Patents
Literature
220 results about "Risk profile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A risk profile is an evaluation of an individual's willingness and ability to take risks. It can also refer to the threats to which an organization is exposed. A risk profile is important for determining a proper investment asset allocation for a portfolio. Organizations use a risk profile as a way to mitigate potential risks and threats.
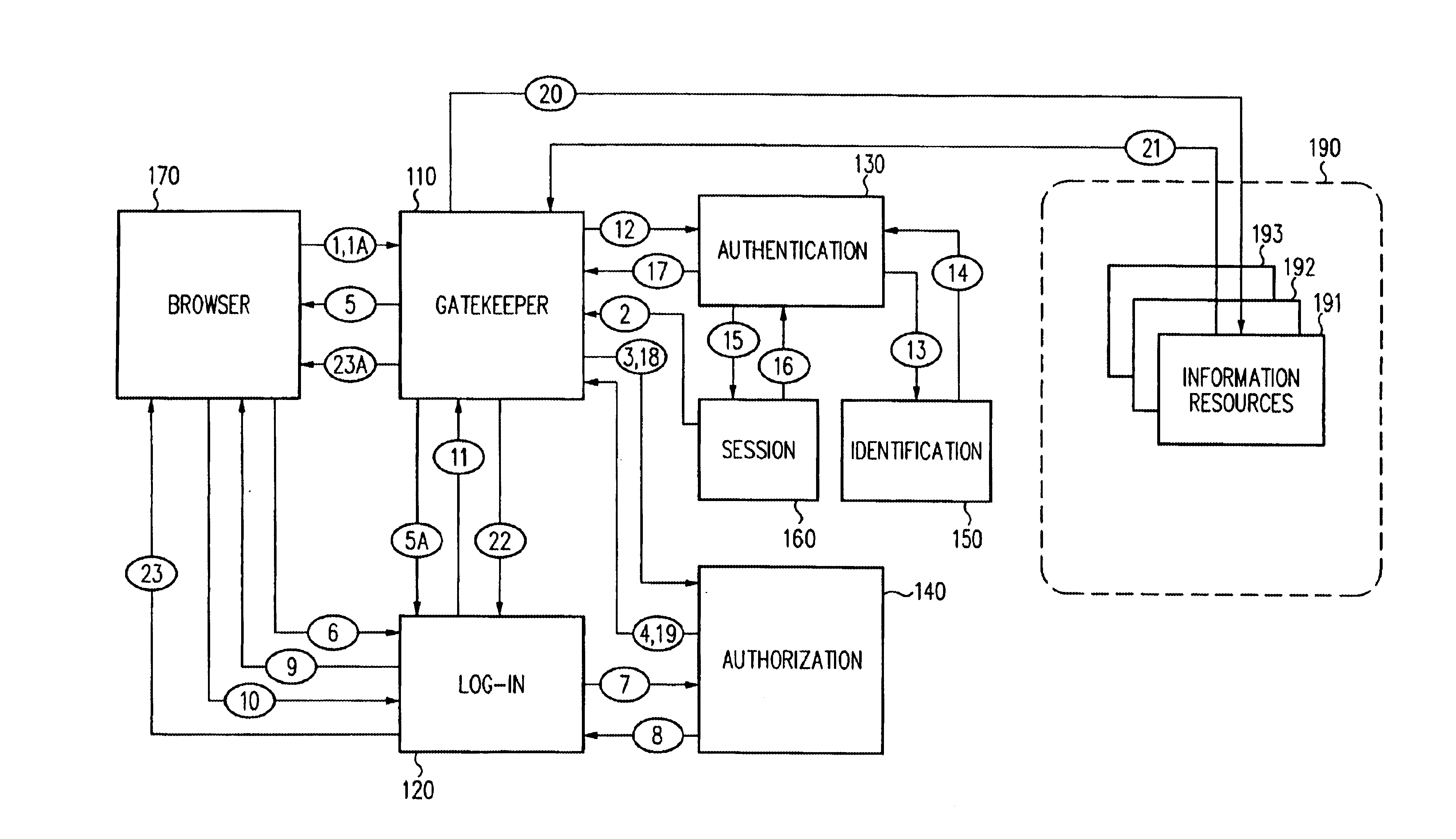
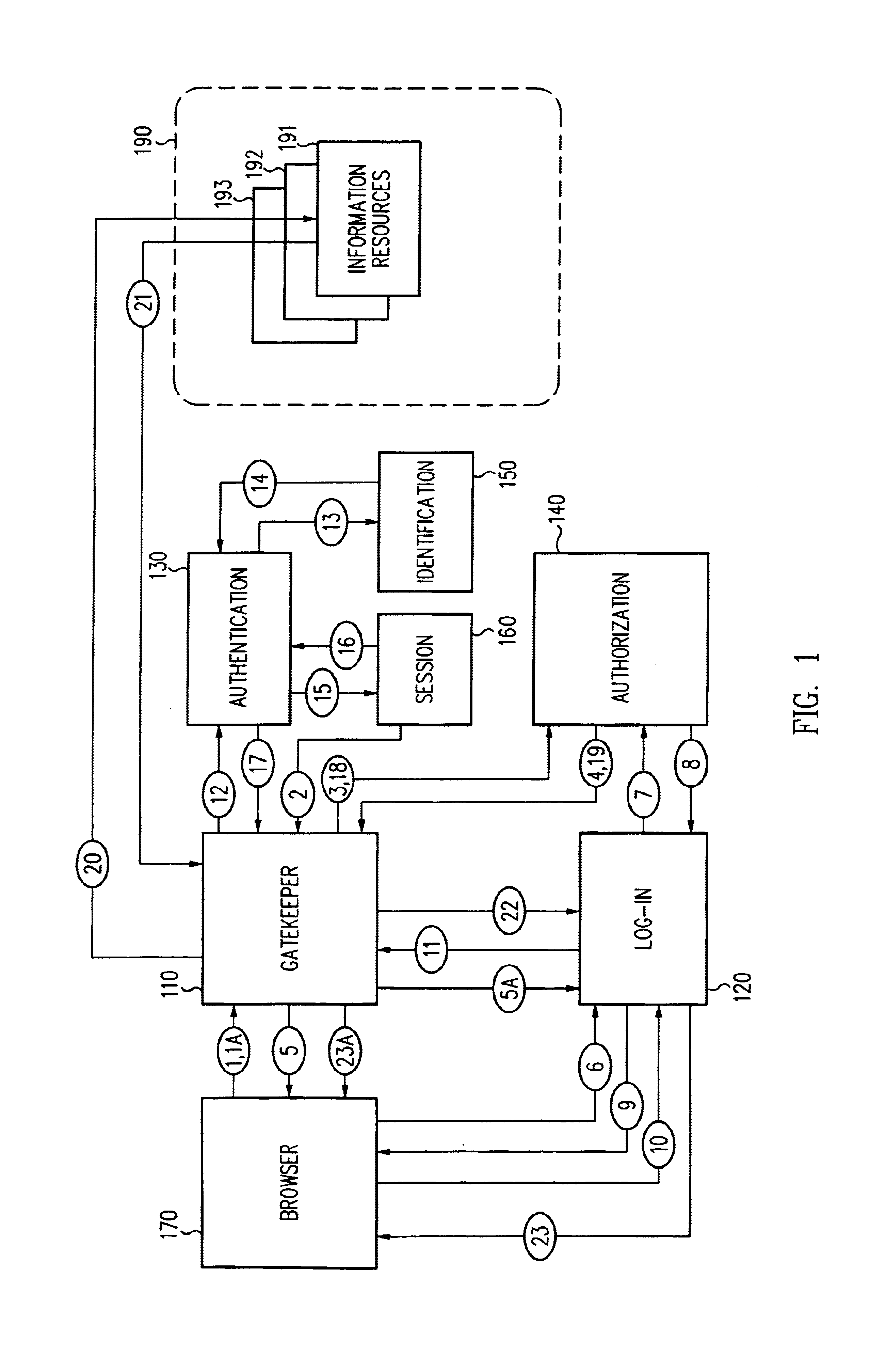
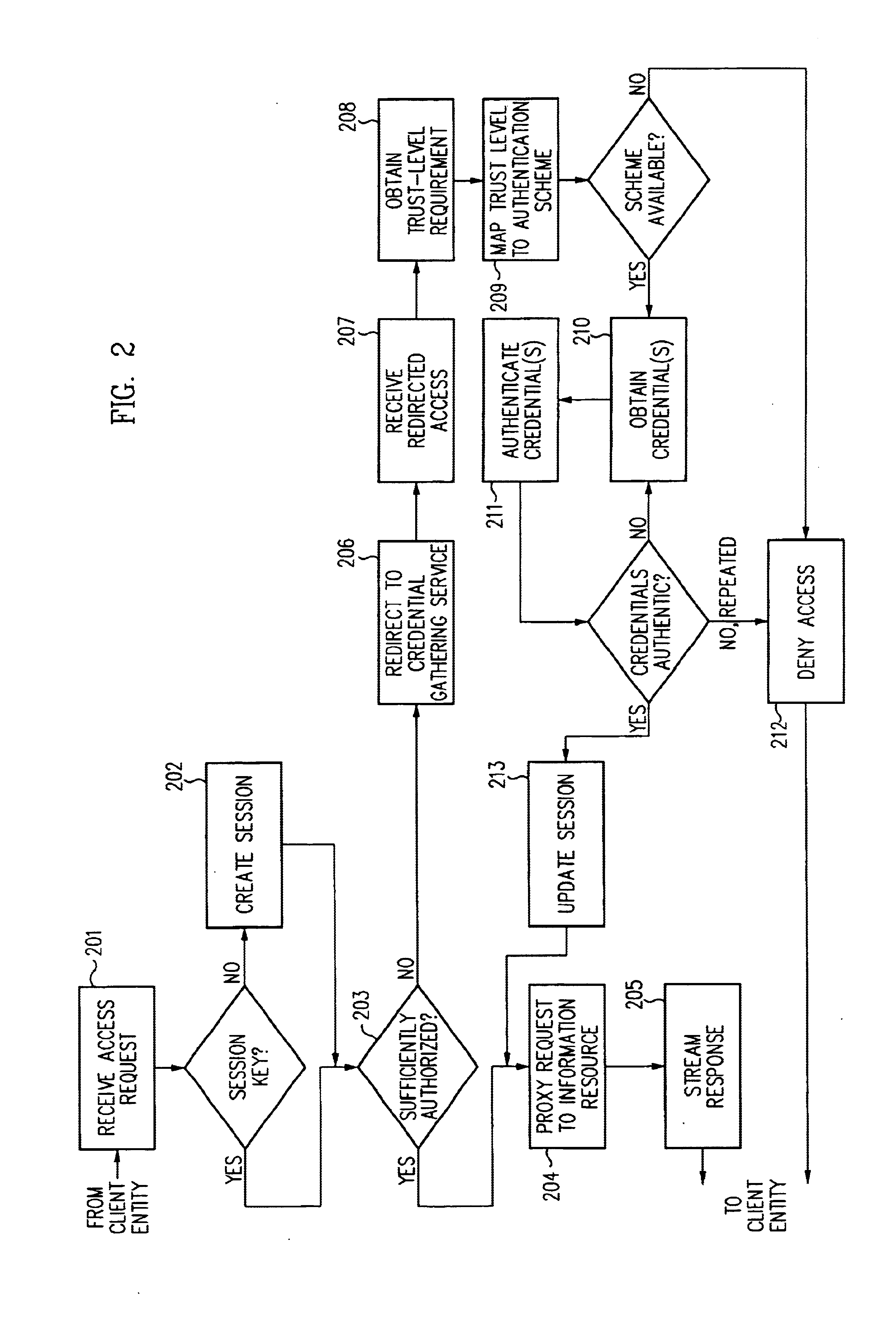
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
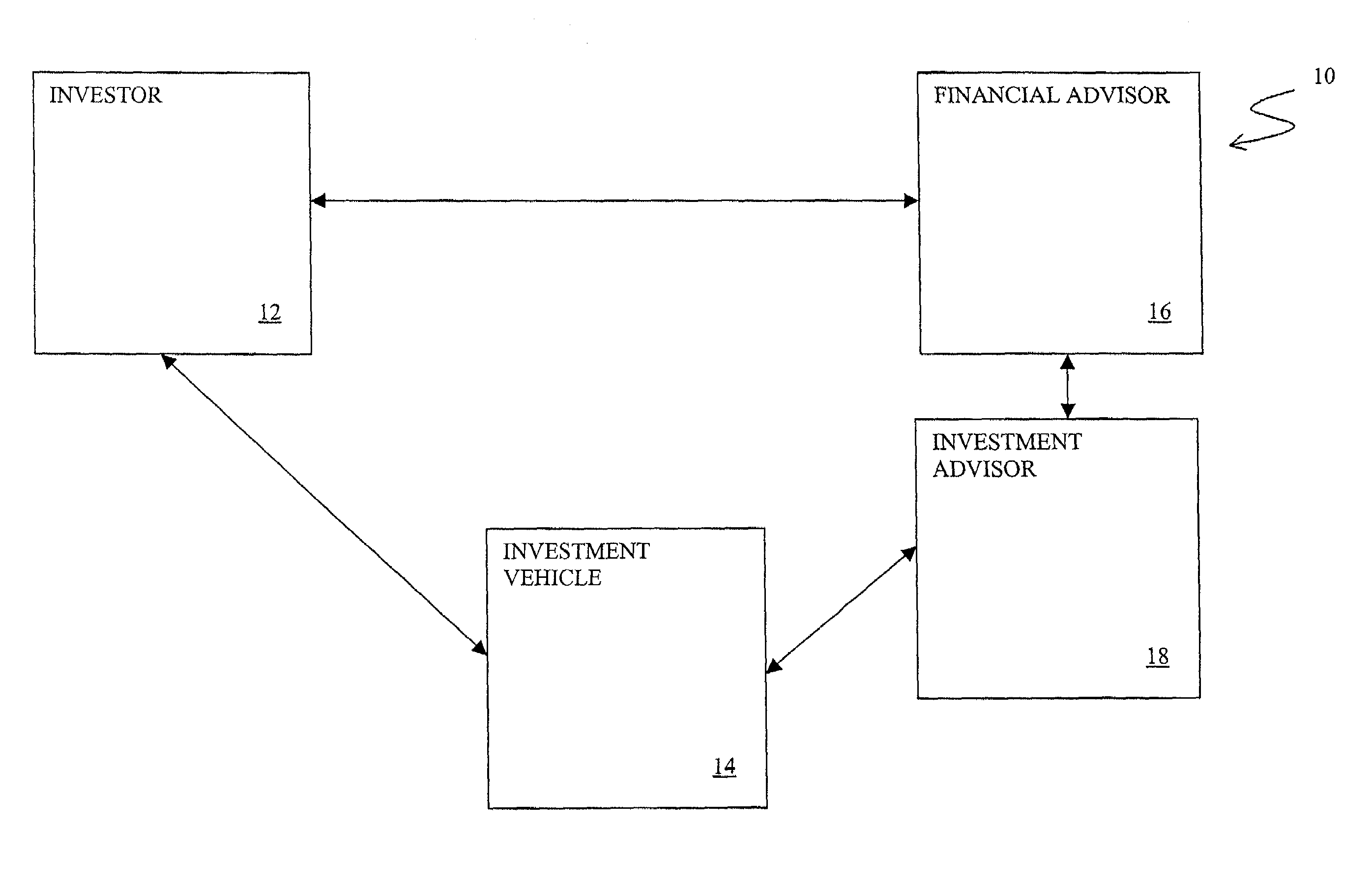
Investment advice systems and methods
The present invention provides investment advice systems. One version of the present invention provides investment advice systems that allow a user to select one or more advisors from a list of investment advisors. According to this version of the invention, the end user can receive advice on a particular transaction either separately from each investment advisor or in consensus. The system offers advice in part on the user's portfolio, tax position and risk profile and in part on the advisors evaluation of current market conditions. Thus, when a user is considering making a transaction, the user can obtain advice that can take into portfolio information including a user's proposed transaction and / or user portfolio information. A user armed with the above-described customized advice can execute a specific transaction and have their portfolio updated to reflect execution of that (those) order(s). In an alternative embodiment, a user's desire to buy or sell a security and / or a need for rebalancing a user's portfolio can generate transaction(s). As a result, the system will generate a buy / sell list (including recommended alternatives) from which a user can select.
Owner:TEGRA118 WEALTH SOLUTIONS INC
Trusted remote attestation agent (TRAA)
ActiveUS20100306107A1Reduce riskFinanceMultiple digital computer combinationsComputer hardwareRisk profiling
Systems and methods for use with a service provider and a consumer electronic device include a trusted remote attestation agent (TRAA) configured to perform a set of checking procedures or mechanisms to help ensure the security status of a consumer electronic device (e.g., a mobile terminal or phone) that holds financial instruments. The checking procedures may include: self-verifying integrity by the TRAA; checking for presence of a provisioning SIM card (one that was present when the financial instruments were enabled on the device); checking that a communication connection between the consumer electronic device and the service provider is available and active; and checking that communication connectivity to a home mobile network is available and active. The frequency of the checking mechanisms may be adjusted, for example, according to a risk-profile of a user associated with the device or the location (e.g., GPS location) of the device. The checks may be used, for example, to temporarily disable or limit the use of the financial instruments from the device.
Owner:PAYPAL INC
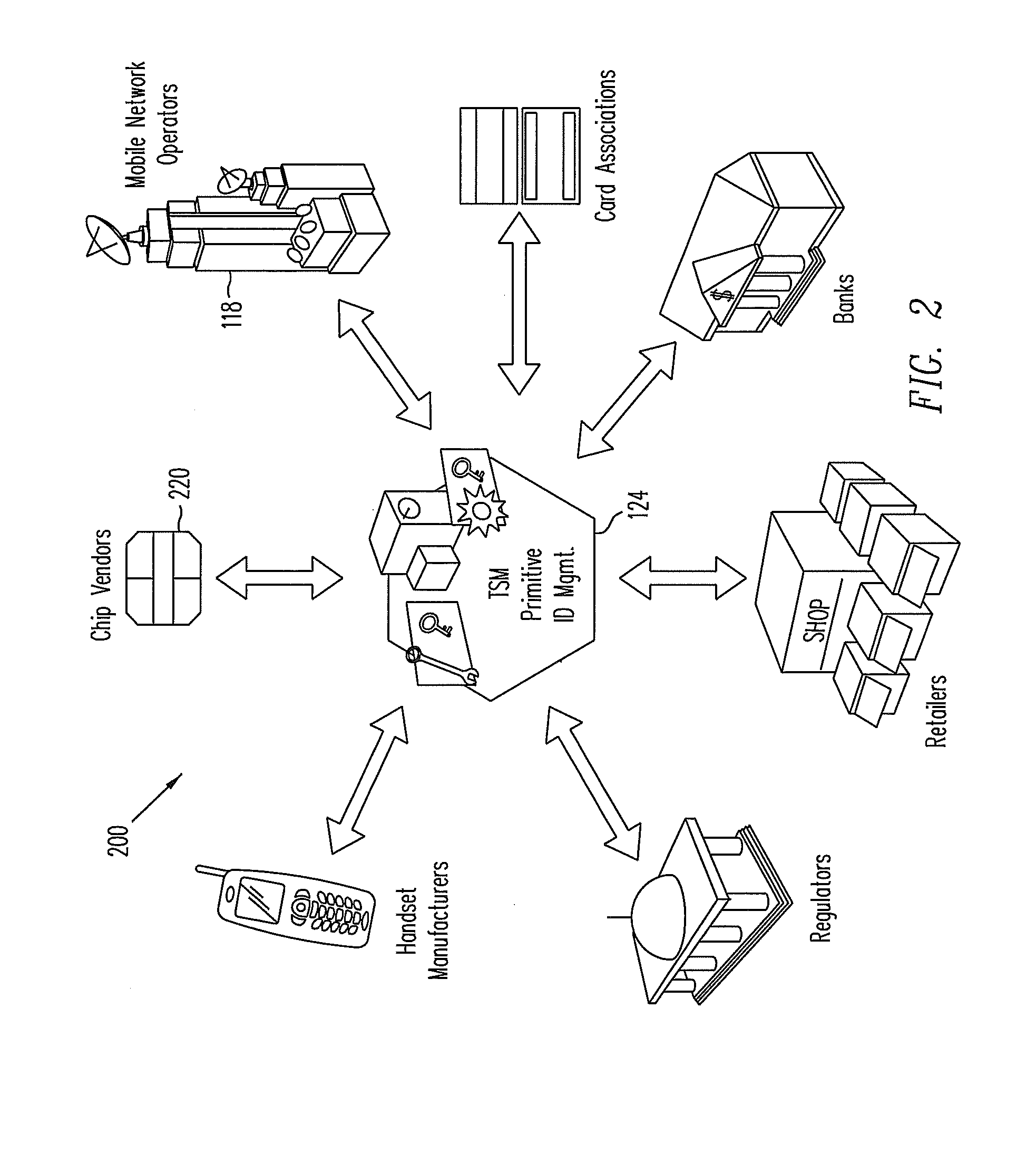
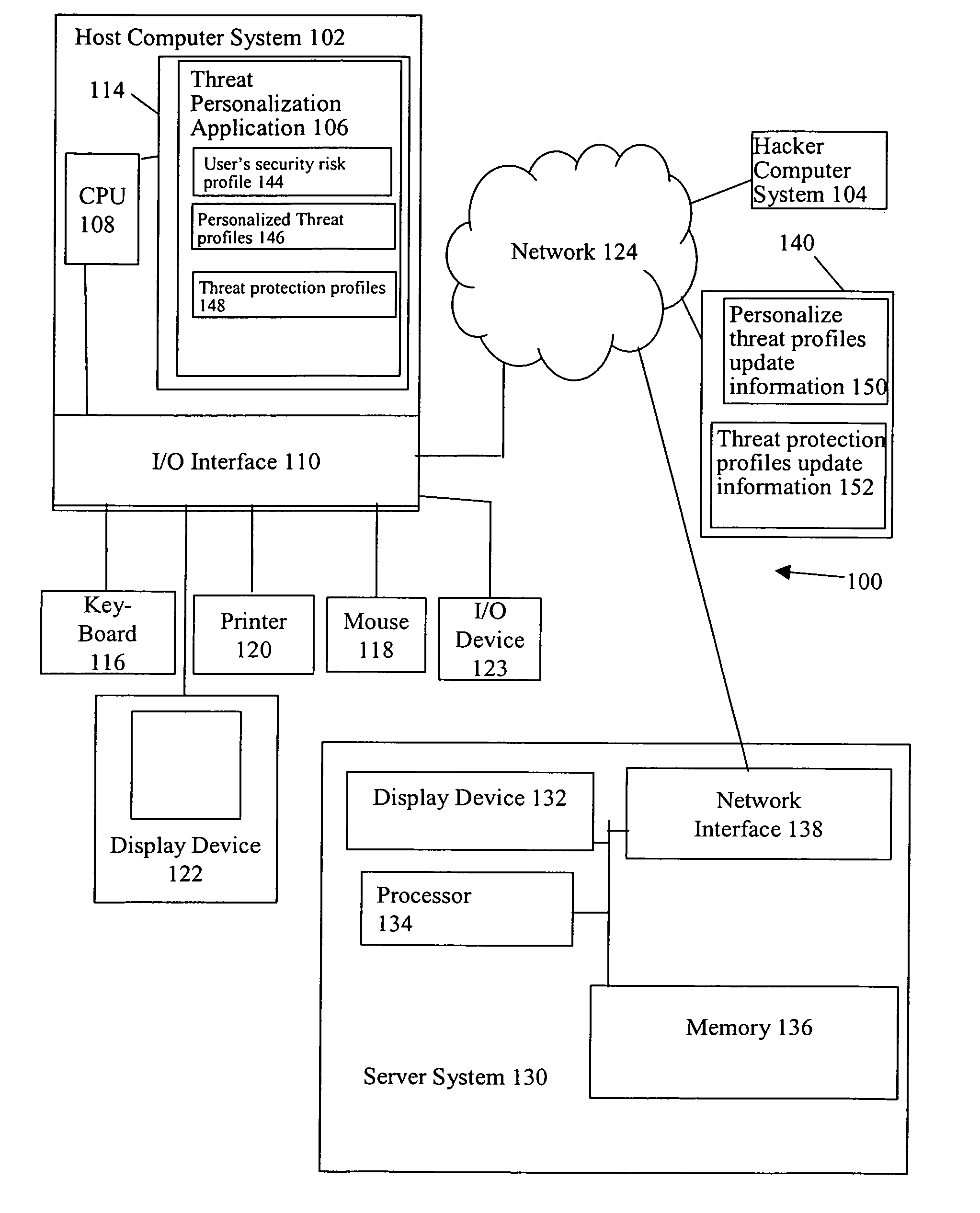
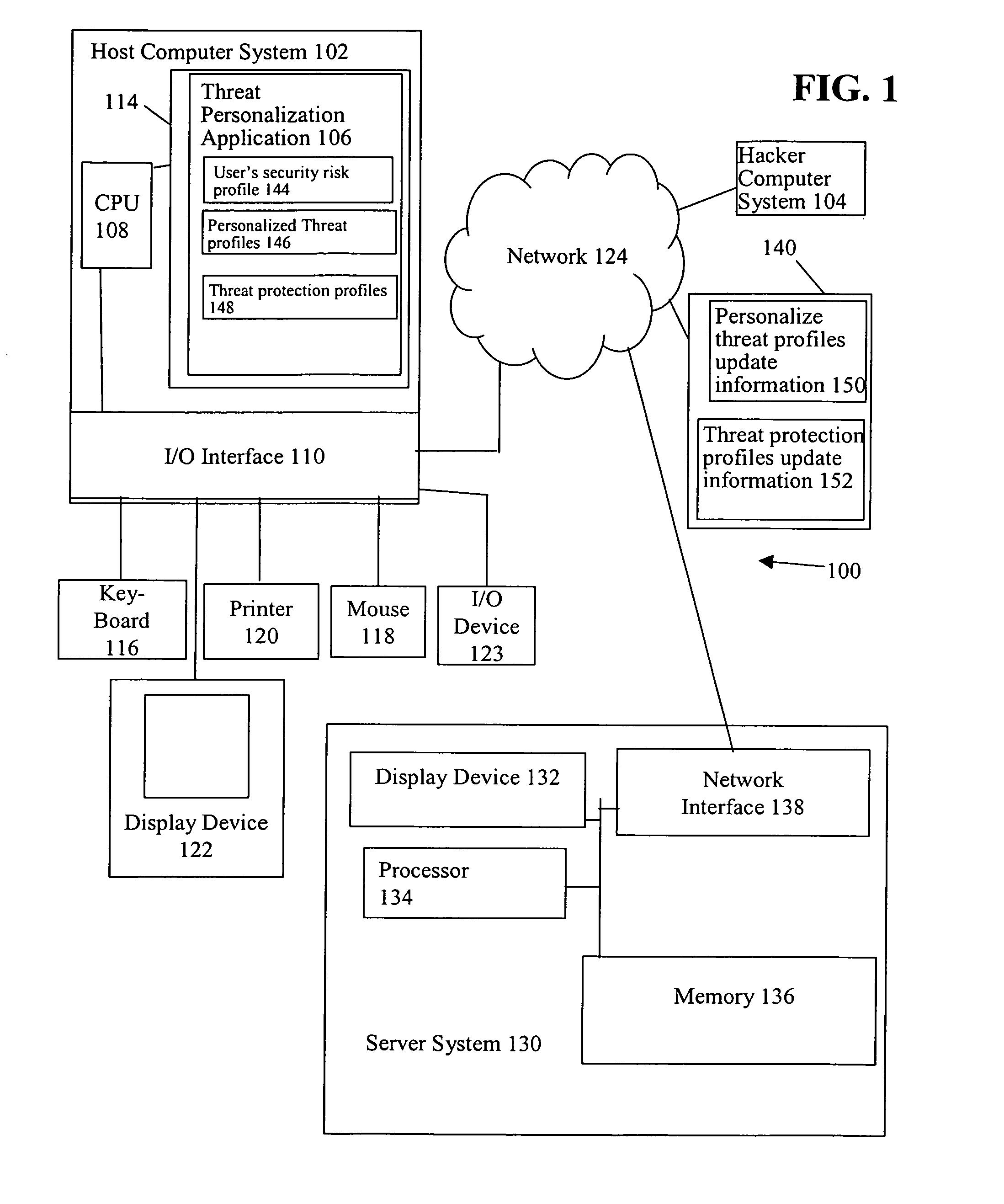
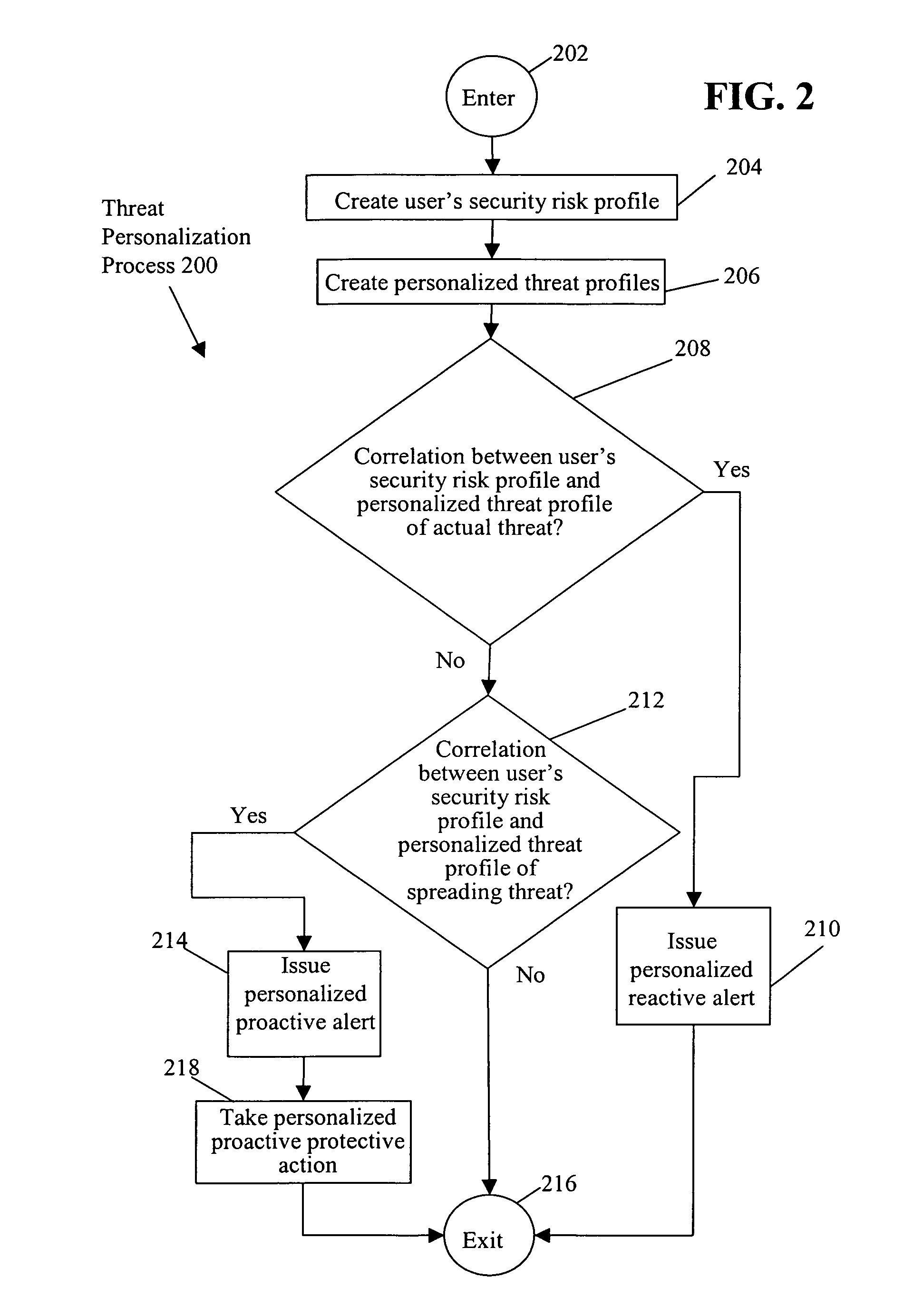
Threat personalization
ActiveUS7841008B1Increase the user's vigilanceMemory loss protectionError detection/correctionPersonalizationRisk profiling
A determination is made as to whether there is a correlation between a user's security risk profile and a personalized threat profile of an actual or spreading threat. If there is a correlation, a personalized reactive alert is issued in the case of an actual threat. The personalized reactive alert informs the user of specific suspected data that may have been compromised by the threat and the specific non-computer related action that the user should take. Further, if there is a correlation, a personalized proactive alert is issued and / or personalized proactive protective action taken in the case of a spreading threat. The personalized proactive alert informs the user of the spreading threat that the user and / or the user's host computer system is particularly susceptible to. Further, the personalized proactive protective action taken provides automated risk mitigation.
