Patents
Literature
1743 results about "Connection type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The four types of connection are…. 1.) Disconnection. 2.) Bad connection. 3.) Fantasy connection. 4.) Real connection. The first three are extremely common, but will bring you nothing but misery. You will thrive only with real connection. Let’s take a closer look at these four types of connection.
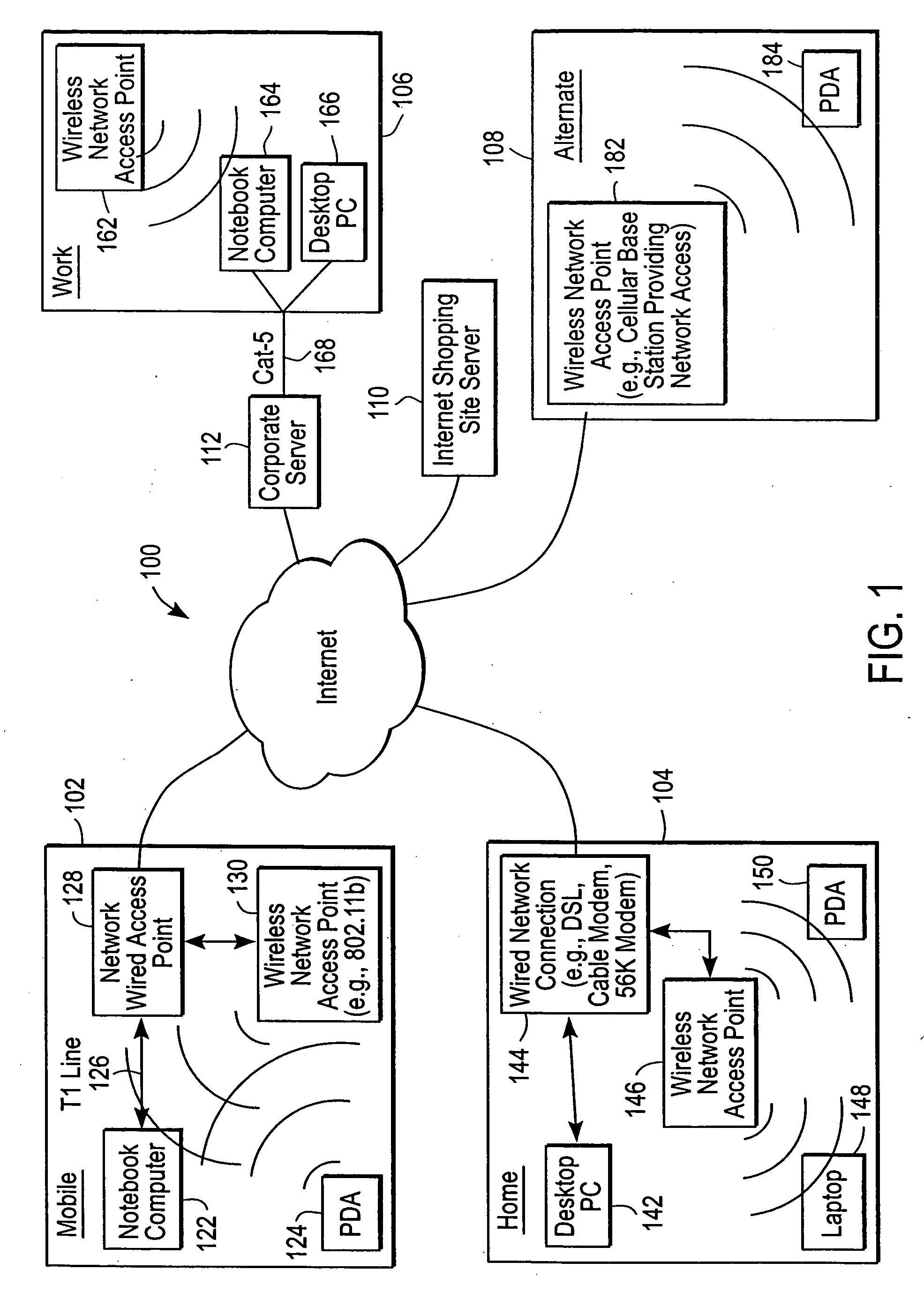
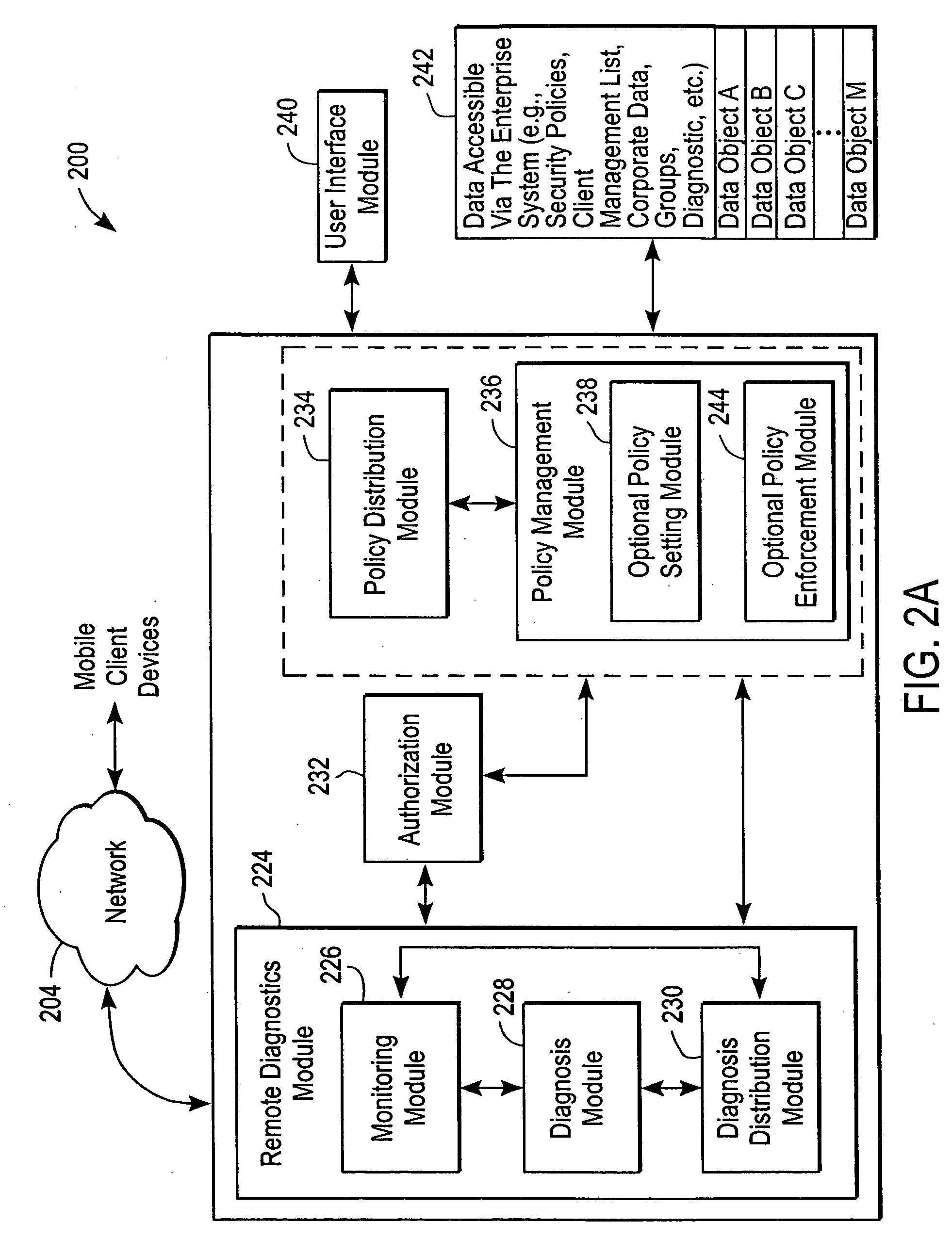
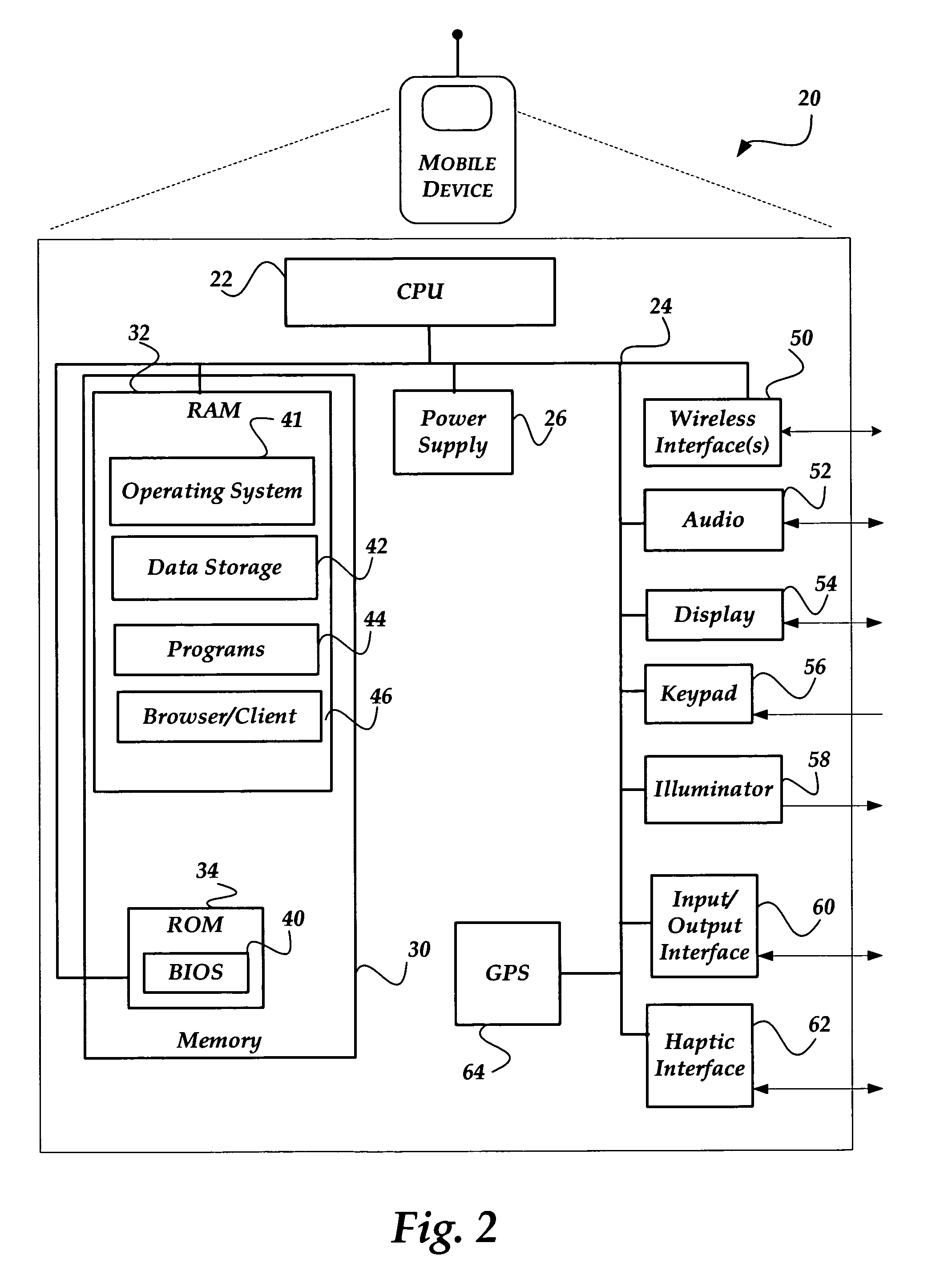
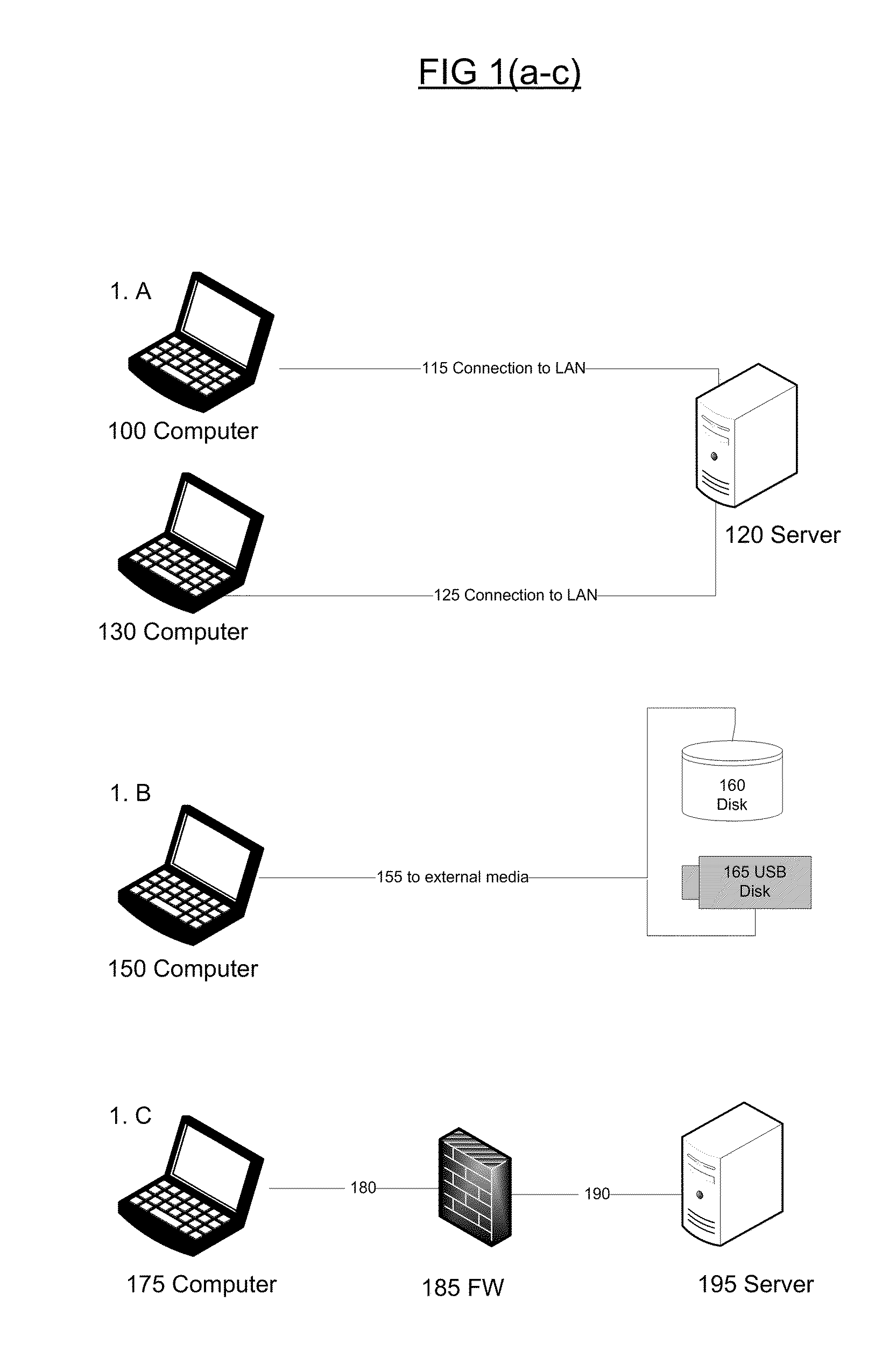
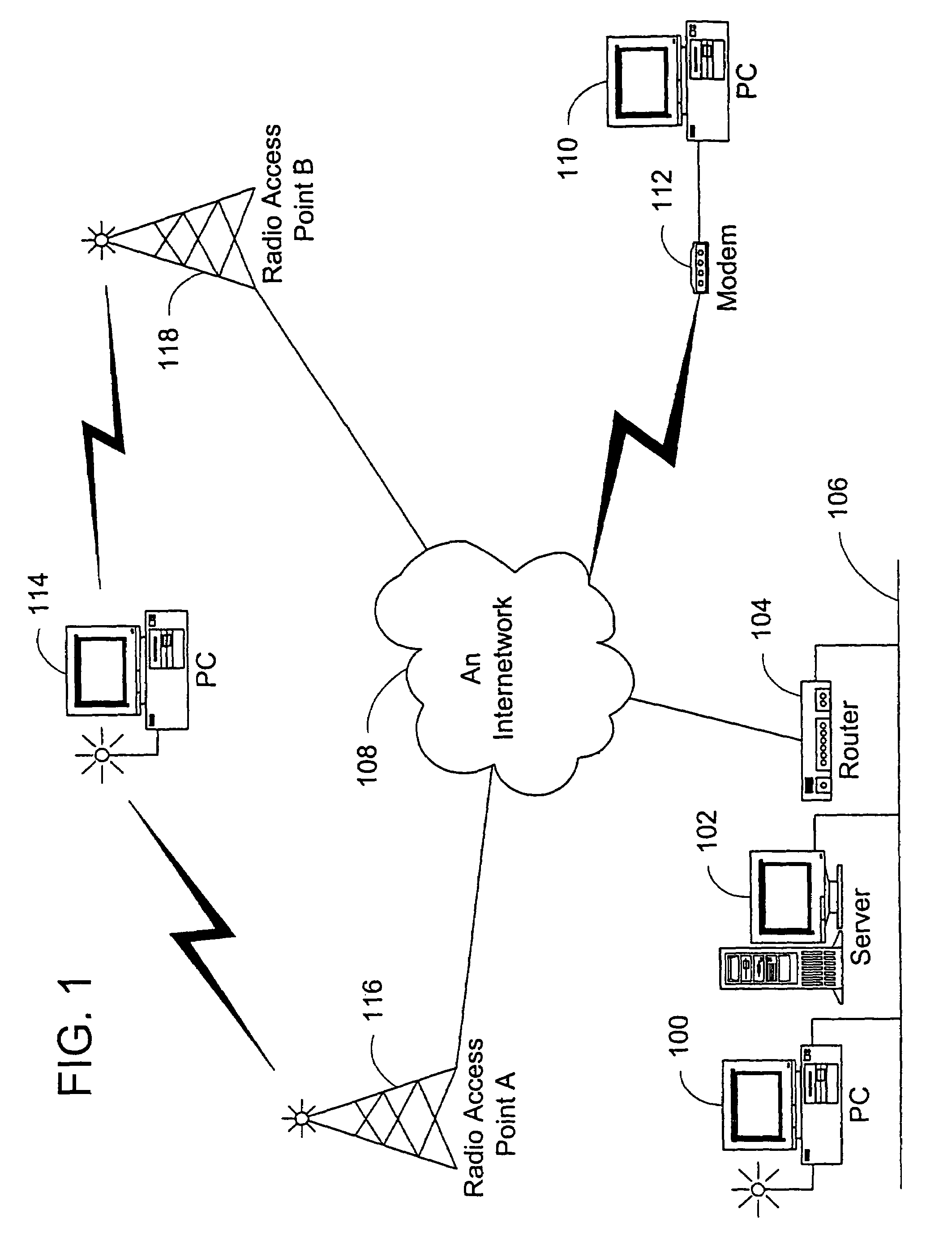
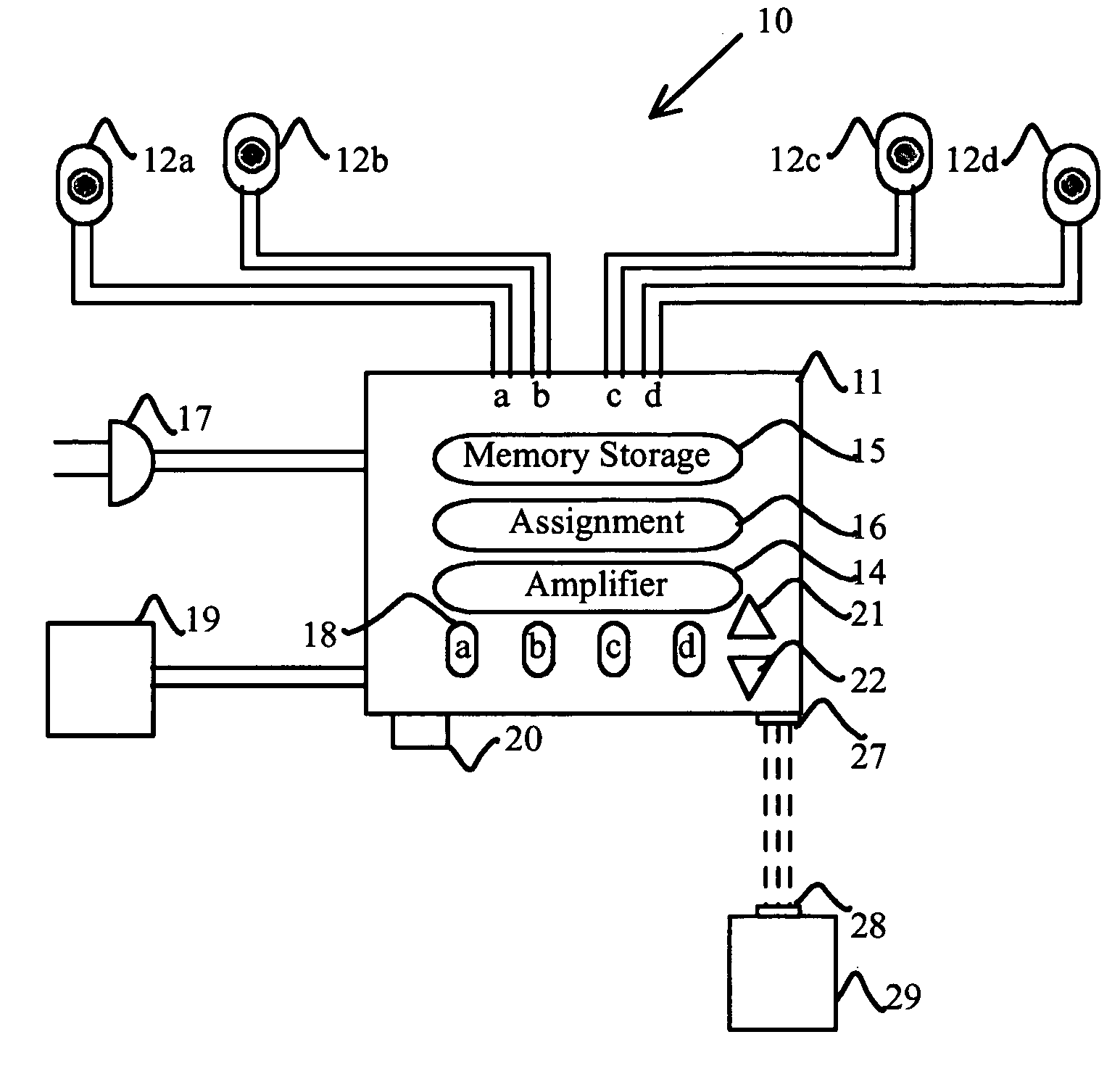
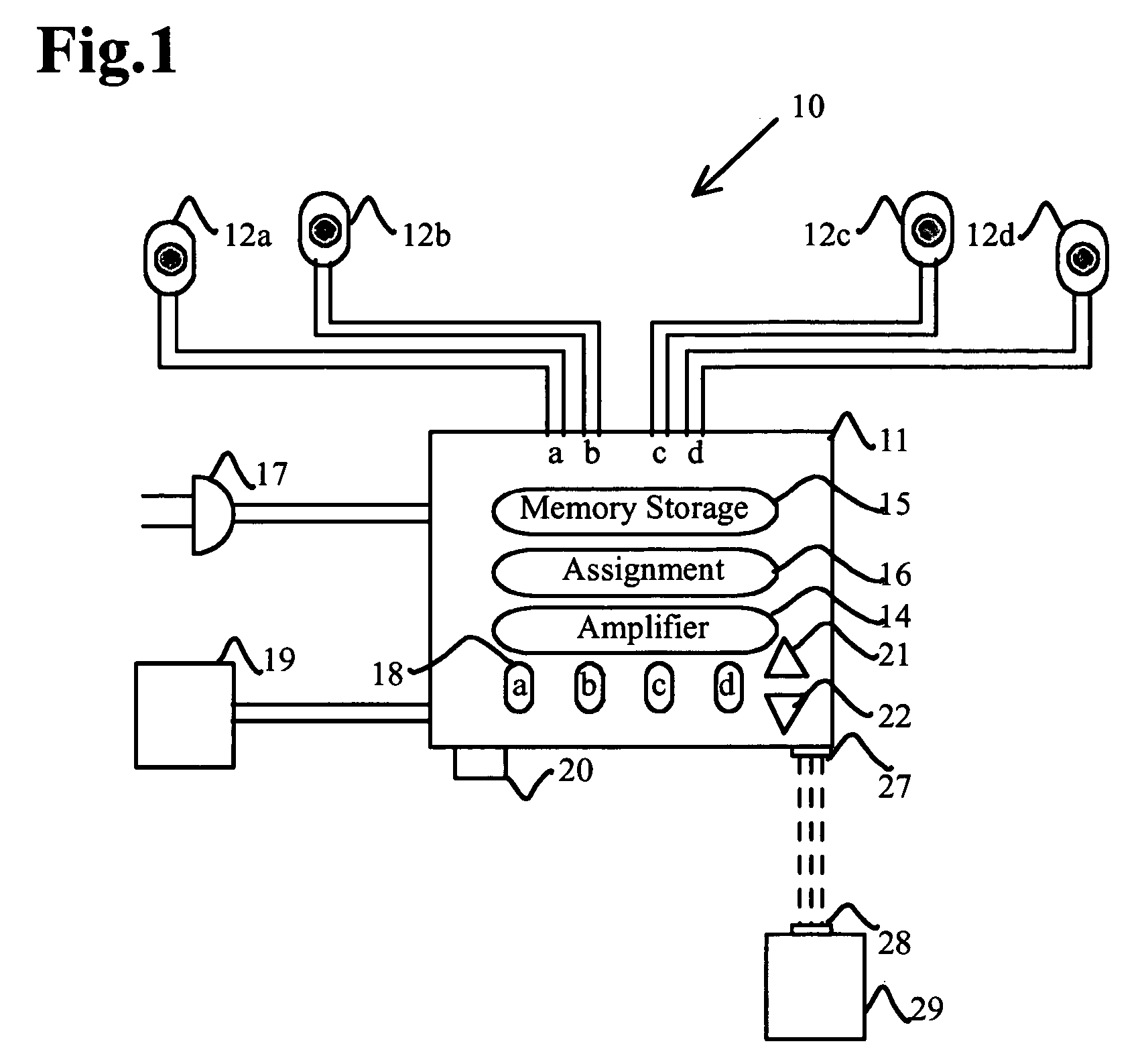
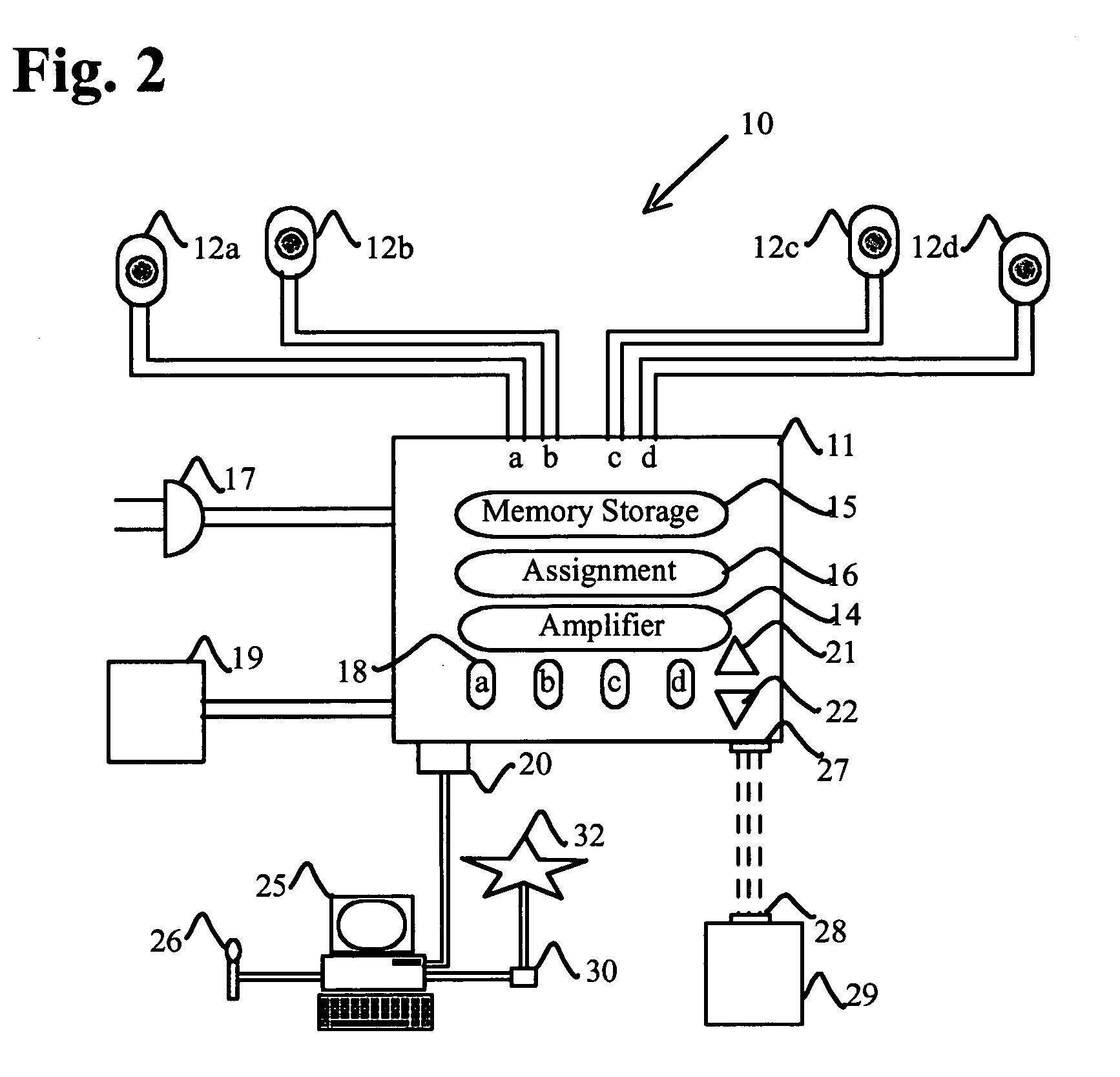
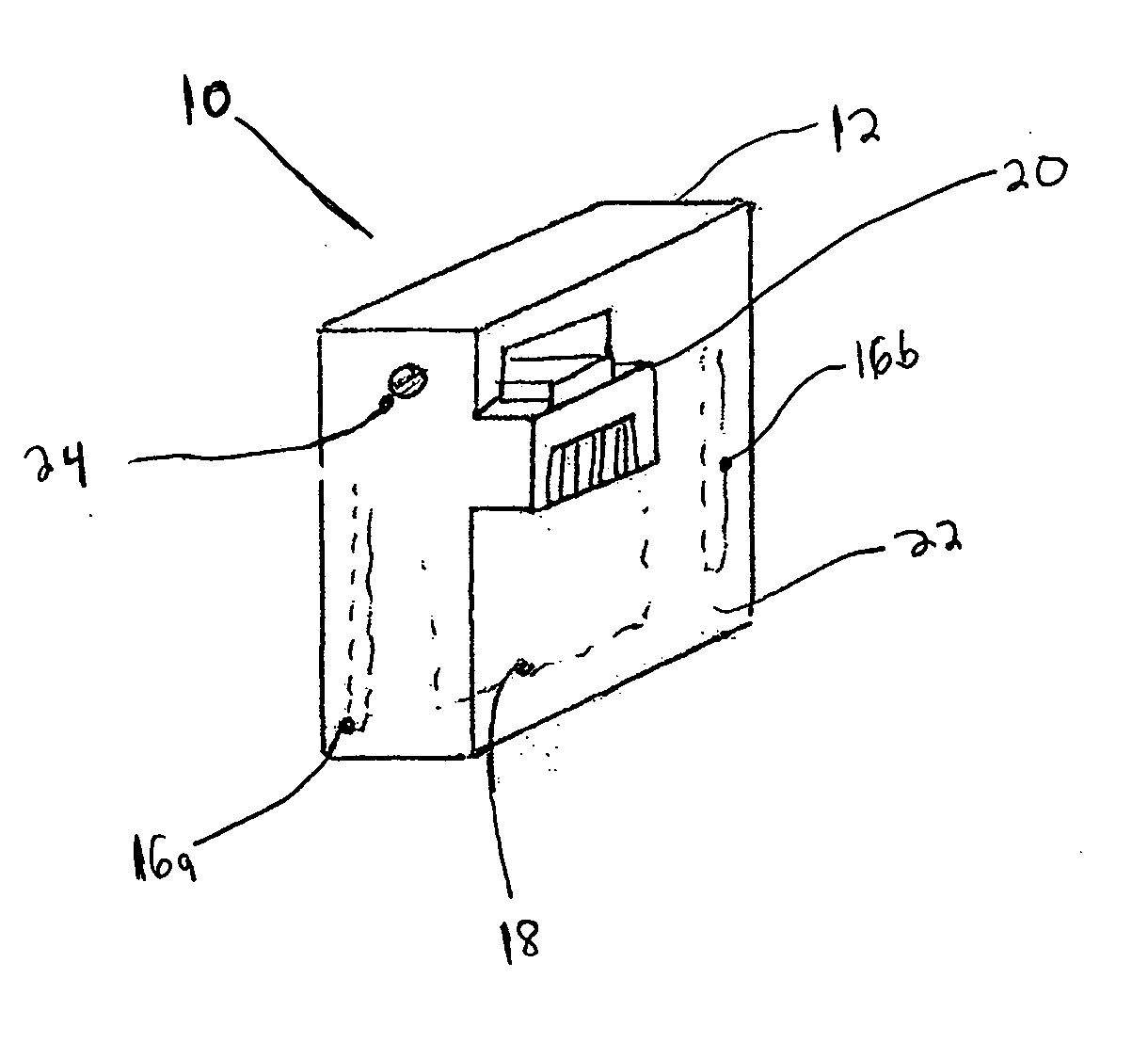
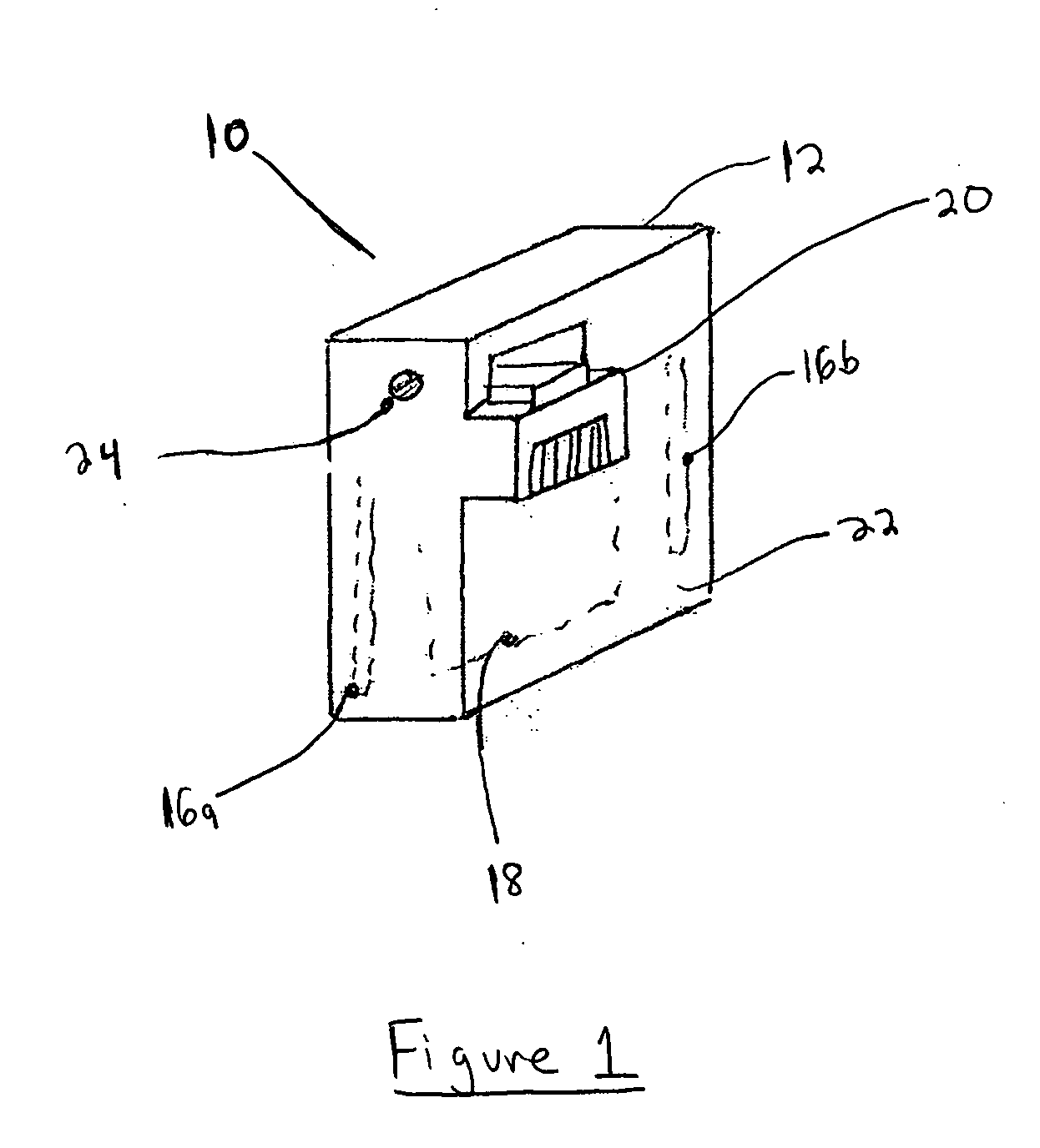
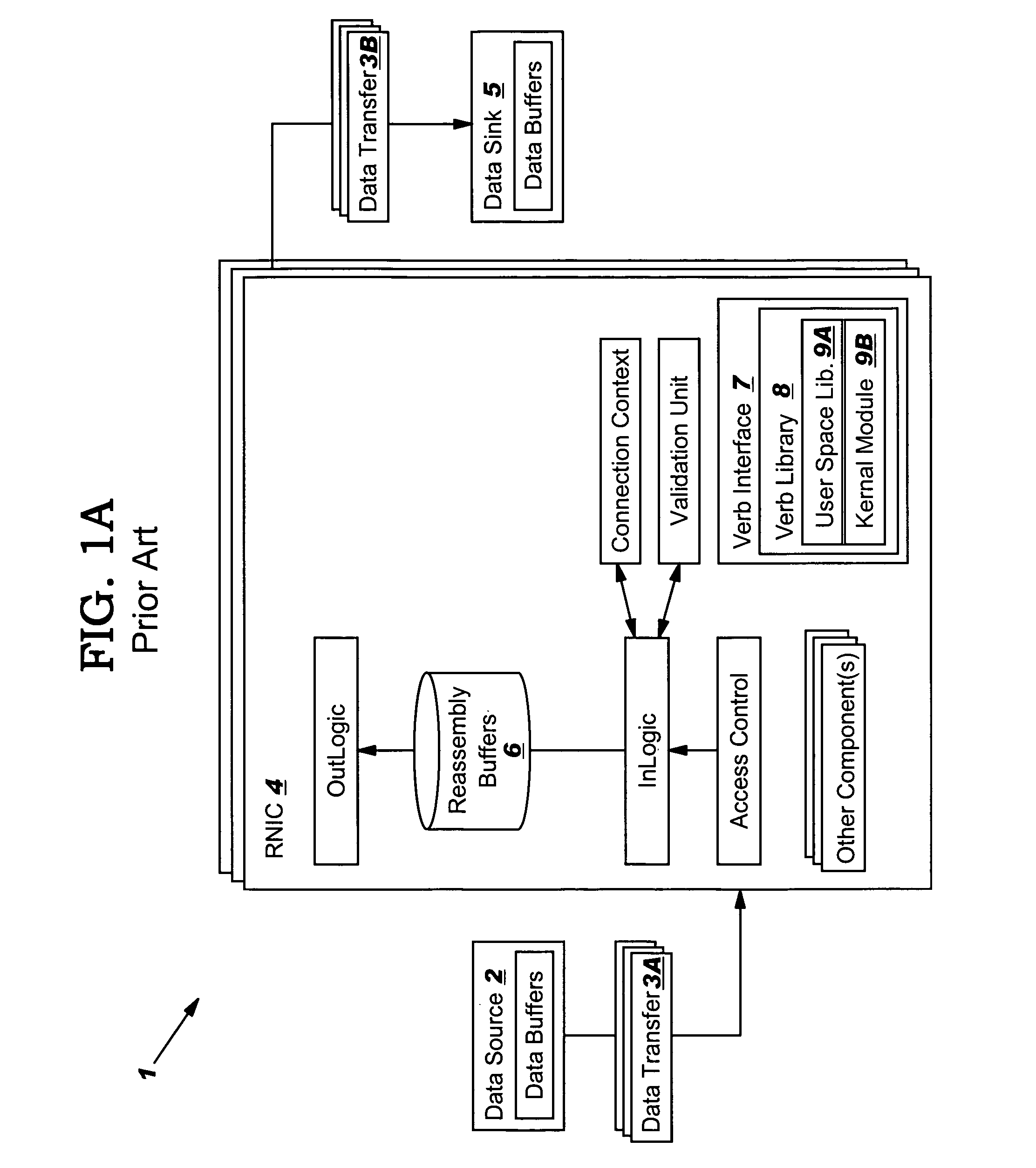
Administration of protection of data accessible by a mobile device
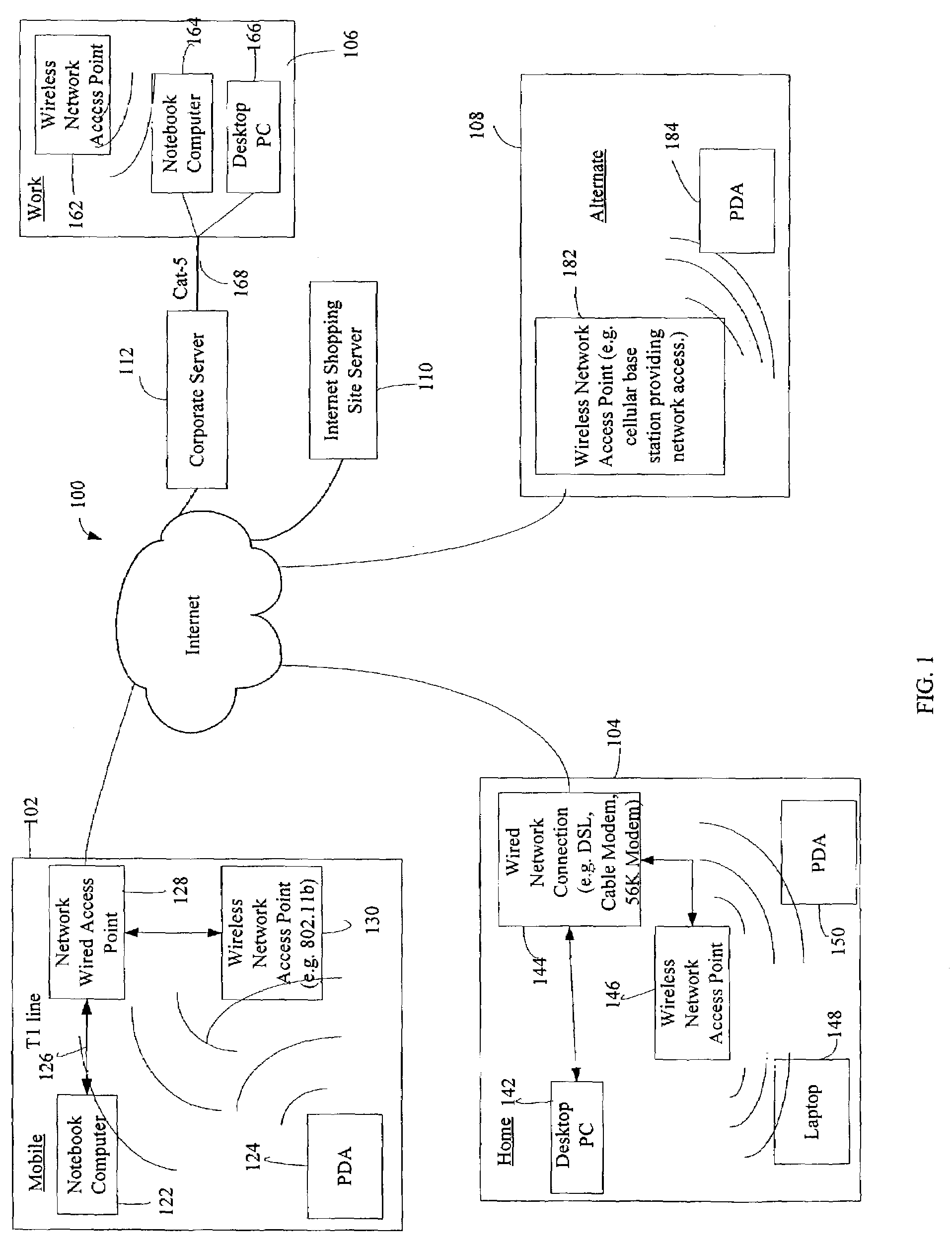
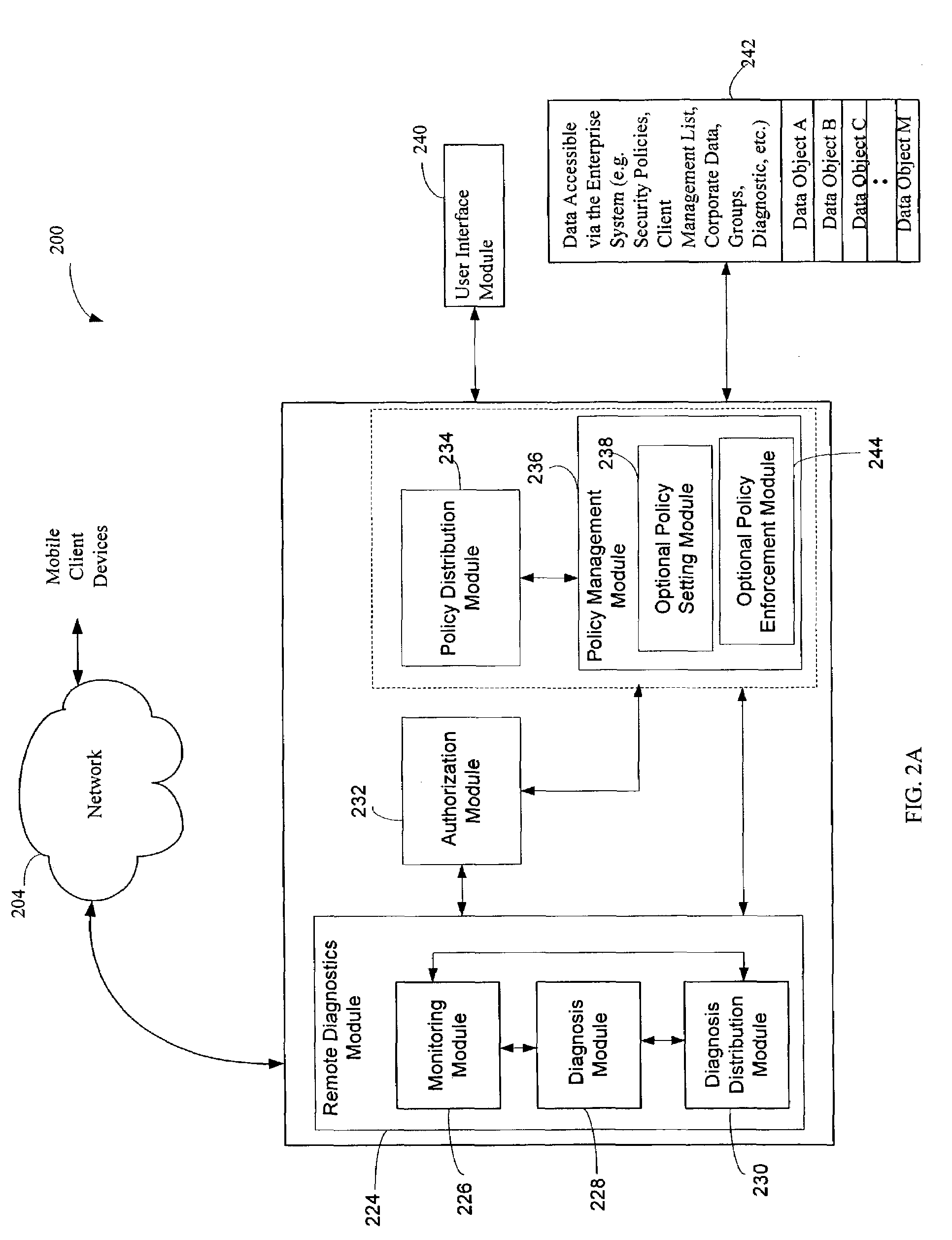
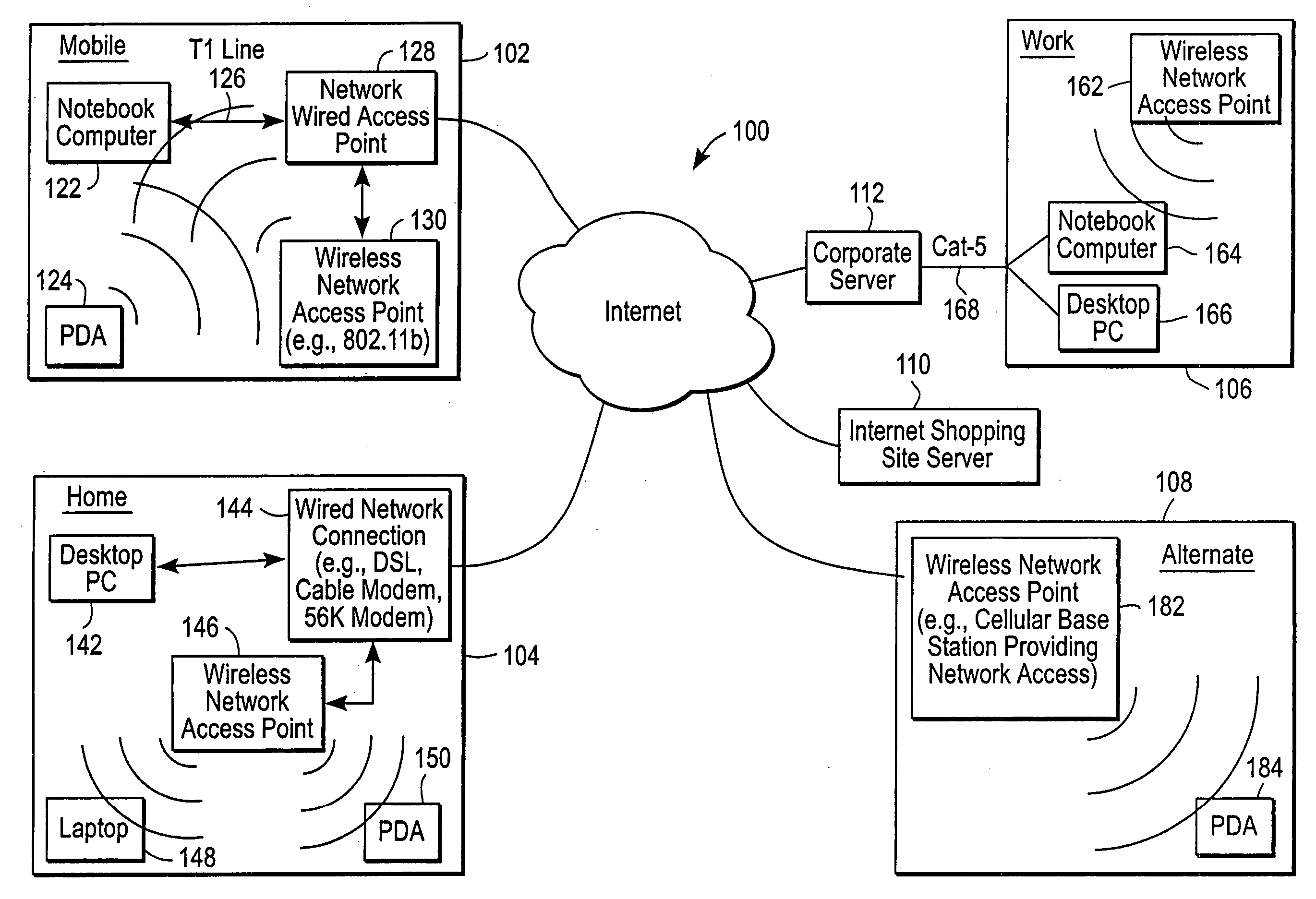
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
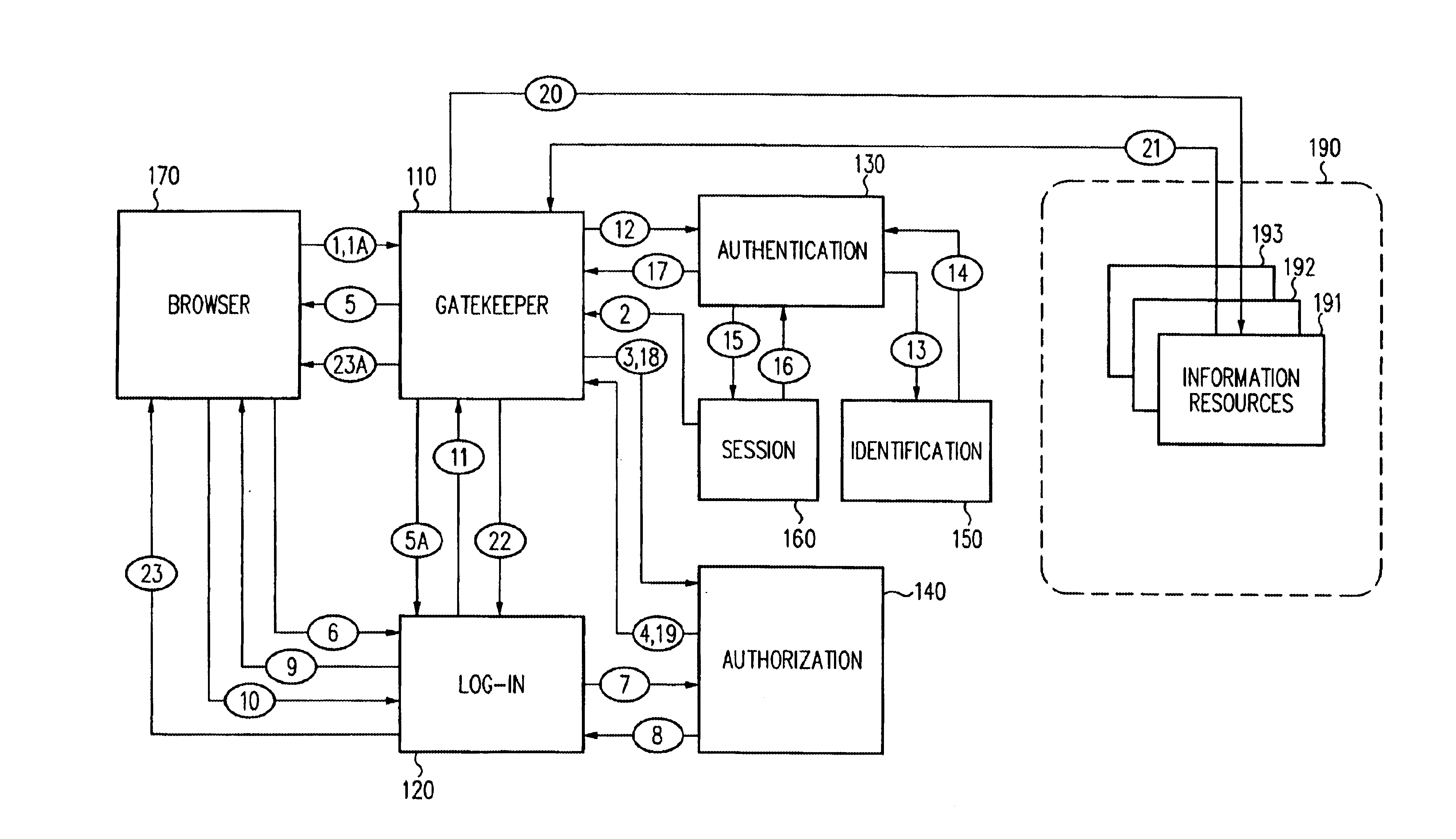
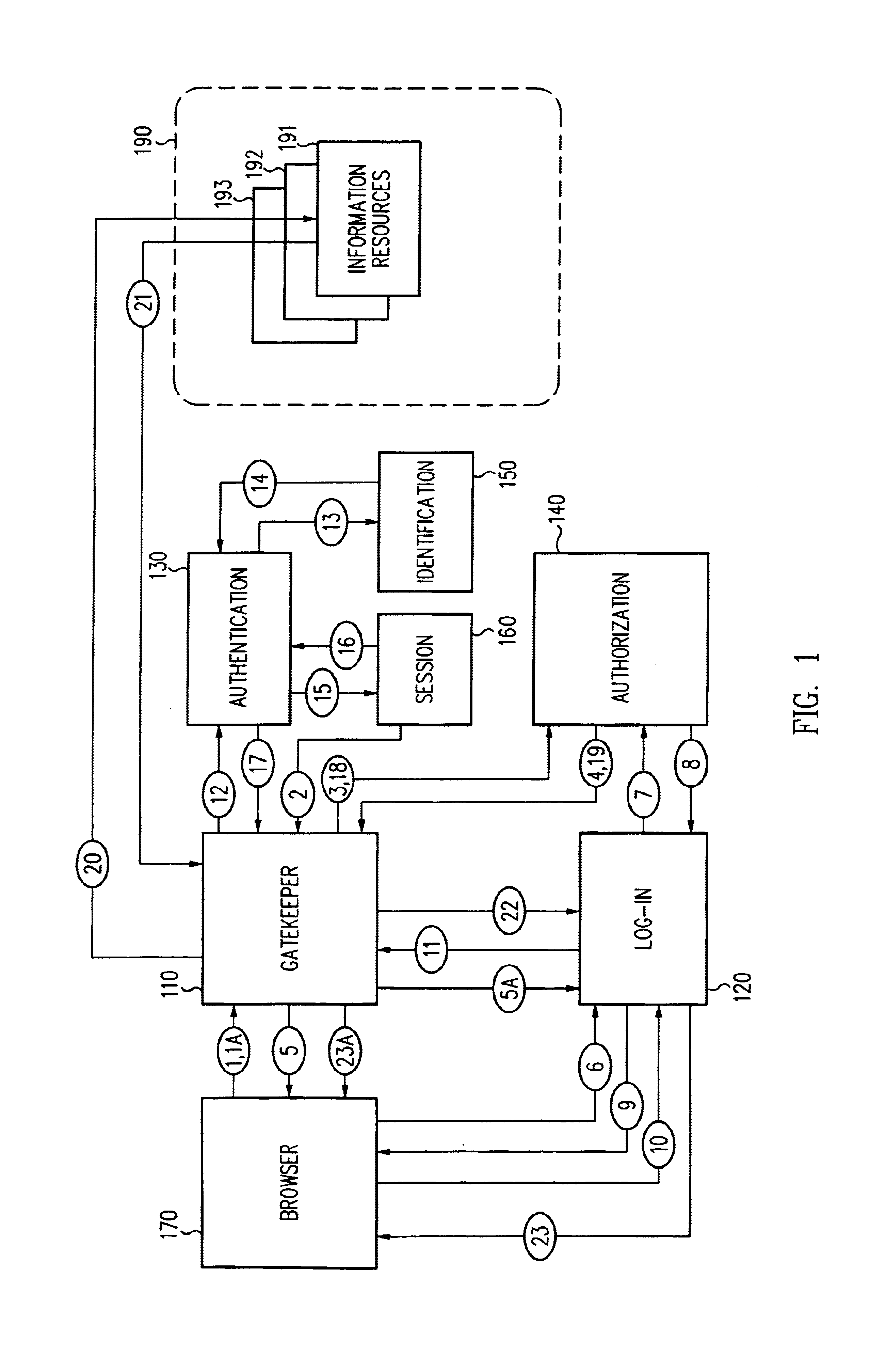
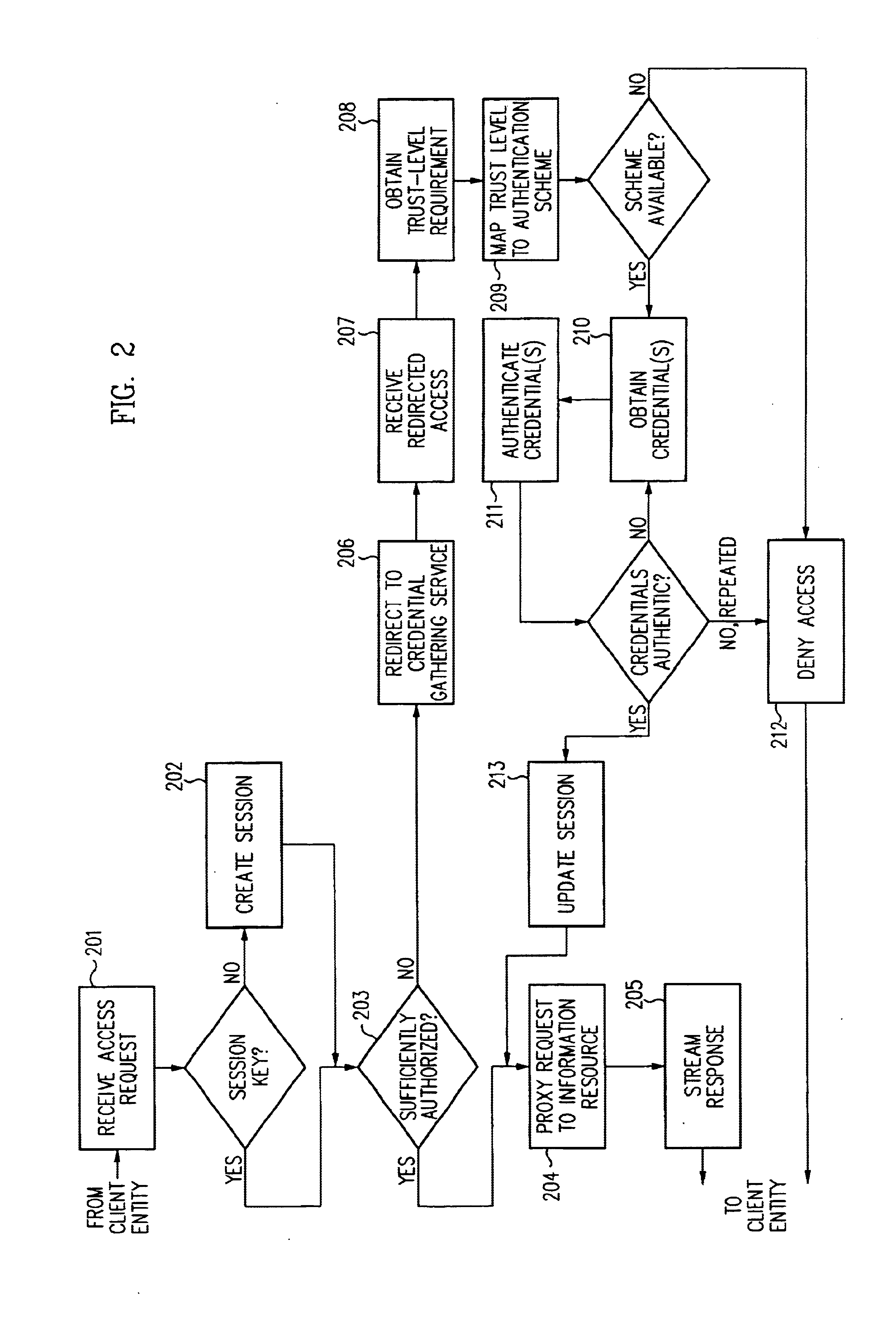
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
