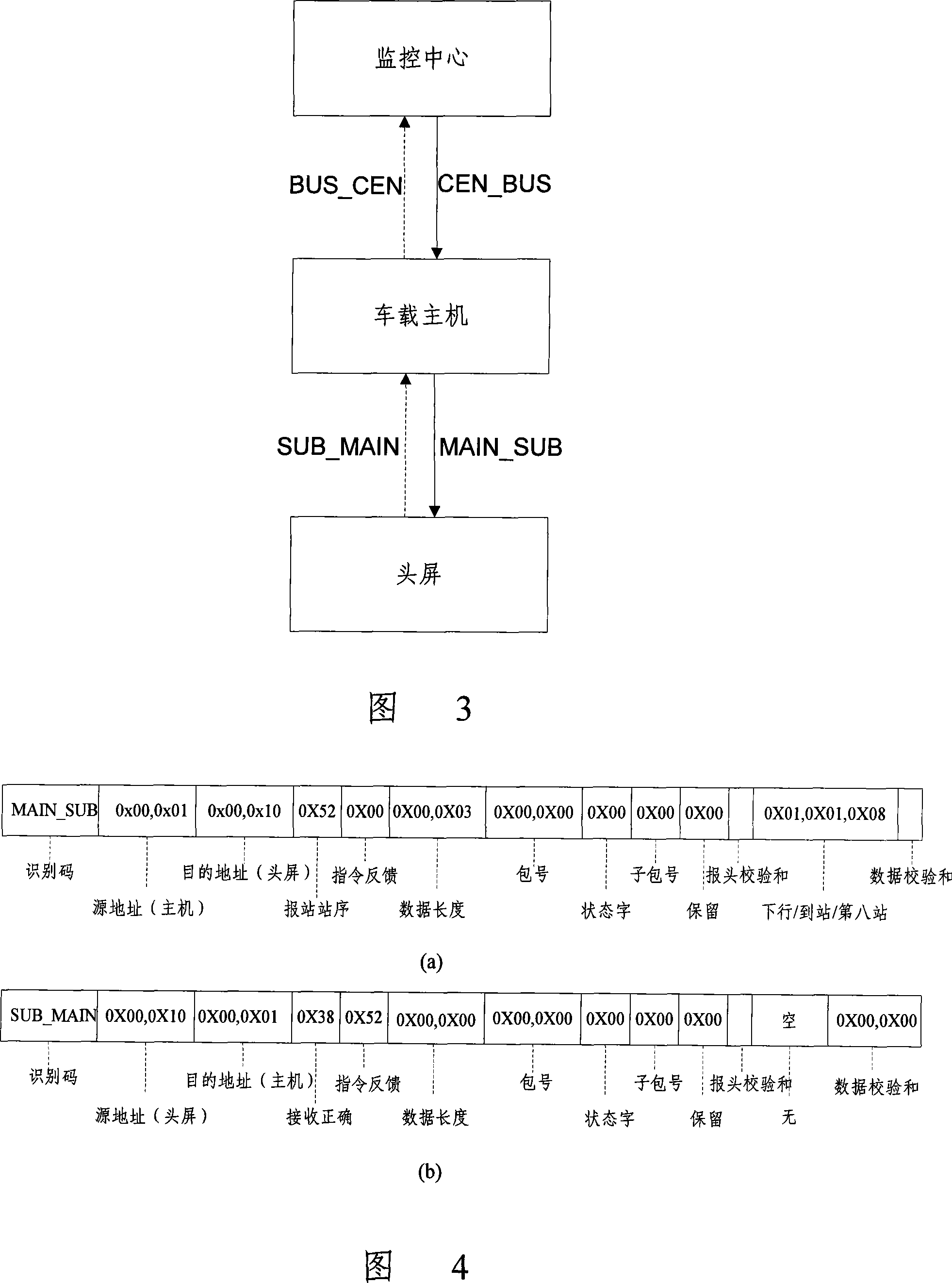Patents
Literature
342results about How to "Simple access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
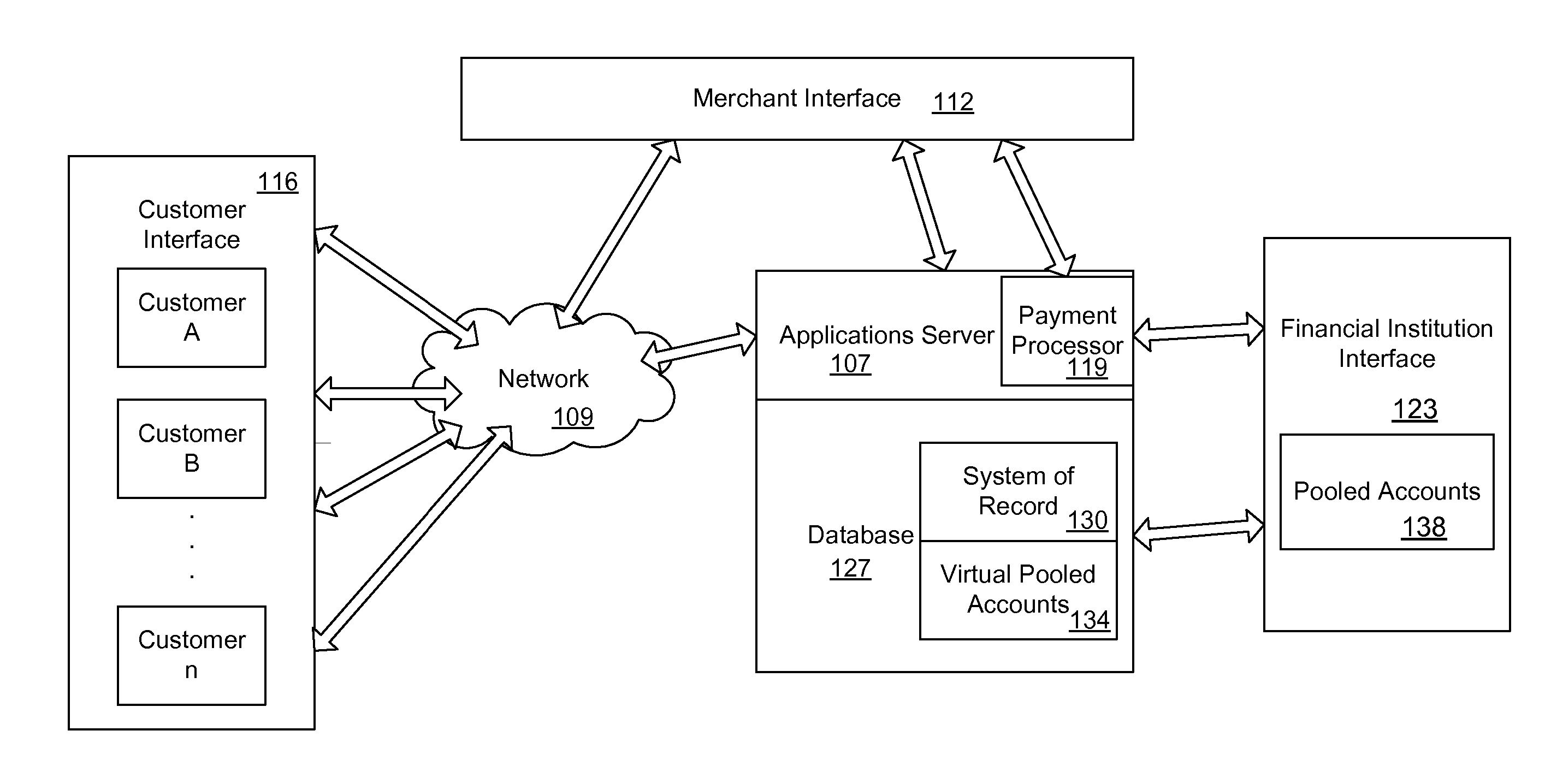
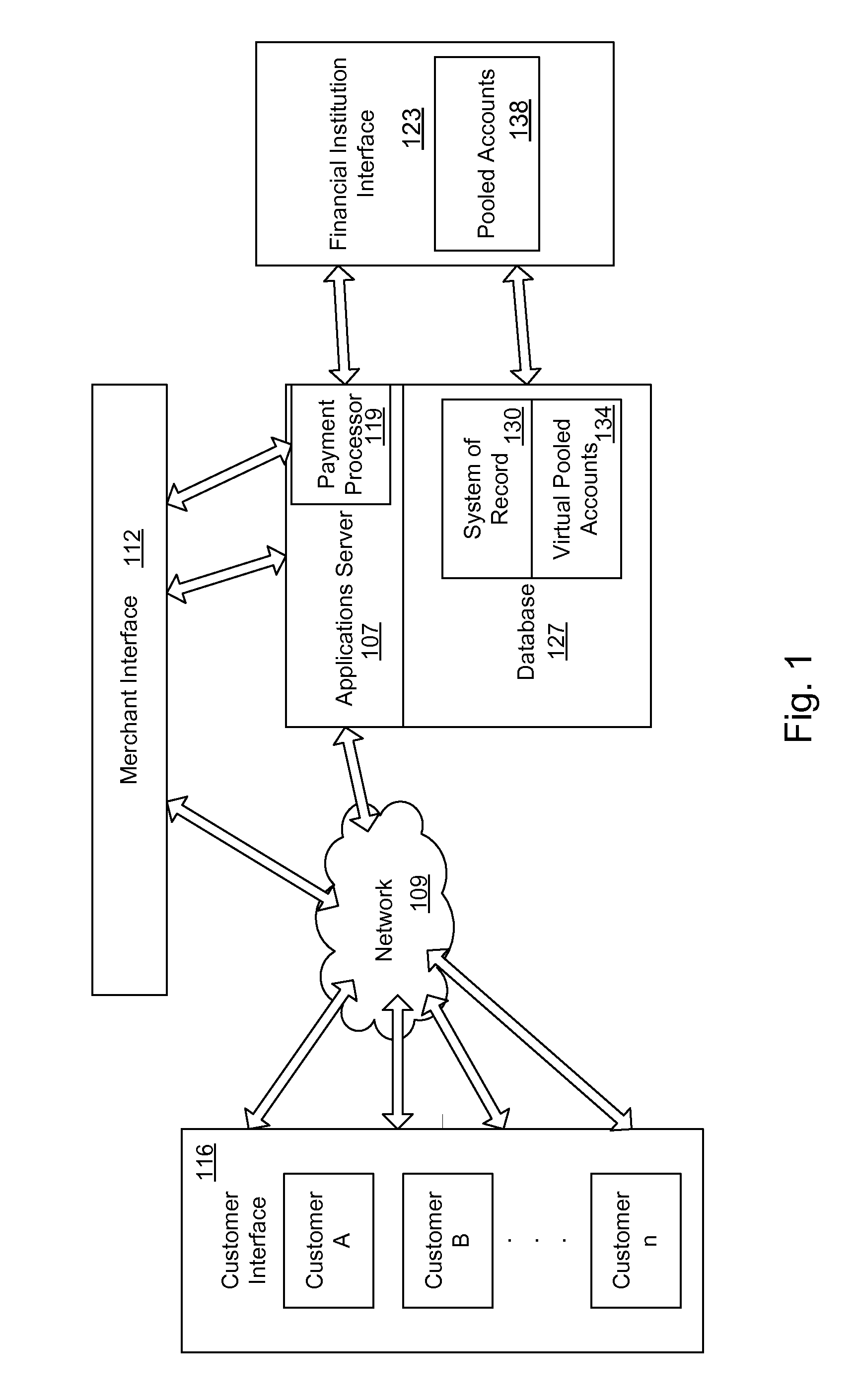
Mobile Person-to-Person Payment System
InactiveUS20070255652A1The process is simple and fastSimple accessFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions may be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions may be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
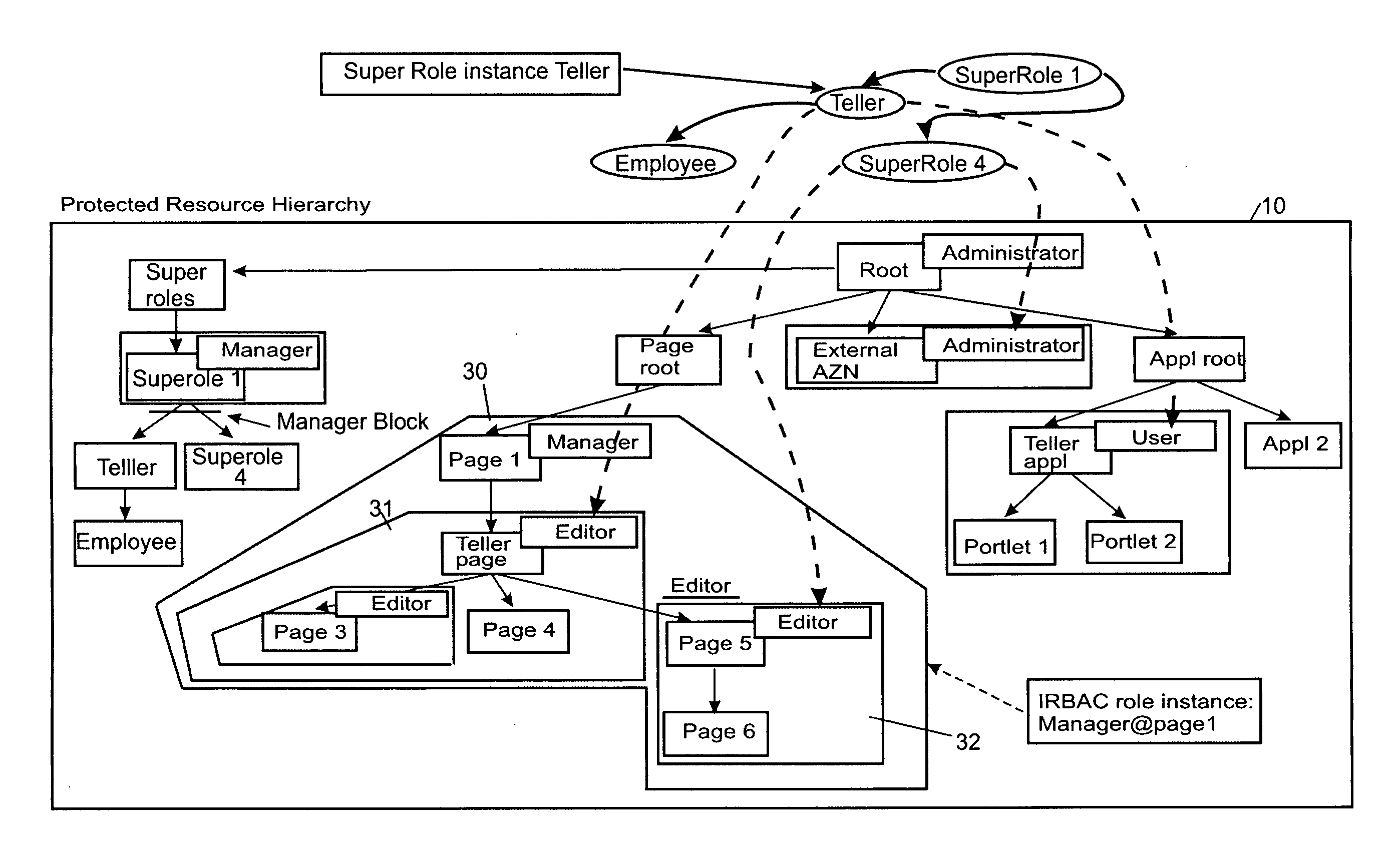
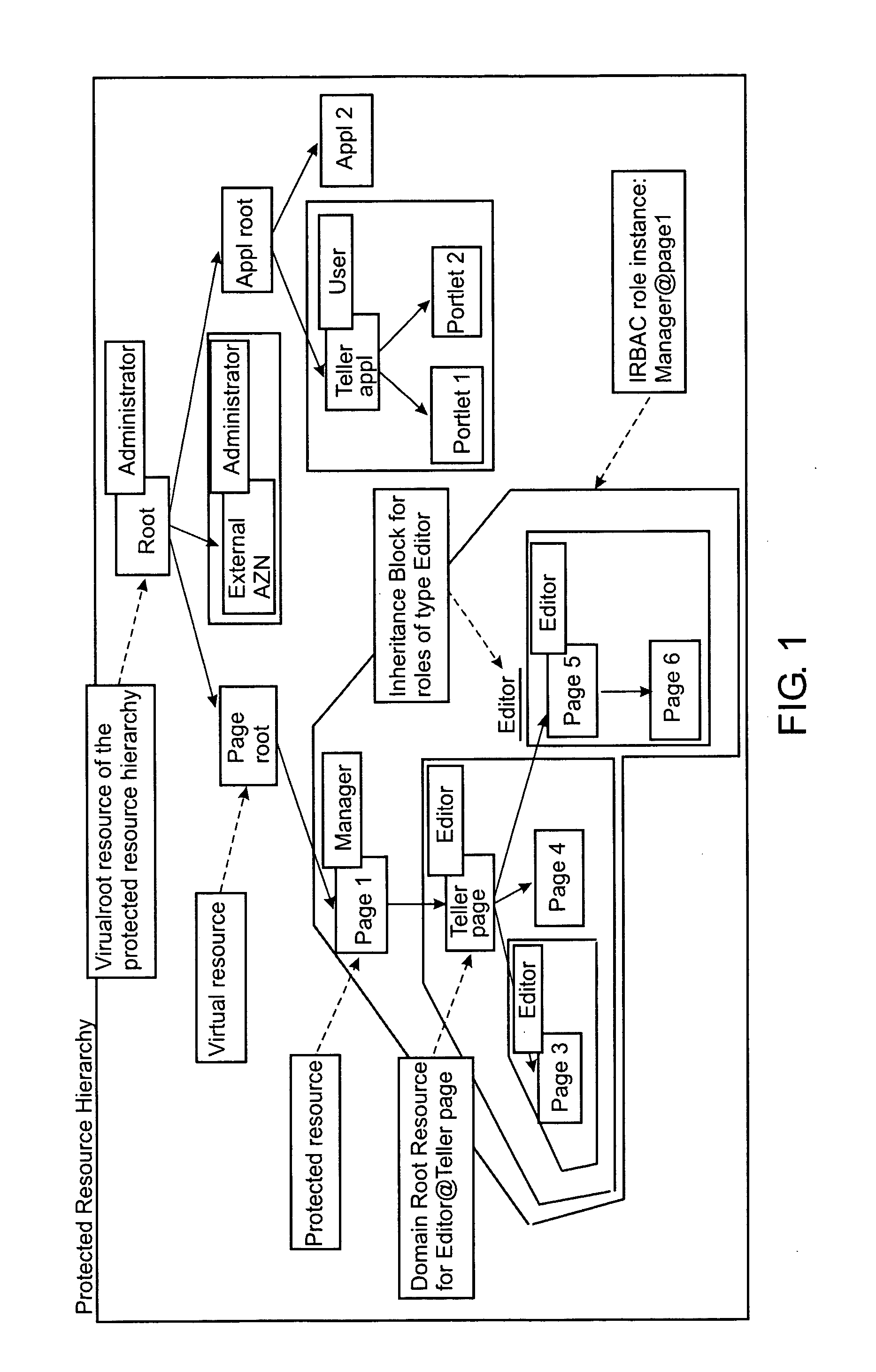
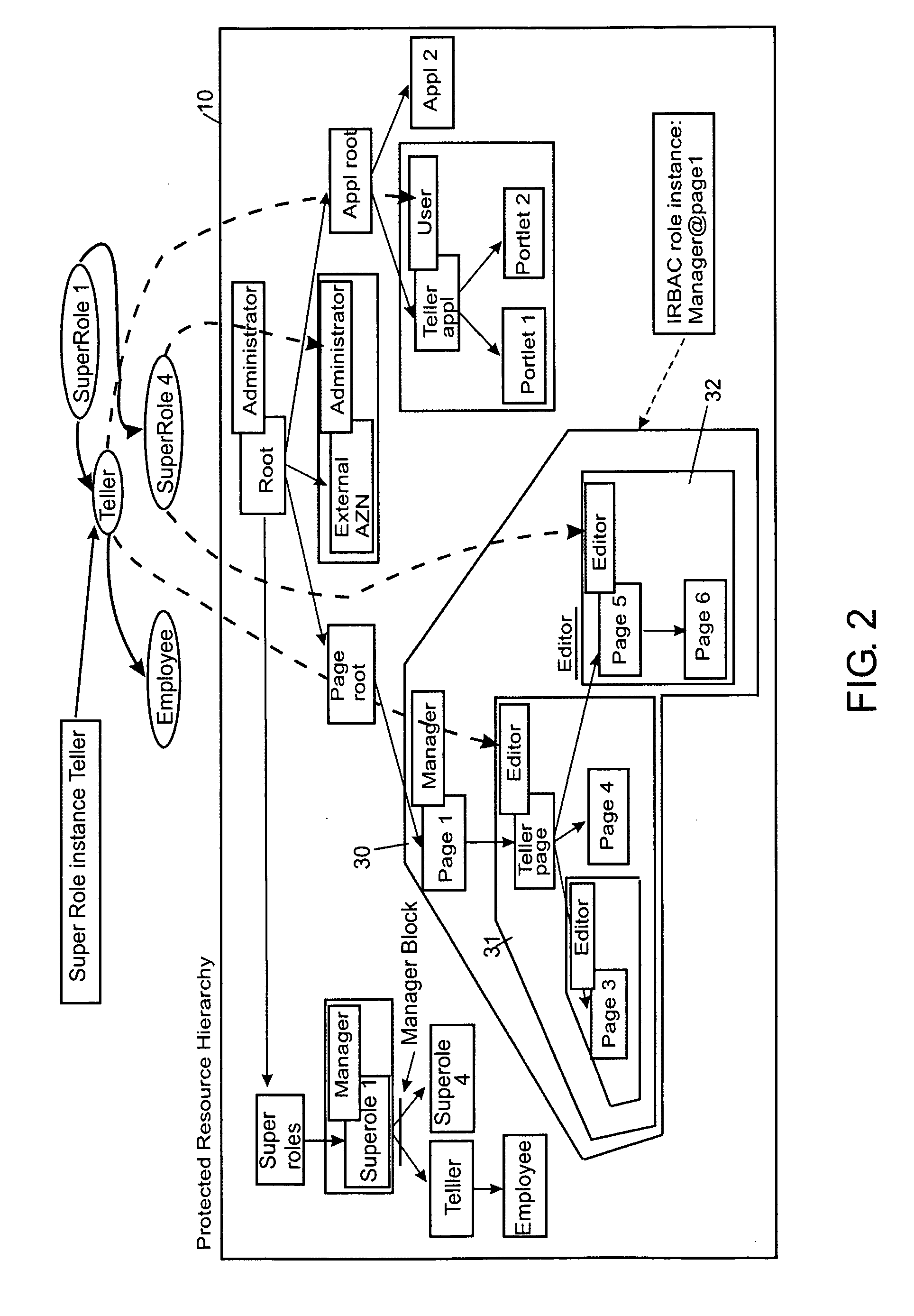
Role-based access control system, method and computer program product
ActiveUS20060089932A1Simplifies consistent dynamic bindingLow costComputer security arrangementsTransmissionControl systemWorld Wide Web
The invention relates to a role-based access control system, including a role definition system for defining roles to be sets of permissions on individual resources thus forming role instances, respectively; and a super role definition system for defining at least one super role by grouping a set of role instances into one super role, wherein the one super role contains all permissions contained in the grouped resource instances. Furthermore, the present invention deals with an appropriate method, a computer program and a computer program product.
Owner:DAEDALUS BLUE LLC
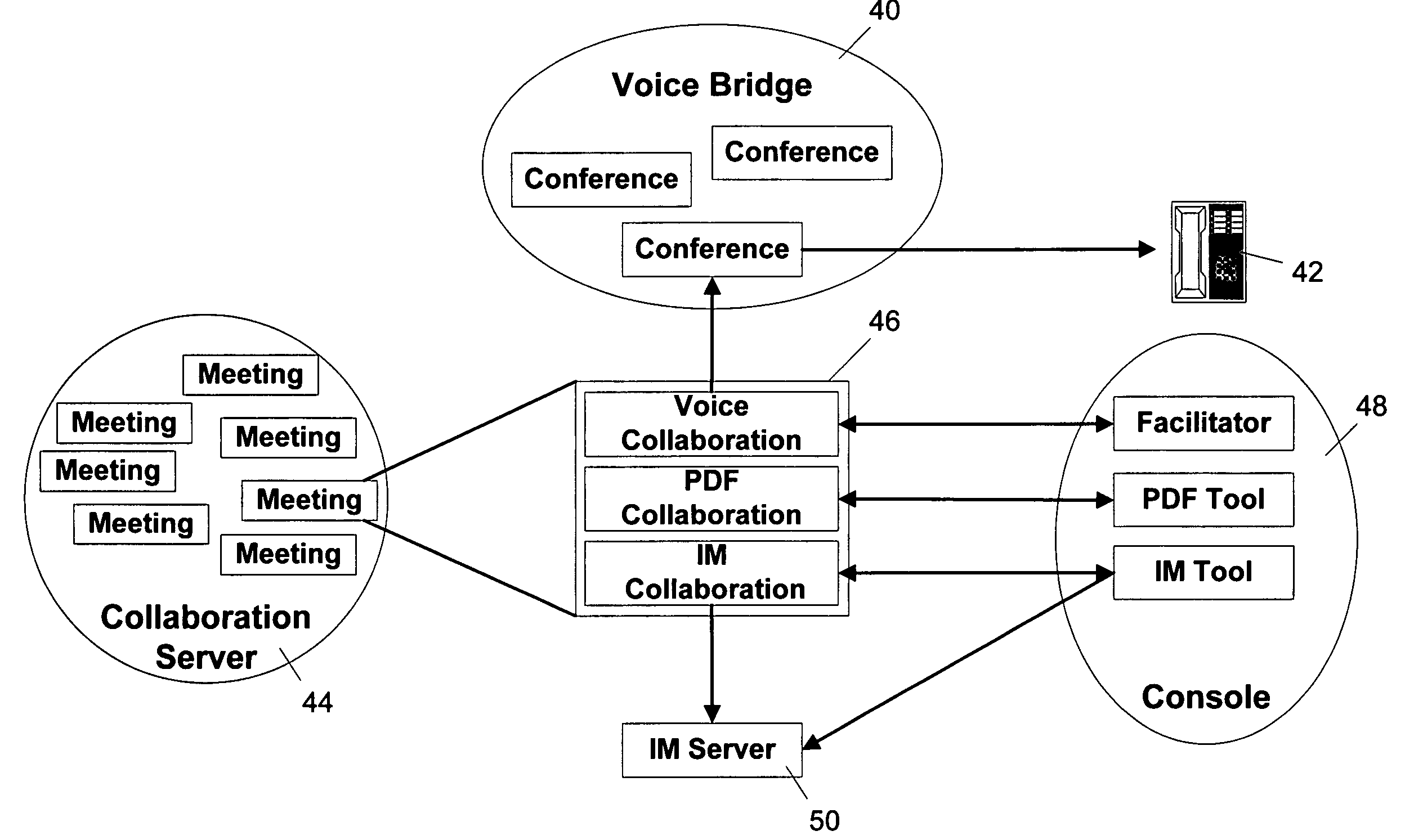
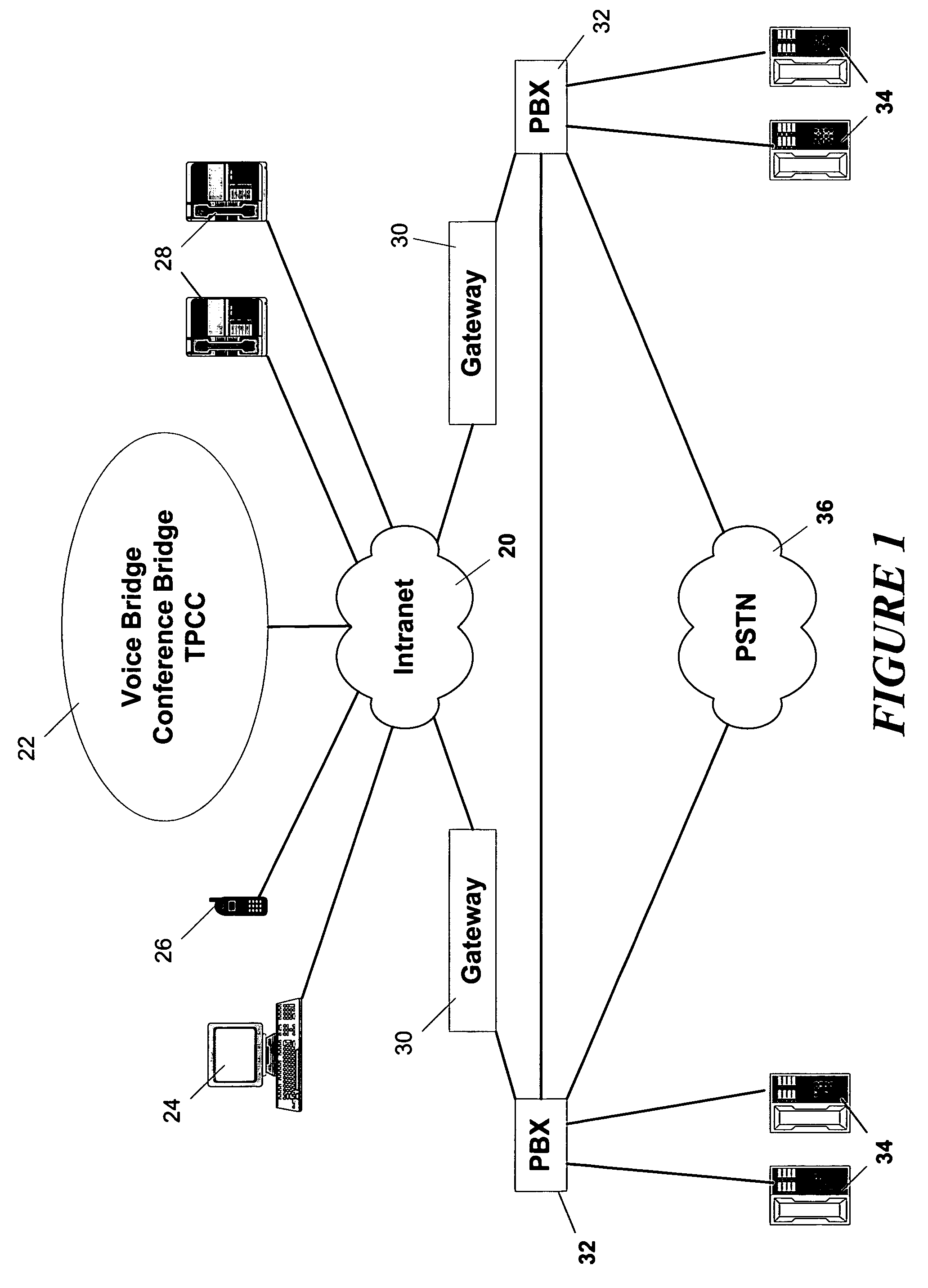
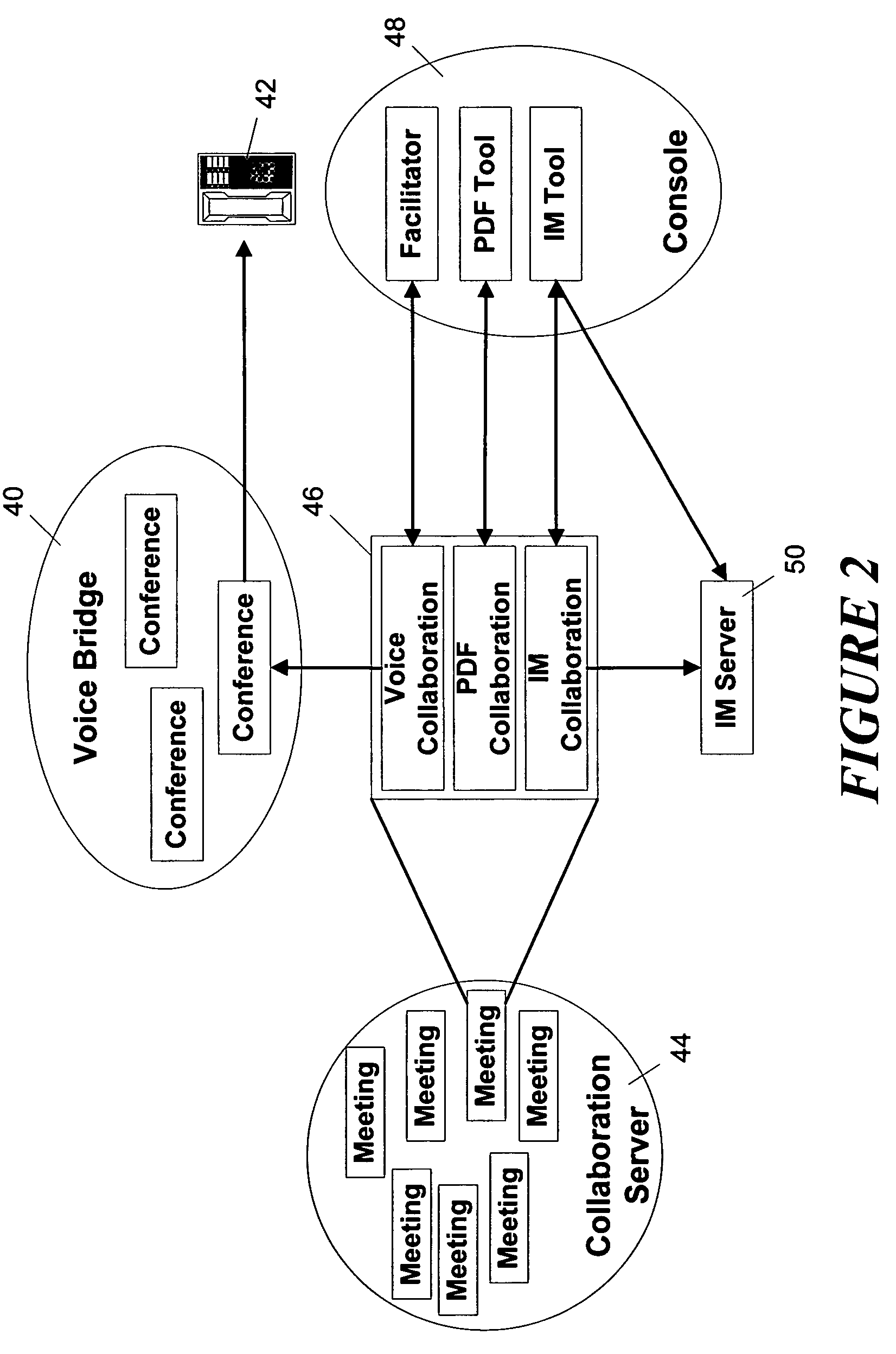
Network collaboration system with private voice chat
ActiveUS7734692B1Enhanced interactionSimple accessSpecial service for subscribersMultiple digital computer combinationsClient-sideSpeech sound
A network collaboration system facilitates collaborations between network clients having access to a digital network. The system uses audio mixes to provide different levels of voice conferences between the meeting participants. In a main collaboration, those participating in the main collaboration receive an audio output that includes audio inputs from the other participants. A subset group of clients may also have a voice chat, in which their audio inputs are removed from the outputs delivered to the clients not participating in the voice chat. Meanwhile, the participants in the voice chat hear each other at full volume, but hear the collaborators who are not part of the voice chat at a reduced volume.
