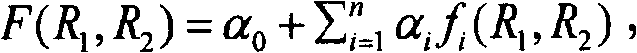Patents
Literature
339 results about "Data scrubbing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data scrubbing is an error correction technique that uses a background task to periodically inspect main memory or storage for errors, then correct detected errors using redundant data in the form of different checksums or copies of data. Data scrubbing reduces the likelihood that single correctable errors will accumulate, leading to reduced risks of uncorrectable errors.
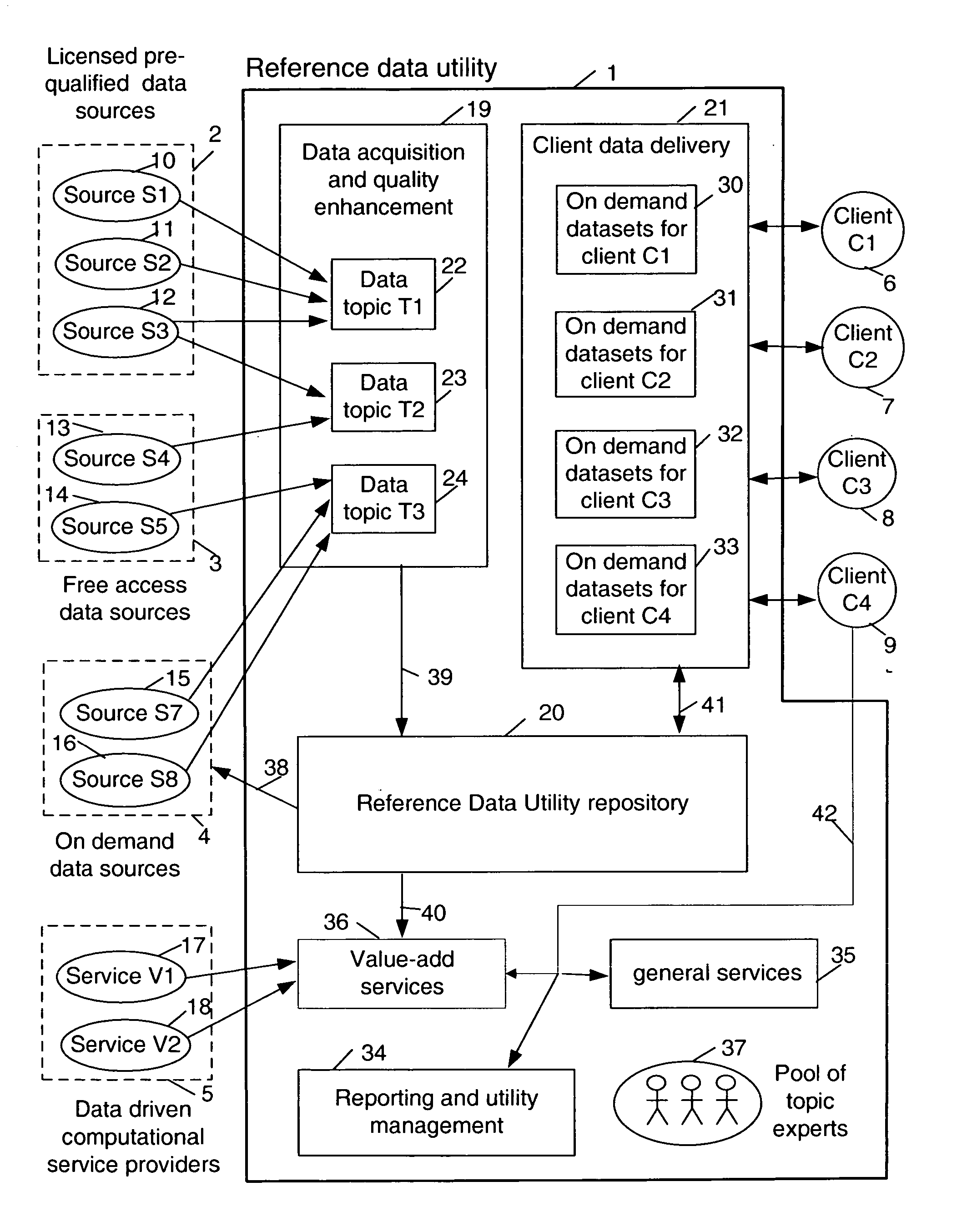
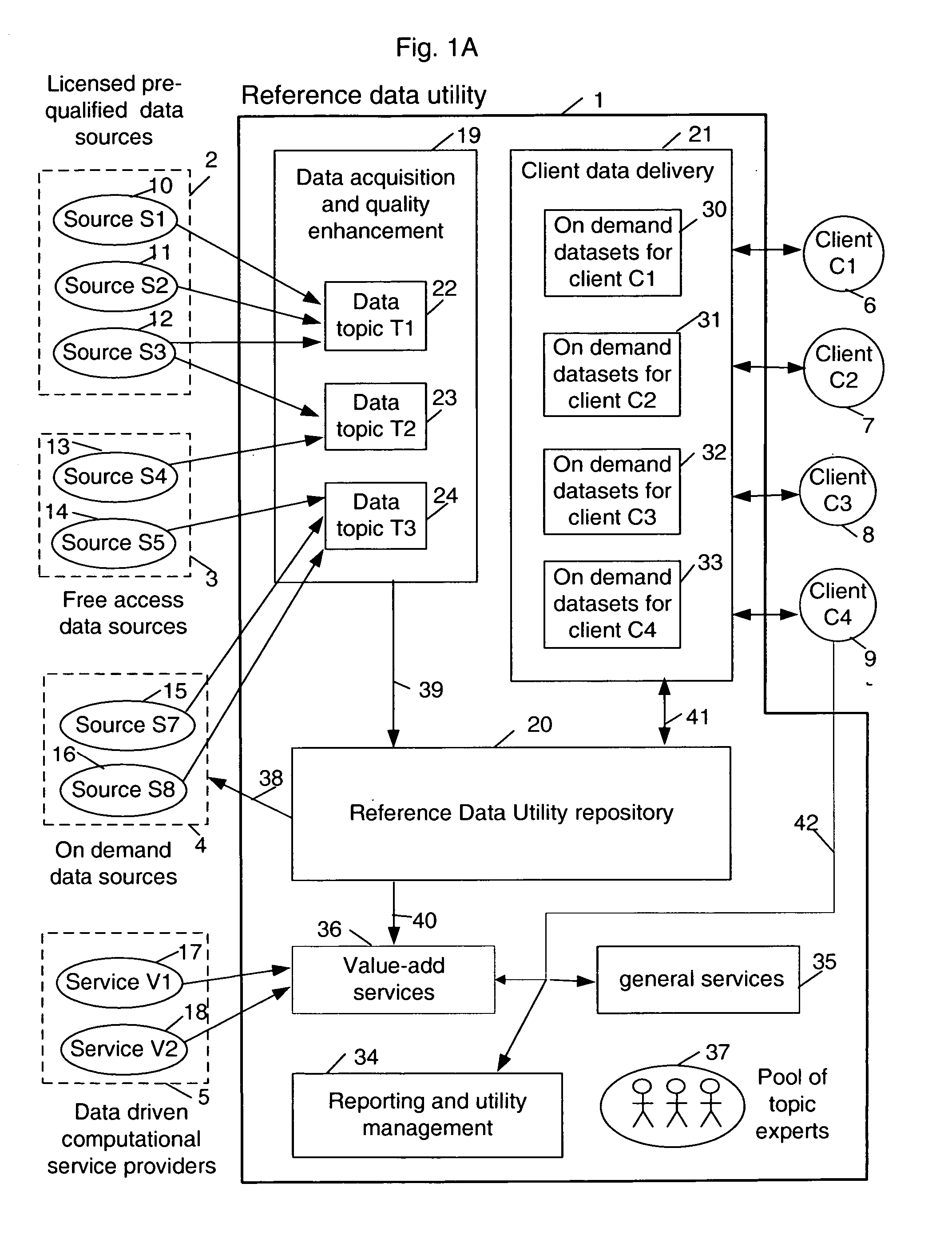
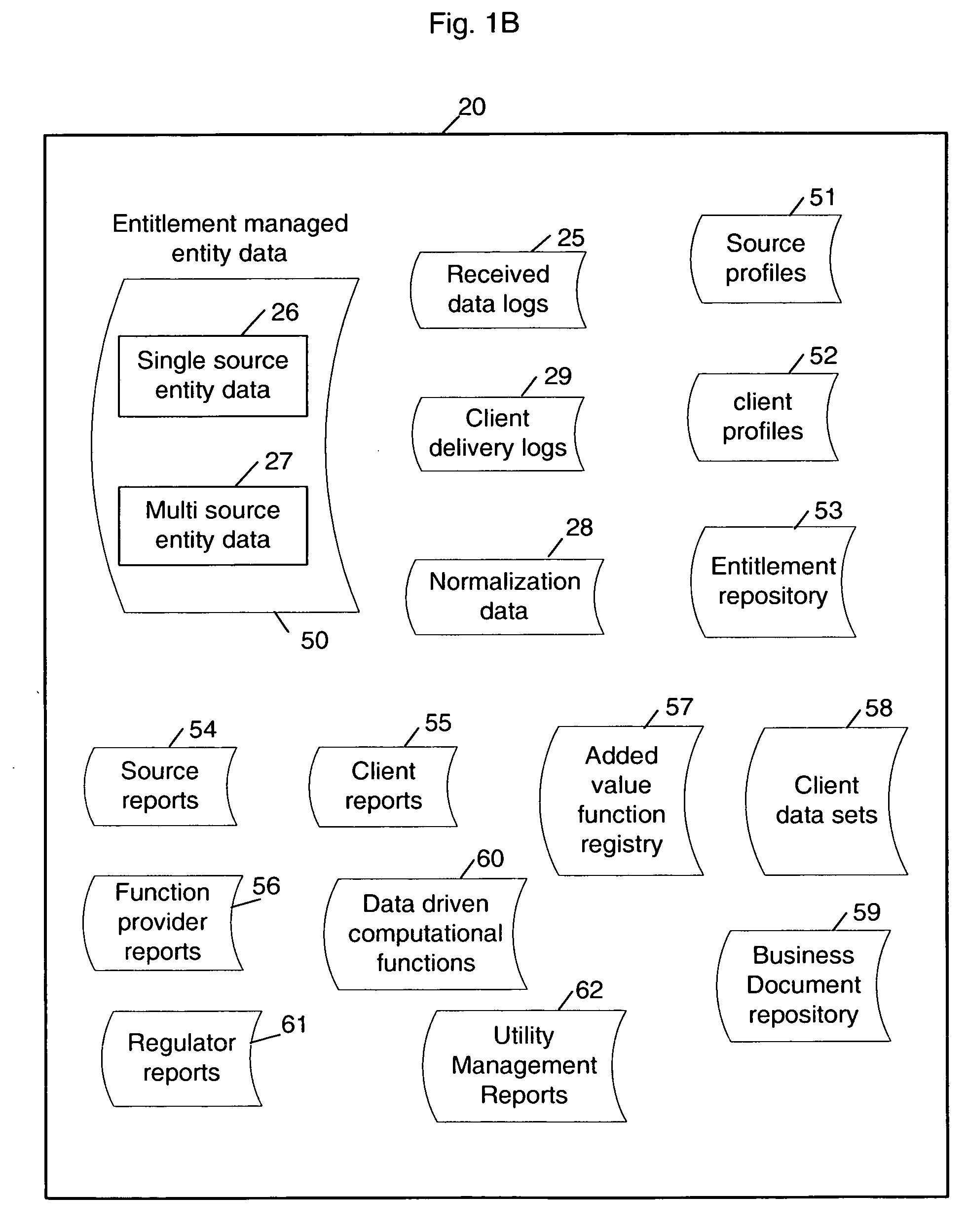
Sharable multi-tenant reference data utility and methods of operation of same
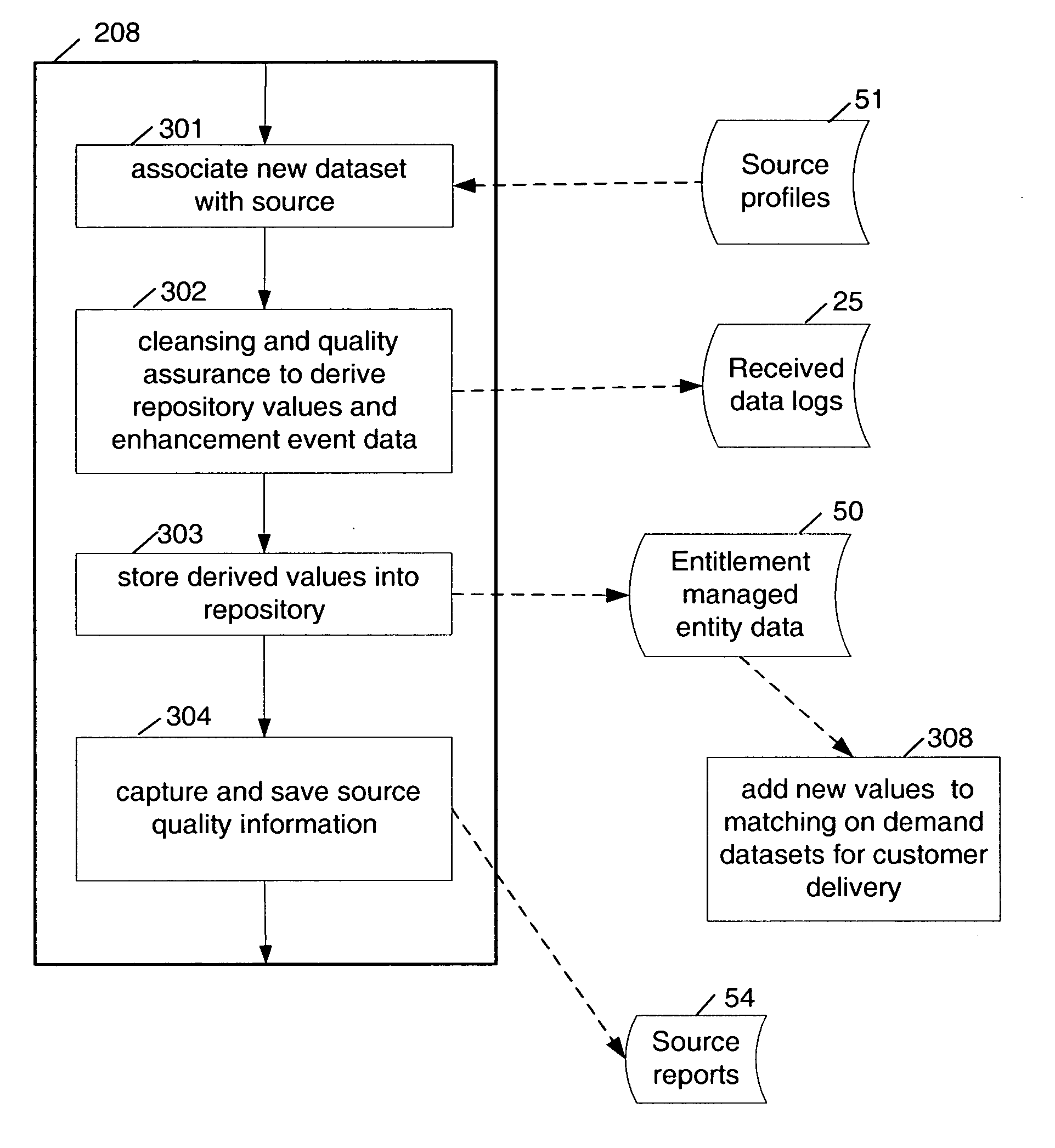
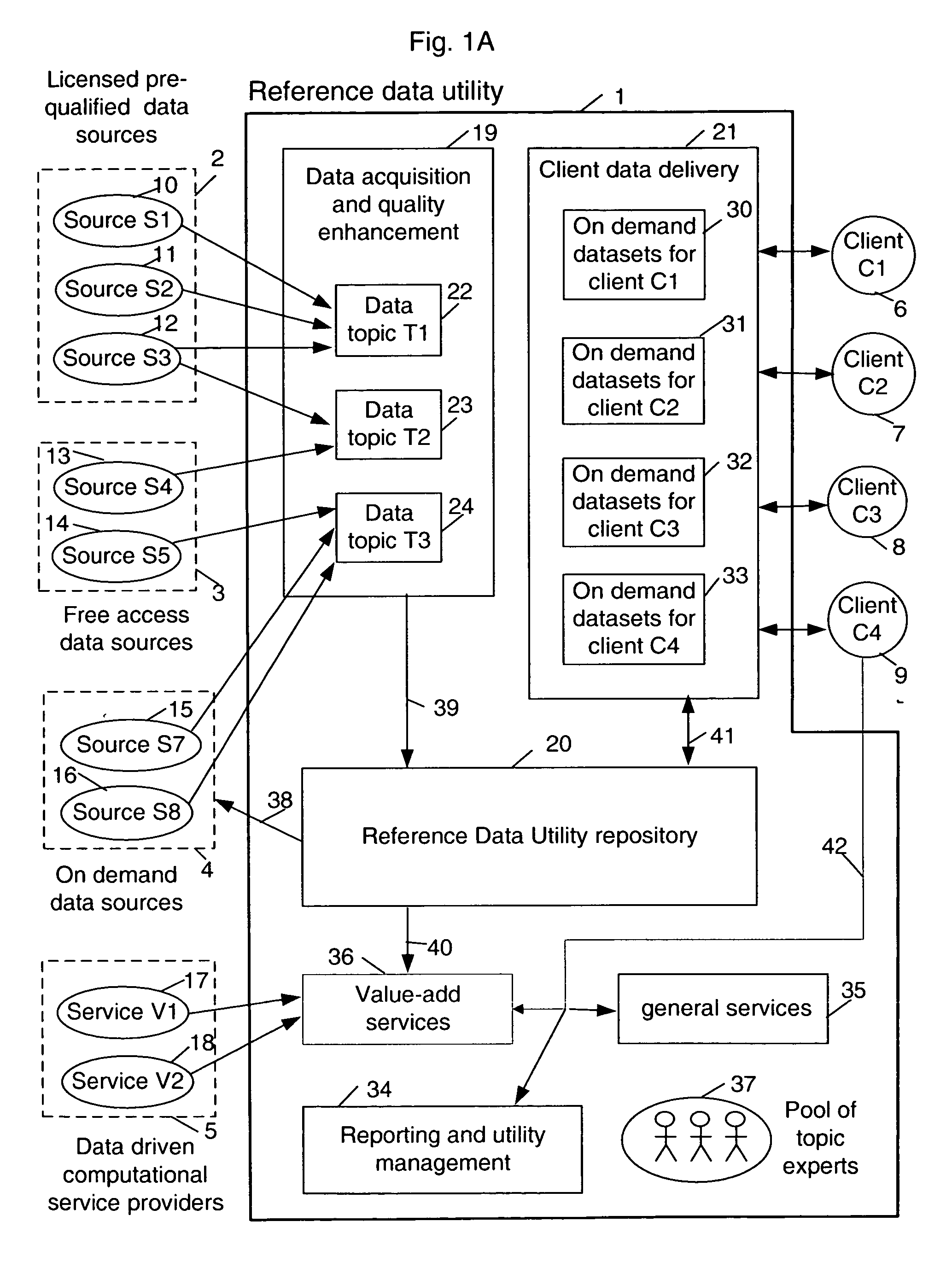