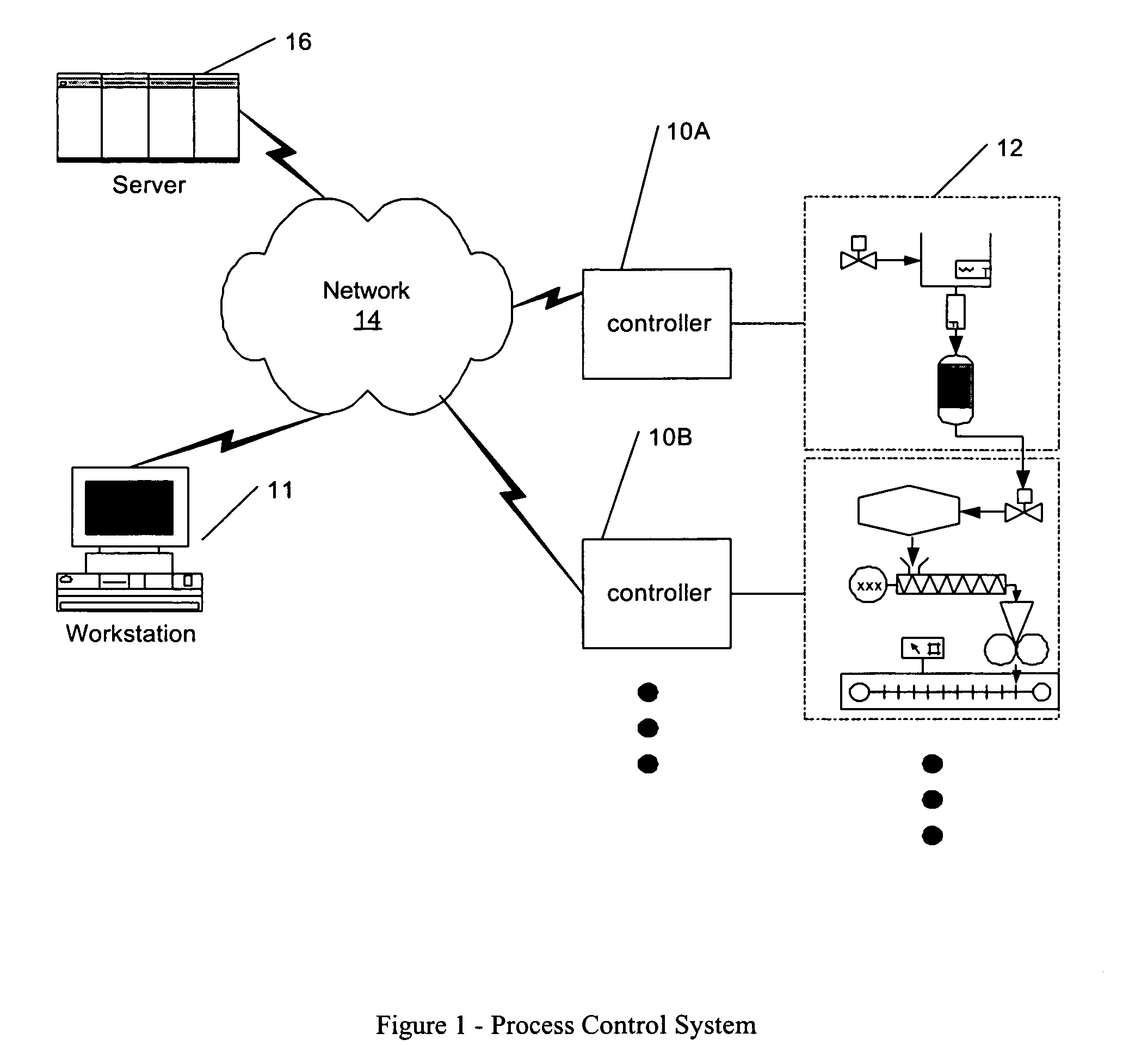
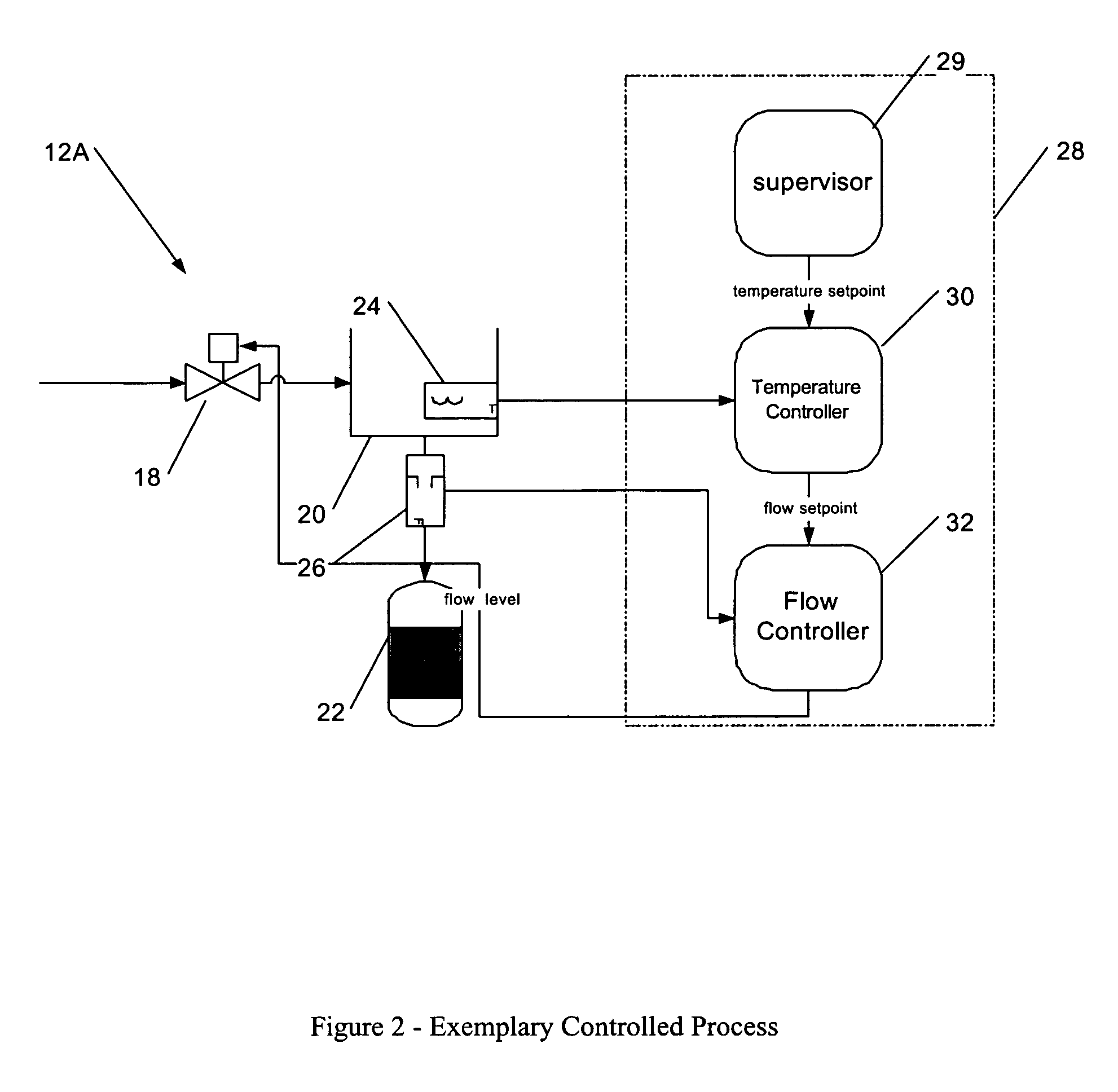
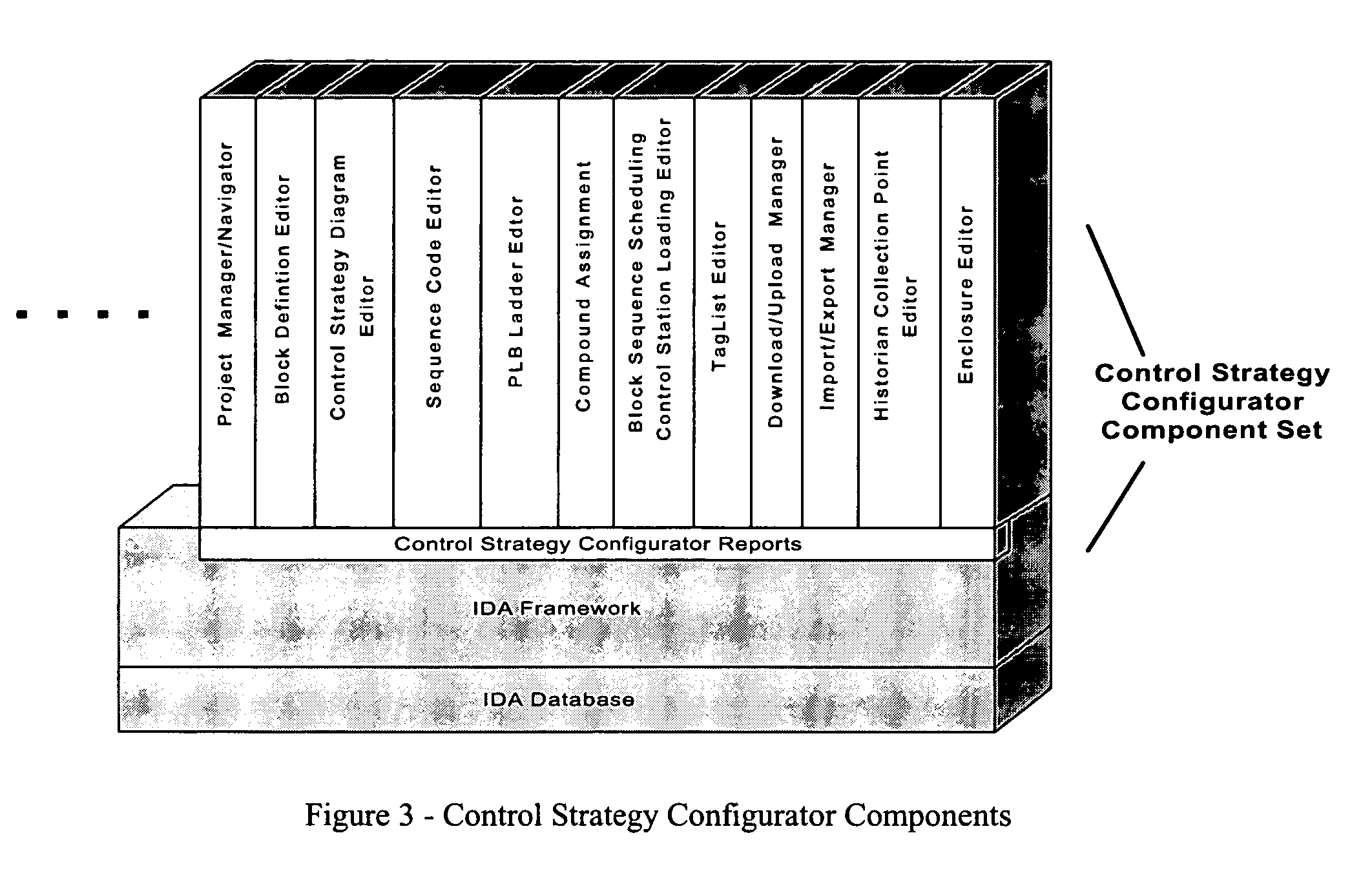
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
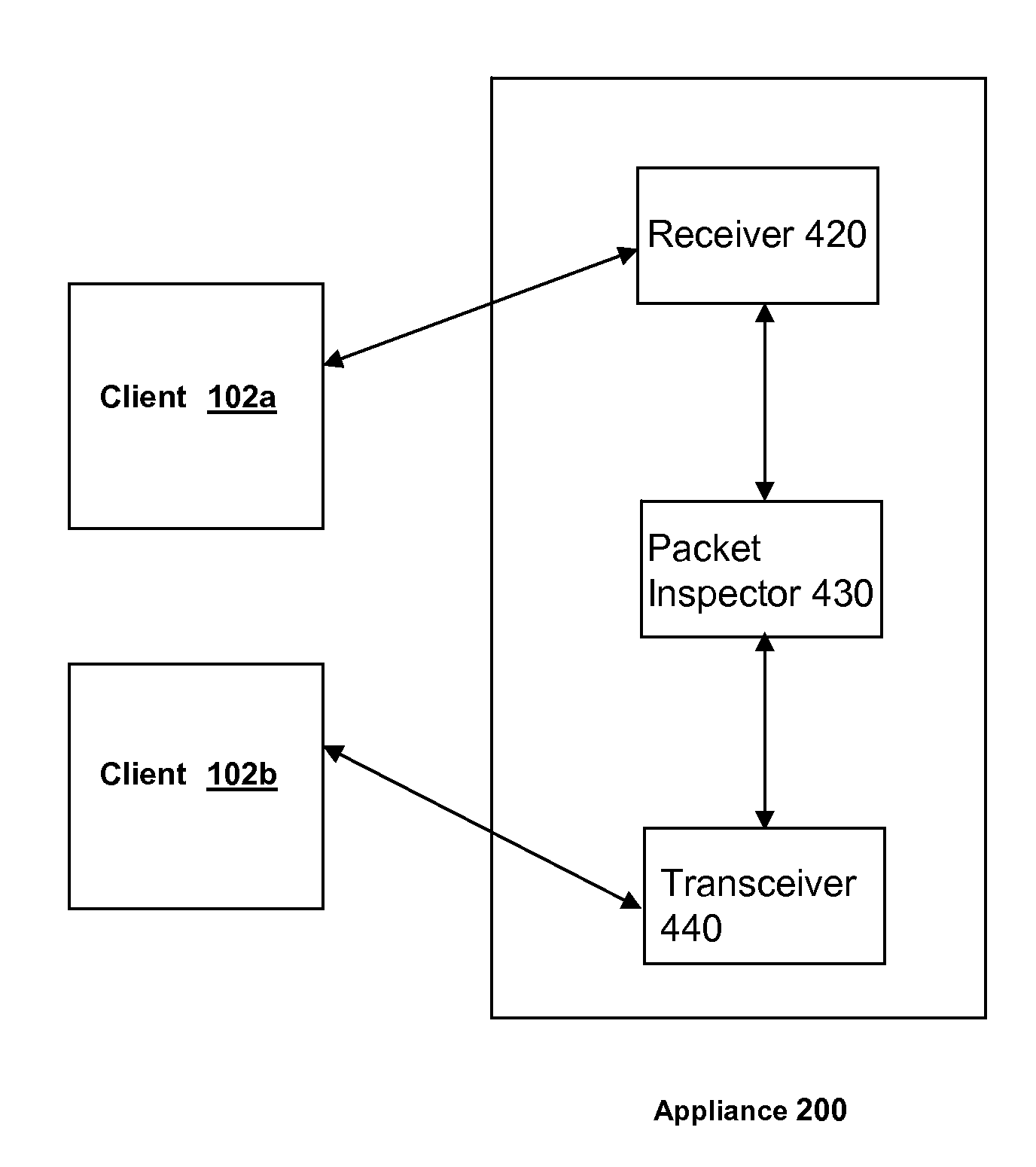
Methods and systems for routing packets in a vpn-client-to-vpn-client connection via an ssl/vpn network appliance
ActiveUS20080034416A1Digital data processing detailsMultiple digital computer combinationsConnection typePrivate network
In a method and system for routing packets between clients, a packet is received from a first client connected to a secure sockets layer virtual private network (an SSL / VPN) network appliance. An identification is made, responsive to an inspection of the received packet, of i) a type of connection required for transmission of the received packet to a destination address identified by the received packet and ii) a second client connected via an SSL / VPN connection to the SSL / VPN network appliance and associated with the identified destination address. A request is made for establishment by the second client of a connection of the identified type within the SSL / VPN connection. The received packet is transmitted to the second client via the established connection of the identified type.
