Patents
Literature
1511 results about "Access frequency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
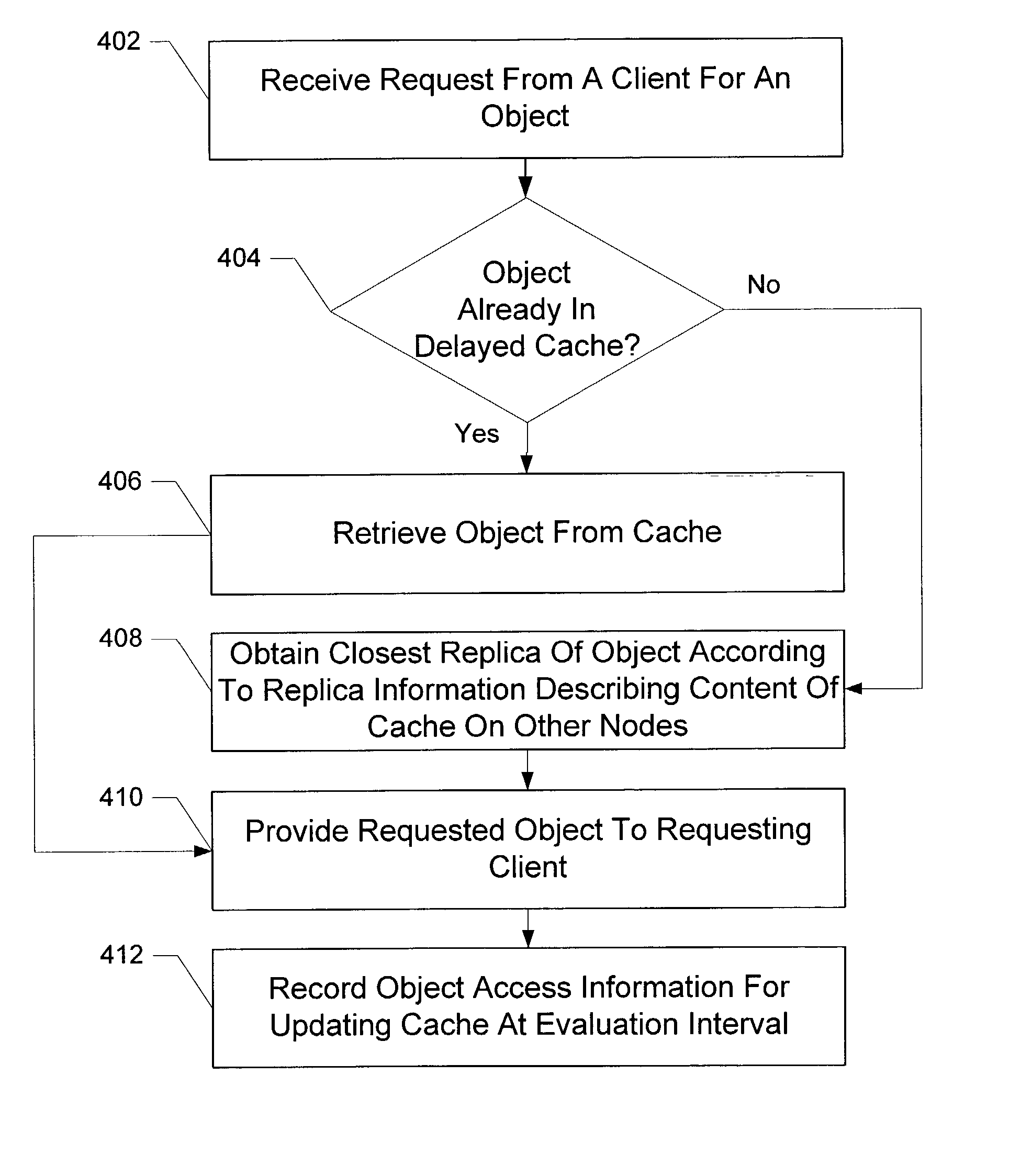
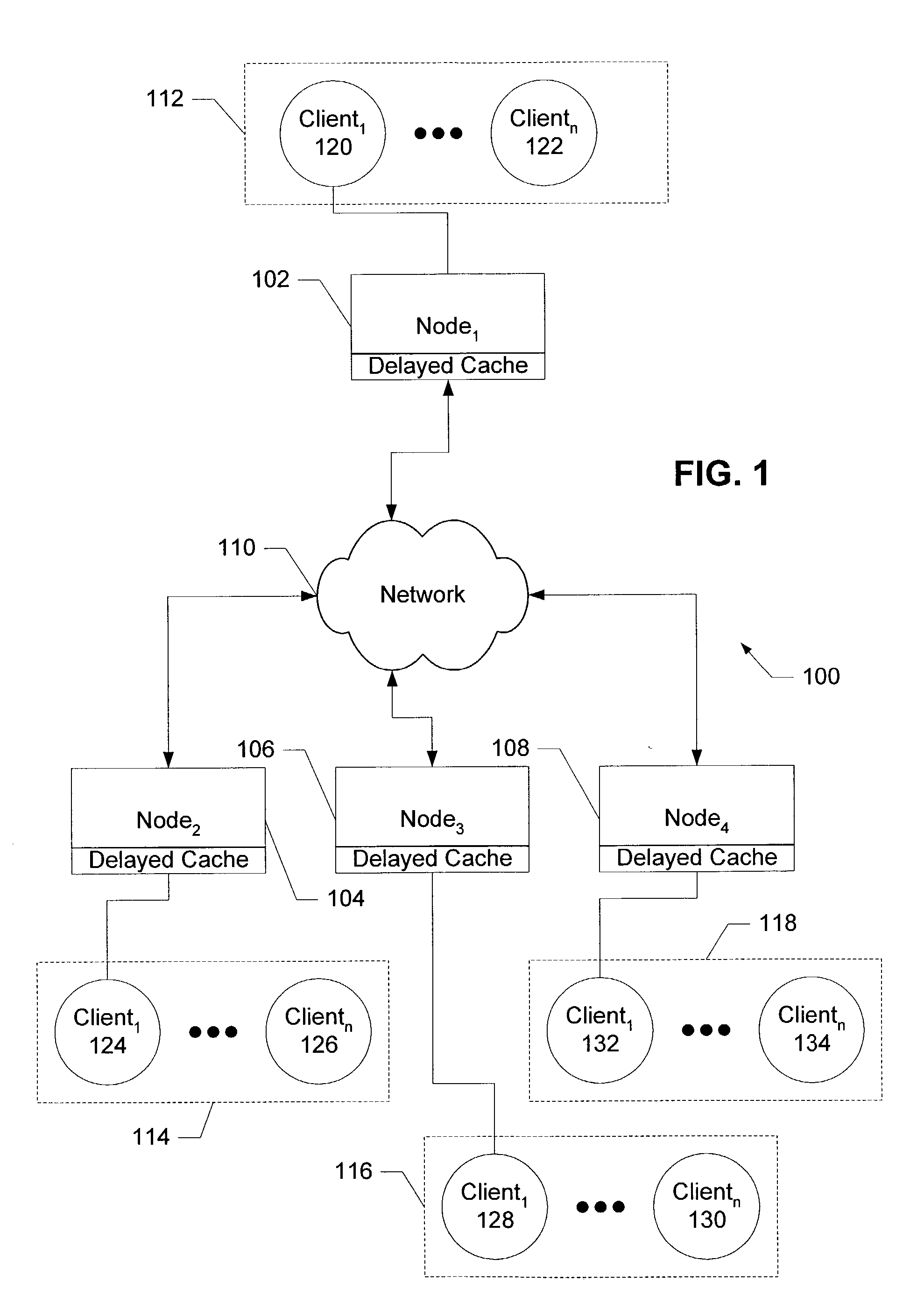
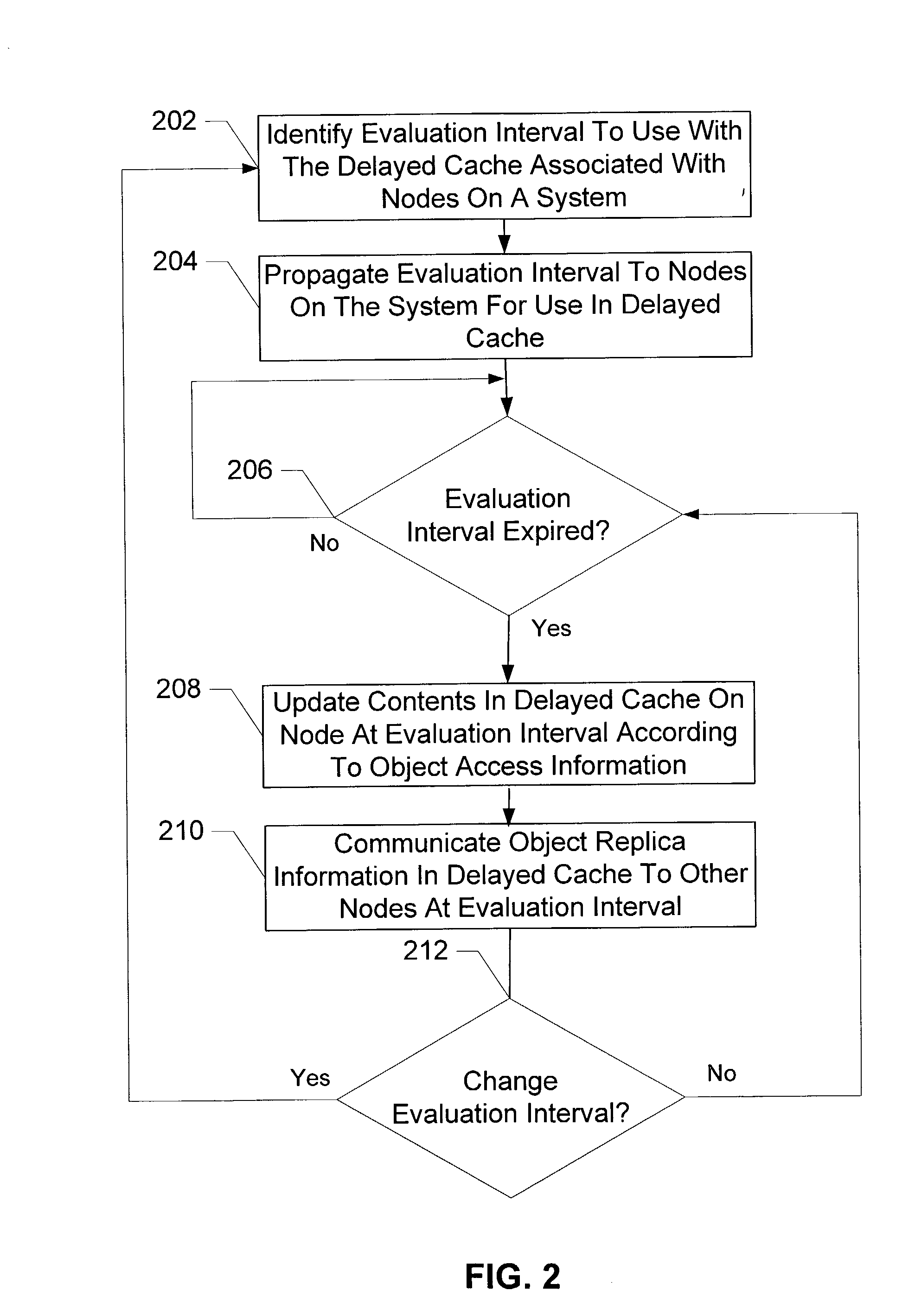
Delay cache method and apparatus
InactiveUS20040034744A1Promote disseminationReduce the amount of processingDigital data information retrievalMemory adressing/allocation/relocationEvaluation IntervalTime segment
Delayed caching receives an evaluation interval to delay updating the objects stored in a delayed cache, delays a time period corresponding to the evaluation interval, and updates the objects stored in the contents of the delayed cache when the time period delay has completed. The configuration operation for the delayed cache selects a time interval to sample a trace having object access frequencies for objects stored in a cache, creates a first working set of objects accessed during the time interval and a second working set of objects accessed during a subsequent time interval based on the historical trace, determines that the difference between the objects contained in the first and second working sets does not exceed a maximum threshold with the selected time interval, and sets a evaluation interval for evaluating the contents of the cache to the selected time interval.
Owner:HEWLETT PACKARD DEV CO LP
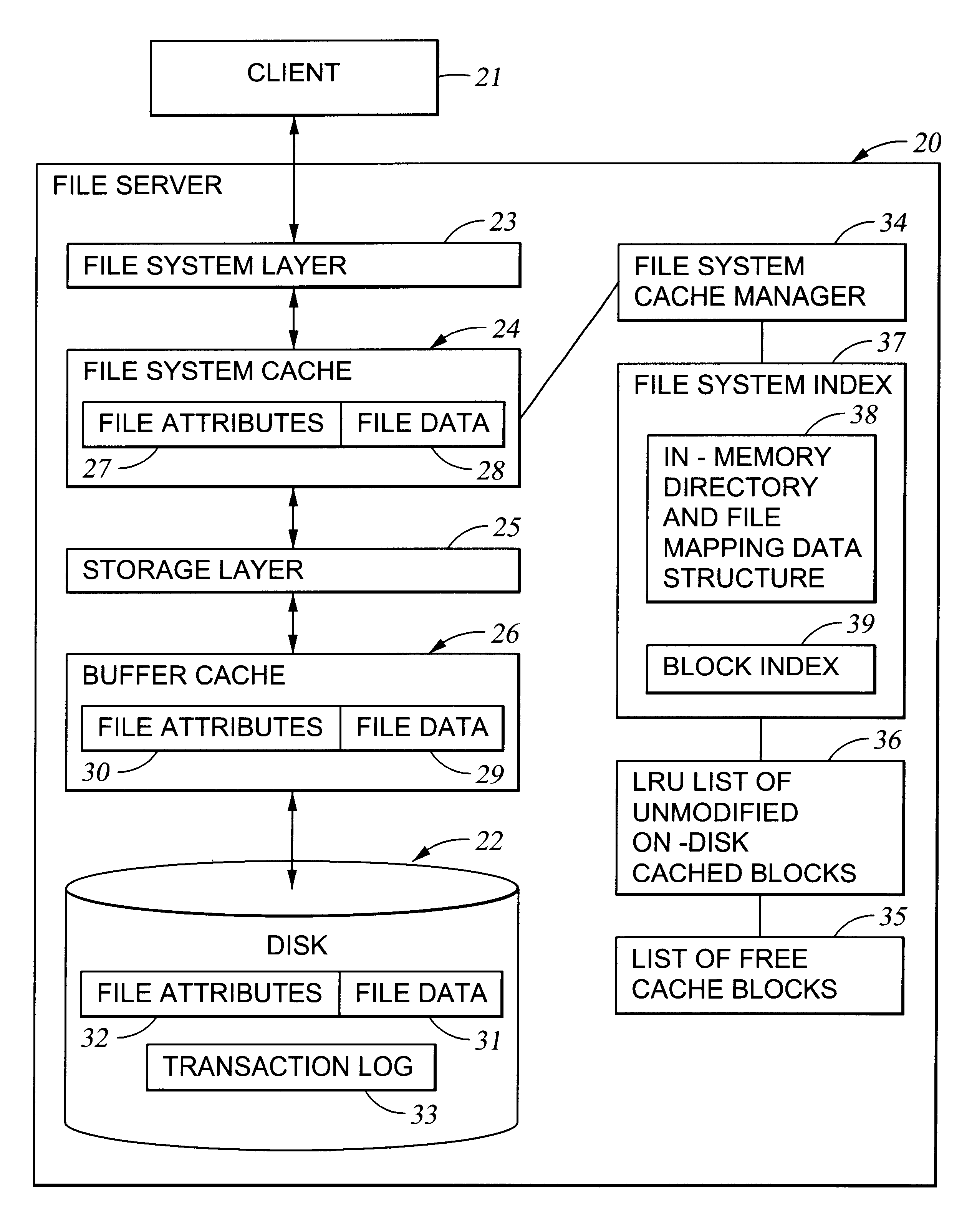
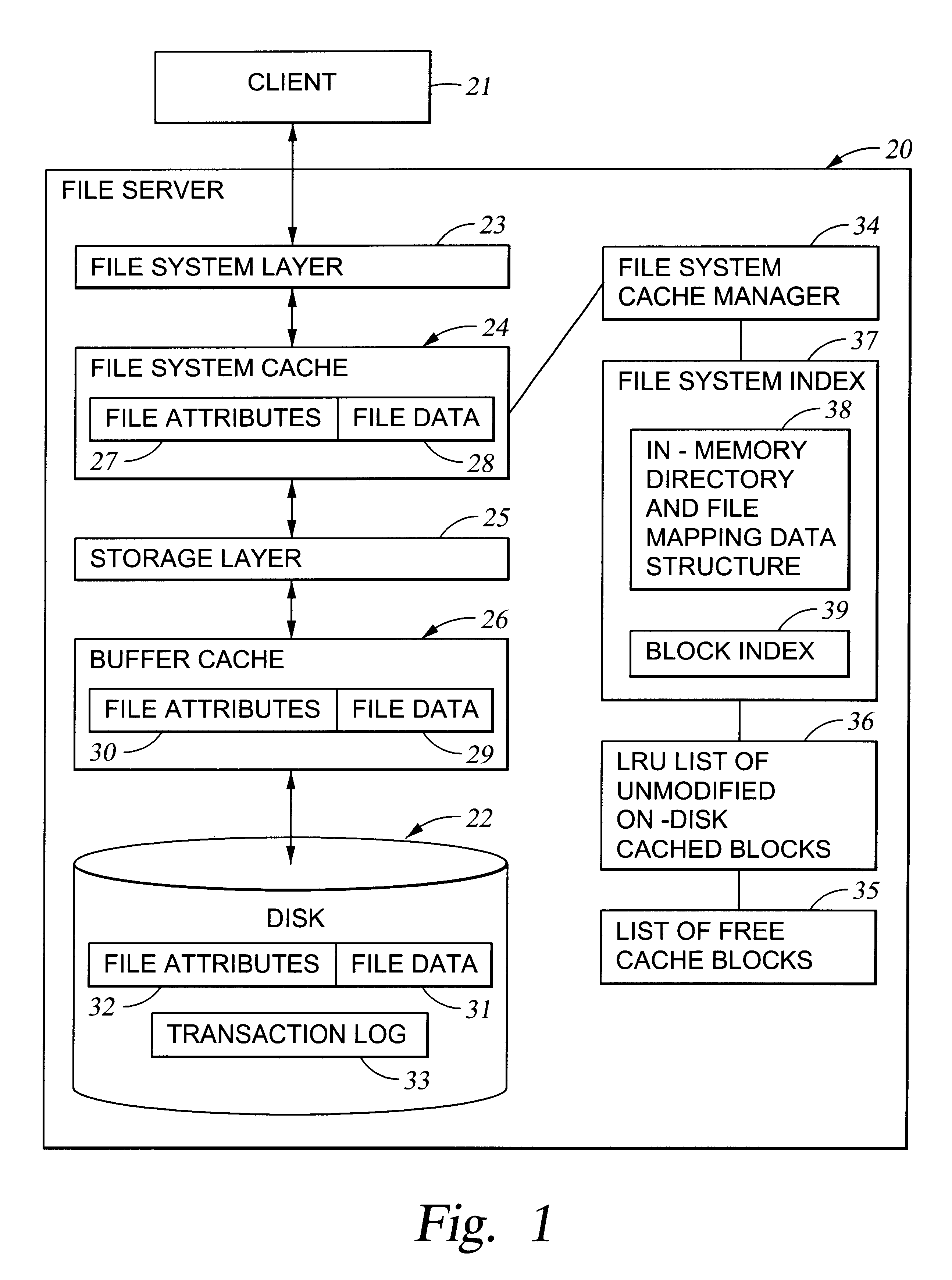
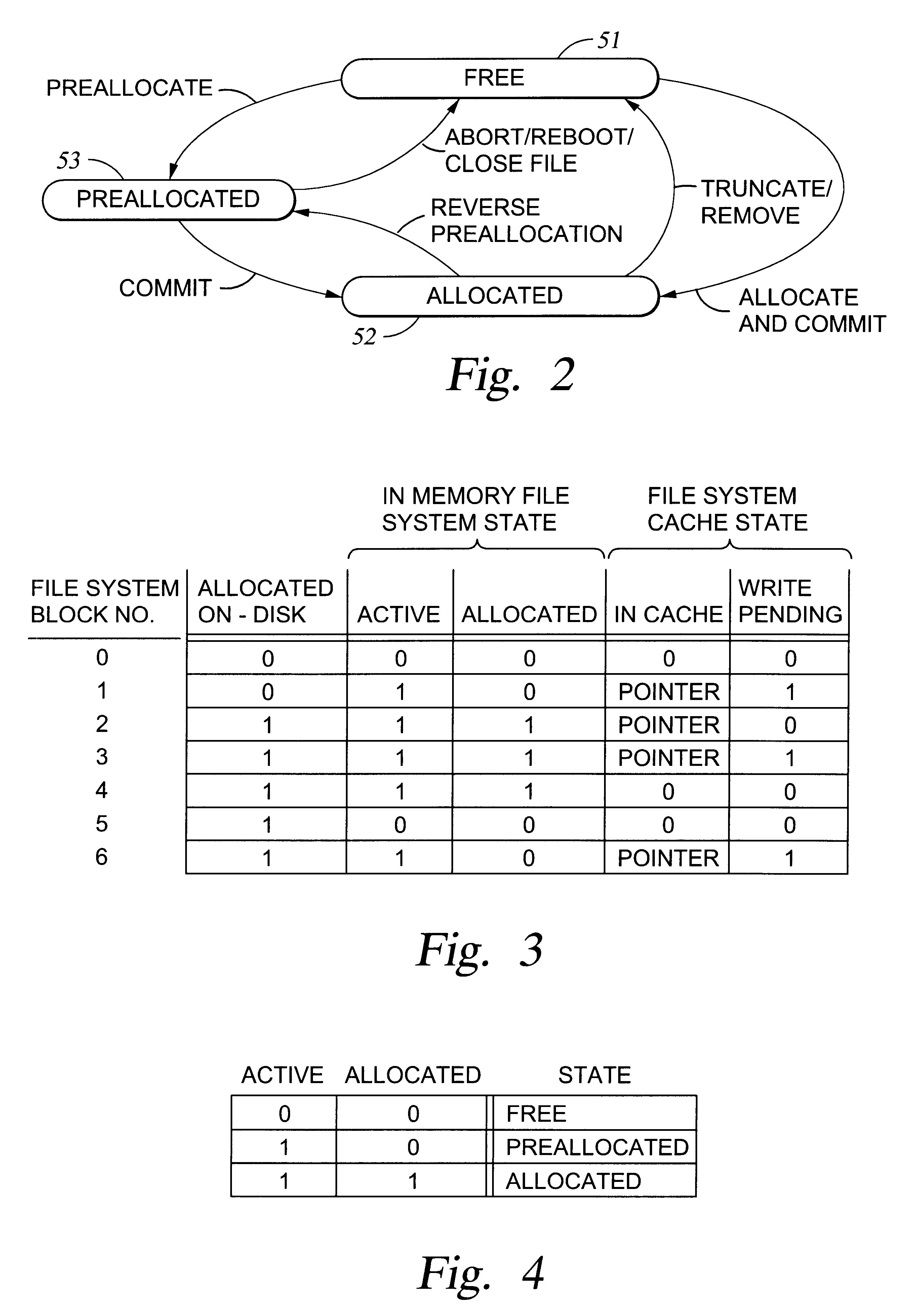
Preallocation of file system cache blocks in a data storage system
InactiveUS6571259B1Data processing applicationsSpecial data processing applicationsOperational systemTransaction log
A file server provides transaction processing capabilities previously supplied by the operating system of a host computer. On-disk file system metadata is changed only at commit time, and a transaction log protects the transition. The disk state can only be a consistent state, resulting from a commit operation. All disk-block reservation and pre-allocation mapping are in the memory, and after a crash, they are automatically discarded. The file server therefore relieves the client of processing burden and also reduces network traffic. In addition, the file server can more efficiently perform the transaction processing capabilities and reduce the frequency of access to storage by judicious allocation of file system blocks and transfer of file system blocks between file system objects, cache memory, and the transaction log. The differentiation between preallocation states and allocation states of in-memory file system blocks also permits application programs to more efficiently transfer data between files.
Owner:EMC IP HLDG CO LLC
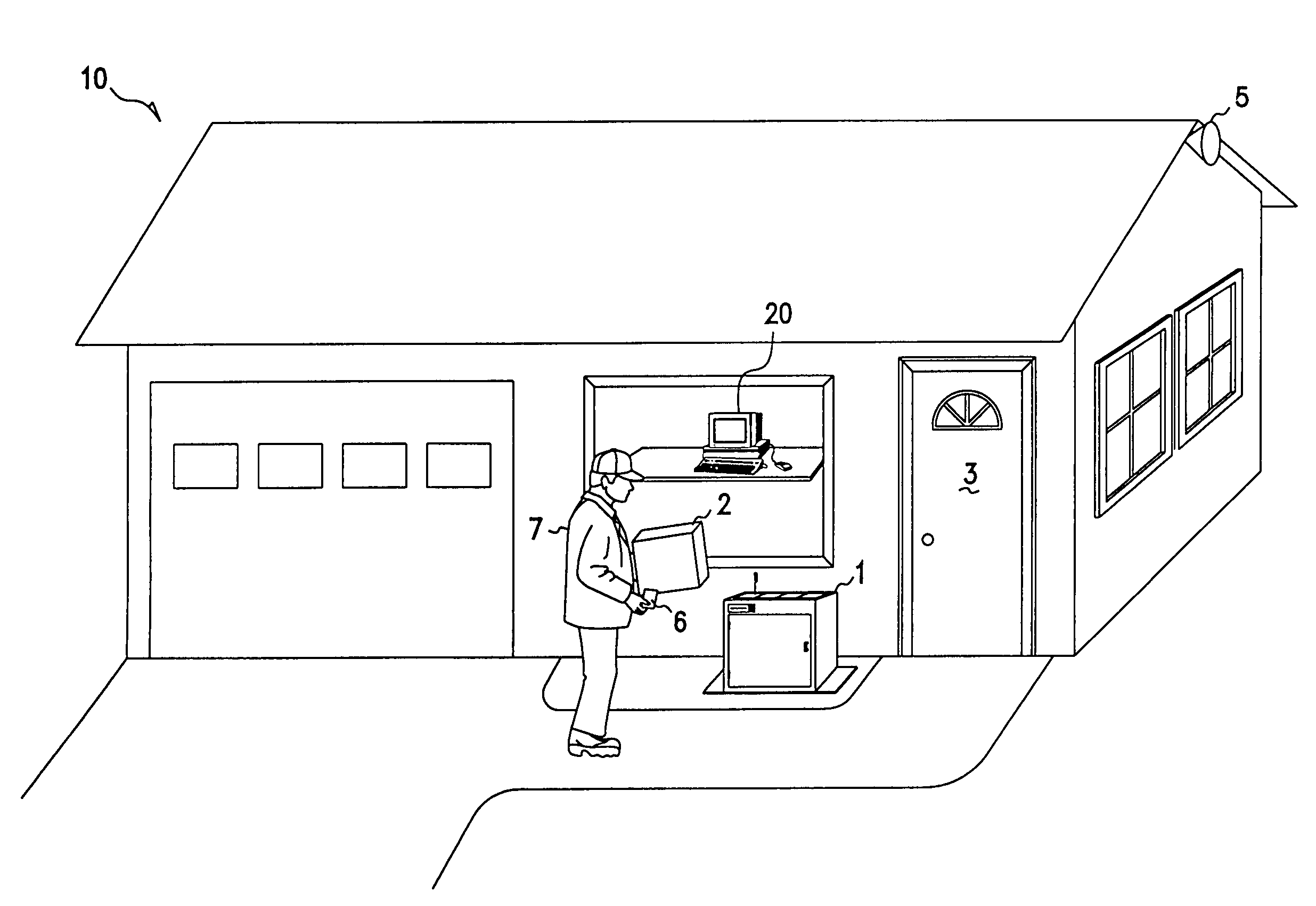
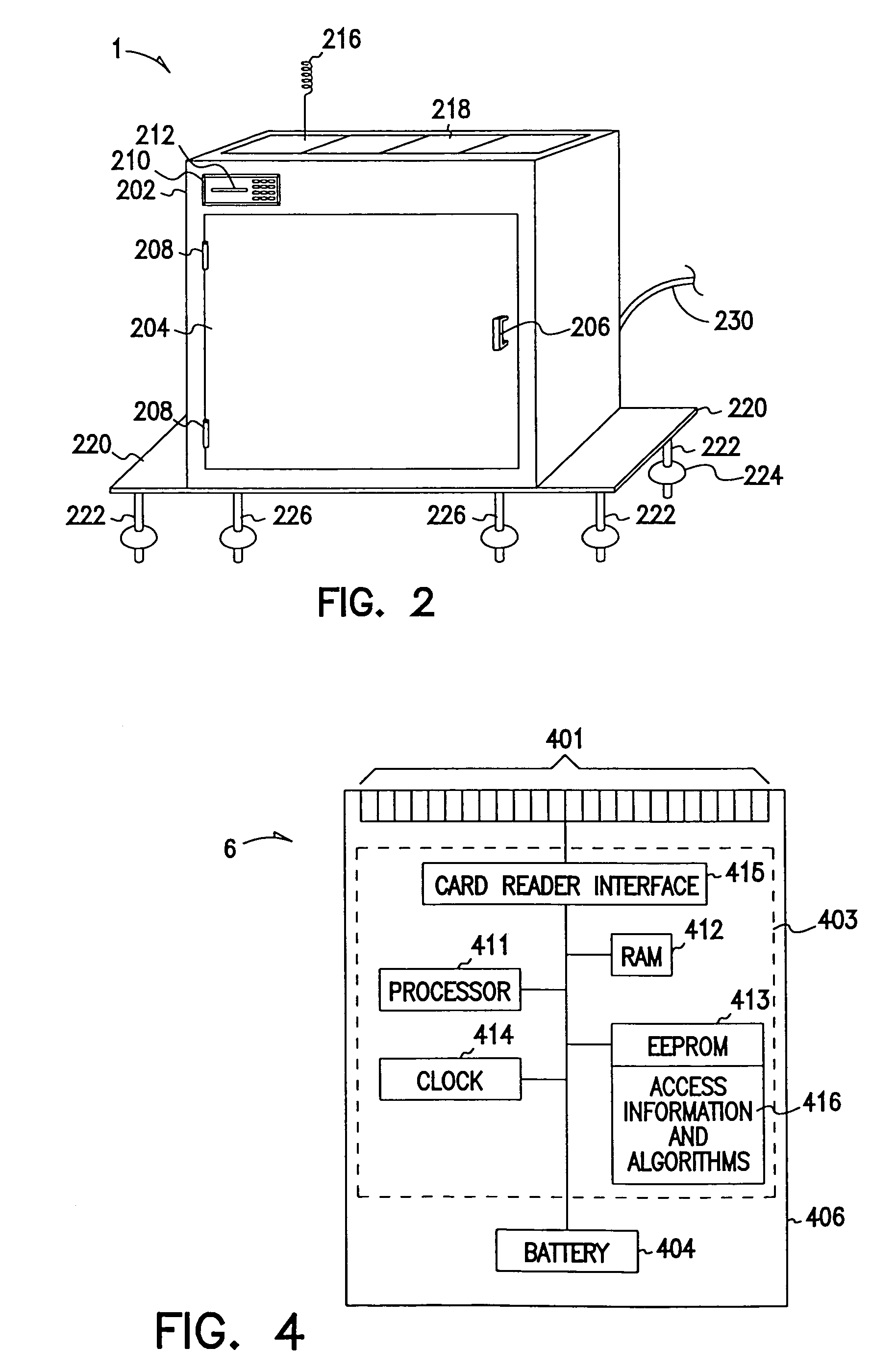
Methods and apparatus for unattended pickups and deliveries
A secure pickup and delivery container includes a lockable door, a control unit, an access element, and an anchoring element, according to one embodiment. The control unit includes a processing element and a memory that can be programmed either on-site or remotely with access privilege information such as identity (e.g. of container, delivery person, etc.), location, date, time, frequency of access, and / or package-specific information. In one embodiment, access privilege information is programmed when an intended recipient of a delivery consummates a point of sale transaction, for example over the Internet or telephone. The access element can be a keypad, a biometric scanner, a card reader, a bar-code reader, and / or a wireless control element to read a programmable token such as a smart card. Delivery personnel can enter access request information into the access element, and if it favorably compares with the access privilege information, the control unit unlocks the door. Notification can be concurrently made via wireline or wireless communications to the intended recipient, who may be situated remote from the secure container. The recipient can optionally return a delivery acknowledgment to the delivery personnel. Details of the delivery transaction can also be recorded electronically on the delivery personnel's token, within the container, or at a remote location.
