Patents
Literature
199 results about "Stream cipher" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
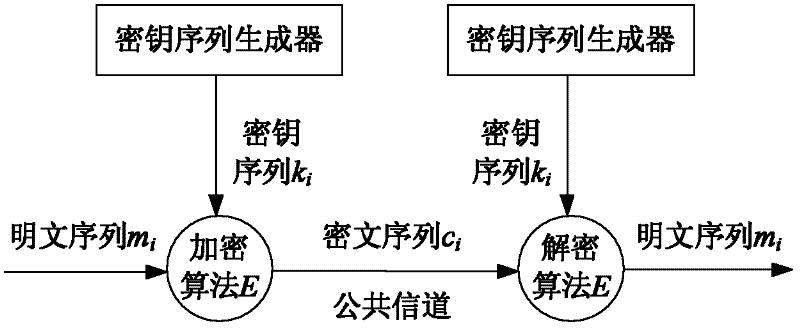
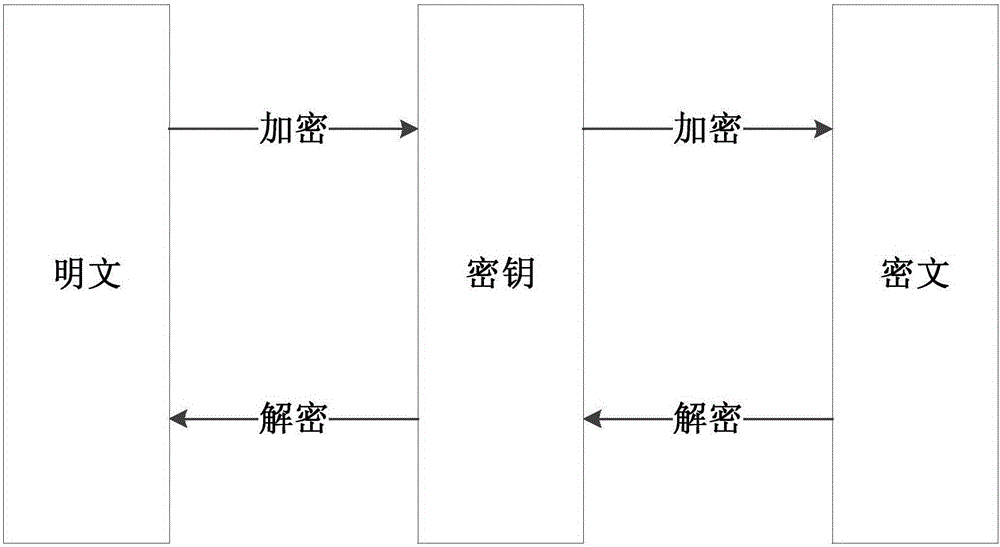
A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation an exclusive-or (XOR).
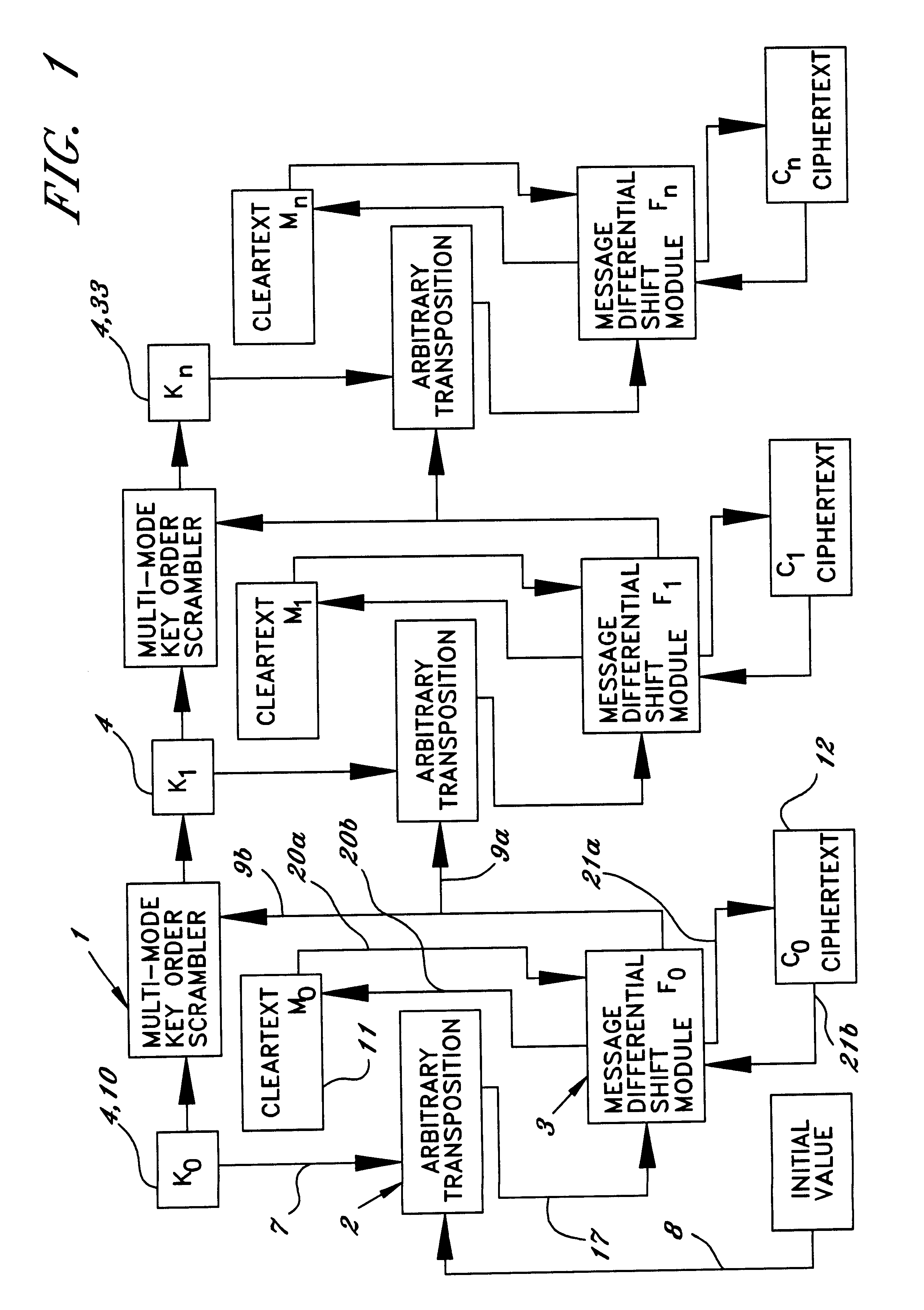
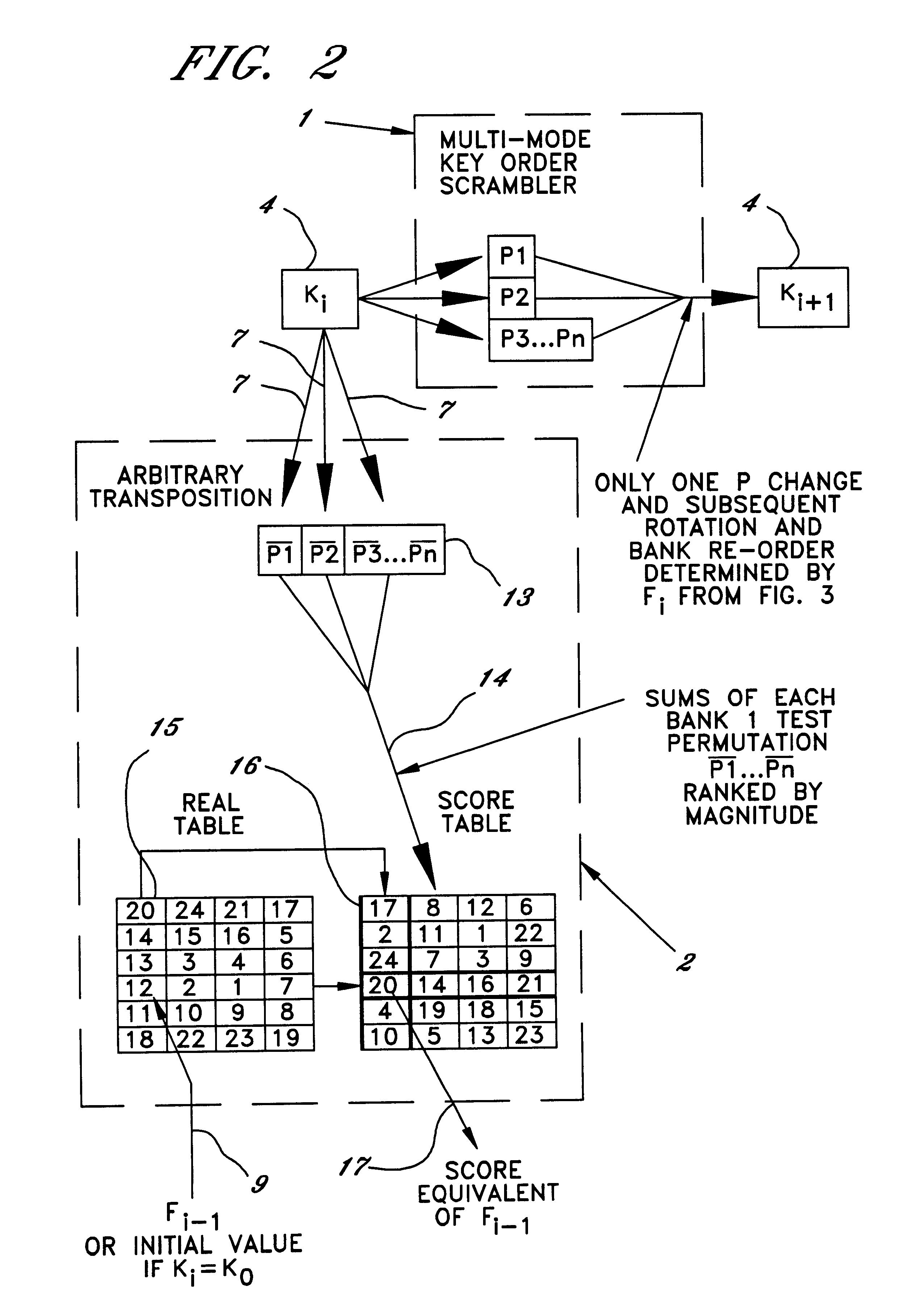
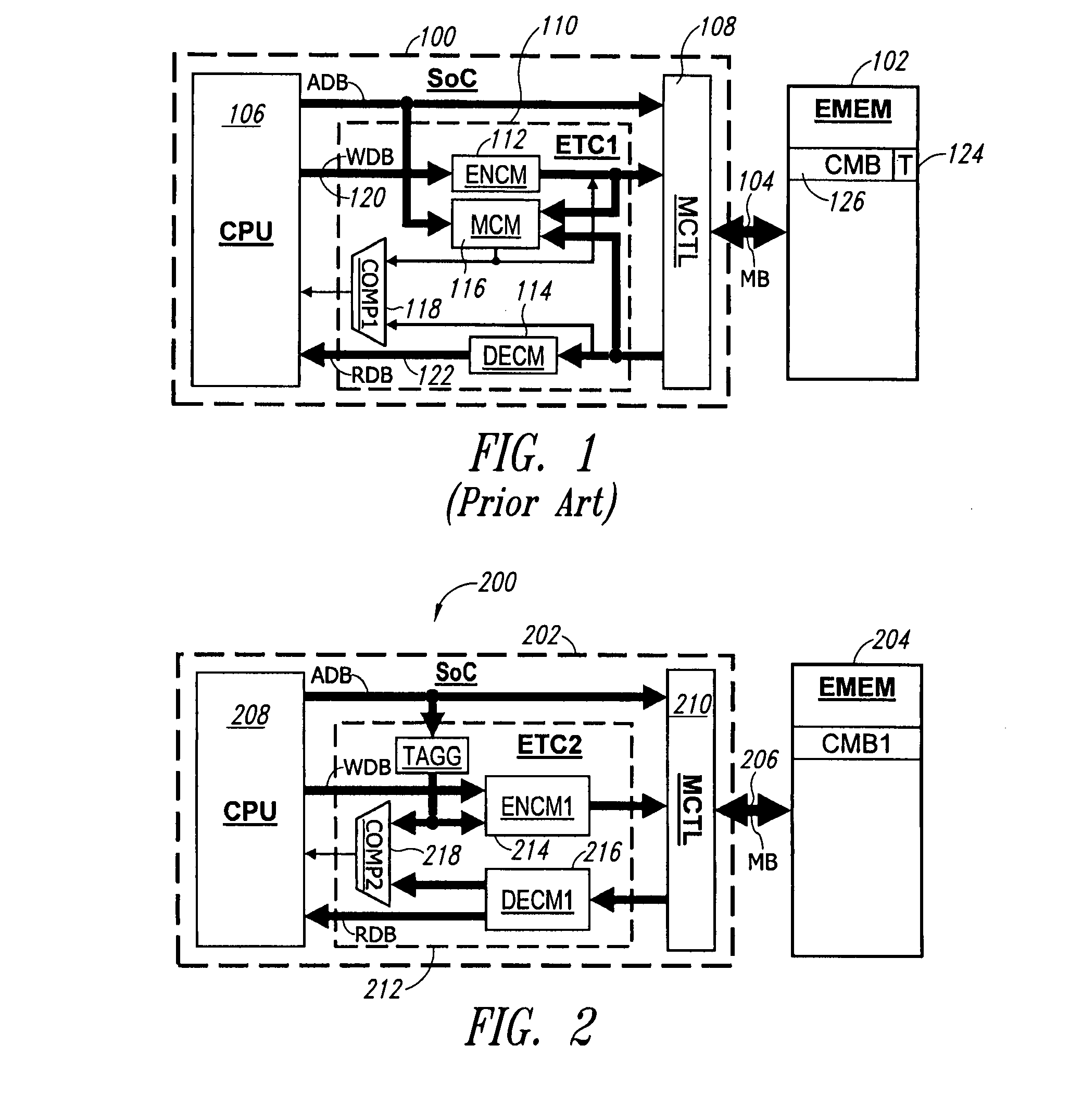
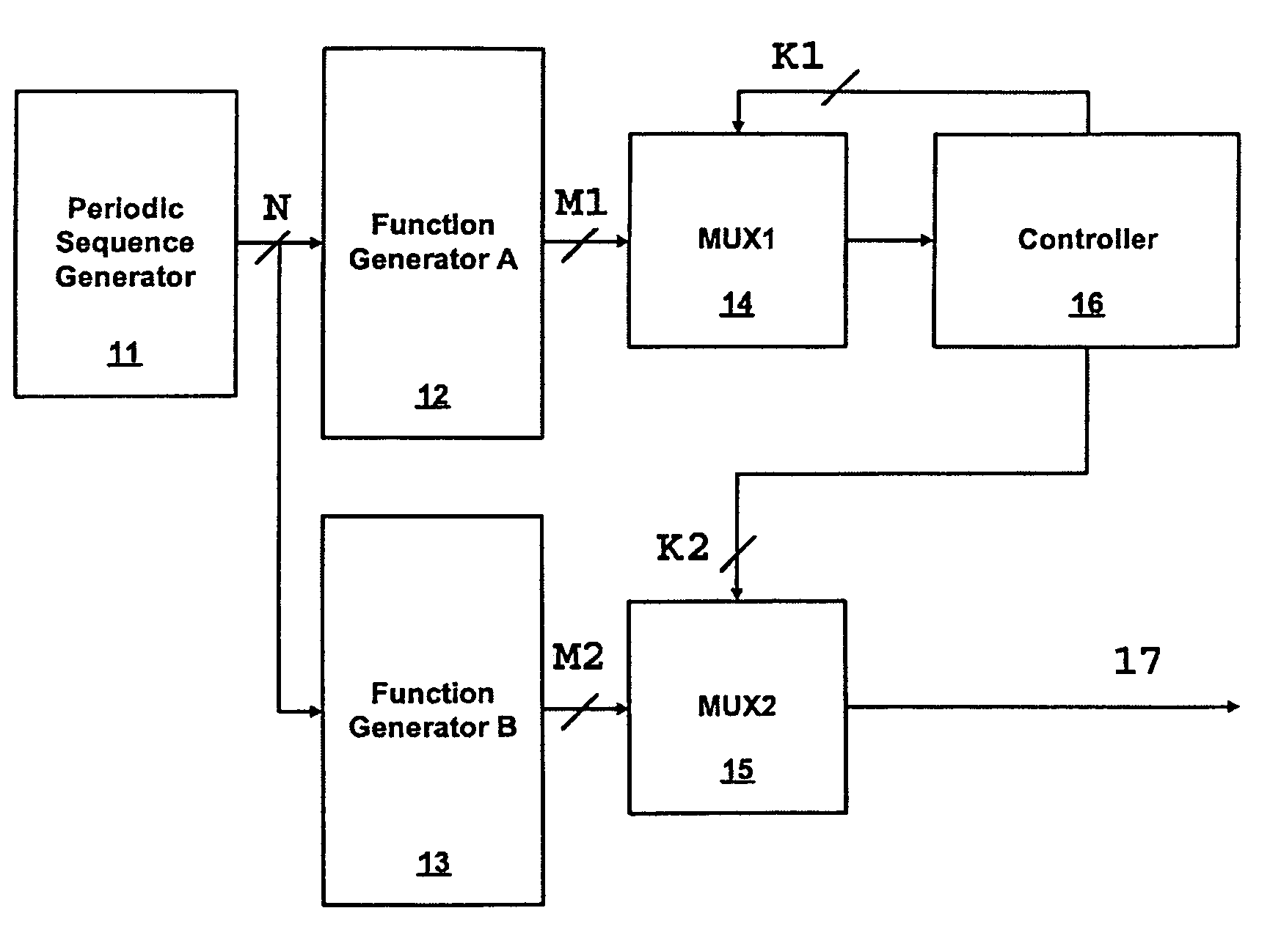
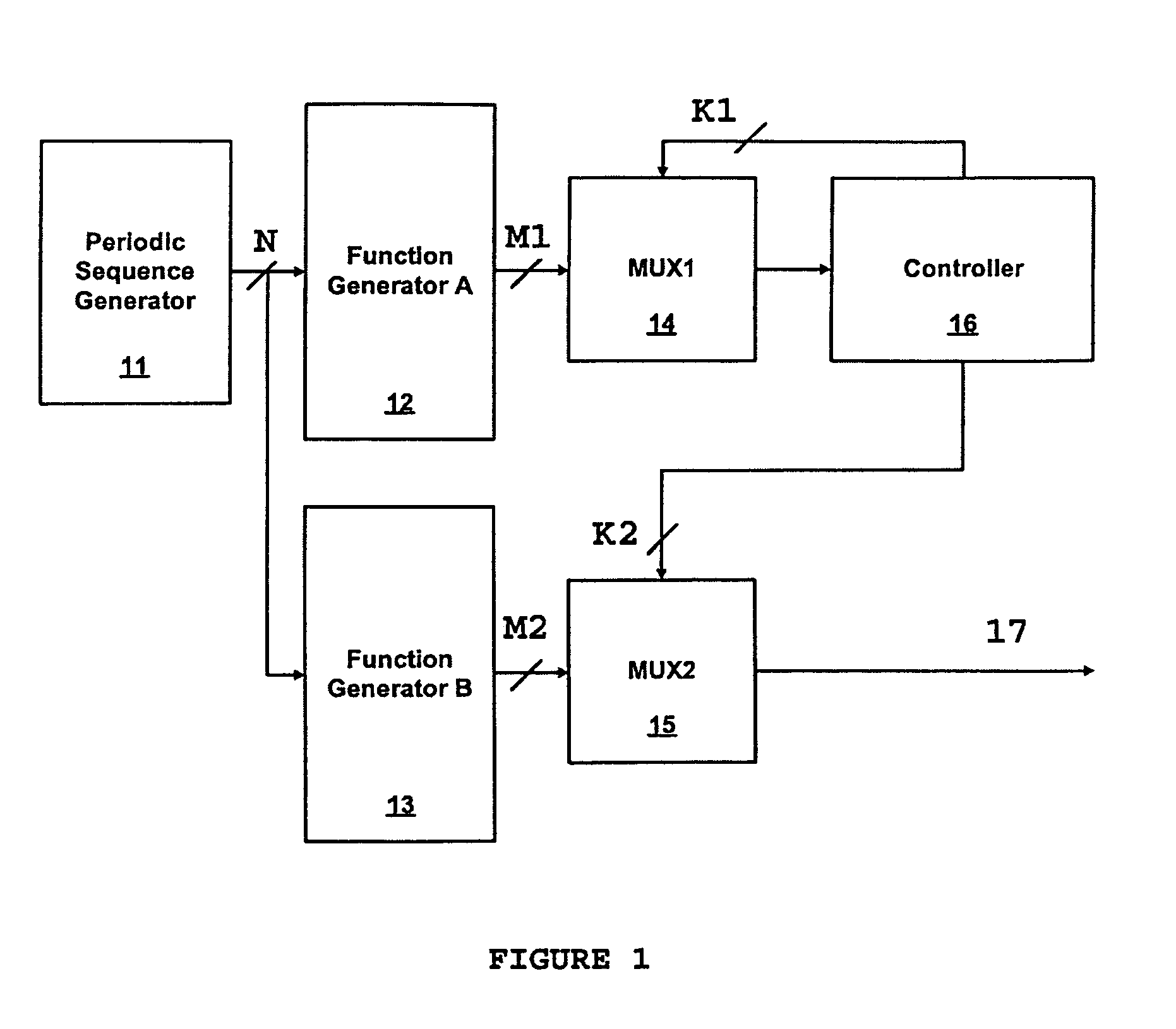
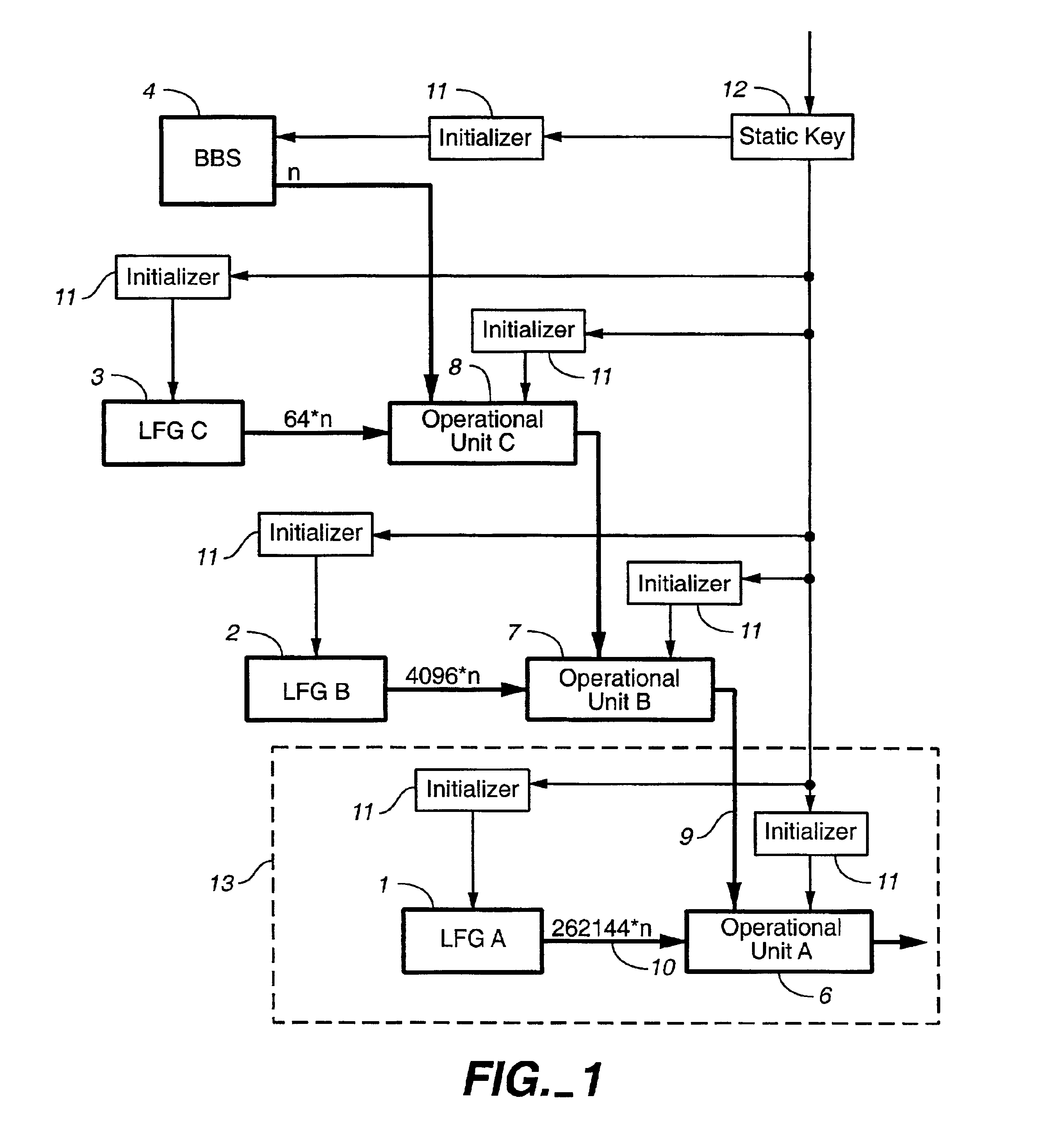
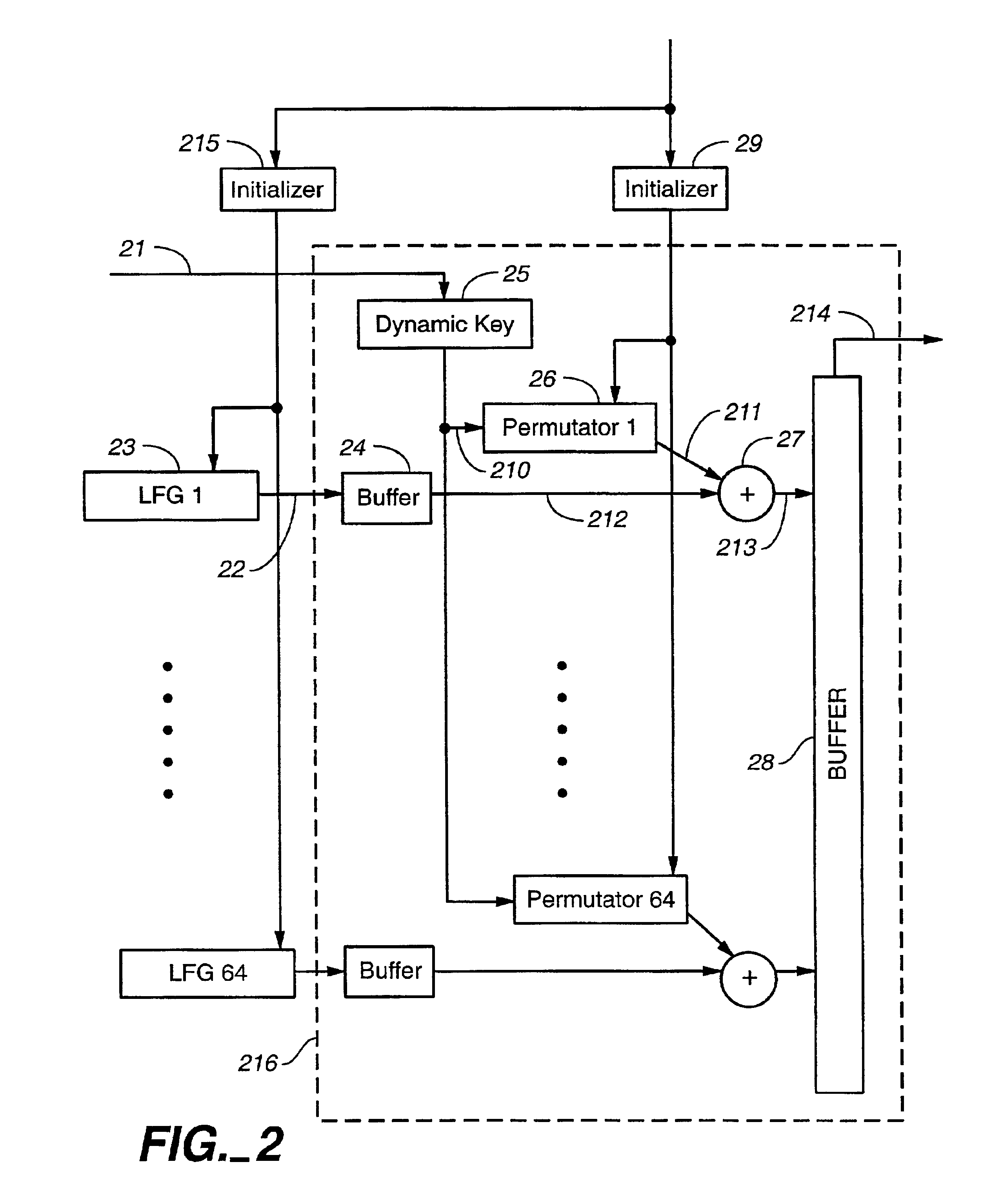
Cryptographic apparatus and method
InactiveUS7177424B1Quick implementationEasy to operateEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPlaintextComputer hardware
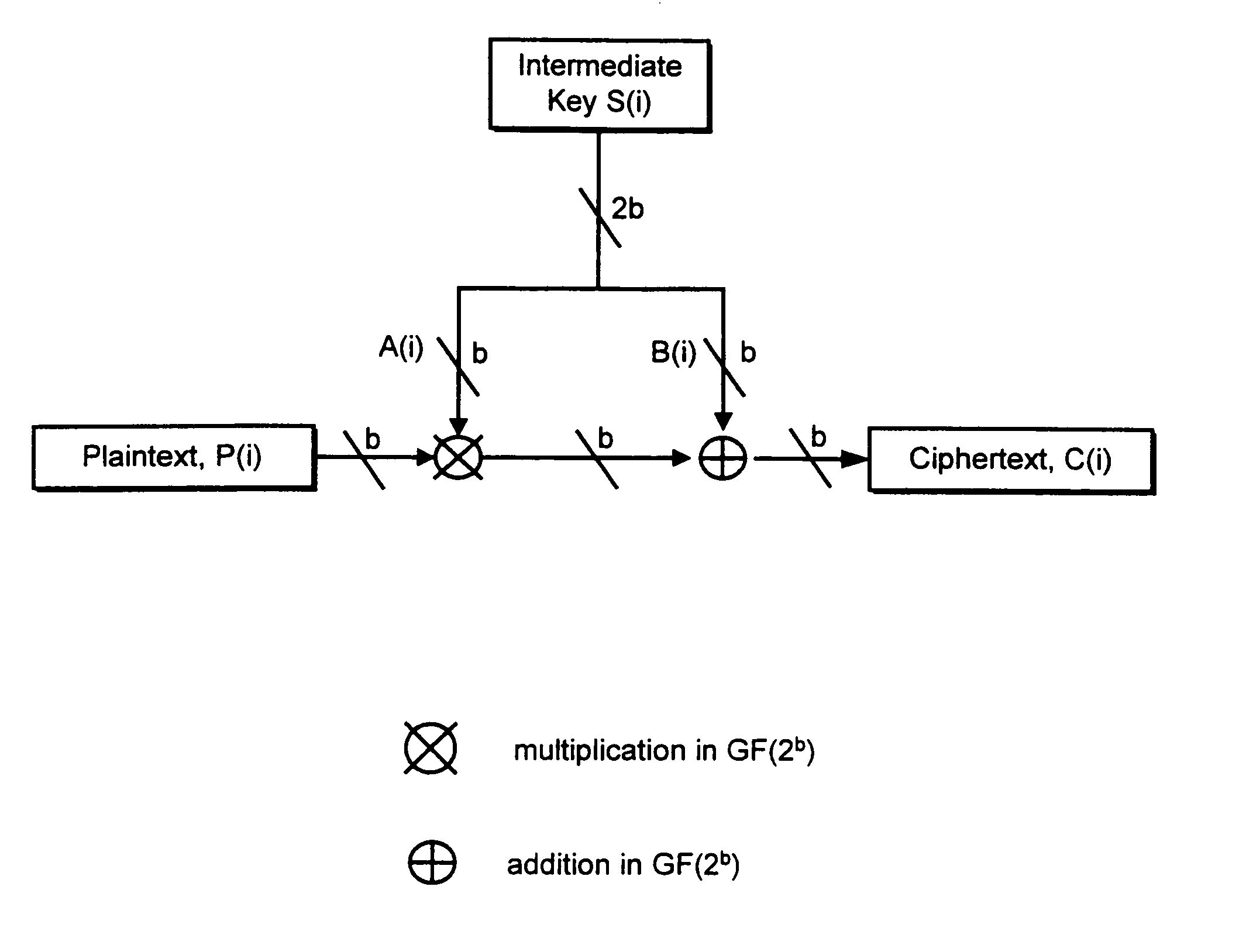
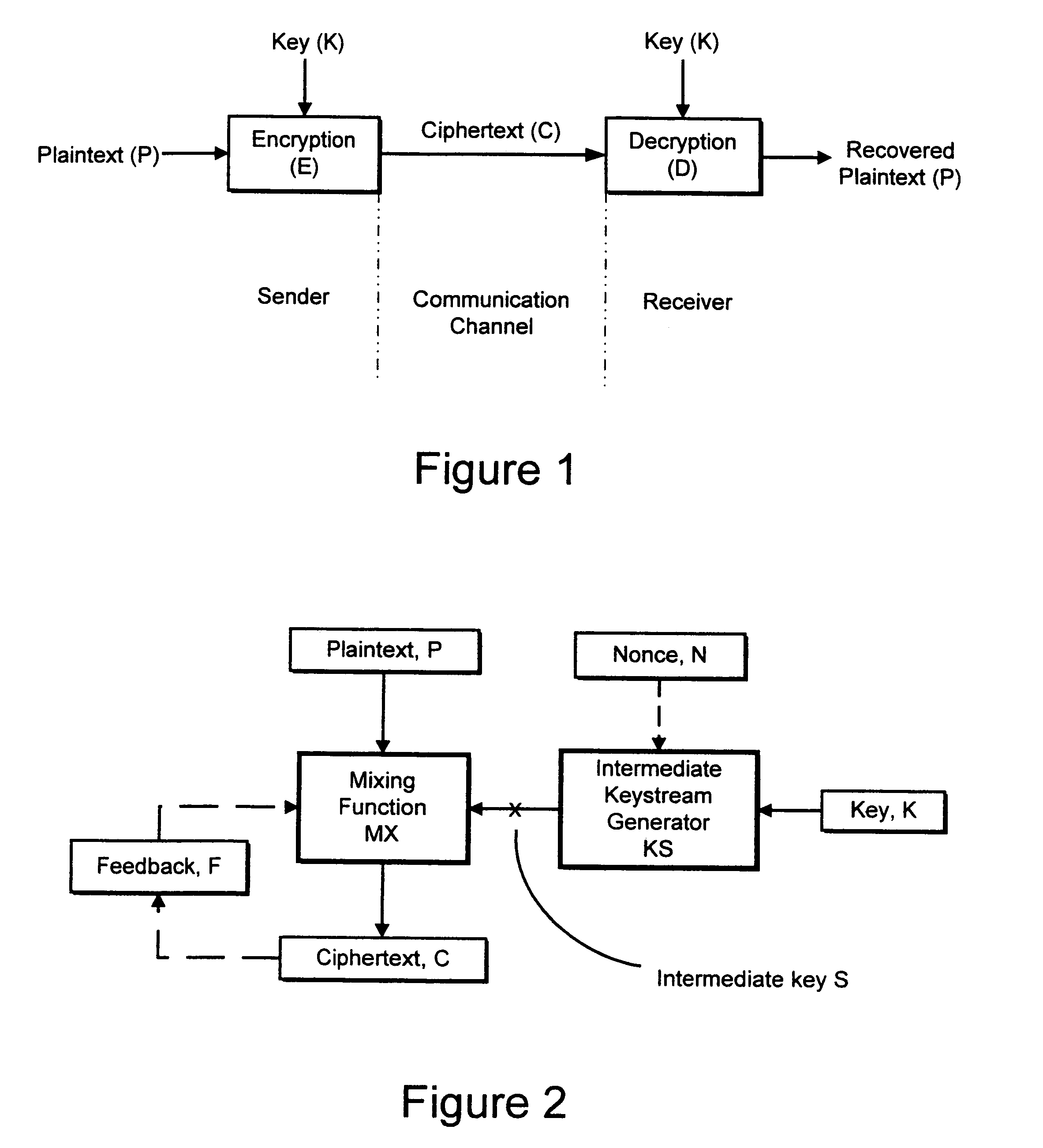
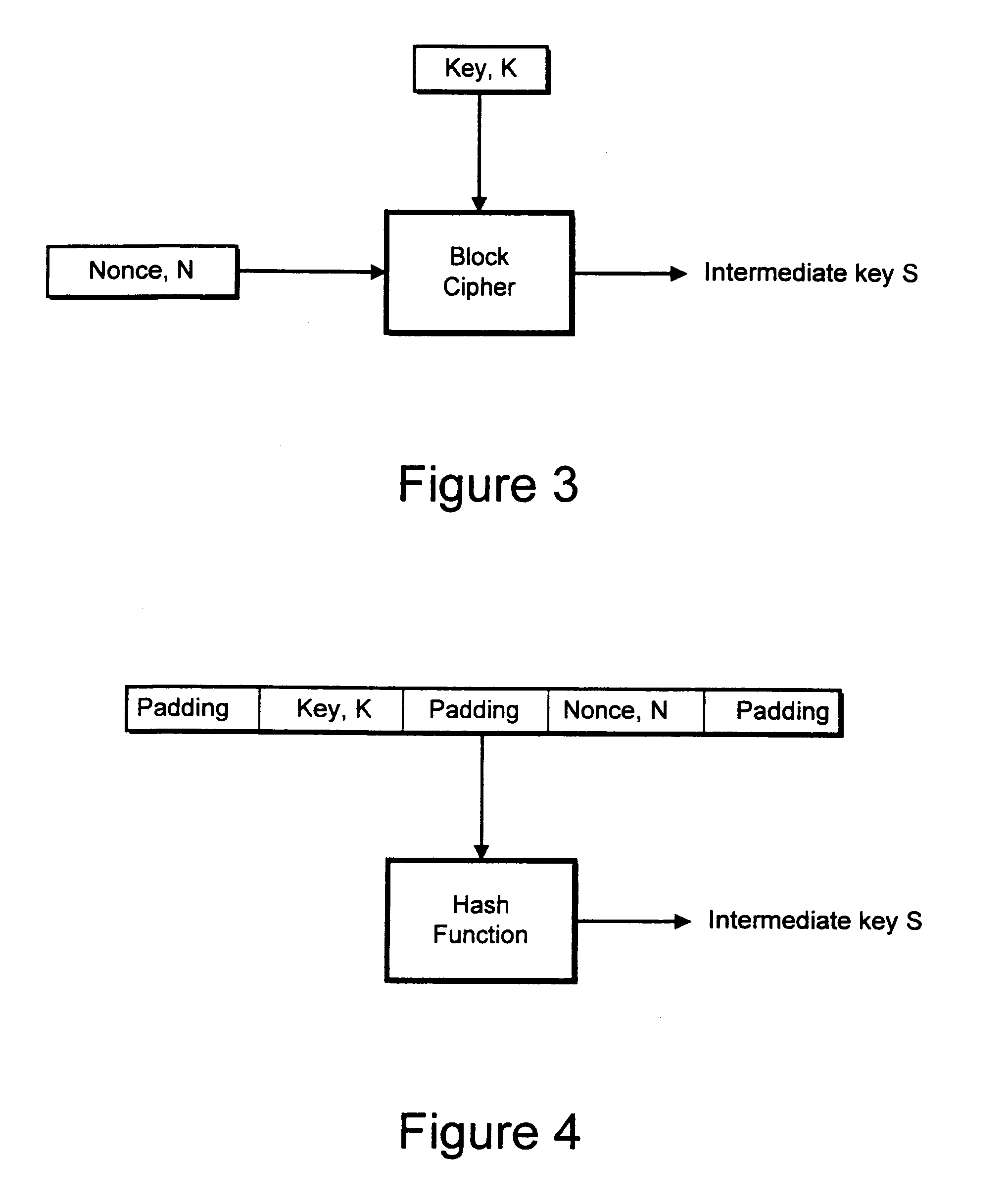
An encryption system comprises a pseudo-random number generator (KS) for generating a long pseudo-random sequence (S) from a shorter encryption key (K) and, if necessary, a nonce value (N), and a mixing function (MX) for combining the sequence with a plaintext message (P) on a block-by-block basis, where successive blocks (S(i)) of 128 bits of the sequence are combined with successive 64-bit blocks of plaintext (P(i)) to produce successive 64-bit blocks of ciphertext. The blockwise use of a long pseudo-random sequence preserves the advantages of a block cipher in terms of data confidentiality and data integrity, as well as benefiting from the speed advantages of a stream cipher.