Owner:CITRIX SYST INC
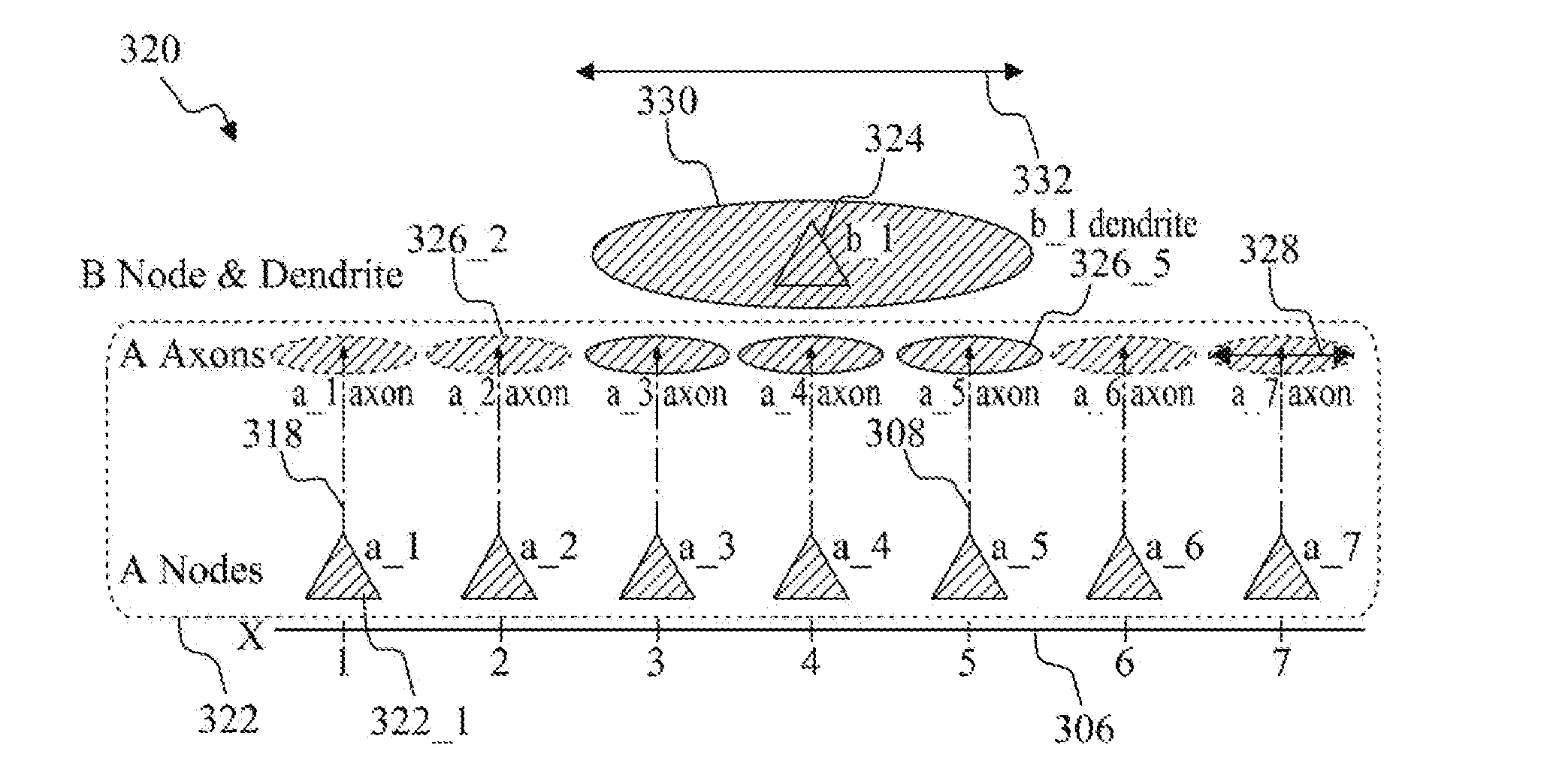
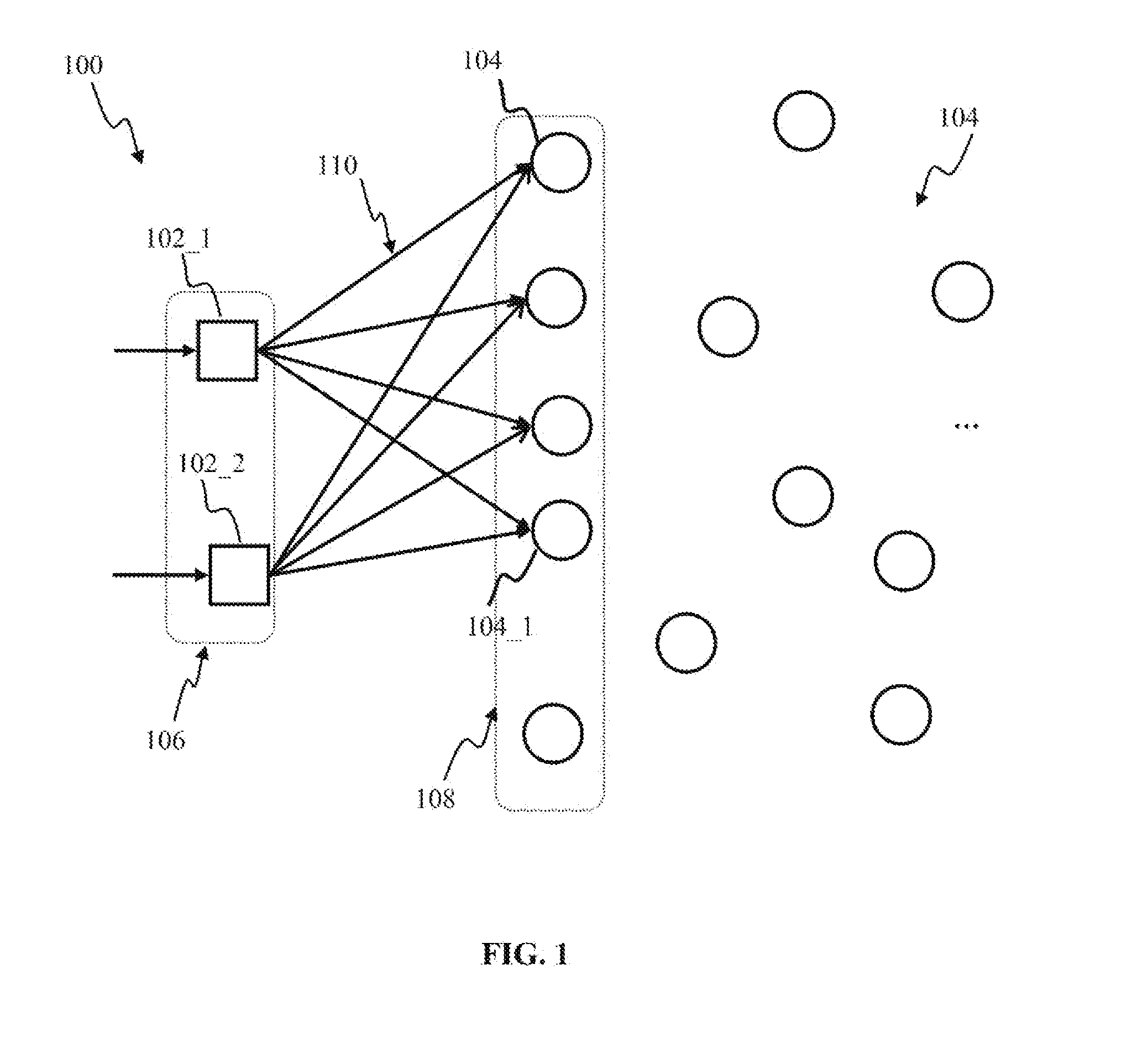
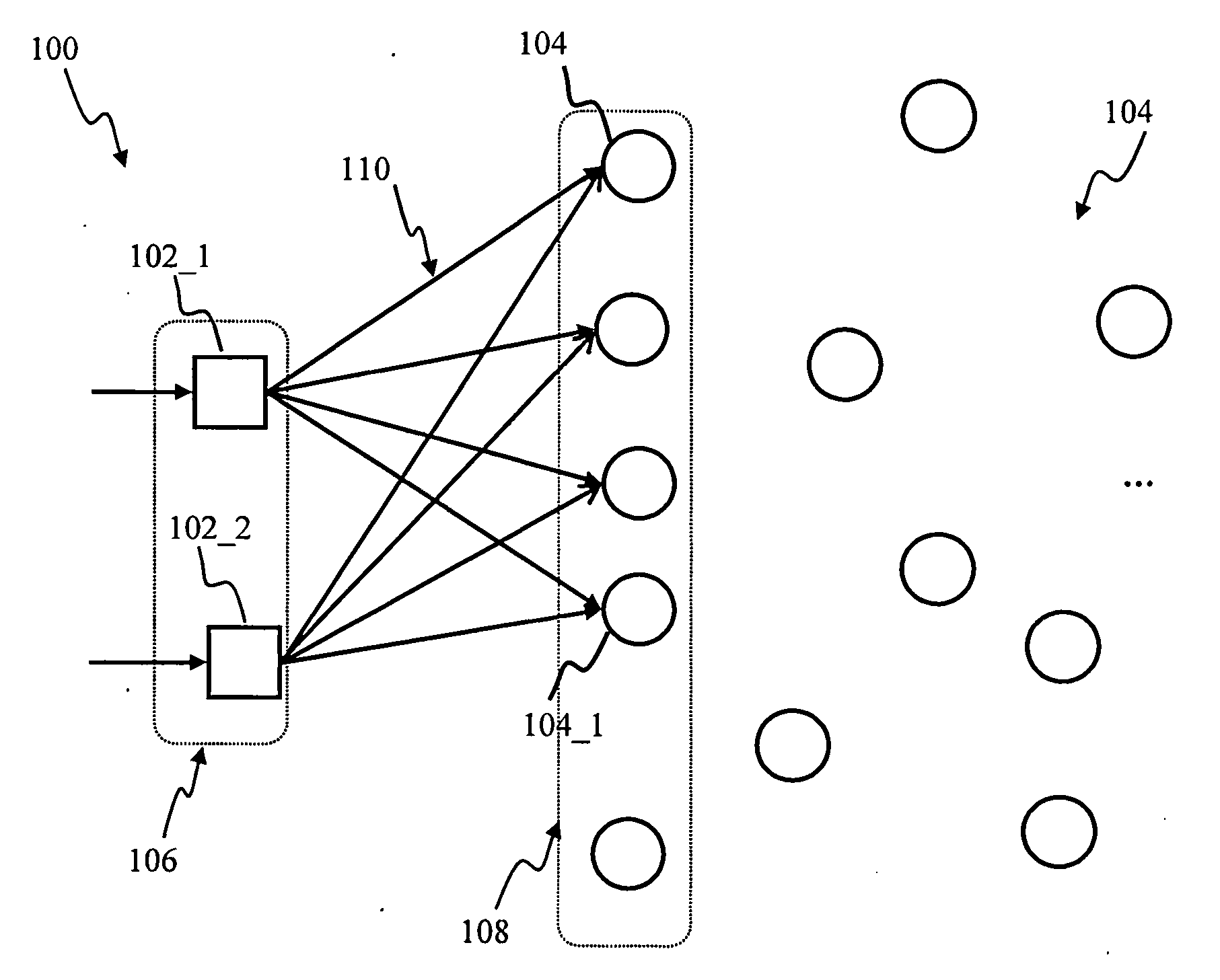
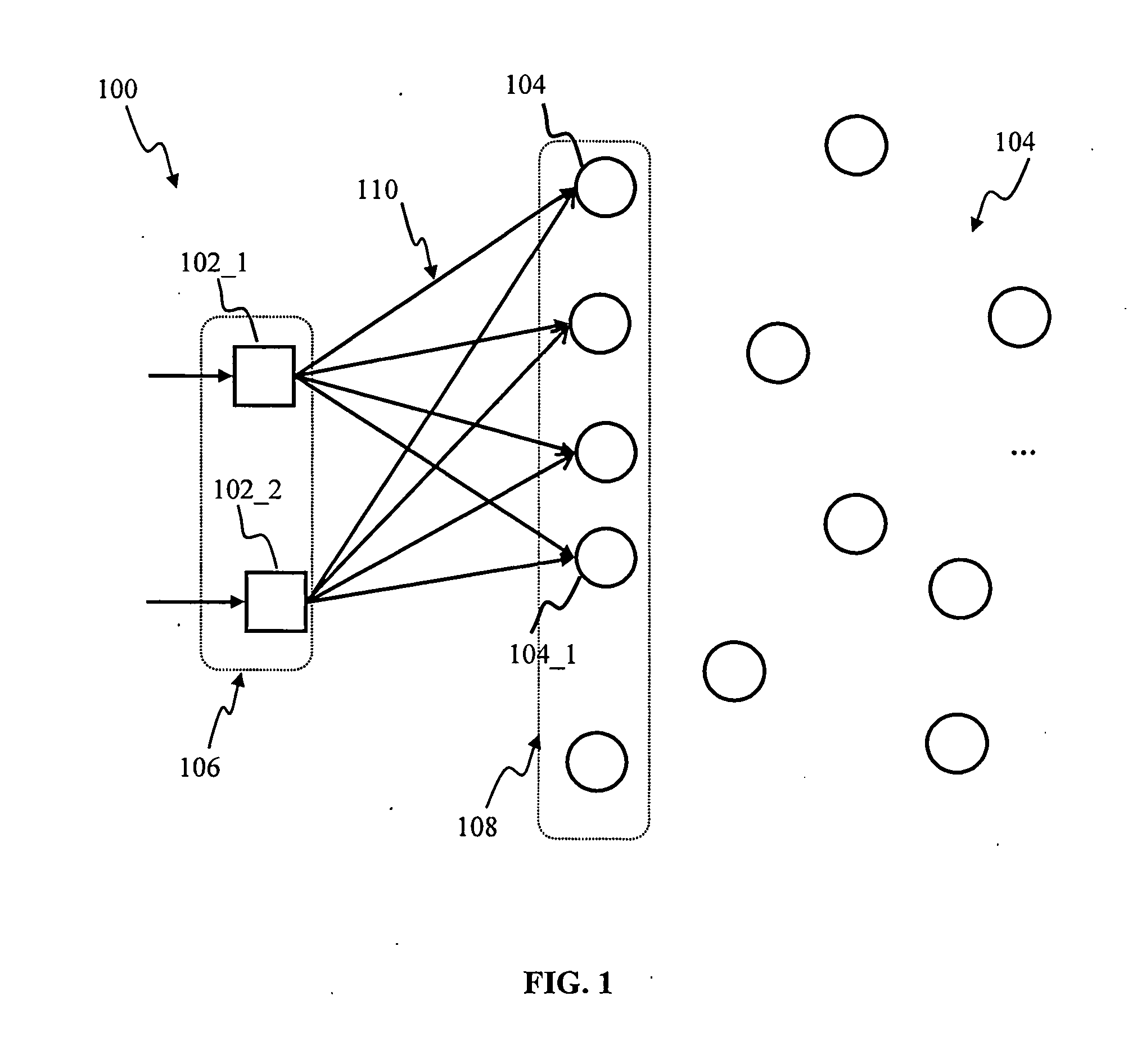
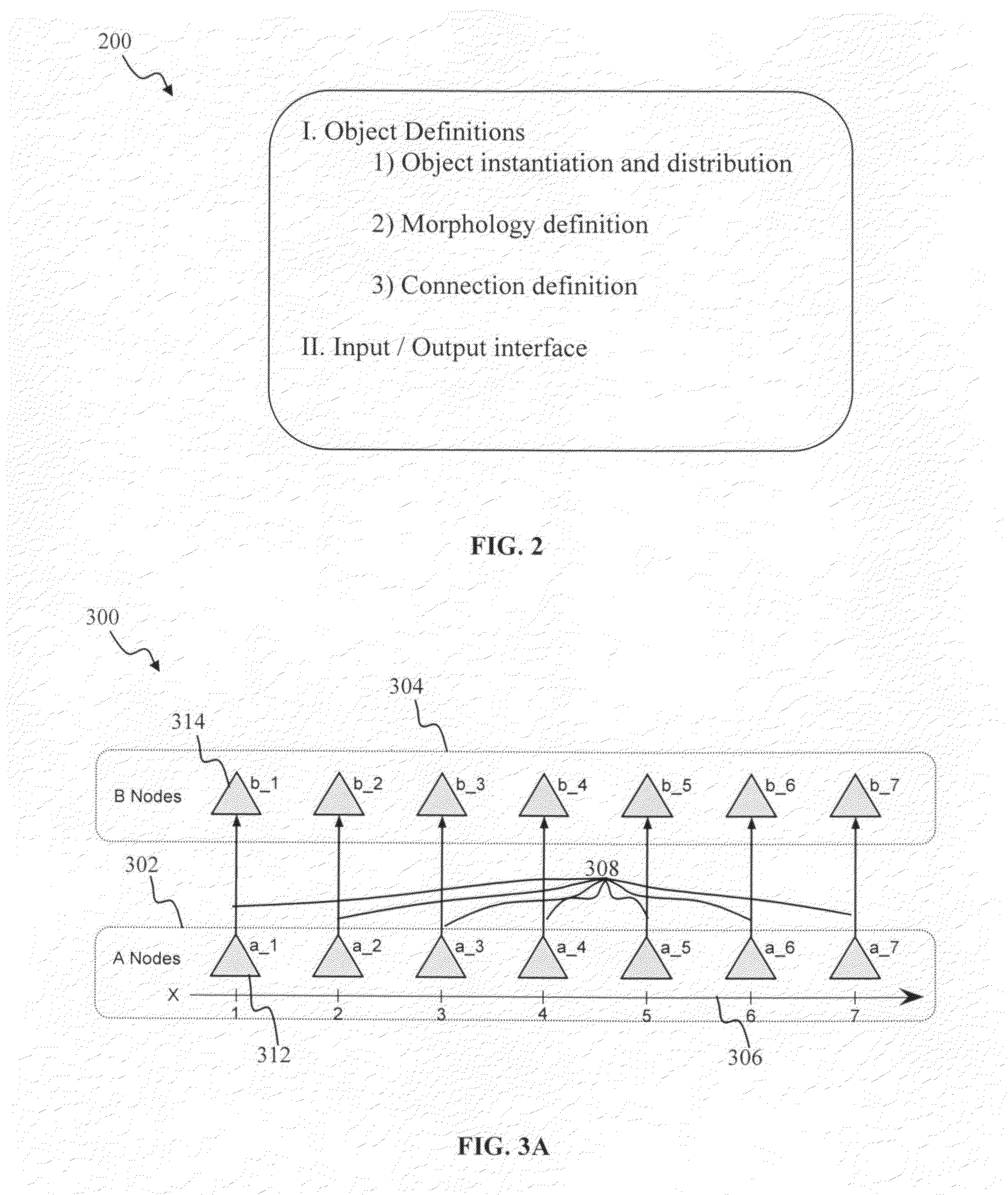
Tag-based apparatus and methods for neural networks
Owner:QUALCOMM INC
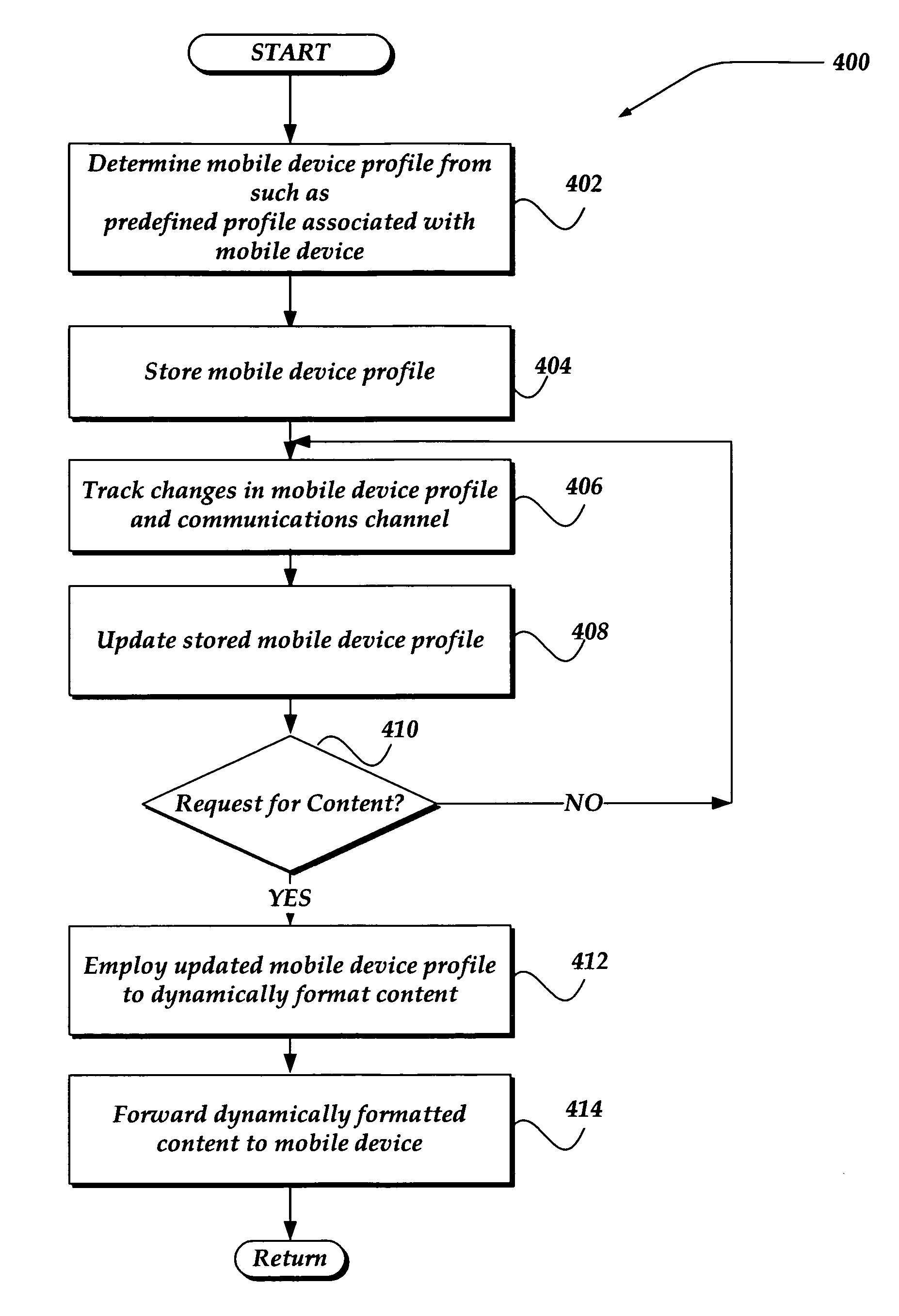
Dynamically generating content based on capabilities of a mobile device
InactiveUS20060274869A1Digital data information retrievalInformation formatConnection typeSpecific test
A system, apparatus, and method is directed to dynamically generating content on the fly based on at least one characteristic of a computing device requesting the content, including a characteristic of a network connection. The invention may receive information from a variety of sources, including a manufacturer of the computing device, a header sent by the computing device, and specific test results performed on computing devices similar to the requesting computing device. The information may include screen size, screen resolution, memory size, browser capabilities, applications supported, and so forth. The network connection information may include bandwidth, delays, degradation, connection type, and so forth. The information may be combined to determine an overall device profile. When a request for content is made, the server may employ the device profile to dynamically format the content and provide it optimized for the computing device.
Owner:OATH INC
Round-trip engineering apparatus and methods for neural networks
Apparatus and methods for high-level neuromorphic network description (HLND) framework that may be configured to enable users to define neuromorphic network architectures using a unified and unambiguous representation that is both human-readable and machine-interpretable. The framework may be used to define nodes types, node-to-node connection types, instantiate node instances for different node types, and to generate instances of connection types between these nodes. To facilitate framework usage, the HLND format may provide the flexibility required by computational neuroscientists and, at the same time, provides a user-friendly interface for users with limited experience in modeling neurons. The HLND kernel may comprise an interface to Elementary Network Description (END) that is optimized for efficient representation of neuronal systems in hardware-independent manner and enables seamless translation of HLND model description into hardware instructions for execution by various processing modules.
