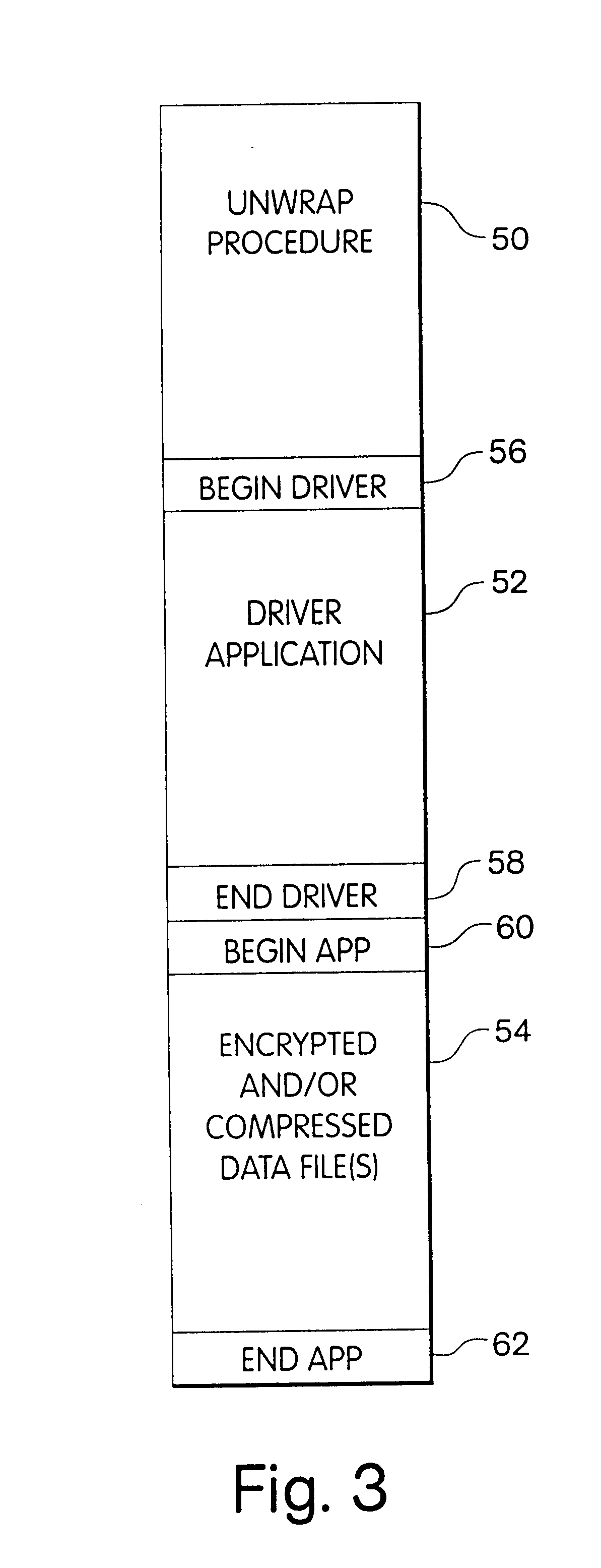
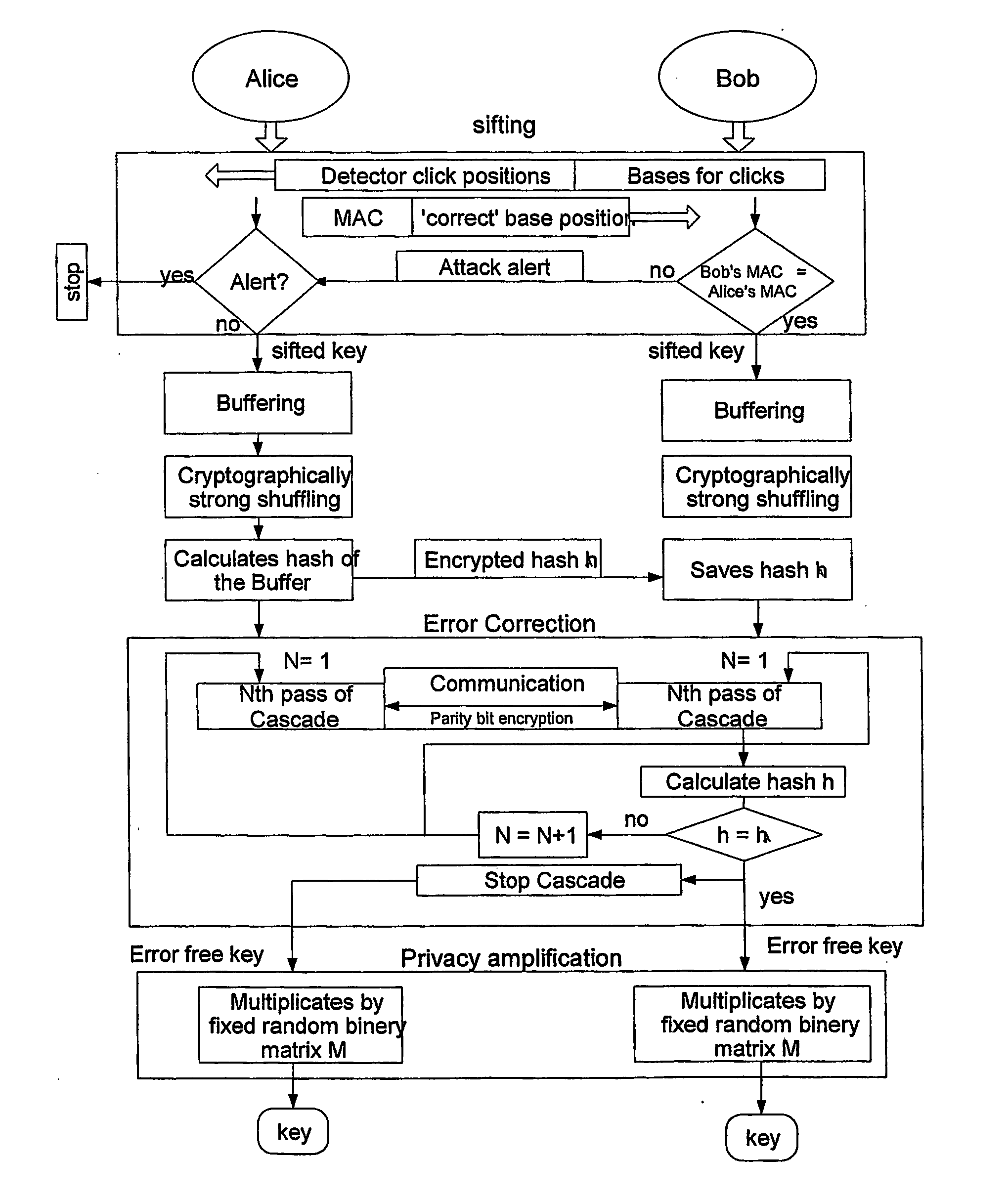
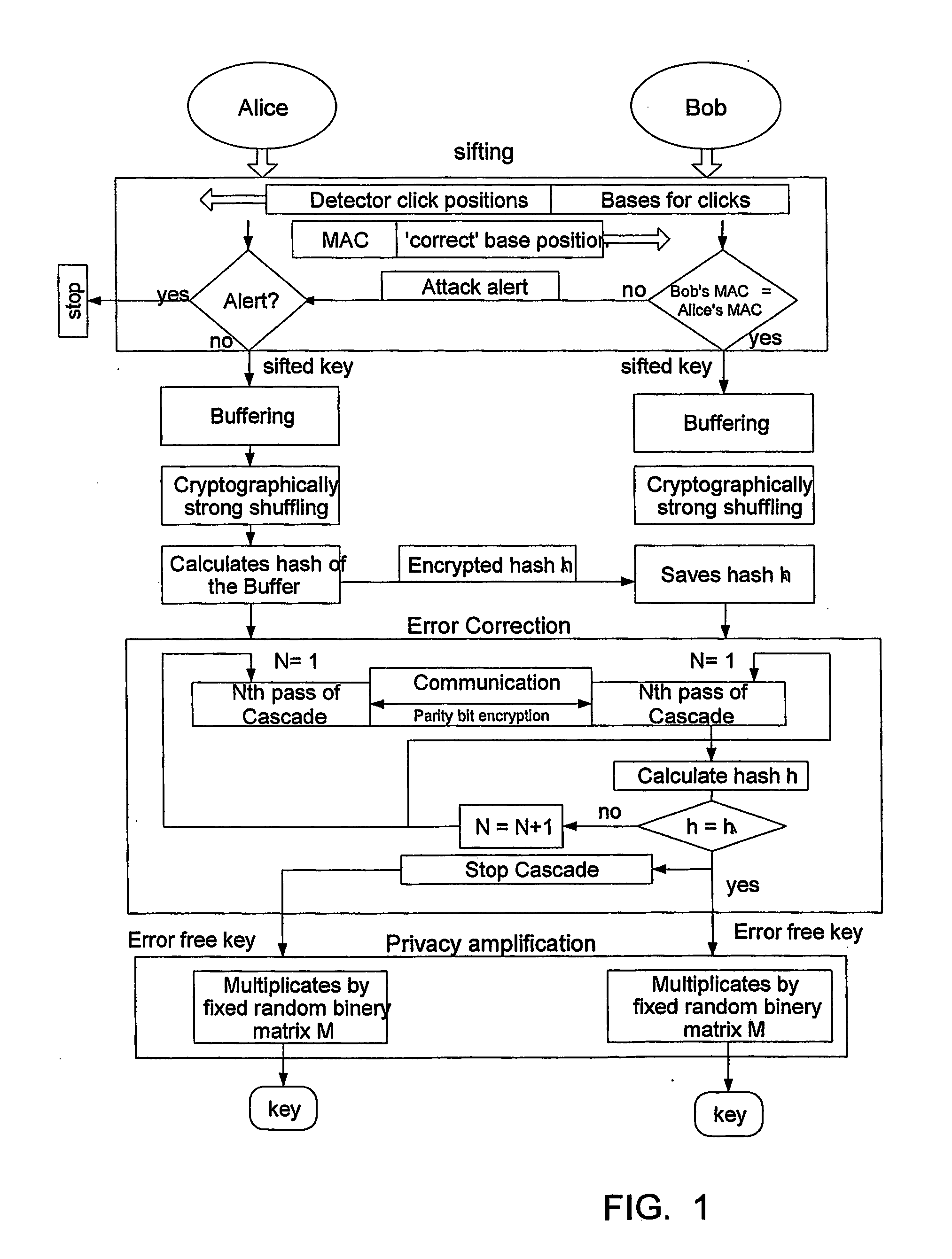
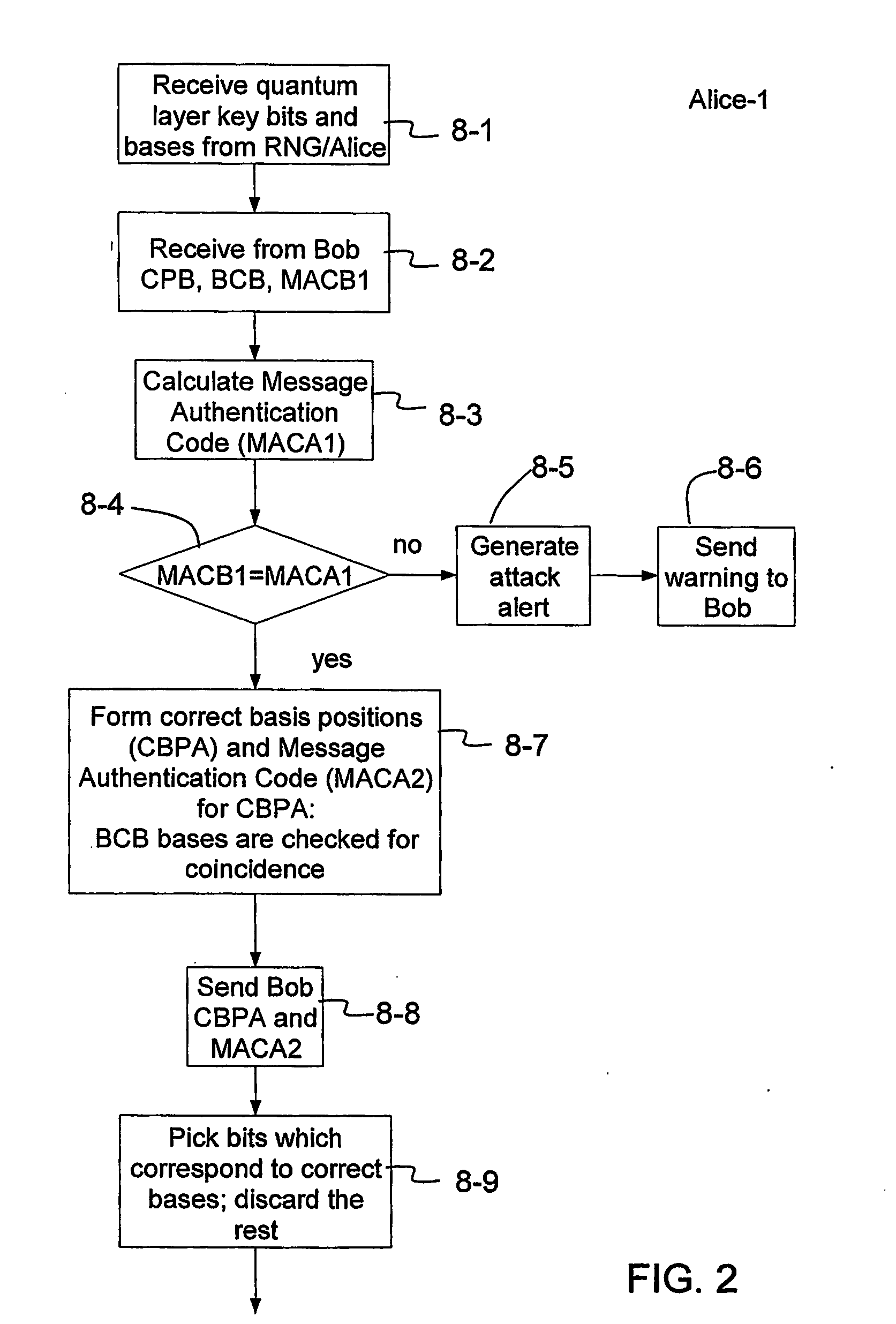
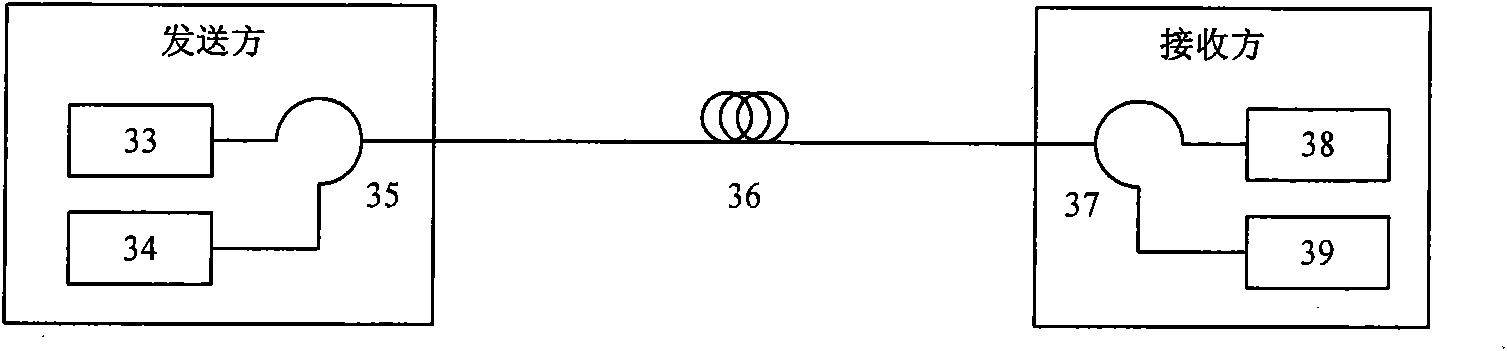Patents
Literature
176 results about "One-time pad" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
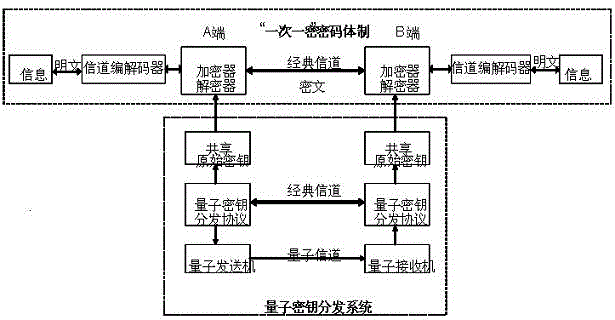
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a one-time pre-shared key the same size as, or longer than, the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition. If the key is (1) truly random, (2) at least as long as the plaintext, (3) never reused in whole or in part, and (4) kept completely secret, then the resulting ciphertext will be impossible to decrypt or break. It has also been proven that any cipher with the property of perfect secrecy must use keys with effectively the same requirements as OTP keys. Digital versions of one-time pad ciphers have been used by nations for critical diplomatic and military communication, but the problems of secure key distribution have made them impractical for most applications.
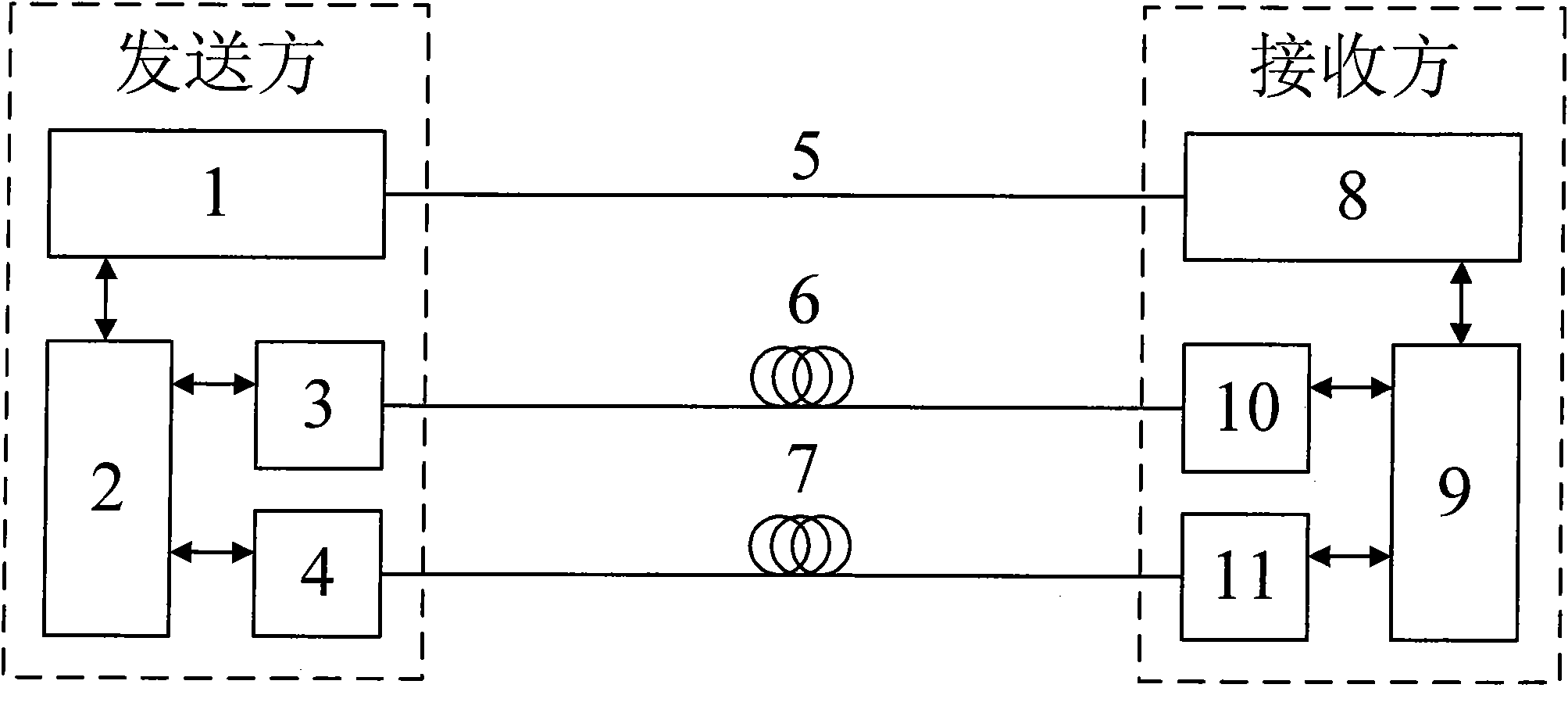
Secure two-way RFID communications
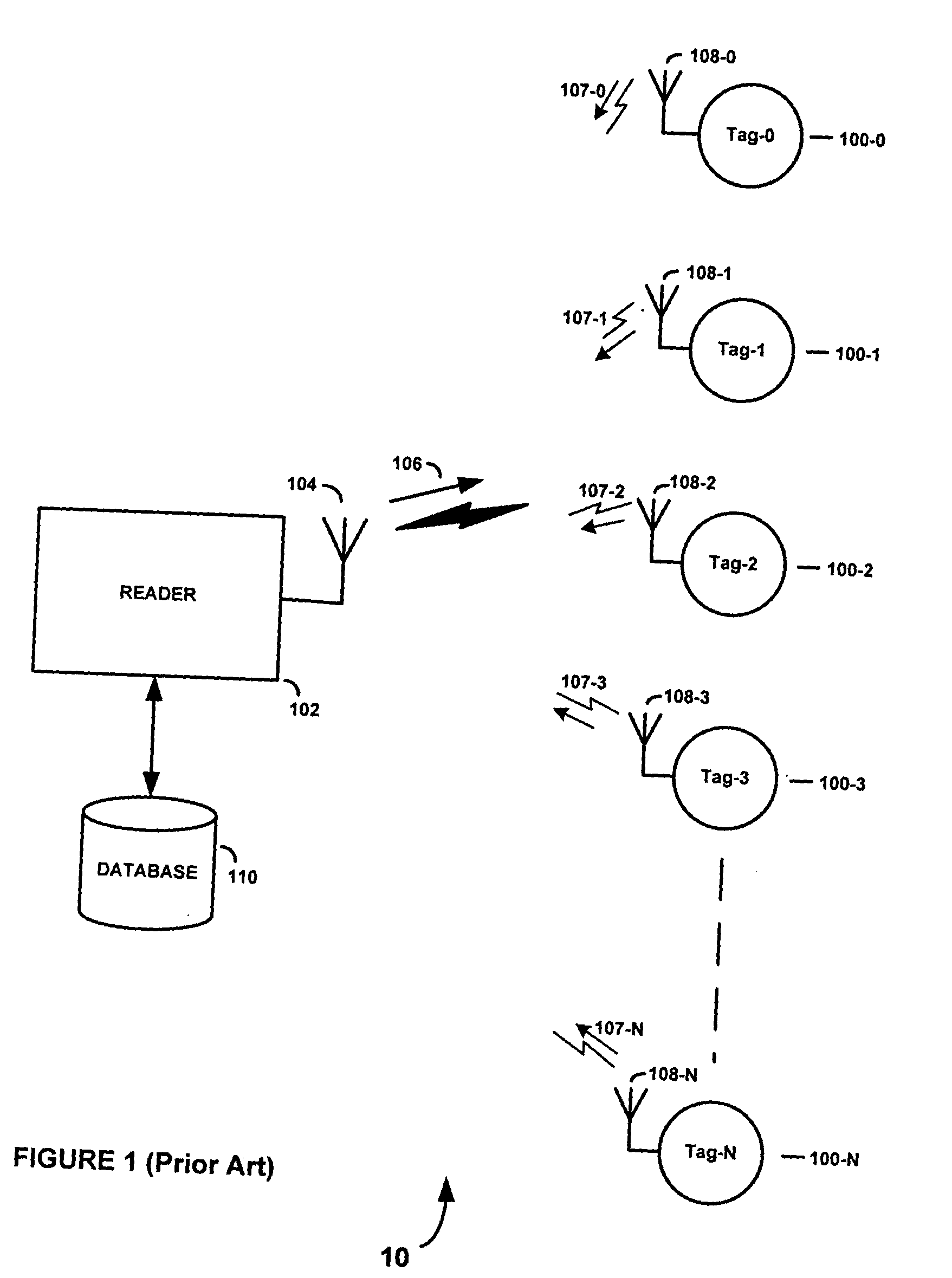
InactiveUS20050058292A1Memory record carrier reading problemsCo-operative working arrangementsComputer hardwareCarrier signal
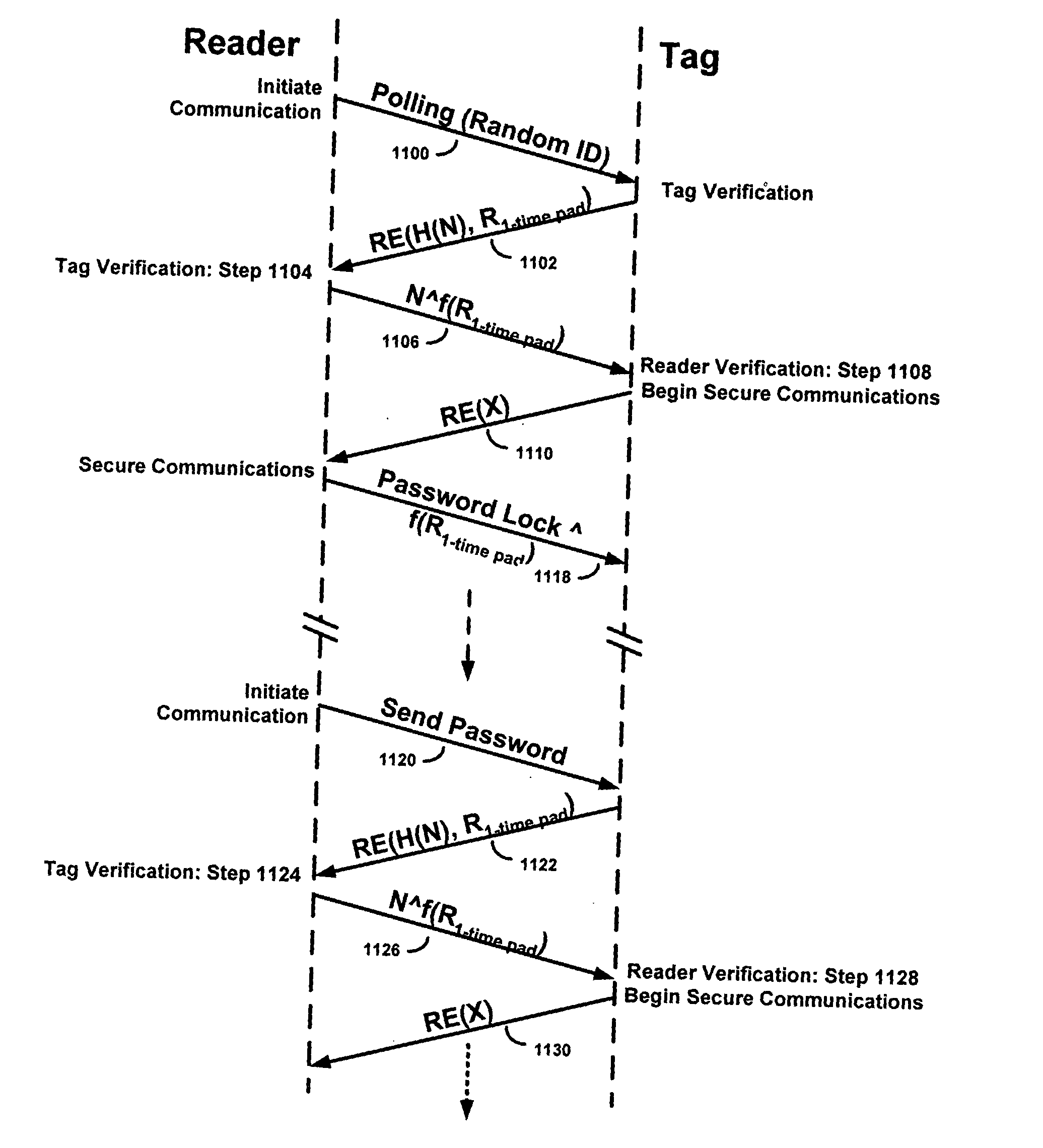
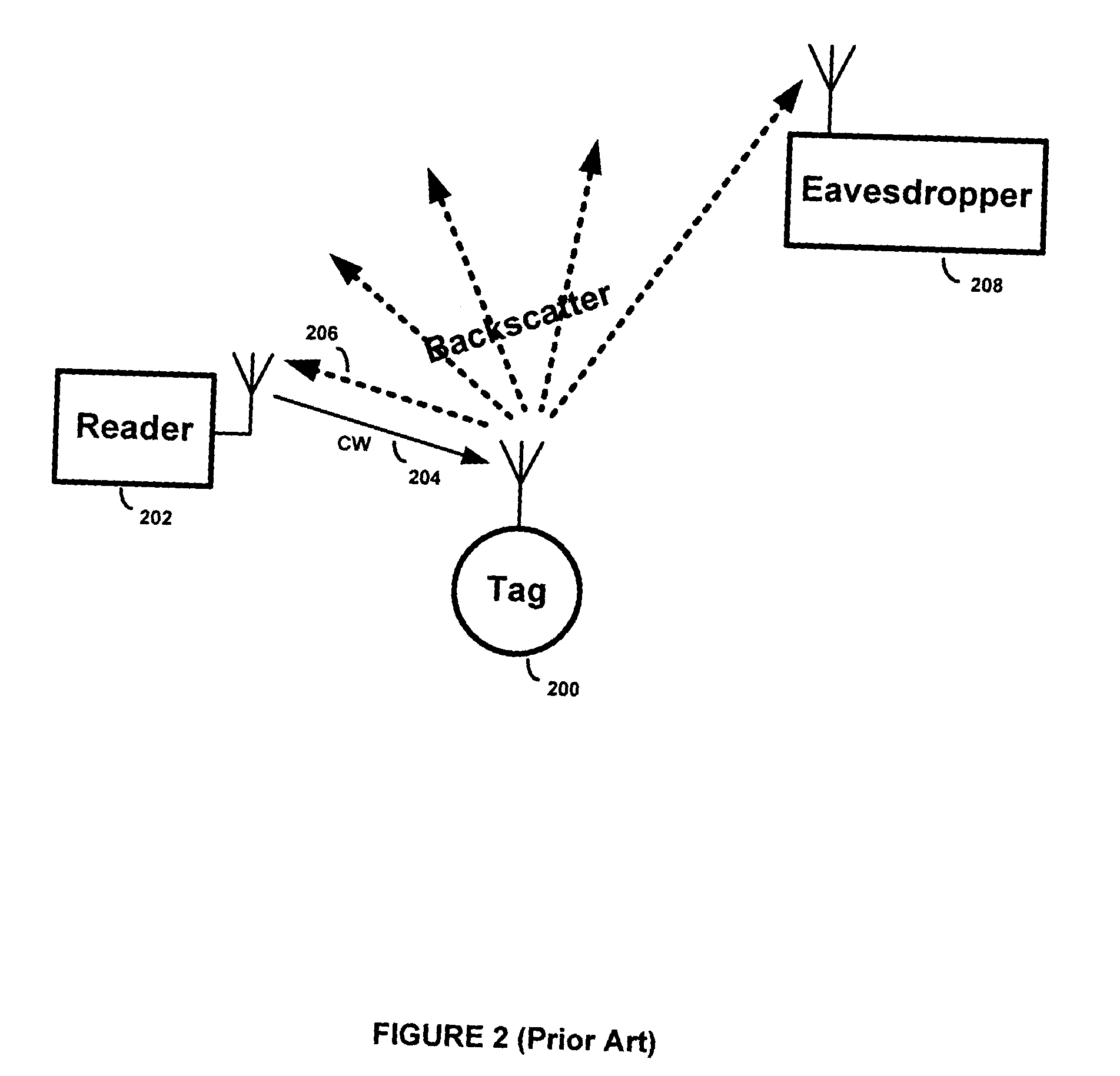
Methods and apparatus for providing secure two-way (reader-to-tag and tag-to-reader) RFID communications. According to one aspect of the invention, a tag receives a noise-encrypted RF carrier signal from a reader and backscatter modulates it with tag information. Eavesdroppers cannot extract the tag information from the backscattered signal because it is masked by the noise encryption. According to another aspect of the invention, establishing a secure two-way RFID communication link includes a reader modulating a carrier signal with a noise encryption signal and broadcasting the noise-encrypted carrier to a singulated tag. The tag backscatter modulates the noise-encrypted carrier with a first portion of a key and / or a one-time pad pseudorandom number. If a key is used, upon receiving the backscattered signal the reader verifies that the tag is authentic, and, if verified as authentic, transmits a second portion of the key, possibly encrypted by a function depending on the one-time pad pseudorandom number, to the tag.