Owner:HITACHI LTD
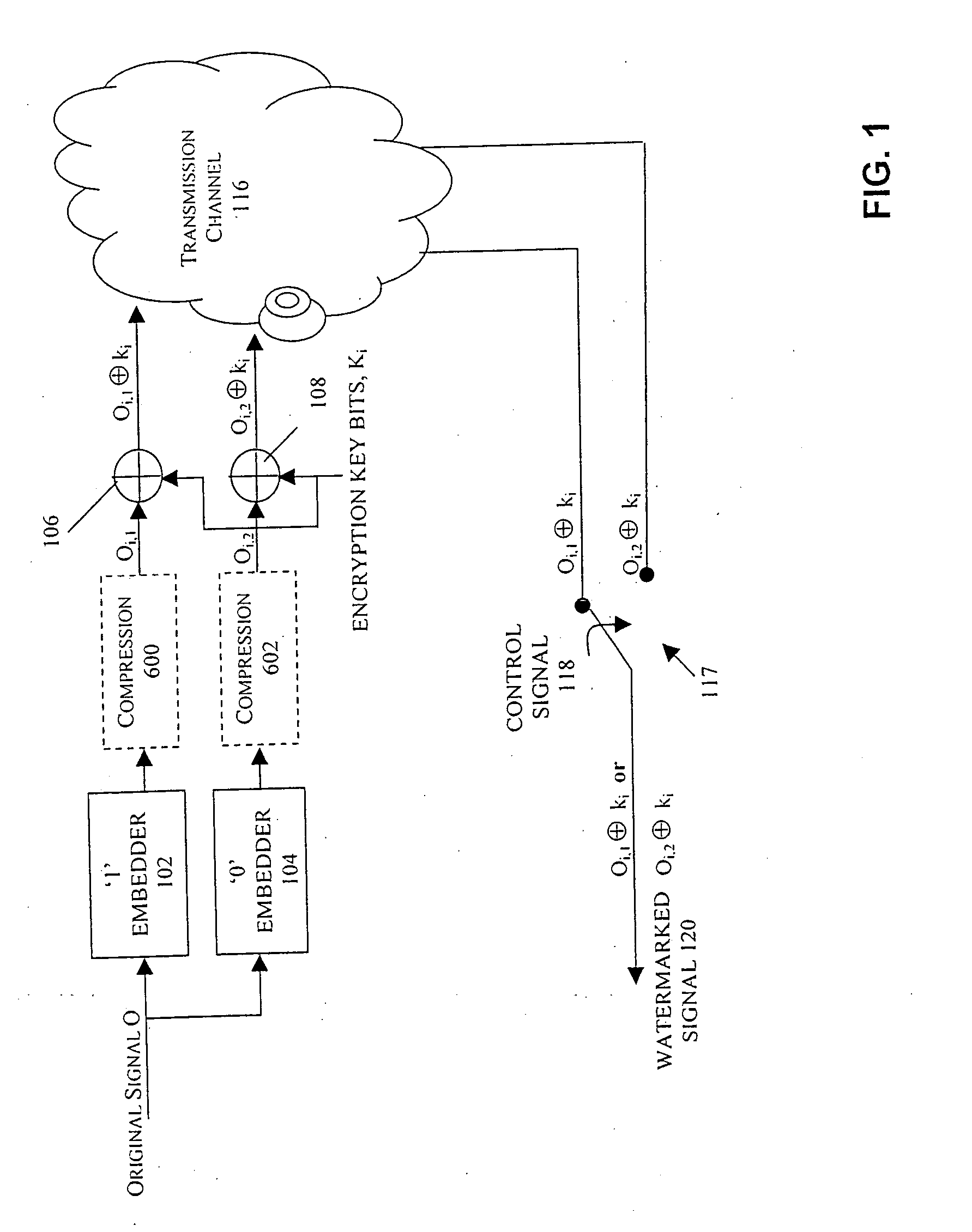
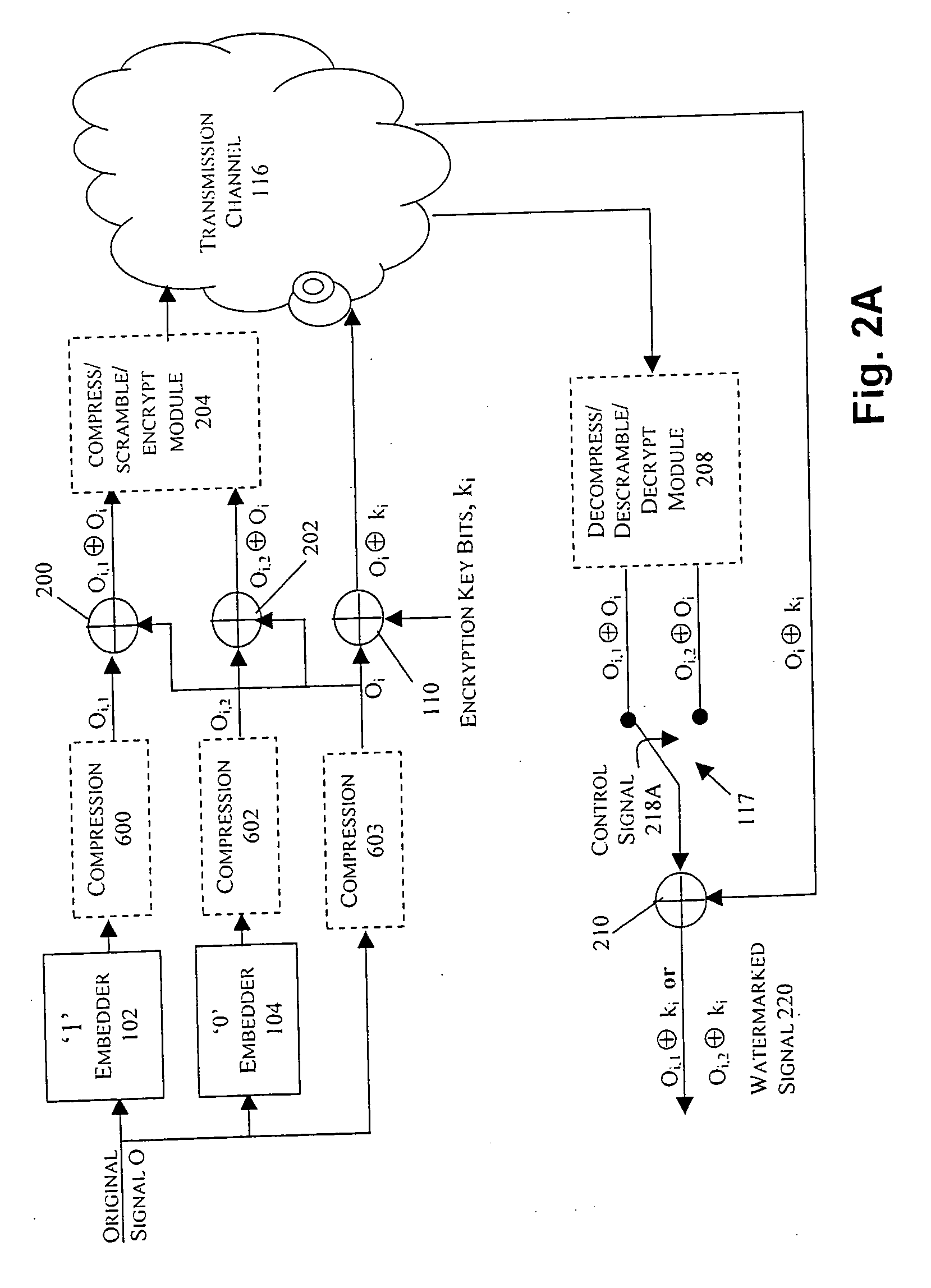
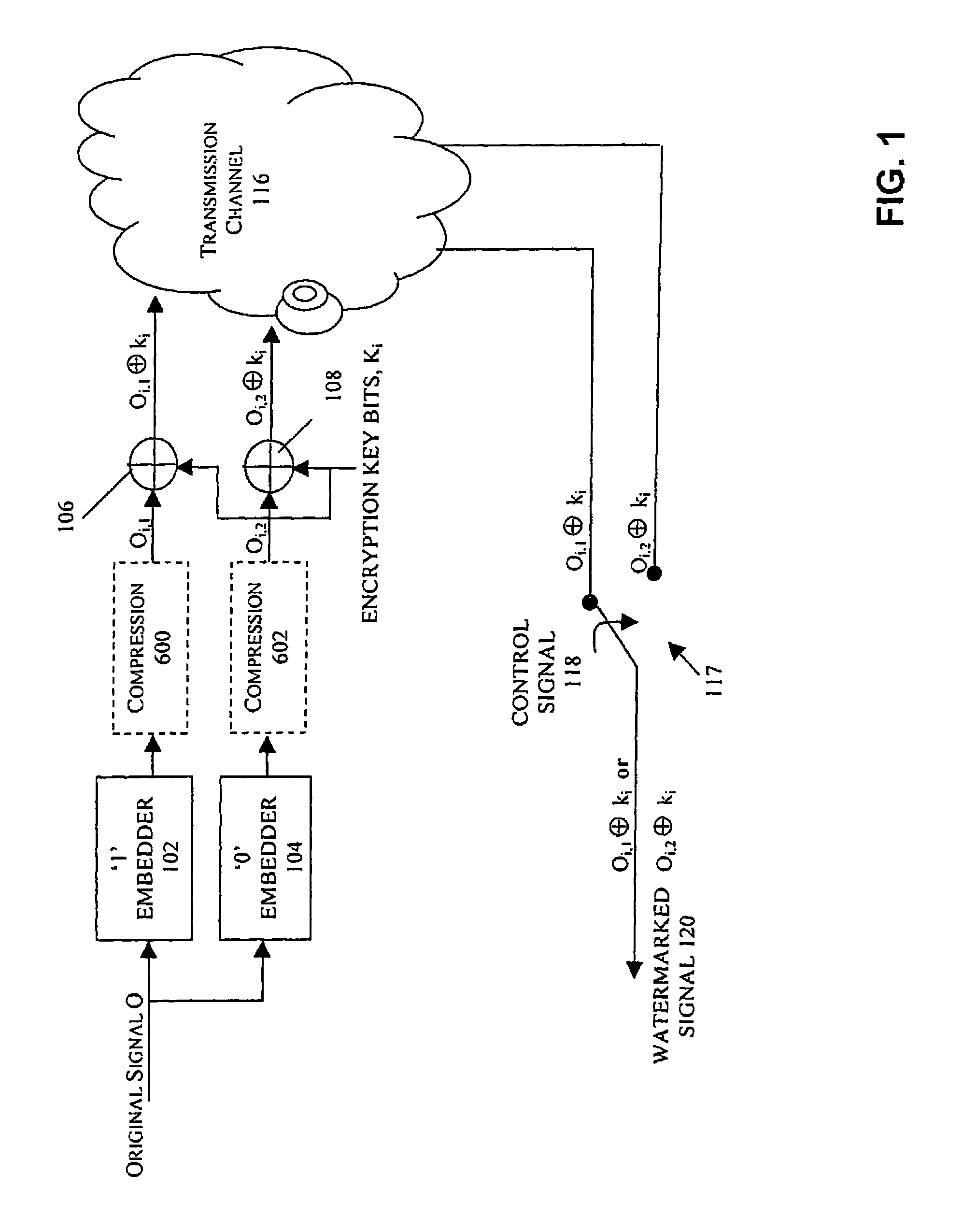
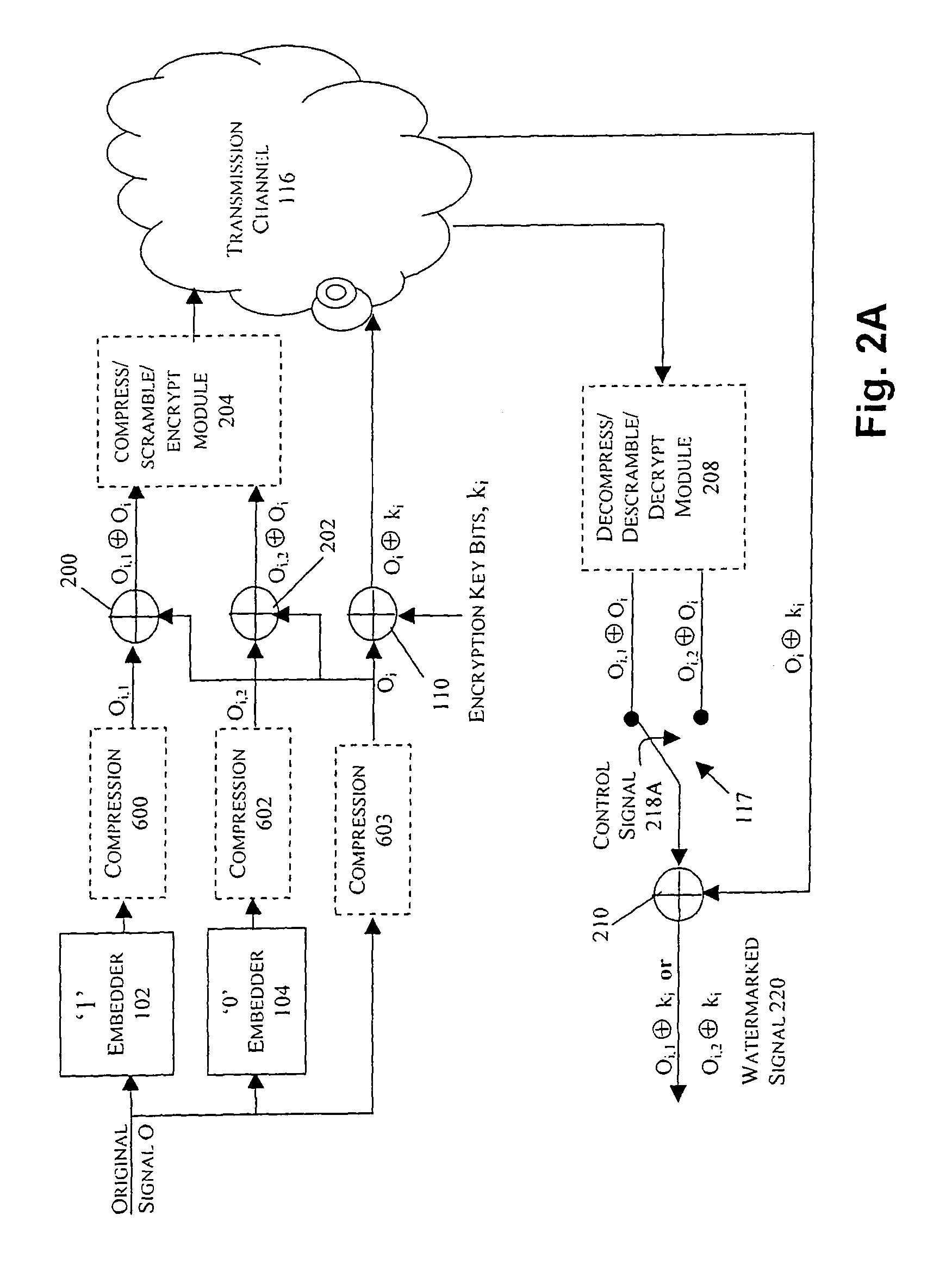
Watermarking in an encrypted domain
InactiveUS20070110237A1Easy to combineTelevision systemsImage data processing detailsDigital contentDigital watermarking
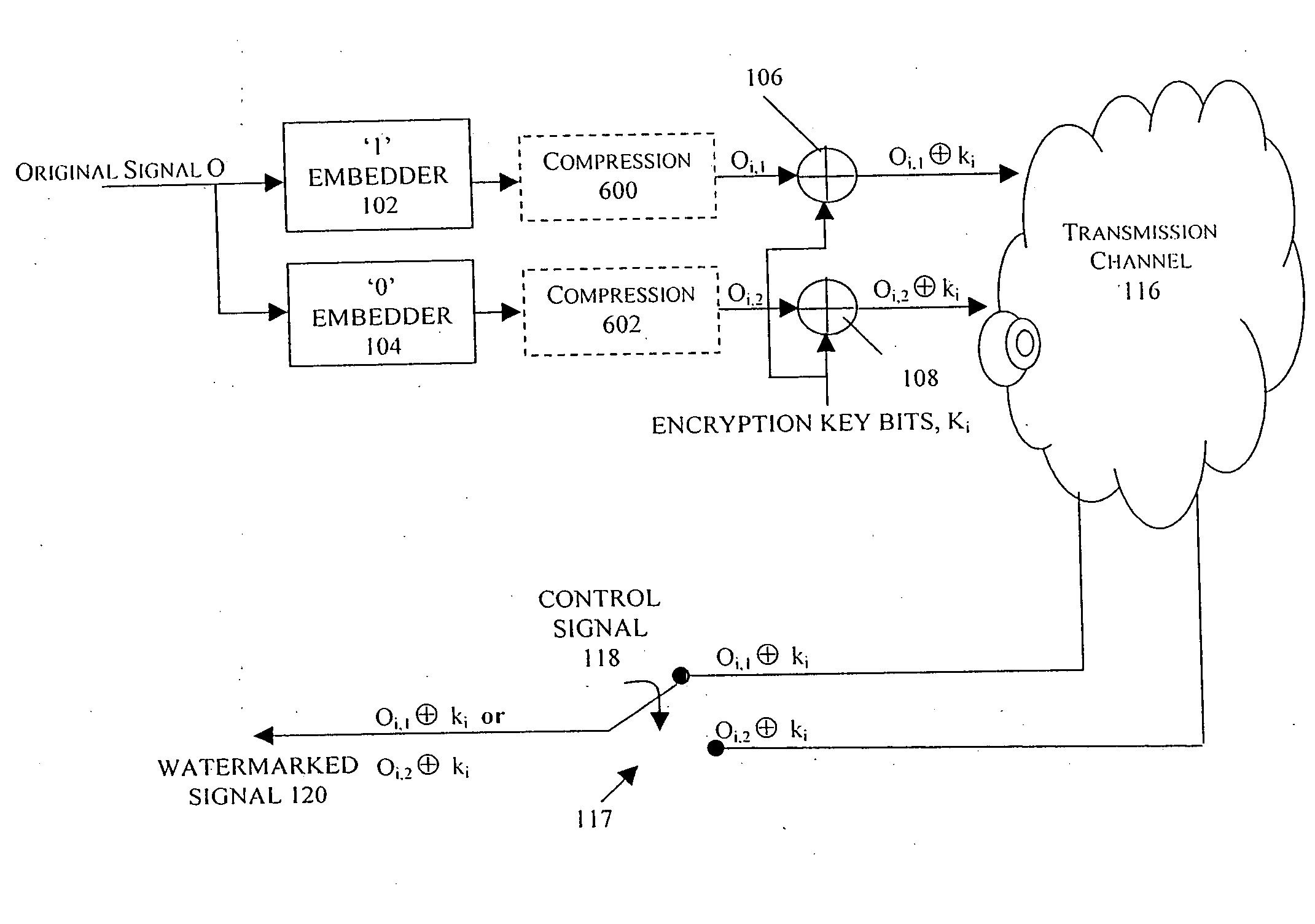
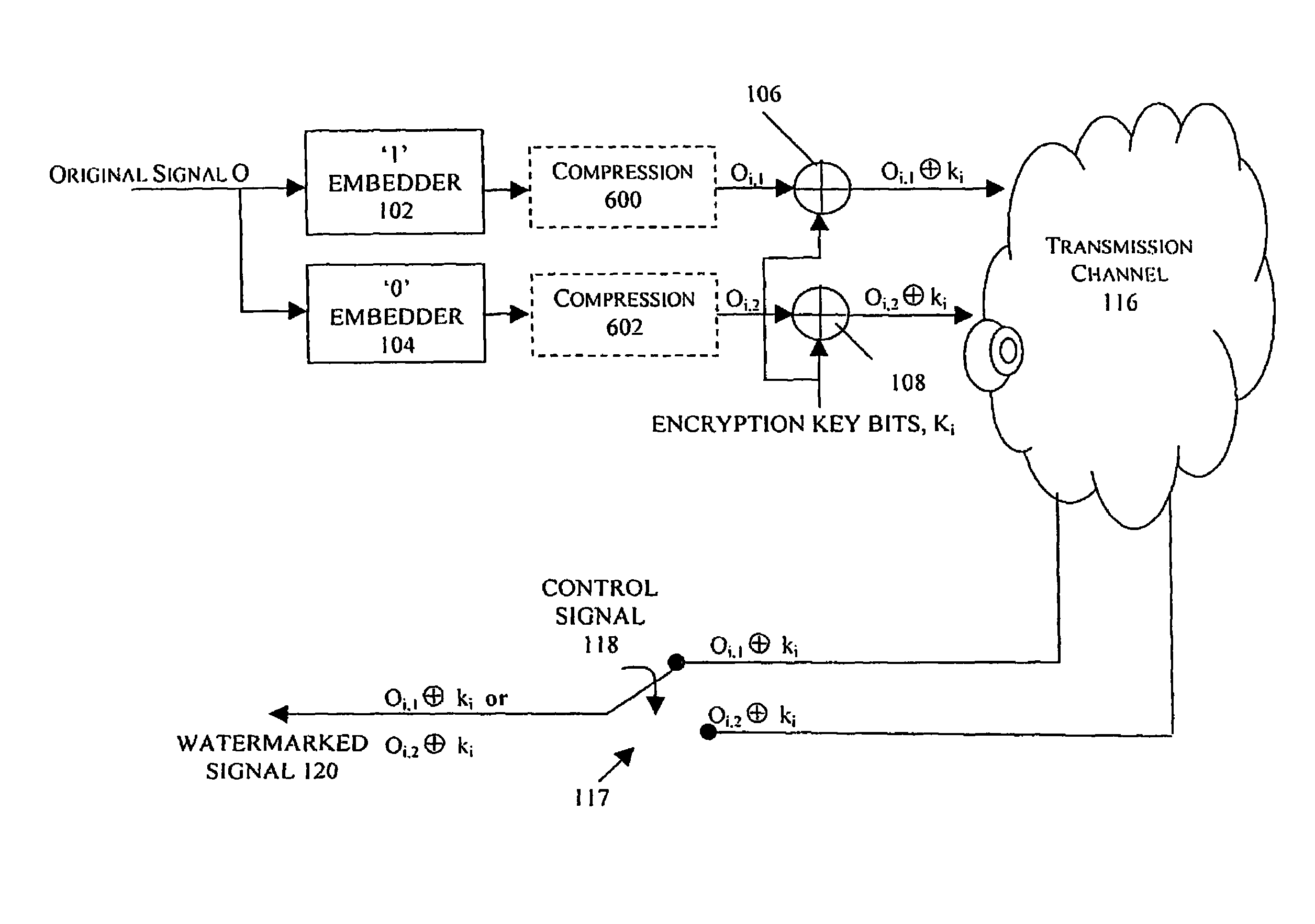
Methods, apparatus and systems for embedding auxiliary information in encrypted host signals are provided. The present invention enables secure application of digital watermarks at any point in the transmission and / or distribution of digital content by enabling the insertion of a plurality of digital watermarks, without the knowledge of the encryption / decryption keys, into a digital host content that has been encrypted with an encryption key. The embedded watermarks persist throughout the content subsequent to the decryption of the content. The disclosed techniques are applicable to content that has been encrypted using a variety of different encryption techniques and algorithms, including stream ciphers, block ciphers, symmetric and asymmetric encryption algorithms. These methods are further adapted to enable the insertion of watermarks into a content that is compressed prior to encryption.
