Patents
Literature
355 results about "Enterprise networking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
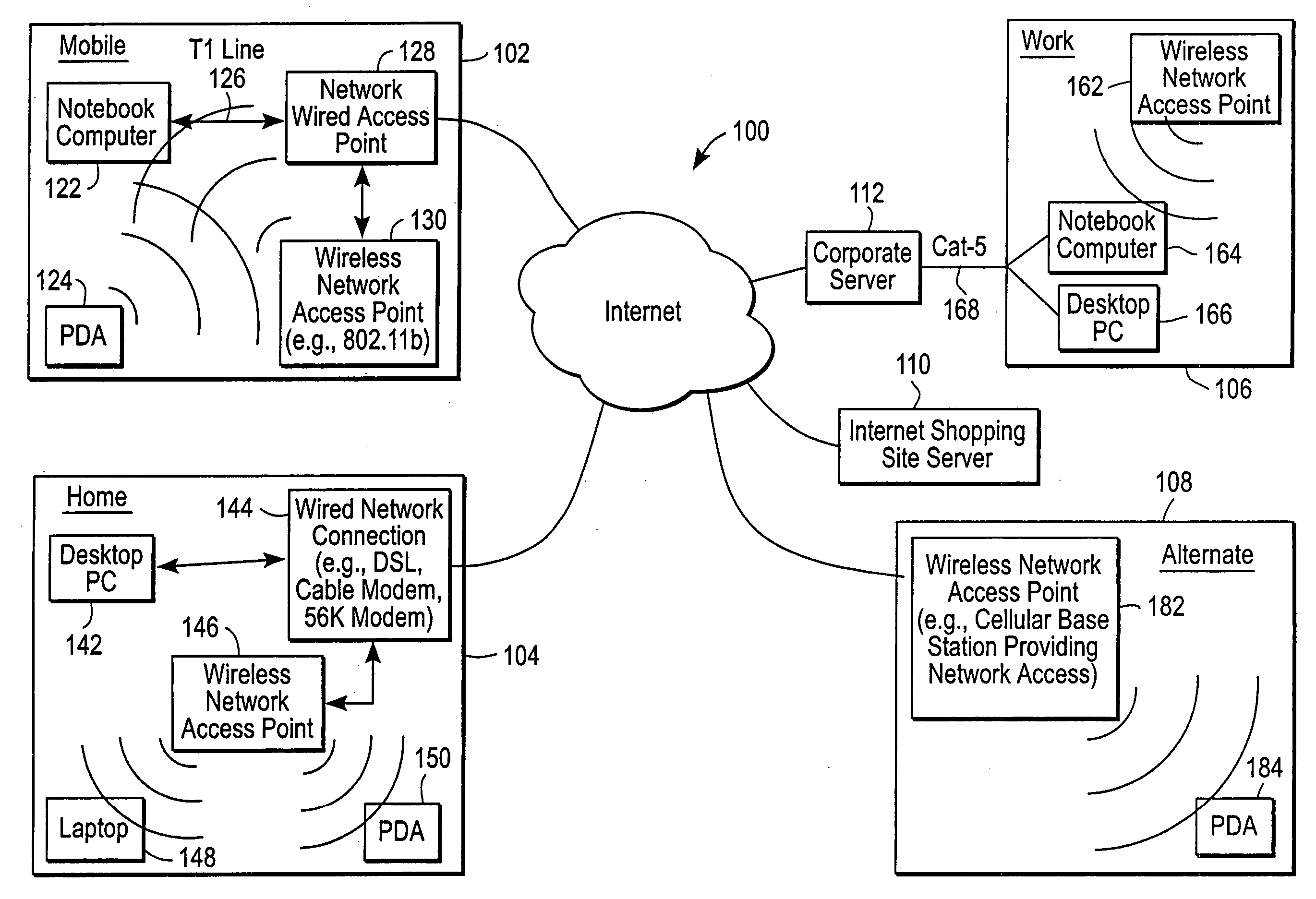
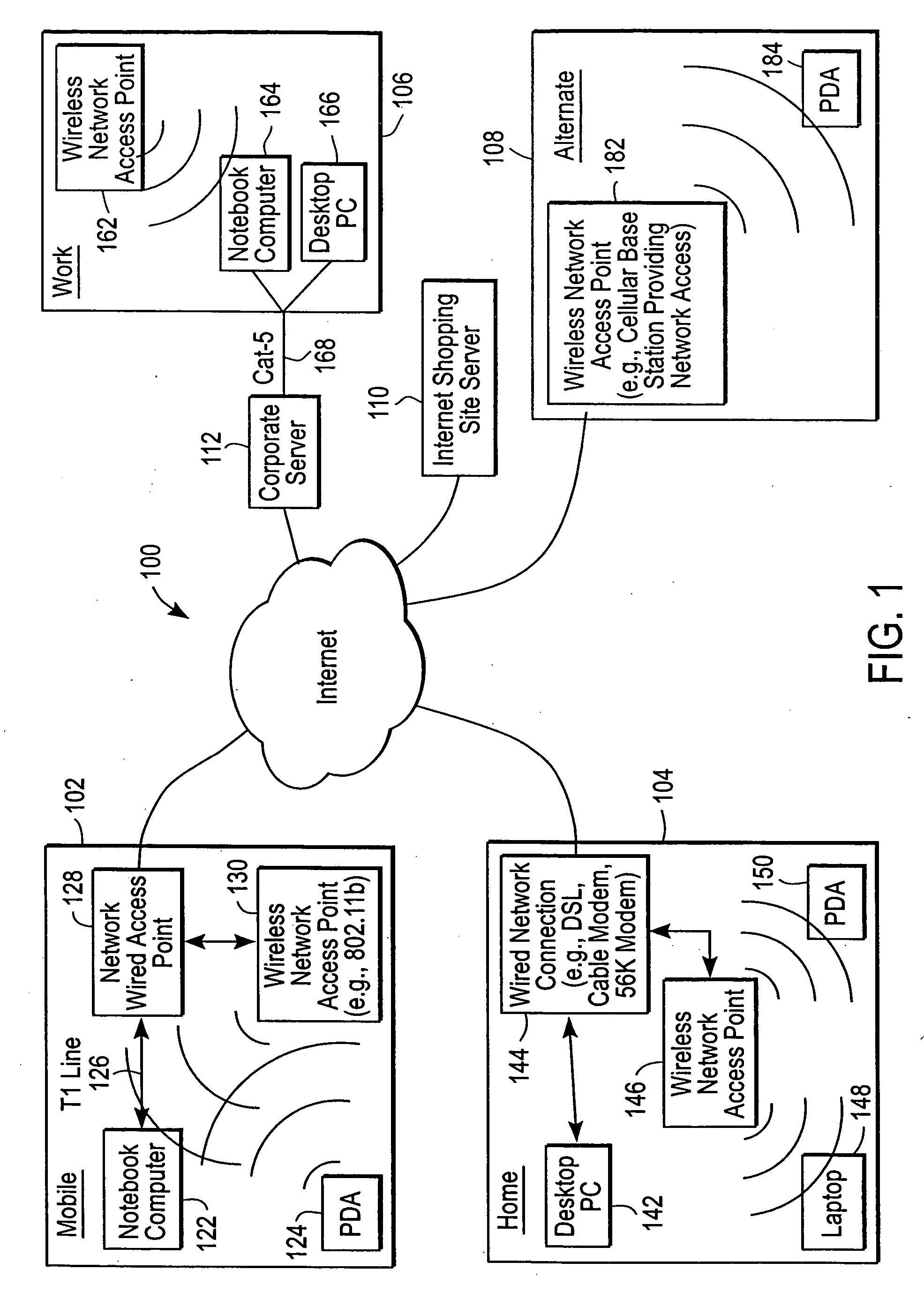
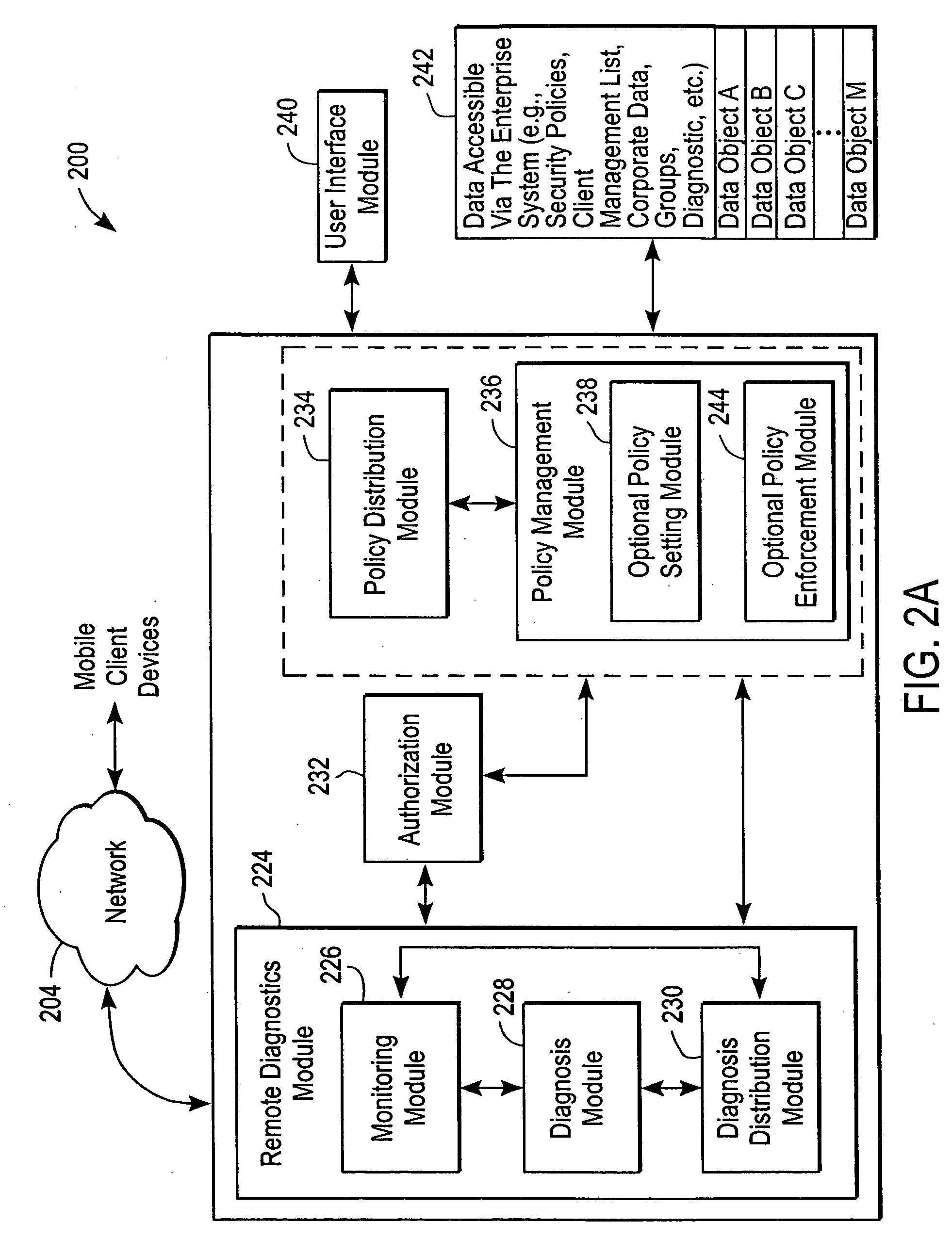
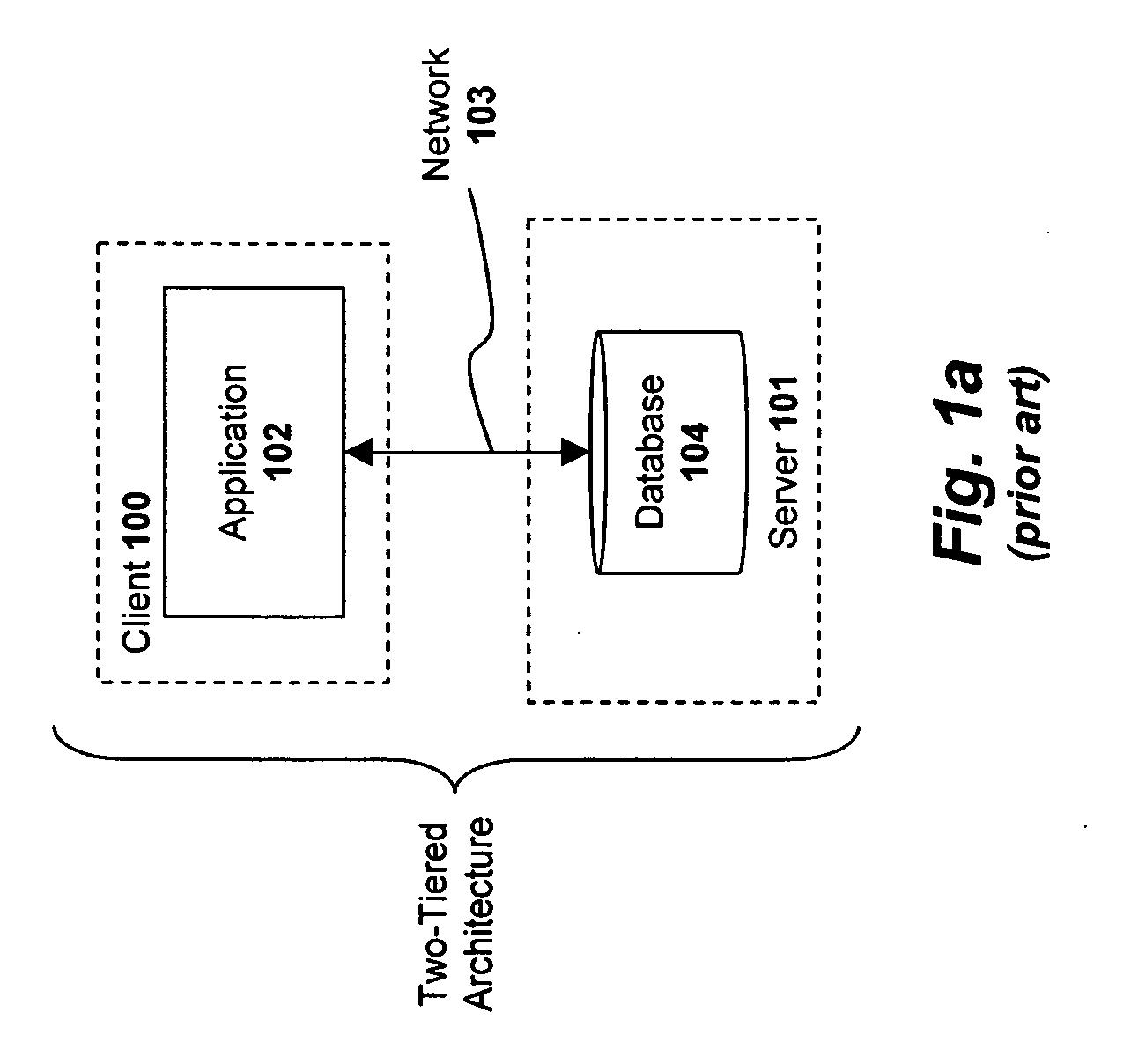
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Method and apparatus for displaying health status of network devices
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
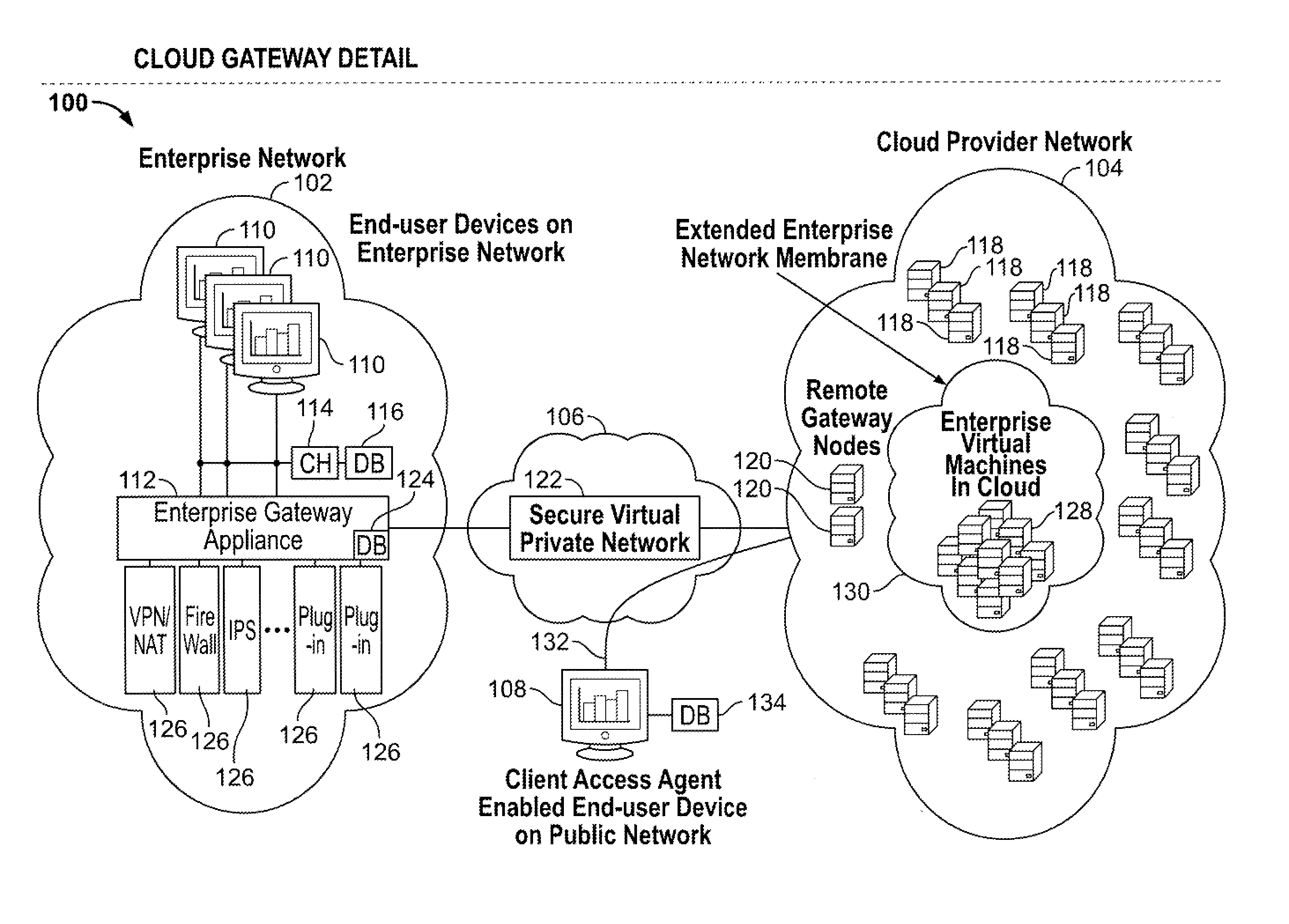
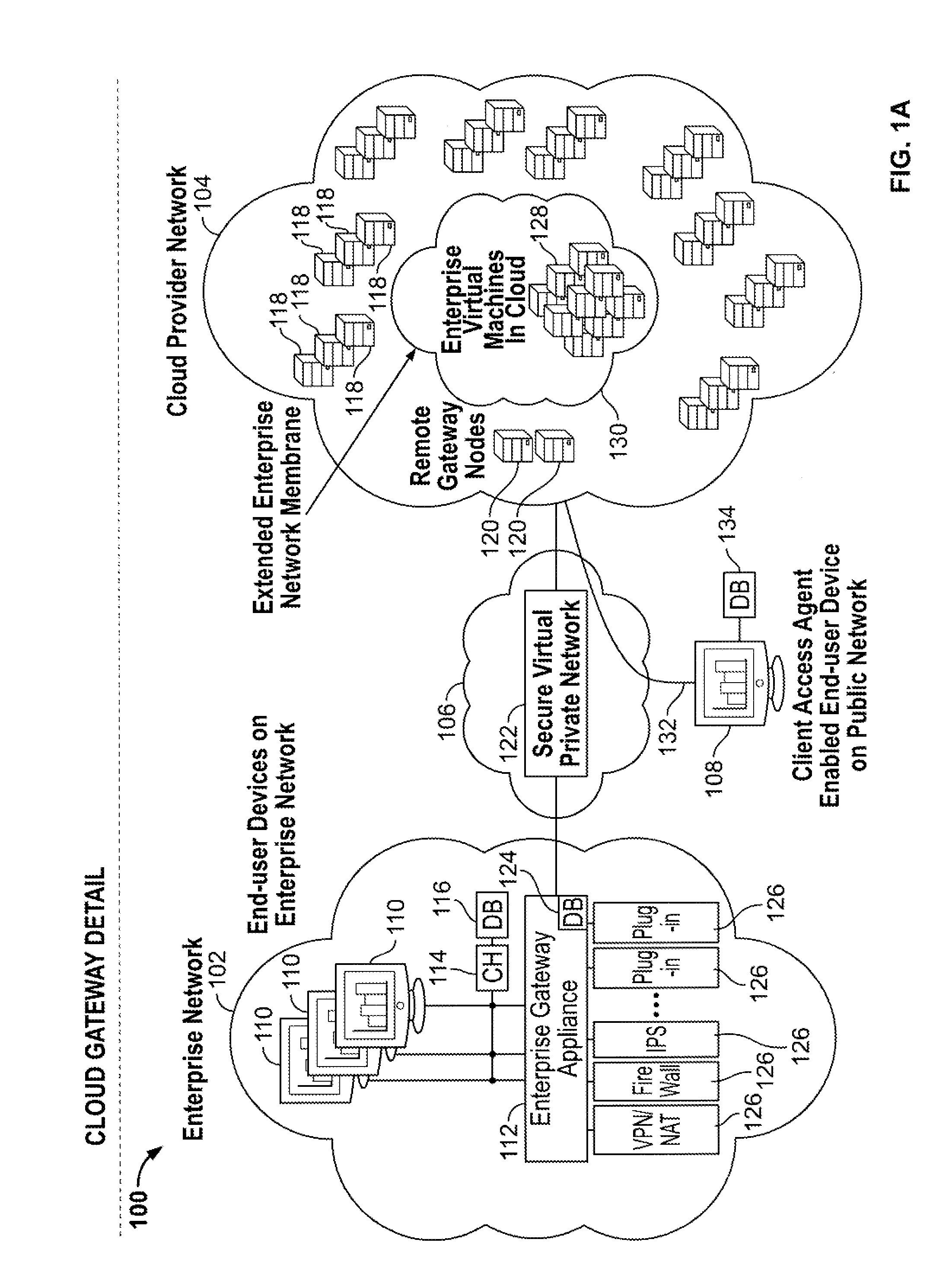
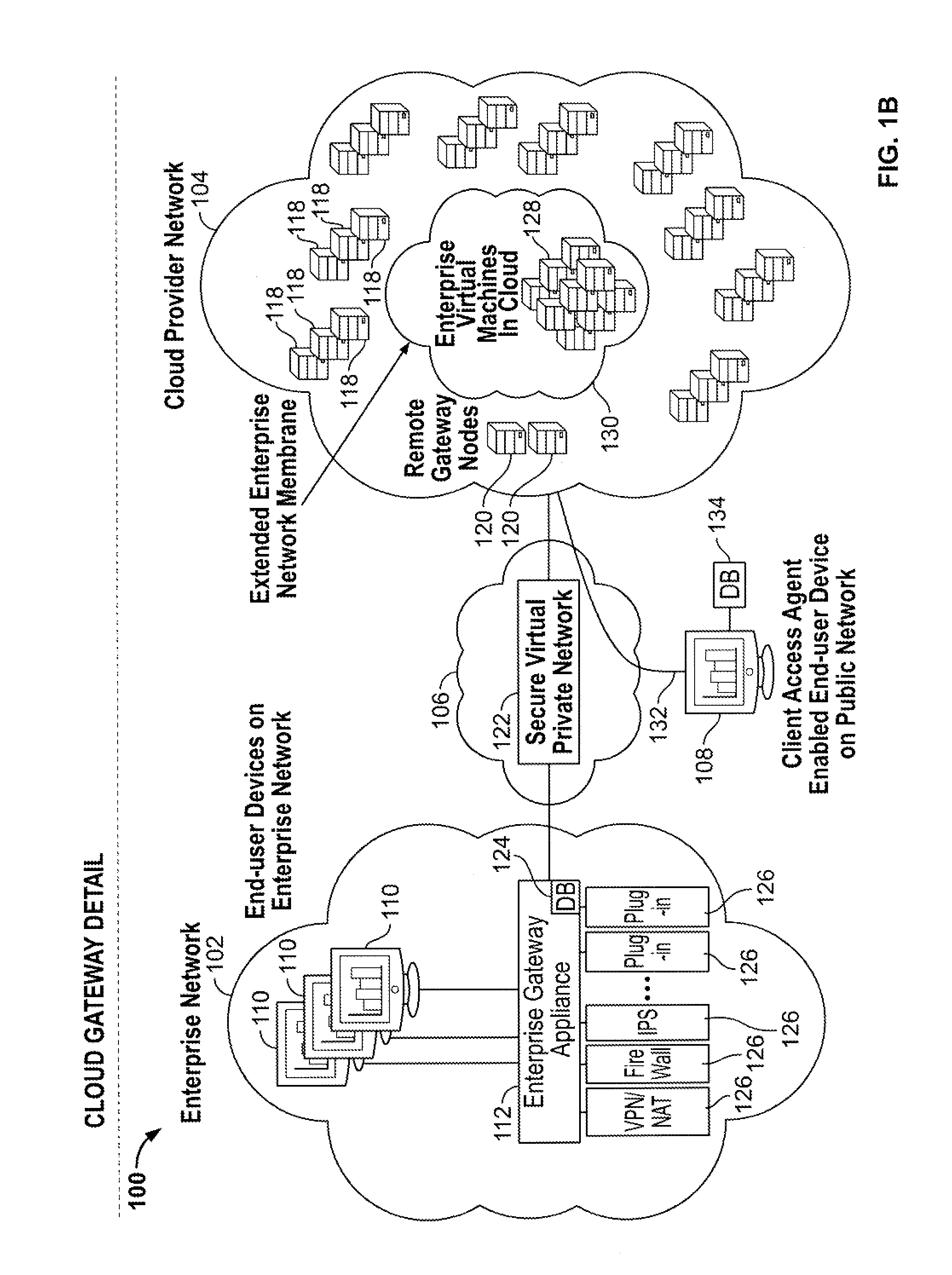
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS20100027552A1Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
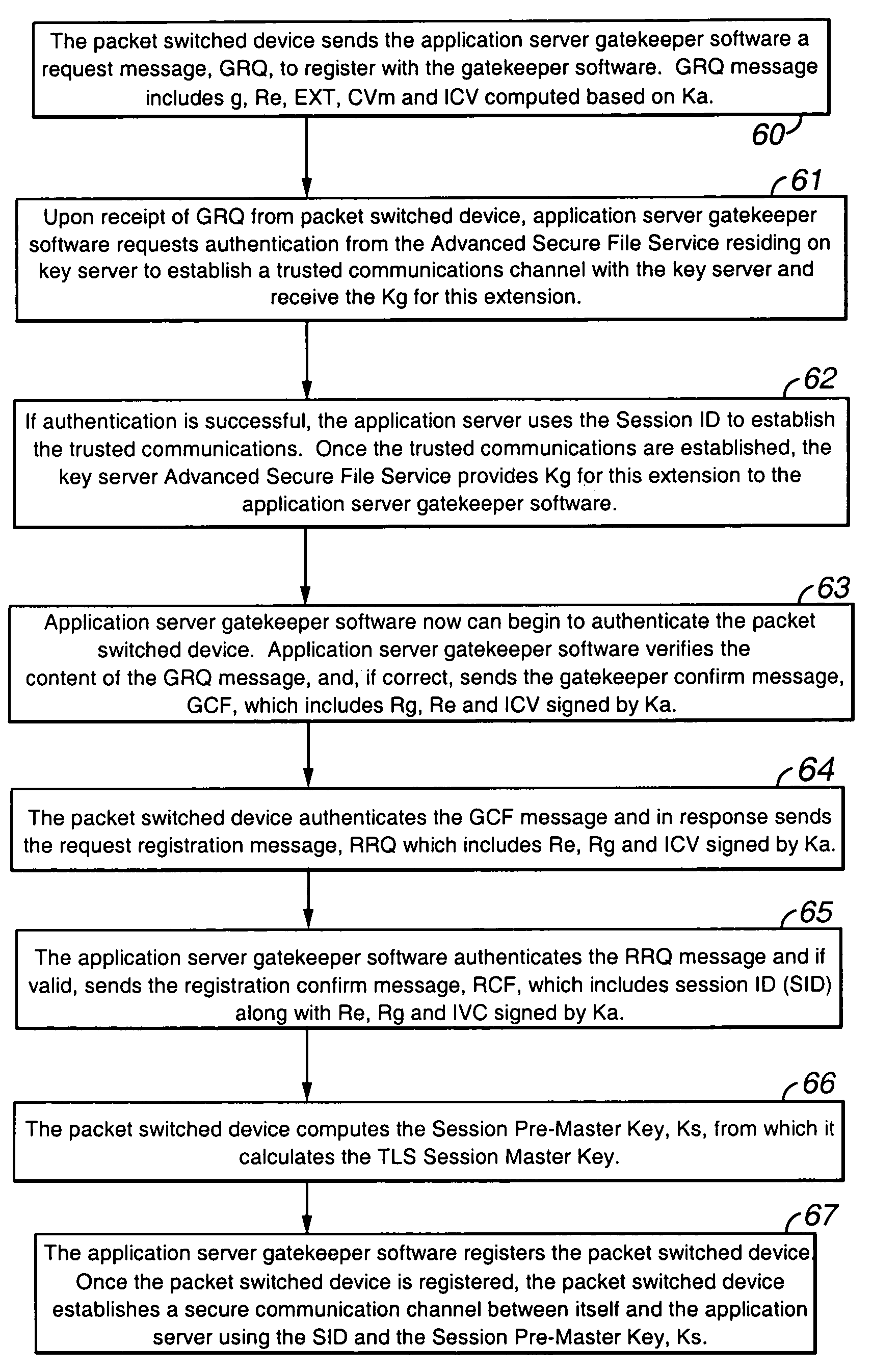
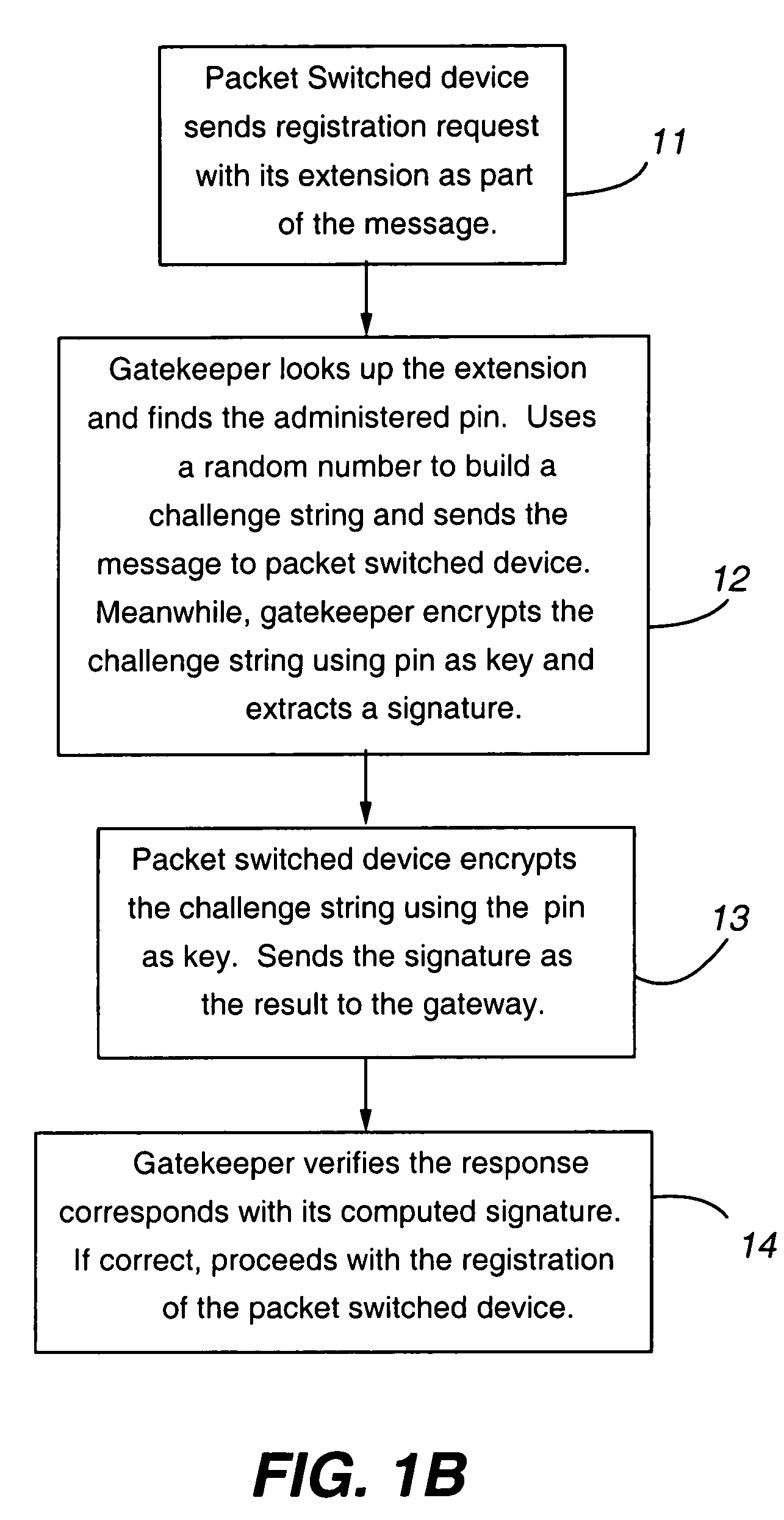
Key server for securing IP telephony registration, control, and maintenance
A packet-switched communications device in an enterprise network is provided. The packet-switched communications device has a corresponding unique identifier, such as an address or extension. The device includes a processor operable to (a) establish a secure communications session with a key generating agent in the enterprise network; (b) provide, to the key generating agent through the session, the unique identifier of the communications device; and (c) receive, from the key generating agent through the session, a secret key and a key identifier. An application server authenticates the packet switched device using the secret key. After authentication is successful, secure communications is established between the packet switched device and the application server.
