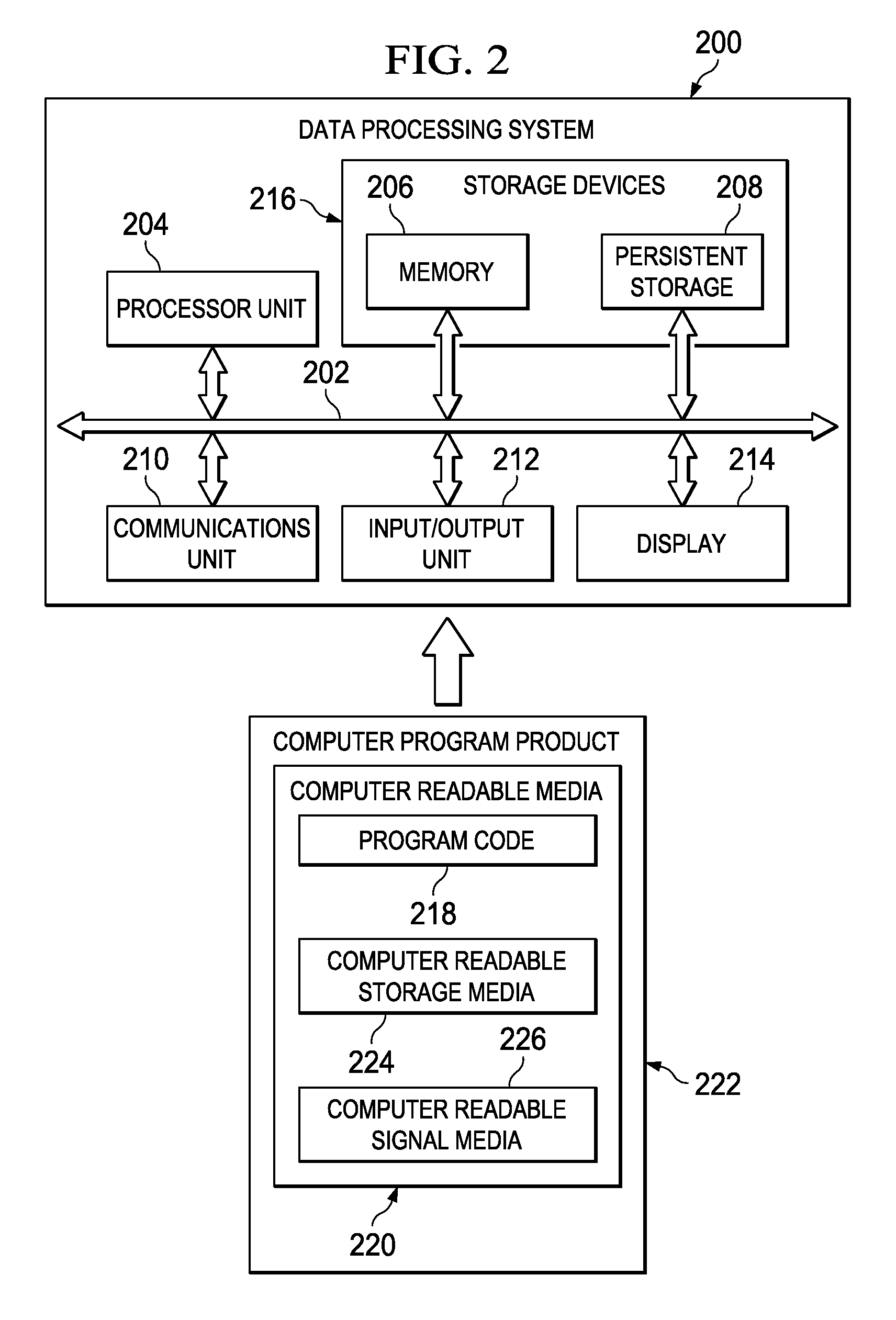
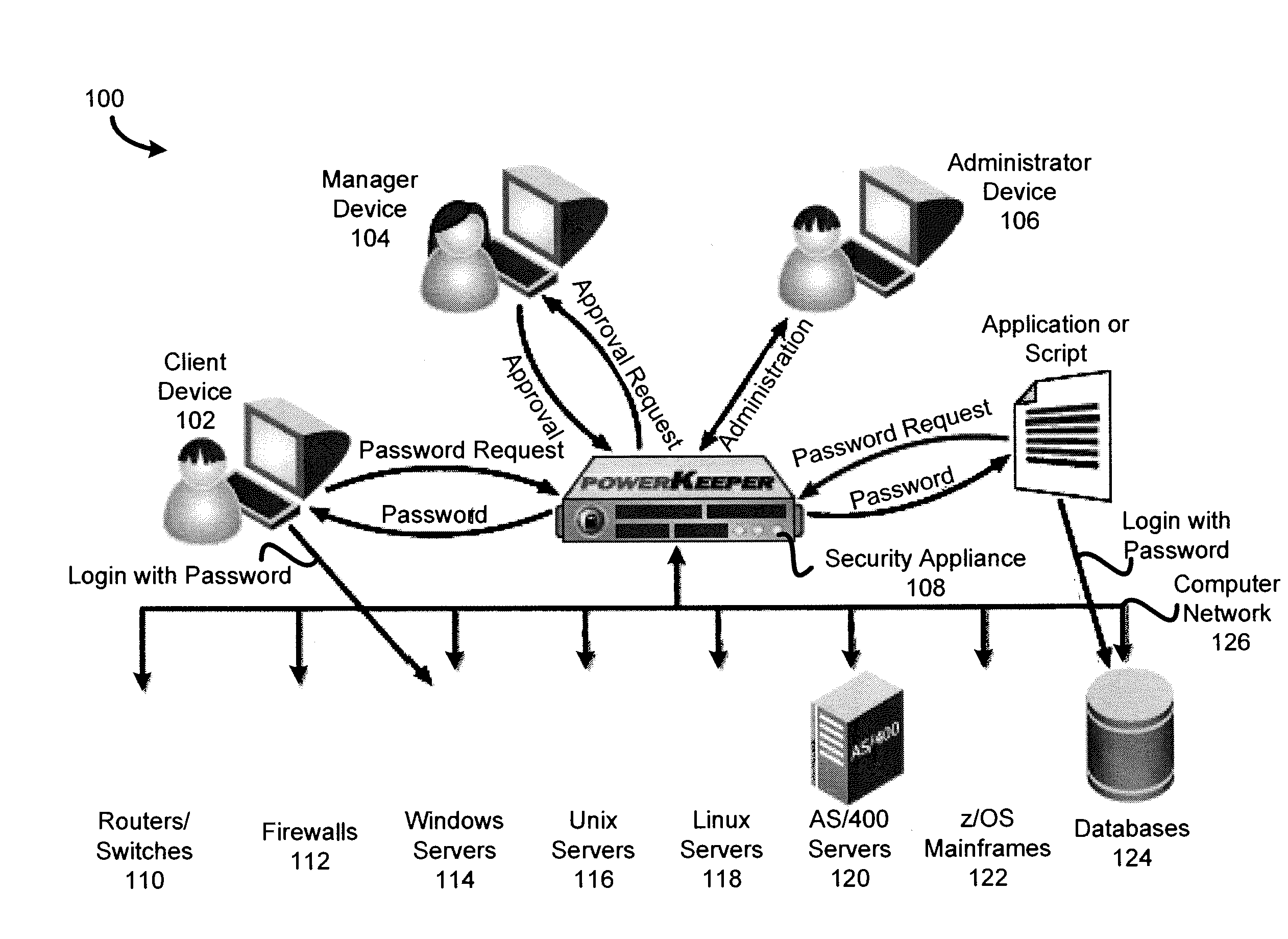
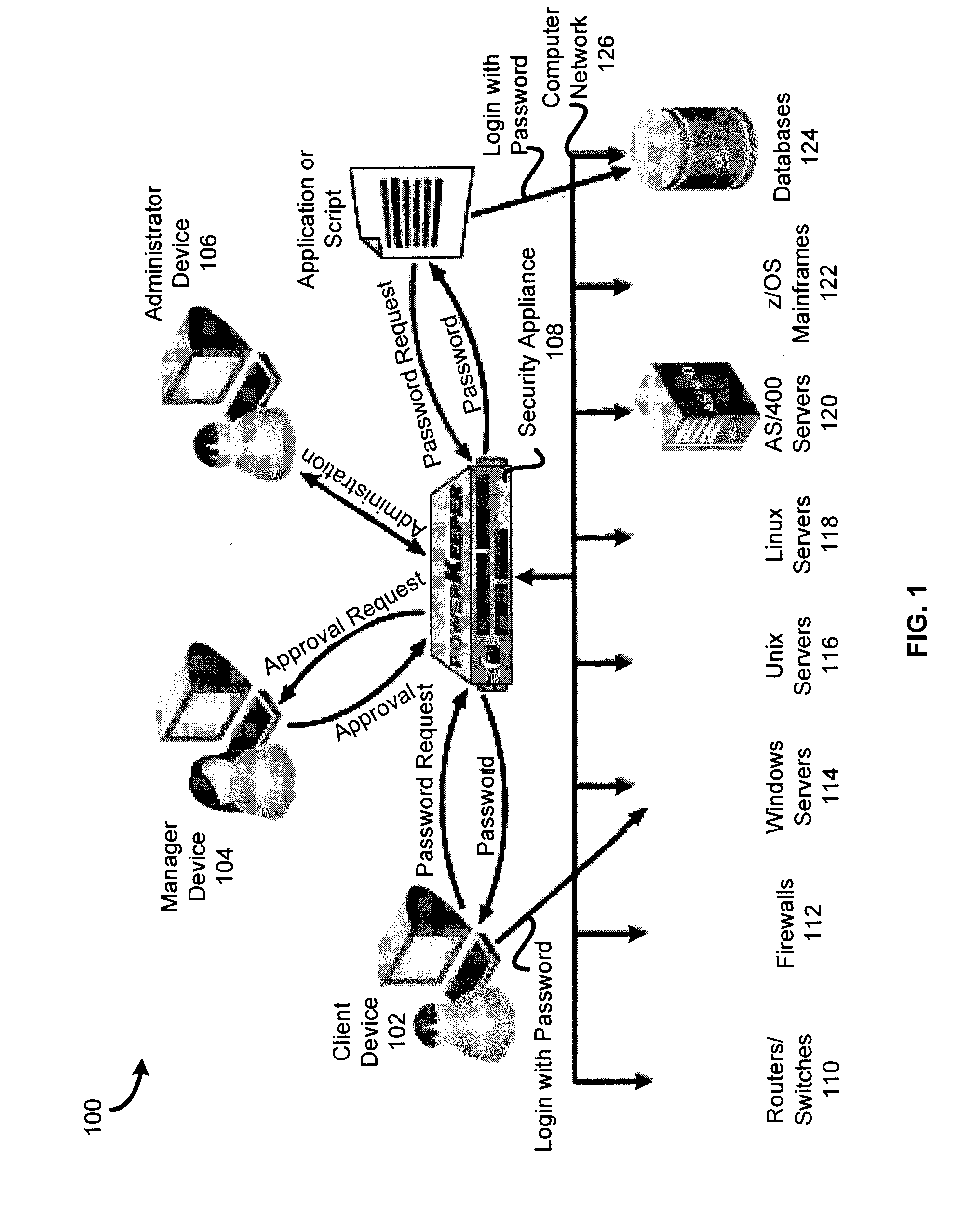
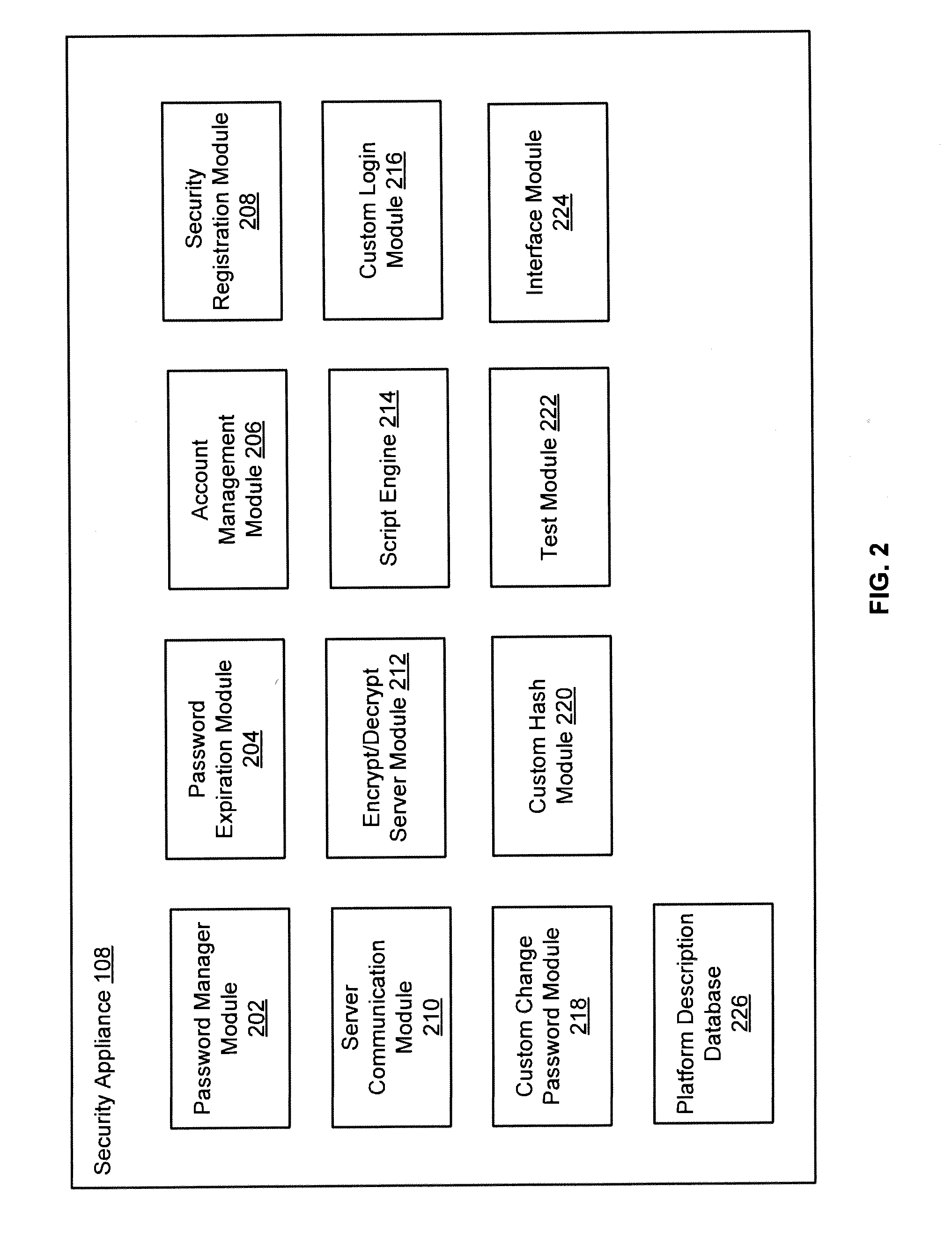
Patents
Literature
546 results about "Password management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
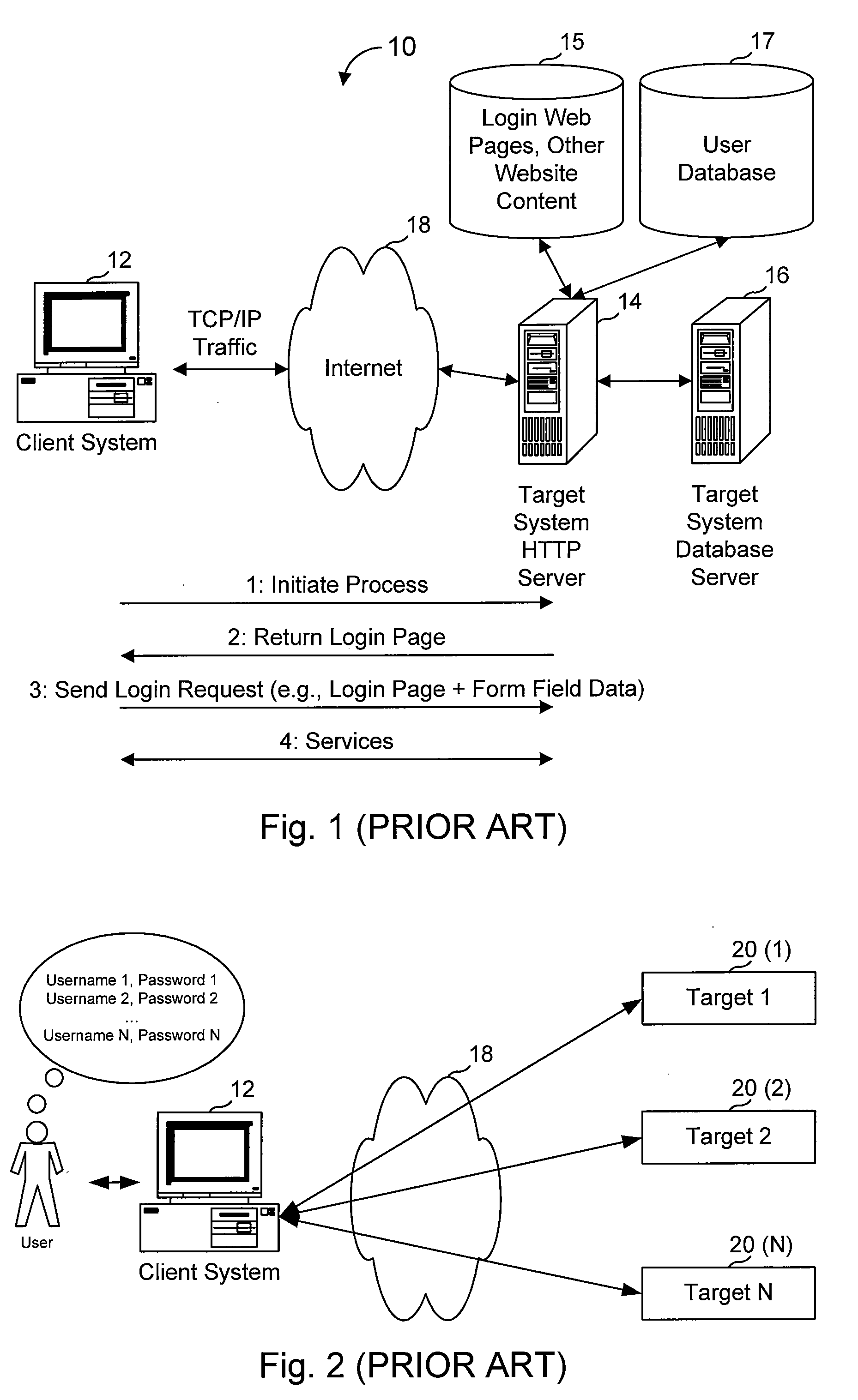
There are several forms of software used to help users or organizations better manage passwords...
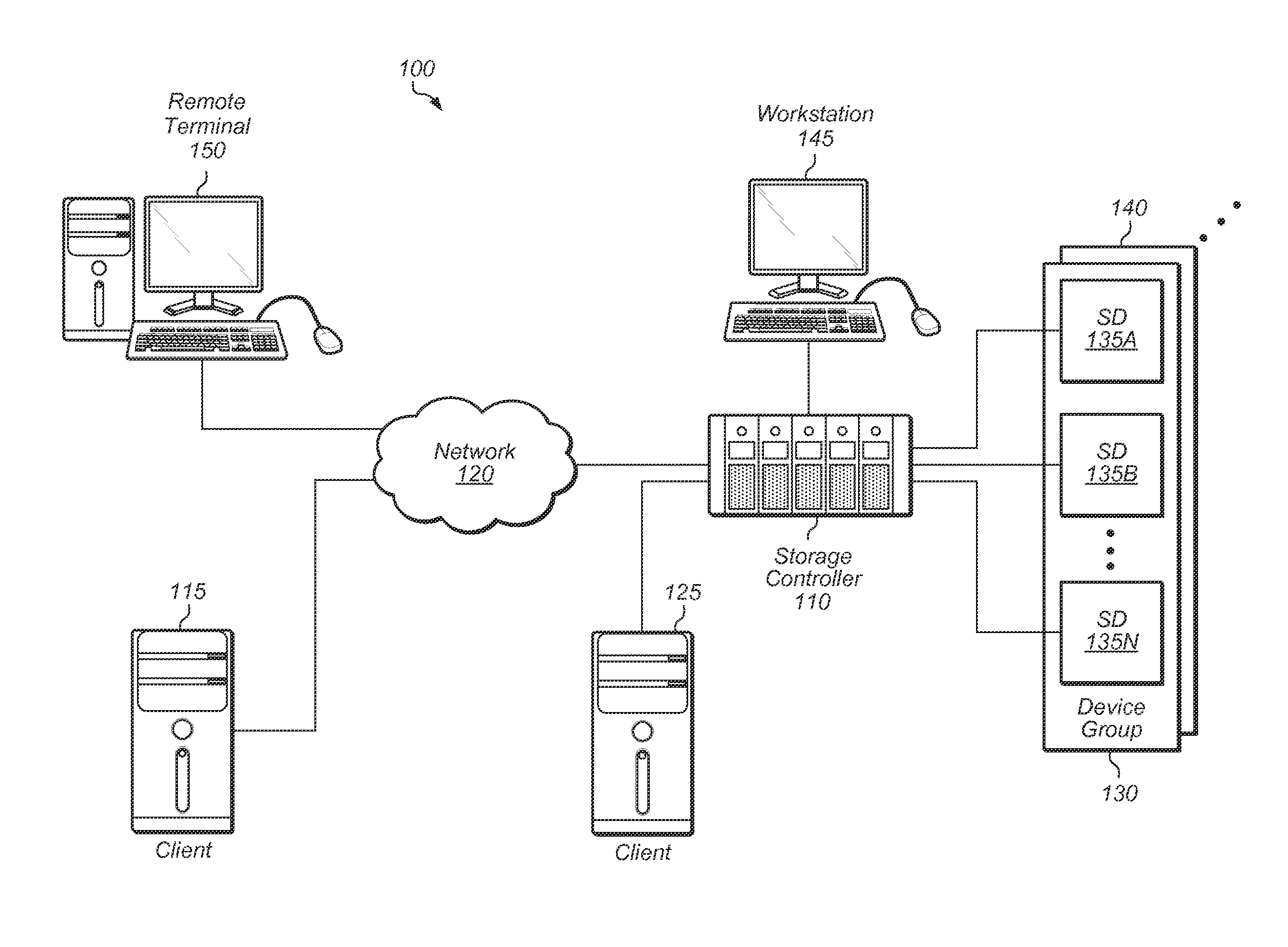
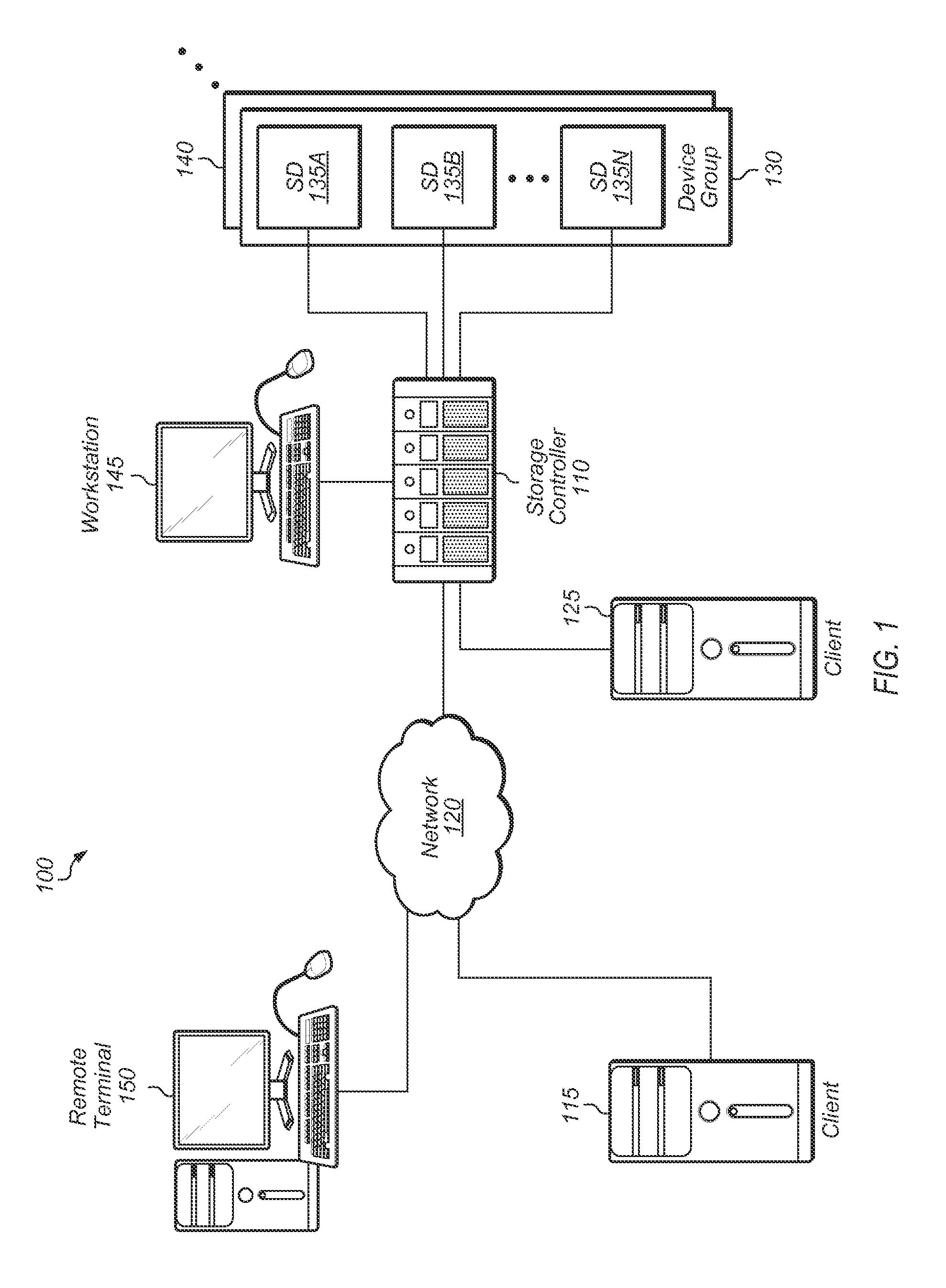
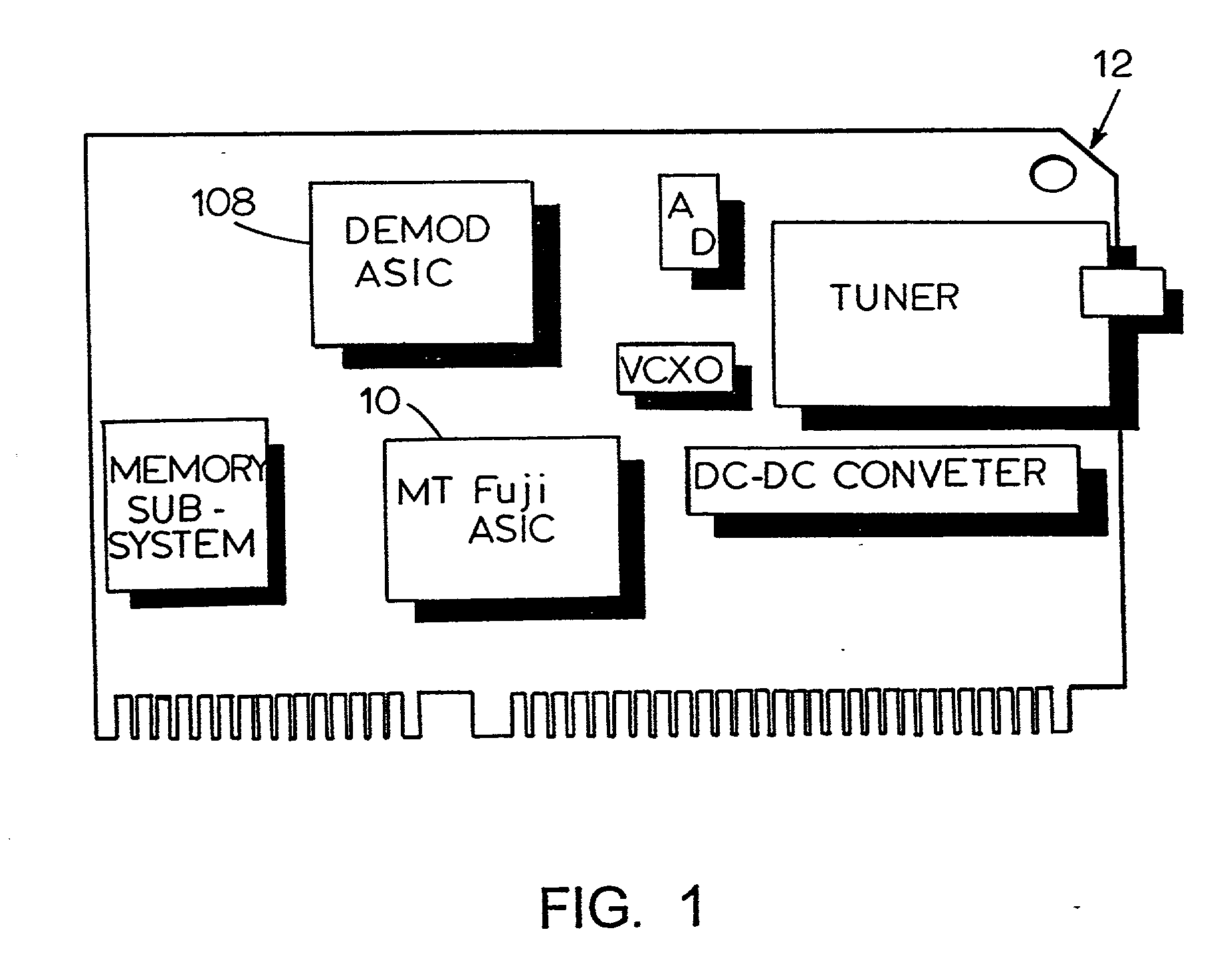
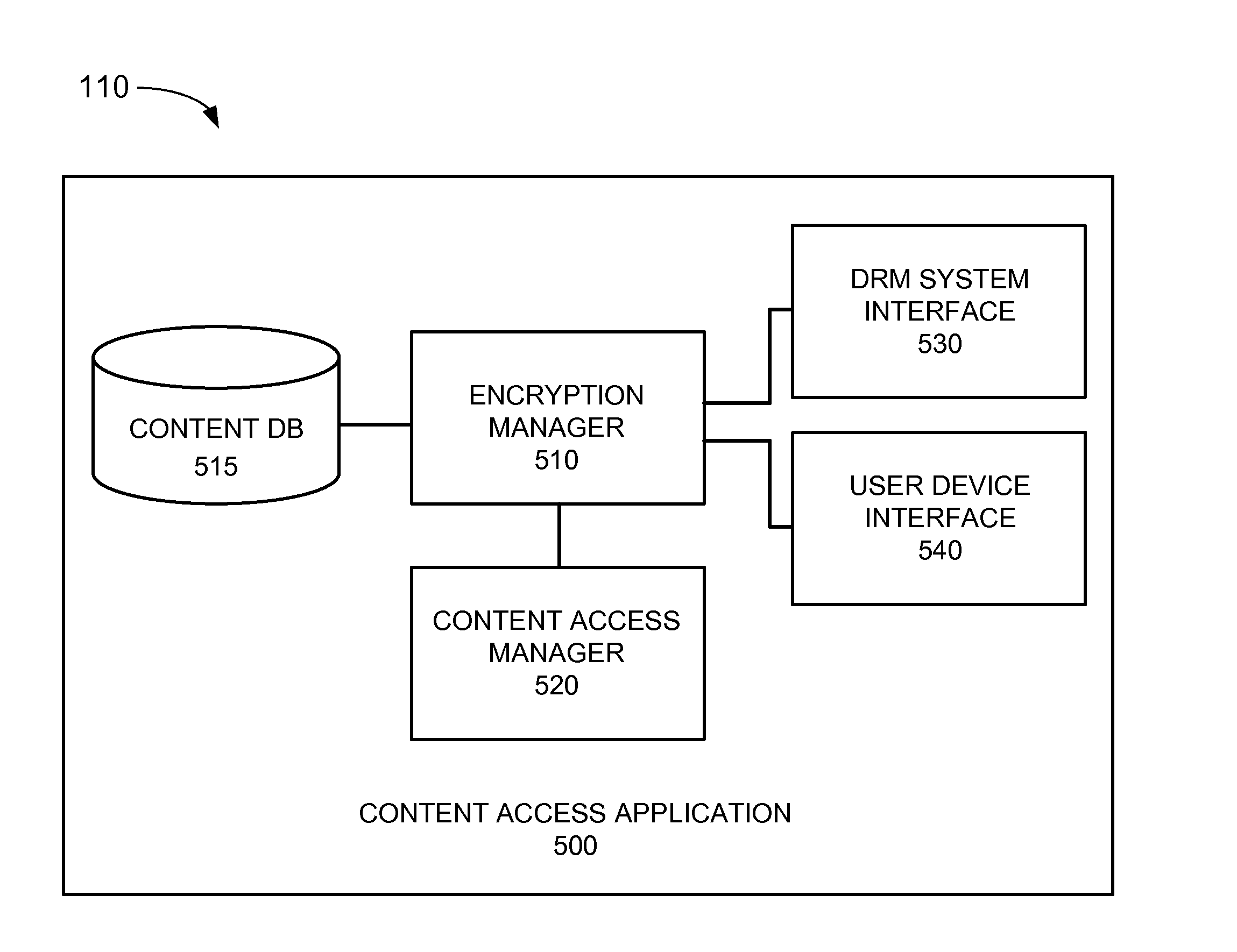
Storage array password management
A system and method for generating passwords for secure login to a storage array. A randomly generated root secret is utilized along with a compartment ID to generate a root password for logging into a storage array with root privileges. The root secret is encrypted with the public key of a public-private key pair and stored on the storage array. The encrypted root secret is then stored in the storage array. When root access is needed, a private key stored externally to the storage array is utilized to decrypt the root secret. The decrypted root secret is then used along with the compartment ID to regenerate the root password.