Owner:VERANCE
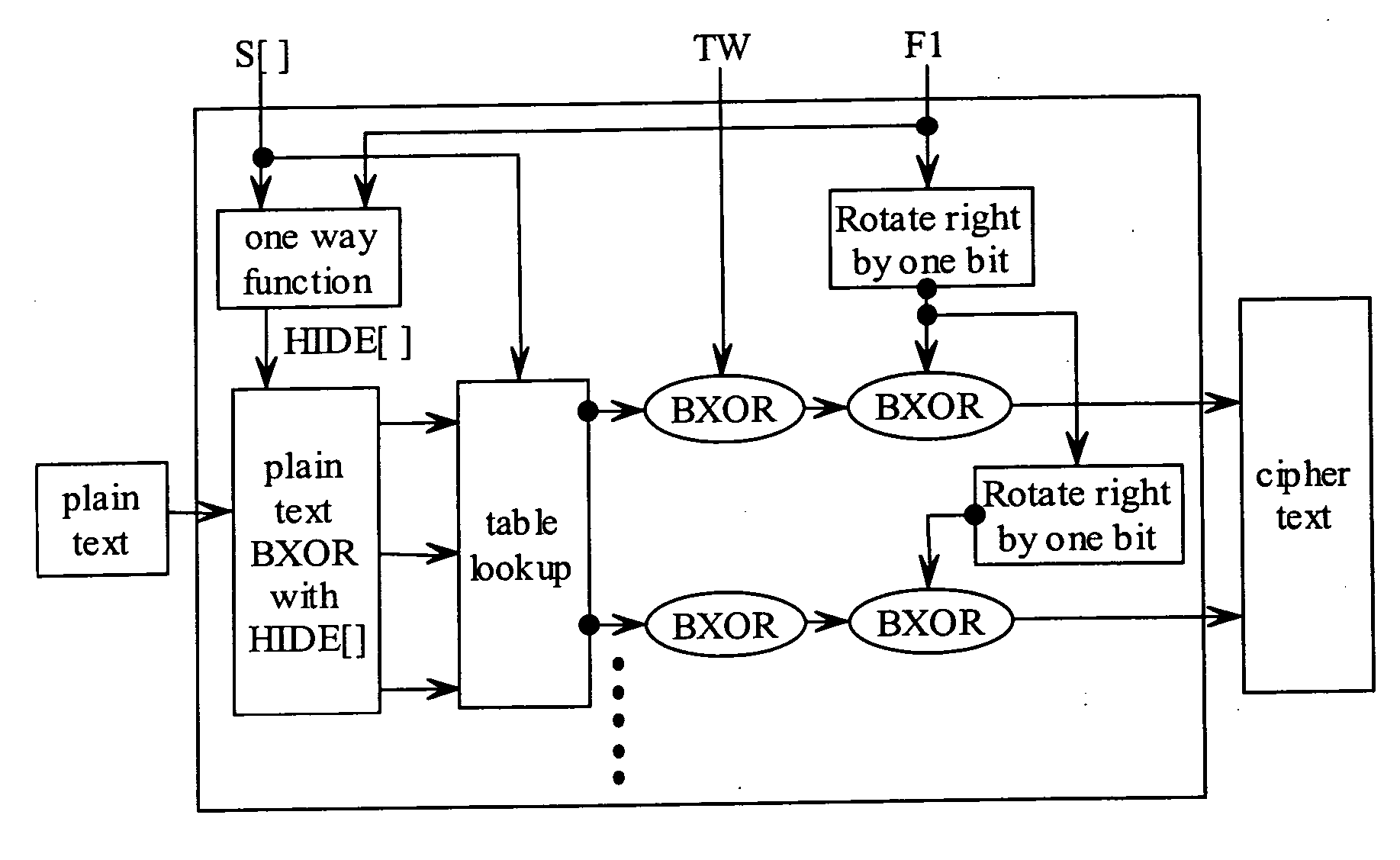
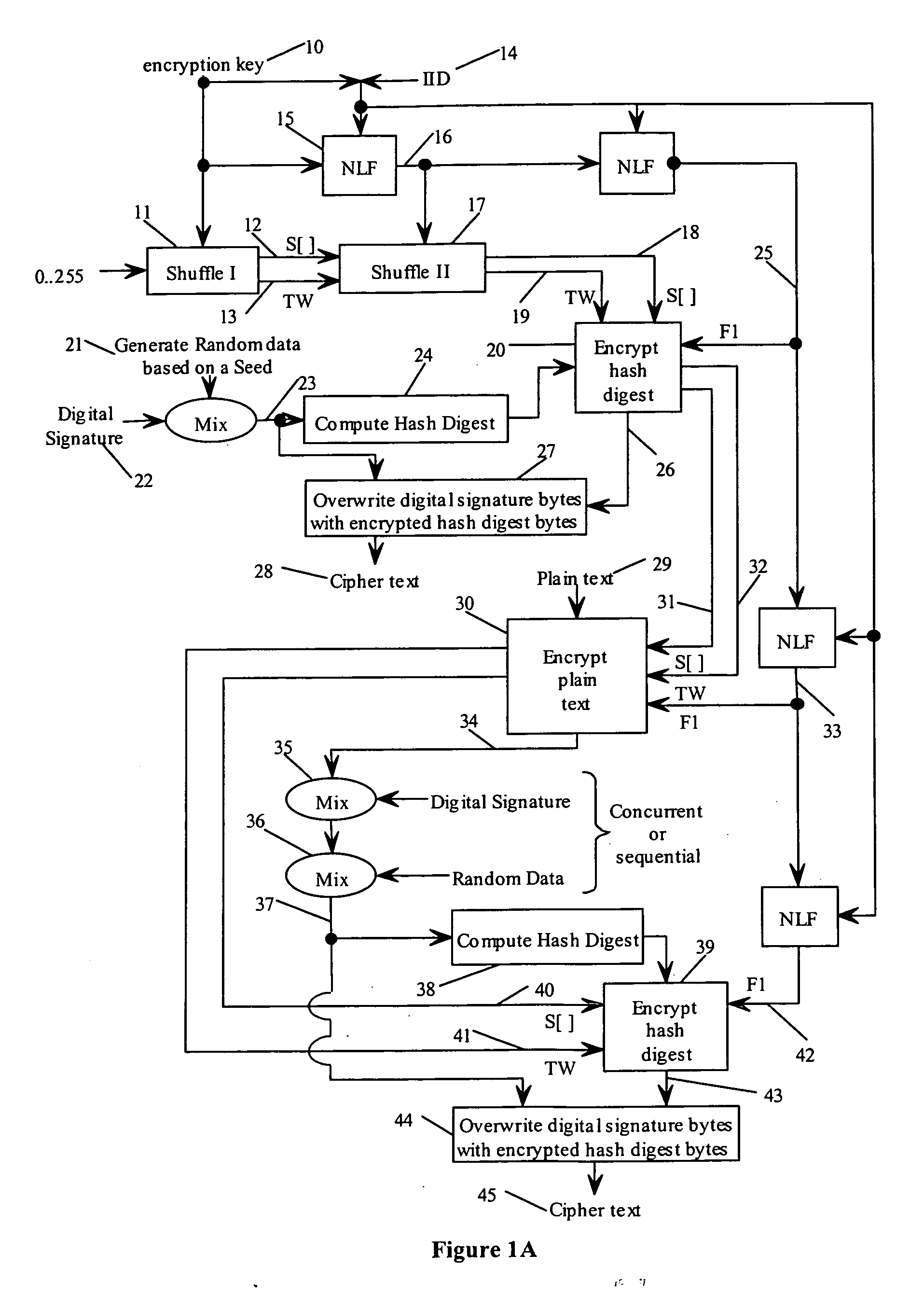
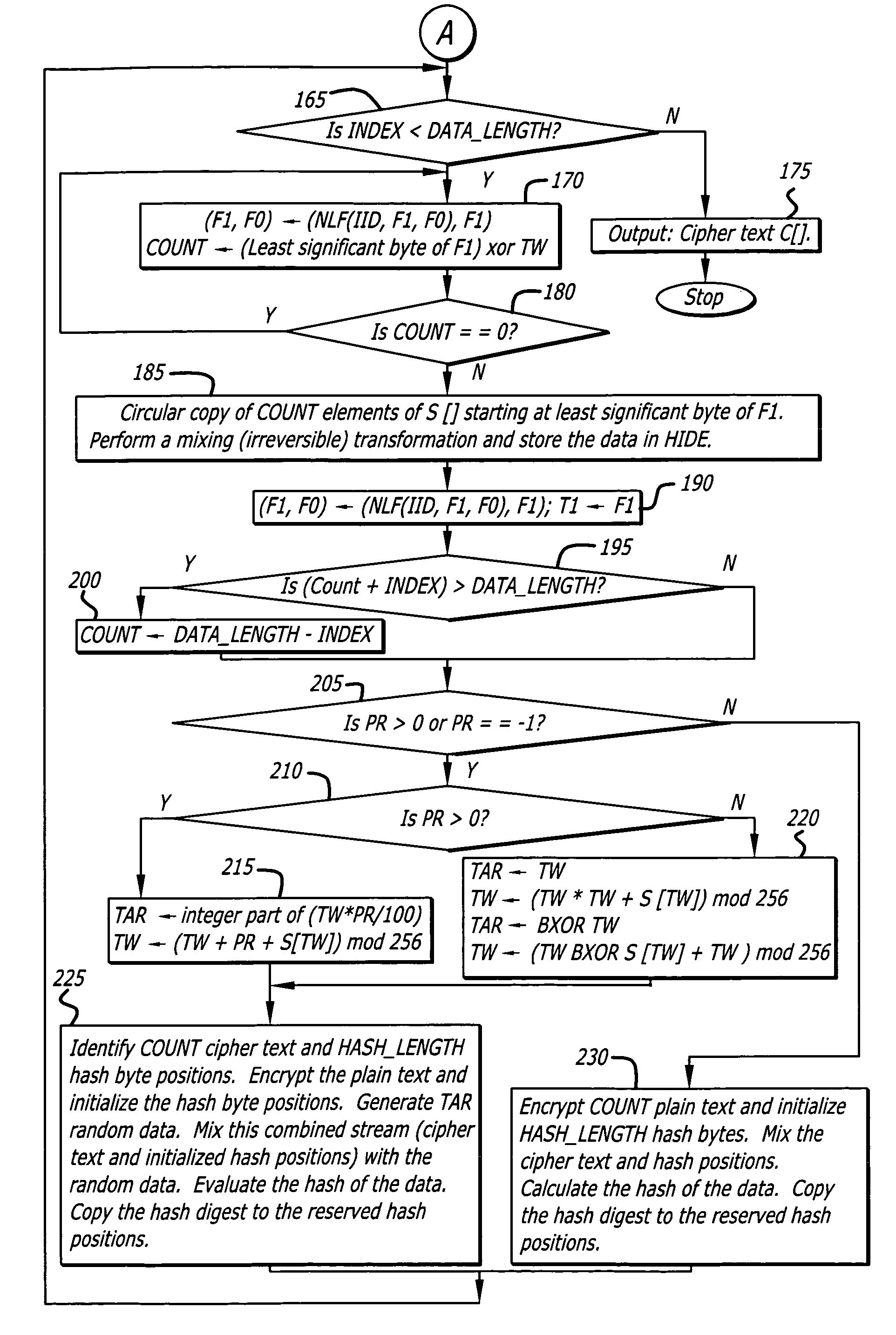
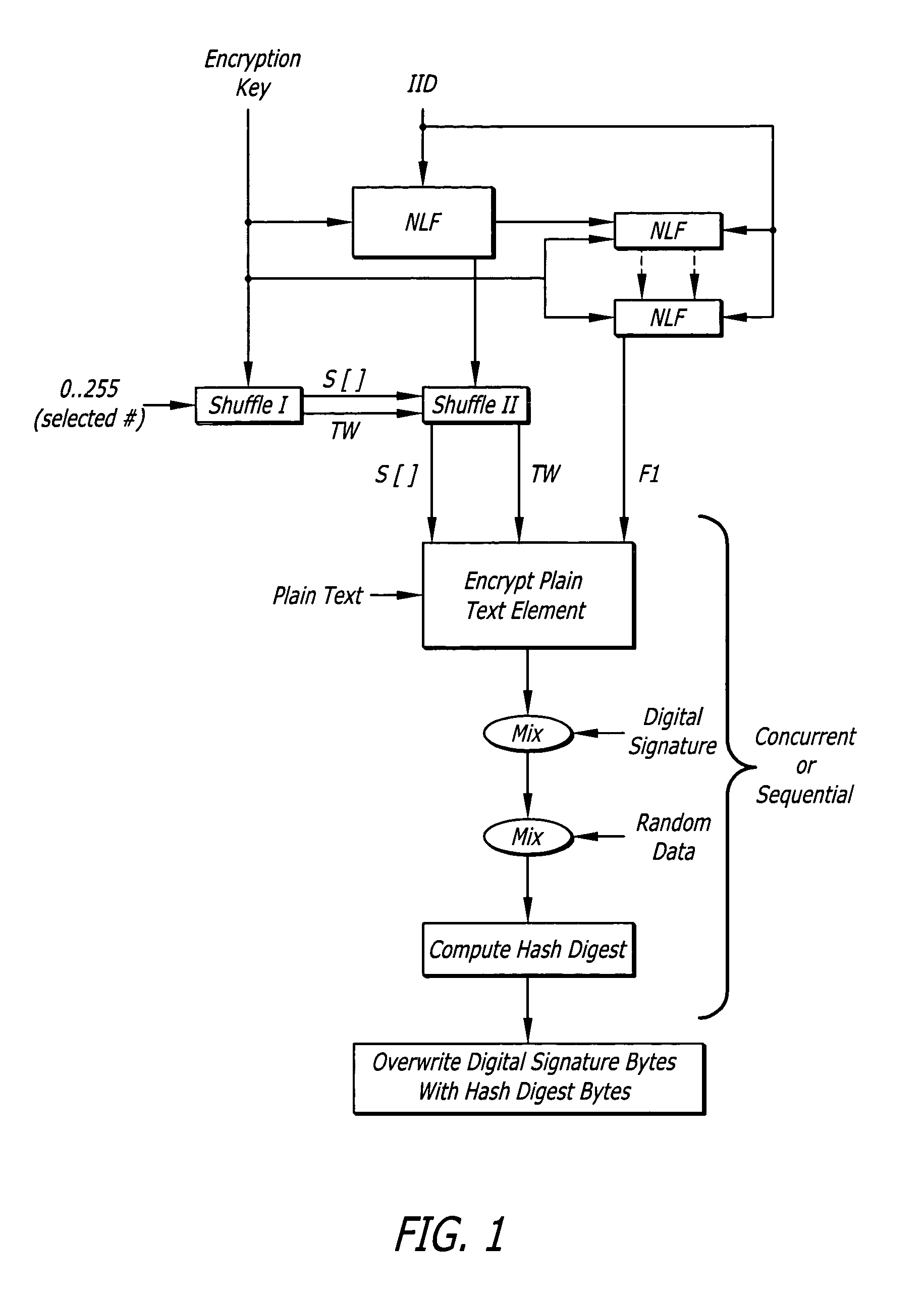
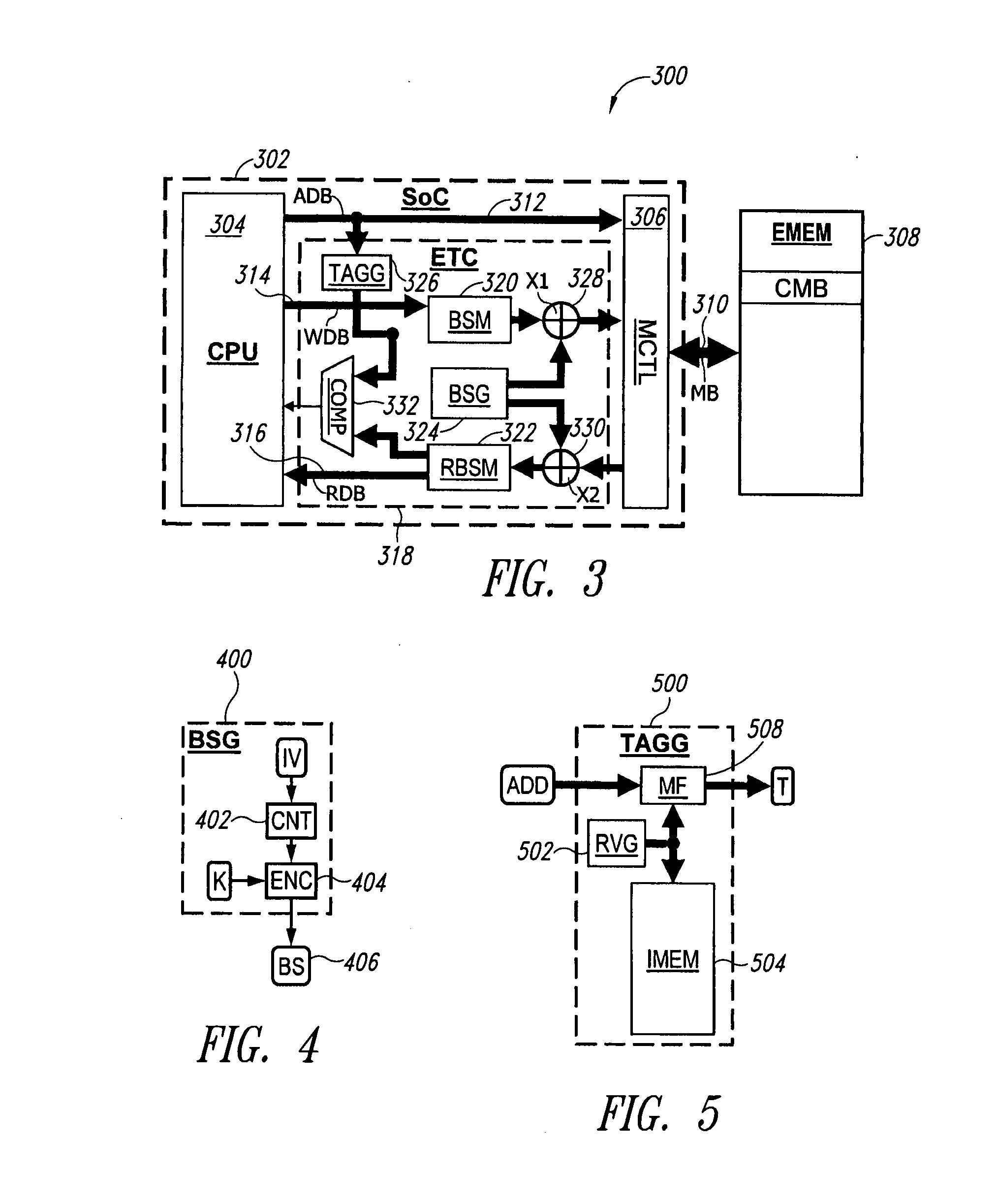
State-varying hybrid stream cipher
InactiveUS7103181B2Data stream serial/continuous modificationSecret communicationAlgorithmCiphertext
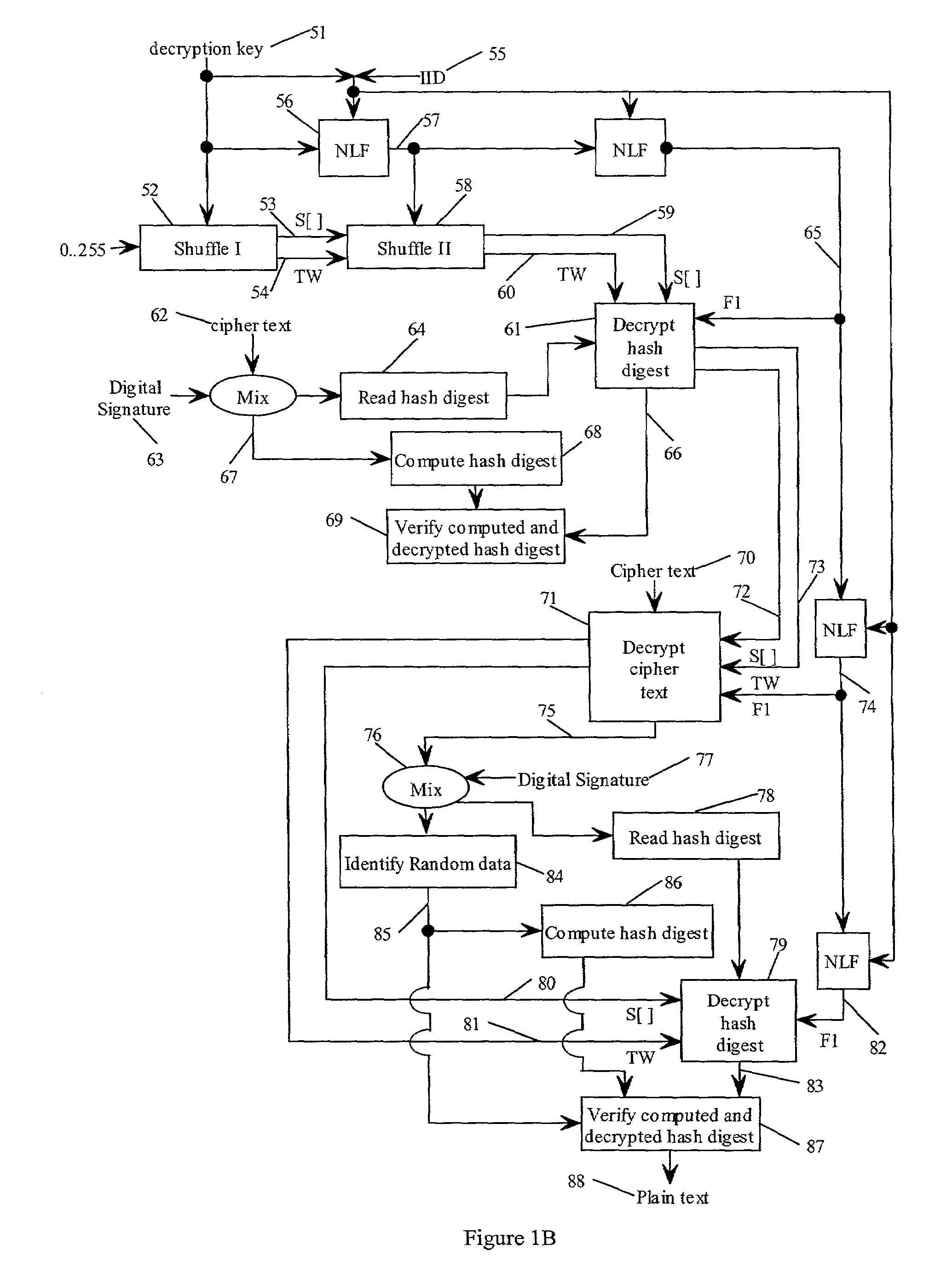
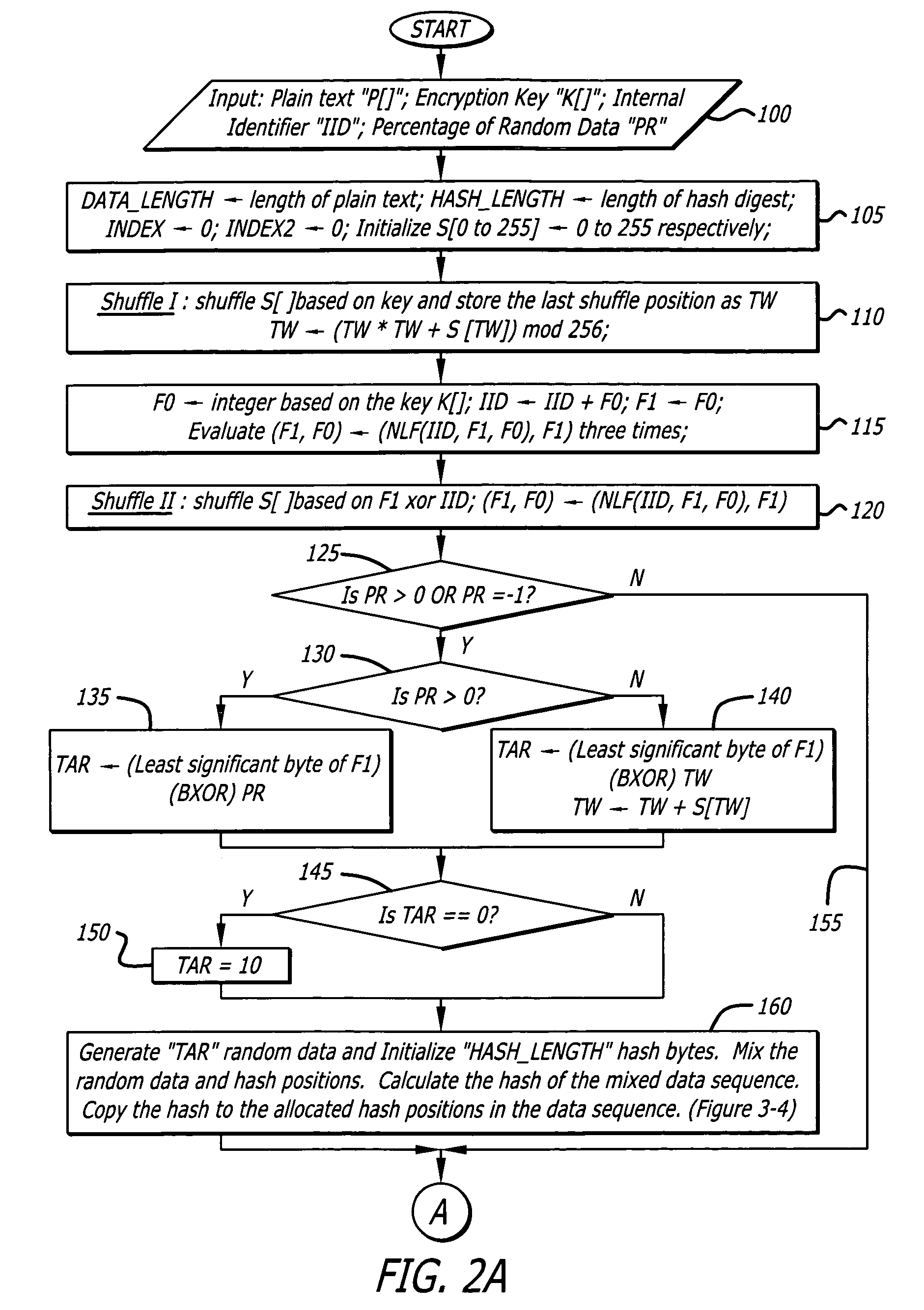
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
Method of and system for encrypting messages, generating encryption keys and producing secure session keys
InactiveUS20020076044A1Easy to provideNever be changedKey distribution for secure communicationMultiple keys/algorithms usagePlaintextCiphertext
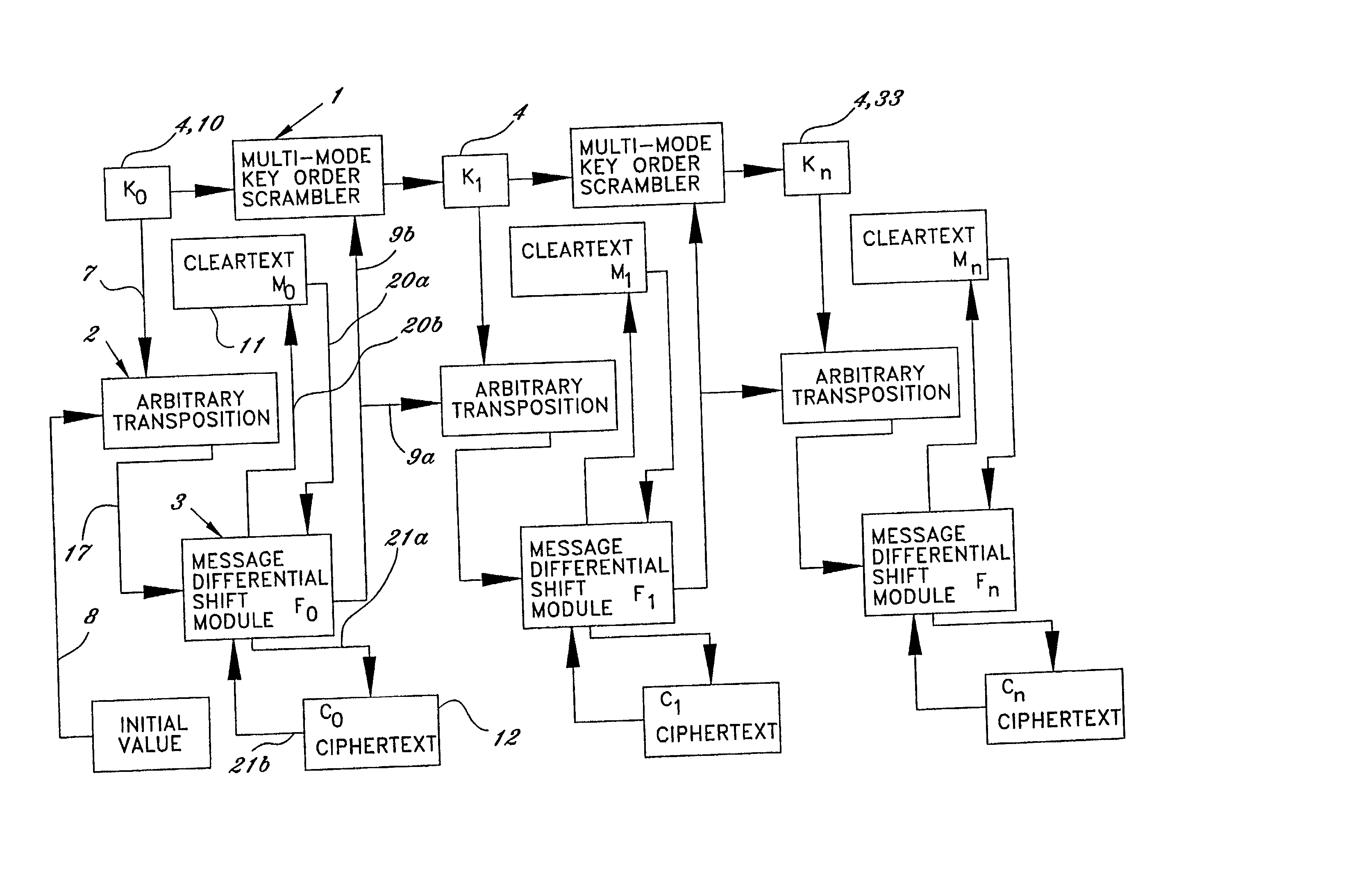
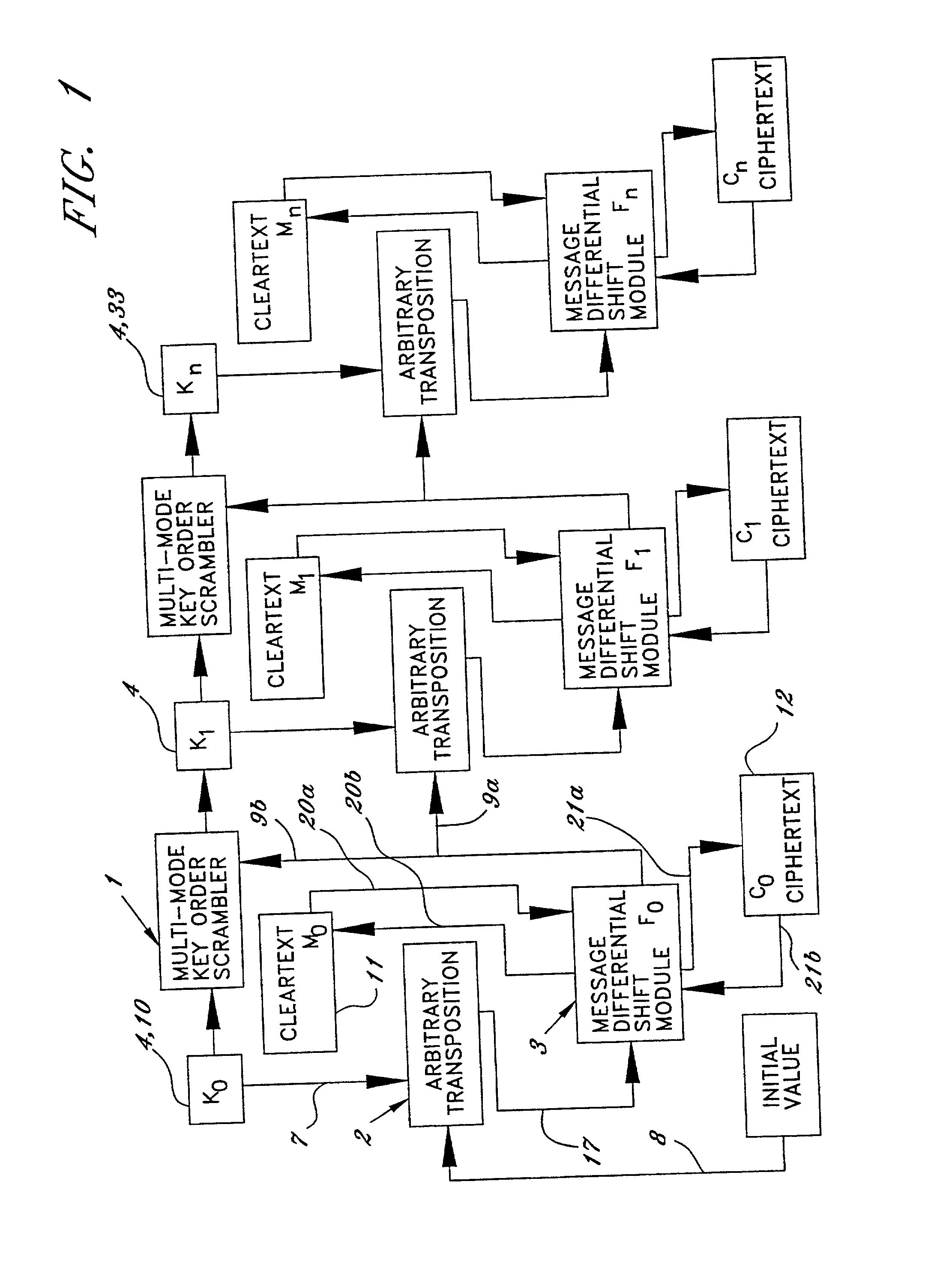
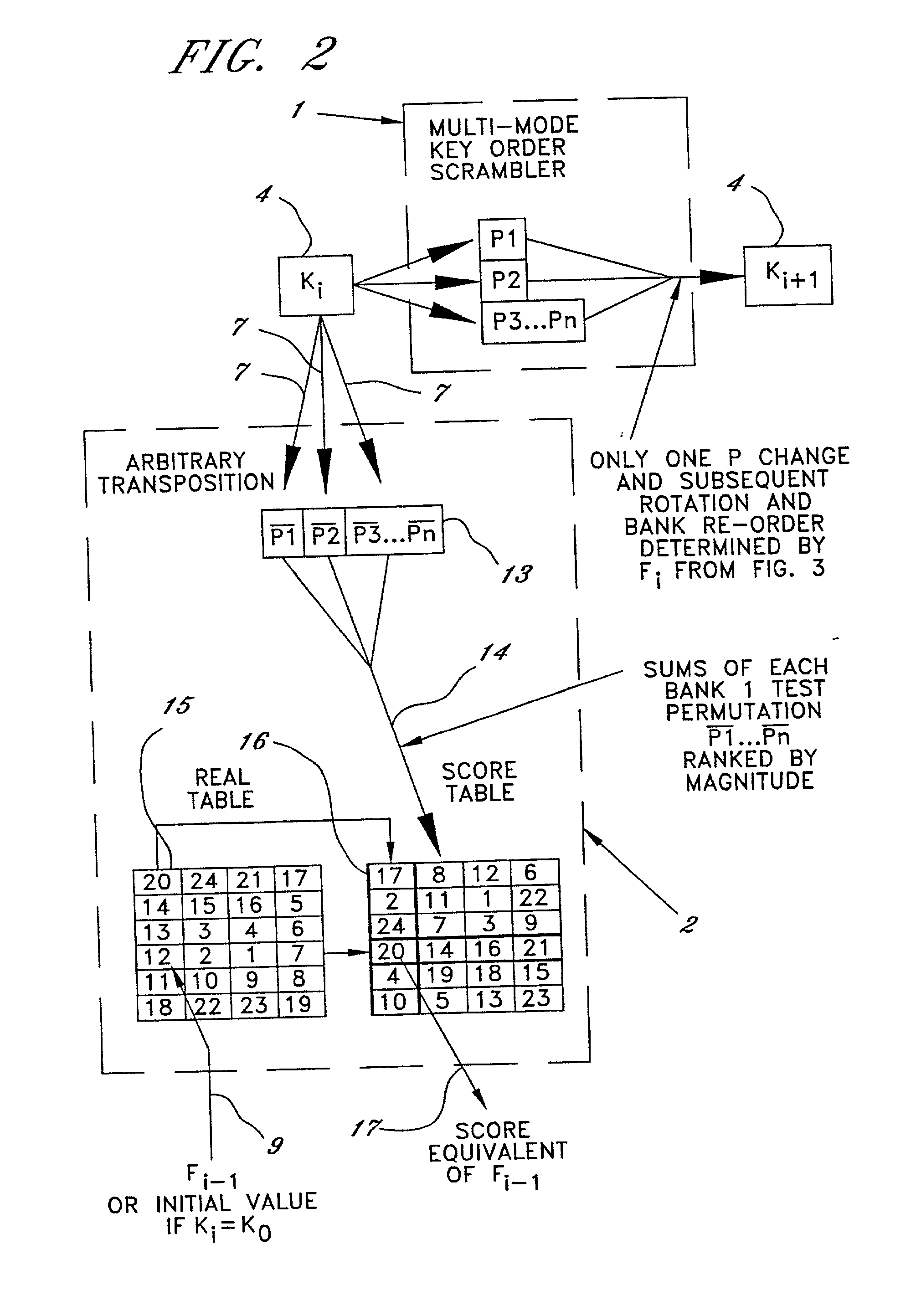
A technique for encrypting and decrypting a data message is described herein and includes a stream cipher, a block cipher, and IV generation embodiment and a key generation embodiment which use a process of Summary Reduction. This overall technique uses a secret key to generate ciphertext from plaintext and in doing so, the technique isolates the nature of the secret key values from the nature of the cipher text created.
Owner:PIRES PAUL
Key expansion for qkd
InactiveUS20060059343A1Key distribution for secure communicationSynchronisation information channelsKey exchangeKey schedule
A method of encrypting information using an encryption pad based on keys exchanged between quantum key distribution (QKD) stations is disclosed. The method includes establishing raw keys between two stations using QKD, processing the keys to establish a plurality of matching privacy amplified keys at each station and buffering the keys in a shared key schedule. The method also includes the option of expanding one or more of the keys in the shared key schedule using a stream cipher to create a supply of expanded keys that serve as pads for one-time-pad encryption.