Owner:AVAYA INC
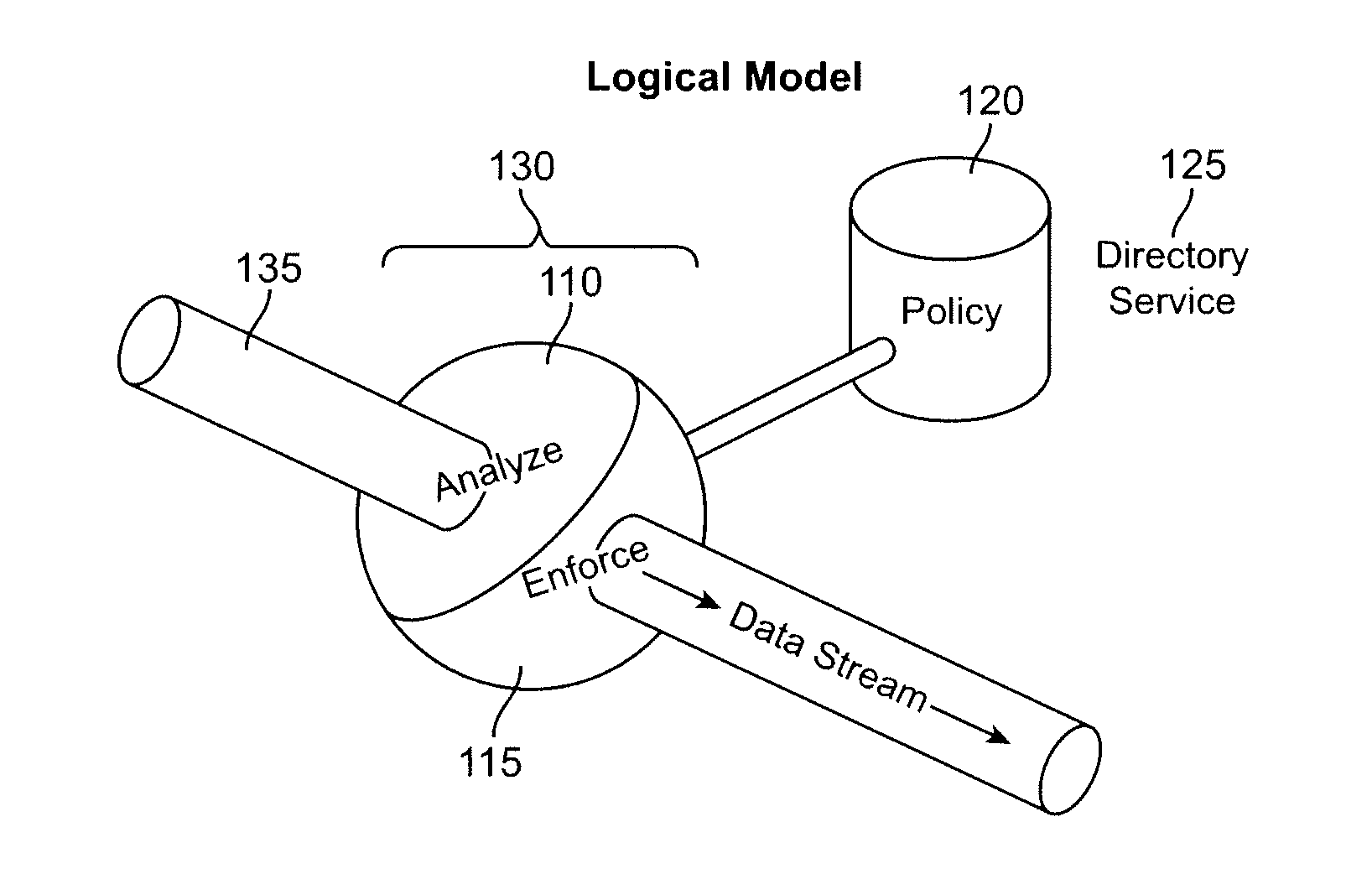
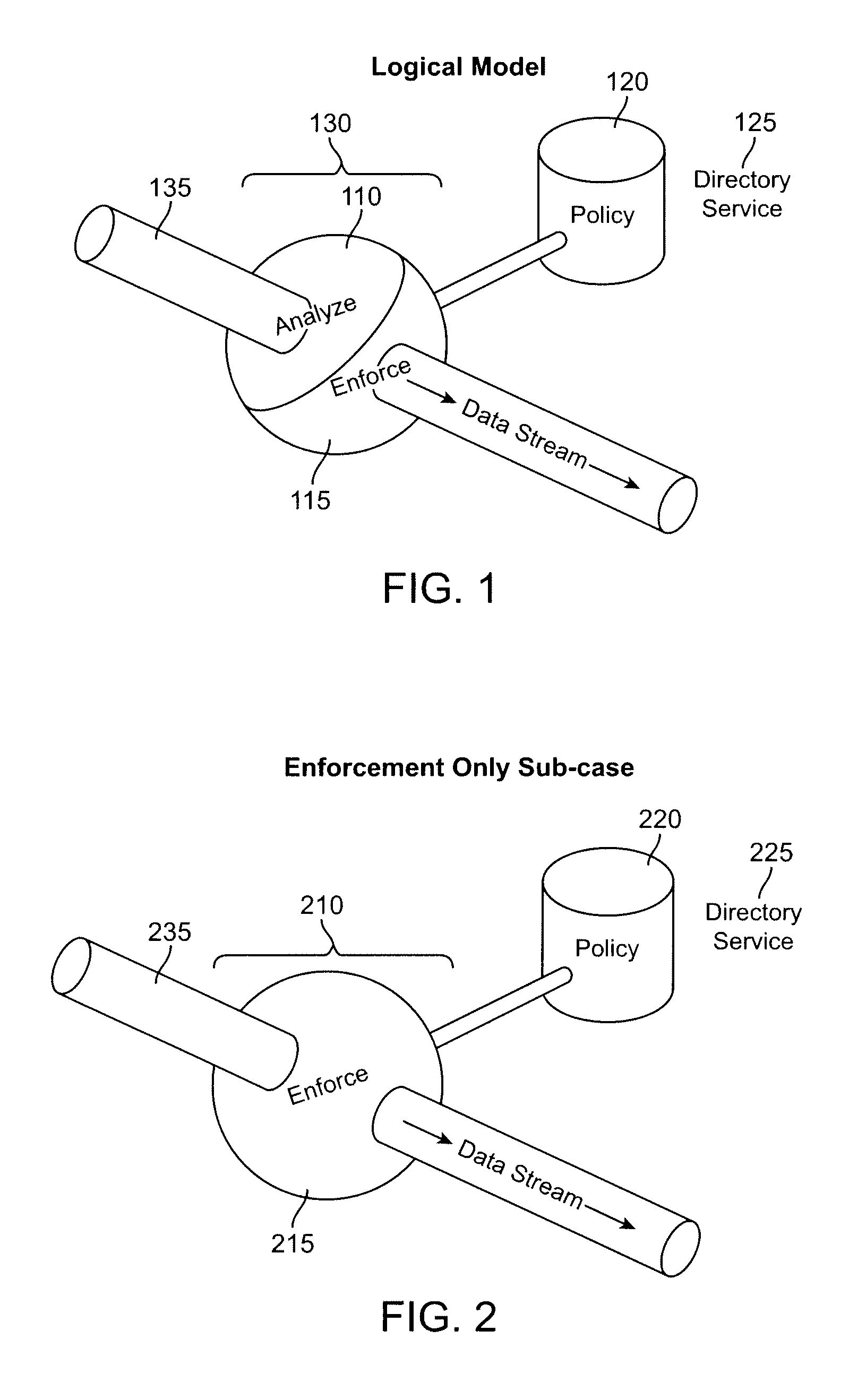
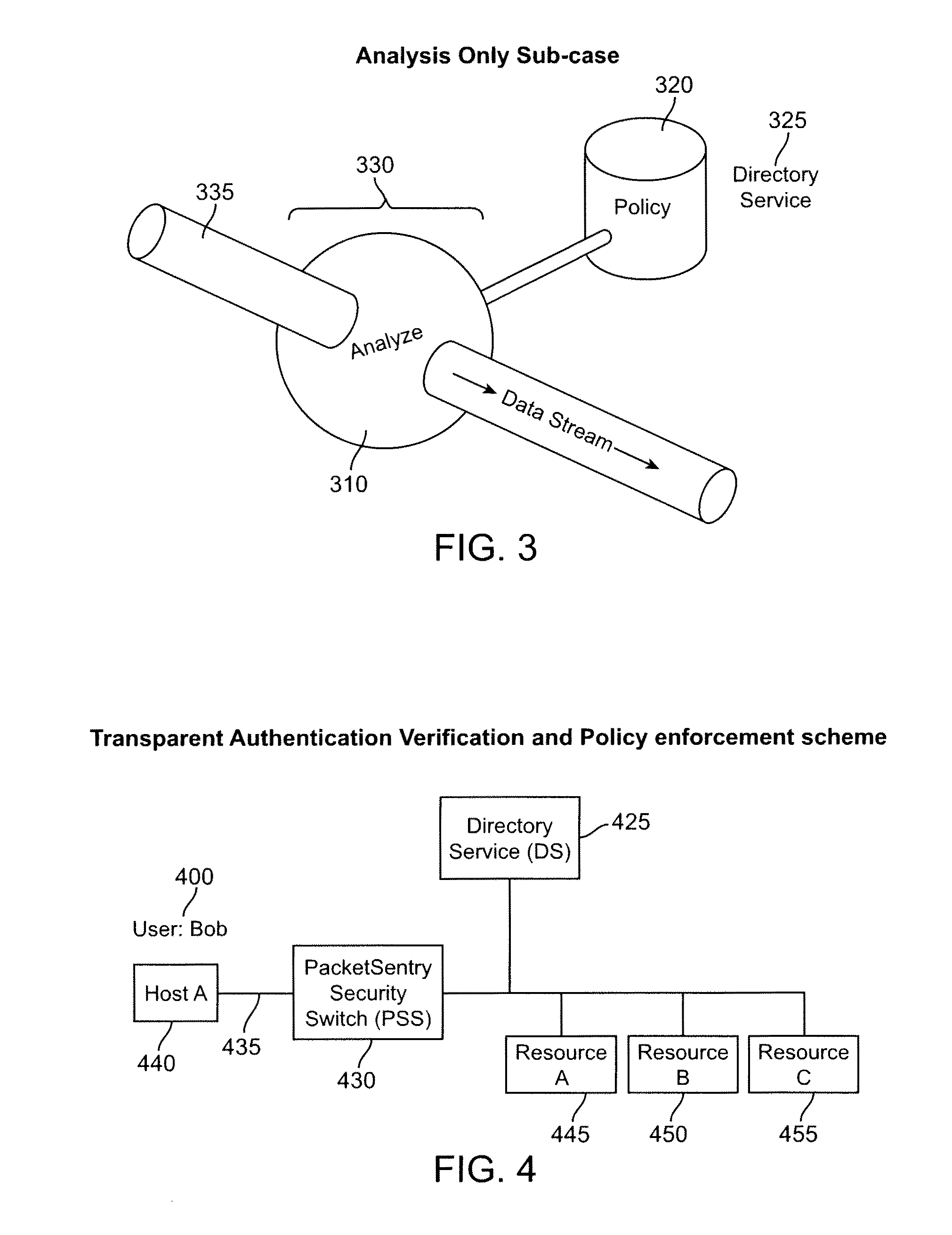
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
Integrated platform for developing and maintaining a distributed multiapplication online presence
InactiveUS7356559B1Various levelMultiple digital computer combinationsWebsite content managementWeb siteCOLA (software architecture)
Software architectures, platforms, and data constructs are disclosed which provide a system for enabling a non-technical or lay user to perform discrete technical tasks necessary to build a complete network-based, multiuser application. The system also allows the user to have a uniform user experience throughout development of the application. For example, the platform can be used to construct and maintain an Internet or online Web site capable of handling e-commerce transactions or can be used to develop a customer relationship management system. A software architecture is described that enables many users to perform a variety of tasks via a wide-area network, such as an enterprise network or the Internet. The architecture has several services, systems, and an extensible database for storing data objects. The database has an underlying structure referred to as a schema that can be extended with previously undefined attributes without having to alter the basic format of the schema. The architecture also includes an integrated platform that enables each of the users to perform the tasks by controlling interaction or communication between the services and systems, and the extensible database.
Owner:HOSTWAY SERVICES INC
Pervasive, user-centric network security enabled by dynamic datagram switch and an on-demand authentication and encryption scheme through mobile intelligent data carriers
InactiveUS20040221163A1Improve reliabilityIncrease flexibilityKey distribution for secure communicationUnauthorised/fraudulent call preventionNetwork connectionEngineering
Methods and systems are provided for improving access control, administrative monitoring, reliability, as well as flexibility of data transmission and remote application sharing over a network. Secure, stable network connections and efficient network transactions among multiple users are supported by an open and distributed client-server architecture. A datagram schema is adapted to enable dynamic datagram switching in support of a multitude of applications and network services. Mobile intelligent data carriers are provided that allow for the implementation of an authentication and encryption scheme. The intelligent data carriers are adapted to target deliver applications to authorized users, thereby achieving access control to not only data but also applications. The authentication and encryption scheme in one embodiment is based on physical or performance biometrics. The methods and systems of this disclosure may be advantageously deployed in an enterprise network environment to support a wide spectrum of business, research, and administrative operations.
Owner:GIRITECH APS
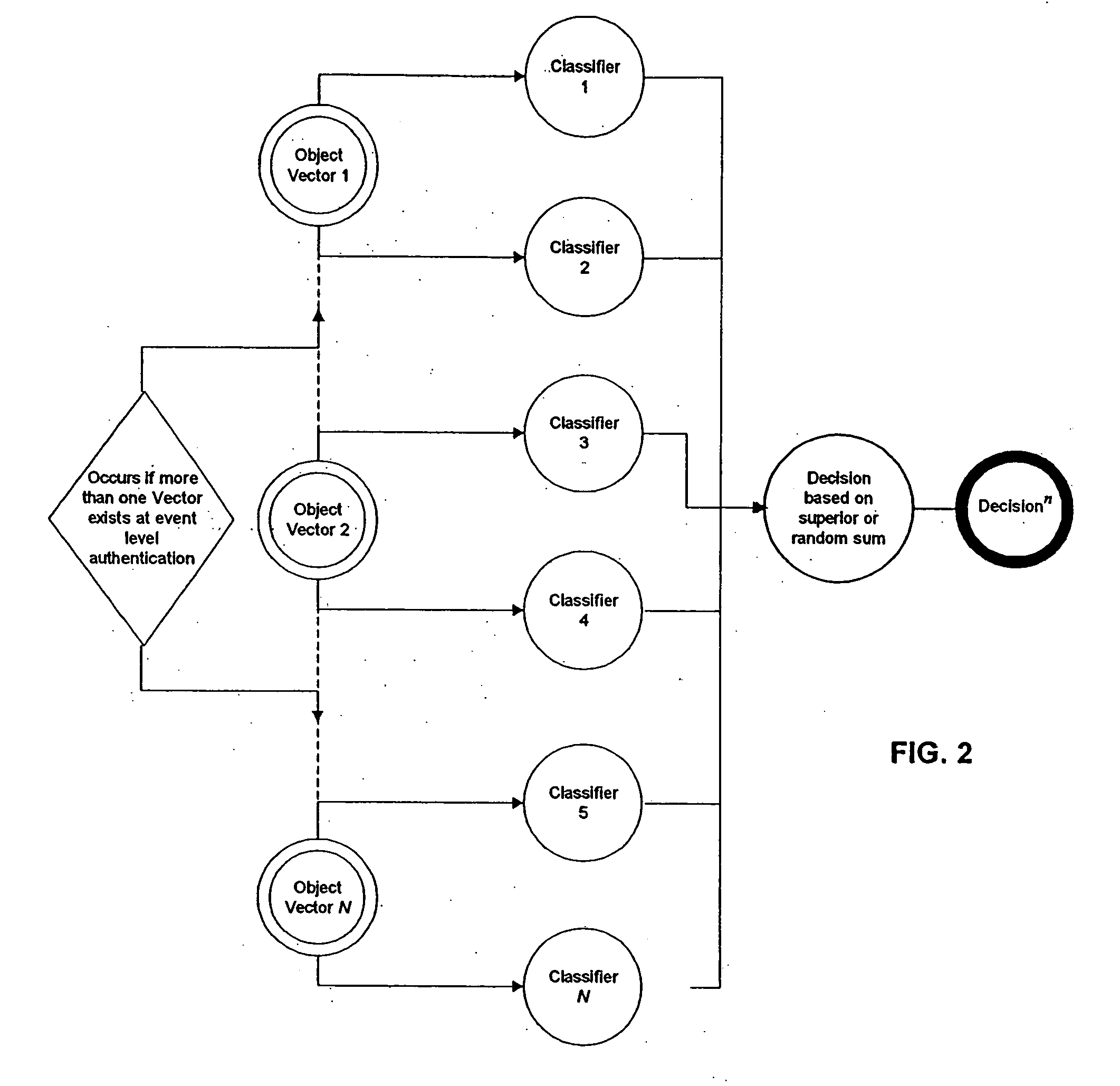
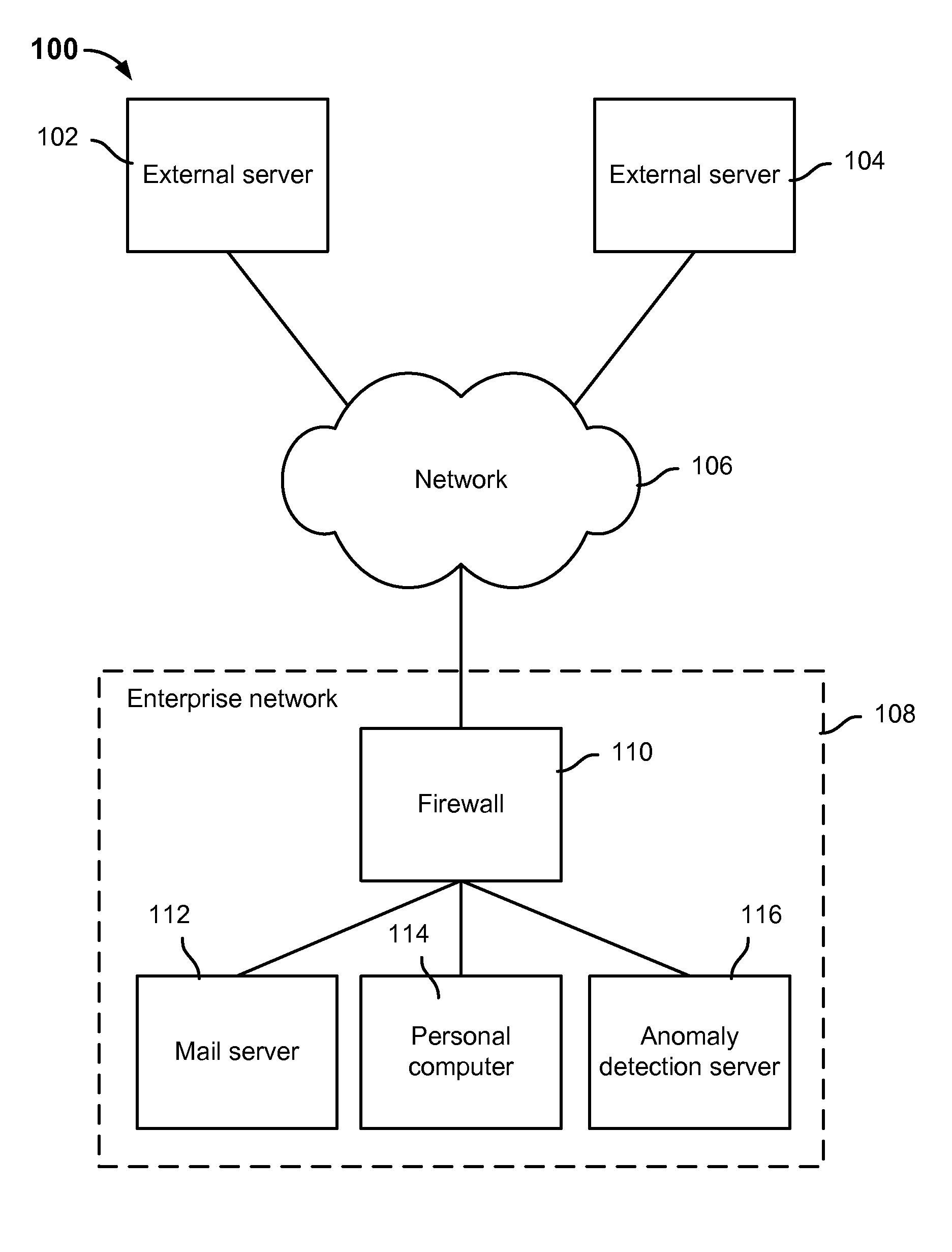
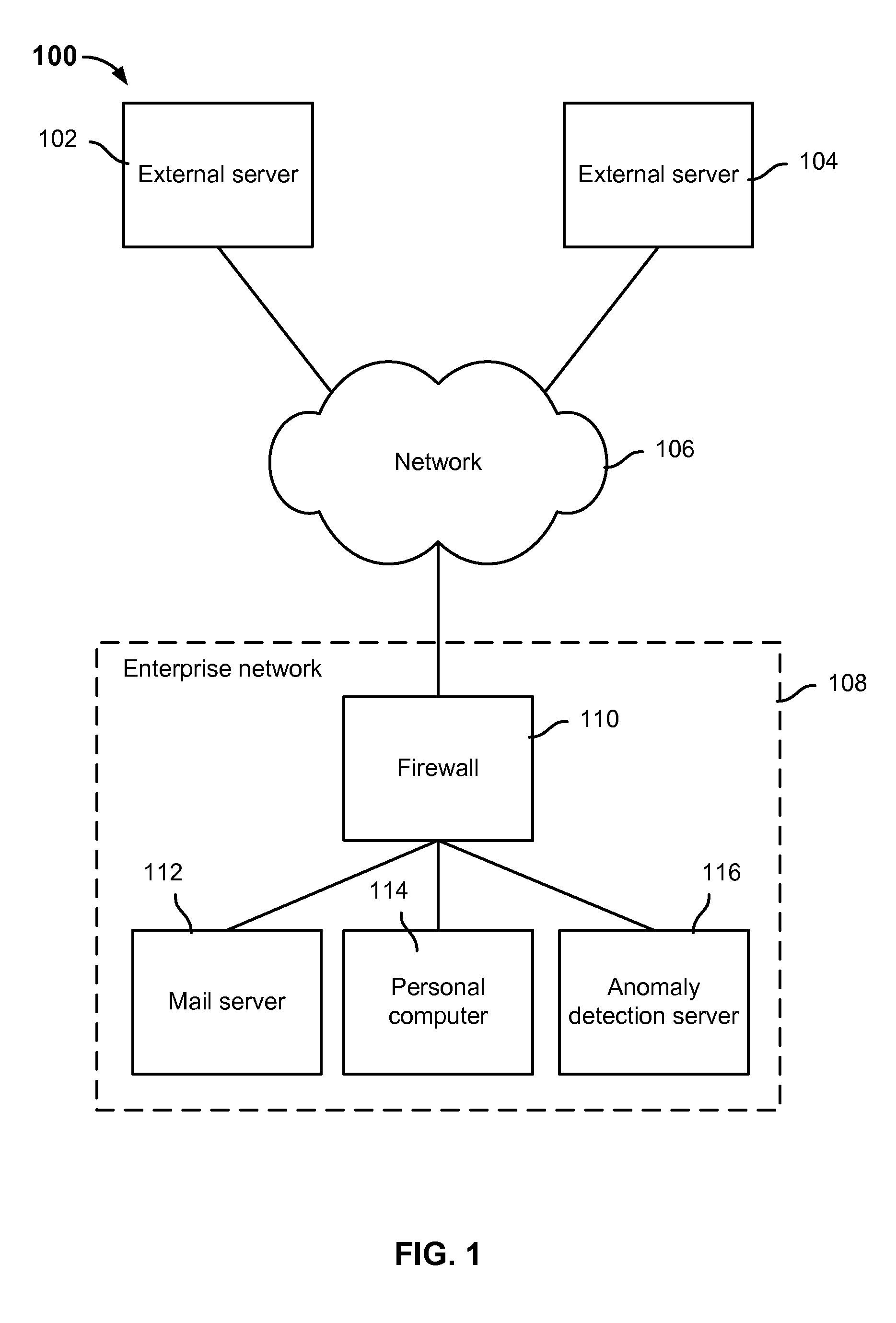
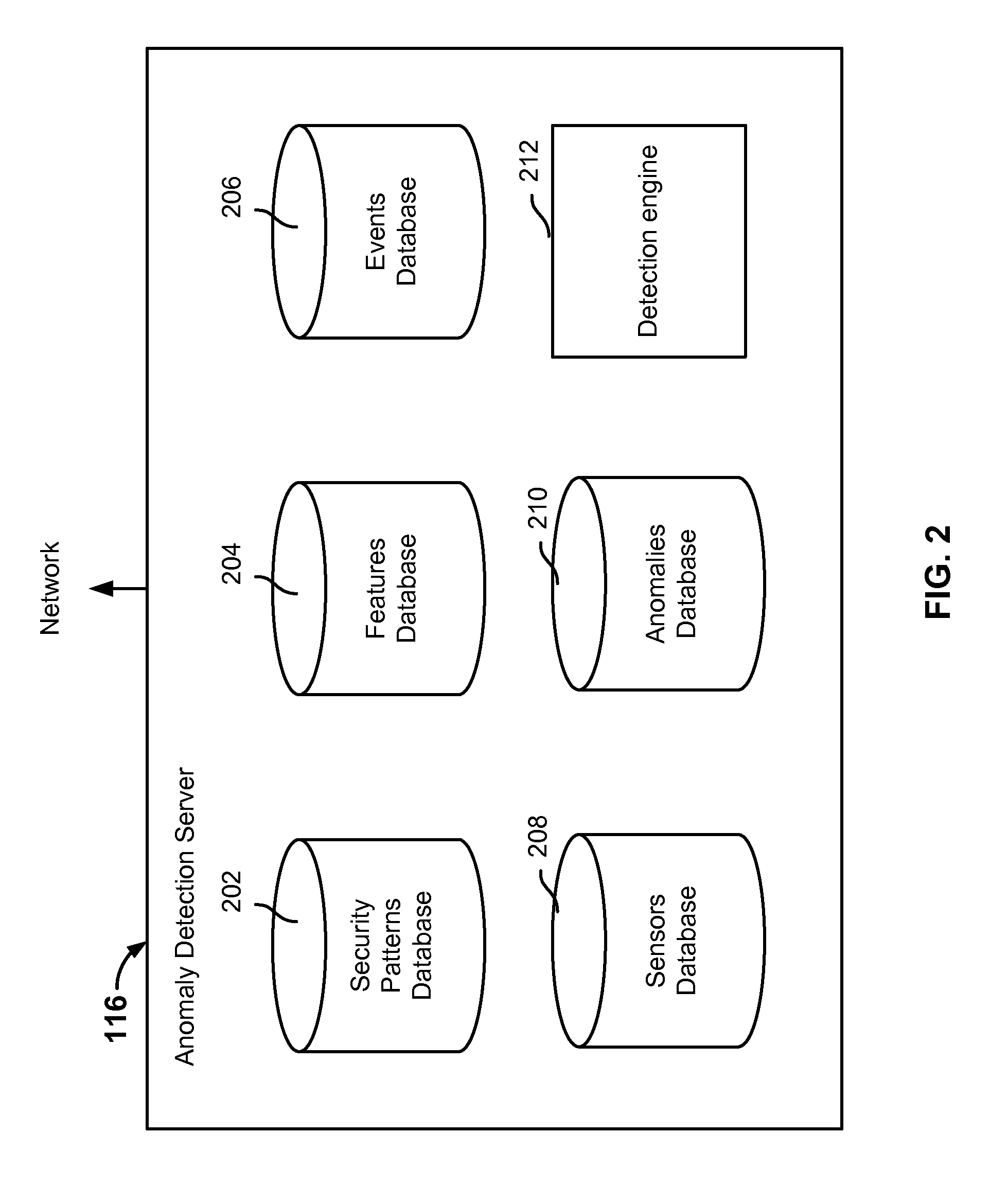
Anomaly detection system for enterprise network security
ActiveUS9112895B1Unauthorized memory use protectionComputer security arrangementsAnomaly detectionEnterprise networking
Anomaly detection is disclosed, including: determining a set of anomalous events associated with an enterprise network; and determining a path of interest based at least in part on at least a subset of the set of anomalous events.