Owner:IMPINJ
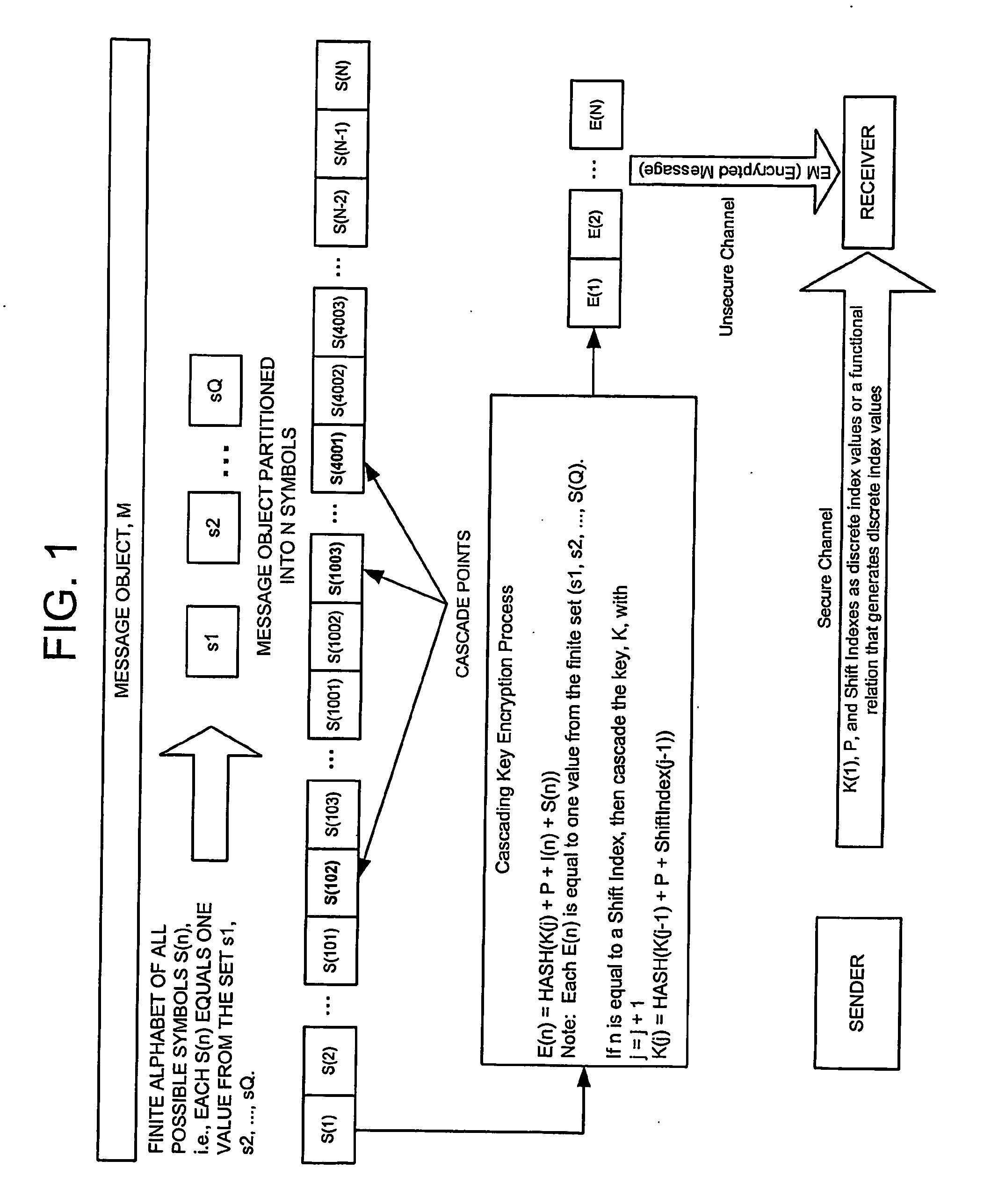
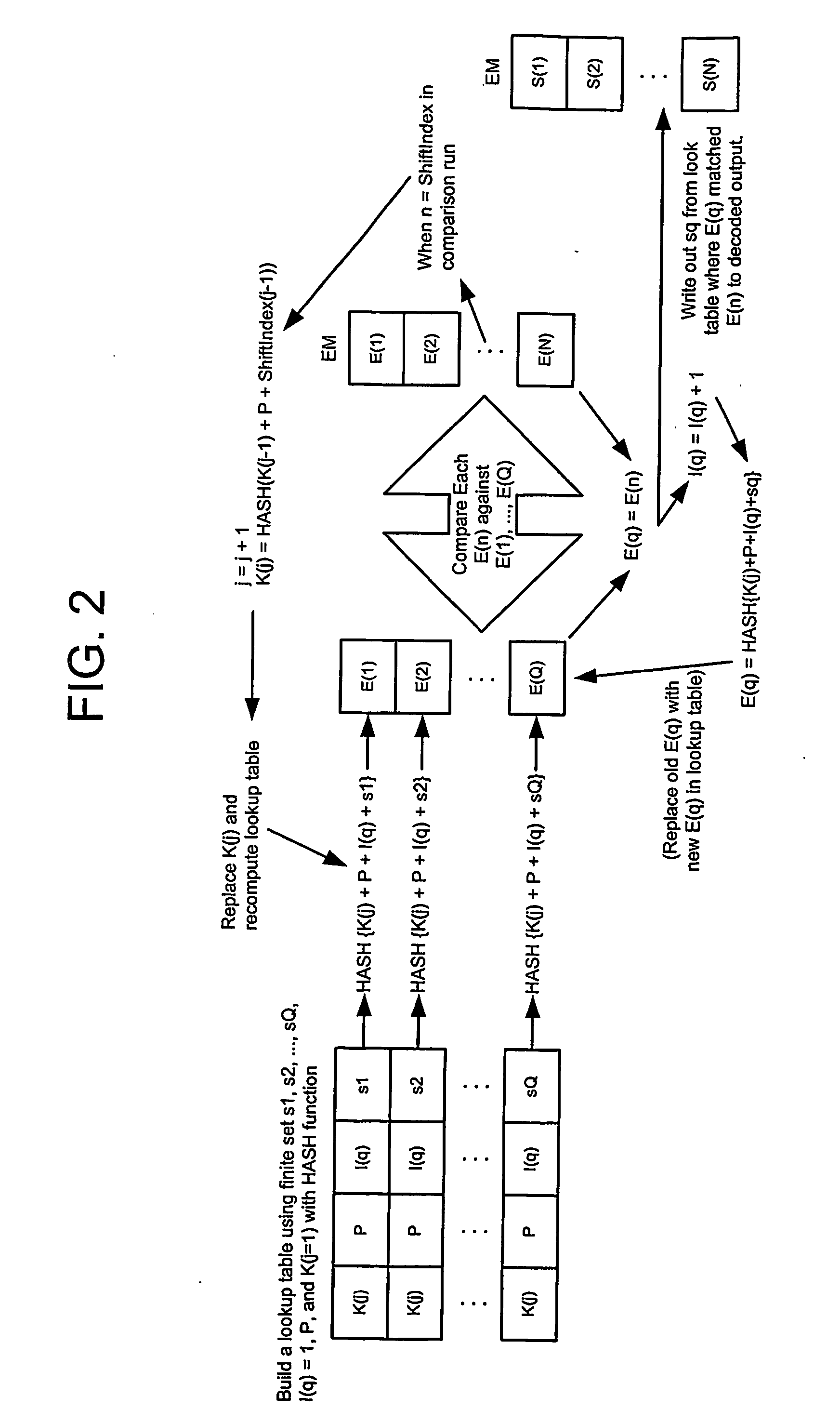
Cascading key encryption
InactiveUS20060265595A1Secure EncryptionSmall sizeKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPasswordSecure transmission
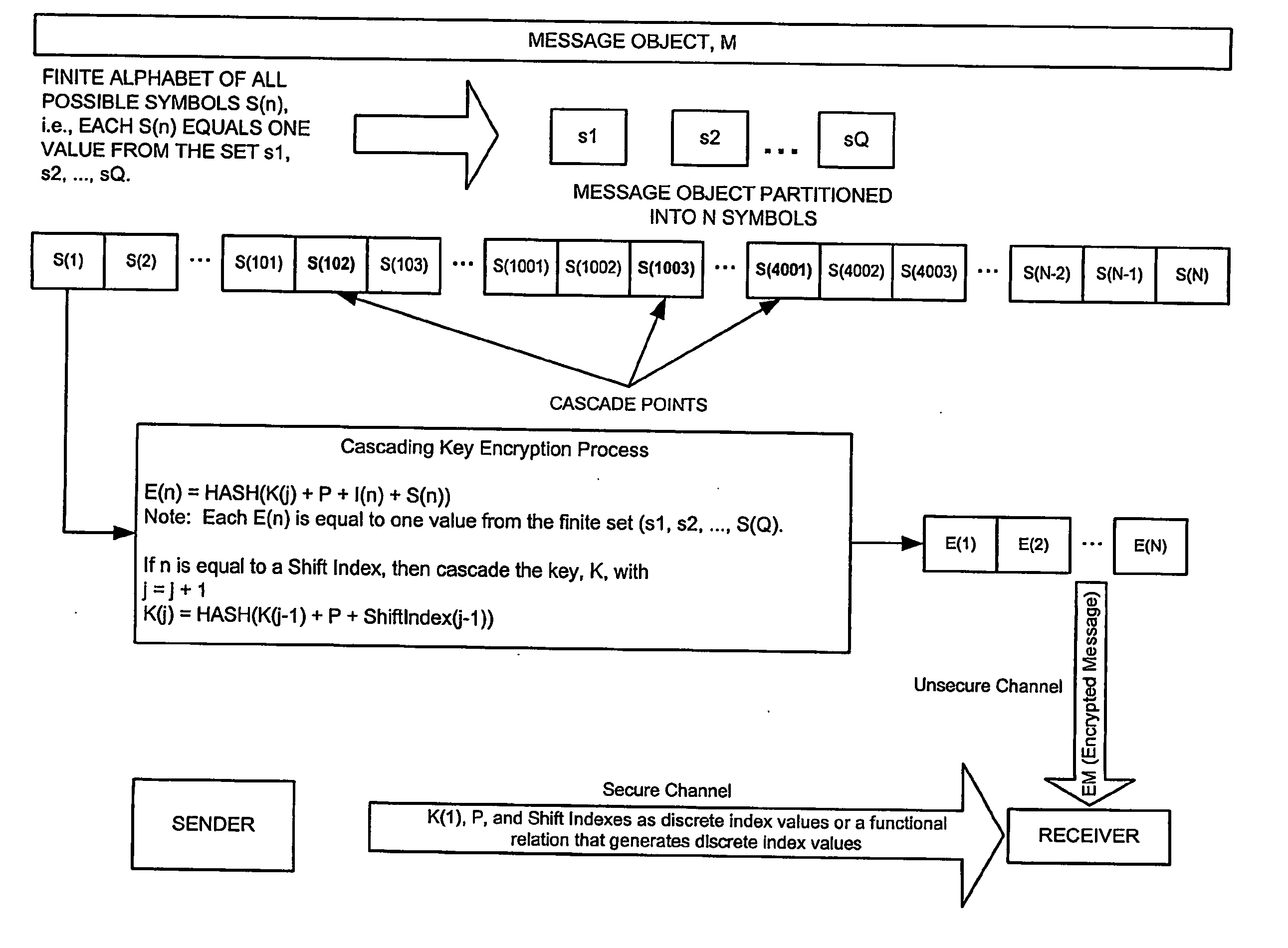
A method for securely transmitting data involves generating keys depending on previous keys and additional information, such as a password, in order to create a pseudo one-time pad. The data is encrypted using the pseudo one-time pad prior to transmission. Only the initial key and minimal additional data are transferred between the sender and receiver in order to synchronize the keys.
Owner:PATHFIRE
One-time pad Encryption key Distribution
InactiveUS6868495B1Ability can be reducedReduce attackKey distribution for secure communicationDigital data processing detailsPaymentSuccessful completion
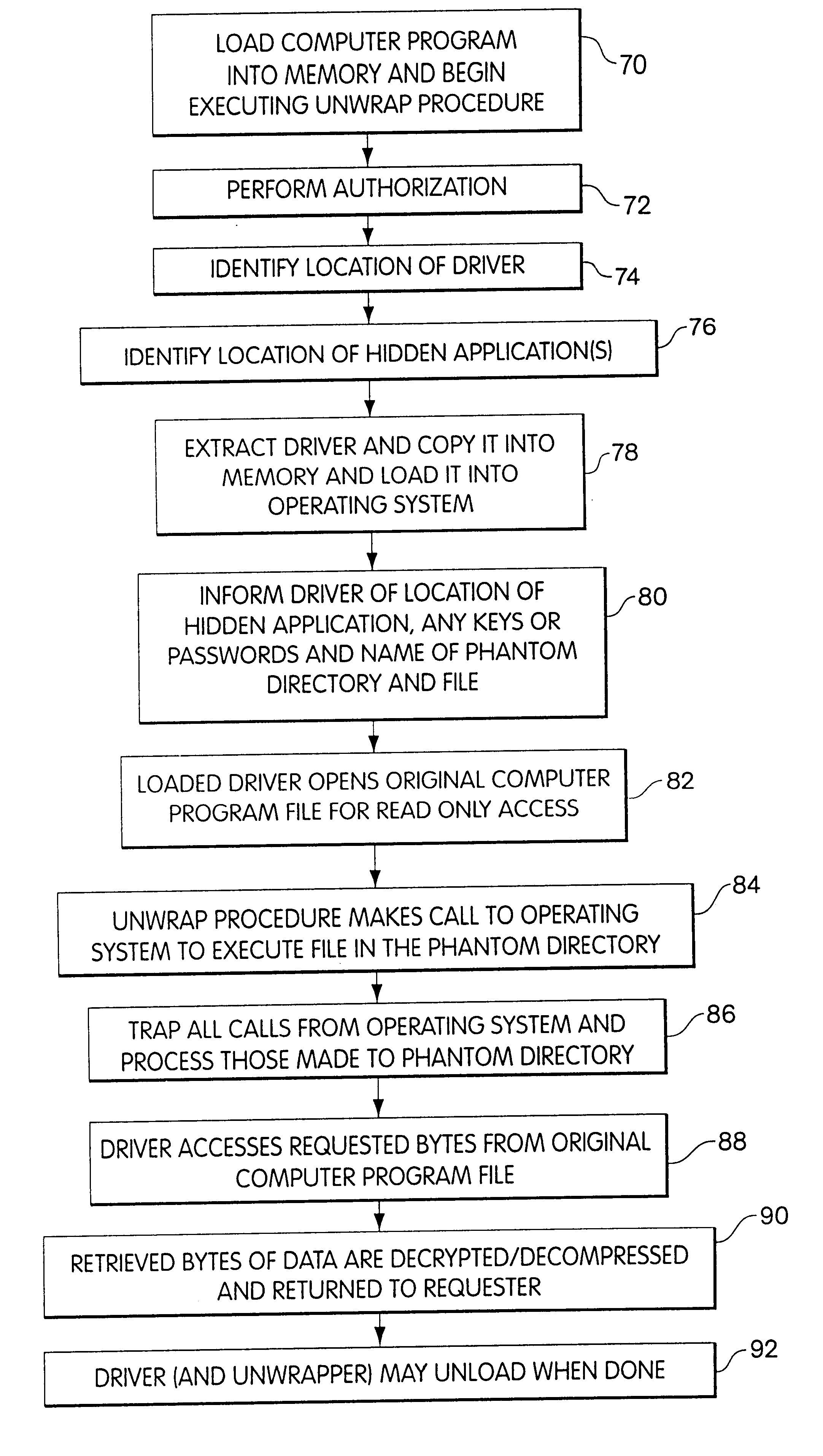
Some of these problems with digital information protection systems may be overcome by providing a mechanism which allows a content provider to encrypt digital information without requiring either a hardware or platform manufacturer or a content consumer to provide support for the specific form of corresponding decryption. This mechanism can be provided in a manner which allows the digital information to be copied easily for back-up purposes and to be transferred easily for distribution, but which should not permit copying of the digital information in decrypted form. In particular, the encrypted digital information is stored as an executable computer program which includes a decryption program that decrypts the encrypted information to provide the desired digital information, upon successful completion of an authorization procedure by the user. In combination with other mechanisms that track distribution, enforce royalty payments and control access to decryption keys, the present invention provides an improved method for identifying and detecting sources of unauthorized copies. Suitable authorization procedures also enable the digital information to be distributed for a limited number of uses and / or users, thus enabling per-use fees to be charged for the digital information.
Owner:RPX CORP
Key expansion for qkd
InactiveUS20060059343A1Key distribution for secure communicationSynchronisation information channelsKey exchangeKey schedule
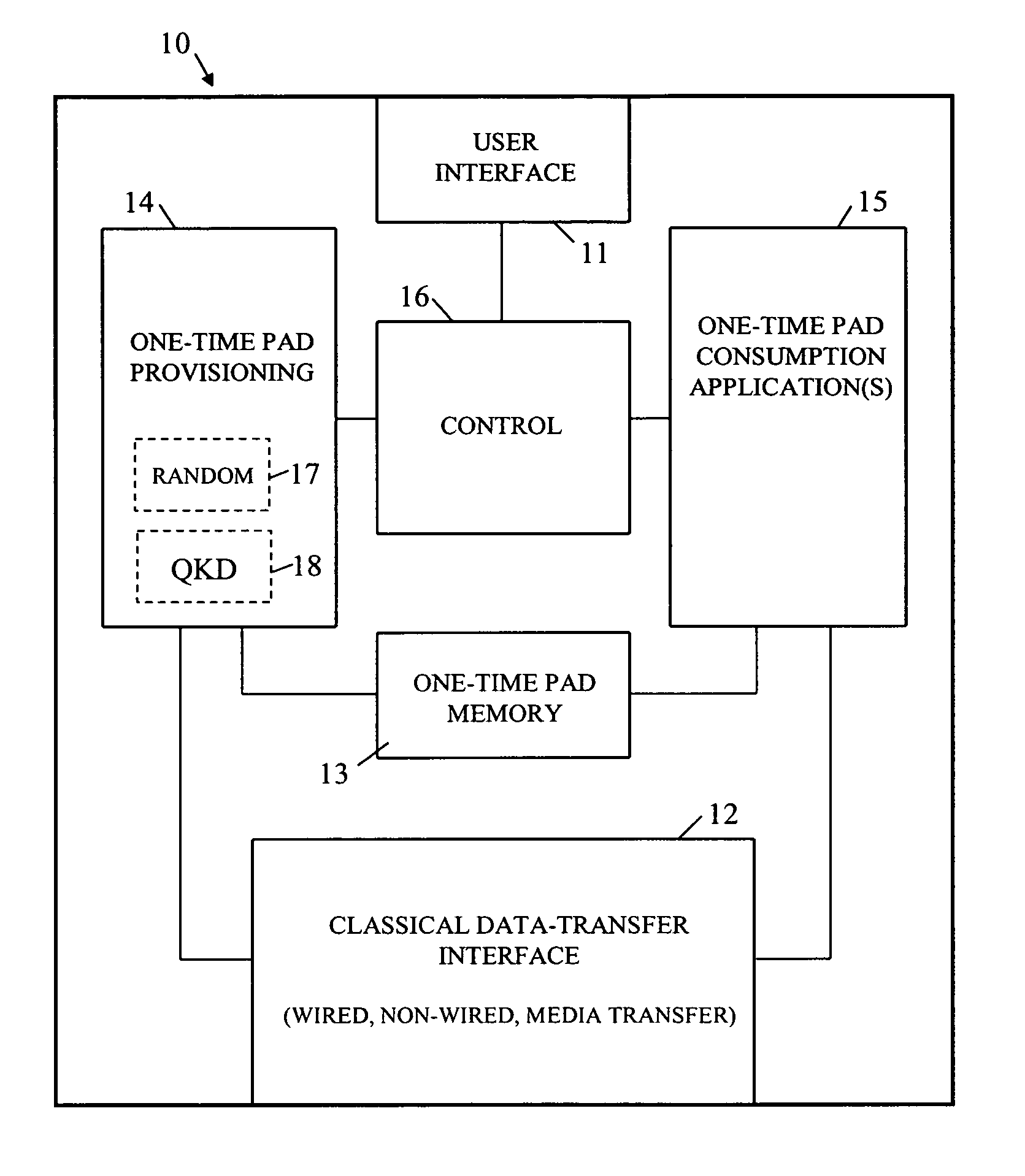
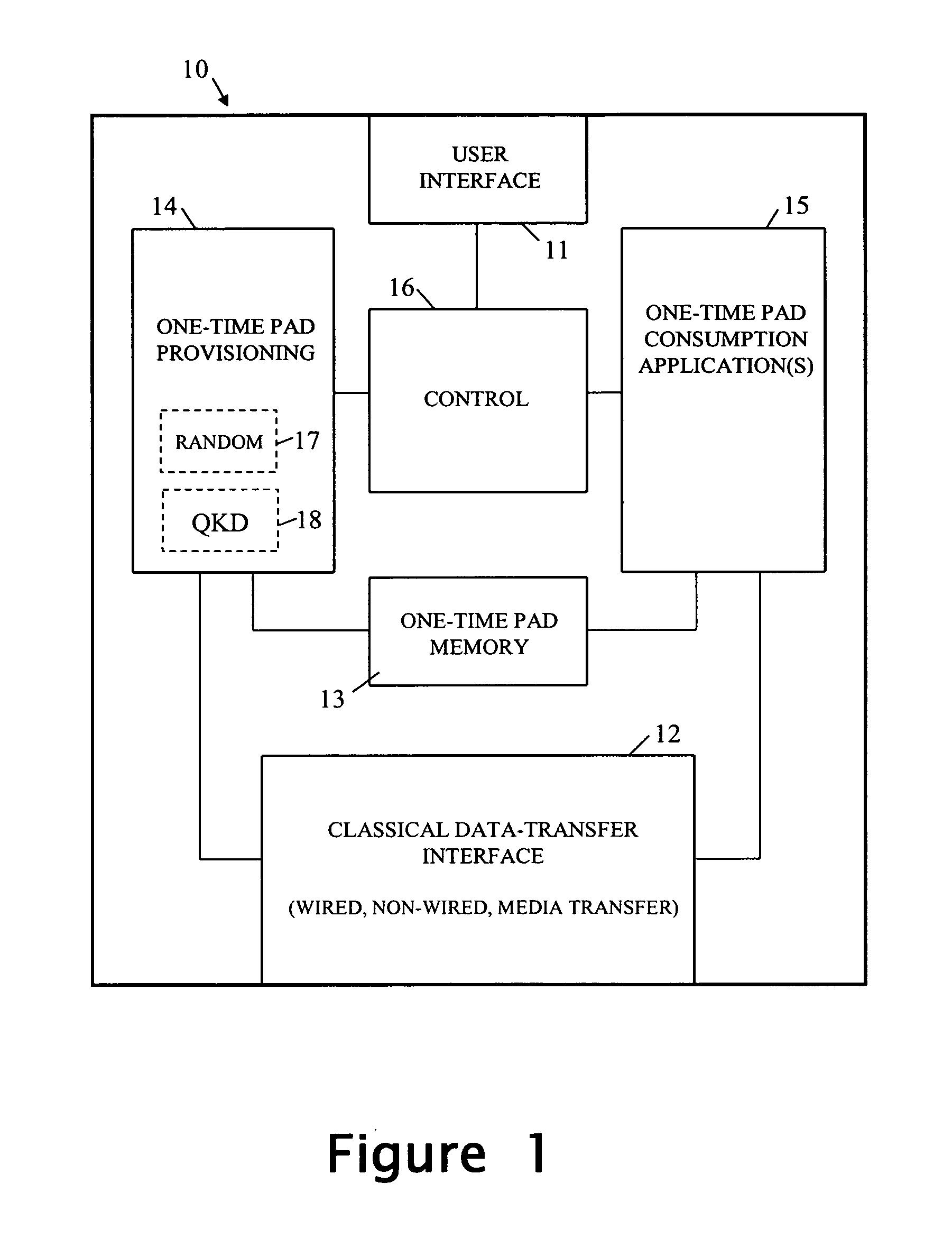
A method of encrypting information using an encryption pad based on keys exchanged between quantum key distribution (QKD) stations is disclosed. The method includes establishing raw keys between two stations using QKD, processing the keys to establish a plurality of matching privacy amplified keys at each station and buffering the keys in a shared key schedule. The method also includes the option of expanding one or more of the keys in the shared key schedule using a stream cipher to create a supply of expanded keys that serve as pads for one-time-pad encryption.
Owner:MAGIQ TECH INC
Method and apparatus for secure transactions
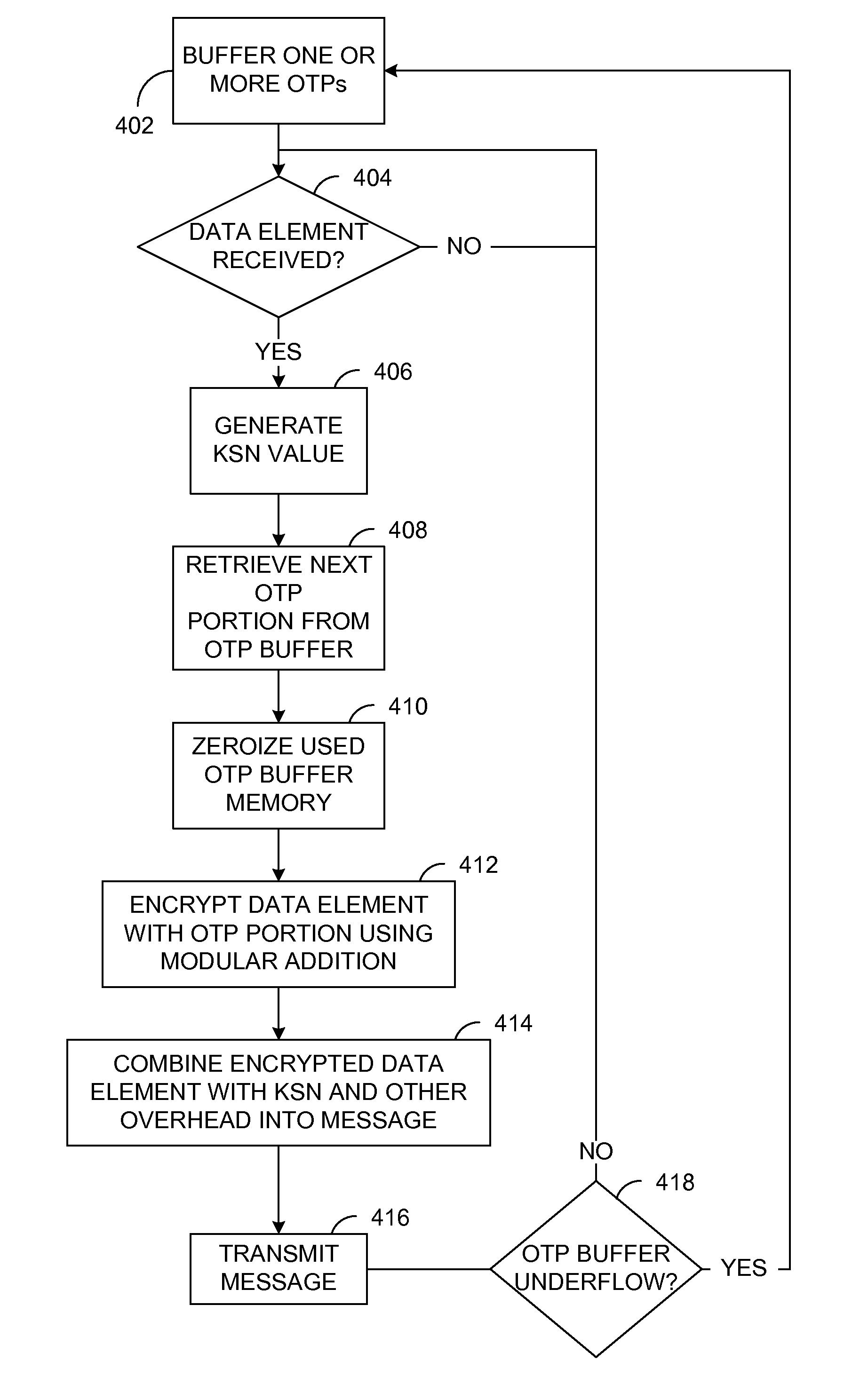
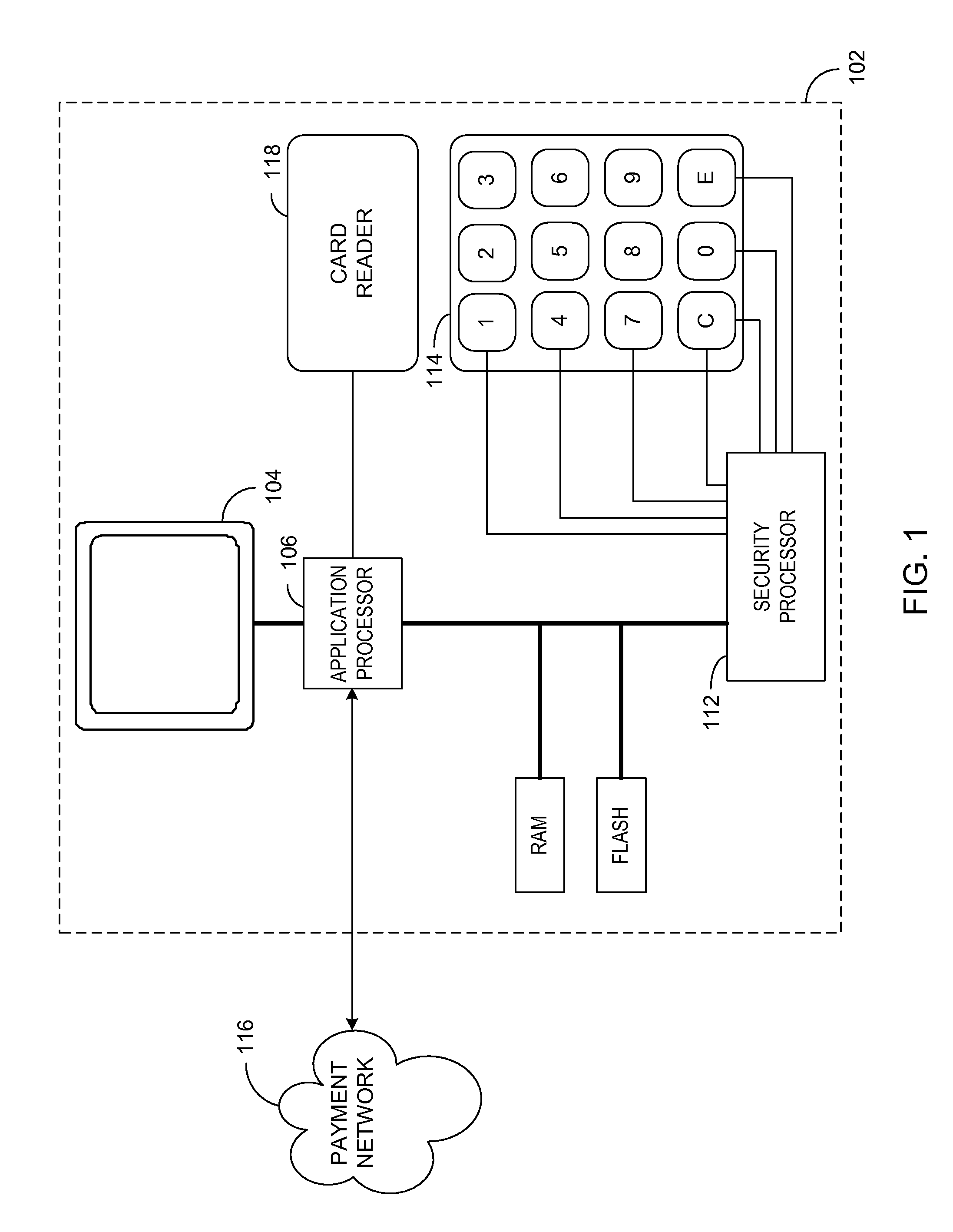
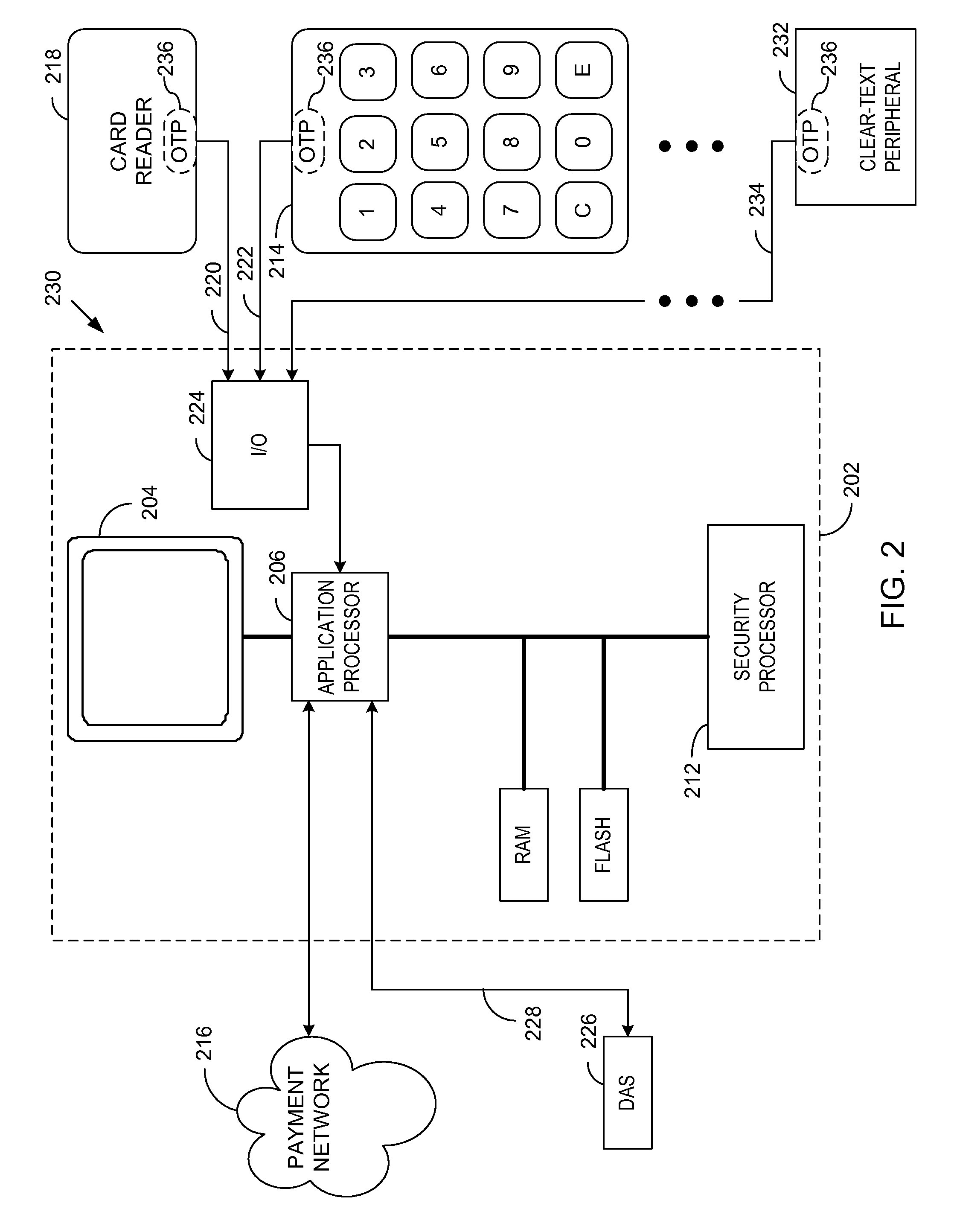
A method and apparatus is provided for secure terminals that facilitate secure data transmission and are compliant with the payment card industry (PCI) data security requirements. A security processor is combined with an application processor and a display into a secure display control unit (SDCU) that provides tamper resistance and other security measures. Modular secure I / O devices are interfaced to the SDCU via a wired, or wireless, medium so as to facilitate secure data transfer to the SDCU during a point-of-sale (POS) transaction or other transaction that requires secure data entry. The secure I / O devices implement one-time-pad (OTP) encryption, where the random keys, or pads, are generated by a derived unique key per transaction (DUKPT) generator. Other embodiments facilitate interconnection of the secure I / O devices to a hardware security module (HSM) or a personal computer (PC) while maintaining a high level of data security.