Owner:MAGIQ TECH INC
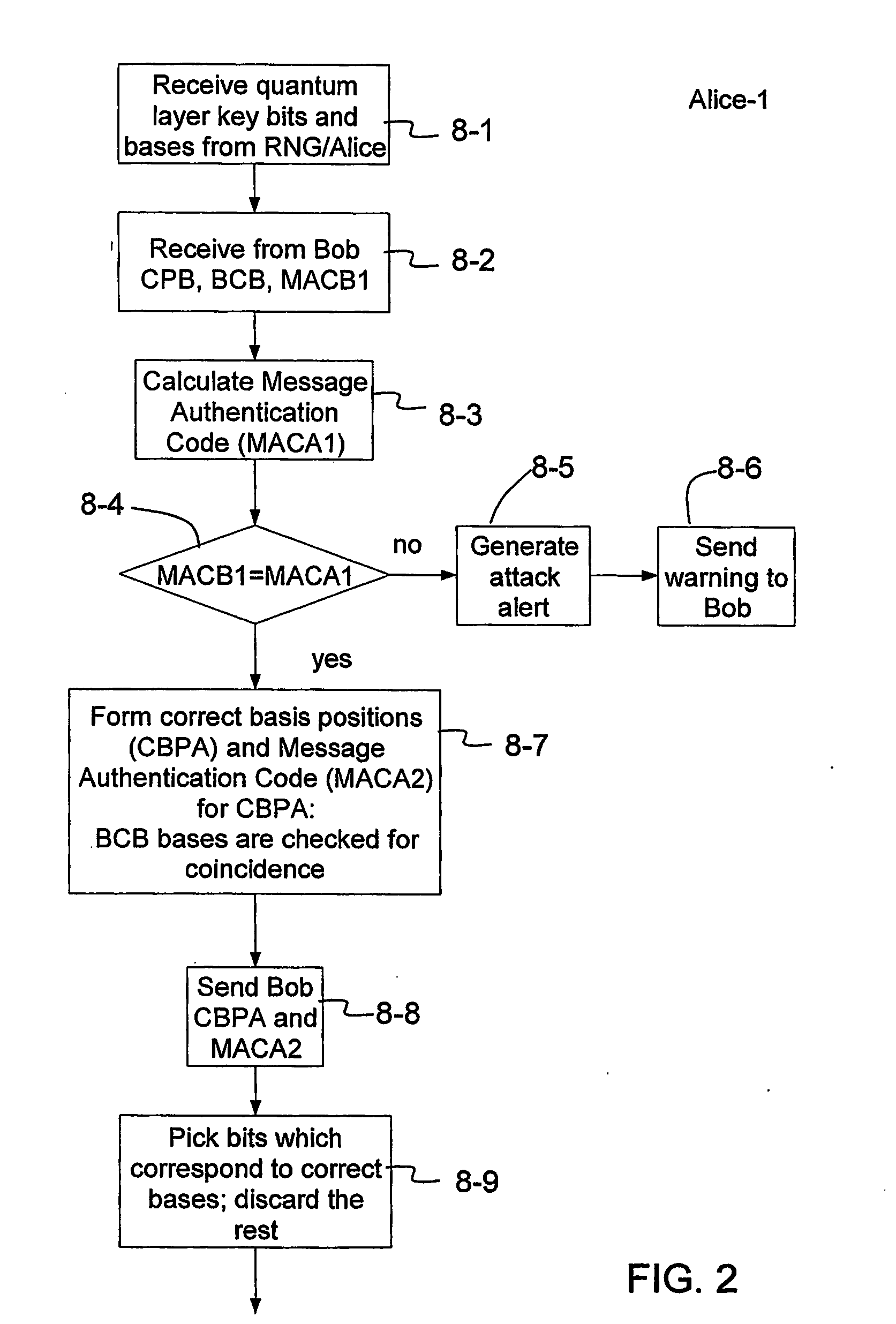
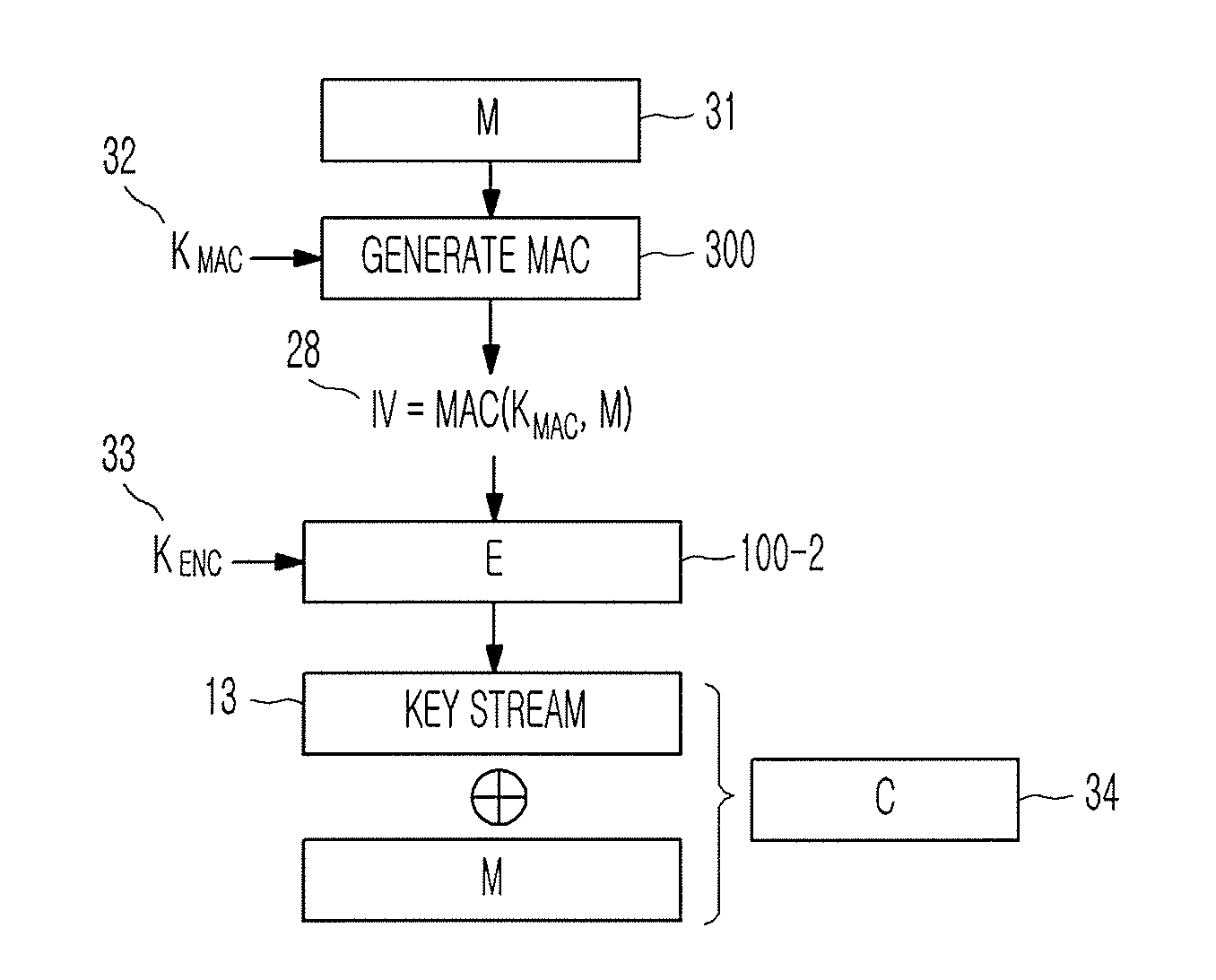
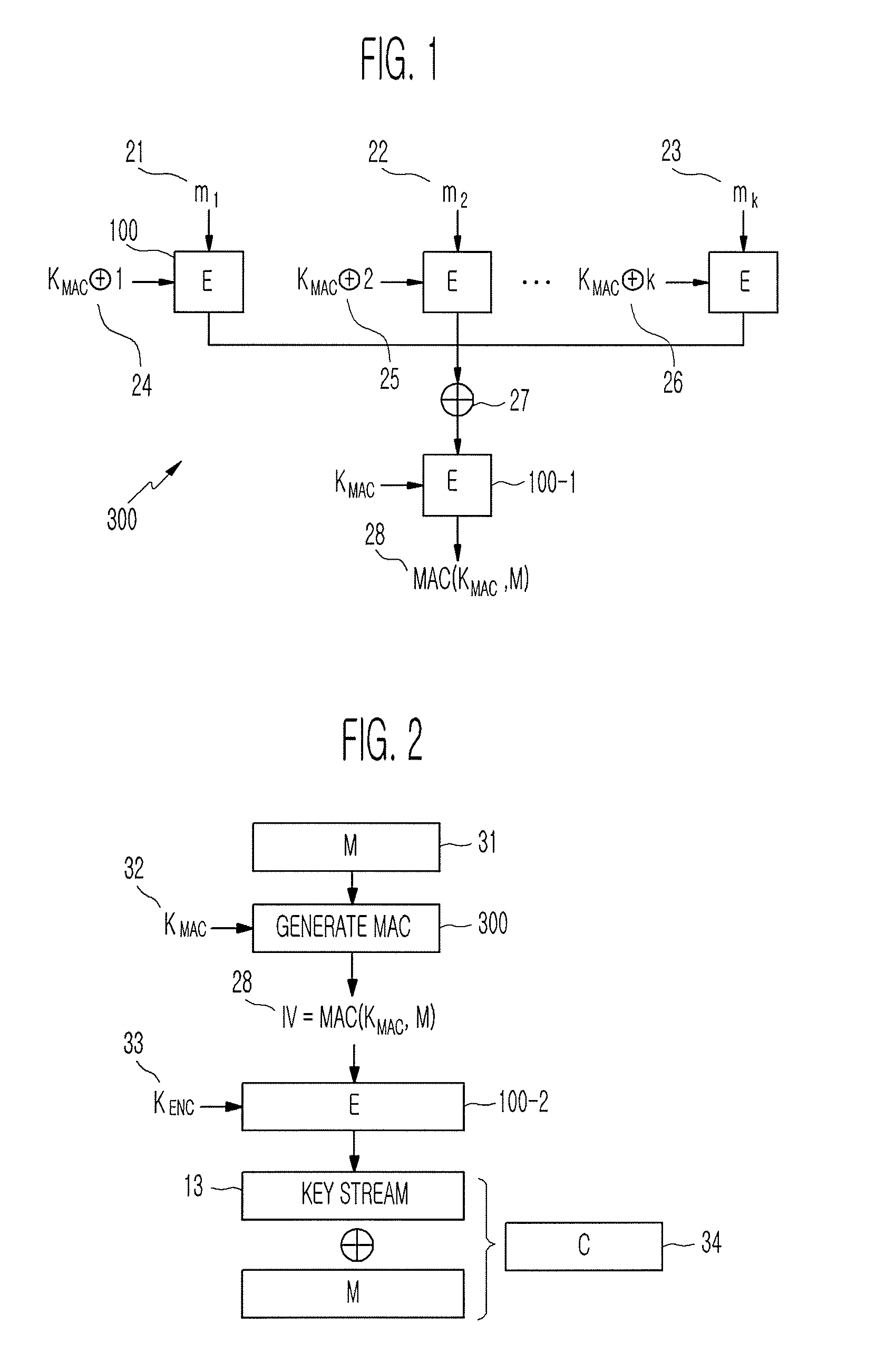
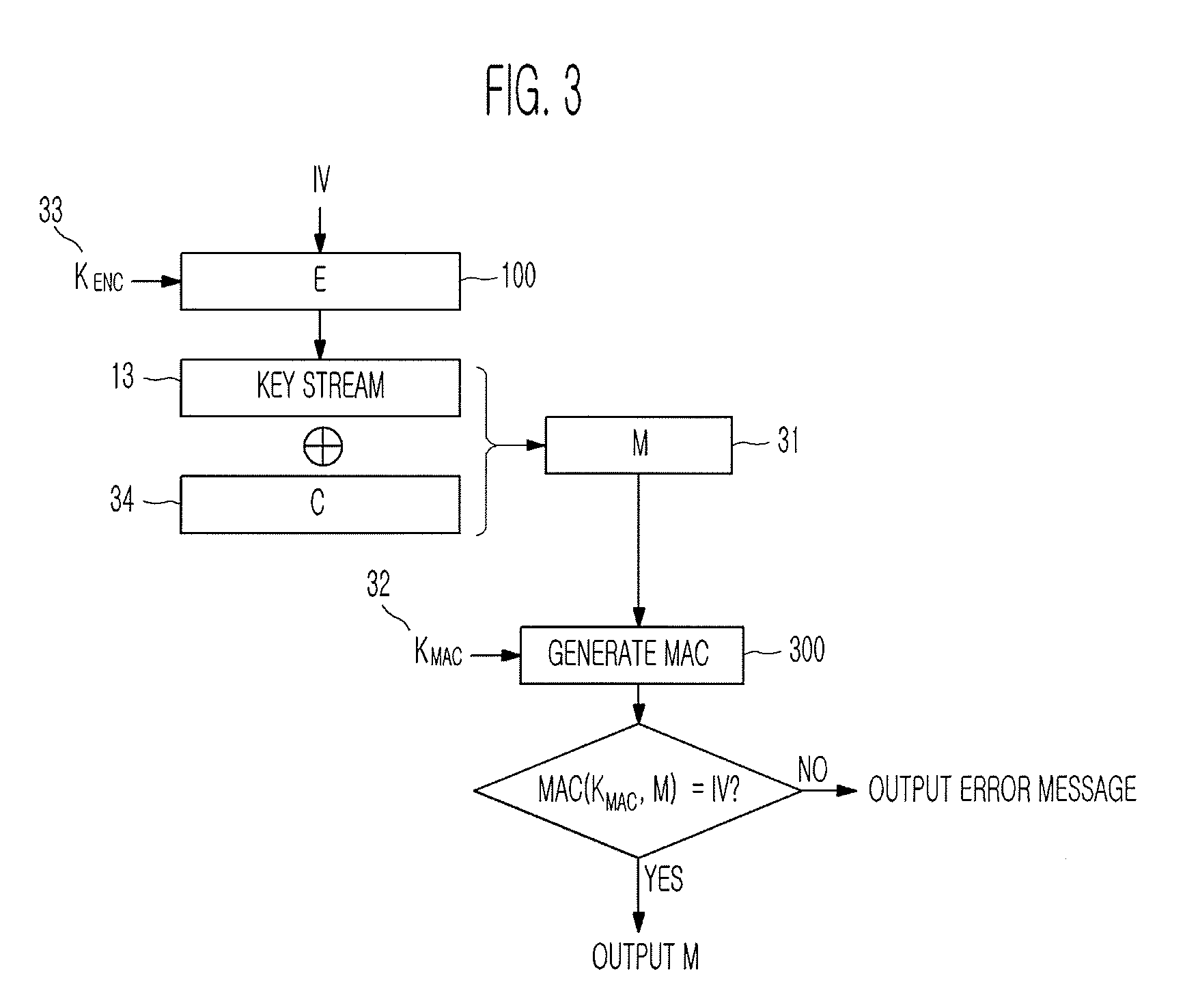
Method of generating message authentication code using stream cipher and authentication/encryption and authentication/decryption methods using stream cipher
InactiveUS20080112561A1Secret communicationSecuring communicationComputer hardwareHash-based message authentication code
Provided are a method of generating a Message Authentication Code (MAC) using a stream cipher, and authentication / encryption and authentication / decryption methods using a stream cipher.According to the methods, authentication / encryption is performed using a MAC generated using a stream cipher as an initialization vector of the stream cipher. Therefore, it is unnecessary to use a random number generation algorithm to generate the initialization vector, and thus implementation efficiency can be improved.In addition, upon generation of a MAC, a plurality of key stream generators perform computation for a plurality of message blocks, respectively. Therefore, the message blocks are computed in parallel at a time, and thus computation efficiency is excellent.
Owner:NAINFOX CO LTD
State-varying hybrid stream cipher
InactiveUS20060291650A1Data stream serial/continuous modificationUser identity/authority verificationState variationCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:ANANTH VISWANATH
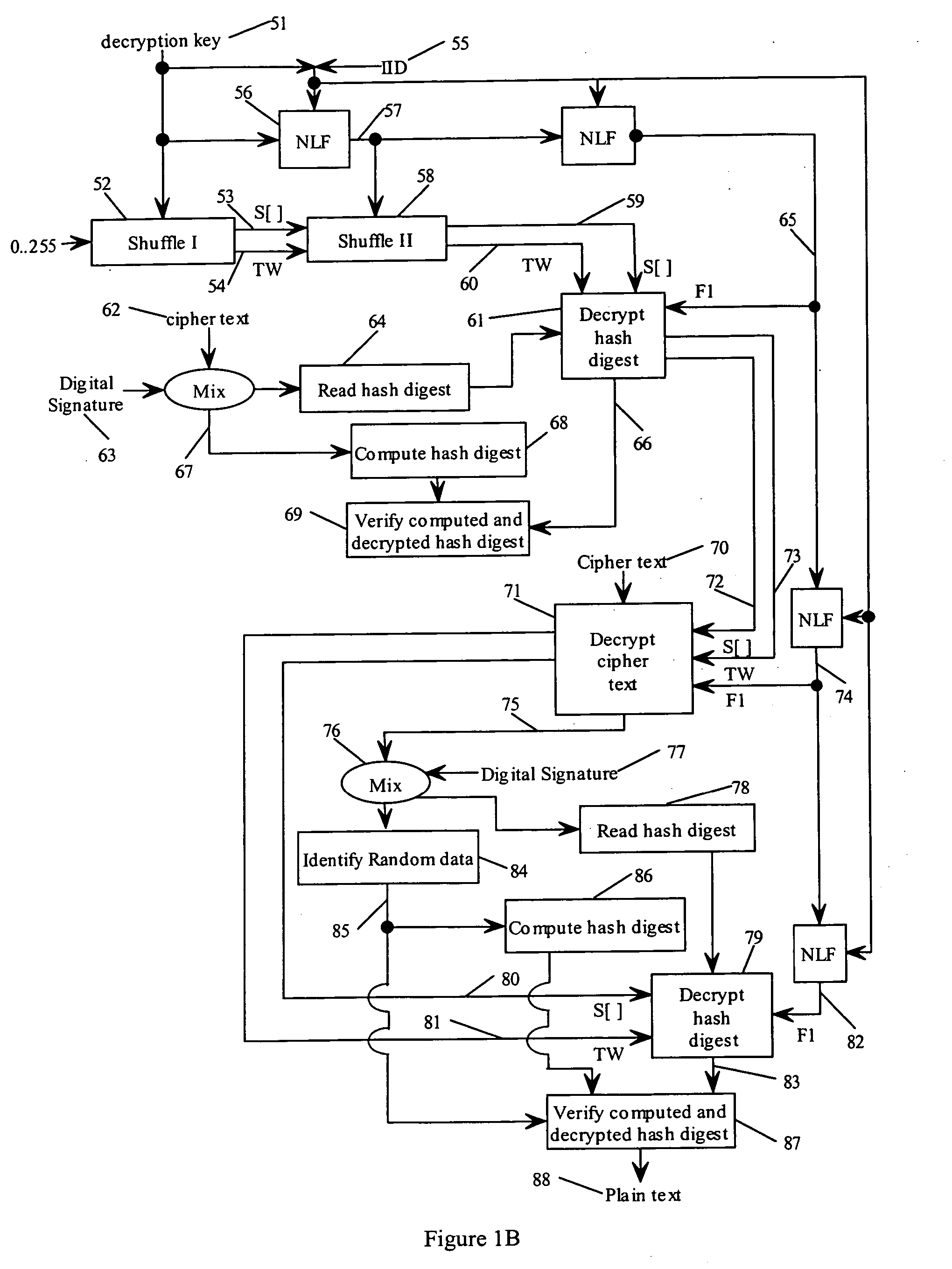
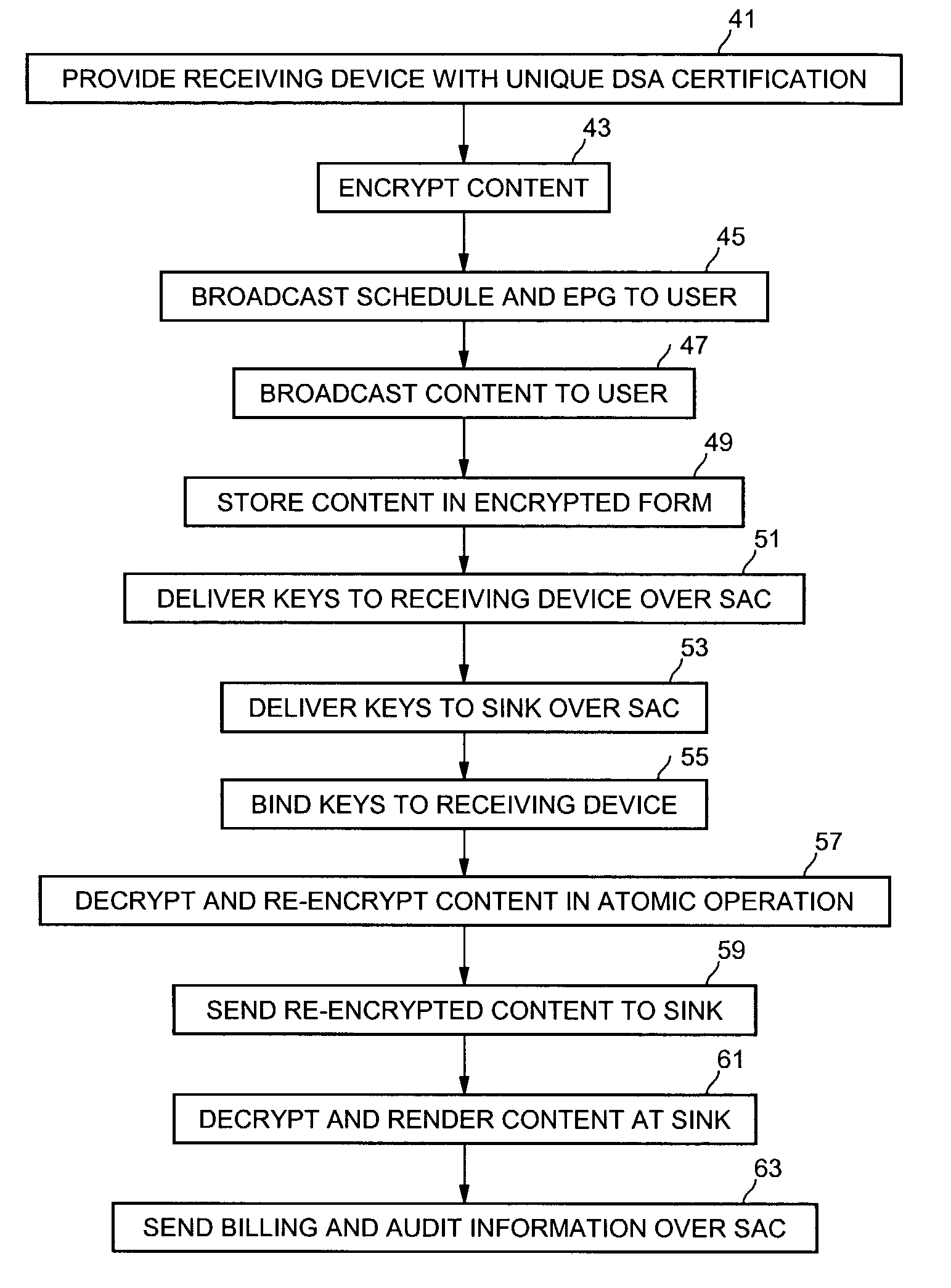
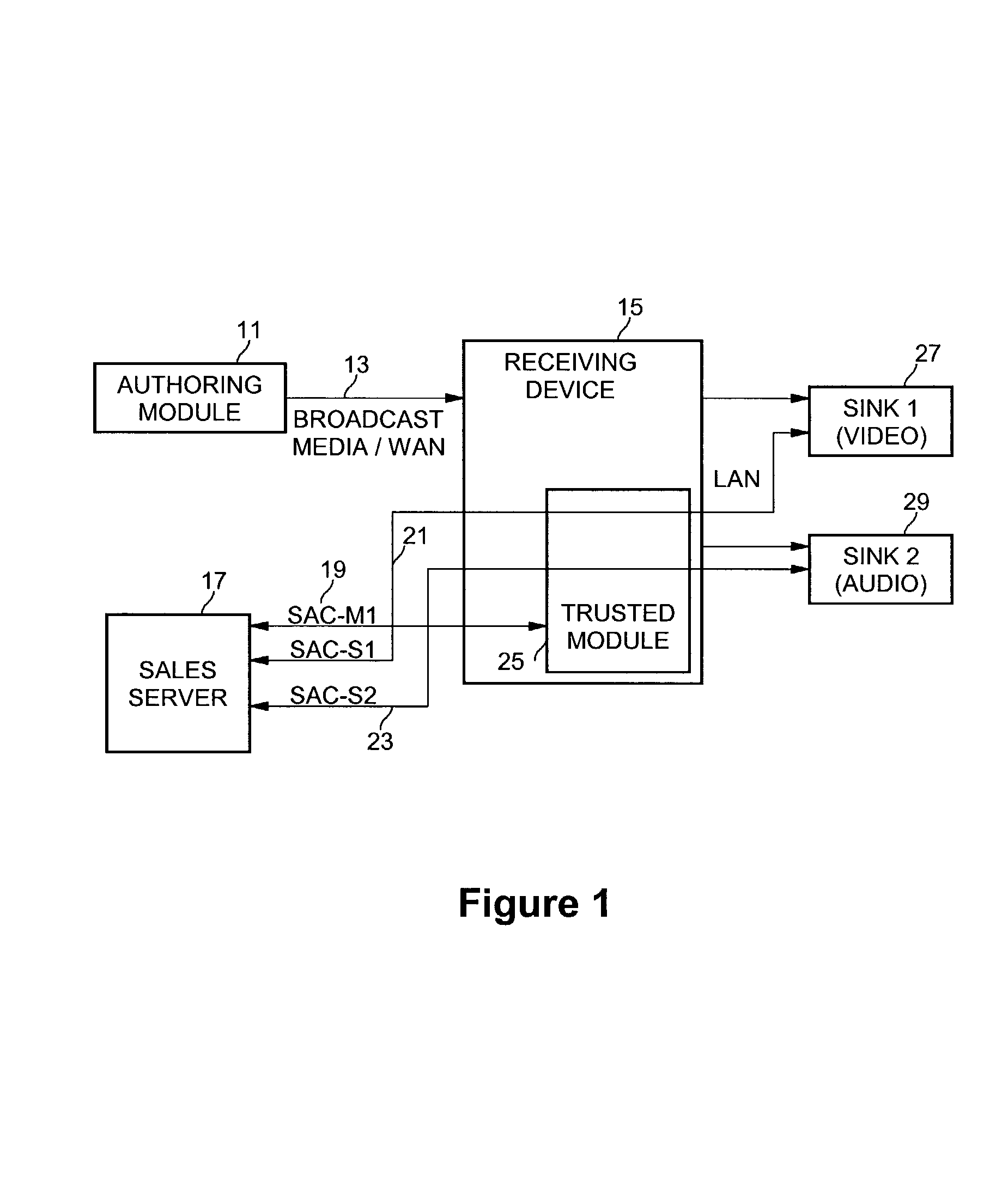
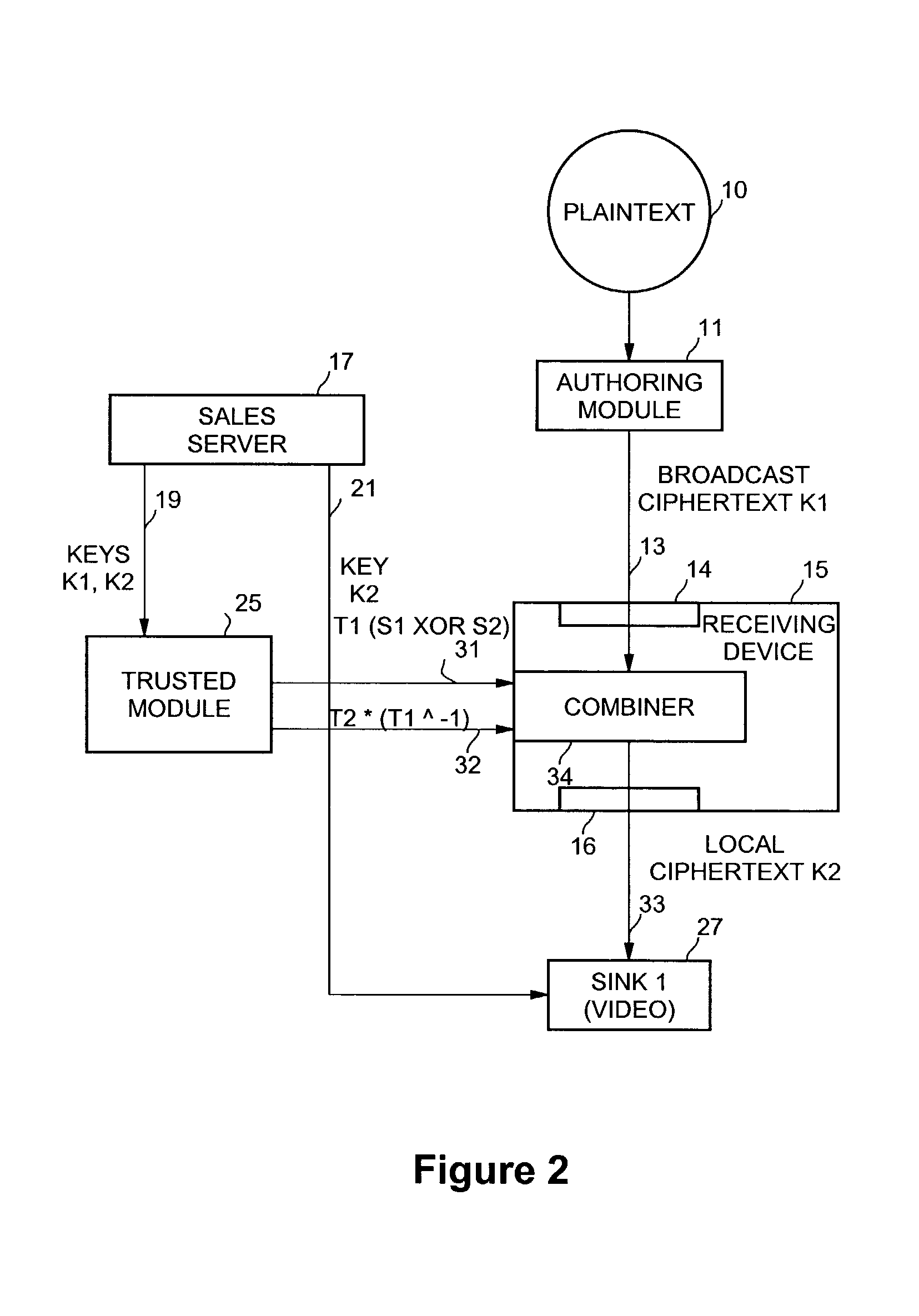
Method and apparatus for simultaneous decryption and re-encryption of publicly distributed content via stream ciphers
InactiveUS7184550B2Key distribution for secure communicationData stream serial/continuous modificationSecure communicationKey generation
Secure communication from one encryption domain to another using a trusted module. In one embodiment, the invention includes receiving encrypted streamed content encrypted with a first key, generating a substitution key stream based on the first key and a second key, generating a transposition key stream based on the first and second keys, and simultaneously decrypting and re-encrypting the encrypted streamed content using a combination of the substitution and transposition streams to produce re-encrypted streamed content encrypted with the second key.
Owner:INTEL CORP
Security data item level database encryption system
ActiveCN102236766ADigital data protectionSpecial data processing applicationsHash functionCiphertext
The invention relates to a security data item level database encryption method. Confidential data is encrypted by a data item level particle size; a hash function is used for deriving an encryption key of each data item according to a derived key and unique positioning information of the data item, even the data item encryption keys for encryption of all integral databases can be derived by using one key to reduce the using amount of the keys and facilitate key management; and a stream cipher algorithm is used for encrypting the data items to avoid filling. A ciphertext index is also encrypted by the stream cipher algorithm; each field (column) is encrypted by using the same key; therefore, searching keywords can be encrypted and then ciphertexts of corresponding fields are matched in spite of precise complete or incomplete searching. The method also has complete security functions of key management, secret sharing, security backup, mandatory access control, security connection and the like.
Owner:WANBANG CHARGING EQUIP CO LTD +1
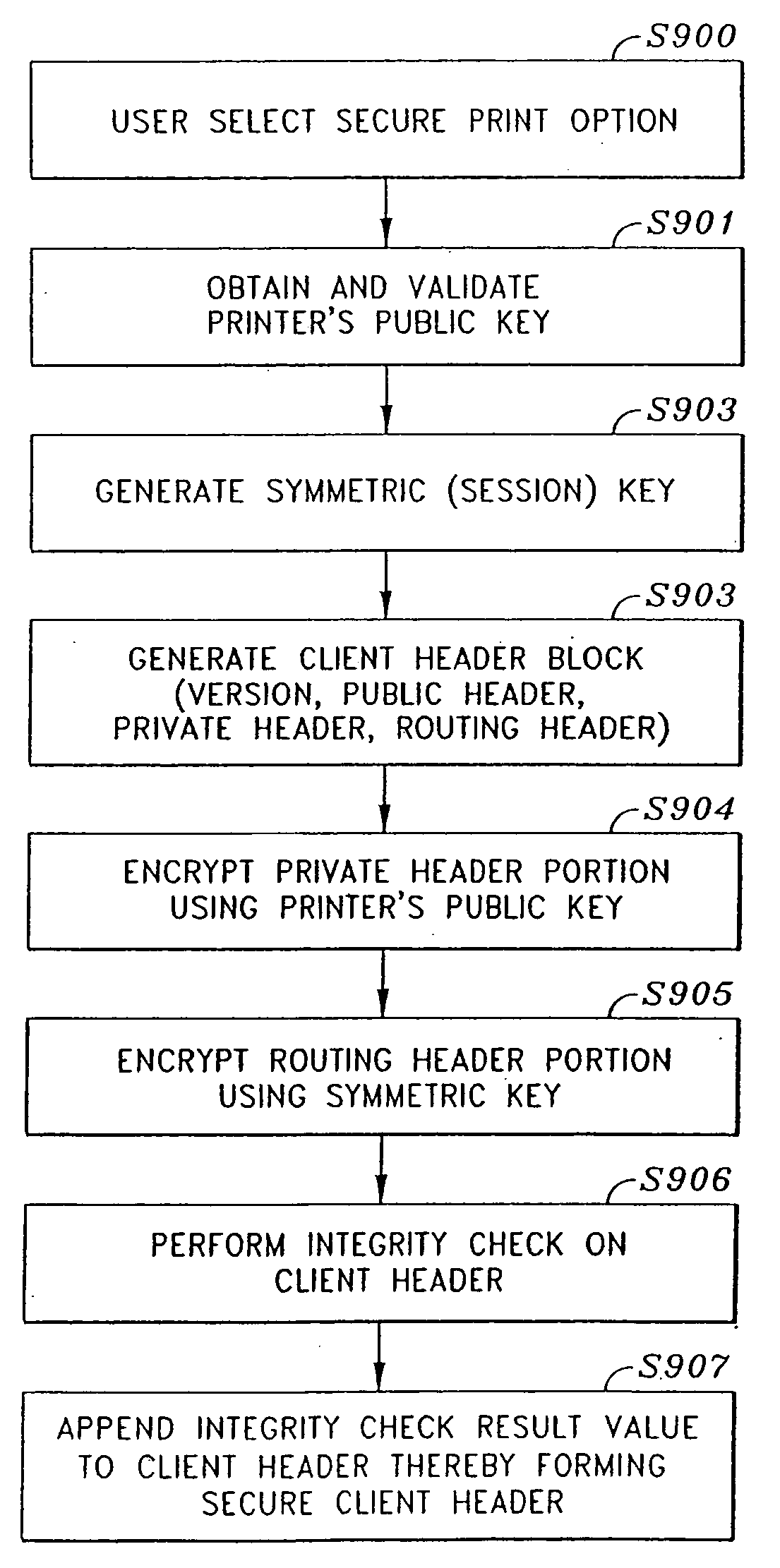
Secure file format
A file format for a secure file for use with a block cipher or a stream cipher, the secure file having a secure client header and a data block appended to the secure client header. The client header has a client information block comprised of a public information block, a private information block and an initialization vector. At least a portion of the private information block is encrypted, and a client information block integrity check value is appended to the client information block, the client information block integrity check value being obtained by performing an integrity check on the client information block. The data block is preferably encrypted and is comprised of a plurality of encrypted data blocks each appended with its own respective integrity check result value. Each of the plurality of data blocks and their respective integrity check result values are obtained by dividing the encrypted data block into n encrypted data blocks, performing an integrity check on a first one of the n encrypted data blocks and the client information integrity check result value appended to the client information block, so as to obtain a first encrypted data block integrity check result value, appending the first encrypted data block integrity check result value to the first encrypted data block, and repeatedly performing, for each of the subsequent n encrypted data blocks, an integrity check on the subsequent encrypted data block and an integrity check result value appended to a previous one of the n encrypted data blocks, so as to obtain an integrity check result value for the subsequent encrypted data block, and appending the subsequent integrity check result value to the subsequent encrypted data block.
