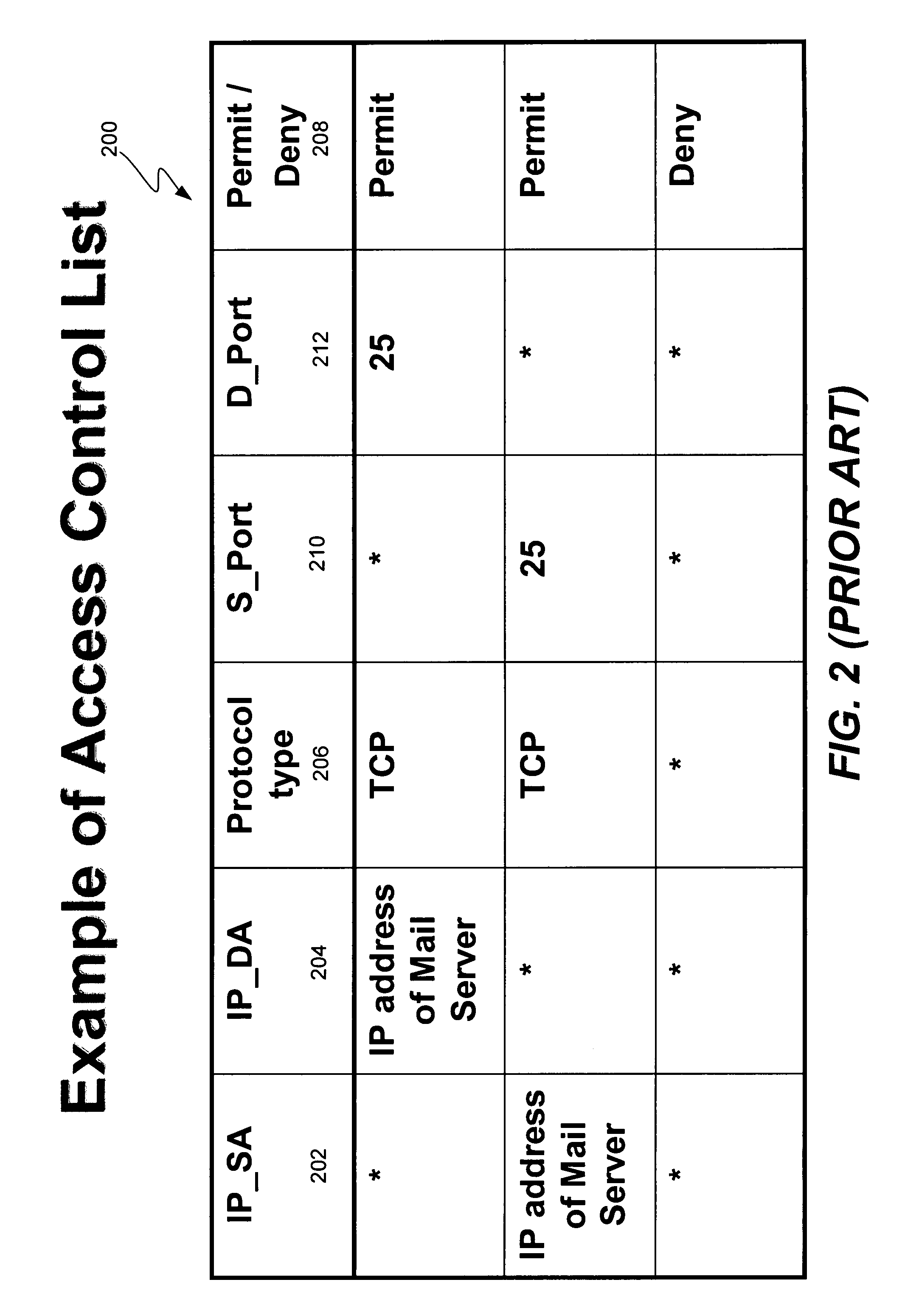
Patents
Literature
234 results about "128-bit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
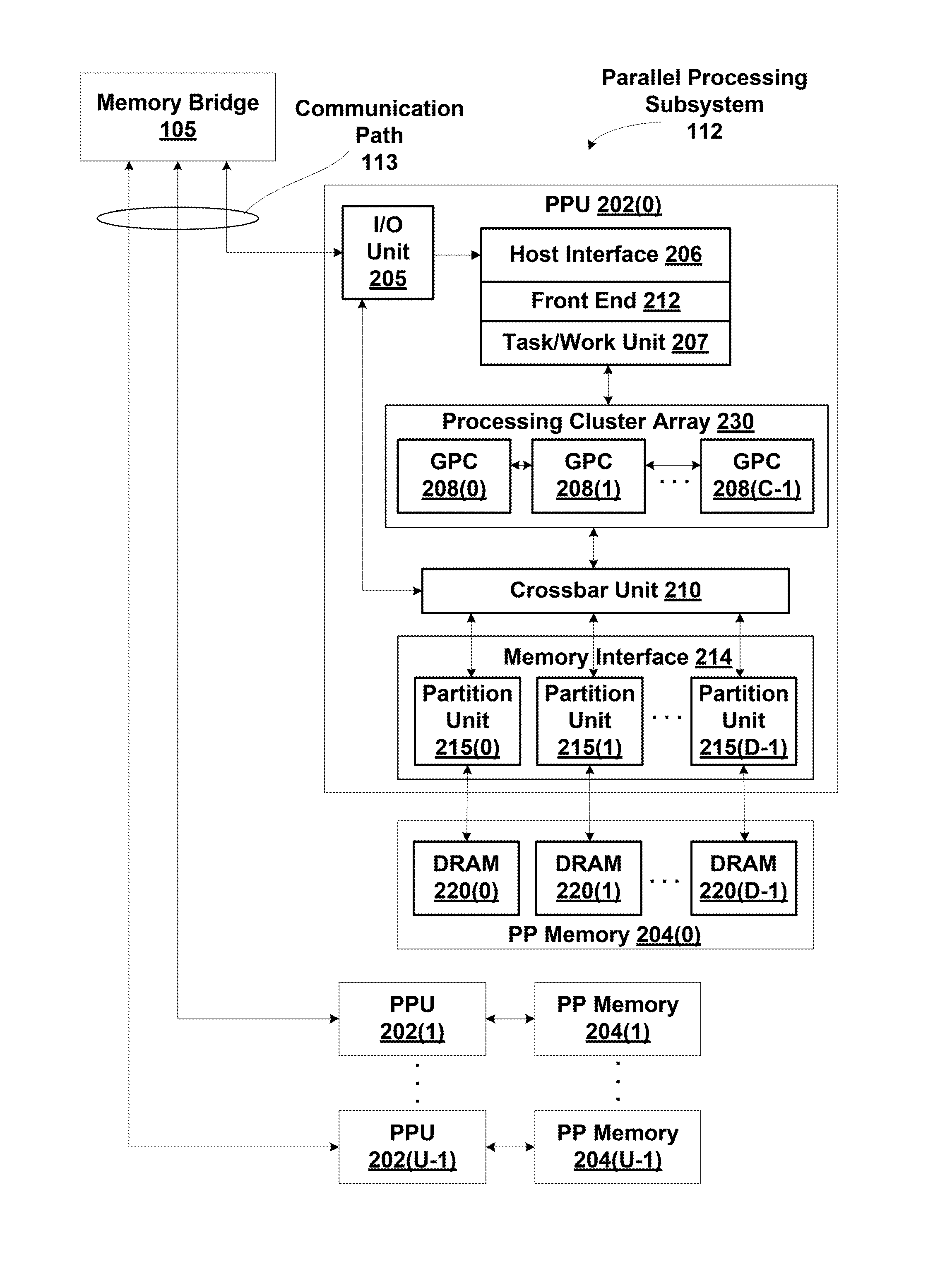
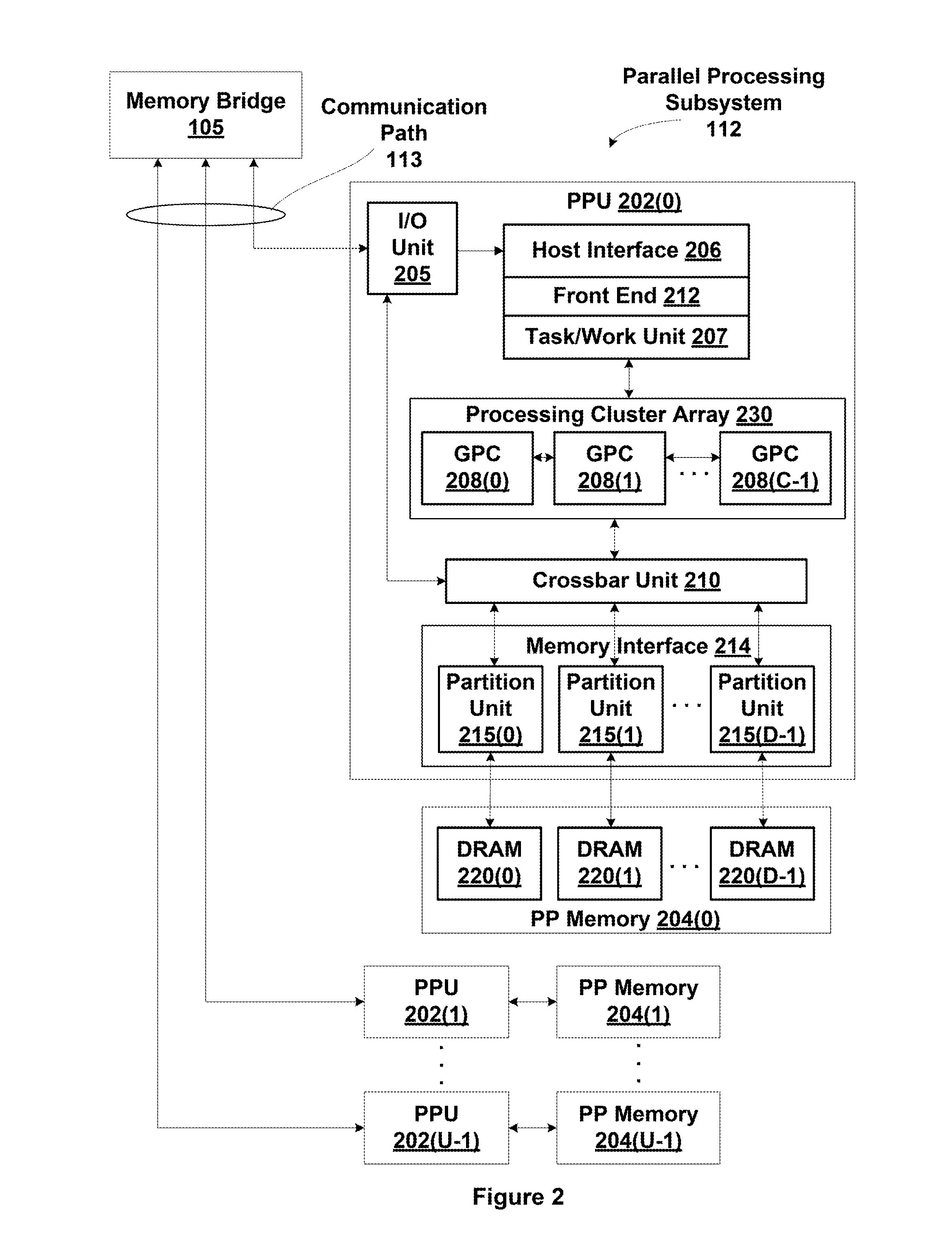
In computer architecture, 128-bit integers, memory addresses, or other data units are those that are 128 bits (16 octets) wide. Also, 128-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
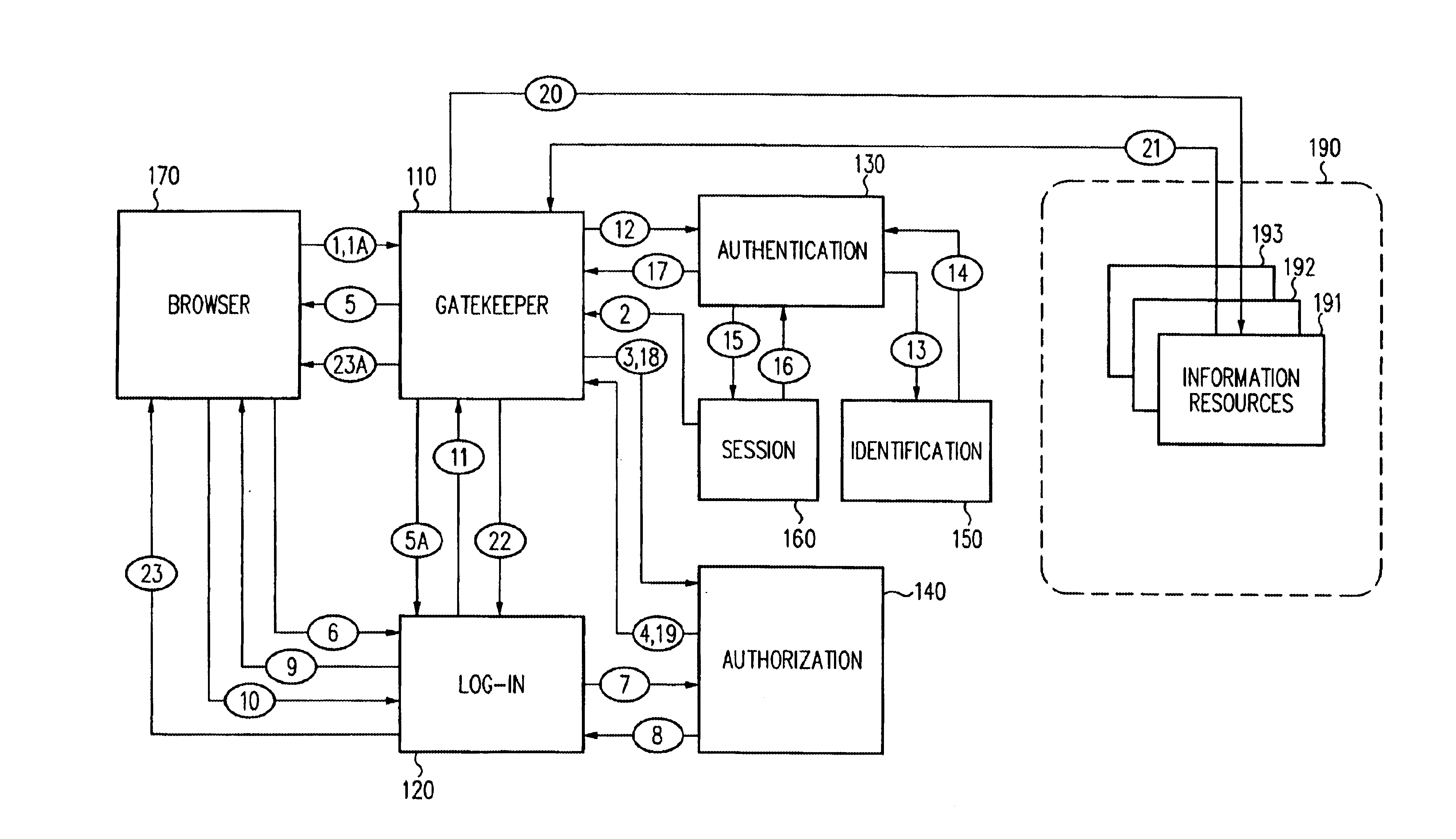
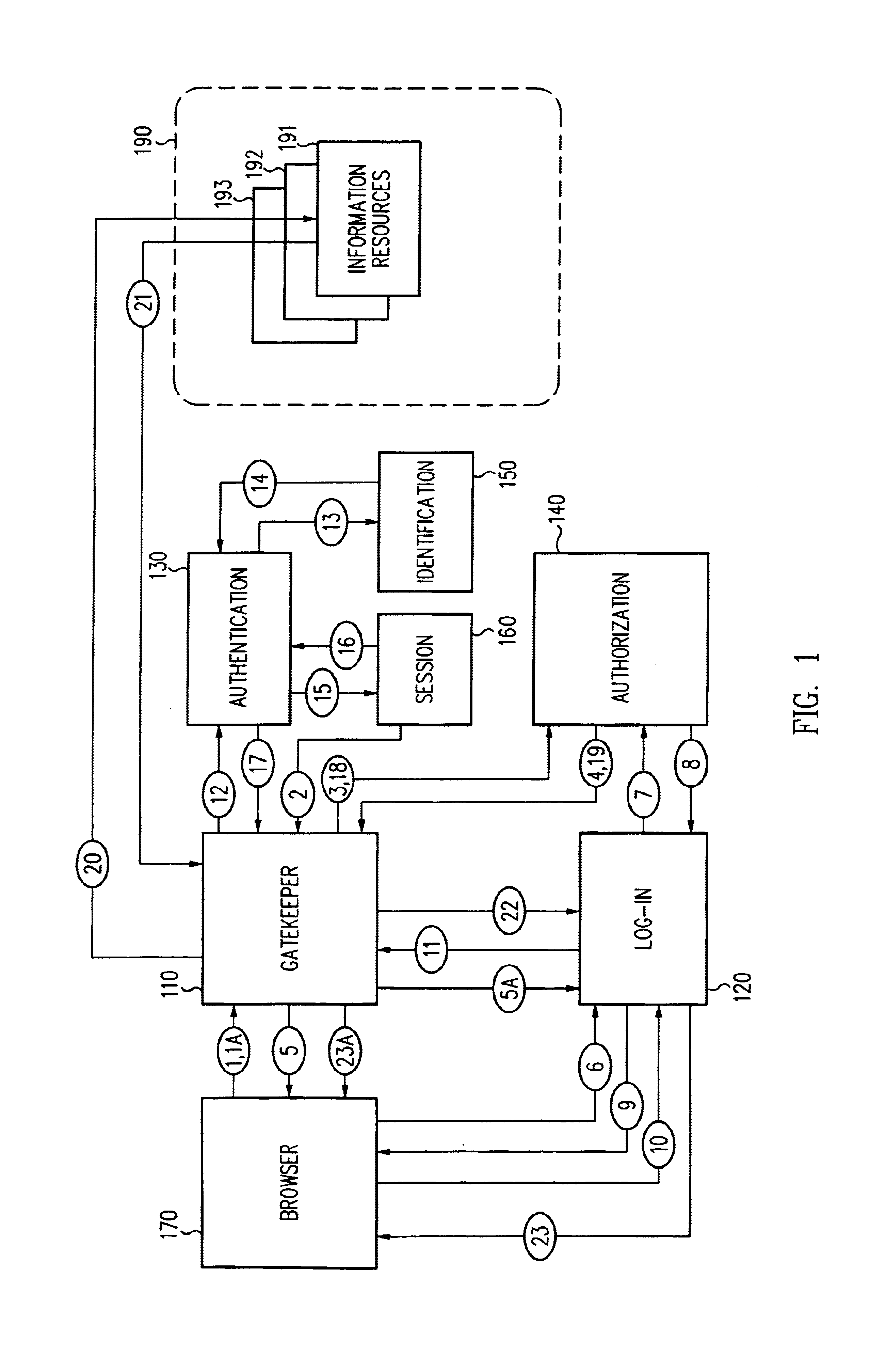
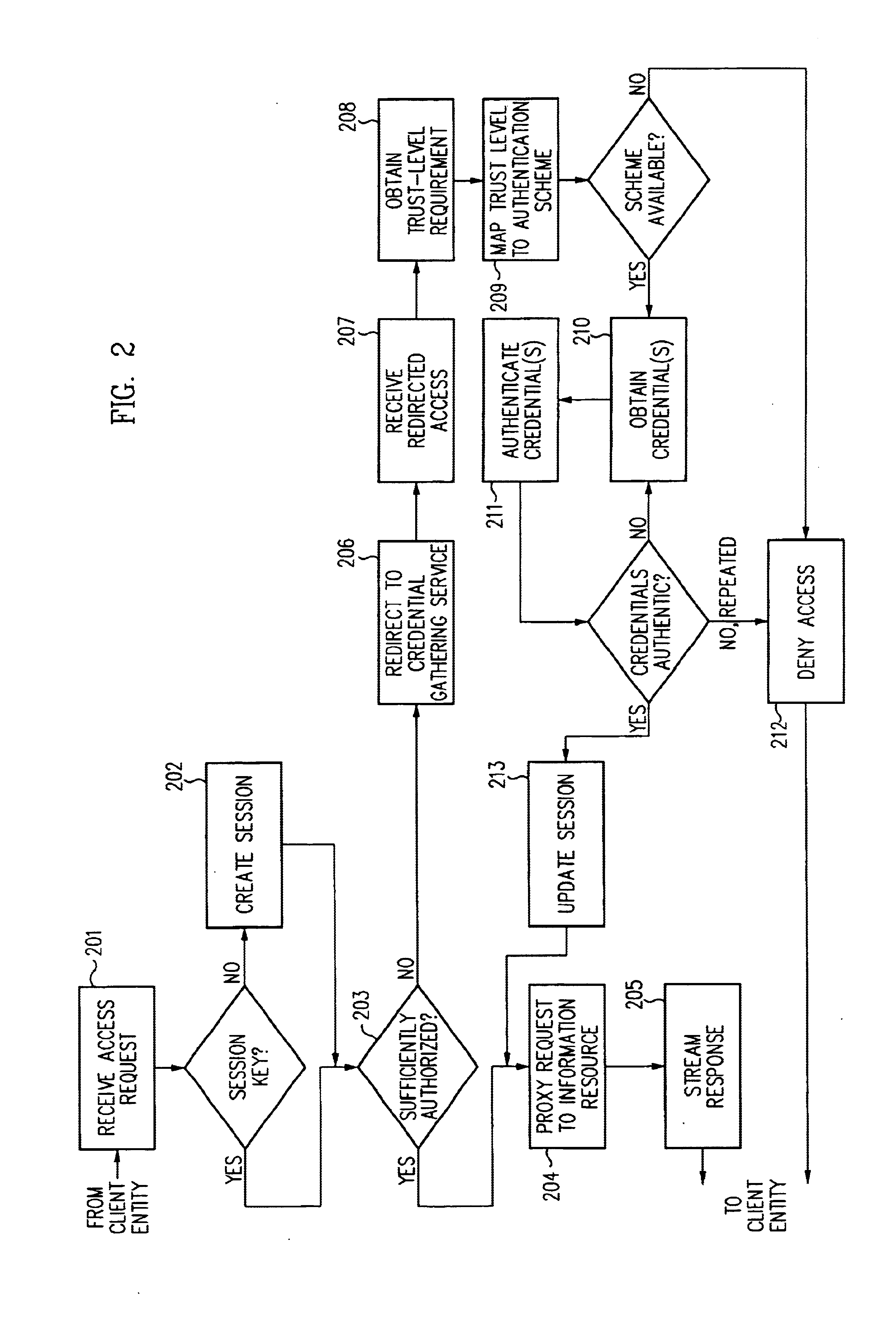
Security architecture with environment sensitive credential sufficiency evaluation
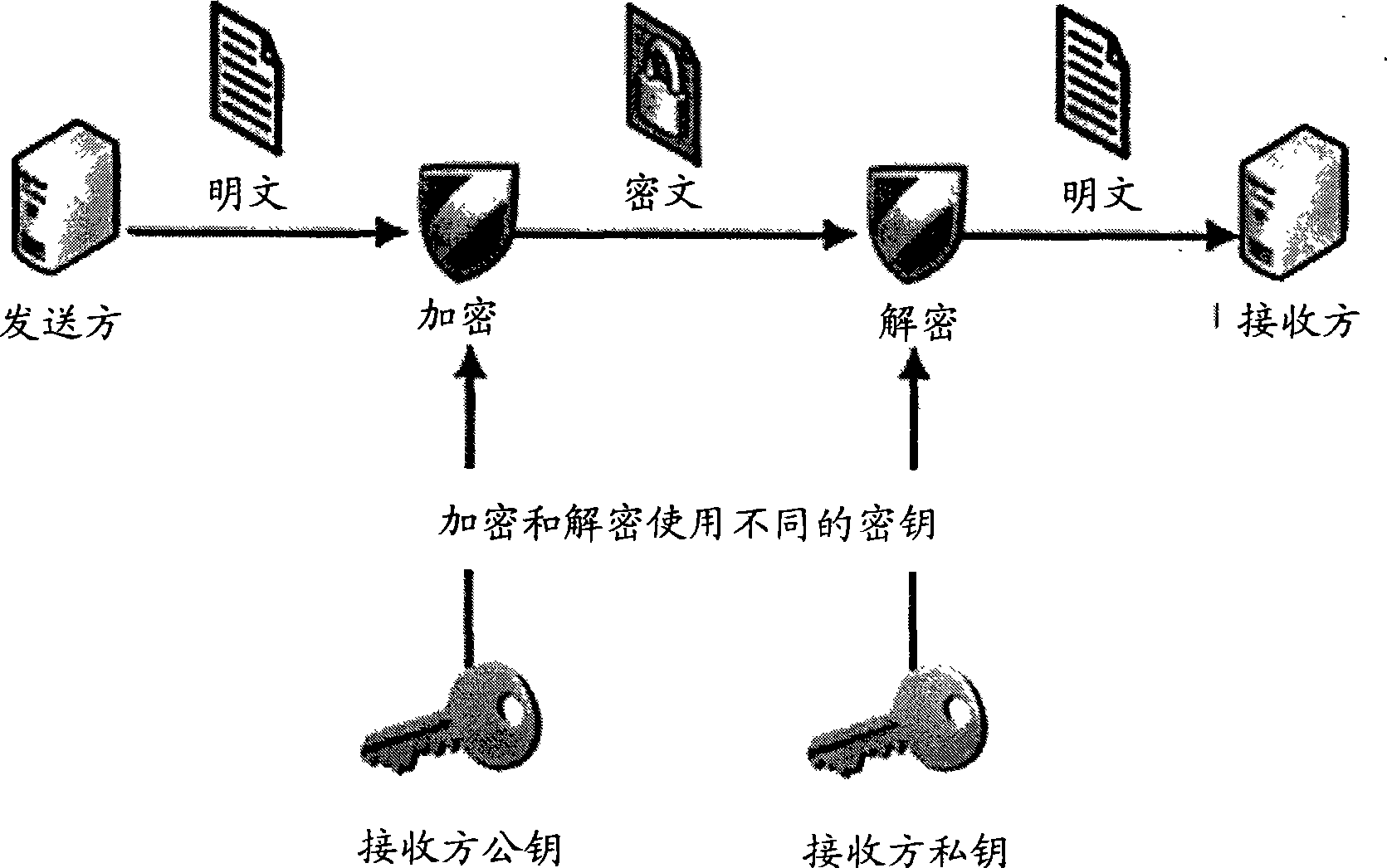
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
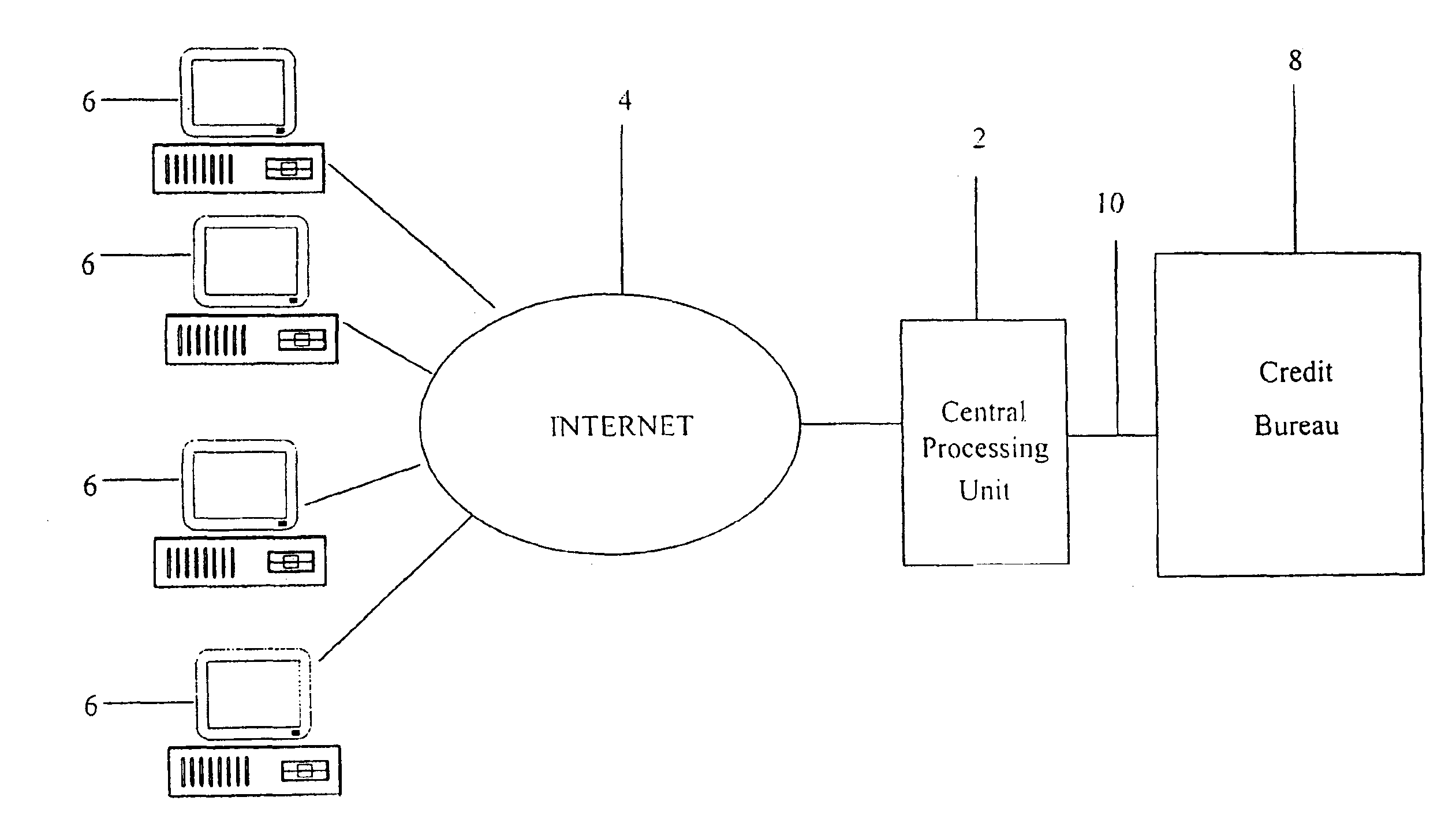
System and method for real-time electronic inquiry, delivery, and reporting of credit information
InactiveUS6988085B2More readable formatSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
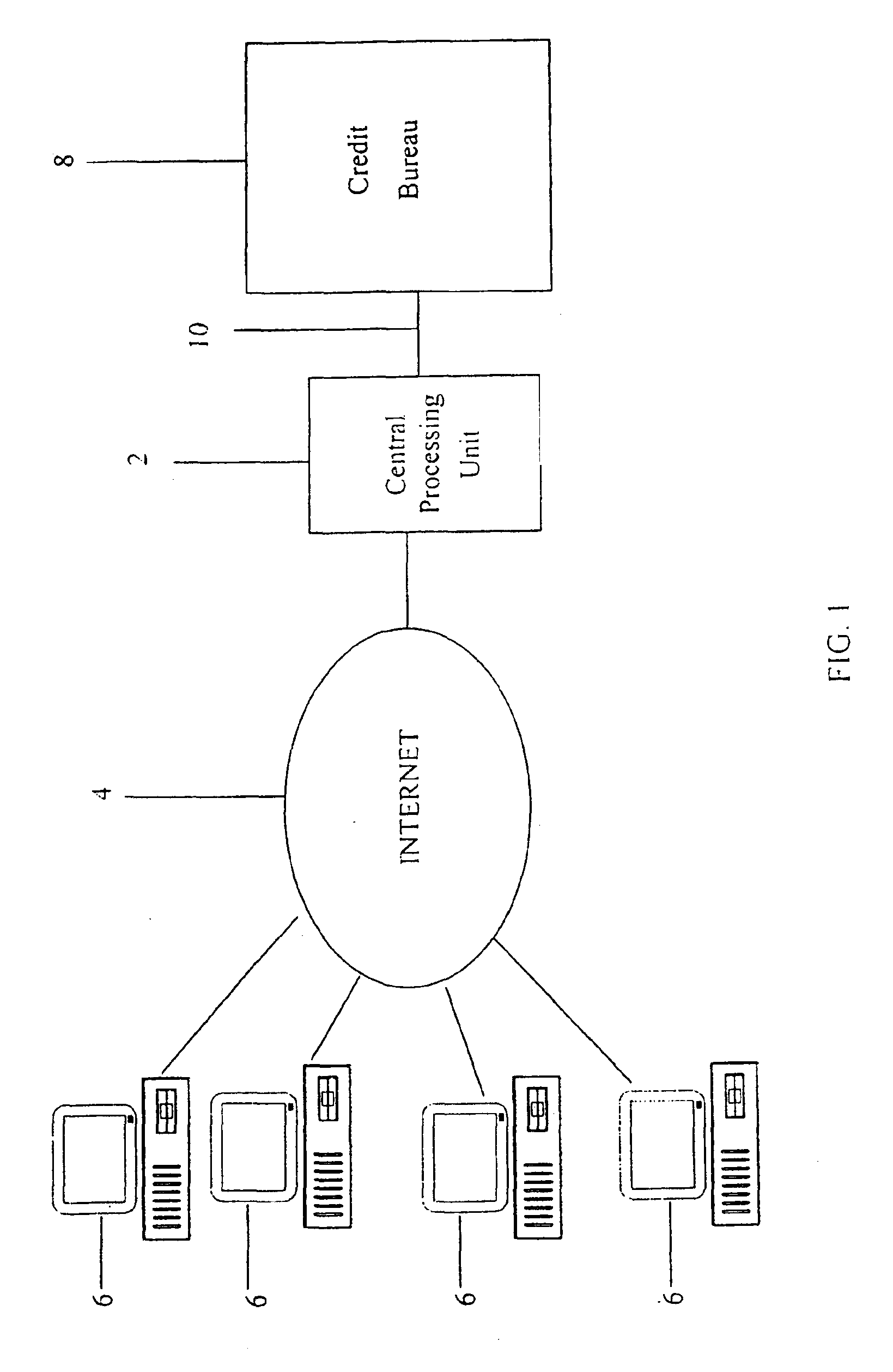
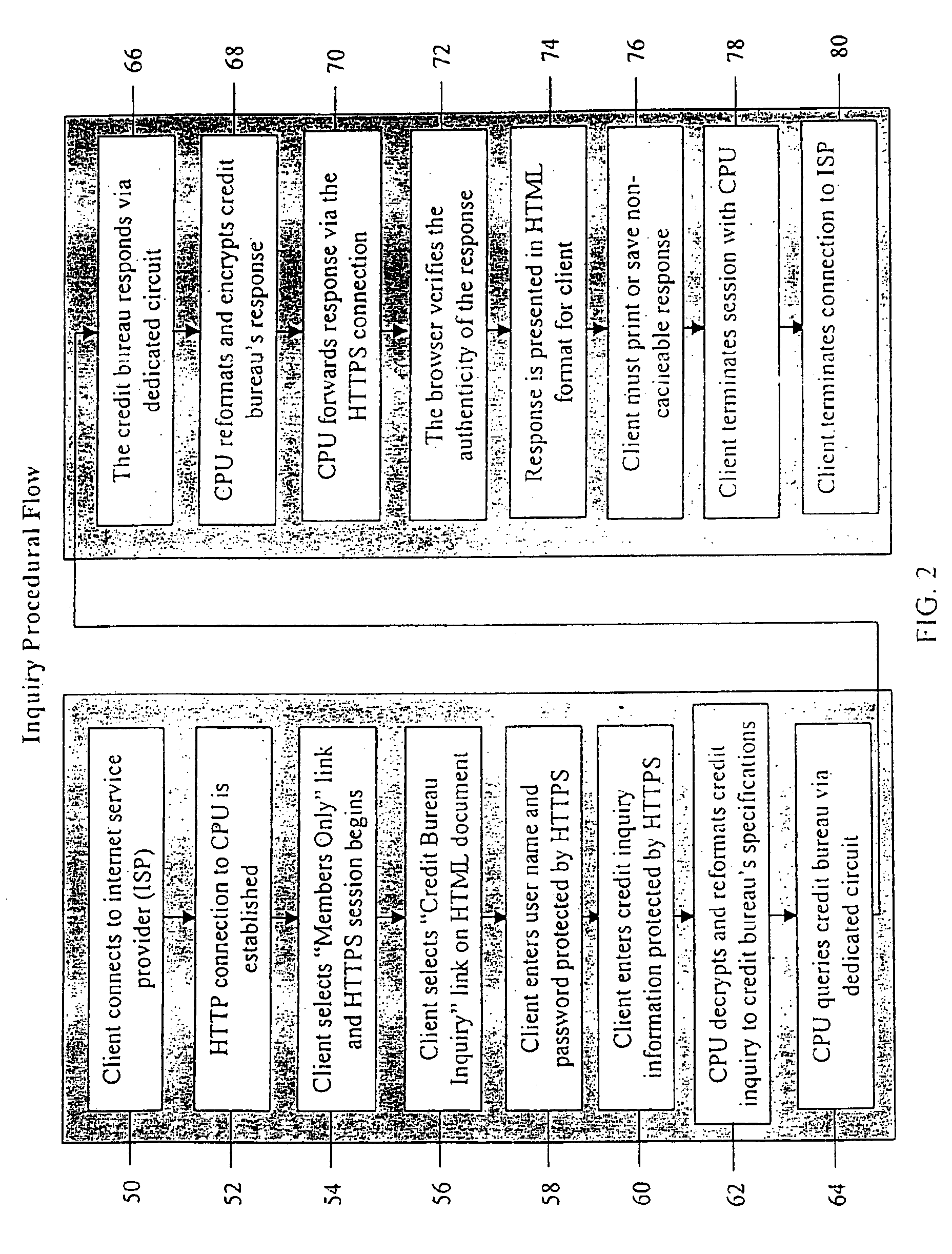
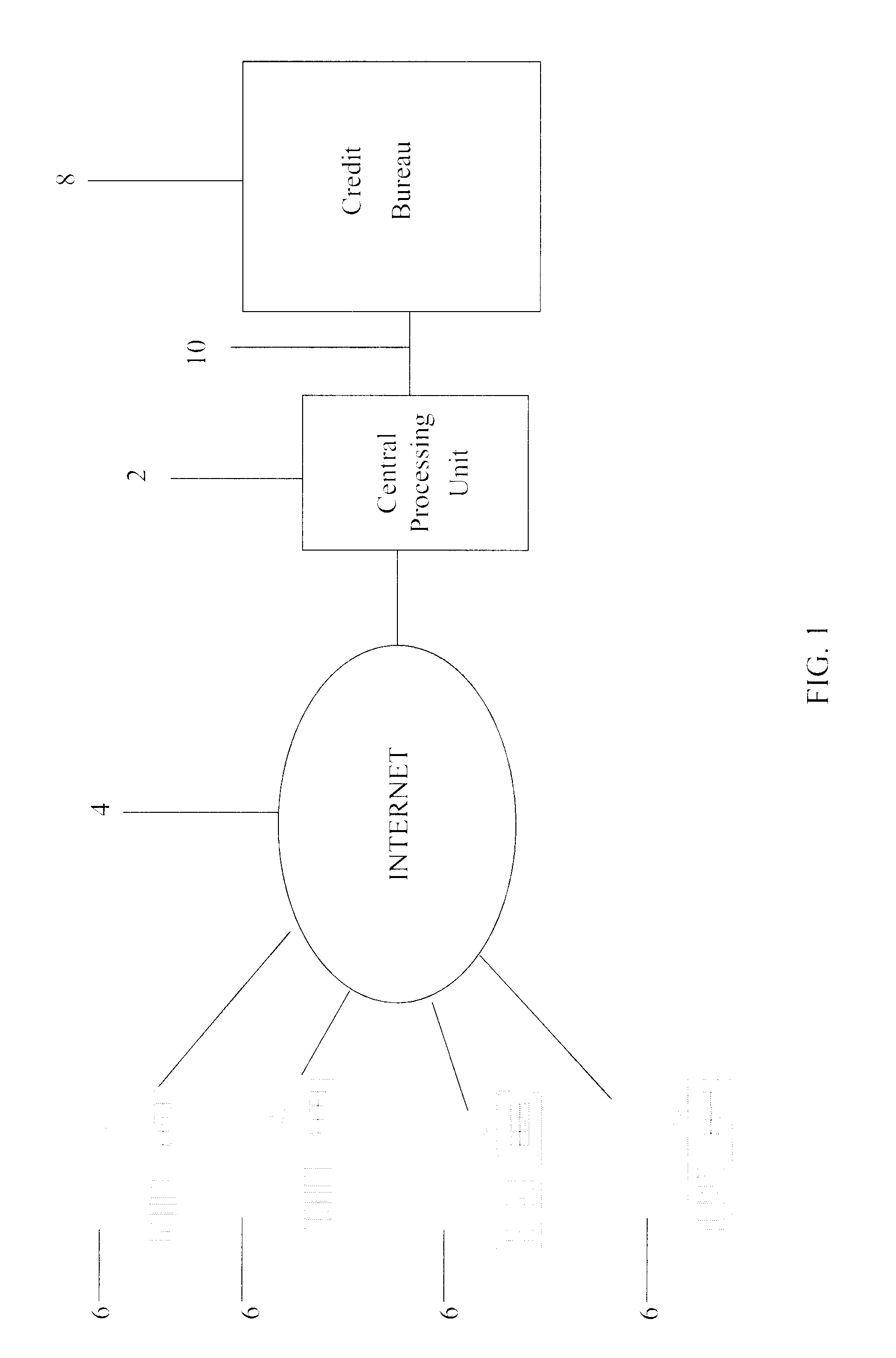
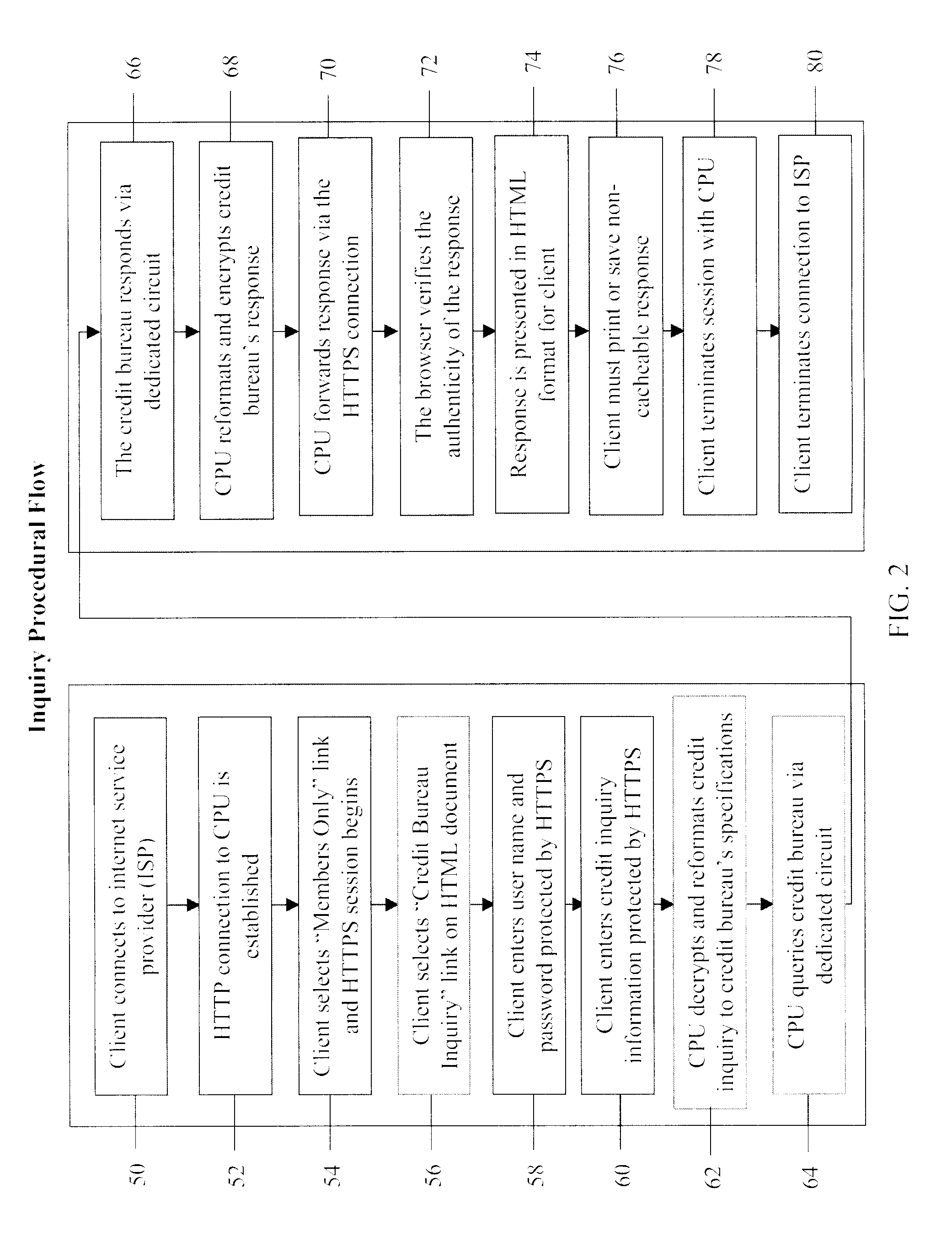
A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
System and method for real-time inquiry, delivery, and reporting of credit information