Owner:INTEL CORP
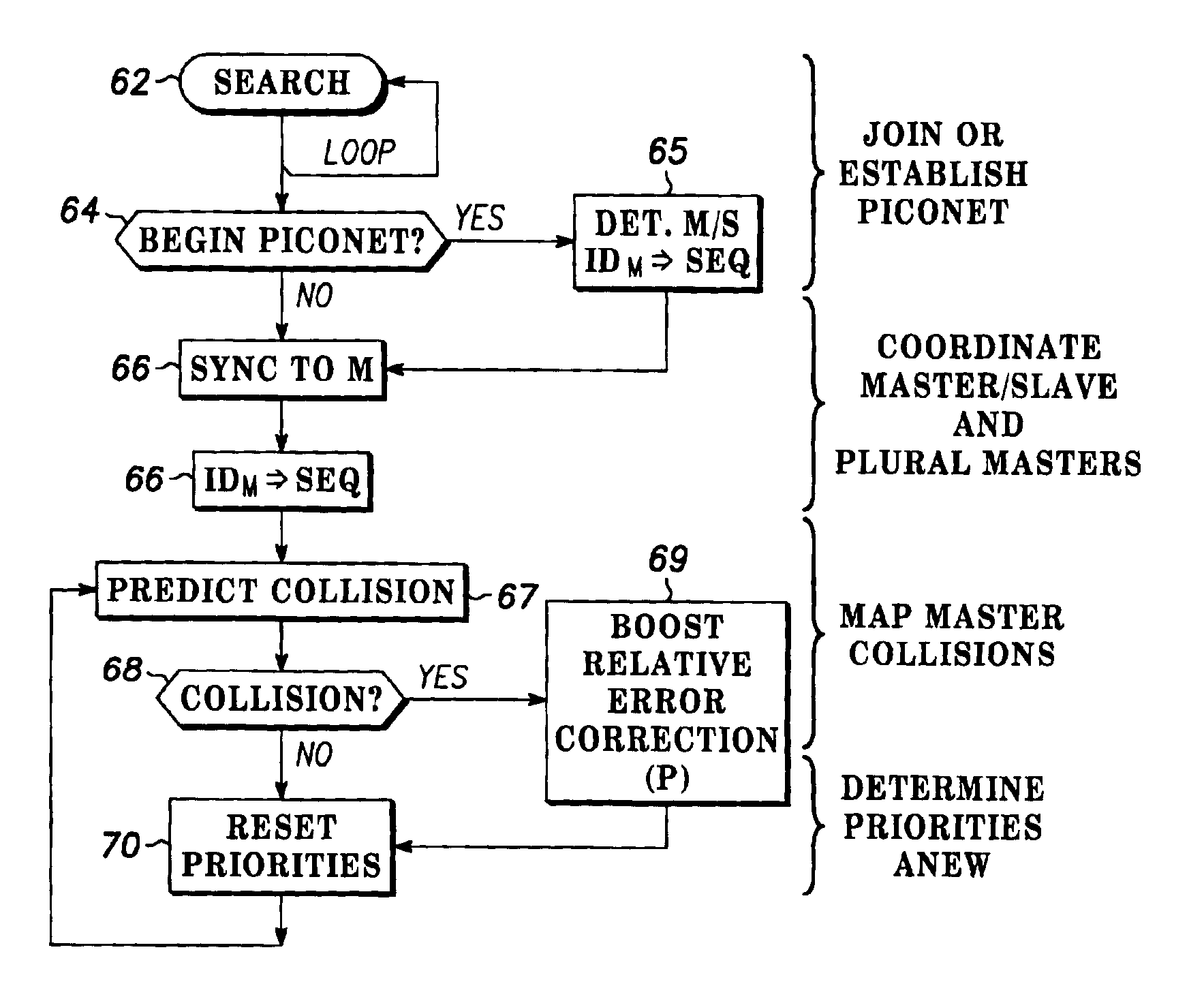
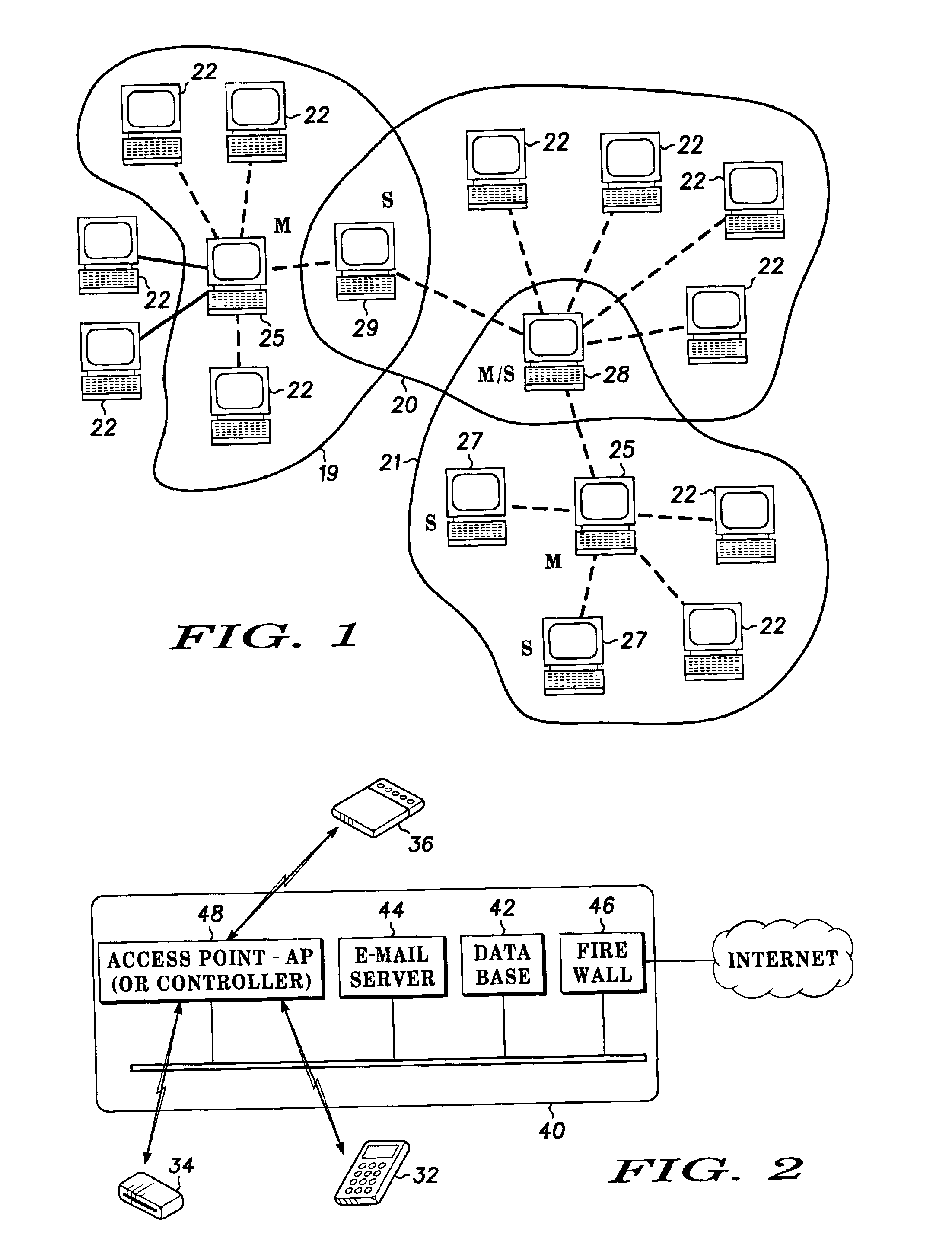
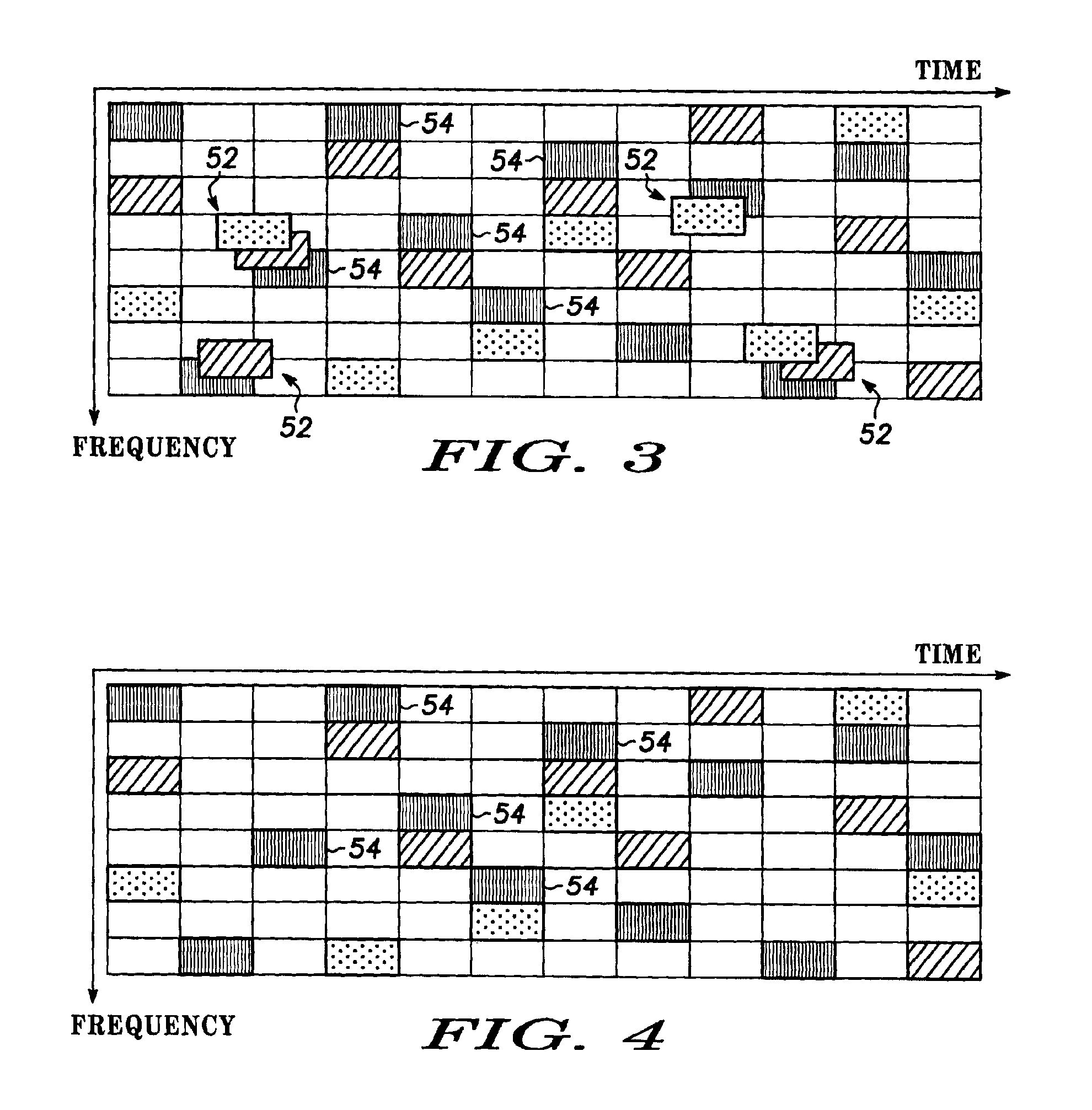
Multiple access frequency hopping network with interference anticipation
InactiveUS6920171B2Spreading over bandwidthSecret communicationMulti-frequency code systemsMessage queueRadio equipment
Spread spectrum packet-switching radio devices (22) are operated in two or more ad-hoc networks or pico-networks (19, 20, 21) that share frequency-hopping channel and time slots that may collide. The frequency hopping sequences (54) of two or more masters (25) are exchanged using identity codes, permitting the devices to anticipate collision time slots (52). Priorities are assigned to the simultaneously operating piconets (19, 20, 21) during collision slots (52), e.g., as a function of their message queue size or latency, or other factors. Lower priority devices may abstain from transmitting during predicted collision slots (52), and / or a higher priority device may employ enhanced transmission resources during those slots, such as higher error correction levels, or various combinations of abstinence and error correction may be applied. Collisions are avoided or the higher priority piconet (19, 20, 21) is made likely to prevail in a collision.
Owner:GOOGLE TECH HLDG LLC +1
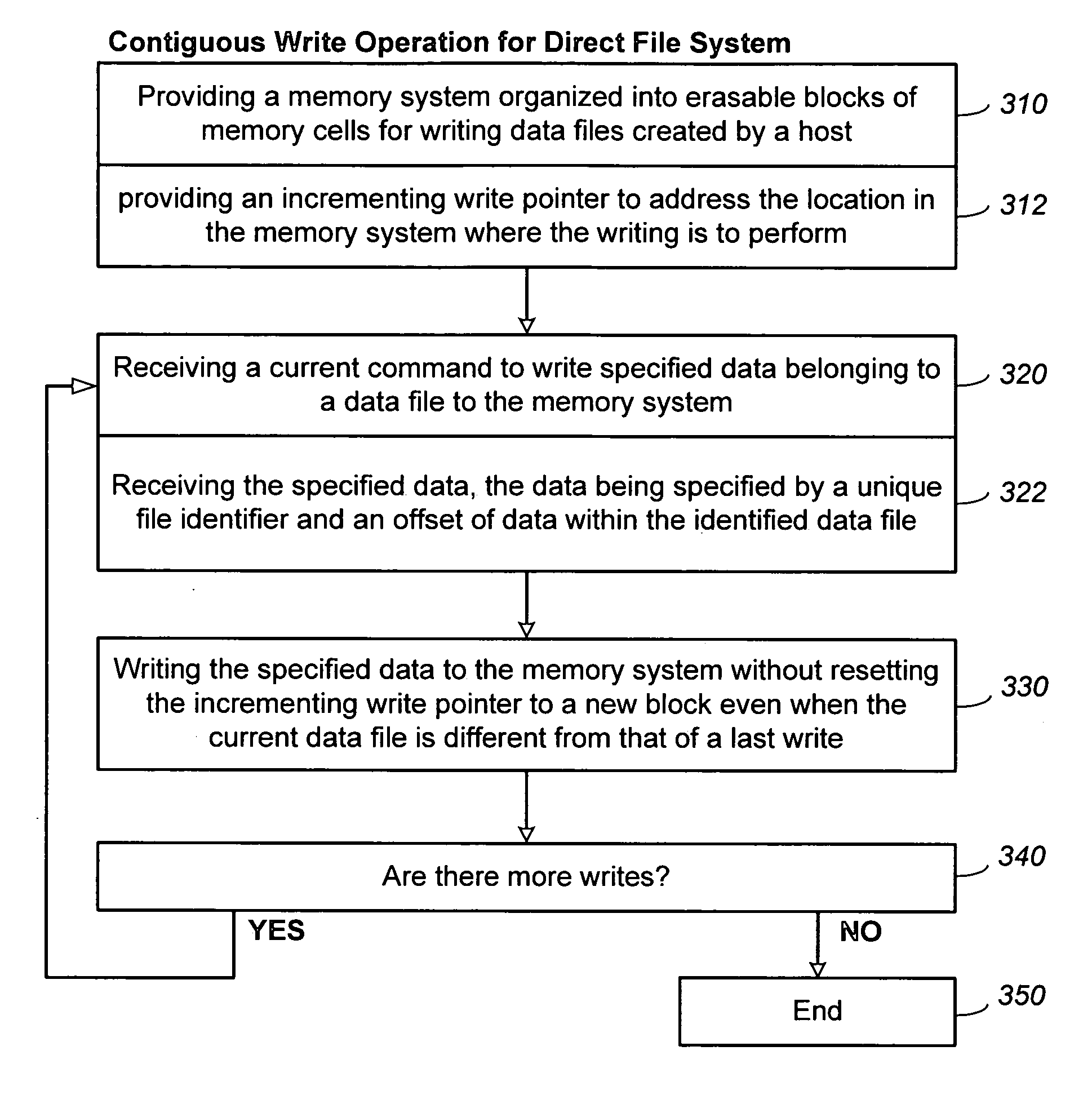
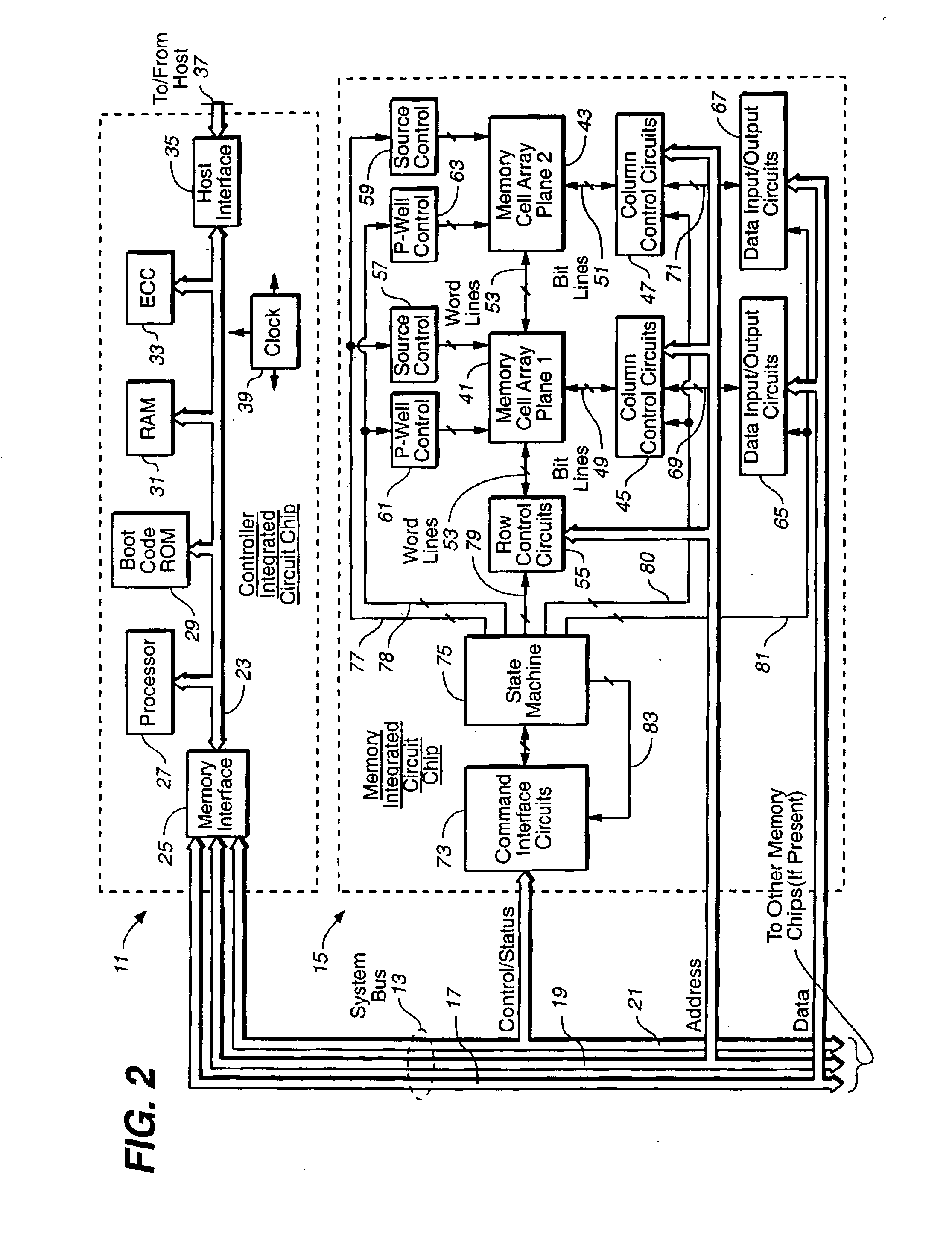
Methods for adaptive file data handling in non-volatile memories with a directly mapped file storage system
InactiveUS20070143561A1Promote high performanceImprove performanceMemory systemsData compressionWaste collection
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
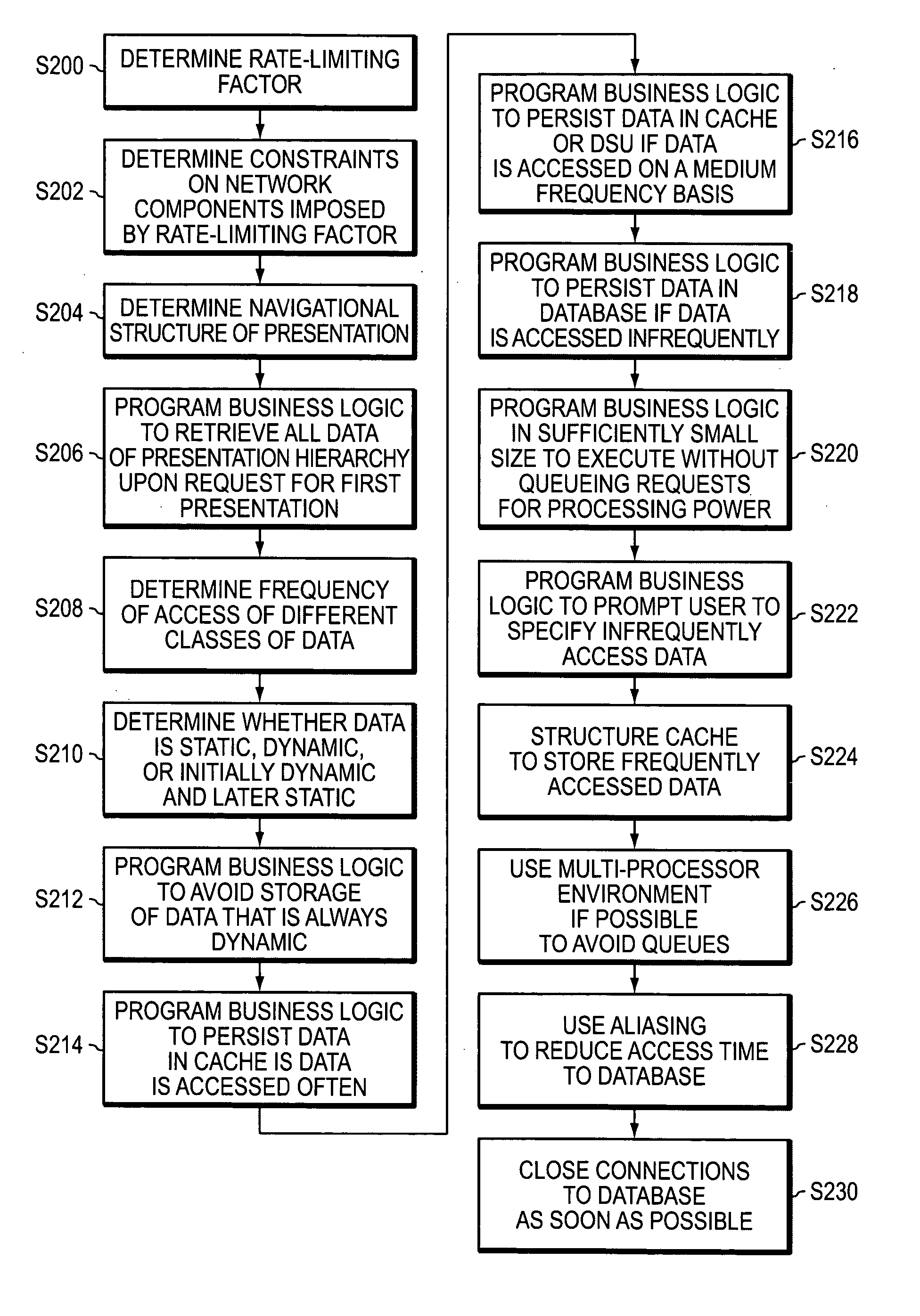
Methods, apparatuses, systems, and articles for determining and implementing an efficient computer network architecture
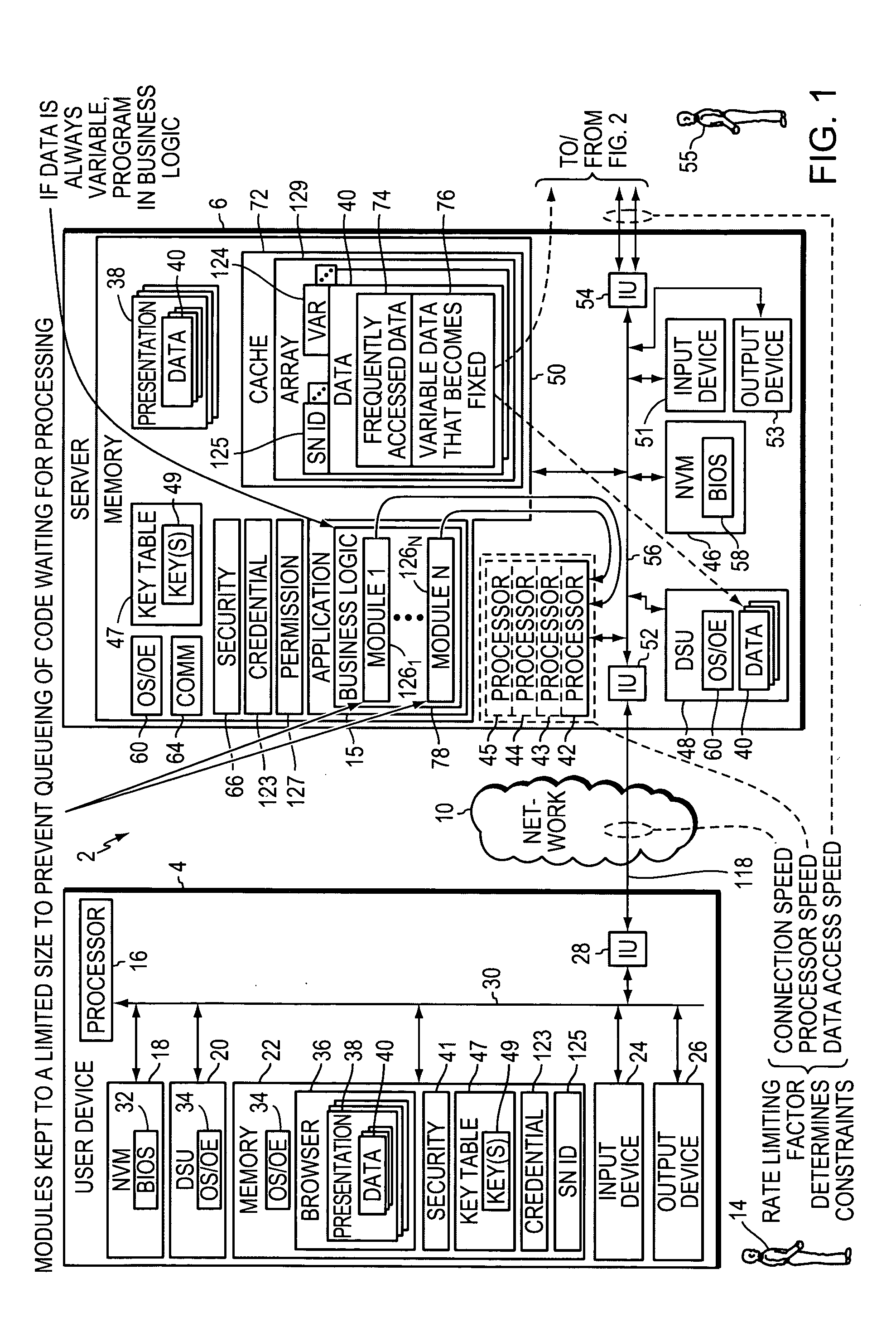
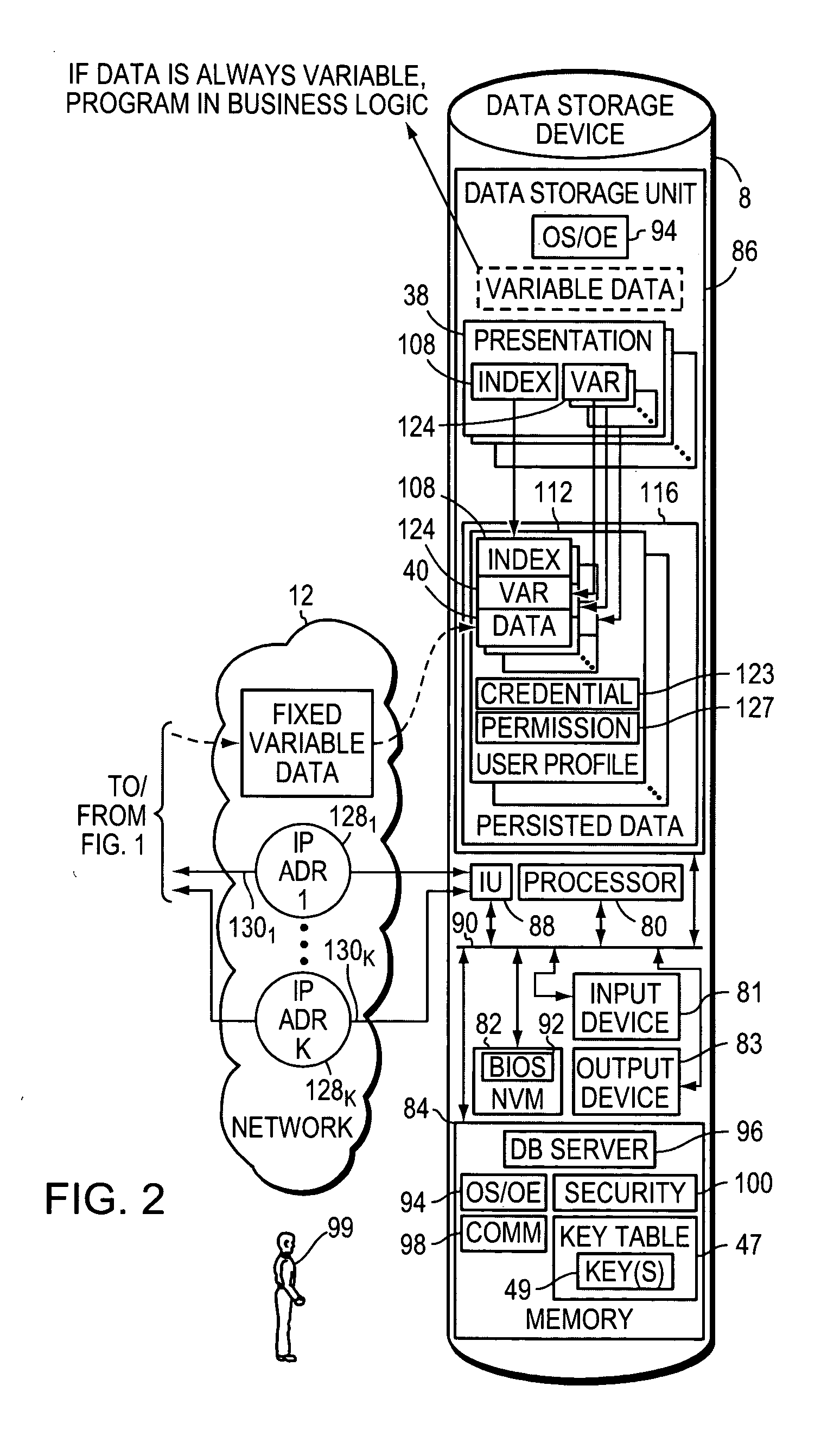
InactiveUS20050138198A1Reduce system performanceAvoid queuingMultiple digital computer combinationsTransmissionRate limitingNetwork architecture
Methods, apparatuses, systems, and articles of the invention are used to enhance the efficiency of a computing environment, and to improve its responsiveness to one or more users. In the invention, queuing of data or computer instructions is avoided since this would detract from best case performance for a network environment. The rate-limiting factor for the network is determined, and all constraints imposed by the rate-limiting factor are determined. Business logic is programmed in modules sufficiently small to avoid queuing of instructions. Data is stored by frequency of access and persistence to increase responsiveness to user requests. Requests for data from a data storage device are fulfilled not only with the requested data, but also additional data which is likely to be requested in the navigational hierarchy of presentations to which the requested data belongs.
