Patents
Literature
259 results about "Hardware security module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
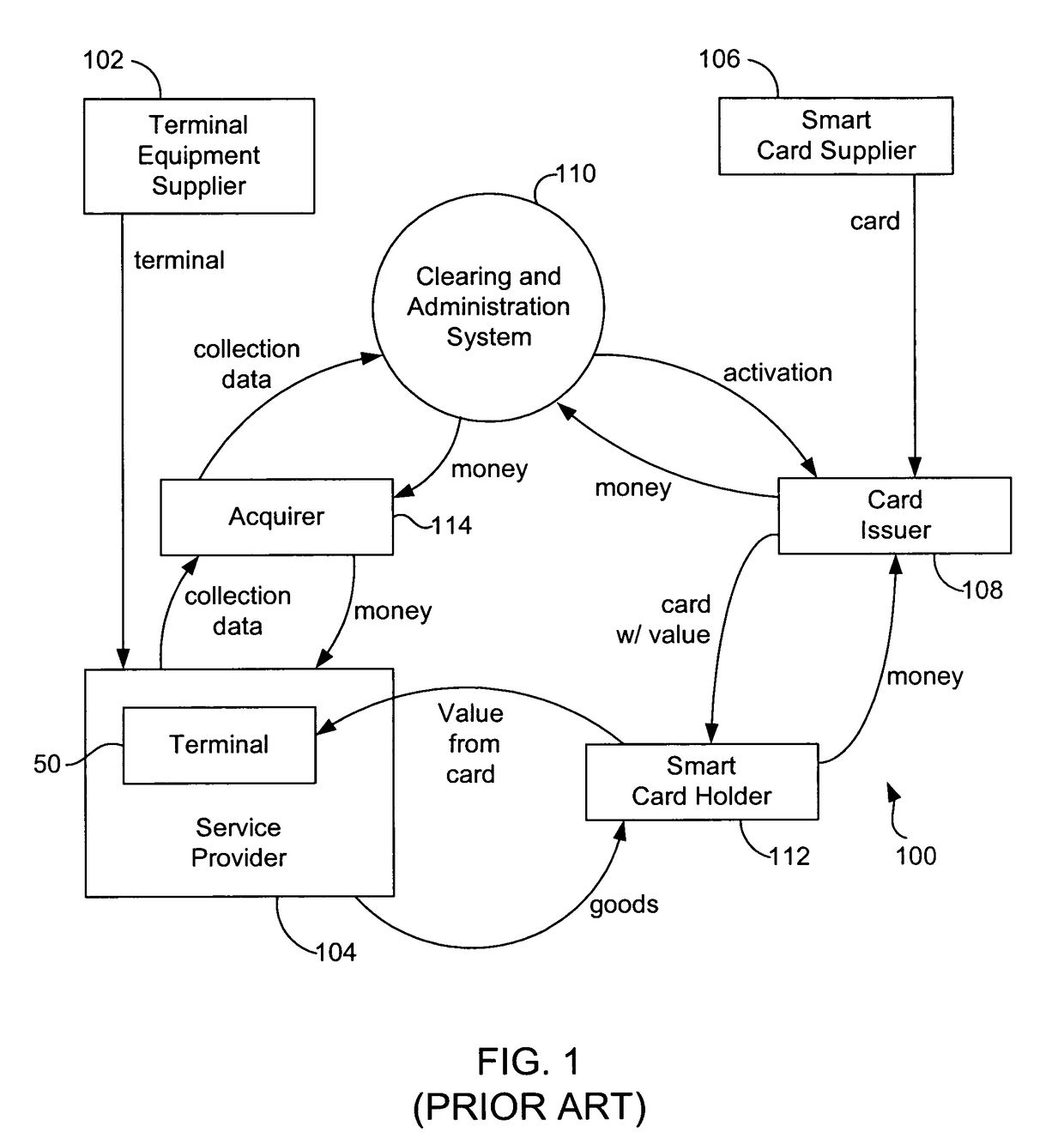
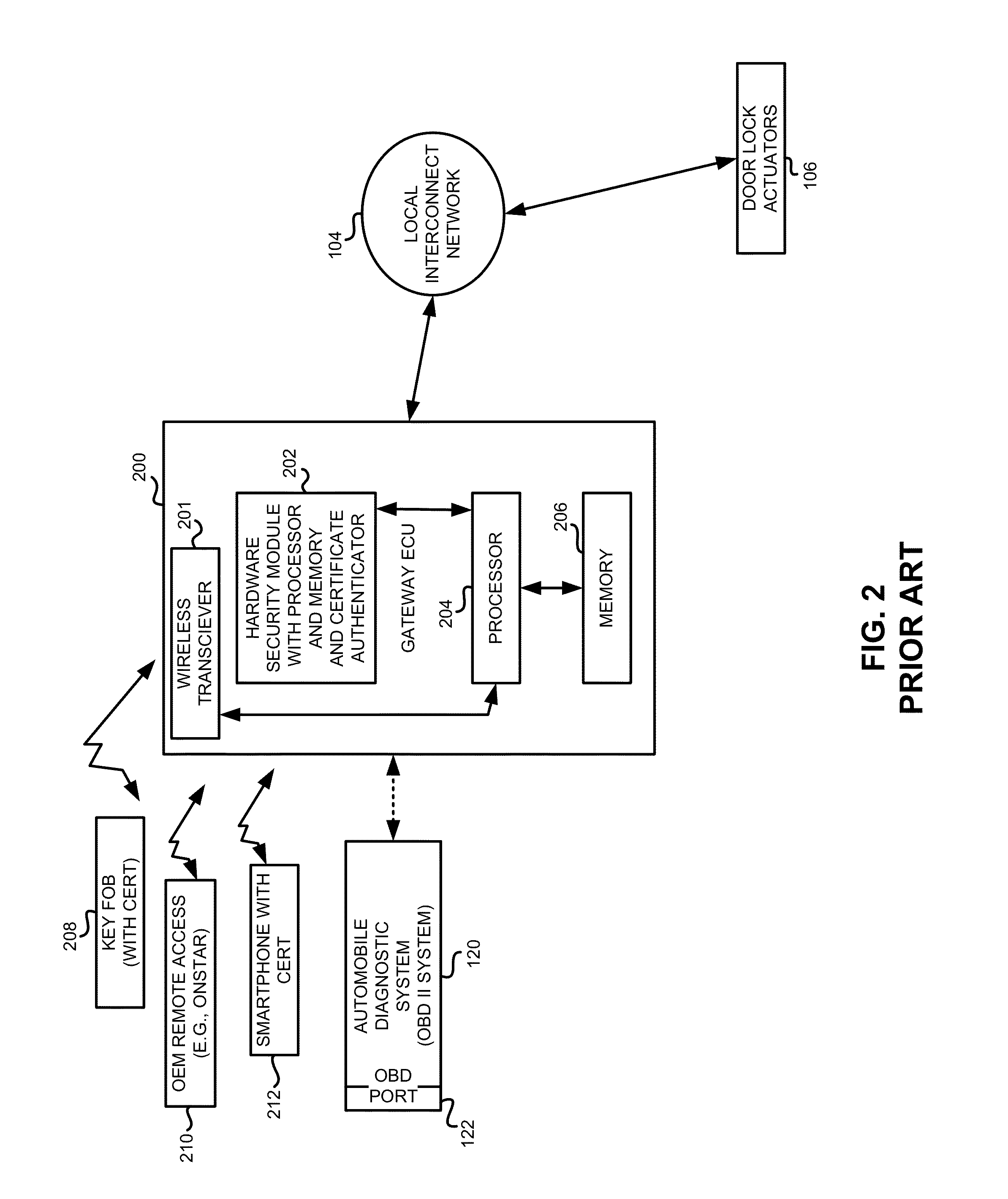
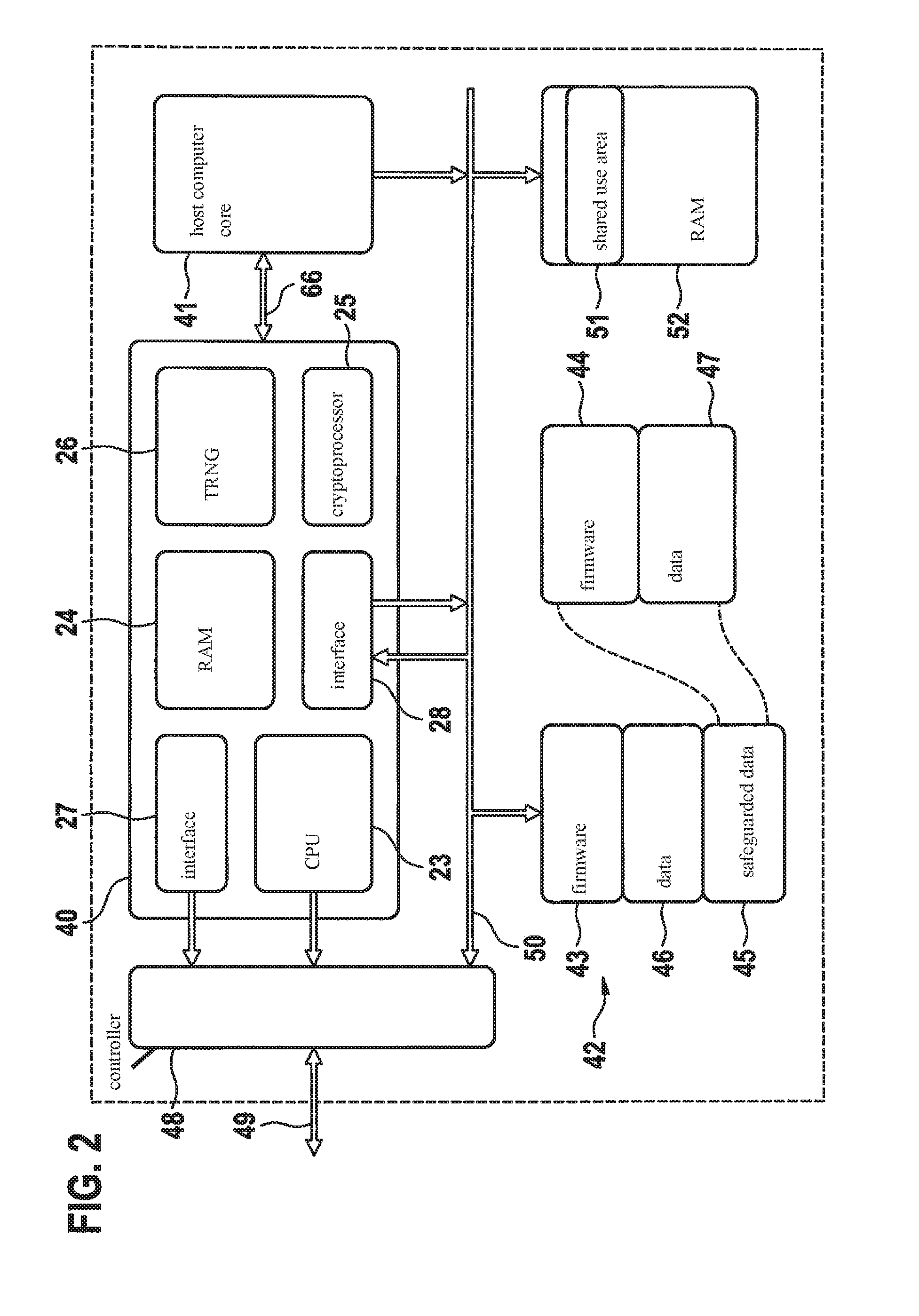
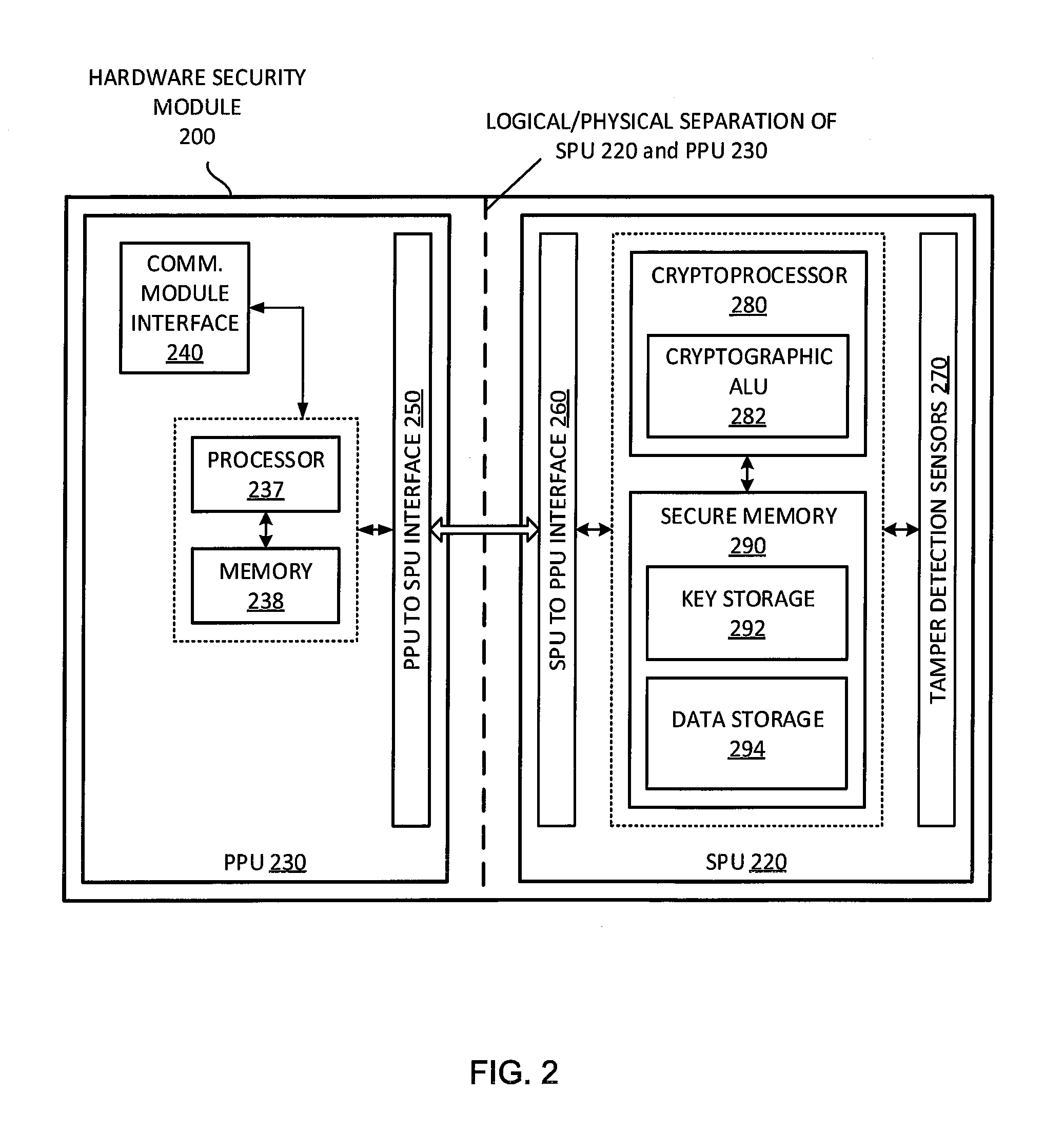
A hardware security module (HSM) is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips.
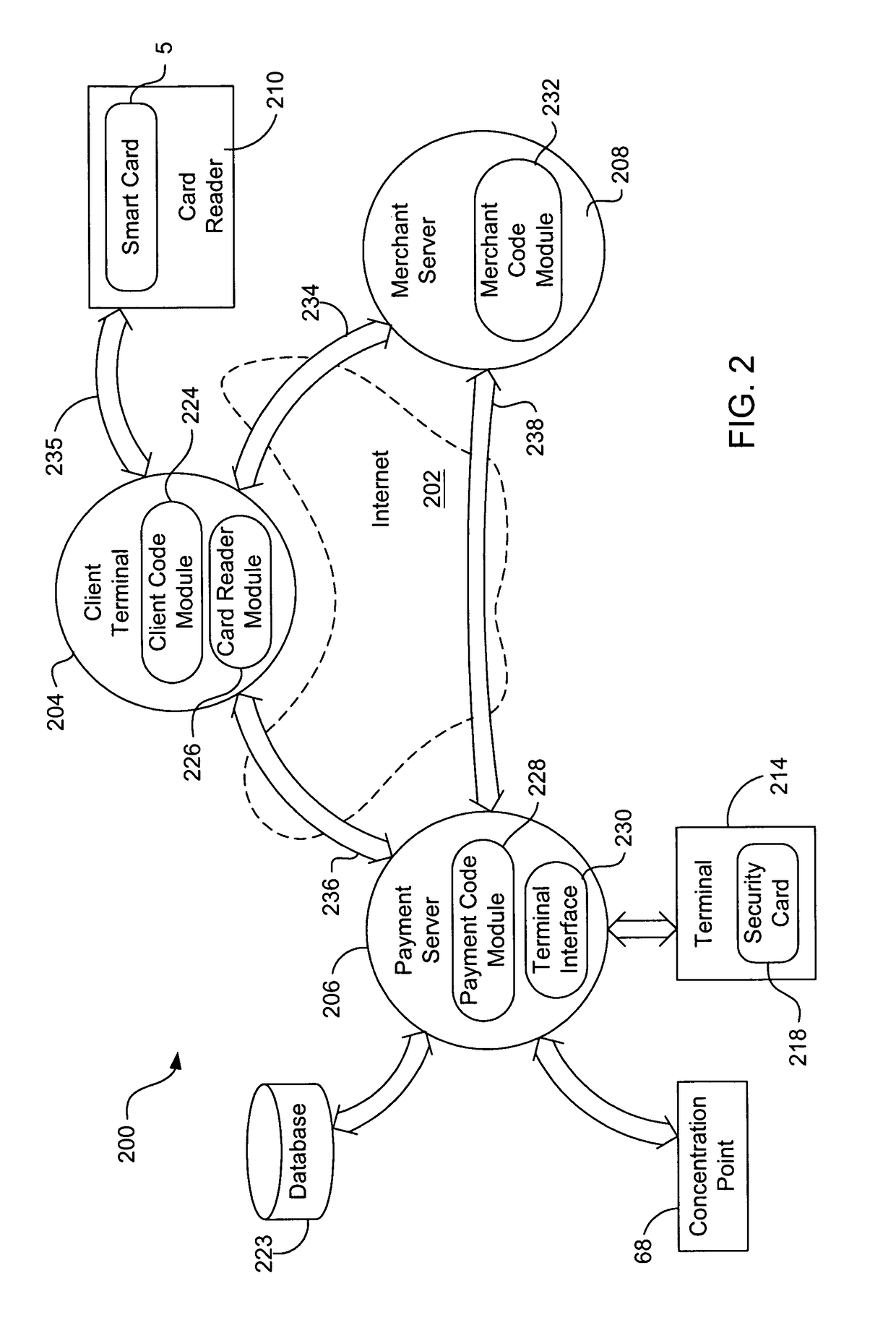
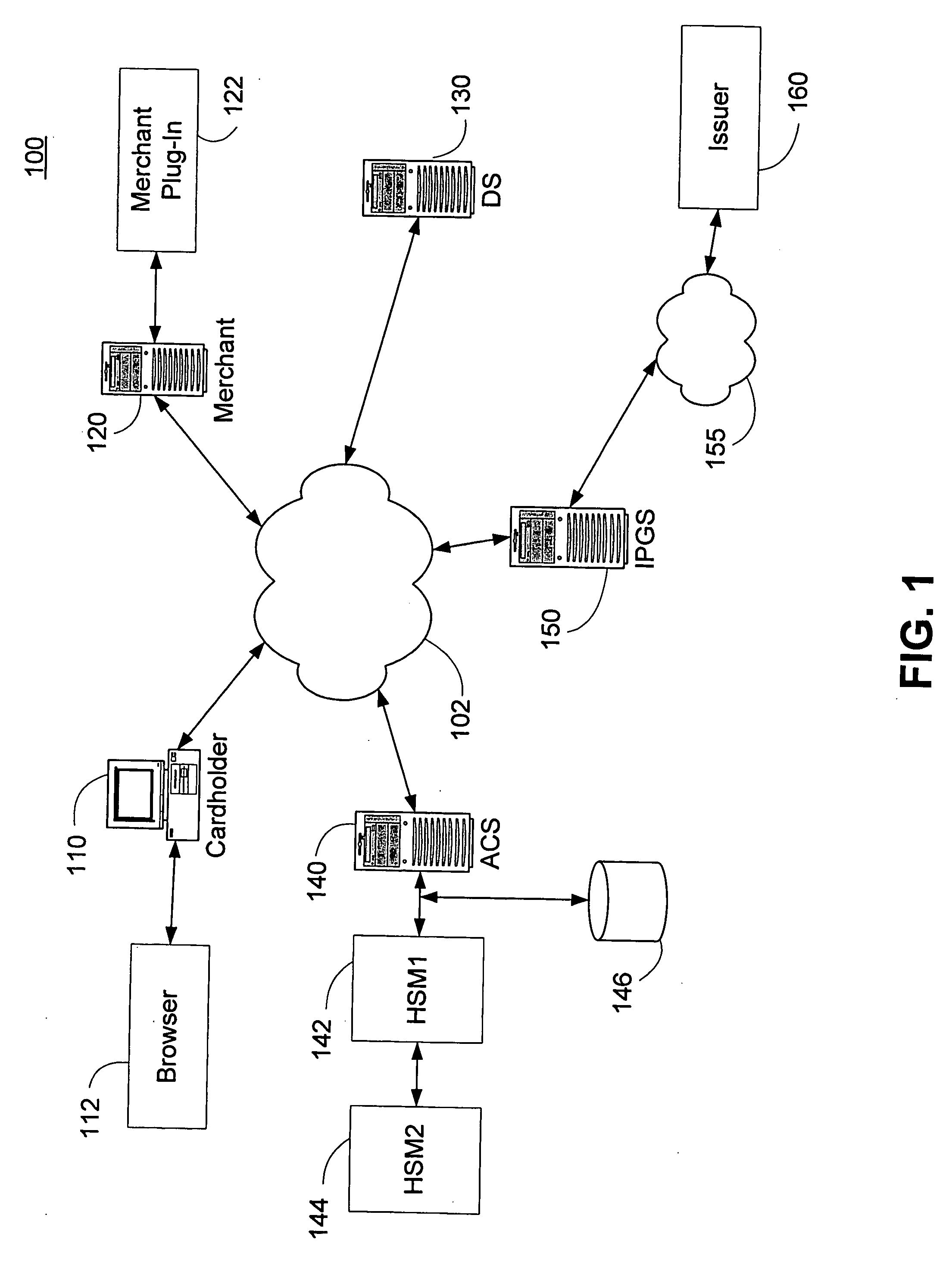
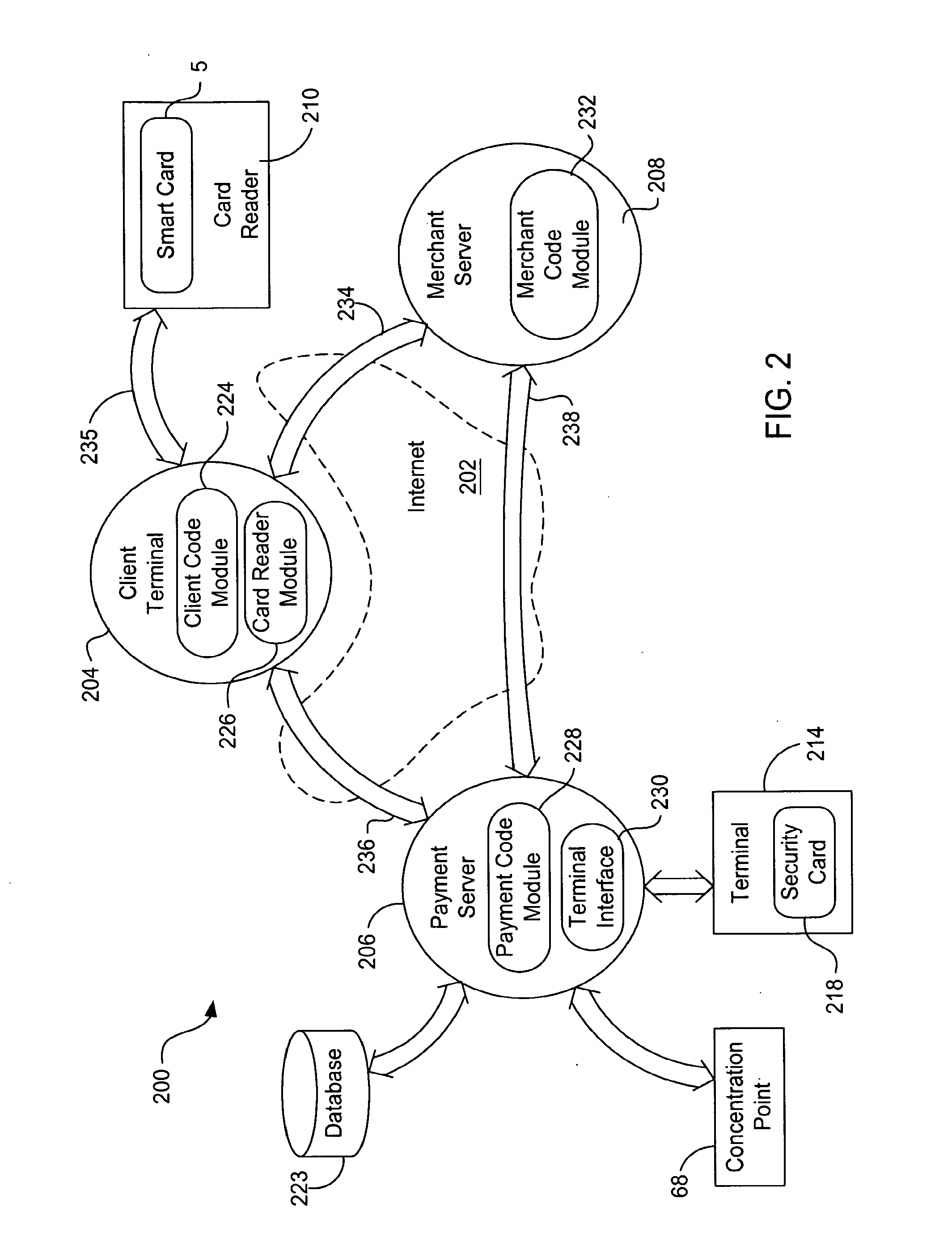
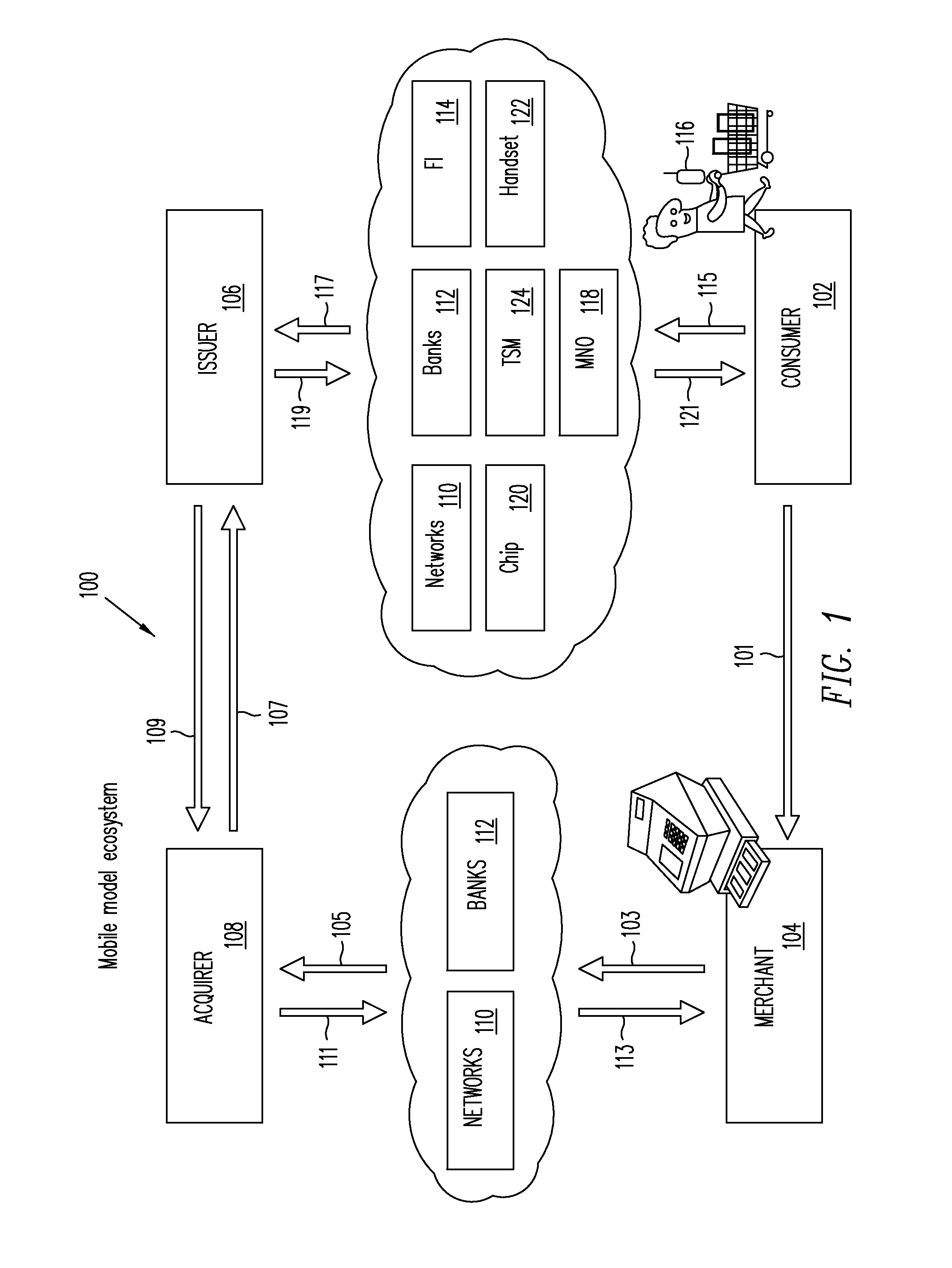
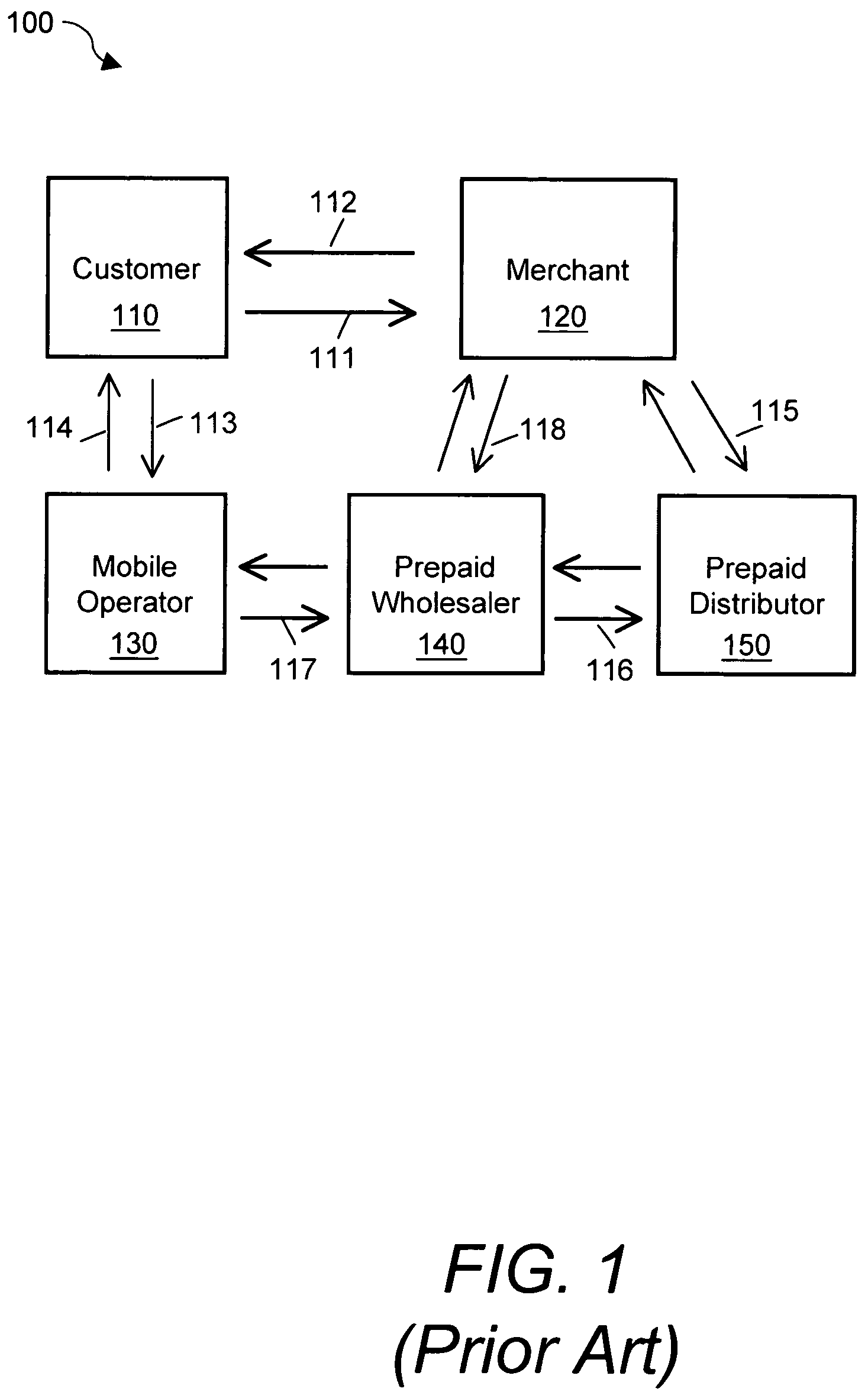
Internet payment, authentication and loading system using virtual smart card
InactiveUS7908216B1Advantageous for small dollar amount transactionMinimal timeFinancePayment circuitsMerchant servicesPayment
A system loads, authenticates and uses a virtual smart card for payment of goods and / or services purchased on-line over the Internet. An online purchase and load (OPAL) server includes a virtual smart card data base that has a record of information for each smart card that it represents for a user at the behest of an issuer. The server includes a smart card emulator that emulates a smart card by using the card data base and a hardware security module. The emulator interacts with a pseudo card reader module in the server that imitates a physical card reader. The server also includes a client code module that interacts with the pseudo card reader and a remote payment or load server. A pass-through client terminal presents a user interface and passes information between the OPAL server and a merchant server, and between the OPAL server and a bank server. The Internet provides the routing functionality between the client terminal and the various servers. A merchant advertises goods on a web site. A user uses the client terminal to purchase goods and / or services from the remote merchant server. The payment server processes, confirms and replies to the merchant server. The payment server is also used to authenticate the holder of a virtual card who wishes to redeem loyalty points from a merchant. To load value, the client terminal requests a load from a user account at the bank server. The load server processes, confirms and replies to the bank server.