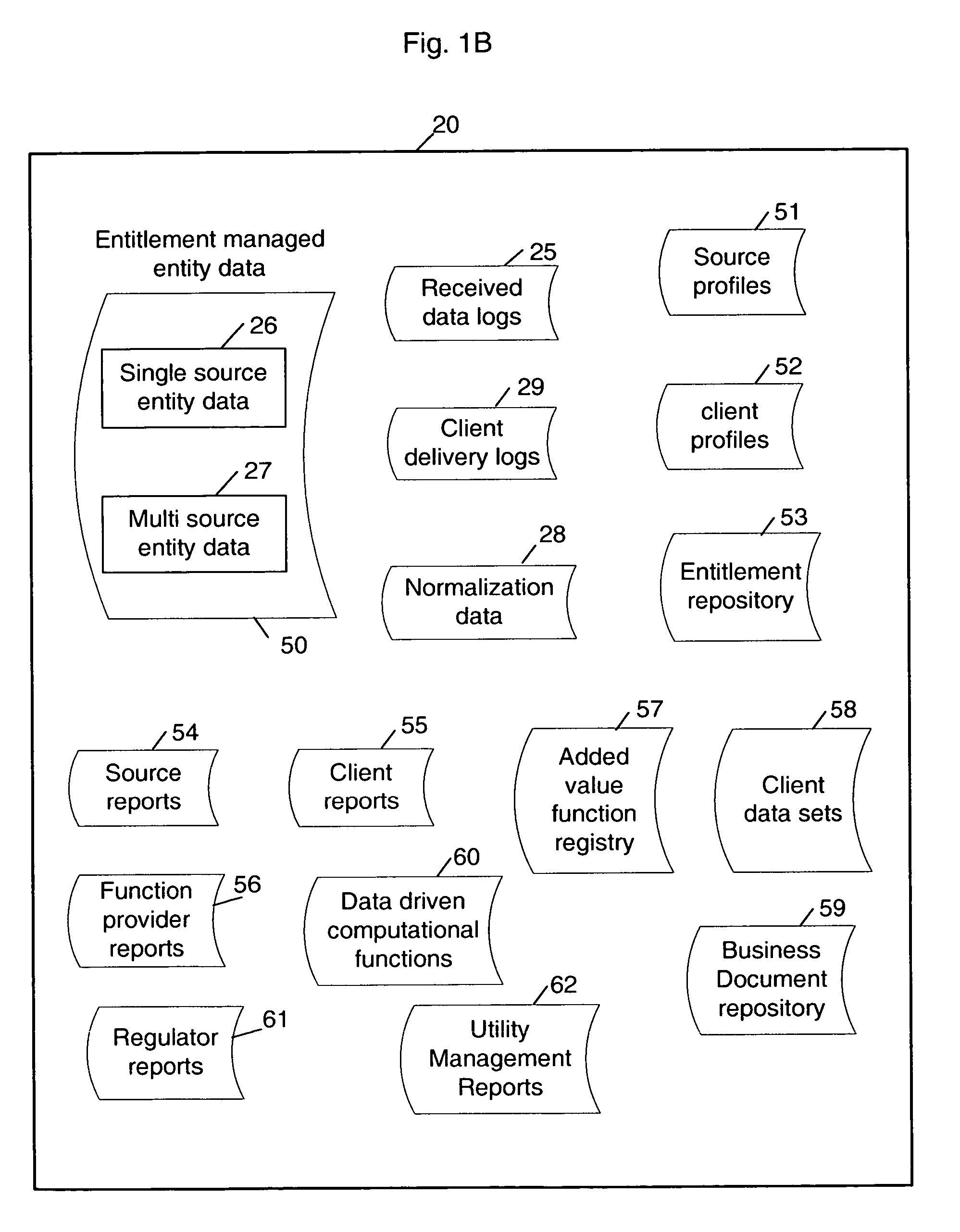
A multi-source multi-tenant reference data utility and methods for forming and maintaining the same, delivering high quality reference data in response to requests from clients, implemented using a shared infrastructure, and also providing added value services using the client's reference data. Included are data cleansing and quality assurance of the received data with full tracking of the sourcing of each value, storage of resulting entity values in a repository which allows retrievals and enforces source based entitlements, and delivery of retrieved data in the form of on demand datasets supporting a wide range of client application needs. An advantageous implementation has additional services for reporting on data