Owner:KEY INNOVATIONS
Secure encryption of data packets for transmission over unsecured networks
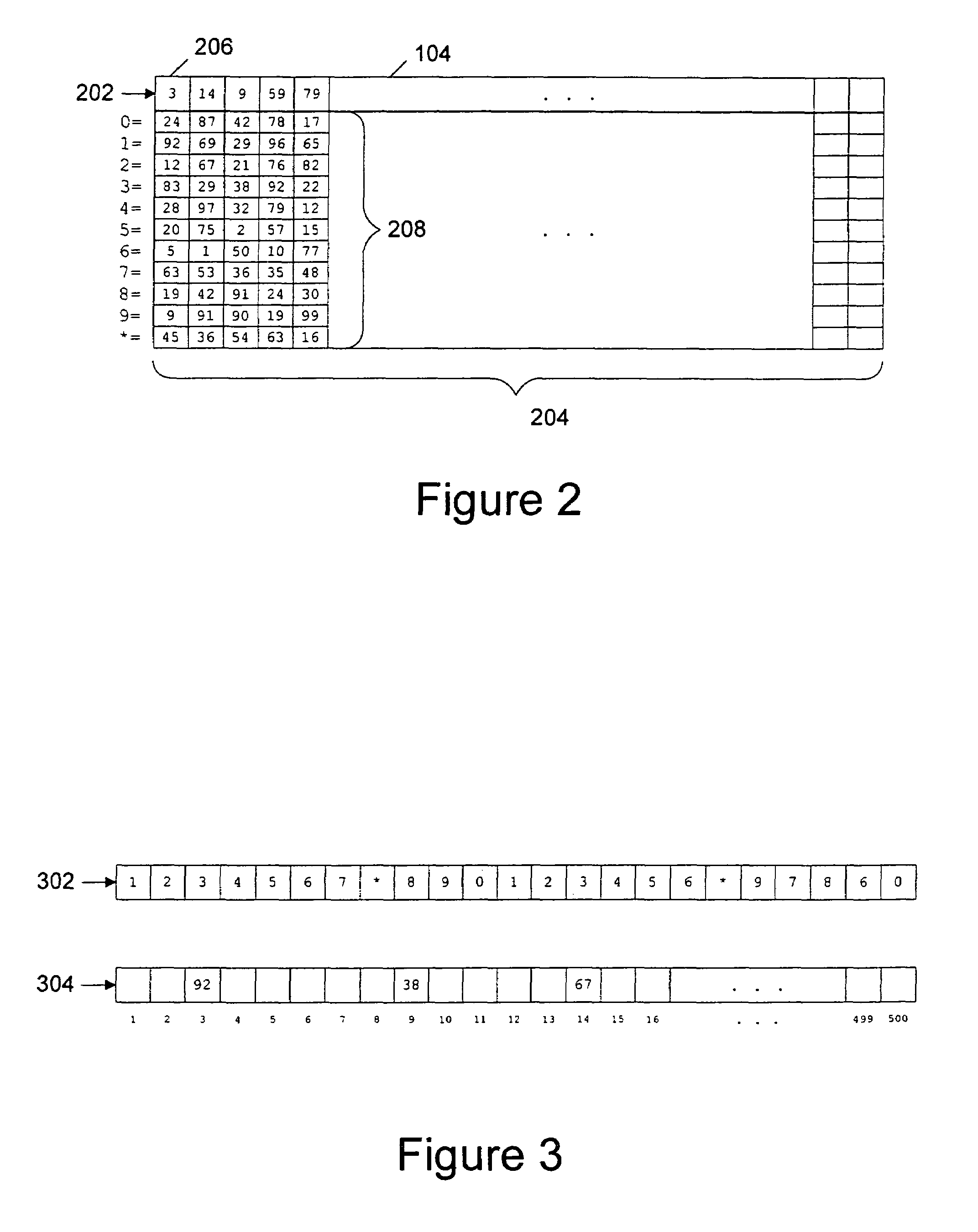
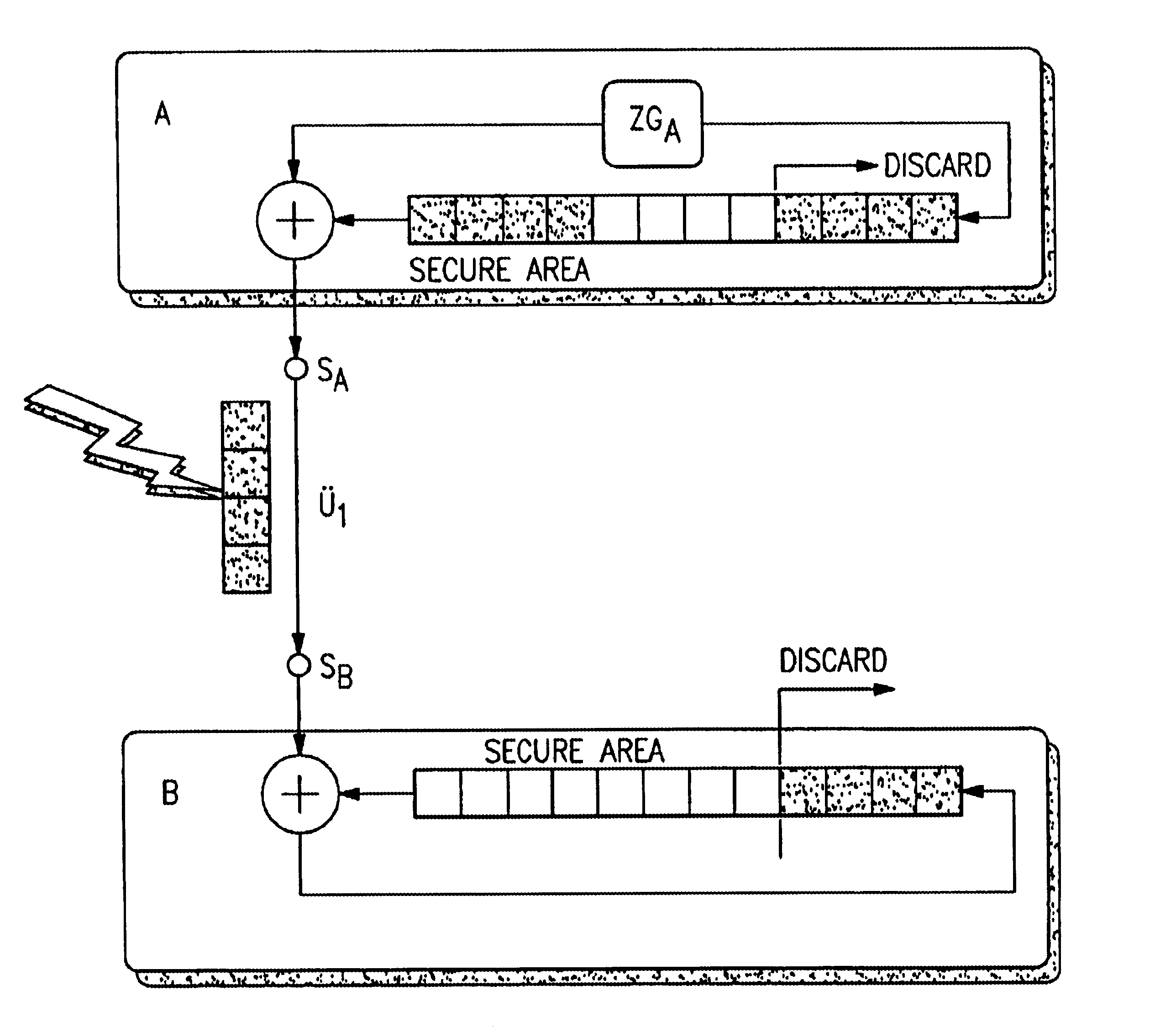
Pure random numbers from a sheet within a one-time pad are employed to encrypt the bytes of a source data packet and to order the encrypted bytes in a random order within the encrypted data packet. Pure random numbers fill remaining positions within the encrypted data packet. The resulting encrypted data packet is unconditionally secure (i.e., unbreakable). Sheets within the one-time pad are utilized only once, and the one-time pad is replaced when exhausted. For electronic checking applications, the one-time pad is distributed to the user stored in an electronic checkbook, with a copy retained by the bank. For cellular telephone applications, the one-time pad is stored in a replaceable memory chip within the mobile unit with a copy retained at a single, secured central computer. For client-server applications or applications involving sales over the Internet, the one-time pad may be provided to the user on a floppy disk or CD-ROM, with a copy retained by the vendor.
Owner:PAYPAL INC
Device with multiple one-time pads and method of managing such a device
ActiveUS20080031456A1More dataFlexible sharingKey distribution for secure communicationComputer scienceTime data
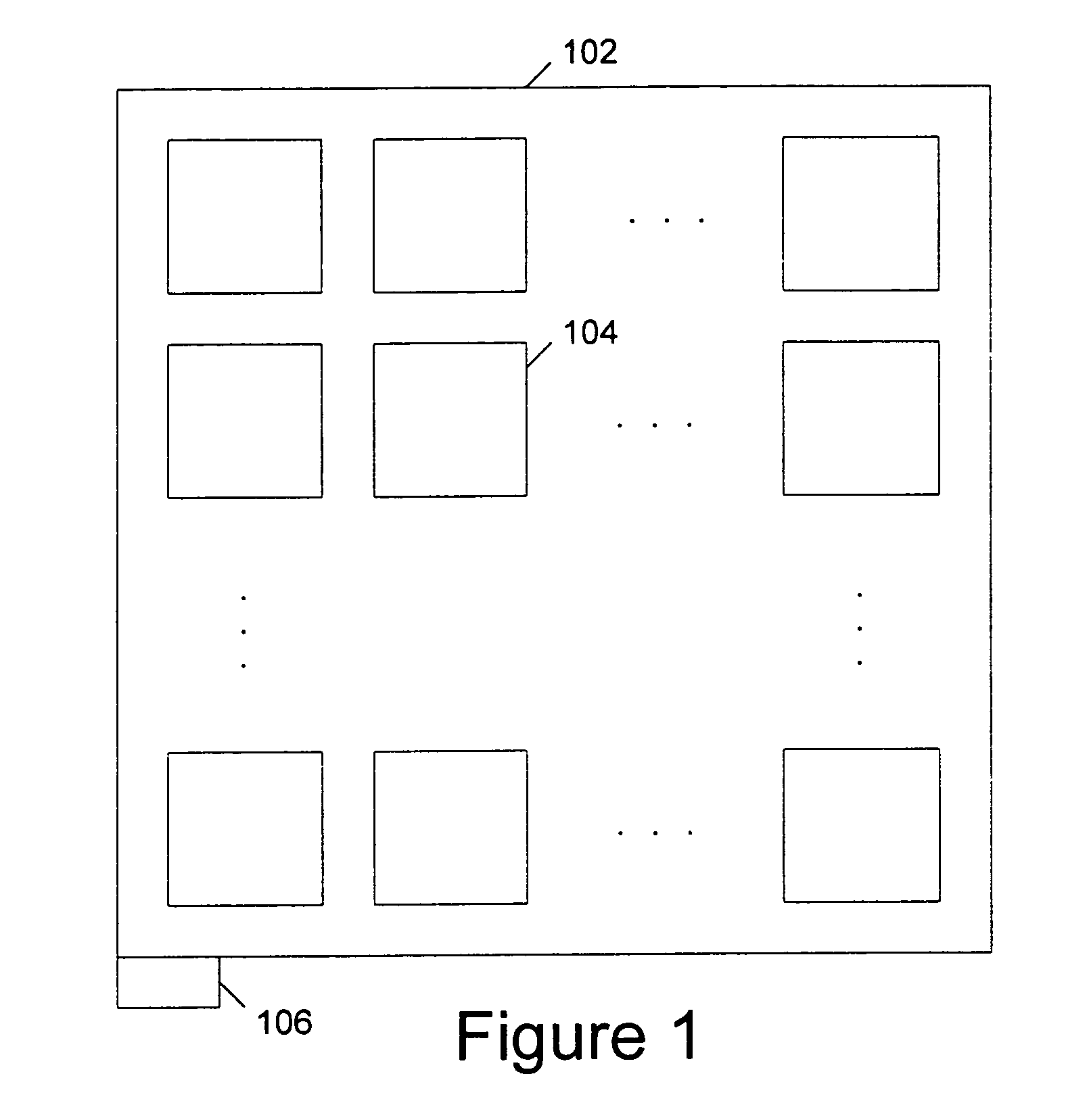
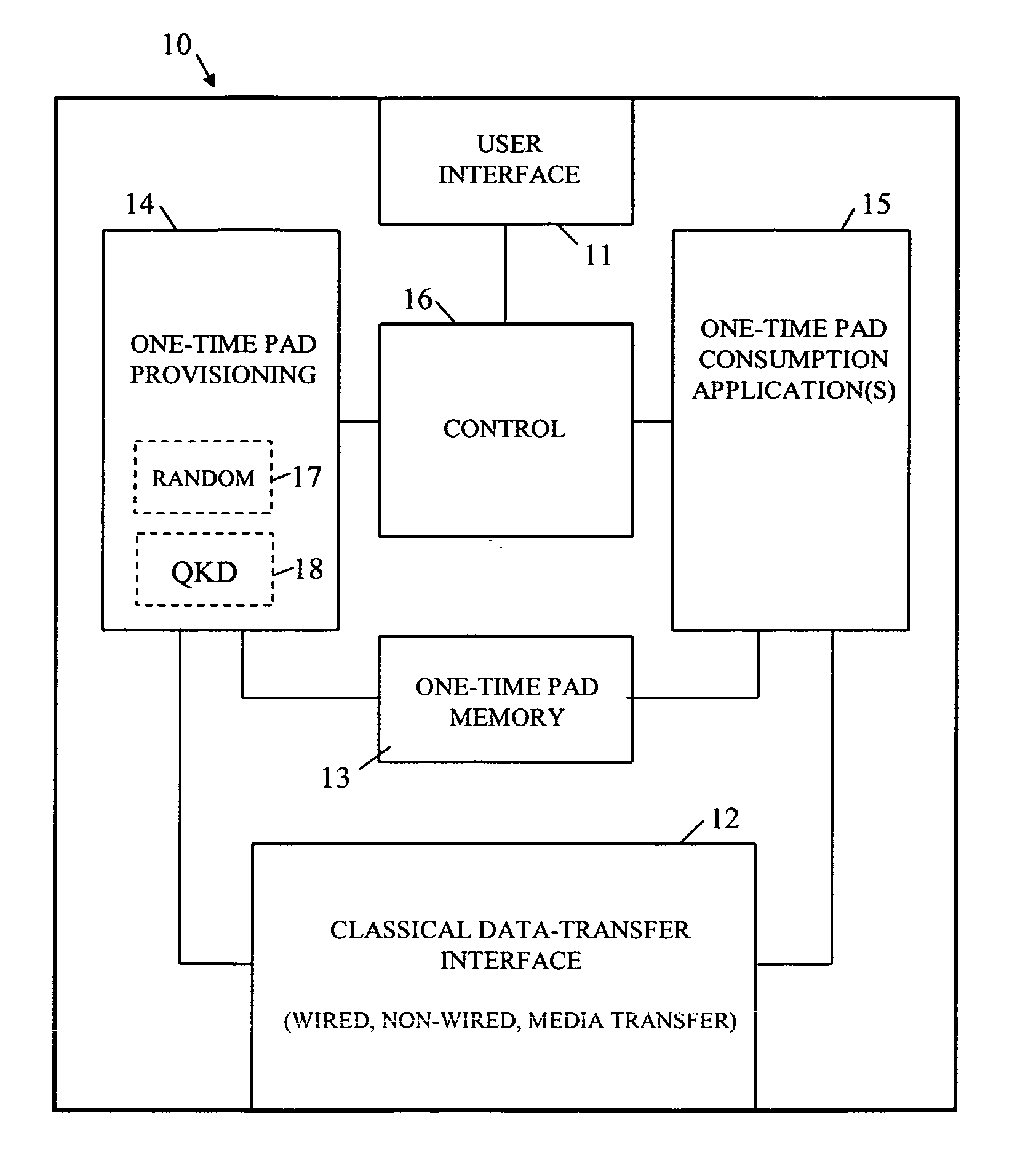
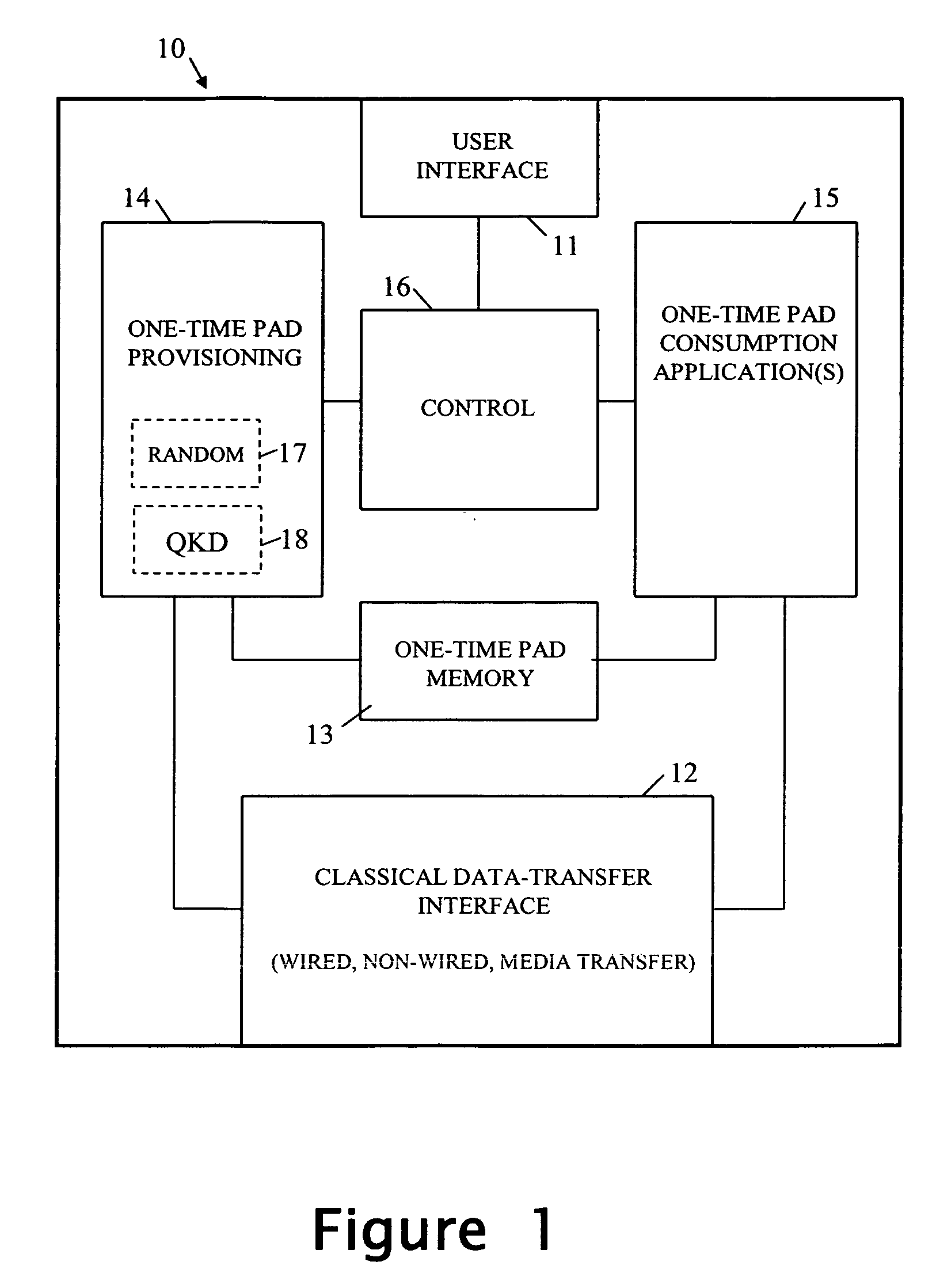
A device is arranged to carry out security-related tasks using one-time pad data. The device has a memory for holding multiple one-time pads, each pad having a different security rating and being intended for use by the device in executing a task to that security rating. Provisioning of the pads with one-time pad data involves carrying out a process for obtaining new secret random data. This process has a security rating with the value of this rating varying according to the nature and parameters of the process concerned. The security rating of the process used to obtain the new secret random data is matched to that of the pad to be provisioned with one-time data, or the other way around, such that the security rating of the process is as least as good as that of the pad to be provisioned.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Replaceable sequenced one-time pads for detection of cloned service client
InactiveUS20050239440A1Reduce service billing usageDiscouraging and reducing illegal cloning activityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUse of servicesClient-side
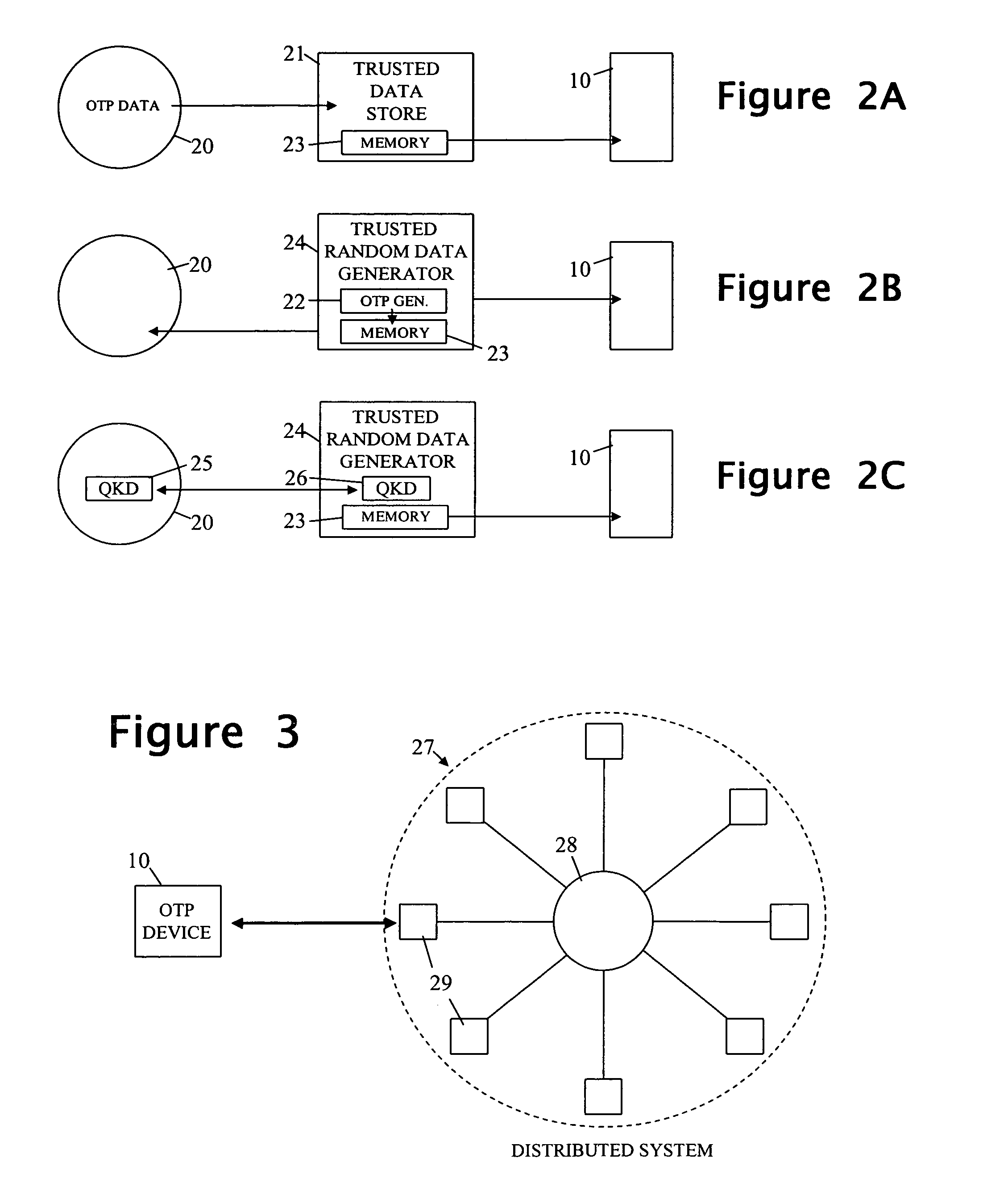
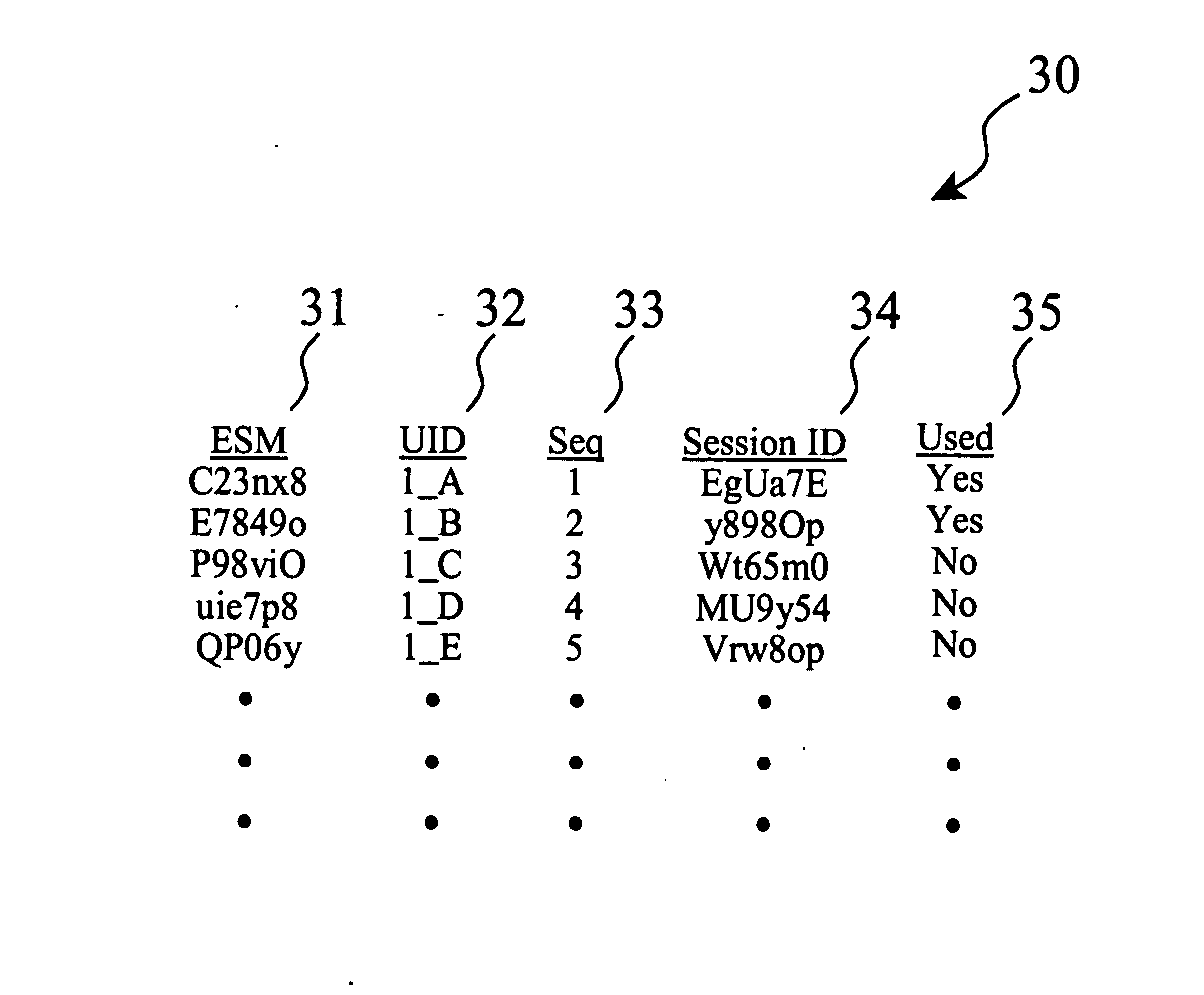
A client device authenticated a one-time pad table stored in the client device, and a matching table maintained by a service provider. When a request for service is posted from the client to the service provider, the next unused pad is exchanged and verified with the current state of the service provider's copy of the table. If the OTP is the next unused code, service is granted, else the user is challenged to identify himself, which when successfully completed results in the client device being downloaded with a new OTP table, replacing the compromised table. Use of service by a cloned device causes the OTP table at the service provider to become out of synchronization with the authentic device's copy of the table, thereby setting up the ability to detect the fraud, stop the service consumption by the clone, and reprogram the authentic device to allow for uninterrupted service.
