Patents
Literature
10782 results about "Electronic mail" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic mail. n. (Communications & Information) the transmission and distribution of messages, information, facsimiles of documents, etc, from one computer terminal to another.
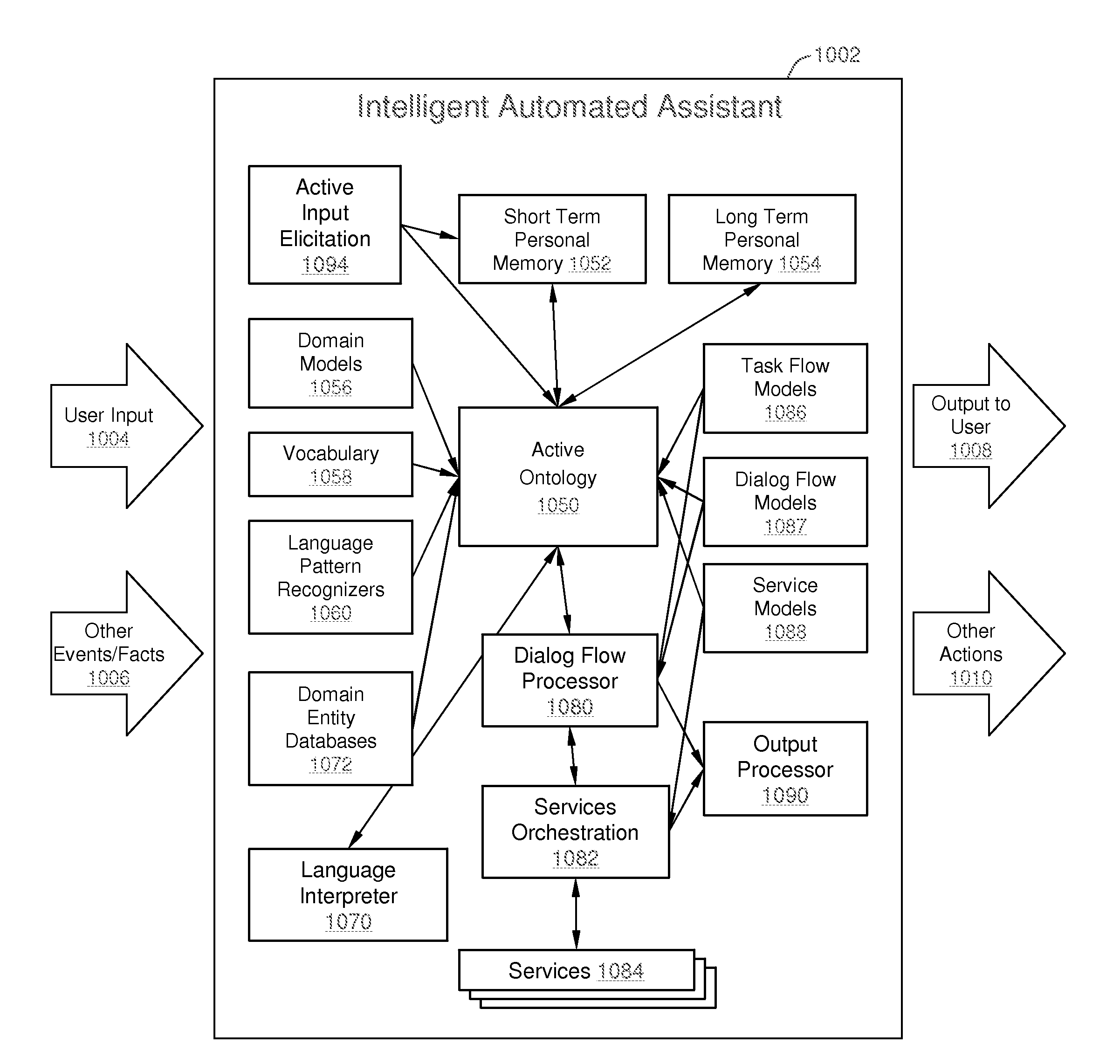
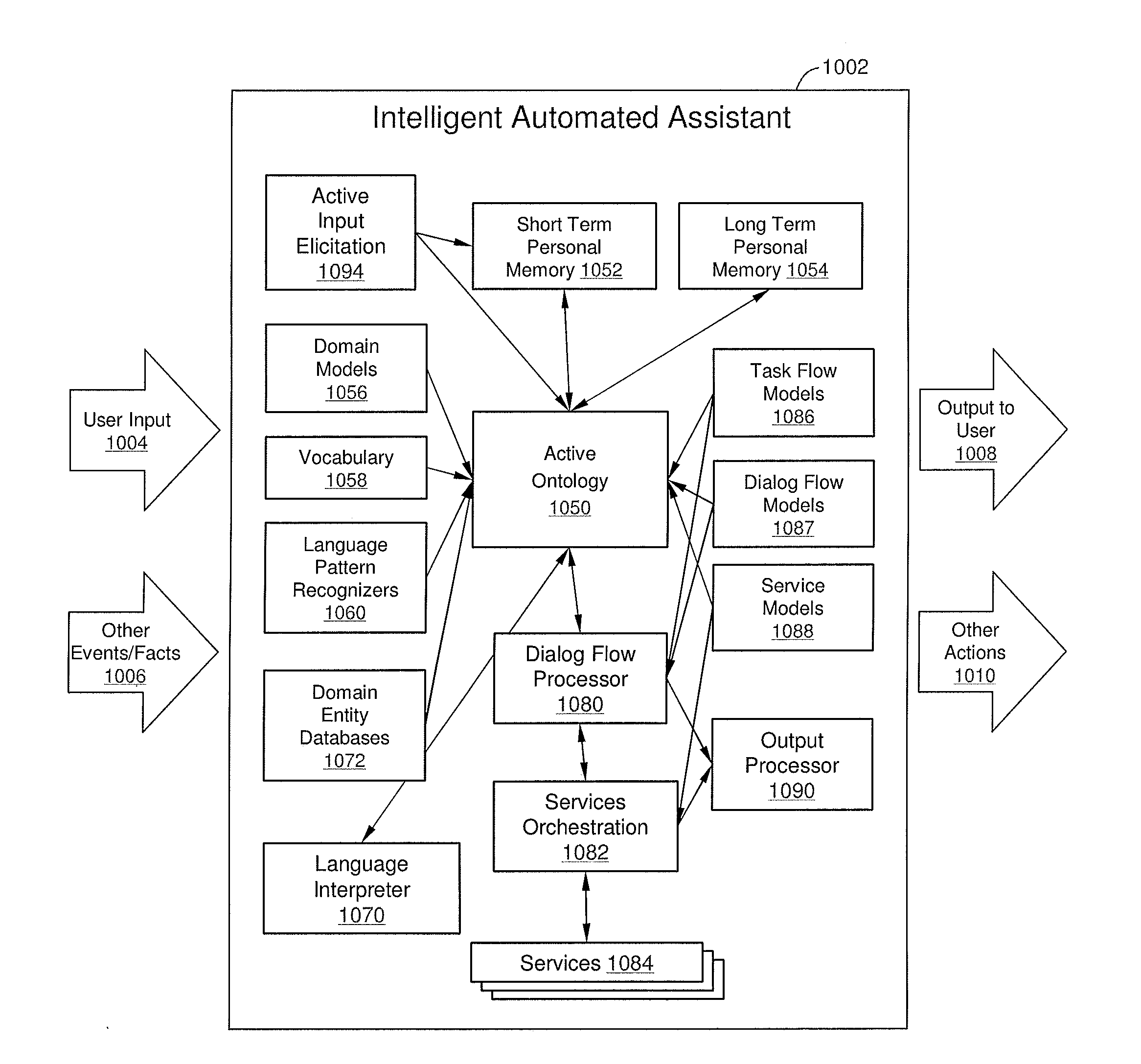
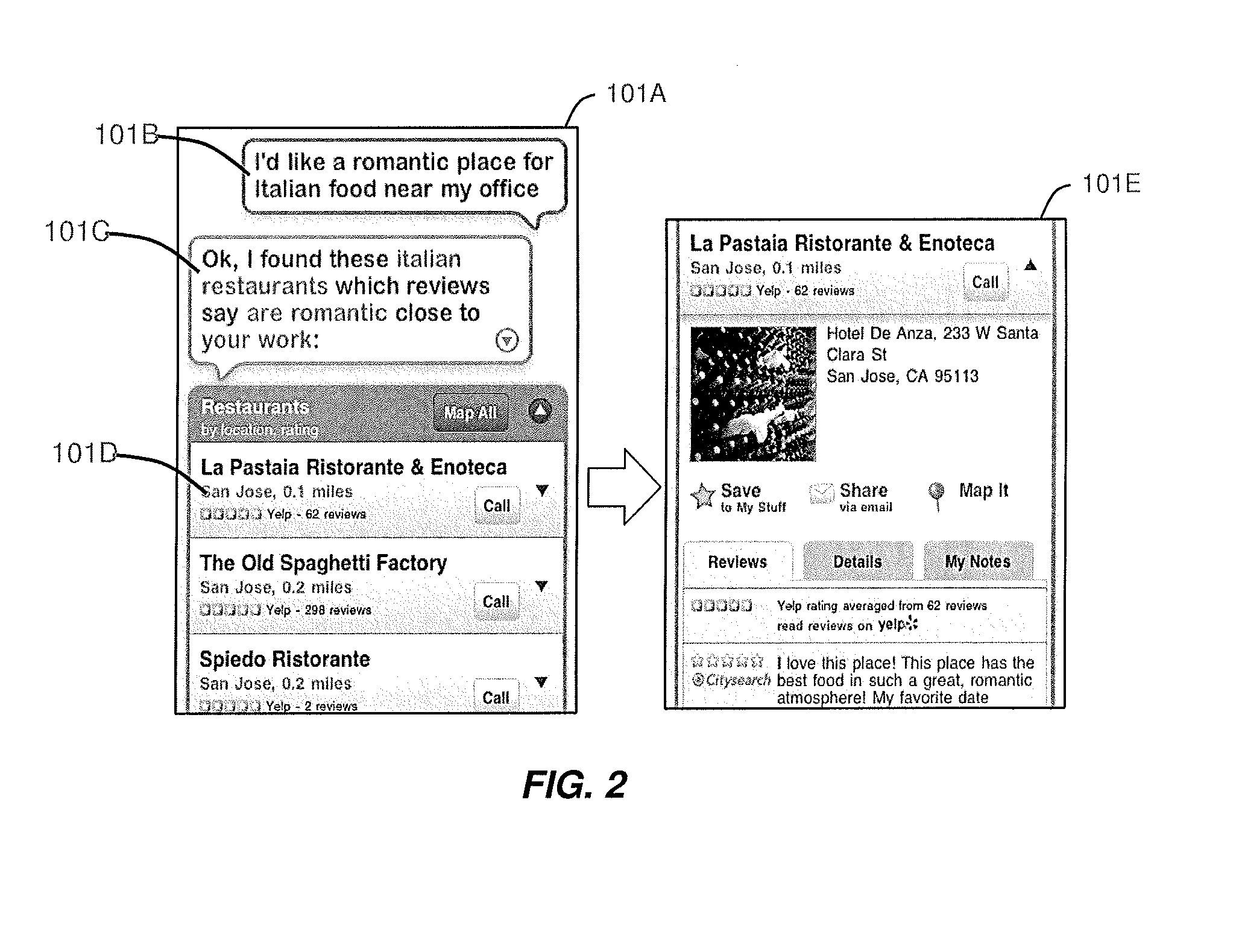
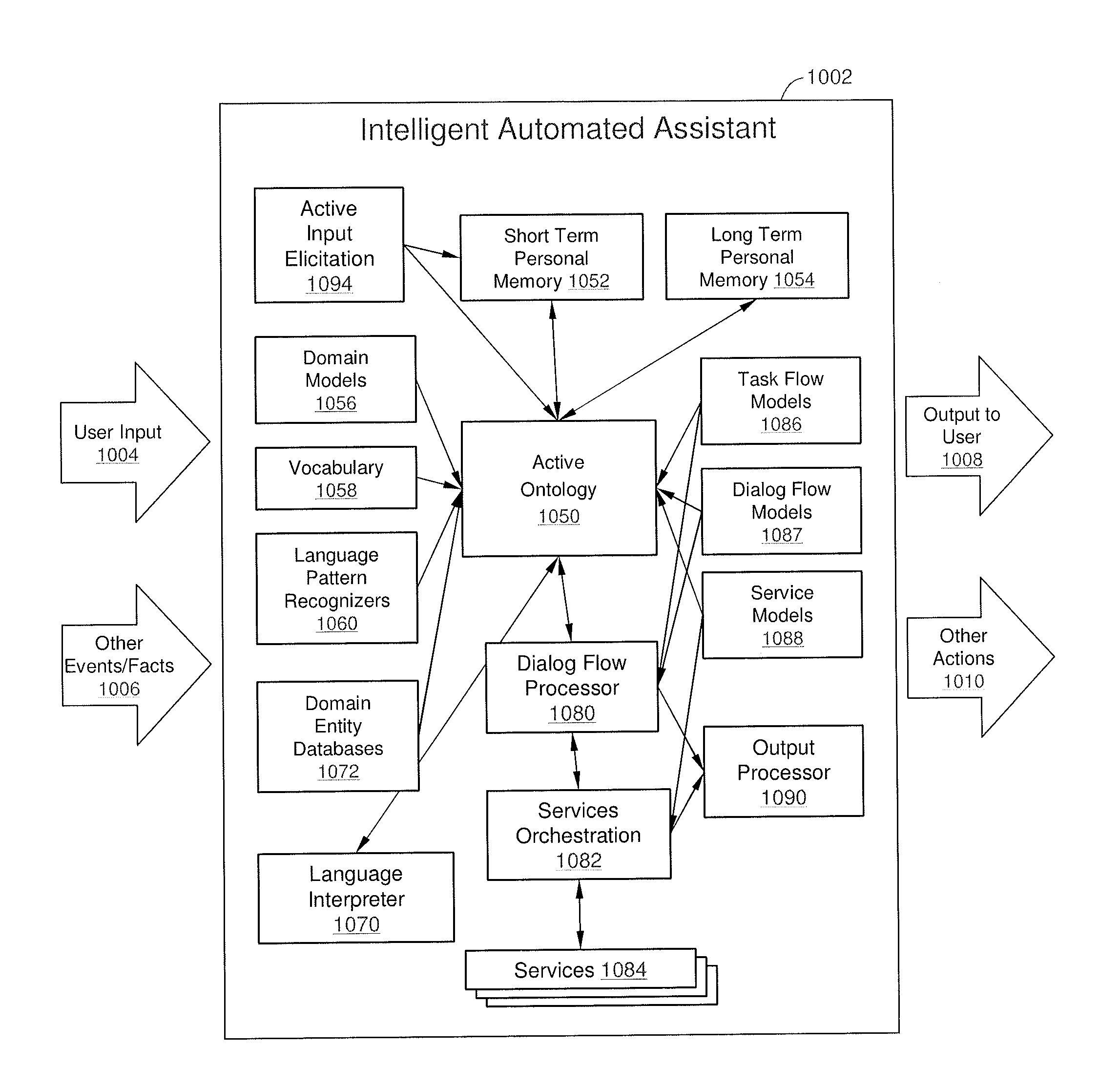
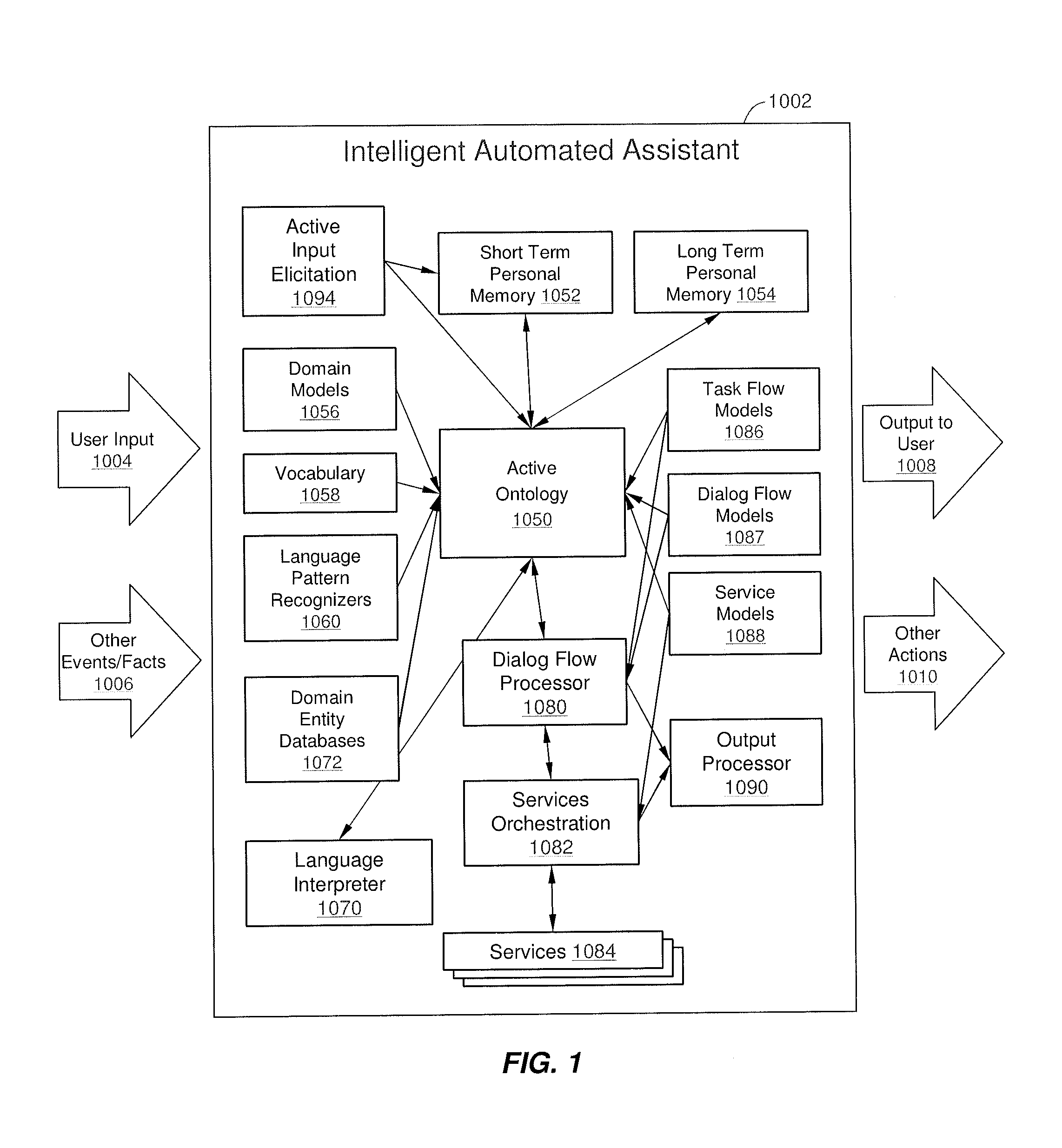
Intelligent Automated Assistant
ActiveUS20120016678A1Improve user interactionPromote effective engagementNatural language translationSemantic analysisService provisionSystem usage
An intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
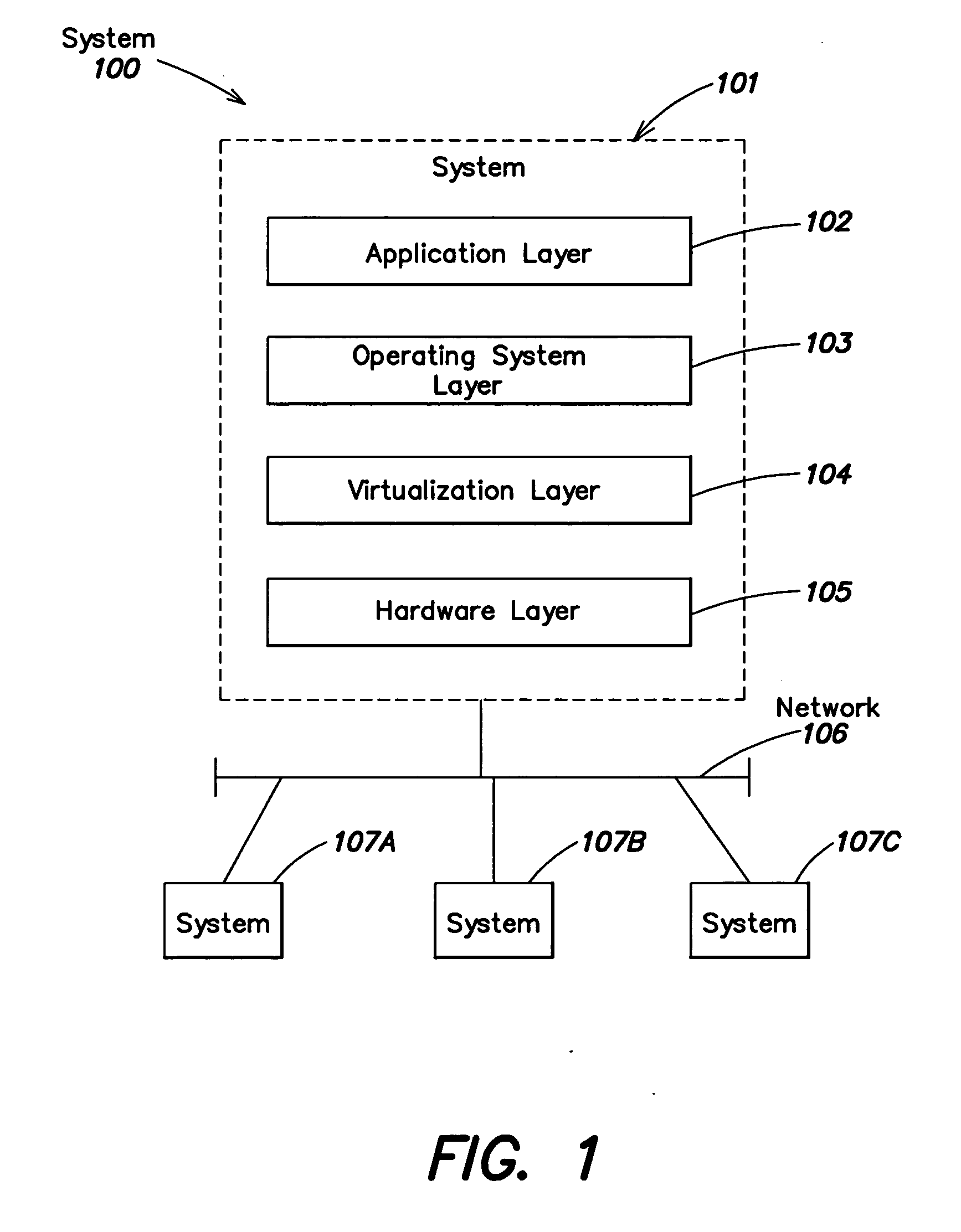
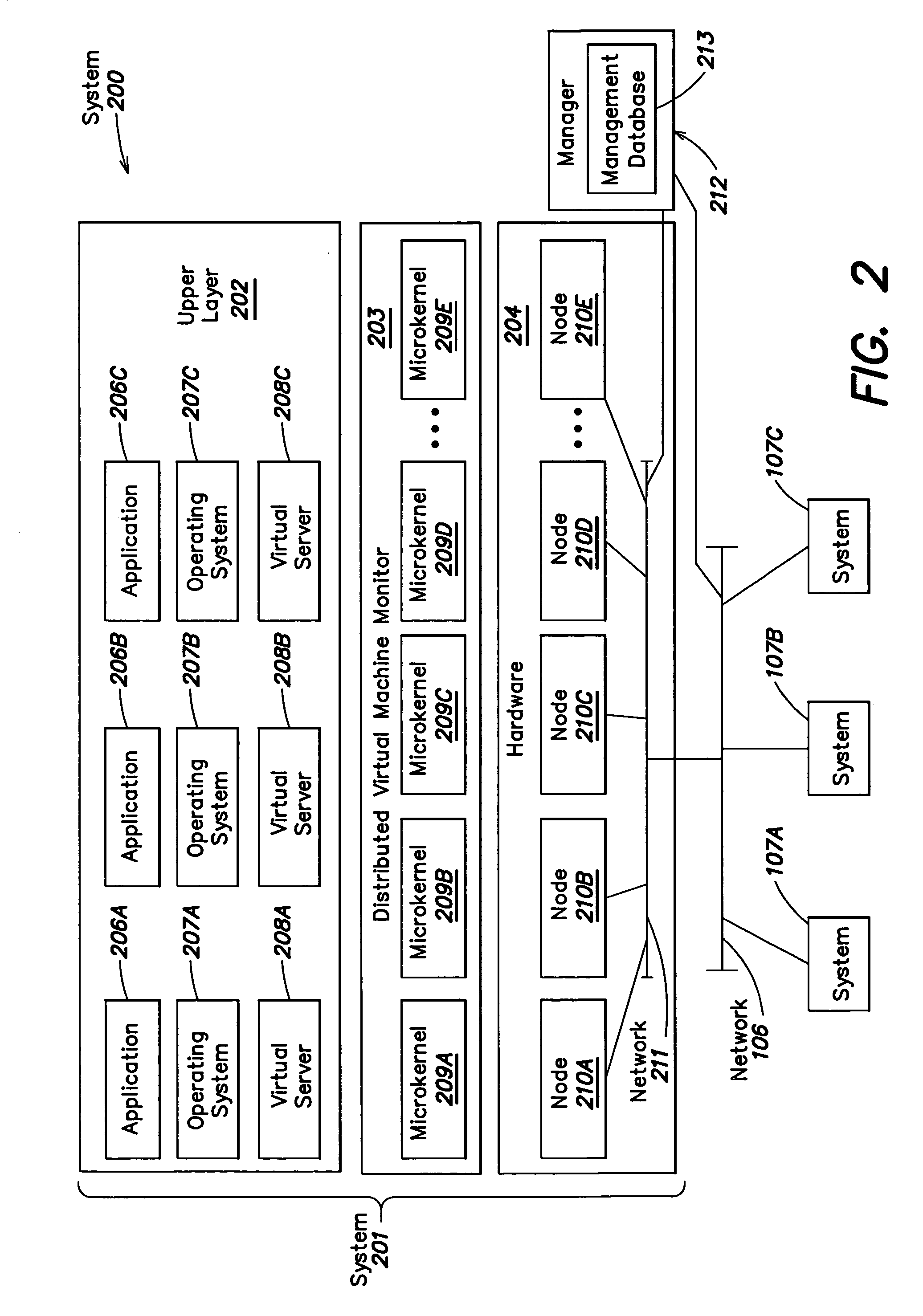
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
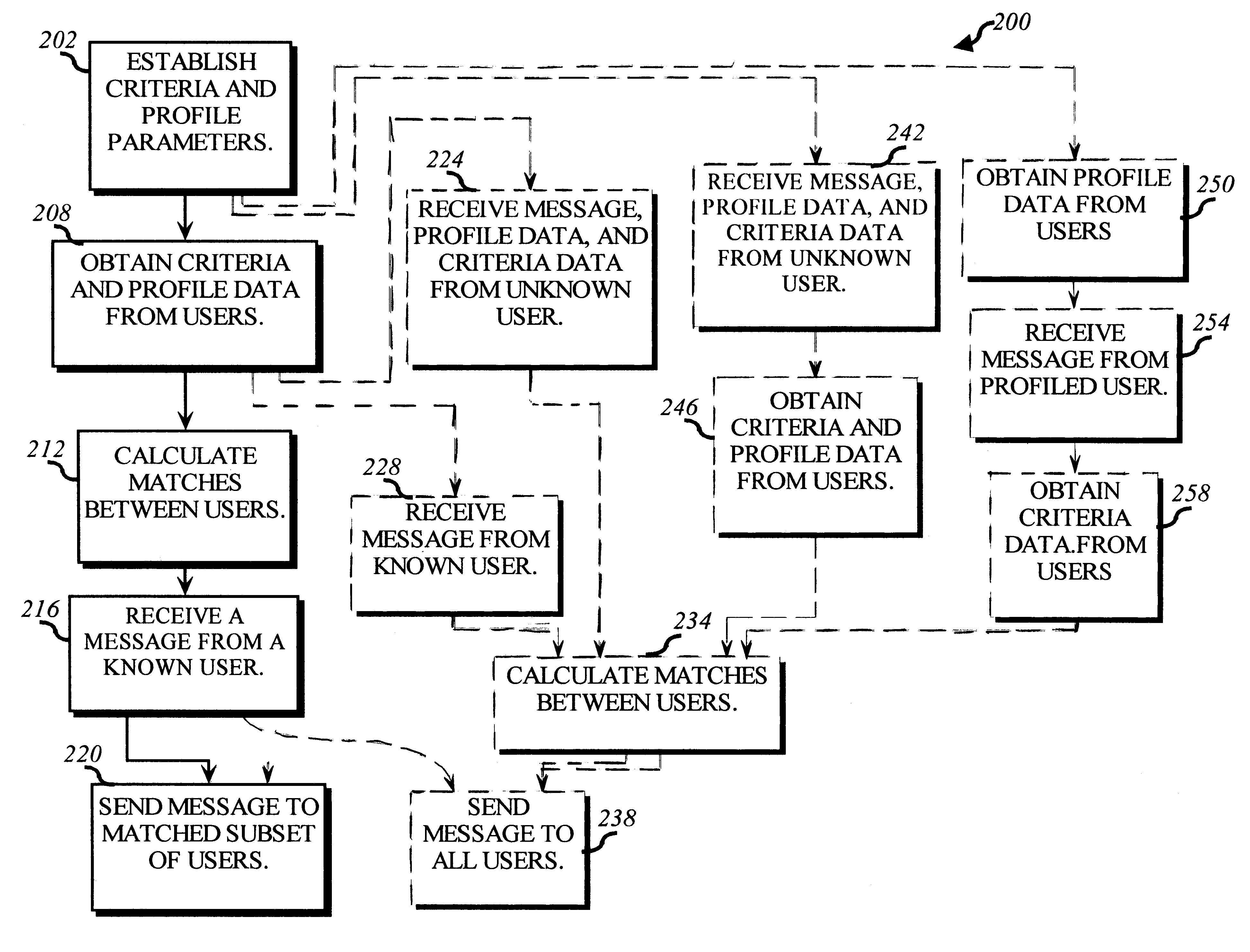
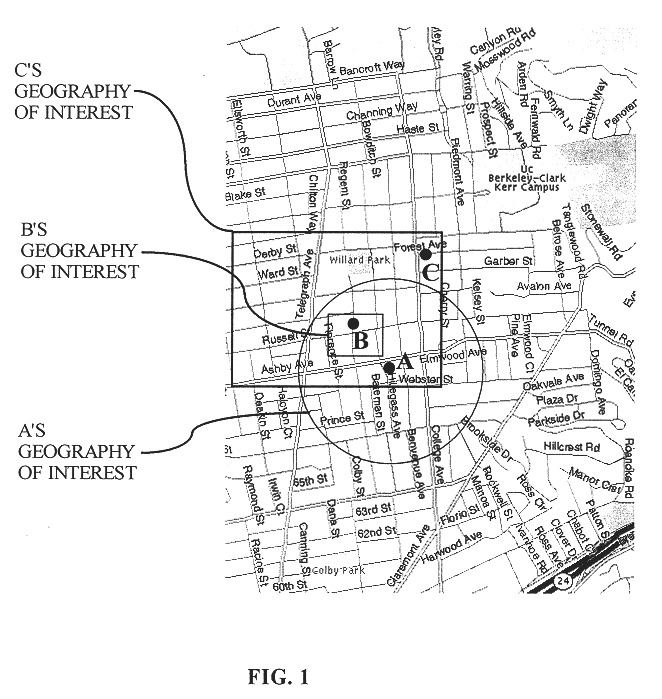
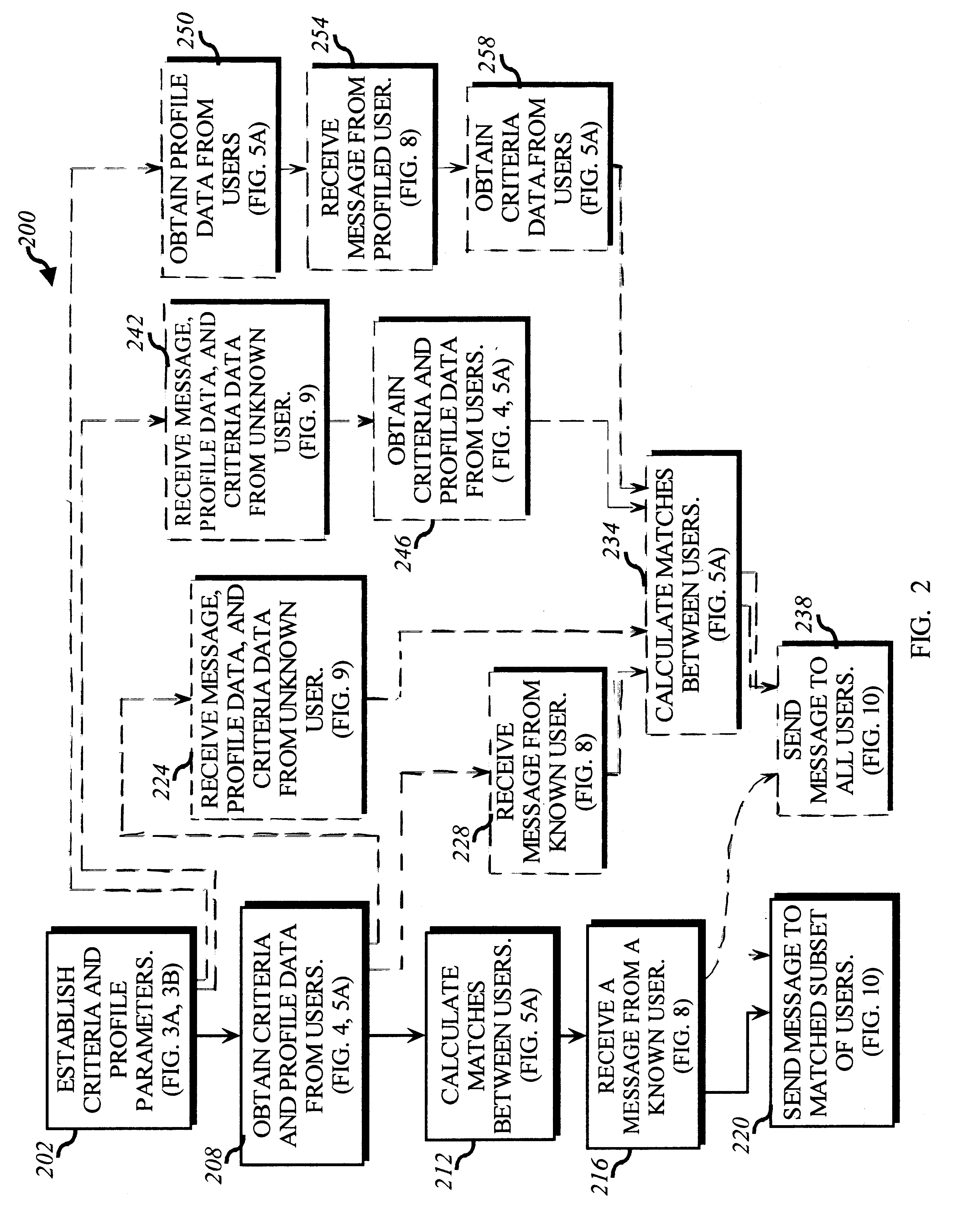
Dynamically matching users for group communications based on a threshold degree of matching of sender and recipient predetermined acceptance criteria
InactiveUS6480885B1Quality of communicationReduce in quantitySpecial service provision for substationMultiprogramming arrangementsPersonalizationWeb service
A method for enabling users to exchange group electronic mail by establishing individual profiles and criteria, for determining personalized subsets within a group. Users establish subscriptions to an electronic mailing list by specifying user profile data and acceptance criteria data to screen other users. When a user subscribes, a web server establishes and stores an individualized recipient list including each matching subscriber and their degree of one-way or mutual match with the user. When the user then sends a message to the mailing list, an email server retrieves 100% her matches and then optionally filters her recipient list down to a message distribution list using each recipient's message criteria. The message is then distributed to matching users. Additionally, email archives and information contributions from users are stored in a database. A web server creates an individualized set of web pages for a user from the database, containing contributions only from users in his recipient list. In other embodiments, users apply one-way or mutual criteria matching and message profile criteria to other group forums, such as web-based discussion boards, chat, online clubs, USENET newsgroups, voicemail, instant messaging, web browsing side channel communities, and online gaming rendezvous.