Owner:IT WORKS
Non-volatile memories with adaptive file handling in a directly mapped file storage system
InactiveUS20070143378A1Promote high performanceImprove performanceMemory architecture accessing/allocationSpecial data processing applicationsData compressionAccess frequency
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
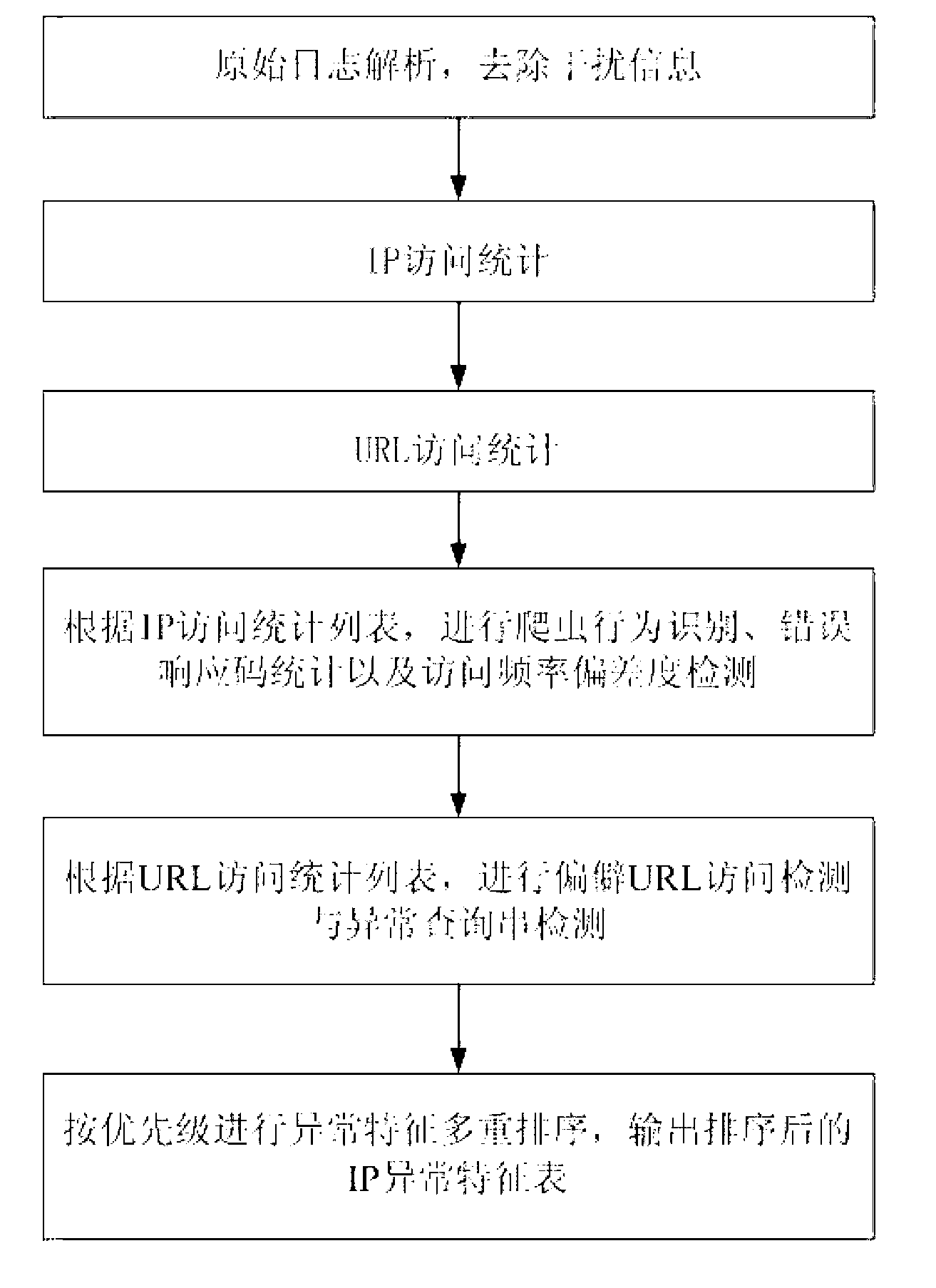
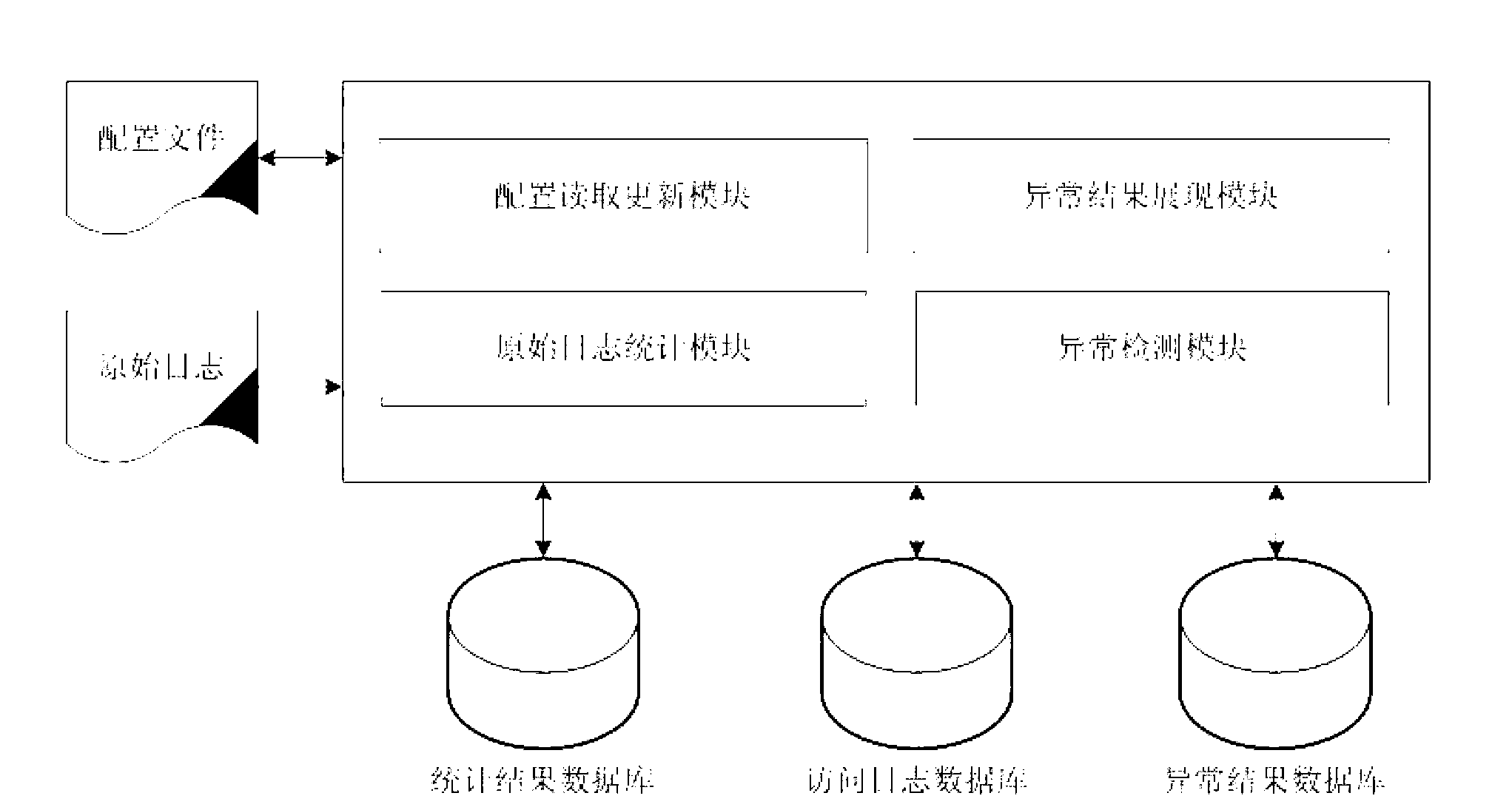
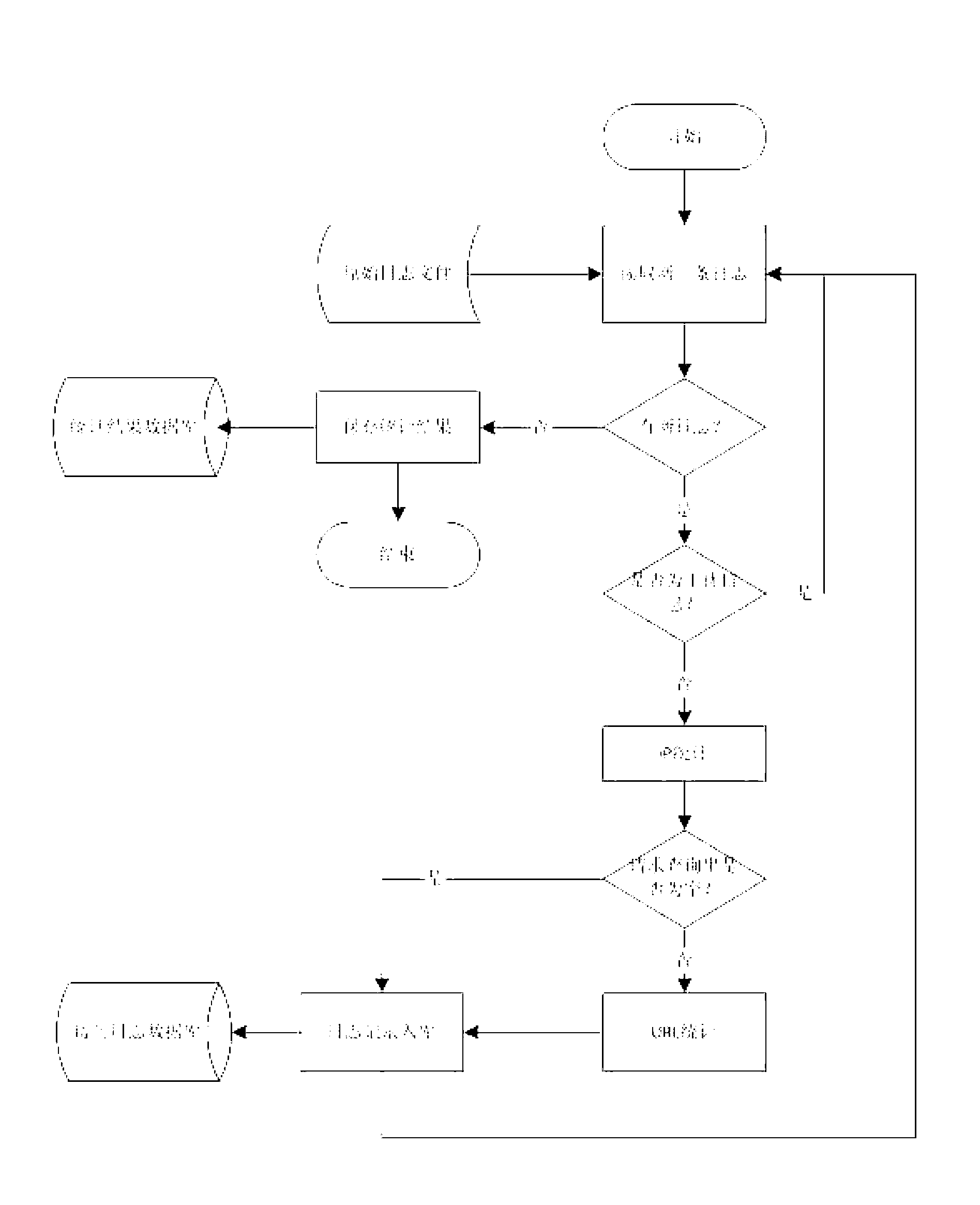
Abnormal access behavior detection method and system on basis of WEB logs
The invention relates to an abnormal access behavior detection method on the basis of WEB logs. The abnormal access behavior detection method includes steps of 1) performing IP(internet protocol) access statistics and URL access statistics after removing interference information by analyzing WEB raw logs so as to acquire an IP access statistic list and a URL access statistic list, 2) according to the IP access statistic list, performing crawler behavior characteristic recognition, error response code statistics and access frequency deviation degree detection while updating IP abnormal characteristic list, and 3) sequencing the abnormal characteristics in the IP abnormal characteristic list according to a set order of precedence, and outputting the sequenced IP abnormal characteristic list to obtain abnormal access results. By the abnormal access behavior detection method, an access model is built with no depending on history access data, abnormal access is checked by lateral comparison, and abnormal parameter detection is performed by voting and referring query strings.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Wireless device and communication method
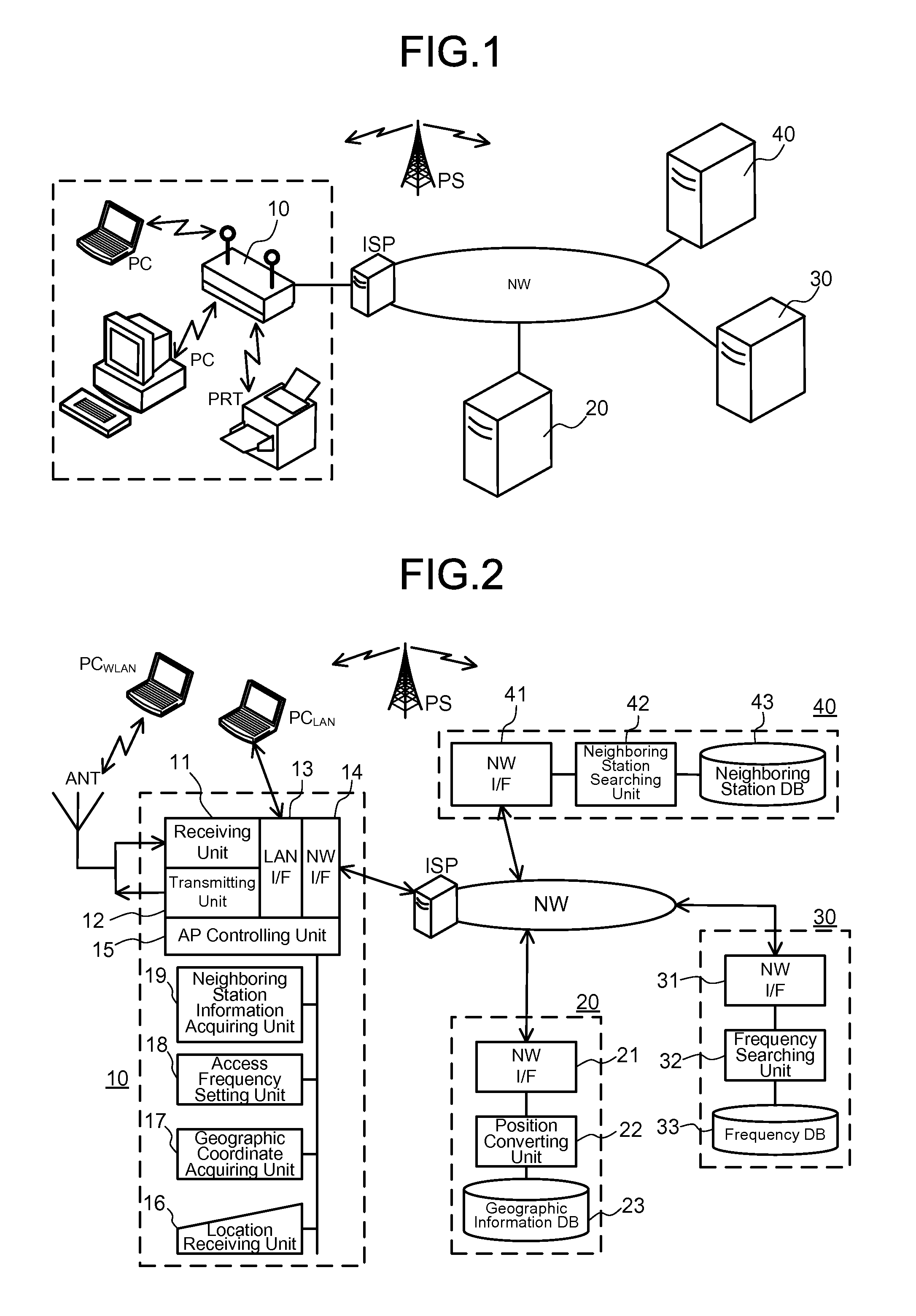
A wireless device and a communication method, which enable a position of the wireless device to be known and enable a frequency which does not interfere with that of another wireless station to be selected, are provided. A wireless device belonging to a second wireless system in which a frequency band to be used overlaps with that of a first wireless system, and a priority with which the overlapping frequency band is used is lower than that of the first wireless system, the wireless device includes: a location receiving unit receiving location information formed of a place name and indicating a location of the wireless device; a geographic coordinate acquiring unit acquiring, based on the location information, geographic coordinates including latitude and longitude corresponding to the location information; and a frequency setting unit accessing a frequency server in which a frequency assigned to a wireless device belonging to the first wireless system and geographic coordinates including latitude and longitude related to a position of the wireless device are stored by being corresponded to each other, by using the geographic coordinates acquired by the geographic coordinate acquiring unit, and acquiring at least one of a frequency that is not assigned to the wireless device belonging to the first wireless system and a frequency which is not at risk of interfering with that of the wireless device, to set the frequency as a transmission / reception frequency.
Owner:NAT INST OF INFORMATION & COMM TECH
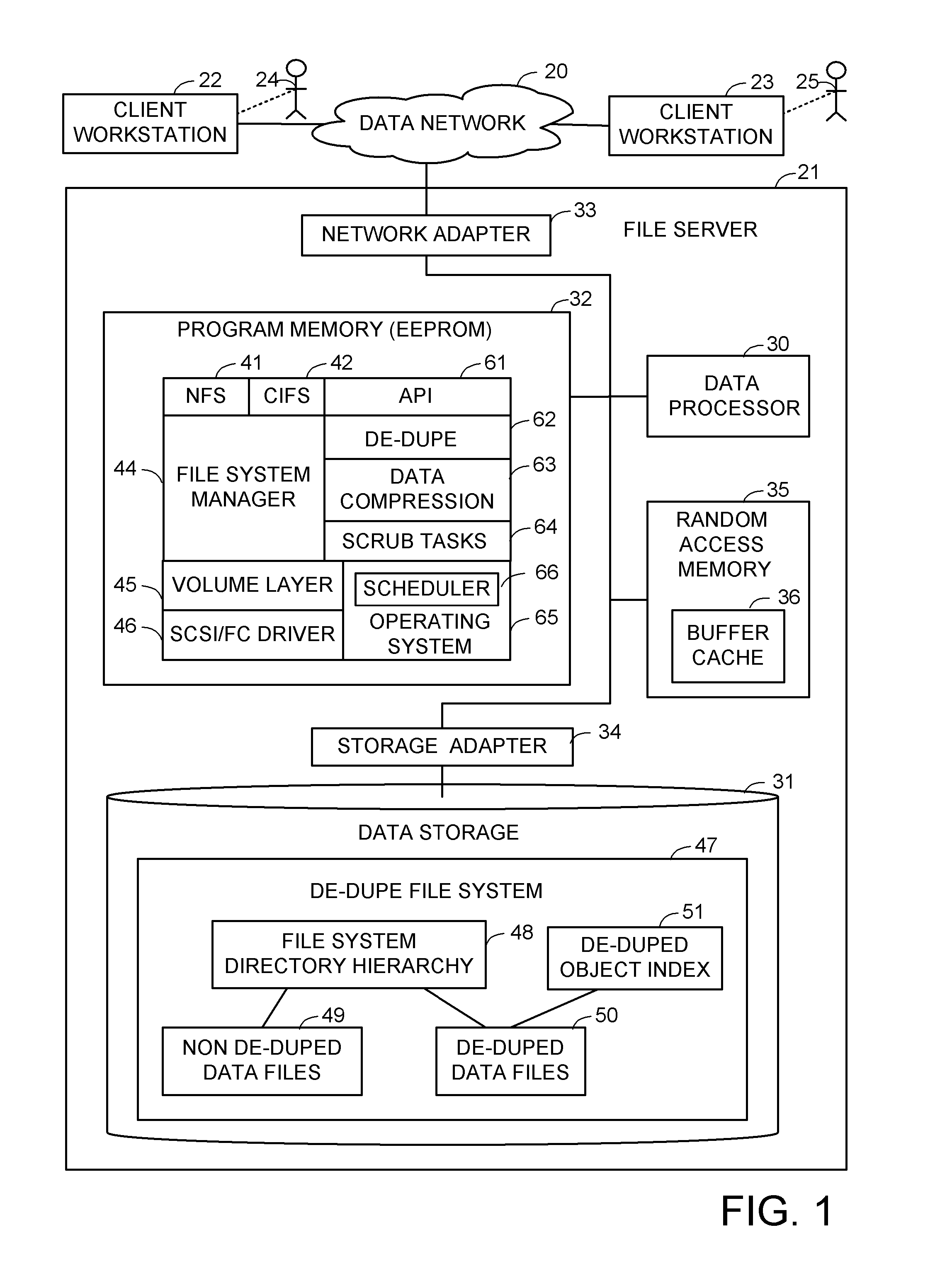
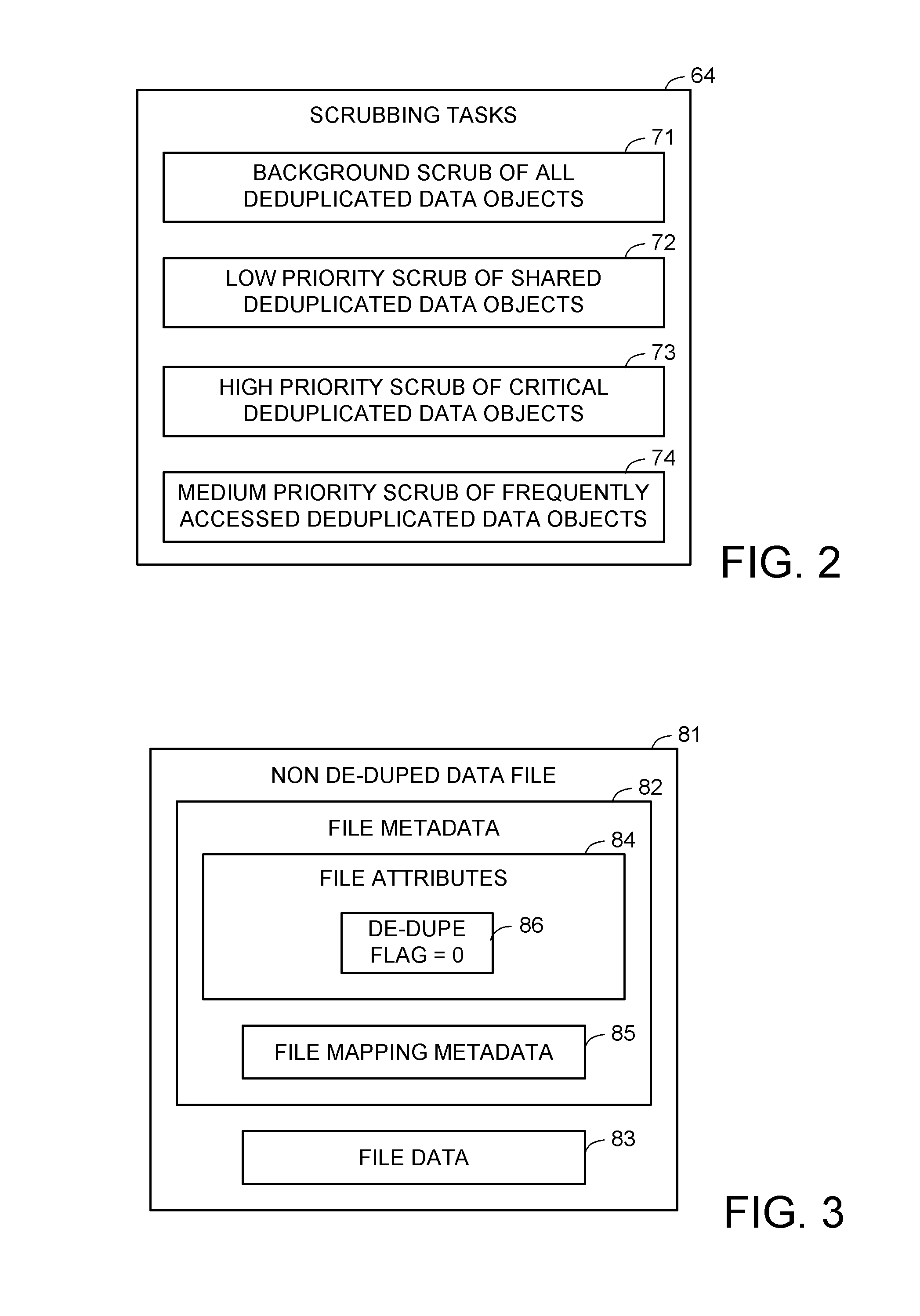
Priority based data scrubbing on a deduplicated data store
ActiveUS8407191B1Digital data information retrievalDigital data processing detailsAccess frequencyData store
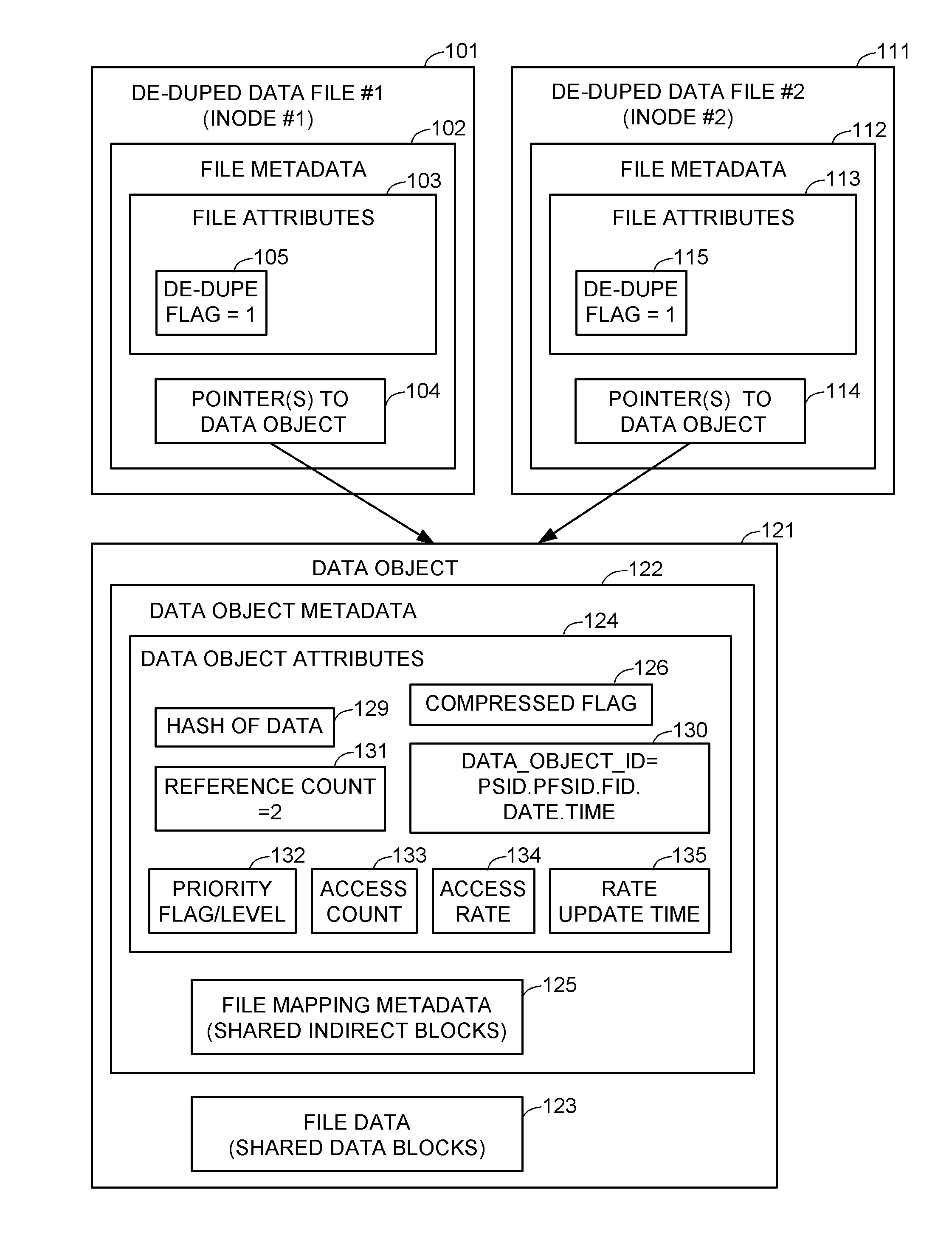
Deduplicated data objects are scrubbed by a executing a priority scrubbing task that scans the deduplicated data objects and applies a condition that enables priority data scrubbing based on the value of at least one attribute of the de-duplicated data objects. For example, a low priority task scrubs a deduplicated data object when a reference count of the deduplicated object reaches a threshold. A high priority task scrubs a deduplicated data object when a priority attribute indicates that the deduplicated data object is used by a critical source data object. A medium priority task scrubs a deduplicated data object when the access frequency of the deduplicated data object reaches a threshold. The condition may encode a scrubbing policy or heuristic, and may trigger further action in addition to scrubbing, such as triggering an update of the access rate.
