Patents
Literature
2362 results about "Read-only memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Read-only memory (ROM) is a type of non-volatile memory used in computers and other electronic devices. Data stored in ROM cannot be electronically modified after the manufacture of the memory device. Read-only memory is useful for storing software that is rarely changed during the life of the system, sometimes known as firmware. Software applications for programmable devices can be distributed as plug-in cartridges containing read-only memory.
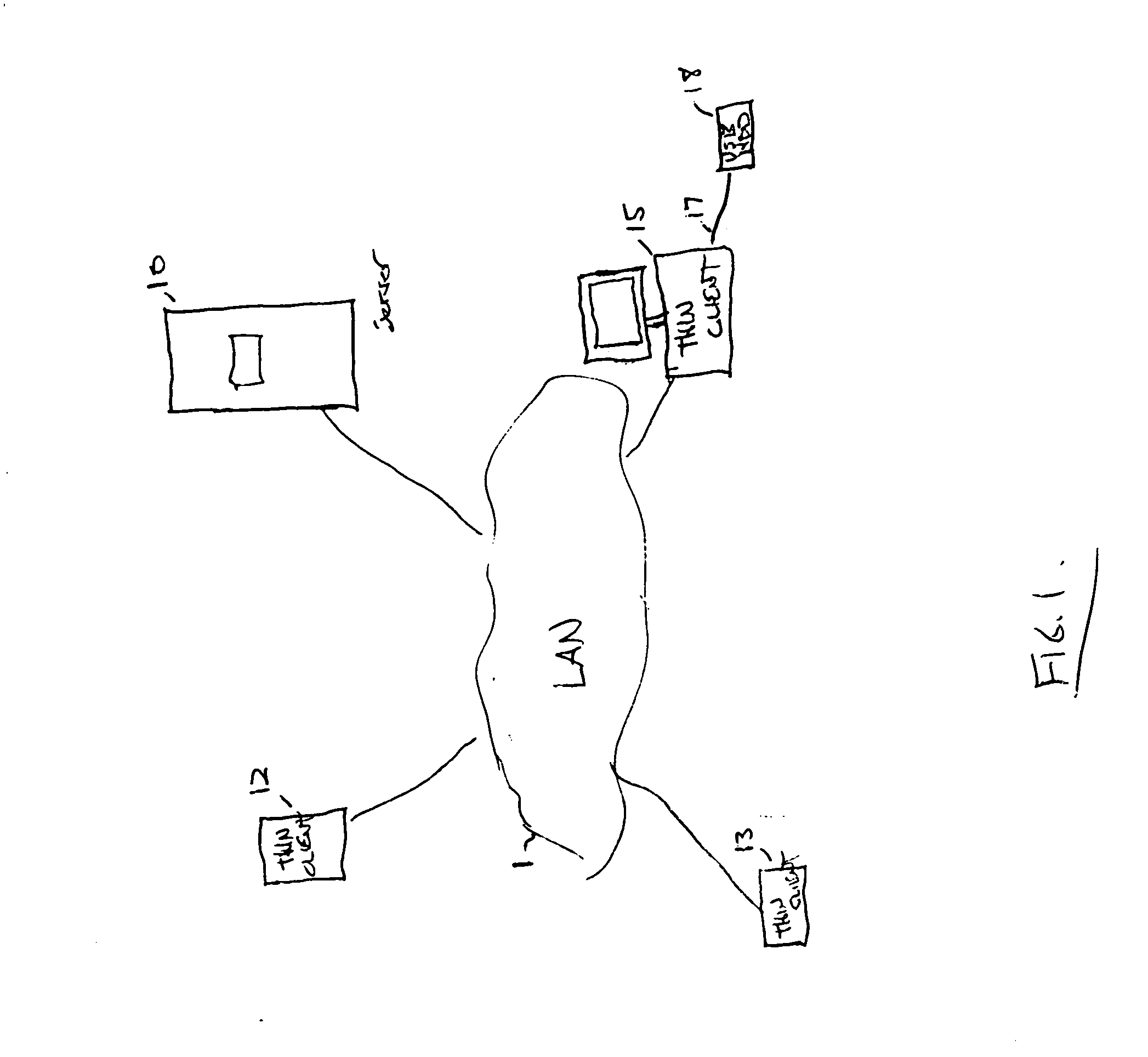
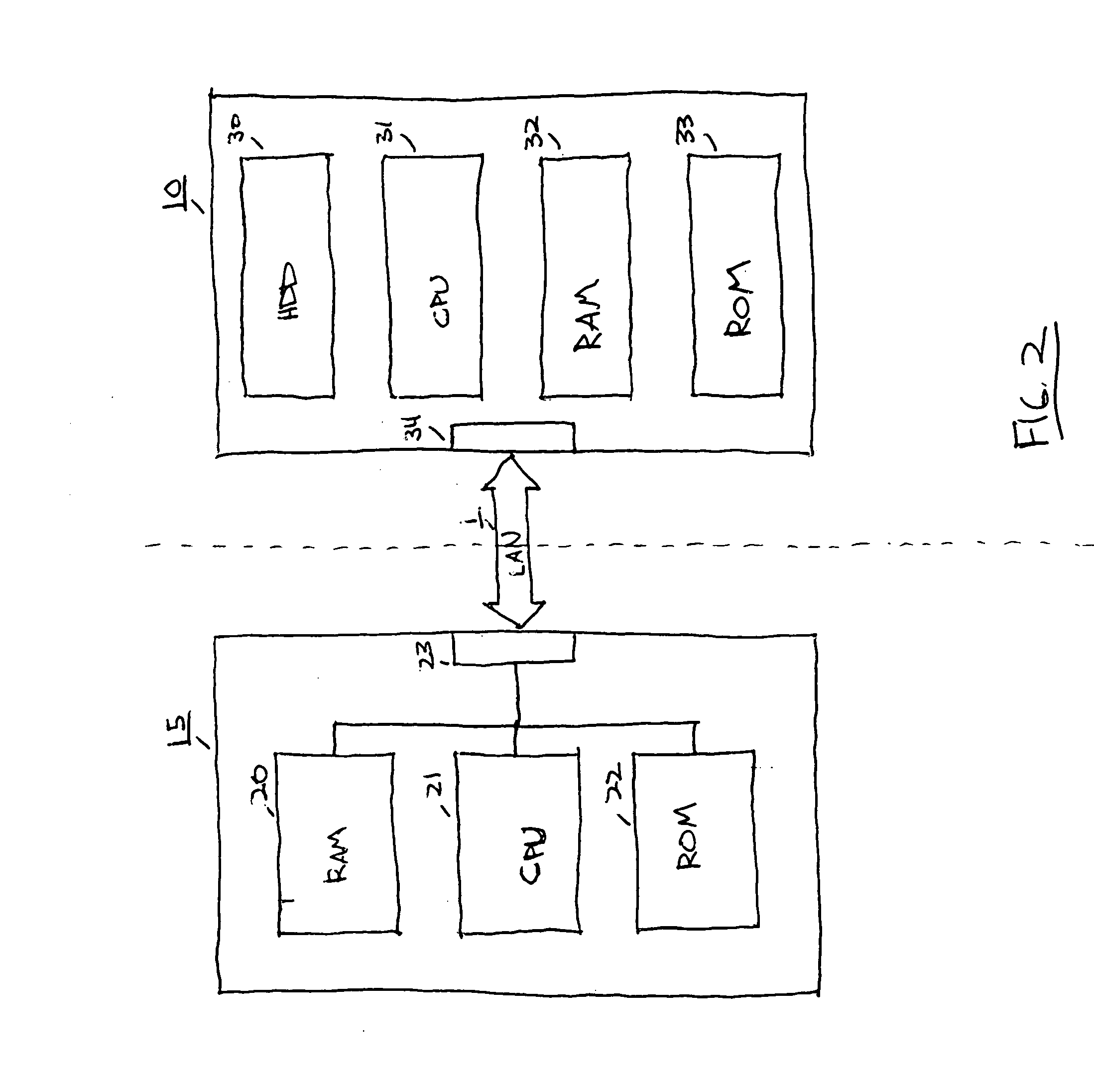
Surgical robotic tools, data architecture, and use
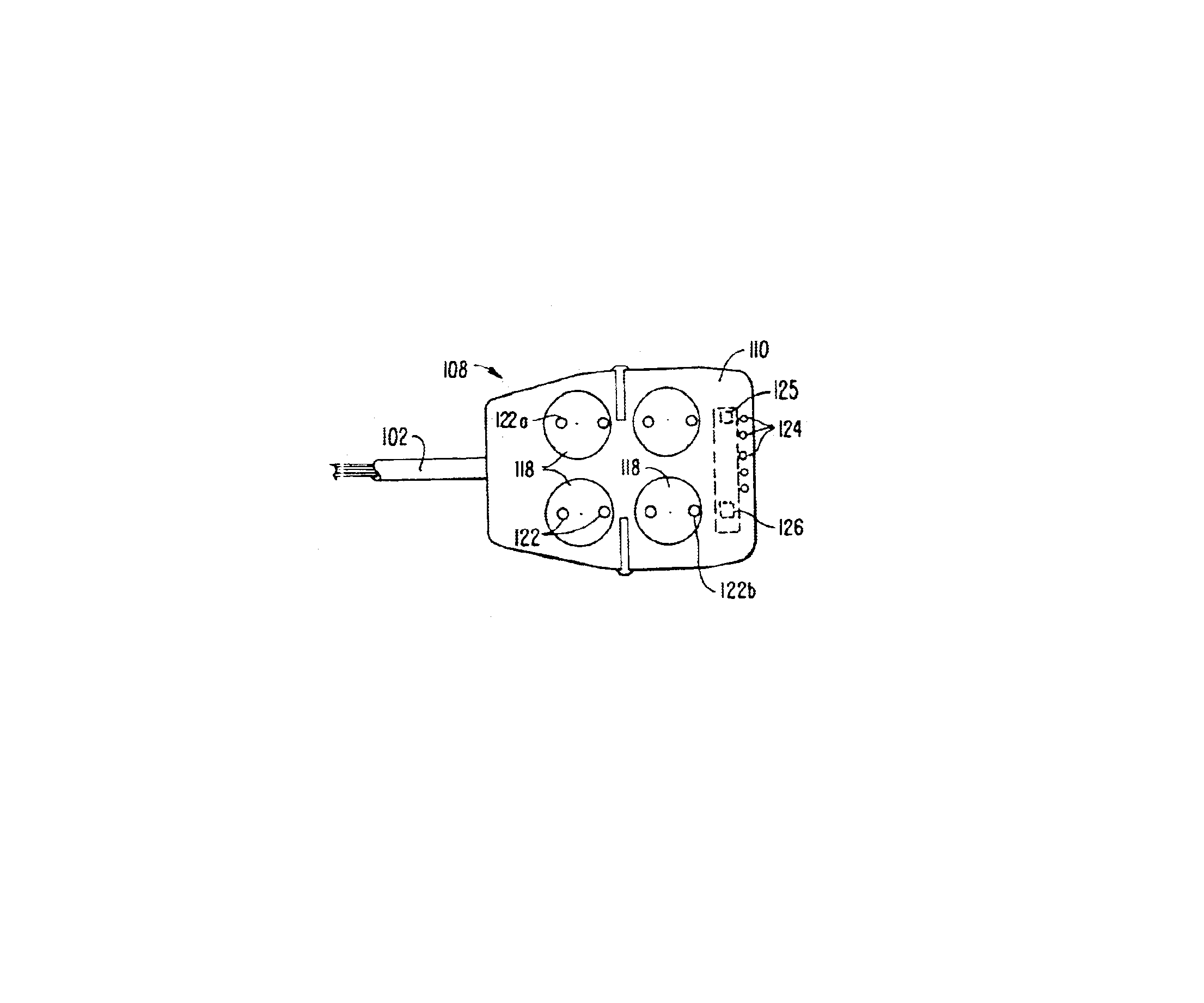
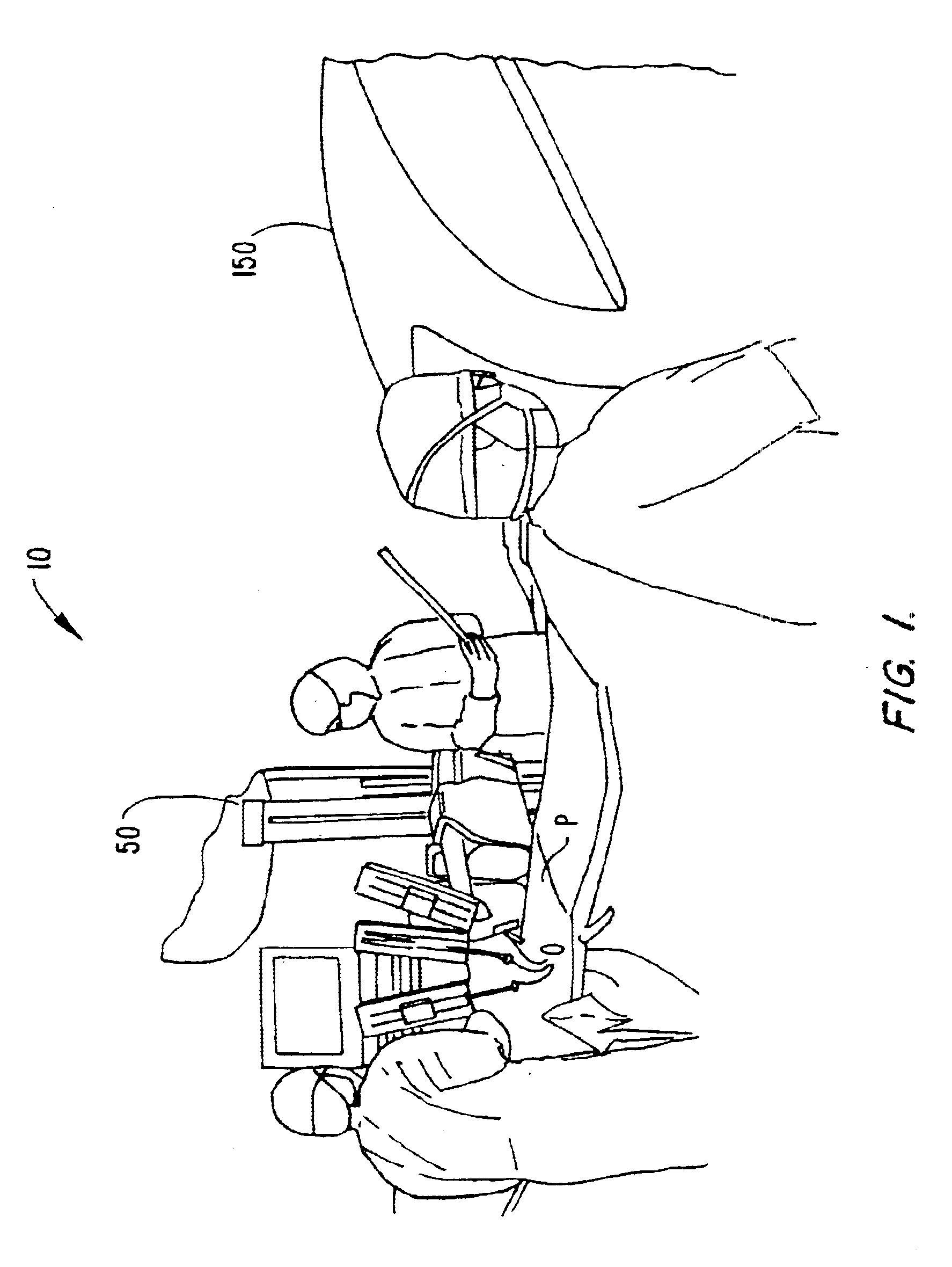
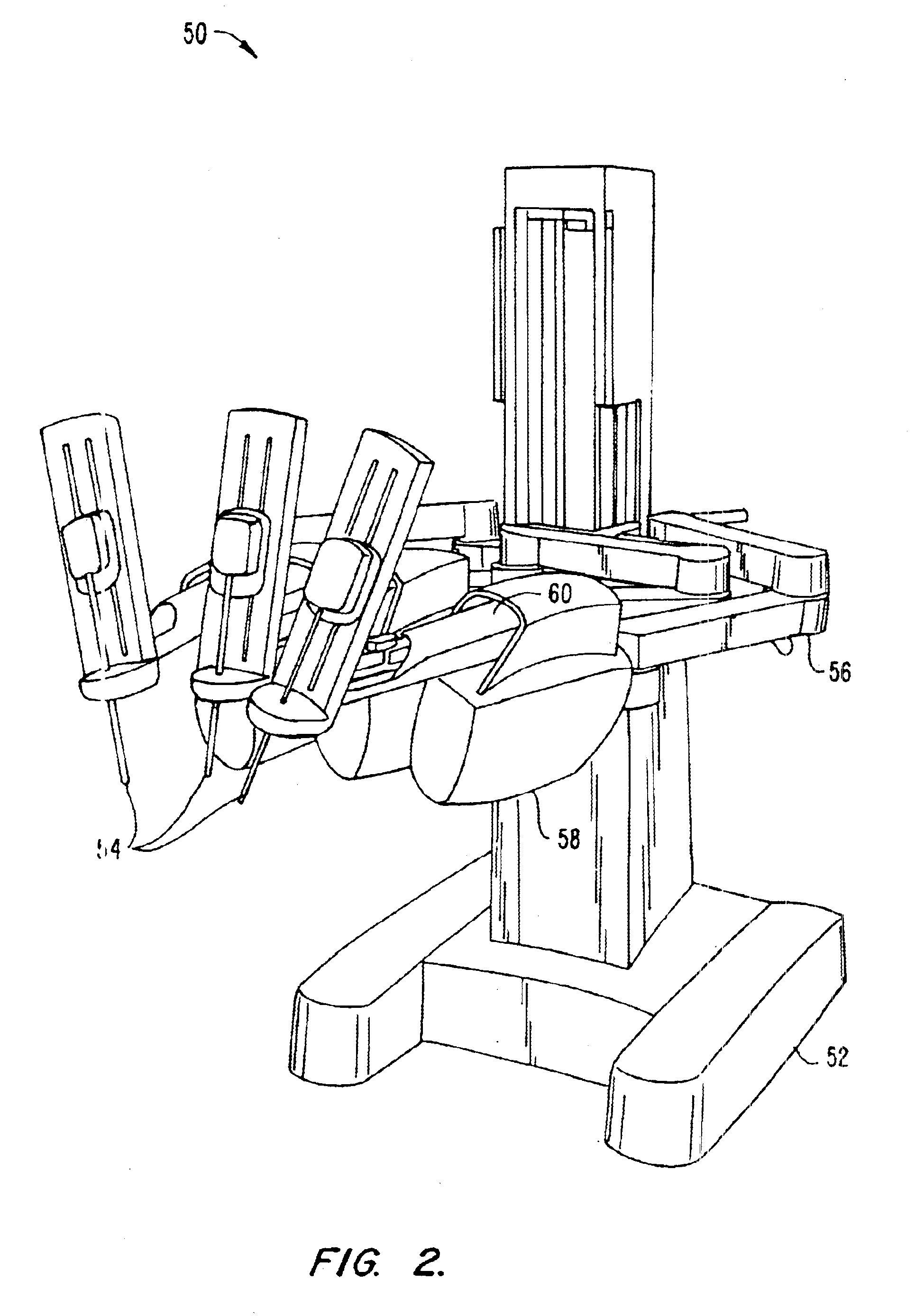
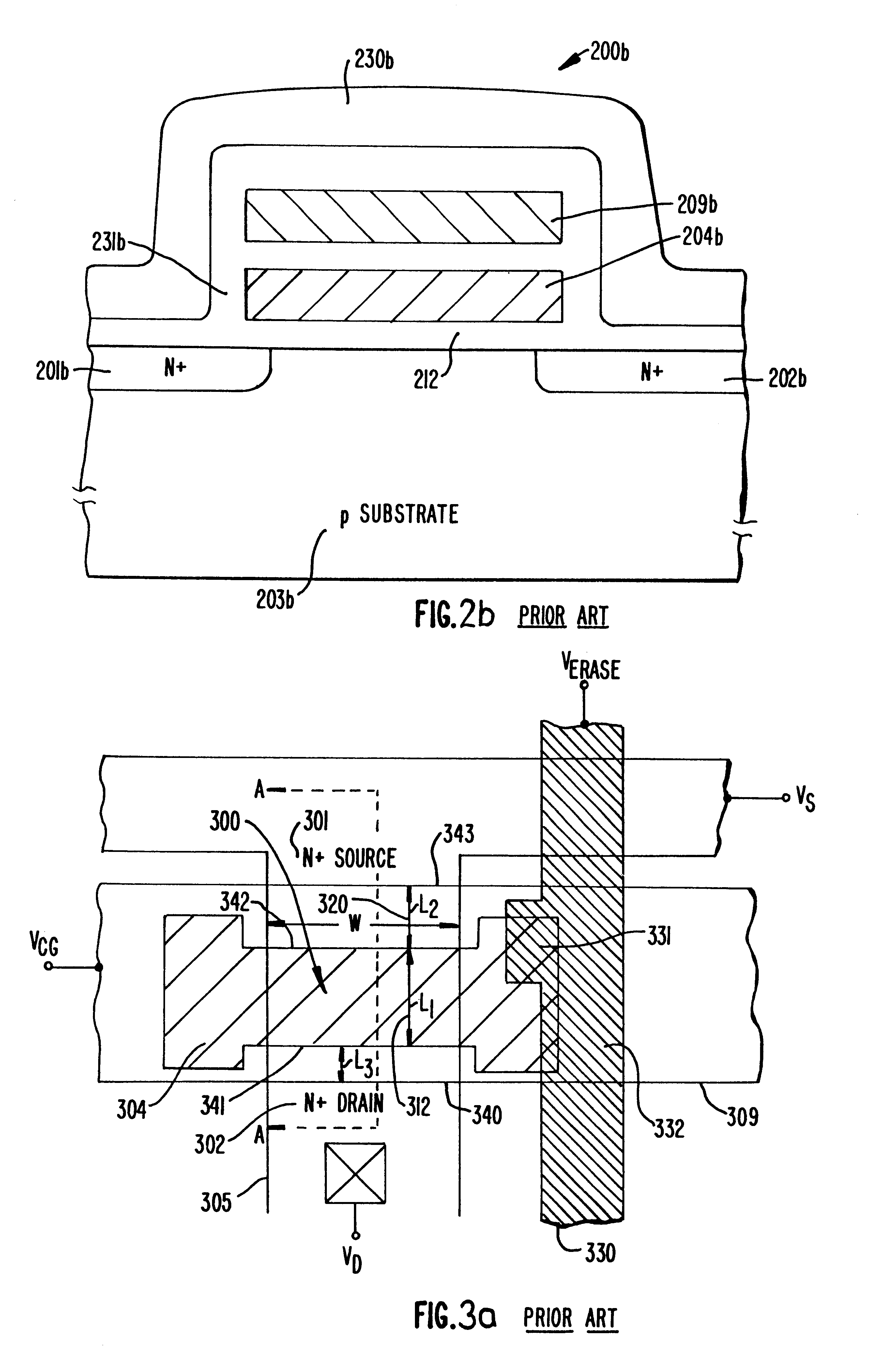
Robotic surgical tools, systems, and methods for preparing for and performing robotic surgery include a memory mounted on the tool. The memory can perform a number of functions when the tool is loaded on the tool manipulator: first, the memory can provide a signal verifying that the tool is compatible with that particular robotic system. Secondly, the tool memory may identify the tool-type to the robotic system so that the robotic system can reconfigure its programming. Thirdly, the memory of the tool may indicate tool-specific information, including measured calibration offsets indicating misalignment of the tool drive system, tool life data, or the like. This information may be stored in a read only memory (ROM), or in a nonvolatile memory which can be written to only a single time. The invention further provides improved engagement structures for coupling robotic surgical tools with manipulator structures.
Owner:INTUITIVE SURGICAL OPERATIONS INC
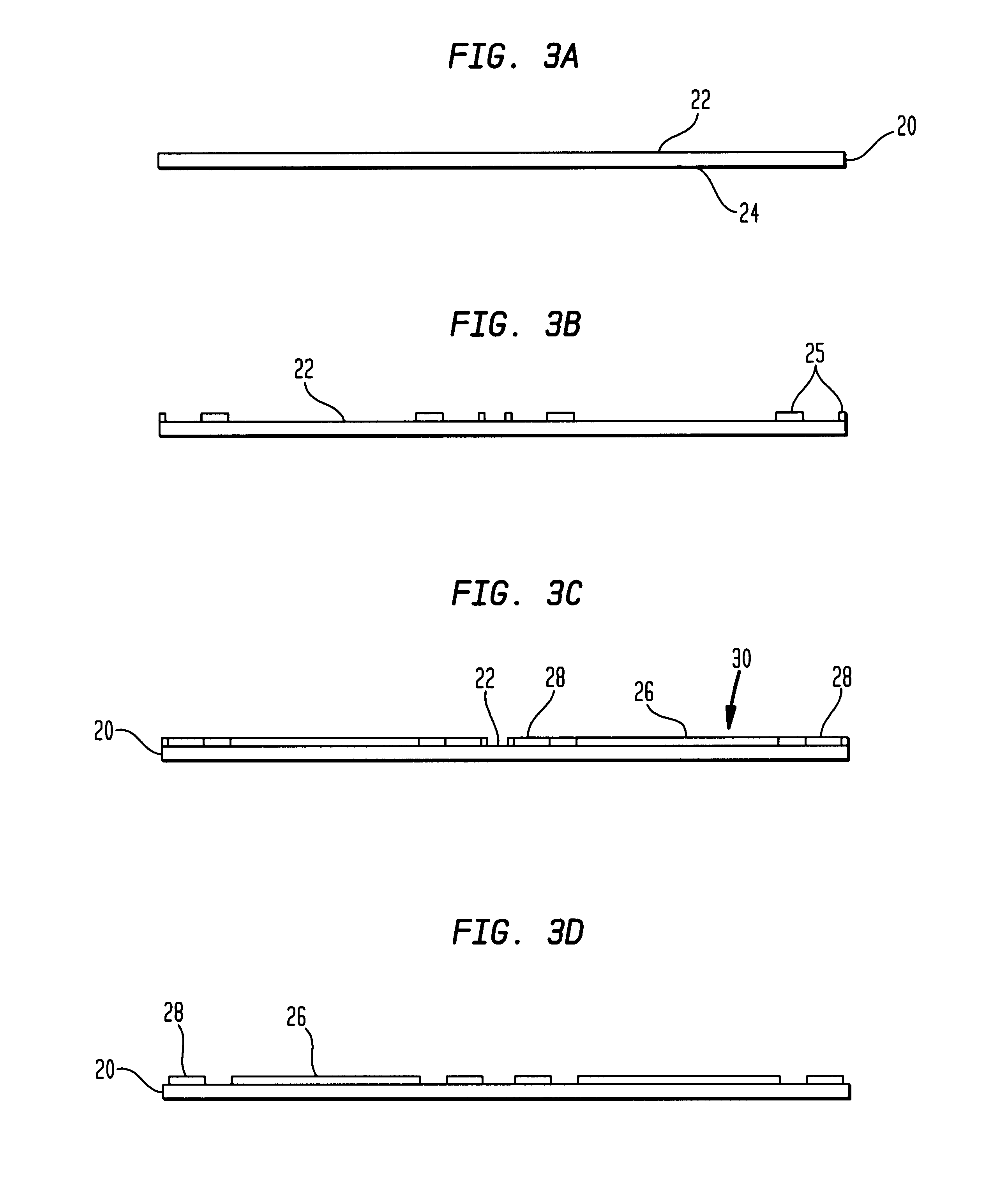
Semiconductor packages having light-sensitive chips
InactiveUS6583444B2Readily flexEasy to moveSemiconductor/solid-state device detailsSolid-state devicesProgrammable read-only memorySemiconductor package
A method of making a microelectronic package includes providing a sacrificial layer having a first surface and providing an optoelectronic element having a front face including one or more contacts and a rear surface and securing the rear surface of the optoelectronic element over the first surface of the sacrificial layer. The one or more contacts are then electrically interconnected with one or more conductive pads on the sacrificial layer and a curable and at least partially transparent encapsulant is provided over the first surface of the sacrificial layer so as to encapsulate the optoelectronic element and the conductive pads. The encapsulant is then cured the sacrificial layer is at least partially removed so as to leave said one or more conductive pads on a bottom surface of the encapsulant, the bottom surface of the encapsulant defining the bottom of the package. The optoelectronic element may include a light sensitive chip such as an ultraviolet-erasable programmable read-only memory (UV EPROM) or a light emitting chip, such as a light emitting diode (LED).