Owner:TUMBLEWEED HLDG LLC
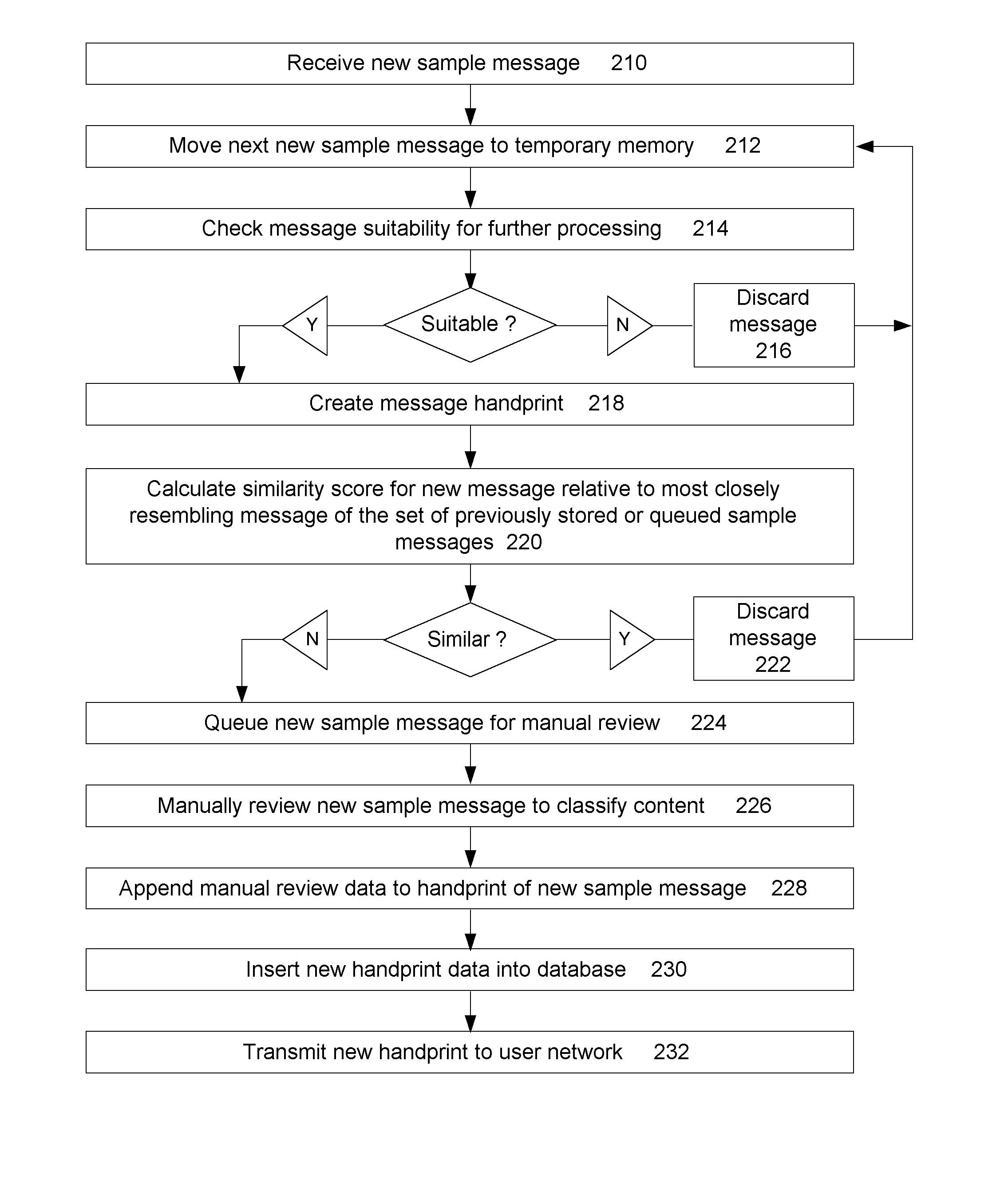
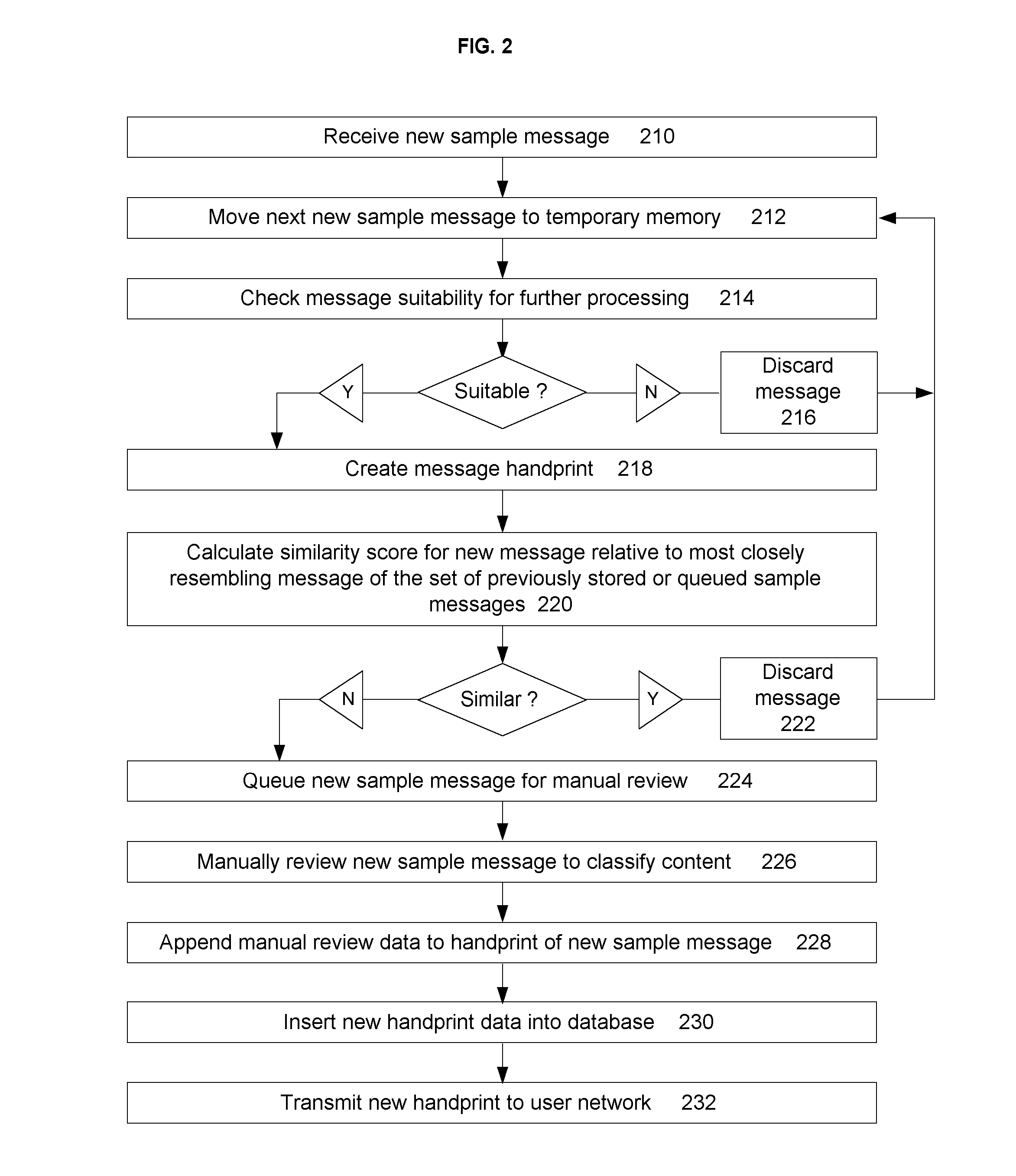
Document similarity detection and classification system
InactiveUS20050060643A1Natural language data processingData switching networksDocument similarityDocument preparation
A document similarity detection and classification system is presented. The system employs a case-based method of classifying electronically distributed documents in which content chunks of an unclassified document are compared to the sets of content chunks comprising each of a set of previously classified sample documents in order to determine a highest level of resemblance between an unclassified document and any of a set of previously classified documents. The sample documents have been manually reviewed and annotated to distinguish document classifications and to distinguish significant content chunks from insignificant content chunks. These annotations are used in the similarity comparison process. If a significant resemblance level exceeding a predetermined threshold is detected, the classification of the most significantly resembling sample document is assigned to the unclassified document. Sample documents may be acquired to build and maintain a repository of sample documents by detecting unclassified documents that are similar to other unclassified documents and subjecting at least some similar documents to a manual review and classification process. In a preferred embodiment the invention may be used to classify email messages in support of a message filtering or classification objective.
Owner:GLASS JEFFREY B MR
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
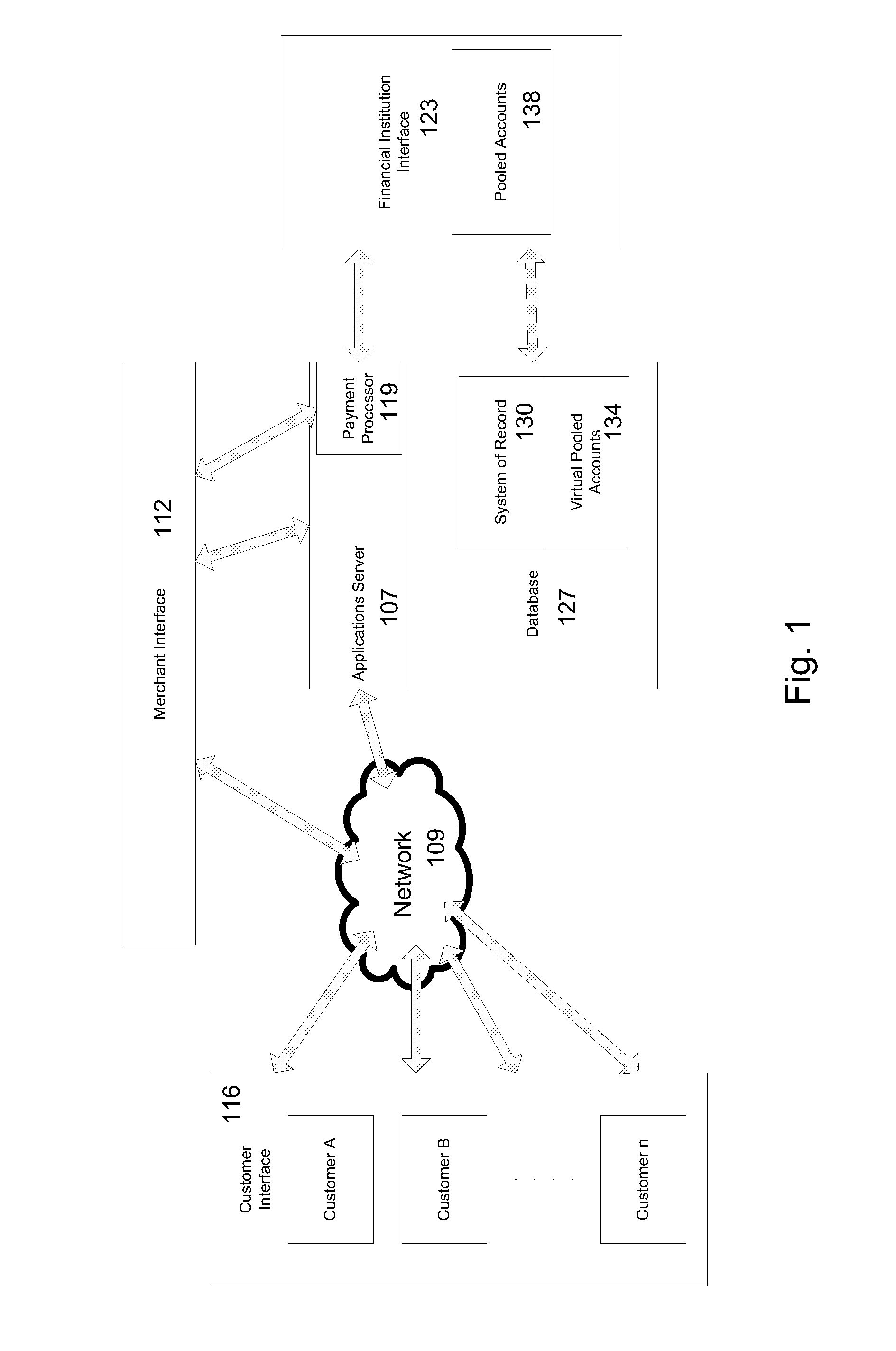
Mobile Person-to-Person Payment System
InactiveUS20070255653A1Easy to useFraudulent transaction is minimizedFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
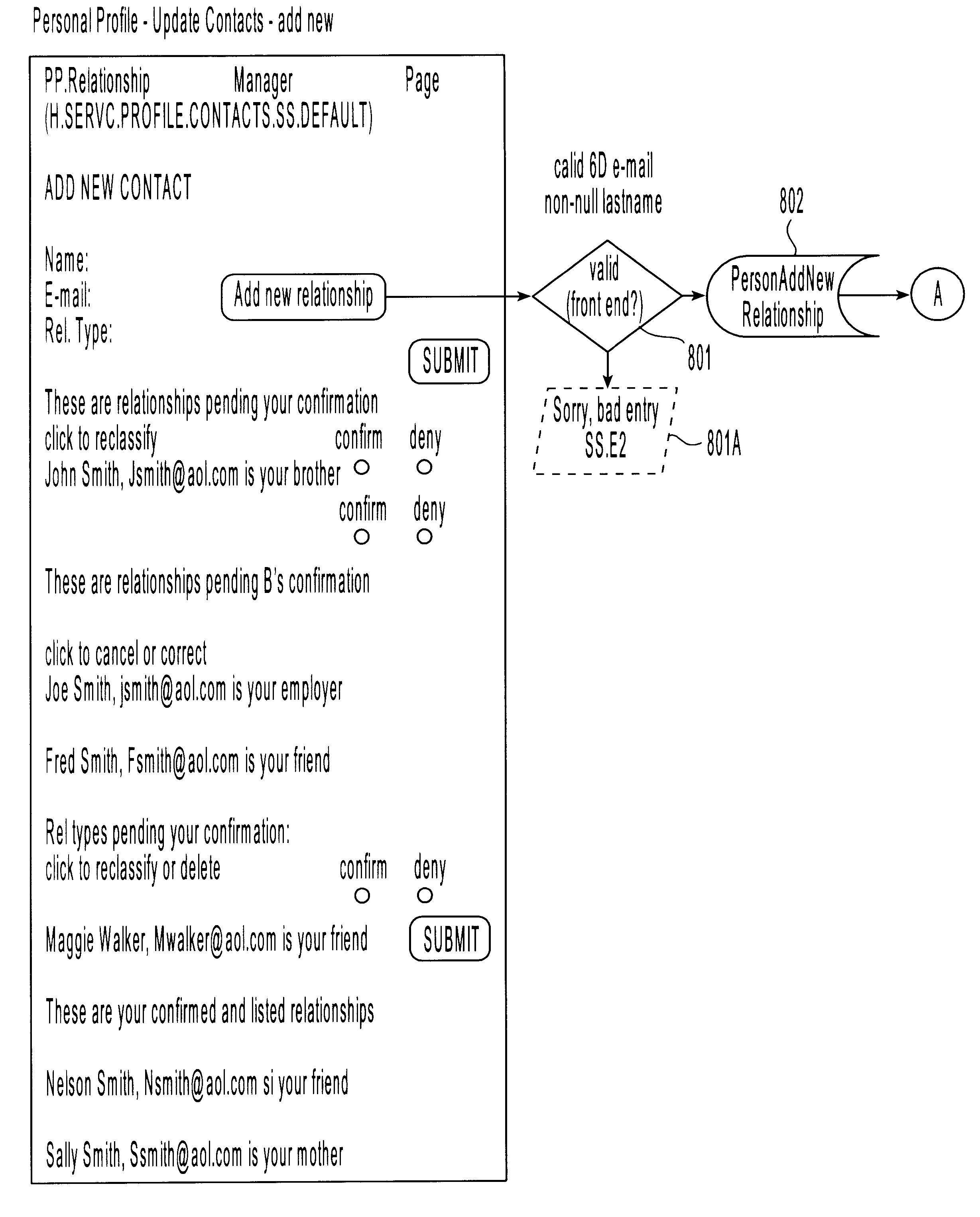
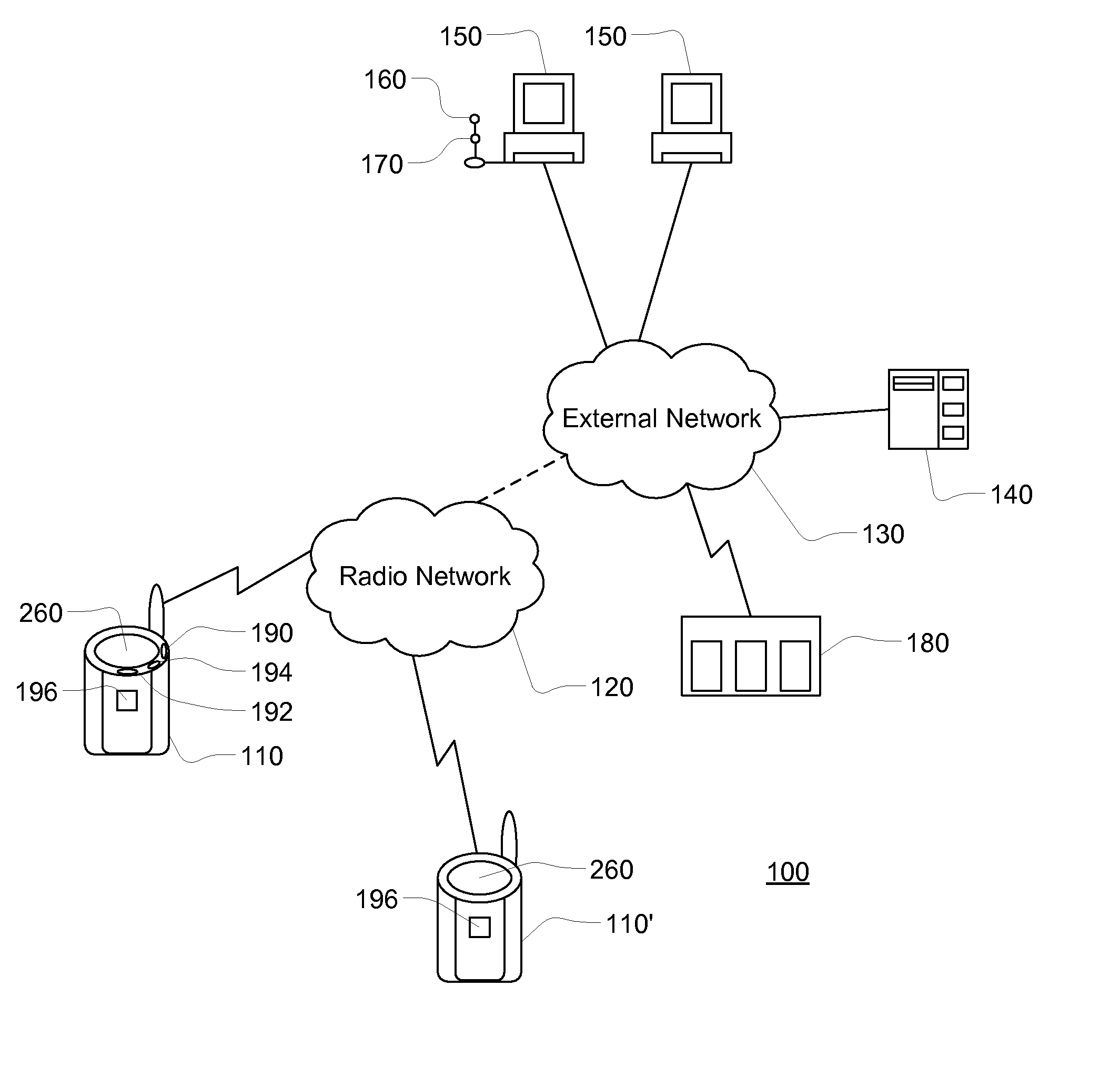
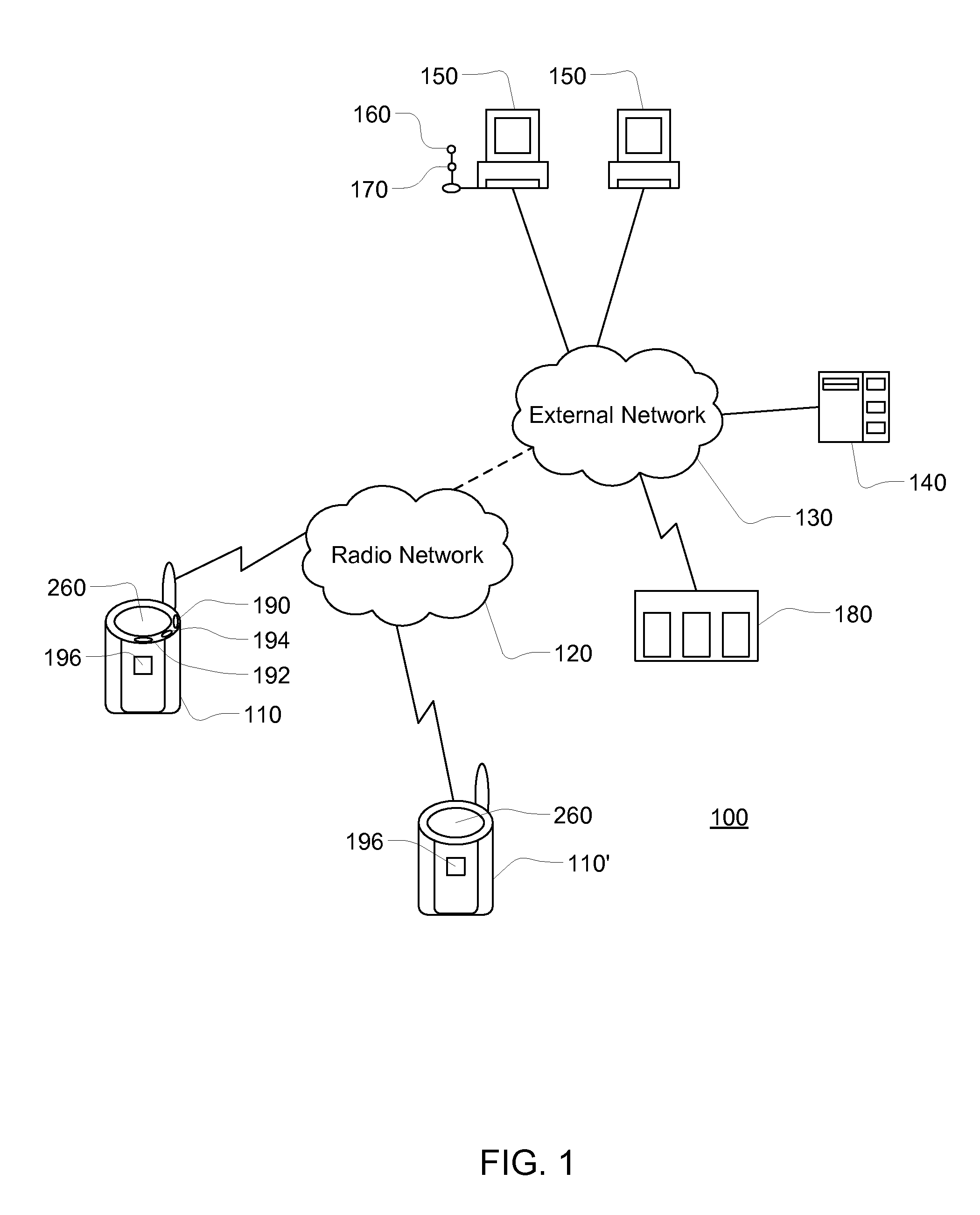
Method and apparatus for constructing a networking database and system
InactiveUS6175831B1Fast constructionGrowthOffice automationSpecial data processing applicationsMutually DefinedDatabase services
A networking database containing a plurality of records for different individuals in which individuals are connected to one another in the database by defined relationships. Each individual has the opportunity to define the relationship which may be confirmed or denied. E-mail messaging and interactive communication between individuals and a database service provider provide a method of constructing the database. The method includes having a registered individual identify further individuals and define therewith a relationship. The further individuals then, in turn, establish their own defined relationships with still other individuals. The defined relationships are mutually defined.