InactiveUS20030041031A1More readableSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
<heading lvl="0">Abstract of Disclosure< / heading> A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
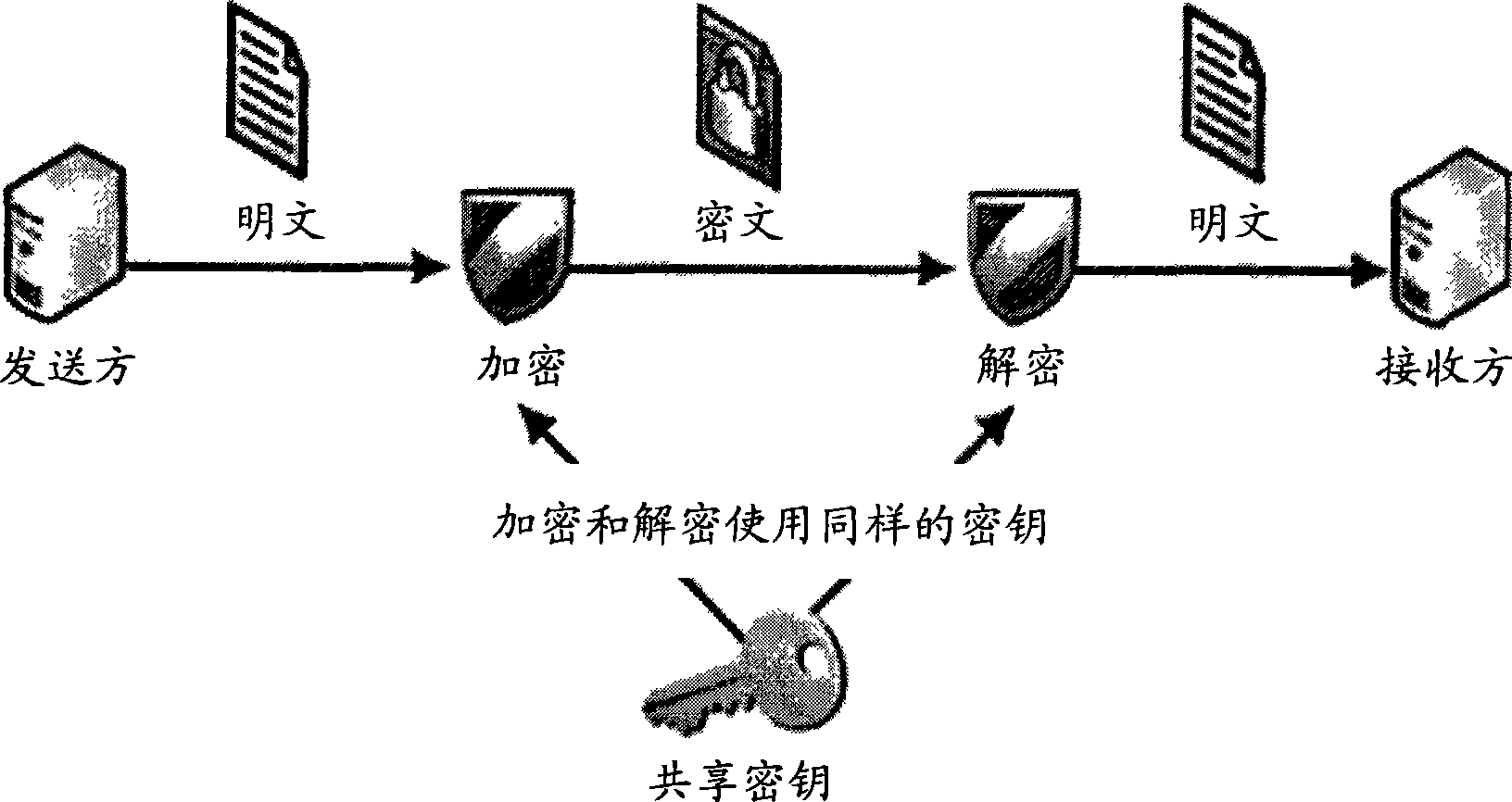
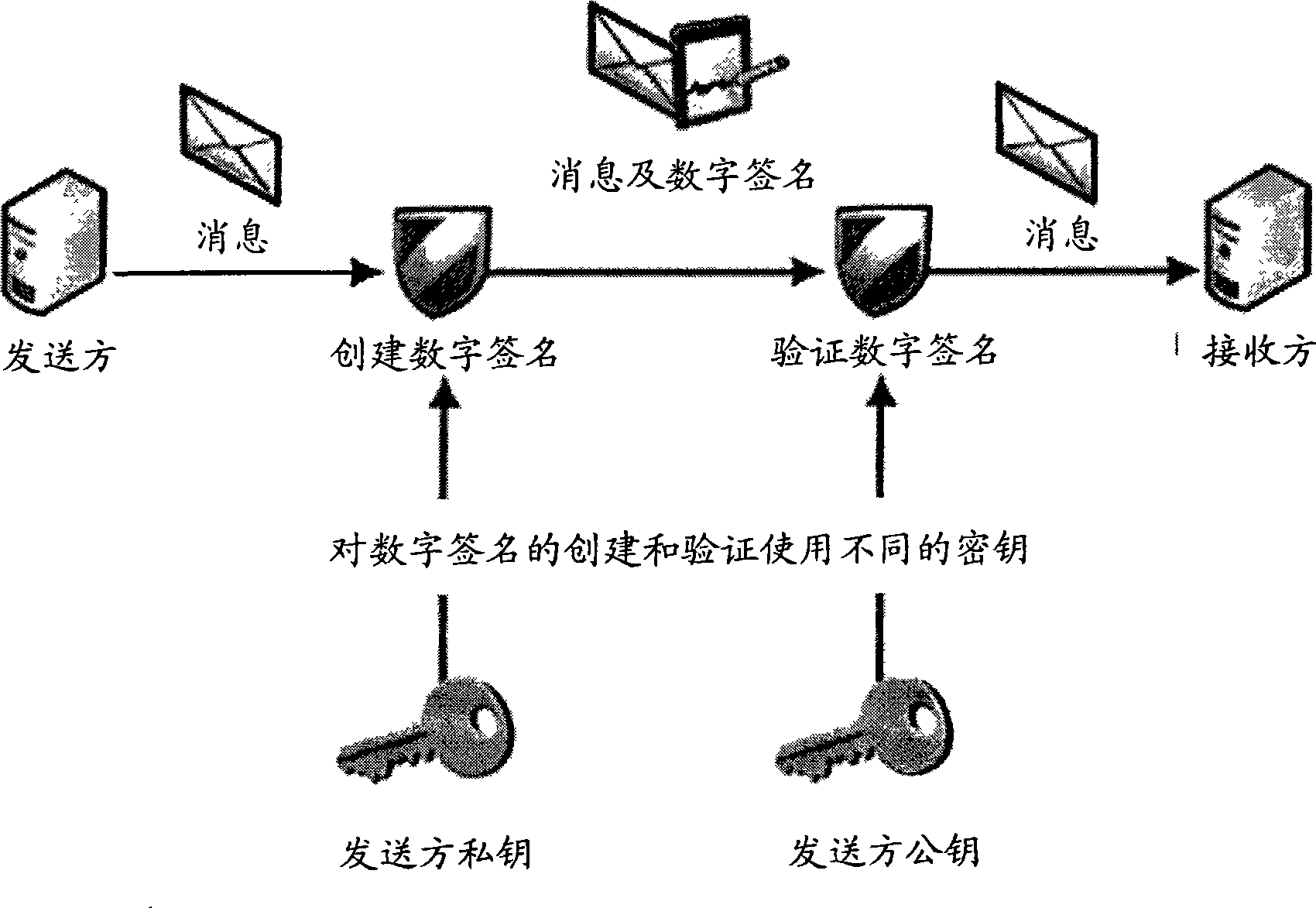
Cryptographic apparatus and method
InactiveUS7177424B1Quick implementationEasy to operateEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPlaintextComputer hardware
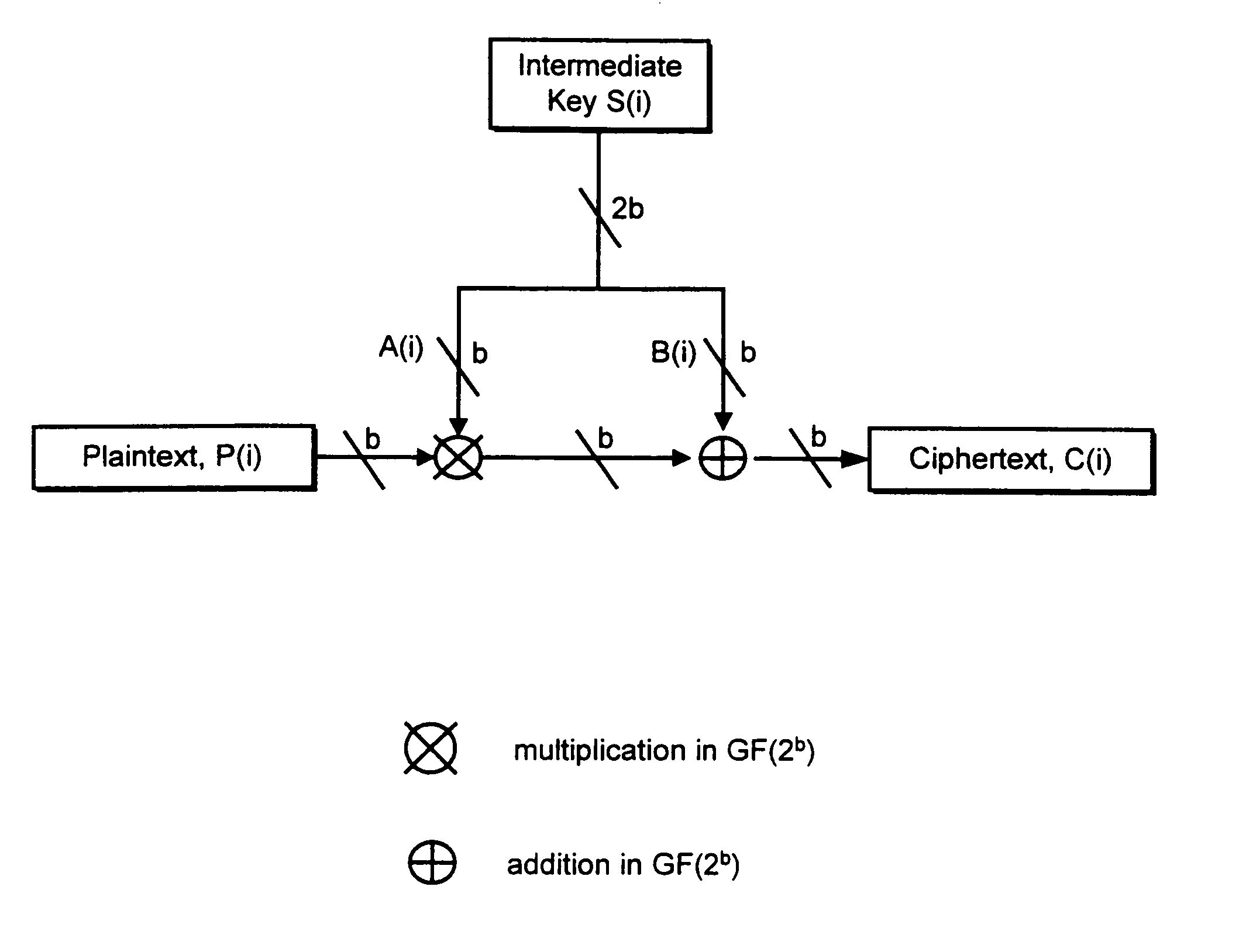
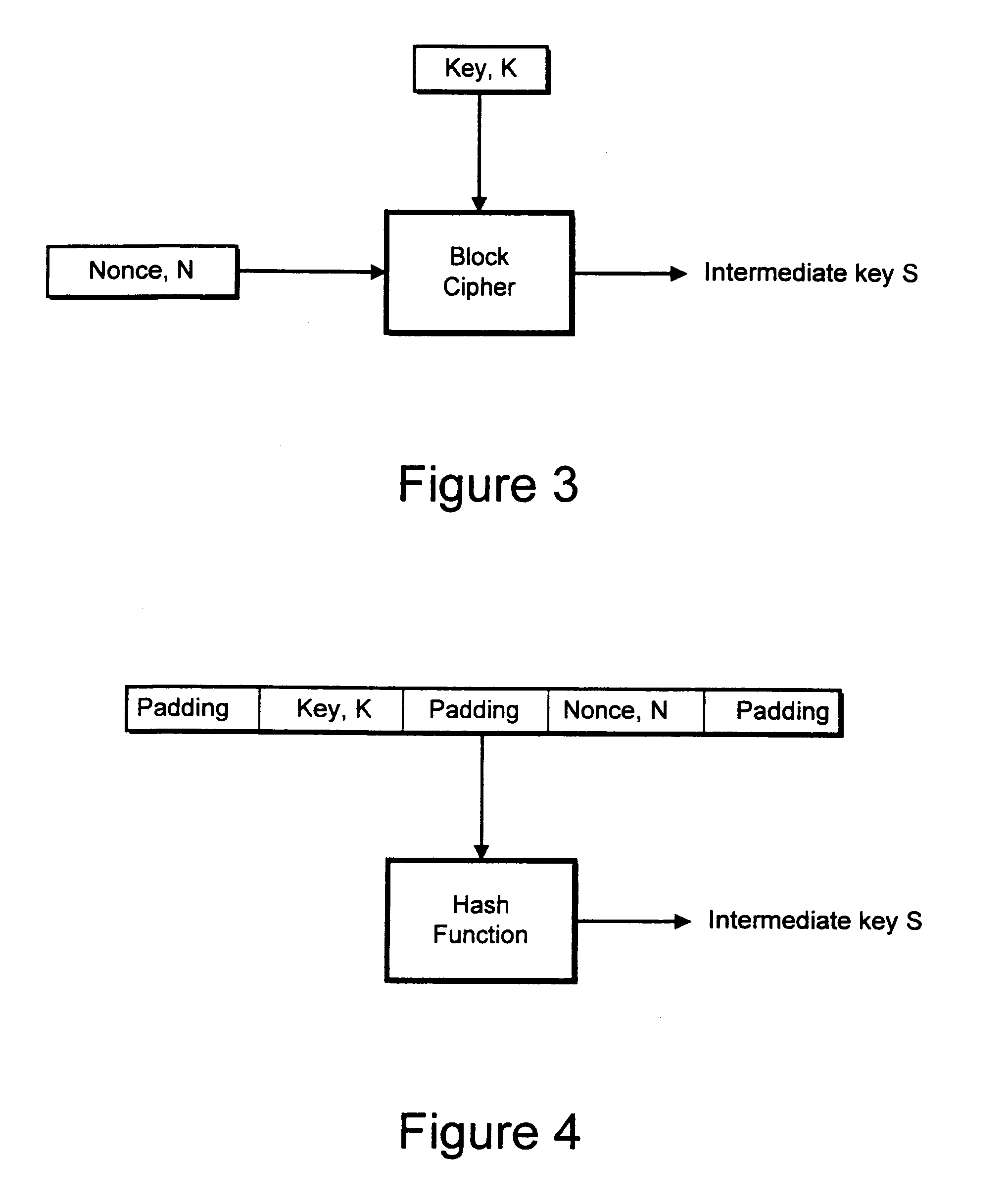
An encryption system comprises a pseudo-random number generator (KS) for generating a long pseudo-random sequence (S) from a shorter encryption key (K) and, if necessary, a nonce value (N), and a mixing function (MX) for combining the sequence with a plaintext message (P) on a block-by-block basis, where successive blocks (S(i)) of 128 bits of the sequence are combined with successive 64-bit blocks of plaintext (P(i)) to produce successive 64-bit blocks of ciphertext. The blockwise use of a long pseudo-random sequence preserves the advantages of a block cipher in terms of data confidentiality and data integrity, as well as benefiting from the speed advantages of a stream cipher.