Owner:IBM CORP
Physical key-protected one time pad
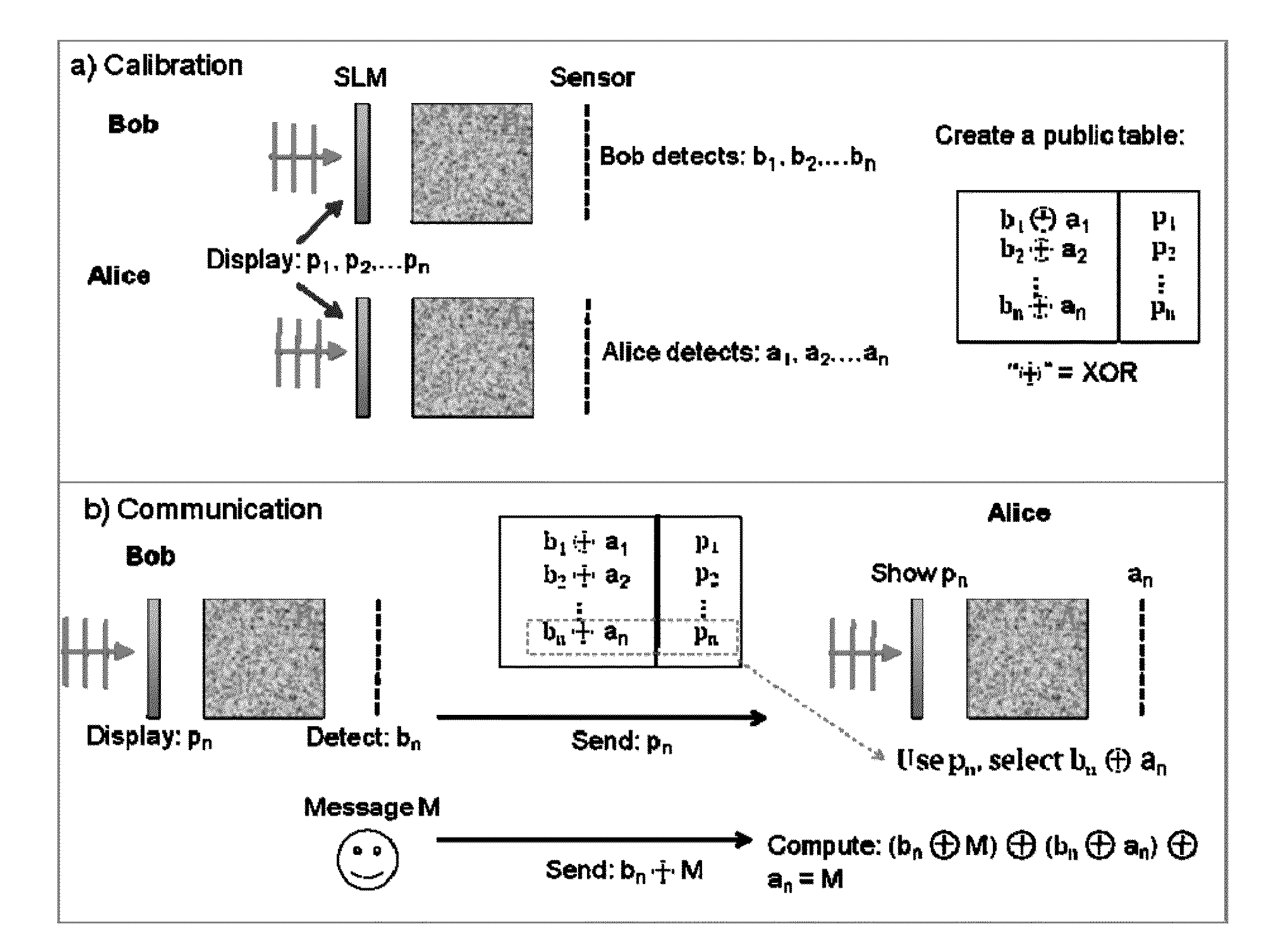
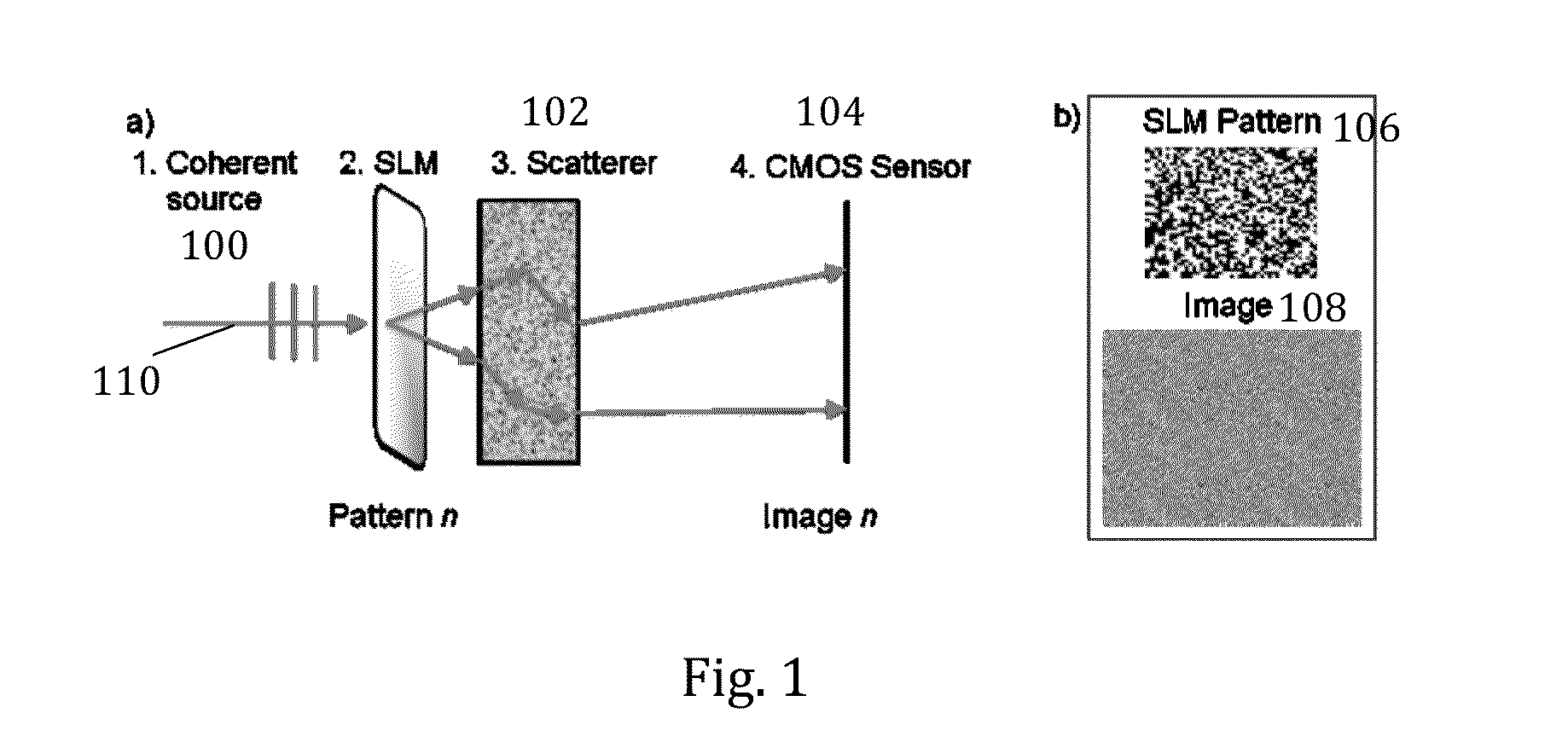
ActiveUS20130243187A1Maximize overlapDetector's pixelsModulated-carrier systemsSecret communicationSpatial light modulatorHemt circuits
A device, including one or more Communication Physical Unclonable Function (CPUF) and key storage devices, the CPUF devices each comprising: a coherent Electromagnetic (EM) radiation source; a spatial light modulator (SLM) connected to the coherent EM radiation source; a volumetric scattering medium connected to the SLM; a detector connected to the volumetric scattering medium; and one or more processors or circuits connected to the detector and one or more processors or circuits connected to the SLM. A communication protocol is also provided.
Owner:LONDON SCHOOL OF HYGIENE & TROPICAL MEDICINE
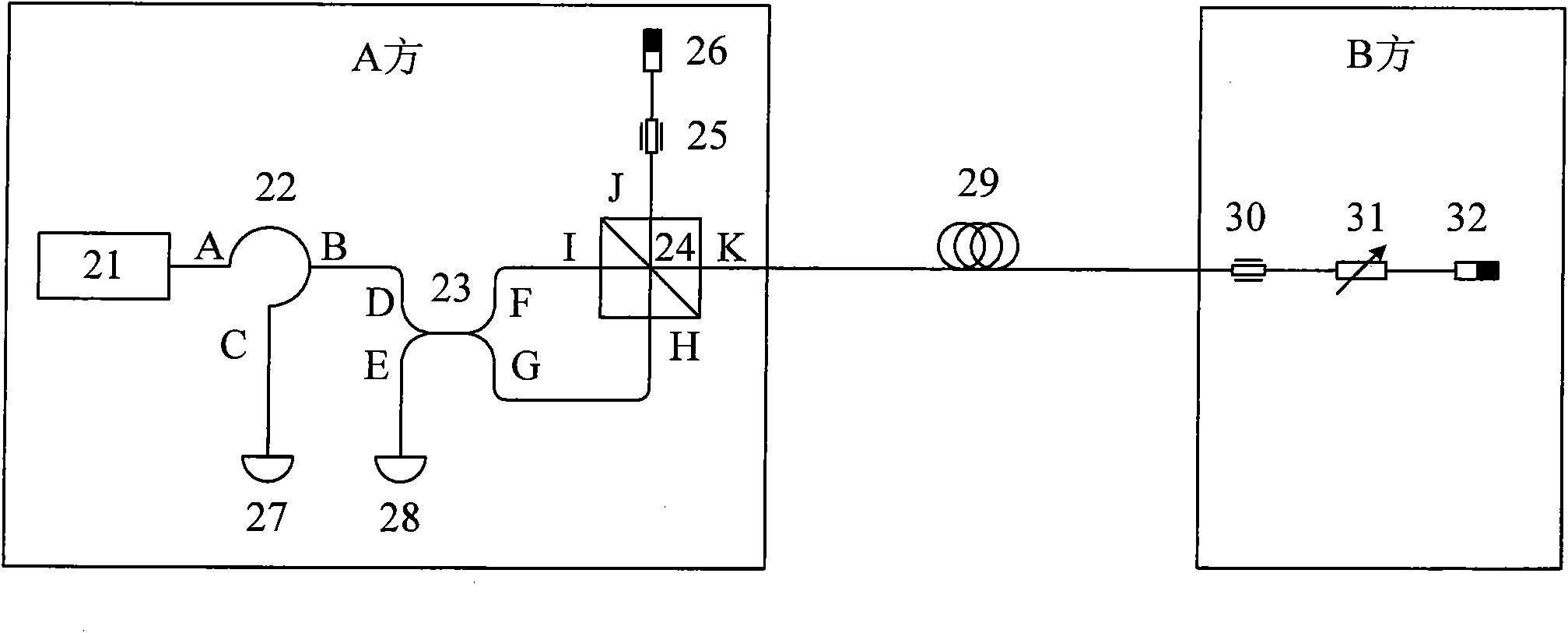
Fast multi-photon key distribution scheme secured by quantum noise
ActiveUS20050152540A1Fast and secure key distributionRaise the ratioKey distribution for secure communicationSecret communicationComputer hardwareQuantum noise
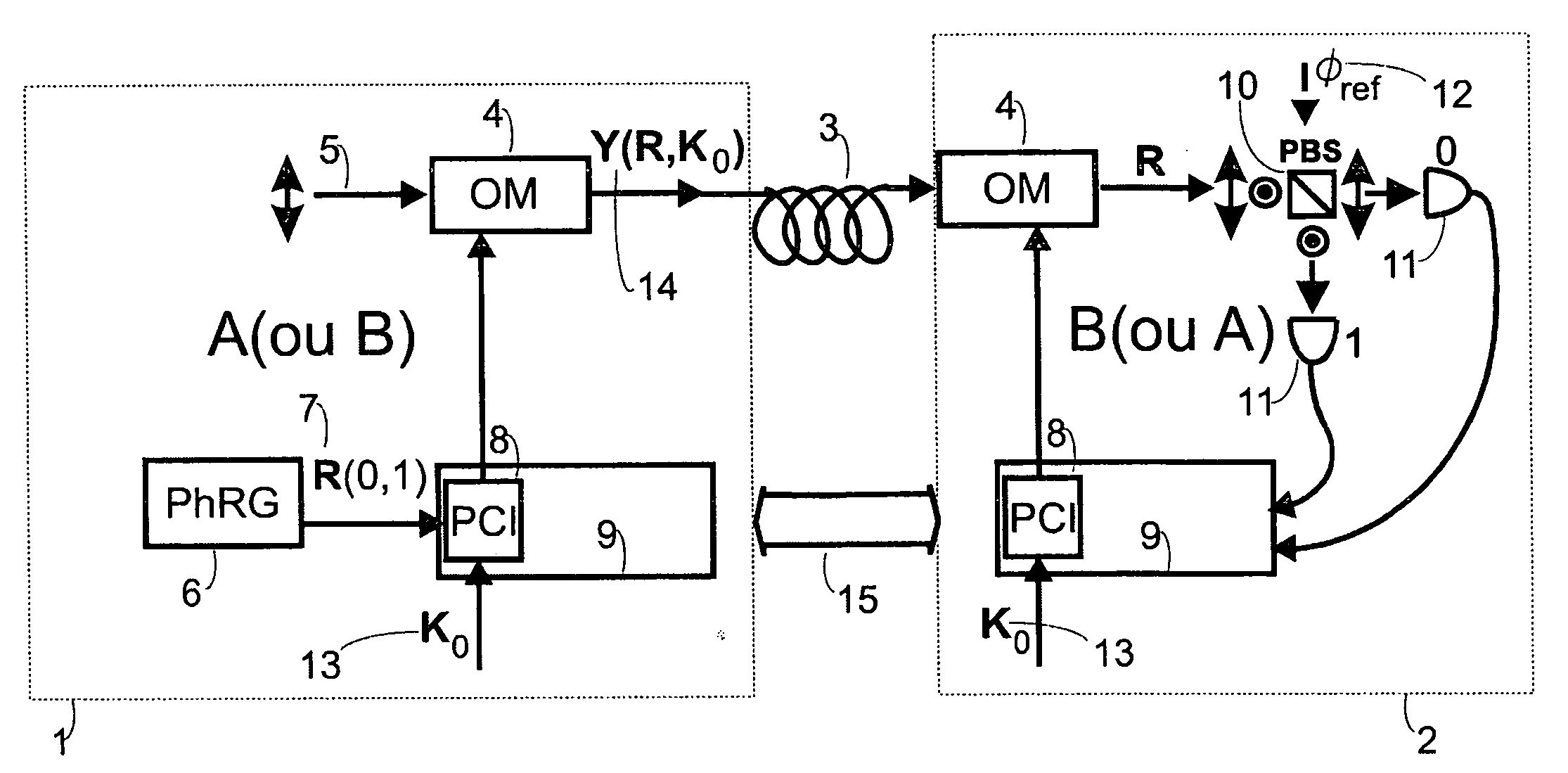
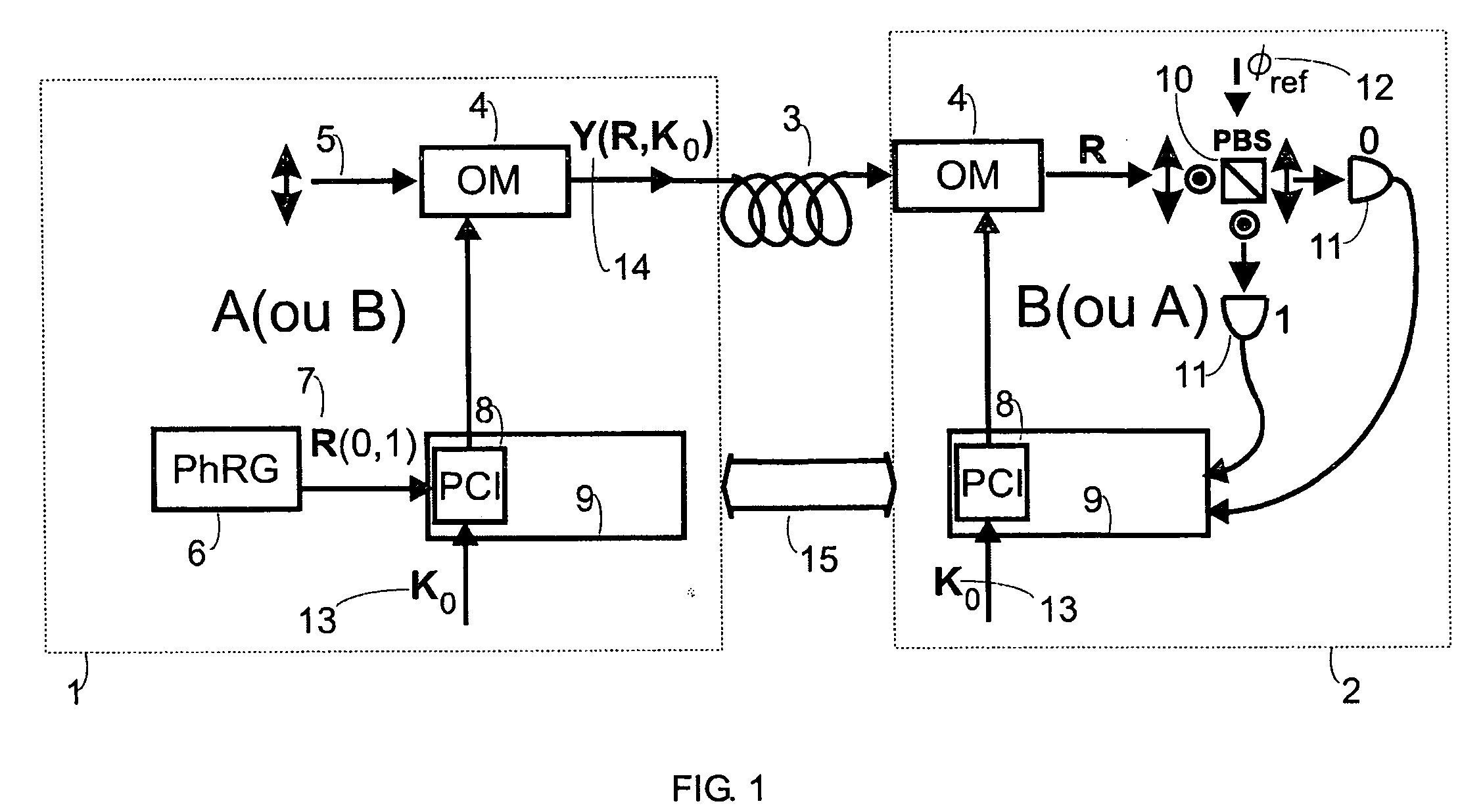
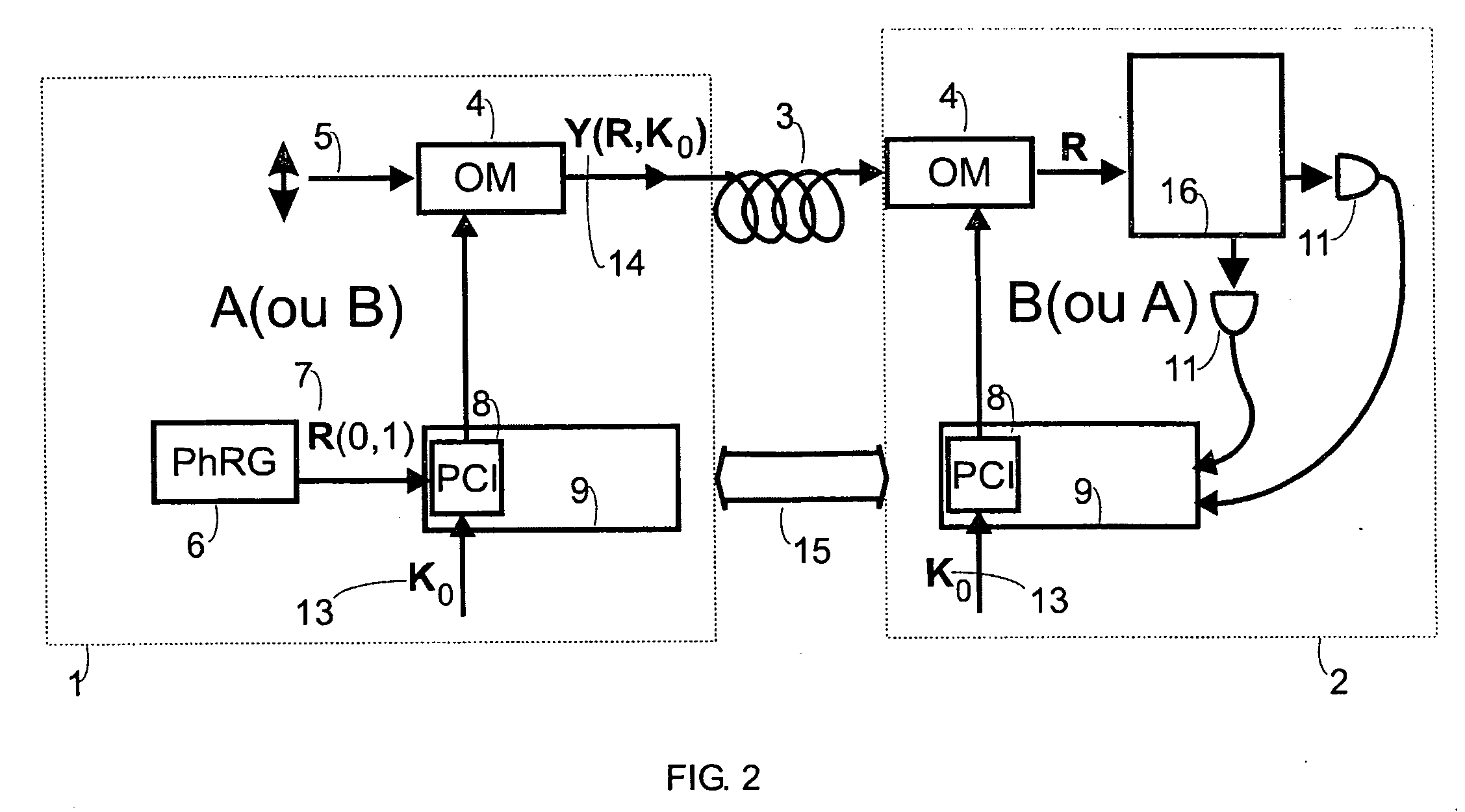
A key distribution scheme comprising a generation and reception system and a specific operation protocol is described. This system allows fast and secure key distribution in optical channels by two stations A and B. One or two true-random physical sources are used to generate random bits and a random sequence received provides the cipher to the following one to be sent. A starting shared secret key is used and the method can be described as a one-time-pad unlimited extender. The minimum probability of error in signal determination by an eavesdropper can be set arbitrarily close to the pure guessing level of one-half and the security of the method comes from the quantum noise of light as well as from the starting secret key. This system allows for optical amplification without security degradation within its operational boundaries.
Owner:SMARTPLUG
Dynamic key generation and confidential synchronization of encryption components
InactiveUS6891952B1Easy and capabilitySynchronising transmission/receiving encryption devicesKey generationOne-time pad
This invention report describes the architecture of a system, which undertakes in a new way the dynamic generation of symmetrical keys and the confidential synchronization of encryption components which use these keys. The basis is formed by the principle of the one-time-pad, with which absolute confidentiality can be ensured in theory. The difficulties with practical implementation of a pure one-time-pad can be avoided by expansions.
Owner:IBM CORP
Method and device using one-time pad data
InactiveUS20070016794A1Computer security arrangementsSecuring communicationArtificial intelligenceOne-time pad
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
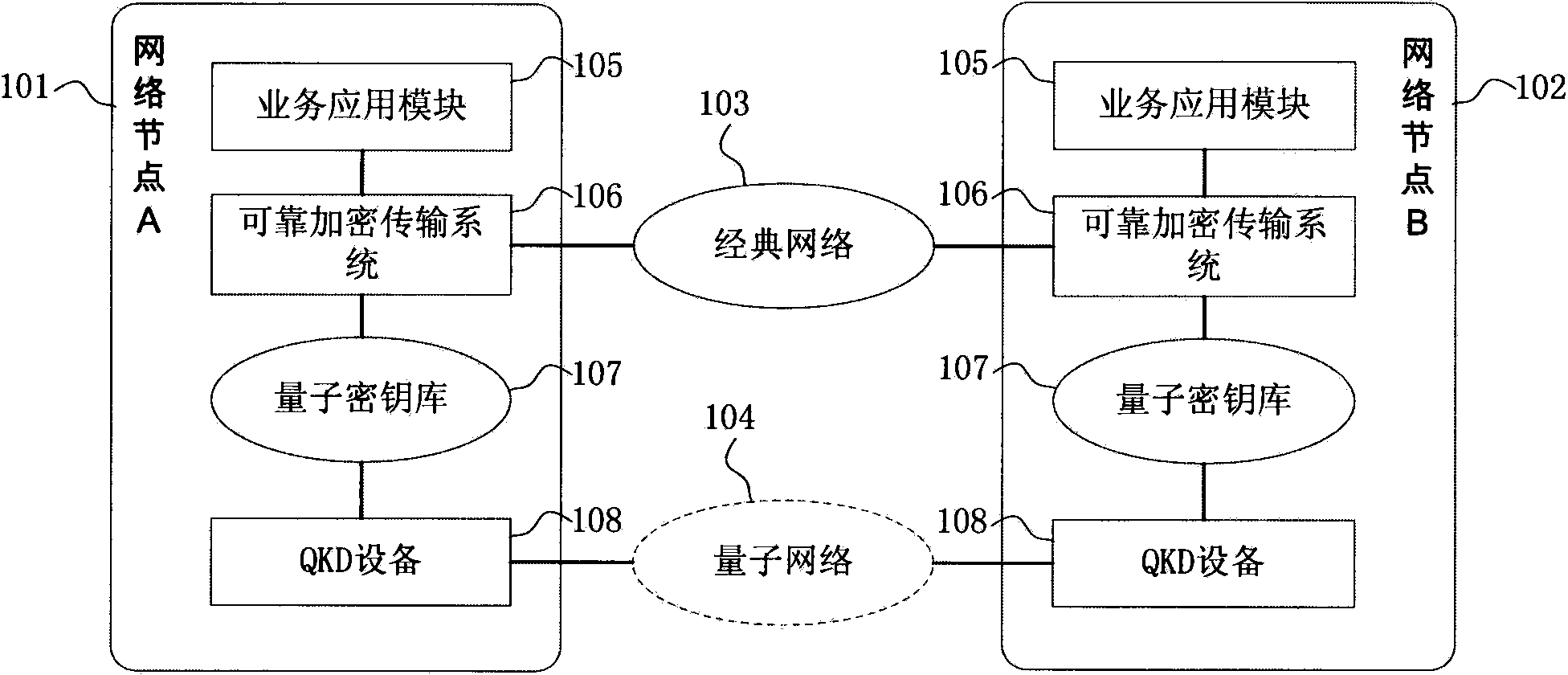
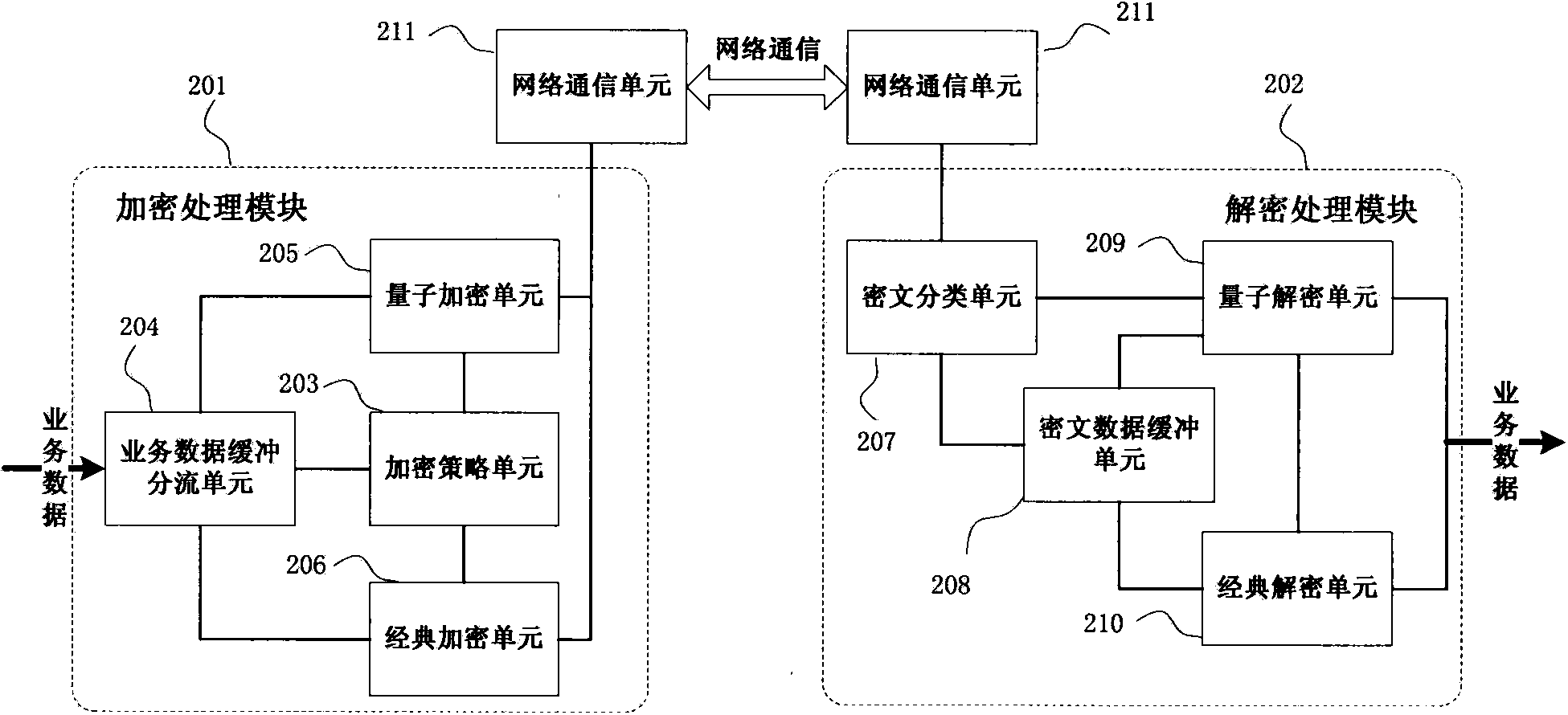
Reliable encryption transmission system and method of quantum cryptography network
ActiveCN103840936AImprove continuityImprove reliabilityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCiphertextDependability
The invention provides a reliable encryption transmission system of a quantum cryptography network. The reliable encryption transmission system comprises an encryption processing module and a decryption processing module, the encryption processing module is composed of an encryption strategy unit, a service data buffering shunt unit, a classic encryption unit and a quantum encryption unit, and the decryption processing module is composed of a cryptograph classification unit, a cryptograph data buffering unit, a classic decryption unit and a quantum decryption unit. Meanwhile, the invention further provides a reliable encryption transmission method of the quantum cryptography network. The classic encryption mode and the quantum one-time pad encryption mode are adopted for transmitting service data in a shunt mode, the shunt proportion of the service data can be timely and correspondingly changed according to changes of the quantum secret key supply-demand relationship, on the basis that the safety is guaranteed, the continuity of service data encryption transmission is improved, and the reliability of service data encryption transmission is improved. Meanwhile, the consumption of quantum secret key data is reduced, quantum secret key generation loads of the quantum cryptography network are reduced, and the cost of service data encryption transmission of the quantum cryptography network is reduced.