Owner:PURE STORAGE
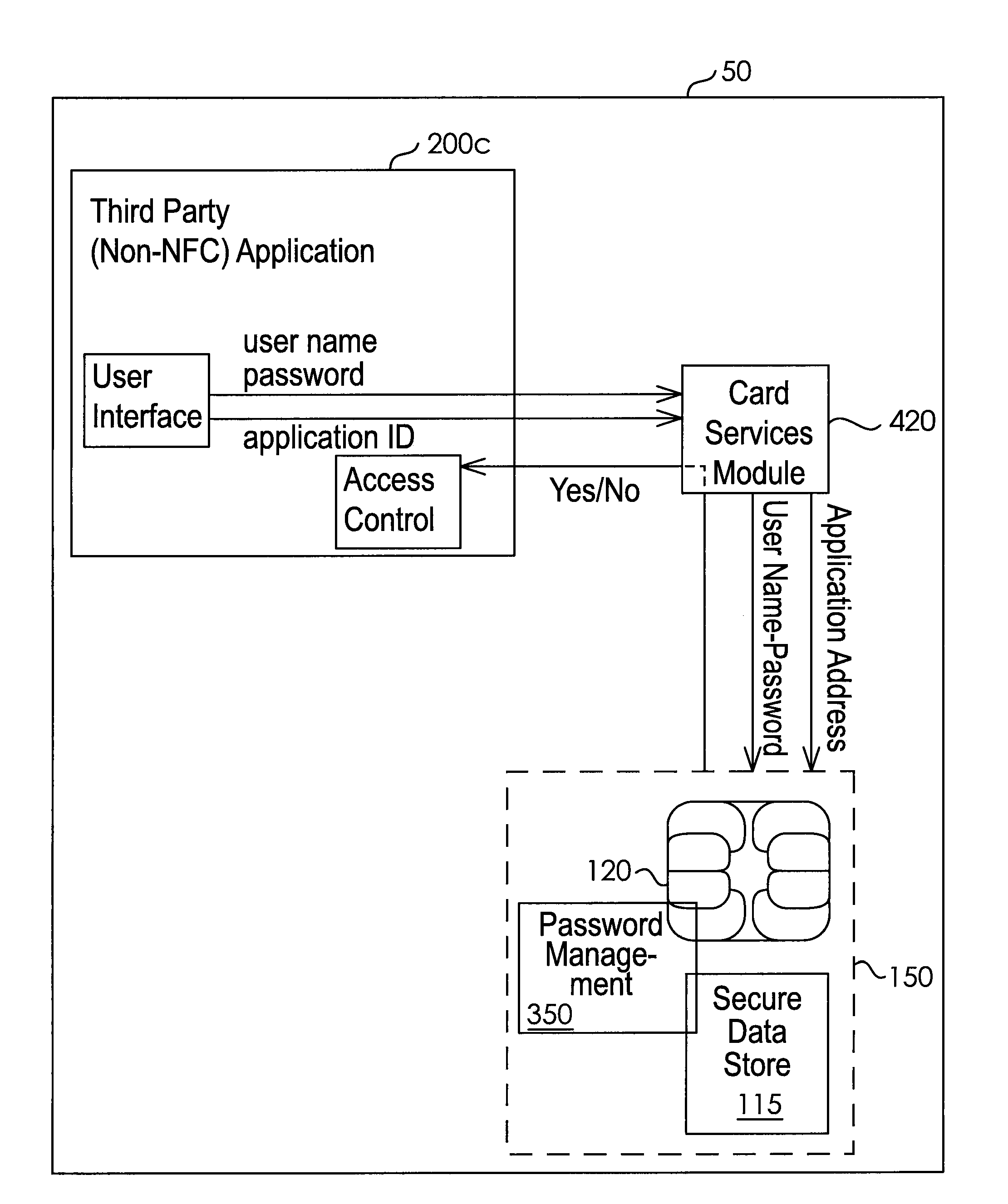
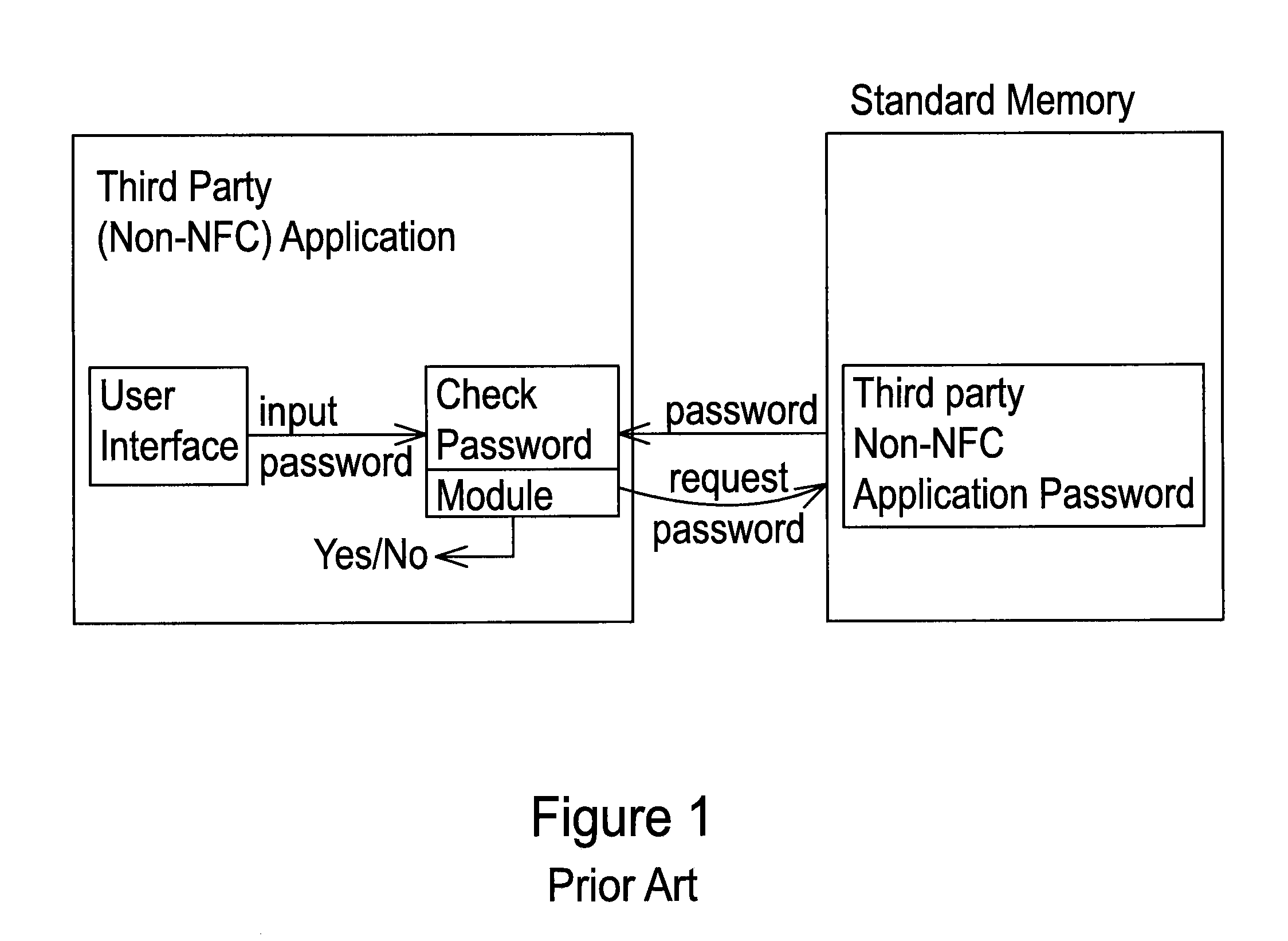
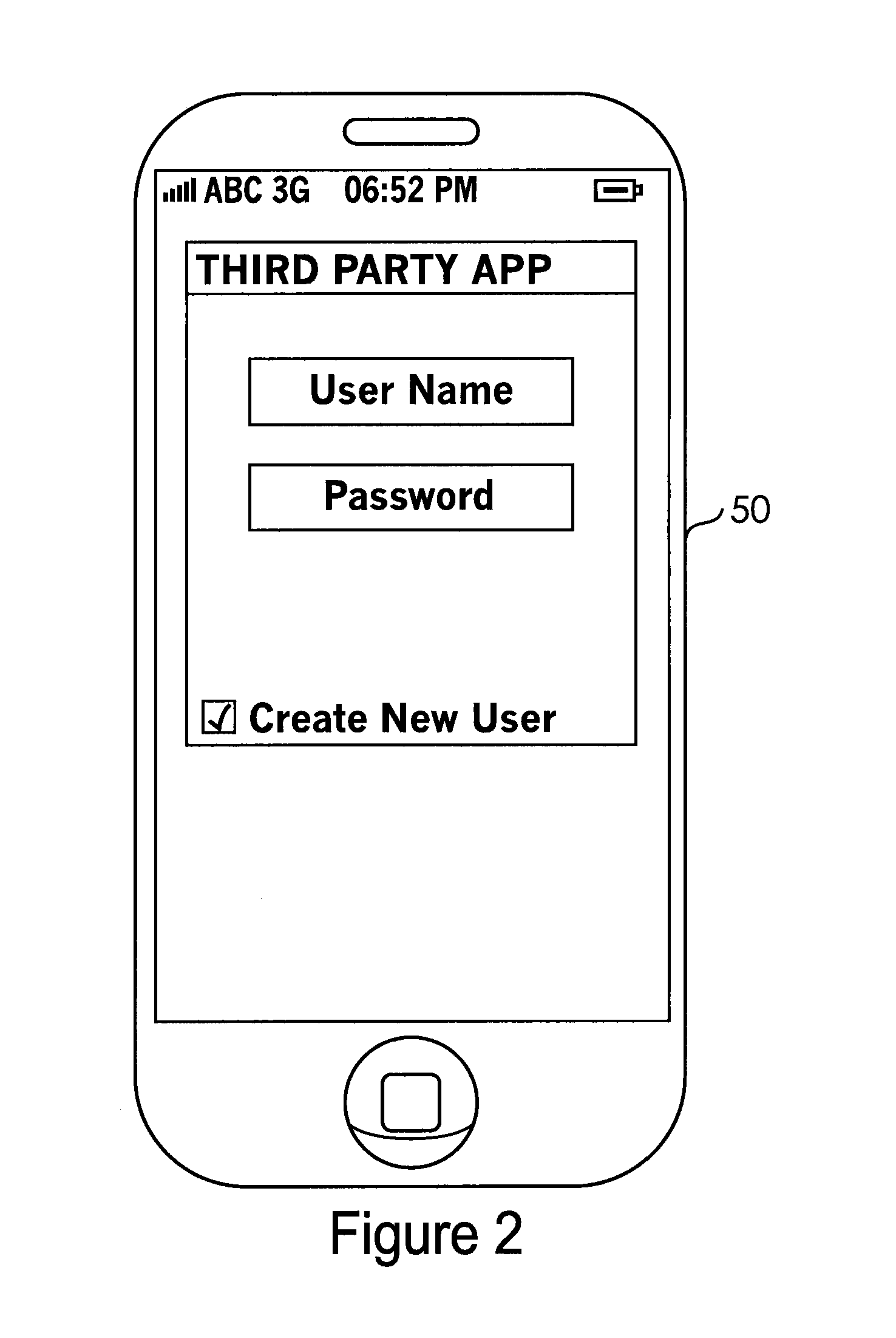
System and Method for Controlling Access to a Third-Party Application with Passwords Stored in a Secure Element
InactiveUS20120266220A1Easy to writeDigital data processing detailsMultiple digital computer combinationsThird partyApplication Identifier
A system for controlling access to an application on a portable communication device having a secured element and a user interface comprises memory associated with the secure element; a card management module operably associated with the portable communication device and with the secure element capable of controlling the secured element to facilitate writing to and reading from the memory; and a password management module operably associated with the card management module, the portable communication device user interface, and the application, the password management module receiving an application identifier associated with the application, a user name, and a password from the user interface, and providing an access command to the application based on whether the received user name and password match information stored in the memory.
Owner:T I S
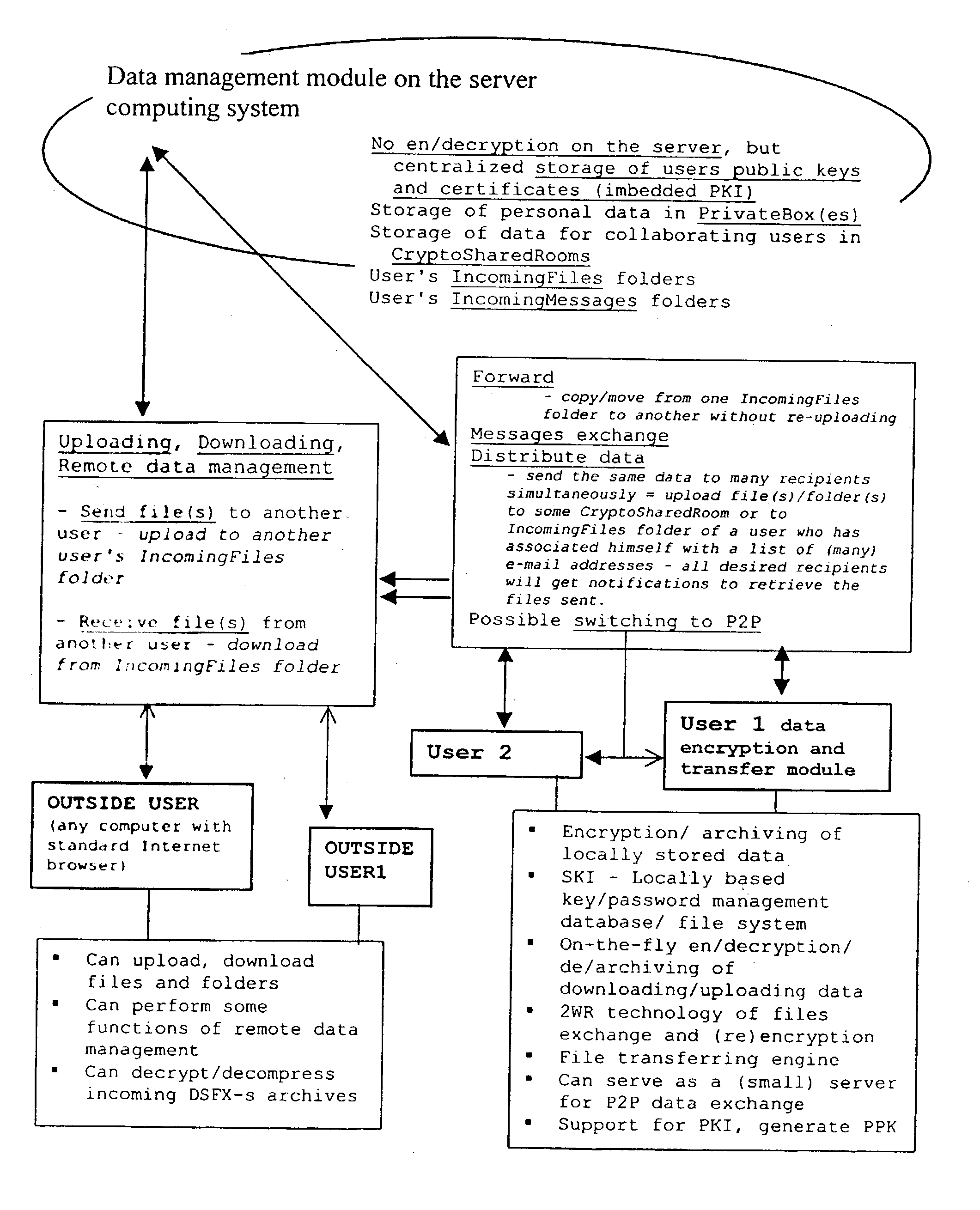
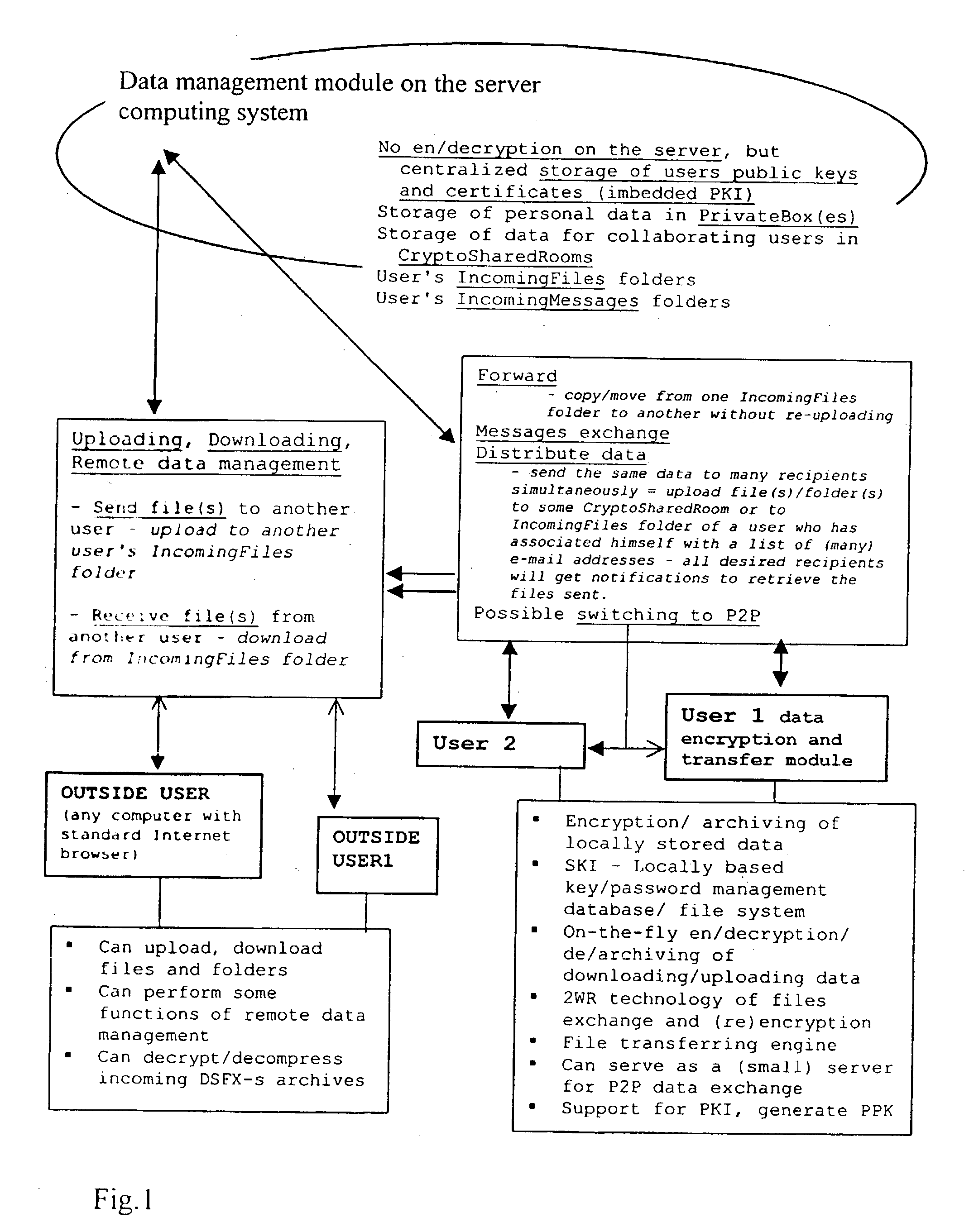
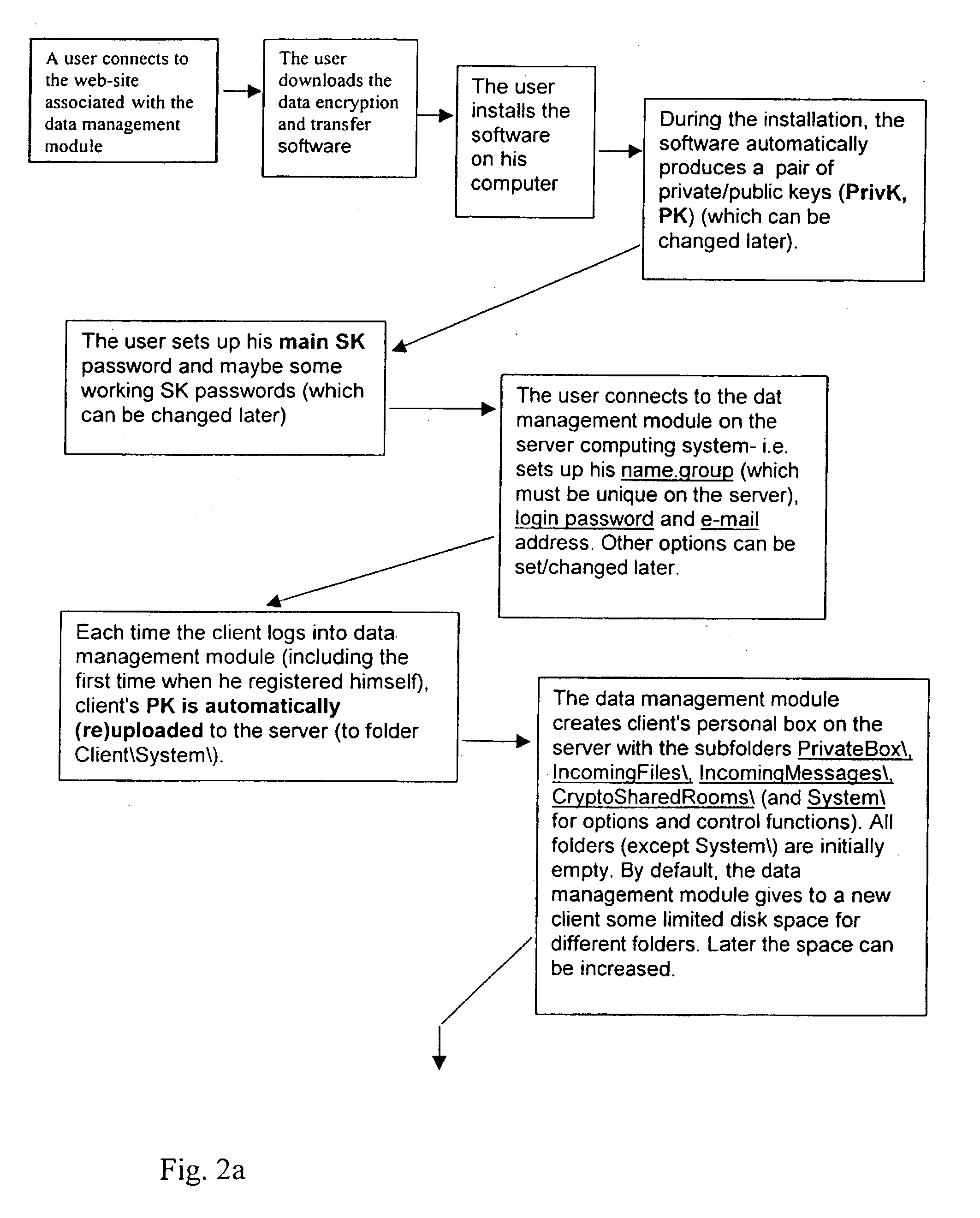
Data transfer and management system
InactiveUS20030177422A1Easily and securely managedEasily downloadableReliability increasing modificationsError preventionMegabyteData file
A system for the secure transfer of data and data management on the Internet has a data encryption and transfer module operable in a user computing system, a data management module operable in a server computing system, the transfer of data between the user and server computing systems being effected on the user computing system through use of the data encryption and transfer module, by moving the data to or from a first desktop window, associated with the user computing system, from or to a second desktop window, associated with the server computing system, each window being associated with a password, such that the step of moving the data from one window to the other causes the data to be encrypted / re-encrypted from one associated password to the other. The system also includes a password management module operable in the user computing system for managing the passwords, which are required to be used by a user of the system. The system uses symmetric key encryption coupled with file transfer protocol (FTP) data transfer and allows for the secure transfer of large data files of 100 megabytes or more.