Owner:TESSERA INC
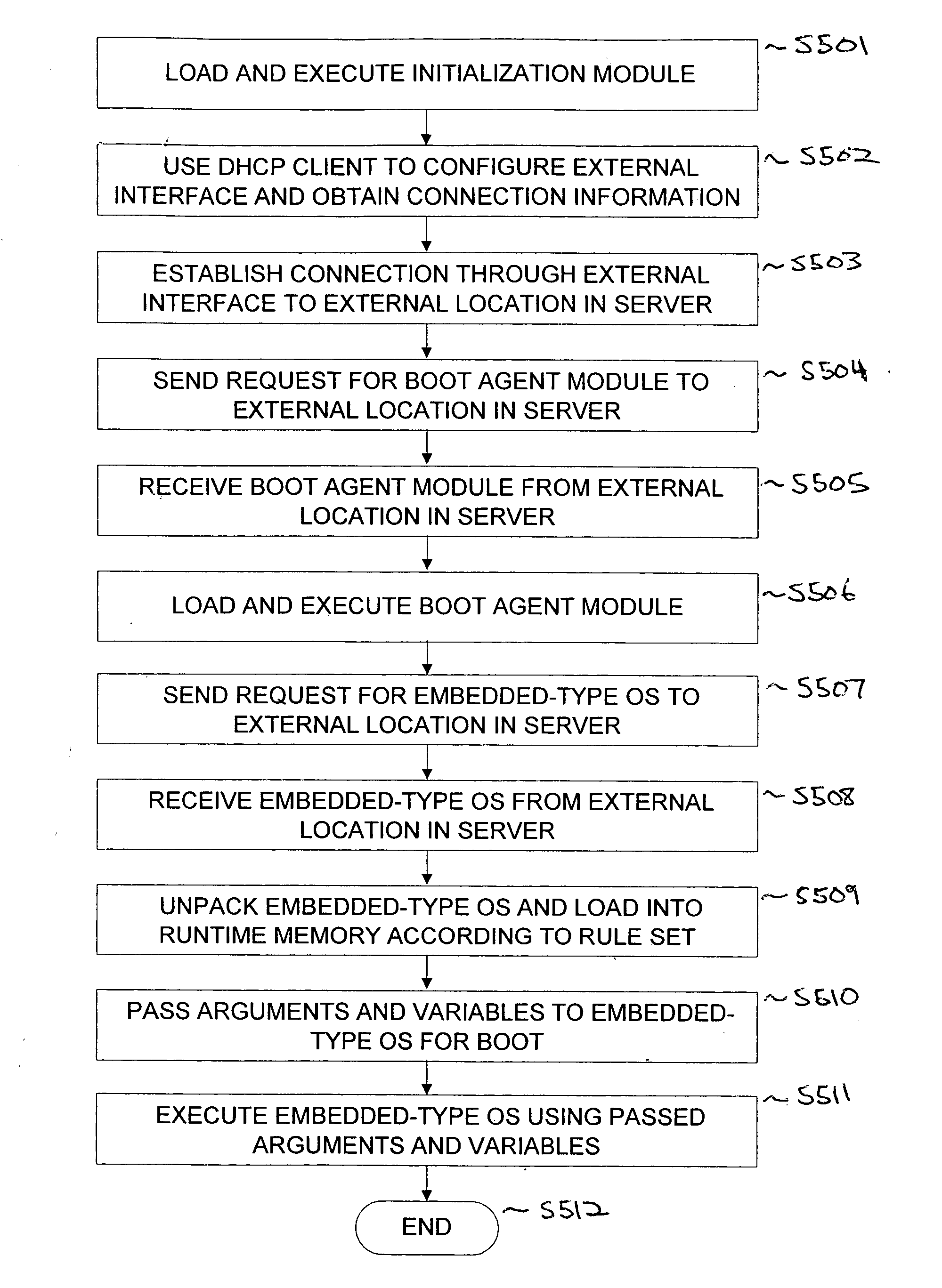
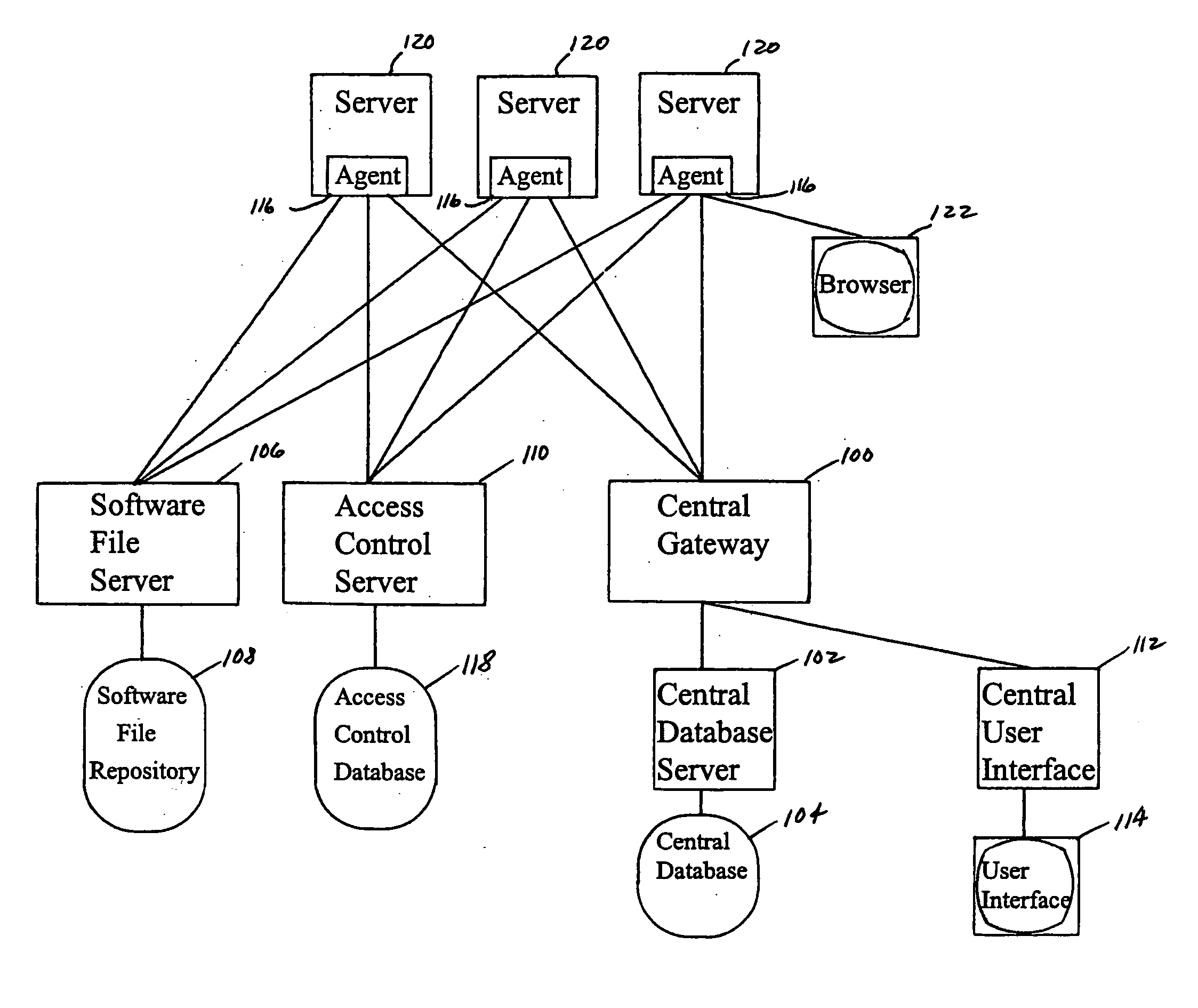
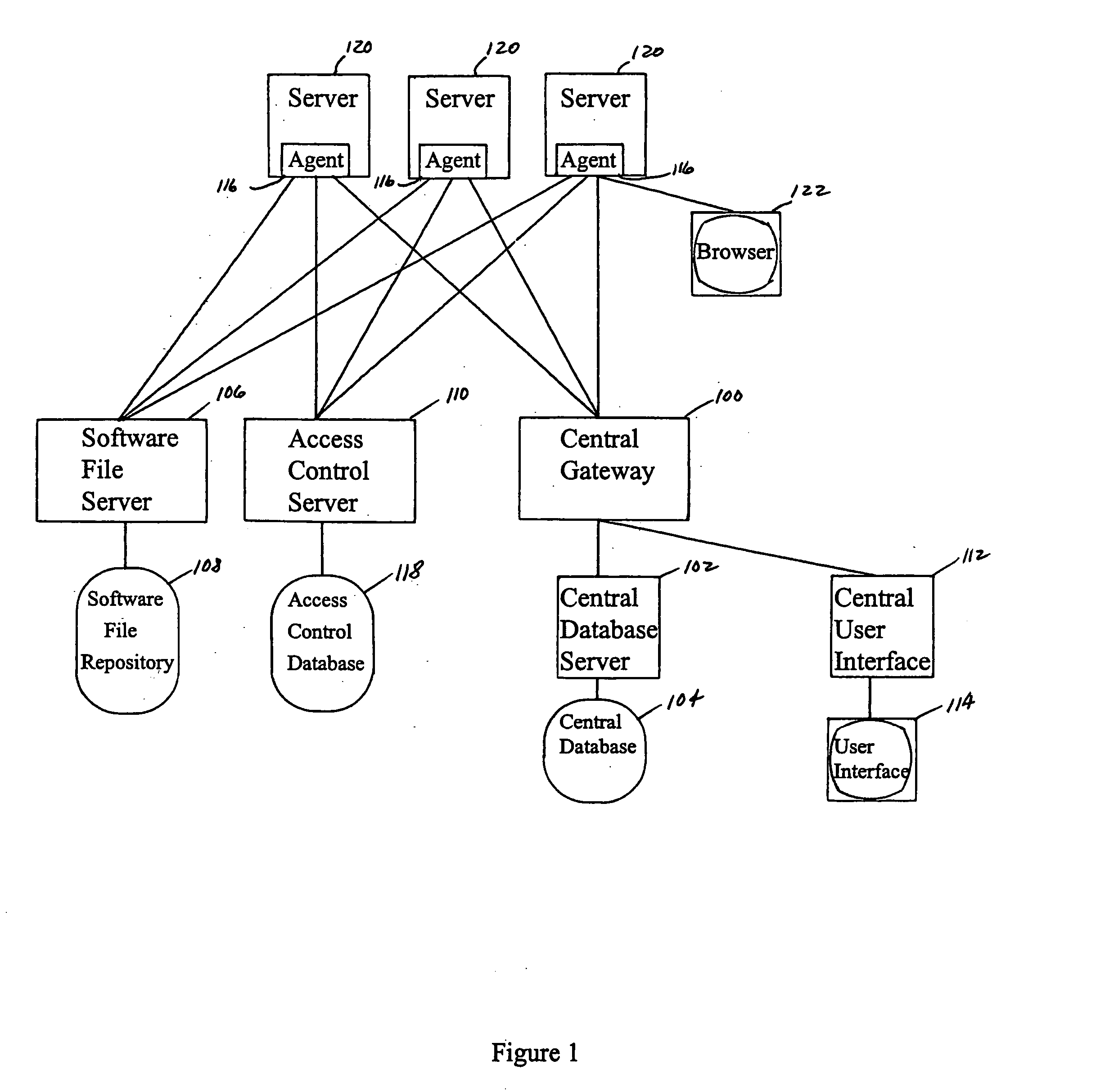
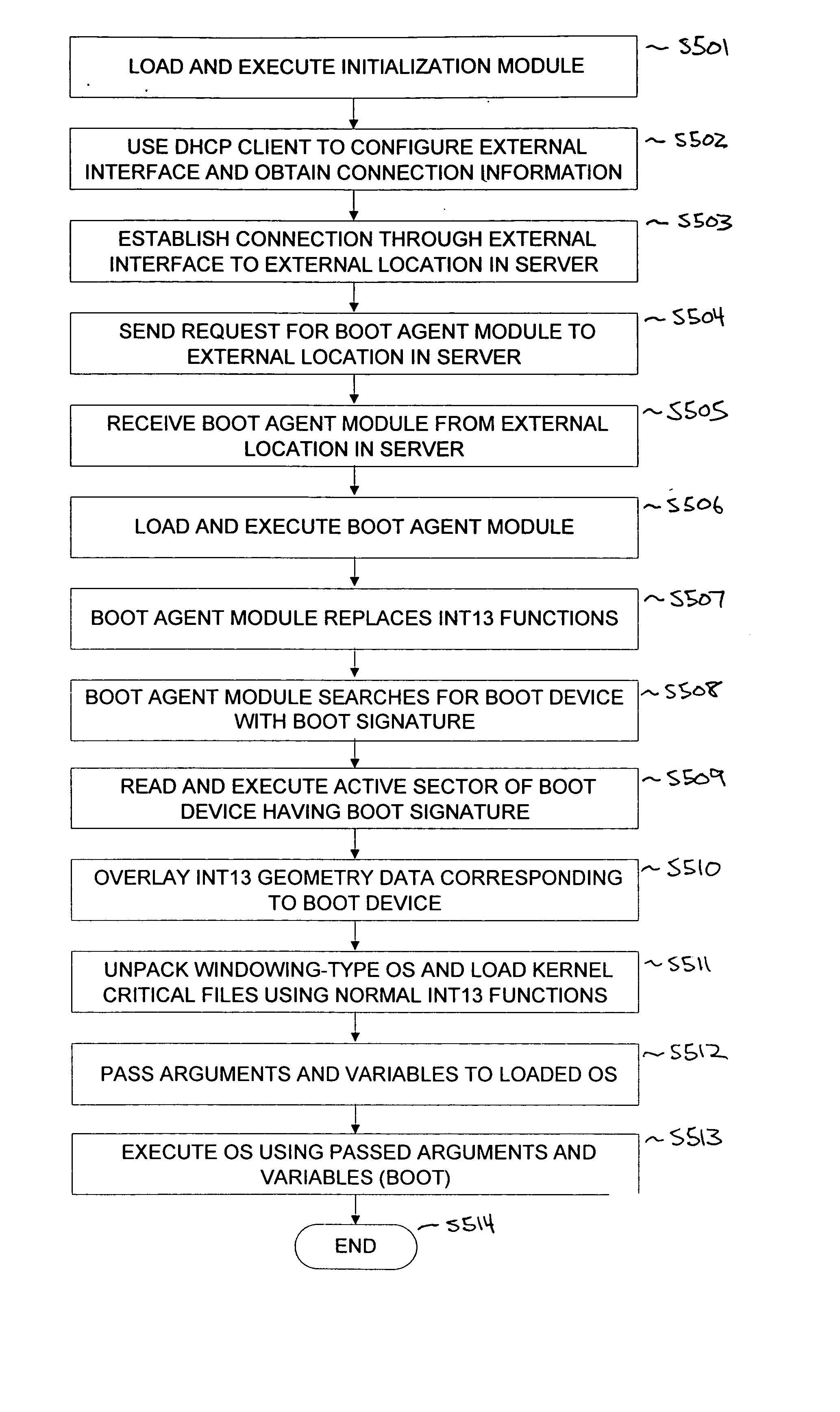
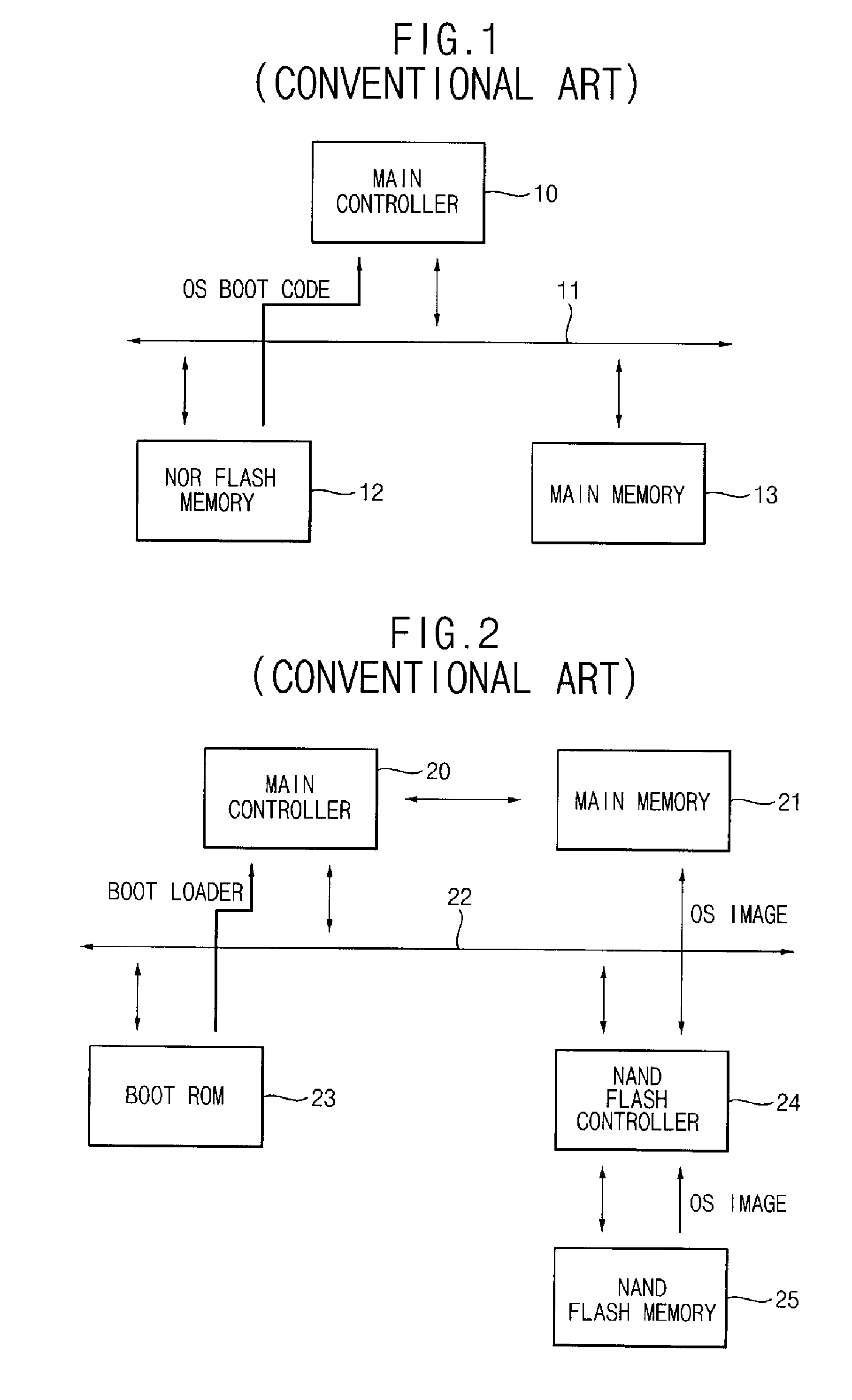
Operating system boot from network location
InactiveUS20060242395A1Easy to manageEasy to storeDigital computer detailsMemory systemsOperational systemInit
The present invention provides a system for booting an intelligent device with an embedded-type operating system obtained through an external interface disposed in the intelligent device, wherein the system includes an initialization module stored in a read-only memory provided in the intelligent device, the initialization module being executed in a processor disposed in the intelligent device and connecting to an external location through the external interface, and a server having a memory media which stores a boot agent module and an embedded-type operating system at the external location, the server sending the boot agent module to the intelligent device through the connection in response to a request from the initialization module, wherein the boot agent module is loaded into a runtime memory in the intelligent device and executed by the processor, the boot agent module then retrieving an embedded-type operating system image from the external location in the sever, whereupon the embedded-type operating system image is loaded into the runtime memory and executed by the processor.
Owner:WYSE TECH LLC
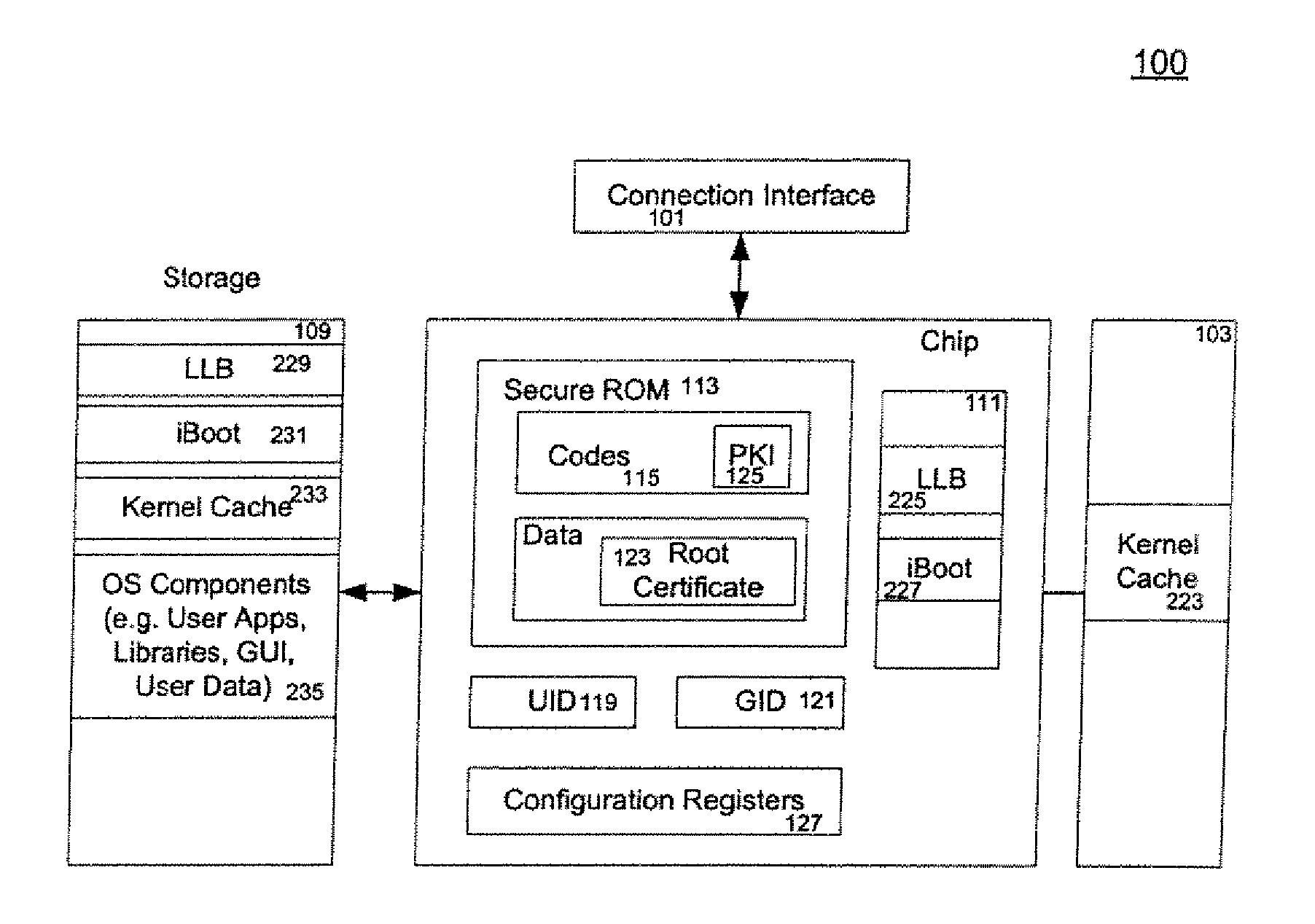
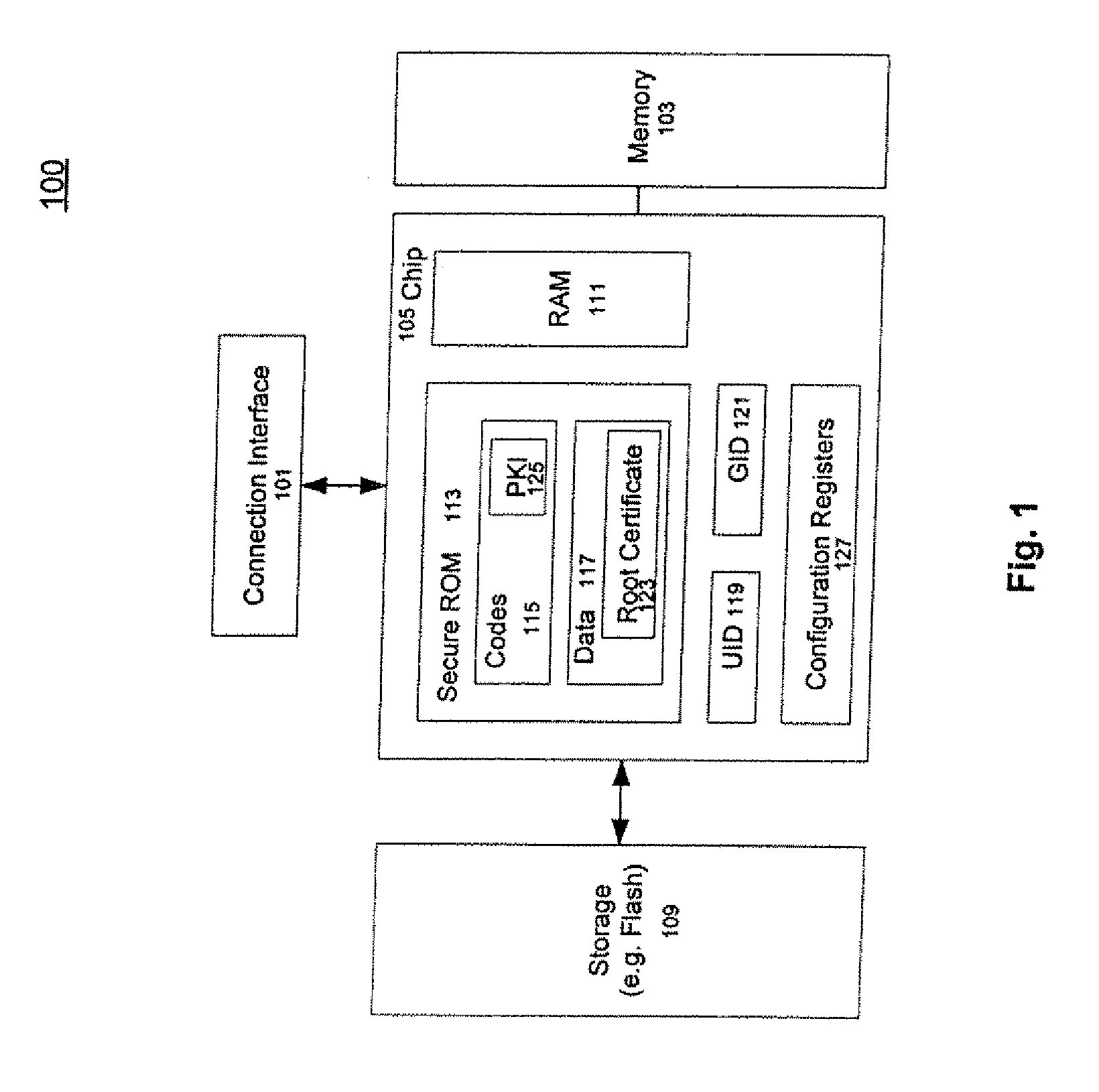
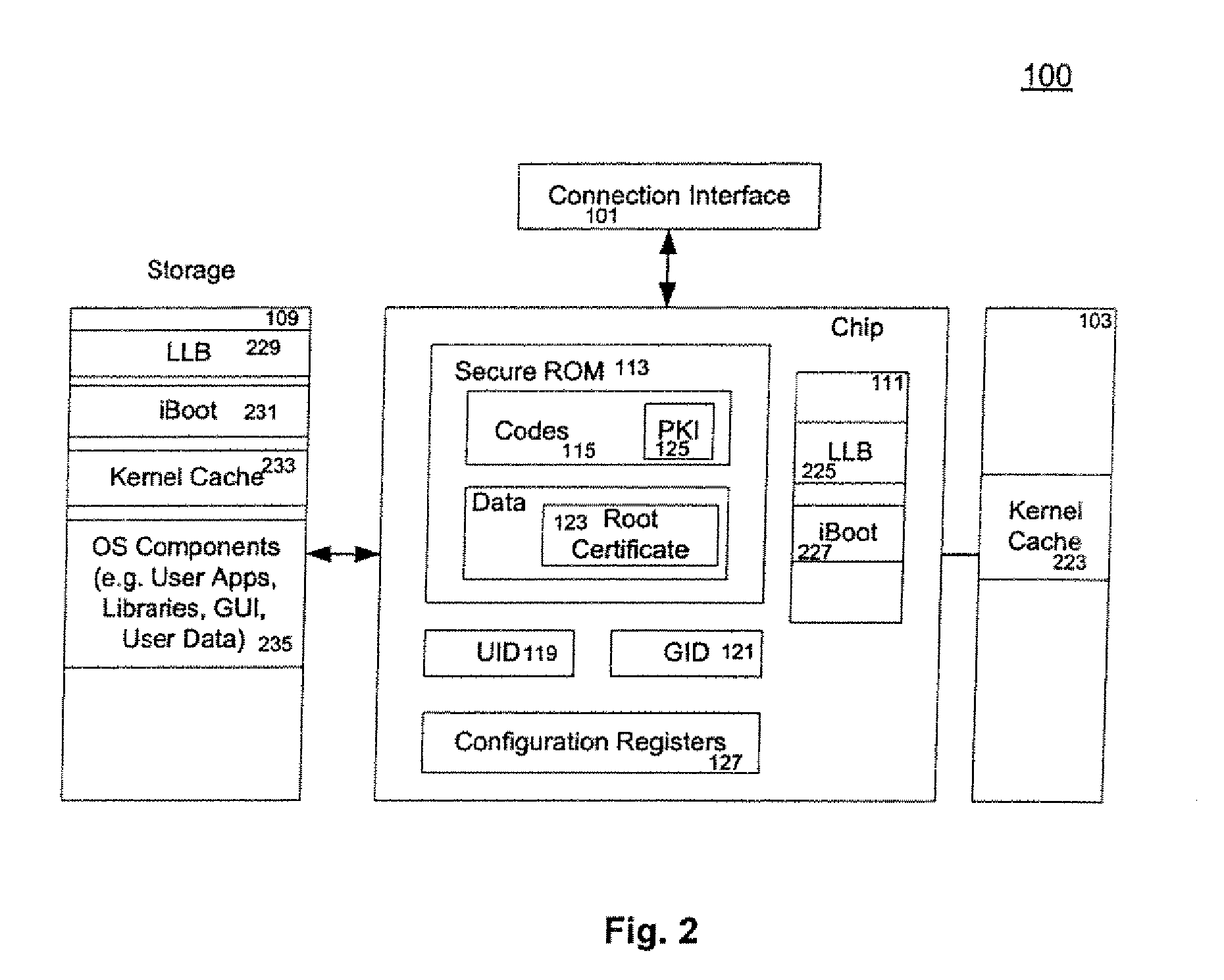
Secure Booting A Computing Device
ActiveUS20080165952A1Multiple keys/algorithms usageDigital computer detailsRead-only memoryOperating environment
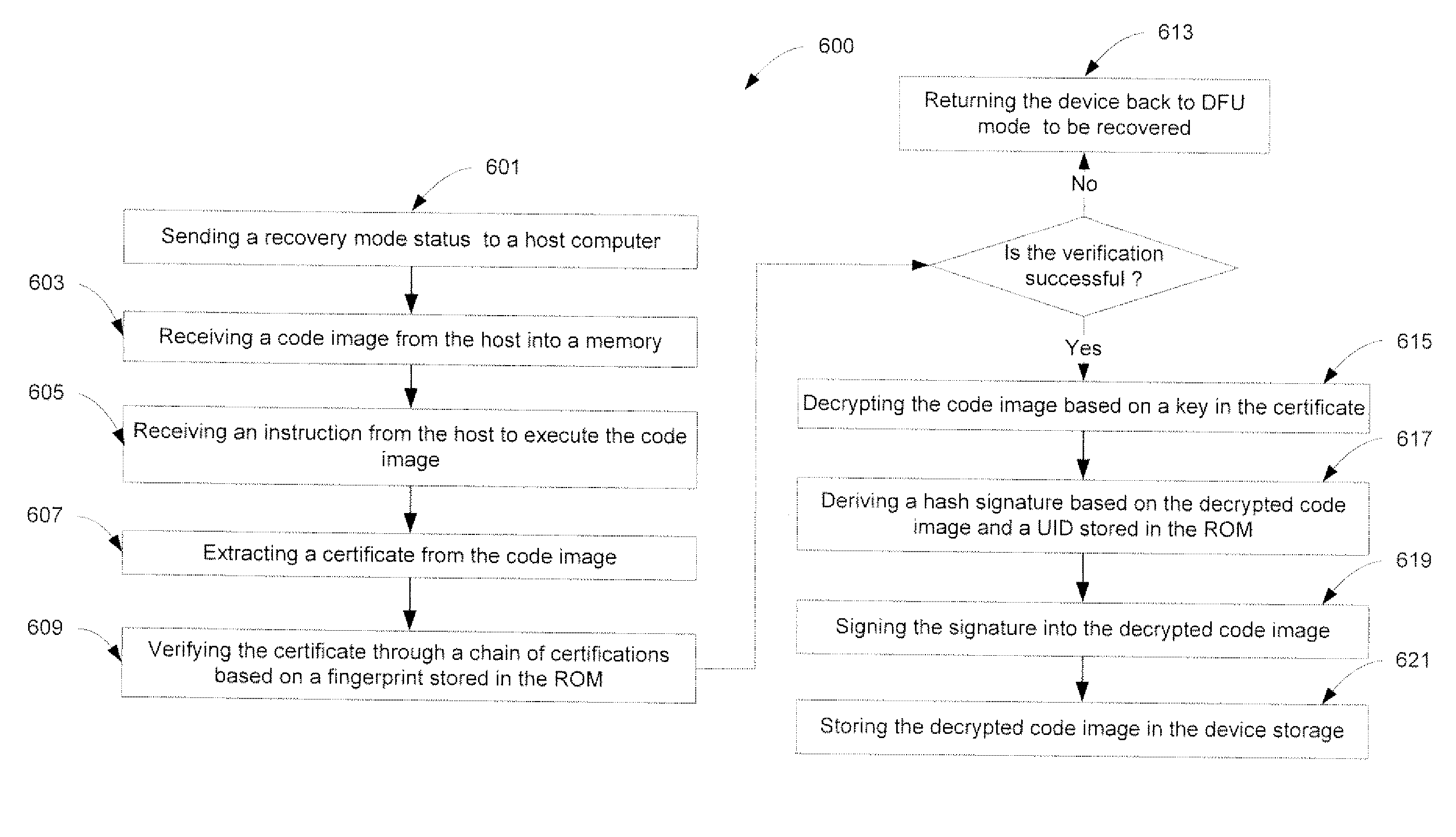
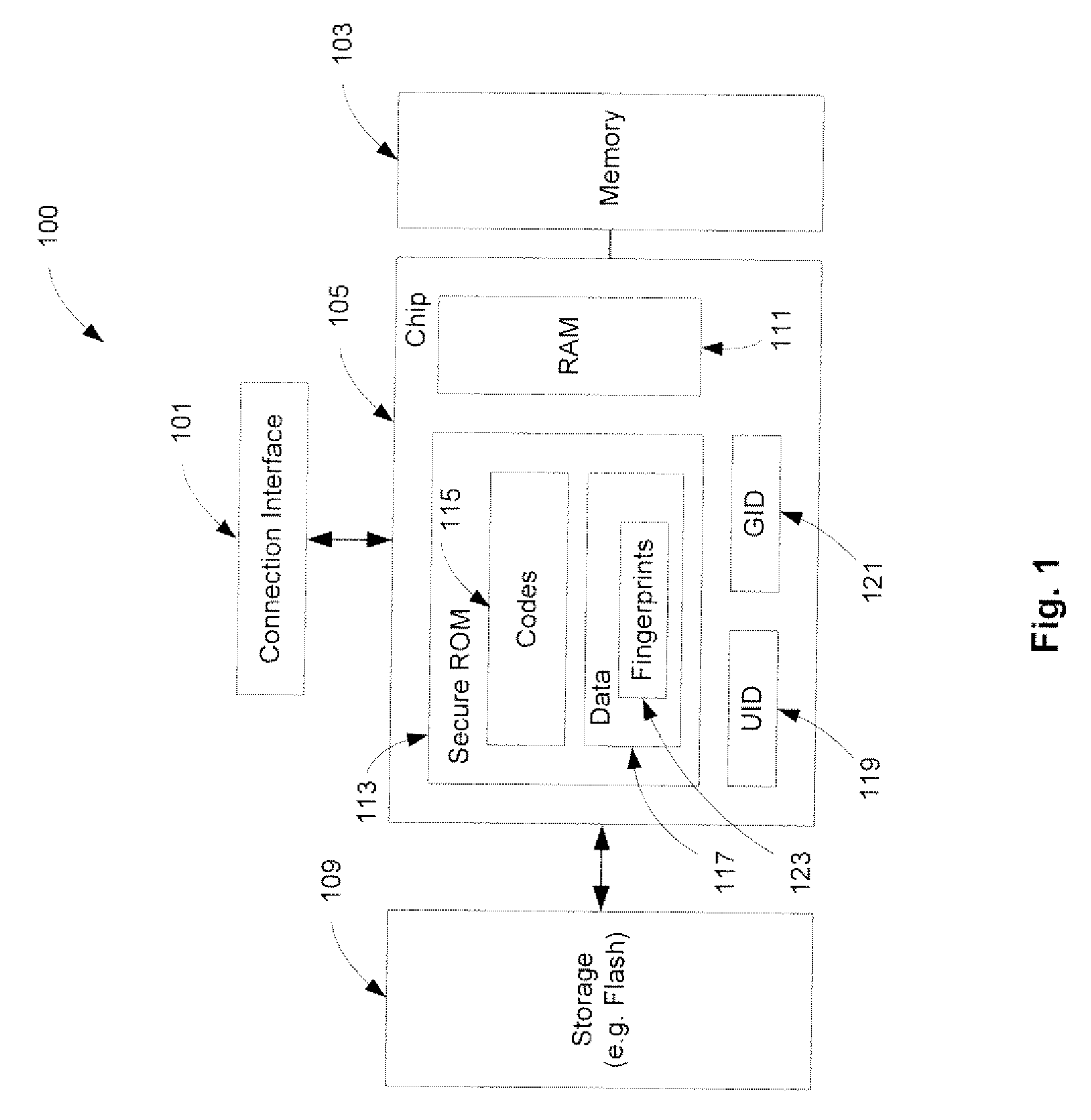
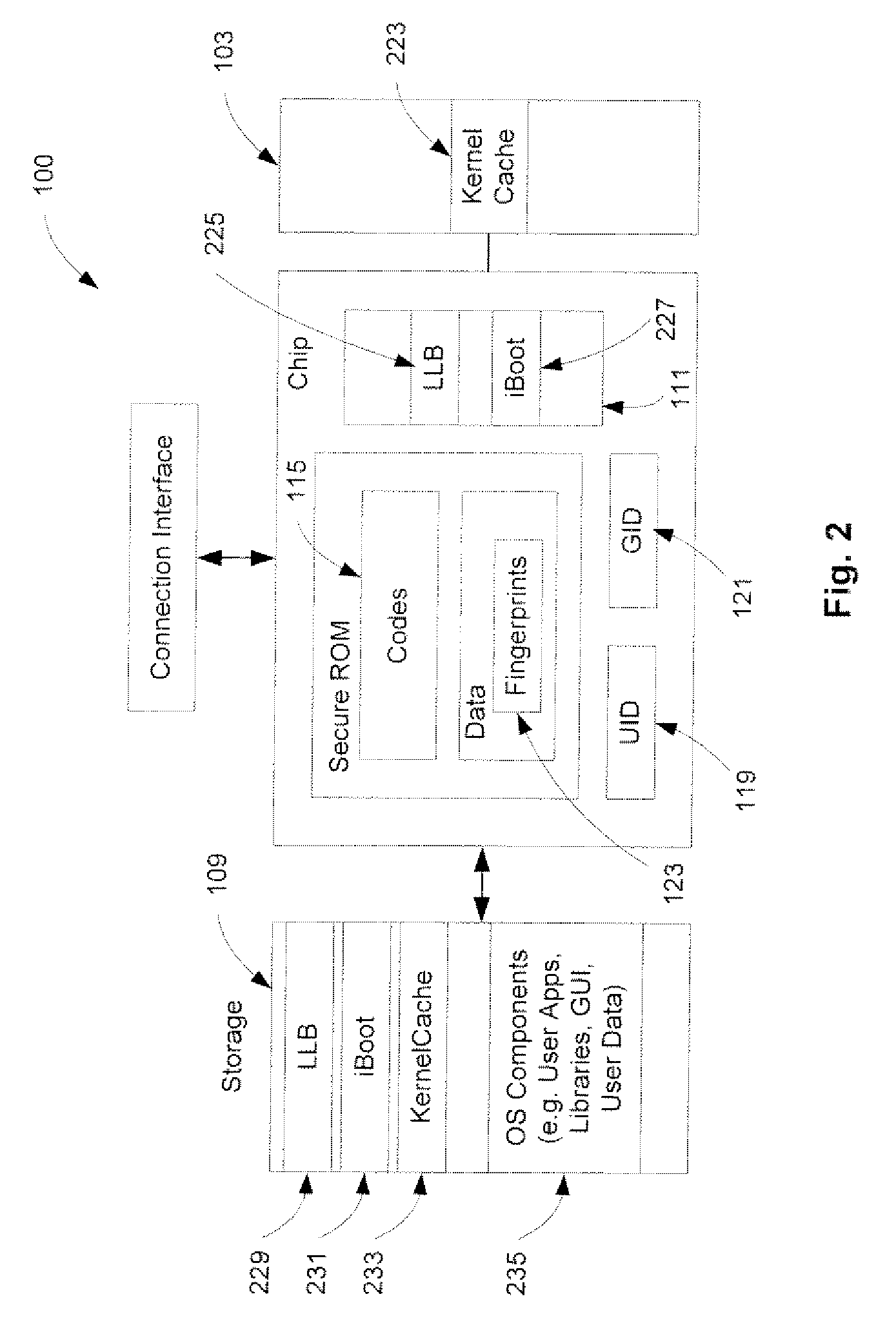
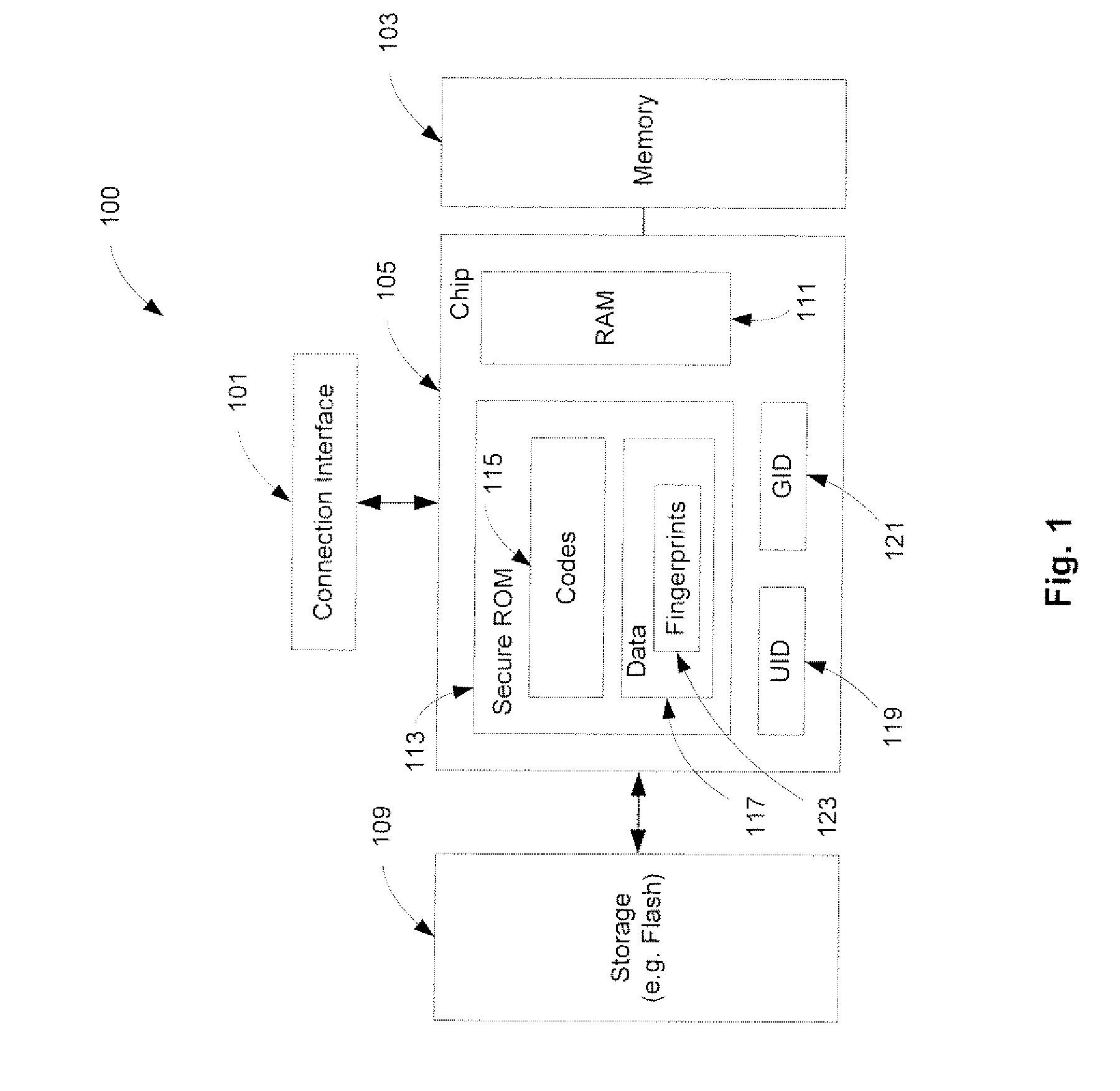
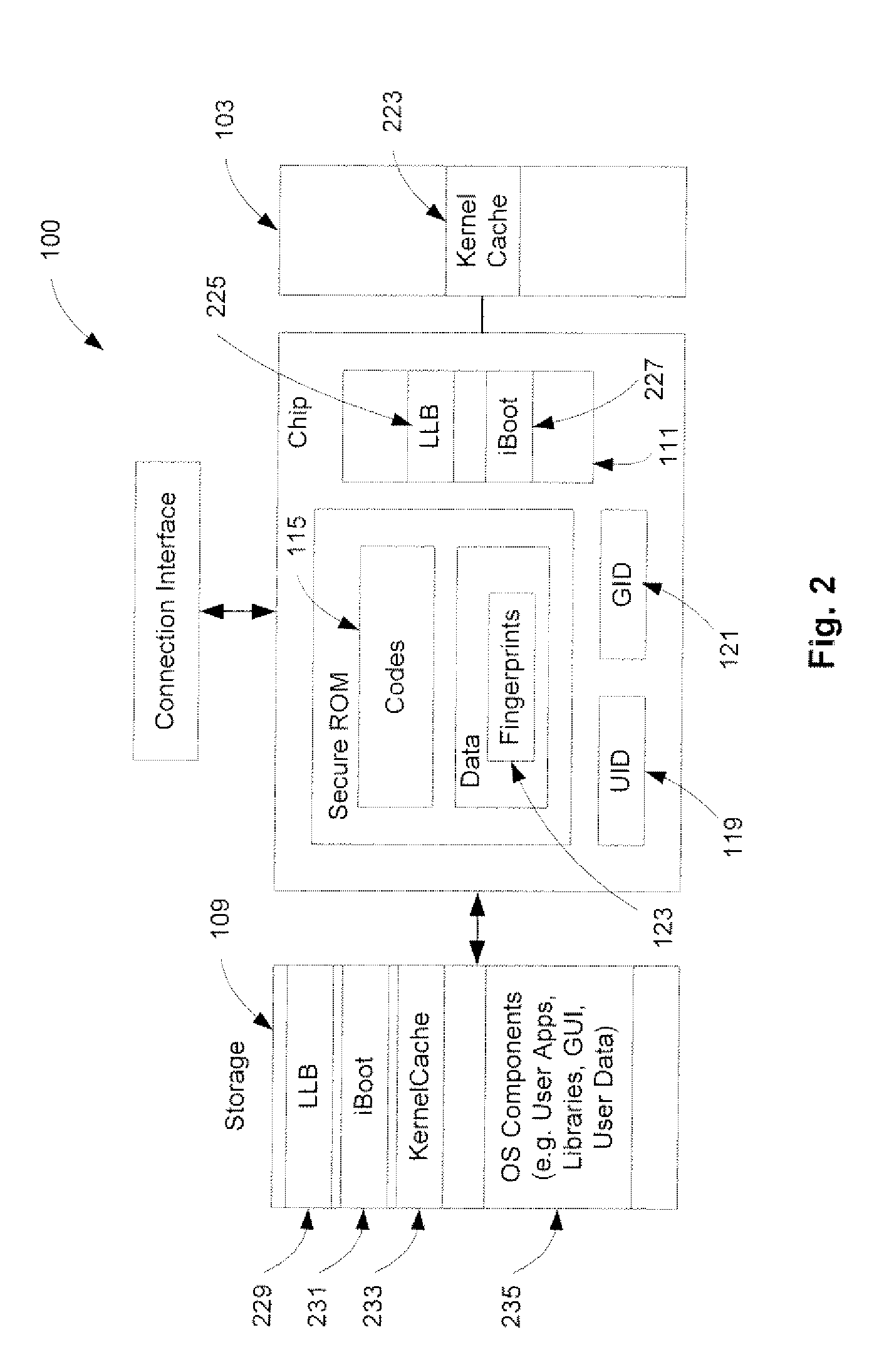
A method and an apparatus for executing codes embedded inside a device to verify a code image loaded in a memory of the device are described. A code image may be executed after being verified as a trusted code image. The embedded codes may be stored in a secure ROM (read only memory) chip of the device. In one embodiment, the verification of the code image is based on a key stored within the secure ROM chip. The key may be unique to each device. Access to the key may be controlled by the associated secure ROM chip. The device may complete establishing an operating environment subsequent to executing the verified code image.