Owner:EMC IP HLDG CO LLC
Trusted Communication Network
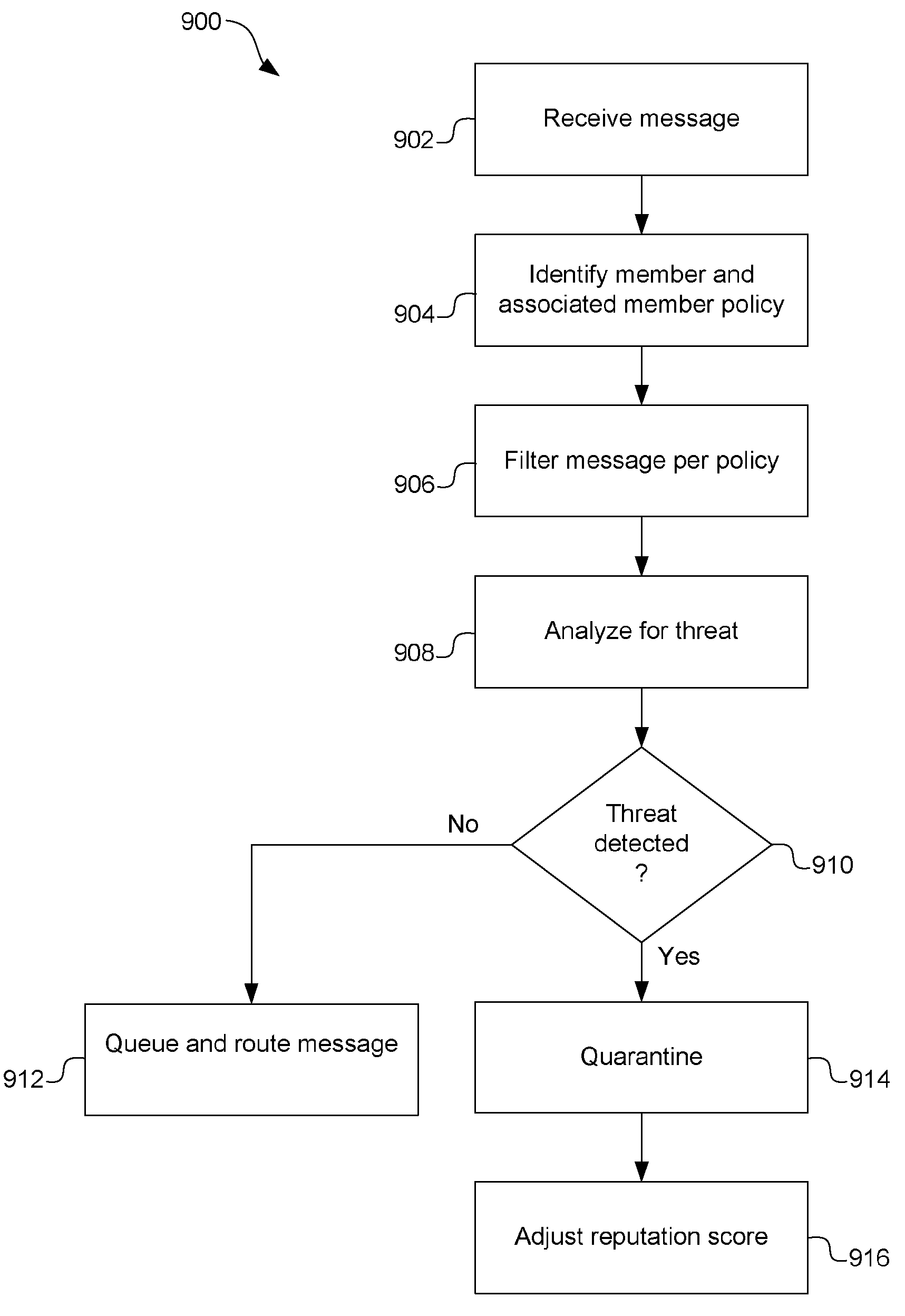
ActiveUS20070107059A1Memory loss protectionError detection/correctionEnterprise networkingSwitched communication network
A system includes a processing node configured to send authorized inbound messages to registered enterprise networks. An authorized message is a message that includes trusted source indicia. Trusted source indicia indicates that the message was sent by one or more of the processing node or an authenticated message transfer node associated with one of the registered enterprise networks. The system may further include an administration node configured to maintain registration of a plurality of message transfer nodes associated with the enterprise networks. A method includes receiving outbound messages from an authenticated message transfer node of an enterprise network, screening the messages for threats to determine whether to send the messages to associated recipients, applying a first message identifier to each message, wherein the first message identifier can be used to track the message and, for each message, sending the message to the associated recipient if no threats are detected in the message.
Owner:GDX NETWORK +1
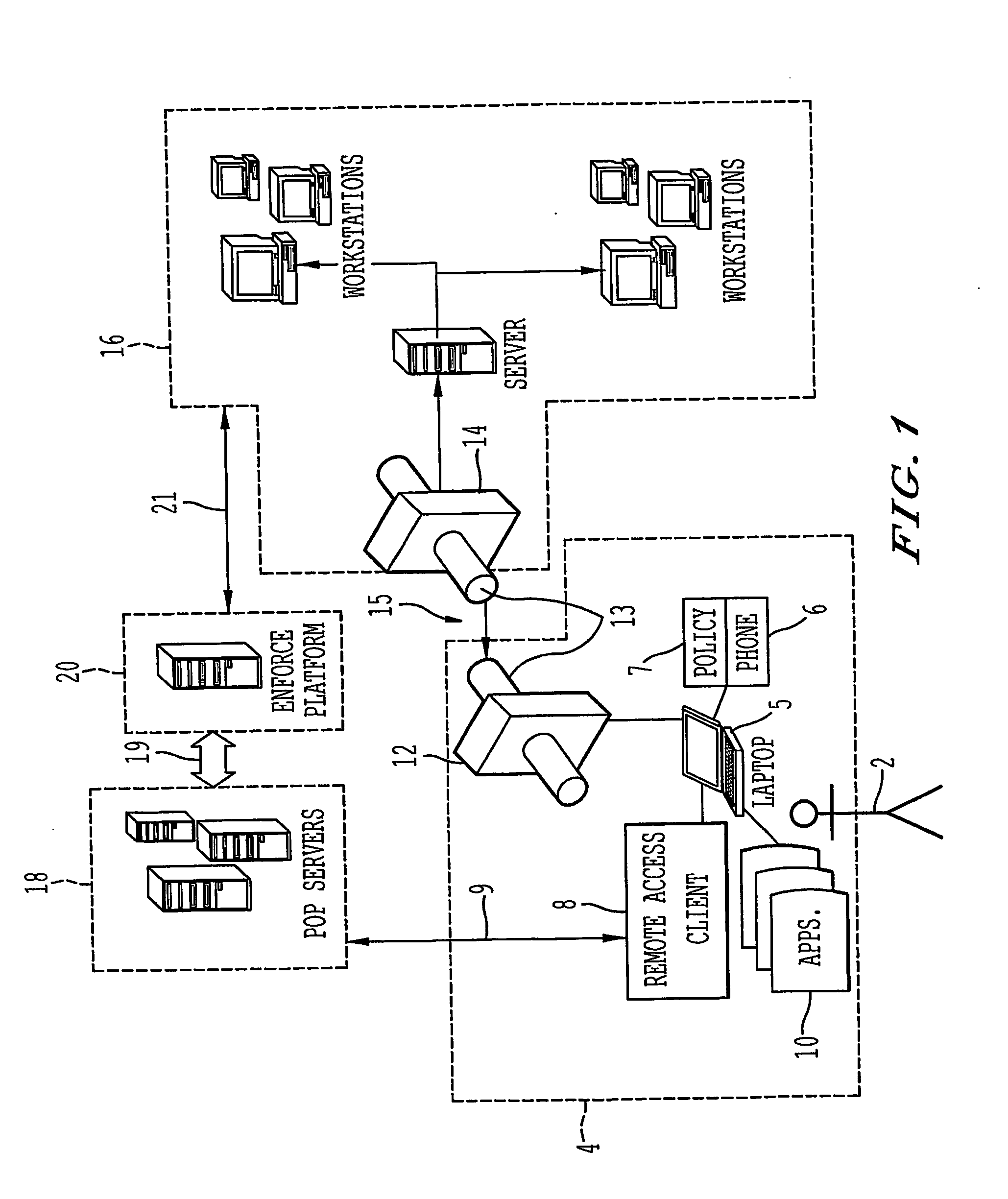
Client-side network access polices and management applications
ActiveUS20050022012A1Digital data processing detailsMultiple digital computer combinationsData terminalPoint of presence
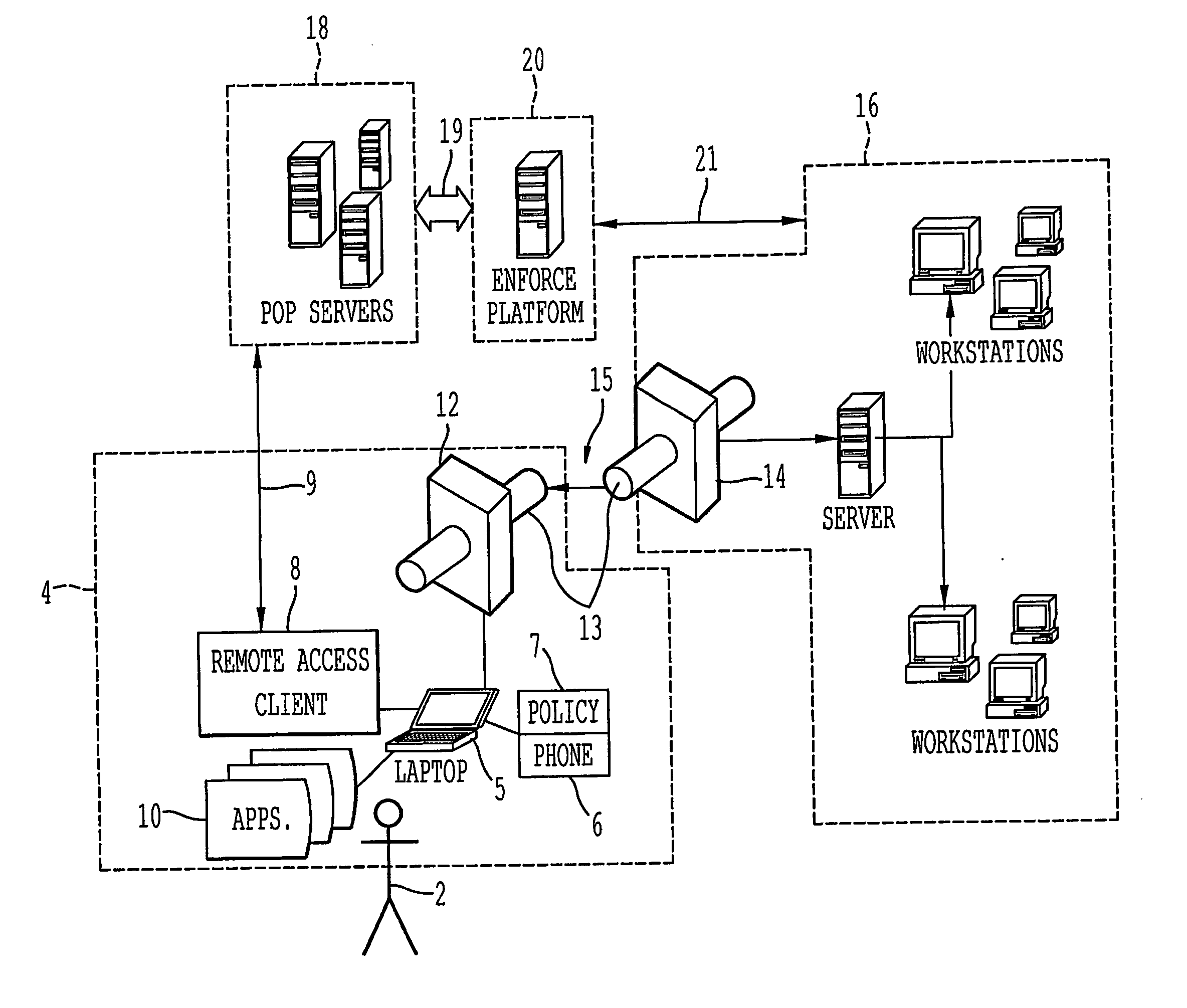
A remote access client is provided for enabling communication between a remote data terminal configured to access a public network, and an enterprise network by way of a VPN tunnel through the public network. The remote access client includes at least one application program interface (API) to receive a first verification of the operating state of a predetermined application of the remote data terminal to enable a connection agent for establishing a point of presence on the public network. Upon connection to the point of presence, the API exchanges data between the remote access client and the predetermined application of the remote data terminal. The remote access client receives a second periodic verification of the operating state of the predetermined application via the API for terminating the connection to the point of presence upon the absence of the second verification. The point of presence enables the VPN tunnel for transporting data from the remote data terminal to the enterprise network across the public network.
Owner:GINEGAR LLC
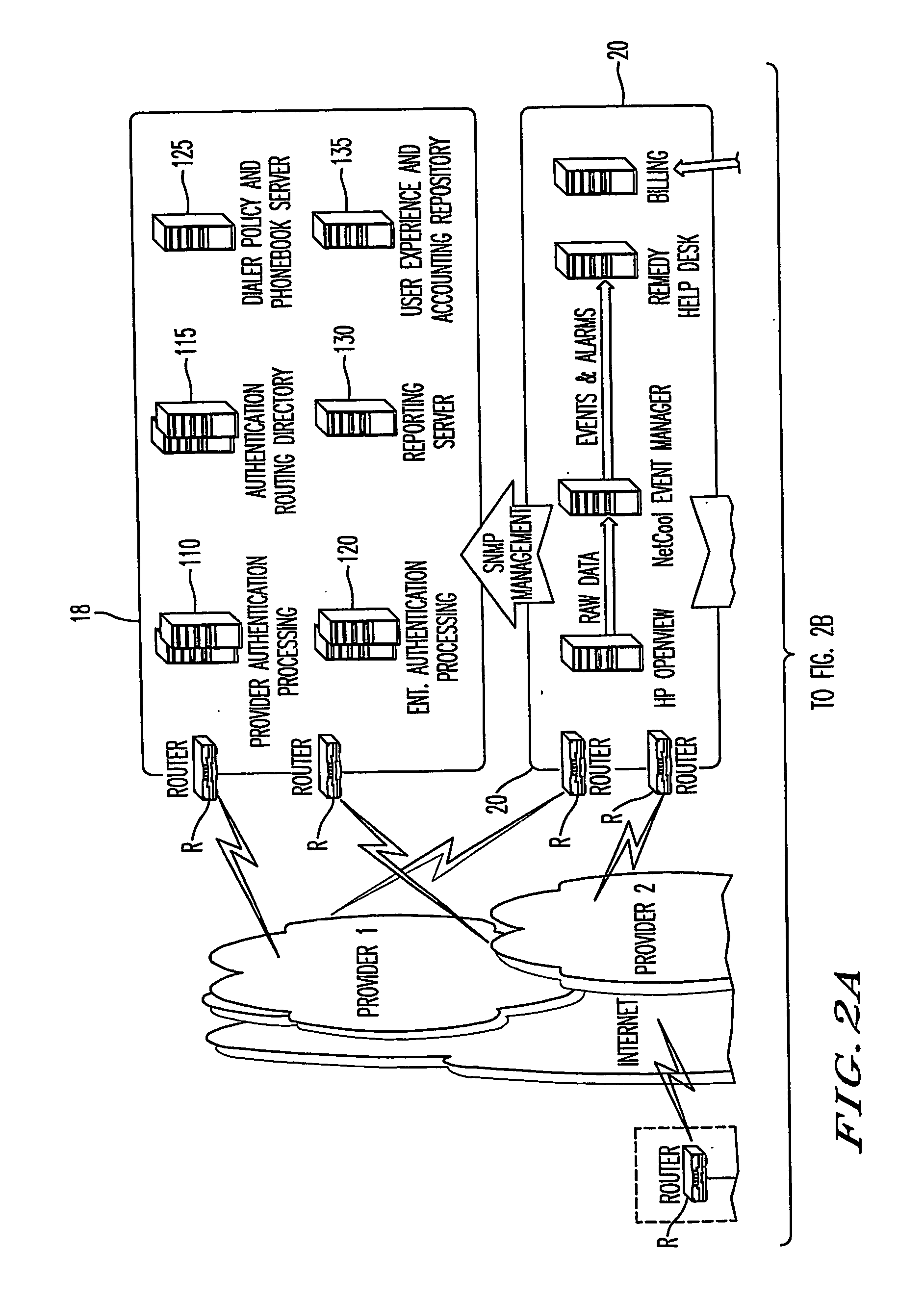
Method and system for enterprise network access control and management for government and corporate entities
InactiveUS20090254392A1Data processing applicationsComputer security arrangementsNetwork Access ControlIdentity management
A method, system, computer program product, and devices for enterprise network access control and management for Government and Corporate entities, including interagency identity management; connectors and controls; an interagency directory services transformation service; a user / duty position resolving service; role-based encryption key management; role-based business process modeling; and proximity-based access control enabled by user-role-track association.
Owner:ZANDER VAN S
Security groups for VLANs
Methods and devices are provided for implementing security groups in an enterprise network. The security groups include first network nodes that are subject to rules governing communications between the first network nodes and second network nodes. An indicator, referred to as a security group tag (SGT), identifies members of a security group. In some embodiments, the SGT is provided in a field of a data packet reserved for layer 3 information or a field reserved for higher layers. However, in other embodiments, the SGT is provided in a field reserved for layer 1 or layer 2. In some embodiments, the SGT is not provided in a field used by interswitch links or other network fabric devices for the purpose of making forwarding decisions.
Owner:CISCO TECH INC
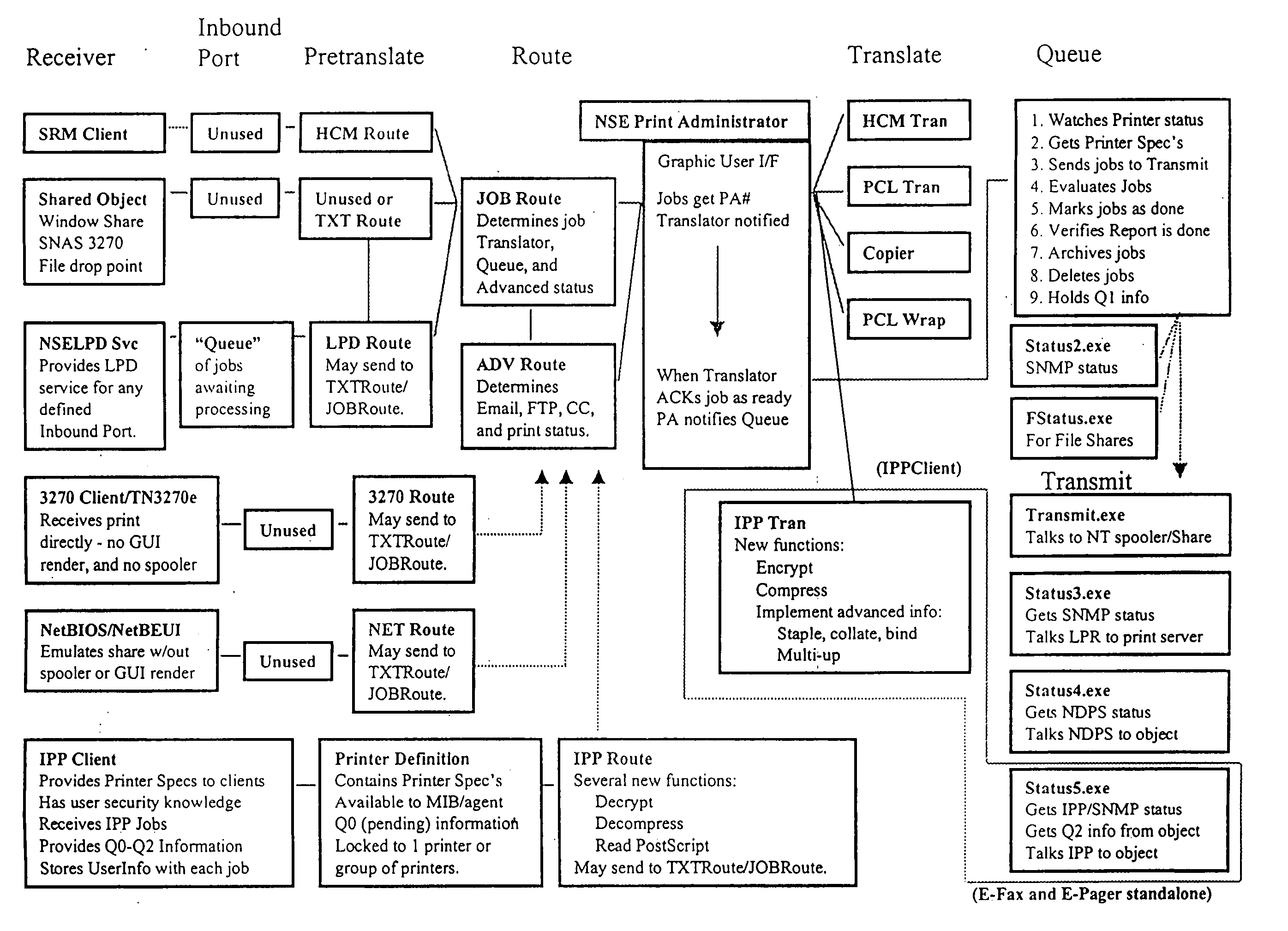
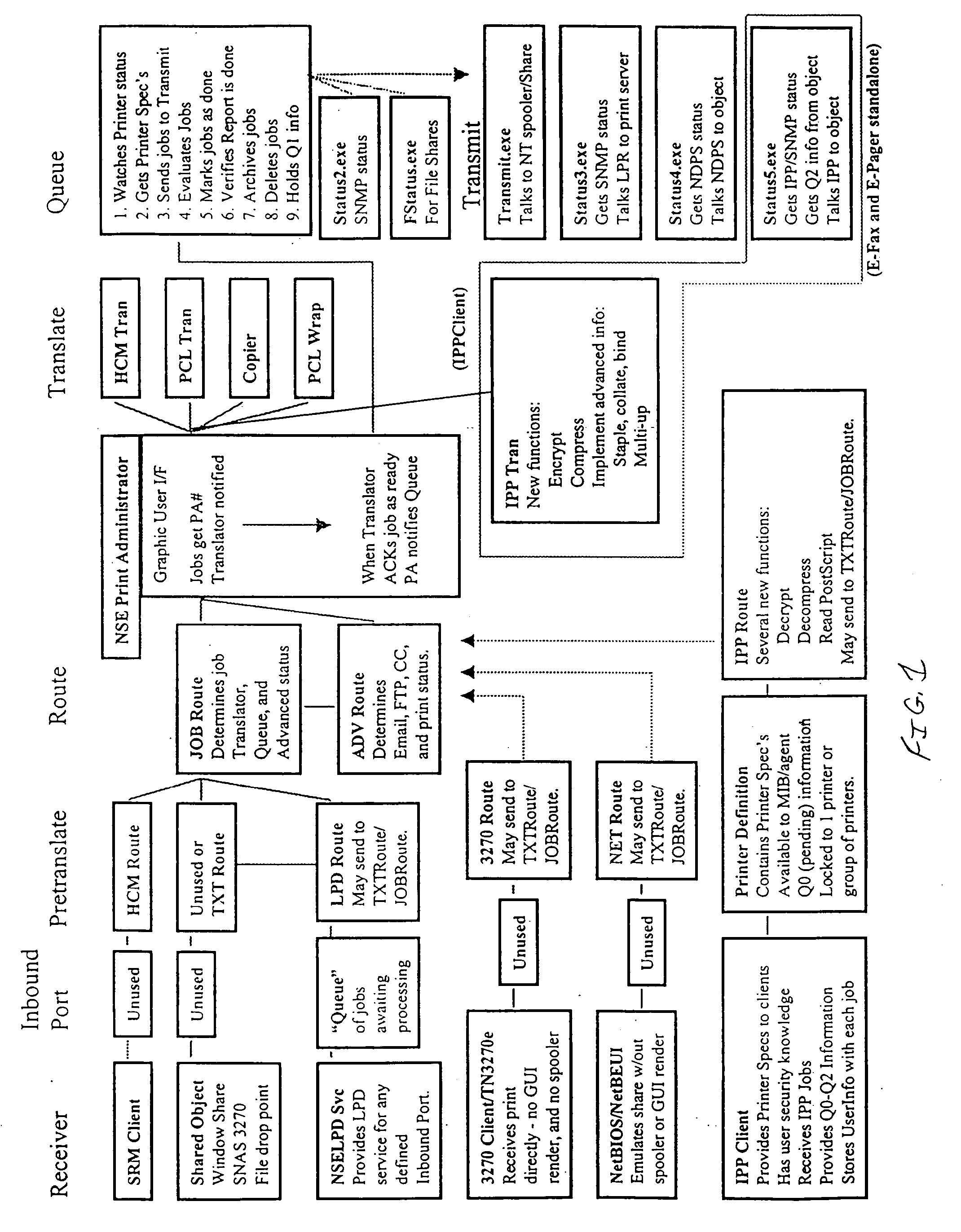
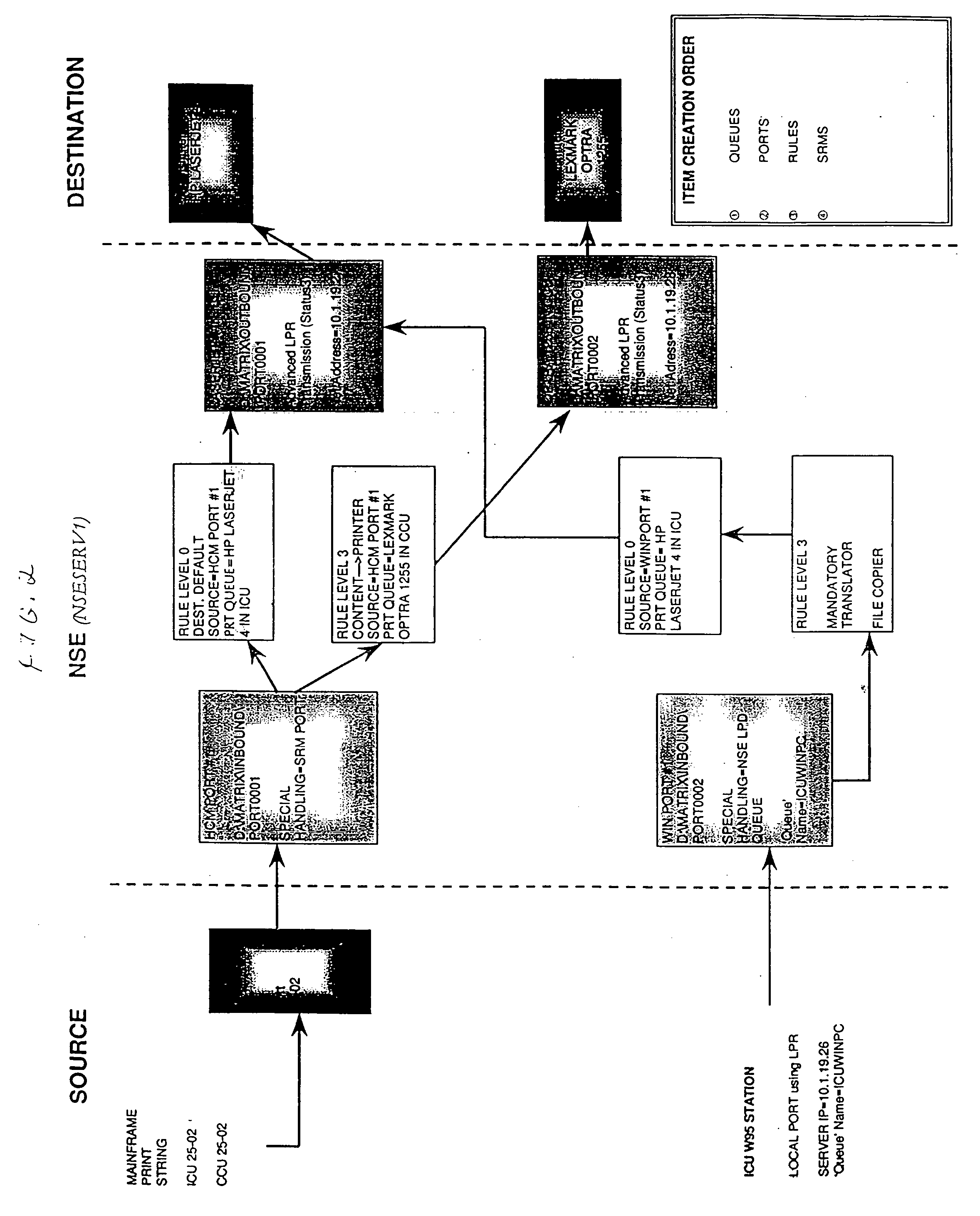
Printer control and document management system
InactiveUS20040105122A1Digital data processing detailsVisual presentation using printersComputer printingElectronic form
A printer control and information management system is provided employing numerous individual satellite modules, and providing an enterprise-wide output system capable of receiving all types of input and redirecting of all types of output. Data can be inputted from any location in an enterprise system and coordinated into a coherent format for reporting and forms processing. Forms can be automatically generated based on the data inputted, which forms can be directed to the appropriate personnel. The system provides for notifications to the appropriate personnel in order to resolve problems which may arise from the operation of the various equipment utilized in the enterprise network system. Information can be redirected to anyone within the system, the user identifying the manner and format of the information to be presented. Thus, inbound reports can be received from different systems and outputs delivered in the format that is preferred by the user. Report recognition is provided for any application, with the ability to merge textual information with electronic forms. Additionally, the forms can be completed with bar code information to prevent inadvertent disclosure of sensitive information. Large and contiguous host generated reports can be electronically distributed to users, as well as the ability to automatically fax any type of report directly to any recipient. The system can be accessed via the Internet for ease of inputting and reviewing information at any location.