Owner:HERBERT STREET TECH
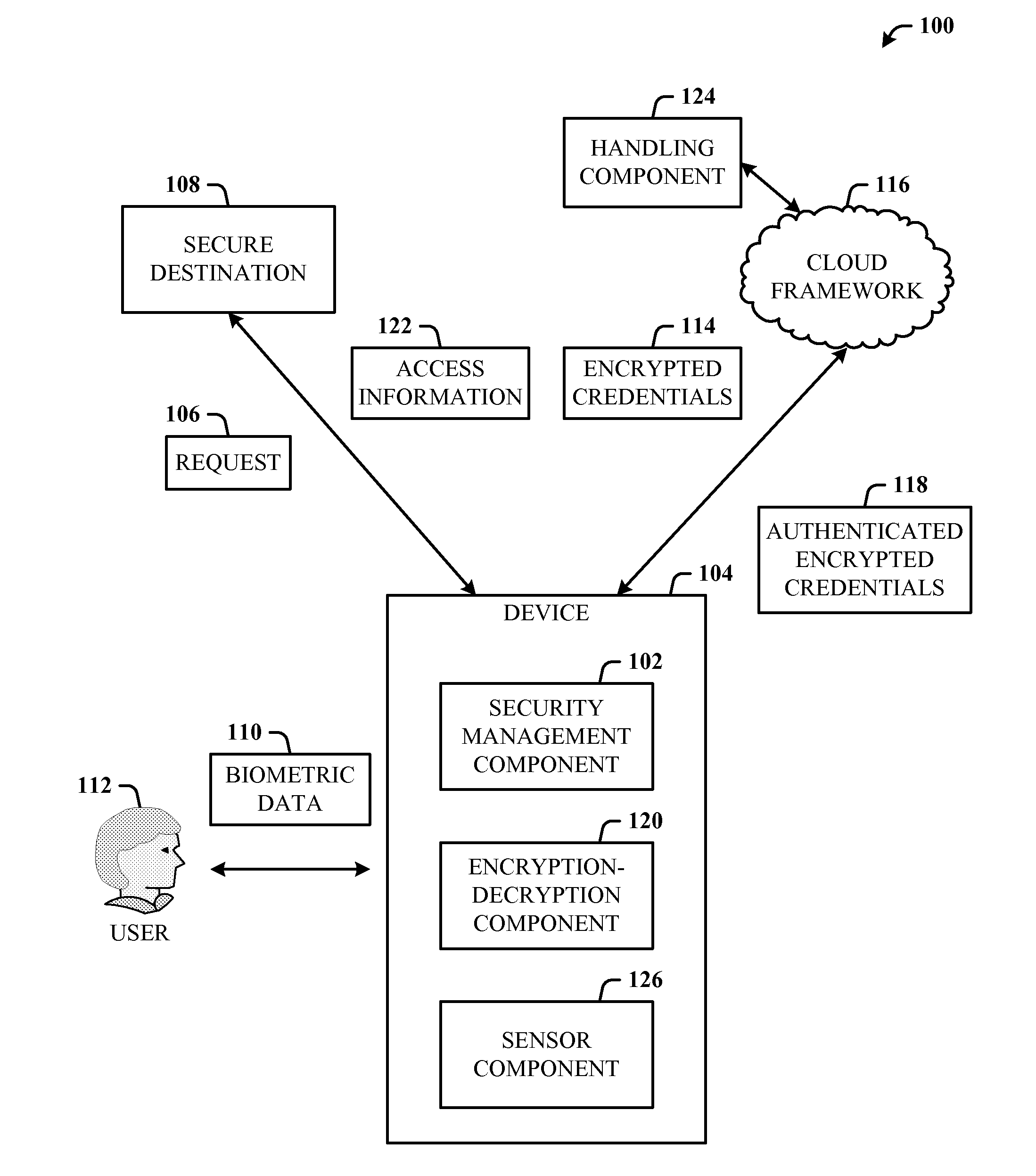
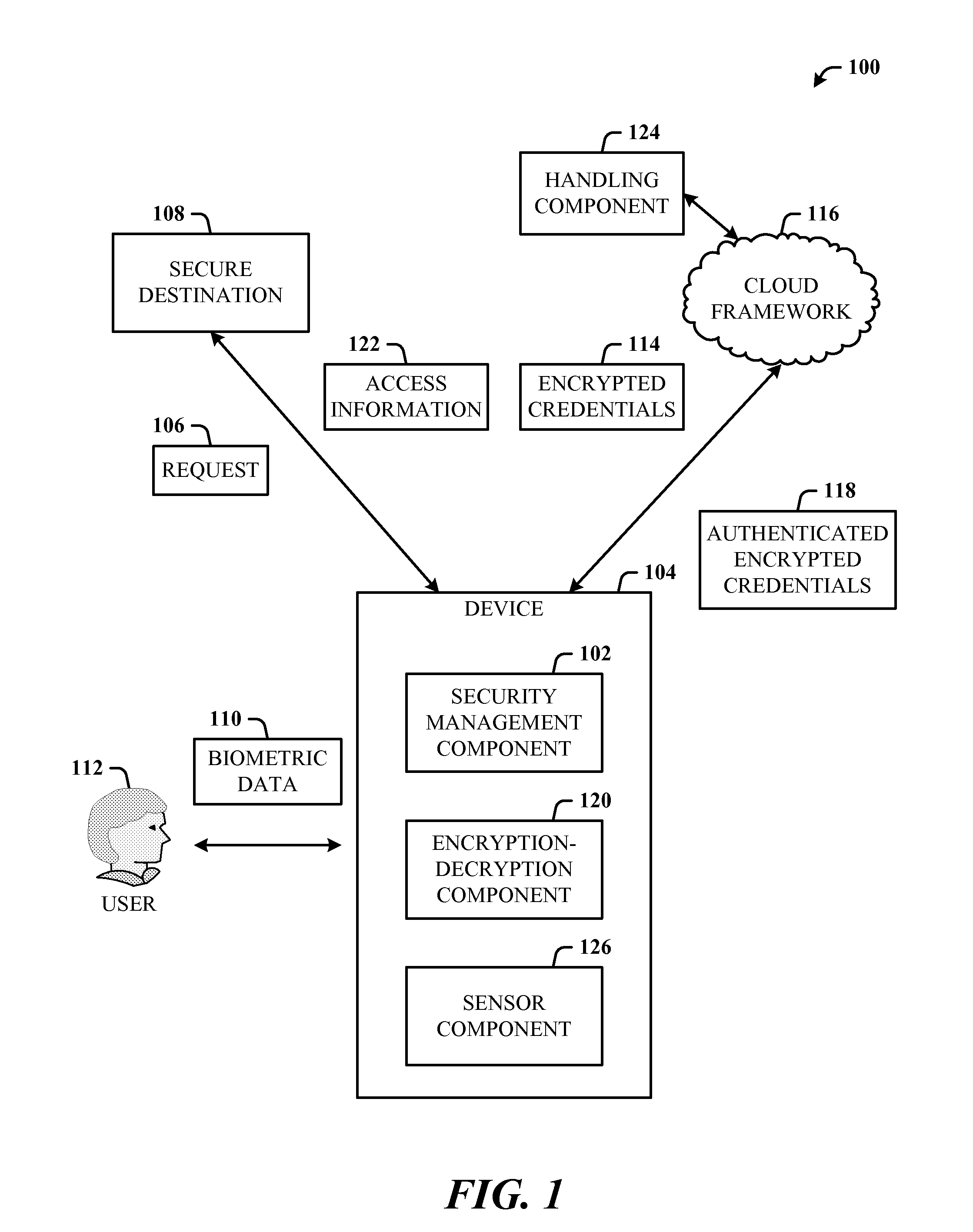
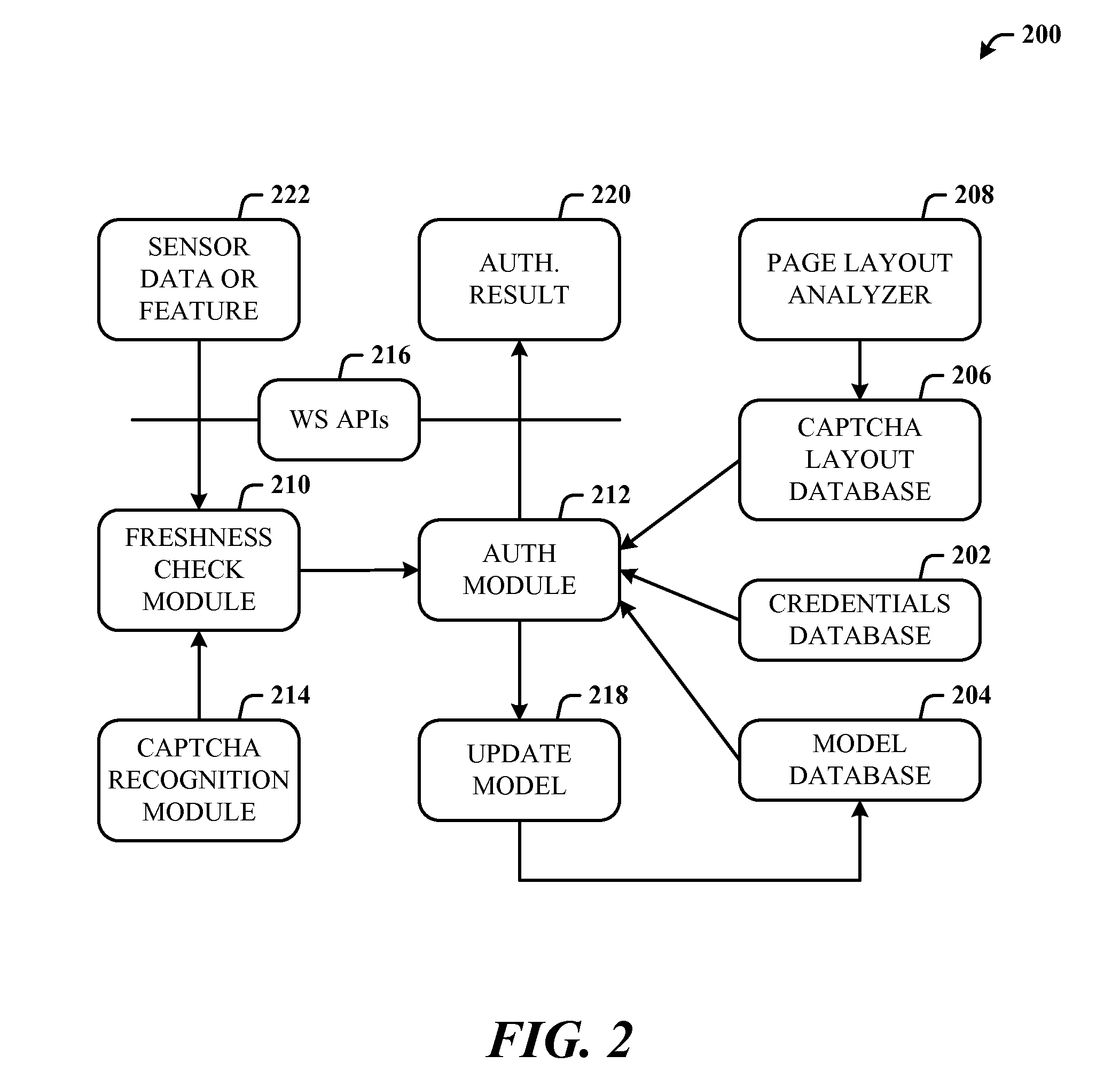
Usable security of online password management with sensor-based authentication
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
User authentication method and system and password management system
InactiveUS20090293119A1Good attackAcutation objectsDigital data processing detailsUser authenticationPassword management
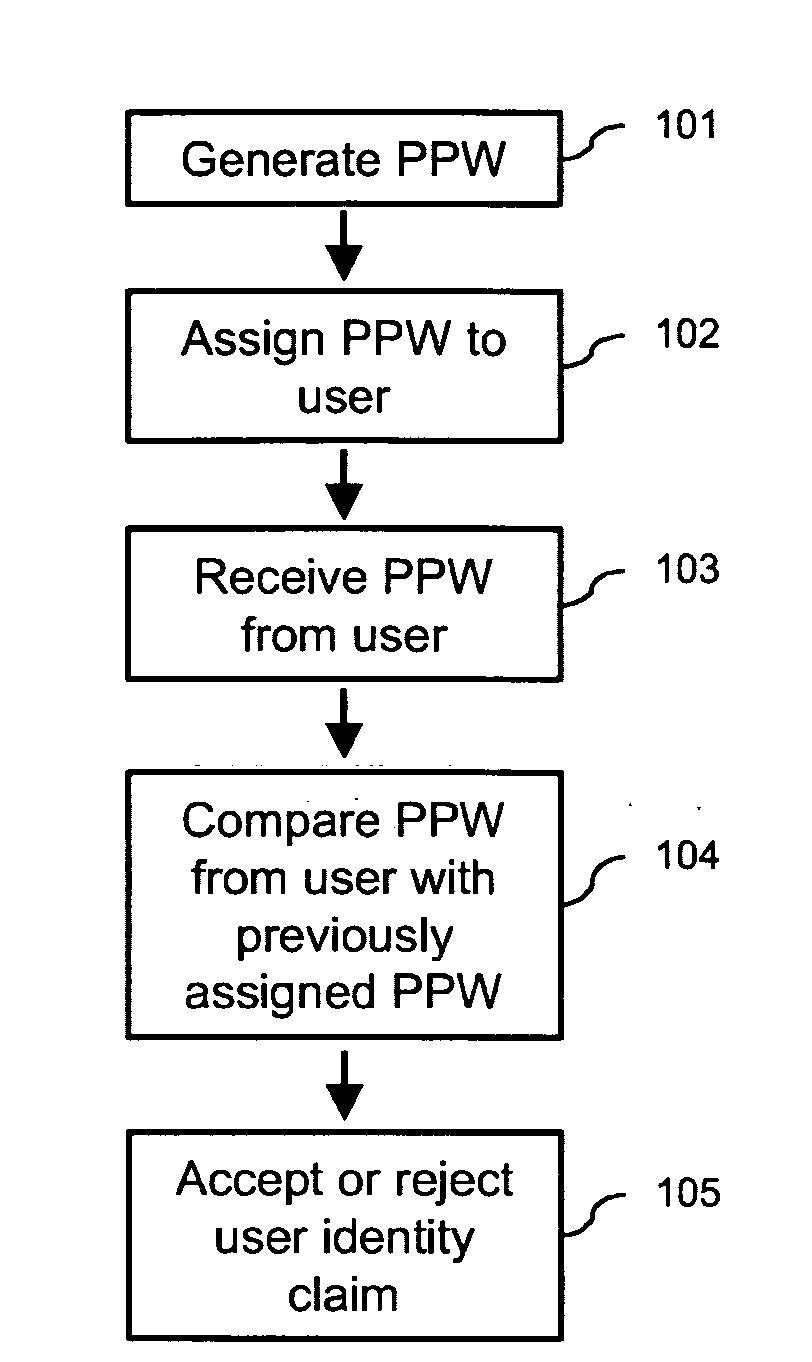
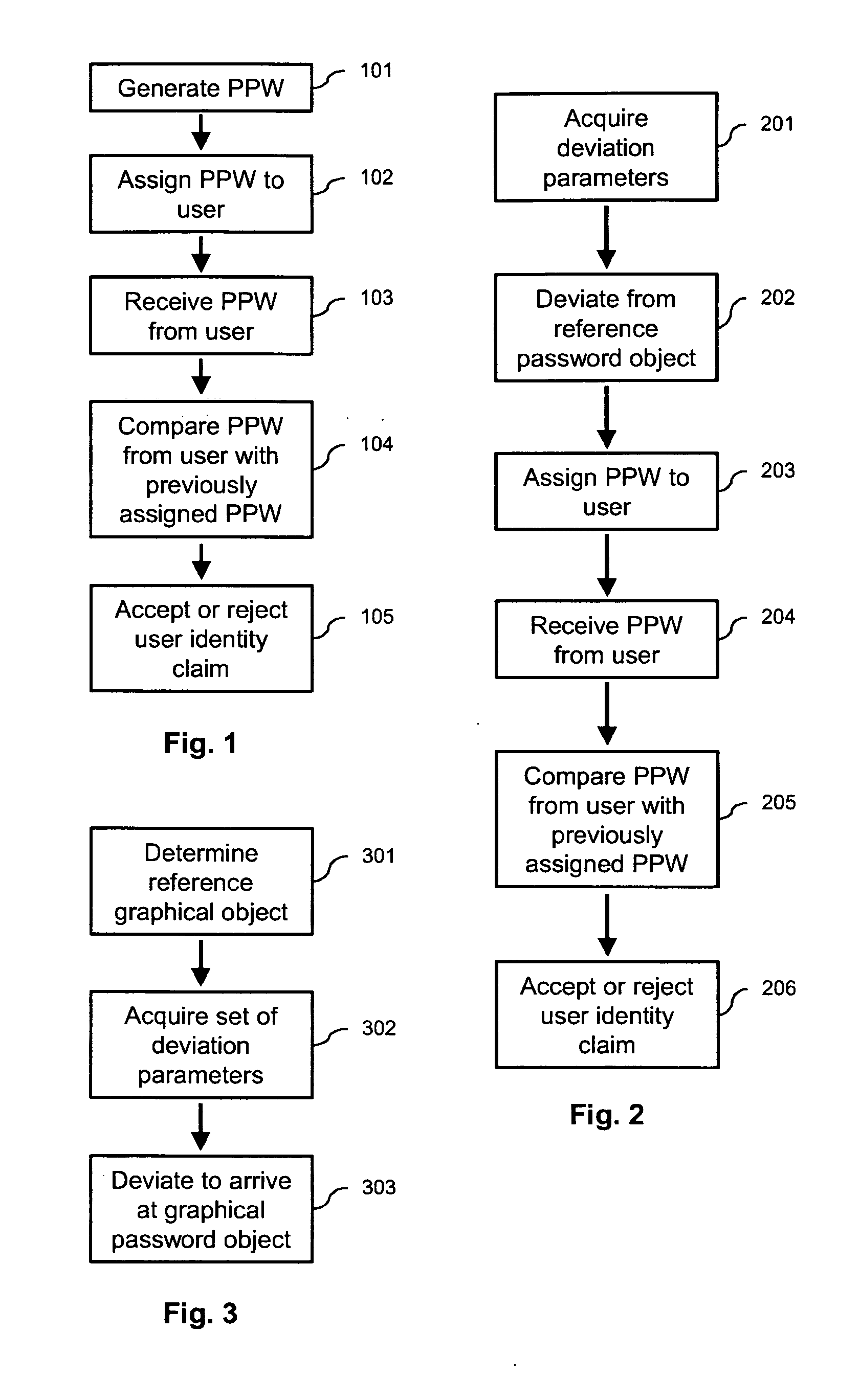
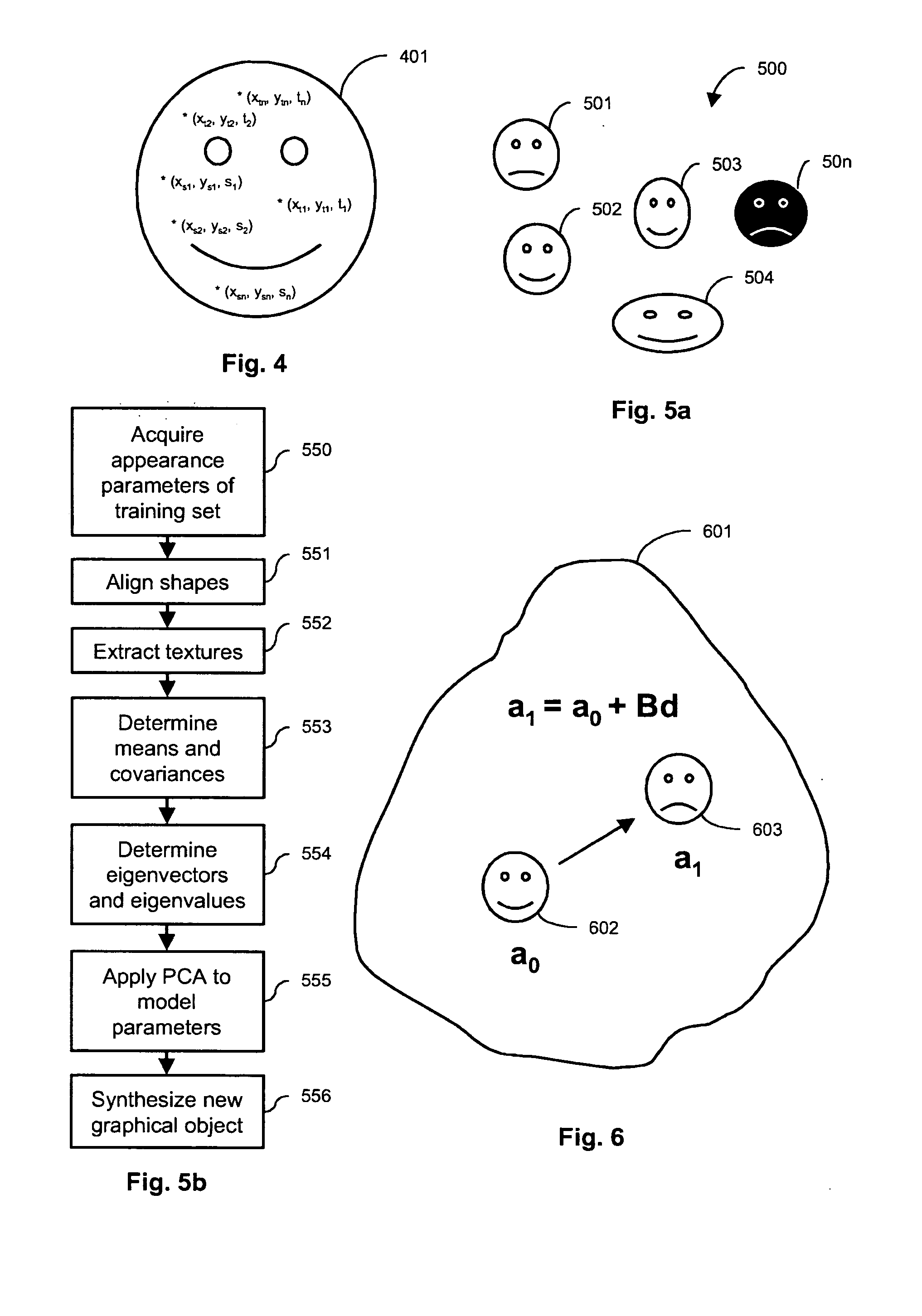
In one embodiment of the present invention, a user authentication method including the steps of automatically generating a set of deviation parameters; deviating from a reference password object, within an object space defined by appearance parameters previously acquired from a training set of objects, in a direction and with an amount determined by the set of deviation parameters, to thereby synthesize a password object; assigning a perceptual password including the password object to a user, and receiving a user identity claim including a user-provided perceptual password. The method further includes the steps of comparing the user-provided perceptual password with the perceptual password assigned to the claimed user, and, based on the result of this comparison, accepting or rejecting the user identity claim.
Owner:CIPHERSTONE TECH
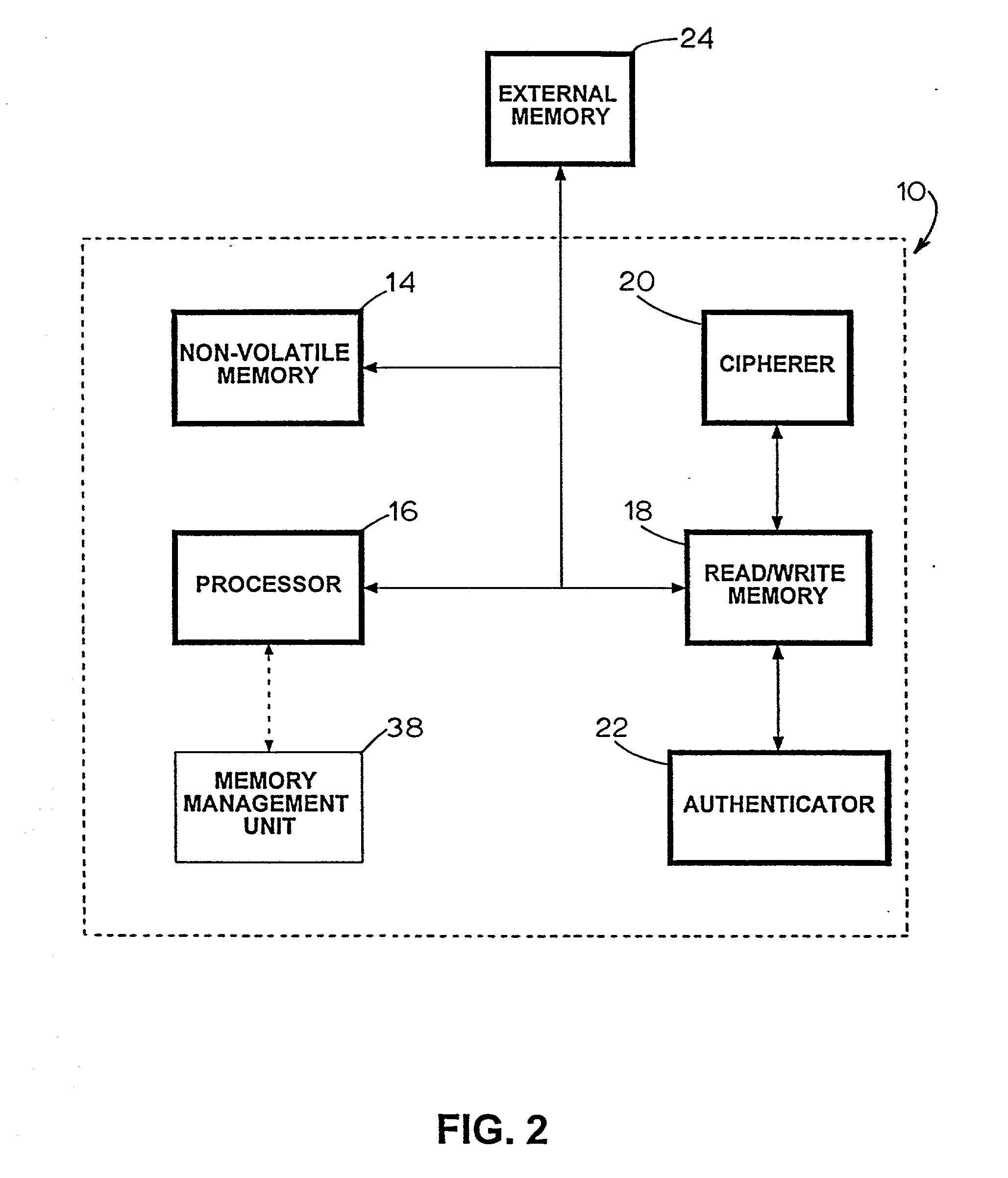
Apparatus for providing a secure processing environment
InactiveUS20020129245A1User identity/authority verificationInternal/peripheral component protectionComputer hardwareSafe handling
An apparatus for providing a secure processing environment is disclosed. In one embodiment, the apparatus includes a read / write memory for storing encrypted information. It also includes a processor, a cipherer and an authenticator. The cipherer is in communication with the read / write memory for receiving encrypted information therefrom and is configured to decrypt the encrypted information into decrypted information to be returned to the memory for subsequent use by the processor. The authenticator authenticates the decrypted information prior to use by the processor and re-authenticates the information prior to re-encryption by the cipherer.
Owner:CASSAGNOL ROBERT D +4
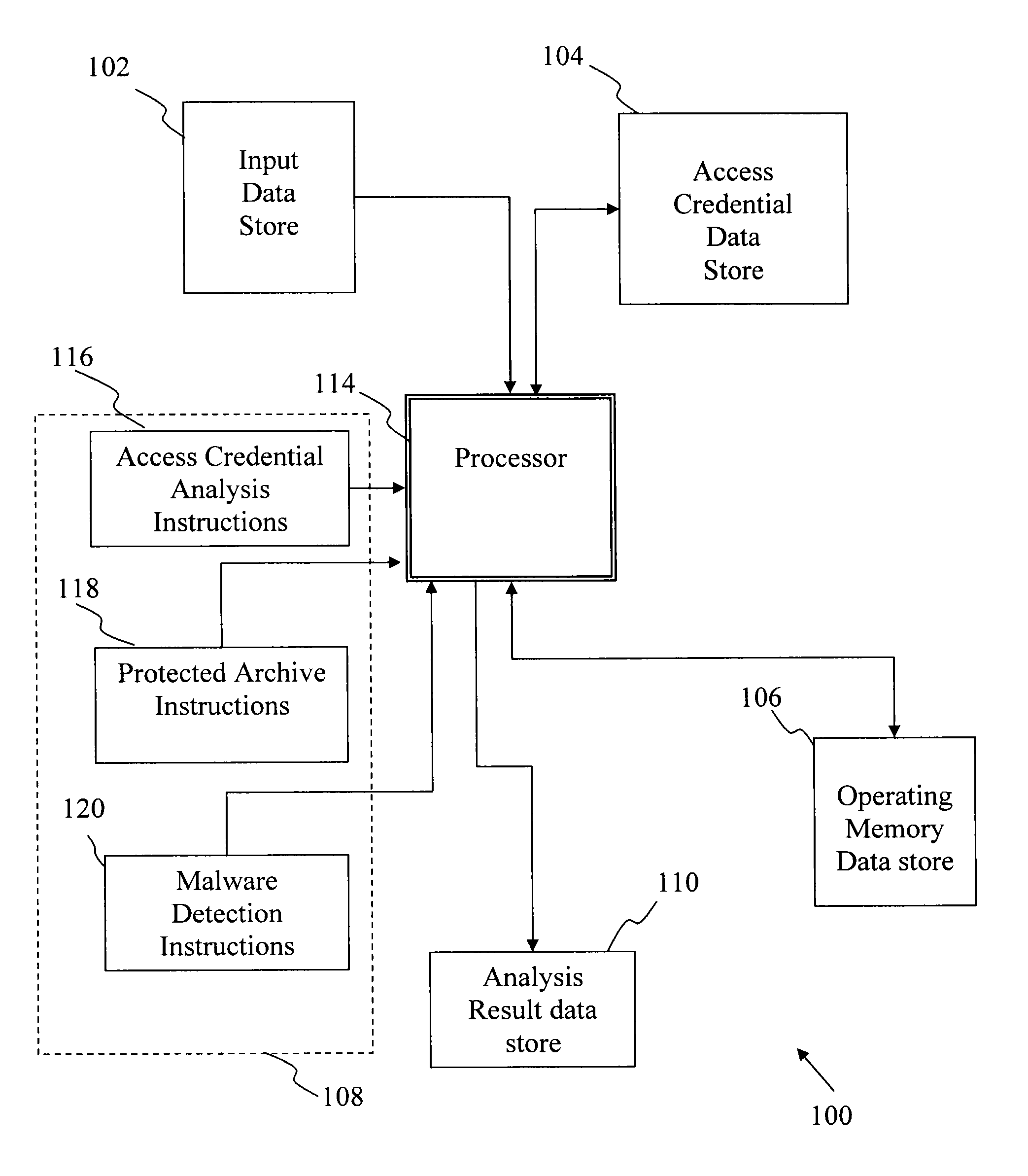
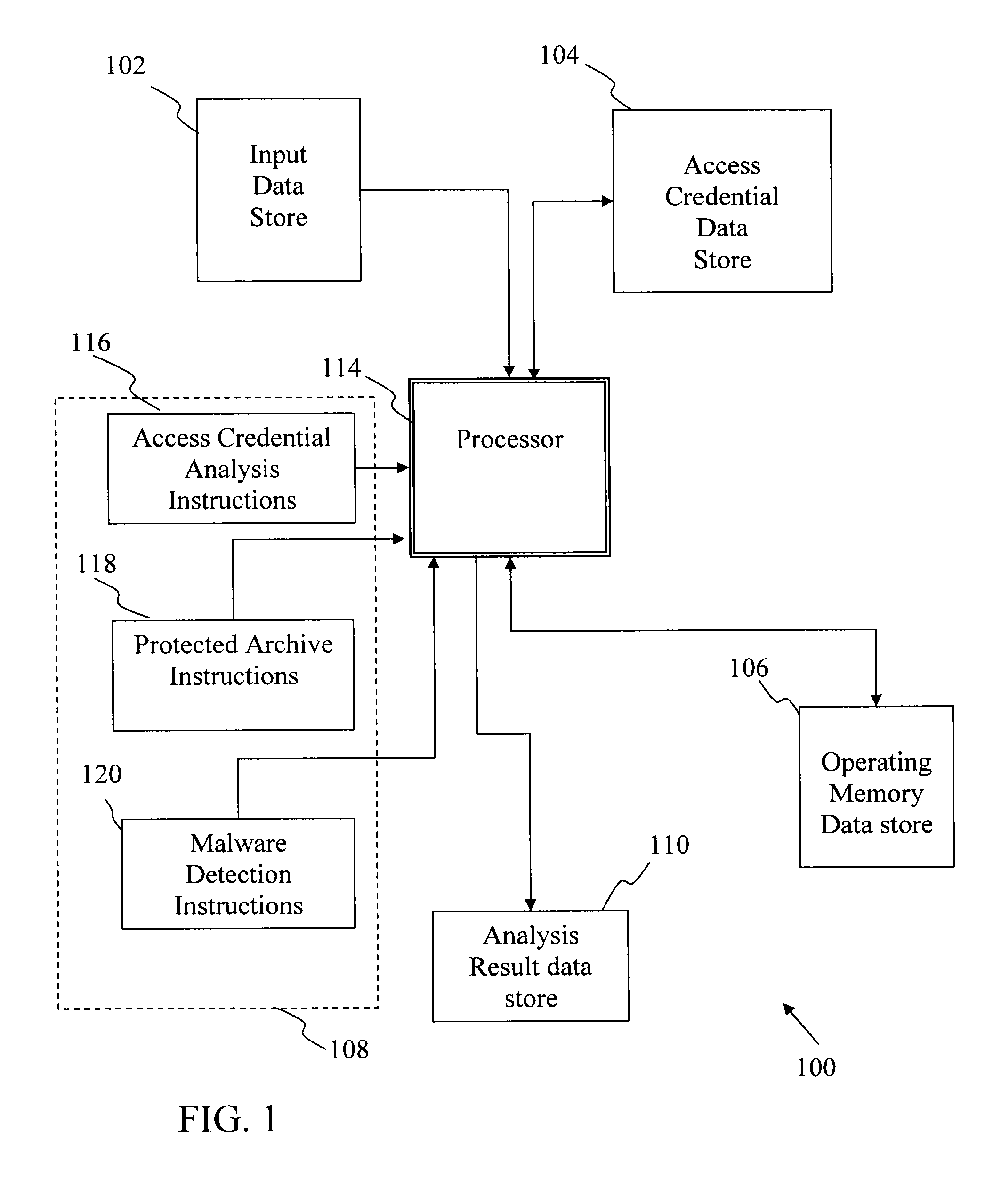
Comprehensive password management arrangment facilitating security
InactiveUS20110083181A1Function increaseMemory loss protectionError detection/correctionData memoryMalware
Computer-implemented process and apparatus for screening data for malware. Received data stored in at least one data store includes at least: (i) a first protected item of data containing contents that are generally inaccessible without specific access credential information, and (ii) specific access credential information corresponding to the first protected item of data. The received data is analyzed to detect any protected items of data therein based on predetermined protected data item identification criteria and to detect any access credential information contained therein based on predetermined access credential identification criteria. In response to a detection of the specific access credential information in the at least one data store, the specific access credential information is stored in the at least one data store in a grouping arrangement with other access credential information. In response to a detection of the first protected item of data, use the specific access credential information is stored in the grouping arrangement to facilitate access to the first protected item of data by a malware screening process to extract its content. The malware screening process is executed to scan the content extracted from the first protected data item to detect a presence of malware.
Owner:AO KASPERSKY LAB
Universal userid and password management for internet connected devices
InactiveUS6859878B1Computer security is enhancedImprove securityKey distribution for secure communicationDigital data authenticationThe InternetApplication software
An improved system, method, and computer program product is provided to manage userid / password combinations by utilizing a universally accessible Internet location. This site stores and manages an encrypted database containing the customers multiple userid and password combinations, and also acts as the repository and distribution center for the software used to access and manage the database by the customer. In one embodiment, these applications are designed to work seamlessly with the Internet connection-software (e.g. a set of buttons on a browsers tool bar). Encryption is used on both the client and / or server side to ensure security and integrity.