Owner:VISA INT SERVICE ASSOC
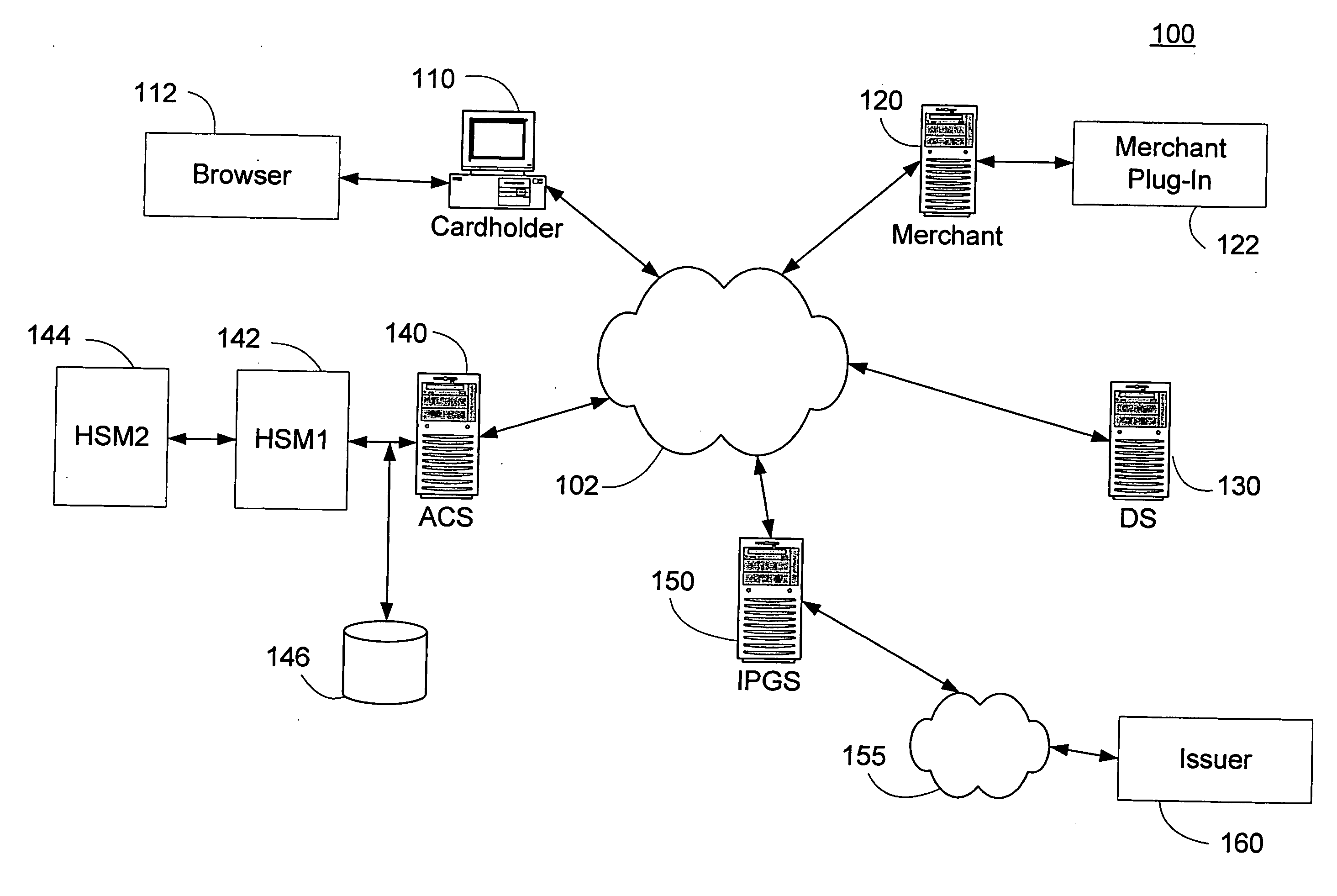
Method and system for secure authentication
ActiveUS20050036611A1Digital data processing detailsMultiple digital computer combinationsPaymentTelecommunications link
A system and method configured to provide secure Personal Identification Number (PIN) based authentication is disclosed. A passcode or PIN associated with a customer value card can be securely authenticated by an issuer prior to authorizing payment. An Access Control Server (ACS) can receive the PIN or passcode from a customer via a secure connection over a public network. The ACS can generate an encrypted PIN and can communicate the encrypted PIN to a remote issuer for authentication. The ACS can use one or more hardware security modules to generate the encrypted PIN. The hardware security modules can be emulated in software or implemented in hardware. The system can be configured such that the PIN is not exposed in an unencrypted form in a communication link or in hardware other than the originating customer terminal.
Owner:VISA USA INC (US)
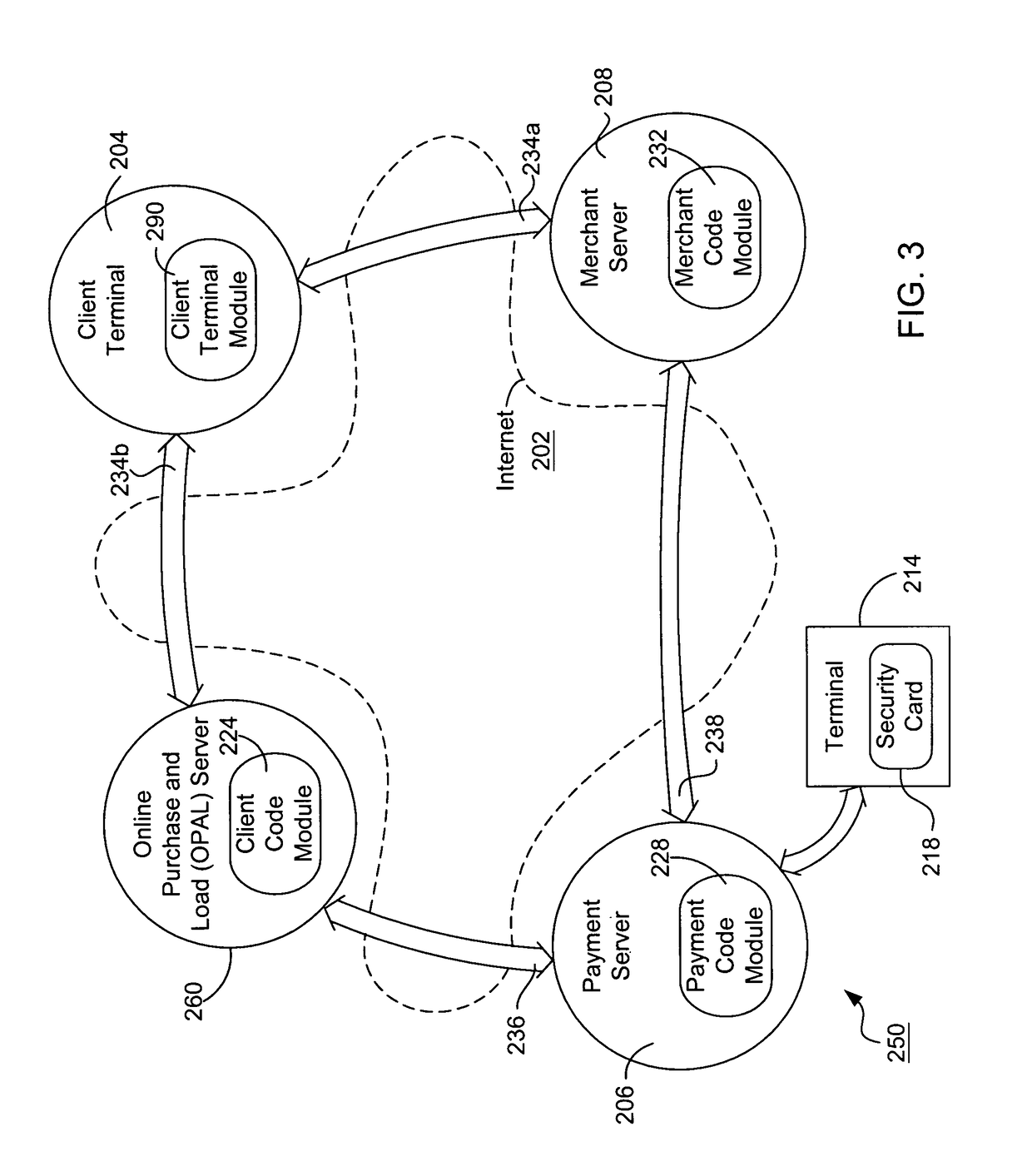
Internet Payment, Authentication And Loading System Using Virtual Smart Card
InactiveUS20110125638A1The process is convenient and fastAdvantageous for small dollar amount transactionFinancePayment circuitsMerchant servicesWeb site
A system loads, authenticates and uses a virtual smart card for payment of goods and / or services purchased on-line over the Internet. An online purchase and load (OPAL) server includes a virtual smart card data base that has a record of information for each smart card that it represents for a user at the behest of an issuer. The server includes a smart card emulator that emulates a smart card by using the card data base and a hardware security module. The emulator interacts with a pseudo card reader module in the server that imitates a physical card reader. The server also includes a client code module that interacts with the pseudo card reader and a remote payment or load server. A pass-through client terminal presents a user interface and passes information between the OPAL server and a merchant server, and between the OPAL server and a bank server. The Internet provides the routing functionality between the client terminal and the various servers. A merchant advertises goods on a web site. A user uses the client terminal to purchase goods and / or services from the remote merchant server. The payment server processes, confirms and replies to the merchant server. The payment server is also used to authenticate the holder of a virtual card who wishes to redeem loyalty points from a merchant. To load value, the client terminal requests a load from a user account at the bank server. The load server processes, confirms and replies to the bank server.
Owner:VISA INT SERVICE ASSOC
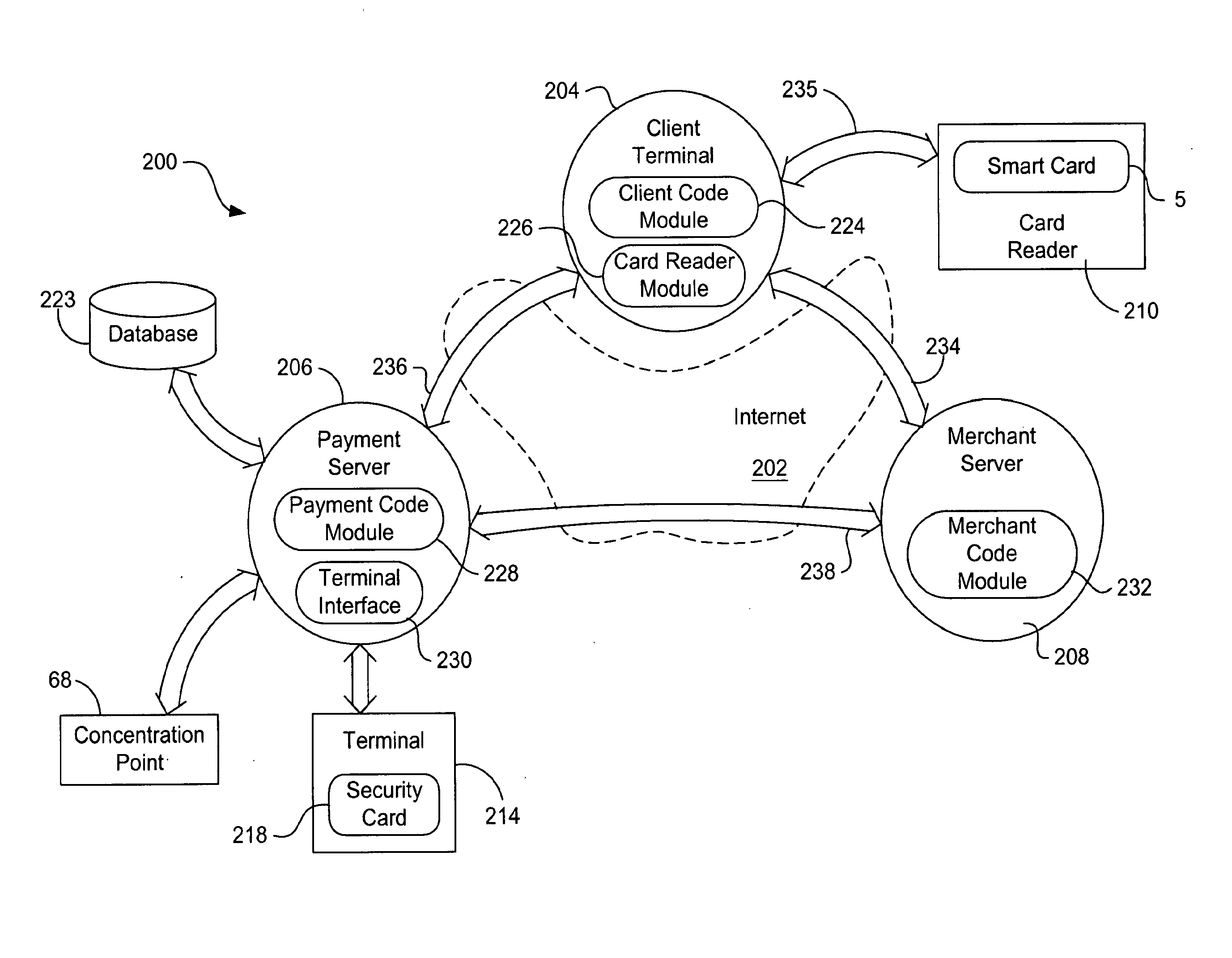
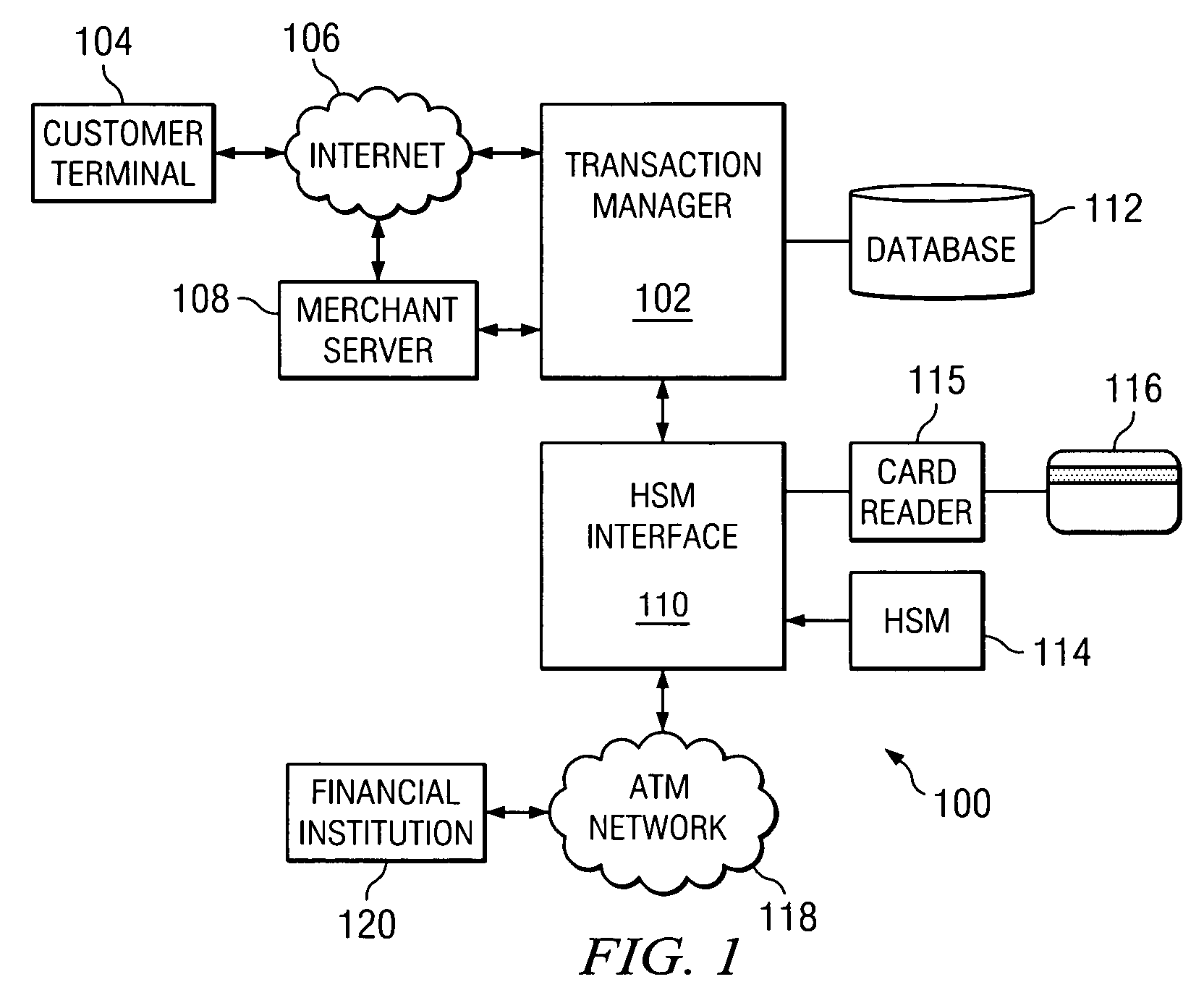
System and method for electronic check verification over a network
A method is disclosed of authenticating a consumer and authorizing a transaction over a network. The method includes first requesting, by a user, performance of a transaction between said user and a merchant, the user and the merchant performing the transaction over a non-secure web page. The user then enters transaction request information into a non-secure general purpose computer, and then enters a PIN into a graphic interface of the non-secure web page on the non-secure general purpose computer. providing, by the non-secure general purpose computer, the transaction request information and a PIN data package, the PIN data package being a digital representation of an impression of the users selection of at least one graphic image representing their PIN to a secure transaction manager via an internet system. The transaction manager then combines at least one of dynamic and corollary data with the PIN data package and securely provides the combination to a hardware security module (HSM). The HSM then distills the PIN data package into a PIN and encrypting the PIN into a PIN Block. Thereafter; the remainder of the transaction is performed.
Owner:ACCULLINK
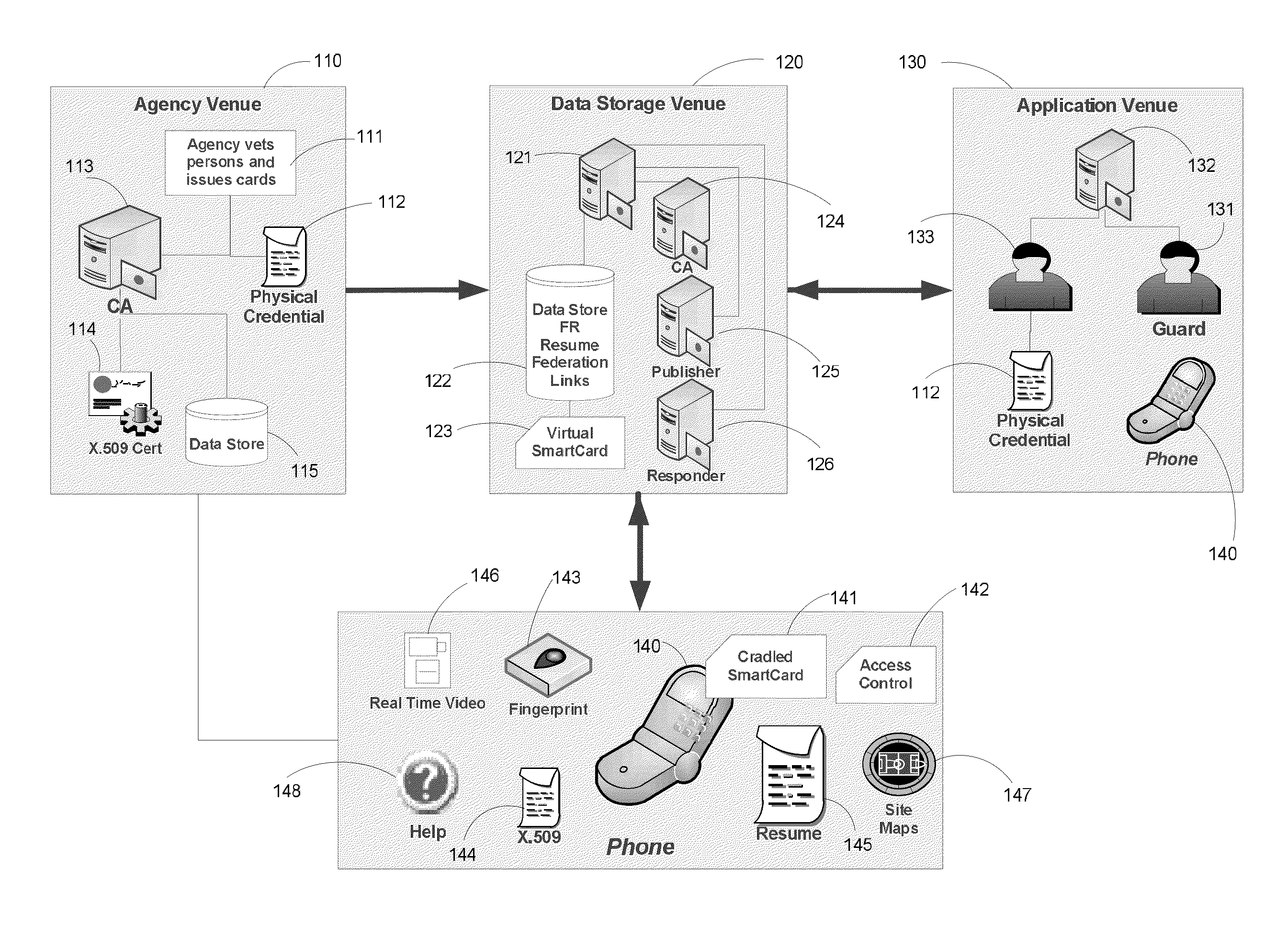
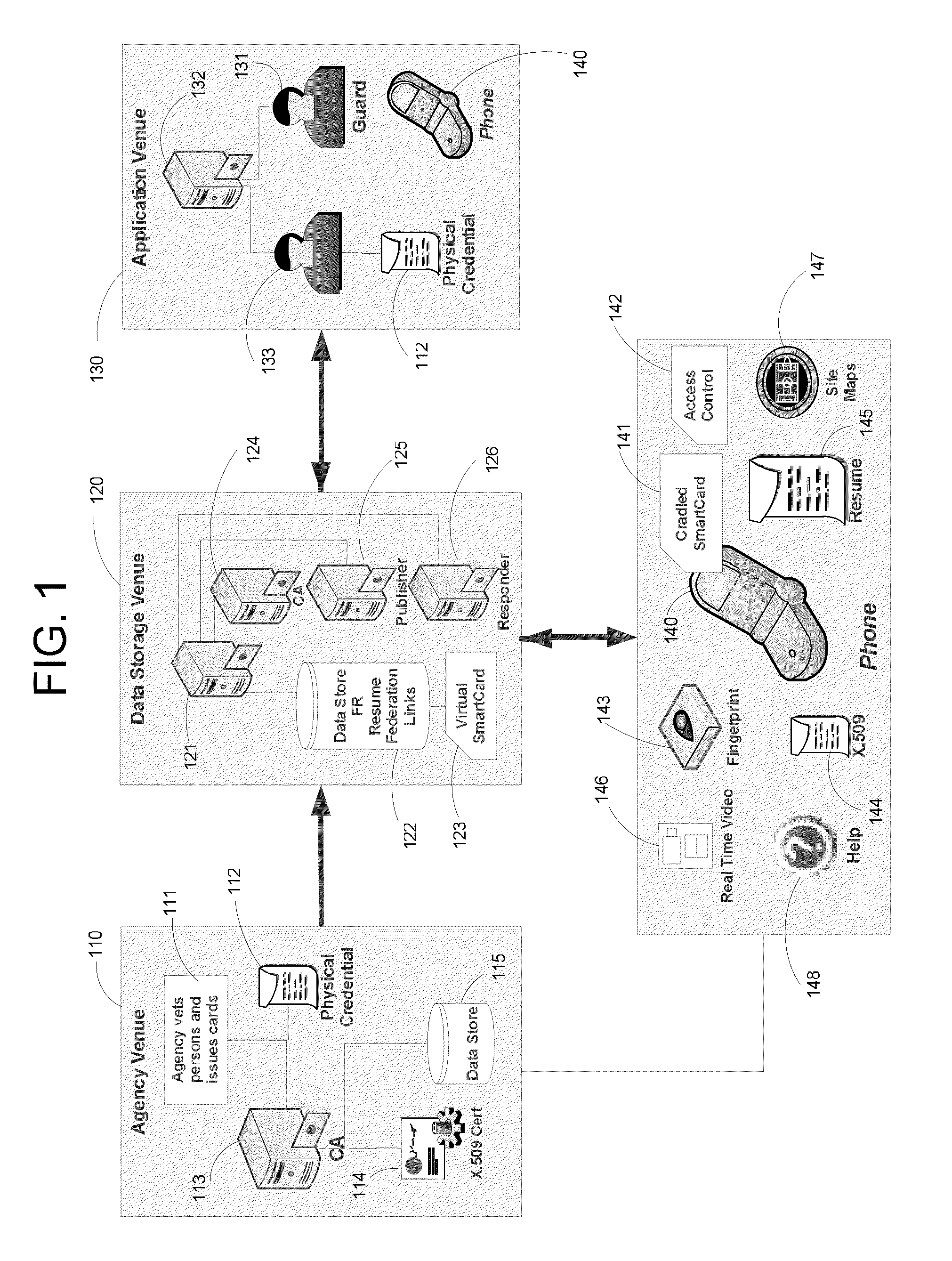
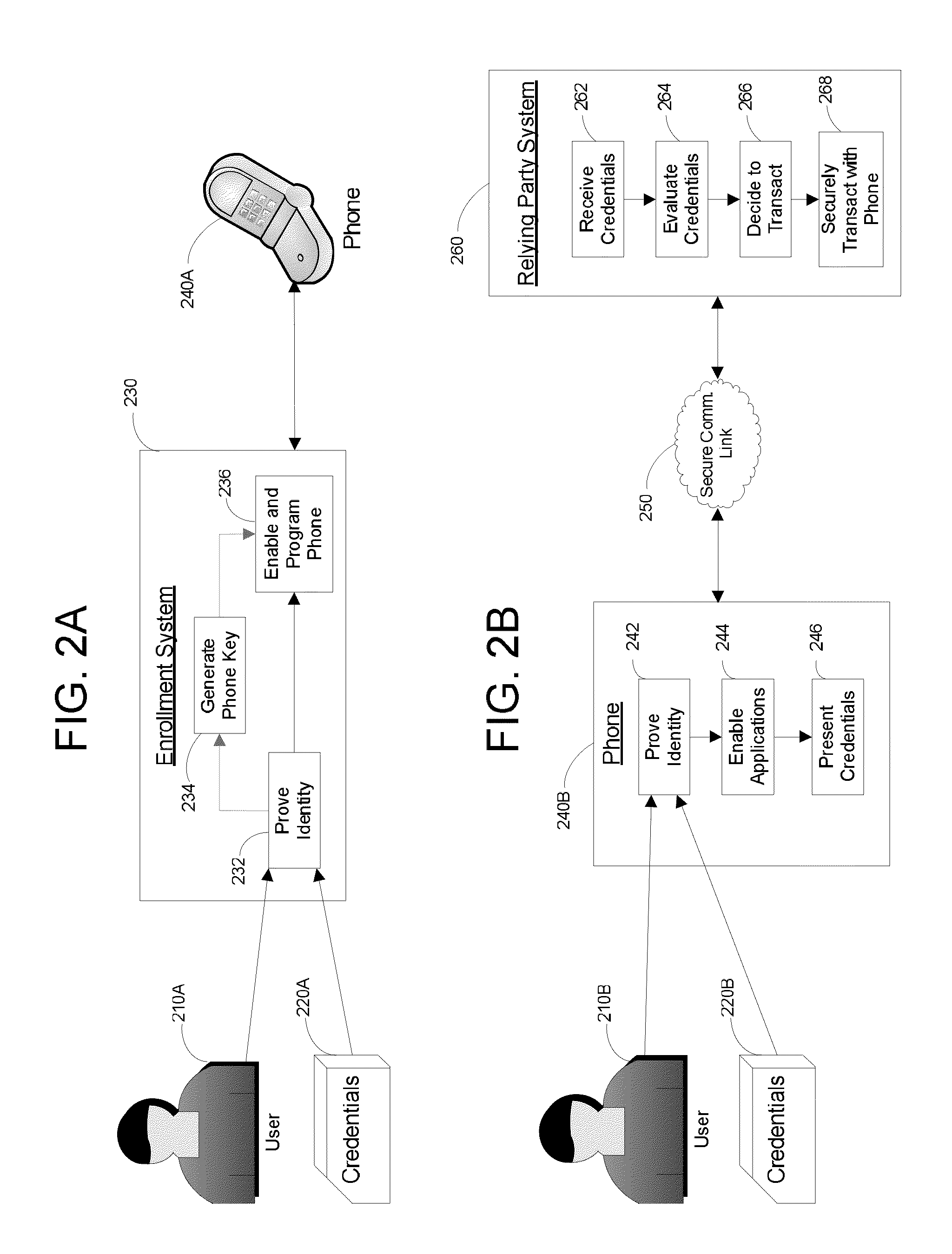
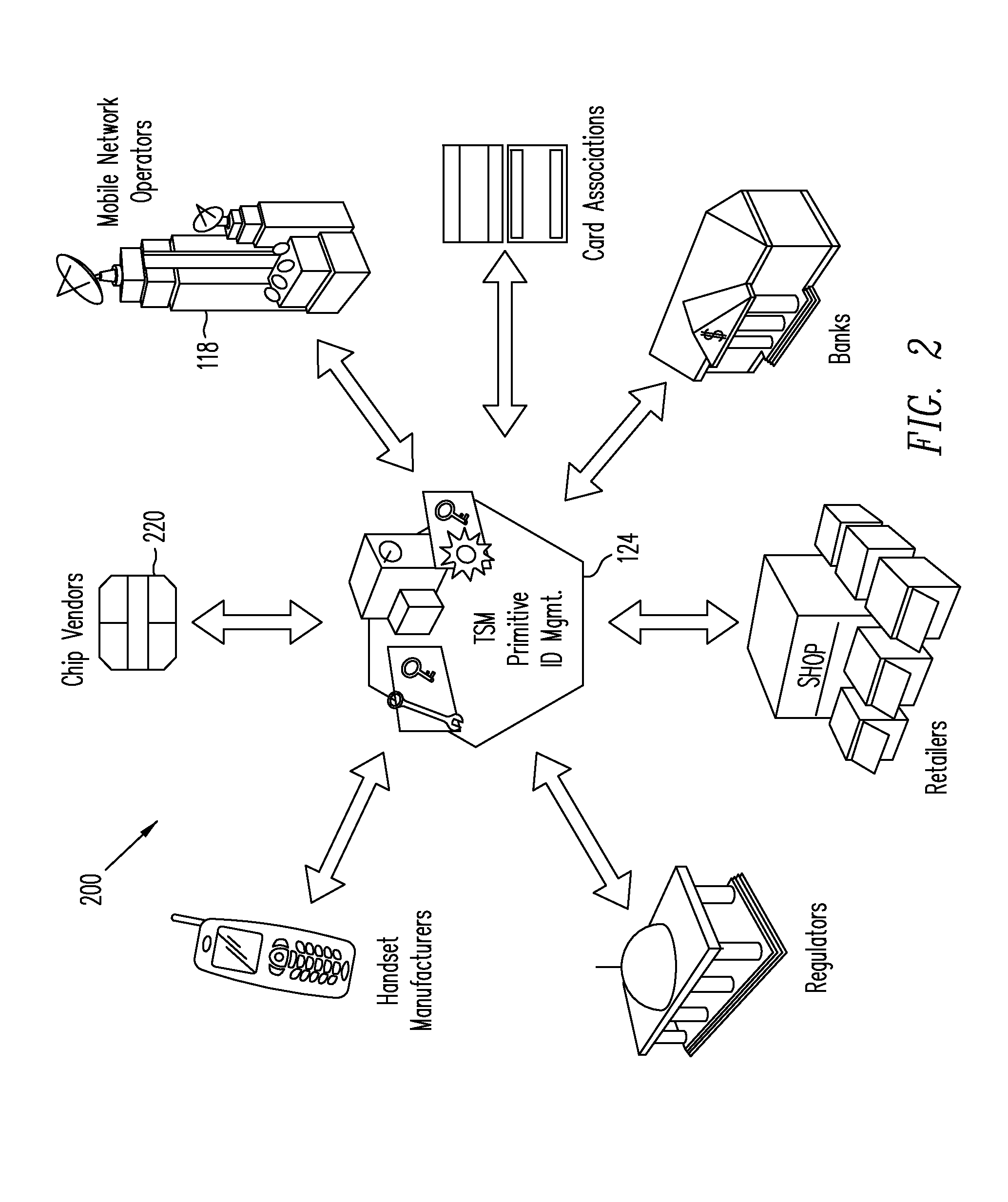
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20130061055A1Reduce computing power requirementsIncrease the number ofDigital data processing detailsUser identity/authority verificationCredit cardHardware security module
A virtual smartcard and methods for creating the same are provided. A virtual smartcard is a set of computer-implemented processes, associated with an individual, which simulate the behavior of a physical smartcard or other authentication token containing a hardware security module. In one embodiment, a computer receives credential data derived from the physical credential and authentication data pertinent to the individual such as a biometric imprint, and creates a virtual smartcard by storing the credential data in association with the authentication data in a network storage. The credential data may later be used for identification and encryption purposes upon the individual providing the authentication data to the network storage, even if the physical credential itself has been lost. Thus, the virtual smartcard provides a network-based method for backing up a passport, driver's license, credit card, public transportation card, or other such identification card or device.