Owner:QUALCOMM INC
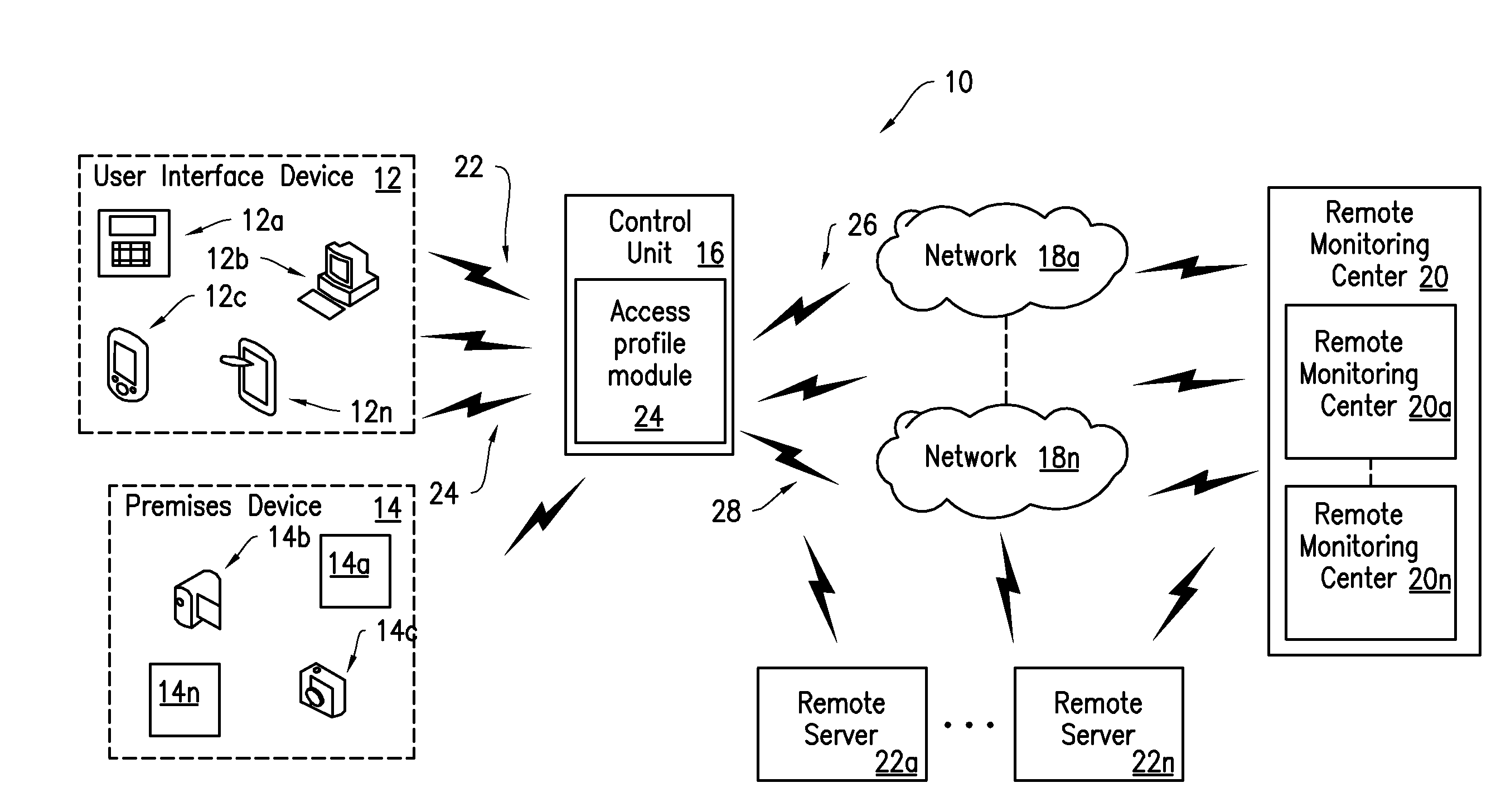
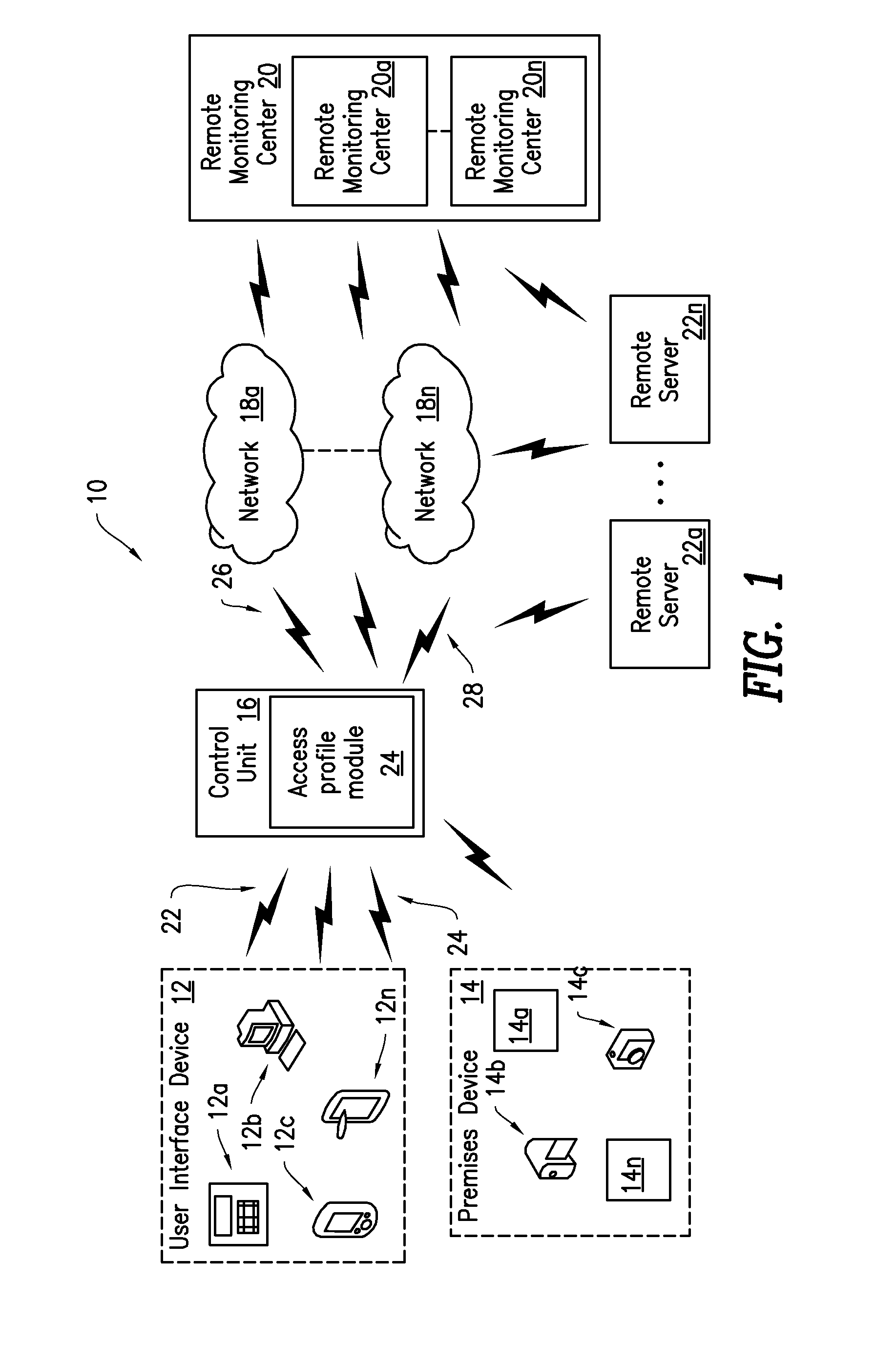
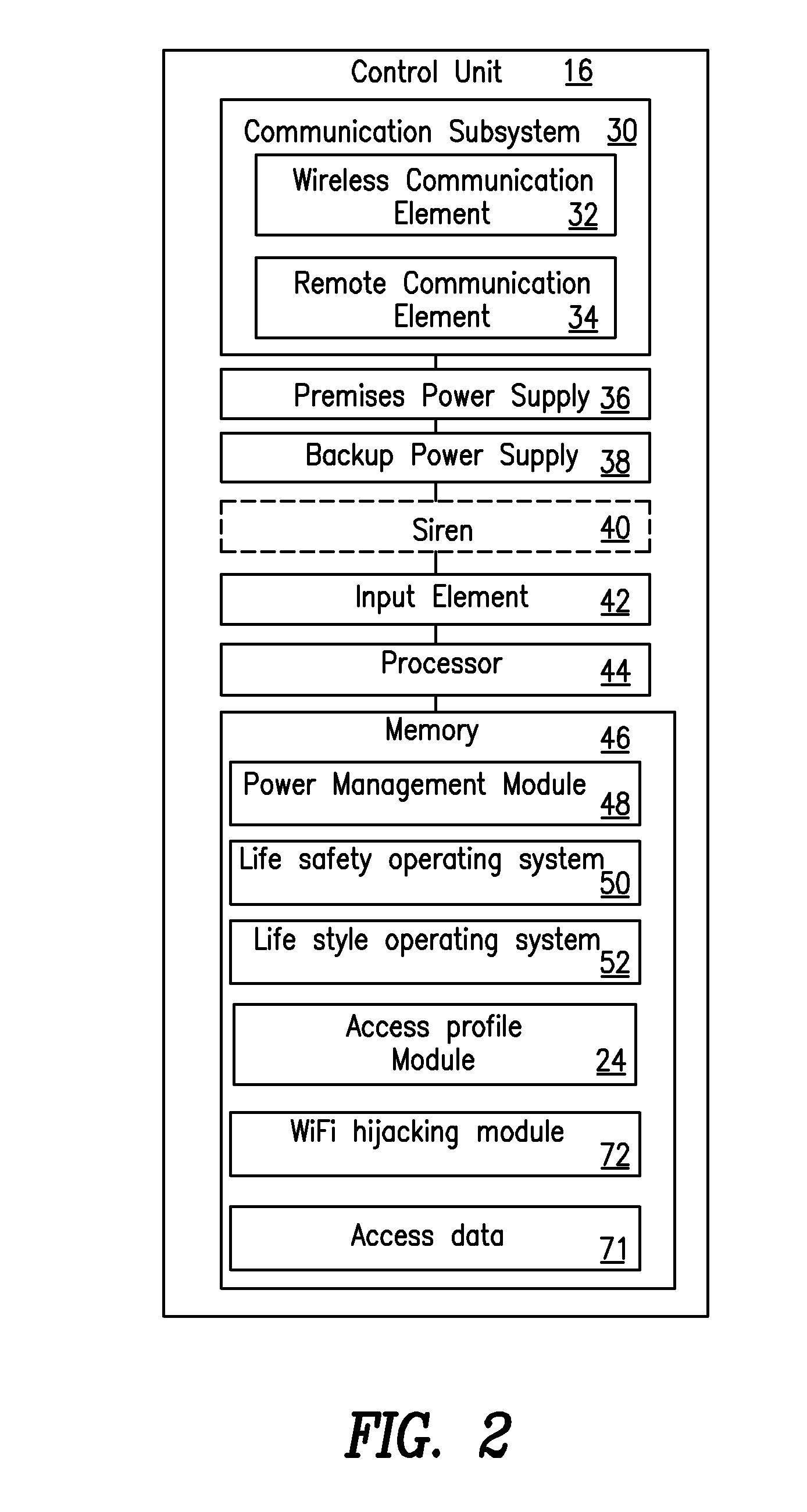
Security system access profiles
An apparatus is provided for controlling access to a premises based system through a user interface device. Criteria are used for establishing a set of system functions that are accessible through the user interface device; and this set of system function is provided by determining an access characteristic associated with the user interface device, comparing the access characteristic to the criteria, and determine the set of system functions to provide the user interface based at least in part on the comparison. The criteria may be defined by an access profile containing a predetermined set of system functions. The access characteristic may include physical location of the user interface device, connection type, device type, and a device identifier. The set of functions may be automatically provided to the user interface device upon with a prompt to arm / disarm the system, and / or control other devices, such as through geo-fencing.
Owner:ADT US HLDG INC
Intelligent storage device for backup system
ActiveUS8099605B1Avoid redundancyDuplicate copies of same informationDigital data processing detailsUnauthorized memory use protectionConnection typeComputer hardware
A data storage and data backup device that offers automatic reduction of duplicate data storage, and that easily can be connected to computing devices, computing systems and networks of computing devices. The device offers high protection against destruction or modification of already stored data, and requires flipping a physical switch and possibly require user authentication in order for the protection to be temporarily bypassed. Several connection types of the device to the computer systems are supported such as wired, wireless like Bluetooth or WI-FI, but not limited to those.
Owner:DATA LOCKER INC +1
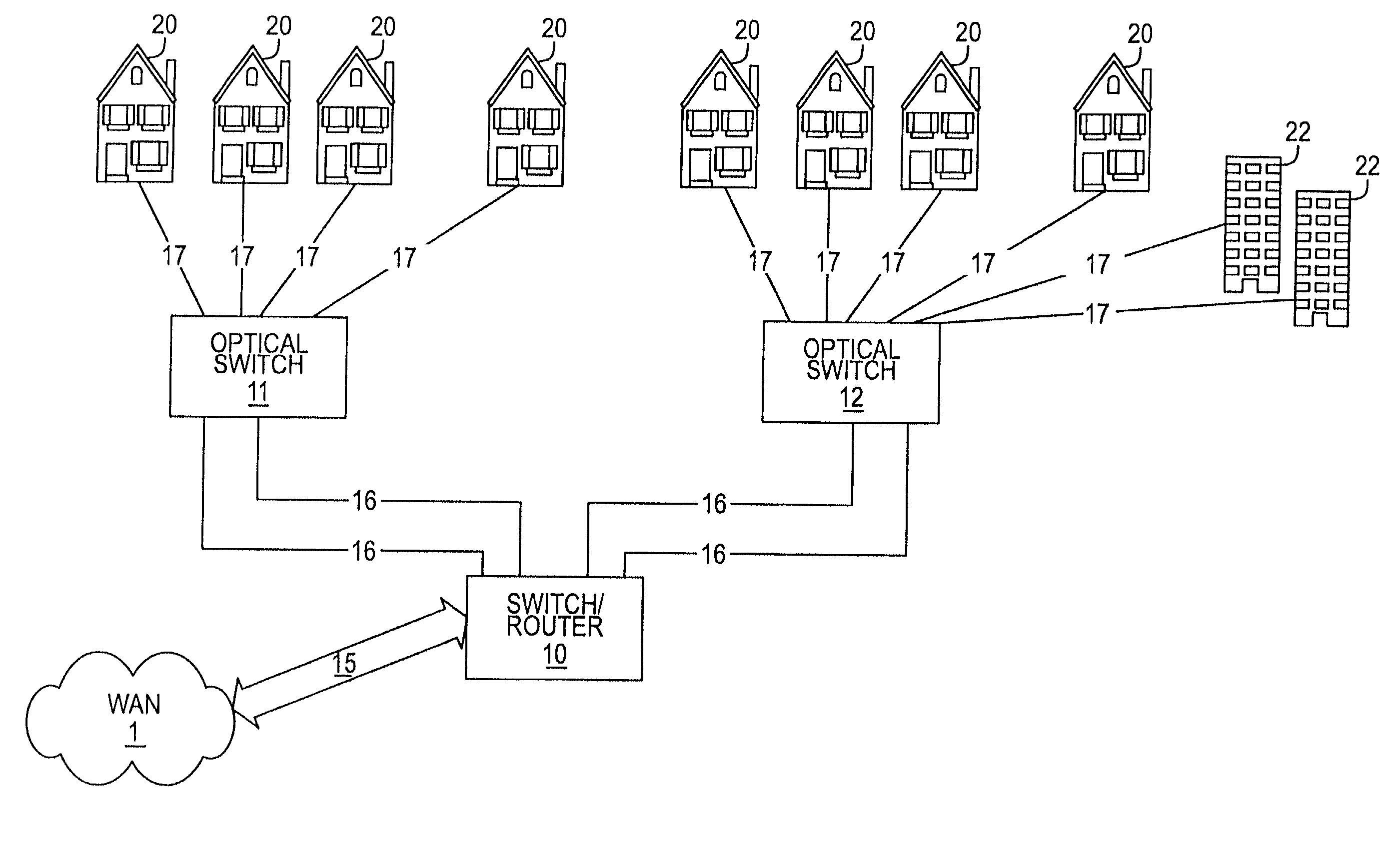
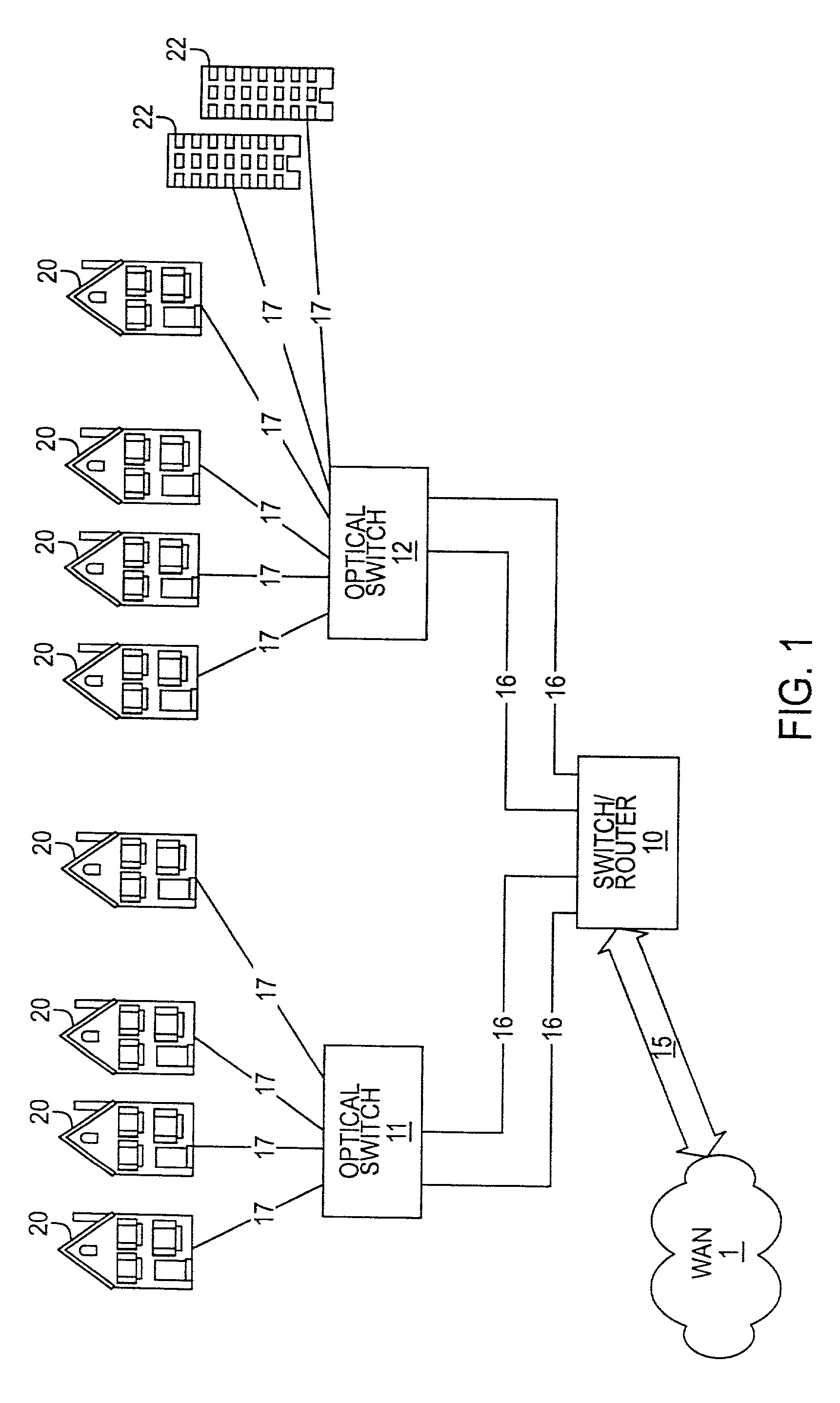
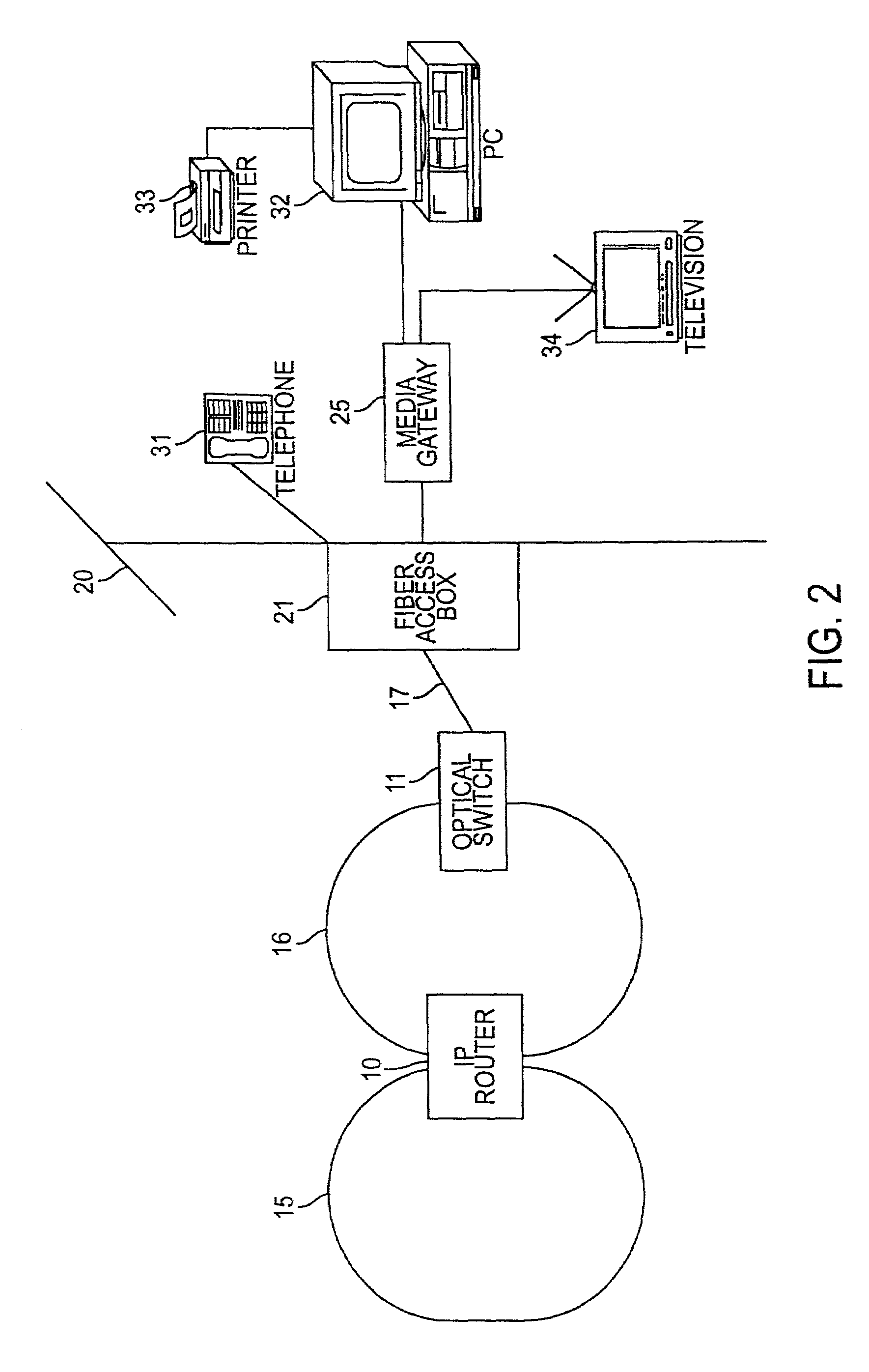
Optical network subscriber access architecture
InactiveUS7171121B1Provides redundancyMultiplex system selection arrangementsOptical multiplexConnection typeFiber
A technique for providing an optical signal to a destination. In one embodiment, the technique is realized through the use of an environmentally hardened, modular switch and a fiber distribution methodology. The modular switch may include fiber access ports, power access ports, dual power supply modules, dual switch fabric modules, dual optical trunking modules, and multiple subscriber service modules that house subscriber service ports and serve a total of up to 96 end points. The dual optical trunking modules may act as an interface between an optical network and the dual switch fabrics, and provide redundancy and variable optical transmission distance between the modular switch and the optical network to which the modular switch is connected. The dual switch fabrics are used for switching and aggregating signals and providing redundancy. Each subscriber service module acts as an interface between one or more subscriber end points and the dual switch fabrics of the modular switch. The subscriber service modules may be coupled to one or both of the dual switch fabrics and a total of up to 96 subscriber end points. Subscriber end point connectivity may be achieved via subscriber service ports (housed within a subscriber service module), one or more of the fiber access ports, external fiber optic splice cabinet, fiber optic trunk cable, and one or more fiber breakout points (housed by pedestals). The subscriber end points may consist of one or more optical or electrical subscriber connection types.
Owner:RPX CLEARINGHOUSE
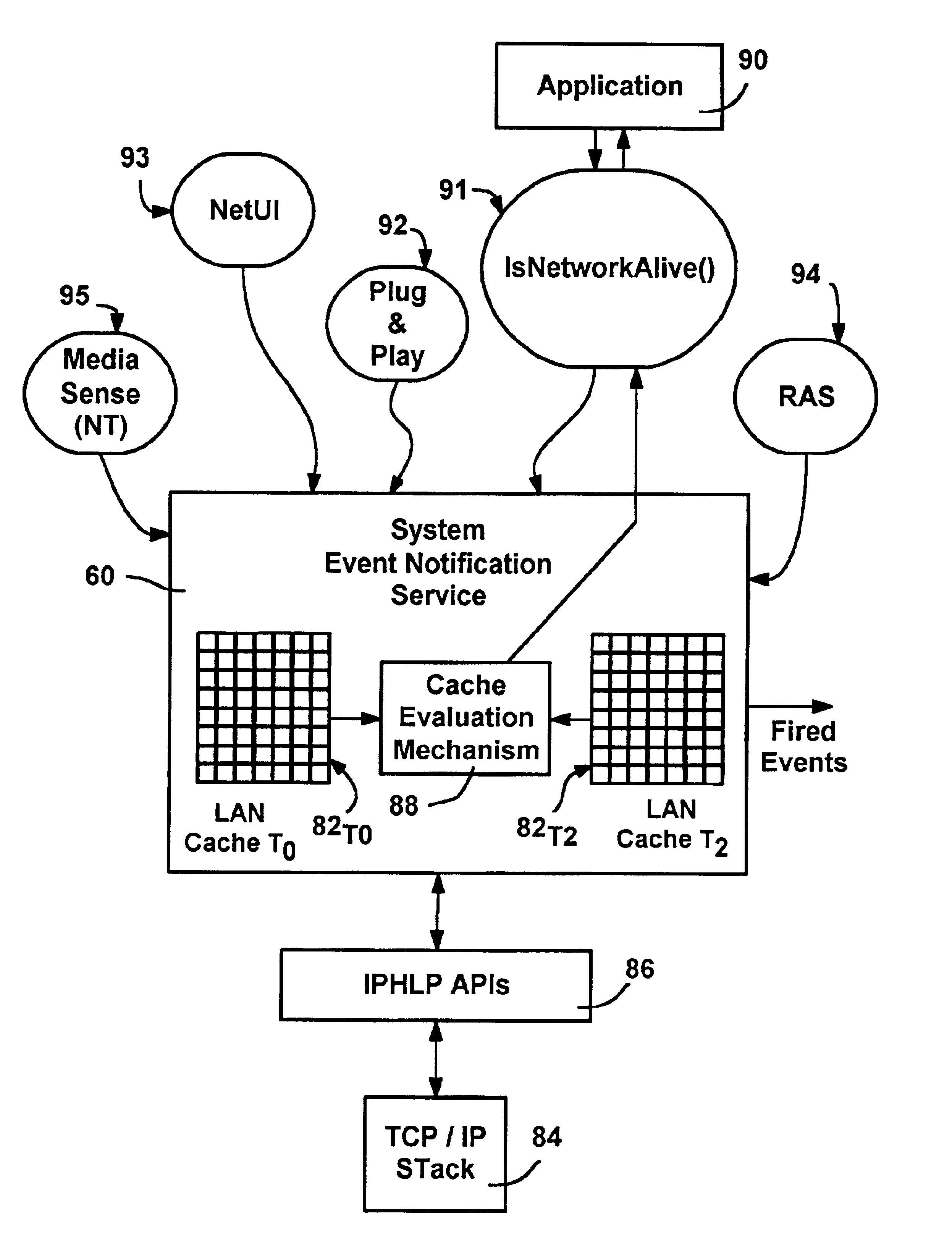
Method and mechanism for providing computer programs with computer system events
InactiveUS6859829B1Special service provision for substationMultiplex system selection arrangementsConnection typeIp address
A method and system for providing system event notifications to clients such as applications. Clients register for notification of one or more types of events with a registration mechanism, and a System Event Notification Service, (SENS), receives system event information and fires event notifications in response thereto. A distribution mechanism selectively communicates the fired event to each client registered for notification thereof based on the type of event. Events include network events, for which the service monitors the connectivity state of the machine, including whether a connection is established or lost, the type of connection (LAN / WAN) and bandwidth information. To monitor a LAN state, the service caches outgoing and incoming network information including errors and packet counts and statistically evaluates this cached information against current information to determine whether the connection is established or lost. The service also determines if a destination (IP address or name) is reachable, by periodically polling destinations. Other system event notifications may be fired, including logon or logoff operations and power management events.
Owner:MICROSOFT TECH LICENSING LLC
Externally connection type USB2.0 interface flash card reader
InactiveUS20020185533A1Sensing record carriersElectric digital data processingConnection typeEngineering
An externally connection type USB2.0 interface flash card reader comprising an insertion cassette housing, and a USB2.0 connection cable, characterized in that one end of the insertion cassette housing is provided with an insertion / connection hole allowing the insertion of various type of solid state flash cards externally to the insertion cassette housing, and connecting to USB ports of a host computer via the USB 2.0 card.