quality and usage, a selection of value adding data driven computations and business document storage. By using a shared infrastructure and amortizing the costs of data quality assurance across a plurality of clients, while ensuring that clients only receive values from data sources to which they are licensed, better quality data at lower cost is delivered.
Owner:IBM CORP
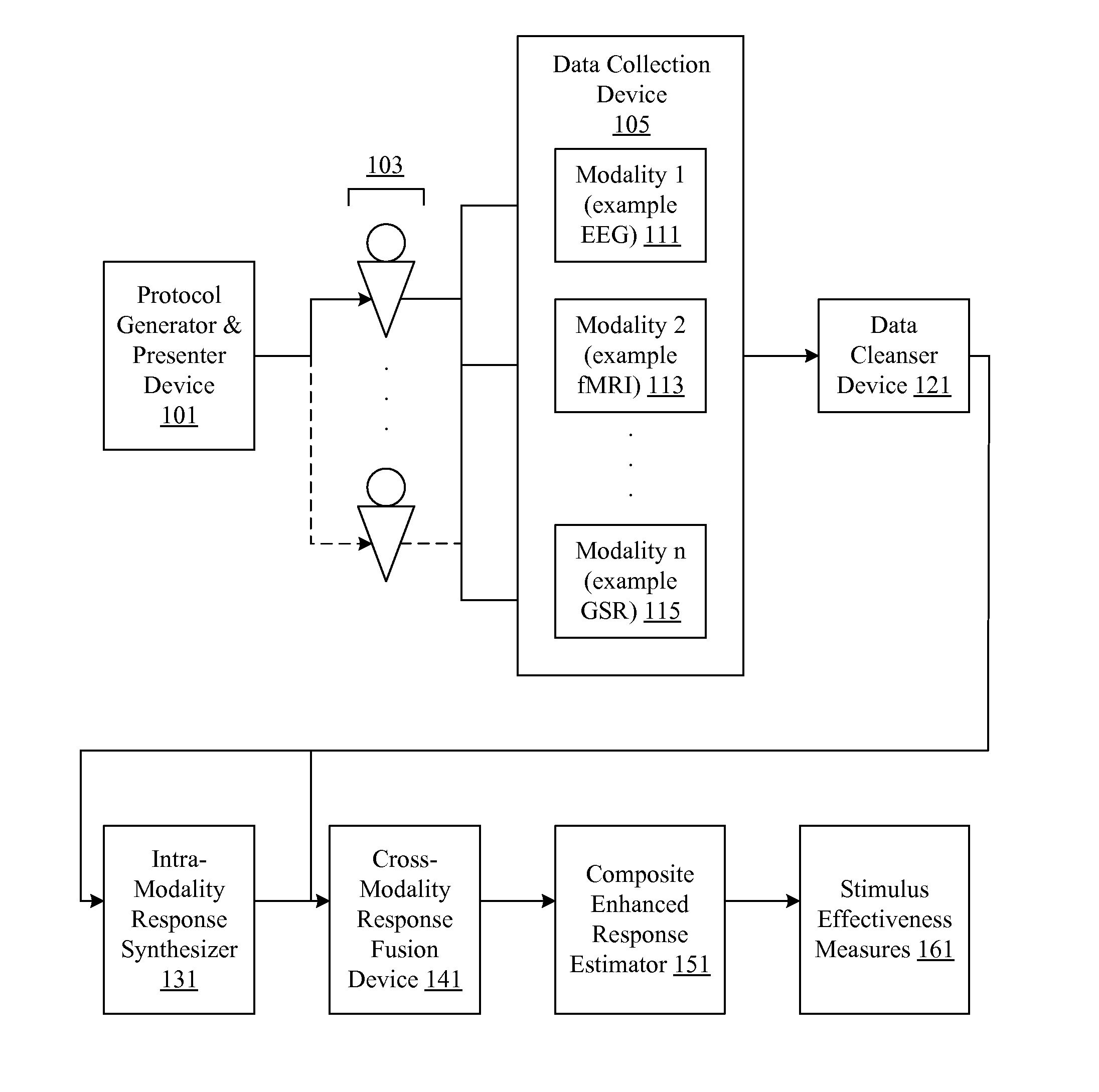
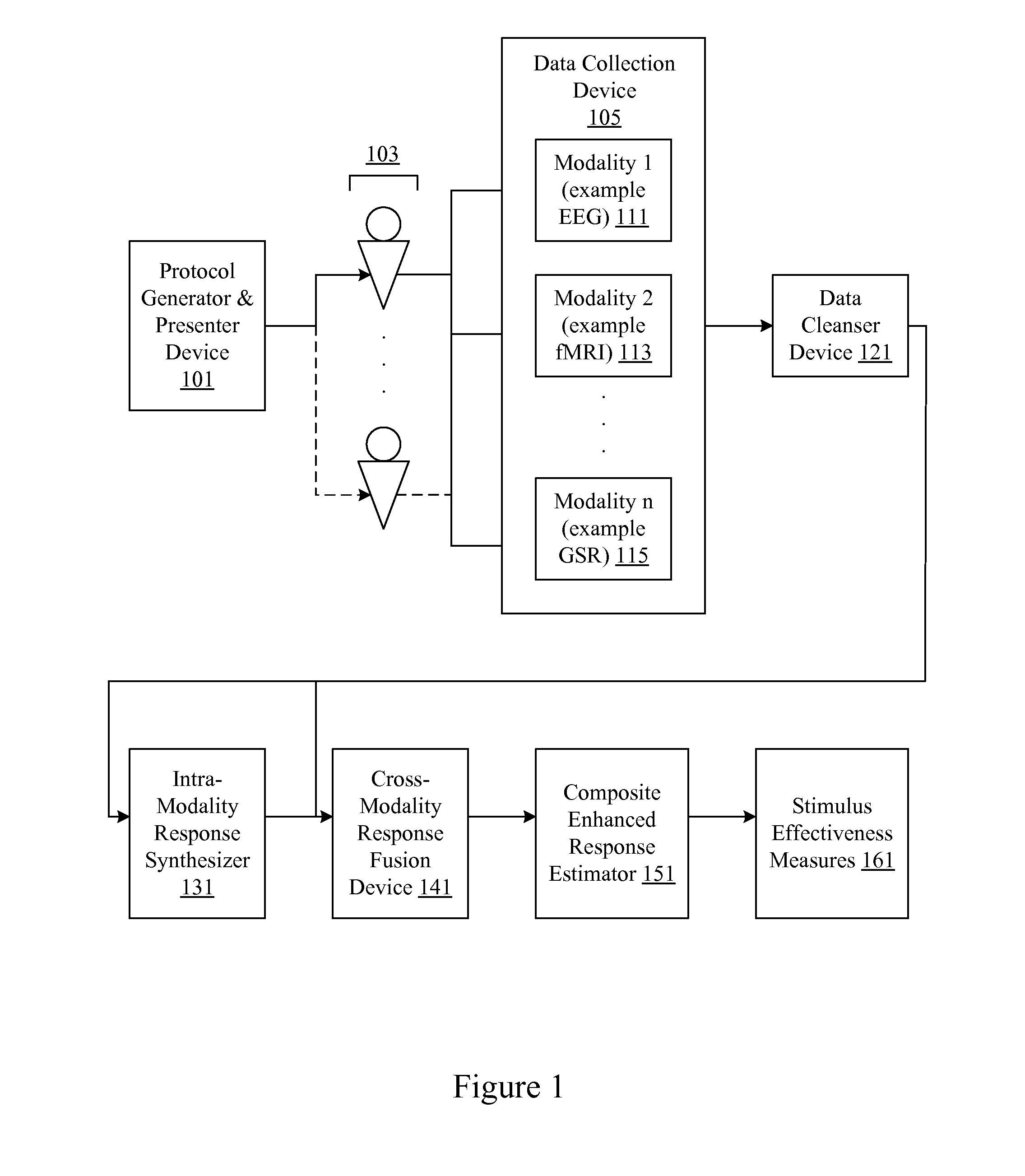
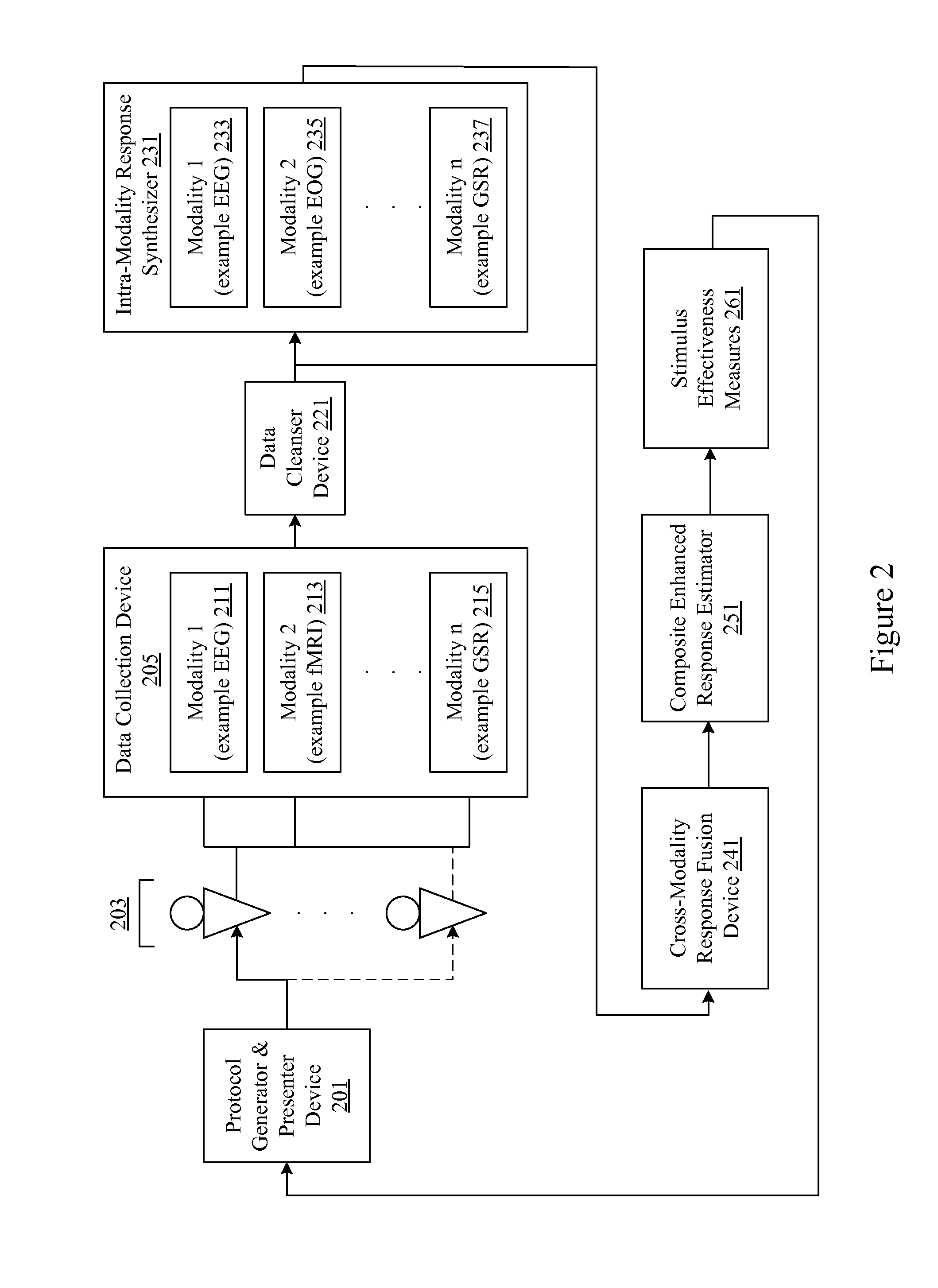
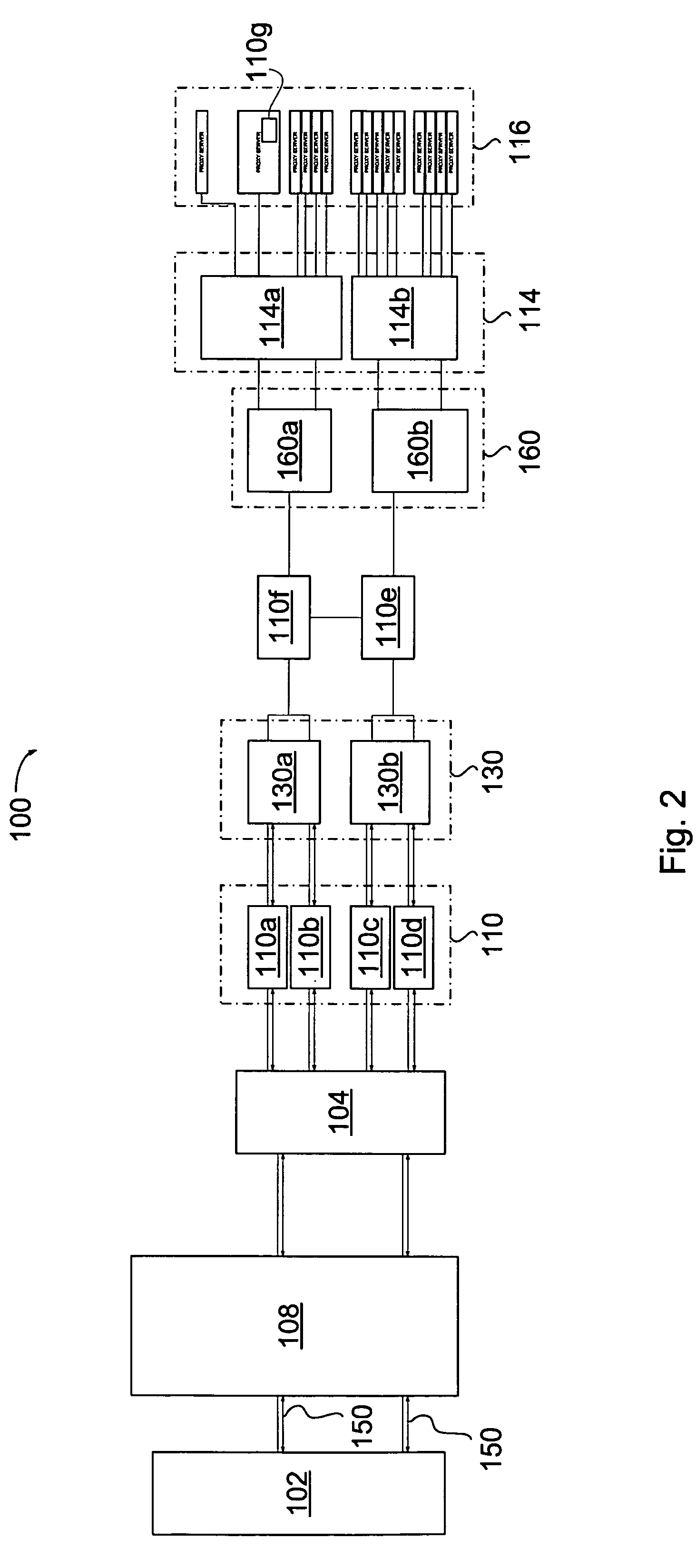
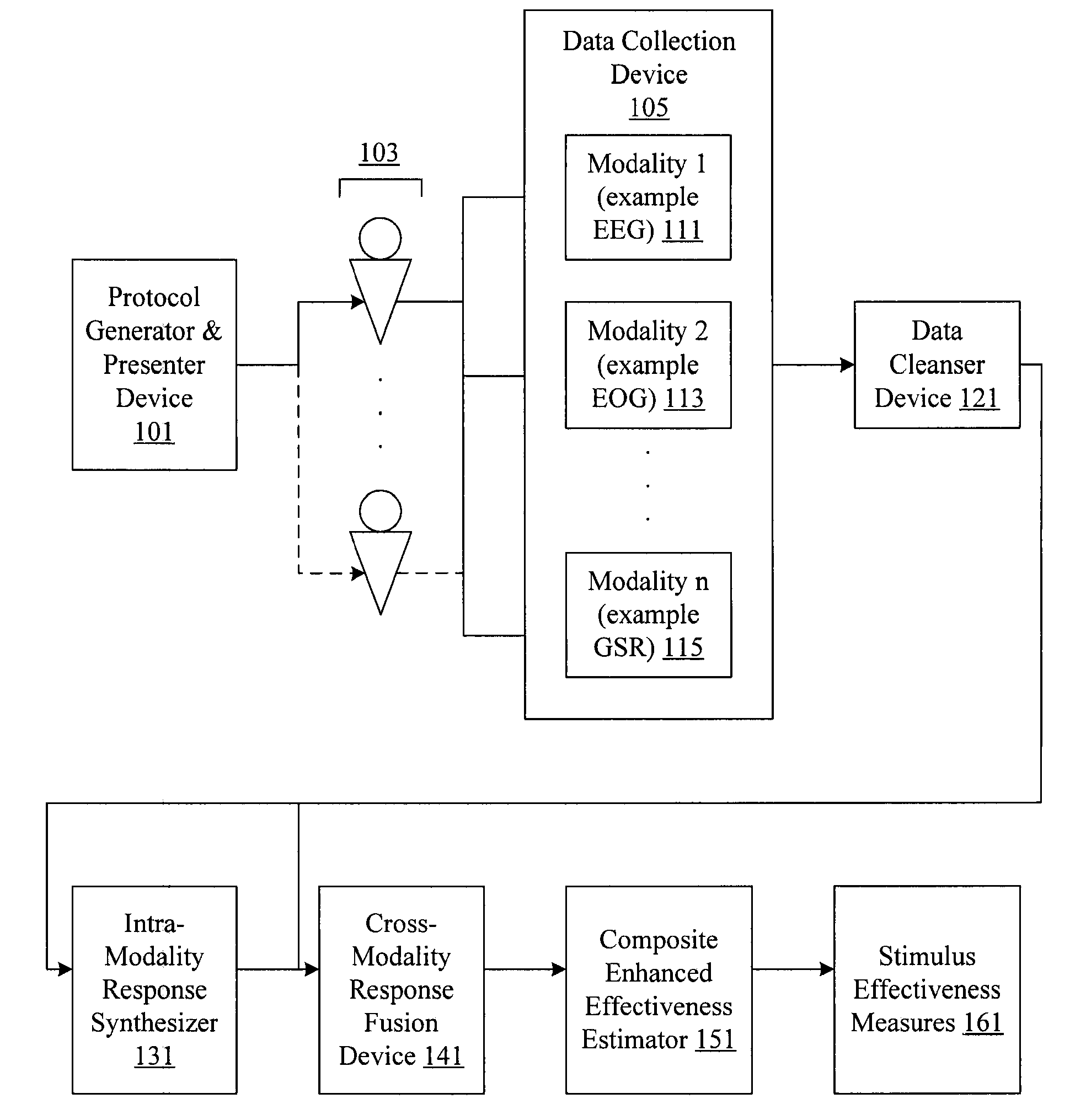
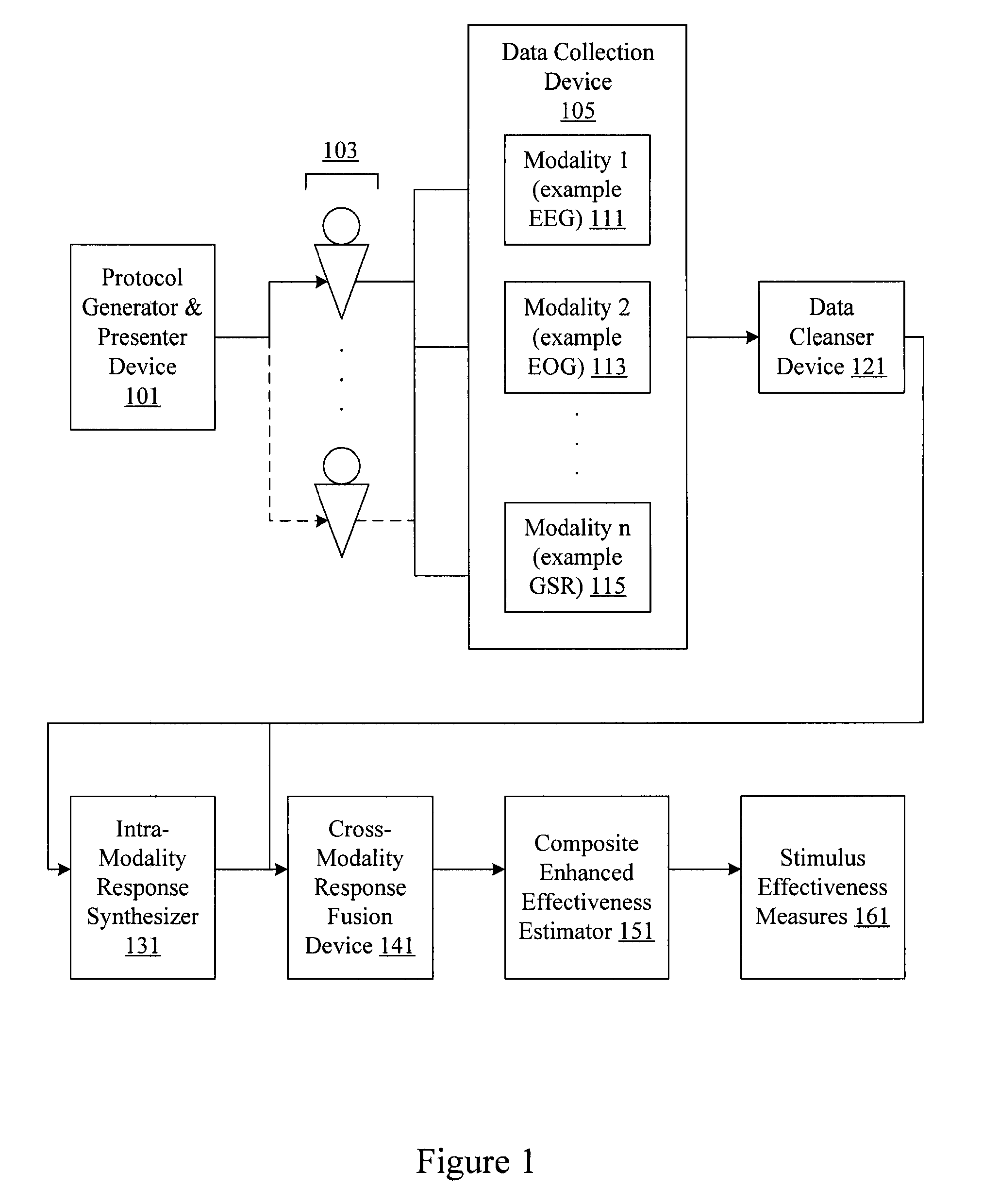
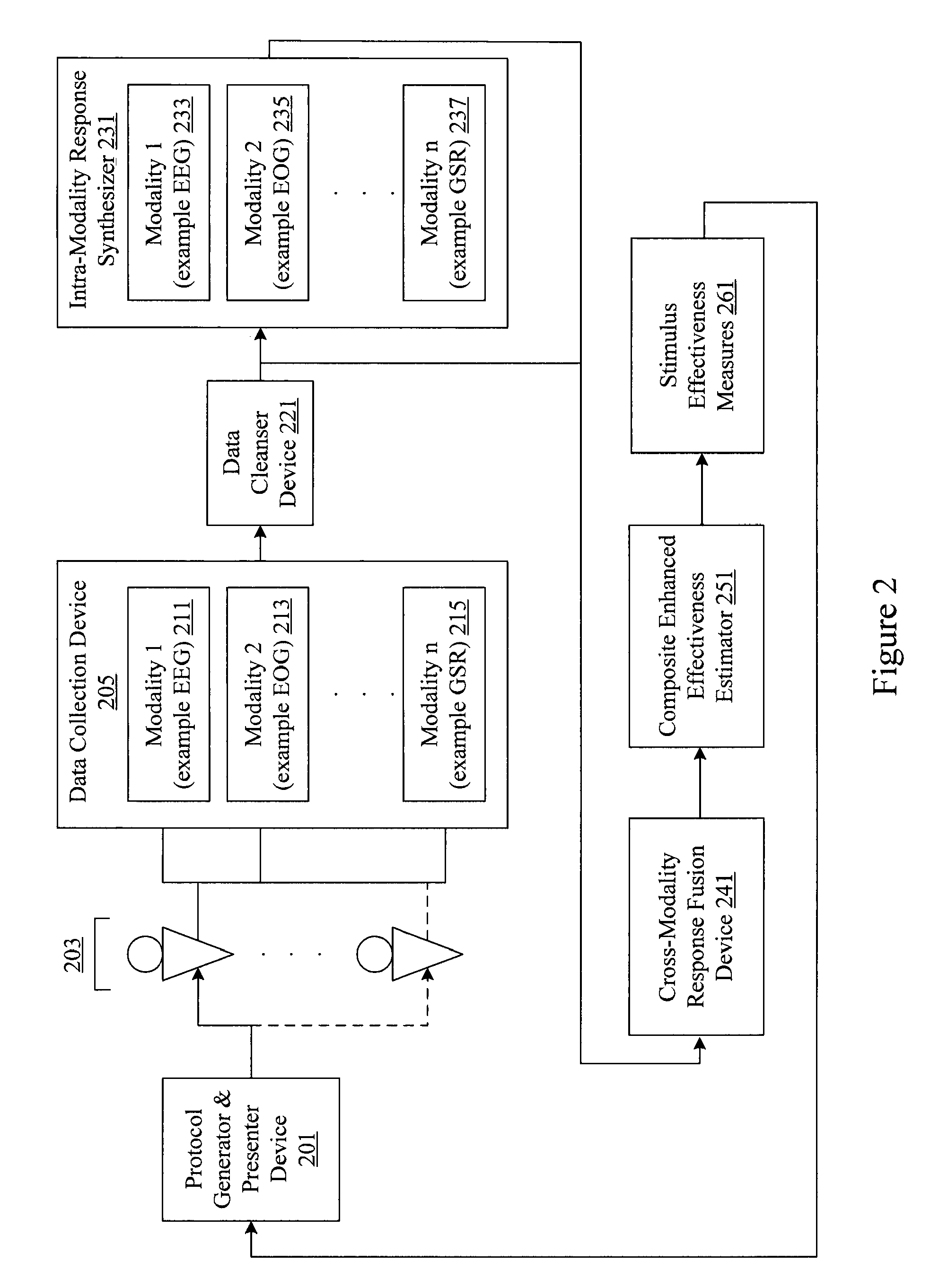
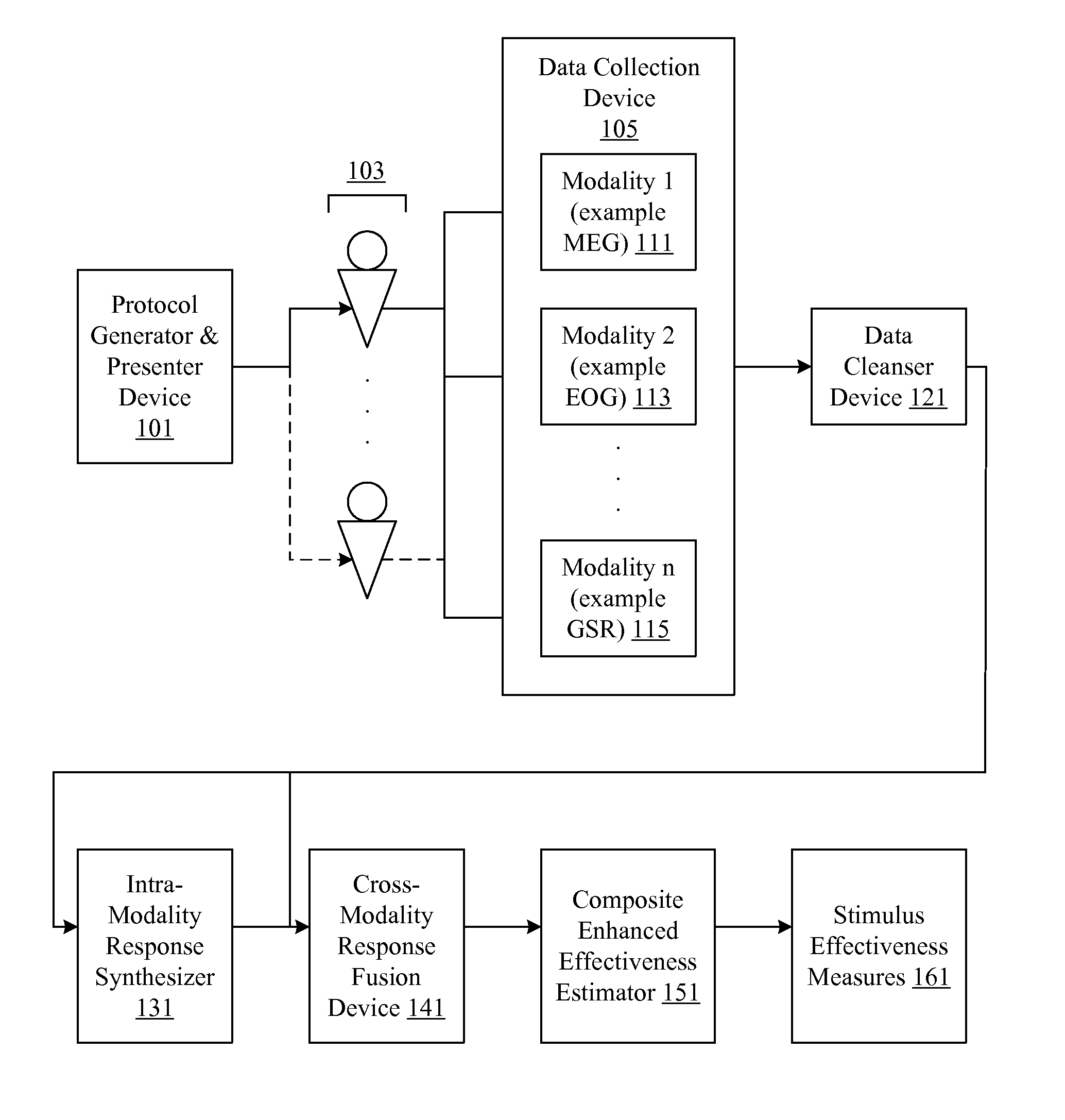
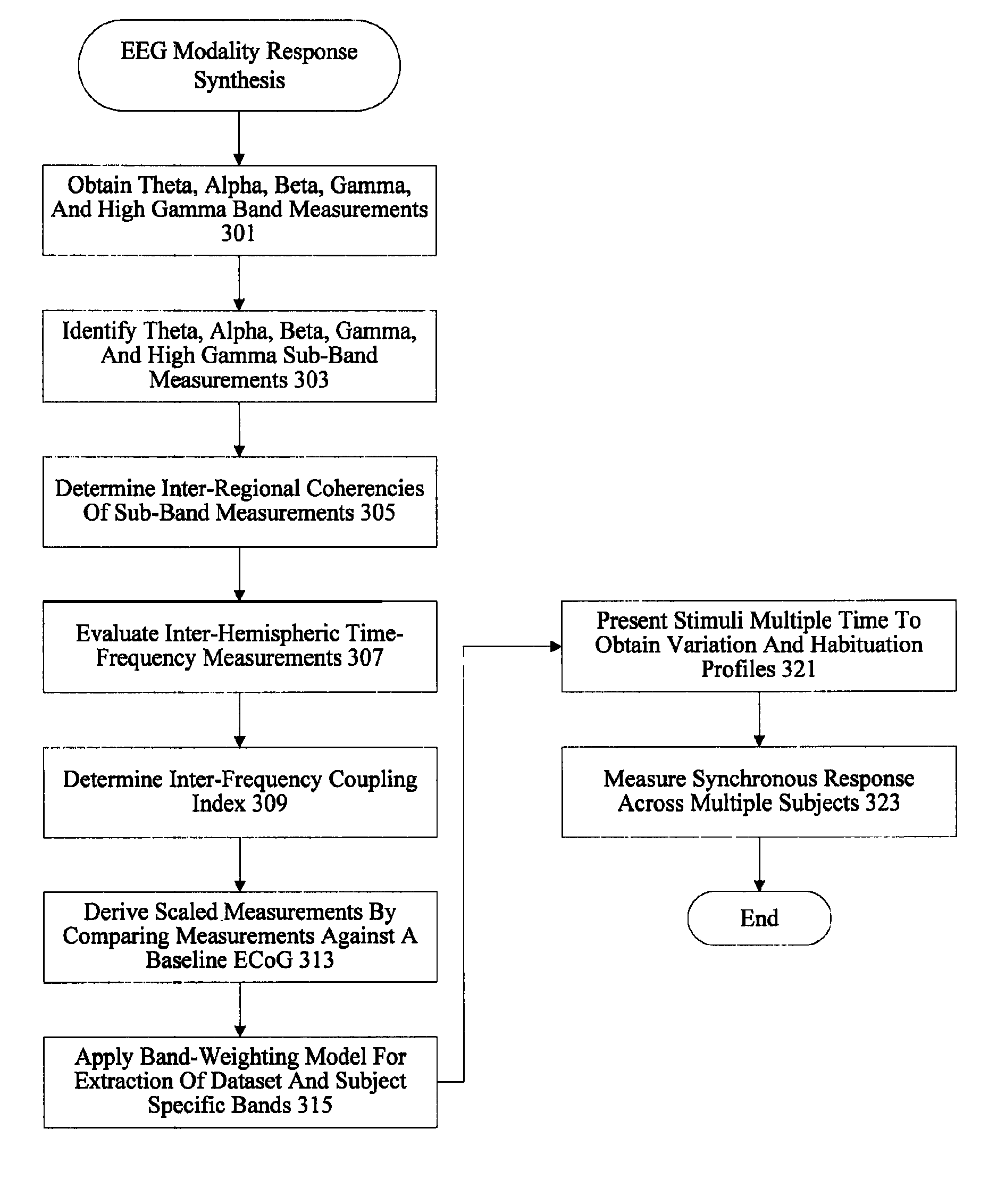
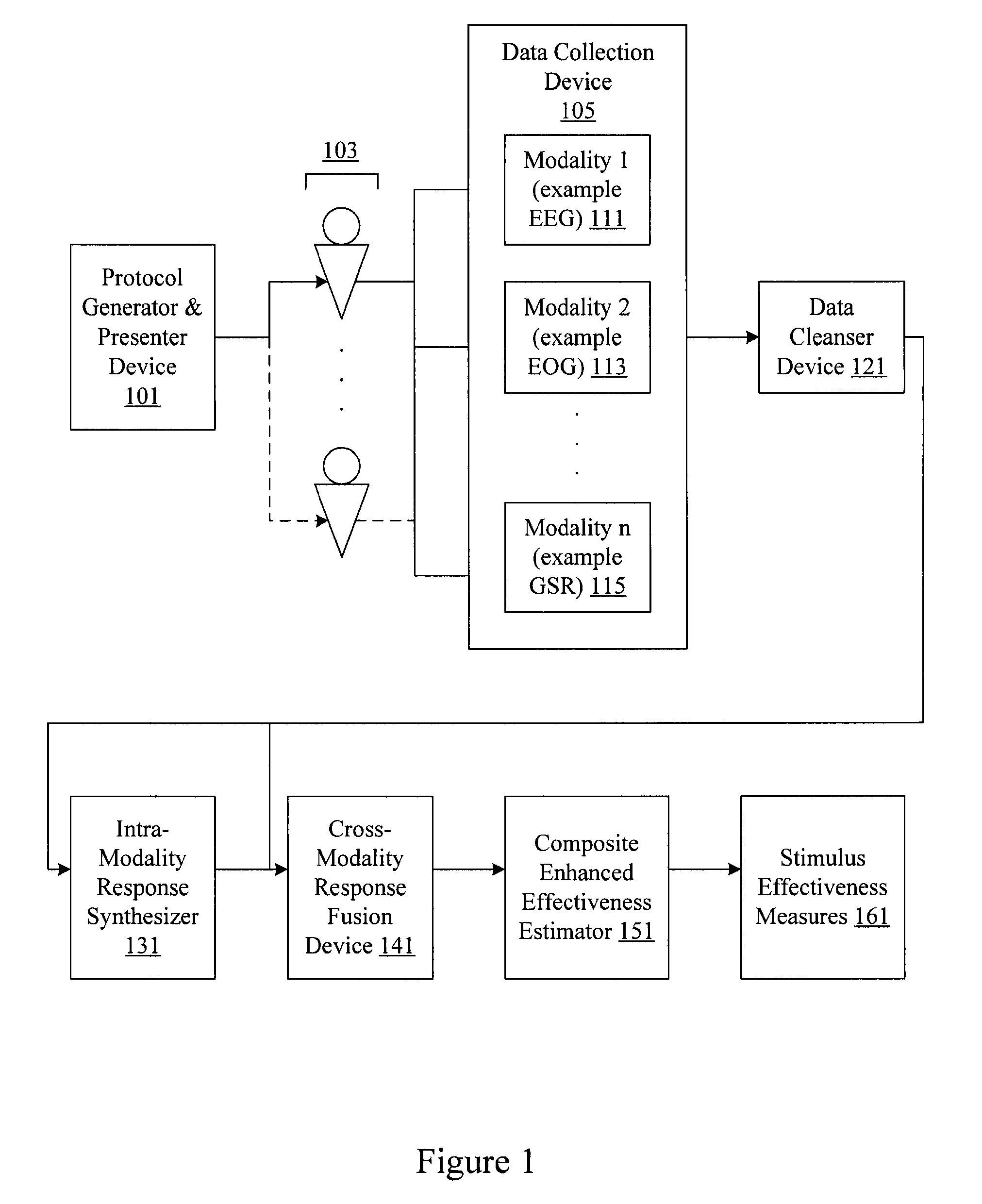