Owner:GEN DIGITAL INC
Applying security policy based on behaviorally-derived user risk profiles
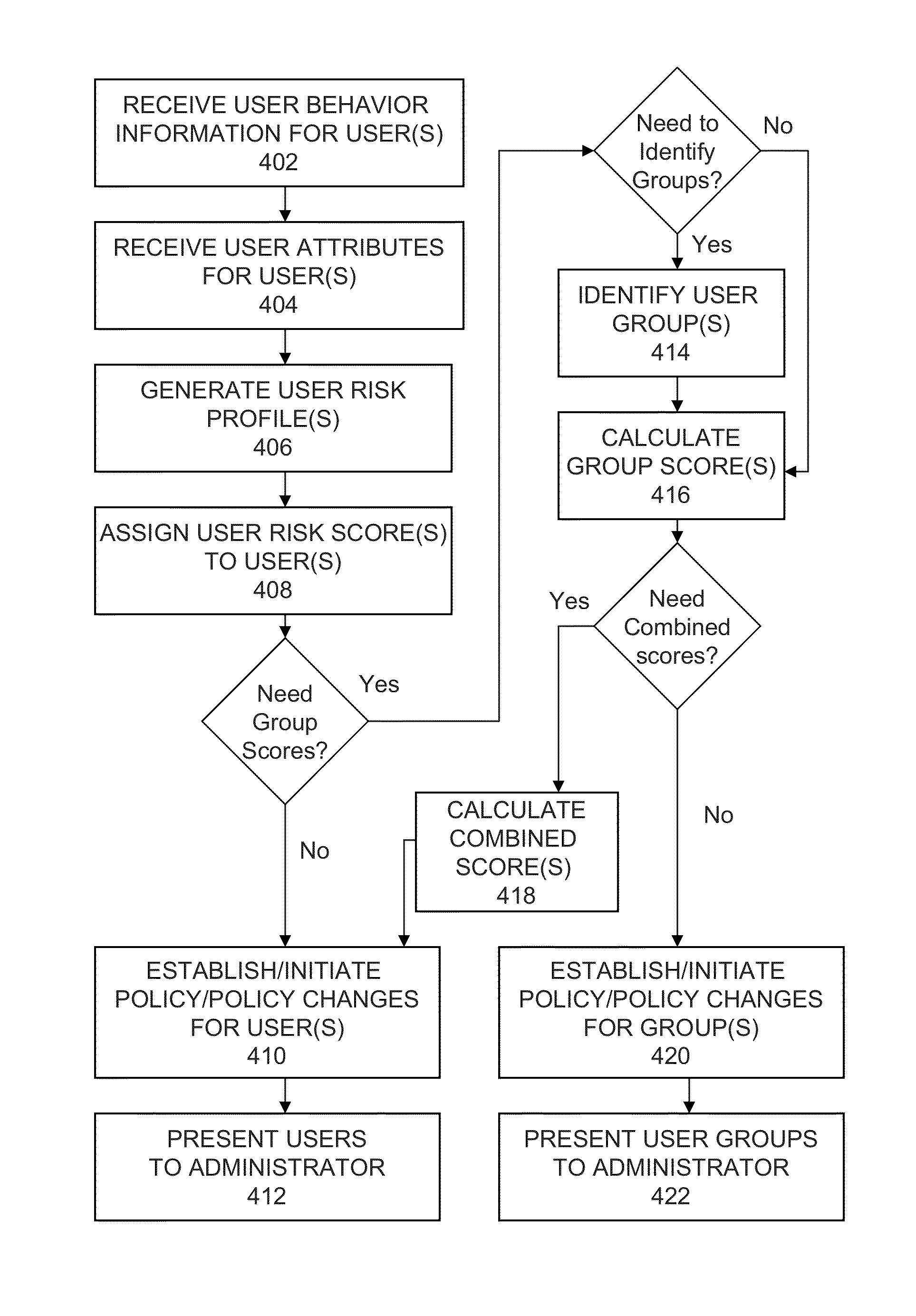
Security policy changes can be implemented for a user or a user group based on behaviorally-derived risk information. A behavior-receiving module receives information about user behaviors for the user across various clients with which the user interacts. An attribute-receiving module receives one or more user attributes identified for a user. A profile-generating module generates a user risk profile for the user based on the received information about the user behaviors and the received user attributes. A user scoring module assigns the user a user risk score based on an evaluation of the user risk profile for the user. Similarly, groups of users can be given group risk scores, or users can have combined group / user scores. Finally, a remediation module automatically establishes a security policy requiring remediative actions for the user (or user group) based on the user risk score or combined score (or group score).
Owner:CA TECH INC
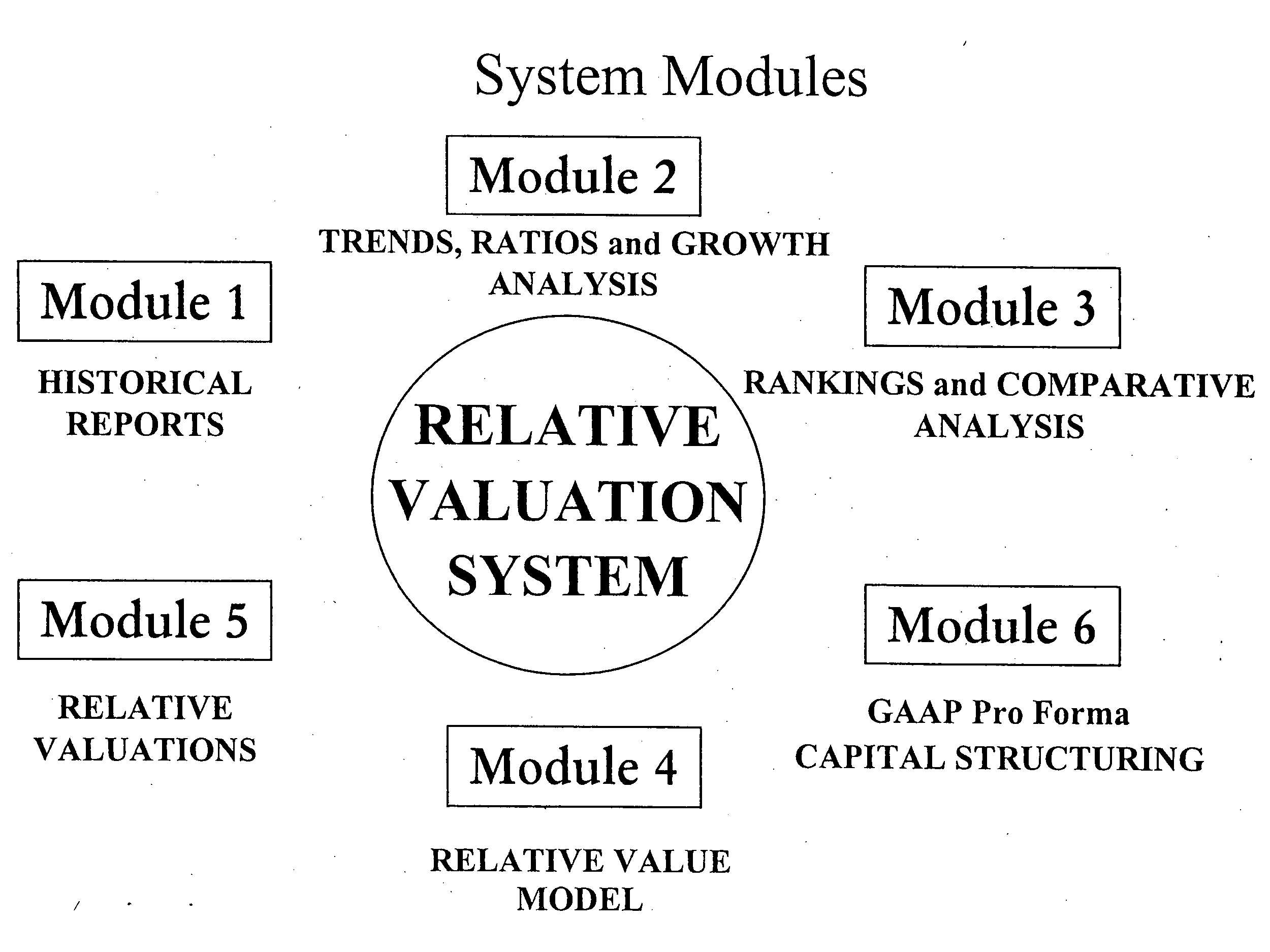
Relative valuation system for measuring the relative values, relative risks, and financial performance of corporate enterprises
InactiveUS20050262014A1The process is convenient and fastFinanceSpecial data processing applicationsRisk profilingDynamic monitoring
A system and method for defining the value of a corporation by its categories of values, and determining the risk profile of the corporation by the relationship between the categories of value, termed the “Risk Signatures.” The system provides for the determination of the “Relative Values” of corporate enterprises, with the capability of dynamically monitoring and measuring the financial performance of an enterprise through the use of artificial intelligence and data mining techniques.
Owner:FICKES STEVEN W
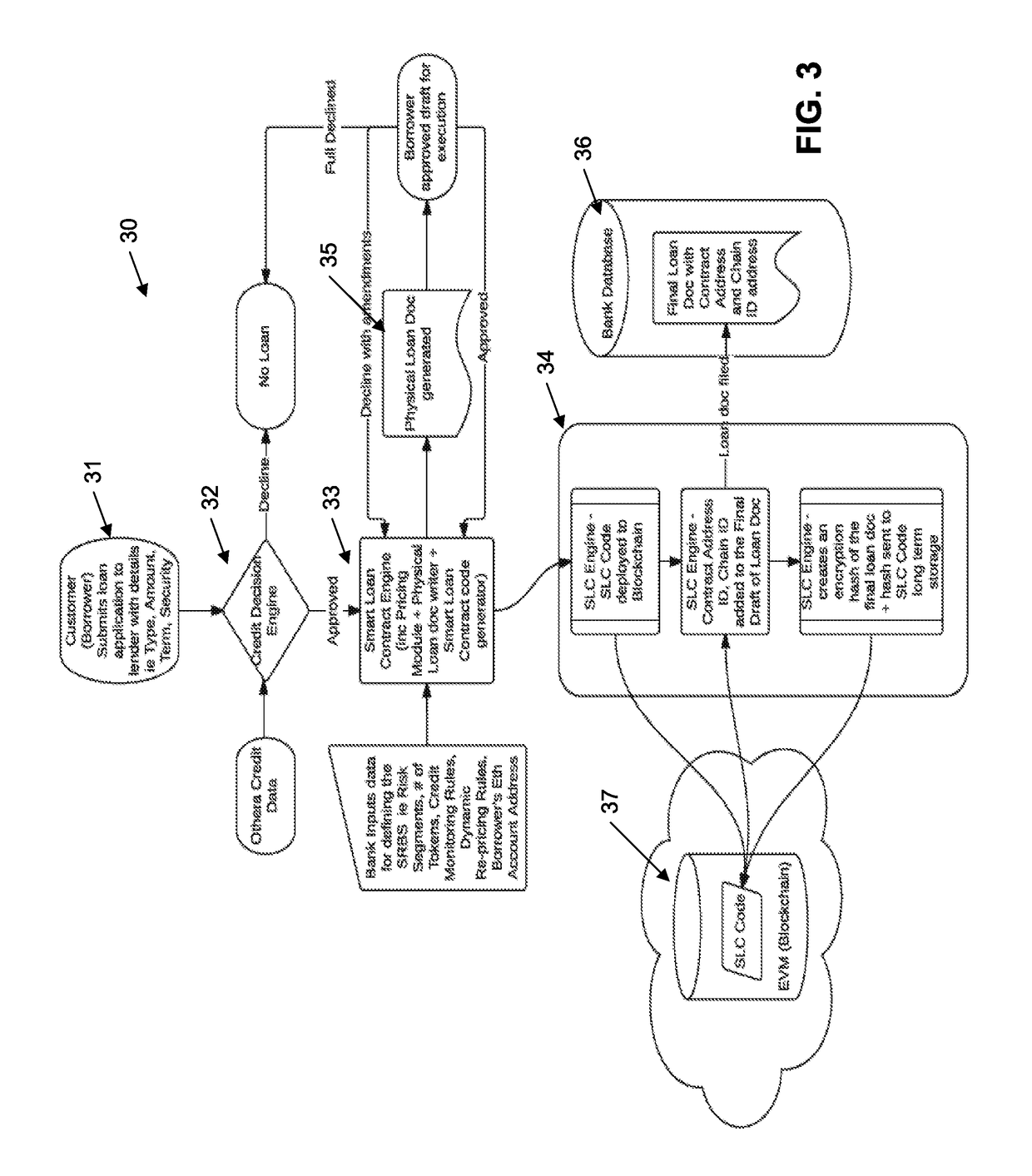
Methods and Systems for Blockchain Based Segmented Risk Based Securities
InactiveUS20190087893A1Easy to purchaseFacilitates saleFinanceEncryption apparatus with shift registers/memoriesDocumentation procedureRisk profiling
A method of providing for a secure financial transaction, the method including the steps of: (a) formulating the documentation associated with the financial transaction, including security for the transaction; (b) dividing the transaction into a series of segments, each segment having an associated expected risk profile and security profile; (c) for each segment, creating an indicative token describing the segment, including associated expected risk profile and security profile; (d) providing a block chain environment for storage of the indicative tokens.
Owner:OTHERA PTY LTD
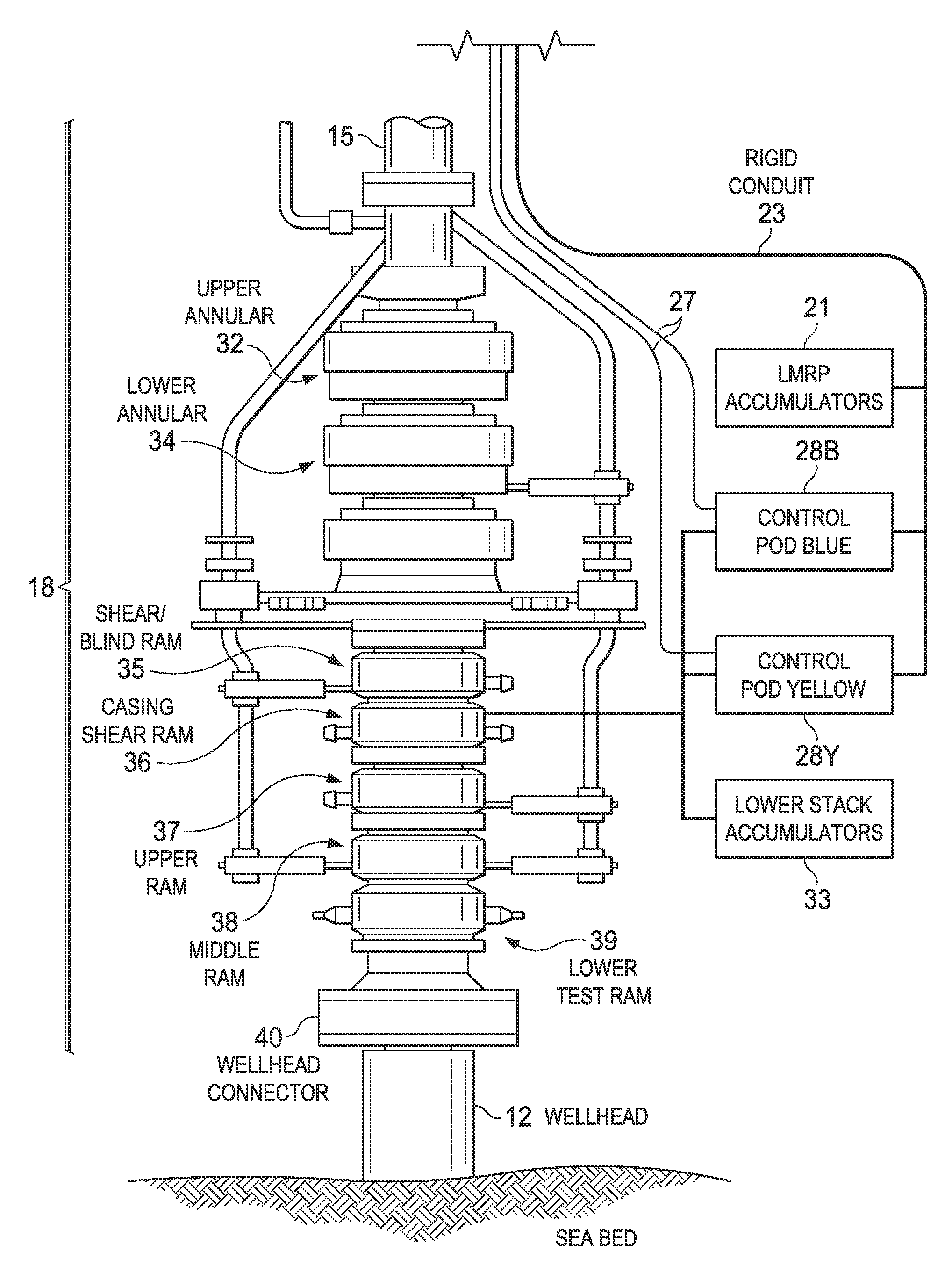
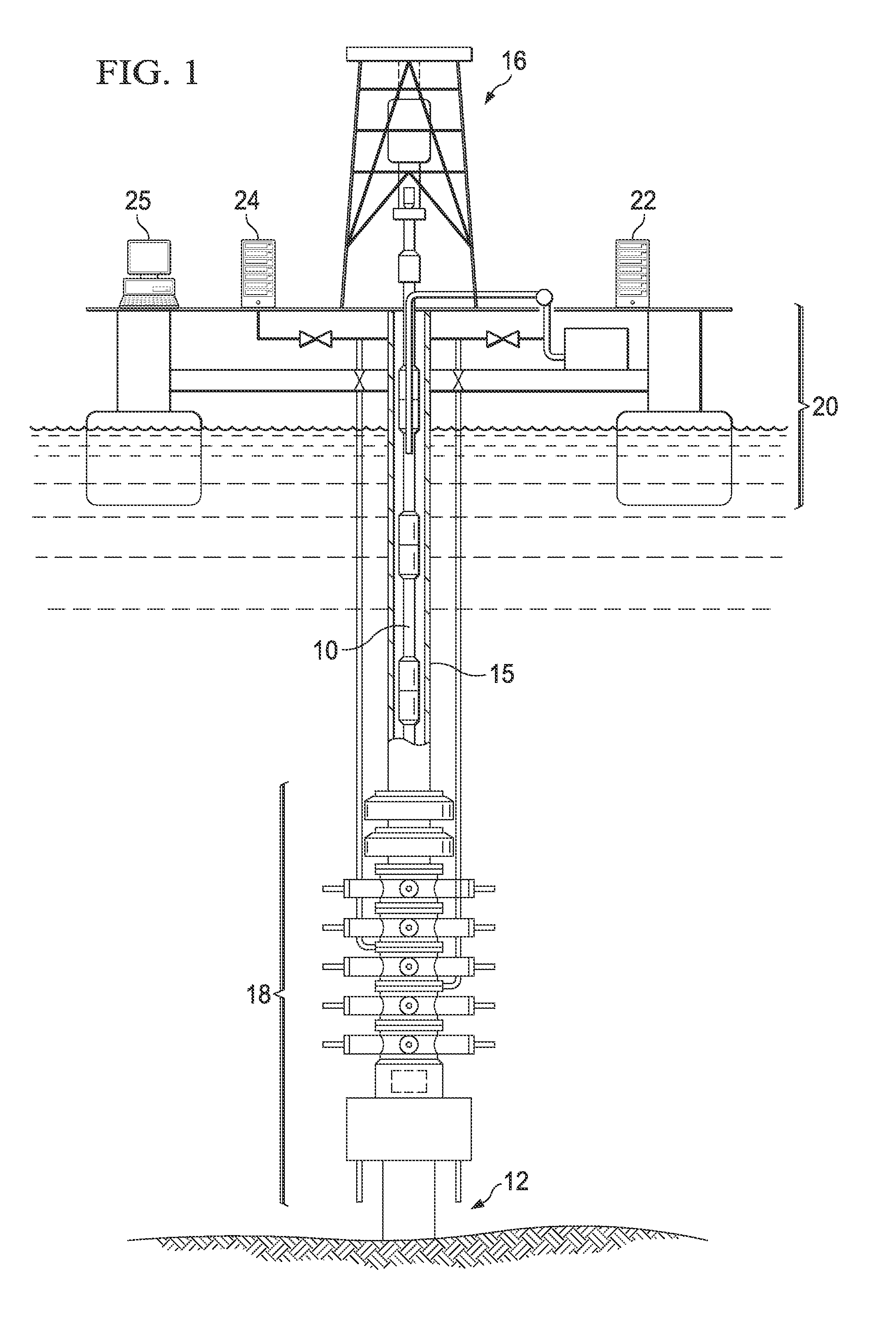
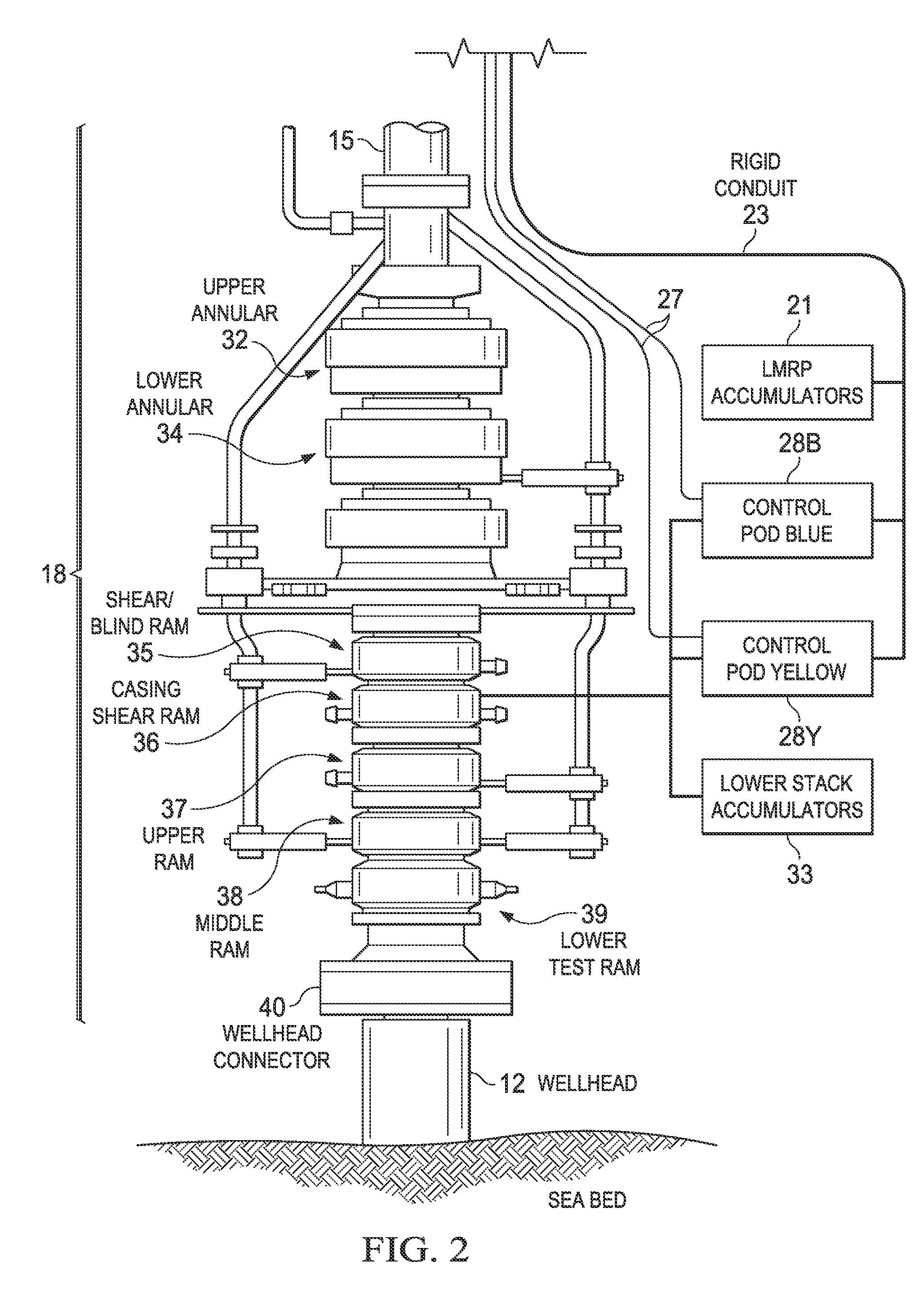
Monitoring the health of a blowout preventer
InactiveUS20120197527A1Electric/magnetic detection for well-loggingFluid removalTraffic signalDisplay device
A computerized monitoring system and corresponding method of monitoring the status and health of a blowout preventer. The system includes a graphics display at which a graphical user interface (GUI) displays the health of various sealing elements and control systems by way of “traffic light” indicators. The health indicators are evaluated, by the monitoring system, based on a risk profile for each of the indicated elements and control systems. The risk profiles are evaluated based on inputs such as measurement inputs, feedback signals, mechanical positions, diagnostic results, drilling conditions, and other status information of the blowout preventer at a given time and based on levels of redundancy and levels of deviation from normal conditions. The GUI includes recent history of changes in operating condition, and alarm indications such as poor health, along with the times of those events.