Owner:HITACHI LTD
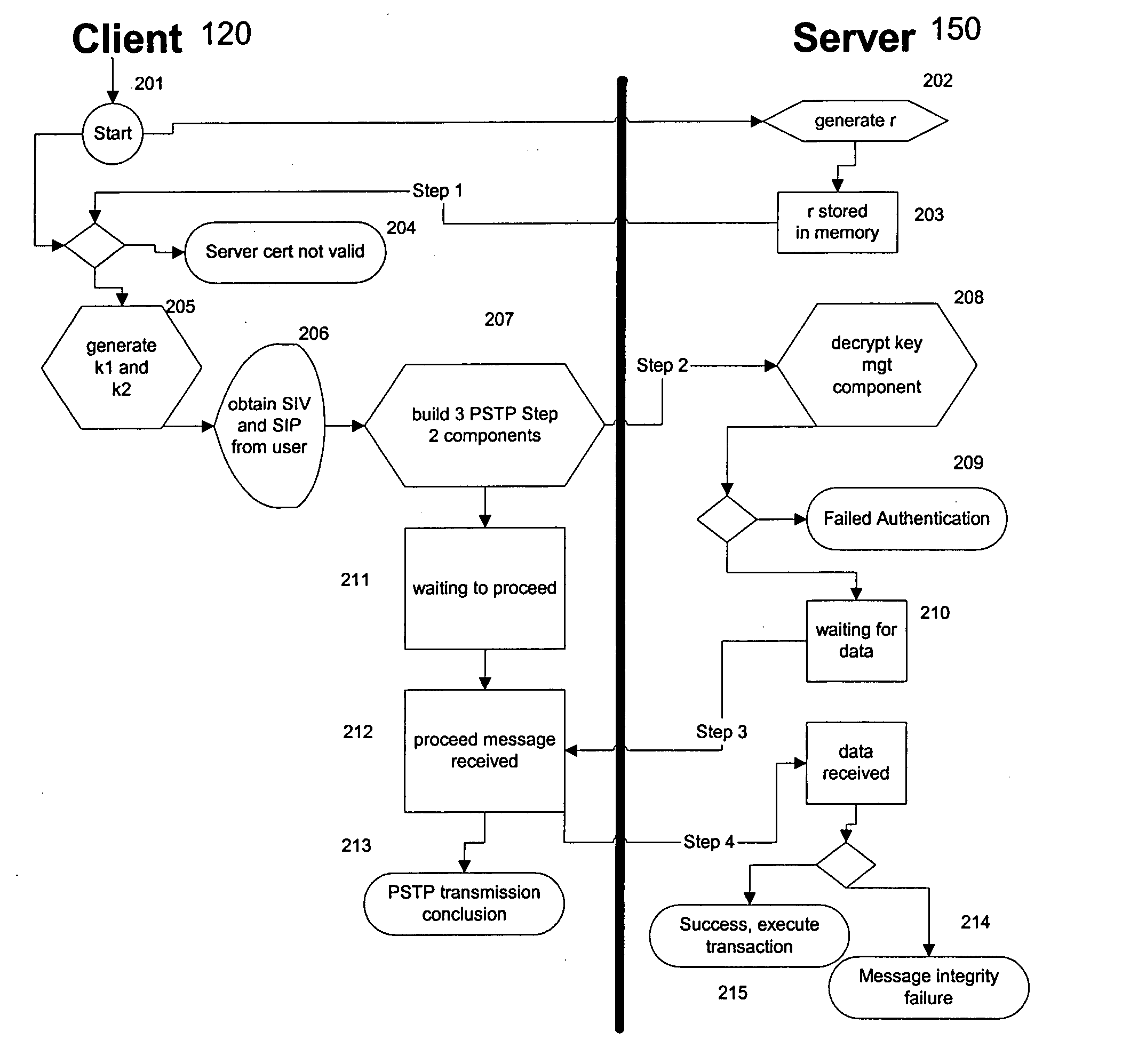
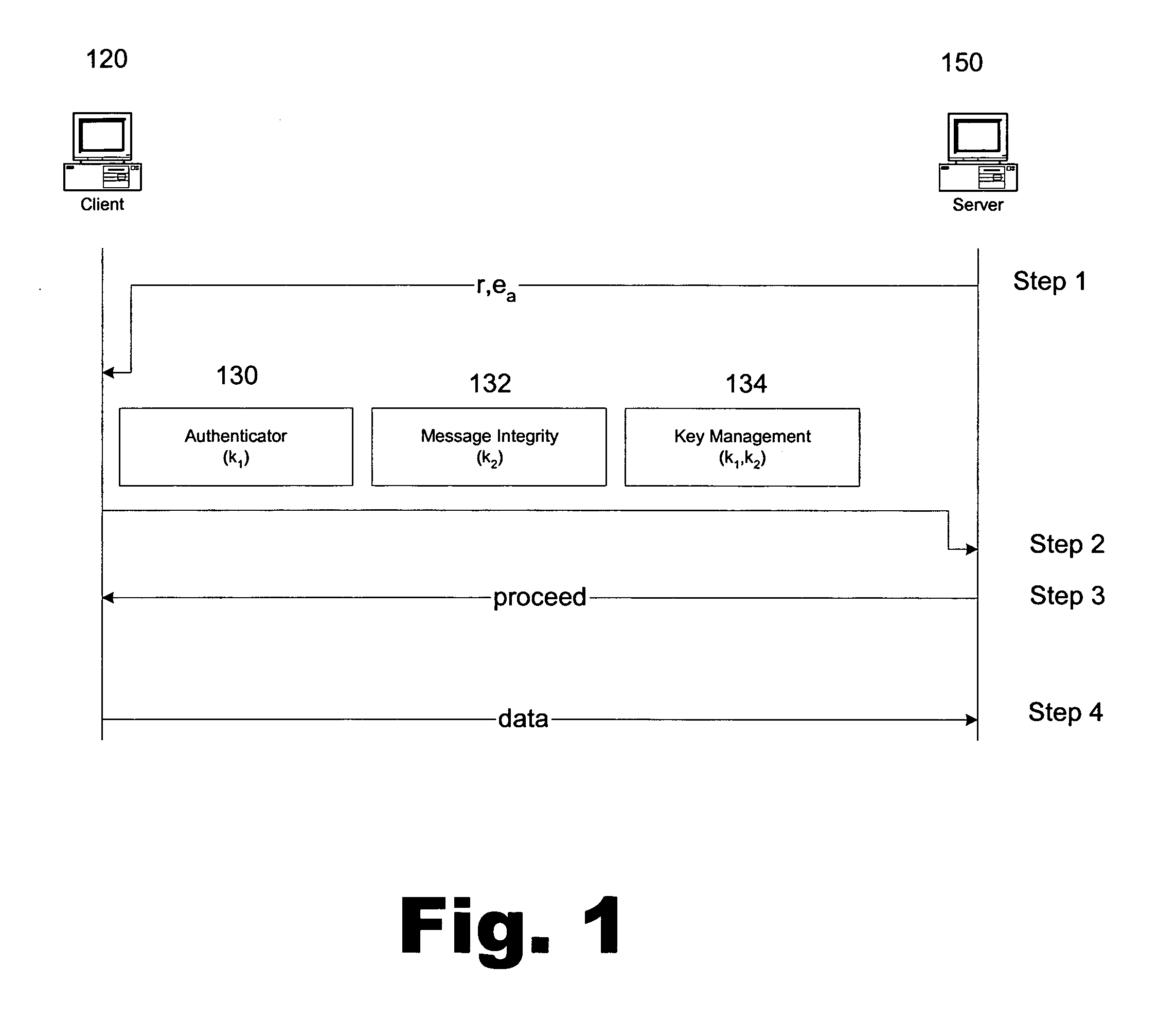
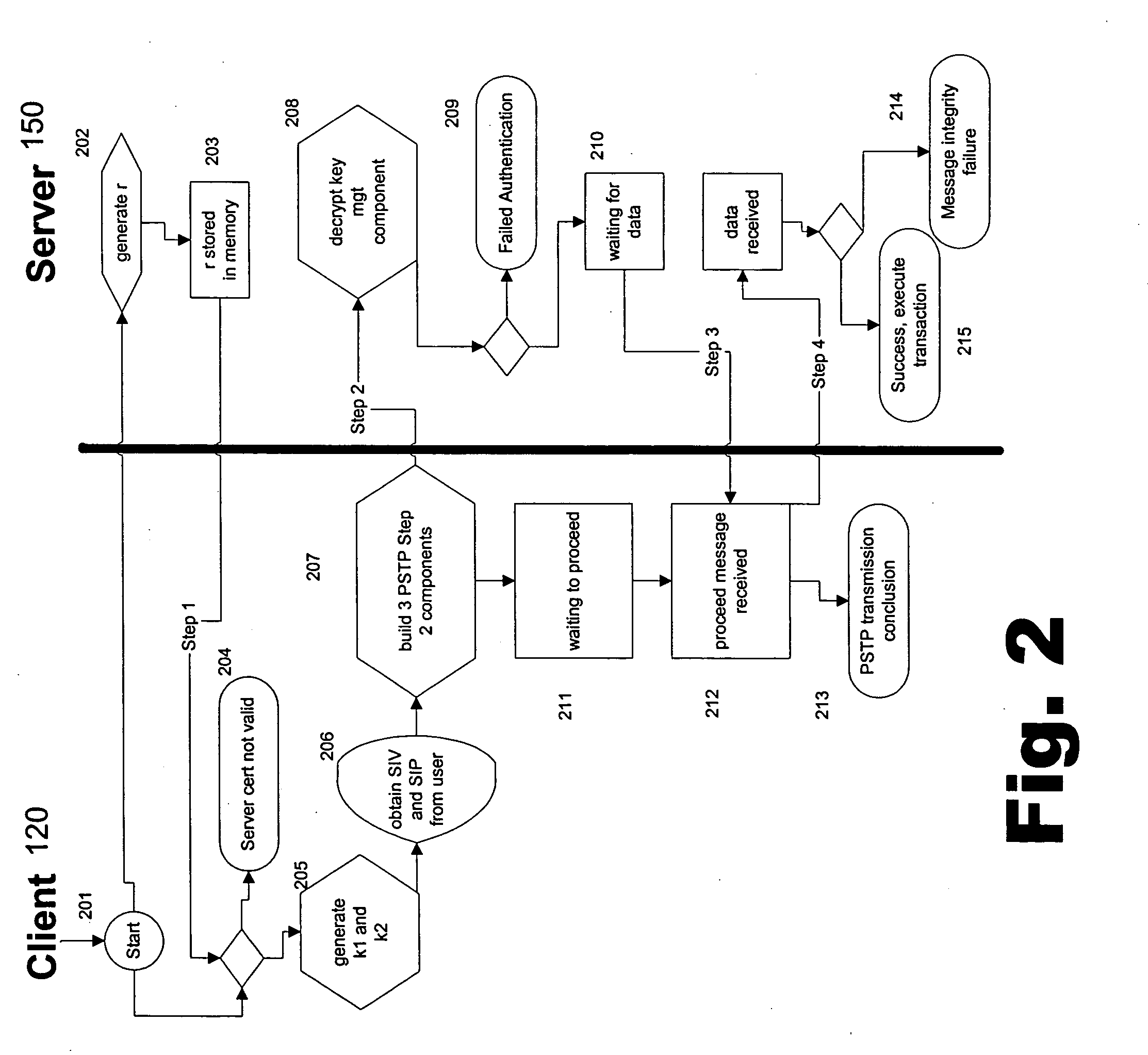
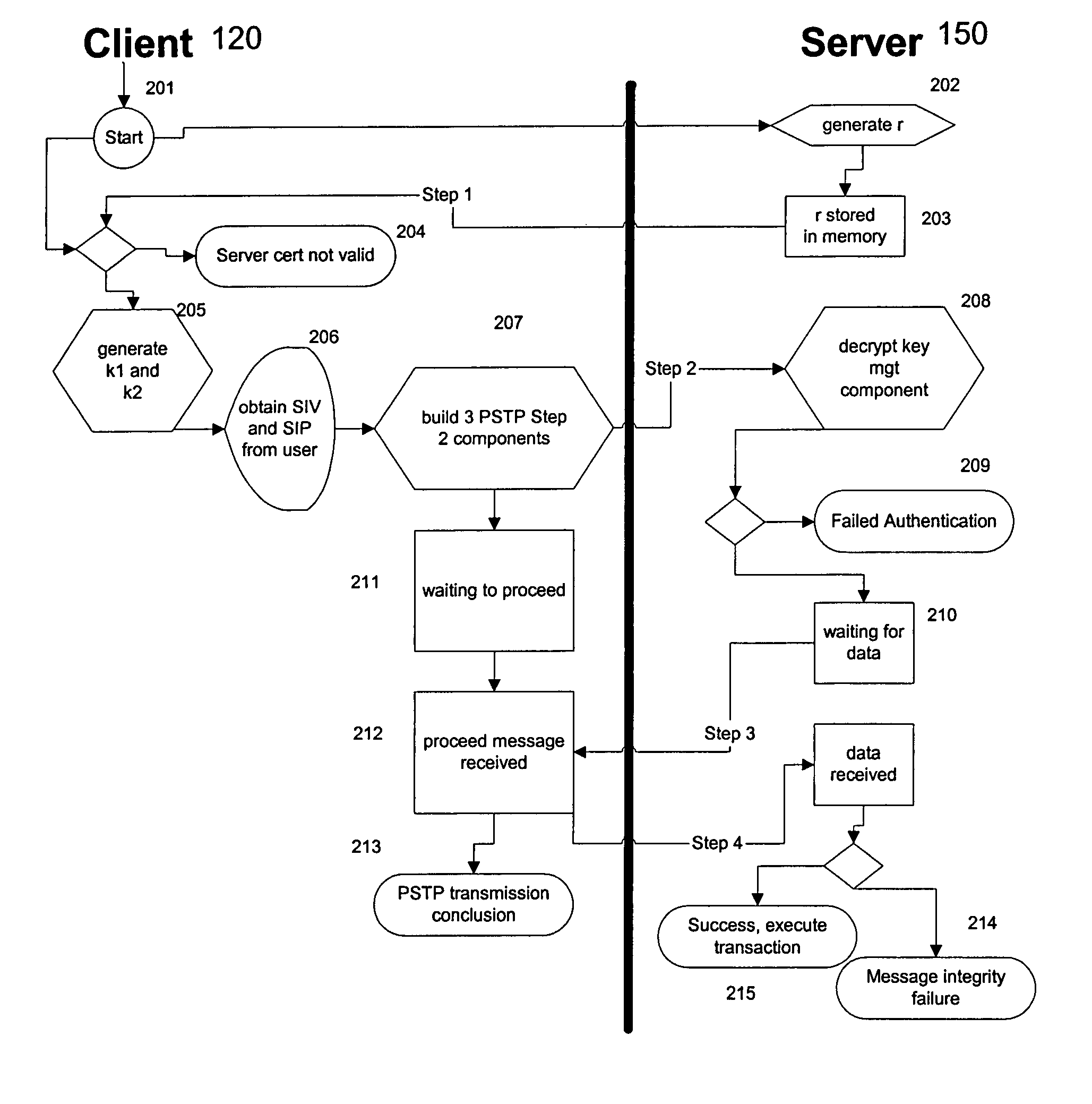
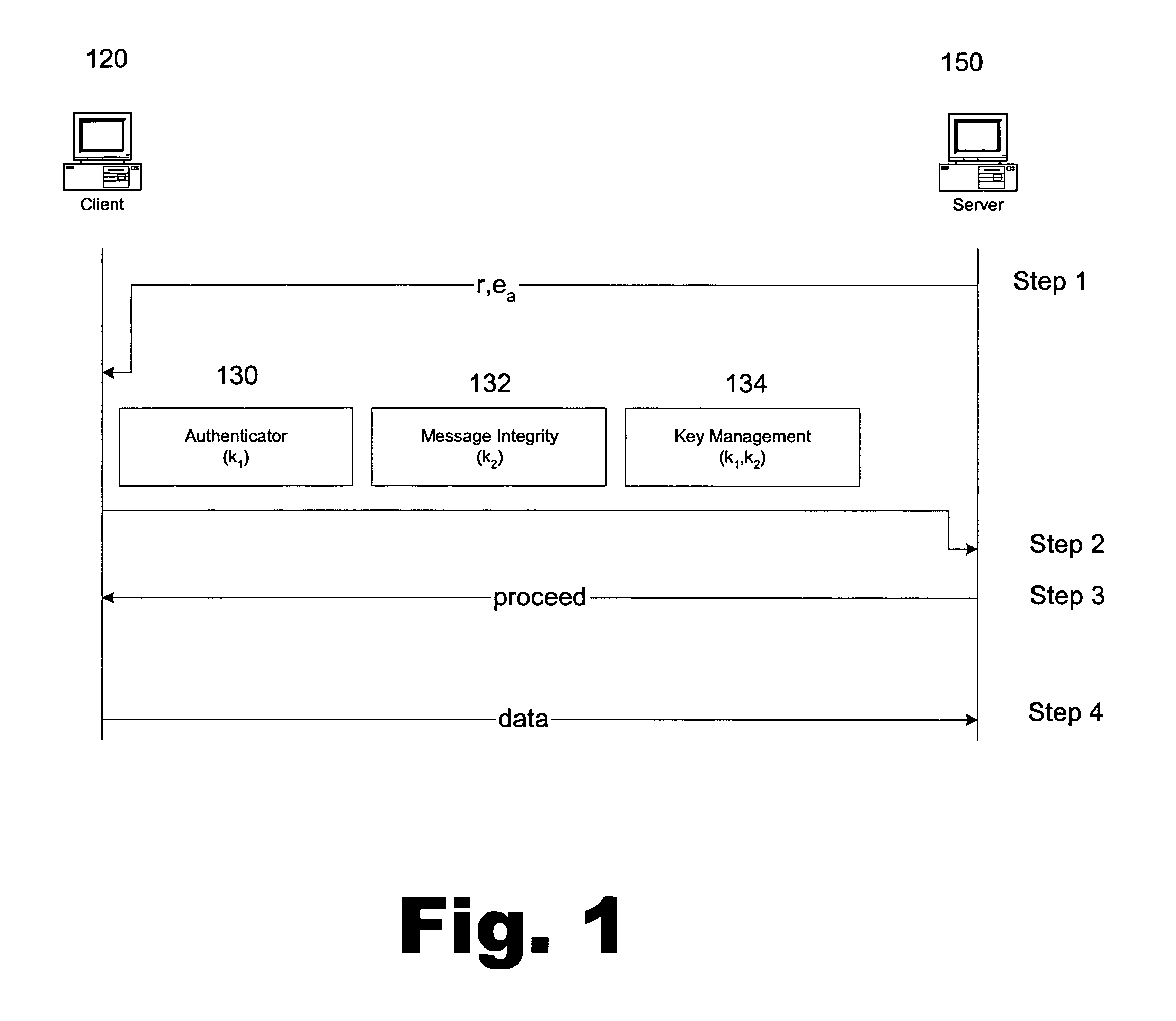
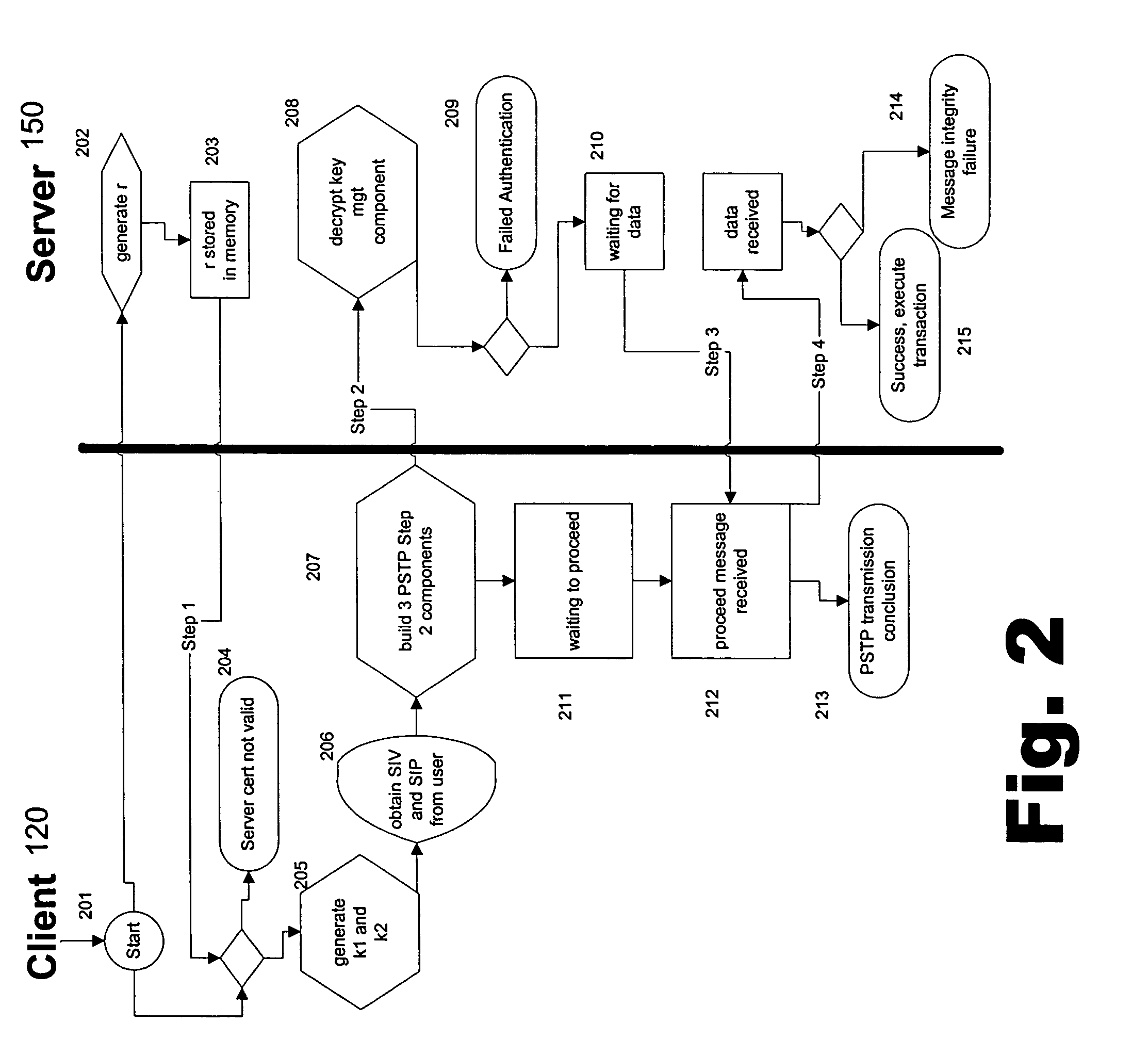
Portable security transaction protocol
ActiveUS20050091492A1Provide authenticityUser identity/authority verificationPayment circuitsThird partyCredit card
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
Portable security transaction protocol
ActiveUS8190893B2Digital data processing detailsUser identity/authority verificationCredit cardThird party
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
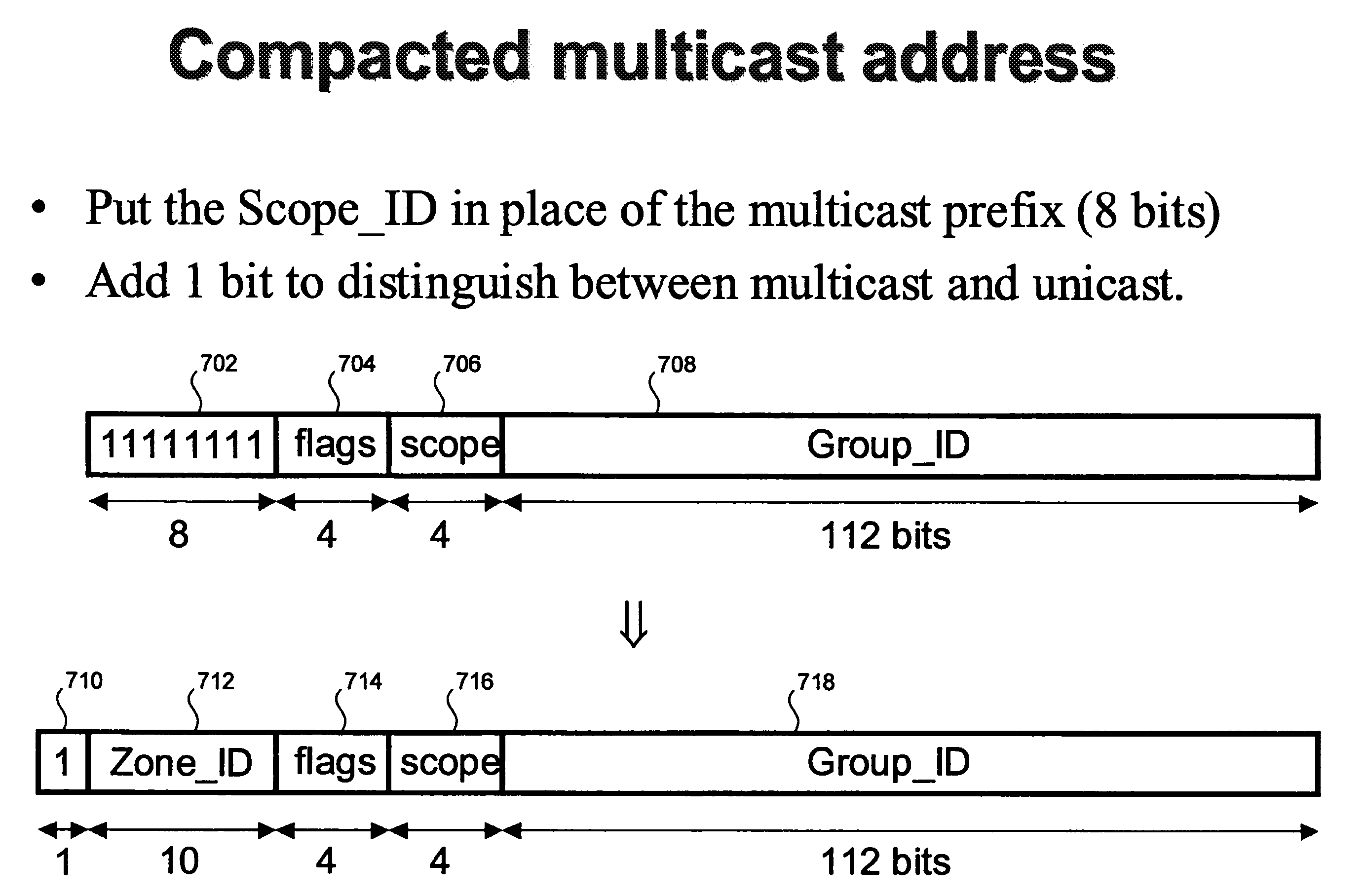
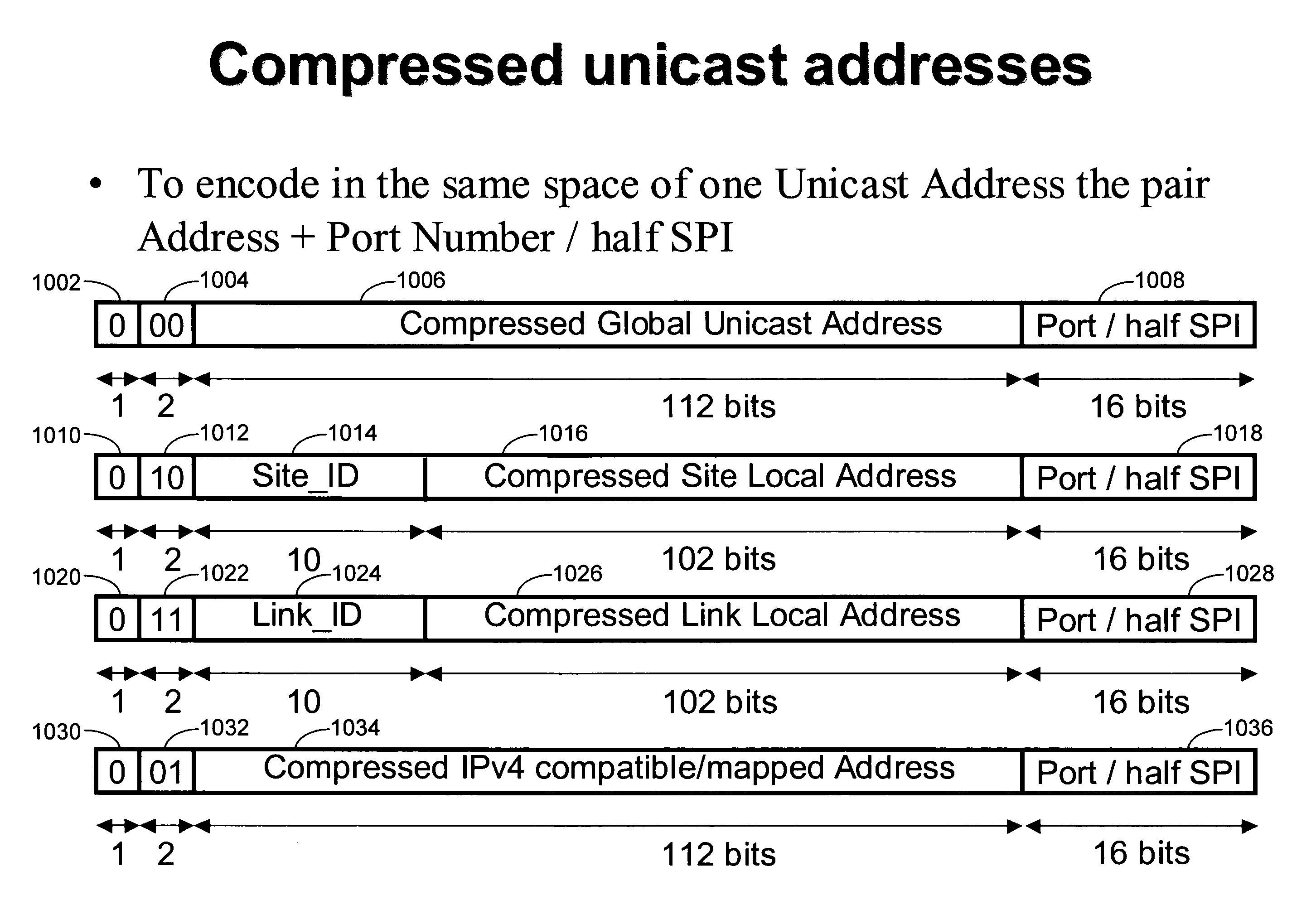
Access list key compression
ActiveUS20080165783A1Time-division multiplexData switching by path configurationComputer networkIPv6
Methods and apparatus for implementing an access list key for accessing information associated with a packet from an access list are disclosed. The packet includes an IP source address field and an IP destination address field, the IP source address field including an IP source address and the IP destination address field including an IP destination address, the IP source address and the IP destination address each having a number of bits (e.g., 128 bits in the case of IPv6). An IP source address is obtained from the IP source address field of the packet and an IP destination address is obtained from the IP destination address field of the packet. A modified IP source address is generated from the obtained IP source address such that the number of bits in the modified IP source address is less than the number of bits in the obtained IP source address. In addition, a modified IP destination address is generated from the obtained IP destination address such that the number of bits in the modified IP destination address is less than the number of bits in the obtained IP destination address. The access list key is then composed from the modified IP source address and the modified IP destination address.