Owner:MACROVIEW COMM CORP +1
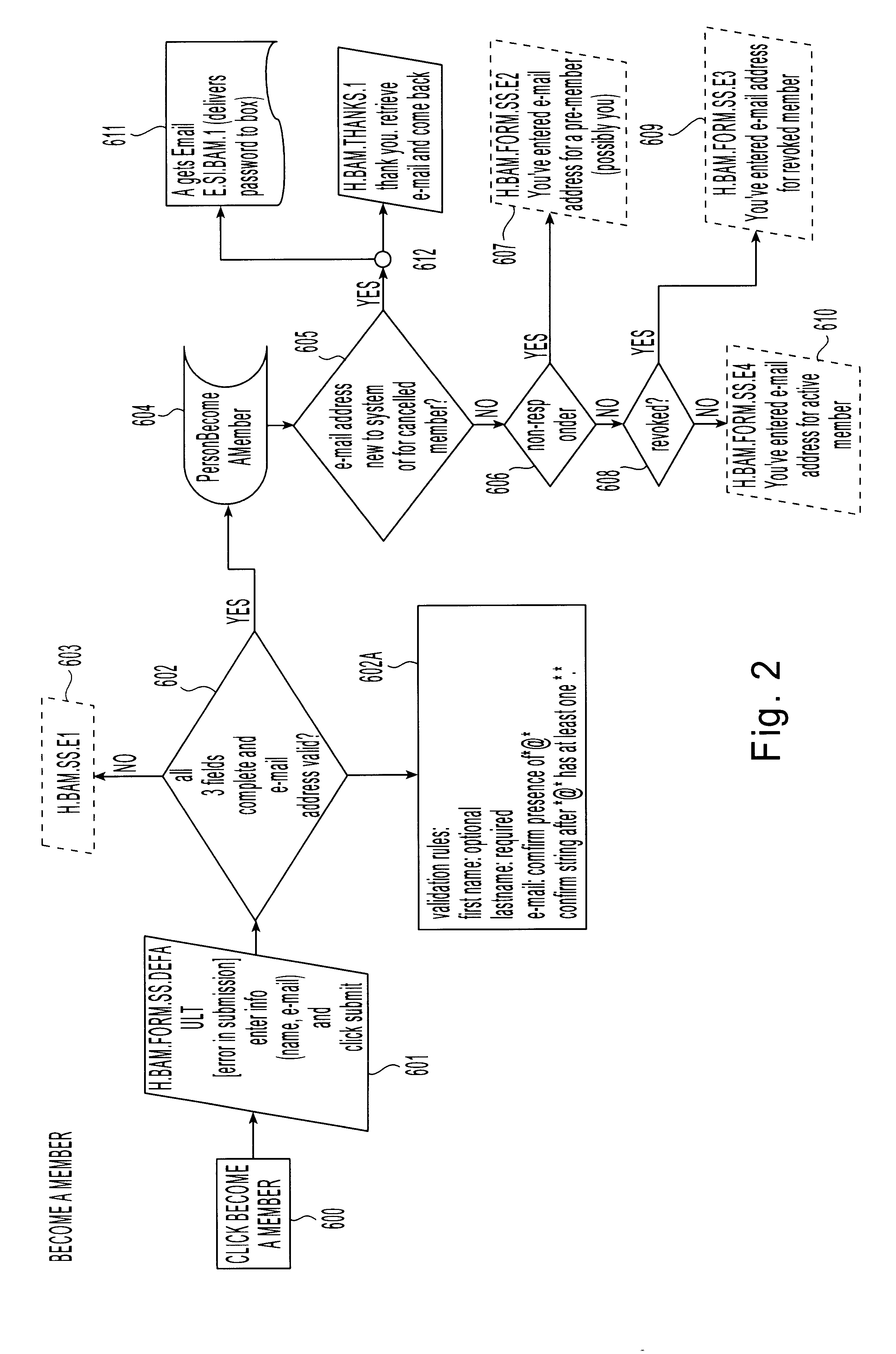
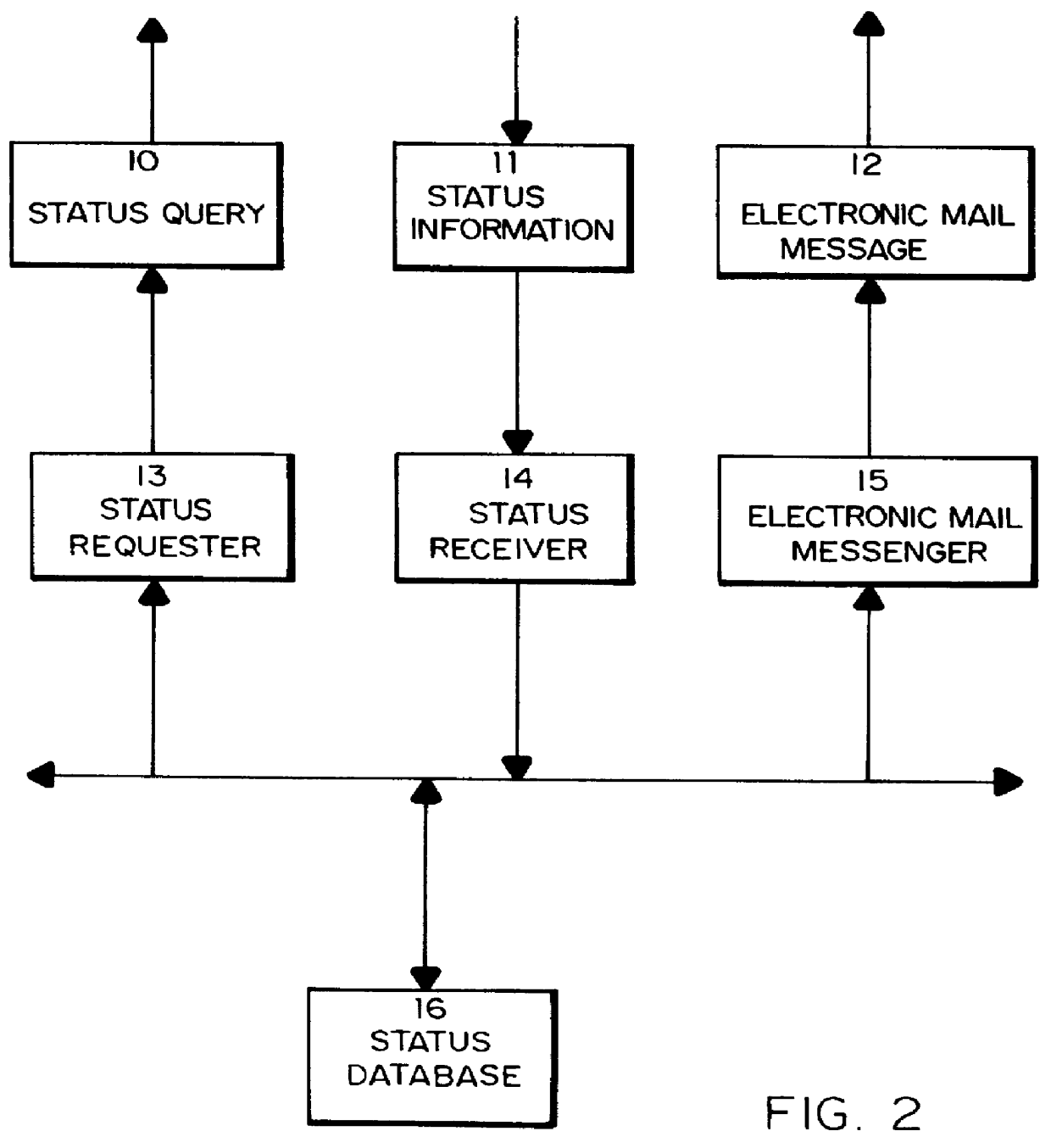
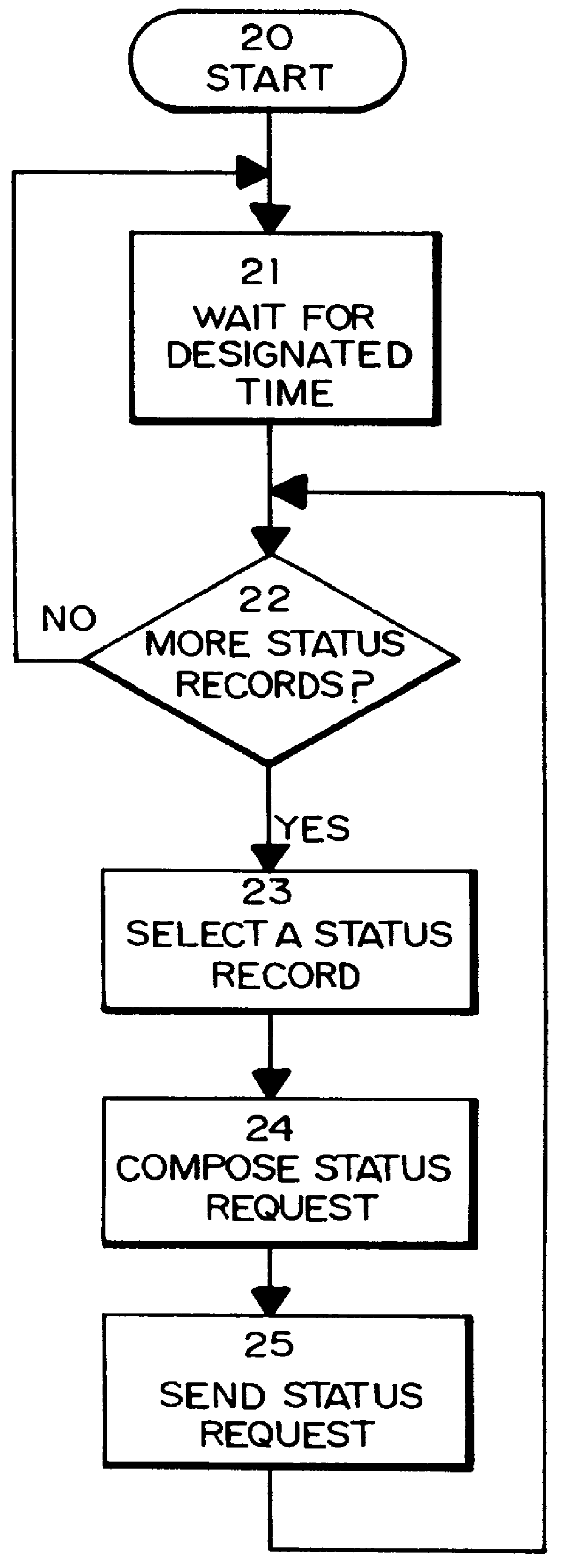
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
Method and system for customized, contextual, dynamic and unified communication, zero click advertisement and prospective customers search engine
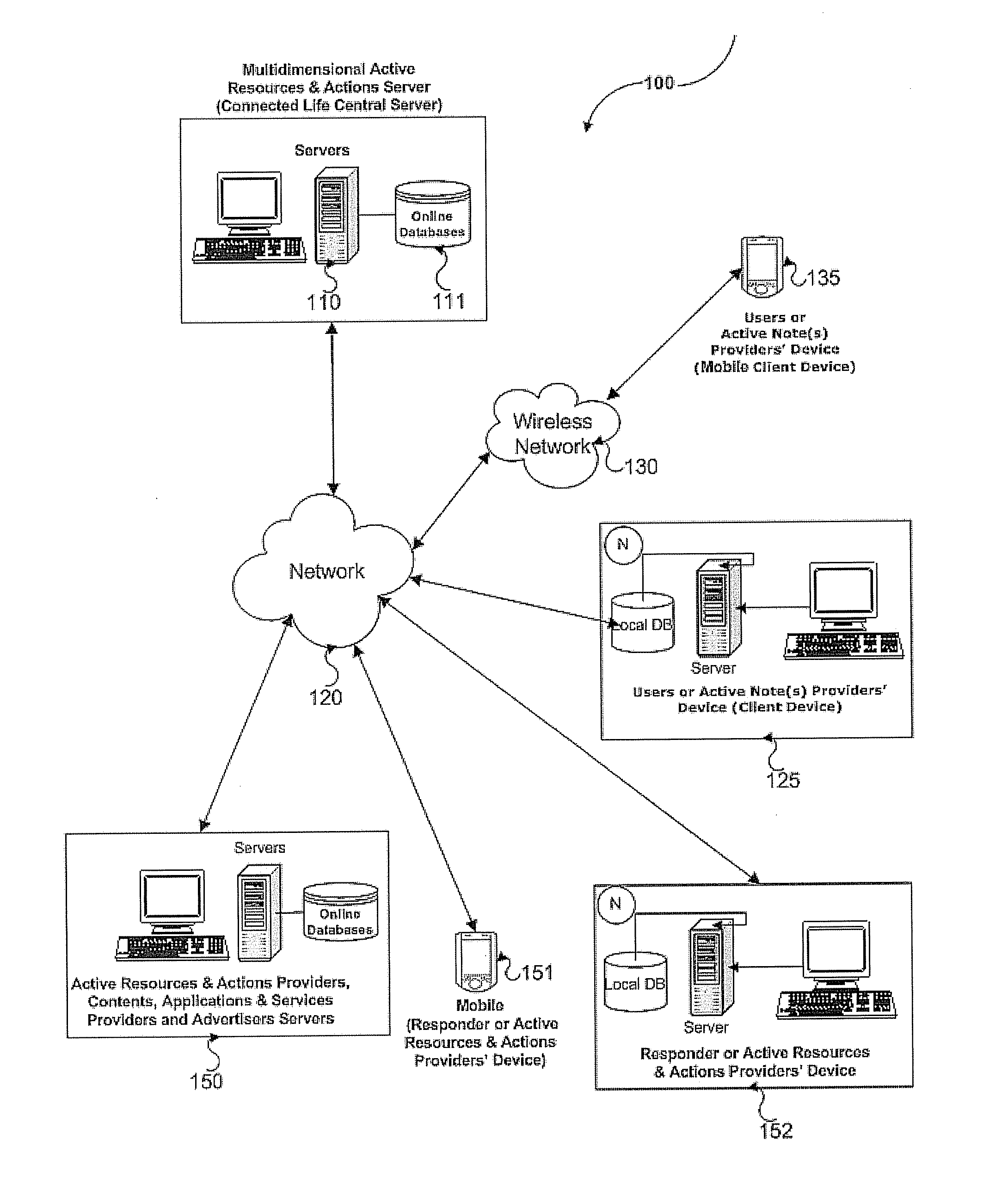
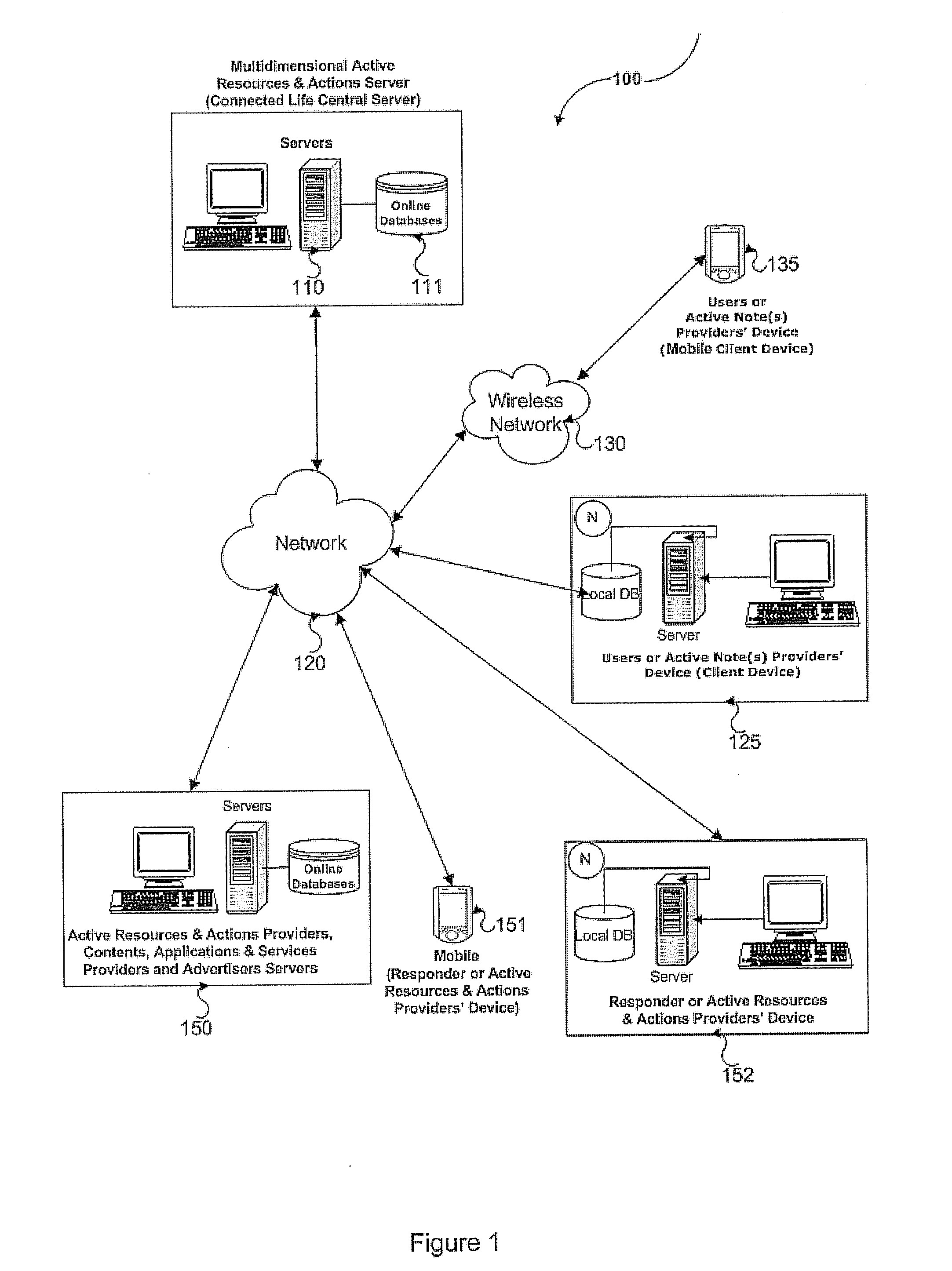
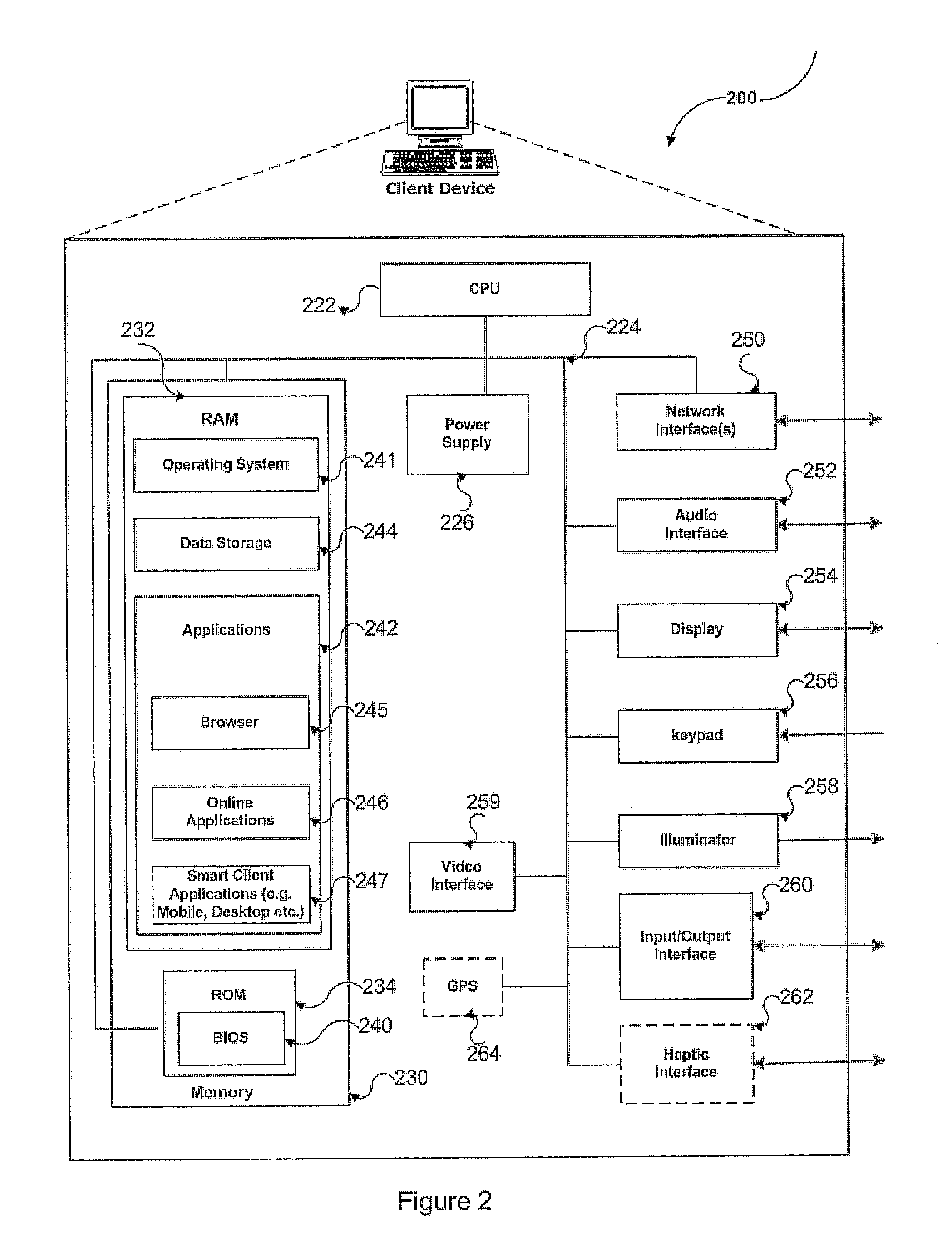
InactiveUS20110208822A1Save energyShorten the timeMultiple digital computer combinationsSpecial data processing applicationsWeb siteUnified communications
The present invention relates device, system and method for facilitating receiving active note(s) from active note(s) provider(s) from the client device and responding multidimensional active resources & actions(s) for said active note(s) by multidimensional active resources & actions(s) provider(s) to the client device. A real time and / or near real communication mechanism such as online, smart and mobile communication applications like web site, smart client, instant messaging, e-mail may be used to communicate with a client device and a community of responders or multidimensional active resources & actions(s) provider(s). One or more Active Note(s) are received from client devices, processed, and sent to responders. Responses from the responders are received, and response is sent to the client device.
Owner:ONEPATONT SOFTWARE LTD
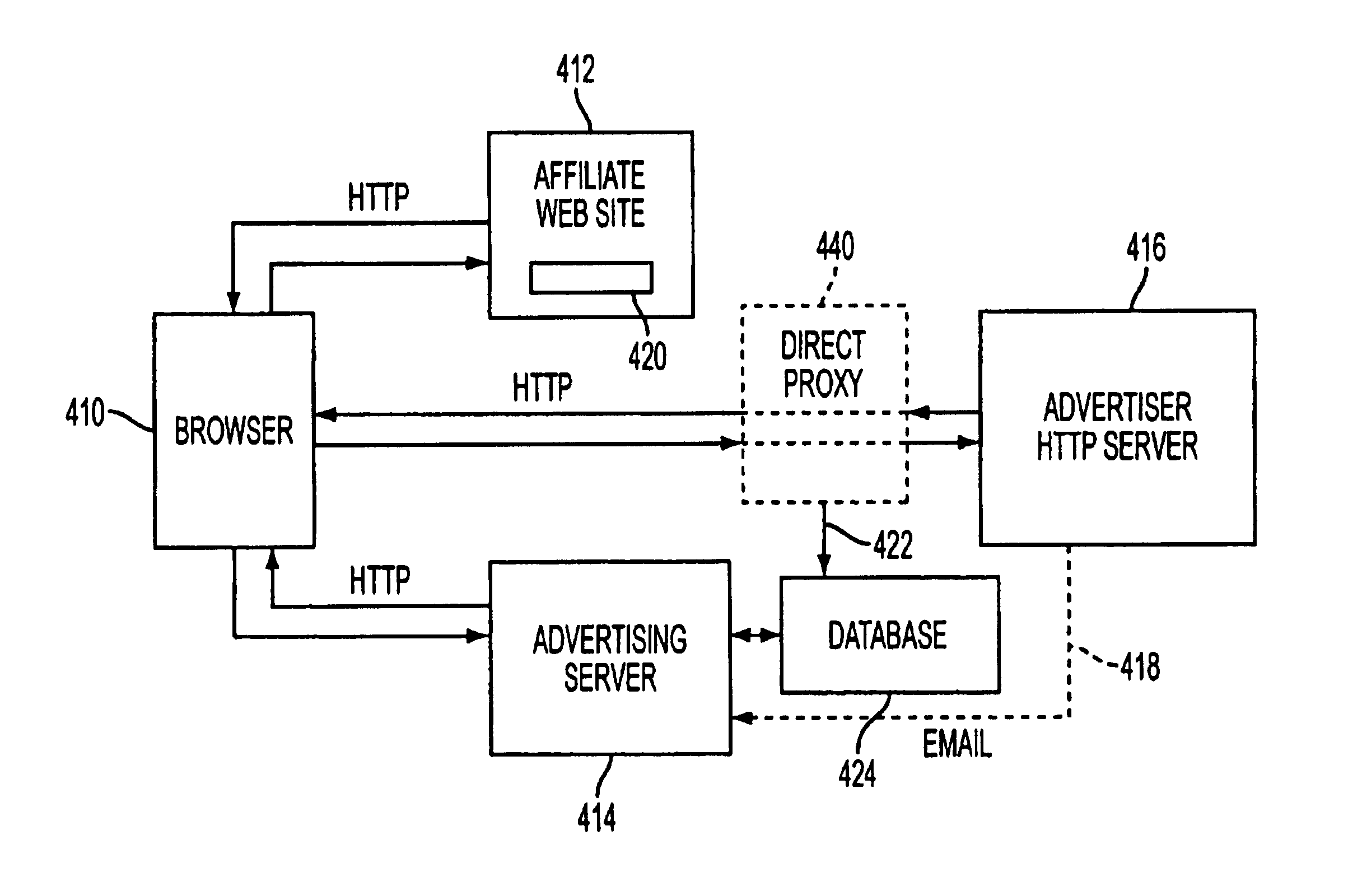
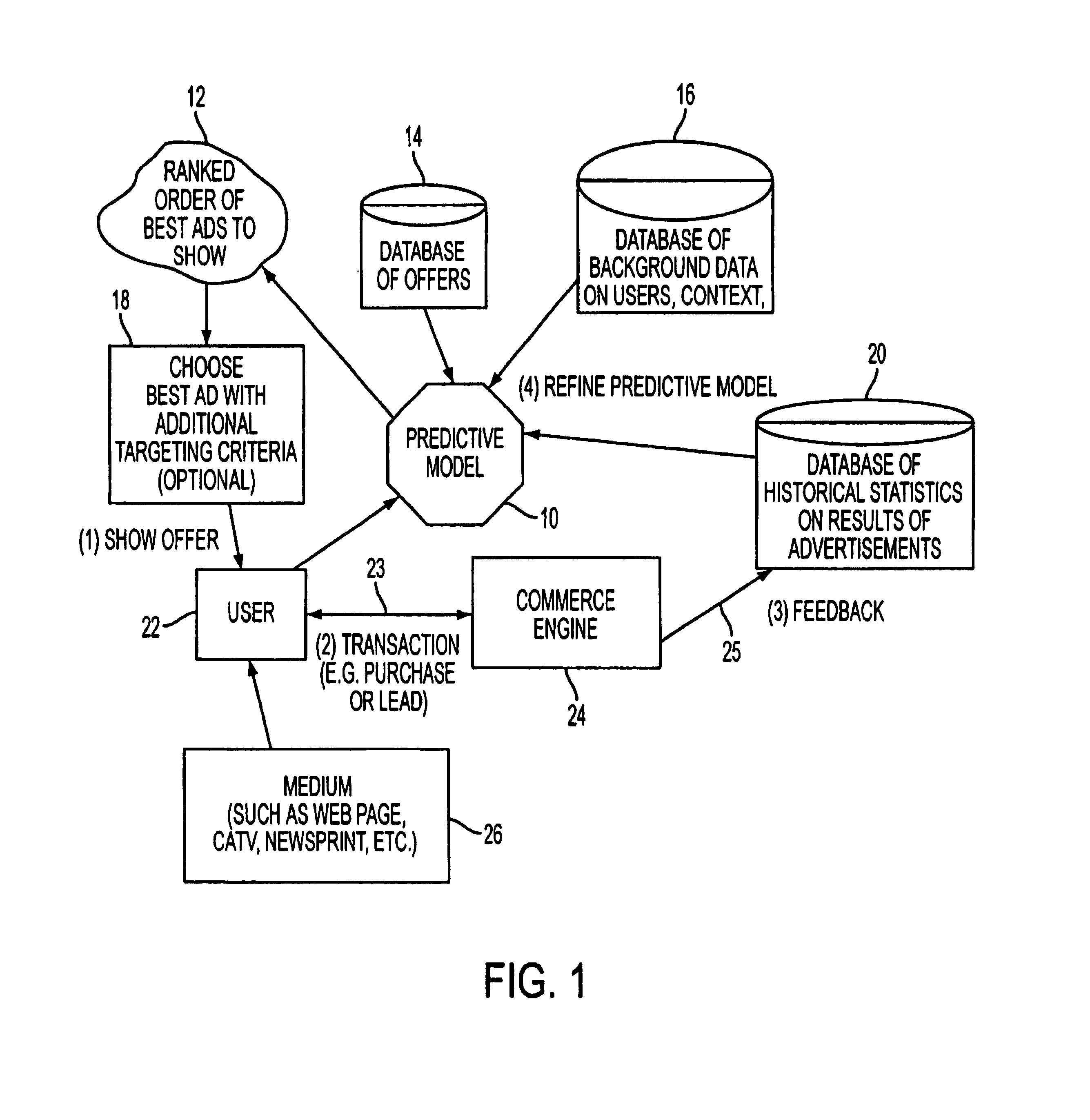
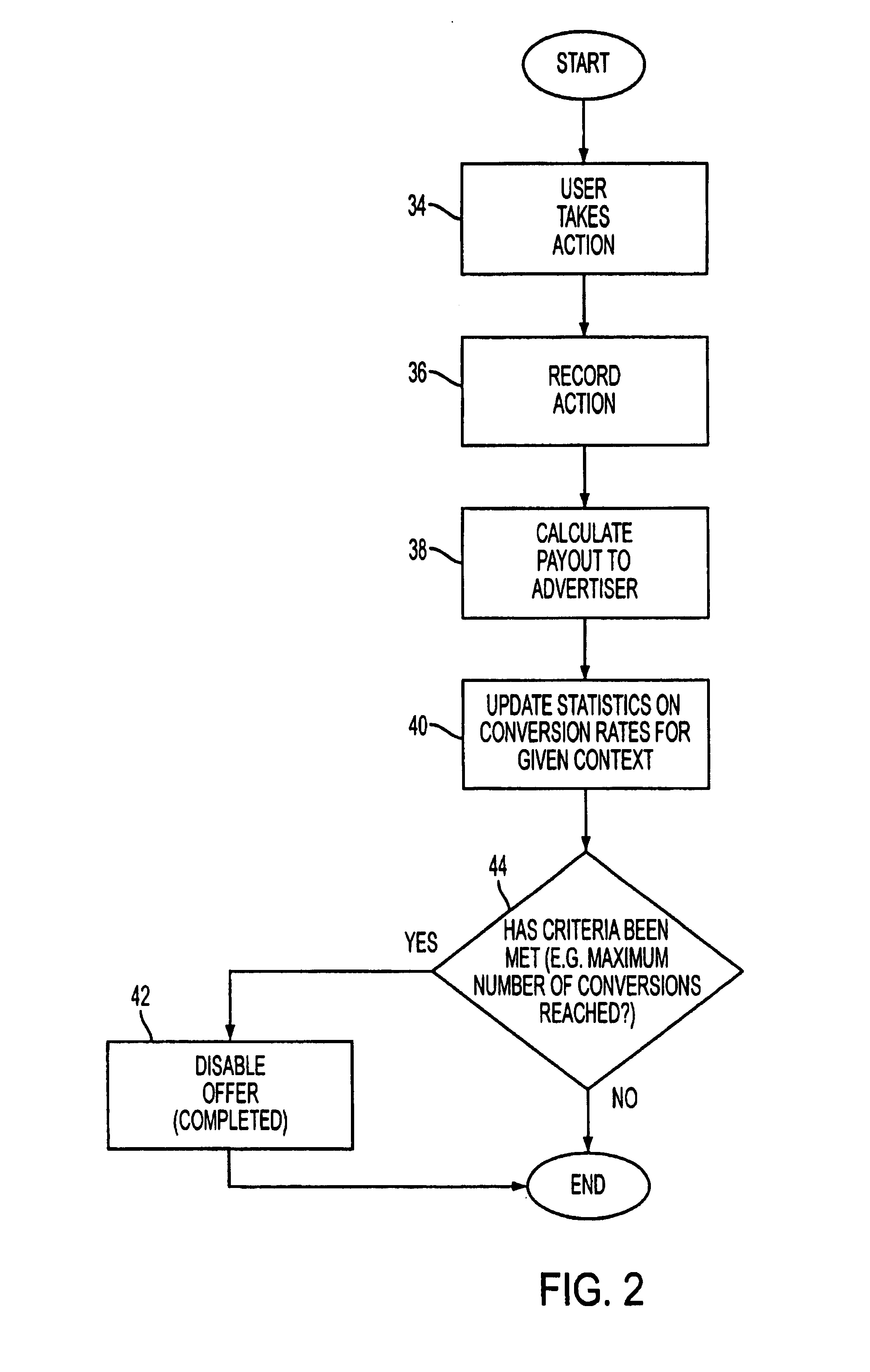
Method and apparatus for automatic placement of advertising
InactiveUS7039599B2Efficient use ofPrevention of ad “burn out.AdvertisementsCash registersWeb siteComputerized system
A computer system for automatic replacement of direct advertisements in scarce media includes an advertising server for selecting a direct advertisement based on certain criteria. Transaction results of the direct advertisement placement are reported back to the advertising server, and an associated accounting system. In one embodiment, the direct advertiser's server reports transactions back to the advertising server by email. In a second embodiment, a direct proxy server brokers the user's session (or interaction) with the direct advertiser's server, including transaction processing and the direct proxy server reports the results of transactions back to the advertising server and its associated accounting system. A direct proxy provides an independent audit of transactions at a remote direct advertiser's web site. The feedback of the results of direct advertisement transactions provides an efficient utilization of direct advertising space by way of an automated computer system with a predictive model for selection and distribution of direct advertising.