Owner:BP CORP NORTH AMERICA INC
Adaptive security for information devices
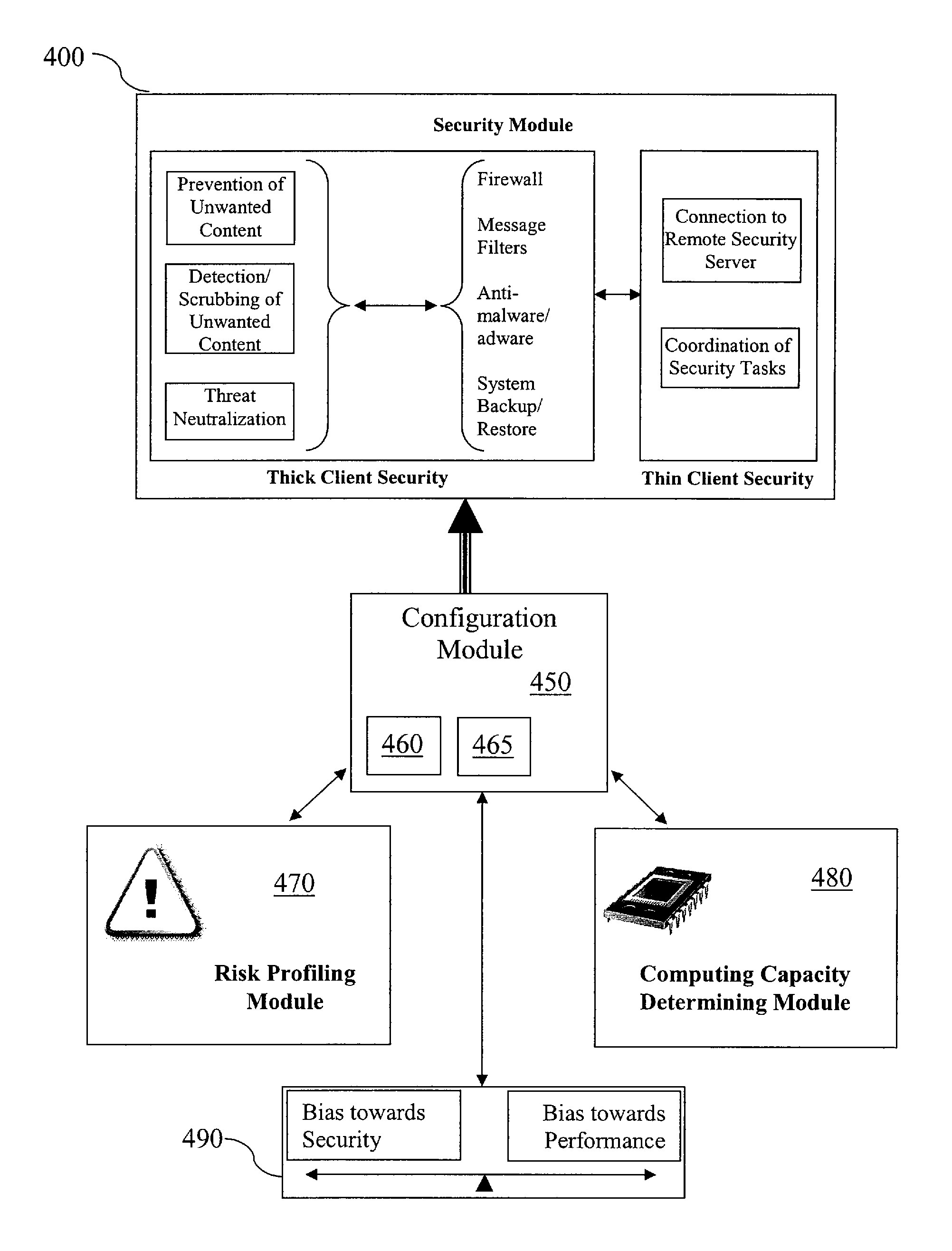
ActiveUS7584508B1Improve usabilityReduce loadMemory loss protectionError detection/correctionRisk profilingInformation device
An information device includes a dynamically configurable security module in which operational settings are automatically and dynamically configured based on risk profile or computing capacity information, or both.
Owner:AO KASPERSKY LAB
Remotely-executed medical diagnosis and therapy including emergency automation
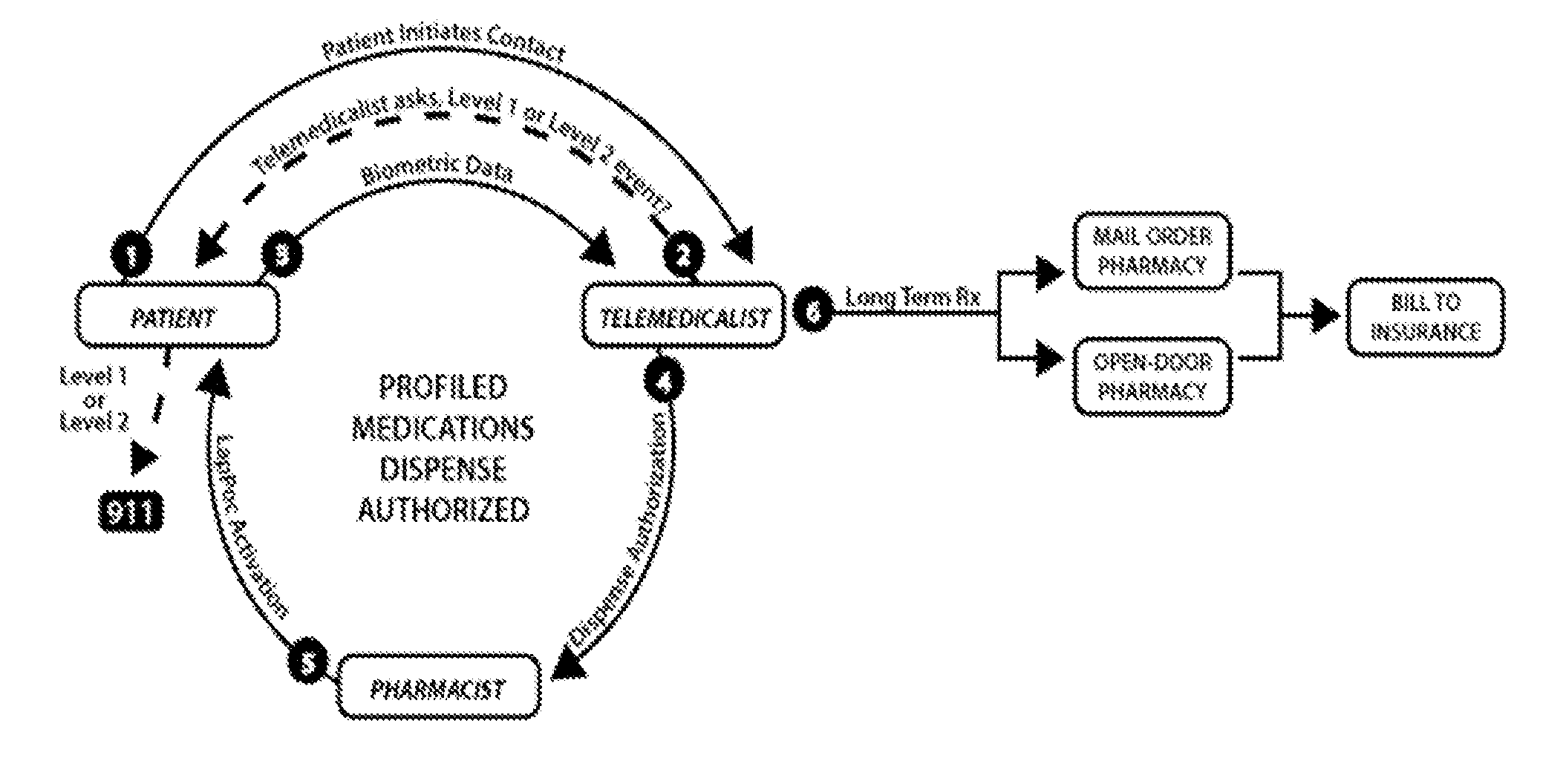
InactiveUS20140058755A1Easy accessUltrasonic/sonic/infrasonic diagnosticsDrug and medicationsRisk profilingMedical diagnosis
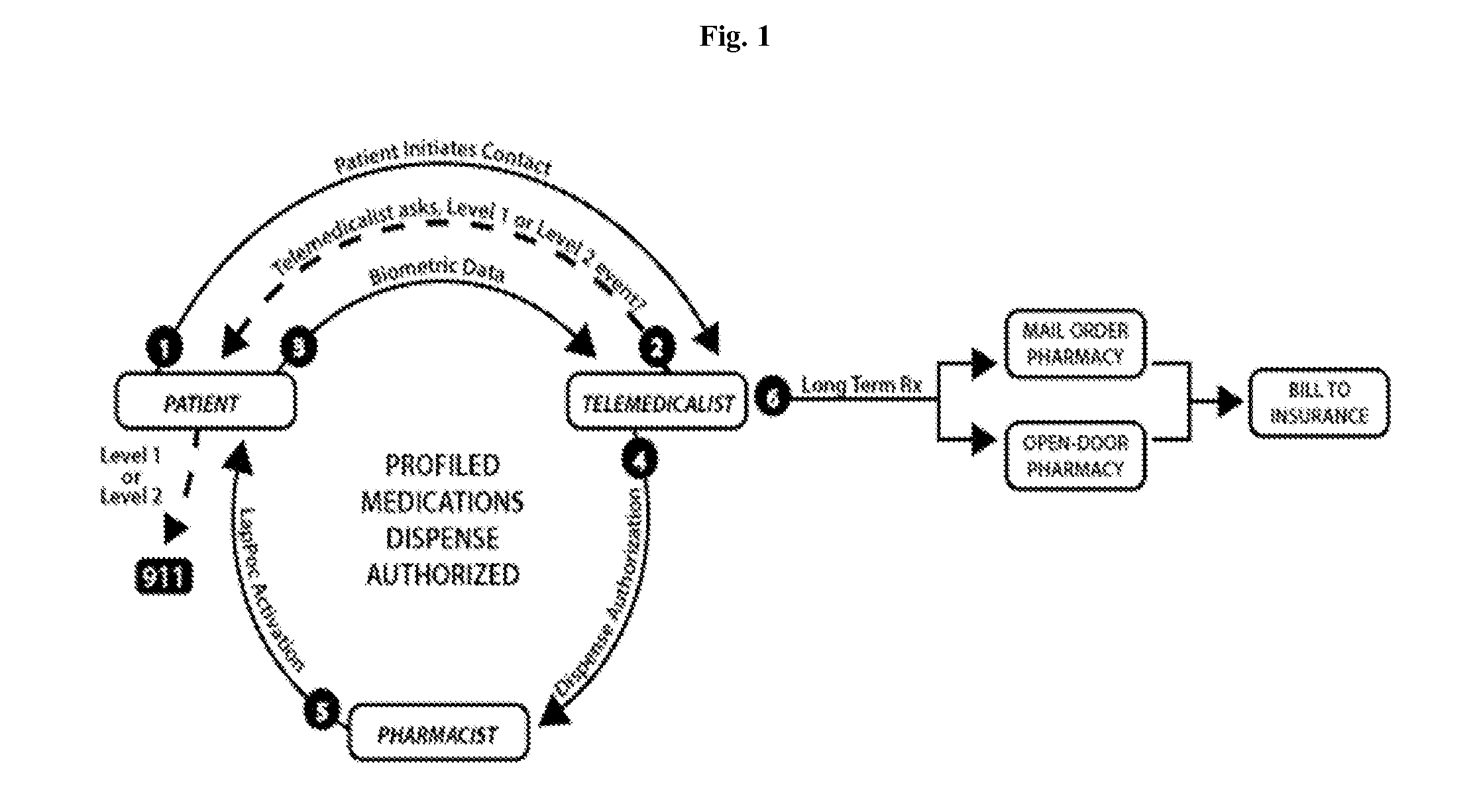
Devices, systems, methods, and software for providing remote medical diagnosis and therapy to a subject comprising: a module for conducting telecommunications with a telemedicalist; a module for applying a diagnostic or a therapeutic analysis; an apparatus for dispensing one or more medical items from an inventory of medical items, the inventory of medical items risk profiled to a subject, a population, a venue, or a situation; and optionally, a biosensor apparatus.
Owner:EXUSMED INC
Game Design Tool
InactiveUS20090100409A1Overcome problemsProvide usageApparatus for meter-controlled dispensingVideo gamesGraphicsRisk profiling
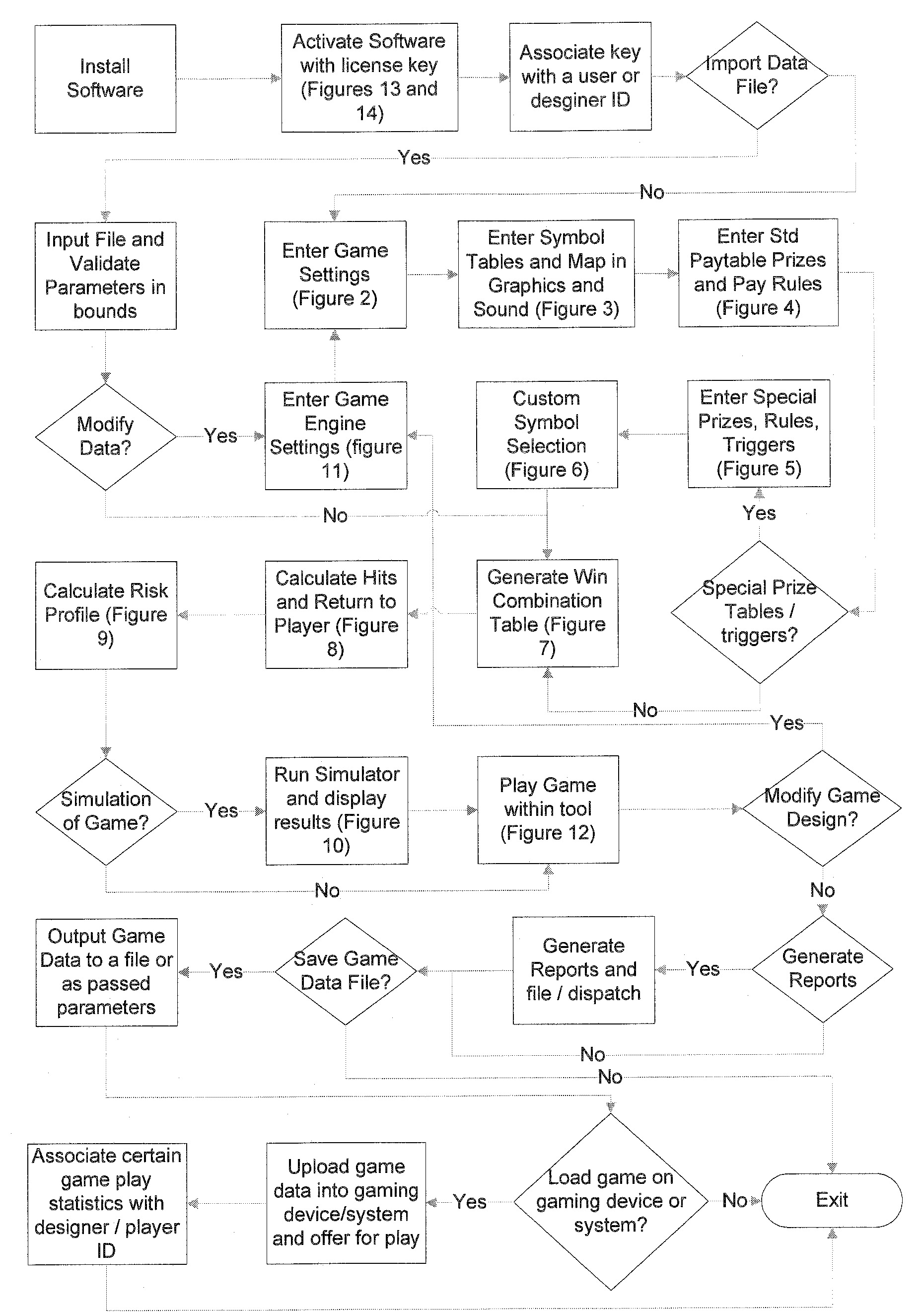
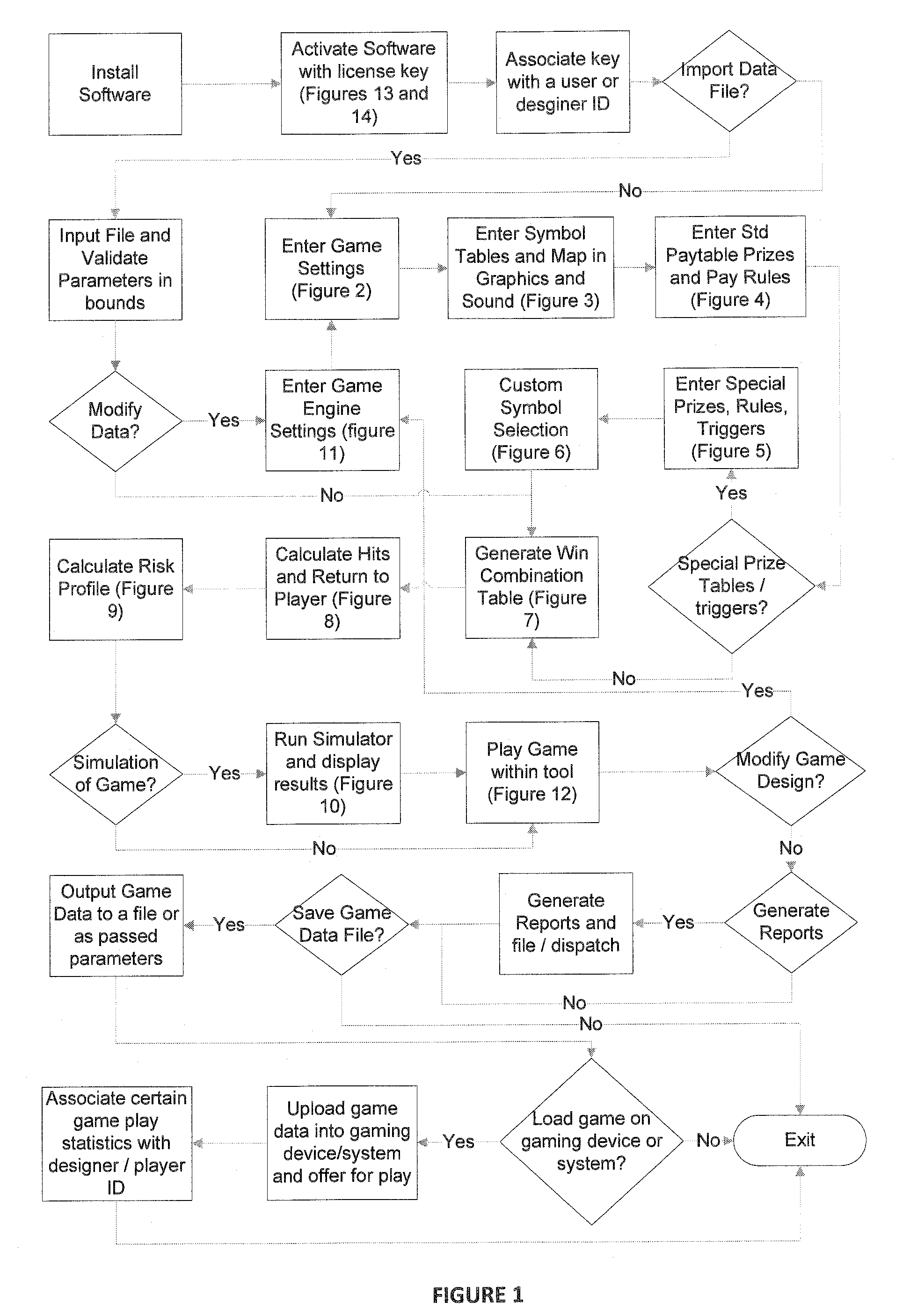
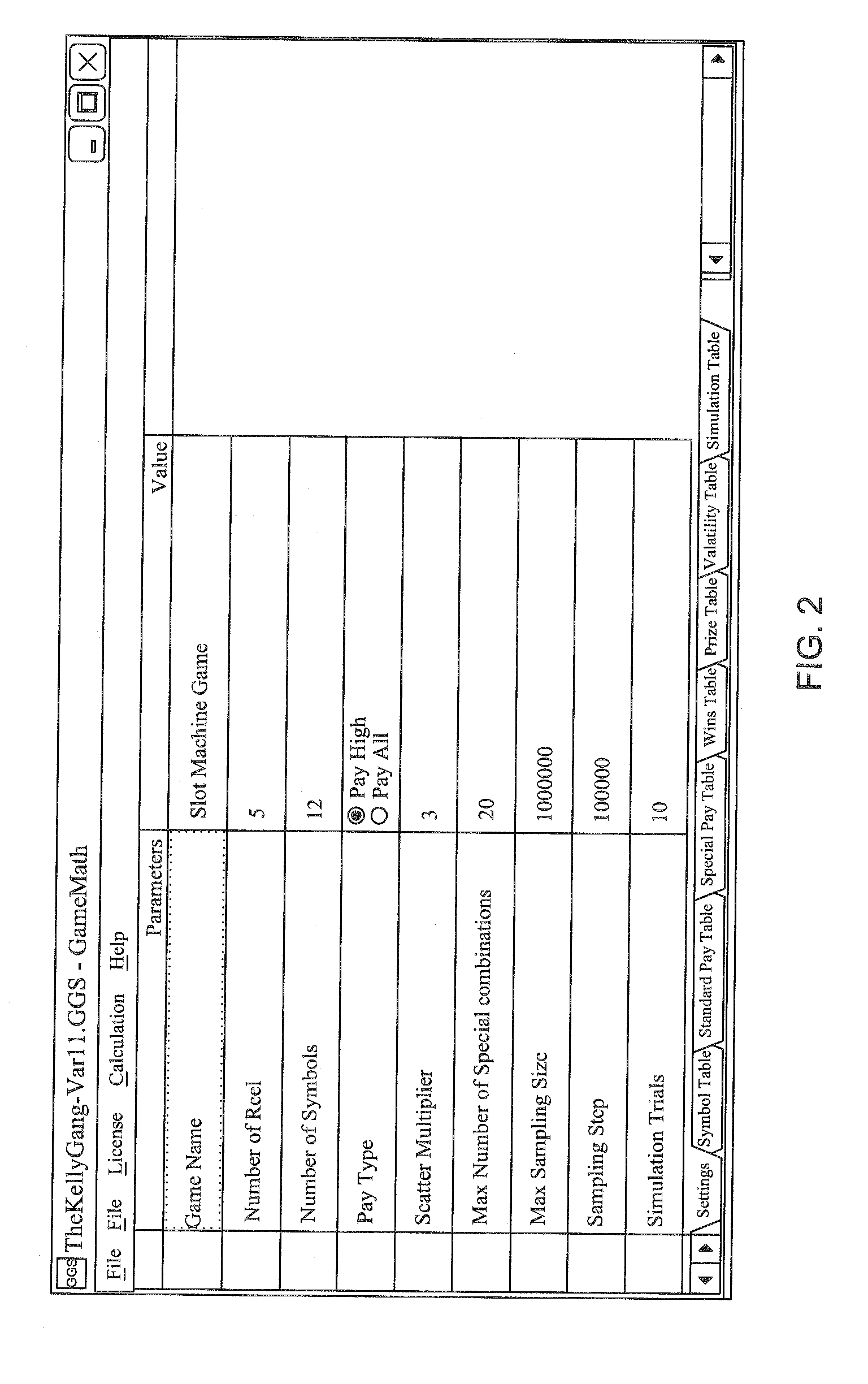
A tool is provided for designing electronic games of chance such as slot or fruit machine games. Software that runs on a computer or remote server takes user inputs and selections such as game rules, input data, and pointers to or import of files (such as sound and graphics files). The output data of such a tool may be a file or parameters that specify one or more of hit rate, return to player, pay-table, symbol mapping, symbols, game theme, risk profile, rules of game play, denomination, language, currency, display, simulation results, pay methods, triggers for game features or jackpots.