Owner:CANON KK
Watermarking in an encrypted domain
Methods, apparatus and systems for embedding auxiliary information in encrypted host signals are provided. The present invention enables secure application of digital watermarks at any point in the transmission and / or distribution of digital content by enabling the insertion of a plurality of digital watermarks, without the knowledge of the encryption / decryption keys, into a digital host content that has been encrypted with an encryption key. The embedded watermarks persist throughout the content subsequent to the decryption of the content. The disclosed techniques are applicable to content that has been encrypted using a variety of different encryption techniques and algorithms, including stream ciphers, block ciphers, symmetric and asymmetric encryption algorithms. These methods are further adapted to enable the insertion of watermarks into a content that is compressed prior to encryption.
Owner:VERANCE
Hybrid stream cipher
InactiveUS7003107B2Data stream serial/continuous modificationSecret communicationCiphertextInternal identifier
In one embodiment, a hybrid stream cipher operating within a computing device. The hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
Unimodular matrix-based message authentication codes (MAC)
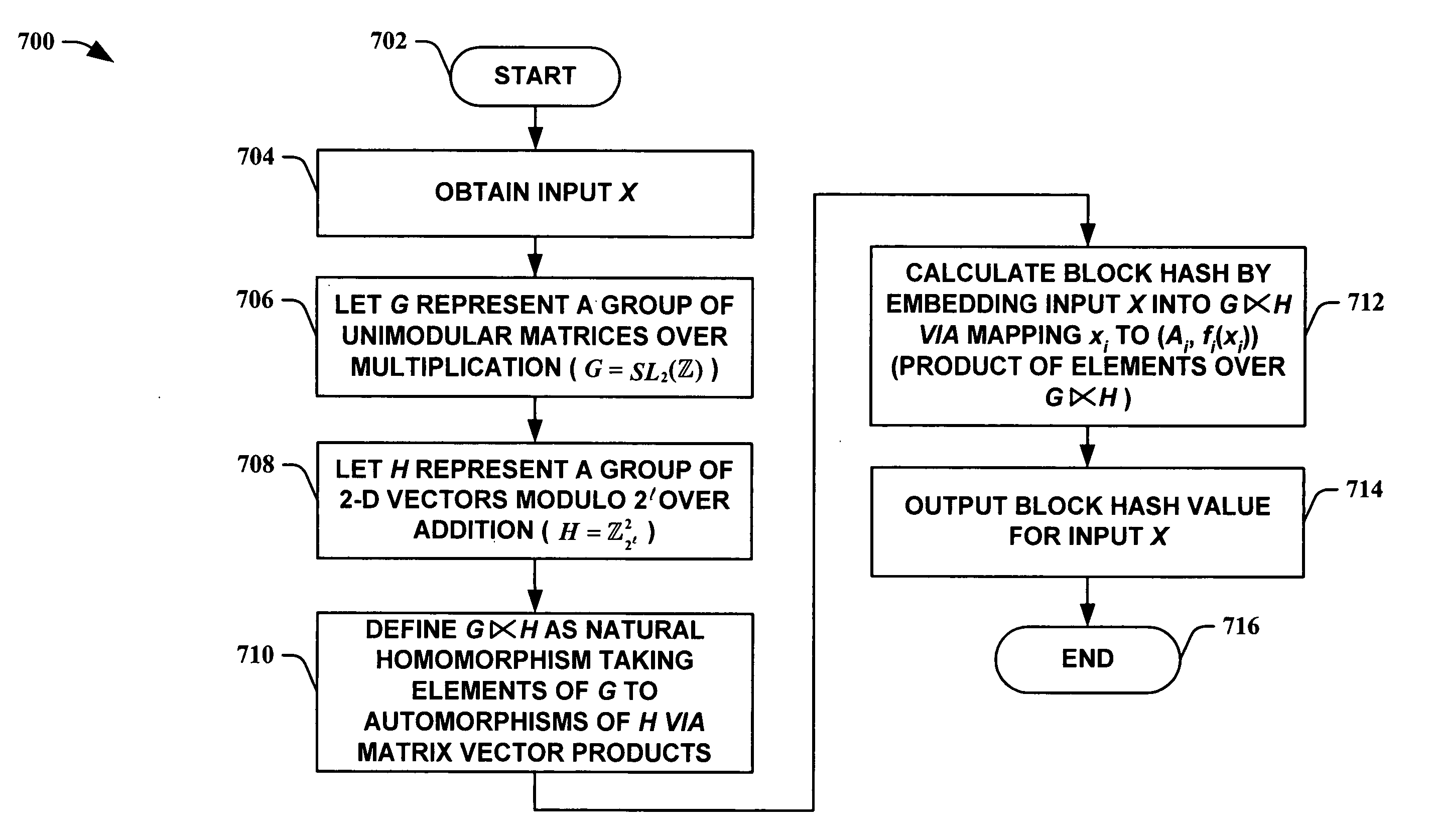
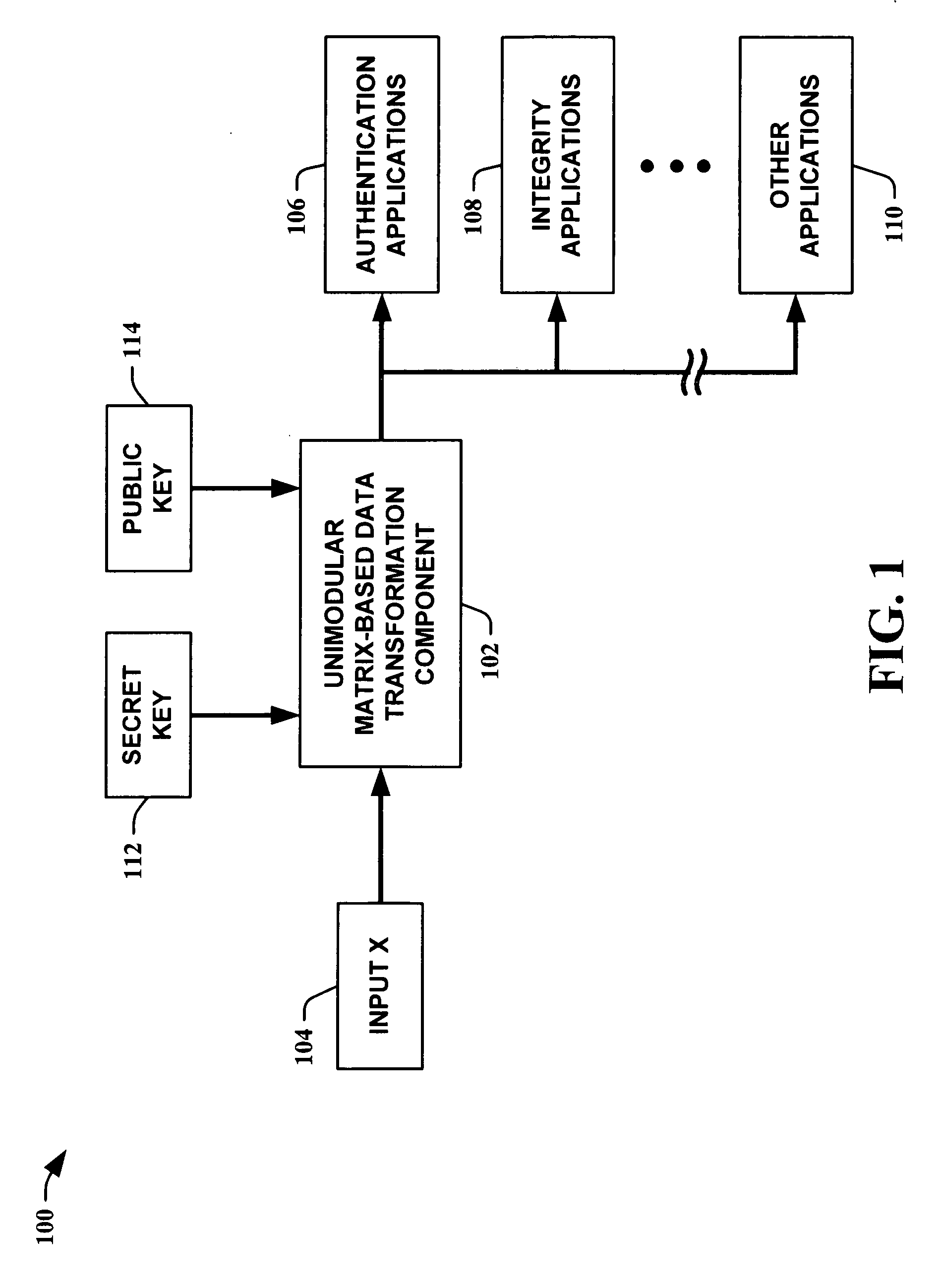
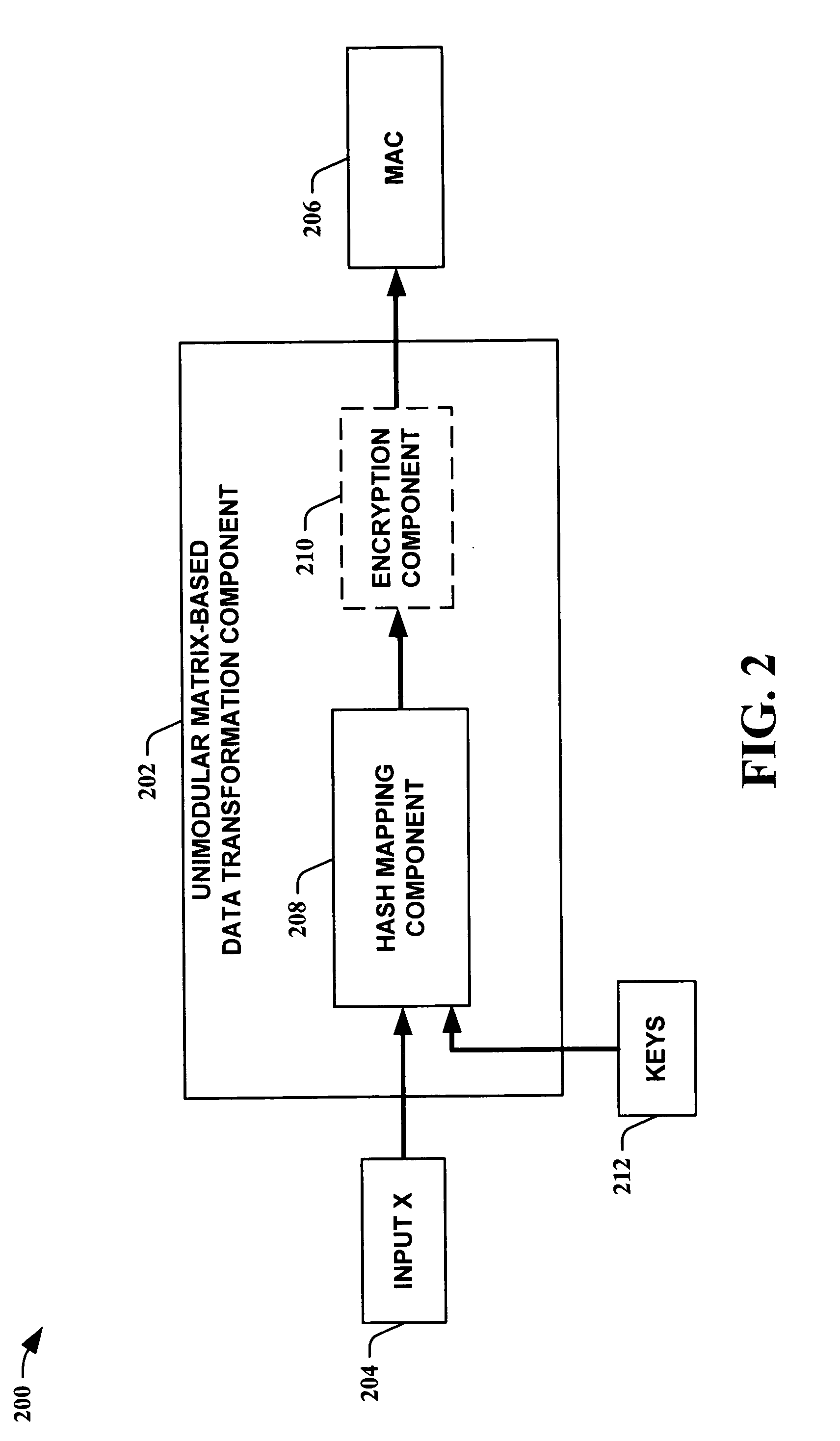
InactiveUS20050210260A1Improve speed performanceHigh performance hash value generationUser identity/authority verificationMemory systemsKey sizeUniversal hashing
The present invention leverages the invertibility of determinants of unimodular matrices to provide a universal hash function means with reversible properties and high speed performance. This provides, in one instance of the present invention, length controllable hash values comprised of vector pairs that can be processed as one instruction in a SIMD (single instruction, multiple data) equipped computational processor, where the vector pair is treated as a double word. The characteristics of the present invention permit its utilization in streaming cipher applications by providing key data to seed the ciphering process. Additionally, the present invention can utilize smaller key lengths than comparable mechanisms via inter-block chaining, can be utilized to double hash values via performing independent hash processes in parallel, and can be employed in applications, such as data integrity schemes, that require its unique processing characteristics.
Owner:MICROSOFT TECH LICENSING LLC
Method of and system for encrypting messages
InactiveUS6269164B1Easy to provideNever be changedData stream serial/continuous modificationSecret communicationPlaintextCiphertext
A technique for encrypting and decrypting a data message is described herein and includes a stream cipher, a block cipher and a key generation embodiment which use a process of Summary Reduction. This overall technique uses a secret key to generate ciphertext from plaintext and in doing so, the technique isolates the nature of the secret key values from the nature of the cipher text created.
Owner:PIRES PAUL
Data parallelized encryption and integrity checking method and device
InactiveUS20080232581A1Improve confidentialityImprove integrityData stream serial/continuous modificationSecret communicationExternal storageConfidentiality
A method and device for encrypting and / or decrypting binary data blocks protecting both confidentiality and integrity of data sent to or received from a memory. The encryption method comprises steps of: applying to the input data block a reversible scrambling process, the scrambling process providing a scrambled data block in which the bits of the input data block are mixed so that a modification of one bit in the scrambled data block impacts on every bit of the input data block, and applying to the scrambled data block a stream cipher encryption algorithm providing an encrypted data block. Application can be made to secured integrated circuits requiring to securely store data in an external memory.
Owner:STMICROELECTRONICS SRL +2
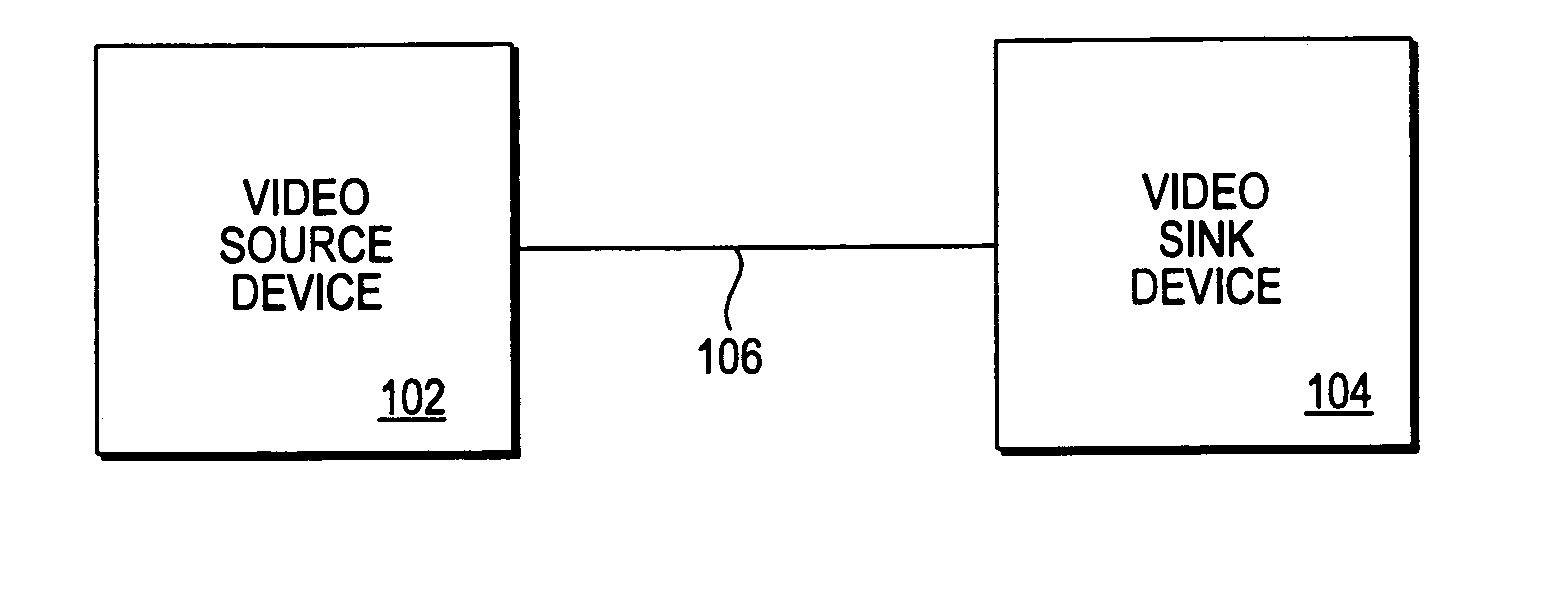
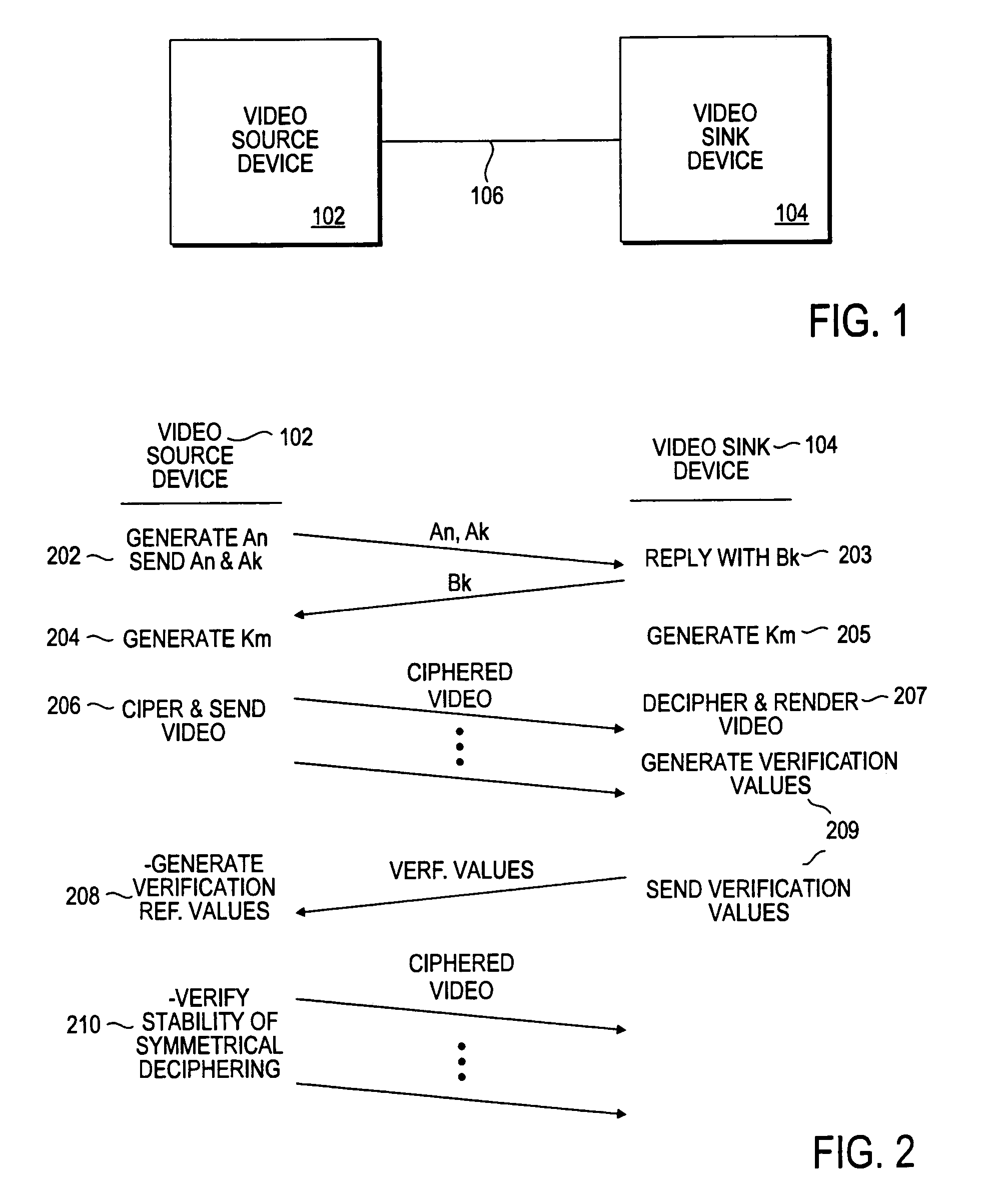
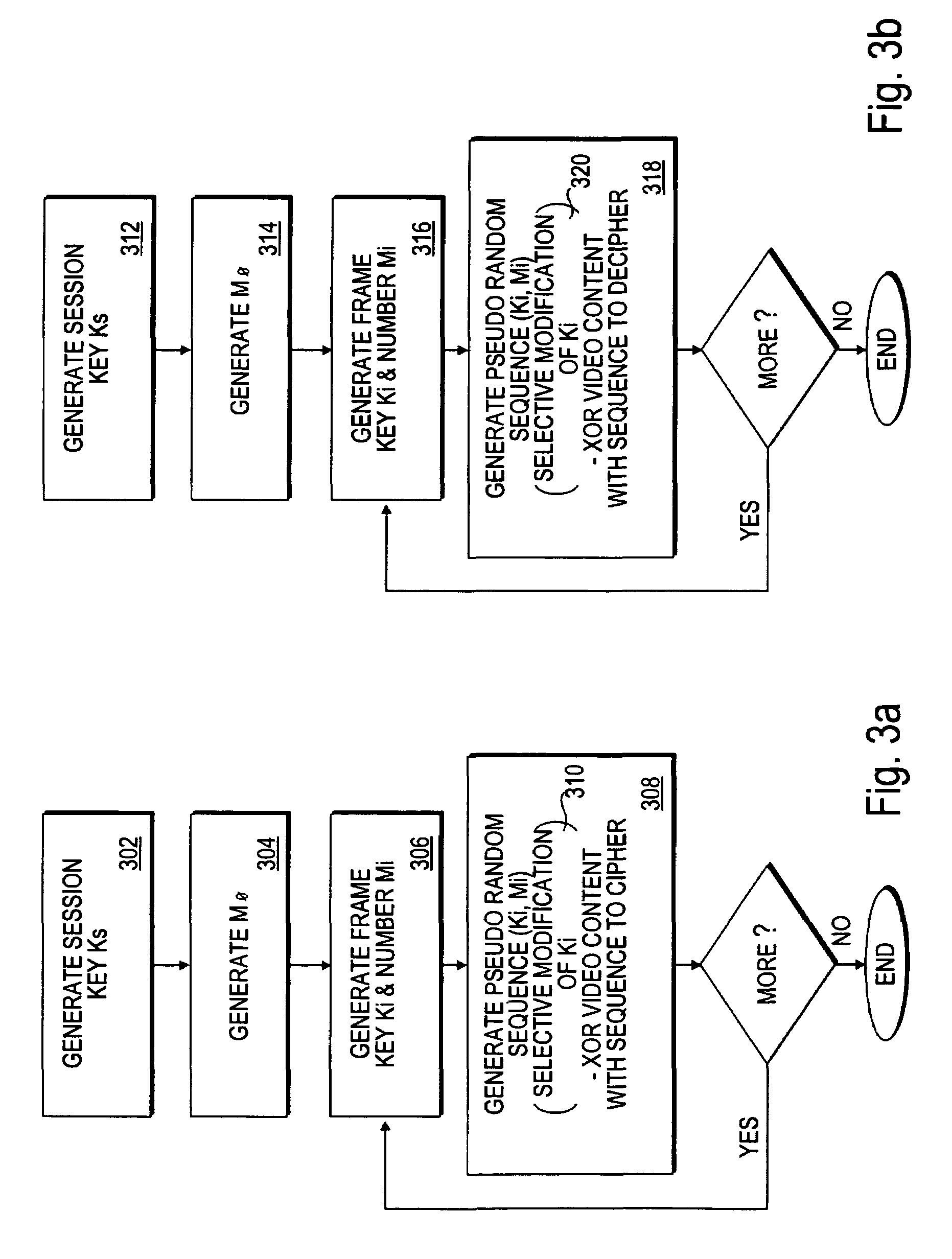
Digital video content transmission ciphering and deciphering method and apparatus
InactiveUS7043021B2Key distribution for secure communicationUser identity/authority verificationDigital videoMultiple frame
A video source device generates a session key for each transmission session wherein a multi-frame video content is to be transmitted to a video sink device. The video source device uses the session key to generate a successive number of frame keys. The frame keys in turn are used to generate corresponding pseudo random bit sequences for ciphering the corresponding frames to protect the video content from unauthorized copying during transmission. The video sink device practices a complementary approach to decipher the received video content. In one embodiment, both devices are each provided with an integrated block / stream cipher to practice the transmission protection method.
Owner:INTEL CORP
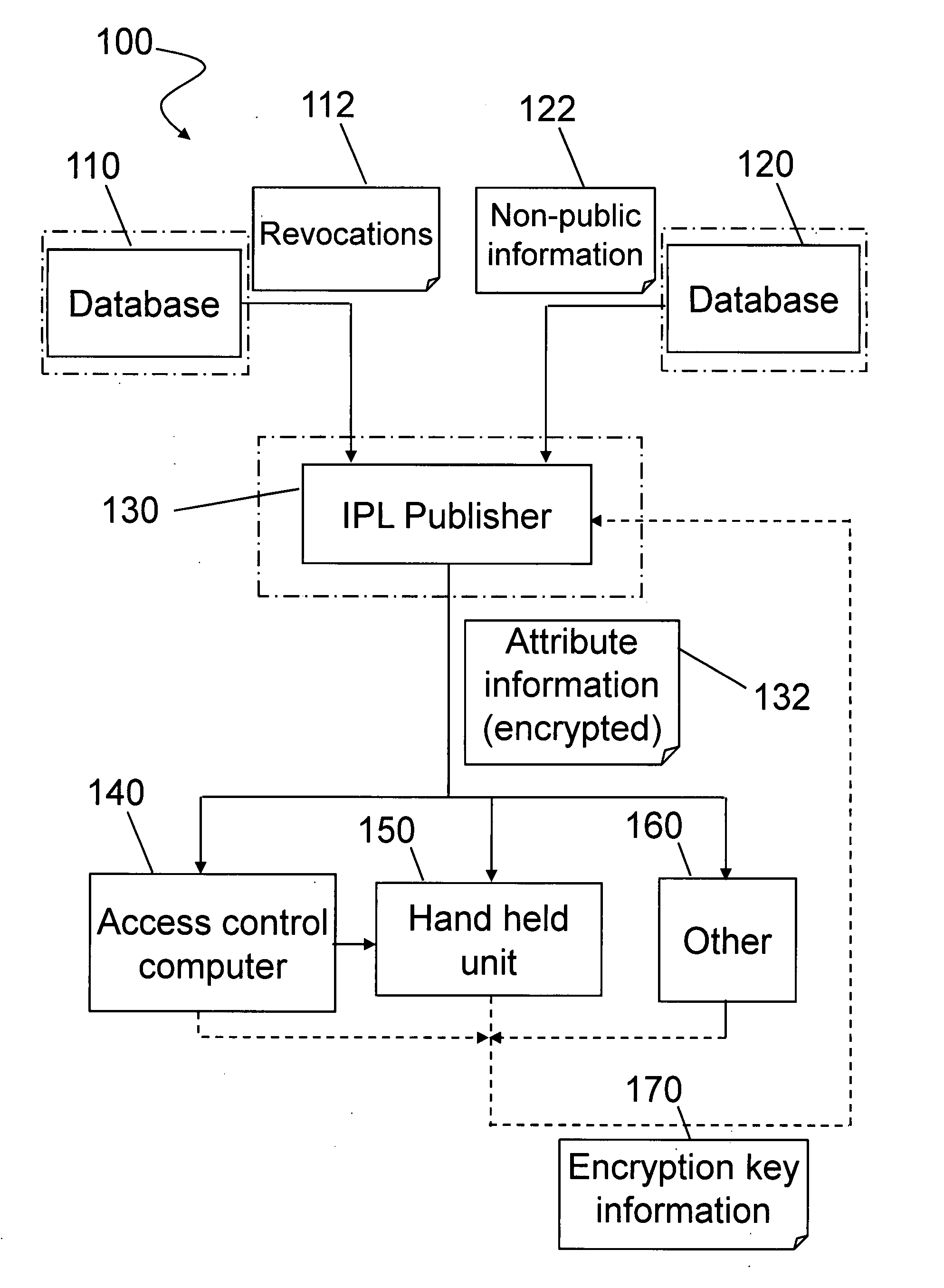
Secure ID checking
ActiveUS20080016370A1Digital data processing detailsUser identity/authority verificationCentralized databaseHand held devices
A cost-effective system that provides for the efficient protection of transmitted non-public attribute information may be used, for example, to control access to a secure area. Encryption of the attribute information may be performed using symmetric encryption techniques, such as XOR and / or stream cipher encryption. A centralized database that stores and transmits the encrypted attribute information may generate the encryption / decryption key based on selected information bytes, for example, as taken from a card inserted into a handheld device used at the secure area. The selected information to generate the encryption key stream may be varied on a periodic basis by the centralized database. Information as to which selected bytes are to be used for a particular access authorization request may be transmitted to the handheld unit or may be input through action of a user of the handheld unit, for example by entry of a PIN code.
