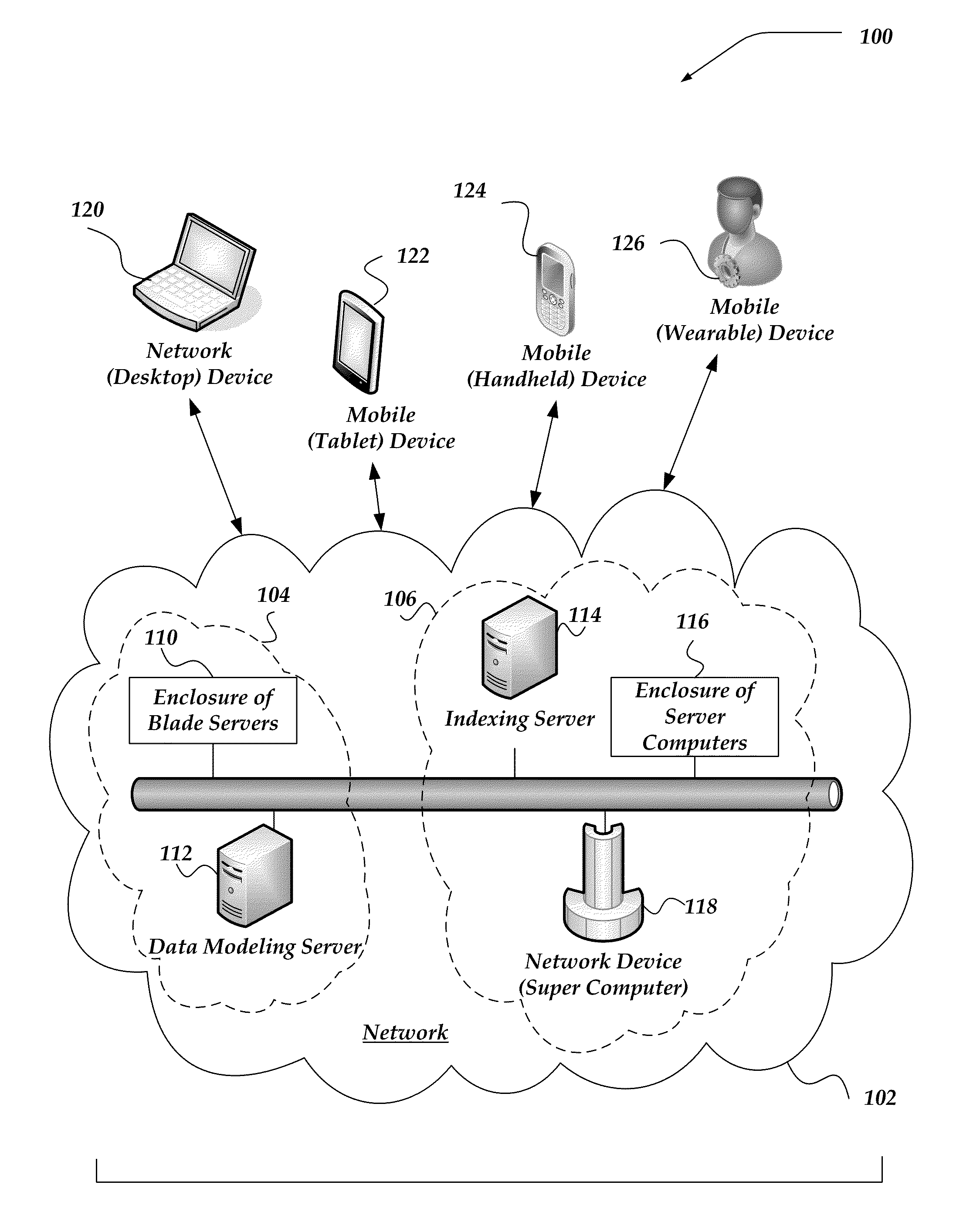
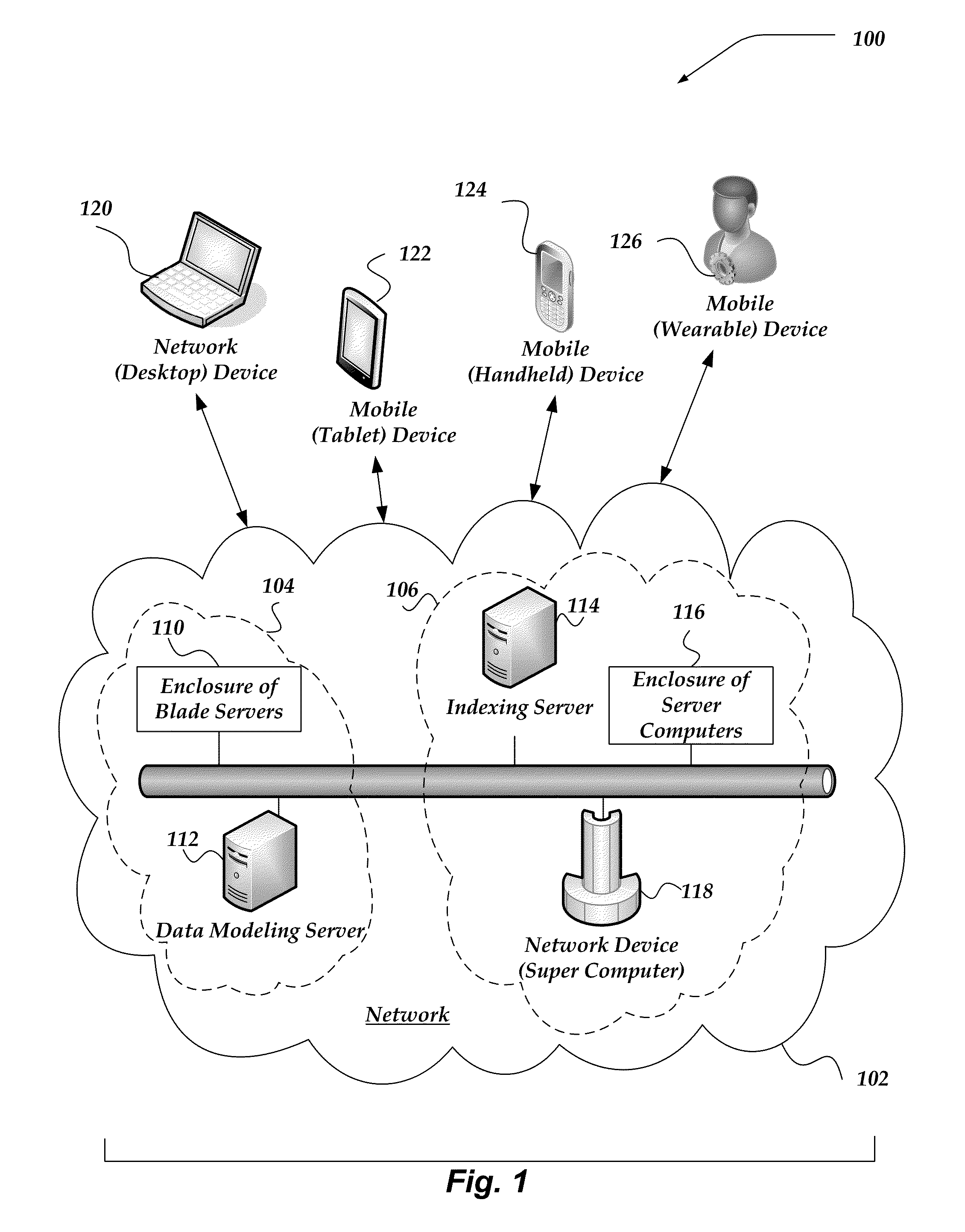
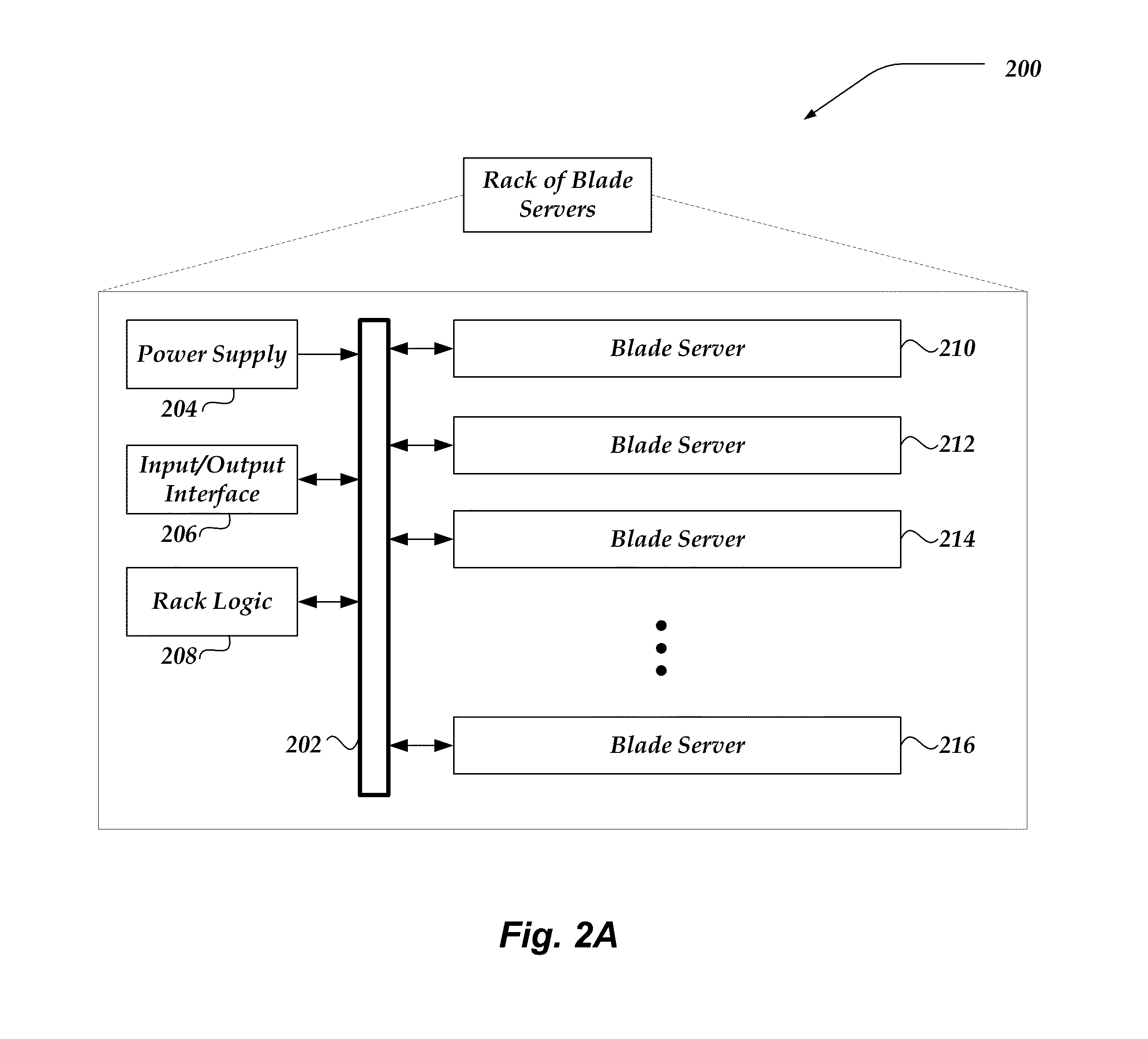
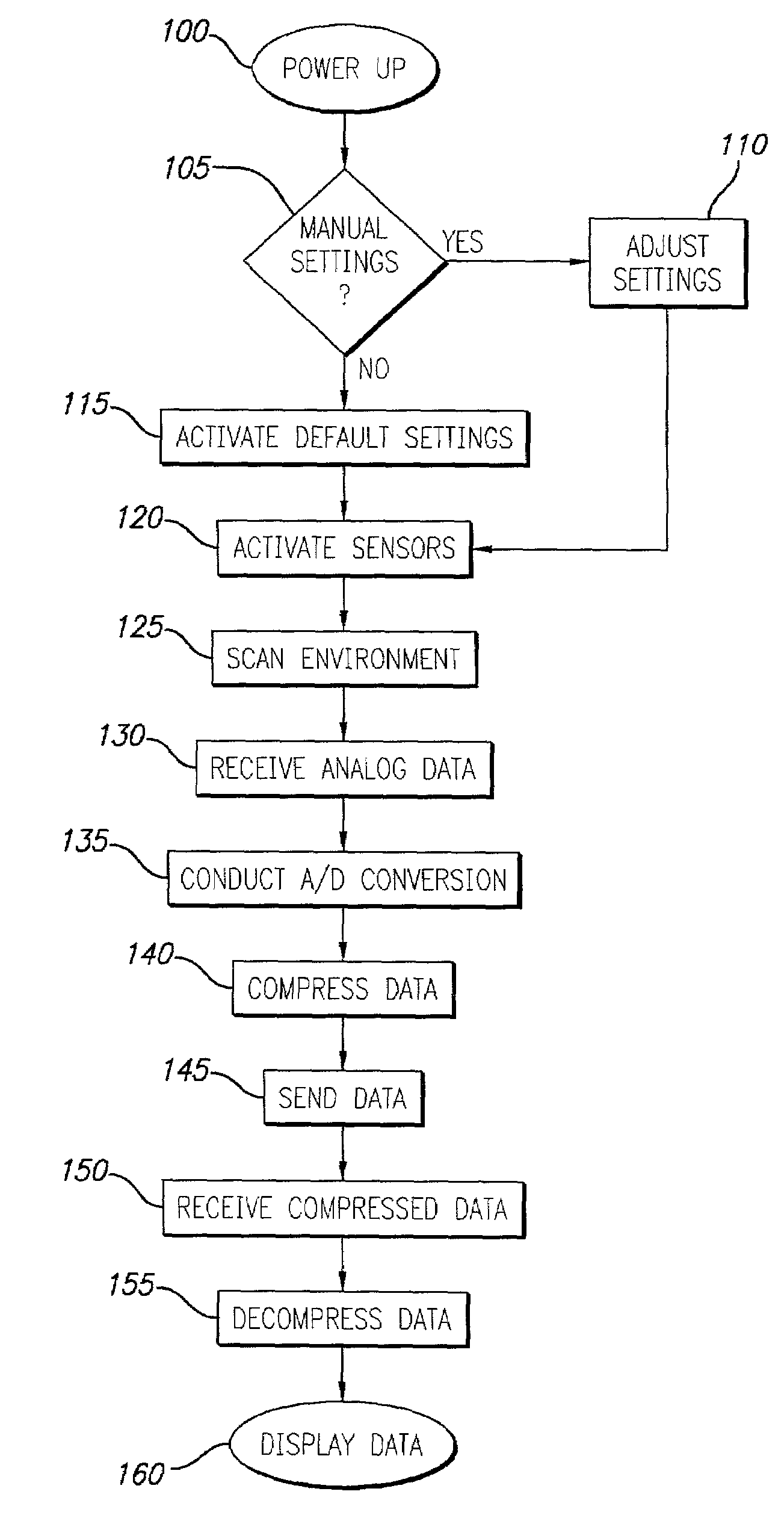
Patents
Literature
290 results about "Query string" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
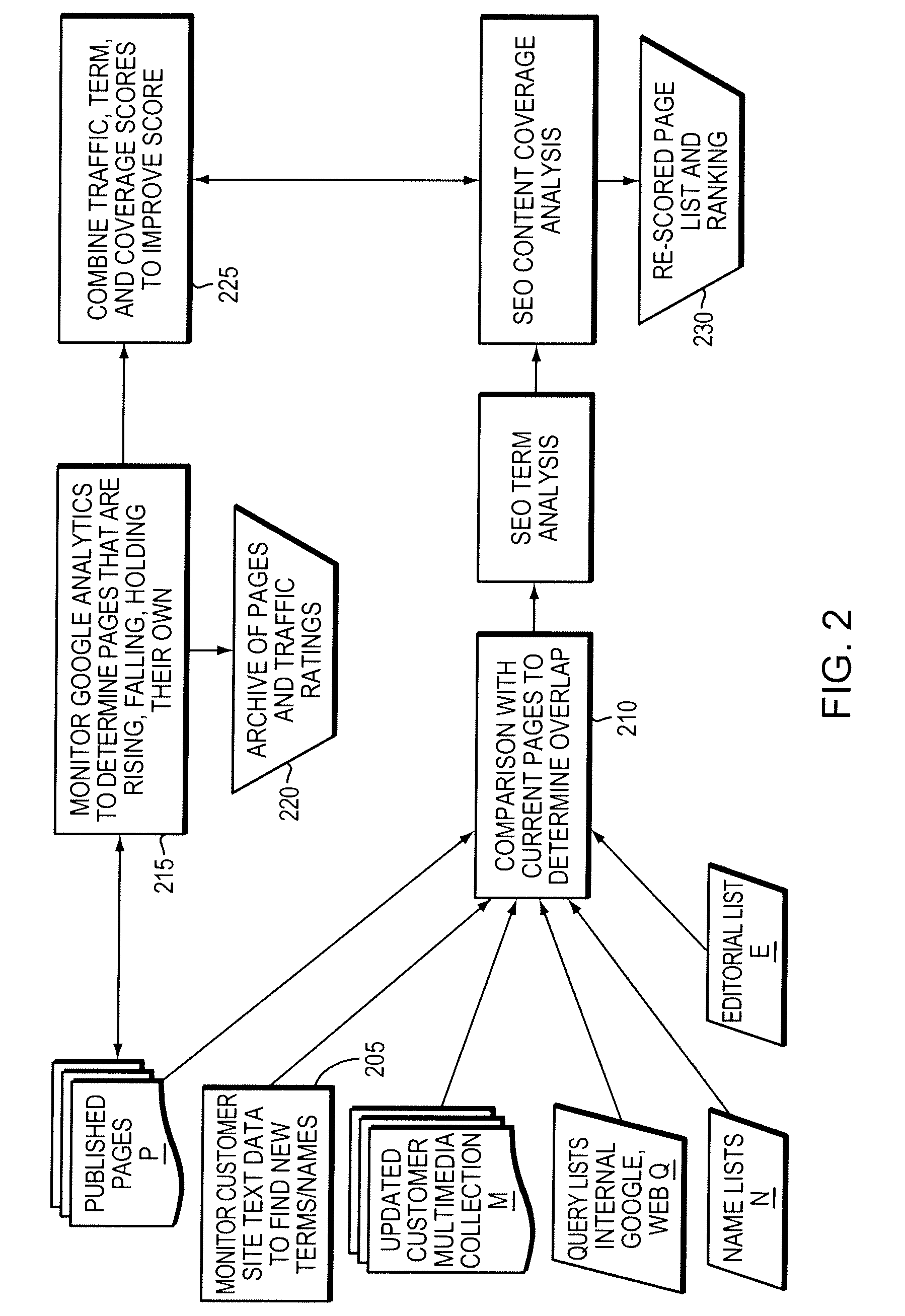
On the World Wide Web, a query string is the part of a uniform resource locator (URL) which assigns values to specified parameters. The query string commonly includes fields added to a base URL by a Web browser or other client application, for example as part of an HTML form.
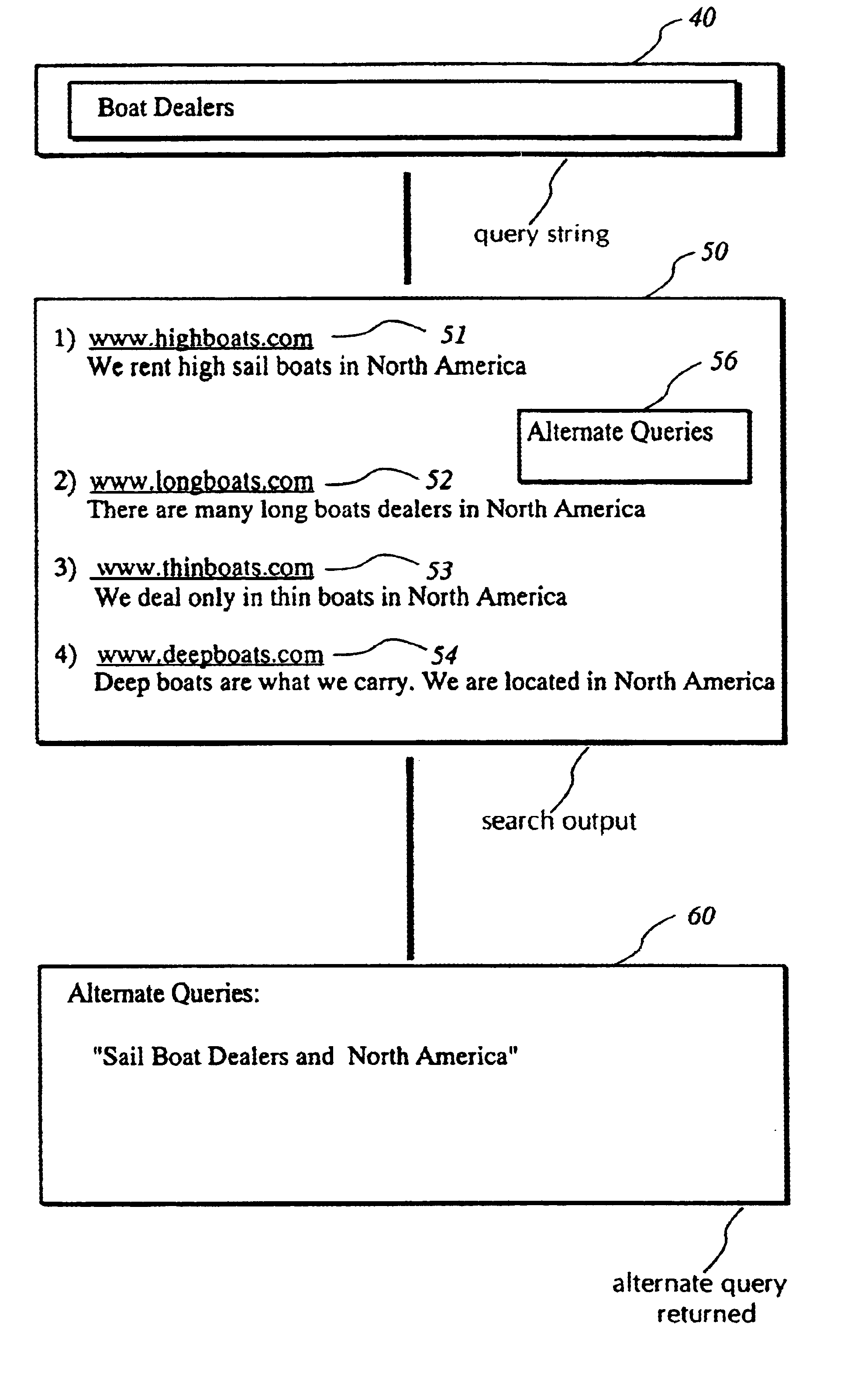
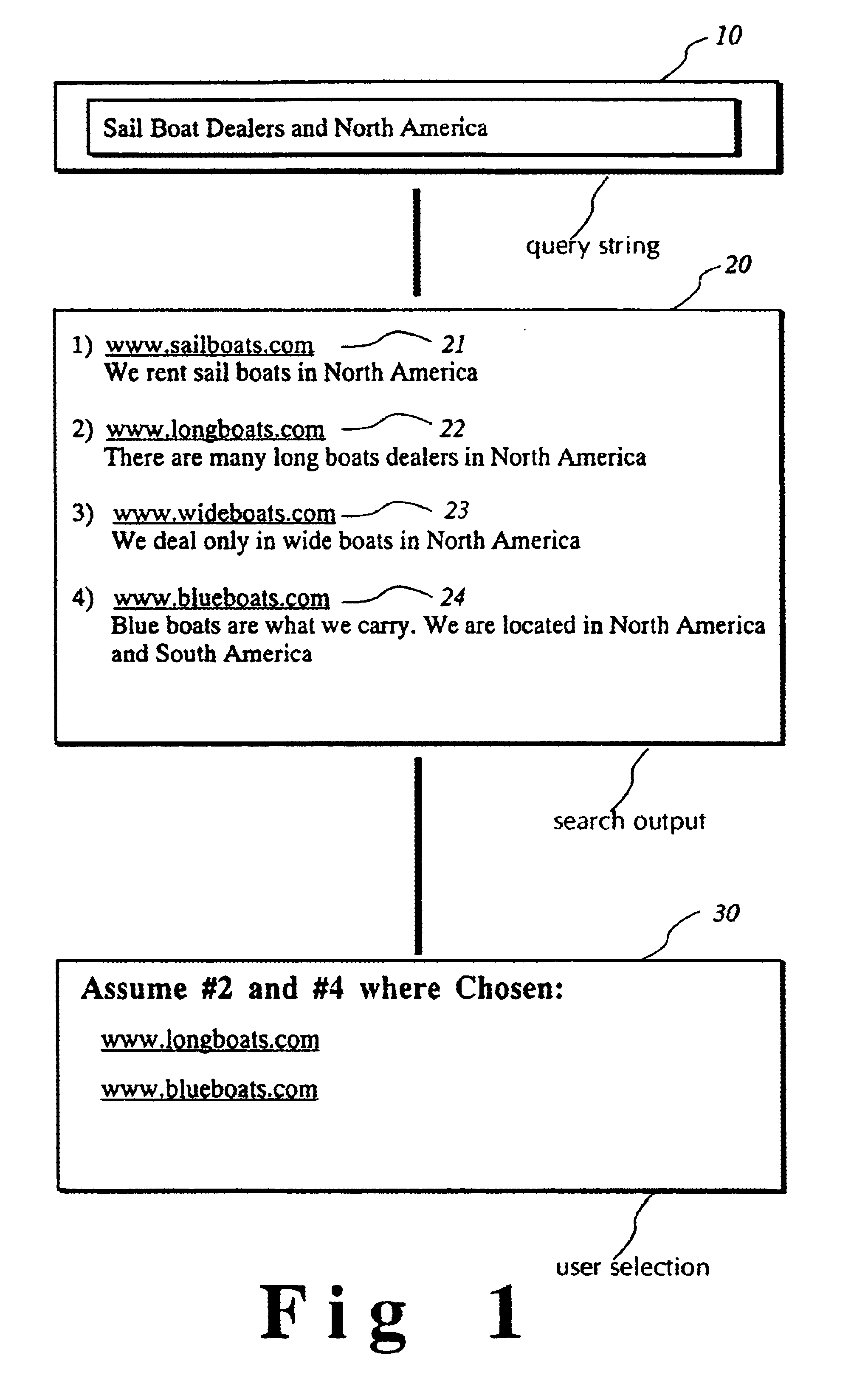
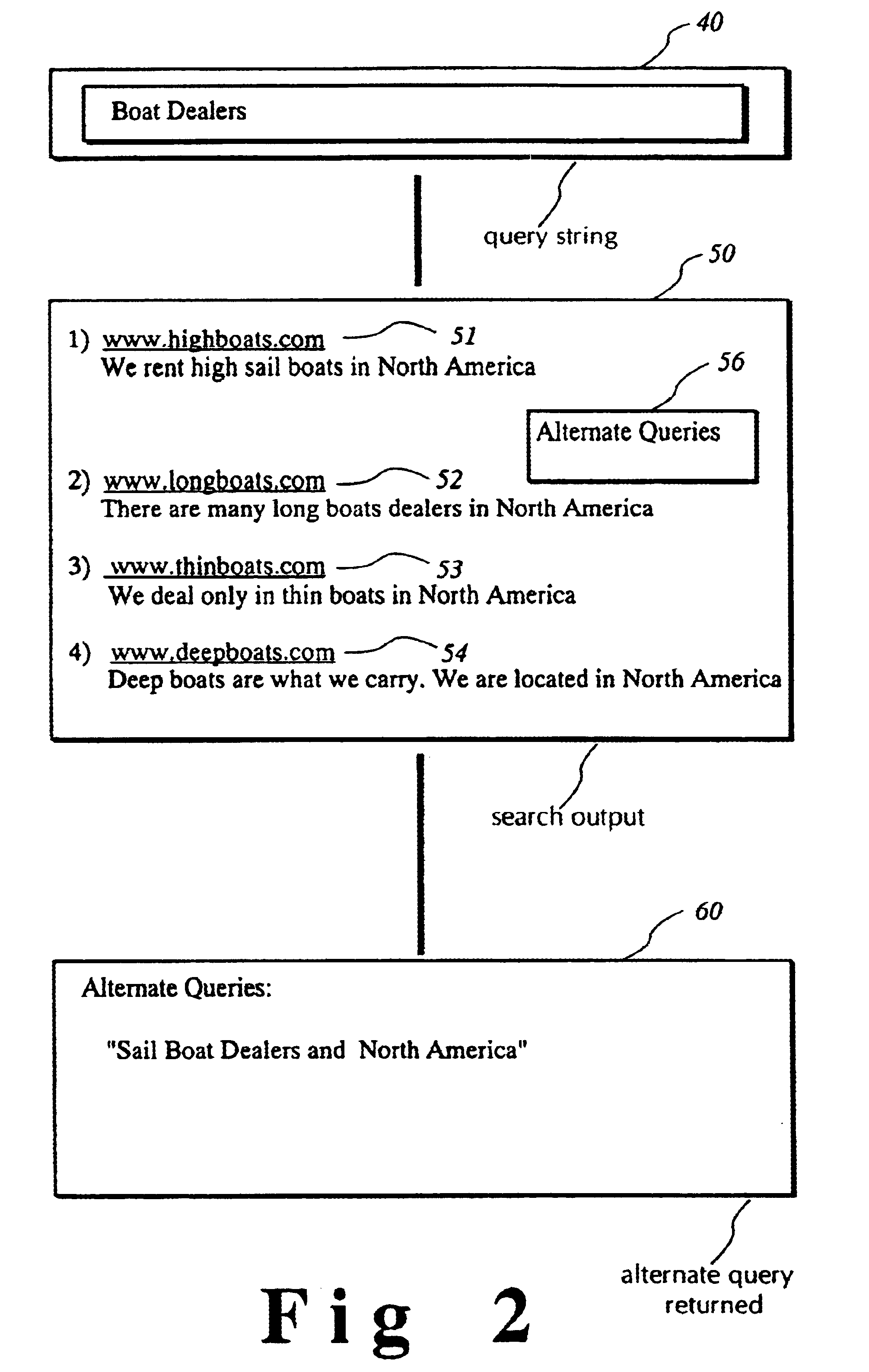
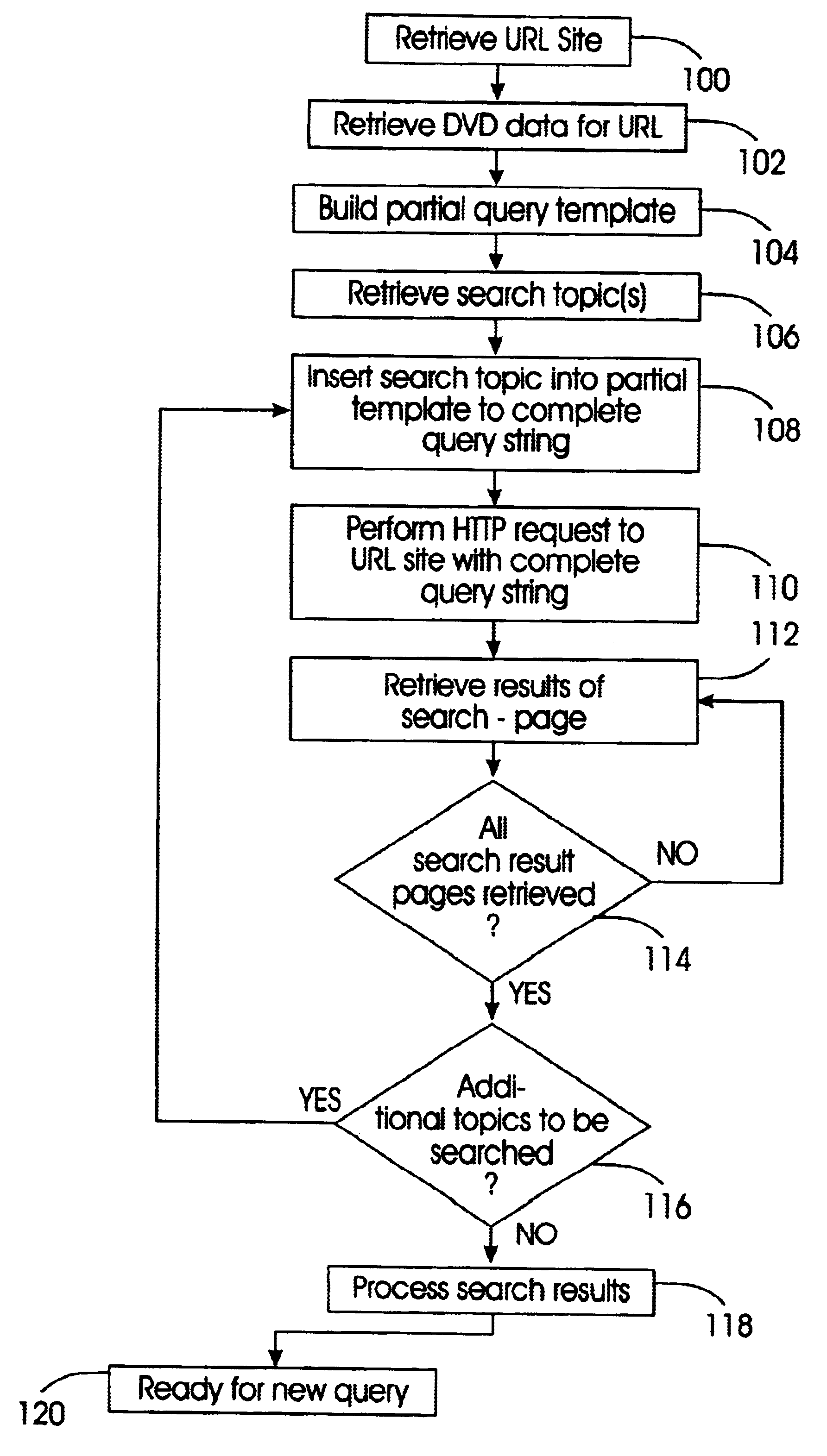
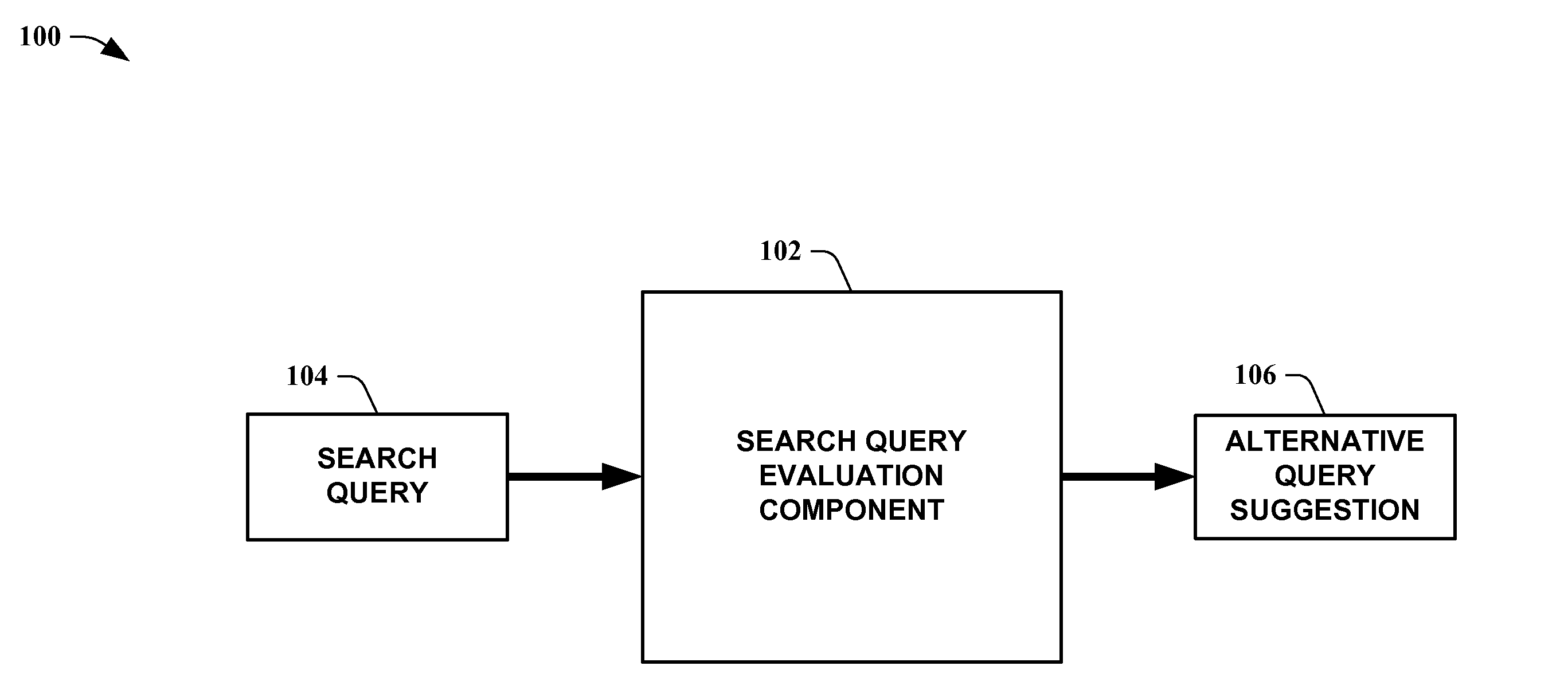
System and technique for suggesting alternate query expressions based on prior user selections and their query strings
InactiveUS6671681B1Increase currentData processing applicationsDigital data information retrievalGraphicsGraphical user interface
An invention for monitoring user choices and selections on a search result web page and providing alternative query expressions to further narrow and enhance the user's search. Monitoring and recording user choices and selections is achieved by a query manager. Query strings are then standardized. The search is performed on an Internet search engine, and each search result item in the result output set is then associated with a list of alternative standardized queries by an alternate query matching manager. Each search result item in the result output set that is associated with the alternate queries is then flagged. The resulting flagged list of alternative queries is displayed to the user by a page presentation manager using a graphical user interface for subsequent user selection. Upon selection of the graphical user interface for alternate query expressions, an alternate query selection manager retrieves and displays each alternate query to the user.