Owner:IBM CORP
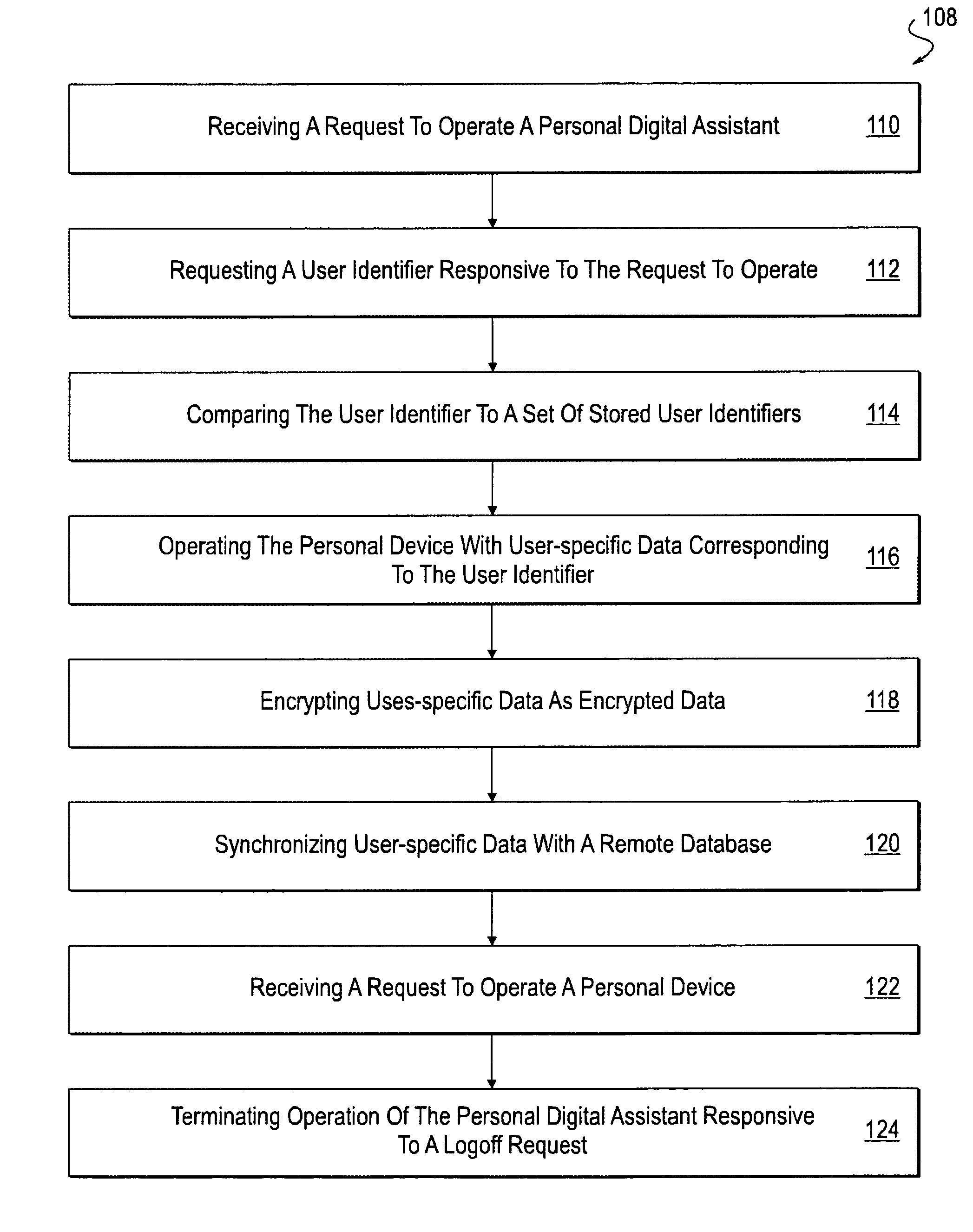
Method and apparatus for storing data on the application layer in mobile devices
ActiveUS7587608B2Safe and efficient data encryption and storageDigital data authenticationSecret communicationComputer hardwareApplication software
The present embodiments provide a system and methods for encrypting and storing data in a mobile device such as a personal digital assistant. The system includes an access controller and a cryptography manager both coupled to the software applications on the mobile device. The system employs a user specific key to encrypt the user specific data. The encrypted file along with header information is stored below the application layer within the mobile system.
Owner:SAP AG
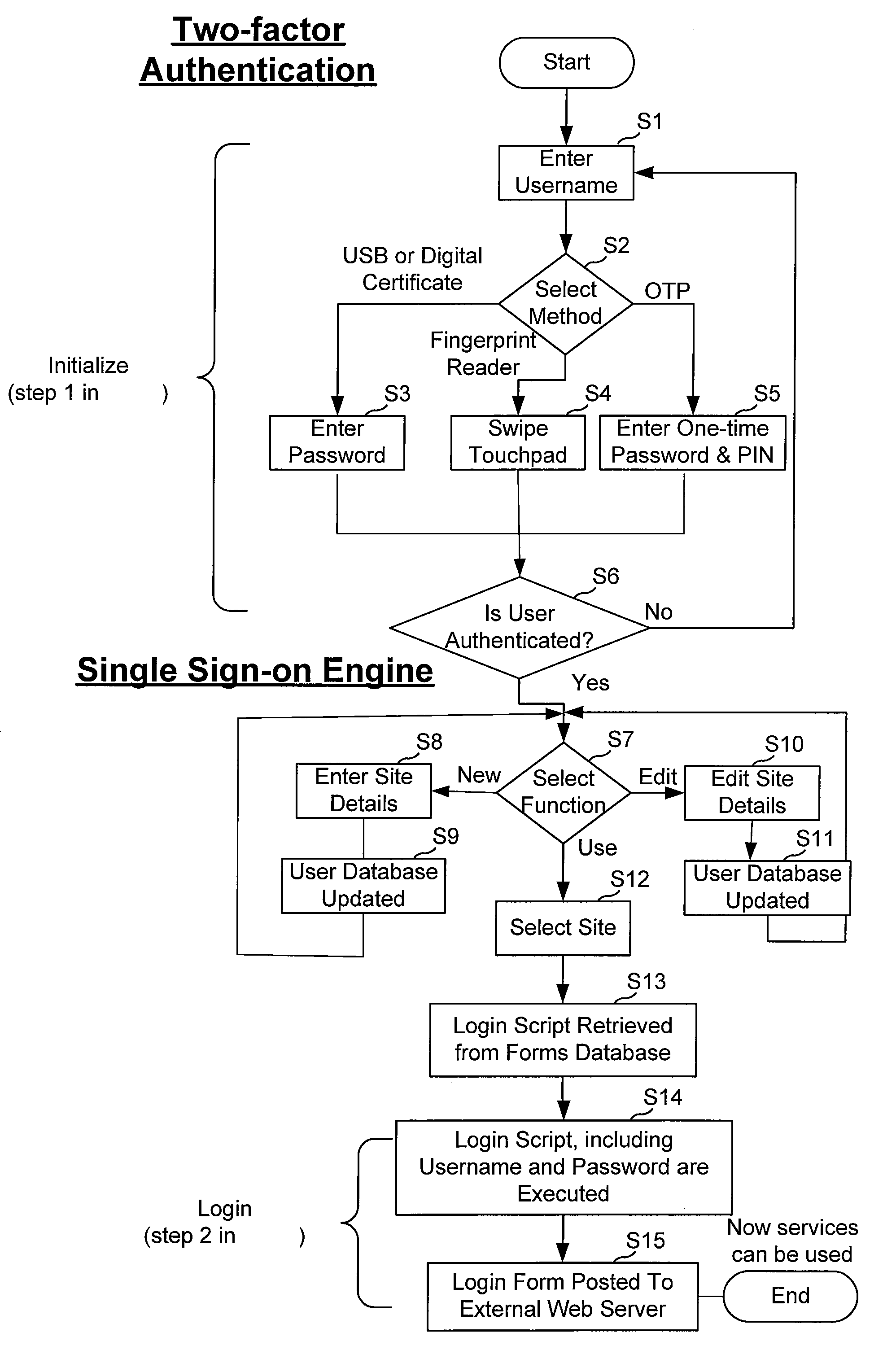
User-administered single sign-on with automatic password management for web server authentication
InactiveUS20070226783A1Digital data processing detailsUser identity/authority verificationWeb serviceNetwork address
A secure login management system is coupled to at least one client system and coupleable to at least one target system and includes a sign-on module for connecting the user to a target system secured against unauthorized access, using at least target system authentication data expected or required by the target system, wherein the secure login management system is at a distinct network address from the user's client system and is accessible by a plurality of client systems available to the user. The secure login management system can provide access by client systems without requiring special preconfiguration of specific client systems or special configuration of target systems. The authentication data can include one or more of a username, password, fingerprint, digital sequence derived from a security device possessed by the user, and / or one-time use password. The secure login management system might perform authentication data management to automatically generate new target system authentication data.
Owner:RABBITS FOOT SECURITY A CALIFORNIA CORP
Radio communication device and user authentication method for use therewith
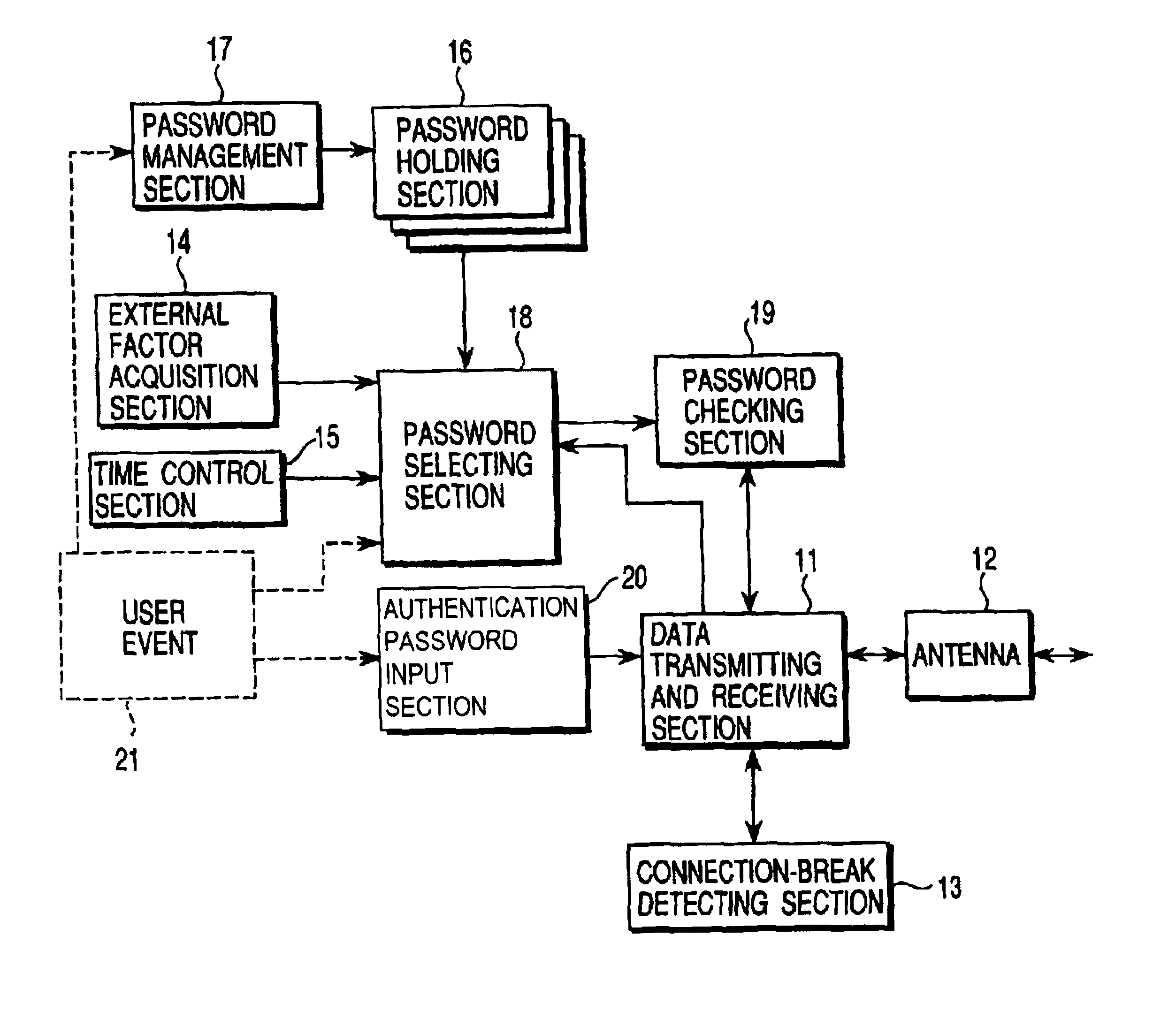
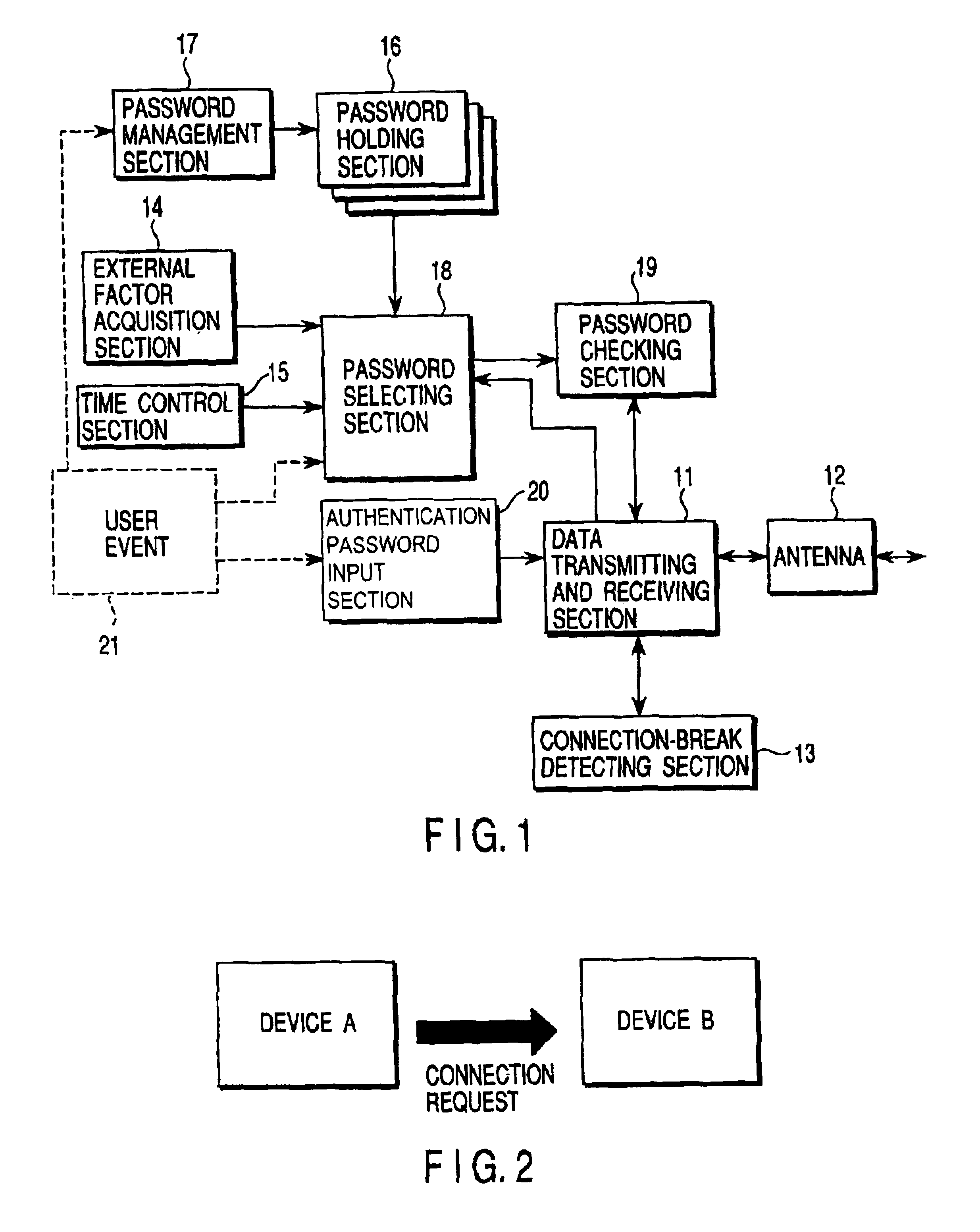
ActiveUS6928166B2Imposing any operating burdenLevel of security can changeMultiple keys/algorithms usageUser identity/authority verificationConfidentialityUser authentication
To allow flexible security level switching according communication situations, a password holding section holds a plurality of device authentication passwords, for example, a temporary password and a private password. The temporary password is valid only under a certain situation and the private password has a high level of confidentiality to increase the device security. A password management section allows the user to add a new password to the password holding section and delete an existing password therefrom. A password selecting section selects the most suitable password for current connection from among passwords in the password holding section according to a user event, information acquired by an external factor acquisition section, and information from a time control section. The selected password is output to a password checking section.
Owner:2BCOM LLC
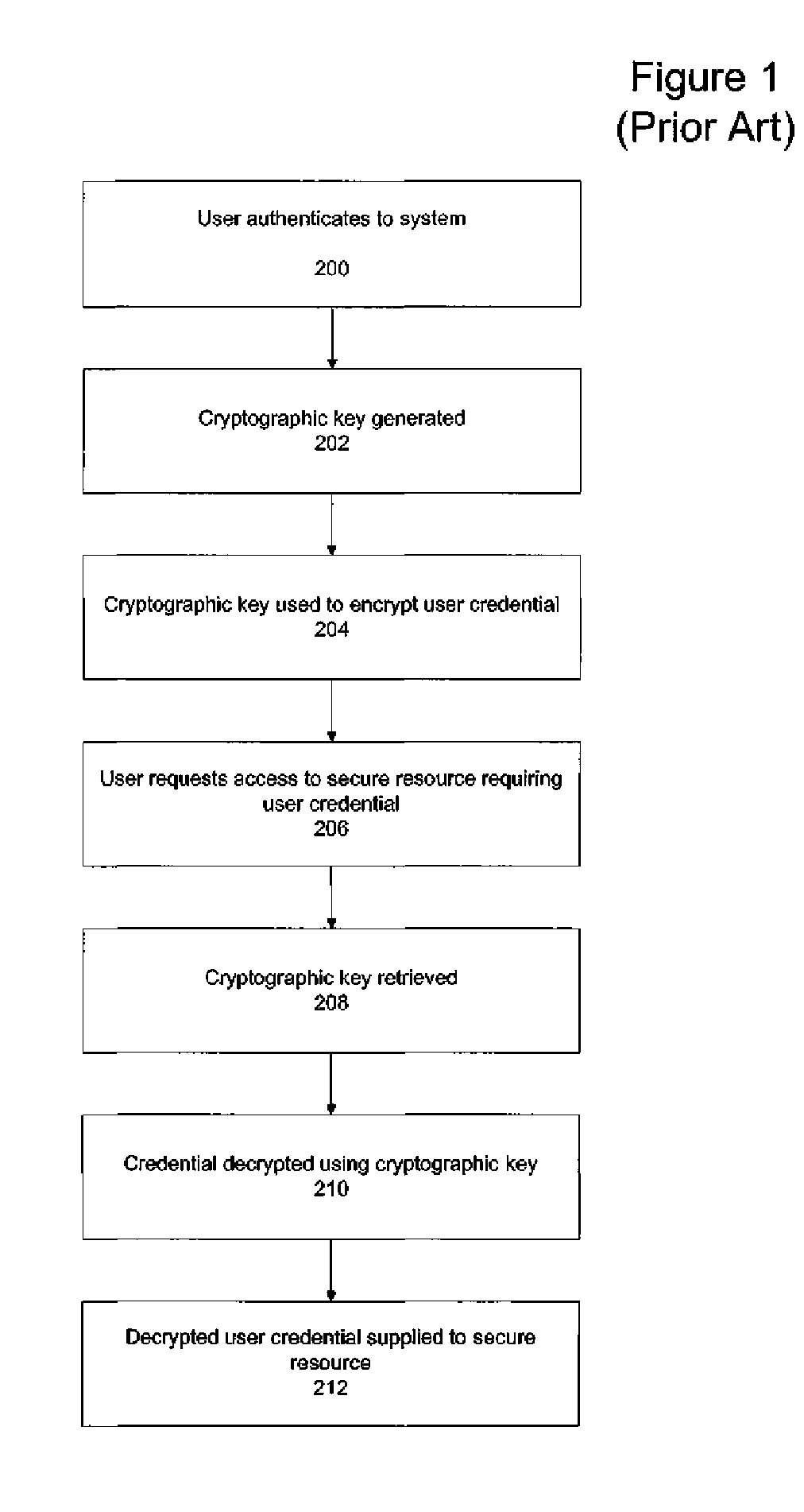
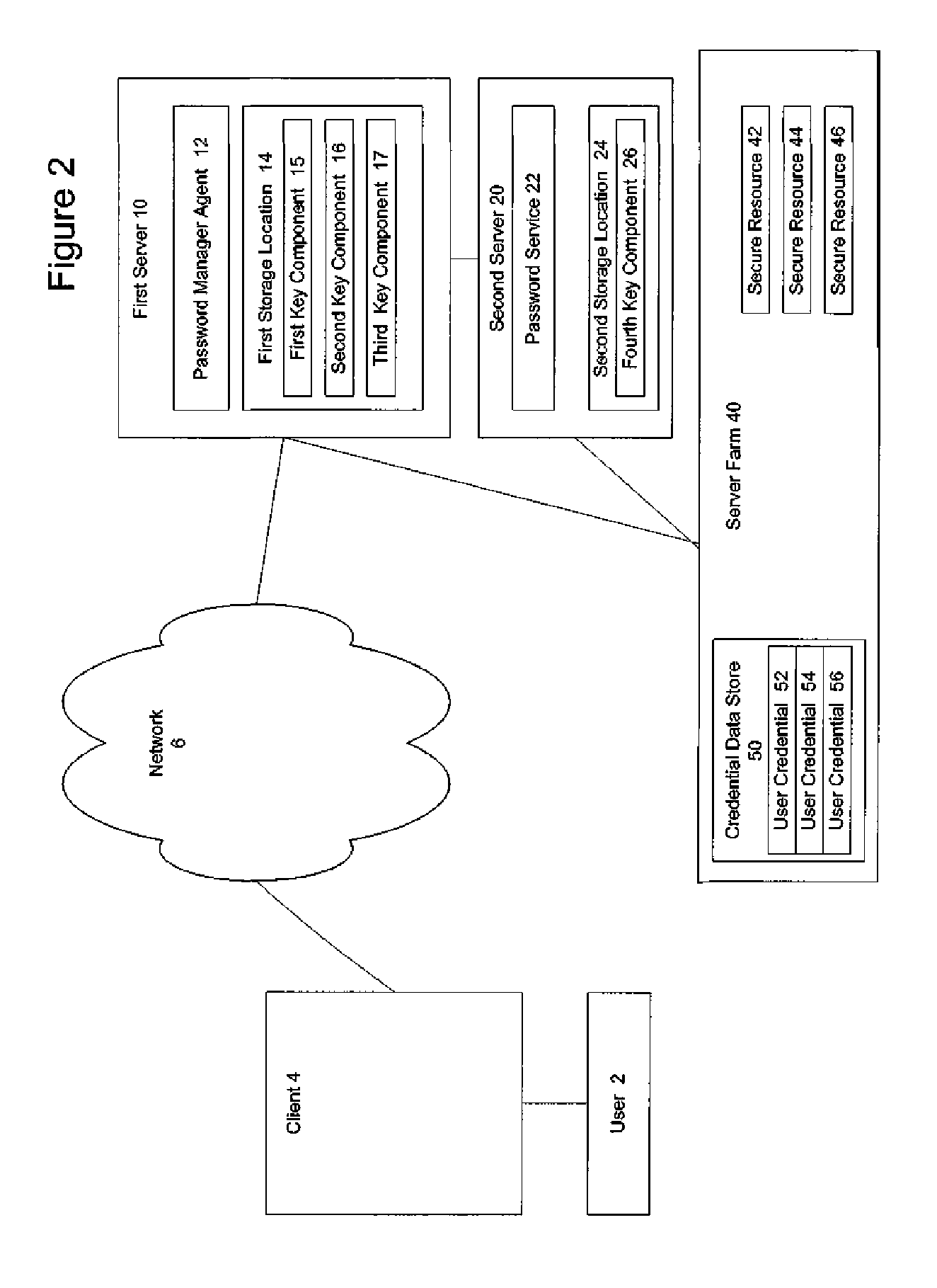
System and method for key recovery
ActiveUS20060242415A1Key distribution for secure communicationDigital data processing detailsPassword managerKey recovery
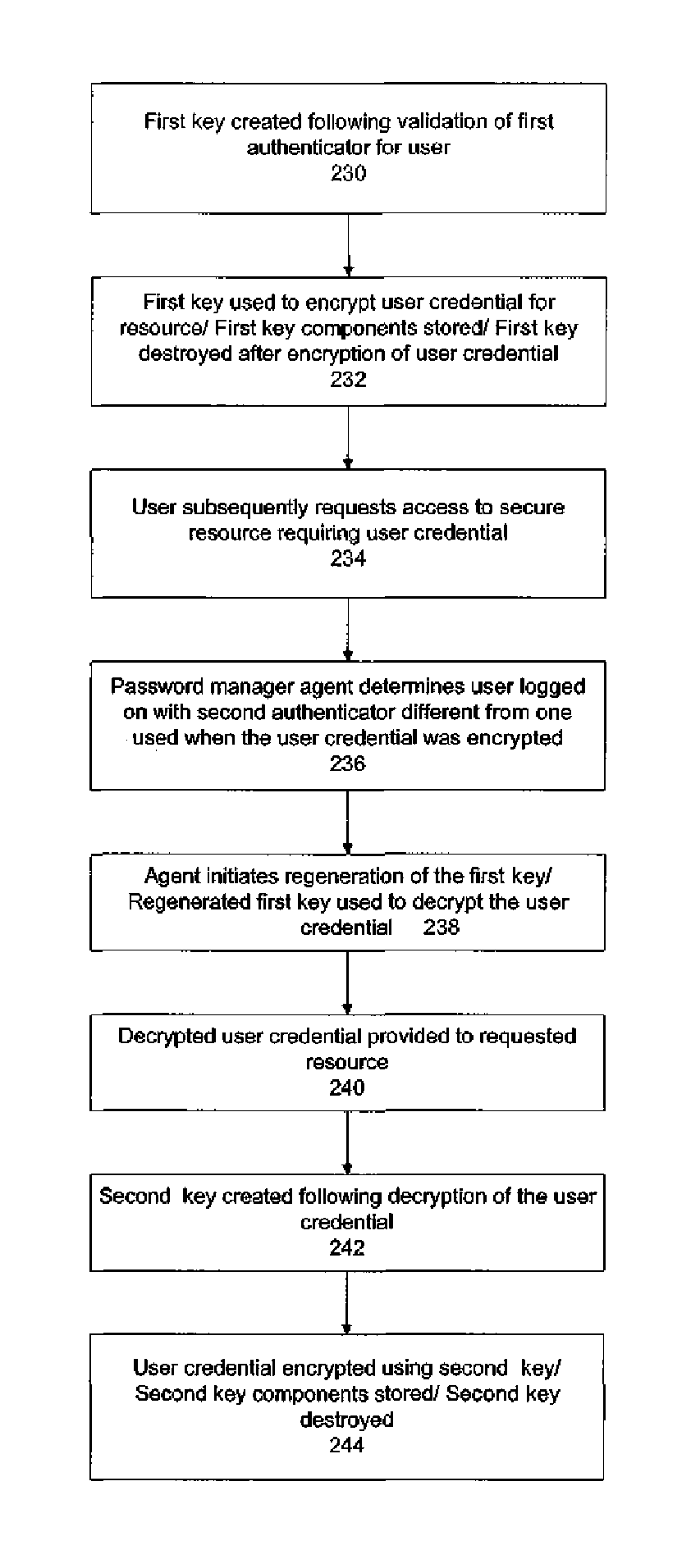
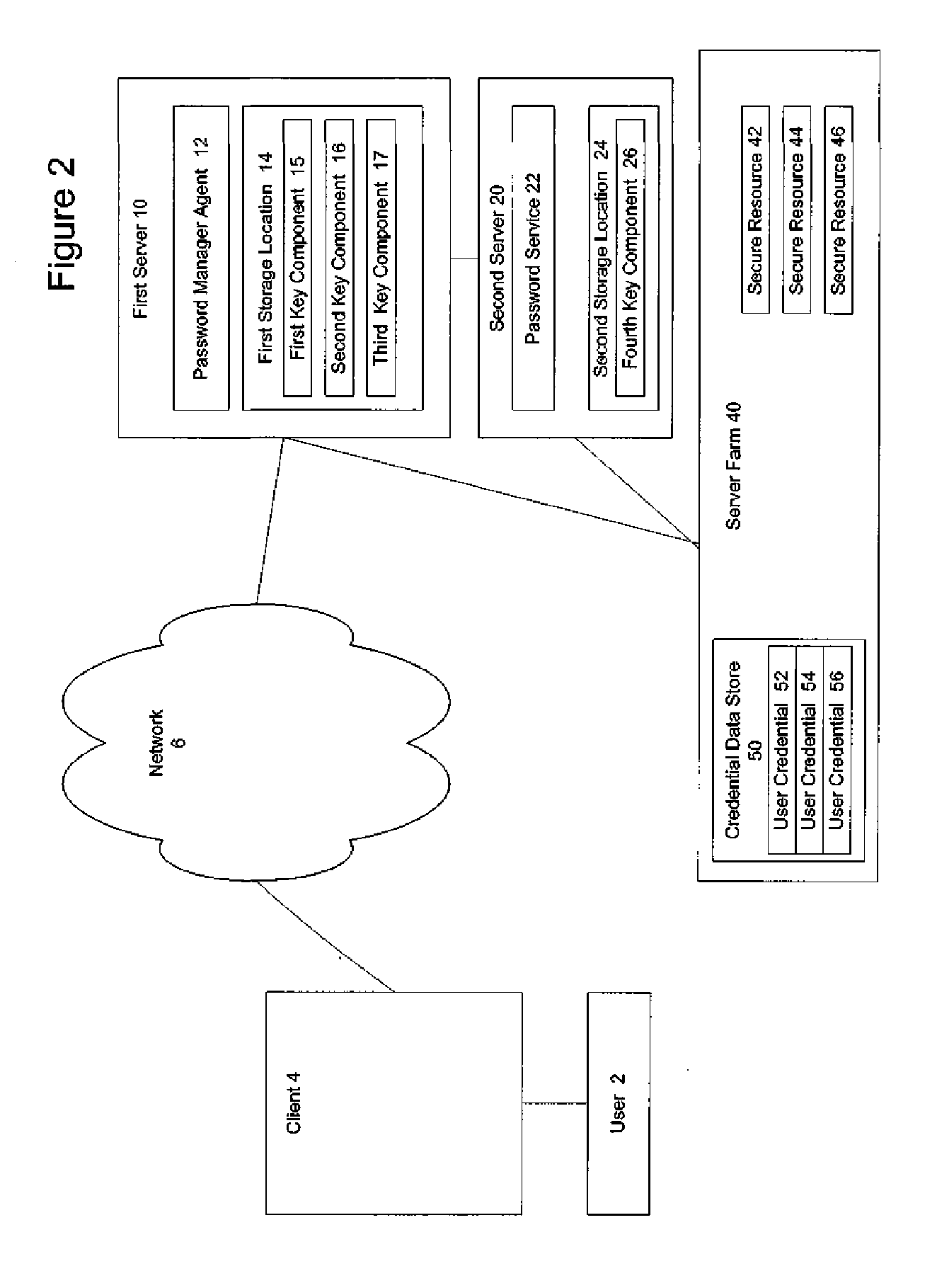
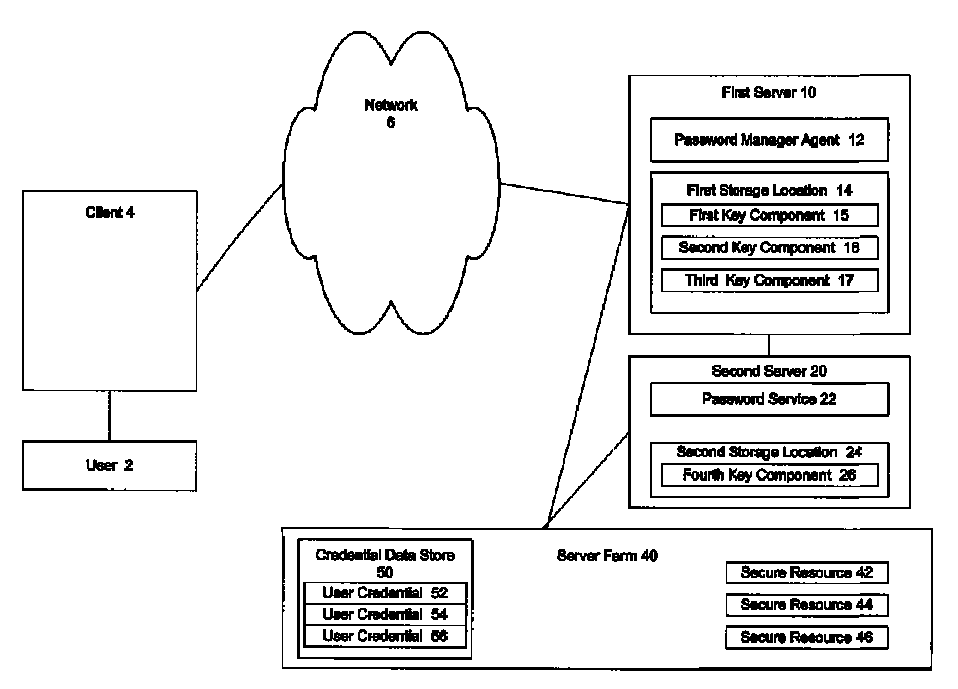
A secure mechanism for transparent key recovery for a user who has changed authentication information is disclosed. A password manager agent intercepts requests by a user to access secure resources that require user credentials. Upon detecting changed authentication information for the user, the password manager agent automatically regenerates the components of a cryptographic key associated with the user that was previously used to encrypt user credentials for the user and then destroyed. After regeneration of the original cryptographic key, the password manager agent uses the key to decrypt the user credentials necessary for the requested application. The regenerated key is then destroyed and the user credentials are re-encrypted by the password manager agent using a new cryptographic key associated with the user made up of multiple components. Following the re-encryption of the user credentials, the components used to assemble the new key are securely stored in multiple locations and the new key is destroyed.