Owner:E SYNERGIES COM
Methods and systems for risk mining and for generating entity risk profiles
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; and aggregating potential risks linked to an entity to an entity risk profile (ERP). A computing device or system for mining risks includes an electronic memory; and a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with a corpus stored in the electronic memory.
Owner:REFINITIV US ORG LLC
Real-time risk management trading system for professional equity traders with adaptive contingency notification
InactiveUS20060047590A1Reduce riskIncreasing their trading volumeFinanceRisk profilingReal-time data
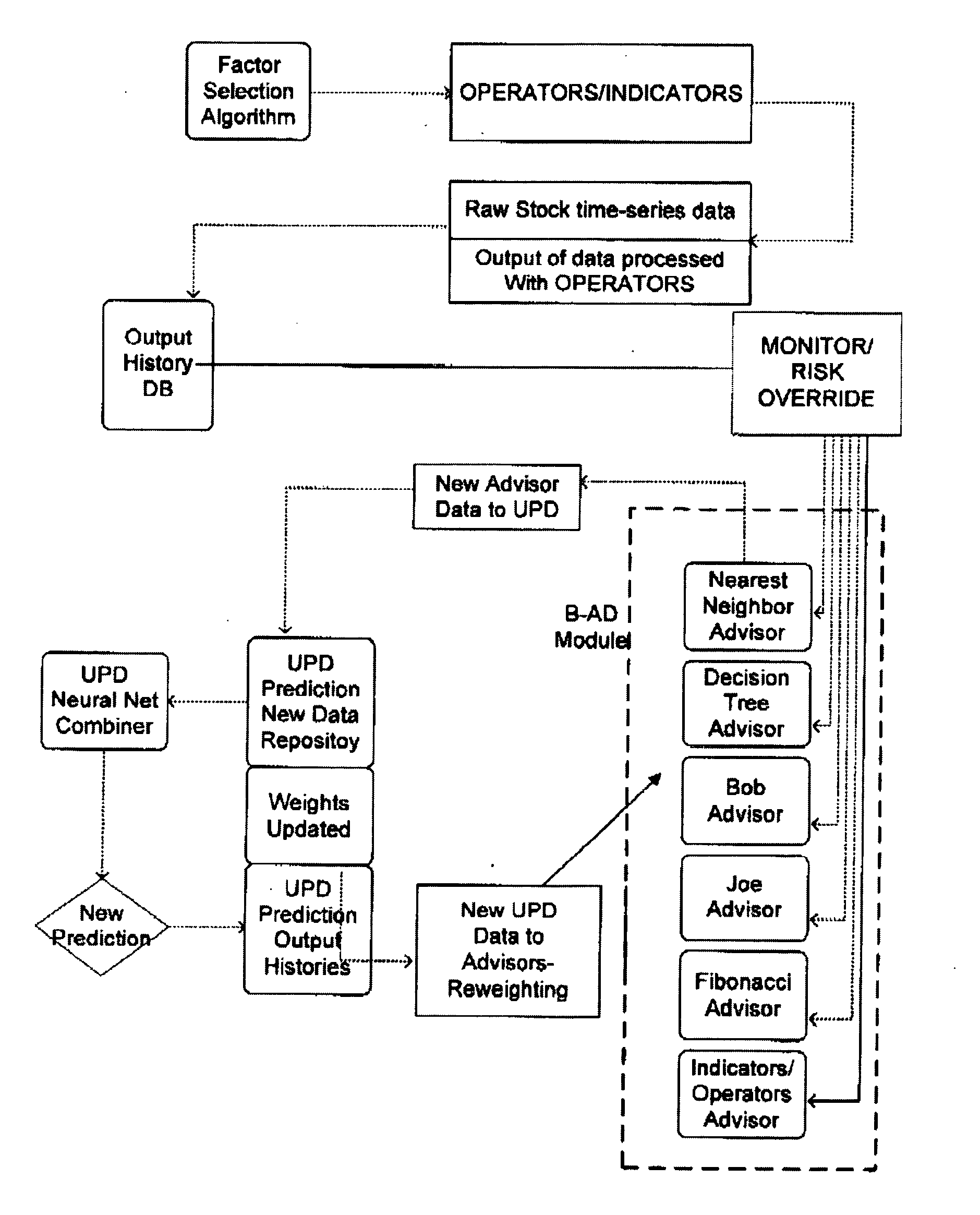
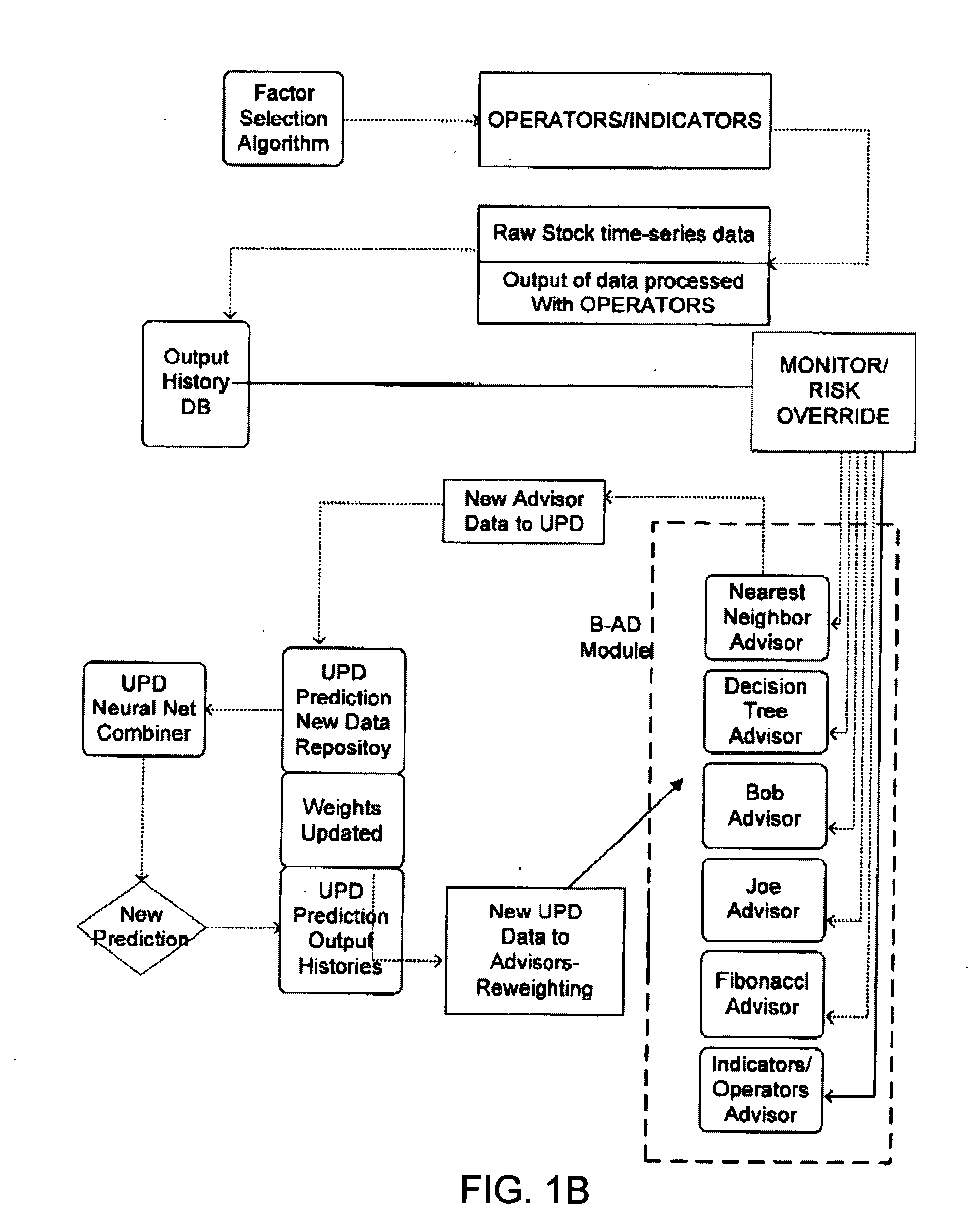
The present invention provides traders with a computer-based neural analysis system for trading commodities based on a traders risk profile, particularly equities, by providing a careful selection of the data to analyze and selecting the correct manipulation of that data. The neural analysis component uses initially selected data components or factors, by manipulating them with operators, or asset specific mathematical functions, a fuzzy or Bayesian advisors help to assist in the genetic learning of the system by being reward and punishment based on the correlation to success and failure, or meta-advisors. A contingency notification system implemented either internally or externally examines the real-time data feed to determine if conditions are such that the trader should be notified that conditions have been met, such that the risk profile requires an immediate action.
Owner:ANDERSON TIMOTHY +1
Robot safety system and a method
ActiveUS20110264266A1Improve securityProgramme-controlled manipulatorComputer controlRisk profilingEngineering
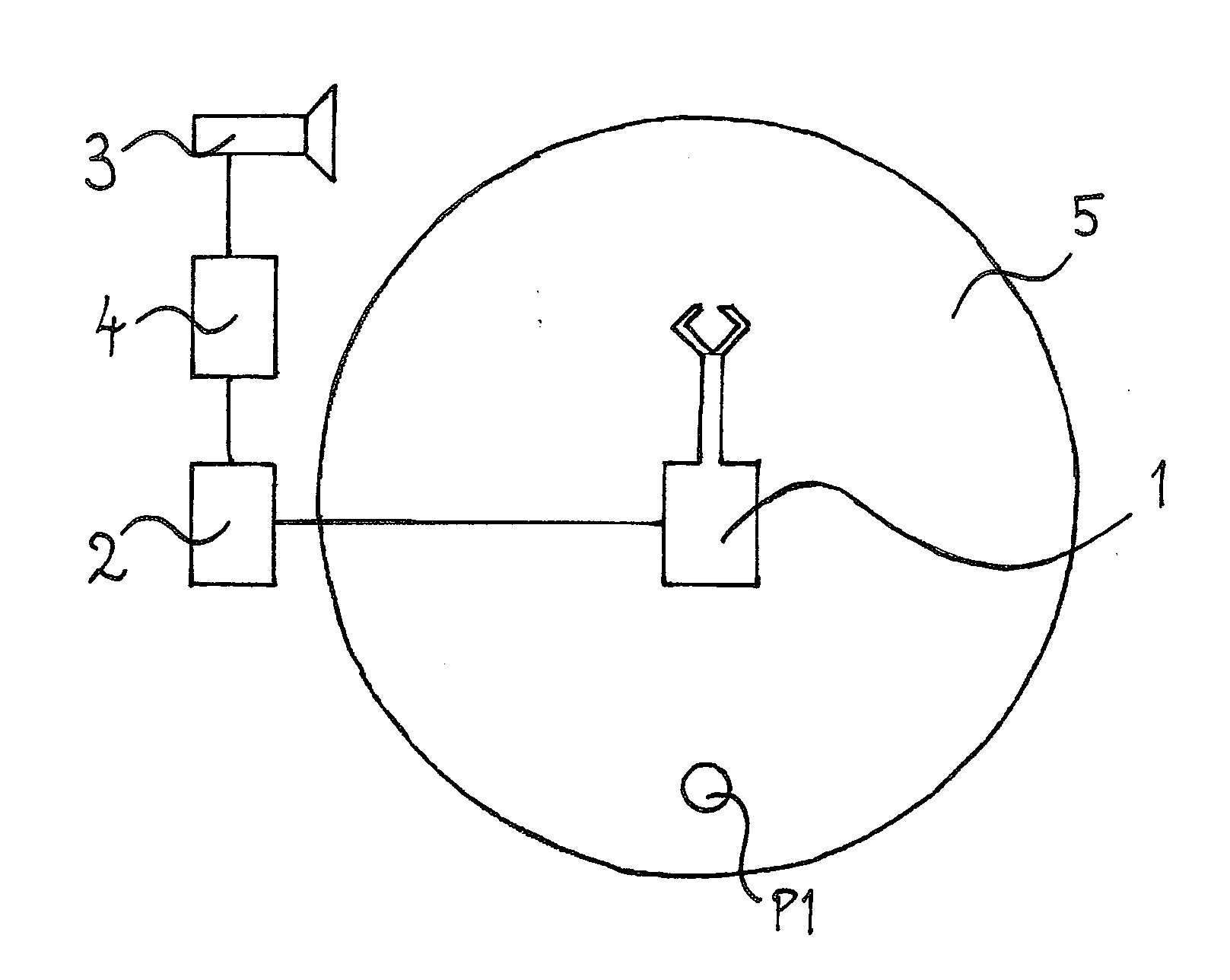
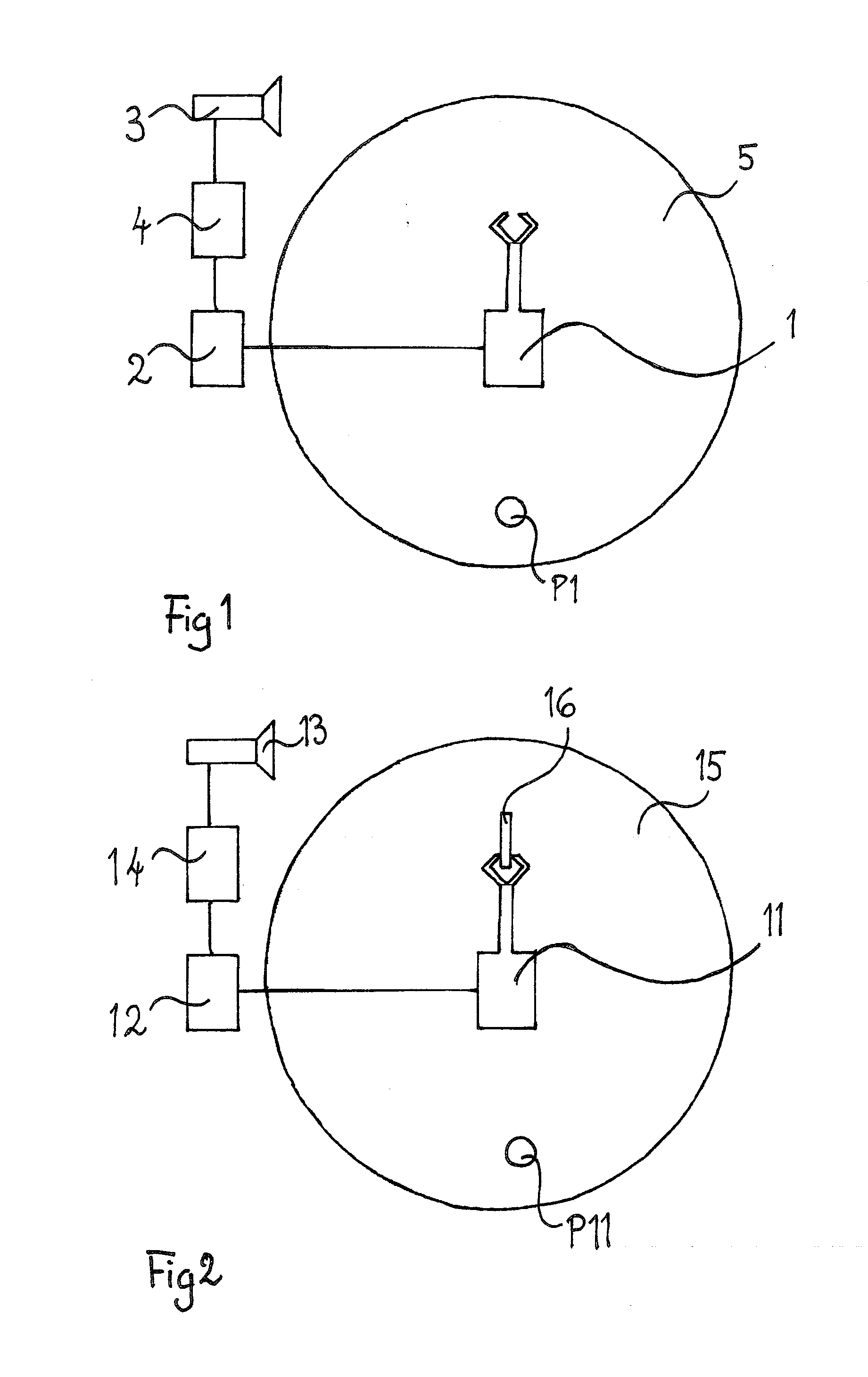
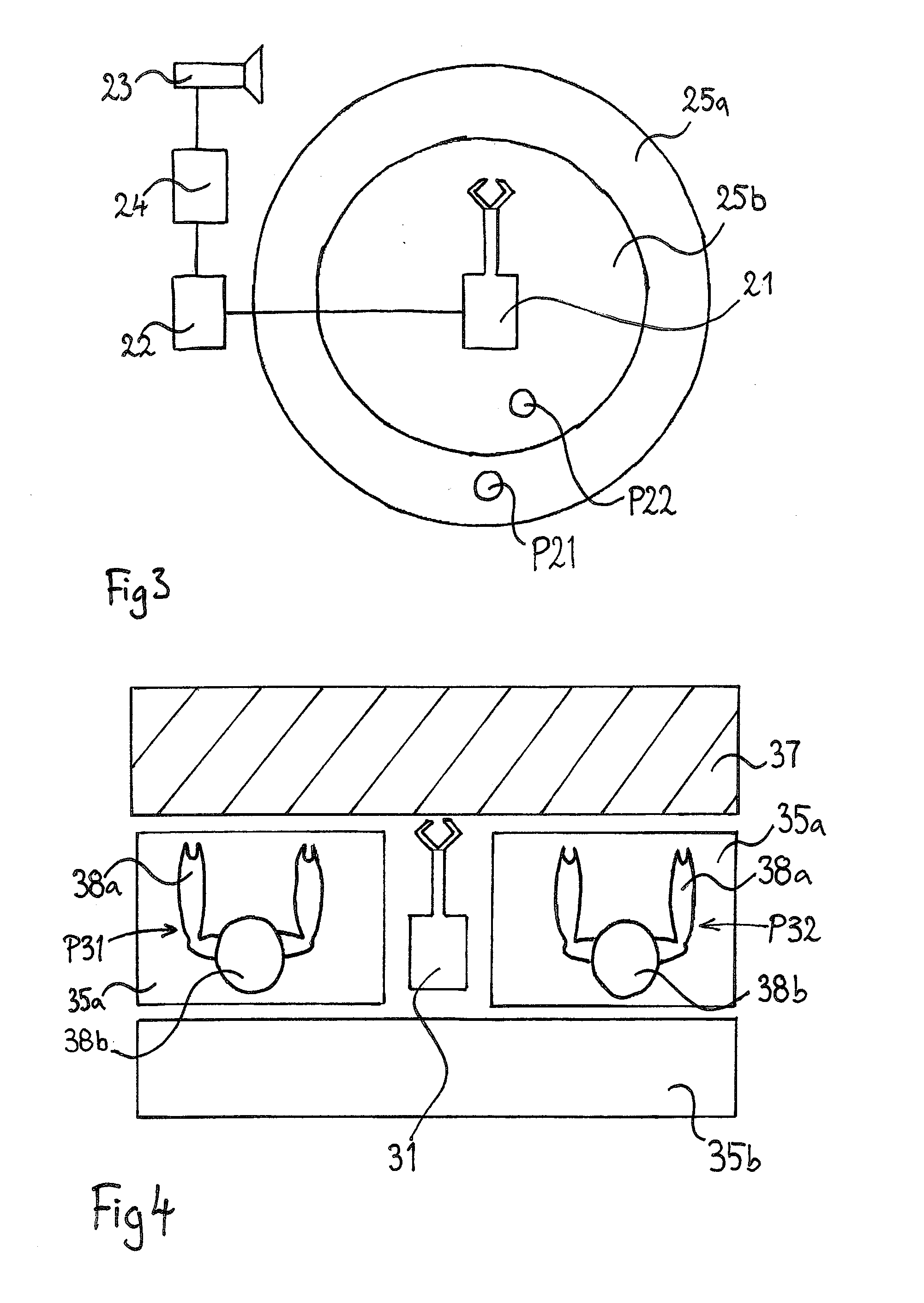
A robot safety system configured to protect humans in the vicinity of a working robot (1, 11, 21, 31) against harmful impacts by said robot (1, 11, 21, 31), said safety system comprising a sensor system (3, 13, 23) and a safety controller (4, 14, 24) configured to establish an impact risk profile of the robot (1, 11, 21, 31) and deliver an operating signal to a robot controller (2, 12, 22) based on said impact risk profile, wherein the safety controller (4, 14, 24) is configured to establish the impact risk profile based on stored data and input signals, and that the stored data and input signals comprise stored impact data, stored data related to the path of the robot (1, 11, 21, 31), and signals from the sensor system of events in the vicinity of the robot (1, 11, 21, 31), such as a detected human (P1, P11, P21, P22, P31, P32) in the vicinity of the robot (1, 11, 21, 31).
Owner:ABB (SCHWEIZ) AG
Method for evaluating system risk
A method for evaluating a system having at least one portal is provided, wherein the method includes examining the at least one portal to identify at least one accessible portal, performing a qualitative analysis responsive to the at least one accessible portal, performing a quantitative analysis responsive to the qualitative analysis and generating a risk profile responsive to the performing a qualitative analysis and the performing a quantitative analysis.