Owner:ST CLAIR MANAGEMENT RESOURCES
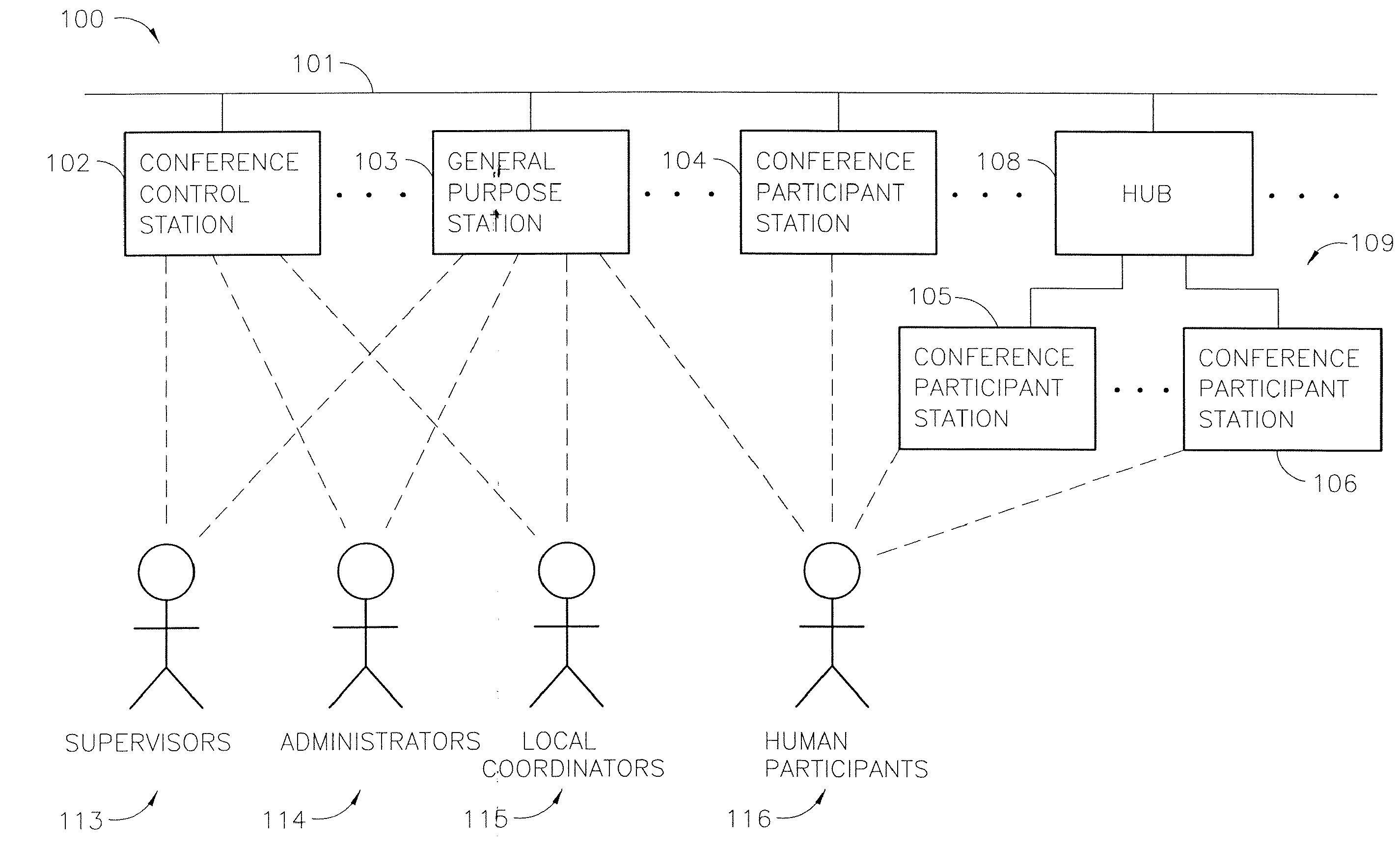
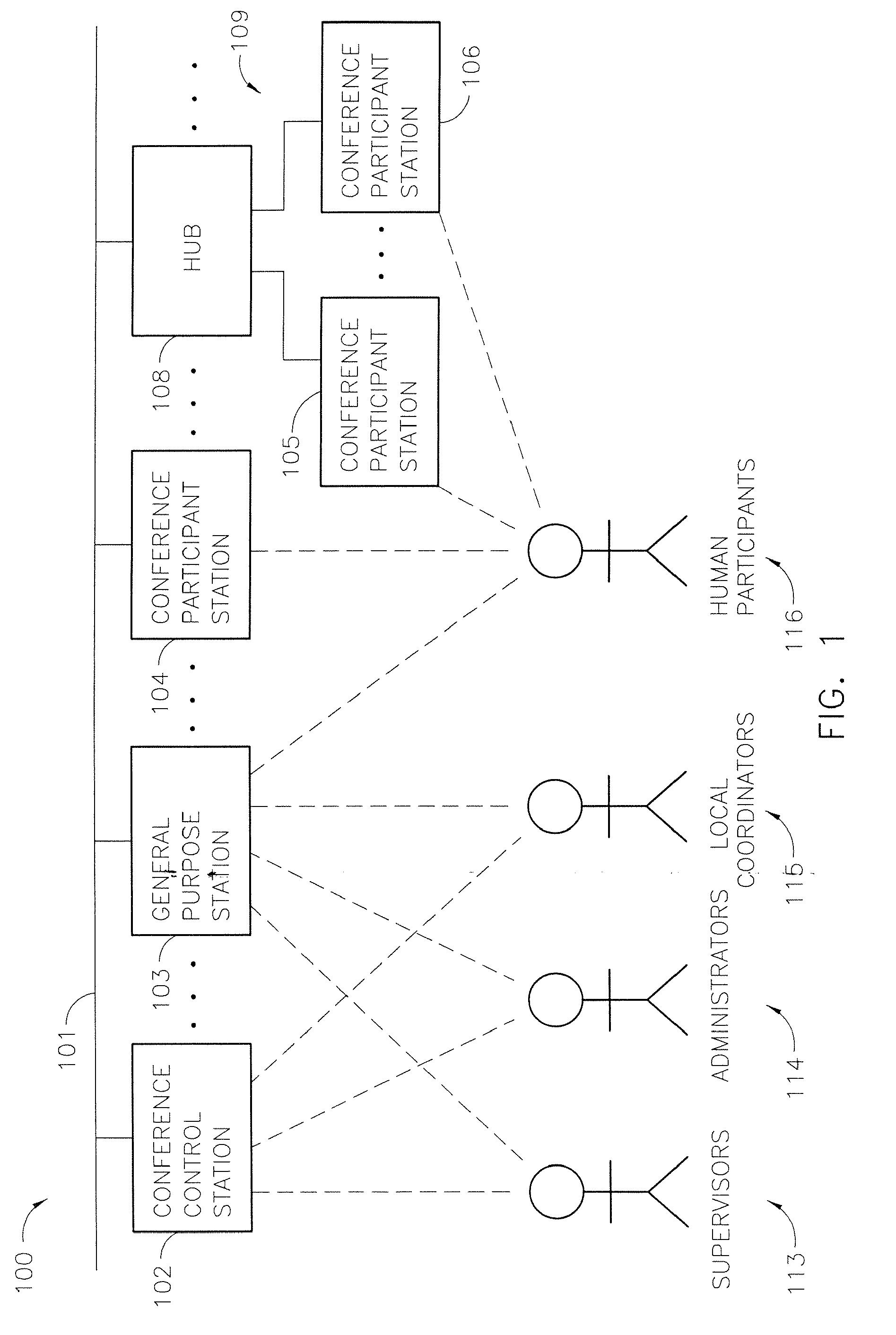
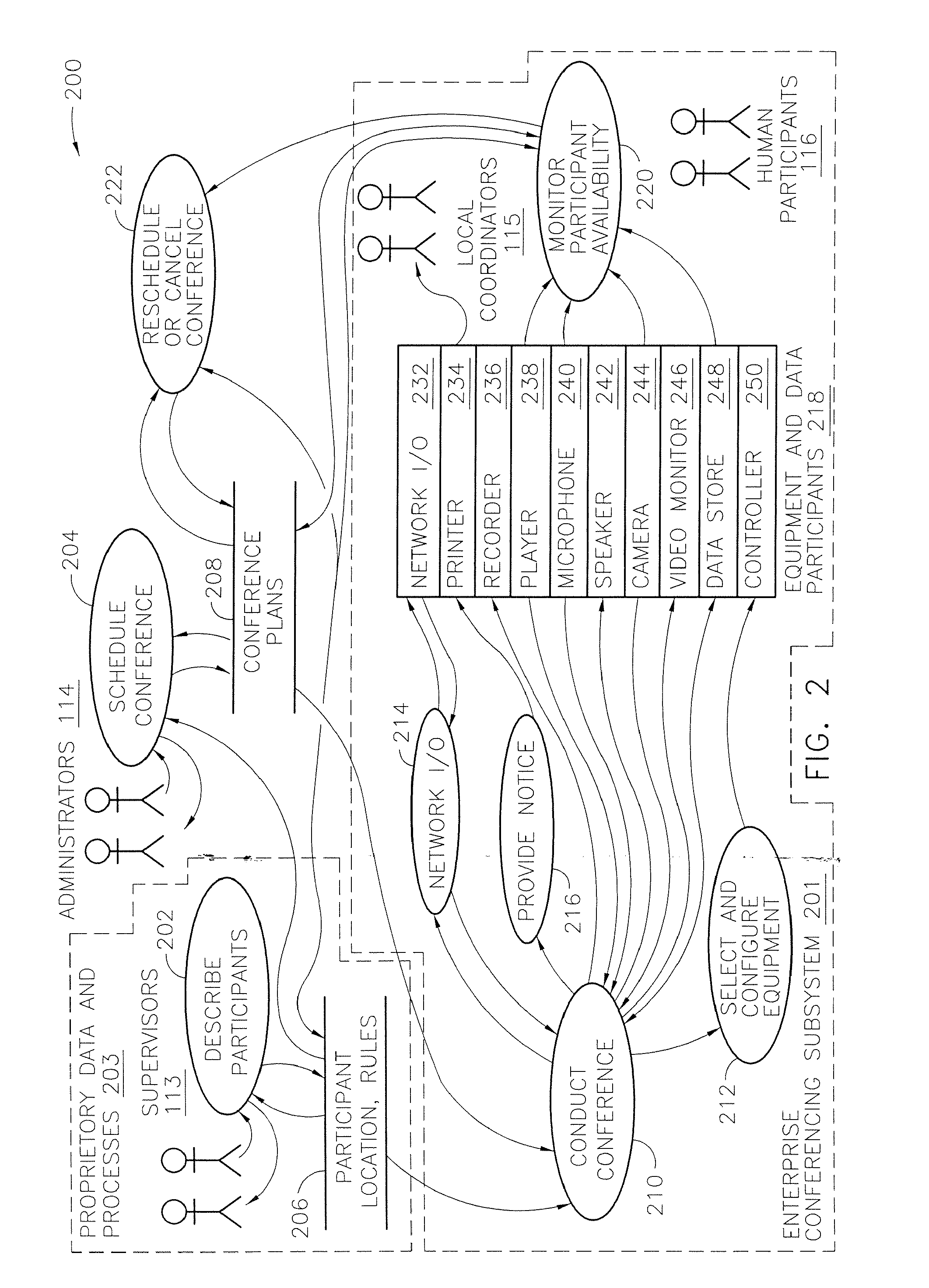
Systems and methods for conferencing among governed and external participants
InactiveUS20070285504A1Highly integratedTelevision conference systemsTwo-way working systemsNetwork linkEnterprise networking
A video conference system for an enterprise facilitates conferences among participants governed by the policies of the enterprise and other participants. The system includes conference participant stations for use by governed participants and a gateway that facilitates linking through a remote network to conference participant stations used by those external to the enterprise. Further, the system may also include an enterprise network having a gateway to facilitate linking through a remote network to conference participant stations and to other enterprise networks. The system includes barriers to access to data and processes proprietary to the enterprise and external participant. A related method may invoke one of a paid, a prepaid or and unpaid video conferencing on a remote network.
Owner:MULTIMEDIA TELESYS
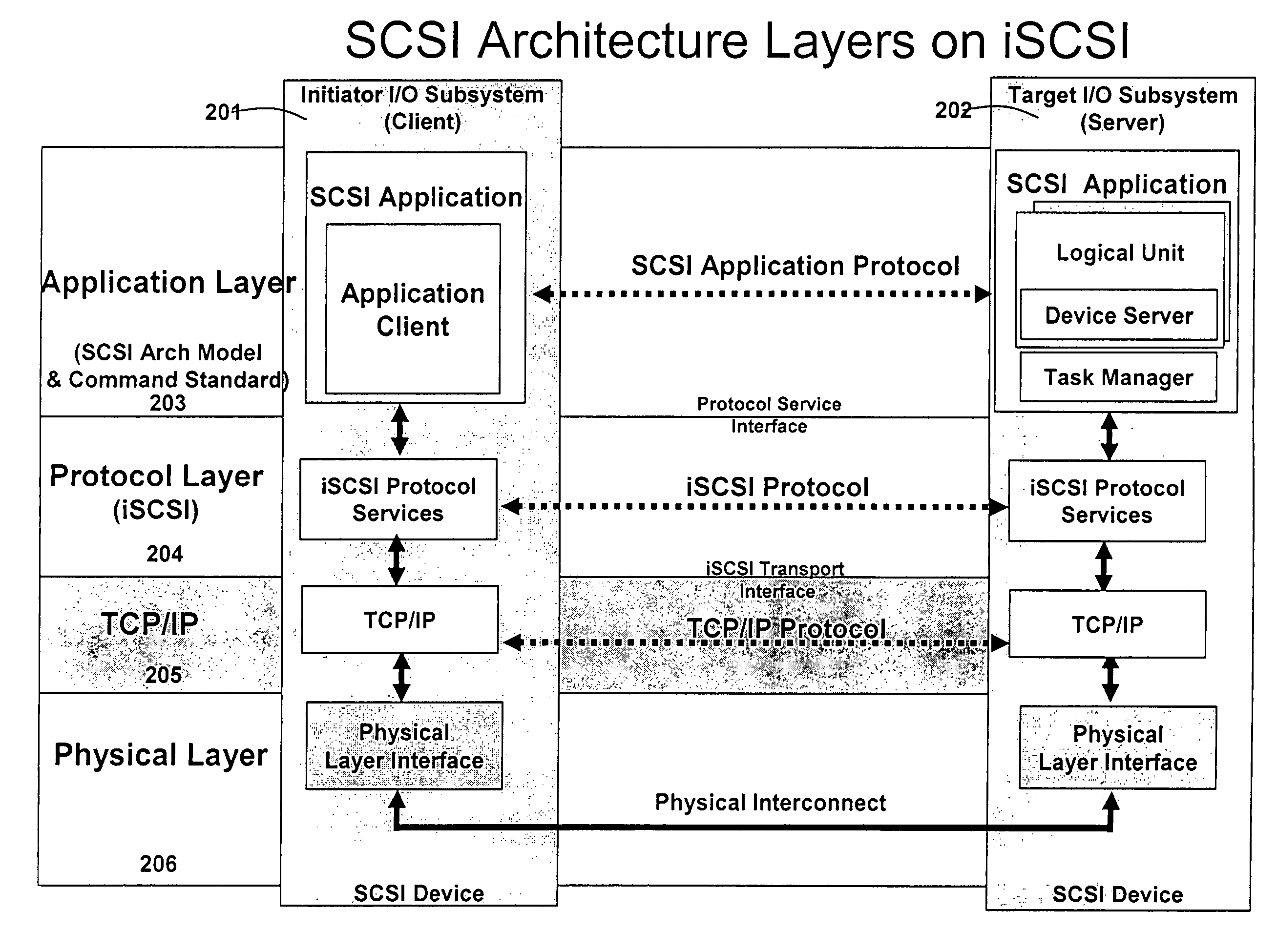
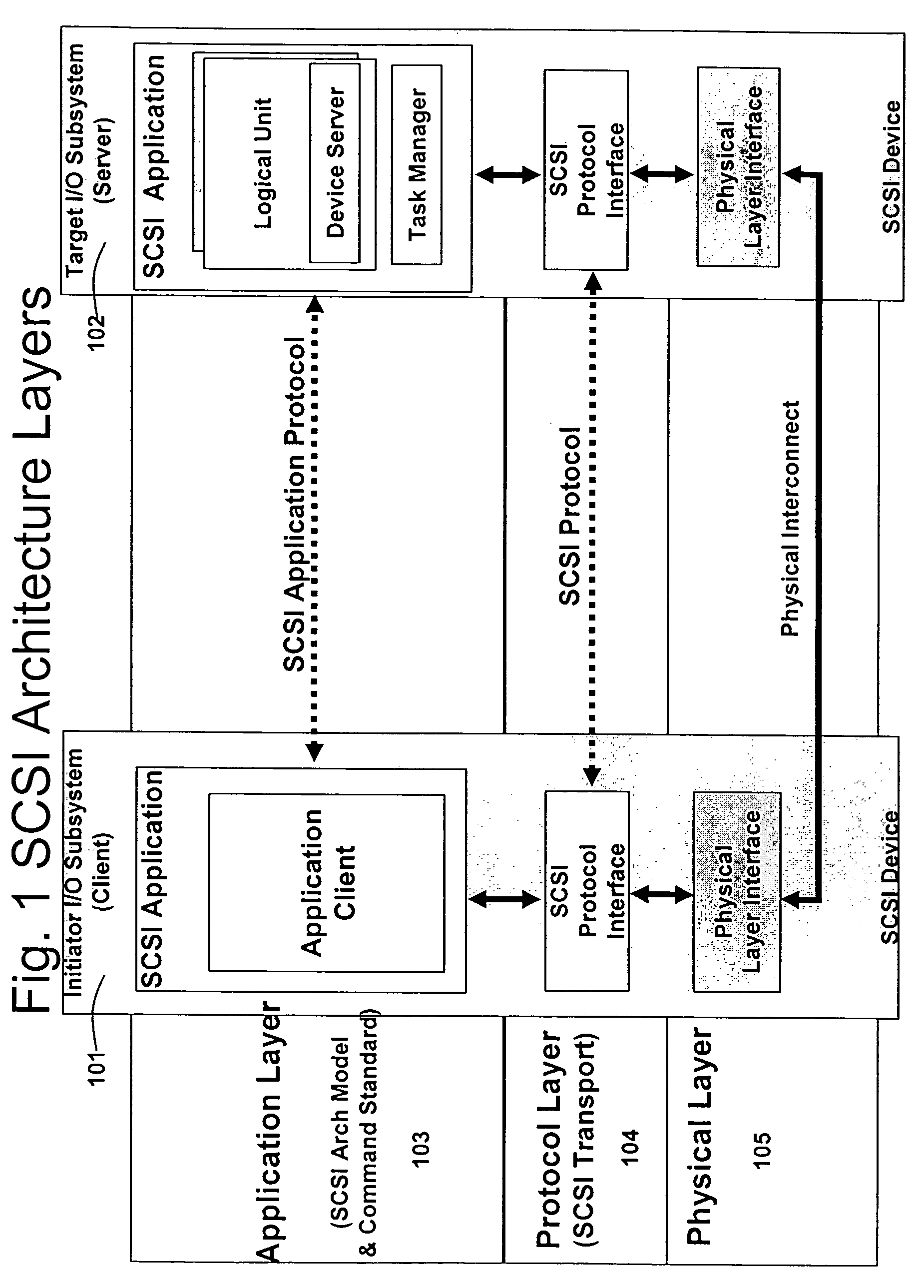
Runtime adaptable protocol processor
ActiveUS7631107B2Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer controlTime-division multiplexInternal memoryData pack
A runtime adaptable protocol processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
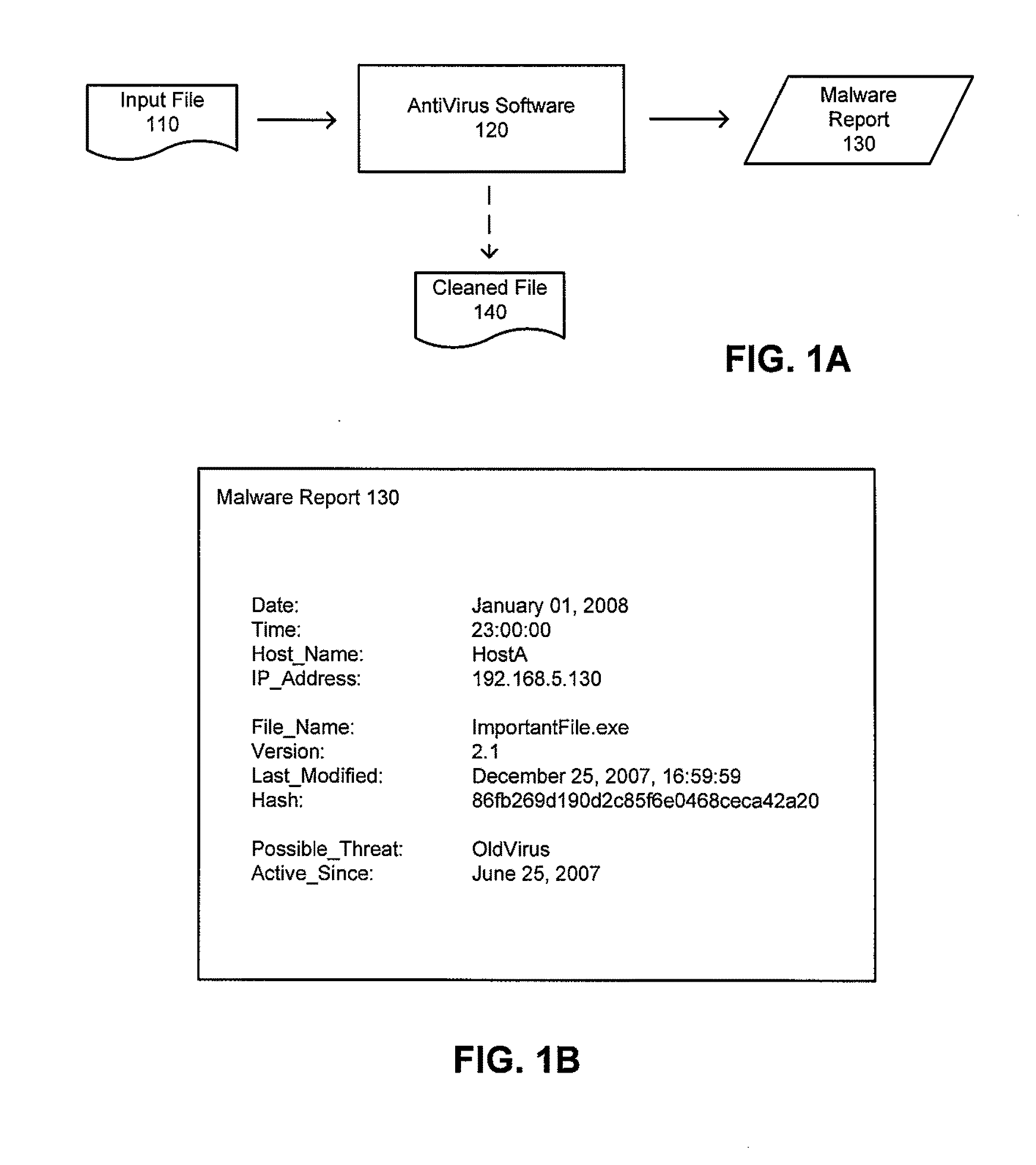
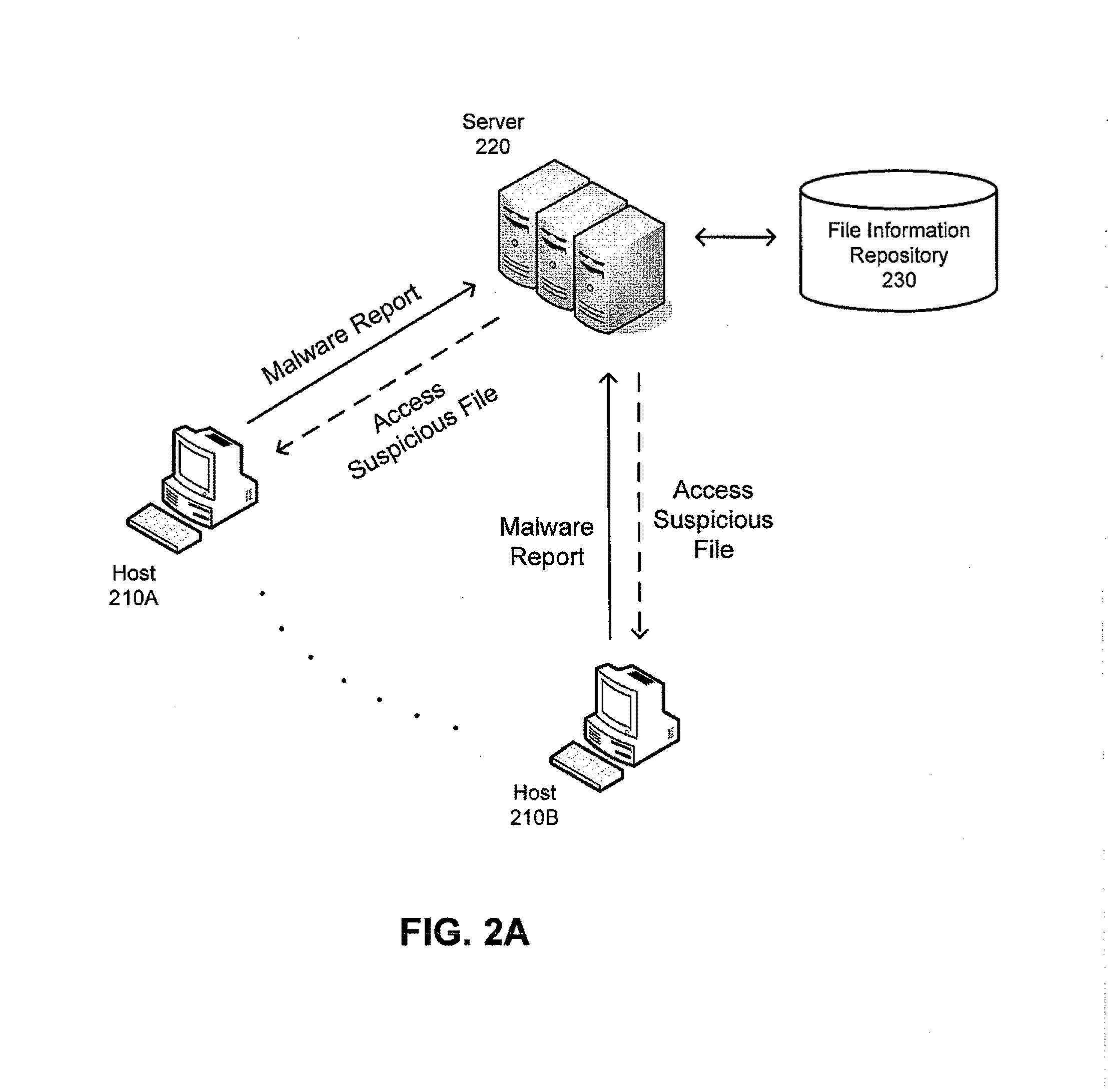
Mitigating false positives in malware detection
ActiveUS20110173698A1Reduce the burden onReducing false positivesMemory loss protectionError detection/correctionMalwareDatabase
An anti-malware system that reduces the likelihood of detecting a false positive. The system is applied in an enterprise network in which a server receives reports of suspected malware from multiple hosts. Files on hosts suspected of containing malware are compared to control versions of those files. A match between a suspected file and a control version is used as an indication that the malware report is a false positive. Such an indication may be used in conjunction with other information, such as whether other hosts similarly report suspect files that match control versions or whether the malware report is generated by a recently changed component of the anti-malware system.