Owner:APPLE INC
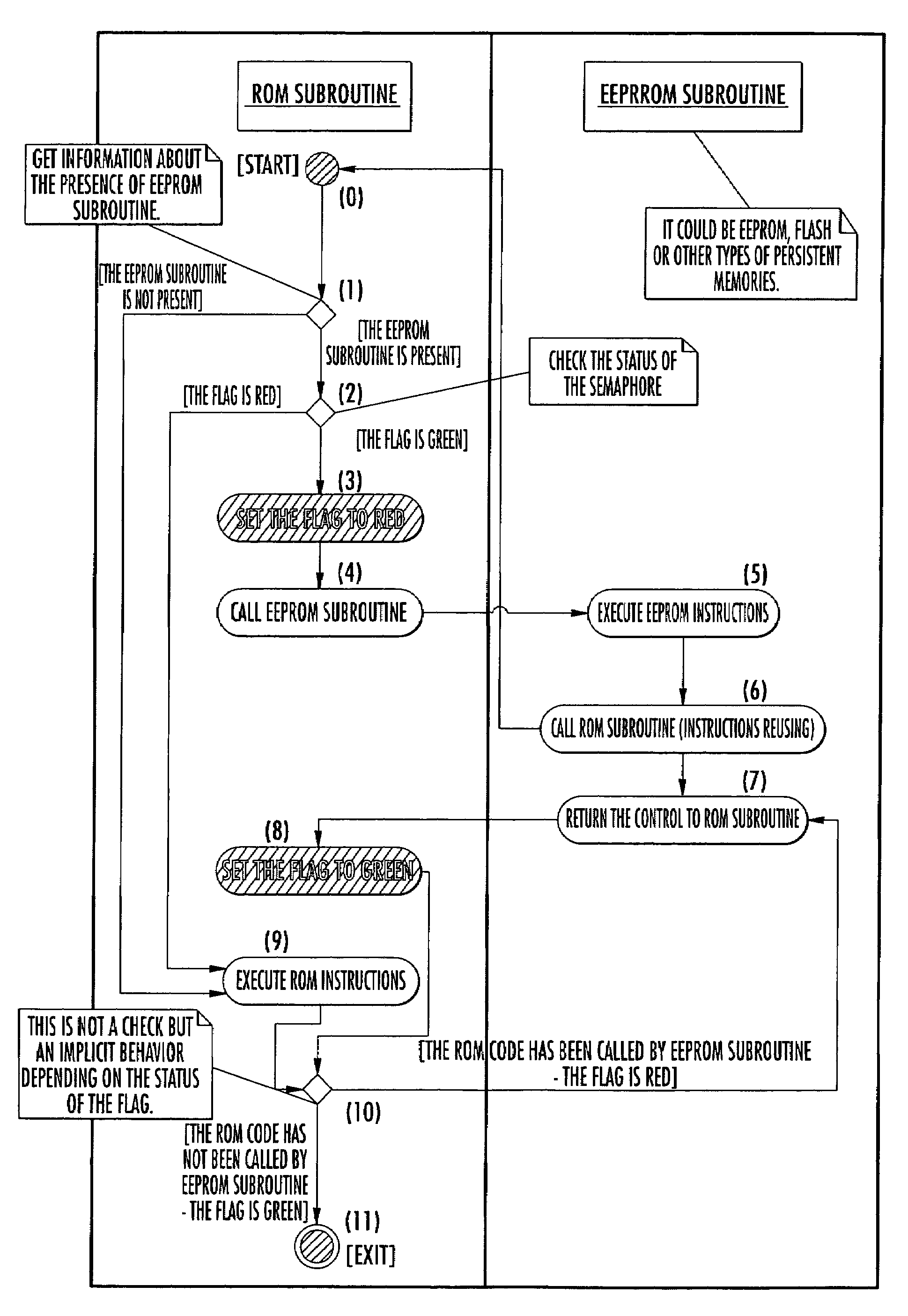
Method for patching ROM instructions in an electronic embedded system including at least a further memory portion
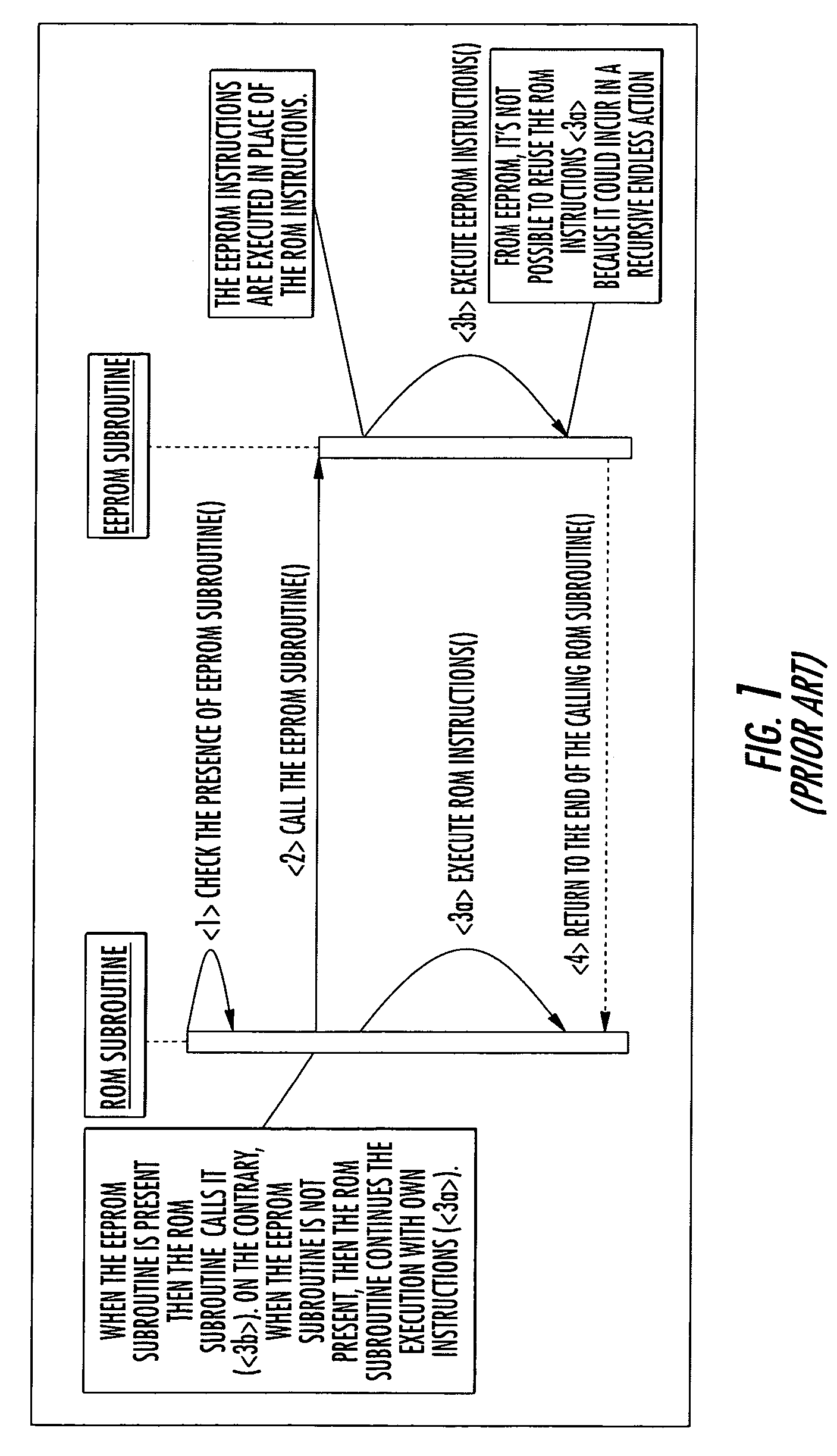
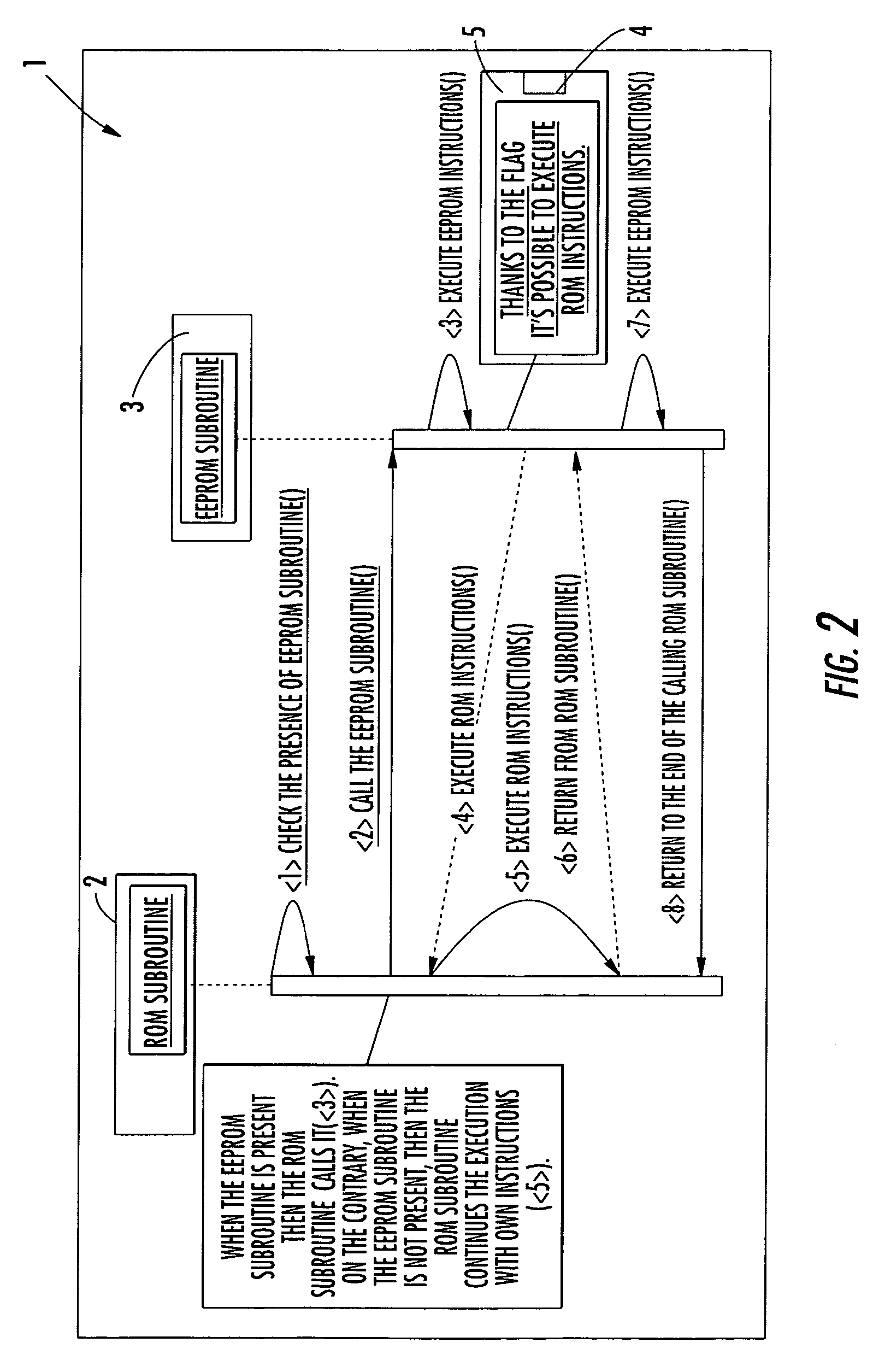
A mechanism for patching read only memory (ROM) instructions in an embedded system is provided. The embedded system includes non-volatile memory such as a ROM, a RAM and an EEPROM. In one configuration, the ROM contains application modules (subroutines) that are subordinate to a flag status. The flag status indicates to the subroutine whether to execute the ROM instructions in the ROM or the extended instructions in the EEPROM. The instructions in the EEPROM may be used to patch or to extend the behaviors masked in the ROM instructions. The extended instructions in the EEPROM may reuse the ROM instructions in the ROM without resulting in recursive actions.
Owner:STMICROELECTRONICS INT NV
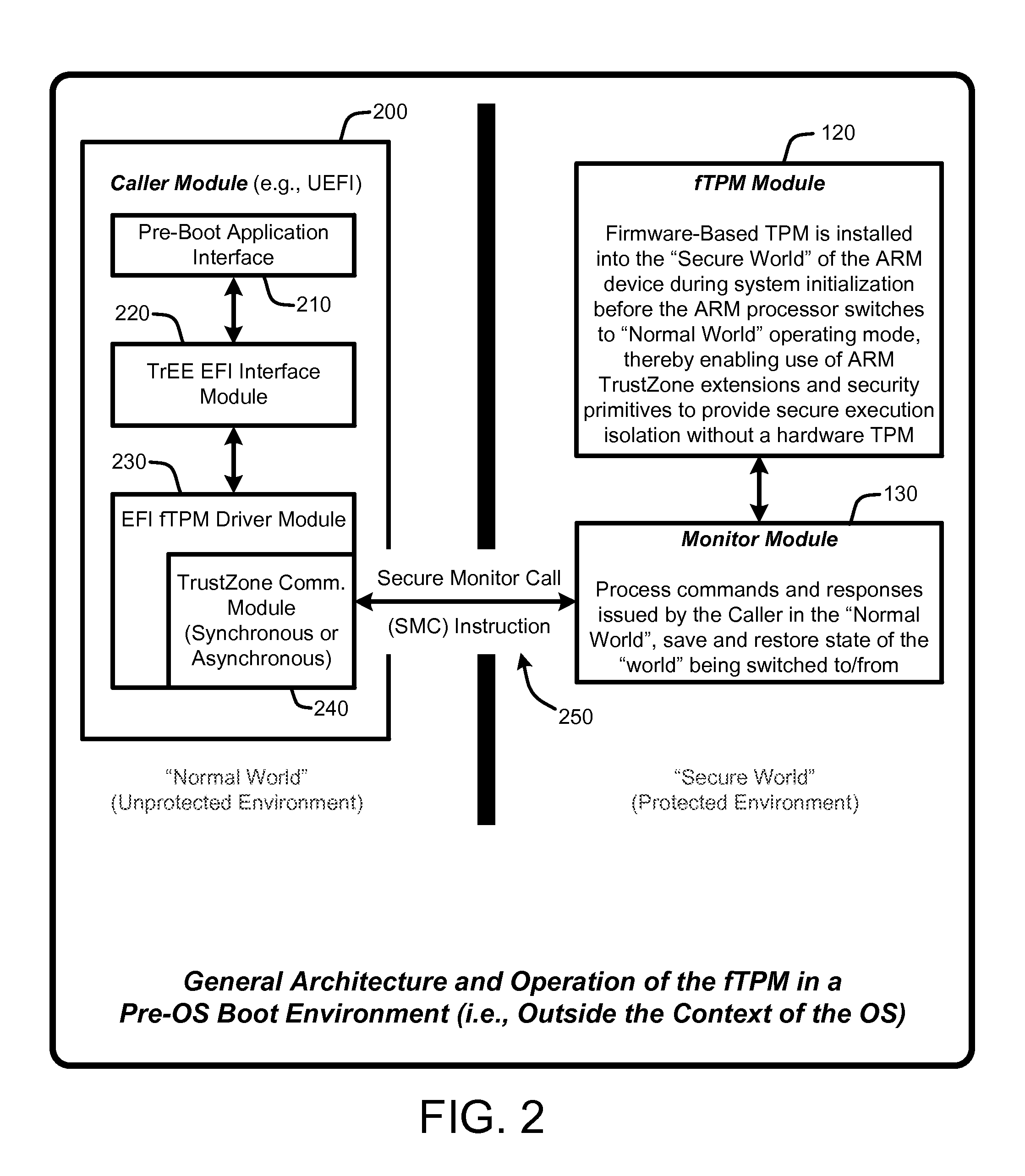
Firmware-based trusted platform module for arm processor architectures and trustzone security extensions
ActiveUS20130031374A1Increase costReduce system costDigital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleSafe handling
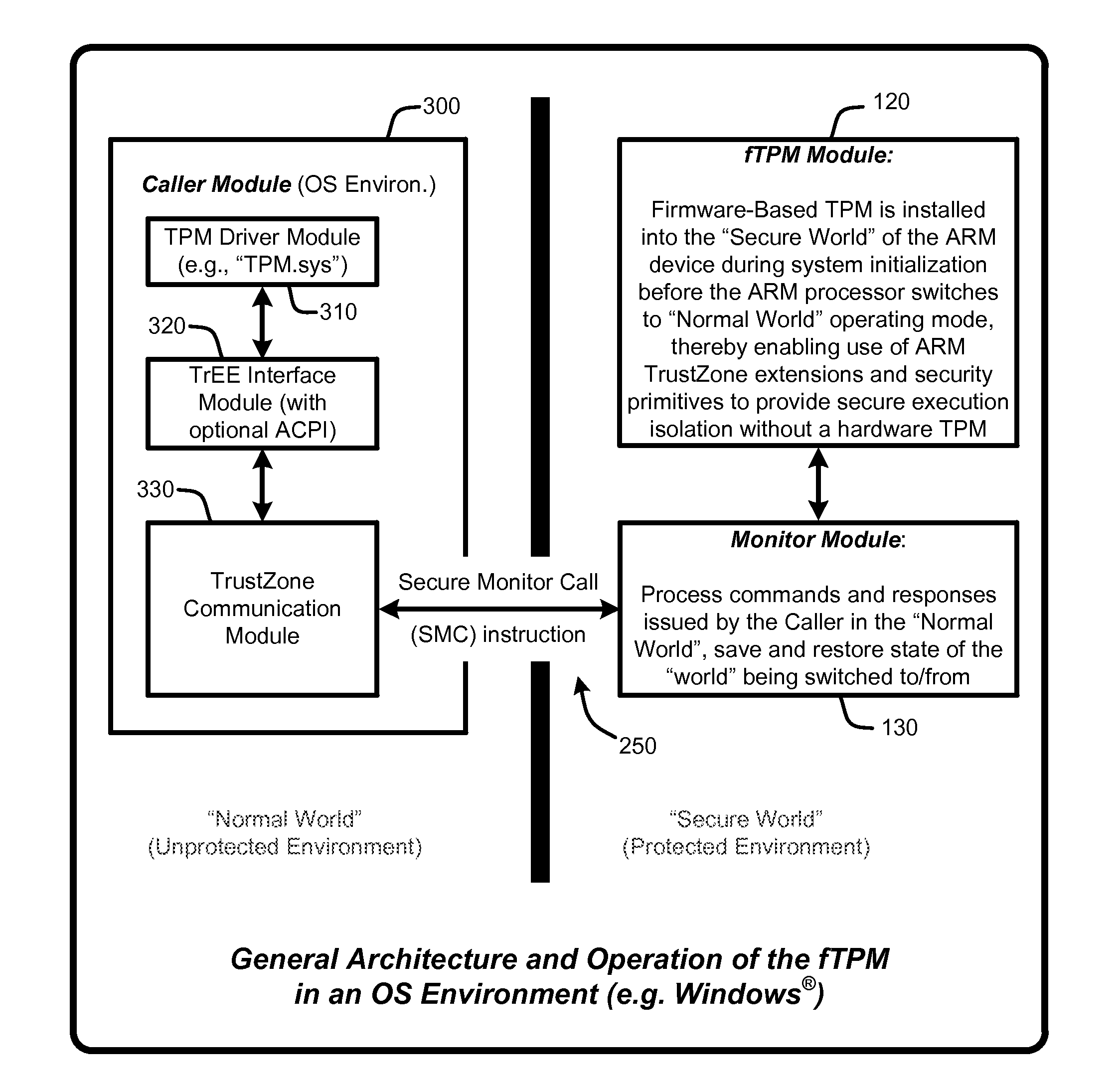
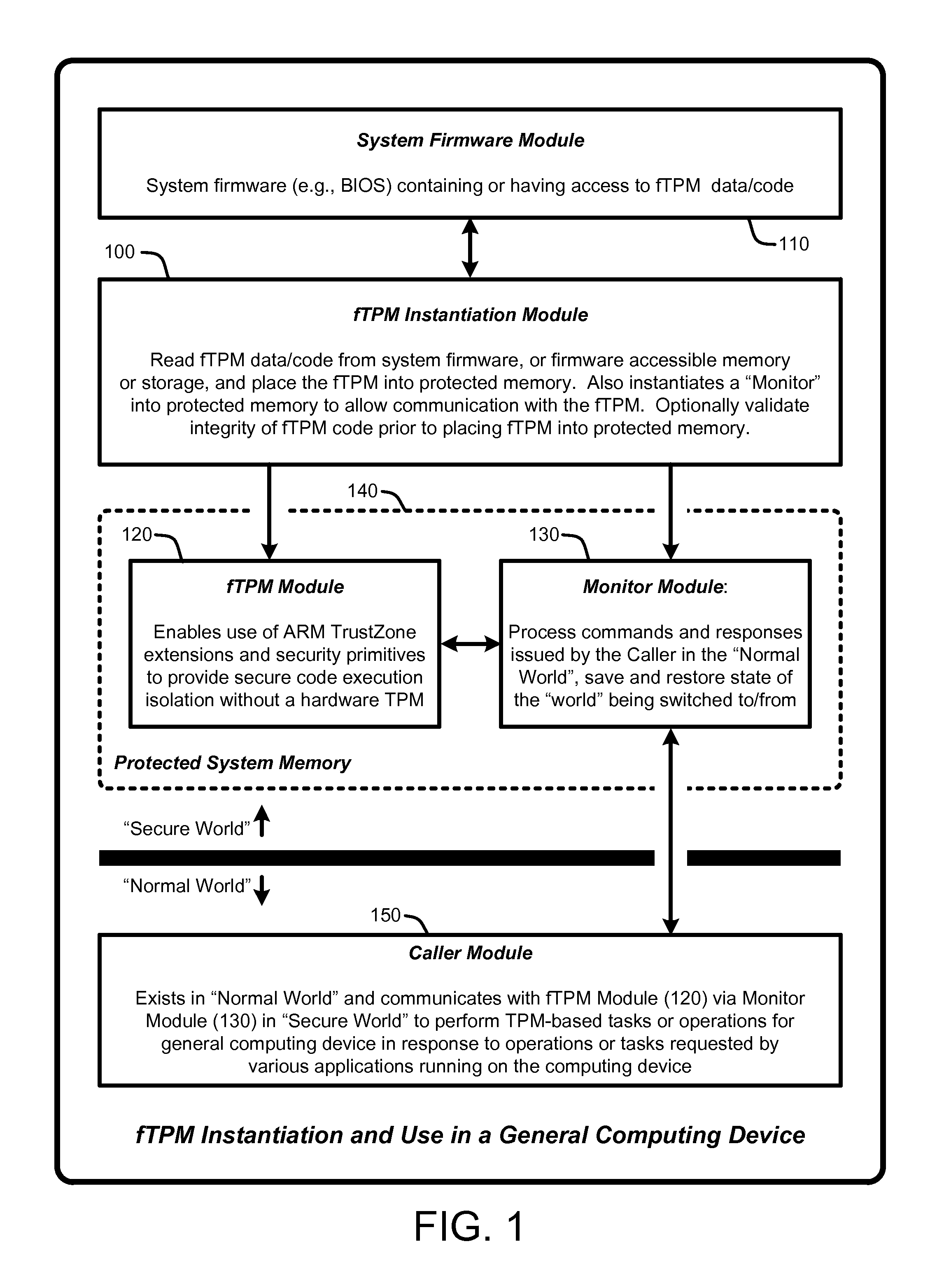
A “Firmware-Based TPM” or “fTPM” ensures that secure code execution is isolated to prevent a wide variety of potential security breaches. Unlike a conventional hardware based Trusted Platform Module (TPM), isolation is achieved without the use of dedicated security processor hardware or silicon. In general, the fTPM is first instantiated in a pre-OS boot environment by reading the fTPM from system firmware or firmware accessible memory or storage and placed into read-only protected memory of the device. Once instantiated, the fTPM enables execution isolation for ensuring secure code execution. More specifically, the fTPM is placed into protected read-only memory to enable the device to use hardware such as the ARM® architecture's TrustZone™ extensions and security primitives (or similar processor architectures), and thus the devices based on such architectures, to provide secure execution isolation within a “firmware-based TPM” without requiring hardware modifications to existing devices.
Owner:MICROSOFT TECH LICENSING LLC
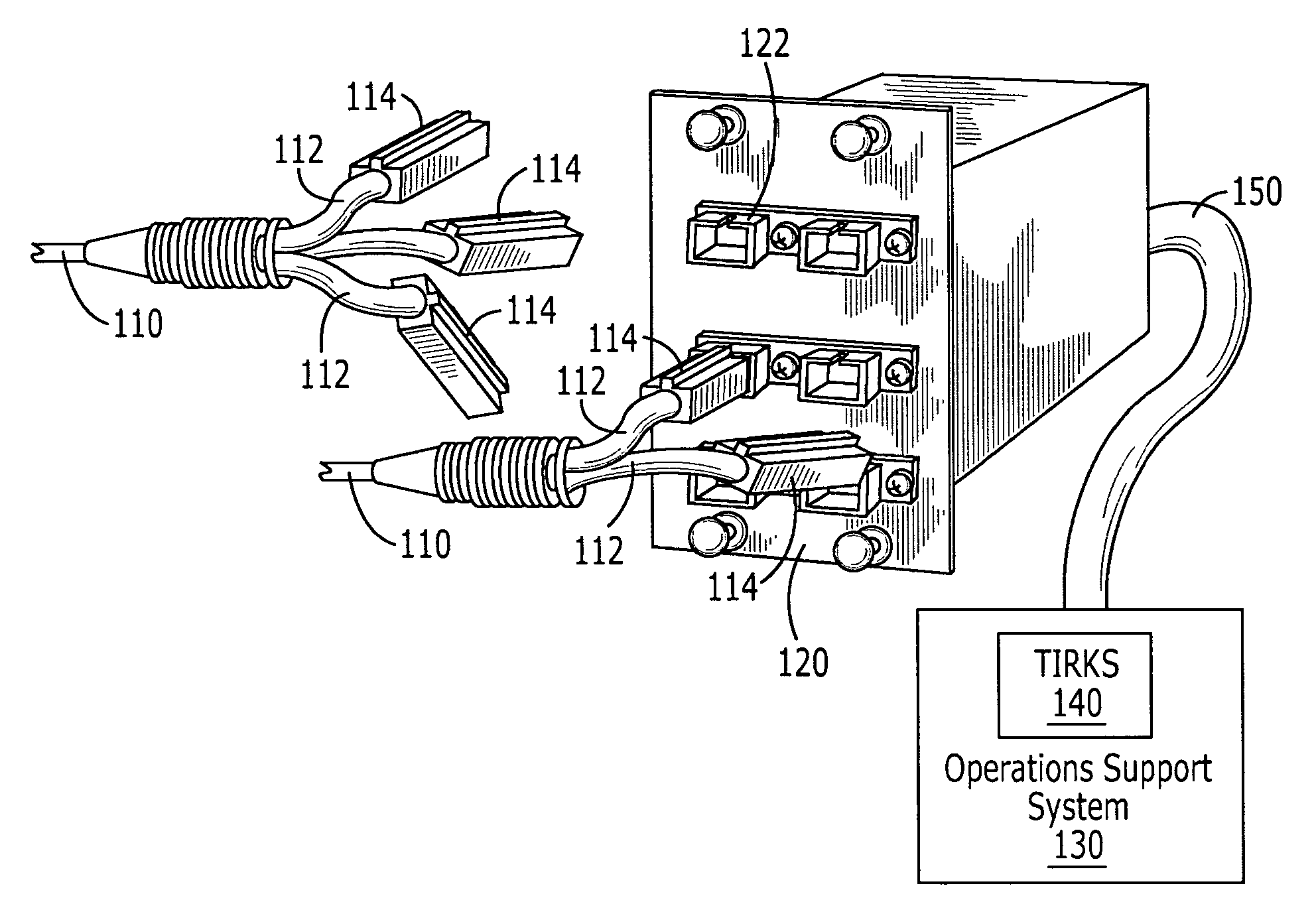
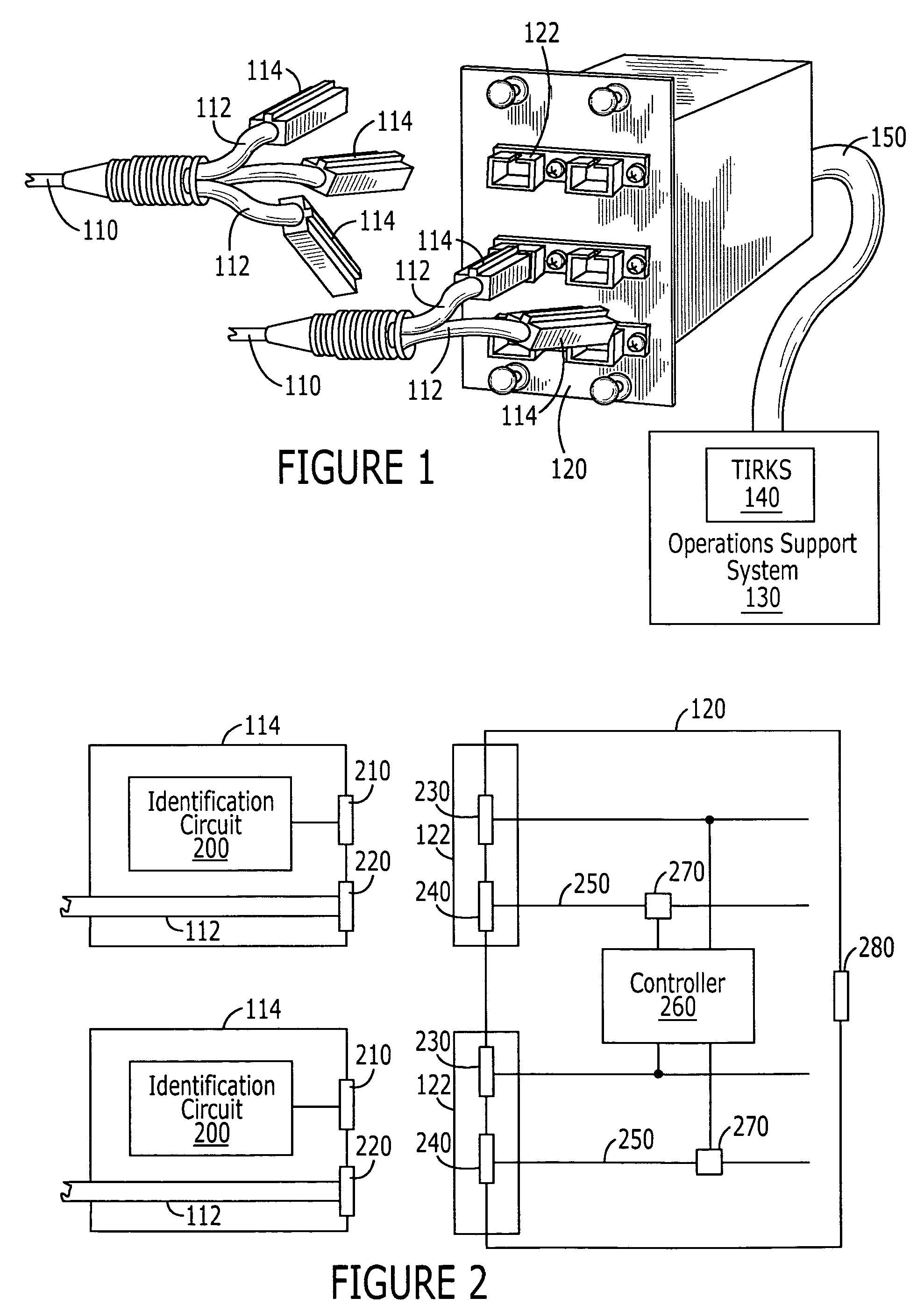
Optical fiber connectors with identification circuits and distribution terminals that communicate therewith
An optical fiber connector can include an optical fiber interface, an identification circuit, and an electrical interface that is communicatively connected to the identification circuit. The identification circuit may be a non-volatile memory such as, for example, a read only memory, a magnetic random access memory and / or a flash-random access memory. The identification circuit may include a housing that can be releasably connected to a Light Guide Cross Connect (LGX). The identification circuit may generate an electrical signal that identifies a fiber, a fiber bundle, a fiber type, a connector type, who manufactured an optical fiber, when an optical fiber was manufactured, and / or when an optical fiber was installed.Related optical fiber distribution terminals are also discussed.