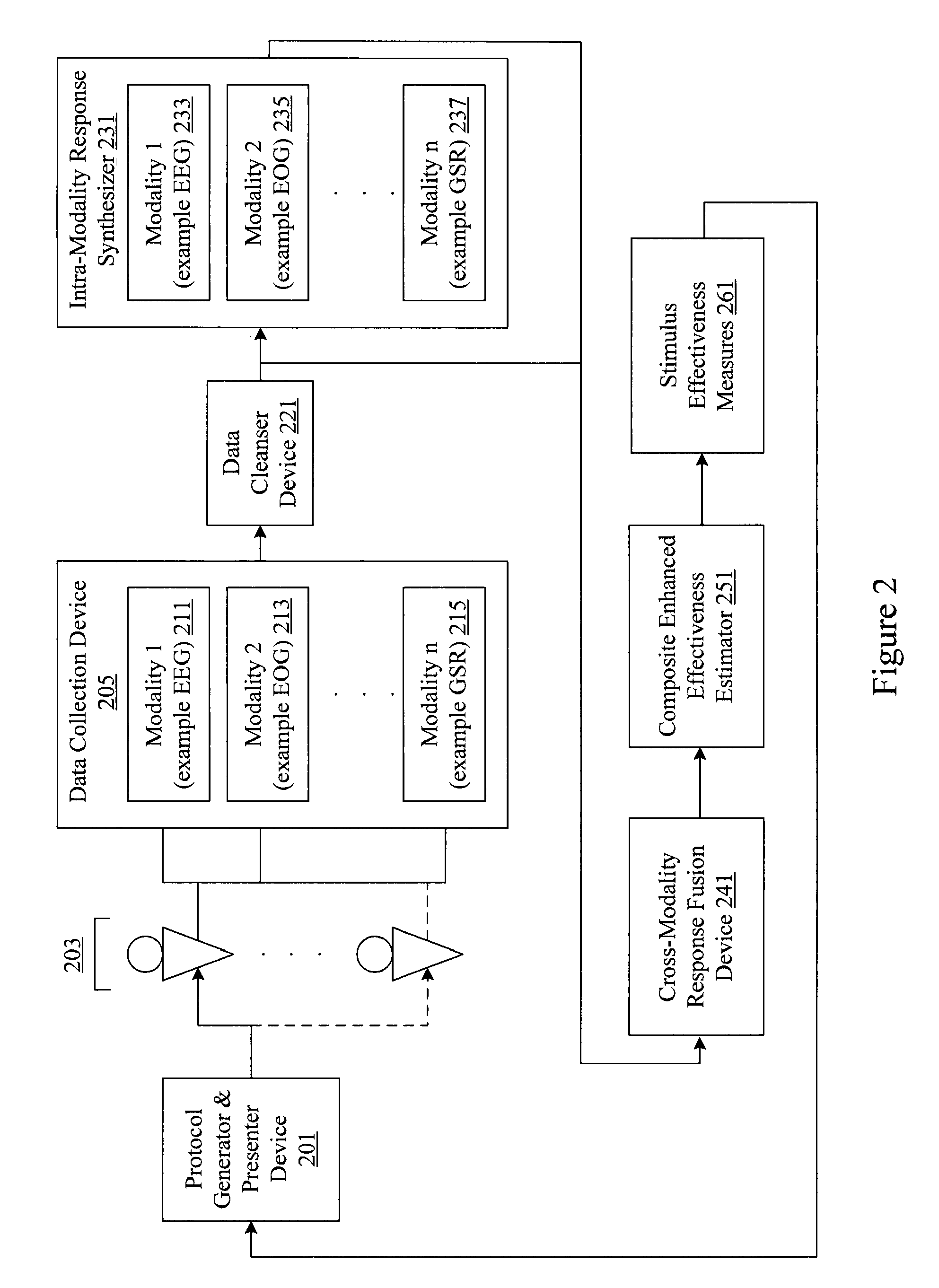
Audience response analysis using simultaneous electroencephalography (EEG) and functional magnetic resonance imaging (FMRI)
Neuro-response data including Electroencephalography (EEG), Functional Magnetic Resonance Imaging (fMRI) is filtered, analyzed, and combined to evaluate the effectiveness of stimulus materials such as marketing and entertainment materials. A data collection mechanism including multiple modalities such as, Electroencephalography (EEG), Functional Magnetic Resonance Imaging (fMRI), Electrooculography (EOG), Galvanic Skin Response (GSR), etc., collects response data from subjects exposed to marketing and entertainment stimuli. A data cleanser mechanism filters the response data and removes cross-modality interference.