Owner:IBM CORP
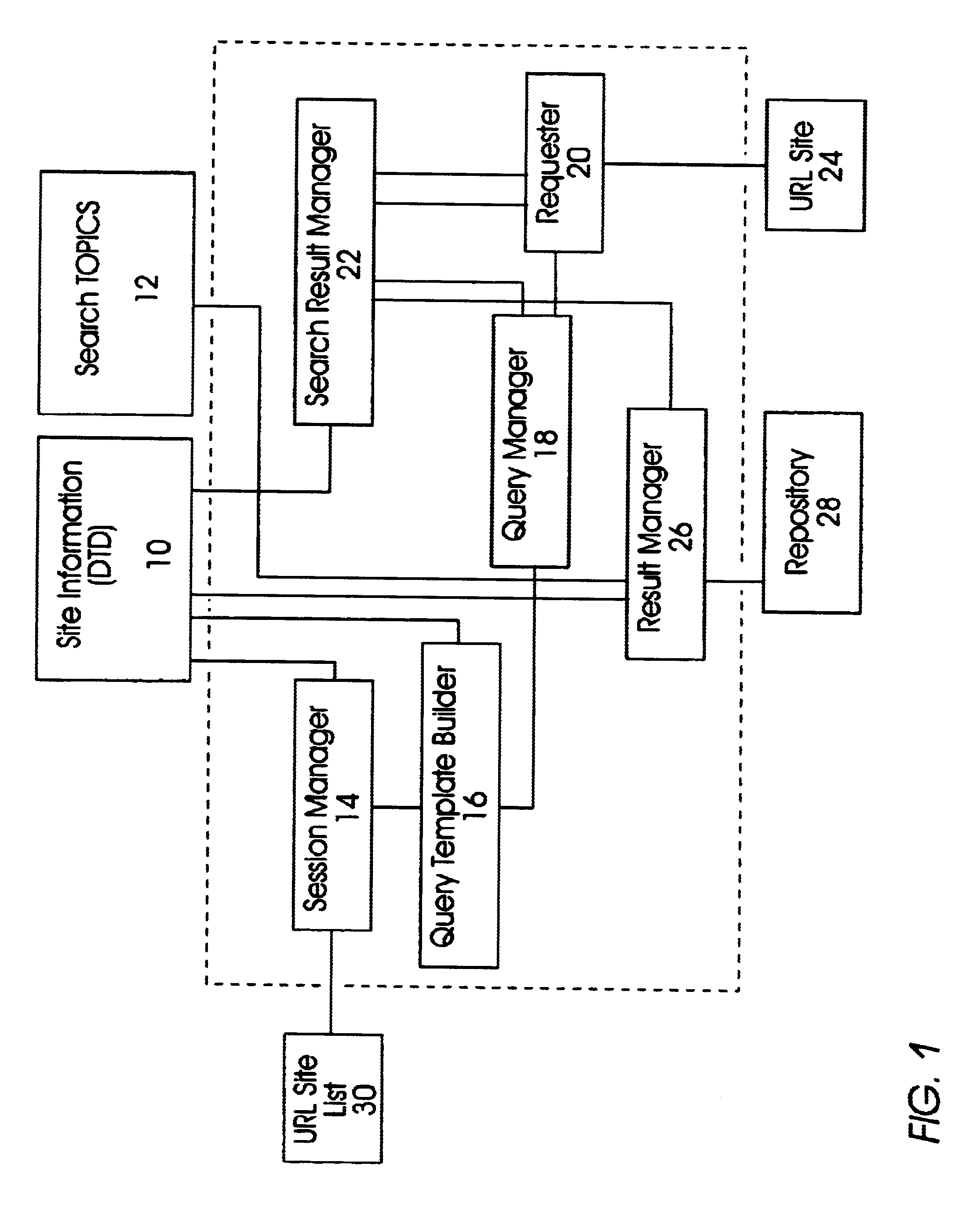
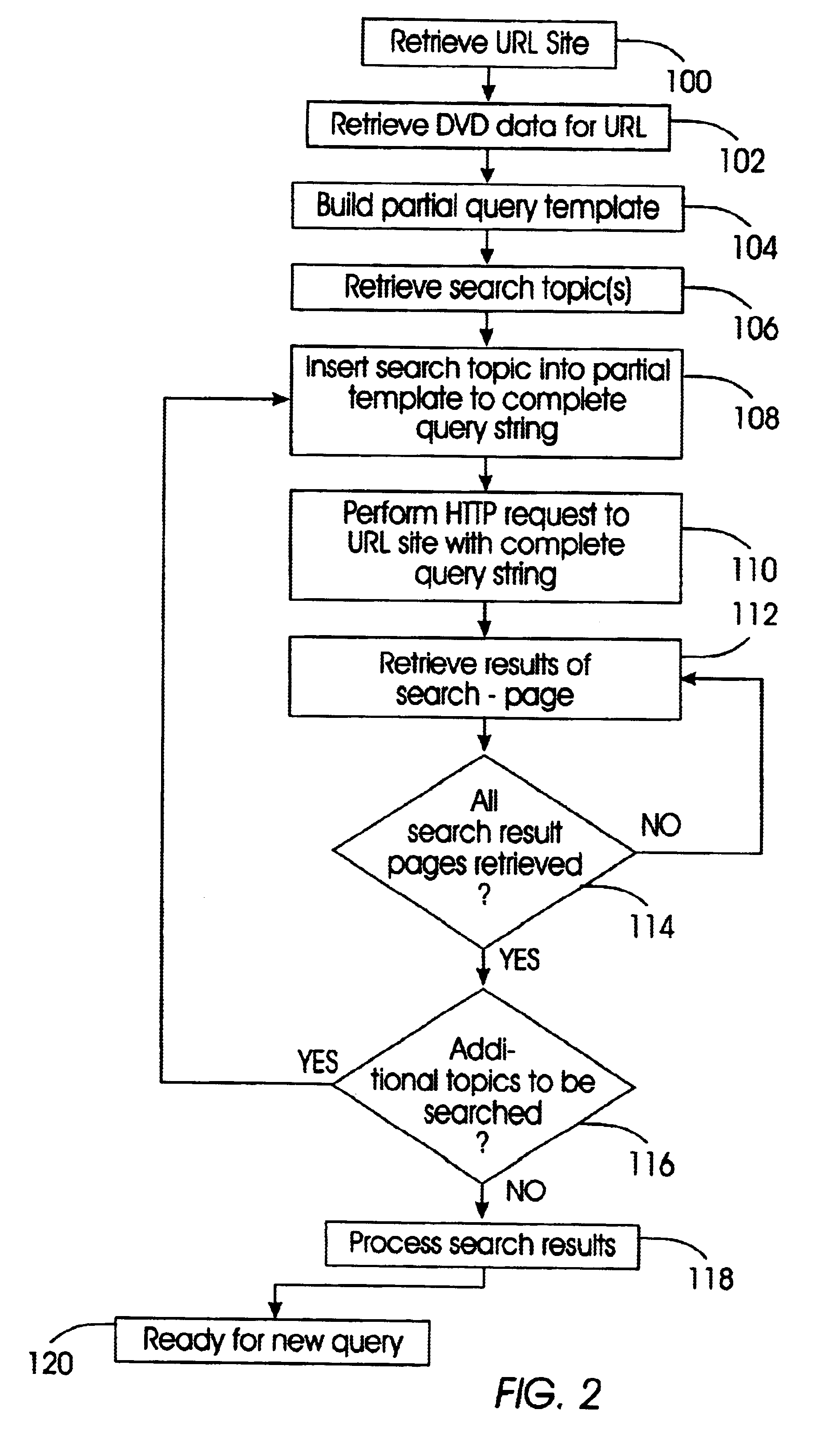
System and method for automatically gathering dynamic content and resources on the world wide web by stimulating user interaction and managing session information
An apparatus and method for a web crawler to automatically simulate user interaction with a dynamic website in order to gather and extract information from the site. This interactive web crawler will be able to create a search query string for any one of a number of desired search topics and systematically crawl dynamic personalized content on a website and retrieve the information desired by the user / client.
Owner:GOOGLE LLC
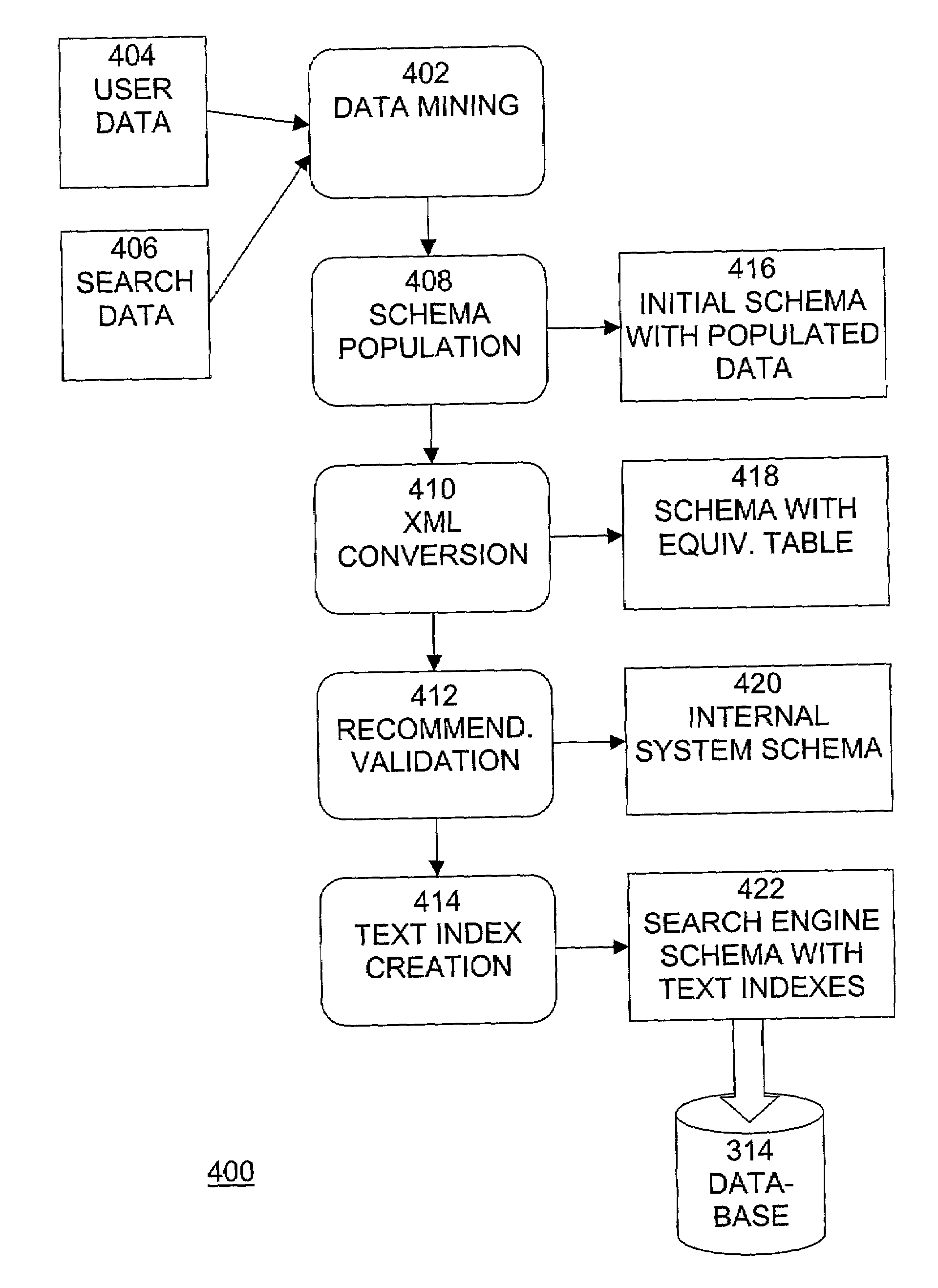
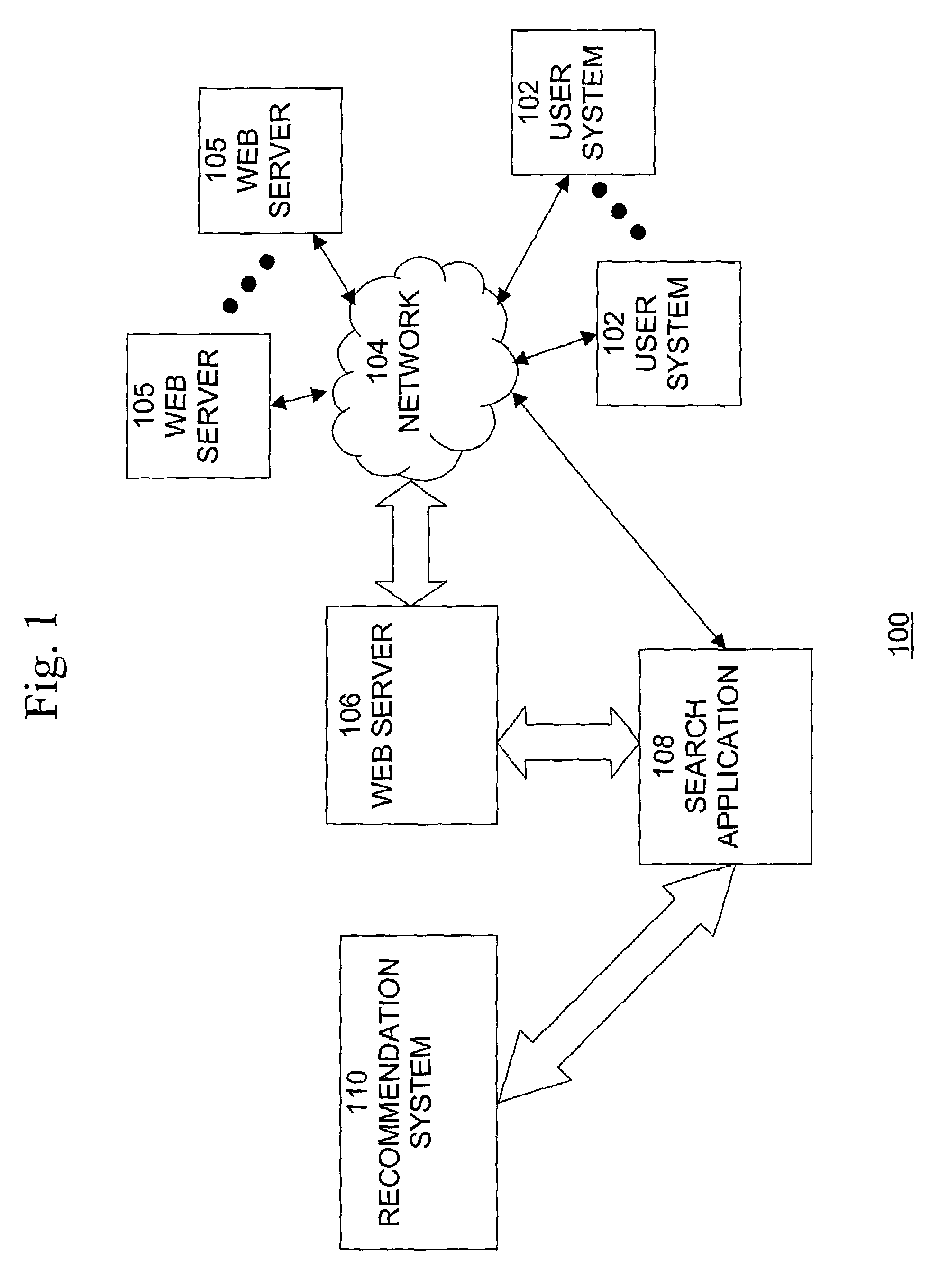
System and method for search and recommendation based on usage mining
InactiveUS7092936B1Data processing applicationsDigital data information retrievalRelevant informationQuery string
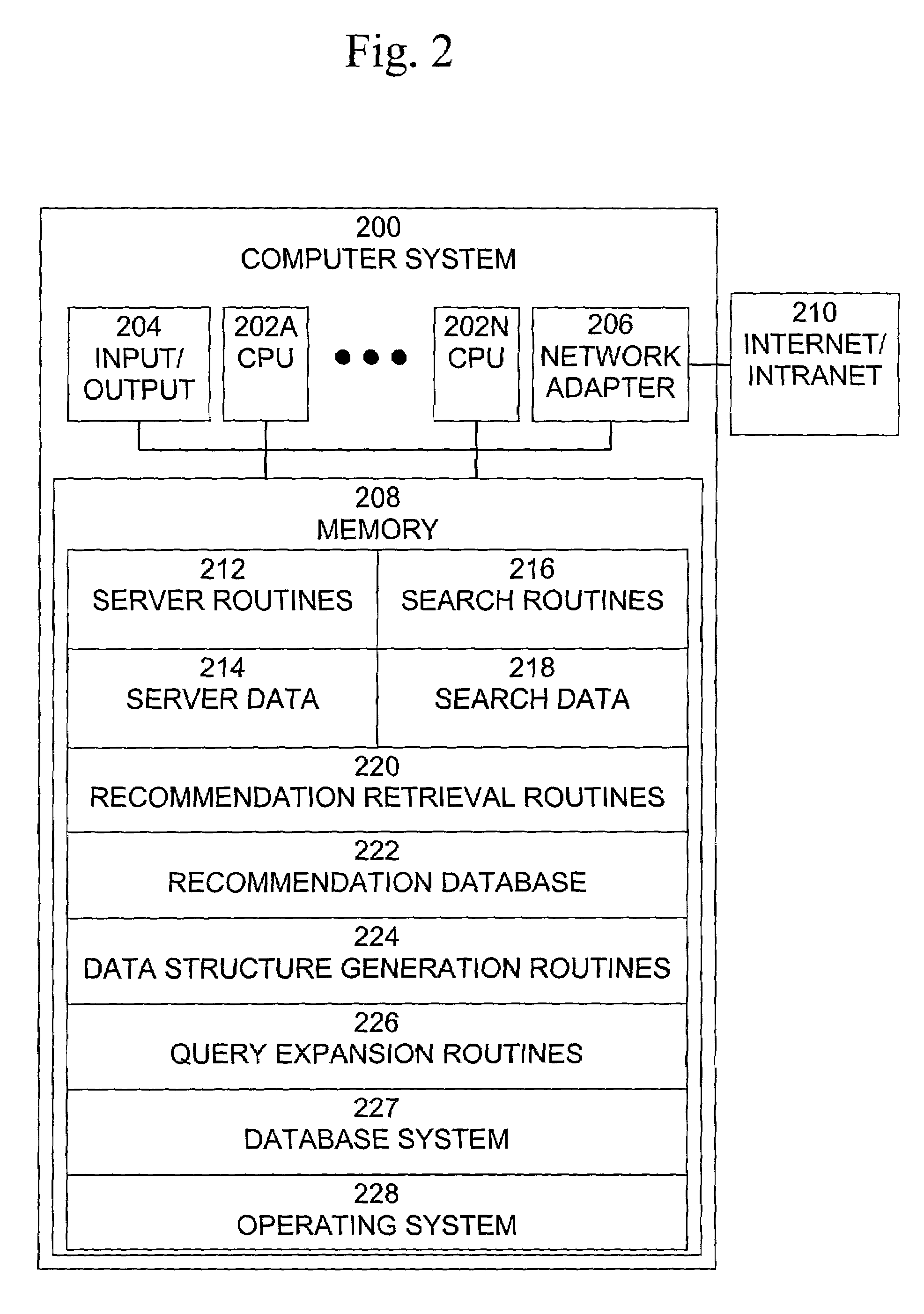
A method, system, and computer program product for performing searching that generates improved queries, retrieves meaningful and relevant information, and presents the retrieved information to the user in a useful and comprehensive manner is described. The method of searching comprises the steps of: receiving from a user a search query requesting information, retrieving at least one recommendation relating to the search query, generating an expanded query based on the received query, performing a search using the expanded query to retrieve documents, and generating themes relating to the retrieved documents. The at least one recommendation relating to the search query is retrieved from a recommendation database. The recommendation database is generated by performing the steps of: performing data mining using users search query logs, user search patterns, and user profile information to generate a plurality of recommendations relating to search query strings, generating a data structure including the recommendations relating to search query strings, and generating a text index based on information in the data structure.
Owner:ORACLE INT CORP
Method and apparatus for performing similarity searching on a data stream with respect to a query string
ActiveUS7917299B2Digital data information retrievalDigital data processing detailsData streamQuery string
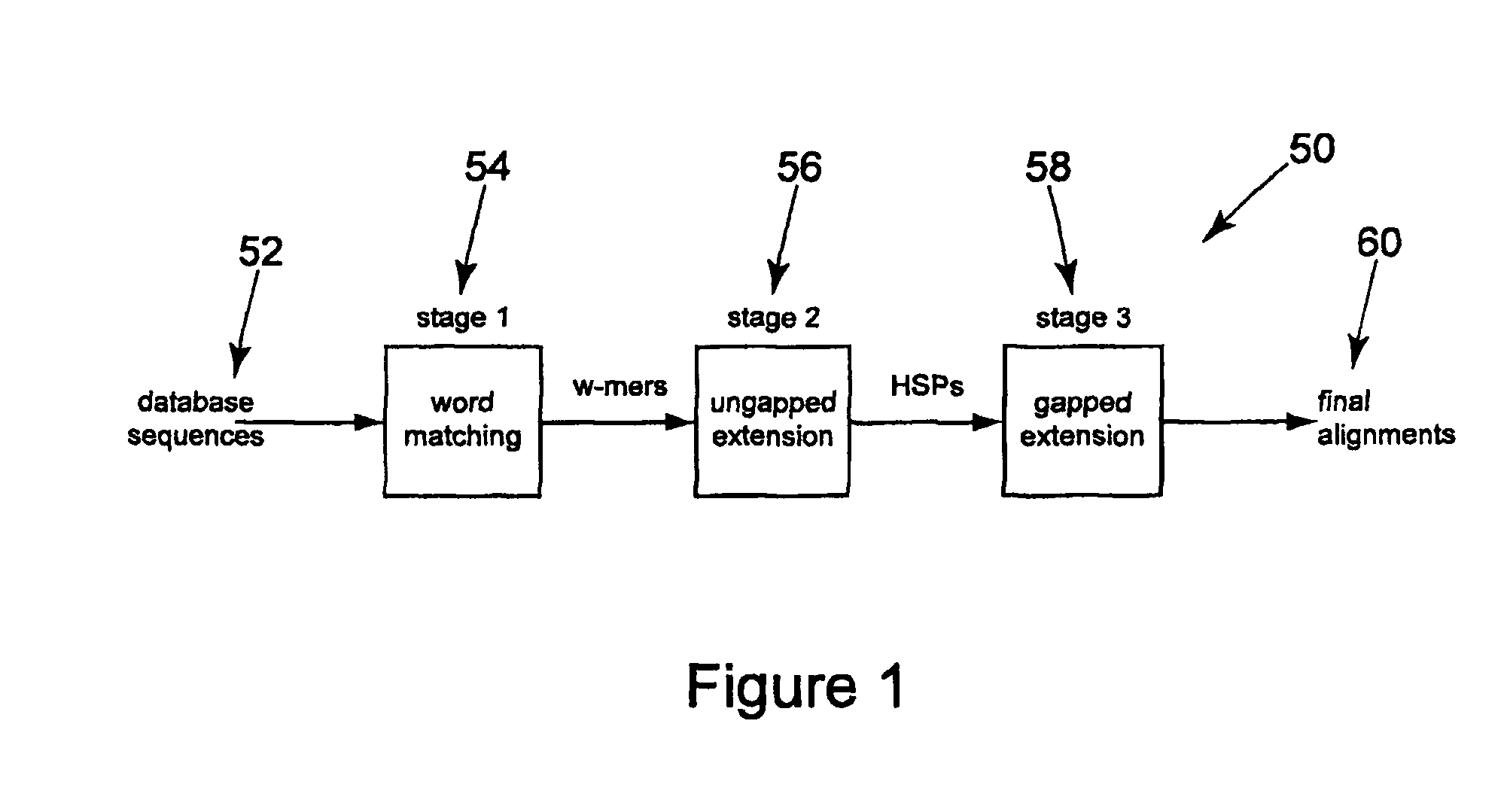
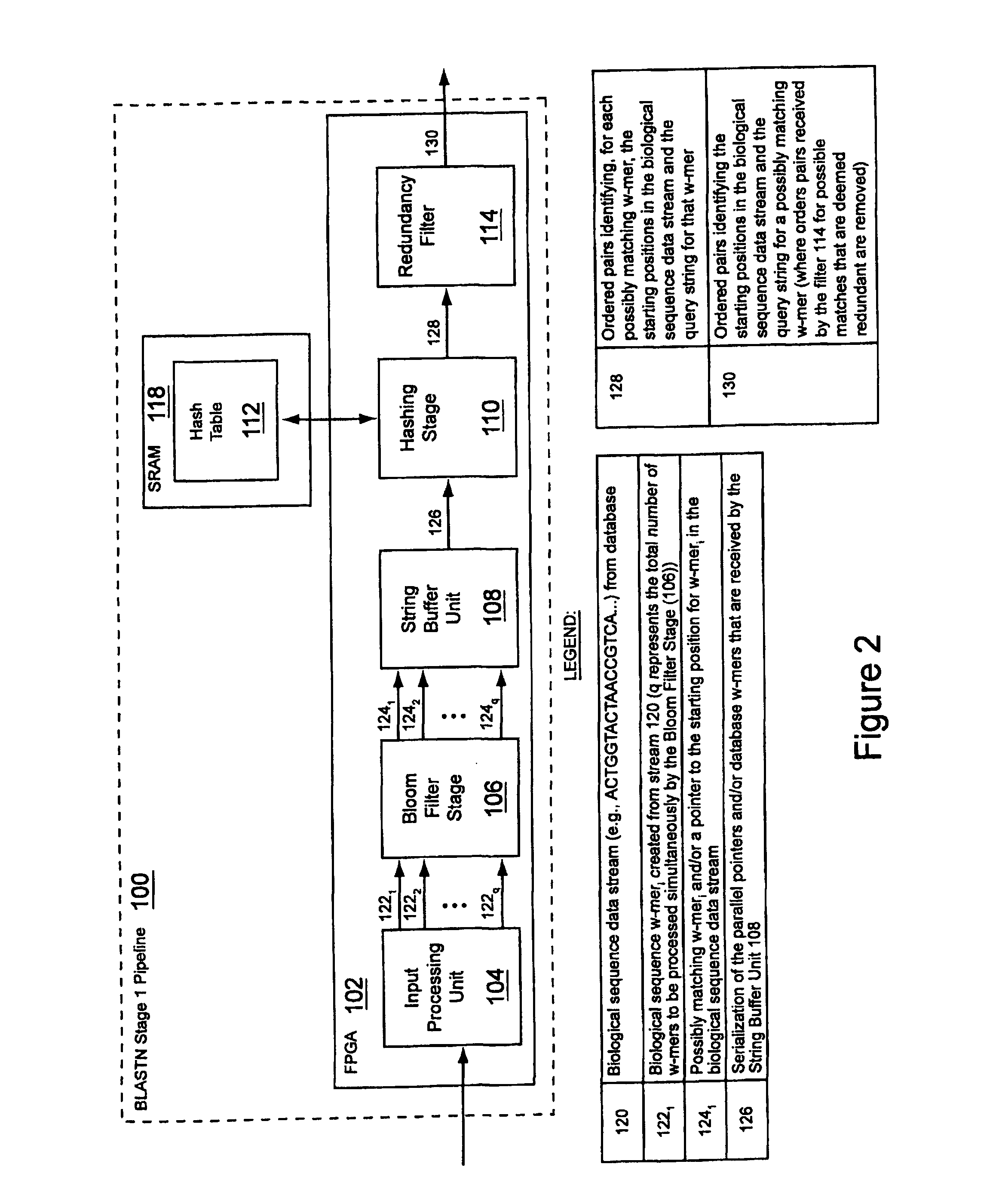
An apparatus and method for performing similarity searching on a data stream with respect to a query string are disclosed, where the data stream comprises a plurality of data substrings, and where the query string comprises a plurality of query substrings. A programmable logic device is used to filter the data stream to find a plurality of possible matches between the data substrings and a plurality of the query substrings, wherein the data substrings and the query substrings comprise a plurality of characters. From these possible matches, a determination can be made as to a similarity between the query string and at least a portion of the data stream.