Owner:CITRIX SYST INC
Secure distributed information and password management
ActiveUS20150127940A1User identity/authority verificationSelective content distributionUser deviceDigital content
A method, performed by a computer device, may include receiving an indication that a first user has acquired rights to access a digital content; generating a key for the digital content; encrypting the digital content using the generated key to generate encrypted digital content; obtaining a first passcode; and providing the first passcode and the encrypted digital content to a user device associated with the first user. The method may further include receiving, from the user device, a request for the key, wherein the request include the first passcode; determining that the first passcode is valid; determining that the key has not expired; and providing the key to the user device, in response to determining that the first passcode is valid and that the key has not expired.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS +1
Cloud based password management
ActiveUS20140173708A1Digital data processing detailsMultiple digital computer combinationsApplication softwareComputer program
The present invention extends to methods, systems, and computer program products for providing a cloud based password manager that automatically logs in users from any computer. The cloud based password manager does not require that the user install a local plug-in or other tool to perform automatic login. In this sense, unlike current password managers, the password manager of the present invention is completely cloud based. By simply using any browser or a dedicated app on any computer, the user can request a website and receive a copy of the website with the user logged in even if the user has never used the computer.
Owner:CROWDSTRIKE
Method for realizing function control on mobile terminal
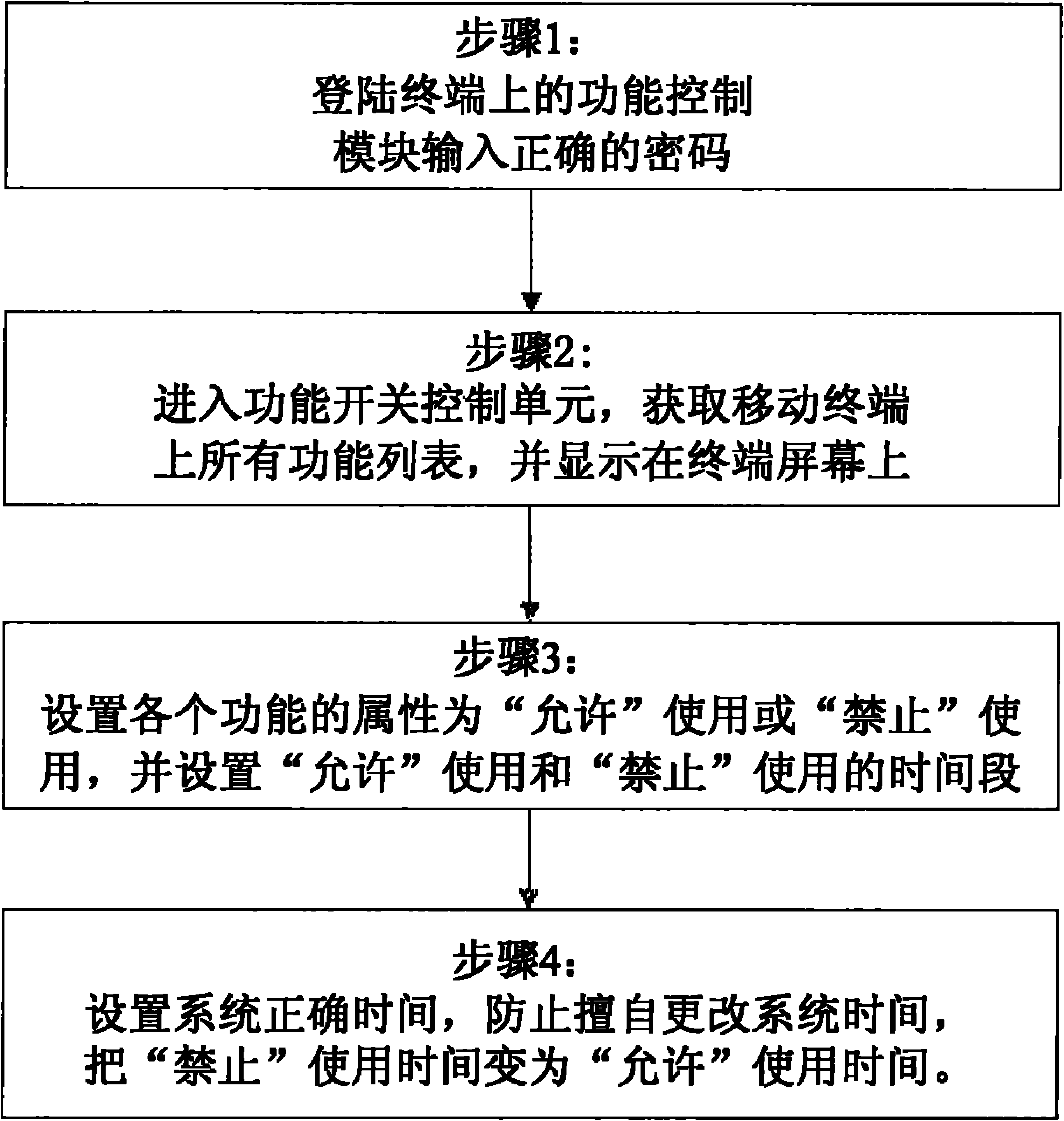
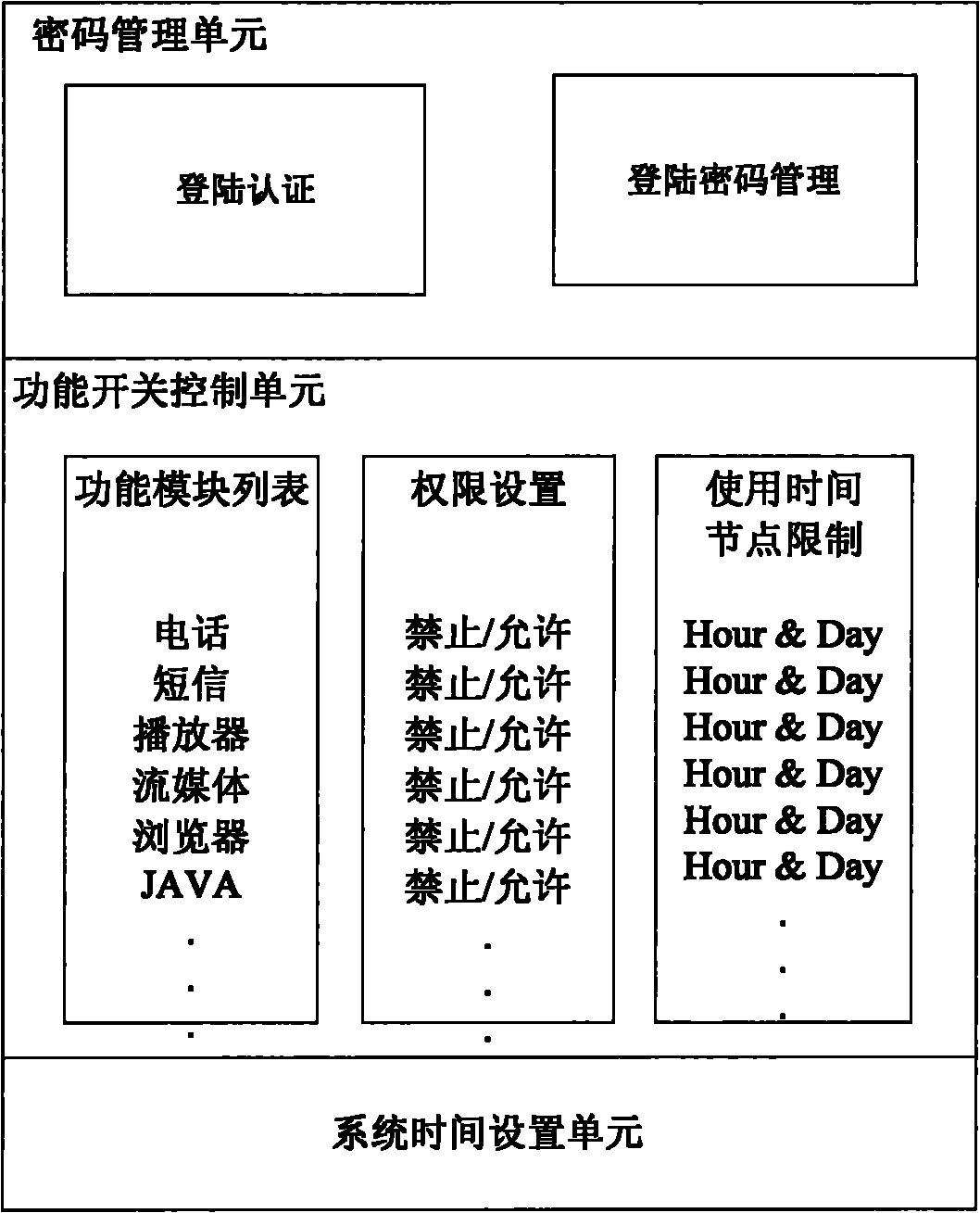
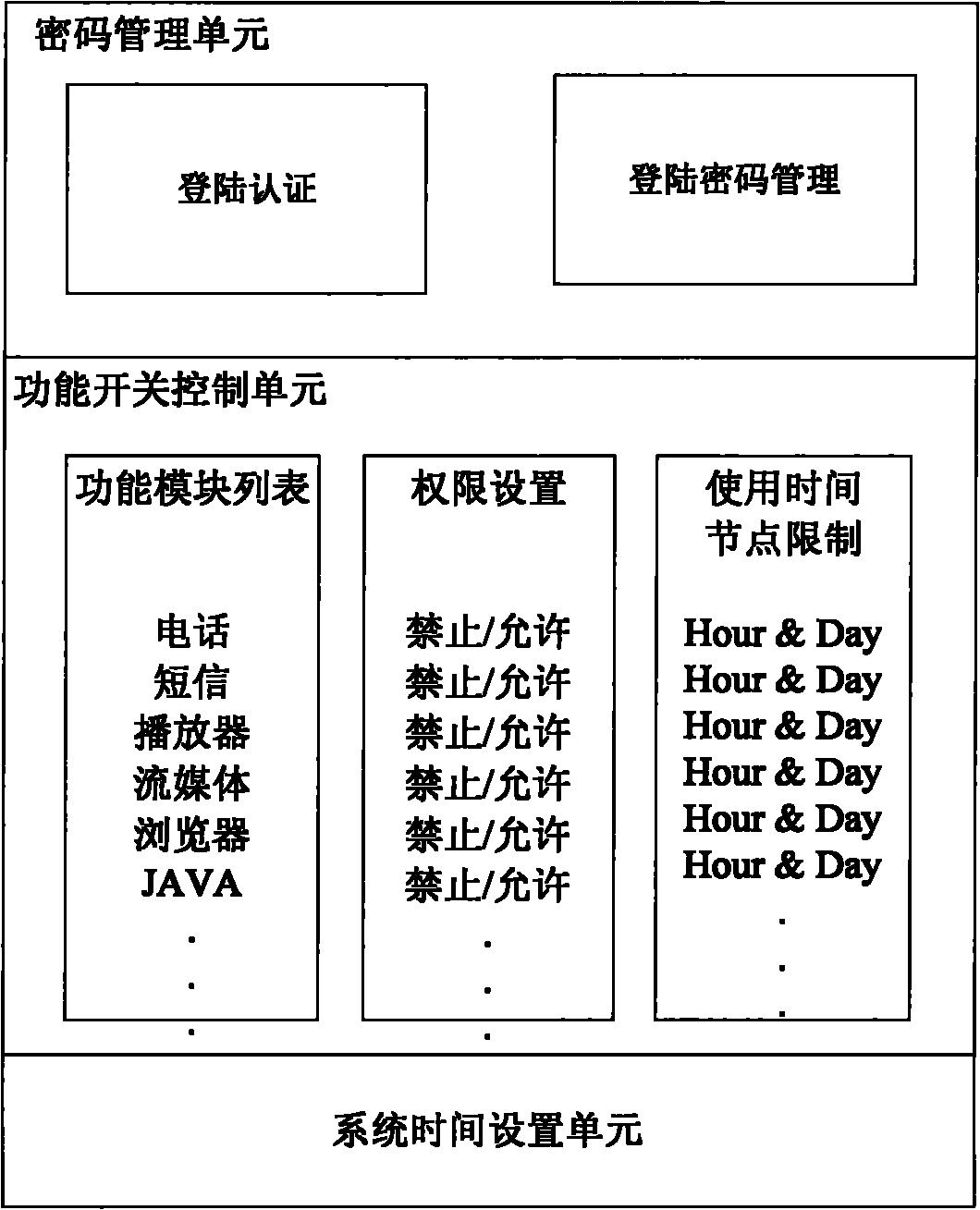
InactiveCN101923614AAvoid entertainment featuresSimple structureDigital data authenticationSubstation equipmentSpecific functionTime segment
The invention relates to a method for realizing function control on a mobile terminal. A function control module is added on the mobile terminal, wherein the function control module comprises a password management unit, a function switch control unit and a system time setting unit; the password contains a character code, fingerprint identification, voice identification or human face identification; the function switch control unit is arranged for displaying a mobile terminal function list, controlling the function permission and limiting by using time node; and the system time setting unit is arranged for setting the system time for the mobile terminal. The method comprises the steps of: after a user logs in the function control module, 1) setting a logging password in the password management unit, 2) choosing the function switch control unit to display the function list on a terminal screen, 3) setting the attributes of each function as 'usage permitted' or 'usage forbidden' or the time for 'usage permitted' or 'usage forbidden', and 4) setting the correct system time. Through the invention, parents can efficiently control the time of the children using a specific function of the mobile terminal so as to prevent study delay.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
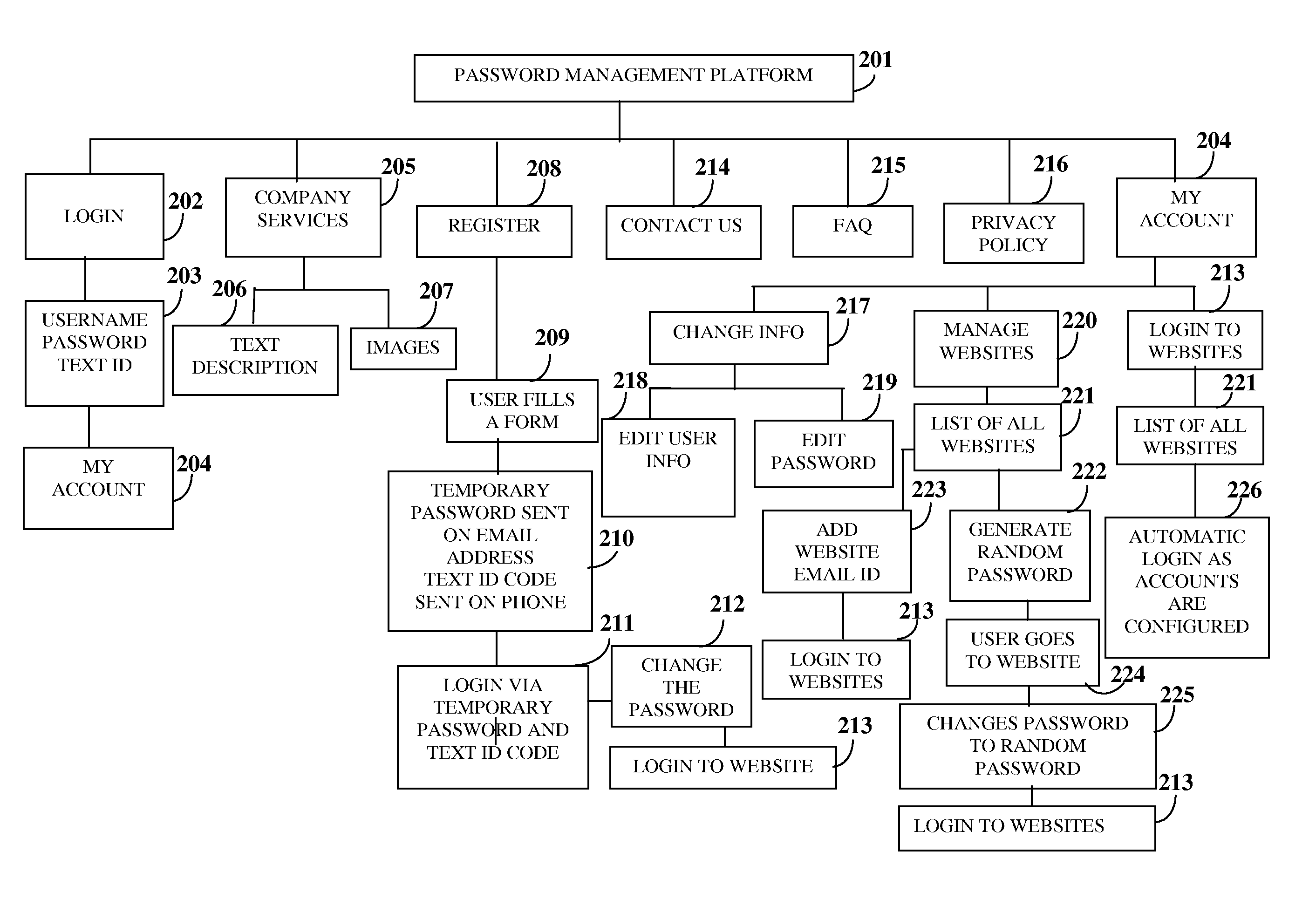
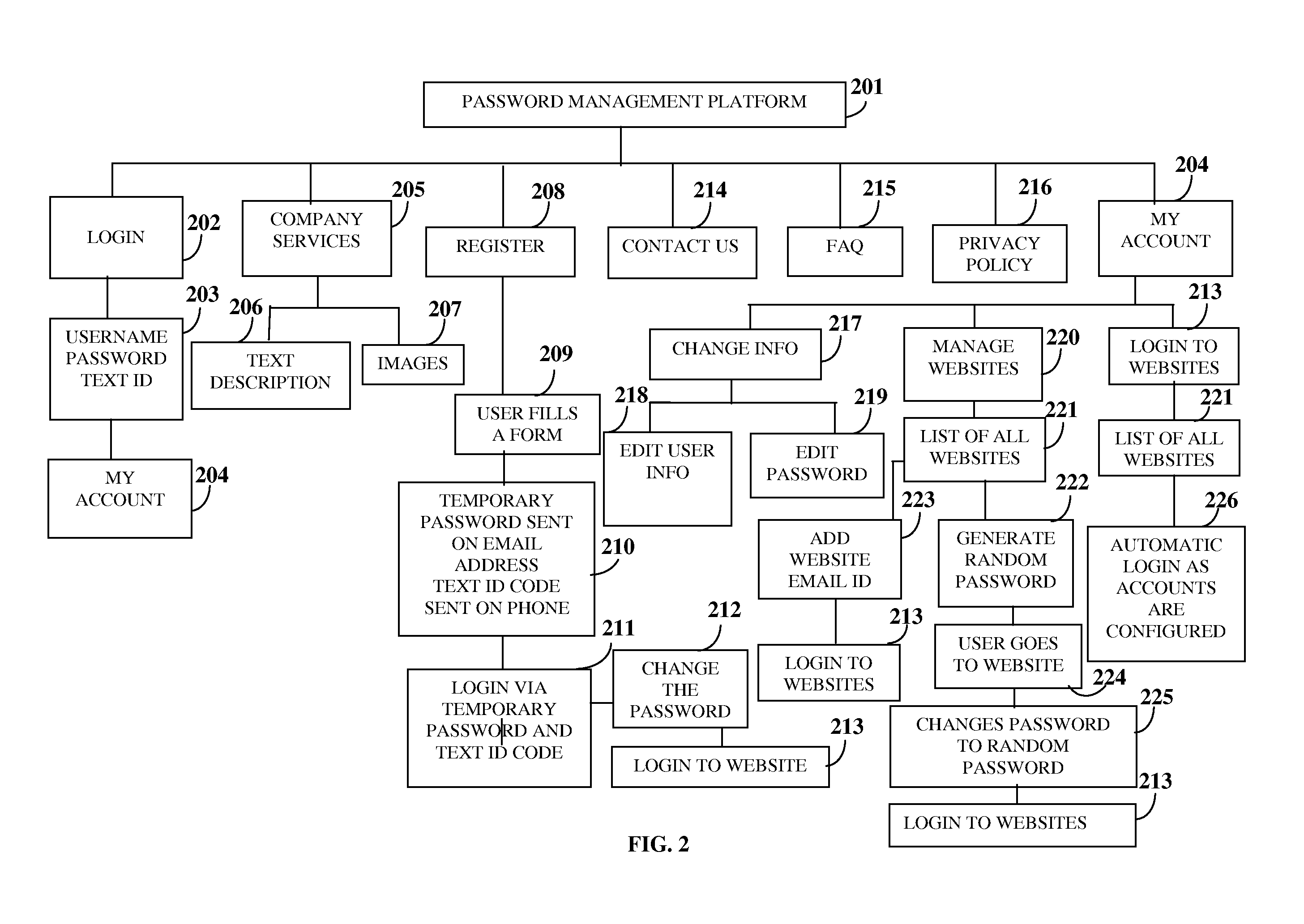
Password Generation And Management
InactiveUS20130254856A1Digital data processing detailsMultiple digital computer combinationsGraphicsGraphical user interface
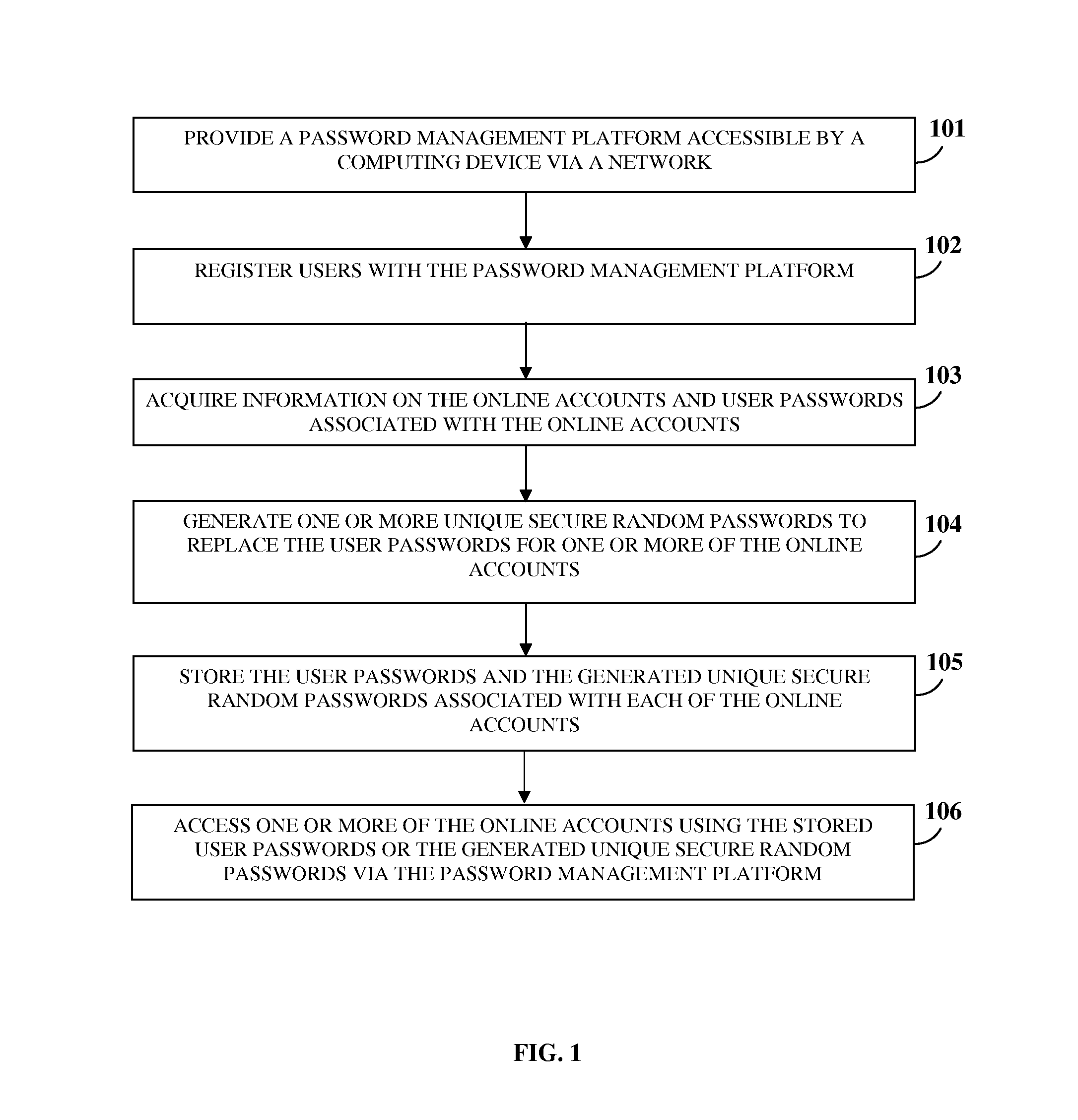
A computer implemented method and system for generating and managing multiple passwords associated with multiple online accounts is provided. The computer implemented method and system provides a password management platform accessible by a computing device via a network. The password management platform acquires information on the online accounts and user passwords associated with the online accounts via a graphical user interface (GUI) provided by the password management platform. The password management platform generates one or more unique secure random passwords to replace the user passwords for each of the online accounts on receiving an indication via the GUI. The password management platform stores the generated unique secure random passwords associated with each of the online accounts for managing access to each of the online accounts. The password management platform provides direct and secure access to the online accounts using the stored user passwords or the generated unique secure random passwords.
Owner:KRISHAN BALDEV
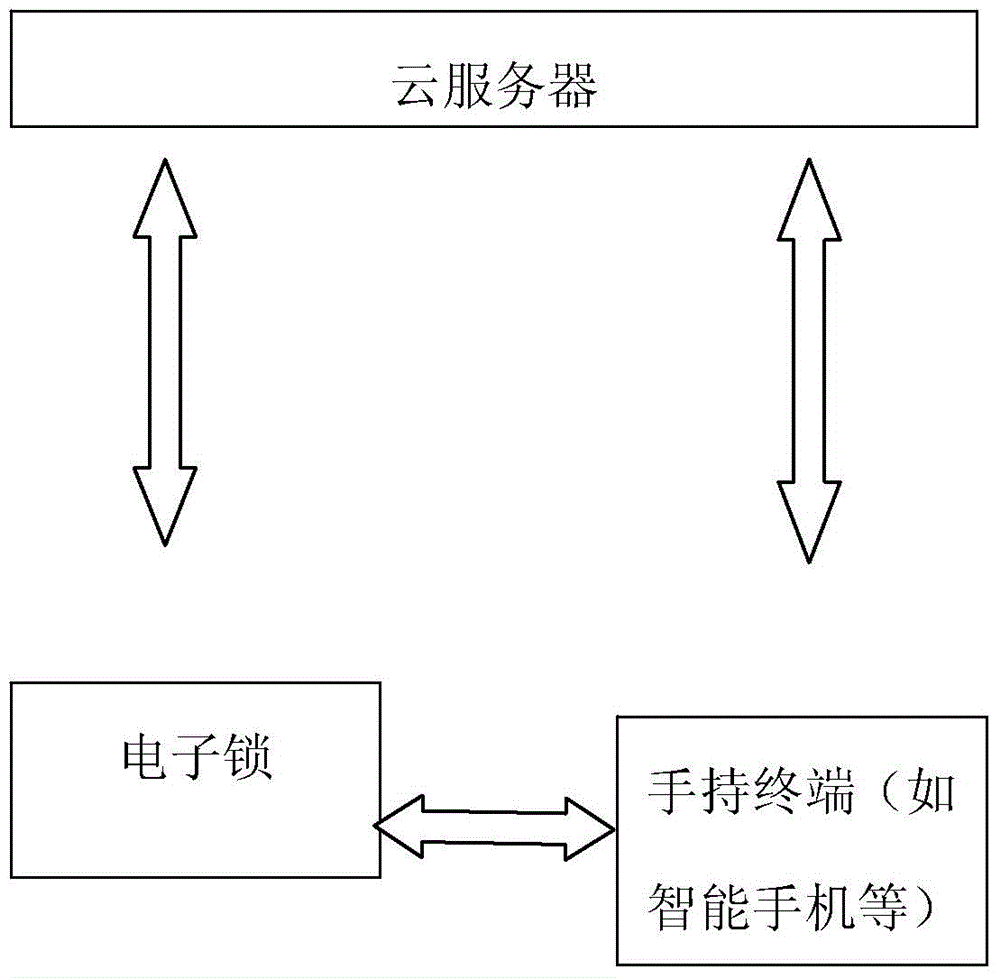
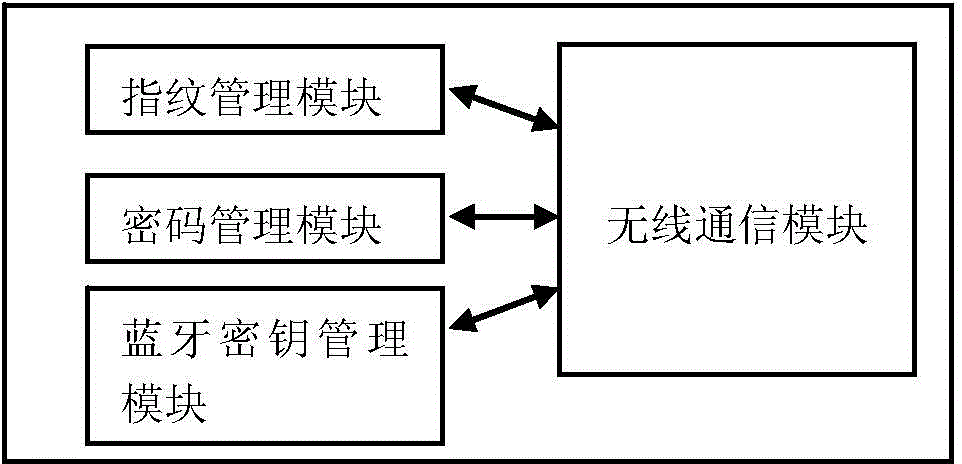
Electronic lock system and intelligent management achieving implementation method thereof
ActiveCN104660719AUser identity/authority verificationIndividual entry/exit registersWireless controlIntelligent management
The invention relates to an electronic lock system and an intelligent management achieving implementation method thereof. The electronic lock system comprises an electronic lock, a handheld terminal and a cloud server, wherein the electronic lock comprises a wireless control communication module, a fingerprint management module, a password management module, a Bluetooth key management module; the handheld terminal is used for sending increase, change, check and delete instructions of a fingerprint, increase, correction, check and delete instructions of a password and increase, correction, check and deletion instructions of a Bluetooth key; the cloud server is used for storing a fingerprint id, a password id and a Bluetooth key id. A user can name the fingerprint, a password and the Bluetooth key through the handheld terminal for memorizing and managing; the increase, correction, check and deletion instructions of the fingerprint, the password and the Bluetooth key, which are sent to a fingerprint lock by the user through the handheld terminal through the cloud server, are identified by the fingerprint id, the password id and the Bluetooth key id, so that the fingerprint, the password and the Bluetooth key of the electronic lock can be relatively intelligently, intuitionally, conveniently and rapidly managed.