Owner:EMC IP HLDG CO LLC
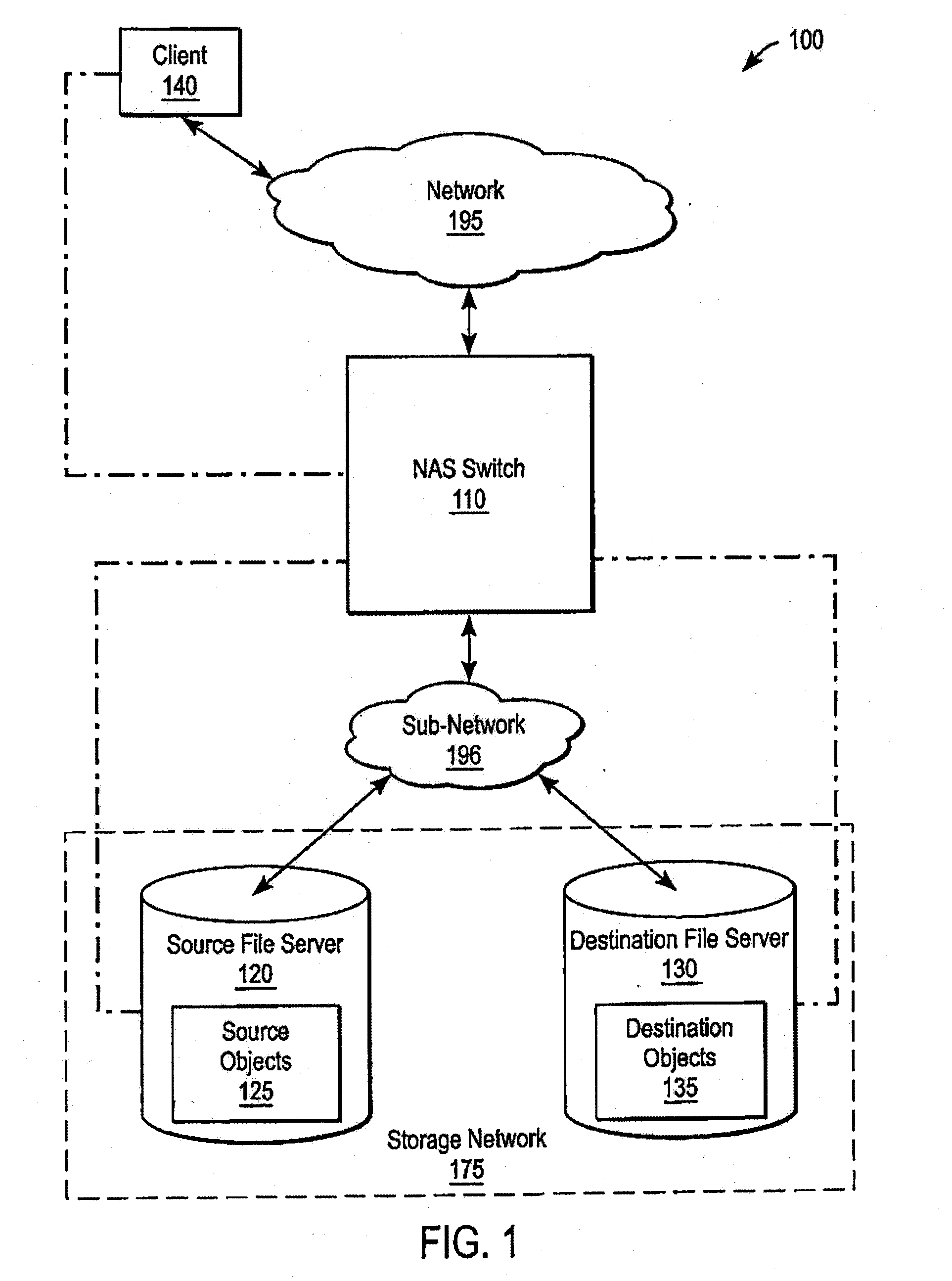
Accumulating access frequency and file attributes for supporting policy based storage management
ActiveUS20070136308A1Digital data information retrievalDigital data processing detailsAccess frequencyStorage management
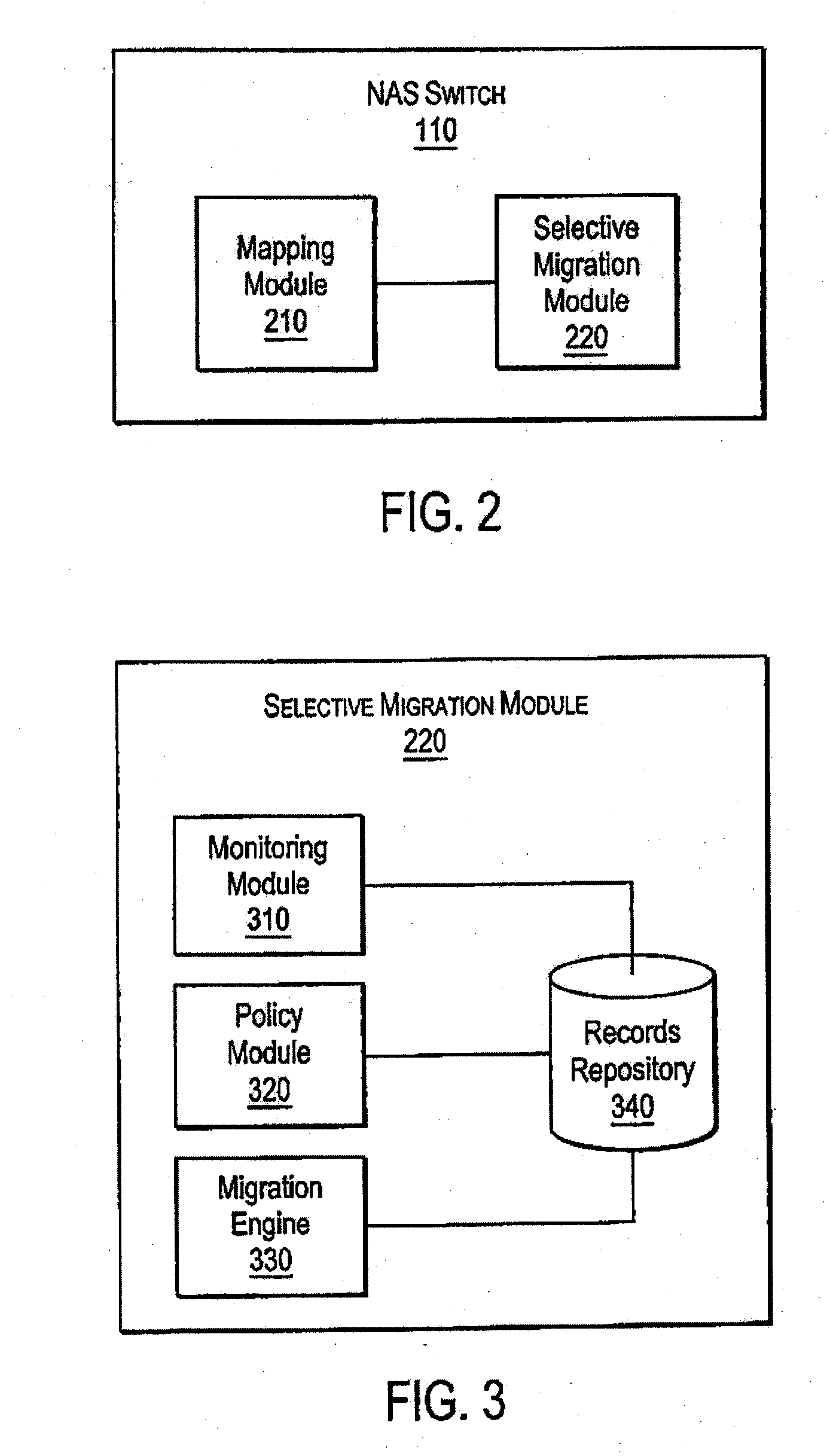
A system and method for performing policy-based storage management using data related to access frequency and file attribute accumulation. A switch device provides transparency for transactions between a client and a storage network. The transparency allows objects (e.g., files or directories) to be moved (e.g., migrated) on the storage network without affecting a reference to the object used by the client (e.g., a file handle). A monitoring module generates accumulation data associated with the transactions for use in policy-based management. The accumulation data can describe uses of the file such as how often certain files are accessed, modifications to files such as creations of new directories or files, and other uses.
Owner:CISCO TECH INC
Storage method and storage device of distributive-type file system
InactiveCN102841931AIOPS pressure equalizationImprove performanceDigital data information retrievalProgram control using stored programsAccess timeFile system
Owner:ZTE CORP
Storage apparatus and control method therefor
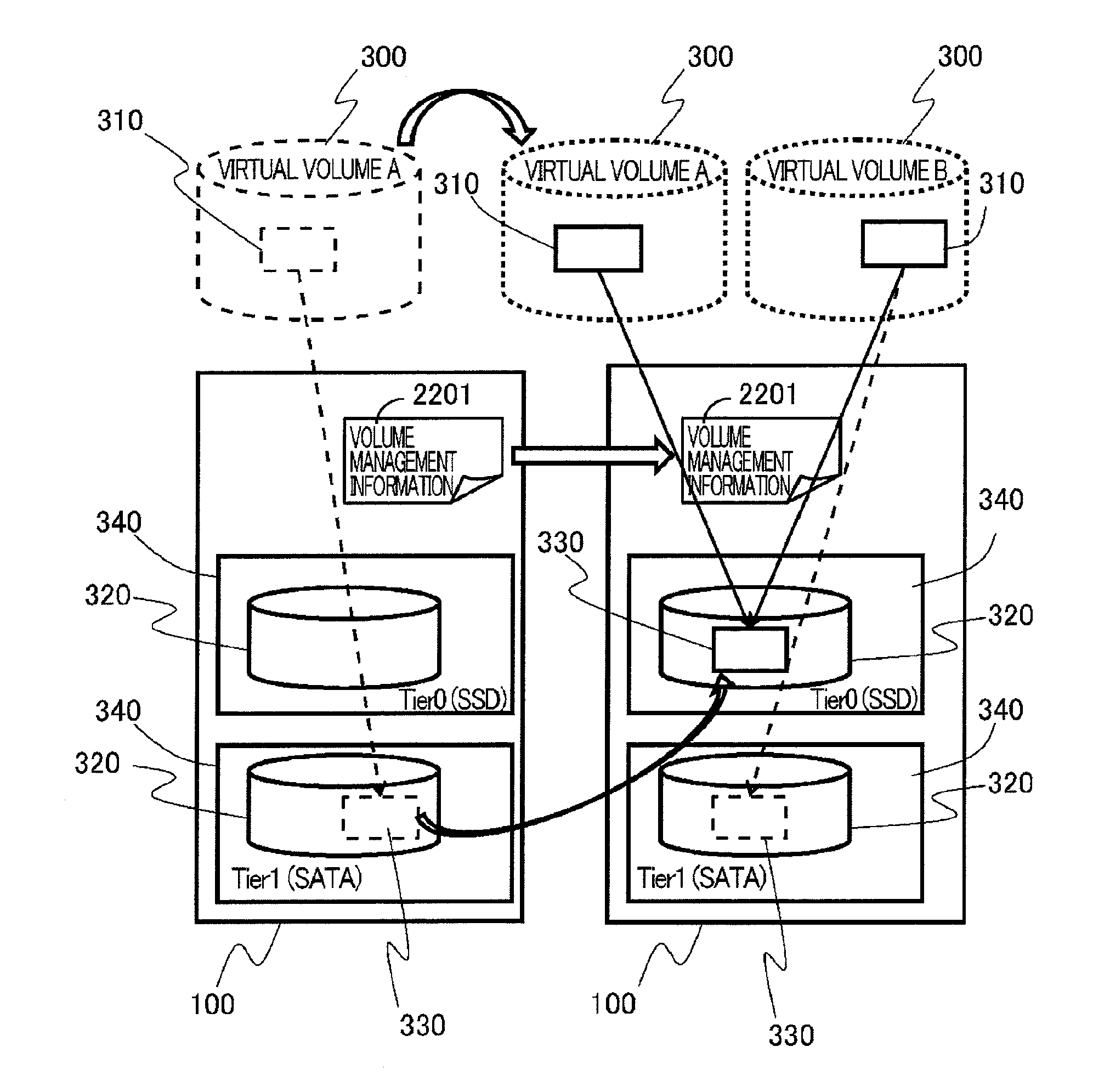
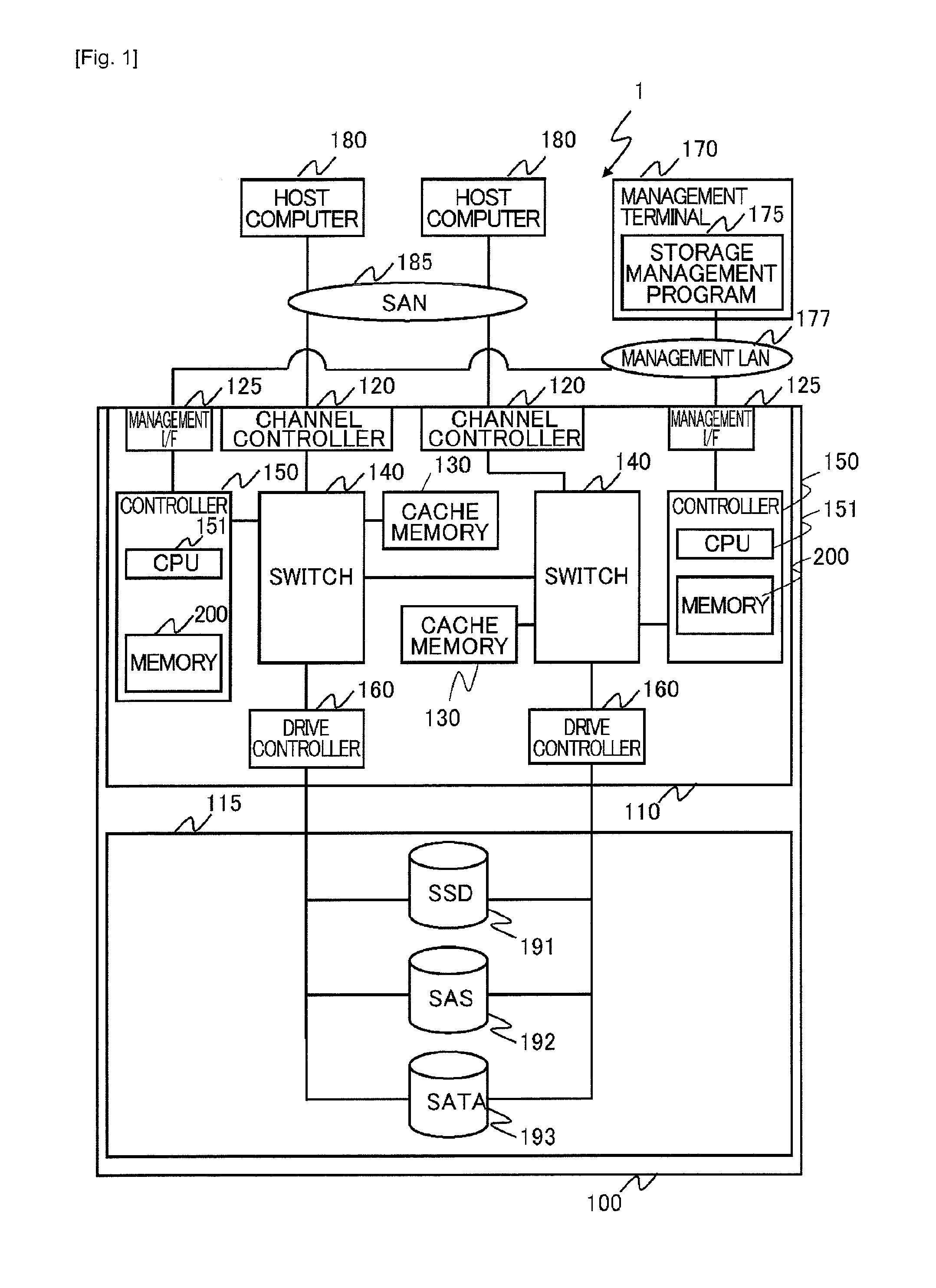
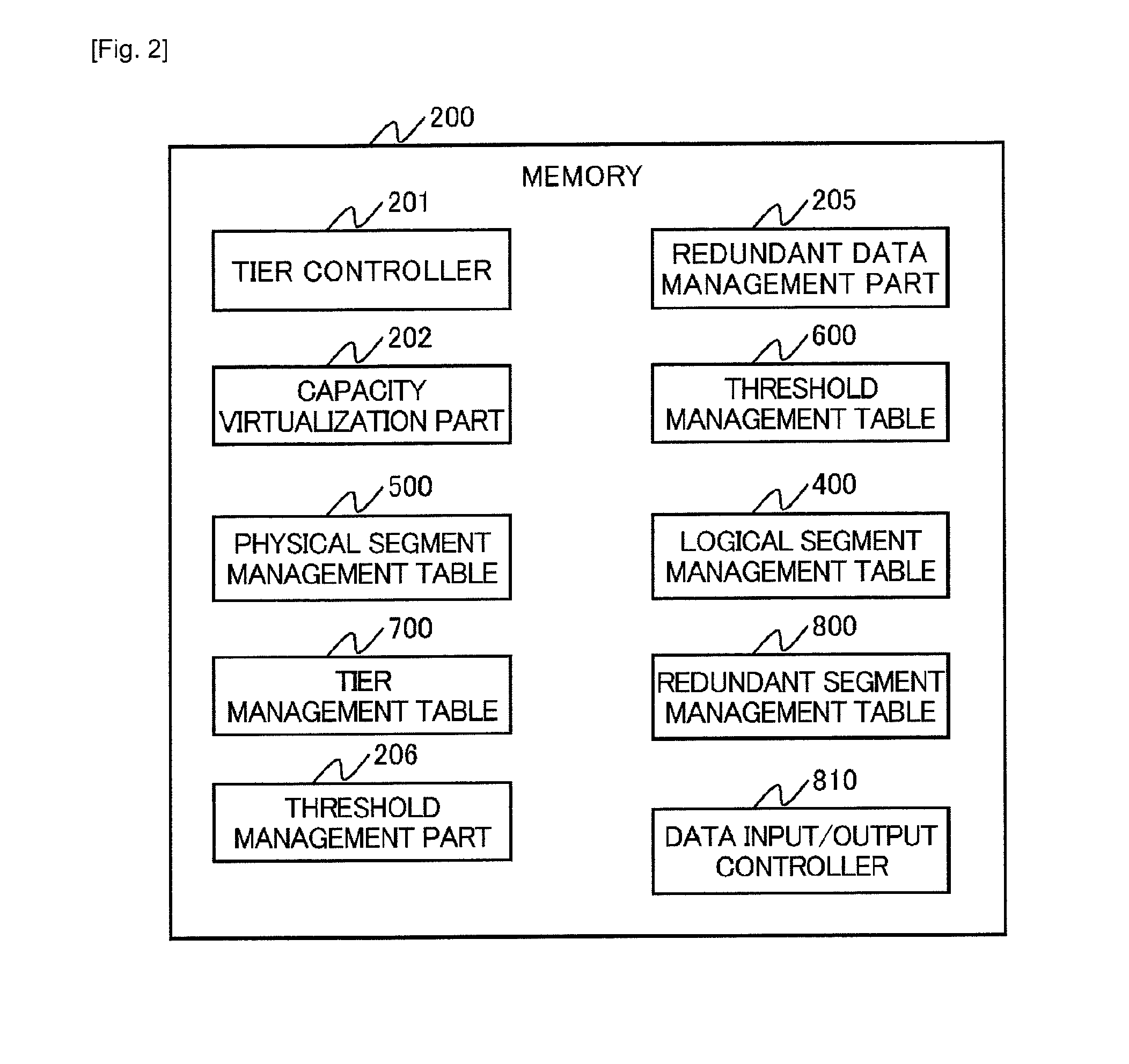
ActiveUS20120278569A1Improve production efficiencyIncreased cost-effectivenessMemory loss protectionError detection/correctionVirtualizationManagement unit
A storage apparatus providing a logical storage area for storing data to an external apparatus, includes a plurality of storage devices each providing a physical storage area for storing the data, the storage devices being different from each other in device property including data input / output performance, a capacity virtualization part managing the physical storage areas of the storage devices as unit physical storage areas each having a predetermined storage capacity and managing the unit physical storage areas in association with a plurality of unit logical storage areas forming the logical storage area, a tier controller managing the plurality of unit physical storage areas by classifying into a plurality of tiers the unit physical storage areas provided by the storage devices having the different device properties, and a redundant data management part managing redundant unit storage areas which are a plurality of the unit physical storage areas storing the same data. The data migration between the tiers is controlled according to, for example, an access frequency to the data from the external apparatus.
Owner:HITACHI LTD
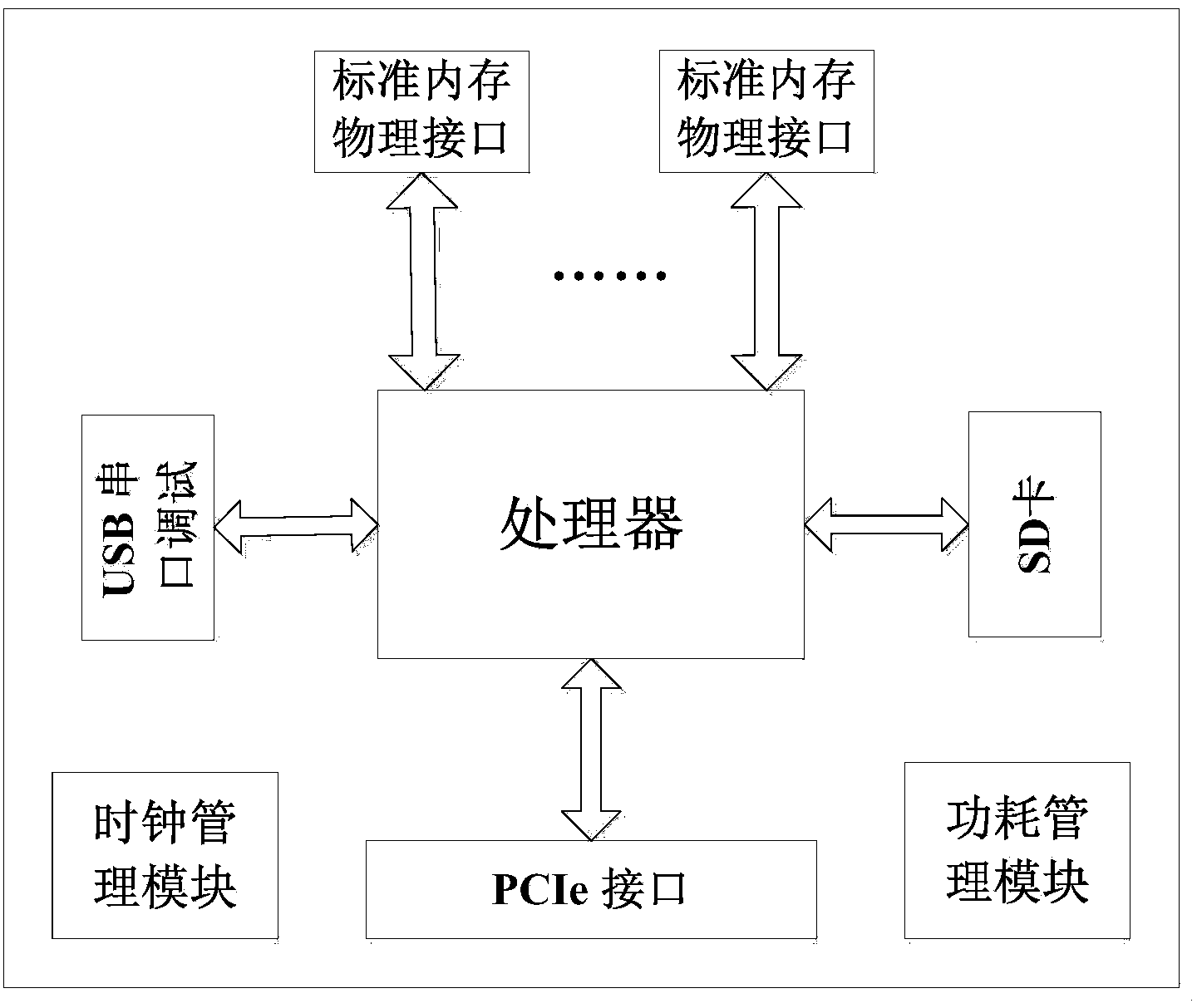
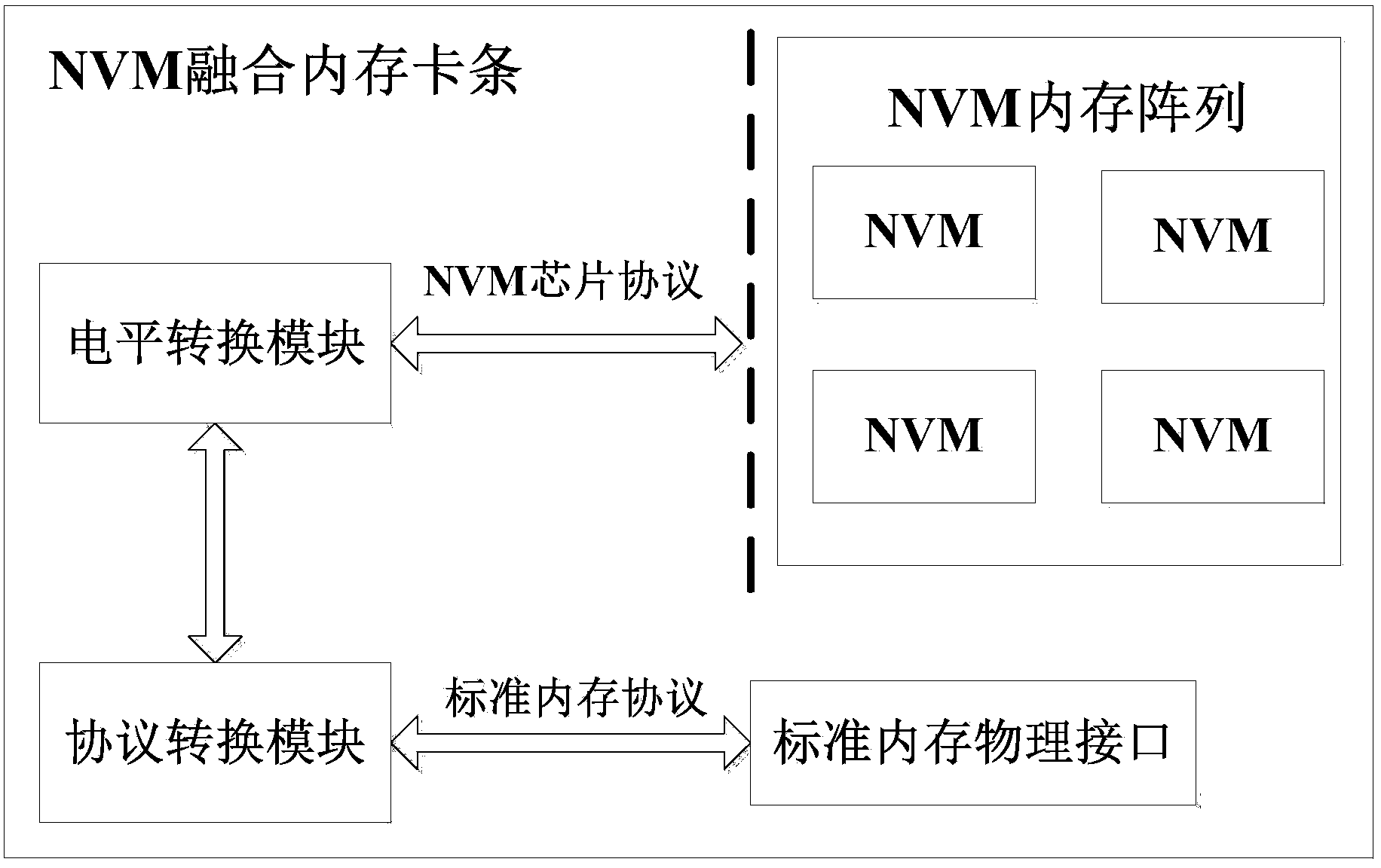
Fusion memory system of nonvolatile memory and dynamic random access memory
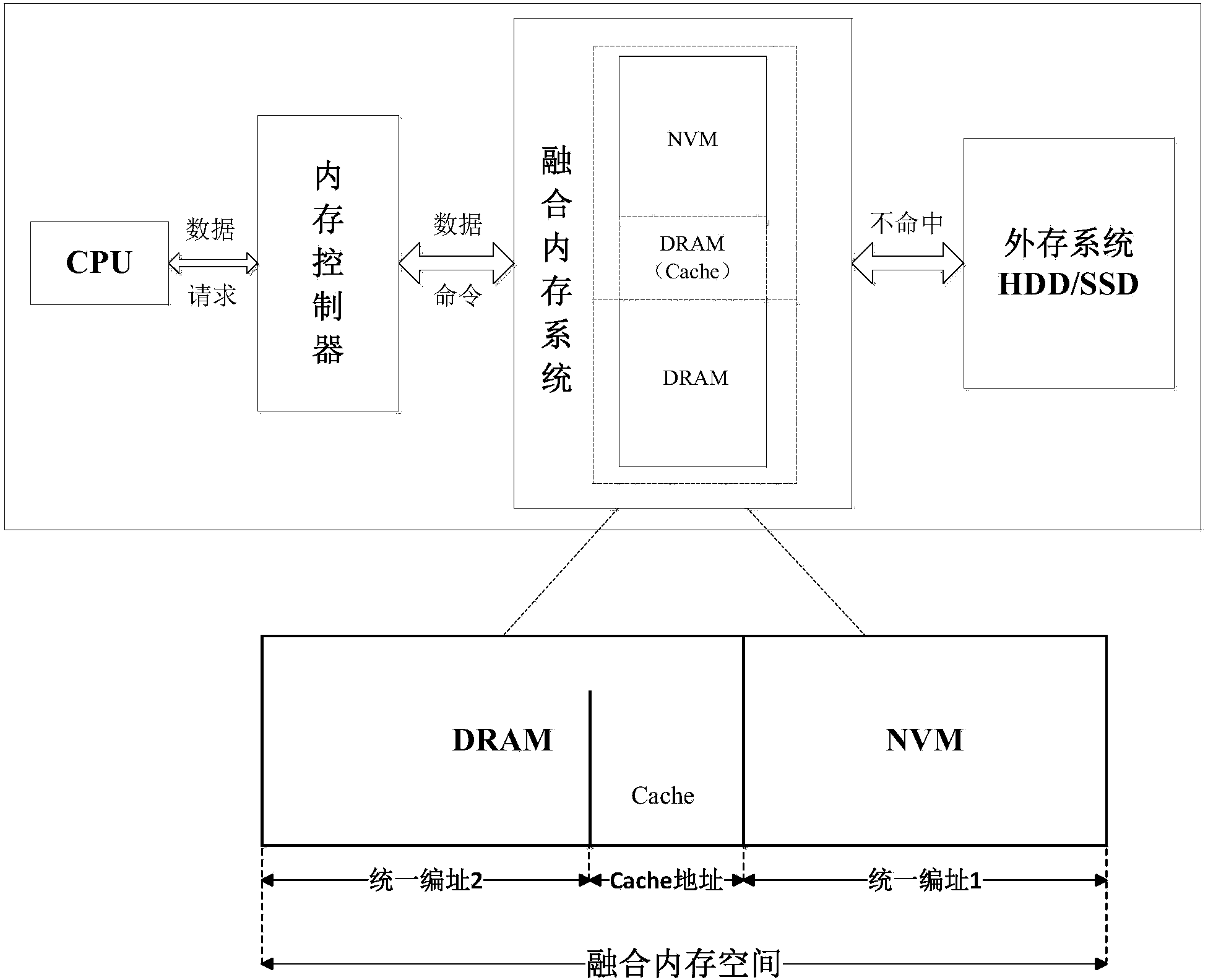
ActiveCN103810113AInput/output to record carriersMemory loss protectionStatic random-access memoryRandom access memory
The invention discloses a fusion memory system of a nonvolatile memory and a dynamic random access memory. The nonvolatile memory and the dynamic random access memory are fused together and are jointly used as a memory of a computer system for unified management, the dynamic random access memory can carry out unified addressing together with the nonvolatile memory, part capacity of the dynamic random access memory can be used as a high-speed cache of the nonvolatile memory, the capacity of cache space adapts to data load characteristics by itself and is dynamically matched, so that the access speed of the nonvolatile memory is improved, access frequency of a disk by an I / O can be lowered, and the overall performance of the computer system is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