Owner:CISCO TECH INC
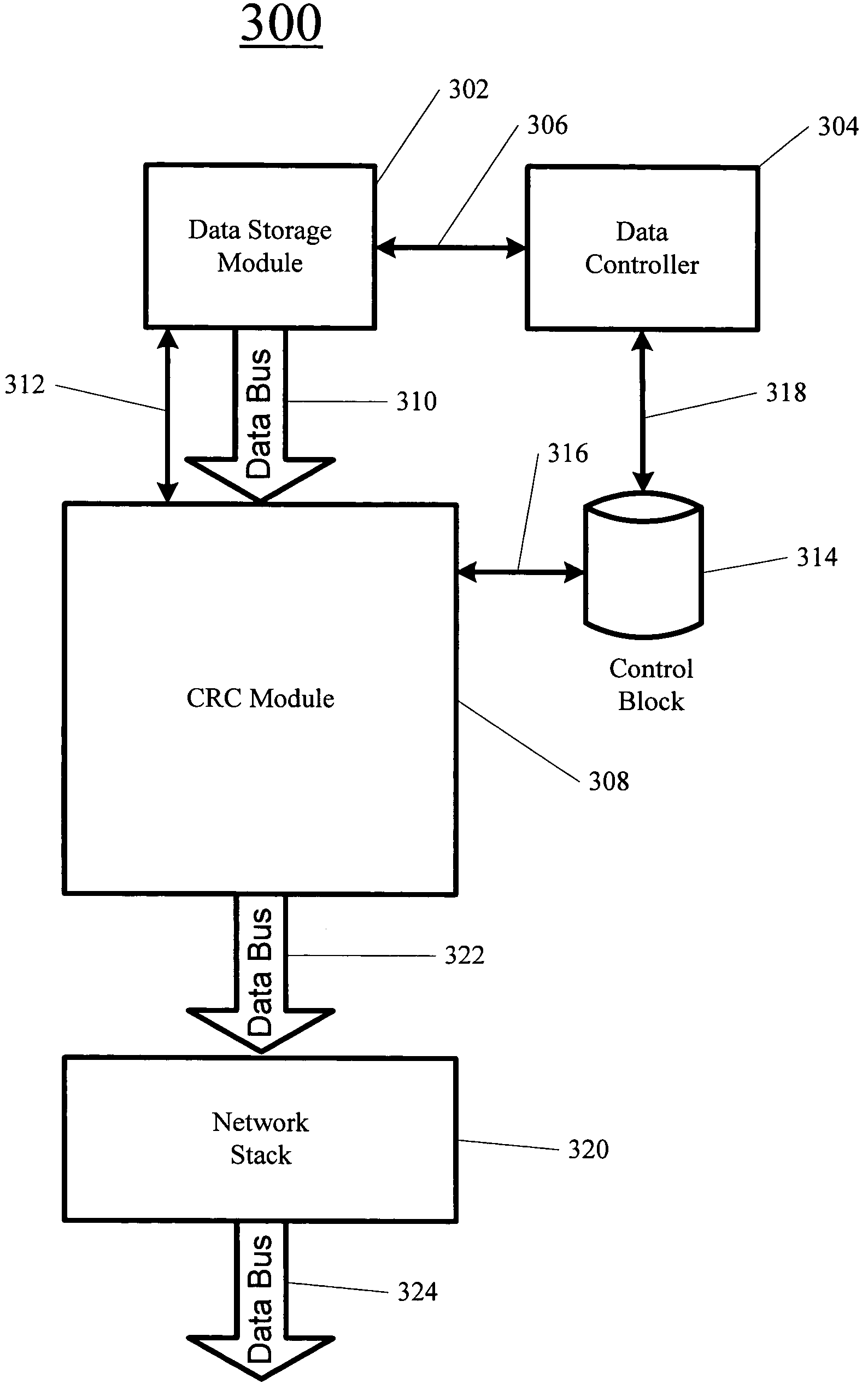
System and method for generating 128-bit cyclic redundancy check values with 32-bit granularity
A System and Method for generating Cyclic Redundancy Check (CRC) values in a system adapted simultaneously handling a plurality of blocks in parallel is described. Included is a memory or other storage device for storing data blocks, wherein the memory or storage device is adapted to output a plurality of data blocks in parallel. A data bus provides a data path wide enough to accommodate the parallel data blocks and is further coupled to a plurality of CRC cores coupled to the data bus, wherein CRC values are calculated for every combination of data blocks on the data bus. A multiplexer coupled to the CRC cores selects the output of one of the CRC cores based on the number of valid data blocks on the data bus. Once the correct CRC value has been calculated, it is appended to a data segment, comprised of a group of data blocks, for transmission to another device.
Owner:NVIDIA CORP
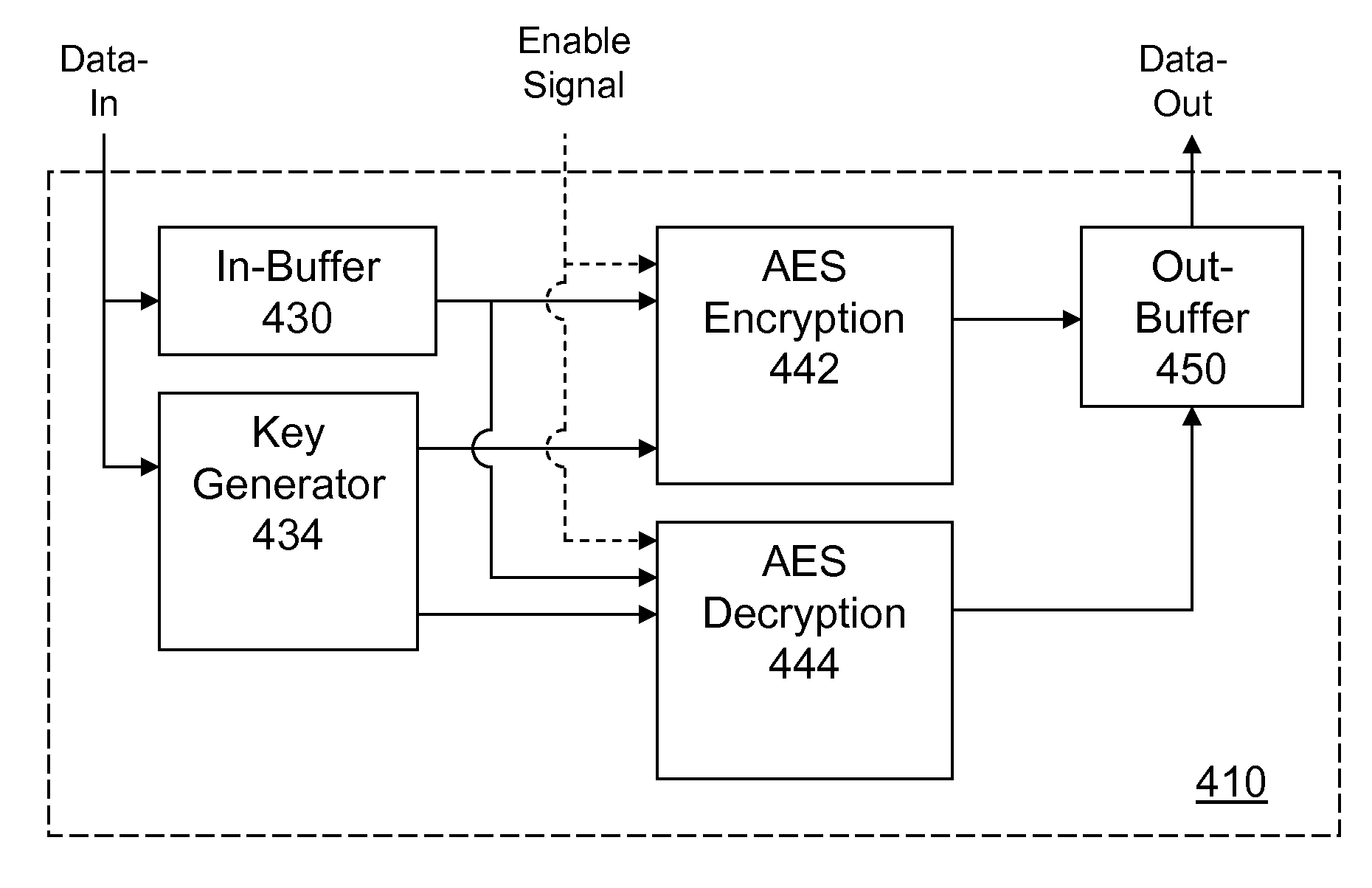
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
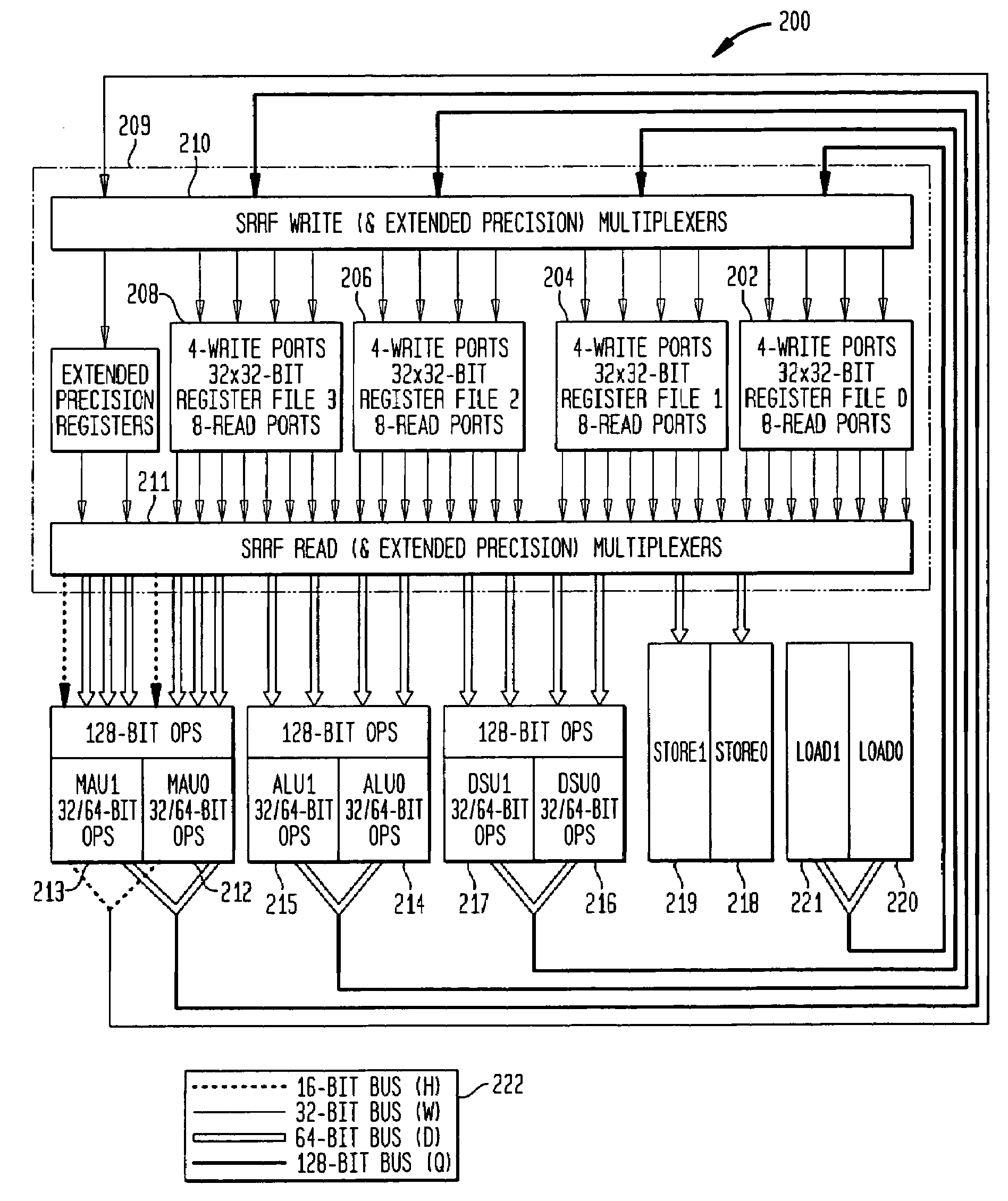
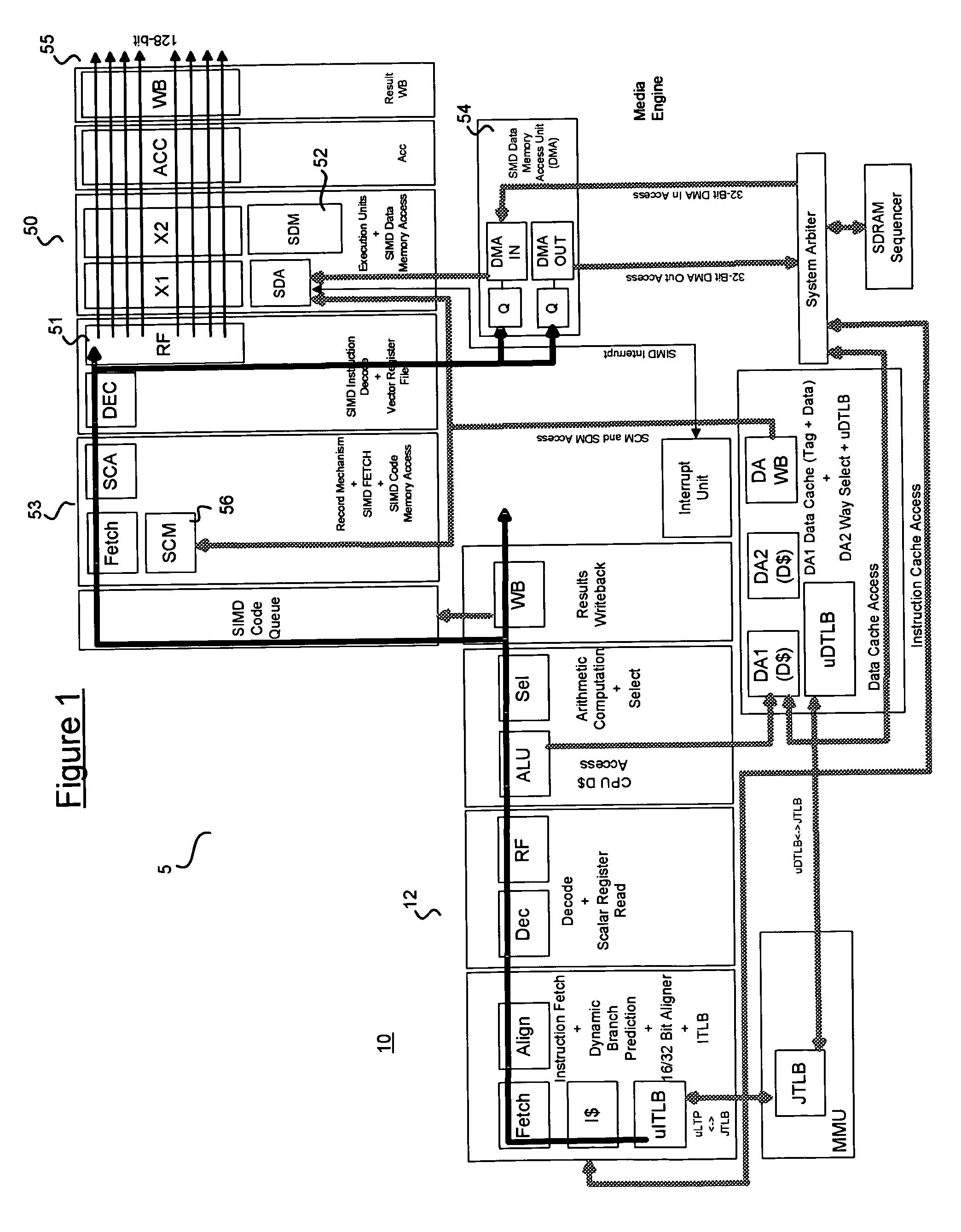
Methods and apparatus for dynamic instruction controlled reconfigurable register file
InactiveUS7398347B1Instruction analysisMemory adressing/allocation/relocationProcessor registerMultiplexer
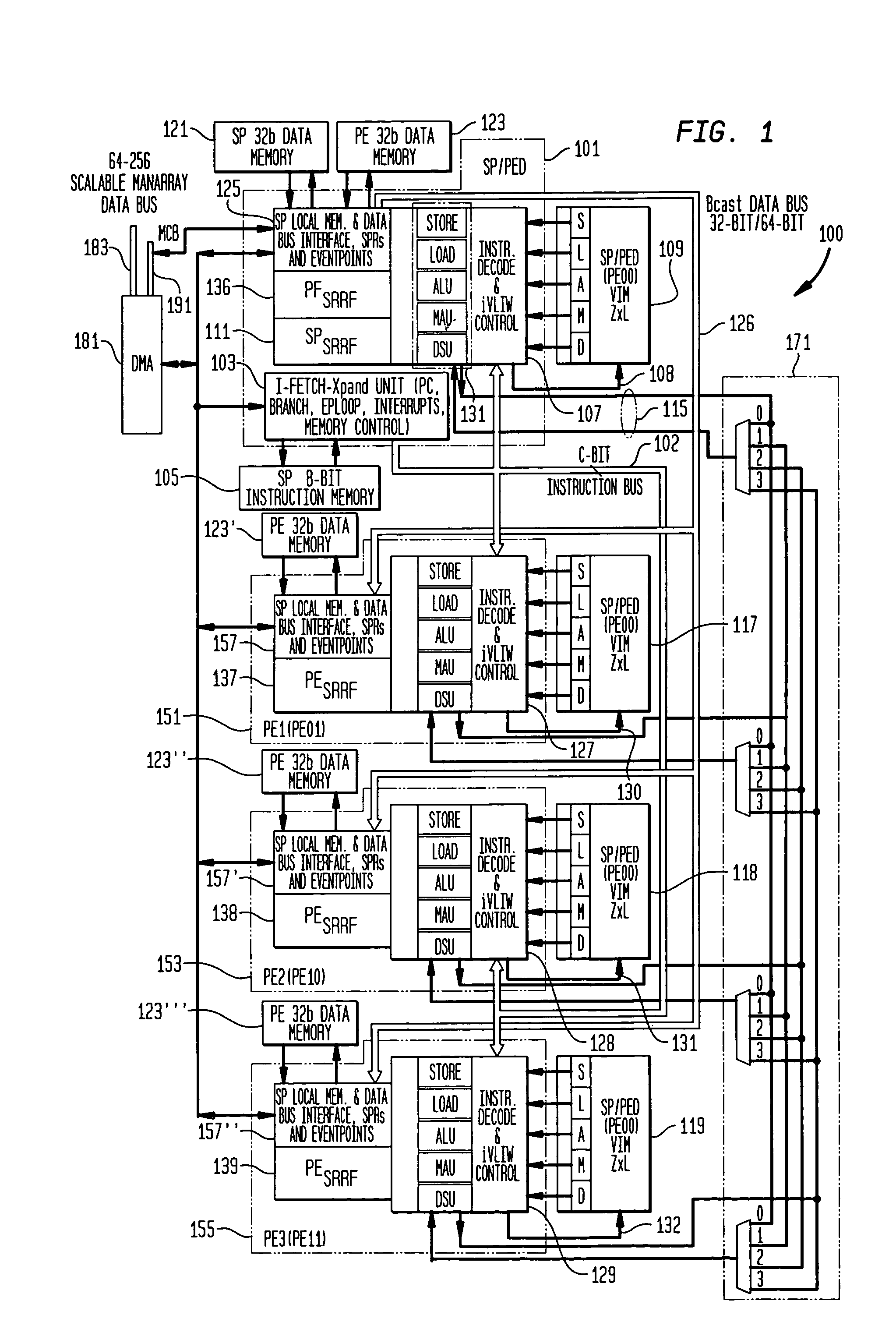
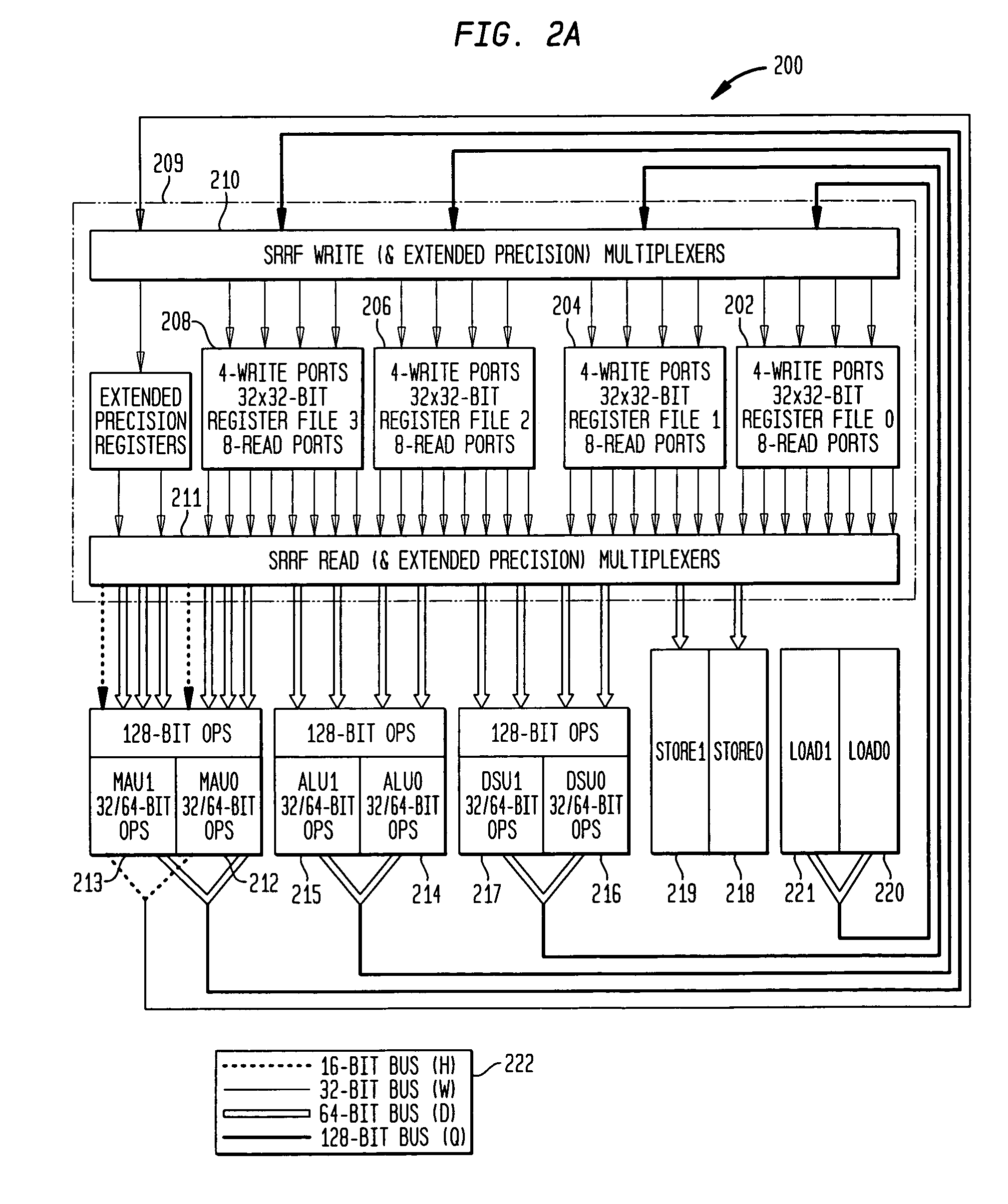
A scalable reconfigurable register file (SRRF) containing multiple register files, read and write multiplexer complexes, and a control unit operating in response to instructions is described. Multiple address configurations of the register files are supported by each instruction and different configurations are operable simultaneously during a single instruction execution. For example, with separate files of the size 32×32 supported configurations of 128×32 bit s, 64×64 bit s and 32×128 bit s can be in operation each cycle. Single width, double width, quad width operands are optimally supported without increasing the register file size and without increasing the number of register file read or write ports.
Owner:ALTERA CORP
Graphics controller integrated circuit without memory interface
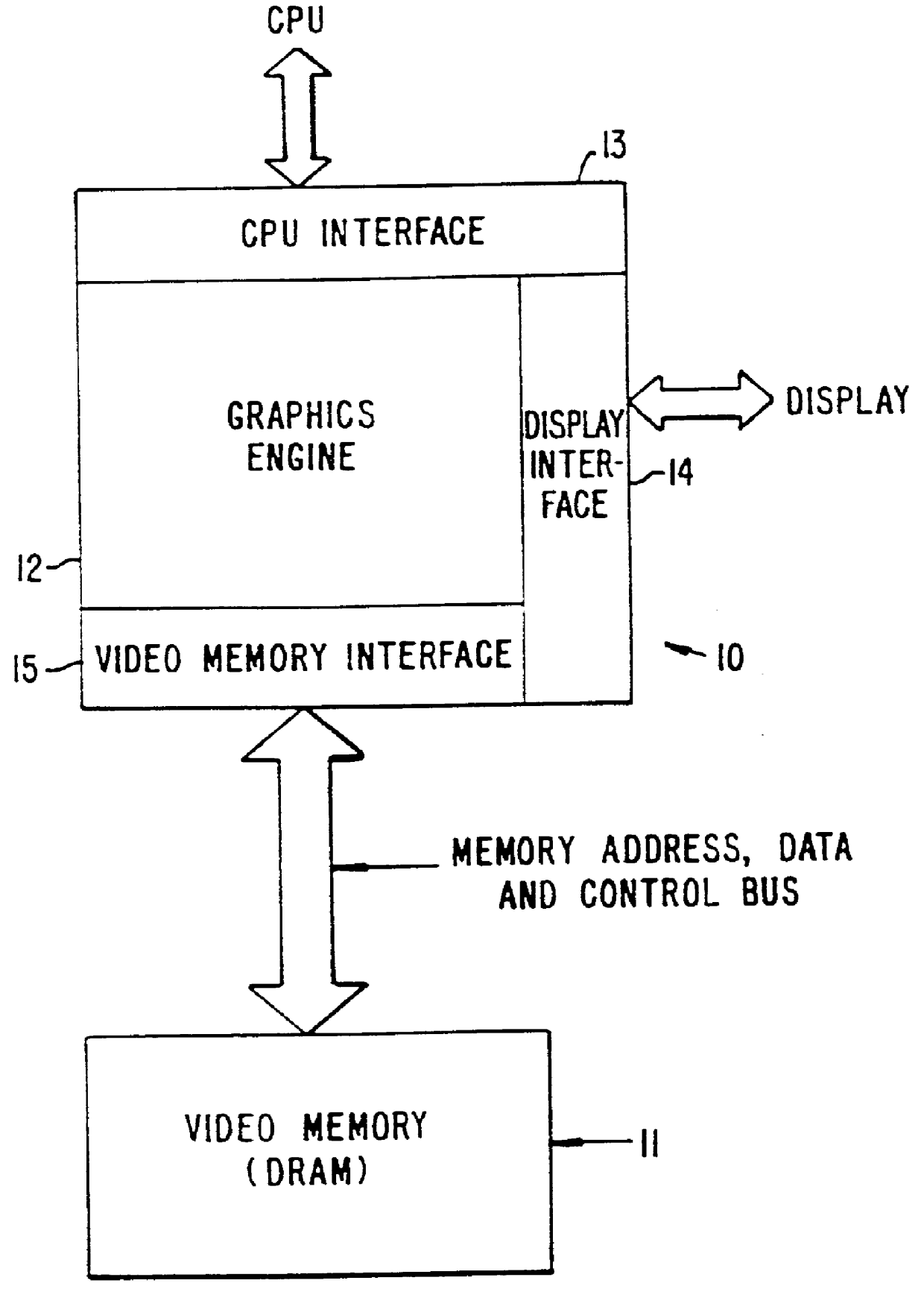
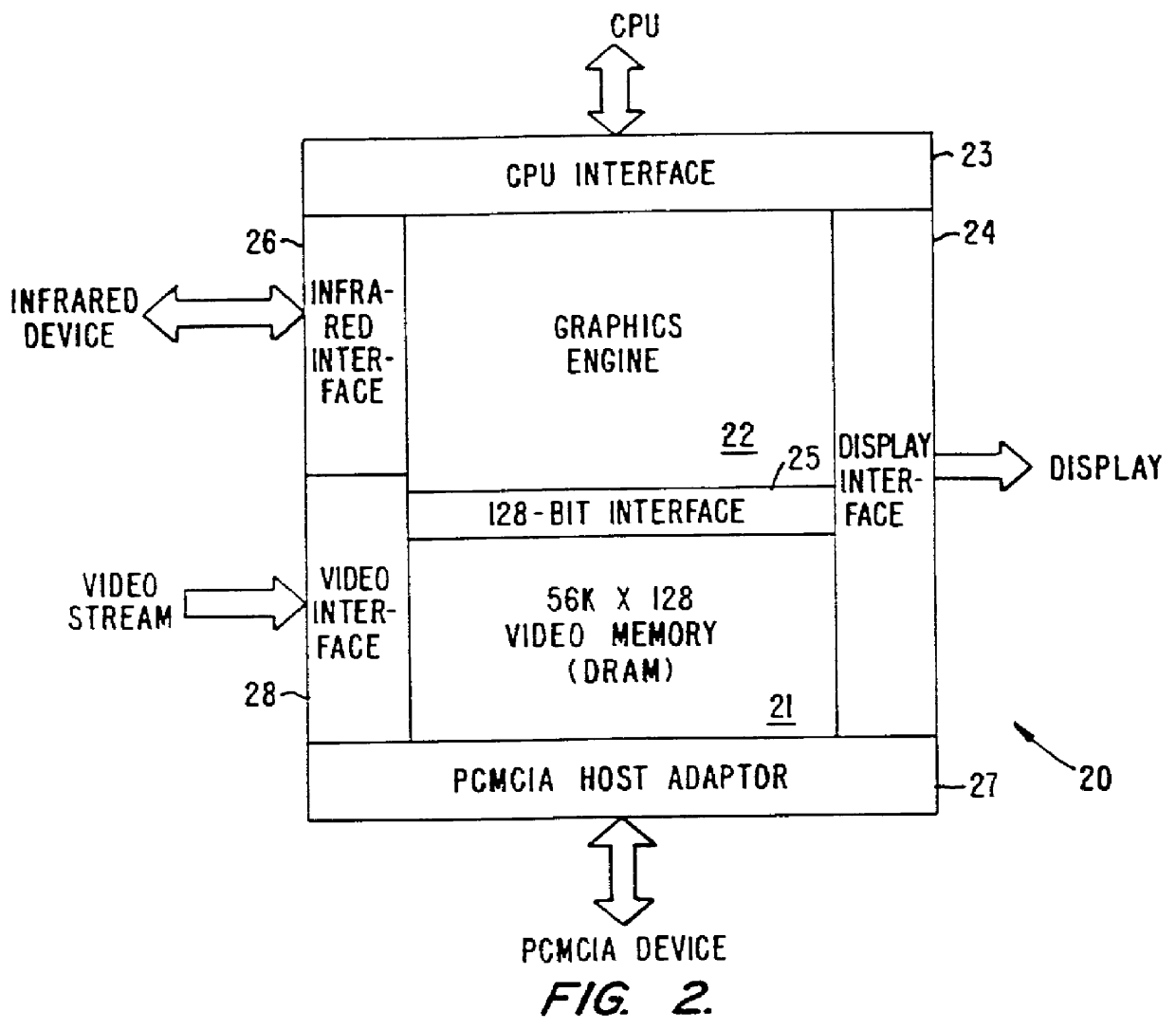
InactiveUS6356497B1Input/output to record carriersCathode-ray tube indicatorsVideo memoryInternal memory
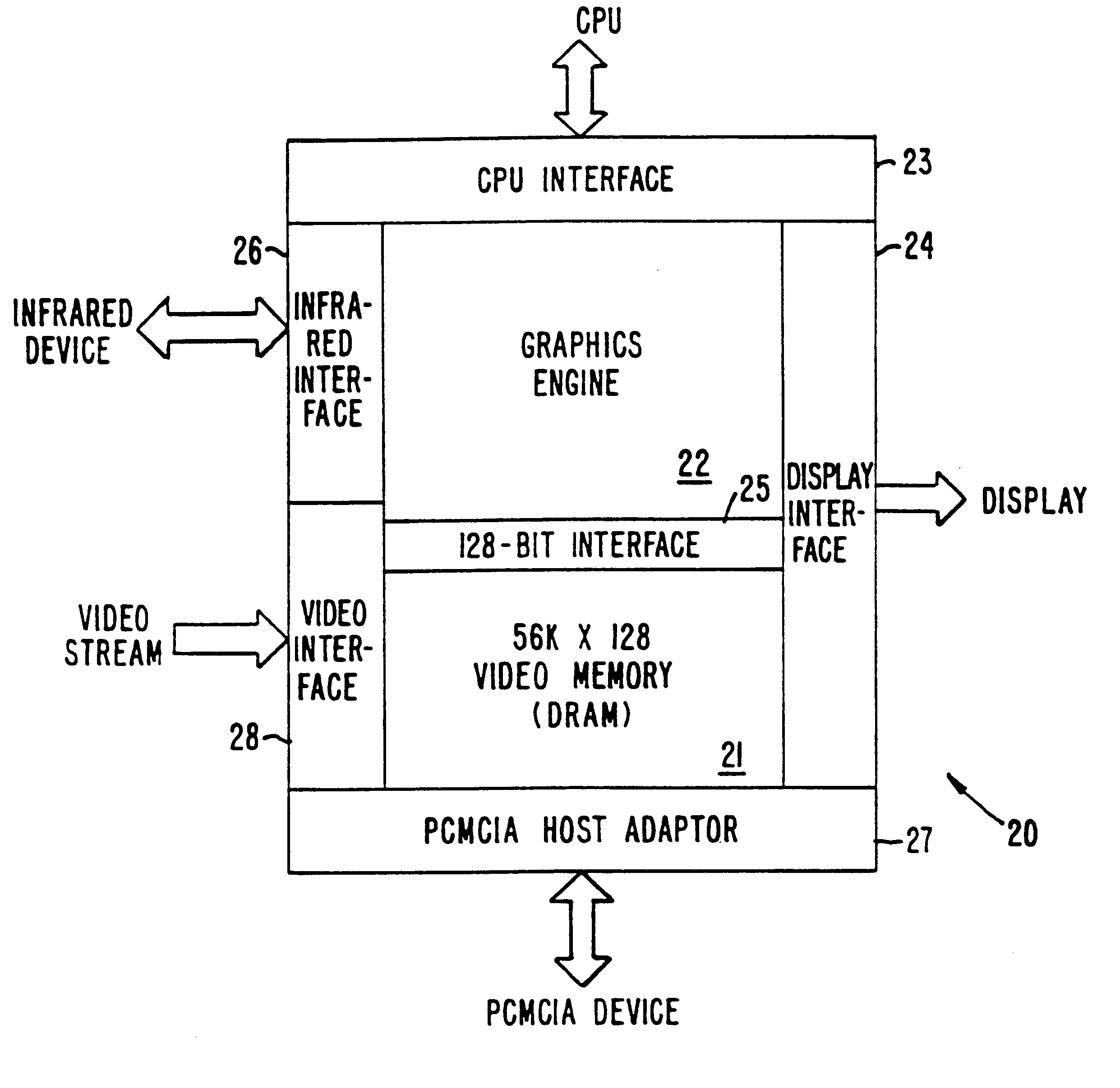
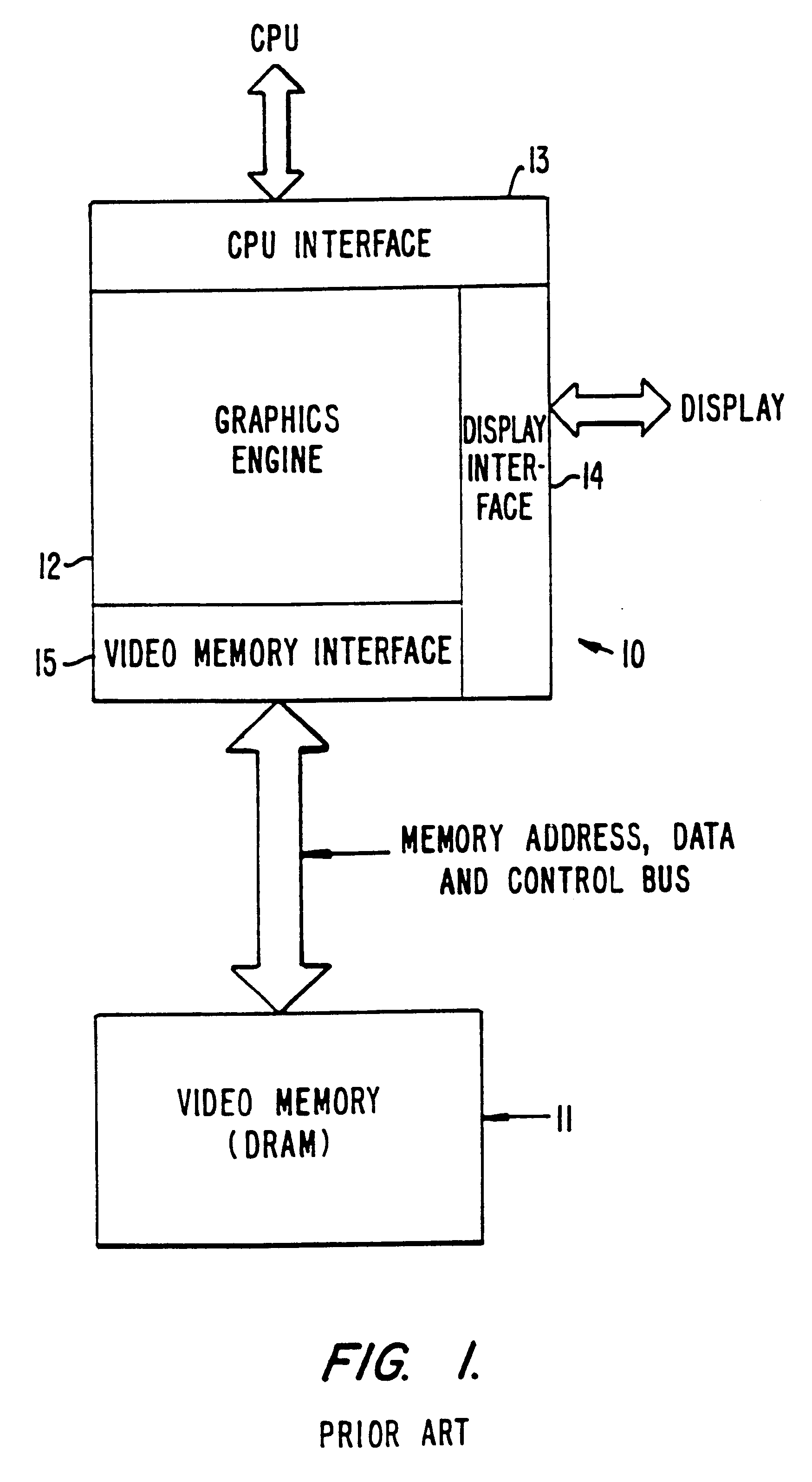
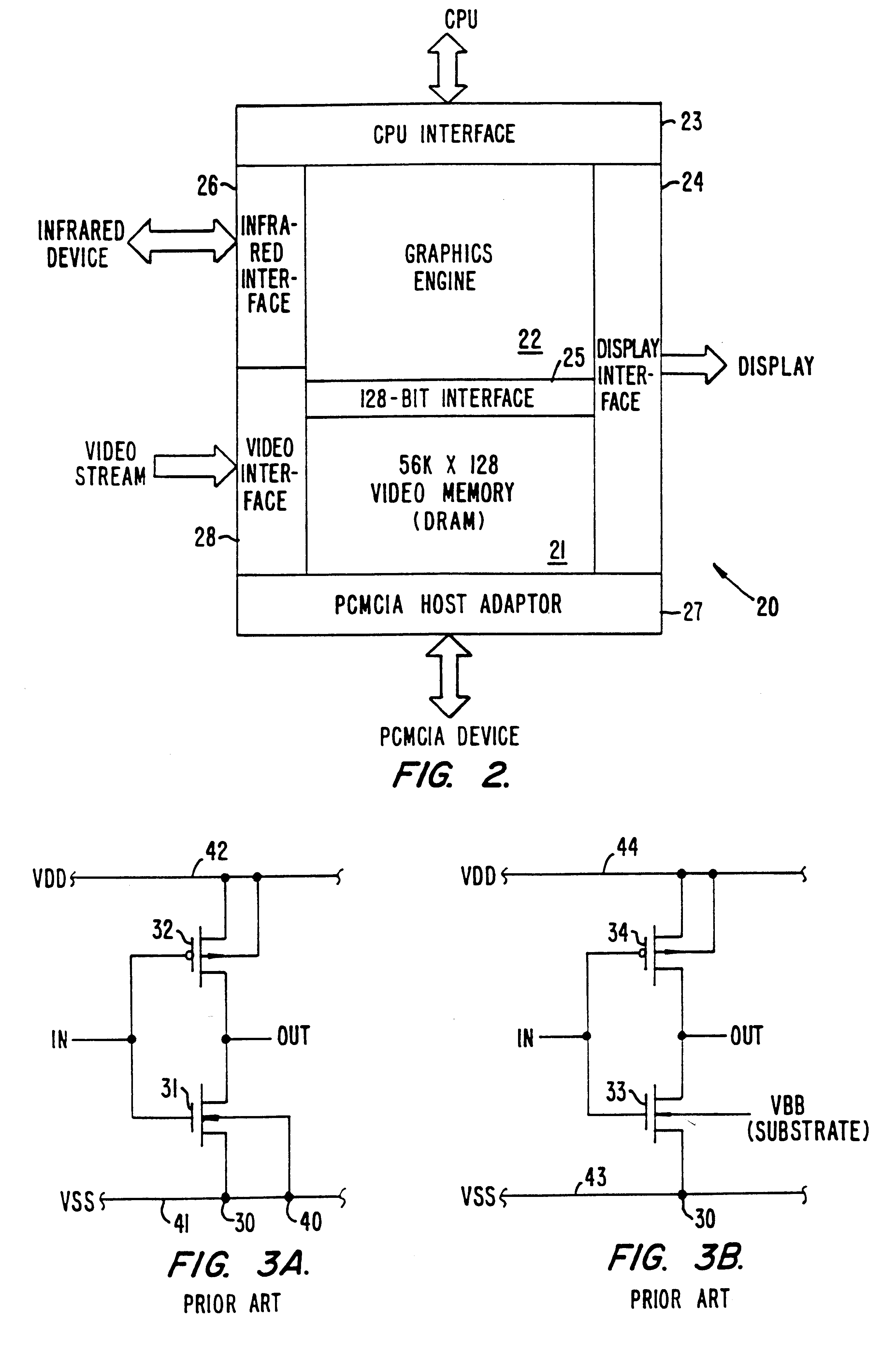
A CMOS integrated circuit that comprises a graphics controller system that consists of a graphics engine and video memory together with some interface blocks, a PCMCIA host adapter, an infrared interface for generating video images on a LCD or CRT display unit, and a video stream interface for receiving video signals. Since the video memory is integrated on the same integrated circuit as the graphics controller, no package pins are required for the memory interface. The pins thus saved are used to provide access to an on-chip PCMCIA host adapter. The internal memory interface is 128 bits wide. Simultaneous performance improvement and power dissipation reduction is achieved because of the wide memory interface and the elimination of the large parasitic capacitances associated with a package pin connection.
Owner:INTELLECTUAL VENTURES I LLC
Method and apparatus for generating ipv6 unique local address
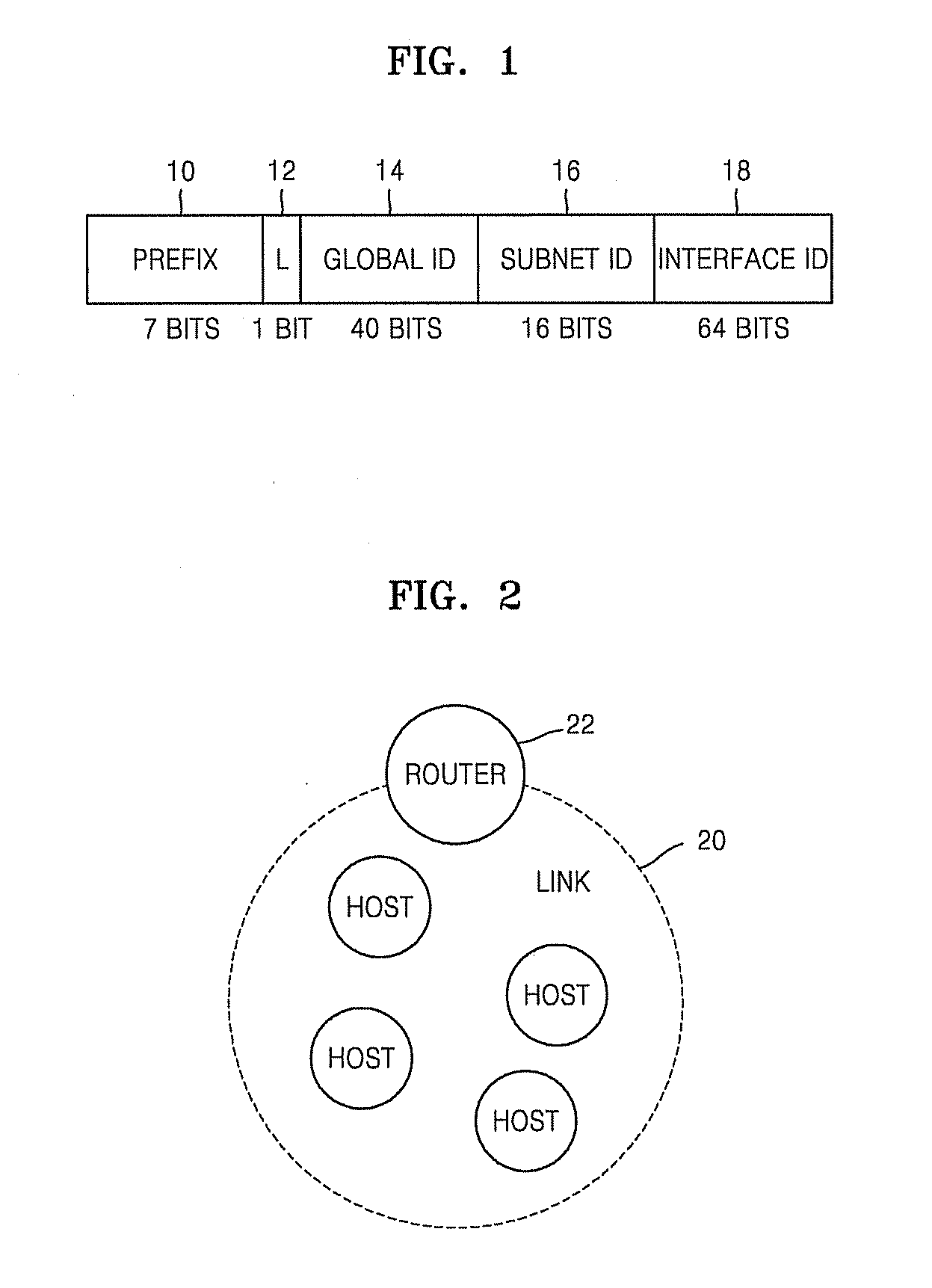
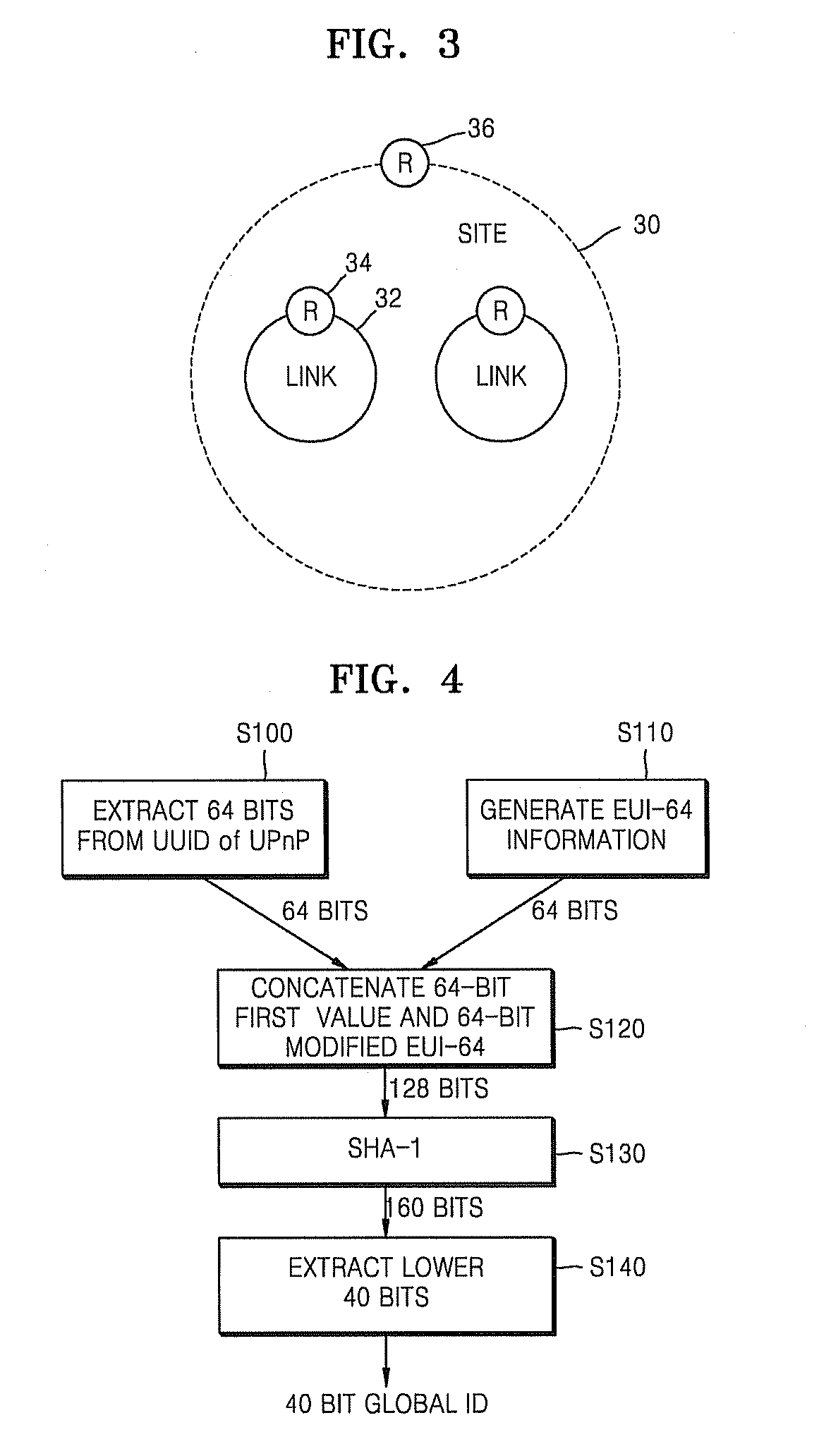
A method and apparatus for generating an IPv6 unique local address (ULA) are provided. The method includes generating a 64-bit first value using unique information on a UPnP device used by a router; generating a modified 64-bit EUI-64 using unique information on an interface device used by the router; generating a 128-bit second value by concatenating the 64-bit first value and the modified EUI-64; generating a 160-bit third value by applying SHA-1 to the 128-bit second value; and generating a global ID by extracting 40 bits from the 160-bit third value. A global ID is generated using unique information on an UPnP device and an interface device and the IPv6 ULA is generated using the global ID, thereby generating the IPv6 ULA having uniqueness in an entire IPv6 address system without an NTP.
Owner:SAMSUNG ELECTRONICS CO LTD
Graphics controller integrated circuit without memory interface pins and associated power dissipation
InactiveUS6041010AInput/output to record carriersCathode-ray tube indicatorsInternal memoryVideo memory
A CMOS integrated circuit that comprises a graphics controller system that consists of a graphics engine and video memory together with some interface blocks, a PCMCIA host adapter, an infrared interface for generating video images on a LCD or CRT display unit, and a video stream interface for receiving video signals. Since the video memory is integrated on the same integrated circuit as the graphics controller, no package pins are required for the memory interface. The pins thus saved are used to provide access to an on-chip PCMCIA host adapter. The internal memory interface is 128 bits wide. Simultaneous performance improvement and power dissipation reduction is achieved because of the wide memory interface and the elimination of the large parasitic capacitances associated with a package pin connection.