Owner:NIELSEN CONSUMER LLC
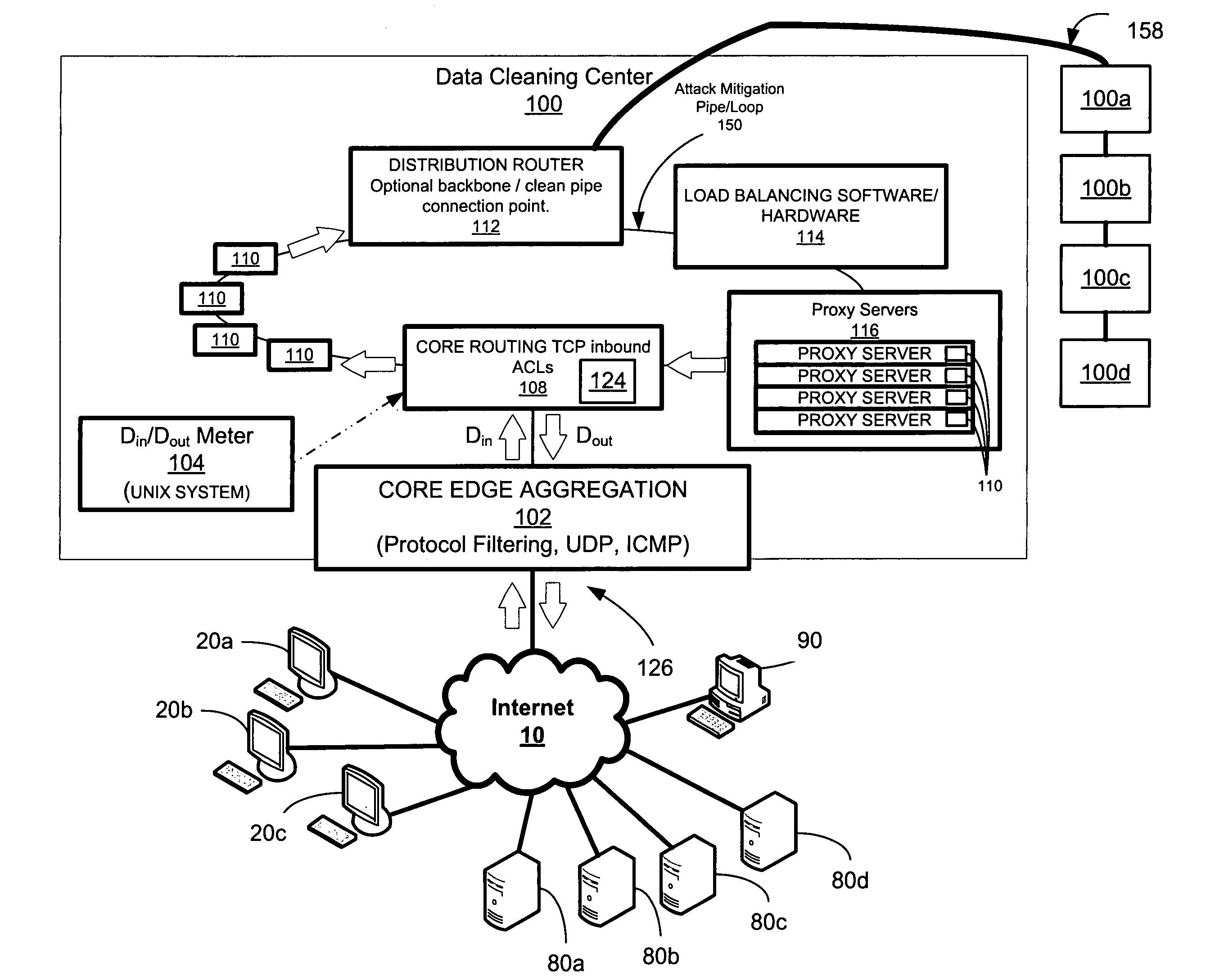
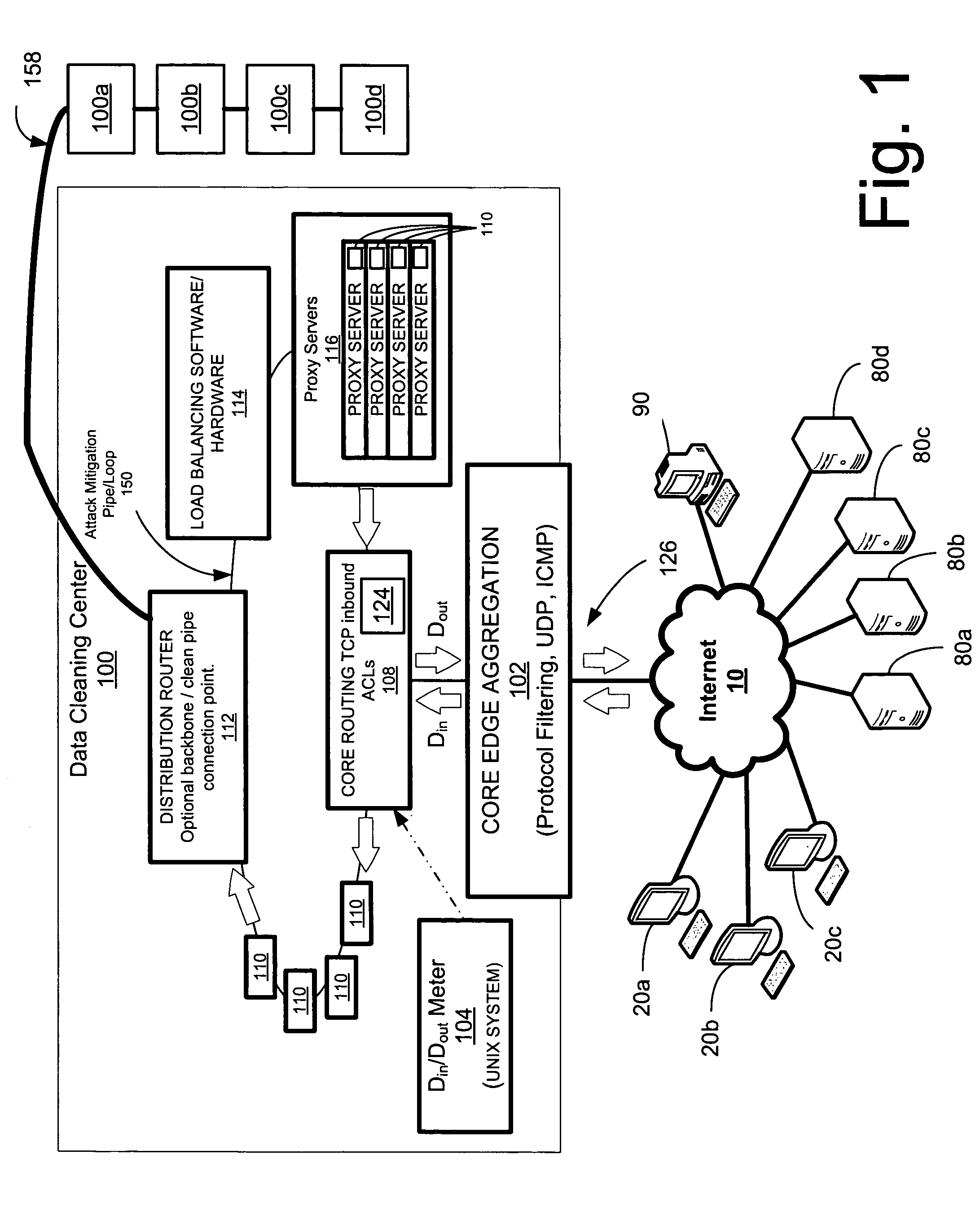
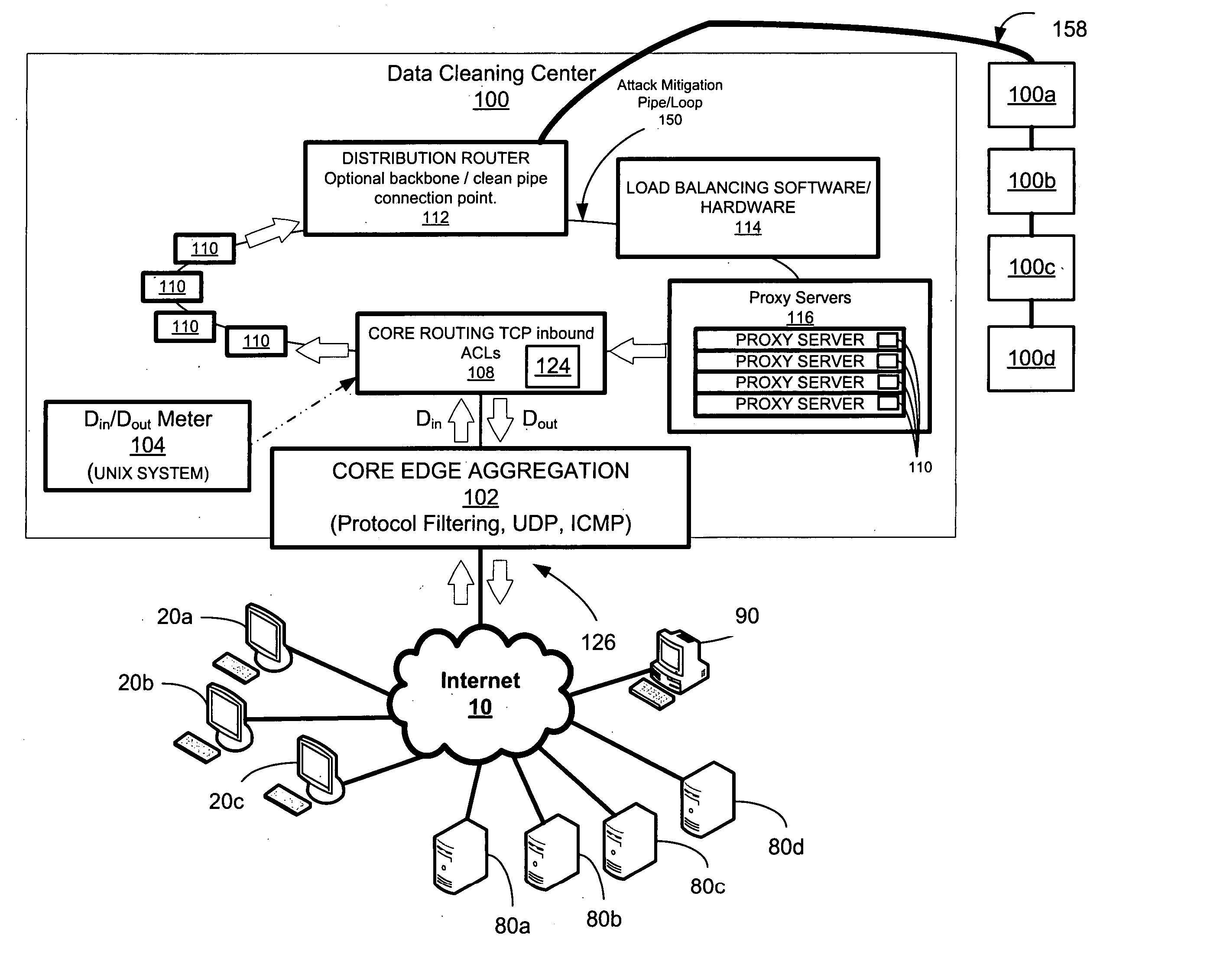
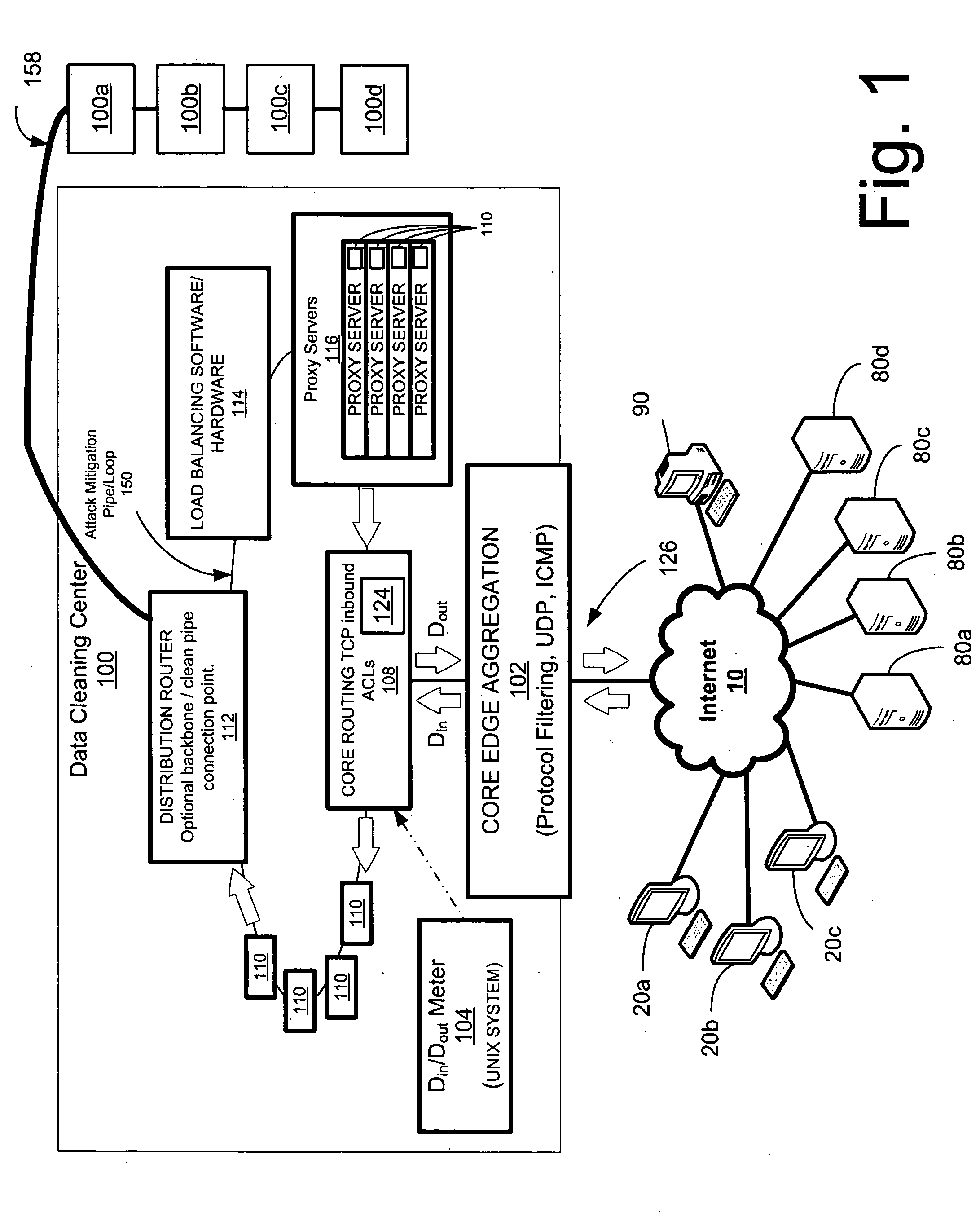
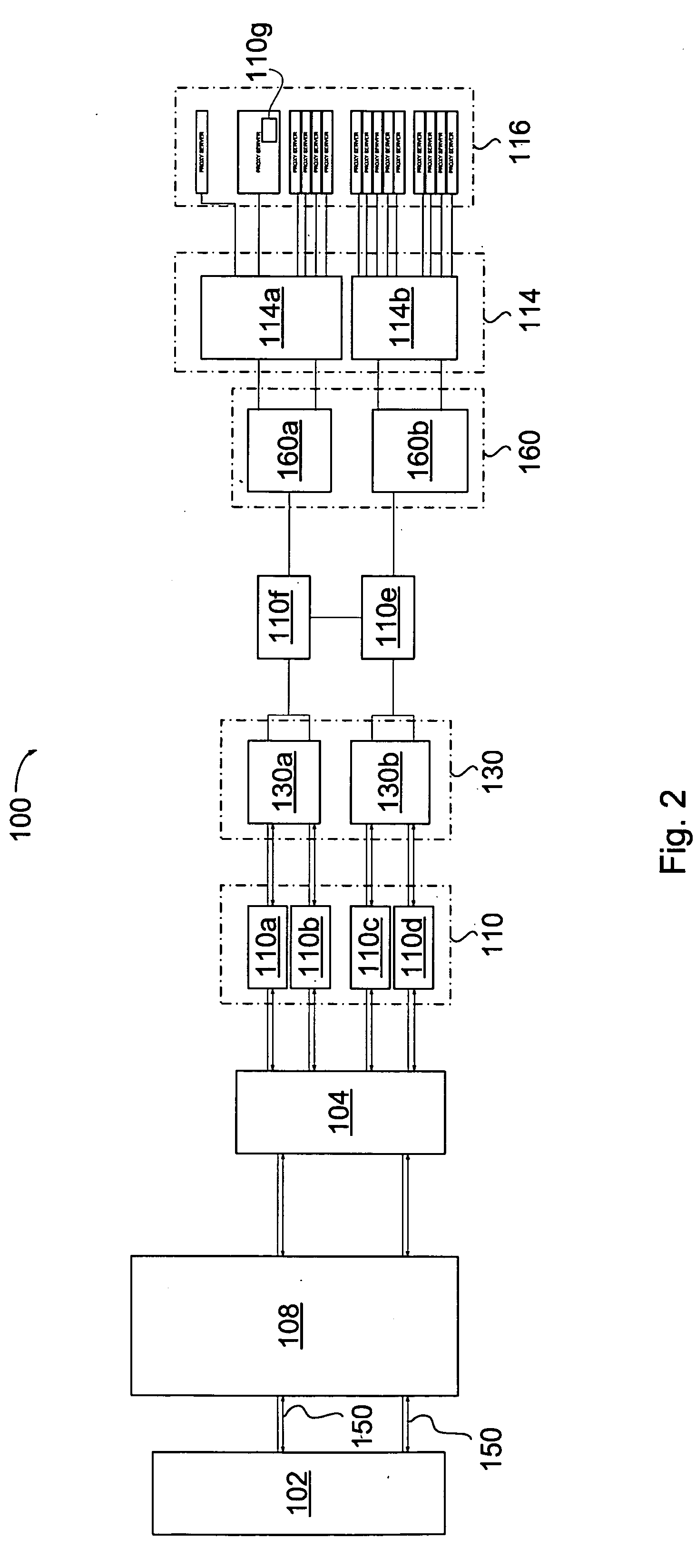
Network overload detection and mitigation system and method
A system and method is disclosed for detecting and / or mitigating an overload condition from one or more first computers, such as a distributed denial of service (DDoS) attack, viral attack, or the like, targeting one or more of a plurality of second computers located on a network. While one or more DDoS attacks are mitigated, a meter, detection apparatus, software, or method, detects the condition being mitigated in a data cleaning center, and provides an alert or notification regarding the mitigated attack.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an overload or attempted overload condition targeting a domain name server. A network connection is provided for receiving one or more DNS requests from one or more client computers located on a network. A preferred embodiment includes a processor for providing a response to the one or more DNS requests to the one or more client computers if more than a threshold number of duplicate DNS requests are received.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an attempted overload condition targeting a networked computer system that uses a redirection module to divert data until it is deemed to be clean.
Owner:AKAMAI TECH INC
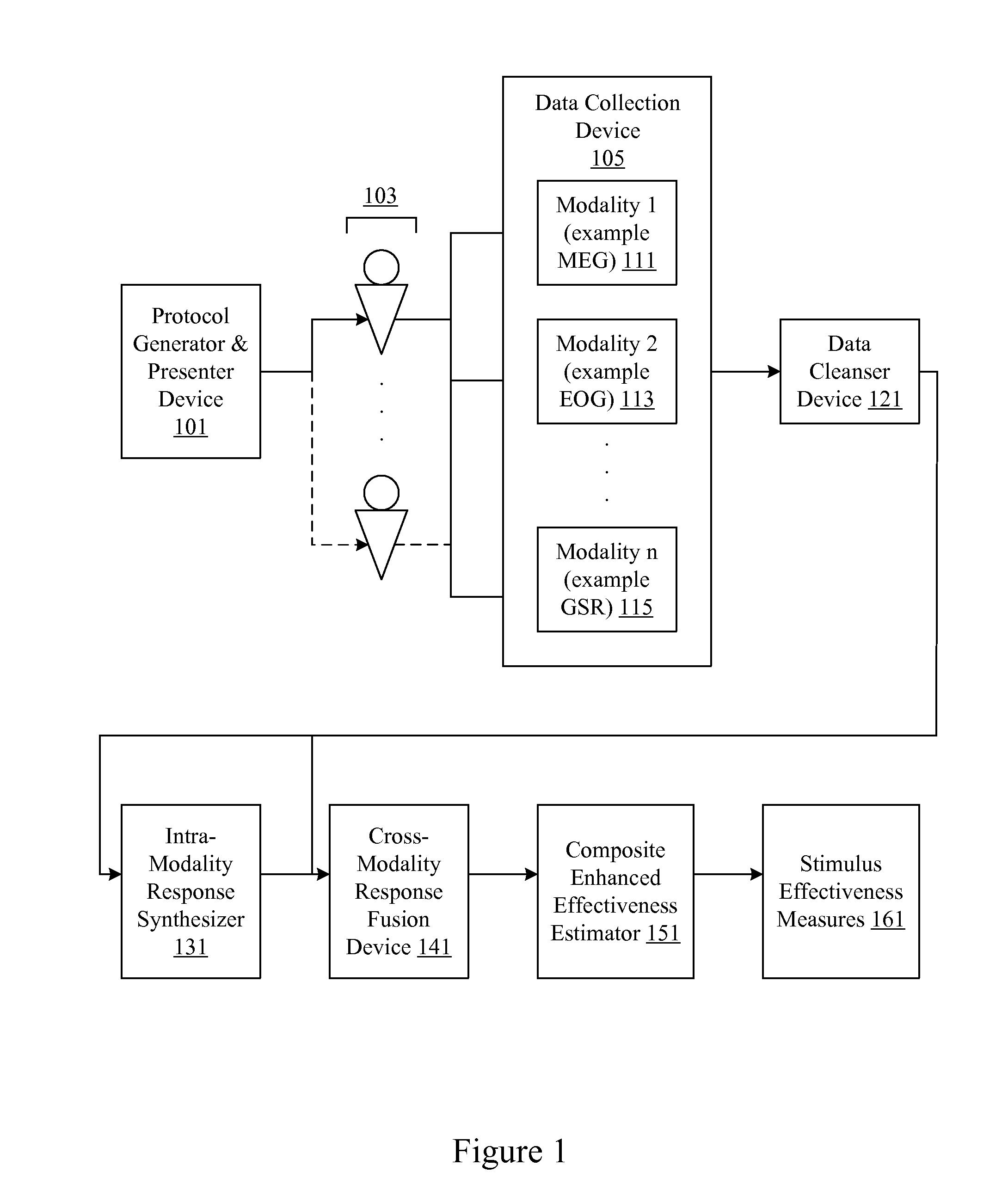
Analysis of marketing and entertainment effectiveness using central nervous system, autonomic nervous sytem, and effector data
ActiveUS20090024447A1Data acquisition and loggingMarket data gatheringCross modalityDiagnostic Radiology Modality
Central nervous system, autonomic nervous system, and effector data is measured and analyzed to determine the effectiveness of marketing and entertainment stimuli. A data collection mechanism including multiple modalities such as Electroencephalography (EEG), Electrooculography (EOG), Galvanic Skin Response (GSR), etc., collects response data from subjects exposed to marketing and entertainment stimuli. A data cleanser mechanism filters the response data. The response data is enhanced using intra-modality response synthesis and / or a cross-modality response synthesis.
