Abnormal access behavior detection method and system on basis of WEB logs
A detection method and log technology, applied in the field of WEB security, can solve problems such as false positives, inability to analyze attacker attack behavior, and inability to detect detection technology.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
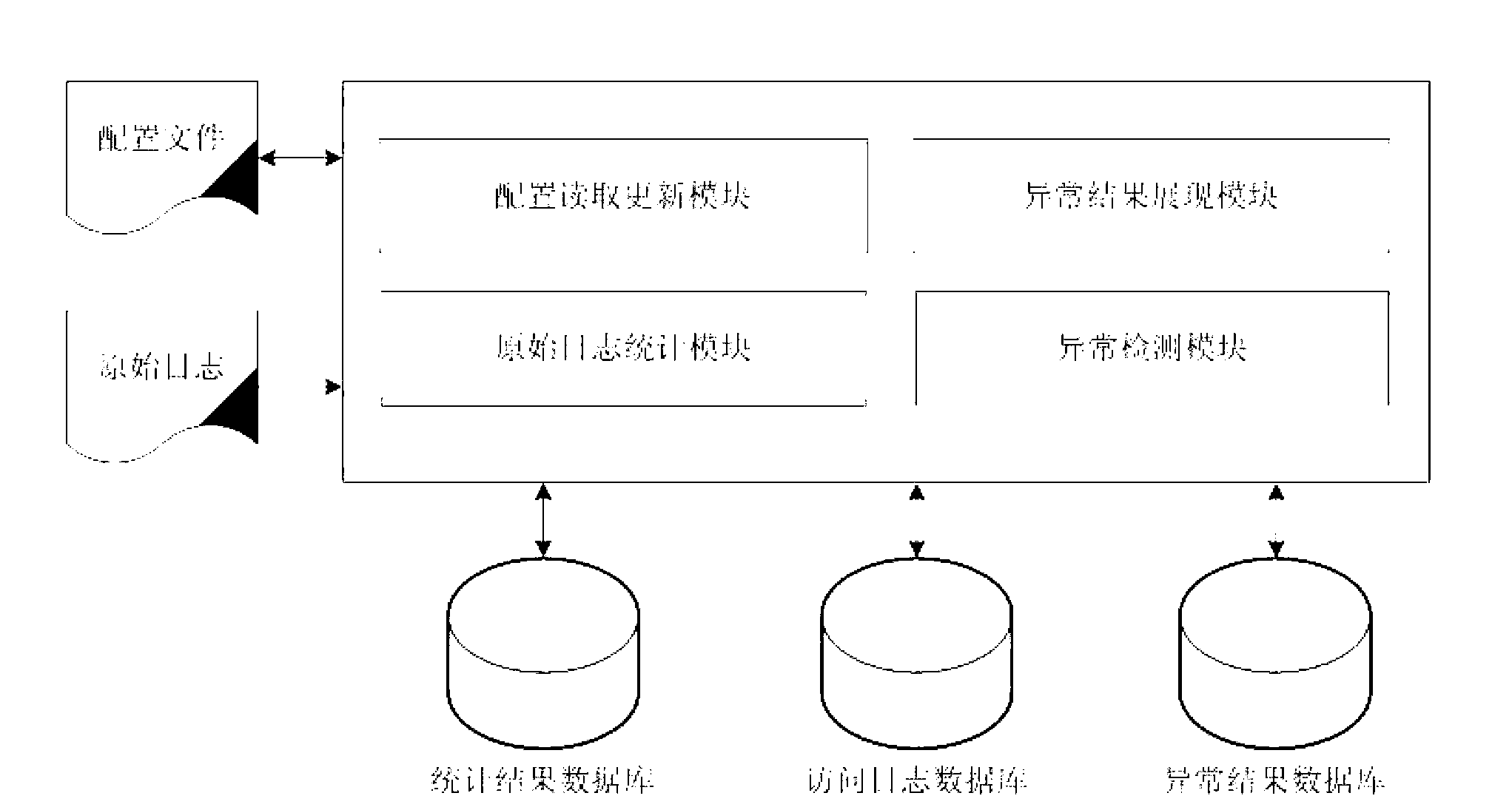
Image
Examples
Embodiment Construction
[0069] The implementation process of the technical solution of the present invention will be described in detail below with reference to the accompanying drawings and specific examples.