Owner:BELLSOUTH INTPROP COR
Securely Recovering a Computing Device
ActiveUS20080168275A1Multiple keys/algorithms usagePublic key for secure communicationTelecommunications linkDigital signature
A method and an apparatus for establishing an operating environment by certifying a code image received from a host over a communication link are described. The code image may be digitally signed through a central authority server. Certification of the code image may be determined by a fingerprint embedded within a secure storage area such as a ROM (read only memory) of the portable device based on a public key certification process. A certified code image may be assigned a hash signature to be stored in a storage of the portable device. An operating environment of the portable device may be established after executing the certified code.
Owner:APPLE INC
Programmable security platform
InactiveUS20060117177A1Internal/peripheral component protectionSecuring communicationRandom access memoryEncryption decryption
A dynamically programmable security device. The device includes: a secure nonvolatile read only memory (NVMROM) for securely storing a unique device cipher key; a secure interface for dynamically loading authenticated application code; a cryptographic engine for encrypting, decrypting data and authenticating the application code; a secure random access memory (RAM) for storing the authenticated application code and application data; and a processor for executing the authenticated application code.
Owner:BROADCOM CORP
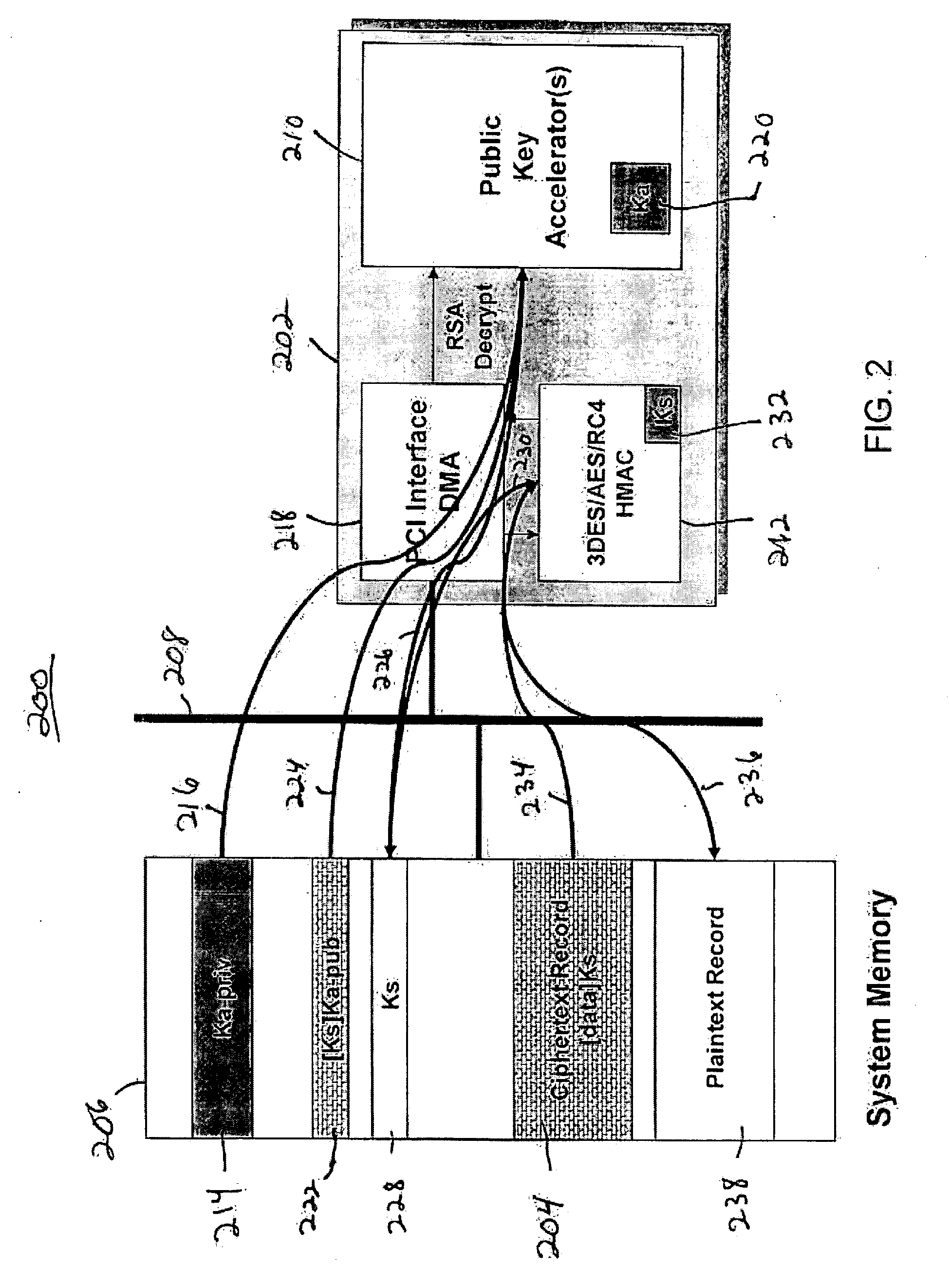
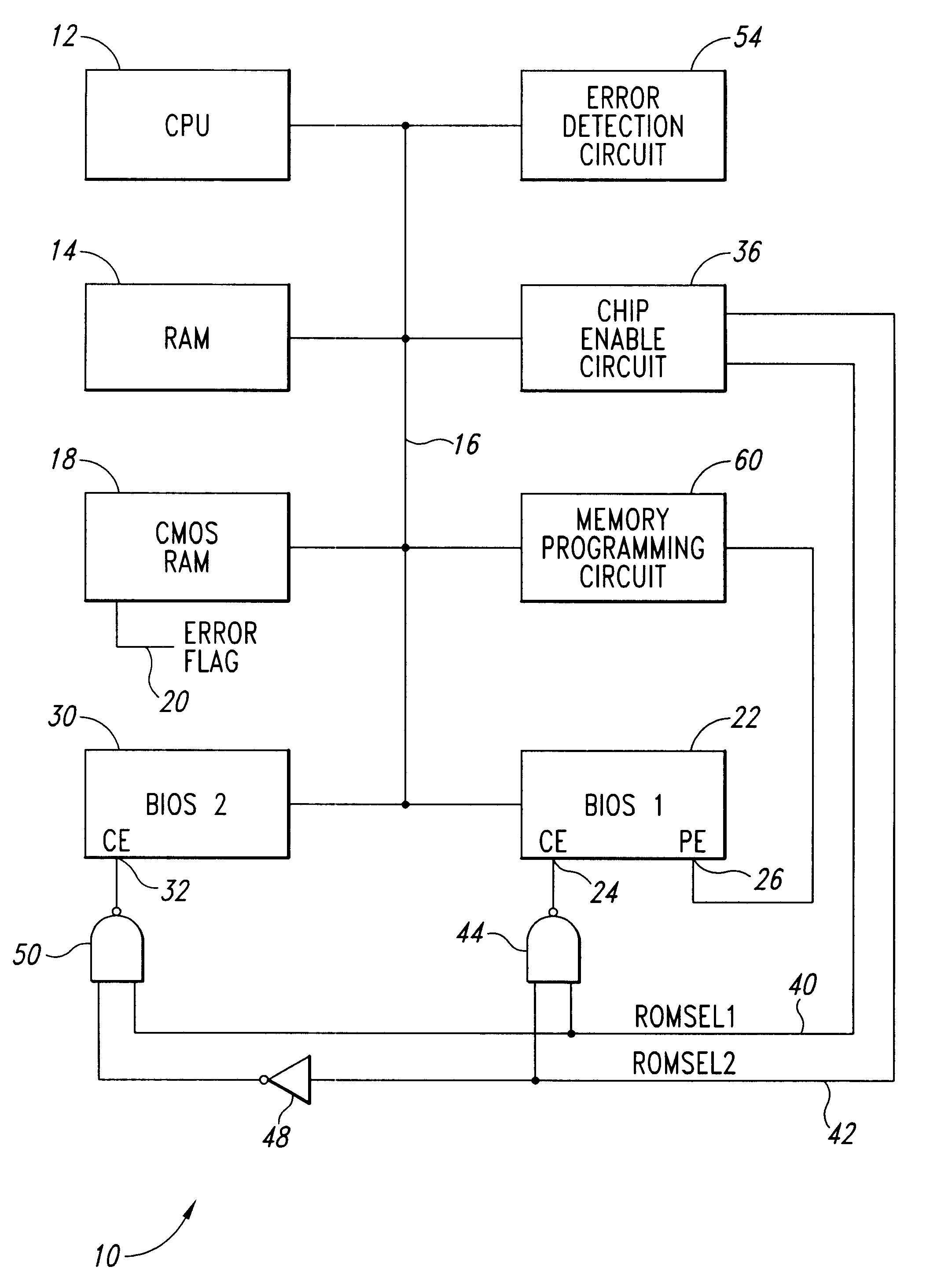
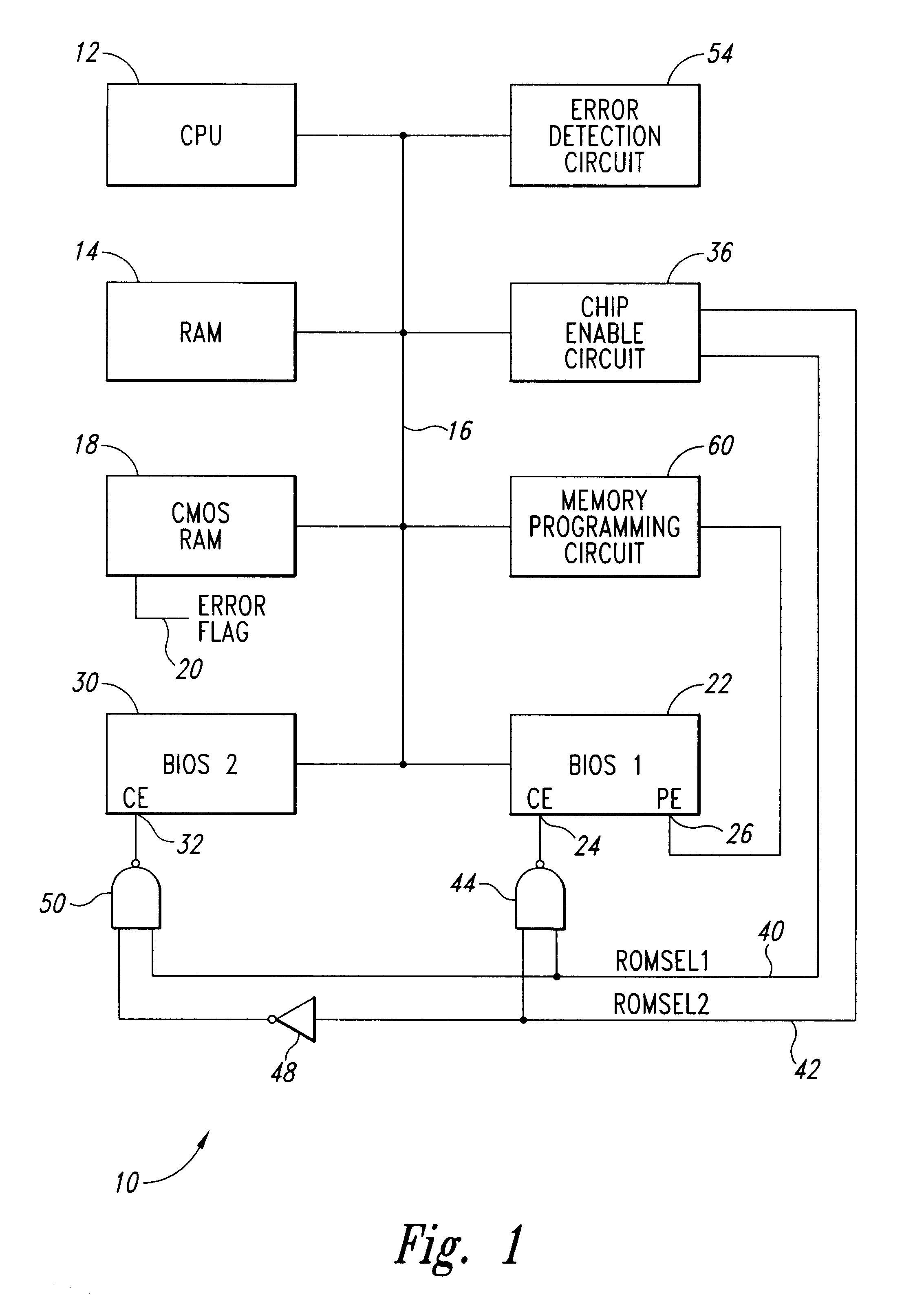
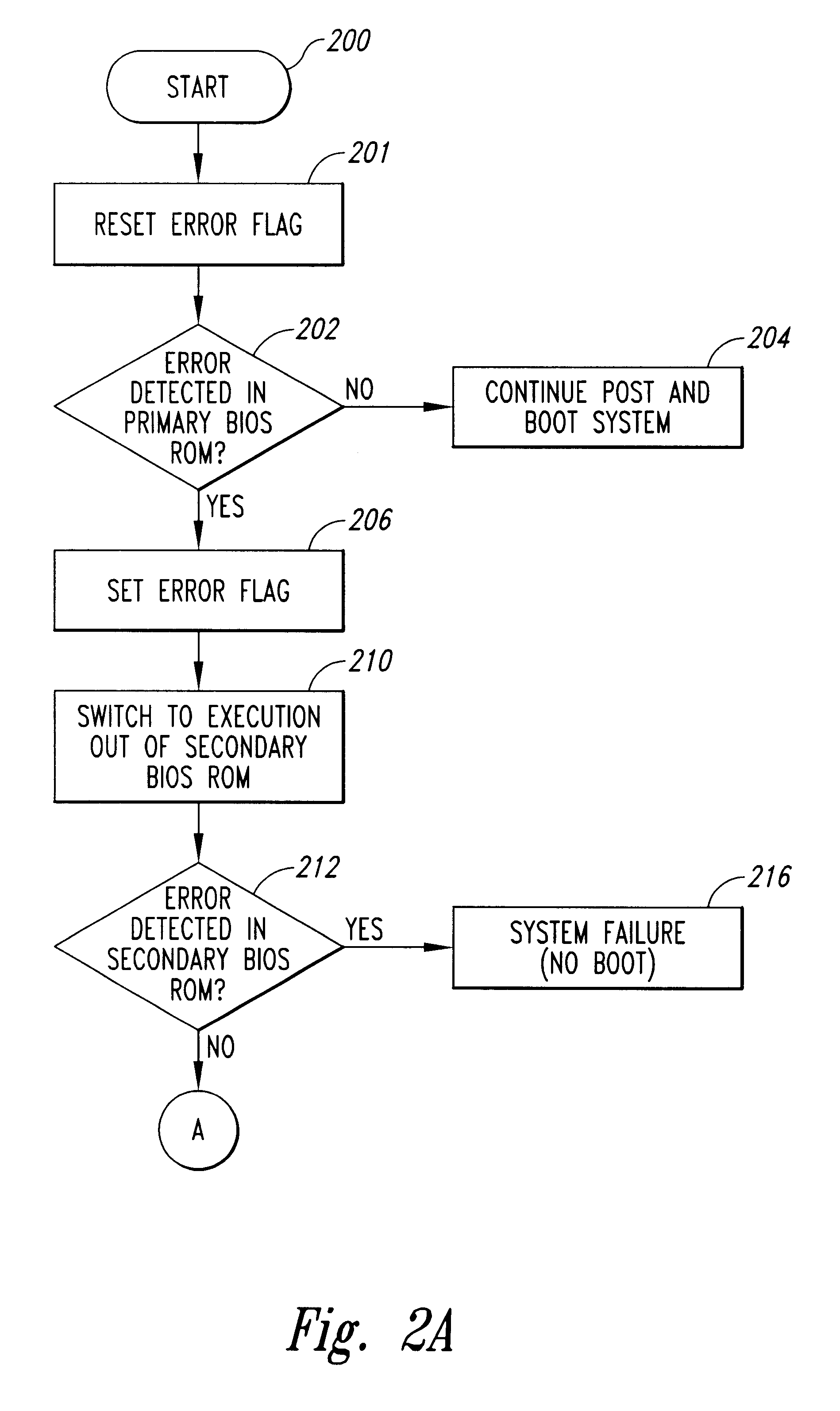
System for a primary BIOS ROM recovery in a dual BIOS ROM computer system
InactiveUS6185696B1Reliability increasing modificationsDetecting faulty hardware by power-on testRandom access memoryComputerized system
A computer system includes a dual basic input-output system (BIOS) read-only memory (ROM) system to initialize the computer. When the computer is first powered on or reset, the primary BIOS ROM is initially enabled. The computer analyzes the contents of the primary BIOS memory to detect data errors. If a data error is detected, a chip enable circuit disables the primary BIOS ROM and enables a secondary BIOS ROM containing essentially the same initialization instructions as the primary BIOS ROM. If no errors are detected in the secondary BIOS ROM, the initialization of the computer proceeds using the secondary BIOS ROM. As part of the initialization procedure, the contents of the secondary BIOS ROM are copied to a random access memory. The primary BIOS ROM can then be reprogrammed with the contents of the secondary BIOS ROM using the copy in random access memory, or from the secondary BIOS ROM itself.
Owner:MEI CALIFORNIA +1
Methods and apparatus for control using control devices that provide a virtual machine environment and that communicate via an IP network
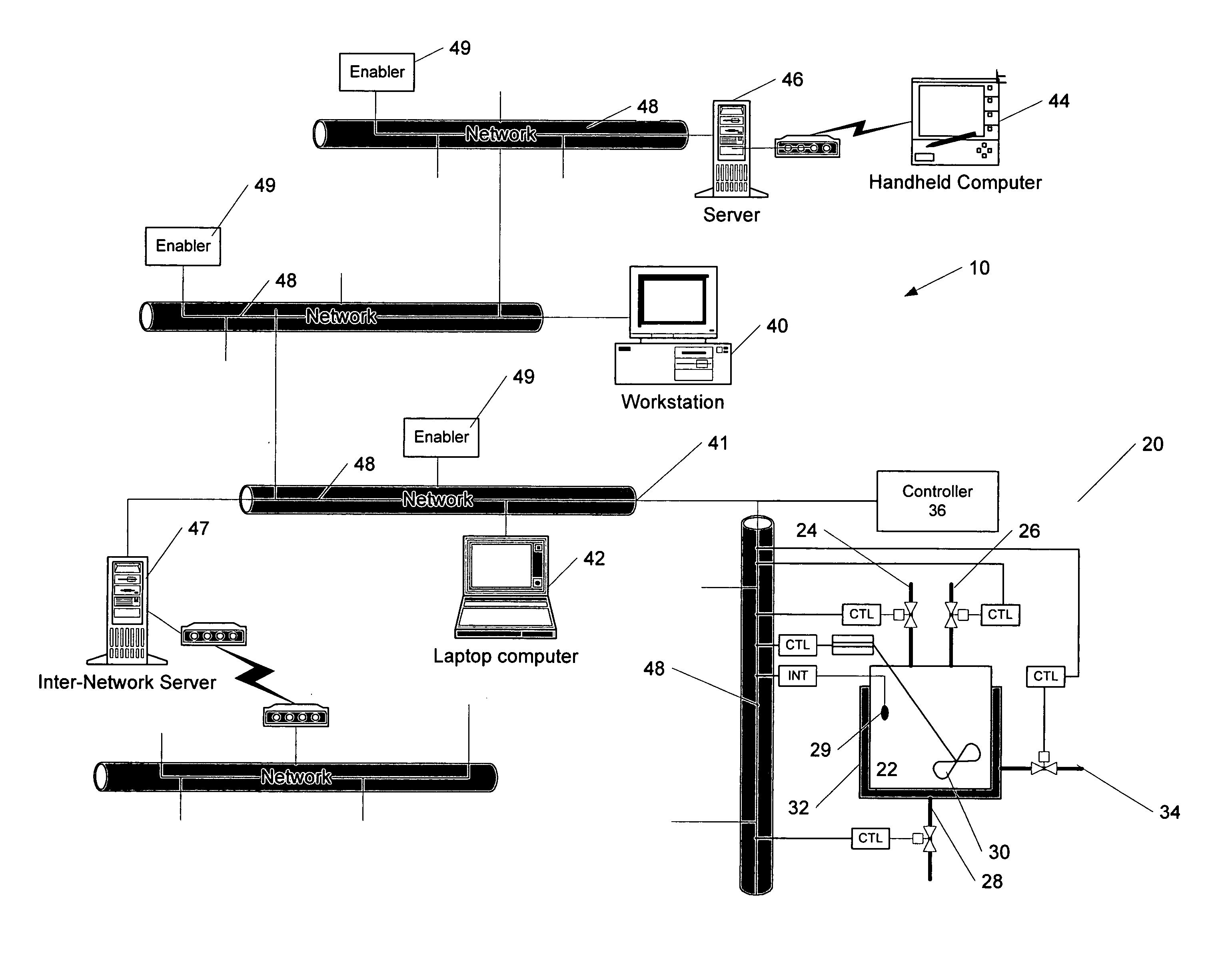
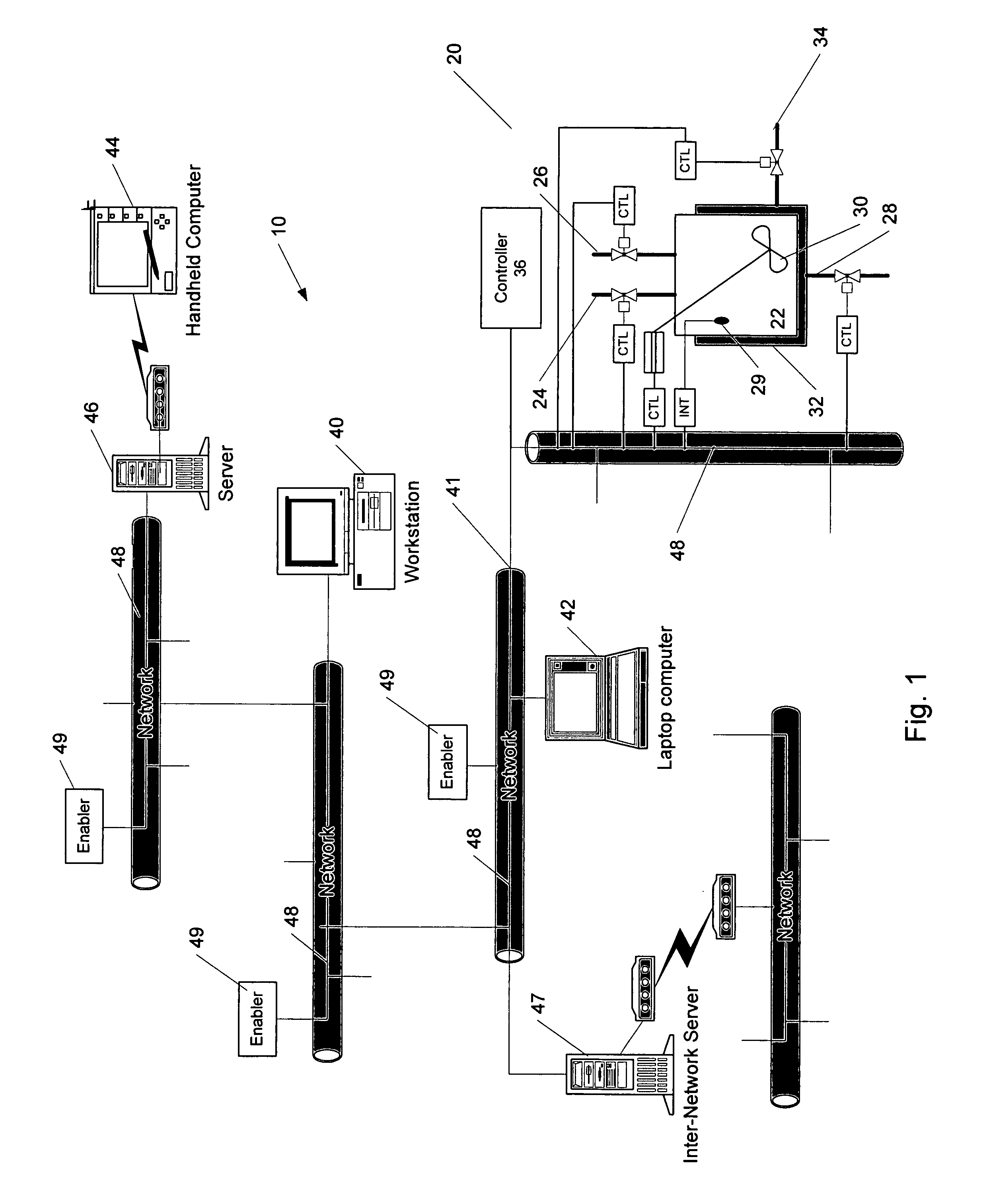
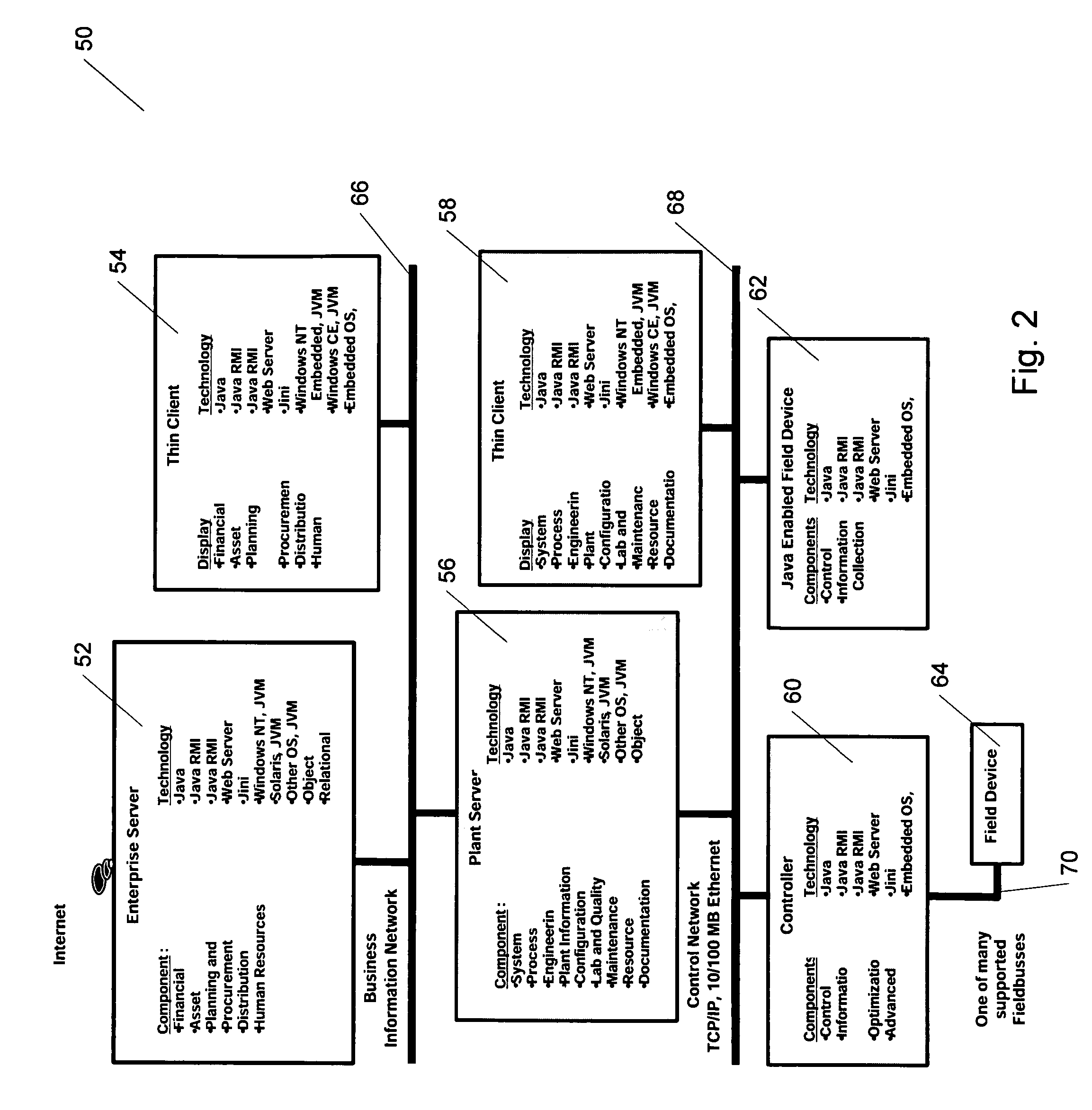
The invention provides improved methods and apparatus for control using field and control devices that provide a virtual machine environment and that communicate via an IP network. By way of non-limiting example, such field device can be an “intelligent” transmitter or actuator that includes a low power processor, along with a random access memory, a read-only memory, FlashRAM, and a sensor interface. The processor can execute a real-time operating system, as well as a Java virtual machine (JVM). Java byte code executes in the JVM to configure the field device to perform typical process control functions, e.g., for proportional integral derivative (PID) control and signal conditioning. Control networks can include a plurality of such field and control devices interconnected by an IP network, such as an Ethernet.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Disk drive and method having cost-effective storage of the disk drive's internal program code
InactiveUS7440214B1Improve data storage performanceFilamentary/web record carriersRecord information storageDisk controllerControl system
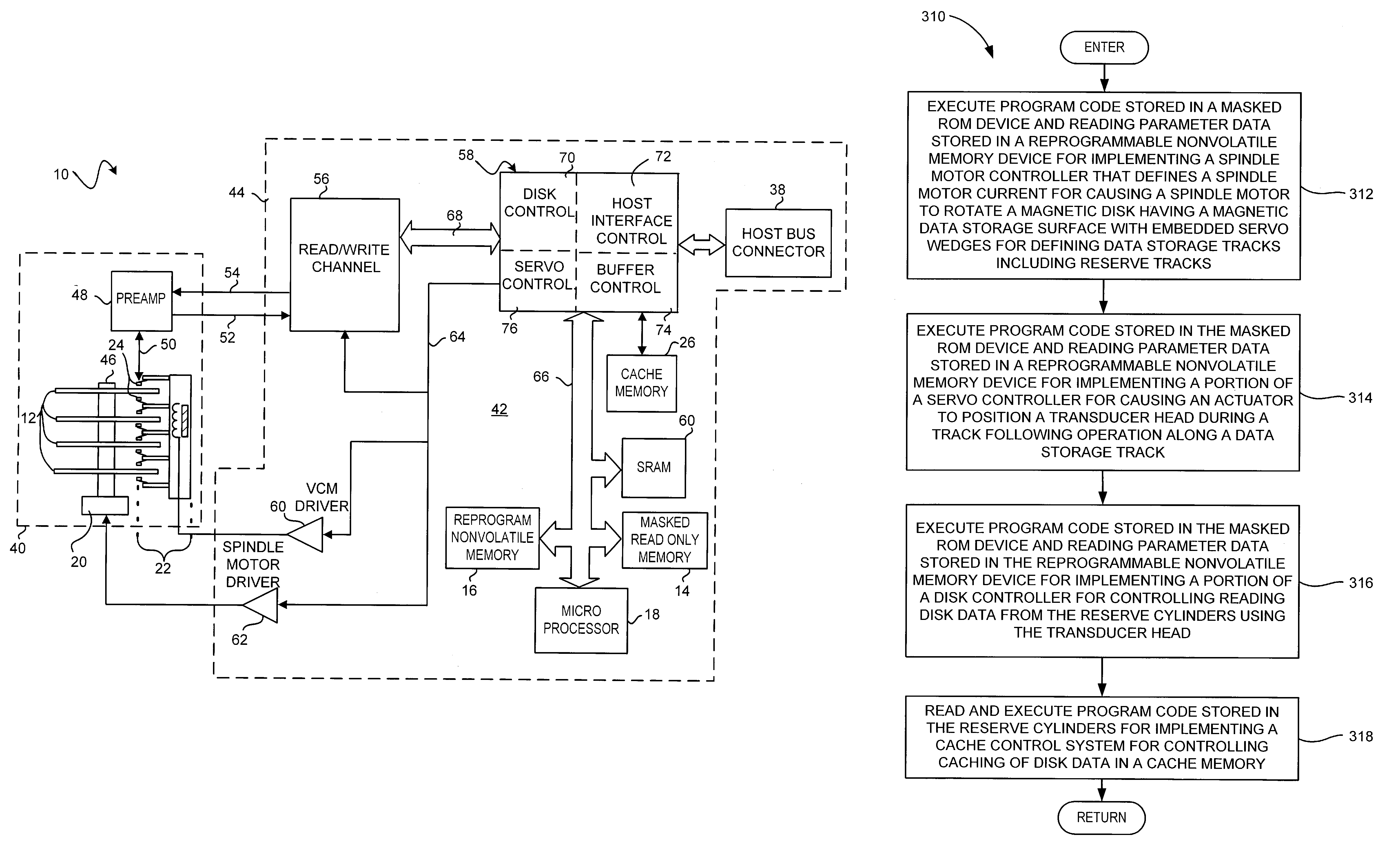
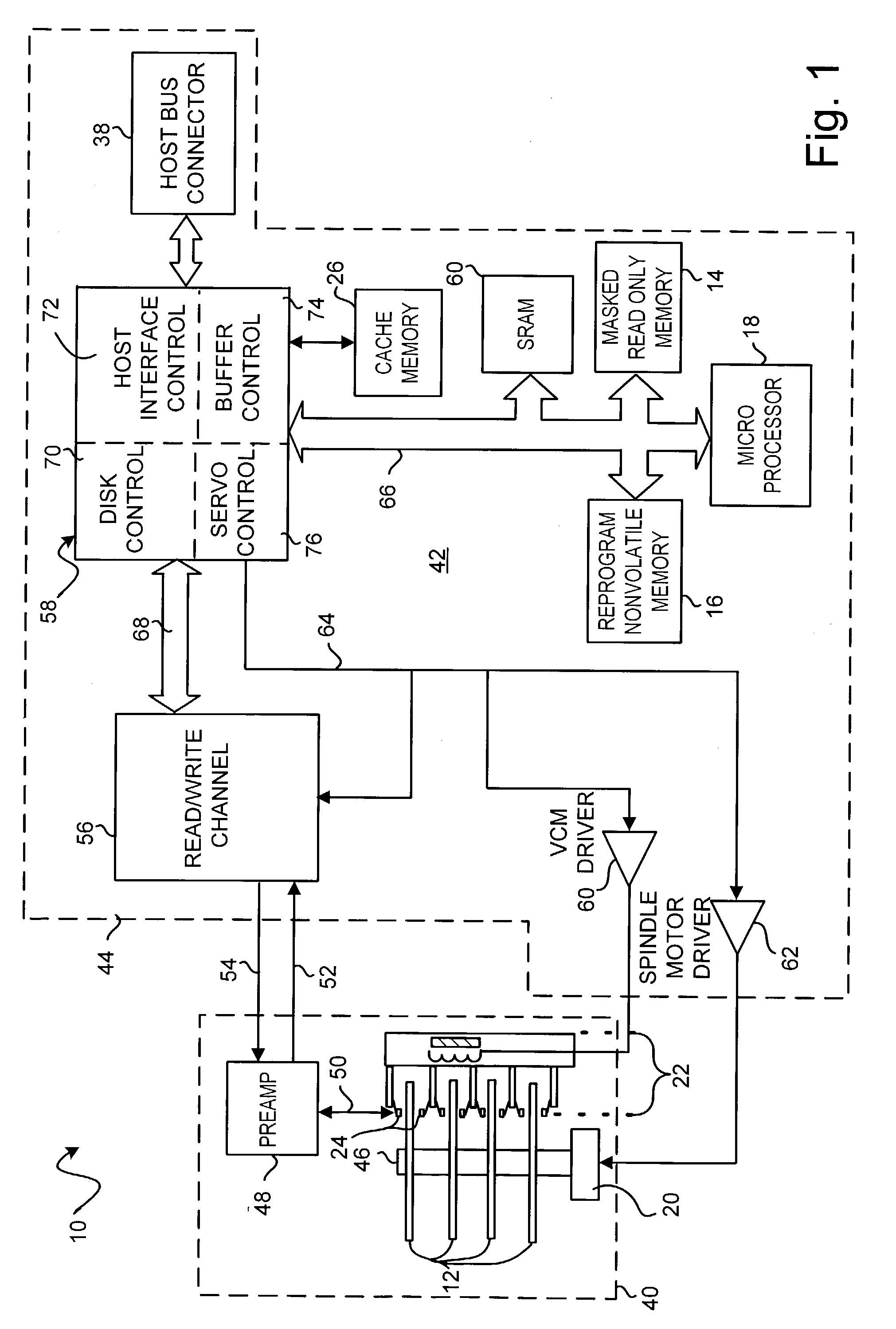
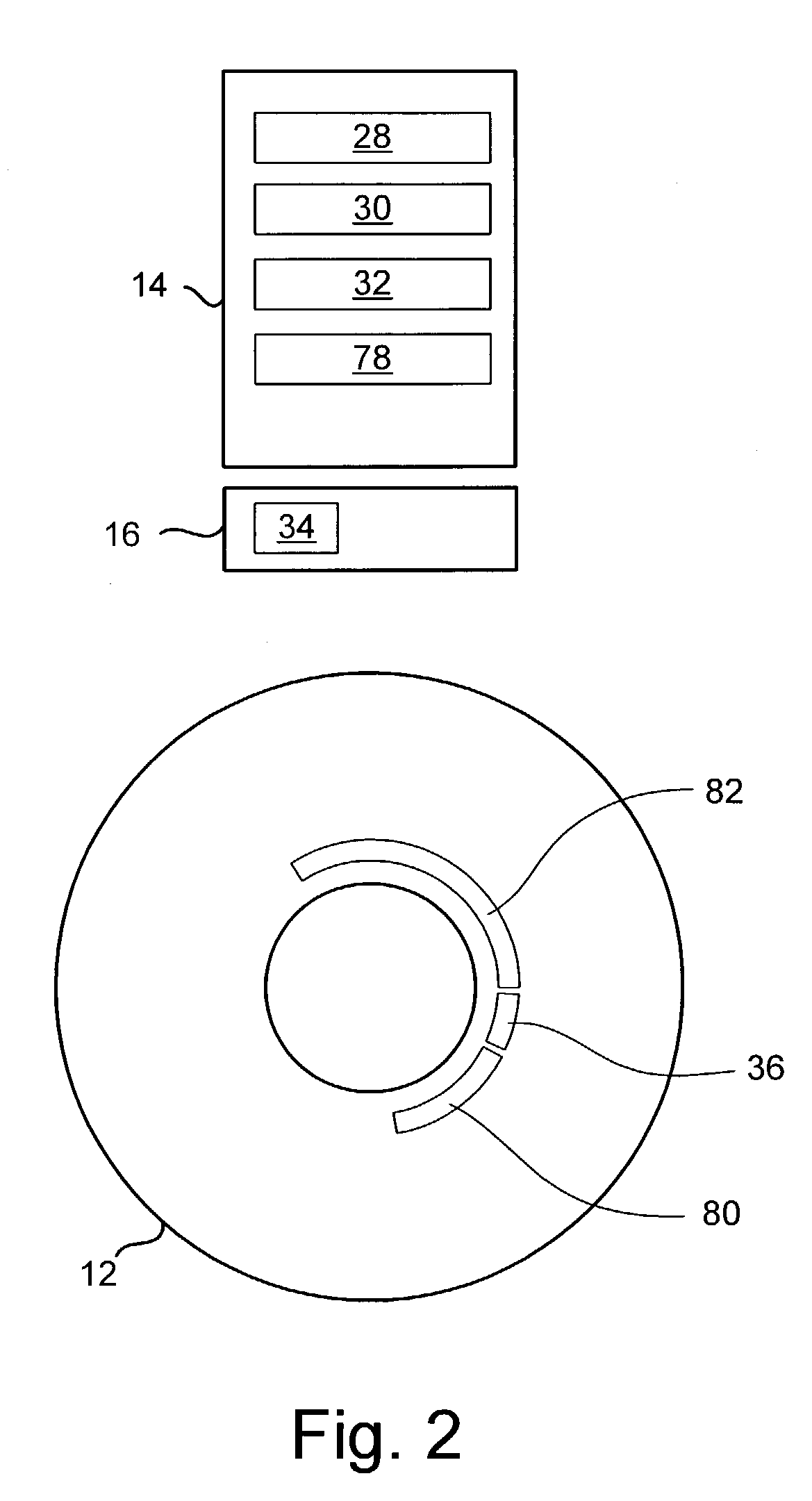
Disclosed is a disk drive having a disk, a masked read-only memory (ROM) device, a reprogrammable nonvolatile memory device, and a microprocessor for executing program code. The disk has a magnetic data storage surface with embedded servo wedges for defining data storage tracks including reserve tracks. The masked ROM device stores program code for implementing a spindle motor controller, program code for implementing a portion of a servo controller for track following along a data storage track, and program code for implementing a portion of a disk controller for controlling writing disk data to and reading disk data from the reserve tracks. The reprogrammable nonvolatile memory device stores data parameters relating to the disk drive's configuration. The reserve tracks store program code for implementing a cache control system for controlling caching of disk data in a cache memory.