Owner:ASSA ABLOY AB
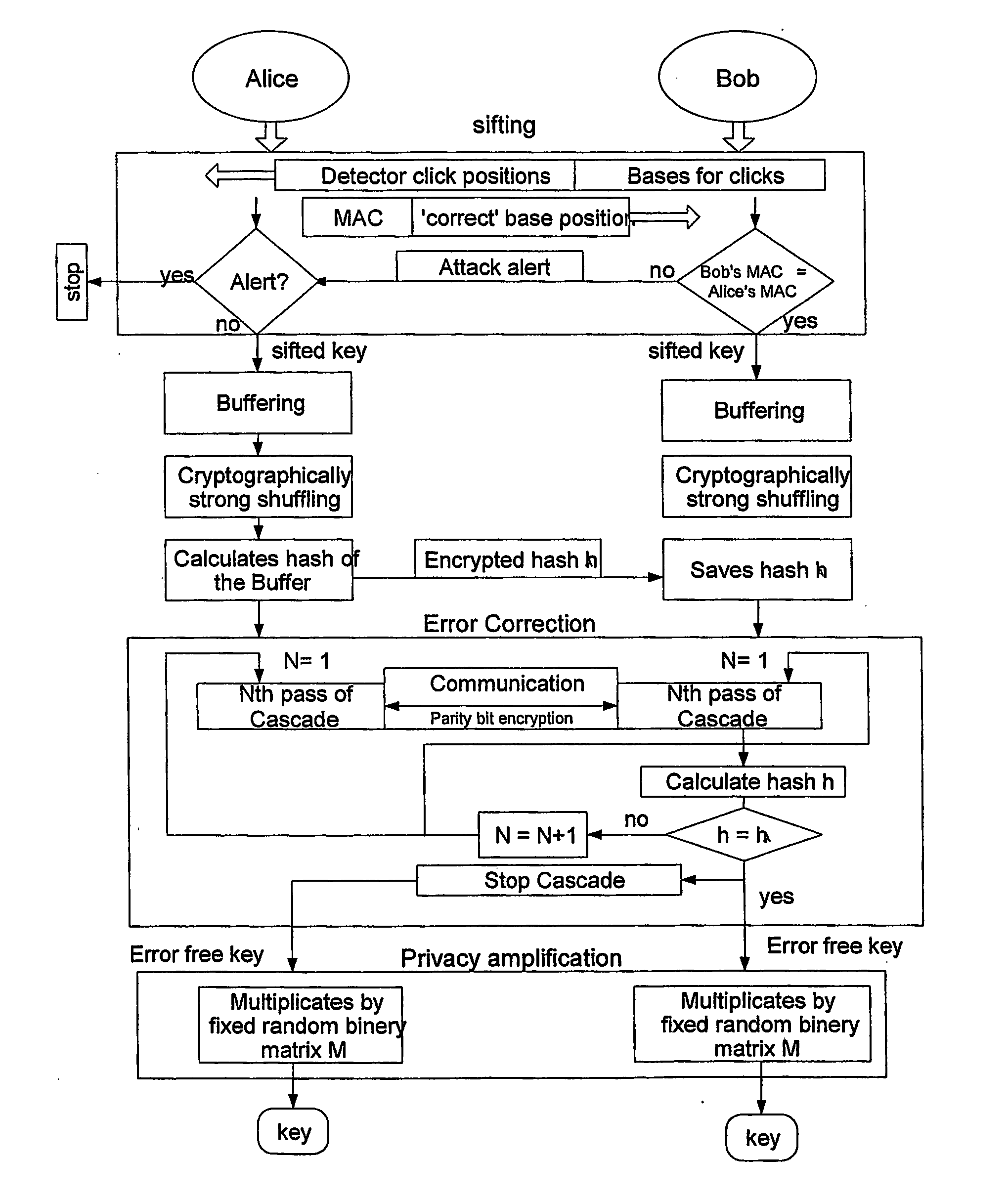
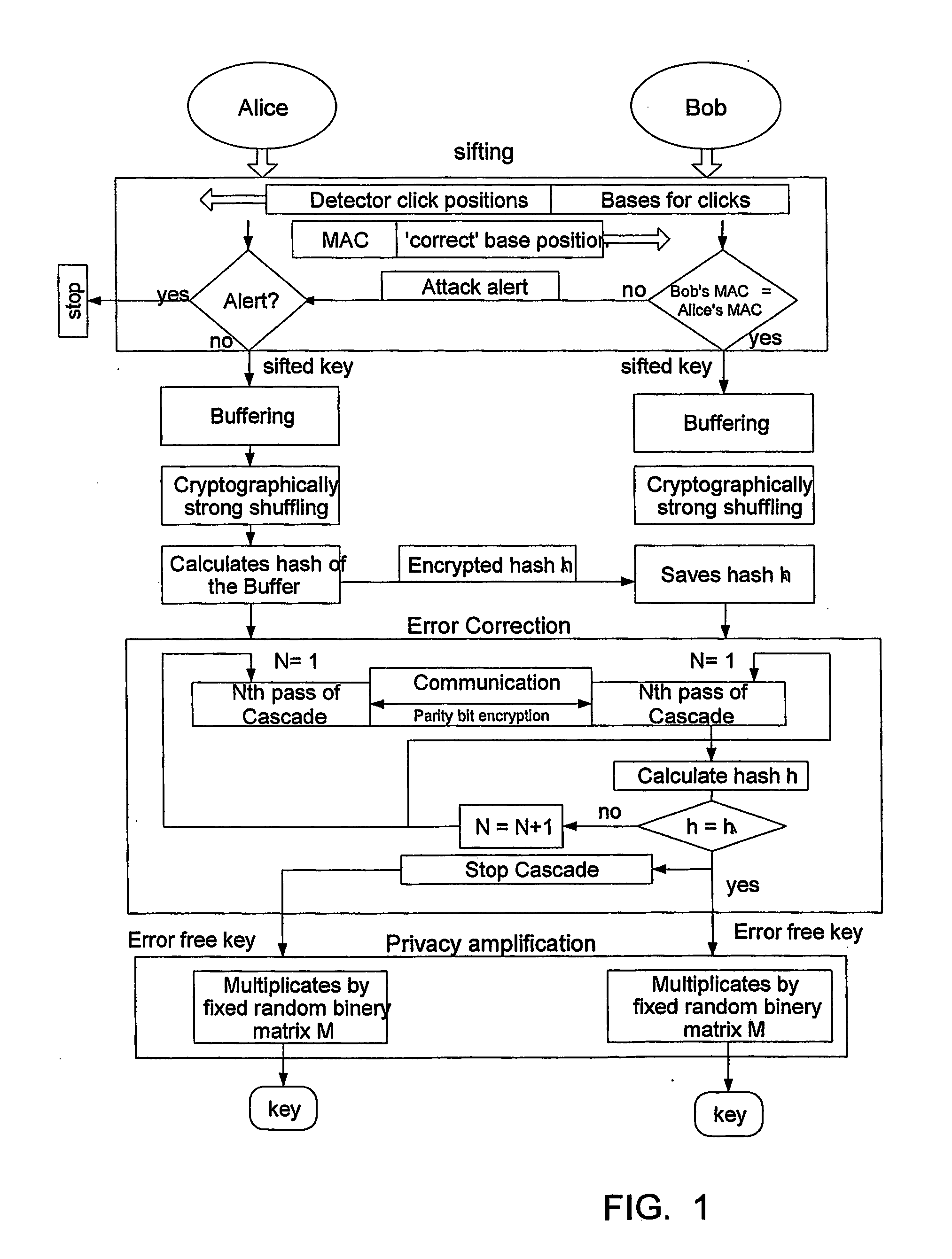
Qkd with classical bit encryption
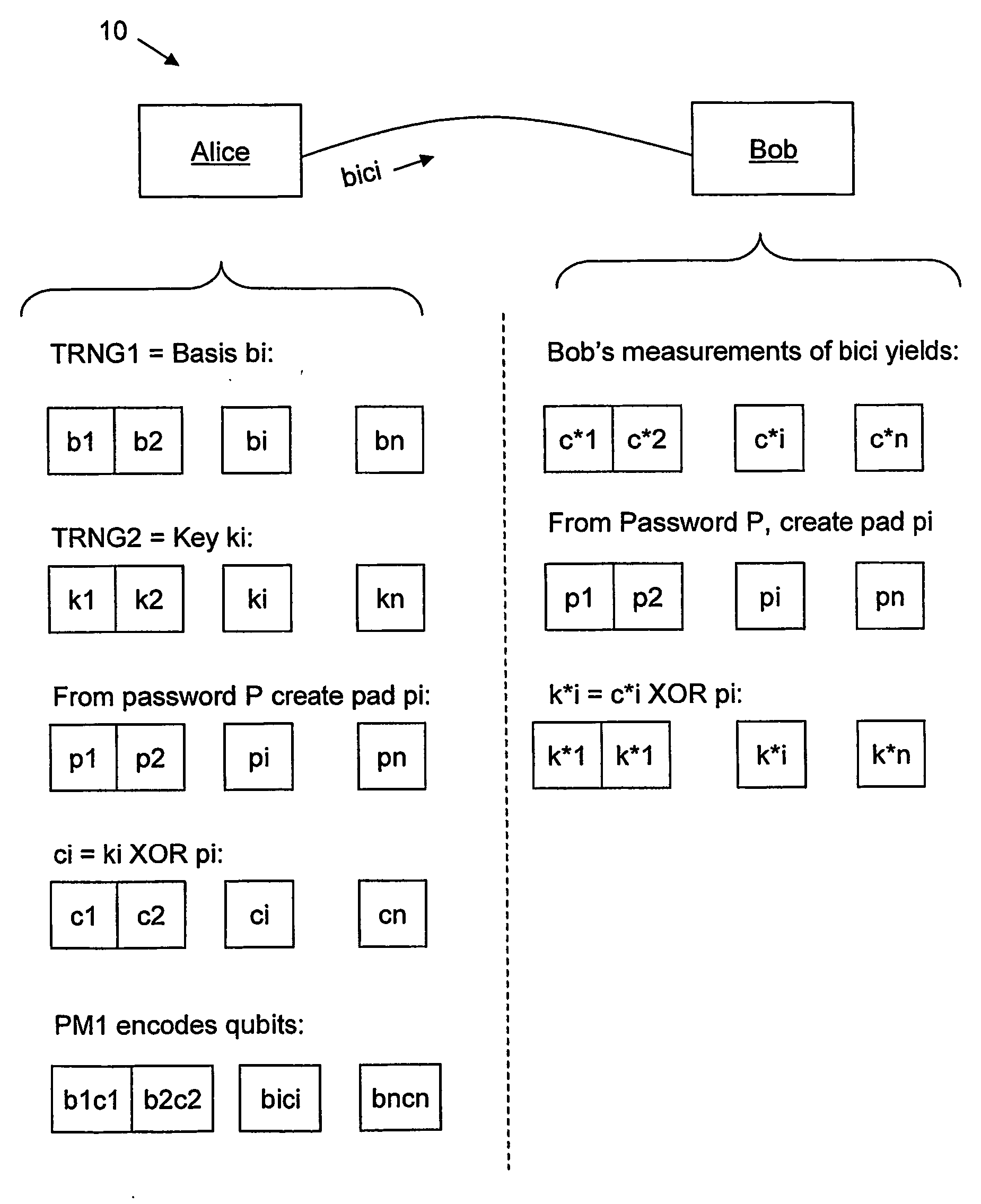
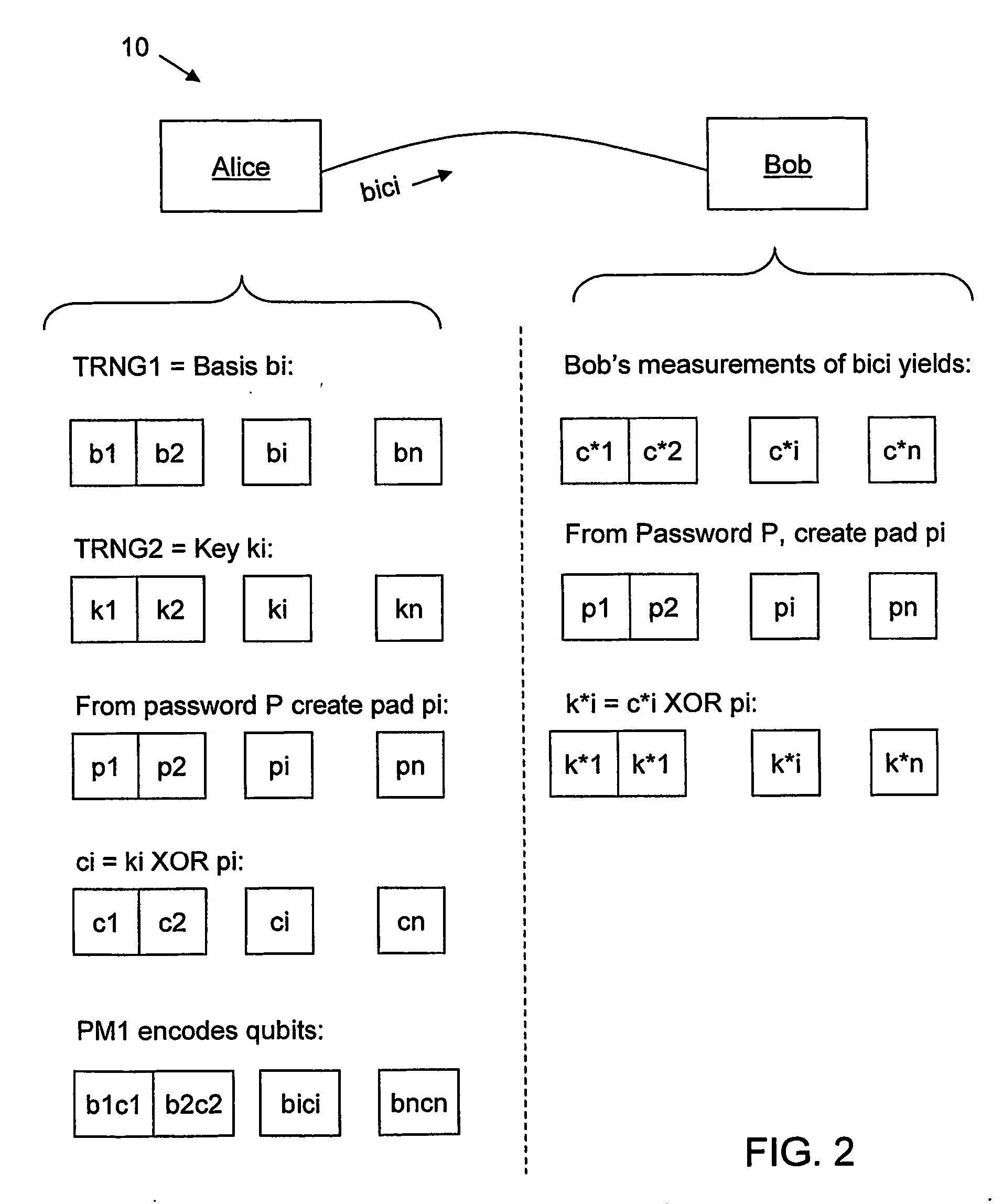
InactiveUS20070140495A1Key distribution for secure communicationData stream serial/continuous modificationComputer hardwareAlice and Bob
A method for enhancing the security of a quantum key distribution (QKD) system having QKD stations Alice and Bob. The method includes encrypting key bits generated by a true random number generator (TRNG) and sent to a polarization or phase modulator to encode weak optical pulses as qubits to be shared between Alice and Bob. Key bit encryption is achieved by using a shared password and a stream cipher. Bob obtains at least a subset of the original key bits used by Alice by utilizing the same stream cipher and the shared password.
Owner:MAGIQ TECH INC
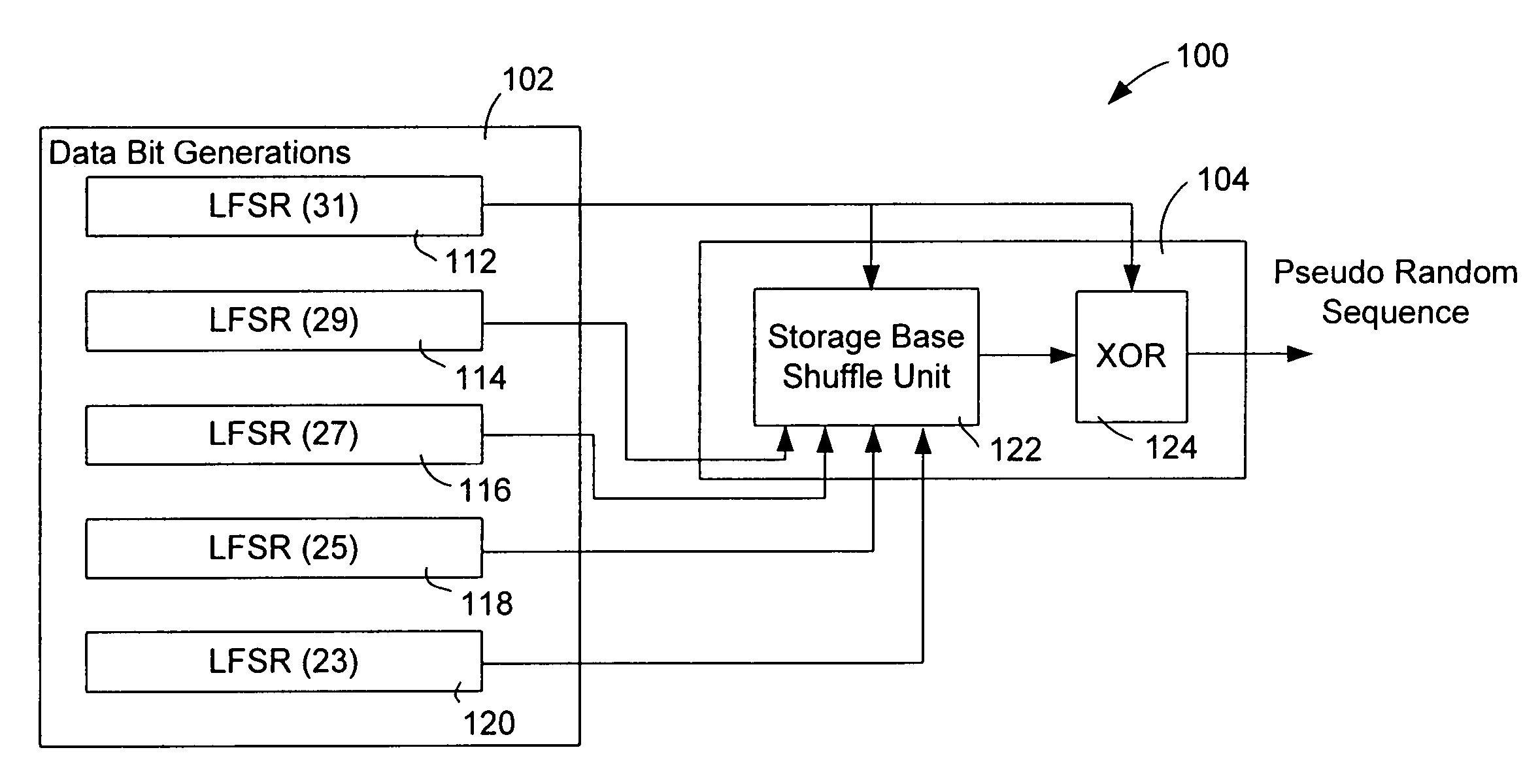
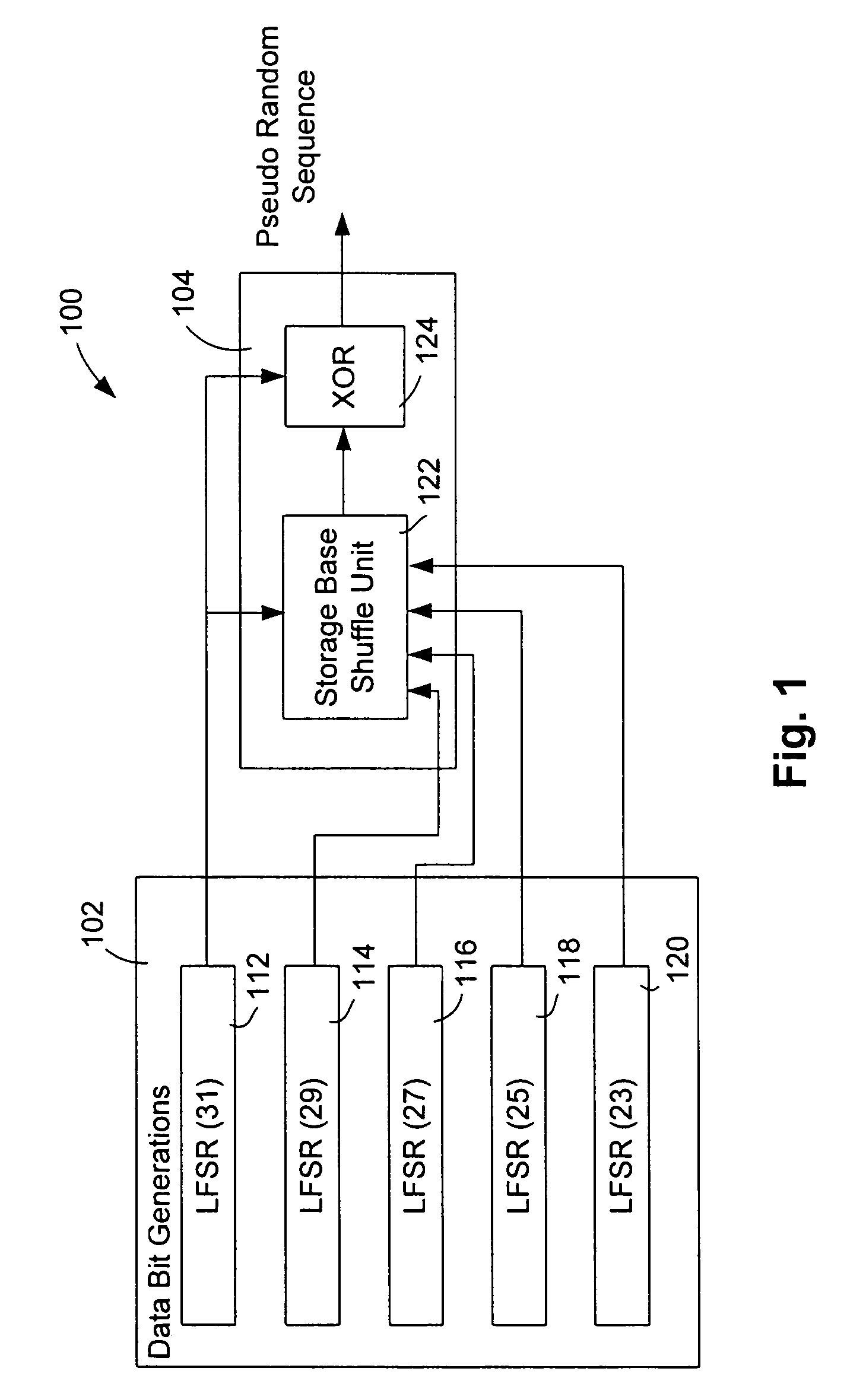
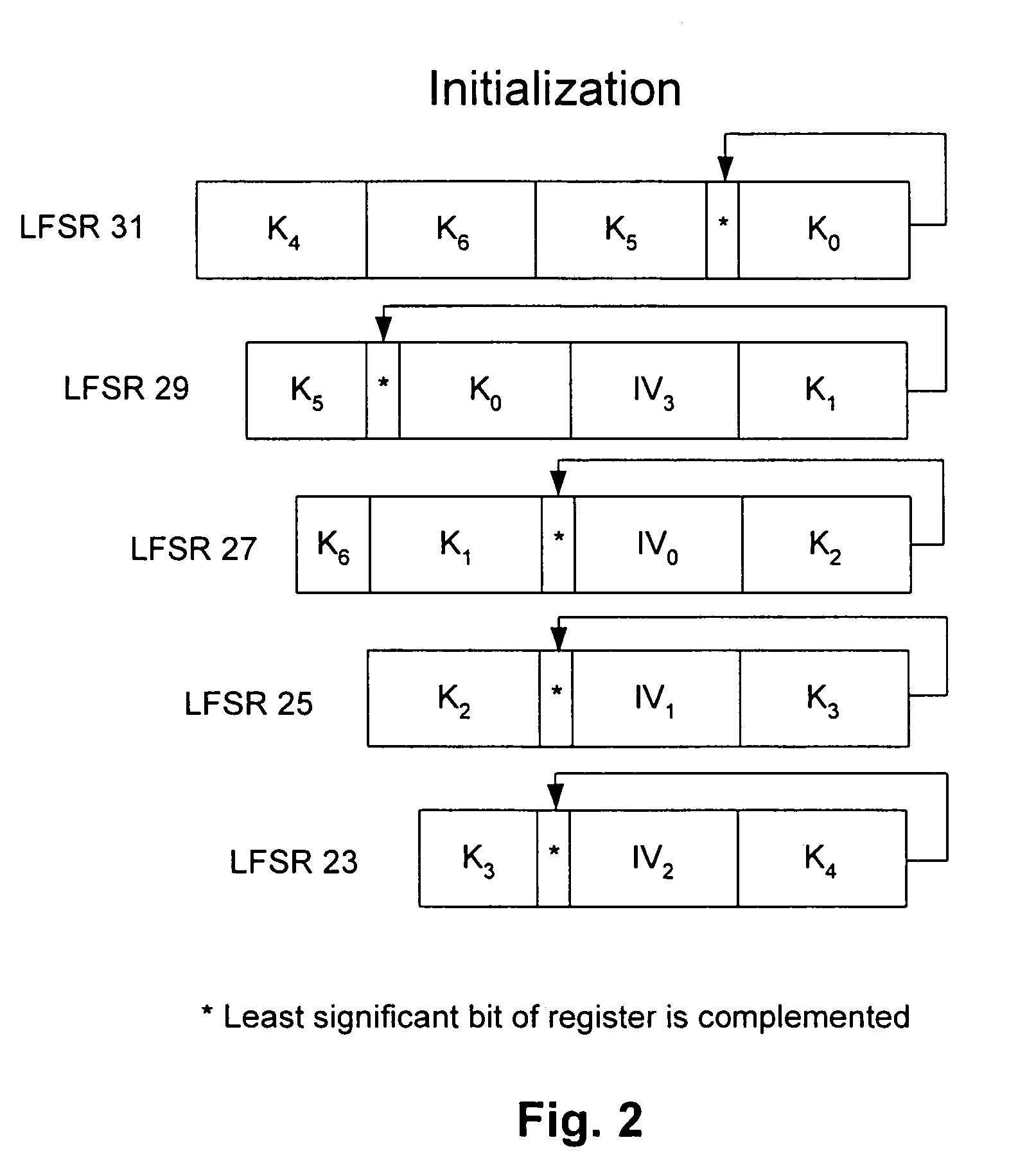
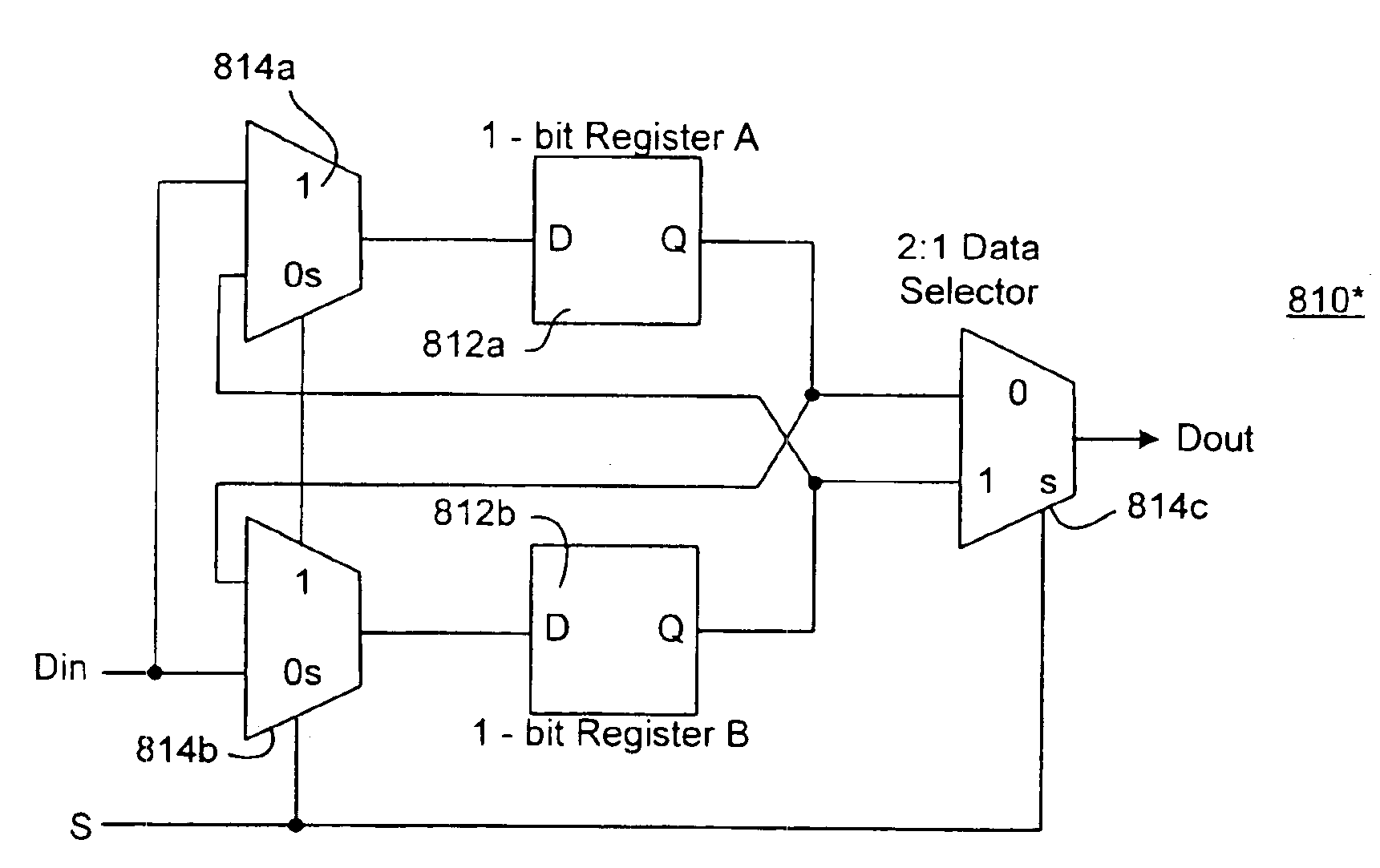
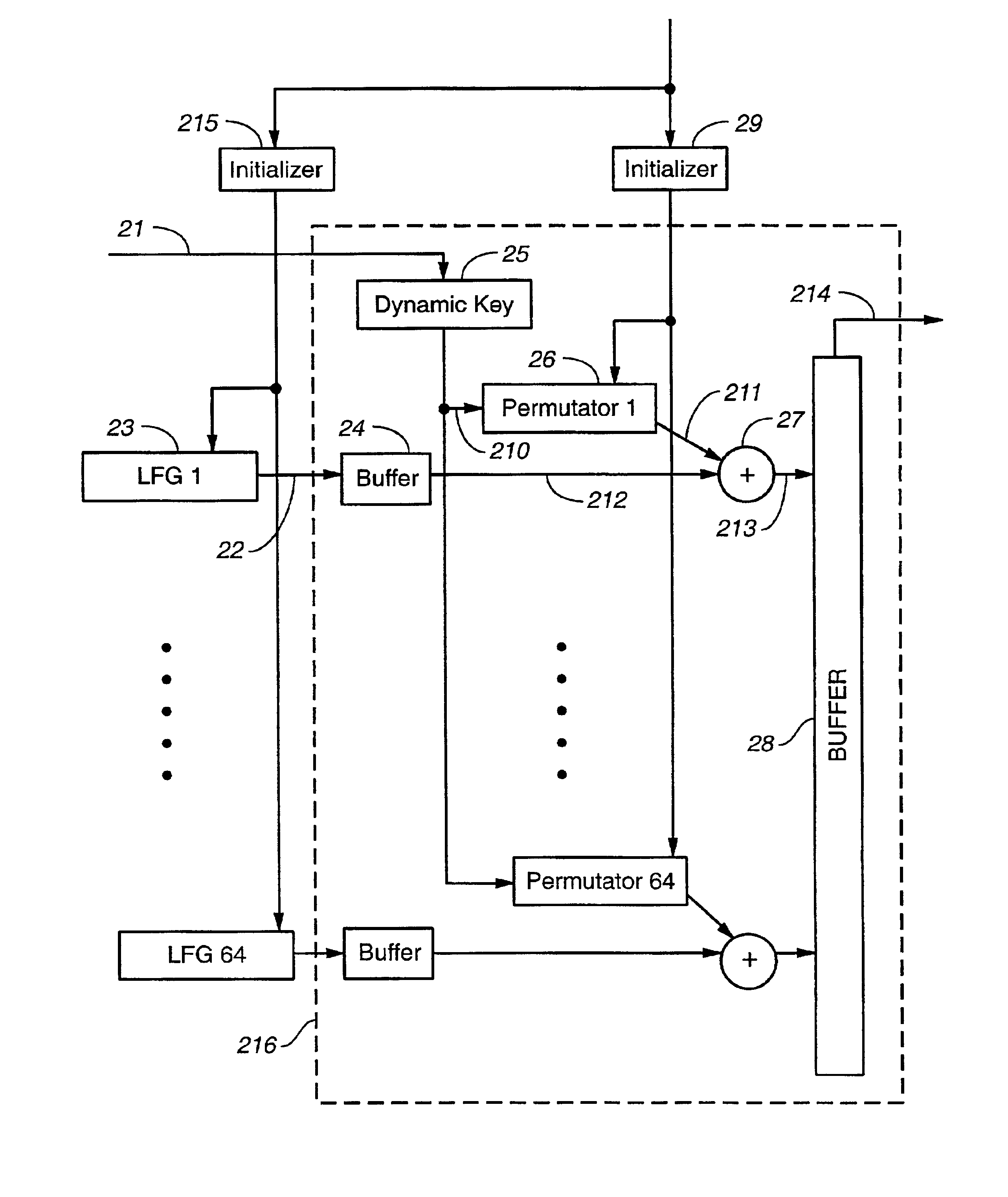
Stream cipher having a combiner function with storage based shuffle unit
A stream cipher is provided with a first and a second data bit generators to generate in parallel a first and a second stream of data bits. The stream cipher is further provided with a combiner function having a shuffling unit including a storage structure to generate a pseudo random sequence, by combining the first stream of data bits with at least stochastically generated past values of the first streams of data bits, generated by using the second stream of data bits to stochastically operate the storage structure of the shuffle unit to memorize and reproduce the data bits of the first stream.
Owner:INTEL CORP
Stream cipher encryption application accelerator and methods thereof
InactiveUS20020037079A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCryptographic acceleratorByte
A system for encrypting and decrypting data formed of a number of bytes using the ARCFOUR encryption algorithm is disclosed. The system includes a system bus and an encryption accelerator arranged to execute the encryption algorithm coupled to the system bus. A system memory coupled to the system bus arranged to store a secret key array associated with the data and a central processing unit coupled to the system bus wherein encryption accelerator uses substantially no central processing unit resources to execute the encryption algorithm.
Owner:AVAGO TECH INT SALES PTE LTD
Stream cipher having a shuffle network combiner function
InactiveUS6947558B1Data stream serial/continuous modificationSecret communicationControl signalStream cipher
A stream cipher is provided with one or more data bit generators to generate a first, second and third set of data bits. The stream cipher is further provided with a combiner function having a network of shuffle units to combine the third set of data bits, using the first and second sets of data bits as first input data bits and control signals respectively of the network of shuffle units. In one embodiment, the shuffle units are binary shuffle units and they are serially coupled to one another.