Owner:ORACLE INT CORP
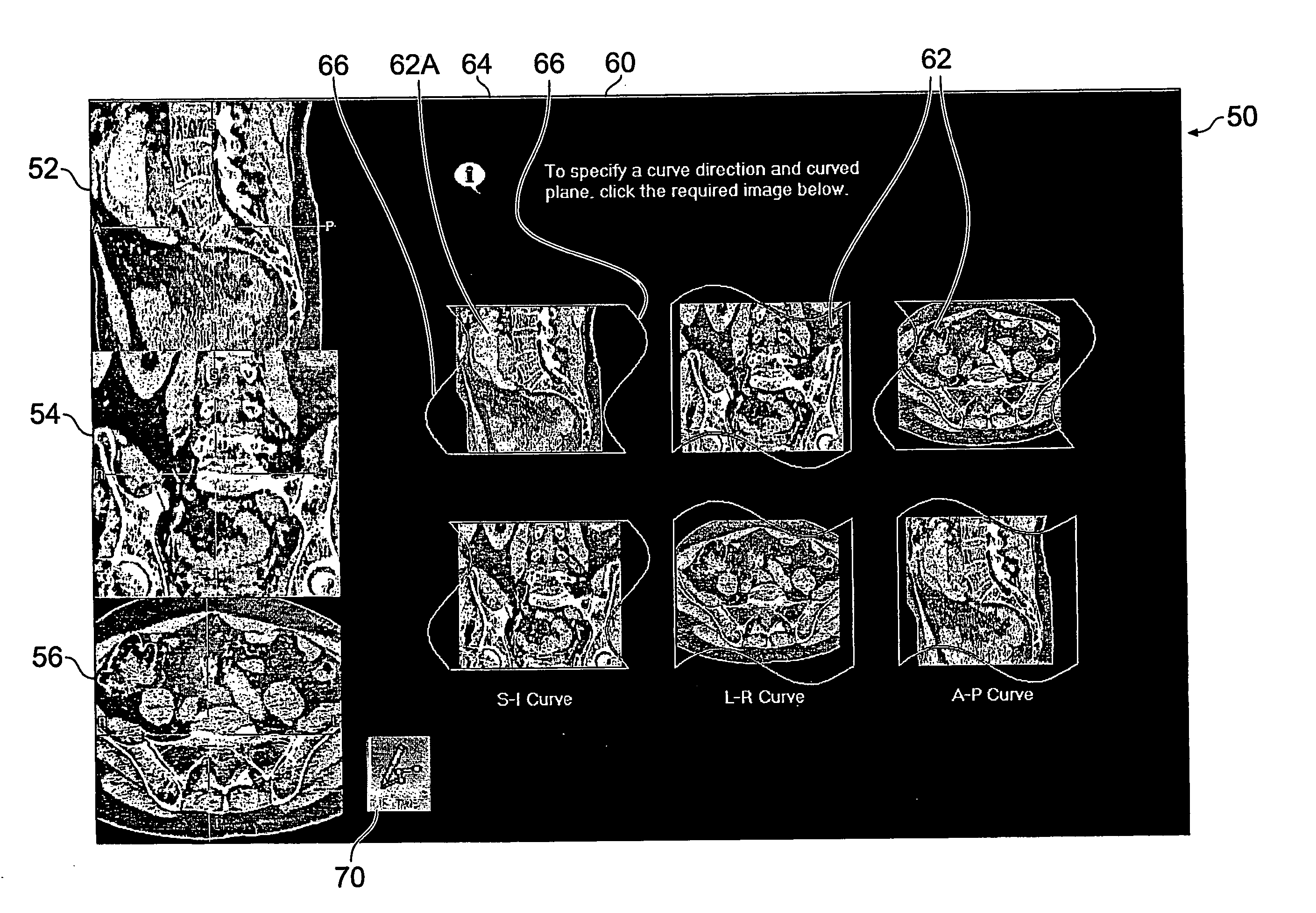
User-interface and method for curved multi-planar reformatting of three-dimensional volume data sets
ActiveUS20050122343A1Simple accessSimplify interfaceGeometric image transformationCathode-ray tube indicatorsVolumetric dataComputer graphics (images)
Owner:TOSHIBA MEDICAL VISUALIZATION SYST EURO
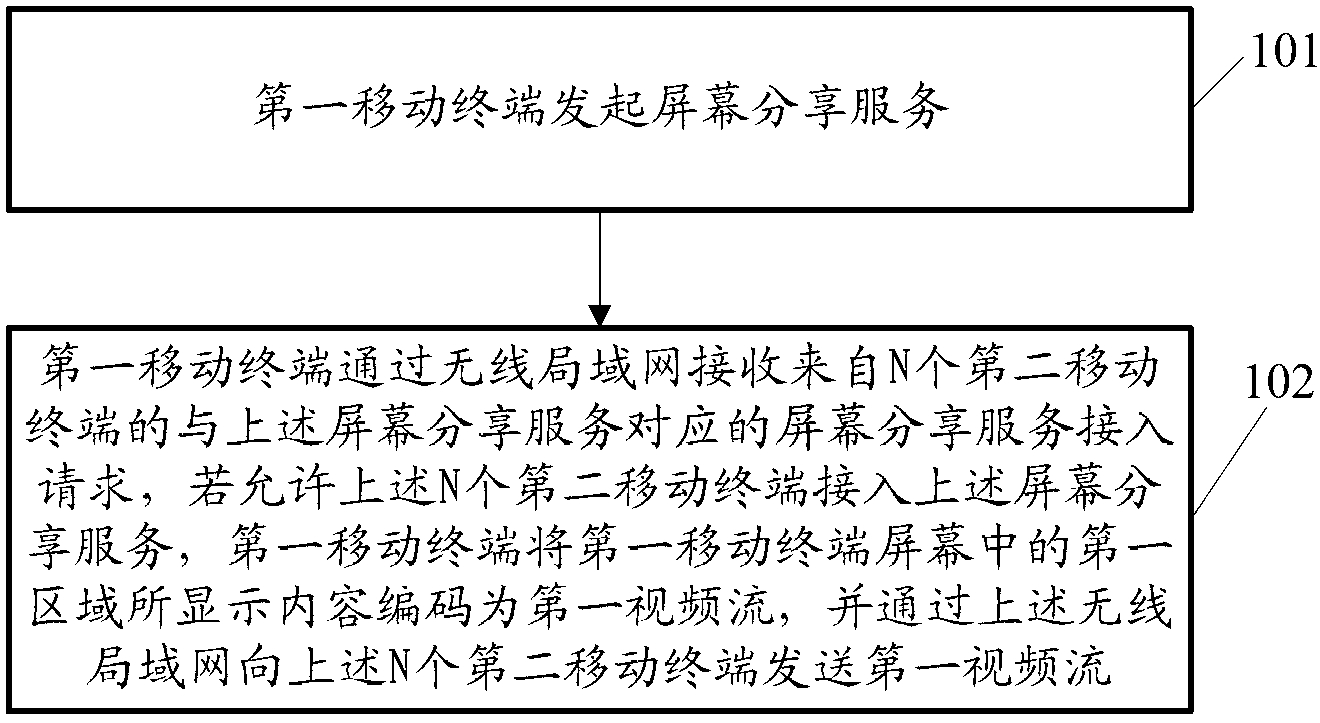
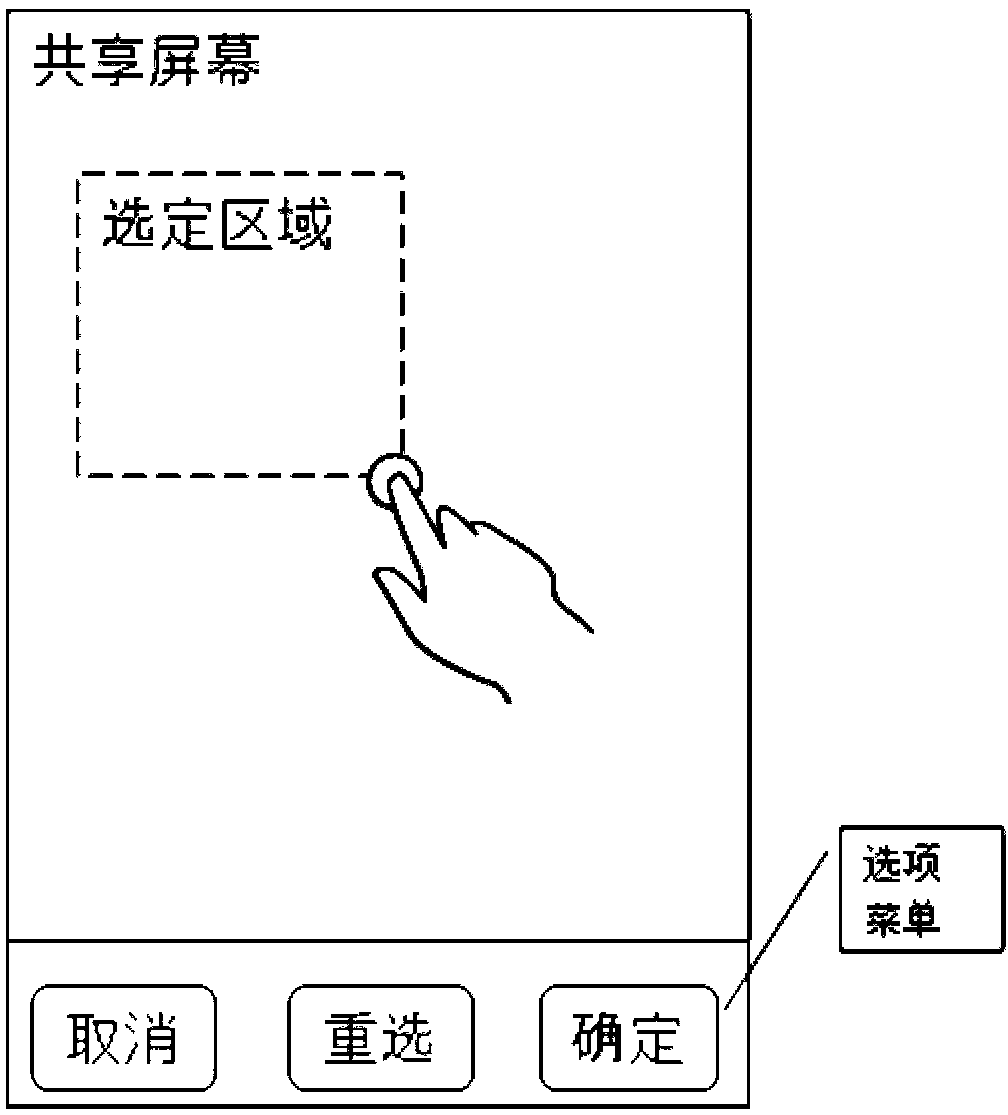
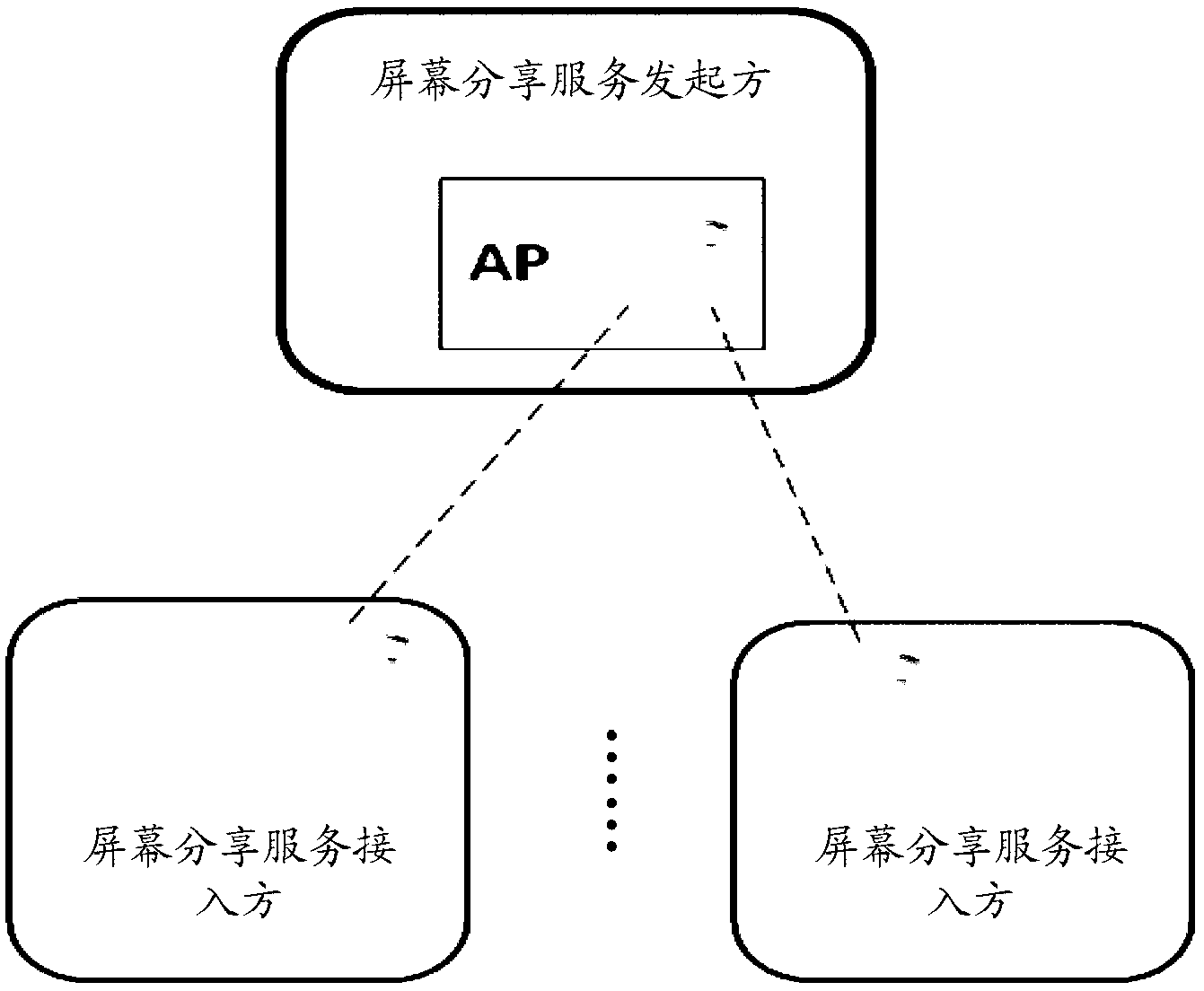
Screen sharing method, associated equipment and communication system
ActiveCN103312804AIncrease the number ofIncrease transfer rateStatic indicating devicesParticular environment based servicesCommunications systemScreen sharing
An embodiment of the invention discloses a screen sharing method, associated equipment and a communication system. The screen sharing method includes that a screen sharing service is started on a first mobile terminal; the first mobile terminal receives a screen sharing service access request coming from N second mobile terminals and corresponding to the screen sharing service through a wireless local area network, wherein the first mobile terminal and the N second mobile terminals are arranged in the wireless local area network, and N is a positive integer; if the N second mobile terminals are allowed to access to the screen sharing service, the first mobile terminal encodes contents displayed in a first region of a first mobile terminal screen into first video streaming and transmits the same to the N second mobile terminals through the wireless local area network. By the screen sharing method, support by a screen sharing technology to scenarios with highly demanded fluency and real-time performance is beneficially improved, and mobile terminal participation and screen sharing flexibility can be enhanced so as to increase the number of screen sharing participants.
Owner:HUAWEI TECH CO LTD
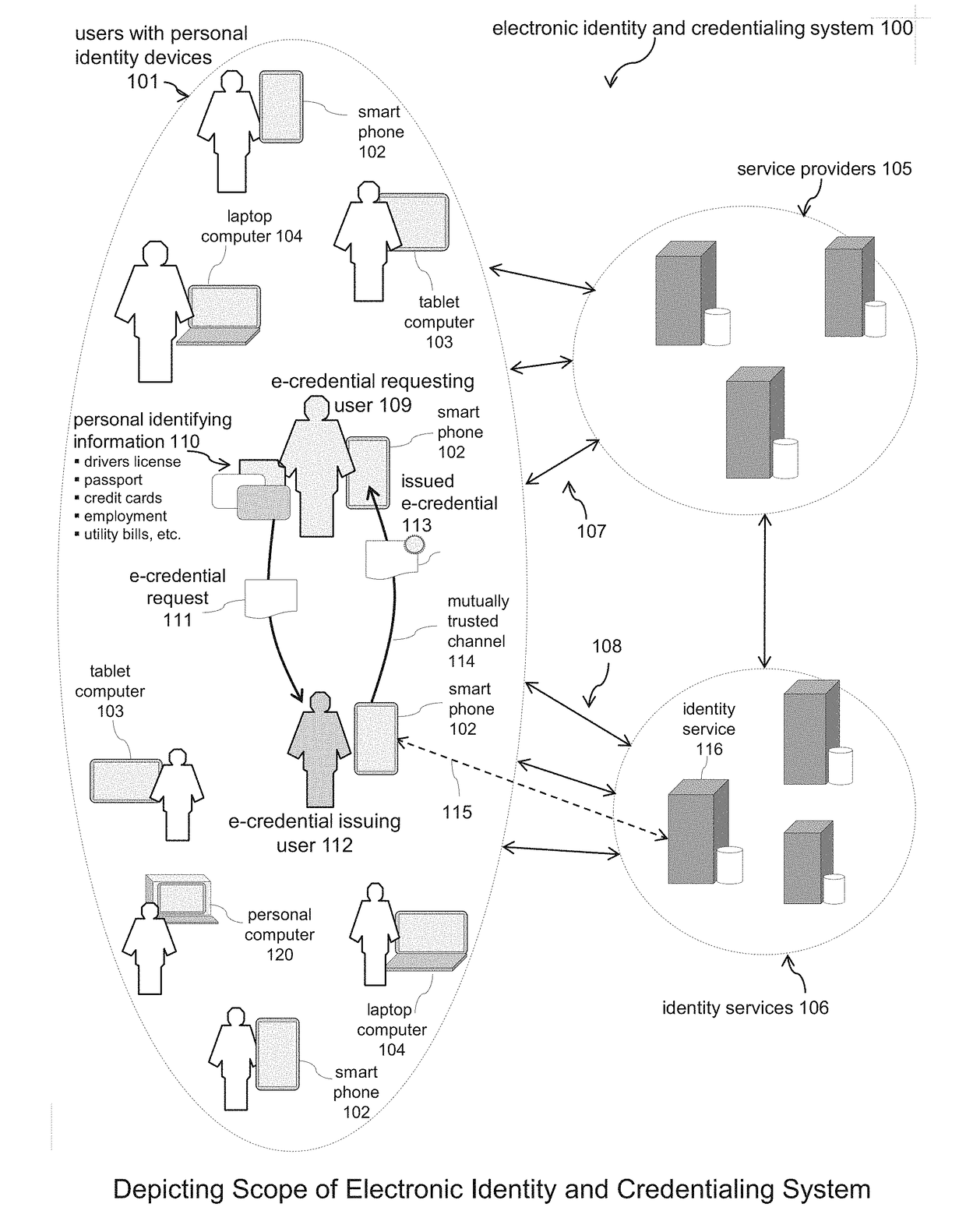
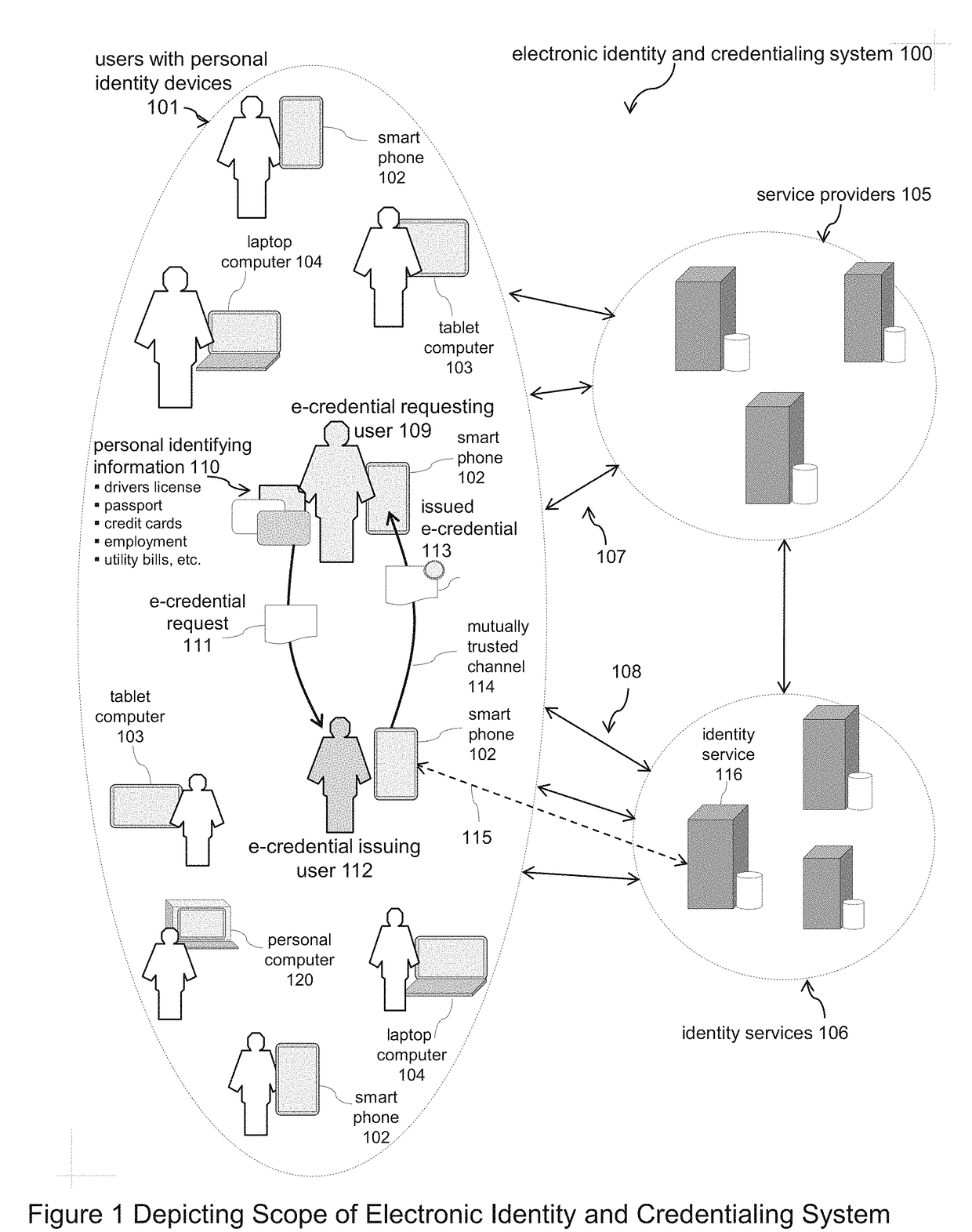
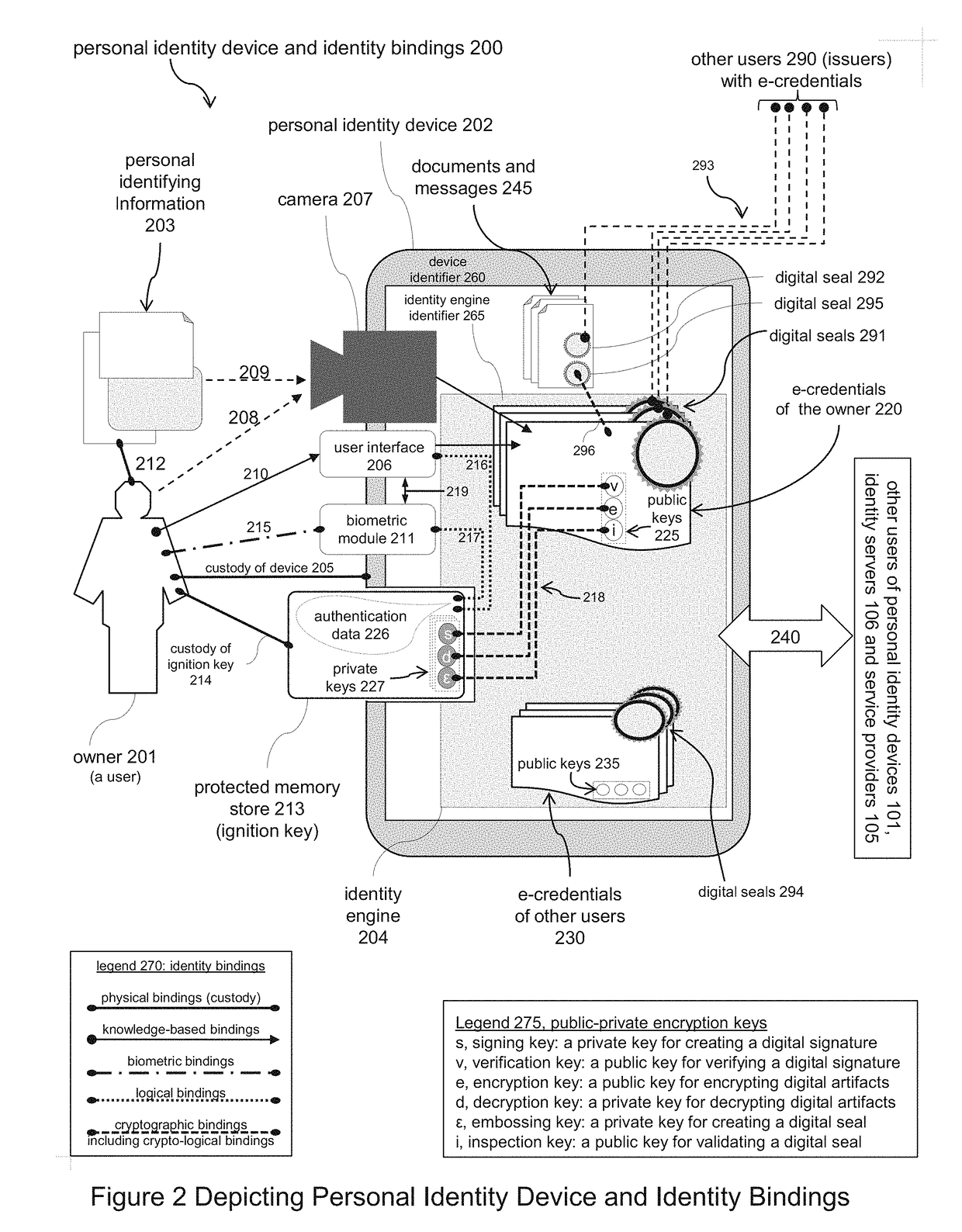
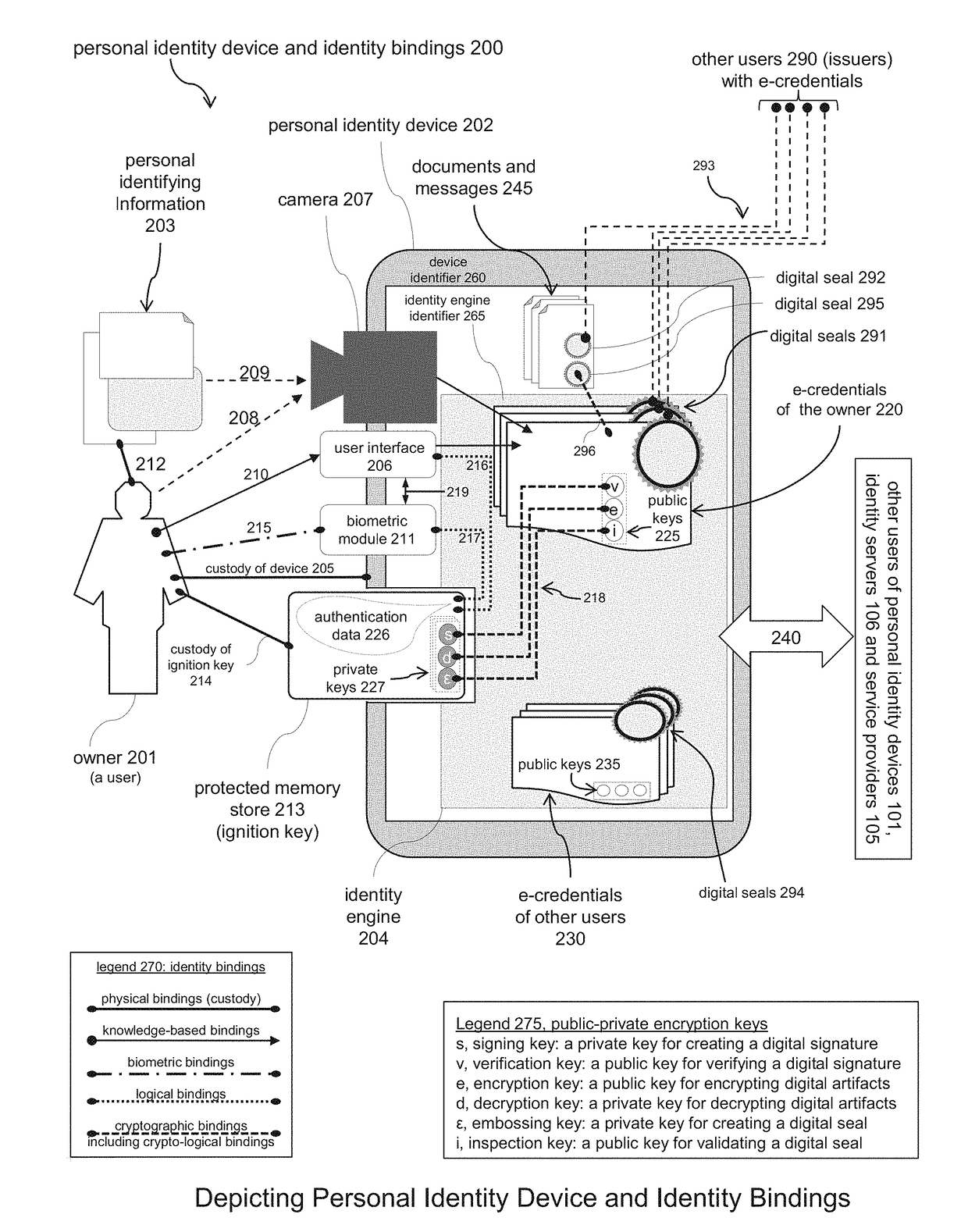
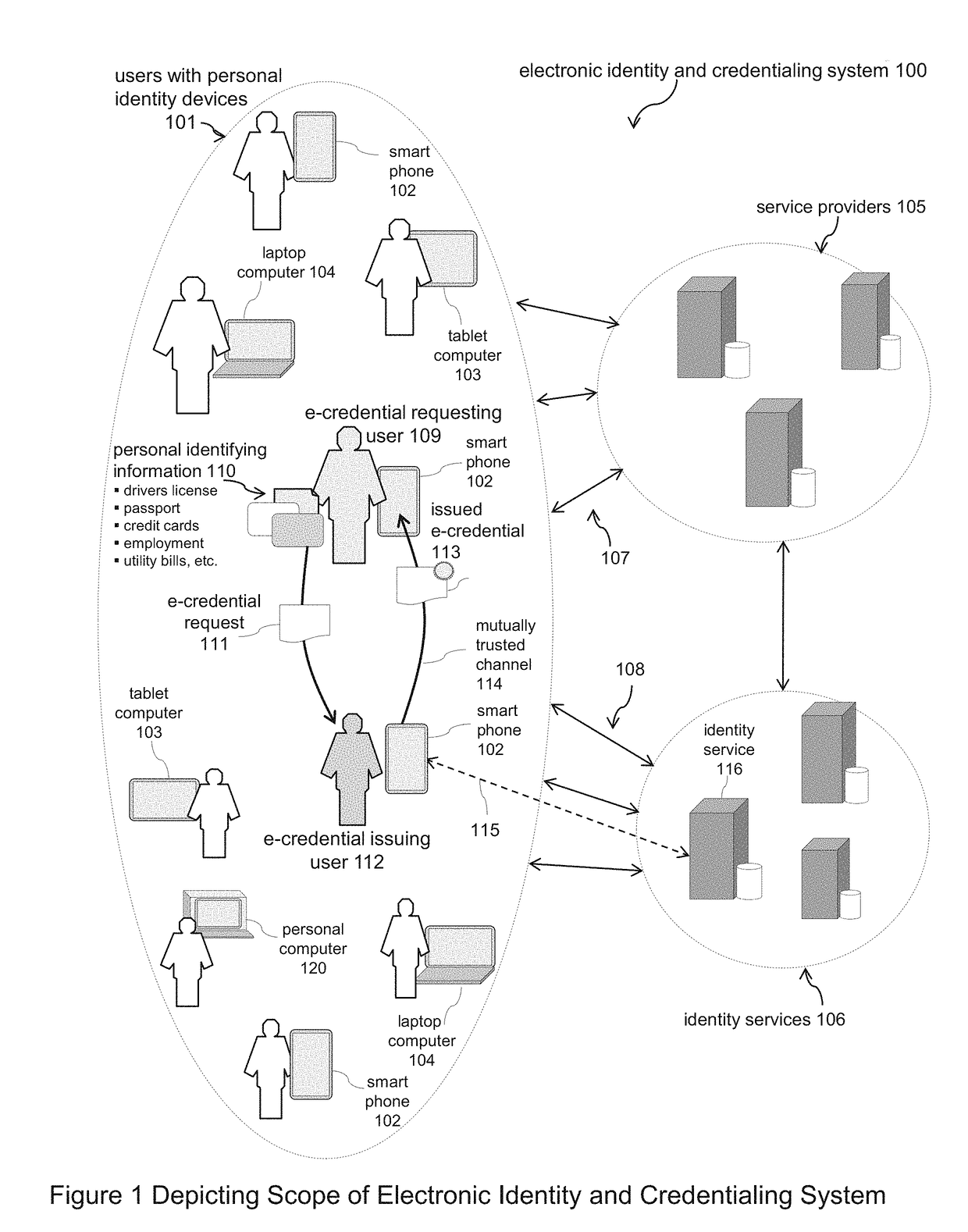
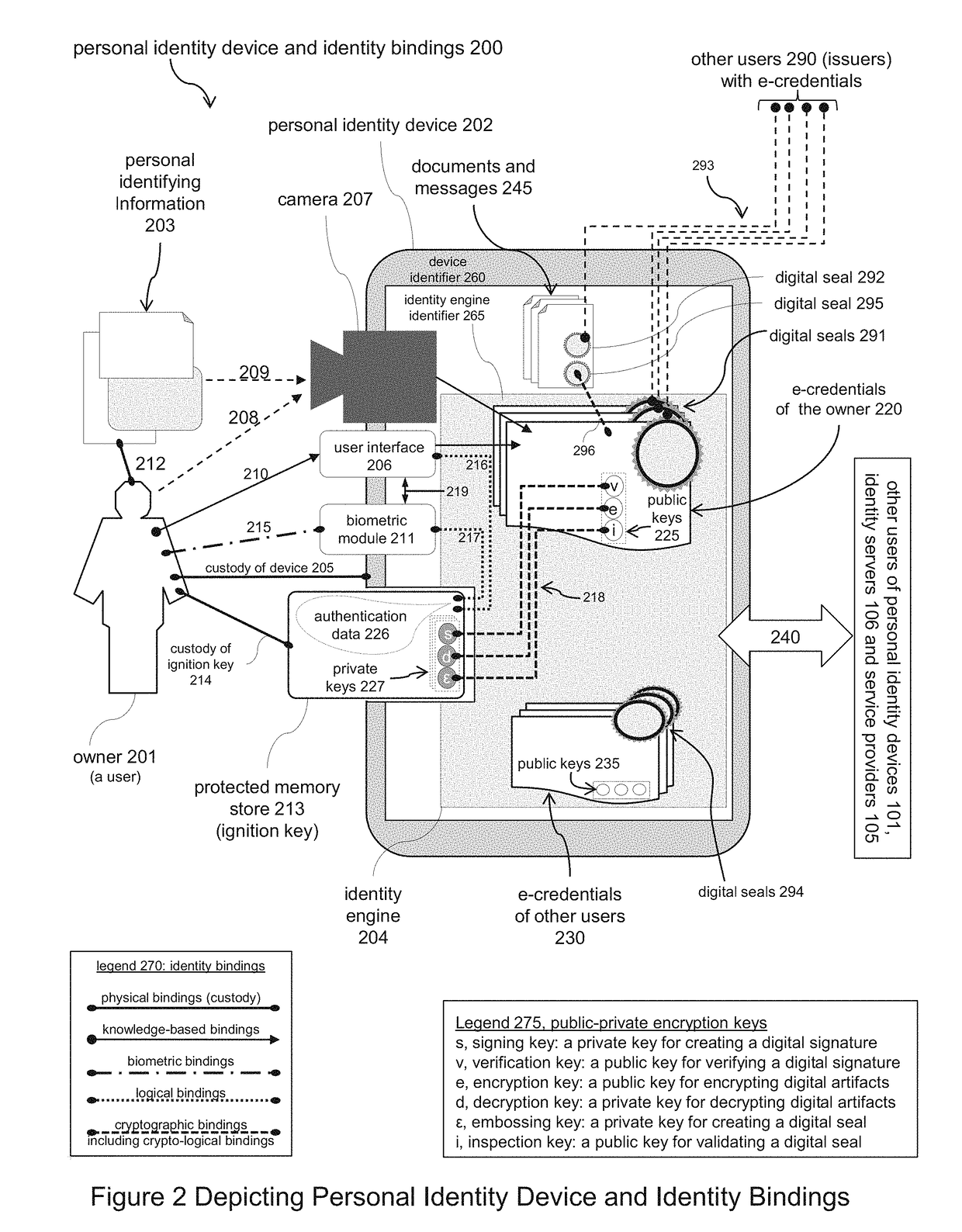
Systems and Methods for Registering and Acquiring E-Credentials using Proof-of-Existence and Digital Seals
ActiveUS20180173871A1Proven reliabilityElevate identityUser identity/authority verificationDigital data authenticationInternet privacyDigitization
Described is a system and methods for registering and acquiring e-credentials using personal devices and an identity registry system that combines the method for handling digital seals with a proof-of-existence method. The identity registry system is used to register and verify e-credentials. Device owners register their e-credentials when created and updated, and verify acquired e-credentials to safeguard against tampering and errors. When registering an e-credential, the e-credential is hashed and digitally sealed creating an identifying thumbprint that is stored in the identity registry system. When verifying an acquired e-credential, the e-credential is hashed, the identity registry system is searched to locate the identifying thumbprint, and the digital seal of the thumbprint is verified. A requesting owner can request an issuing owner to proof, attest, and digitally seal an e-credential of the requester. Both the issuer and requester use the identity registry system to verify e-credentials acquired from the other party.
Owner:TOTH KALMAN CSABA
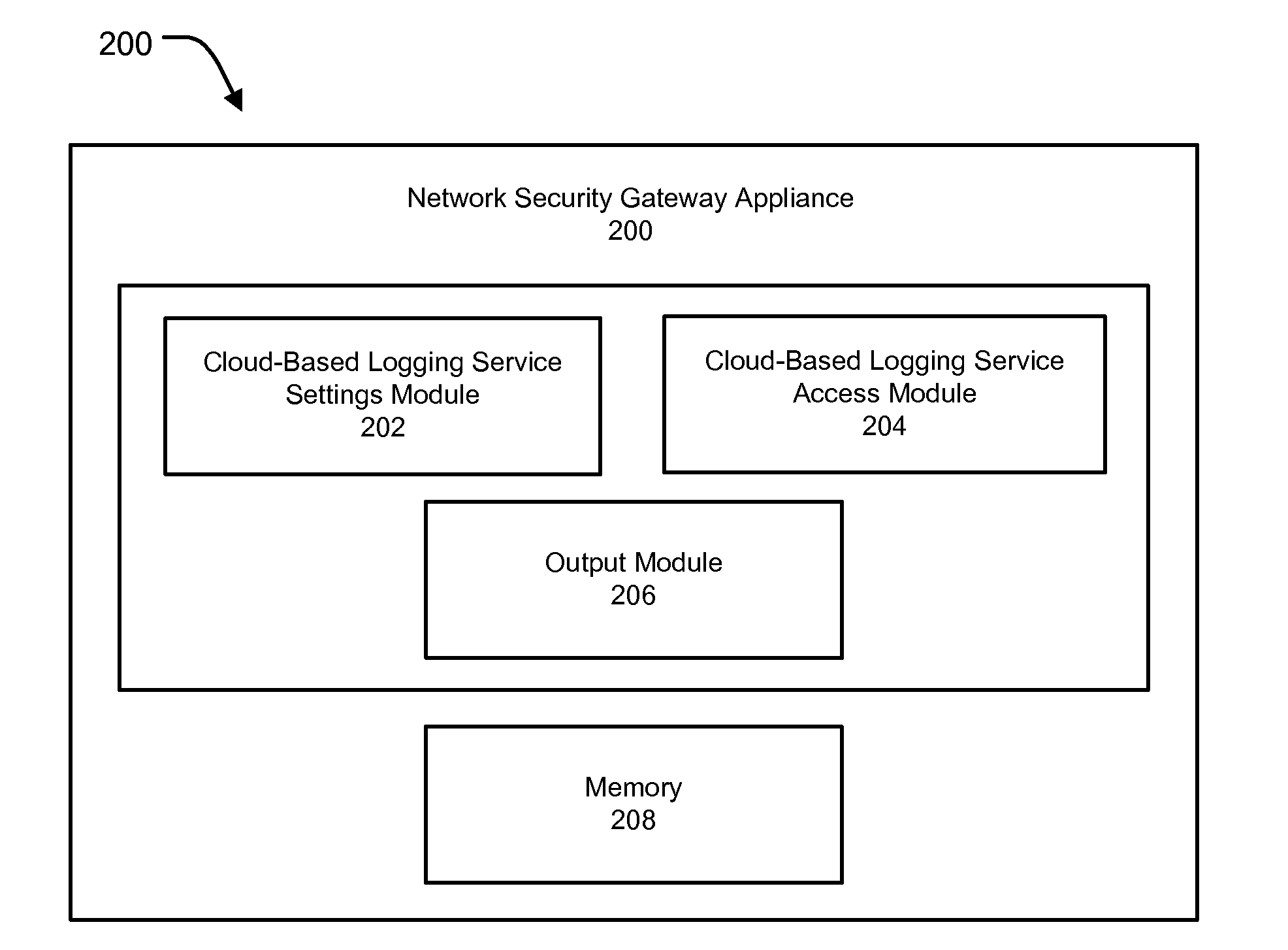
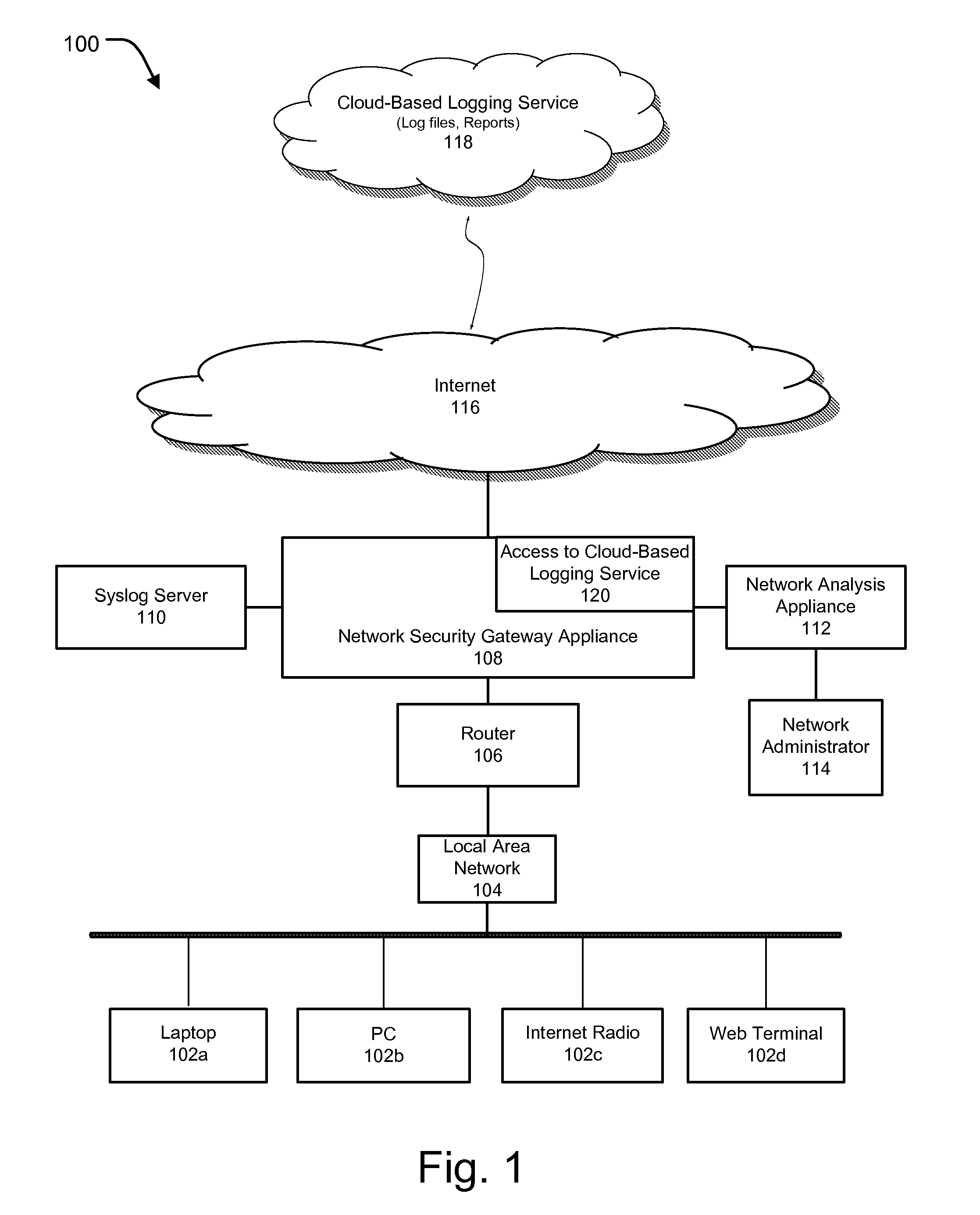
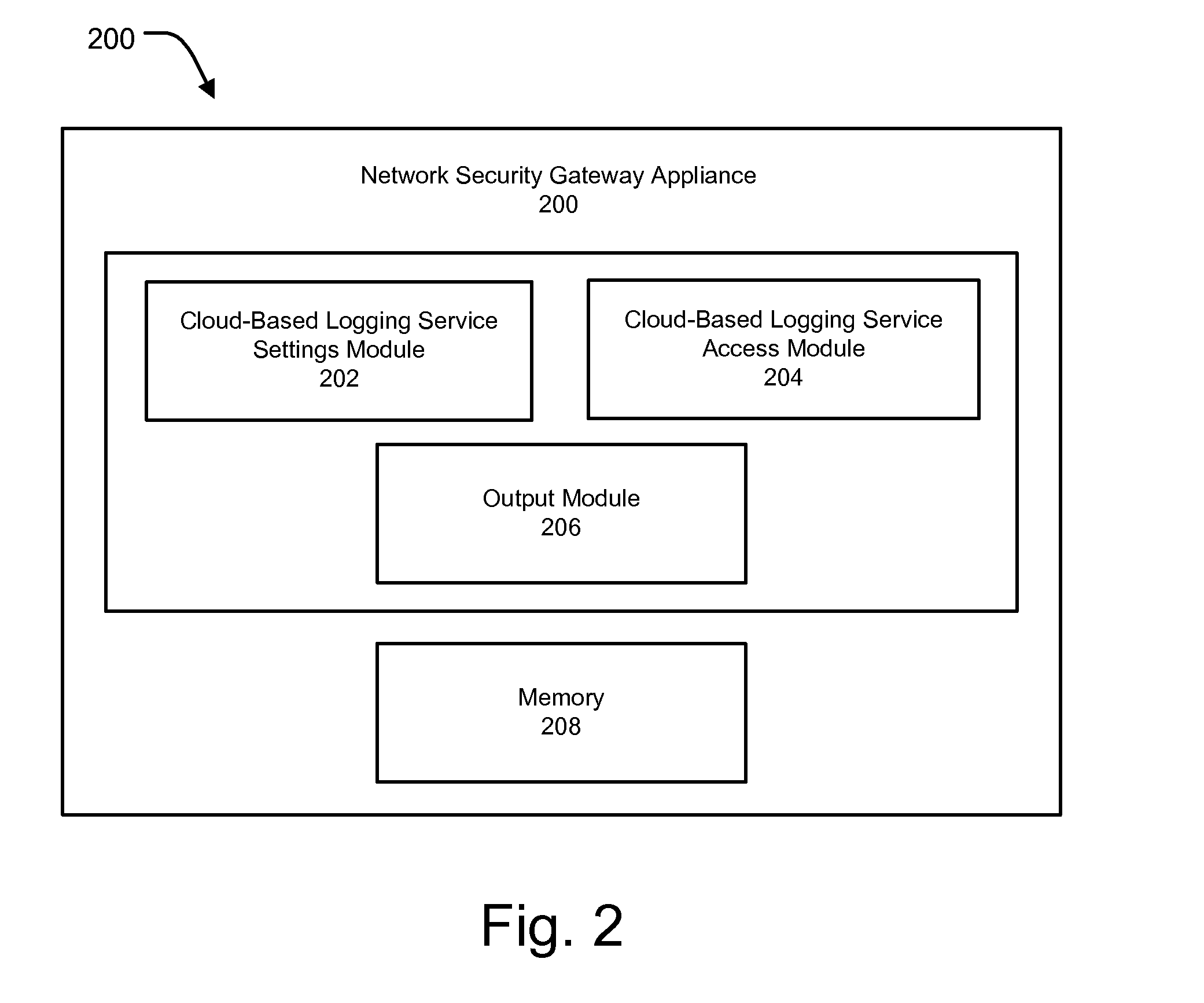
Cloud based logging service
ActiveUS20140366118A1Efficient user accessSimplifying user accessError detection/correctionDigital data protectionApplication programming interfaceNetwork architecture