Owner:STEPHENSON PETER R
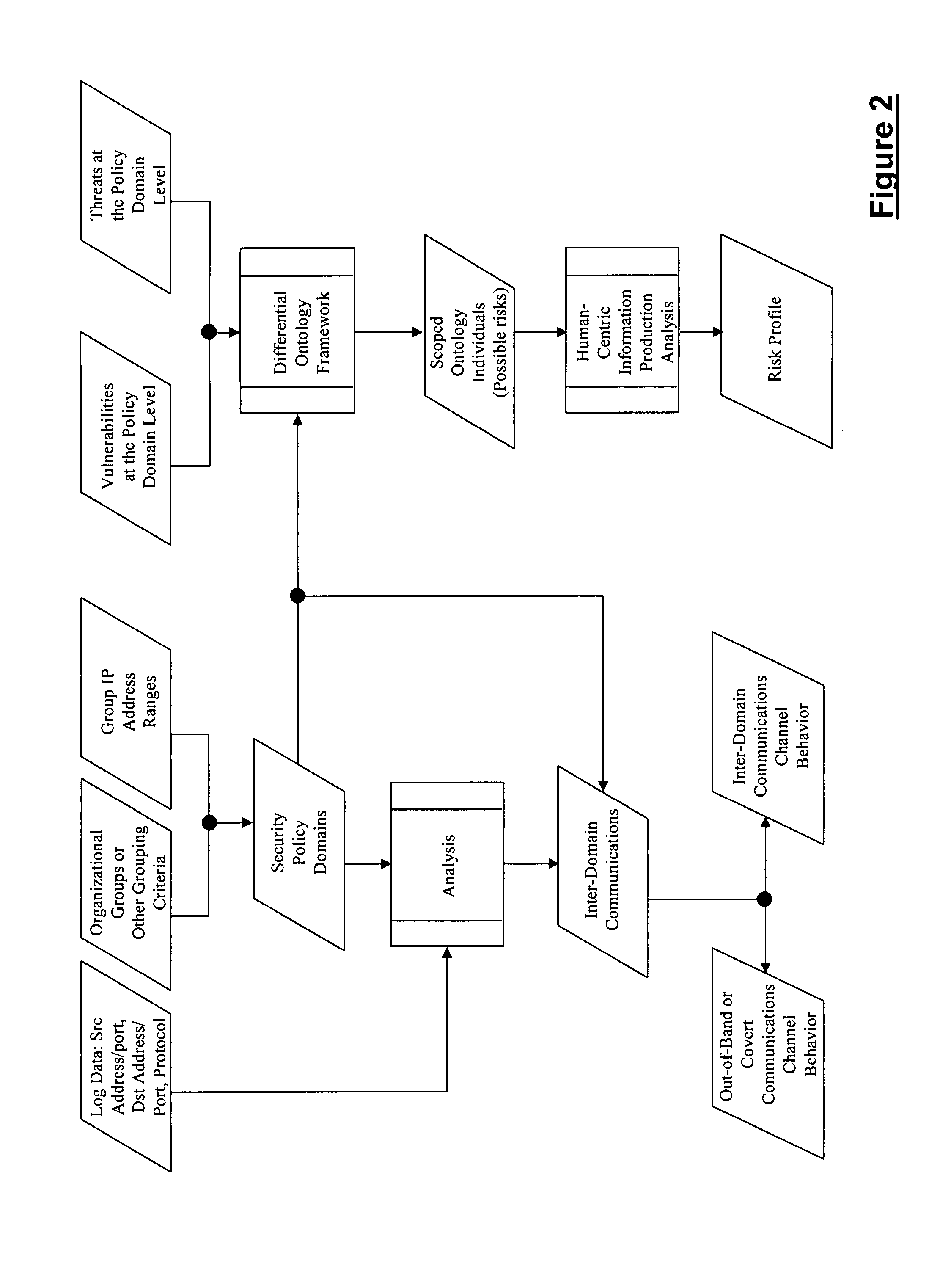
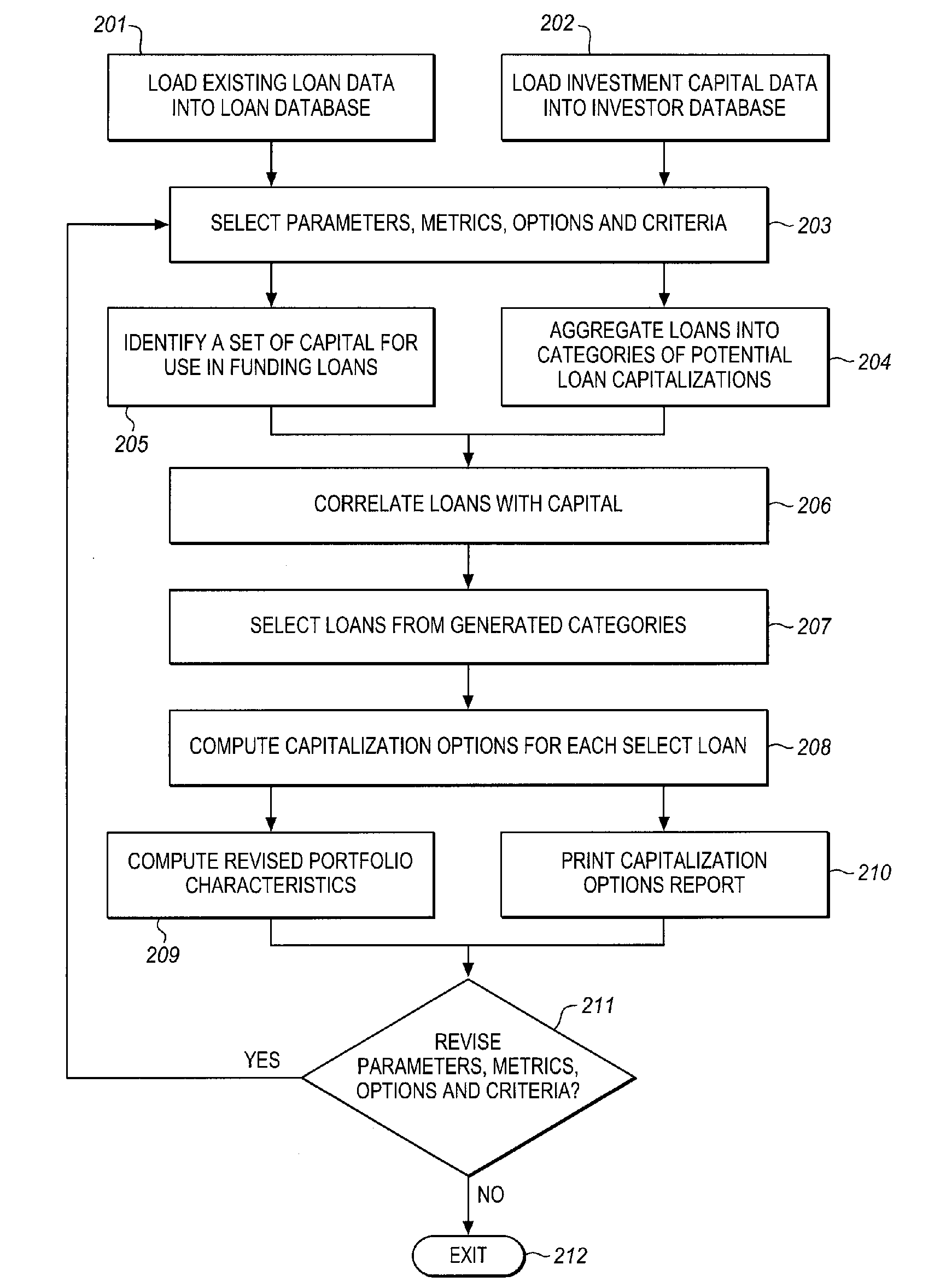
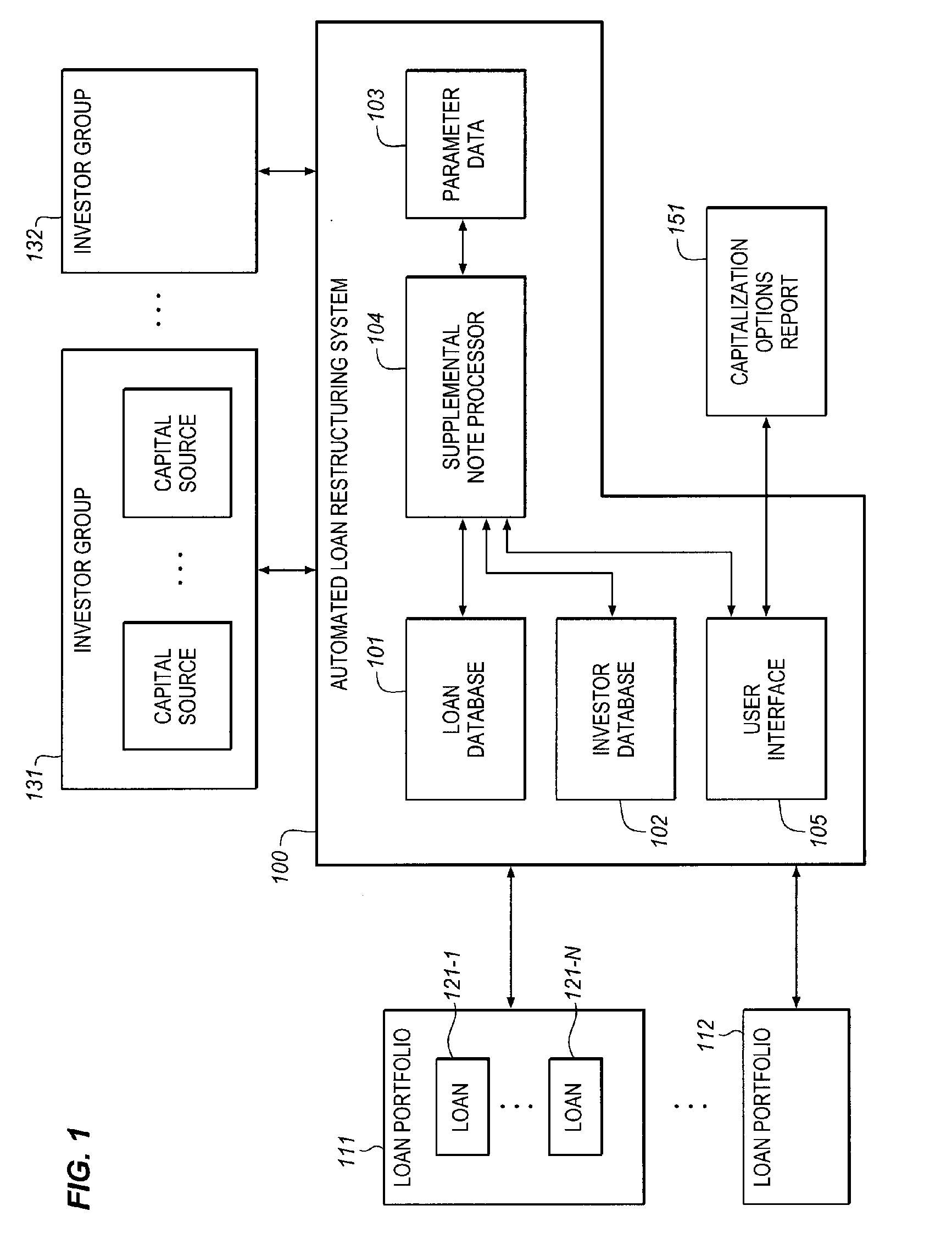
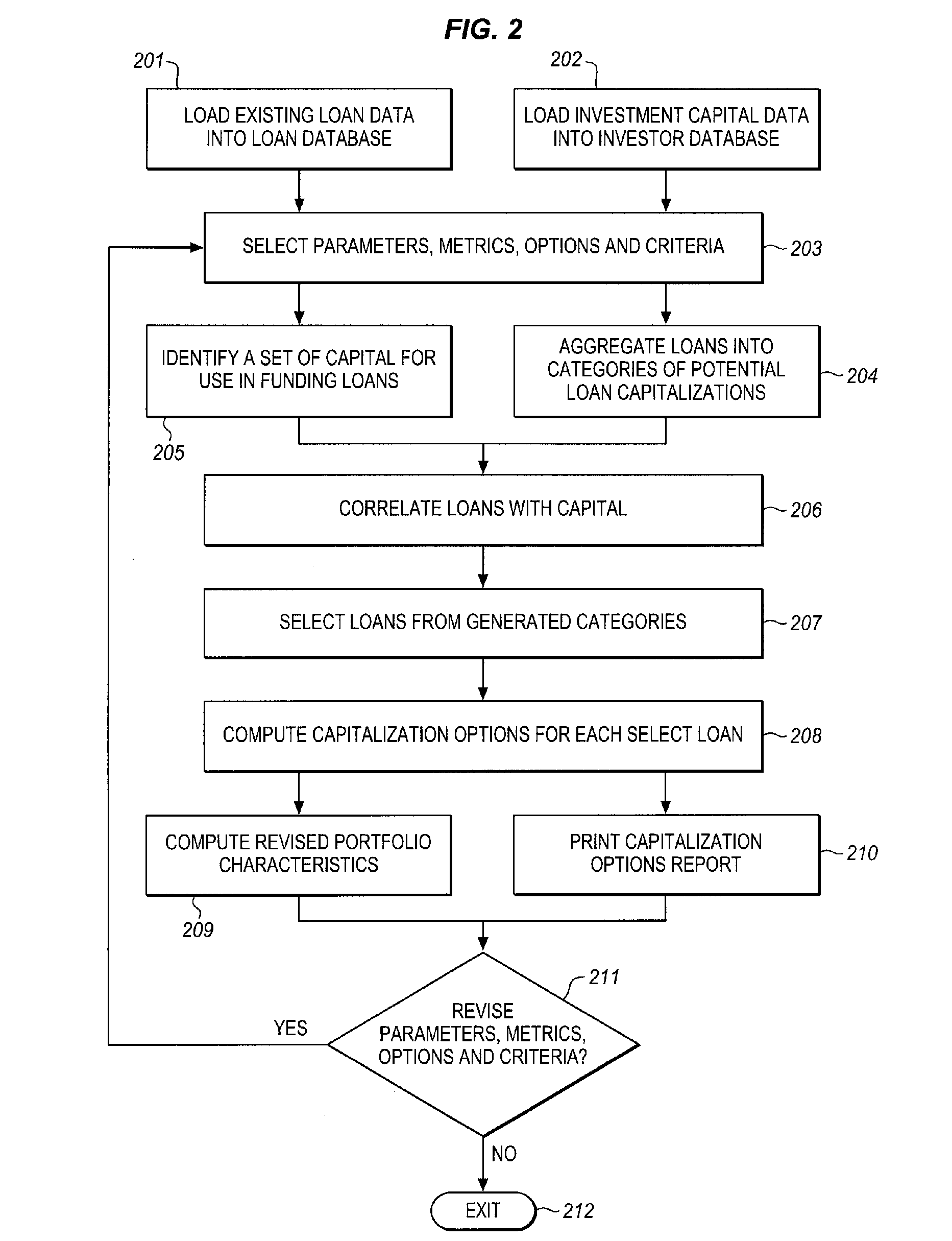
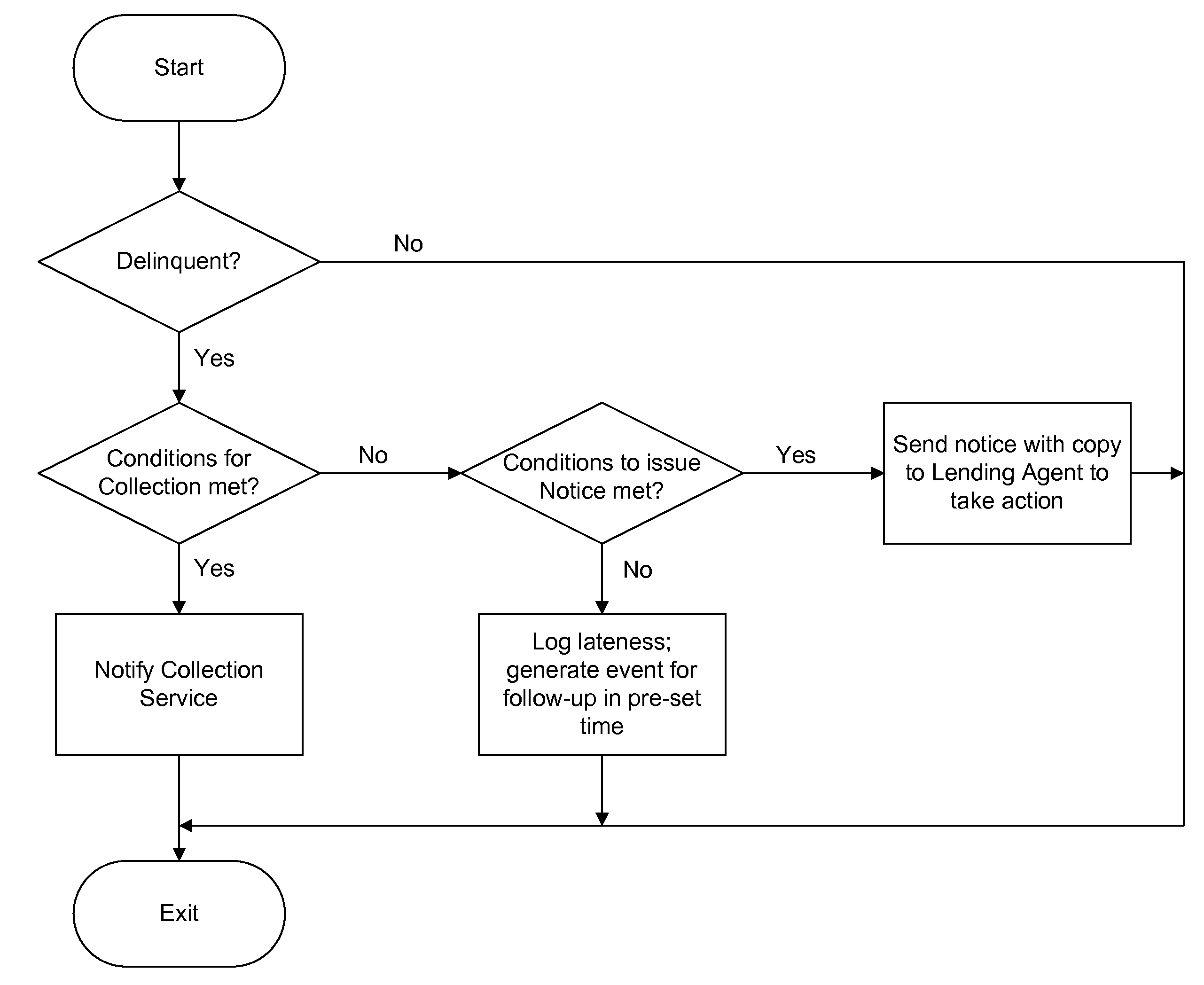
Automated system for compiling a plurality of existing mortgage loans for intra-loan restructuring of risk via capital infusion and dynamic resetting of loan terms and conditions
InactiveUS20100198743A1Facilitates extension of maturitySignificant positive effectFinanceRisk exposureRisk profiling
The CapStratix System operates on a plurality of existing loans (a “designated portfolio”), held by a regulated Lender, using a pool of capital which is available from unregulated Investors, to dynamically re-compute loan packages. The CapStratix System arranges for the disaggregation of a Lender's designated portfolio of Mortgage Loans, each into discrete note amounts, including an A Note and a “RenuNote”, both (or all) secured by the same mortgage lien. This process facilitates the extension of the maturity dates of the loans, at new market pricing, and the restatement of other terms and conditions required for a successful sale of the RenuNote to an Investor, reducing Lender's assets and risk profile, thereby having a positive effect on a Lender's regulatory capital ratios, without requiring a change to the Borrower's ownership structure or risk exposure.
Owner:CAPSTRATIX CAPITAL
Methods and systems for managing investments in complex financial investments
ActiveUS7346573B1Improve developmentFacilitate decision-makingFinanceReservationsRisk profilingEngineering
A metric, Investment Participation at Cost (IPAC) has been developed to determine the amount of money working in an investment vehicle. IPAC has particular application in a complex, private equity investment vehicle. Using IPAC, an investor can get a repeatable, readily understood indication of the amount of working money left in an investment. Further using IPAC, the investor, financial advisor or other interested party can, based on the money still working in any one or more investments, better determine the overall risk profile of an investment portfolio. An investment portfolio can be changed based on the risk profile as so determined.
Owner:GOLDMAN SACHS & CO LLC
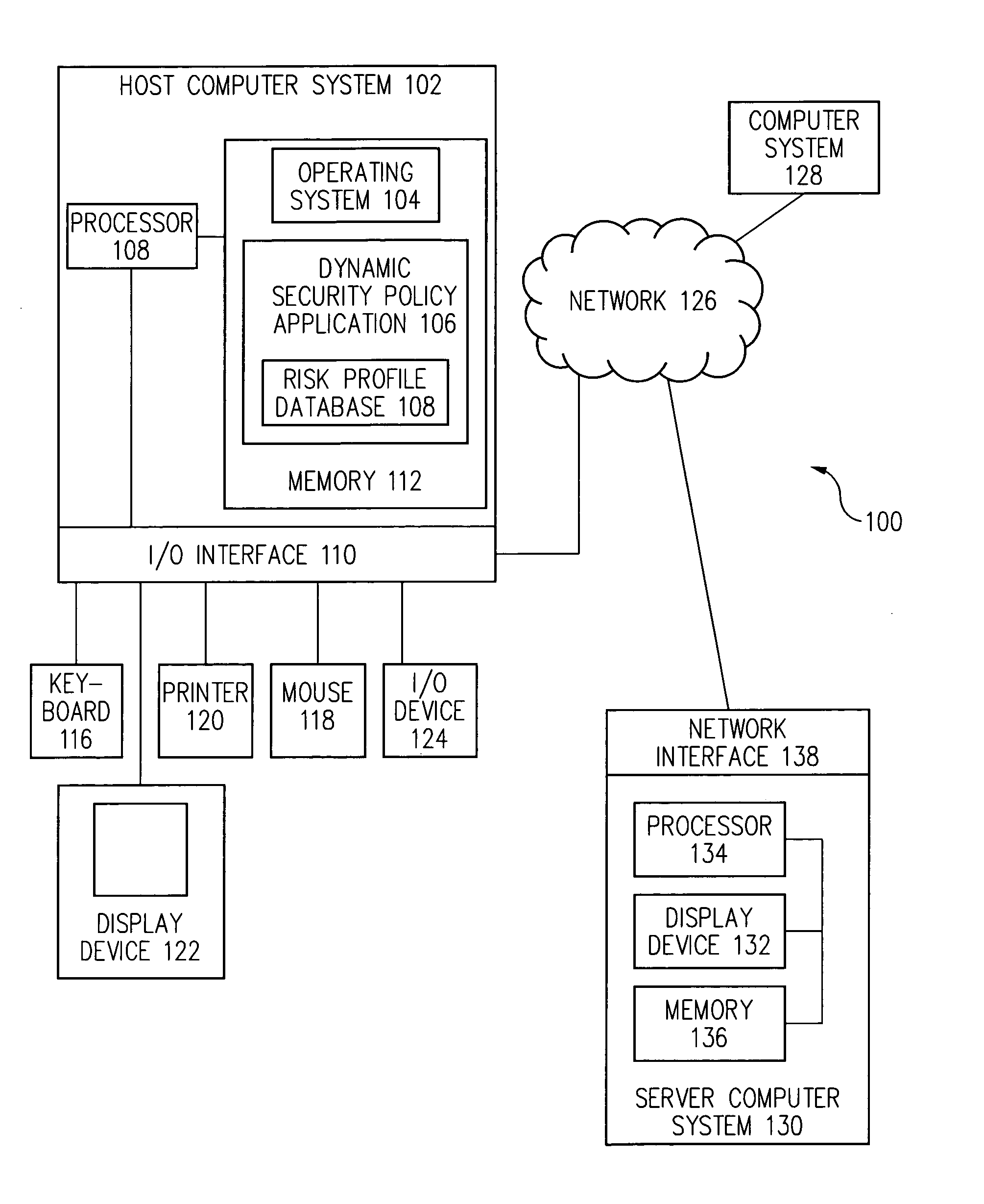
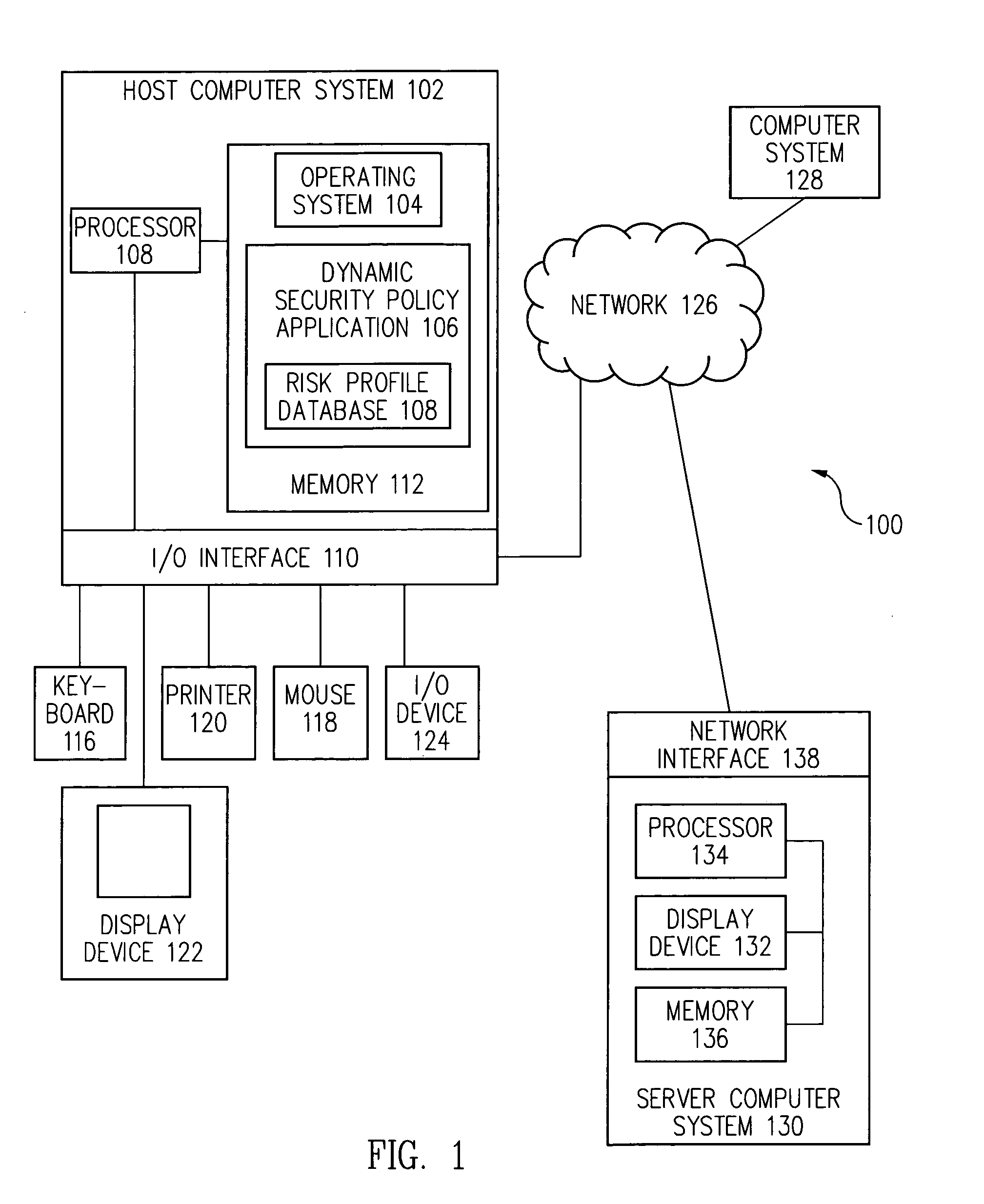
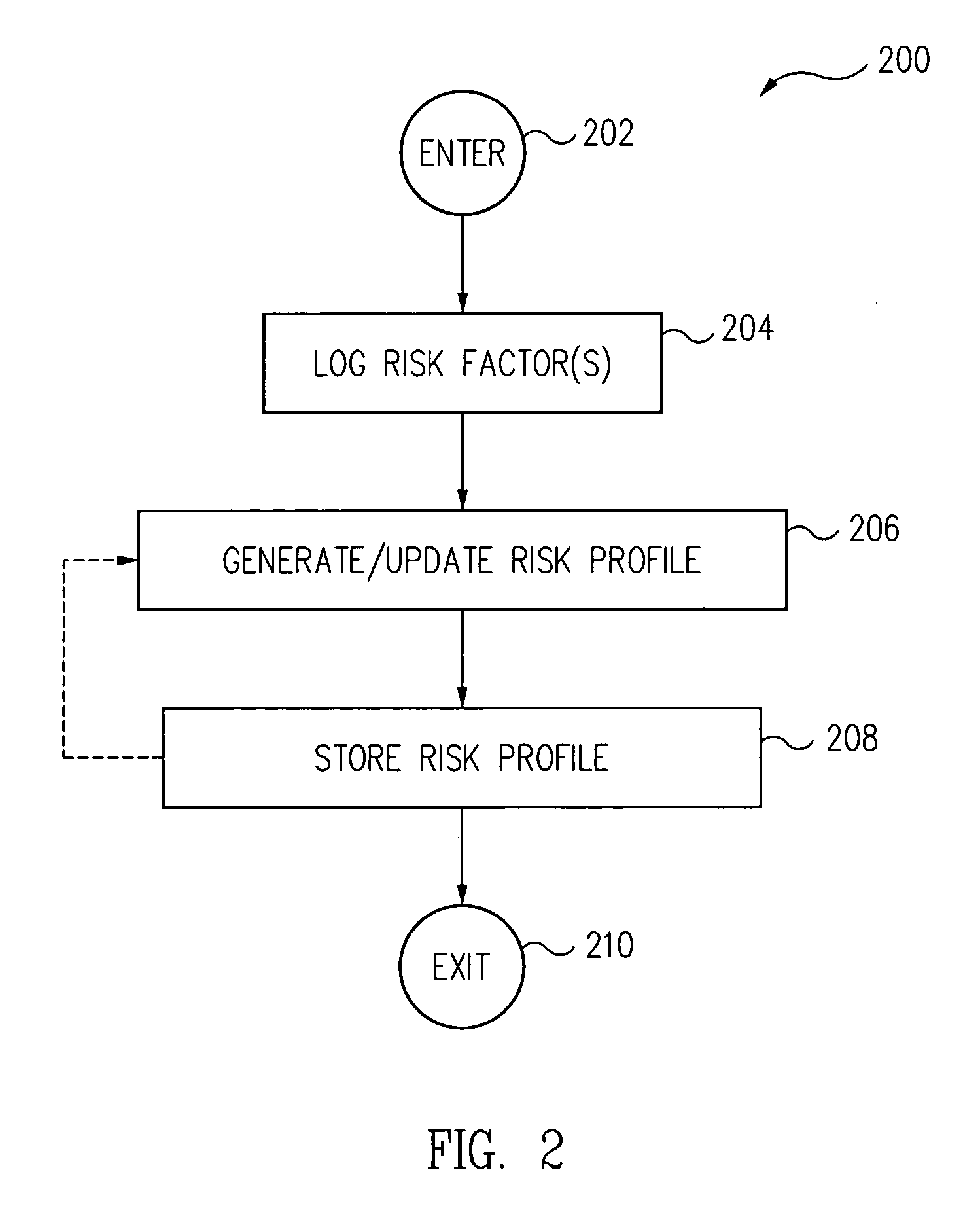
Dynamic security policy through use of empirical security events
Risk events occurring on a computer system are logged over time and a risk profile is dynamically generated and updated based on the logged risk events. In one embodiment, a security policy is dynamically set and updated based on the risk profile.
Owner:CA TECH INC
Methods and systems for risk mining and for generating entity risk profiles and for predicting behavior of security
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; aggregating potential risks linked to an entity to an entity risk profile (ERP); and predicting a movement in a security associated with an entity.