Owner:DATAFAB SYST
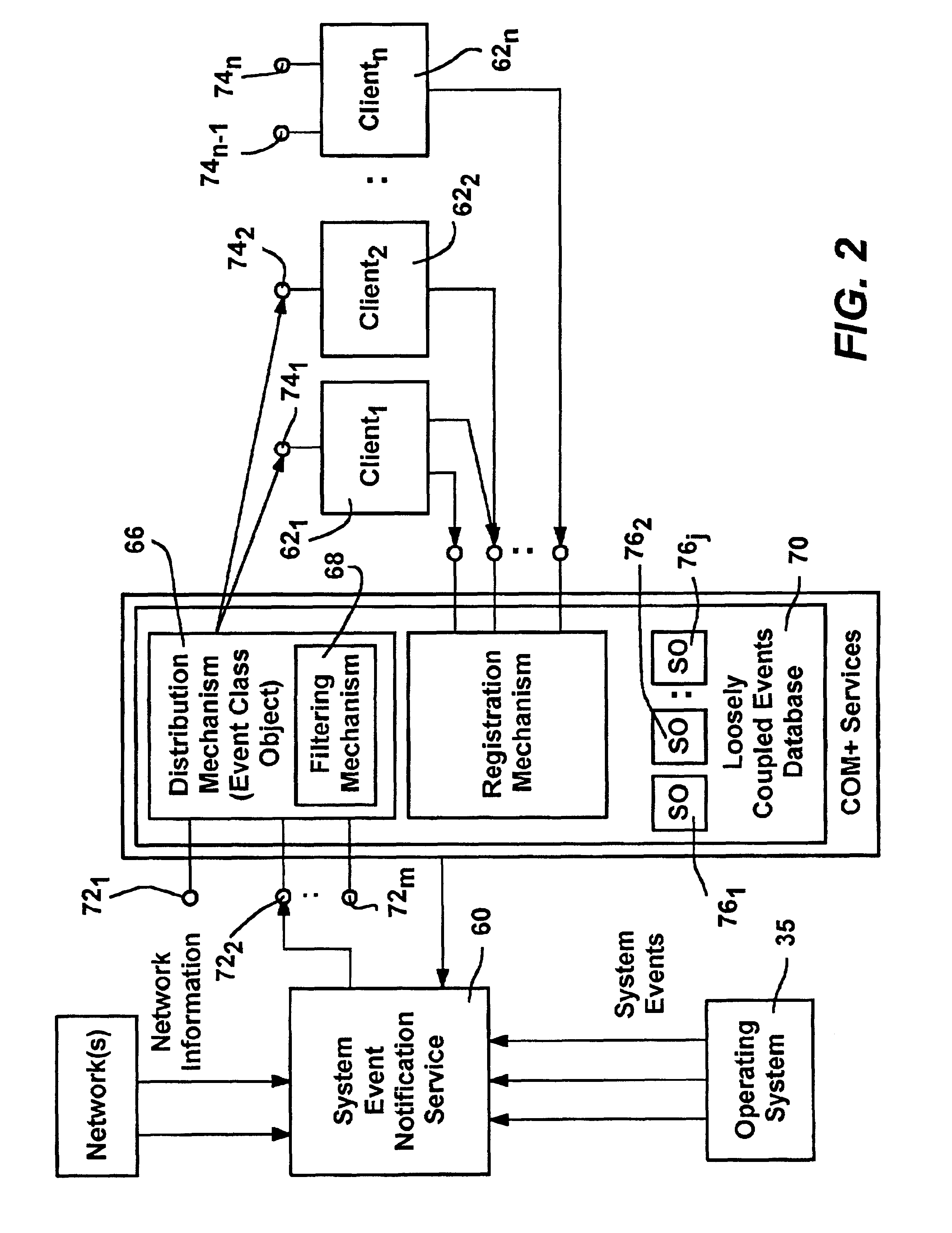
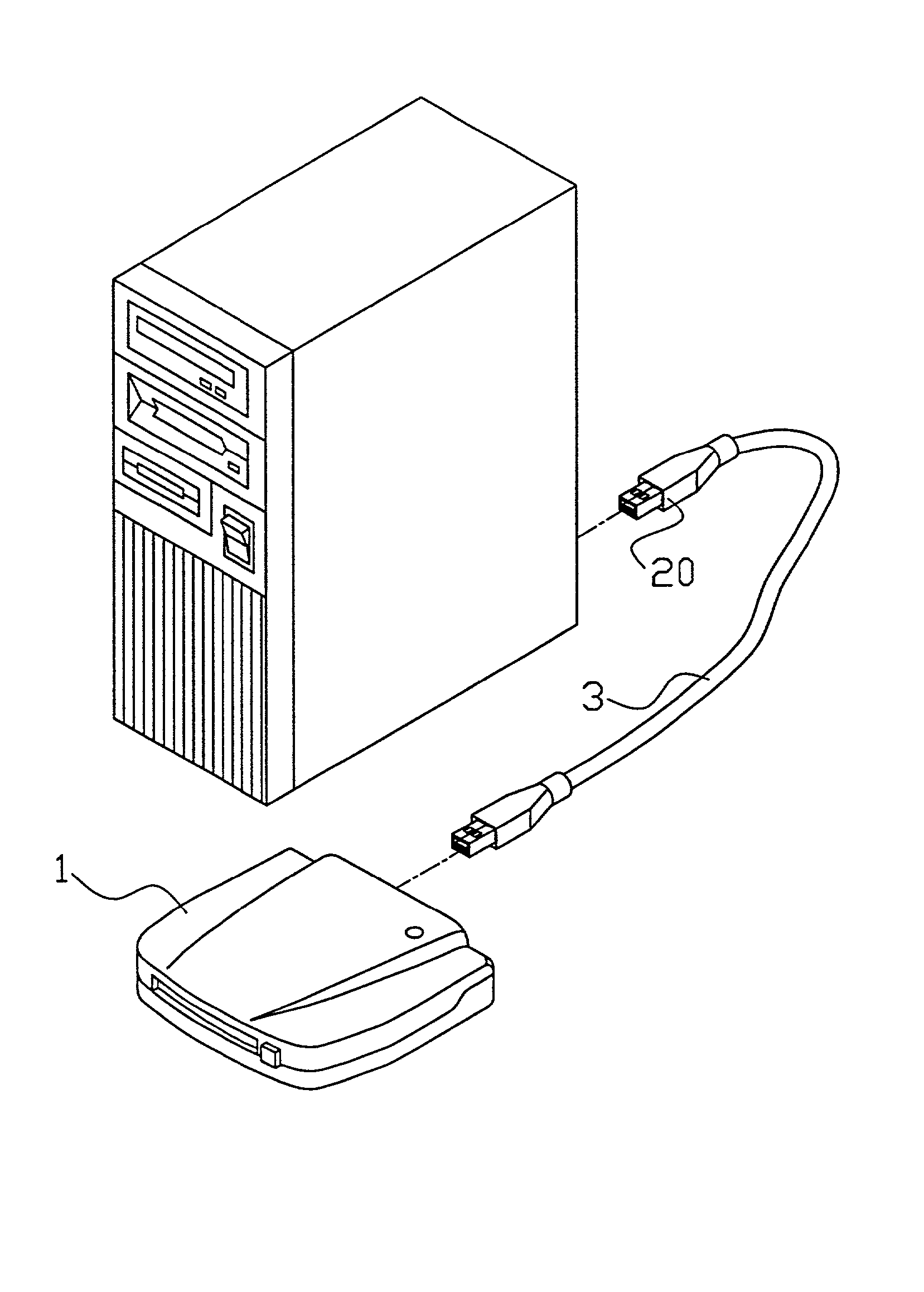
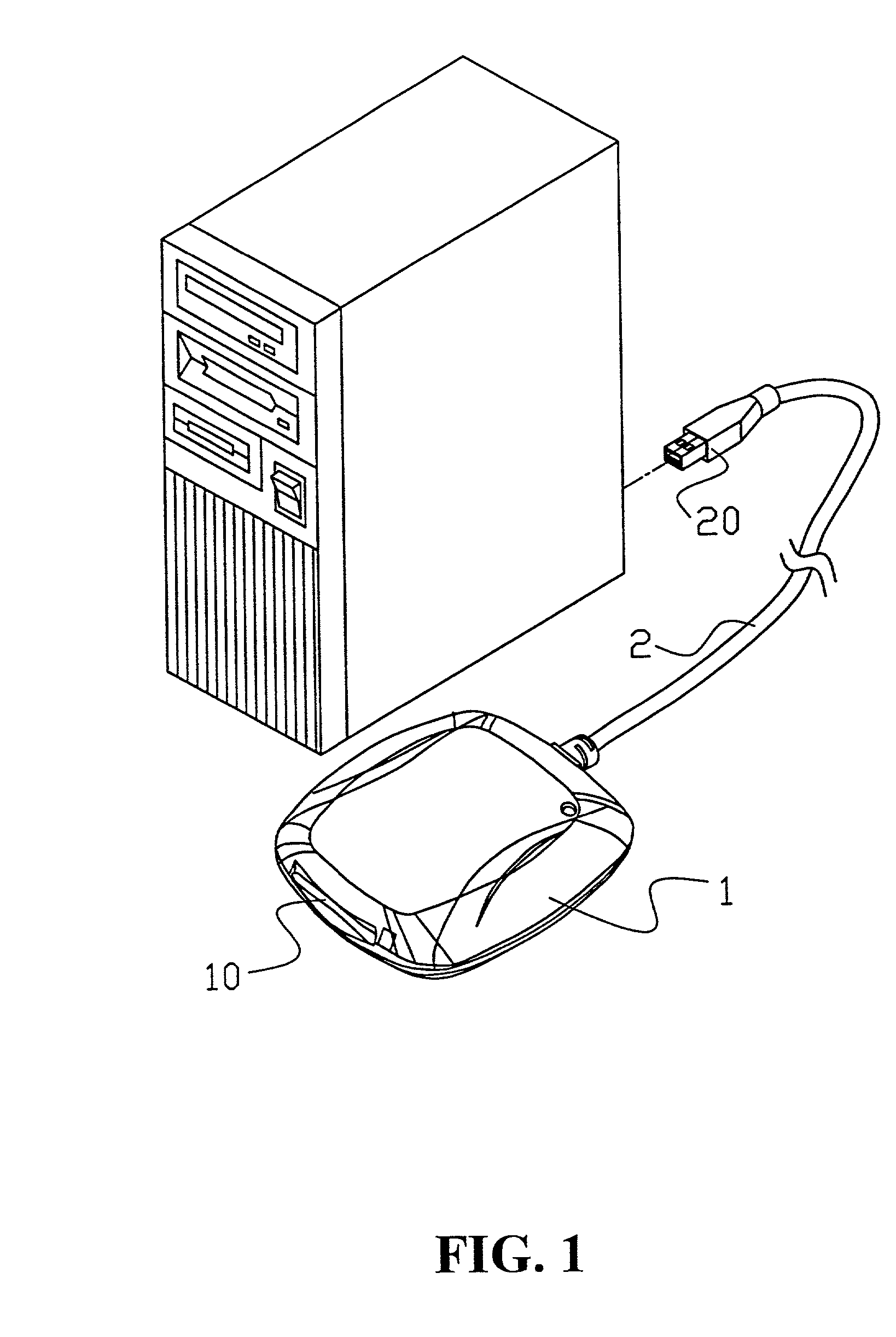
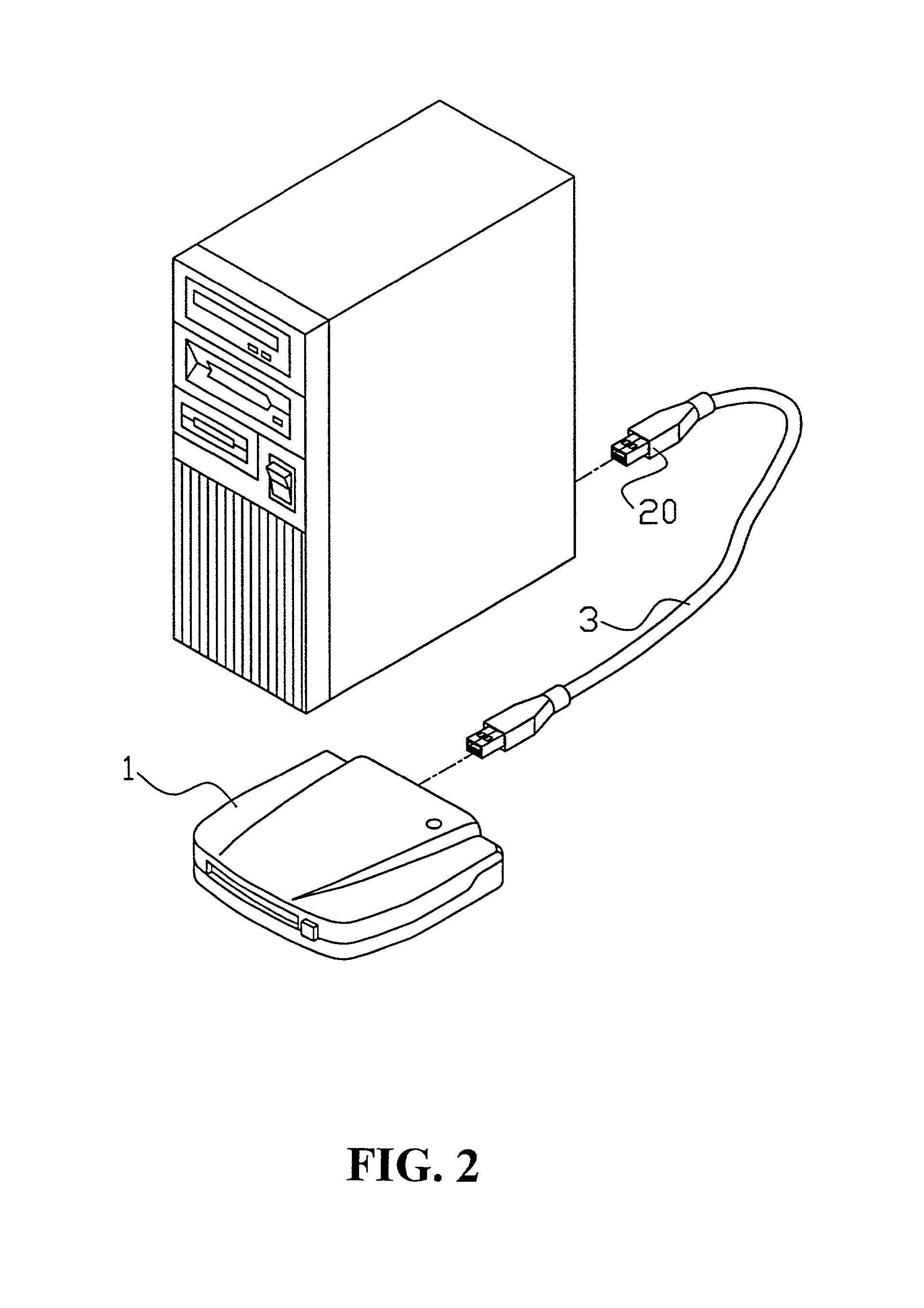
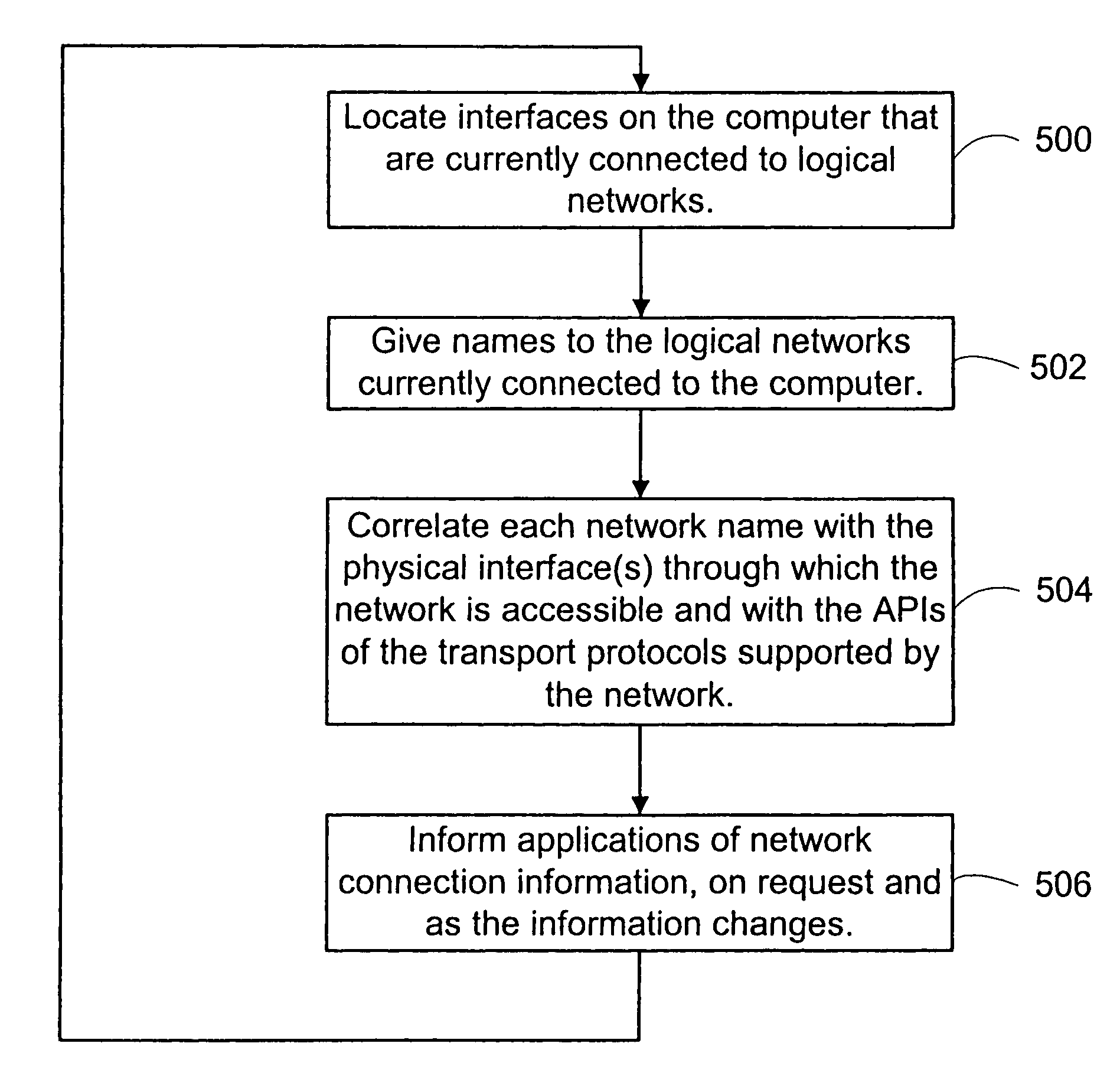
Systems and methods for uniquely identifying networks by correlating each network name with the application programming interfaces of transport protocols supported by the network
InactiveUS7000012B2Broadcast transmission systemsDigital computer detailsConnection typeApplication programming interface
A service is disclosed that discovers information about the logical networks to which a computer is connected and provides that information to applications. The information is keyed to names constructed by the service. There is a mapping between the names and the logical networks. Applications may rely on the names when selecting a configuration to use with a given logical network. The network name may be correlated with other information, such as physical network interface(s) on the computer through which the logical network is accessible, application programming interfaces of the transport protocols supported by the logical network, and the connectivity type of the logical network. Applications are notified when network information provided to them changes or when new information becomes available.
Owner:MICROSOFT TECH LICENSING LLC
Automatically configuring switch ports with appropriate features
ActiveUS7411915B1Error preventionFrequency-division multiplex detailsComputer hardwareConnection type
A method and apparatus for automatically configuring a physical port of a switch with features appropriate to a connection type snoops incoming packets to determine the connection type and executes a port configuration macro installed on the switch to apply appropriate features for the connection type.
Owner:CISCO TECH INC
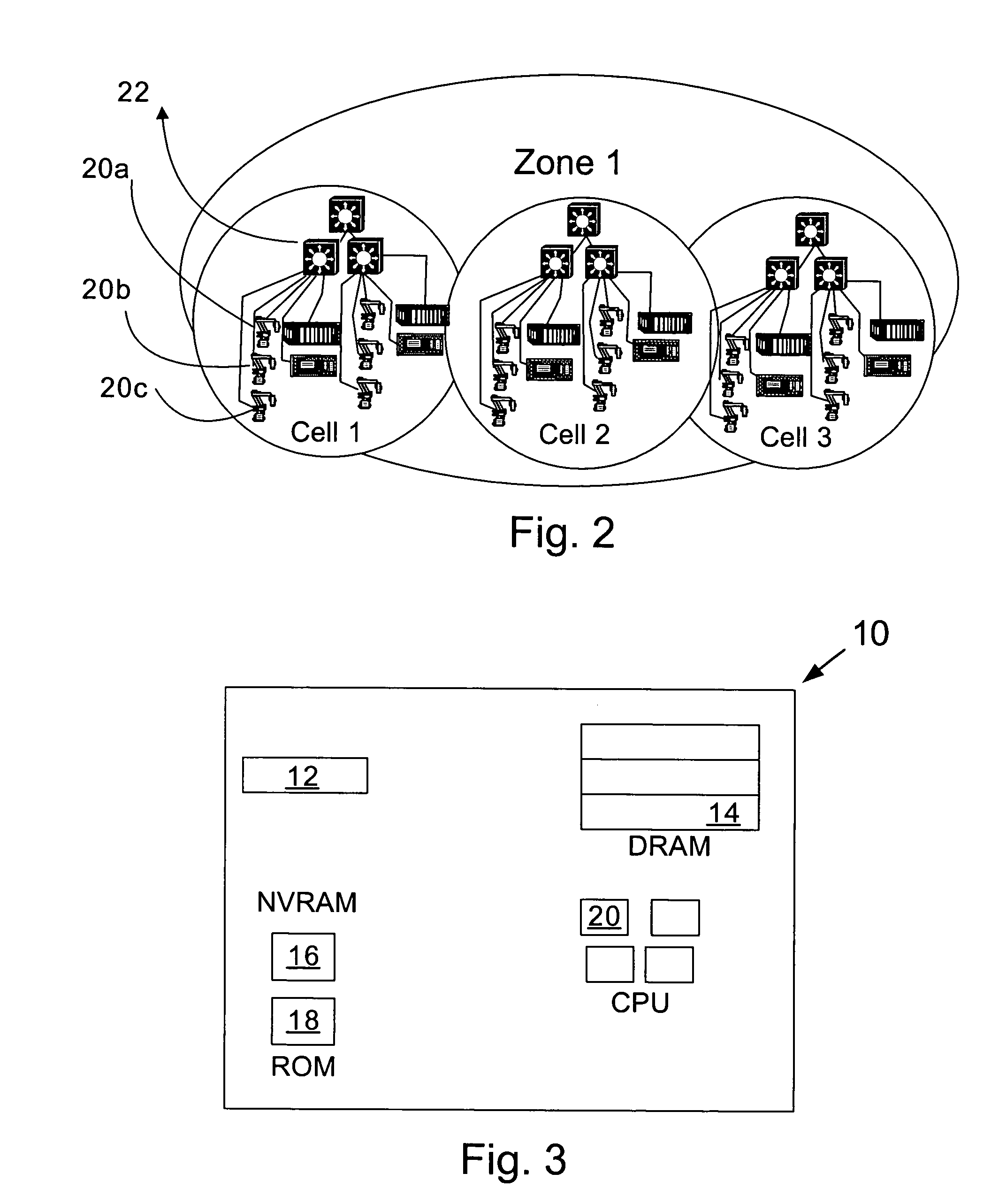
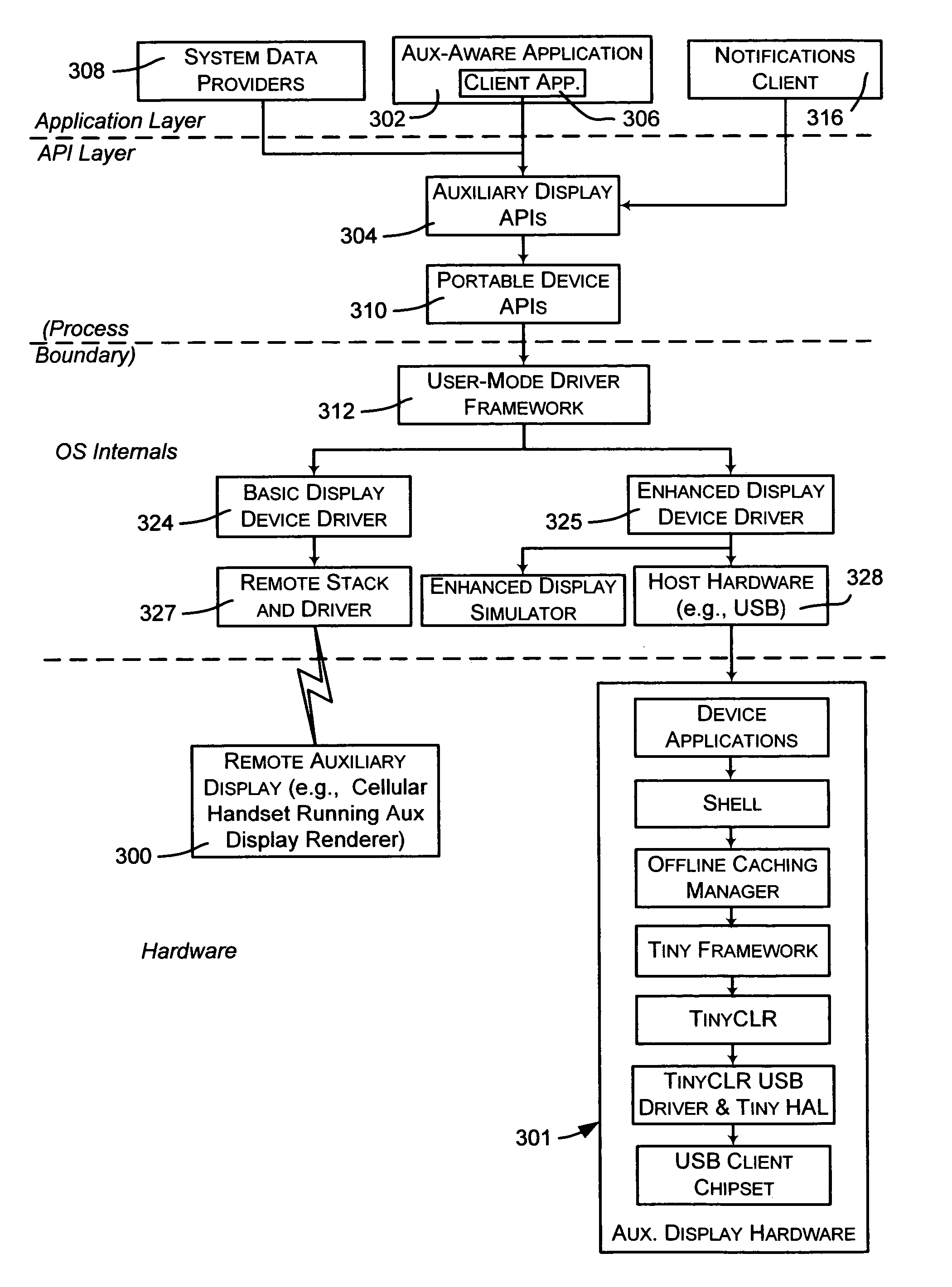
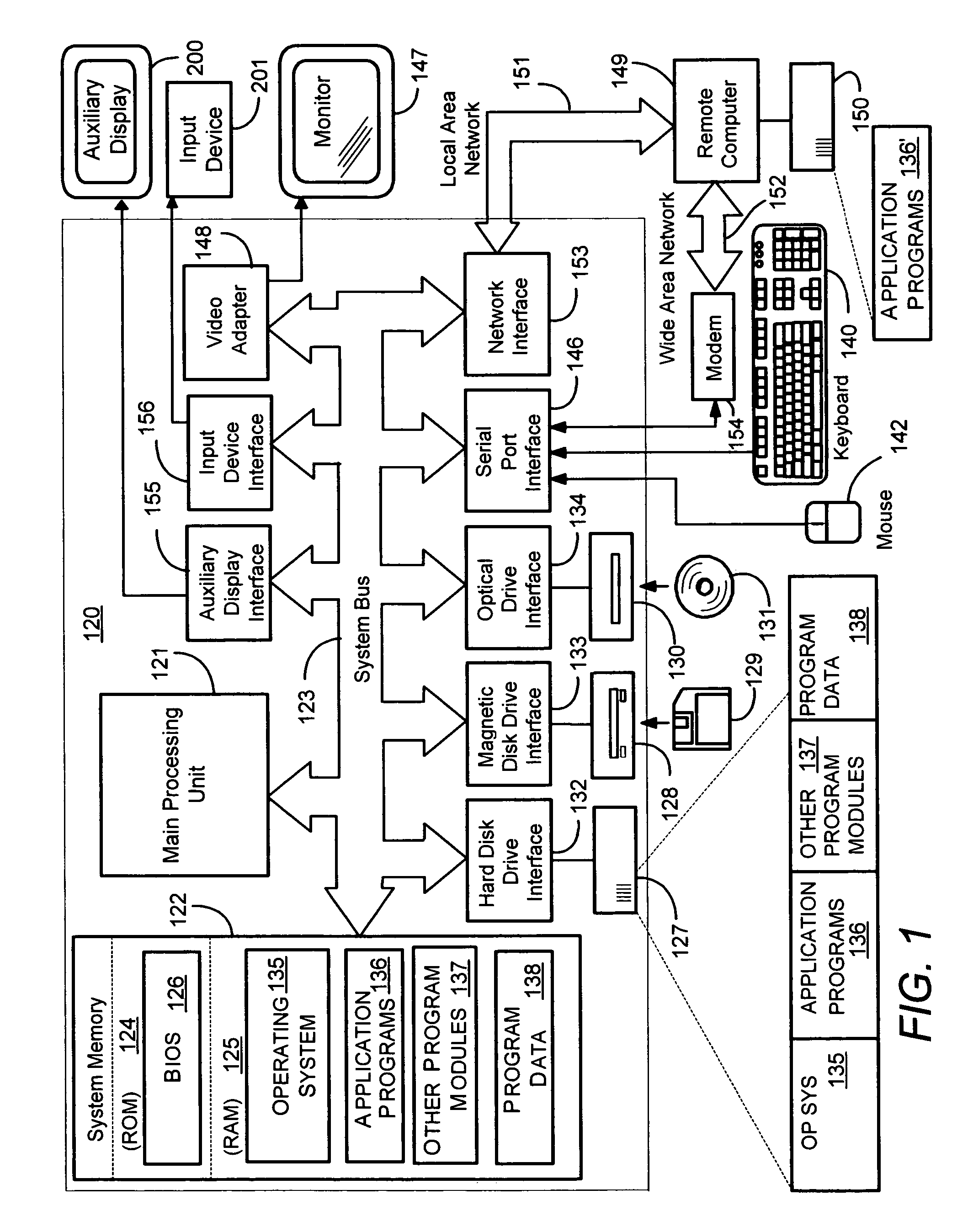
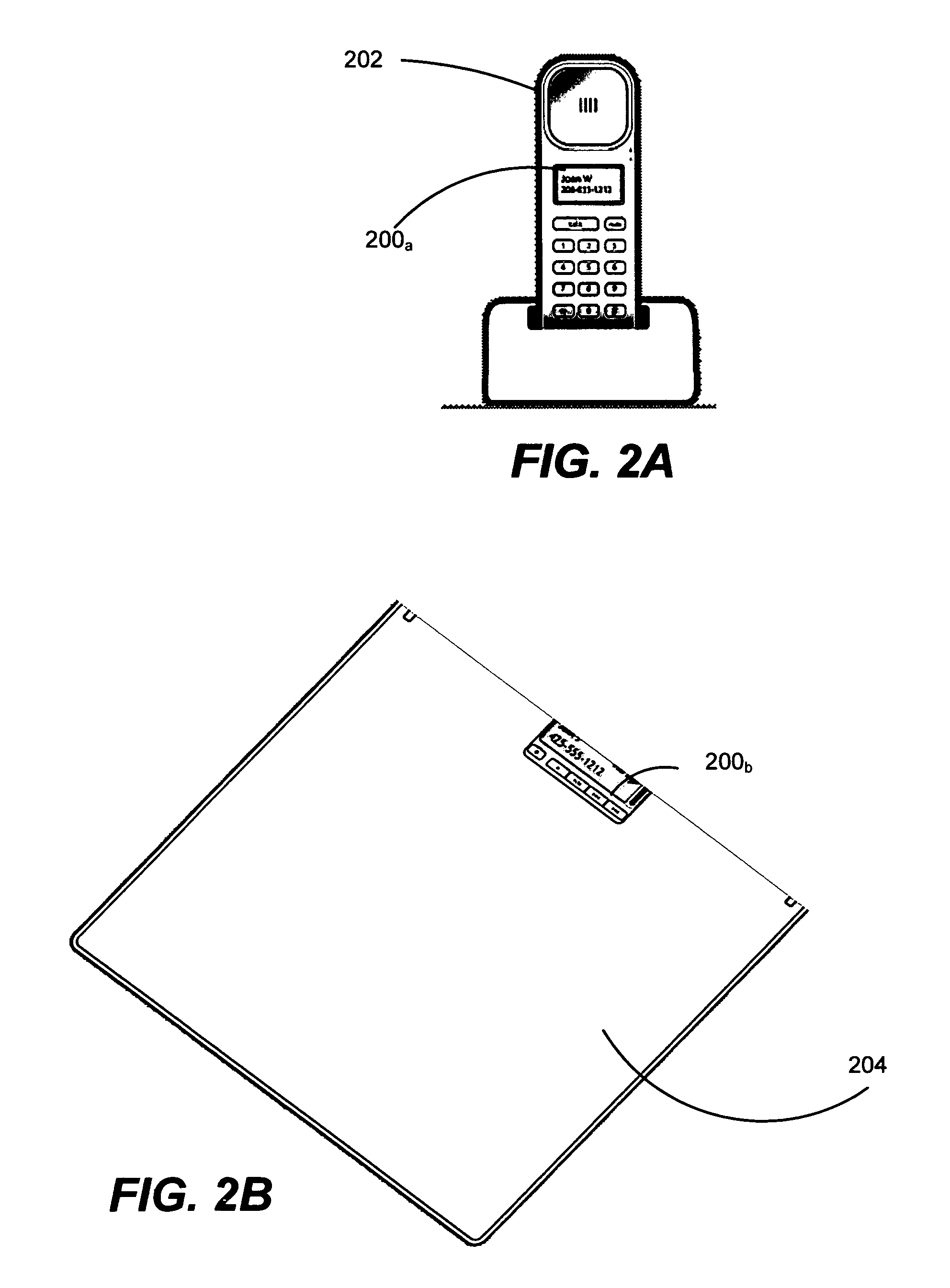
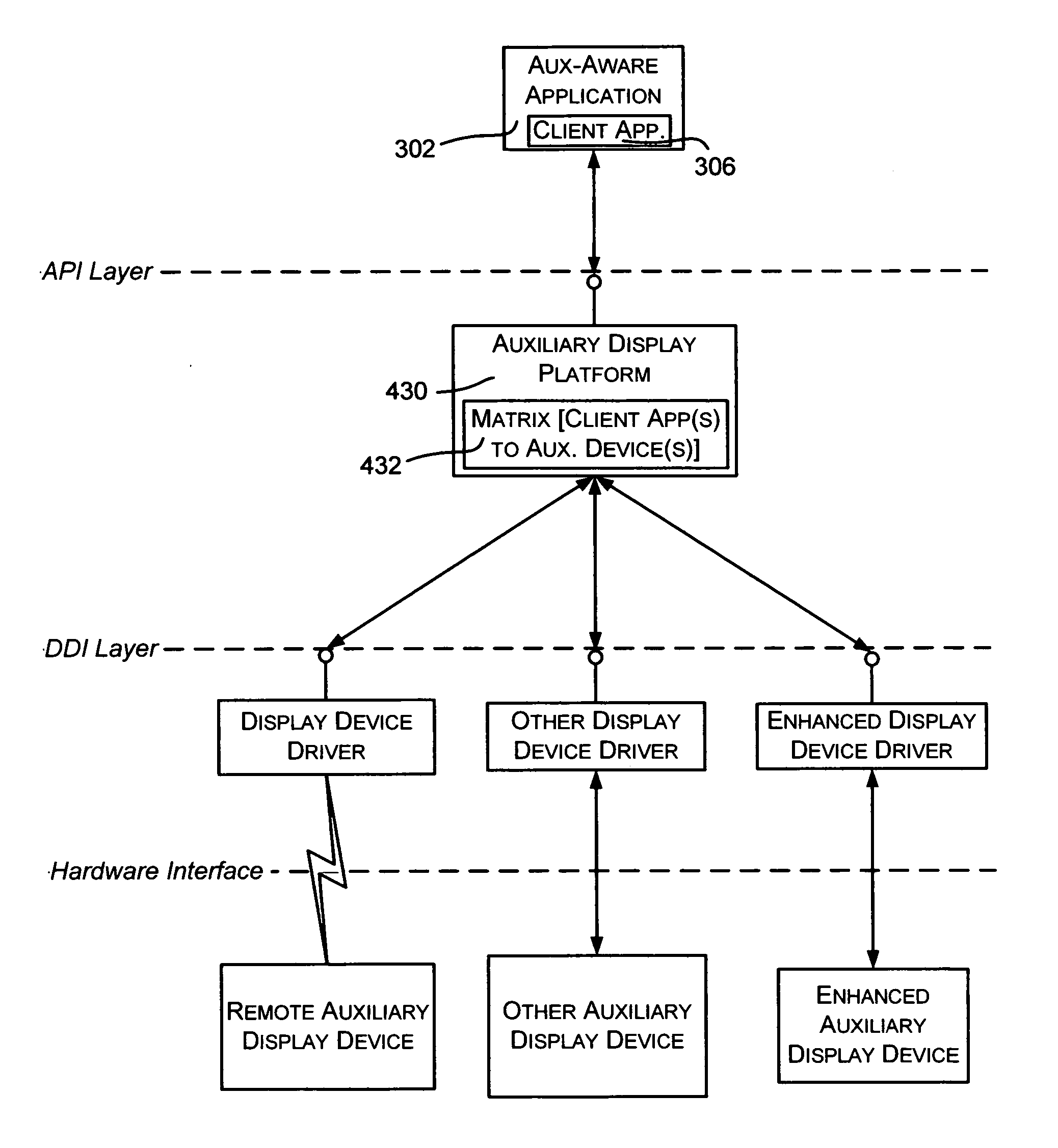
Sending notifications to auxiliary displays
InactiveUS7581034B2Increase profitImprove abilitiesInterprogram communicationCathode-ray tube indicatorsConnection typeRemote control
Described is a system and method by which application programs running on a main computer system communicate with an auxiliary display device (such as a cell phone, pocket-sized computer, alarm clock, television, digital picture frame and so forth) to provide viewable information on the device, remote control capabilities, and notifications. Via API calls, programs provide information in the same format regardless of the device capabilities and / or the connection type. An auxiliary display platform converts a notification into a format understood by a device driver, which then filters the notification as desired for its particular hardware device before the notification is communicated. Return communications return data such as status and user interaction with the displayed information. Software vendors may thus write code once to output notifications on auxiliary displays, while hardware manufacturers can have their devices work as auxiliary displays, with little or no modification to existing hardware.
Owner:MICROSOFT TECH LICENSING LLC
Sending notifications to auxiliary displays
InactiveUS20060164324A1Improve abilitiesIncrease profitInterprogram communicationCathode-ray tube indicatorsConnection typeRemote control
Described is a system and method by which application programs running on a main computer system communicate with an auxiliary display device (such as a cell phone, pocket-sized computer, alarm clock, television, digital picture frame and so forth) to provide viewable information on the device, remote control capabilities, and notifications. Via API calls, programs provide information in the same format regardless of the device capabilities and / or the connection type. An auxiliary display platform converts a notification into a format understood by a device driver, which then filters the notification as desired for its particular hardware device before the notification is communicated. Return communications return data such as status and user interaction with the displayed information. Software vendors may thus write code once to output notifications on auxiliary displays, while hardware manufacturers can have their devices work as auxiliary displays, with little or no modification to existing hardware.