Owner:INFERSPECT
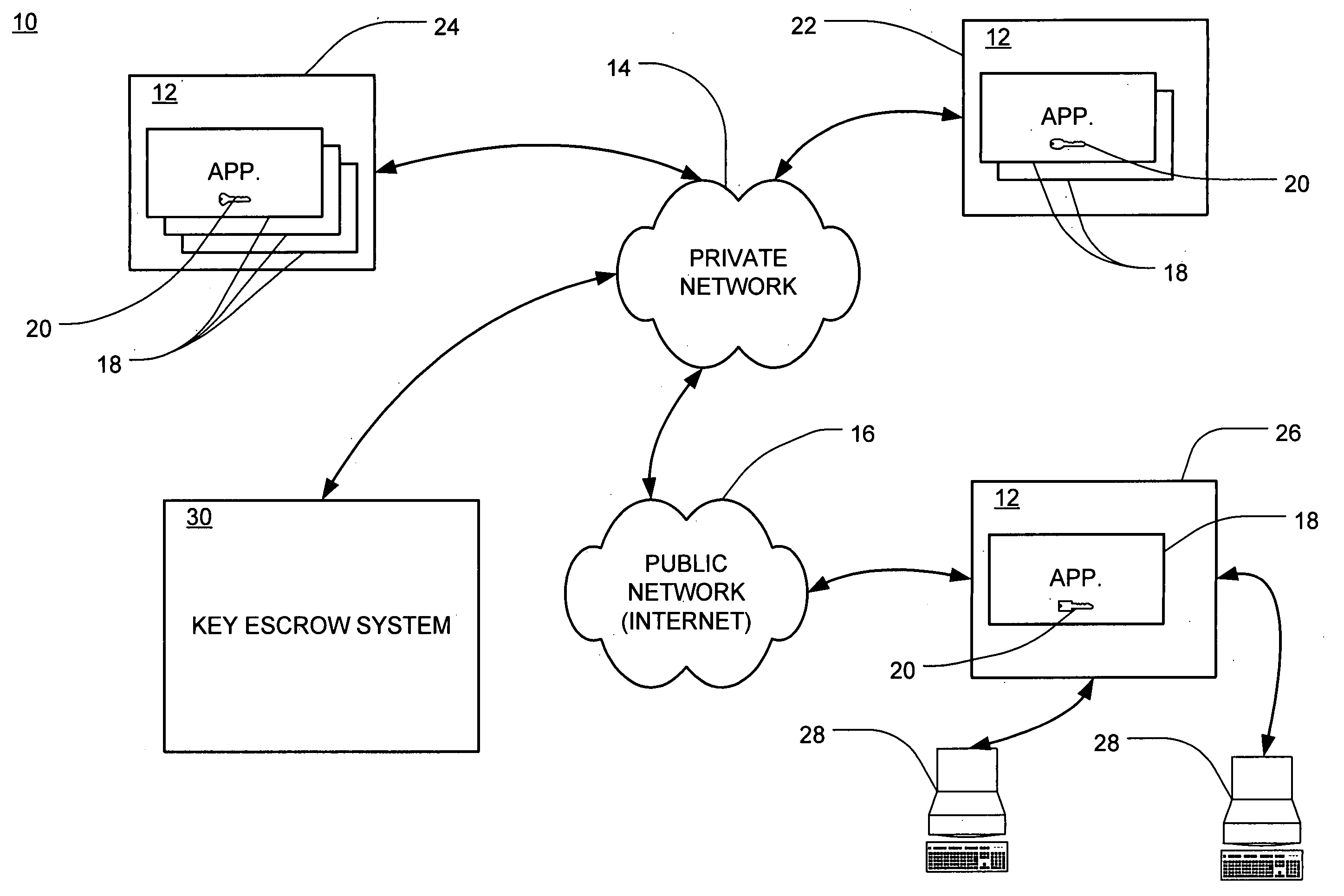
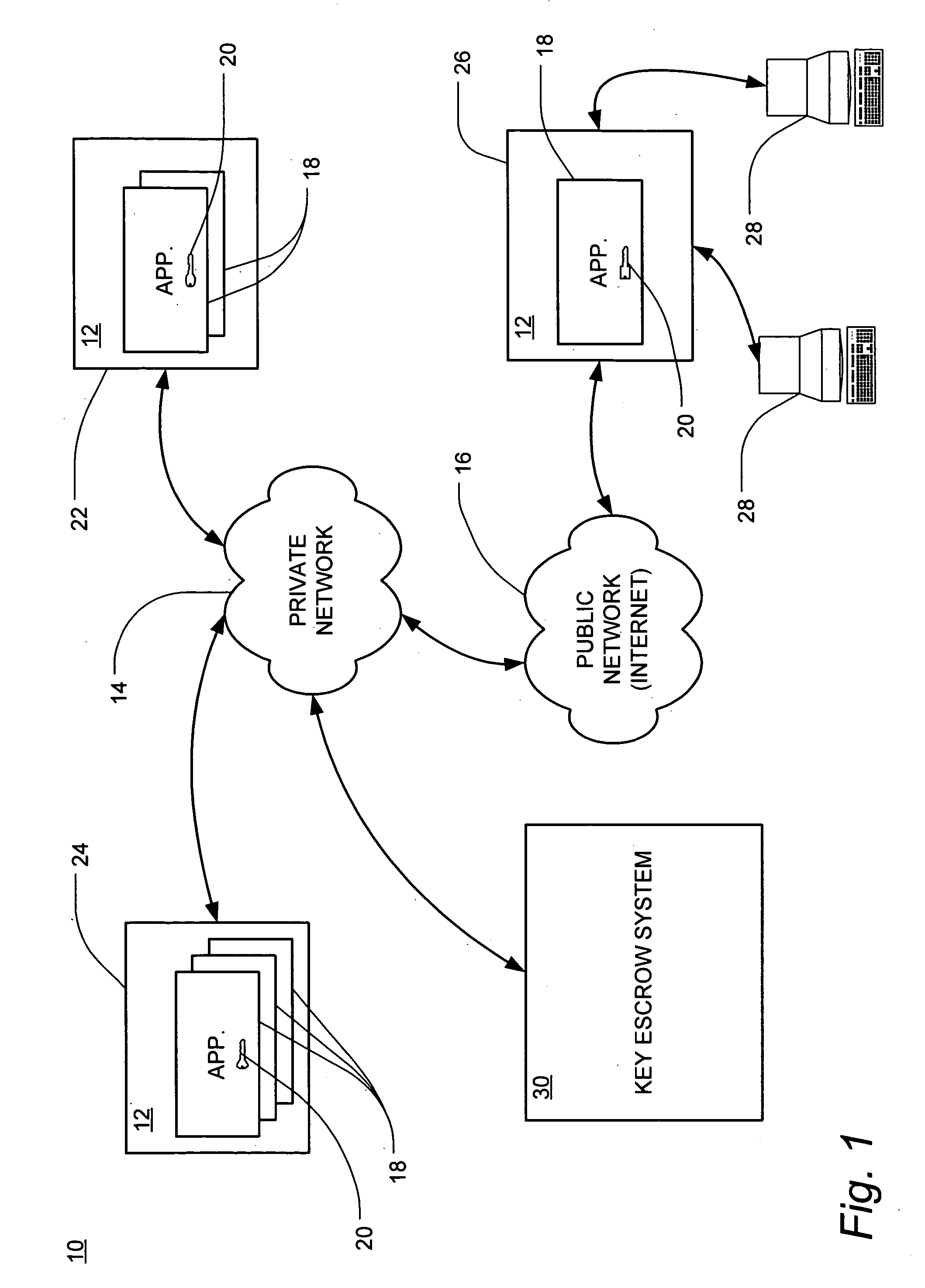
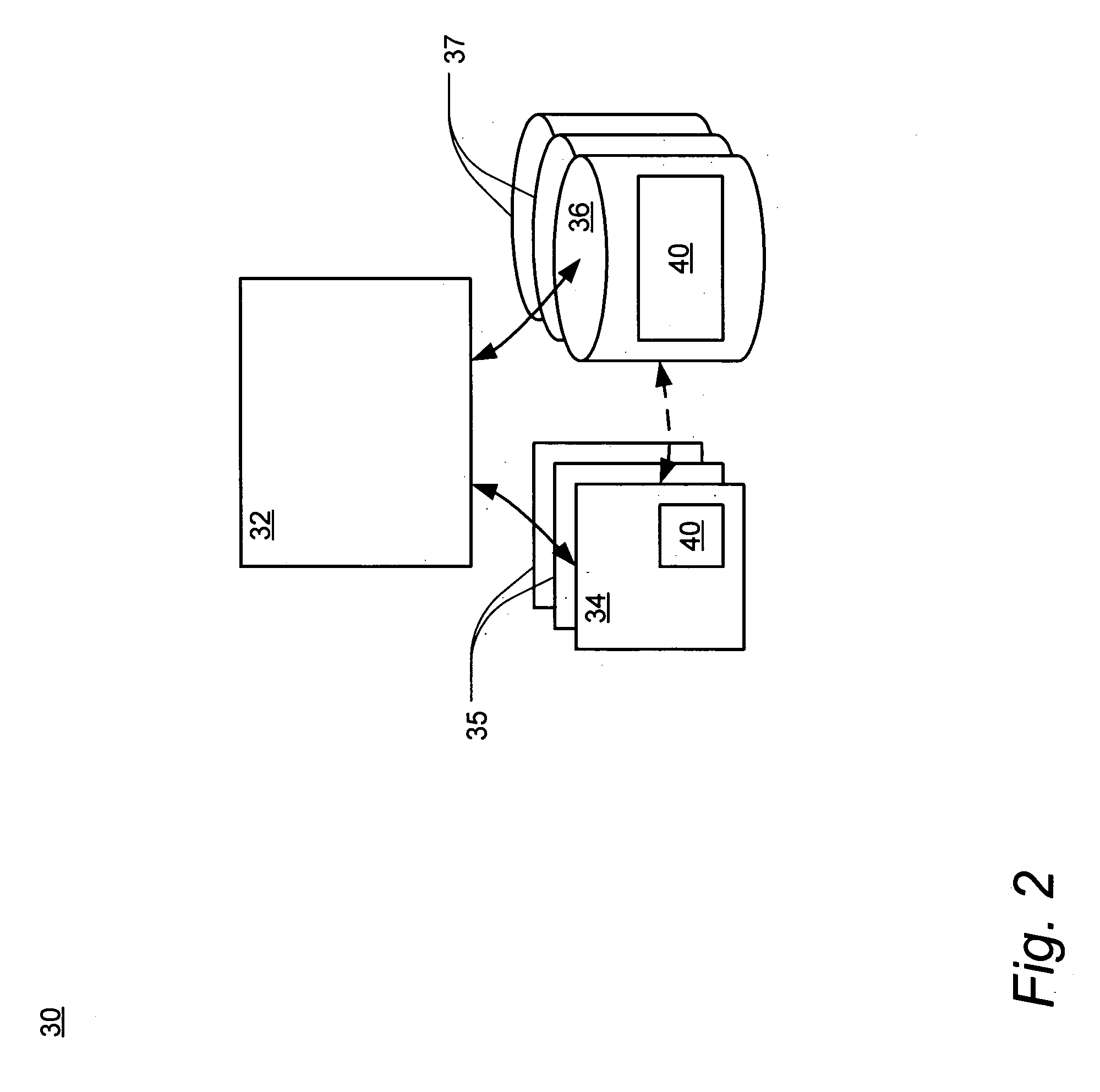
Cryptographic key backup and escrow system
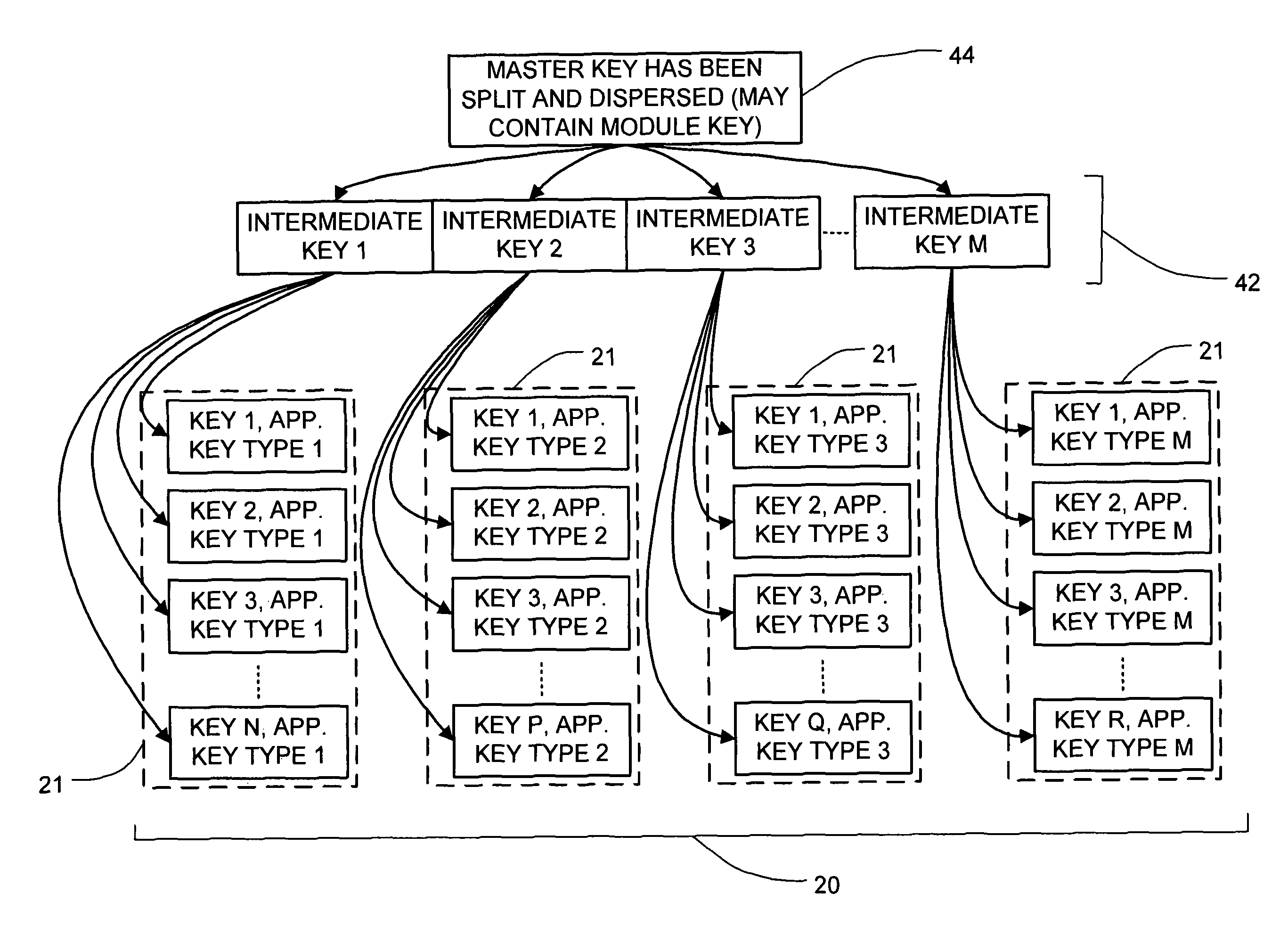
ActiveUS20050138374A1Verify integrityKey distribution for secure communicationHardware security moduleMaster key
A system for securely storing application keys is comprised of a database system, a peripheral hardware security module and cryptographic keys, wherein cryptographic keys comprise application keys, intermediate keys and a master key. Application keys are grouped according to characteristic and are associated with a particular intermediate key, which is utilized to scramble and descramble application keys within the associated group. Intermediate keys are associated with the master key, which is utilized to scramble and descramble the intermediate keys. Scrambling and descrambling of keys is performed within the peripheral hardware security module.
Owner:WELLS FARGO BANK NA
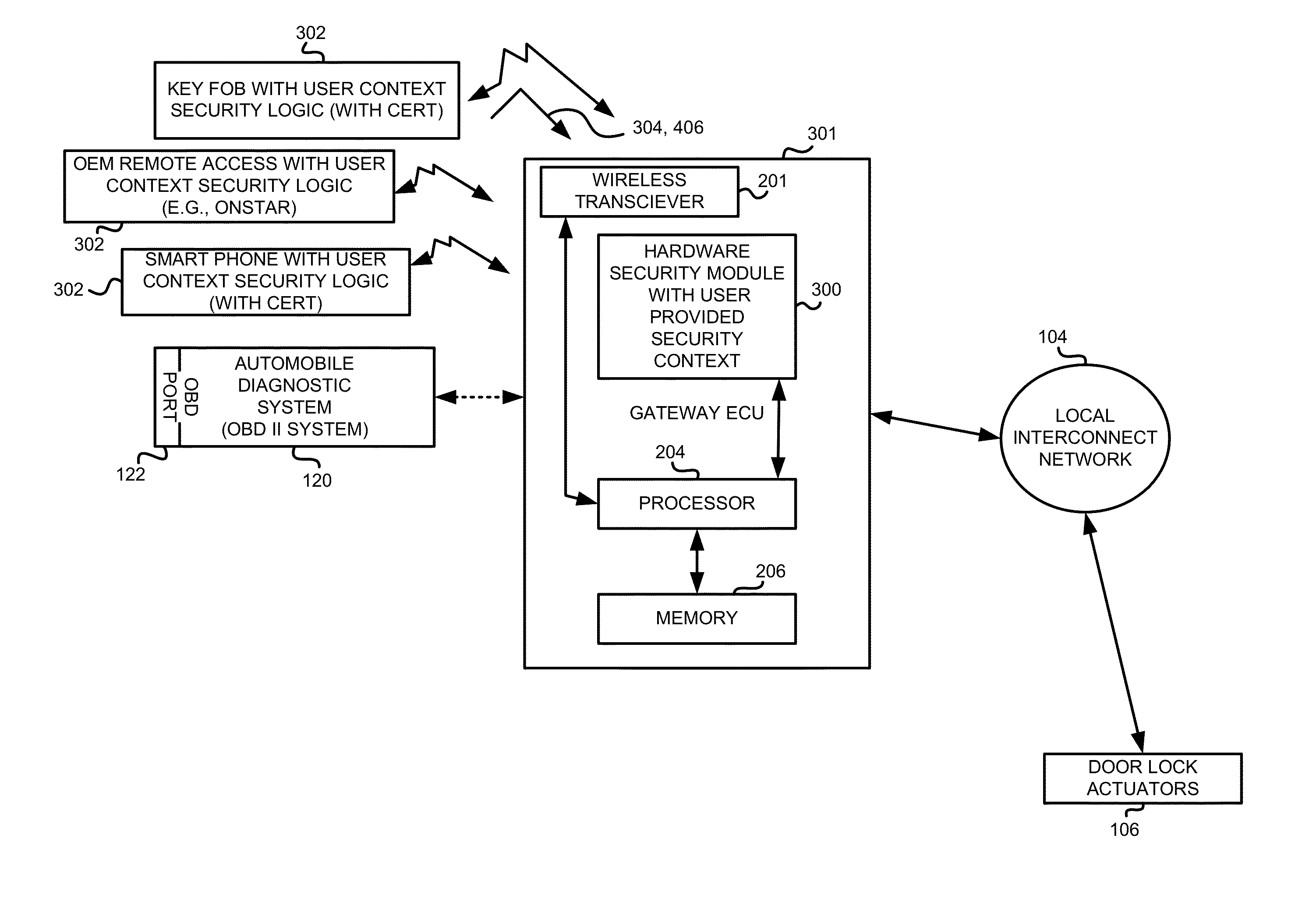
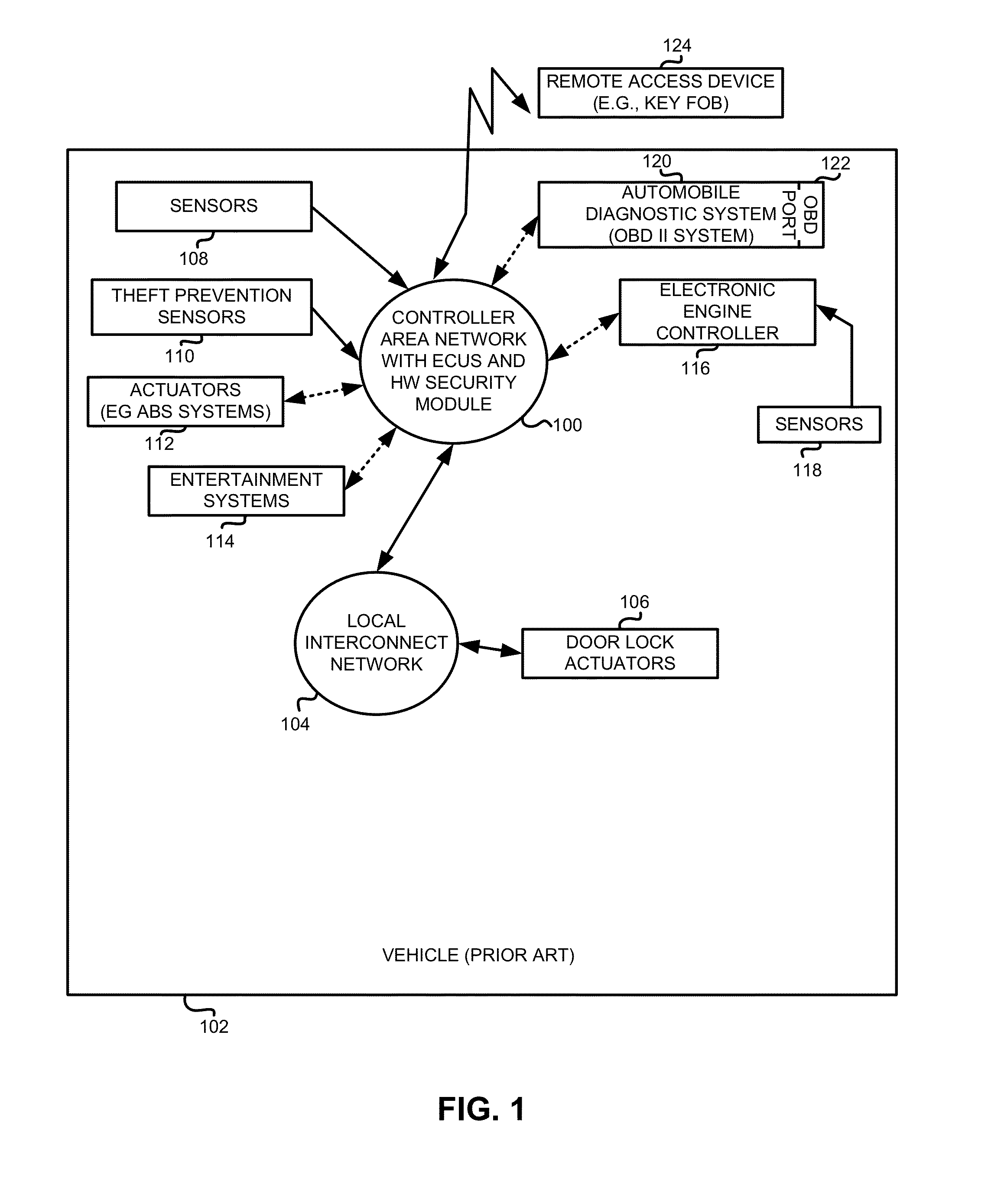
Method and apparatus for providing vehicle security
ActiveUS20160012653A1Electric signal transmission systemsRegistering/indicating working of vehiclesHardware security moduleSecurity level
Apparatus, systems and methods are disclosed that utilize a vehicle user's input to provide logical context of legitimate vehicle usage through a remote access device to defend the vehicle from theft. As such, an additional level of security is employed and may be used in addition to other security and theft prevention technologies of the vehicle. In one example, a legitimate automobile operator signals the context of the vehicle's state to a hardware security module in the vehicle. The states include, for example, to disallow all diagnostic system access or to allow diagnostic access for servicing.
Owner:ENTRUST
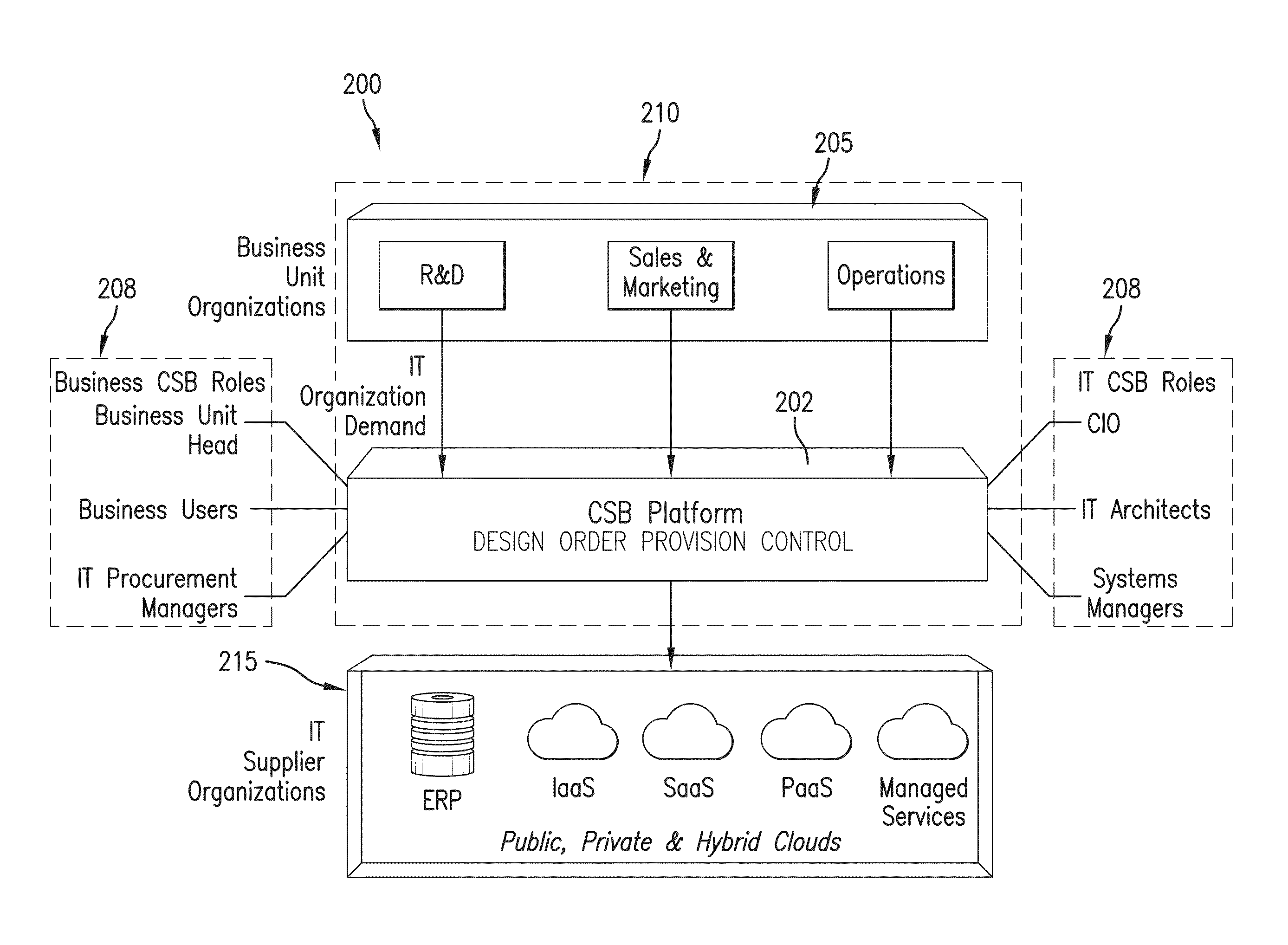
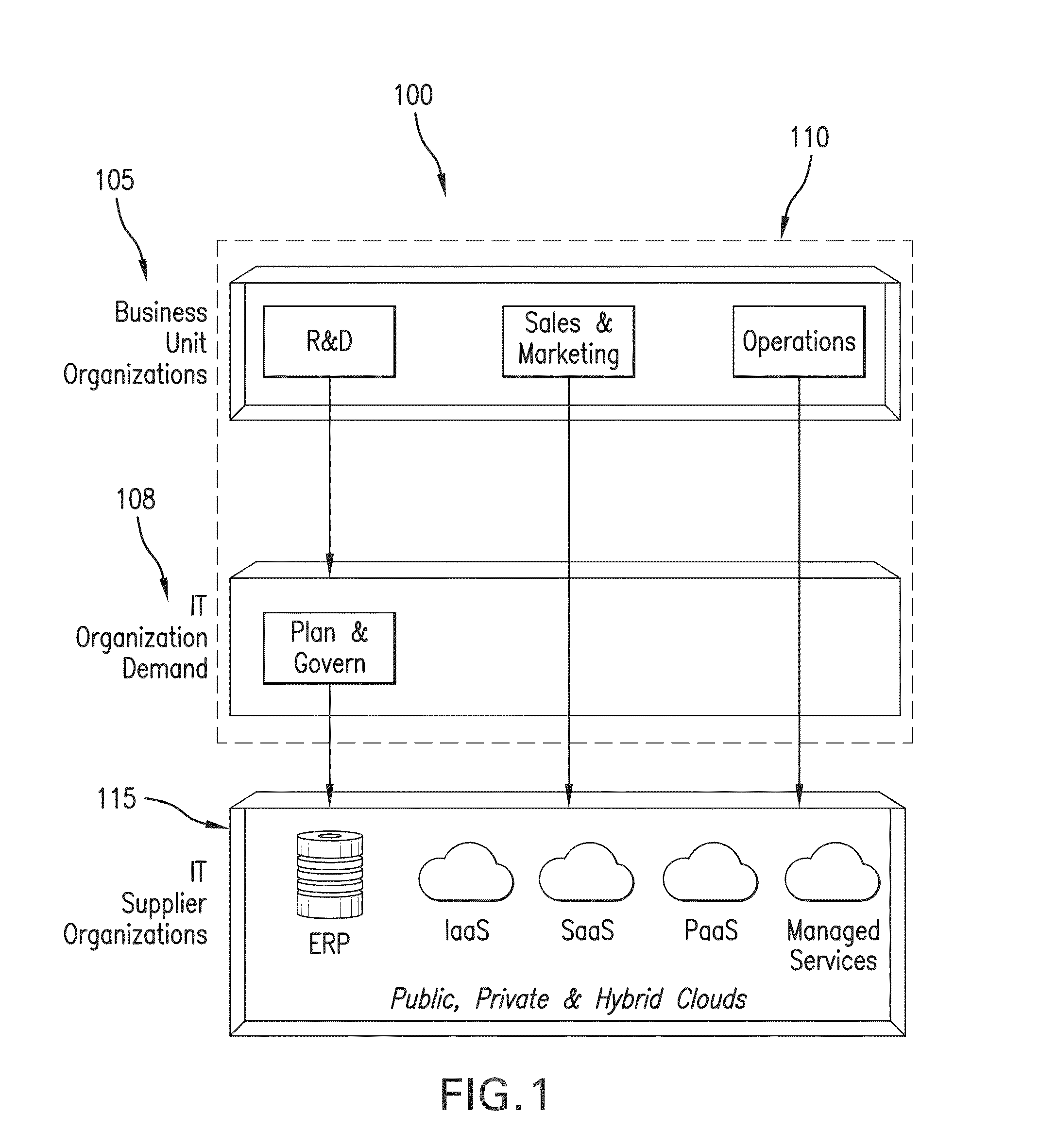
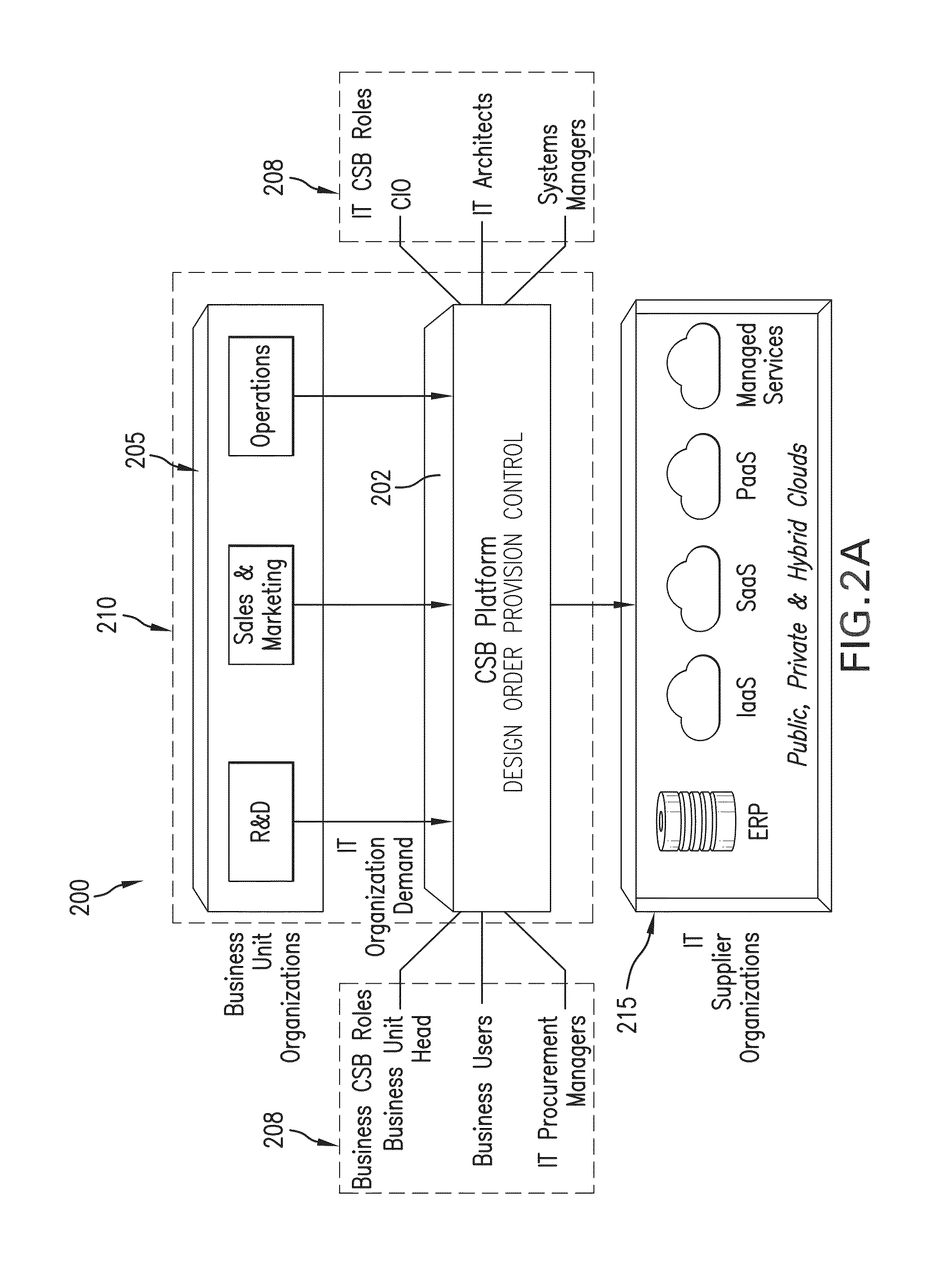
Cross provider security management functionality within a cloud service brokerage platform
ActiveUS20150188927A1Good serviceEfficient and effectiveDigital data processing detailsMultiple digital computer combinationsSystems managementHardware security module
Implementation of cross provider security in accordance with the disclosures made herein enables users of a system (e.g., a cloud services brokerage platform) in a cloud environment provides for system-managed provisioning and management of keys to cloud resources thereby allowing the user to manage data security and enable secured access to their cloud resources. To this end, cross provider security management functionality in accordance with the disclosures made herein can include provisioning system-generated keys across different regions in a provider, provisioning cloud brokerage system-generated keys across different providers; and associating (i.e., managing) the keys from the system to a hardware security module. The keys can be managed by / though a variety of different resources (e.g., brokering system, VDC, user group concepts, etc).