Methods and systems are provided for providing access to a cloud-based logging service to a user without requiring user registration. Methods and systems are also provided for providing cloud-based logging service to users by integrating the cloud-based logging service within a network security gateway appliance, thereby enabling the users to use the cloud-based logging service by accessing the gateway appliance. The cloud-based logging service can be accessed via an Application Programming Interface (API) without requiring user registration and allows easy and efficient access to log files, viewing of log files, and data security to stored log files and generated reports. Methods and systems of the present invention can also be used for multiple other purposes apart from using the cloud-based logging service without registration including, but not limited to, reducing the complexity of a network architecture, providing better and more effective GUI representation and minimizing distribution of data over a controlled network, among other such purposes.
Owner:FORTINET
Method and system for providing information in interworking between mobile communication network and wireless local area network
InactiveCN1674689AEfficient searchSimple accessEnergy efficient ICTAssess restrictionBroadcastingMobile communication network
A method and system for providing information on mobile communication network-WLAN interworking are provided. In the mobile communication network-WLAN interworking system, interworking WLAN information is broadcast from a mobile communication network to a dual terminal, which has a mobile communication network interface and a WLAN interface. Upon receipt of a broadcasting message including information on an interworking WLAN, the dual terminal turns on its WLAN module and periodically scans for a nearby WLAN in a power save mode. Upon receipt of a broadcasting message including no interworking WLAN information, the dual terminal turns off the WLAN module.
Owner:SAMSUNG ELECTRONICS CO LTD
BLOCK SNAPSHOTS OVER iSCSI
InactiveUS20070055710A1Easy accessSimple and flexible and independent accessError detection/correctionSpecial data processing applicationsISCSISoftware engineering
A snapshot of the data of a block storage resource is taken and made available over a network via iSCSI. The snapshot can be either read-only or read-write.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
WebGIS (Web Geographic Information System)-based traffic light fault supervision system
InactiveCN102708699AAutomate regulationImprove maintenance efficiencyTraffic control supervisionTransmissionTime informationWork period
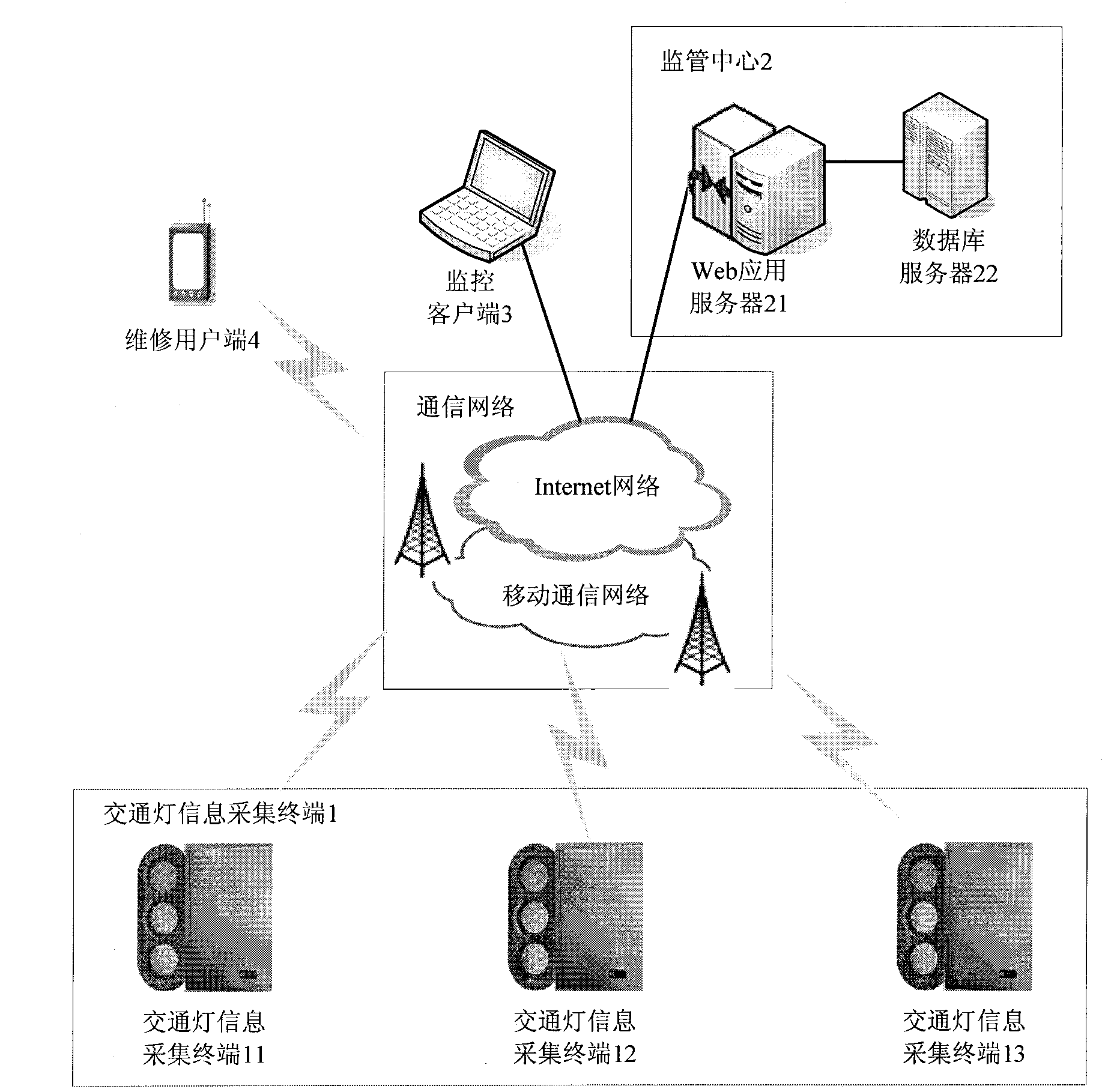
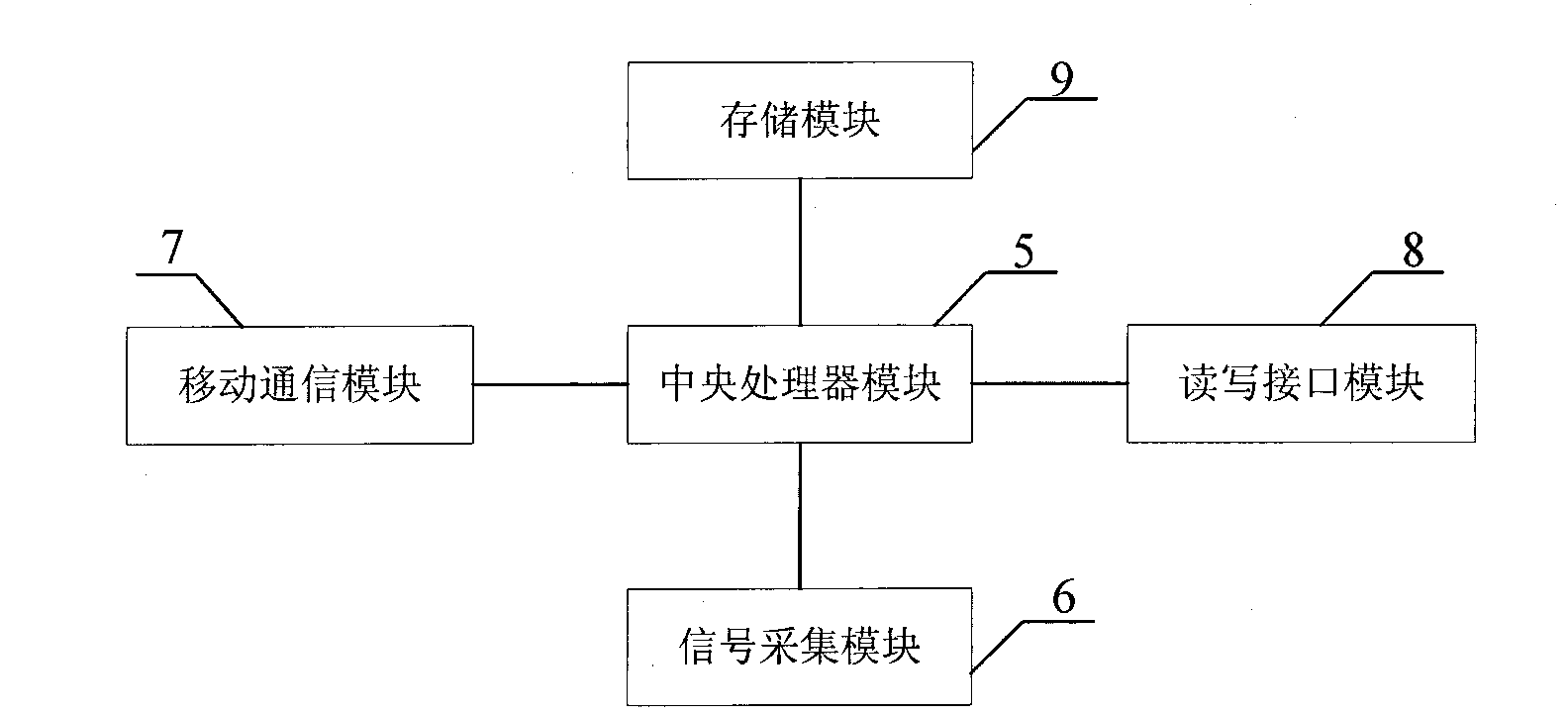
The invention discloses a WebGIS (Web Geographic Information System)-based traffic light fault supervision system. The system mainly comprises a traffic light information collection terminal, a supervision center, a monitoring user side and a maintenance user side which realize two-way information communication by virtue of a mobile communication network and an Internet. The traffic light information collection terminal periodically collects status information of traffic lights and sends the fault information to the supervision center in a text message manner, and the supervision center analyzes and processes the fault information and provides the real-time fault information of the traffic lights in a WebGIS map manner for the monitoring user side logged by a browser, and can automatically perform maintenance task assignment, optimization and calculation after receiving the new fault information, and automatically send a maintenance task command to the maintenance user side after being confirmed by a monitoring personnel. The system can be used for realizing the real-time monitoring and timely maintenance of the traffic lights and increasing the non-fault working time of the traffic lights, thereby further ensuring the safety and smoothing of road traffic..