Owner:MICROSOFT TECH LICENSING LLC
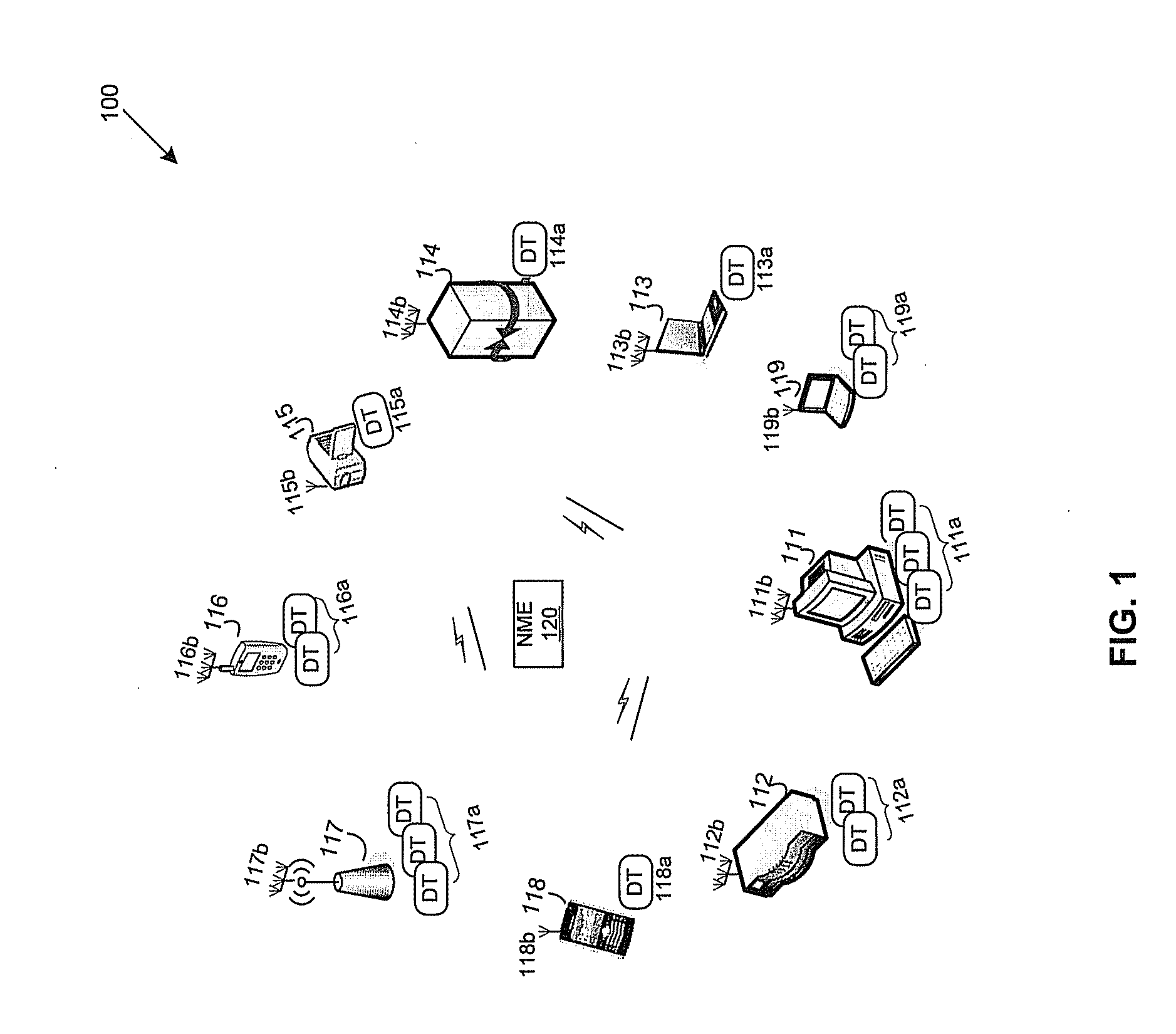
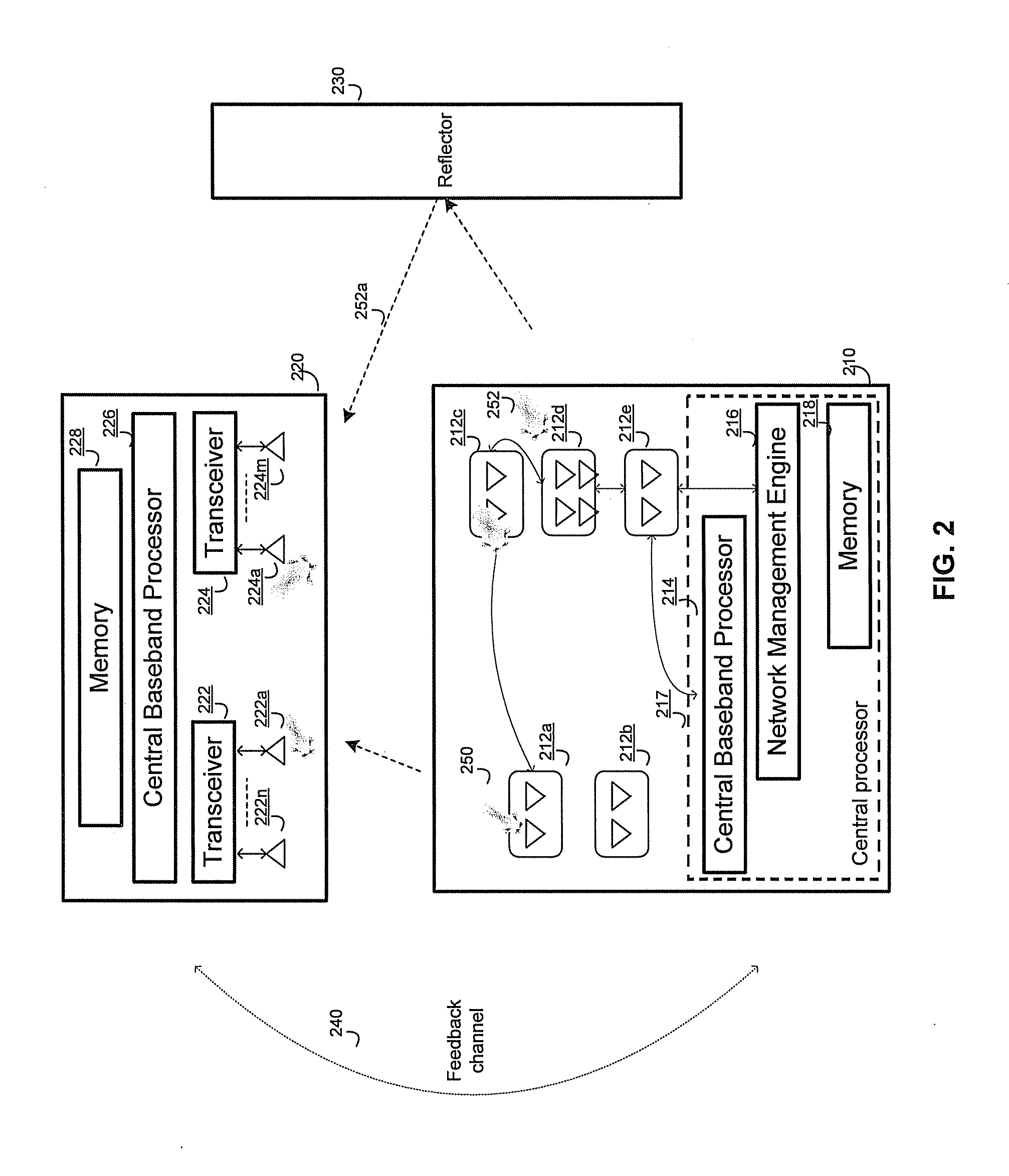
Method and system for centralized distributed transceiver management
A master application device comprises a plurality of distributed transceivers, a central baseband processor, and a network management engine that manages operation of the master application device and end-user application devices. The master application device communicates data streams to the end-user devices utilizing one or more distributed transceivers selected from the plurality of distributed transceivers. The selected distributed transceivers are dynamically configured to switch between spatial diversity mode, frequency diversity mode, multiplexing mode and MIMO mode based on corresponding link quality and propagation environment. Digital signal processing needed for the selected distributed transceivers is performed by the central baseband processor. The network management engine continuously monitors communication environment information to configure beamforming settings and / or antenna arrangement for the selected distributed transceivers. Connection types, communication protocols, and / or transceiver operation modes are determined for the selected distributed transceivers. Resources are allocated to the selected distributed transceivers to continue subsequent data communication.
Owner:GOLBA LLC
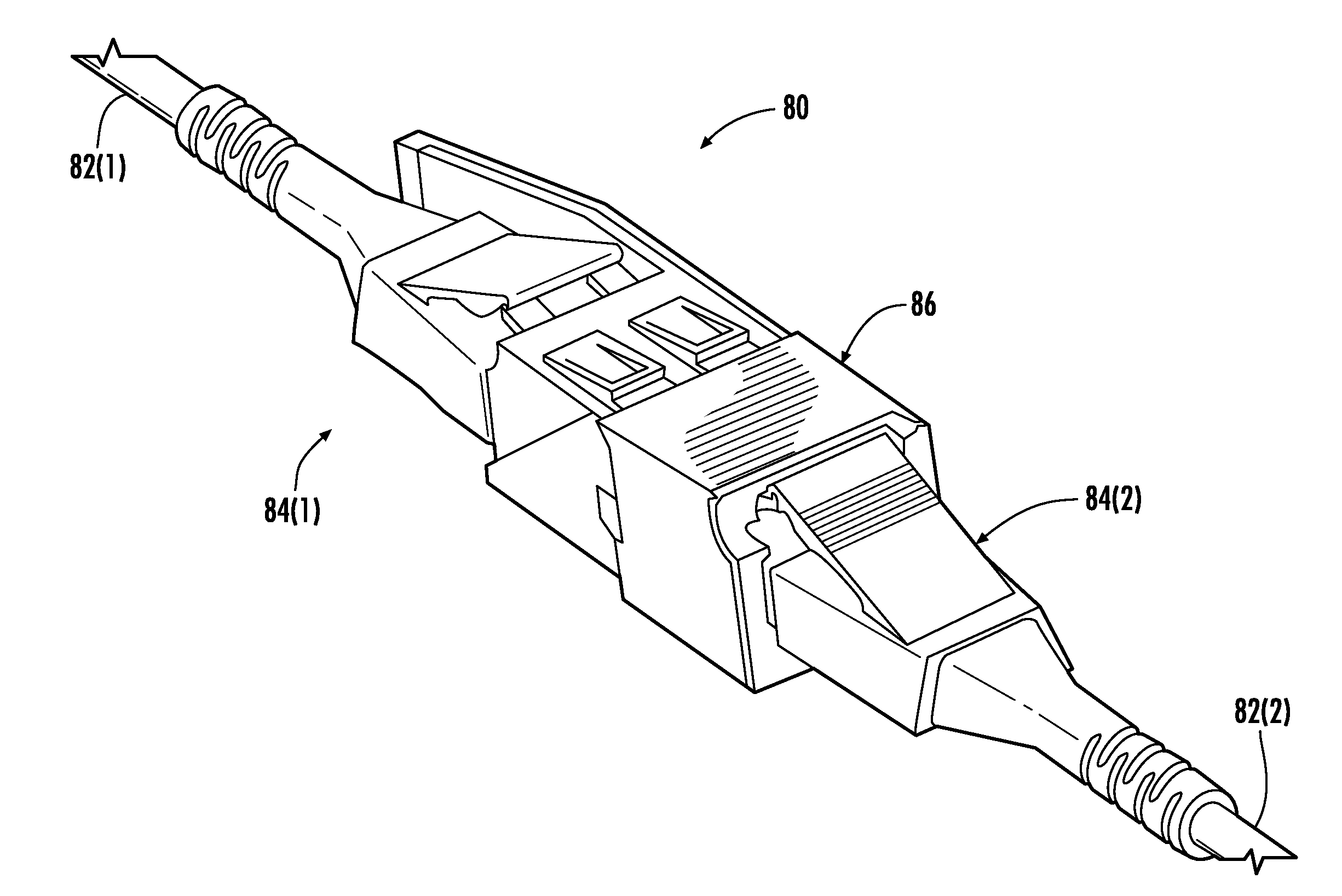
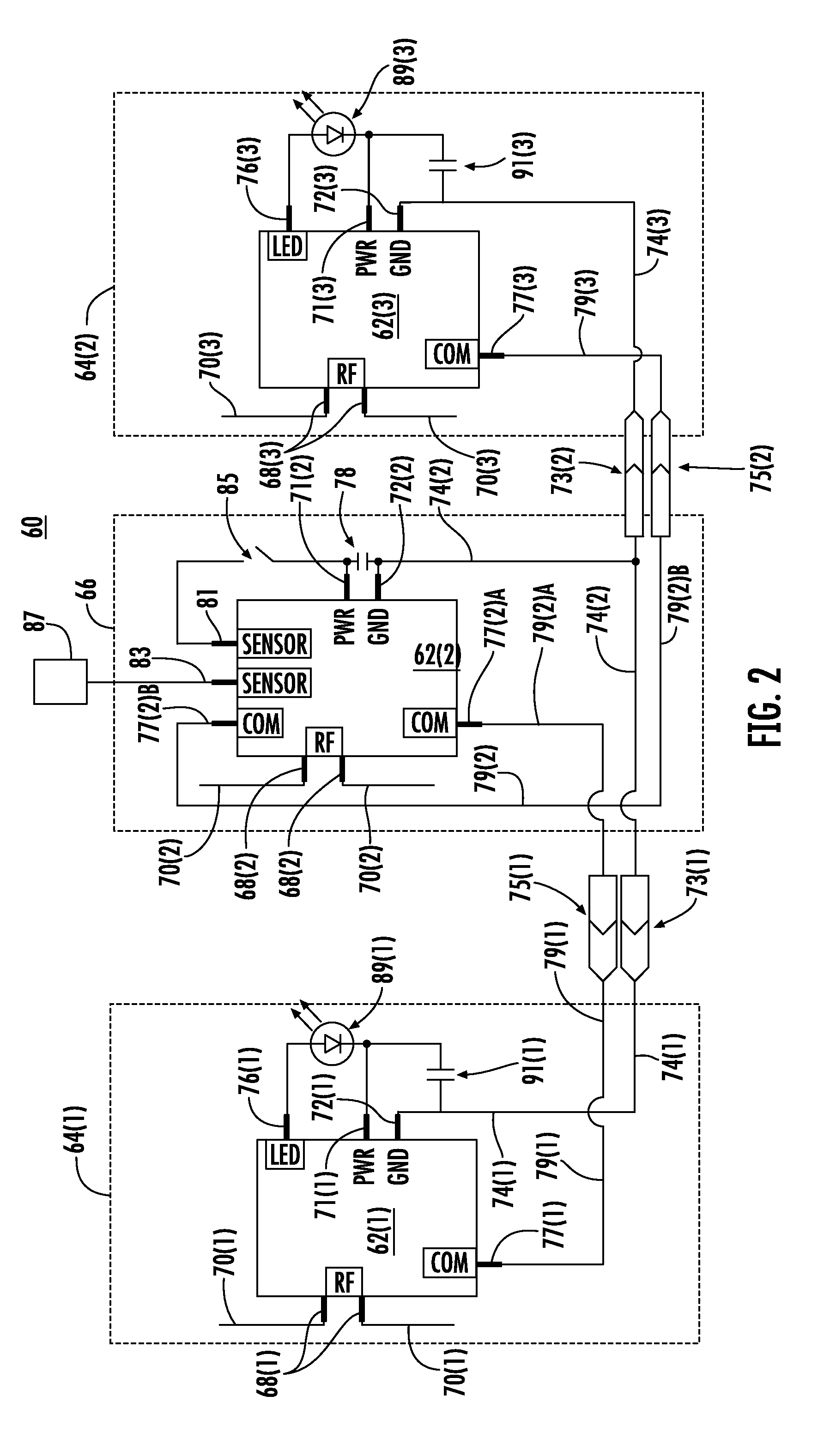
Radio frequency identification (RFID) in communication connections, including fiber optic components
ActiveUS20110274437A1Reduce and eliminate overlapEasy to receiveCoupling light guidesElectromagnetic transmissionElectricityFiber
Radio frequency identification (RFID)-equipped communication components are disclosed. The communication components can include fiber optic components, such as fiber optic connectors and fiber optic adapters as examples. An RFID-equipped circuit is provided in the communication components to communicate information. In order that the electrical circuit be provided in the communication component without altering the communication component connection type, the circuit may be disposed in at least one recessed area of the communication component housing. In this manner, the communication component maintains its connection type such that it is compatible with a complementary communication component connection type for backwards compatibility while also being RFID-equipped. The circuit may also be provided in a substrate containing one or more electrical contacts coupled to the circuit such that a wired coupling is established with one or more electrical contacts provided in another communication component when connected.
Owner:FIBER MOUNTAIN INC
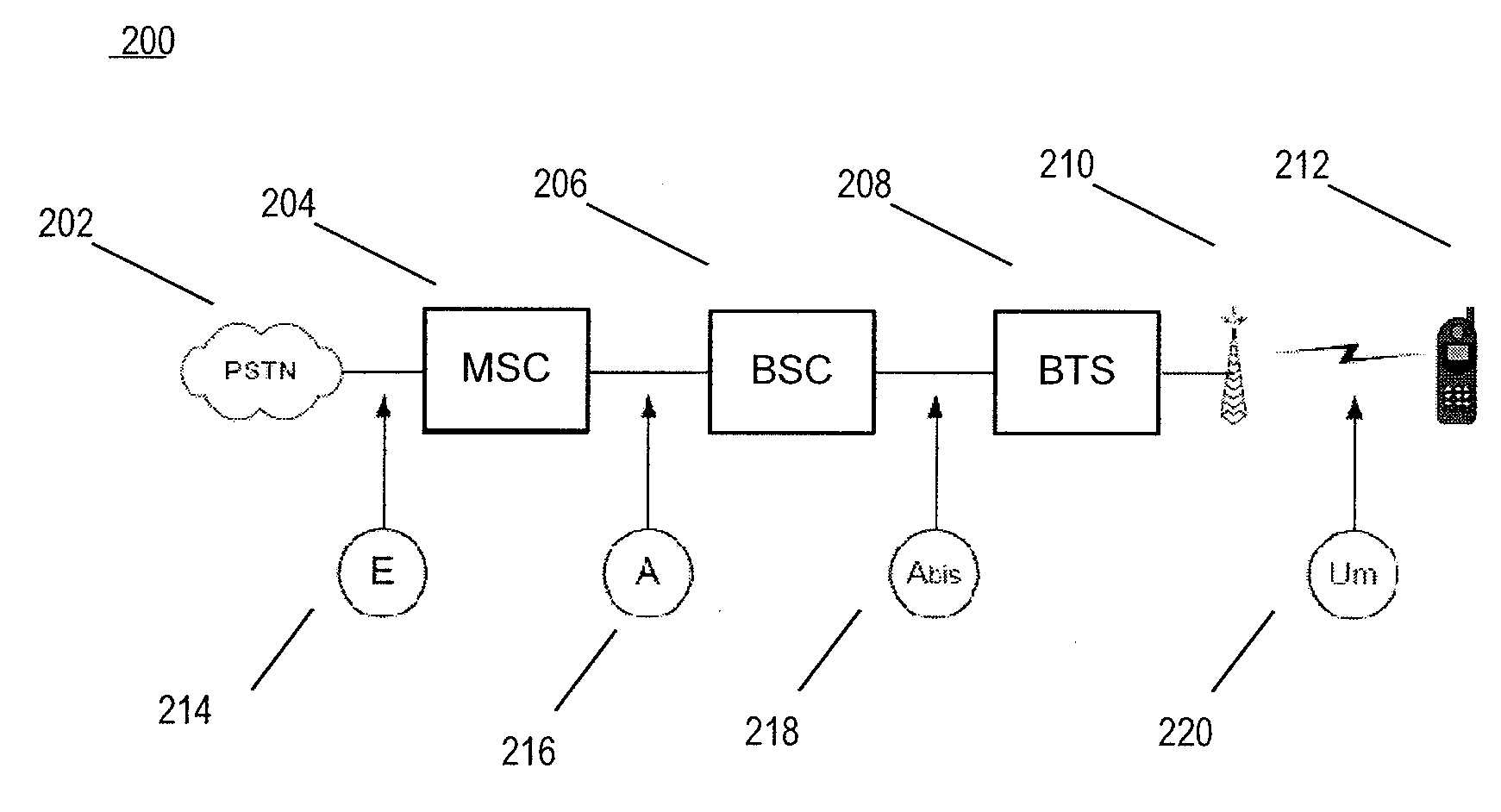
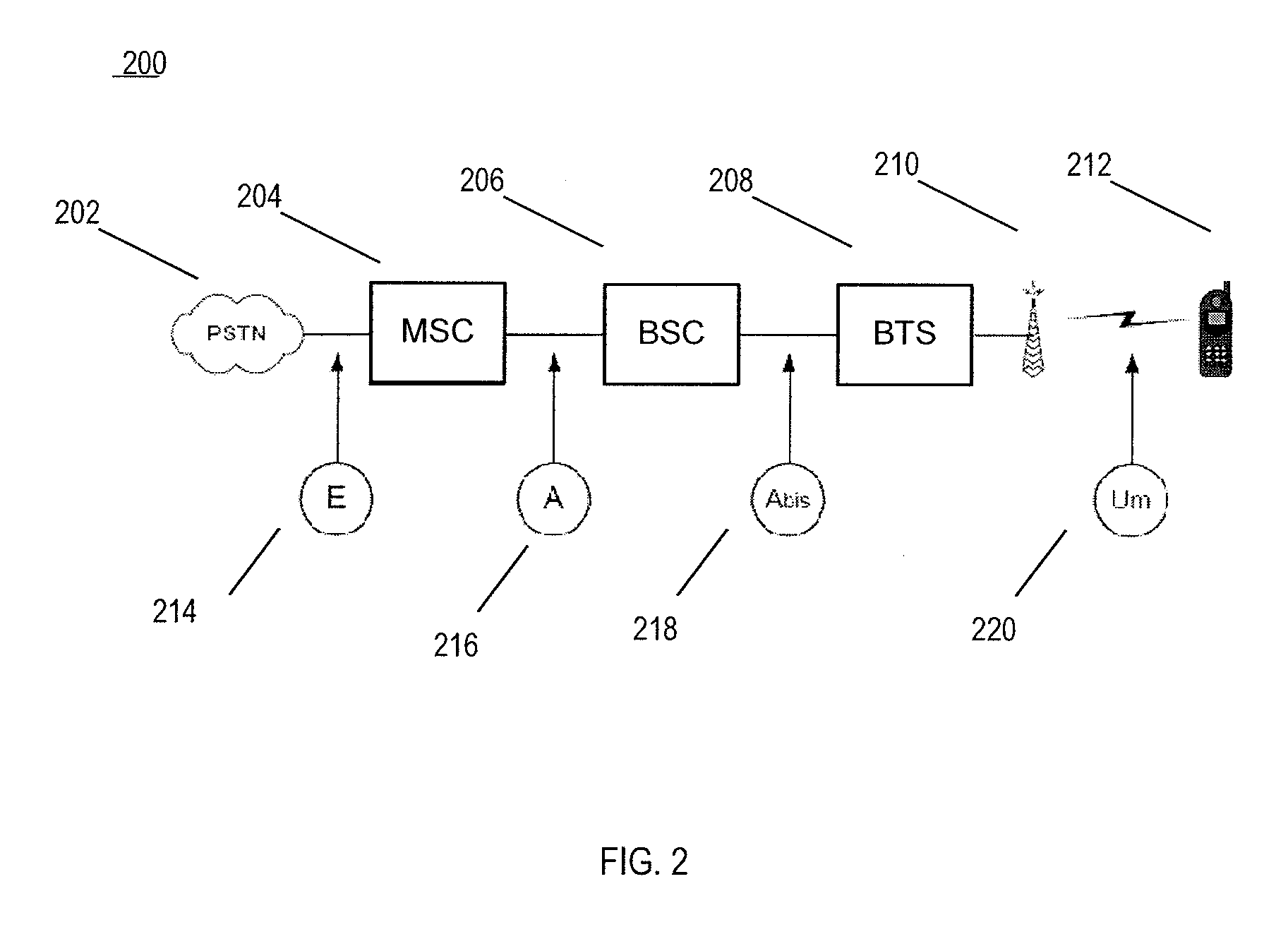
Apparatus, method and computer program product for providing self adapting transport of public switched telephone network (PSTN) circuits over a wireless network
InactiveUS20090257345A1Suppress any silenceError preventionTransmission systemsWireless mesh networkWireless sensor network
An adaptive telecommunications system for transporting communication traffic over a network comprising a means for transmitting communication traffic between a plurality of devices through a network, monitoring the communication traffic between the plurality of devices, and a adaptively changing the mode of operation either before and / or during a call, based on at least one of instantaneous network changes, connection type characteristics, and type of communication traffic. The devices attached to the network may consist of, for example, a fax machine, phone, mobile phone, public branch network exchange, a computer, or a switch. The traffic traveling across the system, voice, fax, or data, for example, may be compressed and / or restricted based on the type of traffic. The system may fully replace the existing PSTN circuits or may be used for overflow when the existing PSTN circuits are at near or full capacity.
Owner:NSGDATACOM
Sampling playback doorbell system
InactiveUS20060038663A1Quality improvementEasy constructionSound producing devicesElectric/electromagnetic audible signallingDocking stationDoorbell
A digital sampling playback doorbell system has two or more doorbell buttons and a central unit with solid state memory storage for multiple digitally sampled sound files. User assignment means are provided for assigning a particular sound file to a particular doorbell button. The digital sampling playback doorbell has computer interface of RS-232, or USB, or infrared wireless connection type and relies on computer installed software to download digitally sampled sound files stored in the computer hard drive to the memory of the digital sampling playback doorbell system central unit. The digitally sampled sound files stored in the computer hard drive are obtained by accessing a web site through the Internet or capturing sound through an audio computer connection to a microphone, CD player, radio broadcast or mass music storage device using software resident in the computer. Alternatively, an IPOD can be used as a source for sounds that can be transferred or sent to play on the doorbell. Such sound transfer can take place via a blue tooth communication link, or by a docking station that resides on the doorbell. Taking advantage of the intelligence contained within the IPOD, one can then select sounds or files that have been previously converted by either the IPOD or the computer that the IPOD was previously attached to, and send them to the doorbell.
Owner:PREDOMINANCE
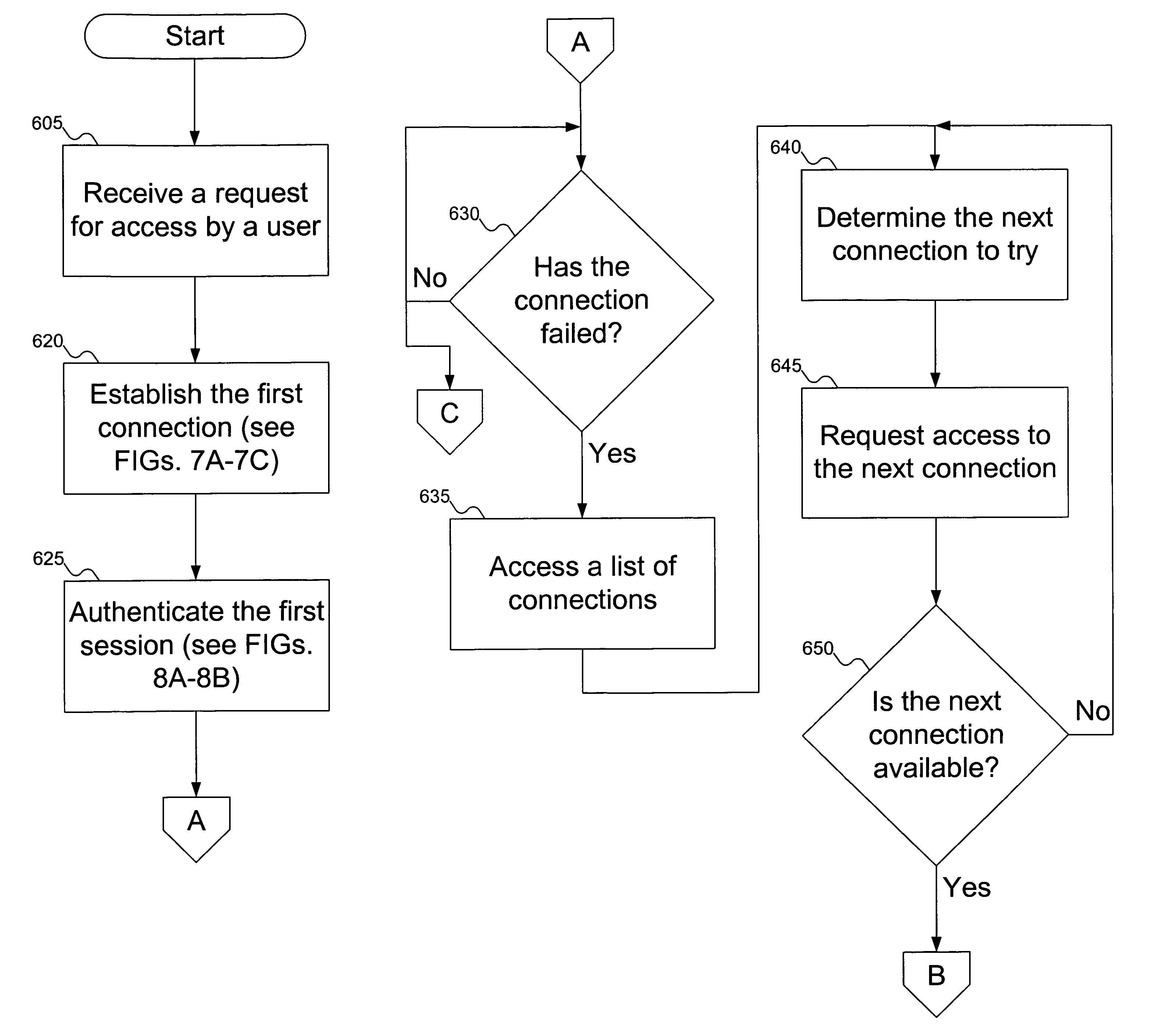
Computing environment failover in a branch office environment
InactiveUS7287083B1Multiple digital computer combinationsTransmissionConnection typeComputerized system
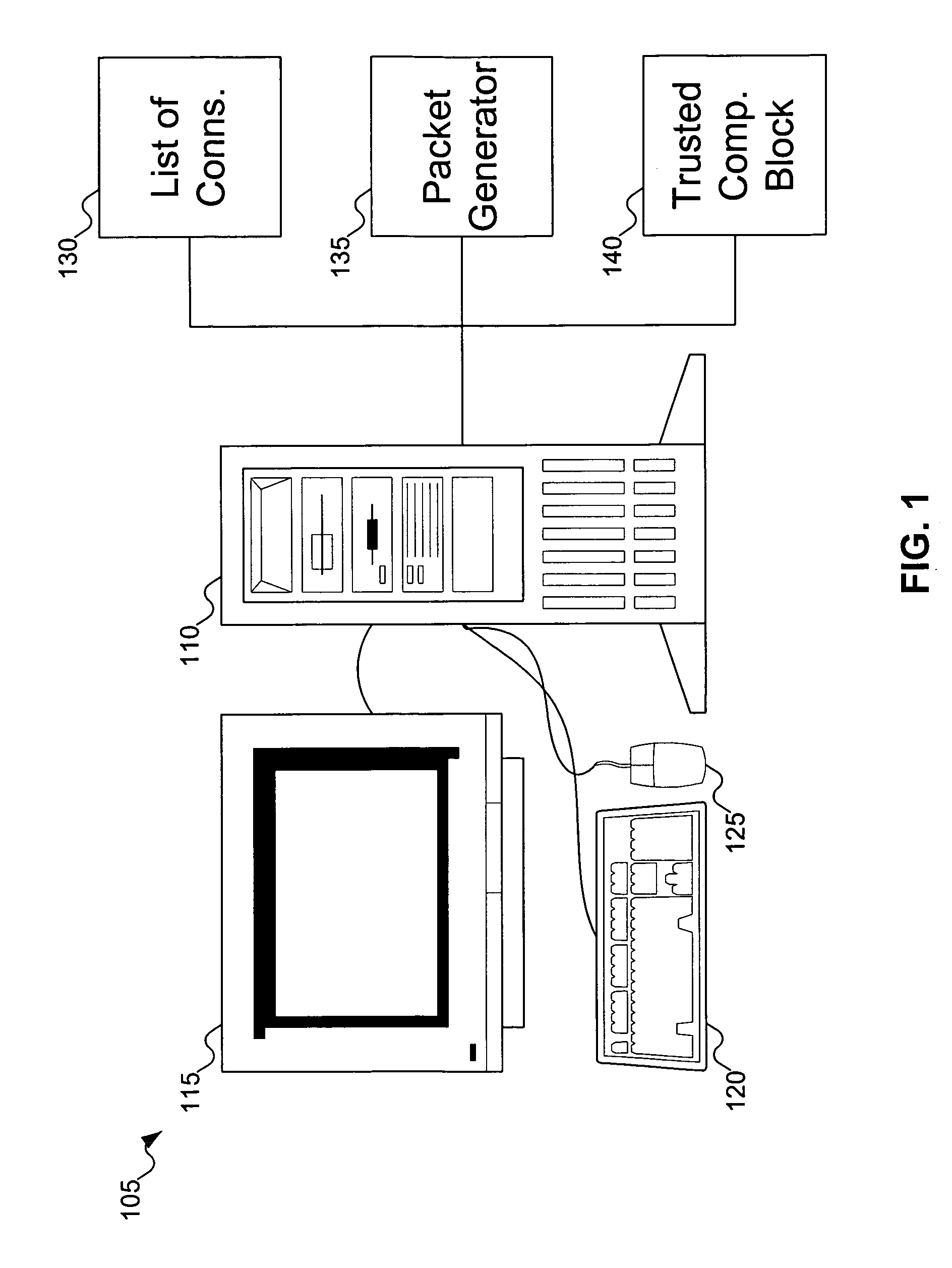
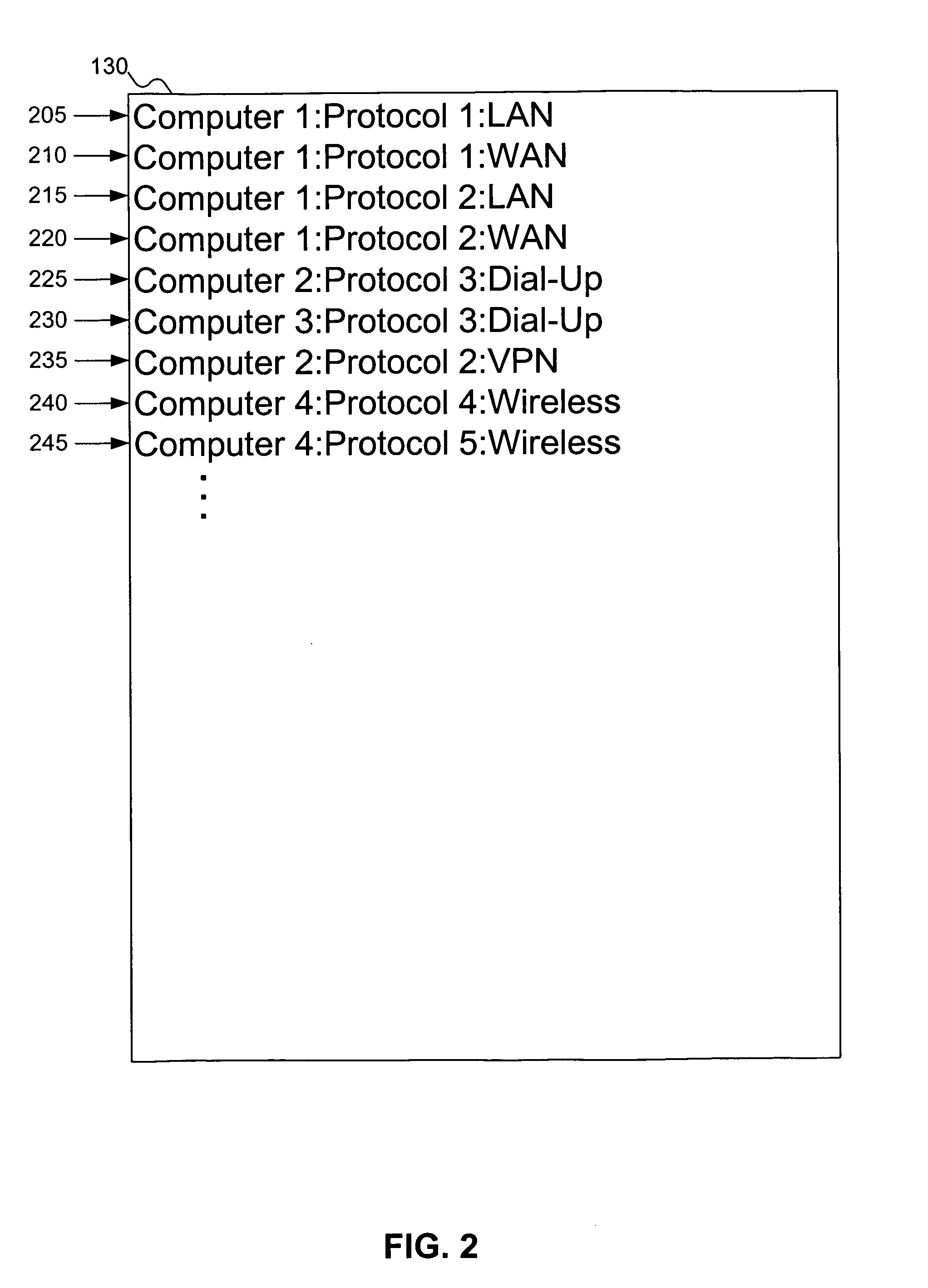
A computer system accesses a list of connections. The list of connections identifies computers, protocols, and / or types of connections that can be used. The computer system attempts to establish a connection to a server. While establishing the connection, the computer system can store a user's credential. If the connection to the server fails, the computer system attempts to access a connection from the list, and uses the stored user credential (if it exists) to authenticate the user on the new connection without requesting the credential anew from the user.