Owner:WASHINGTON UNIV IN SAINT LOUIS
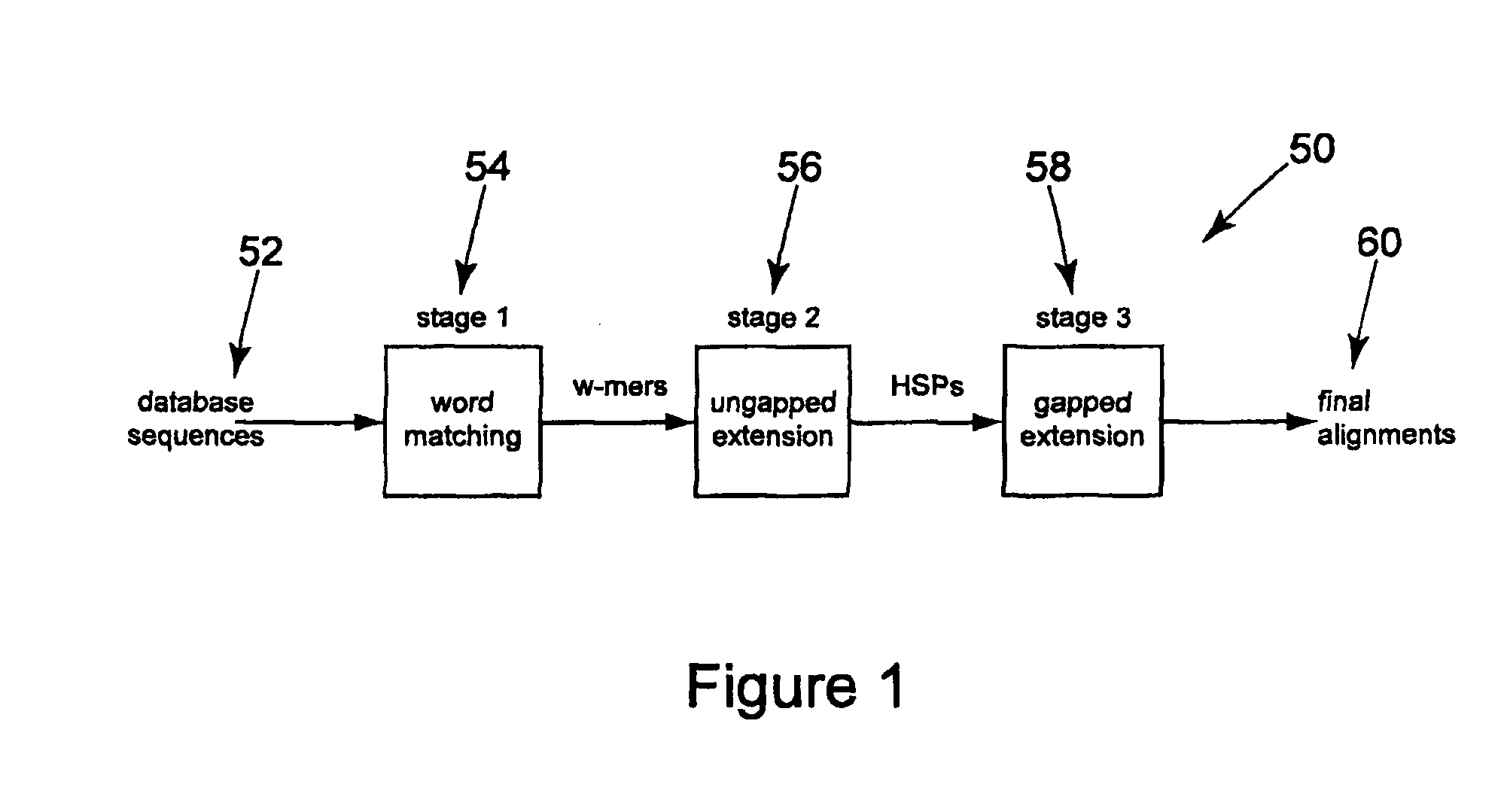
Method and apparatus for performing biosequence similarity searching
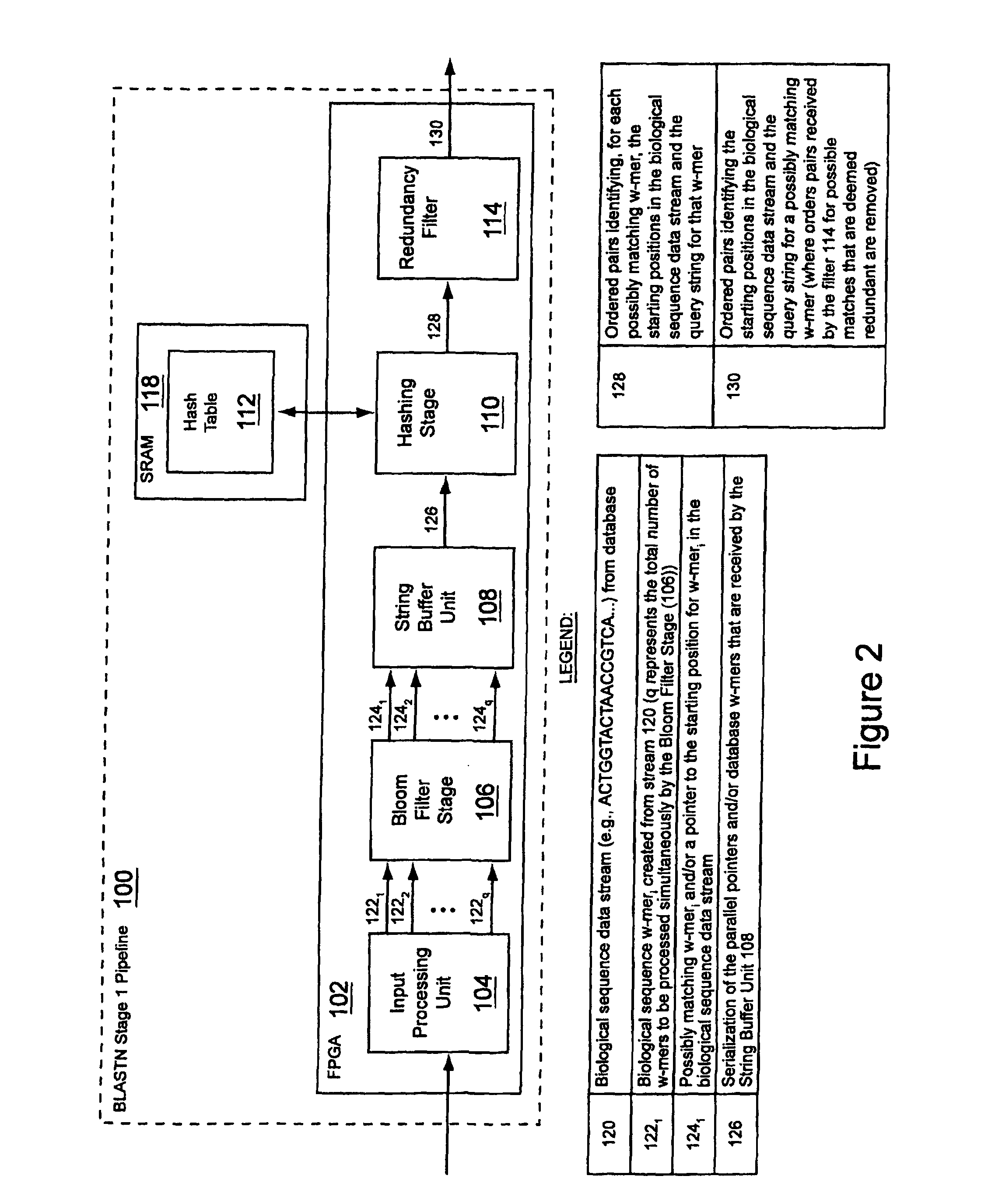
A system and method for performing biological sequence similarity searching is disclosed. This includes a programmable logic device configured to include a pipeline that comprises a matching stage, the matching stage being configured to receive a data stream comprising a plurality of possible matches between a plurality of biological sequence data strings and a plurality of substrings of a query string. The pipeline may further include a ungapped extension prefilter stage located downstream from the matching stage, the prefilter stage being configured to shift through pattern matches between the biological sequence data strings and the plurality of substrings of a query string and provide a score so that only pattern matches that exceed a user defined score will pass downstream from the prefilter stage. The matching stage may include at least one Bloom filter.
Owner:WASHINGTON UNIV IN SAINT LOUIS
Method and system for qualifying keywords in query strings
InactiveUS20080016040A1Improve abilitiesExpand databaseDigital data information retrievalDigital data processing detailsQuery stringDatabase
A method and system for qualifying keyword(s) or phrase(s) to formulate a query string for submitting a search request when the query string contains one or more keywords that may have multiple meanings associated therewith. Database information containing keywords and associated meanings or forms of the keywords is maintained and a requester is prompted to identify one or more of the meanings of a keyword when building the query string. One or more advertisements pertaining to the associated meanings or forms of the keywords in the query string is presented to the requester submitting a search request.
Owner:CHACHA SEARCH
Query string processing
ActiveUS20020099671A1Easy mappingData processing applicationsDigital data processing detailsData matchingQuery string
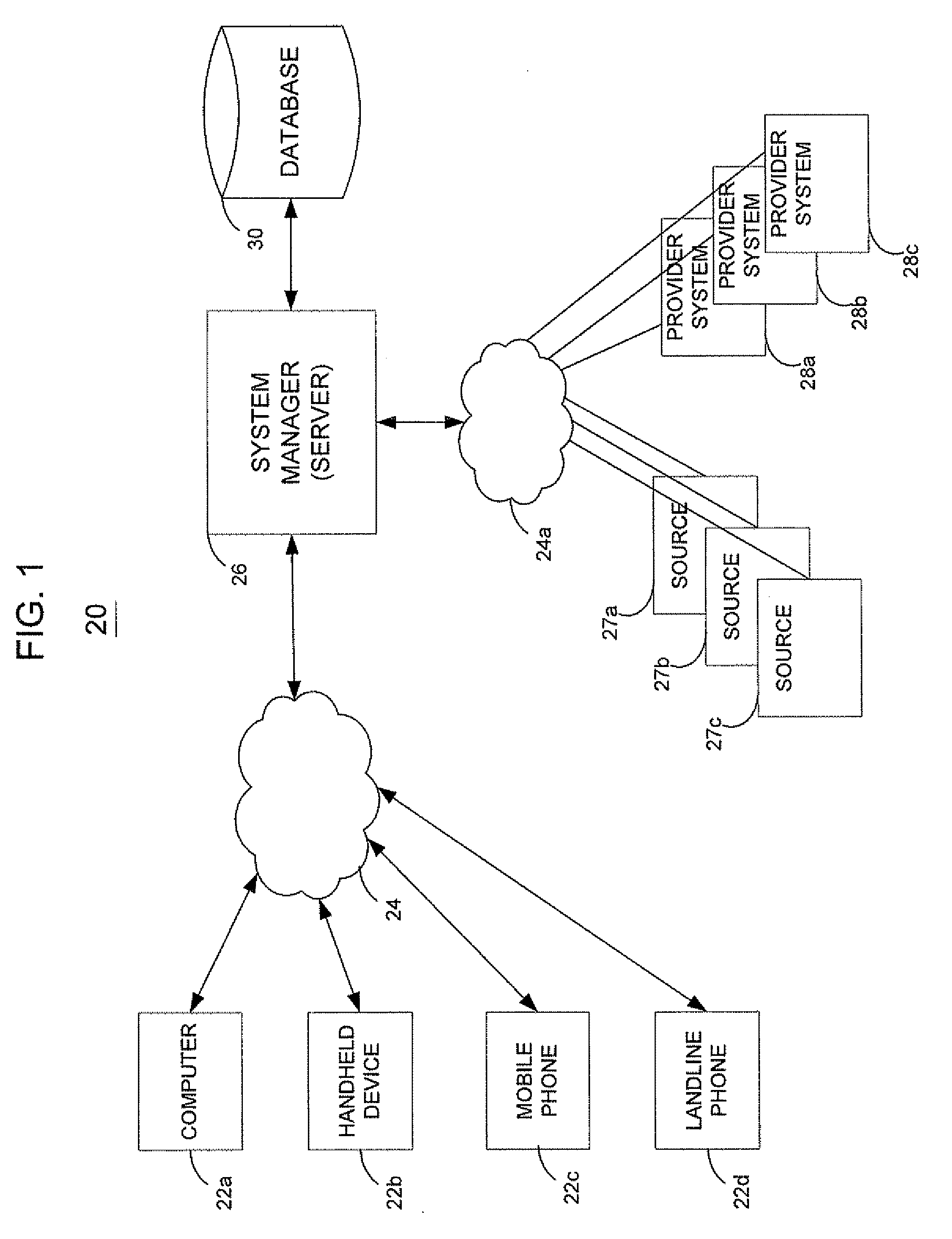
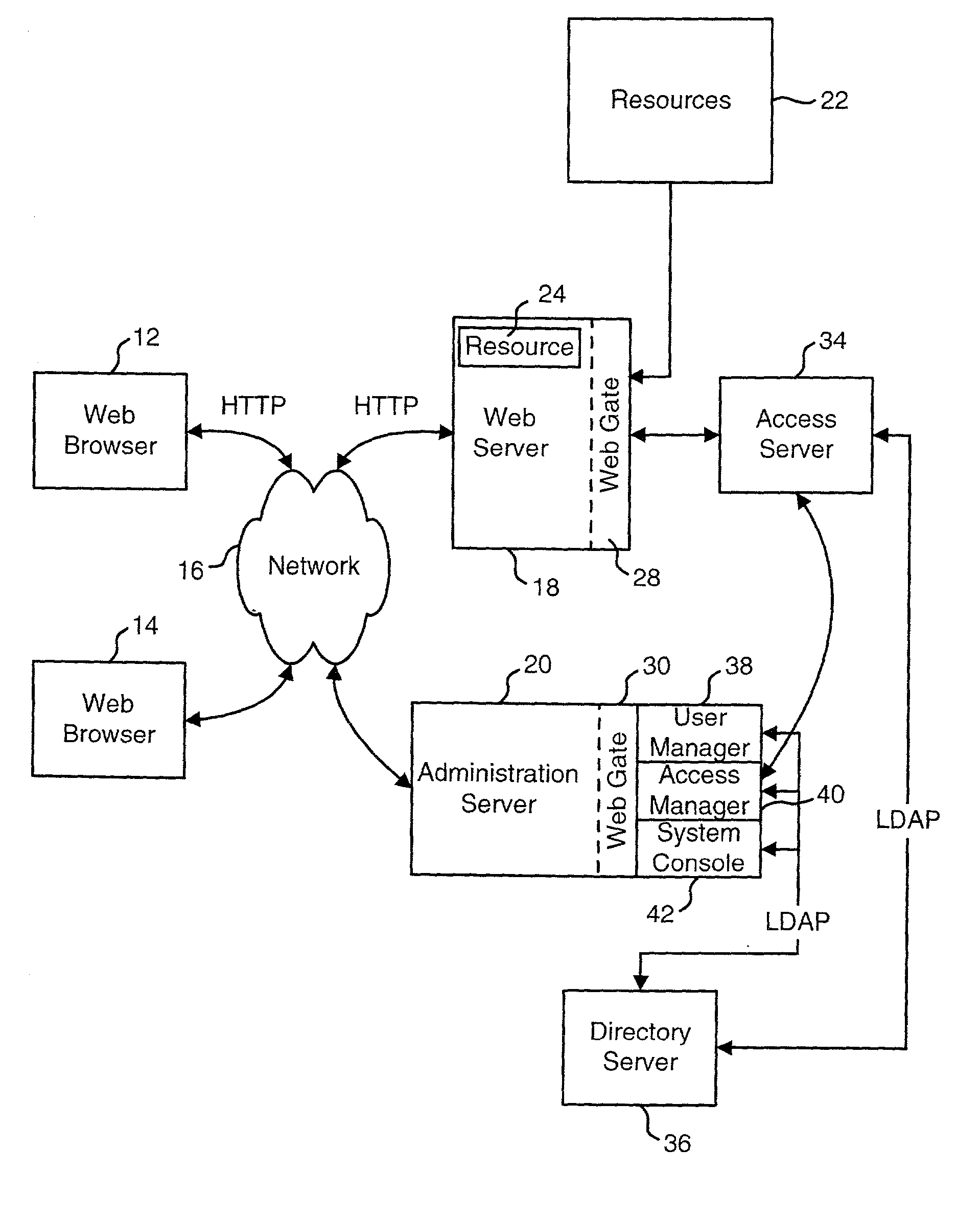
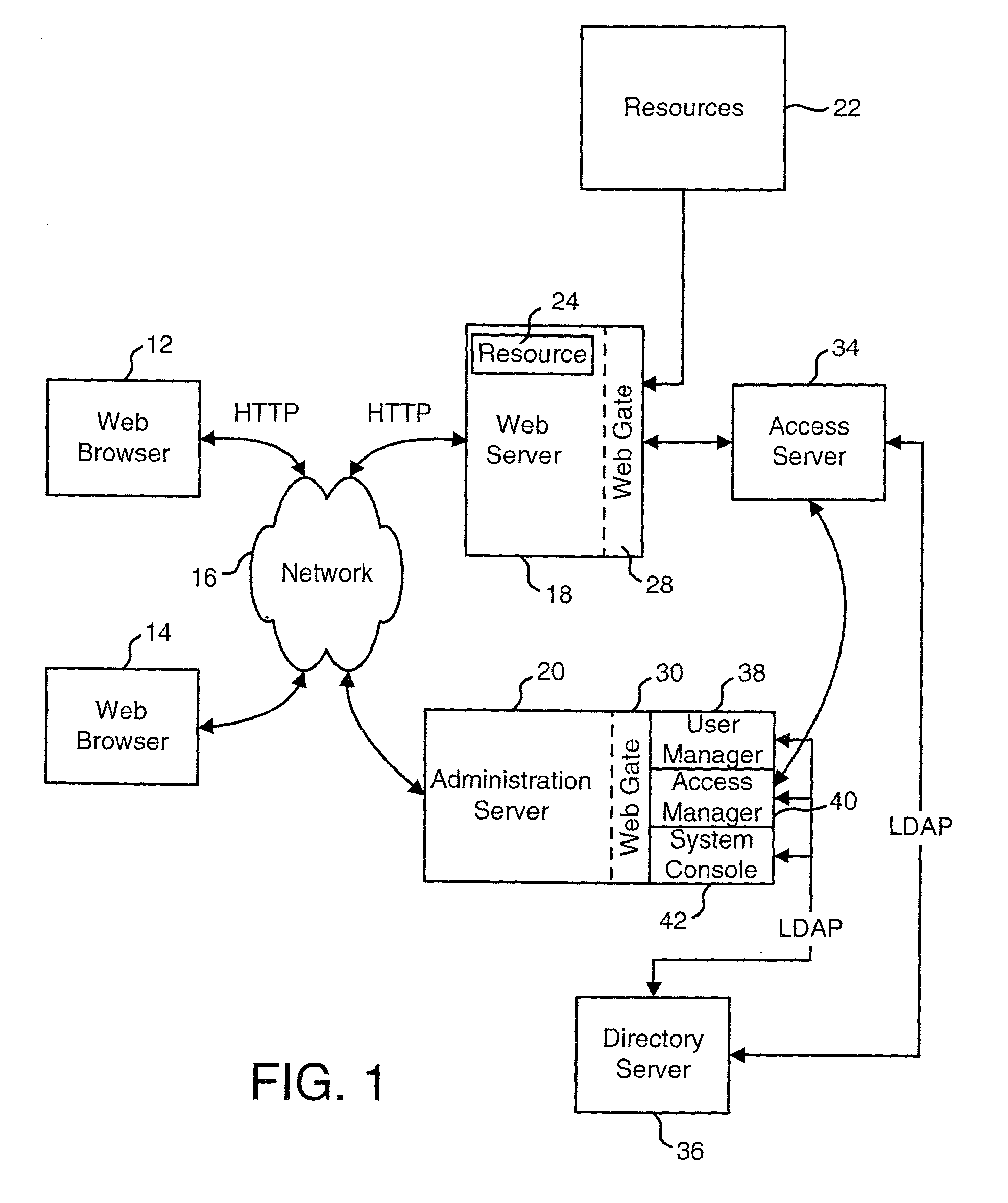
A system is disclosed that is used to provide access management for resources on a network. The system makes use of query data from a URL (or another identification or request) to identify the appropriate access rule. Examples of an access rule include an authentication rule, an authorization rule, or an audit rule. The system can be configured to require the query data to match order dependent variables or order independent variables. In one option, the system can include two levels of rules and the query data can be used to identify first level rules, second level rules or both.
Owner:ORACLE INT CORP
System & method for creating, editing, an on-line publication
InactiveUS20030204814A1Natural language data processingWebsite content managementQuery stringComputation process
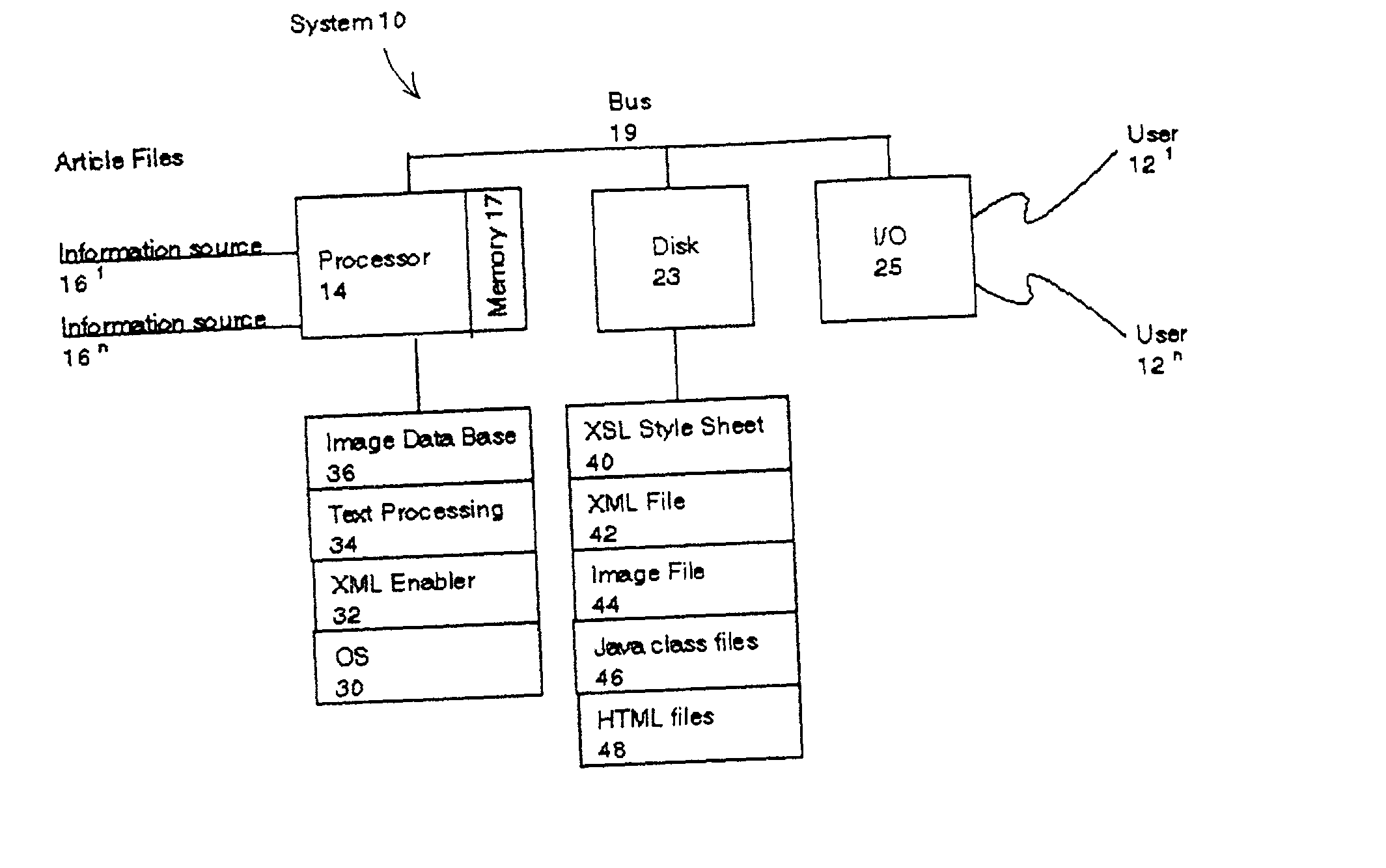
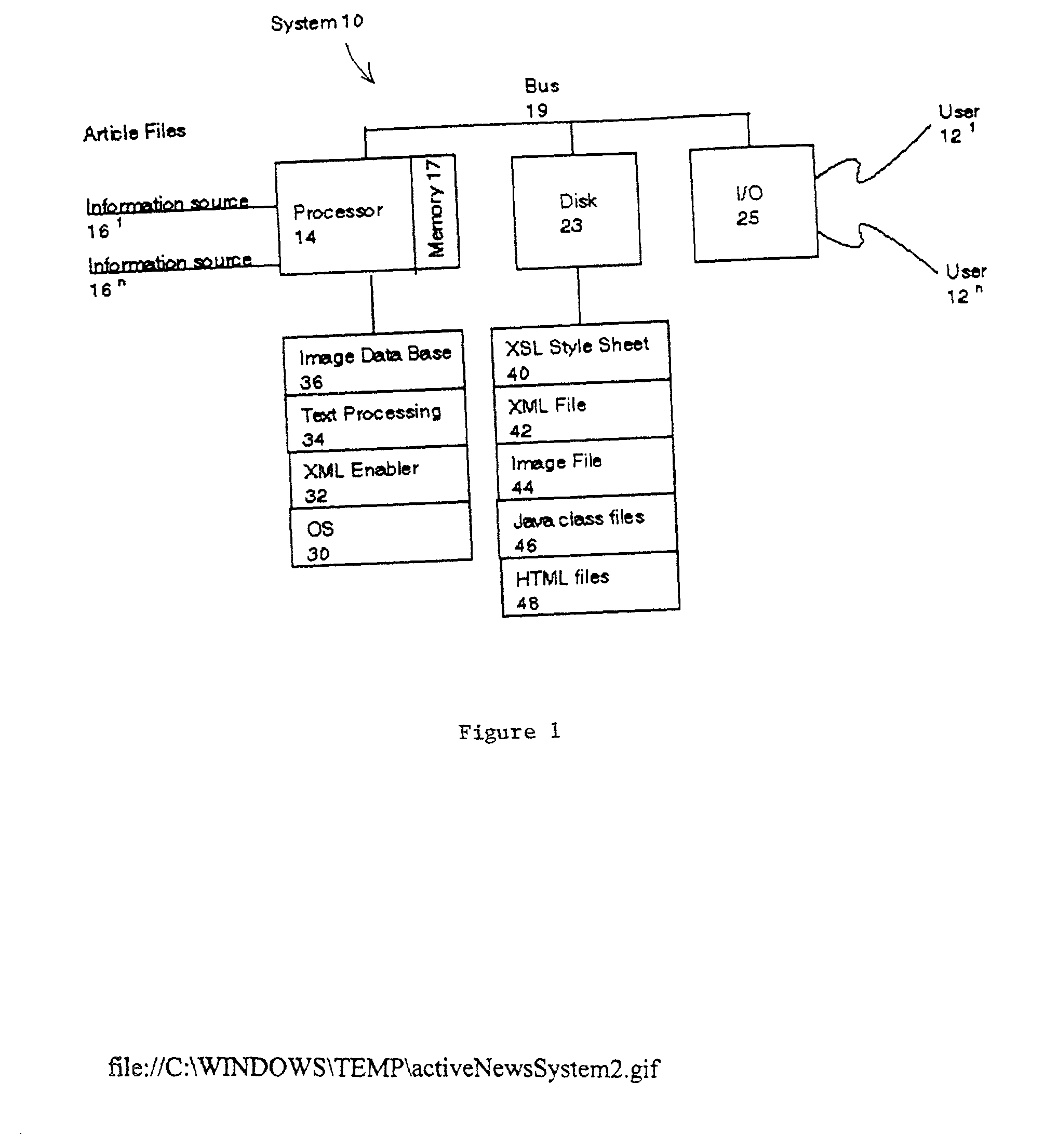
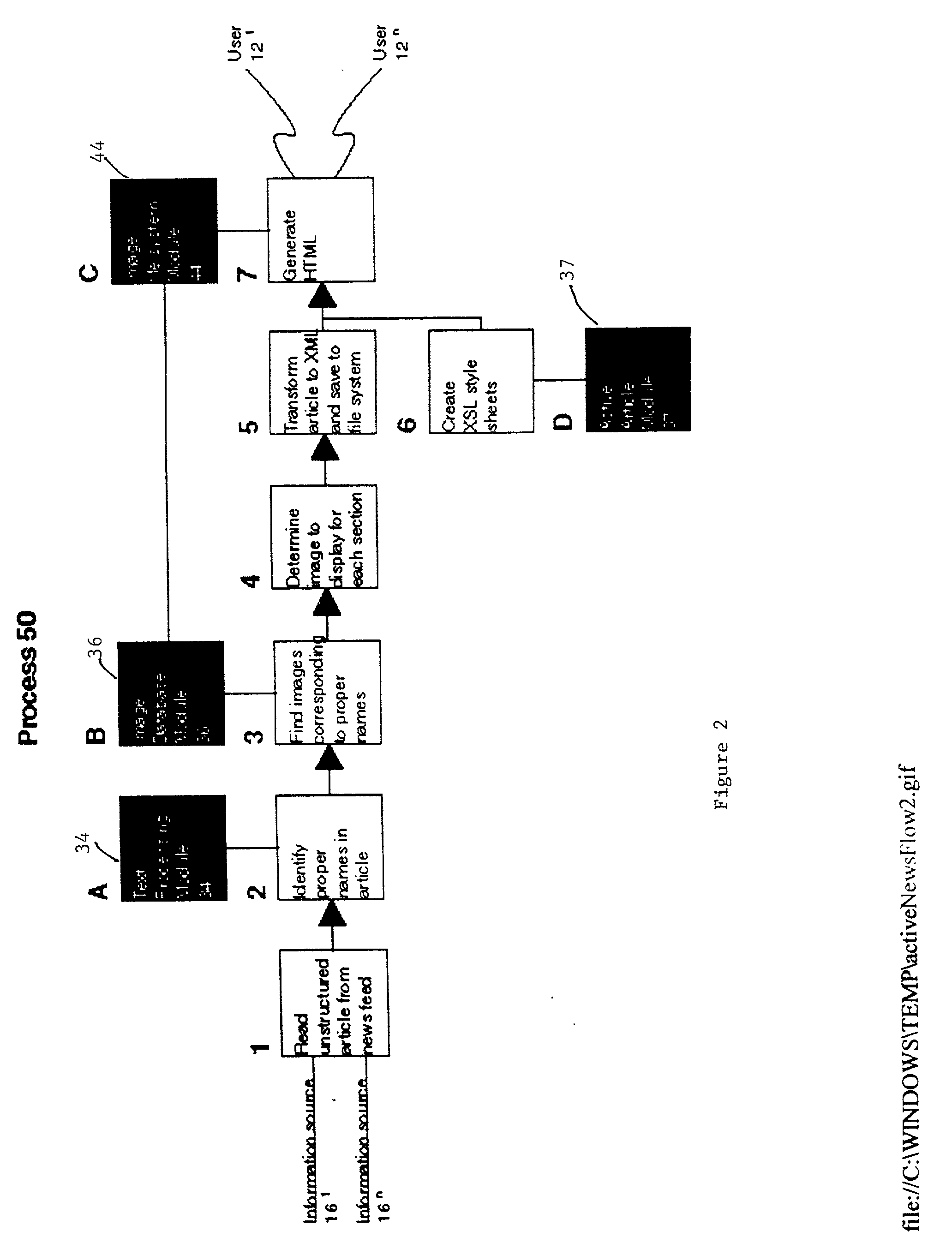
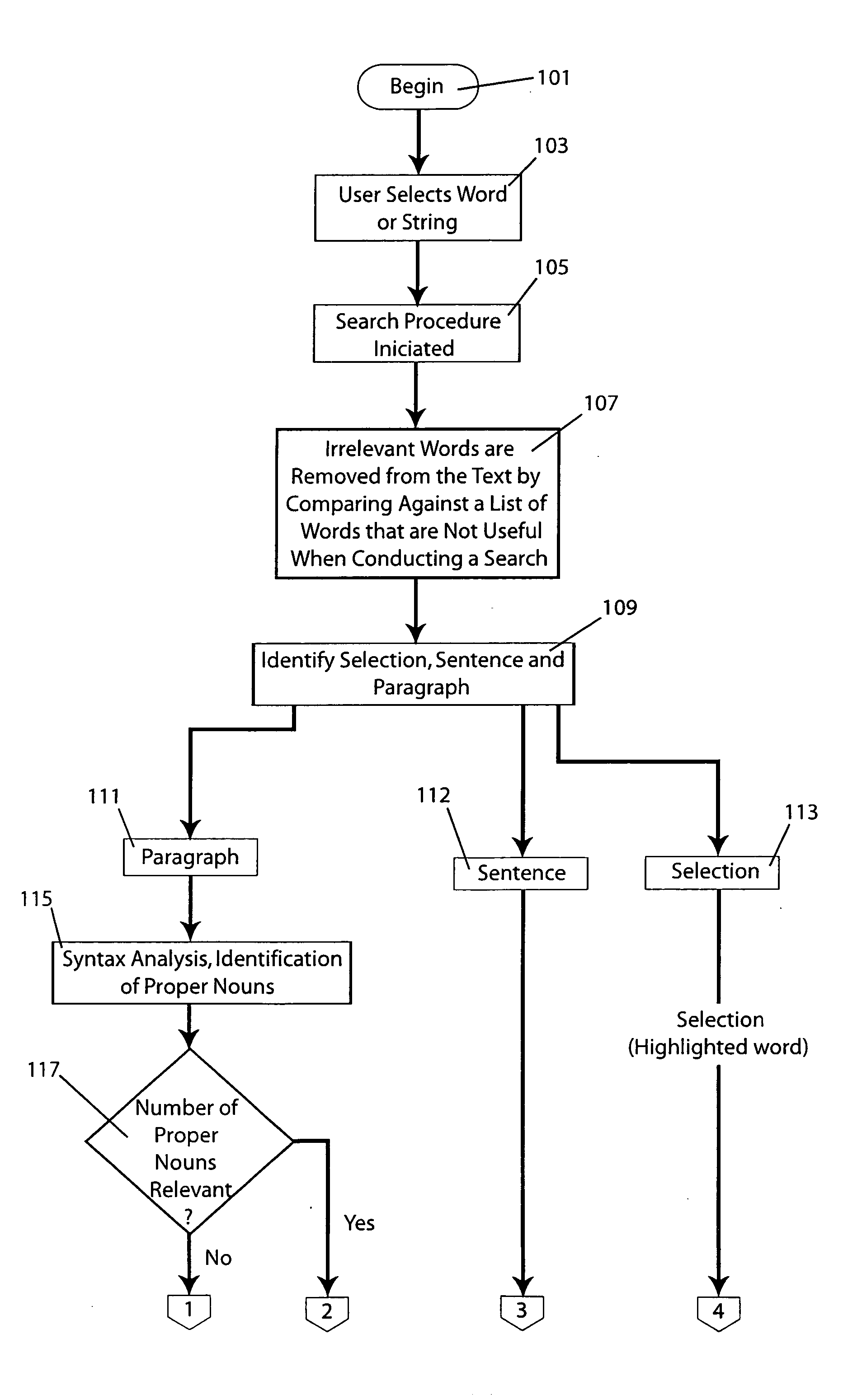
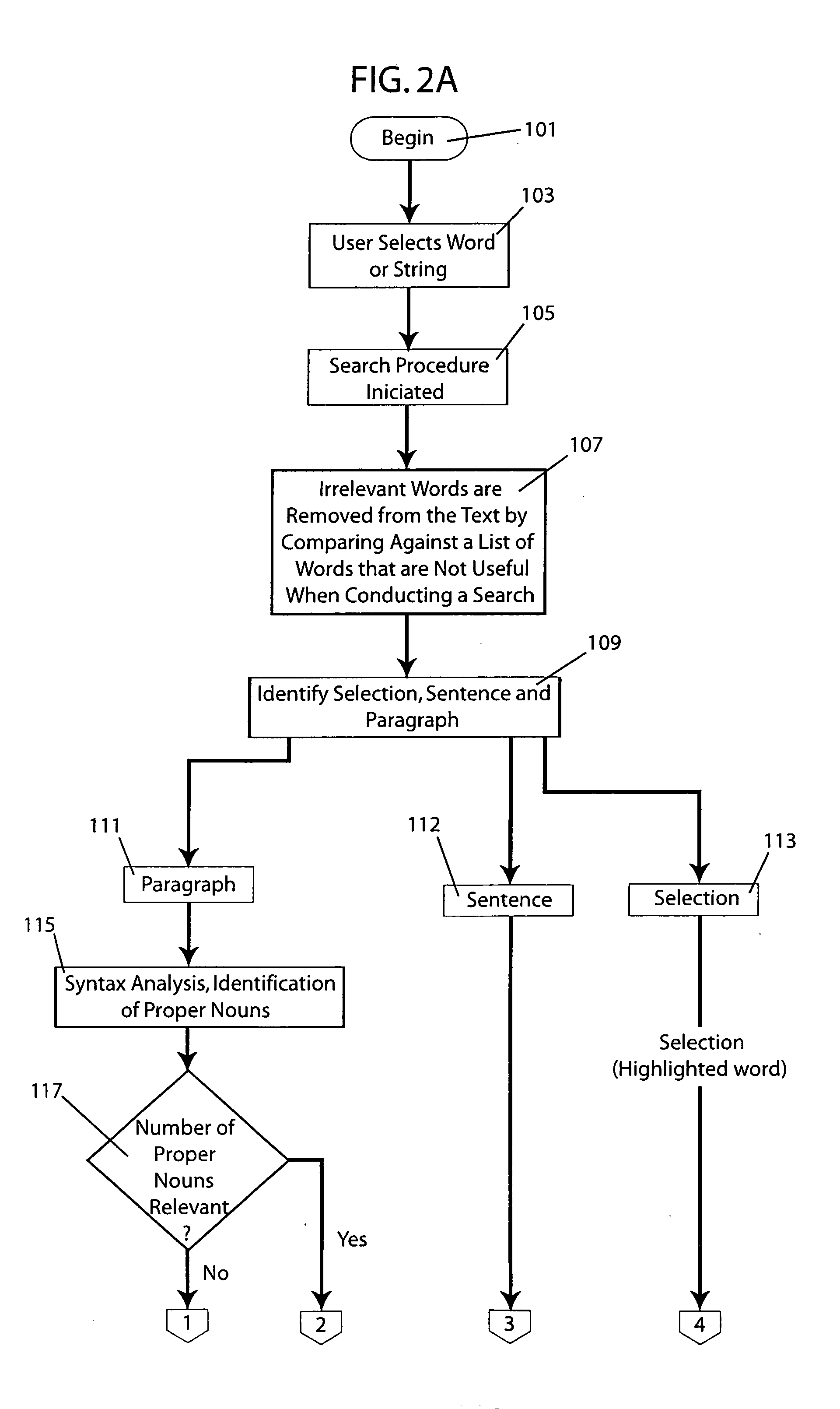
A system and method automatically generate an on-line document from raw text into an engaging, interactive form for a plurality of viewers. Unstructured articles are read from an information feed. A computation process extracts and tags proper names of people, products, organizations, and places and categorizes them. An image database is used to link these proper names with image files. The image database consists of a series of attribute-value pairs for active searching of names. A URL query string is inputted to the database to extract the location of the image in the database file system. An Extensible Markup Language (XML) file is created from the raw text of the article, the list of proper names in the processed data and the image file references. The XML file is stored in a file system. An Extensible Stylesheet Language (XSL) file provides templates containing computational relationships between the text and images. The XML and XSL style sheets are combined to generate a Hypertext Markup Language (HTML) file containing an on-line story of the unstructured articles in a Java Applet which allows the system to provide a variety of interactive behaviors for a final presentation available by a viewer from a browser.