Owner:REFINITIV US ORG LLC
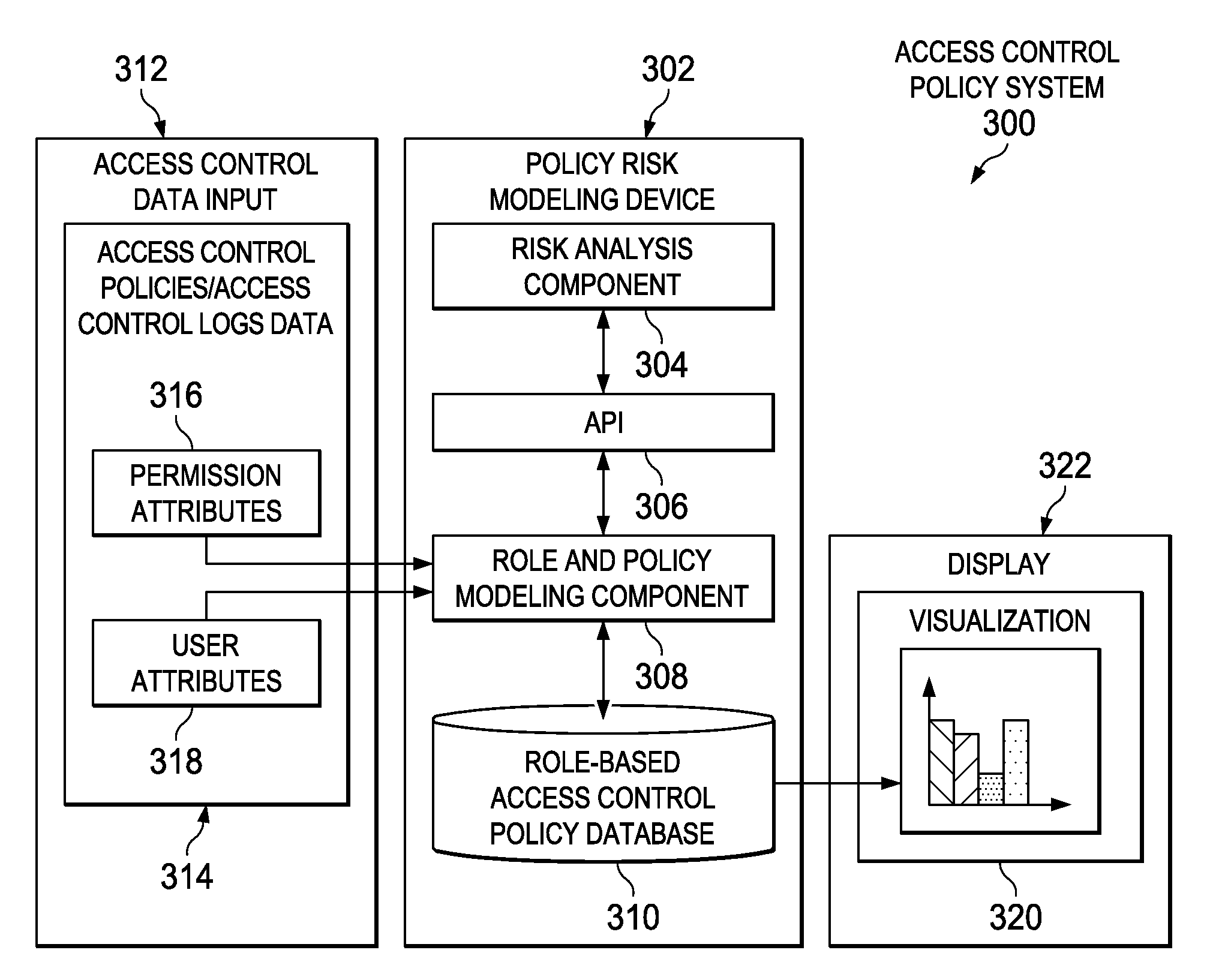
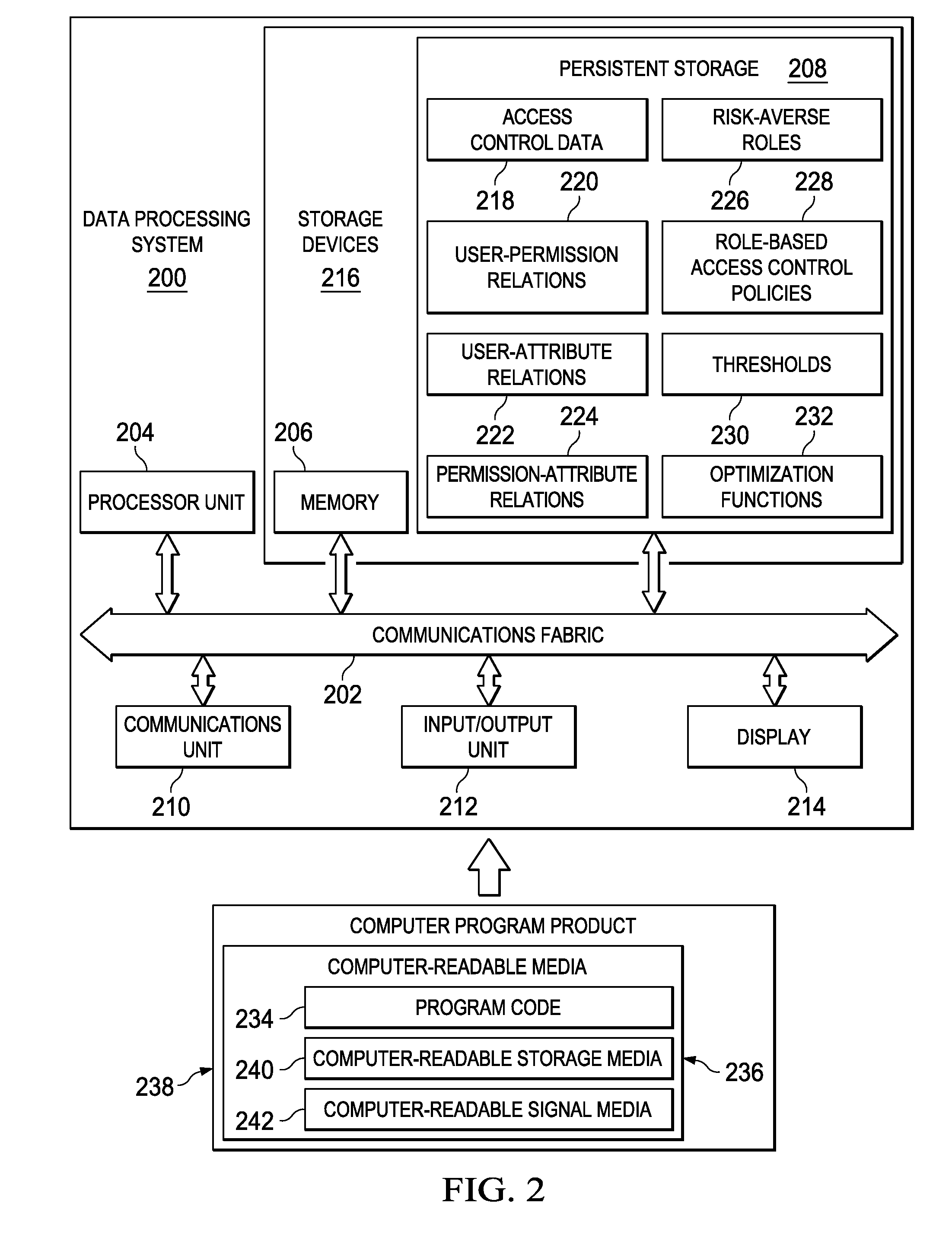
Generating role-based access control policies based on discovered risk-averse roles
InactiveUS20140196104A1Minimize risk profileMinimizes risk profileTransmissionSpecial data processing applicationsUser PrivilegeRisk profiling
Generating role-based access control policies is provided. A user-permission relation is generated by extracting users and permissions assigned to each of the users from a stored access control policy. A user-attribute relation is generated by mapping the users to attributes describing the users. A permission-attribute relation is generated by mapping the permissions to attributes describing the permissions. The set of risk-averse roles, assignment of the set of risk-averse roles to the users, and assignment of the permissions to the set of risk-averse roles are determined based on applying a risk-optimization function to the generated user-permission relation, the generated user-attribute relation, and the generated permission-attribute relation. A role-based access control policy that minimizes a risk profile of the set of risk-averse roles, the assignment of the set of risk-averse roles to the users, and the assignment of the permissions to the set of risk-averse roles is generated.
Owner:IBM CORP
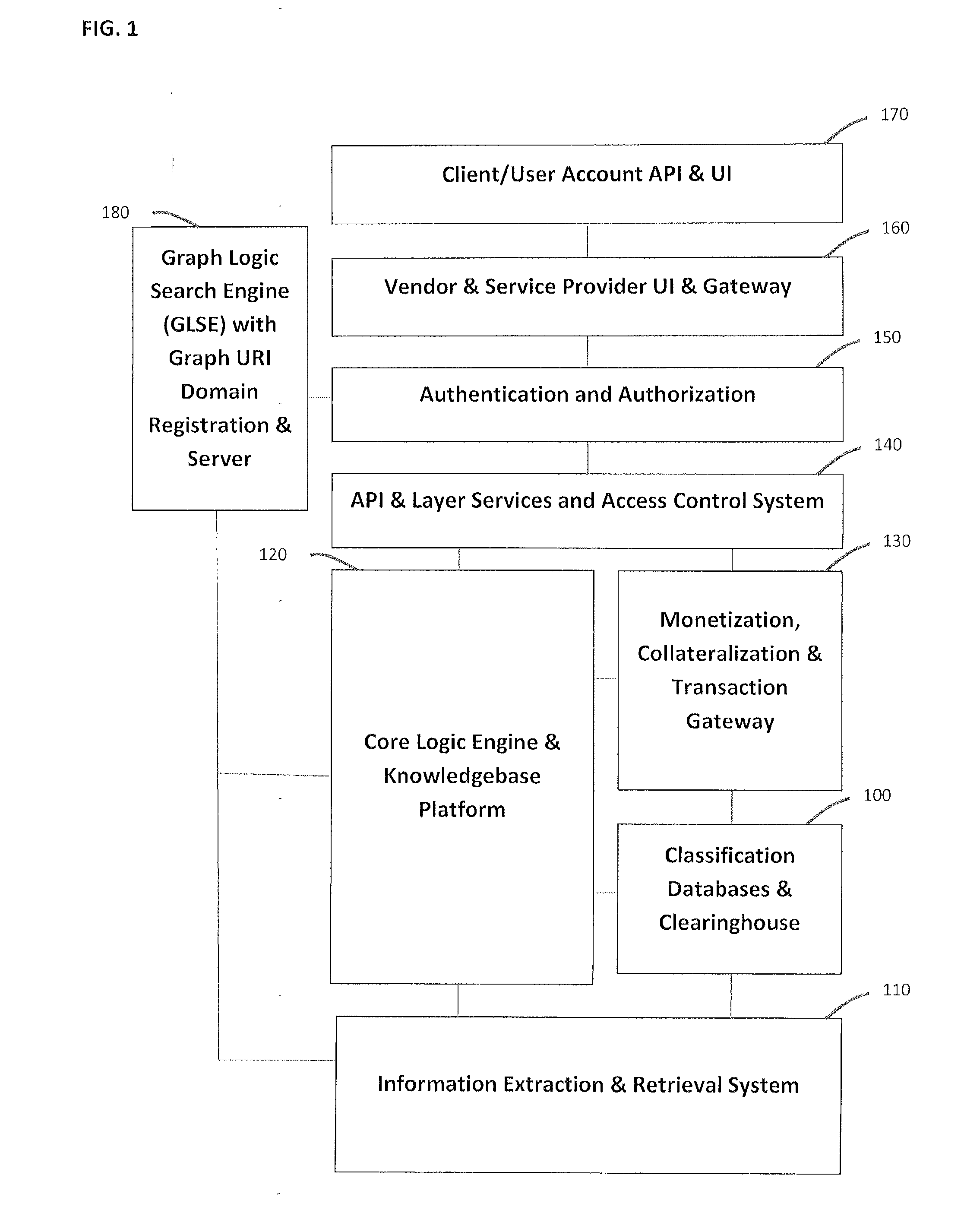
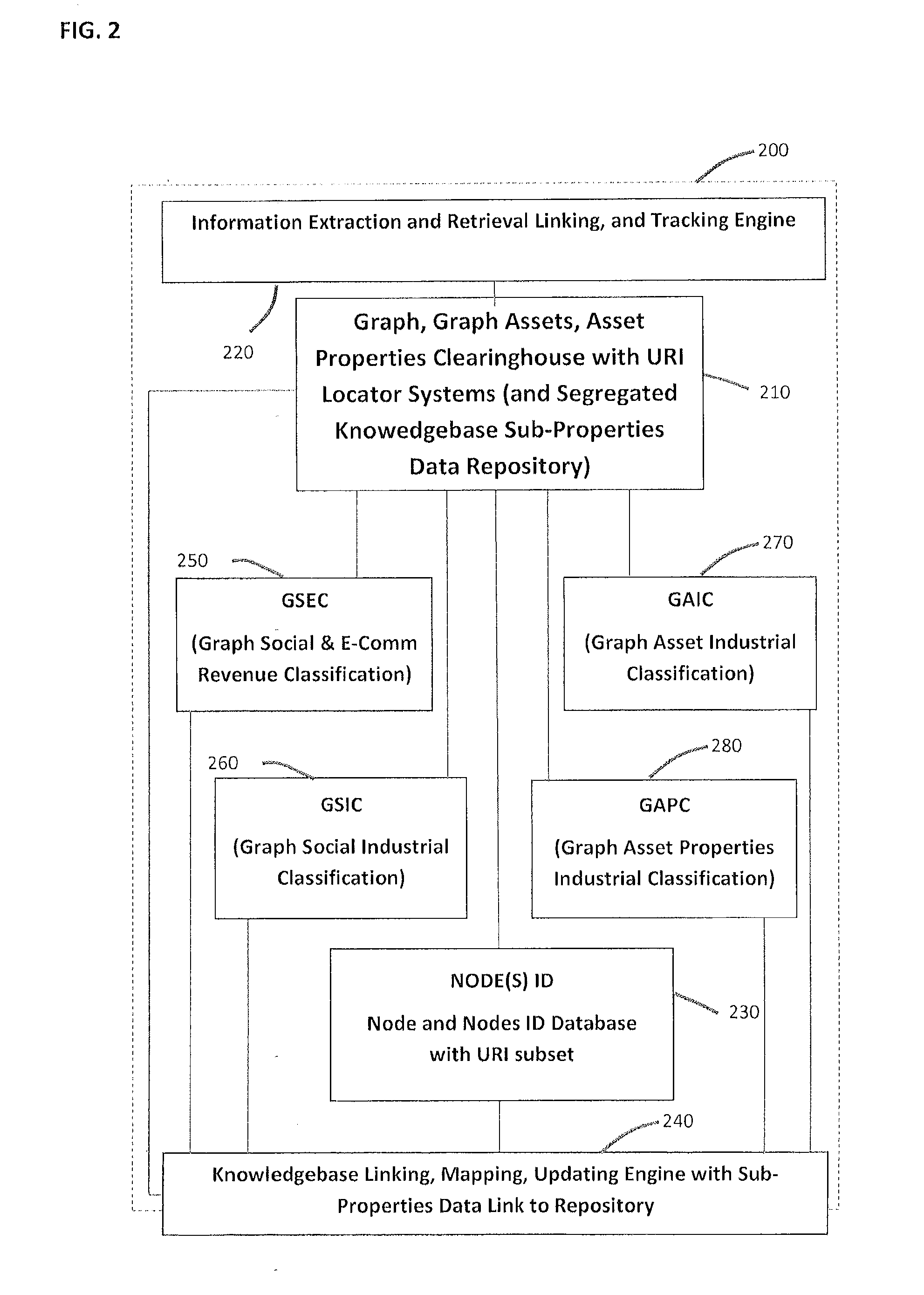
System and method for social graph and graph assets valuation and monetization
InactiveUS20130290226A1Digital computer detailsKnowledge representationReal time analysisContent analytics
A system and method to provide social and graph credit scoring, valuation and monetization. The valuation and monetization system provides users, service providers and other agents with a credit scoring and rating system. An application programming interface provides a platform for integration of all types of financial, business and personal services into the logic and classification infrastructure. A graph assets and collateralization clearinghouse creates a secure platform for collateralization. The graph assets information database provides core classification services for ranking, indexing, and content analysis. In a specific embodiment a financial services provider utilizes the social credit scoring, valuation and monetization platform to process and approve qualified credit line applicants. Approval is primarily based on graph and valuation metrics provided by the system and includes an e-commerce and social metrics real time analysis for knowledge of an applicant's future and present risk profile, including credit and graph properties risks.
Owner:DOKKEN MAYNARD
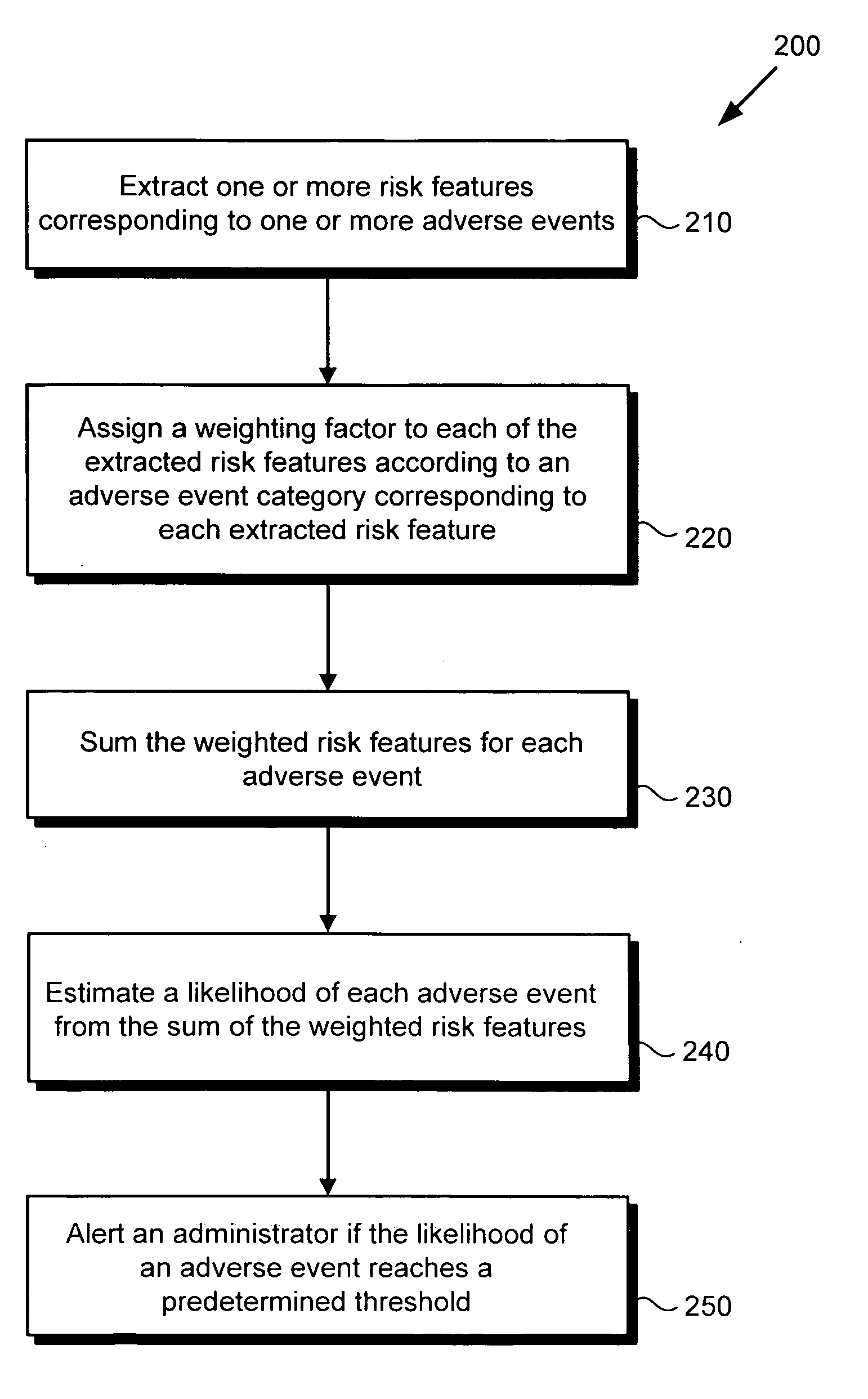
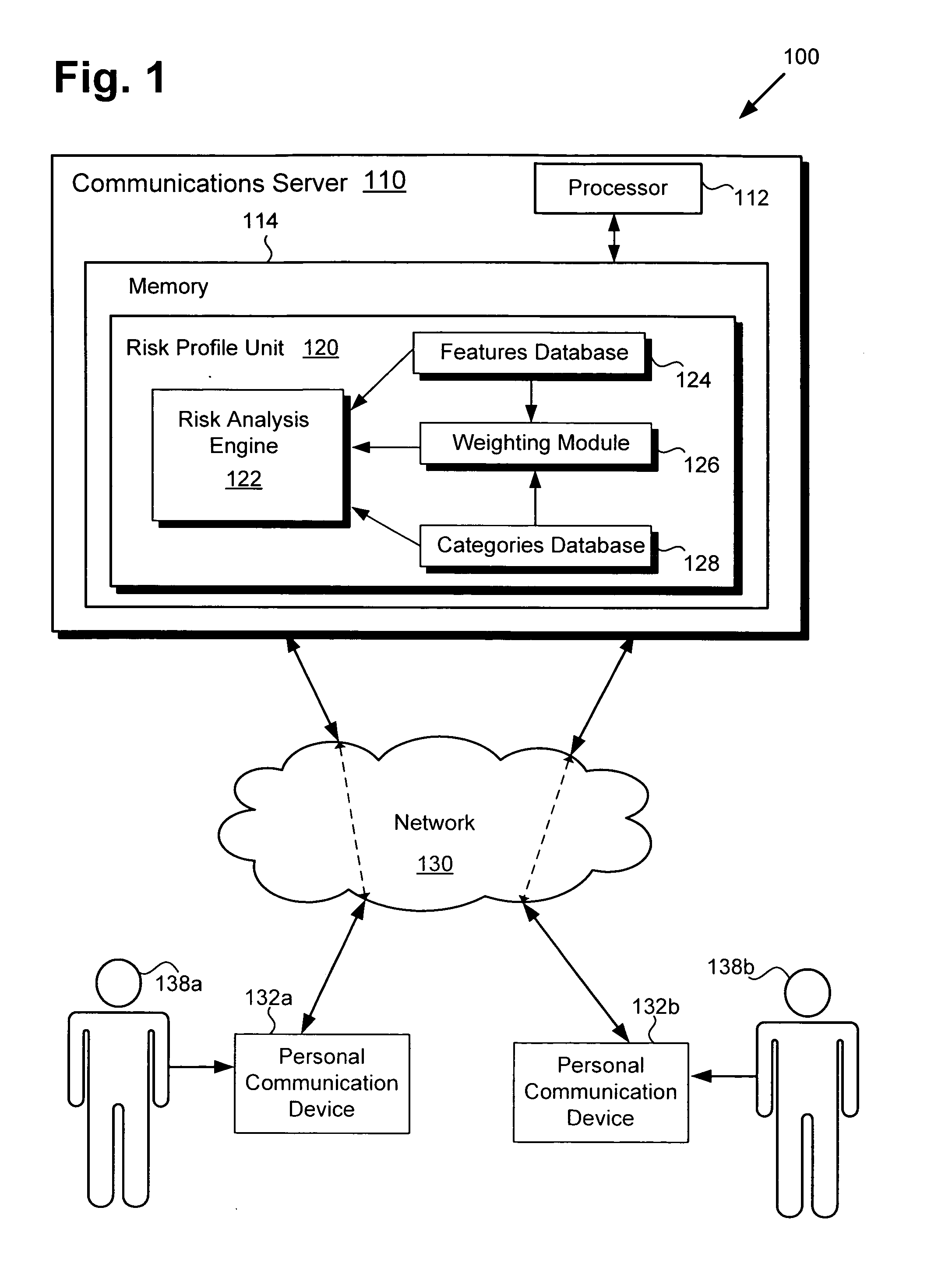
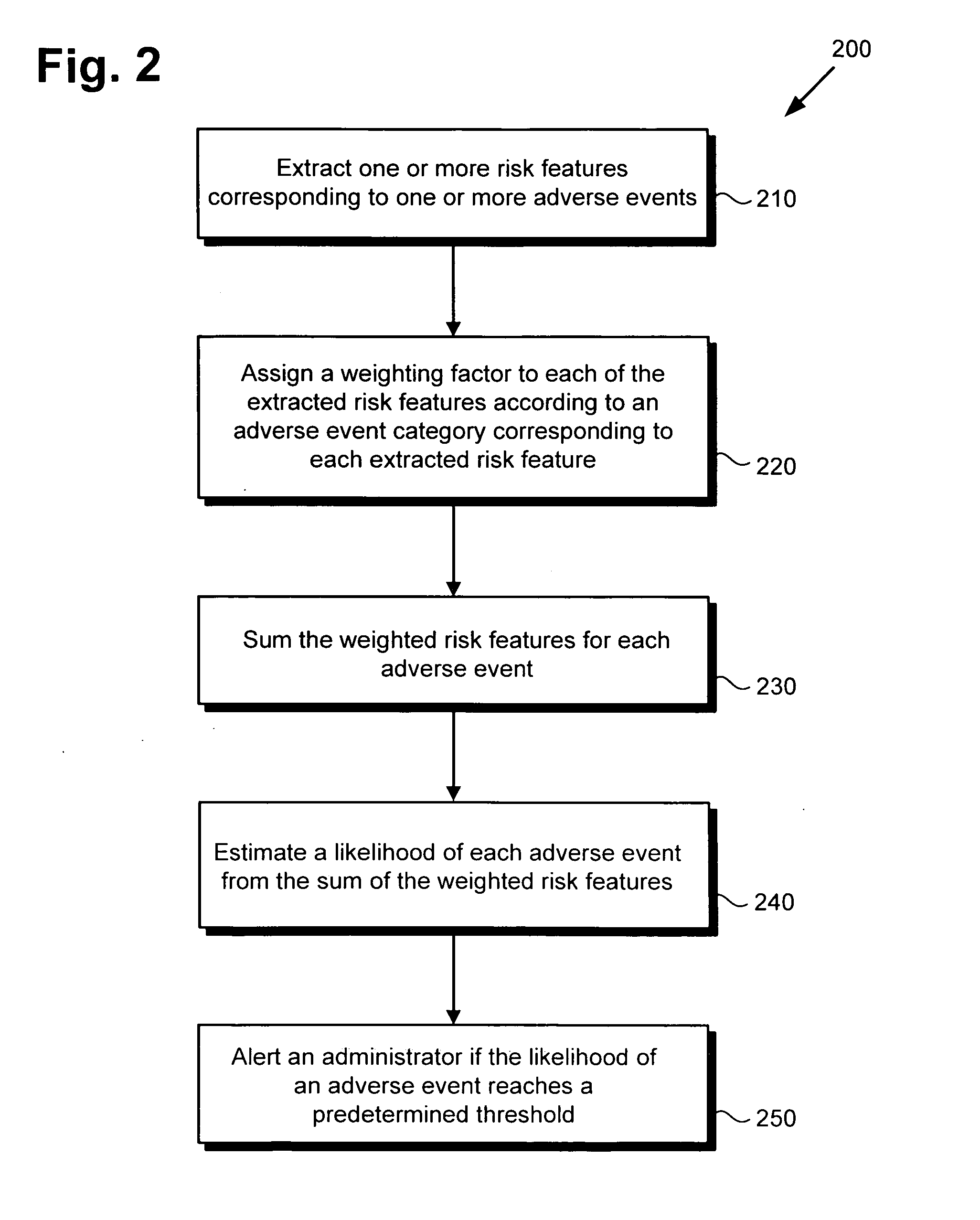
Risk profiling system and method
There is provided a risk profiling system and method. The risk profiling system comprises a system processor, a system memory storing a risk profile unit configured to be controlled by the processor. The risk profile unit includes a risk features database comprising a plurality of risk features corresponding to the adverse event, an aggregation module configured to group risk features detected by the risk profiling system, and a risk analysis engine configured to estimate the likelihood of the adverse event from the grouped risk features.