Owner:MICROSOFT TECH LICENSING LLC
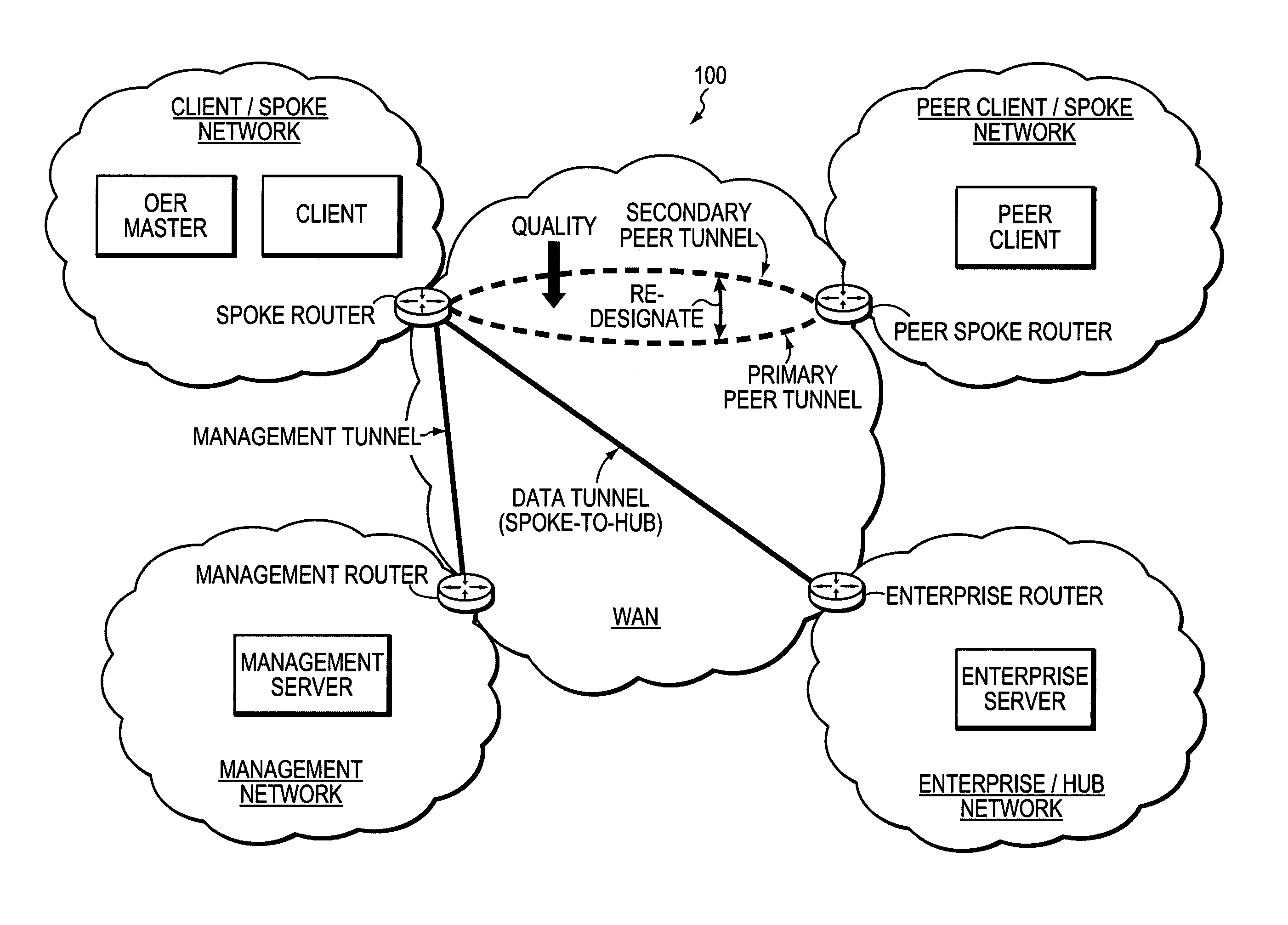
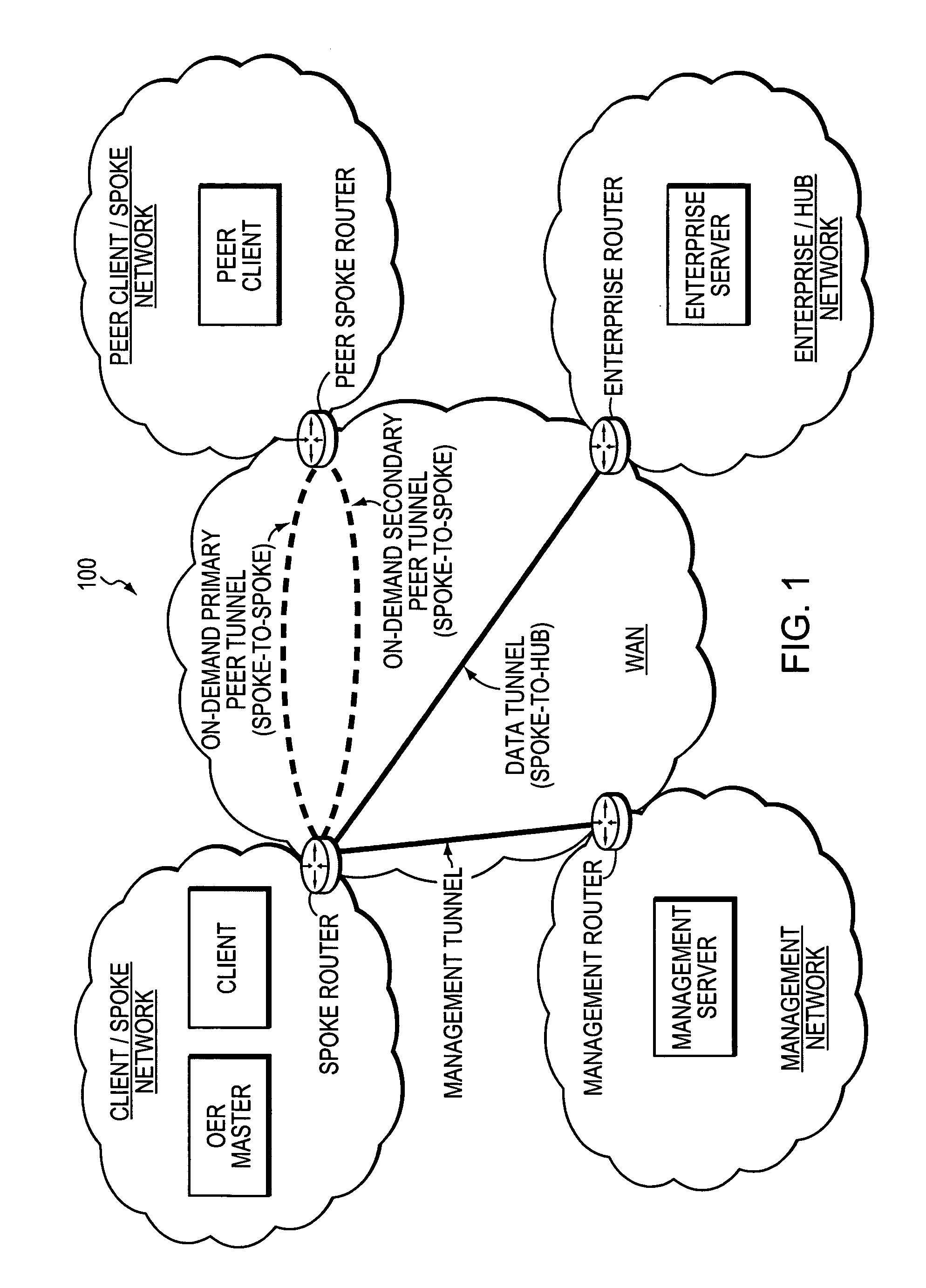
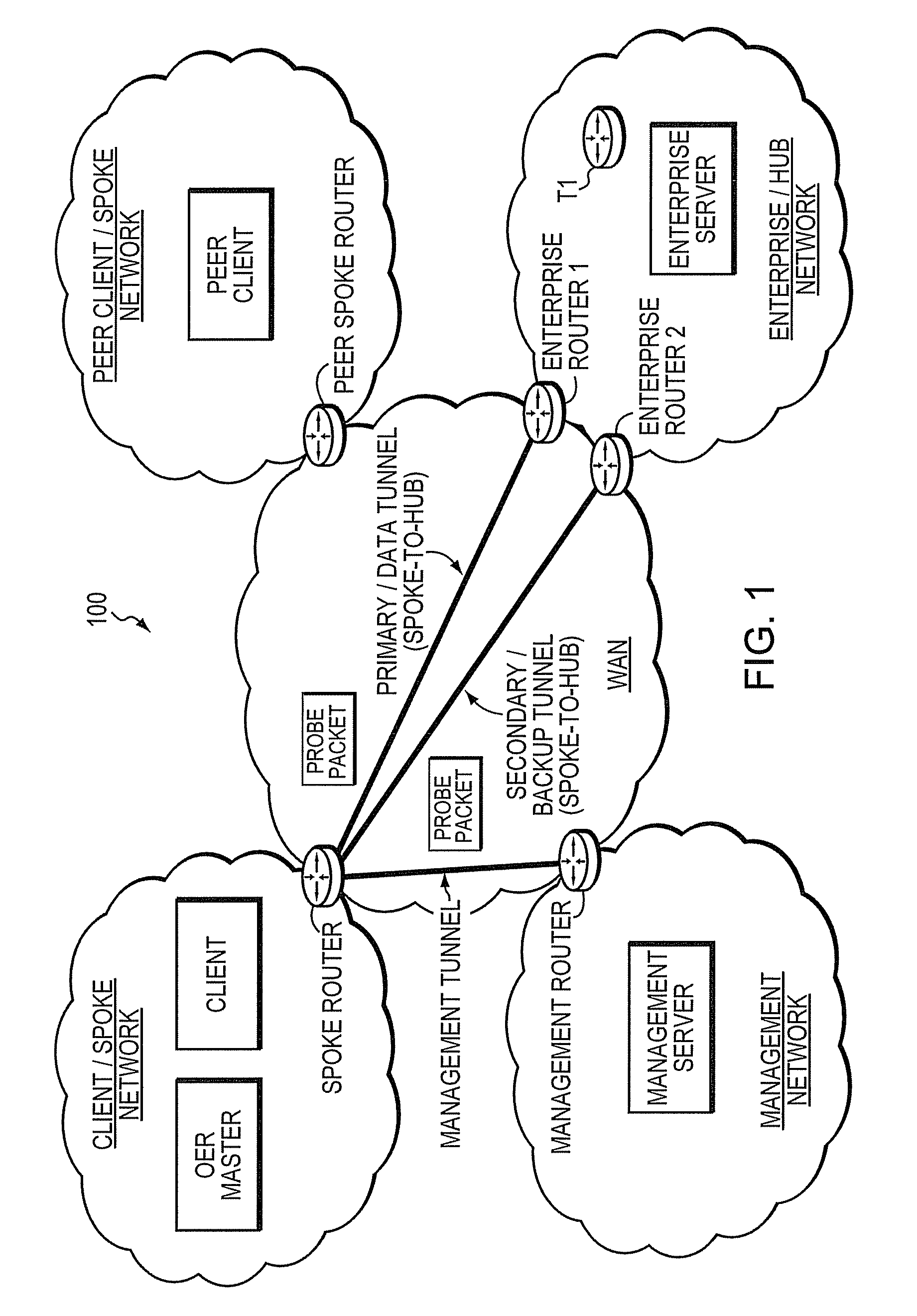
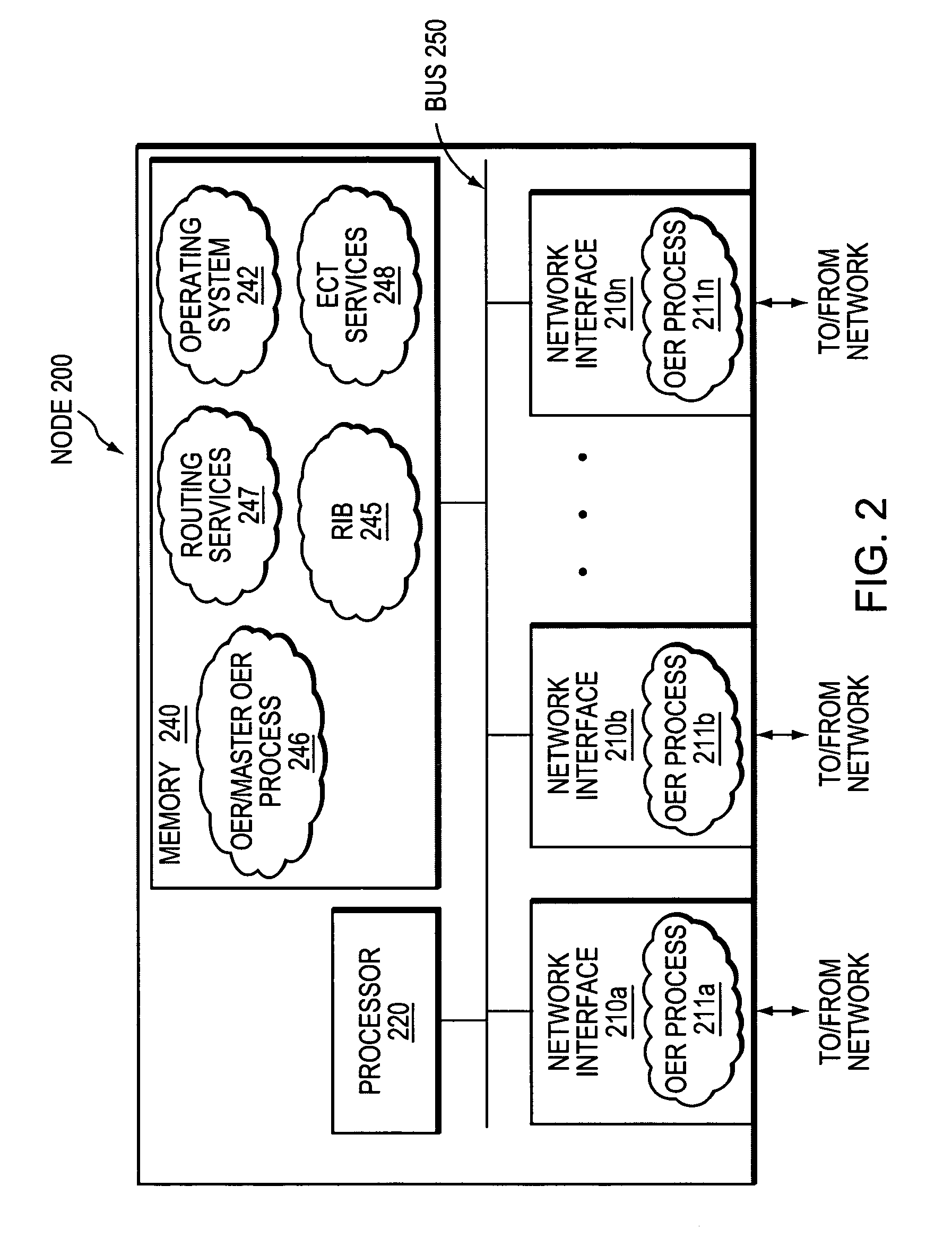
Technique for using OER with an ECT solution for multi-homed spoke-to-spoke sites
InactiveUS7801030B1Extended run timeImprove usabilityError preventionTransmission systemsStationPrivate network
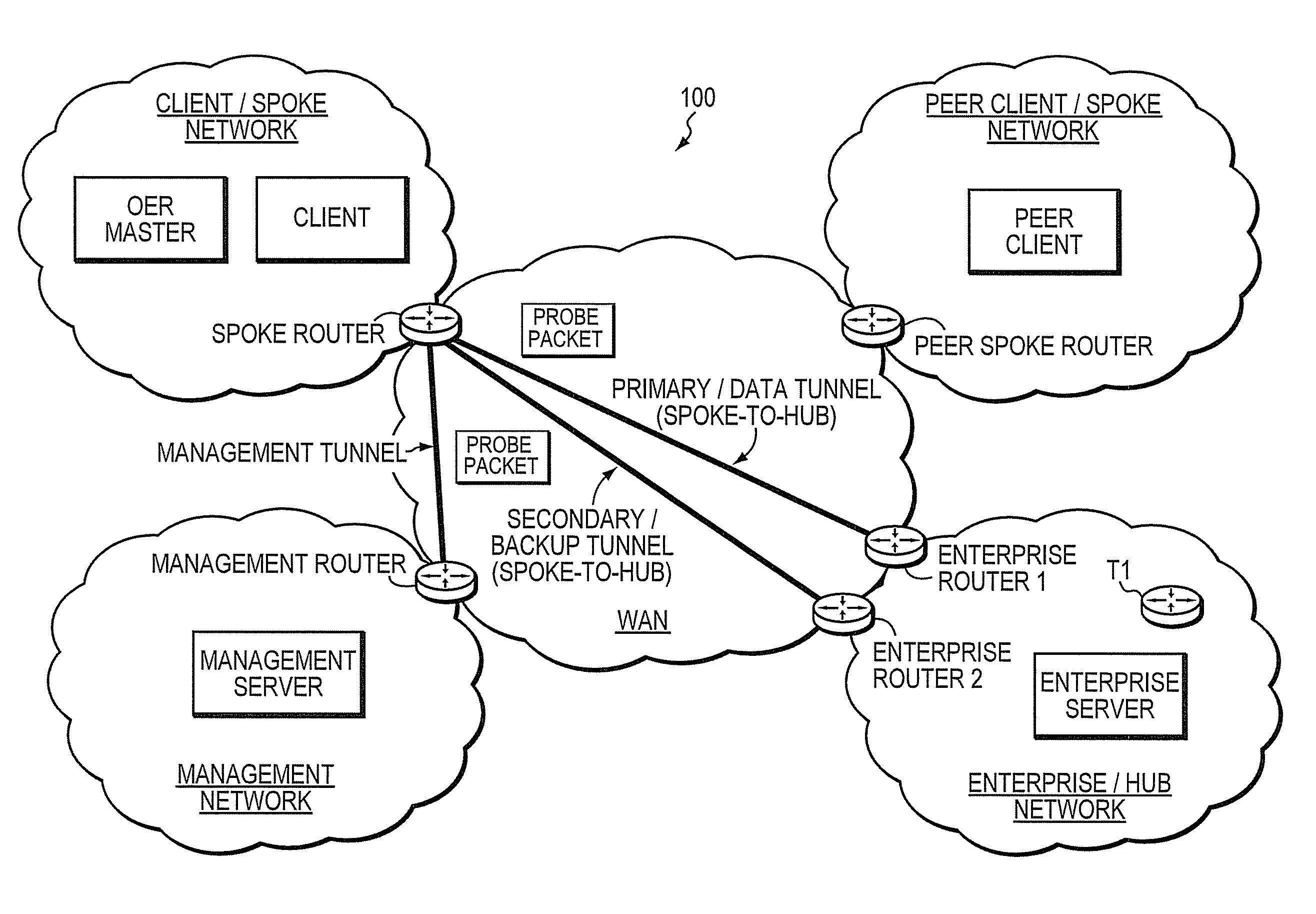
A technique dynamically creates and utilizes a plurality of multi-homed Virtual Private Network (VPN) tunnels from a client node of one spoke network to a client node of another spoke network in a computer network. According to the technique, a VPN client node, e.g., a “spoke,” creates at least one VPN tunnel with an enterprise network, e.g., a “hub.” Once the spoke-to-hub tunnel is established, the spoke may dynamically create a plurality of VPN tunnels with a peer spoke network, e.g., a “peer spoke.” The spoke designates (e.g., for a prefix) one of the tunnels as a primary tunnel and the other tunnels as secondary tunnels, and monitors the quality (e.g., loss, delay, reachability, etc.) of all of the dynamic tunnels, such as, e.g., by an Optimized Edge Routing (OER) process. The spoke may then dynamically re-designate any one of the secondary tunnels as the primary tunnel for a prefix based on the quality of the tunnels to the peer spoke. Notably, the spoke may also dynamically load balance traffic to the peer spoke among the primary and secondary tunnels based on the quality of those tunnels.
Owner:CISCO TECH INC
Access control for federated identities
ActiveUS20050188212A1Digital data processing detailsMultiple digital computer combinationsThird partyFederated identity
An authentication process in a network environment provides a remote user with secured access to an enterprise network based on recognition of a third-party security token. The method includes authenticating the user against a plurality of third-party security tokens, wherein the third-party security tokens originate from a range of different partner home sites. The remote user, prior to obtaining secured access to the enterprise network, is not known to the enterprise network, and does not need to be associated with any security tokens previously originating from the enterprise network. The enterprise network is provided with the ability to rely upon third-party security tokens to authenticate the remote user.
Owner:GOOGLE LLC
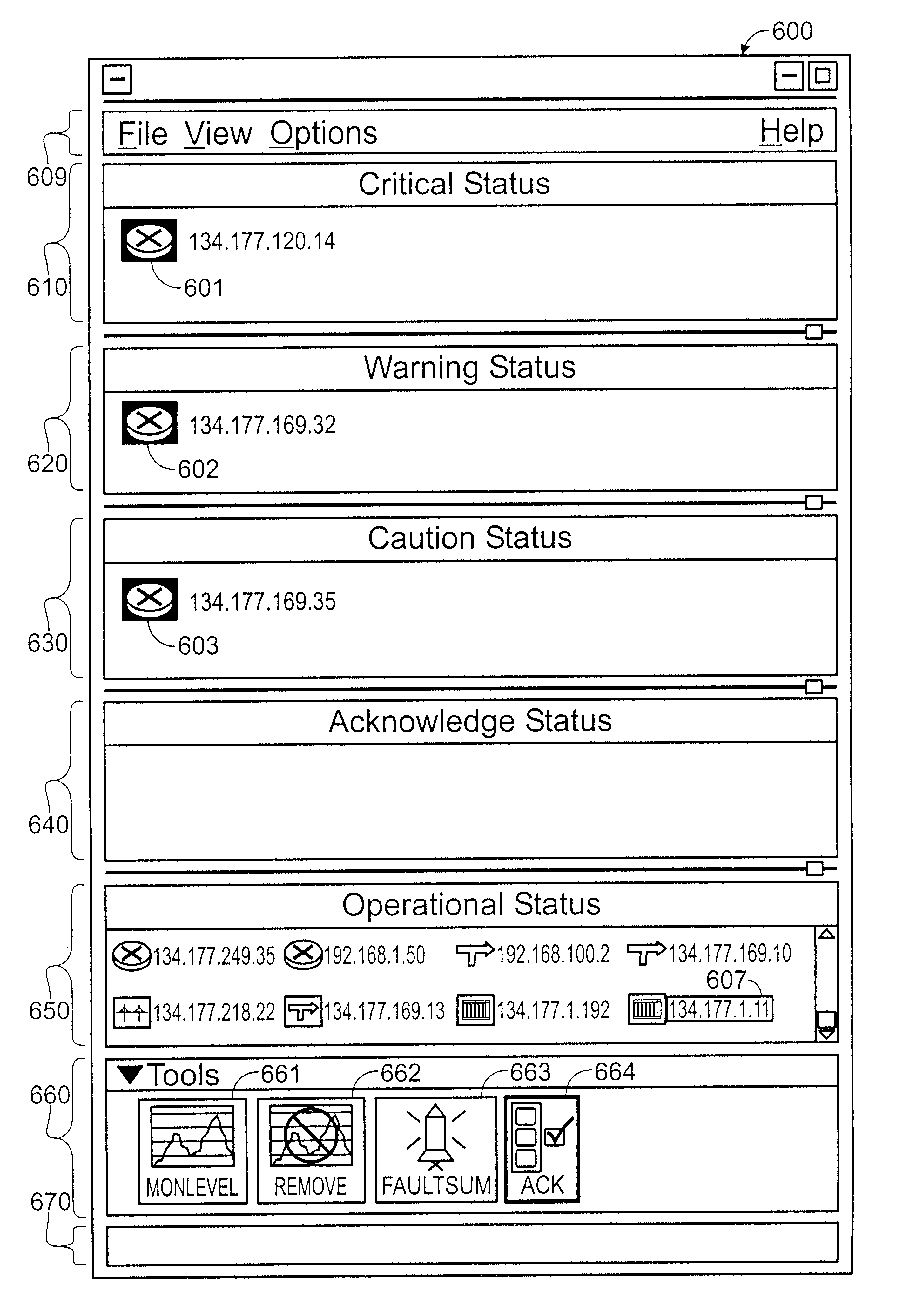
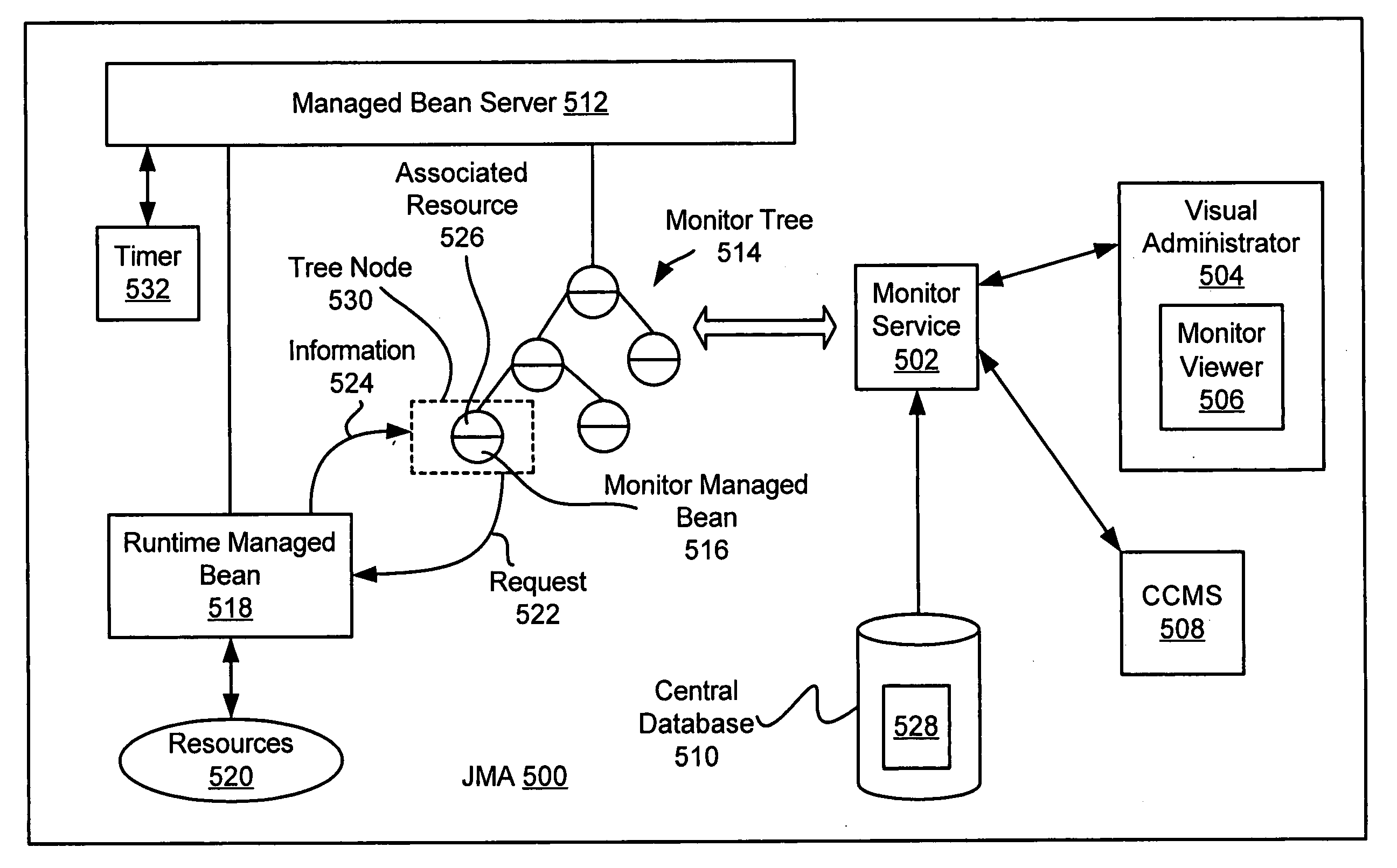
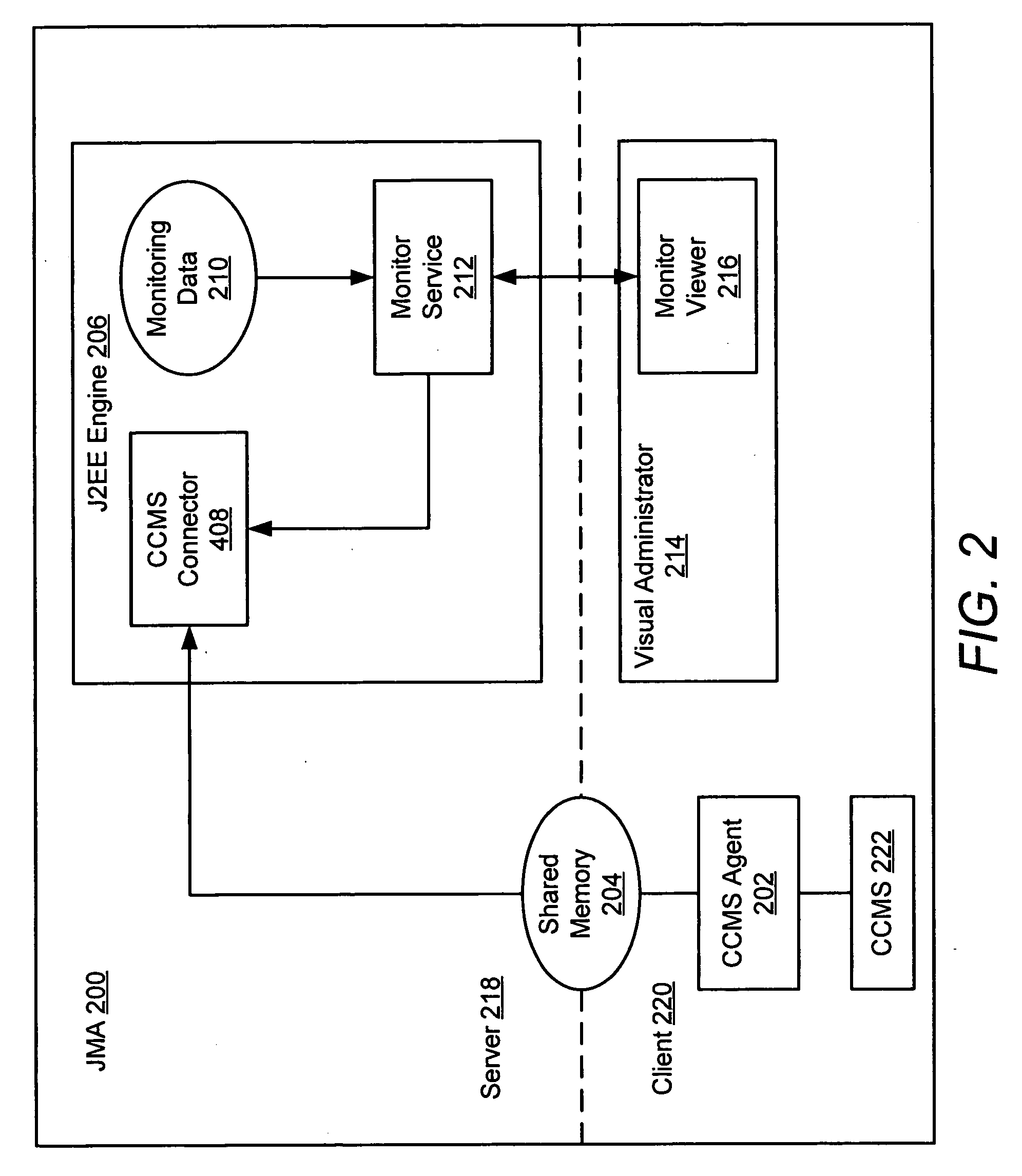
Monitor viewer for an enterprise network monitoring system
InactiveUS20050216585A1Digital computer detailsData switching networksGraphicsGraphical user interface
A method, apparatus, and system are provided for a monitor viewer in an enterprise network monitoring system. In one embodiment, upon selecting a monitor service tree node, a monitor tree (e.g., a graphical representation of one or more monitored / managed resources) is displayed in a graphical user interface. The displayed monitor tree may have one or more selectable monitor tree nodes, wherein each of the monitor tree nodes is a graphical representation of a monitored / managed resource. In an embodiment, a monitor tree node may be selected and configured in the graphical user interface.