Owner:CHINA JILIANG UNIV
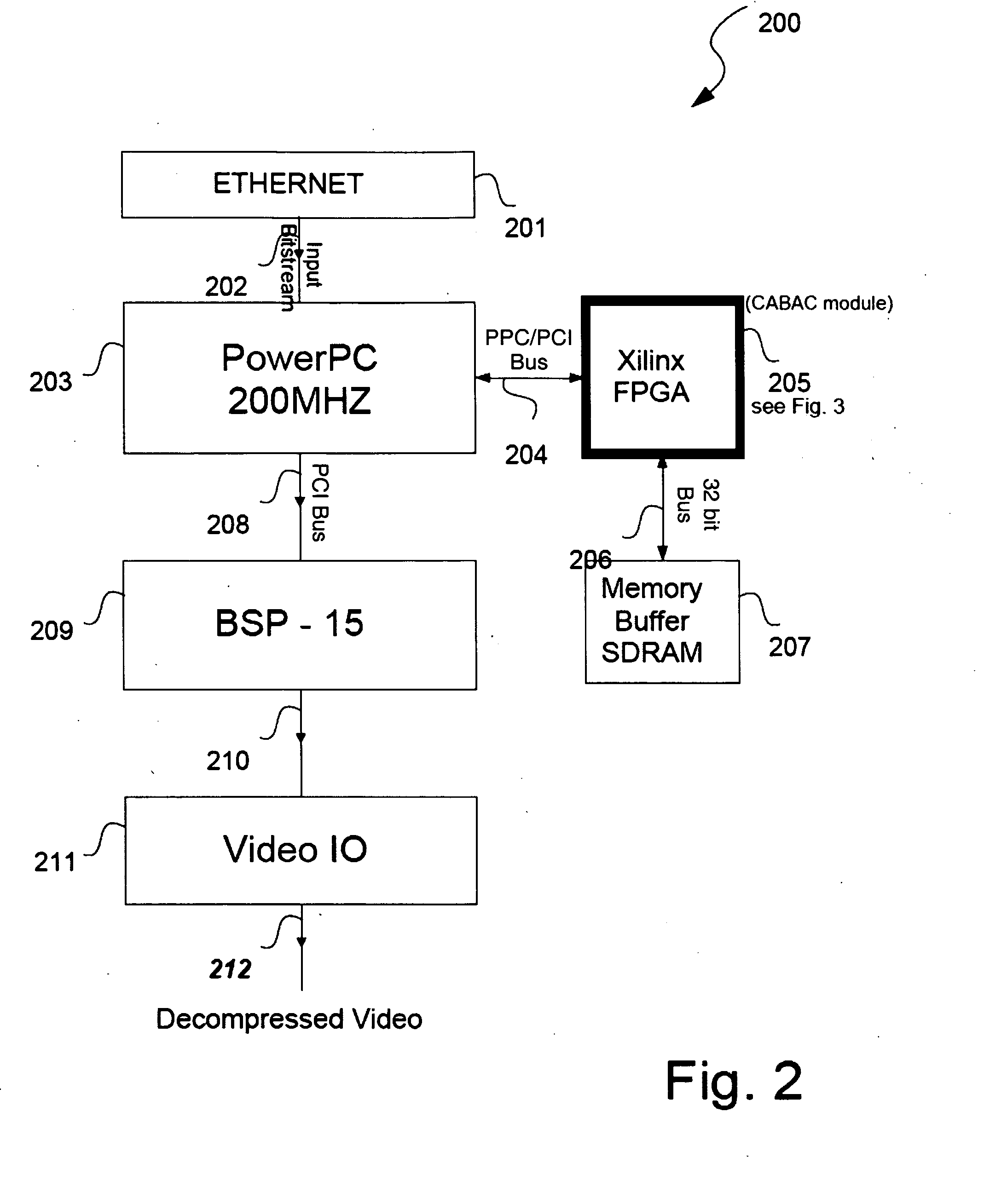
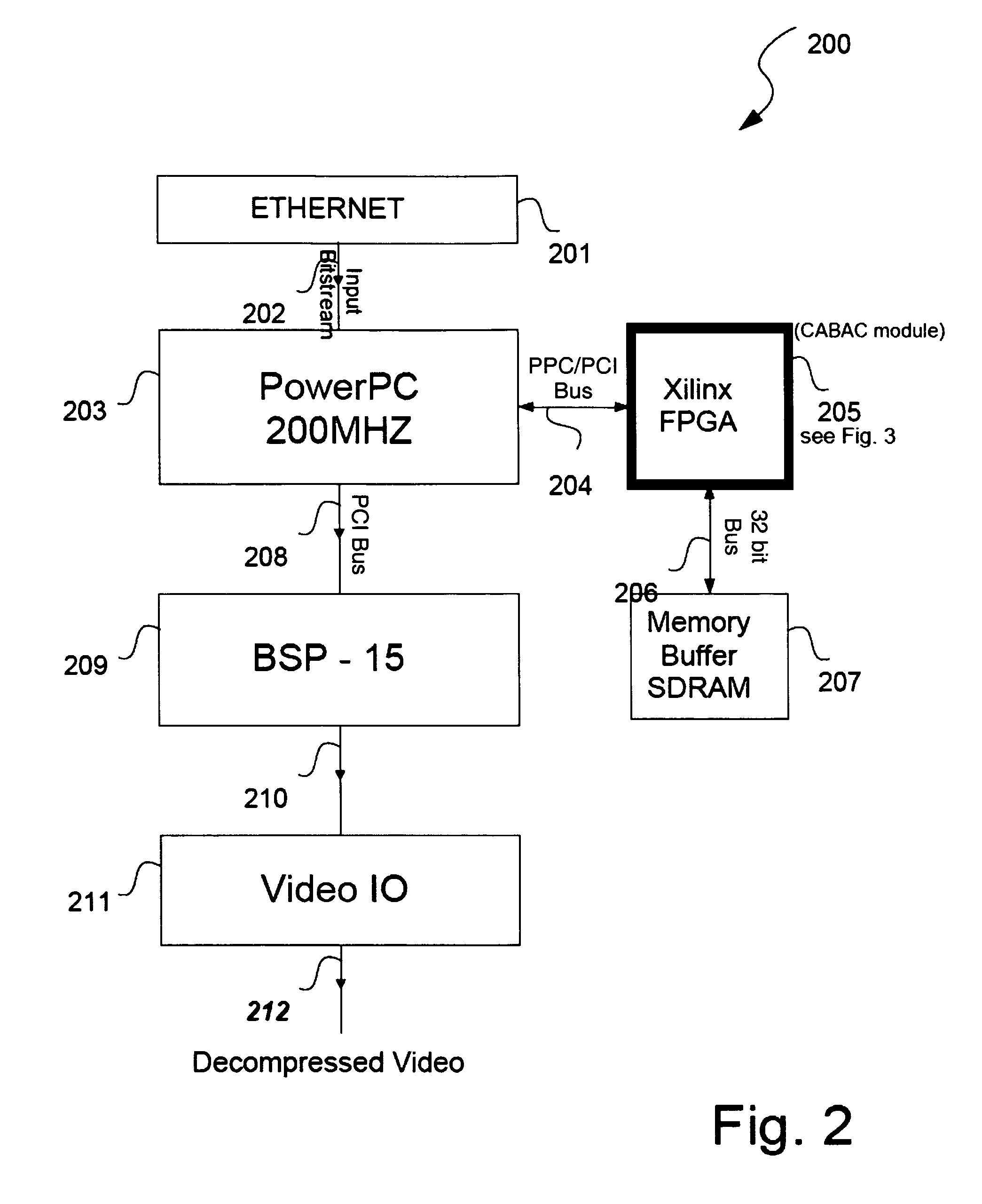
Memory reduced H264/MPEG-4 AVC codec
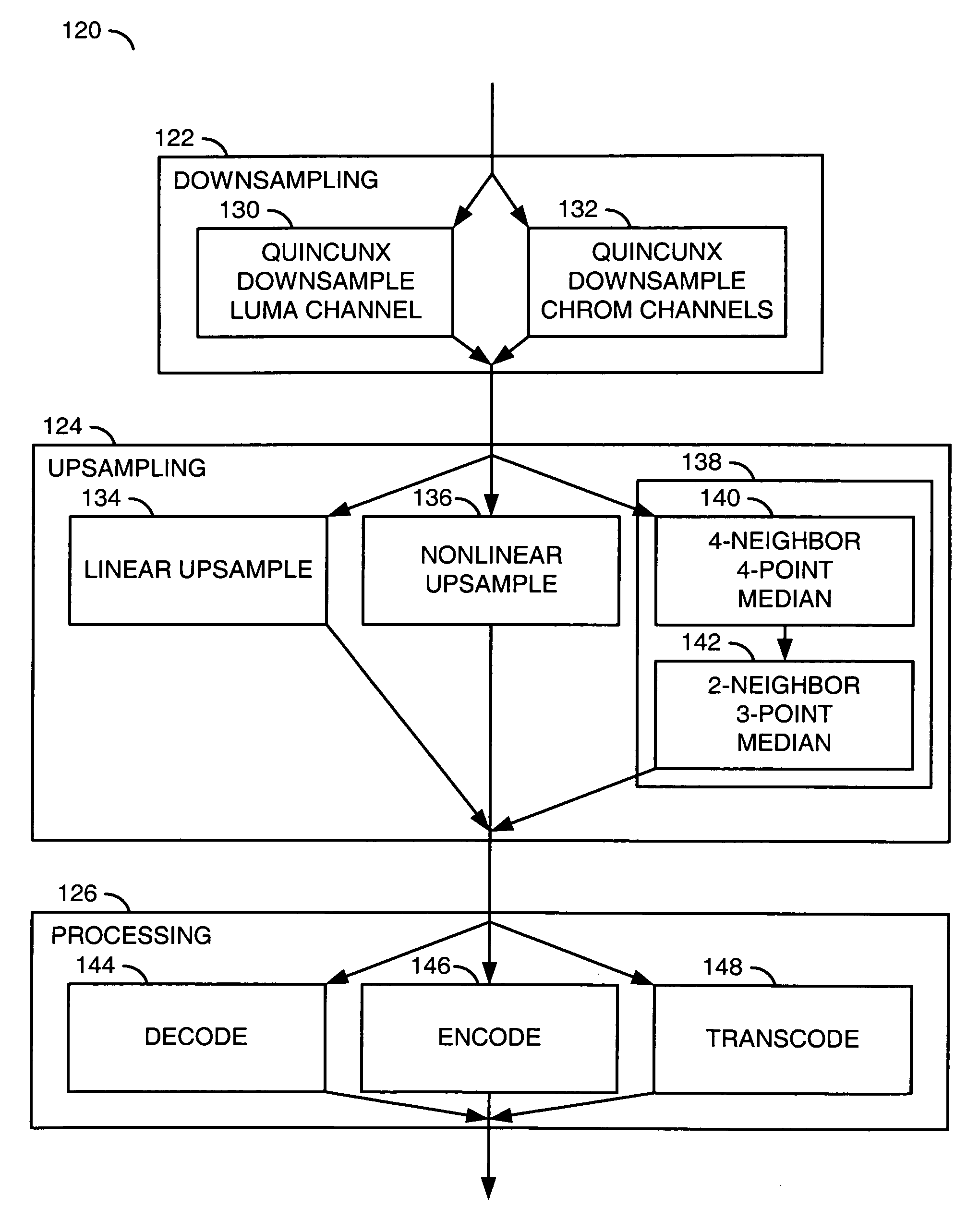
ActiveUS20080130754A1Reduce utilizationImprove performanceColor television with pulse code modulationColor television with bandwidth reductionDigital videoReference map
A method for reducing memory utilization in a digital video codec. The method generally includes the steps of (A) generating a second reference picture by downsampling a first reference picture using a pattern, wherein the pattern (i) comprises a two-dimensional grid and (ii) is unachievable by performing a vertical downsampling and separately performing a horizontal downsampling, (B) generating a third reference picture by upsampling the second reference picture and (C) processing an image in a video signal using the third reference picture.
Owner:AVAGO TECH INT SALES PTE LTD
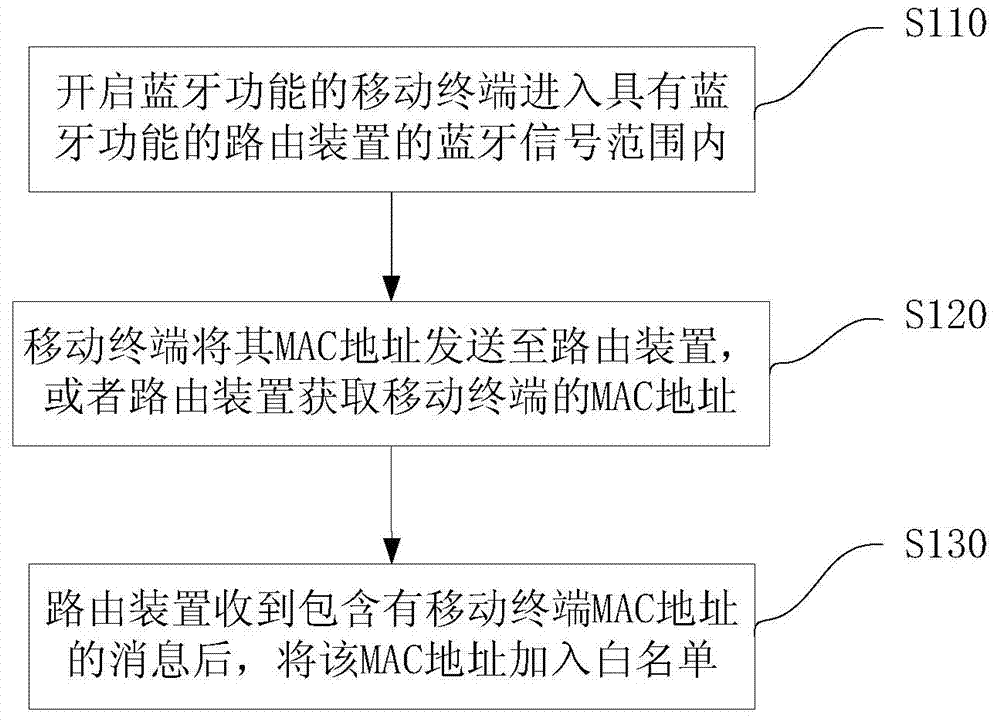
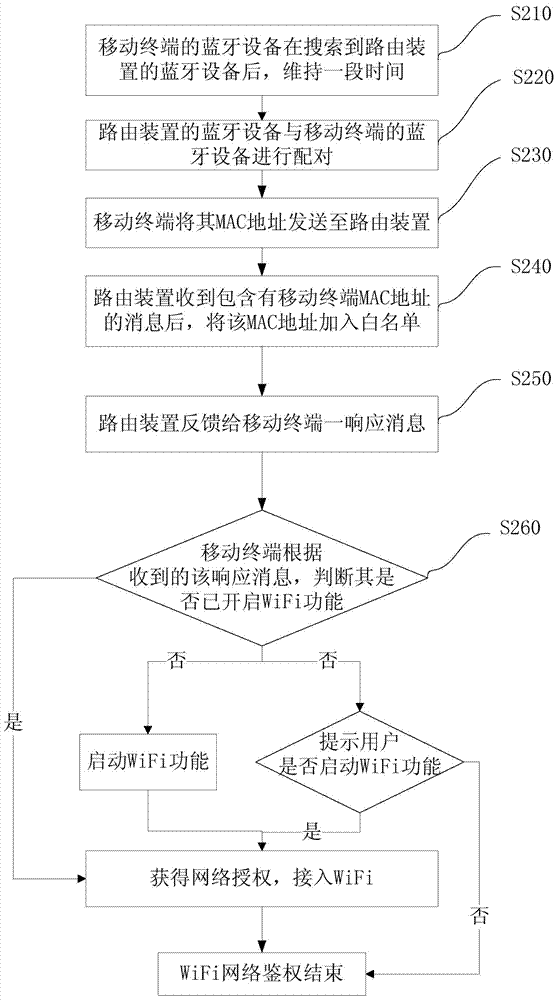
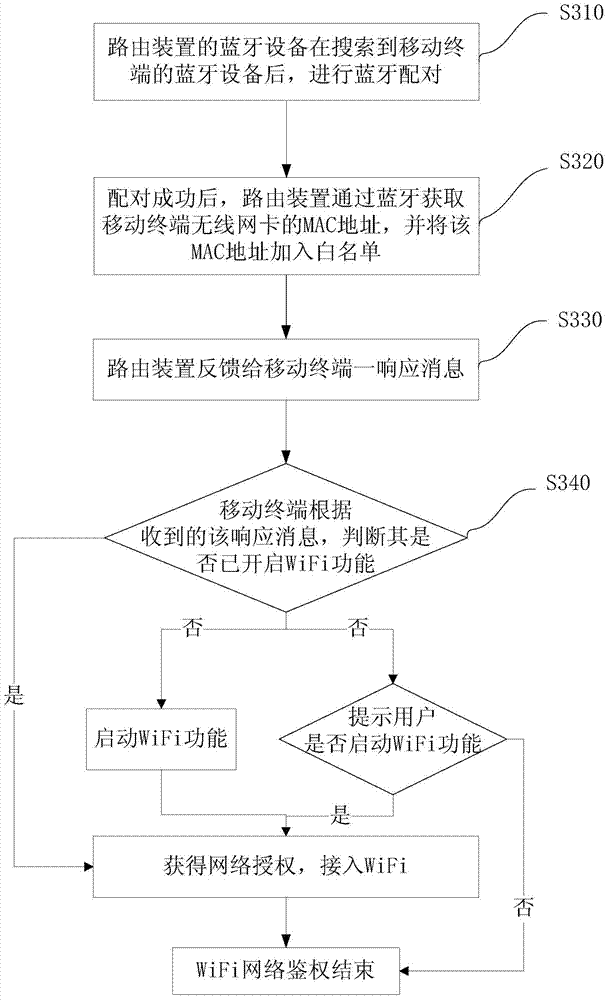
Method and routing device for realizing network authentication through Bluetooth matching
InactiveCN103874168AImprove efficiencyEasy accessNear-field transmissionAssess restrictionClient-sideMedia access control
The invention provides a method and a routing device for realizing network authentication through Bluetooth matching. A Bluetooth function is added to a router, a Bluetooth signal is set in a specified range, the concrete distance can be adjusted according to the magnitude of Bluetooth power, and the distance is used for replacing password authentication. When a mobile phone enters a signal range of the Bluetooth of the router, the MAC (media access control) address of a wireless network card of the mobile phone is transmitted to the router through the Bluetooth by the Bluetooth function of the mobile phone, and after the routing device receives the MAC address, the MAC address of the mobile terminal is used as a client side capable of being accessed to network authority, and is stored on storing equipment. Through the method and the routing device, a user in a limited region can conveniently access a WiFi (wireless fidelity) network, and the working efficiency is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
Method, apparatus, device and system for network access
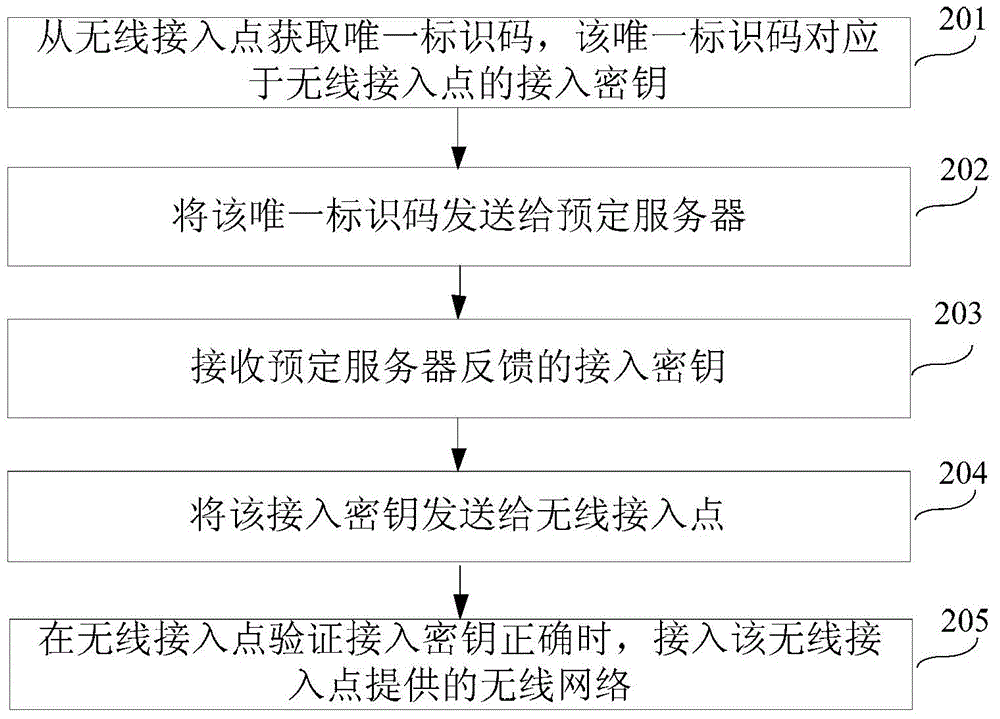
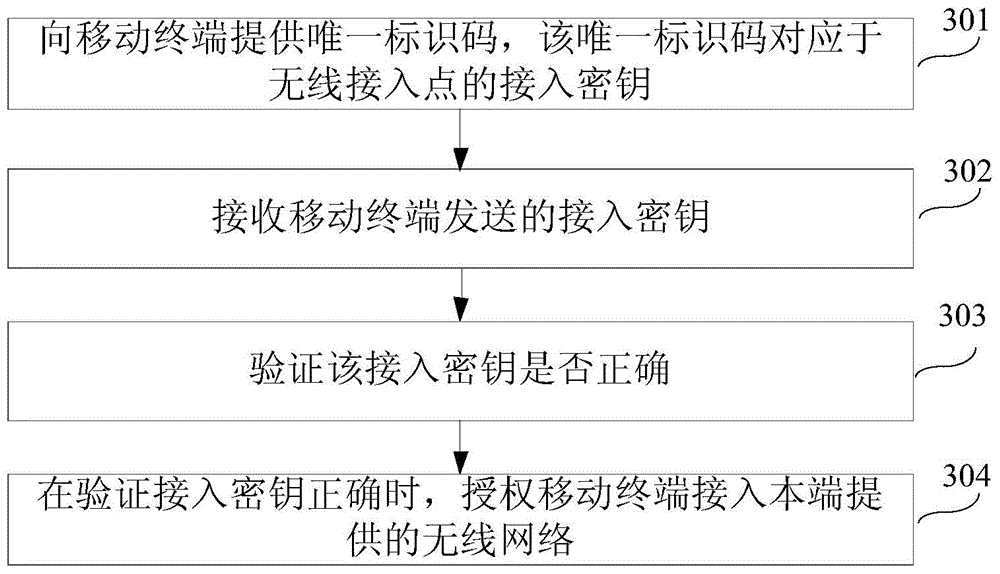
InactiveCN103607713ASimple accessSolve the problem that the access method is still not concise and efficientConnection managementSecurity arrangementAccess methodUser input
The disclosure relates to a method, apparatus, device and system for network access and belongs to the field of computer networks. The network access method includes: acquiring a unique identification code from a wireless access point; sending the unique identification code to a predetermined server; receiving an access secret key fed back by the predetermined server; sending the access secret key to the wireless access point; and accessing a wireless network provided by the wireless access point when the wireless access point verifies that the access secret key is correct. The method, apparatus, device and system for the network access solve a problem that network access methods provided by related technologies are not simple and highly-efficient enough and effects that a user is neither required to input a comparatively long PIN code nor required to press a button for twice and only the step that the user acquires the unique identification code at the wireless access point through a mobile terminal is required so that the wireless network can be accessed simply and highly efficiently are achieved.