Owner:DISNEY ENTERPRISES INC
System, computer program, and method of cooperative response to threat to domain security
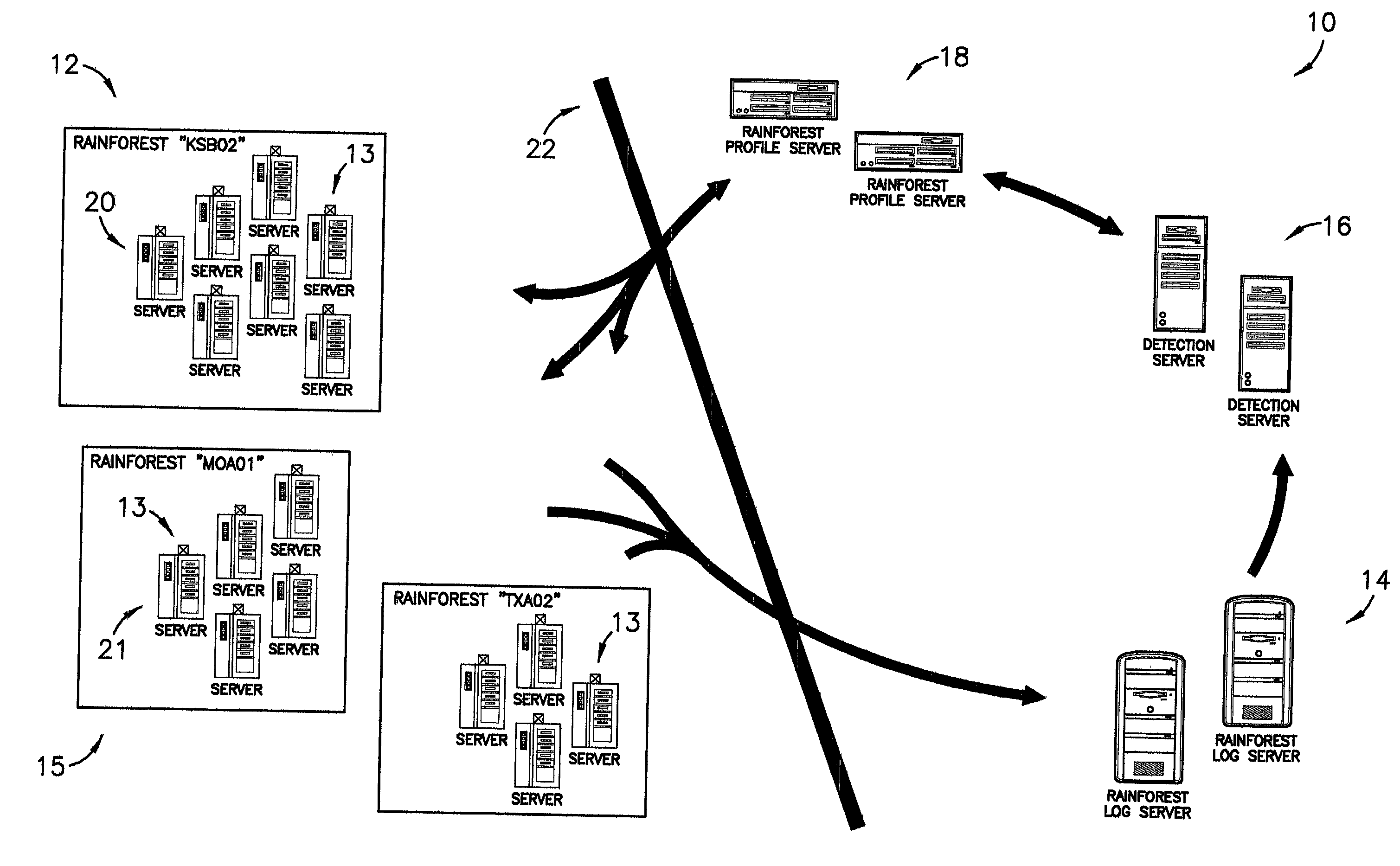
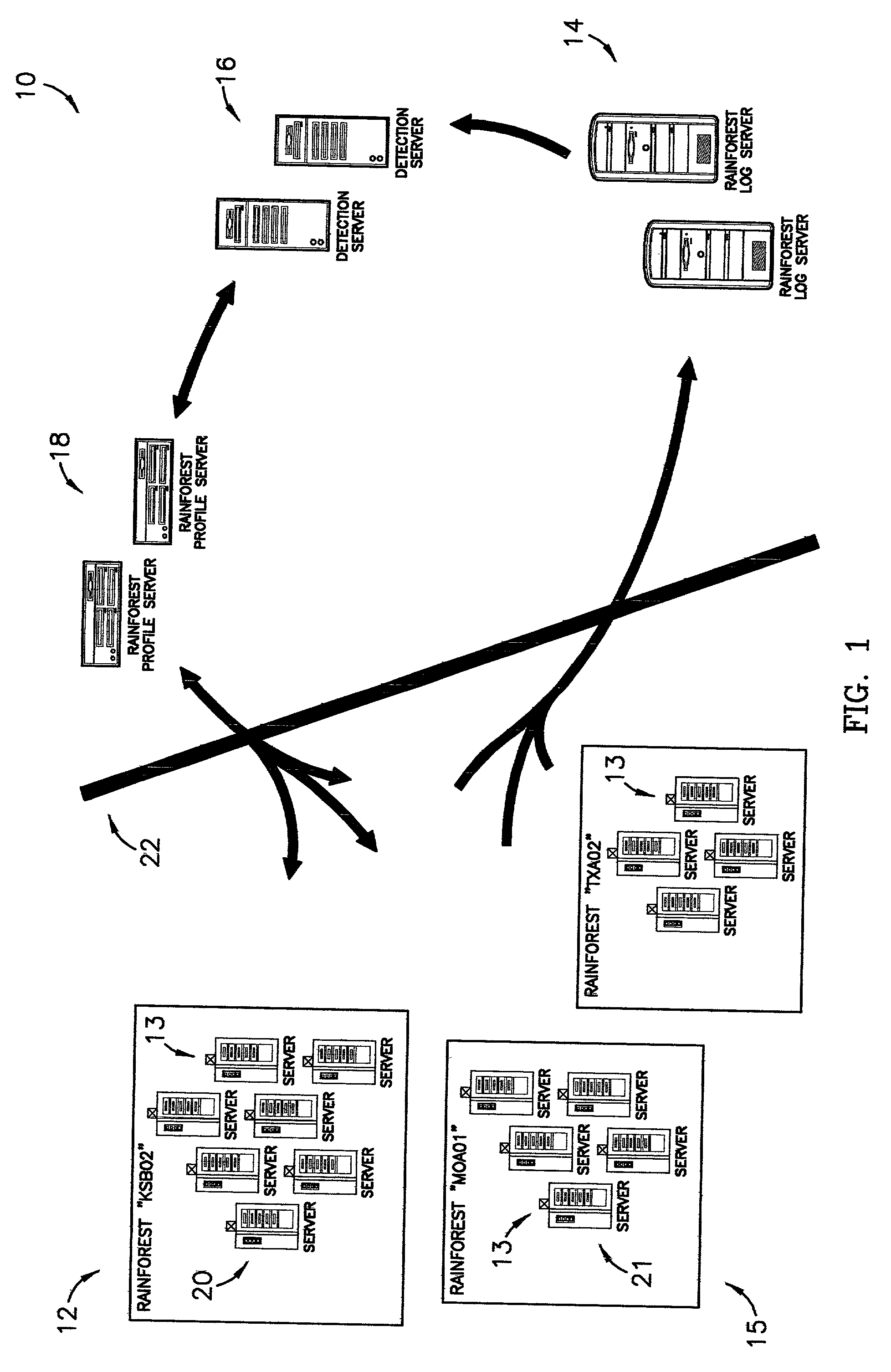
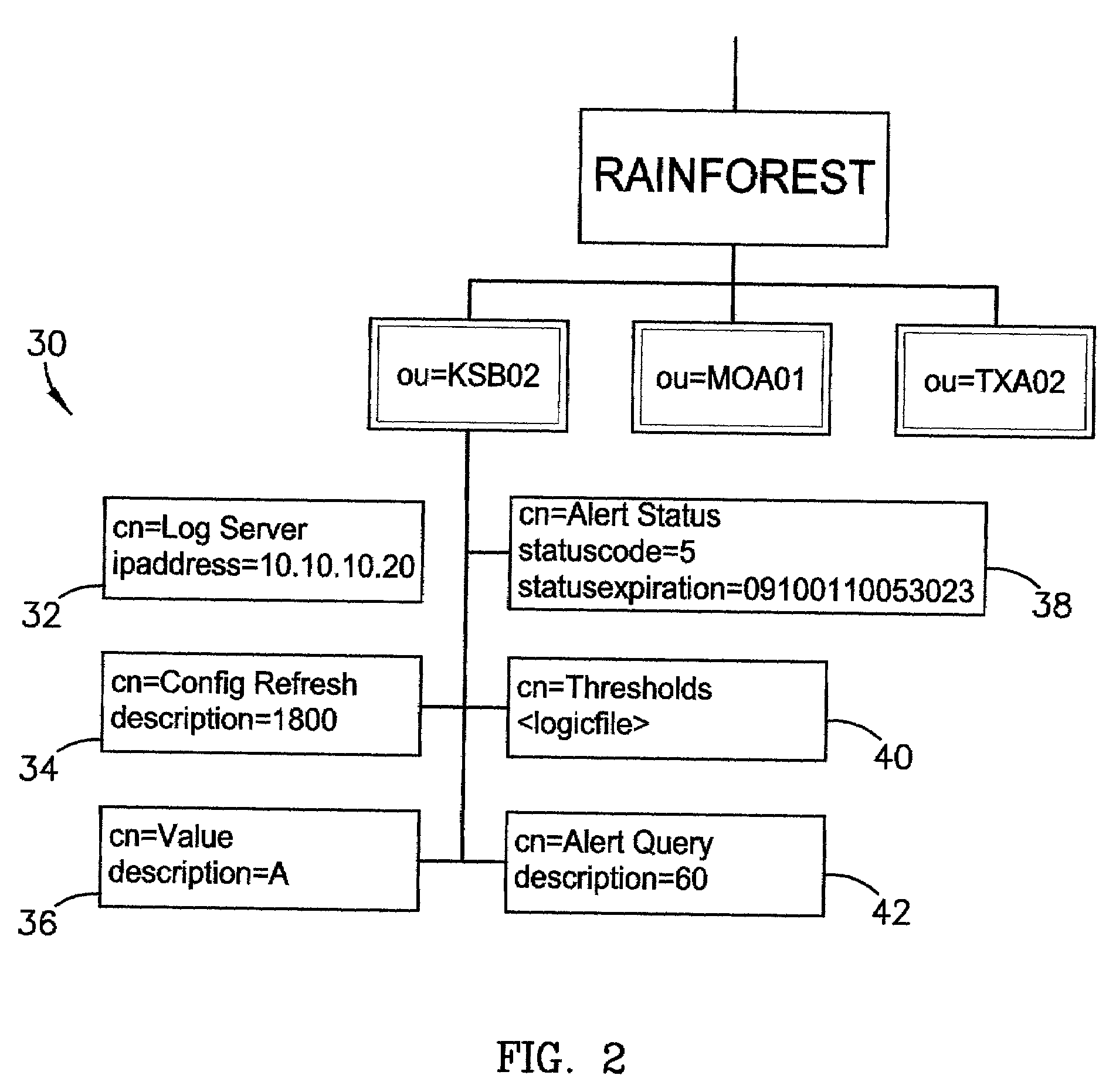
ActiveUS7028338B1Minimize impactMinimizes resourceMemory loss protectionDigital data processing detailsDomain nameRisk profiling
A system, computer program, and method of providing an automatic cooperative response ability to all members of a domain in light of a detected threat or other suspicious activity, such as, for example, a virus or denial of service attack, directed, at least initially, at less than all members of the domain. The system broadly comprises the domain; a log server; a detection server; and a profile server. The domain comprises a logical grouping of members having similar risk profiles. The detection server monitors and parses log and audit records generated by the members and copied to the log server. When the detection server identifies threatening or other suspicious activity it sets an alert status in a security profile stored on the profile server. The members periodically query the profile server for updates to the alert status and are thereby apprised of the alert.
Owner:SPRING SPECTRUM LP
Bioinformatic transaction scheme
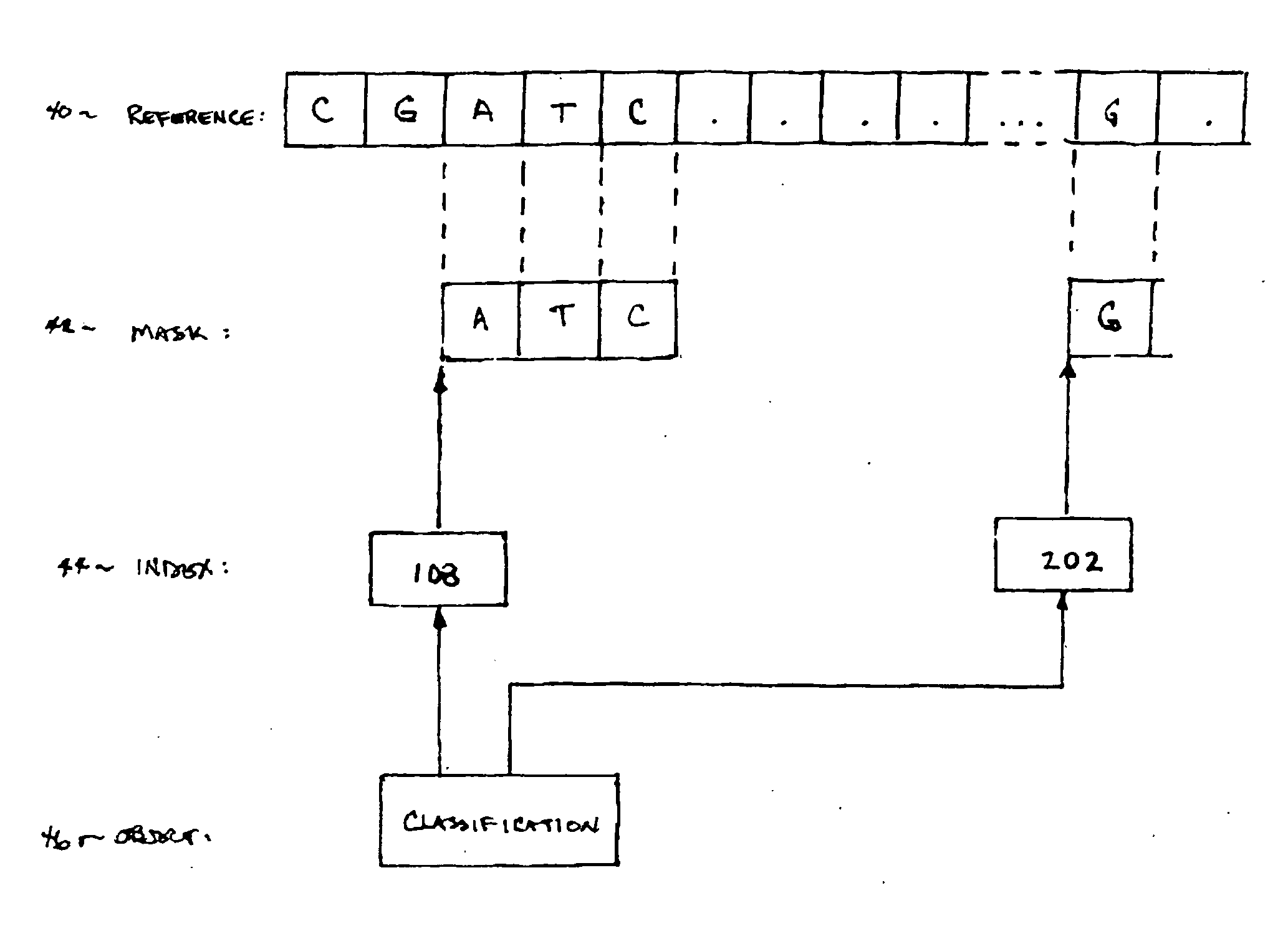
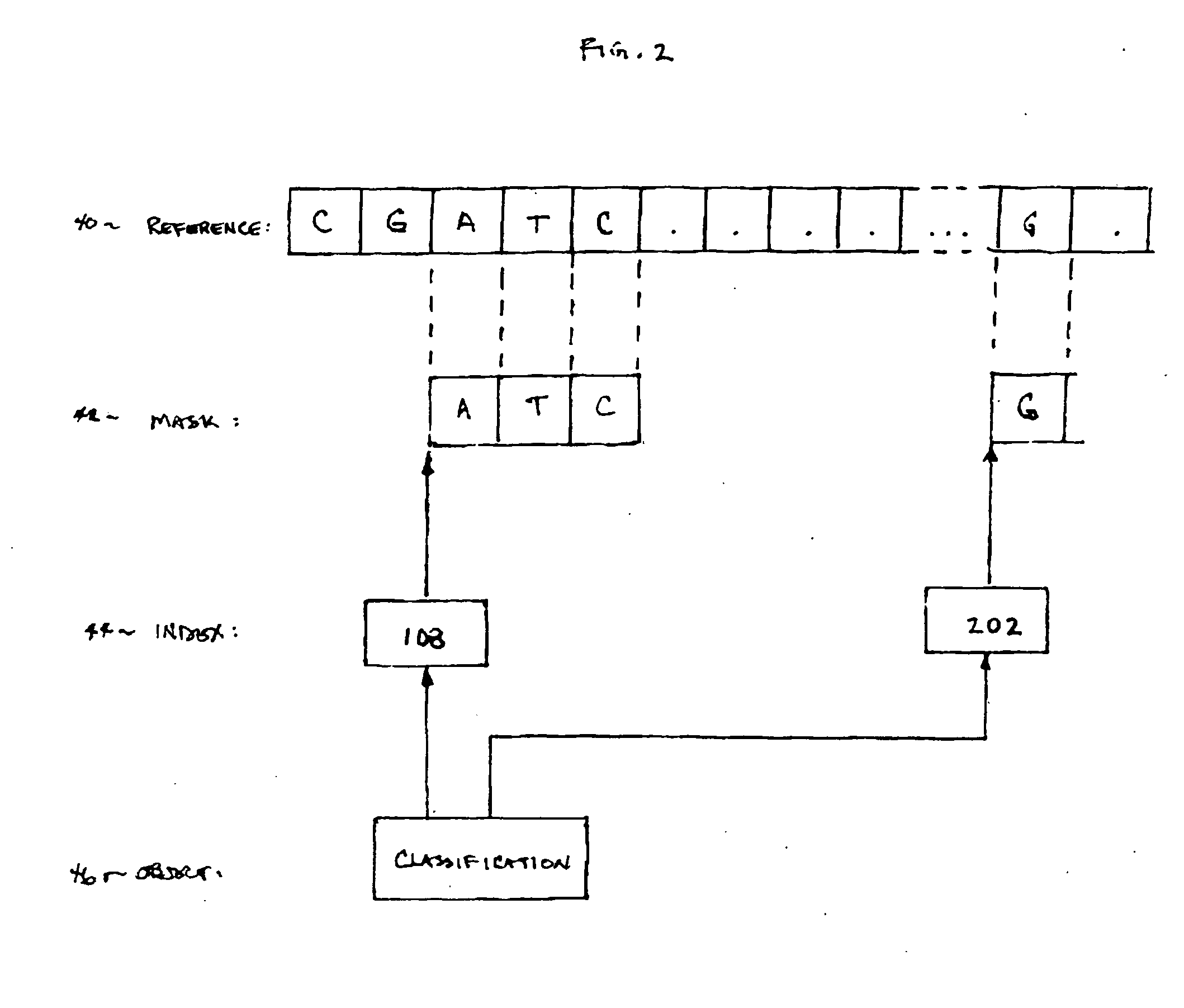
InactiveUS20070061085A1Digital data authenticationSpecial data processing applicationsRisk profilingUser device
Secure network transaction system obtains user-authorized genetic term or bioinformatic profile, and transacts online service according to genetically-based user medical or other risk determined therefrom. Insurance policy, promotional offer, or other service may dynamically address genetically-based condition. Bioinformatic data classifies user per personal mask which filters subset of user genetic sequence. Risk profile may be calculated according to actuarial statistics, genetics and / or heredity using non-discriminatory rules specified for users in temporal or jurisdictional groups. User transactions are modifiable according to bioinformatic data representing genetically-based risk increase or decrease. Data is securely processed, modulated, and stored by network server for remote access and transaction using various portable user devices.
Owner:FERNANDEZ DENNIS S
Mobile device security policy based on authorized scopes
A technique to enforce mobile device security policy is based on a“risk profile” of the individual device, where the risk profile is fine-grained and based on the types of applications installed on the device, the services they are accessing, and the operation(s) the user granted the device authorization to perform. Thus, the approach takes into account not only the actual applications installed on the device (and those actively in use), but also the services those applications are accessing, and the scope of operations the user has granted the device authorization to perform. By combining this information to create the risk profile, a suitable security policy, including one that does not unnecessarily degrade device usability, may then be applied.
Owner:IBM CORP
Methods and systems for assessing financial personality
One or more aspects comprise a computer system comprising one or more servers that: (a) provide a financial personality assessment questionnaire to a user; and (b) receive data describing said user's responses to one or more questions in said questionnaire; and one or more processors in communication with said one or more servers that: (a) based on said data describing said user's responses, assess said user's investment-related attitudes across a plurality of scales and produce a multi-dimensional financial personality identifier for said user; and (b) construct a user risk profile for said user derived from said multi-dimensional financial personality identifier.
Owner:BARCLAYS BANK
Investment advice systems and methods
The present invention provides investment advice systems. One version of the present invention provides investment advice systems that allow a user to select one or more advisors from a list of investment advisors. According to this version of the invention, the end user can receive advice on a particular transaction either separately from each investment advisor or in consensus. The system offers advice in part on the user's portfolio, tax position and risk profile and in part on the advisors evaluation of current market conditions. Thus, when a user is considering making a transaction, the user can obtain advice that can take into portfolio information including a user's proposed transaction and / or user portfolio information. A user armed with the above-described customized advice can execute a specific transaction and have their portfolio updated to reflect execution of that (those) order(s). In an alternative embodiment, a user's desire to buy or sell a security and / or a need for rebalancing a user's portfolio can generate transaction(s). As a result, the system will generate a buy / sell list (including recommended alternatives) from which a user can select.