Owner:NIELSEN CONSUMER LLC
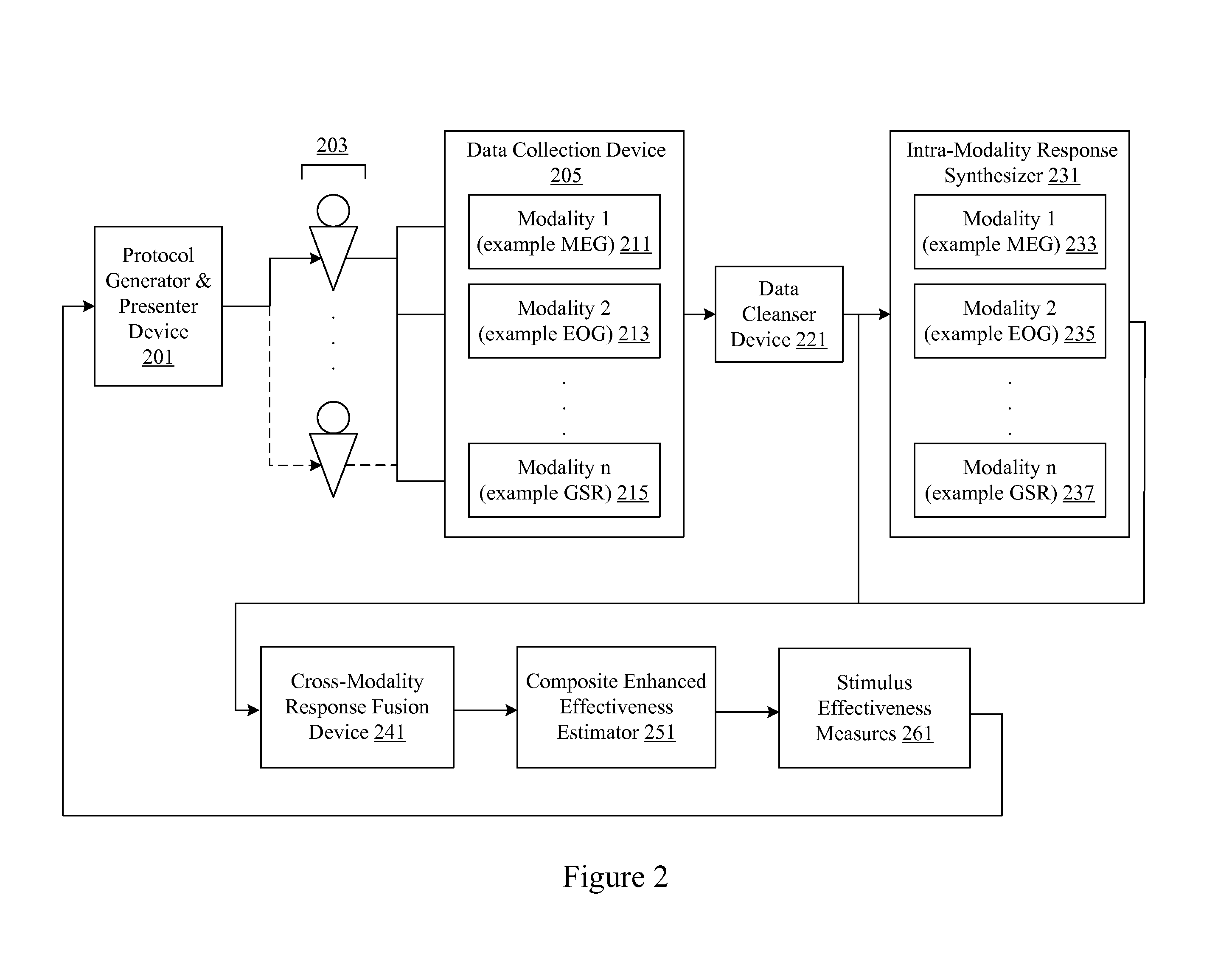
Analysis of marketing and entertainment effectiveness using magnetoencephalography
ActiveUS20090082643A1Analogue secracy/subscription systemsDiagnostic recording/measuringDiagnostic Radiology ModalityCross modality
Central nervous system, autonomic nervous system, and effector data is measured and analyzed to determine the effectiveness of marketing and entertainment stimuli. A data collection mechanism including multiple modalities such as Magnetoencephalography (MEG), Electrooculography (EOG), Galvanic Skin Response (GSR), etc., collects response data from subjects exposed to marketing and entertainment stimuli. A data cleanser mechanism filters the response data. The response data is enhanced using intra-modality response synthesis and / or a cross-modality response synthesis.
Owner:NIELSEN CONSUMER LLC
Enabling value enhancement of reference data by employing scalable cleansing and evolutionarily tracked source data tags
Provision for scalable cleansing and value enhancement of data in the context of a multi-source multi-tenant data repository. The source data comes from multiple sources and on multiple topics. Evolutionarily tracked source data tags are used to hold tracking information reflecting the nature and sources of each change to the data, as it is affected during the various stages of data processing. The stages of processing include validation, normalization, single-source cleansing and cross-source processes. Various rules are applied during these stages, and evolutionarily tracked source data tags are used to record sources and agents of all changes to the data. As information is processed, transformed, and added to the repository, corresponding evolutionarily tracked source data tags are stored in association with the various information elements. The information contained in these tags can be used to enforce data entitlements in a multi-tenant data repository environment.