Owner:SHANDONG INST OF QUANTUM SCI & TECH
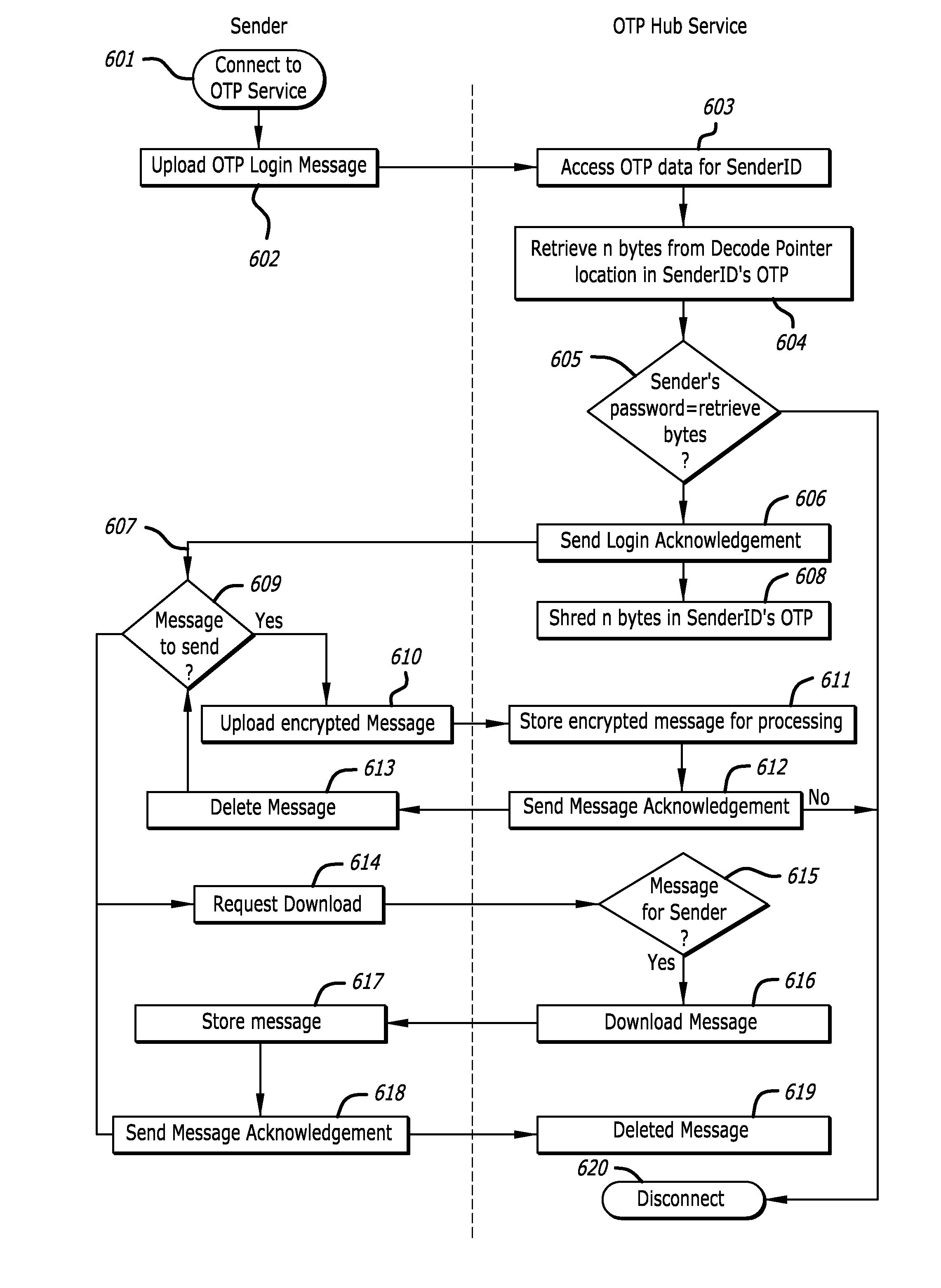
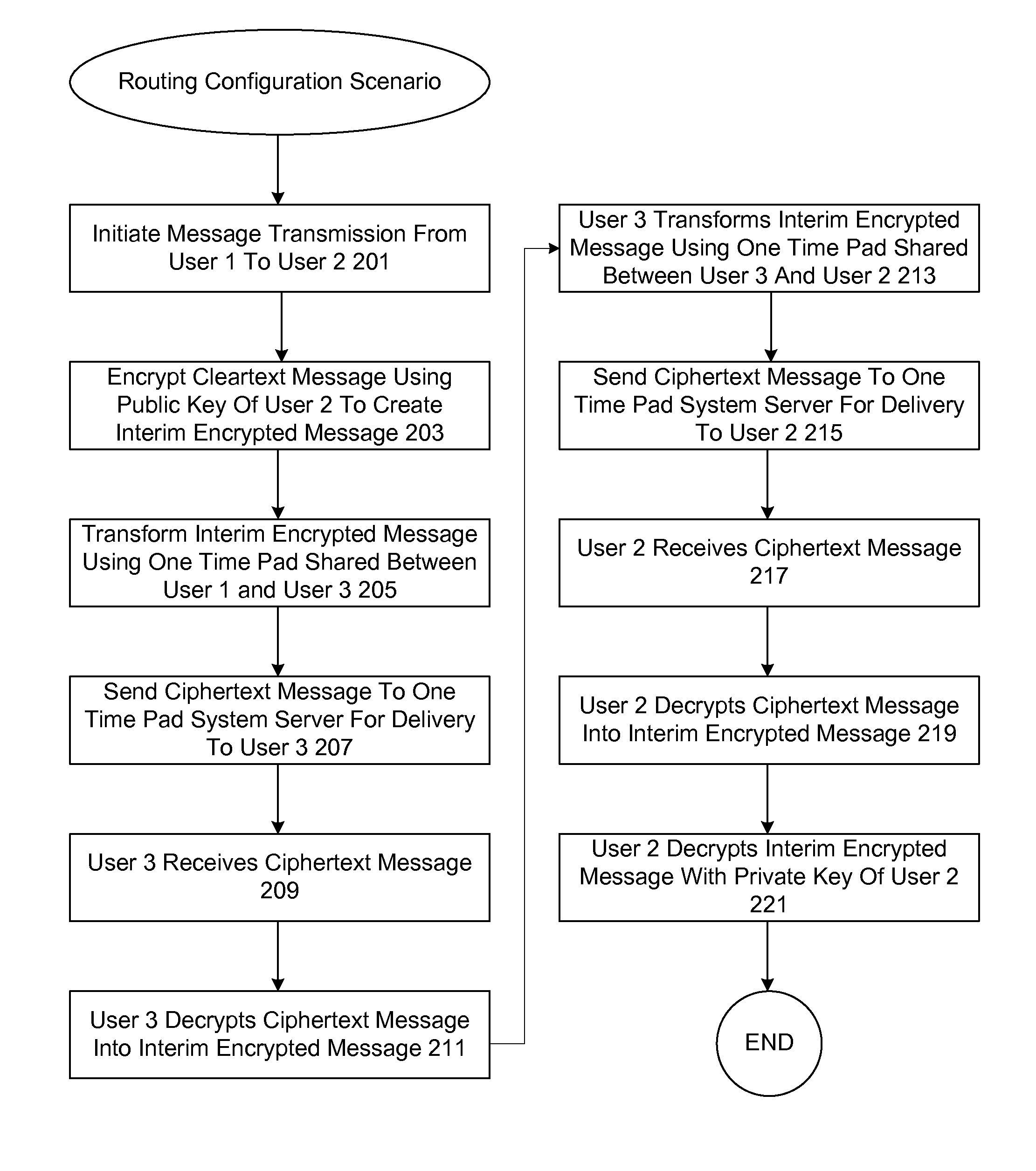
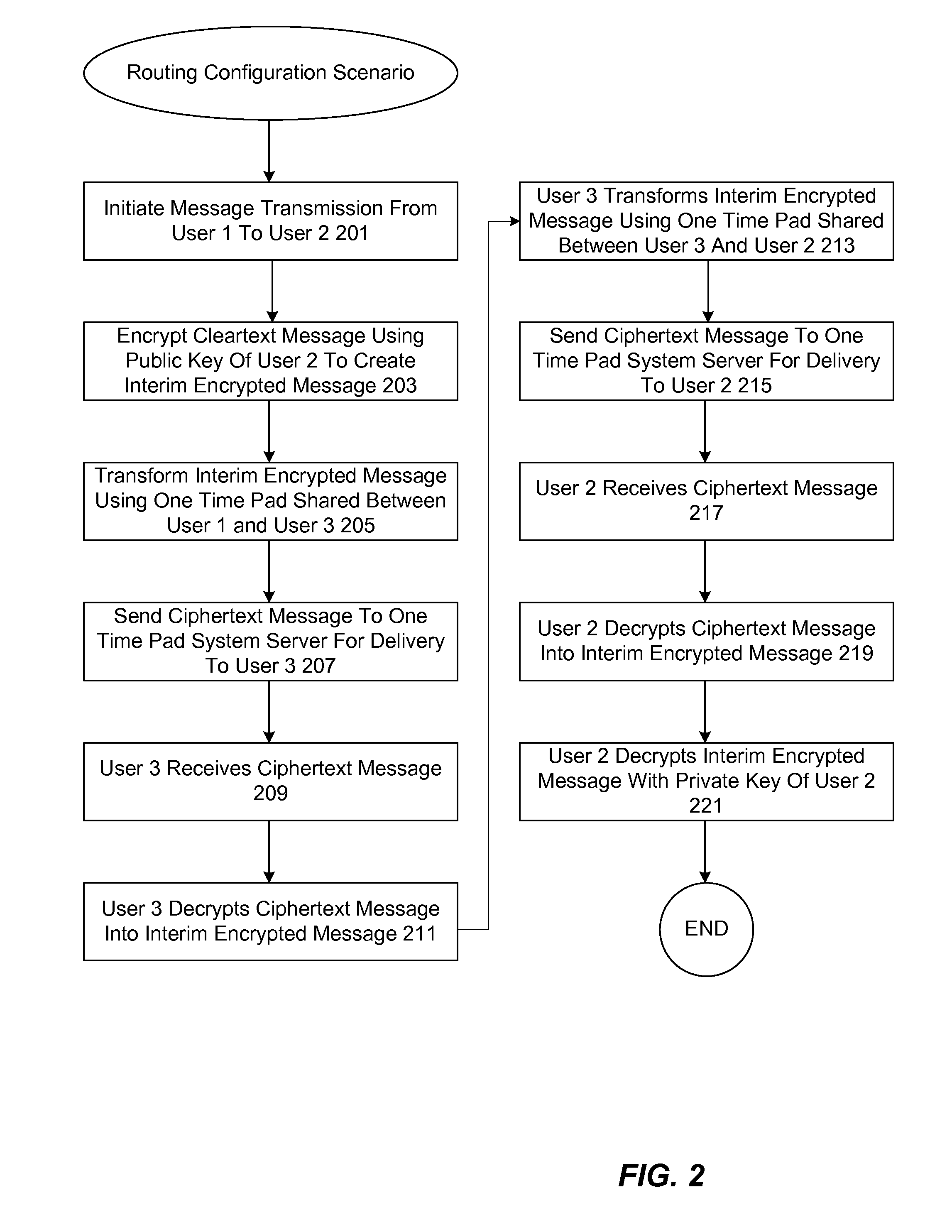
One-time pad communications network
ActiveUS20140337615A1Low costLarge capacityComputer security arrangementsSecurity arrangementService provisionOne-time password
A system and method for providing secure and anonymous communication between a plurality of individuals relying on the cryptographic method of the one-time pad (OTP) is described. Unique, randomly generated blocks of data are generated to serve as one-time pads, and each is given a unique identification that serves as a system address. One-time pads are anonymously distributed to communicants with a copy of each being retained by a service provider that operates a One-Time Pad Hub. Messages may be exchanged among holders of one-time pads through the Hub using the identifier addresses.
Owner:TOMKOW ROBERT JOHN
Method and system for securely storing and transmitting data by applying a one-time pad
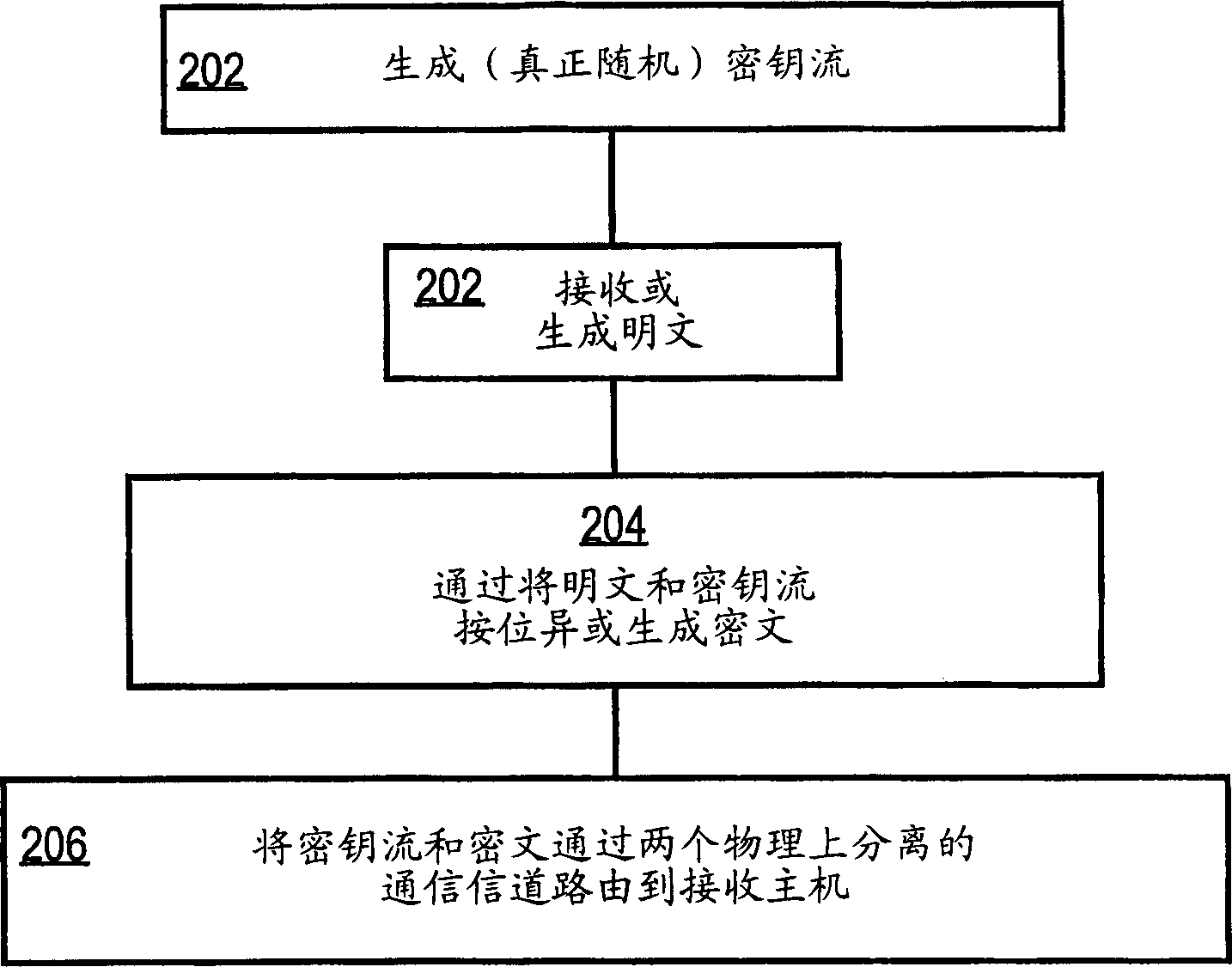
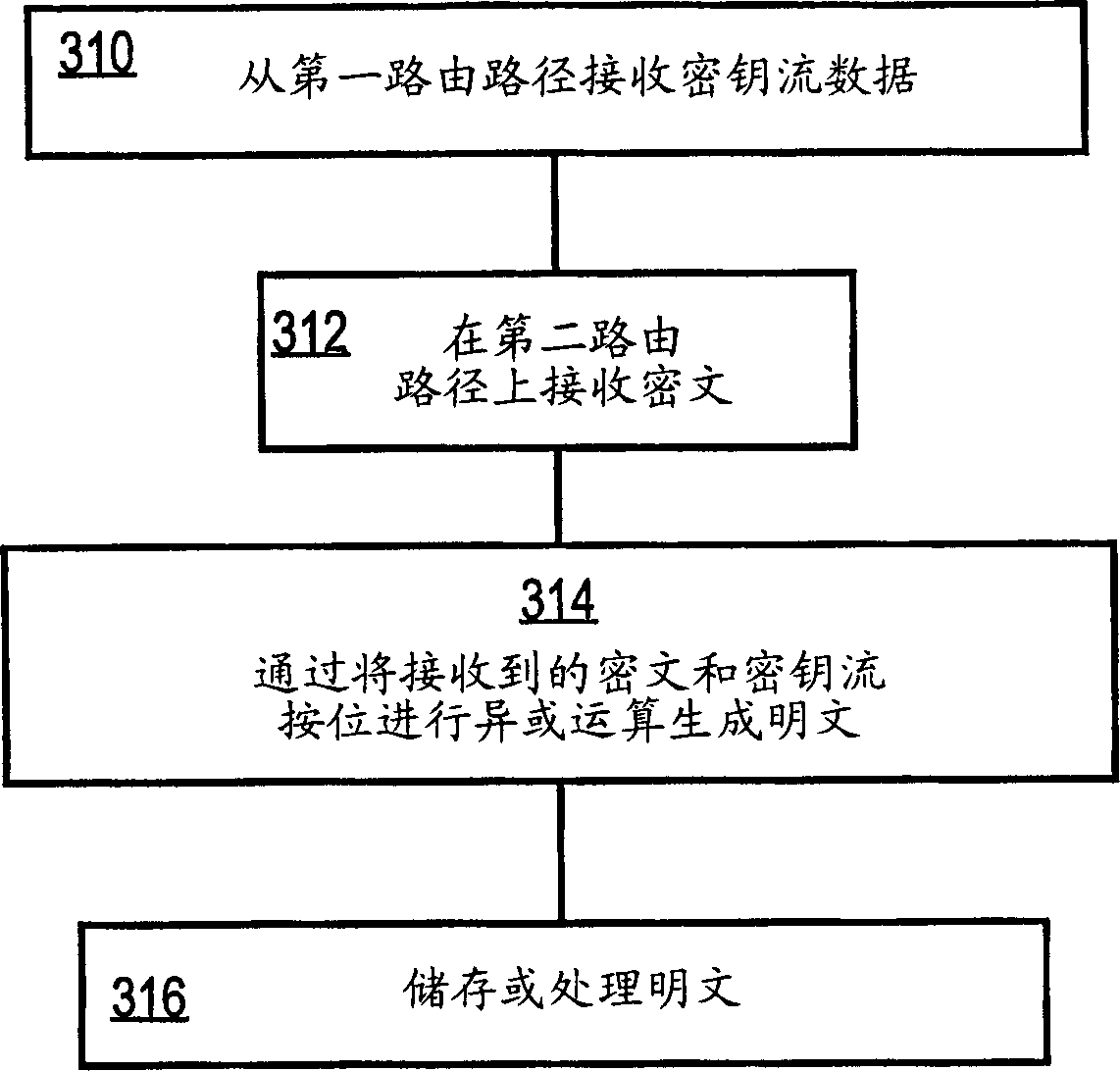
InactiveCN1593033ASimple methodEase of evaluationKey distribution for secure communicationData stream serial/continuous modificationPlaintextKeystream
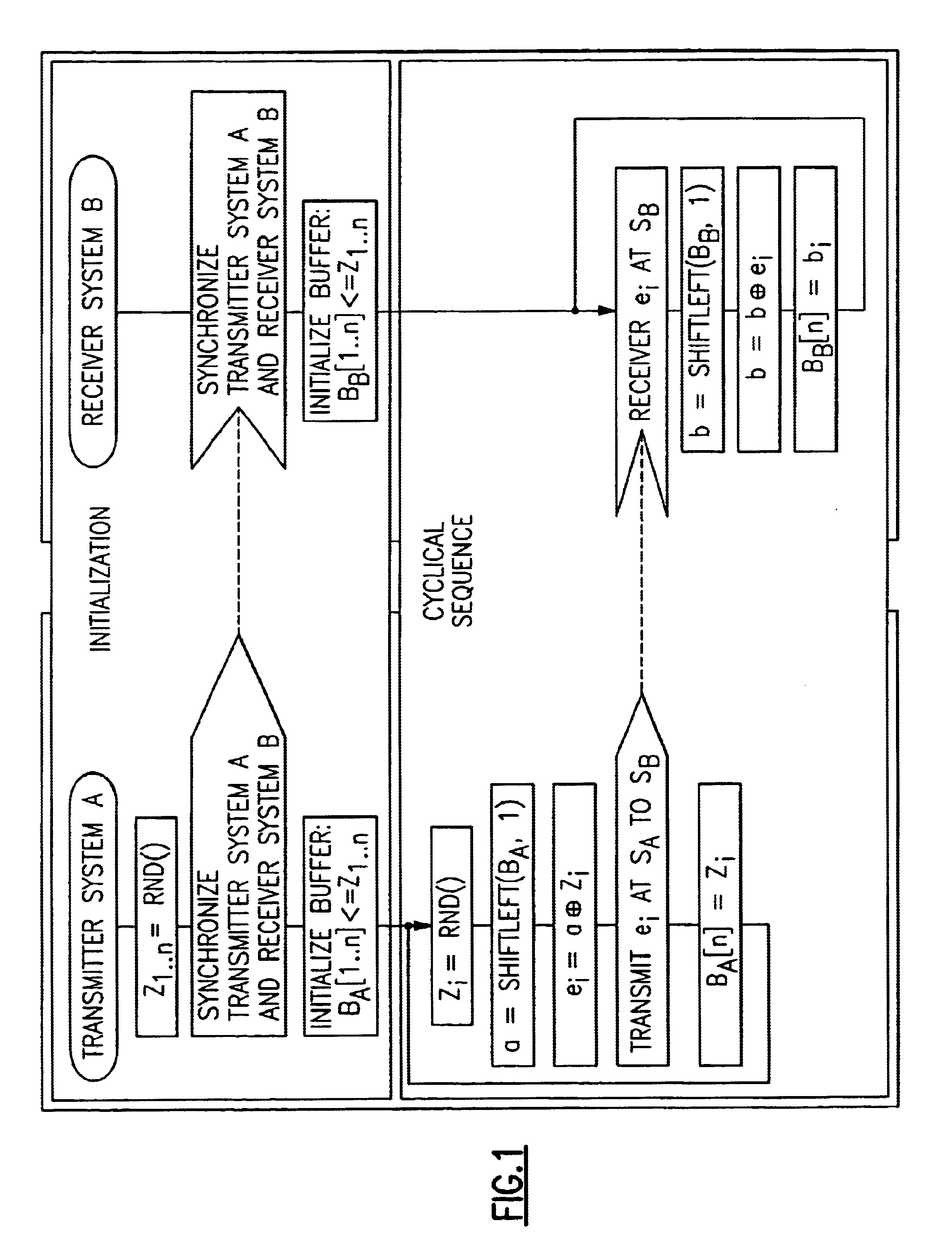
An approach for securely transmitting and storing data is described. A sending host generates a random sequence of characters as a keystream as a one-time pad. The keystream is bitwise combined with plaintext using an exclusive-OR operation to create ciphertext. The keystream and ciphertext are routed over physically separate communication paths to a receiving host, which decrypts by applying the keystream to the ciphertext using exclusive-OR, The separately routed paths may be established using MPLS labeling or strict route options.
Owner:CISCO TECH INC
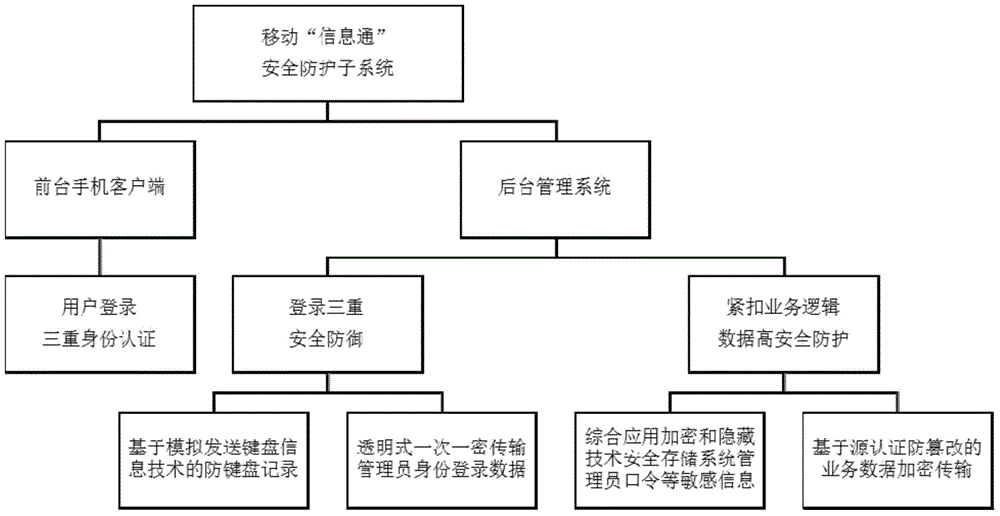
Implementation method for integrated security protection subsystem of mobile office system
ActiveCN104469767AImprove data securityRealize multi-factor authentication security defenseTransmissionSecurity arrangementInformation securityOne-time pad
The invention discloses an implementation method for an integrated security protection subsystem of a mobile office system. The implementation method includes the steps of triple mobile phone client identity authentication, triple background management system login security defense and tight service logic data security protection. The step of triple mobile phone client identity authentication includes password authentication, face recognition authentication and pattern password authentication. The step of triple background management system login security defense includes keyboard record prevention based on the simulative transmission keyboard information technology, a transparent one-time pad administrator login identity information encryption transmission mode based on RSA, and a double-factor authentication mode based on cloud pushing and combining dynamic passwords with static user names / passwords. Various kinds of security technology is transparently adopted, the data security is improved, multi-identity-authentication security defense is achieved, the access control capacity is enhanced, and notice announcement and news browsing of enterprises are safe and efficient through the integrated information security protection subsystem.
Owner:杭州安新立行网络科技有限公司
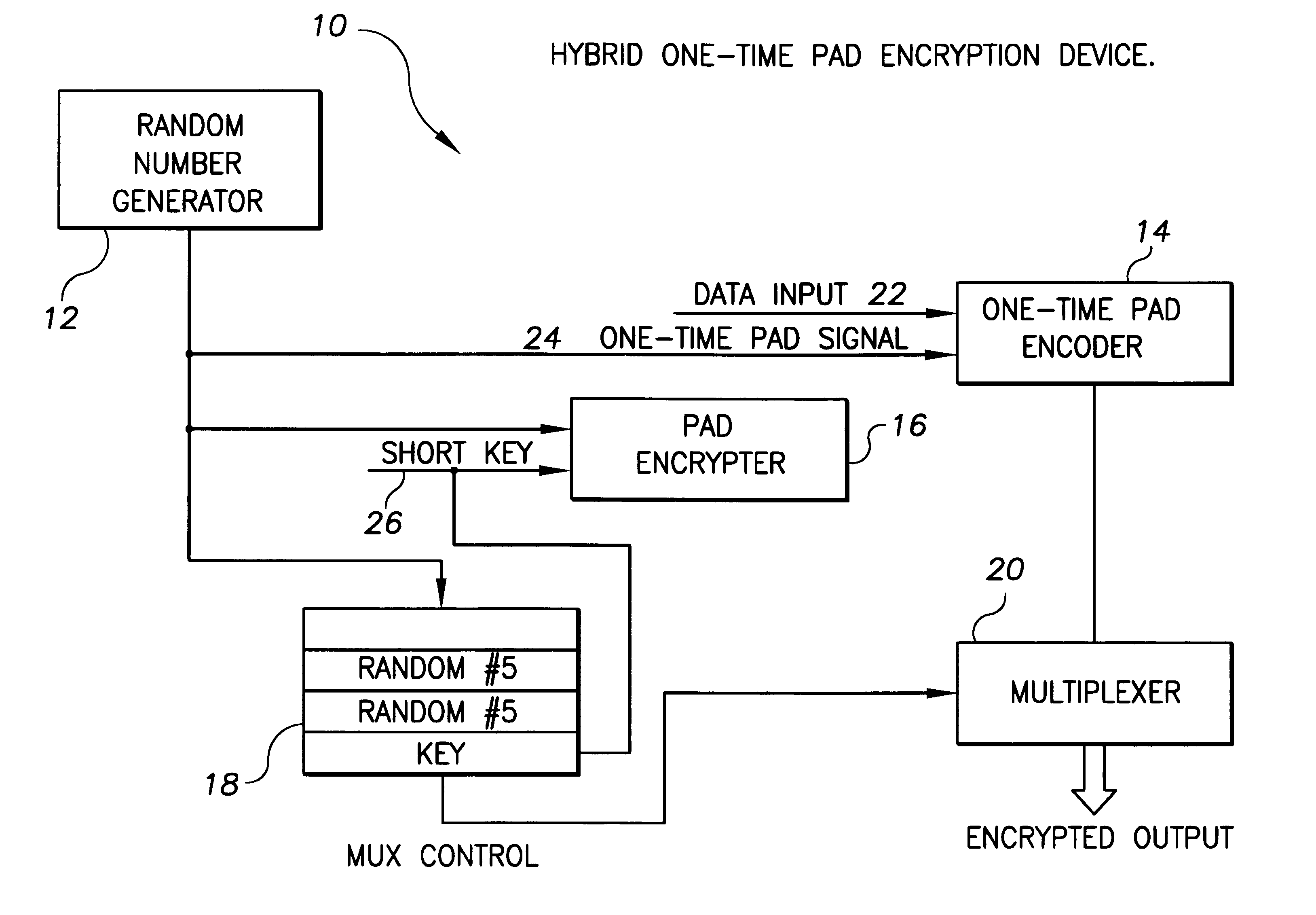
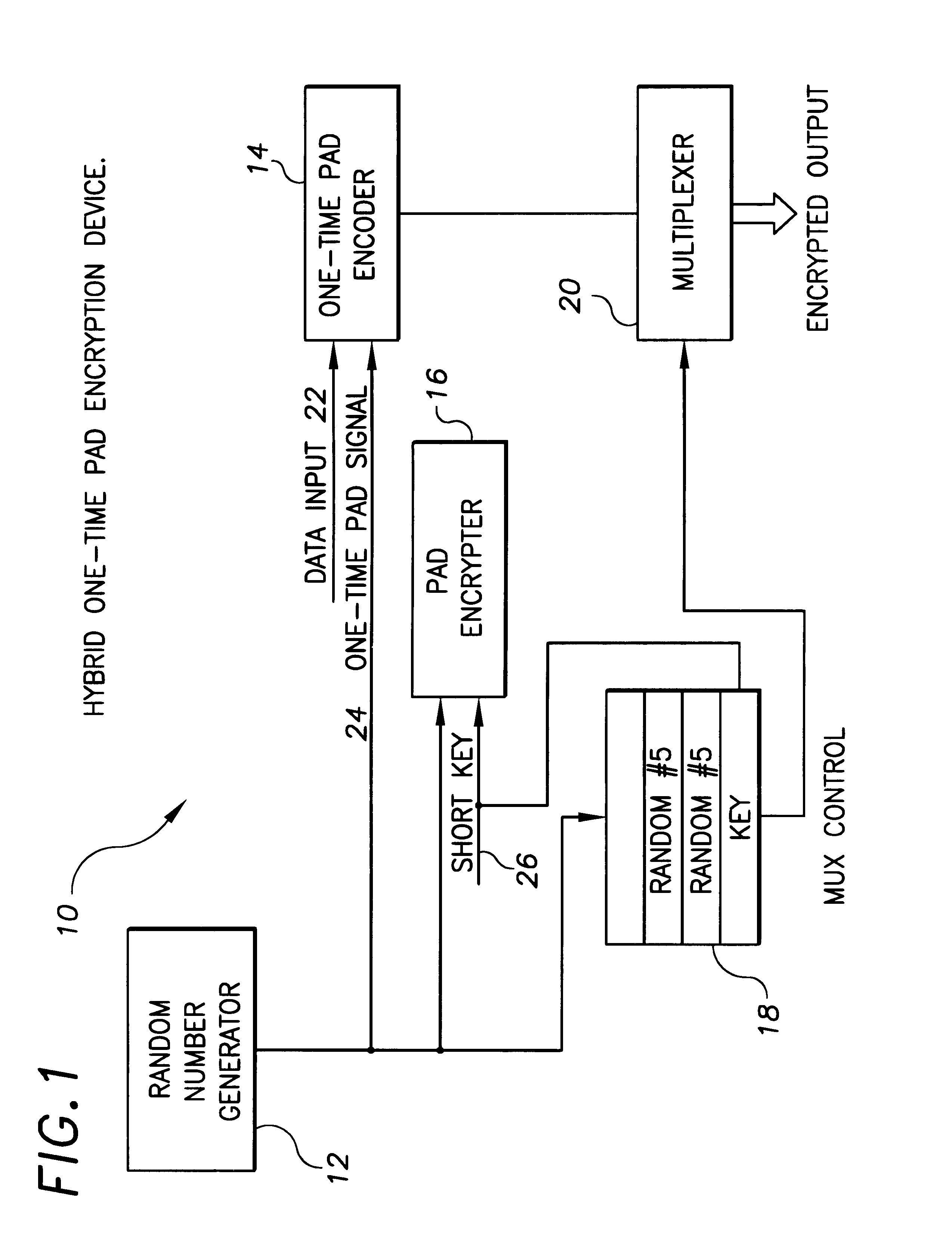
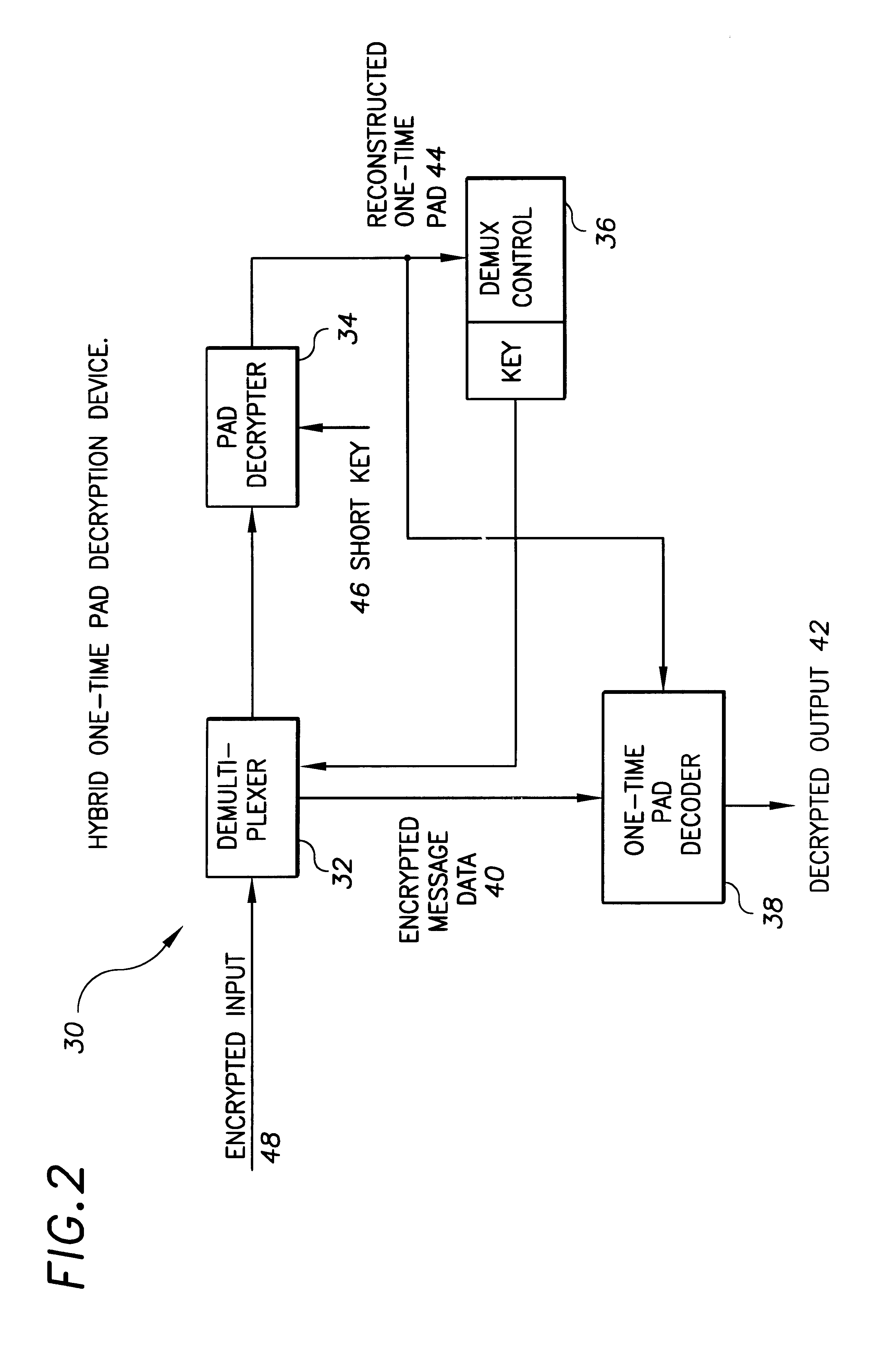
Hybrid one time pad encryption and decryption apparatus with methods for encrypting and decrypting data
InactiveUS6363152B1Key distribution for secure communicationUser identity/authority verificationComputer hardwareOne-time pad
A hybrid one time pad encryption and decryption apparatus with methods for encrypting and decrypting data wherein a one time random number pad provides high security encryption. The random number sequence is encrypted using DES, RSA or other technique and embedded in the message as a function of the random pad itself. This generates an encryption message that is impervious to attempts to directly decode the message text as the message is randomly dispersed throughout a message and the message contains as much quasi-random data as text. The message is also relatively impervious to attempts to decode the cipher, as the cipher is randomly interrupted by the encrypted data.