Owner:GOOGLE LLC
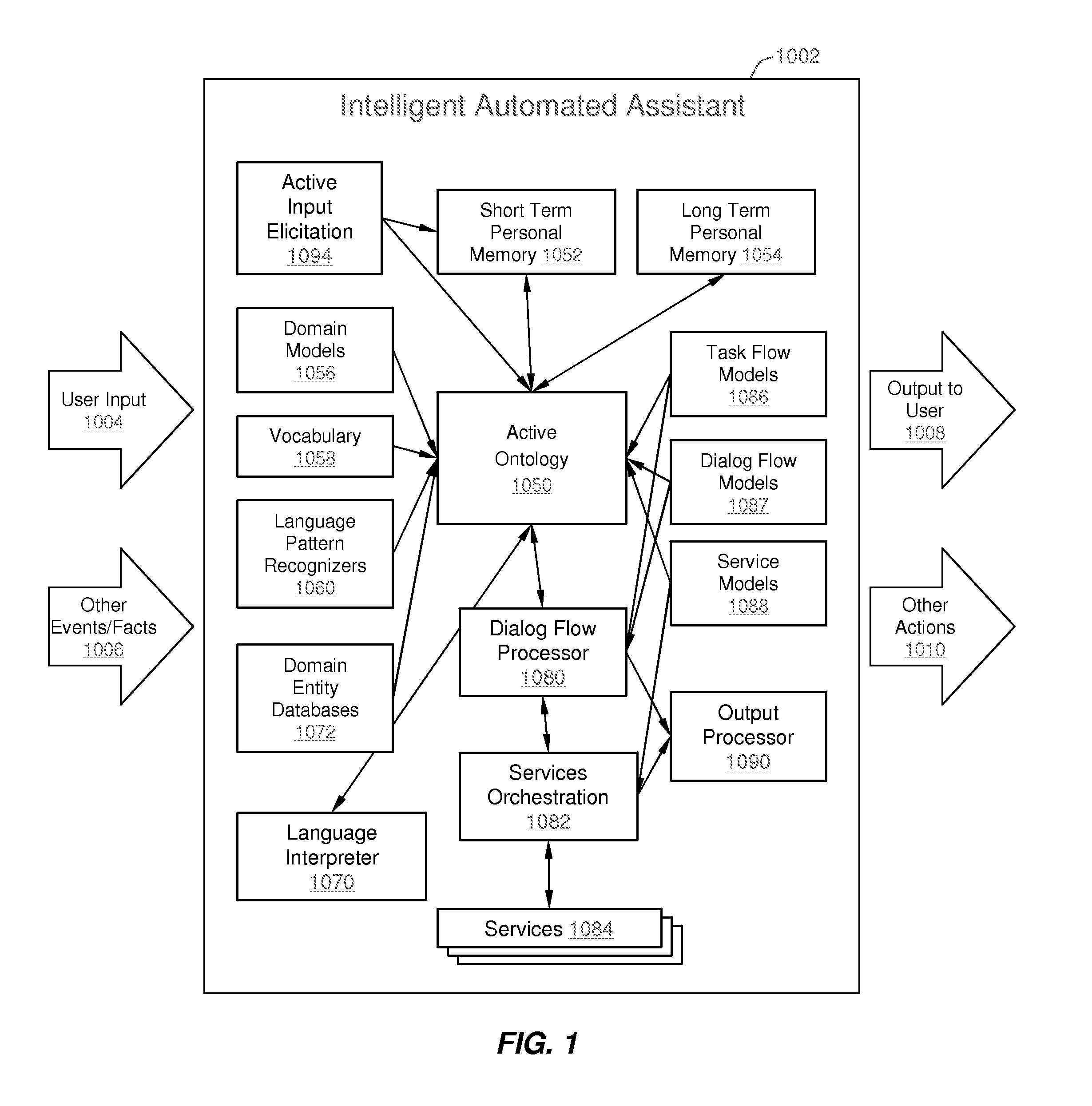
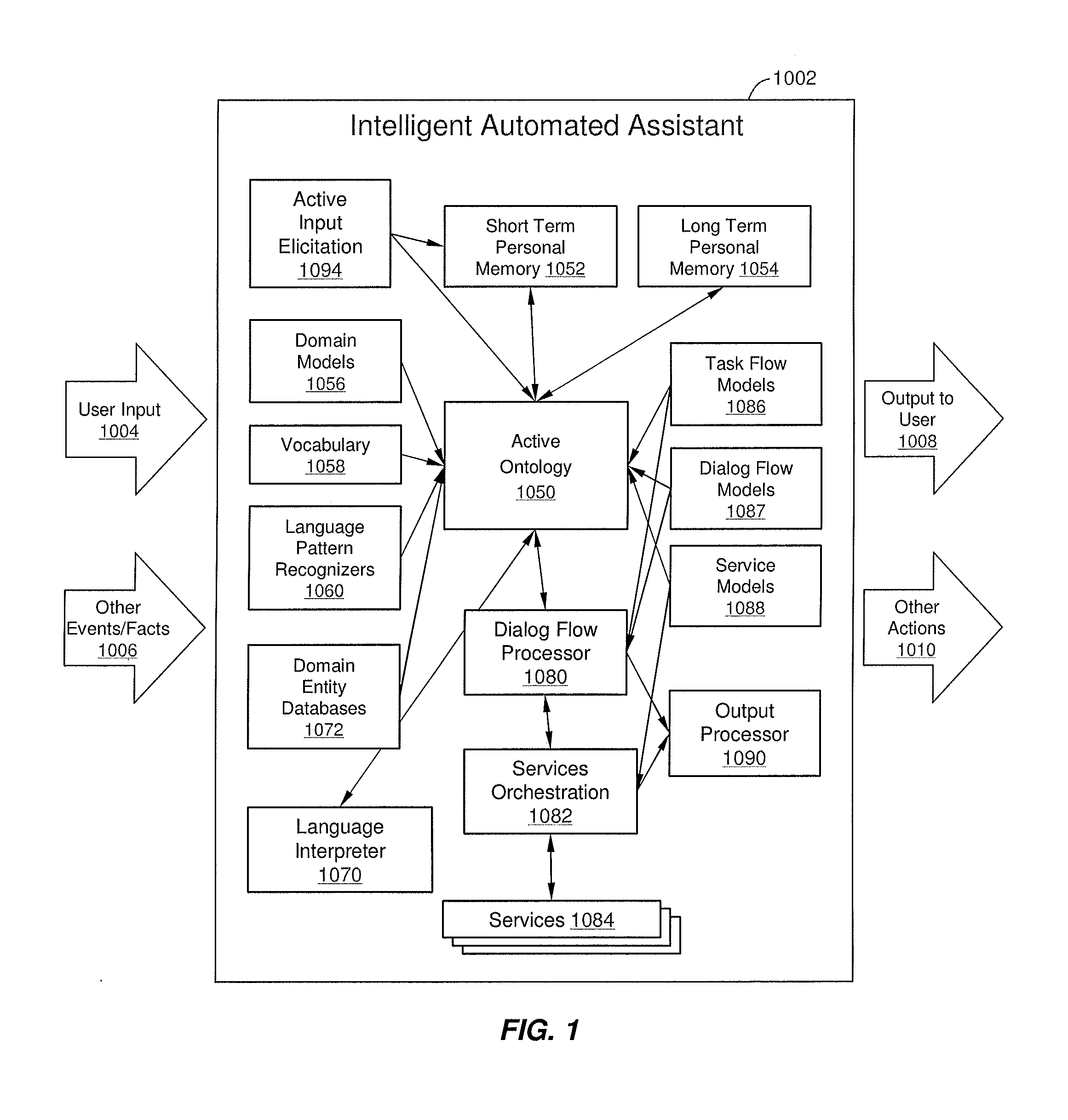
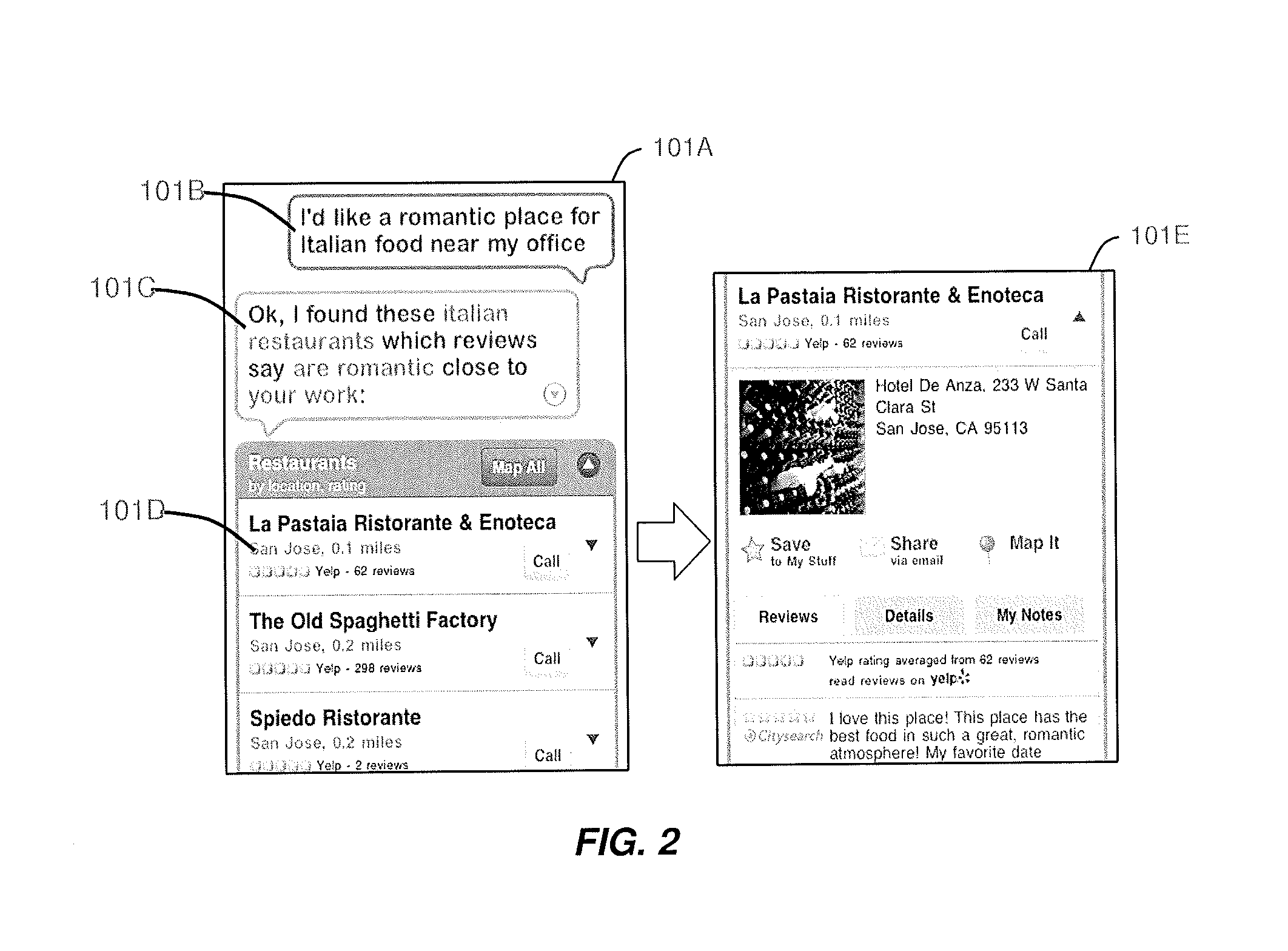
Intelligent Automated Assistant
ActiveUS20130275164A1Improve user interactionPromote effective engagementReservationsSpeech recognitionService provisionComputer science
The intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
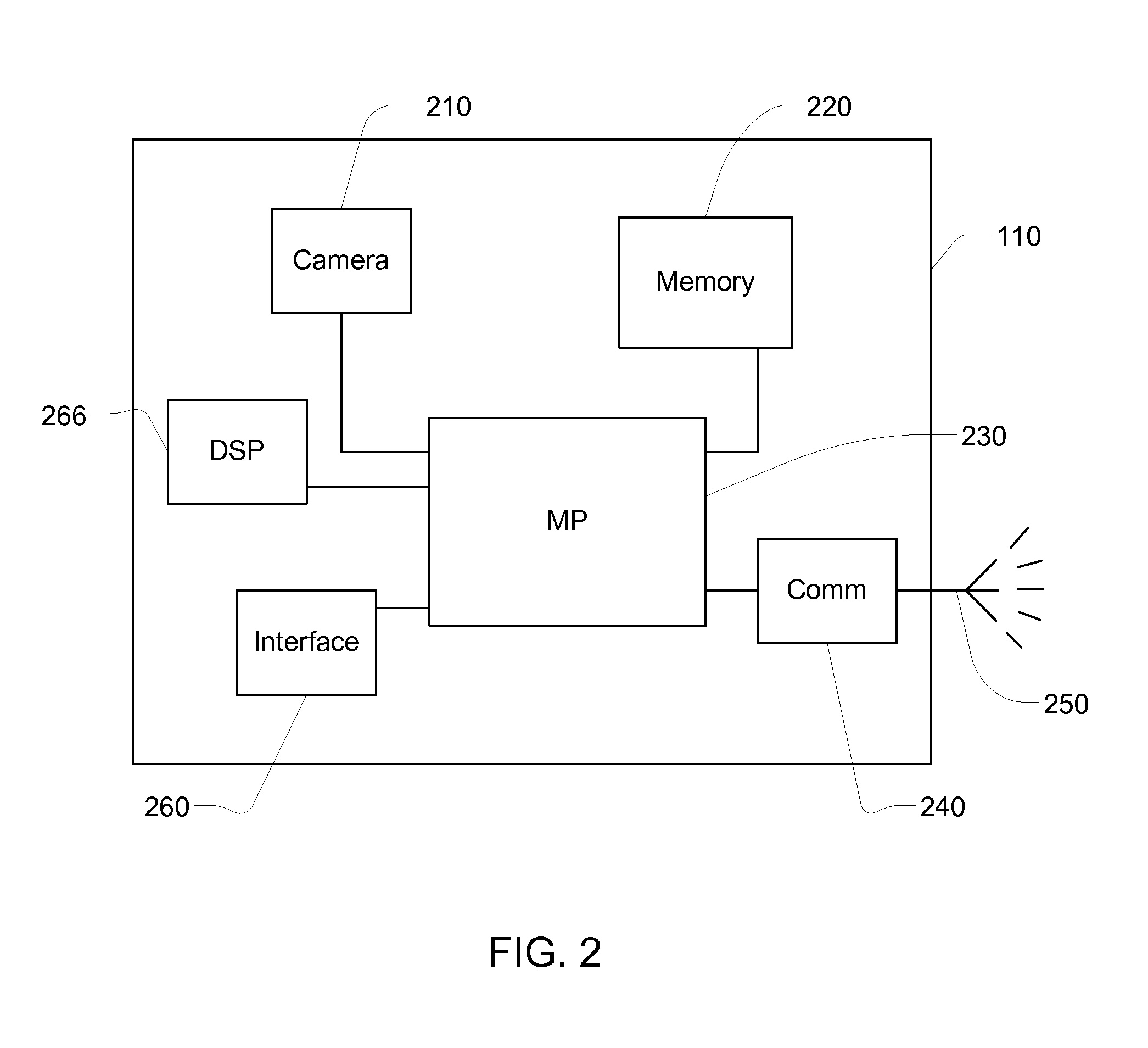
Apparatus and system for prompt digital photo delivery and archival
InactiveUS7173651B1Minimize the numberSimple processTelevision system detailsColor television detailsMessage handlingRemote system
The invention comprises a wireless camera apparatus and system for automatic capture and delivery of digital image “messages” to a remote system at a predefined destination address. Initial transmission occurs via a wireless network, and the apparatus process allows the simultaneous capture of new messages while transmissions are occurring. The destination address may correspond to an e-mail account, or may correspond to a remote server from which the image and data can be efficiently processed and / or further distributed. In the latter case, data packaged with the digital message is used to control processing of the message at the server, based on a combination of pre-defined system and user options. Secured Internet access to the server allows flexible user access to system parameters for configuration of message handling and distribution options, including the option to build named distribution lists which are downloaded to the wireless camera. For example, configuration data specified on the server may be downloaded to the wireless camera to allow users to quickly specify storage and distribution options for each message, such as archival for later retrieval, forwarding to recipients in a distribution list group, and / or immediate presentation to a monitoring station for analysis and follow-up. The apparatus and system is designed to provide quick and simple digital image capture and delivery for business and personal use.
Owner:FO2GO
Apparatus and method for delivering information to an individual based on location and/or time
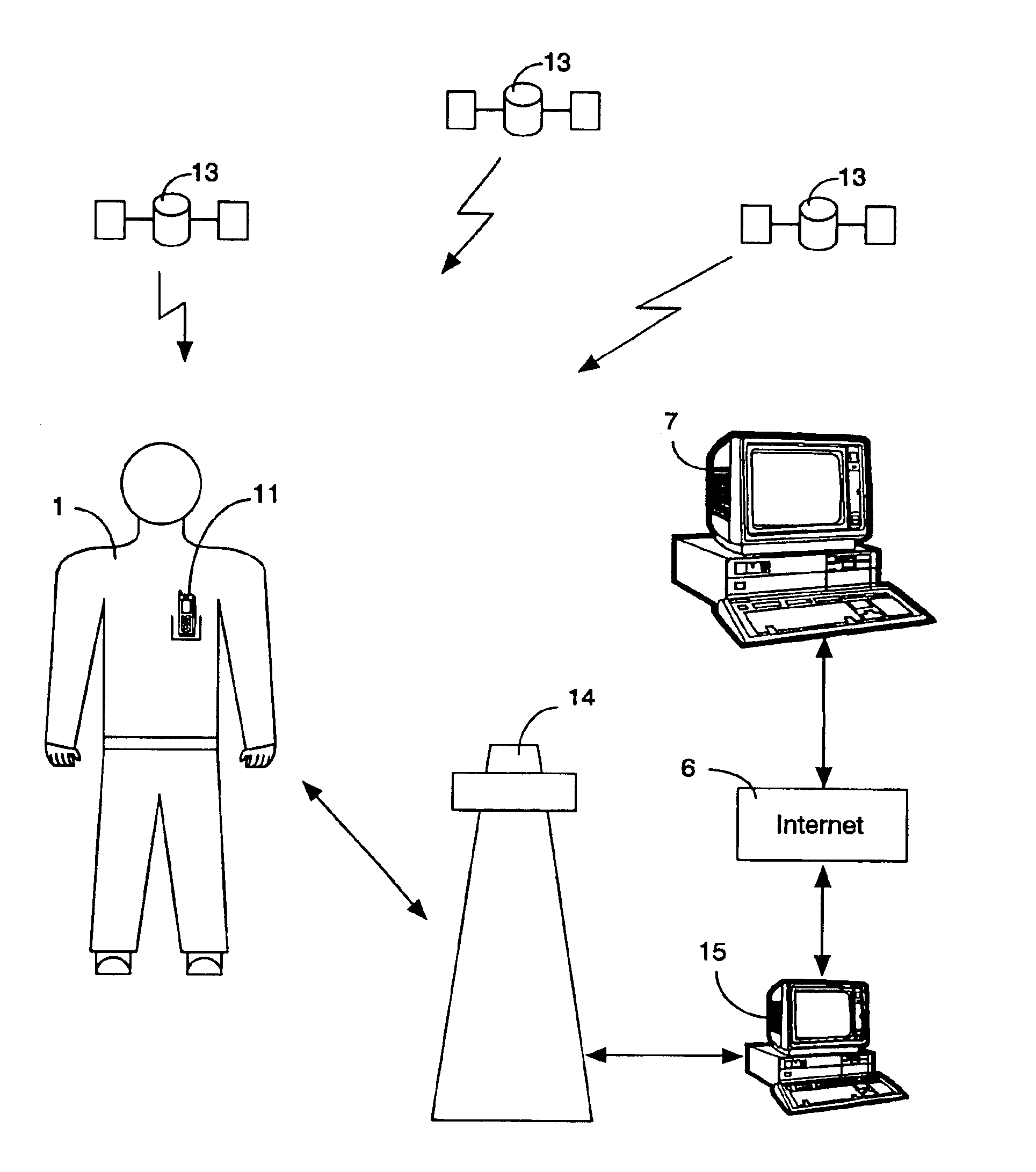
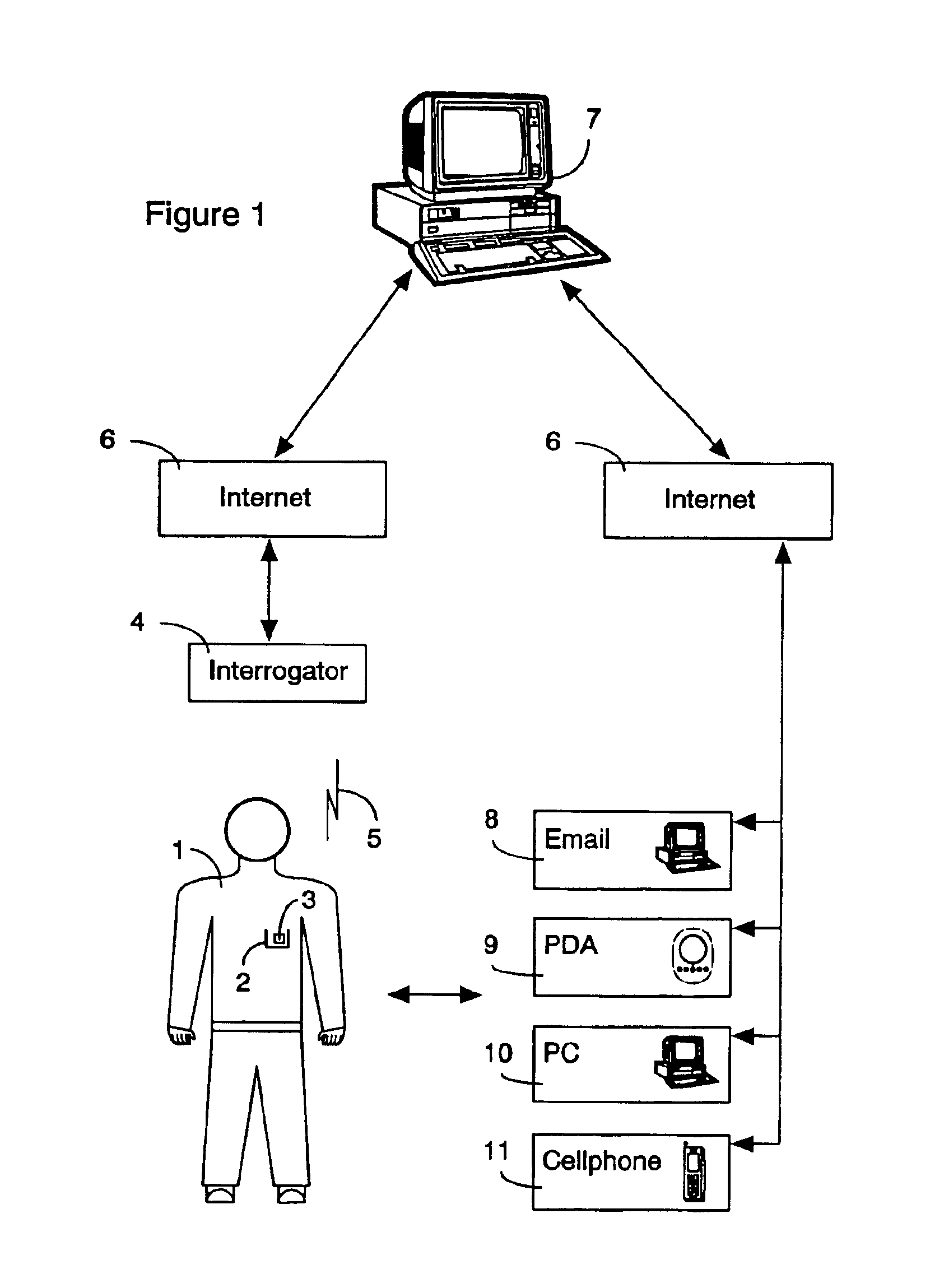
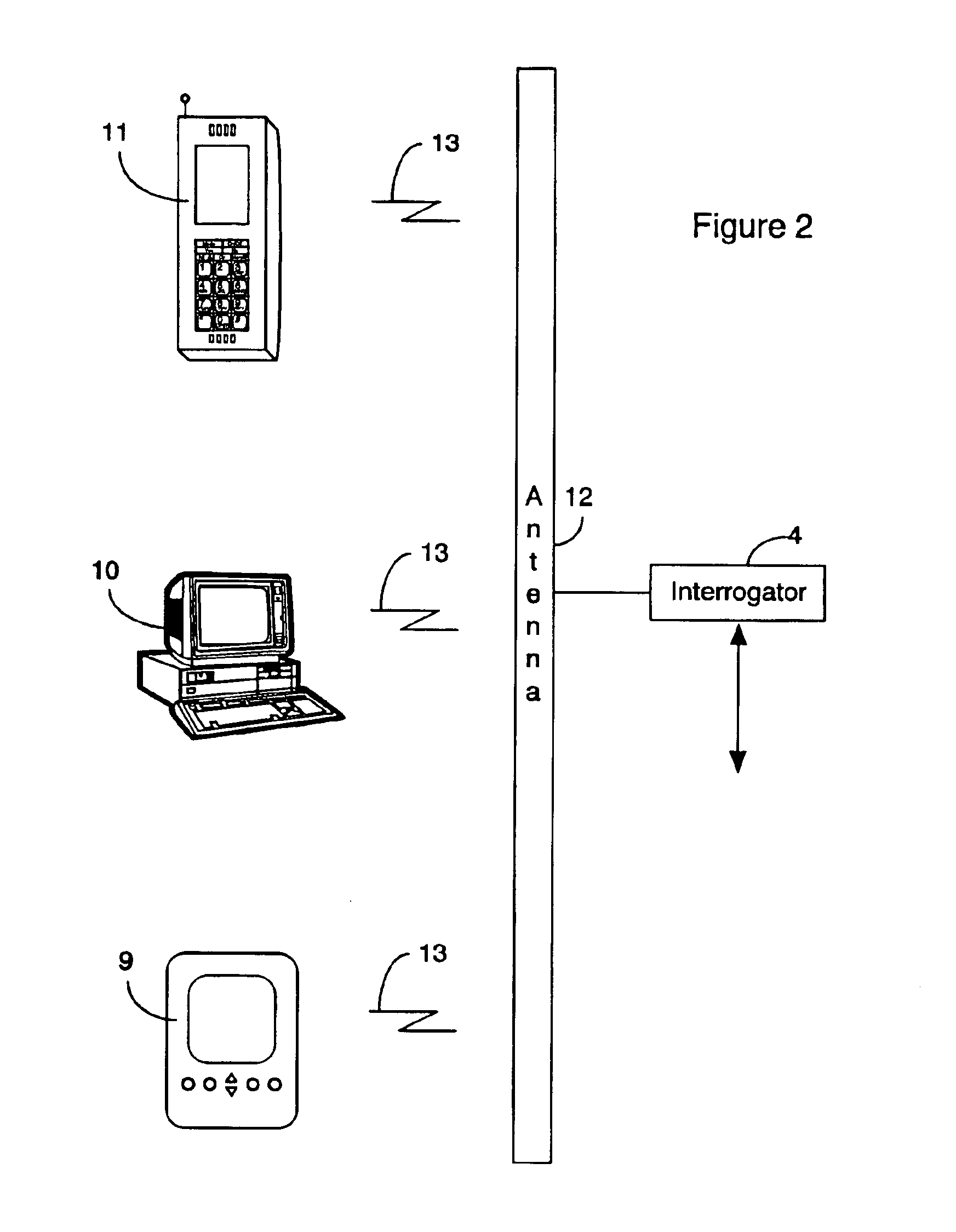
InactiveUS6912398B1The location information is accurateWireless commuication servicesMarketingPagerThe Internet
A time / location information delivery system that provides focused advertising and / or other information to individuals based on the time and their location. A wireless identification device is carried by an individual and can be read from or written to when the individual passes by interrogators in a specific geographic location. The detectors read ID information embedded in the wireless identification device. A computer uses the ID and location information to select, from a list of information providers, those information providers which provide information content identifiable or correlated to a location and / or time, and is of interest to the individual. The information content can be forwarded to the individual by a variety of information channels. One channel uses conventional Internet email to deliver advertisements and other information to the individual's Internet mailbox. The email can be delivered to a conventional PC, a portable computer, a PDA, an intelligent telephone, pager or other suitable device. For ease of discussion, a pager and a PDA will be referred to collectively as a PDA. The wireless identification device can be an RFID tag embedded in a card, or even a wireless telephone. The RFID tag is read or written to by fixed interrogators and the location of the wireless telephone is detected by triangulating information from cell towers or by embedding the GPS receiver in the wireless telephone thereby providing the location information directly from the telephone. Of course, other nearly identical location determination means, such as quadrangulation could also be used. The location determination can be performed through similar means with other devices such as PDAs, laptops, pagers, etc.
Owner:CDN INNOVATIONS LLC +1
System and methodology for optimizing delivery of email attachments for disparate devices
InactiveUS20020016818A1Digital data information retrievalMultiple digital computer combinationsDevice typeWireless handheld devices
An e-mail system that re-packages message attachments optimized for delivery to wireless handheld devices is described. The preferred embodiment provides an optimization of the e-mail deliveries to allow for the recipients to receive e-mail attachments at a time and in a size / format as desired. The preferred embodiment compares the size of attached images to the capabilities of the type of the recipient client device, and preempts delivery of the original format of those attachments if they are determined to be burdensome or overwhelming. In cases wherein these attachments would strain the capabilities of the recipient devices' wireless bandwidth and / or display features, the original attachments are removed from the messages and do not accompany the e-mail delivery. Any detached attachment is saved in a network media-sharing repository, and can be subsequently accessed via a link (e.g., URL) referencing that storage address. Recipients can specify their wireless handheld device types, and opt to receive transformations of this type of attachment as a default substitute in subsequent e-mail deliveries. In cases wherein the recipient has previously used multiple types of client devices when receiving messages from the system, the present invention applies a transformation on the current attachment that corresponds to the least capable in the set of those multiple devices. Recipients may also elect to receive the URL for the network storage address of copies of either the original and / or transformed attachments.
Owner:SYNIVERSE ICX CORP
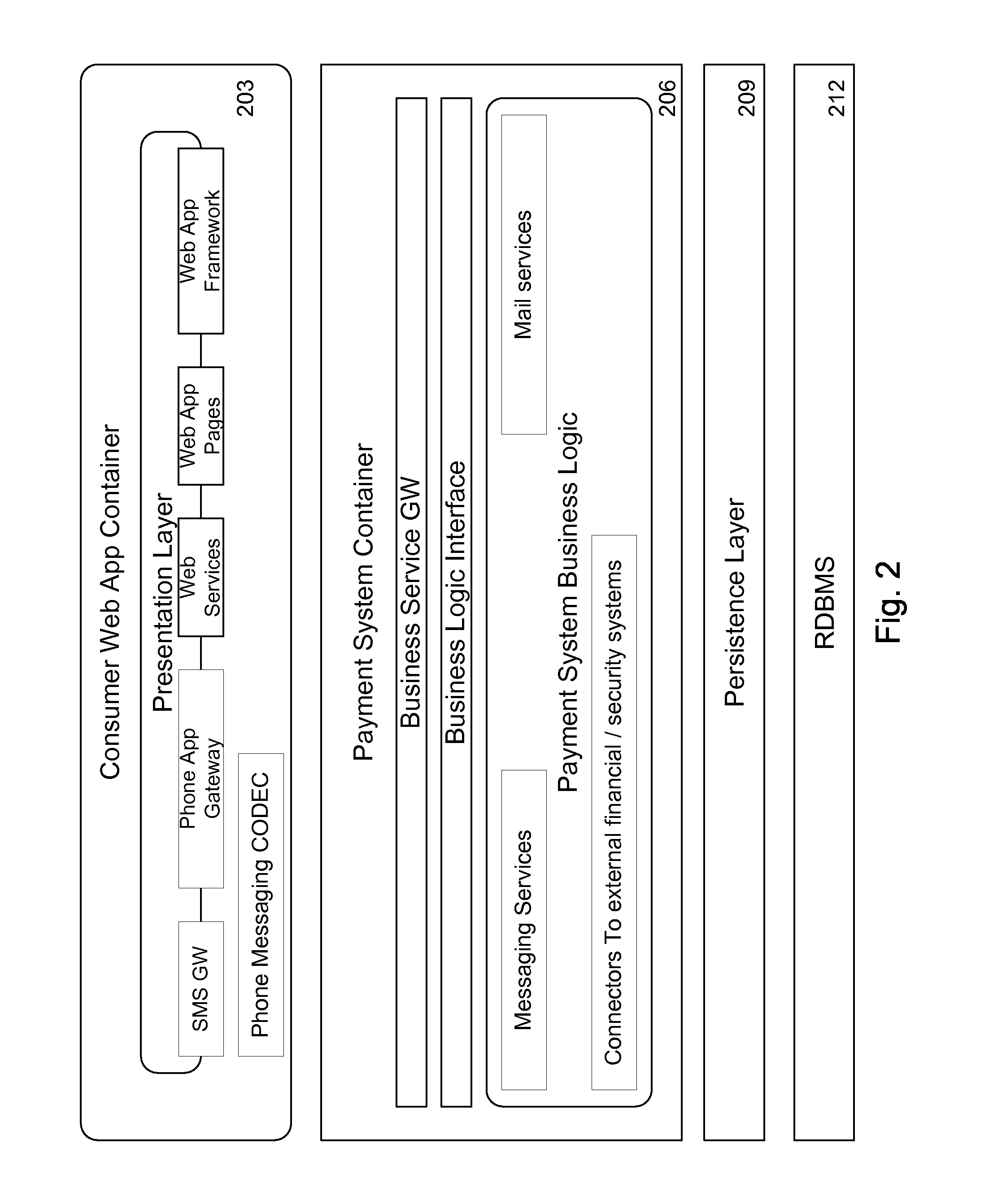
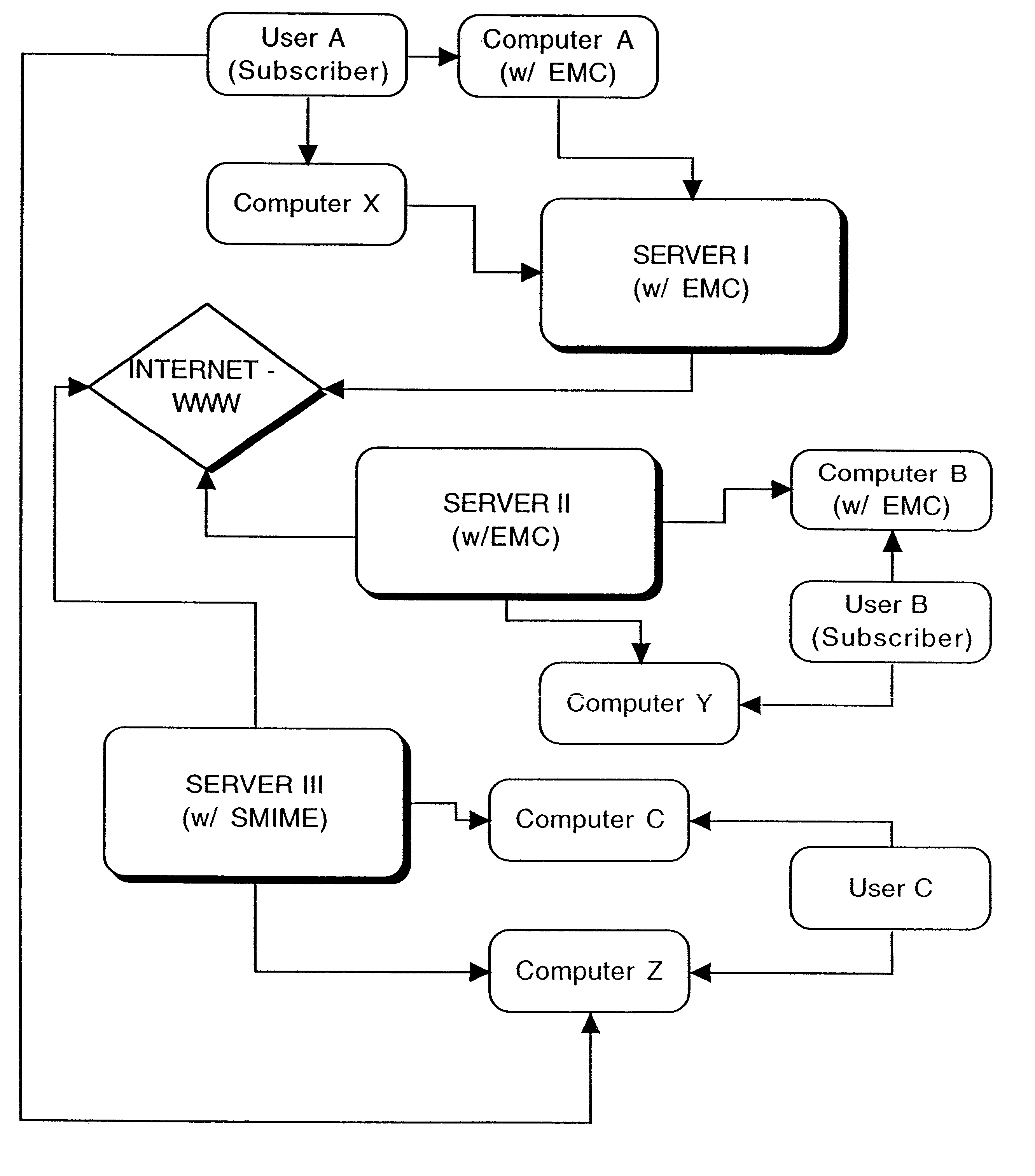
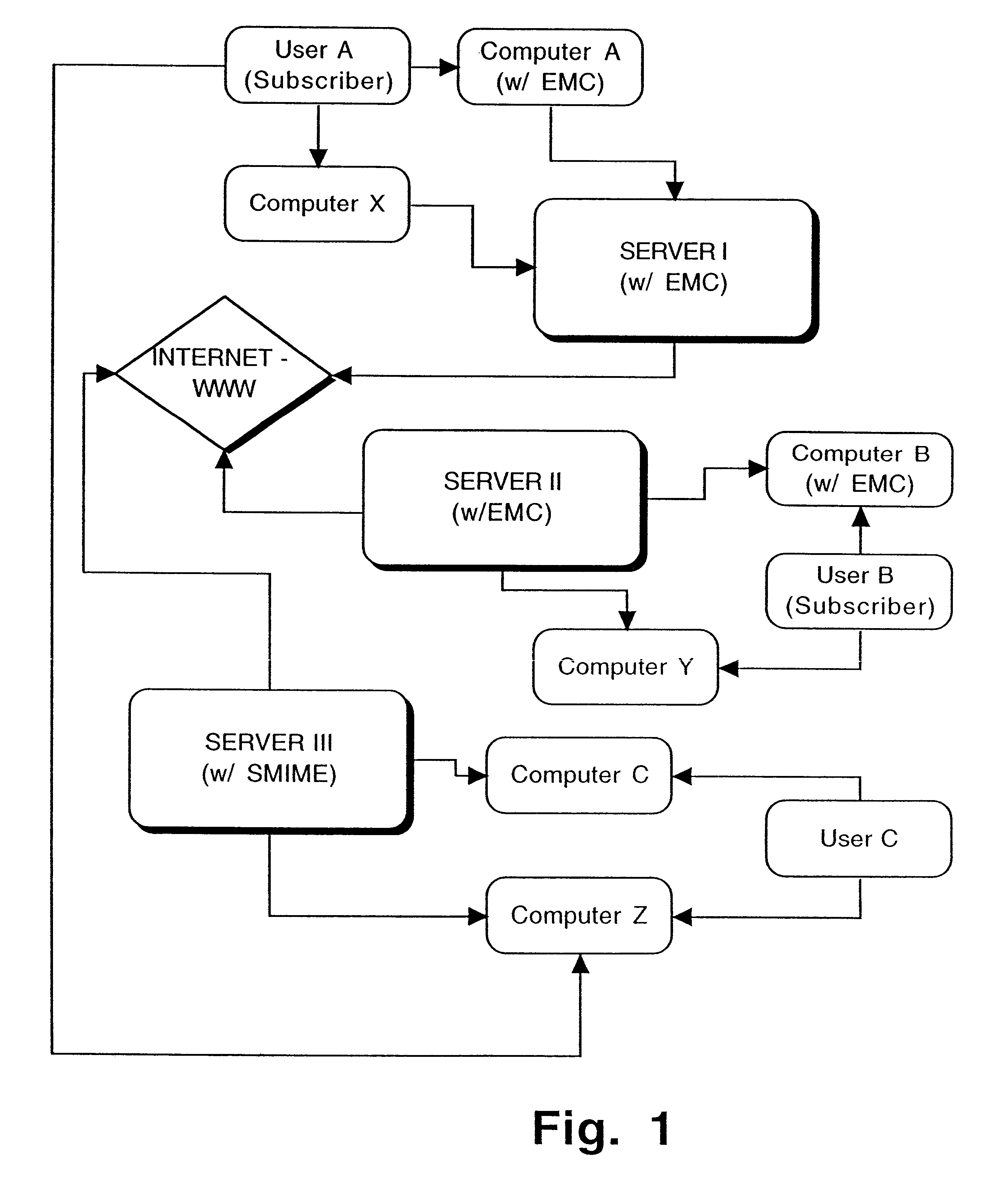
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
System and method for creating and delivering customized multimedia communications
InactiveUS20030191816A1Unprecedented personalization, expression and advertising opportunitiesMultiple digital computer combinationsMarketingPersonalizationGraphics
A system and business methodology for providing interactive and customizable digital full-motion, animated and static multimedia content, to be used for communicating unique personalized entertainment, information, and messages and advertising to be delivered via the internet, electronic mail, or any other methods of delivering interpersonal communications and messages. The communications and messages are initiated and received by senders and recipients visiting a host site of the system through the internet. Content within the customized communication includes content personally relevant to a user which is integrally associated with sponsorship or advertising information. Creation of a customized communication begins by selection of a content item by a user, which content may be personalized by graphical editing techniques. Personalized or non-personalized content may be executed in parallel or in series with other content items in a multilinear playback sequence compiled according to a predetermined script to produce a finished customized multimedia communication. The host site also provides other features and products desirable to users, such as screensavers, reminder services, etc.