Owner:XIAOMI INC
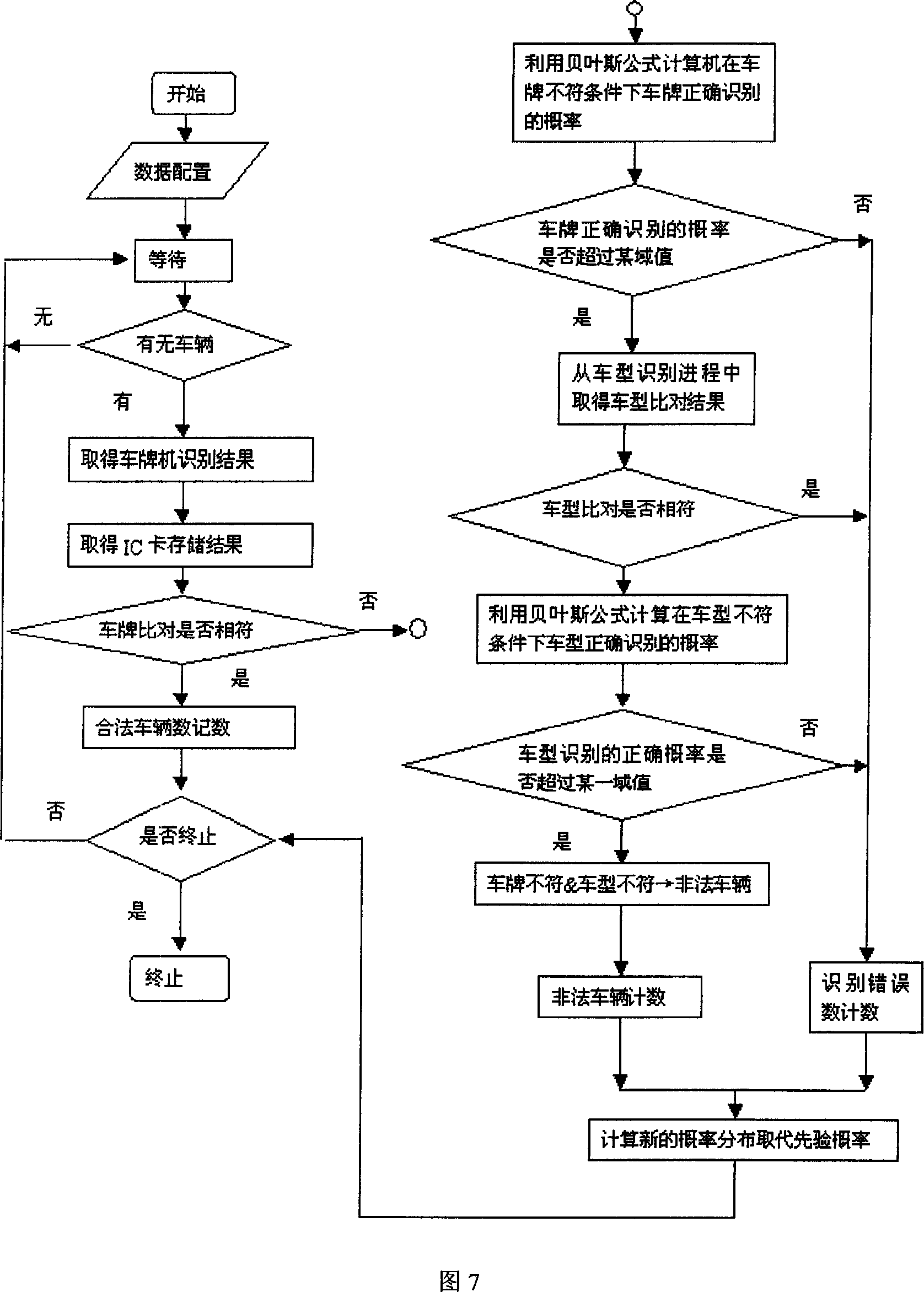
Vehicle personal identification system of ETC electric no-parking charge
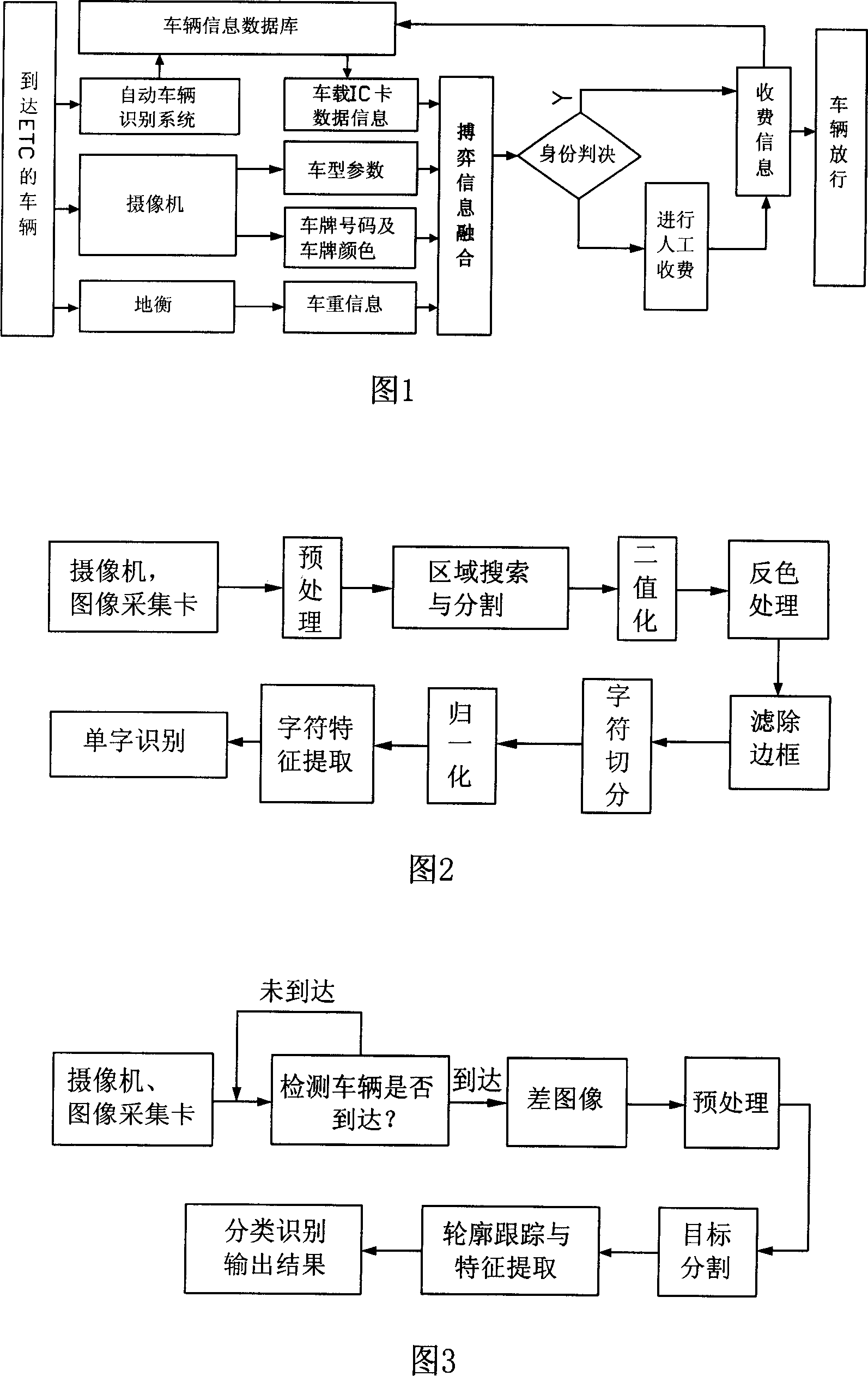
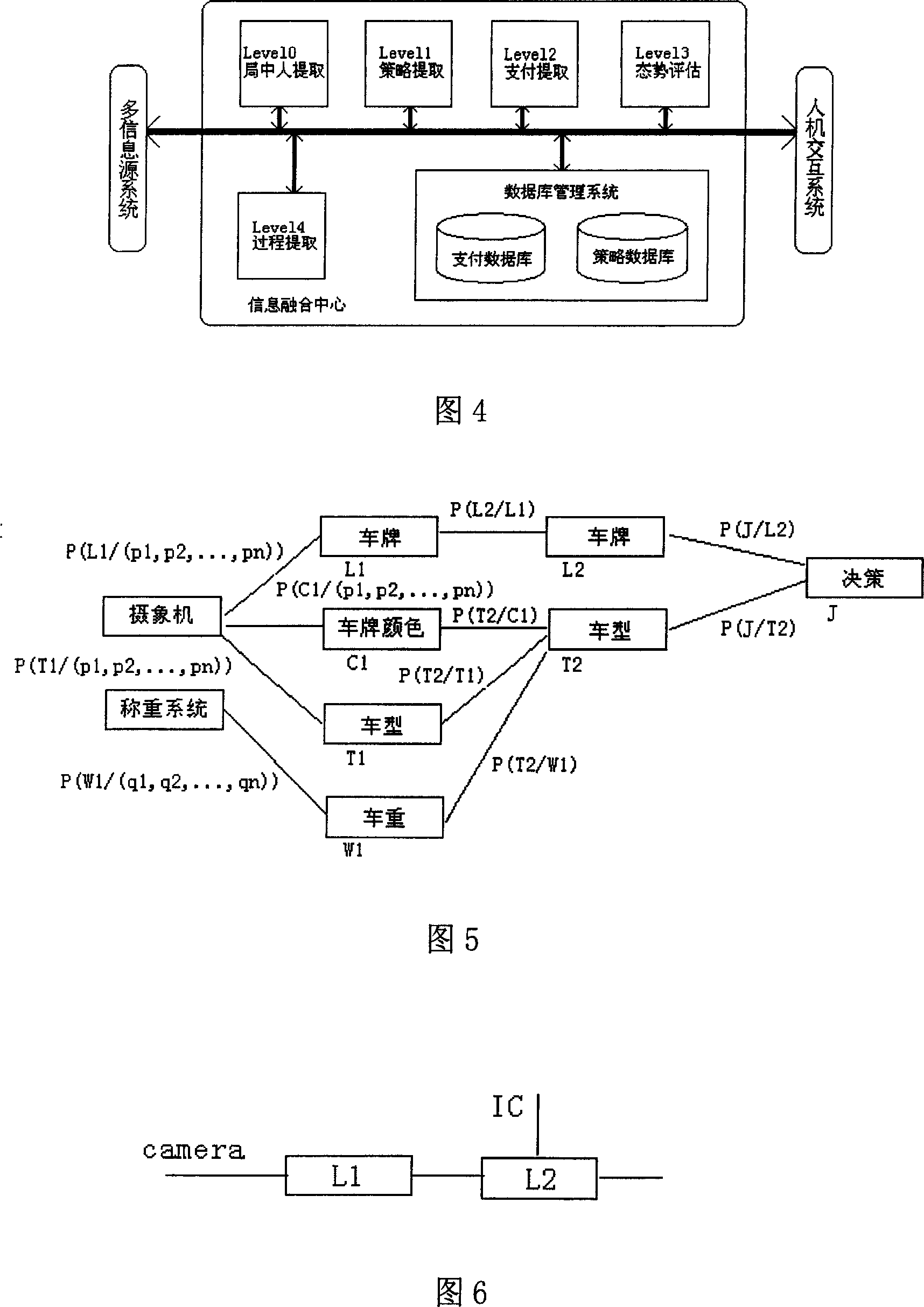
InactiveCN101097605AGuaranteed reliabilityHigh precisionTicket-issuing apparatusRecord carriers used with machinesInformation integrationRadio frequency
The invention discloses a kind of recognition system of vehicle ID of ETC electron without stopping to charging, which includes IC card of vehicle-carrying radio frequency containing the basic information of vehicle and several information channels connect with several sensors, and the information channels is combined by anabranch model of play chess information and the ratiocination algorithm of Bayes's network to complete the precious identification for vehicle ID. The invention anabranches the information of vehicle ID in non-contact intelligent IC card based on the anabranch theory of playing chess information, and the several source information can reach the optimized reliable judgment by the competition and the corporation in the anabranch model, and identify the real ID of vehicle, and ensures the reliability of identification, and the precision can reach above 99.99%, and the invest is little, and the reliability is well. The recognition system of vehicle ID does not occupy the source of host computer and improve the work efficiency of host computer. The identifying device is small and easy to install.
Owner:HENAN UNIVERSITY OF TECHNOLOGY
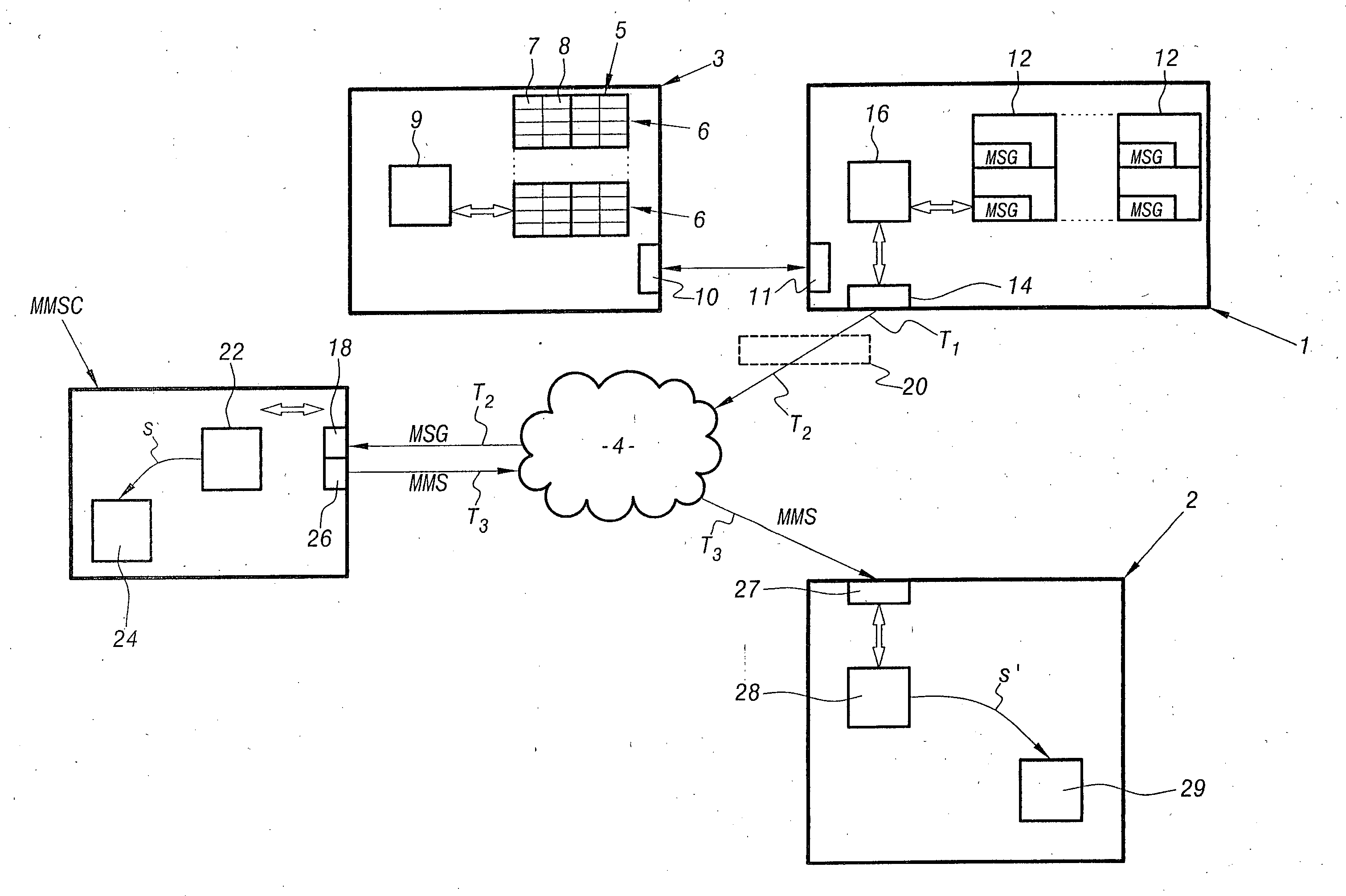
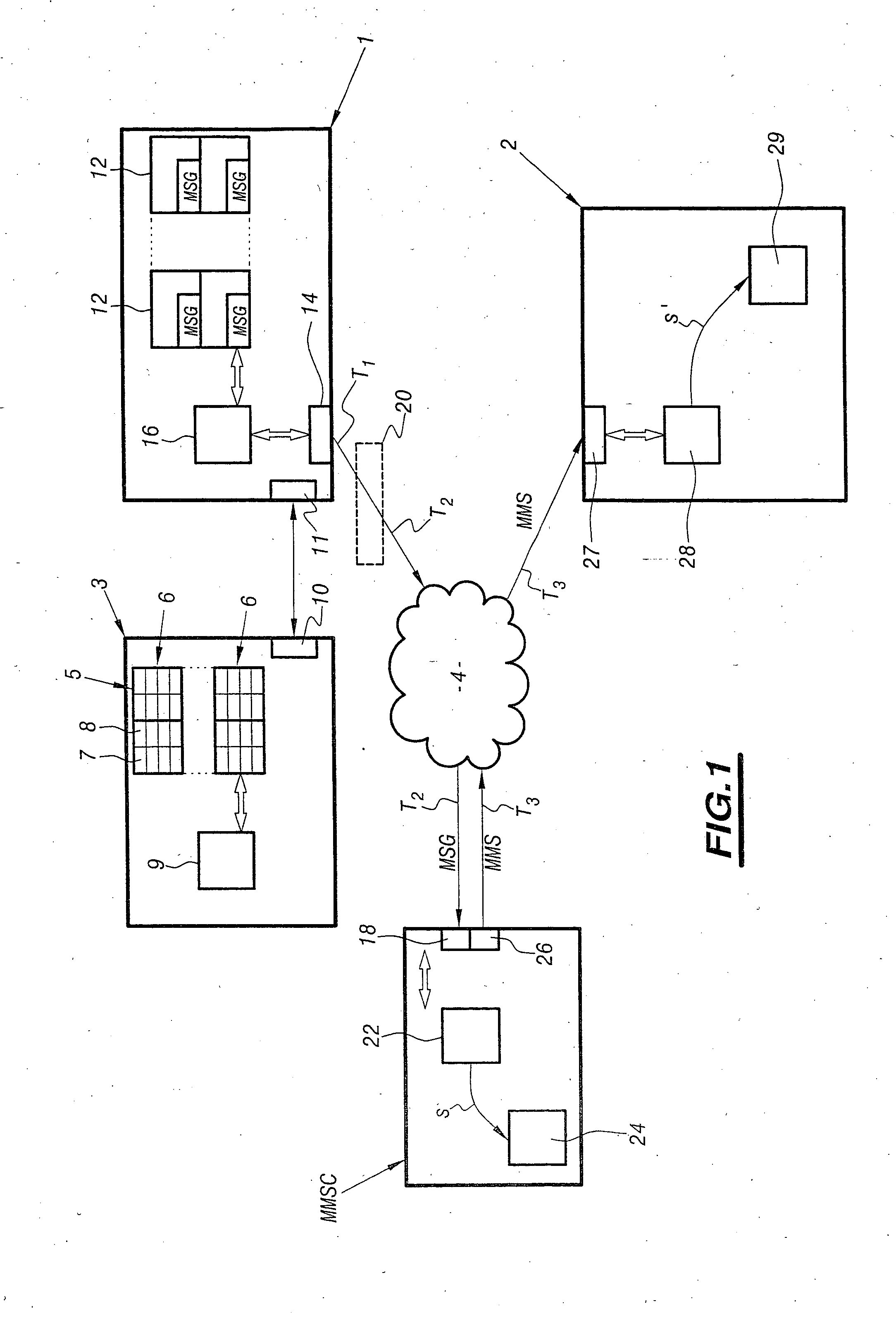
Method and a system for submitting messages deposited in an inbox of a messaging service
InactiveUS20050018821A1Improve notificationsMore user-friendlyAutomatic call-answering/message-recording/conversation-recordingDigital computer detailsEngineeringDirectory
This invention relates to a system and to a method for submitting a message (MSG) to a telecommunications terminal (2) of an addressee, which message has been deposited by a caller in an inbox (12) of a messaging server (1) of the addressee. The method comprises the following successive steps: a step of sending a request to search for an illustration (8) from the voice messaging server (1) to a directory device (3), a step of sending said illustration (8) from the directory device (3) to the messaging server (1), a step of sending the deposited message (MSG) and said illustration (8) from the messaging server (1) to a multimedia messaging server centre (MMSC), and a step of sending a multimedia message (MMS) containing at least said deposited message (MSG) and said illustration (8) from the multimedia messaging server centre (MMSC) to the terminal (2).
Owner:FRANCE TELECOM SA
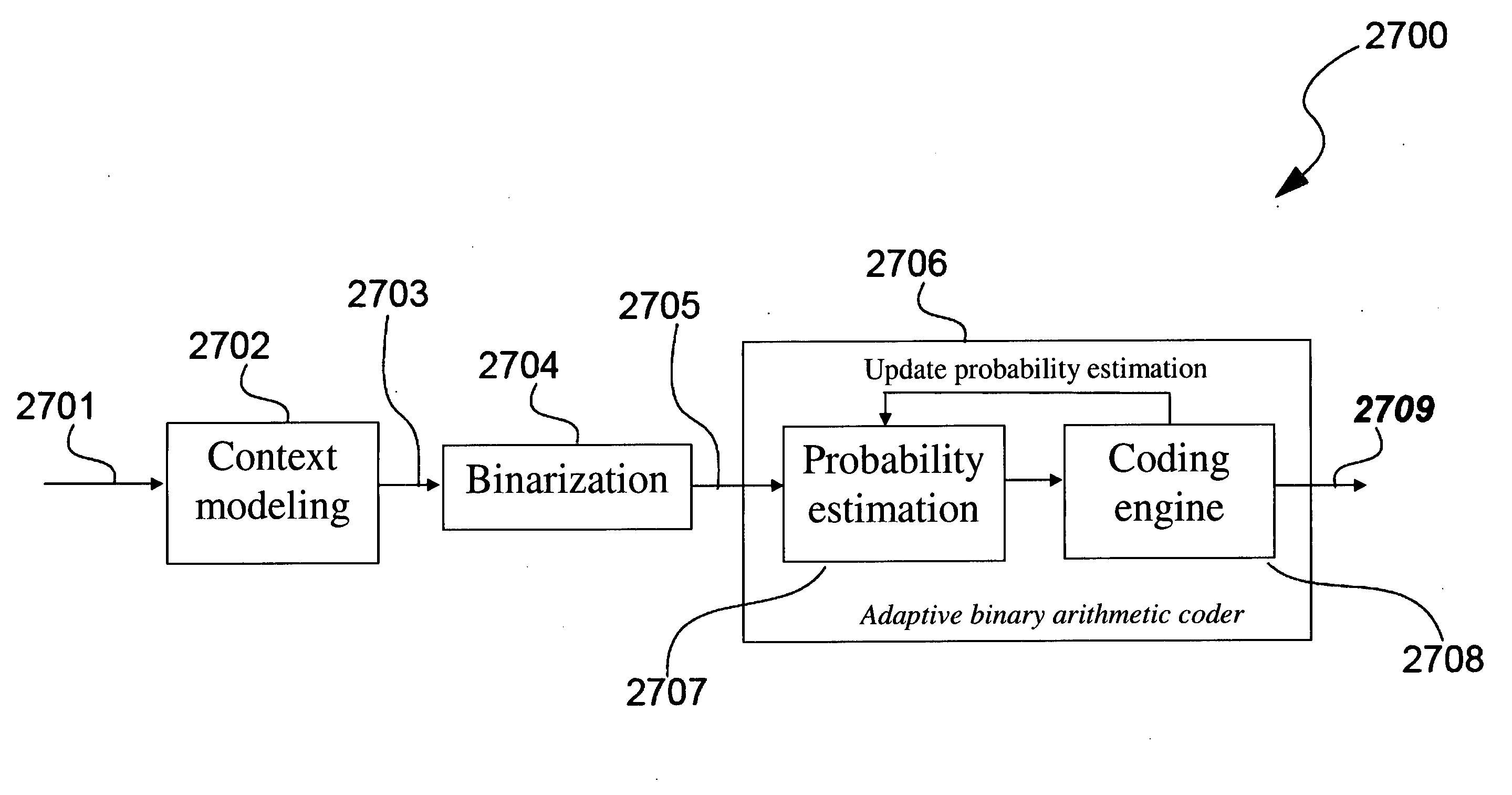
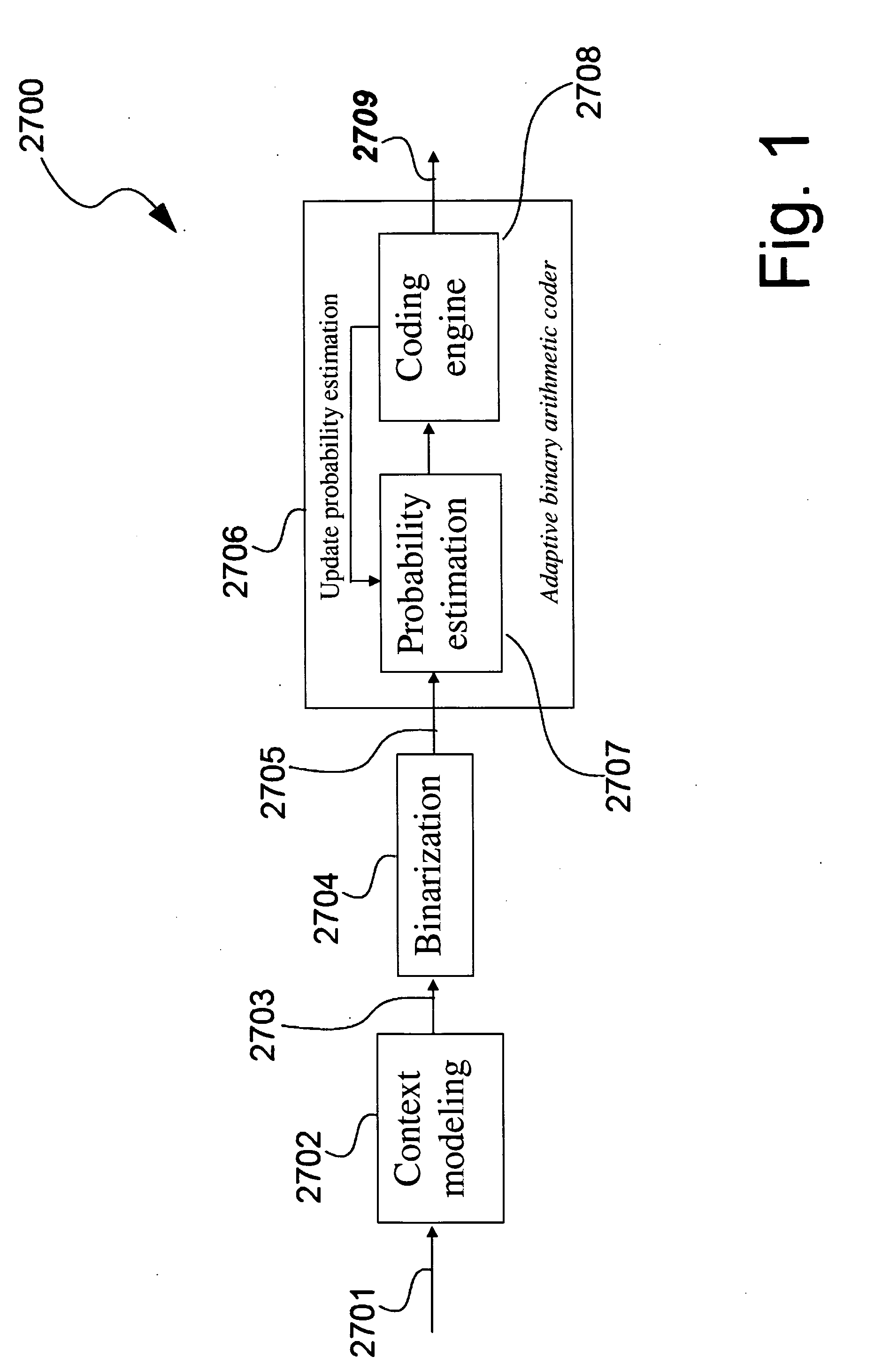
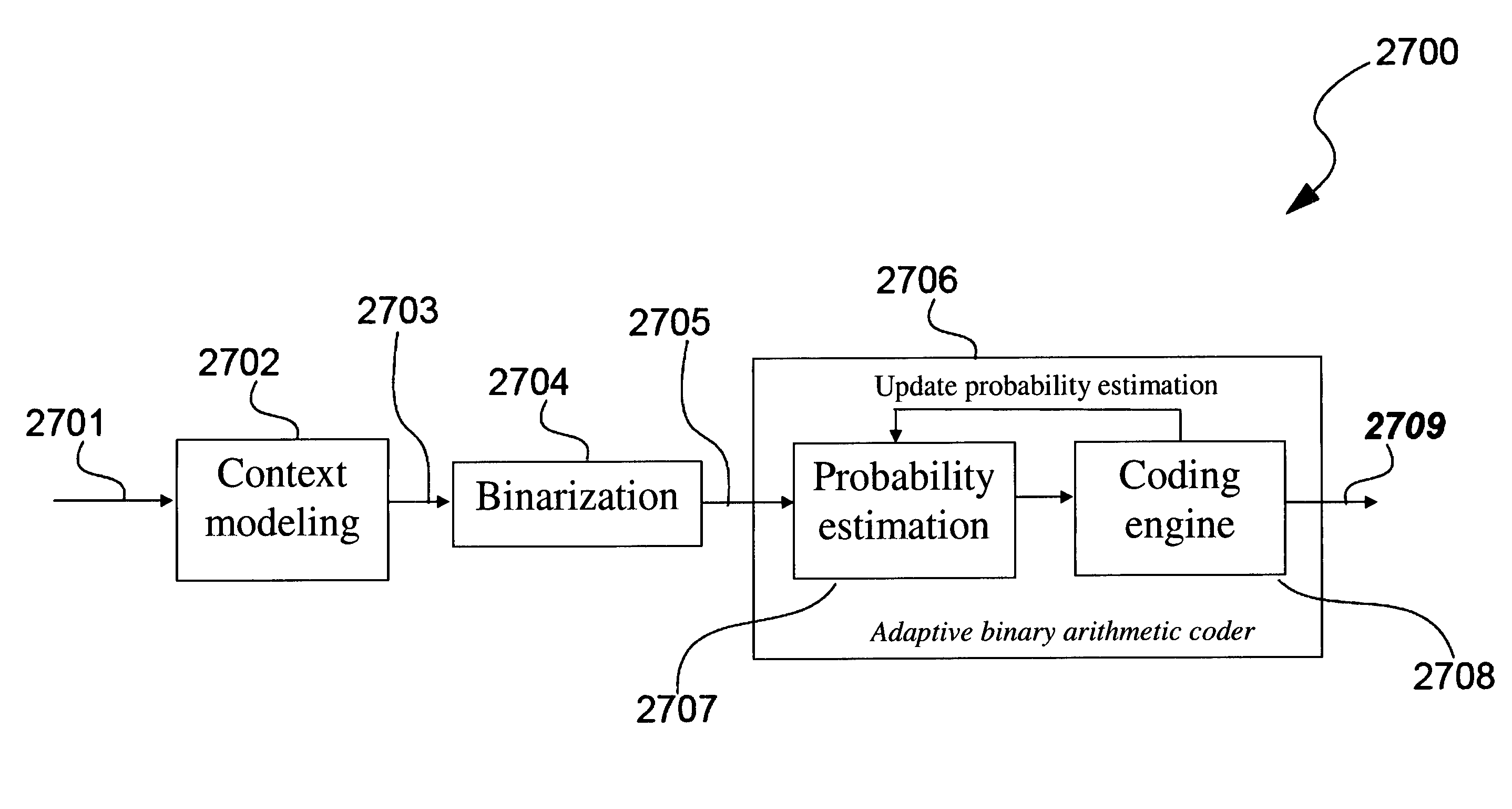
High speed context memory implementation for h.264
ActiveUS20080240234A1Improve speedEnhance hardware performanceColor television with pulse code modulationColor television with bandwidth reductionRead-only memoryMemory controller
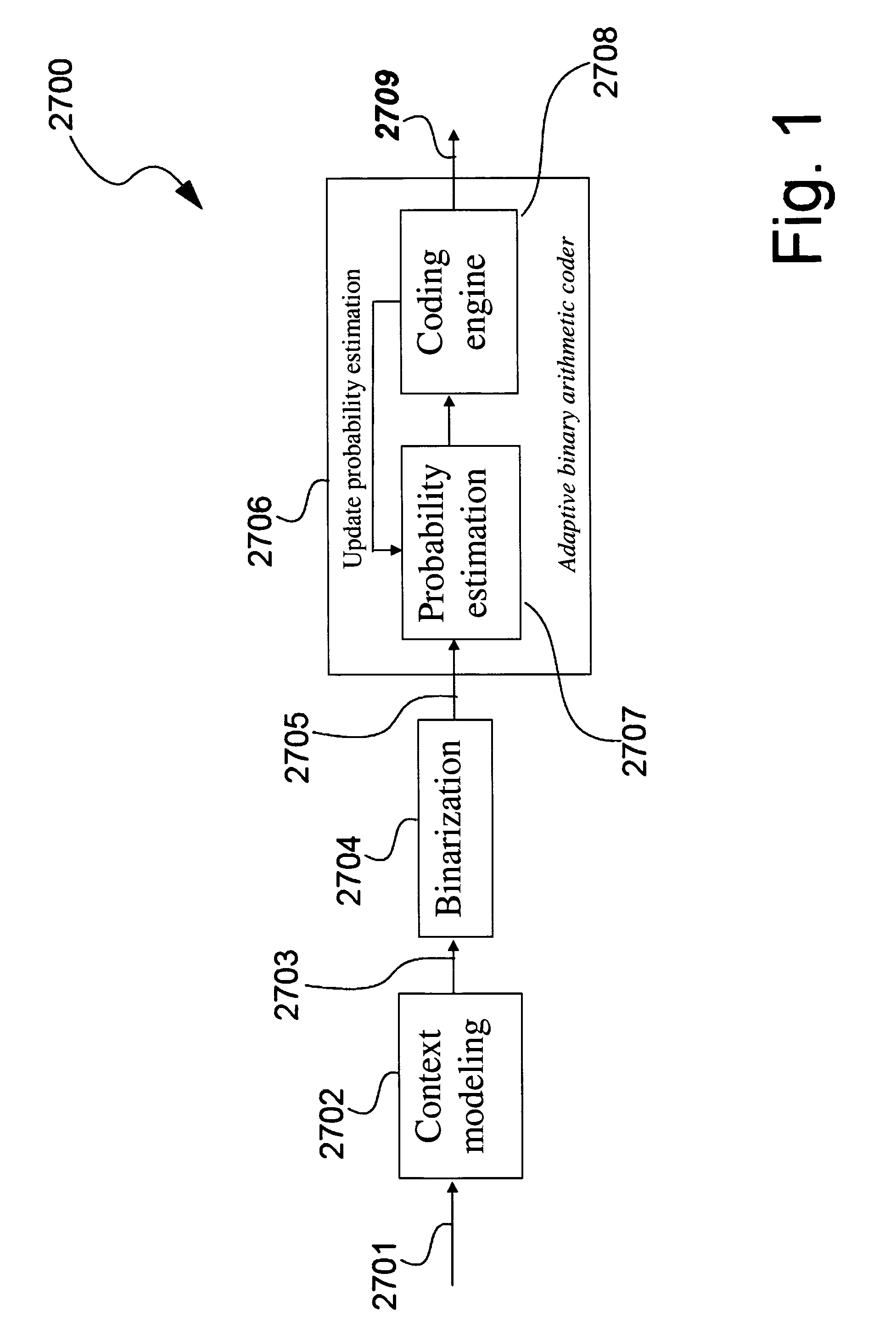
Disclosed is a context modeller (103) used in decoding data (202) encoded using Context Adaptive Binary Arithmetic Coding, said context modeler (103) comprising a Read Only Memory (1001) for storing uninitialized context model values, said uninitialized context model values being stored in the Read Only Memory (1001) in a manner that enables a plurality of uninitialized context model values to be read from the Read Only Memory (1001) in a single clock cycle, an Arithmetic Logic Module (1003) comprising a plurality of parallel processing paths (2202-2207), each said processing path comprising a plurality of pipeline stages, a Random Access Memory (1005) and a memory controller (1008) for determining, using the Arithmetic Logic Module (1005) operating on said plurality of uninitialized context model values read from the Read Only Memory (1001) in each clock cycle, initialized context model values for storage in the Random Access Memory (1001) based upon header information in said incoming encoded data (202).