Owner:WESTERN DIGITAL TECH INC
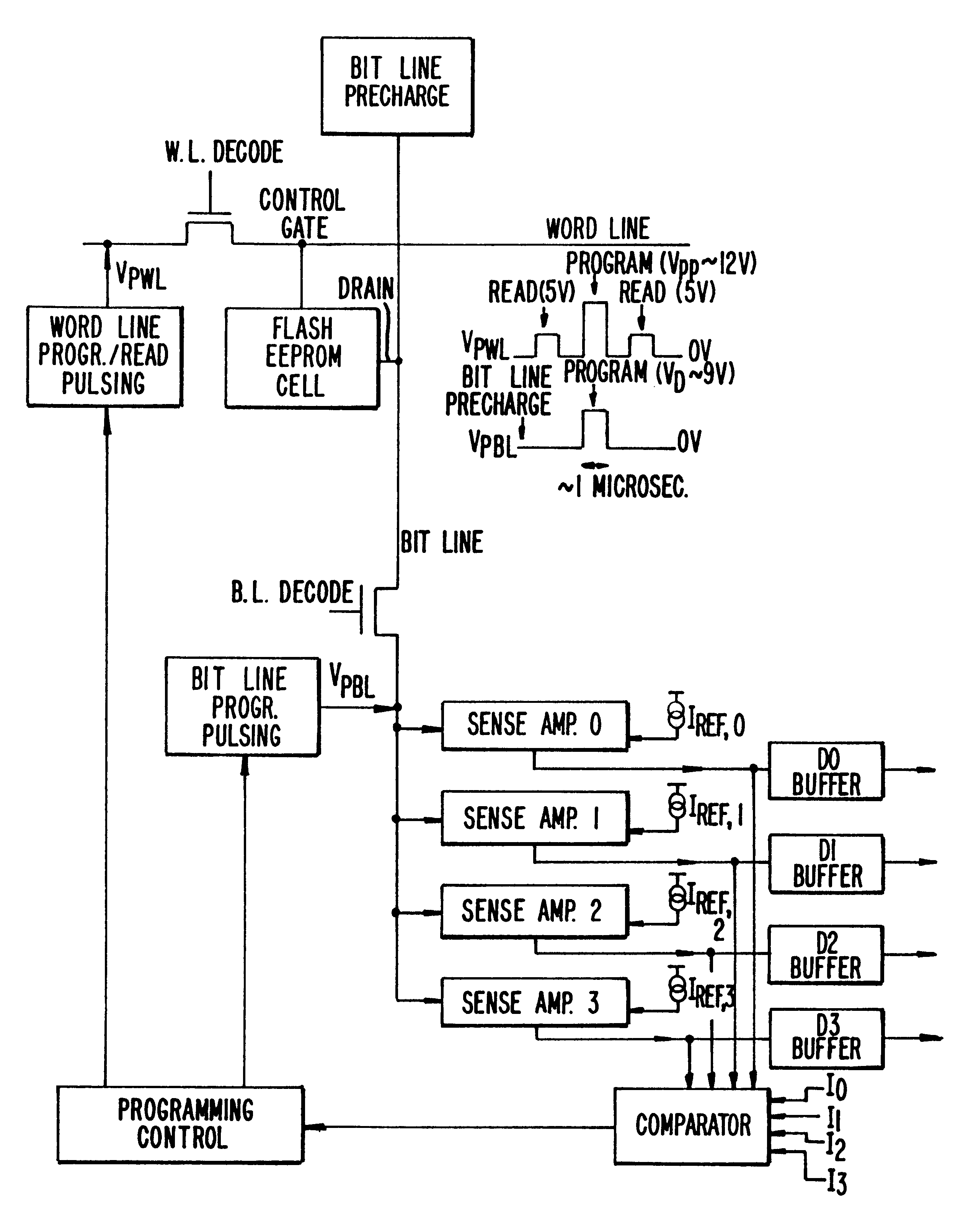
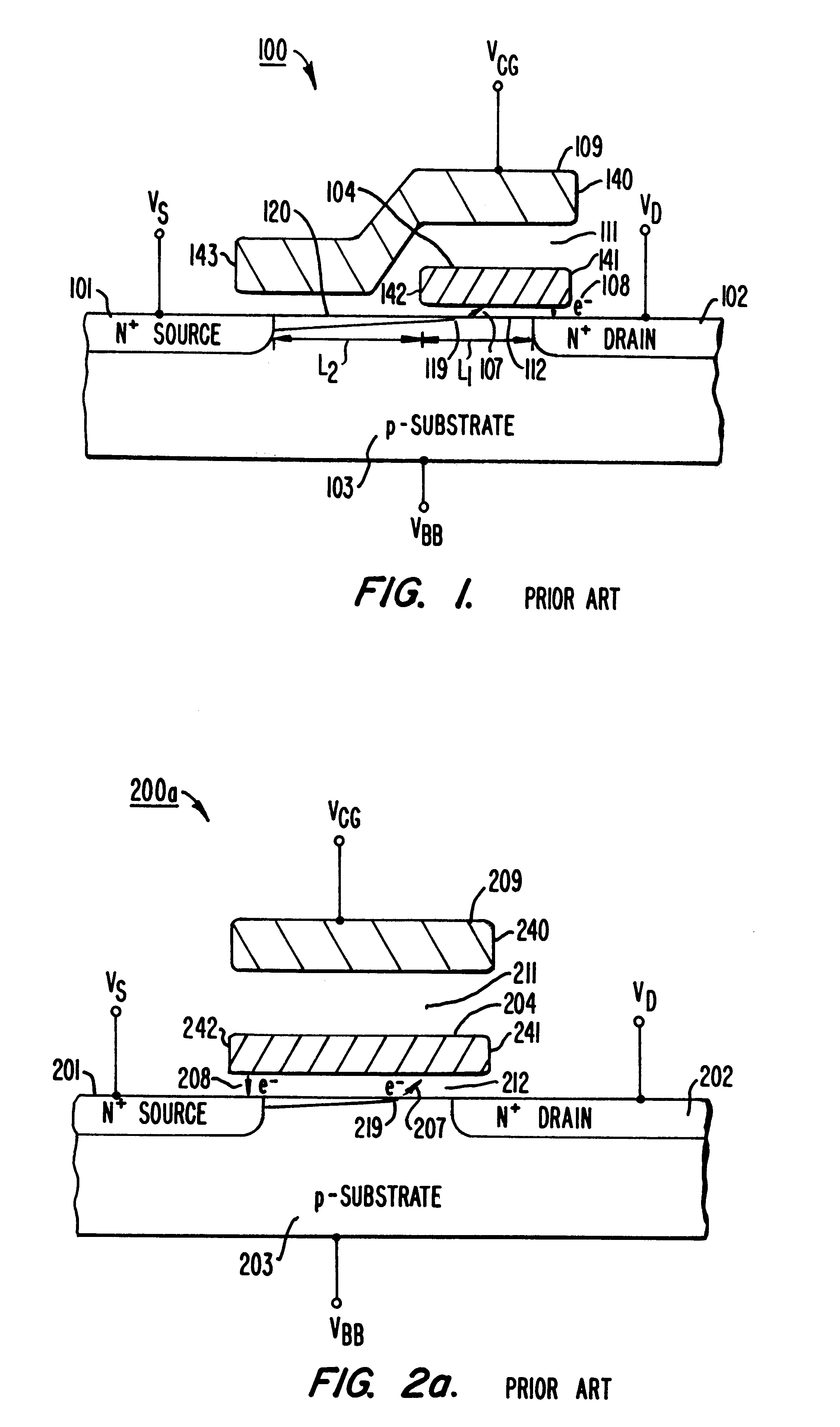
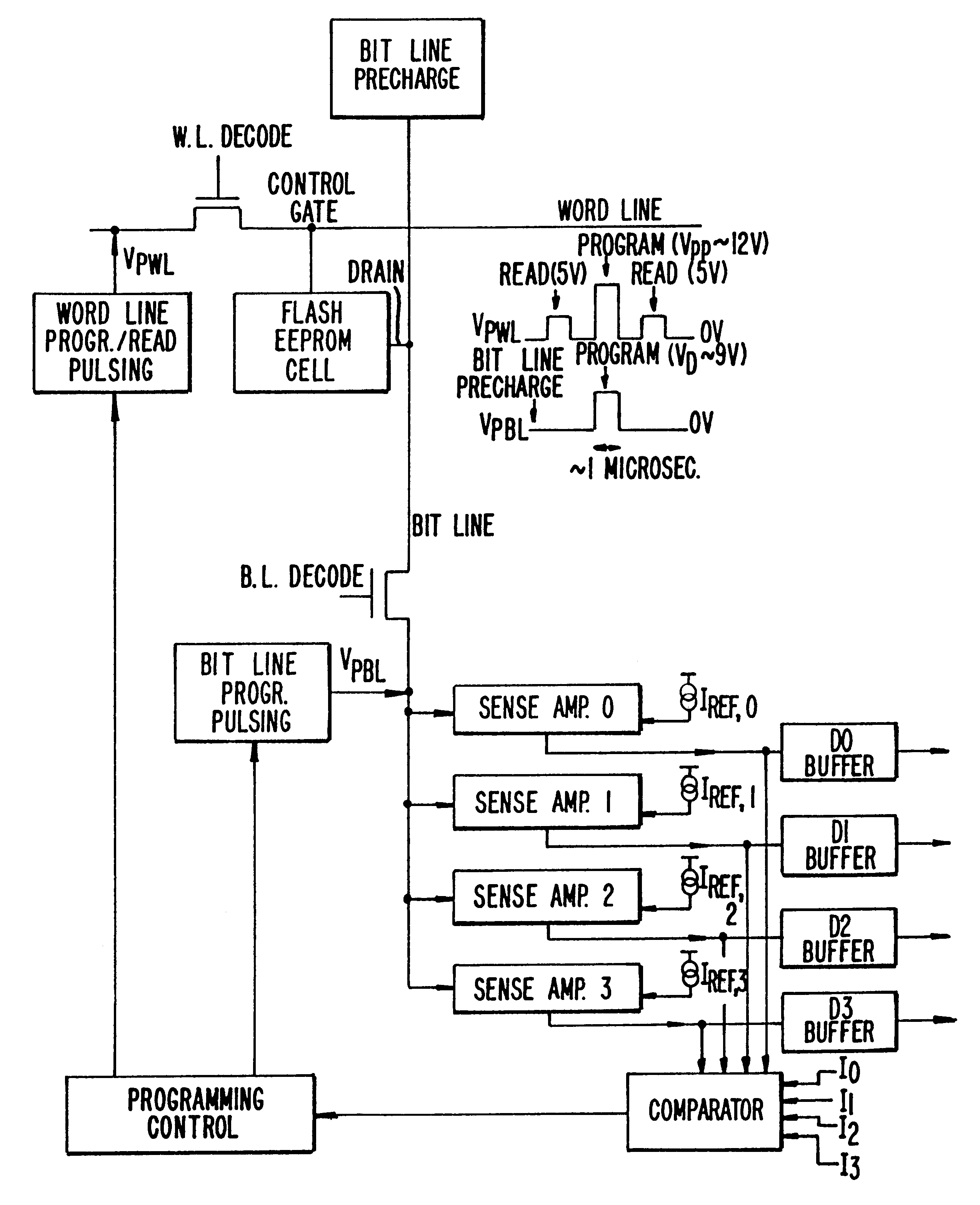
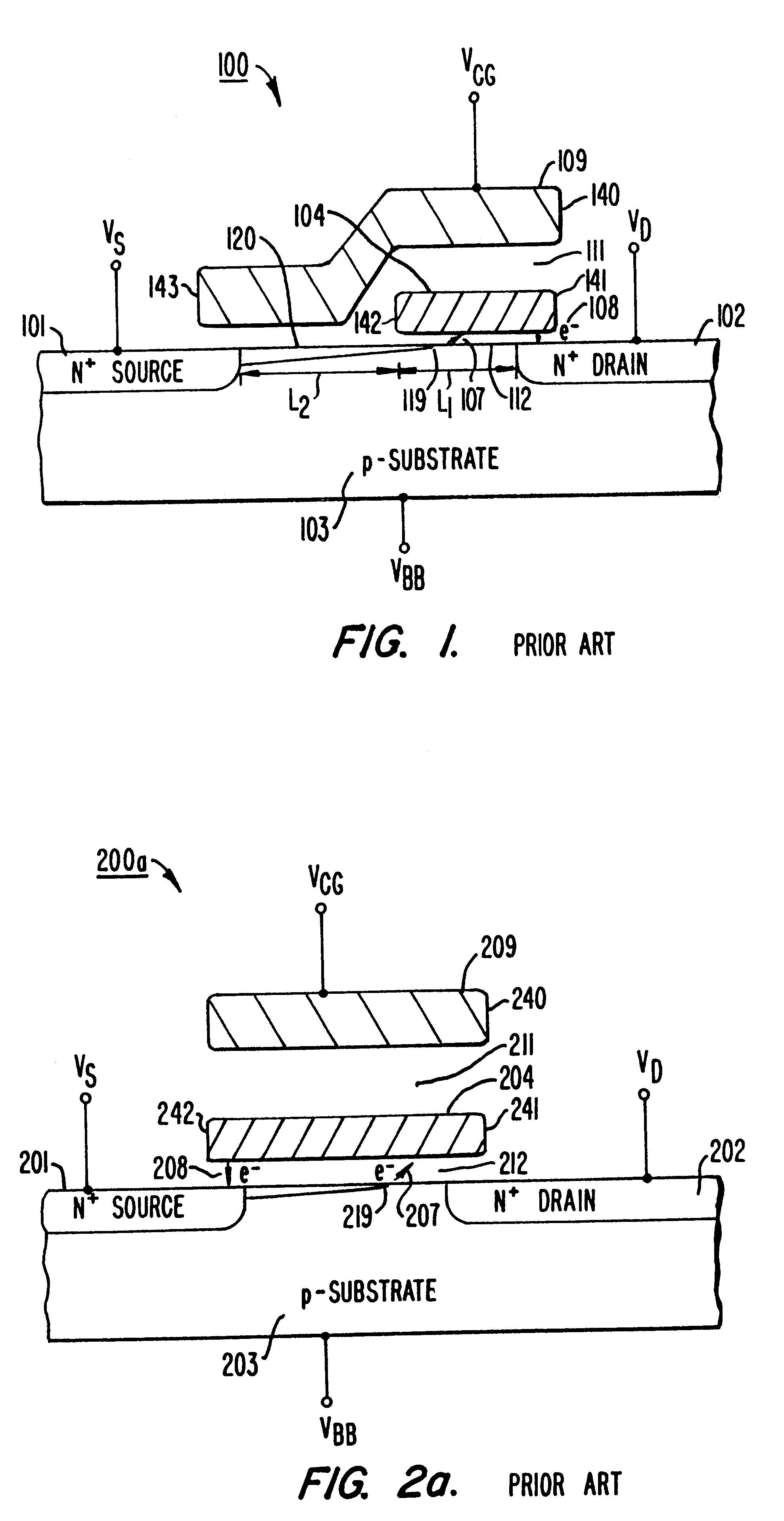
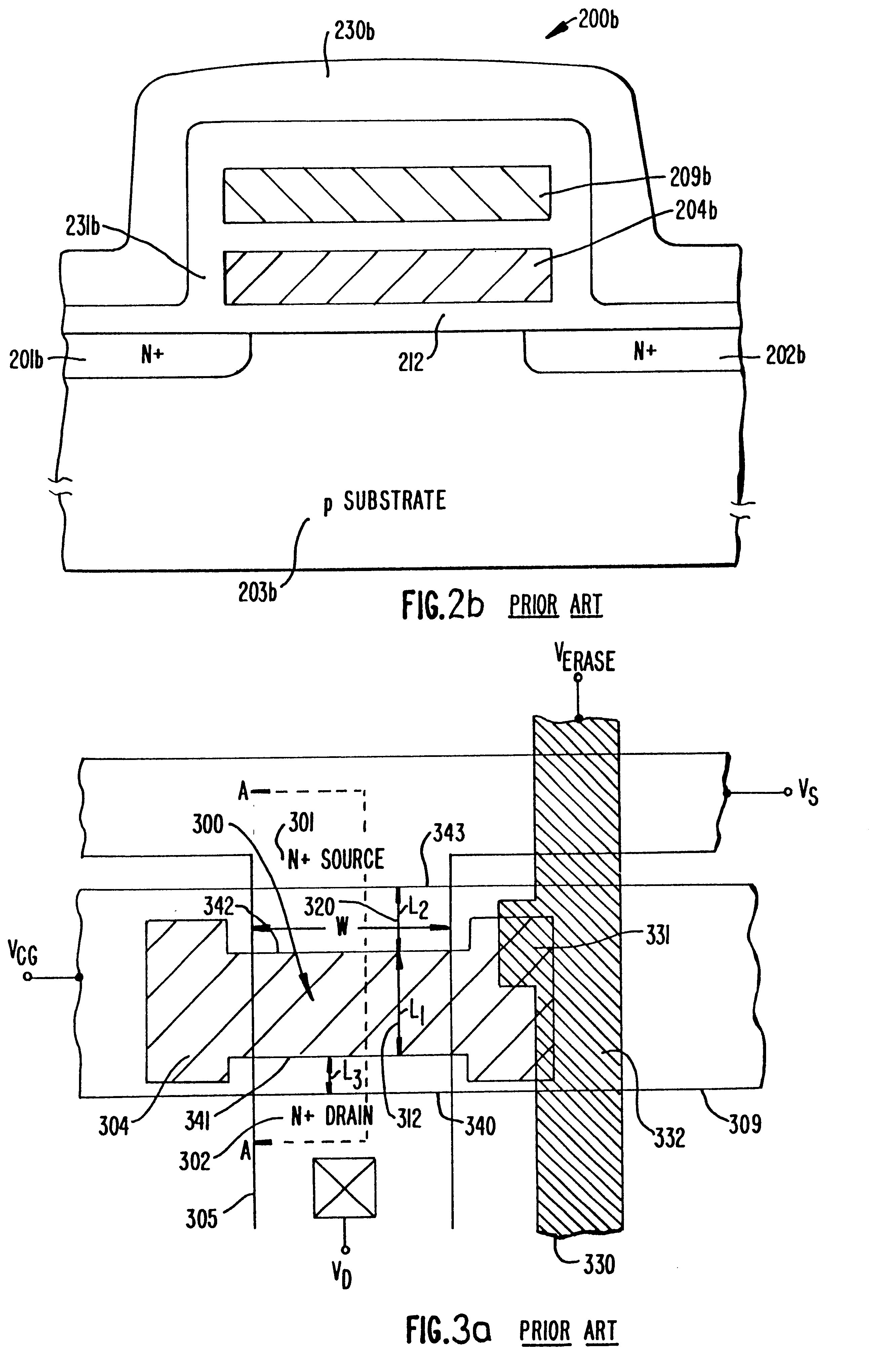
Highly compact EPROM and flash EEPROM devices
Structures, methods of manufacturing and methods of use of electrically programmable read only memories (EPROM) and flash electrically erasable and programmable read only memories (EEPROM) include split channel and other cell configurations. An arrangement of elements and cooperative processes of manufacture provide self-alignment of the elements. An intelligent programming technique allows each memory cell to store more than the usual one bit of information. An intelligent erase algorithm prolongs the useful life of the memory cells. Use of these various features provides a memory having a very high storage density and a long life, making it particularly useful as a solid state memory in place of magnetic disk storage devices in computer systems.
Owner:SANDISK TECH LLC
Surgical robotic tools, data architecture, and use
InactiveUS20050149003A1Avoids frequent delayMechanical apparatusDiagnosticsRobotic systemsEngineering
Robotic surgical tools, systems, and methods for preparing for and performing robotic surgery include a memory mounted on the tool. The memory can perform a number of functions when the tool is loaded on the tool manipulator: first, the memory can provide a signal verifying that the tool is compatible with that particular robotic system. Secondly, the tool memory may identify the tool-type to the robotic system so that the robotic system can reconfigure its programming. Thirdly, the memory of the tool may indicate tool-specific information, including measured calibration offsets indicating misalignment of the tool drive system, tool life data, or the like. This information maybe stored in a read only memory (ROM), or in a nonvolatile memory which can be written to only a single time. The invention further provides improved engagement structures for coupling robotic surgical tools with manipulator structures.
Owner:INTUITIVE SURGICAL OPERATIONS INC
System for registering, locating, and identifying network equipment
The present invention is directed toward providing a system for registering, locating, and identifying network servers within a data center containing many such servers. Parallel and serial port couplers with an erasable, programable read-only memory are encoded with a unique ID number, and a label with a bar code corresponding to the ID number is affixed to each coupler. A server to be installed in a data center has an encoded coupler attached to one of its communication ports, and information related to that particular server is stored in a system database. Upon encountering a problem with a network server, the system displays the logical name of the server at issue. The location and identification information for the server are retrieved from the system database and displayed to a technician responsible for the server at issue. Using the displayed location information, the technician reads the label on the coupler connected to the suspected server and verifies that the ID number on the coupler matches the ID number displayed for the server requiring service.
Owner:OPSWARE
Operating system boot from external media
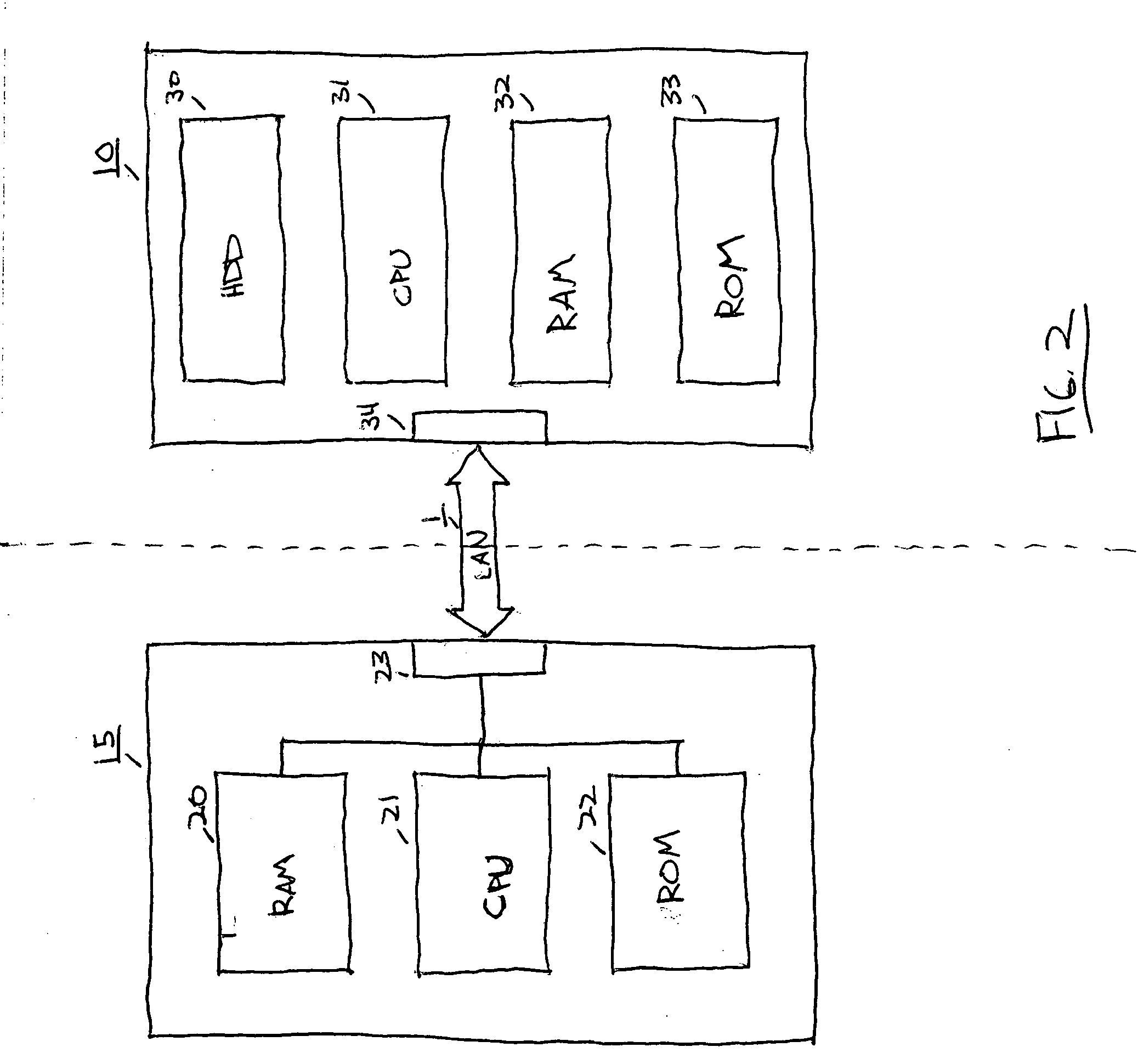
ActiveUS20060206702A1Easy to manageLow costDigital computer detailsMemory systemsData connectionOperational system
A system for booting an computing device with a windowing operating system obtained from an external memory media via an external interface, wherein the system includes an initialization module stored in a read-only memory provided in the computing device, the initialization module being executed in a processor disposed in the computing device and establishing a data connection to the external memory media through the external interface, and an external device in which the external memory media is disposed, the external memory media storing a windowing operating system at an external location, the external device sending the windowing operating system image from the external memory media to the computing device via the external interface in response to a request from the computing device, the request being based on memory geometry information of the external memory media, wherein the windowing operating system image is received by the computing device, loaded into a runtime memory in the computing device and then executed by the processor in order to boot the windowing operating system in the computing device.