Owner:INTEL CORP
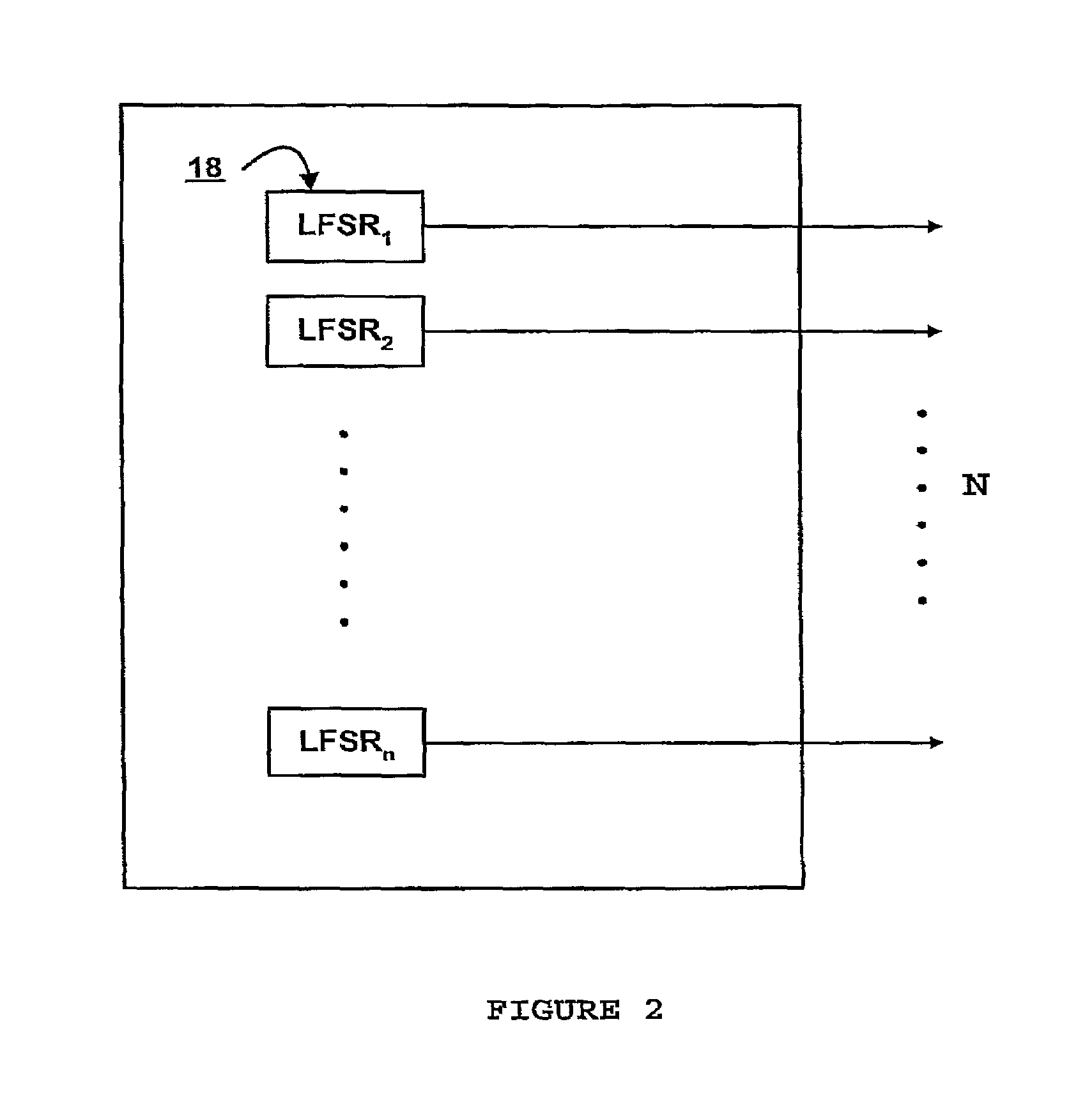
Sequence generator and method of generating a pseudo random sequence
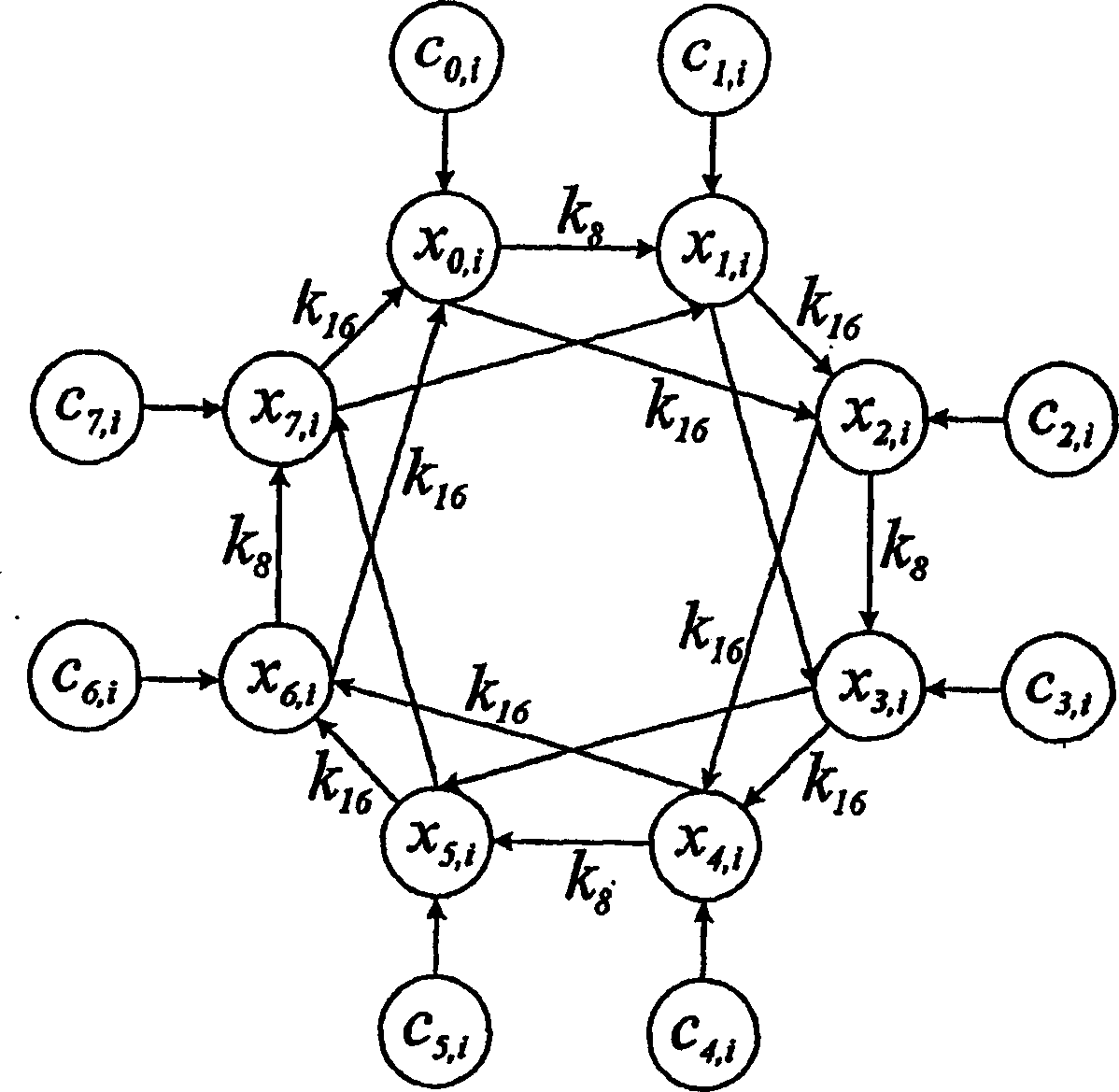
InactiveUS7142675B2Increased complexityRandom number generatorsEncryption apparatus with shift registers/memoriesLinear feedback shift registerNon linear functions
A sequence generator for generating a pseudo random sequence for random number generation or a stream cipher engine includes a plurality of linear feedback shift registers operable to generate a plurality of binary sequences. A plurality of nonlinear functions having the binary sequences as their input and operable to generate a second plurality of binary sequences. There are at least two switches and a controller including a shift register operable to control said first and second switches. The first switch is operative to select one of the second plurality of binary sequences to the first bit of the shift register, and the second switch is operative to select one of said second plurality of binary sequences to the output of the sequence generator.
Owner:INTELLECTUAL VENTURES II
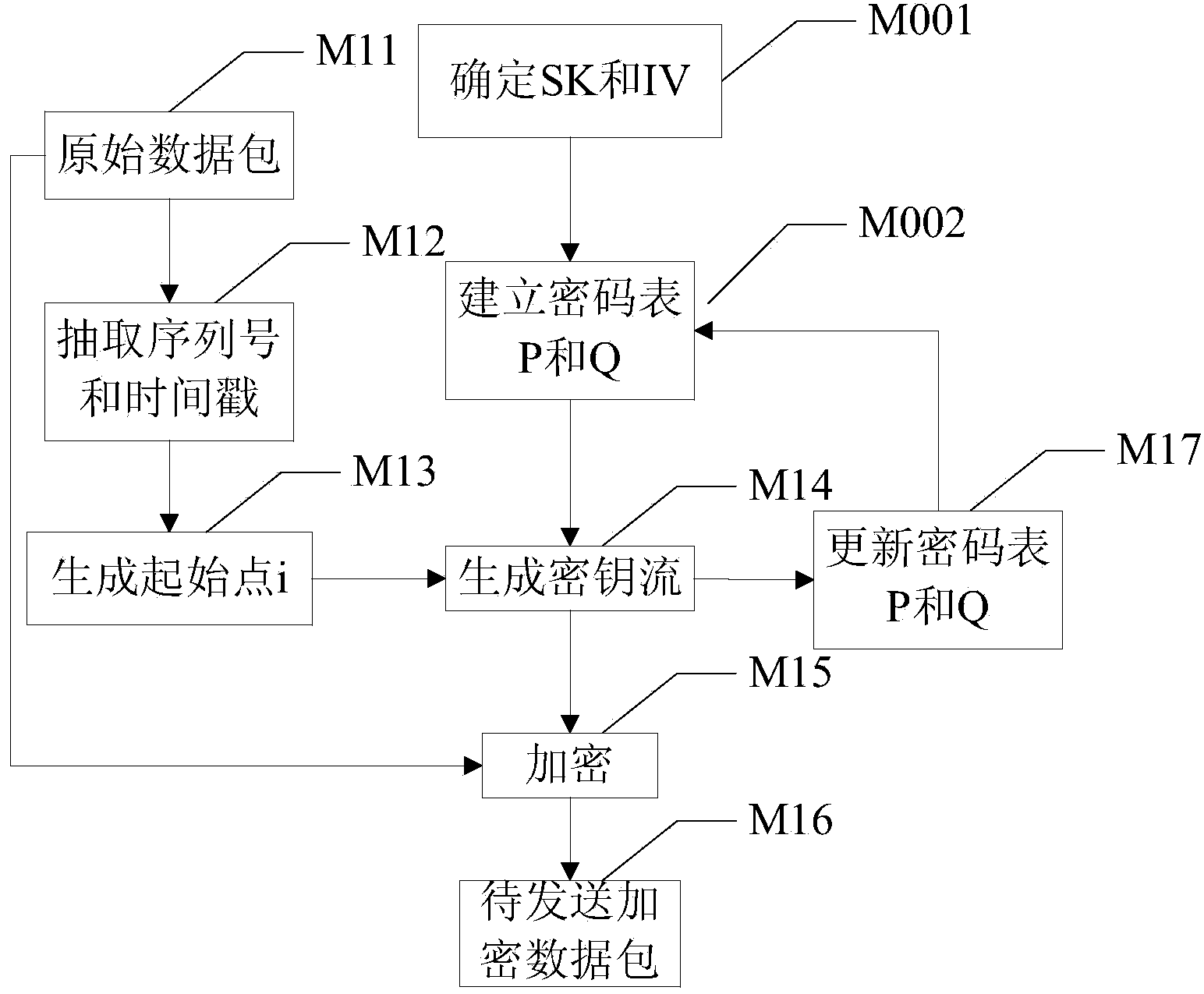
Encryption-decryption method and terminal of data pack based on network transmission
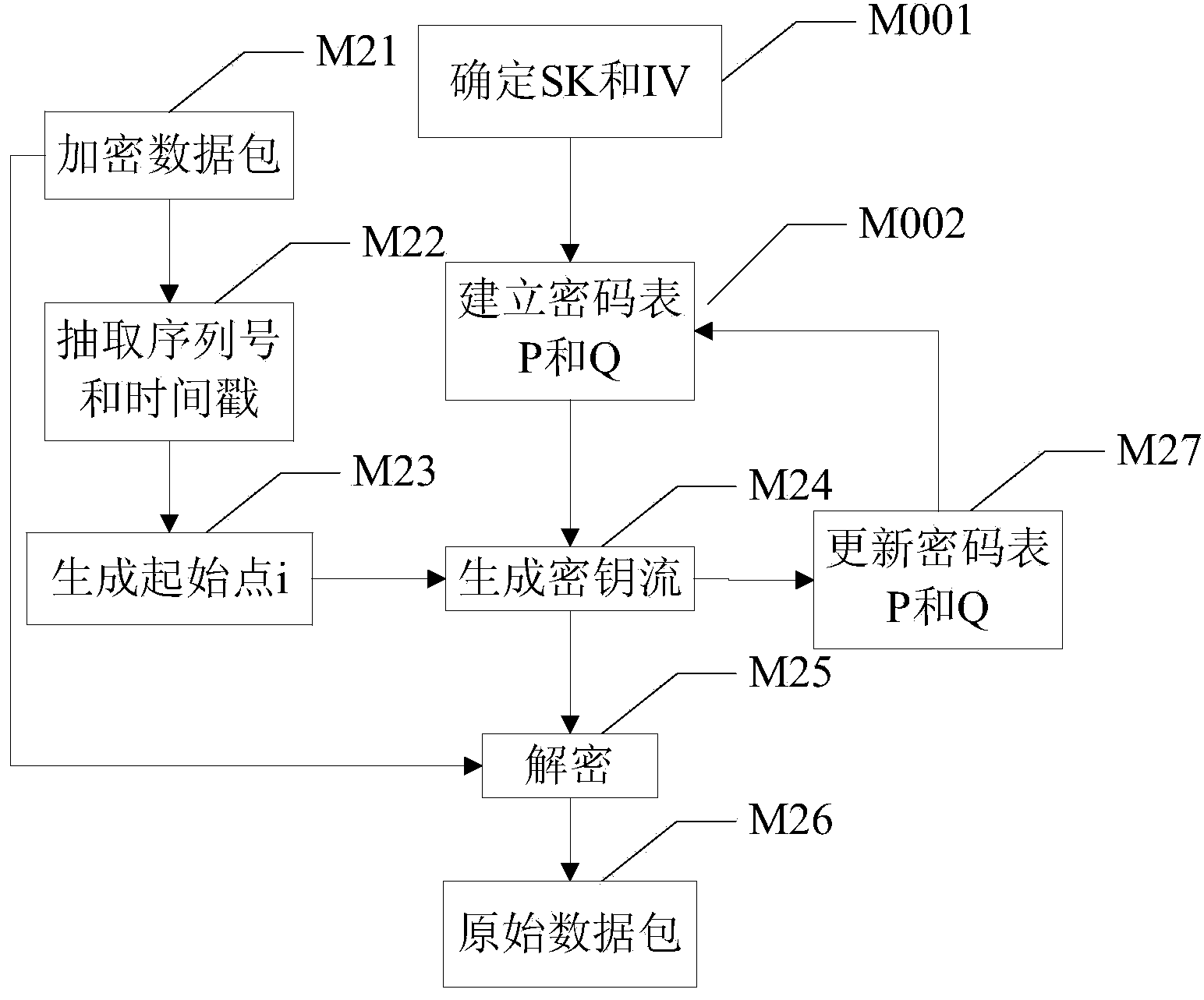
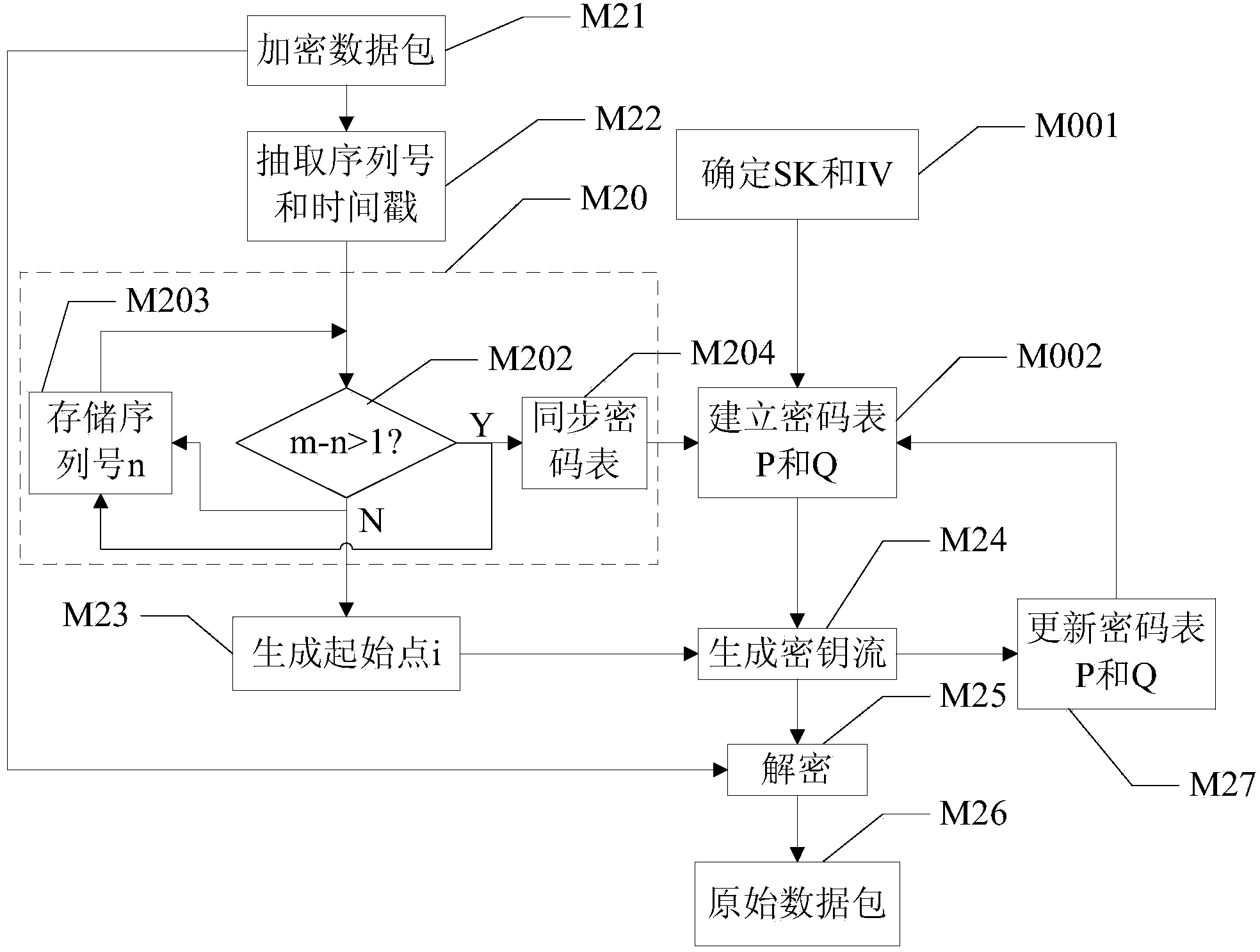
ActiveCN103684787AAvoid pitfalls that increase network trafficImprove securityUser identity/authority verificationTraffic capacityNetwork packet
The invention discloses an encryption-decryption method and terminal of a data pack based on network transmission. A terminal-to-terminal real-time encryption method based on a stream cipher algorithm is used, both sides of communication carry out negotiation on session parameters at an initial session stage, and cipher tables are established respectively. A sending side extracts data pack head information, a key stream starting point is generated, and according to the cipher tables and the starting point, a section of key stream is generated to encrypt data pack load. A receiving side judges whether network pack loss exists according to the data pack head information, when network pack loss exists, the receiving side completes cipher table synchronization at first, and then based on the updated cipher tables and the starting point, a synchronous key is generated to decrypt data pack load. On the basis that extra network communication flow is not increased and the key stream is generated on line in real time, the real-time encryption technology with key self-synchronizing function under the network condition that pack loss exists is achieved.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Method for improving unpredictability of output of pseudo-random number generators
InactiveCN1668995AGood bit mixingImprove unpredictabilityRandom number generatorsChaos modelsData setTheoretical computer science
A method for performing computations in a mathematical system which exhibits a positive lyapunov exponent, or exhibits chaotic behavior, comprises varying a parameter of the system. When employed in cryptography, such as, e.g., in a pseudo-random number generator of a stream-cipher algorithm, in a block-cipher system or a HASH / MAC system, unpredictability may be improved. In a similar system, a computational method comprises multiphying two numbers and manipulating at least one of the most significant bits of the number resulting from the multiplication to produce an output. A number derived from a division of two numbers may be used for deriving an output. In a system for generating a sequence of numbers, an array of counters is updated at each computational step, whereby a carry value is added to each counter. Fixed-point arithmetic may be employed. A method of determining an identification value and for concurrently encrypting and / or decrypting a set of data is disclosed.
Owner:克瑞迪科公司
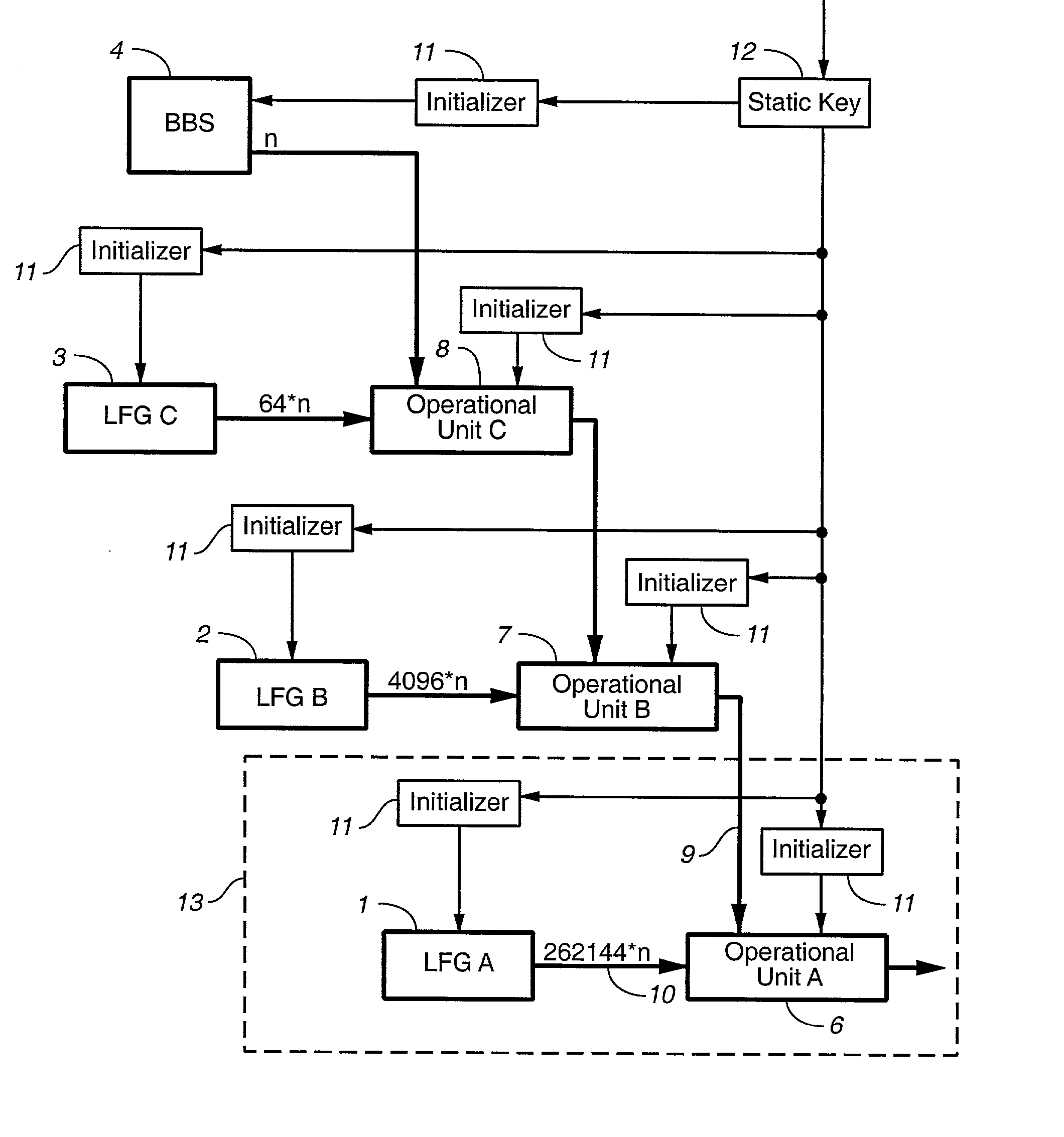
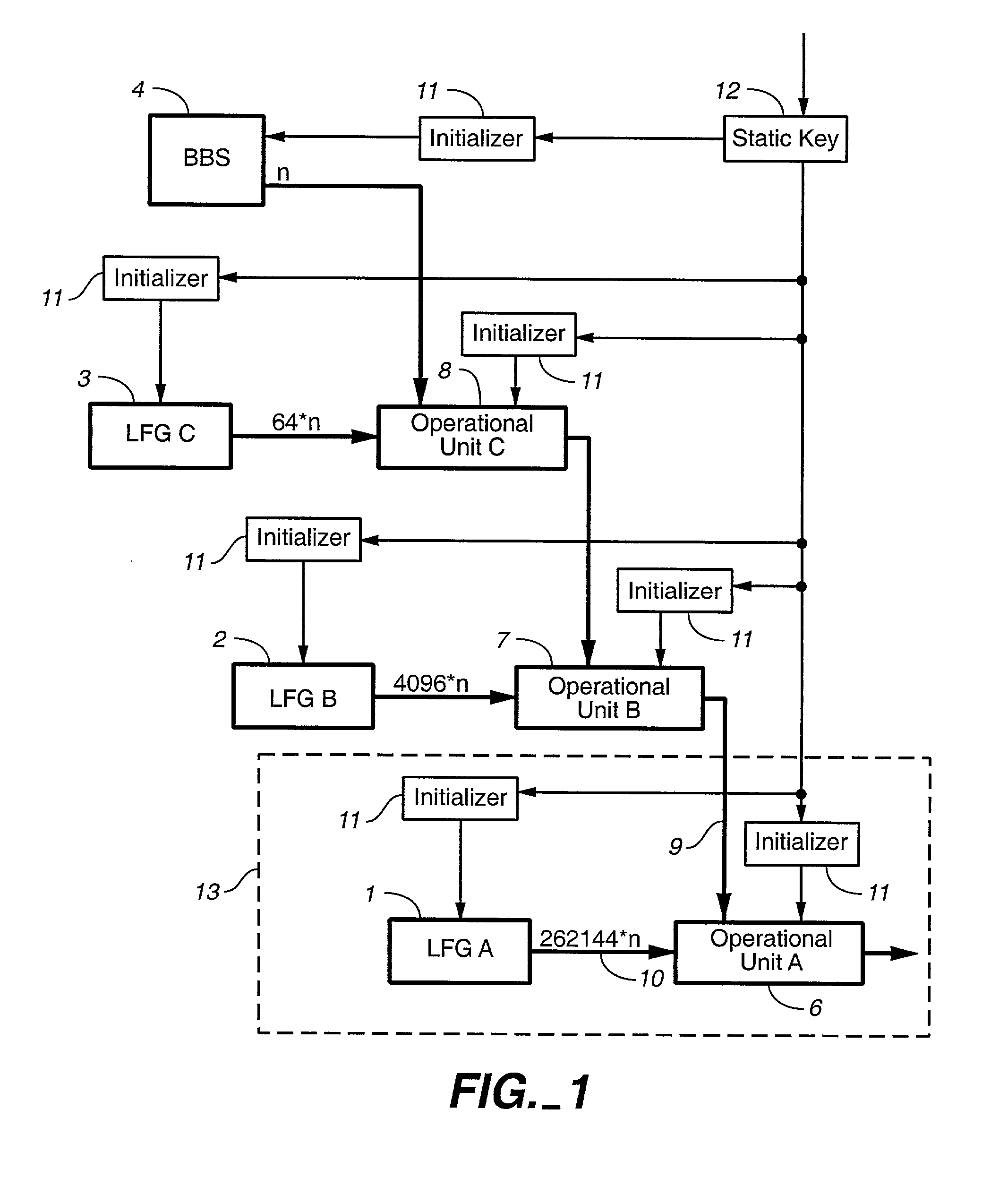
Cascaded stream cipher
ActiveUS20020054679A1Random number generatorsSecret communicationNumber generatorPseudo random number generation
A pseudo-random number generating circuit and method, comprising: a plurality of pseudo-random number generator (PRNG) units combined in a cascade structure of several layers to produce a pseudo-random output stream, the PRNG units of any given layer running more slowly than those PRNG units of more downstream layers of the cascade structure and running more quickly than those PRNG units of more upstream layers of the cascade structure, the PRNG units including a relatively slow but cryptographically very secure PRNG unit feeding the most upstream layer of the cascade structure, and very fast, but possibly cryptographically insecure PRNG unit at the most downstream layer.
Owner:VESELY IVAN
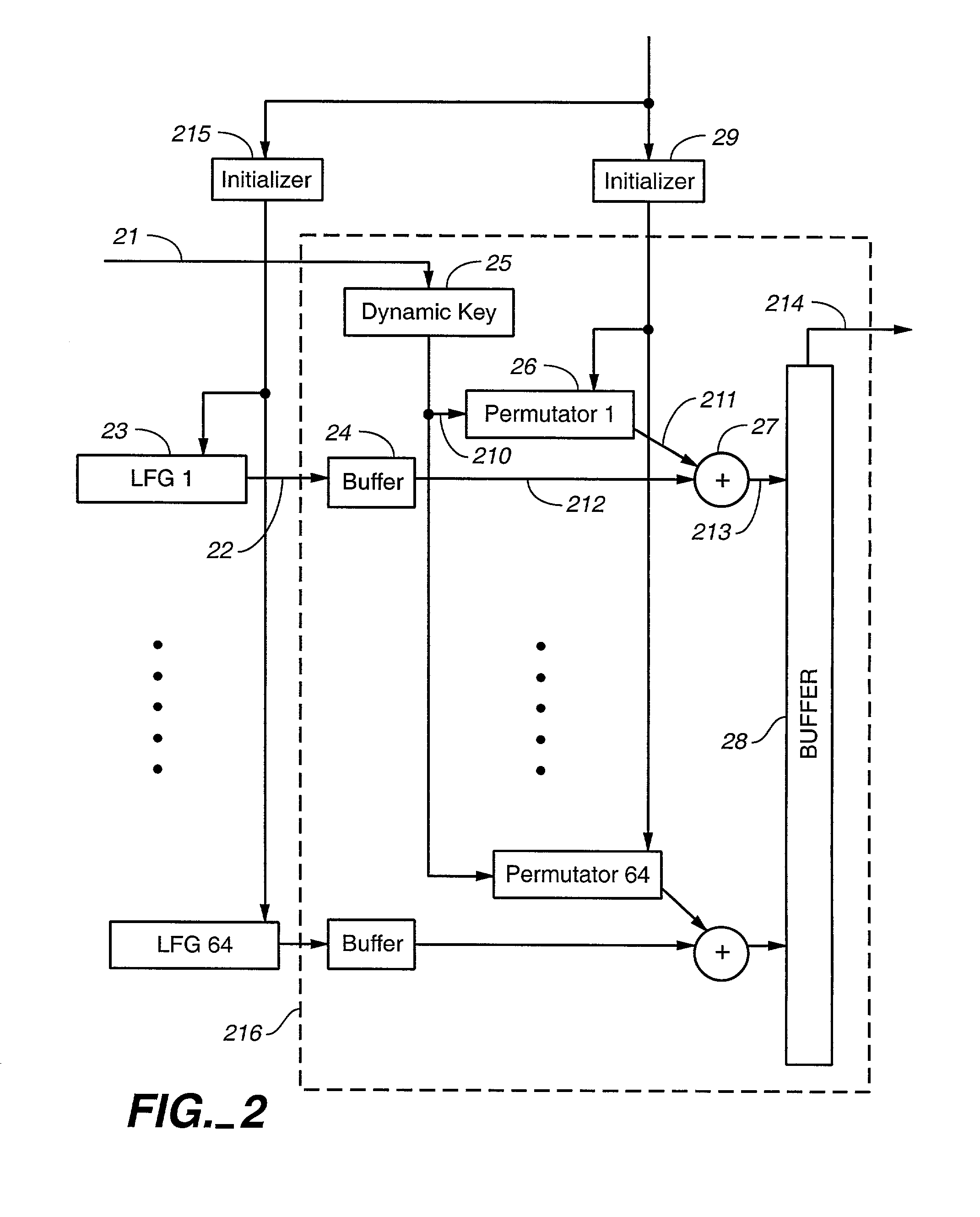
Pseudorandom number generator for a stream cipher
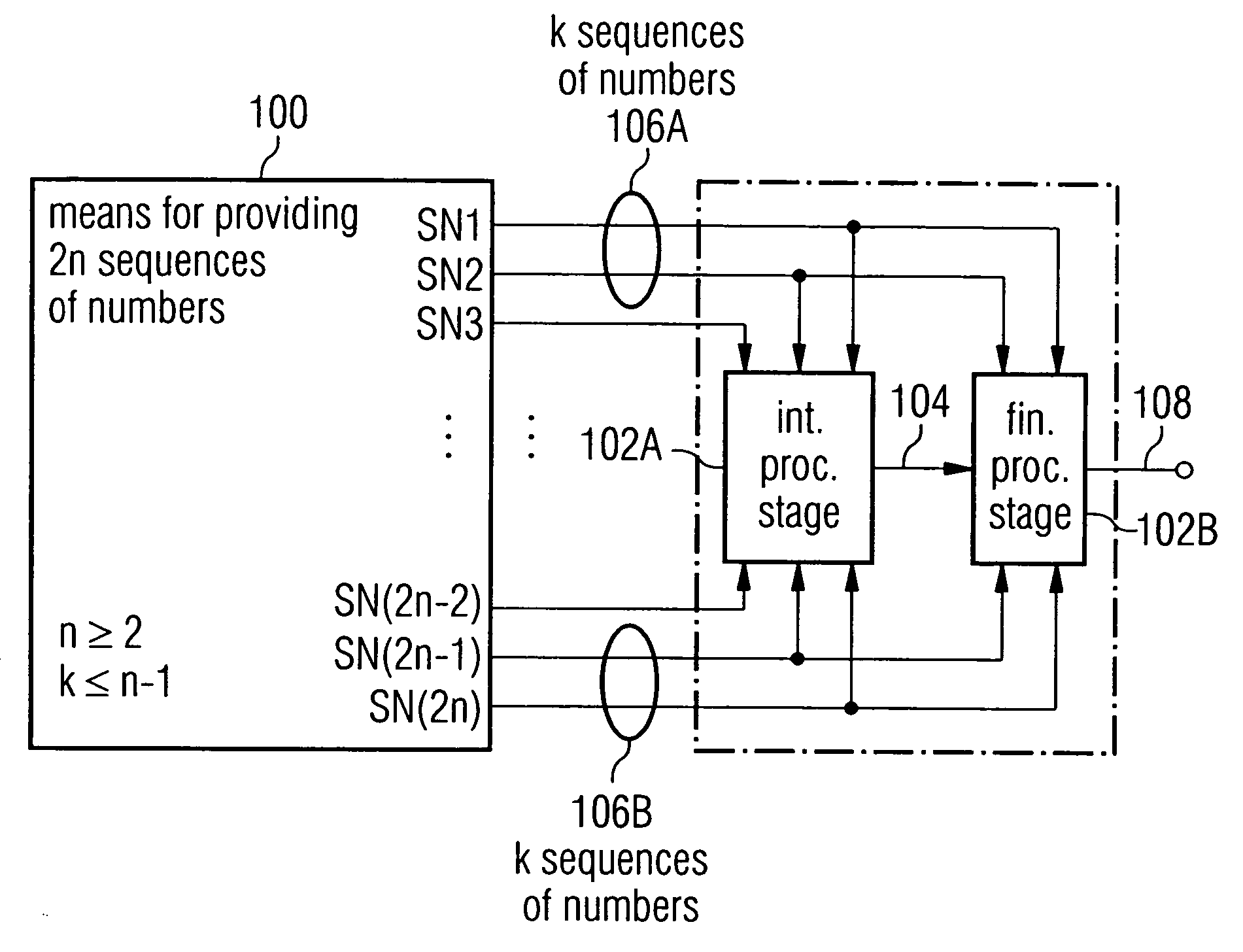
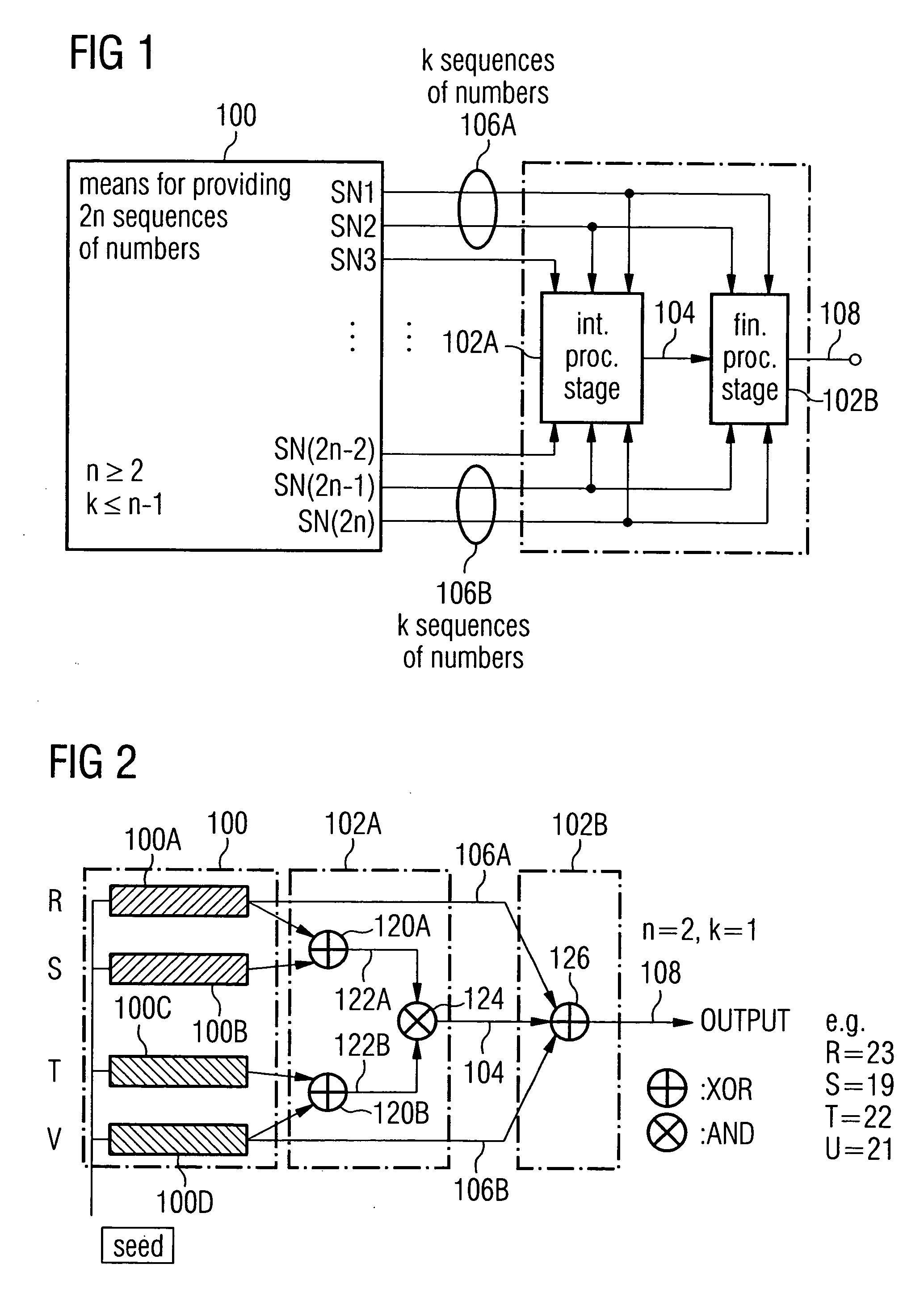
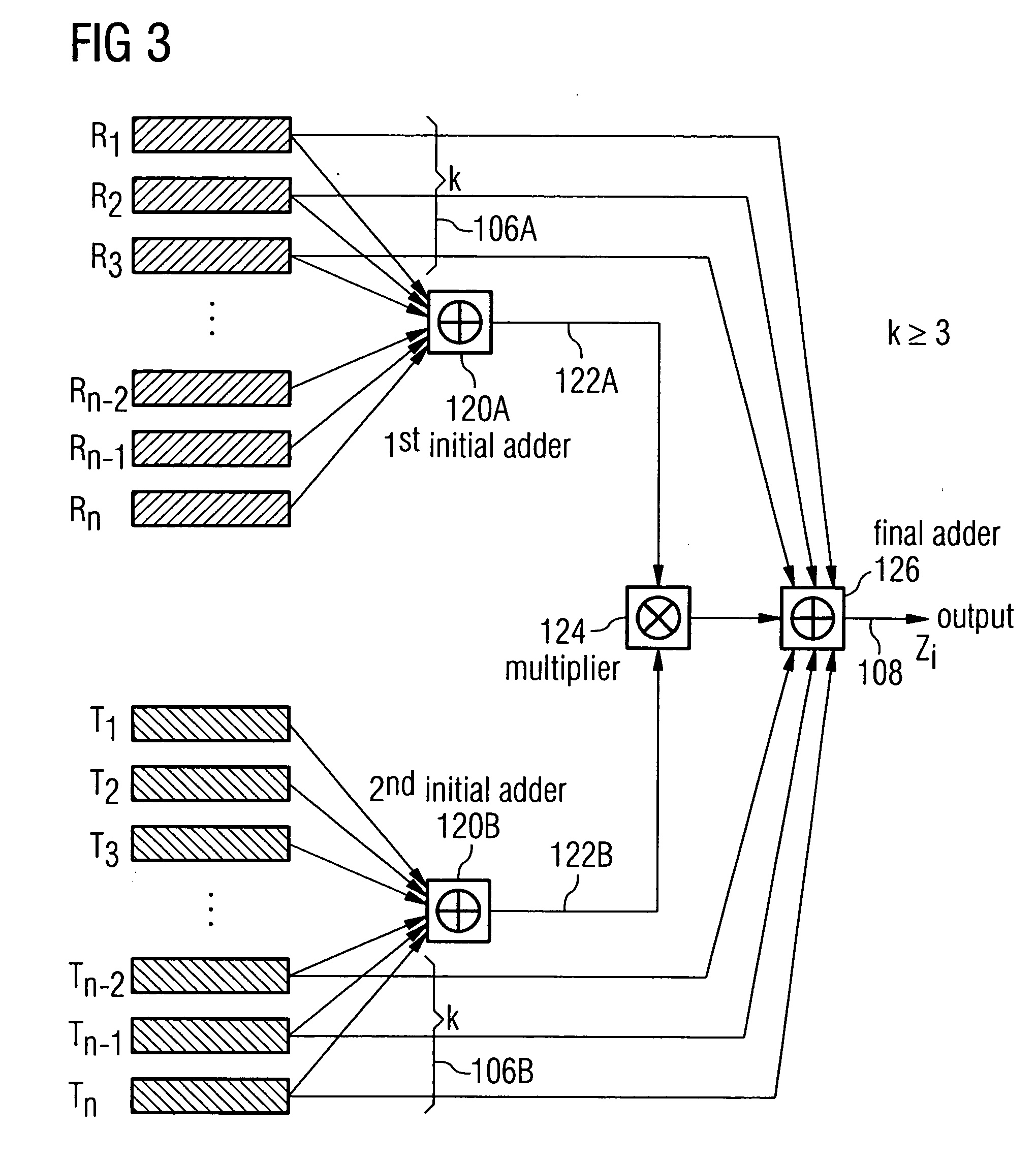
ActiveUS20050120065A1Random number generatorsSecuring communicationStream cipherPseudorandom generator
A pseudorandom number generator includes a unit for providing a number of 2n sequences of numbers, n being greater than or equal to 2. The sequences of numbers are combined by a unit such that at first all the sequences of numbers are combined with one another in an intermediate processing stage to obtain an intermediate processing sequence, and that subsequently a subgroup of k sequences of numbers is combined with the intermediate processing sequence in a final processing stage to obtain the output sequence.
