Apparatus for providing a secure processing environment
a technology of processing environment and apparatus, applied in the direction of digital transmission, program/content distribution protection, instruments, etc., can solve the problems of inability to decrypt encrypted information in a reasonable amount, inability to frustrate or "hack" the security measures of these devices, and attackers having access to all information about the system except for the keys, etc., to achieve the effect of ensuring the security of the environmen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
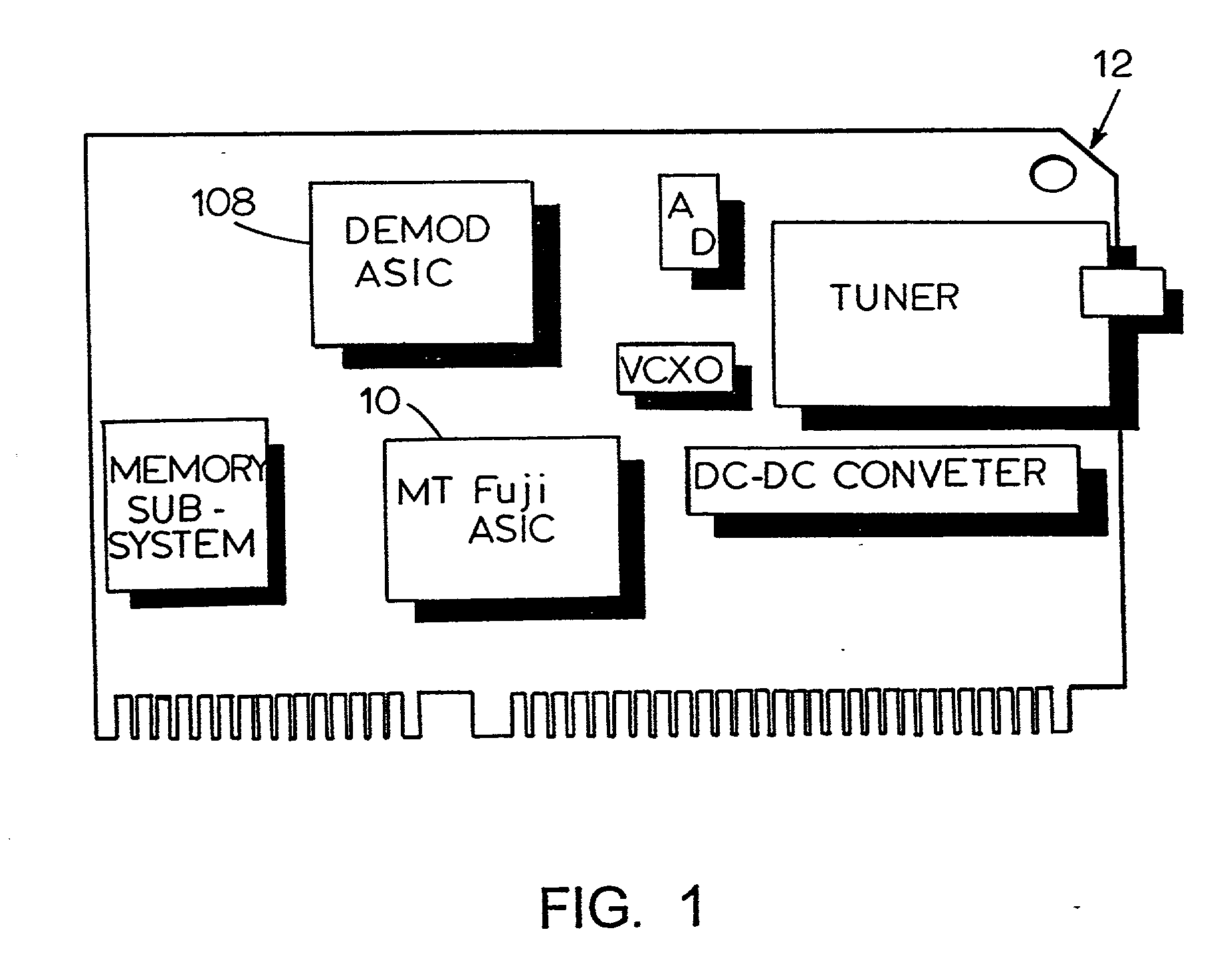
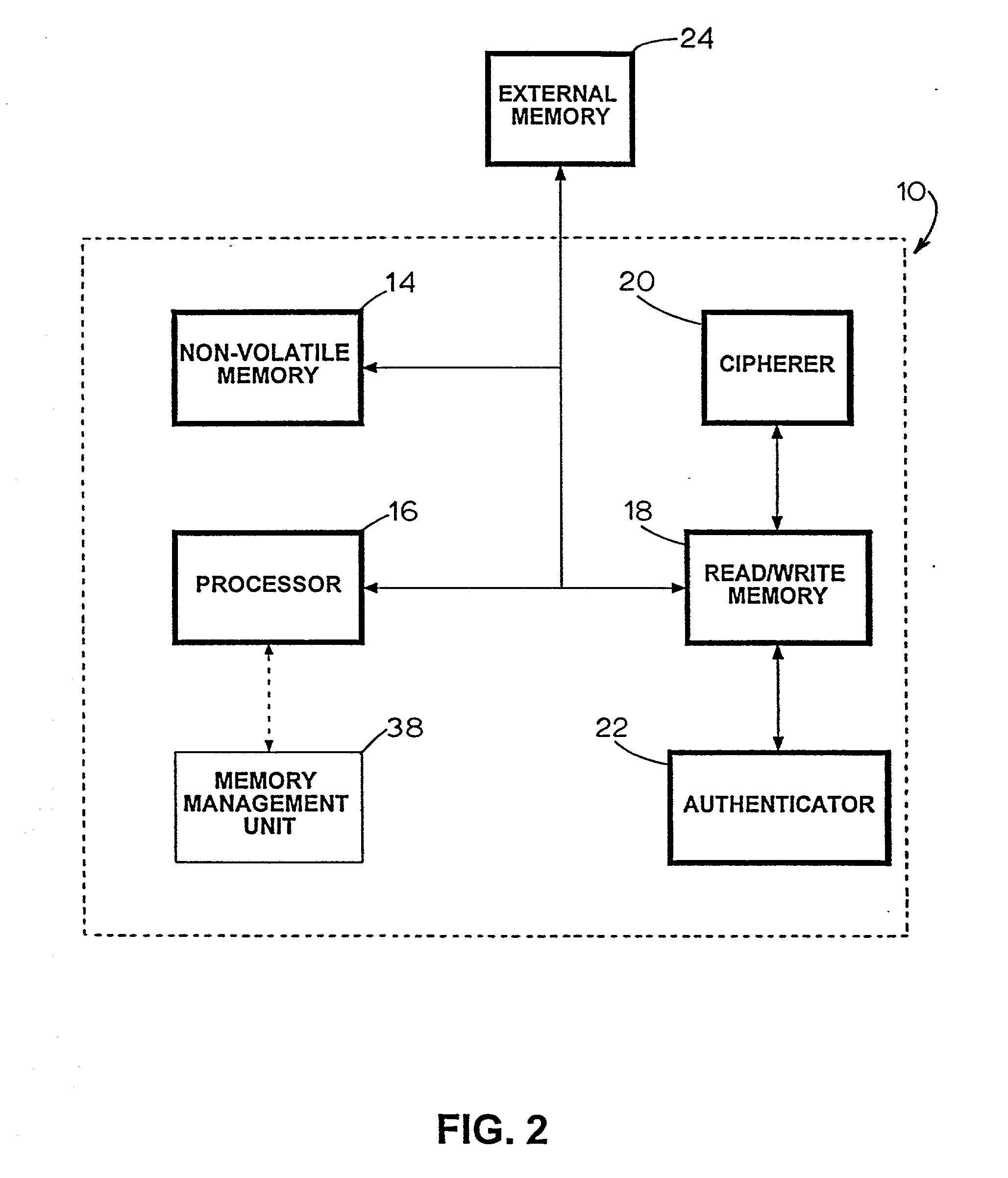
[0040] An apparatus 10 constructed in accordance with the teachings of the invention is schematically illustrated in FIG. 1 in one possible environment of use, namely, on a DirecPC.TM. module 12 for use in a personal computer (not shown). As explained in detail below, the apparatus 10 is constructed to provide a secure environment for processing sensitive information. As used throughout this description and appended claims, the term "information" refers to data, programmed instructions (e.g., software, firmware) or both. Although the apparatus 10 is capable of use in the DirecPC.TM. product, persons of ordinary skill in the art will appreciate that the apparatus 10 is not limited to use in any specific environment or with any specific application. On the contrary, without departing from the scope or spirit of the invention the illustrated apparatus 10 can be used in any application or environment which would benefit from the enhanced processing security it provides. For example, it ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com