Owner:DELL MARKETING CORP
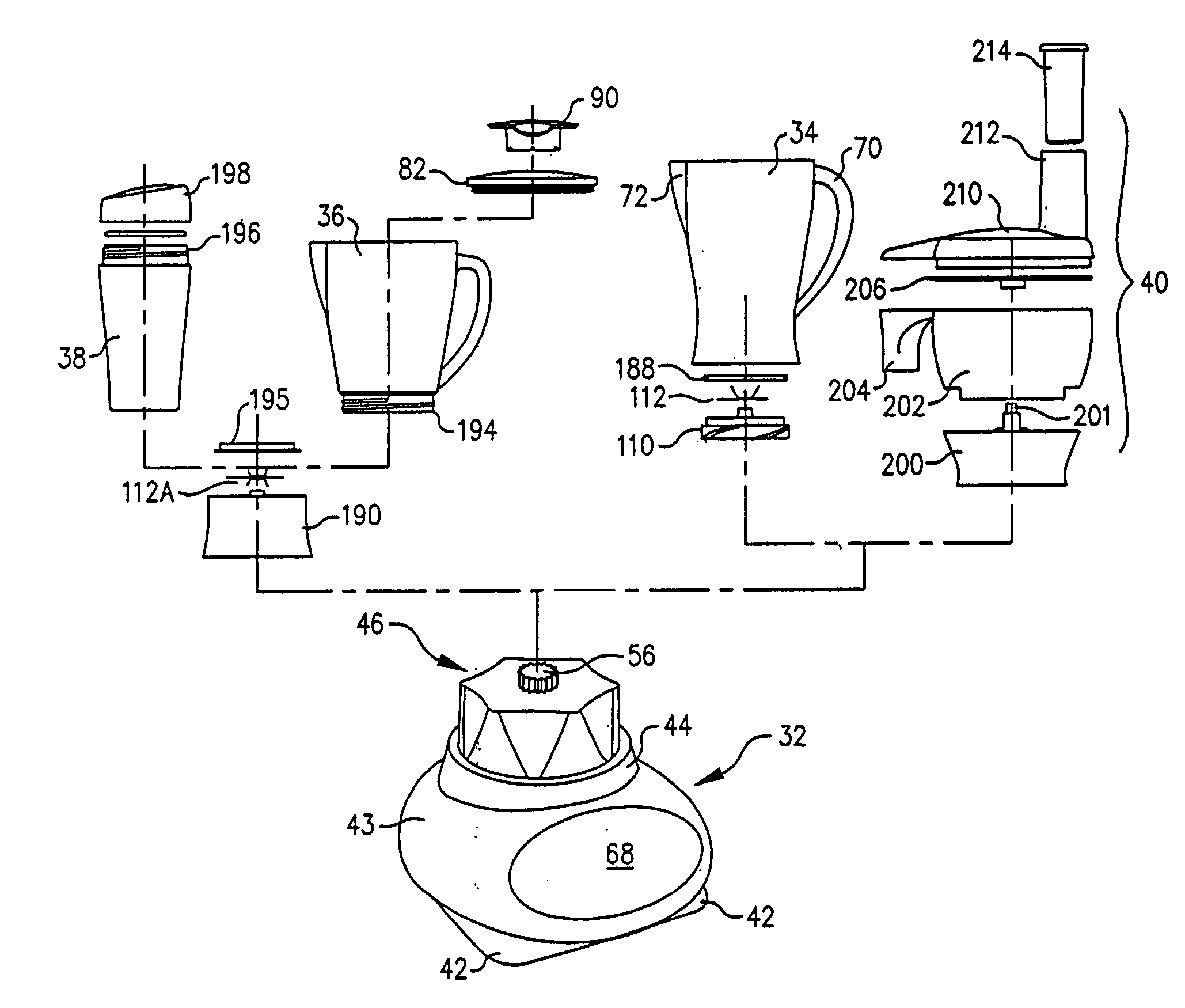
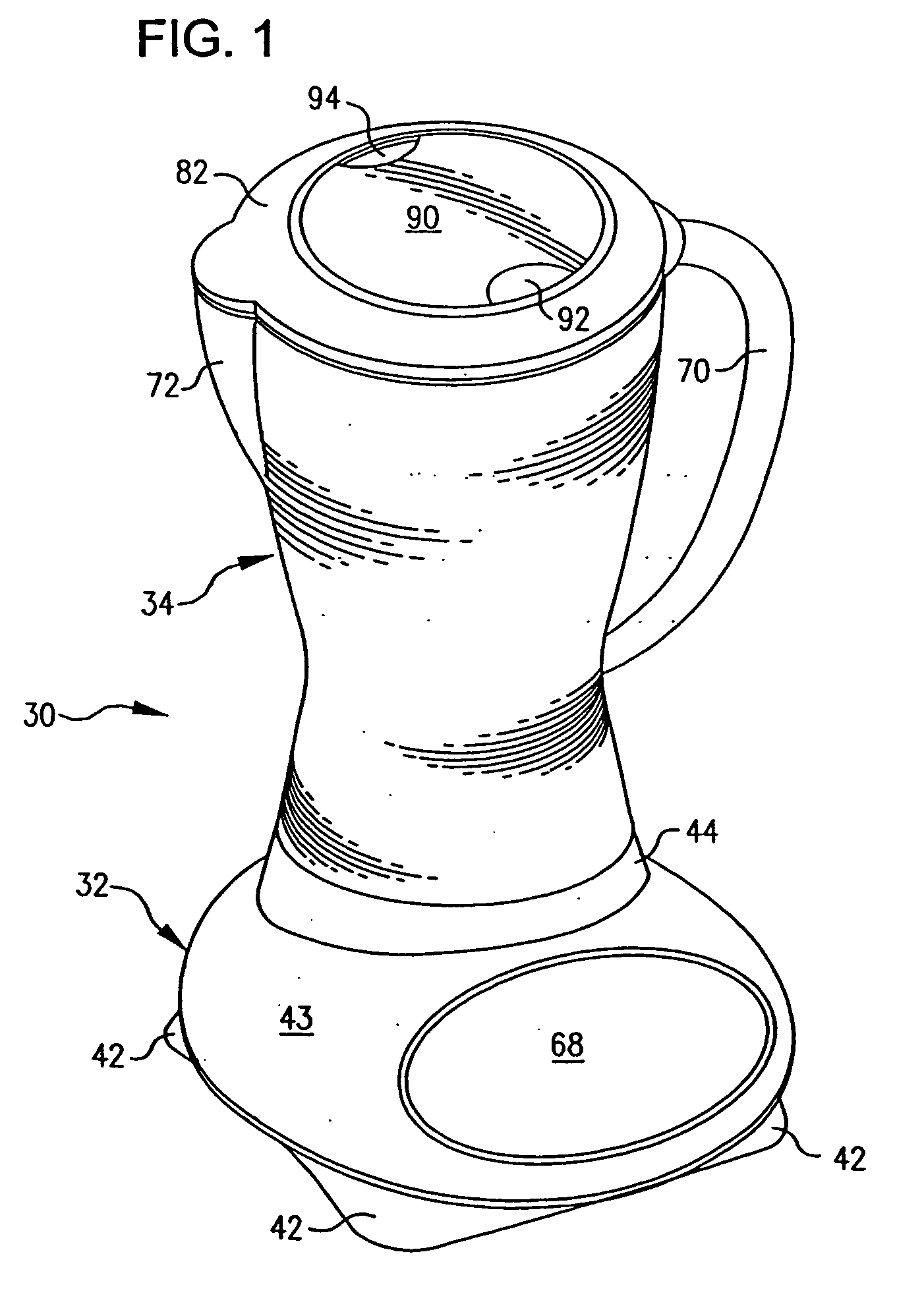
Blender base with food processor capabilities
InactiveUS20050068846A1Avoid vibrationImprove stabilityGas current separationTransportation and packagingMicrocontrollerLiquid-crystal display
A blender base that may be used with a food processor container, a blender container, and a single use beverage container. The blender container includes a novel blade unit having a food processor-style blade and blender type blades. Programs with preprogrammed motor commands for desired operations are stored in memory and may be selected by a user on a user interface. The user interface may include a liquid crystal display, or function switches and light emitting diodes. Upon selection of a particular pre-defined function, the microcontroller retrieves the appropriate program from the read only memory and specifies the preprogrammed motor commands to accomplish the selected function.
Owner:WULF JOHN DOUGLAS +5
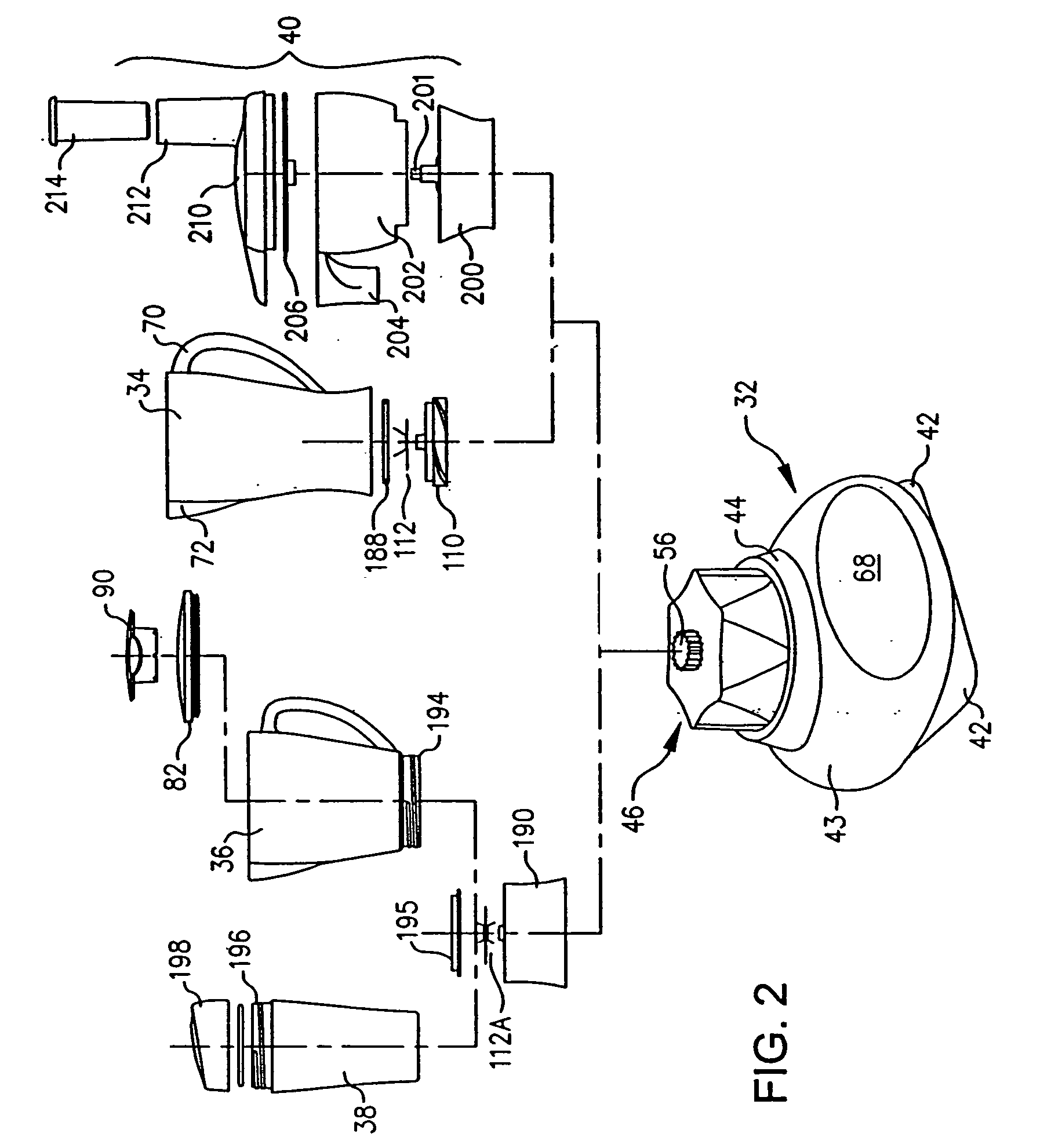
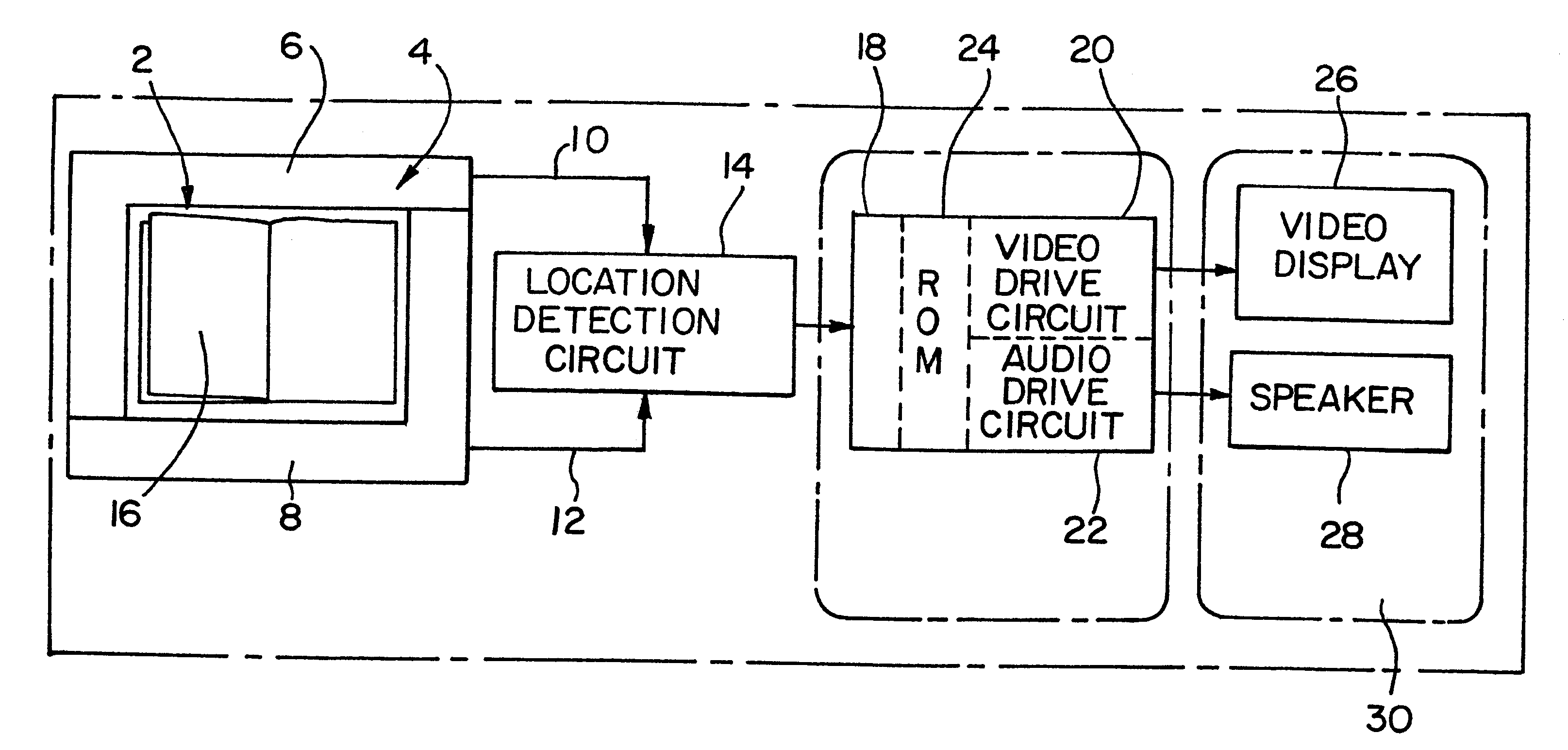
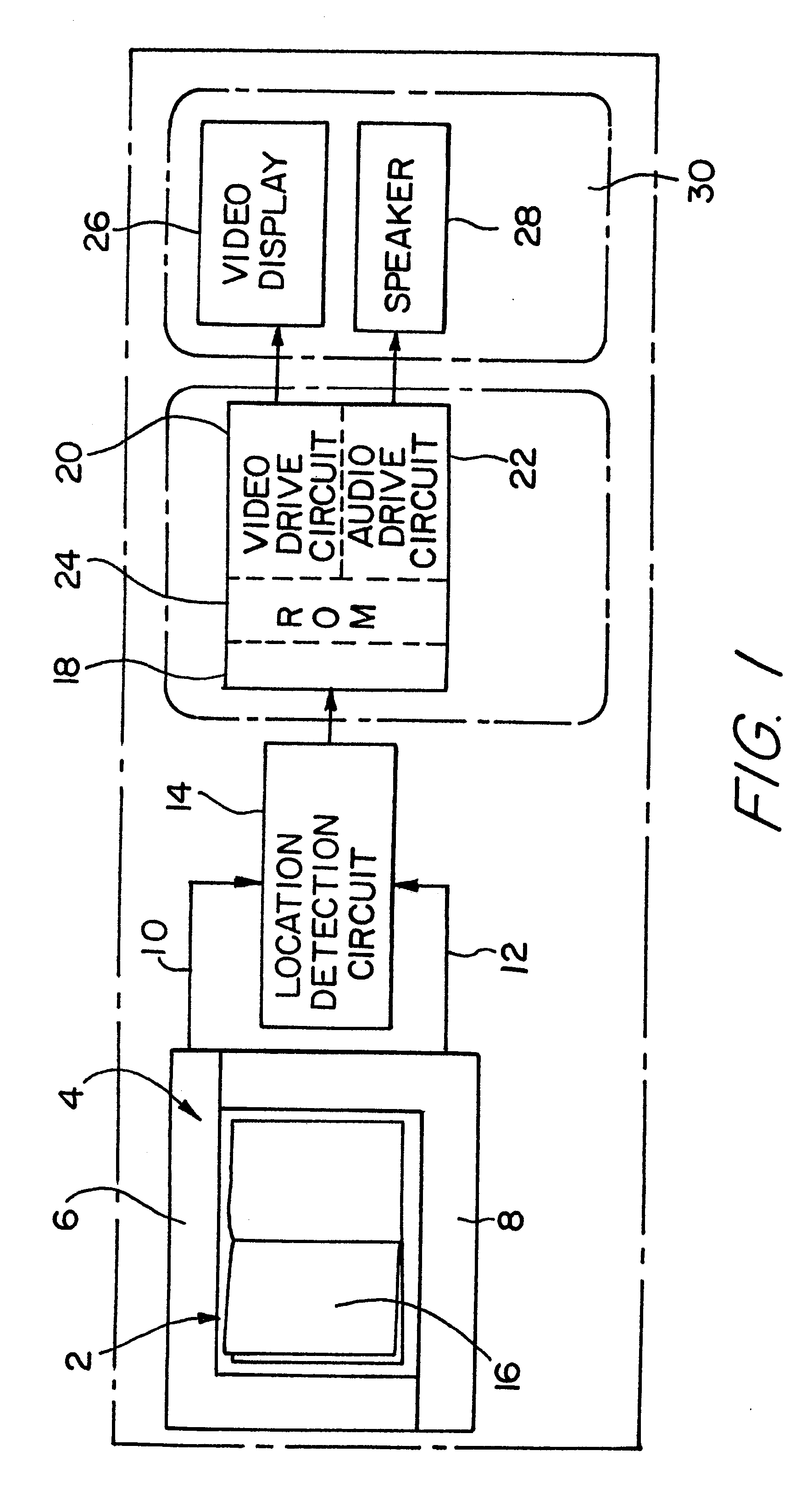
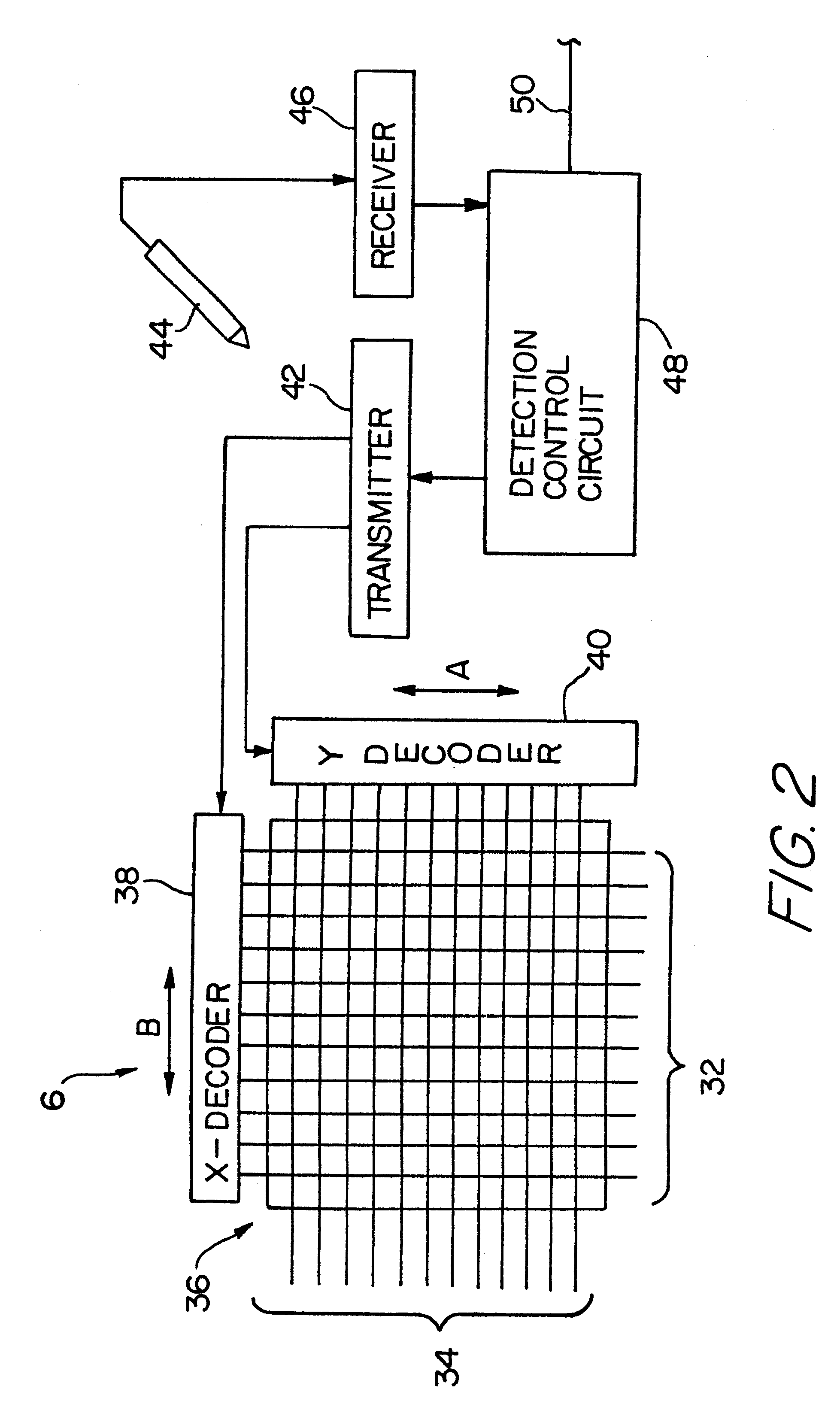
Information display system for electronically reading a book
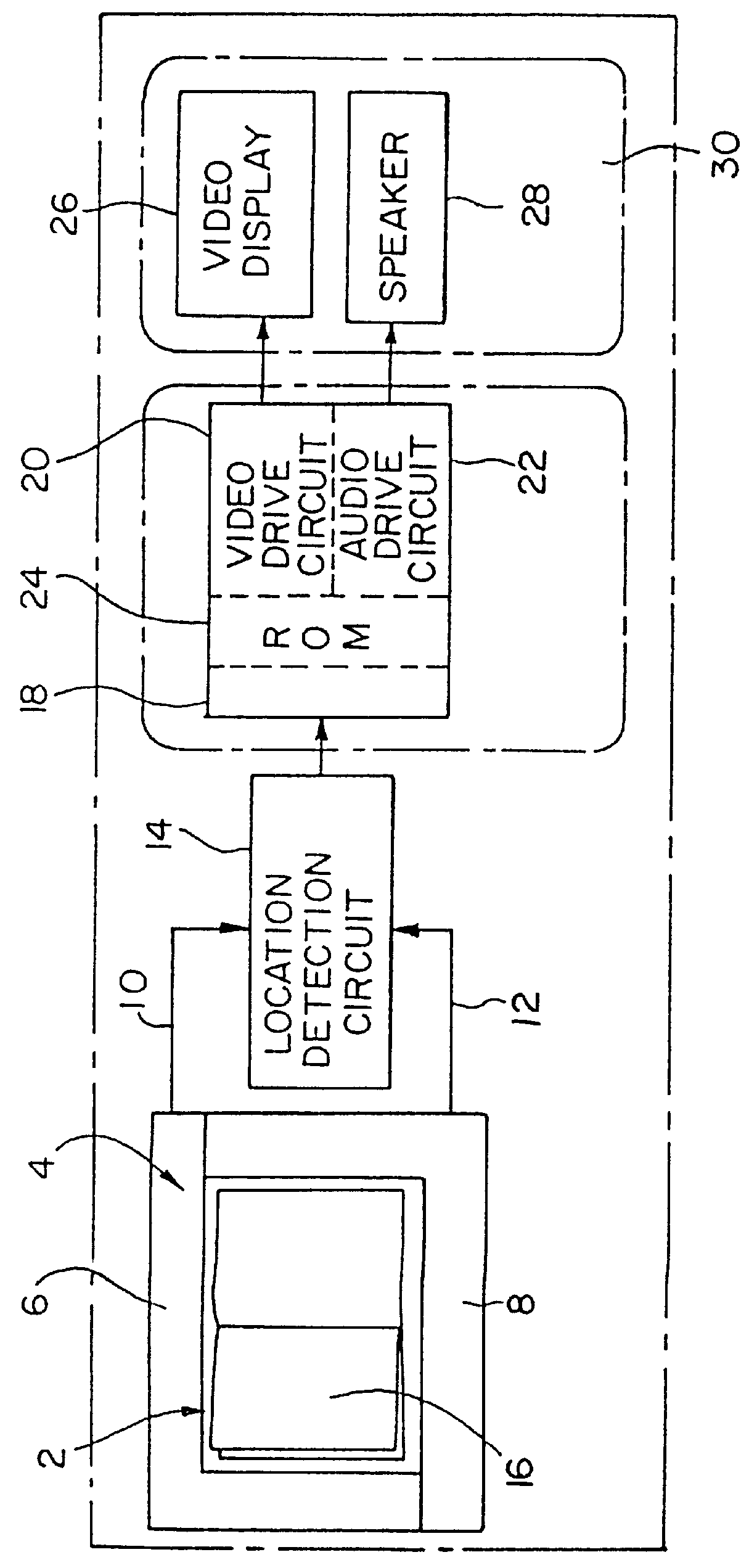
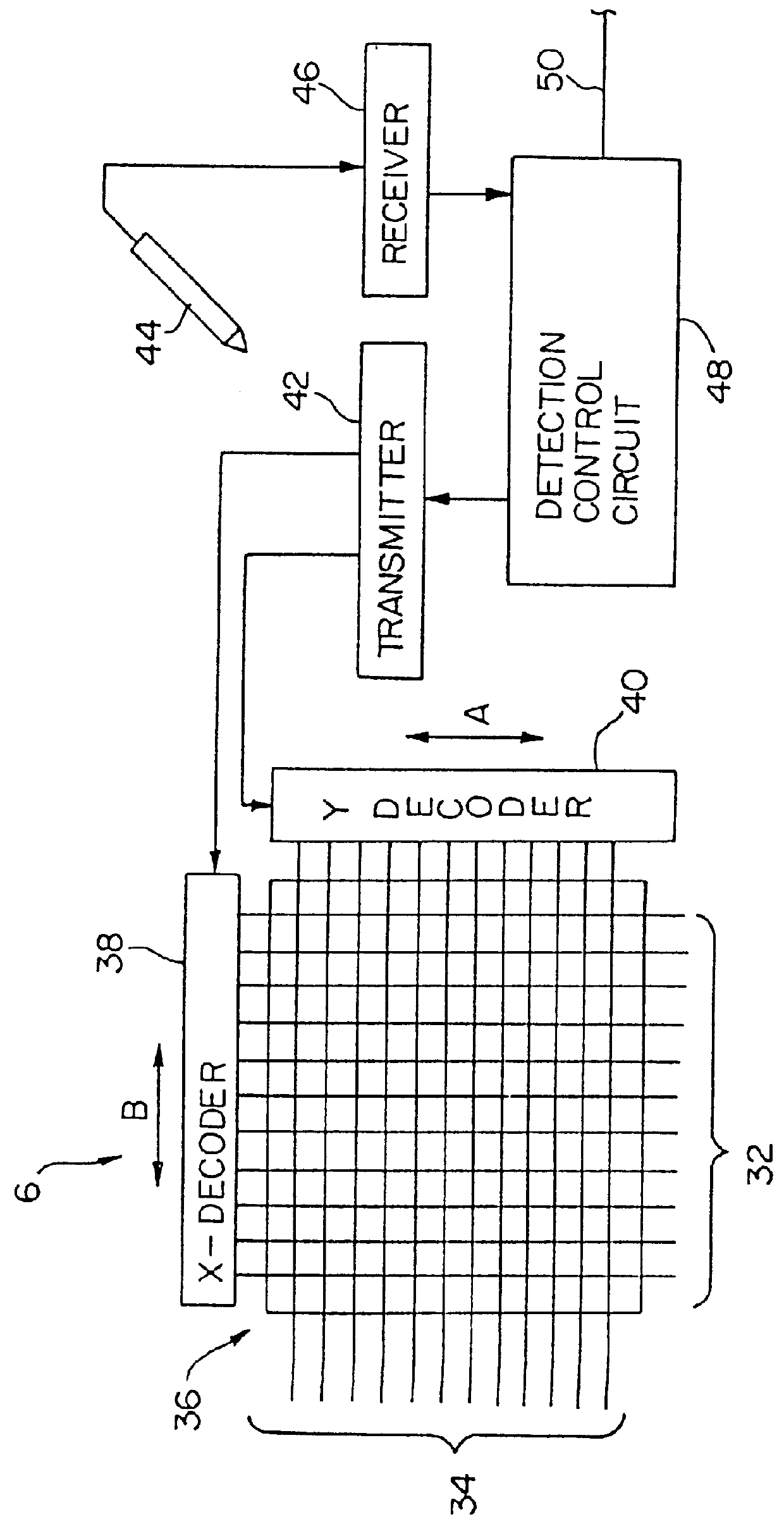
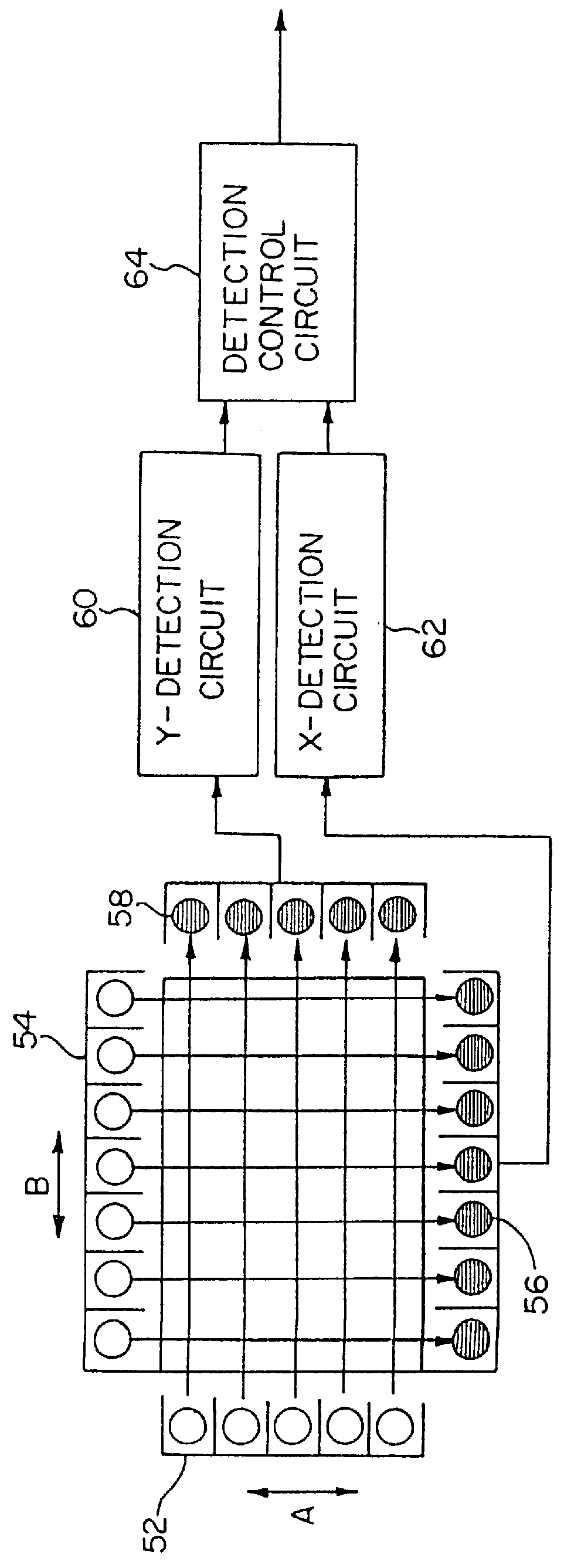
InactiveUS6297812B1Co-operative working arrangementsToysLocation detectionInformation display systems
An information display system having a housing with a location for receiving a document such as a book is provided. A location detection circuit is mounted on the housing adjacent the document and can determine any subjective selection of a location on the document. The document can have a plurality of indicia. When such indicia is selected, a control circuit can retrieve the information from a read only memory and appropriately display the information in an audible or visual manner.
Owner:SEGA CORP
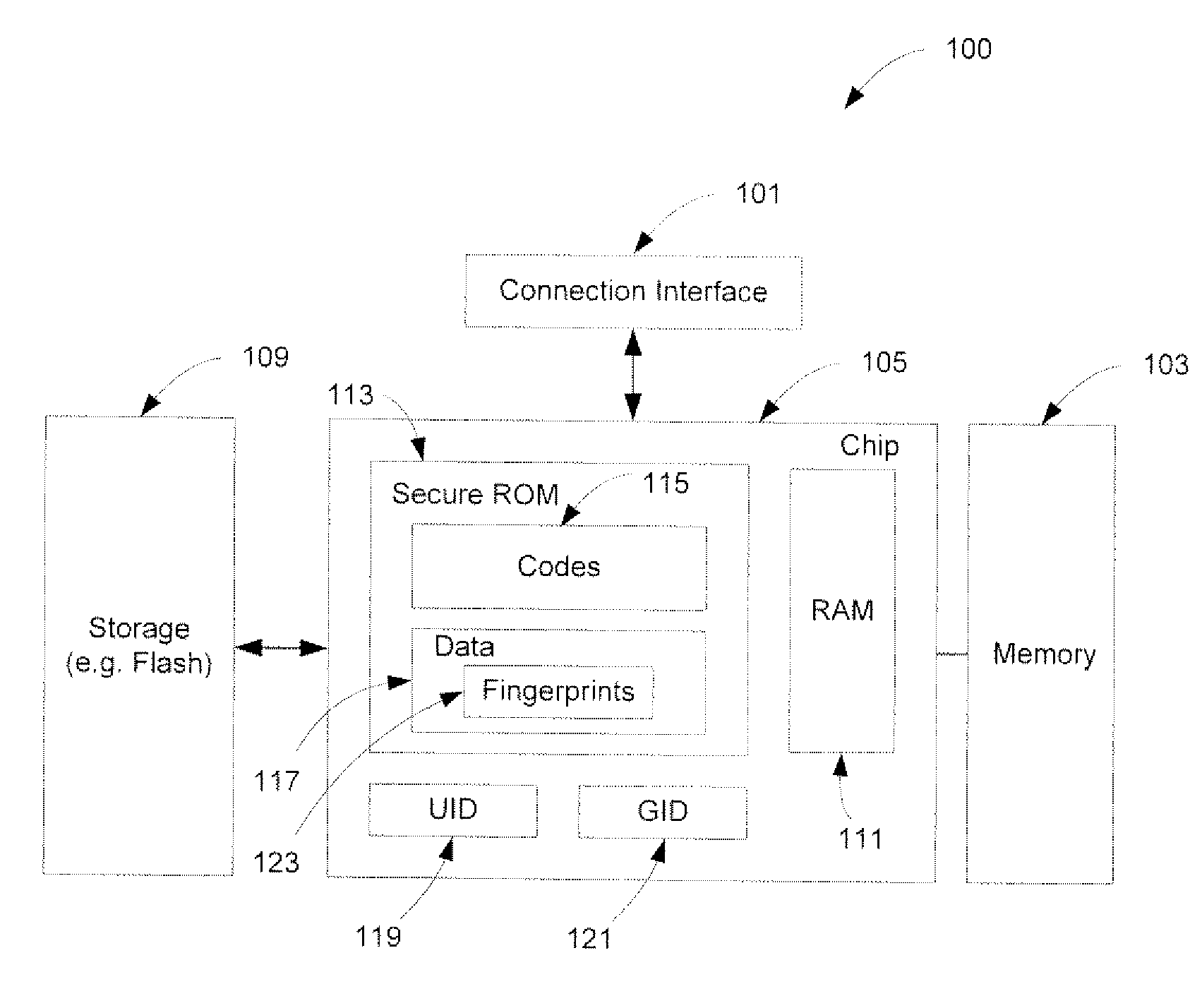
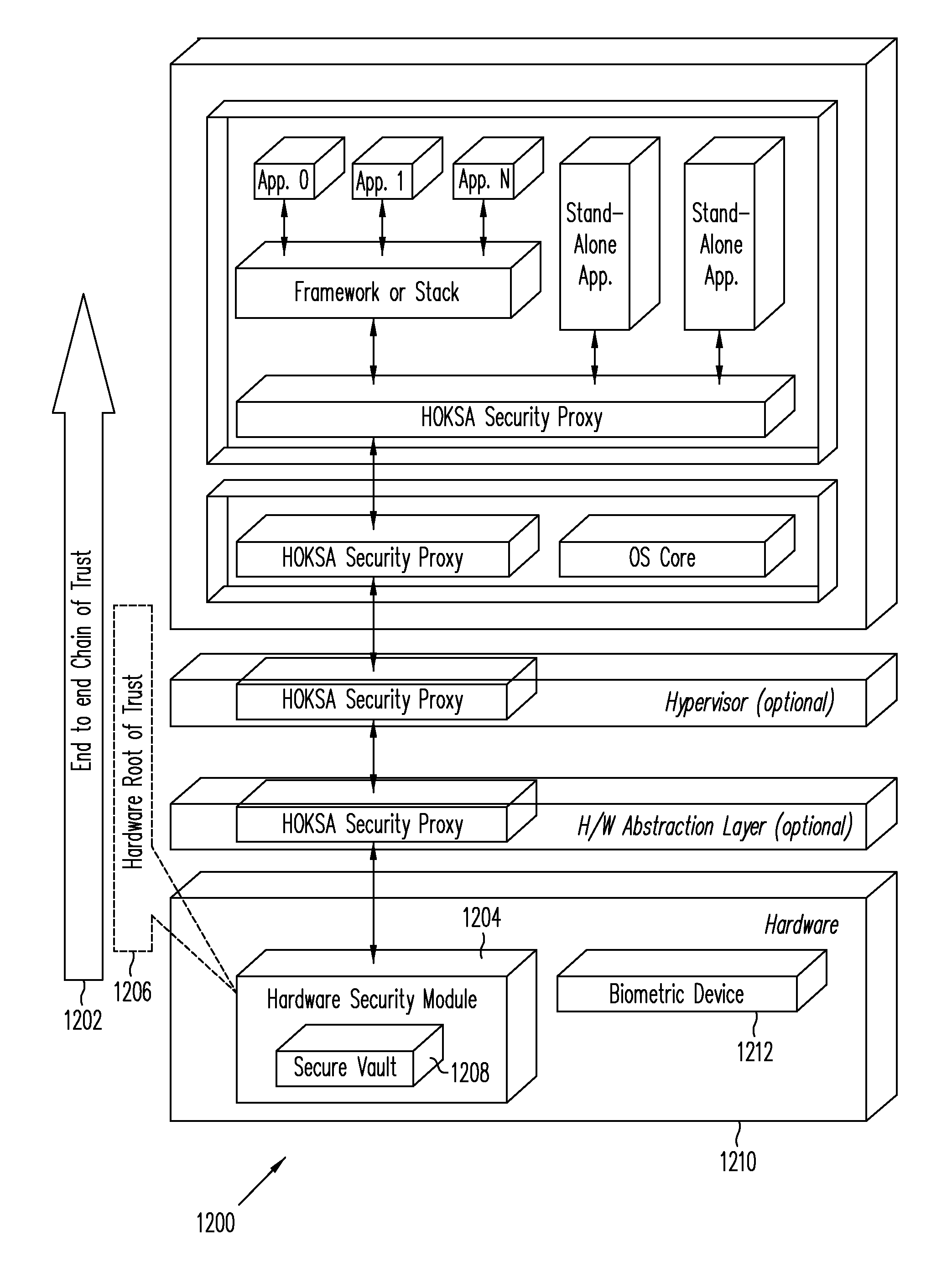
Hardware-Based Zero-Knowledge Strong Authentication (H0KSA)
InactiveUS20100306531A1Reduce riskUser identity/authority verificationDigital data authenticationHardware security moduleChain of trust
Systems and methods are provided for a device to engage in a zero-knowledge proof with an entity requiring authentication either of secret material or of the device itself. The device may provide protection of the secret material or its private key for device authentication using a hardware security module (HSM) of the device, which may include, for example, a read-only memory (ROM) accessible or programmable only by the device manufacturer. In the case of authenticating the device itself a zero-knowledge proof of knowledge may be used. The zero-knowledge proof or zero-knowledge proof of knowledge may be conducted via a communication channel on which an end-to-end (e.g., the device at one end and entity requiring authentication at the other end) unbroken chain of trust is established, unbroken chain of trust referring to a communication channel for which endpoints of each link in the communication channel mutually authenticate each other prior to conducting the zero-knowledge proof of knowledge and for which each link of the communication channel is protected by at least one of hardware protection and encryption.
