Key expansion for qkd
a key expansion and key technology, applied in the field of quantum cryptography, can solve the problems of limited data bandwidth, low data bandwidth achievable, and low secure key rate of qkd system, and achieve the effect of increasing the number of keys and reducing the number of keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
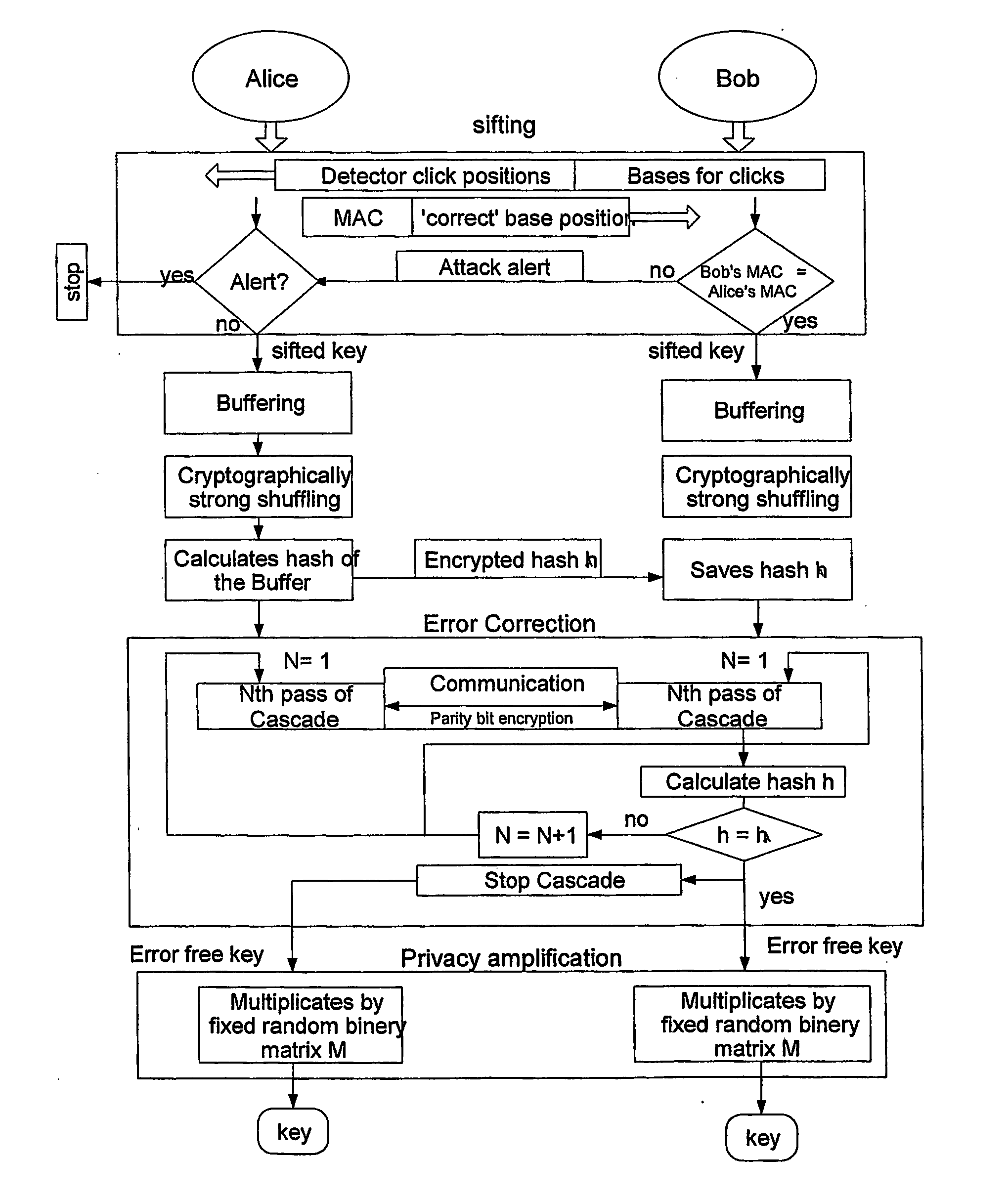
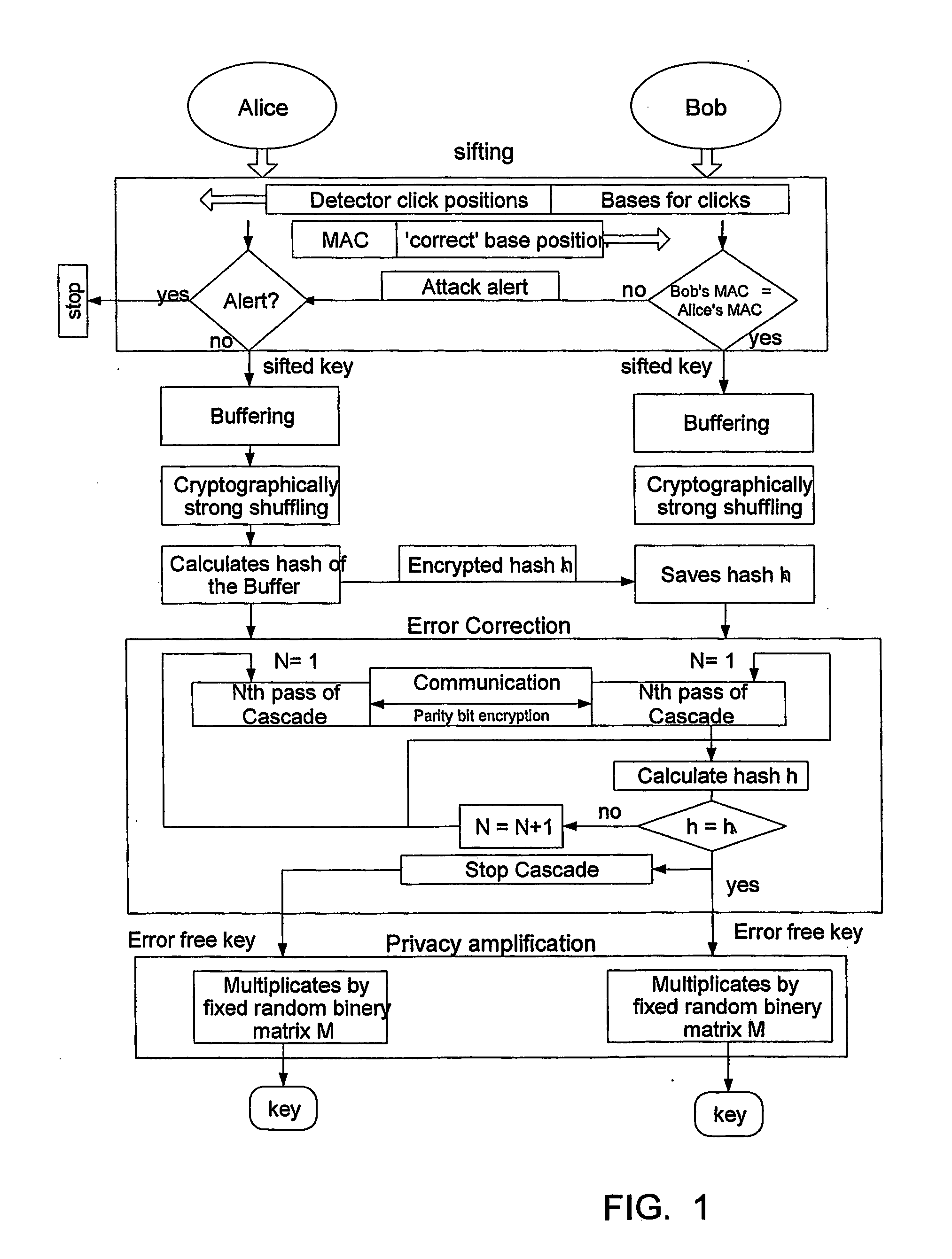
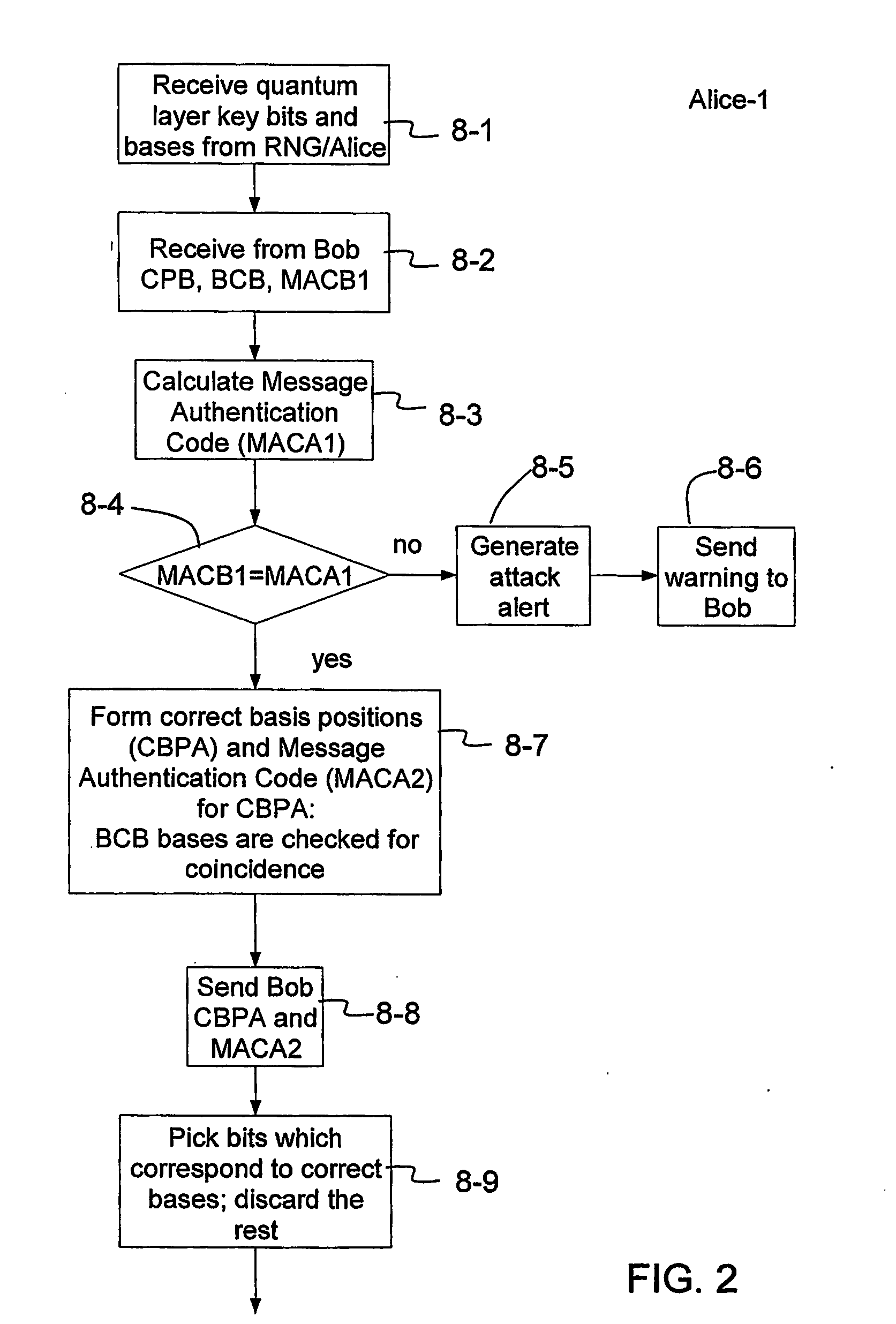
[0021] The present invention has industrial utility in the fields of quantum cryptography, quantum key distribution, and data encryption. In particular, the present invention has industrial utility in combining quantum, cryptography and classical cryptography. The present invention provides protection from not only eavesdroppers that utilize passive tapping of transmitted information from a carrier such as, but not limited to, an optical photon, but from any type of intrusion attack including involved active types of attacks wherein an eavesdropper probes the Alice and Bob nodes (stations) using a probe signal sent through an optical fiber used to transmit data.
[0022] As described in greater detail below, the present invention includes a method for generating a cryptographically secure key between two stations. An example method includes exchanging single photon signals between two QKD stations to establish a plurality of matching raw keys at each station. The method also includes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com