Owner:HCL TECH LTD
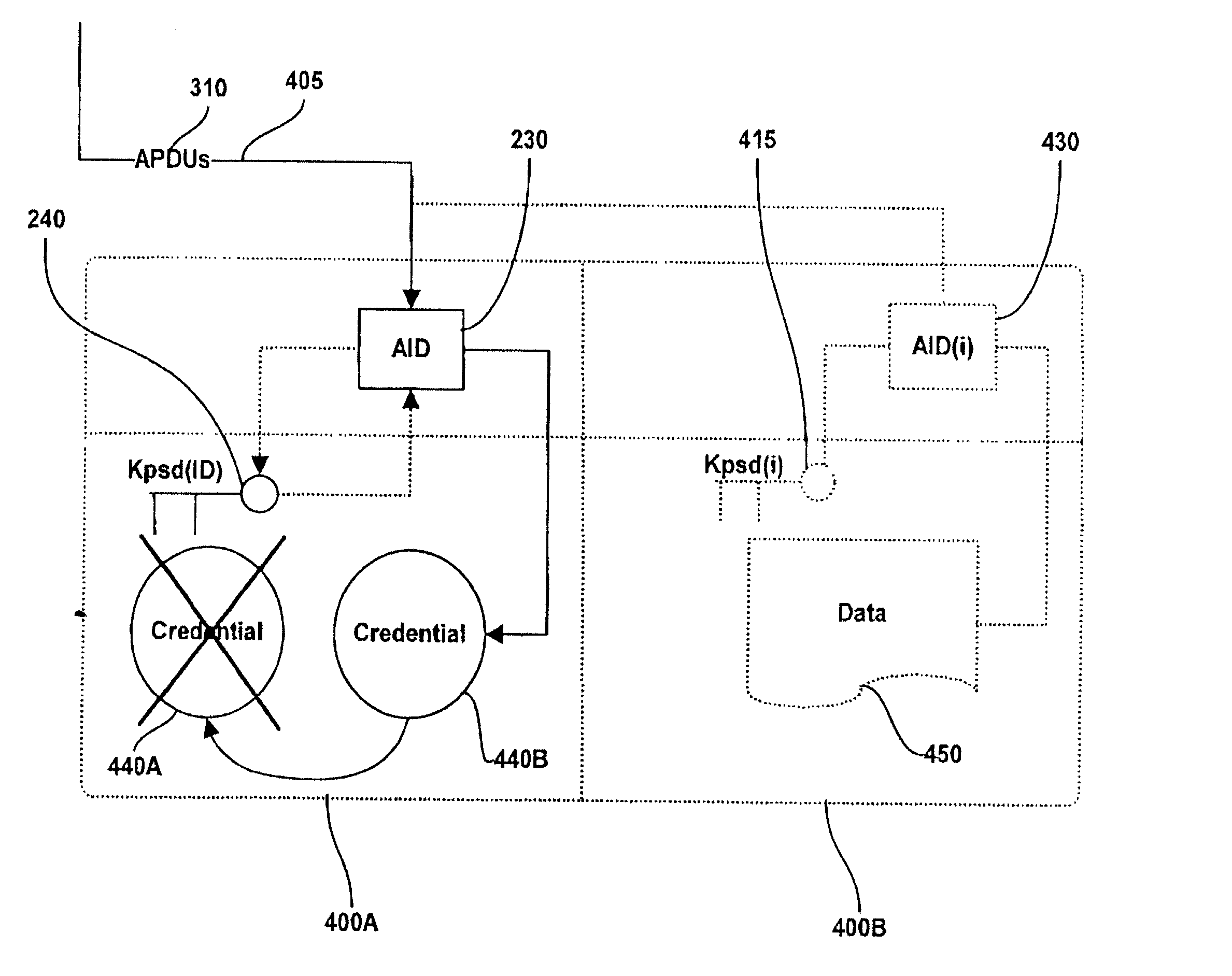
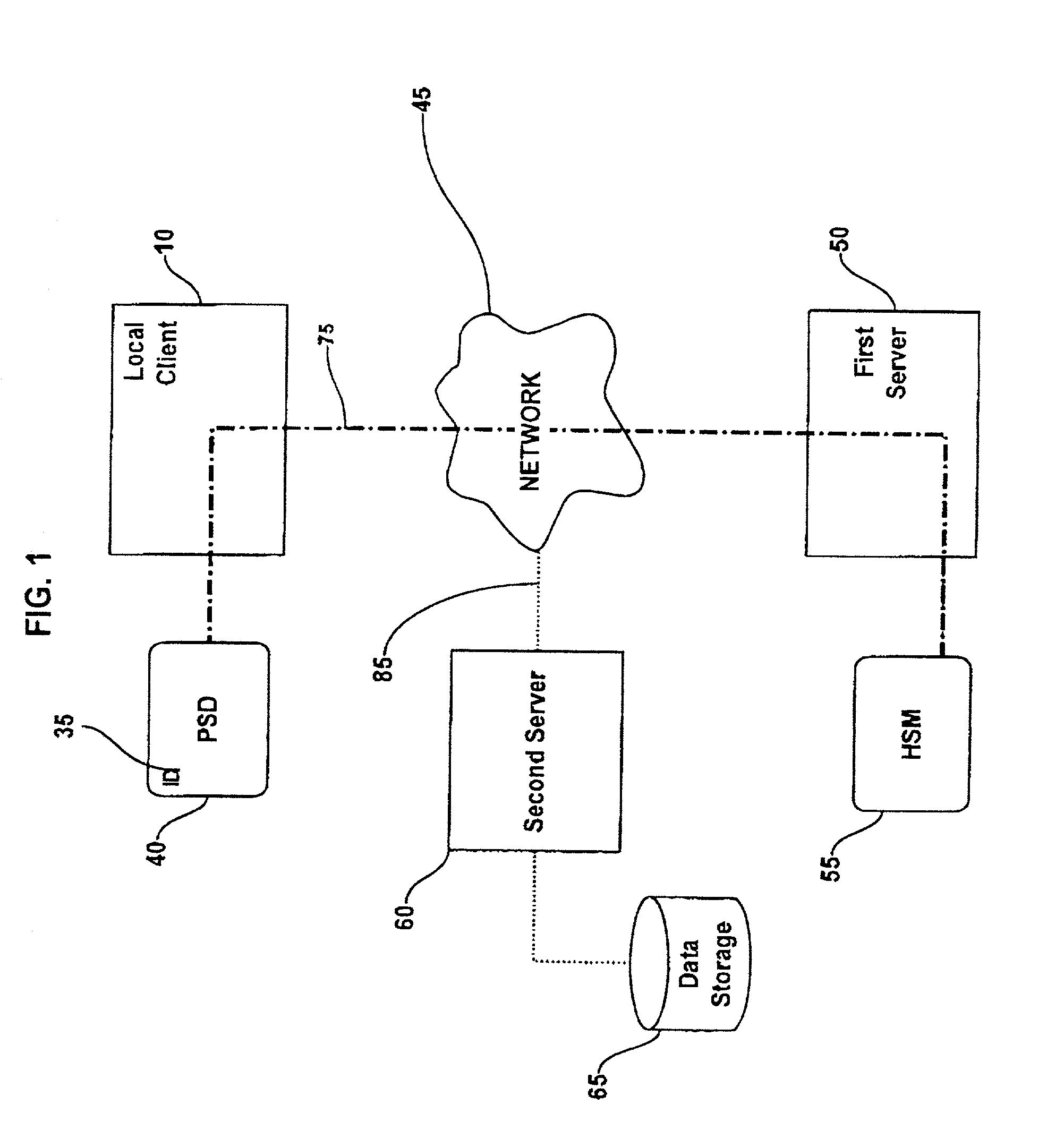
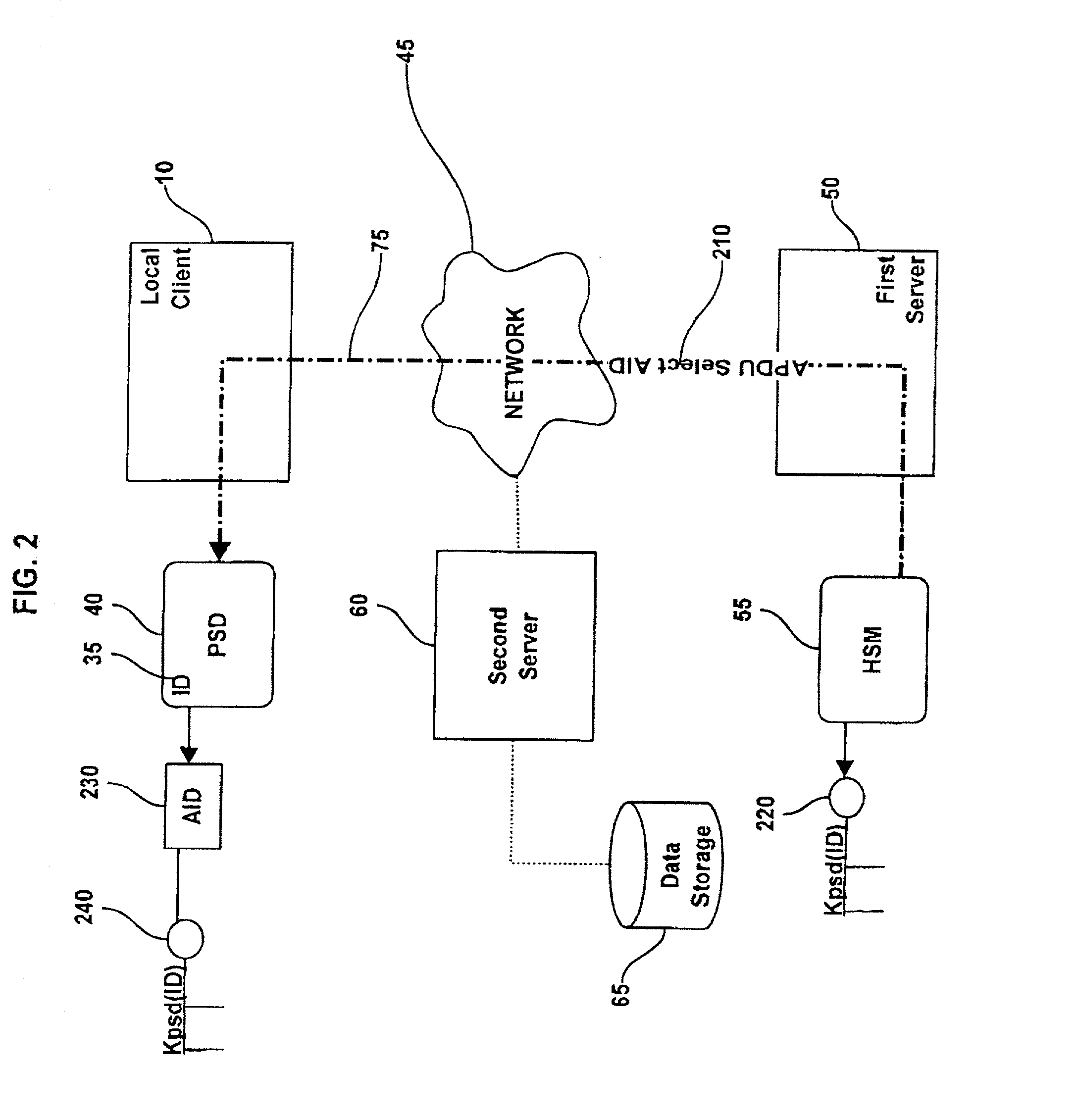
Method and system for performing post issuance configuration and data changes to a personal security device using a communications pipe
InactiveUS20030167399A1User identity/authority verificationUnauthorized memory use protectionHardware security moduleDigital credential
This invention provides a mechanism for performing secure configuration and data changes between a PSD and a hardware security module (HSM) using a communications pipe established between said PSD and said HSM. The data changes and configuration changes include but are not limited to installing, updating, replacing, deleting digital certificates, cryptographic keys, applets, other digital credentials, attributes of installed objects, or other stored proprietary information.
Owner:ACTIVCARD
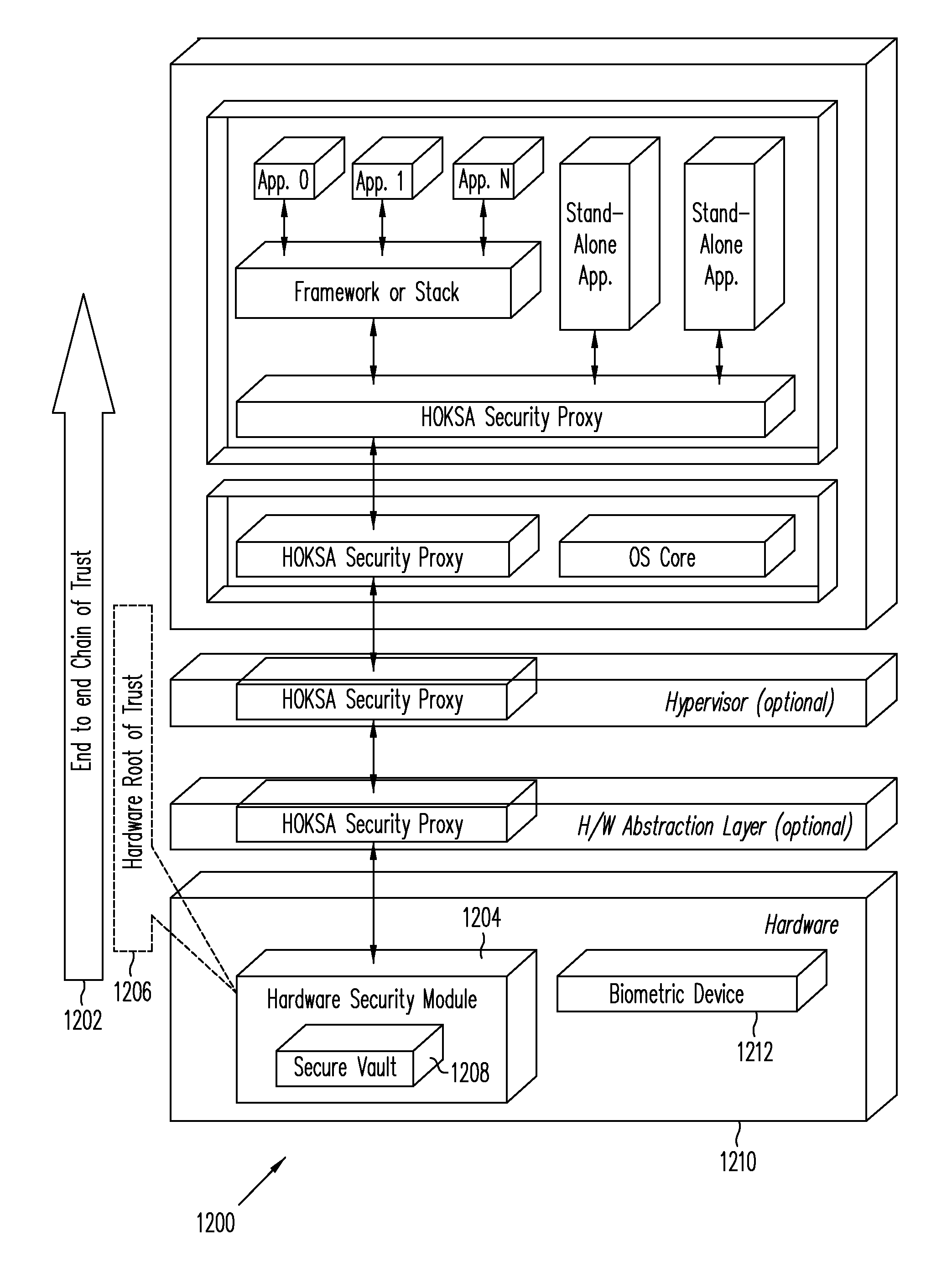
Hardware-Based Zero-Knowledge Strong Authentication (H0KSA)
InactiveUS20100306531A1Reduce riskUser identity/authority verificationDigital data authenticationHardware security moduleChain of trust
Systems and methods are provided for a device to engage in a zero-knowledge proof with an entity requiring authentication either of secret material or of the device itself. The device may provide protection of the secret material or its private key for device authentication using a hardware security module (HSM) of the device, which may include, for example, a read-only memory (ROM) accessible or programmable only by the device manufacturer. In the case of authenticating the device itself a zero-knowledge proof of knowledge may be used. The zero-knowledge proof or zero-knowledge proof of knowledge may be conducted via a communication channel on which an end-to-end (e.g., the device at one end and entity requiring authentication at the other end) unbroken chain of trust is established, unbroken chain of trust referring to a communication channel for which endpoints of each link in the communication channel mutually authenticate each other prior to conducting the zero-knowledge proof of knowledge and for which each link of the communication channel is protected by at least one of hardware protection and encryption.
Owner:PAYPAL INC
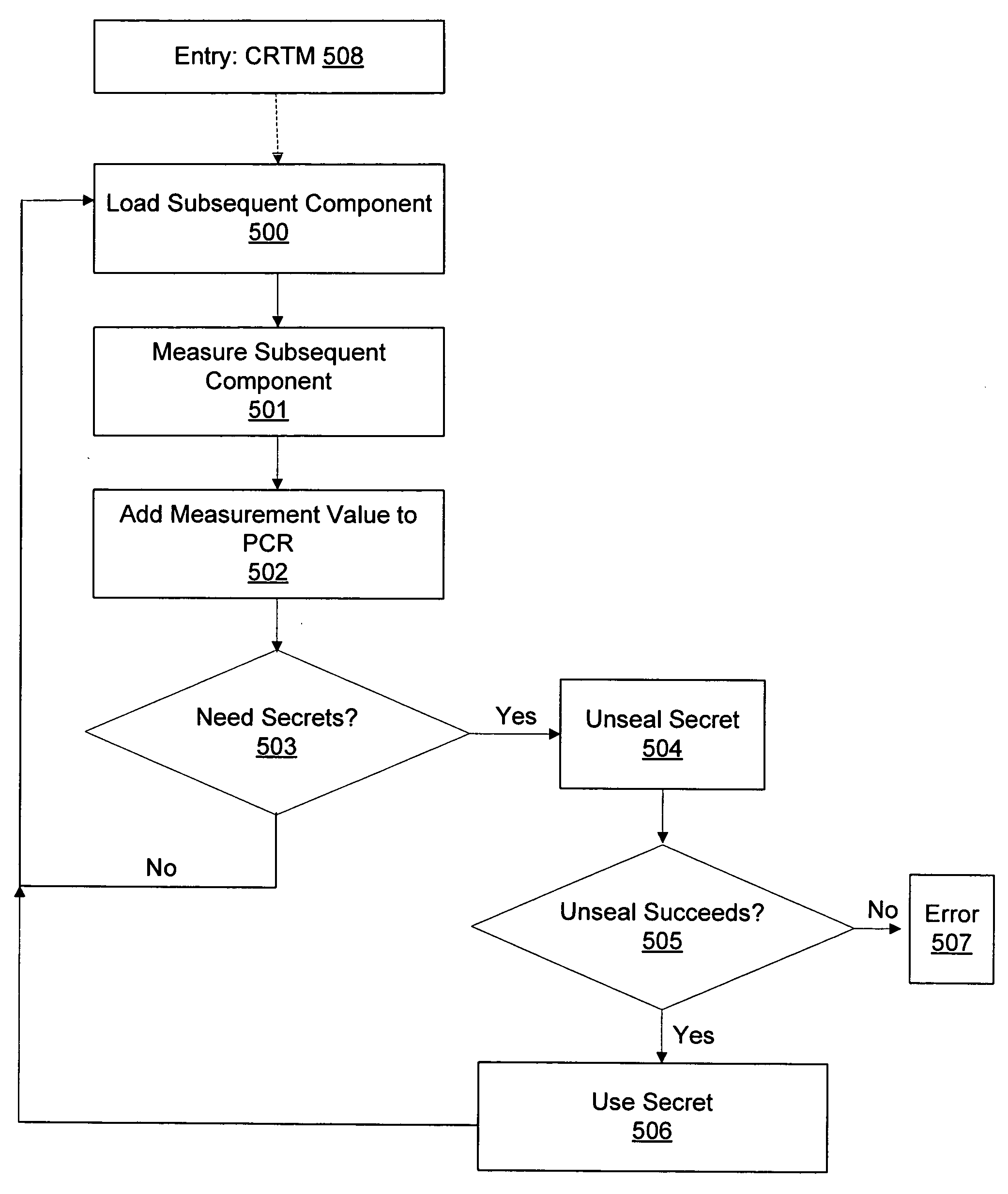
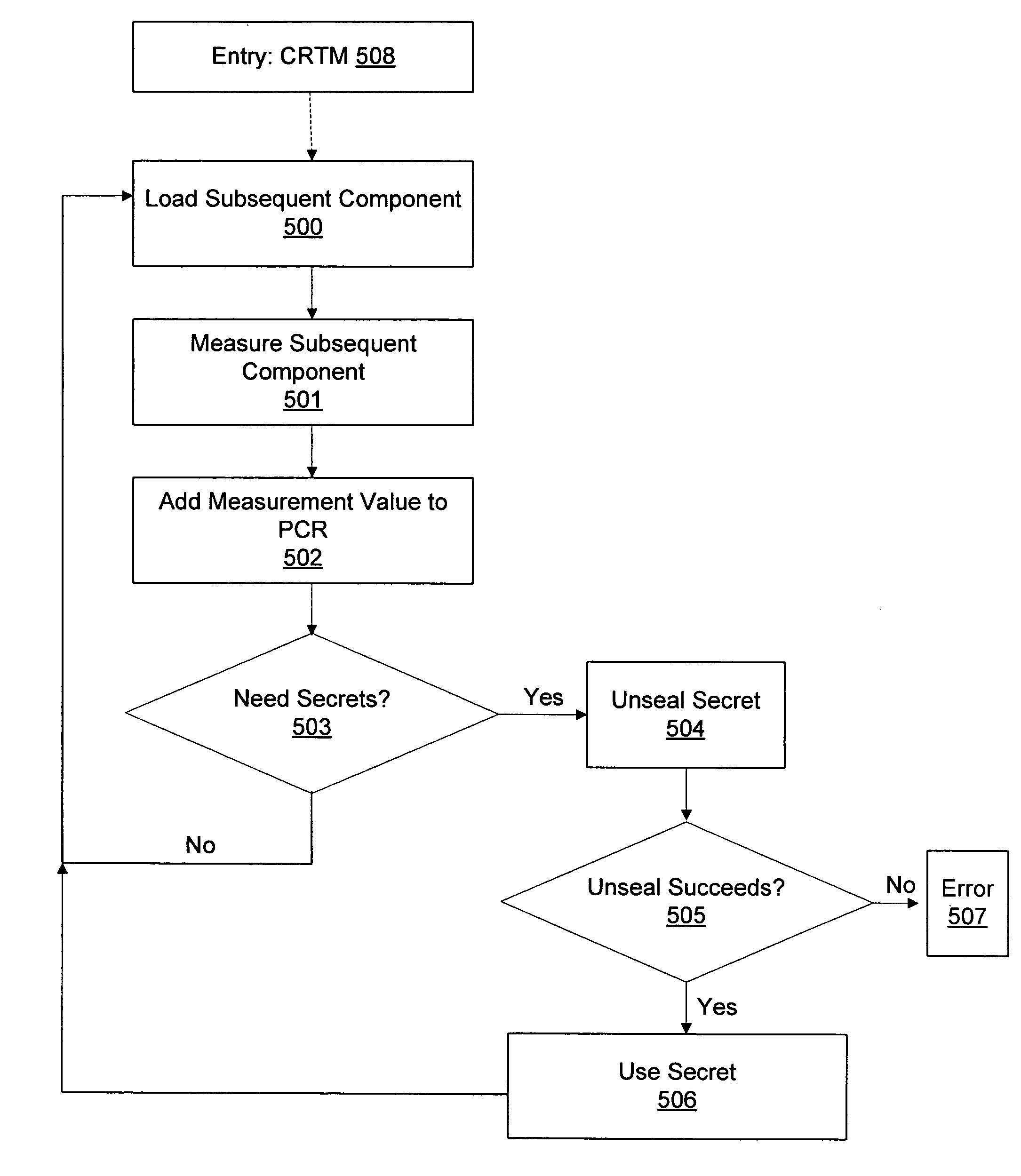
Systems and methods for updating a secure boot process on a computer with a hardware security module
ActiveUS20060161784A1Unauthorized memory use protectionHardware monitoringComputer hardwareTrusted Platform Module
Systems and methods are provided for maintaining and updating a secure boot process on a computer with a trusted platform module (TPM). A boot process may be maintained by inspecting a log of TPM activity, determining data that prevented a secret to unseal, and returning the data to an original state. In situations where this type of recovery is not workable, techniques for authenticating a user may be used, allowing the authenticated user to bypass the security features of the boot process and reseal the boot secrets to platform configuration register (PCR) values that may have changed. Finally, a secure boot process may be upgraded by migrating TPM sealed secrets to a temporary storage location, updating one or more aspects of a secure boot process, and resealing the secrets to the resulting new platform configuration. Other advantages and features of the invention are described below.
Owner:MICROSOFT TECH LICENSING LLC
Cross provider security management functionality within a cloud service brokerage platform
ActiveUS9832205B2Good serviceEfficient and effectiveFinanceProgram loading/initiatingSystems managementHardware security module
Implementation of cross provider security in accordance with the disclosures made herein enables users of a system (e.g., a cloud services brokerage platform) in a cloud environment provides for system-managed provisioning and management of keys to cloud resources thereby allowing the user to manage data security and enable secured access to their cloud resources. To this end, cross provider security management functionality in accordance with the disclosures made herein can include provisioning system-generated keys across different regions in a provider, provisioning cloud brokerage system-generated keys across different providers; and associating (i.e., managing) the keys from the system to a hardware security module. The keys can be managed by / though a variety of different resources (e.g., brokering system, VDC, user group concepts, etc).
Owner:HCL TECH LTD
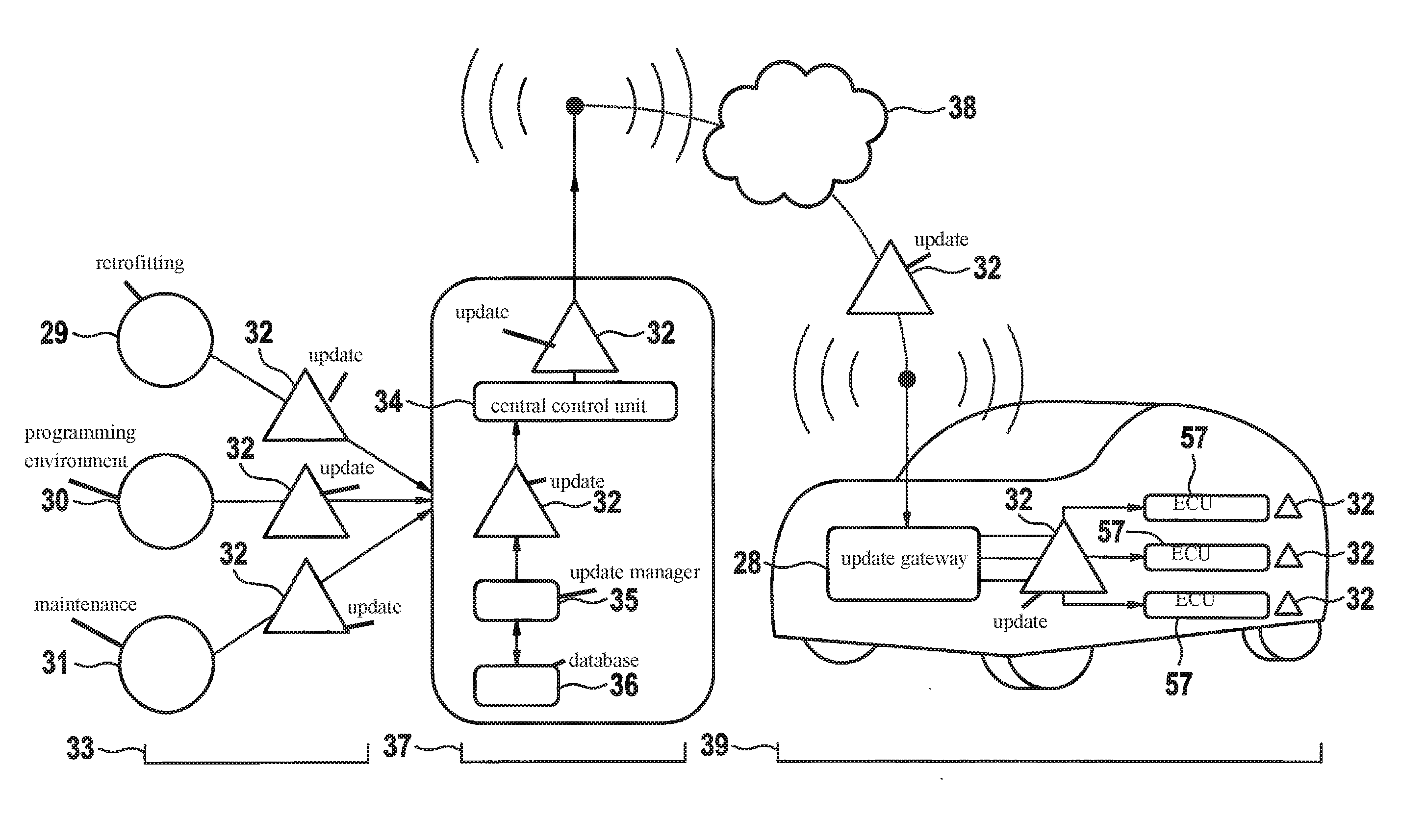
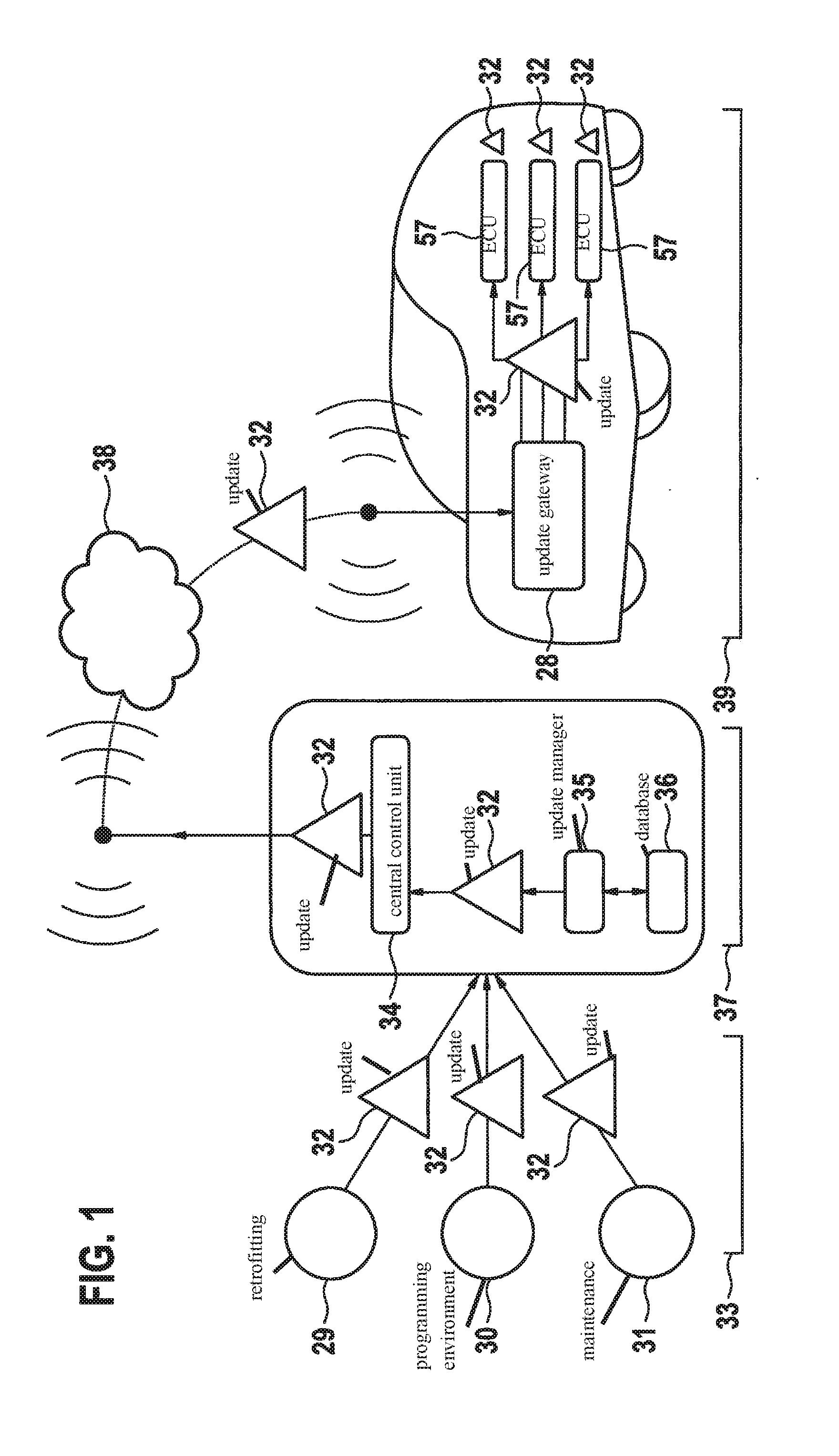
Method and update gateway for updating an embedded control unit
ActiveUS20160344705A1Not be counterfeitedMultiple keys/algorithms usagePublic key for secure communicationHardware security moduleComputer module
A method for updating an embedded electronic control unit, including an update gateway requests from a hardware security module an update request destined for the electronic control unit, the update gateway receives from the hardware security module the update request, which is signed by the hardware security module, the update gateway creates a communication channel, based on a cryptographic identity of the update gateway, to a backend, the update gateway sends the update request to the backend, the update gateway receives from the backend via the communication channel an update ticket which corresponds to the update request and is signed by the backend, in addition to associated update data, validates the update data, initiates a validation of the update ticket, checks the result of the validation, and depending on the result, the update gateway updates the electronic control unit with the update data.