Owner:INTELLECTUAL VENTURES I LLC
Encipher method and system for B2B data exchange
InactiveCN101442409AMeet the integration conditionsPublic key for secure communicationUser identity/authority verificationPlaintextNetwork packet
The invention discloses an encryption method for B2B data exchange, which is used for encrypted data exchange between two service entities in a plurality of service entities. The method comprises the following steps: transmitting party encryption, in which a 128 bit random key is generated by a random algorithm; a clear text requiring transmission is symmetrically encrypted by the random key and a symmetric cryptographic algorithm to generate a cryptograph; the random key is encrypted to a key by an asymmetric cryptographic algorithm of a digital certificate public key of a receiving party; a digital signature is generated on cryptograph by a digital certificate private key of the transmitting party; and a data packet consisting of the cryptograph, the key and the digital signature is accessed to a data to be read area of the receiving party; the receiving party decryption, in which validity of the digital signature is authenticated by the digital certificate public key of the transmitting party so as to determine that the data is real and valid; the key is decrypted by the digital certificate private key and the asymmetric cryptographic algorithm of the receiving party so as to acquire the random key through calculating; and the cryptograph is decrypted by the random key and the symmetric cryptographic algorithm to acquire the clear text.
Owner:上海欧冶供应链有限公司
Access list key compression
ActiveUS7367052B1Efficient processingDigital data processing detailsMultiple digital computer combinationsComputer networkIPv6
Methods and apparatus for implementing an access list key for accessing information associated with a packet from an access list are disclosed. The packet includes an IP source address field and an IP destination address field, the IP source address field including an IP source address and the IP destination address field including an IP destination address, the IP source address and the IP destination address each having a number of bits (e.g., 128 bits in the case of IPv6). An IP source address is obtained from the IP source address field of the packet and an IP destination address is obtained from the IP destination address field of the packet. A modified IP source address is generated from the obtained IP source address such that the number of bits in the modified IP source address is less than the number of bits in the obtained IP source address. In addition, a modified IP destination address is generated from the obtained IP destination address such that the number of bits in the modified IP destination address is less than the number of bits in the obtained IP destination address. The access list key is then composed from the modified IP source address and the modified IP destination address.
Owner:CISCO TECH INC
Encryption method for network and information security
ActiveCN101764686AHigh speedDiffusion is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareKey size
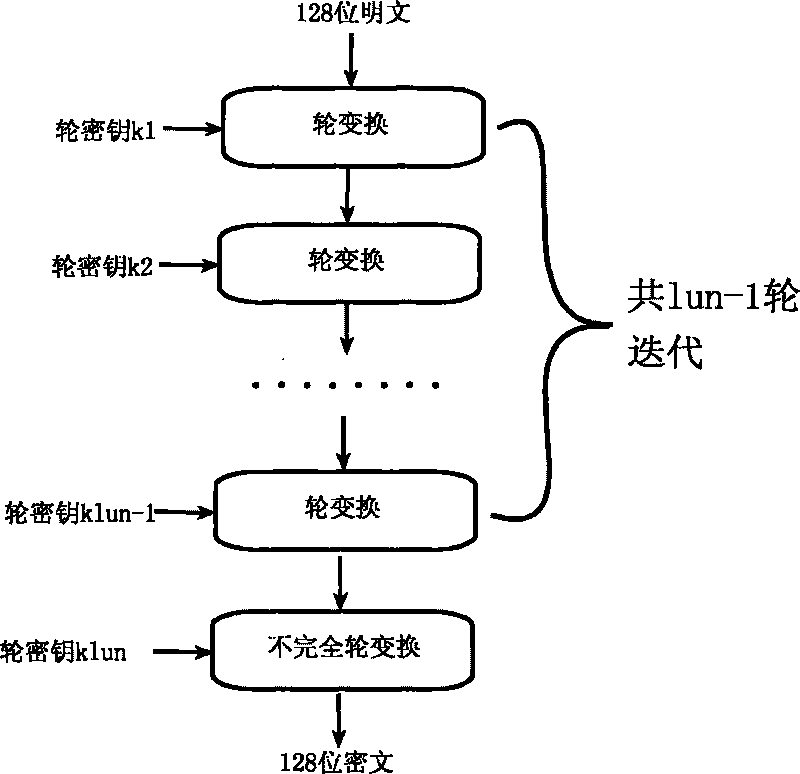
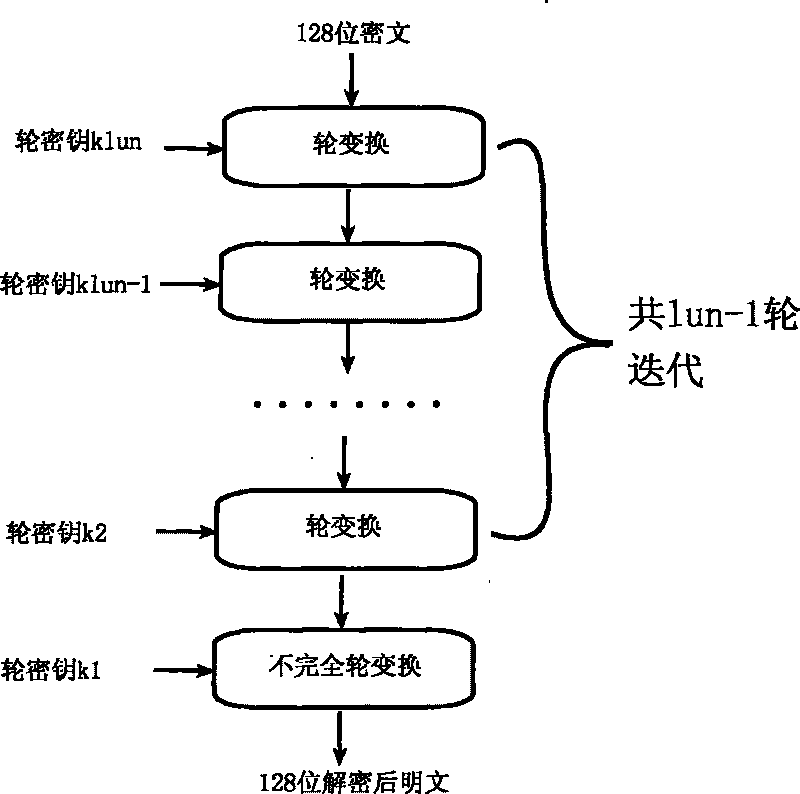
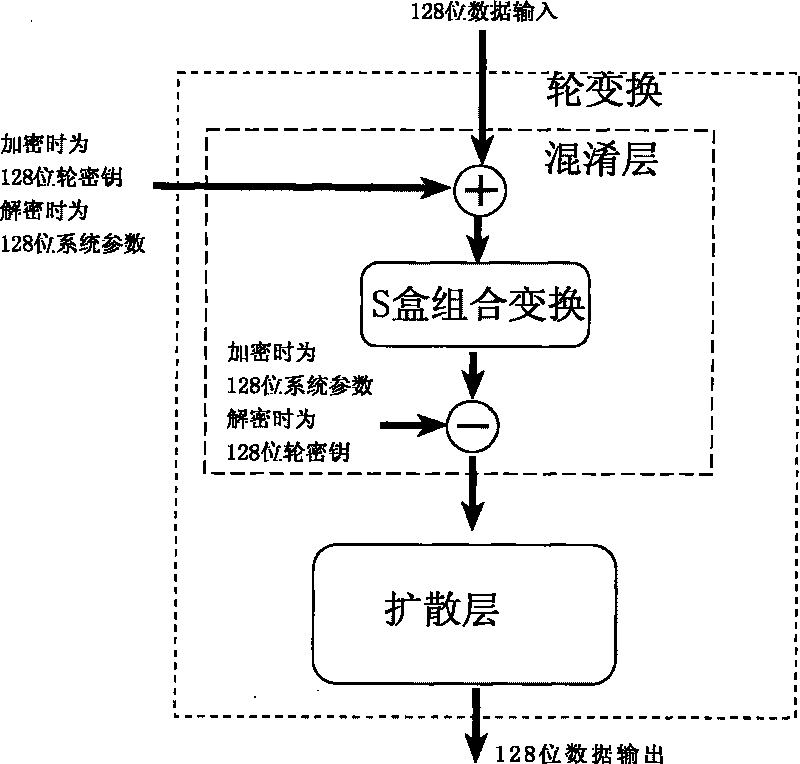
The invention relates to an encryption method for network and information security; the adopted packet length and key length are 128 bits, and a 128-bit system parameter is added; encryption algorithm comprises a plurality of rounds of round transform iteration consisting of mixed layers and diffusion layers, wherein the last round is incomplete round transformation, and the incomplete round transformation consists of the mixed layer; the mixed layer comprises key plus, S box portfolio transform and system parameter minus; the S box portfolio transform comprises 8-input 8-output reversible S box transform and inverse S box transform in the same number which are output by parity exchange; the diffusion layer can construct linear transformation with a reversible re-model polynomial matrix; an encryption round key is generated by an encryption key through encryption round transformation; and decryption algorithm is the inverse transformation of encryption algorithm. The encryption methodfor network and information security has the advantages of high diffusion speed, good security strength, hardware resource saving, and very high speed when being realized by hardware and on a software platform.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Connectivity verification of IC (integrated circuit) mask layout database versus IC schematic; LVS check, (LVS: IC layout versus IC schematic) via the internet method and computer software
InactiveUS20060200789A1Avoid repetitive drawingShorten the timeCAD network environmentCAD circuit designThe InternetLayout Versus Schematic
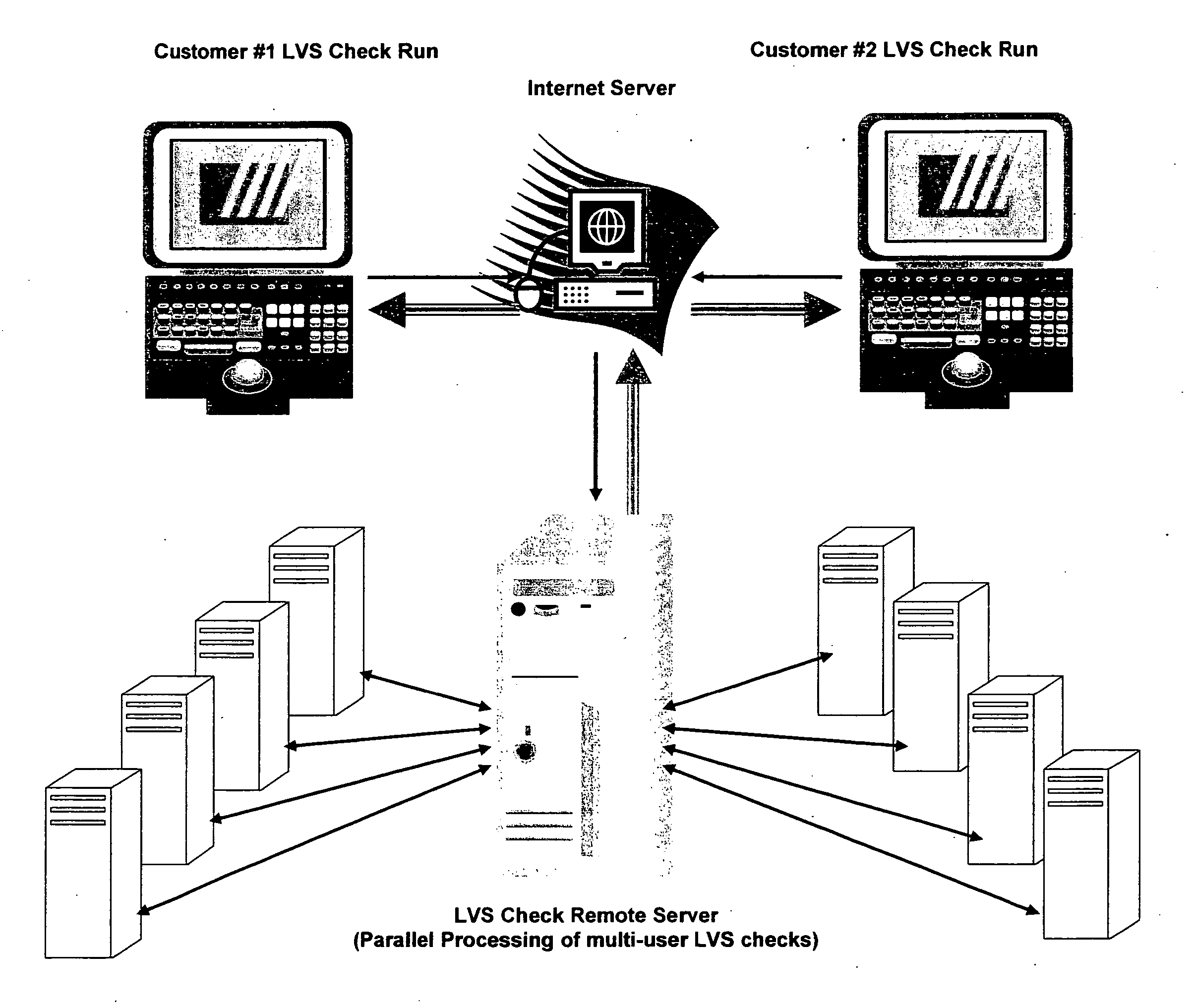
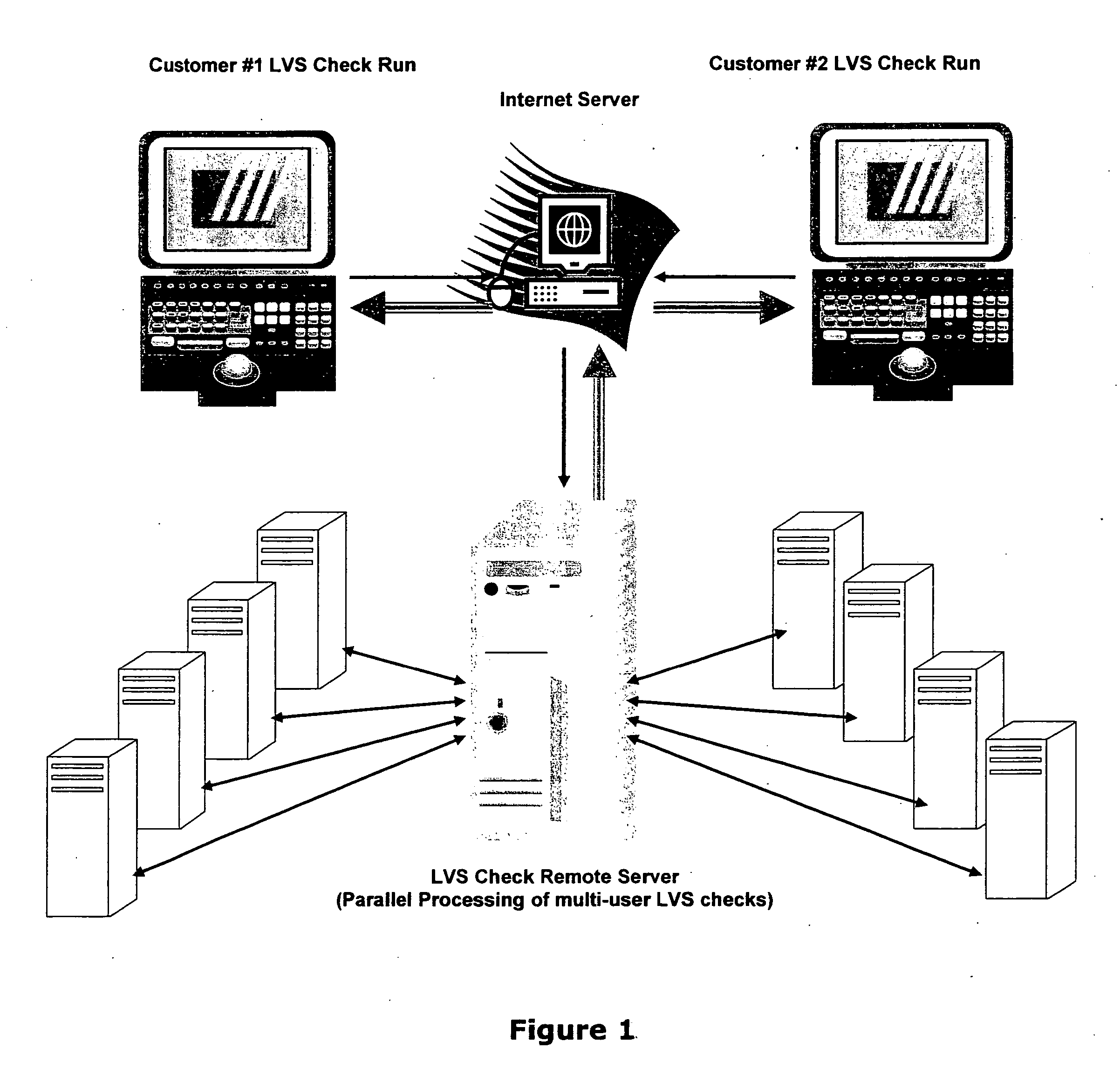
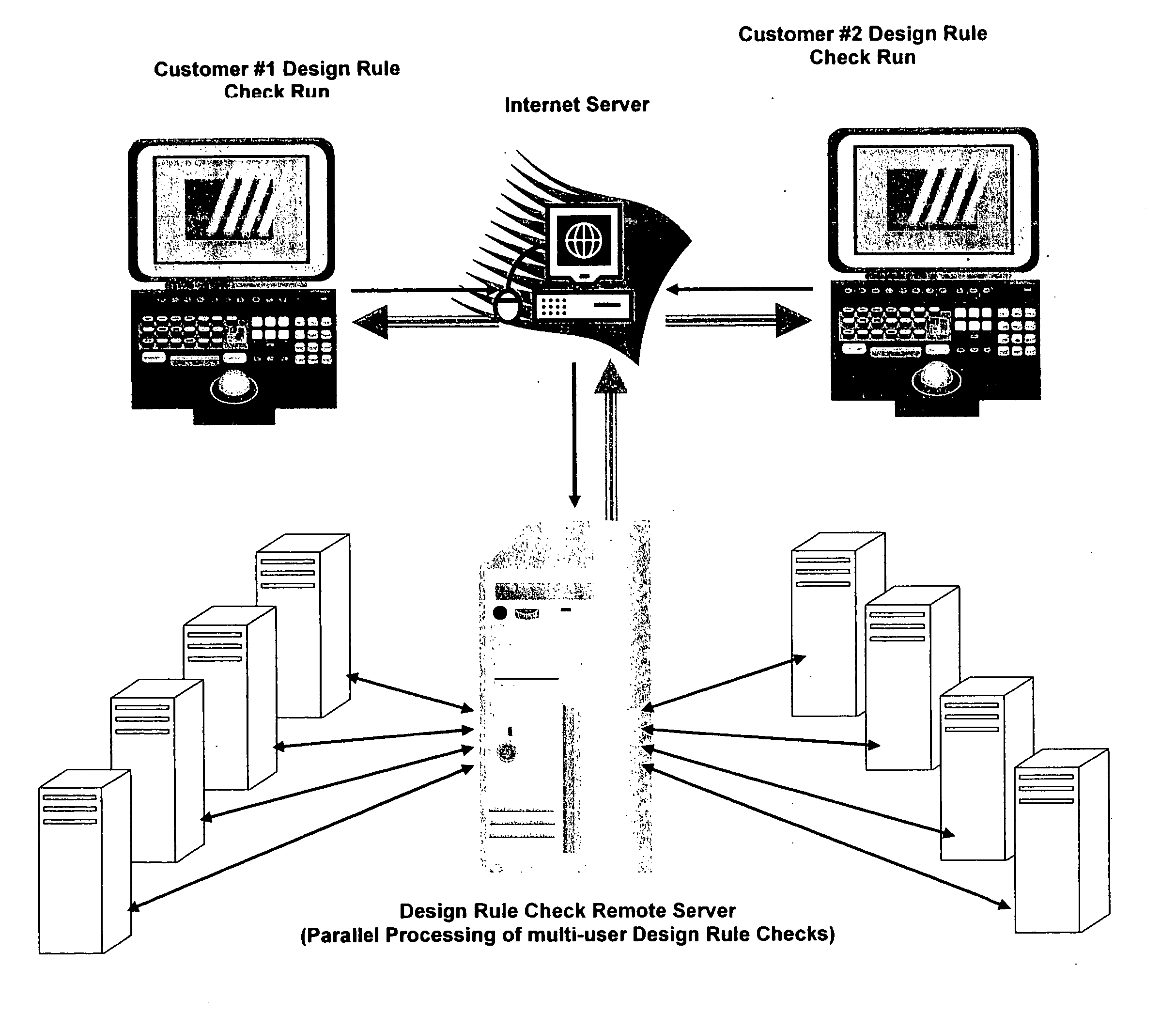