Owner:PAYPAL INC
Highly compact EPROM and flash EEPROM devices
Structures, methods of manufacturing and methods of use of electrically programmable read only memories (EPROM) and flash electrically erasable and programmable read only memories (EEPROM) include split channel and other cell configurations. An arrangement of elements and cooperative processes of manufacture provide self-alignment of the elements. An intelligent programming technique allows each memory cell to store more than the usual one bit of information. An intelligent erase algorithm prolongs the useful life of the memory cells. Use of these various features provides a memory having a very high storage density and a long life, making it particularly useful as a solid state memory in place of magnetic disk storage devices in computer systems.
Owner:SANDISK TECH LLC
Virtual universe supervisory presence
ActiveUS8176421B2Video gamesInput/output processes for data processingStatic random-access memoryMagnetic tape
It is understood that the terms computer-readable medium or computer useable medium comprise one or more of any type of physical embodiment of the program code. In particular, the computer-readable / useable medium can comprise program code embodied on one or more portable storage articles of manufacture (e.g., a compact disc, a magnetic disk, a tape, etc.), on one or more data storage portions of a computing device, such as the memory 316 and / or the storage system 332 (e.g., a fixed disk, a read-only memory, a random access memory, a cache memory, etc.).
Owner:ACTIVISION PUBLISHING
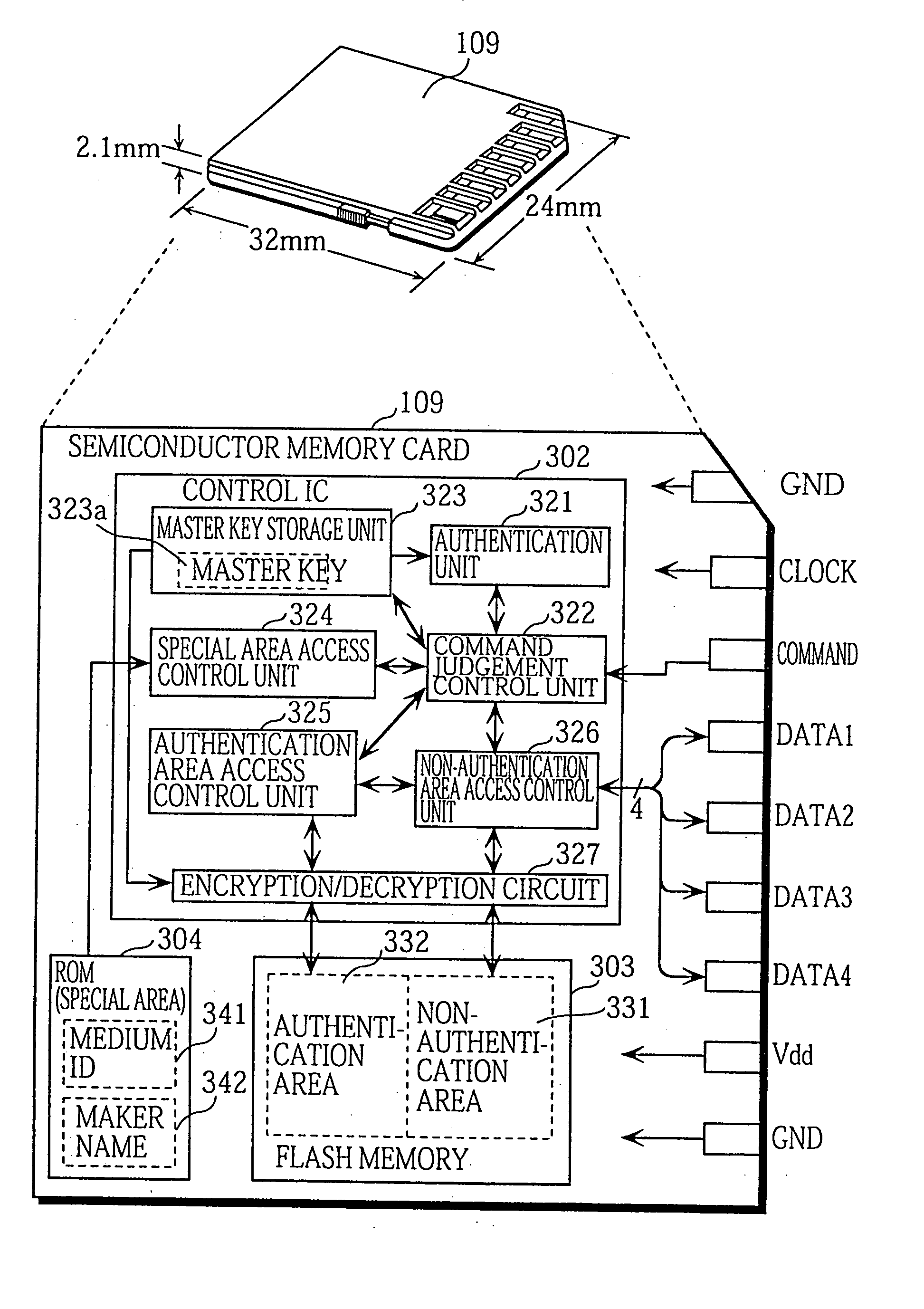
Semiconductor memory card and data reading apparatus
InactiveUS20050005149A1Secures healthy distribution of digital contentKey distribution for secure communicationDigital data processing detailsRead-only memorySemiconductor
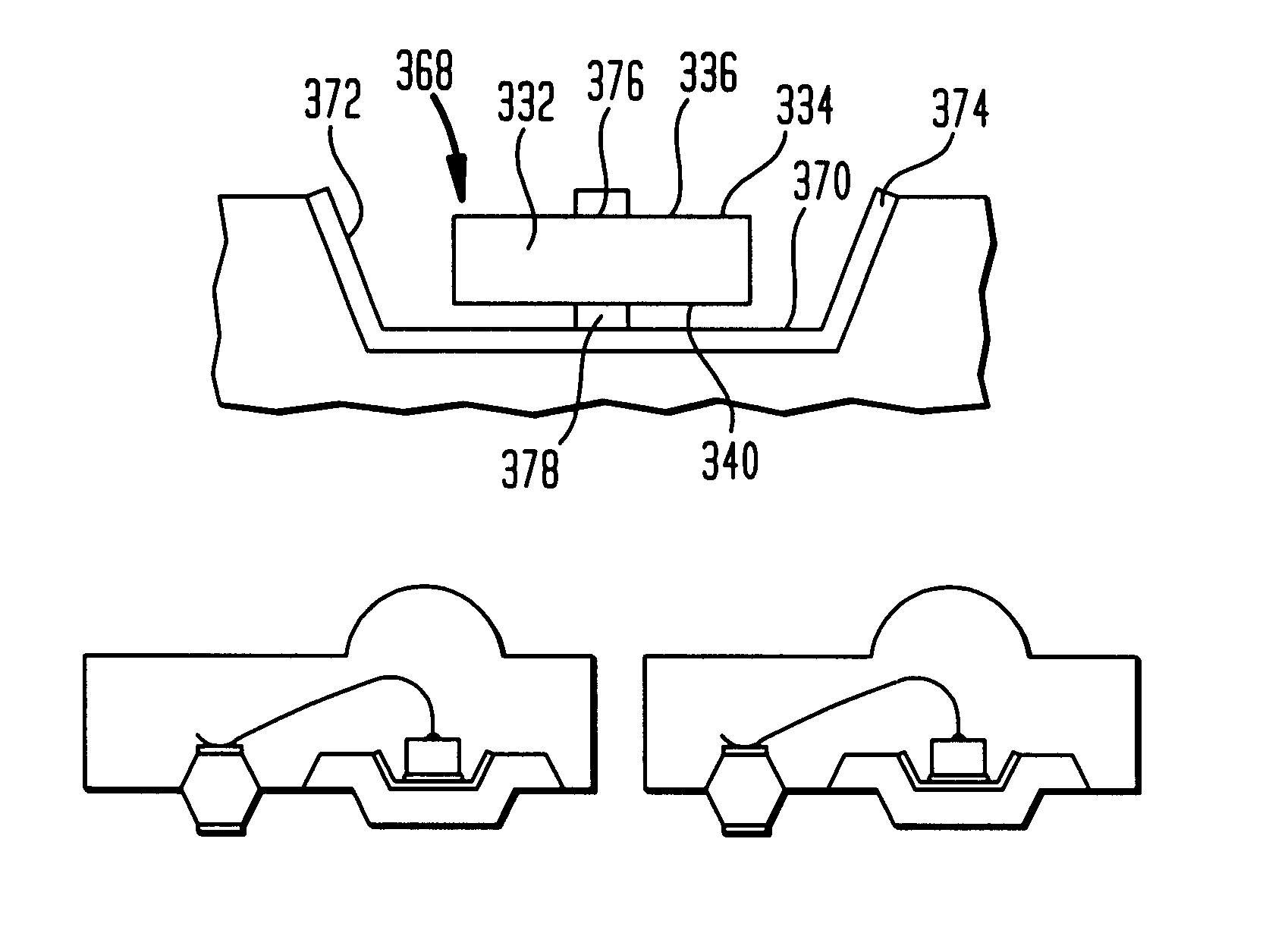
A semiconductor memory card comprising a control IC 302, a flash memory 303, and a ROM 304. The ROM 304 holds information such as a medium ID 341 unique to the semiconductor memory card. The flash memory 303 includes an authentication memory 332 and a non-authentication memory 331. The authentication memory 332 can be accessed only by external devices which have been affirmatively authenticated. The non-authentication memory 331 can be accessed by external devices whether the external devices have been affirmatively authenticated or not. The control IC 302 includes control units 325 and 326, an authentication unit 321 and the like. The control units 325 and 326 control accesses to the authentication memory 332 and the non-authentication memory 331, respectively. The authentication unit 321 executes a mutual authentication with an external device.
Owner:PANASONIC CORP
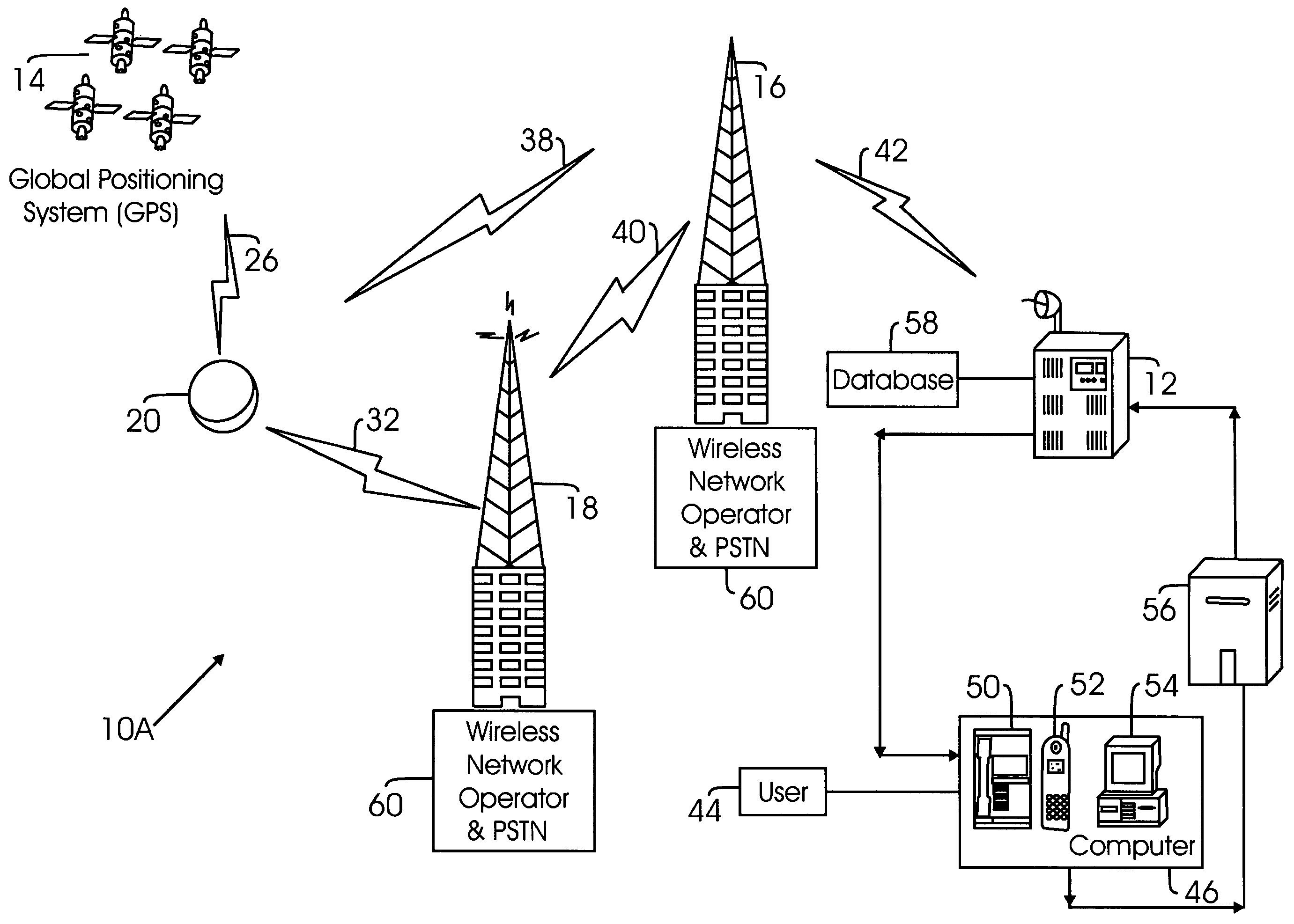
System for locating individuals and objects
ActiveUS7728724B1Position fixationElectric/electromagnetic visible signallingProgrammable read-only memoryGlobal Positioning System
A positioning and tracking system may comprise a monitoring station for receiving a location request and a user's identification code and transmitting a signal; a tracking device, which includes a signal receiver for receiving a signal from the monitoring station, including the user's identification code, a microprocessor / logic circuit for storing a first identification code, and generating a position signal; an erasable programmable read-only memory; a global positioning system logic circuit; a signal transmitter; and a plurality of transmitter / receiver stations for communicating between the tracking device and the monitoring station; wherein the tracking device compares the user's identification code to the stored identification code and upon determining that the user's identification code matches the stored identification code, the signal transmitter transmits the position signal to the monitoring station.
Owner:LBT IP II LLC
Single Security Model In Booting A Computing Device
ActiveUS20090257595A1Secure bootKey distribution for secure communicationMemory loss protectionRead-only memoryOperating environment
A method and apparatus for securely booting software components in an electronic device to establish an operating environment are described herein. According to an aspect of the invention, software components are to be executed in sequence in order to establish an operating environment of a device. For each software component, a security code is executed to authenticate and verify an executable code image associated with each software component using one or more keys embedded within a secure ROM (read-only memory) of the device and one or more hardware configuration settings of the device. The security code for each software component includes a common functionality to authenticate and verify the executable code image associated with each software component. In response to successfully authenticating and verifying the executable code image, the executable code image is then executed in a main memory of the device to launch the associated software component.
Owner:APPLE INC
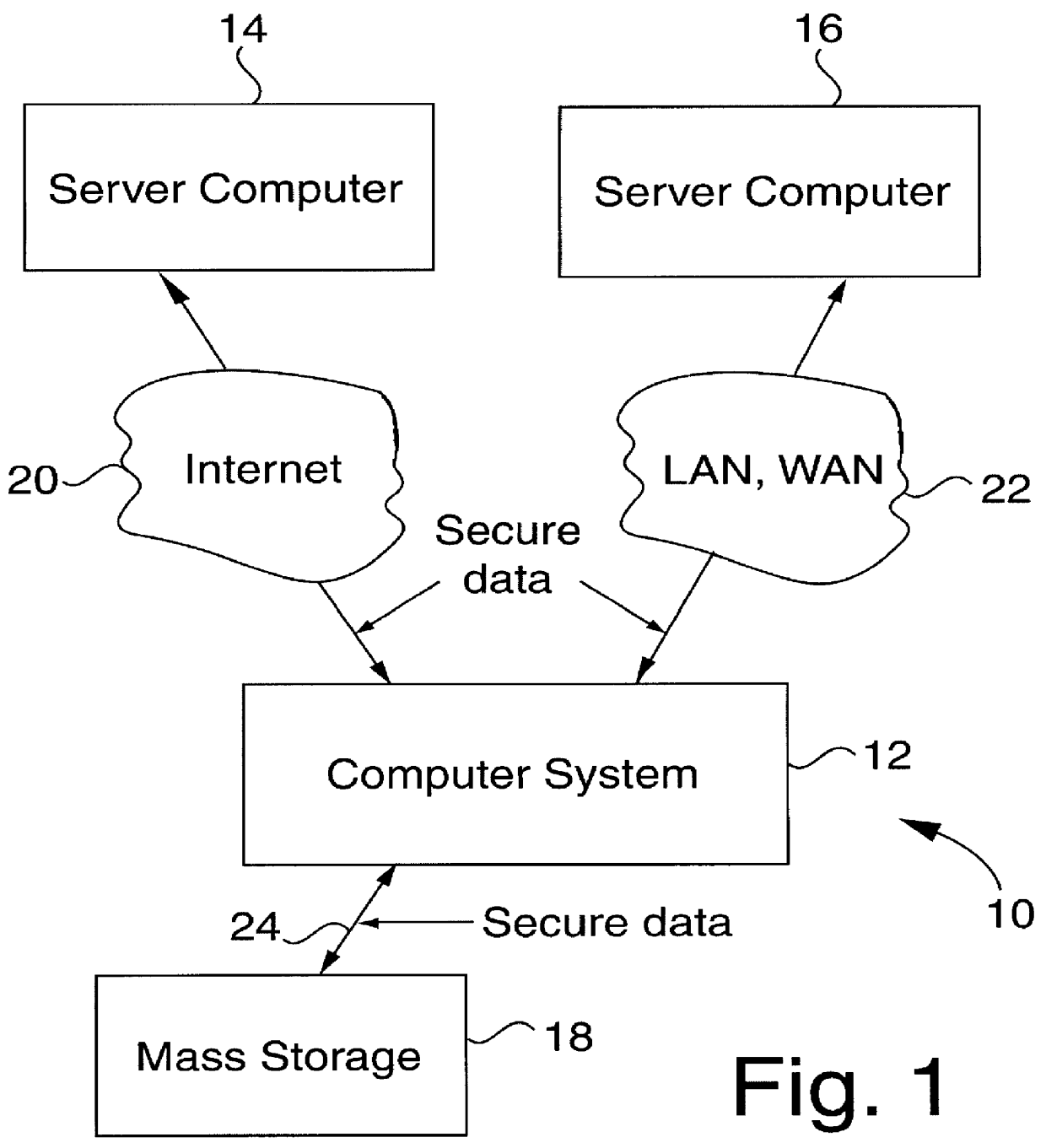
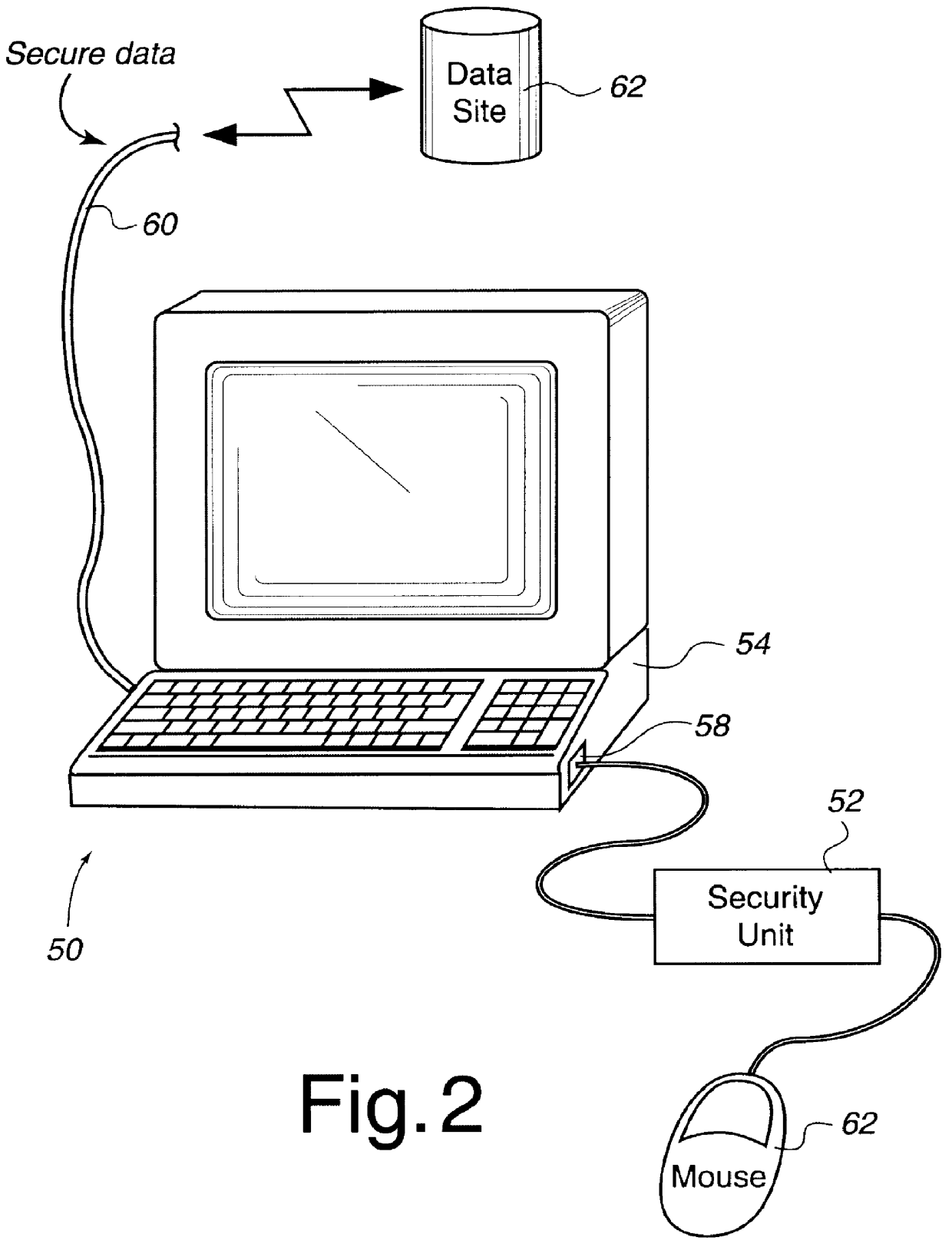
Security apparatus for data transmission with dynamic random encryption
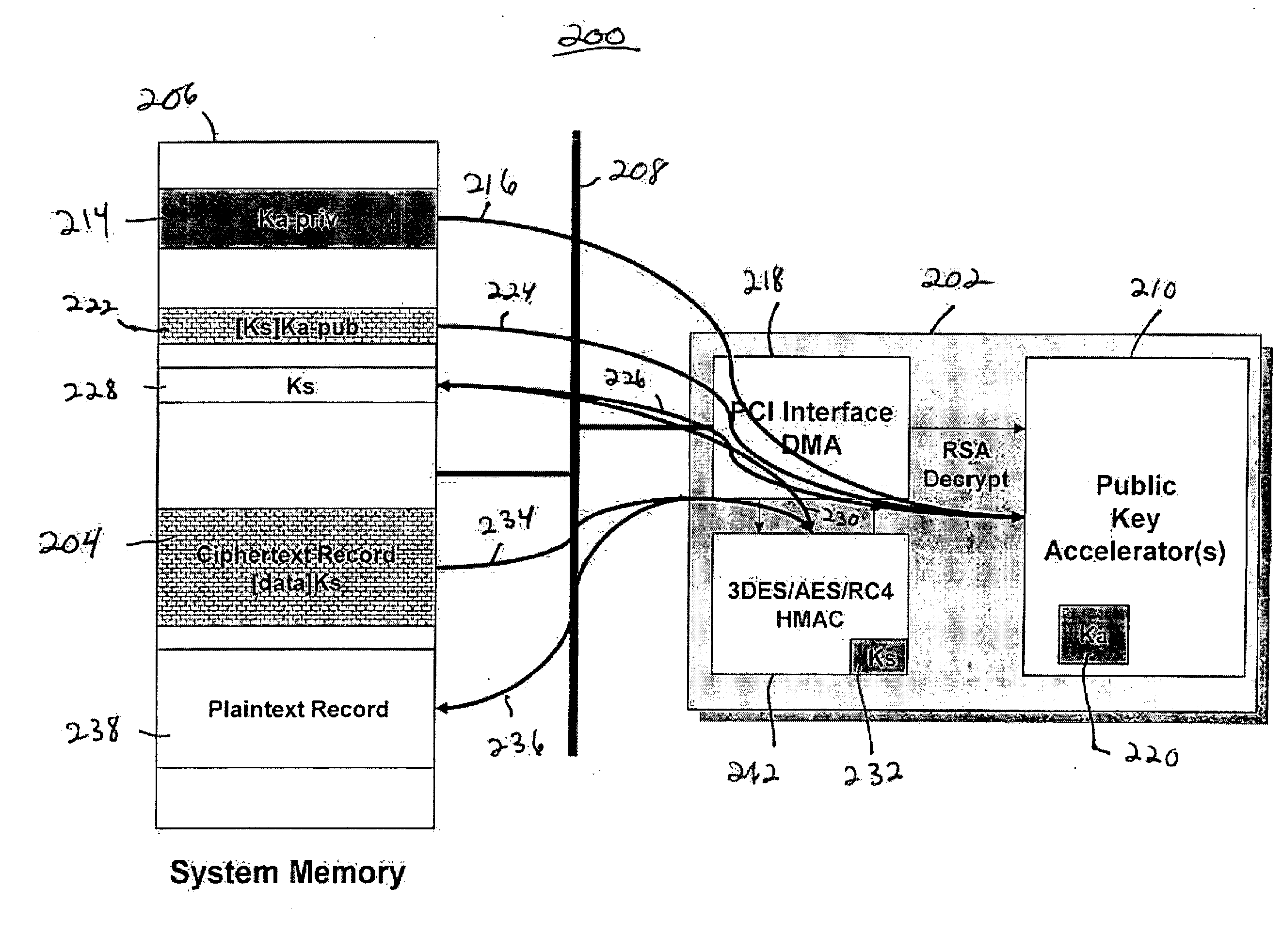
InactiveUS6094486ASimple equipmentBuilt inexpensively and smallEqual length code transmitterDigital data processing detailsPage address registerShift register
A security apparatus including a number input device (302), an address register (312) responsive to the number input device, an encryption schema memory (316) addressable by the address register to produce an output code and a relative address code, and address incrementing logic (310) responsive the relative address code and operative to increment the address register. The apparatus also preferably includes a PIN register (304) coupled to the number input device, a public code register (306) coupled to the number input device, and merging logic (308) merging outputs of the PIN register and the public code register to be input to the address register. The apparatus also preferably includes an output shift register operative to shift out the output code of the encryption schema memory. The encryption schema memory can be read only memory, writeable memory, or both.