Owner:ROBERT BOSCH GMBH
Method and apparatus for secure transactions
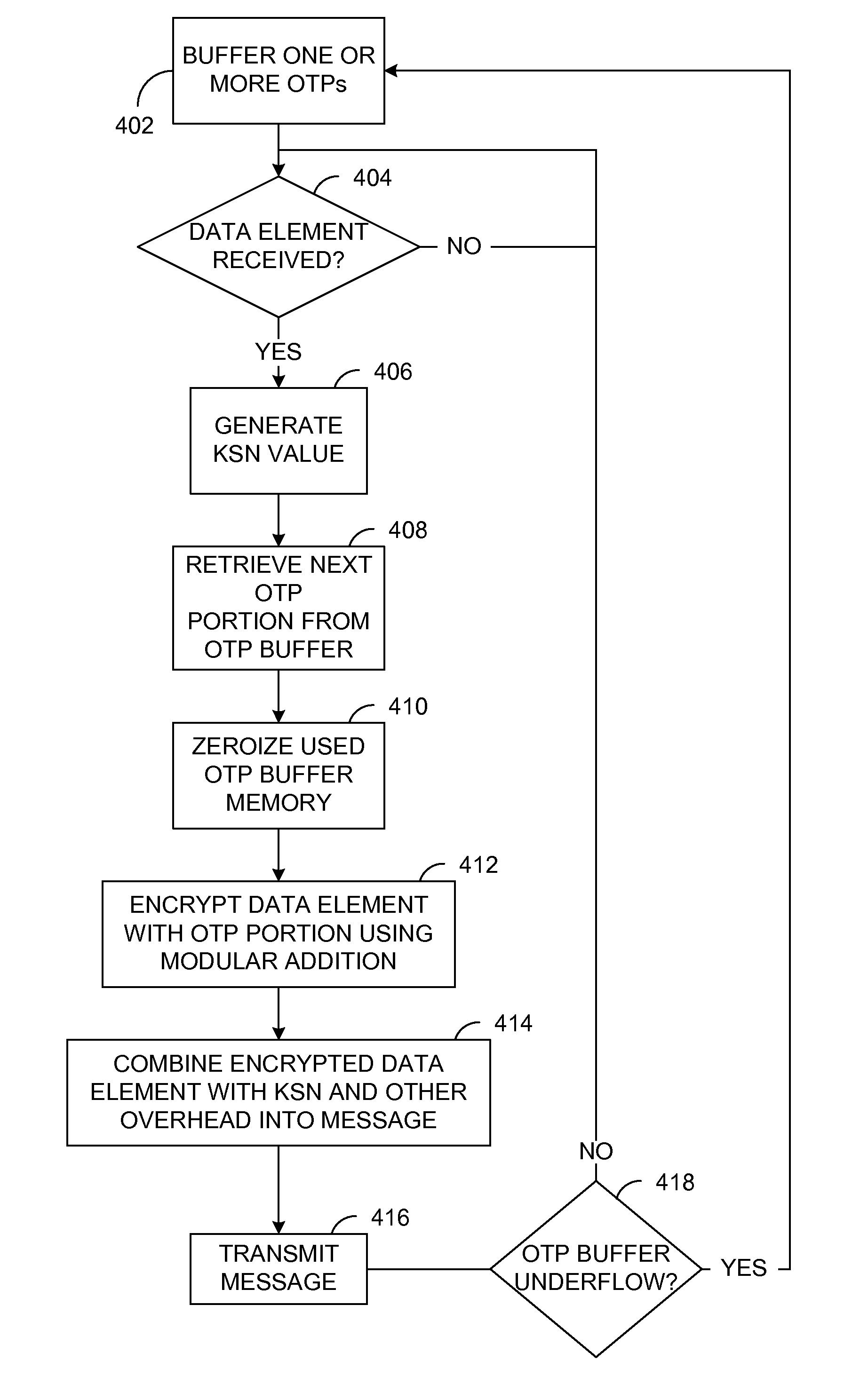
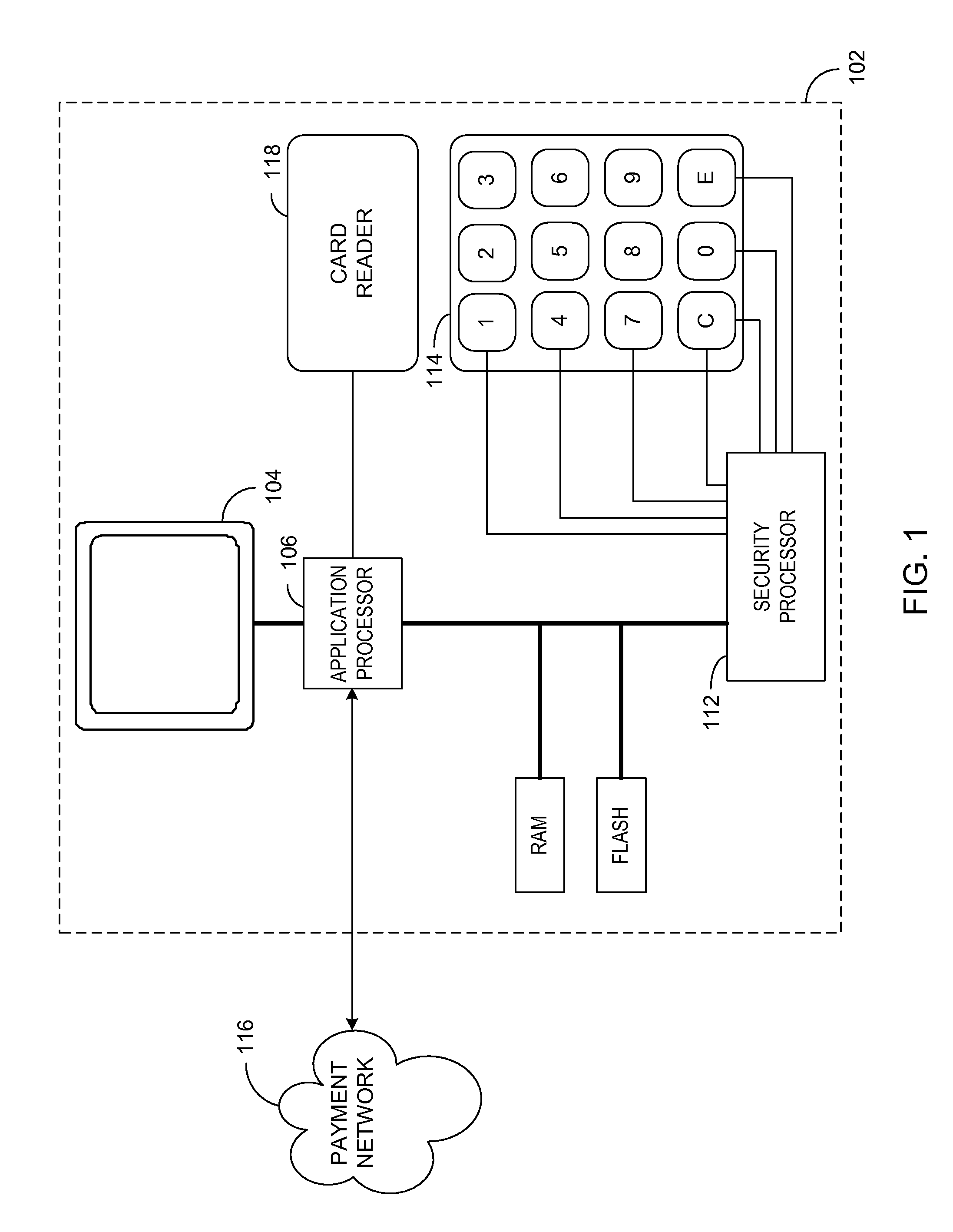
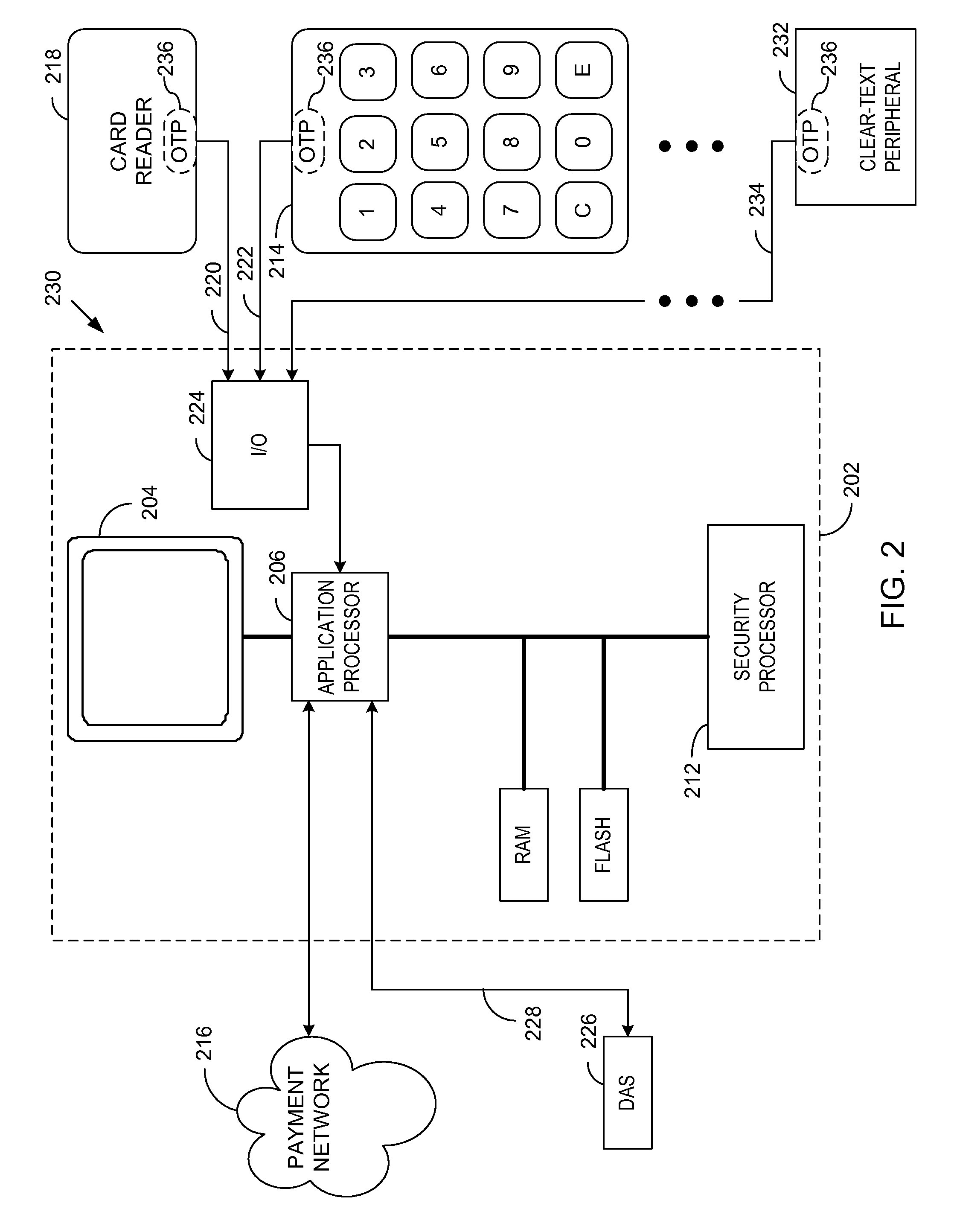
A method and apparatus is provided for secure terminals that facilitate secure data transmission and are compliant with the payment card industry (PCI) data security requirements. A security processor is combined with an application processor and a display into a secure display control unit (SDCU) that provides tamper resistance and other security measures. Modular secure I / O devices are interfaced to the SDCU via a wired, or wireless, medium so as to facilitate secure data transfer to the SDCU during a point-of-sale (POS) transaction or other transaction that requires secure data entry. The secure I / O devices implement one-time-pad (OTP) encryption, where the random keys, or pads, are generated by a derived unique key per transaction (DUKPT) generator. Other embodiments facilitate interconnection of the secure I / O devices to a hardware security module (HSM) or a personal computer (PC) while maintaining a high level of data security.
Owner:KEY INNOVATIONS
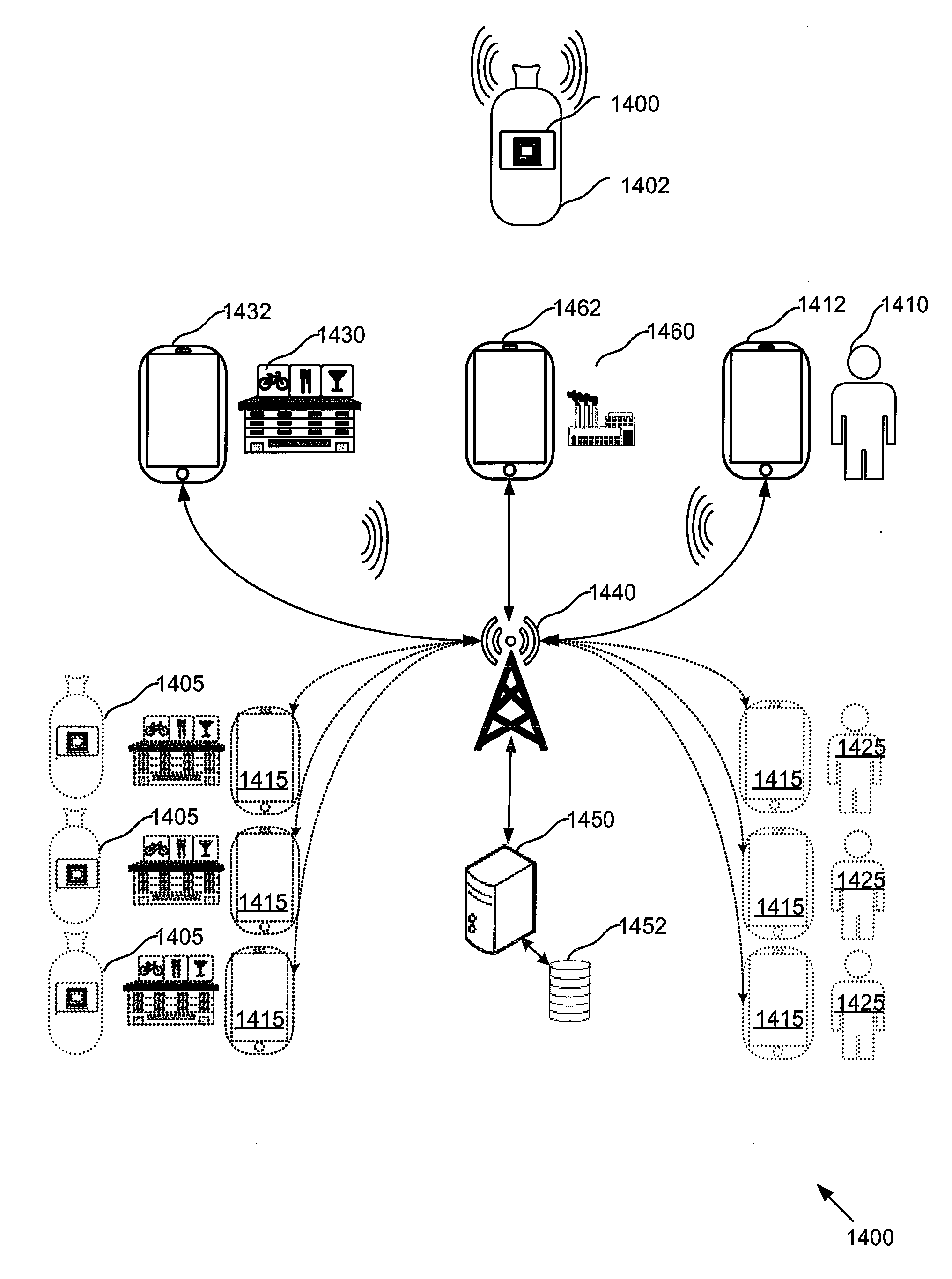
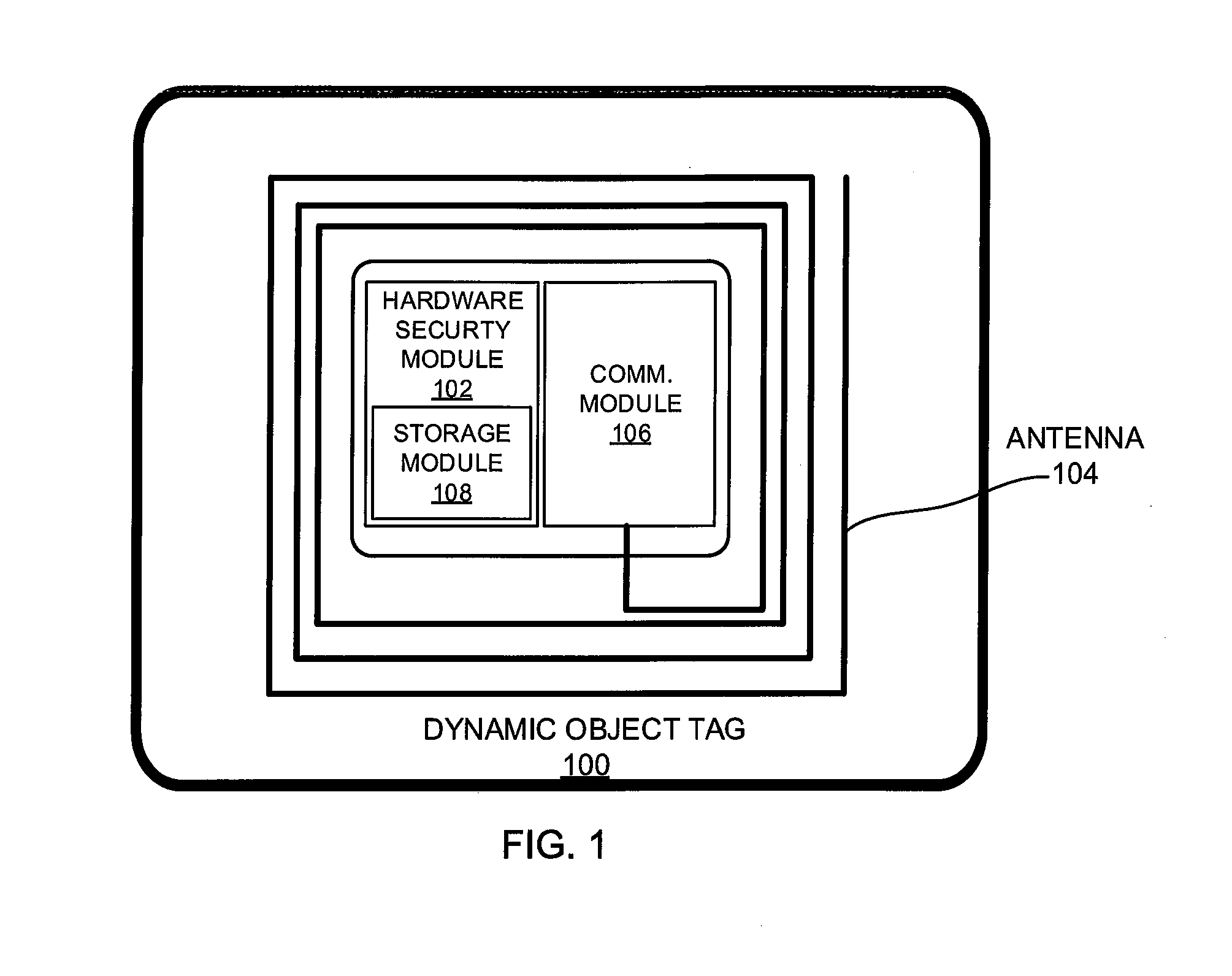
Dynamic object tag and systems and methods relating thereto
ActiveUS20150254677A1Cryptography processingDigital data processing detailsHardware security moduleSecure communication channel
A dynamic object tag for a product and systems and methods relating thereto is disclosed. The dynamic object tag comprises a hardware security module, including an electronic storage module, and a communication module for communicating with an interrogation device. The hardware security module is adapted to establish a secure communication channel with the interrogation device, to exchange dynamic authentication parameters with the interrogation device, and to communicate product information stored on the electronic storage module to the interrogation device over the secure communication channel.
Owner:VISA INT SERVICE ASSOC
Systems and methods for securing data
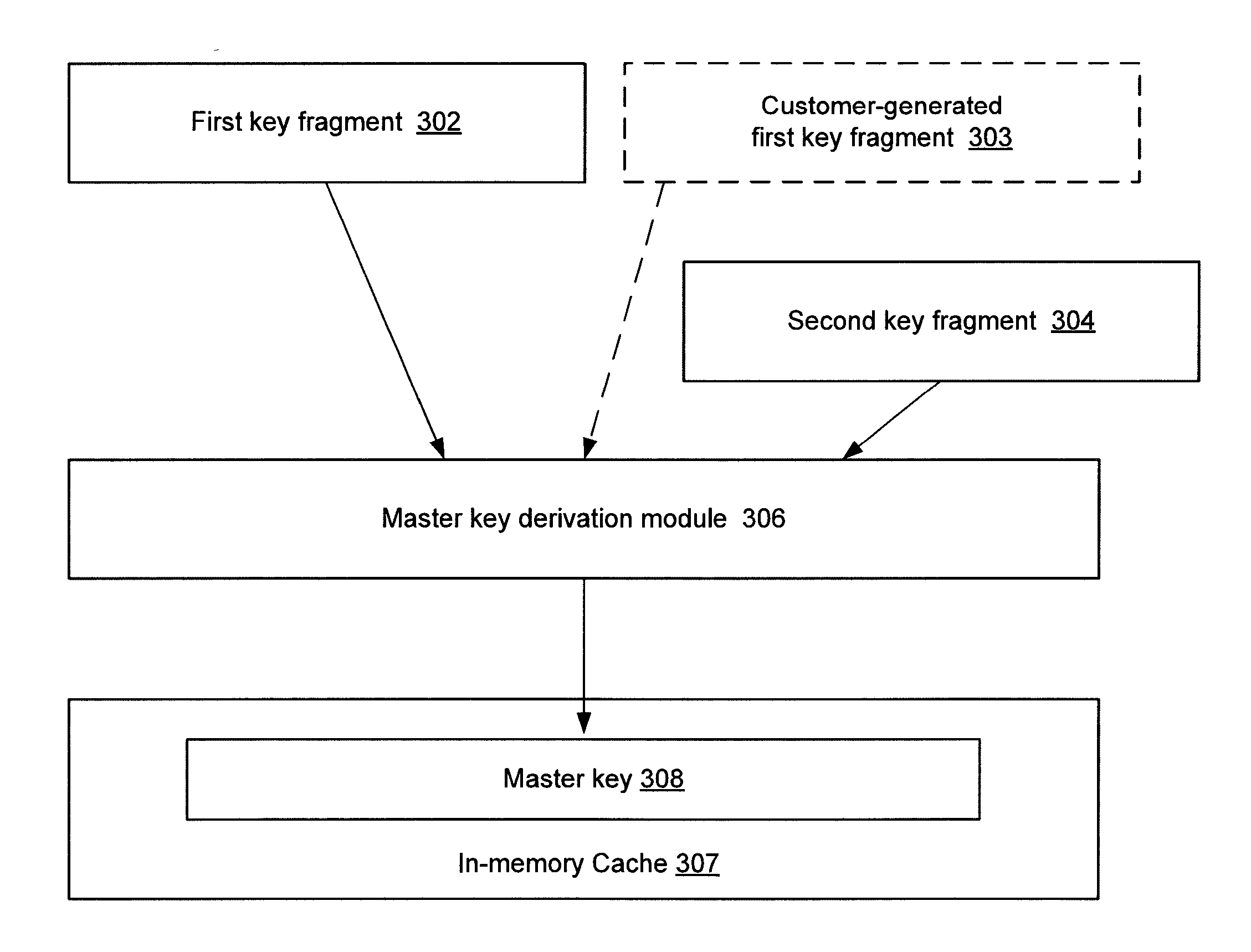
Embodiments include an apparatus for securing customer data and include a processor, and one or more stored sequences of instructions which, when executed, cause the processor to store an encrypted first key fragment in a first storage area, store an encrypted second key fragment in a separate second storage area, wherein access to the first storage area and to the second storage area is mutually exclusive. The instructions further cause the processor to decrypt the encrypted first key fragment and the encrypted second key fragment using a key set and keys associated with a hardware security module based on receiving a request to derive a master key. The master key is derived using the decrypted first key fragment and the decrypted second key fragment and stored in an in-memory cache. The master key is used to encrypt or to decrypt encrypted customer data.
Owner:SALESFORCE COM INC
Cryptographic key backup and escrow system
A system for securely storing application keys is comprised of a database system, a peripheral hardware security module and cryptographic keys, wherein cryptographic keys comprise application keys, intermediate keys and a master key. Application keys are grouped according to characteristic and are associated with a particular intermediate key, which is utilized to scramble and descramble application keys within the associated group. Intermediate keys are associated with the master key, which is utilized to scramble and descramble the intermediate keys. Scrambling and descrambling of keys is performed within the peripheral hardware security module.
Owner:WELLS FARGO BANK NA
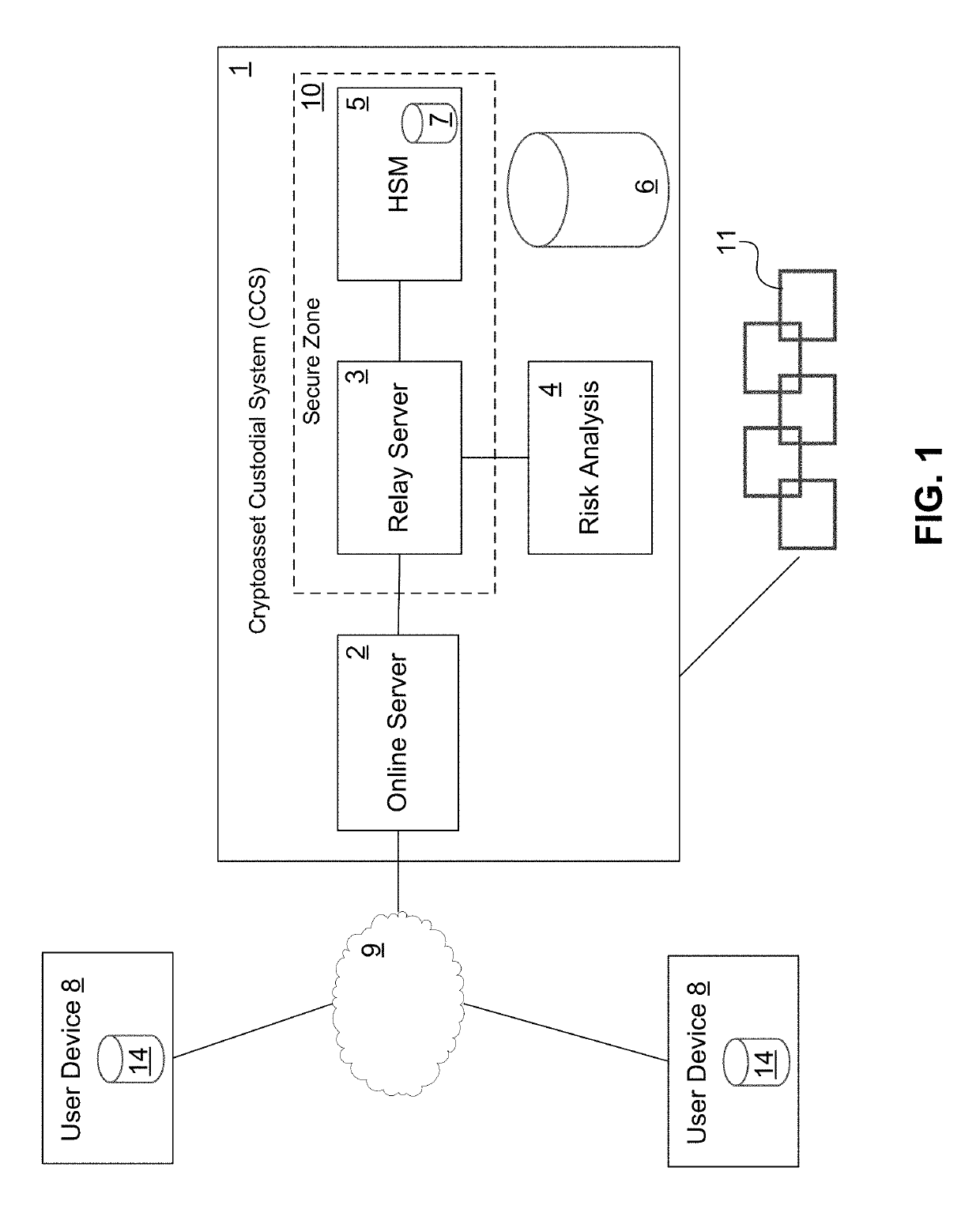
Digital Asset Custodial System
PendingUS20190266576A1Cryptography processingDigital data authenticationHardware security moduleAuthentication
A digital asset custodial system for maintaining custody of, and controlling access to, cryptocurrencies and / or other digital assets, is disclosed. The digital asset custodial system includes multiple layers of security to enable large volumes of digital assets to be maintained in a secure manner. The digital asset custodial system can include a combination of biometric-based multi-user validation, transaction risk analysis, and a hardware security module (HSM) that provides authentication / validation functionality and secure storage of private keys of digital assets.
Owner:ANCHOR LABS INC
Method and system for establishing a trust framework based on smart key devices
ActiveUS20050154875A1User identity/authority verificationUnauthorized memory use protectionTrust relationshipSecure unit
A mechanism is provided for securing cryptographic functionality within a host system such that it may only be used when a system administrator physically allows it via a hardware security token. In addition, a hardware security unit is integrated into a data processing system, and the hardware security unit acts as a hardware certificate authority. The hardware security unit may be viewed as supporting a trust hierarchy or trust framework within a distributed data processing system. The hardware security unit can sign software that is installed on the machine that contains the hardware security unit. Server processes that use the signed software that is run on the machine can establish mutual trust relationships with the hardware security unit and amongst the other server processes based on their common trust of the hardware security unit.
Owner:META PLATFORMS INC
Secure multi-party protocol
A requestor and a responder may conduct secure communication by making API calls based on a secure multi-party protocol. The requestor may send a request data packet sent in a API request to the responder, where the request data packet can include at least a control block that is asymmetrically encrypted and a data block that is symmetrically encrypted. The responder may return a response data packet to the requestor, where the response data packet can include at least a control block and a data block that are both symmetrically encrypted. The requestor and the responder may derive the keys for decrypting the encrypted portions of the request and response data packets based on some information only known to the requestor and the responder. The secure multi-party protocol forgoes the need to store and manage keys in a hardware security module.