Owner:SPOOVY
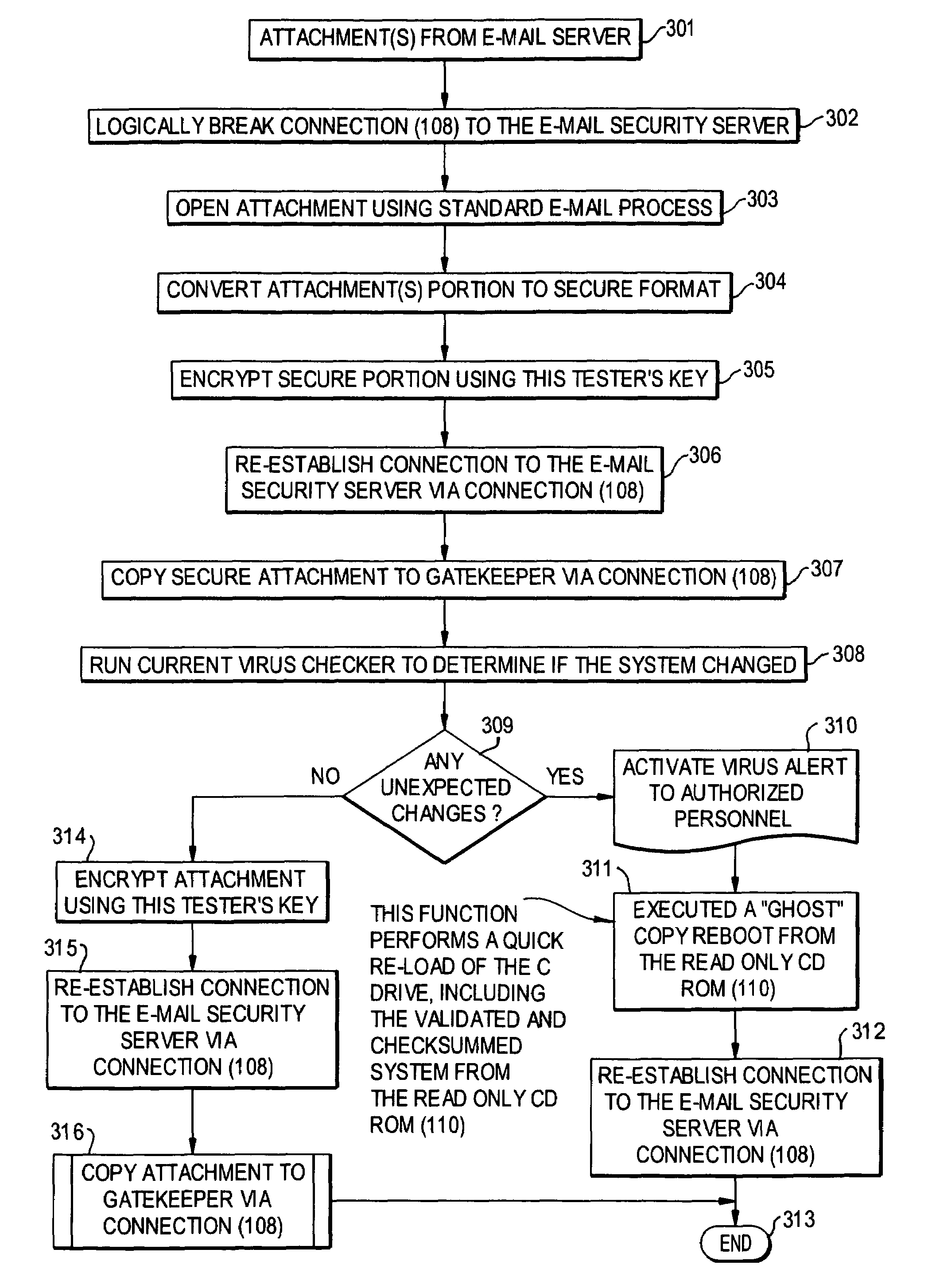
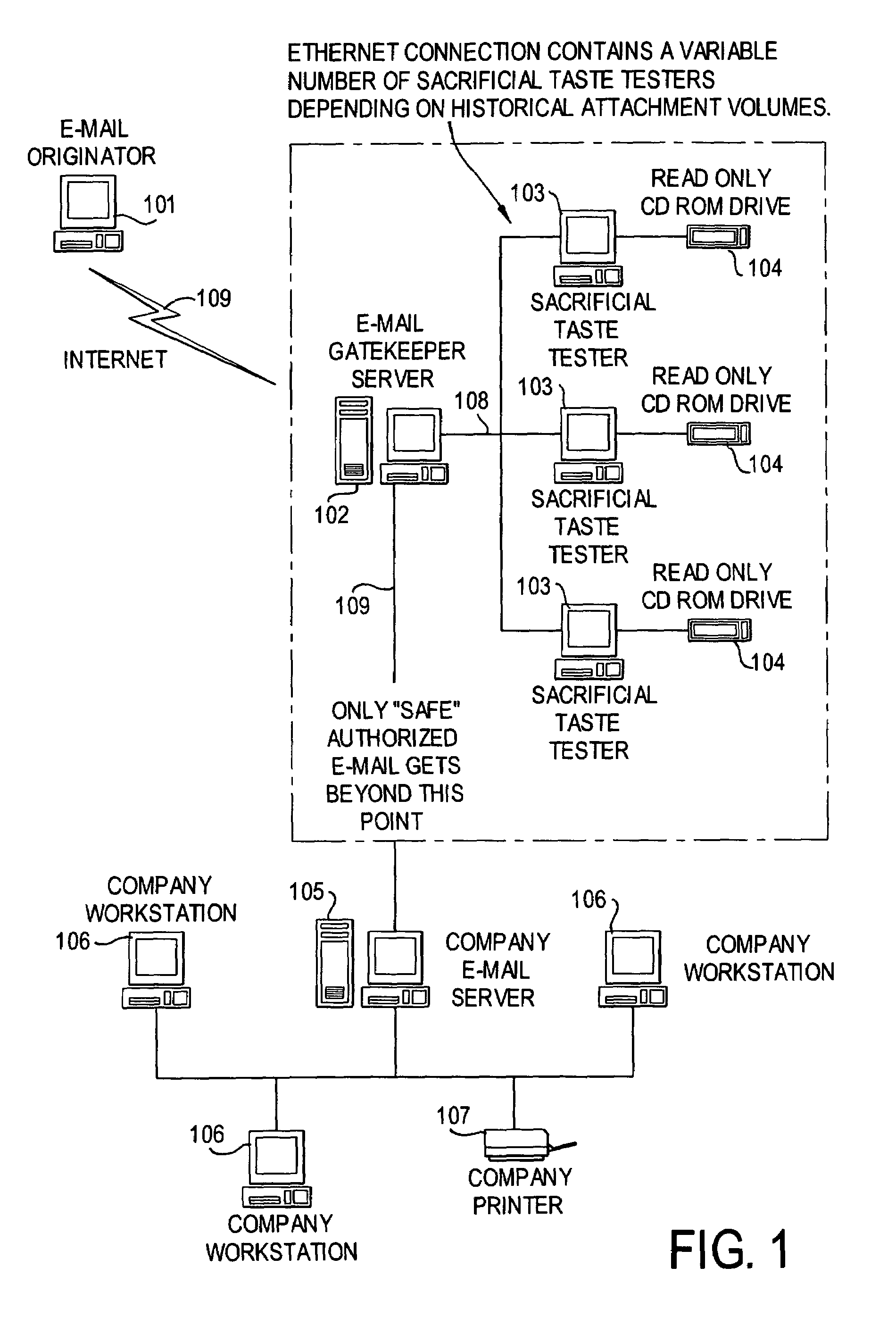
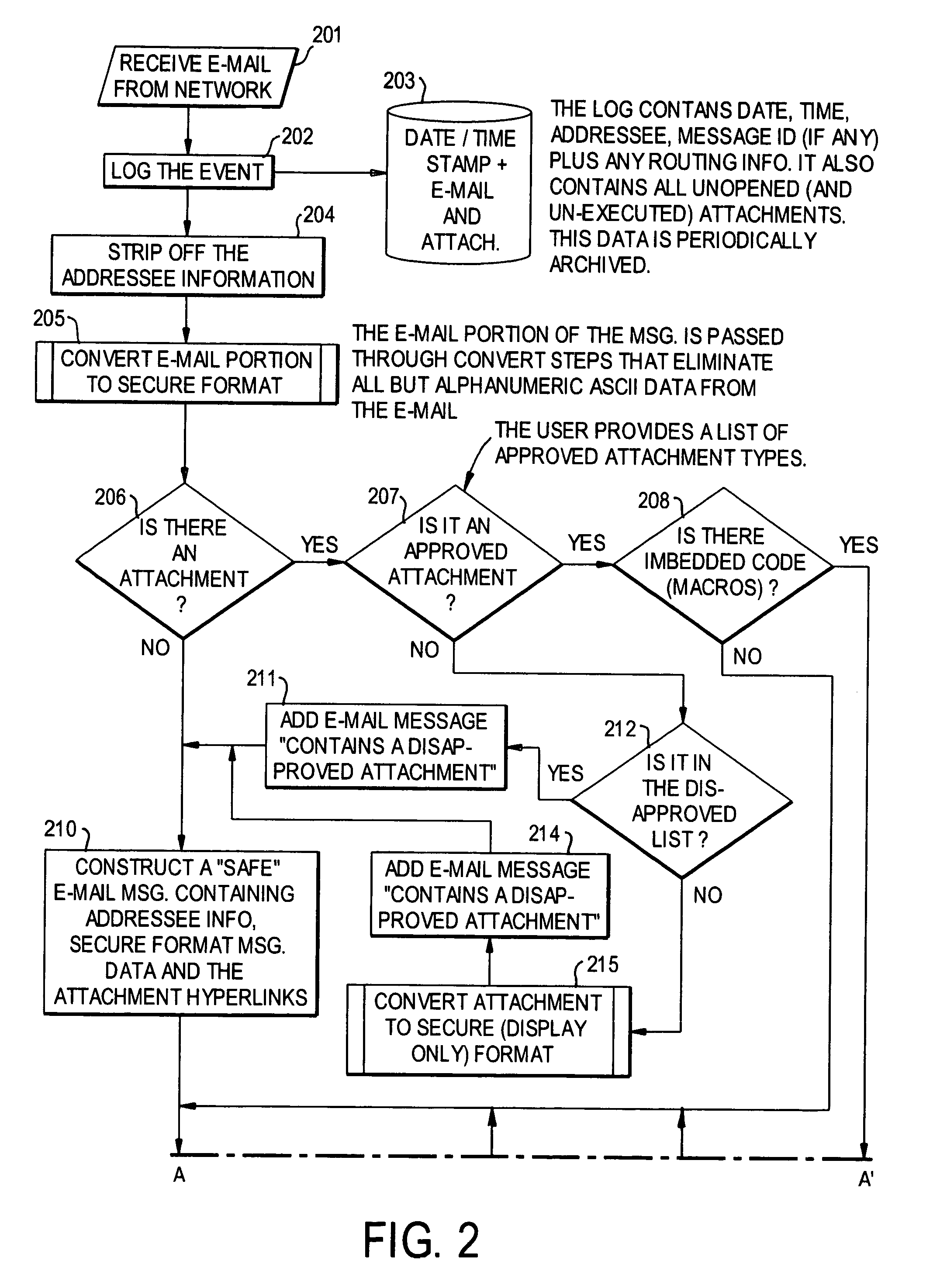
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
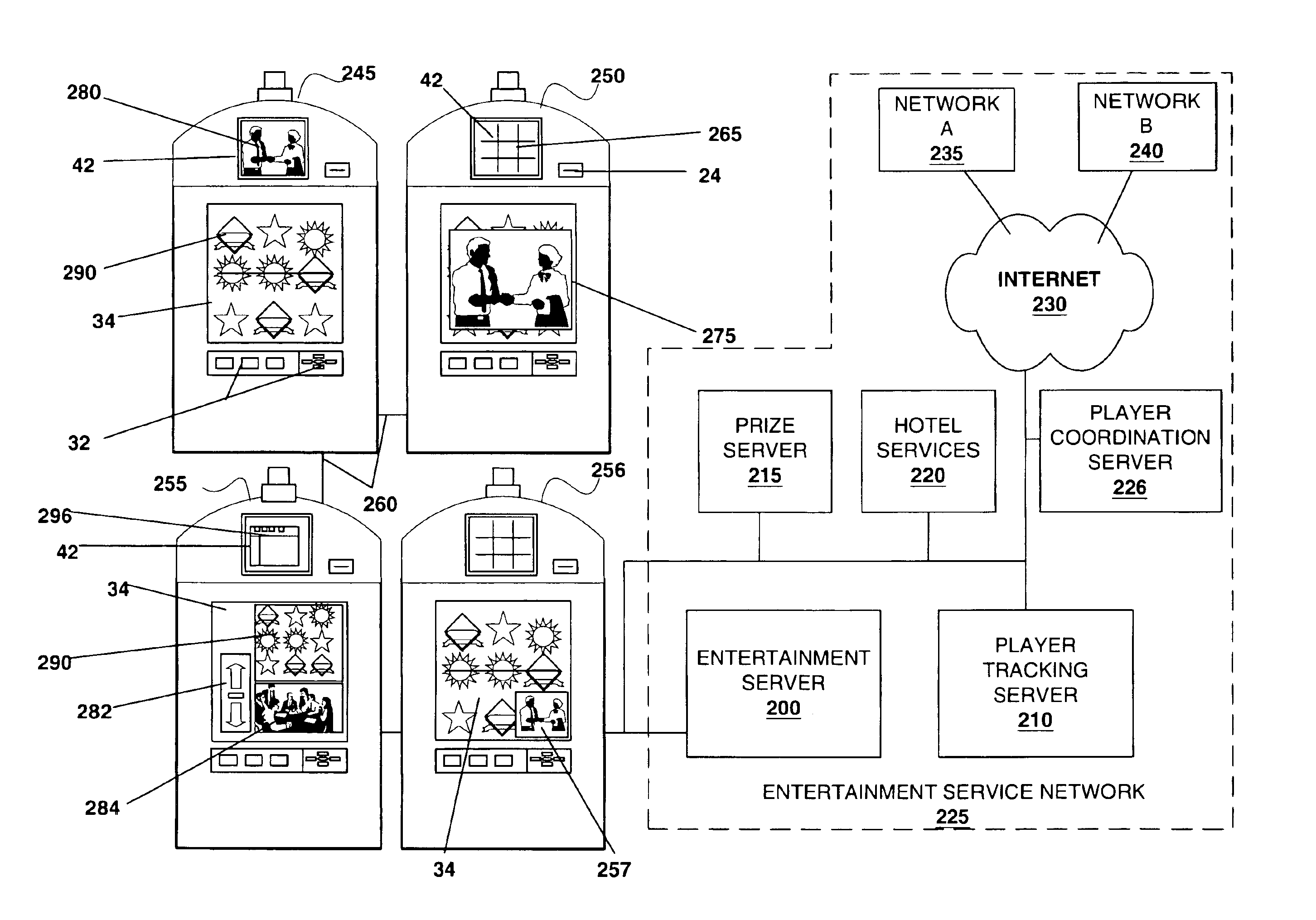
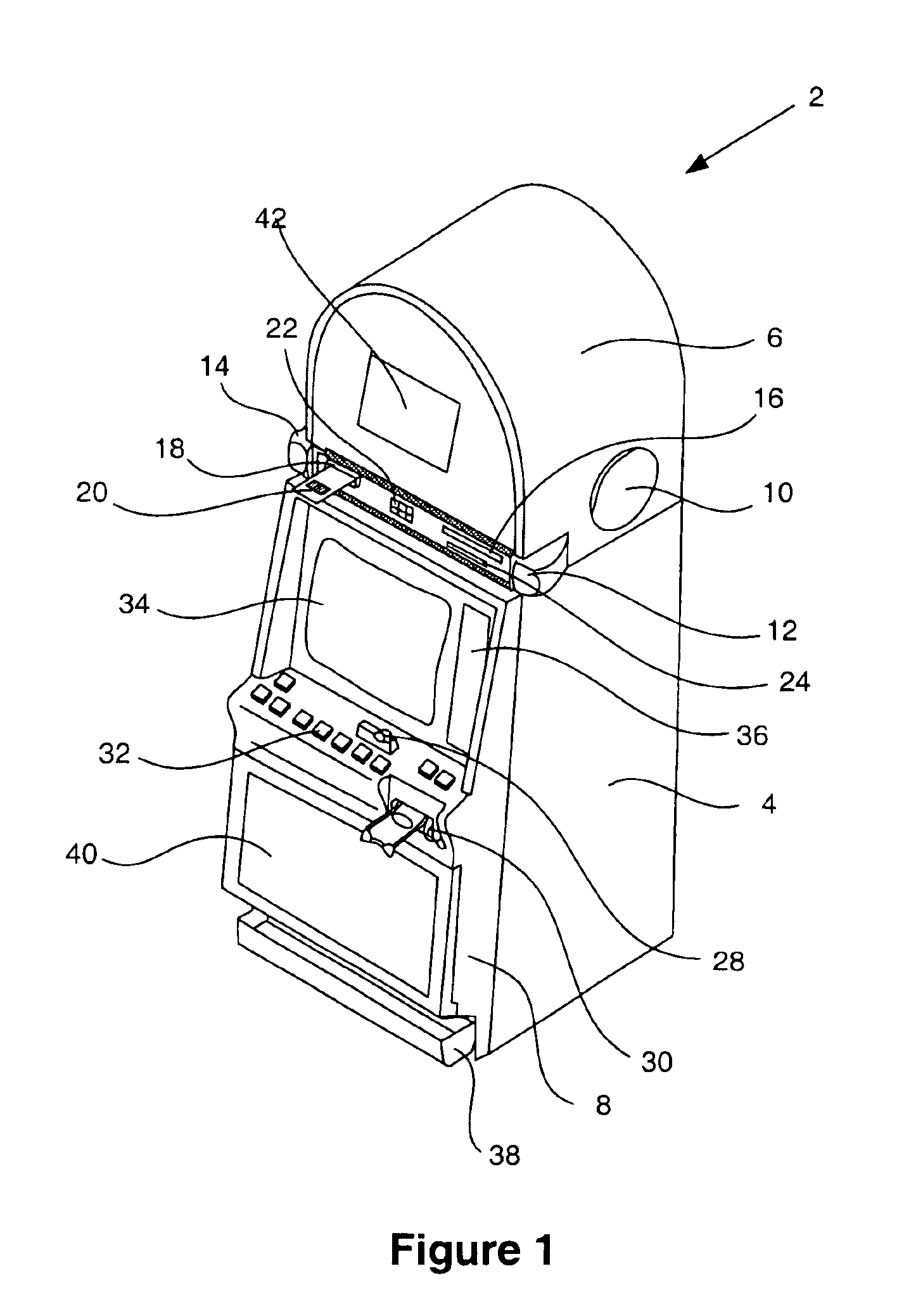
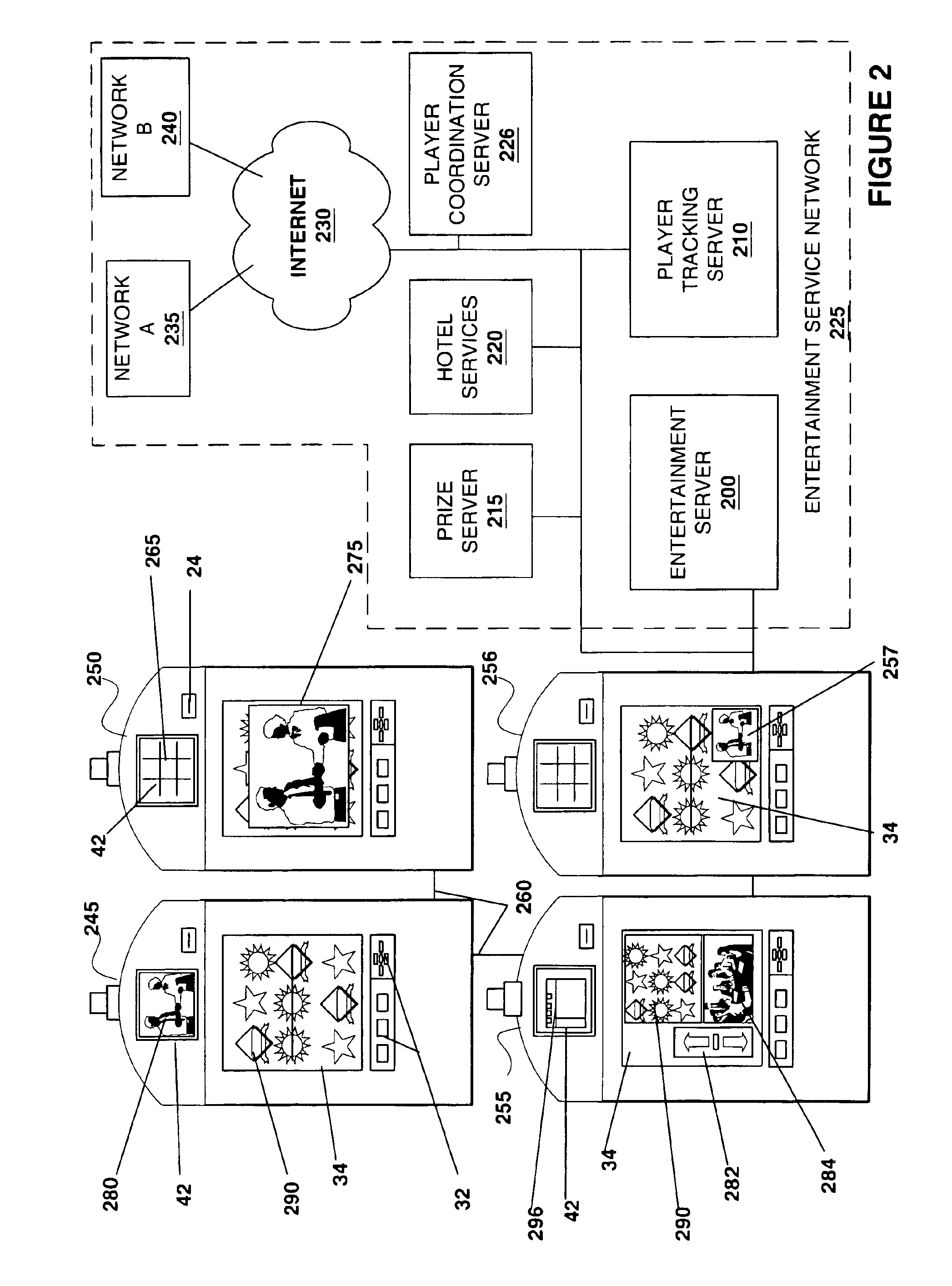
Method and apparatus for providing entertainment content on a gaming machine
A gaming machine with devices able to output entertainment content (e.g. movies, TV programming, audio programs and advertising) from entertainment content sources located within the gaming machine or outside of the gaming machine is described. A player utilizing the gaming machine may access, independently of game play, entertainment content on the gaming machine where access to the entertainment content is granted according to a predetermined fee. In addition, the player utilizing the gaming machine may receive personal messages on the gaming machine. For example, while utilizing the gaming machine, a player may receive, e-mail, stock quotes, news and advertising that is of particular interest to the player utilizing the gaming machine.
Owner:IGT
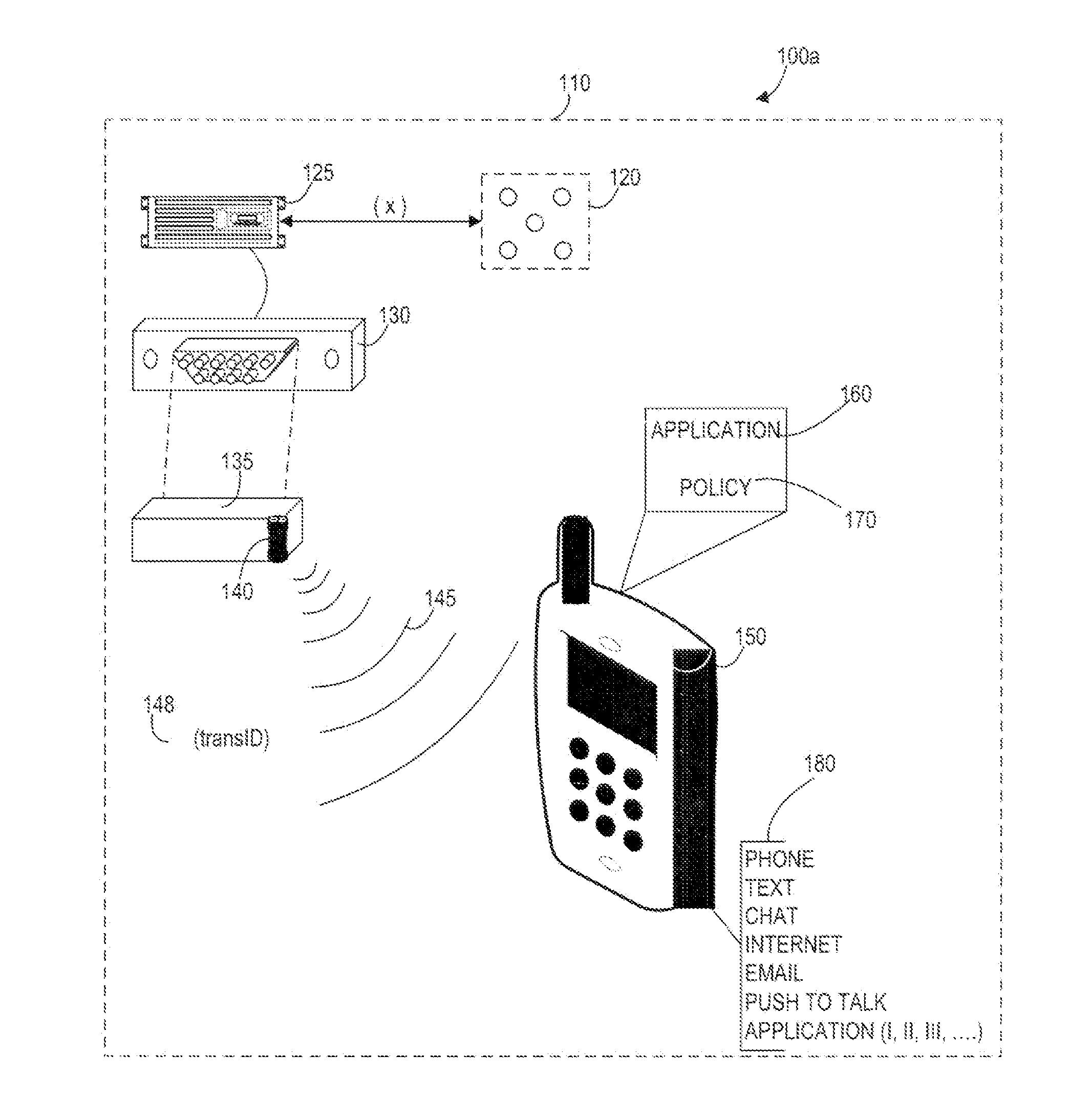
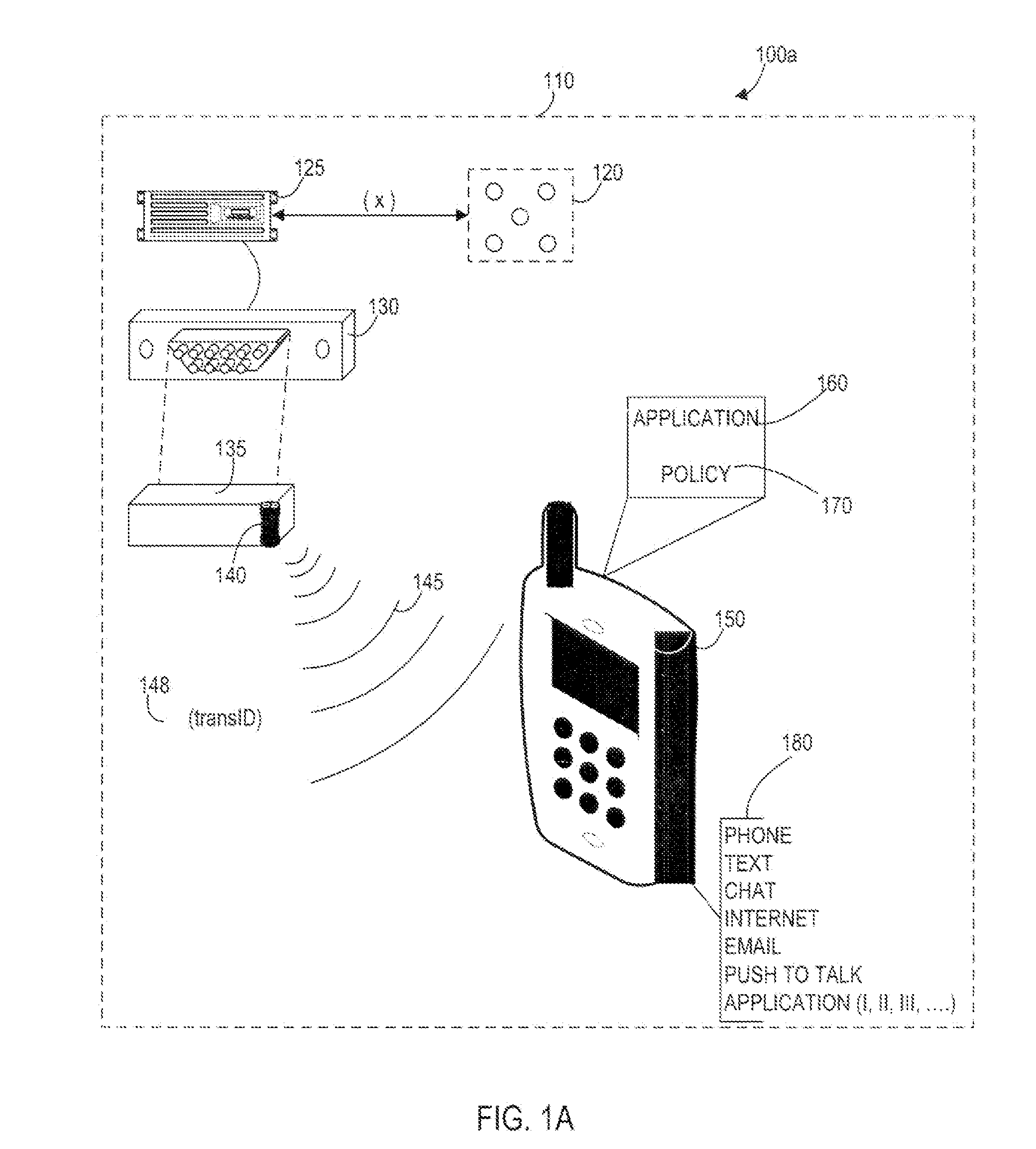
Systems, Methods, And Devices For Policy-Based Control and Monitoring of Use of Mobile Devices By Vehicle Operators
ActiveUS20110009107A1Reduce the cost of insuranceSpecial service provision for substationRoad vehicles traffic controlMobile vehicleOn board
Systems, methods, and devices for controlling and limiting use of functions, such as calling, texting, chatting, emailing, Internet surfing, and similar applications, on a mobile device when the mobile device is in a moving vehicle, includes use of an on-board computer installed within the vehicle, a transmitter in electronic communication with the on-board computer that periodically transmits speed data of the vehicle to a receiver installed on the mobile device, wherein the mobile device includes suitable software and a rules-based policy that define and control when and which functions of the mobile device are disabled or interrupted by the software when the vehicle is in motion above a minimum threshold speed. Policies are set by default but may be customized for particular individuals, devices, or circumstances. Policies may also be customized for particular groups or subgroups of employees or contractors for company or legal compliance to reduce distracted driving.