Owner:CALUSINSKI EDWARD PATRICK JR +9
Text joins for data cleansing and integration in a relational database management system
InactiveUS20050027717A1Relational databasesComparison of digital valuesCosine similarityRelational database management system
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
Adaptive data cleaning
InactiveUS20060238919A1Digital data information retrievalRecord information storageAnalysis dataData system
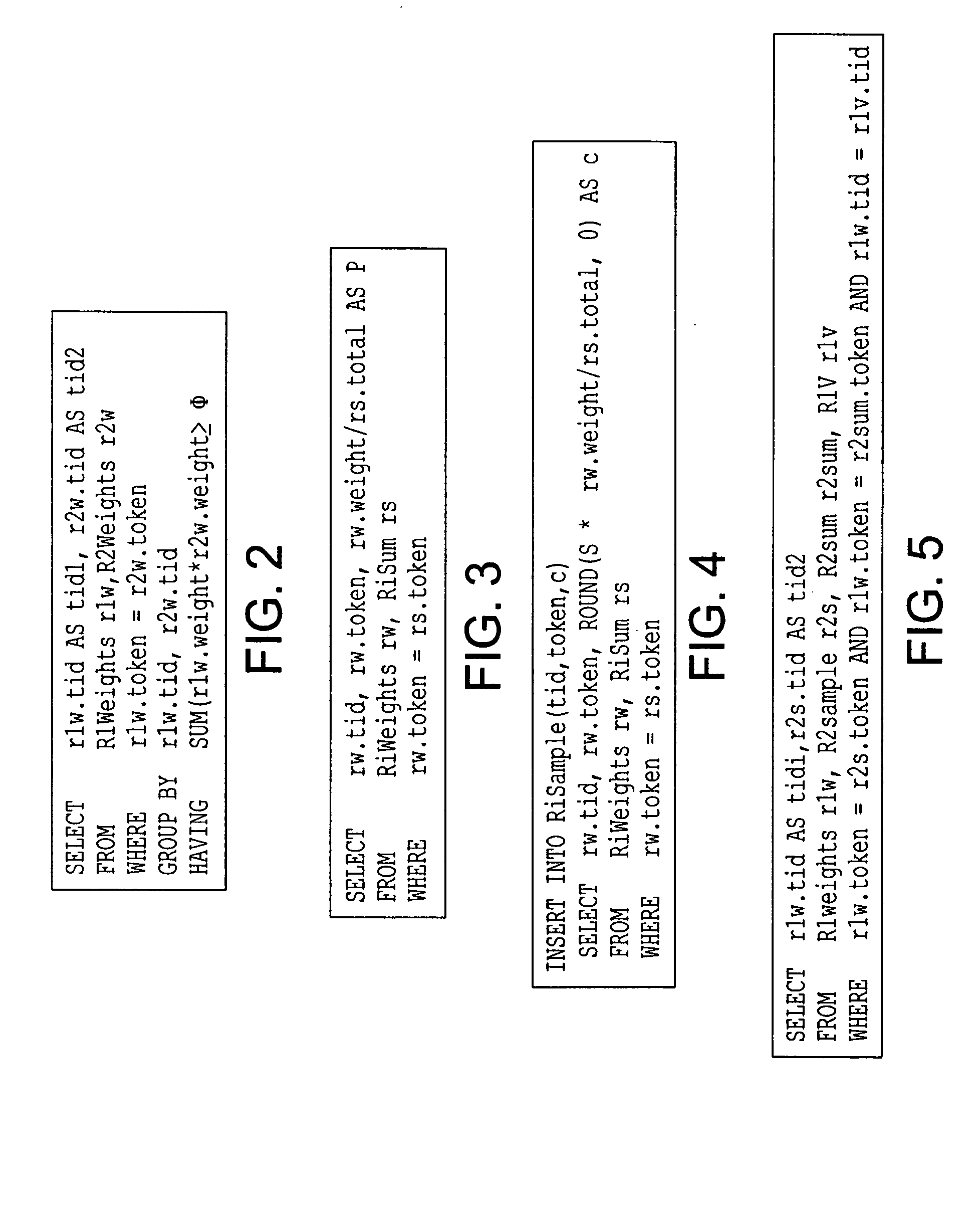
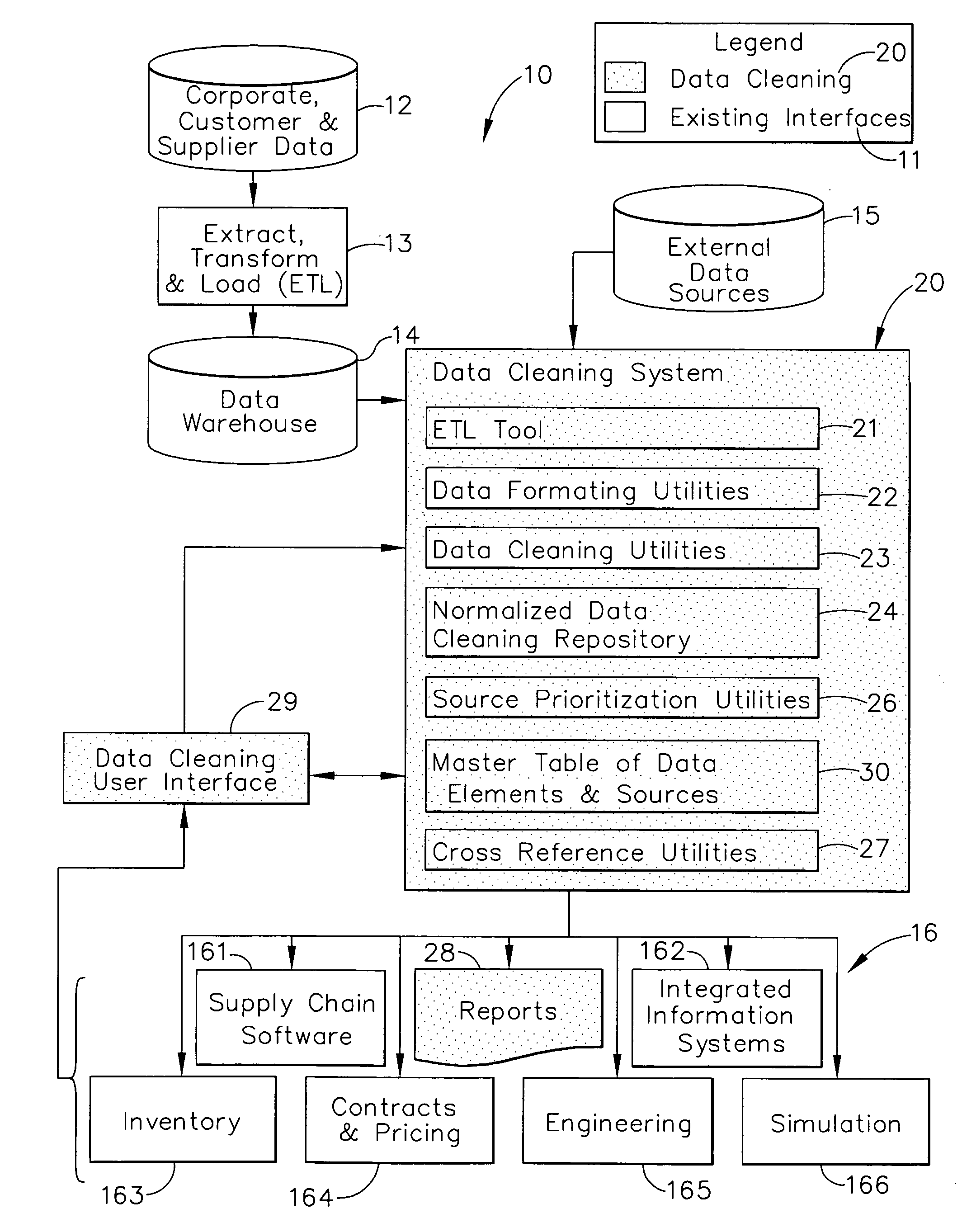
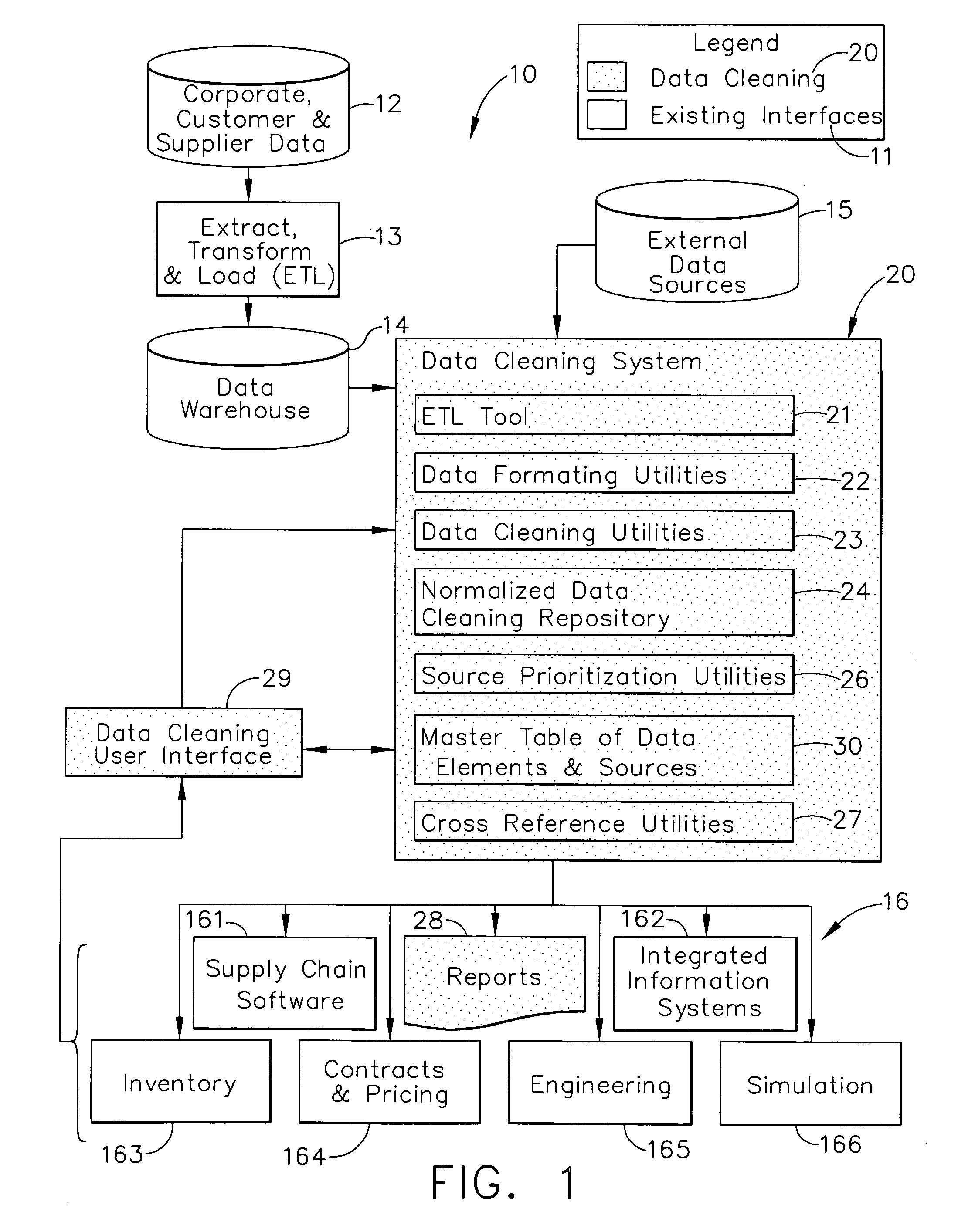
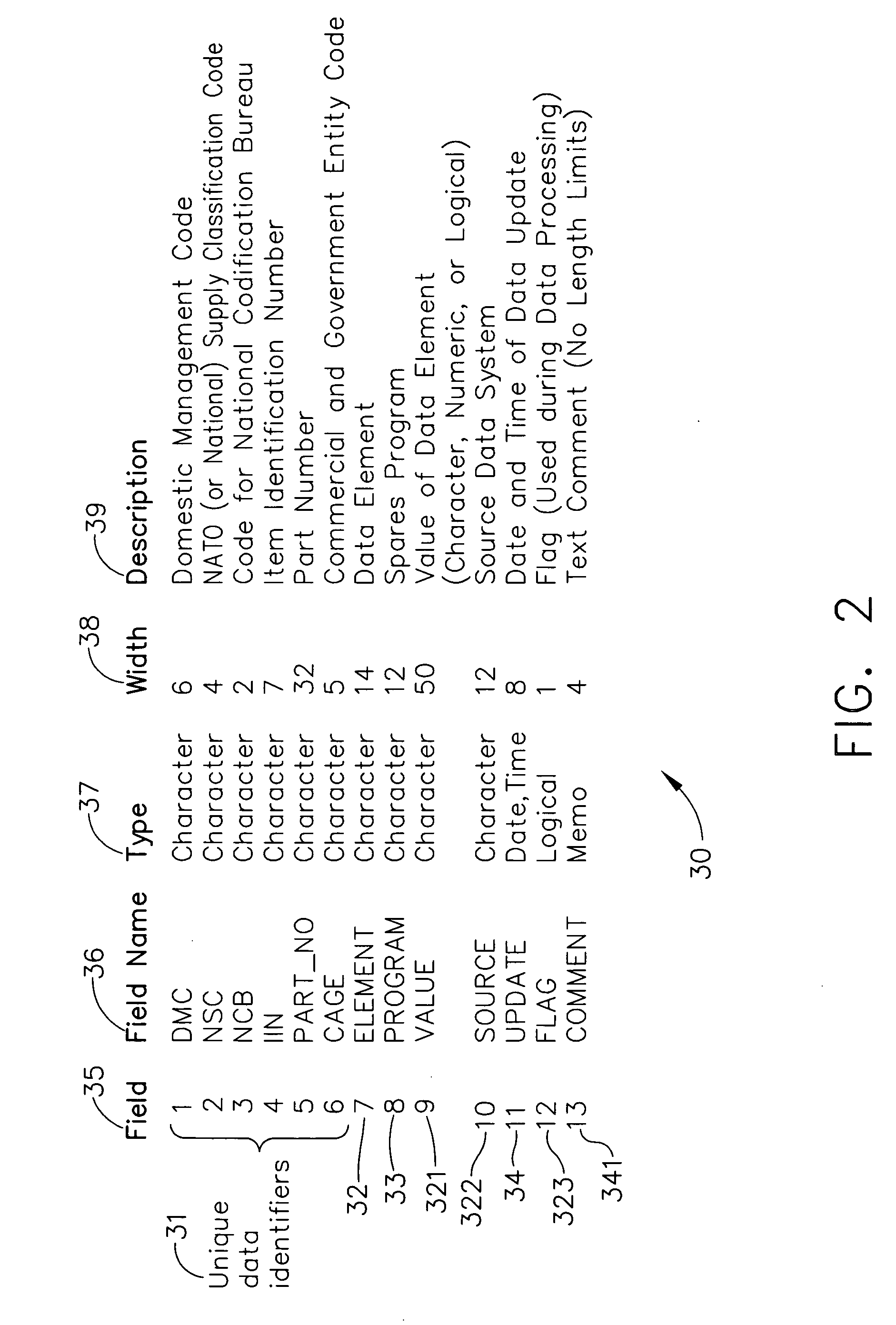
A data cleaning process includes the steps of: validating data loaded from at least two source systems; appending the validated data to a normalized data cleaning repository; selecting the priority of the source systems; creating a clean database; loading the consistent, normalized, and cleansed data from the clean database into a format required by data systems and software tools using the data; creating reports; and updating the clean database by a user without updating the source systems. The data cleaning process standardizes the process of collecting and analyzing data from disparate sources for optimization models enabling consistent analysis. The data cleaning process further provides complete auditablility to the inputs and outputs of data systems and software tools that use a dynamic data set. The data cleaning process is suitable for, but not limited to, applications in aircraft industry, both military and commercial, for example for supply chain management.