Owner:VISA INT SERVICE ASSOC
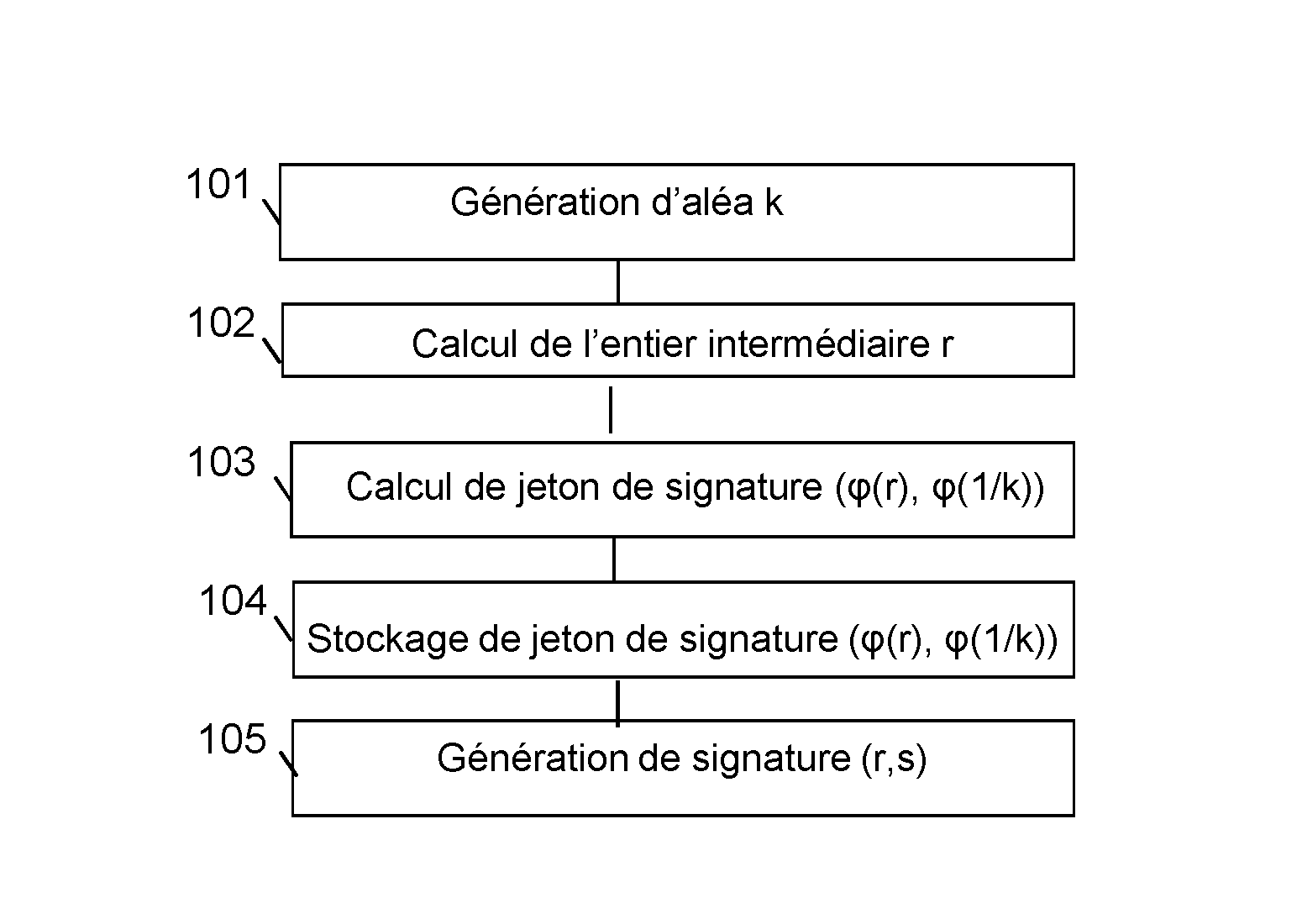
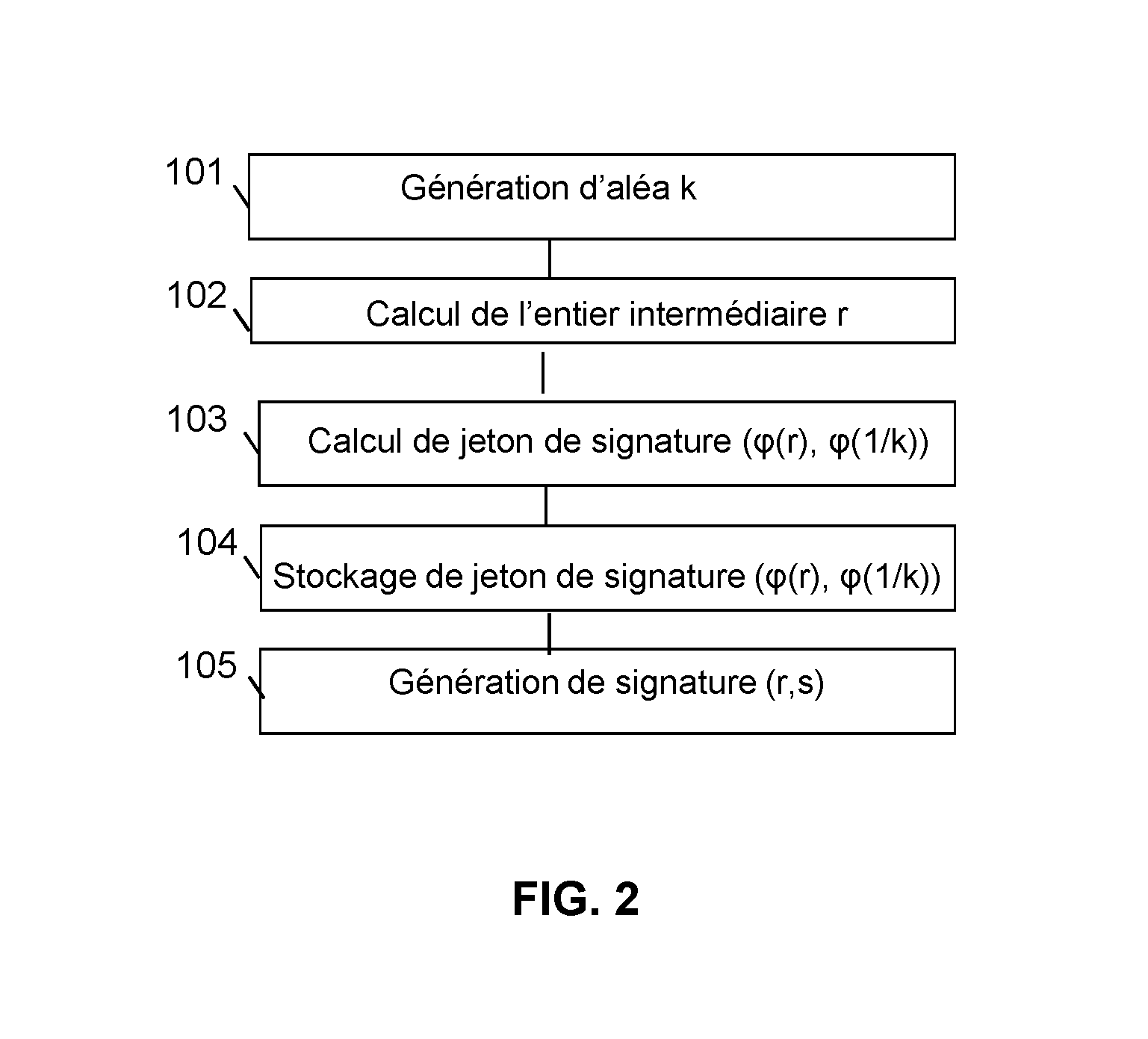
Method for generating a message signature from a signature token encrypted by means of a homomorphic encryption function
ActiveUS20160344557A1Not to endanger securityReduce power generation costsPublic key for secure communicationUser identity/authority verificationHardware security modulePrecomputation
The invention relates to a method for generating a message signature intended to be validated by a verifier server, a client device being configured to hold a private key and a corresponding public key and comprising steps of:offline precomputation (103) by a hardware security module of a signature token, a result of encryption by means of a homomorphic encryption function,storage (104) of said signature token;generation (105) of said signature of said encrypted message by means of said homomorphic encryption function from the result of the encryption by said homomorphic encryption function of the private key stored by the client device, of the signature token and of said message, said signature being intended to be validated by said verifier server by means of said public key.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
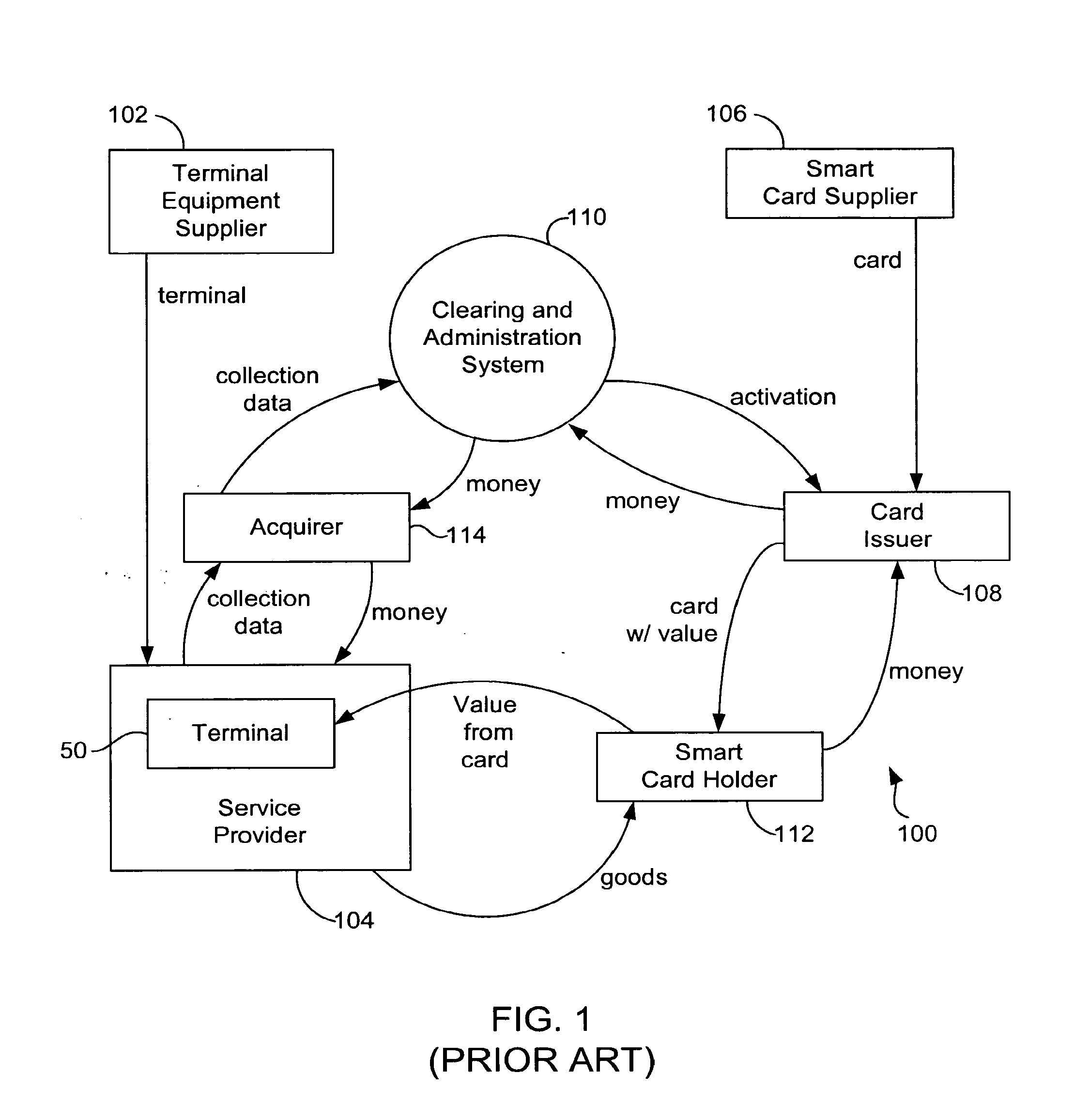
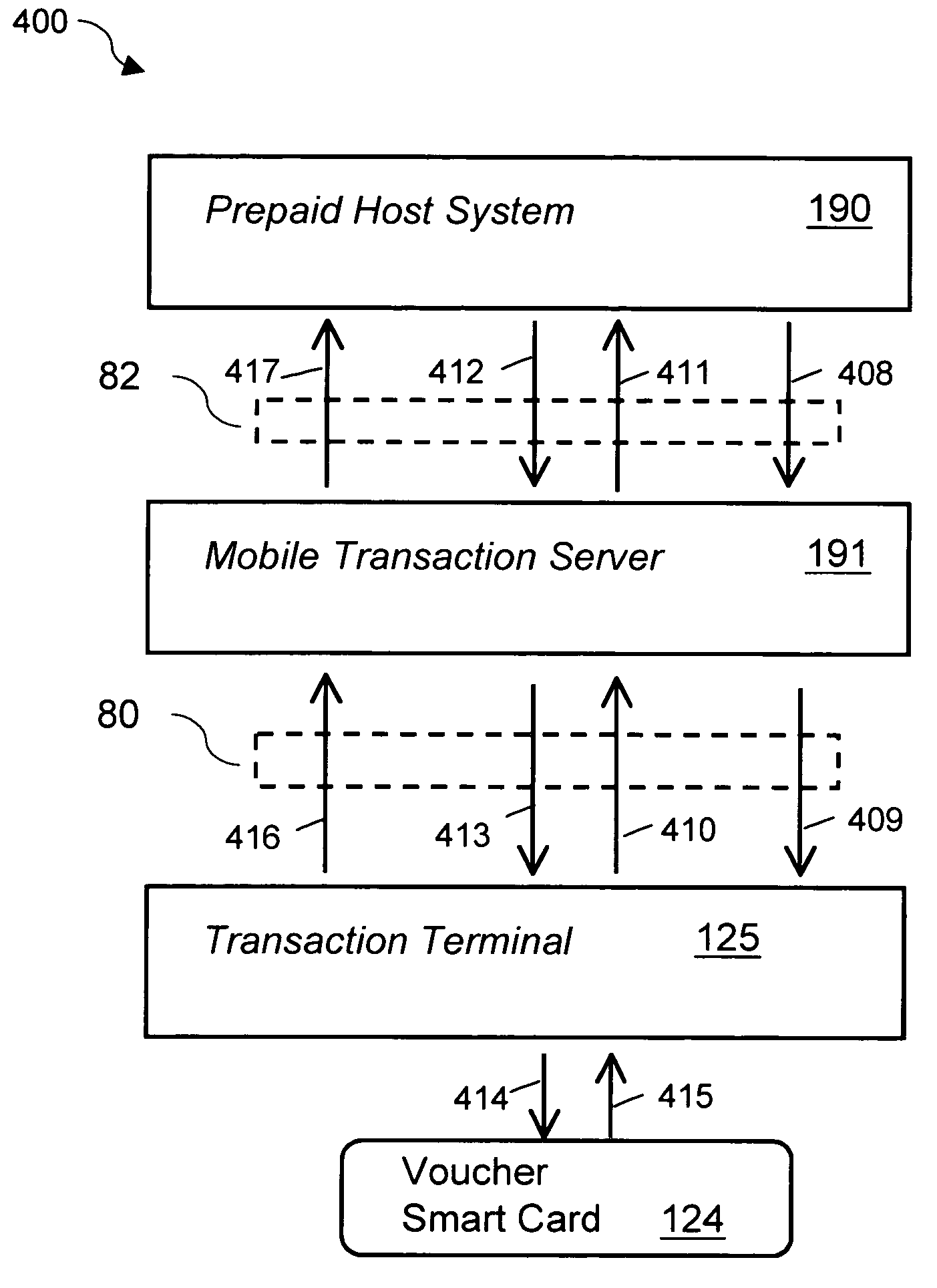
System and method for securely storing, generating, transferring and printing electronic prepaid vouchers
InactiveUS7188089B2Security is importantTimelyCredit registering devices actuationDevices with card reading facilityHardware security moduleMobile transaction
A system and a method that utilizes transaction terminals equipped with smart card readers to download and store a batch of multiple prepaid electronic vouchers to a smart card, retrieve and decrypt individual prepaid vouchers from the smart card and print a voucher receipt with a printer in connection with the transaction terminal. The transaction terminals are in connection with a mobile transaction server that acts as a gateway to a prepaid system and routes transactions between transaction terminals and the prepaid system and between transaction terminals. A method for storing a voucher encryption key on a second smart card or hardware security module. The voucher encryption key is utilized to decrypt encrypted vouchers on a voucher repository smart card. The transaction terminals are mobile devices communicating to the mobile transaction server over wireless networks.
Owner:VERIFONE INC
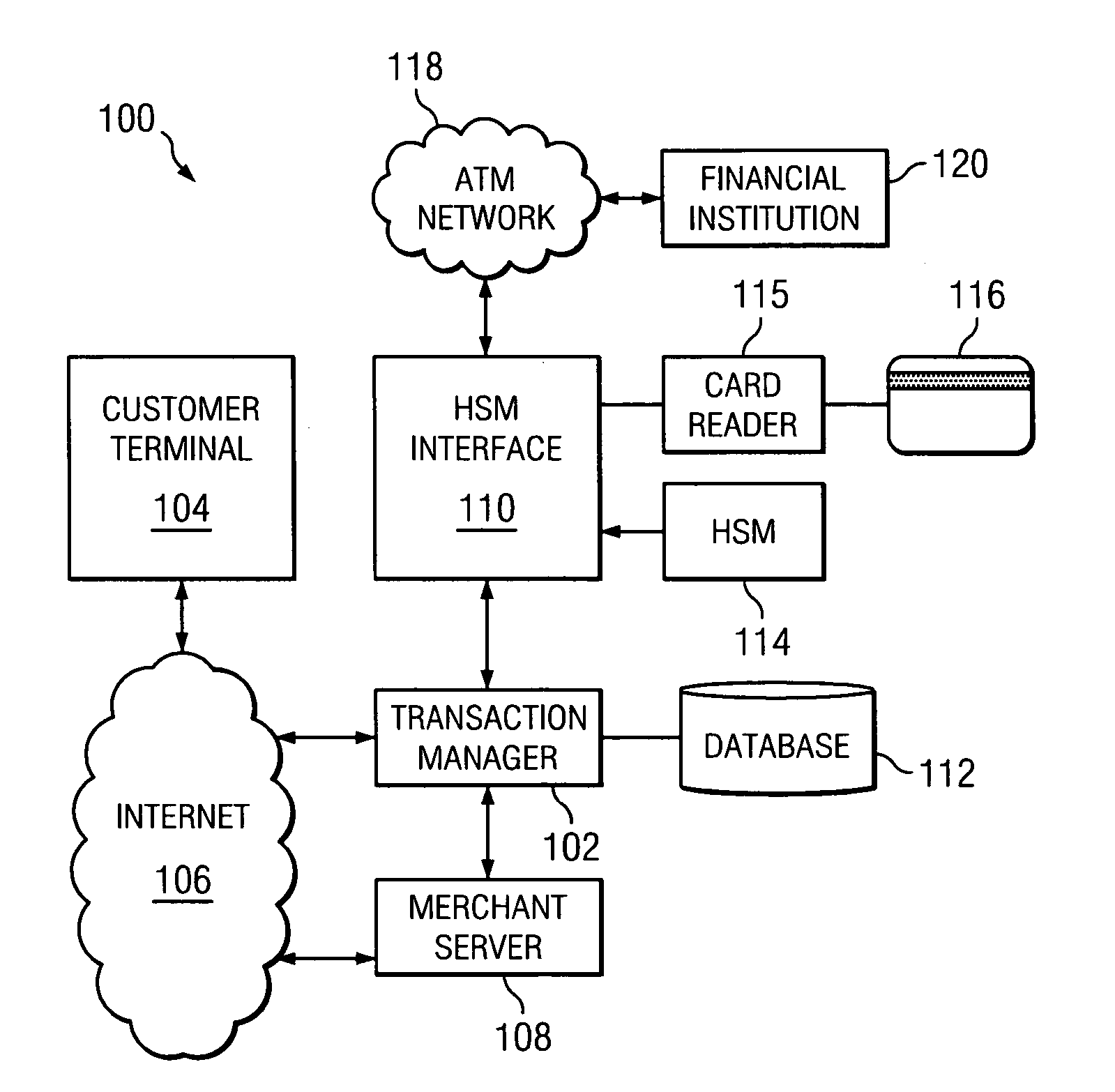
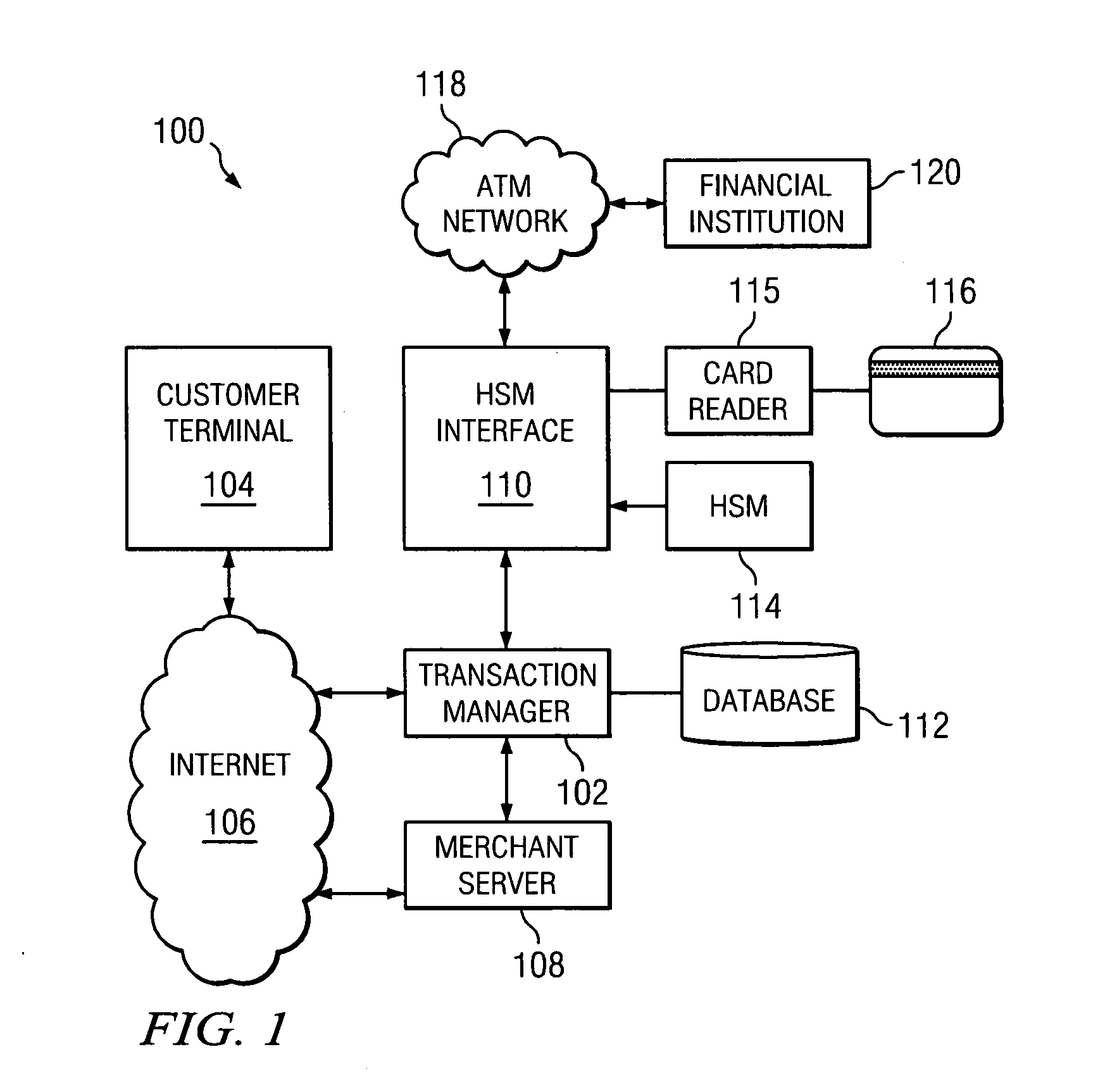
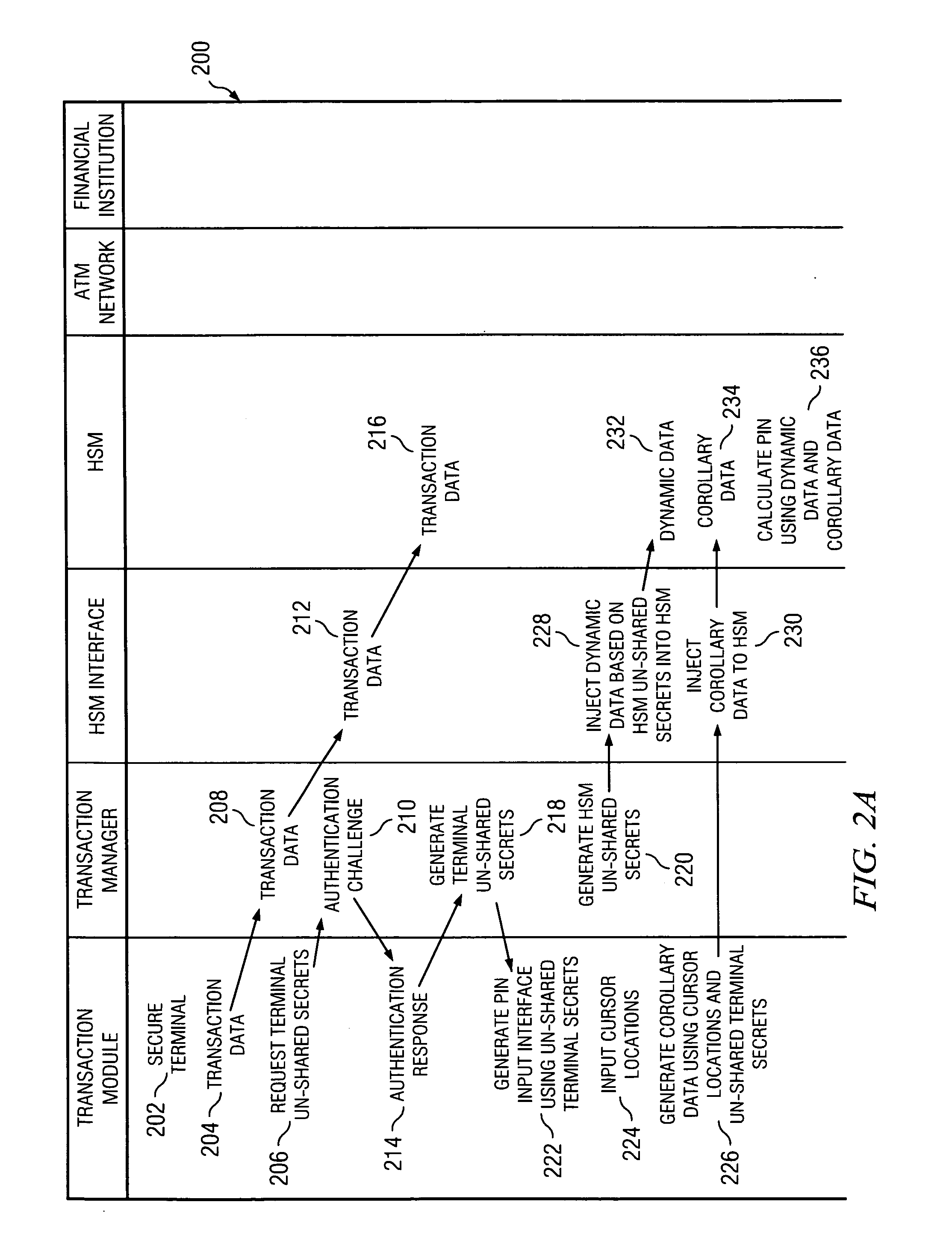
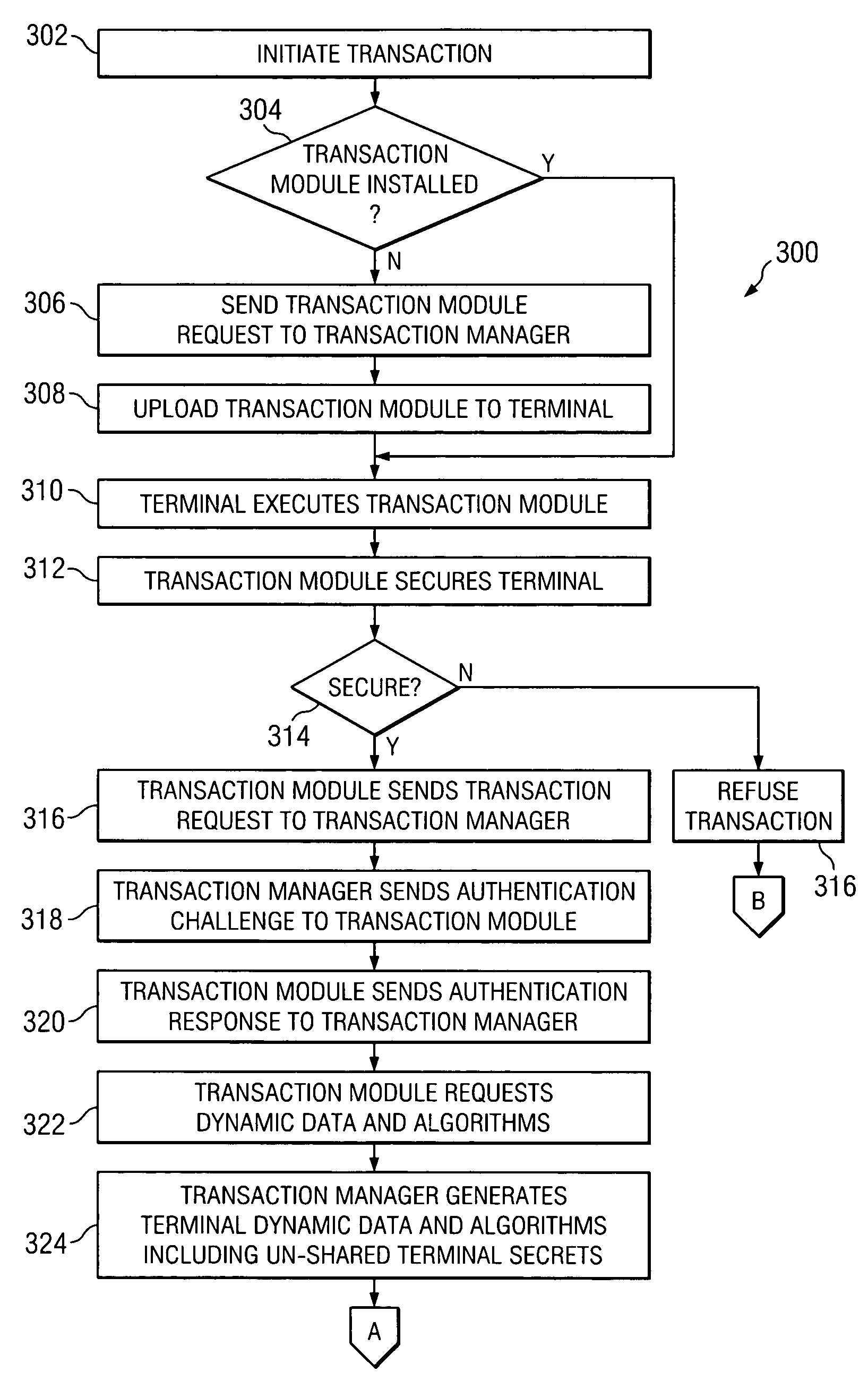
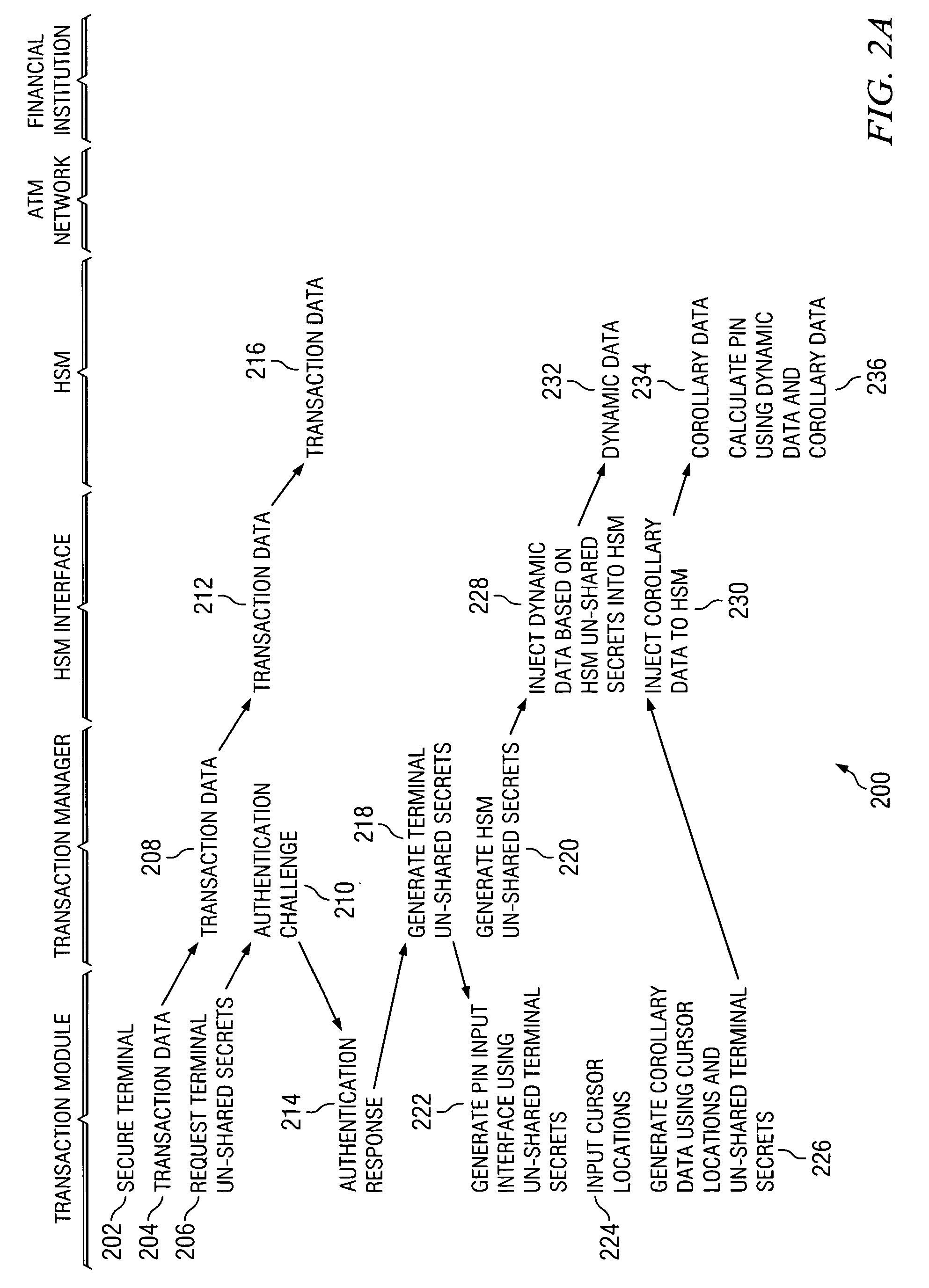
Secure PIN management
ActiveUS7526652B2Key distribution for secure communicationDigital data processing detailsComputer hardwareHardware security module
A system and method of secure PIN processing in a network transaction includes a transaction manager that sends terminal data to a terminal. The terminal generates corollary data from user input and the terminal data. The corollary data is sent to the transaction manager. The transaction manager then sends the corollary data and HSM data to a hardware security module. The hardware security module generates a PIN from the corollary data and the HSM data, encrypts the PIN and generates a PIN block. The transaction manager uses the PIN block and transaction data to send a transaction request to the ATM Network.