Owner:VLSI TECHNOLOGY
Method and system using one-time pad data to evidence the possession of a particular attribute
InactiveUS20070101410A1Digital data processing detailsUser identity/authority verificationData matchingOne-time pad
A method and system are provided for evidencing to a first entity, such as a visa-checking authority, that a second entity, such as a traveller, possesses a particular attribute, such as right of entry to a specific country. The method involves a preliminary phase of verifying that the second entity has the attribute of interest; associating that attribute with a first one-time pad held by the first entity; and arranging for the second entity to possess a second one-time pad that is at least a subset of the first one-time pad. Thereafter, when the second entity wishes to prove to the first entity that it has the attribute of interest, it passes evidence data derived from the second one-time pad to the first entity. The first entity can then check for the presence, in the first one-time pad, of data matching, or usable to produce, the evidence data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods and apparatus for implementing a communications system secured using one-time pads
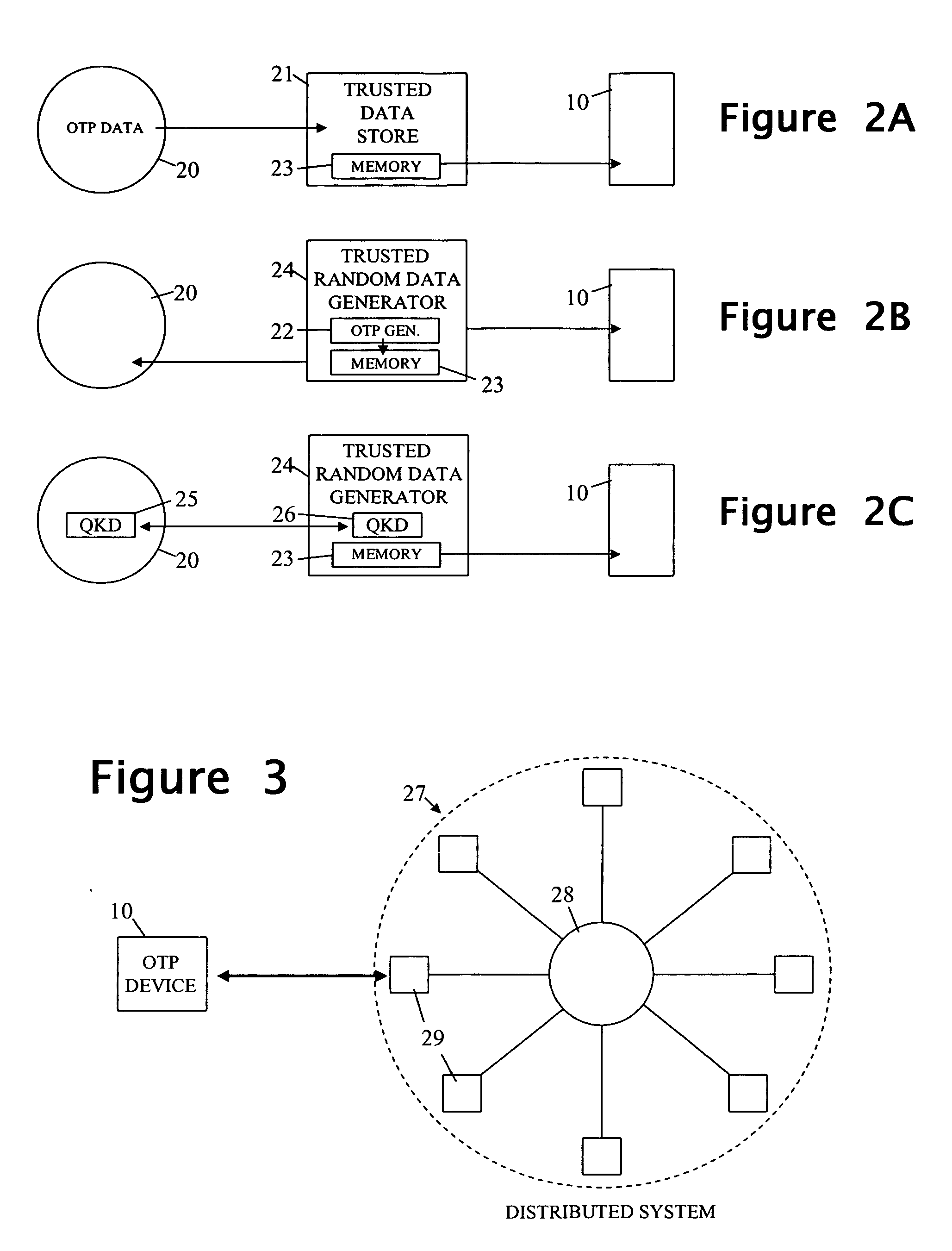
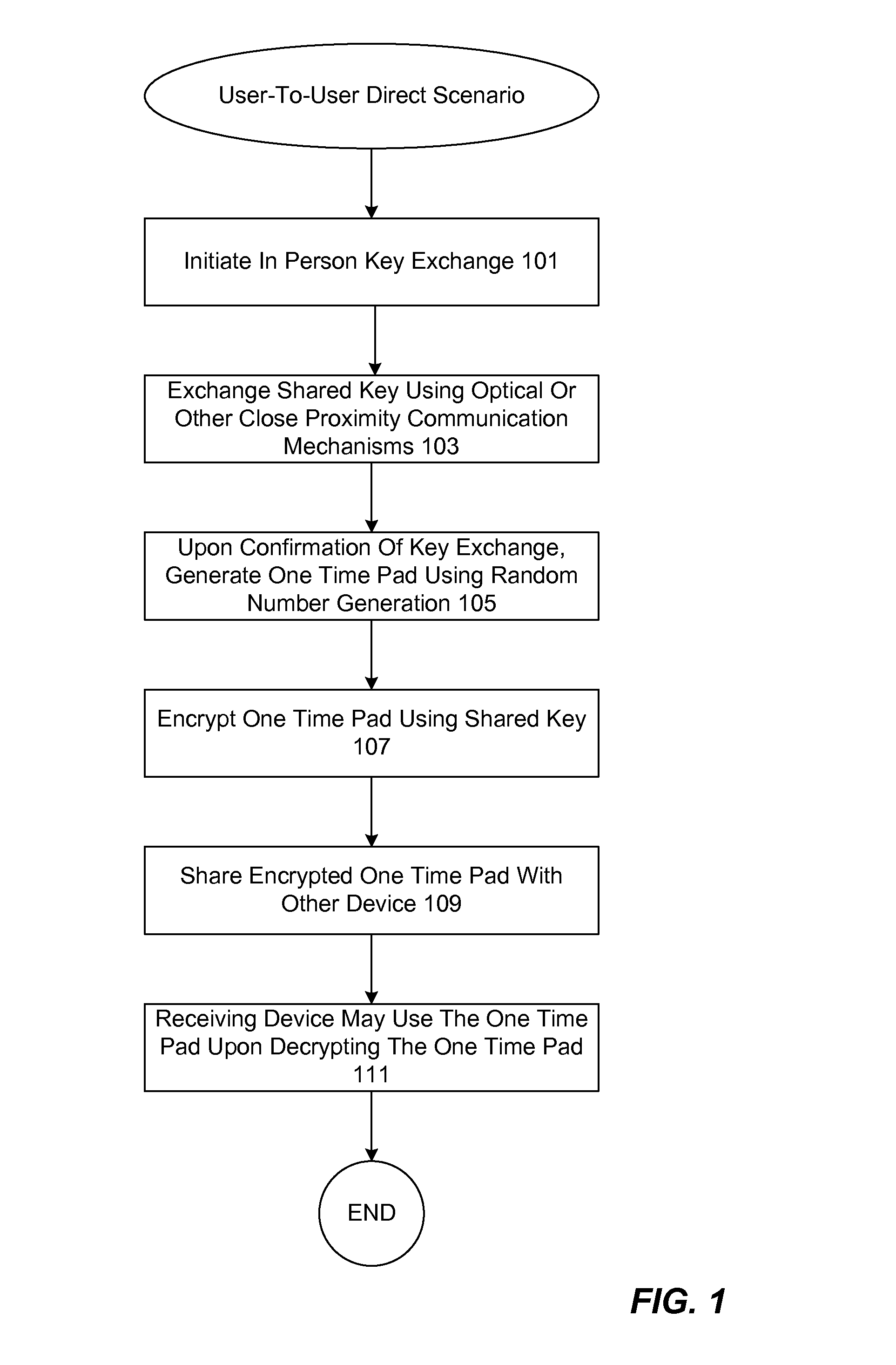
InactiveUS20170033925A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCommunications systemOptical communication
The present invention relates generally to mechanisms for securing a communication system by using one-time pads. One-time pads may be generated and exchanged in person using proximity based mechanisms including optical communication mechanisms on mobile devices. In particular examples, a quick response (QR) code on one party's mobile device is scanned by the other party's mobile device to securely exchange a randomly-generated symmetric key. The symmetric key is used to encrypt a randomly generated one-time pad transmitted from one party's mobile device to the other party's mobile device. The one-time pad may be shared in encrypted form using proximity based mechanisms including Bluetooth, WiFi, etc.
Owner:OSCAR TANGO PAPA
Security instant communication system
InactiveCN101645770AImprove securityAdjustable parametersKey distribution for secure communicationData switching networksSequence signalCommunications system
The invention discloses an instant communication system, which comprises a sender and a receiver. Instant communication modules of the sender and the receiver carry out parameter setting on a controlcircuit, generate encrypted data for transmission, and decrypt the received data; a control circuit modulates a quantum key module, acquires an original key and controls a synchronous timing sequence;the quantum key module generates the original key synchronously according to a trigger signal, modulation voltage and a timing sequence signal of the control circuit; a clock synchronous module generates a synchronous clock signal according to the trigger signal of the corresponding control circuit, and sends the synchronous clock signal to the clock synchronous module of the receiver; the clocksynchronous module of the receiver returns the clock synchronous signal and completes the synchronization of the sender and the receiver; and the sender and the receiver encrypt and decrypt information by a real-time security key generated by a quantum key generation system according to an one-time pad memo-type encryption scheme; therefore, the instant communication system has high security, andcan realize the off-site absolutely-secure instant communication.
Owner:INST OF PHYSICS - CHINESE ACAD OF SCI
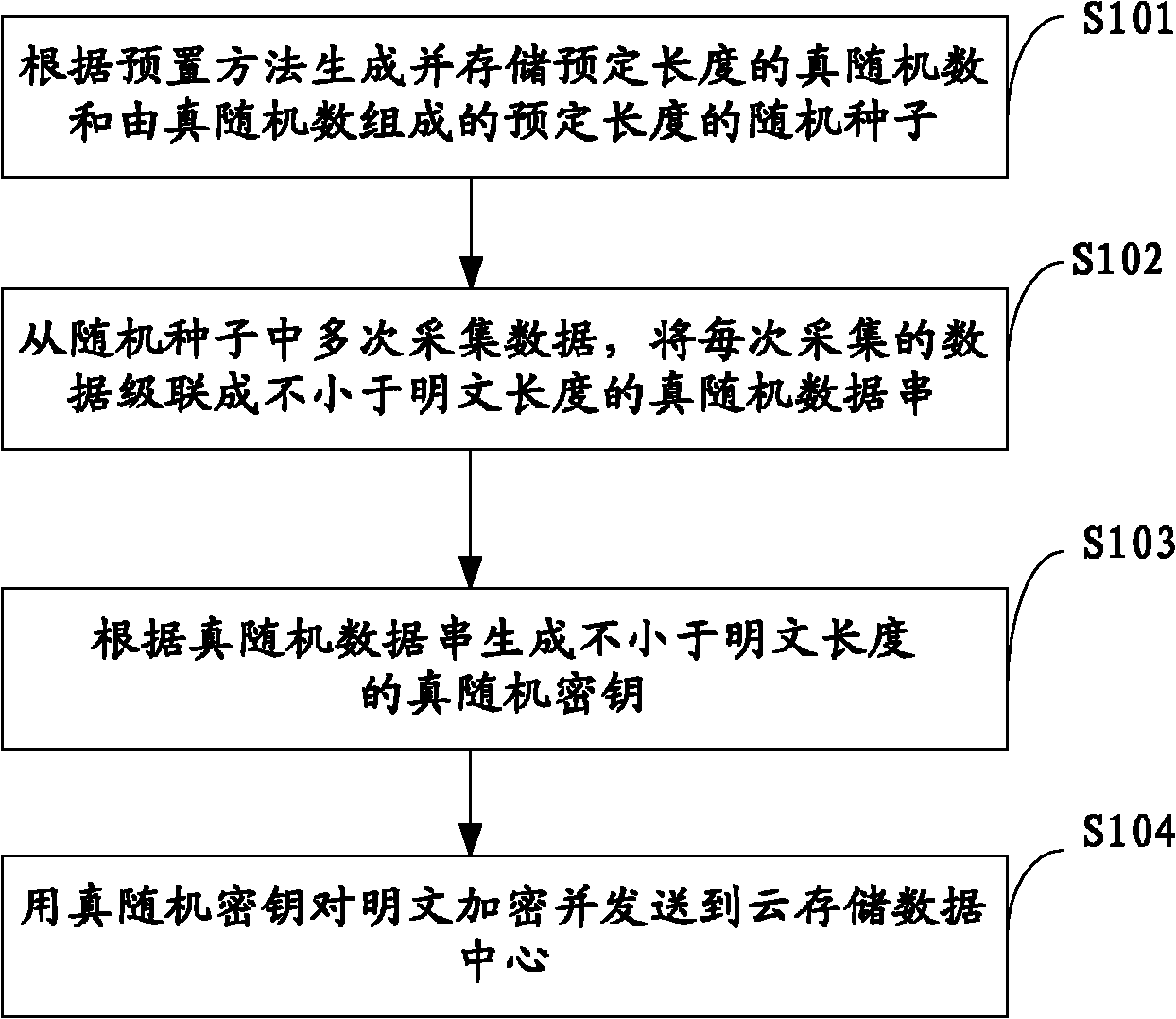
OTP-based cloud storage data storing method, device and system
InactiveCN101986663AProtection securityPrivacy protectionUser identity/authority verificationConfidentialityData center
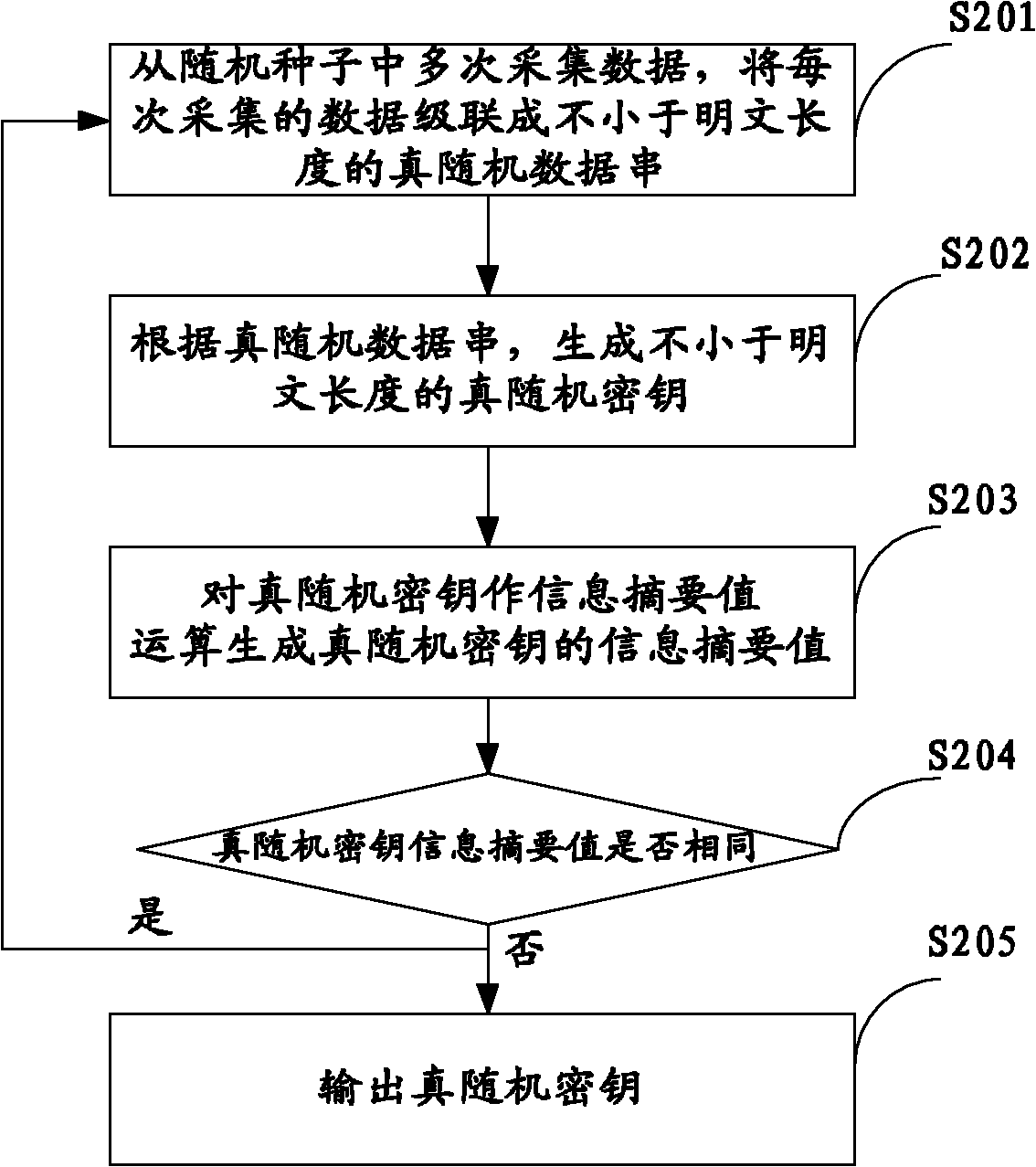
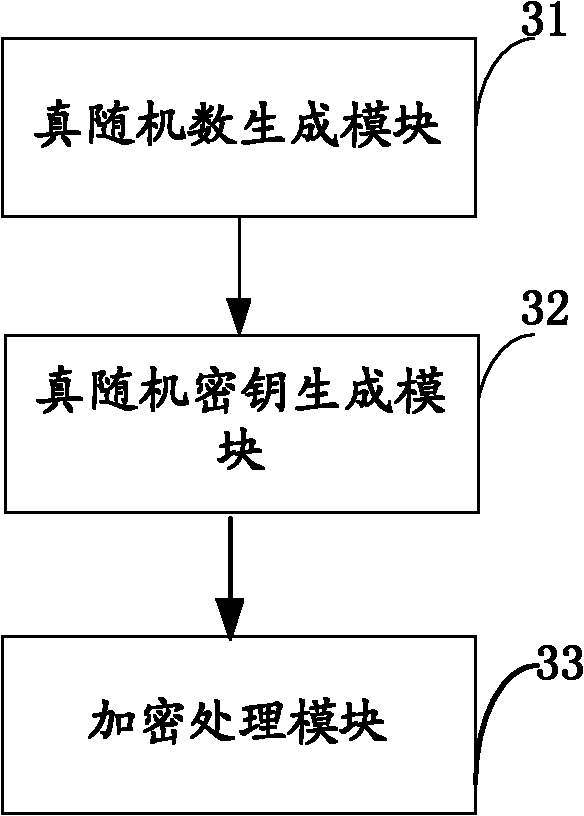
The invention belongs to the technical field of cloud storage security, and particularly relates to an OTP-based (one-time pad-based) cloud storage data storing method, an OTP-based cloud storage data storing device and an OTP-based cloud storage data storing system. The method comprises the following steps of: generating and storing a true random number of predetermined length and a random seed consisting of the true random number and with predetermined length according to a preset method; repeatedly acquiring data from the random seed, and cascading the data acquired each time into a true random data string not shorter than a plain text length; and generating a true random key not shorter than the plain text length according to the true random data string, encrypting the plain text and sending the encrypted plain text to a cloud storage data center. The invention also provides the OTP-based cloud storage data storing device and the OTP-based cloud storage data storing system. The method, the device and the system generate and store the true random key with enough number and without repeated use by using relatively small plain text storage space, effectively protect the security and the privacy of the cloud storage data and improve the confidentiality of the cloud storage data.
Owner:BEIJING Z & W TECH CONSULTING
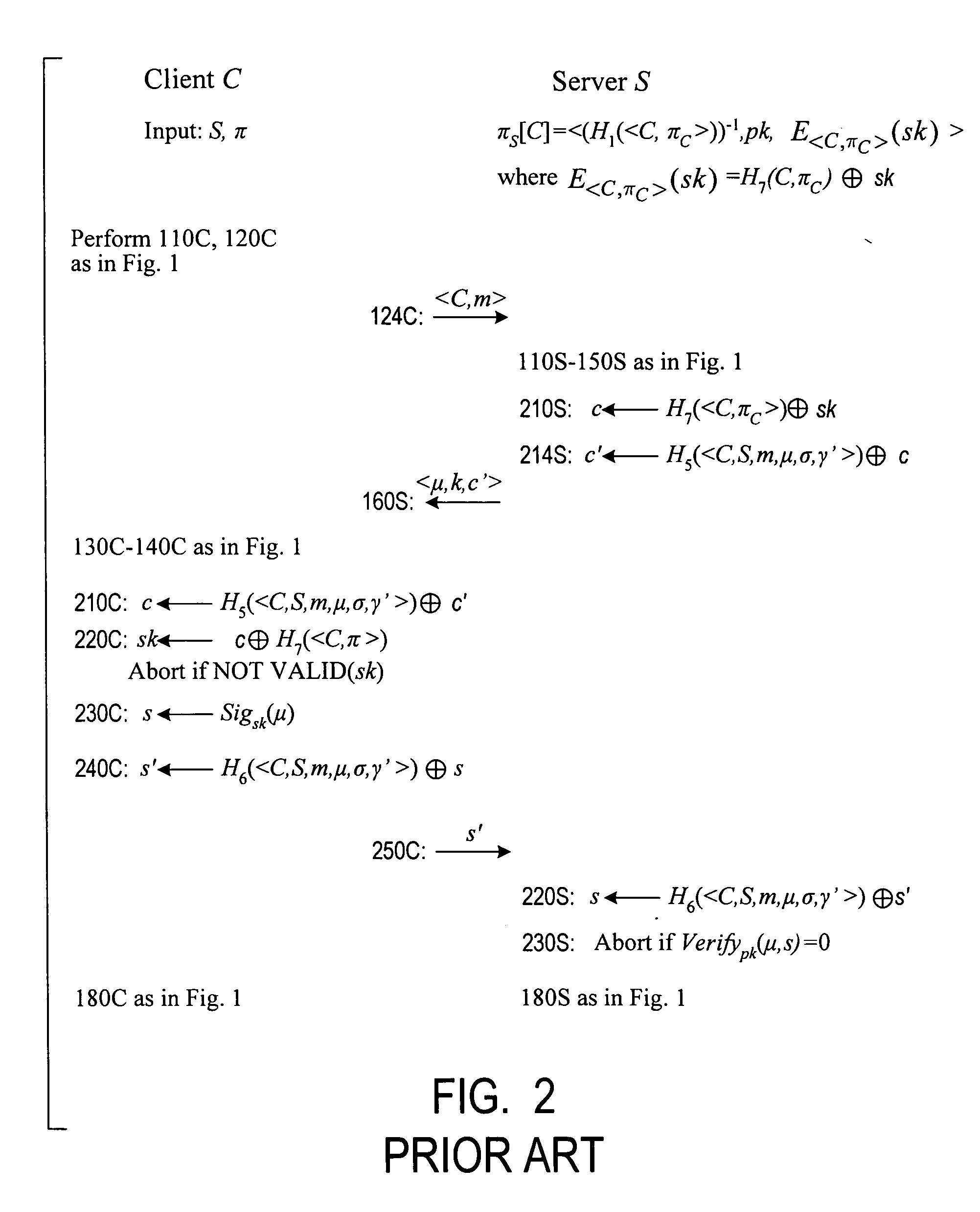
Cryptographic authentication, and/or establishment of shared cryptographic keys, using a signing key encrypted with a non-one-time-pad encryption, including (but not limited to) techniques with improved security against malleability attacks
InactiveUS20070067629A1Effective attackUser identity/authority verificationComputer security arrangementsOne-time passwordClient-side
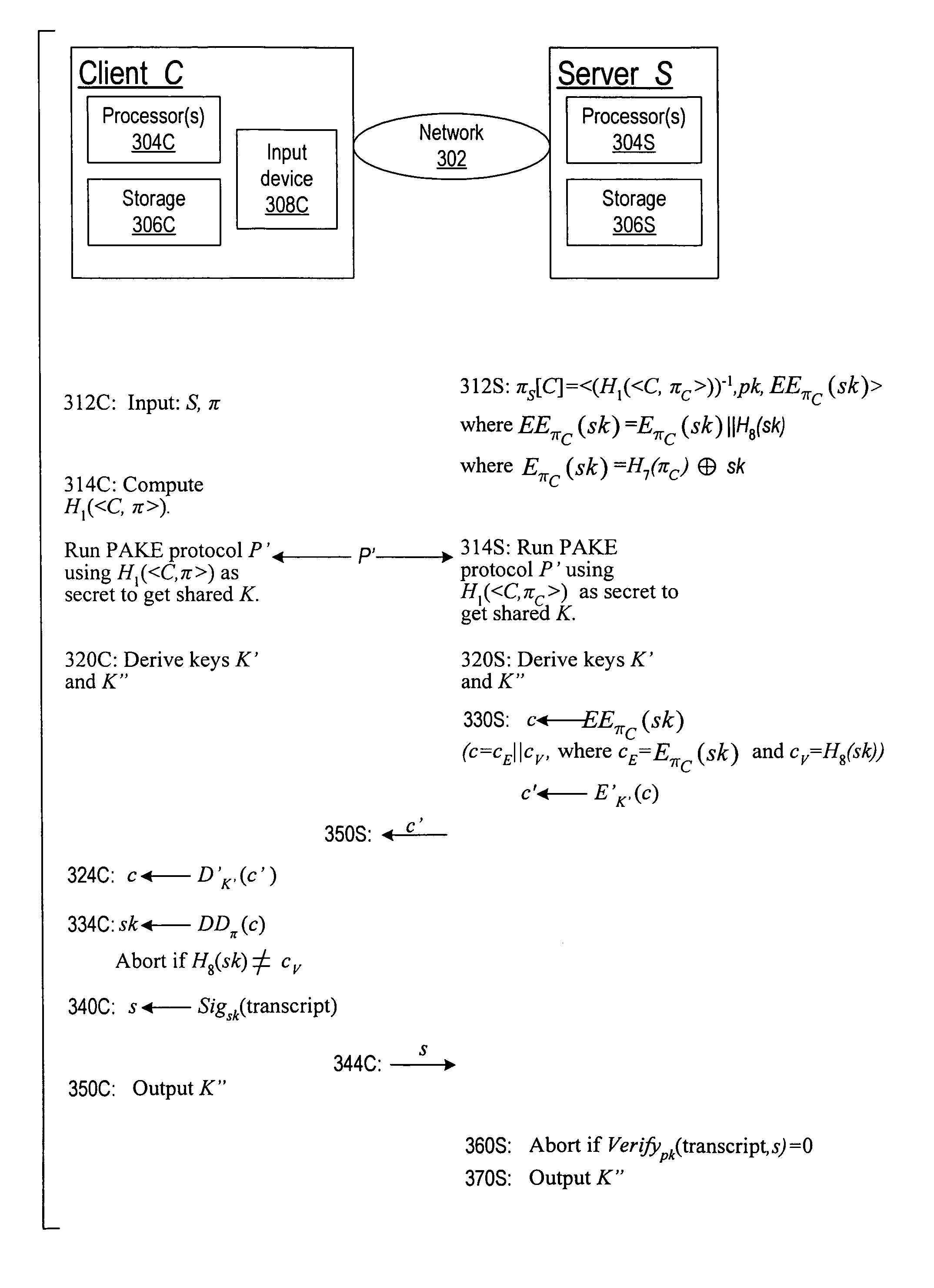
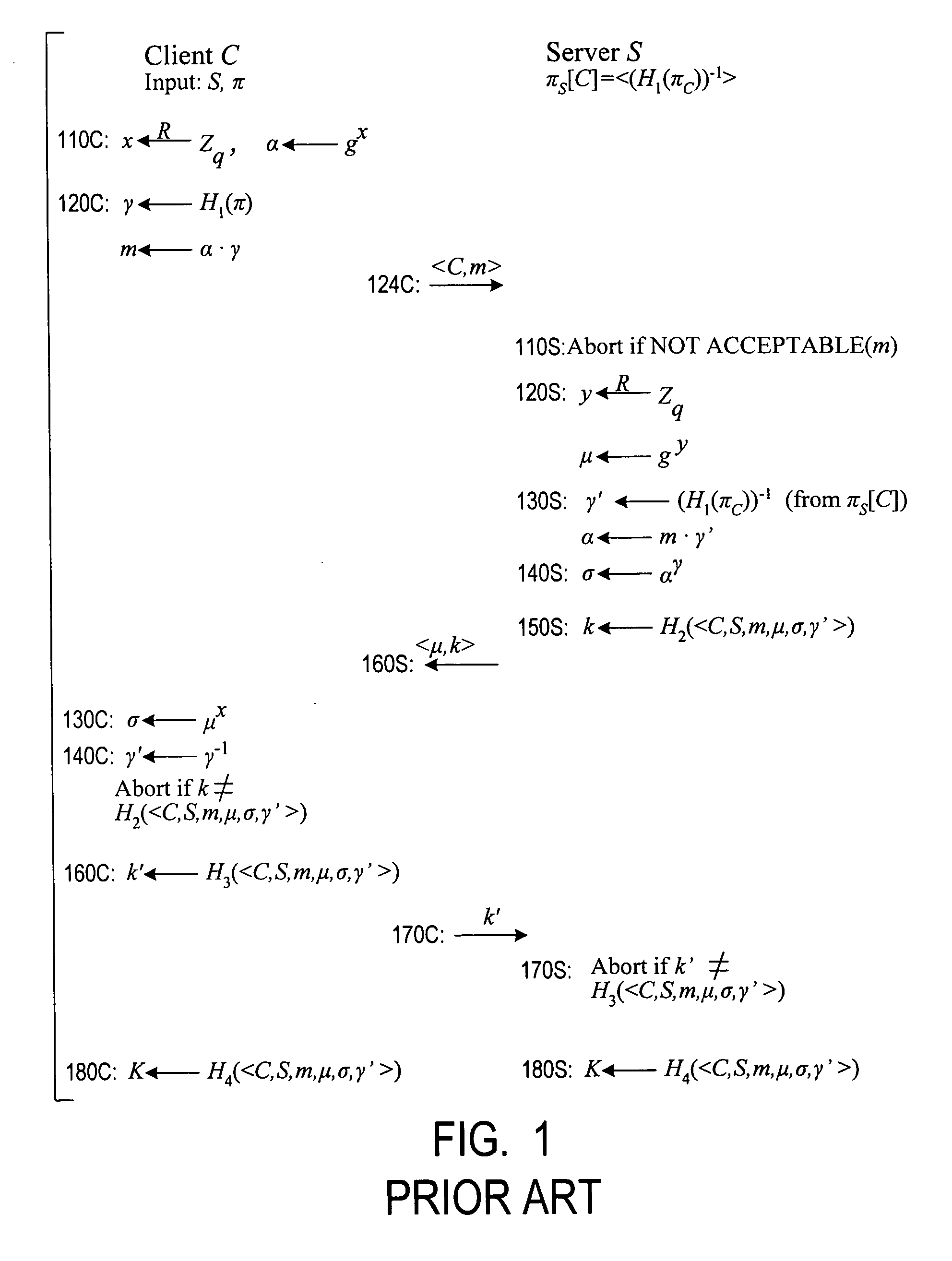
Using a password (π), a client (C) computes part (H1(<C,πC>) of the password verification information of a server (S), and together they use this information to authenticate each other and establish a cryptographic key (K′), possibly using a method resilient to offline dictionary attacks. Then over a secure channel based on that cryptographic key, the server sends an encryption (EE<C,π>(sk)) of a signing key (sk) to a signature scheme for which the server know a verification key (pk). The encryption is possibly non-malleable and / or includes a decryptable portion (E<C,π>(sk)) and a verification portion (H8(sk)) used to verify the decrypted value obtained by decrypting the decryptable portion. The signing key is based on the password and unknown to the server. The client obtains the signing key using the password, signs a message, and returns the signature to the server. The server verifies this signature using the verification key, hence getting additional proof that the client has knowledge of the password. The client and the server generate a shared secret key (K″), more secure than the password, for subsequent communication.