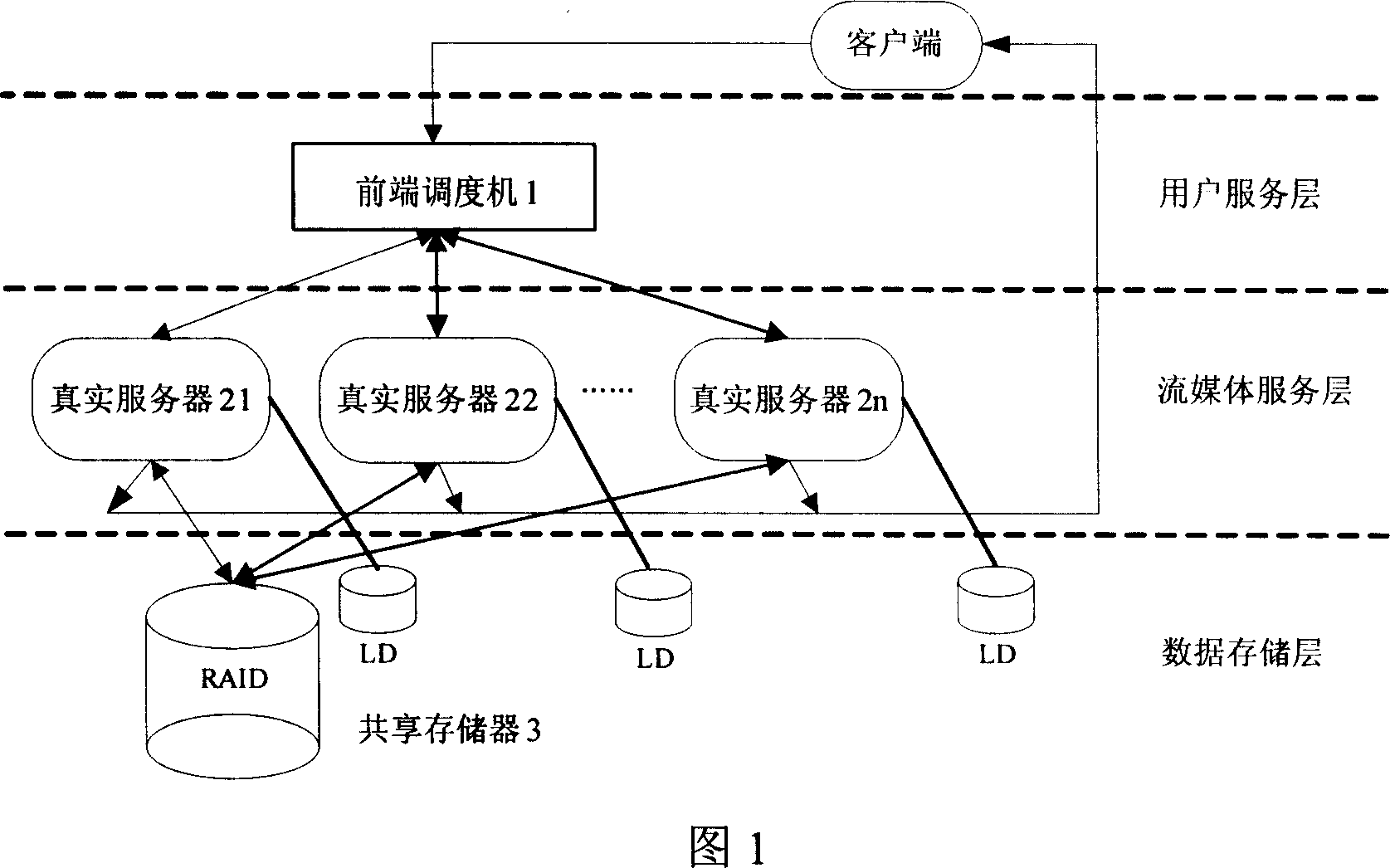
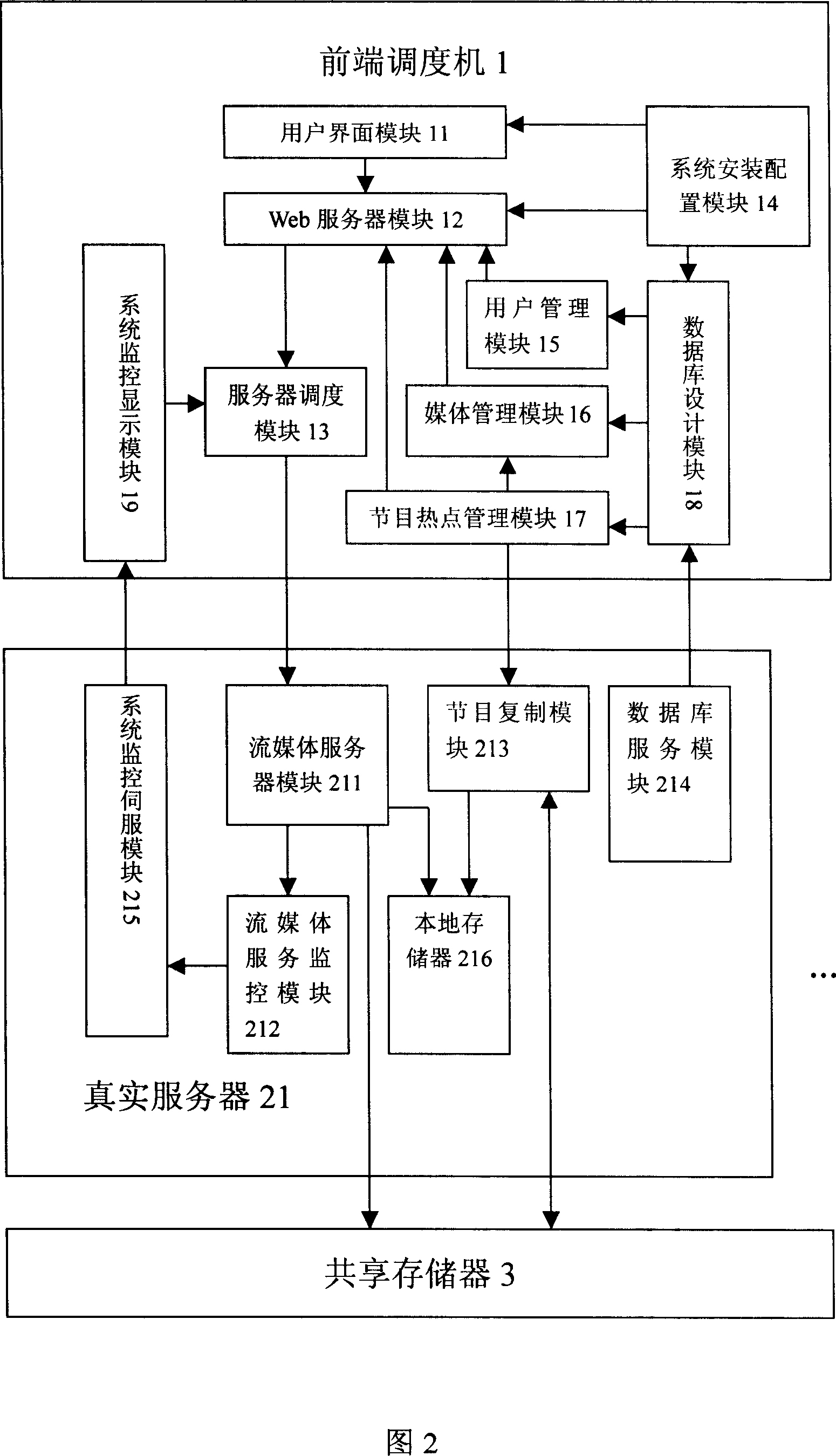
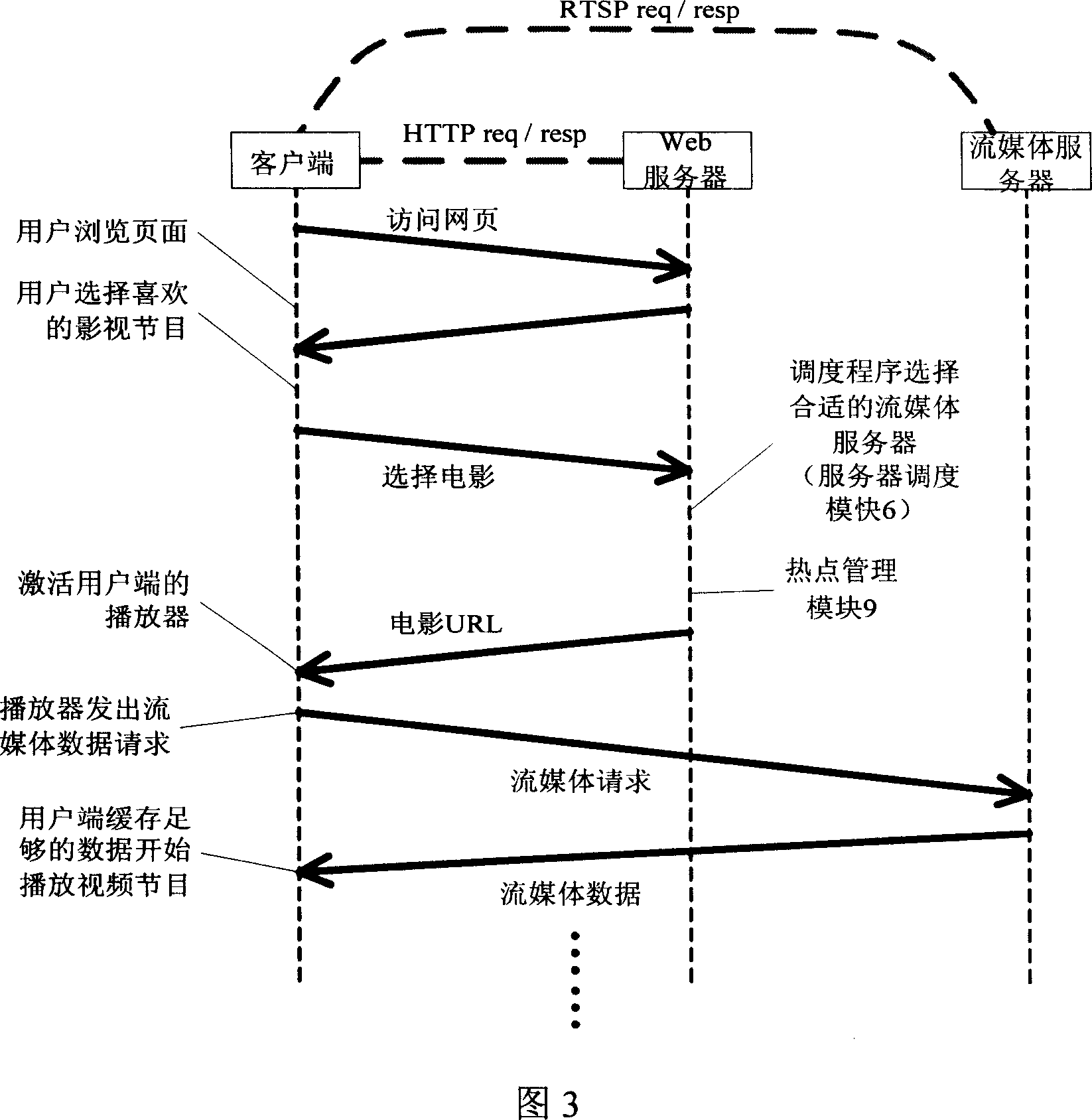
A stream media server system based on cluster balanced load
This invention relates to flow media servo system based on group balance load, which comprises front transfer machine, n real servo and common memory, wherein, the transfer machine provides user visit interacting interface and system manager entrance and selects minimum load for user according to current each real servo status; real servo receives front transfer visual frequency point require to provide media service for user and for utility rate onto local database; in system spare, according to hot video information copying information from common memory into real servo local memory.
Owner:HUAZHONG UNIV OF SCI & TECH
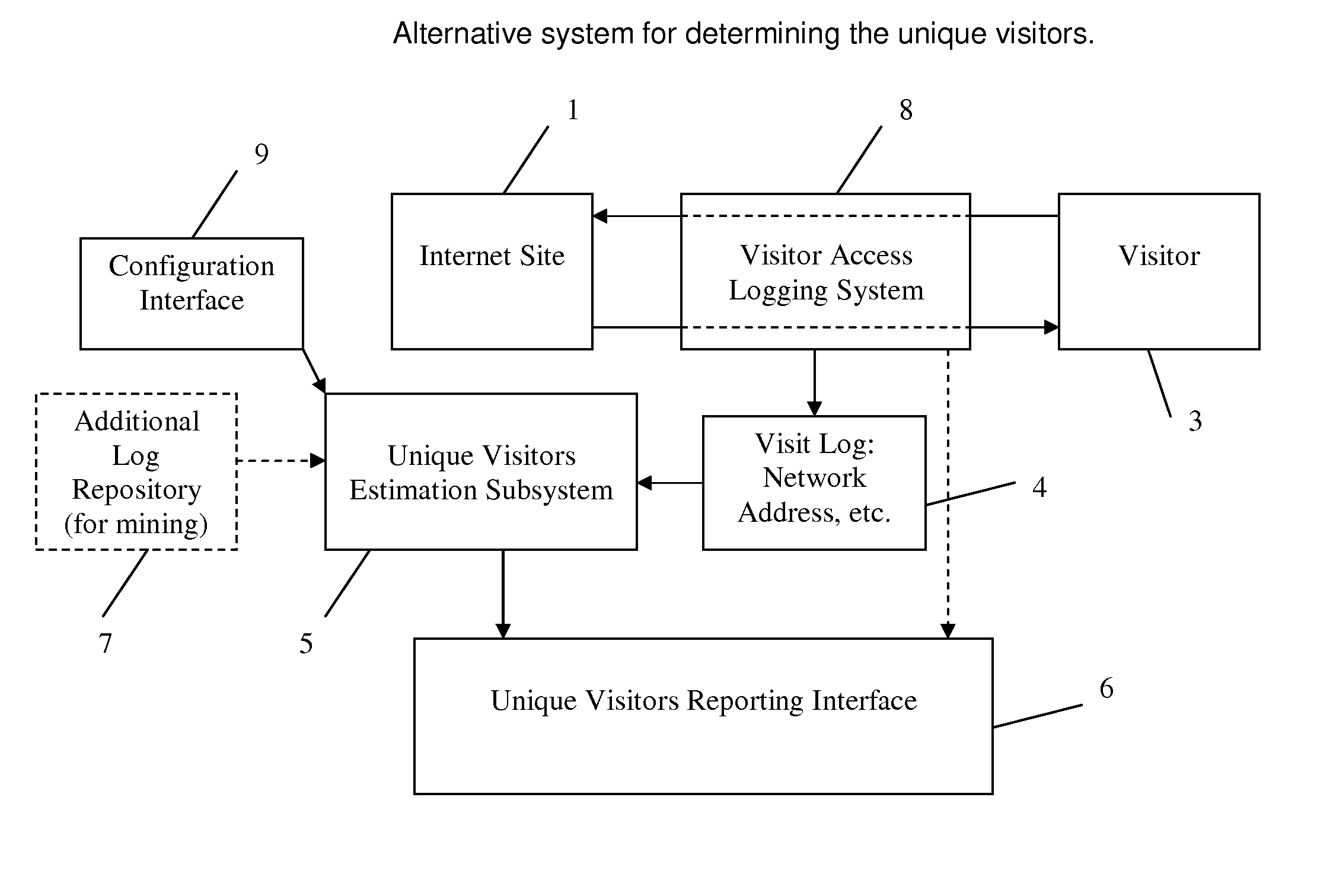
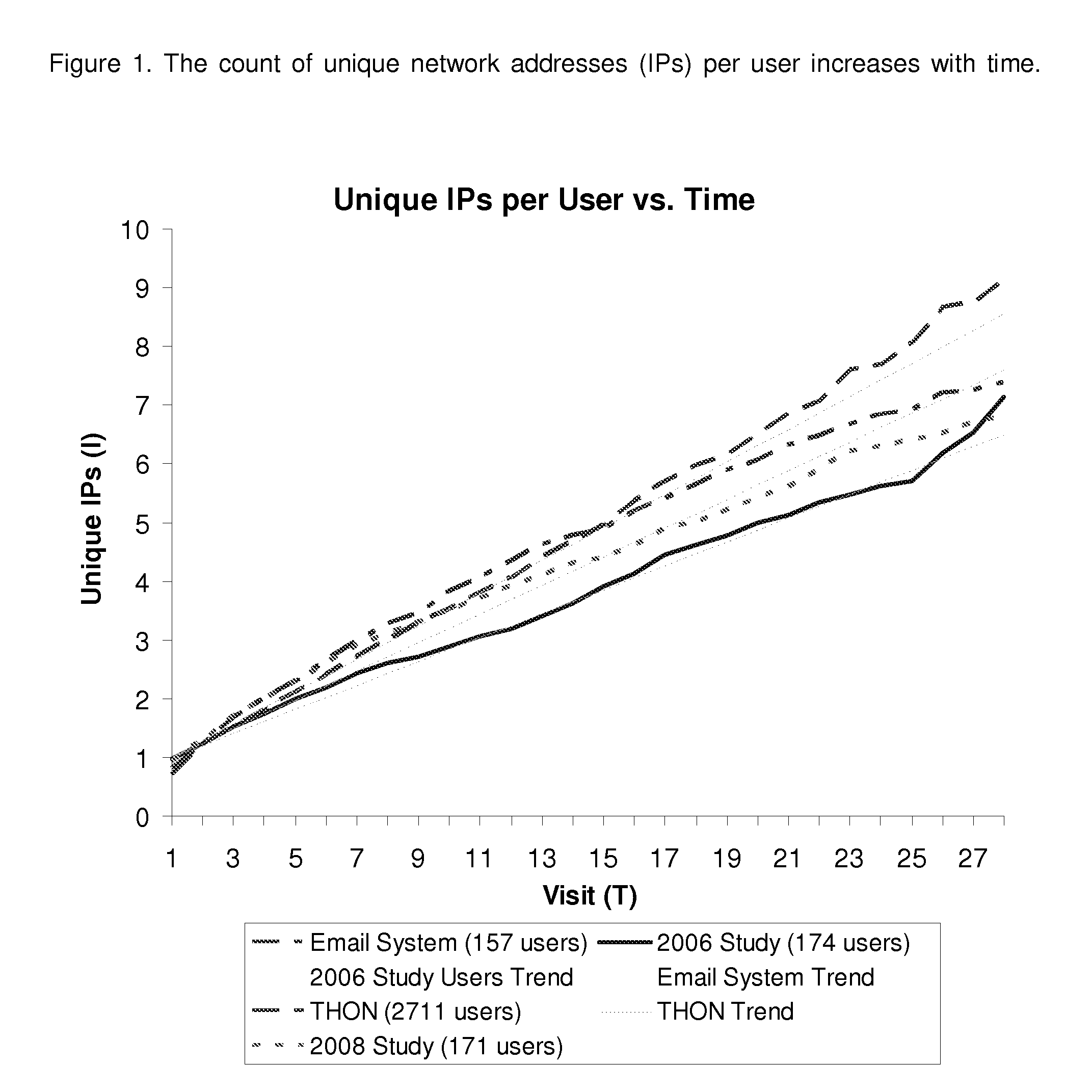
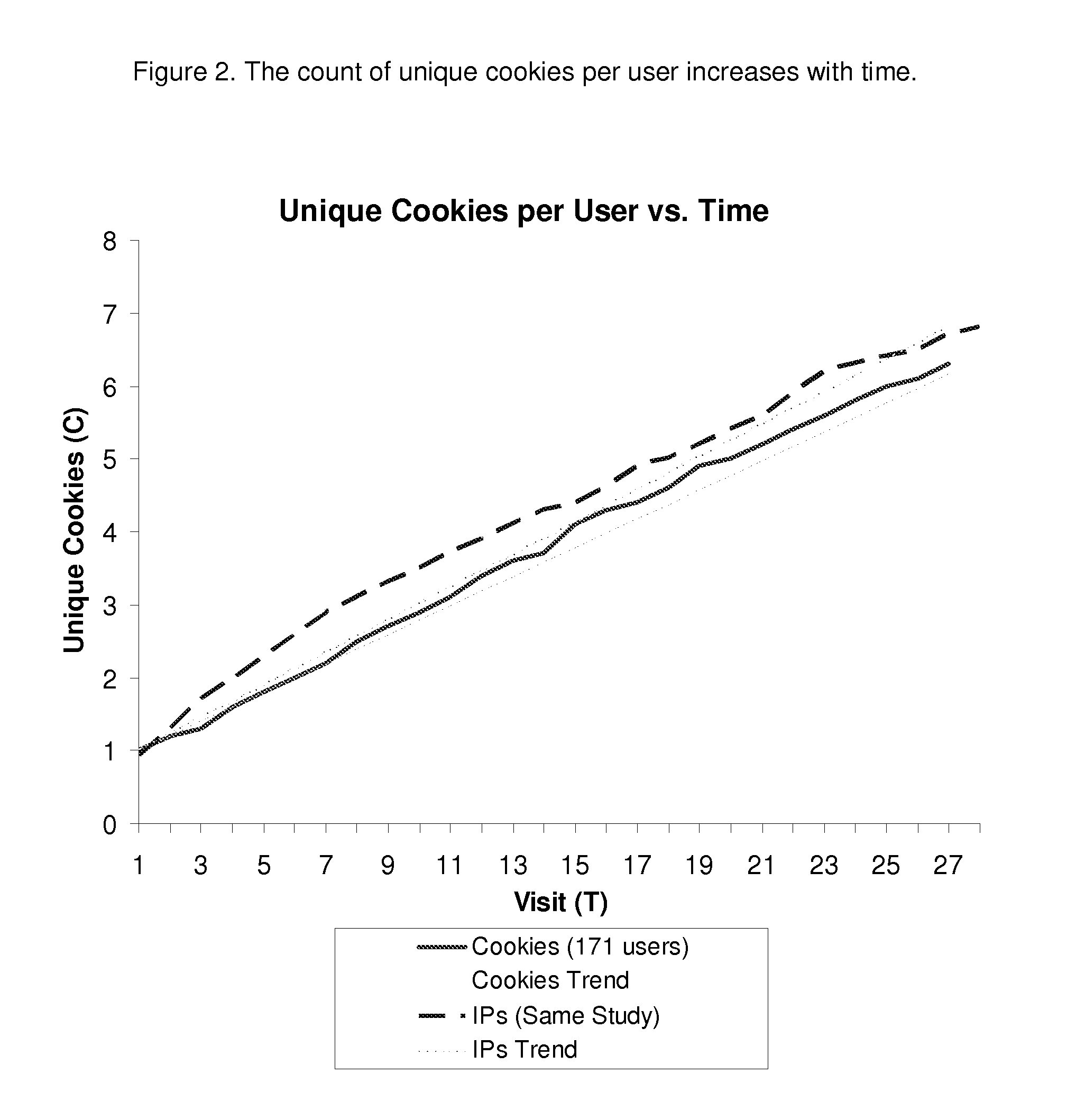
Method and System for Estimating Unique Visitors for Internet Sites
InactiveUS20100228850A1Ensure effective implementationSimplicity easeDigital computer detailsElectric testing/monitoringThird partyNetwork addressing
This invention comprises a method and system for estimating unique visitors for Internet sites that is more accurate than the existing unique cookie / unique address counting methods. The invented method relies on the count of unique user identifiers (such as network addresses or preferably cookies)—I—that can be obtained from an existing cookie tracking / user access logging system. The number of unique visitors U is calculated substantially as a ratio of the count of unique cookies (or unique network addresses) to the number of visits N times the inflation factor X plus constant on that is approximately one (exactly one in the case of cookies). The number of visits is calculated by multiplying the sampling period t to the visitation frequency T1 minus one. The resulting estimate of the unique visitors is stable and does not diverge with sampling time unlike estimates directly obtained from the unique network address or unique cookie counts. The method is also applicable when there are multiple dominant visitation frequencies by accounting to the sum by all significant visitation frequencies. All key parameters of the method can be established before hand by mining a multitude of the site's historical visit logs and / or third party site access logs; the parameters can be corrected / calculated dynamically by mining the site's current access log (or current third party logs) while focusing on unambiguously identified visitors (such as return visitors identified by their login ID or unchanged cookie value).
Owner:FOMITCHEV MAX
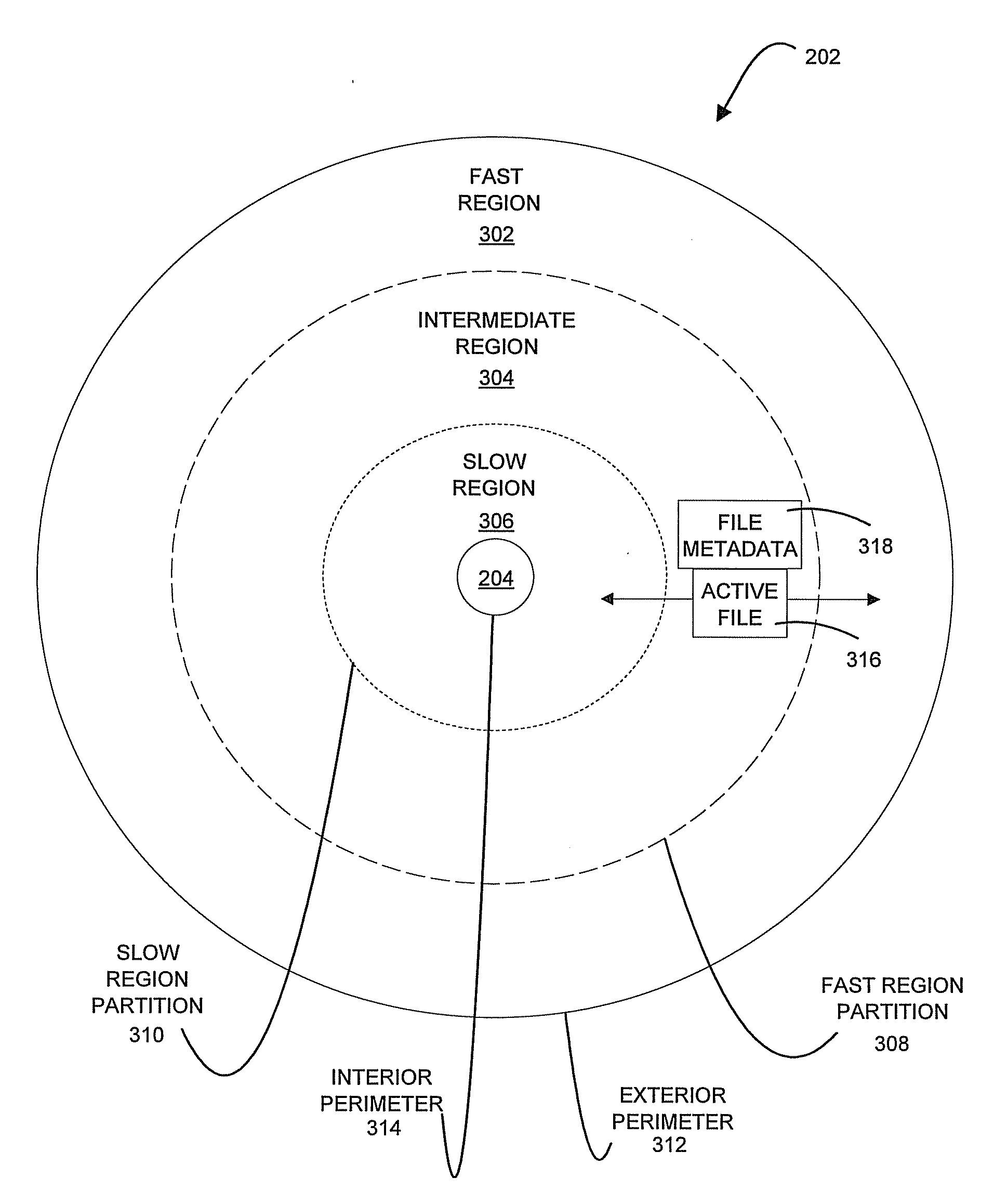
Methods, systems, and computer program products for file relocation on a data storage device
InactiveUS20090106518A1Memory adressing/allocation/relocationInput/output processes for data processingAccess frequencyData store
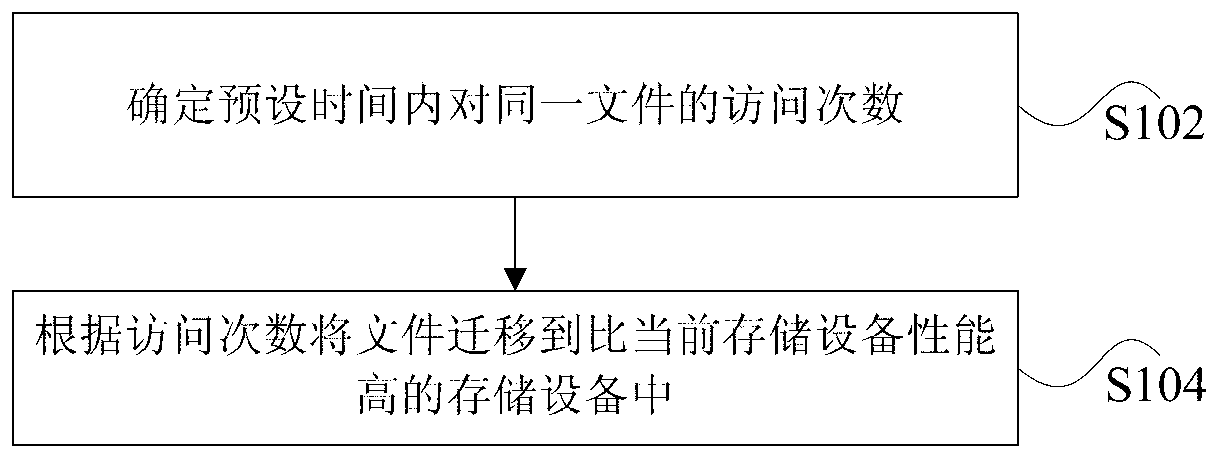
A method, system, and computer program product for file relocation on a data storage device are provided. The method includes initiating file relocation in response to invoking a cleaner function for a data storage device. The method also includes examining metadata associated with a file on the data storage device to determine an access frequency of the file, and classifying the file as a function of the access frequency. The method further includes relocating the file to a fast region of the data storage device when the file is classified as frequently accessed, and relocating the file to a slow region of the data storage device when the file is classified as infrequently accessed.