Owner:TODOROVA TSVETELINA +2
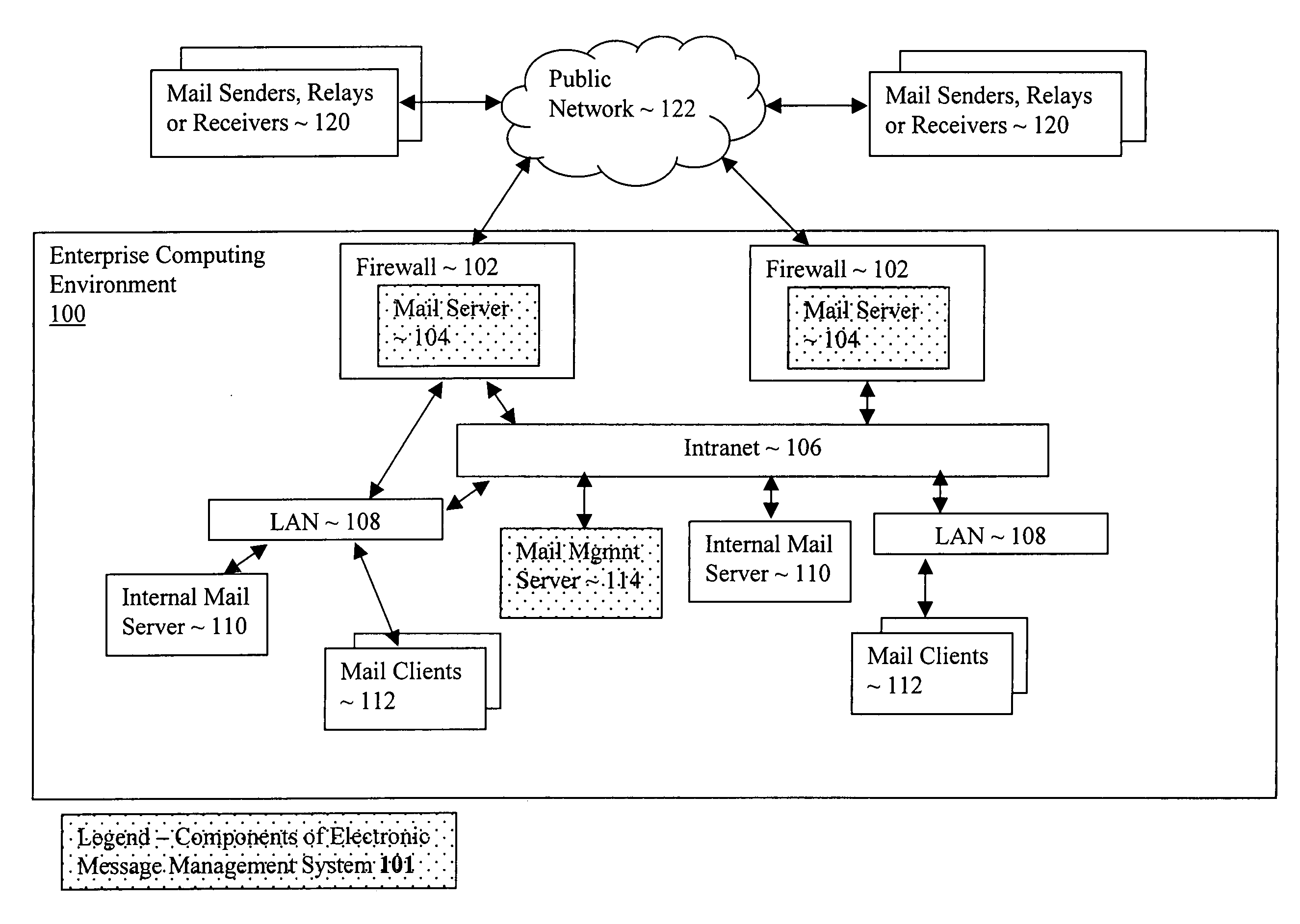
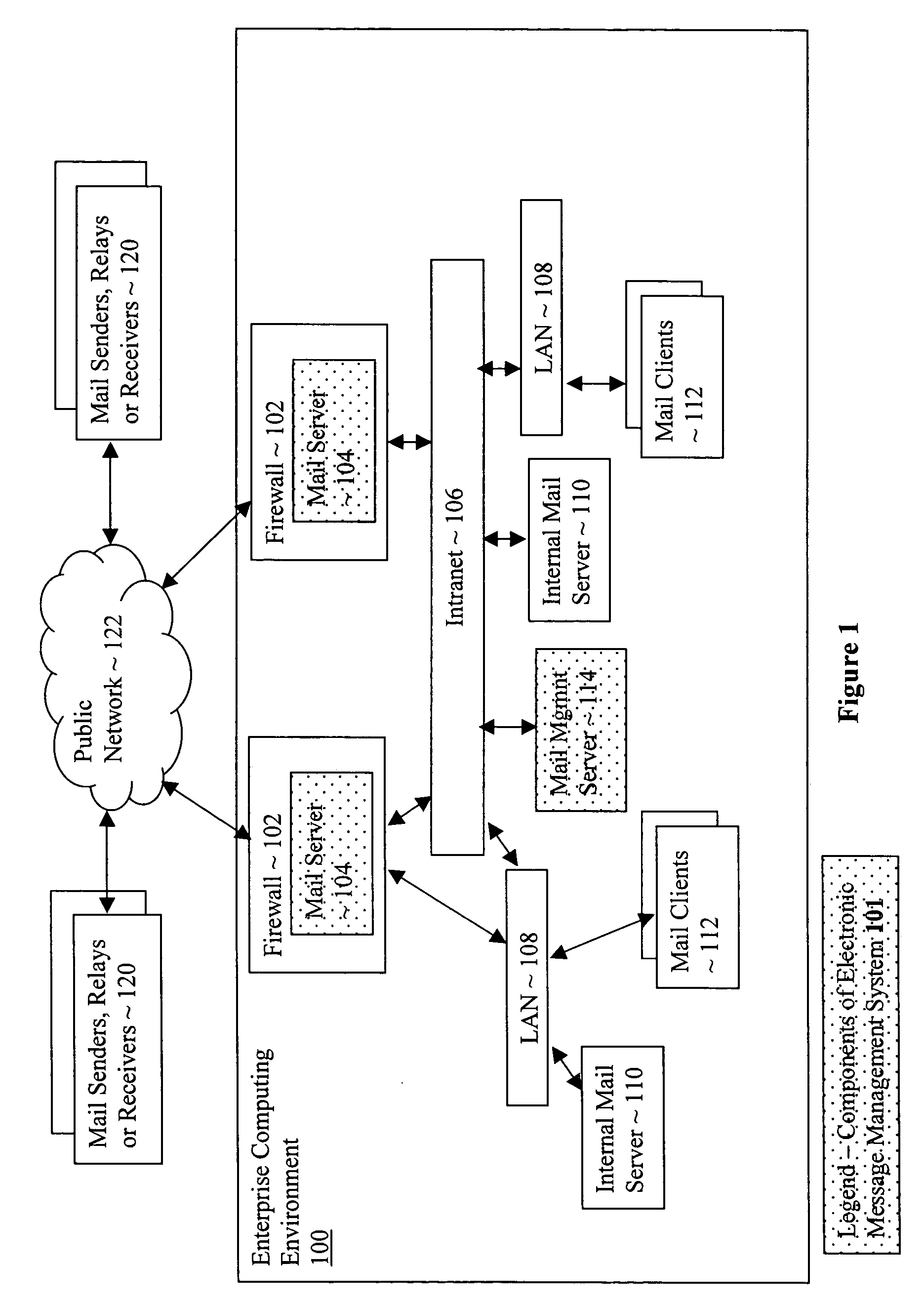
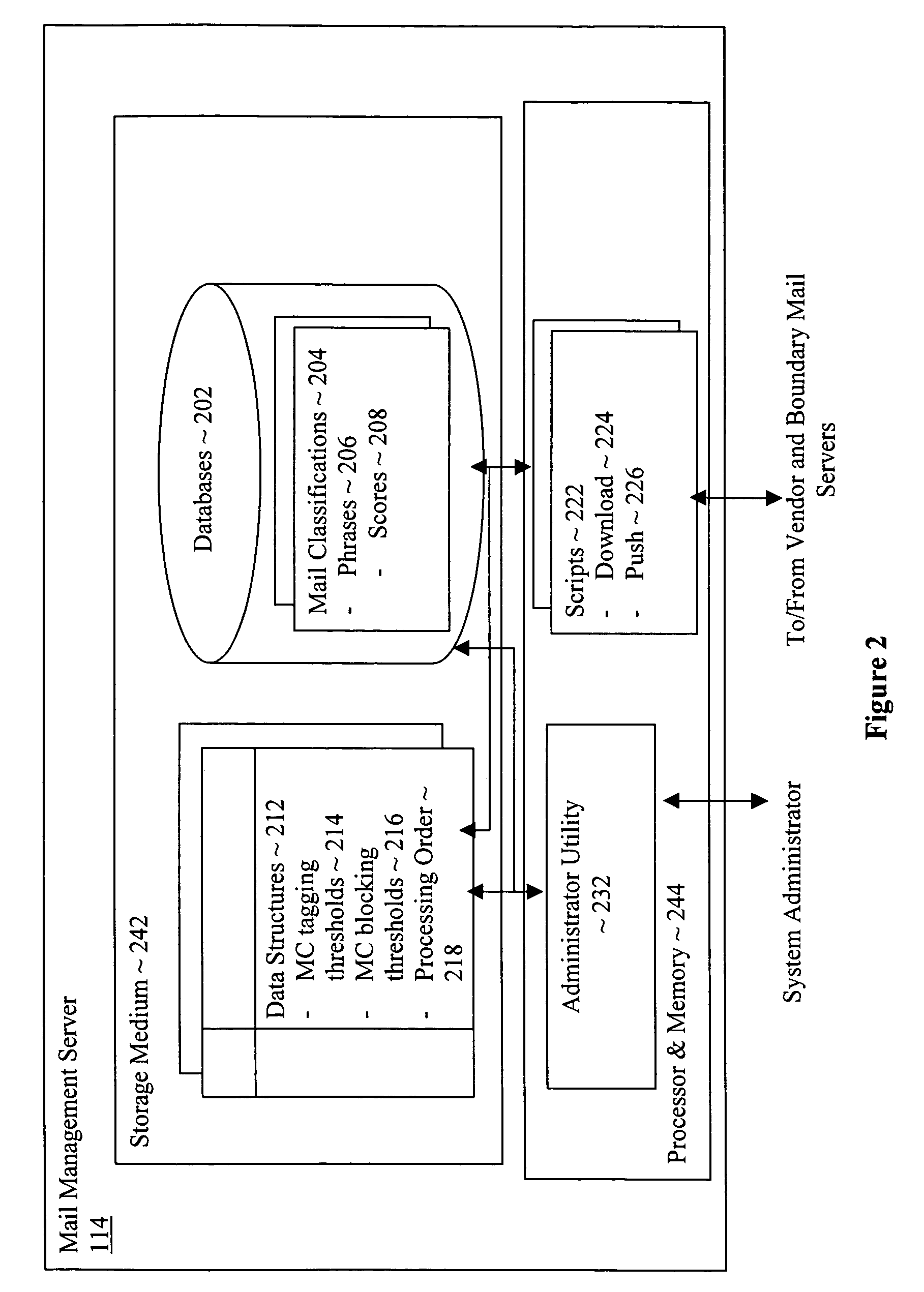
Electronic message management system
An electronic message management system, including in one embodiment, servers disposed at boundary points of an enterprise network, and employment of phrases of various message classifications, is disclosed and described herein.
Owner:MESSAGEGATE
System and method to improve the resiliency and performance of enterprise networks by utilizing in-built network redundancy
ActiveUS7188189B2Improve reliabilityImprove performanceData switching by path configurationMultiple digital computer combinationsService provisionNetwork packet
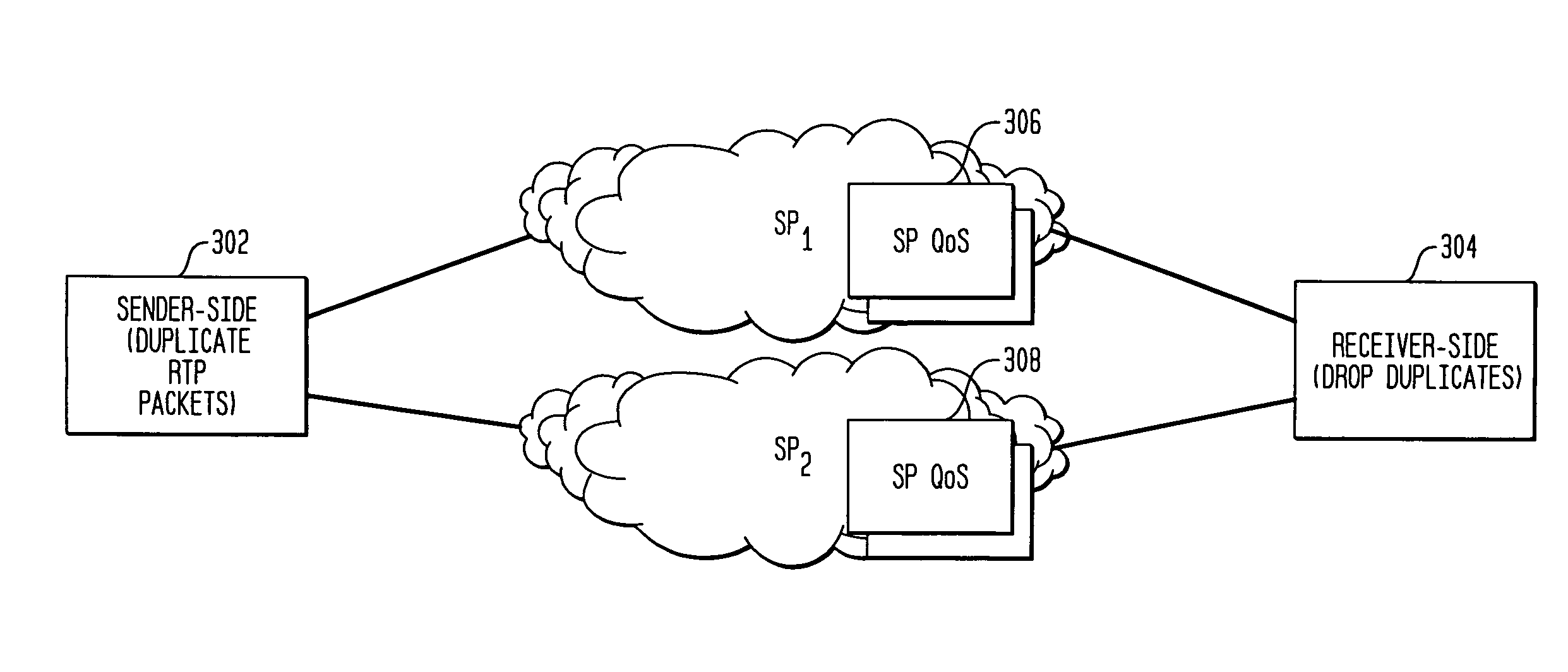
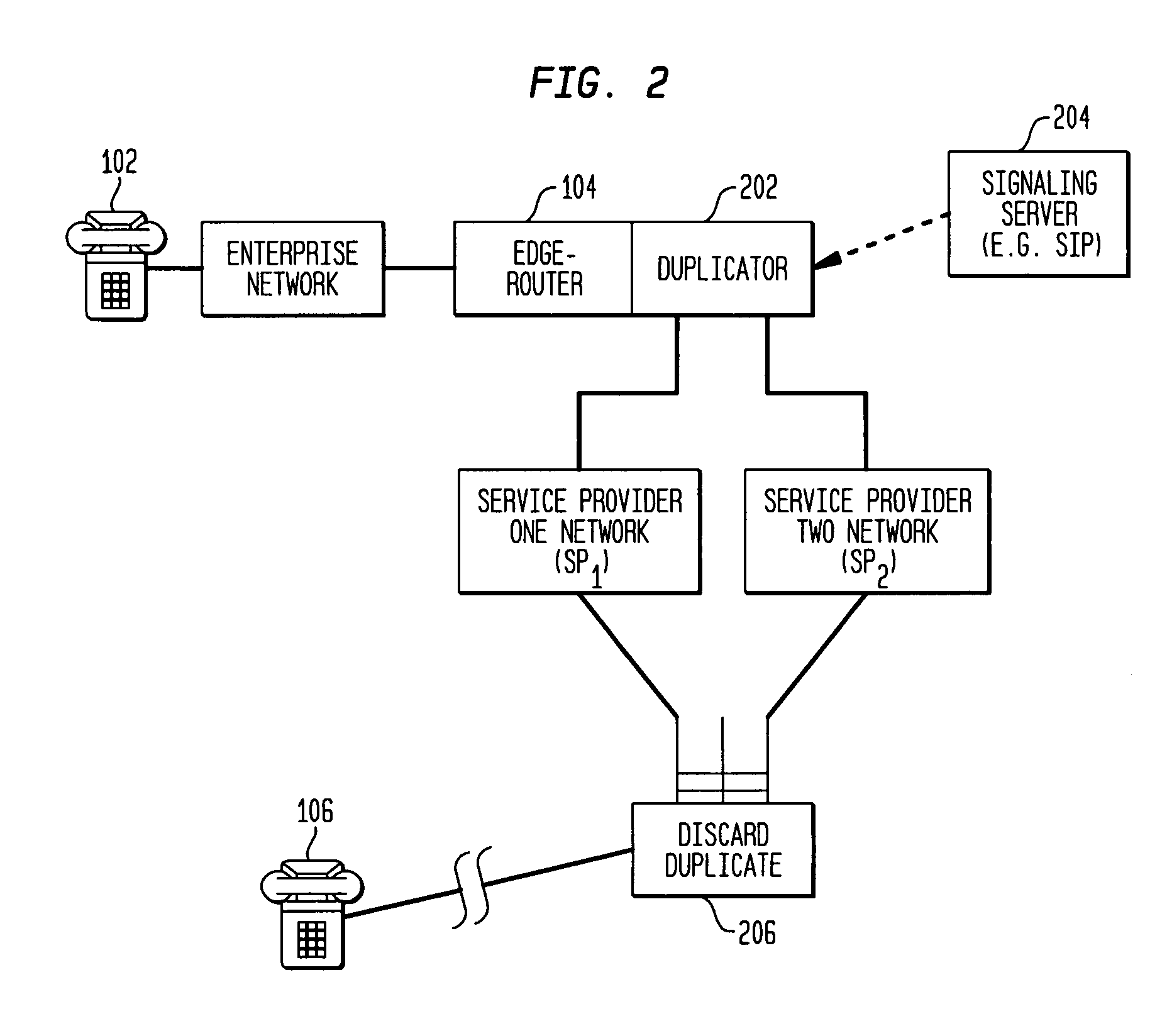
The present invention is a system and method to improve the reliability and performance of existing enterprise IP networks which have dual-homed (or multi-homed) network architectures. In one aspect of the invention packets related to a selected category of transmission (e.g., VoIP) are duplicated at an edge router and sent over both (multiple) service providers. After traversing the service provider networks, only the first-to-arrive packets are kept and the later-arriving copies are discarded. In so doing, the result is better protection against node failures, link failures, and packet errors, and also better QoS performance under normal (fault-free) operation.
Owner:AVAYA INC
Technique for using OER with an ECT solution for multi-homed sites
ActiveUS8260922B1Extended run timeImprove usabilityDigital computer detailsTransmissionTraffic capacityReachability
A technique dynamically utilizes a plurality of multi-homed Virtual Private Network (VPN) tunnels from a client node to one or more enterprise networks in a computer network. According to the technique, a VPN client node, e.g., a “spoke,” creates a plurality of multi-homed VPN tunnels with one or more servers / enterprise networks, e.g., “hubs.” The spoke designates (e.g., for a prefix) one of the tunnels as a primary tunnel and the other tunnels as secondary (backup) tunnels, and monitors the quality (e.g., loss, delay, reachability, etc.) of all of the tunnels, such as, e.g., by an Optimized Edge Routing (OER) process. The spoke may then dynamically re-designate any one of the secondary tunnels as the primary tunnel for a prefix based on the quality of the tunnels to the enterprise. Notably, the spoke may also dynamically load balance traffic to the enterprise among the primary and secondary tunnels based on the quality of those tunnels.
Owner:CISCO TECH INC
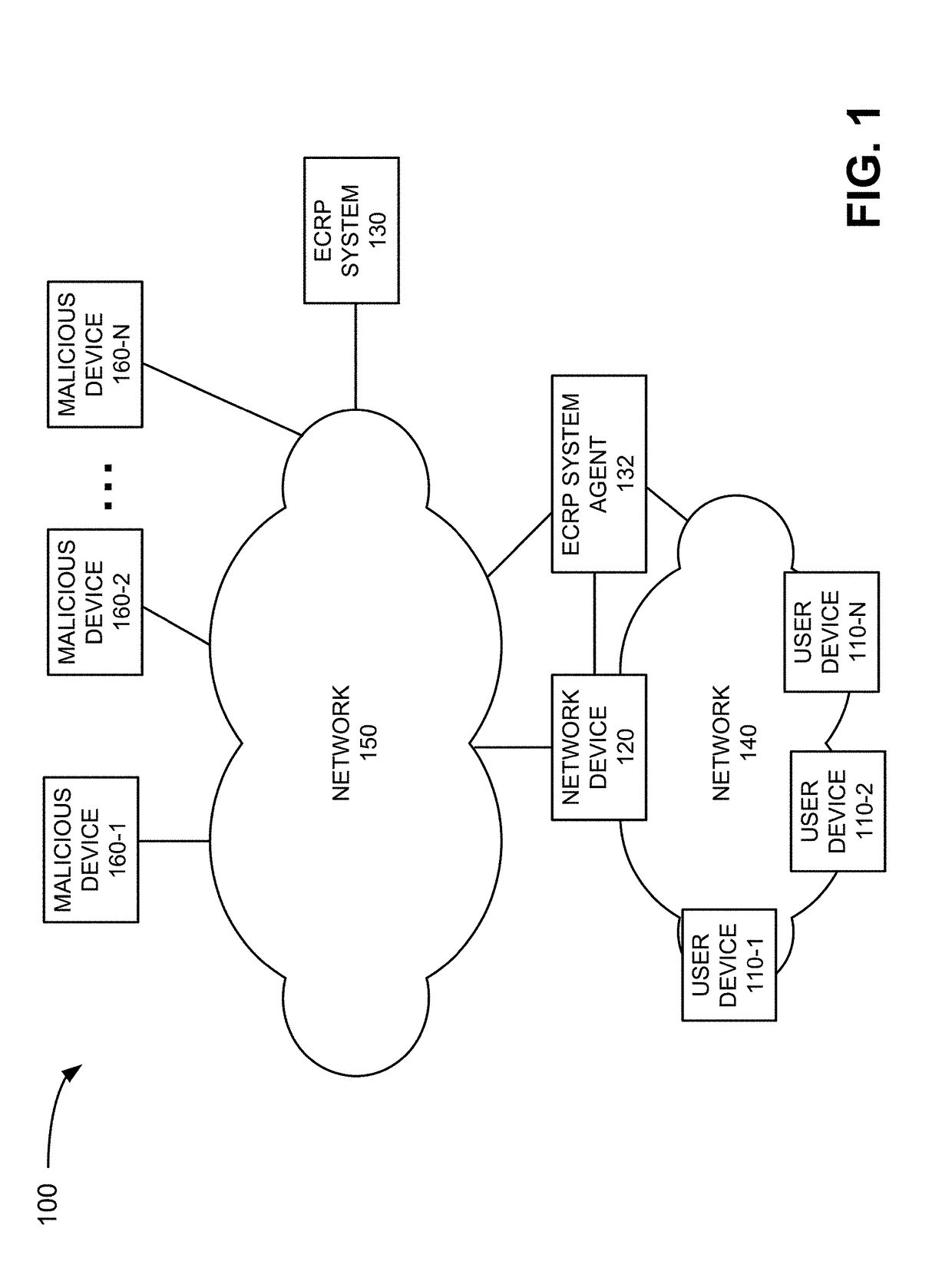
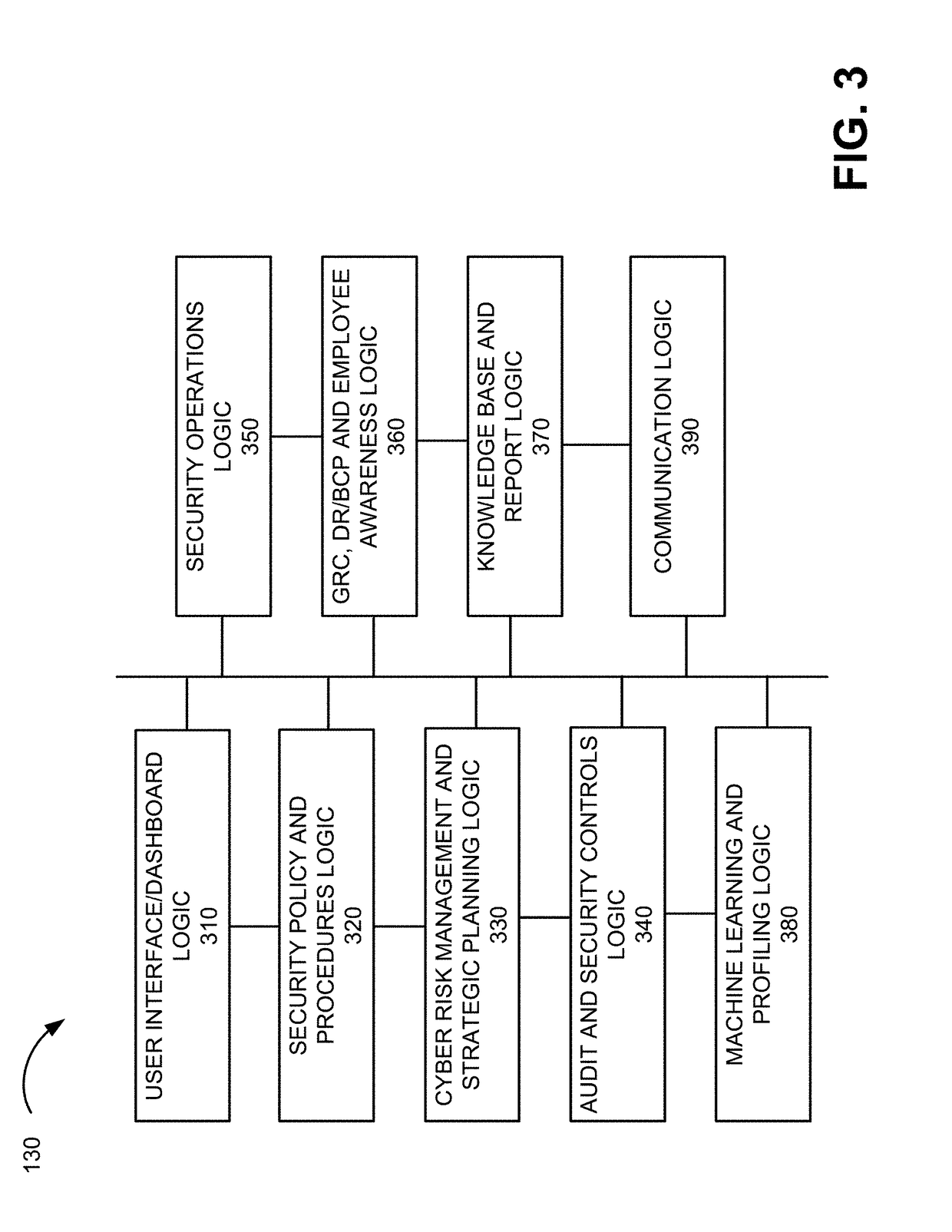
Enterprise cyber security risk management and resource planning
A system includes a memory to store network-related security policies and procedures associated with an enterprise, a display and at least one device. The device is configured to monitor enterprise activity associated the enterprise's networked and determine, based on the enterprise activity, whether the enterprise is complying with the security policies and procedures. The device is also configured to calculate a risk exposure metric for an asset of the enterprise based on the enterprise activity and whether the enterprise is complying with the security policies and procedures, and output, to the display, a graphical user interface (GUI) identifying the risk exposure metric. The device may also be configured to receive, via the GUI, an input to initiate a change with respect to at least one of the enterprise's networked devices or initiate the generation of a plan to make a change to at least one of the networked devices.
