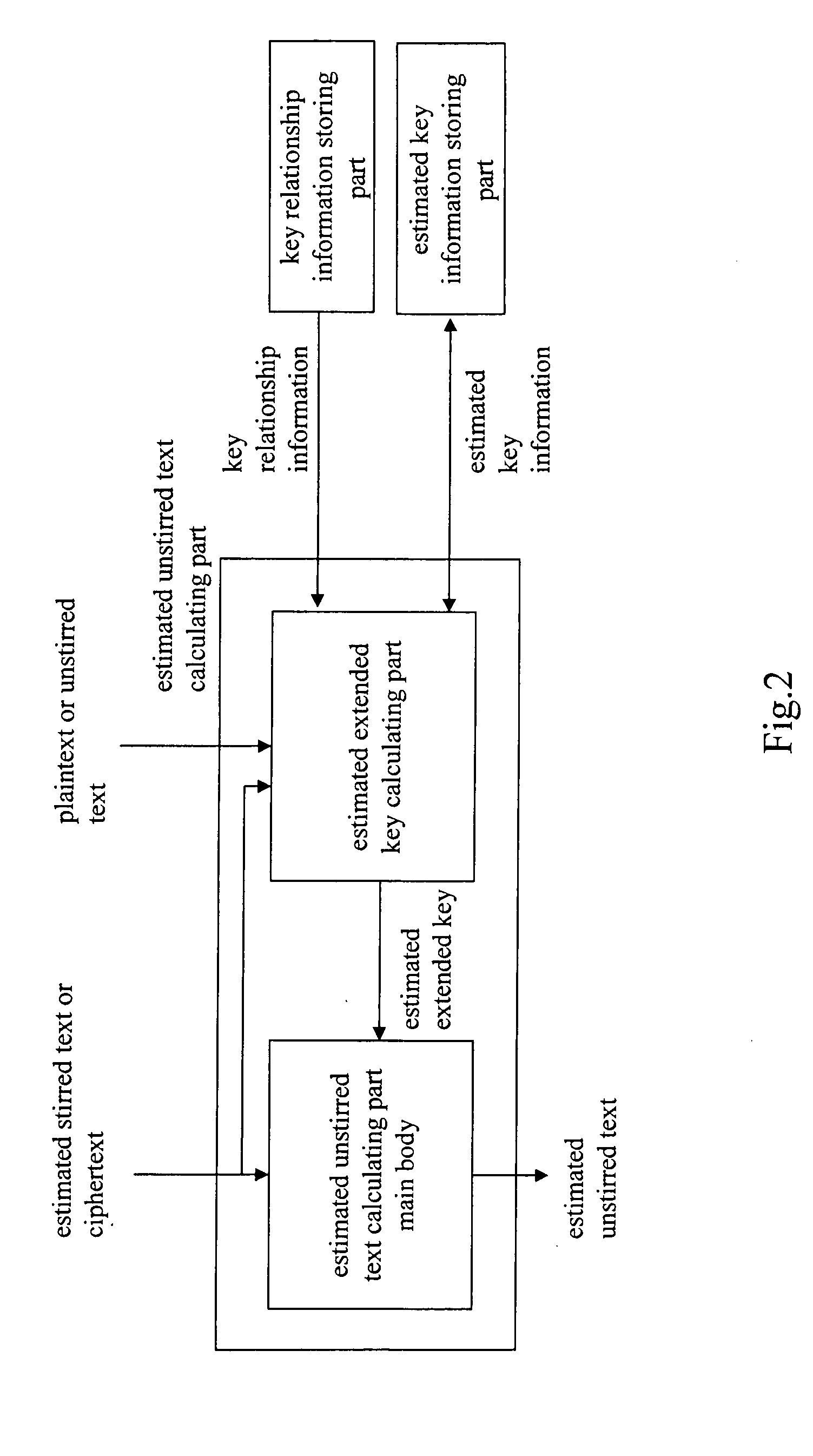
InactiveUS20050157879A1Improve bindingLow difficulty of decryptionKey distribution for secure communicationMemory loss protectionCiphertextKey schedule
An object is to evaluate the strength in consideration of the relationship held between keys, to allow the detection of a weak key condition to lower the difficulty in decrypting ciphertext, and to detect a weak key based on the weak key condition. Based on the relationship between keys in a key schedule and based on estimated keys, a certain estimated extended key can be calculated by utilizing the relationship between the estimated extended key in the key schedule and an estimated extended key having been calculated, and cost information required for calculation is outputted to allow the verification of a weak key condition. A weak key can be detected based on the weak key condition, and the difficulty in decrypting ciphertext can be increased without modifying an encryption apparatus.
Owner:NAT INST OF INFORMATION & COMM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com