Owner:IBM CORP
Generation of a data model applied to queries
ActiveUS9128980B2Database distribution/replicationNatural language data processingQuery stringData modeling
Embodiments include generating data models that may give semantic meaning for unstructured or structured data that may include data generated and / or received by search engines, including a time series engine. A method includes generating a data model for data stored in a repository. Generating the data model includes generating an initial query string, executing the initial query string on the data, generating an initial result set based on the initial query string being executed on the data, determining one or more candidate fields from one or results of the initial result set, generating a candidate data model based on the one or more candidate fields, iteratively modifying the candidate data model until the candidate data model models the data, and using the candidate data model as the data model.
Owner:SPLUNK INC
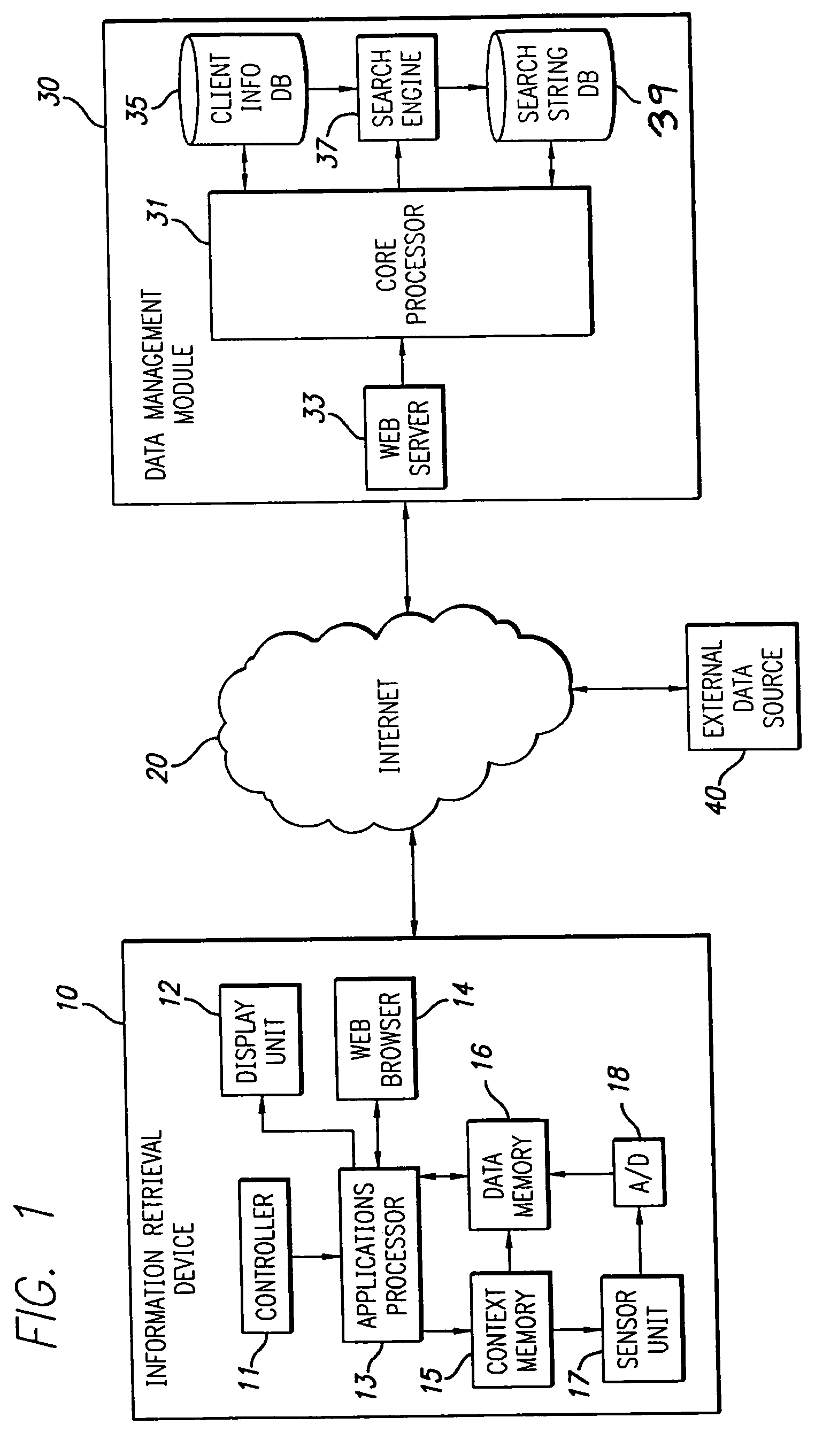
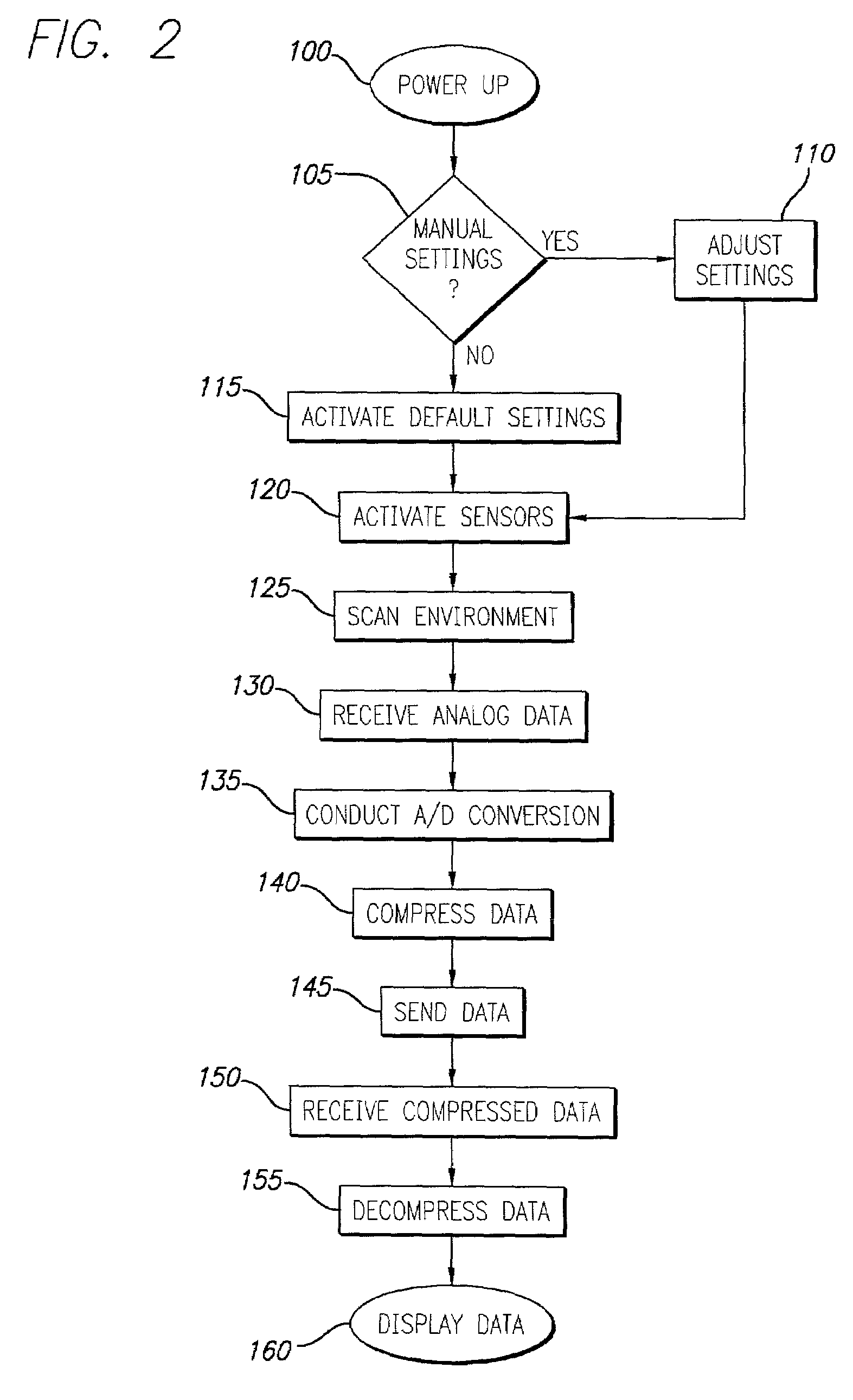
Method and apparatus for delivering content via information retrieval devices
InactiveUS7228327B2Digital data information retrievalElectrical apparatusInformation typeReal-time data
A method for anticipating a user's desired information using a PDA device connected to a computer network is provided. This method further comprises maintaining a database of user tendencies within the computer network, receiving sensor data from the user's physical environment via the PDA device, generating query strings using both tendency data and sensor data, retrieving data from external data sources using these generated query strings, organizing the retrieved data into electronic folders, and delivering this organized data to the user via the PDA device. In particular, a data management module anticipates the type of information a user desires by combining real time data taken from a sensor unit within a PDA and data regarding the history of that particular user's tendencies stored within the data management module.
Owner:INTELLECTUAL VENTURES I LLC
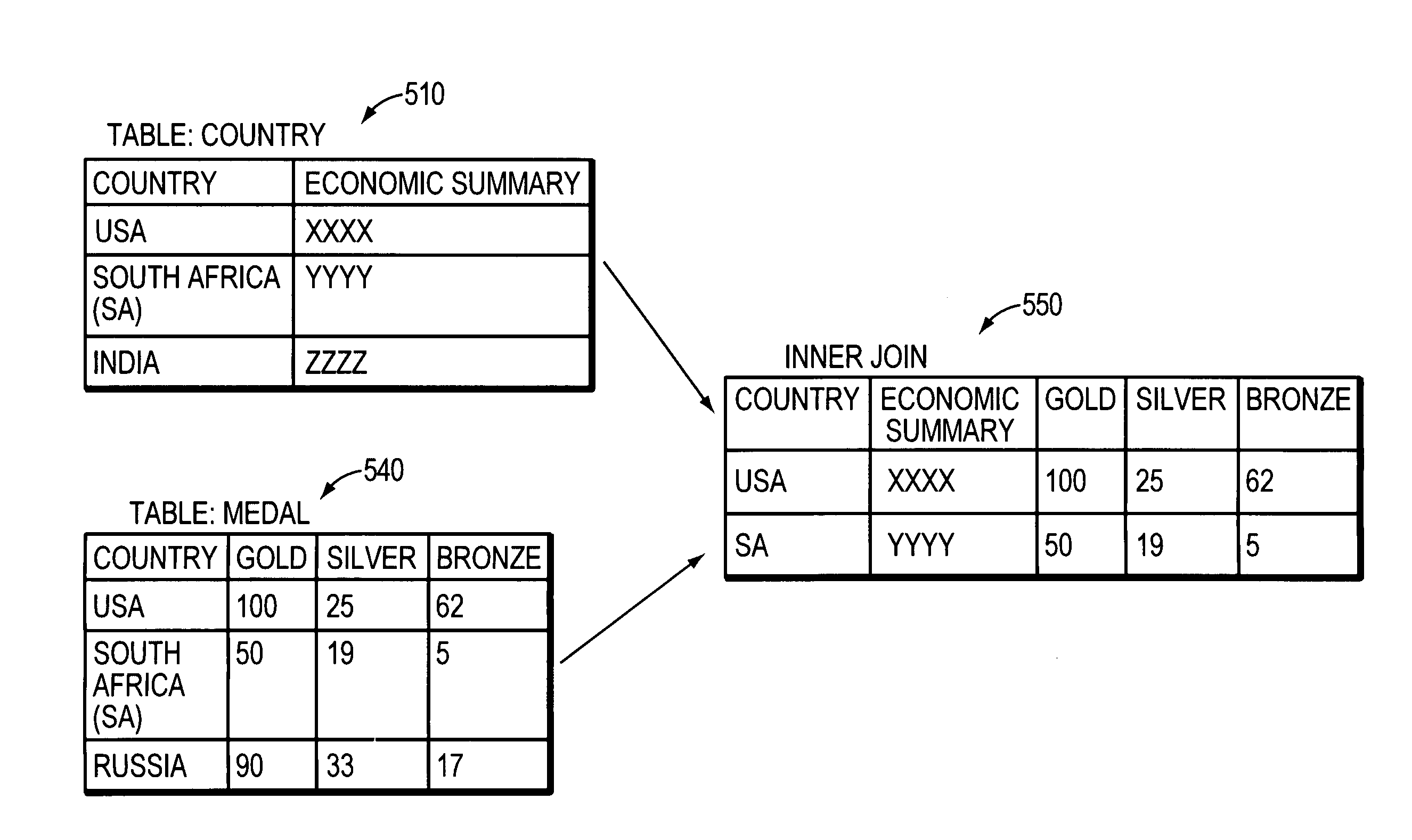
Querying joined data within a search engine index
ActiveUS20100005054A1Efficient queryEfficient retrievalDigital data information retrievalDigital data processing detailsQuery stringDocument preparation
Techniques and systems for indexing and retrieving data and documents stored in a record-based database management system (RDBMS) utilize a search engine interface. Search-engine indices are created from tables in the RDBMS and data from the tables is used to create “documents” for each record. Queries that require data from multiple tables may be parsed into a primary query and a set of one or more secondary queries. Join mappings and documents are created for the necessary tables. Documents matching the query string are retrieved using the search-engine indices and join mappings.
Owner:SERVICENOW INC
Method and system for accessing search services via messaging services
InactiveUS20090006333A1Web data indexingMultiple digital computer combinationsQuery stringService provision
A user using a chat or instant message, mobile message or email type of interface, for example, an information seeker, can connect via an instant message, mobile message, email or chat type of service provider, for example, an America On-line Instant Messenger (AIM) server. The message server connects the user to a routine that allows the user to utilize his or her service interface in combination with the services provided by the information search system. After connection has been established via the message interface, for example, an instant message is received via the chat process. A query string can then be extracted from the instant message and passed to the search system, which can respond with search results.
Owner:CHACHA SEARCH
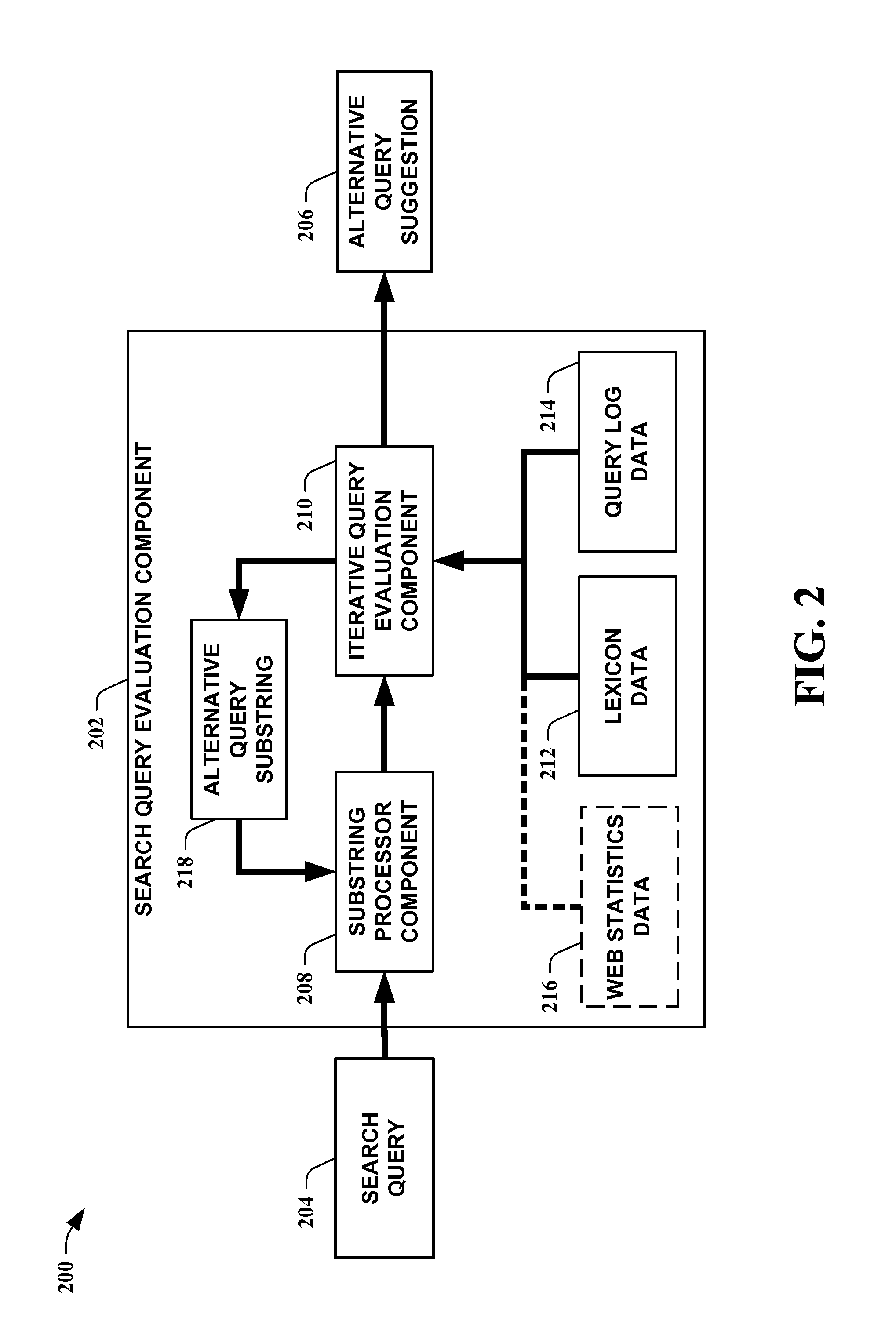
Systems and methods for improved spell checking
InactiveUS20070106937A1Raise checkQuality improvementDry-dockingDigital data information retrievalPersonalizationQuery string
The present invention leverages iterative transformations of search query strings along with statistics extracted from search query logs and / or web data to provide possible alternative spellings for the search query strings. This provides a spell checking means that can be influenced to provide individualized suggestions for each user. By utilizing search query logs, the present invention can account for substrings not found in a lexicon but still acceptable as a search query of interest. This allows a means to provide a higher quality proposal for alternative spellings, beyond the content of the lexicon. One instance of the present invention operates at a substring level by utilizing word unigram and / or bigram statistics extracted from query logs combined with an iterative search. This provides substantially better spelling alternatives for a given query than employing only substring matching. Other instances can receive input data from sources other than a search query input.
Owner:MICROSOFT TECH LICENSING LLC
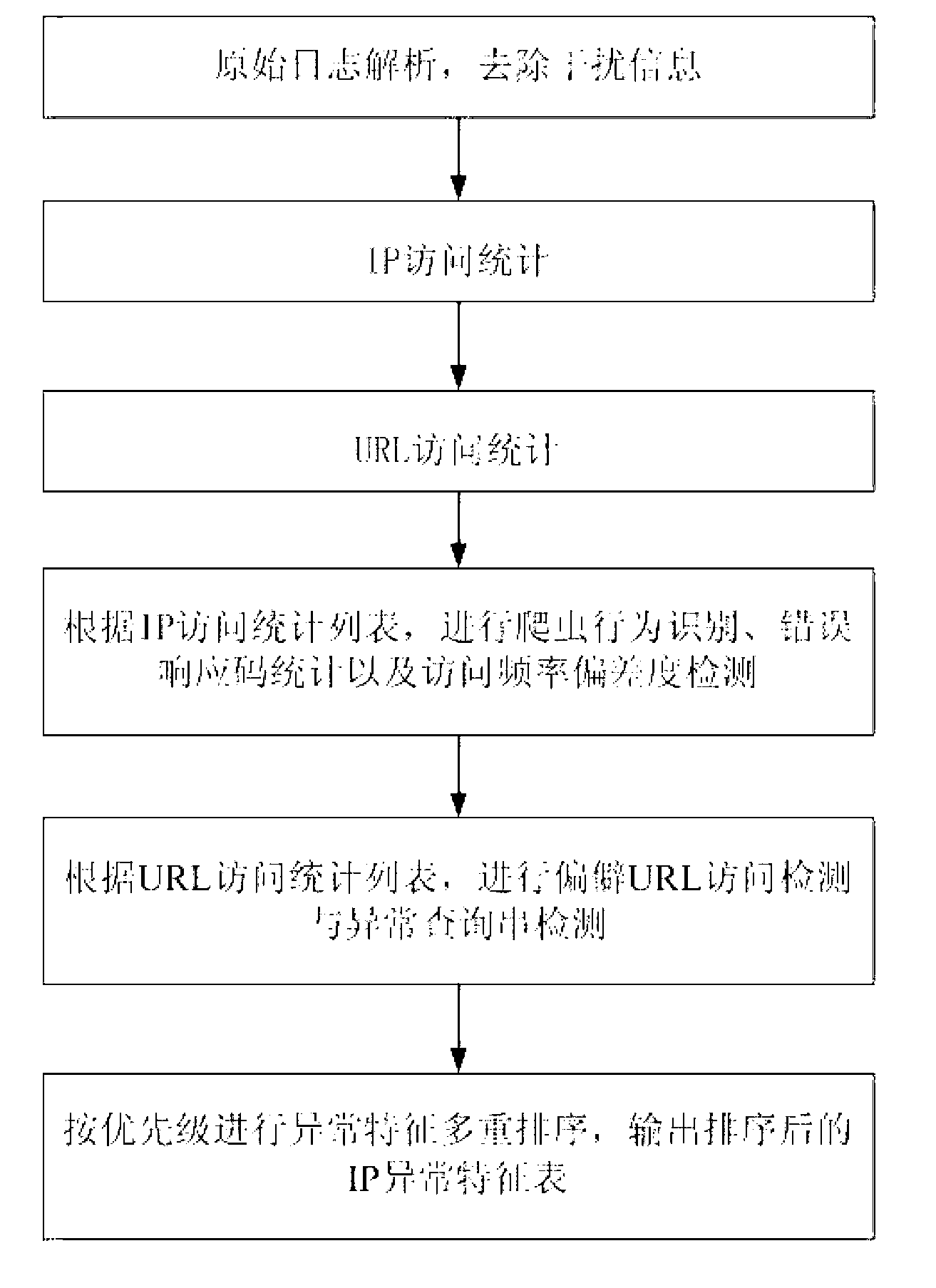
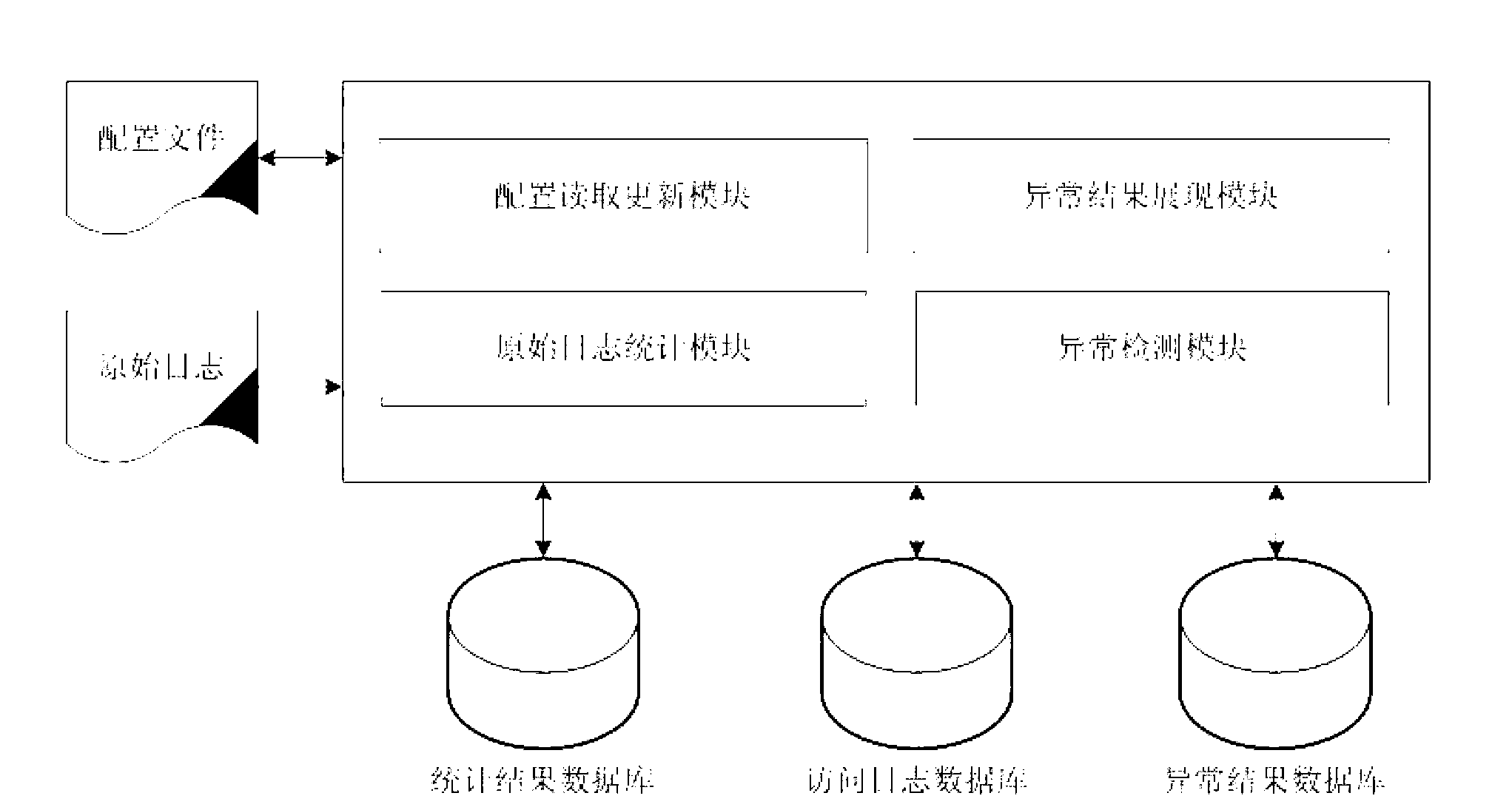
Abnormal access behavior detection method and system on basis of WEB logs
The invention relates to an abnormal access behavior detection method on the basis of WEB logs. The abnormal access behavior detection method includes steps of 1) performing IP(internet protocol) access statistics and URL access statistics after removing interference information by analyzing WEB raw logs so as to acquire an IP access statistic list and a URL access statistic list, 2) according to the IP access statistic list, performing crawler behavior characteristic recognition, error response code statistics and access frequency deviation degree detection while updating IP abnormal characteristic list, and 3) sequencing the abnormal characteristics in the IP abnormal characteristic list according to a set order of precedence, and outputting the sequenced IP abnormal characteristic list to obtain abnormal access results. By the abnormal access behavior detection method, an access model is built with no depending on history access data, abnormal access is checked by lateral comparison, and abnormal parameter detection is performed by voting and referring query strings.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
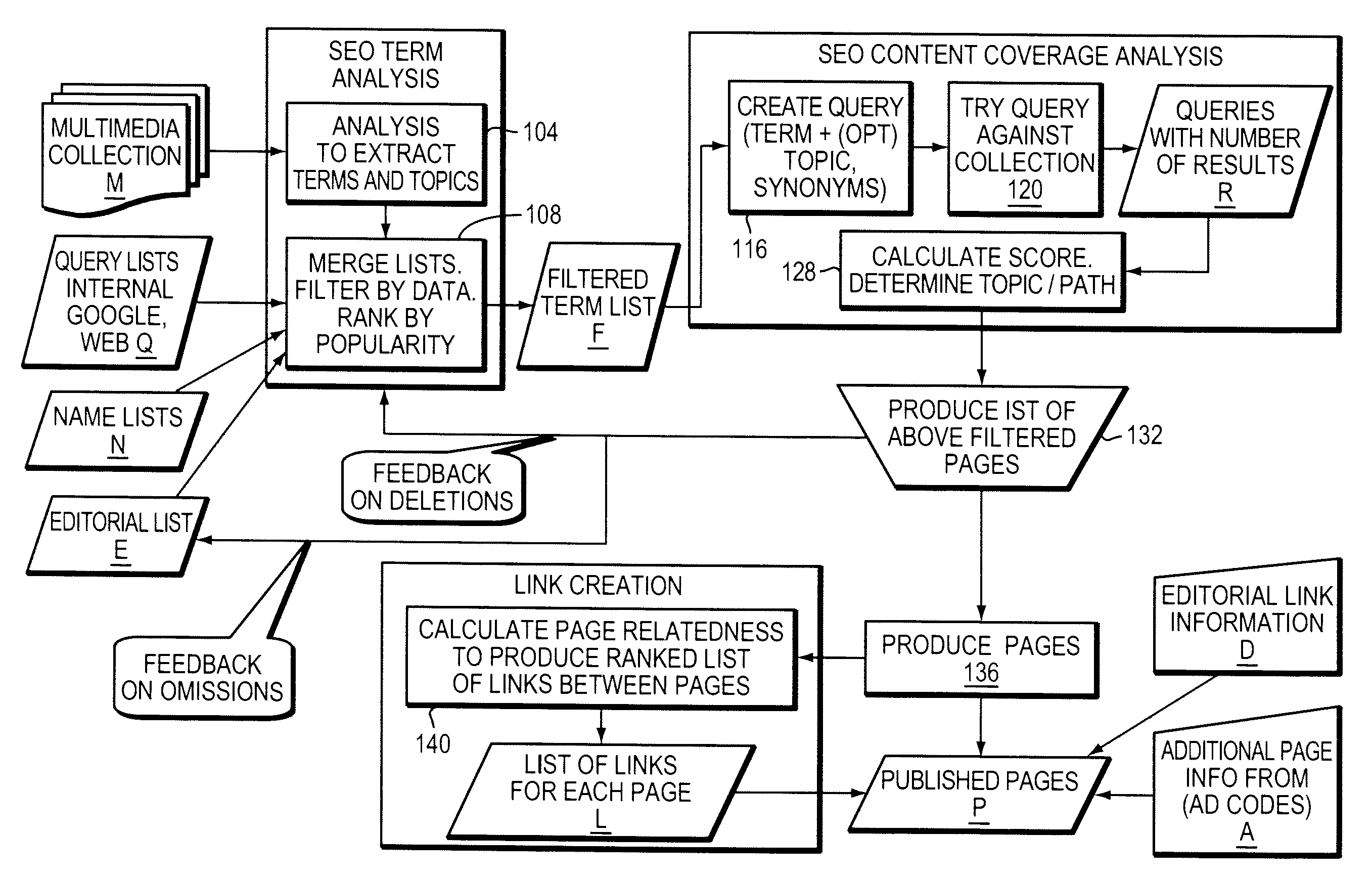
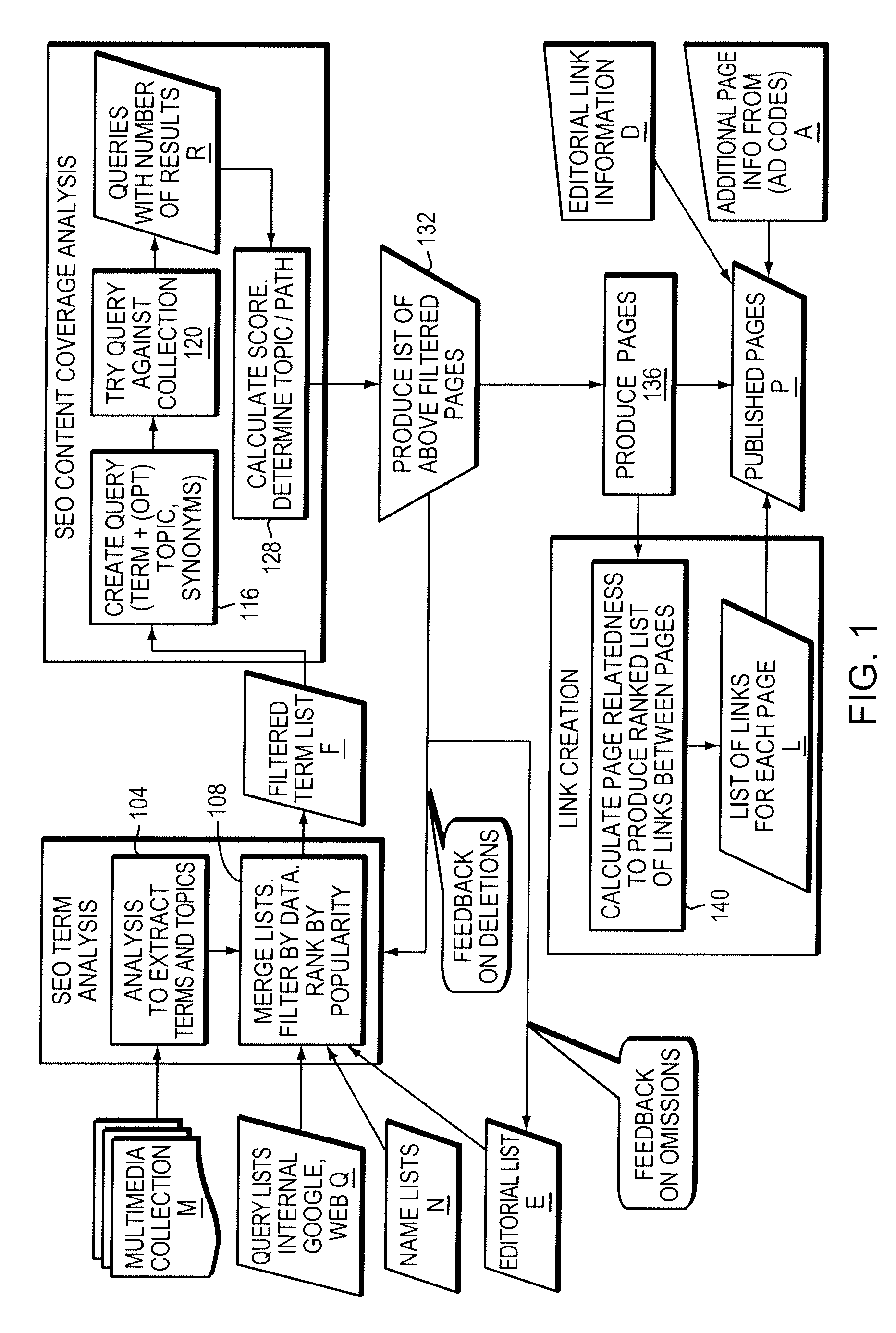
Search Engine Optimization
ActiveUS20090240674A1Digital data processing detailsNatural language data processingQuery stringWeb page
Topic-centric, dynamically-created web pages are compiled from links to multimedia content elements. Keywords are identified within the content elements and used to identify a set of topics related to the content elements. A query string comprising the keywords is executed against the content elements and in response to a request to display information about a topic the query string associated with the topic is executed against the collection of multimedia content elements to identify content elements related to the topic. A dynamically-created web page is displayed that includes computer-executable links to the set of related multimedia content elements.