Owner:CISOTERIA LTD
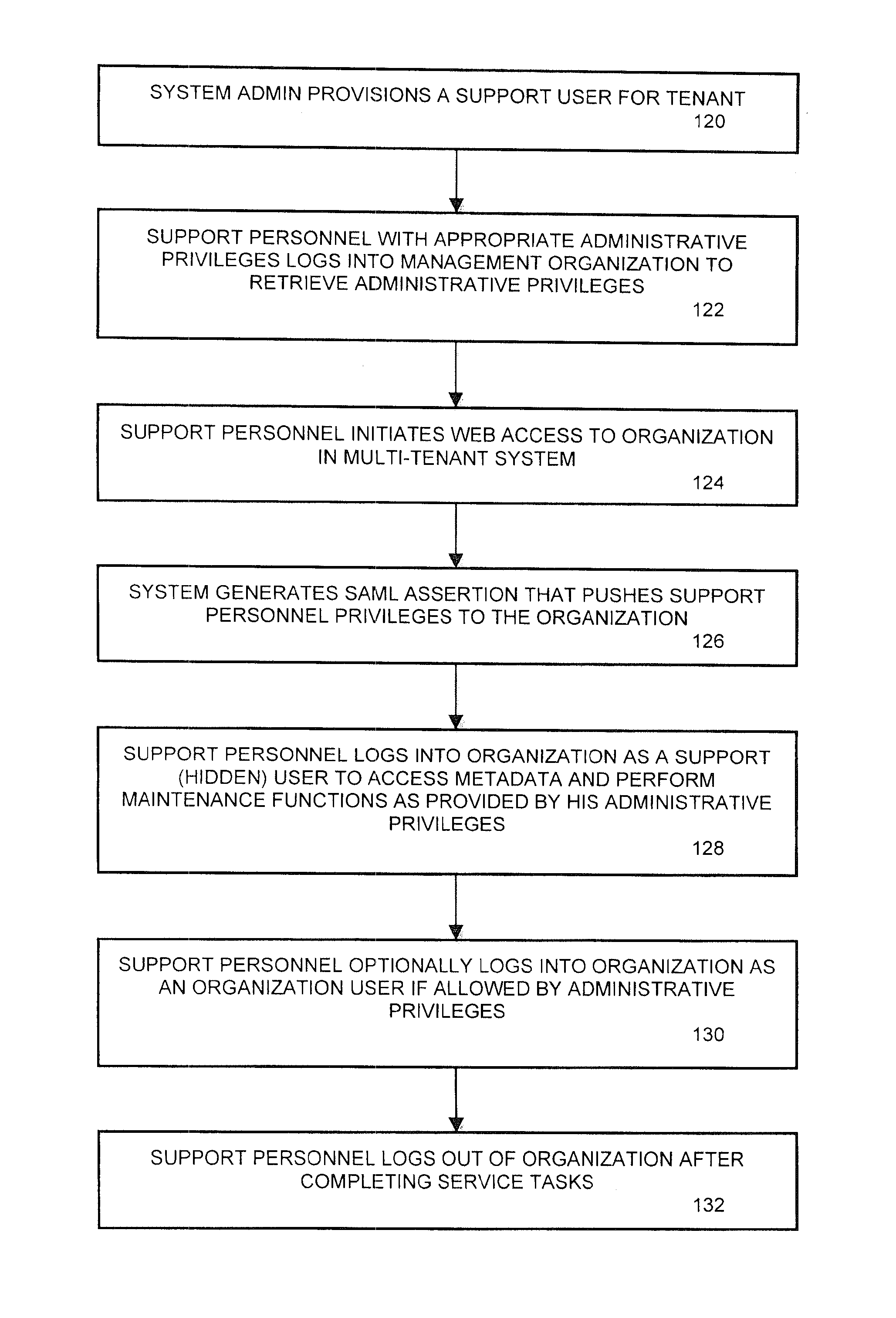
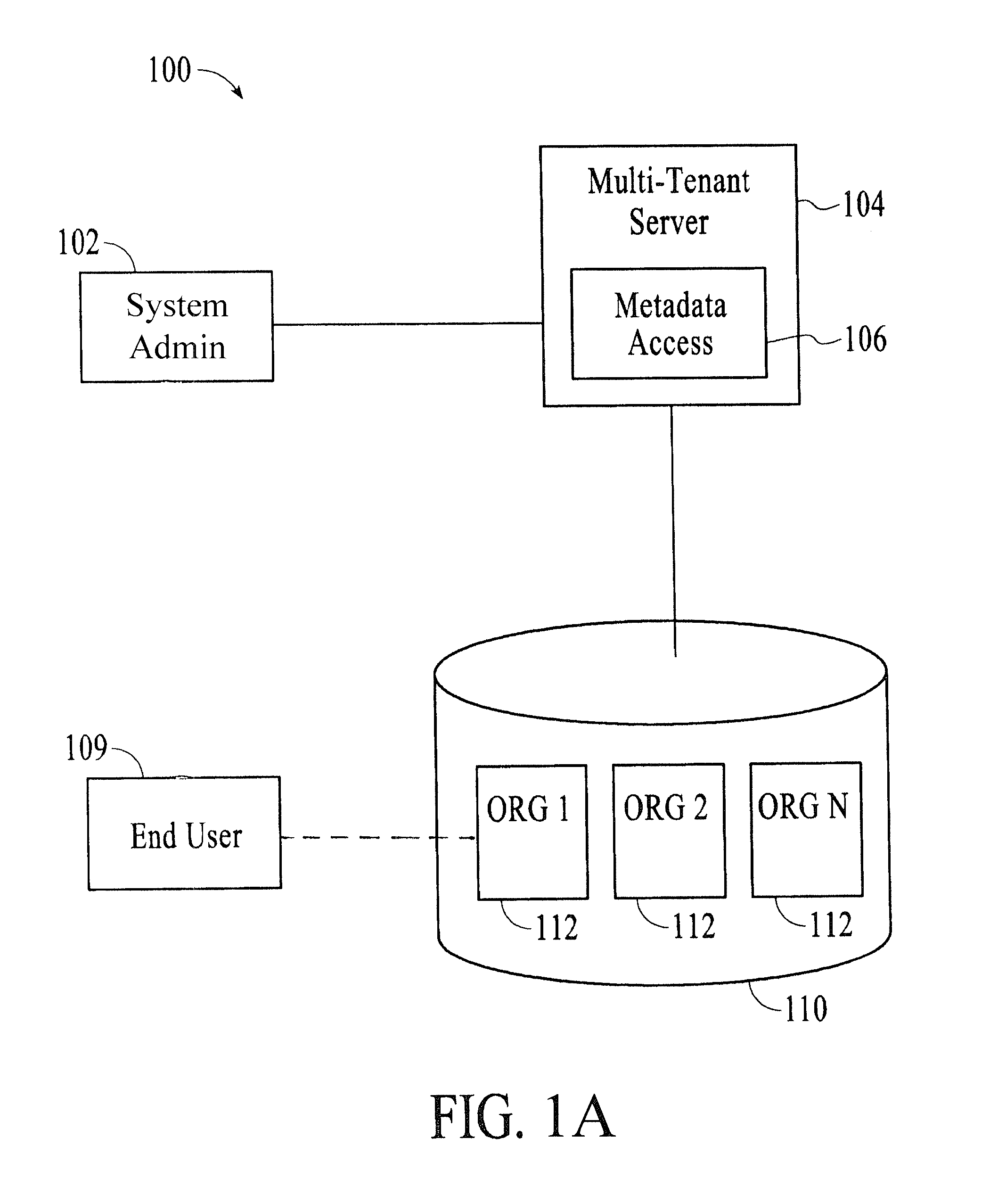
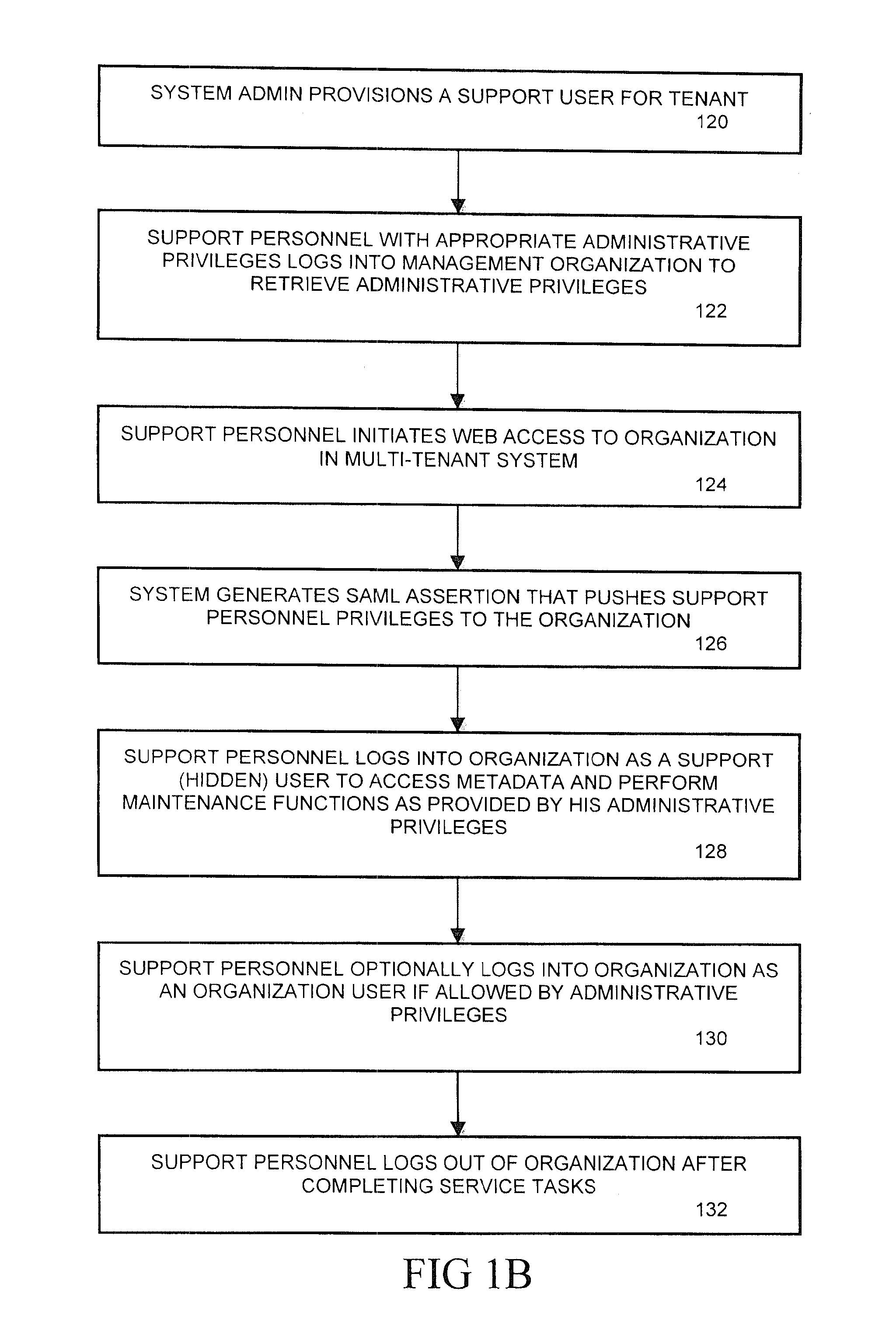
Methods and systems for provisioning access to customer organization data in a multi-tenant system
ActiveUS8949939B2Digital data processing detailsDigital data protectionClient organizationUser profile
Methods and systems are described for providing support representative access to applications deployed in an enterprise network environment. An access provisioning system defines a support user class in a user profile database for an application executed on an organization partition within the network. The support user is granted read only privileges to metadata of the application. An organization administrator can grant support personnel access to the application as a support user, thus the ability to view, analyze, and possibly modify the metadata. The access provisioning system generates a Security Assertion Markup Language (SAML) assertion upon request by the support personnel to enable access to the data to the extent of the granted privileges. The SAML protocol includes authentication of the support representative as an authorized support user within the system.
Owner:SALESFORCE COM INC
Methods for Associating an IP Address to a User Via an Appliance
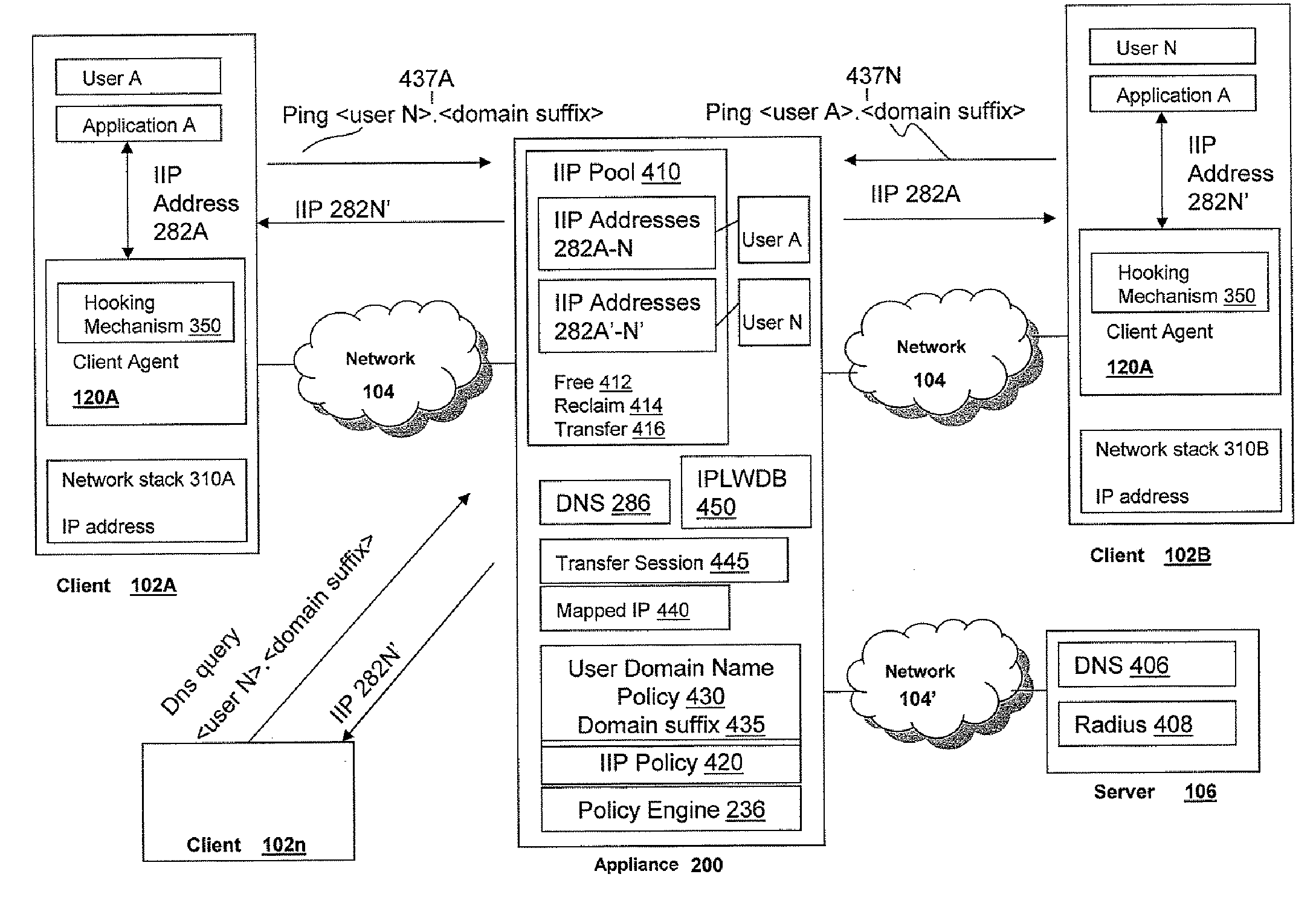
ActiveUS20080043749A1Efficiently assigning and managing and queryingData switching by path configurationMultiple digital computer combinationsClient agentPrivate network
The intranet IP address management solution of the appliance and / or client described herein provides an environment for efficiently assigning, managing and querying virtual private network addresses, referred to as intranet IP (IIP) addresses of virtual private network users, such as a multitude of SSL VPN users on an enterprise network. The appliance provides techniques and policies for assigning previously assigned virtual private network addresses of a user to subsequent sessions of the user as the user logs in multiple times or roams between access points. This technique is referred to IIP stickiness as the appliance attempts to provide the same IIP address to a roaming VPN user. The appliance also provides a configurable user domain naming policy so that one can ping or query the virtual private network address of a user by an easily referenceable host name identifying the user. The appliance and / or client agent also provide techniques to allow applications to seamlessly and transparently communicate on the virtual private network using the virtual private network address of the user or client on the private network.
Owner:CITRIX SYST INC
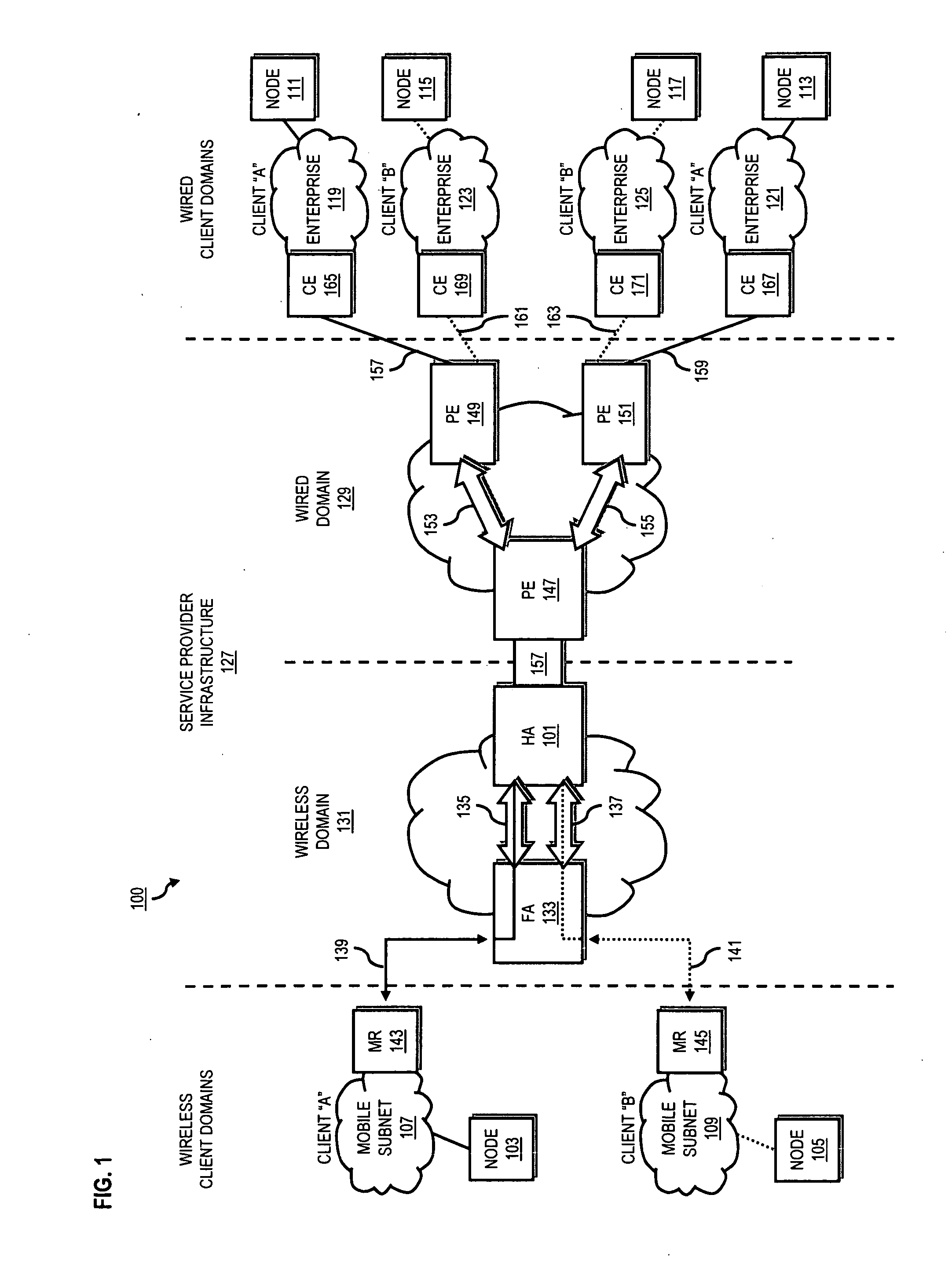
System and method for providing network mobility
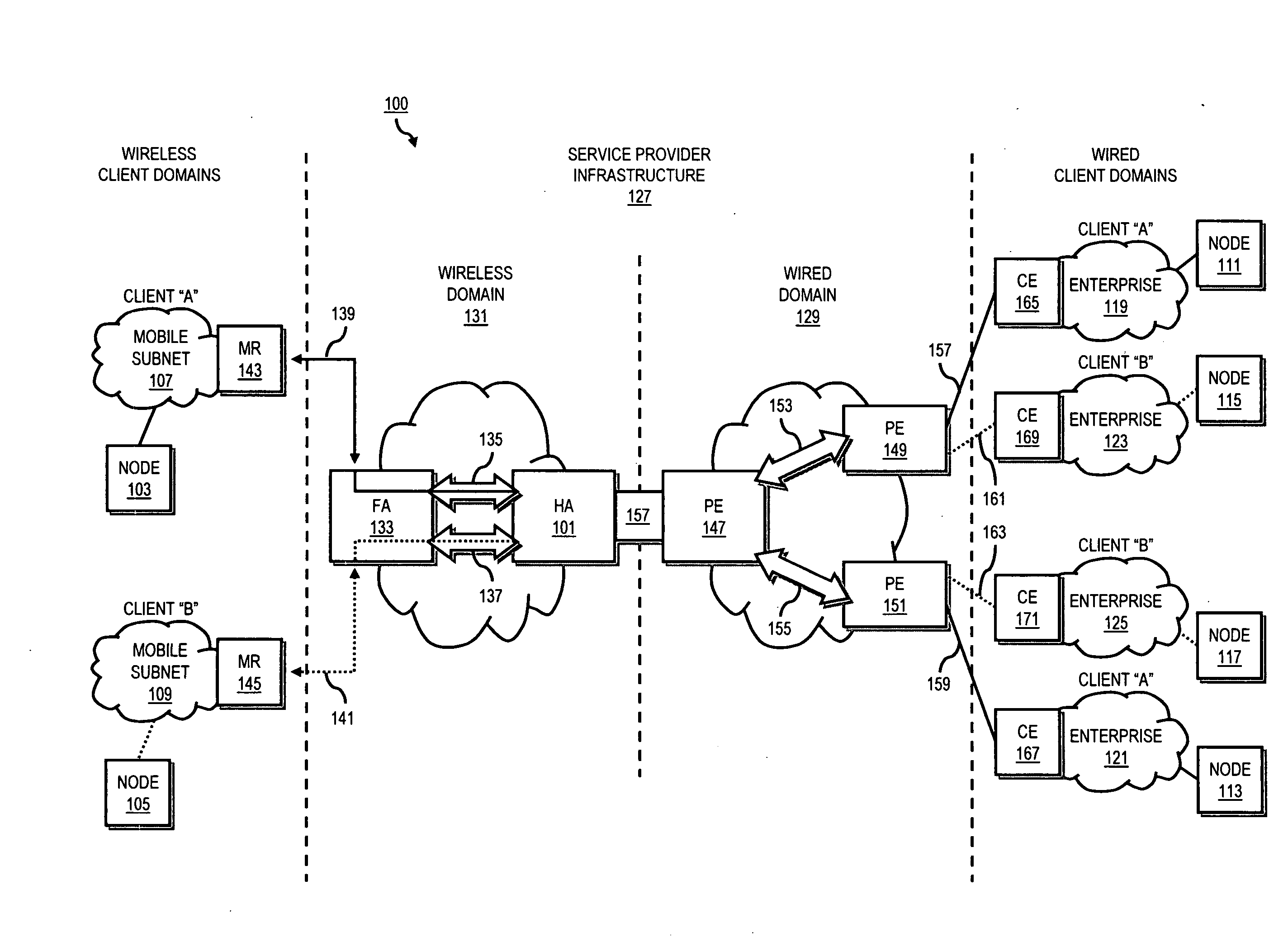
An approach is provided for extending private enterprise networking to wireless interconnecting domains. A home agent maintains a first routing table for a first wireless router configured to route according to a first address space. The home agent also maintains a second routing table for a second wireless router configured to route according to a second address space. The first address space and the second address space are overlapping.
Owner:VERIZON PATENT & LICENSING INC
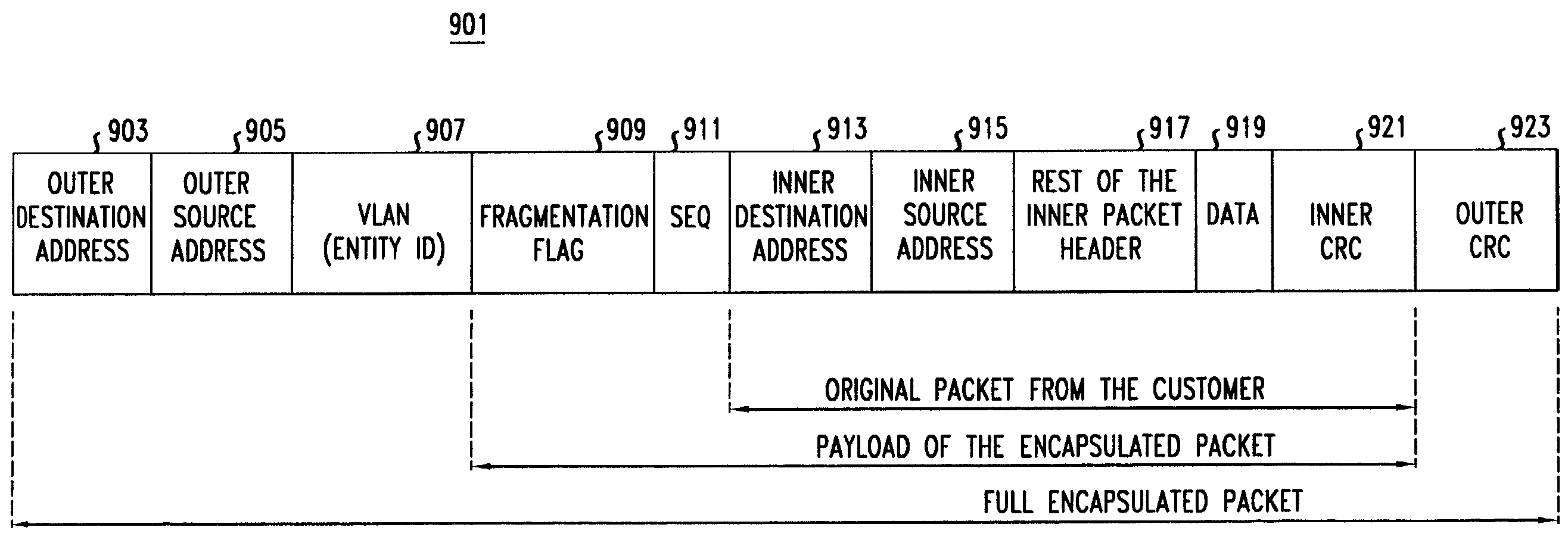
Ethernet packet encapsulation for metropolitan area ethernet networks
InactiveUS7130303B2Efficient mannerTime-division multiplexNetworks interconnectionEncapsulated dataMetro Ethernet
The problems of large tables in Ethernet switches used on a metropolitan area scale, and the exposure of the enterprise network topologies, can be avoided by encapsulating each original Ethernet packet, which originates in a first network of an entity, e.g., an enterprise, a customer, or a network service provider, within another Ethernet packet which is given a source address that identifies the new encapsulating packet as originating at a port of a switch that is located at the interface between the first network in which the original packet originated and a second Ethernet network, e.g., the metropolitan area Ethernet network, which is to transport the encapsulating packet. When the encapsulating packet would exceed the allowable Ethernet packet length, the original packet may be split up at the interface between the first and second network and the resulting parts encapsulated into two encapsulating packets.