Owner:WESTERN ALLIANCE BANK
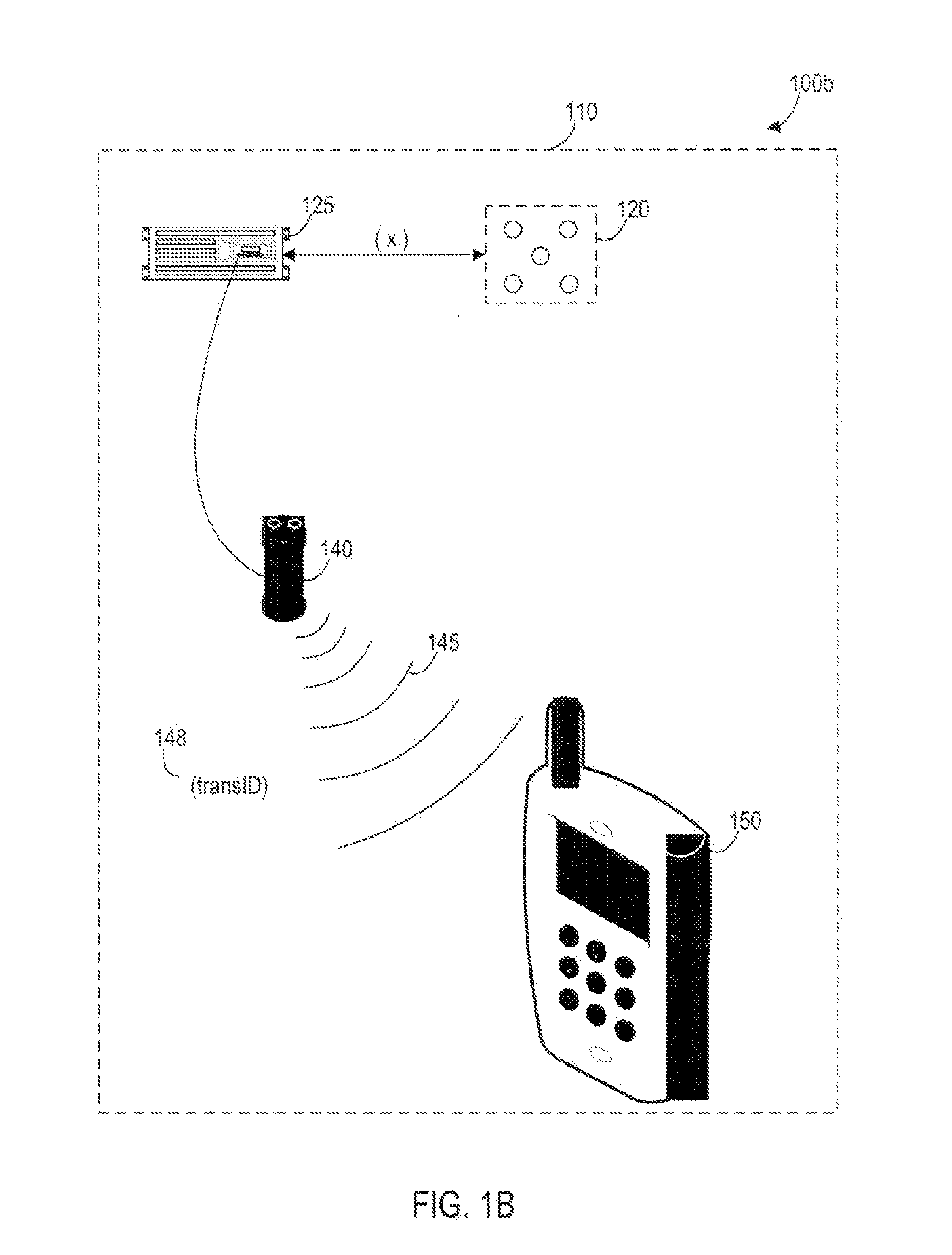
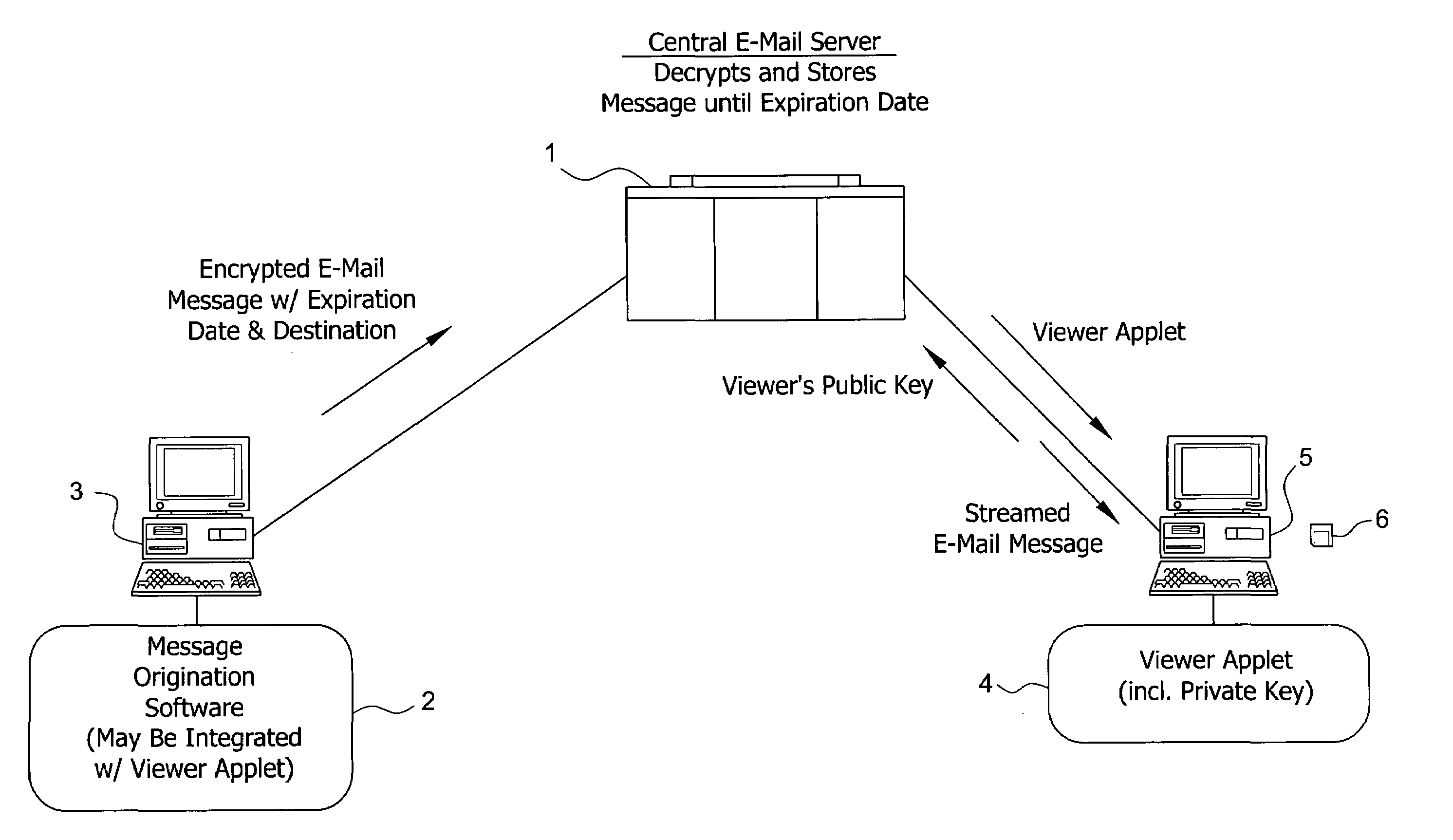
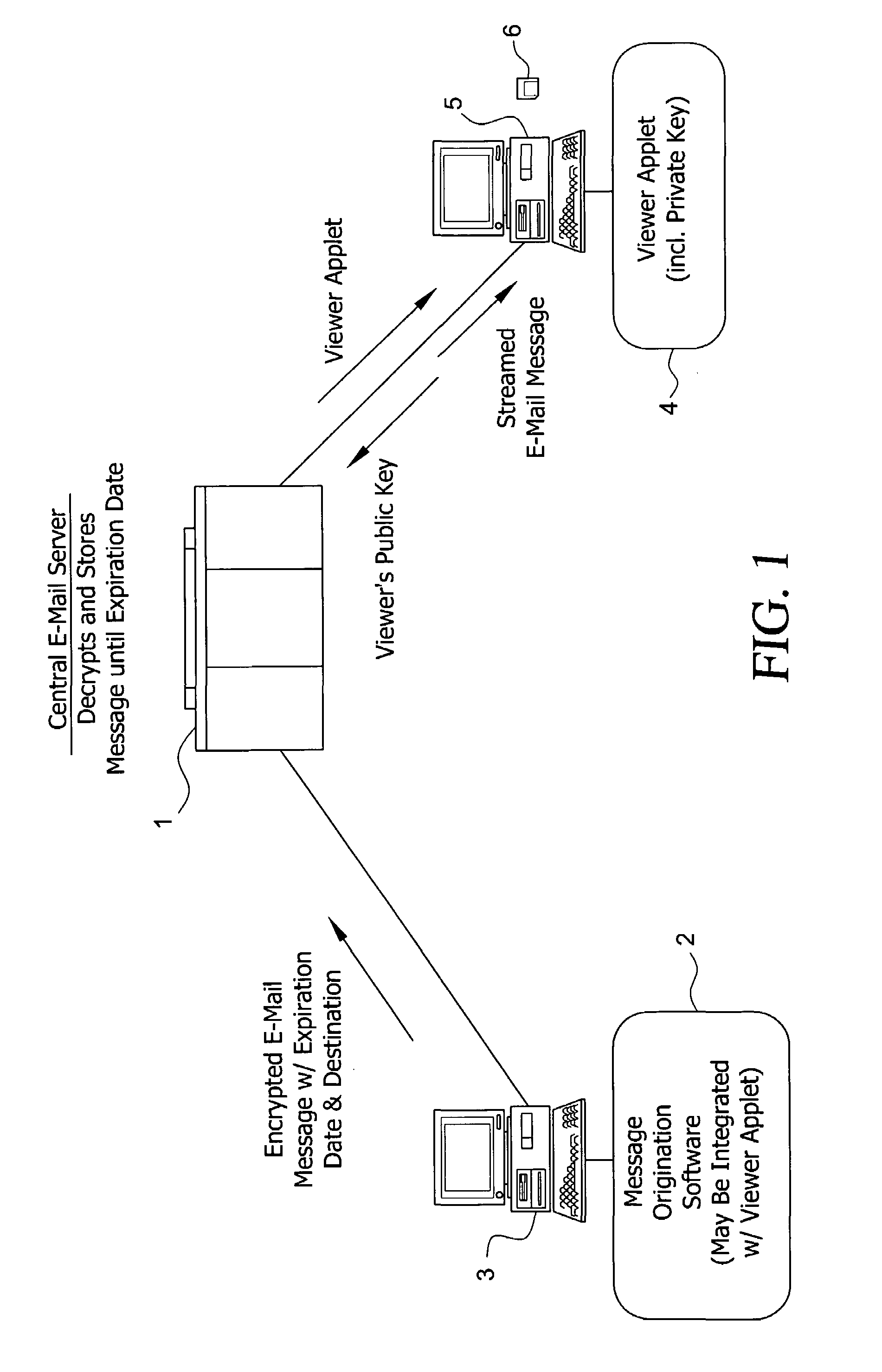
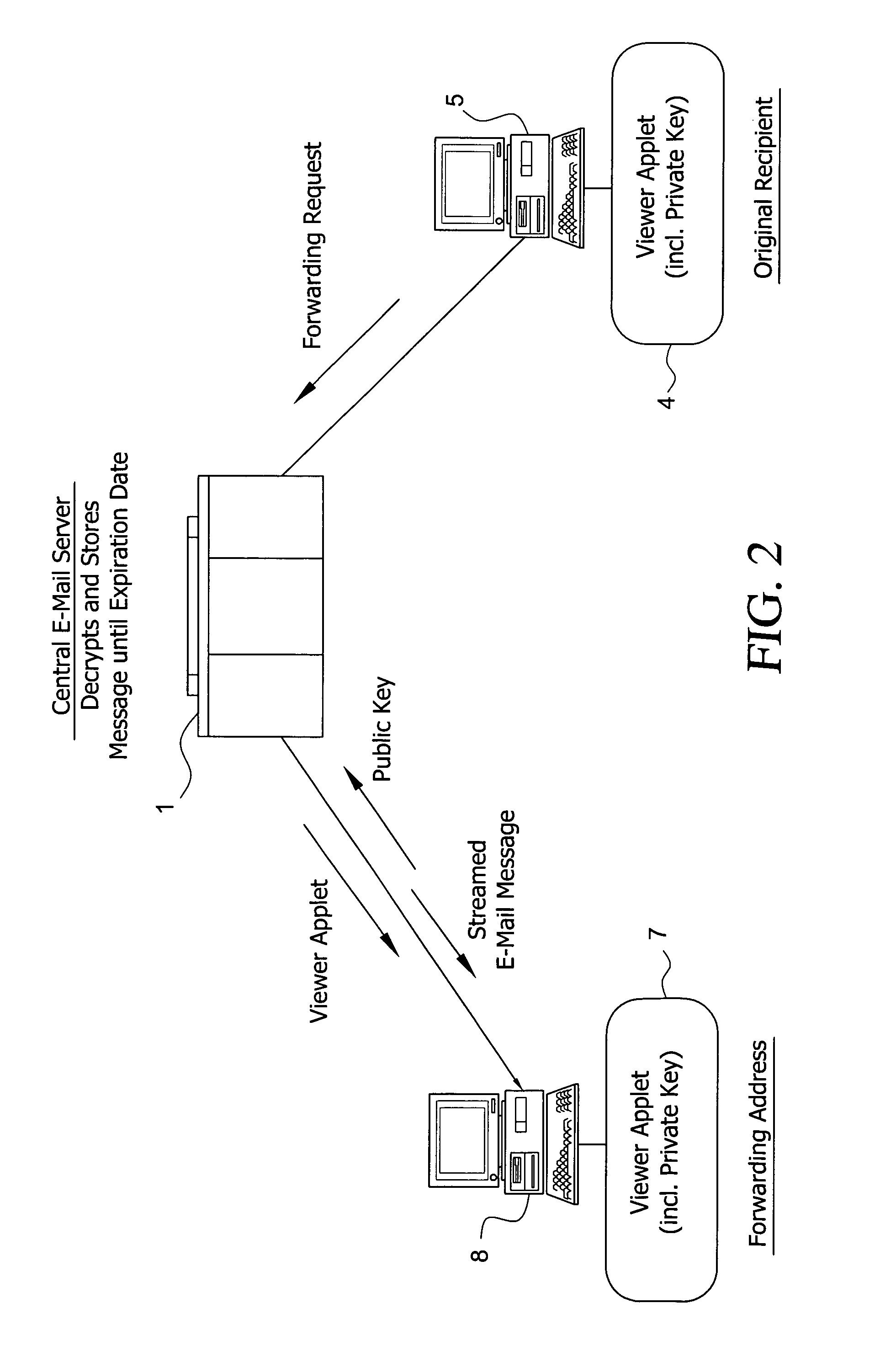
System and method for enabling the originator of an electronic mail message to preset an expiration time, date, and/or event, and to control processing or handling by a recipient
InactiveUS7149893B1Limited lifespanRapid and efficient mannerDigital data processing detailsAnalogue secracy/subscription systemsExpiration TimeComputer hardware
An electronic mail system and method enables the originator of a message sent by electronic mail to select a date, time, or event at which the message and all incarnations of the message to self-destruct, regardless of the number and types of computers or software systems that may have interacted with the message. The system and message also permits the originator to include processing and handling limitations. The necessary control over the message is achieved by encrypting the message and enabling viewing only through a viewer applet arranged to facilitate destruction of the message upon the occurrence of the selected expiration time, date, or event, and to implemented the handling and processing limitations. A central server can be used to exercise additional control over the message by serving as a proxy destination, and by streaming the encrypted message to the viewer applet. The viewer applet can be transmitted to new recipients with the message so that the system and method can direct mail to any electronic mail user.
Owner:RESOURCE CONSORTIUM LTD LLC
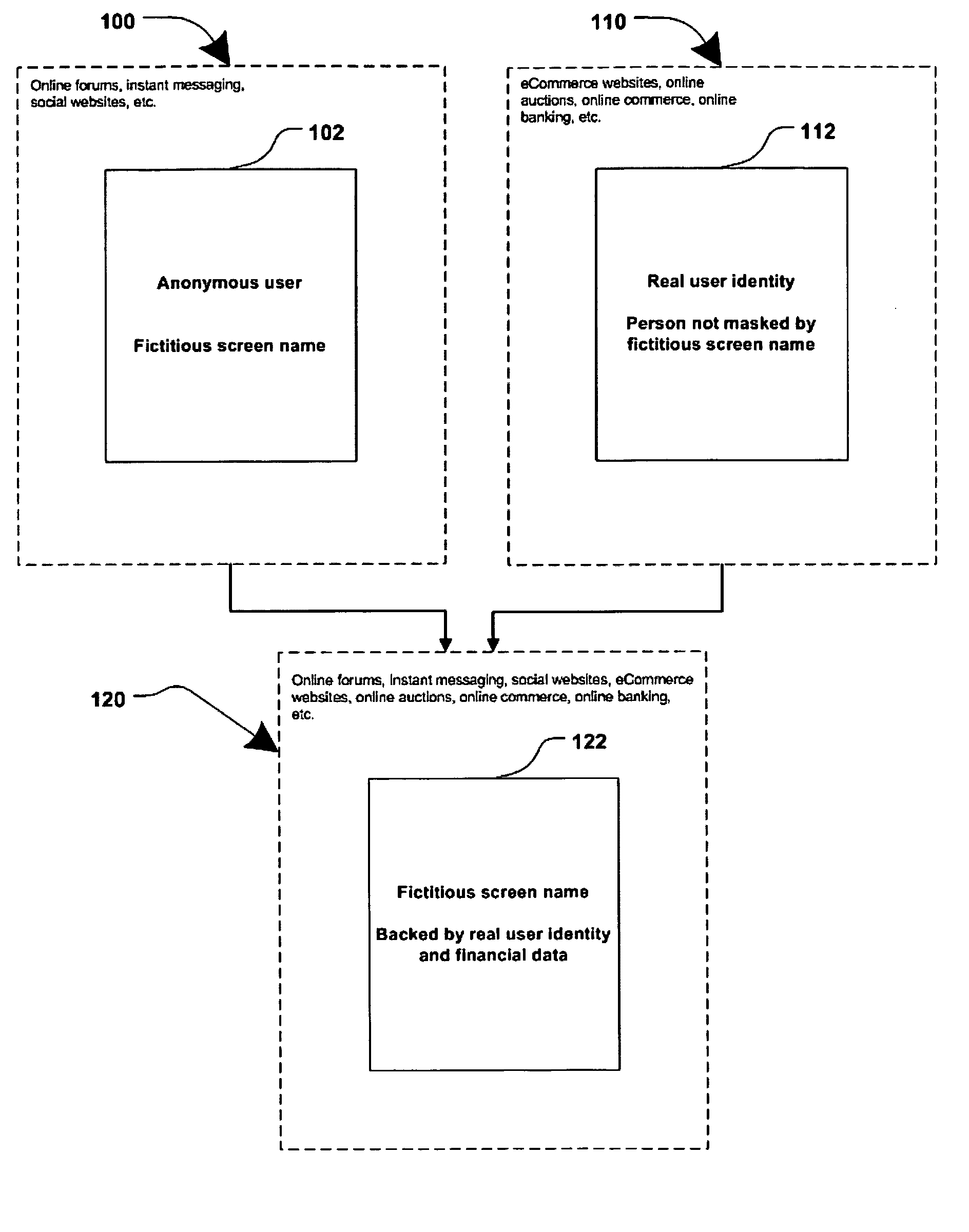
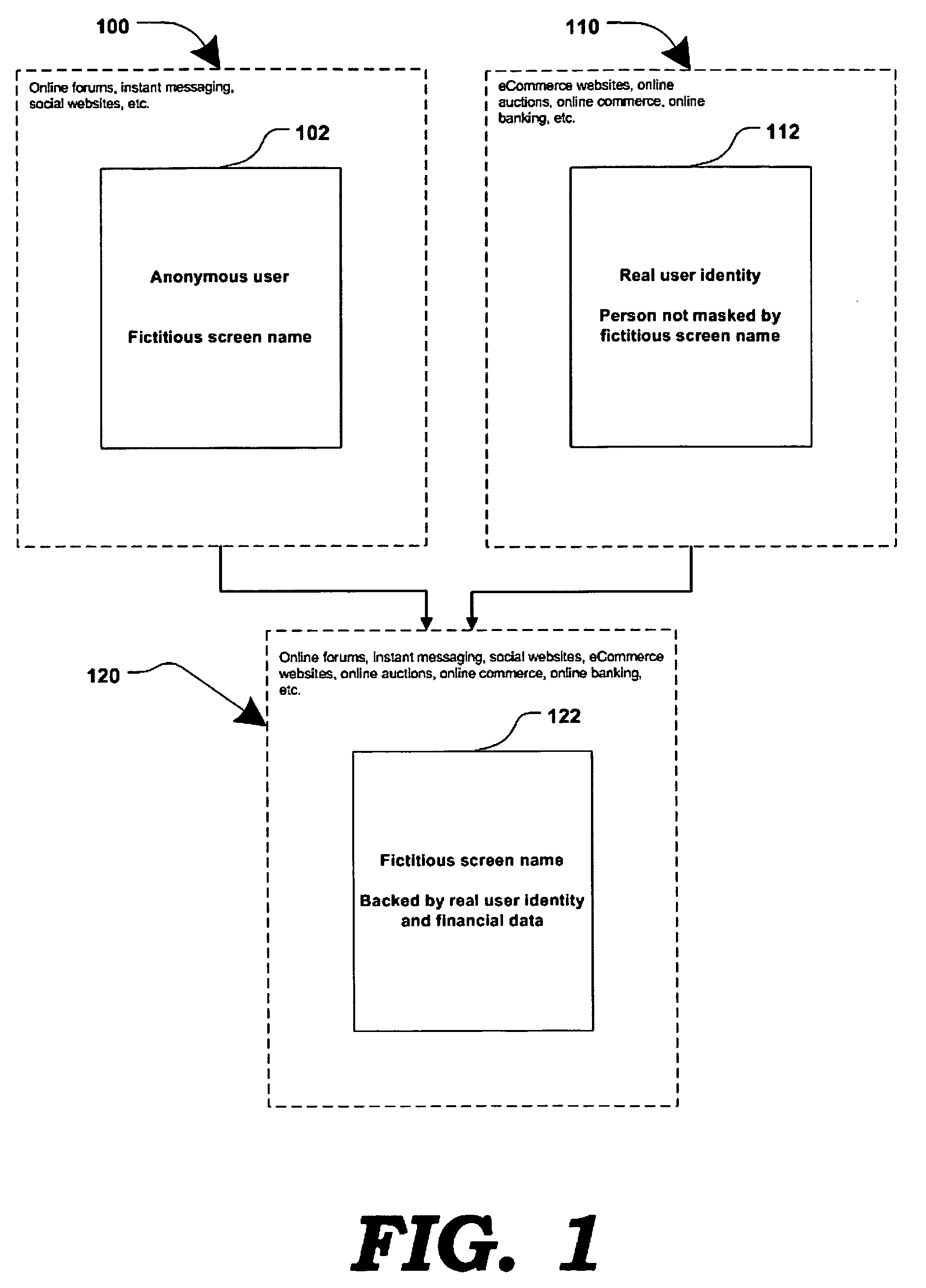
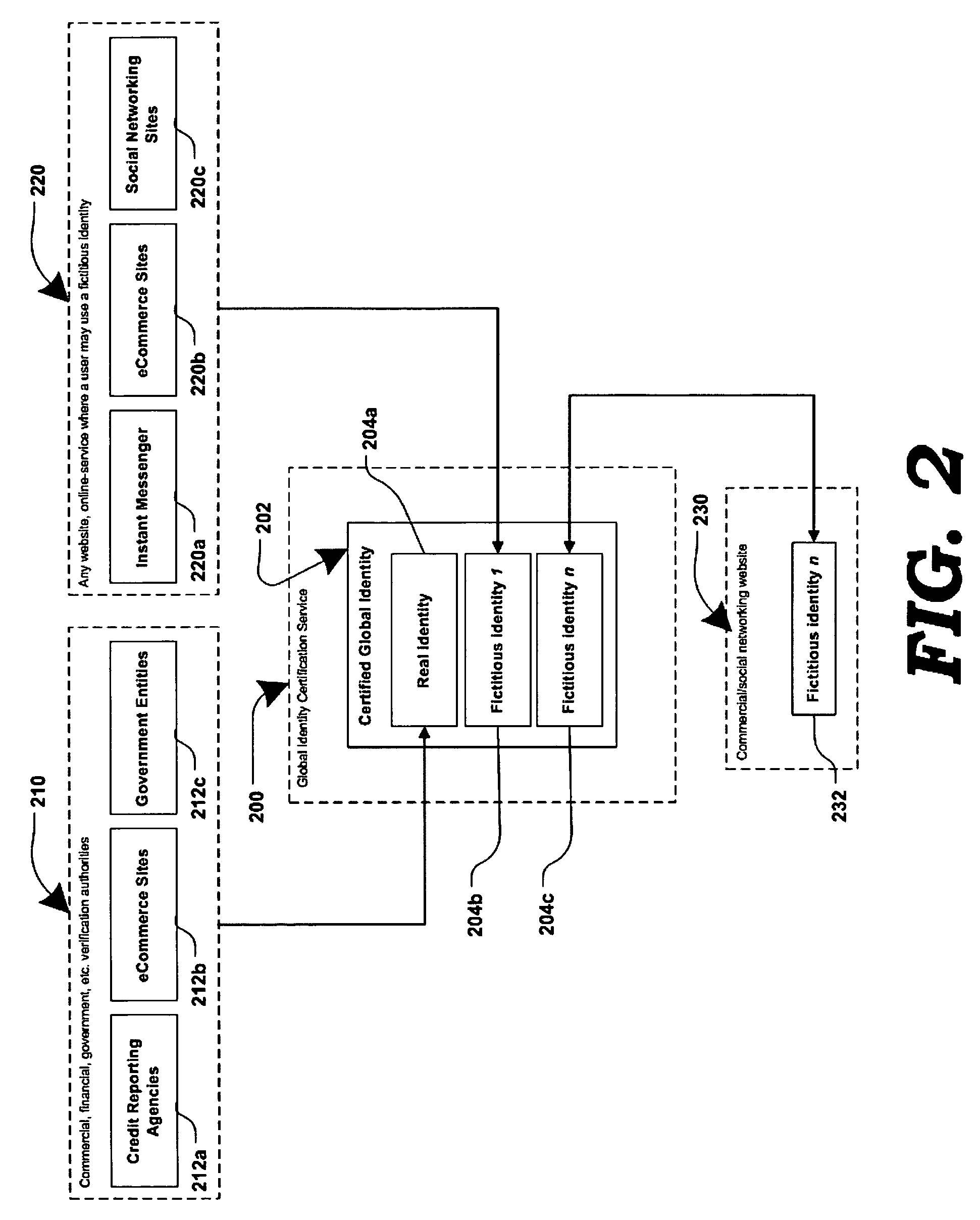
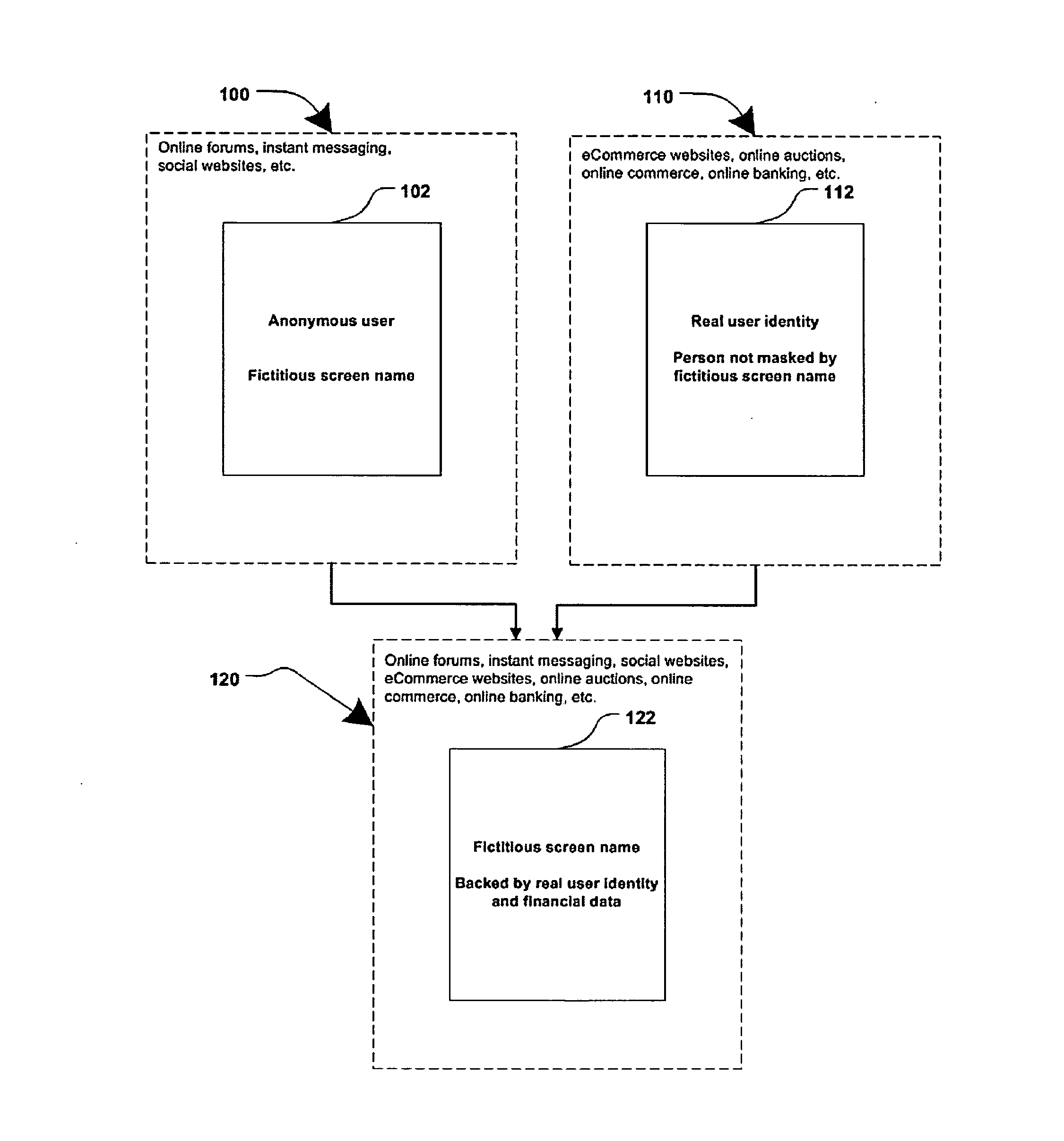
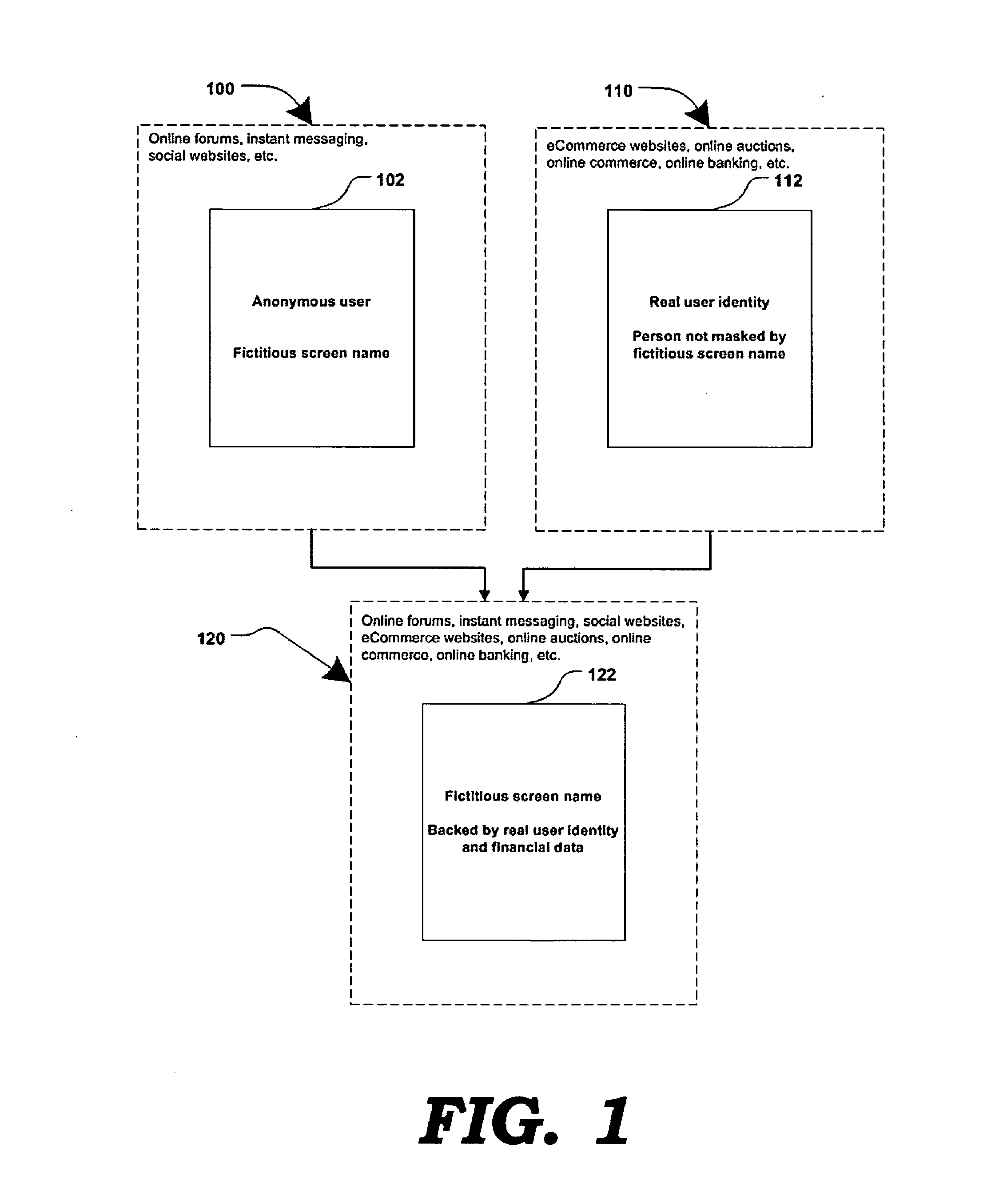
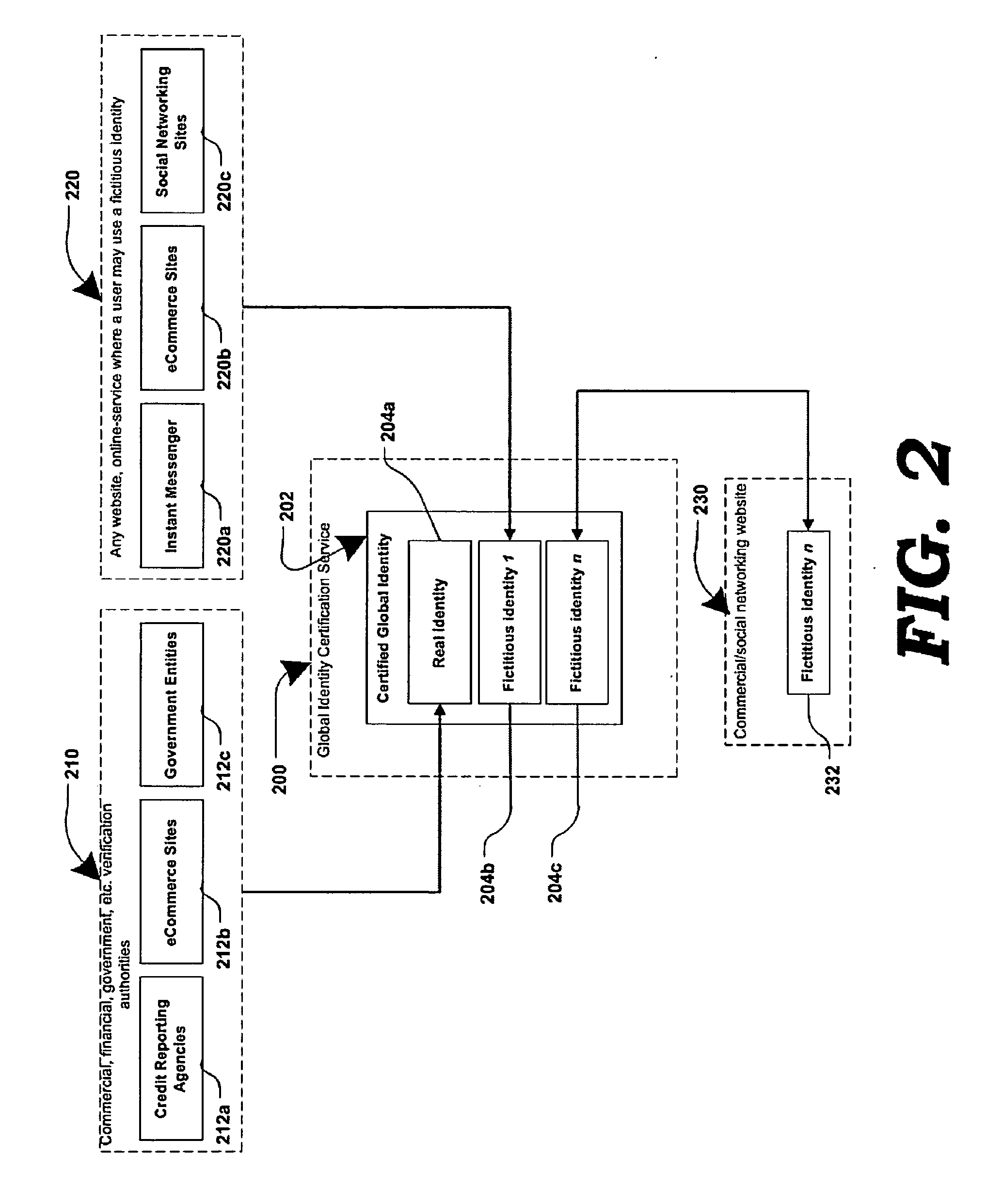
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
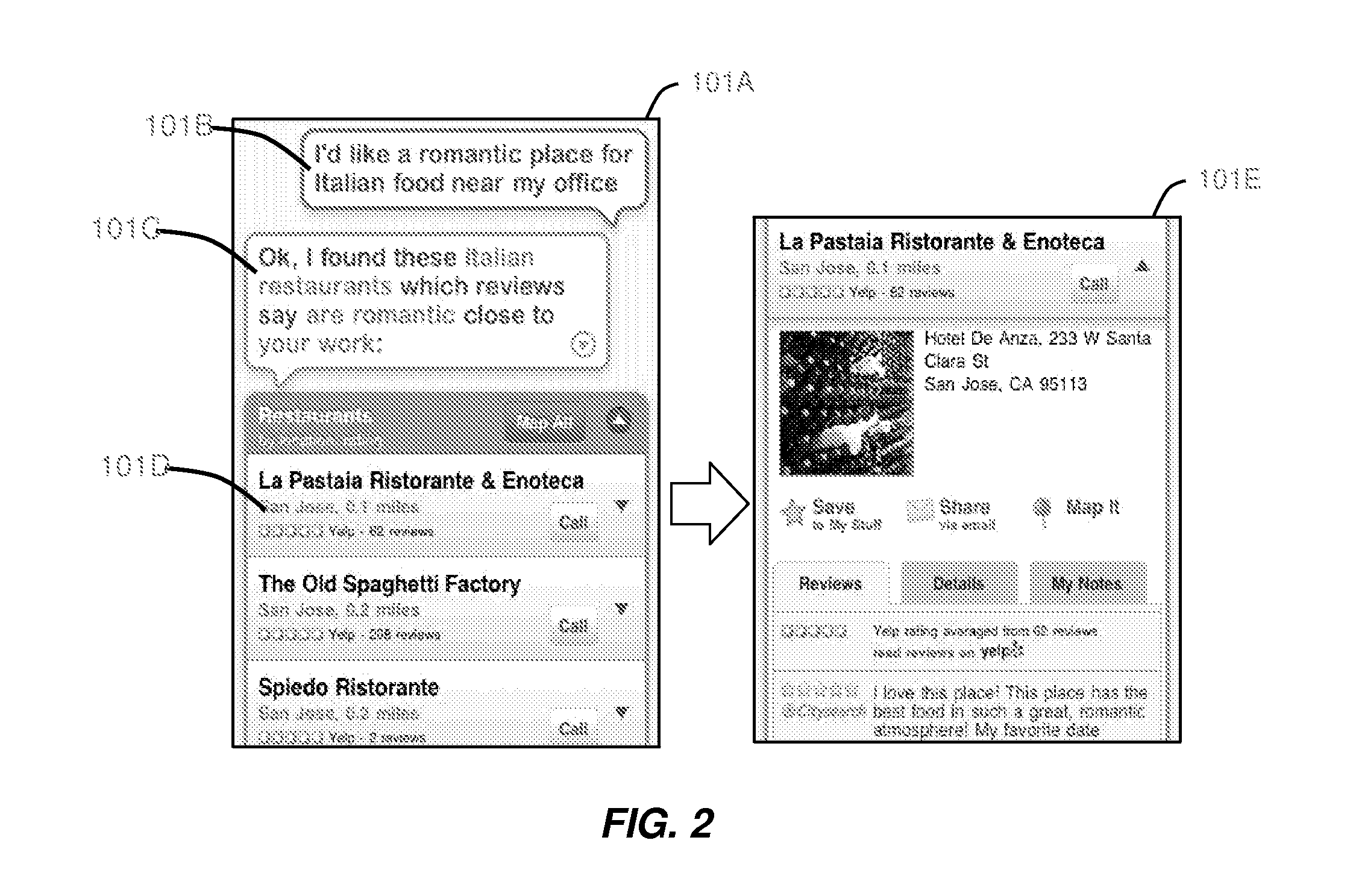