Owner:APPLE INC
Data transfer error checking
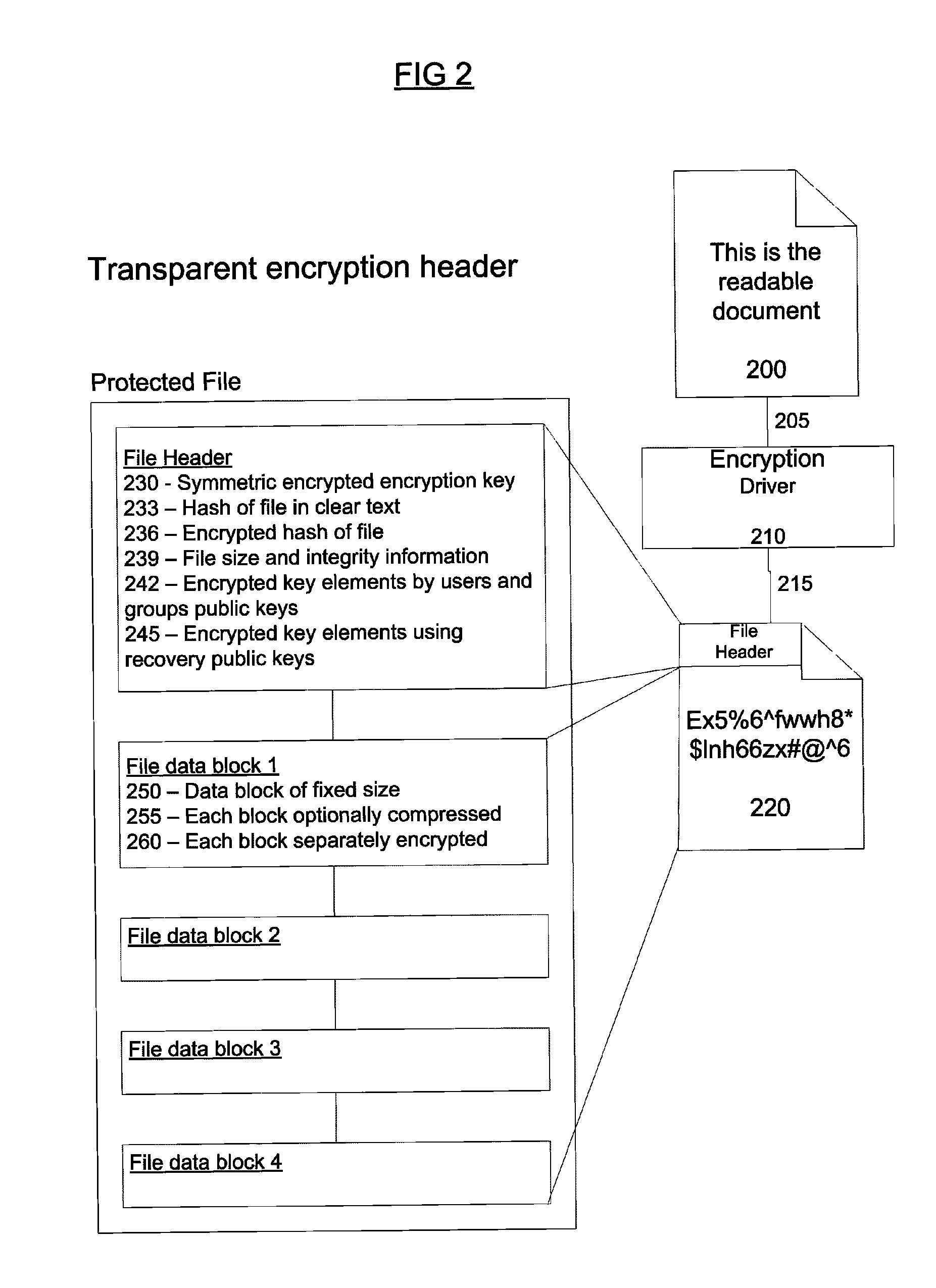
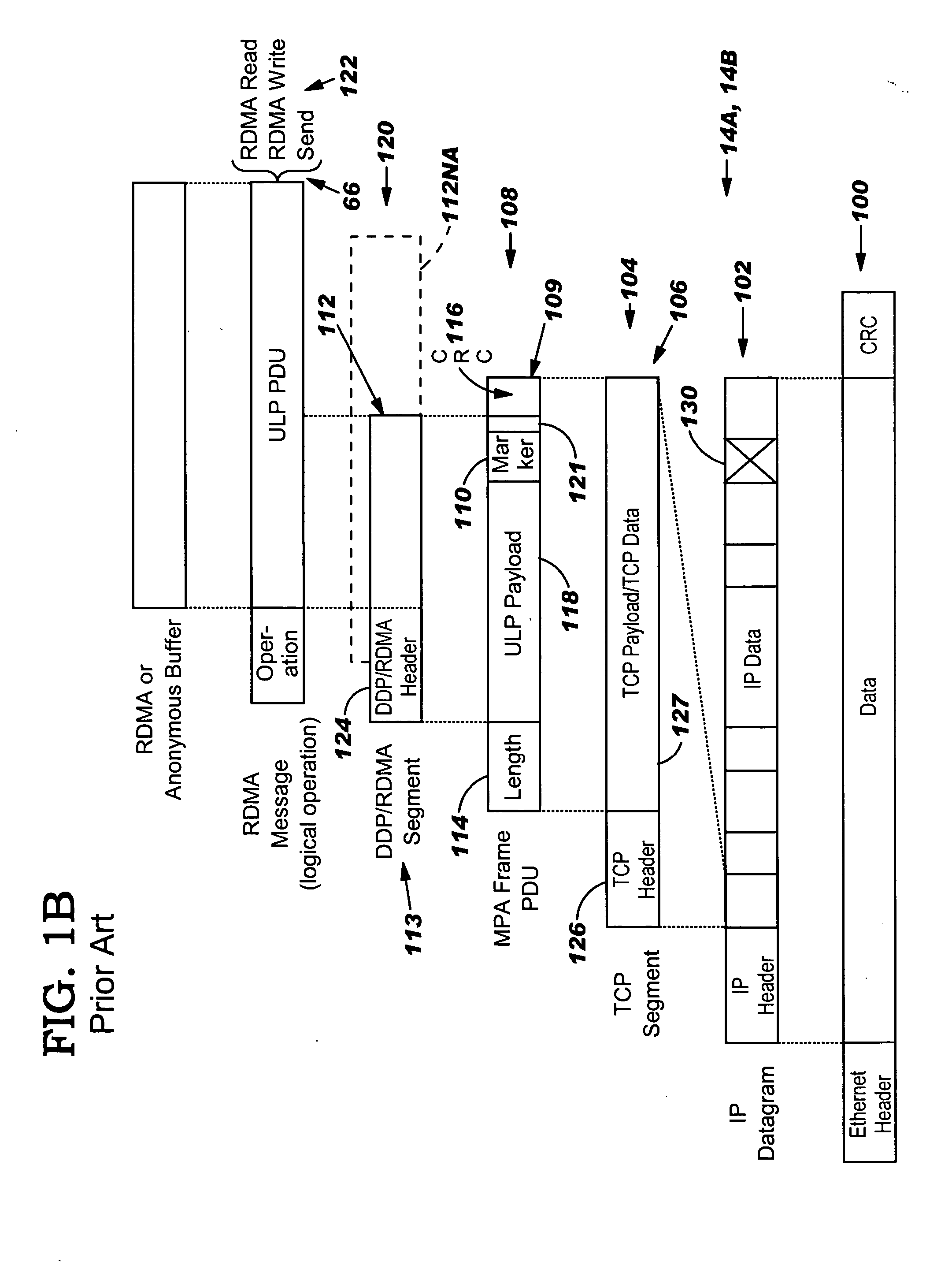
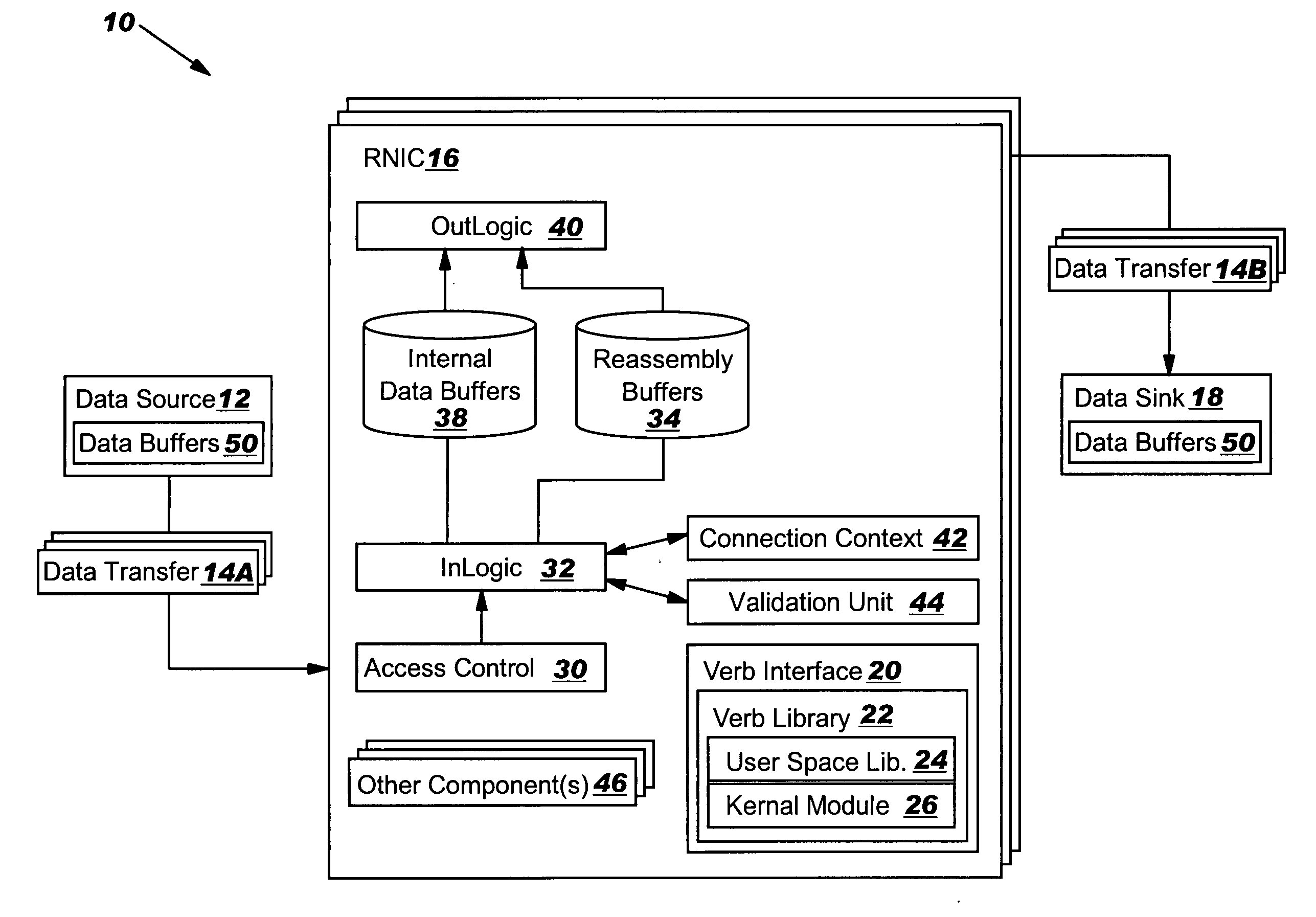
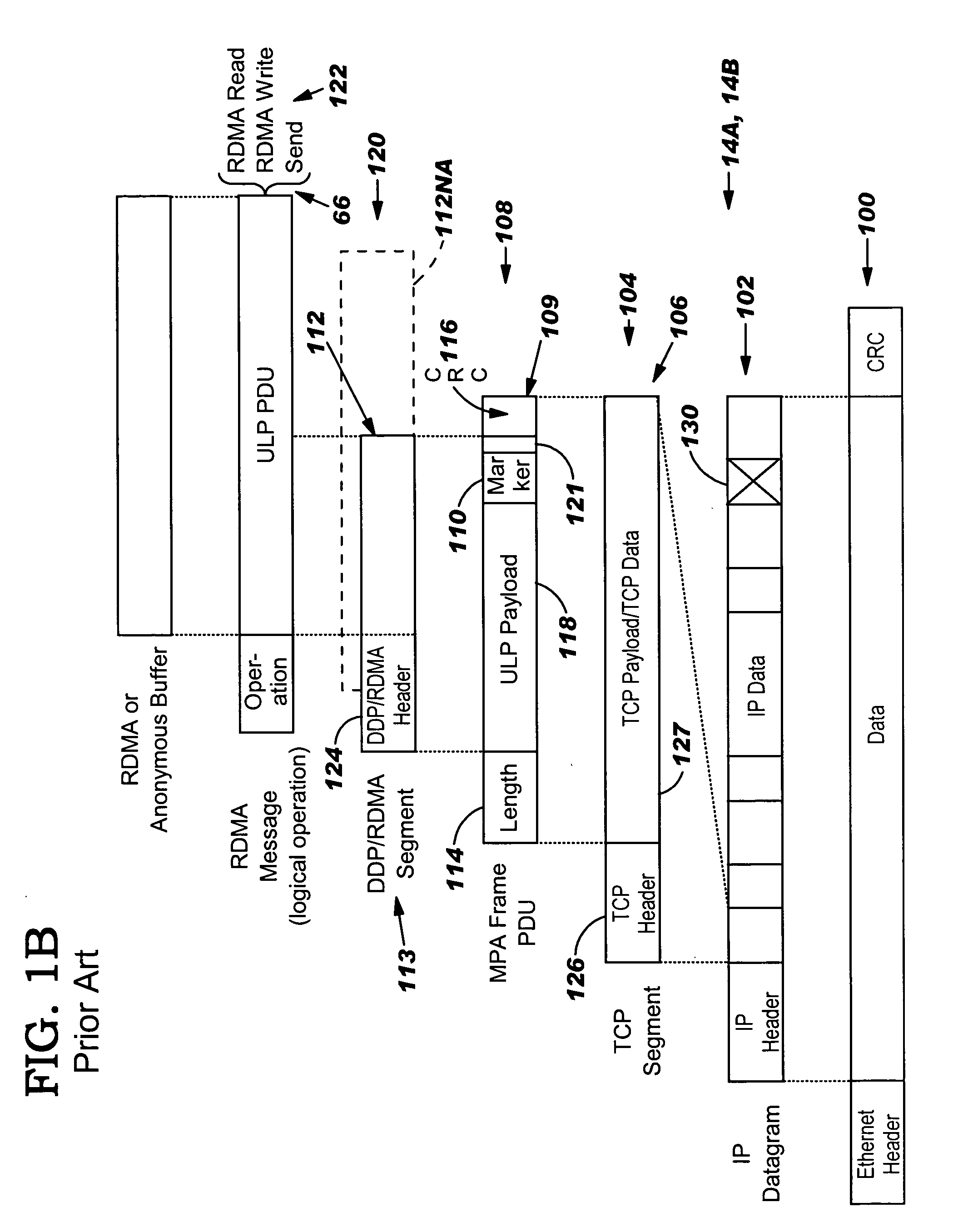
InactiveUS20050149817A1Reduce memory bandwidthReduce latencyCode conversionError detection onlyConnection typeData placement
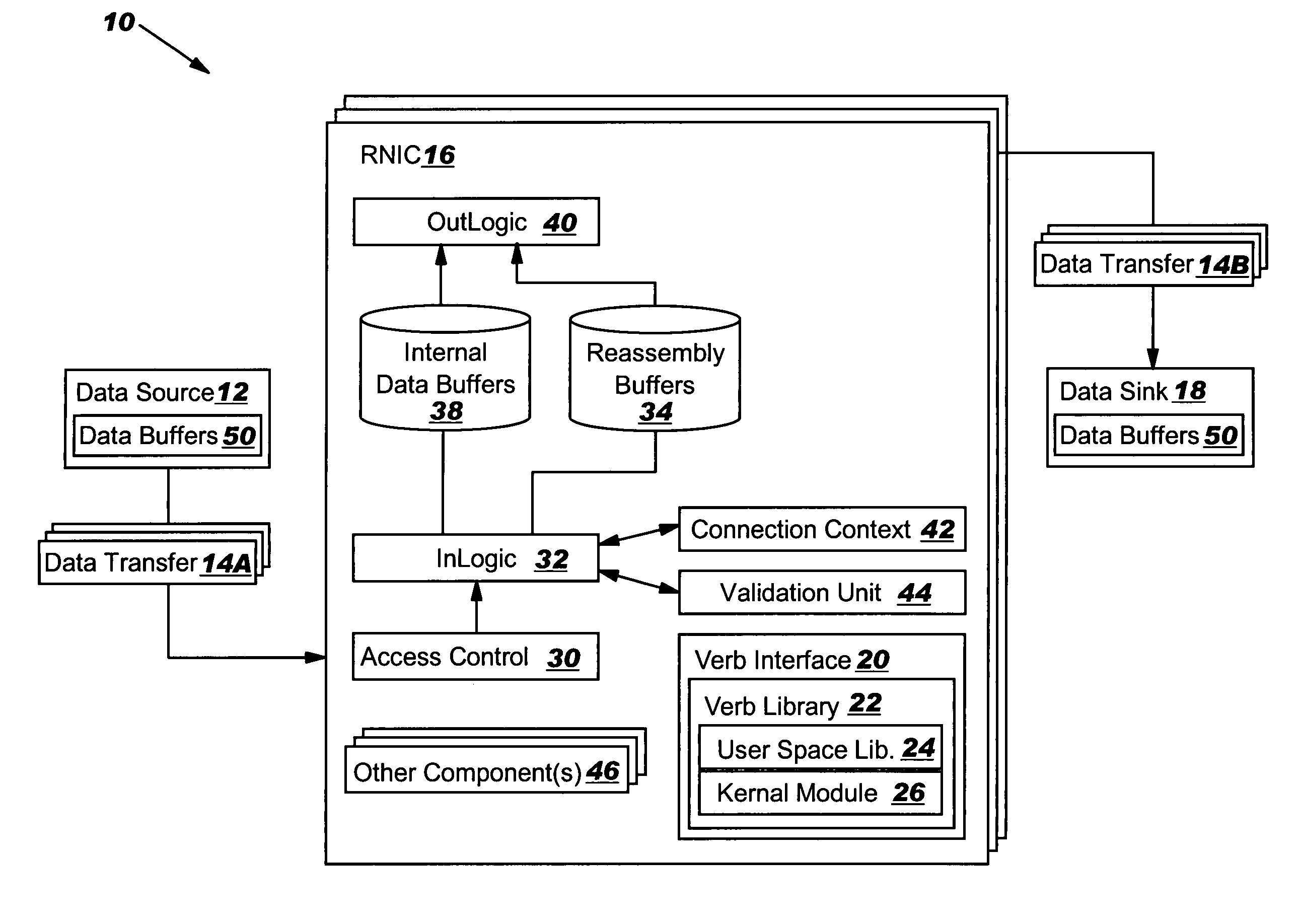
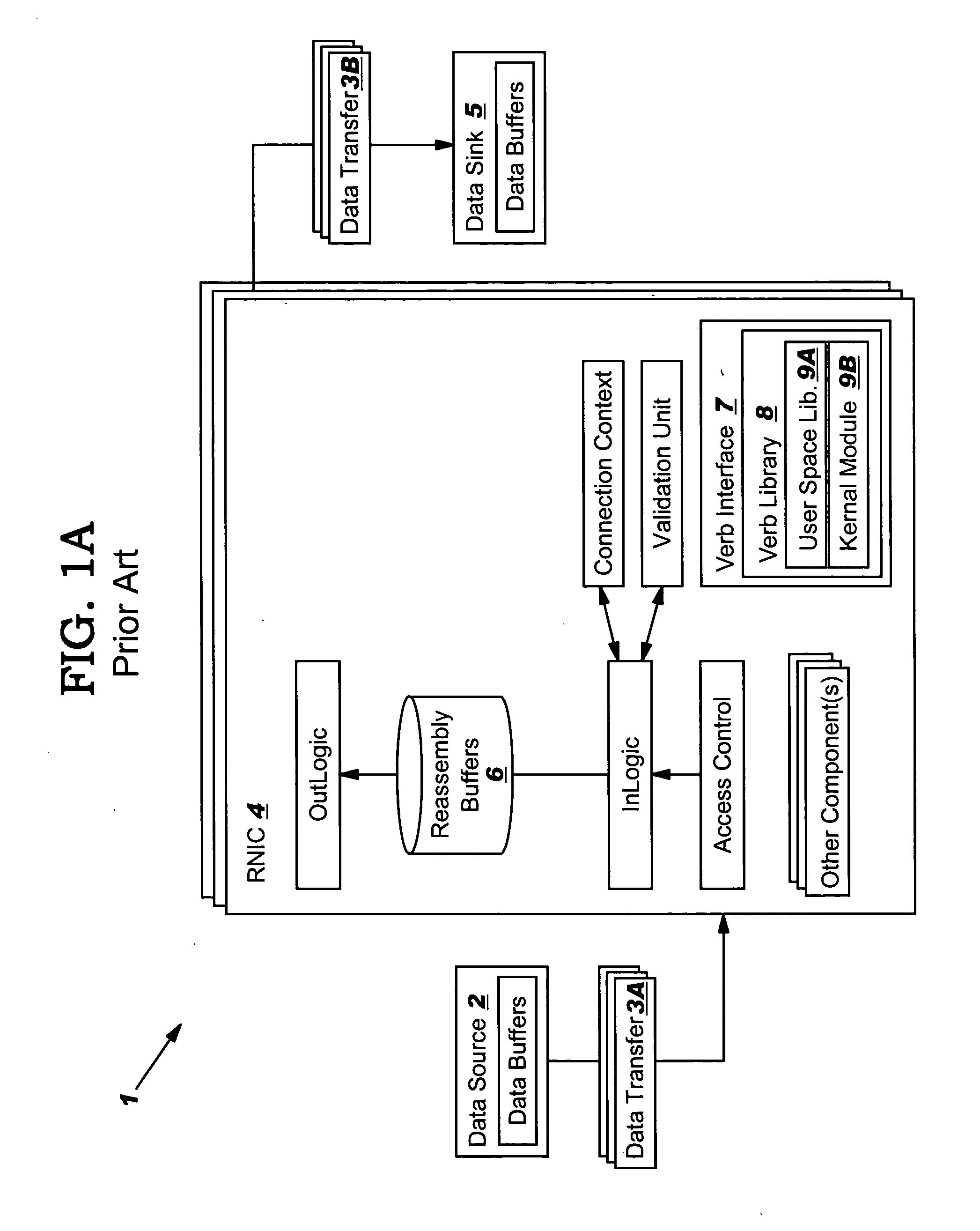
An RNIC implementation that performs direct data placement to memory where all segments of a particular connection are aligned, or moves data through reassembly buffers where all segments of a particular connection are non-aligned. The type of connection that cuts-through without accessing the reassembly buffers is referred to as a “Fast” connection because it is highly likely to be aligned, while the other type is referred to as a “Slow” connection. When a consumer establishes a connection, it specifies a connection type. The connection type can change from Fast to Slow and back. The invention reduces memory bandwidth, latency, error recovery using TCP retransmit and provides for a “graceful recovery” from an empty receive queue. The implementation also may conduct CRC validation for a majority of inbound DDP segments in the Fast connection before sending a TCP acknowledgement (Ack) confirming segment reception.
Owner:IBM CORP
Automated configuration of network device ports
ActiveUS20050264420A1Network traffic/resource managementSensing record carriersConnection typeComputer hardware
Owner:CISCO TECH INC
Plug-in Wi-Fi access point device and system
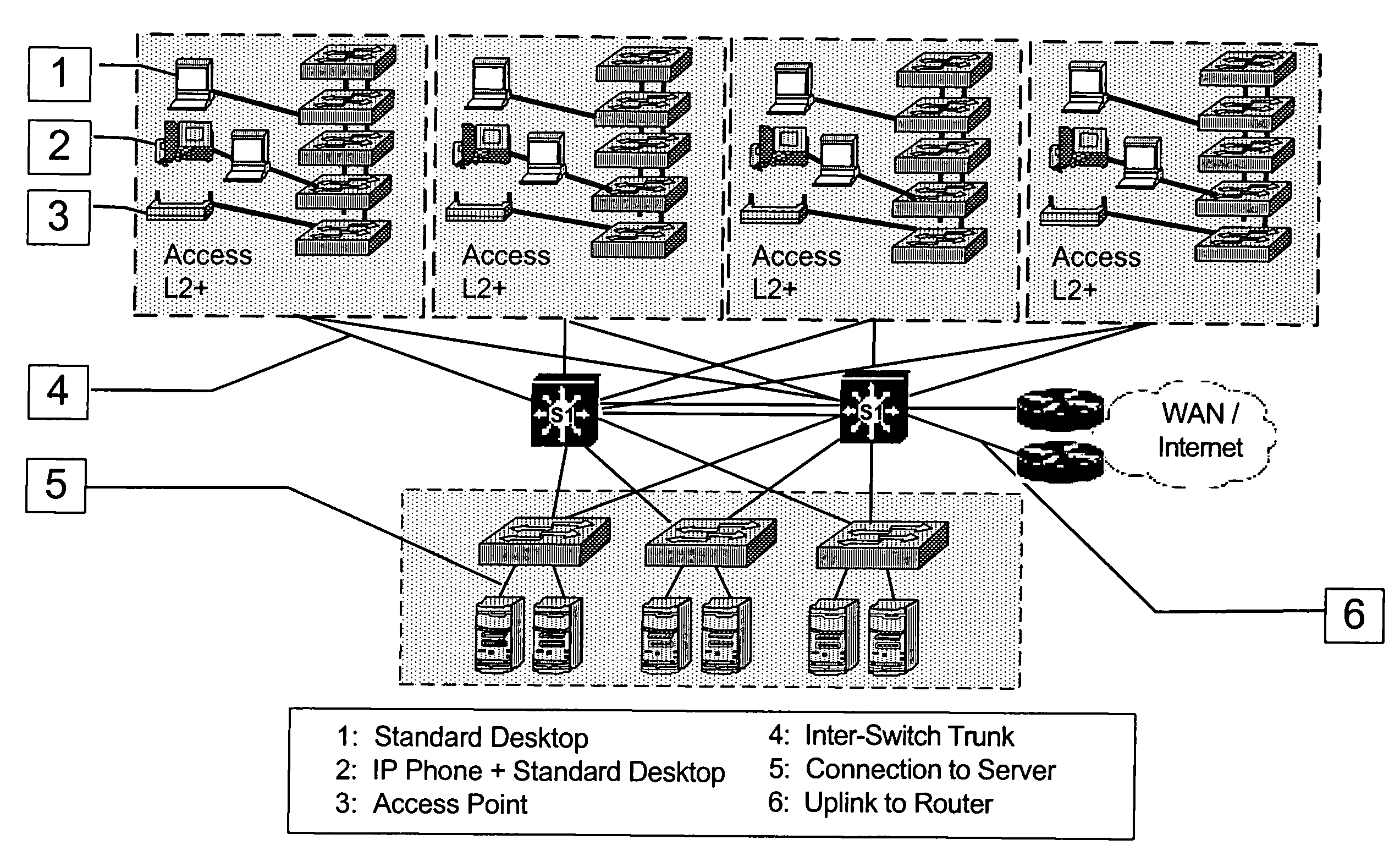
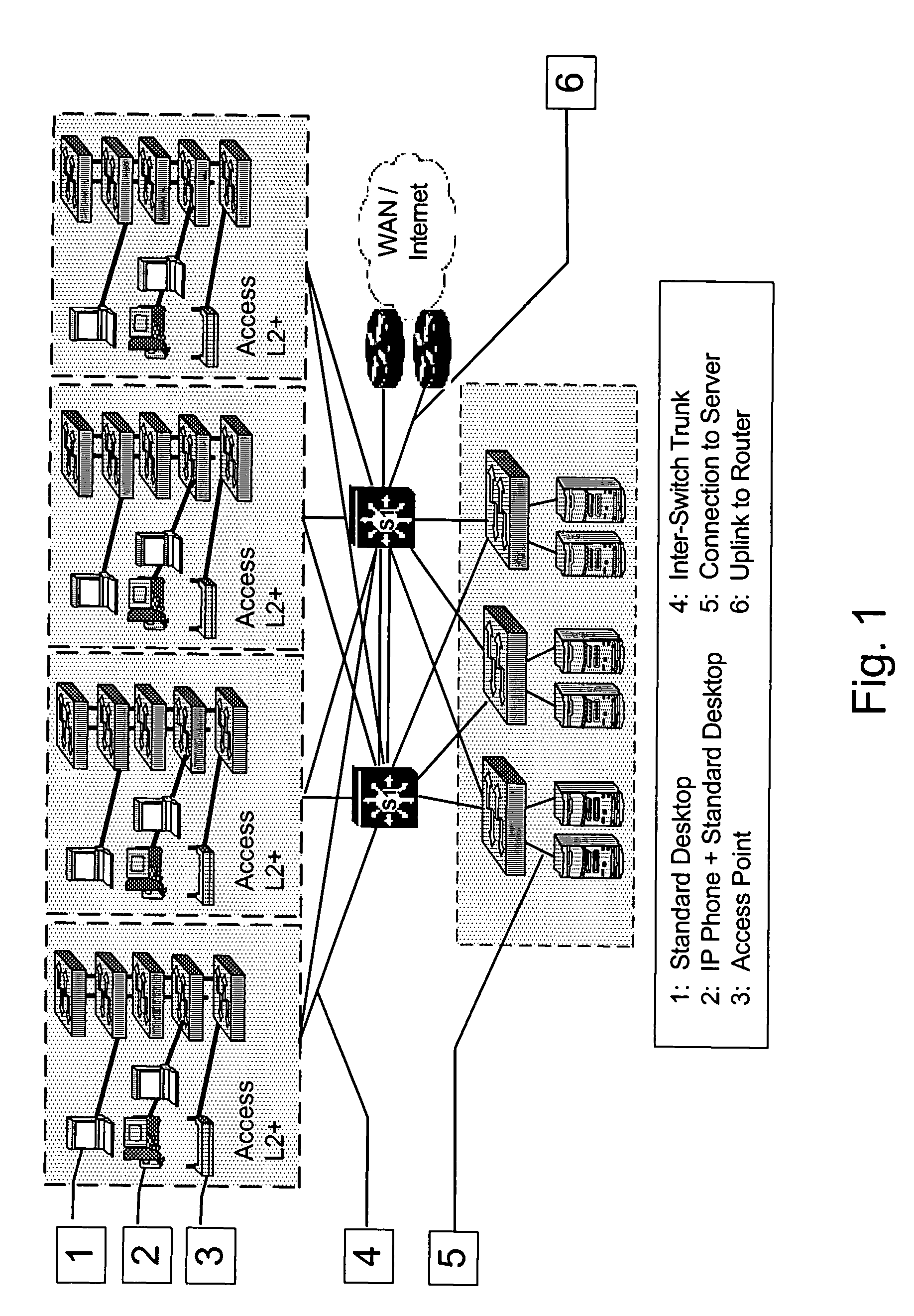
A plug-in Wi-Fi access point device and system is provided that is configured for Wi-Fi or other wireless network and to be directly plugged into a face plate / workstation. The plug-in Wi-Fi access point device and system advantageously provides ease of integration into an existing wired network without the use of a patch cord, security from removal by unauthorized personnel, non obtrusiveness in relation to other face plate / workstation jacks, and the ability to be powered through an Ethernet connection to avoid the need for a separate power source. Furthermore, the plug-in Wi-Fi access point device and system may beneficially permit the integration of complementary connections within the access point including, for example, data, voice, and video connection types. The plug-in Wi-Fi access point device includes a housing for accommodating Wi-Fi access point circuitry, Wi-Fi access point circuitry mounted within the housing, and a connector mounted on side of the housing for direct plug-in into an Ethernet jack of a face plate / workstation. The plug-in Wi-Fi access point device may further include a locking or self-locking mechanism, an integrated hub / switch / router, and at least one integrated voice, video and / or data jack for voice, video or data communication.
Owner:ORTRONICS INC
Limiting number of retransmission attempts for data transfer via network interface controller
ActiveUS20050129045A1Reduce memory bandwidthReduce latencyError prevention/detection by using return channelTransmission systemsConnection typeData placement
An RNIC implementation that performs direct data placement to memory where all segments of a particular connection are aligned, or moves data through reassembly buffers where all segments of a particular connection are non-aligned. The type of connection that cuts-through without accessing the reassembly buffers is referred to as a “Fast” connection because it is highly likely to be aligned, while the other type is referred to as a “Slow” connection. When a consumer establishes a connection, it specifies a connection type. The connection type can change from Fast to Slow and back. The invention reduces memory bandwidth, latency, error recovery using TCP retransmit and provides for a “graceful recovery” from an empty receive queue. The implementation also may conduct CRC validation for a majority of inbound DDP segments in the Fast connection before sending a TCP acknowledgement (Ack) confirming segment reception.