Owner:CXENSE
Method and system for recommending query based on user log
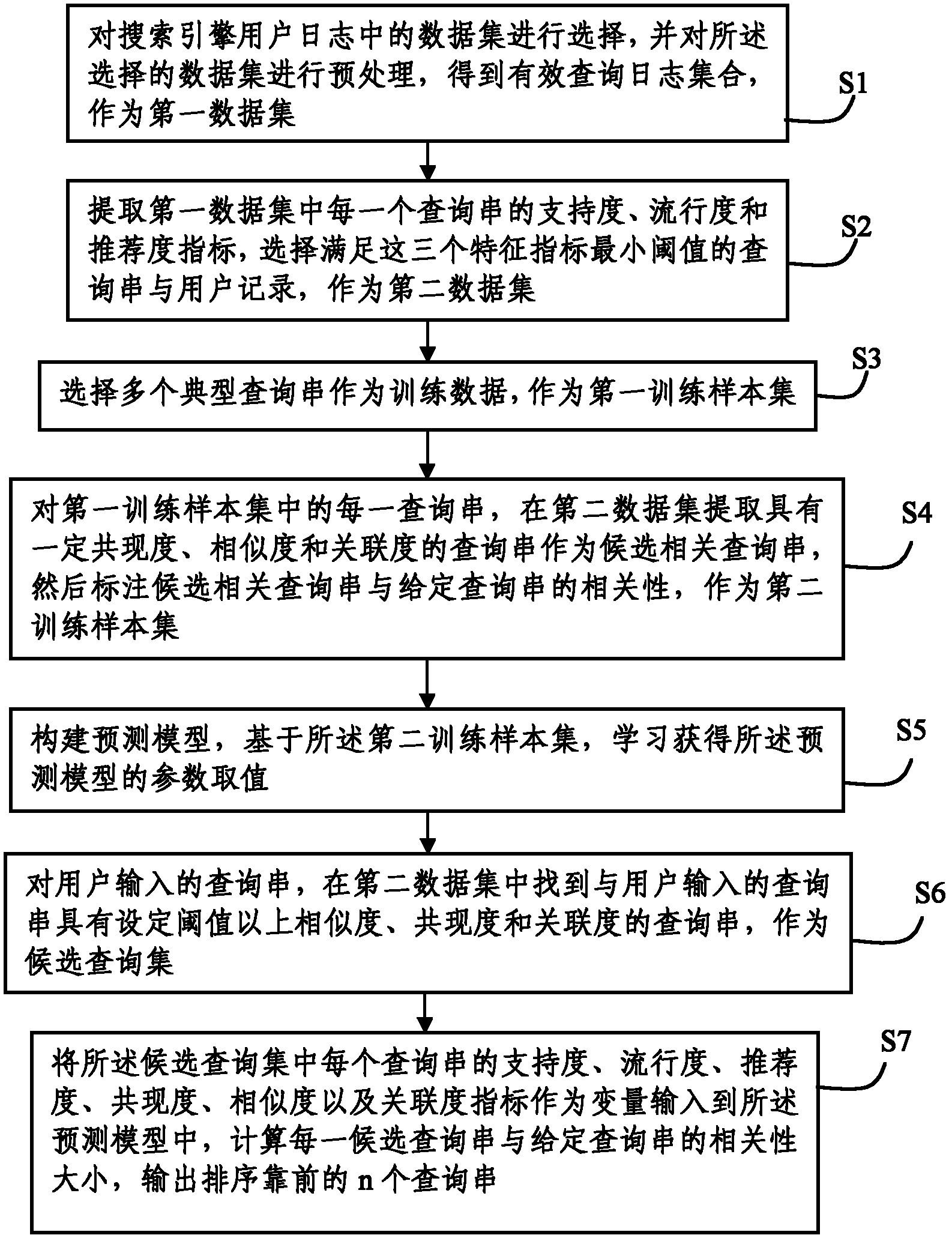
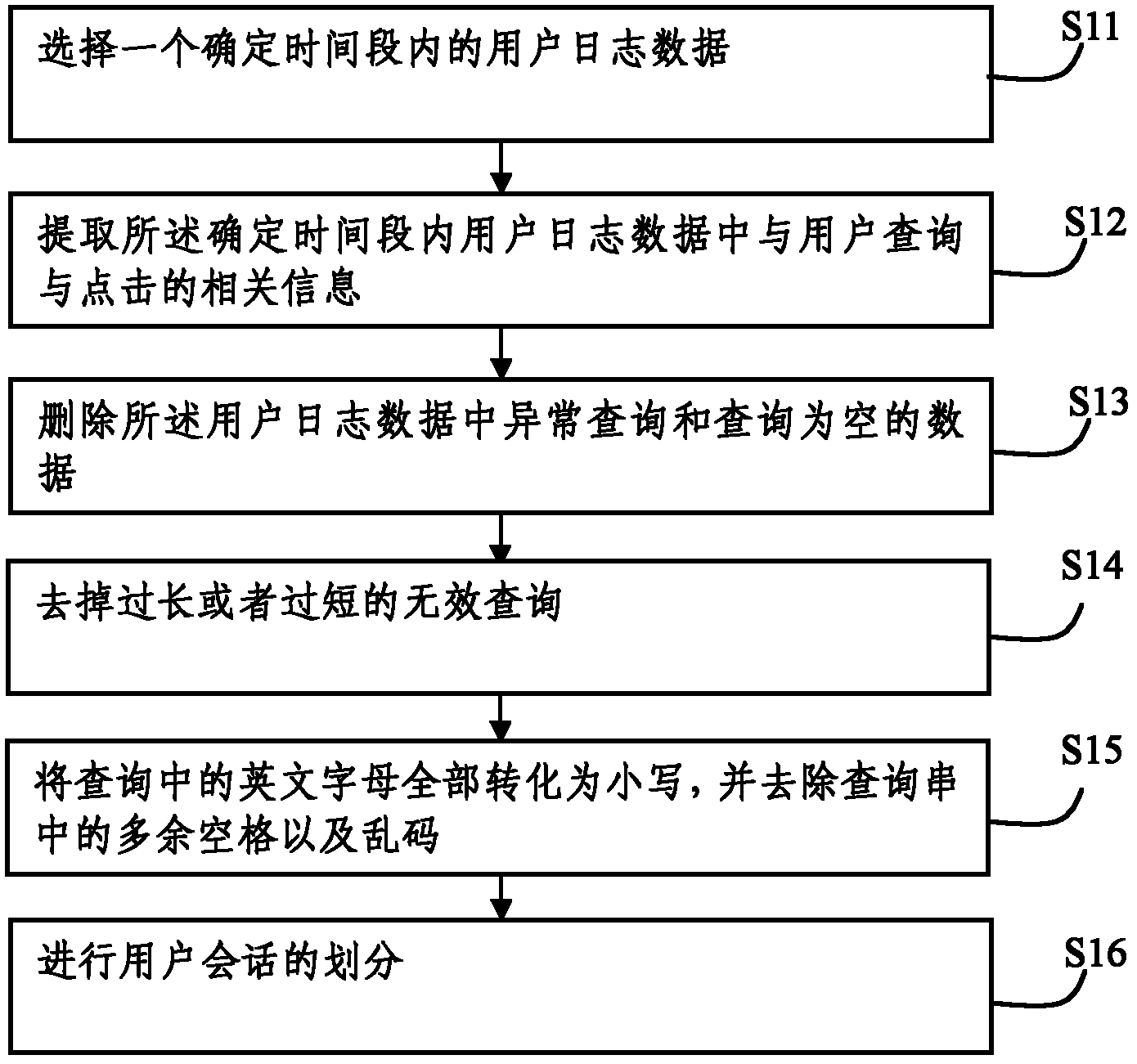
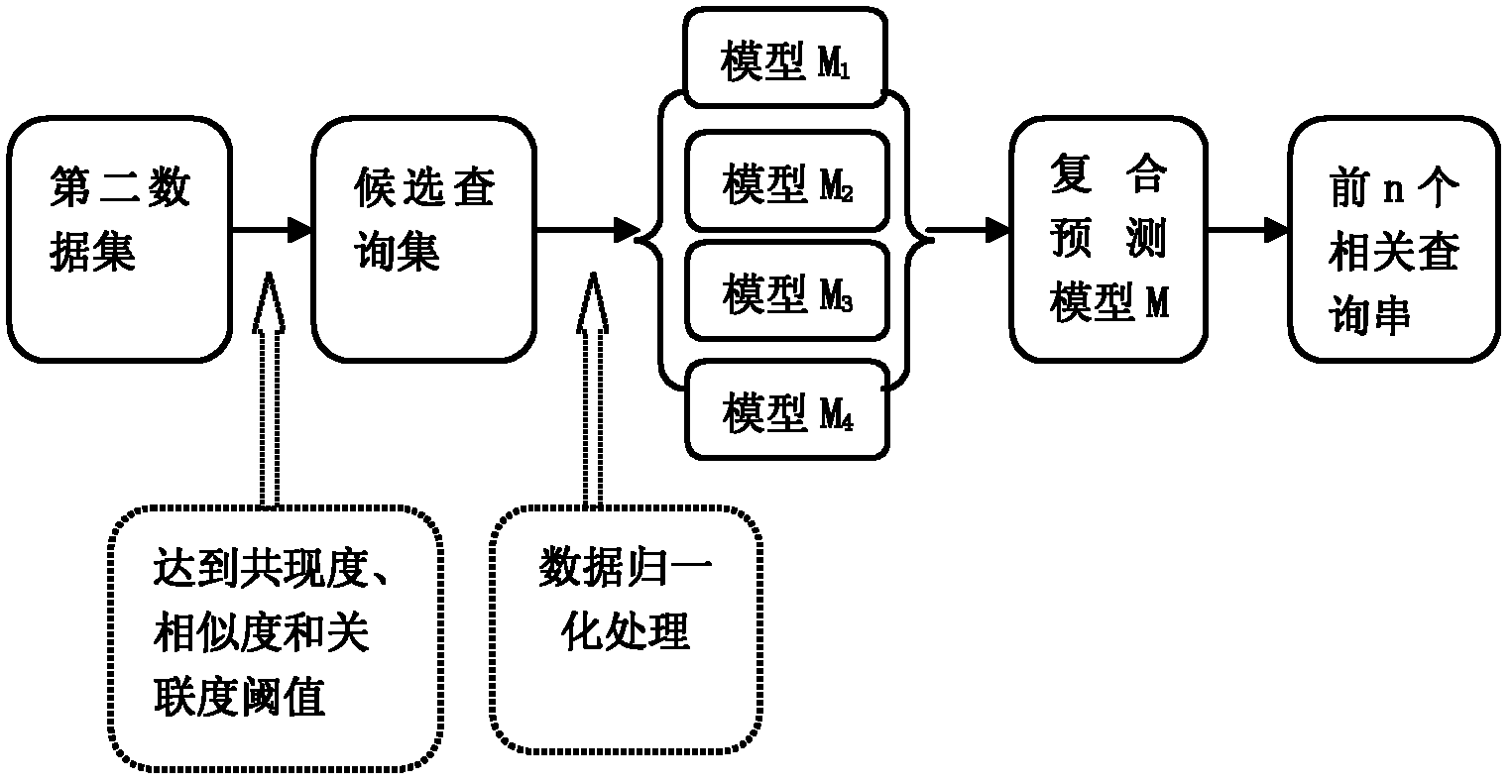
ActiveCN102609433AEasy to findRapid responseSpecial data processing applicationsData setQuery string
The invention discloses a method and system for recommending query based on user log. The method comprises acquiring an effective query log set according to the data set in the user log; selecting a typical query string as the training set, extracting 6 characteristic indexes of each query string in the effective query log set, such as support degree, popularity, recommendation degree, co-occurrence degree, similarity, and association degree, and constructing a composite prediction model based on the training set; and extracting the 6 characteristic indexes of candidate query strings inputted by a user, inputting the extracted characteristic indexes into the composite prediction model as variables, calculating the relevancy between each candidate query string and a given query string, and outputting n query strings with higher rank. The system comprises a data preparation module, a prediction model construction module, and a processing output model for realizing the above method. By fully utilizing the user log of a search engine, the method and system can recommend query strings with higher quality for the user.
Owner:PEKING UNIV
Using Private Threat Intelligence in Public Cloud
ActiveUS20170272469A1Preserving data integrityPreserving securityComputer security arrangementsTransmissionUser deviceQuery string
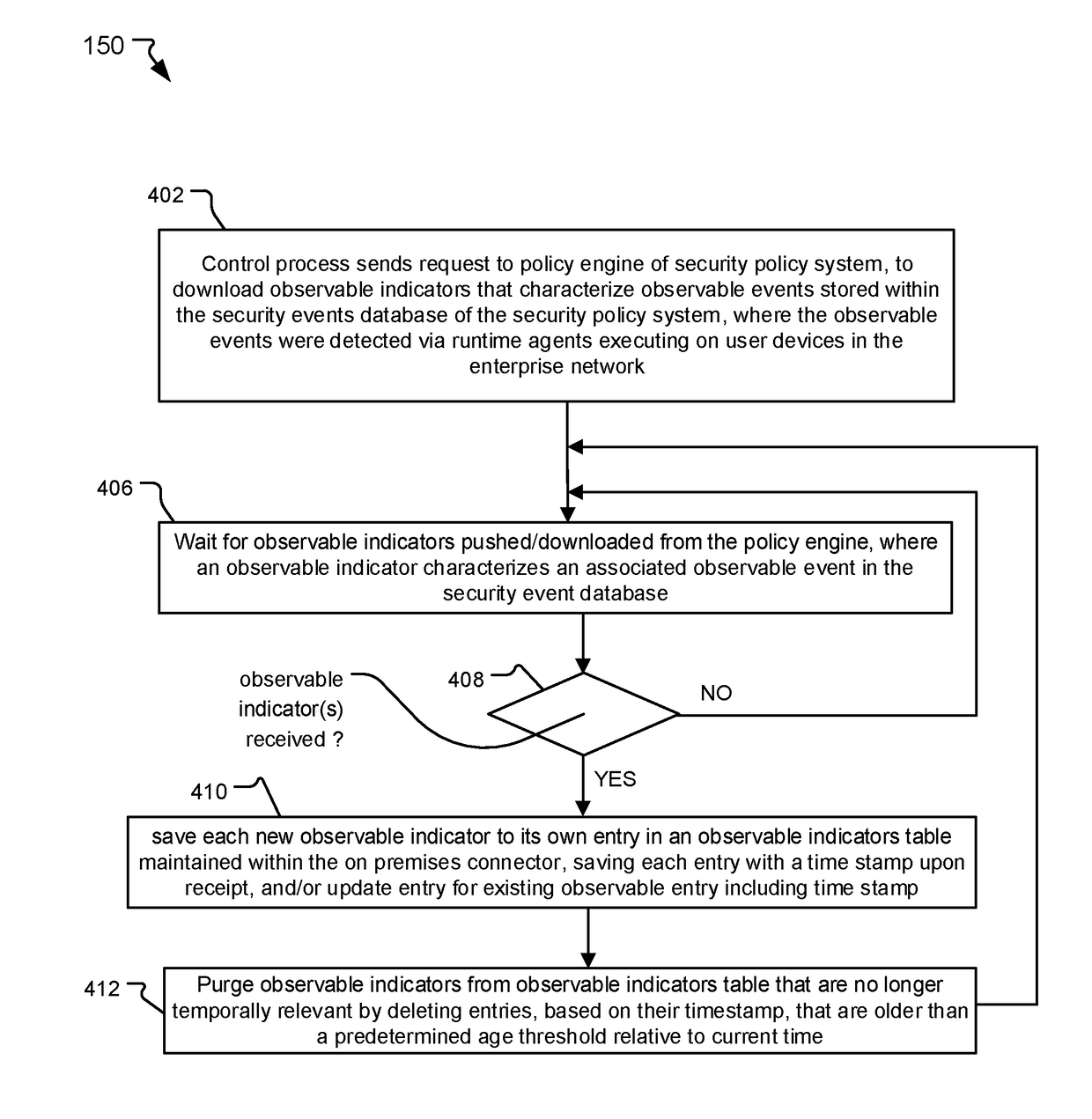
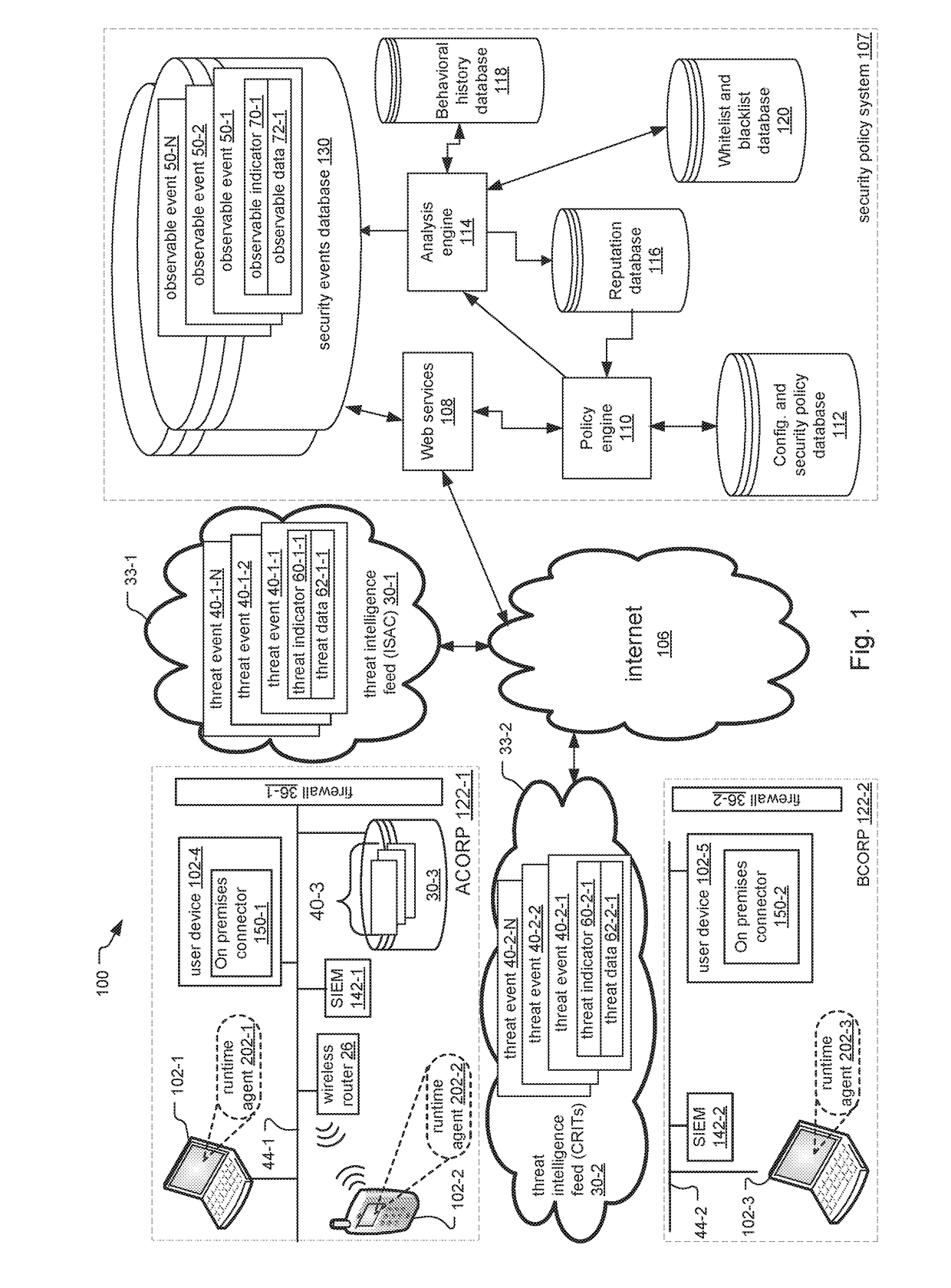
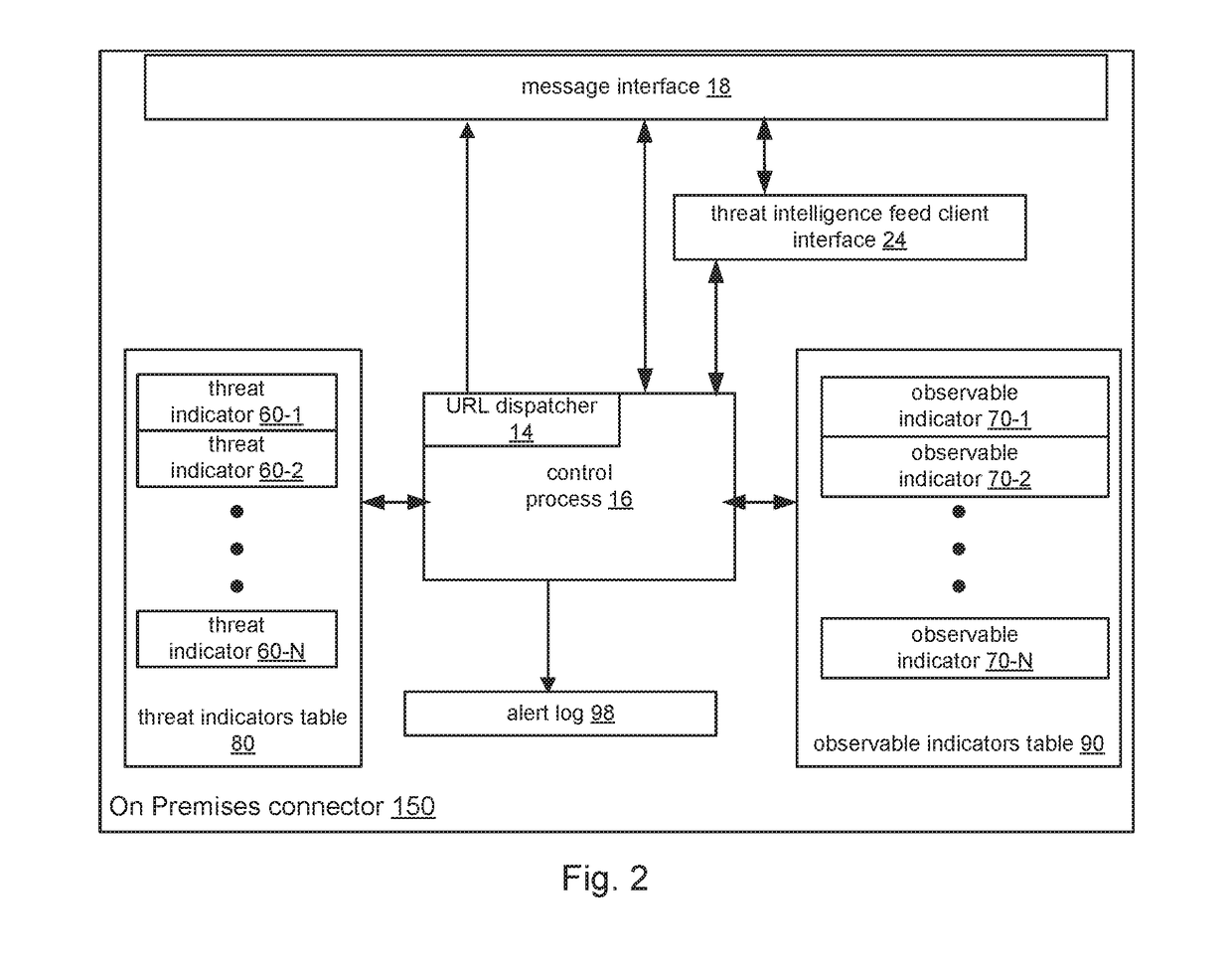
A distributed security system and method are disclosed that enable access to known threat events from threat intelligence feeds when the system includes public cloud components. A cloud-based security policy system stores observable events for security incidents detected by and sent from user devices within an enterprise network. The observable events include observable indicators for characterizing the observable events. The threat events within the feeds include threat indicators for characterizing the threat events. An on-premises connector within the enterprise network downloads the observable indicators from the security policy system and the threat indicators from the feeds. In response to determining that any observable indicators match any threat indicators, the on-premises connector provides access to the threat events and / or the observable events having the matching indicators. In one example, the on-premises connector generates opaque query strings for users on user devices to access the threat events / observable events having the matching indicators.