Intelligent Automated Assistant
ActiveUS20120245944A1Improve user interactionEffectively engageNatural language translationSemantic analysisService provisionComputer science
The intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
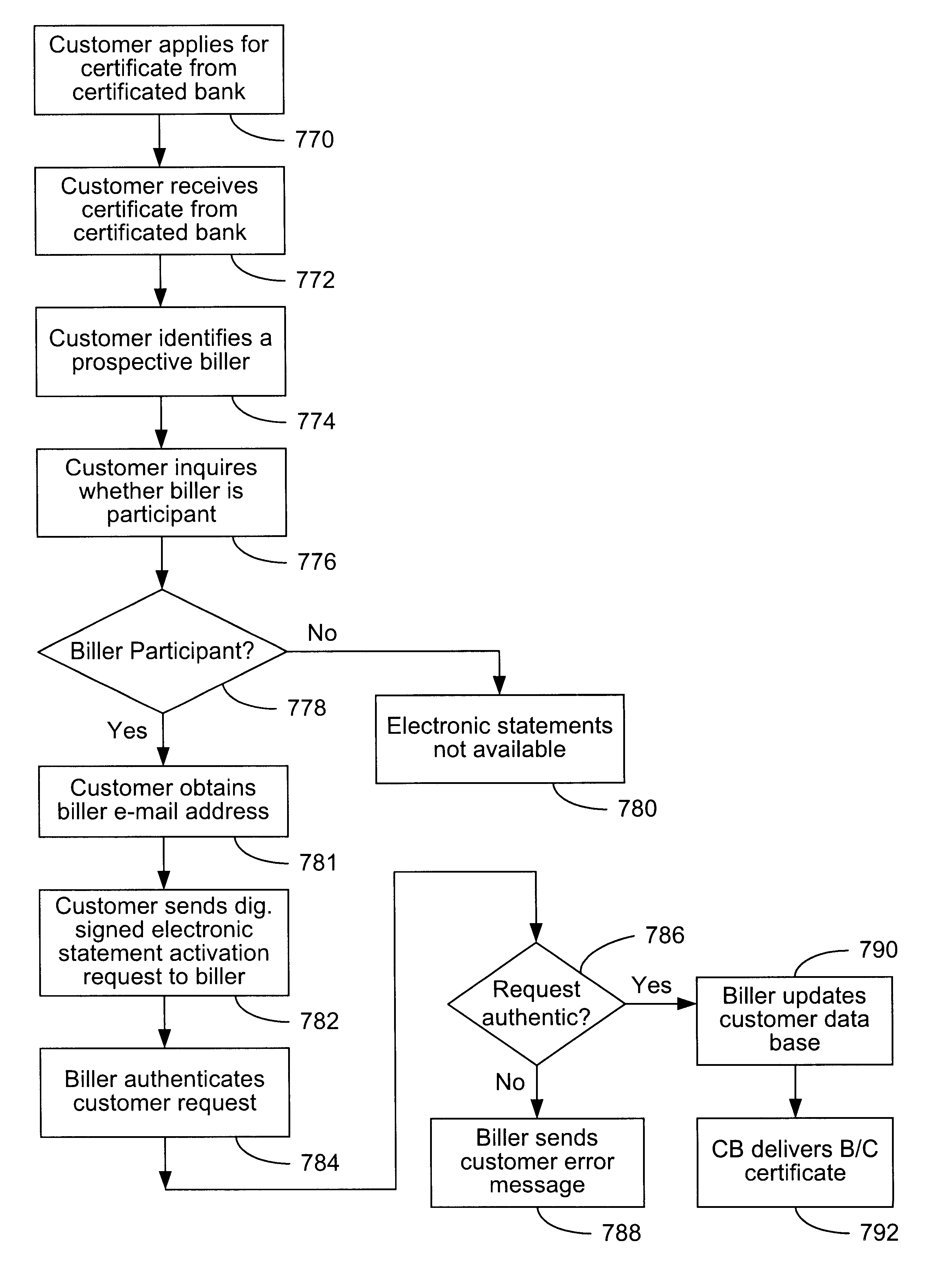
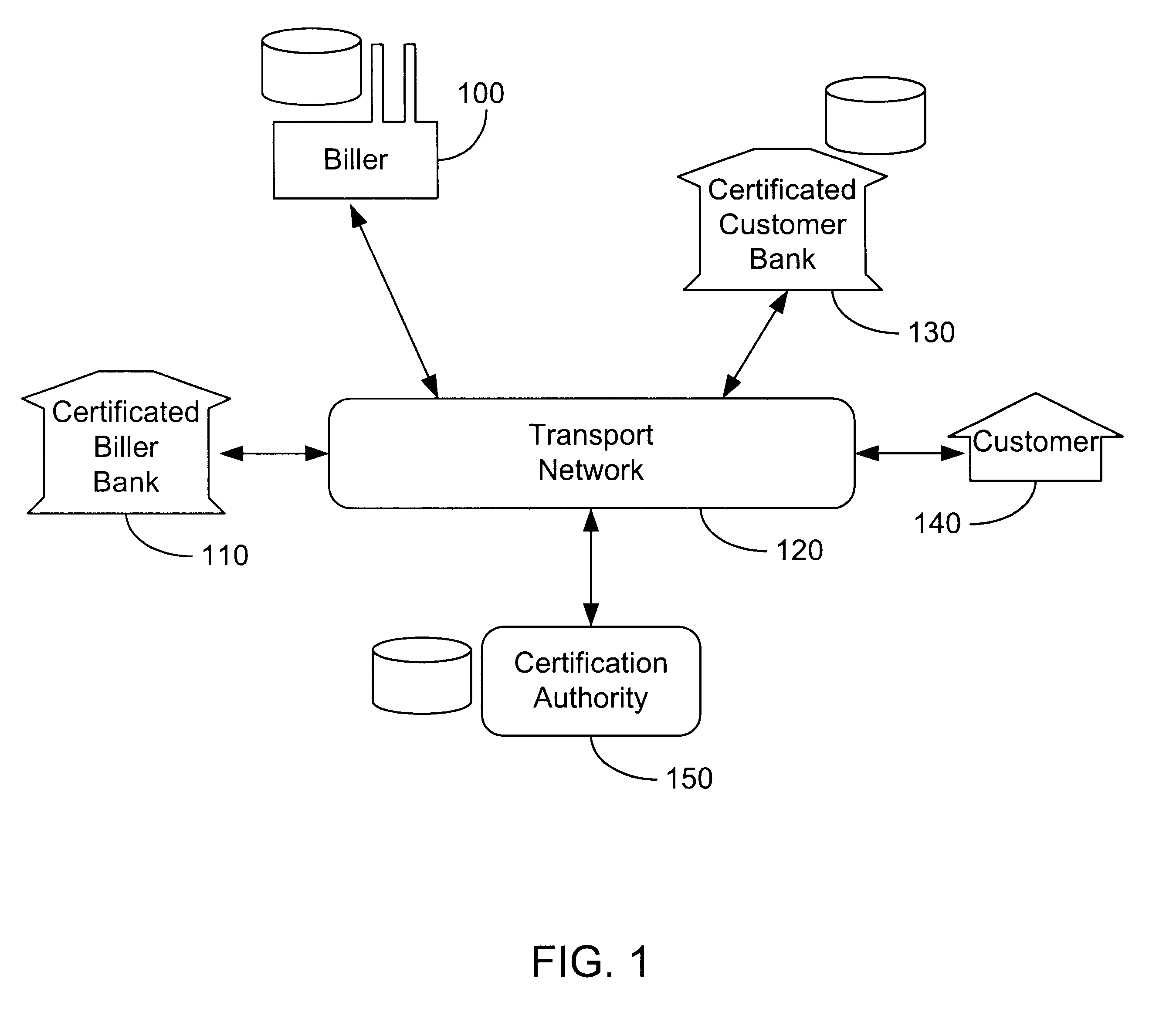
Secure interactive electronic account statement delivery system
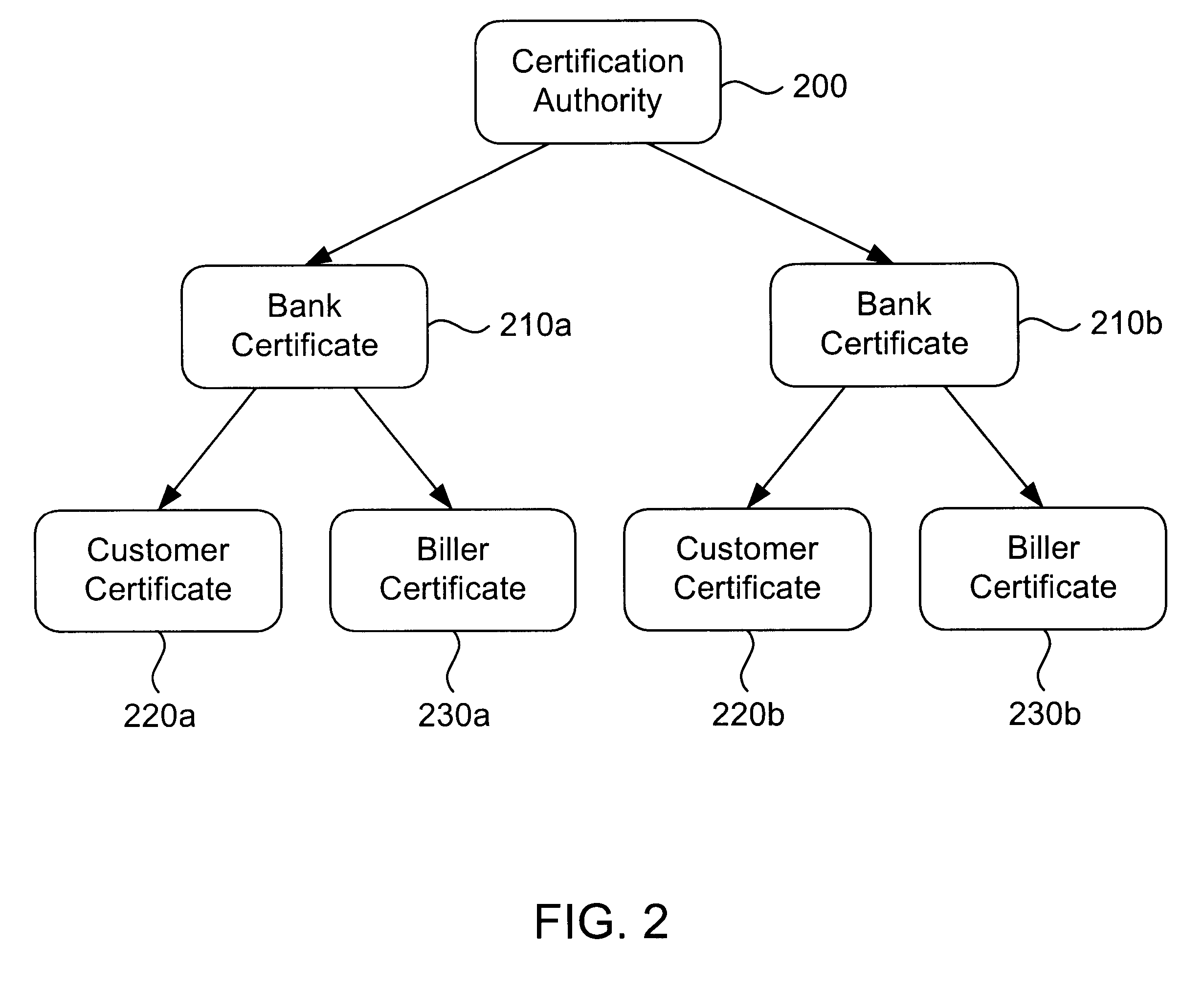
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
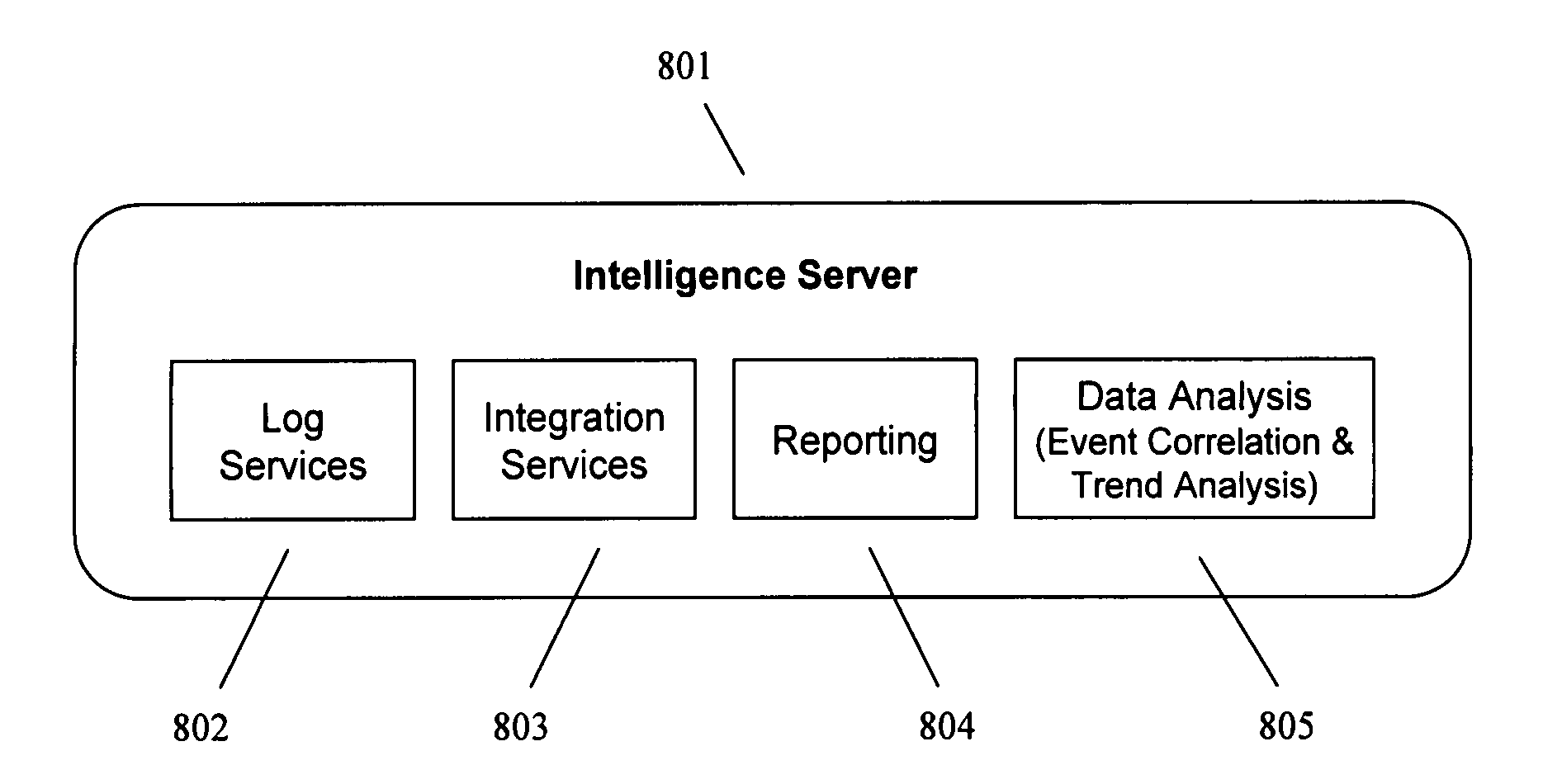
Detecting Behavioral Patterns and Anomalies Using Activity Profiles
ActiveUS20080059474A1Potential security breachError detection/correctionDigital data processing detailsBehaviour patternActivity profile
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
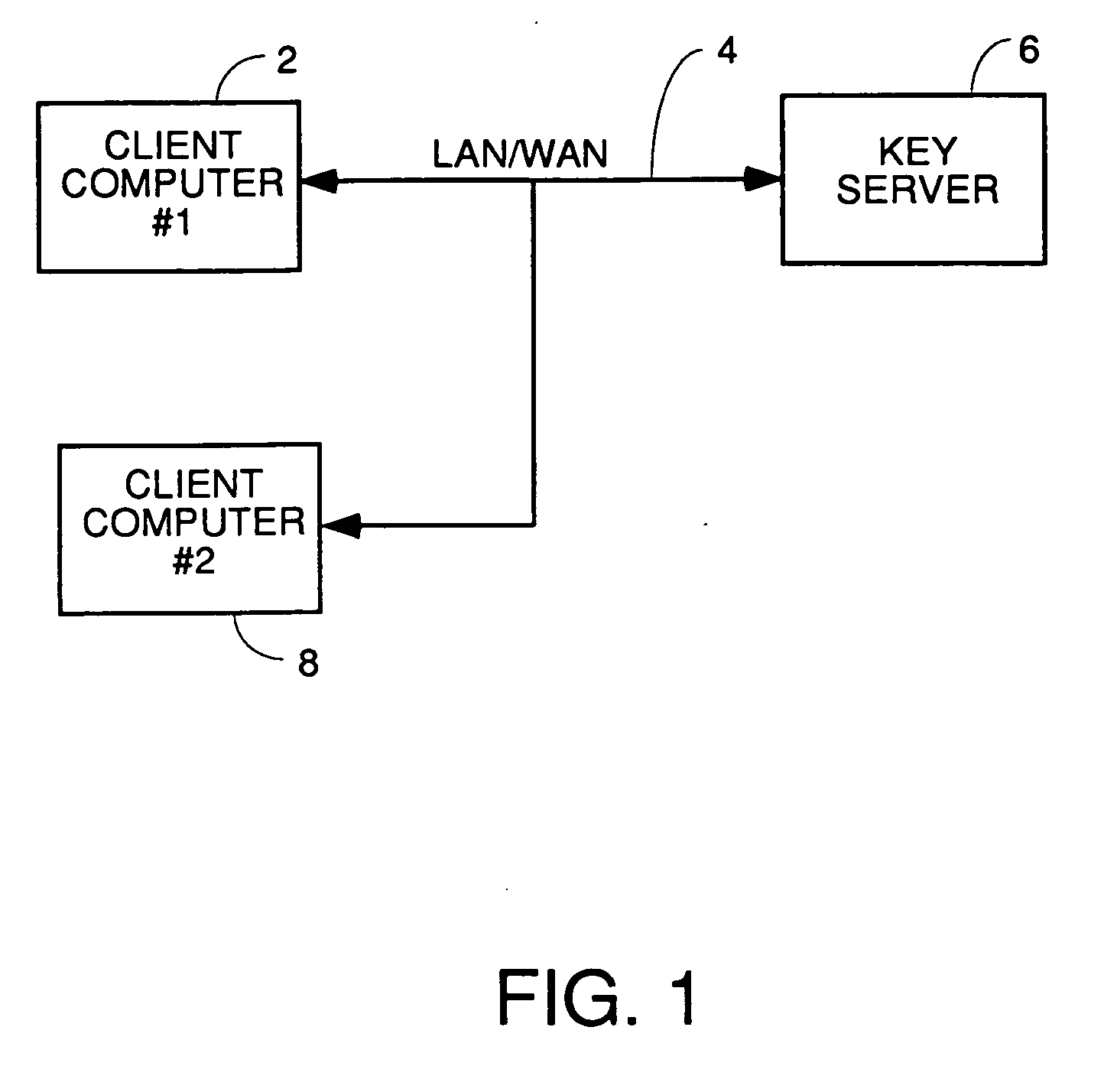
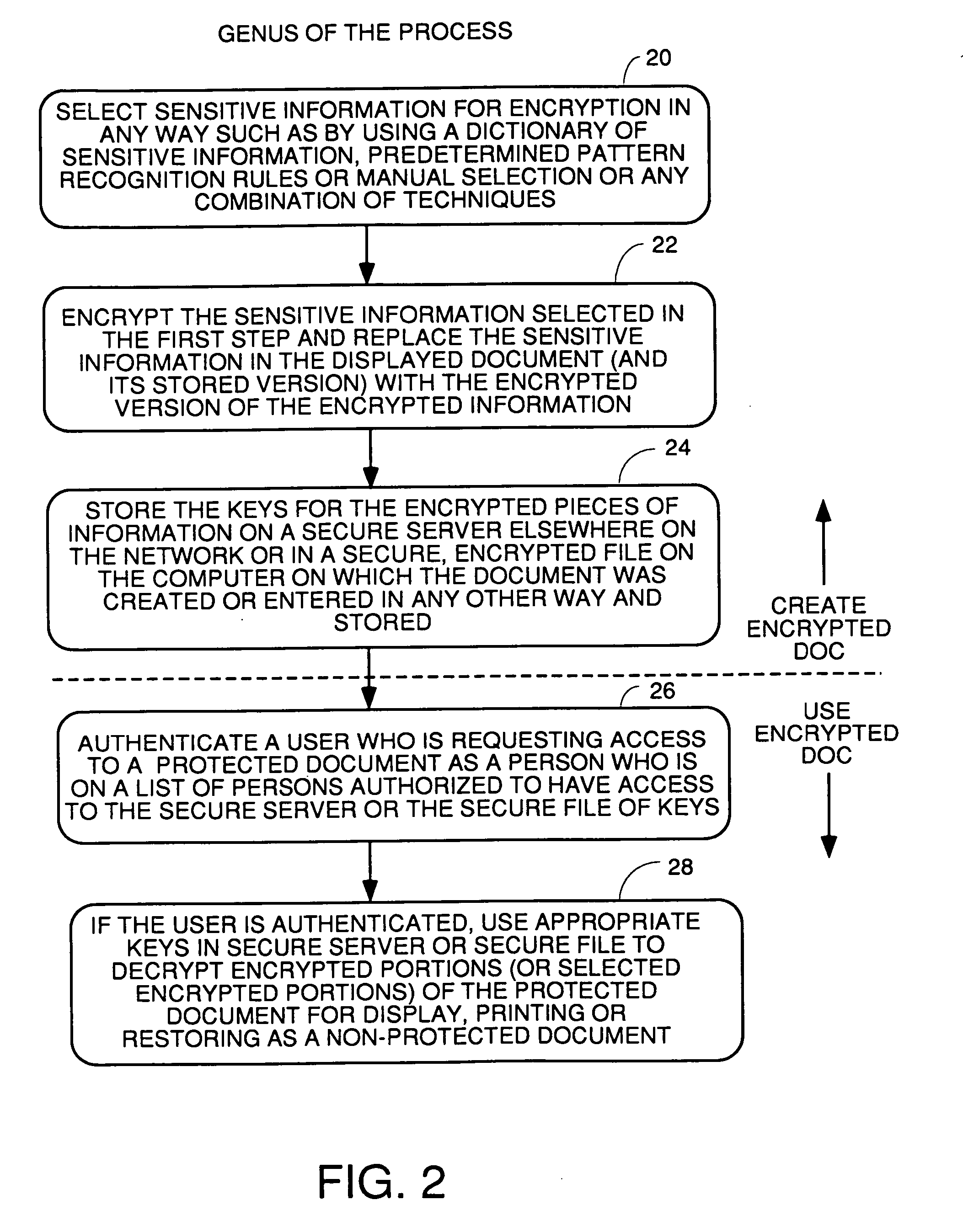
Method and apparatus for recognition and real time protection from view of sensitive terms in documents
InactiveUS20060075228A1Computer security arrangementsSecuring communicationInternet privacyClient-side
A process for automatically selecting sensitive information in any form of document being displayed and / or generated on a computer to select sensitive information for protection by encryption, redaction or removal of only the sensitive text. Selection is done by using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically protected on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted or redacted version or a space and a pointer to where the decryption key or the original of the redacted or removed text is stored. Other embodiments require manual approval of automatically selected text prior to protection. For encryption embodiments, the keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially redacted document is stored. Embodiments to protect the body of emails and attachments in either the email client or web mail environment are also disclosed.