Owner:INFINEON TECH AG
Cascaded stream cipher
InactiveUS6961426B2Random number generatorsSecret communicationPseudo random number generationNumber generator
Owner:VESELY IVAN
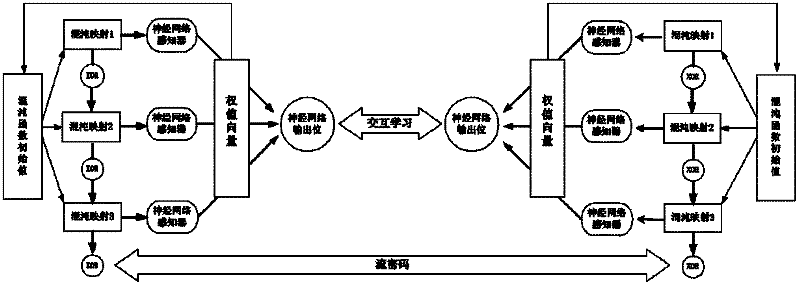
A Stream Cipher Key Control Method Fused with Neural Network and Chaotic Map
ActiveCN102263636AImprove security featuresImprove securityKey distribution for secure communicationKey generatorComputer science
The invention provides a stream cipher key control method for fusing a neural network with chaotic mappings. A sending party and a receiving party are configured to have neural network weight synchronization models with same parameters and three chaotic mapping functions with the same initial value, and the sending party and the receiving party are set to have the same initial value of the chaotic functions. The method comprises the following steps: (1) determining a hybrid stream key generator based on three chaotic mappings; and (2) realizing a chaotic function initial value update mechanism based on neural network weight synchronization. The method provided by the invention can be used for updating the chaotic initial values and strengthening the safe application of stream ciphers.
Owner:ZHEJIANG UNIV OF TECH
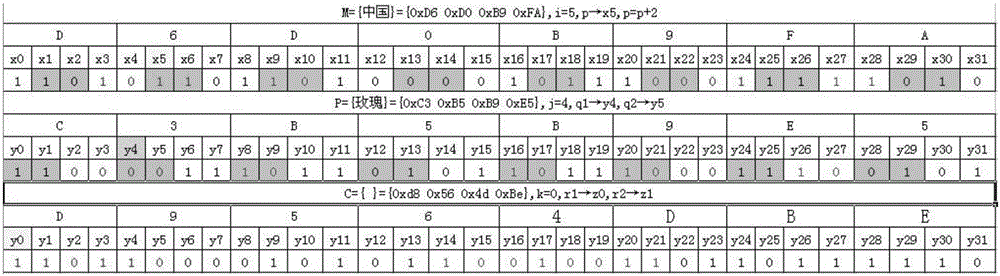
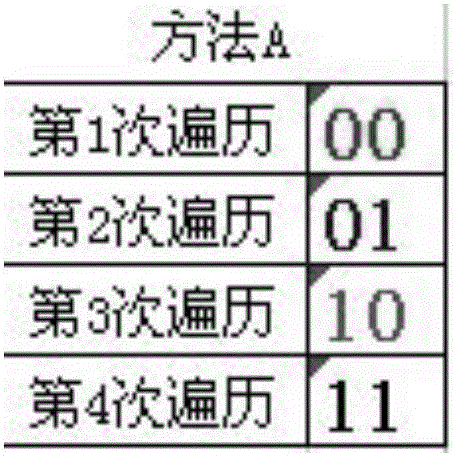
Double-bit unidirectional circular linked list encryption and decryption method based on stream ciphers
InactiveCN105959118ASimple methodDifficult to decipherMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesRound complexityCiphertext
The stream cipher-based double-bit one-way circular linked list encryption and decryption method of the present invention includes: opening up memory space, performing initialization and setting values for setting; generating corresponding first pointers and second pointers; running an algorithm program to perform the first The pointer and the second pointer are shifted and read; the first pointer and the second pointer are traversed through the one-way circular linked list four times, and the ciphertext file is obtained according to the XOR result of the character bits pointed to by the first pointer and the second pointer. The decryption scheme of the present invention is consistent with the encryption method. The beneficial effects of the invention are: it is extremely difficult to decipher, easy to implement, and the security system is more secure. This encryption method is out-of-order encryption, which can be transmitted in the existing and open communication channels; it does not need auxiliary hardware equipment, and is completely realized by software; the key byte can be of any length, with the length of the key byte As it increases, its encryption complexity also increases.
Owner:JILIN UNIV
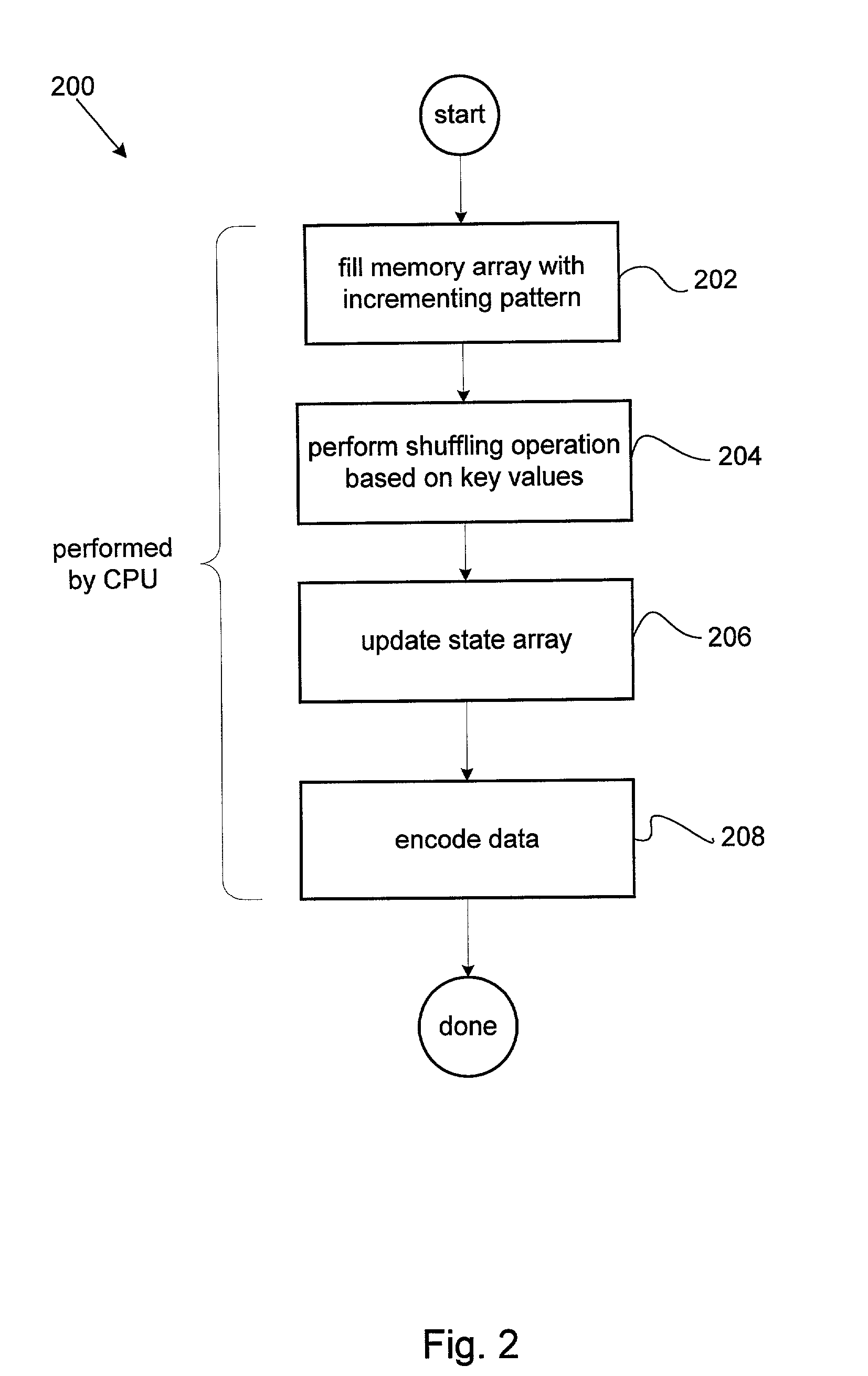
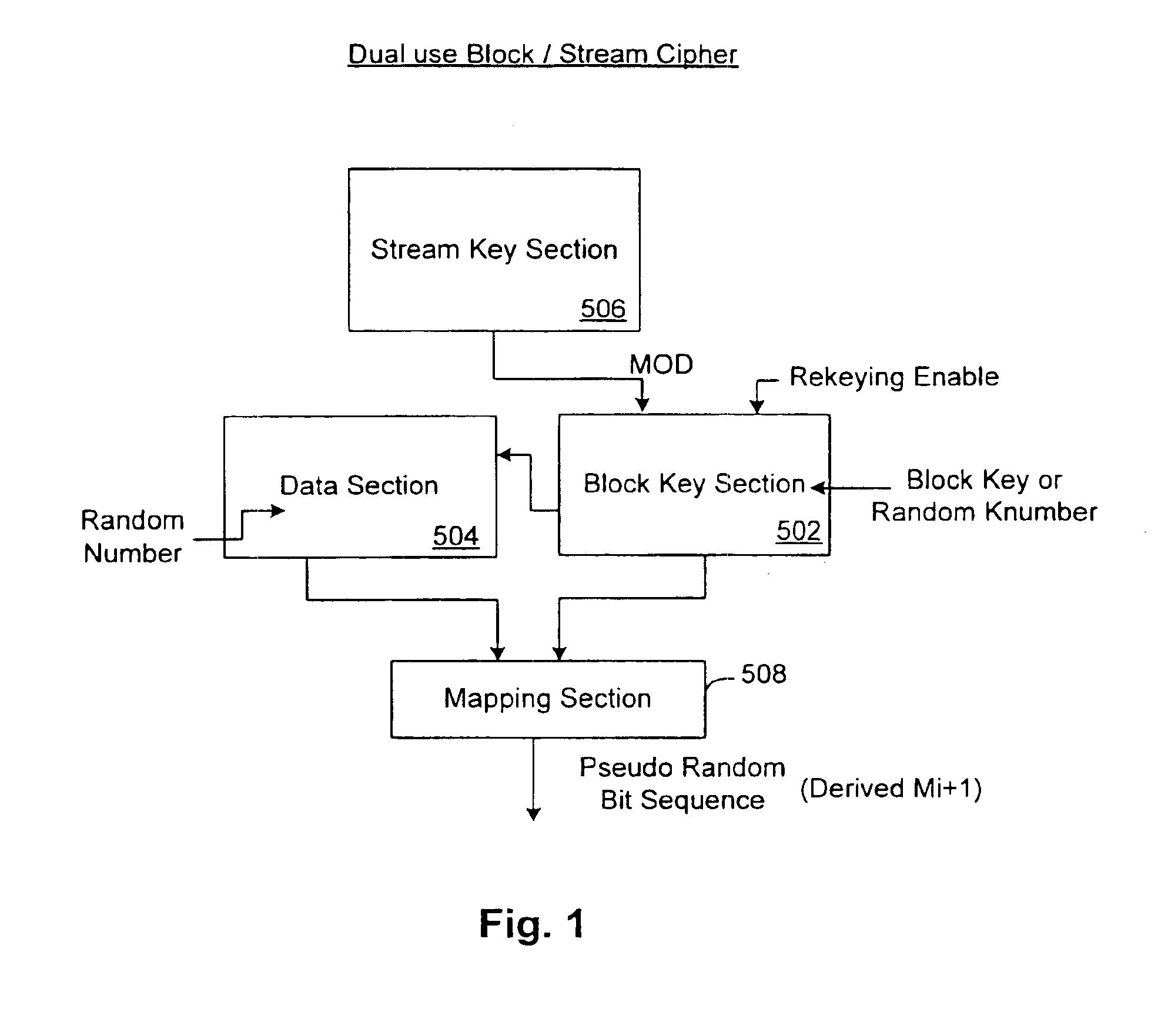
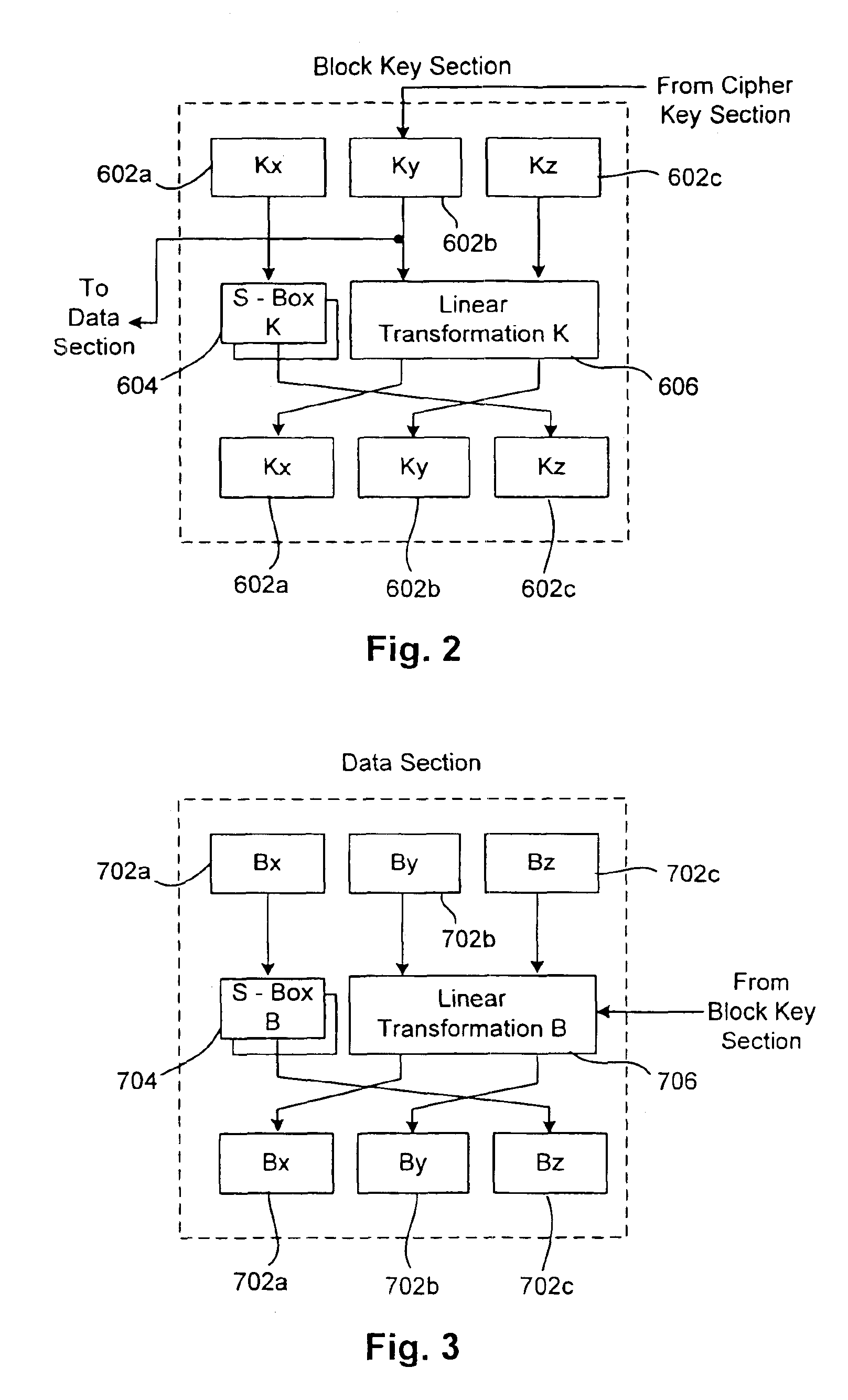
Dual use block/stream cipher
InactiveUS7068786B1Random number generatorsData stream serial/continuous modificationComputer hardwarePlain text
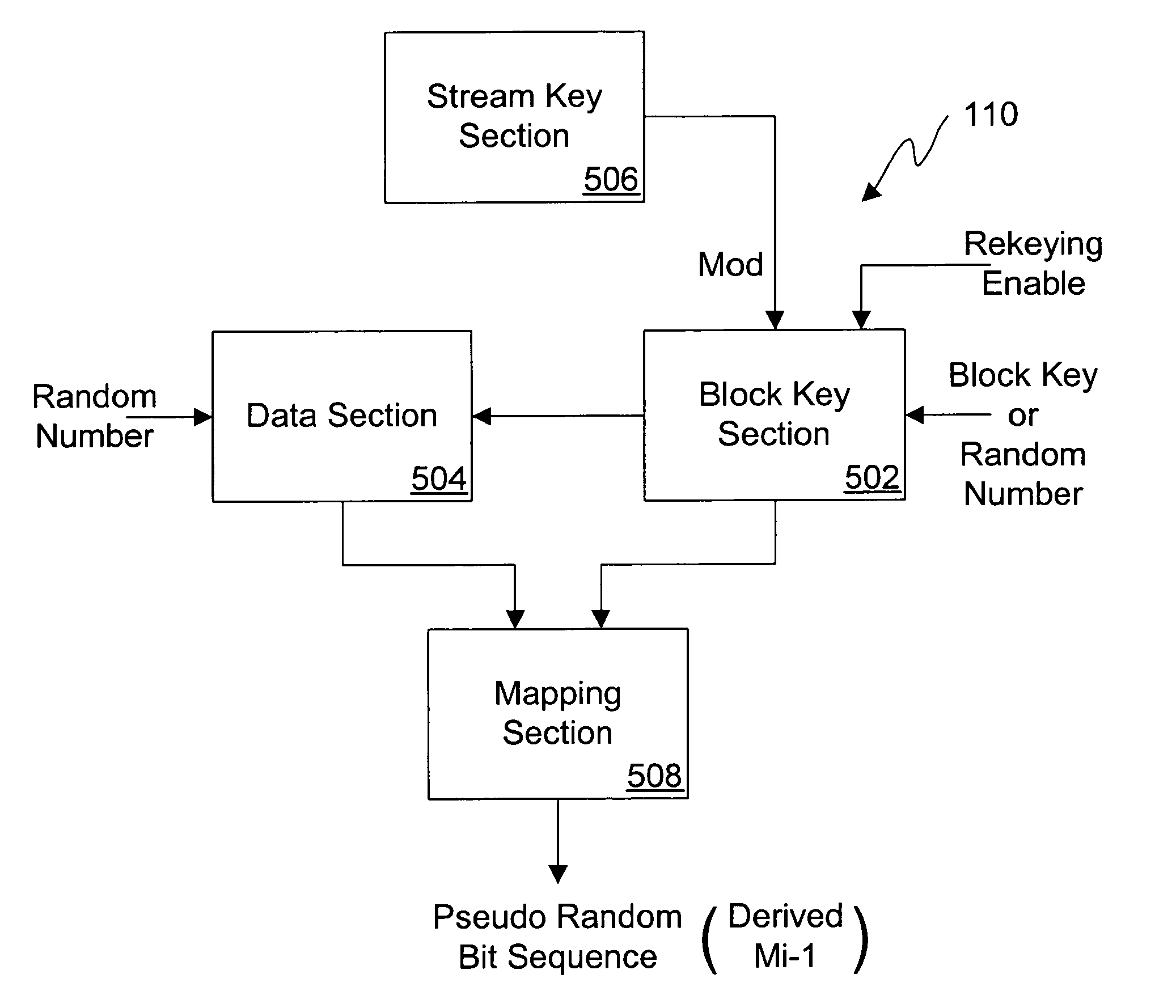
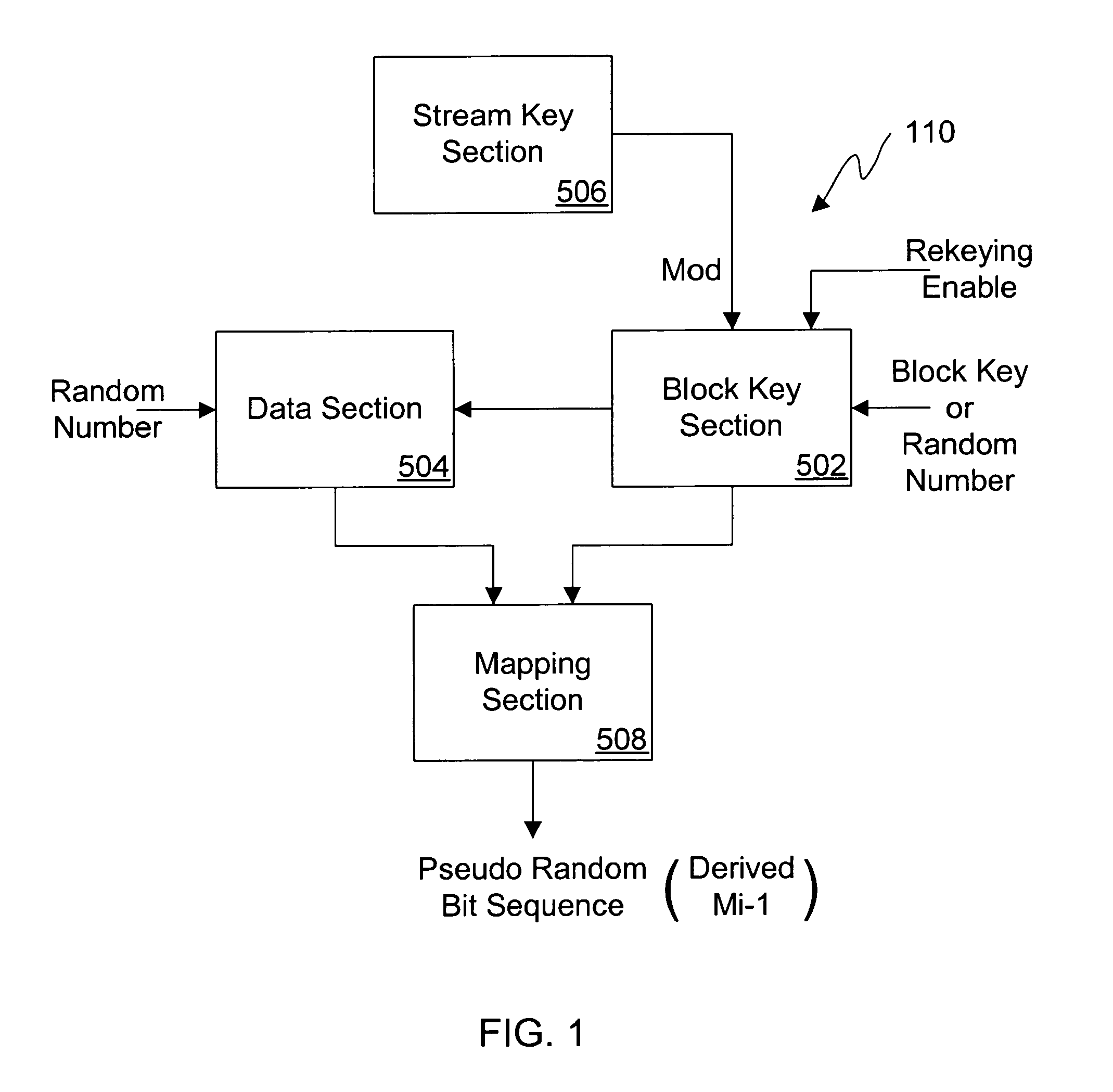
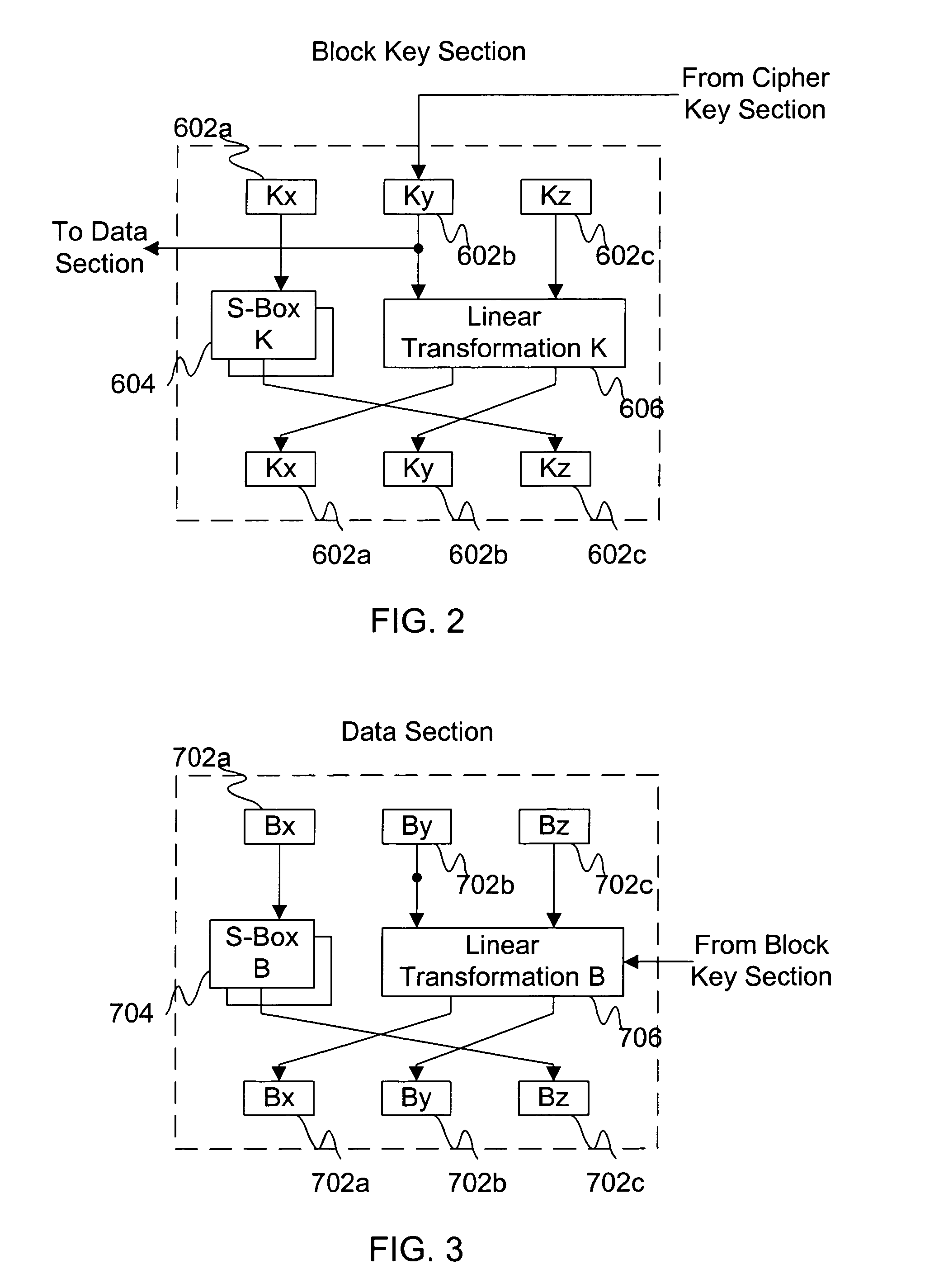
A dual use block / stream cipher is provided with a first key section and a data section. The first key section is to be initialized with a first cipher key, and to successively transform the first cipher key or a modified version of the first cipher key. The data section, coupled to the first key section, is to be initialized with either a block of plain text or a random number, and to successively and dependently, on the first key section, transform the plain text / random number. The cipher is further provided with a second key section and a mapping function. The second key section, coupled to the first key section, is selectively enableable to modify the first cipher key. The mapping section, coupled to the first key section, is to generate a pseudo random bit sequence when the second key section is selectably enabled to modify the stored first cipher key.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com