Owner:MARCHANT BRIAN E
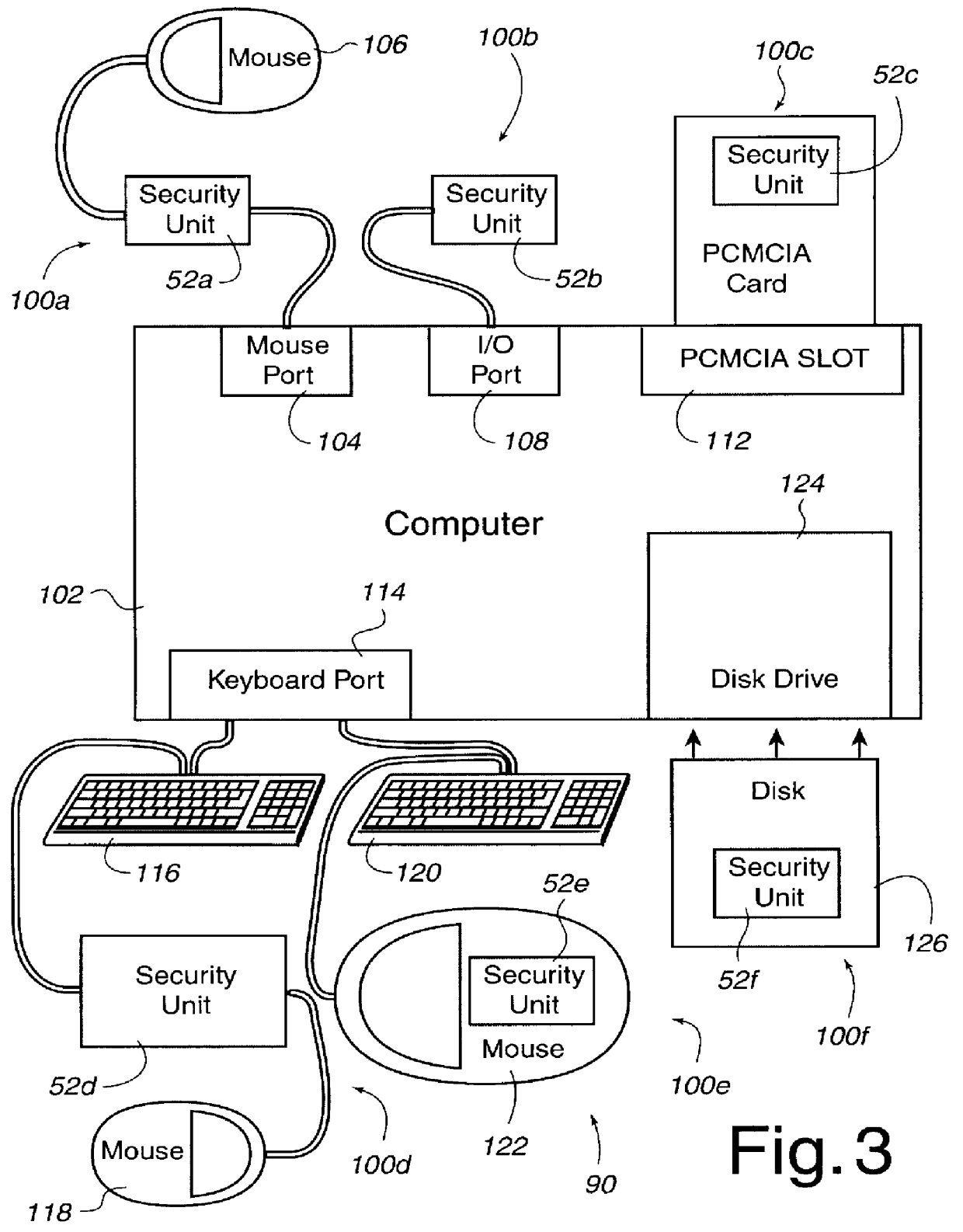
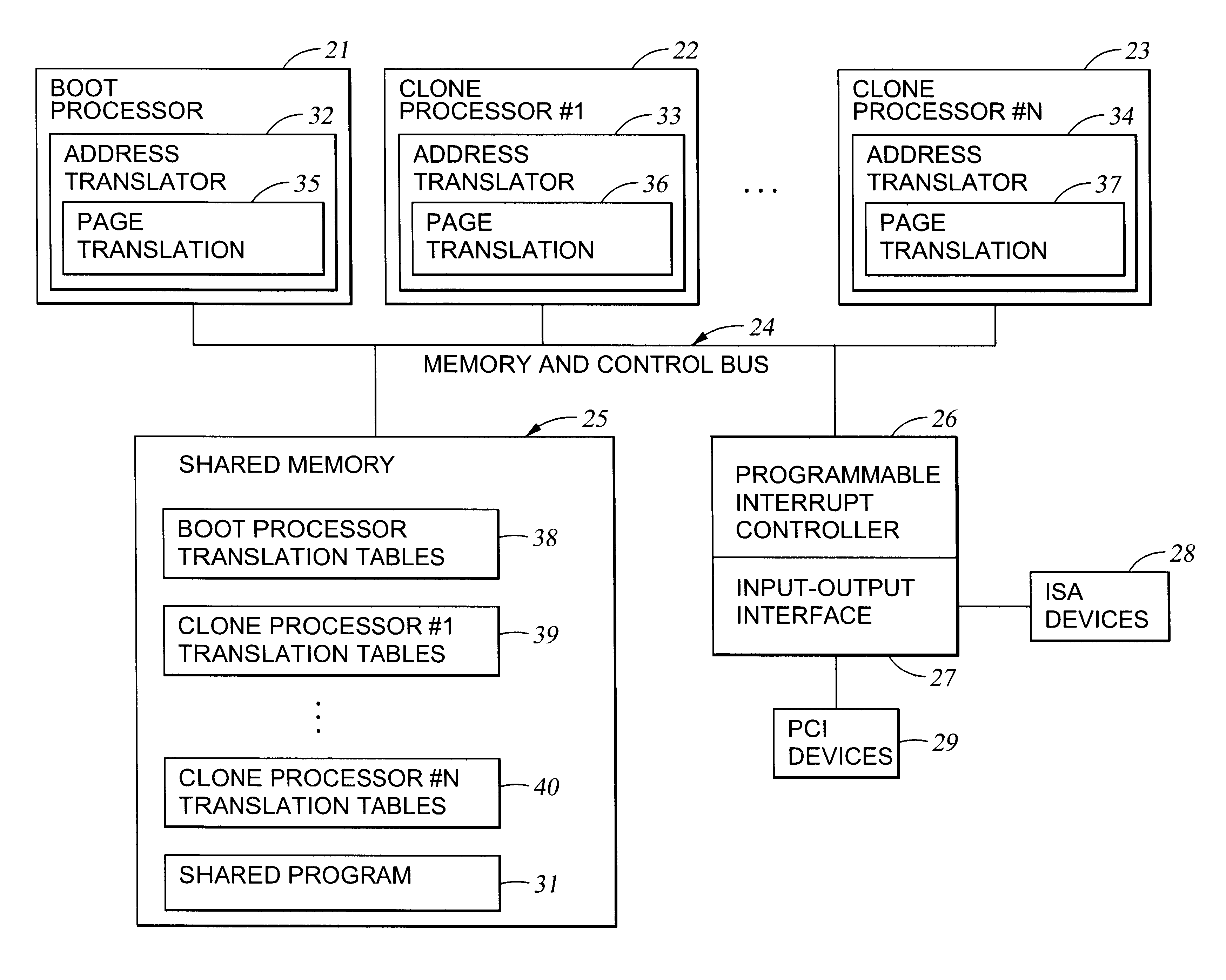
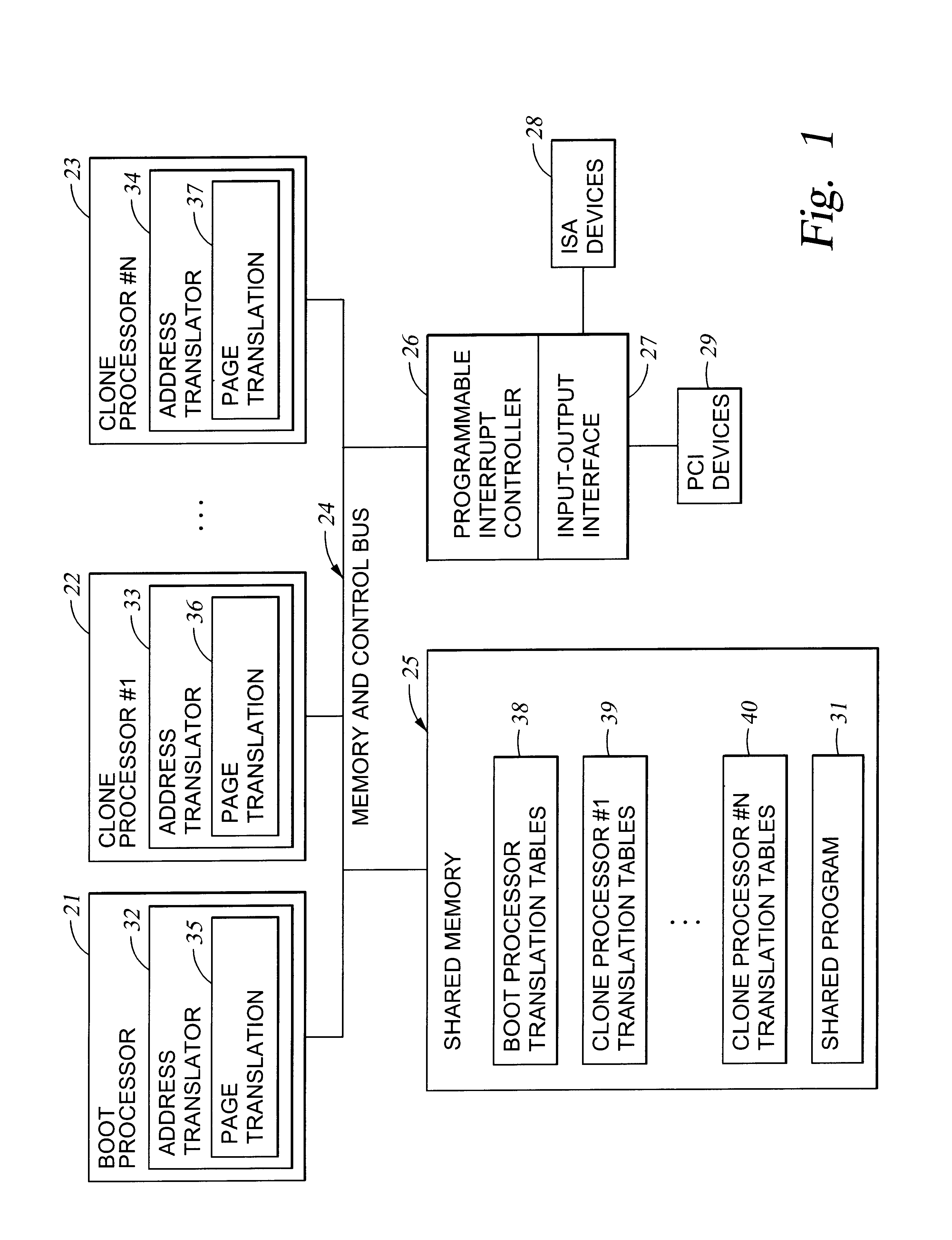
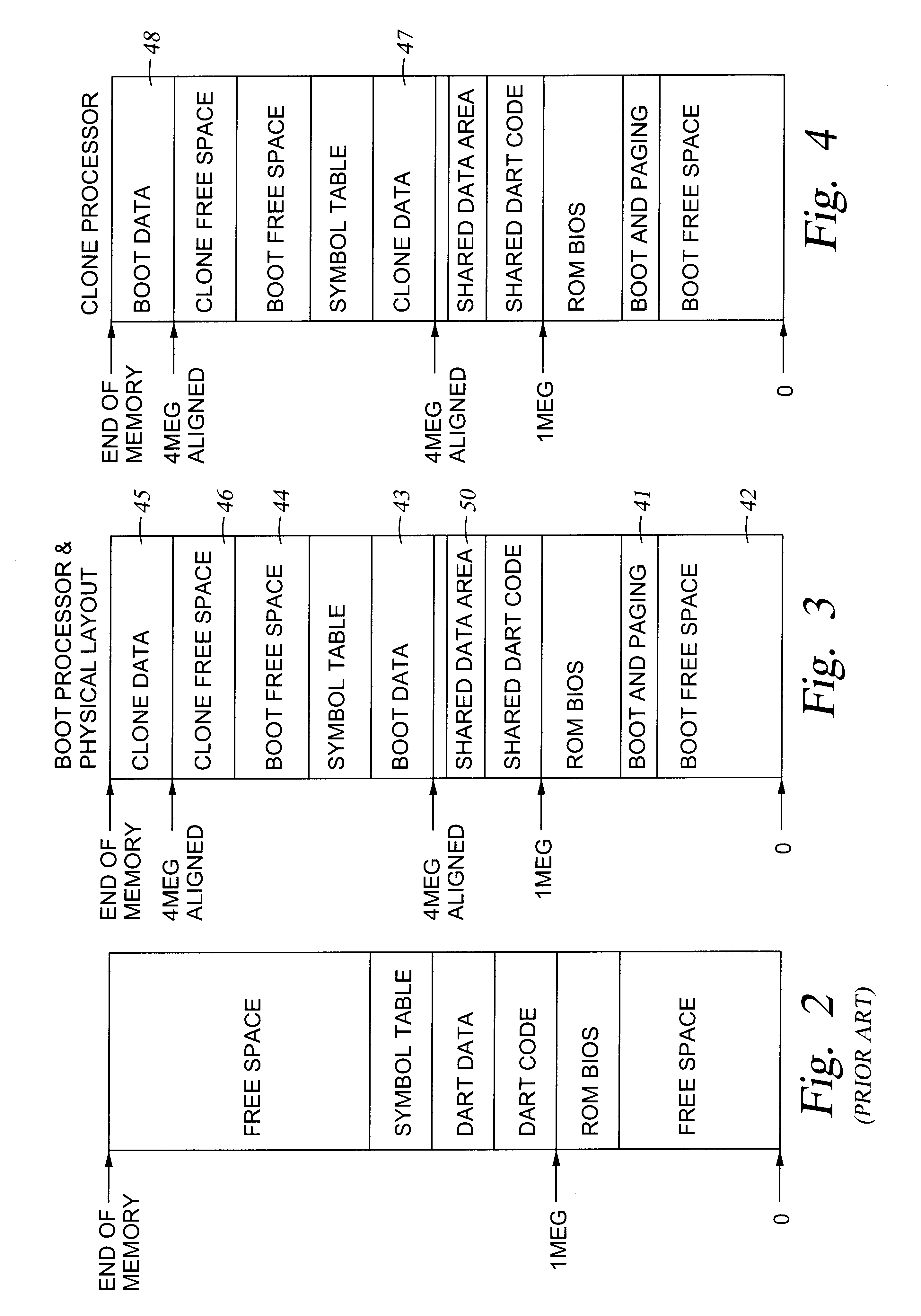
Method of sharing memory in a multi-processor system including a cloning of code and data
InactiveUS6813522B1Memory architecture accessing/allocationComputer controlMulti processorRead-only memory
Code and data are cloned in a multiprocessor system in order to permit each processor to run concurrently a separate invocation of a program. Each processor uses the same address translation for shared access to the program code in a shared memory, and a different address translation for access to a respective private read-write data region in the shared memory. Initialization of a private data region is performed by copying data from a shared read-only memory region, such as the program region, to the private data region. Some static constructors may access a shared read-write data area that should not be reinitialized by the clone processor. In this case, a working copy of a data region is made, the address translation is remapped for access to the working copy, the static constructors are run, and then the mapping is returned for normal access to the shared data.
Owner:EMC IP HLDG CO LLC
Information display system for electronically reading a book
InactiveUS6052117AToysCo-operative working arrangementsLocation detectionInformation display systems
An information display system having a housing with a location for receiving a document such as a book is provided. A location detection circuit is mounted on the housing adjacent the document and can determine any subjective selection of a location on the document. The document can have a plurality of indicia. When such indicia is selected, a control circuit can retrieve the information from a read only memory and appropriately display the information in an audible or visual manner.
Owner:SEGA CORP
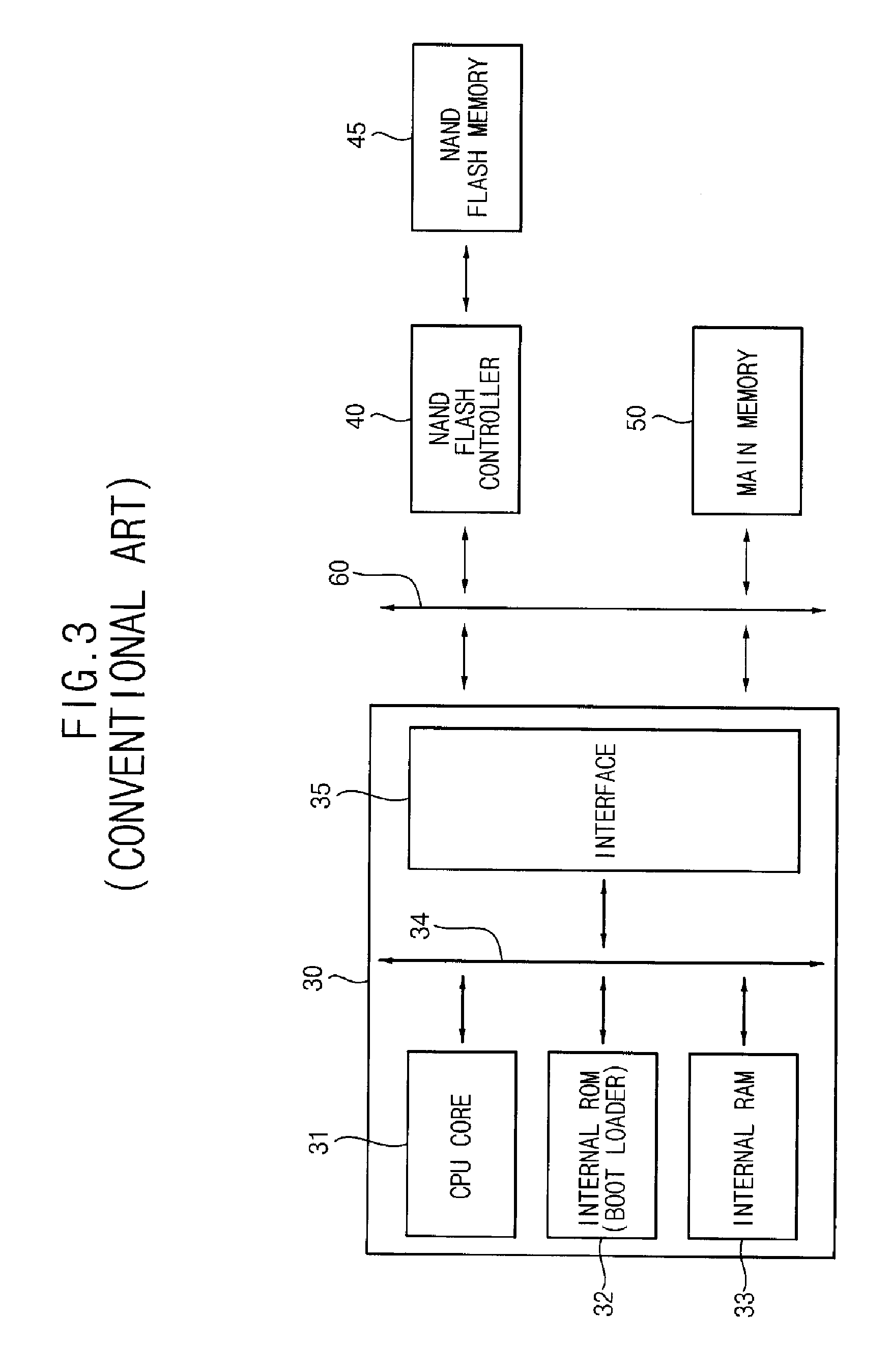
Method and apparatus for booting a microprocessor system using boot code stored on a serial flash memory array having a random-access interface
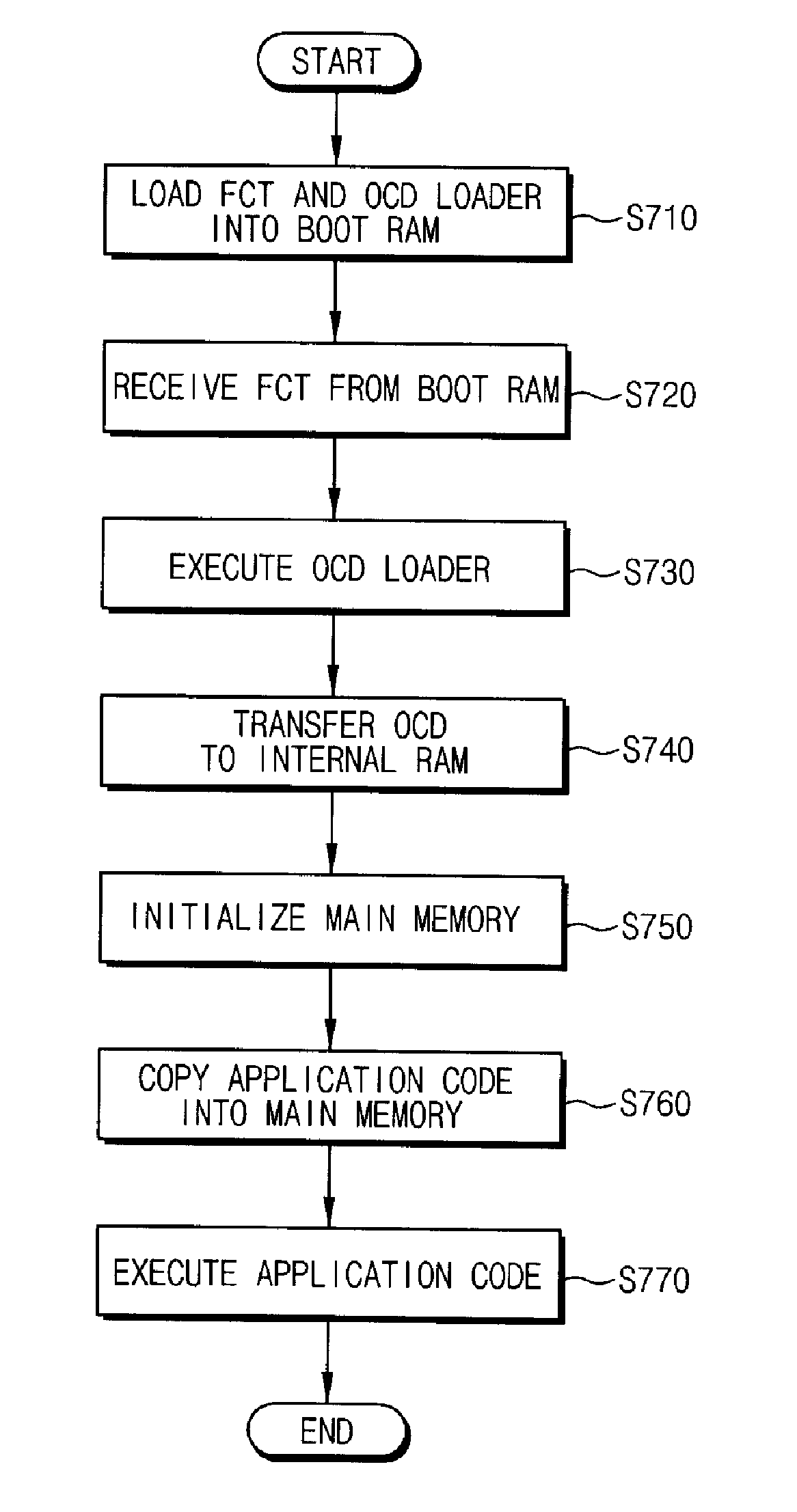
ActiveUS20070113067A1Ensure flexibilityLow costDigital computer detailsData resettingRead-only memoryProgram code
A method and apparatus for booting a microprocessor system using a serial (e.g., NAND-type) flash memory array having a random-access (parallel, e.g., NOR-flash type) interface. The method includes loading a boot code loader stored in the serial (e.g., NAND-type) flash memory array into a RAM when power is turned on, according to a routine of a read-only memory (ROM) of the microprocessor; loading boot code stored in the serial flash memory into an internal or external (main) RAM of the microprocessor according to the boot code loader; loading application code stored in the serial flash memory into the main (RAM) memory according to the boot is code; and executing the application code. The system may be manufactured at a low cost compared to NOR-Flash based systems, while ensuring flexibility of a microprocessor.
Owner:SAMSUNG ELECTRONICS CO LTD
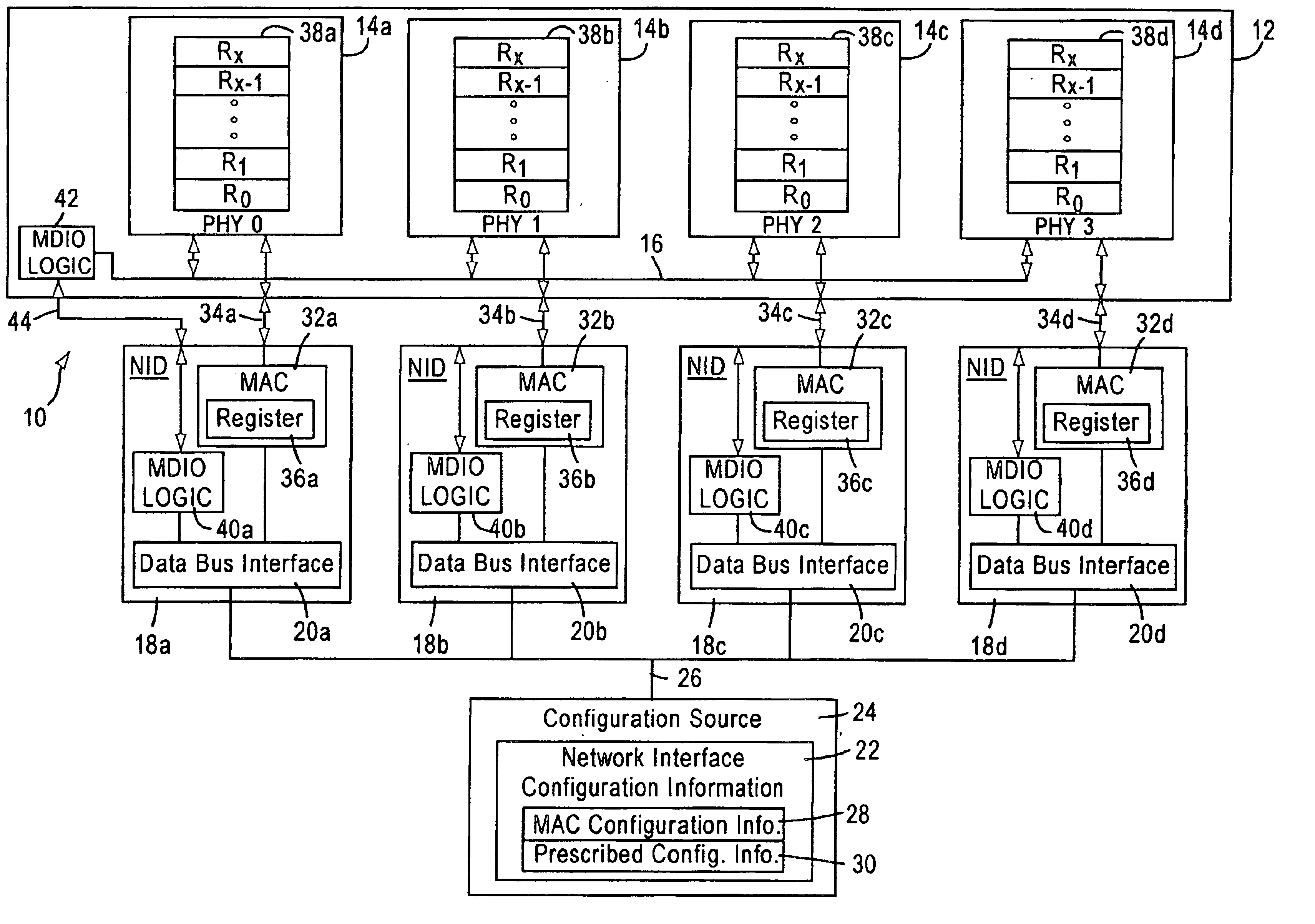
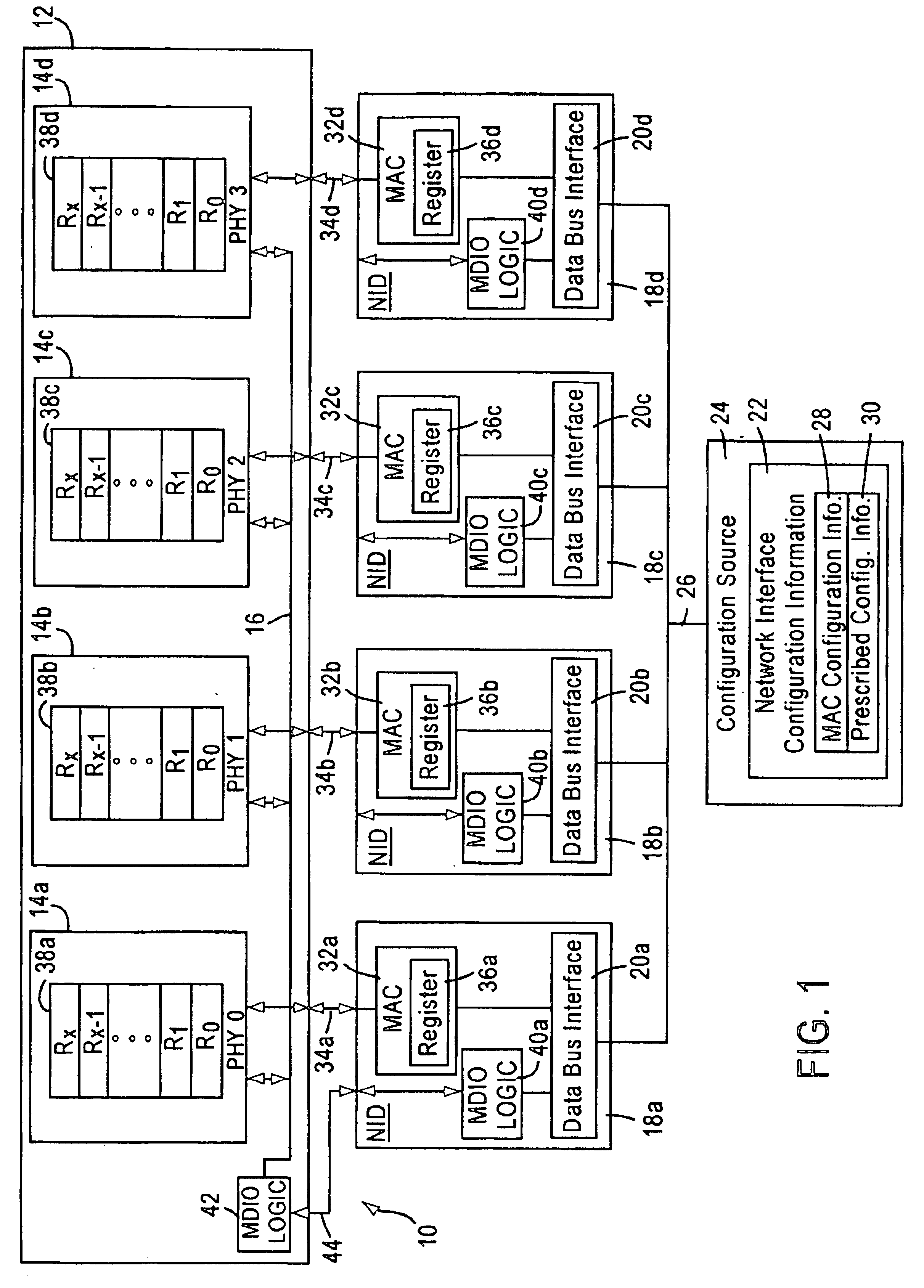
System and method enabling configuration of physical layer devices and corresponding link partners for communicating network data via a configuration source or auto-negotiation
InactiveUS6859825B1Multiple digital computer combinationsData switching networksProgrammable read-only memoryNetwork interface device
A network interface configures a plurality of physical layer devices and a corresponding plurality of network interface devices to allow for the communication of network data between the physical layer devices and corresponding link partners. At least one of the network interface devices is configured as a master device that communicates management information and autonegotiation results with the physical layer devices, while the other network interface devices do not. A configuration source, such as a central processing unit (CPU) or electronic erasable programmable read only memory (EEPROM), receives the autonegotiation results from the physical layer devices, through the master device, and configures the media access controllers (MACs) of each of the network interface devices in accordance with the autonegotiation results. This forces the MACs into their respective proper configurations even though the network interface devices that are not master devices do not receive the autonegotiation results directly from their corresponding physical layer devices.
Owner:ADVANCED MICRO DEVICES INC
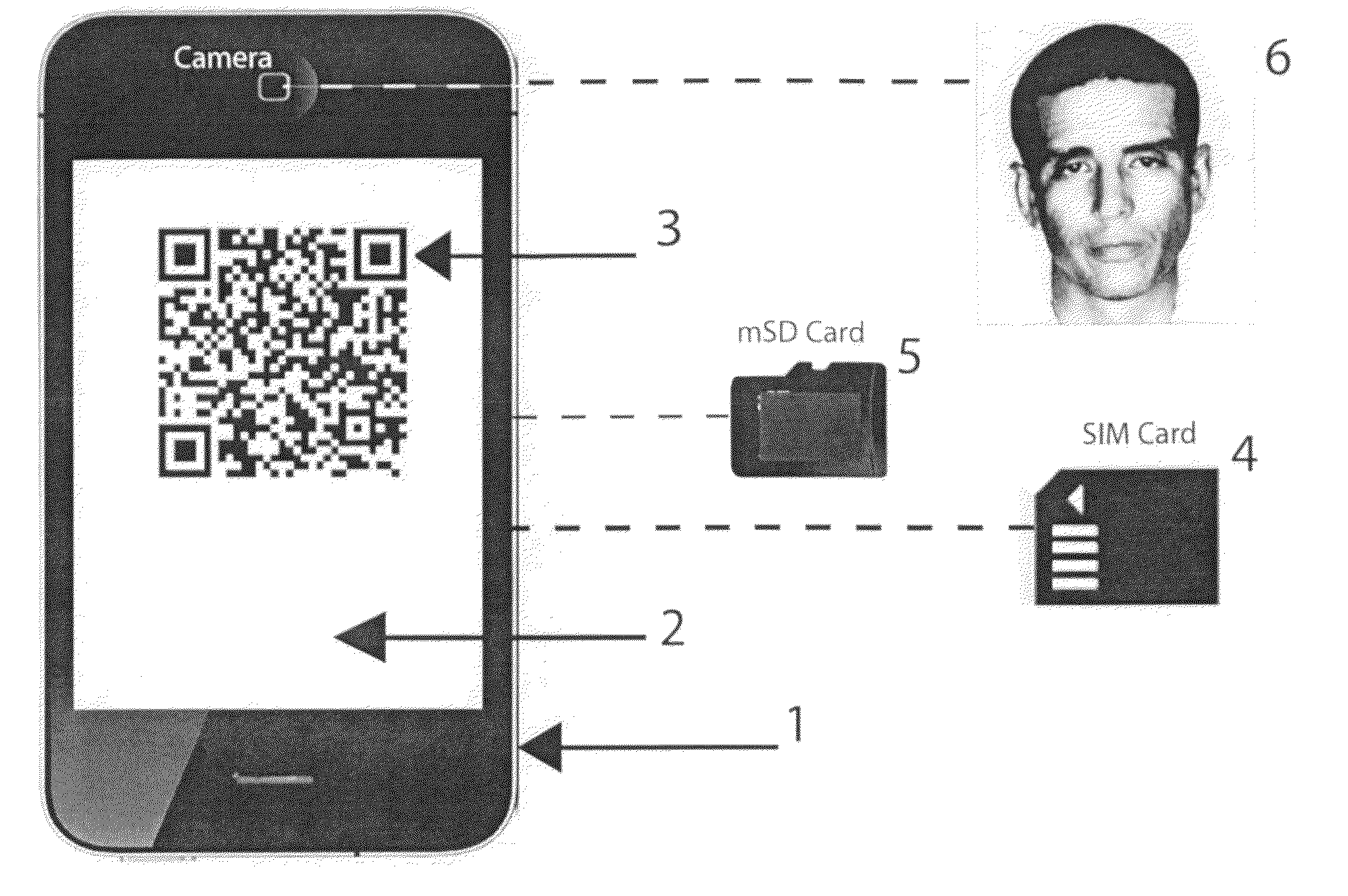
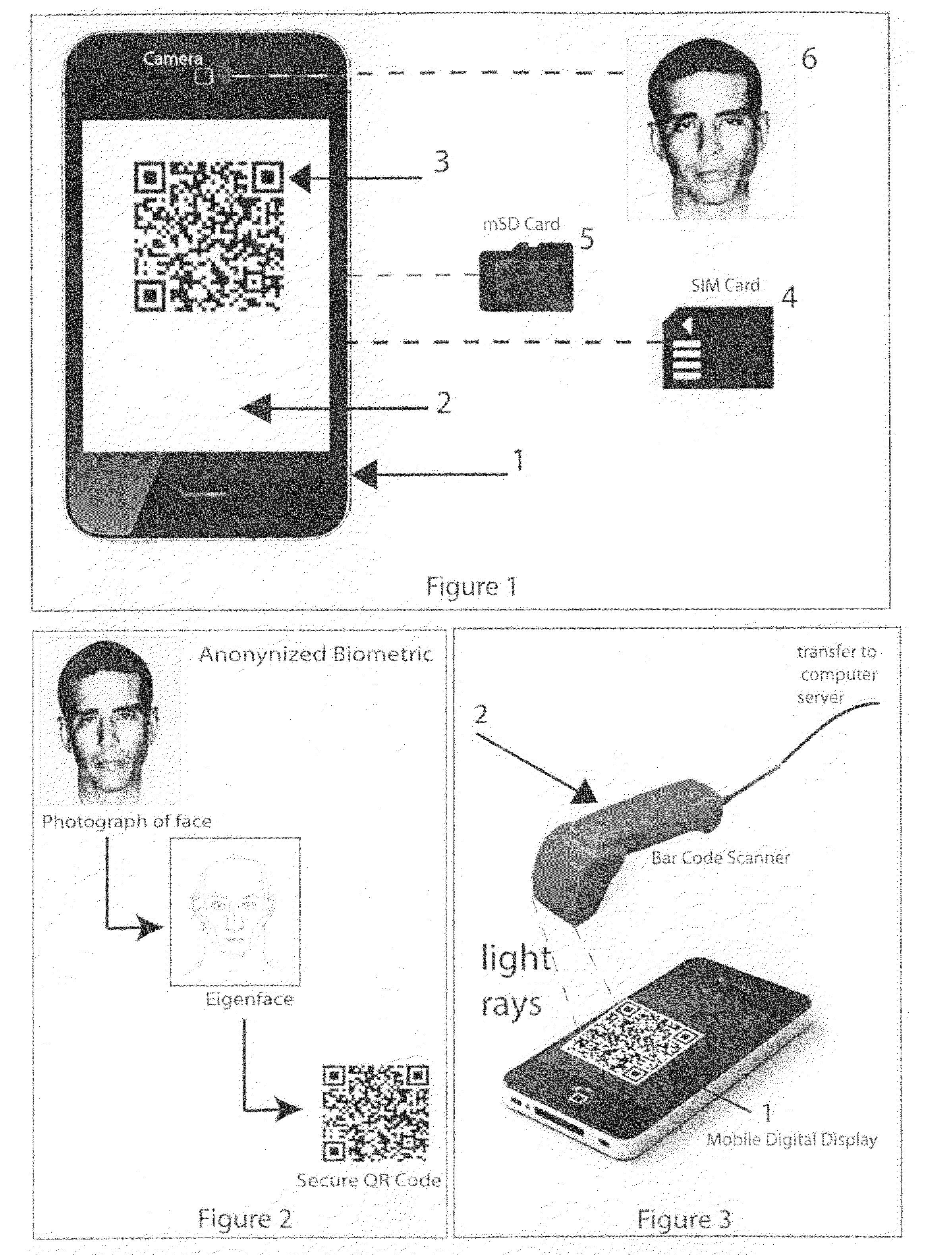
Secure two dimensional bar codes for authentication
InactiveUS20120138679A1Record carriers used with machinesVerifying markings correctnessBiometric dataPhysical Marking
The invention is a method for creating one time-use highly secure 2D barcodes, or secure two-dimensional barcodes, by utilizing machine readable physical tokens such as read only memory (ROM) or biometric data as a precursor and then applying a public key encryption algorithm and a time-stamp to otherwise standard 2D barcode generation schemas.
Owner:YODO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com