Owner:CARBON BLACK
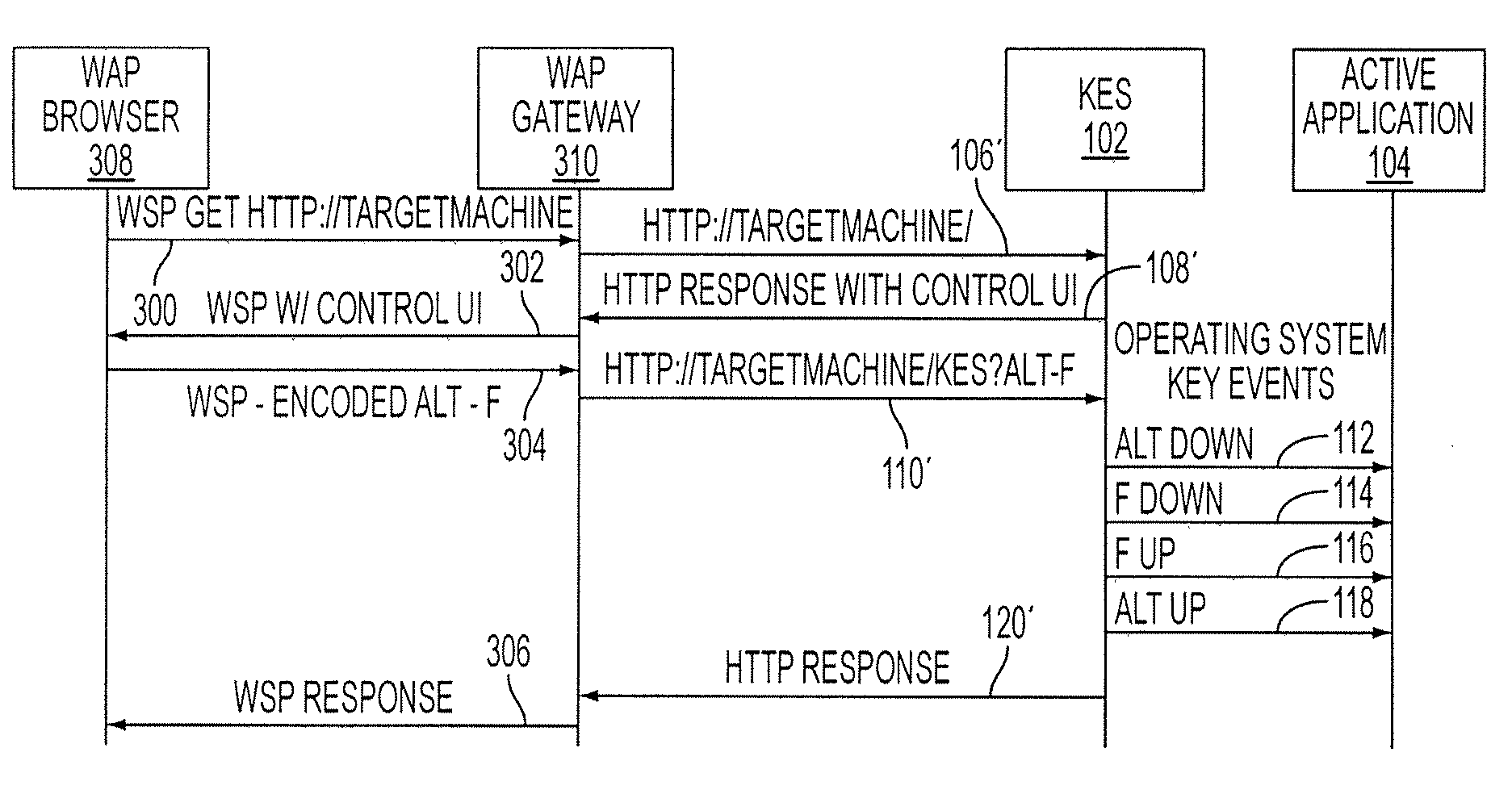
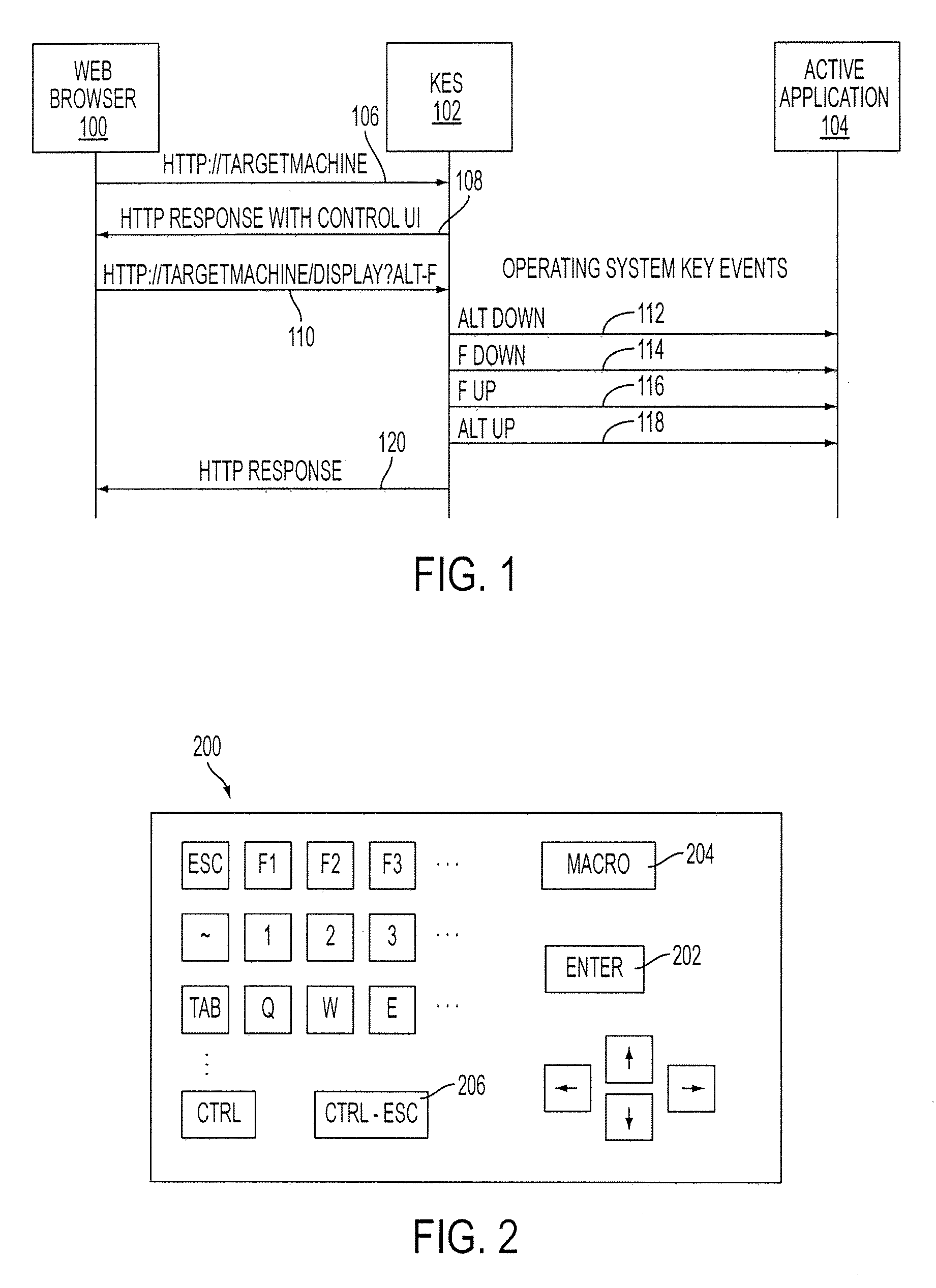
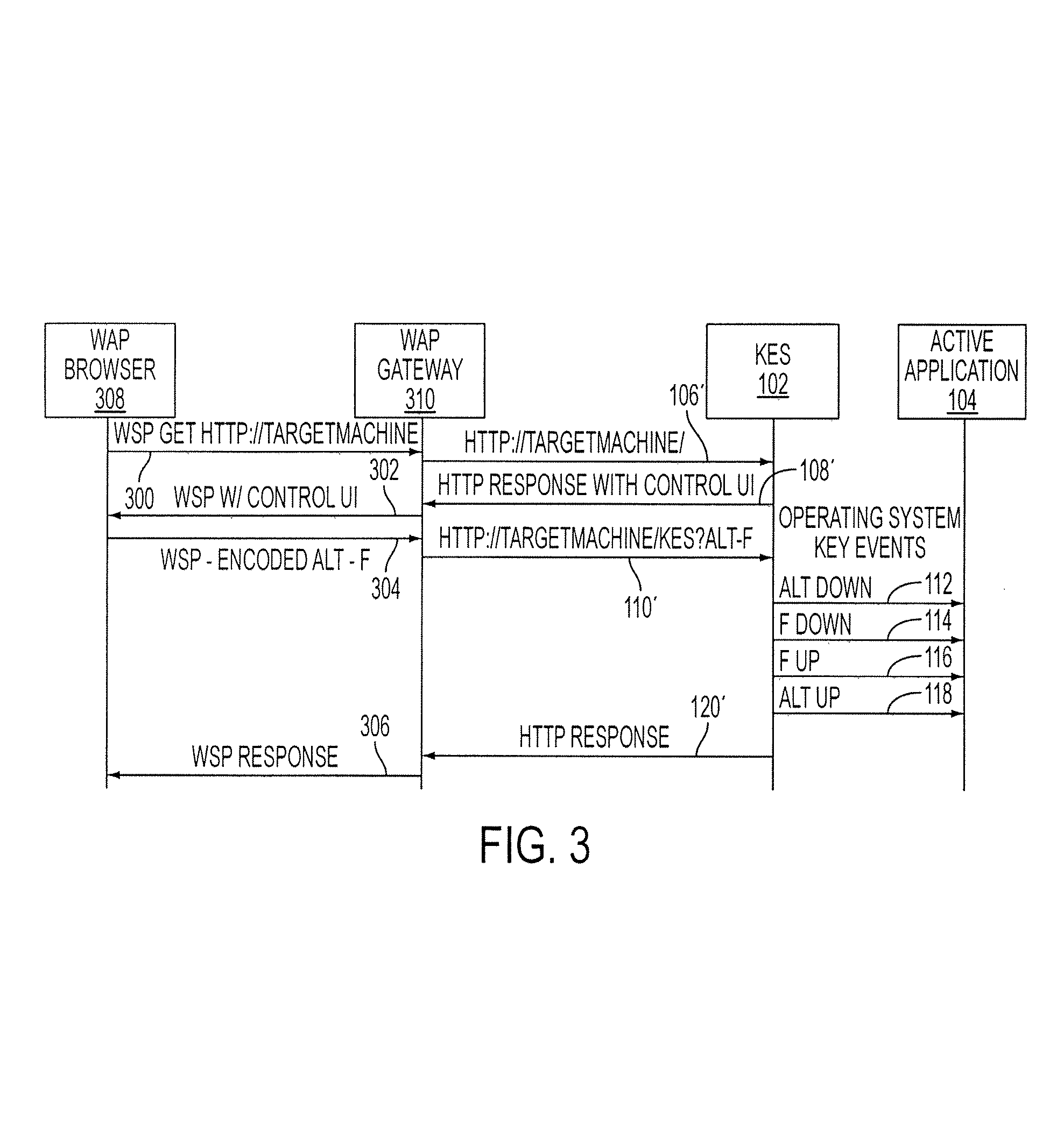
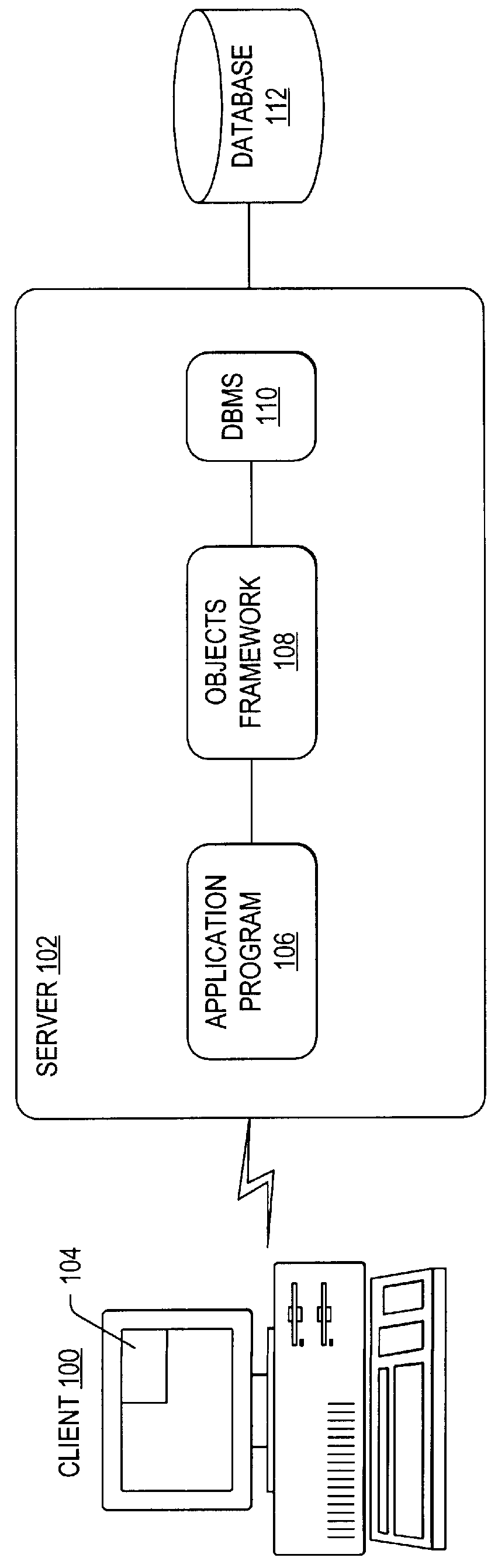
Remotely controlling a computer via simulated keyboard events
A keyboard event server (KES) allows an end user to remotely control a computer. The KES accepts a uniform resource locator having a query string that specifies one or more keyboard events to be simulated. The query string may include mnemonics corresponding to one or more keyboard-key presses that can be simulated one after another and / or simultaneously. An end user can use a wireless-access browser running on a wireless-client device to remotely control a target computer through a wireless-access gateway.
Owner:NOKIA INC
Internet-enabled generic application program for accessing hierarchical data
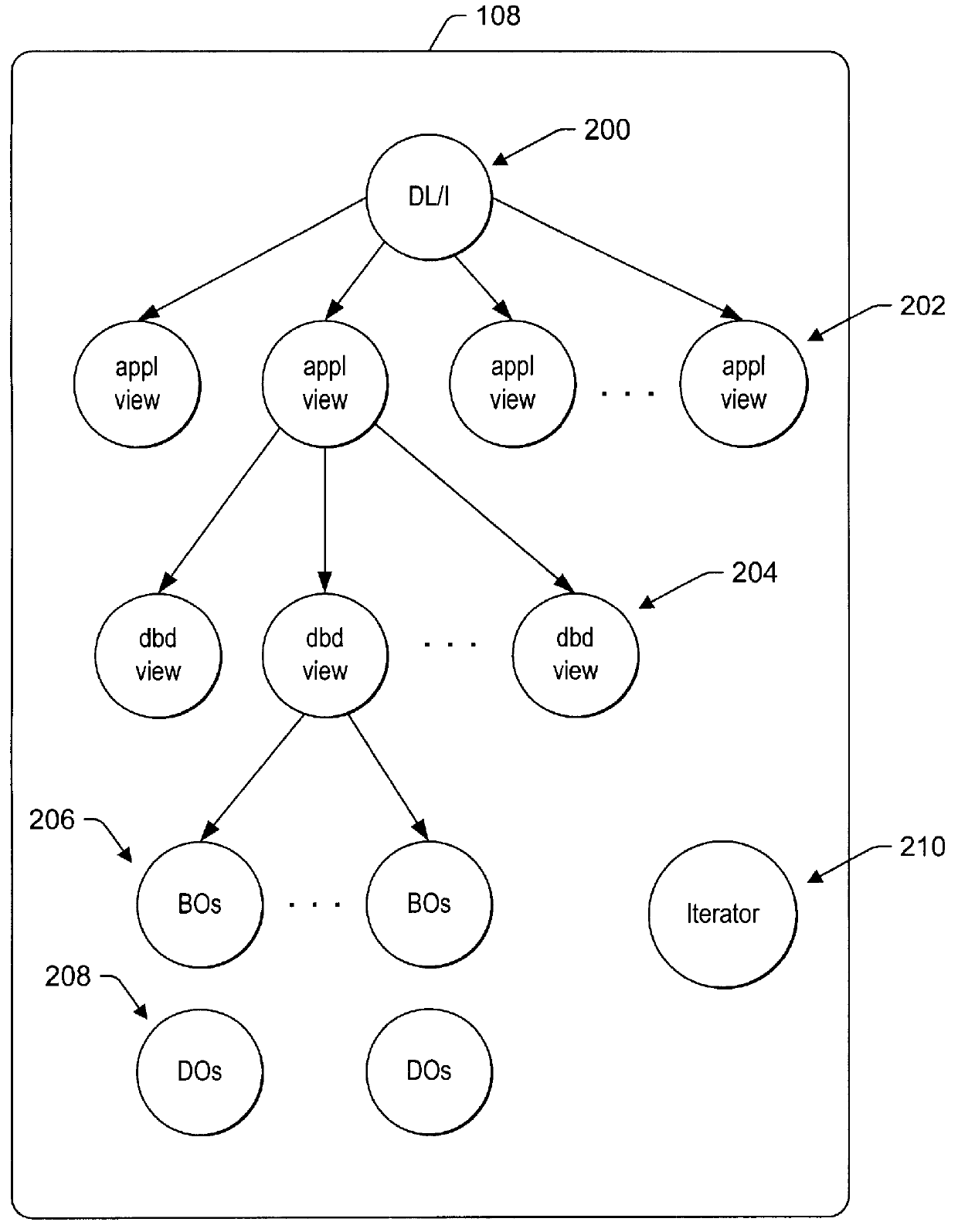
InactiveUS6128611AData processing applicationsDigital data processing detailsQuery stringBatch processing
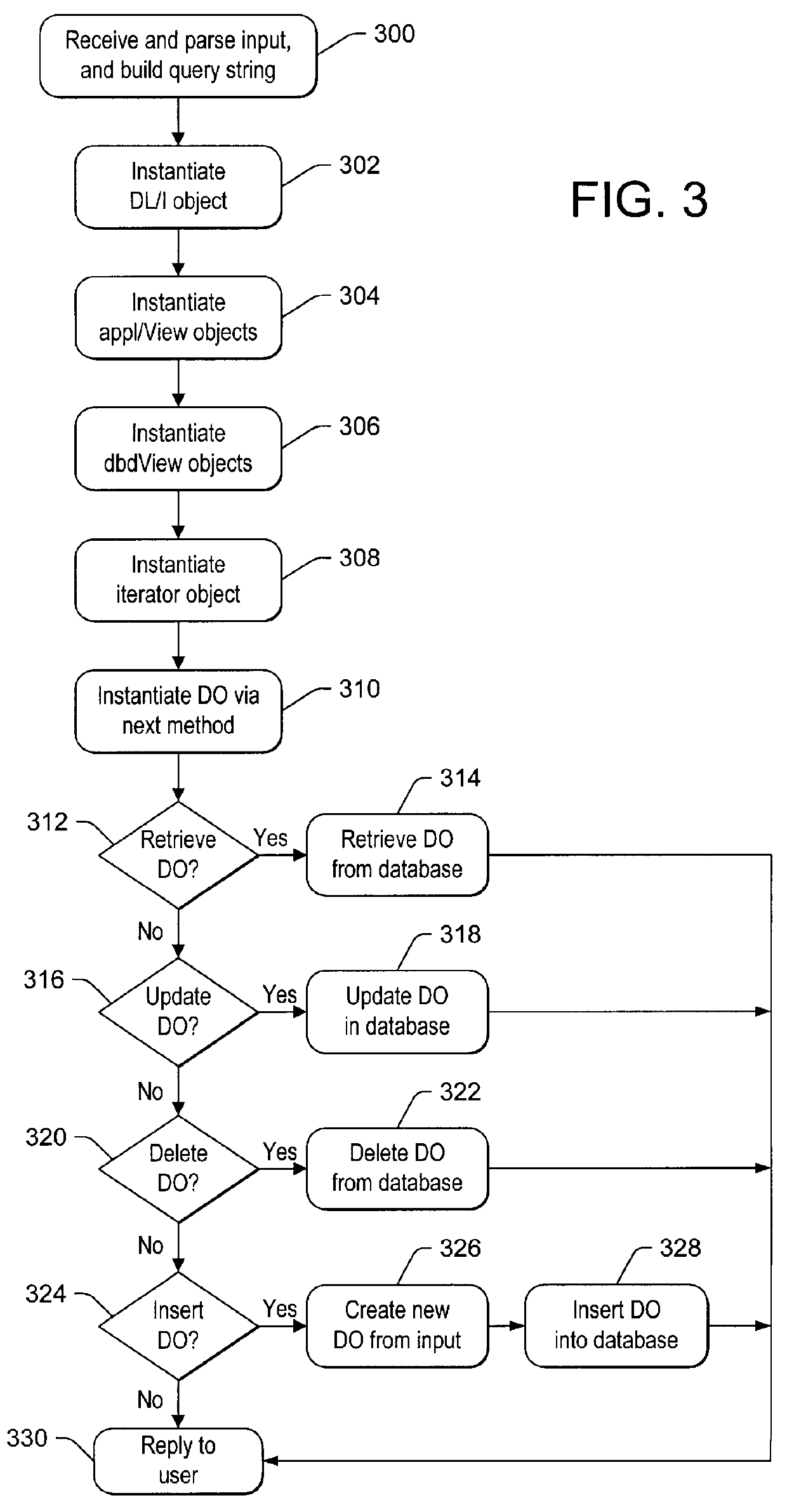
A method, apparatus, and article of manufacture for accessing a hierarchical database. An objects framework models the database as one or more objects. An Internet-enabled generic application program accesses the database via the objects framework. The present invention introduces an Internet-enabled generic application program for accessing hierarchical databases, such as an IMS TM database, by modeling the database into an objects framework and then accessing the database via the objects framework using standard tools, such as the DL / I TM query language for the IMS TM database. The Internet-enabled generic application program dynamically builds a DL / I TM query string based on web browser inputs. The generic application program loads the objects framework to instantiate IMS TM objects and dynamically constructs DL / I TM calls to access the IMS TM database. The generic application program can be used in a number of different environments, such as: (1) DL / I TM batch processing and (2) on-line transactions including both IMS TM and CICS TM transactions. Moreover, the generic application program and objects framework can be executed in any MVS address space, including IMS TM and non-IMS TM address spaces, such as web server address spaces. With this invention, customers can continue to access their business data in IMS TM databases using the latest Internet technology, without relying on legacy application programs and without developing new application programs. Thus, the present invention offers improved IMS TM application programming productivity by supporting IMS TM business objects and data objects, by eliminating complicated DL / I TM programming, and by supporting use of object-oriented programming tools.
Owner:IBM CORP
Method and System for Detecting Changes in Geographic Information
InactiveUS20090100031A1Easy to prepareInstruments for road network navigationDigital data processing detailsQuery stringGeolocation
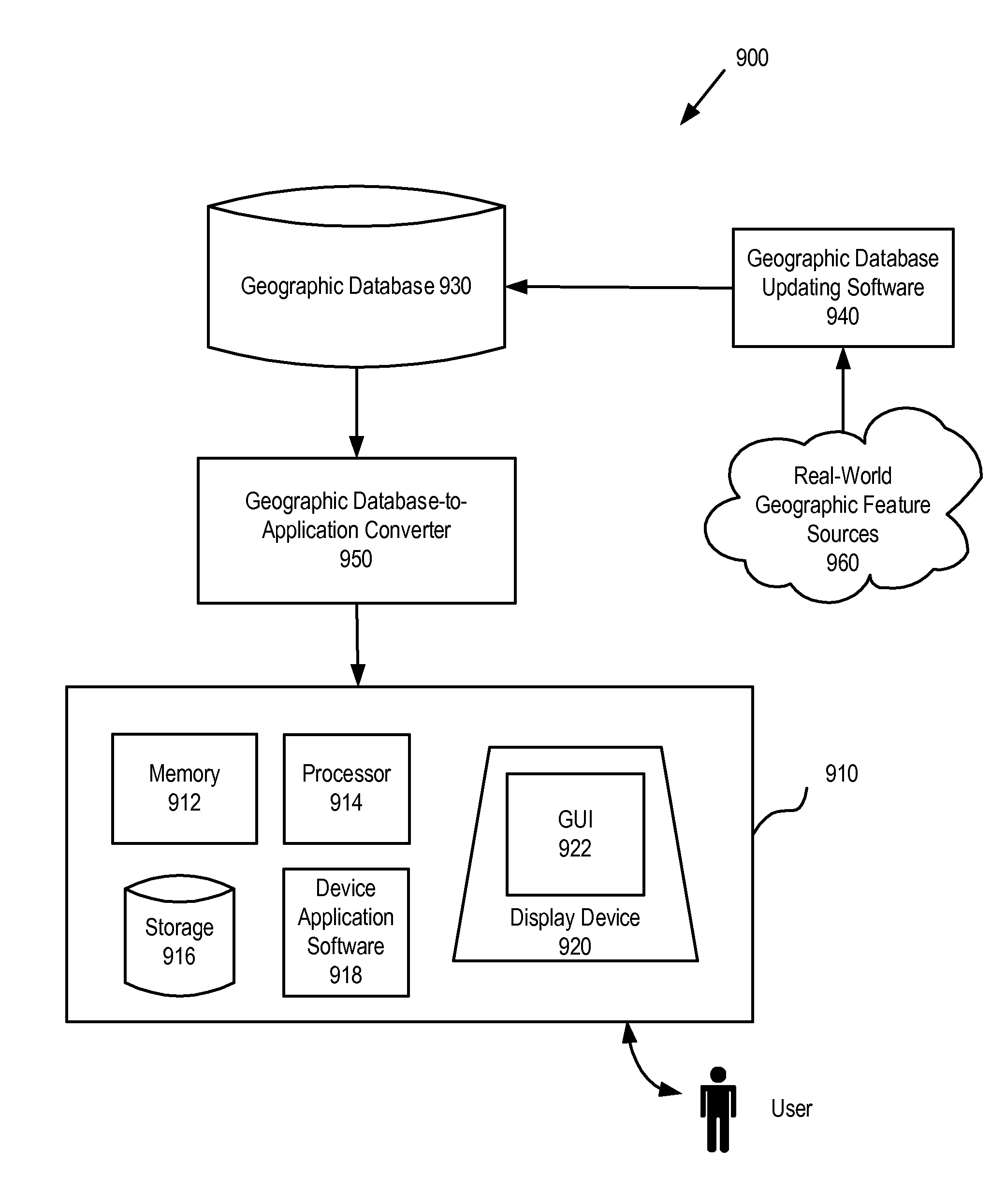
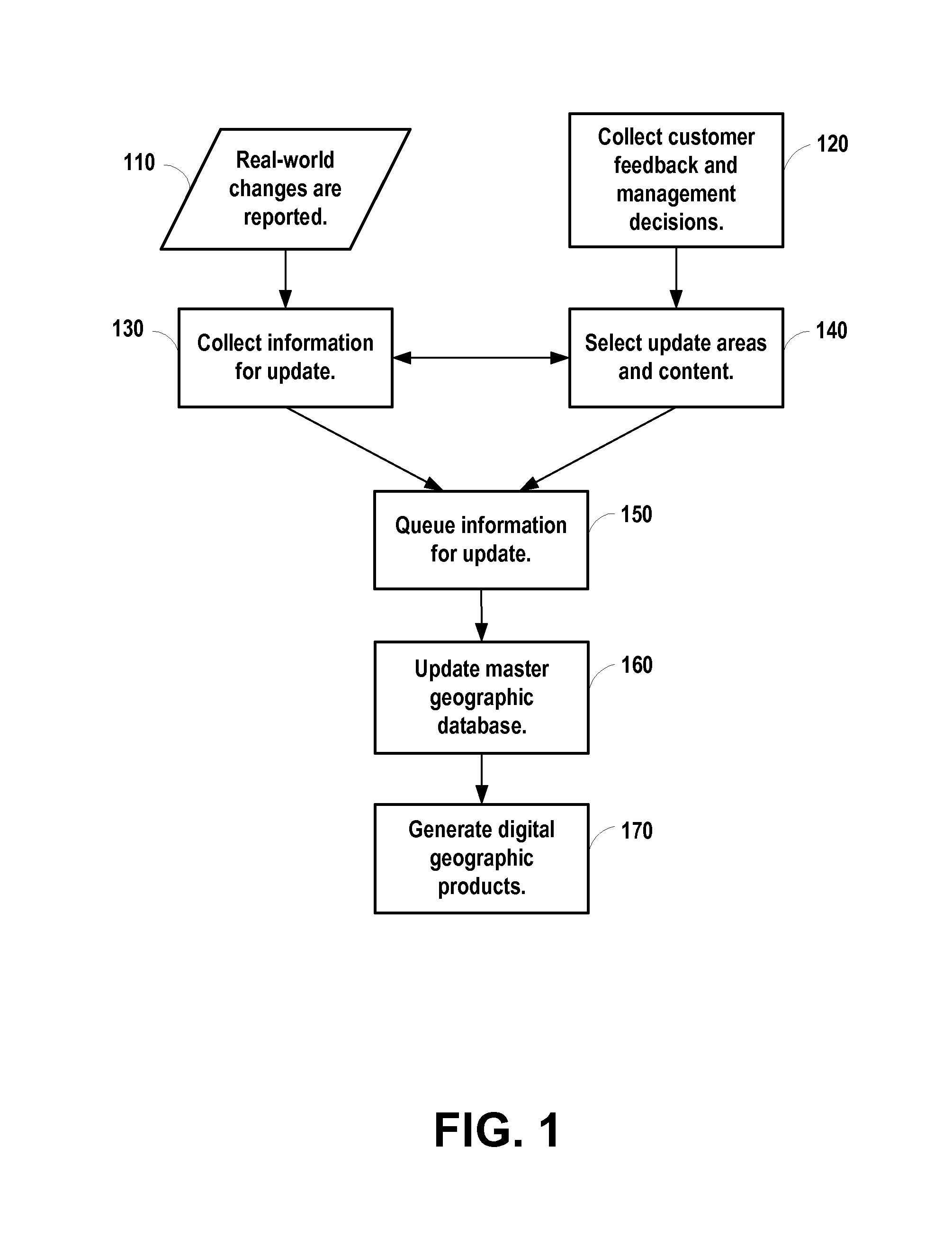
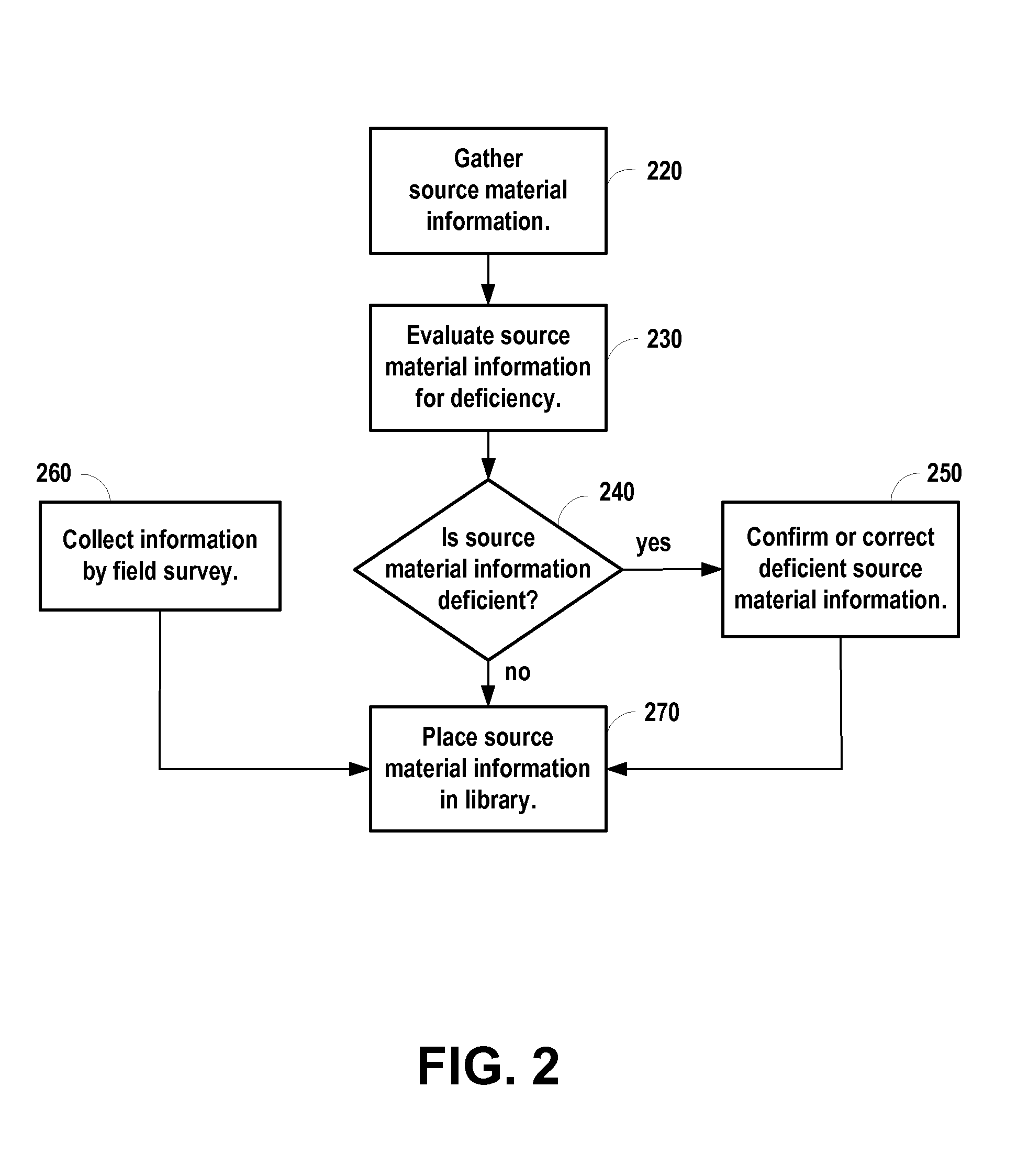
Data related to changes in real-world geography are collected promptly for incorporating into a geographic database. Query strings are created using keywords targeted to detect data related to changes in real-world geography. Automatic Web search technology is utilized to search the World Wide Web for instances that match the created query strings. References to Web pages, references to Web pages accompanied by brief abstracts, Web pages, and hard copies of documents by mail are automatically collected that potentially refer to changes in real-world geography.