Owner:HONG KONG APPLIED SCI & TECH RES INST
High speed context memory implementation for H.264
ActiveUS7443318B2Increase speedSimple methodColor television with pulse code modulationColor television with bandwidth reductionRandom access memoryMODELLER
Owner:HONG KONG APPLIED SCI & TECH RES INST
Cell communication method, system and radio network controller
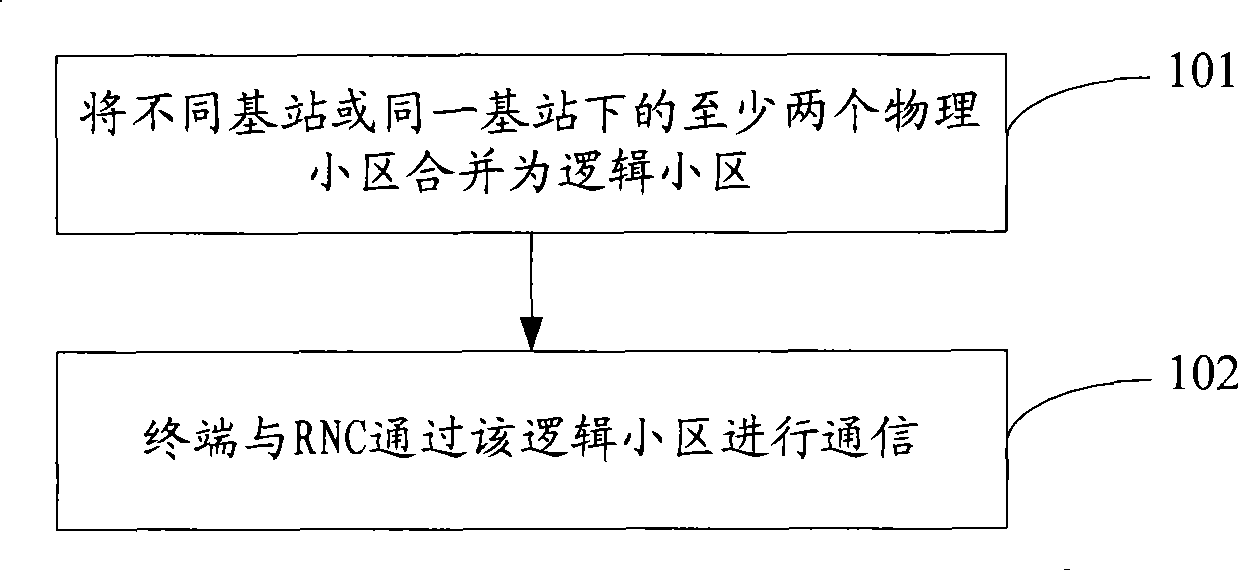
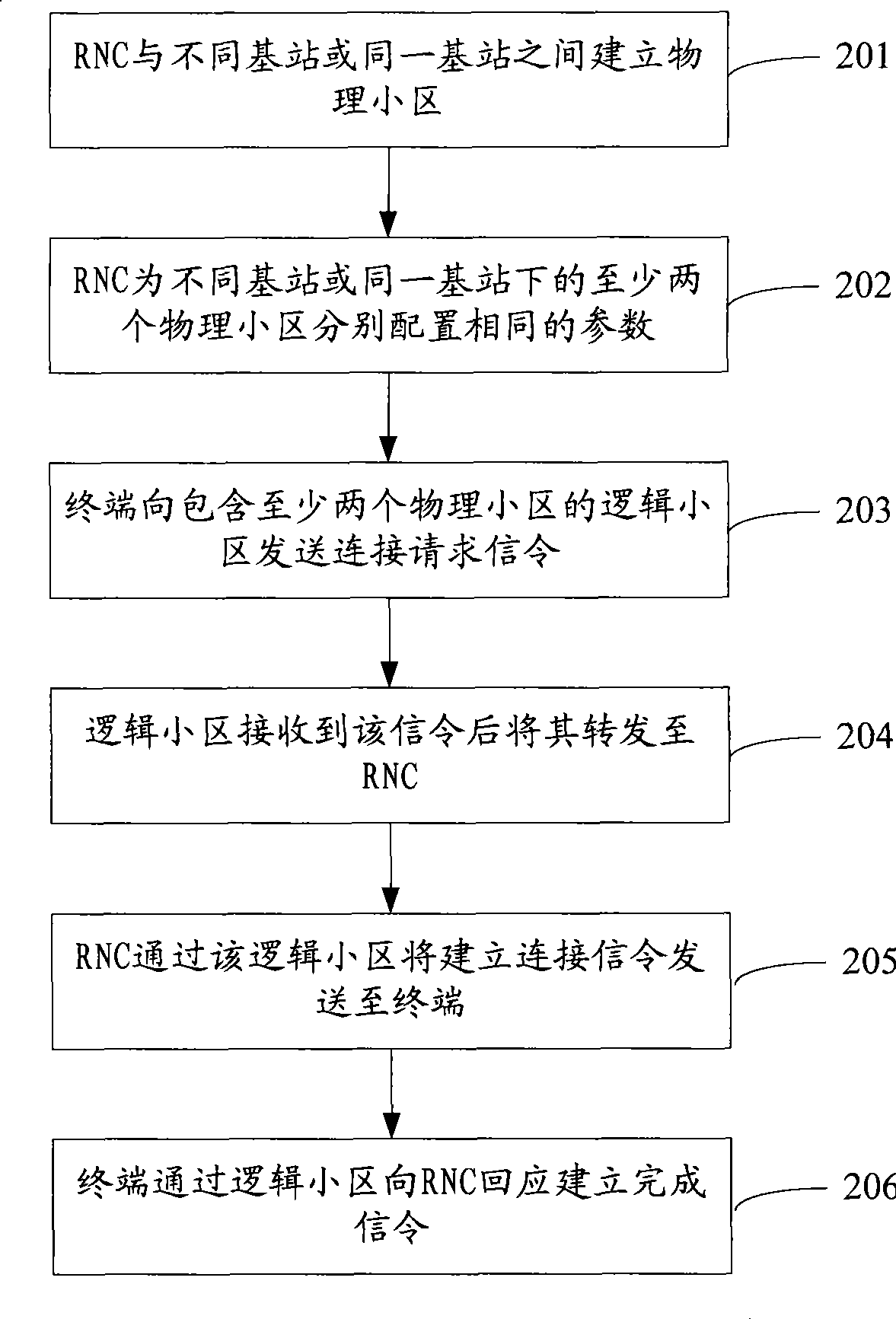
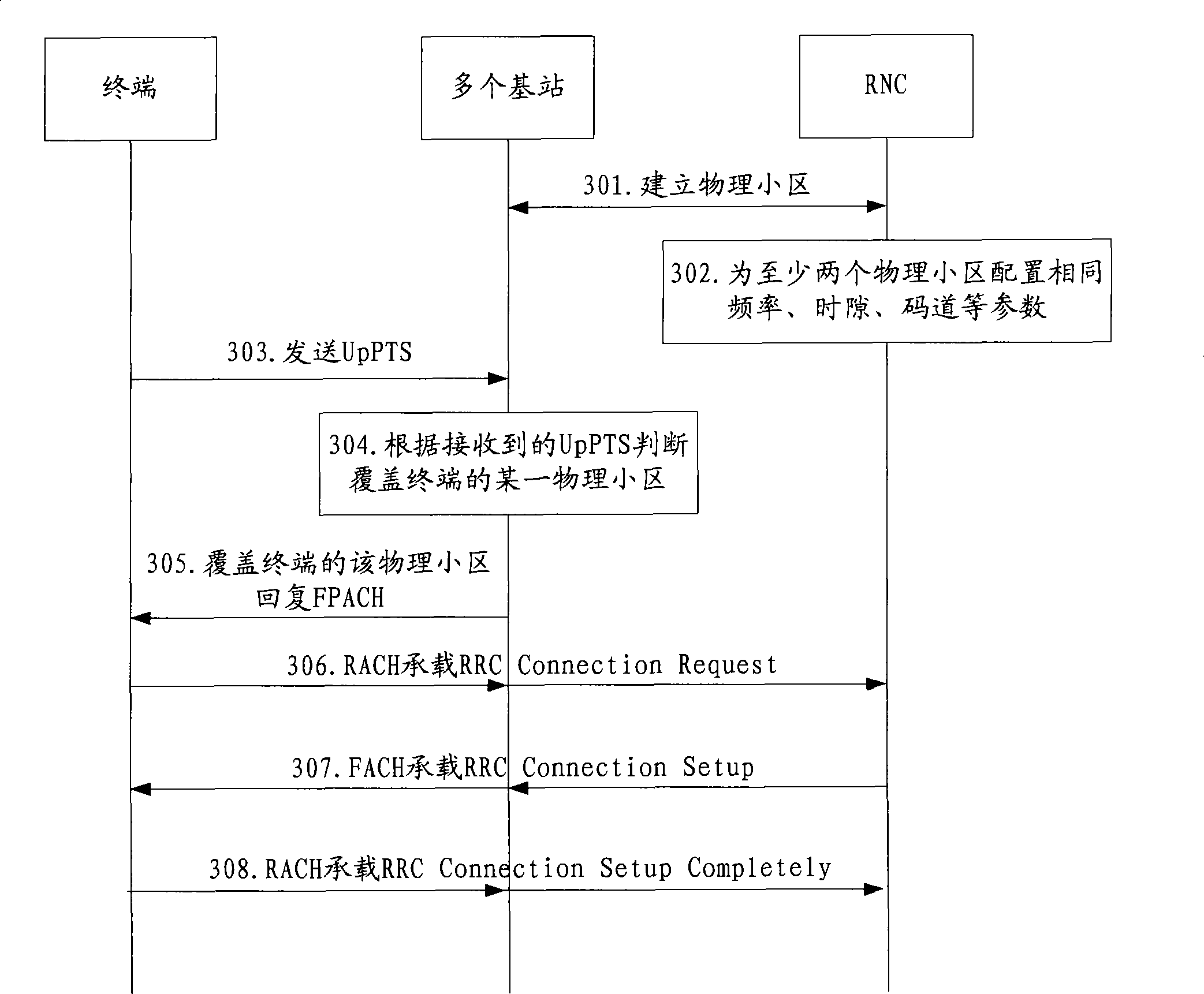
InactiveCN101400111AImprove communication qualitySimple accessAssess restrictionNetwork planningCommunications systemRadio Network Controller
The invention discloses a method of district communication, comprising: combining at least two physical districts under different base stations or the same base station into a logic district; communicating through the logic district between terminals and a radio network controller RNC. The invention also discloses a district communication system and a radio network controller. According to the invention, district coverage range of the wireless communication system is added through the logic district constituting a plurality of physical districts, avoiding restrict of a transmitting device and special terminals to increasing transmitting power and receiving sensitivity, requirement of distributivity antennas or repeater stations on transmission bandwidth is adopted, wherein realization is convenient. Due to the increased coverage range of the district after combining the logic district, the terminal are easy to access into the district, increasing switching success ratio, avoiding drop call.
Owner:CHINA ACAD OF TELECOMM TECH
Alternating-direct current series-parallel port distribution network and comprehensive dispatching control method thereof
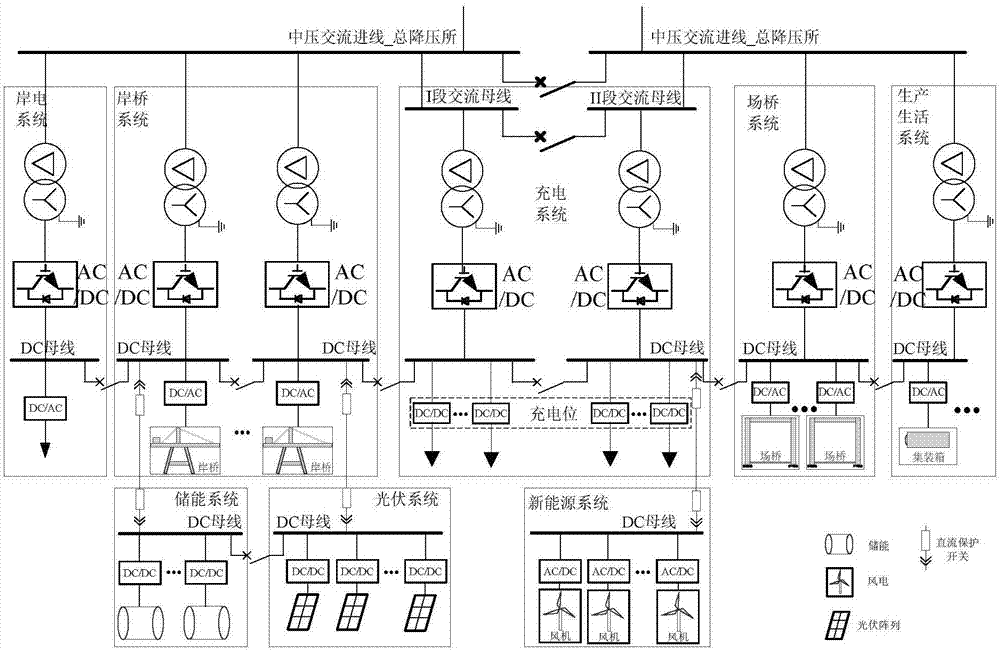
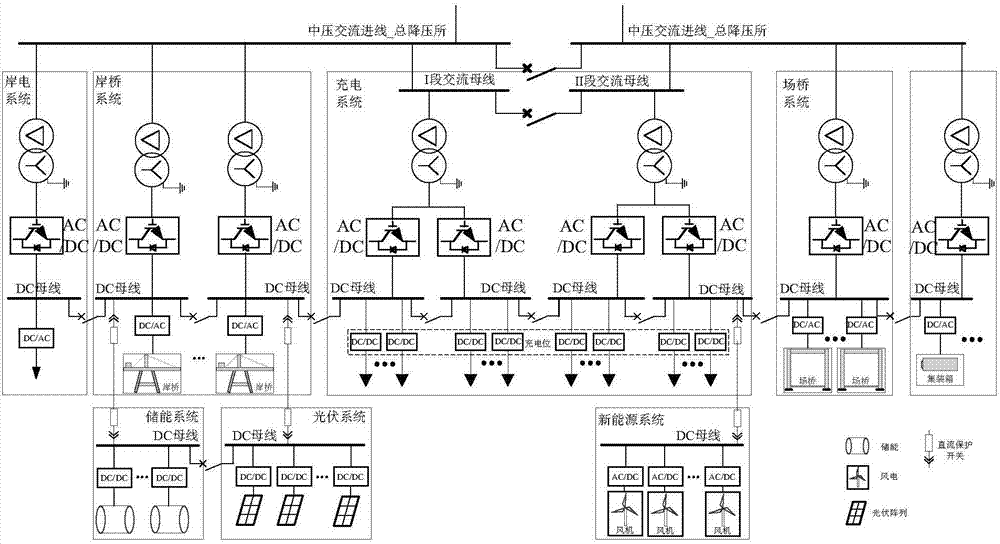
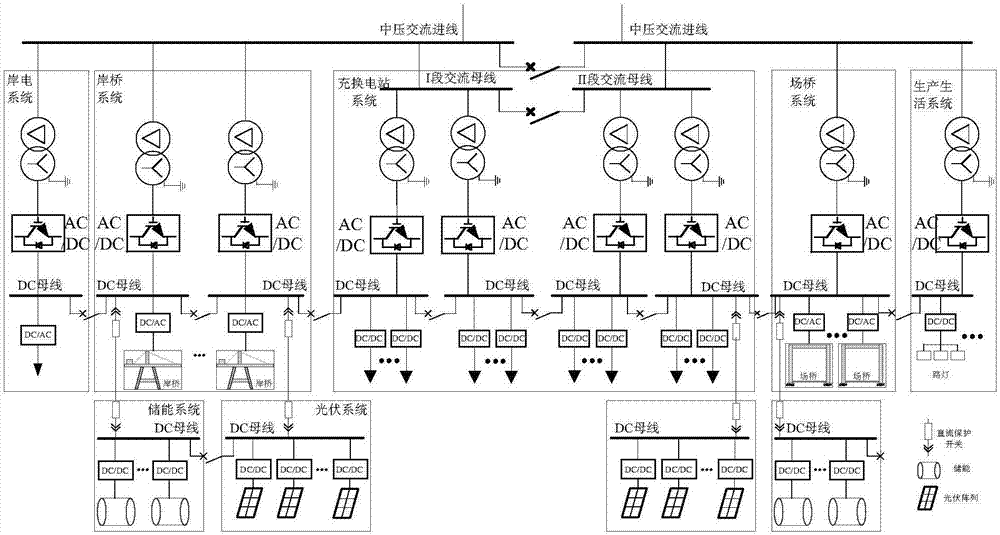
PendingCN107394831ADesign capacity and cost reductionIncrease flexibilitySingle network parallel feeding arrangementsDc source parallel operationDc converterDistribution transformer
The invention discloses an alternating-direct current series-parallel port distribution network and a comprehensive dispatching control method thereof, and belongs to the field of port distribution power and distribution network automation. The distribution network comprises a general step-down station, a branch substation or a switch-on / switch-off station and various distribution subsystems; a multi-channel feeder of the general step-down station provides alternating current power for the various distribution subsystems through the branch substation or the switch-on / switch-off station; each distribution subsystem comprises a shore electronic system, a shore bridge subsystem, a field bridge subsystem, a power charging and converting station subsystem for electric port trailers, a new energy subsystem and a production life subsystem; each distribution subsystem utilizes an alternating current distribution transformer and an AC / DC converter to construct a direct current bus of the distribution subsystem, and the direct current buses of the distribution subsystems are in direct current interconnection through direct current interconnection protection switches; each distribution subsystem is internally provided with multiple sections of direct current buses, and the multiple sections of direct current buses are in direct current interconnection through direct current interconnection protection switches. According to the alternating-direct current series-parallel port distribution network and the comprehensive dispatching control method thereof, the optimal power supply and comprehensive dispatching control of the port distribution network can be achieved.
Owner:STATE GRID CORP OF CHINA +2
Method and device for accessing mobile network and user device
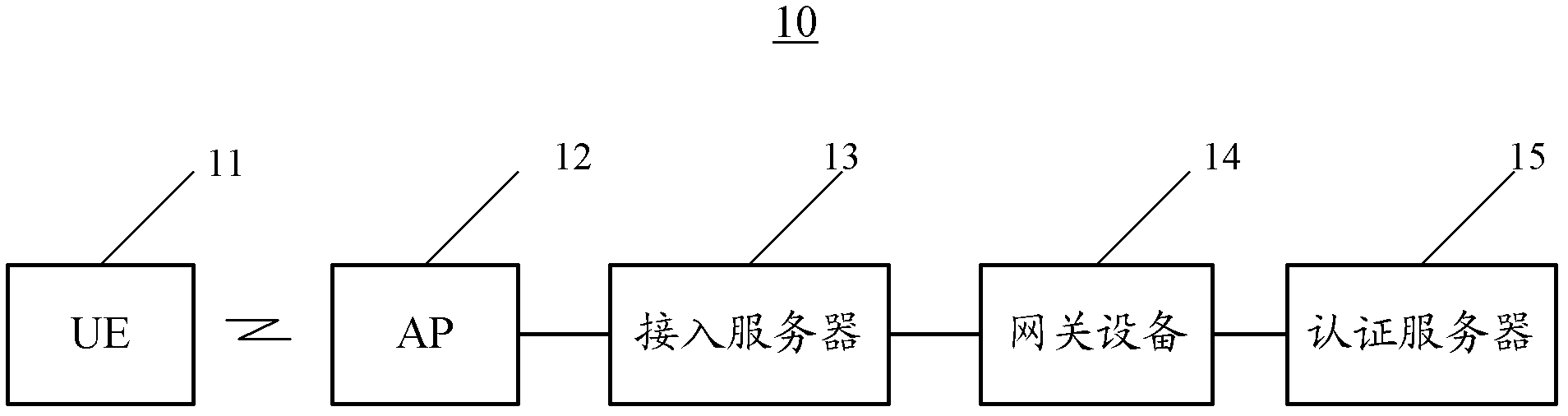
ActiveCN102388639ASimple accessRetrofit smallAssess restrictionSecurity arrangementAccess networkIp address
The embodiments of the invention provide a method and device for accessing mobile network and a user device. The device comprises a receiving module for receiving EAP successful responding messages from an authentication server, and a sending module for seding EAP successful responding messages and Internet protocol IP address to a user device to an access server. The embodiments of the invention can send EAP successful responding messages returned by the authentication server and Internet protocol IP address to a user device to the access server by utilizing the device for accessing a mobile network. Since basic functions supported by the access server during said process, the modification of an access service can be minimized and accessing to a mobile network can be easily realized.
Owner:HUAWEI TECH CO LTD
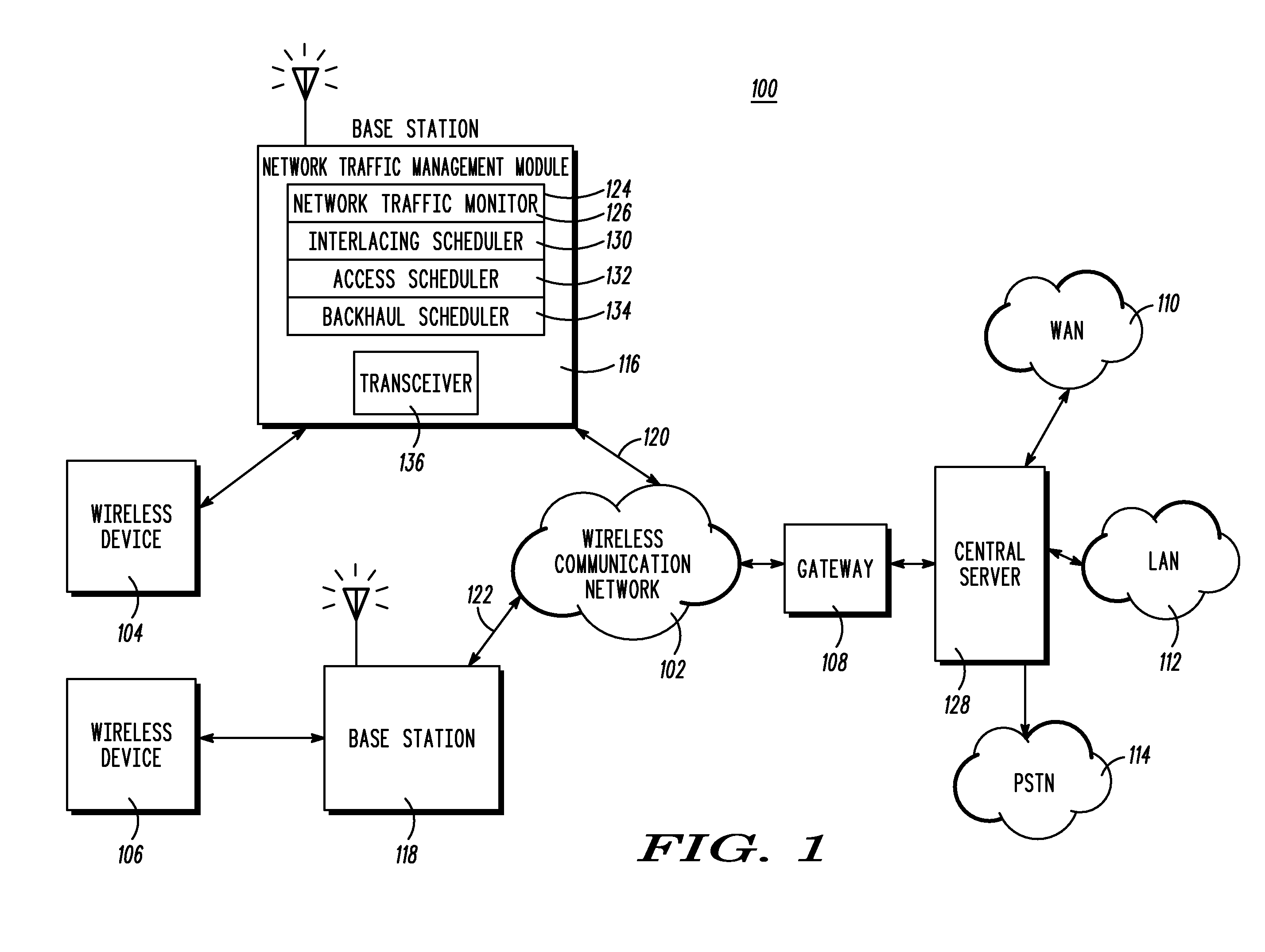
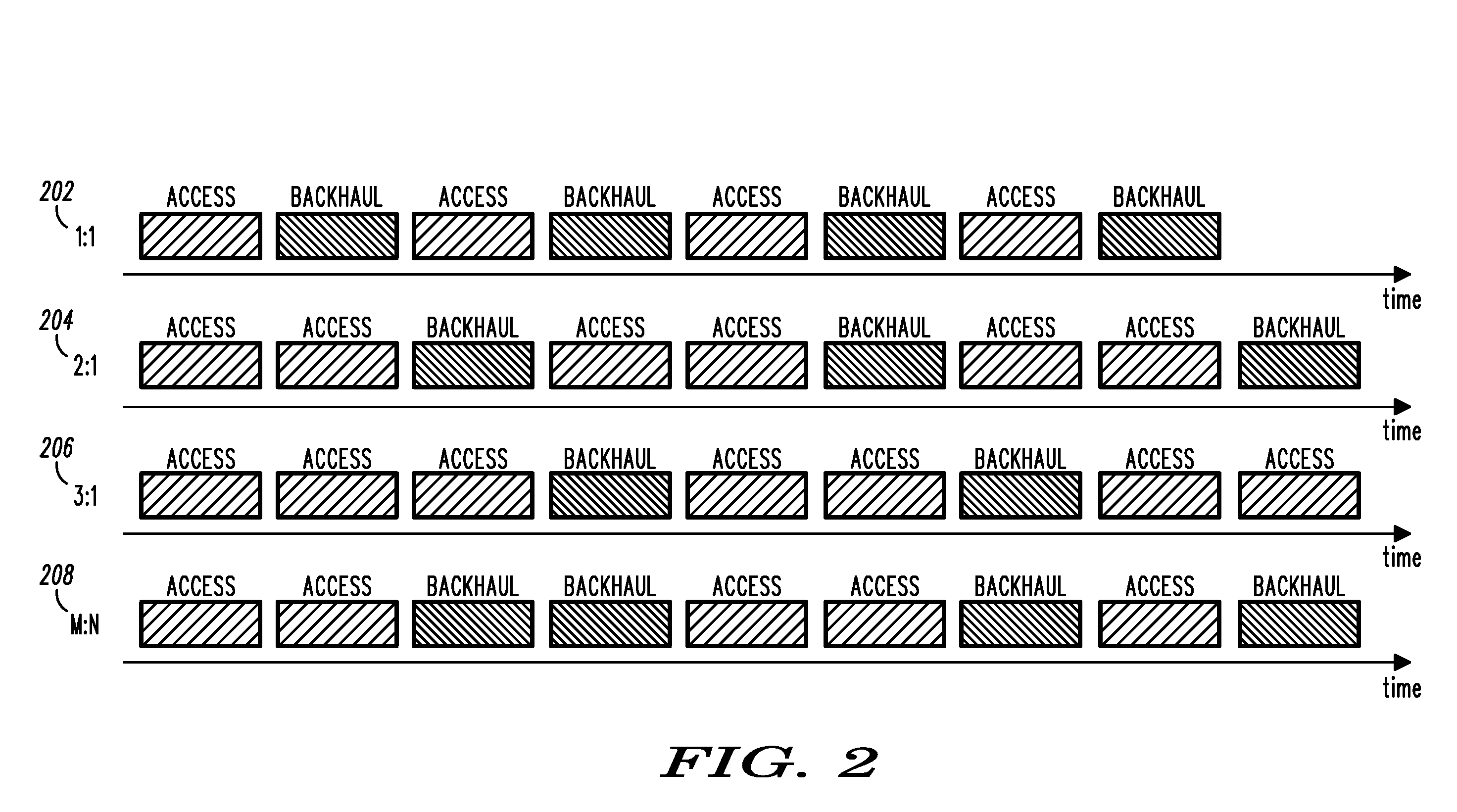
Access and backhaul frame interlacing from time division duplex wireless communication system
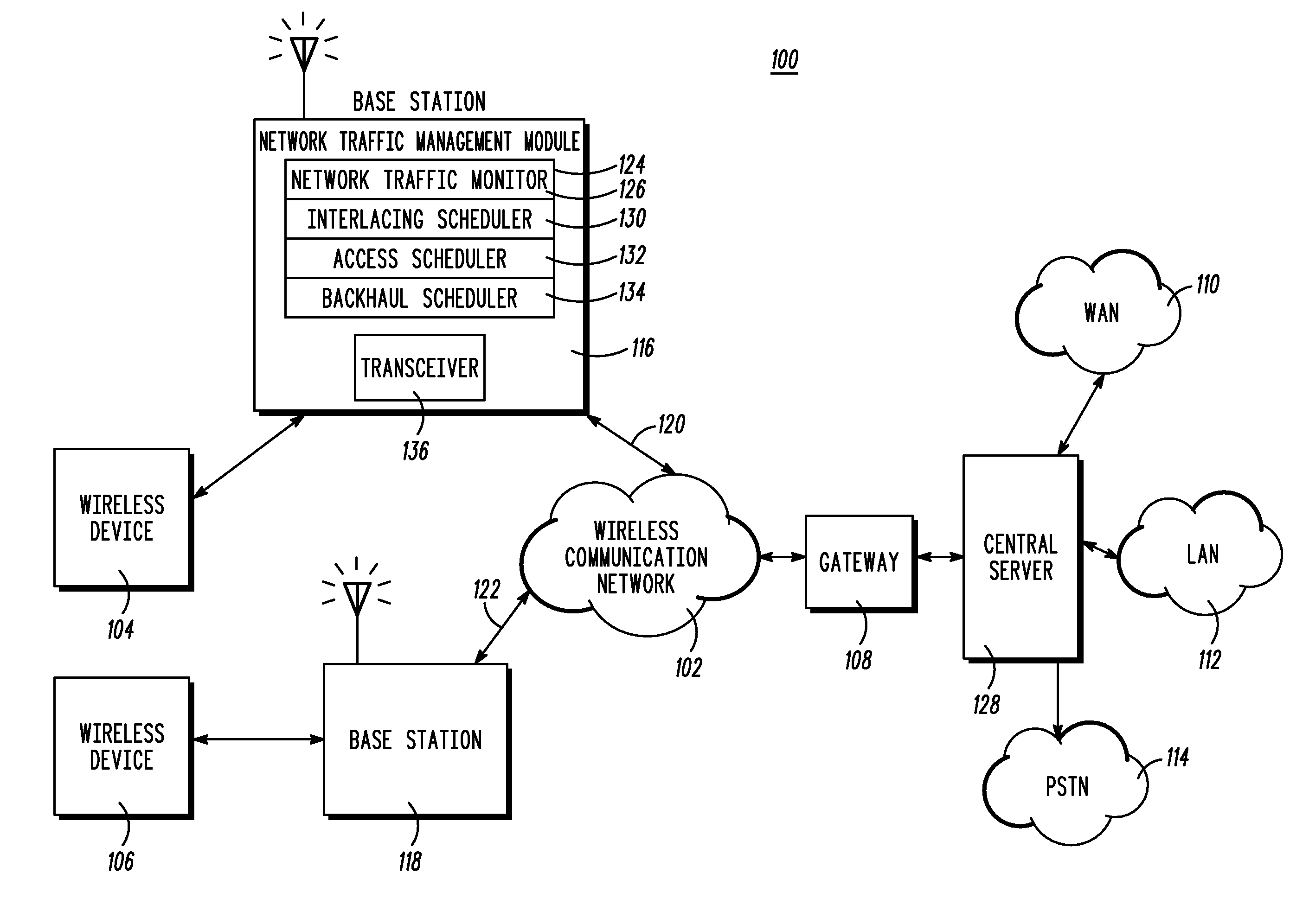
InactiveUS20080285473A1Characteristic is differentModification can be complexError preventionTransmission systemsTraffic capacityTraffic characteristic
A method, base station, and wireless communications system for interlacing Access and Backhaul frames in a Time Division Duplex wireless communication system. The method includes monitoring Access traffic and Backhaul traffic (604). Access traffic characteristics, Backhaul traffic characteristics, and corresponding frame control overhead information are determined in response to the monitoring (606). The method also includes determining an amount of time required to deliver a substantially equal amount of bearer Access traffic and Backhaul traffic (608). A frame interlacing ration is determined (608) in response to determining the amount of time required to deliver a substantially equal amount of bearer Access traffic and Backhaul traffic. A set of Access frames (302) and a set of Backhaul frames (304) are interlaced on a frequency band using the determined frame interlacing ratio.