Owner:YUNDING NETWORK TECH BEIJING
Method for managing identities across multiple sites
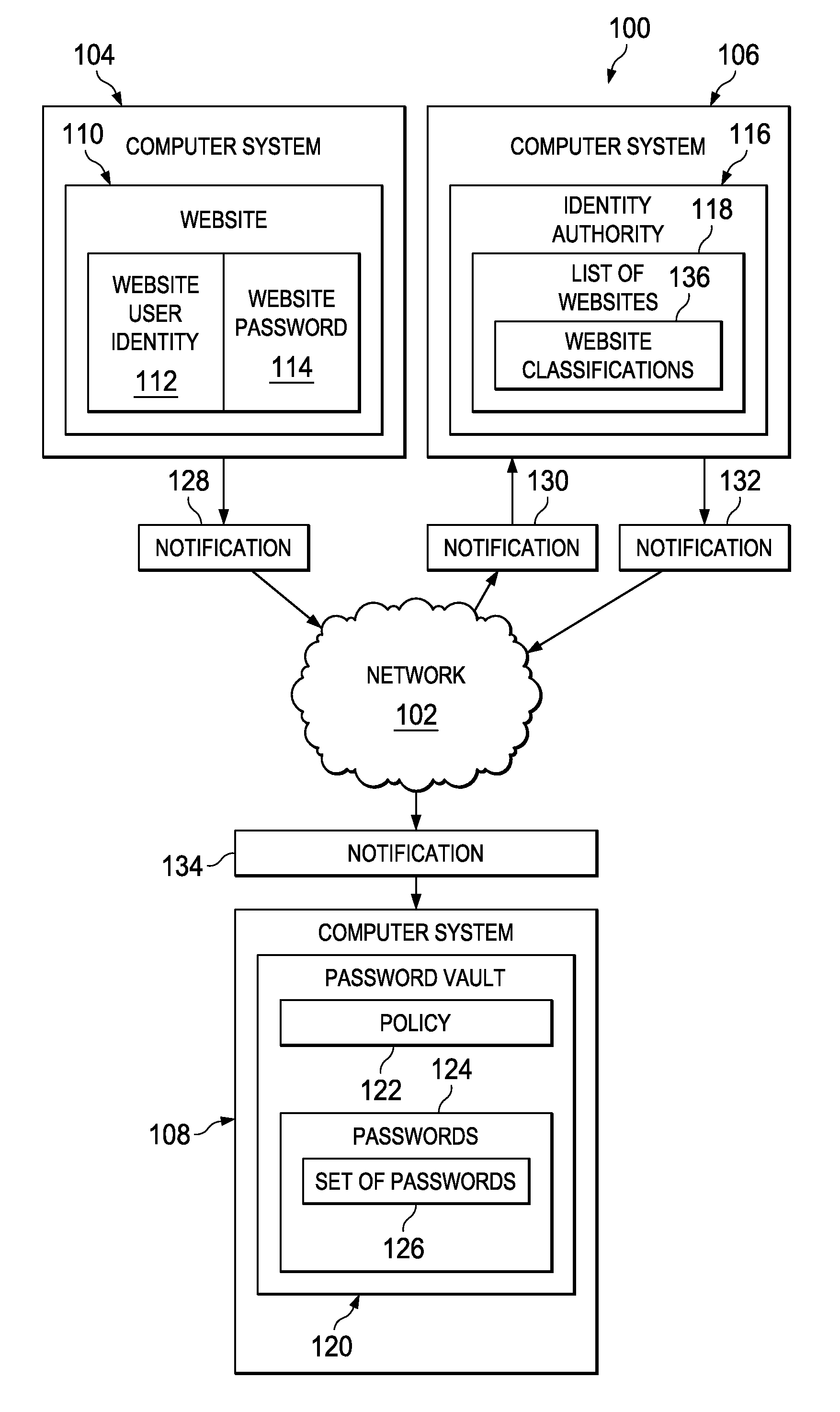
InactiveUS20130014236A1Digital data processing detailsUser identity/authority verificationData processing systemInternet privacy
A method, data processing system, and computer program product for managing passwords. A computer system receives a notification from a website that indicates a password for the website needs to be changed. If the computer system determines the website is in a list of websites and a classification of the website matches one or more of a set of website classifications, a notification is sent to a password vault that indicates the password for the website needs to be changed. A set of passwords in the password vault is selected based upon the set of passwords meeting a policy for password management.
Owner:IBM CORP
Systems and Methods for Custom Device Automatic Password Management
InactiveUS20100325687A1Digital data processing detailsUser identity/authority verificationDigital devicePassword management
In various embodiments, a method comprises receiving a custom login script from a first user, receiving a custom change password script from the first user, logging onto an account on a digital device using the custom login script from the first user, changing an old password on the account to a new password at predetermined intervals using the custom change password script from the first user, receiving a password request from a second user, approving the password request, and checking out the new password to the second user.
Owner:BEYONDTRUST SOFTWARE
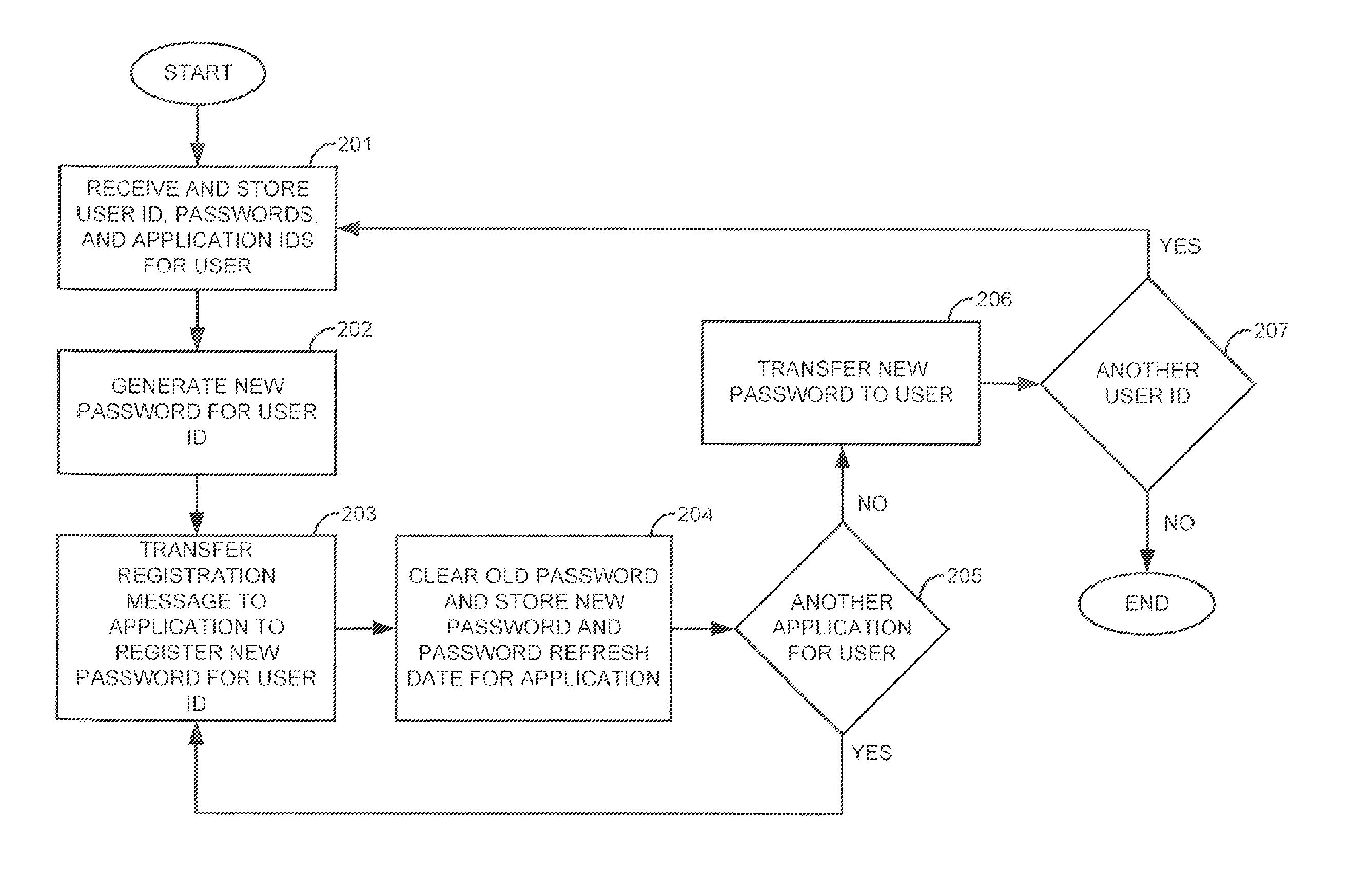
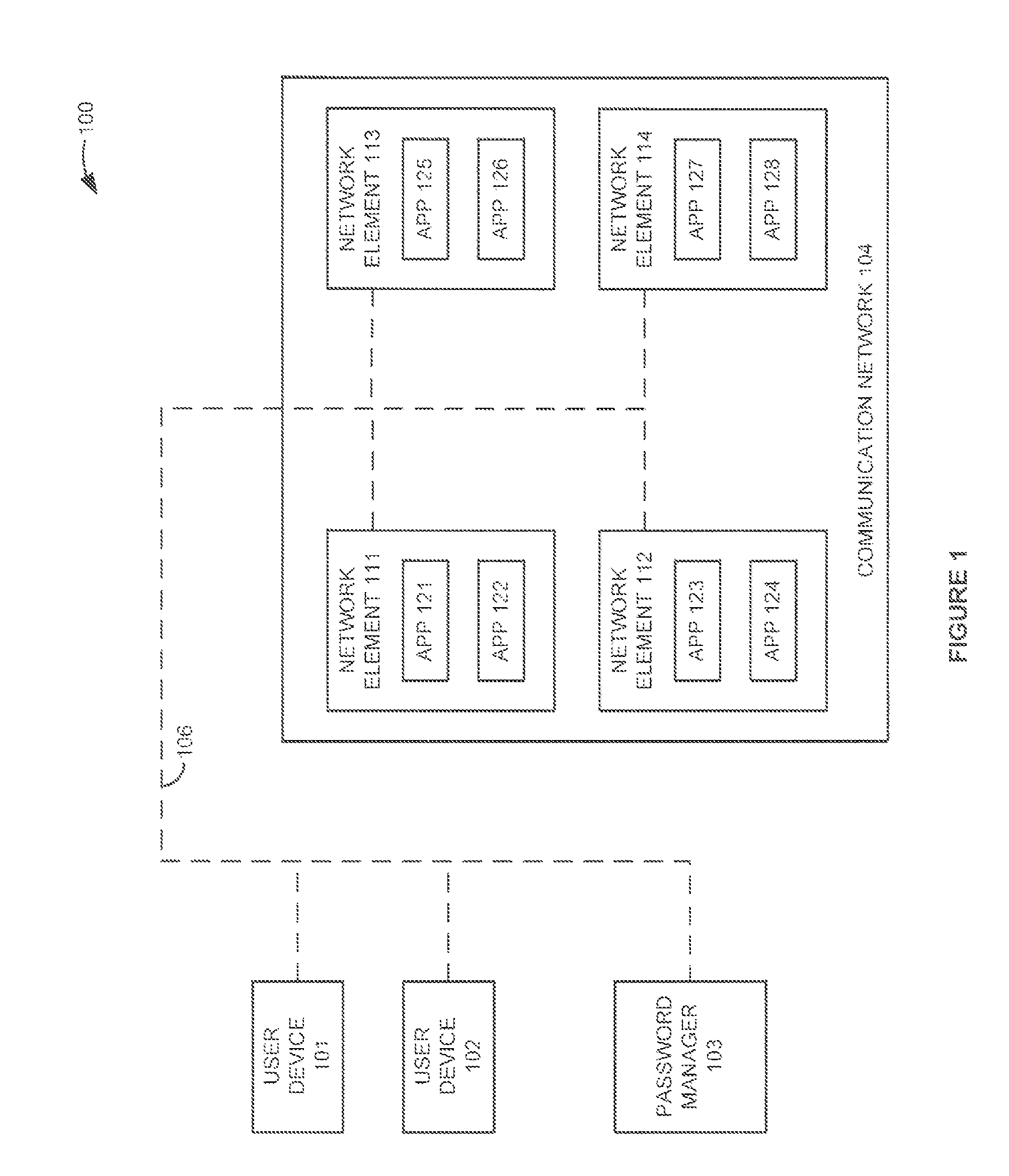
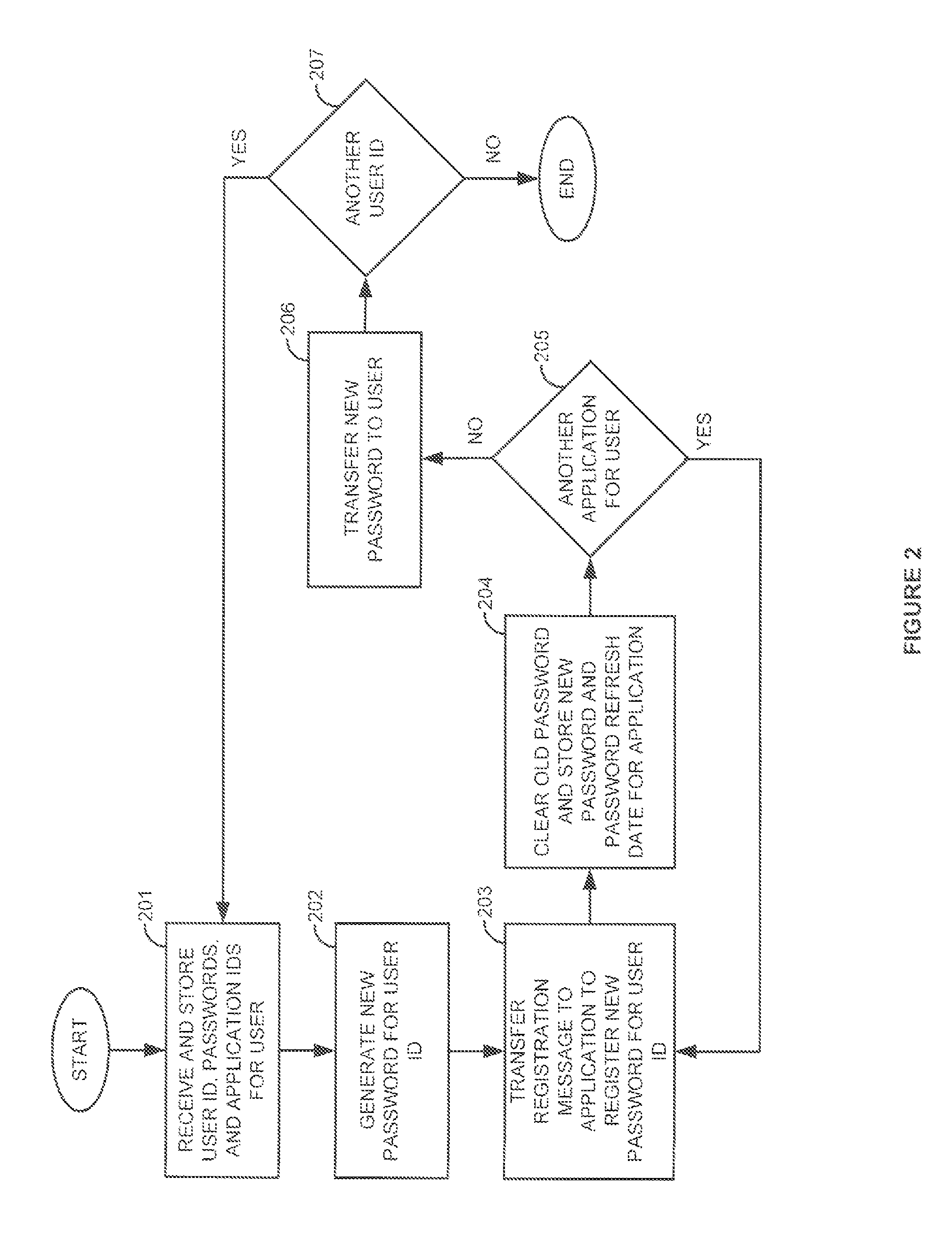
Password management for a communication network
InactiveUS7950051B1Digital data processing detailsMultiple digital computer combinationsNetwork addressingNetwork address
A password management system generates passwords for users. The system registers the passwords with applications in network elements in a communication network. The system indicates the passwords to the users who use the passwords to access the applications. The system generates new passwords before the old passwords expire. The system registers the new passwords with the applications and indicates the new passwords to the users before the old passwords expire. The users use the new passwords to access the applications. The system may also register network addresses with the applications for the users.
Owner:SPRINT CORPORATION
System and method for key recovery
ActiveUS7831833B2Key distribution for secure communicationDigital data processing detailsApplication softwareComputer science
A secure mechanism for transparent key recovery for a user who has changed authentication information is disclosed. A password manager agent intercepts requests by a user to access secure resources that require user credentials. Upon detecting changed authentication information for the user, the password manager agent automatically regenerates the components of a cryptographic key associated with the user that was previously used to encrypt user credentials for the user and then destroyed. After regeneration of the original cryptographic key, the password manager agent uses the key to decrypt the user credentials necessary for the requested application. The regenerated key is then destroyed and the user credentials are re-encrypted by the password manager agent using a new cryptographic key associated with the user made up of multiple components. Following the re-encryption of the user credentials, the components used to assemble the new key are securely stored in multiple locations and the new key is destroyed.
Owner:CITRIX SYST INC
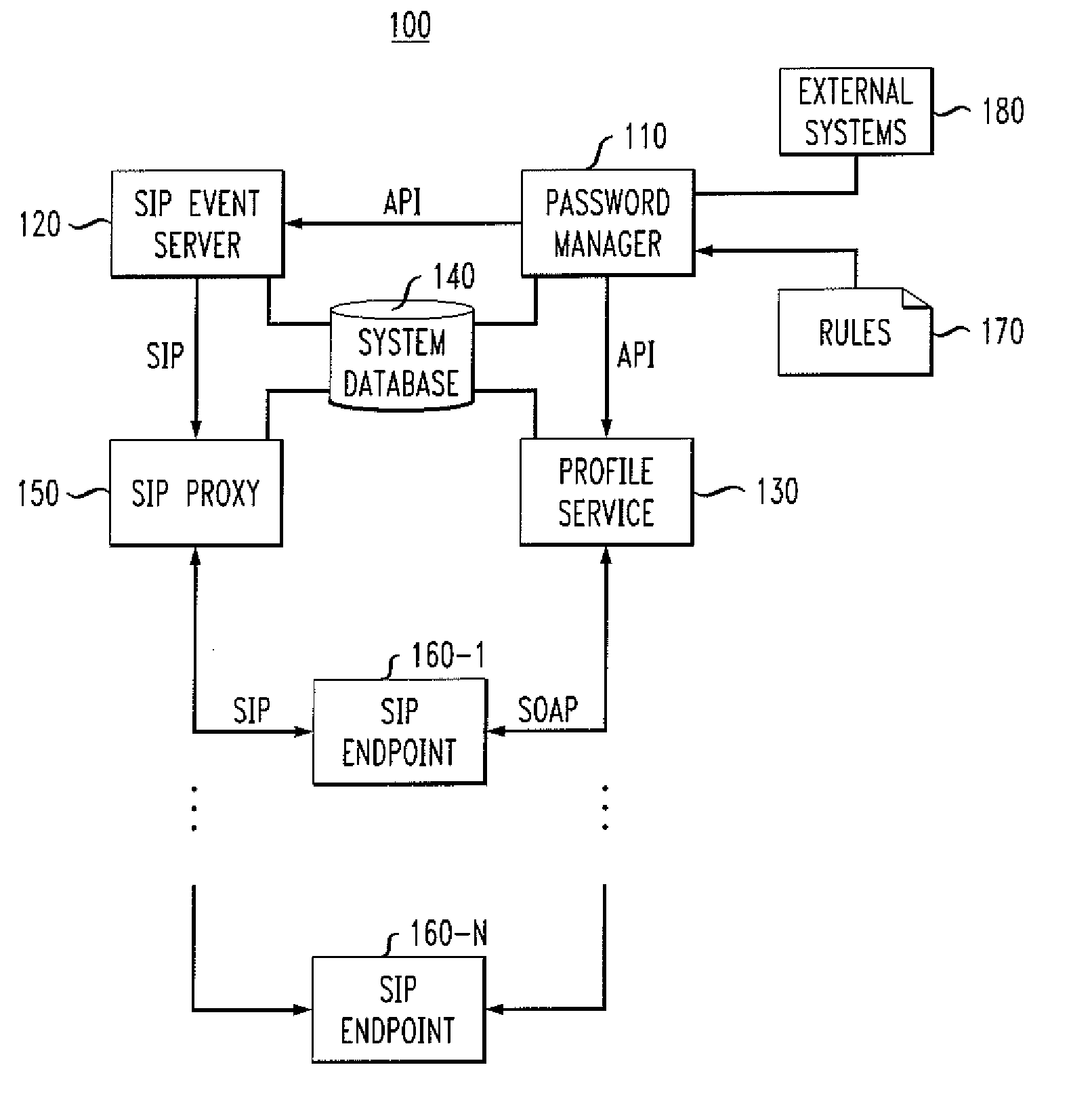
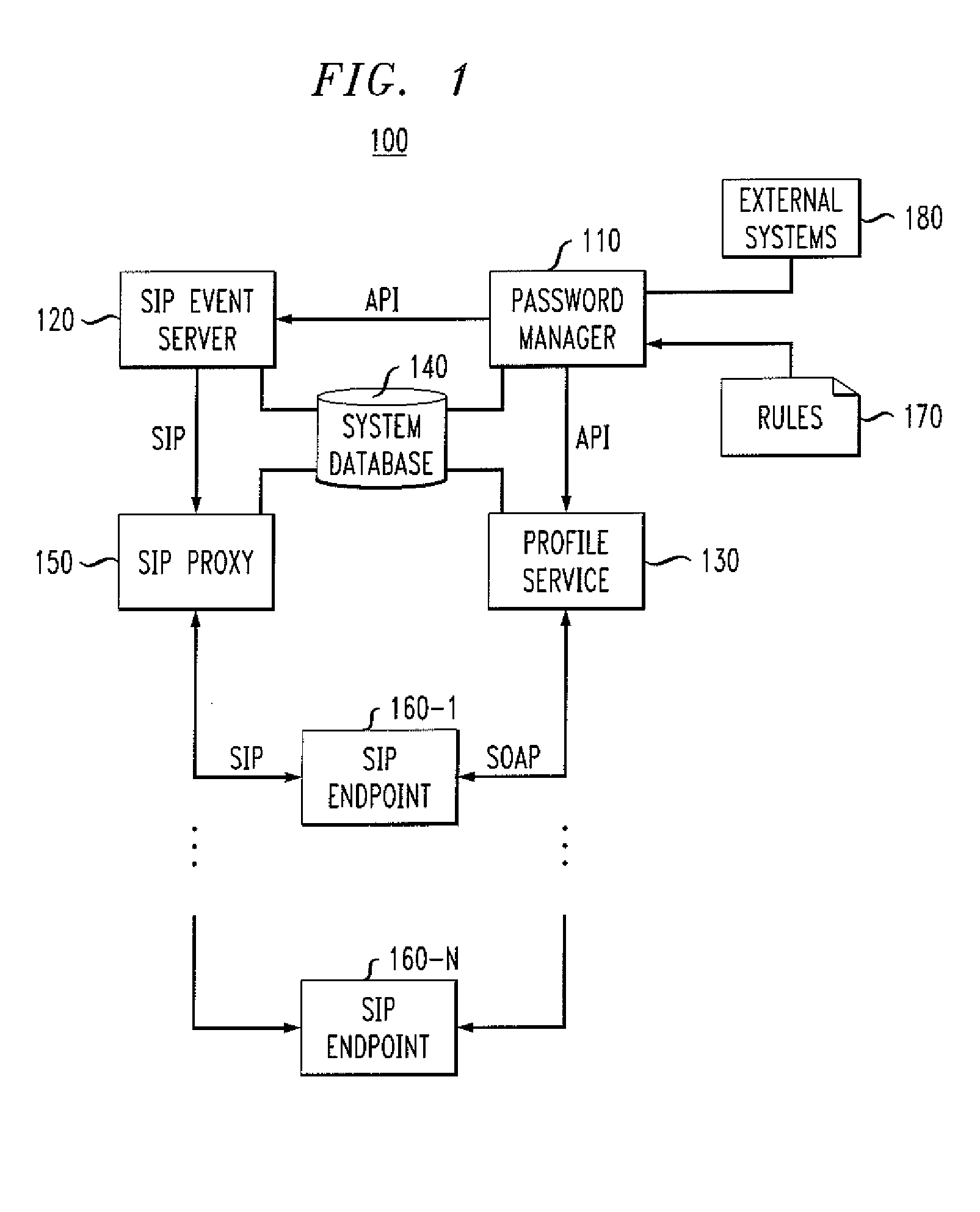
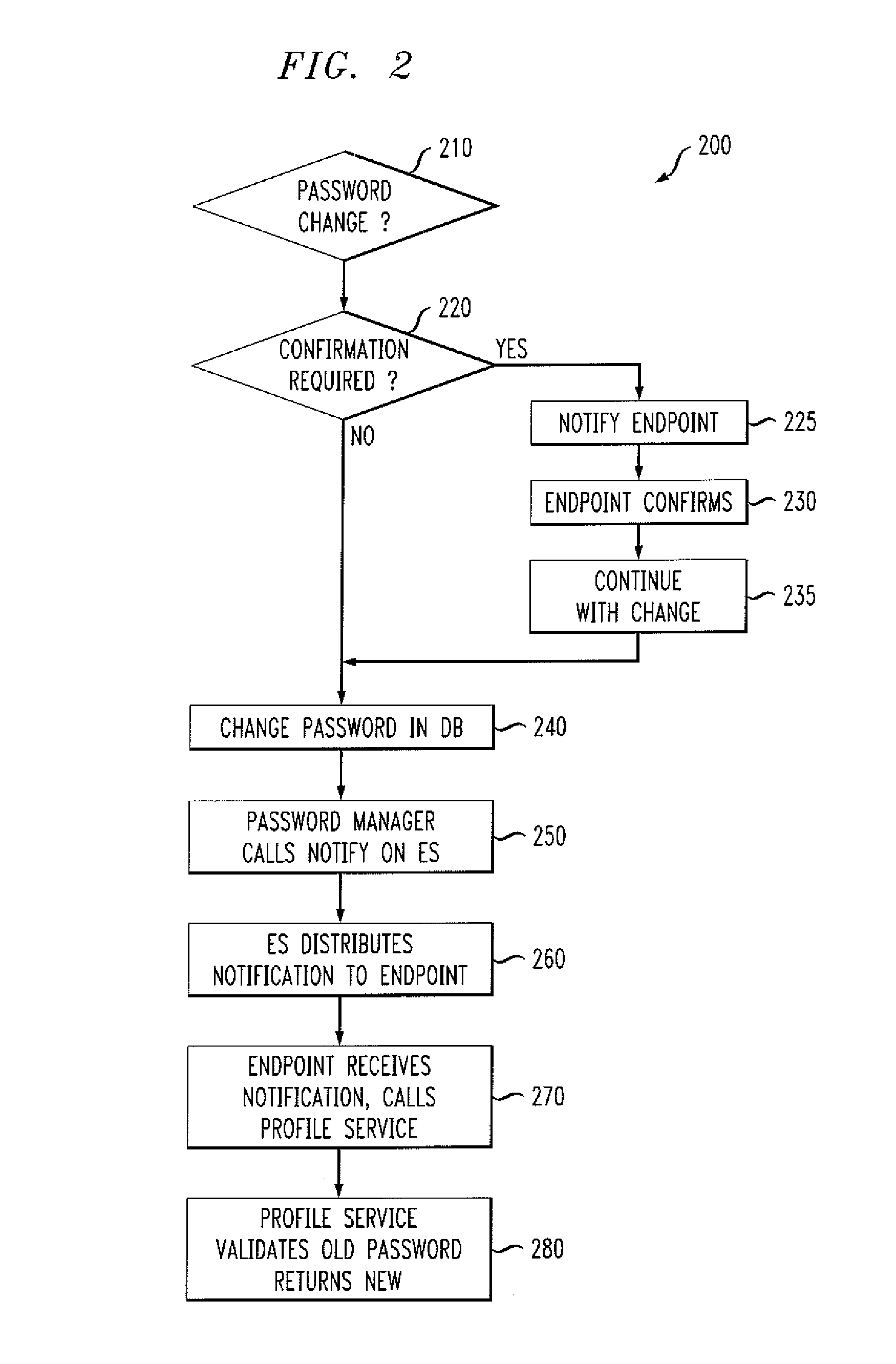
Methods and apparatus for changing passwords in a distributed communication system
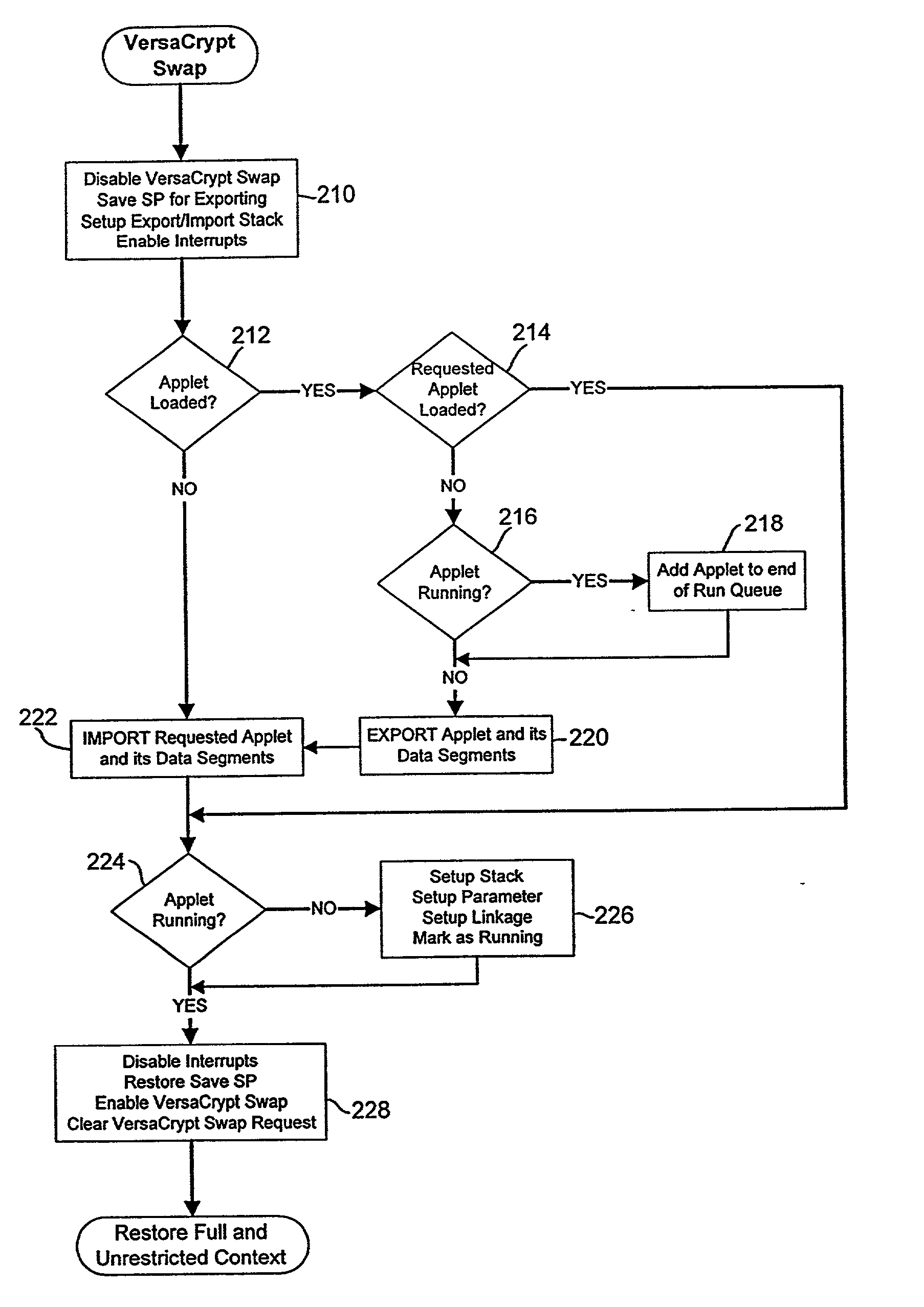
InactiveUS20080104411A1Random number generatorsUser identity/authority verificationPassword managerPassword management
Methods and apparatus are provided for changing passwords in a distributed communication system. The disclosed password management system includes an event server for receiving one or more subscriptions to a password change event from one or more endpoints associated with a user and for notifying the endpoints that subscribed to the password change event of a password change; and a profile service for (i) receiving a request for a new password from one or more of the endpoints in response to the subscription notification from the event server of the password change event; (ii) authenticating the one or more of the endpoints based on an existing password; and (iii) providing a new password to the one or more of the endpoints following the authentication. A password manager notifies the event server and profile service of a password change.