Owner:TELE ATLAS NORTH AMERICA
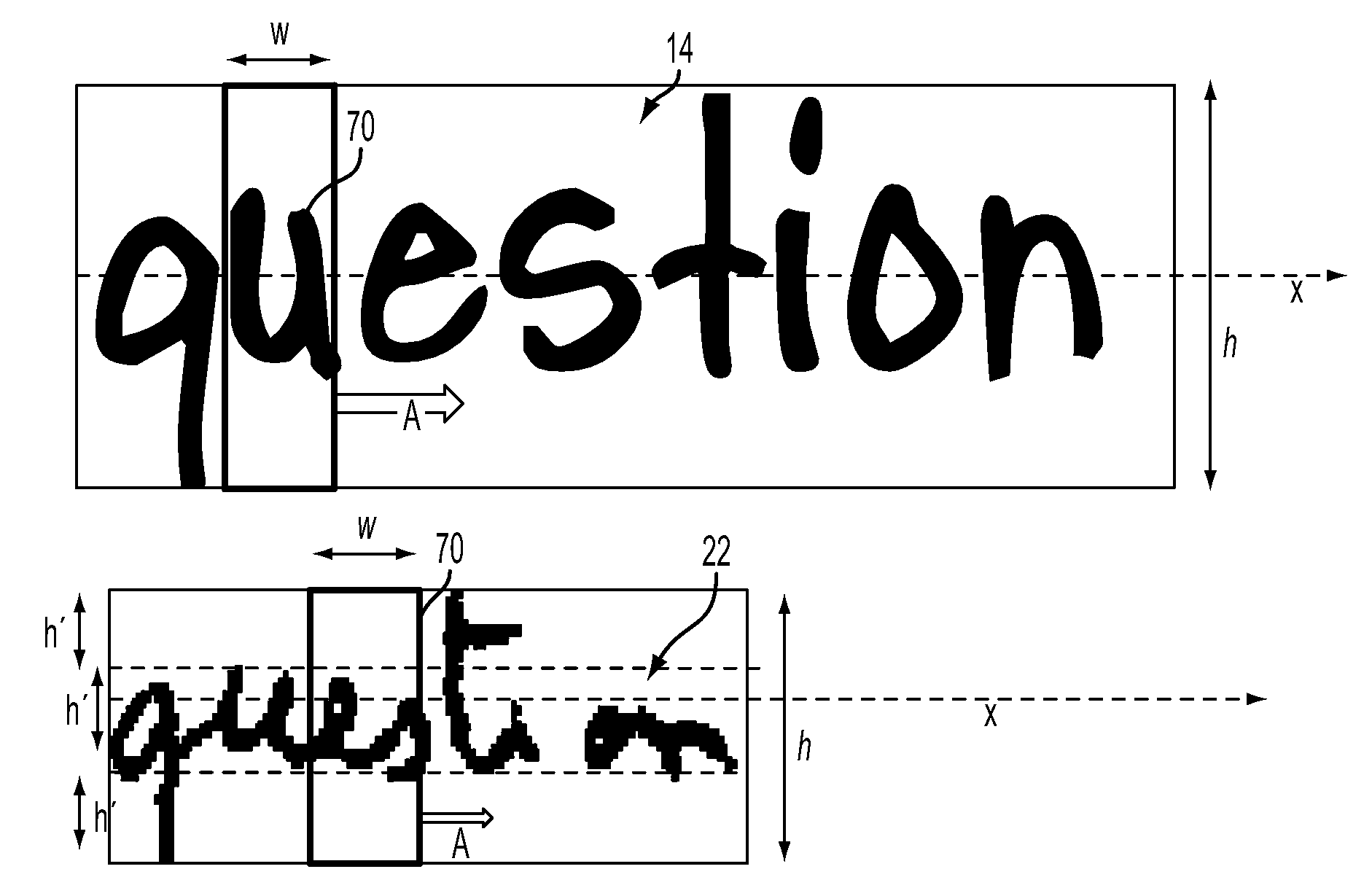
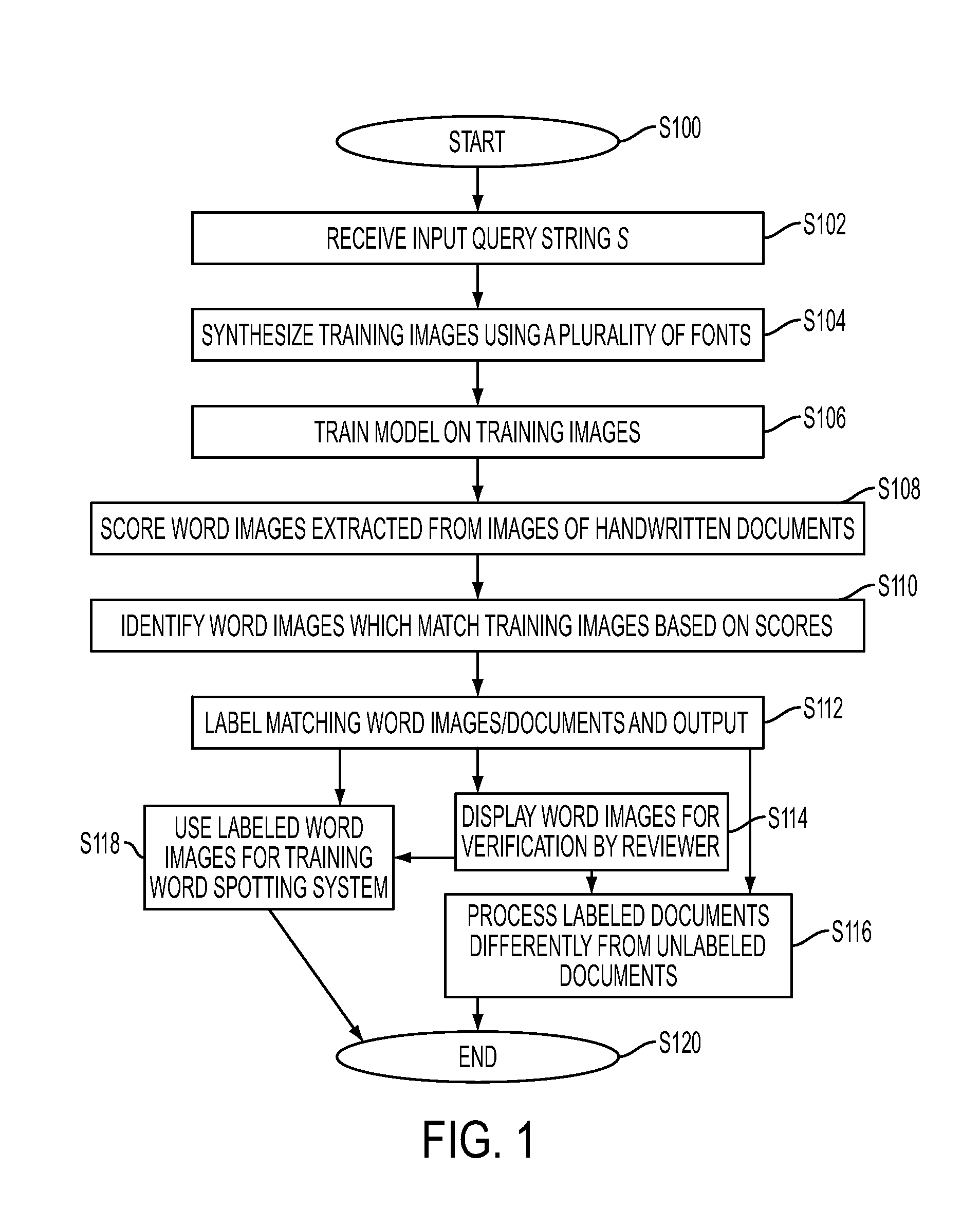
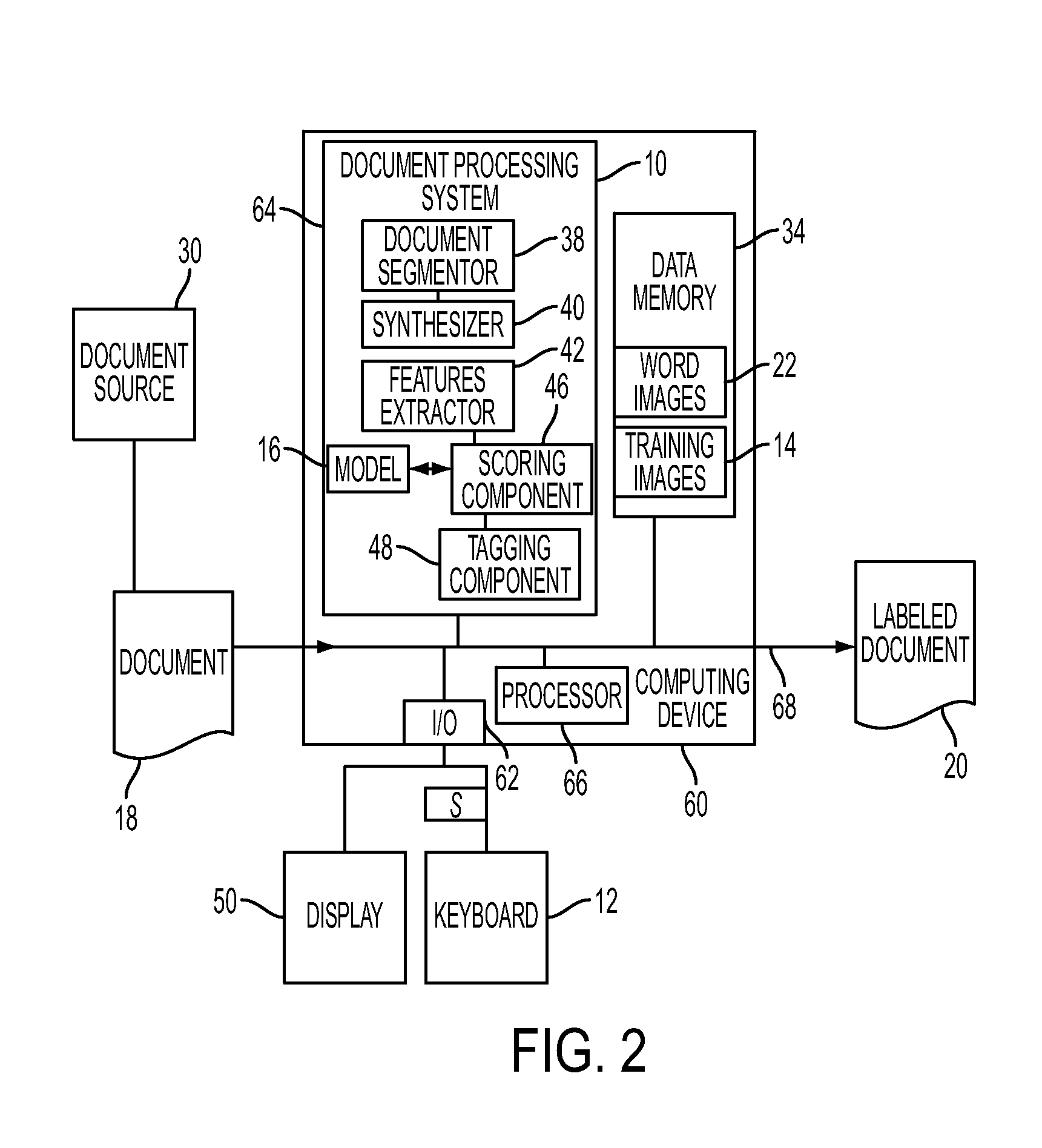
Handwritten word spotter using synthesized typed queries
A wordspotting system and method are disclosed for processing candidate word images extracted from handwritten documents. In response to a user inputting a selected query string, such as a word to be searched in one or more of the handwritten documents, the system automatically generates at least one computer-generated image based on the query string in a selected font or fonts. A model is trained on the computer-generated image(s) and is thereafter used in the scoring the candidate handwritten word images. The candidate or candidates with the highest scores and / or documents containing them can be presented to the user, tagged, or otherwise processed differently from other candidate word images / documents.
Owner:XEROX CORP
Point-in-time query method and system
InactiveUS20070271242A1Efficient queryEfficient storageSemi-structured data queryingSpecial data processing applicationsTimestampQuery string
Embodiments of the present invention include storing a plurality of subtrees in a database, the plurality of subtrees representing one or more structured documents. At least one subtree has a birth timestamp indicating a time at which the at least one subtree was created. If a subtree has been obsoleted, the subtree has a death timestamp indicating a time at which the subtree was obsoleted. Embodiments further include receiving a database query comprising a query string and a query timestamp, the query timestamp indicating a historical time for which the query is to apply, and determining an intermediate result list of subtrees. The intermediate result list is filtered to generate a final result list responsive to the database query, the filtering comprising removing subtrees that do not have a birth timestamp, have a birth timestamp later than the query timestamp, or have a death timestamp earlier than the query timestamp.
Owner:MARKLOGIC
Multidimensional interval querying method and system thereof
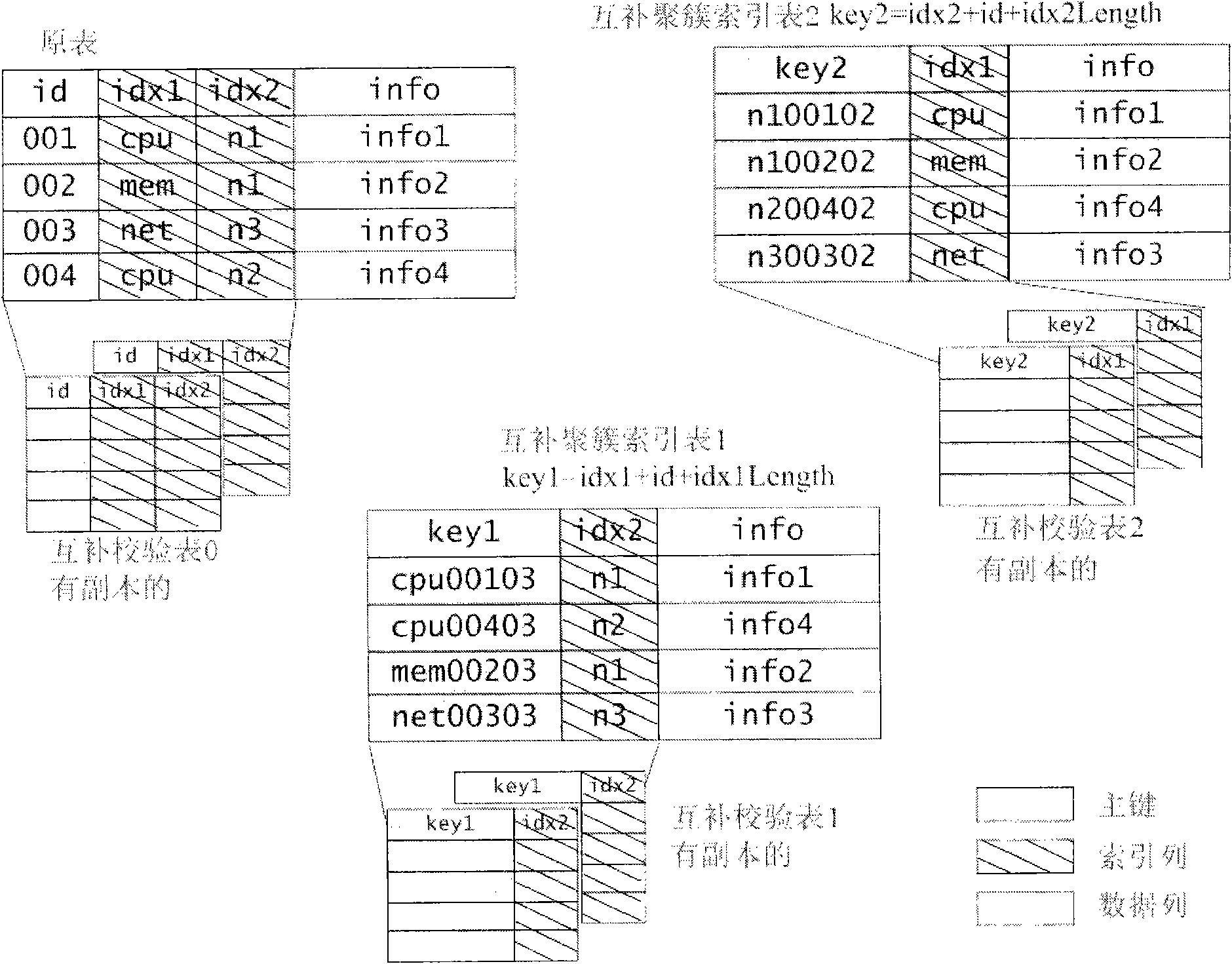
ActiveCN101866358AResilience remains the sameFast executionSpecial data processing applicationsQuery stringQuery optimization
The invention relates to a multidimensional interval querying method and a system thereof. The method comprises the following steps of: 1. organizing a transcript for copying data to be a plurality of complementary cluster index tables which are mutually compensated and verified, wherein each complementary cluster index table builds a sequence table which takes the length of a column value, an original line primary key and a column value as a primary key by means of each index column, completely stores the data of the other columns in the original line, and is used for continuously scanning when querying; and 2. converting a query string into a query plane tree, and performing query optimization to complete the query. The invention can simultaneously meet the requirements of high performance, low storage cost and high reliability.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Word Association Method and Apparatus
InactiveUS20100211567A1Facilitate efficient translationImprove translationNatural language translationDigital data processing detailsNatural language processingQuery string
Owner:MEANINGFUL MACHINES
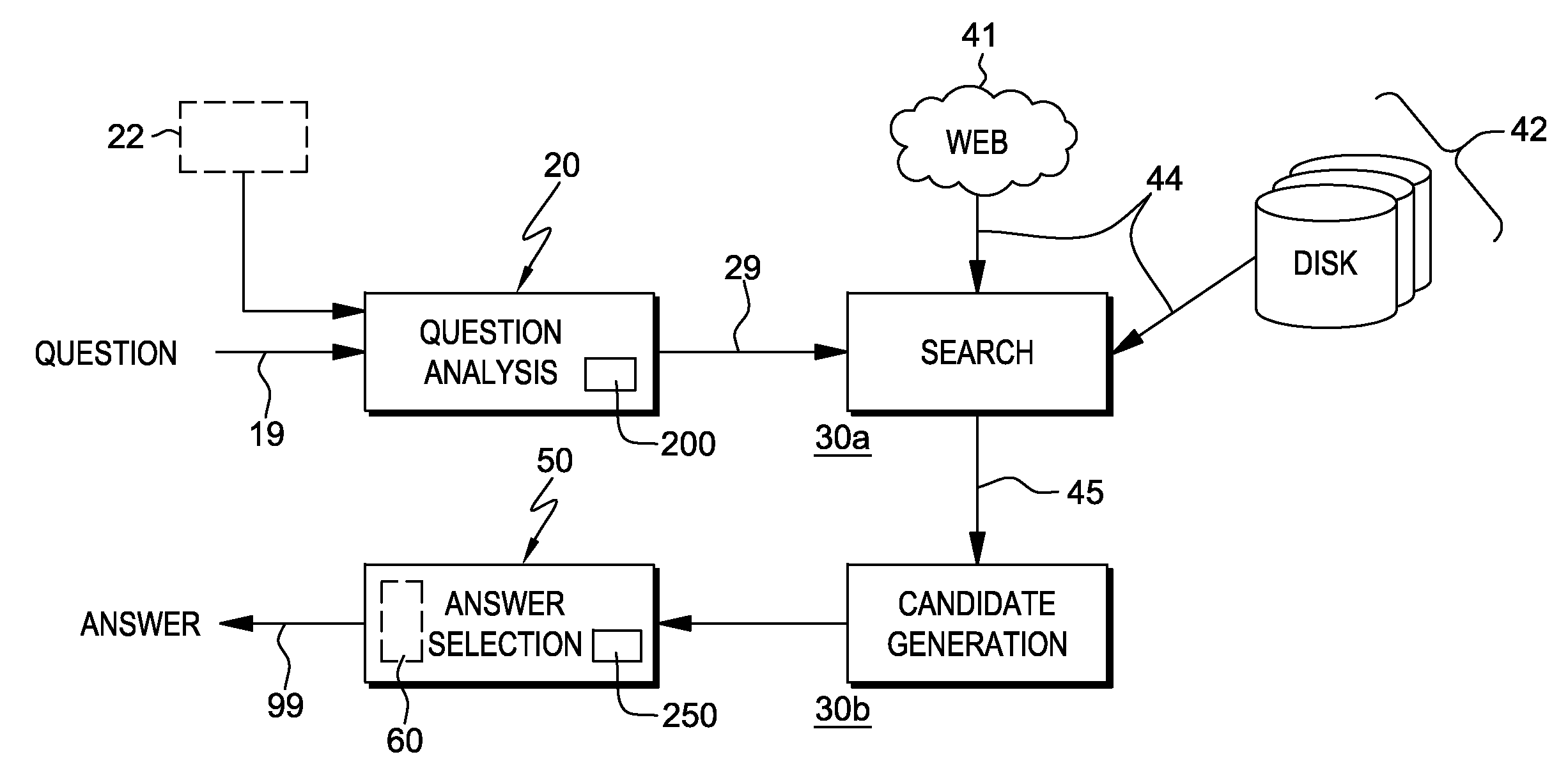
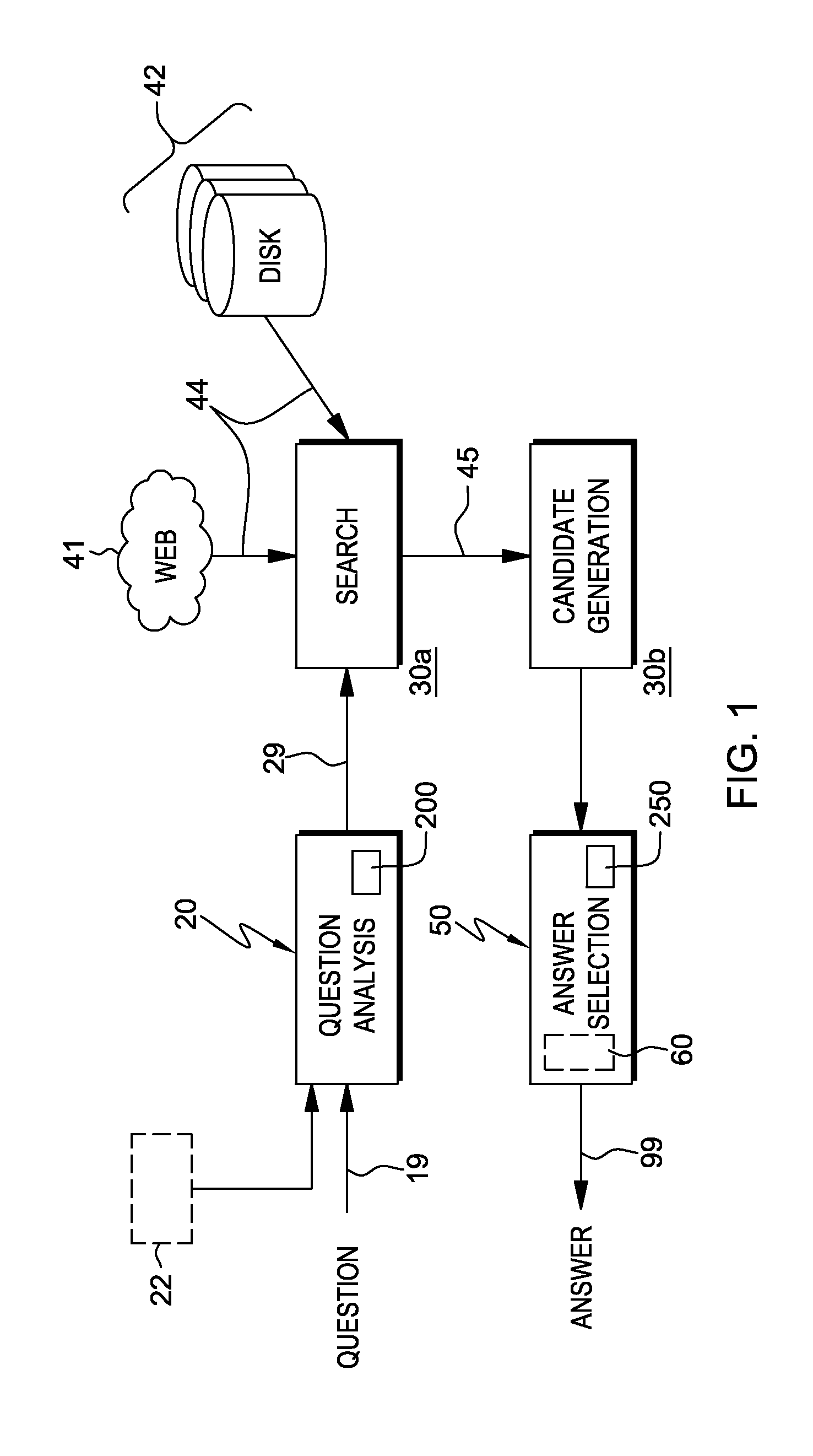
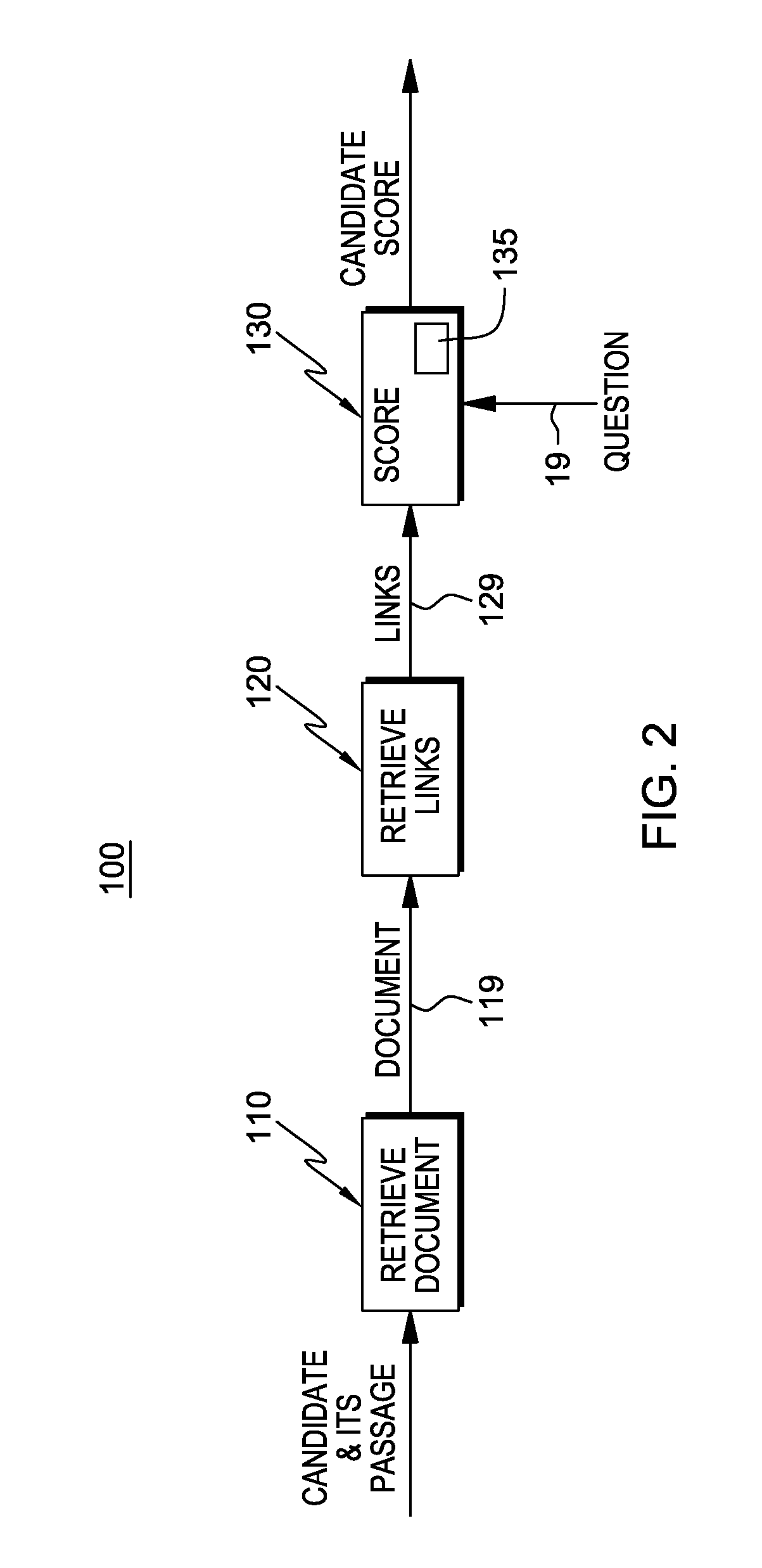
Scoring candidates using structural information in semi-structured documents for question answering systems
ActiveUS20120089622A1Improve system efficiencyHigh scoreDigital data information retrievalDigital data processing detailsStructured contentQuery string
A system, program product, and methodology automatically scores candidate answers to questions in a question and answer system. In the candidate answer scoring method, a processor device performs one or more of receiving one or more candidate answers associated with a query string, the candidates obtained from a data source having semi-structured content; identifying one or more documents with semi-structured content from the data source having a candidate answer; and for each identified document: extracting one or more entity structures embedded in the identified document; determining a number of the entity structures in the identified document that appear in the received input query; and, computing a score for a candidate answer in the document as a function of the number Overall system efficiency is improved by giving the correct candidate answers higher scores through leveraging context-dependent structural information such as links to other documents and embedded tags.