Owner:NTT DOCOMO INC
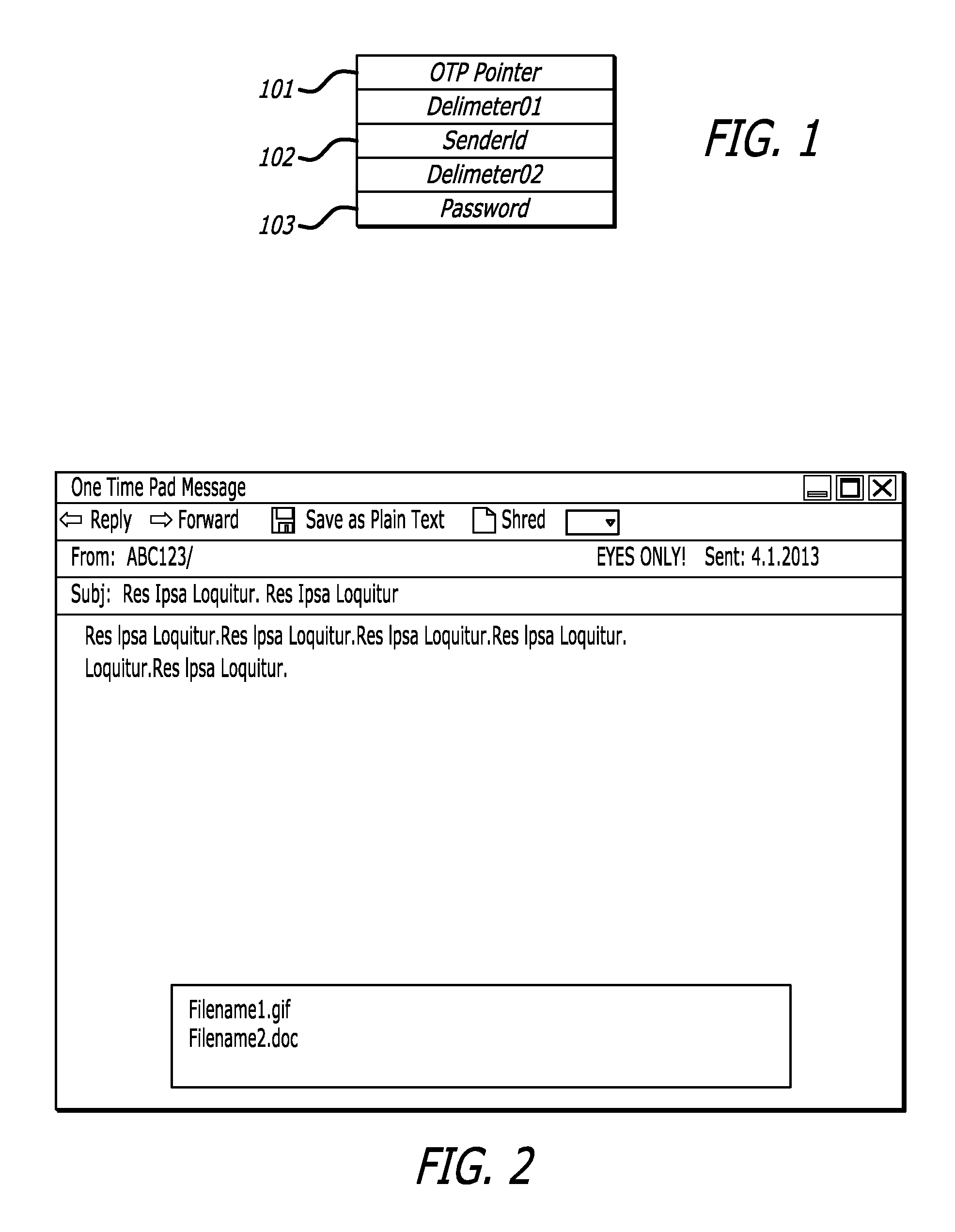
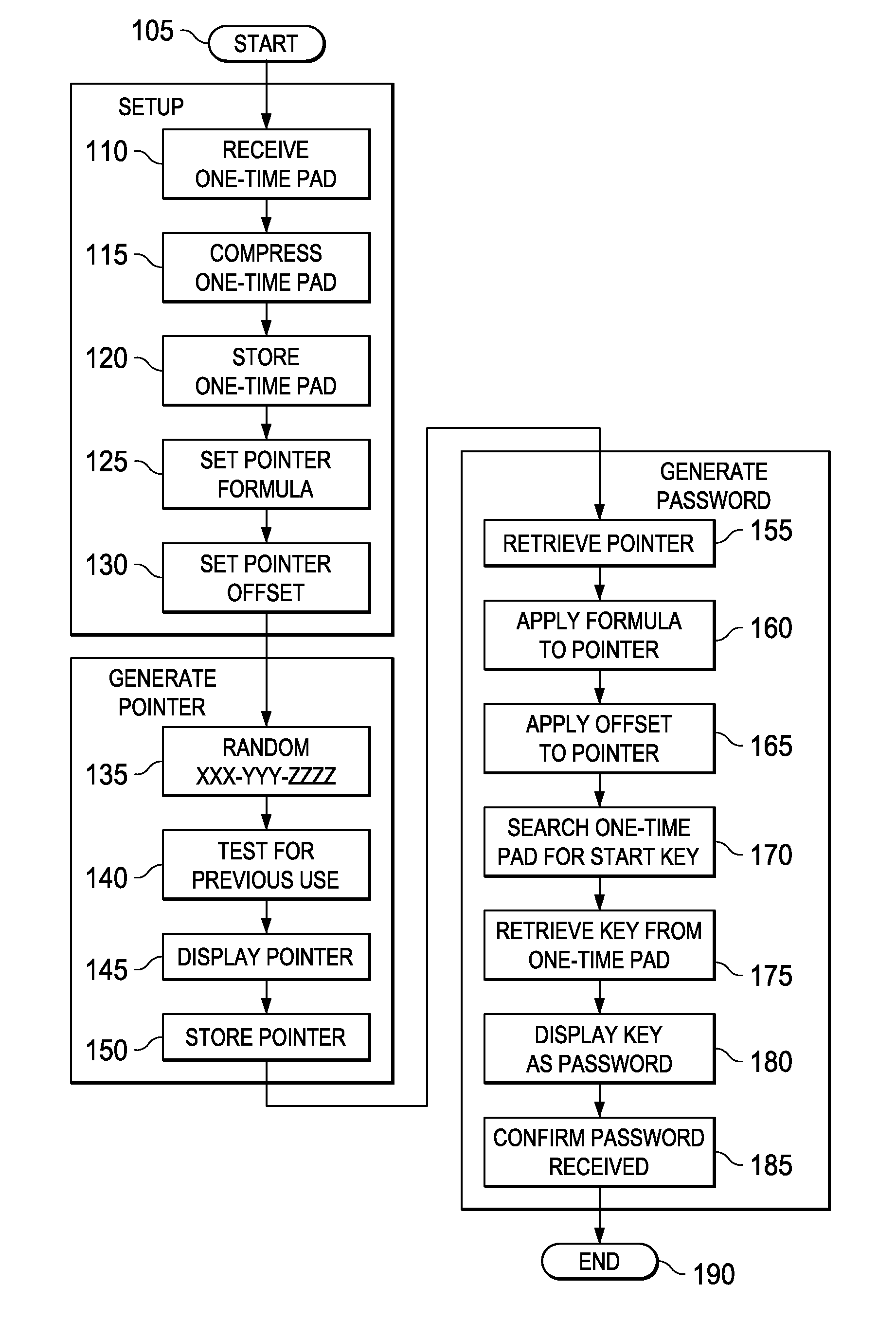
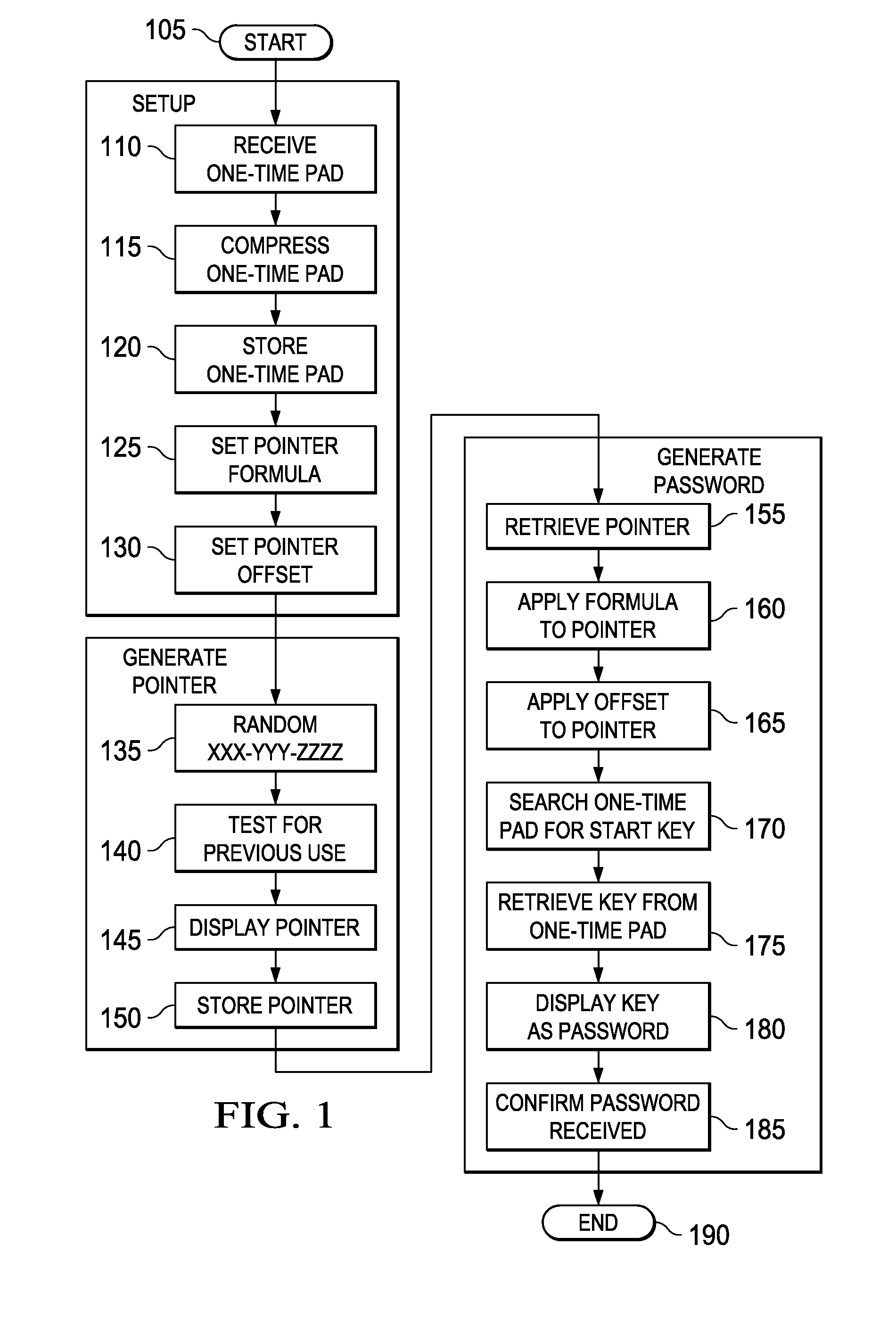
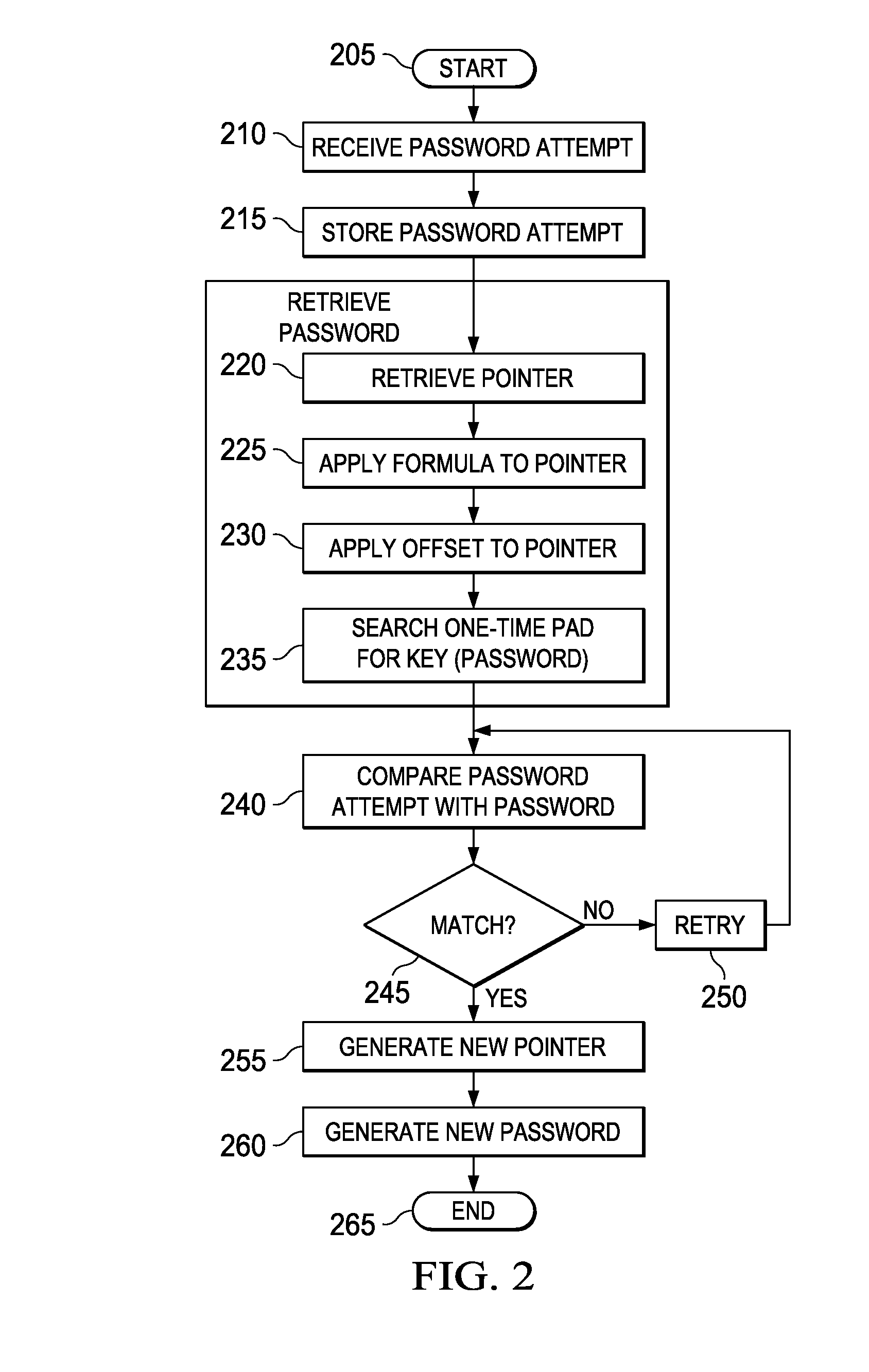
Systems and methods for information security using one-time pad
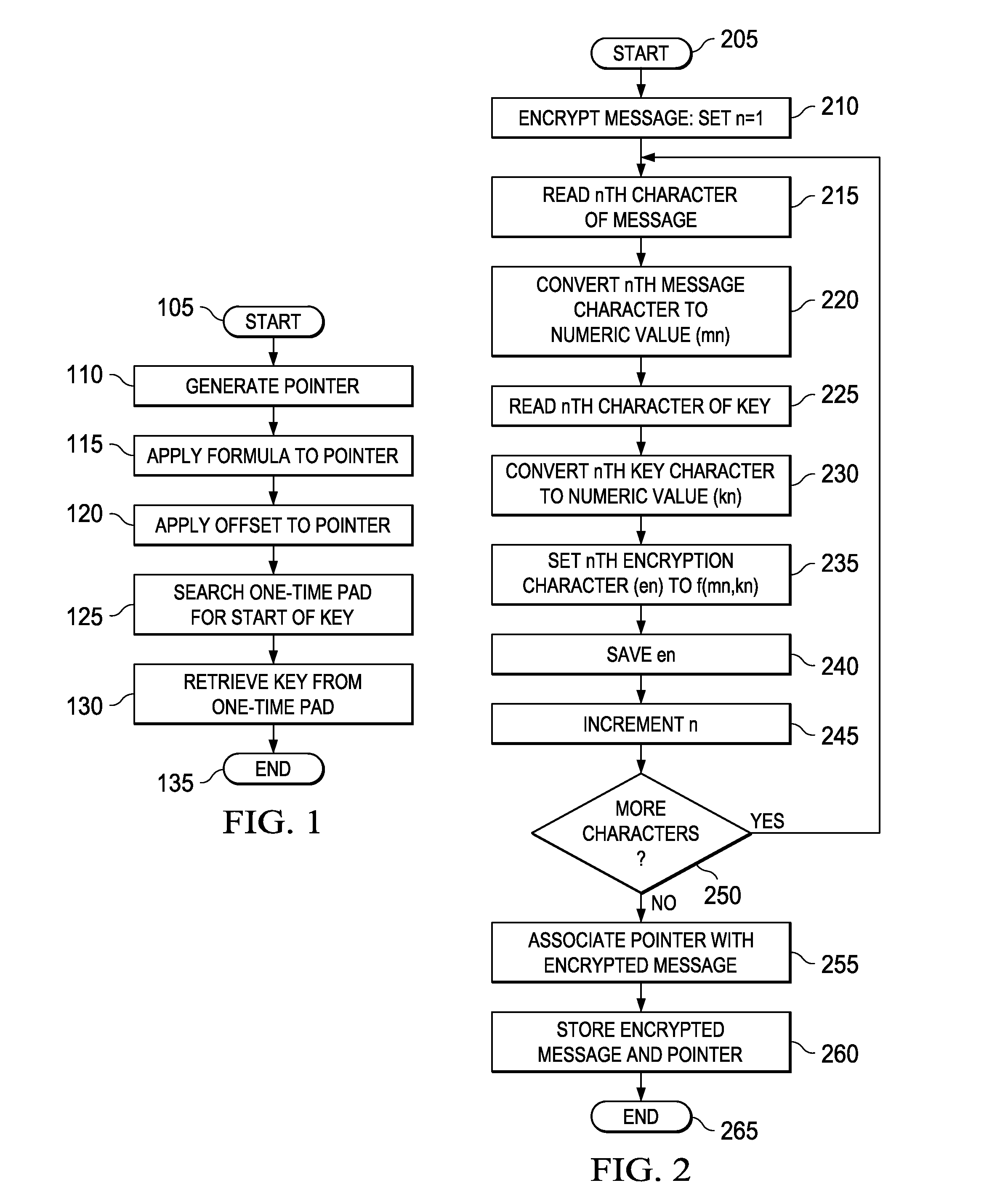
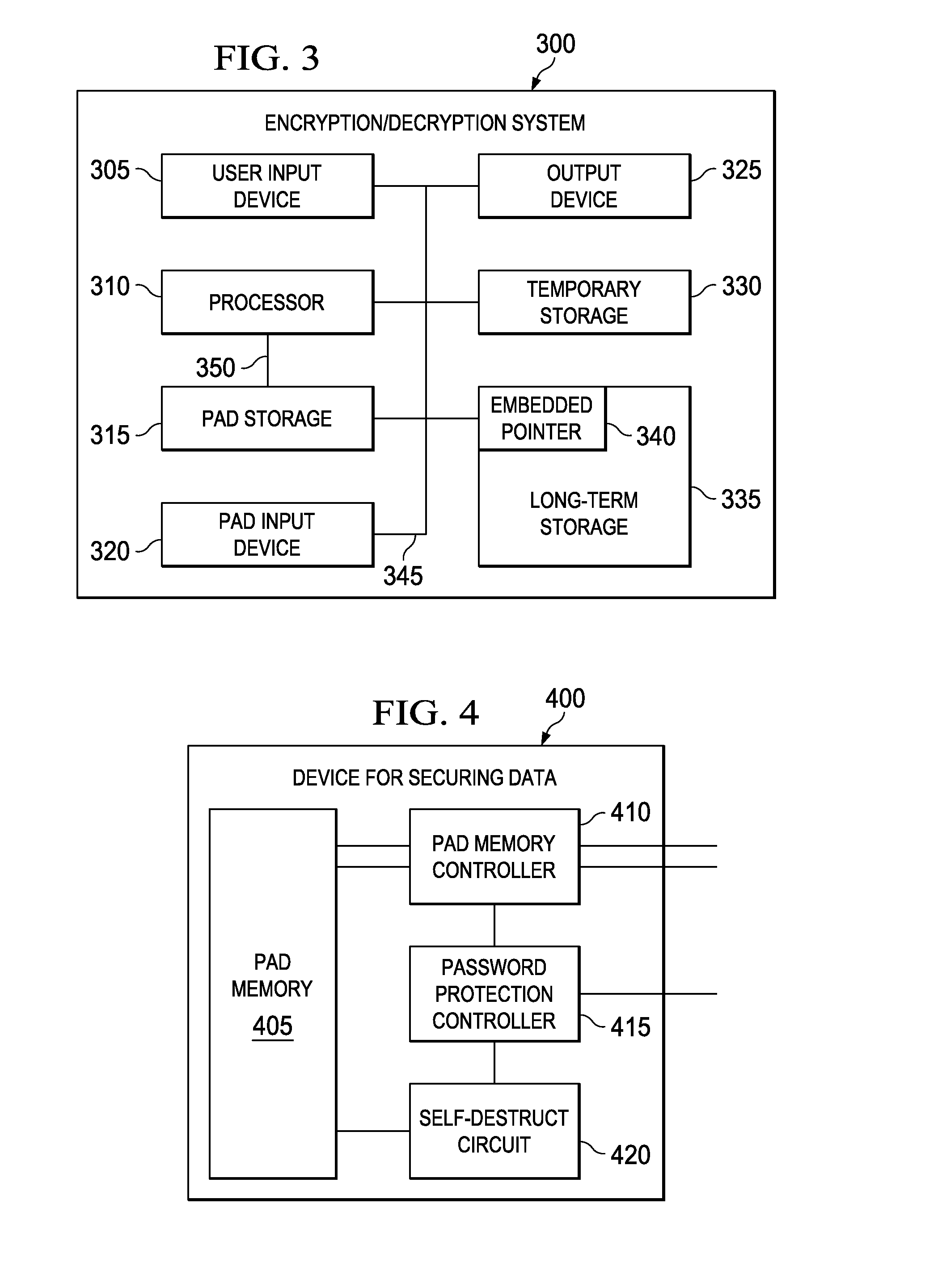
ActiveUS20100246811A1Digital data processing detailsUser identity/authority verificationValidation methodsOne-time password
A method of verifying a password and methods of encryption and decryption using a key generated from a one-time pad. In one embodiment, the method of verifying includes: (1) receiving a password attempt, (2) retrieving a pointer from memory, (3) searching a one-time pad based on the pointer to retrieve a password, (4) comparing the password attempt with the password and (5) generating a new pointer if the password attempt matches the password.
Owner:LSI CORPORATION
Device for data security using user selectable one-time pad
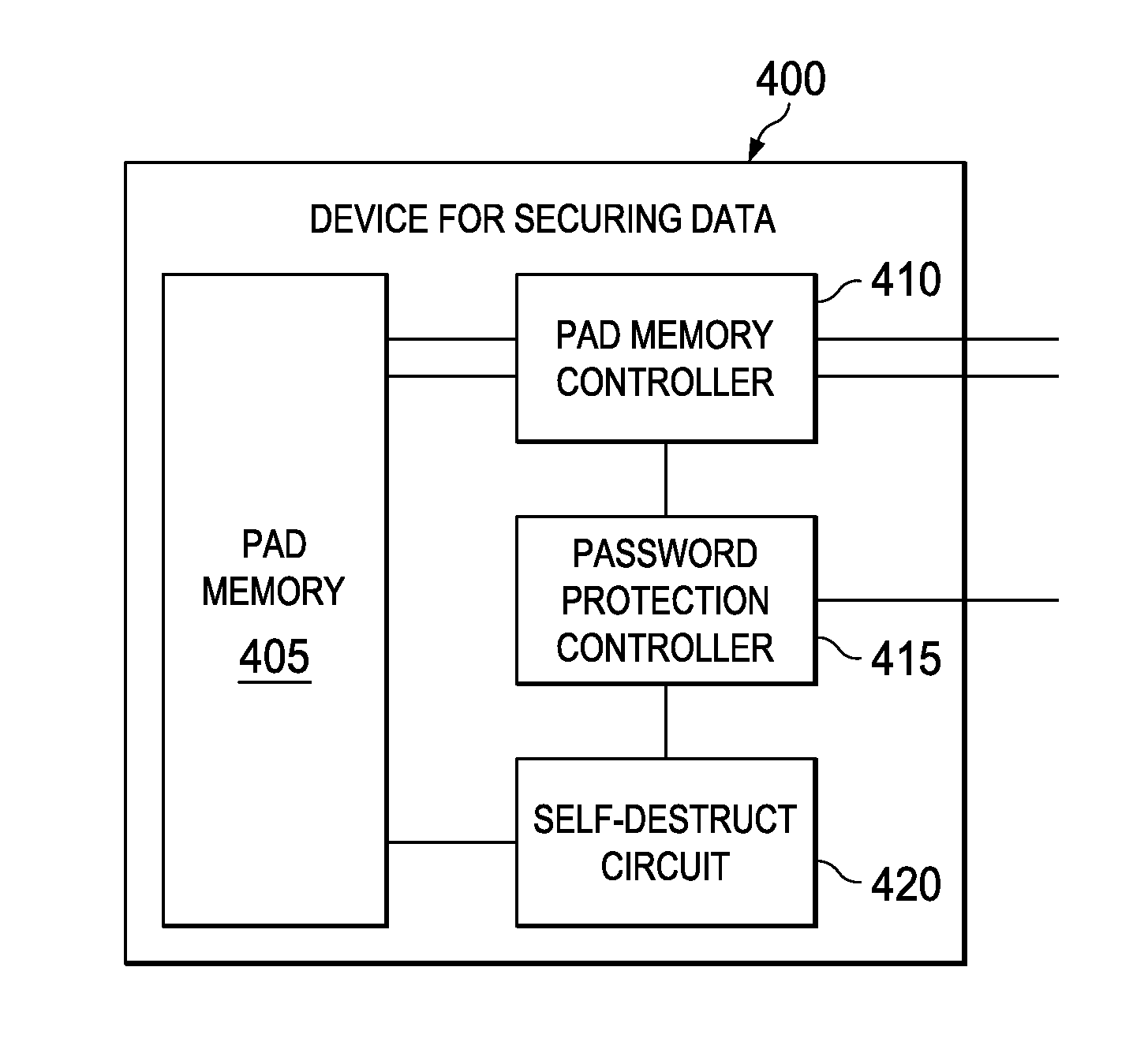
InactiveUS20100250968A1Digital data processing detailsUnauthorized memory use protectionPasswordMemory controller
Devices for securing data and method of managing a one-time pad stored in nonvolatile memory of a device. In one embodiment, the device for securing data includes: (1) a nonvolatile memory, (2) a nonvolatile memory controller coupled to the nonvolatile memory and configured to cooperate with the nonvolatile memory to make a key available when a password provided to the device is valid and (3) a self-destruct circuit coupled to the nonvolatile memory and configured to corrupt at least part of the nonvolatile memory when the password is invalid.
Owner:LSI CORPORATION
Security data communication achieving method based on quantum key distribution
InactiveCN104468097AReduce lossIncrease spawn rateKey distribution for secure communicationError preventionComputer hardwareKey distribution
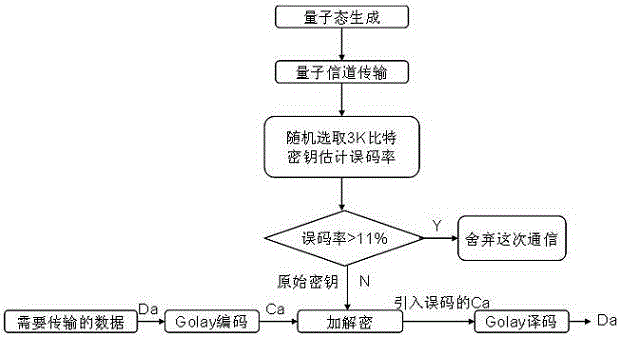
The invention discloses a security data communication achieving method based on quantum key distribution. In traditional data communication based on quasi single-photon source quantum key distribution, a large number of quantum bits will be consumed in the data reconciliation process, and quantum key distribution efficiency is low. According to the security data communication achieving method based on quantum key distribution, a new quantum security communication model is built, the data reconciliation process is omitted, original key error codes are equivalent to channel error codes, and data secrecy transmission is achieved by exchanging the encryption and decryption sequence and the channel coding frequency. Dolay coding with the high error correcting capability is adopted for channel coding, original keys are used for encrypting and decrypting the coded data in a one-time pad mode, Dolay decoding is carried out on the decrypted data with error codes, and verification is carried out in an experiment system. Research results show that the quantum key distribution process is simplified, the key security is enhanced, computing and communication resources are saved, the key generating rate is improved, and a new idea is provided for quantum key distribution.