Owner:AVAYA INC
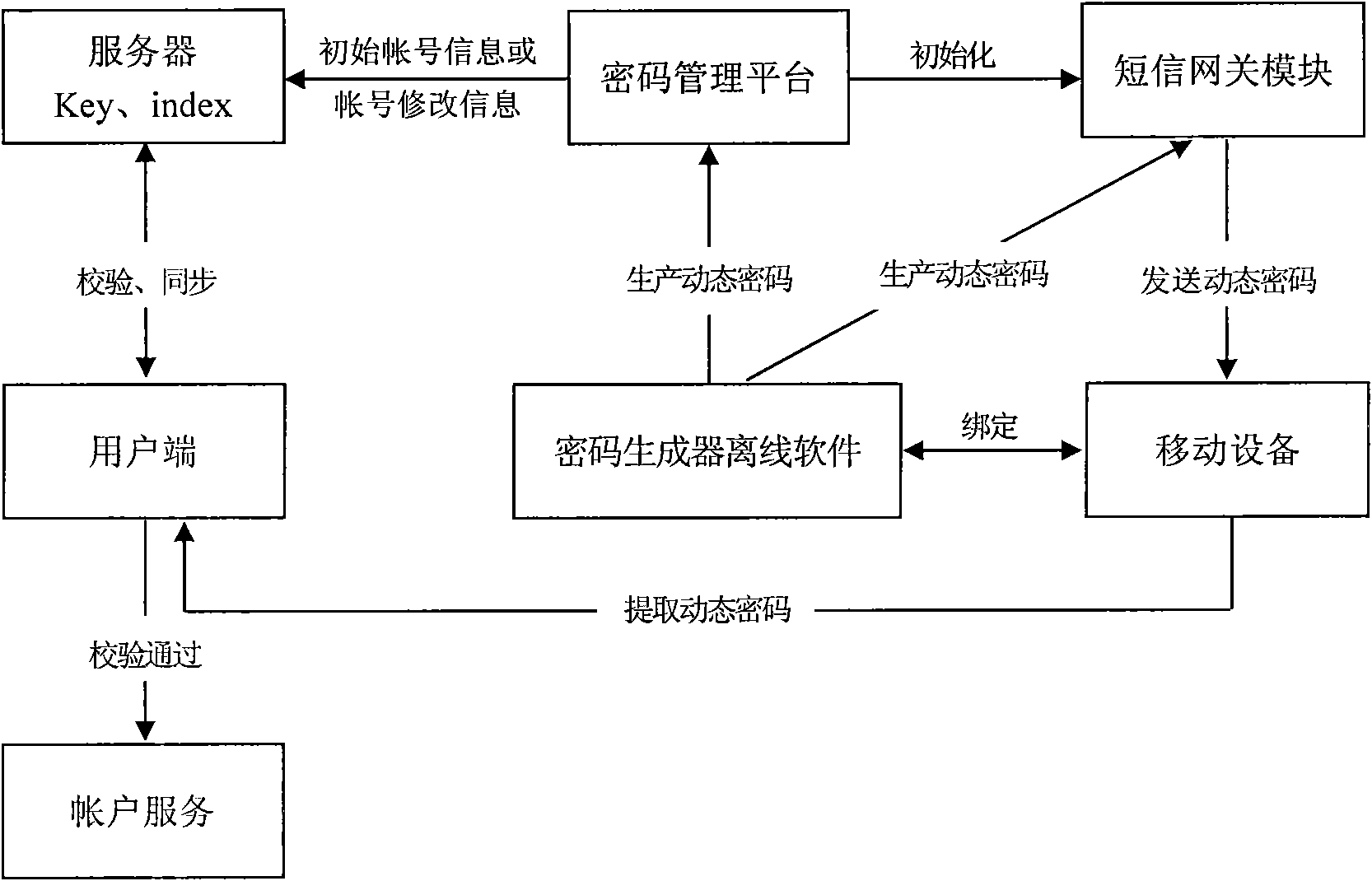
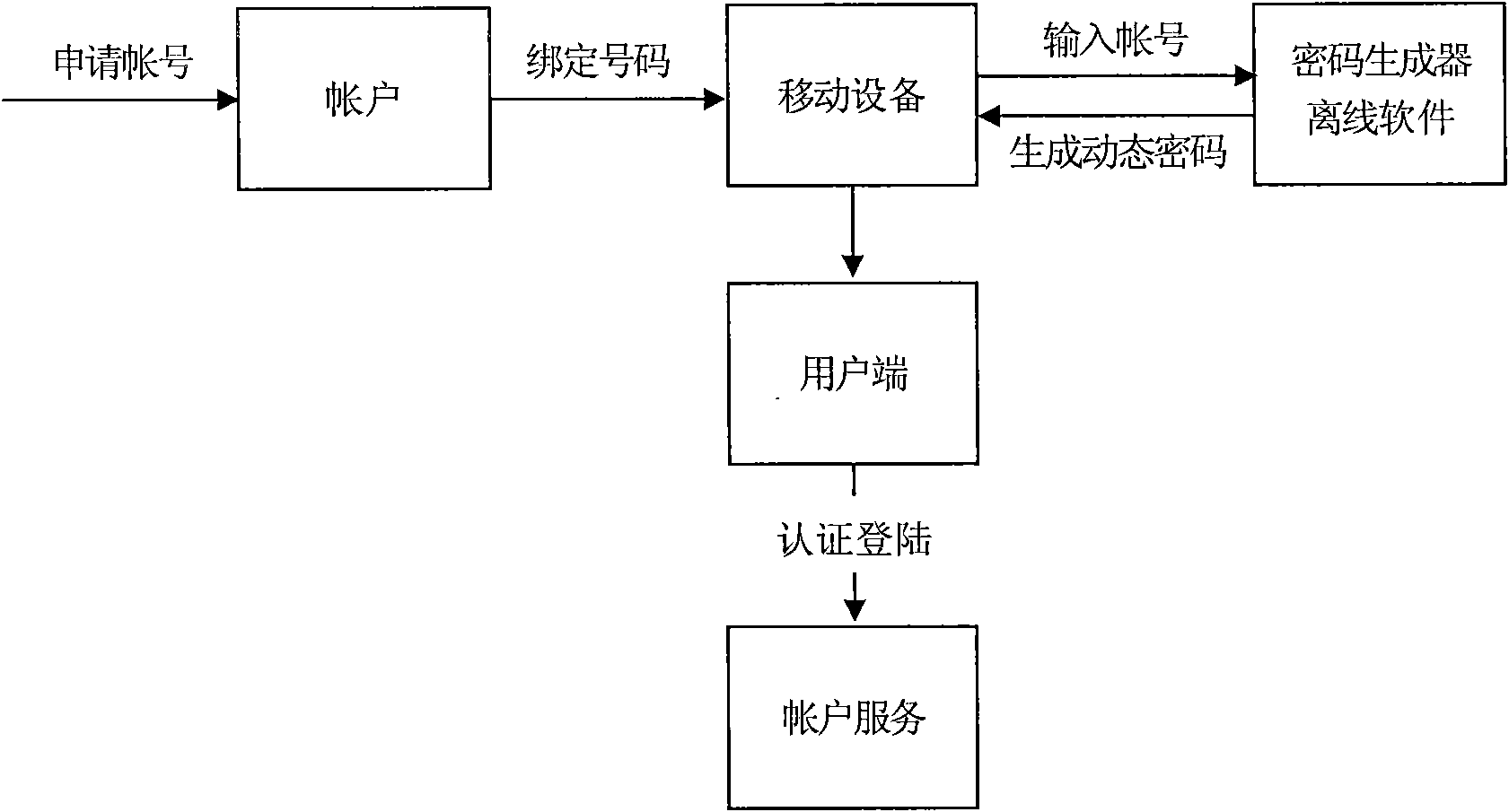
Method for off-line generation of dynamic password and debarkation authentication and synchronization of server
InactiveCN101651546ANo problem of being stolenImprove securityUser identity/authority verificationMobile deviceServer-side
The invention discloses a method for off-line generation of a dynamic password and debarkation authentication and synchronization of a server, which is realized by the following steps: initialized information of the dynamic password is subject to application, acquisition, reset, cancel and other operations by a password management platform; the password management platform is connected with the server; a password generator saves an initial random number parameter key and a sequence number parameter index which are randomly generated and encrypted by the server; every time the password generator is used, two parameters are utilized to generate a new dynamic password; and when a user end uses an account, the account number or the user name and the dynamic password are input, computed, and authorized whether to pass and synchronously carry out the feedback of continuous debarkation or error with the same random number parameter key and the sequence number index which are saved in the server end, wherein off-line software of the password generator is arranged on equipment of a security environment with software running, storage and computation capabilities, binds a mobile equipment number for each account number name which is received and authorized by a short message gateway module, sends a short message to the bond mobile equipment number, provides binding data and generates andsends the dynamic password.
Owner:FUZHOU BOYUAN WIRELESS NETWORK TECH
System and method for temporary password management
ActiveUS20190036914A1Key distribution for secure communicationUser identity/authority verificationUser deviceManagement system
A system and method for of temporary password management may include: obtaining, by a password management entity, a request to login a local device into an authentication authority; generating, by the password management entity, a temporary password; sending, by the password management entity, the temporary password to the authentication authority; sending, by the password management entity, the temporary password to a user device; obtaining, at the authentication authority the temporary password from the local device; comparing, by the authentication authority, the temporary password obtained from the local device with the temporary password obtained from the password management entity; and authorizing the login if a match is found.
Owner:SECRET DOUBLE OCTOPUS LTD
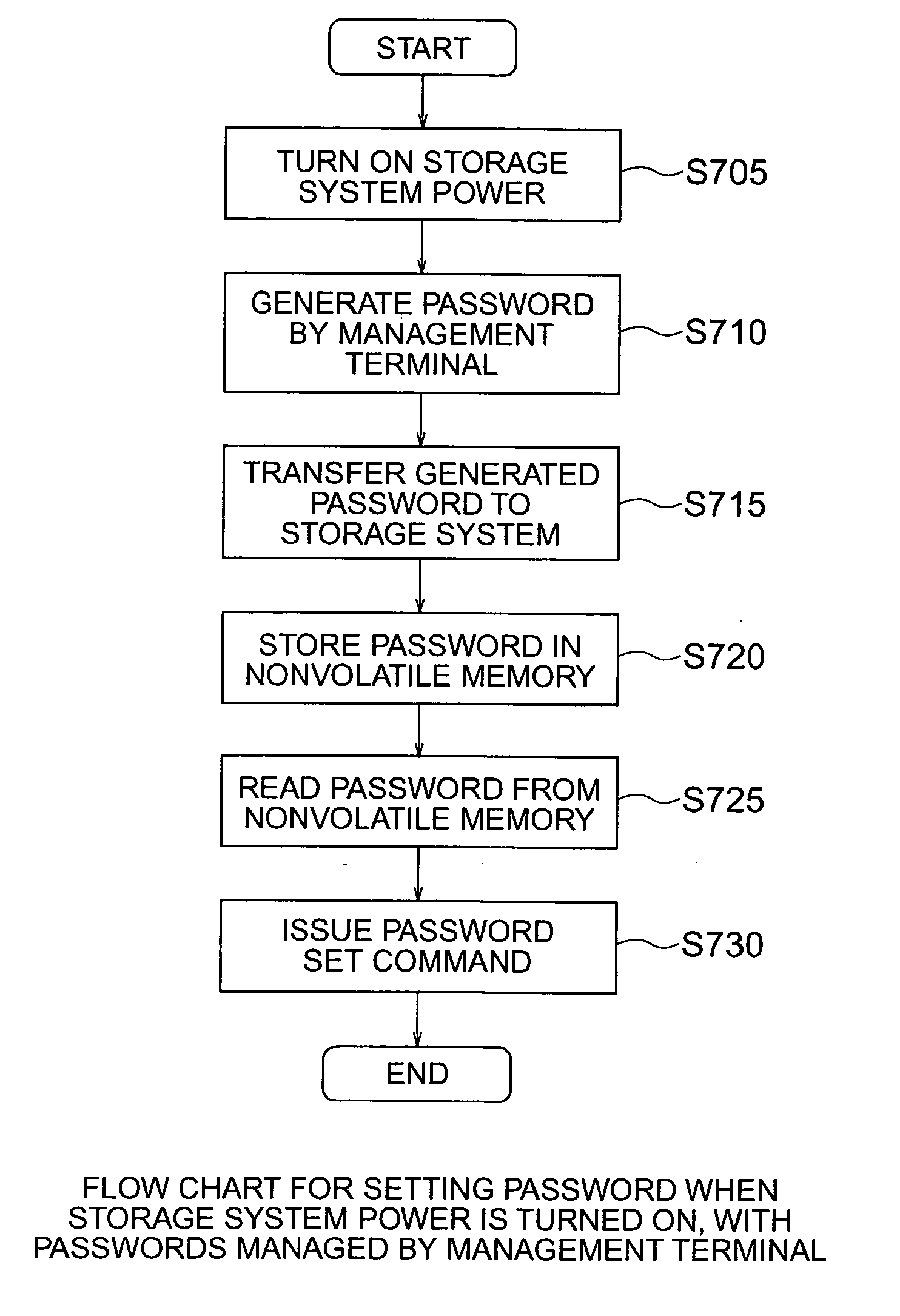
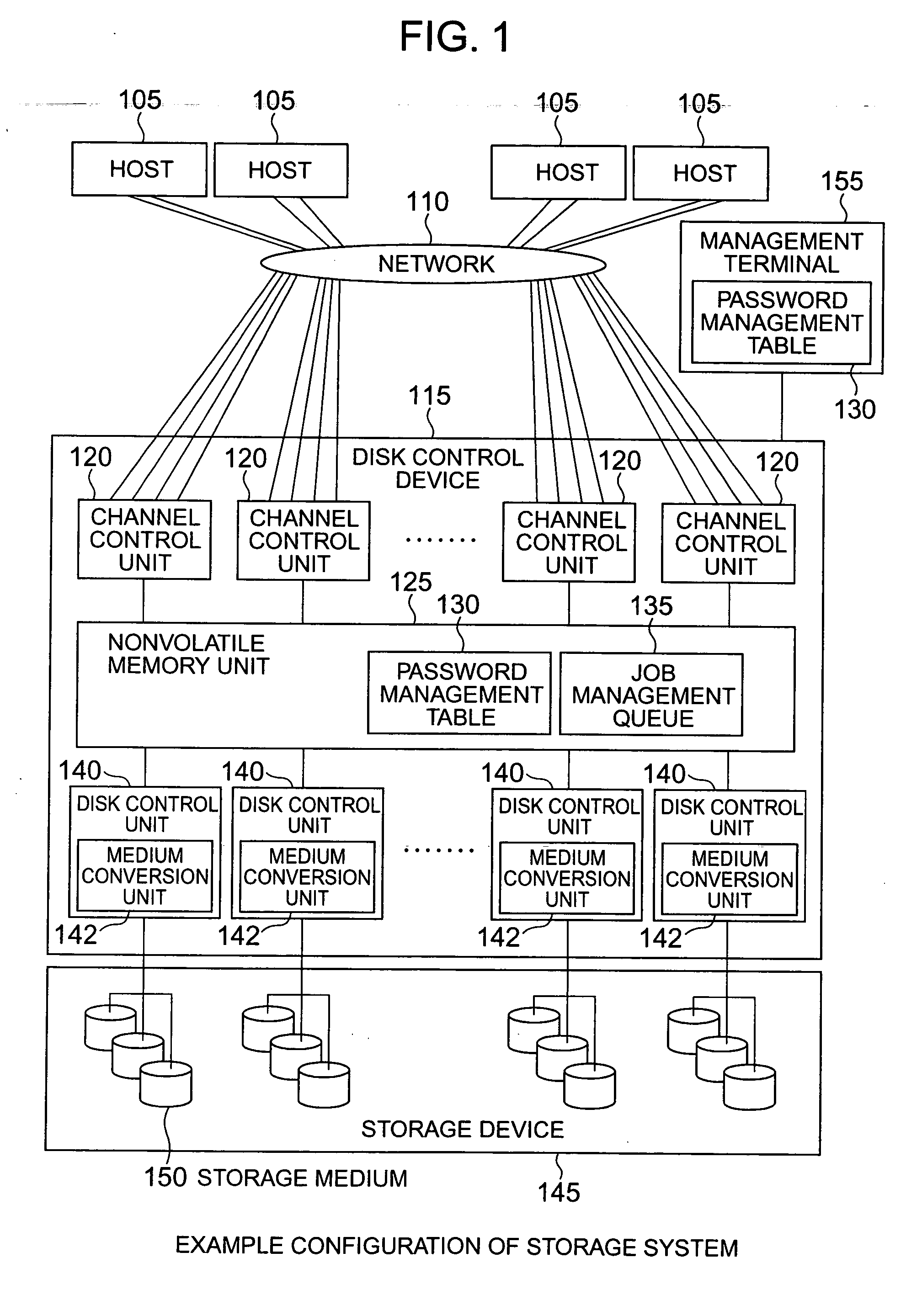
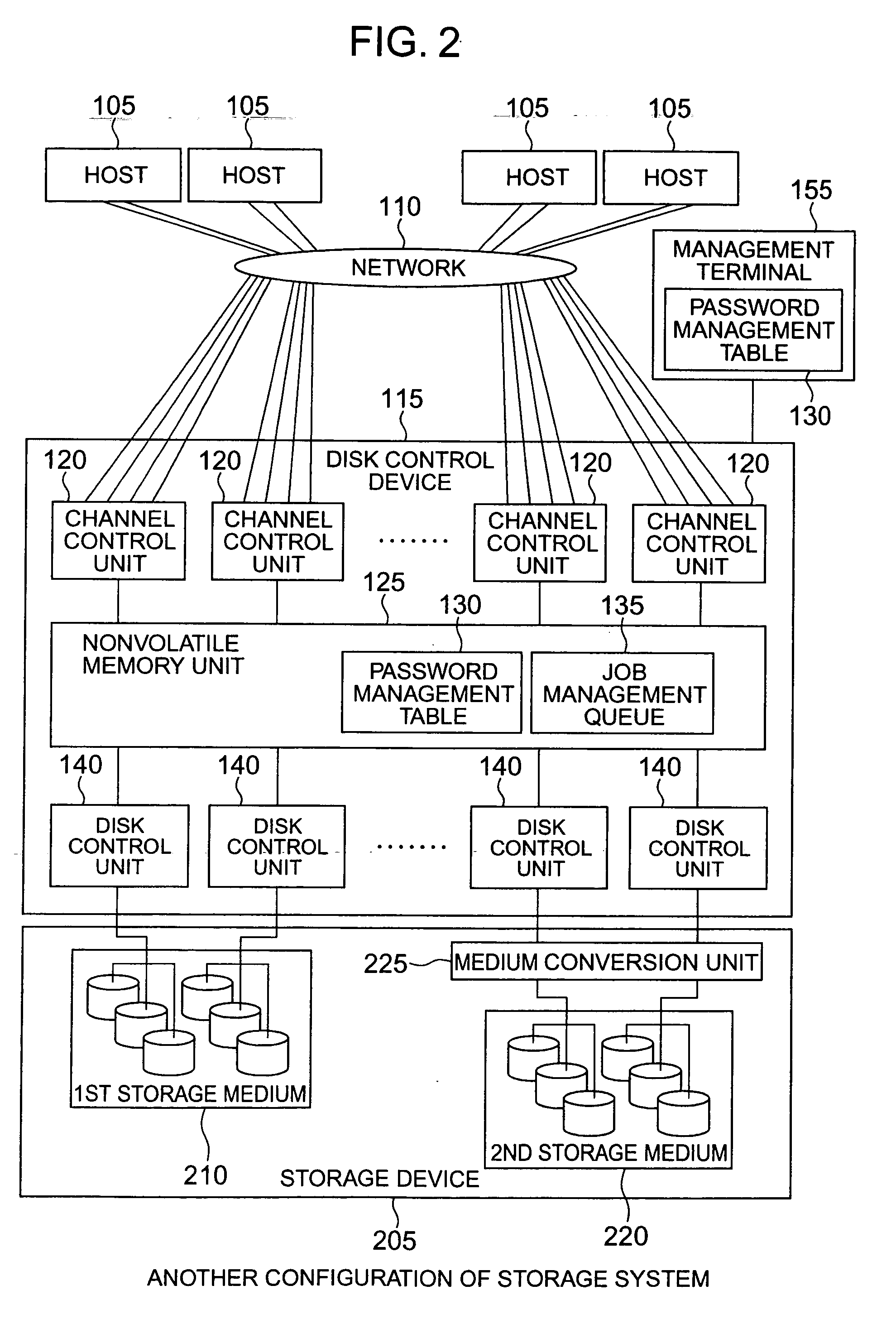
Storage system and storage control method
InactiveUS20060064560A1Improve securityStored informationUnauthorized memory use protectionDigital data protectionComputer hardwareData transmission
In a storage system, which includes a storage device and a disk control device that controls data transfer between the storage device and a host computer, a security of storage medium making up the storage device is enhanced. For this purpose, the storage system is provided with a password management table, that manages a password for the entire storage device, for each storage medium or for each logical device, and also with a function of setting and unlocking the password for the entire storage device, for each storage medium or for each logical device.
Owner:HITACHI LTD
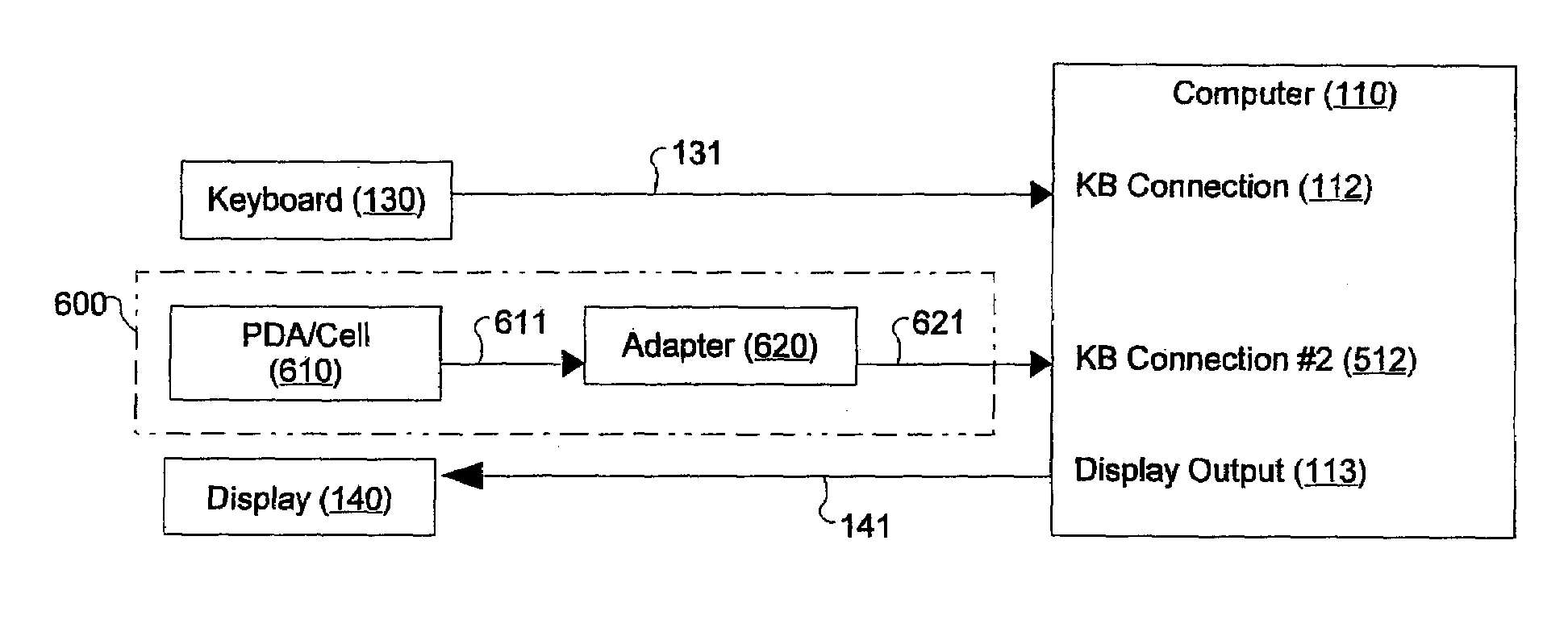
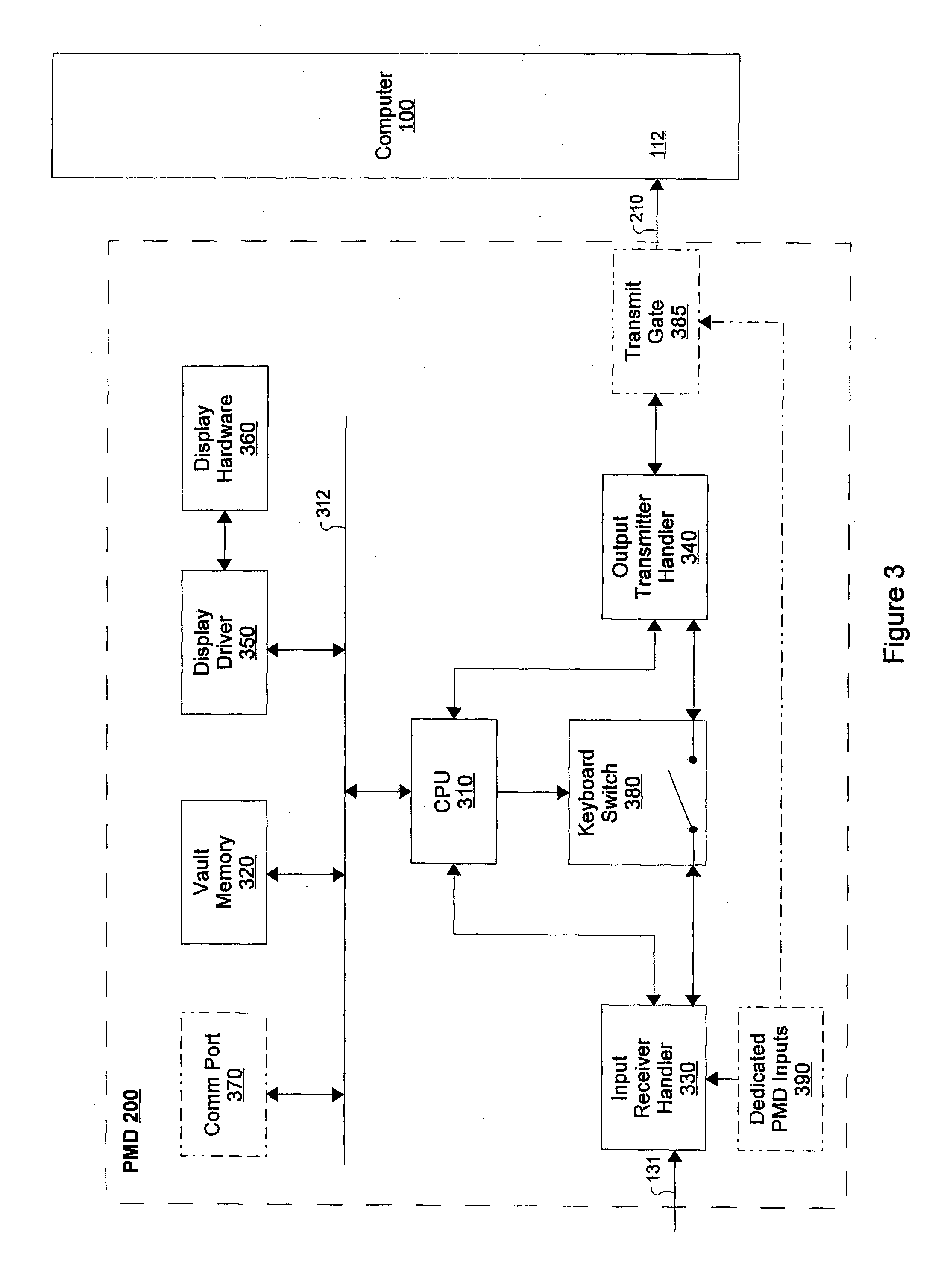
Device for Transmission of Stored Password Information Through a Standard Computer Input Interface
InactiveUS20090222908A1Less vulnerableAvoid attackDigital data processing detailsUser identity/authority verificationPush technologyTraffic capacity
A novel password management device is interposed between a computer and a conventional computer input device such as a keyboard. Passwords are defined at the input device, stored in a preferably encrypted password vault and forwarded to a secure application. When the user is prompted for a password, the device retrieves the password from the vault and provides it to the computer in a manner indistinguishable from conventional data traffic, mitigating the likelihood that the innocuous data stream will be monitored to recover the password. The transmission of a password is push technology and may be enhanced by a gating feature. Automatic password retrieval from the vault is convenient to the user, particularly if the device automatically generates random passwords. No software is installed on the computer; the device is operating system, application and platform independent. The device may be integrated within the input device or within the computer itself.