Owner:INT BUSINESS MASCH CORP
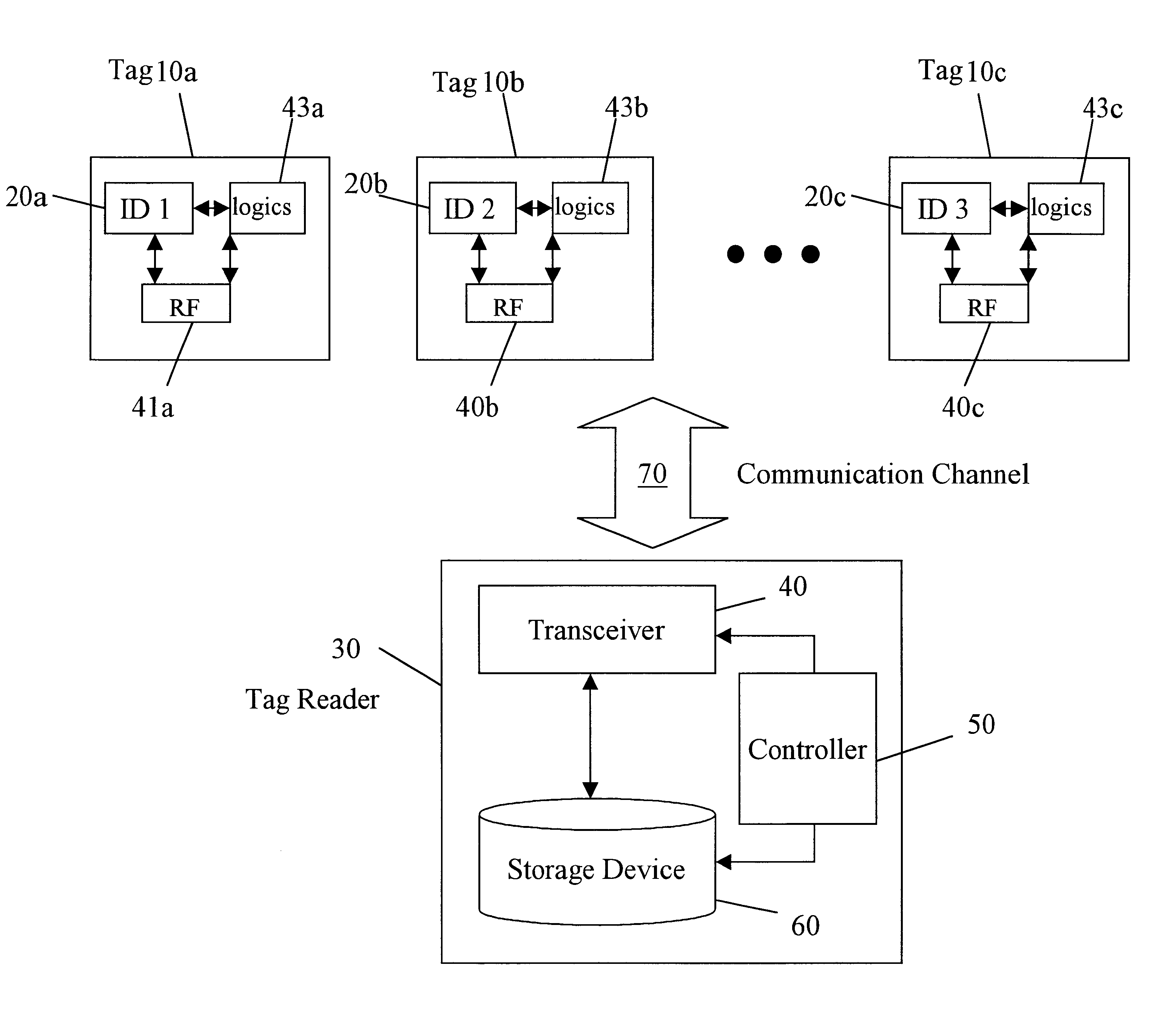
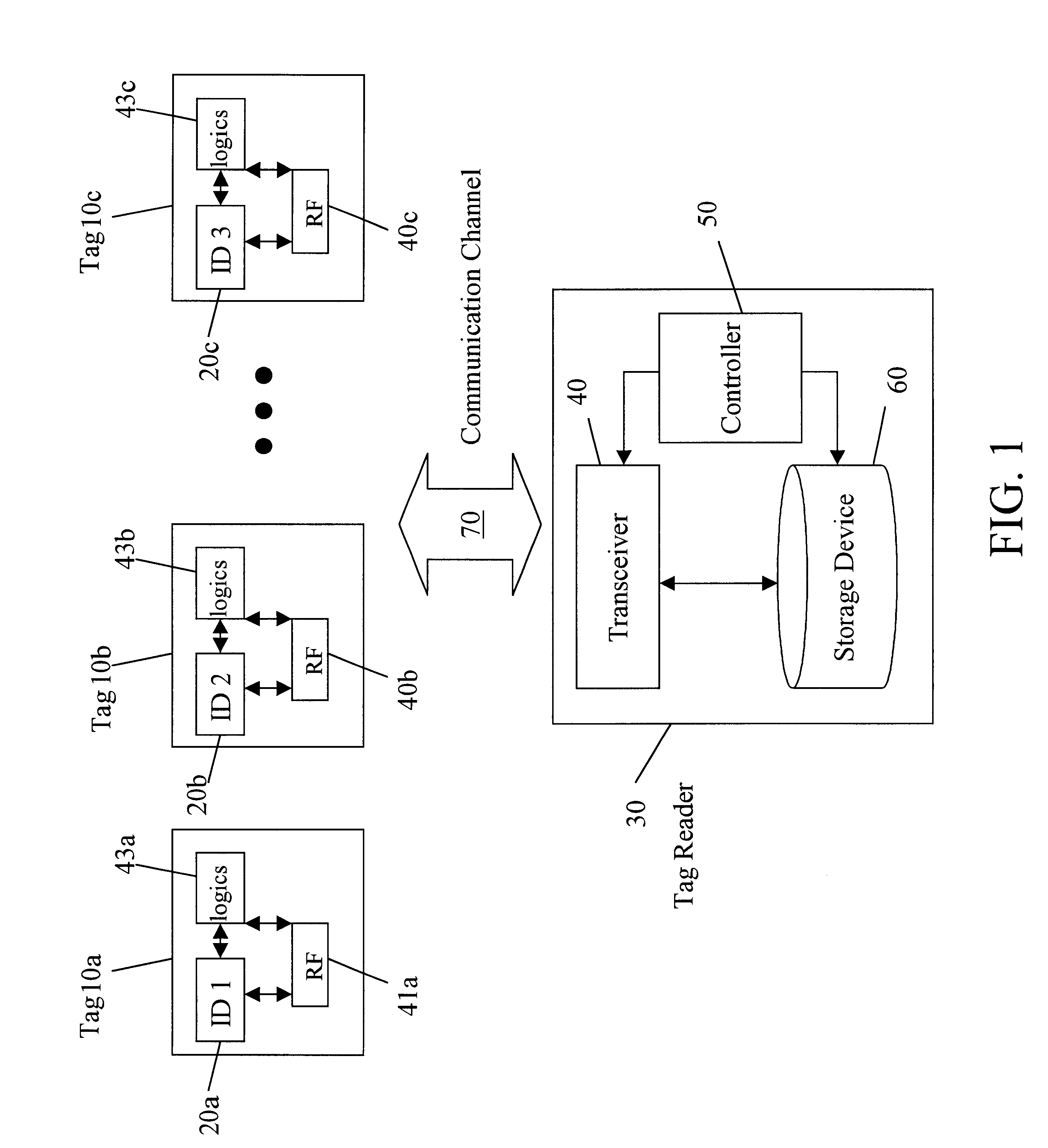
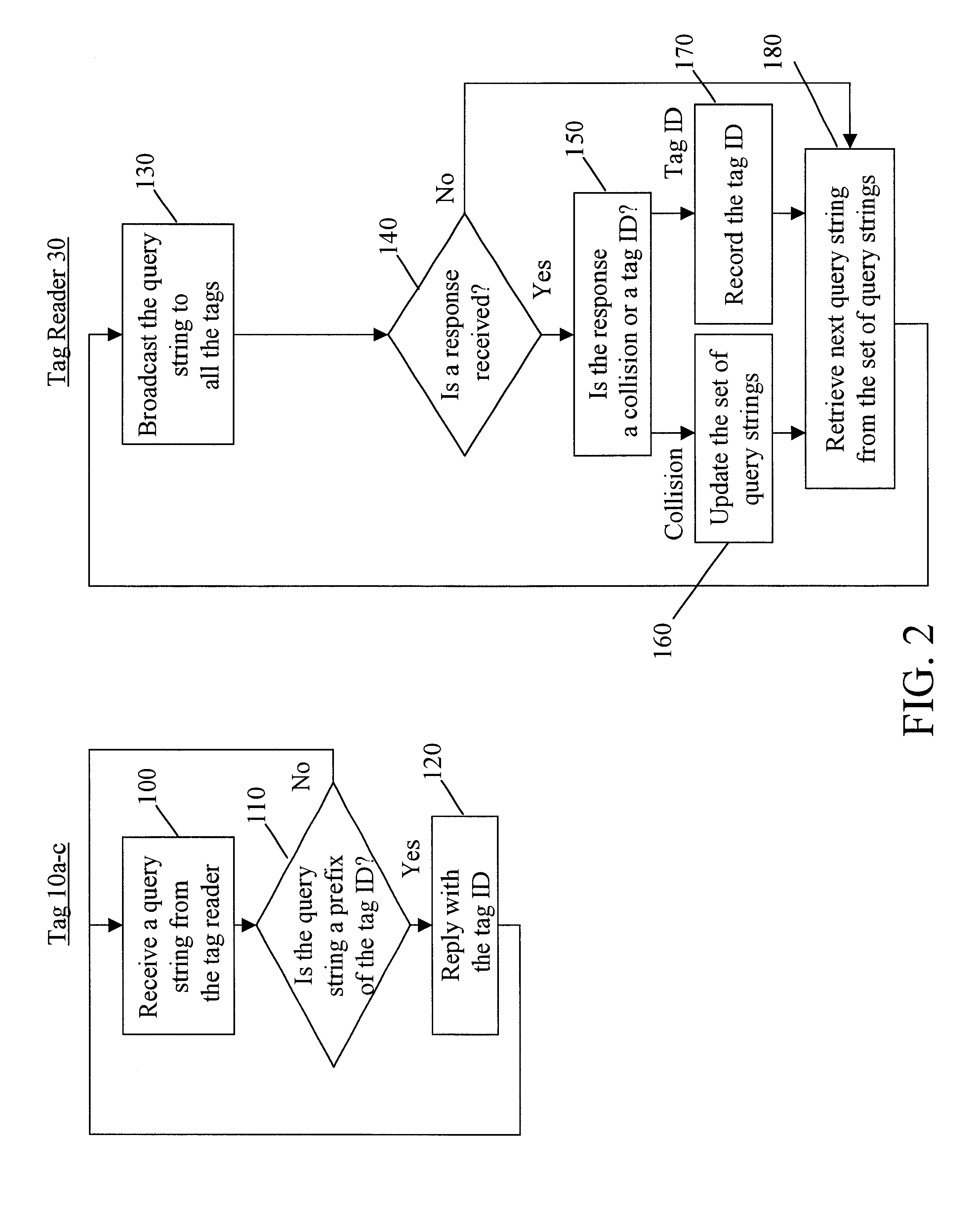
Efficient memoryless protocol for tag identification
InactiveUS6859801B1Data processing applicationsPosition fixationQuery stringCommunication complexity
The invention features a method and system for identifying a plurality of tags using an efficient memoryless protocol. The system includes a reader and a plurality of tags. The reader is adapted to maintain an ordered set of query strings; select a string from the set of query strings; broadcast a query message containing the selected string or a portion of the selected string to the tags; and receive a response from one of the tags. The tags operate without batteries and are adapted to respond to the selected string broadcast by the reader. Accordingly, the tag identification methods are efficient in terms of both time and communication complexities.
Owner:MASSACHUSETTS INST OF TECH
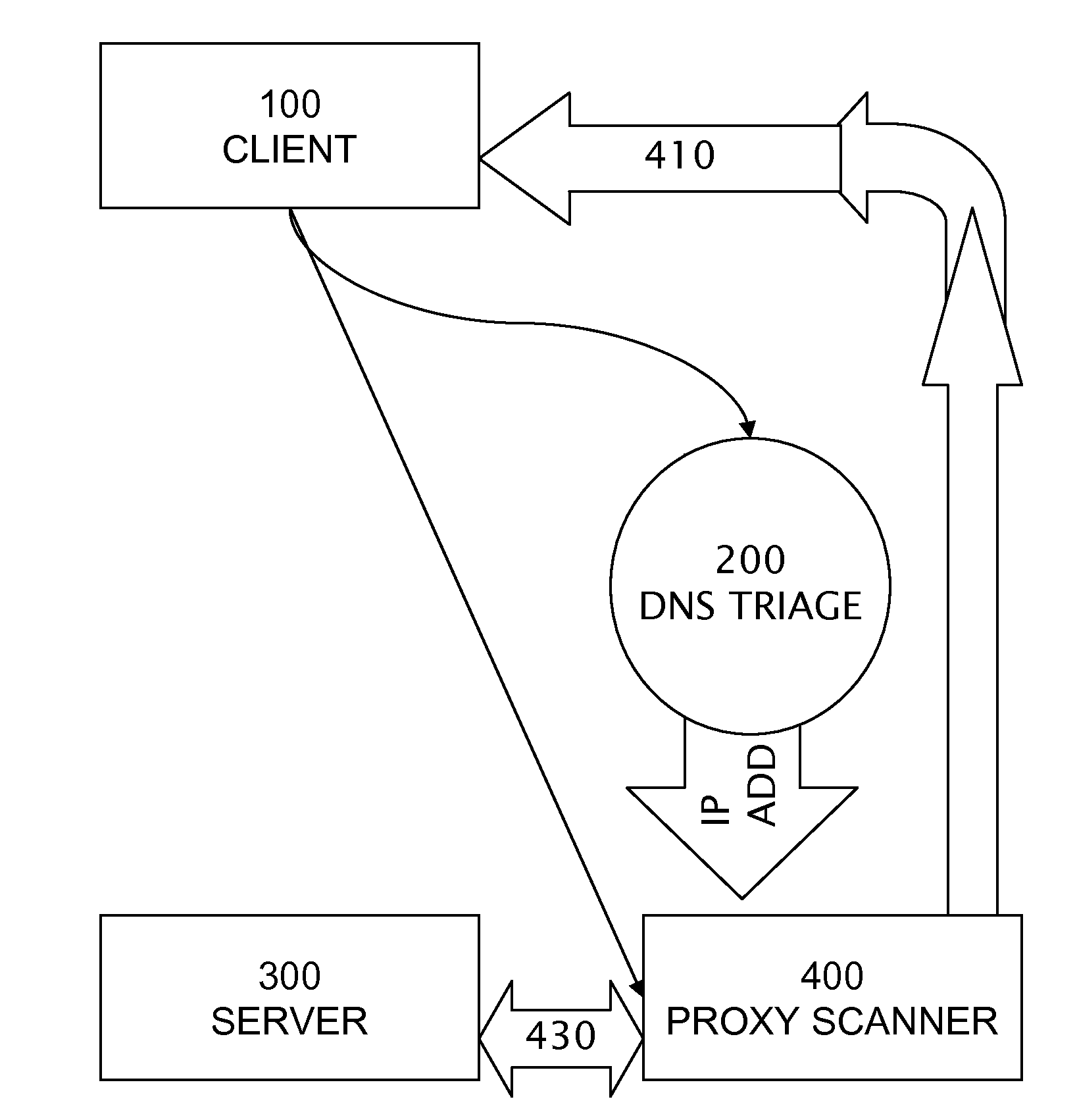
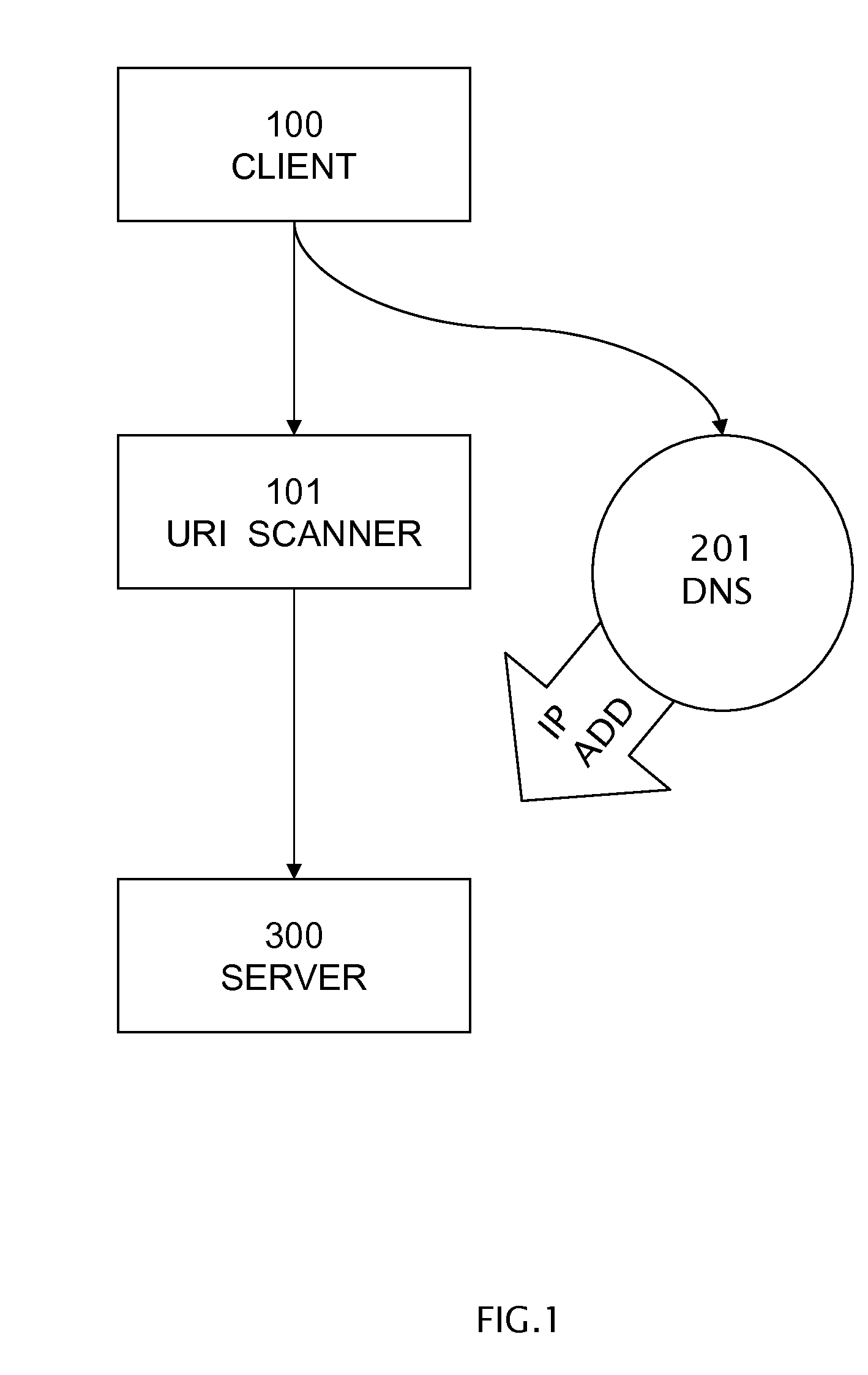
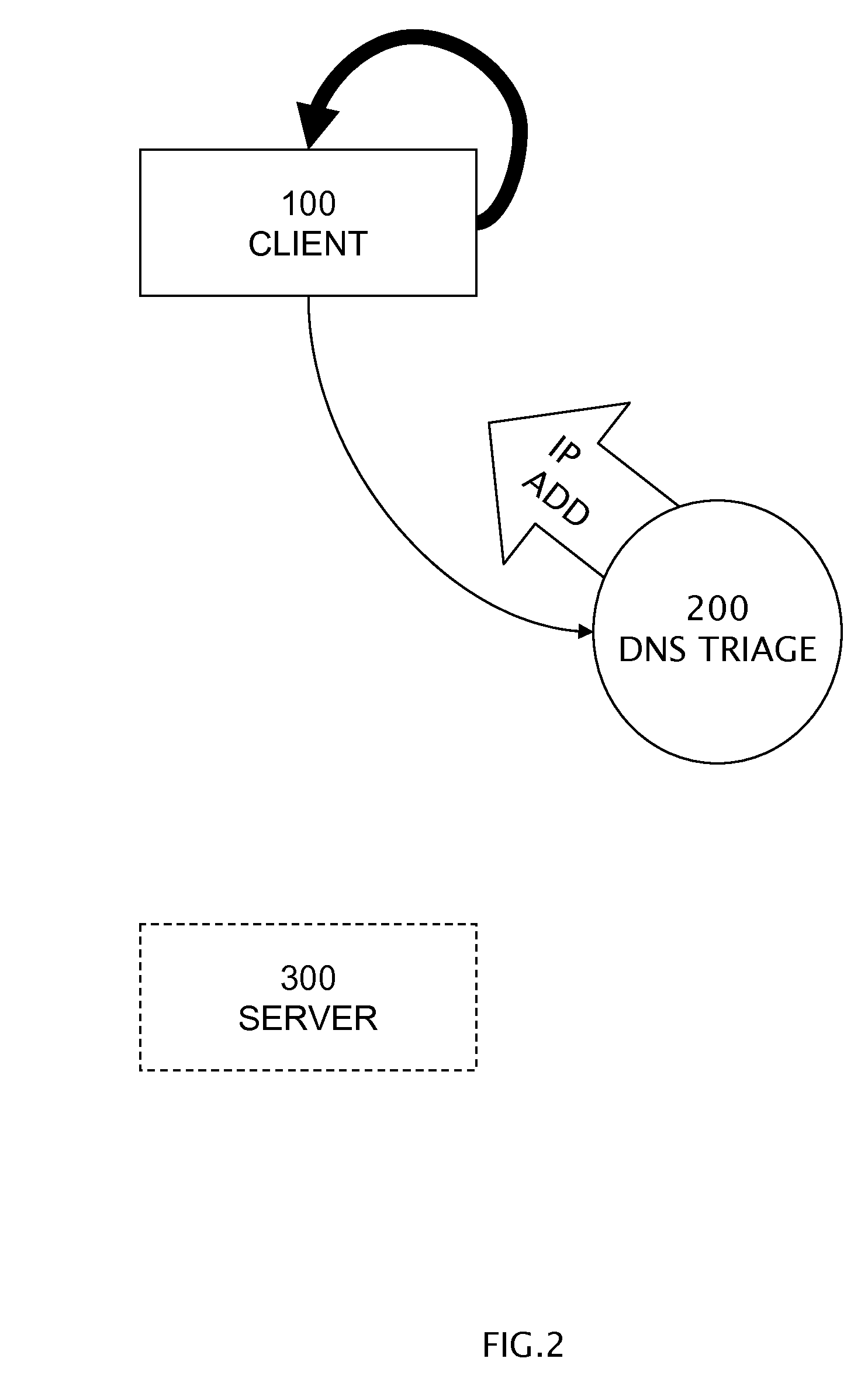
Protocol-independent, mobile, web filter system provisioning DNS triage, uri scanner, and query proxy services
A system comprising three services: query string proxy, URI path scanner, and domain name system triage. A query string proxy sends a request on behalf of a client and analyzes the response from a remote server. A URI path scanner performs keyword matching on the entire path of a uniform resource identifier. A domain name system triage service receives a UDP request prior to establishing any protocol session between a client and a server and returns one IP address selected from the following: a block IP address, a trusted IP address, and a redirection to enhanced filter service IP address.
Owner:BARRACUDA NETWORKS
Contextual searching
InactiveUS20050187920A1Improve relevanceEnhance the search itselfWeb data indexingSpecial data processing applicationsQuery stringPaper document
A method of improving the relevance of search results includes the steps of selecting search terms from a document under review for performing a search, and incorporating text surrounding the search terms in the document and the search terms into a query string. A search is then imitated using the expanded query string. As a result, the information retrieved depends not only on the search terms but also on the context in which they were found in the original document.
Owner:PORTO RANELLI
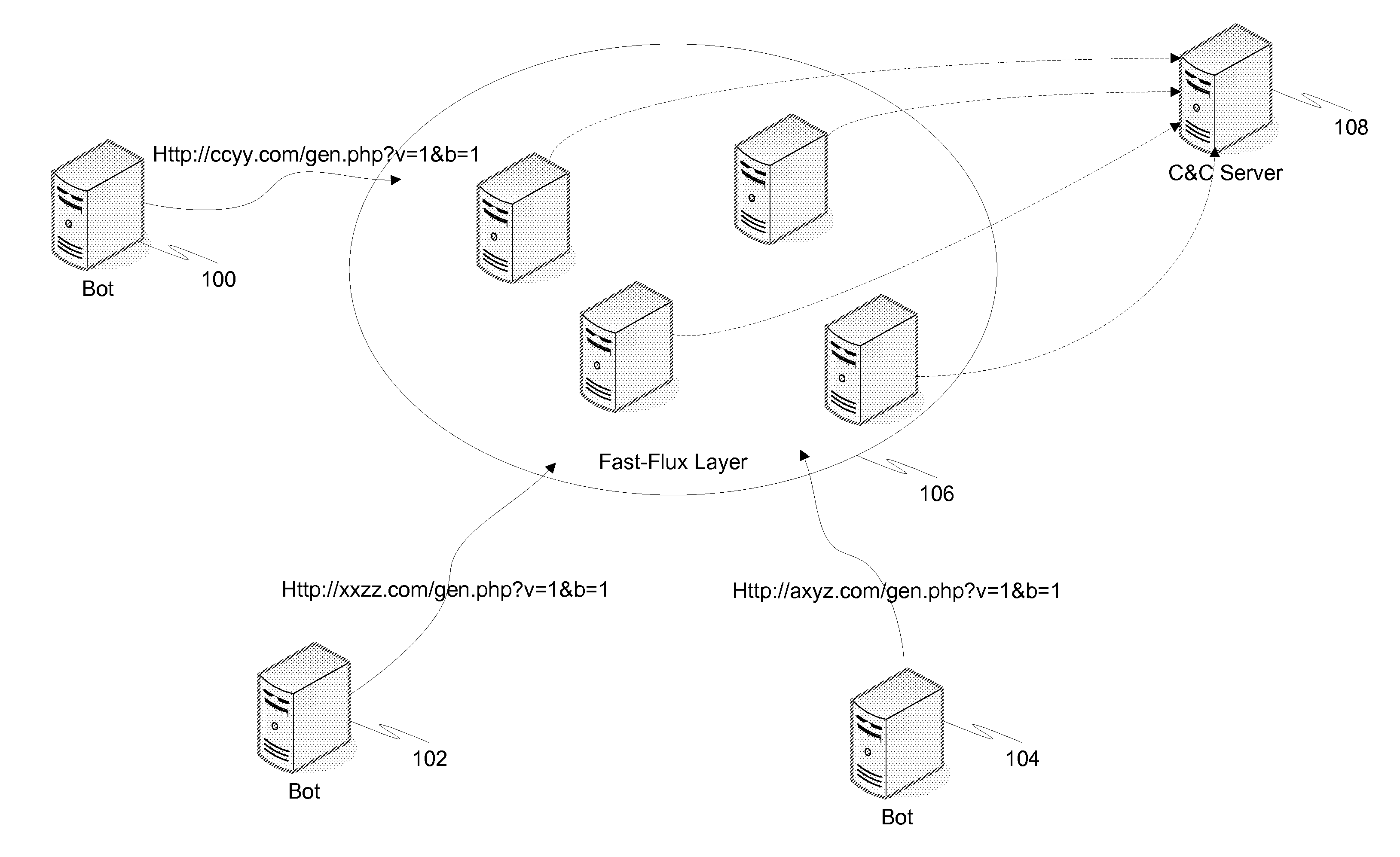
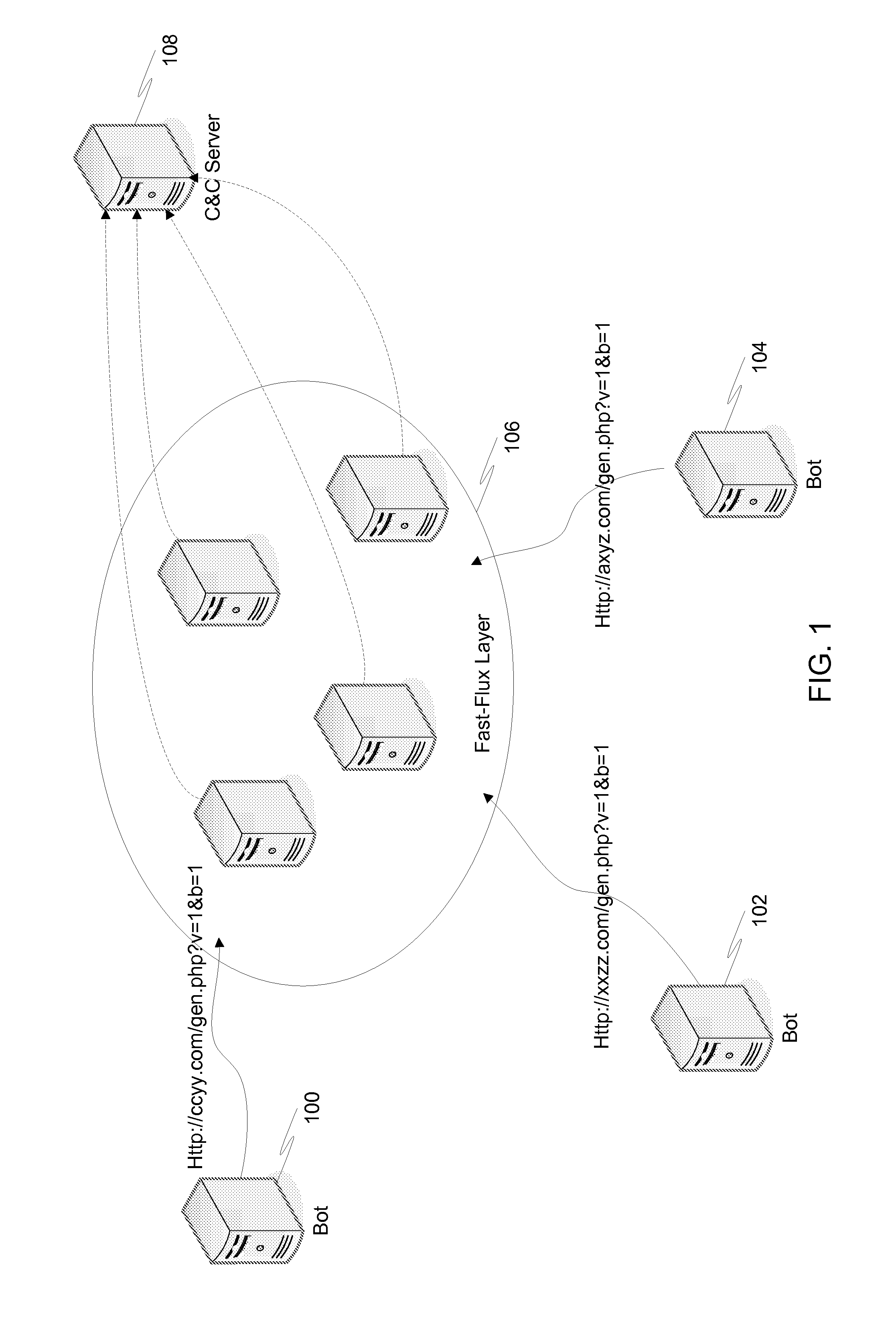
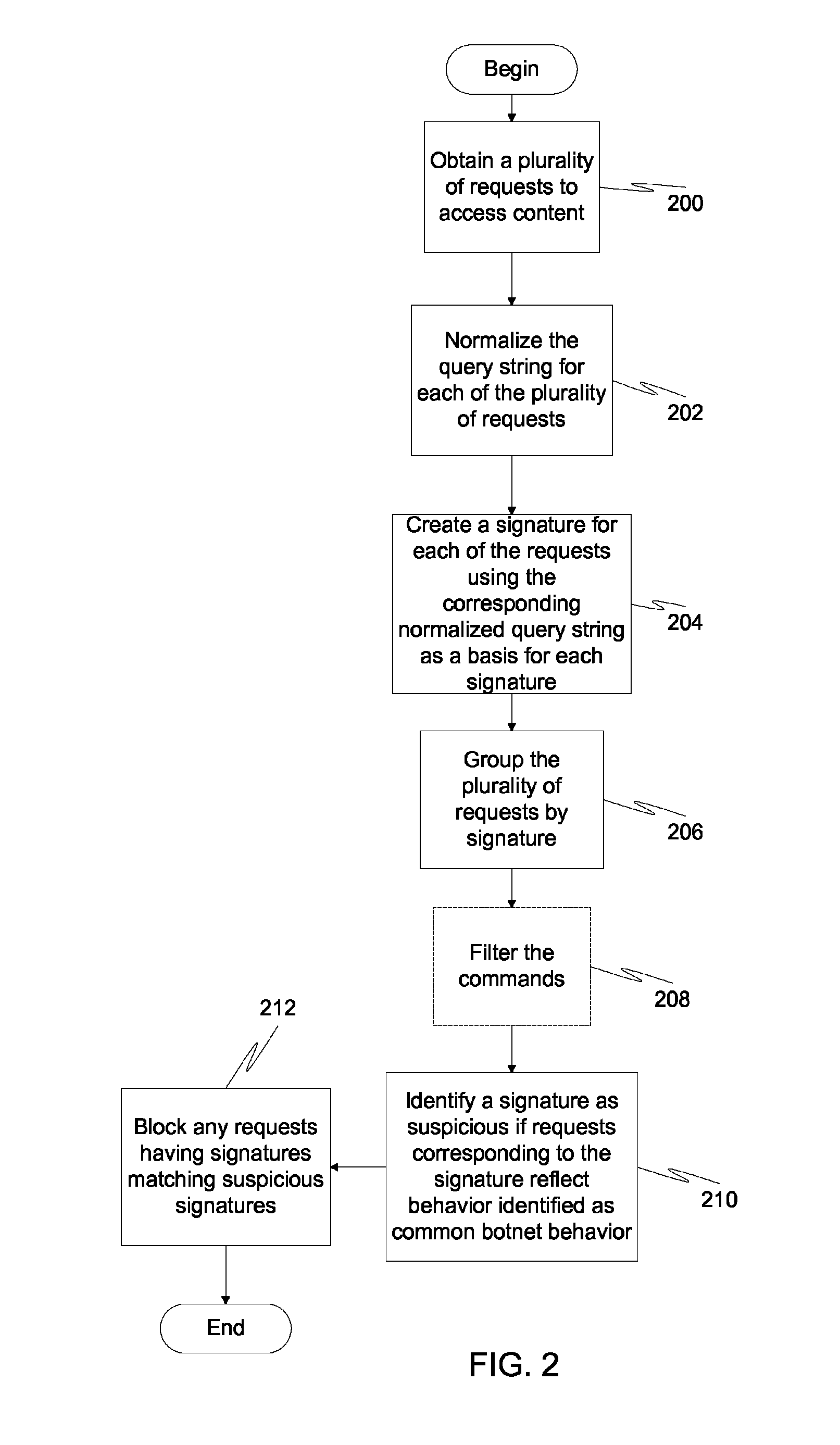
Command and control channel detection with query string signature
Detection and prevention of botnet behavior is accomplished by monitoring access request in a network. Each request includes a domain of content to access and a path of content to access, and each path includes a file name and query string. Once obtained, the query strings for each of these requests are normalized. A signature is then created for each of the normalized query strings. The obtained requests can then be grouped by signature. Once the requests have been grouped by signature, each grouping is examined to identify suspicious signatures based on common botnet behavior. Suspicious requests are used in back-end and front-end defenses against botnets.
Owner:TREND MICRO INC
Method and device for ordering information records
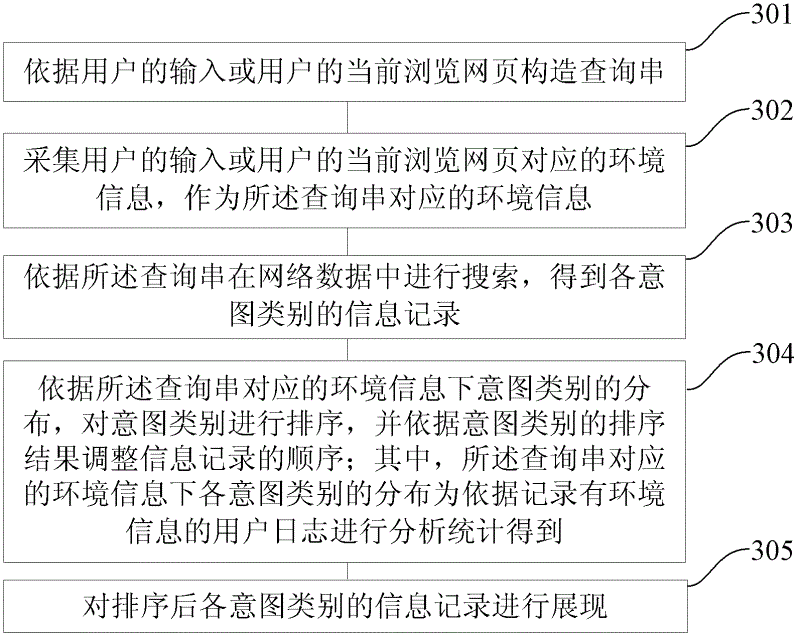
ActiveCN102622417AFulfilling real information needsNo consideration of individual needsSpecial data processing applicationsPersonalizationQuery string
The invention provides a method and a device for ordering information records. The method specifically includes: acquiring environmental information corresponding to a query string; acquiring information records about intention categories according to the query string; and ordering the intention categories according to distribution of the intention categories under the environmental information corresponding to the query string, and reordering the information records according to the result of ordering the intention categories, wherein the distribution of the intention categories under the environmental information corresponding to the query string is obtained by statistically analyzing a user log which records the environment information. By the method and the device, the intention categories can be ordered according to the environment information, and the intention categories that the current user is interested in are ordered in the front. In addition, according to the factor of individuality of the user, the latter information records are more likely true information required by the user.
Owner:BEIJING SOGOU INFORMATION SERVICE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com