Owner:IBM CORP
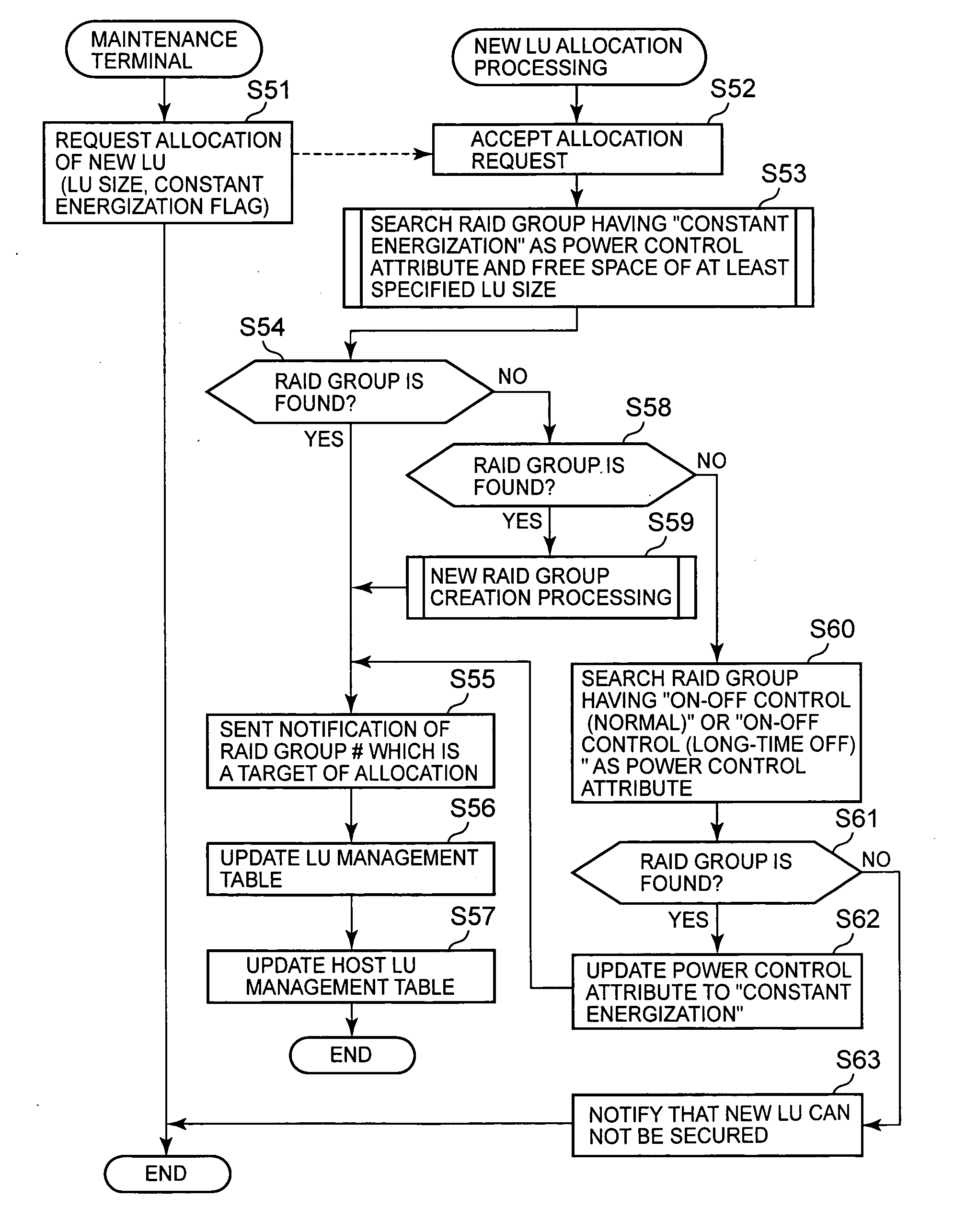
Storage controller, and method of controlling storage controller
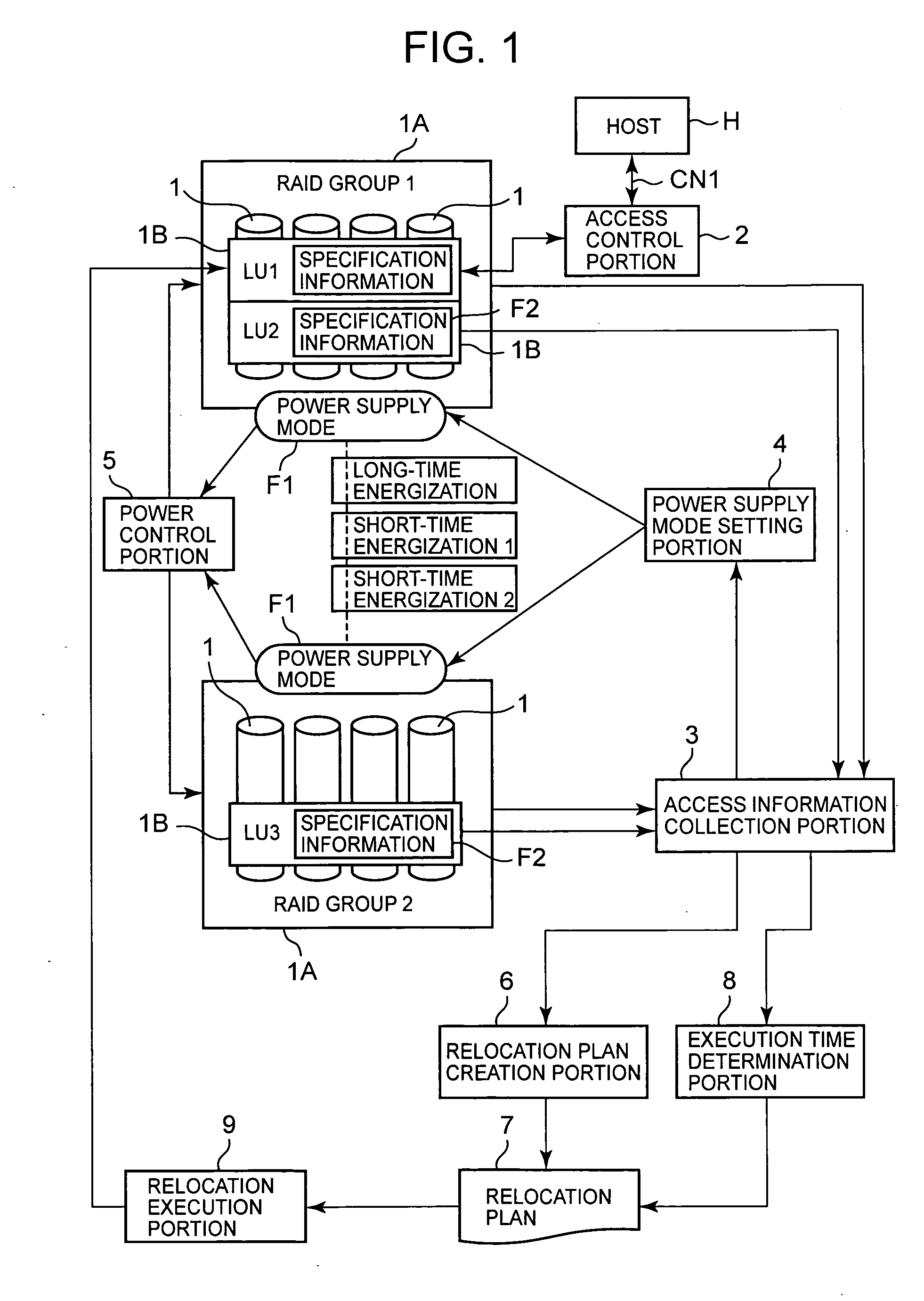
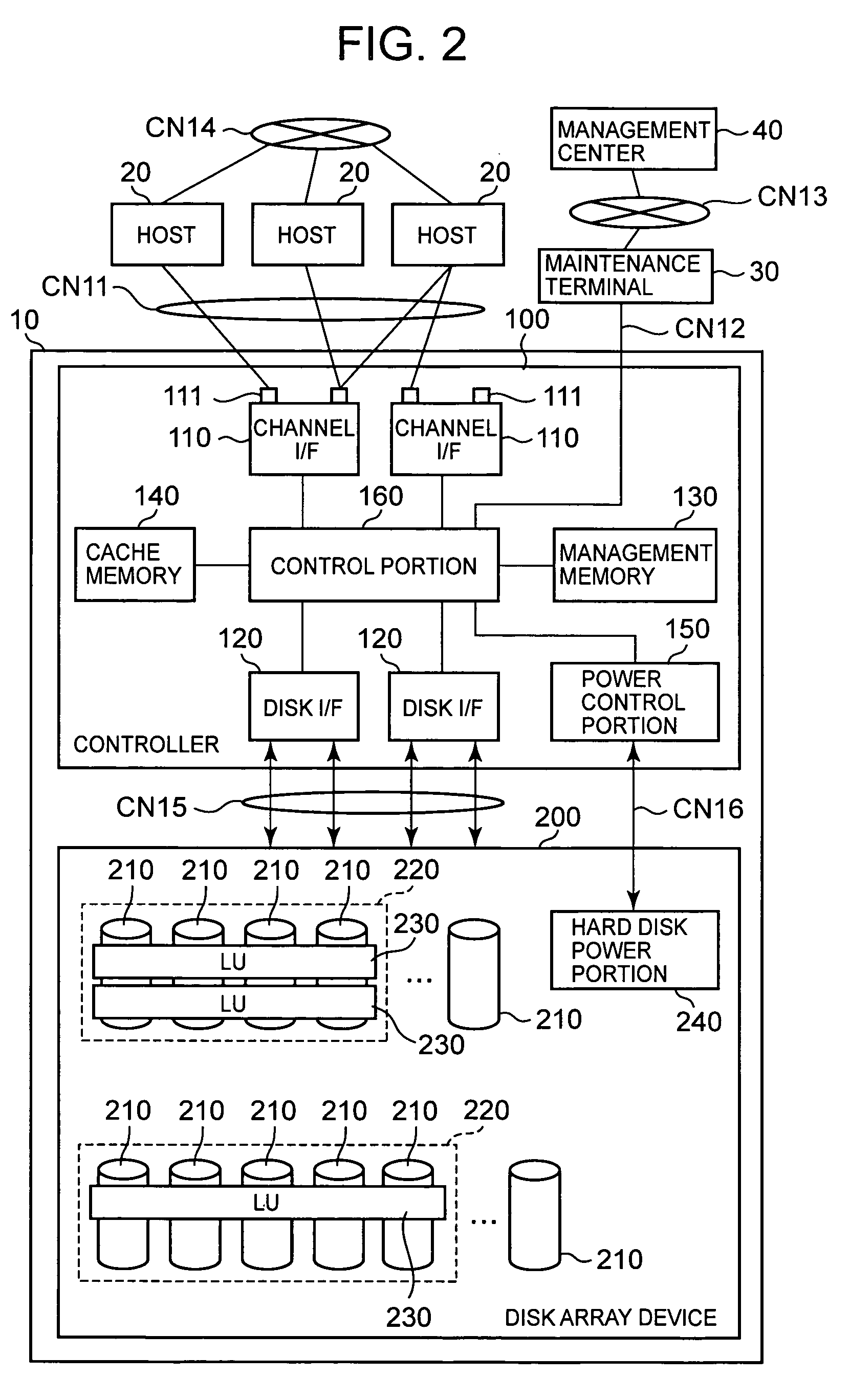
InactiveUS20070143542A1Improve reliabilityCut total energization timeEnergy efficient ICTMemory loss protectionRAIDControl store
The present invention controls supply of power to a storage device on the basis of an access status, moves a logical storage device between physical storage devices having different power supply modes, reduces energization time, and improves the reliability. A relocation plan creation portion creates a relocation plan by disposing a logical volume with high access frequency in a RAID group which is in a long-time energization mode, disposing a logical volume with moderate access frequency in a RAID group which is in a first short-time energization mode, and disposing a logical volume with low access frequency in a RAID group which is in a second short-time energization mode. An execution time determination portion determines an execution time for executing the relocation plan, on the basis of the access frequency to the RAID groups. The volumes with higher access frequency are disposed in the RAID group in which the power supply time is long, and the volumes with lower access frequency are disposed in the RAID group in which the power is supplied in an on-demand fashion.
Owner:HITACHI LTD
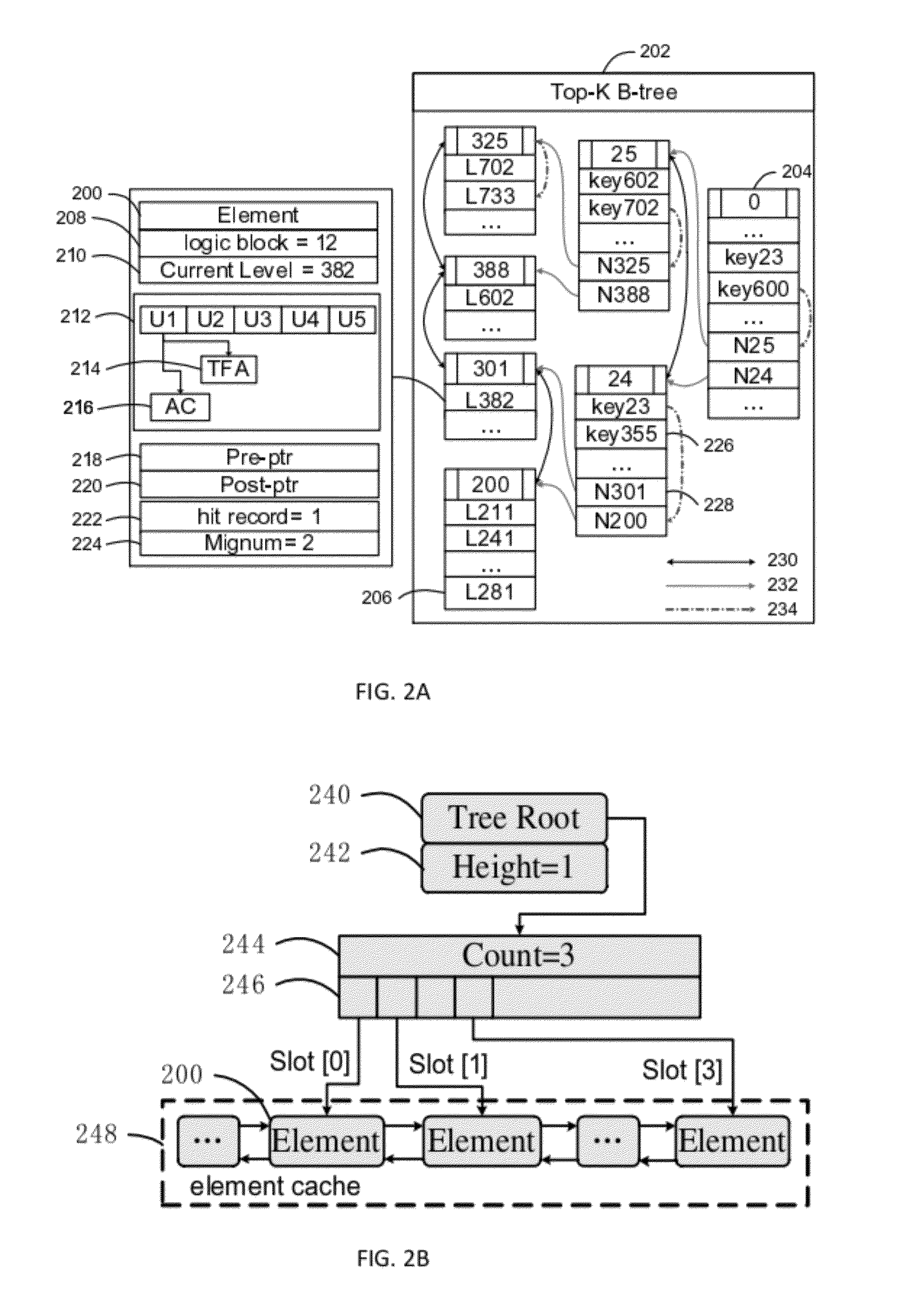
Solid-State Disk Caching the Top-K Hard-Disk Blocks Selected as a Function of Access Frequency and a Logarithmic System Time
InactiveUS20120317338A1Memory architecture accessing/allocationMemory loss protectionAccess frequencySystem time
A solid state disk (SSD) caches disk-based volumes in a heterogeneous storage system, improving the overall storage-system performance. The hottest data blocks are identified based on two factors: the frequency of access, and temporal locality. Temporal locality is computed using a logarithmic system time. IO latency is reduced by migrating these hottest data blocks from hard-disk-based volumes to the solid-state flash-memory disks. Some dedicated mapping metadata and a novel top-K B-tree structure are used to index the blocks. Data blocks are ranked by awarding a higher current value for recent accesses, but also by the frequency of accesses. A non-trivial value for accesses in the past is retained by accumulating the two factors over many time spans expressed as a logarithmic system time. Having two factors, access frequency and the logarithmic system time, provides for a more balanced caching system.
Owner:21VIANET GRP INC
Method and system for managing digital assets
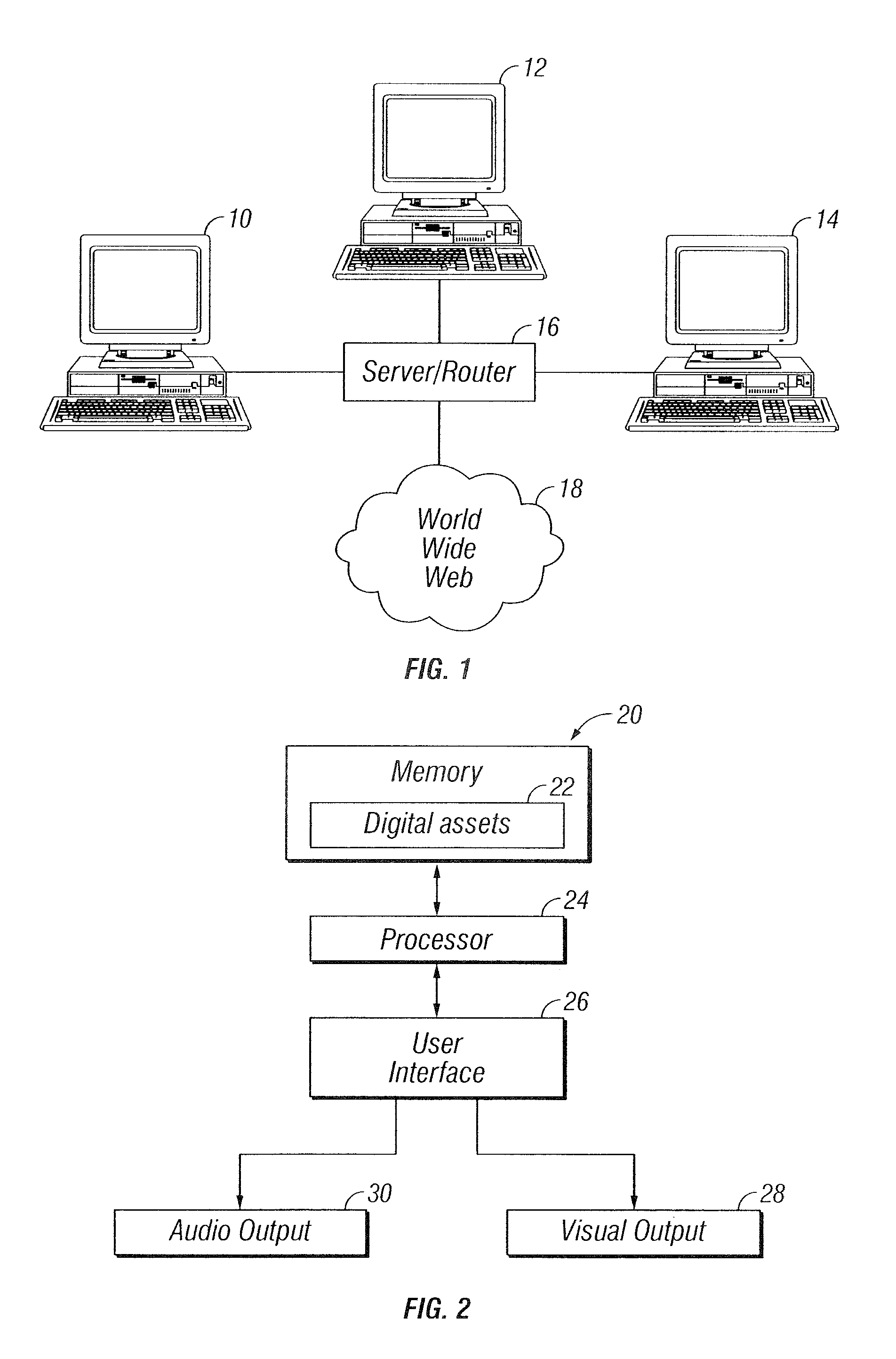
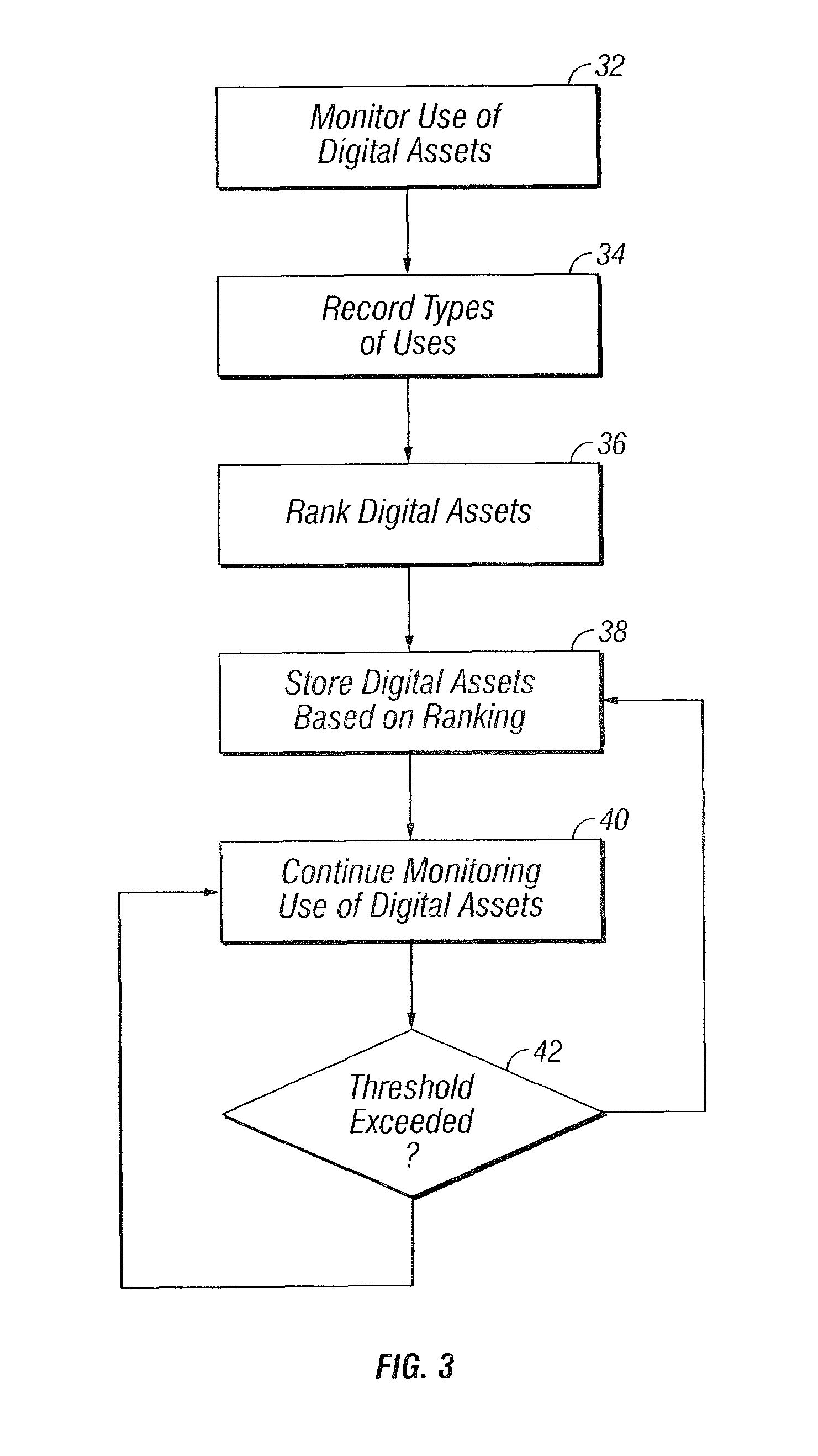
InactiveUS20050028104A1Efficient accessDigital data information retrievalCathode-ray tube indicatorsRankingAccess frequency
The claimed invention enables digital asset management that is responsive to a user's interactions with digital assets. Based on the user's interaction, the invention generates a ranking of the digital assets that is intended to reflect the value of the digital assets to the user. The ranking is based in part on the access frequency and recency, and the number and types of uses of the digital assets. An access hierarchy is derived from the ranking that stores the digital assets so that the higher ranked digital assets are more easily accessed than the lower ranked digital assets. The digital assets can include any of digital images, audio files, and Uniform Resource Locators. The invention can also distinguish between different types of uses so that some types of uses imbue an asset with greater value than others. The types of uses include passive viewing or playback, file sharing, transport, and editing. The invention also allows the user to assign subjective values to each digital asset that can be factored into the ranking independently of usage patterns. A volatility-dampening attribute is provided to moderate volatility in the access hierarchy.