Owner:MOTOROLA INC
Systems and methods for registering and acquiring E-credentials using proof-of-existence and digital seals
ActiveUS10127378B2Proven reliabilityElevate identityEncryption apparatus with shift registers/memoriesUser identity/authority verificationInternet privacyDigitization
A system and methods for registering and acquiring e-credentials using personal devices and an identity registry system that combines the method for handling digital seals with a proof-of-existence method. The identity registry system is used to register and verify e-credentials. Device owners register their e-credentials when created and updated and verify acquired e-credentials to safeguard against tampering and errors. When registering an e-credential, the e-credential is hashed and digitally sealed creating an identifying thumbprint that is stored in the identity registry system. When verifying an acquired e-credential, the e-credential is hashed, the identity registry system is searched to locate the identifying thumbprint, and the digital seal of the thumbprint is verified. A requesting owner can request an issuing owner to proof, attest, and digitally seal an e-credential of the requester.
Owner:TOTH KALMAN CSABA
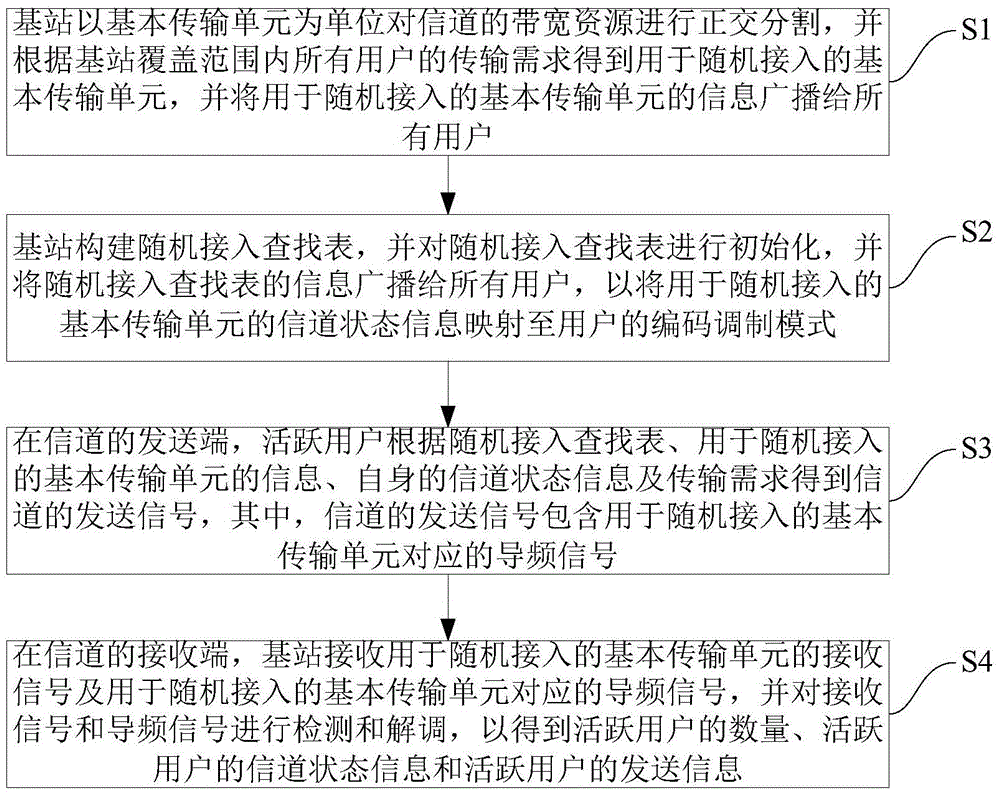
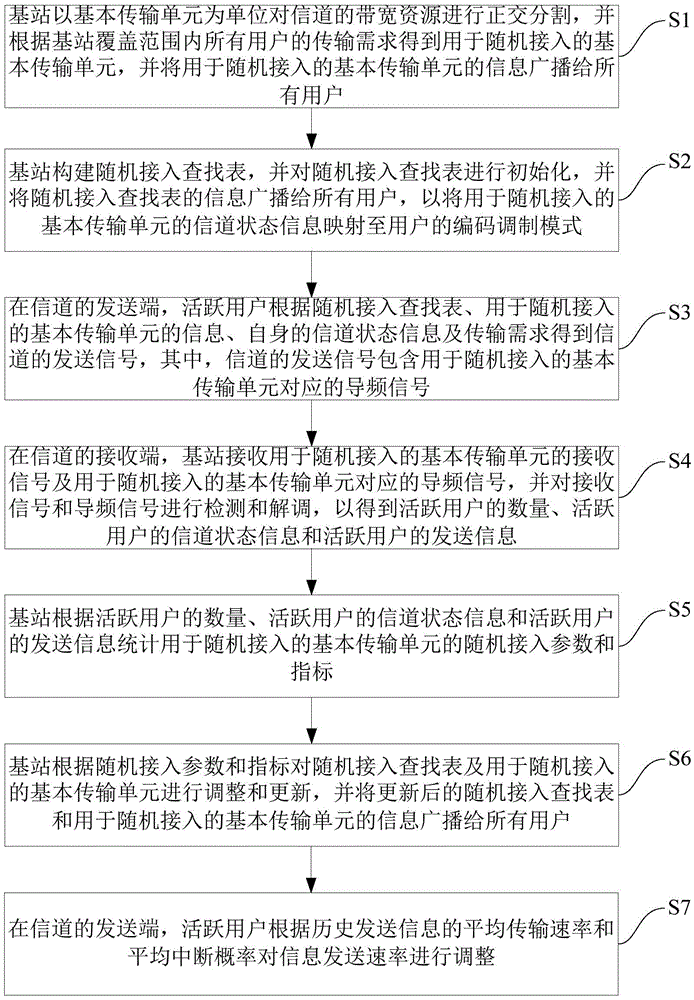
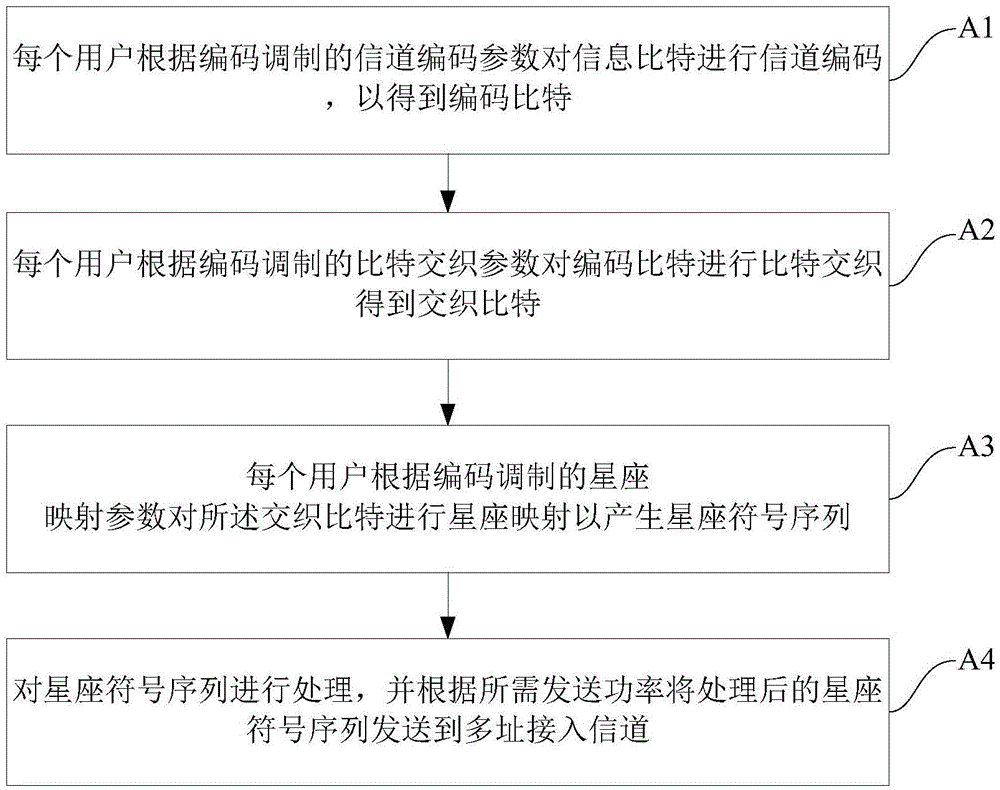
Random access method
ActiveCN105554901ASimple accessPilot signal allocationWireless communicationChannel state informationRandom access memory
The invention provides a random access method. The method comprises steps: orthogonal segmentation is carried out on bandwidth resources of a channel, a basic transmission unit for random access is obtained according to all users in a base station coverage range, and the information of the basic transmission unit is broadcasted to all users; a random access lookup table is initialized, and the information of the random access lookup table is broadcasted to all users; at a transmitting end of the channel, active users obtain channel transmitting signals according to the random access lookup table, the information of the basic transmission unit, the self channel state information and transmission requirements; and at the receiving end of the channel, the base station carries out detection and demodulation on the obtained basic transmission unit receiving signals and pilot signals corresponding to the basic transmission unit, and the number of the active users, the channel state information of the active users and the transmitting information of the active users can be obtained. The base station control and the user access for random access are simple and effective, and the multiple access technology approaching the channel capacity can be made full use of.
Owner:TSINGHUA UNIV
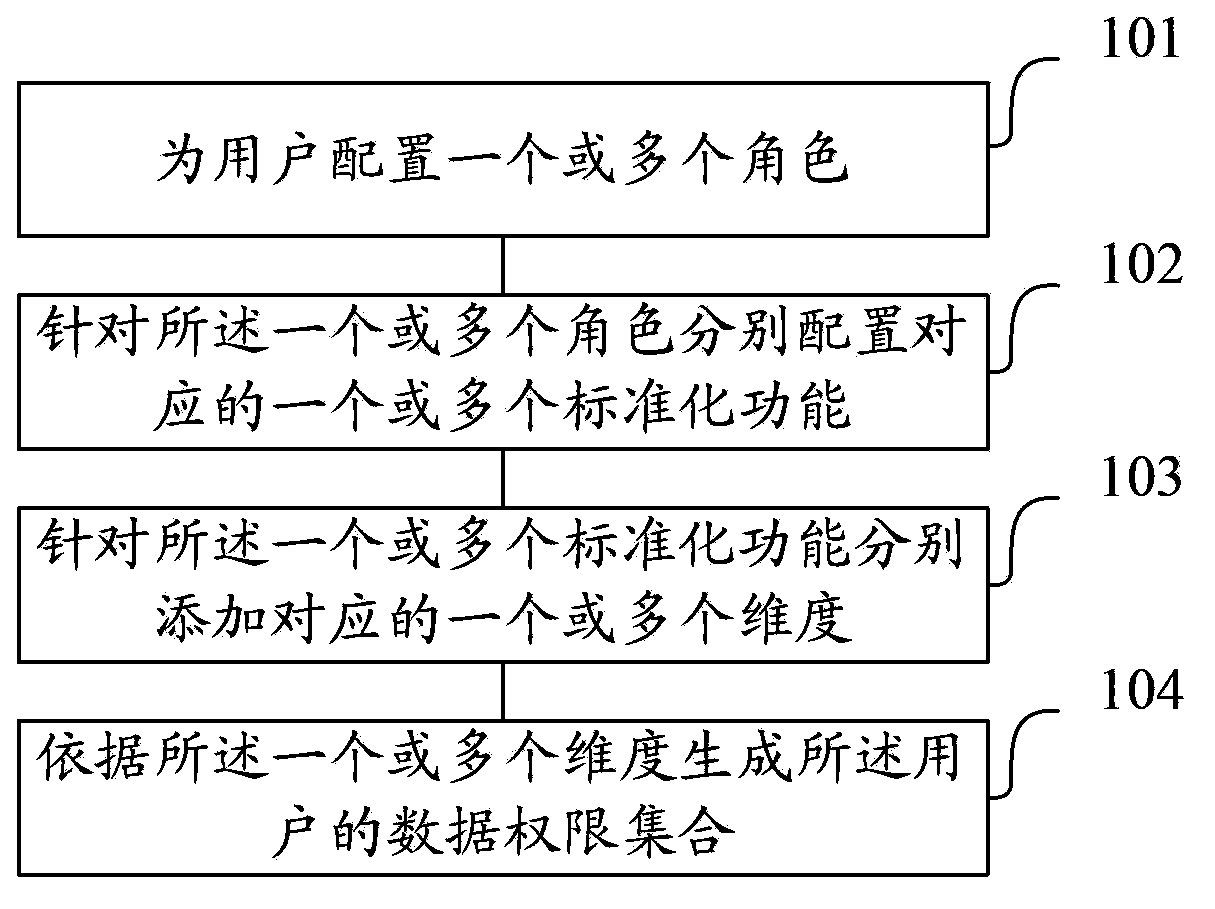
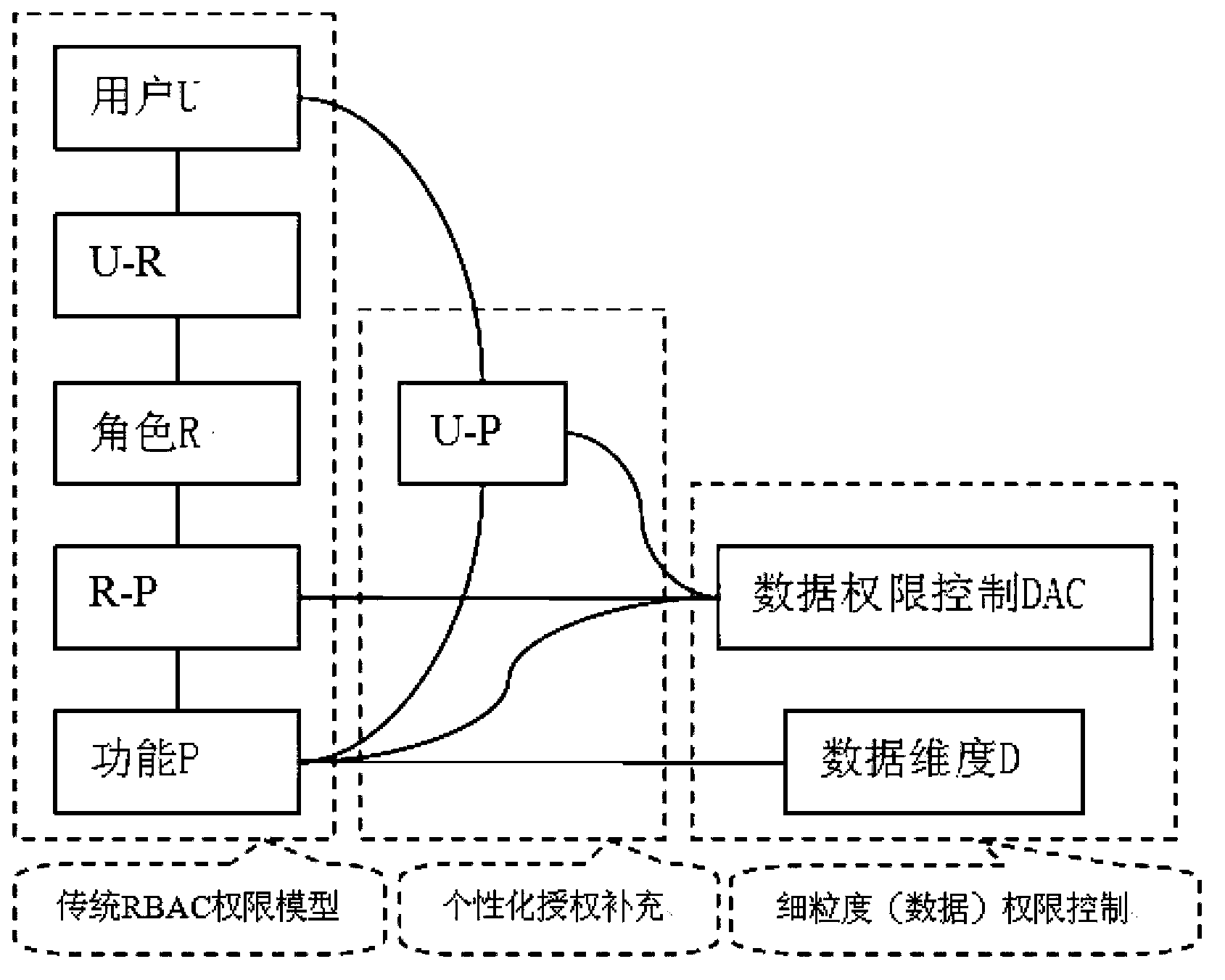
Data permission control method and device for application system clusters
InactiveCN104112085ARetrofit smallLess intrusiveDigital data authenticationStandard functionMultiple dimension
An embodiment of the invention provides a data permission control method and device for application system clusters. The method includes: receiving an access request which a user submits in an application system cluster; when the fact that the user has data permissions is determined according to the access request, acquiring a data permission set corresponding to the user, to be specific, searching for one or multiple characters corresponding to the user, searching for one or multiple standard functions corresponding to the one or multiple characters and searching for one or multiple dimensions corresponding to the one or multiple standard functions; acquiring a current data permission set of the user according to the one or multiple dimensions. The data permission set includes standard data permission sets. The data permission control method and device for application system clusters according to the embodiment has the advantages that parameter-based fine-grained permission control is achieved, few modifications are made to the application system clusters, few invasions are caused to the application system clusters, and accessing is simple.
Owner:ALIBABA GRP HLDG LTD
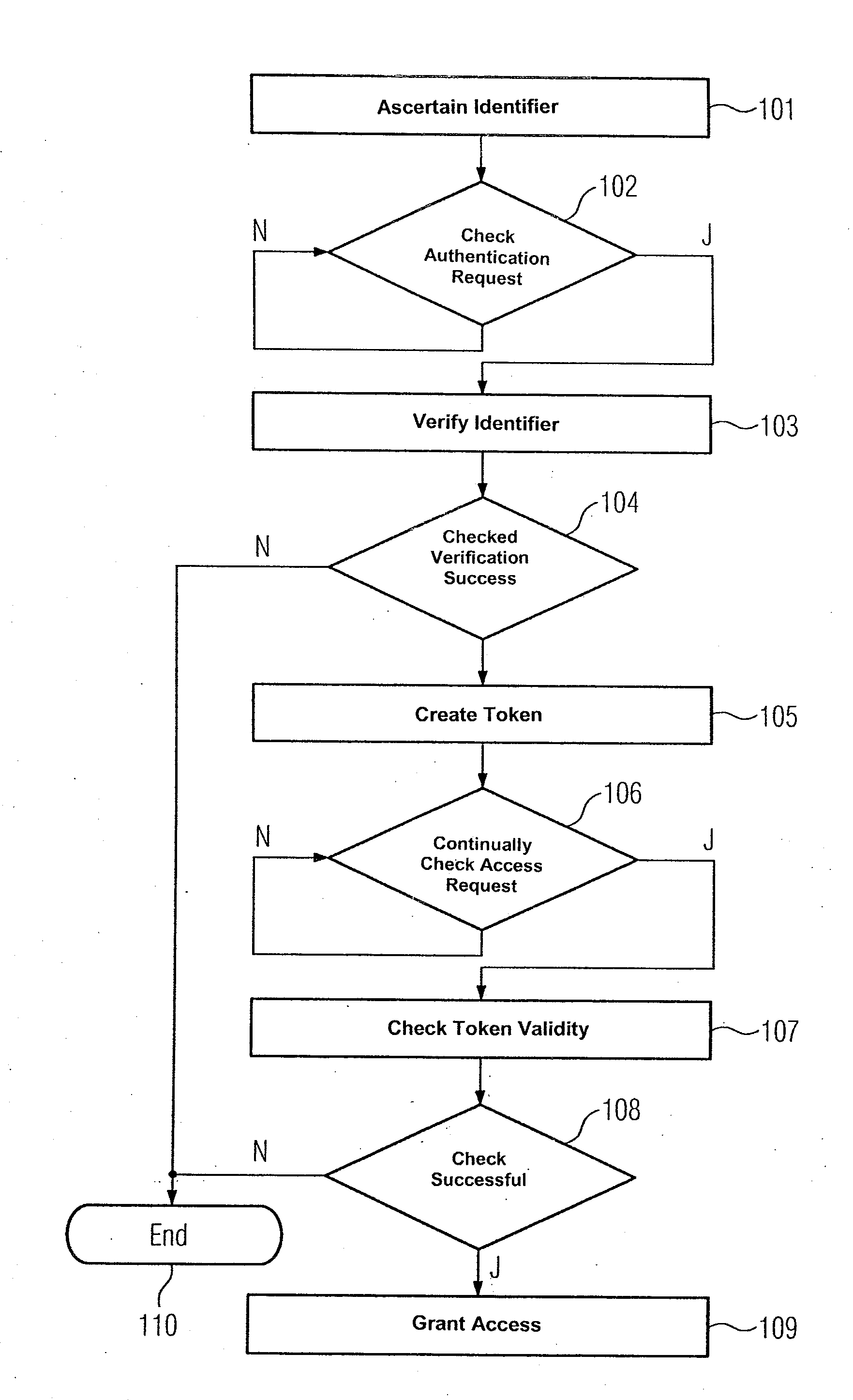
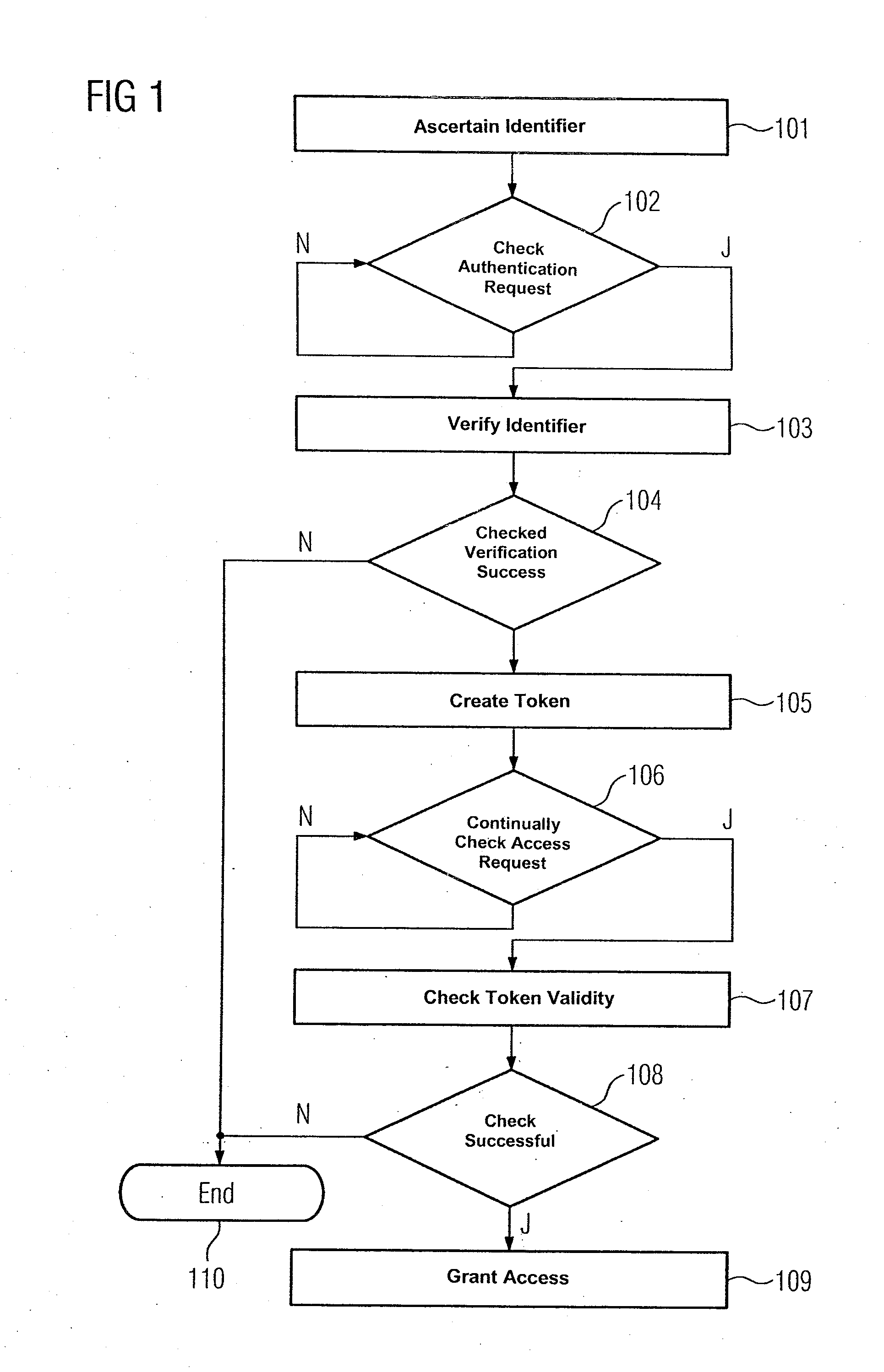
Method for Granting Authorization to Access a Computer-Based Object in an Automation System, Computer Program, and Automation System
InactiveUS20120117380A1The process is fast and efficientFast wayProgramme controlUser identity/authority verificationAuthorizationAuthentication
An identifier is determined for a control program, and the identifier is encrypted based on a private digital key associated with a control and monitoring unit of the automation system to grant authorization to access a computer-based object in an automation system. A first service of the automation system is provided based on the computer-based object, and a second service of the automation system is provided based on the control program. The encrypted identifier is decrypted when being transmitted to an authentication service and is verified by the authentication service. If the verification process has been successful, the authentication service transmits a temporarily valid token to the second service. When the control program requests access to the computer-based object, the token is transmitted to the first service for checking purposes. The control program is granted access to the computer-based object if the result of the checking process is positive.
Owner:SIEMENS AG
Control circuit and method for backlight sources, and image display apparatus and lighting apparatus using the same
ActiveUS20100102752A1Reduce numberManufacturing cost be reduceElectrical apparatusStatic indicating devicesData transmissionLight source
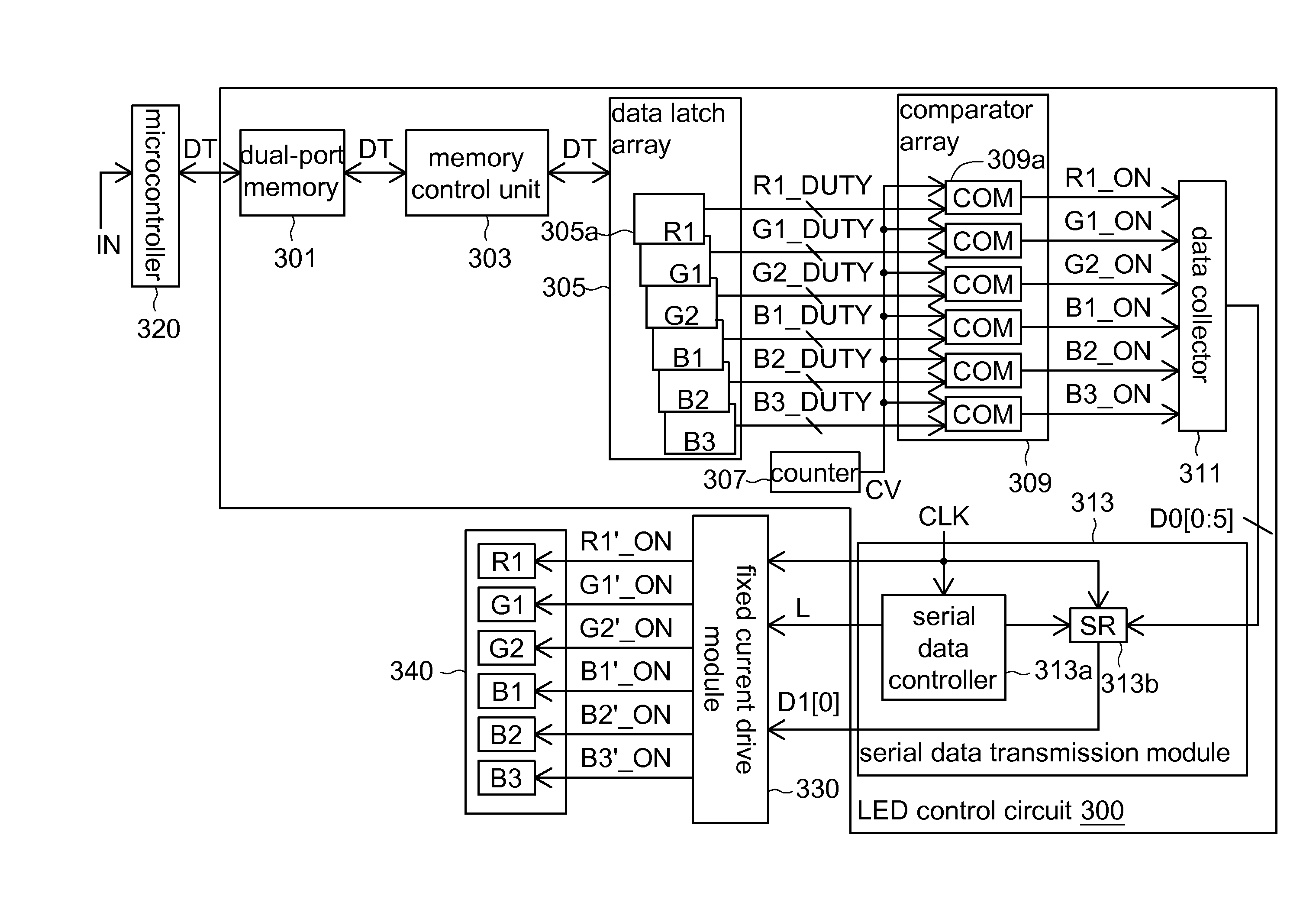
In light emitting diode (LED) control, a plurality of duty cycle signals corresponding to a plurality of LEDs are stored in a dual-port memory by memory mapping. By sampling, the stored duty cycle signals are outputted to generate a plurality of parallel single-bit data each having one single bit. After the single-bit data are converted by a data transmission module, each bit of the single-bit data is serially outputted to a drive module to drive the LEDs. Thus, the ON duty cycles of the LEDs are modulated by pulse width modulation (PWM), light emitted from the LEDs are mixed in time-domain, and the brightness of the LEDs can be controlled.