Owner:LUCENT TECH INC
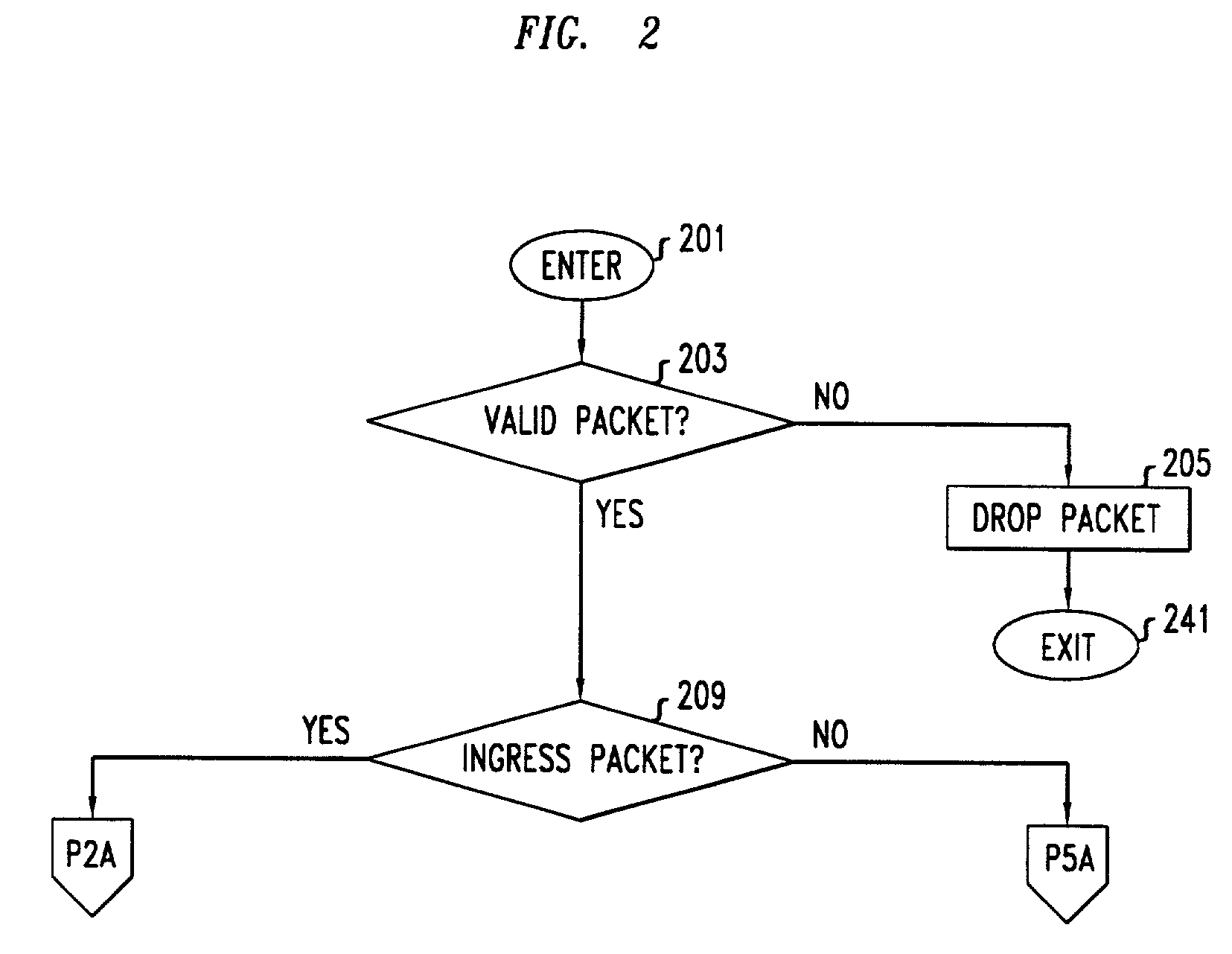
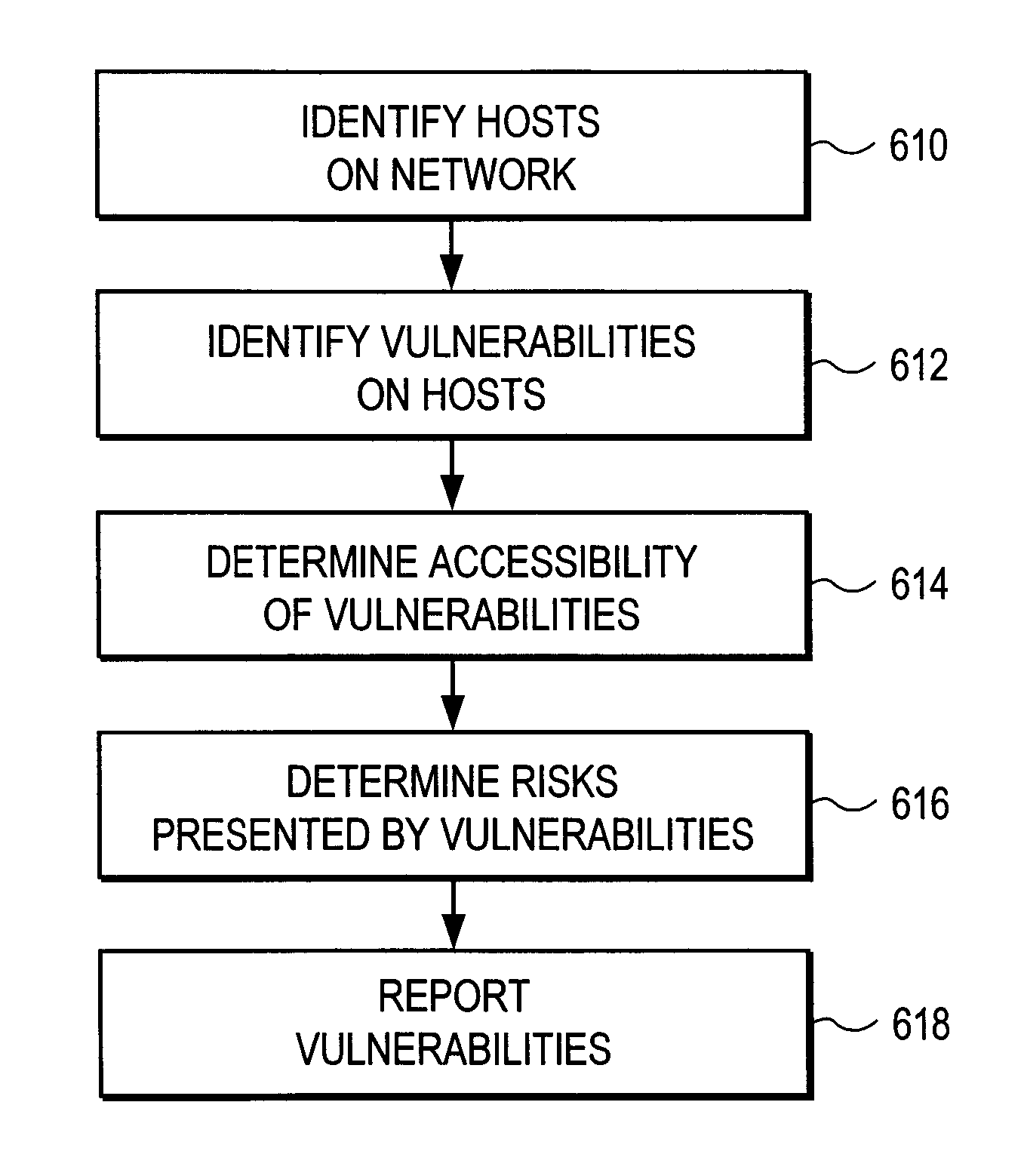
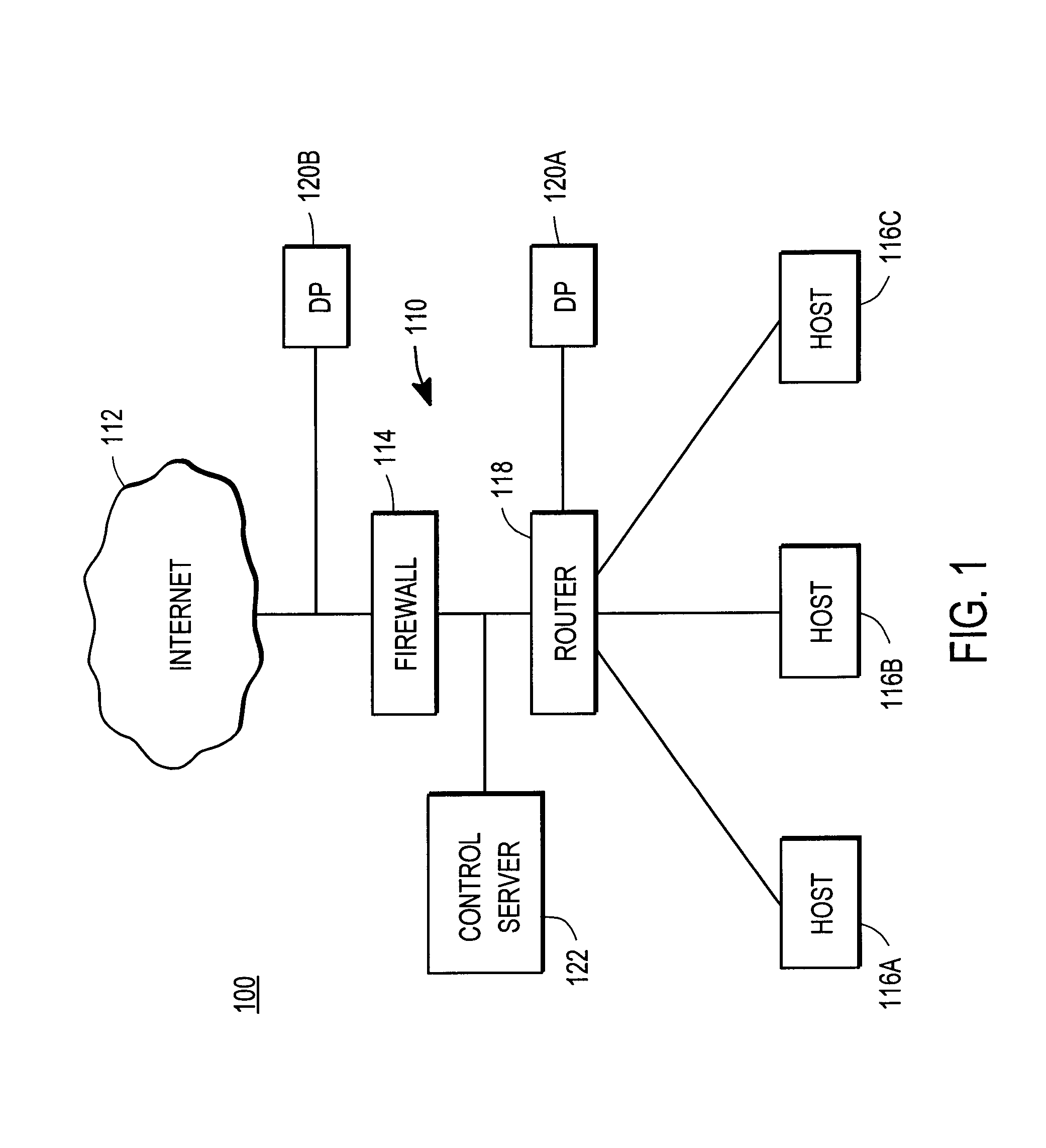
Prioritizing network security vulnerabilities using accessibility
ActiveUS8918883B1Memory loss protectionError detection/correctionInternet privacyBusiness enterprise
An enterprise network includes hosts running services. Some of the services have security vulnerabilities. There are one or more threat zones associated with the network. For example, a firewall may create two threat zones, one internal to the firewall and one external to it. A device profiler in the first threat zone profiles the hosts on the network and identifies the vulnerabilities that are present. A device profiler in the second threat zone determines which of the identified vulnerabilities are accessible from its zone. A risk module calculates the risk associated with a vulnerability based on the vulnerability's severity, threat level metrics for the threat zones, and an asset value of the host with the vulnerability. A reporting module prioritizes the vulnerabilities based on their risks.
Owner:TRIPWIRE
Using Private Threat Intelligence in Public Cloud
ActiveUS20170272469A1Preserving data integrityPreserving securityComputer security arrangementsTransmissionUser deviceQuery string
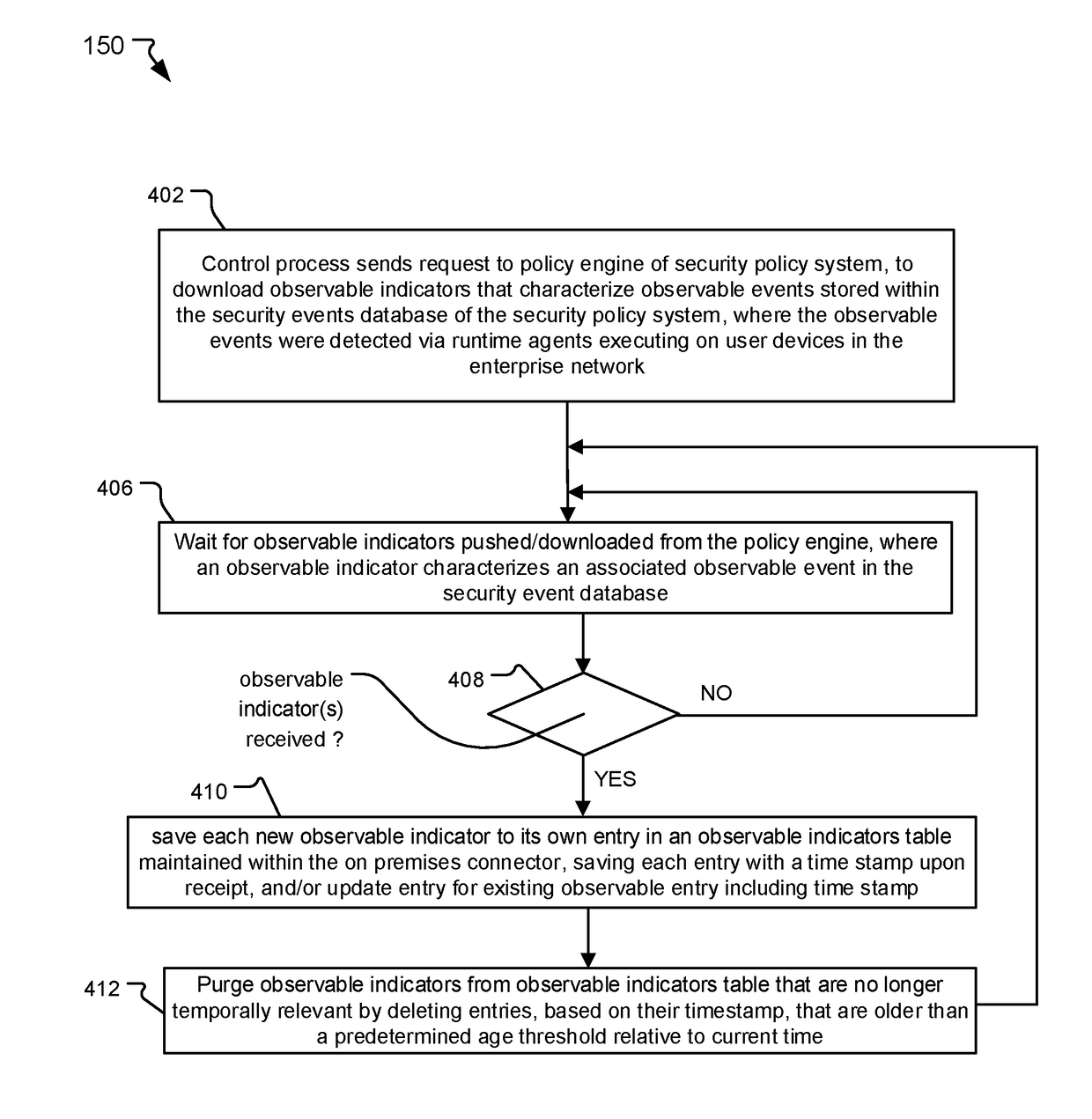
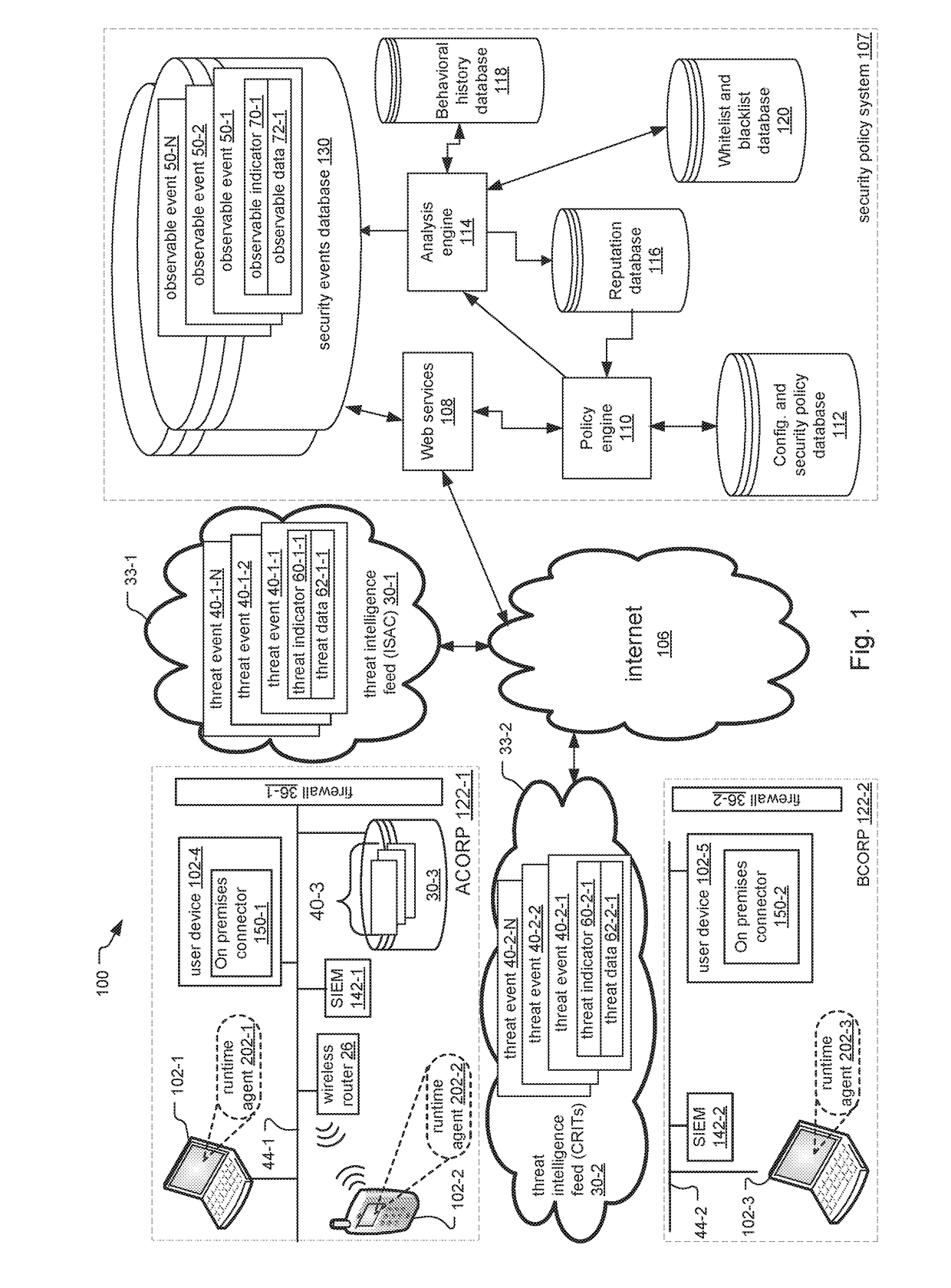
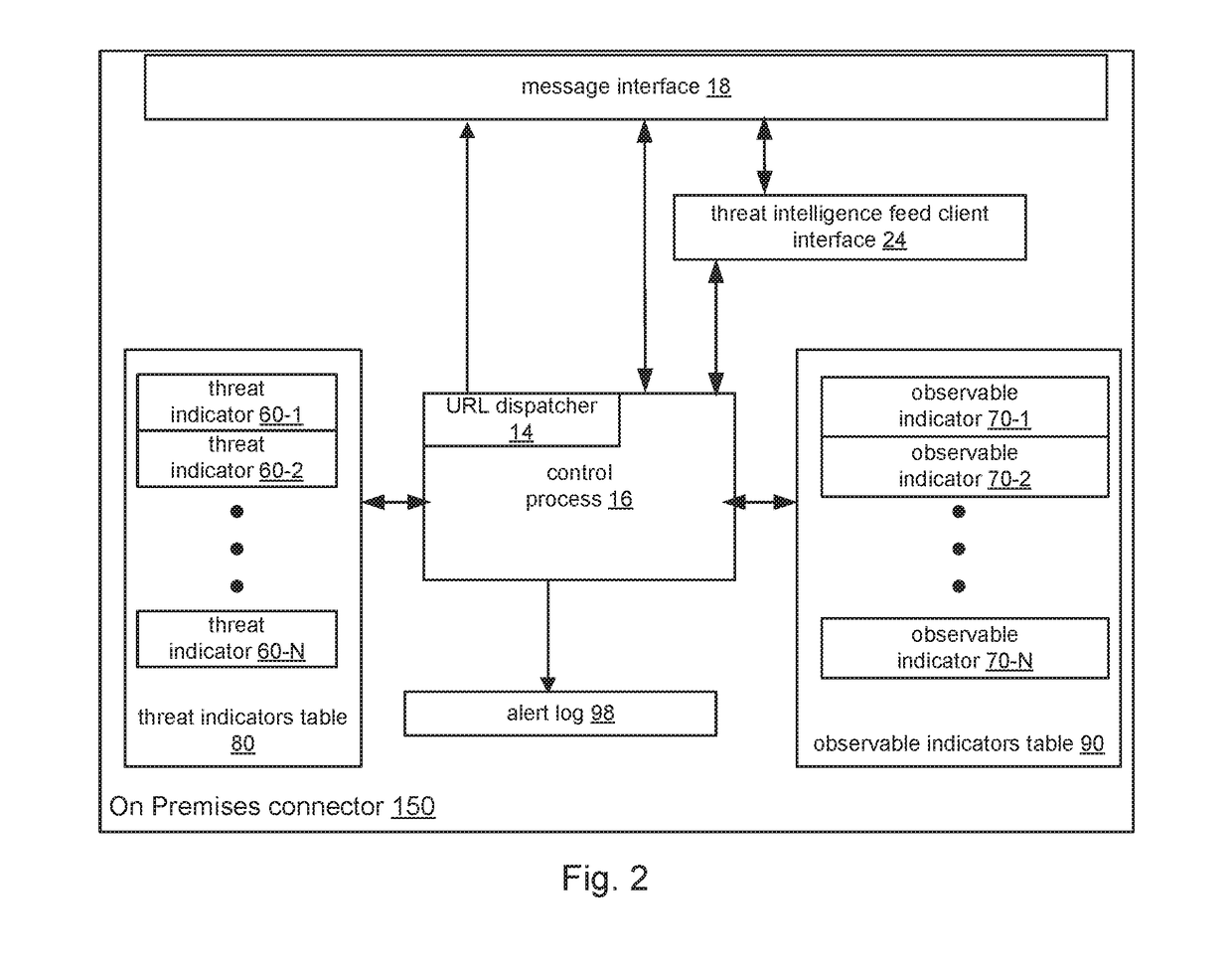
A distributed security system and method are disclosed that enable access to known threat events from threat intelligence feeds when the system includes public cloud components. A cloud-based security policy system stores observable events for security incidents detected by and sent from user devices within an enterprise network. The observable events include observable indicators for characterizing the observable events. The threat events within the feeds include threat indicators for characterizing the threat events. An on-premises connector within the enterprise network downloads the observable indicators from the security policy system and the threat indicators from the feeds. In response to determining that any observable indicators match any threat indicators, the on-premises connector provides access to the threat events and / or the observable events having the matching indicators. In one example, the on-premises connector generates opaque query strings for users on user devices to access the threat events / observable events having the matching indicators.
Owner:CARBON BLACK
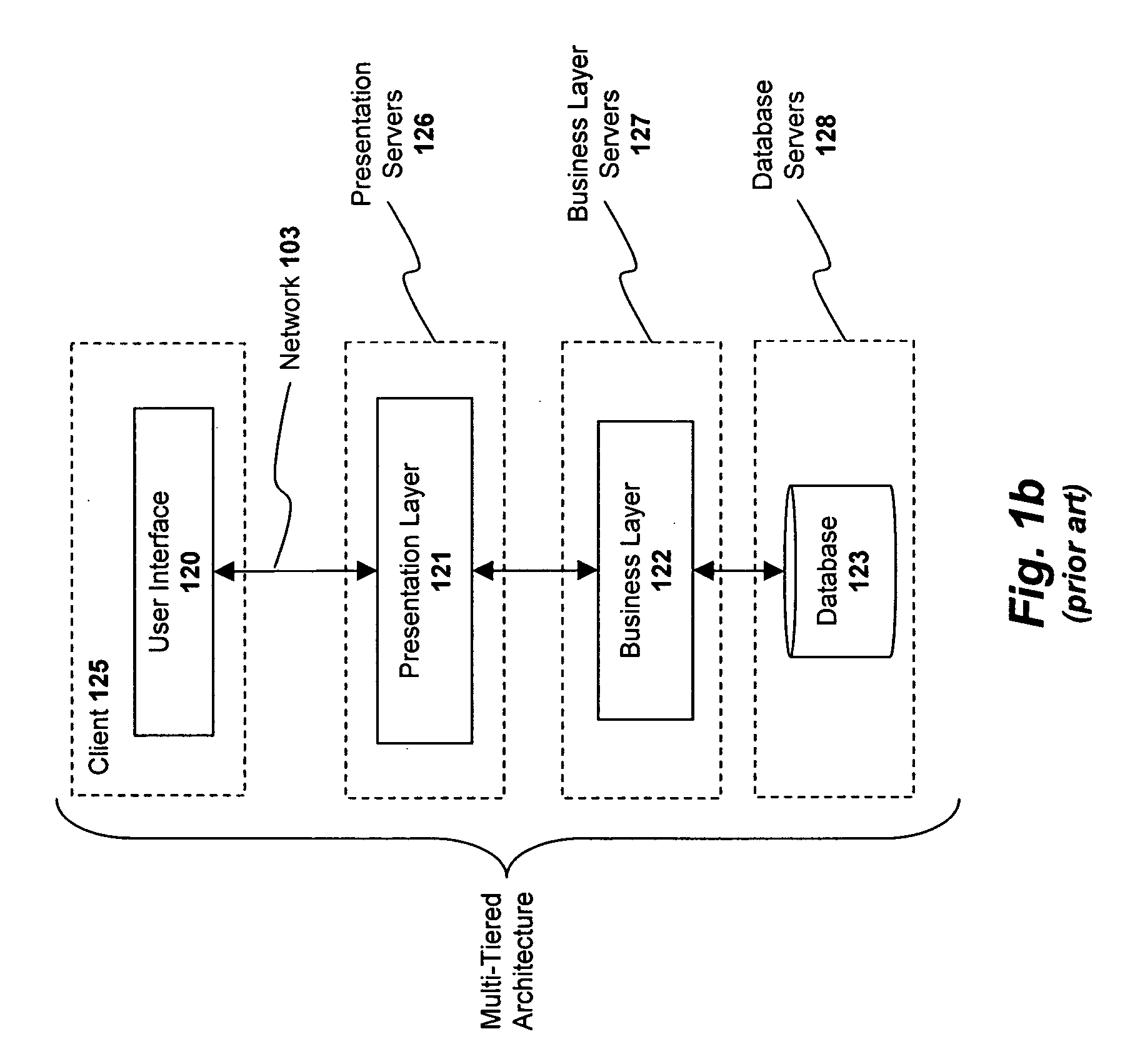
Session lifecycle management within a multi-tiered enterprise network
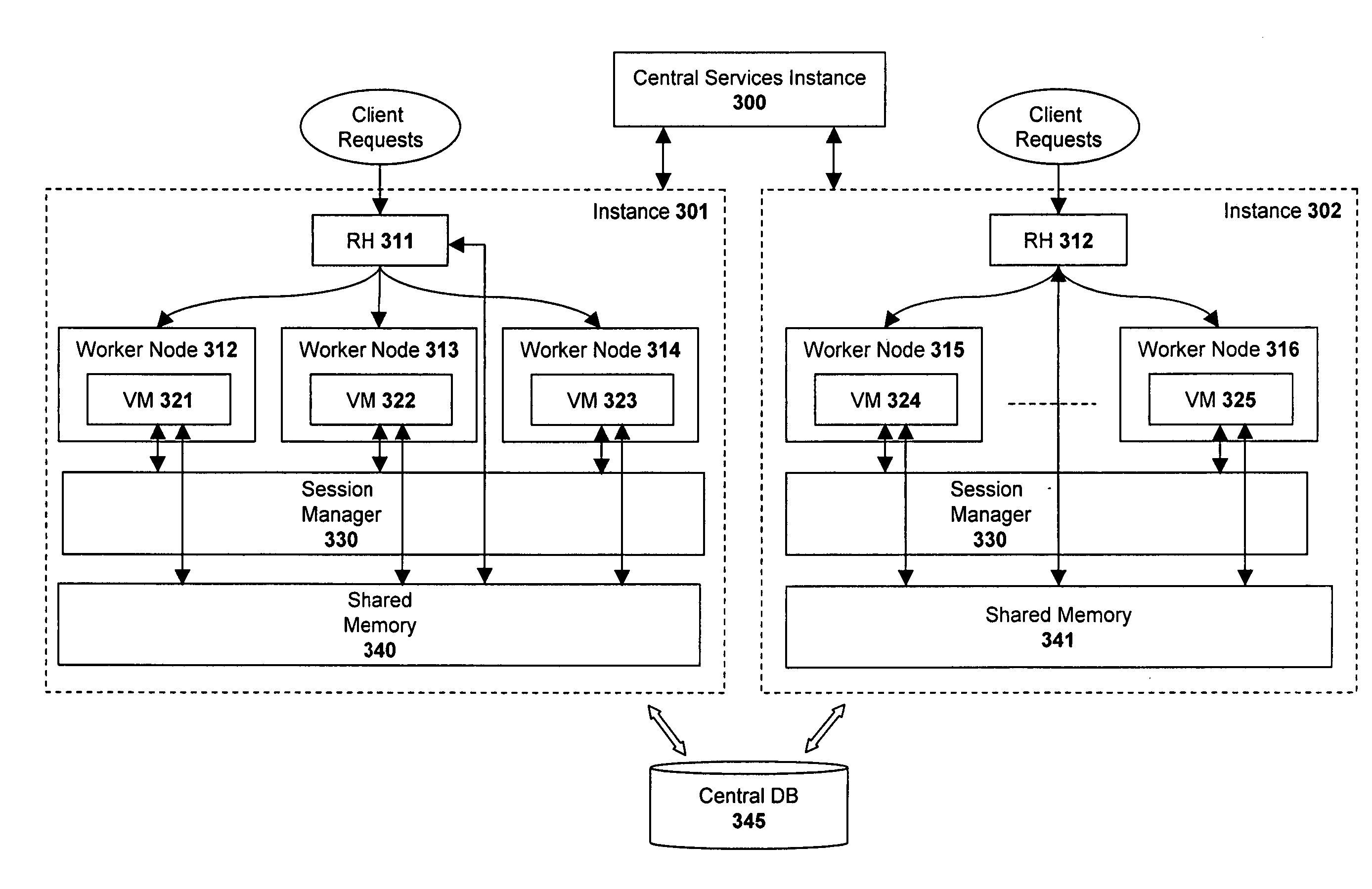
ActiveUS20060155756A1Multiple digital computer combinationsTransmissionApplication lifecycle managementObject based
A system and method are described for managing session lifecycles within a multi-tiered enterprise network. In one embodiment, a plurality of session objects are generated at different layers of the enterprise network in response to a client request. Each of the session objects store session data defining a state of interaction with the client. In addition, one embodiment of the invention manages the lifecycle of a first session object based on corresponding lifecycles of one or more related session objects and also the type of relationship existing between the first session object and the one or more related session objects. In one embodiment, the defined relationship types include strong references, weak references, and soft references.
Owner:SAP AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com