Owner:META PLATFORMS INC
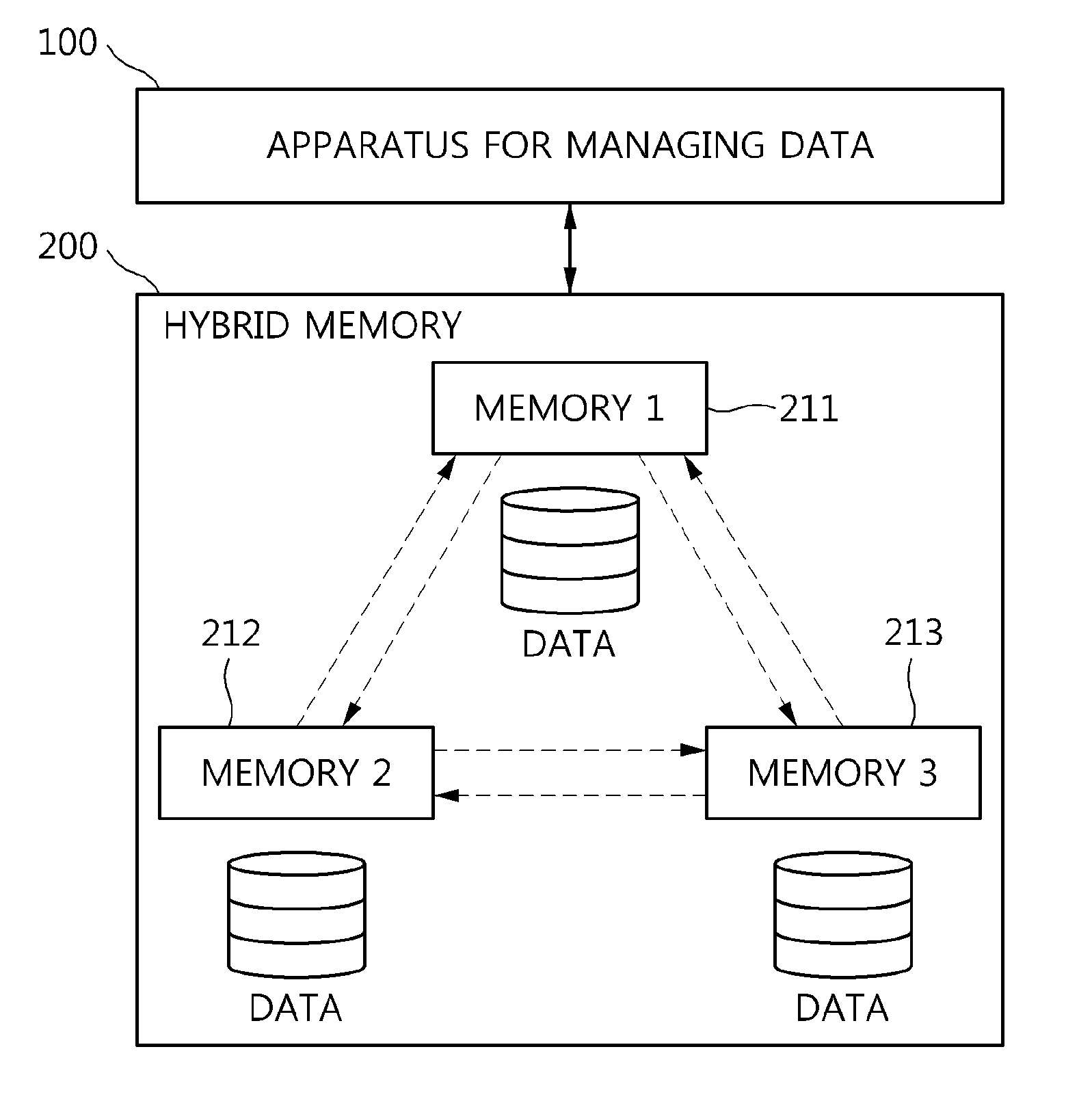
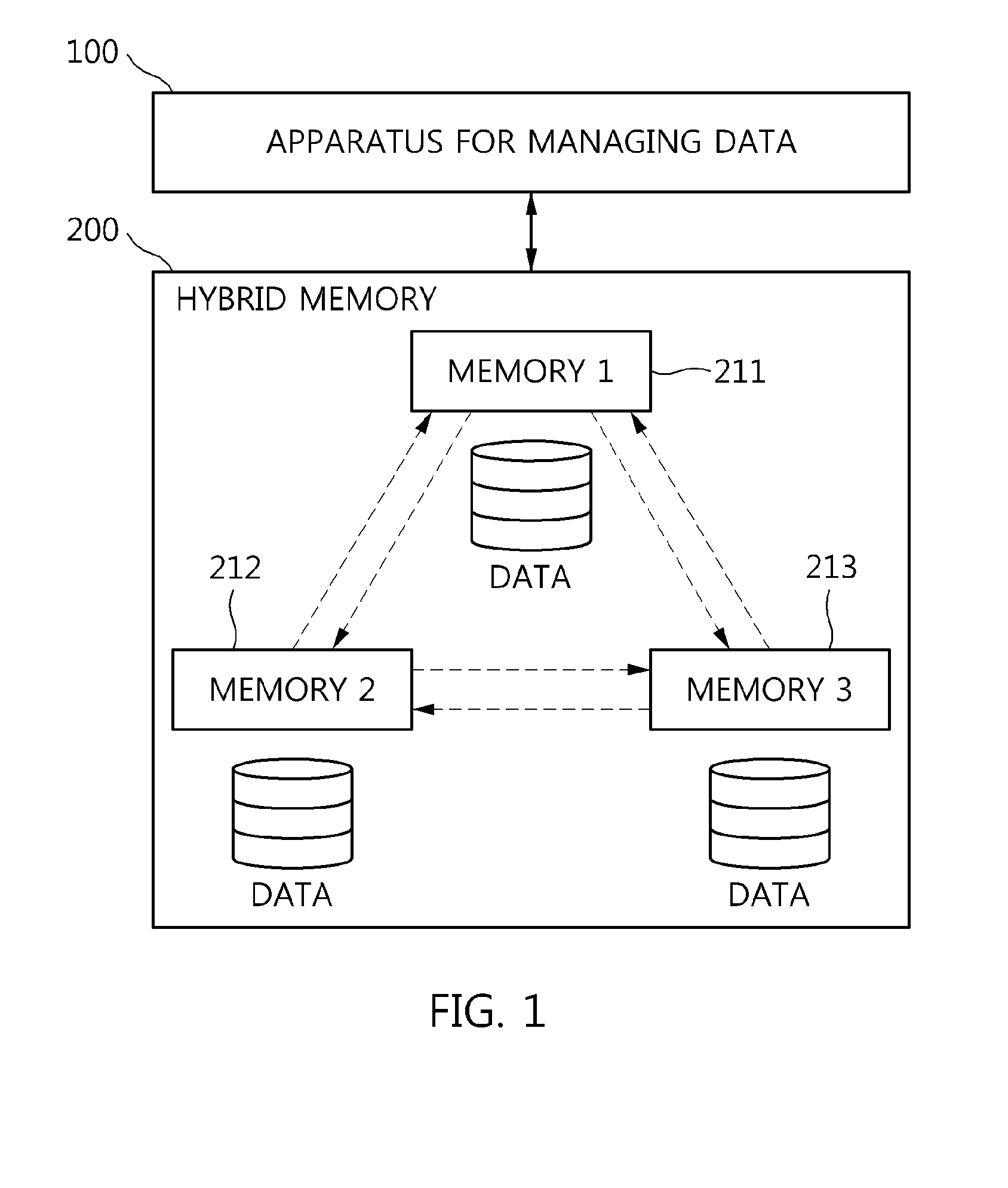
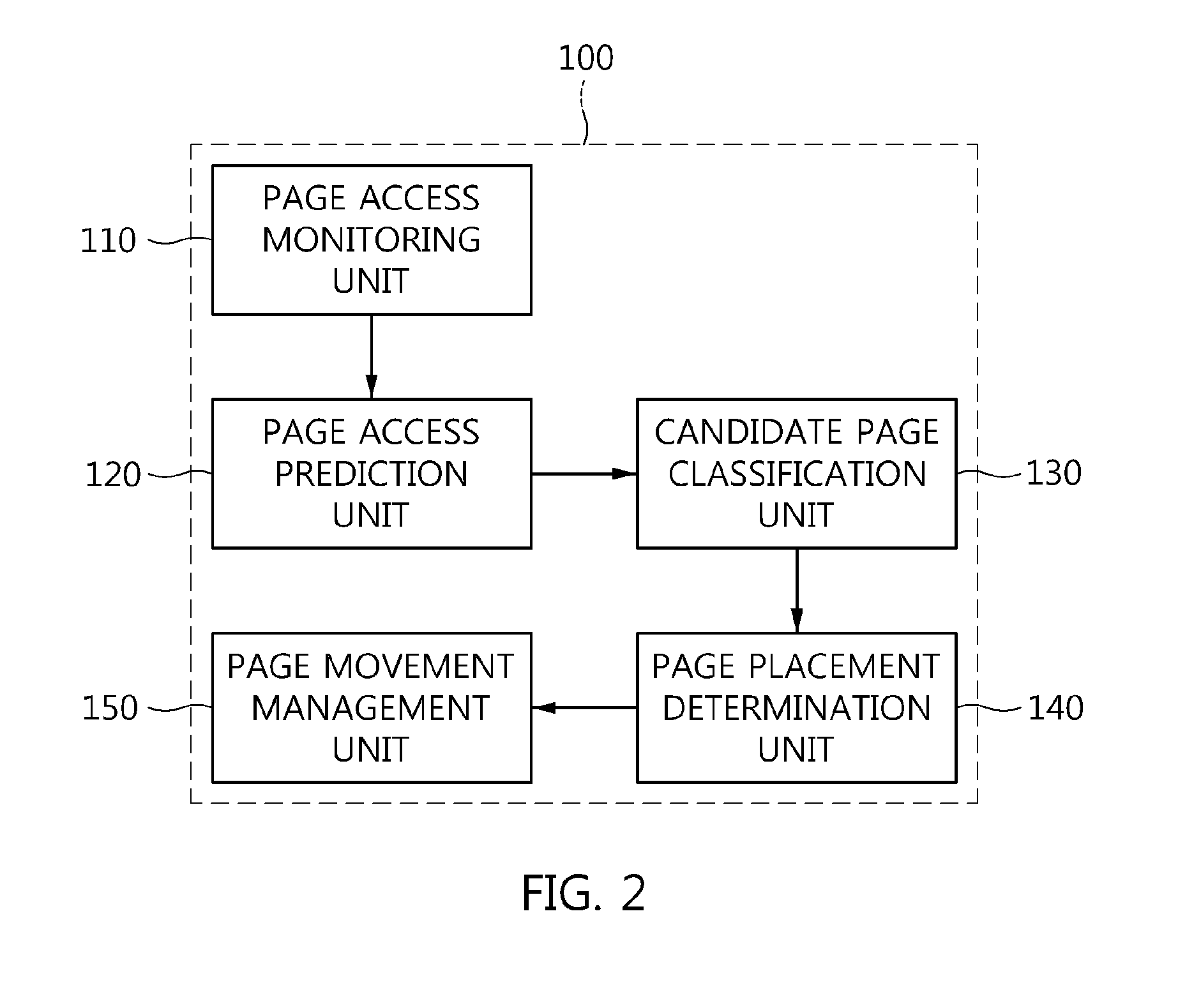
Apparatus and method for managing data in hybrid memory
InactiveUS20150106582A1Efficient managementMemory architecture accessing/allocationInput/output to record carriersAccess frequencyEngineering
An apparatus and method for managing data in hybrid memory are disclosed. The apparatus for managing data in hybrid memory may include a page access prediction unit, a candidate page classification unit, and a page placement determination unit. The page access prediction unit predicts an access frequency value for each page for a specific period in a future based on an access frequency history generated for the page. The candidate page classification unit classifies the page as a candidate page for migration based on the predicted access frequency value for the page. The page placement determination unit determines a placement option for the classified candidate page.
Owner:ELECTRONICS & TELECOMM RES INST
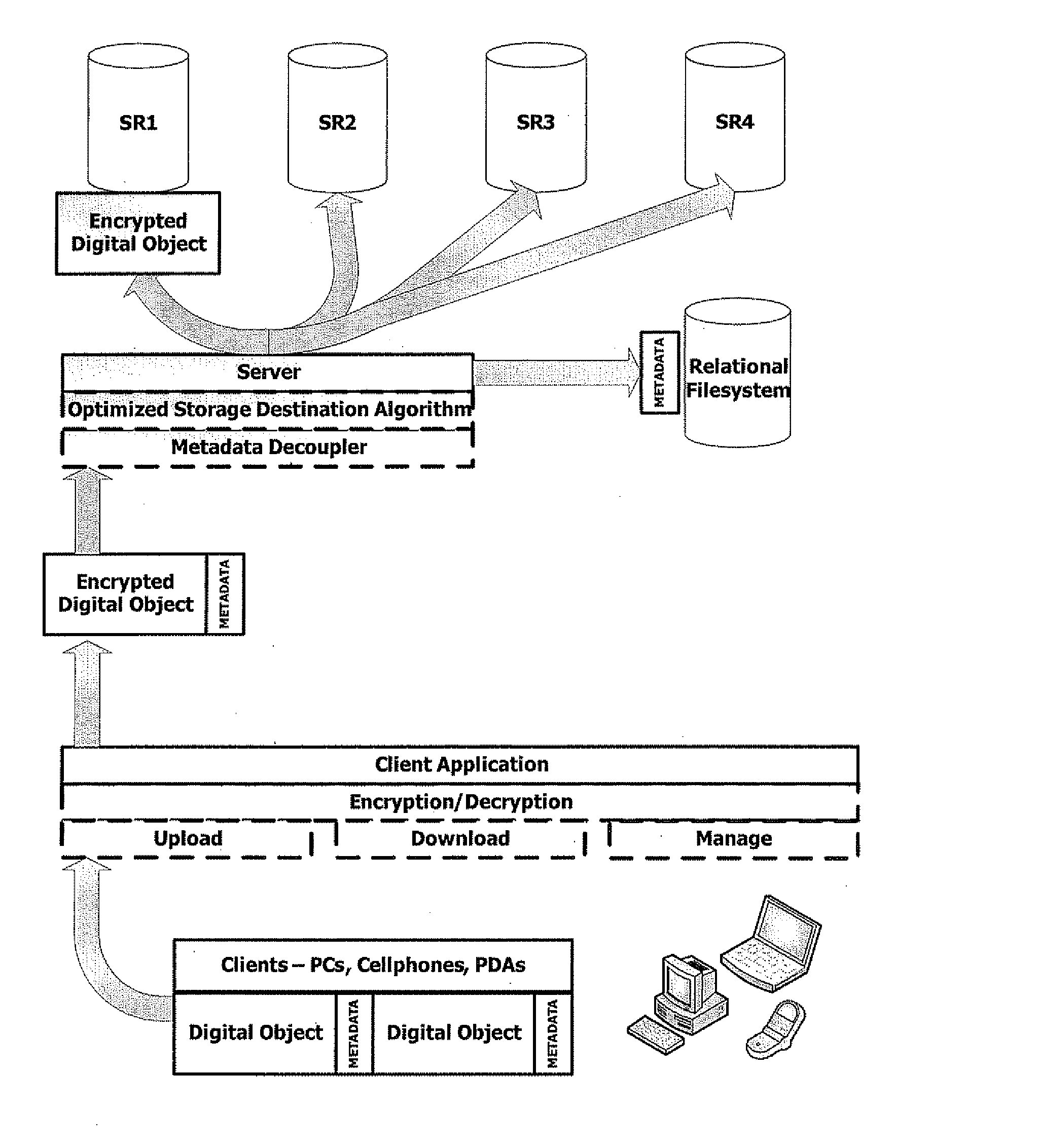
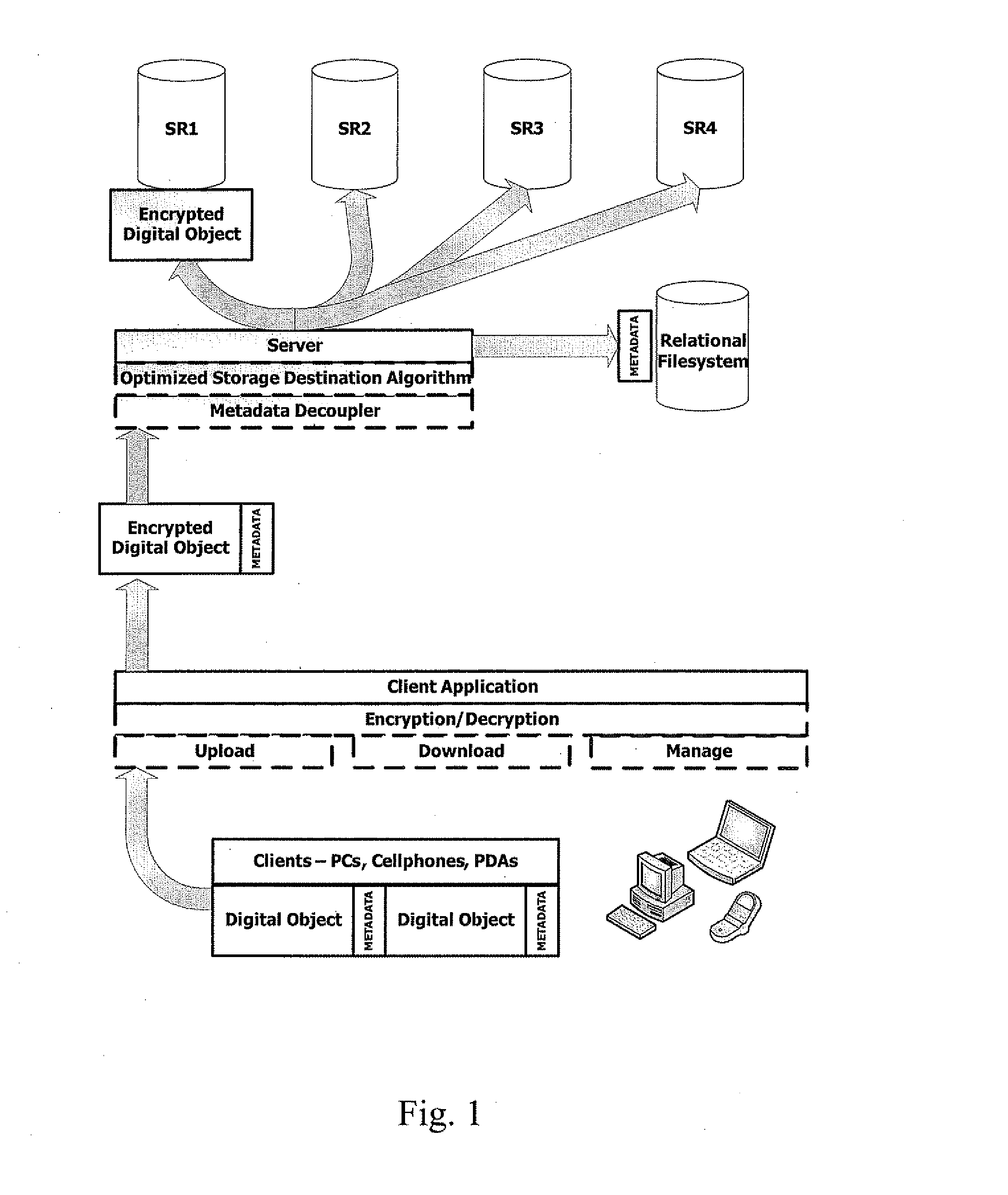
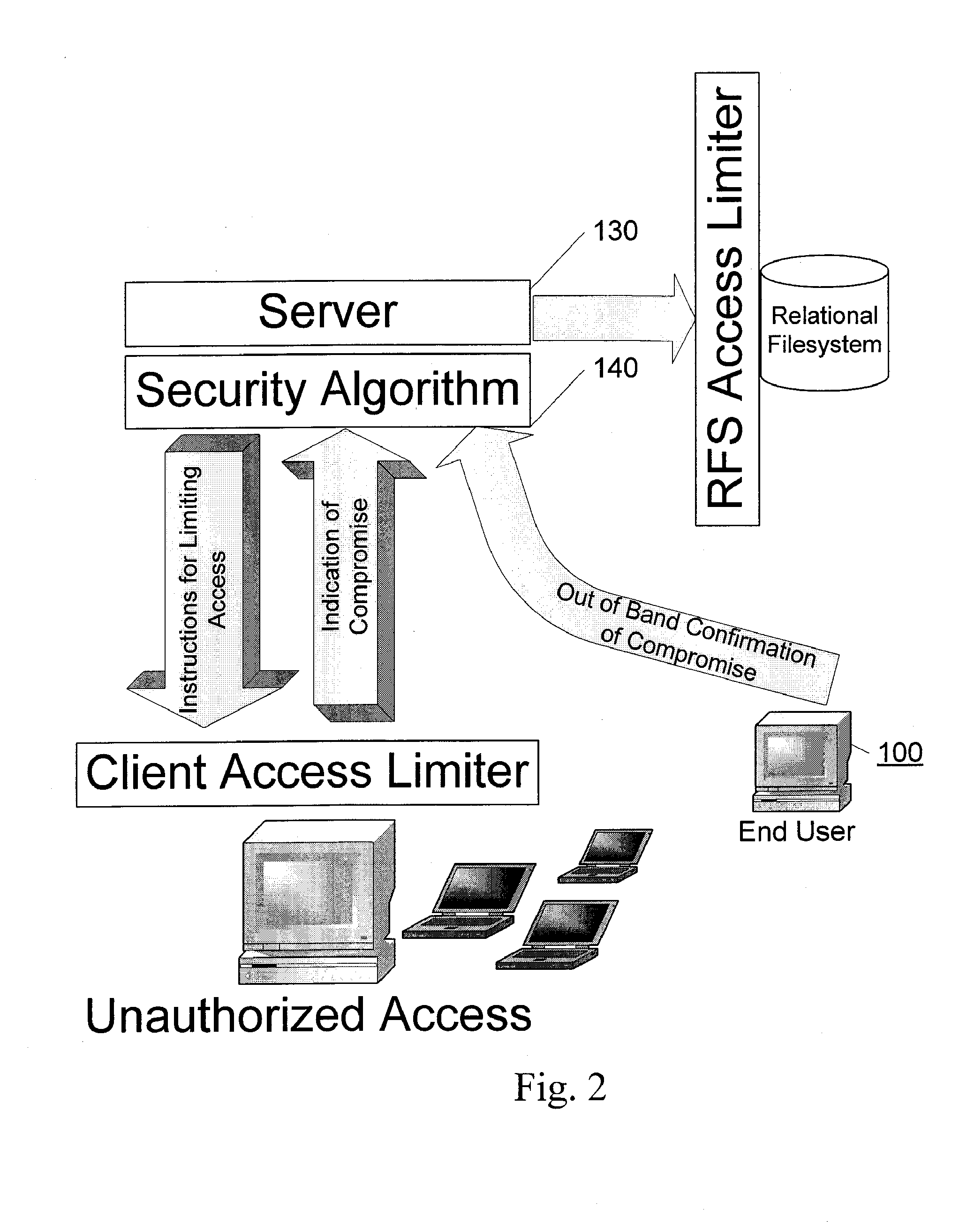
Abstracted and optimized online backup and digital asset management service
InactiveUS20080052328A1Overcome deficienciesLow costDigital data information retrievalDigital data processing detailsRelational databaseAccess frequency
A system and method for providing online storage and security. Digital assets are sent from client applications to server applications. The server implements an algorithm that optimizes the storage of digital assets. The server extracts the meta-data from digital assets and stores the meta-data in a relational database. The storage of digital assets will depend on analyzing the meta-data; factors such as file type, frequency of usage, and frequency of access are considered by the storage destination optimizing algorithm. The server also implements an algorithm that protects the digital assets from unauthorized network access. Upon detection of network intrusion by the security algorithm, the digital assets of the compromised users will be frozen, then either be destroyed or render unreadable by the unauthorized user. The security algorithm may then send an instance of the digitals assets to the compromised user to ensure that the digital assets remain accessible.
Owner:ELEPHANTDRIVE
Method for Exchanging Location-Relevant Information Using a Mobile Device with an Interactive Map Display
InactiveUS20090258656A1Promote generationEasy to specifyServices signallingLocation information based serviceRelevant informationBattery charge
A method is disclosed for wirelessly providing easily accessed and comprehended location-relevant information to a mobile device or web browser by displaying a map showing locations of interest. Simply by touching the map, a user can specify locations and regions used for queries and for uploading peer-to-peer information such as blogs, reviews, items for sale, etc. The device can request information, receive synchronously or asynchronously pushed responses, and display them with symbols that indicate category, age, etc. Location-aware devices can automatically specify their locations and provide location histories. Regions of interest can be adjusted according to visitation frequency, or region boundaries can simply be traced on the map. Limits can be placed on requested information and on distribution of uploaded information. Queries can use fuzzy logic, transactions can be completed using the devices, and requested information can be delivered when battery charge level and wireless link quality are appropriate.
Owner:WANG YIN +1
Method and system for optimizing data access in a database using multi-class objects
ActiveUS20090210445A1Save computing resourcesEasy to classifyDigital data information retrievalSpecial data processing applicationsData setRelational database
Methods for optimizing data access in a row-oriented relational database containing data sets having attributes using a computer are presented the method including: causing a computer to analyze a database workload to determine an access frequency for each of the attributes; causing the computer to assign each of the attributes to a priority classes corresponding with the access frequency, where the priority classes include a higher priority class and a lower priority class, and where a higher priority class corresponds with a higher access frequency and a lower priority class corresponds with a lower access frequency; causing the computer to store the attributes in accordance with the classes, where the attributes assigned to the higher priority class are stored in a high priority storage medium, and where the attributes assigned to a lower priority class are stored in a low priority storage medium.
Owner:IBM CORP
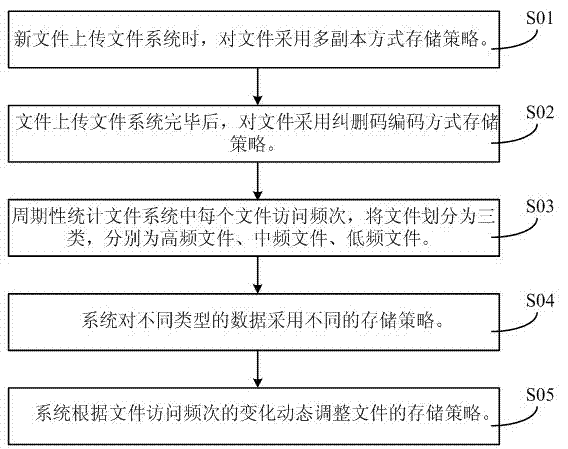
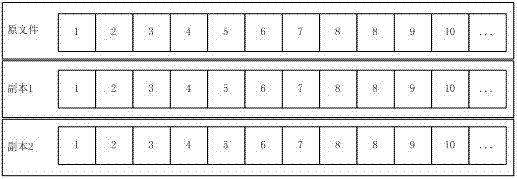
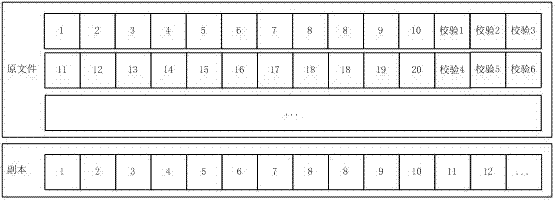
Mixed cloud storage method based on file access frequency
ActiveCN103118133AGuaranteed speedEnsure data reliabilityTransmissionFile systemResource utilization
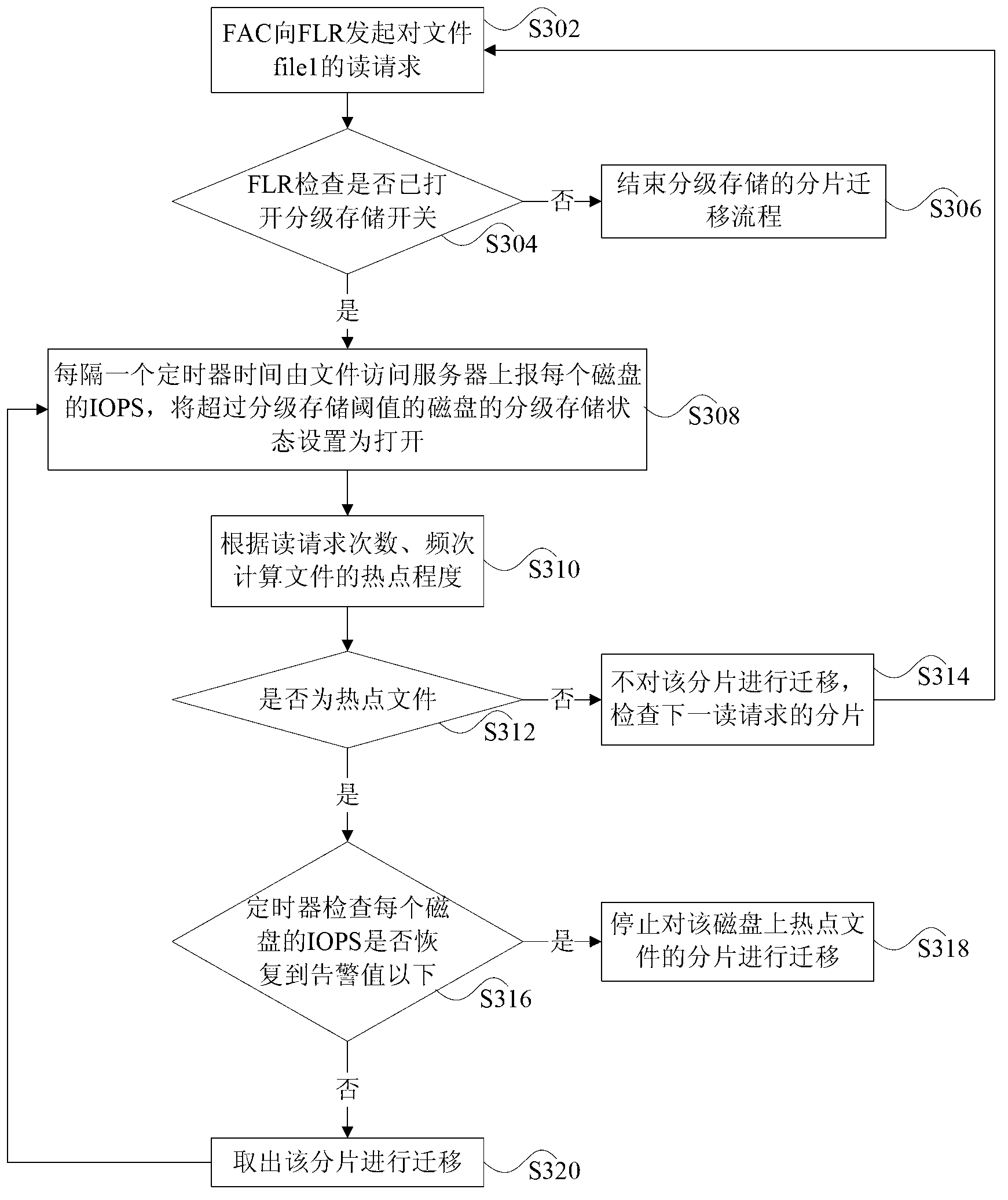
The invention discloses a mixed cloud storage method based on file access frequency. The mixed cloud storage method based on the file access frequency includes the following steps: adopting a multi-copy mode storage strategy for a new file when the new file is uploaded to a file system; adopting an erasure code coding mode storage strategy for the file after the file is completely uploaded to the file system; periodically counting access frequency of each file in the file system, and dividing files into three categories which are respectively high frequency files, medium frequency files and low frequency files; adopting different storage strategies for different types of data and different types of files in the system; and dynamically adjusting the storage strategies of the files according to changes of the access frequency of the files in the system. The mixed cloud storage method based on the file access frequency classifies the files by periodically counting the access frequency of each file in the file system, adopts different storage strategies for different types of files, and adjusts the storage strategies of the files according to the changes of the access frequency of the files, and therefore the whole file system wholly improves system storage resource utilization rate on the premises of guaranteeing data reliability and access speed.
Owner:ZHEJIANG UNIV
Method and system for managing digital assets
InactiveUS7082573B2Efficient accessDigital data information retrievalDigital computer detailsAccess frequencyRanking
The digital asset management system is responsive to user interactions with digital assets. Based on user interaction, the system generates a ranking of digital assets to reflect the value of the digital assets to the user. The ranking is based in part on access frequency and recency, and the number and types of uses of the digital assets. An access hierarchy is derived from the ranking that stores the digital assets so that higher ranked digital assets are more easily accessed from storage than lower ranked digital assets. The digital assets can include any of digital images, audio files, and Uniform Resource Locators. The system can also distinguish between different types of uses, such as passive viewing or playback, file sharing, transport, and editing. The system preferably allows subjective values to be assigned to digital assets that can be factored into the ranking independently of usage patterns.