Owner:FIRST DATA MERCHANT SERVICES LLC
Systems and methods for boot recovery in a secure boot process on a computer with a hardware security module
ActiveUS20060161769A1Digital data processing detailsDigital computer detailsComputer hardwareHardware security module
Systems and methods are provided for maintaining and updating a secure boot process on a computer with a trusted platform module (TPM). A boot process may be maintained by inspecting a log of TPM activity, determining data that prevented a secret to unseal, and returning the data to an original state. In situations where this type of recovery is not workable, techniques for authenticating a user may be used, allowing the authenticated user to bypass the security features of the boot process and reseal the boot secrets to platform configuration register (PCR) values that may have changed. Finally, a secure boot process may be upgraded by migrating TPM sealed secrets to a temporary storage location, updating one or more aspects of a secure boot process, and resealing the secrets to the resulting new platform configuration. Other advantages and features of the invention are described below.
Owner:MICROSOFT TECH LICENSING LLC
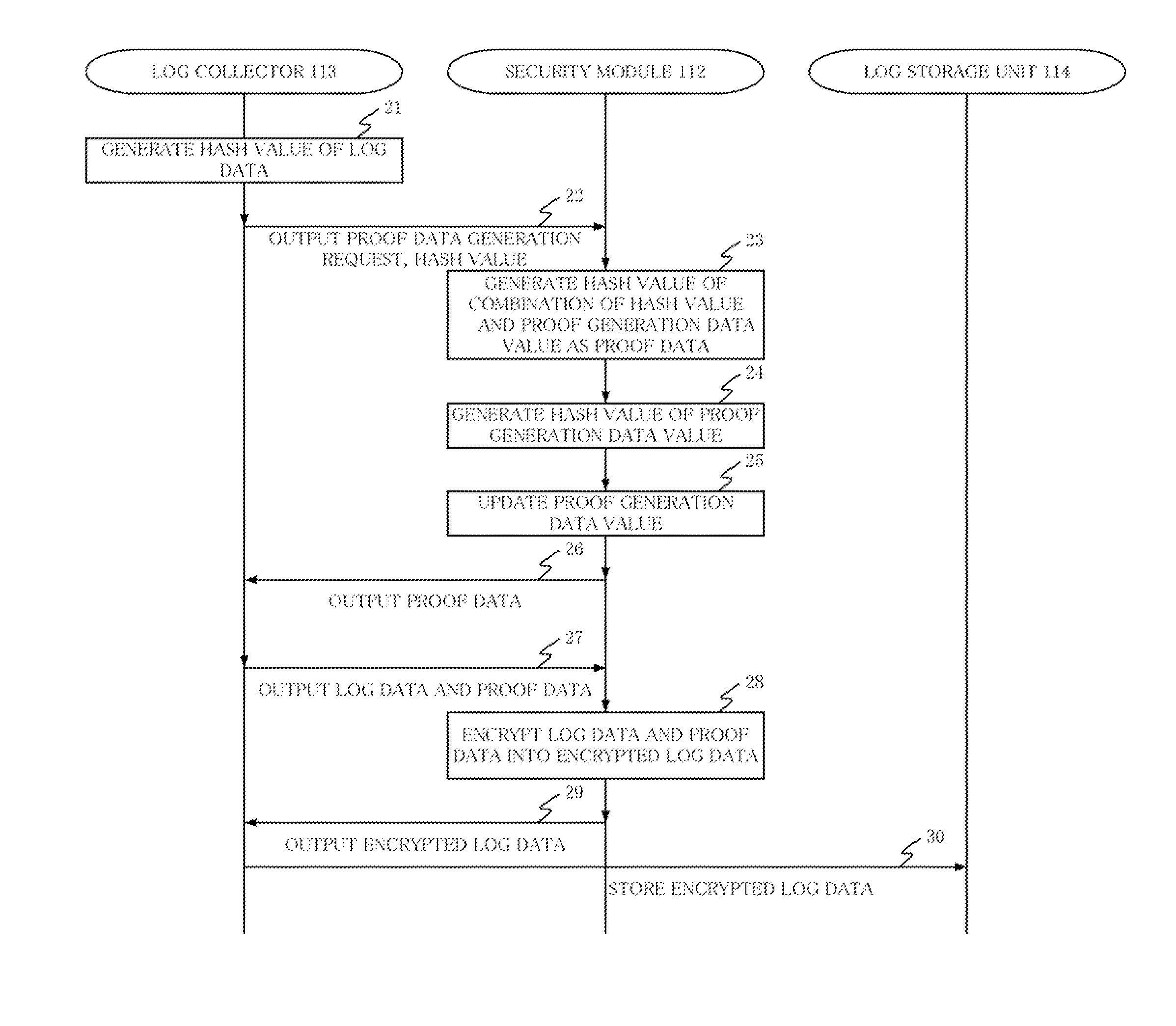
Log acquisition system, log collection terminal, log acquisition terminal, and log acquisition method and program using the same system and terminals
InactiveUS20100070769A1Log information is preventedInhibition of informationKey distribution for secure communicationUser identity/authority verificationHardware security moduleComputer module
In a log acquisition system comprising a log collection terminal for collecting log data and a log acquisition terminal for acquiring the log data collected by the log collection terminal from the log collection terminal, the log collection terminal stores a common key between the log collection terminal and the log acquisition terminal in a hardware security module inherently mounted in the log collection terminal, encrypts the collected log data as encrypted log data using the stored common key, and stores the encrypted log data, and the log acquisition terminal stores the common key in a hardware security module inherently mounted in the log acquisition terminal, acquires the encrypted log data from the log collection terminal, and decrypts the acquired encrypted log data with the common key.
Owner:NEC CORP
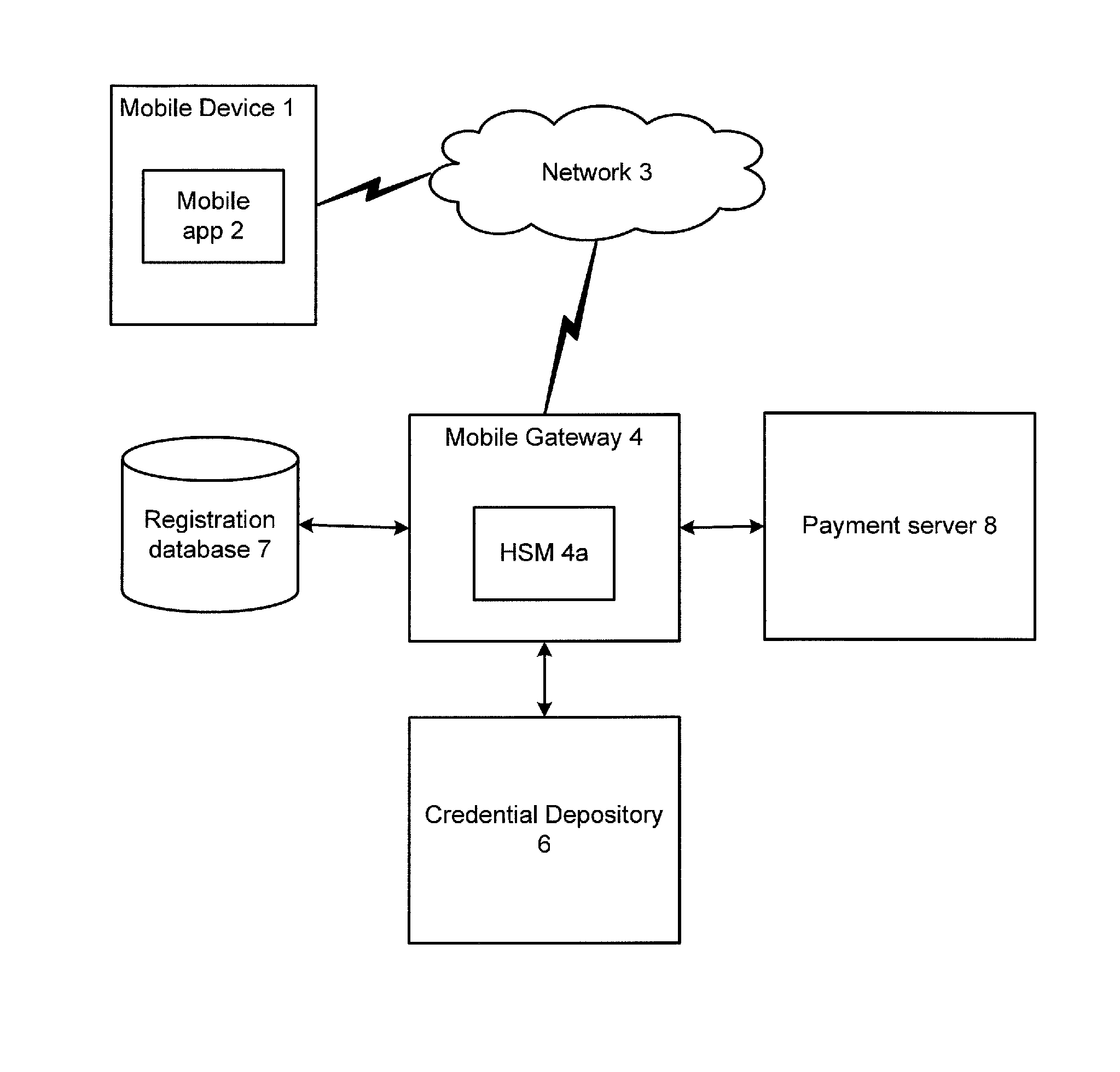
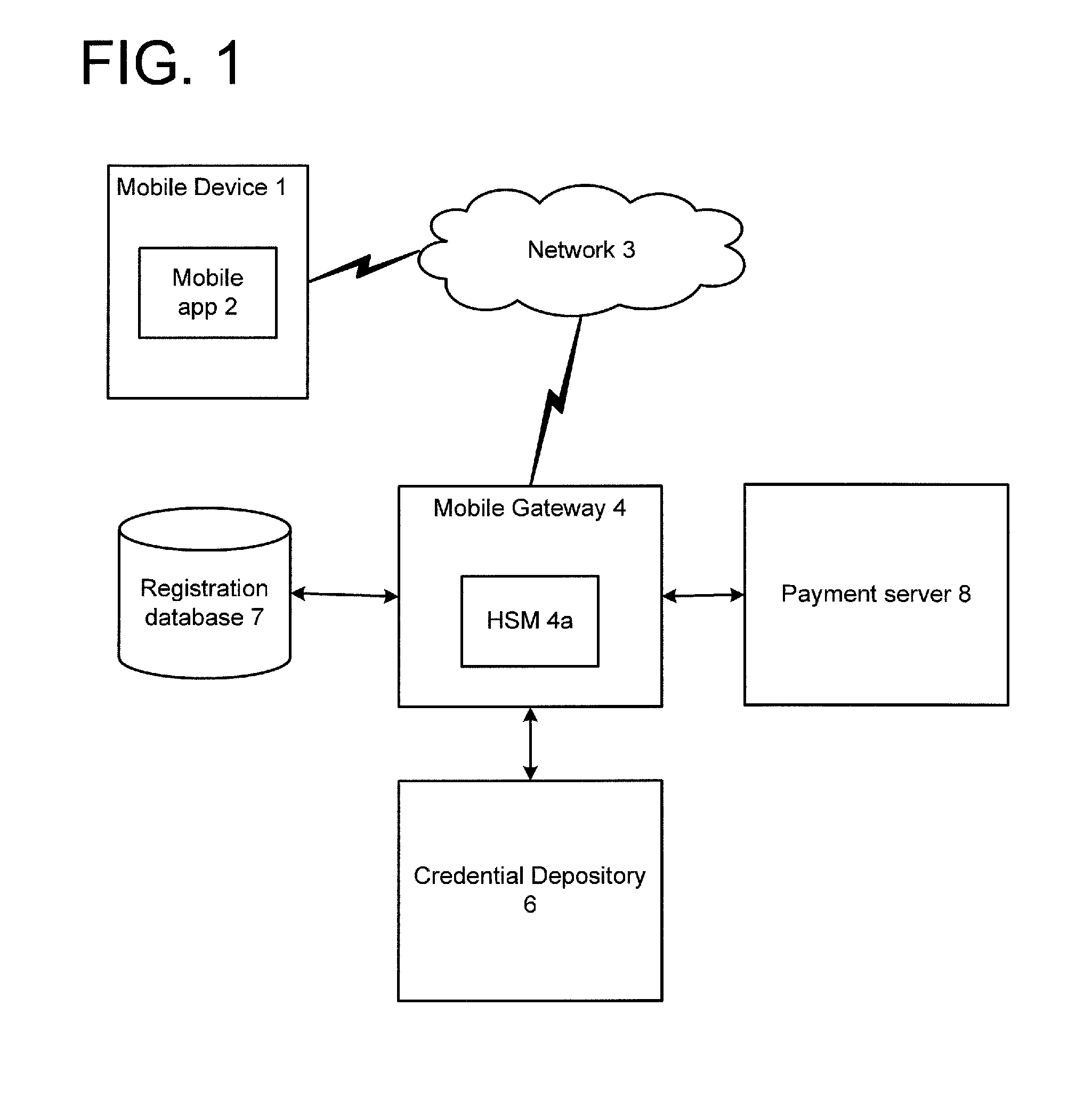
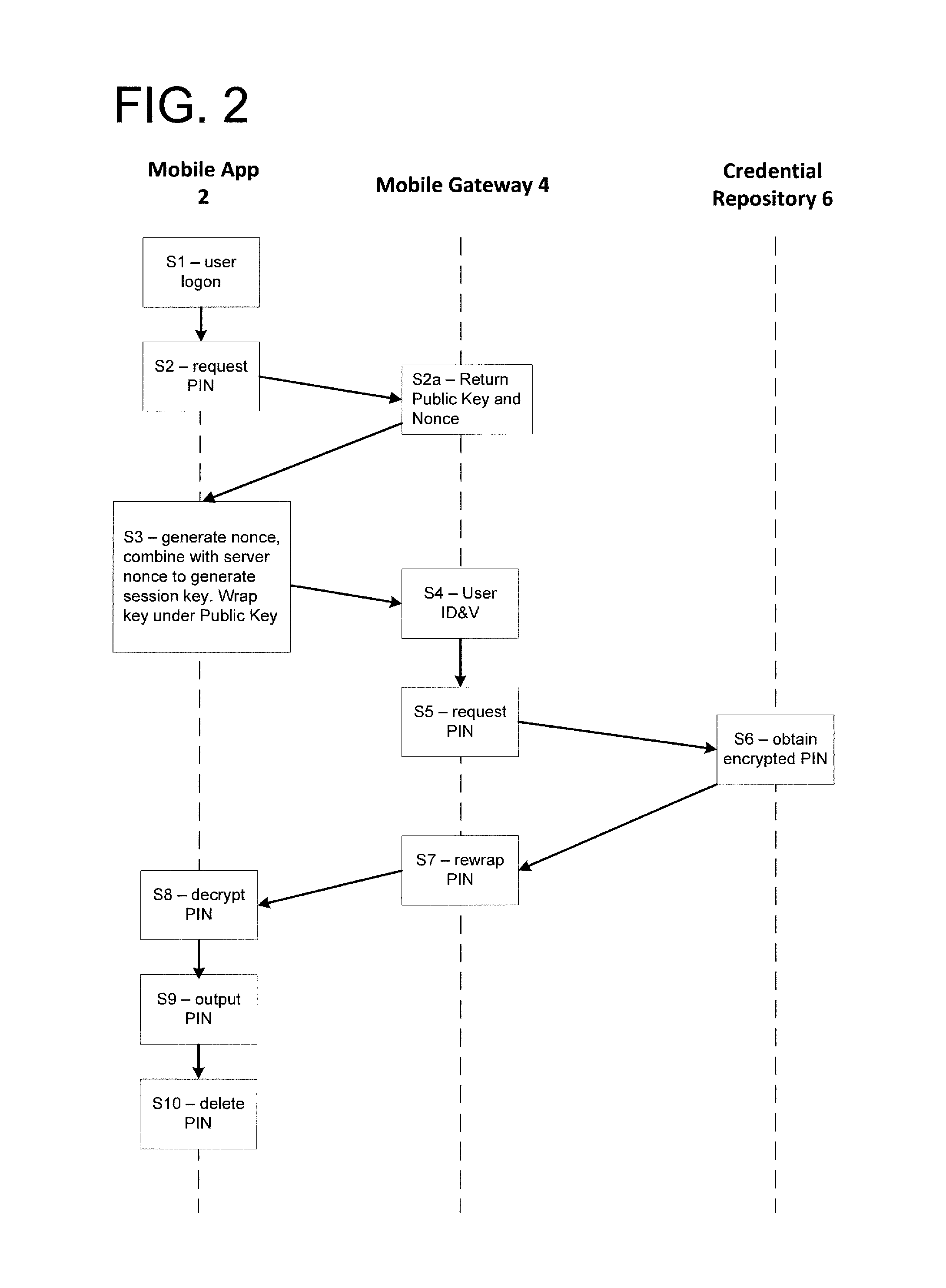
Credential Recovery
ActiveUS20140156989A1Key distribution for secure communicationDigital data authenticationHardware security moduleCommunication device
In a credential recovery process, a user is authenticated using an application running on a mobile communications device, and requests recovery of a credential. The application generates a session key encrypted with the public key of a gateway, and sends the encrypted key to the gateway. The gateway recovers the credential from a depository, encrypted using a symmetric key shared with the depository. The gateway decrypts the credential and re-encrypts the credential using the session key. Preferably, the decryption and re-encryption is performed within a hardware secure module within the gateway. The re-encrypted credential is sent to the application, which decrypts the credential and outputs it to the user. In this way, the credential is provided securely to the user and may be made available for use immediately, or nearly so.
Owner:BARCLAYS EXECUTION SERVICES LTD
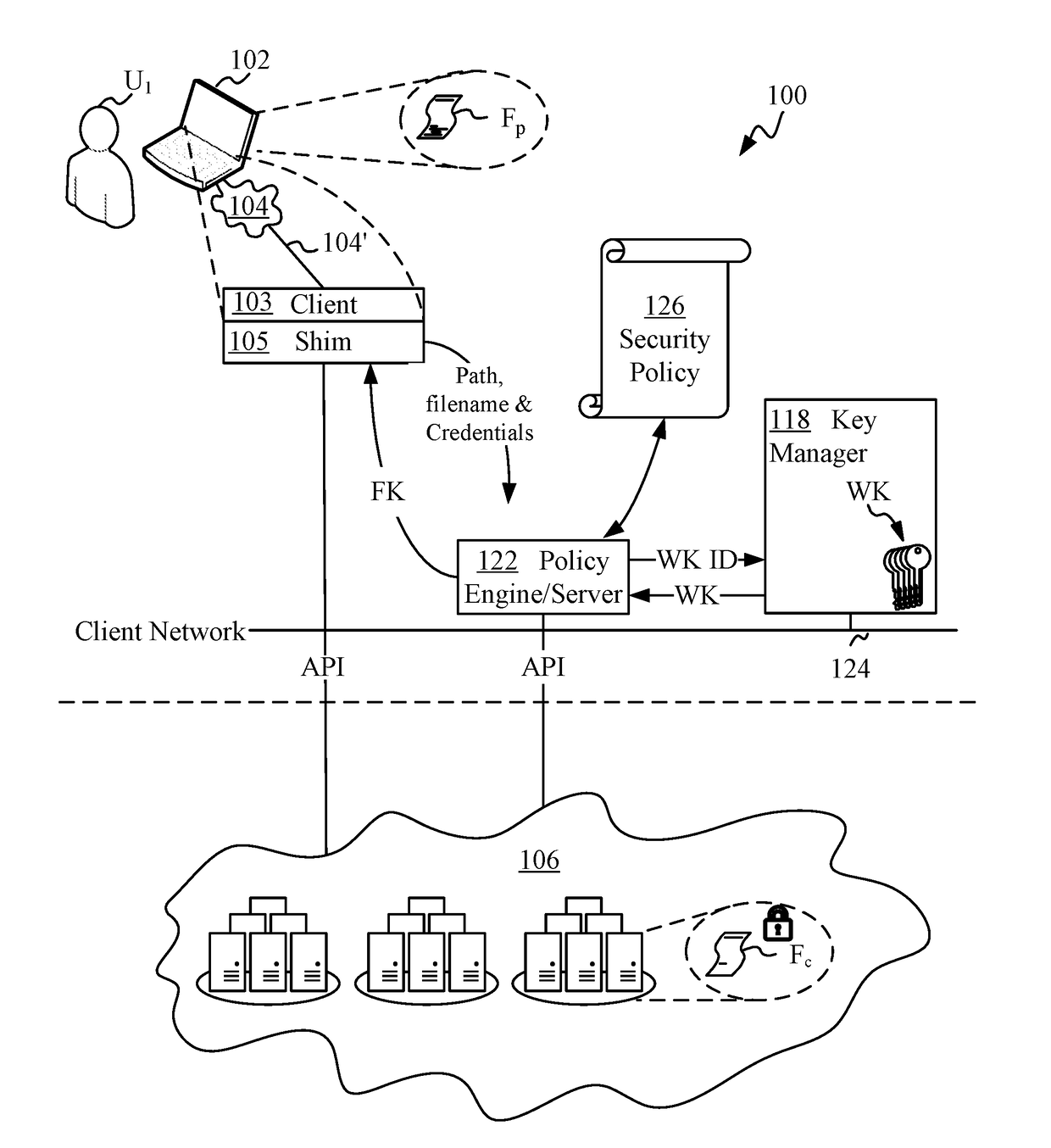
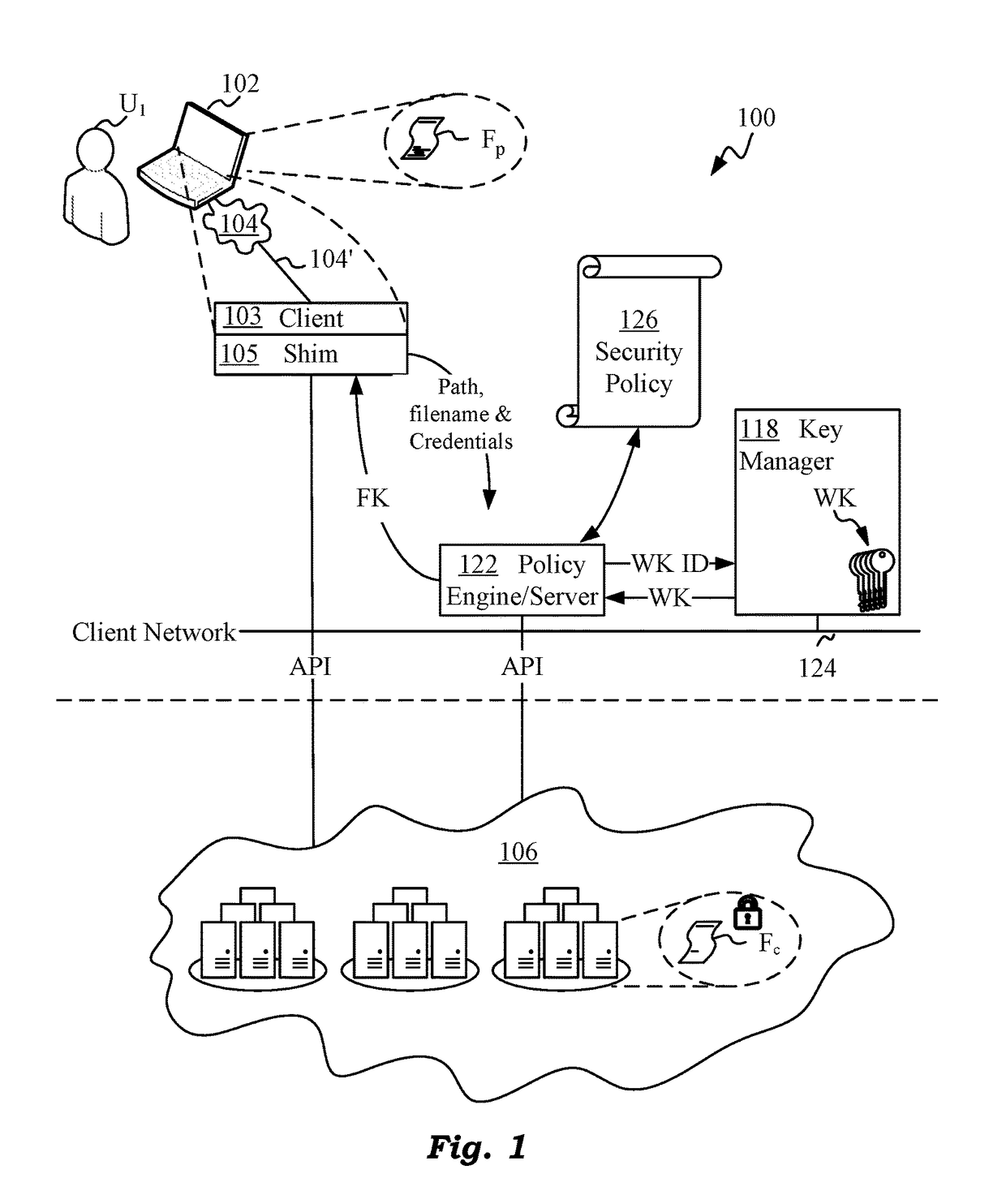
Cloud Storage Encryption
ActiveUS20180082076A1Improve integrityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesManagement toolHardware security module
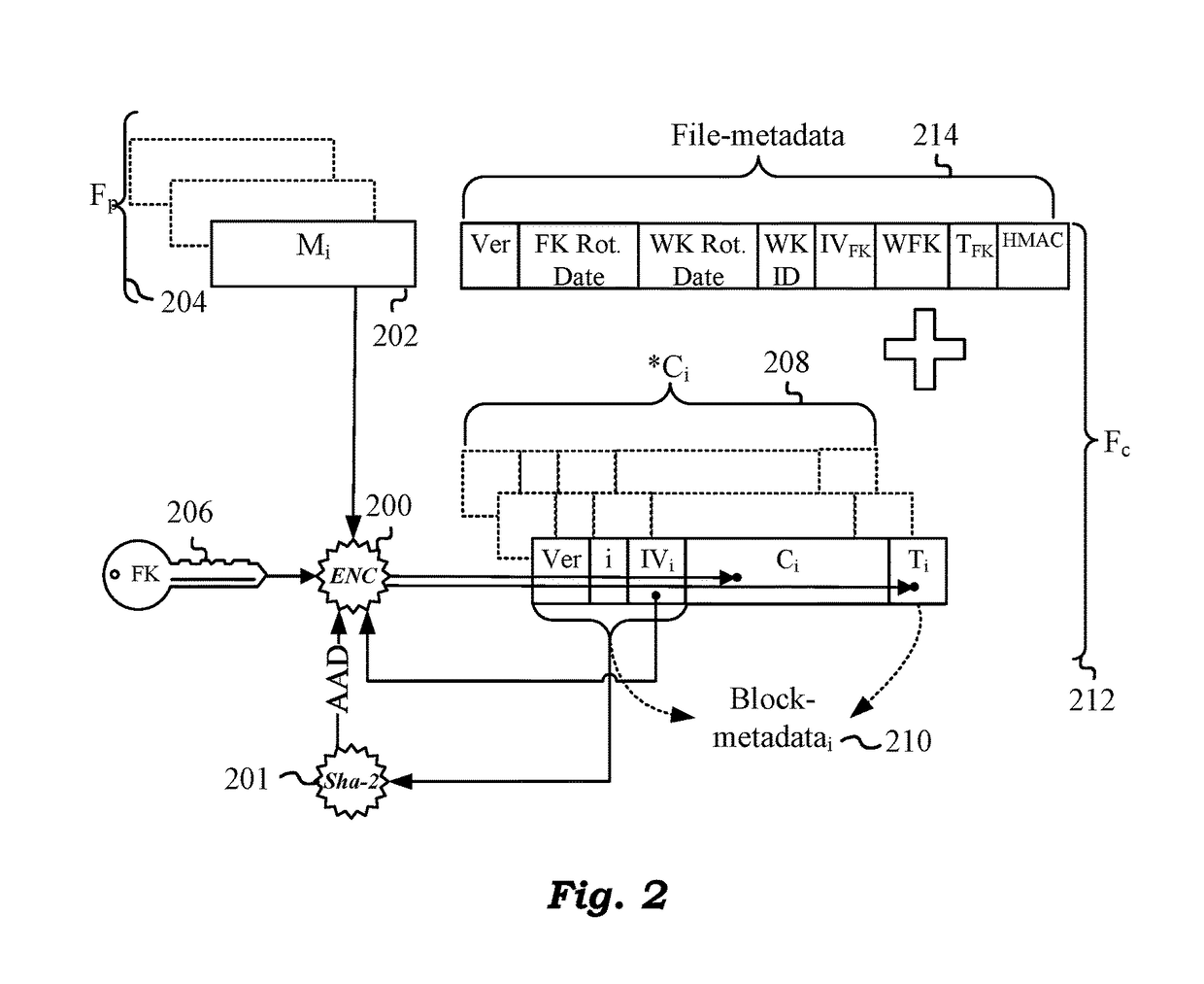
Techniques are disclosed for securing data in a cloud storage. Plaintext files are stored as secured, encrypted files in the cloud. The ciphering scheme employs per-block authenticated encryption and decryption. A unique file-key is used to encrypt each file. The file-key is wrapped by authenticated encryption in a wrapping-key that may be shared between files. A centralized security policy contains policy definitions which determine which files will share the wrapping-key. Wrapping-keys are stored in a KMIP compliant key manager which may be backed by a hardware security module (HSM). File metadata is further protected by a keyed-hash message authentication code (HMAC). A policy engine along with administrative tools enforce the security policy which also remains encrypted in the system.