Owner:IND TECH RES INST
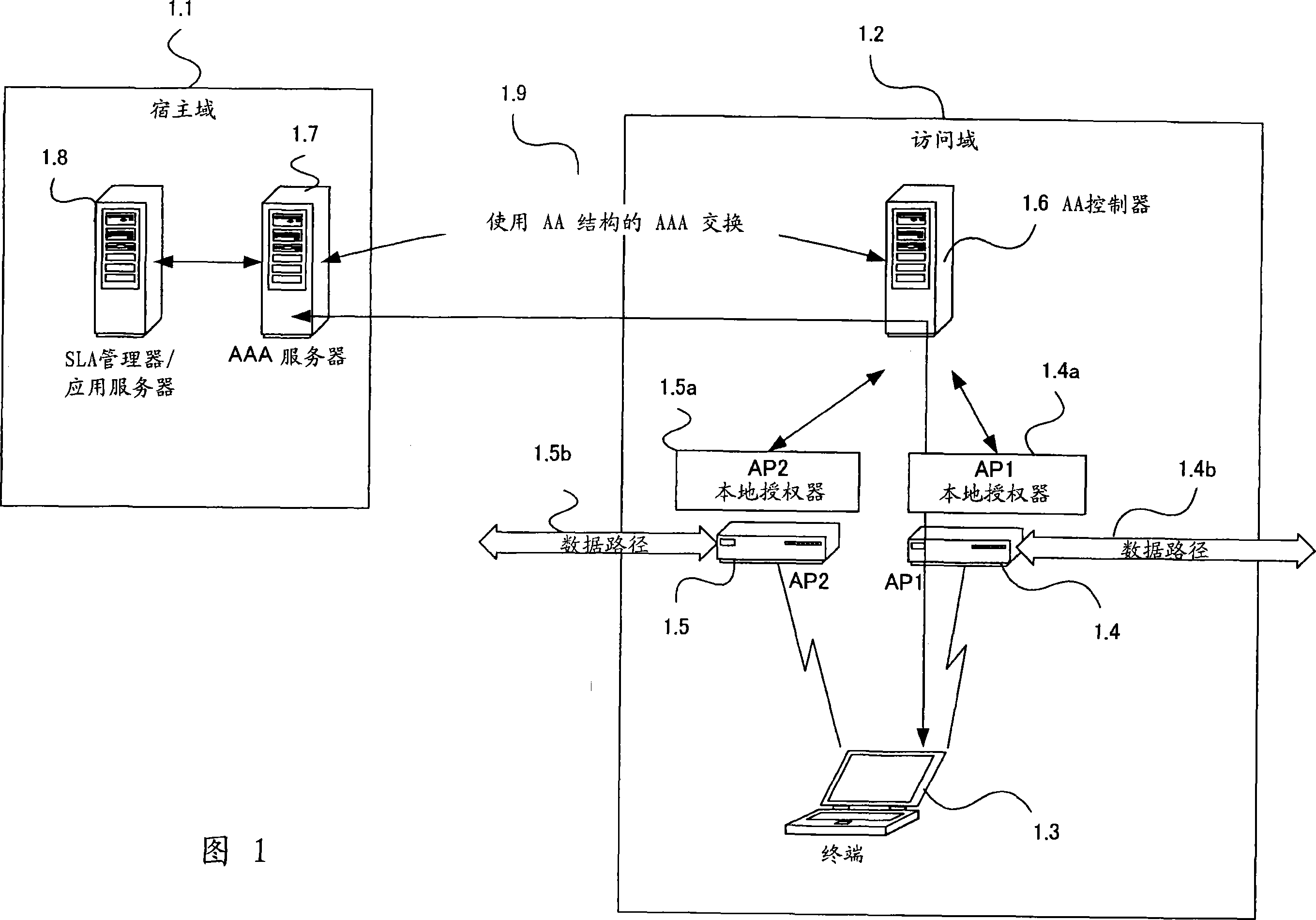
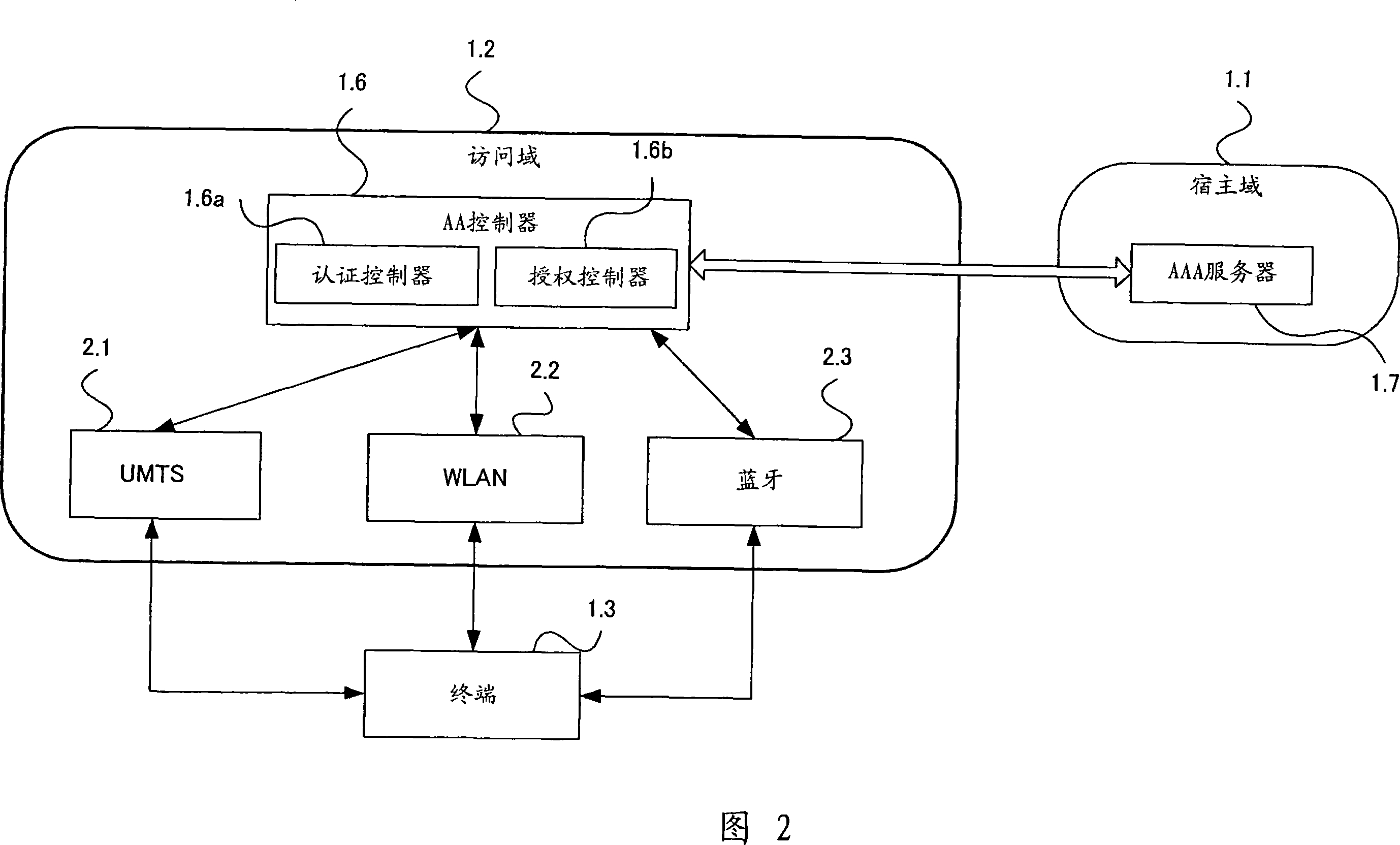
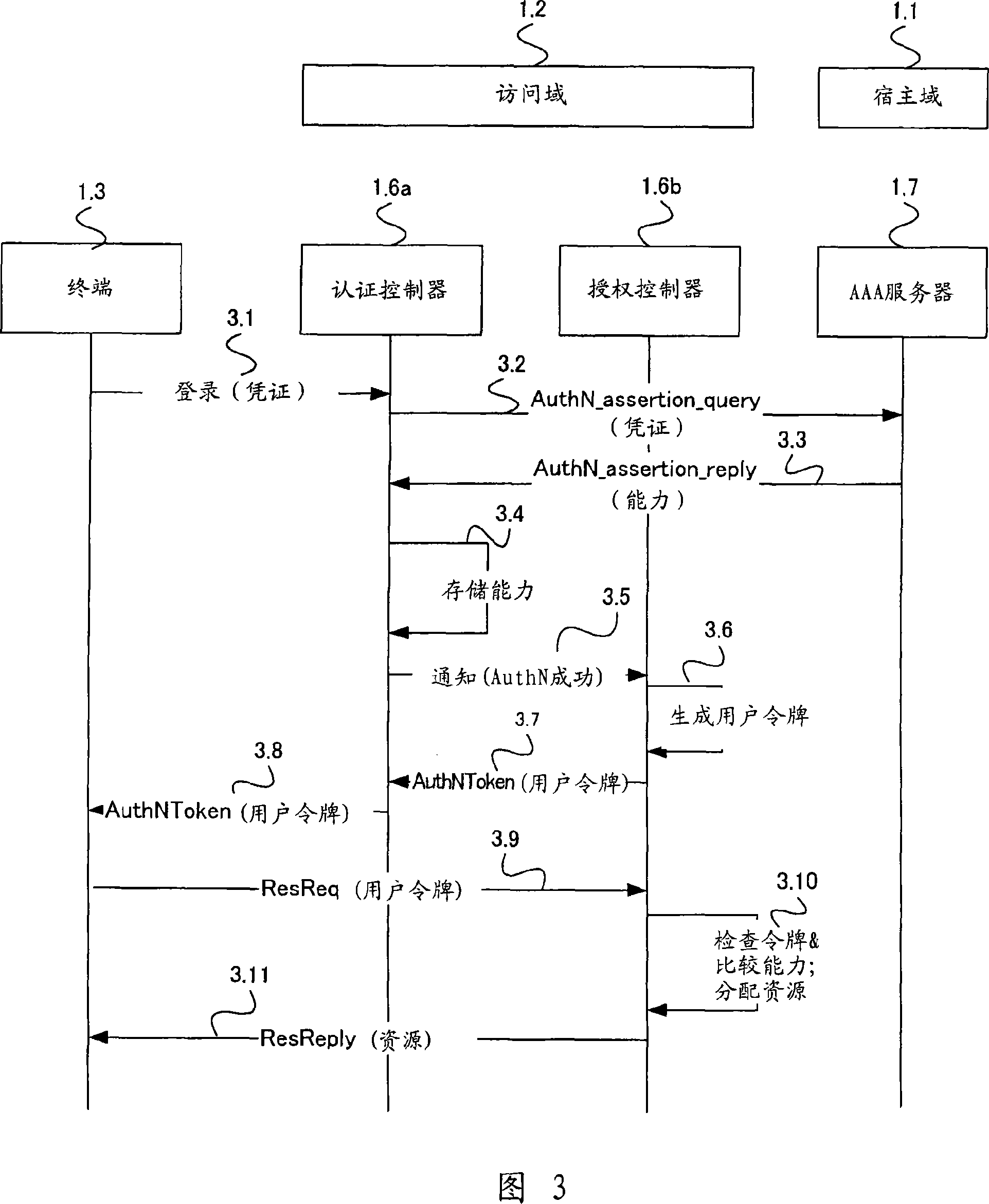
System and method for managing user authentication and service authorization to achieve single-sign-on to access multiple network interfaces
InactiveCN101014958AReduce processing overheadSimple accessUser identity/authority verificationMultiple digital computer combinationsNetwork managementUser authentication
A single-sign-on to access multiple networks residing at multiple domains is disclosed. In particular the single-sign-on features refers to the authentication and the authorization process carried out among the different network administration domains so that the terminal using the end service need not explicitly initiate the authentication process each time it accesses a new service. This invention's single-sign-on feature can be extended for usage in a federated domain environment and non-federated domain environment. The non-federated domains are able to form an indirect federation chain through other domains in order to utilize this invention. Therefore discovery of intermediate domains to form a federation chain is also covered. The management of user credentials to allow a Visited Domain to perform authetication is also covered in this invention.
Owner:PANASONIC CORP
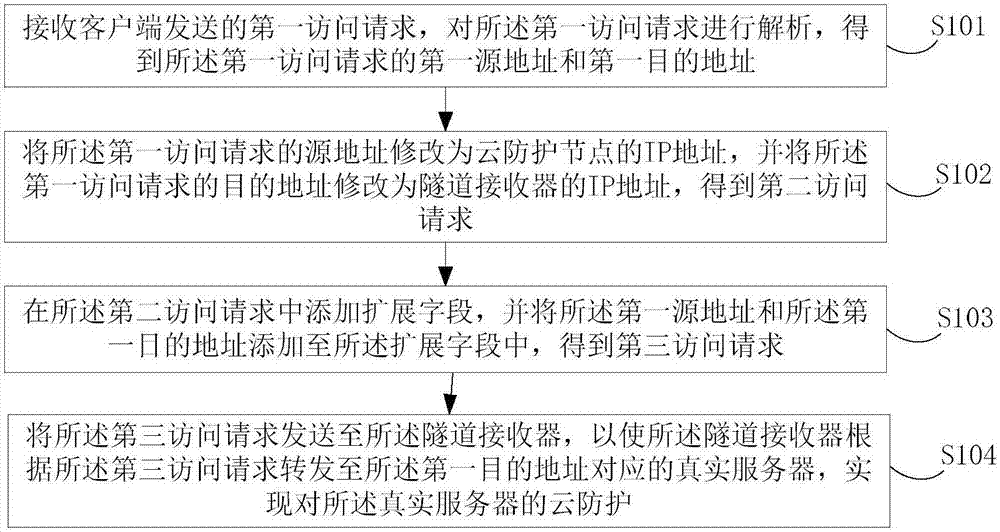
Cloud protection method and device based on tunnel mode
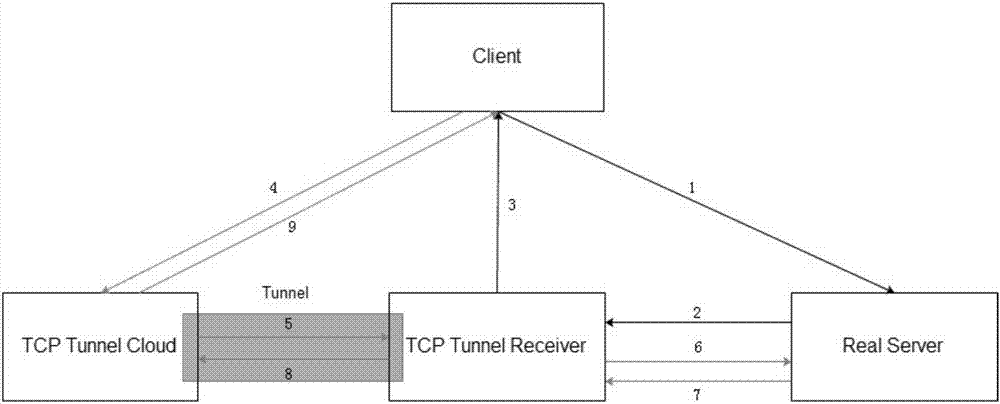
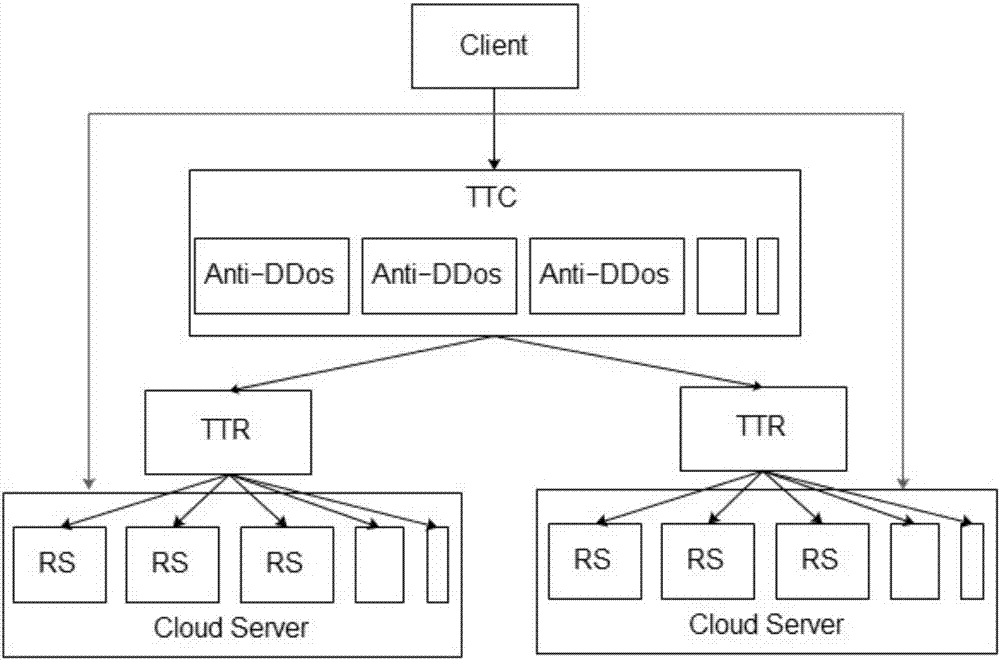
ActiveCN107995324ASimple accessReduce operation and maintenance costsTransmissionIp addressClient-side
The embodiment of the invention discloses a cloud protection method and device based on a tunnel mode. The method comprises the steps of analyzing a first access request sent by a client, thereby acquiring a first source address and a first destination address; modifying the source address of the first access request into an IP address of a cloud protection node and modifying the destination address of the first access request to the IP address of a tunnel receiver, thereby acquiring a second access request; adding an expansion field to the second access request and adding the first source address and the first destination address to the expansion field, thereby acquiring a third access request; and sending the third access request to the tunnel receiver, thereby enabling the tunnel receives to forward the third access request to a true server. The expansion field is added to the access request and the first source address and the first destination address, namely the address of the client and the address of the true server, are stored to the expansion field, so the true address of the client can be acquired, an access mode is simple, the configuration of a great deal of port mapping is avoided, and the operation and maintenance cost is greatly reduced.
Owner:BEIJING QIANXIN TECH
Intelligent public transportation system and implementing method thereof
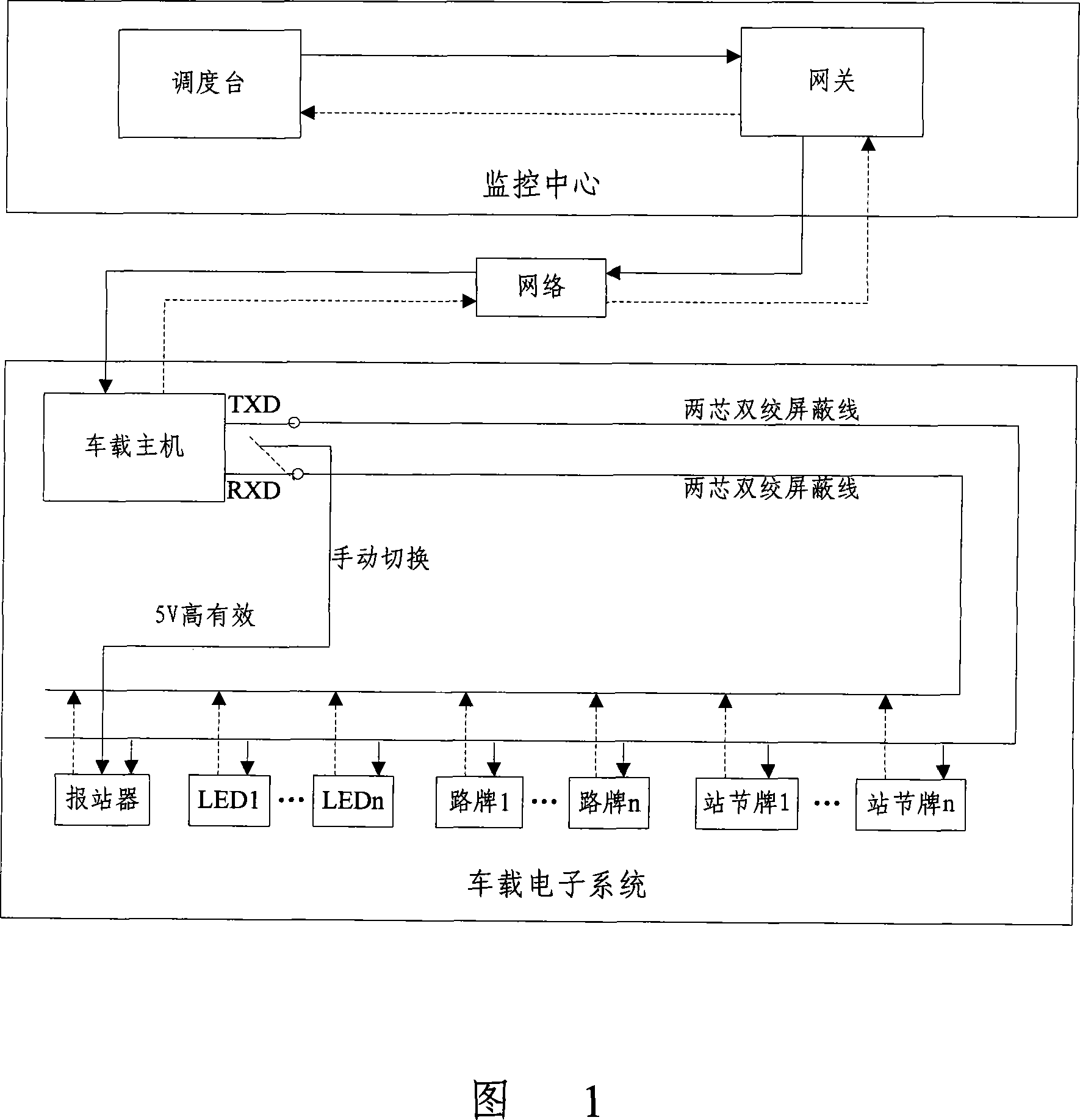
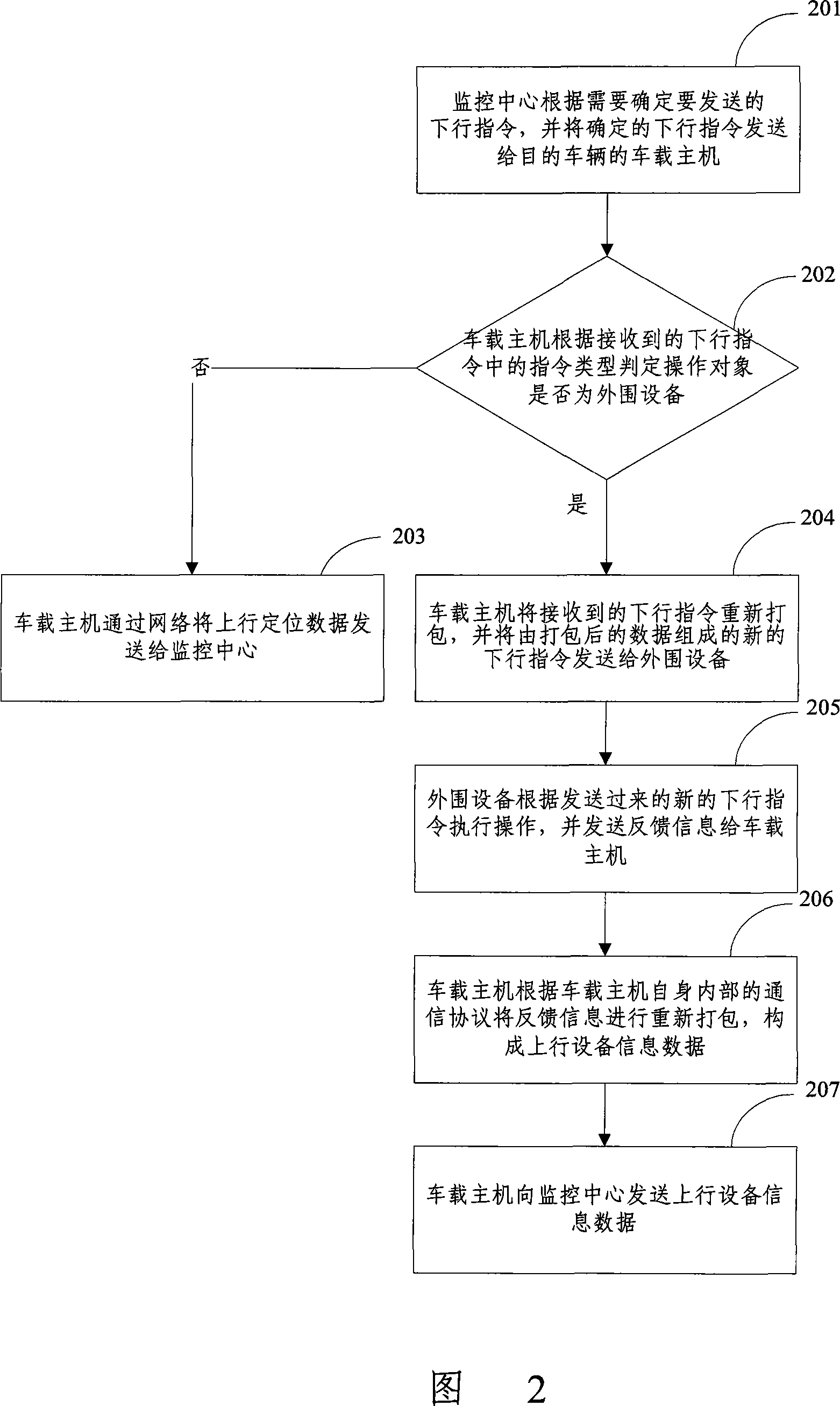
InactiveCN101131795AAchieve integrationRealize information interactionRoad vehicles traffic controlFar distanceLED display
This invention disclose a intelligent bus system and its realize method, the monitor center of the system and the bus electric system change their information in network, the peripheral equipment of the bus electric system includes report station implement, LED display screen, the guidepost, station sign, all of these equipment are linked with the bus host computer; the monitor center can send the related dictate to the bus host computer in network, the bus host computer doing related operation to the related peripheral equipment according to the received dictate, the peripheral equipment uploads the feed back information to the monitor center, by the way, the bus host computer can locate in real time, and upload the orientation information according to the dictate of the monitor center. The monitor center can realize the far distance, real time monitor to the bus electric system, at the same, realize the entirety information alternate and share in the system.
Owner:BEIHANG UNIV +1
Distributed industrial data distribution method based on DDS
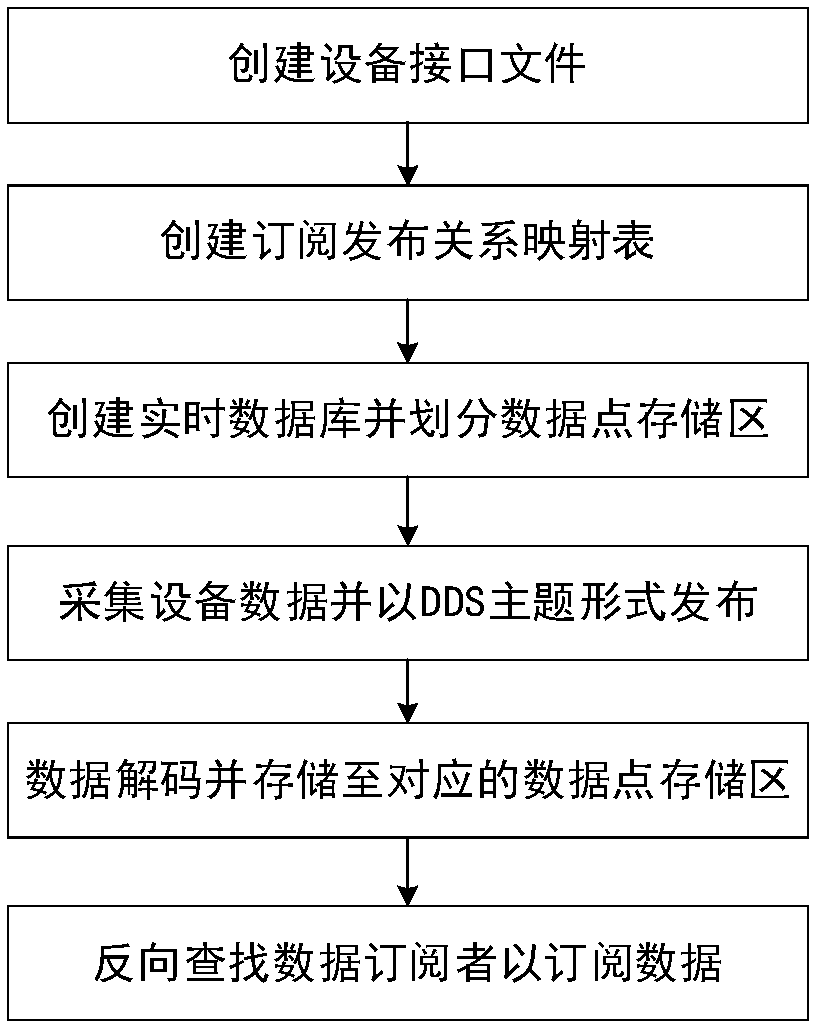
ActiveCN109547529AEasy to integrateConsistent Data CollectionTransmissionDistribution methodData acquisition
The invention discloses a distributed industrial data distribution method based on a DDS. The method comprises the following steps: S1, creating a device interface file for each abstract device; S2, creating a subscription and issuing relation mapping table, and building a mapping relation between a data subscriber and a data issuer and the mapping relation between the data subscriber and a DDS theme; S3, creating a real-time database; S4, acquiring interface data of the data issuer and issuing the interface data in a network through a form of the DDS theme; S5, decoding the DDS theme data andwriting the decoded data into the real-time database; S6, reversely finding out the data issuer corresponding to the DDS theme according to the subscription and issuing relation mapping table, and calling a device interface of the data subscriber to notify the data subscriber to read the DDS theme data. With the method provided by the invention, software interfaces of industrial sensors are unified, consistent data acquisition and output processing is realized, and integration of the sensors, miniature devices, virtual devices and non-standard devices of different models and different types is facilitated.
Owner:NO 719 RES INST CHINA SHIPBUILDING IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com