Owner:META PLATFORMS INC
Distribution type file system multi-file copy management method
InactiveCN101187931AImprove usabilityImprove reliabilitySpecial data processing applicationsDistributed File SystemFile system
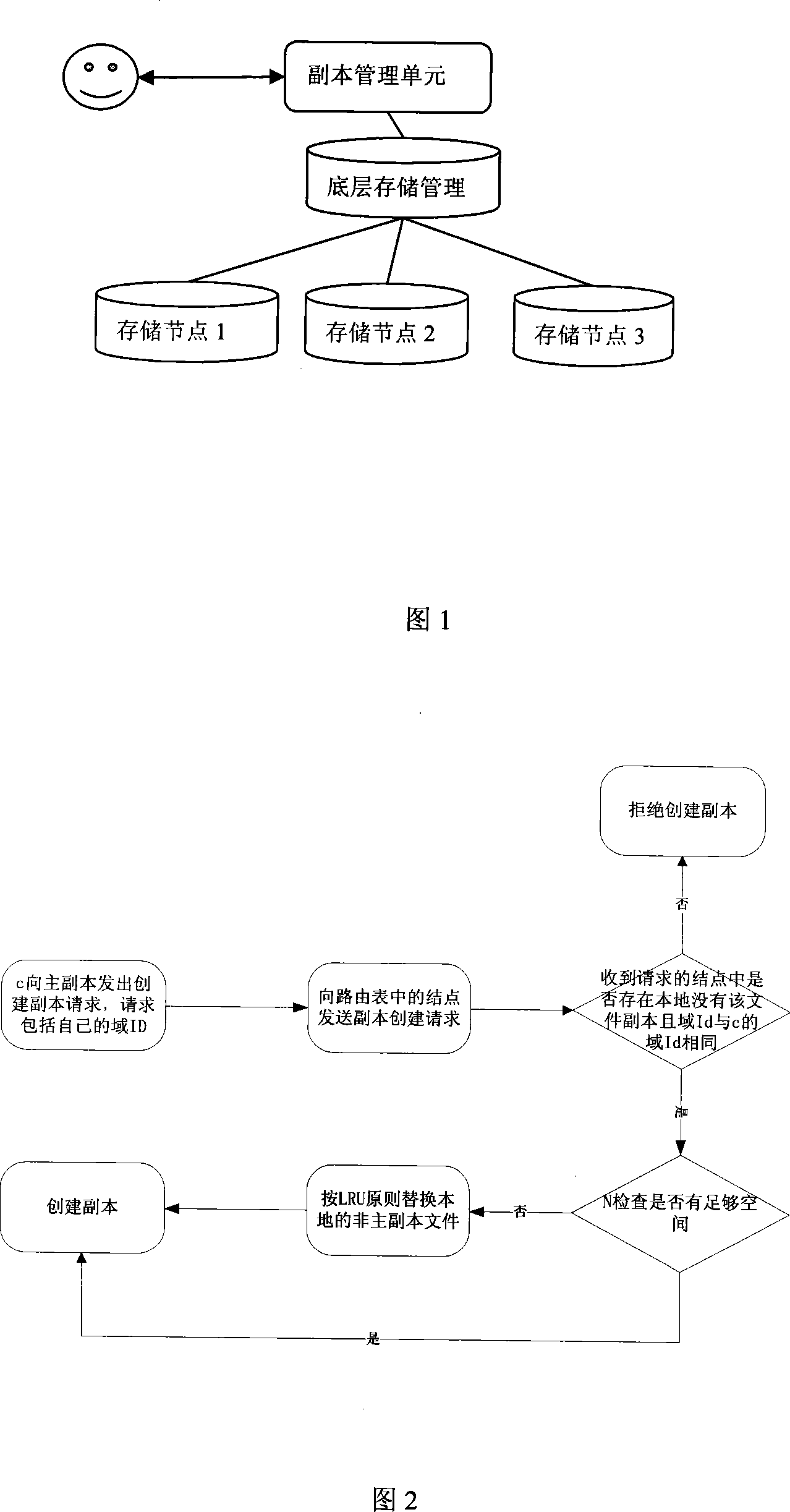
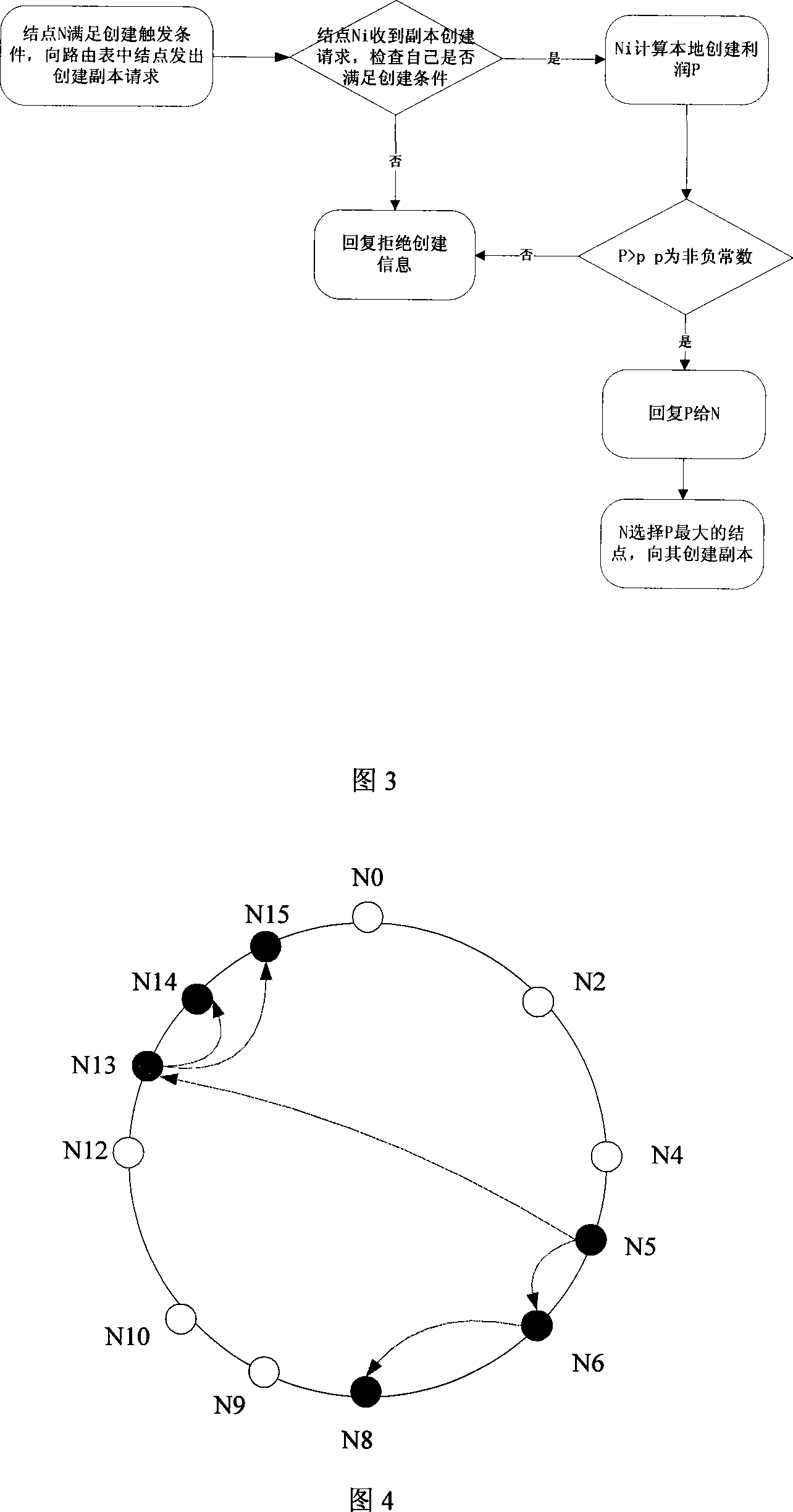
The invention relates to a management method of a multifile copy of a distributed file system. A copy management mechanism based on a frequency is adopted, the state of a file copy is changed according to the read-write access frequency of the file and the information trend of an access resource, and the position transference is increased / reduced and stored through the trend of the quantity of the file copy. The management method includes copy grading management, copy creating policy, copy selection and orientation, and a copy consistency maintenance method. The creating method of the file copy includes the creating initiated by the user and the creating initiated by a crunodes, and adopts a data gridding method and a policy based on the benefit drive. The orientation of the copy maps a logic file on an appropriate copy, and a copy with minimum cost and highest access efficiency is selected to be provided to the user for using. The invention has the advantages that the provided service carries on the excellent characteristics of the distributed file system, which includes loose coupling, high usability, high reliability and high cost performance.
Owner:ZHEJIANG UNIV
Computer system security using file system access pattern heuristics
InactiveUS20090144545A1Provide securityComputer security arrangementsSecuring communicationFile systemHeuristic
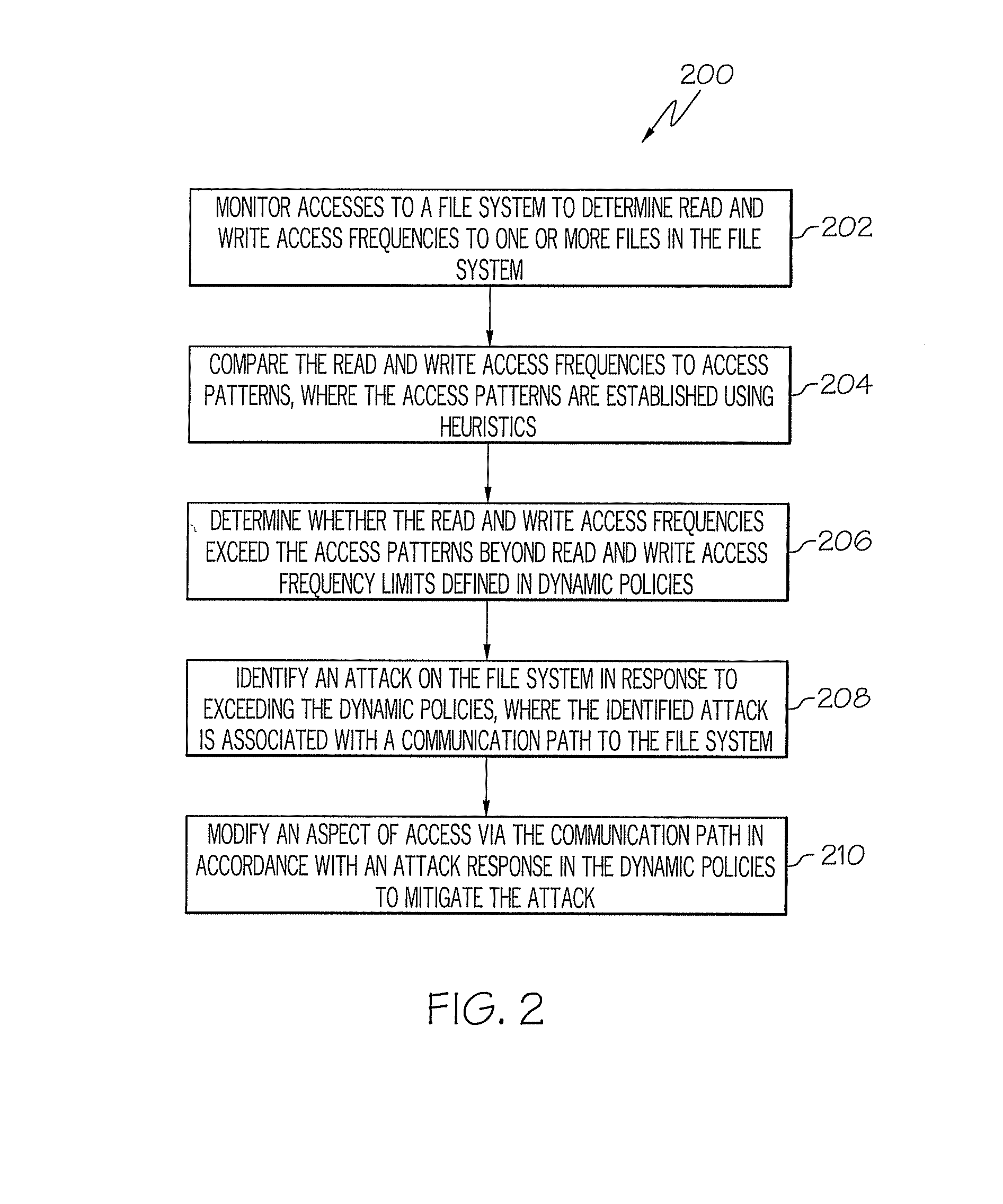
A system for computer system security using file system access pattern heuristics is provided. The system includes access patterns to establish nominal read and write frequencies to a file system using heuristics, dynamic policies, and a policy manager. The policy manager monitors accesses to the file system to determine read and write access frequencies to the file system. The policy manager also compares the read and write access frequencies to the access patterns, and determines whether the read and write access frequencies exceed the access patterns per the dynamic policies. The policy manager further identifies an attack on the file system in response to exceeding the dynamic policies, where the identified attack is associated with a communication path to the file system. The policy manager additionally modifies an aspect of access via the communication path in accordance with the attack response in the dynamic policies to mitigate the attack.
Owner:IBM CORP
Apparatus and method for memory management
InactiveUS20040139282A1Memory loss protectionMemory adressing/allocation/relocationData accessAccess frequency
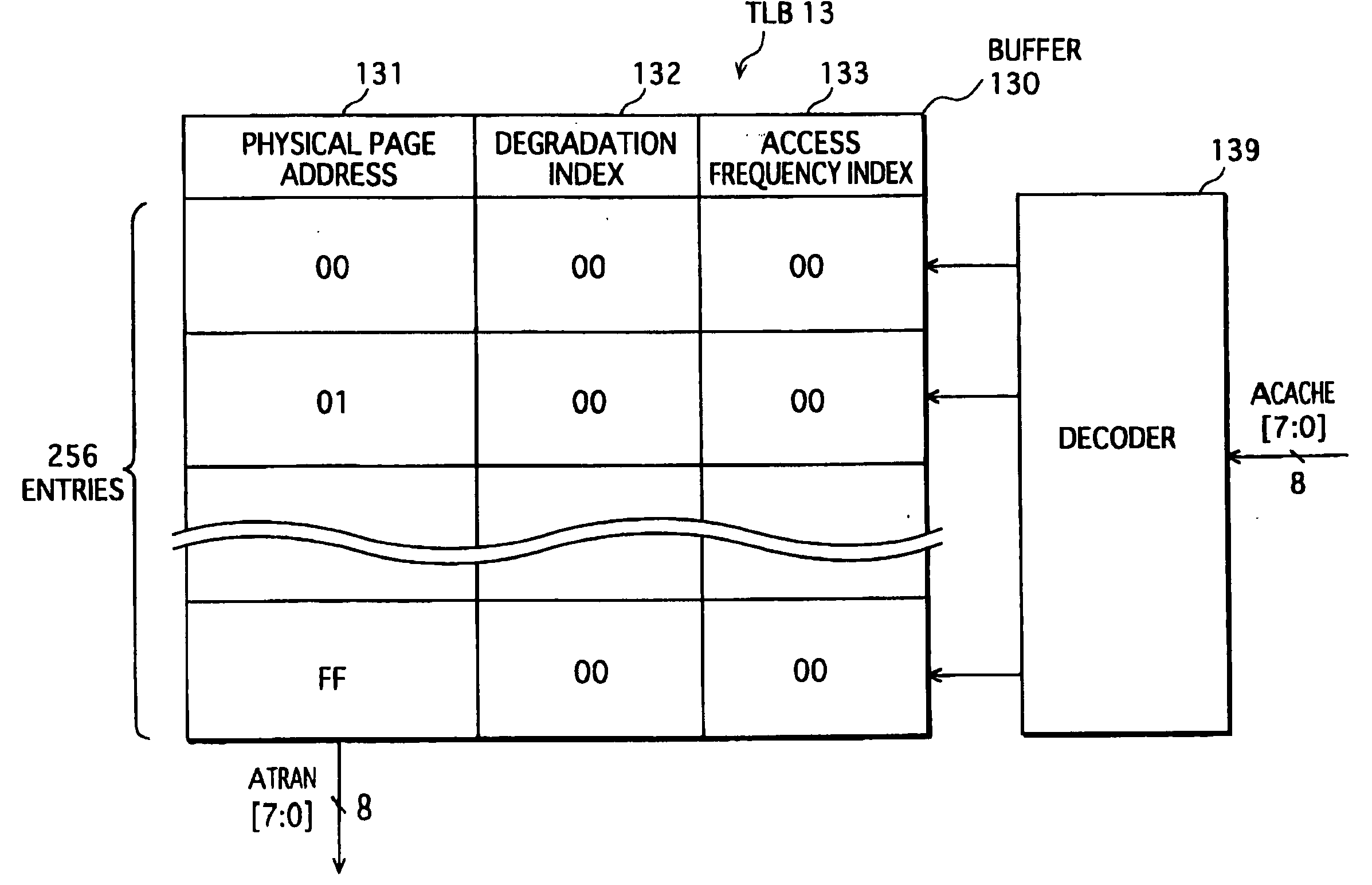
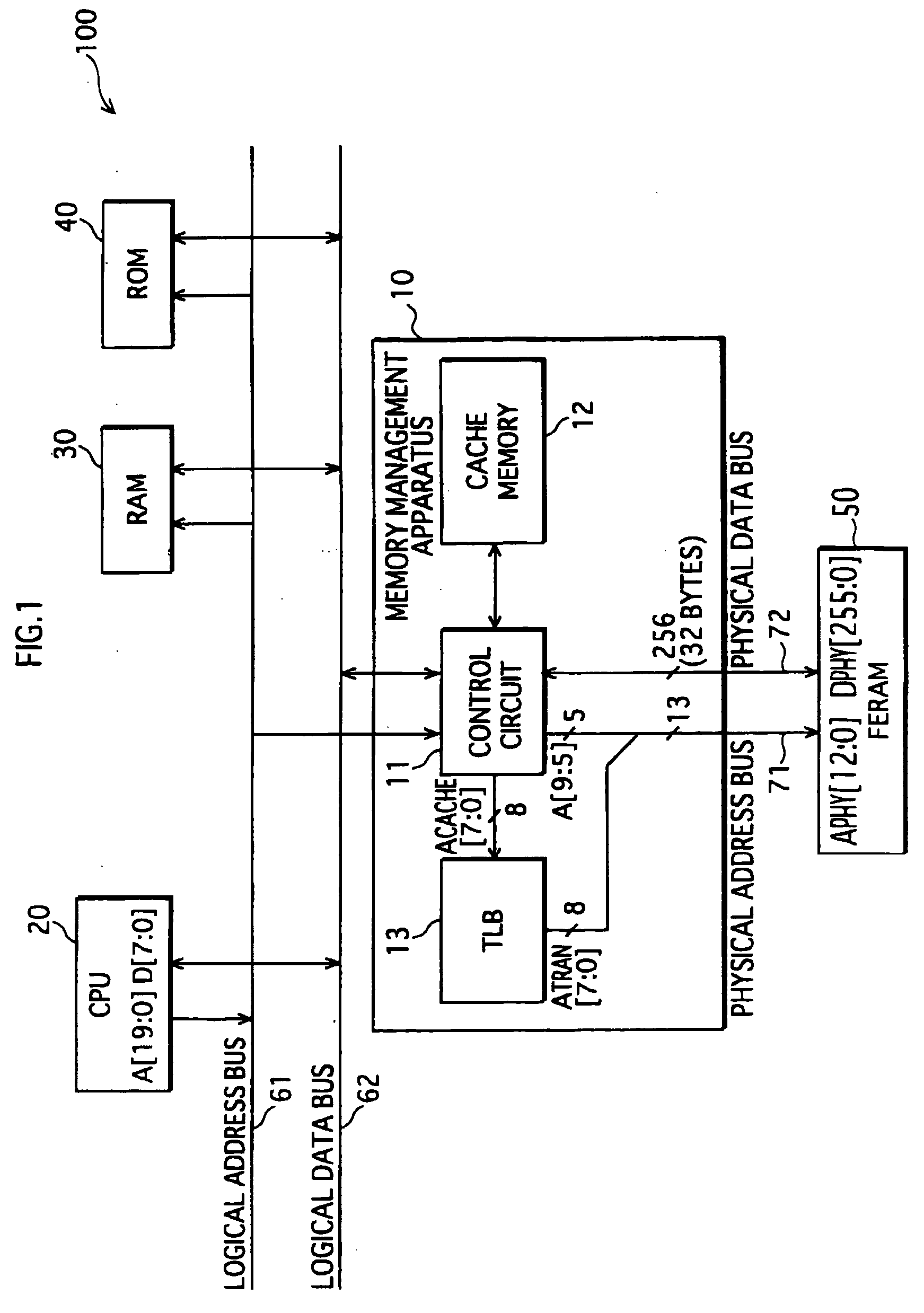
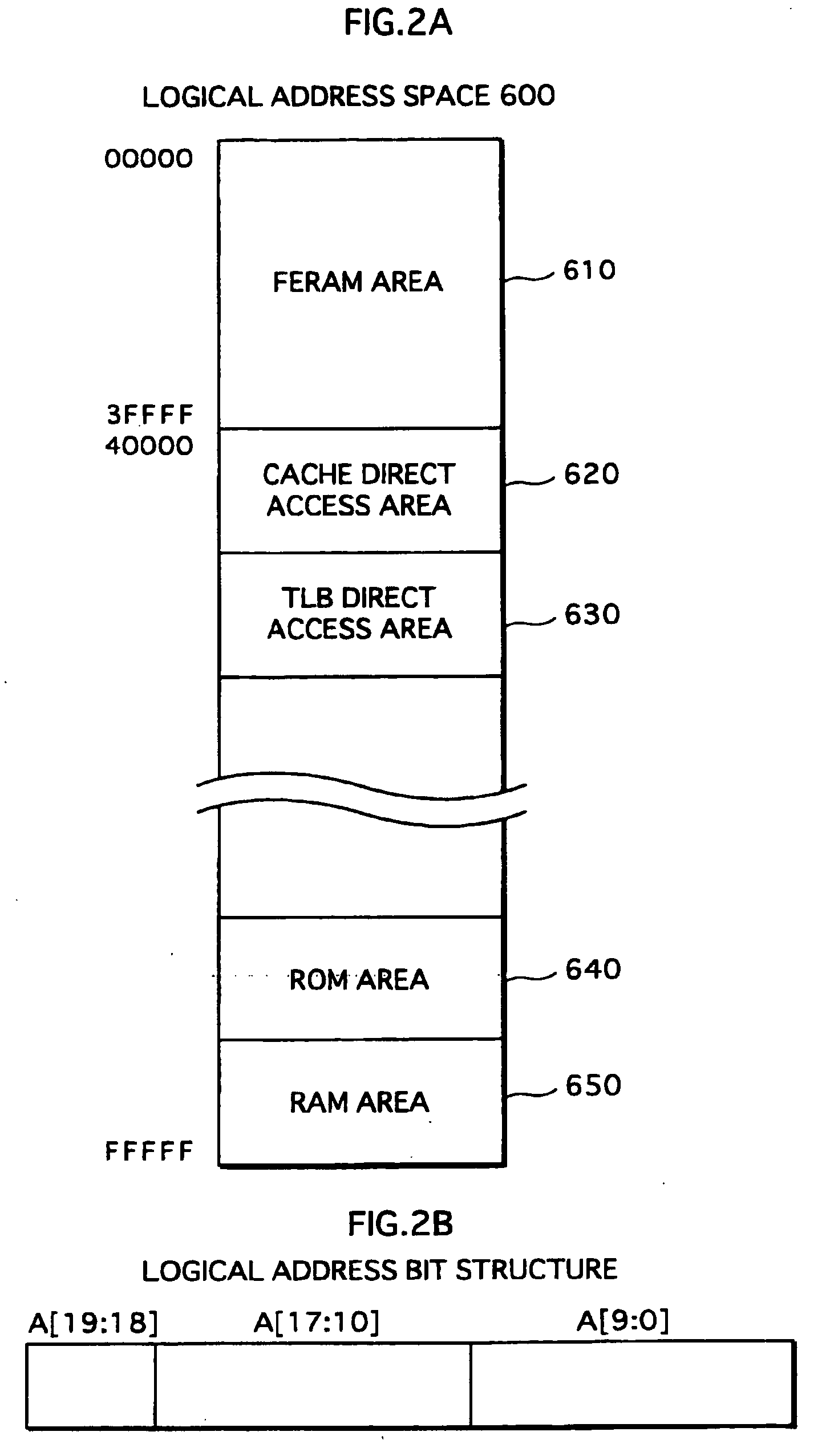
A TLB provided in a memory management apparatus stores an entry for each logical page, and each entry holds an address of a physical page mapped to a corresponding logical page, an index showing the degradation degree of the physical page, and an index showing the access frequency to the logical page. The memory management apparatus accesses a physical page mapped to a desired logical page according to the data stored in the TLB, periodically exchanges the contents between a first physical page mapped to a specific logical page having a largest access frequency index and a second physical page having a smallest degradation index, and then maps the specific logical page to the second physical page. Through the physical page exchange and corresponding mapping process, accesses to each physical page are distributed, so that degradation in storage function is substantially equalized.
Owner:SOCIONEXT INC
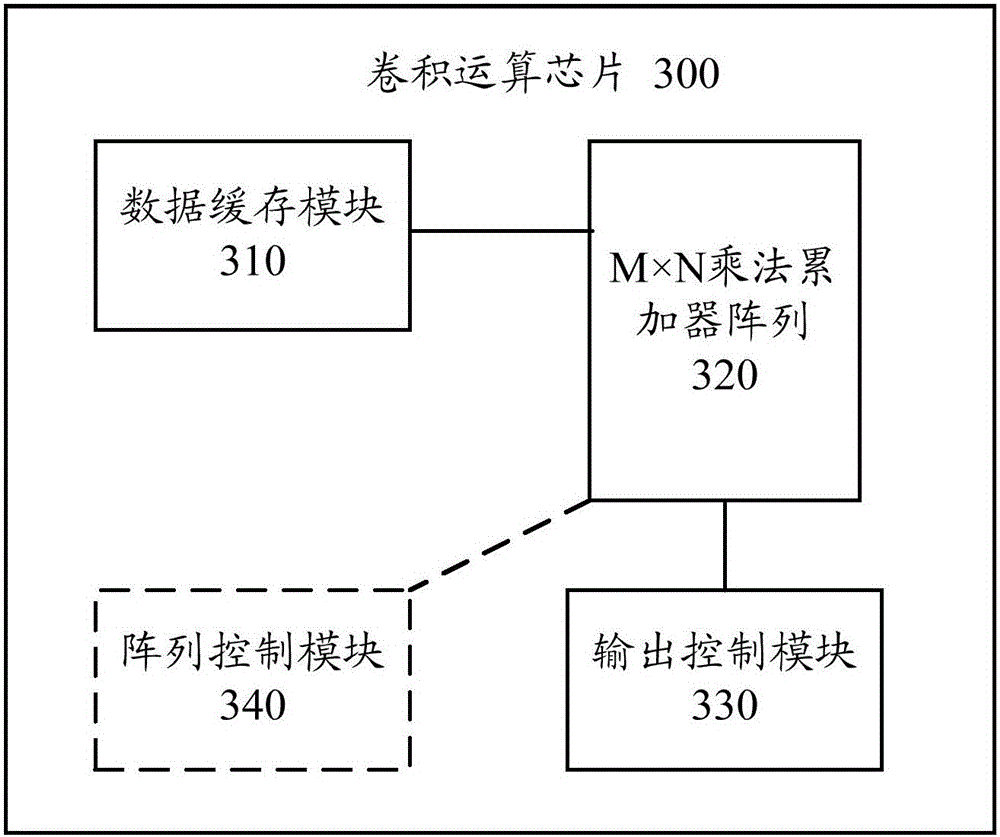
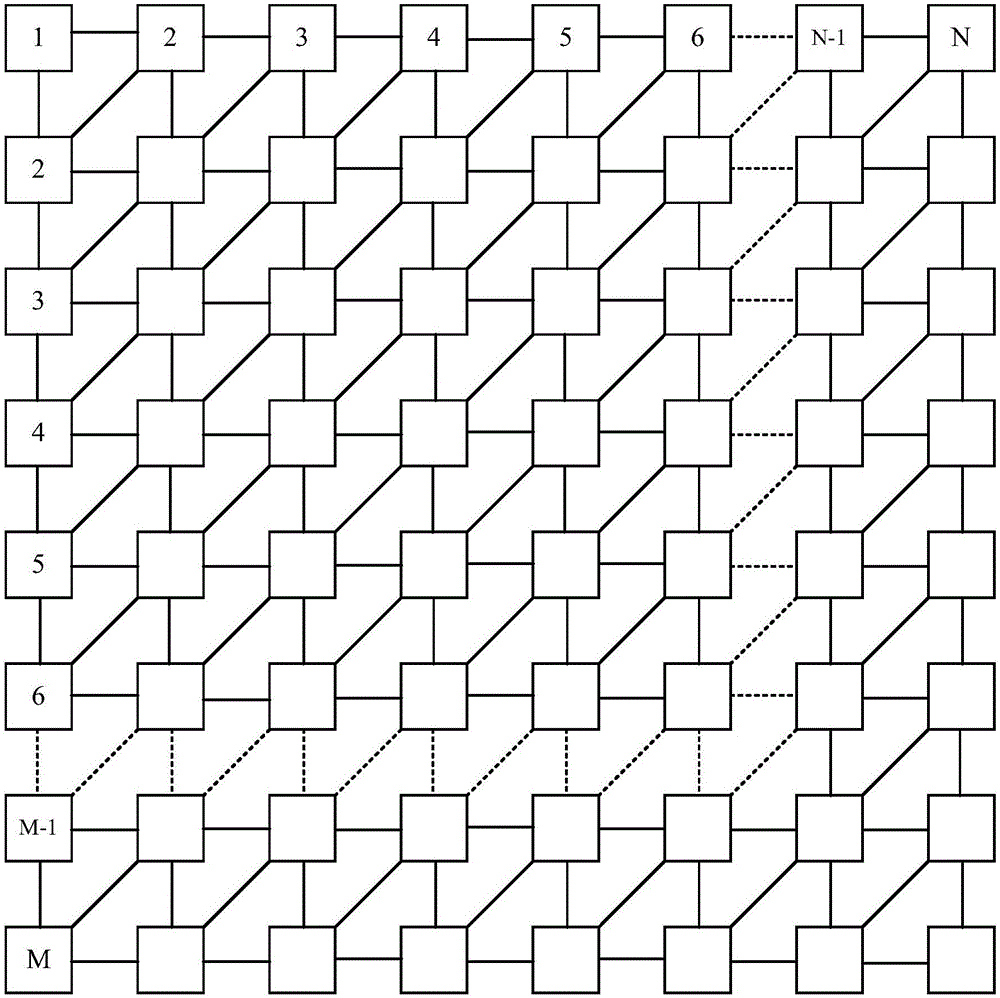
Convolution operation chip and communication equipment
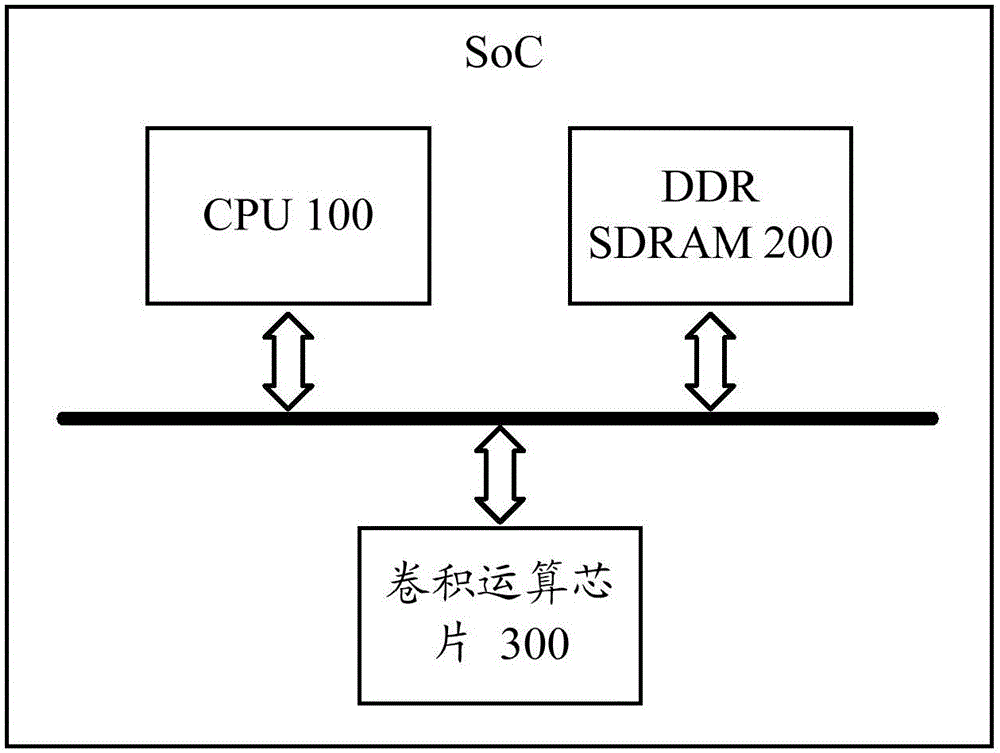
ActiveCN106844294AReduce visitsReduce access pressureDigital data processing detailsBiological modelsResource utilizationComputer module
The invention provides a convolution operation chip and communication equipment. The convolution operation chip comprises an M*N multiplier accumulator array, a data cache module and an output control module; the M*N multiplier accumulator array comprises a first multiplier accumulator window, and a processing unit PE<X, Y> of the first multiplier accumulator window is used for conducting multiplication operation on convolution data of the PE<X, Y> and convolution parameters of the PE<X, Y> and transmitting the convolution parameters of the PE<X, Y> to PE<X, Y+1> and transmitting the convolution data of the PE<X, Y> to PE<X-1, Y+1> to serve as multipliers of multiplication operation between the PE<X, Y+1> and the PE<X-1, Y+1>; the data cache module is used for transmitting the convolution data and the convolution parameters to the first multiplier accumulator window; the output control module is used for outputting a convolution result. According to the convolution operation chip and the communication equipment, the RAM access frequency can be decreased and the RAM access stress can be relieved while the array resource utilization rate is increased.
Owner:HUAWEI MACHINERY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com