Bulk password grading priori check method
A verification method and password technology, applied in the field of information security, can solve the problems of relying on weak password dictionaries and accuracy dependence of Markov model method, and achieve the effect of effectively evaluating password strength and protecting the overall security of the system.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
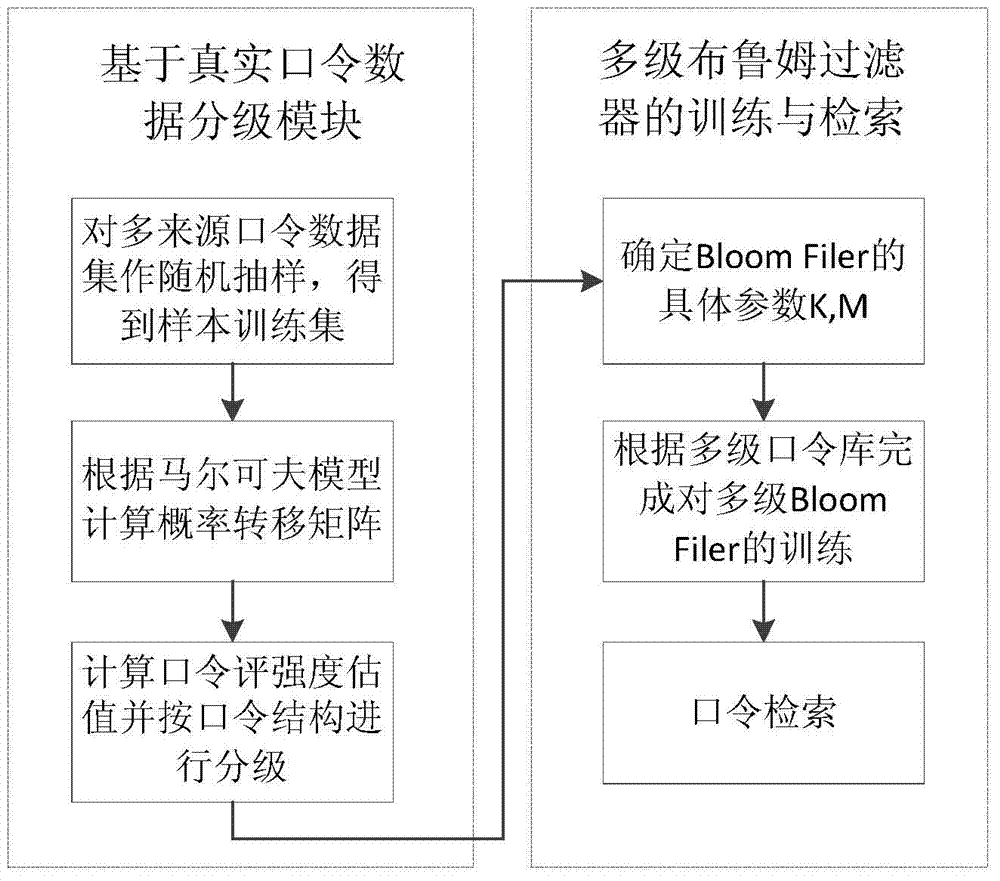
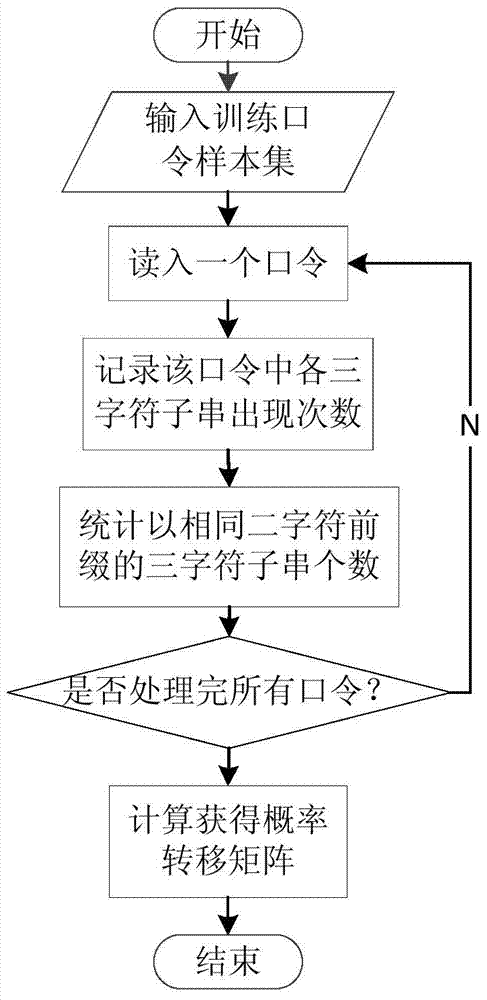
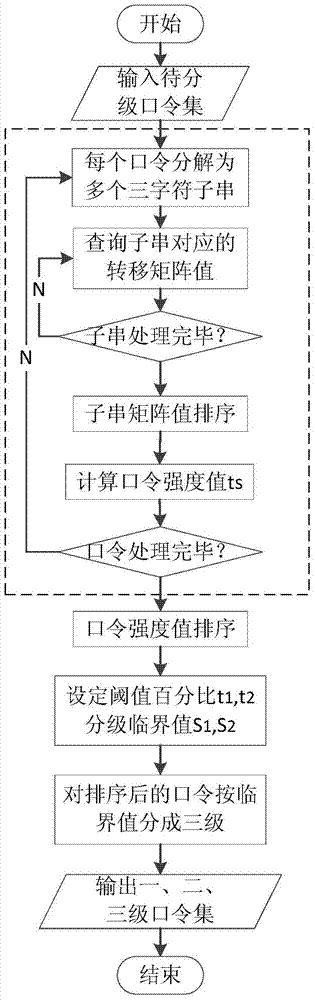
[0138] Import the real password data of 10 million Chinese users, apply this method to do 0.1% random sampling first (the degree of agreement between the classification effect and the complete password set training effect reaches 0.96), and obtain the second-order Markov probability transition matrix after training, and then import All 10 million passwords, starting with t 1 =0.2,t 2 =0.8 Set the threshold, divide into 3 levels, and decompose about 2 million, 6 million and 2 million passwords of the first level, second level and third level respectively. Corresponding to the use of three-stage Bloom filter, using the above nine hash functions, the false positive rate is 0.005, and the bit vector M of the first, second, and third-stage Bloom filter is calculated 1 , M 2 , M 3 24 million, 72 million, and 24 million bits, after obtaining the specific parameters of the 3-stage Bloom filter, initialize it. And map the corresponding password set to the corresponding Bloom filter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com