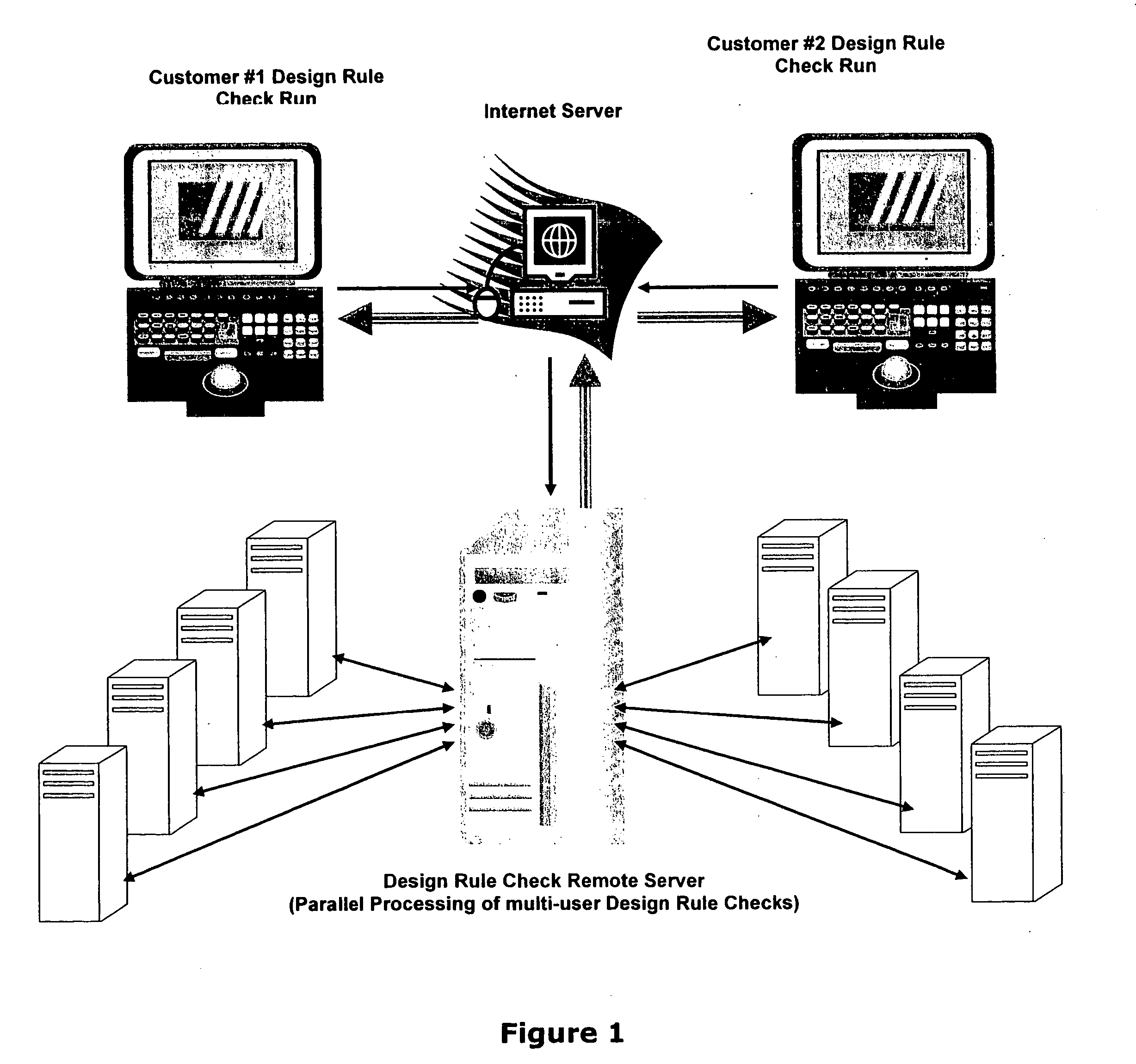
This paper describes an EDA (Electronic Data Automation) method and computer software invention for connectivity verification of IC mask Layout database versus IC Schematic; LVS Check (LVS: IC Layout versus IC Schematic) over the internet. The technique takes advantage of a unique algorithm to check the mask layout database connectivity, compare it with its corresponding schematic diagram for any mismatches in the mask layout polygons connections. The input of the tool is a mask layout database blocks (i.e.: IC layout) that were made manually and / or automatically using synthesized tools. These blocks may have some connectivity mismatches that need to be fixed in order to match the corresponding integrated circuit (IC) schematic diagrams. The output of the software tool is a text based descriptive log file and errors markers pointers that may be read into the mask layout database in order to point any connectivity mismatches of the mask layout database, comparing it to its corresponding schematic diagram. The end result is a mask layout set of markers and a text format log file that describes any mismatched connections in the mask layout database, comparing it to its corresponded schematic diagram. The software performs on individual mask layout blocks and / or on hierarchical structure of mask layout blocks. The system works hierarchically and / or flat. System also checks mask layout database incrementally, means only blocks that have been changed are checked. The system can be run via the internet using our secured protocol. The system offer a web based control panel to execute all necessary setups for submitting LVS check over the internet. The system offers the option to run on a local machine (user's computer) or on the main server over the internet. (Inventor's computer) The system also offers a PDA (Personal Digital Assistant) interface to launch LVS runs via industry's standard PDA's. The procedure is fully secured by 128 bit security protocol. All necessary file including mask layout GDSII (or GDSIII) file, netlist and technology file are securely encrypted using 128 bit protocol and send to the remote server. These files are decrypted and submitted for LVS check on the remote servers. The main remote server is distributing the task among other computer system for advanced parallel processing to achieve fast results. All results log files are encrypted using 128 bit security protocol and available for download by the user. In case of local LVS check the results files are available on the user's local machine.
Owner:RITTMAN DAN
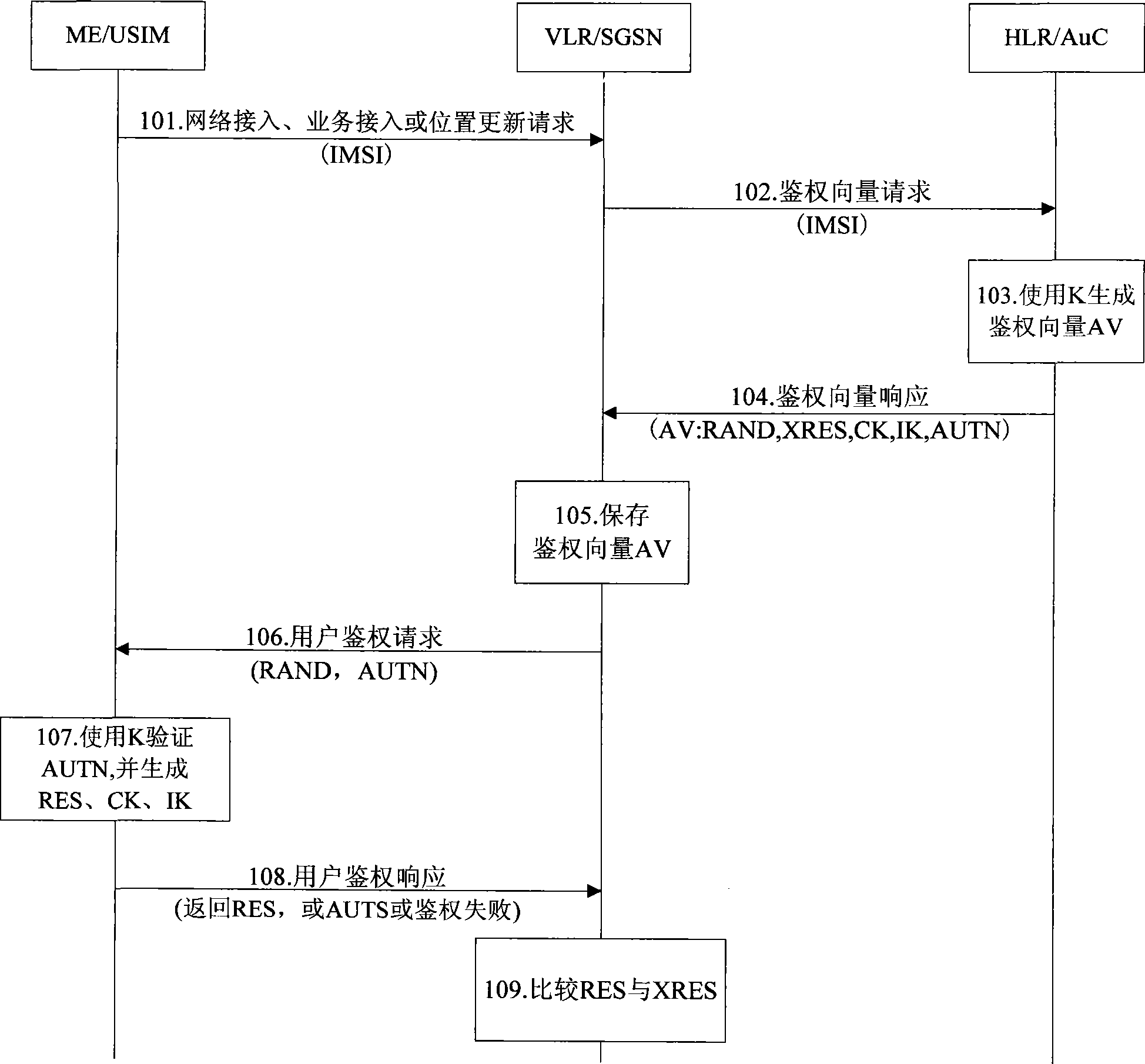
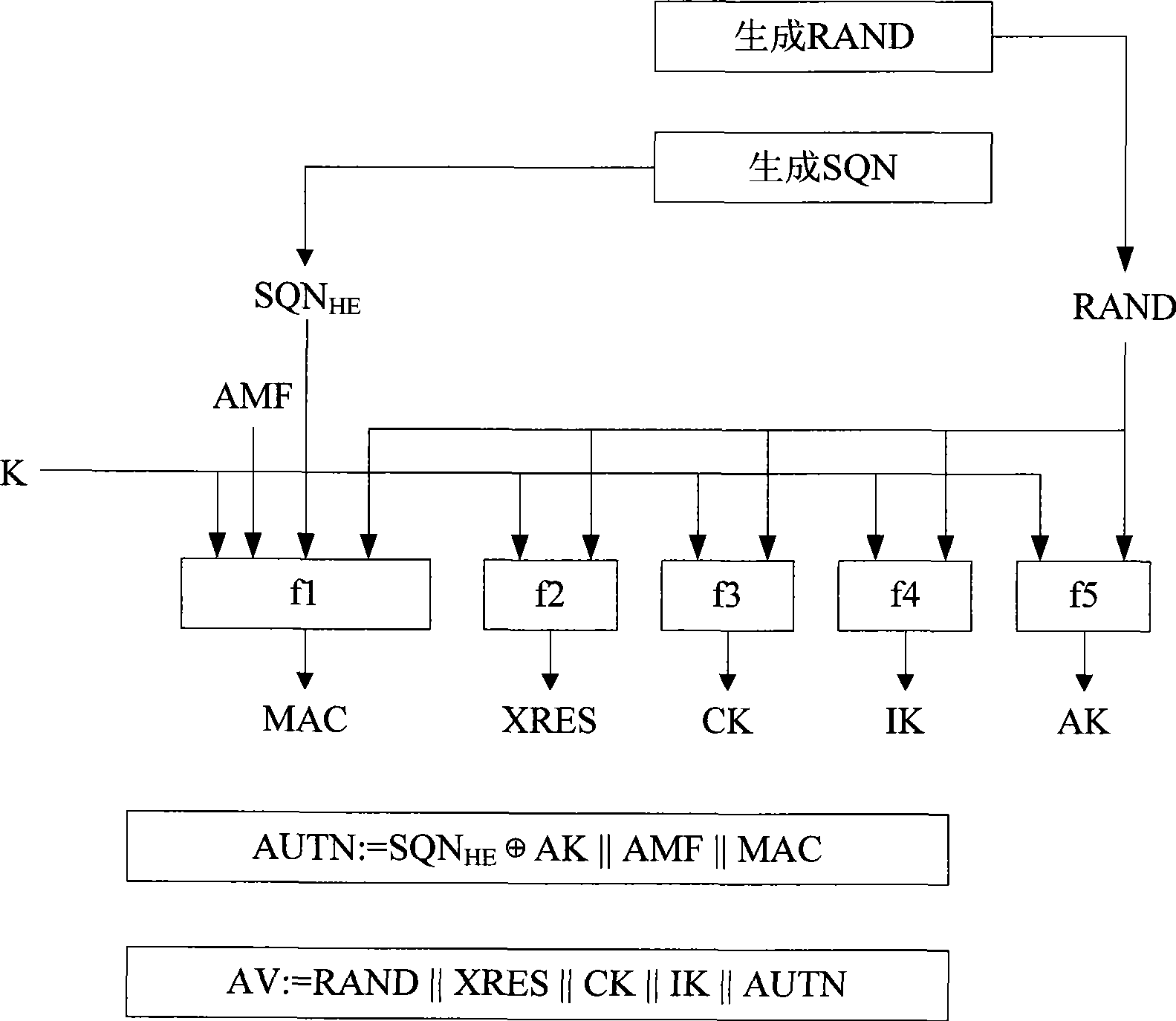
Authentication and cipher key negotiation method of mobile communication system
ActiveCN101511084AIncrease the difficultyReduce security risksUser identity/authority verificationSecurity arrangementMobile communication systemsSerial code
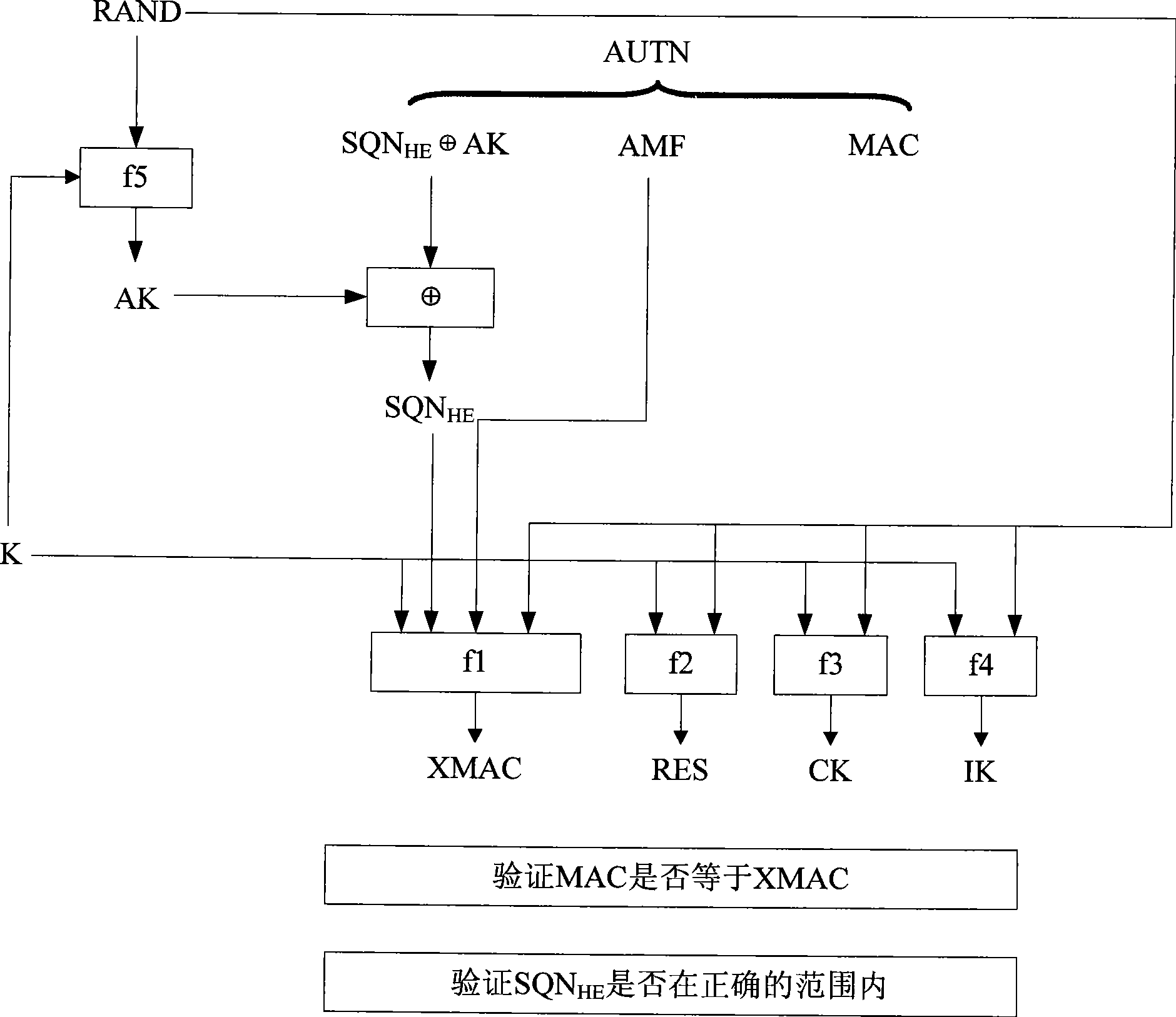
The invention provides an authentication and key arranging method in a mobile communication system. A network side and a mobile terminal side use a boot authentication key K kept by both sides respectively, and same random number RAND and a sequence number SQN with 128 bits length for generating a temporary key(*)=fxk(RAND,SQN), and use K(*) for generating MAC and RES respectively to process dual-way authentication of the network side and the mobile terminal side; wherein, fx is a group arithmetic with 128 bits key length; K is the key used by fx arithmetic function. The AKA enhancement authentication method one time one encryption can increase difficulty for decoding the authentication key greatly, accordingly, reduce safe risk of decoding the authentication boot key.
Owner:CHINA MOBILE COMM GRP CO LTD +1
A secure and efficient face recognition method based on depth learning and homomorphic encryption
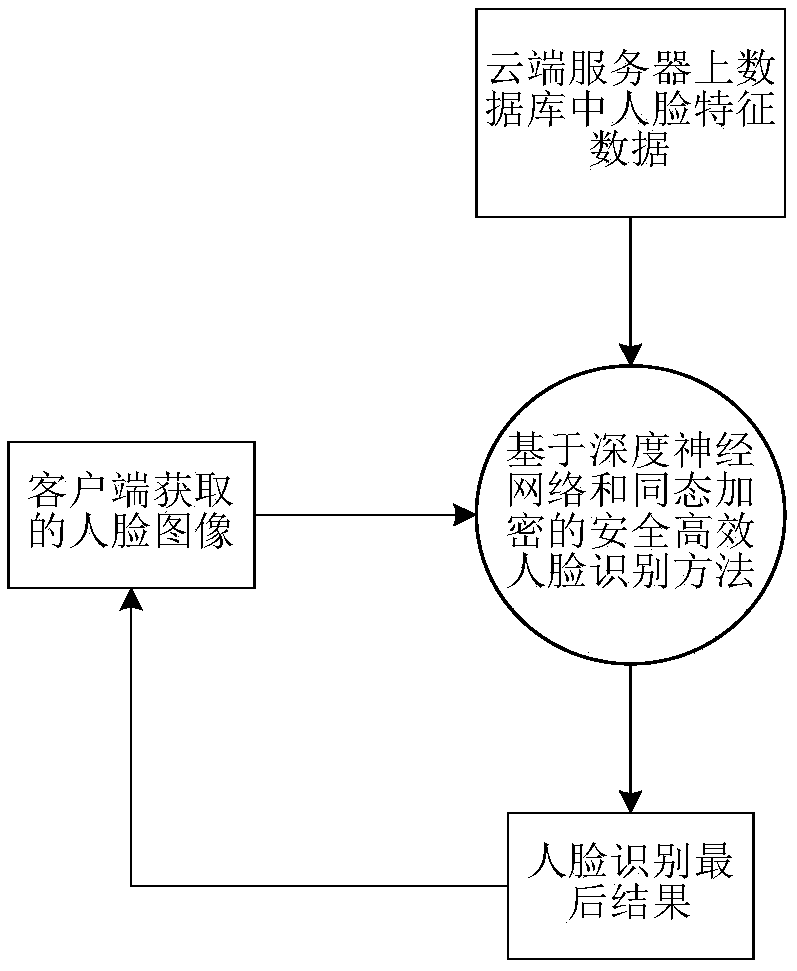
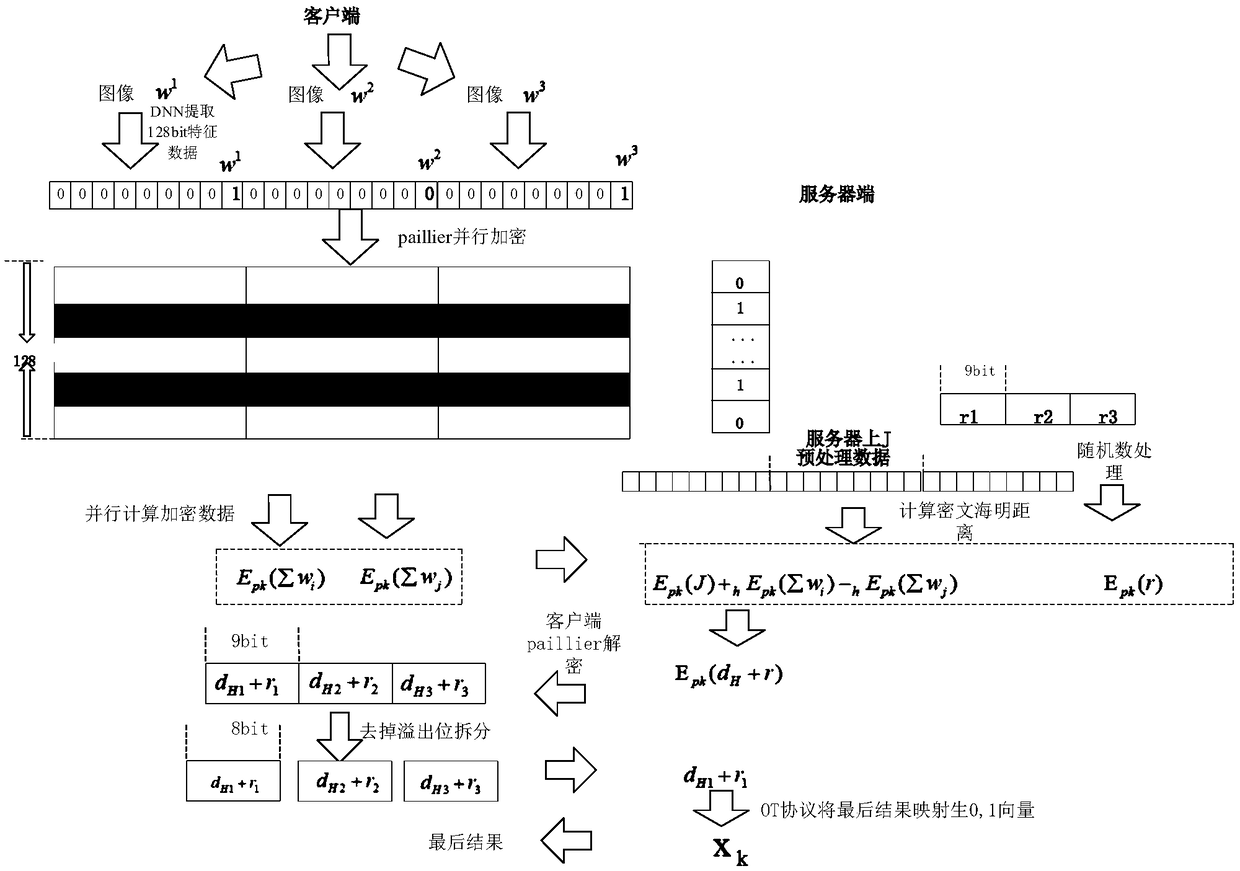
InactiveCN109145829AReduce data volumeSimple calculationCharacter and pattern recognitionNeural learning methodsFeature extractionCiphertext
The invention provides a safe and efficient face recognition method based on depth learning and homomorphic encryption. Each terminal is responsible for acquiring face images by using depth neural network, extracting face features from the acquired face images, extracting 128-bit feature data, encrypting the feature data by paillier encryption algorithm and sending the ciphertext data to the cloud. The server at a cloud end receives the ciphertext data from the terminal, and calculates the Hamming distance by the formula of efficient hidden Hamming distance in this ciphertext state, and finally returns the recognition result to the terminal by OT protocol, which effectively protects the privacy. In the process of facial feature data encryption and Hamming distance computation, a parallel computing mode is introduced, which can encrypt multiple facial feature data and compute the corresponding Hamming distance in parallel, thus greatly improving the efficiency of the whole scheme and achieving the goal of high efficiency, and the method is easy to be implemented by software.