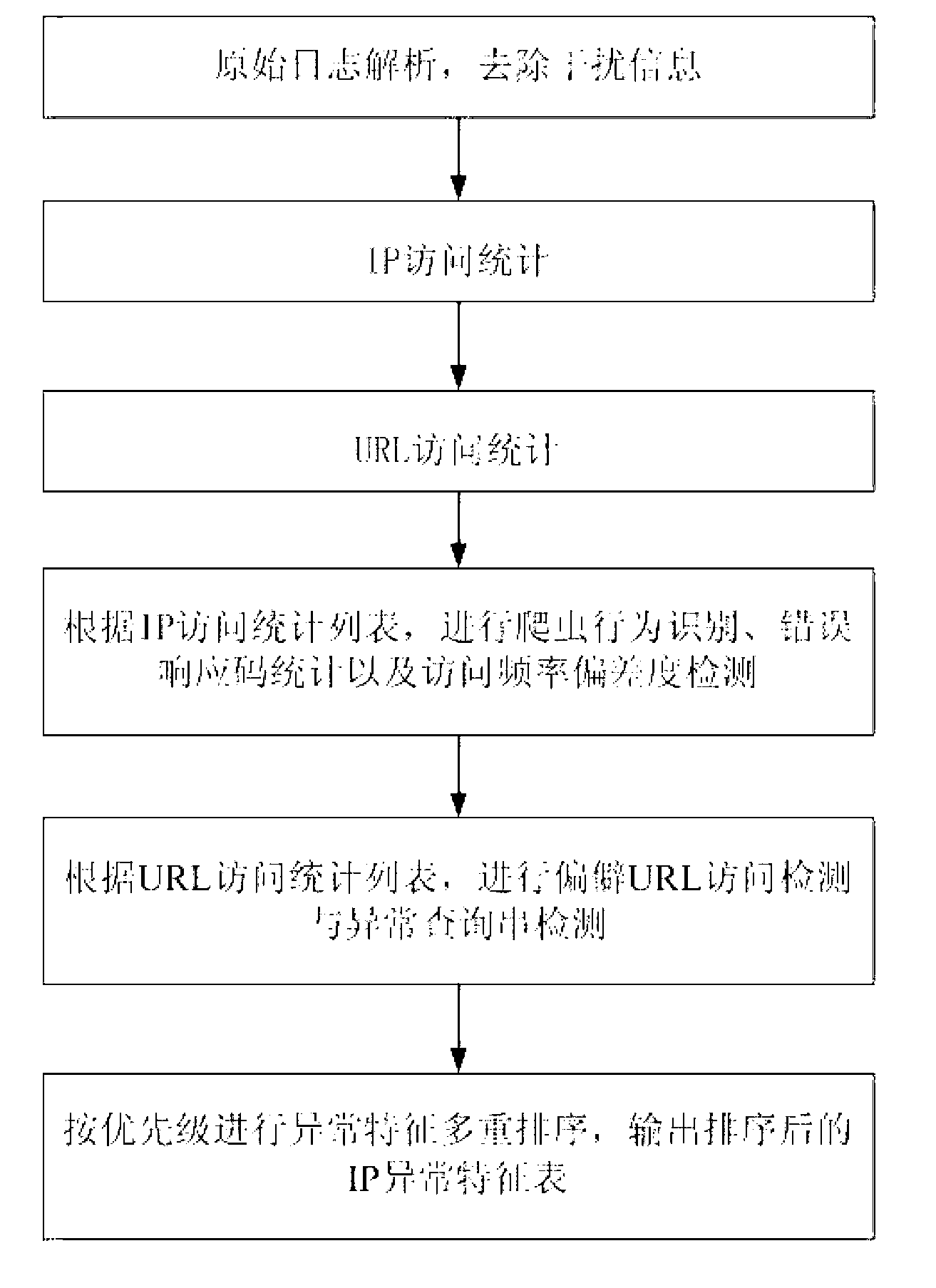
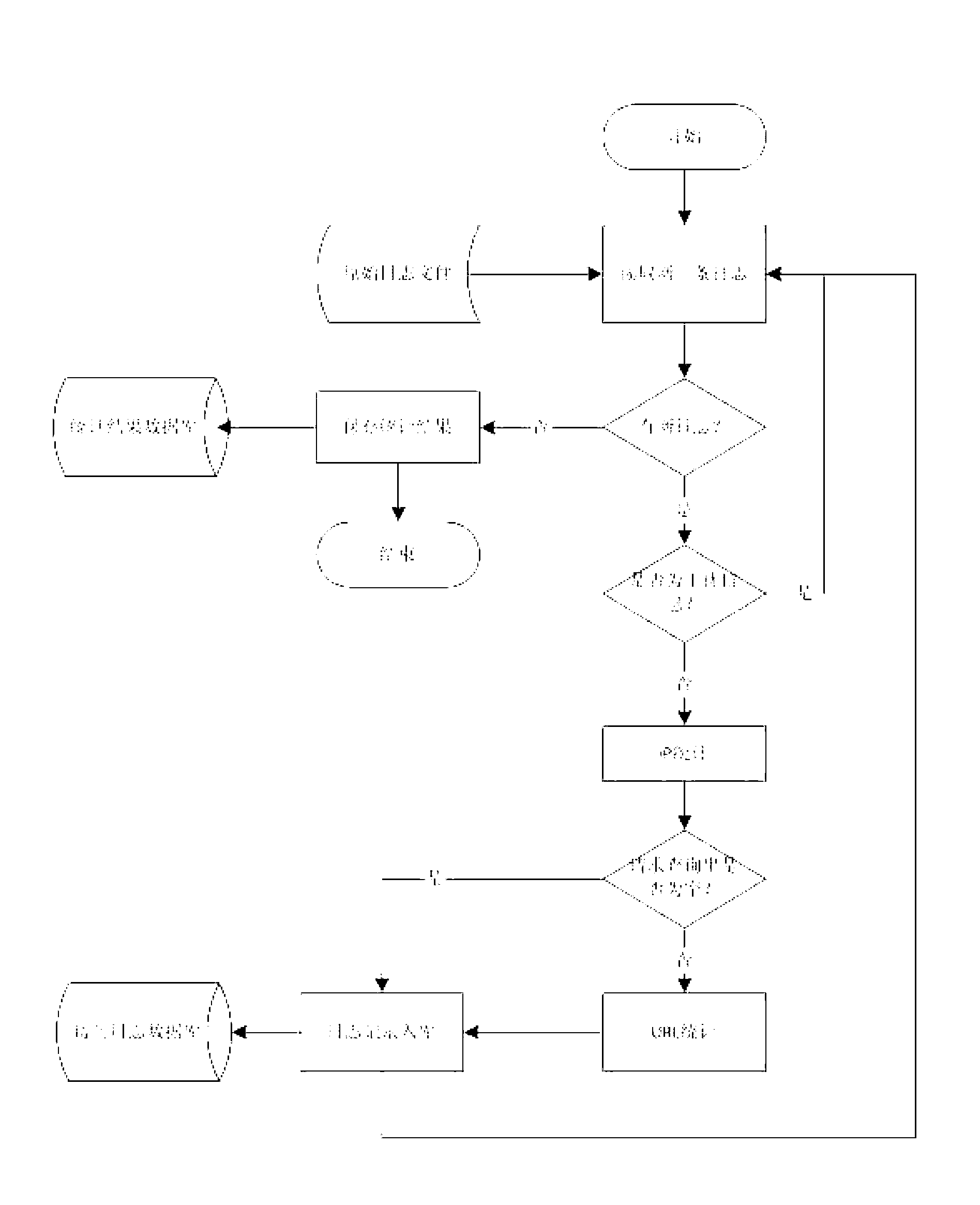
[0070] Such as figure 1 Shown is a schematic flow chart of an embodiment of a method for detecting abnormal access behavior based on WEB logs of the present invention, and its specific steps include:
[0071] 1. Analyze the original WEB log and remove the interference information;
[0072] 2. IP access behavior statistics, get the IP access statistics list, including the total number of sessions, duration, number of visits, non-page access ratio, error response code ratio, download access ratio of each IP;
[0073] 3. URL access statistics, get URL access statistics list, including visitor information dictionary table and query string dictionary table for each URL;
[0074] 4. According to the IP access statistics list, carry out crawler behavior feature identification, error response code ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com