Owner:INFOSAFE
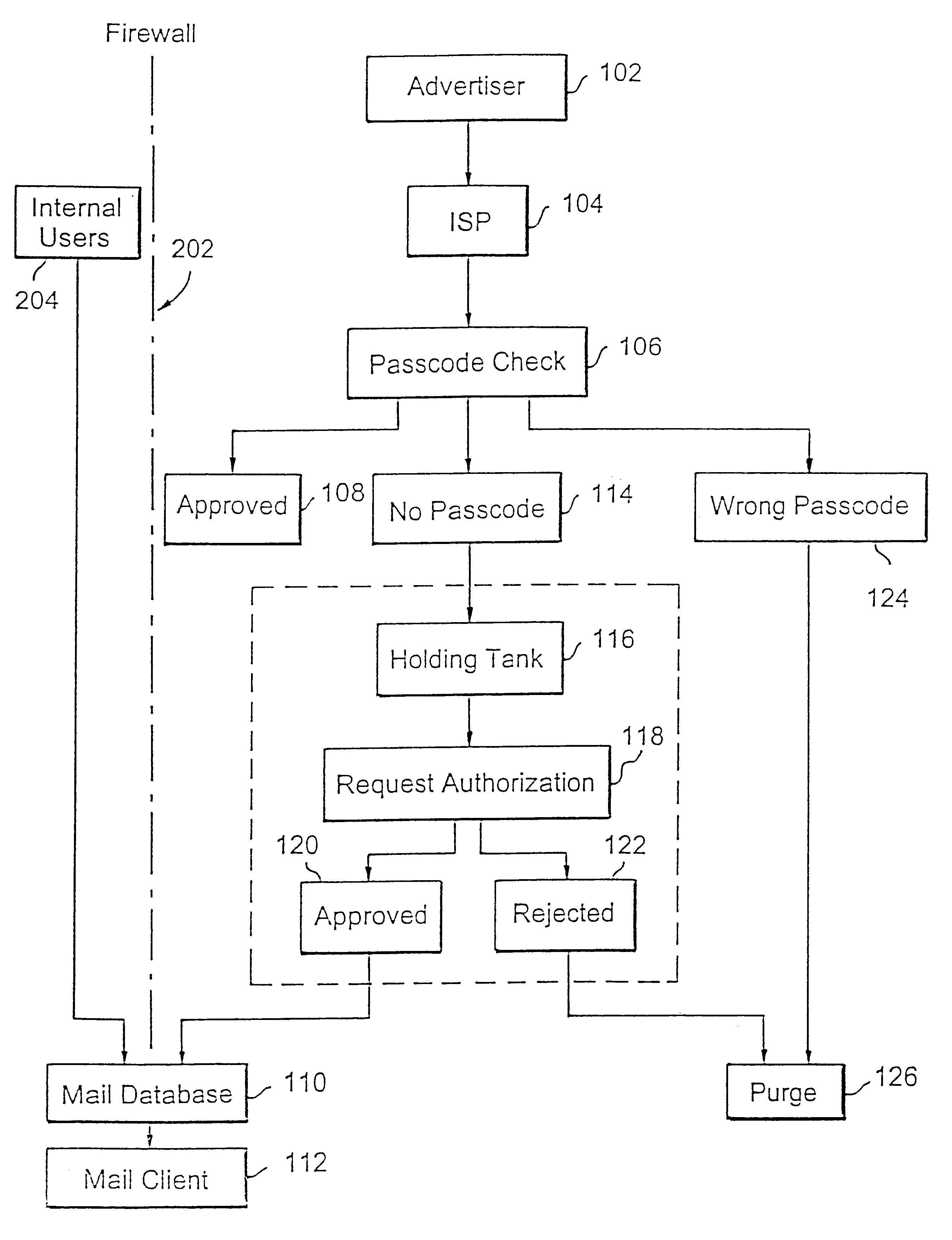
Method for blocking all unwanted e-mail (SPAM) using a header-based password
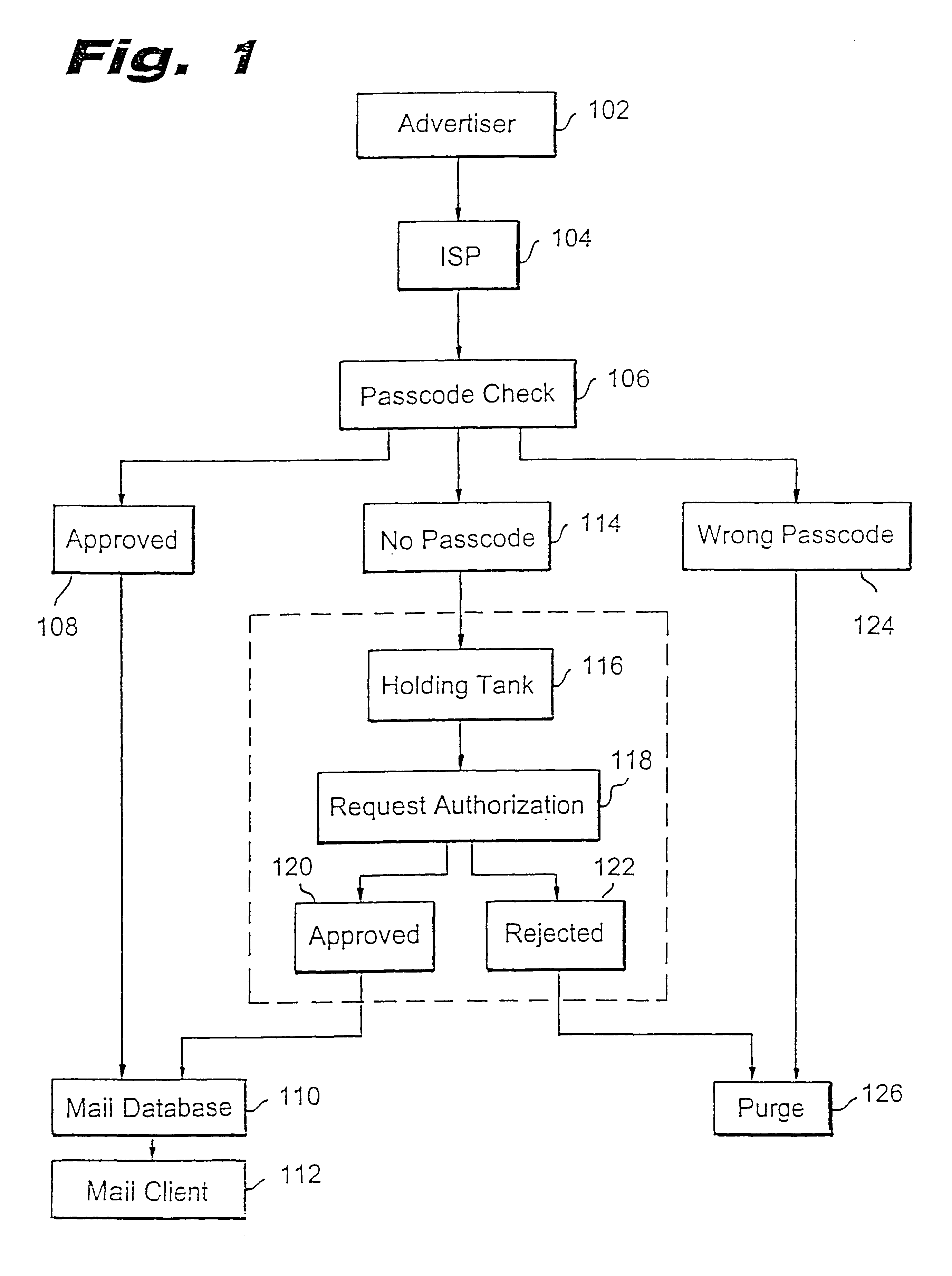
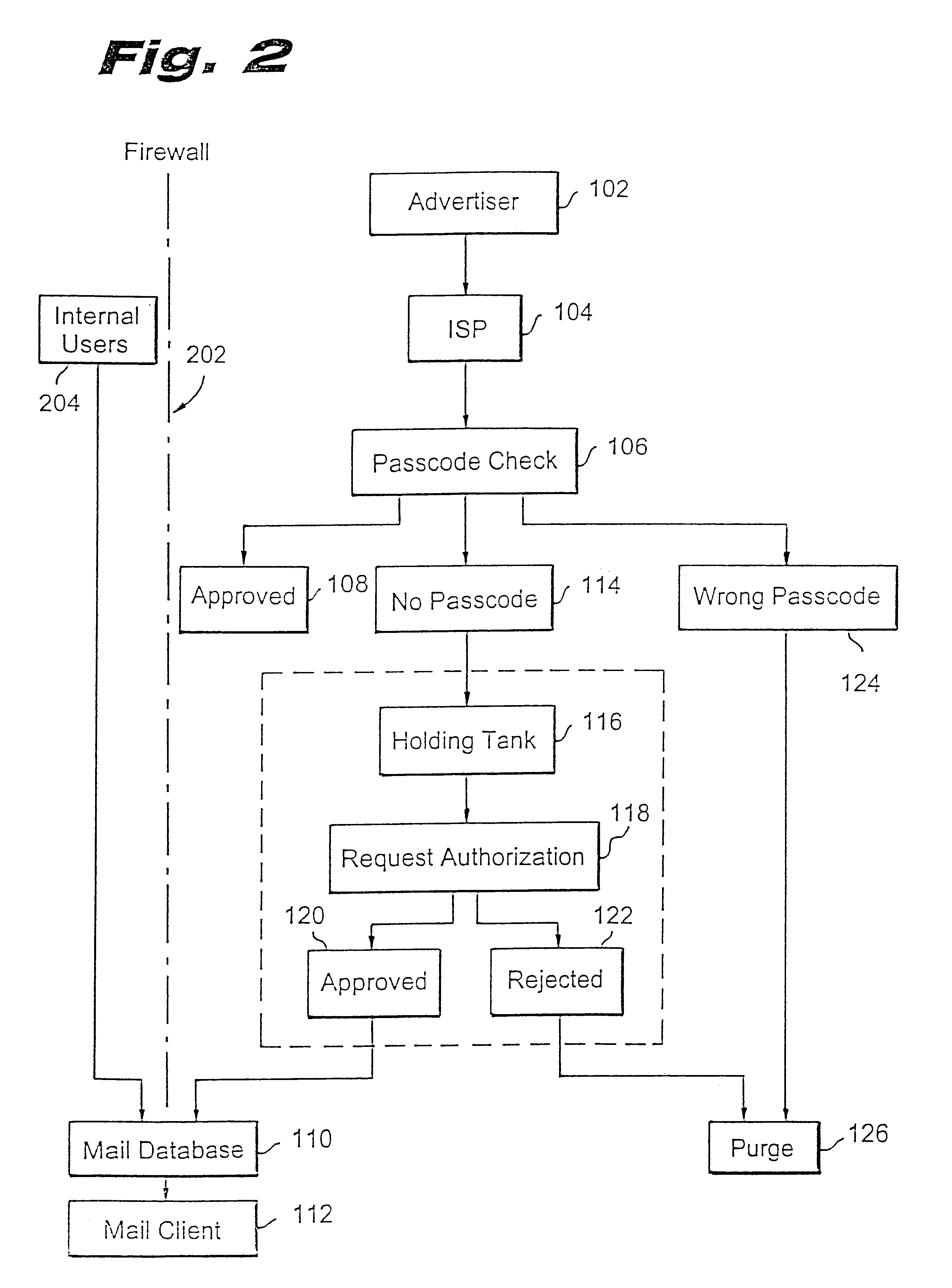
InactiveUS6266692B1Easy to sendEasy to solveOffice automationData switching networksEmail addressPassword
A method for blocking and / or filtering electronic mail. Selected senders are provided with a valid passcode associated with an e-mail address. When an e-mail is received at a mail server node, a field in a header of the e-mail is checked for a valid passcode associated with the destination e-mail address. If a valid passcode is detected, the e-mail is automatically sent to a receiver at the e-mail address. If an incorrect passcode is detected, the e-mail is automatically deleted at the server node and does not reach the receiver. If there is no passcode in the e-mail header, the e-mail is held temporarily, until the receiver approves to receive the e-mail. If the receiver rejects the e-mail, the e-mail is deleted. The present invention includes an additional capability for the senders of e-mails to request a passcode associated with a specific e-mail address in a lookup directory, before sending an e-mail to that address. Furthermore, the present invention enables firewall servers to block incoming e-mails only if they are received from the public Internet, thereby allowing all internal e-mails to reach the receiver without having to include valid passcodes.
Owner:TREND MICRO INC
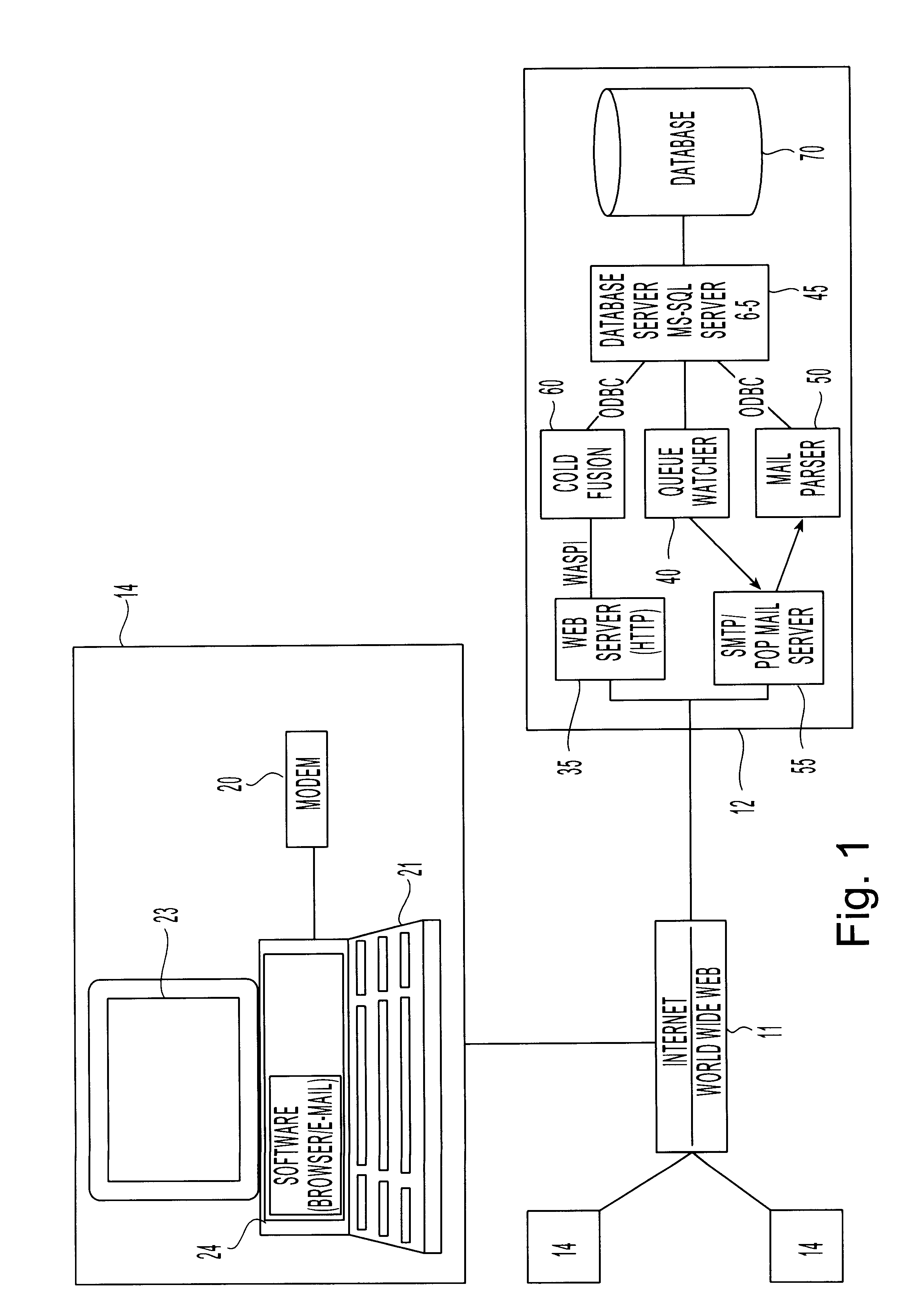
Electronic mail distribution system for integrated electronic communication
InactiveUS6023700ASpecial service for subscribersSubstation equipmentElectronic communicationDistribution system
A system is disclosed for integrated electronic mail, voice mail, and fax mail messaging. A common message format is defined for use by an electronic mail service and a telecommunications service so electronic mail messages that may include voice and fax mail attachments may be exchanged between the services. Message senders and receivers may choose from a variety of filter and forward options that allow them to manage their communications and specify a preference for receiving messages at the electronic mail or telecommunications service. Forwarding and conversion of messages is performed automatically. The options are used to define a set of rules to be applied to inbound and outbound messages so that messages are sent and received in accordance with the preferences of the senders and receivers.
Owner:OATH INC
Mobile Person-to-Person Payment System
InactiveUS20070255652A1The process is simple and fastSimple accessFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions may be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions may be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
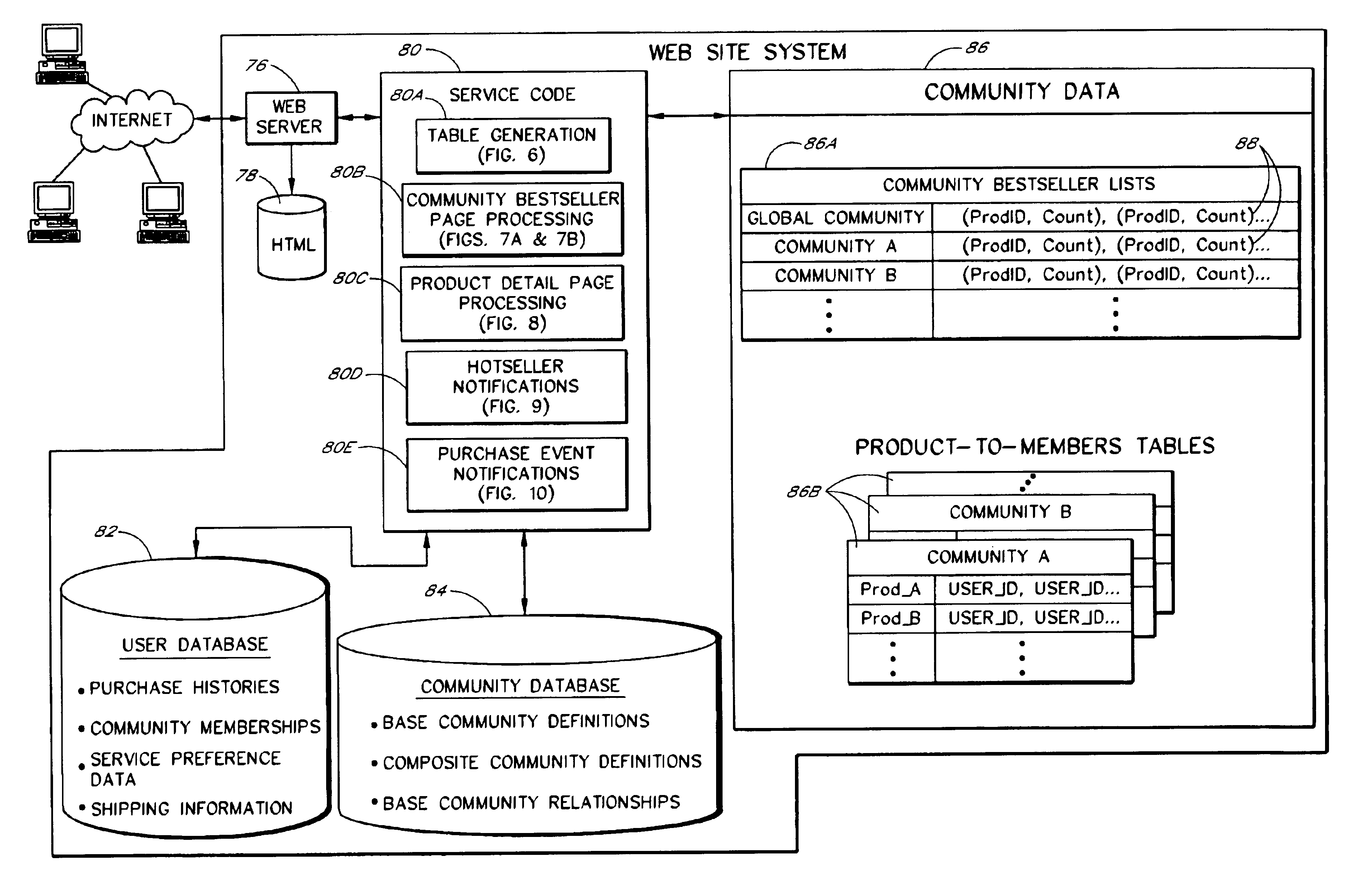
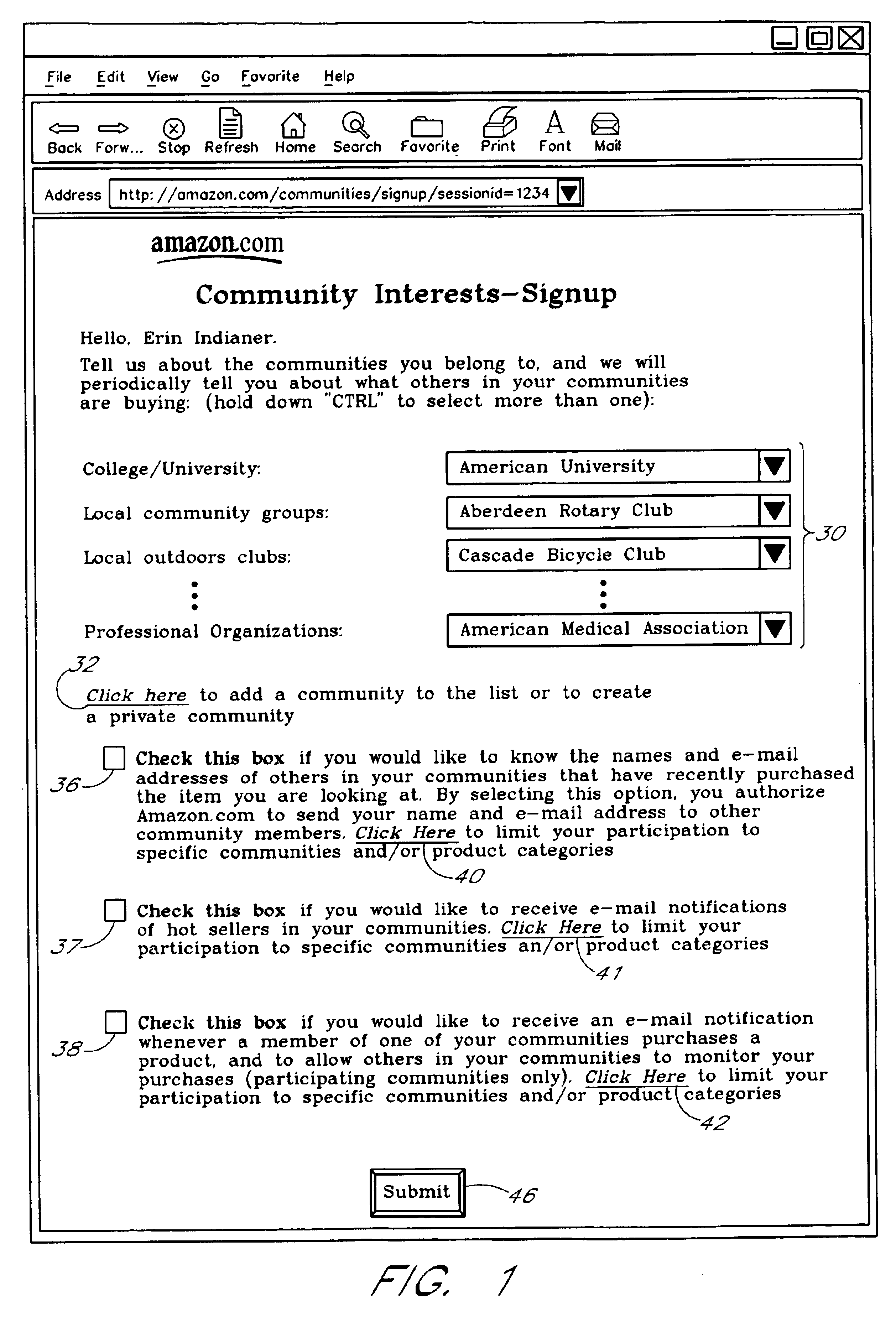
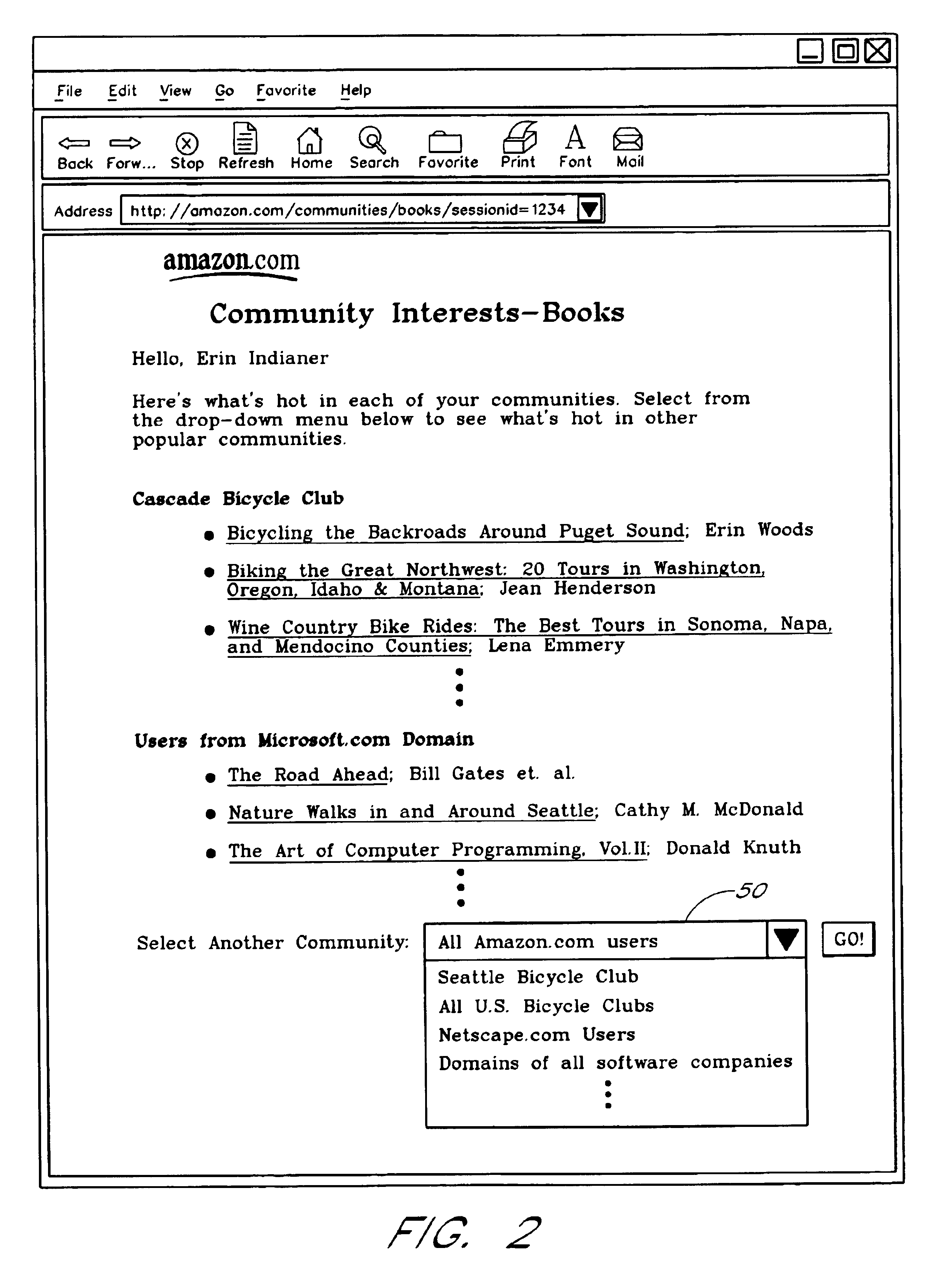
Computer services for assisting users in locating and evaluating items in an electronic catalog based on actions performed by members of specific user communities
A Web based system provides informational services for assisting customers in selecting products or other types of items from an electronic catalog of a merchant. Users of the system can create and join user communities, such as communities based on user hobbies, localities, professions, and organizations. The system also supports implicit membership communities that are based on email addresses (e.g., all users having a “nasa.com” email address), shipping / billing addresses, and other known user information. Using purchase history data collected for online users, the system automatically identifies and generates lists of the most popular items (and / or items that are becoming popular) within particular communities, and makes such information available to users for viewing. For example, in the context of an online book store users of the nasa.com community may automatically be presented a Web page which lists the bestselling book titles among nasa.com users, or may be sent email notifications of purchase events or hotselling books within the community. Another feature involves automatically notifying users interested in particular products of other users (preferably other members of the same community) that have purchased the same or similar products. For example, in one embodiment, when a user accesses a book detail page, the detail page is customized to include the names and email addresses of other members of the user's community that recently purchased the same book.
Owner:AMAZON TECH INC
Method and system for seeding online social network contacts
A method, apparatus, and system are directed towards seeding a user's contacts for their online social network. The invention is arranged to automatically recommend to the user a set of seed contacts that the user may employ to invite to join their social network. The set of seed contacts may be harvested from the user's existing portal activities, as well as other sources. In one embodiment, the invention analyzes portal activity, such as email exchanges with the user, and the like, to determine a frequency of contact with the user. Other sources may include but not be limited to emails, names within an address book of the user, names within an address book of another person, a buddy list, an instant messaging list, an activity, a mailing list, an online discussion group, a membership in a category, chat group, and the like.
Owner:SLACK TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com