Owner:WARREN RUSSELL
Password management systems and methods
InactiveUS20110265160A1Digital data processing detailsMultiple digital computer combinationsPassword managementCipher
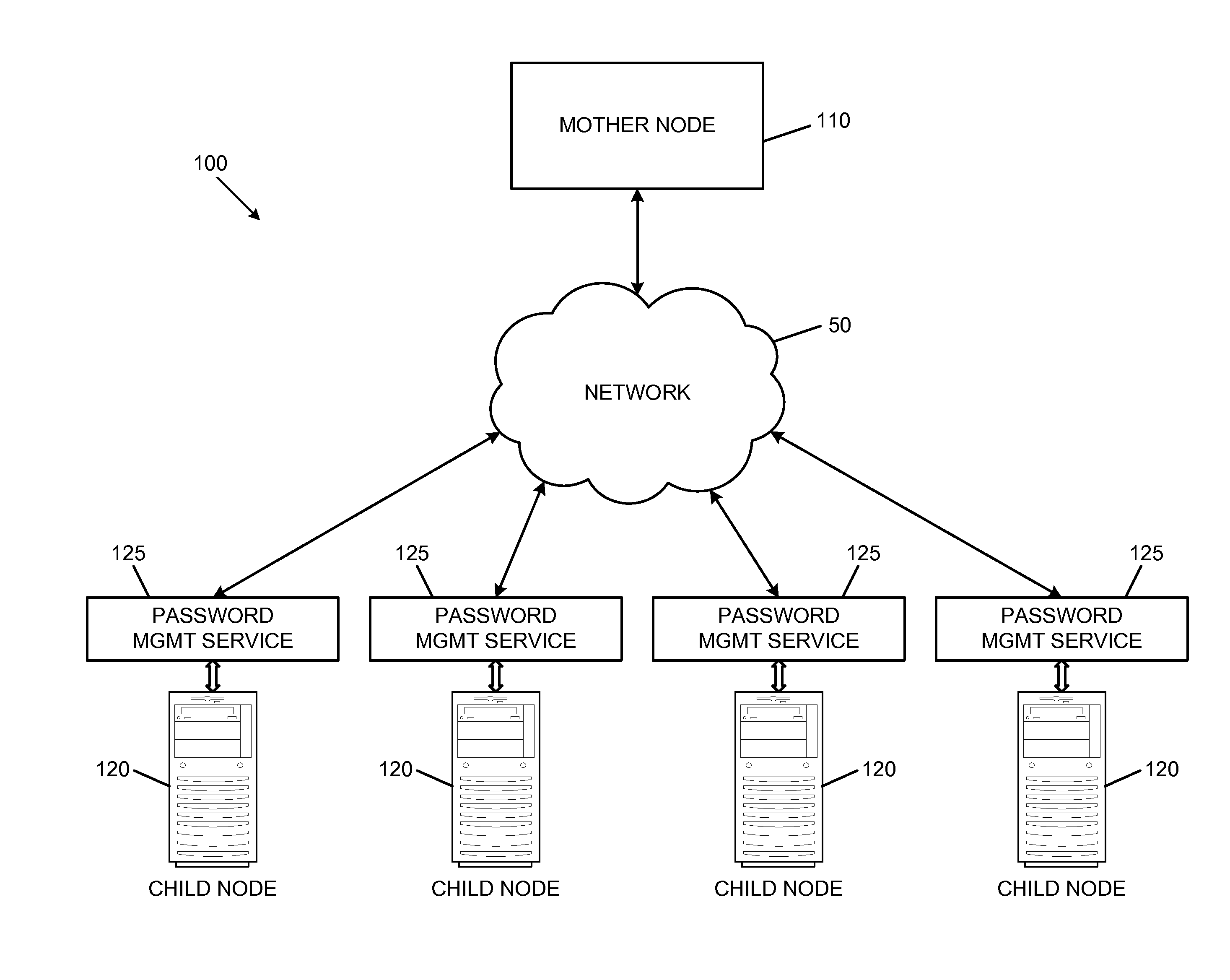
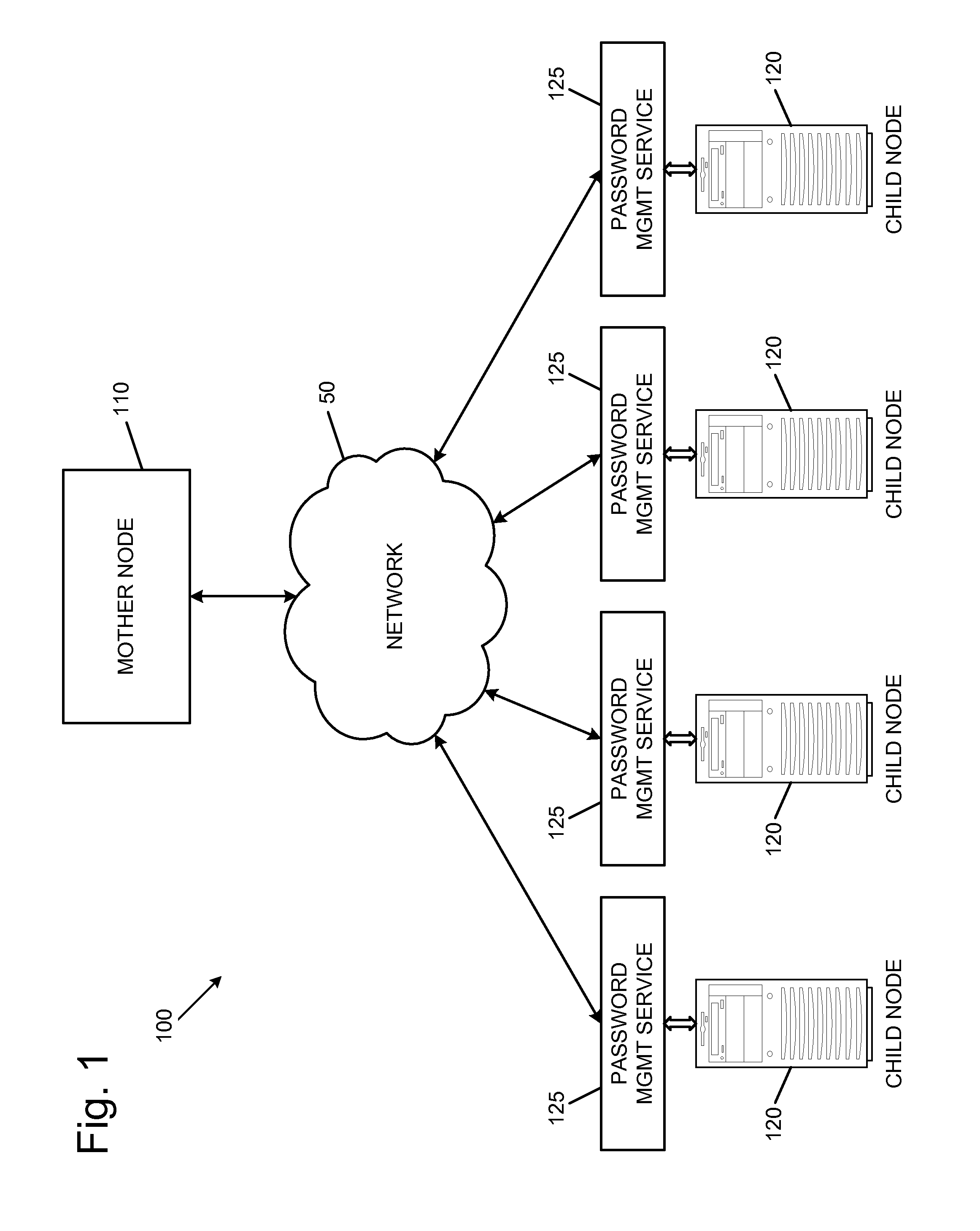
Password management systems include a plurality of child nodes and a mother node. Each child node includes a secure resource, a target account, and a password management service. The target account can be password-protected, and the secure resource can be accessible through the target account. The password management service can periodically update a password of the target account by requesting a new password from the mother node. In response to such requests, the mother node can generate new passwords and forward the new passwords to the appropriate child nodes. The mother node can store the new passwords in a database of current passwords. When an authorized user of the mother node requests a current password for a target account of a child node, the mother node can provide the requested current password to the authorized user. Other aspects, features, and embodiments are also claimed and described.
Owner:PEER 1 NETWORK ENTERPRISES
System and method for distributed network acess and control enabling high availability, security and survivability
InactiveUS7278023B1Public key for secure communicationUser identity/authority verificationSurvivabilityWide area network
Owner:NORTHROP GRUMMAN SYST CORP
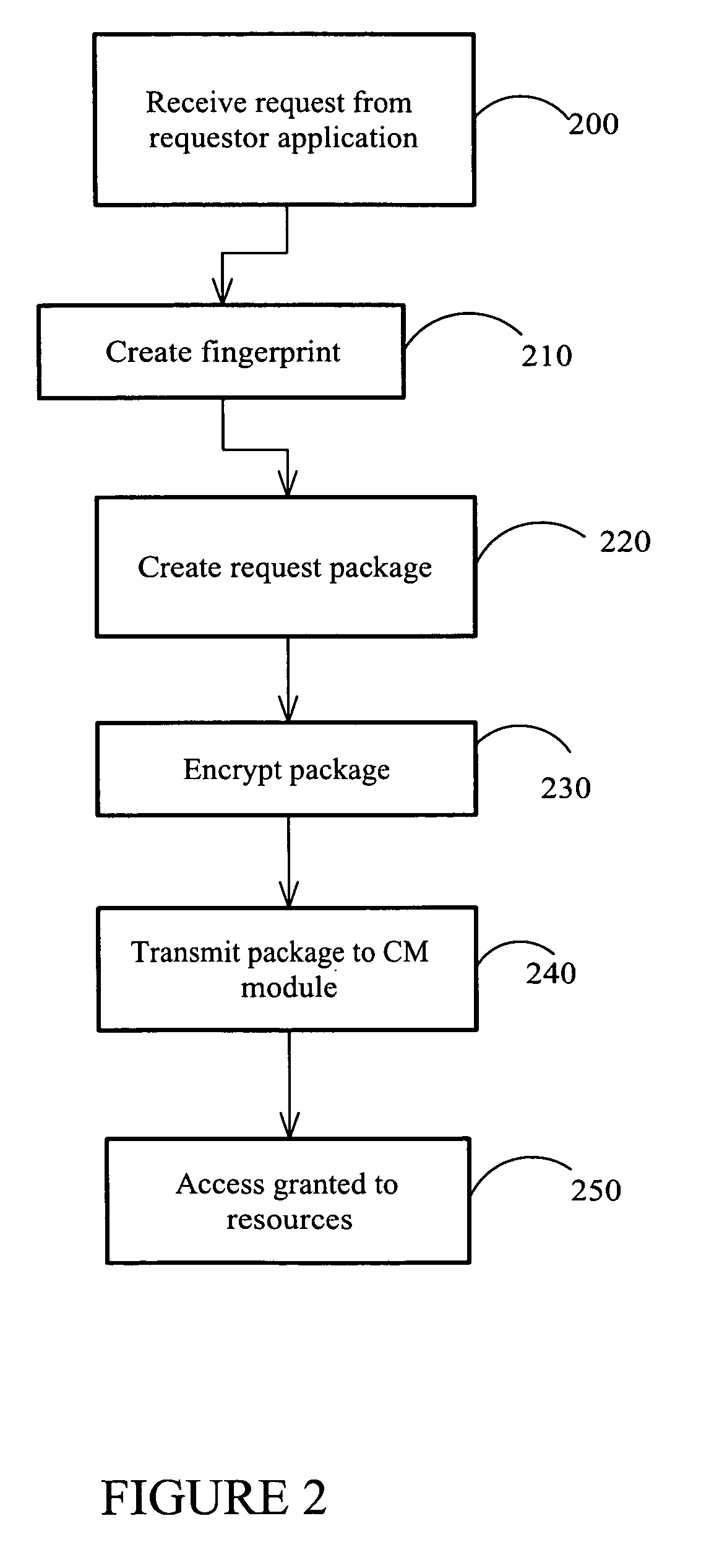
Simplified management of authentication credentials for unattended applications
ActiveUS20080148373A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsData matchingData storing
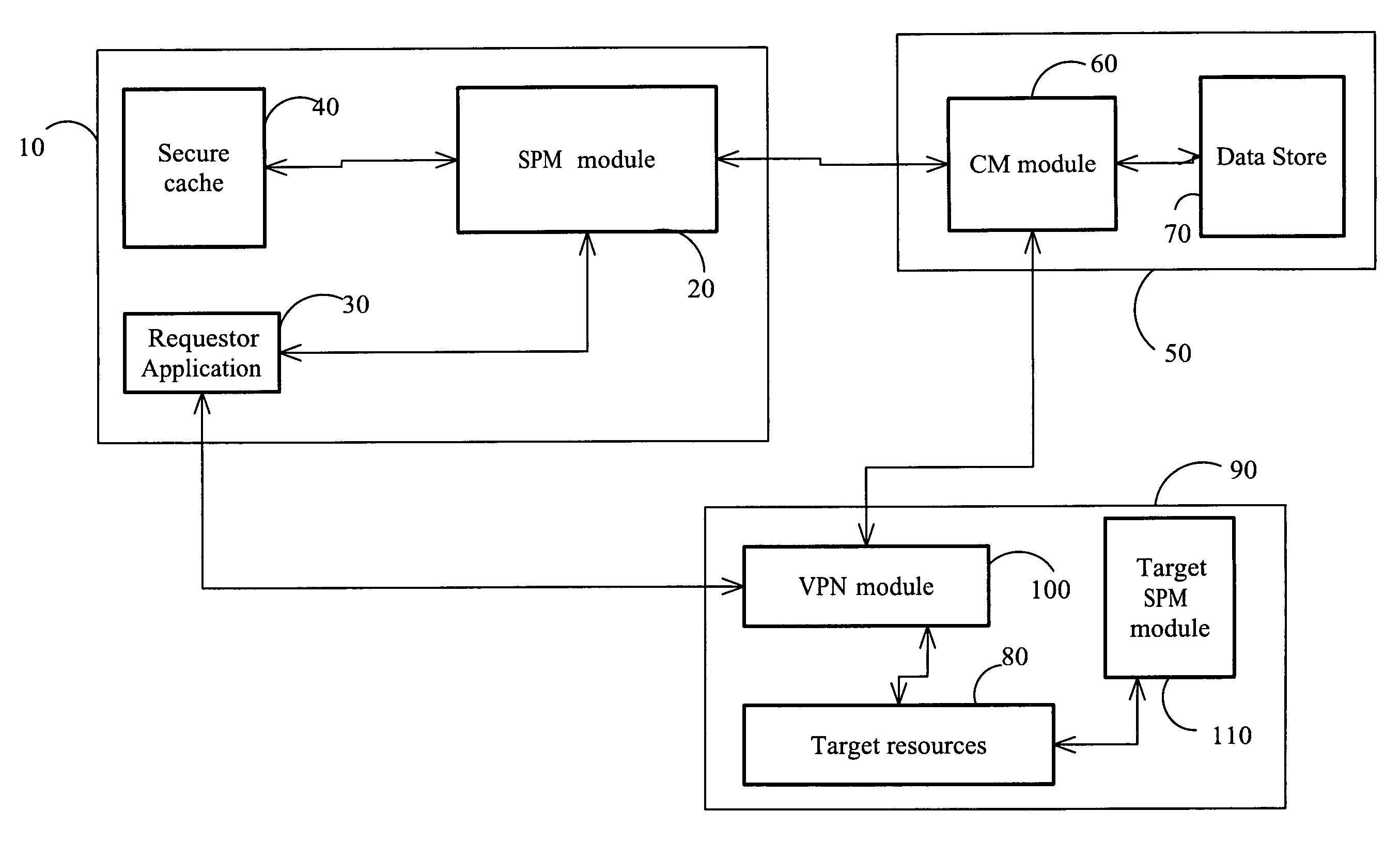
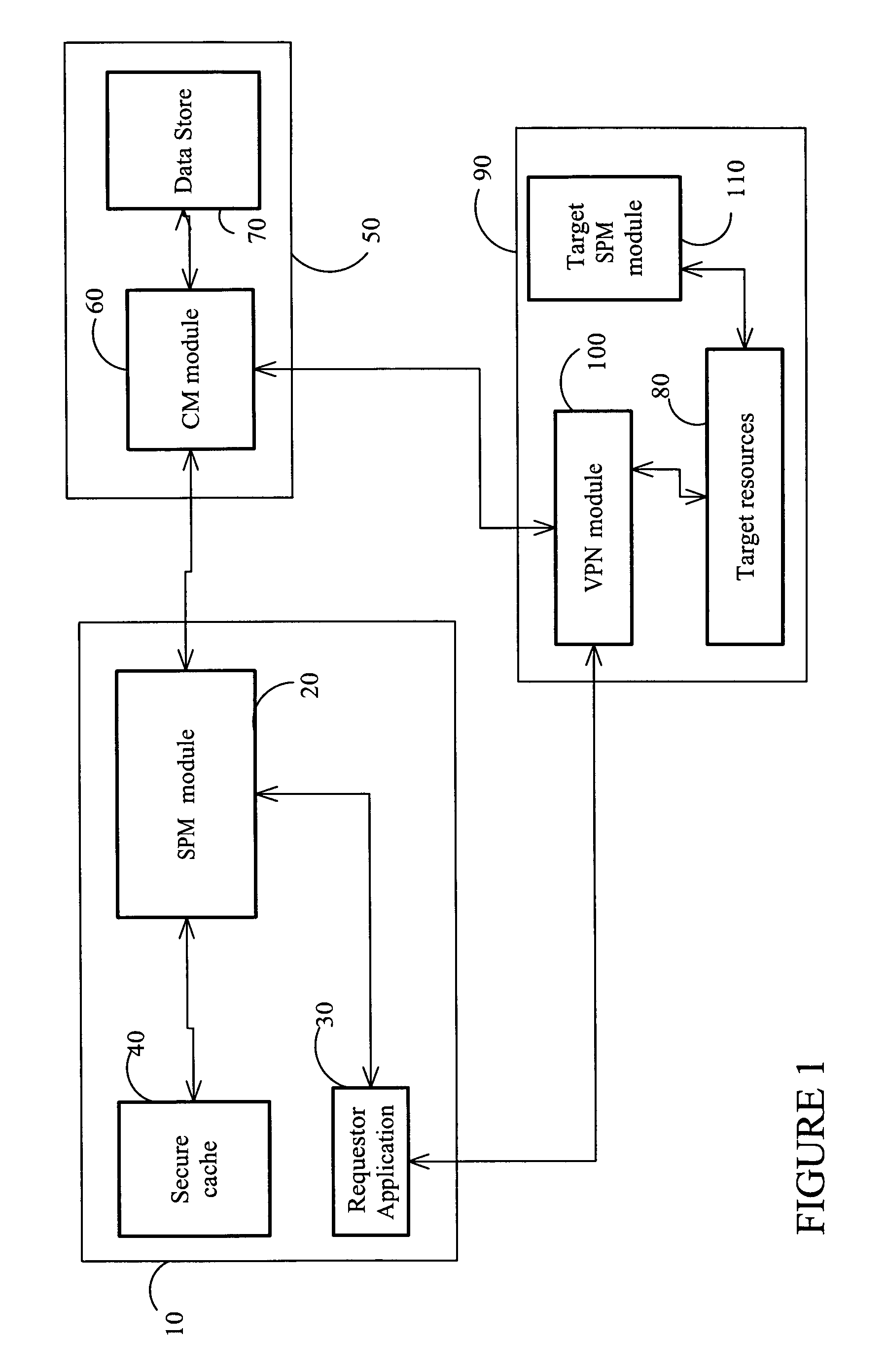
Systems and methods for unattended authentication of software applications to provide these applications with access to shared resources. A server password manager (SPM) module resident on a node also occupied by a requester software application requesting access to resources receives the requestor's request. The SPM module creates a request package containing the requestor's information as well as the node's identifying information. The request package is then transmitted to a credentials manager (CM) module in a CM node. The request package, encrypted by the SPM module with encryption keys previously generated by the CM module, is decrypted by the CM module. The contents are checked against data stored by the CM module regarding the SPM module and the requestor application when these were registered with the CM. If the data matches, then the CM provides credentials which are used to give the requestor application access to the requested resources.
Owner:IRDETO ACCESS
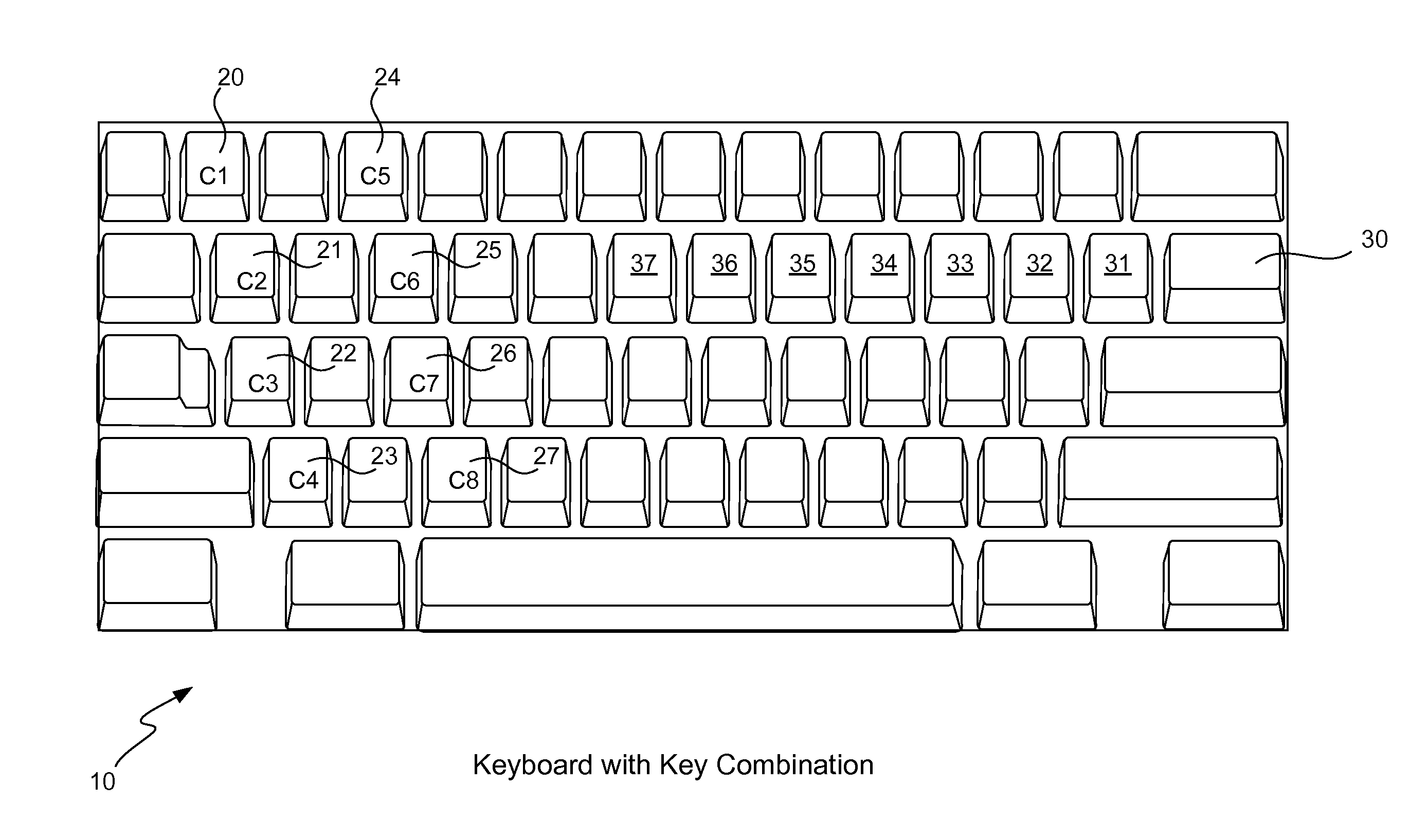
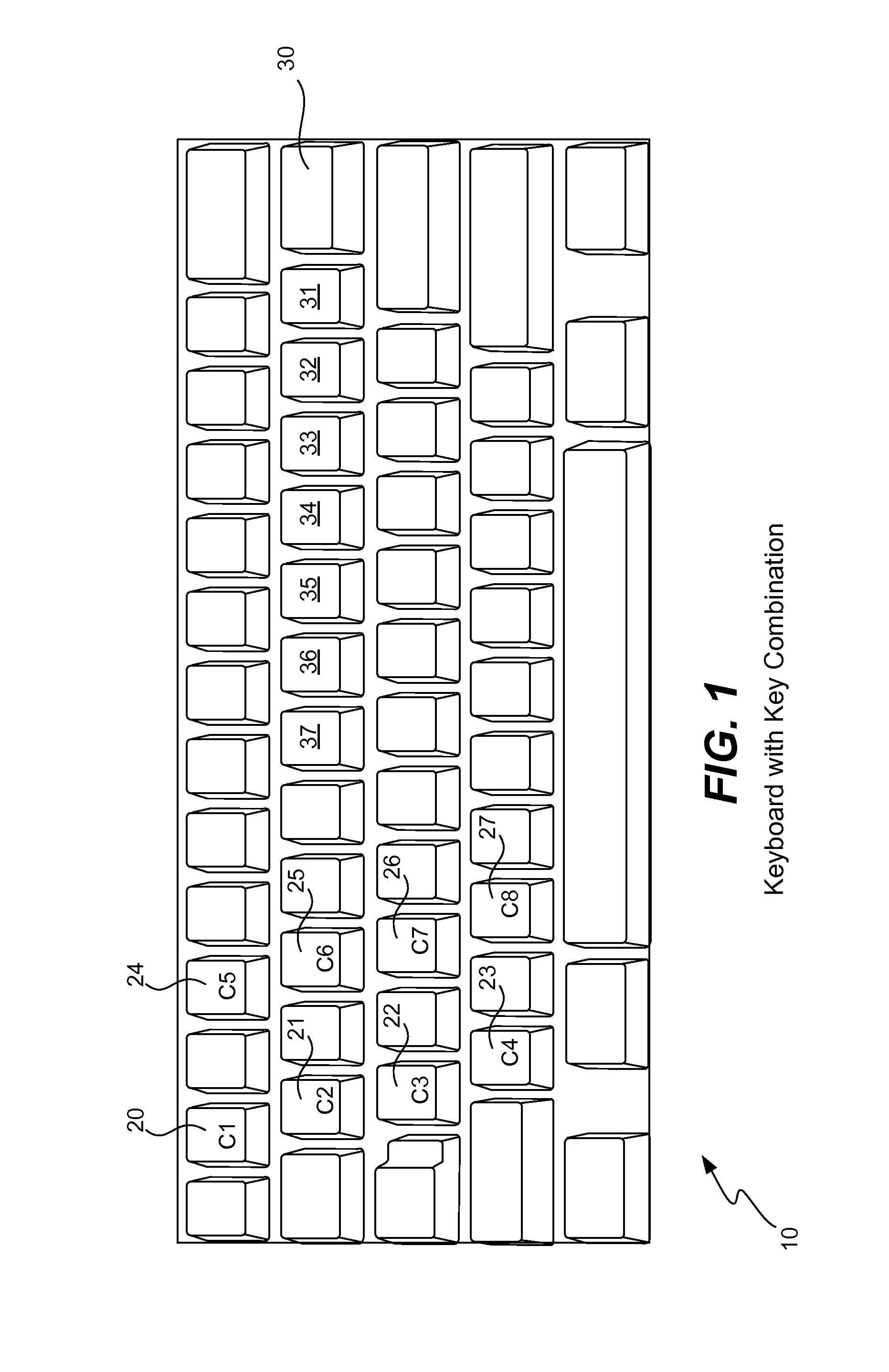
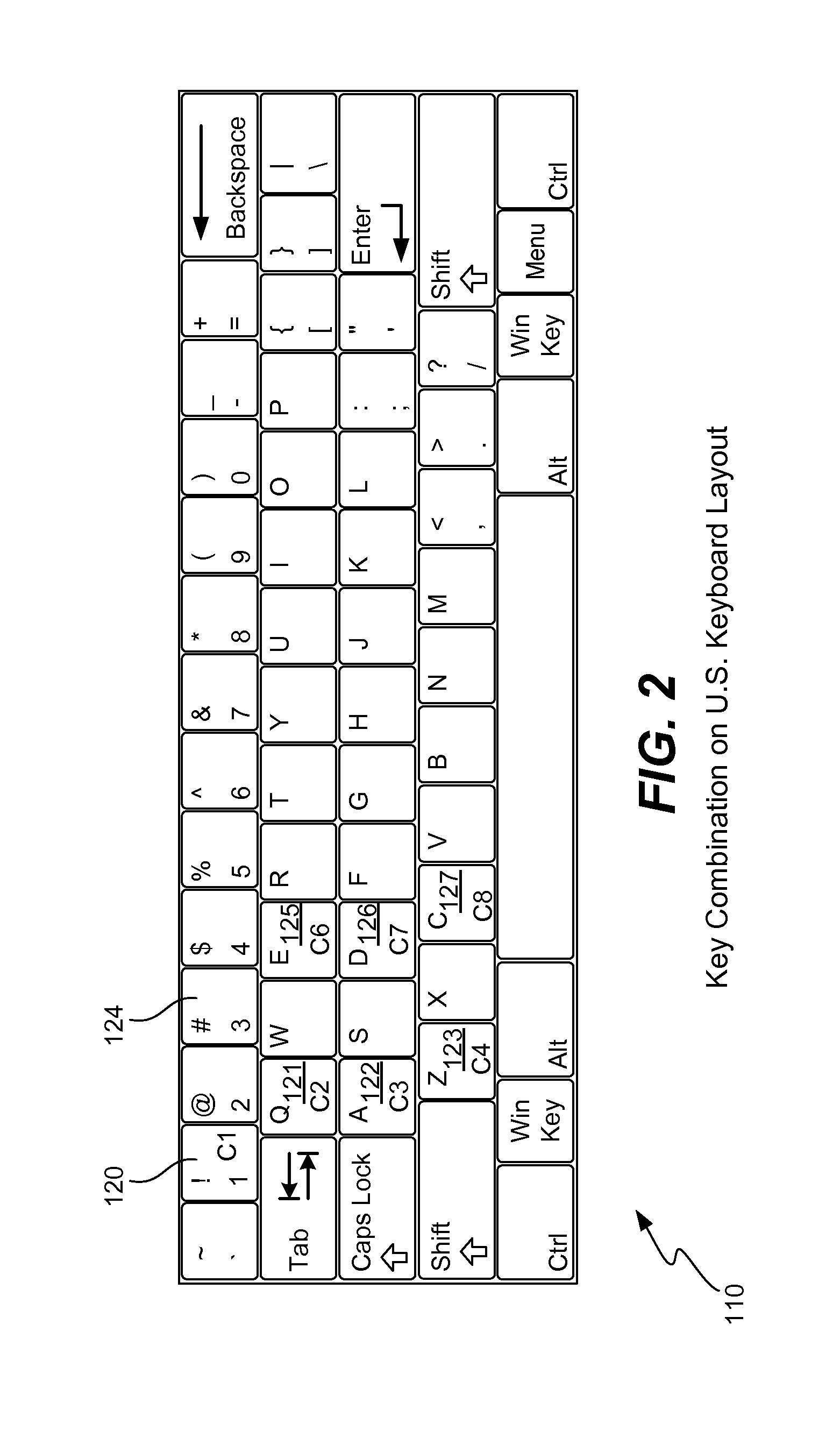
Secure password management using keyboard layout
ActiveUS8520848B1Improve securityImprove password securityDot-and-dash transmission apparatusEqual length code transmitterWeb siteTyping
A password management service located either on a user computer or in the cloud intercepts a user's attempt to create an account on a Web site. The user enters a sequence of a physical key combination and the service assigns a particular keyboard layout for this Web site. The service generates a password by combining the key combination with the assigned keyboard layout and returns this password to the user or to the Web site. The service stores the name of the Web site in association with the designated keyboard layout. Upon a subsequent login attempt, the service again intercepts the user's typing of the same physical key combination, generates the same password by combining the key combination with the previously assigned and stored keyboard layout, and returns the generated password to the Web site for authentication. A keyboard layout for a site may be chosen by the user, may be selected by the service, or a random layout may be generated. The service enforces a password constraint of a site by adding in the required characters, by requiring the user to choose a new key combination, or by using a different keyboard layout.
Owner:TREND MICRO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com