Owner:中共中央办公厅电子科技学院
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
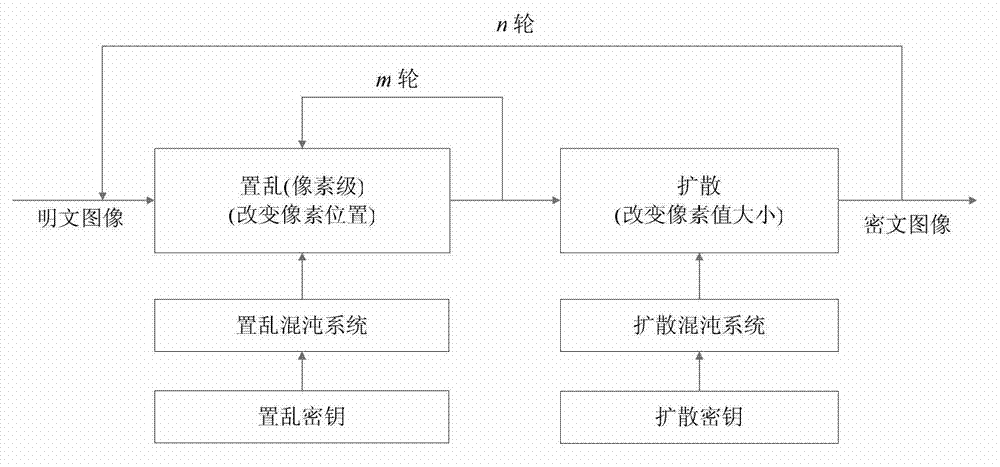
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
Design rule violations check (DRC) of IC's (integrated circuits) mask layout database, via the internet method and computer software
InactiveUS20060253813A1Fast resultsLow costComputer aided designSpecial data processing applicationsGuidelineSoftware design
This paper describes method and EDA (Electronic Data Automation) computer software invention for design rule violations check of mask layout database (integrated circuits layout) via the internet. The technique takes advantage of a unique algorithm to analyze the mask layout database to find mask layout polygons that are less than the minimum design rules (distances) that are determined by the fabrication process. The computer program then creates an output file that marks all design rule violations location and type. The input of the tool is a mask layout database (i.e.: layout block / s) that is made manually by a mask design specialist or automatically by automatic IC layout tools. The output of the software tool is a guideline mechanism and file to mark all design rule violations for correction. This markers file can be loaded into any industry's standard IC mask layout database editor for viewing and correction. The software performs on individual mask layout blocks and / or on hierarchical structure of mask layout blocks. The system also checks mask layout database incrementally, means only blocks that have been changed are checked. The system is activated via the internet using secured protocol. In order to reduce the cost of DRC (design rule check) computer program, corporations may log in to a main server to submit complete DRC (Design Rule Check) run. User point reference files at a local location (User's local computer) and setup all parameters on a web based interface. The system collects all local information and run a complete design rule check locally or on remote server. The system offer a web based control panel to execute all necessary setups for submitting design rule check over the internet using any secured internet browser like MS Explorer and Netscape. The system offers the option to run on a local machine (user's computer) or on the main server over the internet. The system also offers a PDA (Personal Digital Assistant) interface to launch DRC runs via industry's standard PDA's. The procedure is fully secured by 128 bit security protocol. The system supports existing industry standard rule decks like: Mentor's Calibre, Cadence's Assura and Synopsys's Hercules. All design rules can be easily imported from these rule decks to be used by DRC program on the main server. All necessary files including mask layout GDSII (or GSIII) file and technology file are securely encrypted using 128 bit protocol and send to the remote server. These files are decrypted on the remote computer and submitted for design rule check. The main remote server is distributing the task among other computer system for advanced parallel processing to achieve fast results. All results log files are encrypted using 128 bit security protocol and available for download by the user. In case of local design rule check the results files are available on the user's local machine. This approach eliminates the purchase of a full local license and enables affordable price for small and medium size chip design firms. This fact significantly reduces integrated circuits design cost and time to market factor for chip design corporations, enabling faster deliveries to their end customers.
Owner:MICROLOGIC DESIGN AUTOMATION
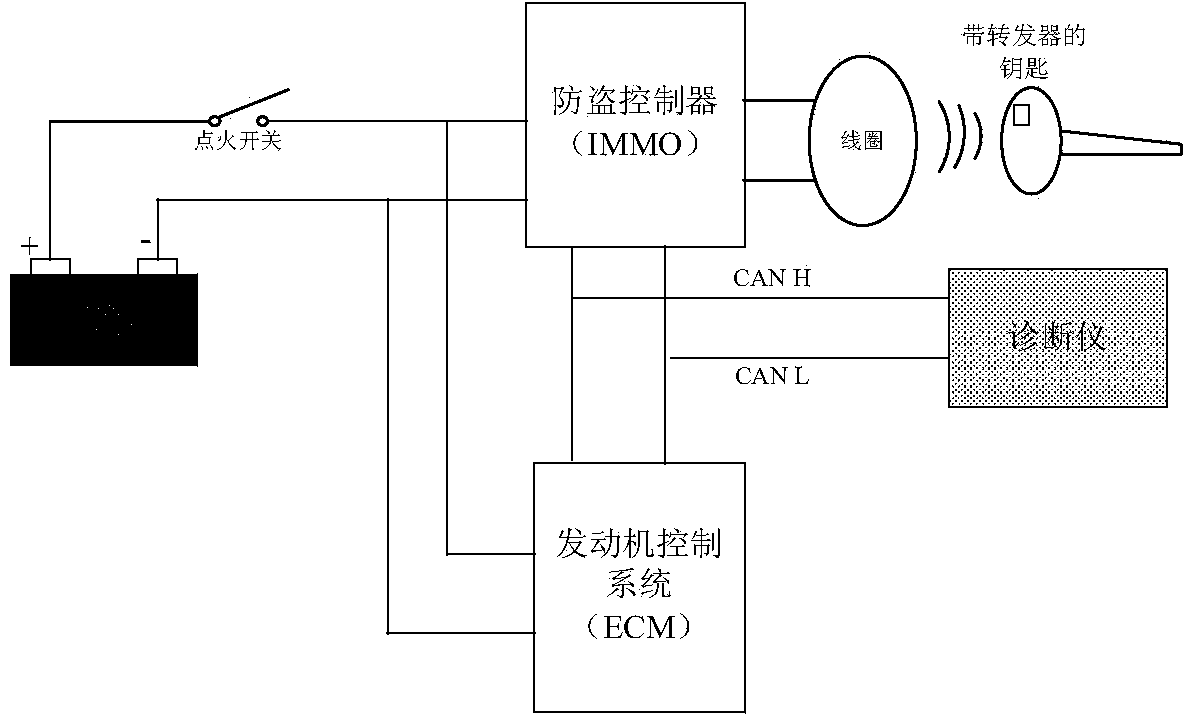
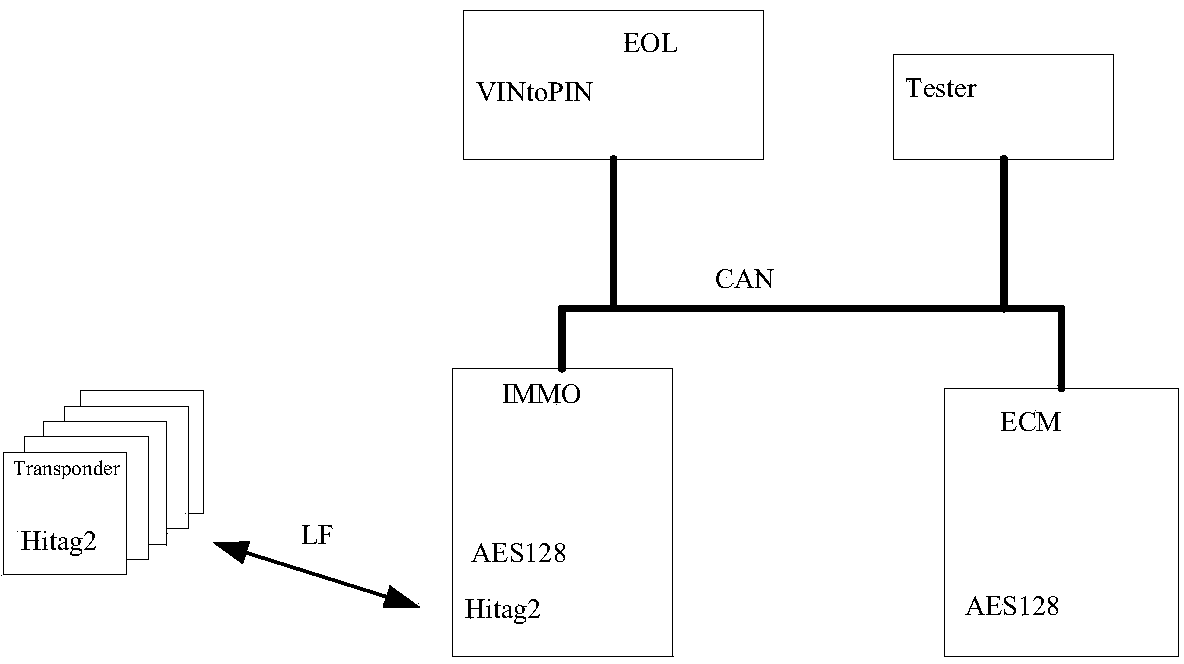
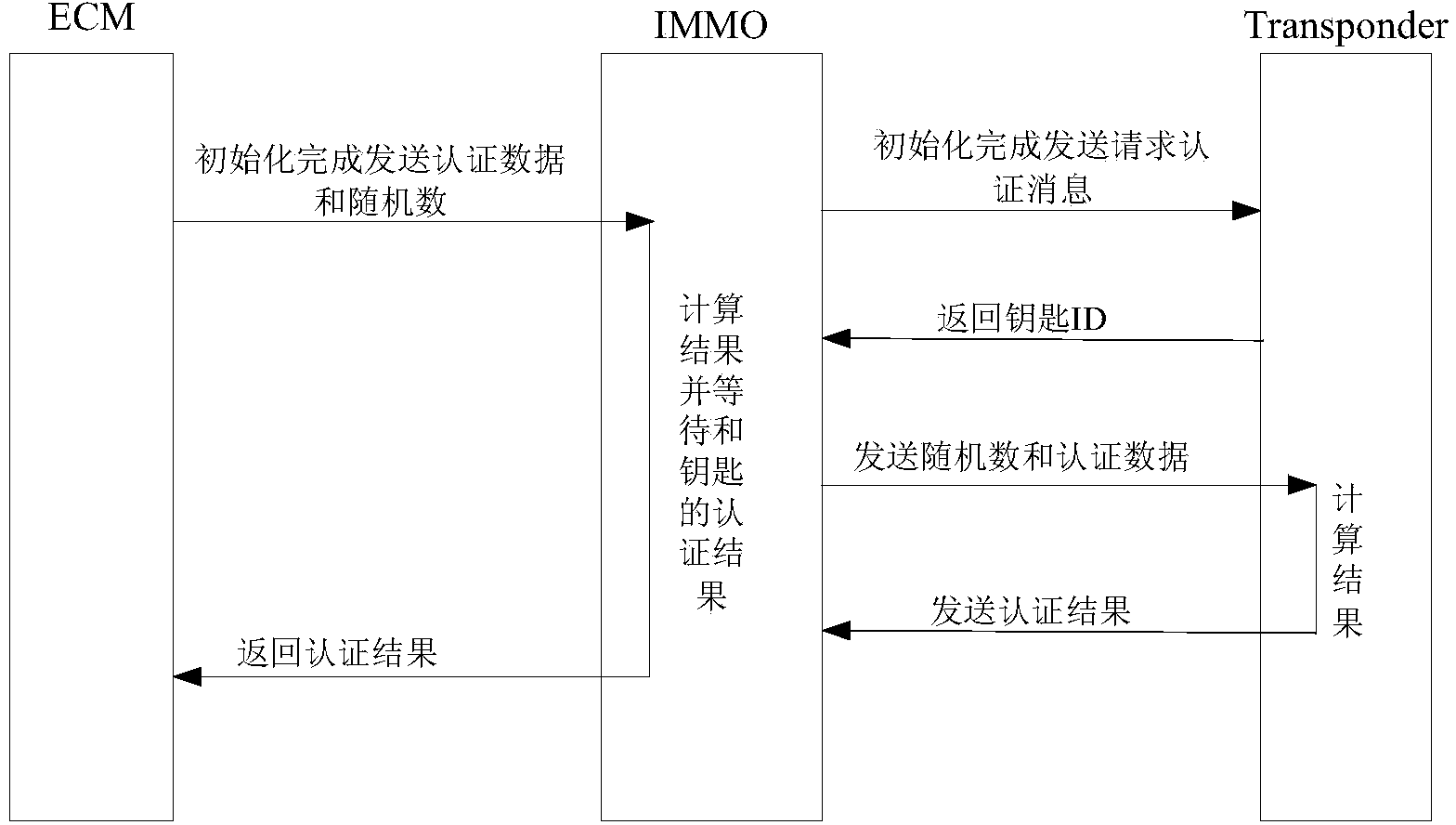
CAN (controller area network)-bus automobile-engine IMMO (immobilizer) system and authentication method thereof
InactiveCN104029652AIncrease the difficulty of crackingImprove securityAnti-theft devicesArea networkEngineering
The invention relates to a CAN (controller area network)-bus automobile-engine IMMO (immobilizer) system and an authentication method thereof. The CAN-bus automobile-engine IMMO system comprises an engine control unit, an IMMO controller unit and a key assembly, the engine control unit is in communication connection with the IMMO controller unit and is used for verifying authentication algorithm with the IMMO controller unit and controlling whether to start the engine or not, the IMMO control unit in communication connection with the engine control unit stores the authentication algorithm between the key assembly and the engine controller, and is used for transmitting commands and encrypted data in the IMMO system. The key assembly comprises a transponder and an IMMO coil. Transmitting of the IMMO system is realized through a CAN bus, AES128 algorithm is added into the authentication process of the IMMO system, 128-bit encrypted data are used as operators, and cracking difficulty of the IMMO system is increased. By the aid of two IMMO authentication algorithms, the cracking difficulty of the CAN-bus automobile-engine IMMO system is increased as compared with that of the IMMO system with only one authentication algorithm.
Owner:CHERY AUTOMOBILE CO LTD
Chaotic sequence generation method and sequence generator of high speed high-precision chaotic function
InactiveCN101222318AGood statistical propertiesOvercome short cycle responseSecuring communicationComplex mathematical operationsPlaintextMultiplexer
The invention discloses a chaotic sequence generation method and a sequence generator for high-speed high-accuracy chaotic functions. An initial key circuit stores the initial value of a chaotic latch unit, a u value key circuit stores a sequence ui value; each cp chaotic function finishes one-time interactive operation: a bitwise conversion circuit outputs a bitwise XOR to the chaotic latch unit, the bitwise XOR is used to realize a subtraction operation N minus one and minus the absolute value of xi and so on; a shift data selector takes the ui as an address code of the data selector, the data is shifted with a plurality of bits toward right, then the subtraction is used to realize a multiplication that the ui is multiplied by the data; the subtraction result is stored into the chaotic latch unit at the rising edge of the cp, each cp generates a 160-bit chaotic output; the randomness is good due to the existence of an initial key and a u value key; the precision is far greater than that of the double type, the cycle of the cp can reach 90ns, the encryption of a 128-bit plaintext needs 1.7us; the invention can be realized by using FPGAs, GPLDs and ASICs and so on, and is used in the network security technical field, particularly in the wireless networks and the wireless sensor networks.
Owner:HEILONGJIANG UNIV
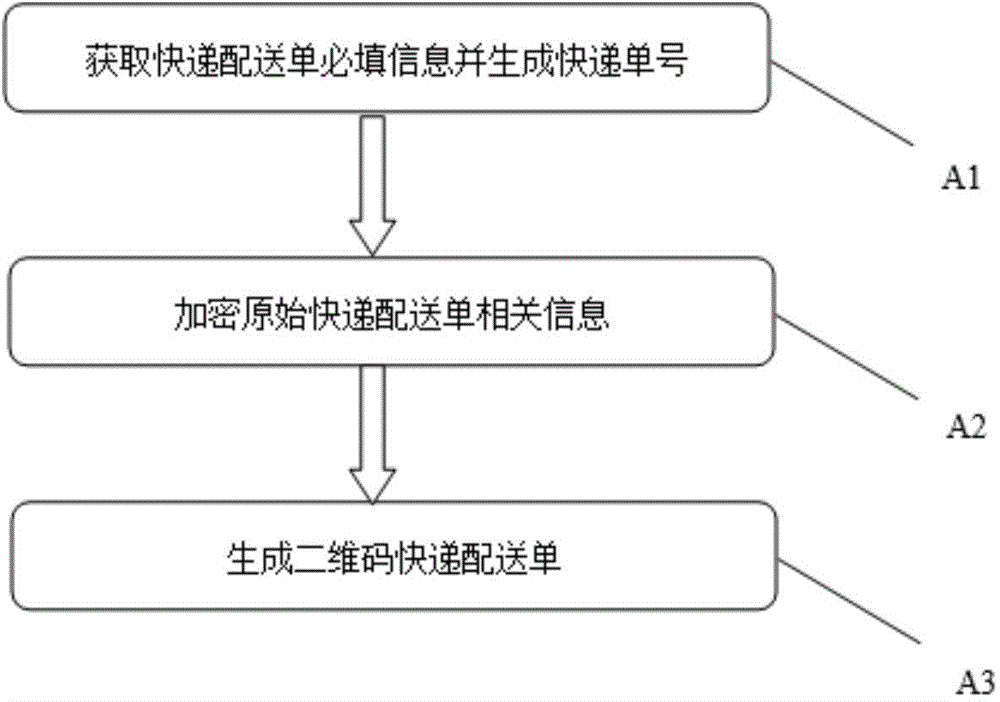
Logistics distribution bill generating method based on two-dimension code and encryption technology
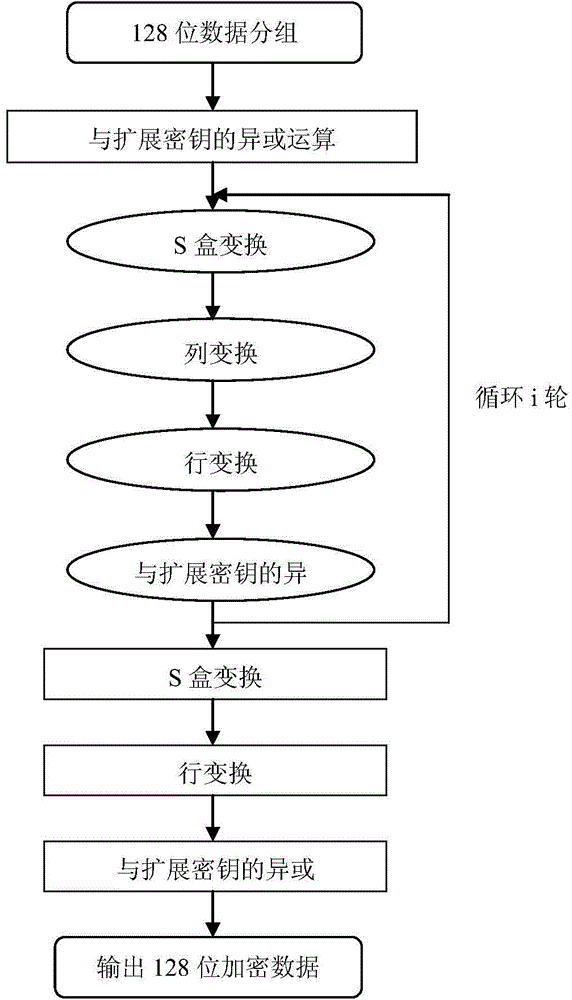
InactiveCN104463529AEncryption/decryption okImprove protectionEncryption apparatus with shift registers/memoriesLogisticsLogistics managementS-box
A logistics distribution bill generating method based on a two-dimension code and an encryption technology includes the following steps that A1, required basic information of an original express distribution bill is obtained, and an express bill number is automatically generated; A2, the symmetric encryption algorithm AES algorithm is adopted for encrypting the related information of the original express distribution bill, and the process includes the steps that (1), 128-bit data are grouped; (2), xor calculation of an and expansion secrete key is performed; (3), S box transformation is performed; (4), row transformation is performed; (5), column transformation is performed; (6), xor is performed in the and expansion secrete key; (7), S box transformation is performed; (8), row transformation is performed; (9), xor is performed on the and expansion secrete key; (10), the 128-bit data are output; A3, a two-dimension code express distribution bill is generated through a two-dimension code generator. The distribution efficiency and safety degree of logistics can be improved.
Owner:ZHEJIANG UNIV OF TECH
Dynamic bank mode addressing for memory access
ActiveUS20130268715A1Avoid bank conflictsMemory adressing/allocation/relocationConcurrent instruction executionParallel computing64-bit computing
One embodiment sets forth a technique for dynamically mapping addresses to banks of a multi-bank memory based on a bank mode. Application programs may be configured to perform read and write a memory accessing different numbers of bits per bank, e.g., 32-bits per bank, 64-bits per bank, or 128-bits per bank. On each clock cycle an access request may be received from one of the application programs and per processing thread addresses of the access request are dynamically mapped based on the bank mode to produce a set of bank addresses. The bank addresses are then used to access the multi-bank memory. Allowing different bank mappings enables each application program to avoid bank conflicts when the memory is accesses compared with using a single bank mapping for all accesses.
Owner:NVIDIA CORP
Systems and methods for performing deblocking in microprocessor-based video codec applications
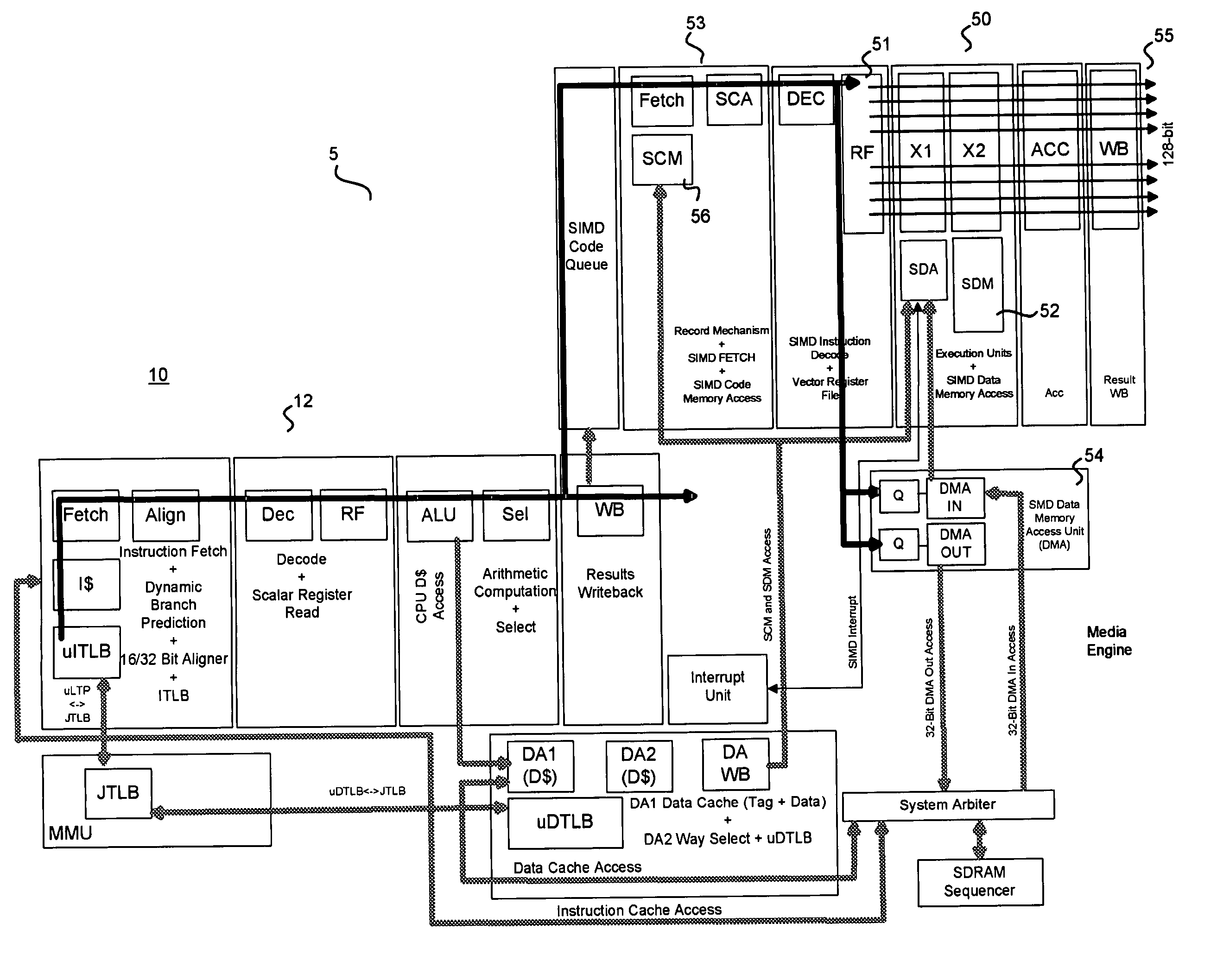
ActiveUS20070071106A1Geometric image transformationPicture reproducers using cathode ray tubes16-bitOperand
Two pairs of deblock instructions for performing deblock filtering on a horizontal row of pixels according to the H.264 (MPEG 4 part 10) and VC1 video codec algorithms. The first instruction of each pair has three 128-bit operands comprising the 16-bit components of a horizontal line of 8 pixels crossing a vertical block edge between pixels 4 and 5 in a YUV image, a series of filter threshold parameters, and a 128-bit destination operand for storing the output of the first instruction. The second instruction of each pair accepts the same 16-bit components as its first input, the output of the first instruction as its second input and a destination operand for storing an output of the second instruction as its third input. The instruction pairs are intended for use with the H.264 or VC1 video codecs respectively.