Owner:CHECKFREE SERVICES CORP
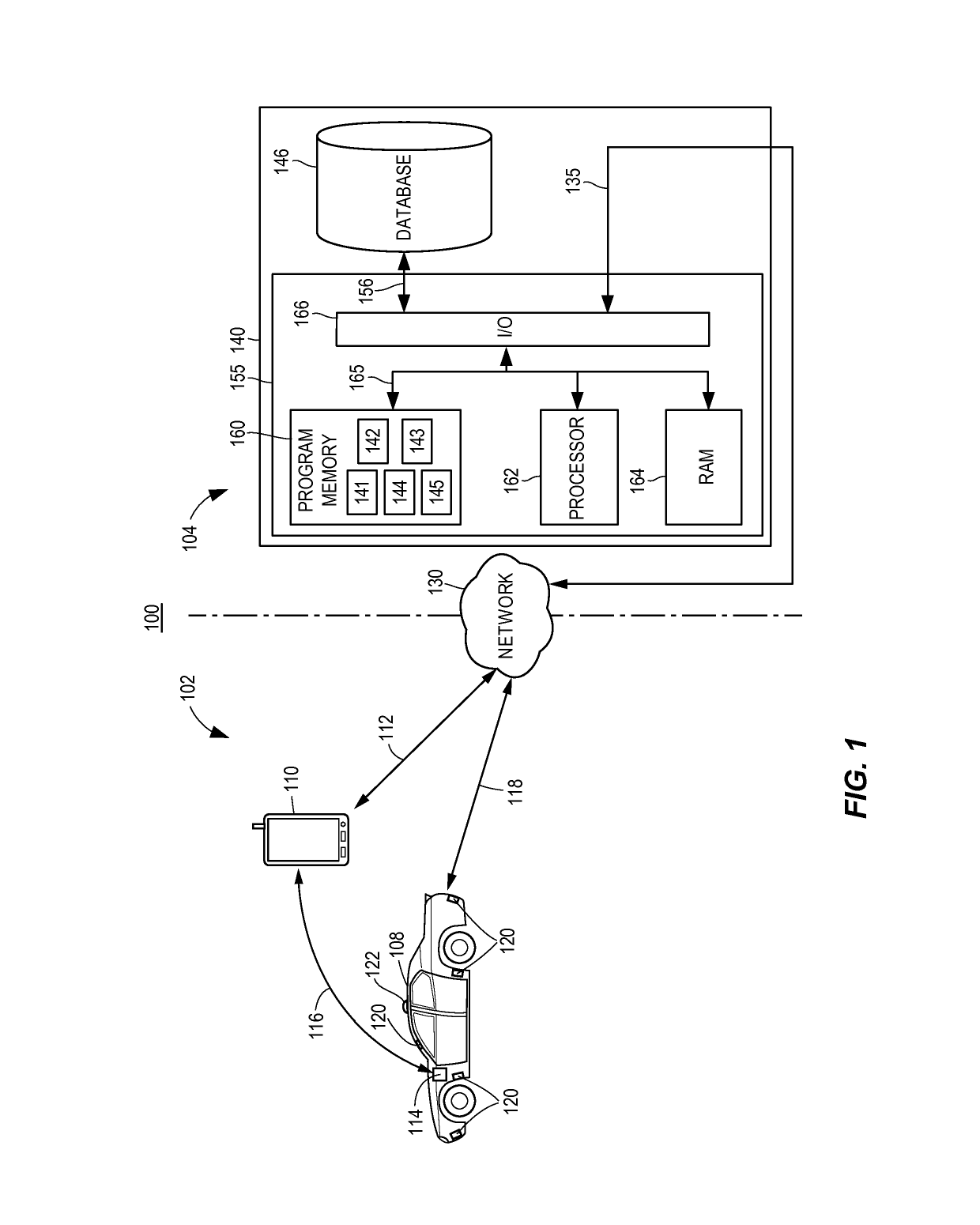
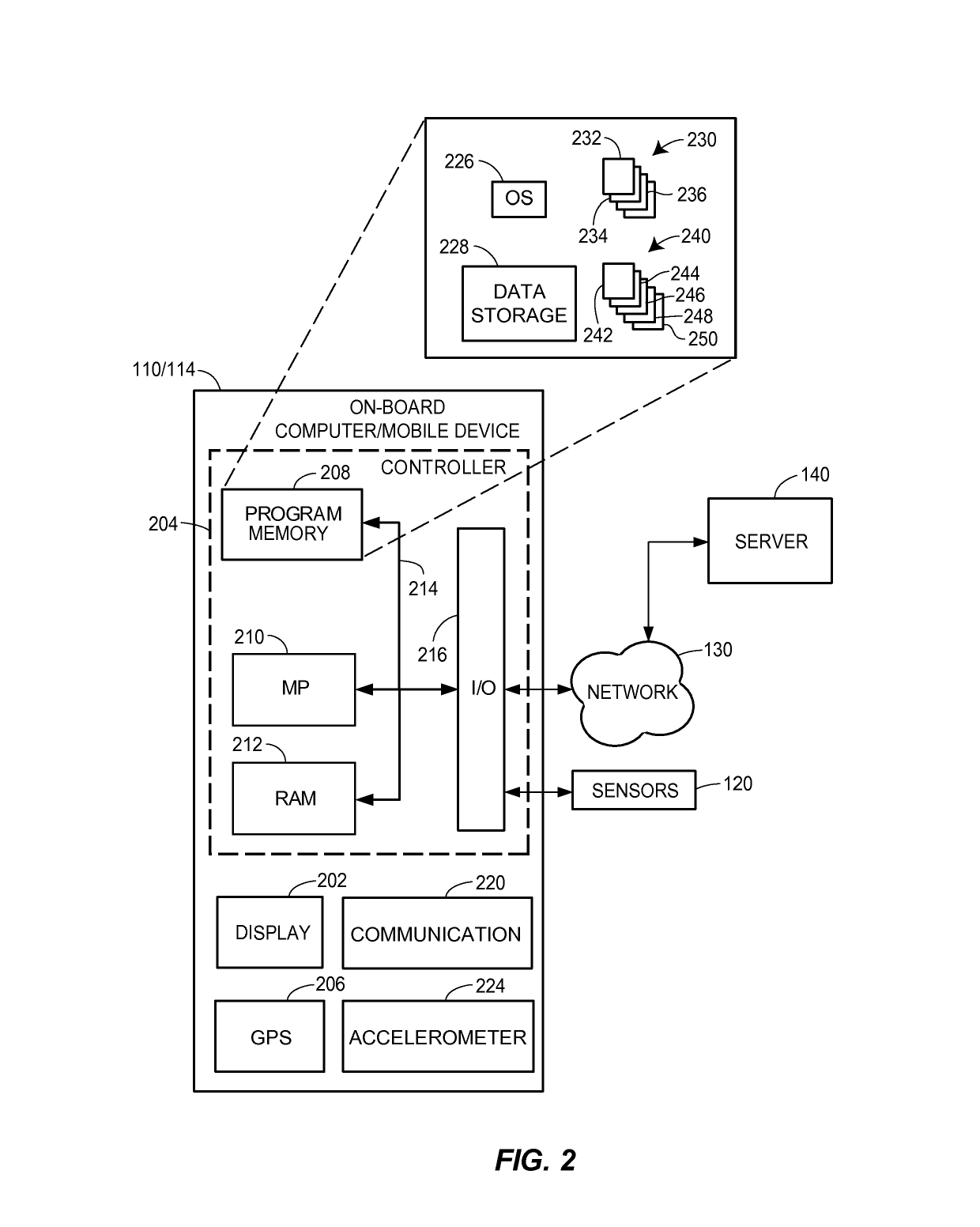
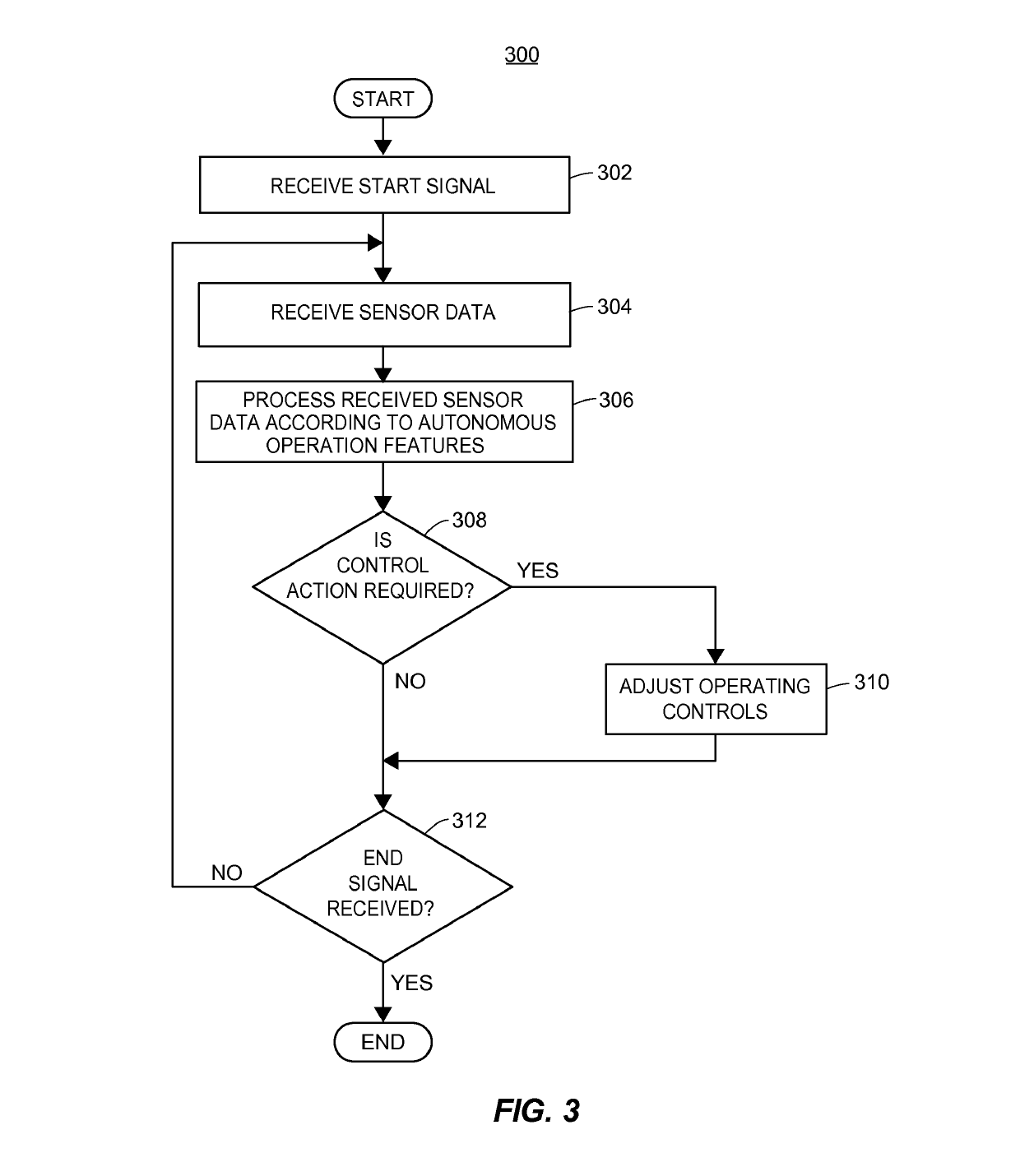
Fully autonomous vehicle insurance pricing
ActiveUS10373259B1Facilitate risk assessmentFacilitate premium determinationFinanceRisk levelTotal risk
Methods and systems for determining risk associated with operation of fully autonomous vehicles are provided. According to certain aspects, autonomous operation features associated with a vehicle may be determined, including types and version of sensors, control systems, and software. This information may be used to determine a risk profile reflecting risk levels for a plurality of features, which may be based upon test data regarding the features or actual loss data. Expected use levels may further be determined and used with the risk profile to determine a total risk level associated with operation of the vehicle by the autonomous operation features. The expected use levels may indicate expected vehicle use, as well as traffic, weather, or other conditions in which the vehicle is likely to operate. The total risk level may be used to determine or adjust aspects of an insurance policy associated with the vehicle.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
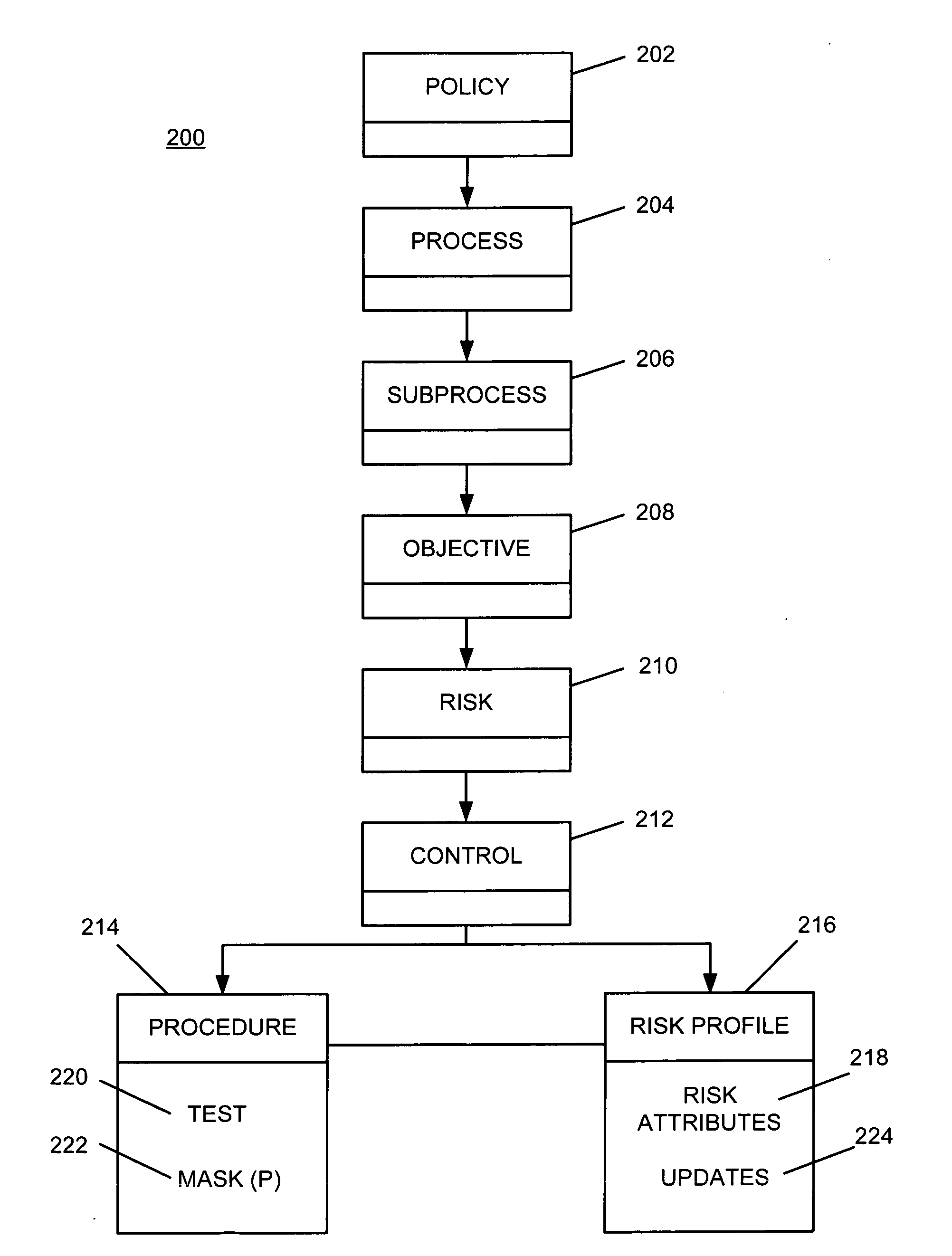
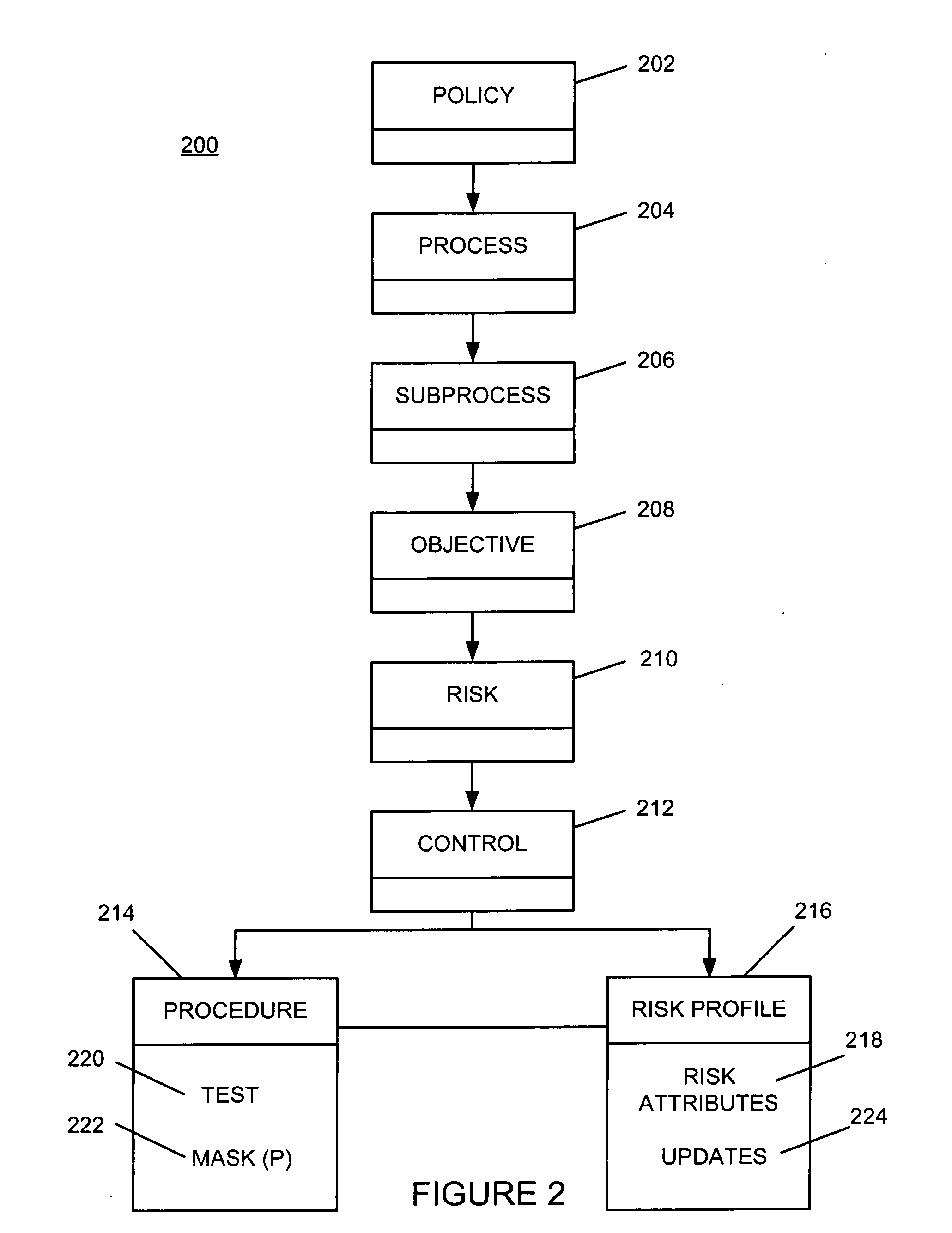
Risk profiling for enterprise risk management
ActiveUS20090228316A1Increased riskImproves risk and opportunity managementFinanceResourcesRisk profilingRisk rating
A risk profile element is created and associated with a control element within a risk hierarchy associated with an organization. A risk attribute is updated automatically within the risk profile element in response to an event associated with the control element. The updated risk attribute is processed to evaluate risk associated with the control element.
Owner:IBM CORP
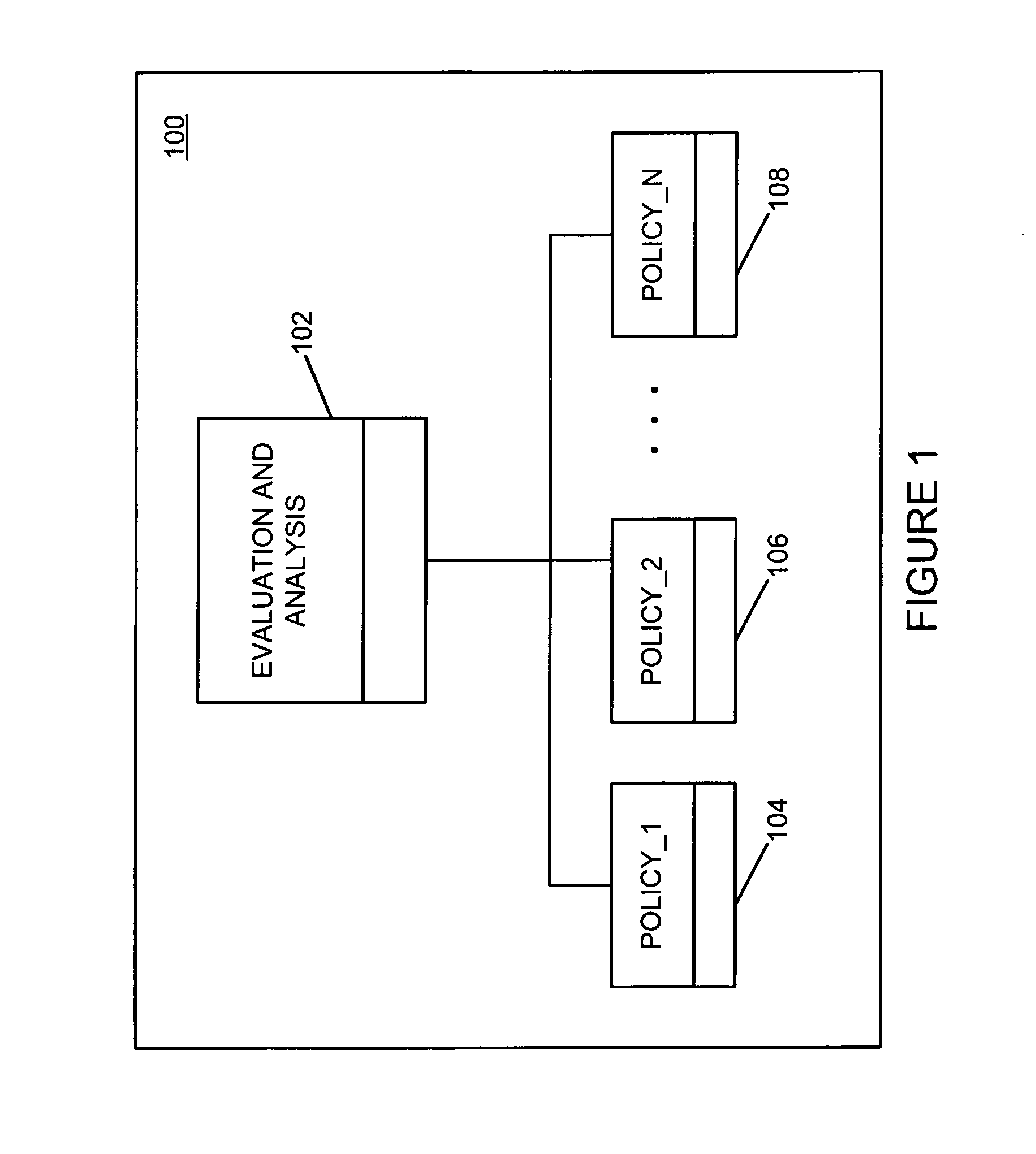
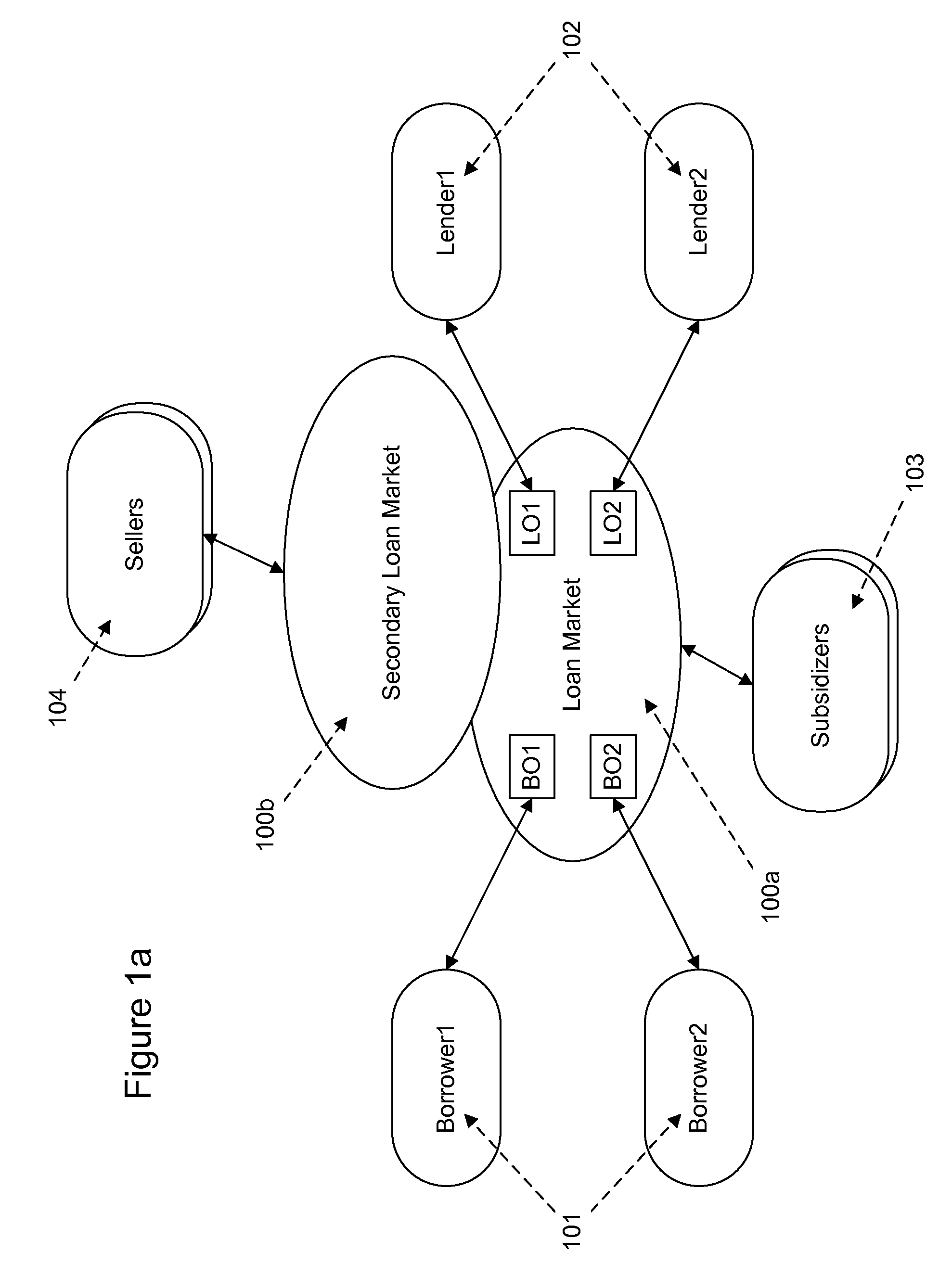
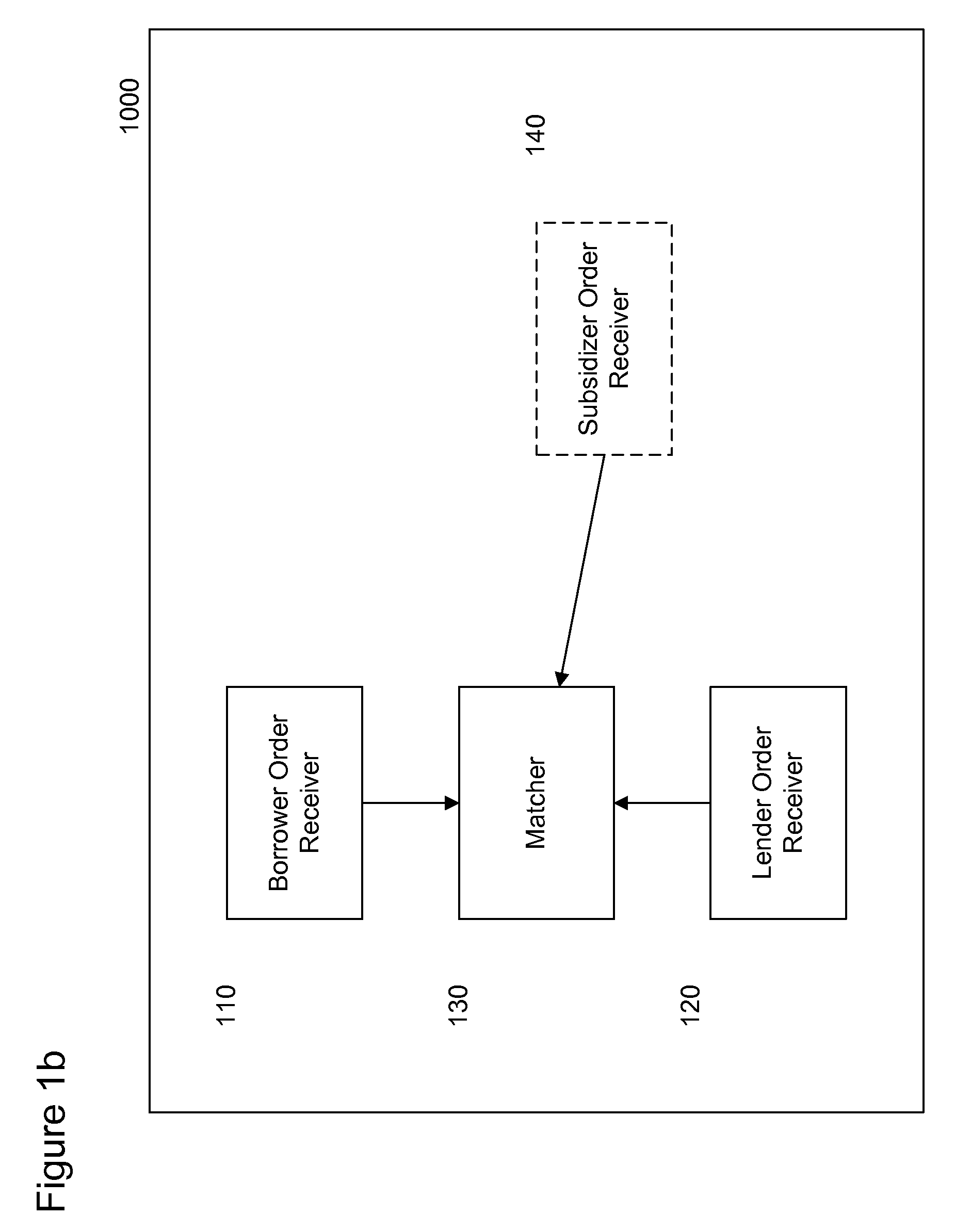
Risk profiles in networked loan market and lending management system
Systems, methods, and apparatus for receiving, from a lender, a lending order that specifies a desired risk profile, end term, and interest rate for a loan, the risk profile specifying a plurality of parameters used to determine a risk of a loan; and generating a portfolio loan that includes a plurality of atomic loans with a plurality of different borrowers or borrower requests that, in combination, satisfy the desired risk profile, term, and rate specified in the lending order, wherein the atomic loans each comprise a direct contractual agreement between the lender and a borrower.
Owner:AXCESSNET INNOVATIONS LLC (US)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com