Owner:PLA UNIV OF SCI & TECH
Virtual genome-based cryptosystem (VGC)
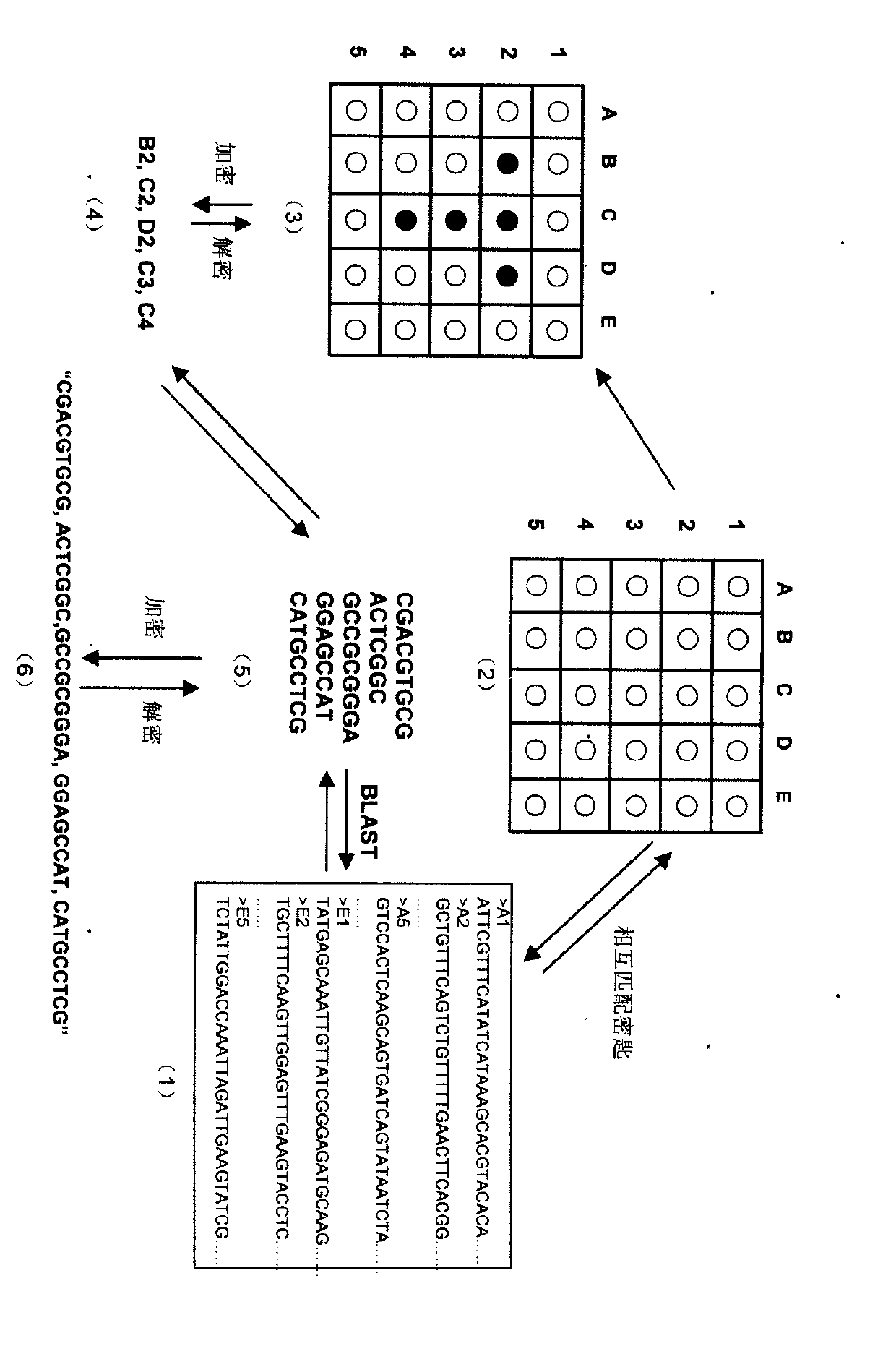
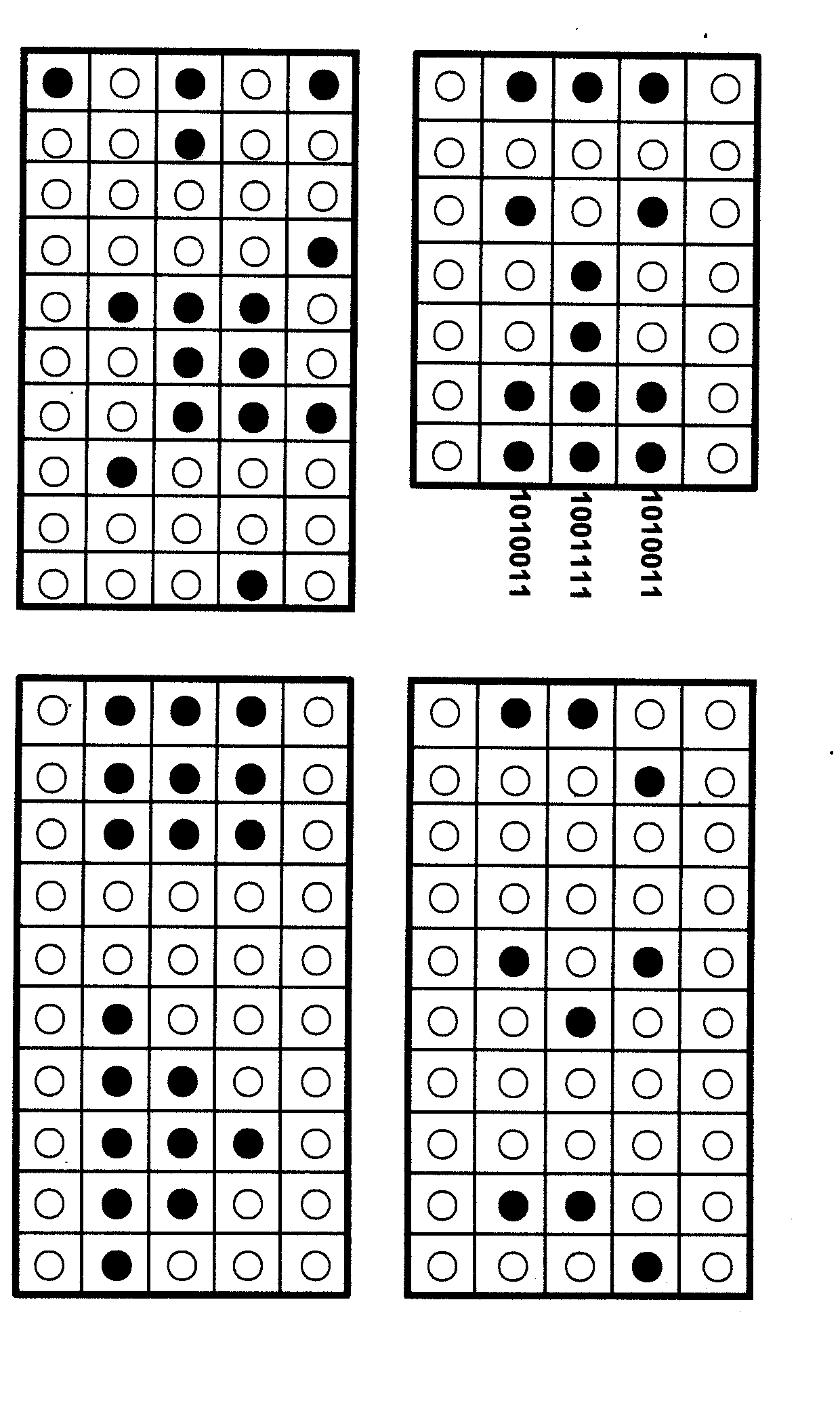
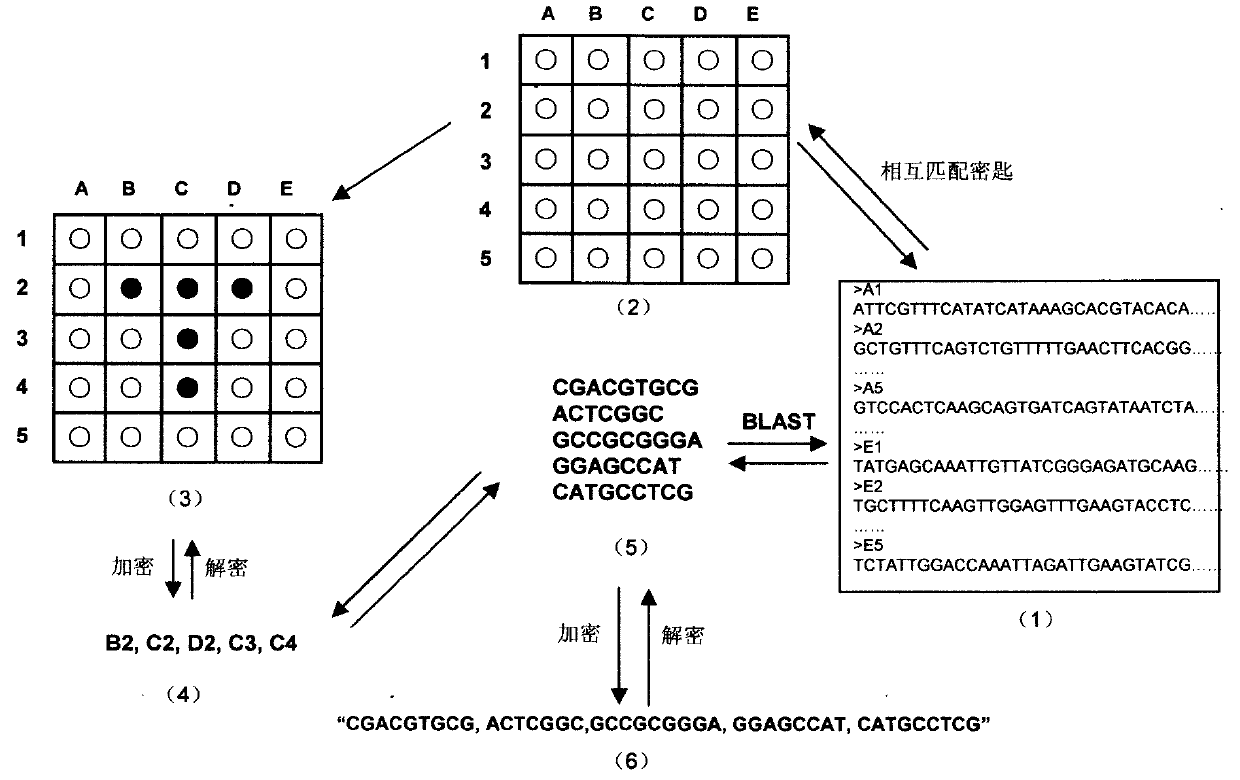
InactiveCN102025482ASolve the first sharing problemHuge key spaceGenetic modelsSecuring communicationPlaintextDNA Microarray Chip
The invention relates to information security technology, in particular to a virtual genome-based cryptosystem (VGC). The cryptosystem is provided with two matched keys, of which one is a virtual genome database (VGDB) consisting of random deoxyribonucleic acid (DNA) sequences and the other one is a position table that virtual genes of the VGDB are randomly distributed in a two-dimensional microarray, namely a virtual DNA microarray chip (VDMC). Any plaintext information can be freely written on the VDMC, namely points for forming the plaintext information are selected from the VDMC microarray. The selected points correspond to the virtual genes in the VGDB; small segments of DNA sequences are randomly selected from the virtual genes; and the uniqueness of the small segments of DNA sequences in the VGDB is determined by using a common tool of the bioinformatics, namely a basic local alignment search tool (BLAST), or other character string search algorithms such as a Knuth-Morris-Pratt (KMP) algorithm and the like. A cipher text is combined by the small segments of DNA sequences. The small segments of DNA sequences need only to perform BLAST on the VGDB during decryption, namely the points for forming the plaintext information can be discovered, and the plaintext information can be restored according to the VDMC. Any non-VGDB sequence can be randomly inserted into the cipher text and does not have any influence on the encryption. Thus, the VGC is an excellent information hiding system. In addition, the VGC key can be updated automatically so as to realize an indecipherable one-time-pad system. The cryptosystem is used for real-time quick secret information communication, digital signature and identity authentication.
Owner:SOUTH CHINA BOTANICAL GARDEN CHINESE ACADEMY OF SCI
IPSec VPN method used for realizing quantum safety
ActiveCN107453869AImproving Quantum SecurityImplement converged applicationsKey distribution for secure communicationOne-time padQuantum
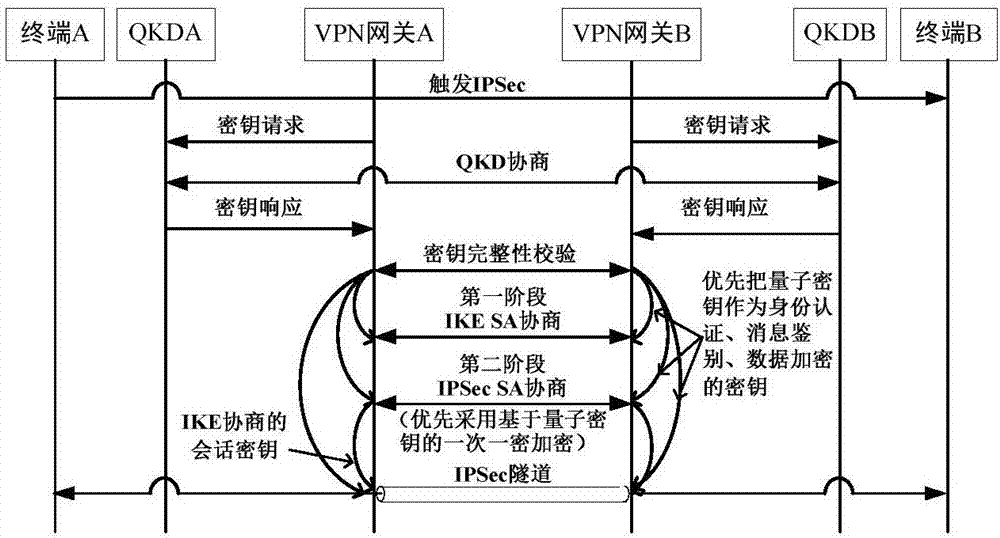
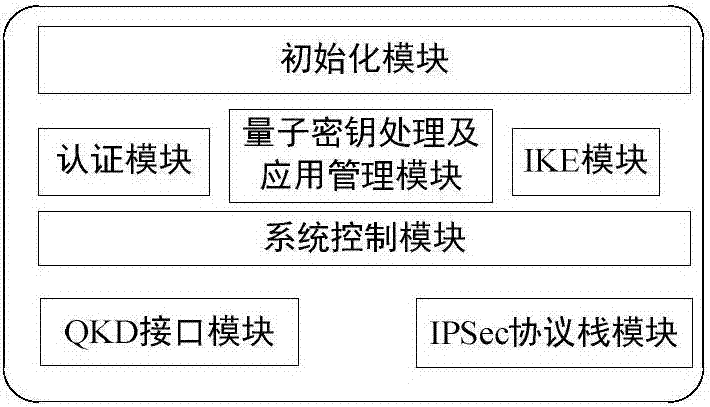
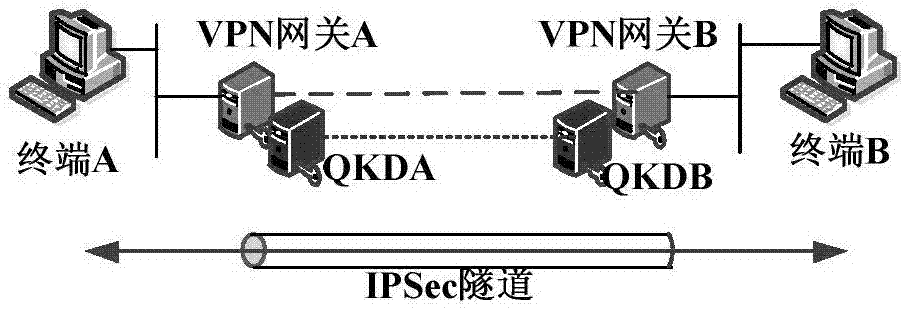
The invention discloses an IPSec VPN method used for realizing quantum safety. The method is characterized by adding a safe interface of QKD in an IPSec VPN gateway; adding a quantum key access and application mechanism in an IPSec VPN safety strategy; adding a one-time pad encryption option based on a quantum key in an IPSec encryption component and adding a strategy which preferentially adopts the quantum key as a pre-shared key, and adopts a session key of a data encryption algorithm and a shared key of an HMAC algorithm; and realizing fusion application of the QKD, quantum encryption and an IPSec protocol, and increasing quantum safety of identity authentication, message authentication and data encryption of an IPSec VPN system. The safety of the system is high, application access is flexible, and a good application prospect is possessed in fields of party, government, industrial control, finance, military and the like.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Cryptographic one time pad technique
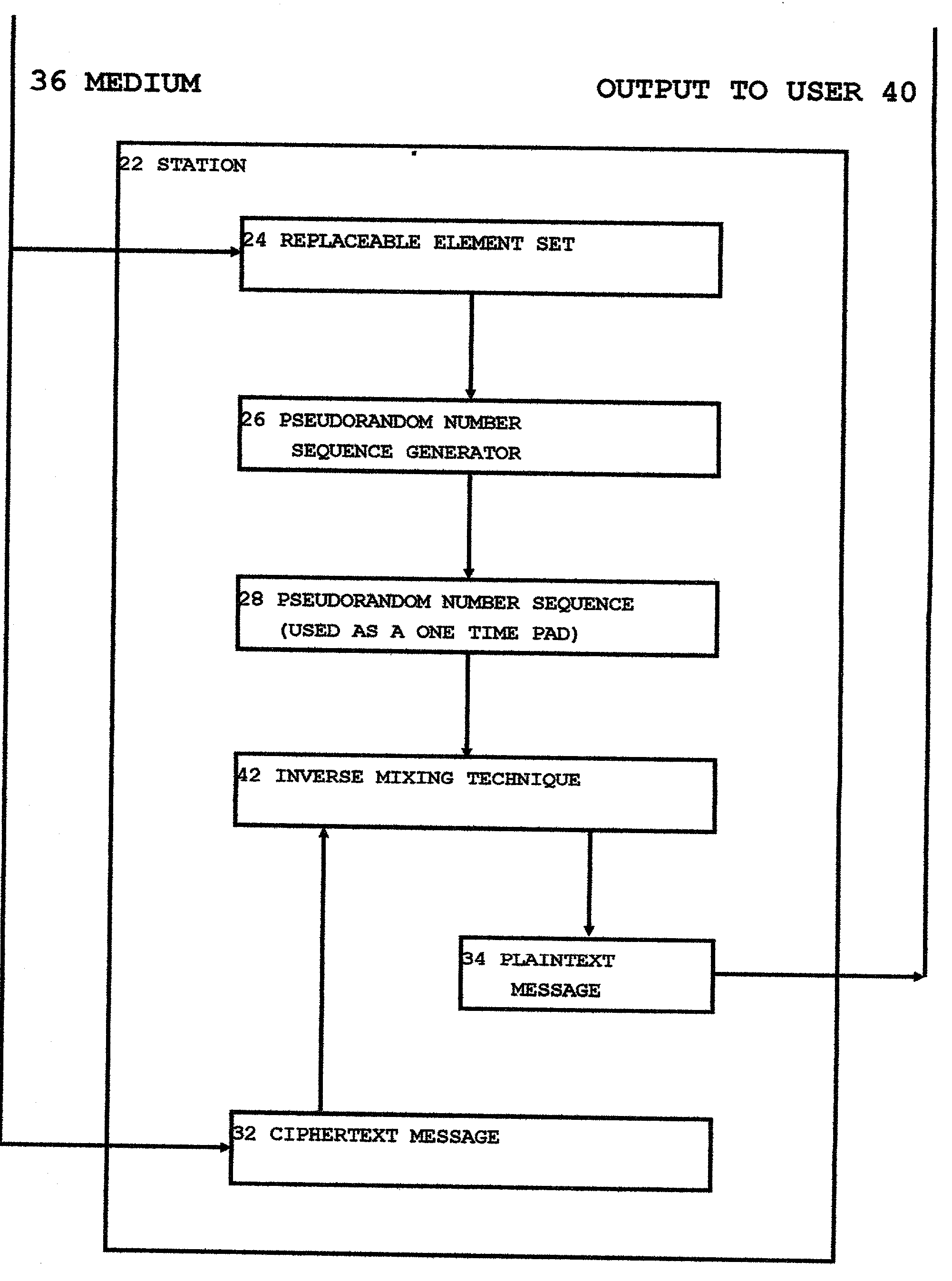
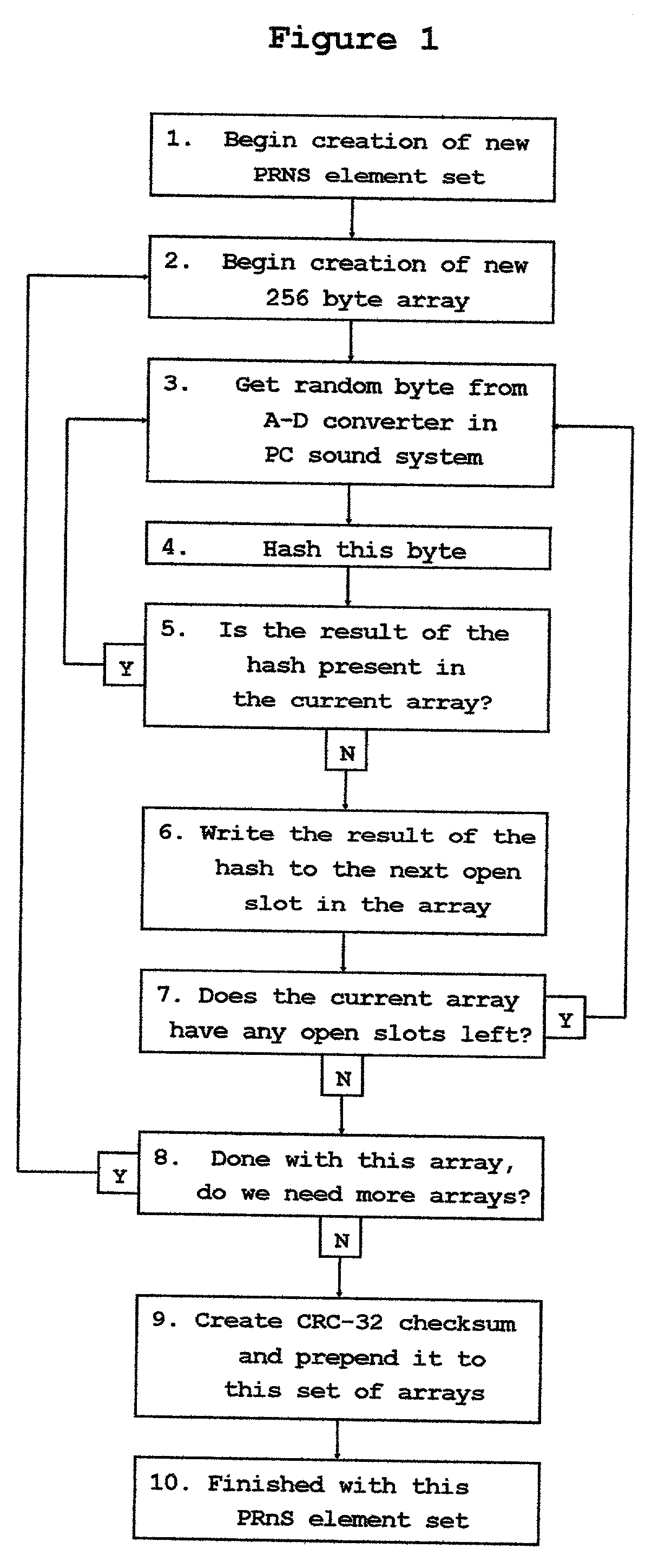
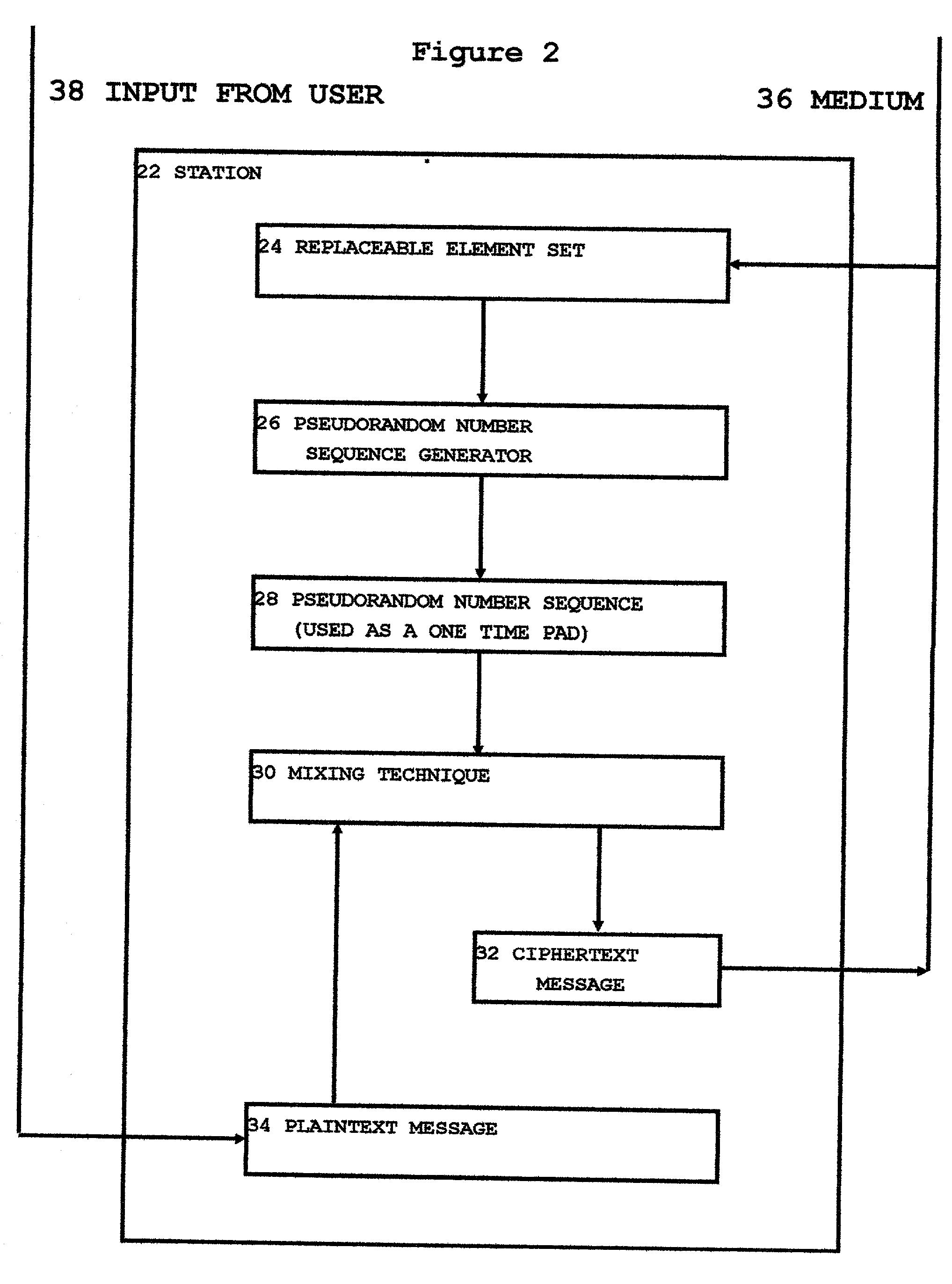
InactiveUS20030142821A1Tighter requirementSynchronising transmission/receiving encryption devicesKey escrowKey distribution
A variant on the "One Time Pad' cipher is used to provide an encrypted link between two or more stations. The main feature of this variant is the use of a unique and easily created Pseudo-Random Number Sequence segment not having any internal repeats. At one station, a mixing function is used to combine a locally created stream of truly random bytes with a portion of this unique PRNS segment, yielding a fresh stream of truly random data. This freshly created stream of truly random data is operated on in such a way as to create a new and unique PRNS element set which is used to control the functioning of a PRNS generator. The PRNS generator is used to create a new and unique PRNS segment which has a repeat period much longer than the length of the PRNS element set used to create it. It is then useful to treat the PRNS element set as a message and transfer it across the encrypted link to other stations. In this fashion, this OTP cipher variant can be re-keyed and used for as long as there is a continuing source of truly random data available at one of the stations on the network. This technique of using unique and freshly created PRNS segments rather than the classic One Time Pad allows encrypted networks to function independently of any central key distribution regimens or Public Key Infrastructures, making such an encrypted network proof against security breaches perpetrated upon, or key escrow schemes propagated through, such external key distribution infrastructures. This technique also provides certain securities against willful betrayals by tempted users or coerced revelations by users under duress.
Owner:ROSS DAVID MARSHALL
Two-way CA system of digital TV-set and method for ordering and cancelling programm based on it
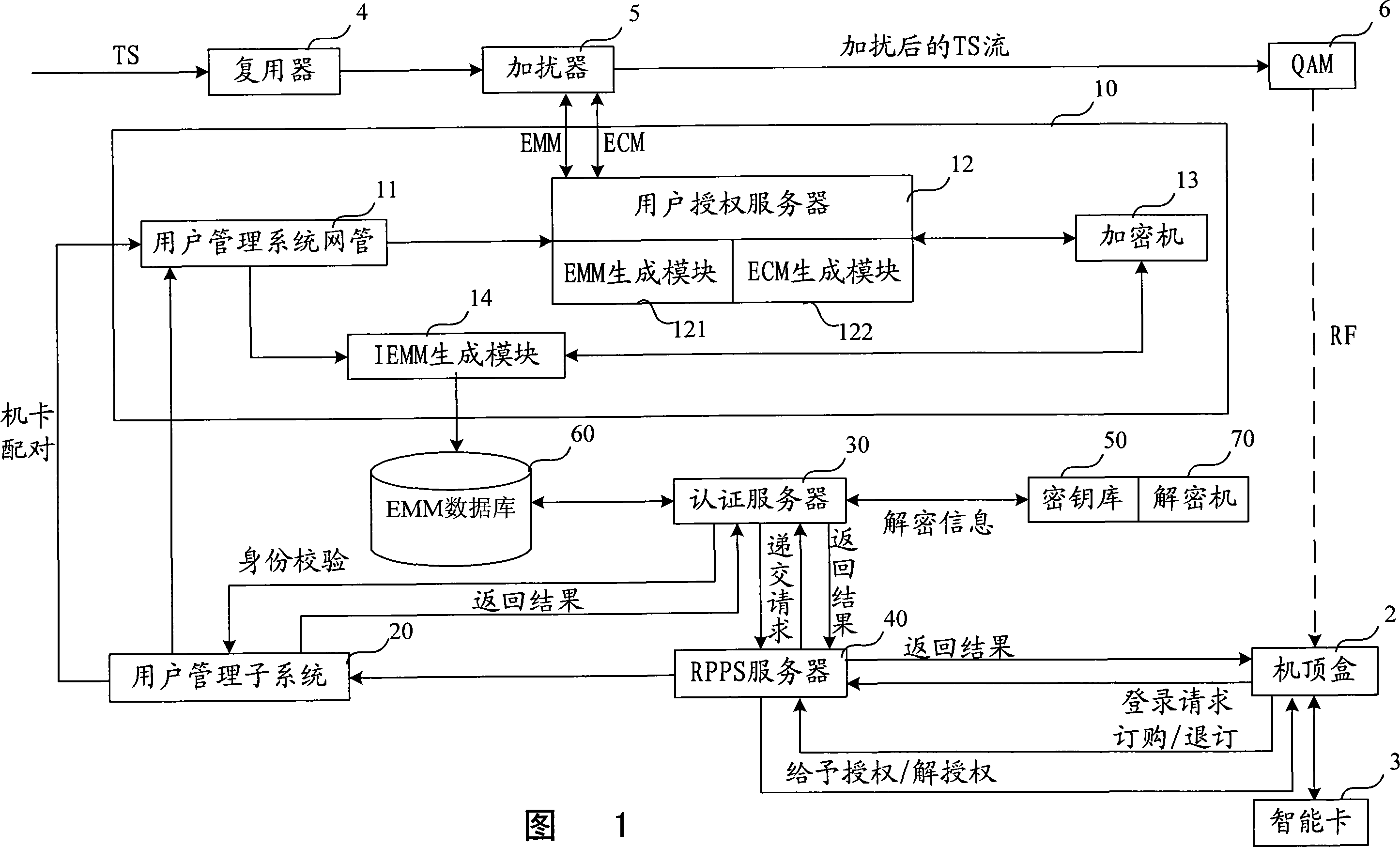
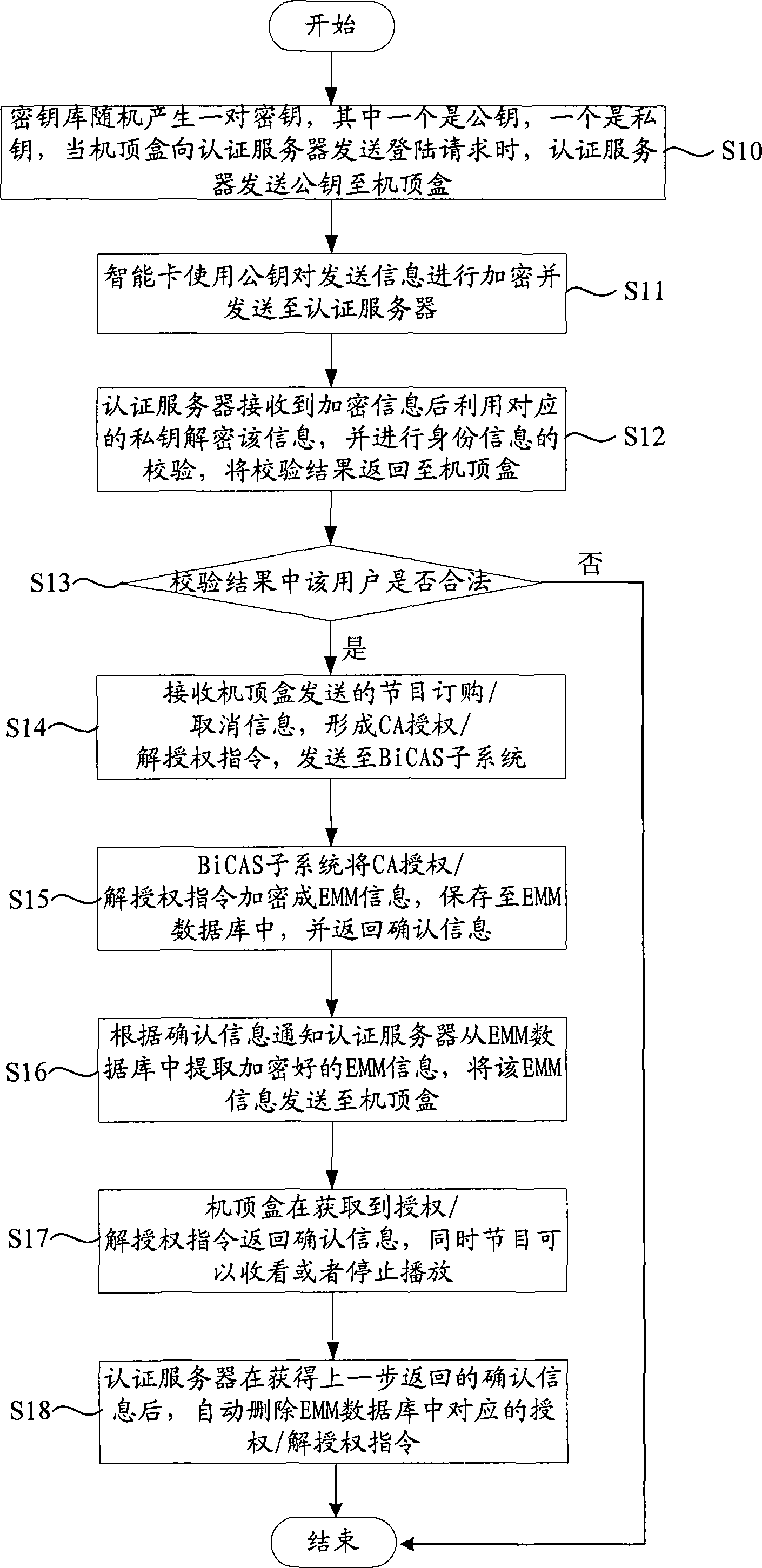
ActiveCN101076109AStrong complementarityImprove securityUser identity/authority verificationAnalogue secracy/subscription systemsSmart cardAuthentication server
The invention is used for providing a security authentication between the content provider, network service supplier and users in digital TV system. The method comprises: based on the active authentication of client side, a bidirectional authentication is adopted in order to realize the one-time-pad in the authentication process; said authentication information is encrypted with public key in the smart card of set-top box, and the encrypted authentication information is decrypted with private key in the front end authentication server.
Owner:上海云视科技股份有限公司
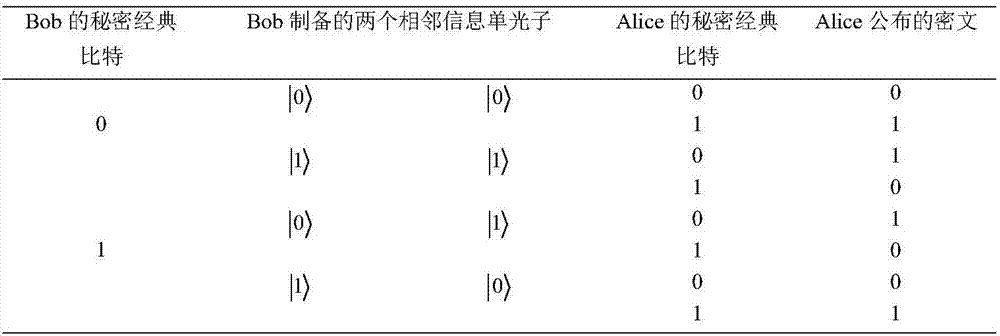
Semi-quantum dialogue method without classical correspondent with measurement capability based on single photons
The invention provides a semi-quantum dialogue method without a classical correspondent with the measurement capability based on single photons. Bidirectional communication between one quantum correspondent and one classical correspondent is achieved. The active-attack security of external Eve is guaranteed through scrambling operation of the classical correspondent, the complete robustness of an existing semi-quantum key distribution method and classical one-time-padding encryption. Through classical base measurement of every two adjacent information single photons of the quantum correspondent, the initial states of the quantum correspondent and the classical correspondent are shared by the quantum correspondent and the classical correspondent, and therefore the information leakage problem can be solved with the semi-quantum dialogue method. Compared with a traditional information-leakage-free quantum dialogue method, the semi-quantum dialogue method has the advantage that only one correspondent has the quantum capacity. Compared with an existing semi-quantum dialogue method, the semi-quantum dialogue method has the advantages that the single-photon entangled state but not two-photon entangled states is used as a quantum carrier, and has the good practical performability.
Owner:嘉兴市顺凯鹿科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com