Owner:SYNOPSYS INC
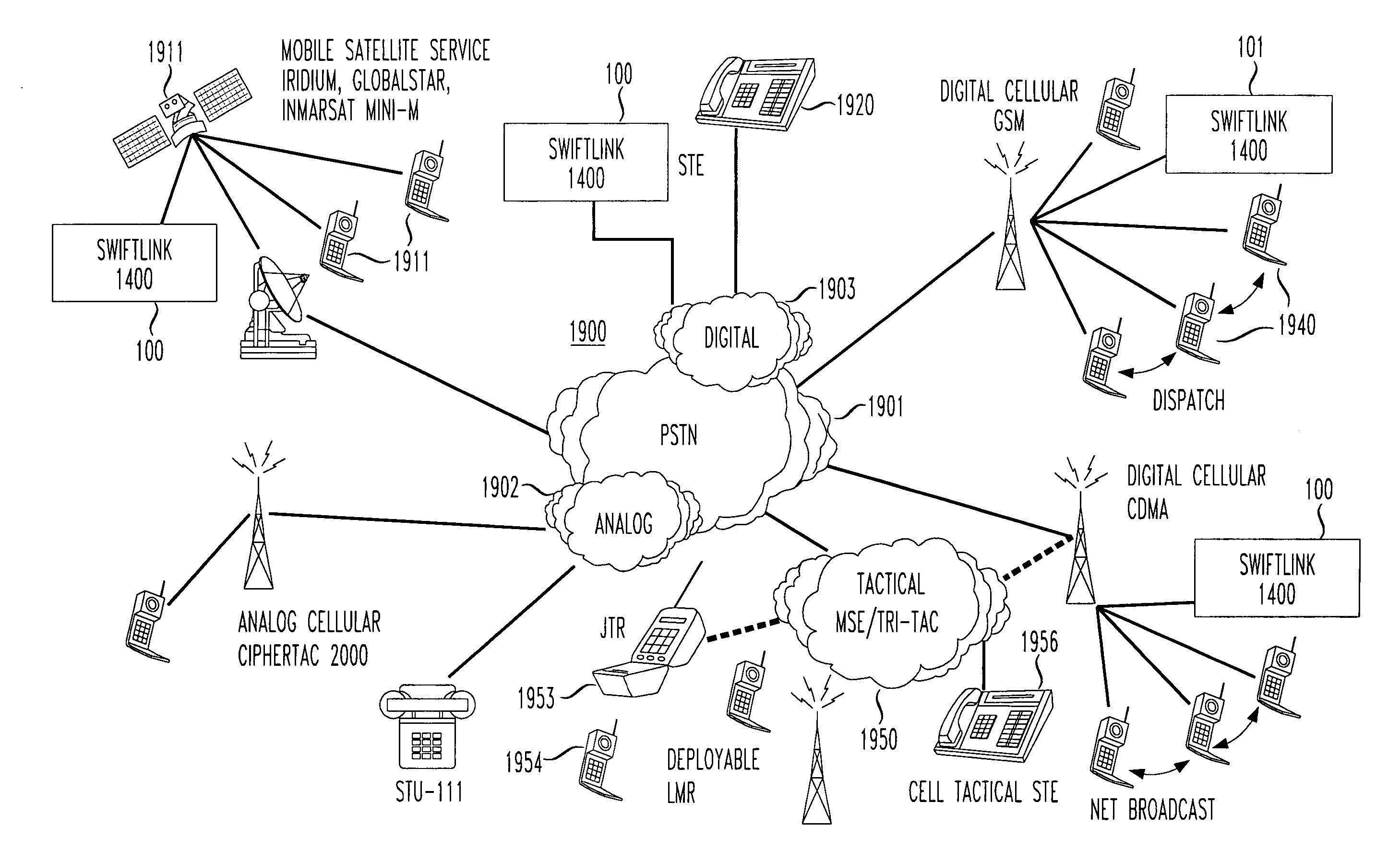
Reach-back communications terminal with selectable networking options
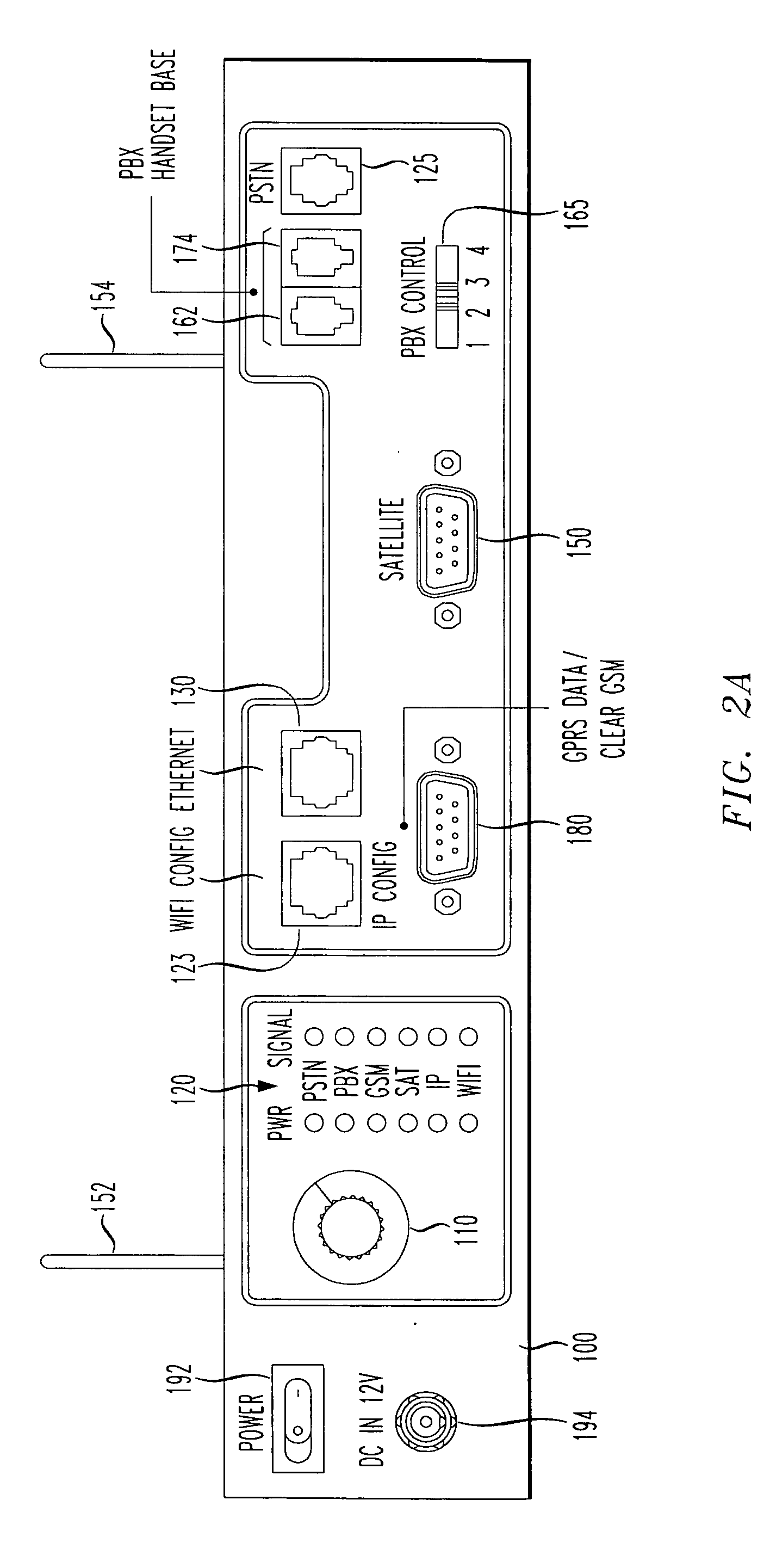
InactiveUS20050210234A1Public key for secure communicationSecret communicationSecure communicationTelecommunications network
A reach back secure communications terminal that offers immediate and secure voice, data and video connectivity to multiple telecommunications networks, high availability and reliable connectivity, total access to vital resources, and secure extension to the home office. Integrated components simplify access to varied networks allowing deployed users to select and connect quickly to a network that best supports their present mission. Commercial or optional NSA Type 1 encryption may be implemented. Networking options include any of PSTN, PBX, GSM (or CDMA or other cell telephone standard), SAT, IP and WiFi. During secure call setup, the reach-back communications terminal exchanges public keys with a remote terminal using FNBDT signaling. Traffic encryption is performed using the NIST approved Advanced Encryption System (AES) standard (Rijndael) and a 128-bit random key (2{circumflex over ( )}128 possible keys).
Owner:TELECOMM SYST INC
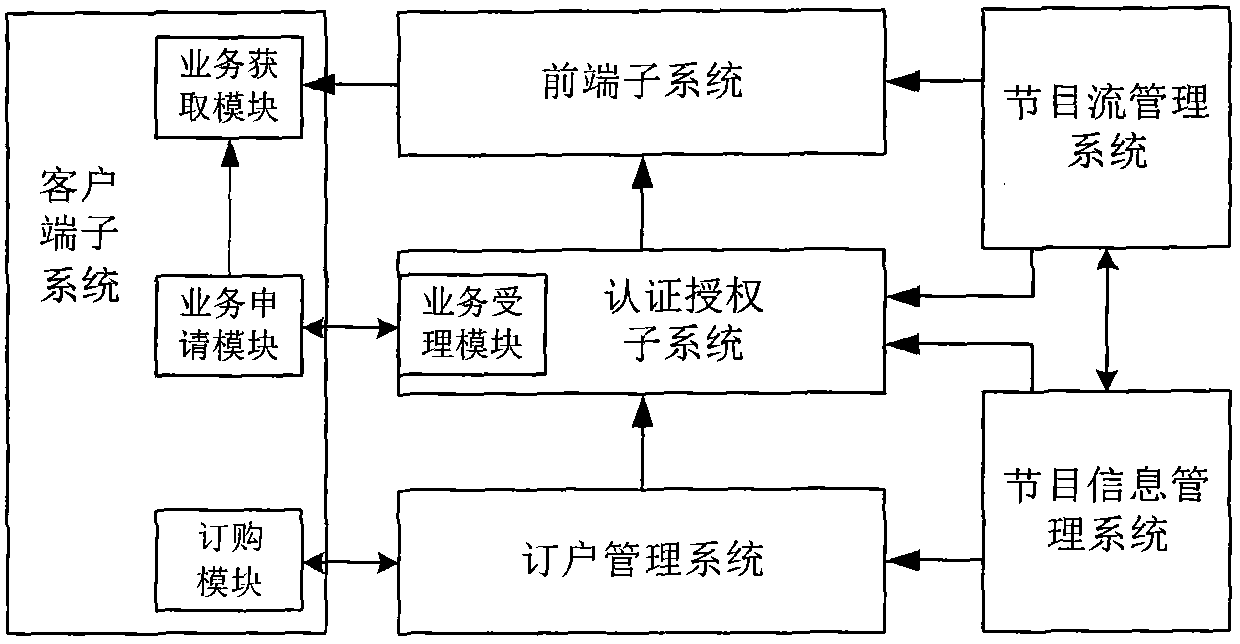
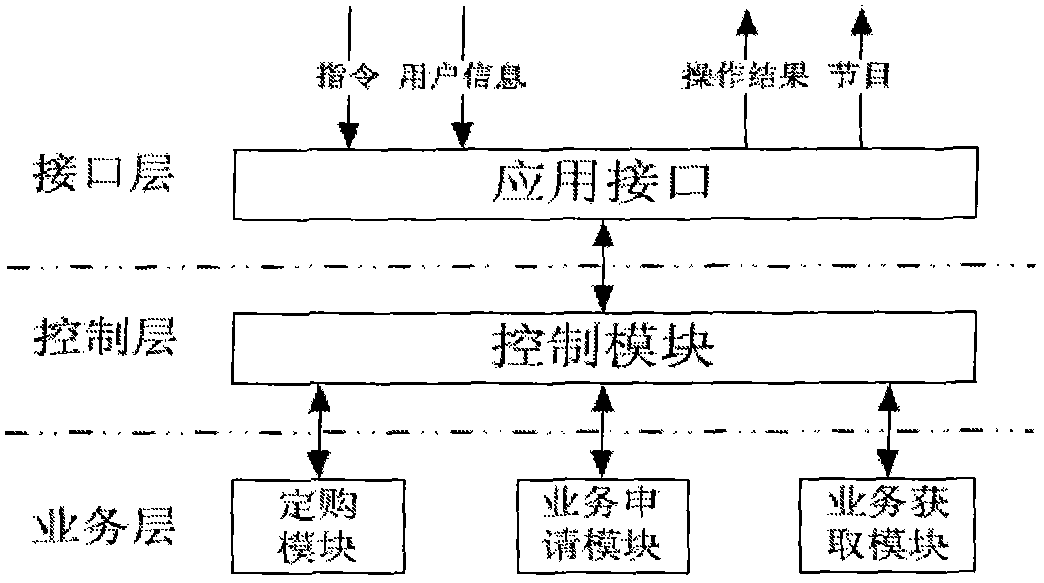
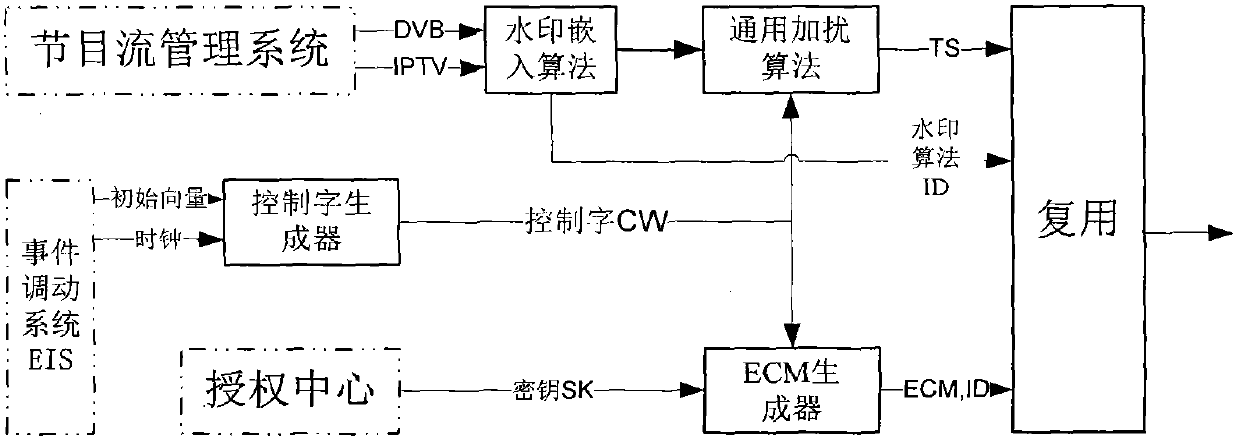
DVB/IPTV dual-mode interactive business protection system
A DVB / IPTV dual-mode interactive business protection system comprises a client end subsystem, a front end subsystem, an authentication authorization subsystem, a subscriber management system, a program stream management system, and a program information management system; the client end subsystem, the CA front end subsystem and the authentication authorization subsystem are the main portion; the subscriber management system, the program stream management system, and the program information management system belong to a peripheral auxiliary system. The DVB / IPTV dual-mode interactive business protection system supports DVB and IPTV video scrambling, provides a controllable scrambling depth control strategy and adaptive scrambling of program content, and supports more than three secret key management modes; secret key length selection above 128 bits and distributed packaging of large size content are realized; the protection system supports safety and business monitoring of the content based on digit watermarking. The DVB / IPTV dual-mode interactive business protection system supports DVB / IPTV dual modes, introduces secret key update batch processing strategy and a distributed authentication authorization scheme, provides secret key real time update and distribution in a million user scale, reduces system overhead, enhances whole secret key updating capacity, improves system safety, and provides a flexible changeable protection mechanism for pay TV business.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Method for password protection for constructing unidirectional hash function based on infinite dimension ultra-chaos
InactiveCN101237320AImprove scrambling performanceIncreased sensitivitySecuring communicationPlaintextHash function
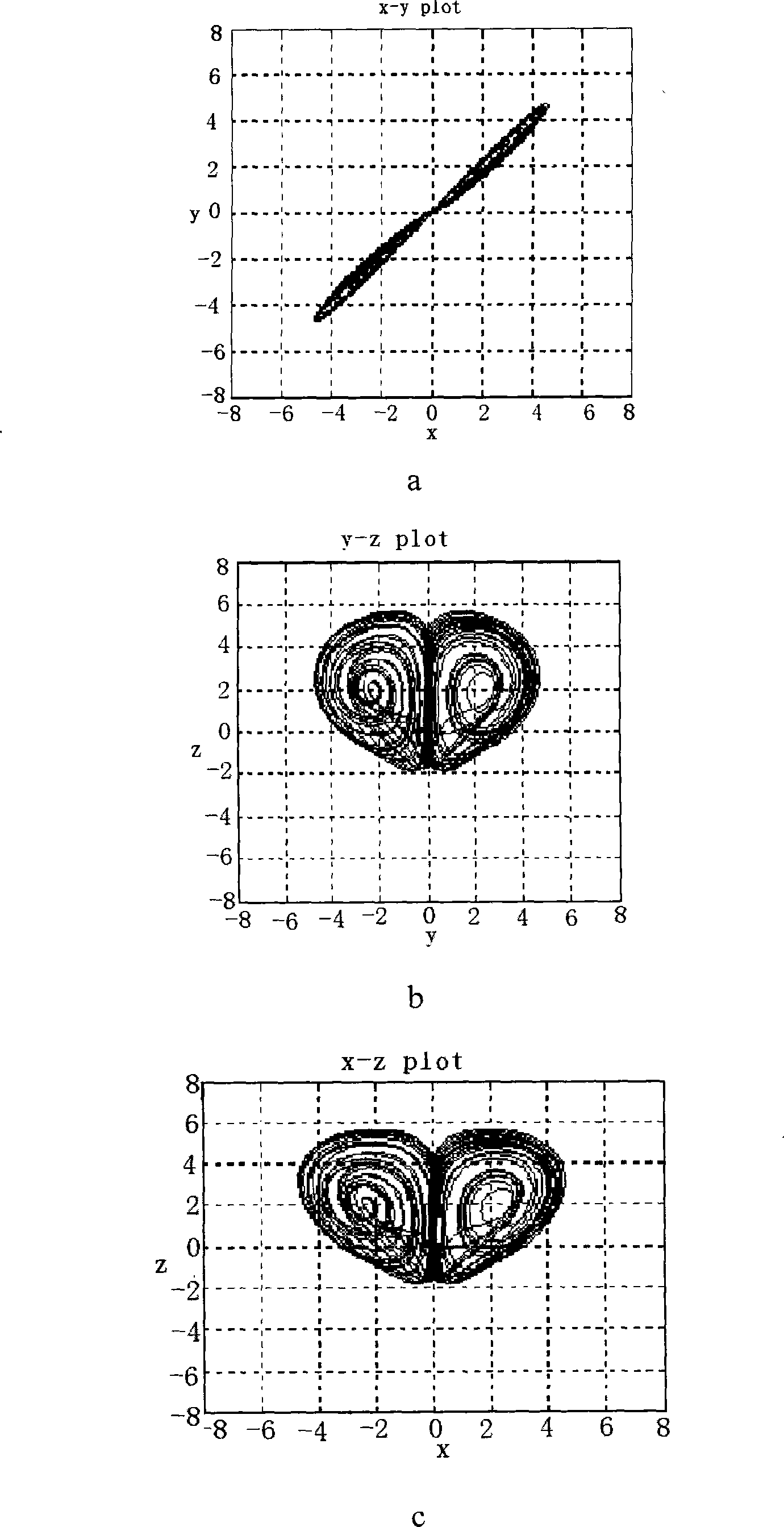
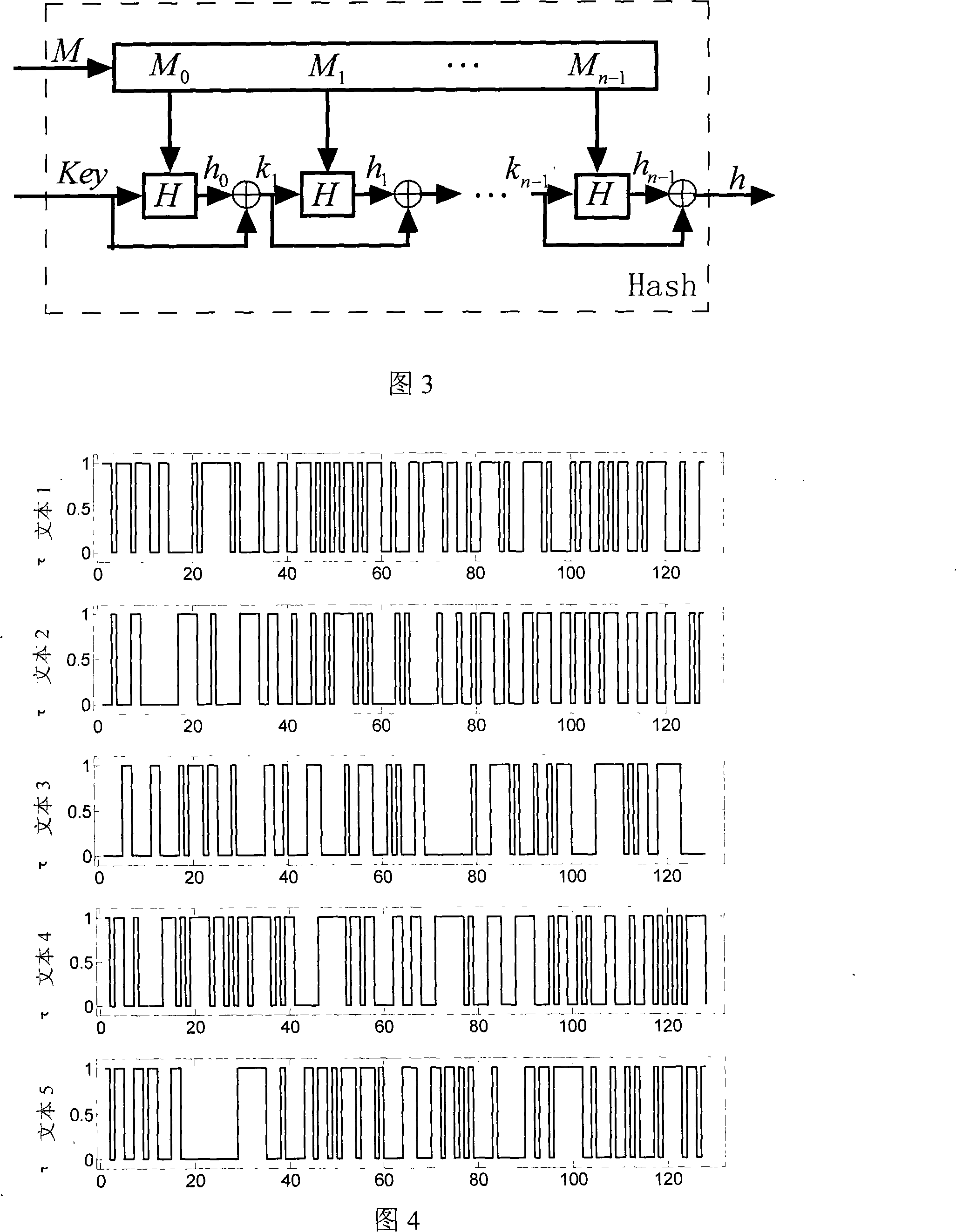
The invention discloses a method for cryptoguard by utilization of infinite dimensional hyperchaos for construction of unilateral hash functions, wherein, a plaintext and a key are taken as initial values of two hyperchaos Chen systems provided with delay feedback at first; evolvement is performed according to characteristics of chaotic dynamics of the system; a final result of evolvement is quantized; the quantized value is substituted into key streams for iteration; confusion and diffusion of plaintext information and key information are realized, and a 128-bit Hash value of the plaintext with any length is generated on the basis of a cipher block chain mode. The method of the invention performs cryptoguard by construction of the Hash functions, fully utilizes signals generated by an infinite dimensional hyperchaos system to improve the scrambling performance of the signals and the sensitivity of parameters, and has stronger attack resistance and better safety to predicted attacks.
Owner:XIAN UNIV OF TECH
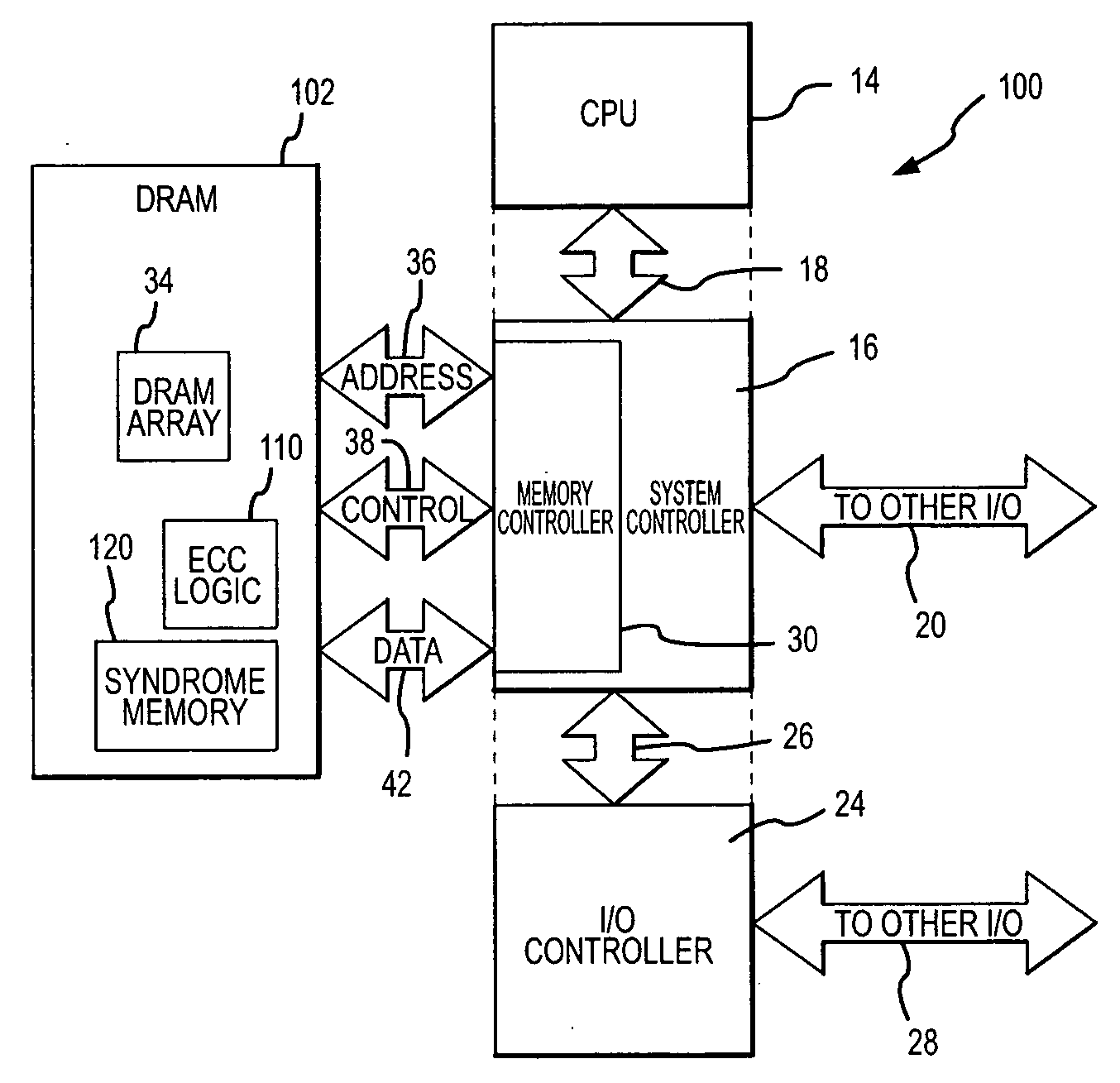
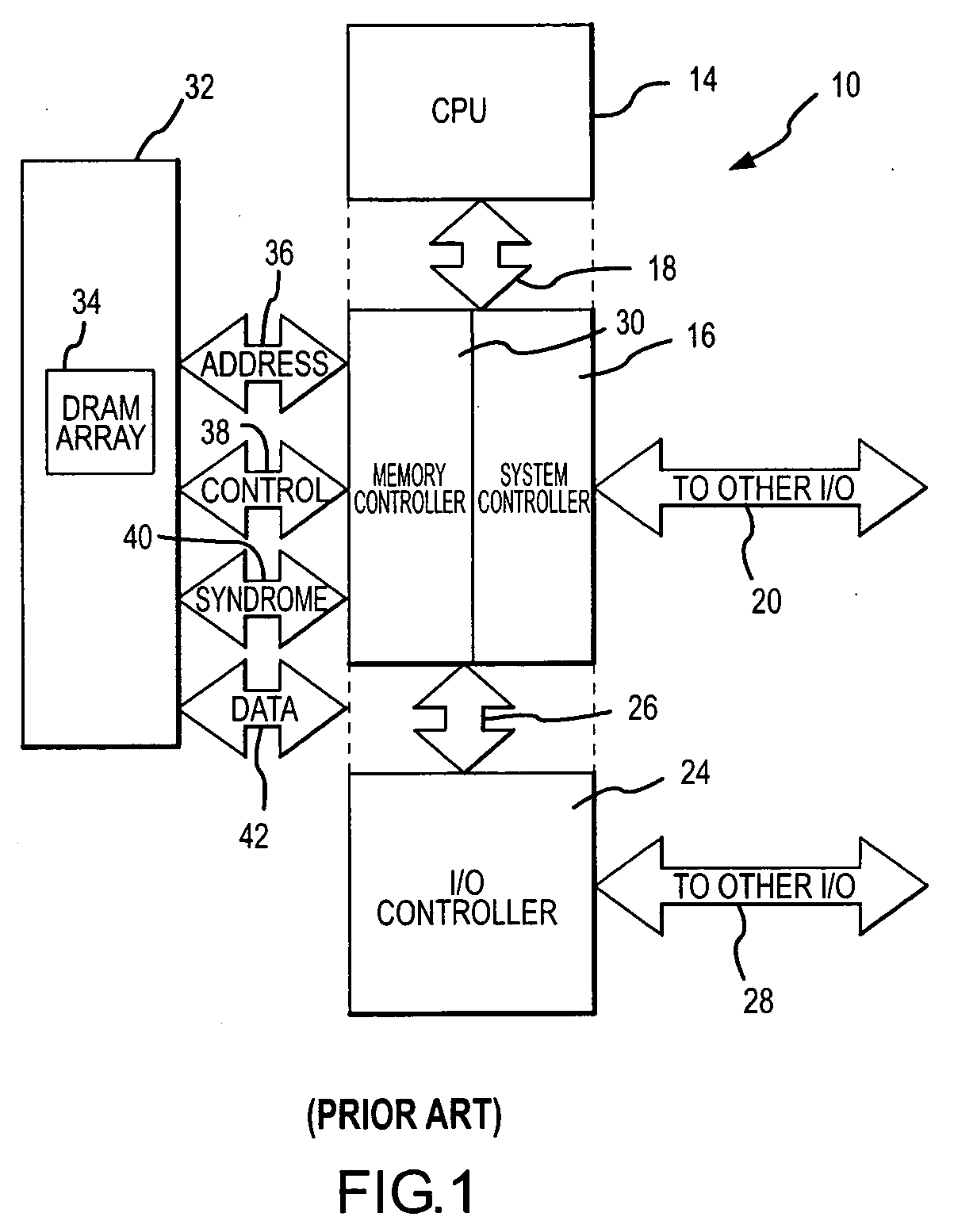
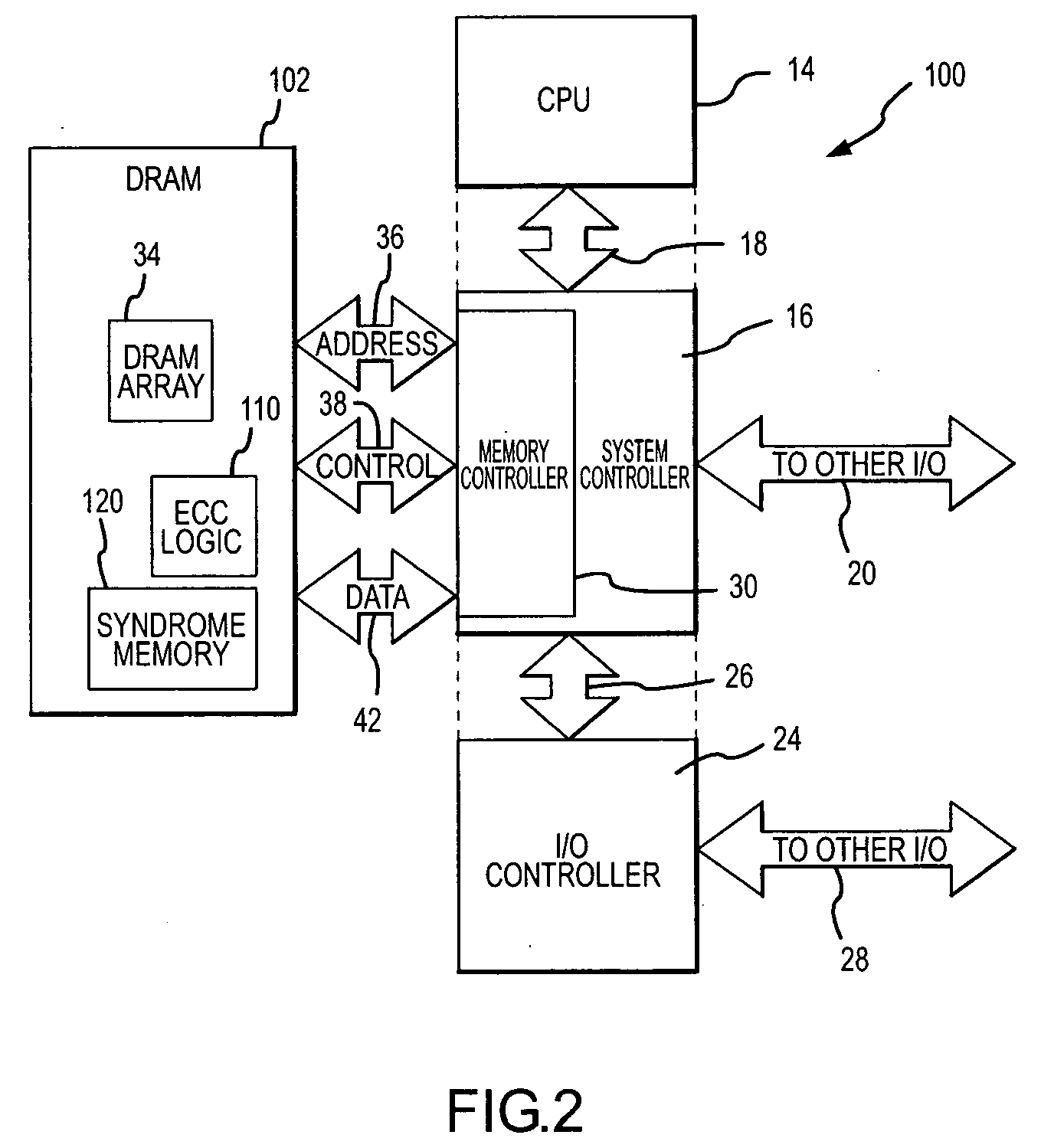
Low power cost-effective ECC memory system and method
ActiveUS20060218469A1Reduce overheadData representation error detection/correctionMemory loss protectionError checkingMemory controller
Owner:MICRON TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com