Owner:ZETTASET
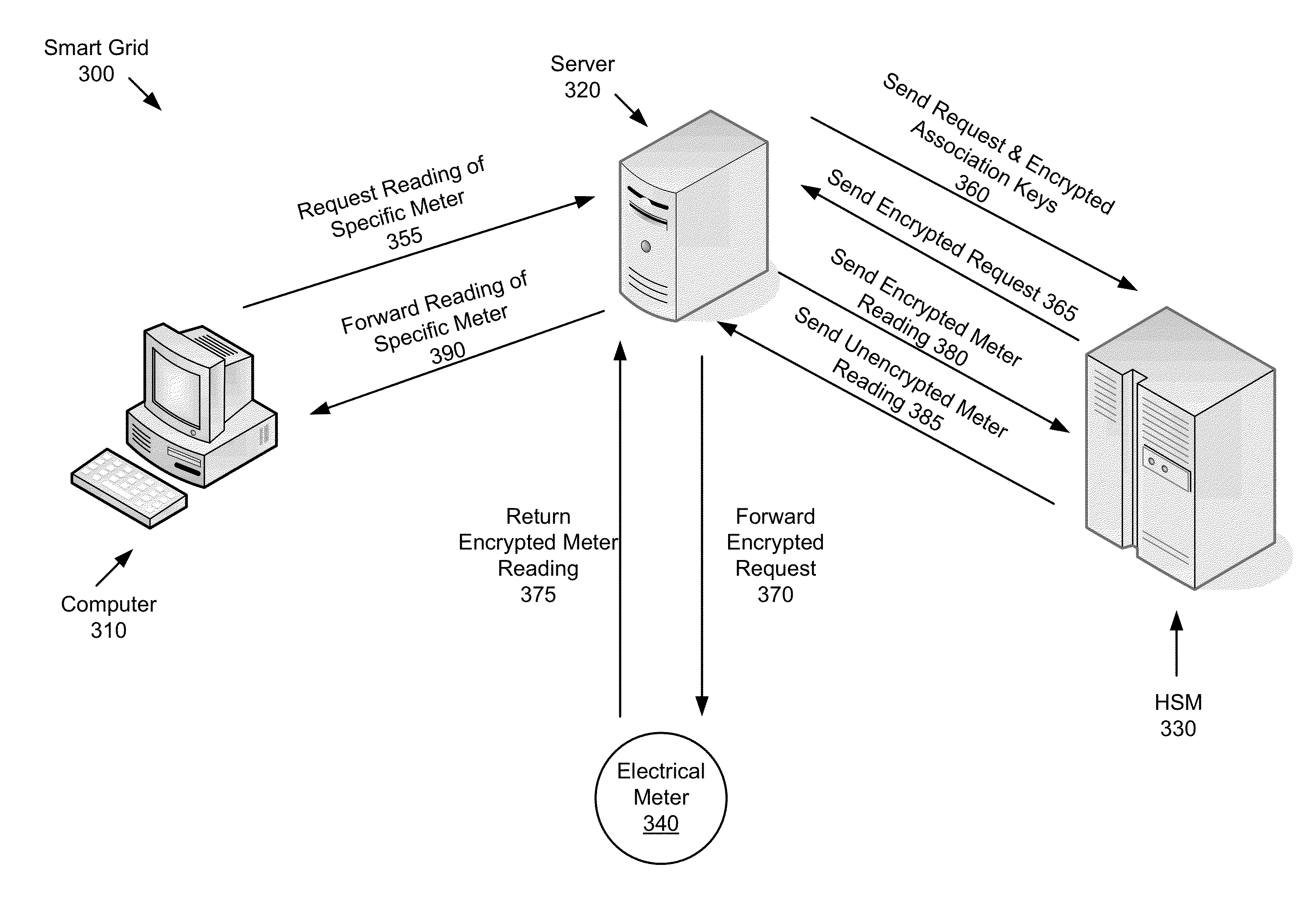
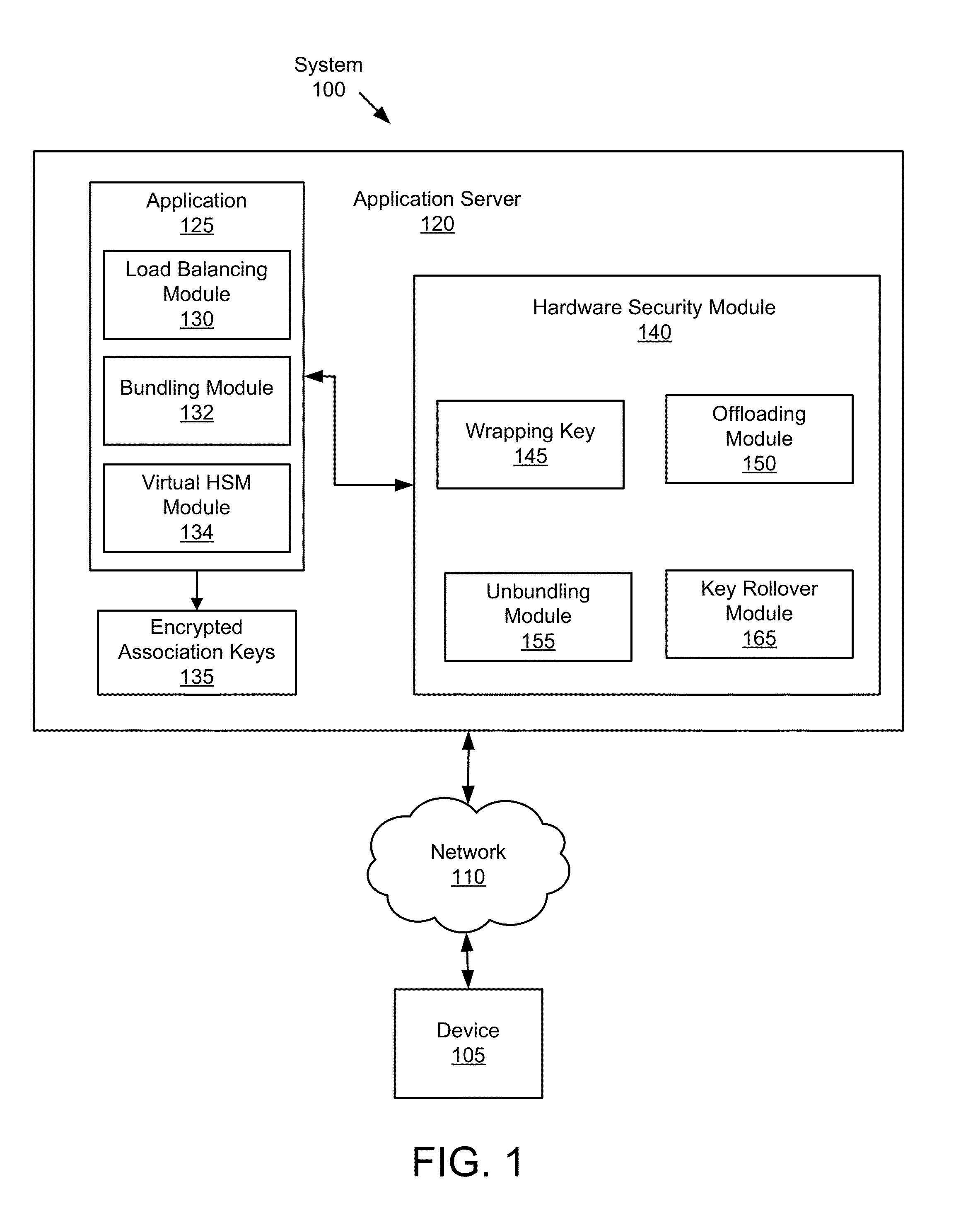
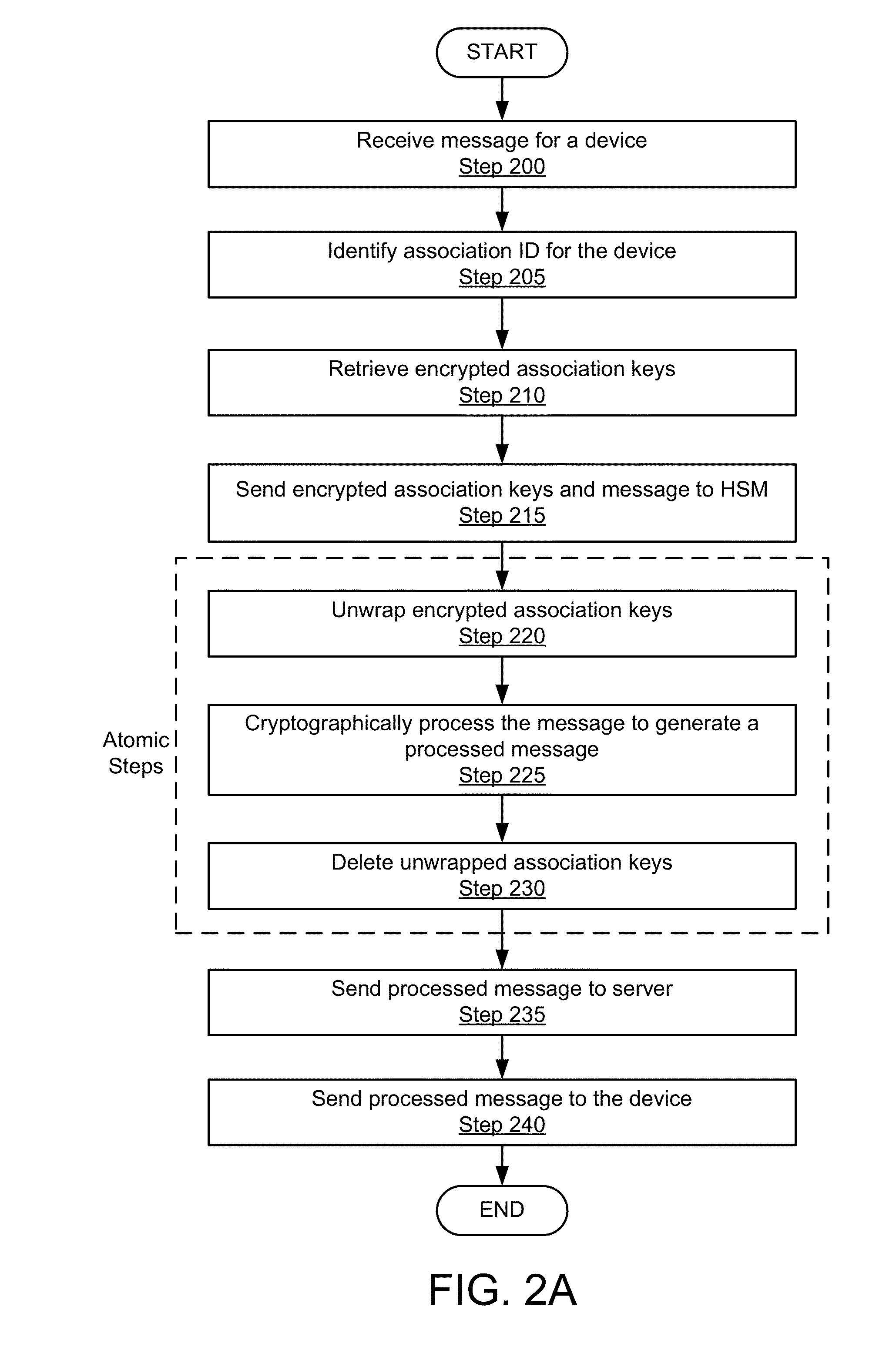
System and method for enabling a scalable public-key infrastructure on a smart grid network
ActiveUS20140281483A1Remote meteringInformation technology support systemComputer hardwareHardware security module
A method for enabling a scalable public-key infrastructure (PKI) comprises invoking a process of receiving a message for a device, identifying an association ID for the device, retrieving encrypted association keys stored on the server for communicating with the device, the encrypted association keys encrypted using a wrapping key stored on a Hardware Security Module (HSM). The method further comprises sending the message and the encrypted association keys to the HSM, unwrapping, by the HSM, the encrypted association keys to create unwrapped association keys, cryptographically processing the message to generate a processed message, deleting the unwrapped association keys, sending the processed message to the device, and invoking, concurrently and by a second application, the process.
Owner:SILVER SPRING NETWORKS
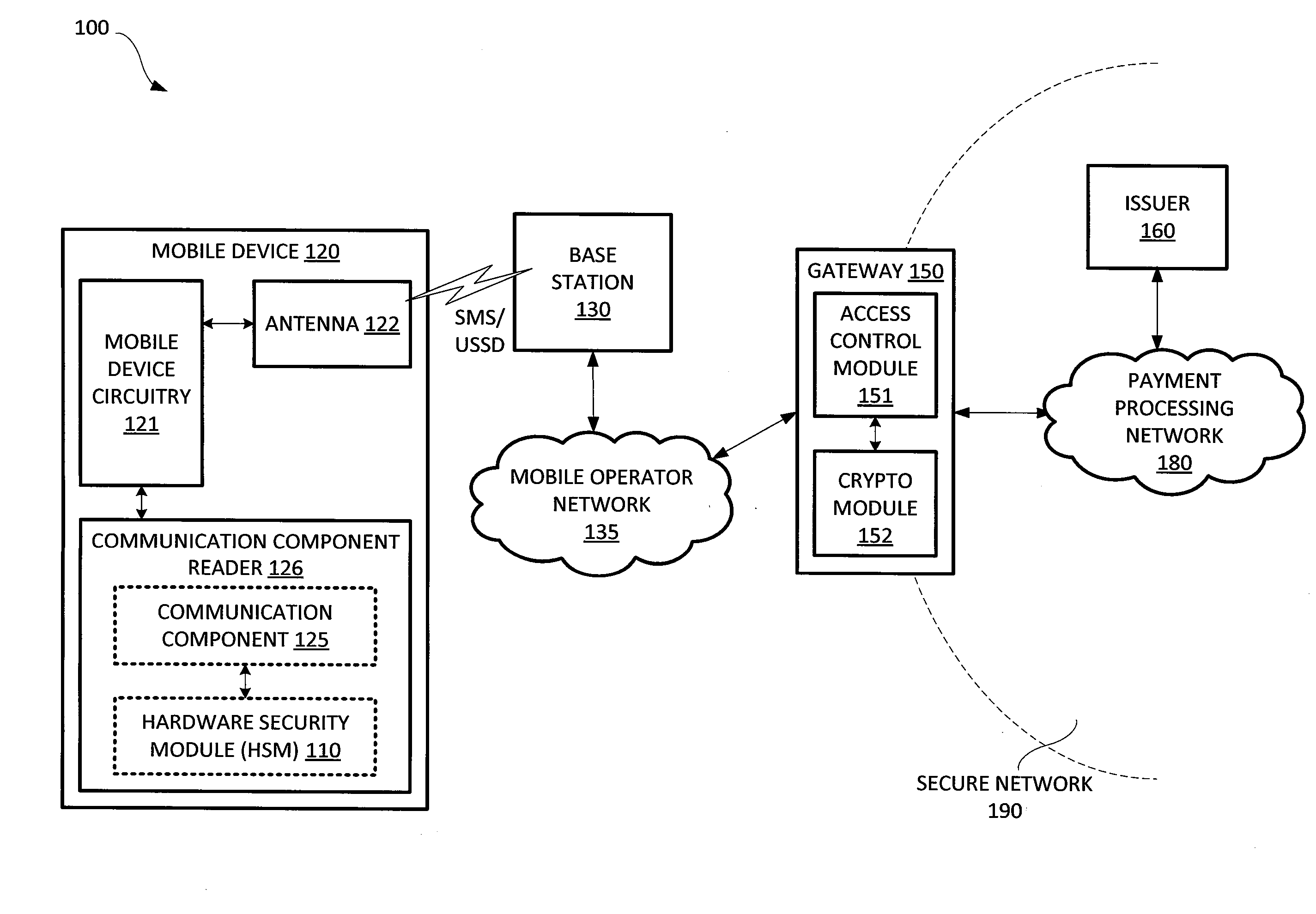
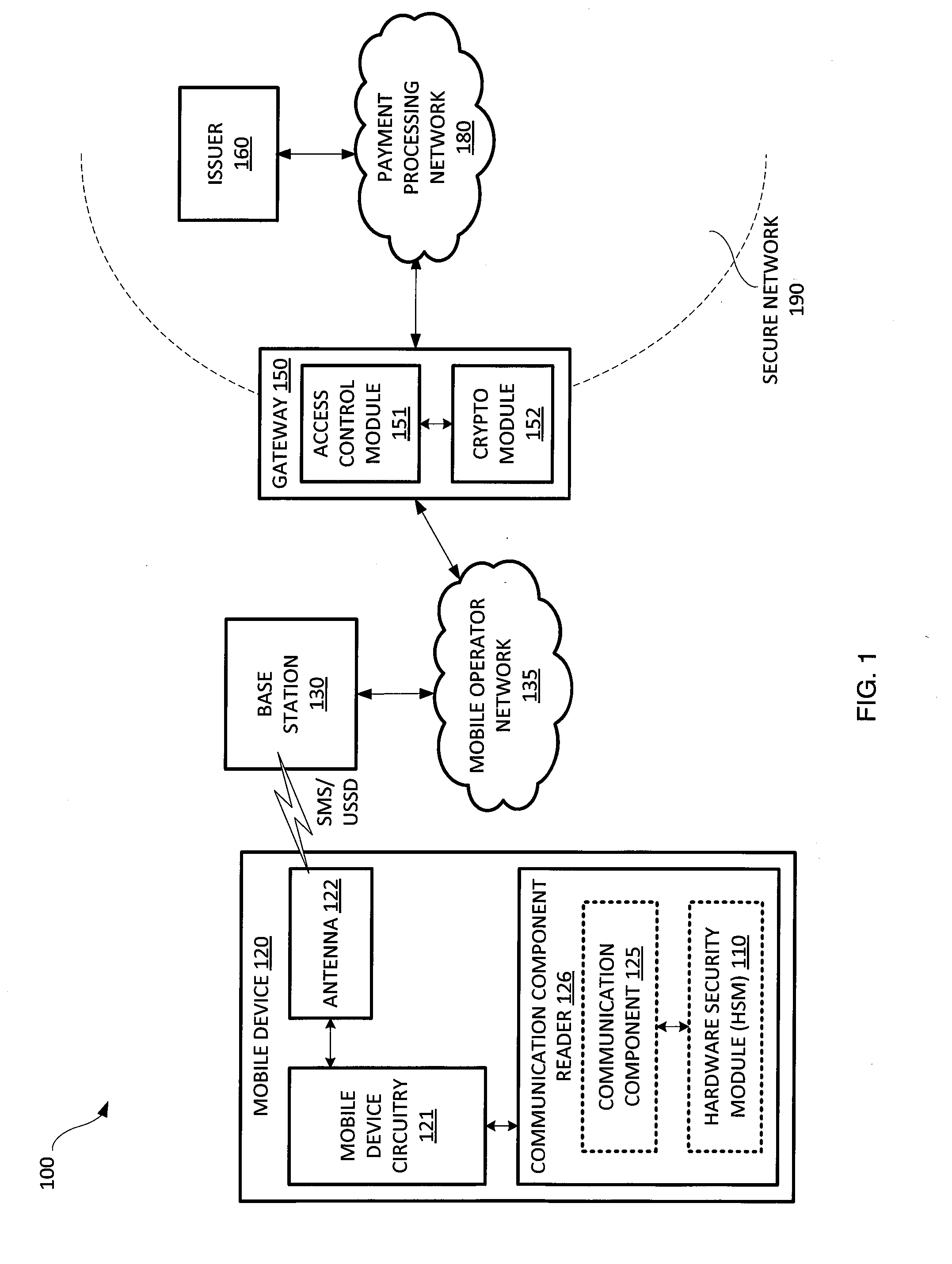
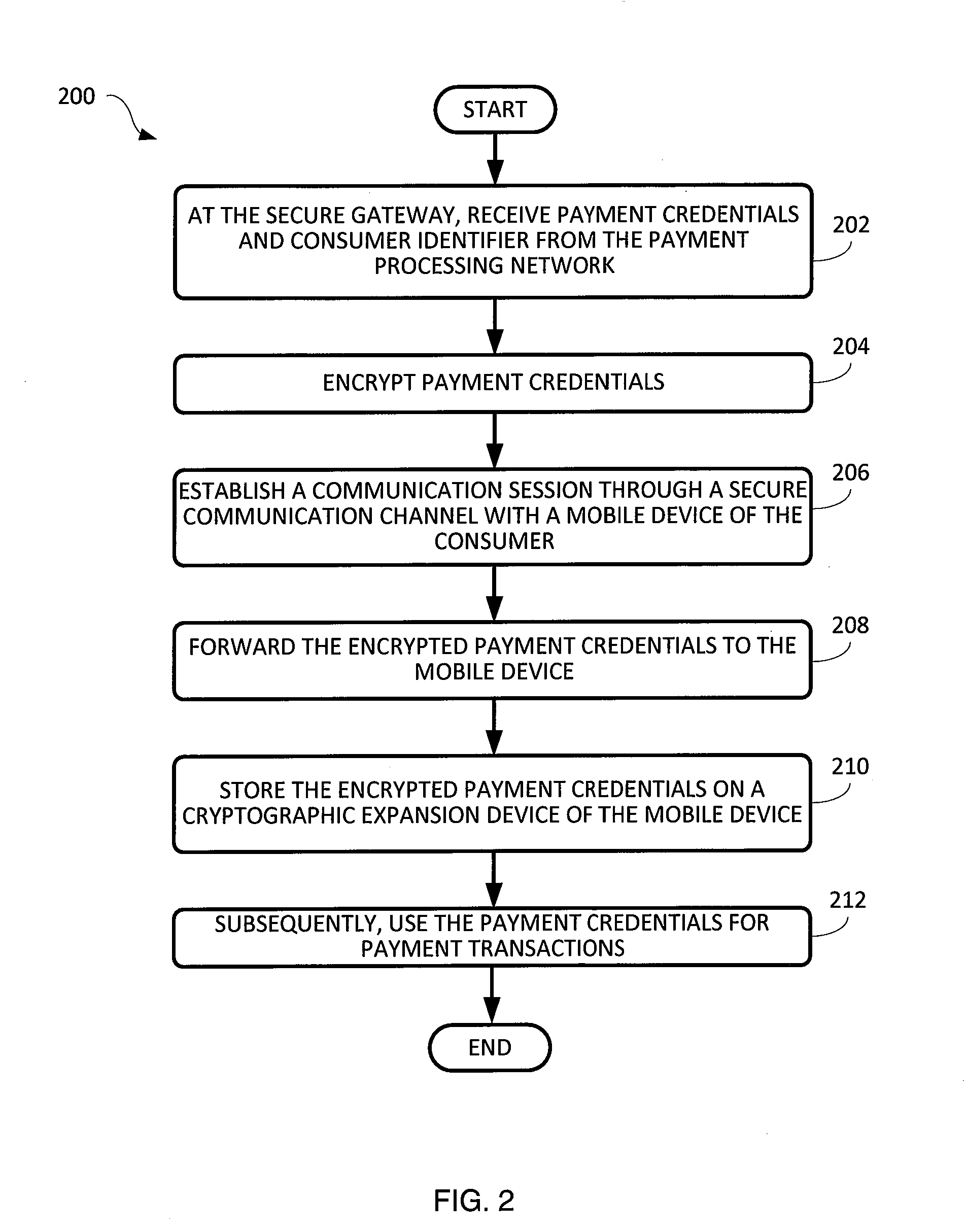
Issuing and storing of payment credentials
A system and method of issuing payment credentials to a consumer is disclosed. A payment processing network sends payment credentials and an identifier of a consumer to whom the payment credentials belong to a secure gateway. The secure gateway encrypts or zone translates the payment credentials and sends them to a mobile device of the consumer through a secure communication channel. The mobile device includes a hardware security module (HSM) which stores the payment credentials to be used for subsequent financial transactions by the consumer. Multiple sets of payment credentials may be stored on the HSM, corresponding to multiple payment accounts belonging to the consumer.
Owner:VISA INT SERVICE ASSOC
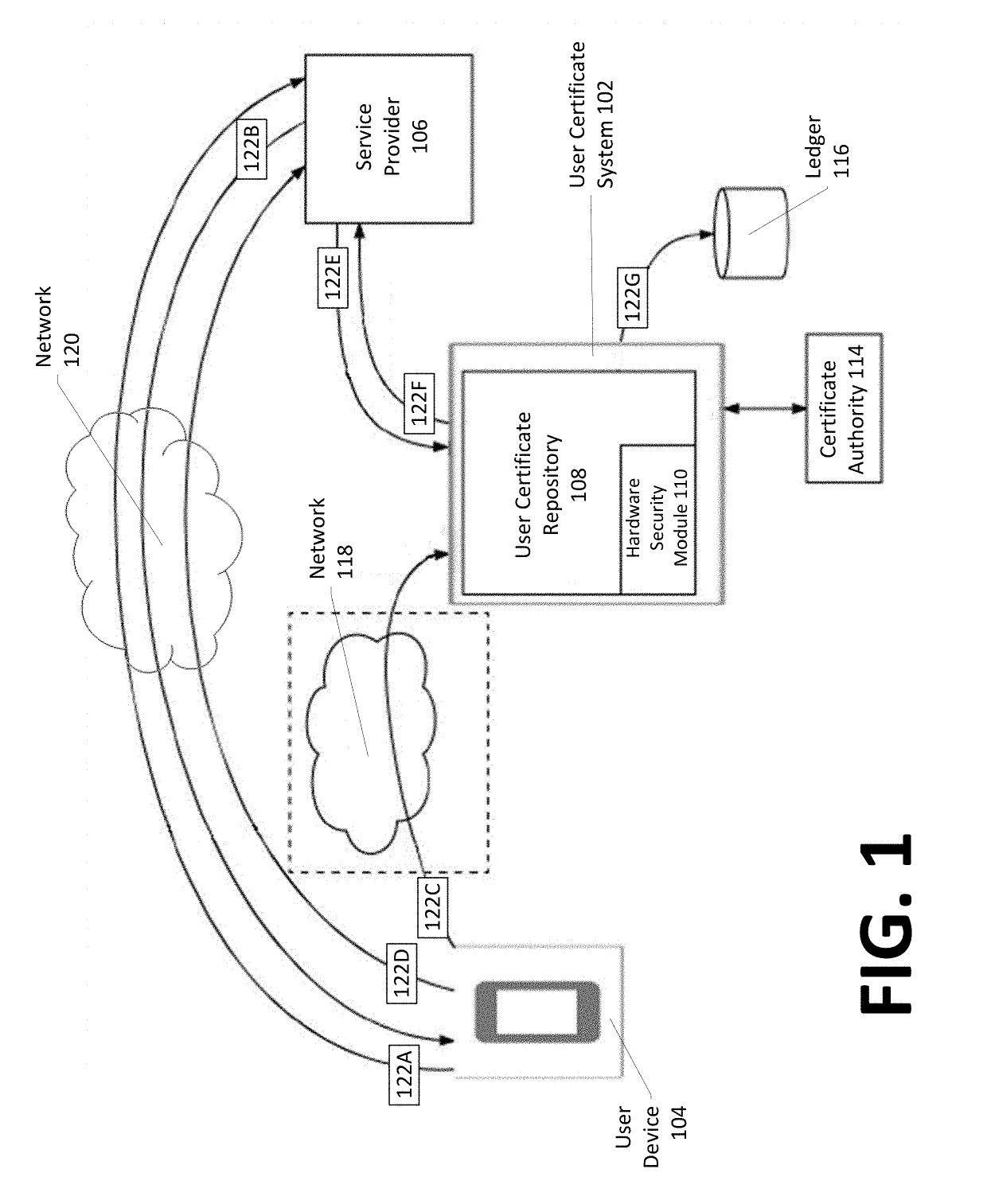
Identity-linked authentication through a user certificate system
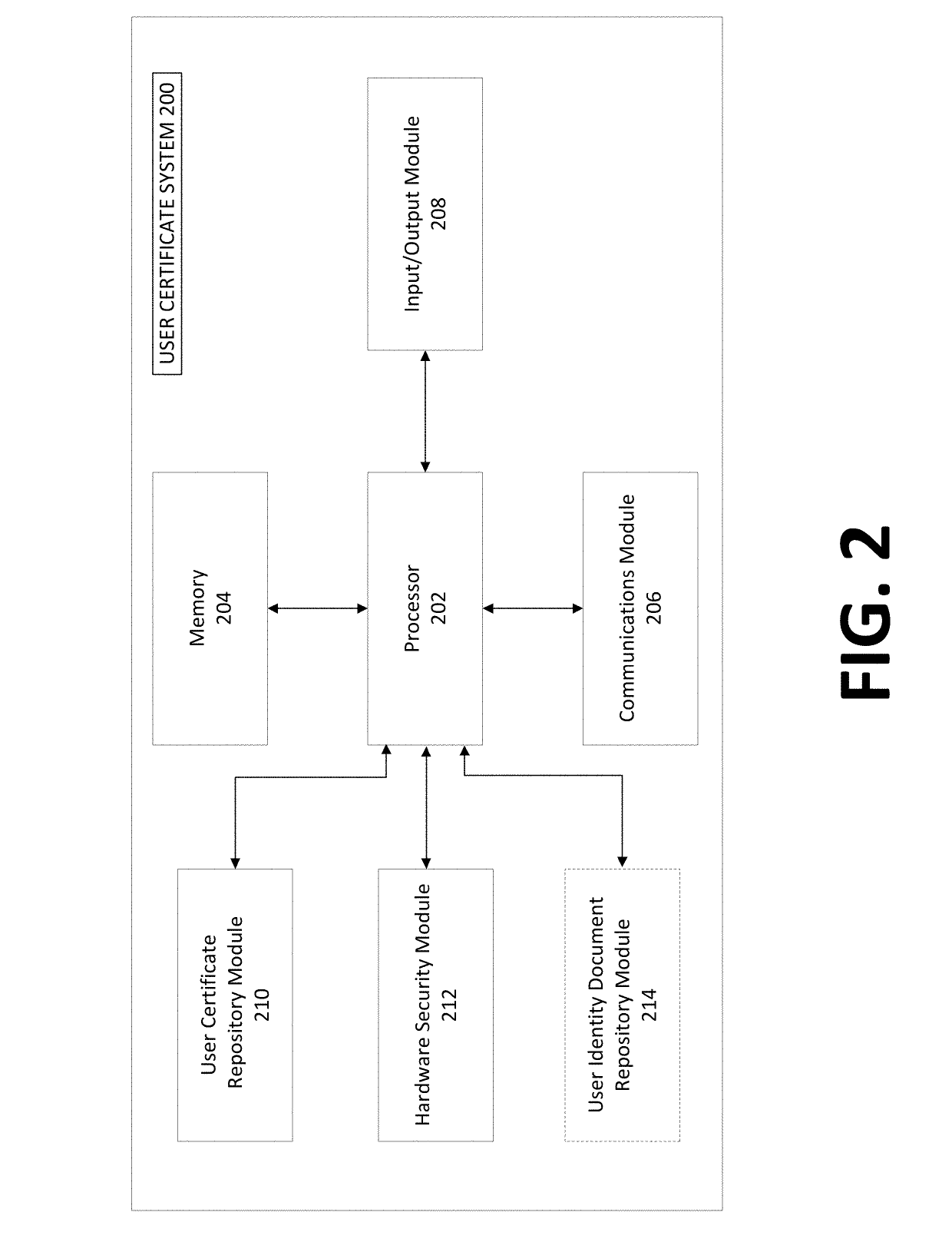
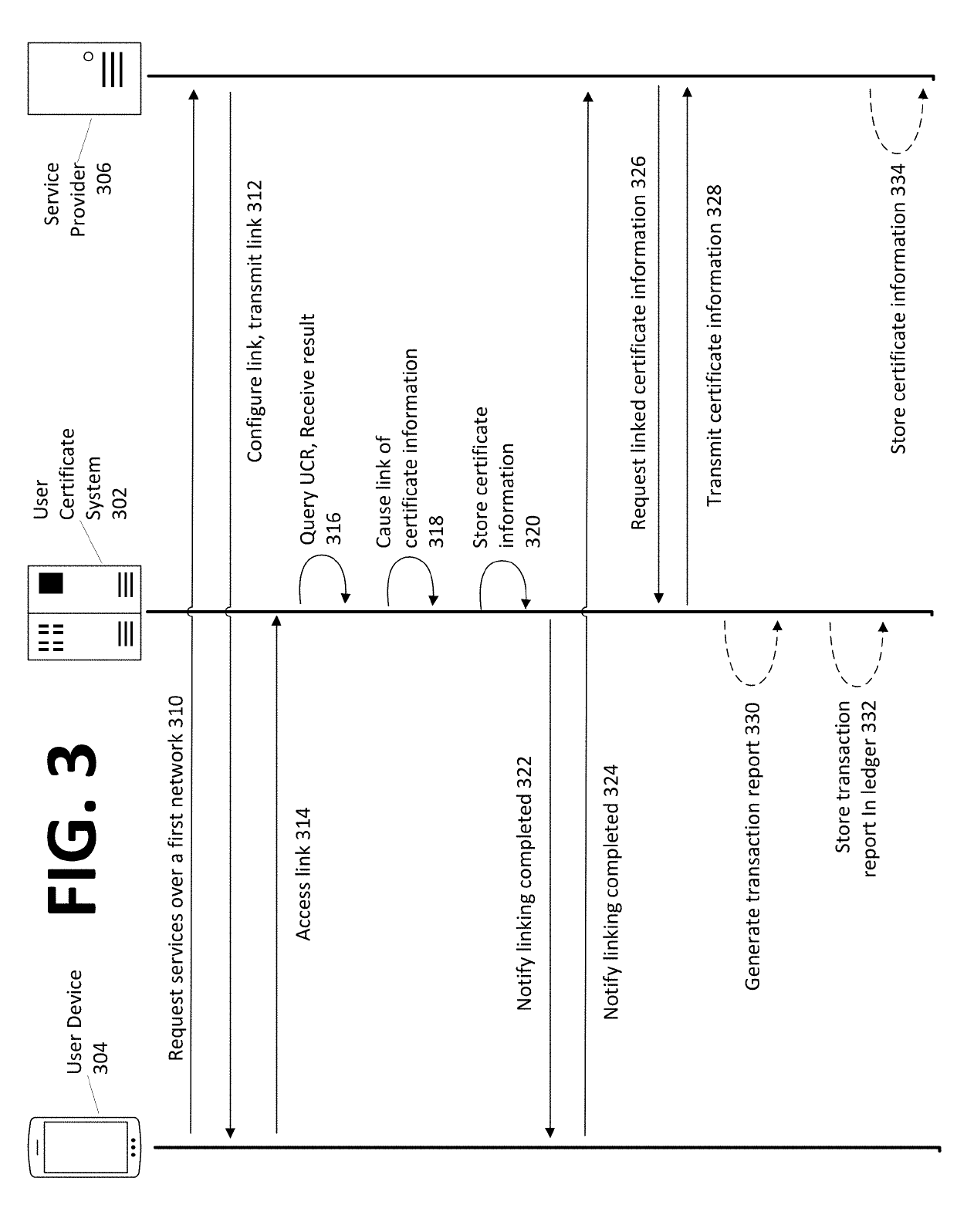
InactiveUS20190140844A1Easy accessKey distribution for secure communicationUser identity/authority verificationInternet privacyHardware security module
Systems, methods, apparatuses, and computer readable media for facilitating user identity authentication to a service provider by linking, on a user certificate system, identity-linked information to certificate information, such that the certificate information may be used to generate an identity message that the service provider may verify to confirm a user identity. An exemplary method comprises receiving identity-linked information, retrieving public certificate information, retrieving, from a hardware security module, a private key, causing transmission, over a second network to the service provider, of a notification that an identity message is available for access, the identity message based on the retrieved public certificate information and the retrieved private key, and upon reception, from the service provider, of a request for the identity message, generating and transmitting the identity message, wherein the identity message comprises at least an encrypted portion of the identity message encrypted using at least the private key.
Owner:AVERON US INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com