Owner:MELLANOX TECHNOLOGIES LTD
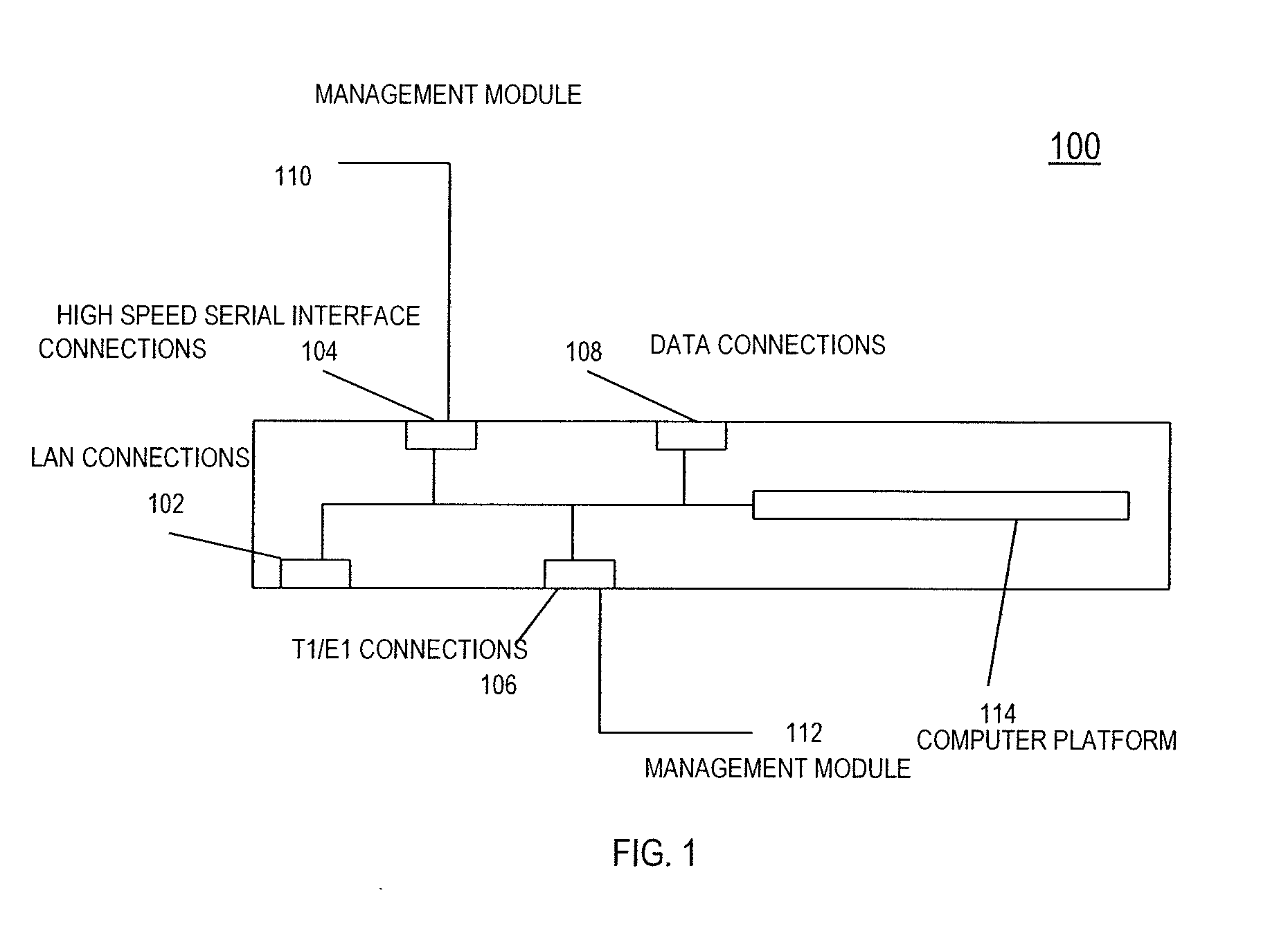
Universal computer management interface
ActiveUS20070206630A1Efficient cablingEliminate needDigital computer detailsTime-division multiplexOperational systemNetwork connection
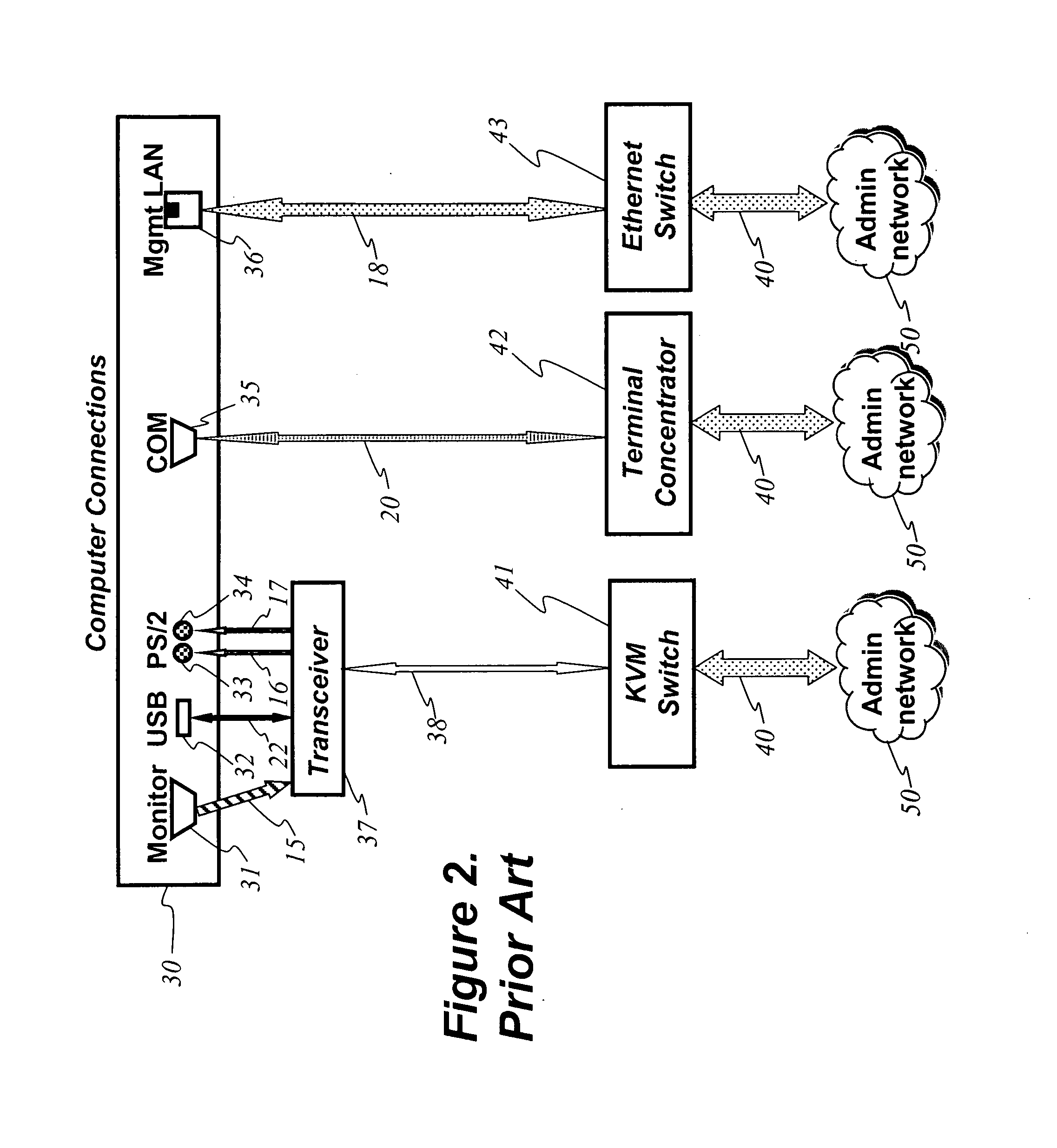
An integrated computer management apparatus allowing a networked administrator to manage a computer via multiple connection types and protocols. A preferred embodiment of the device has a network connection for the administrative users, coupled via an internal Ethernet switch and a processor to keyboard-video-mouse, serial, and Ethernet computer connections. Depending on hardware characteristics, operational status, OS, and administrator preferences any of these may be used to provide remote computer system management functions. Software running on the processor can provide direct logical connection between the remote administrator and a management port; may serve web pages graphically interpreting data gleaned from one or more of the connections; can provide protocol translation or proxy services; or locally execute an intelligent management agent. The device can be physically small enough to be supported by its connecting cables, and receives power from the attached computer.
Owner:LANTRONIX
Wireless communication device, communication system and method for establishing data connectivity between a wireless communicaiton device and a first access network
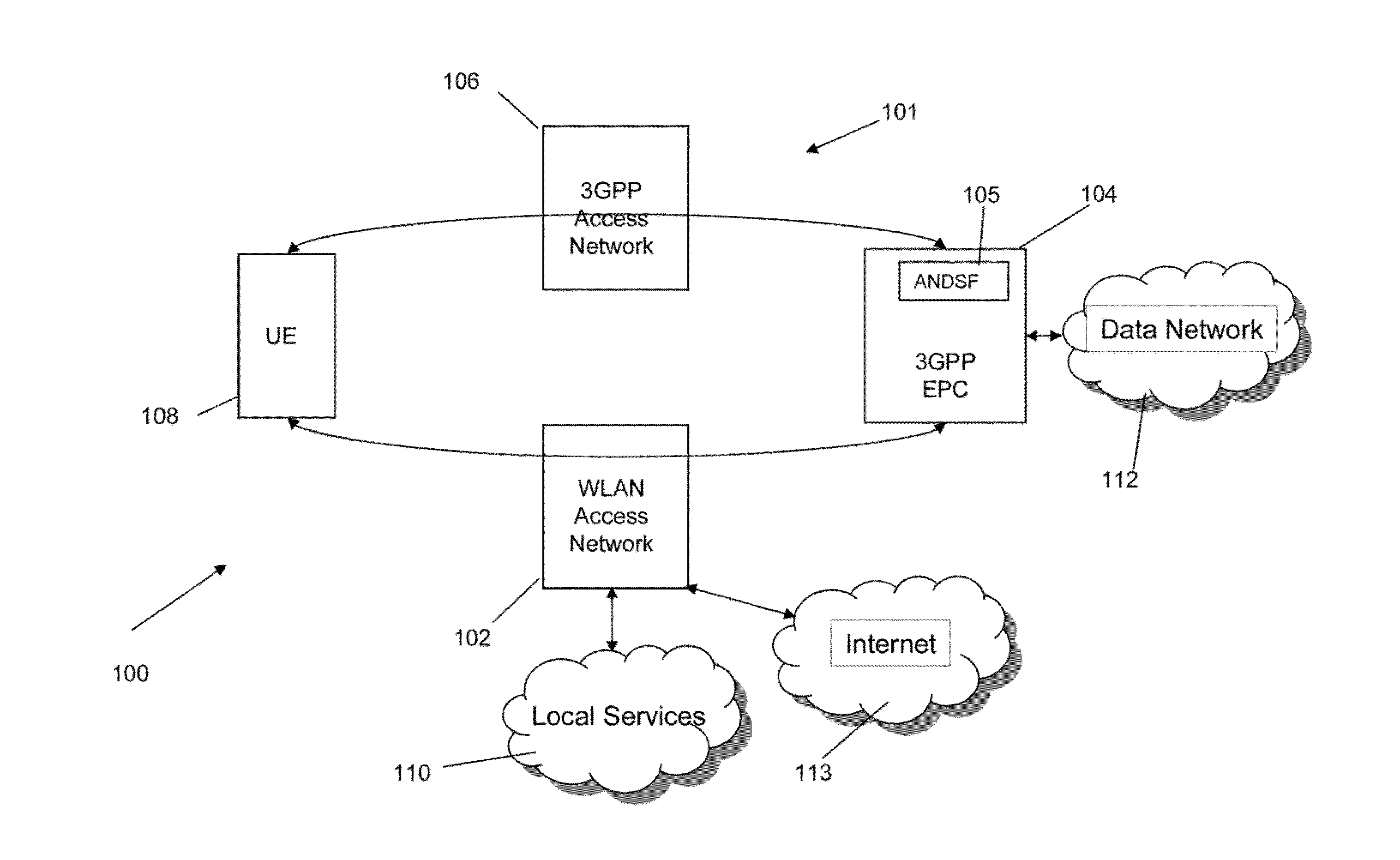
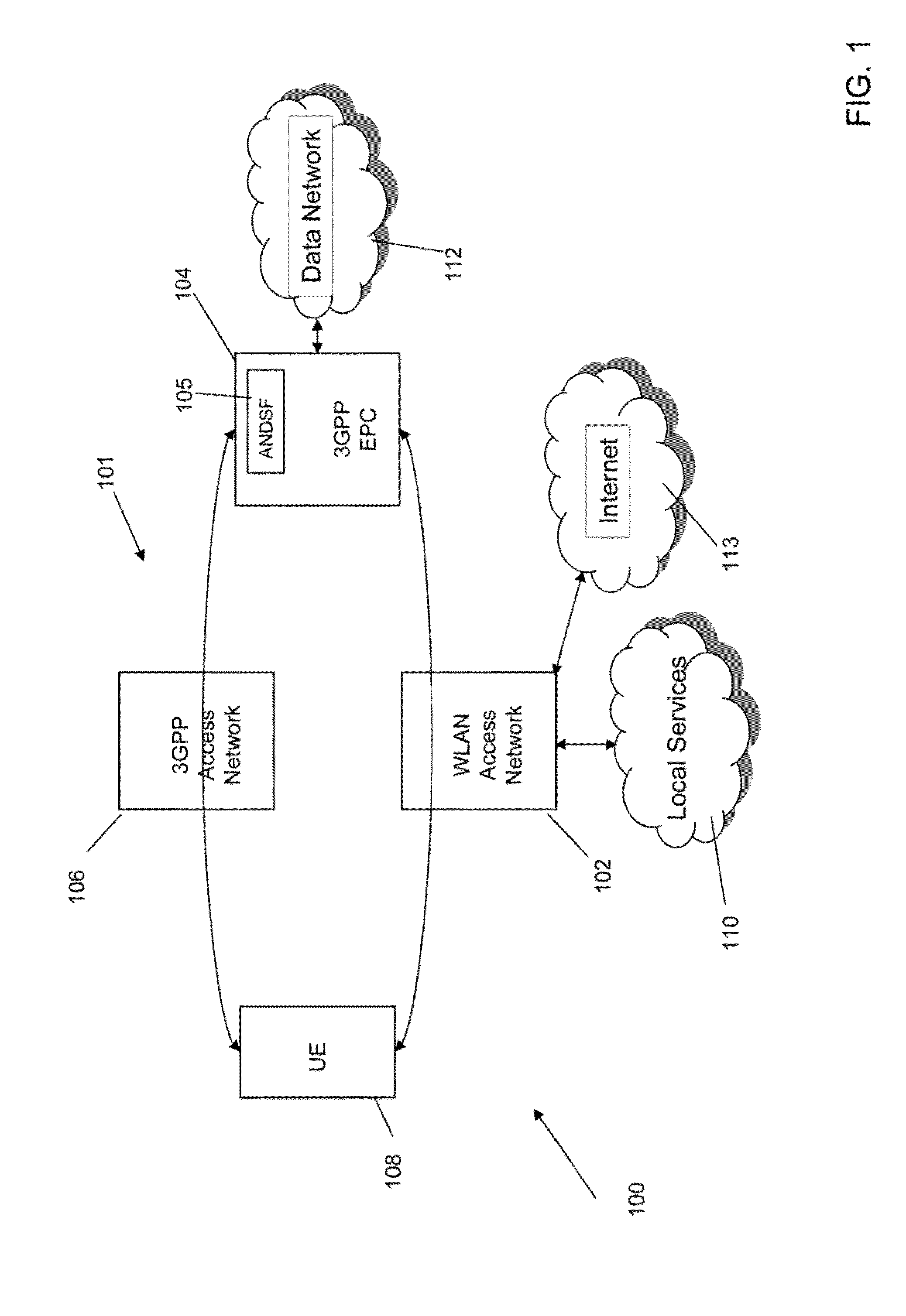
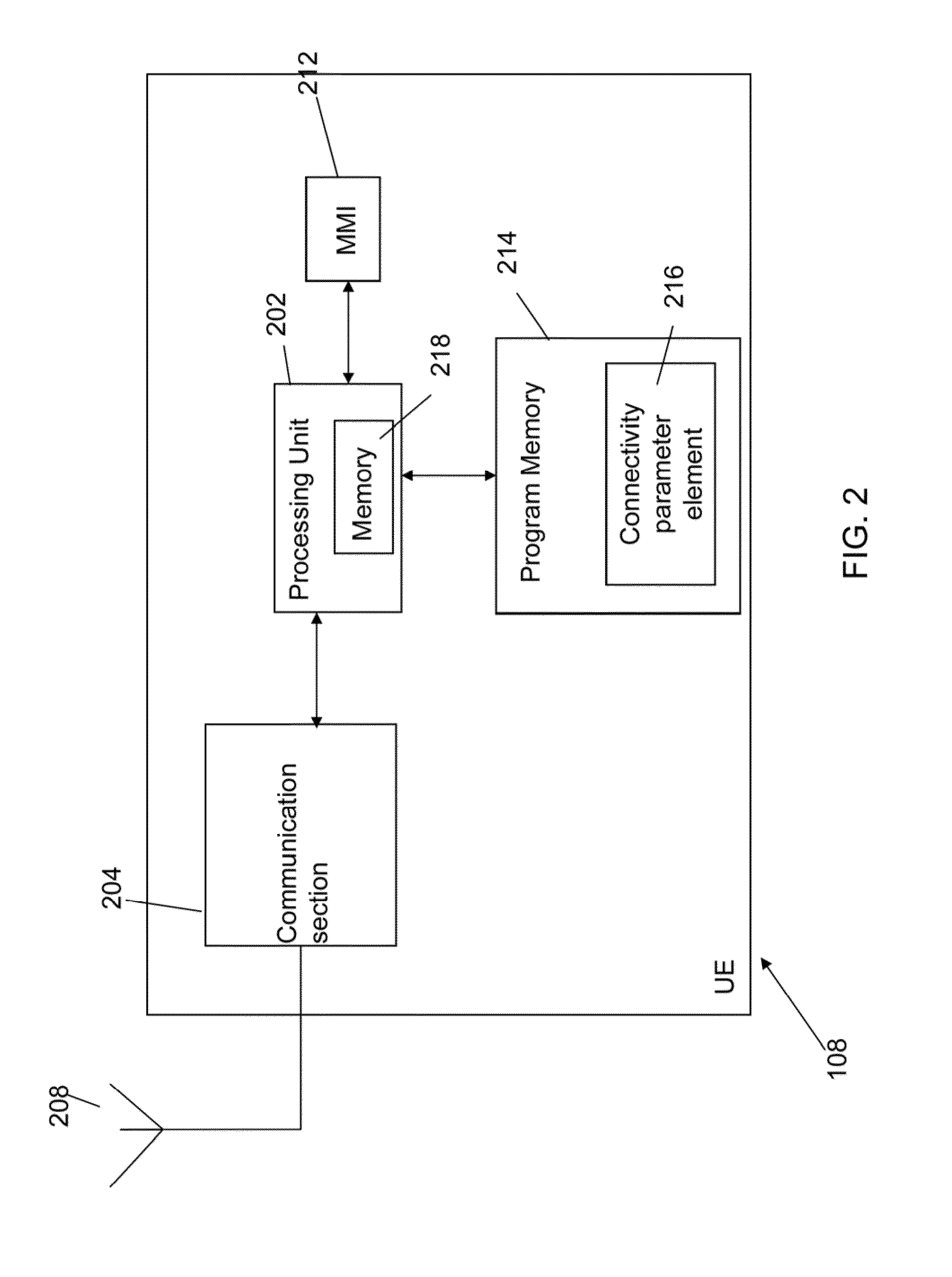
A device, method and system for establishing data connectivity between the device (108) and a first access network (102). The method includes receiving (300) information associated with at least the first access network (102). The information includes a first connectivity type when the first access network is configured to establish a connection to a second access network (104) and tunnel all data traffic from the device (108) to the second access network (104) and a second connectivity type when the first access network (102) is configured to not establish a connection to the second access network (104) and provide direct access to services. When a request to establish data connectivity with the first access network (102) that supports the first connectivity type is received (302), the device provides connectivity parameters to be used to establish a connection between the first (102) and second (104) access networks.
Owner:GOOGLE TECH HLDG LLC
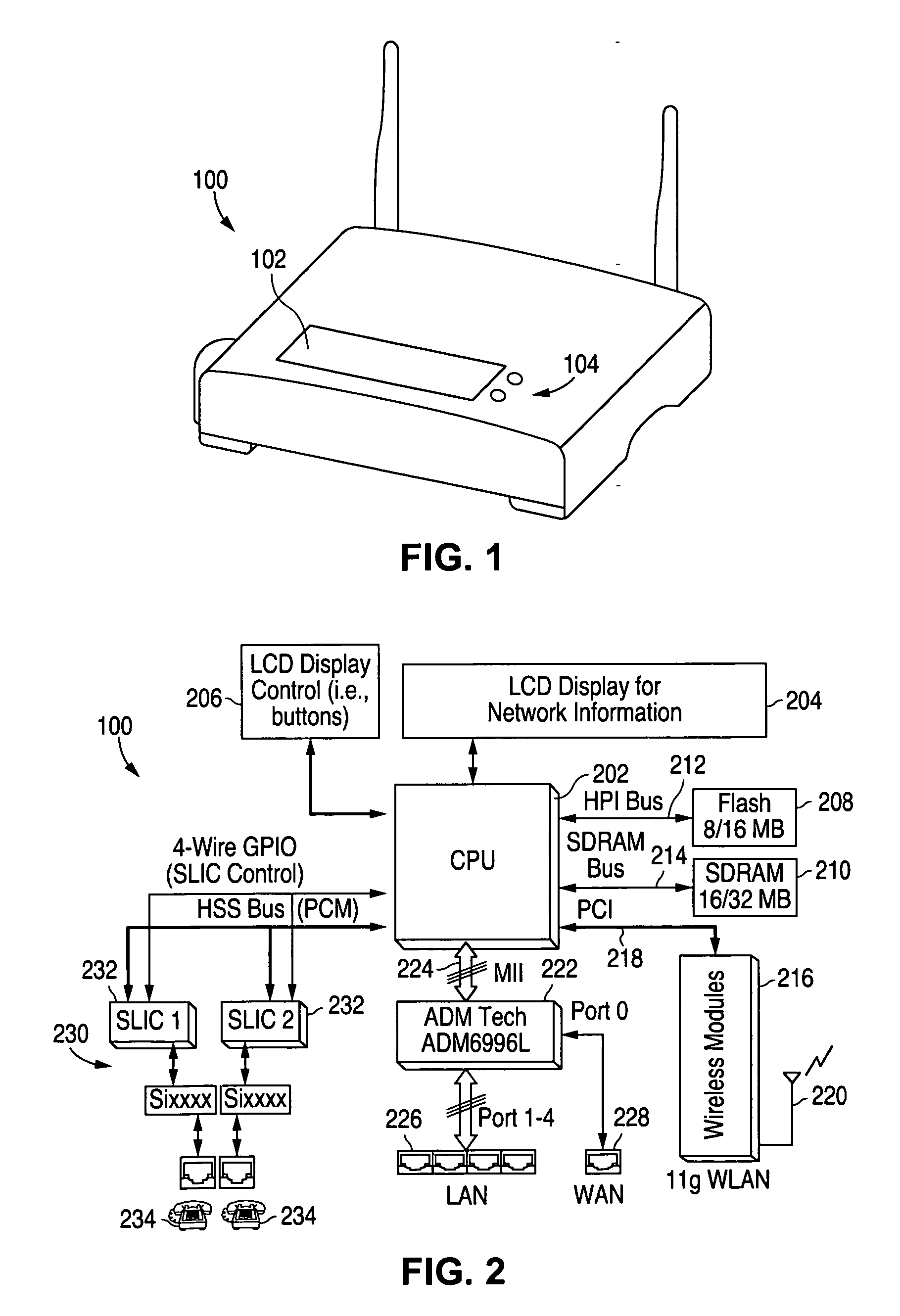
LCD display on wireless router
InactiveUS20060187890A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless routerConnection type
Owner:CISCO TECH INC
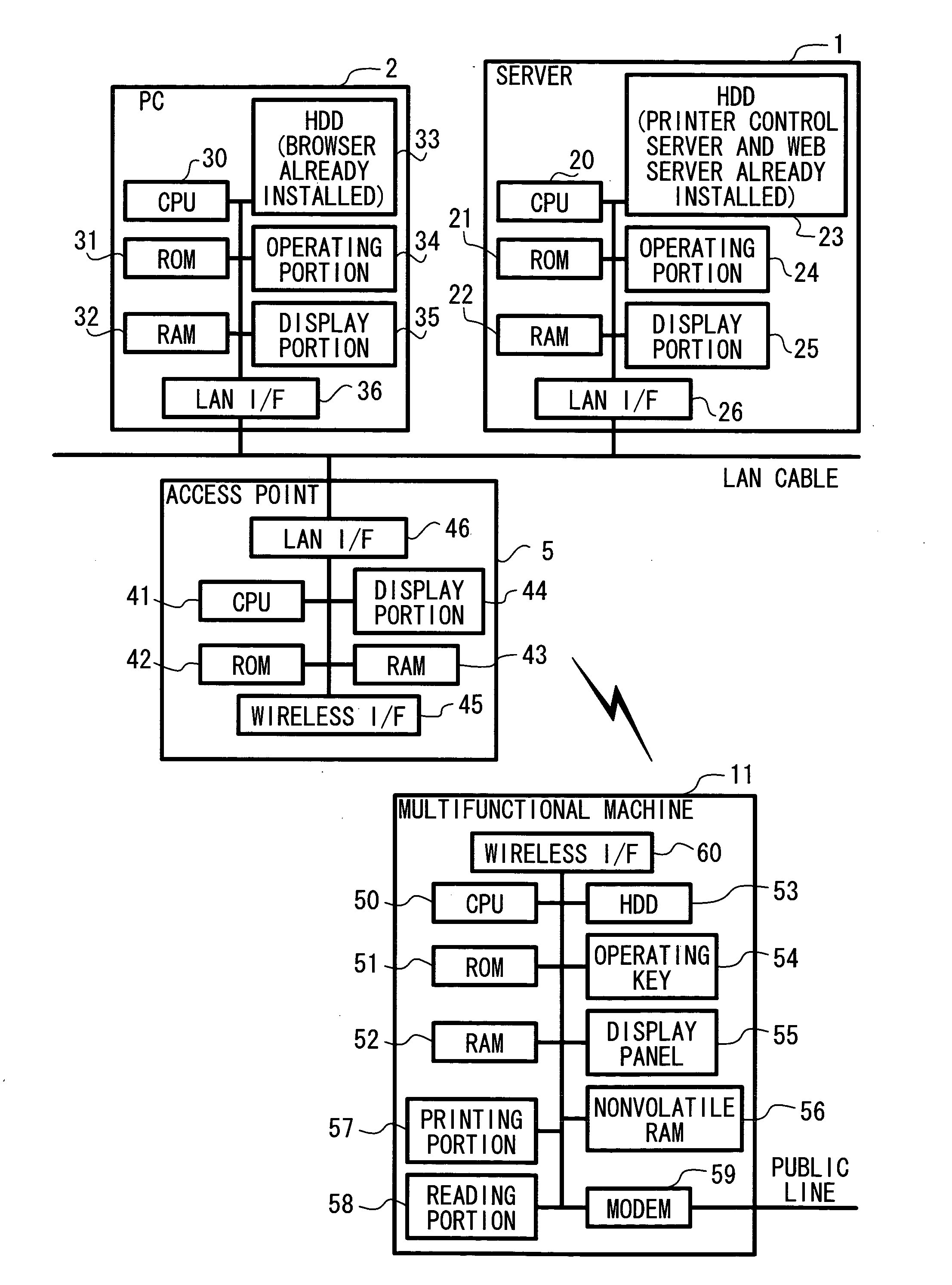
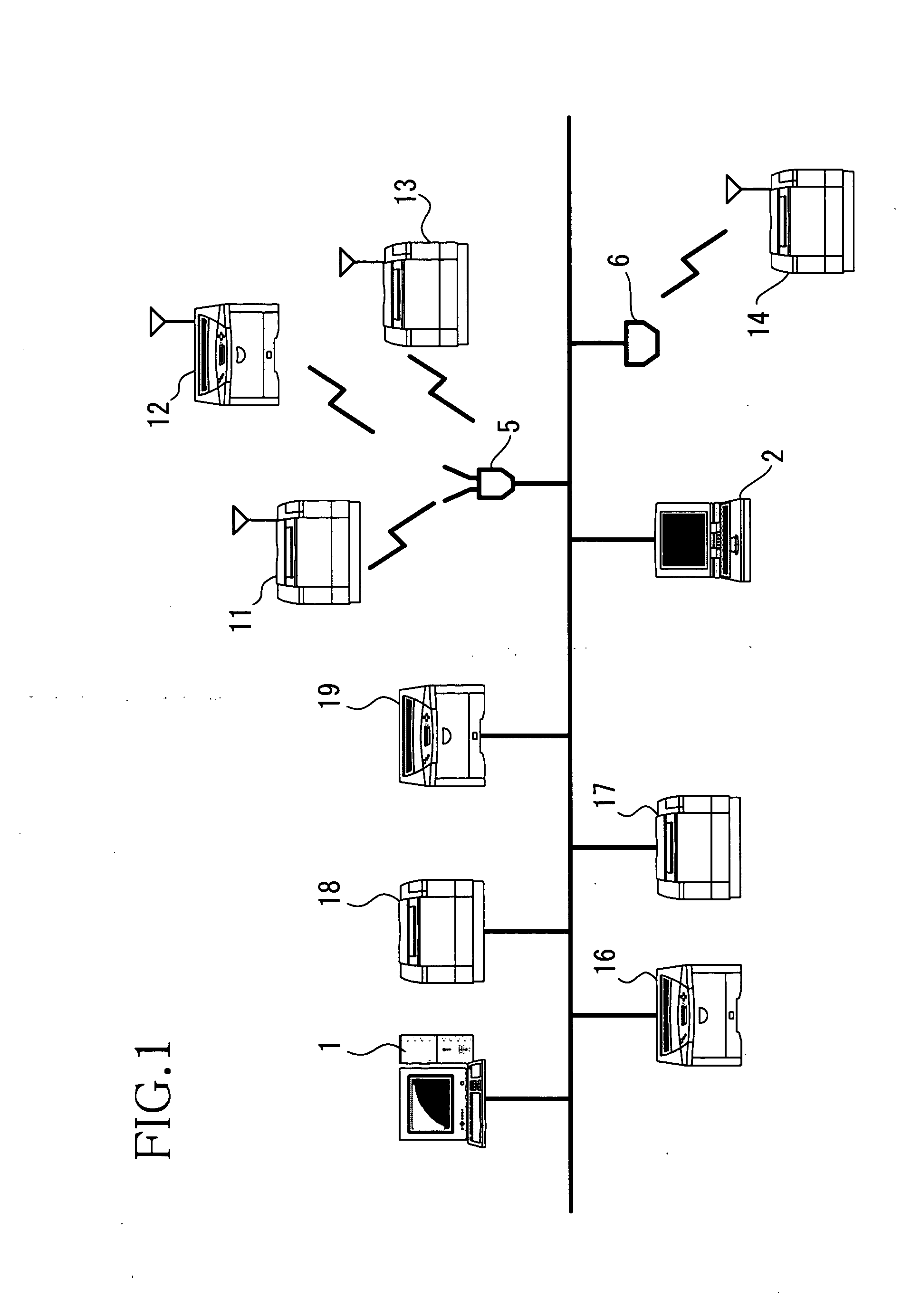
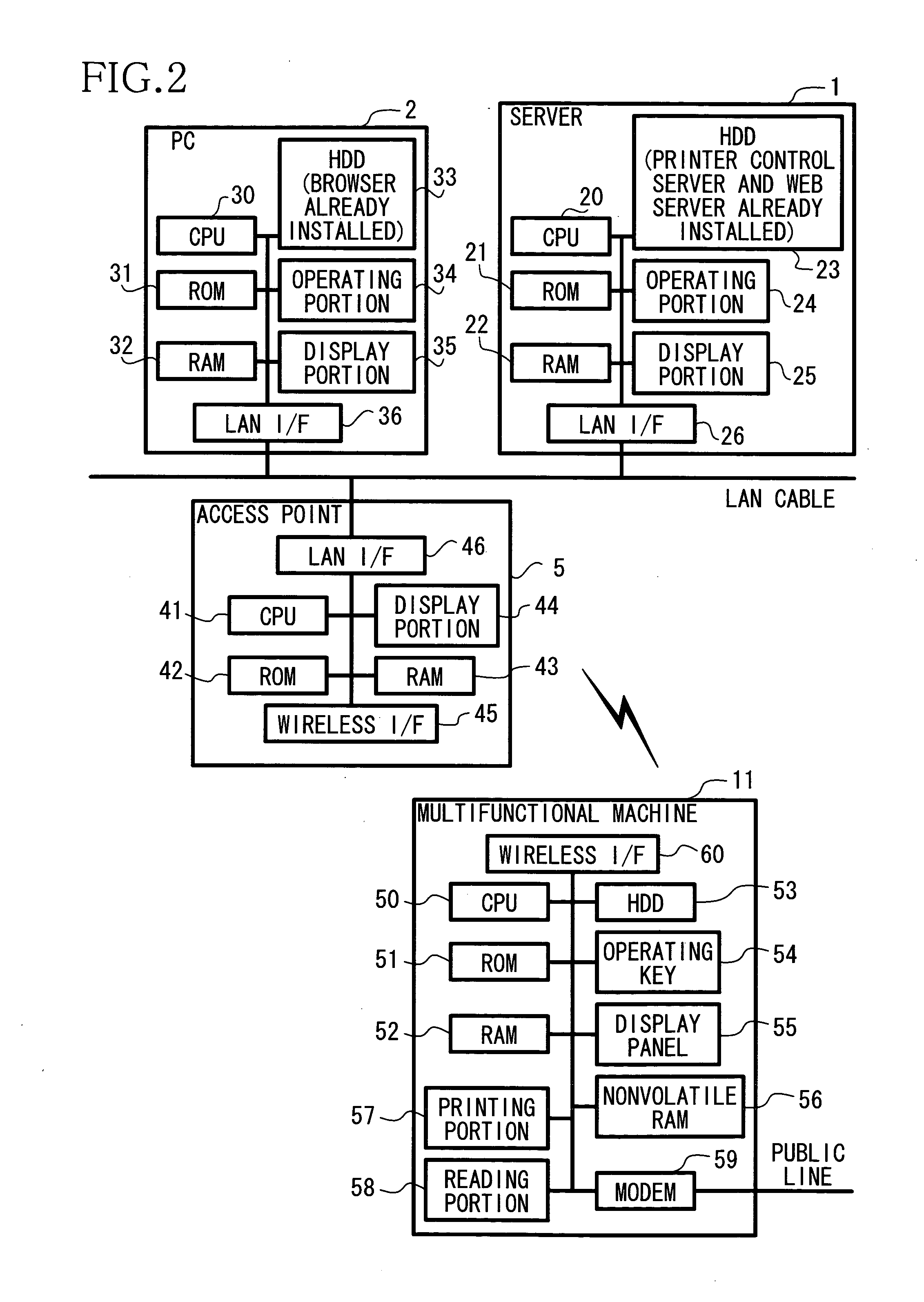
Network device management system, network device management device, and network device management program
ActiveUS20050099962A1Easy to identifyDigital computer detailsComputer security arrangementsConnection typeComputer network
A network device management system includes a computer that is connected to a network and at least one network device that is connected to the network and is capable of communicating with the computer via the network. Each network device includes a network device controller that provides the computer with network device information about settings and conditions of each network device of the at least one network device, via the network. The network device information includes connection type information that indicates whether each network device is a wired connection type or a wireless connection type. The computer includes a computer controller that obtains the network device information from each network device via the network and outputs a part or all of contents of the network device information including at least the connection type information, based on the obtained network device information.
Owner:BROTHER KOGYO KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com