Owner:THE BOEING CO
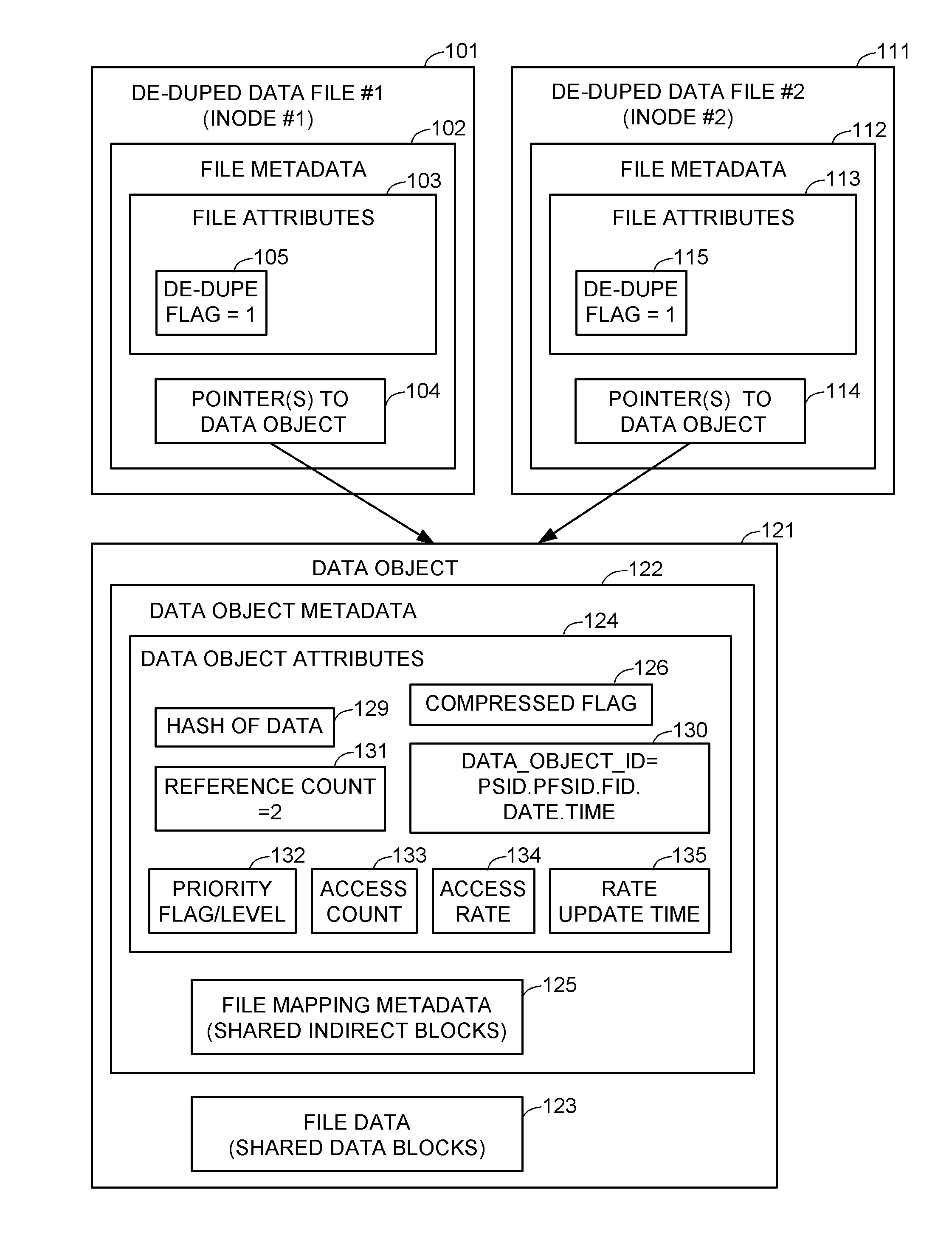
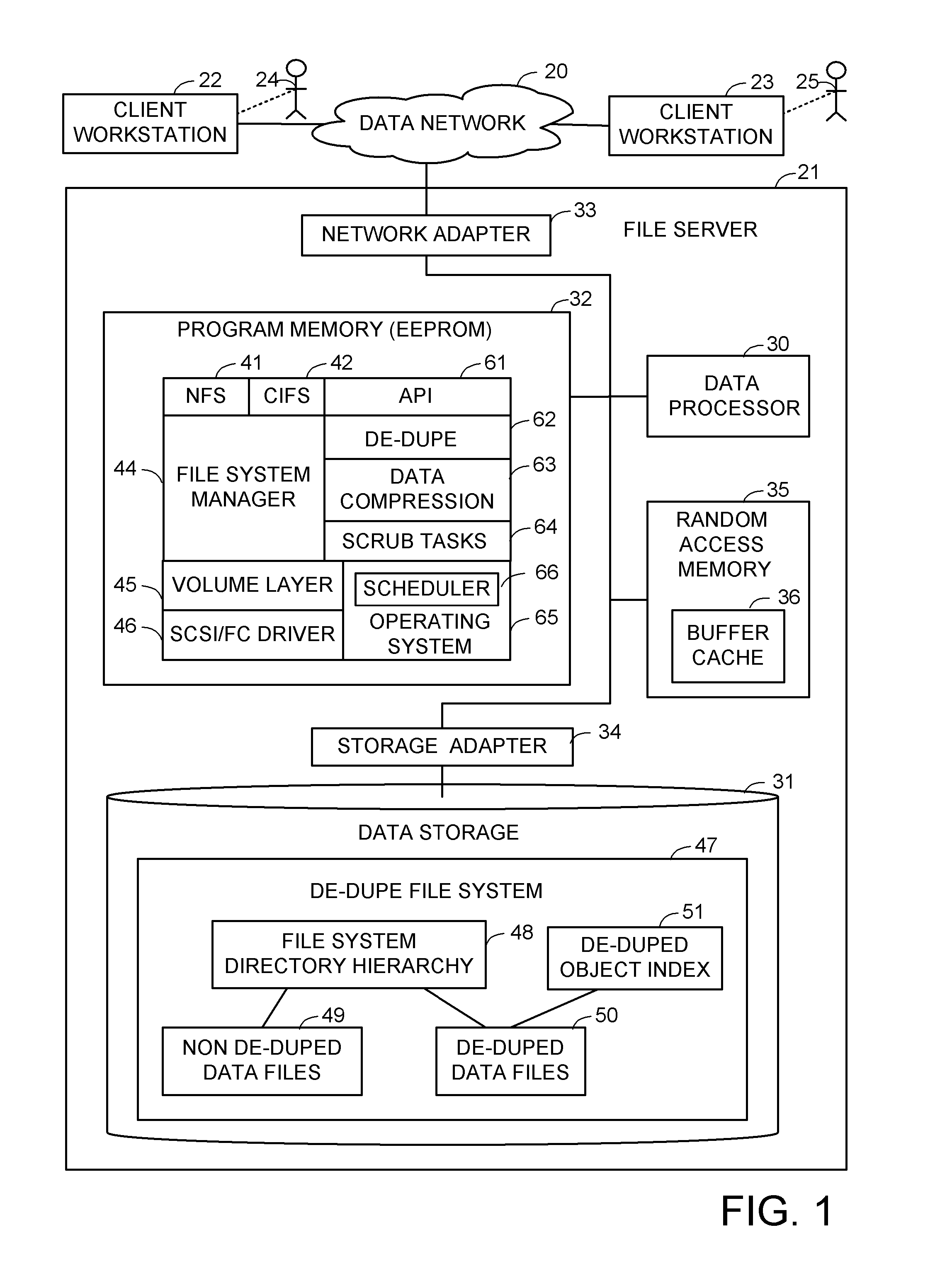
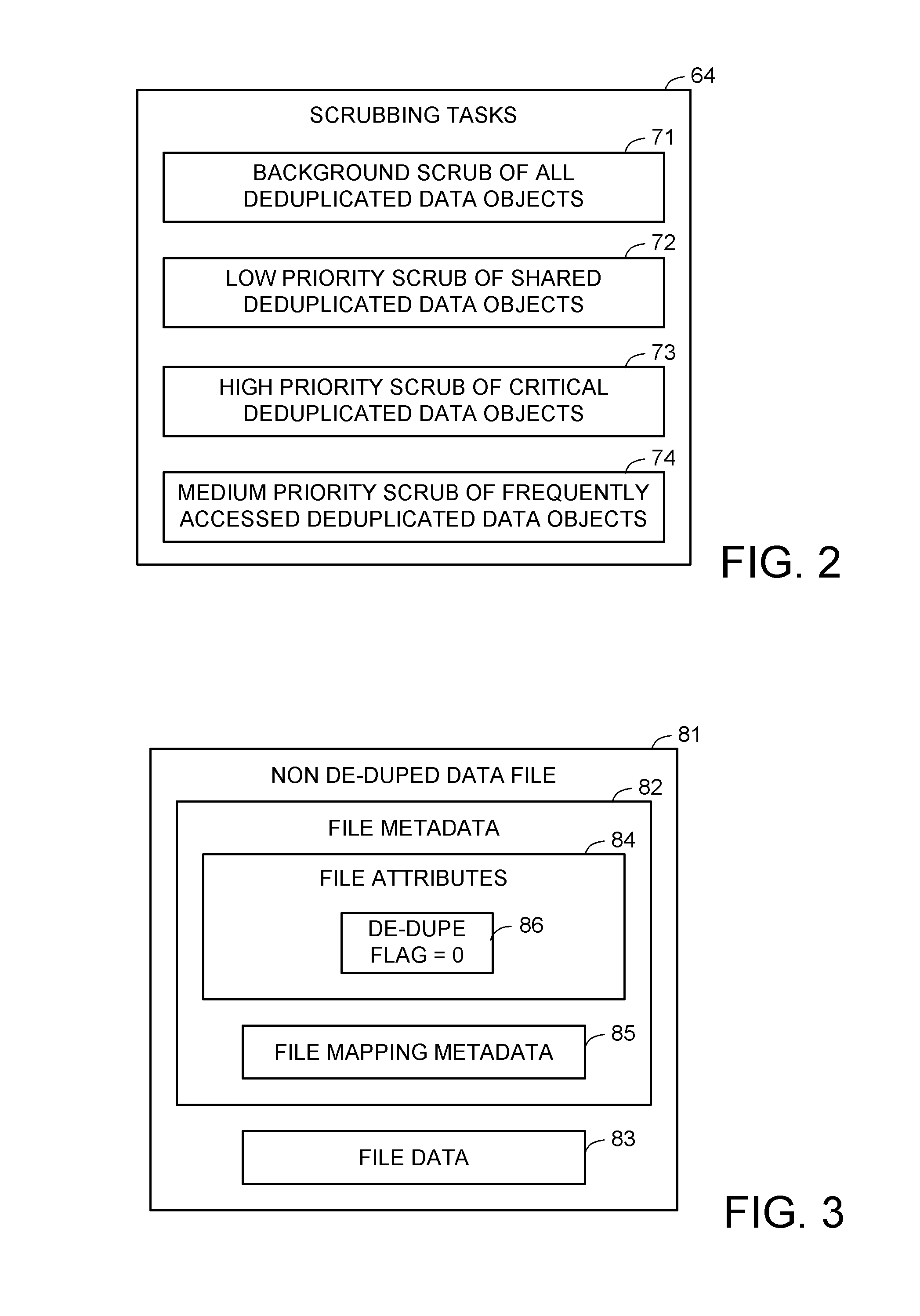
Priority based data scrubbing on a deduplicated data store
ActiveUS8407191B1Digital data information retrievalDigital data processing detailsAccess frequencyData store
Deduplicated data objects are scrubbed by a executing a priority scrubbing task that scans the deduplicated data objects and applies a condition that enables priority data scrubbing based on the value of at least one attribute of the de-duplicated data objects. For example, a low priority task scrubs a deduplicated data object when a reference count of the deduplicated object reaches a threshold. A high priority task scrubs a deduplicated data object when a priority attribute indicates that the deduplicated data object is used by a critical source data object. A medium priority task scrubs a deduplicated data object when the access frequency of the deduplicated data object reaches a threshold. The condition may encode a scrubbing policy or heuristic, and may trigger further action in addition to scrubbing, such as triggering an update of the access rate.
Owner:EMC IP HLDG CO LLC
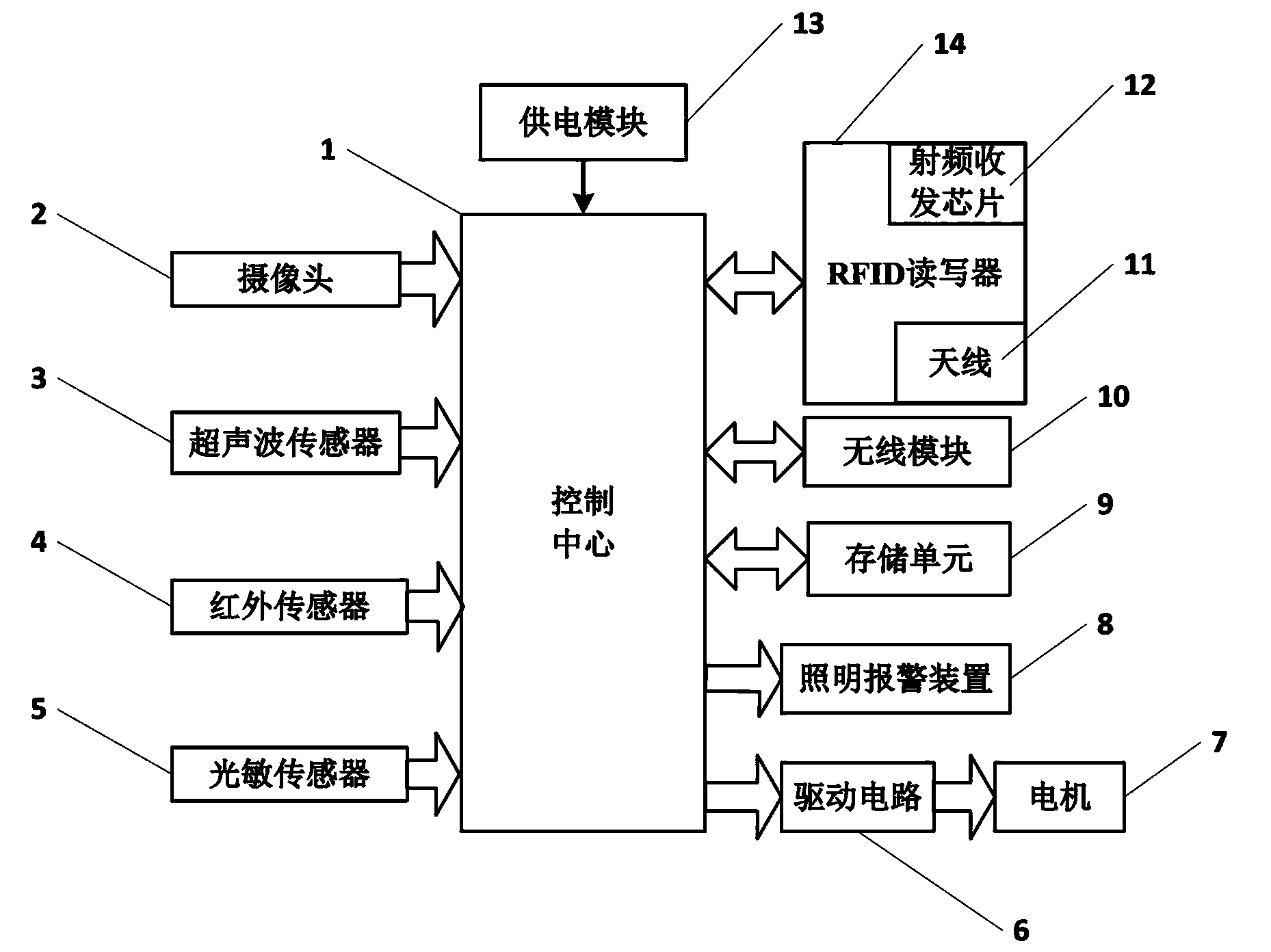
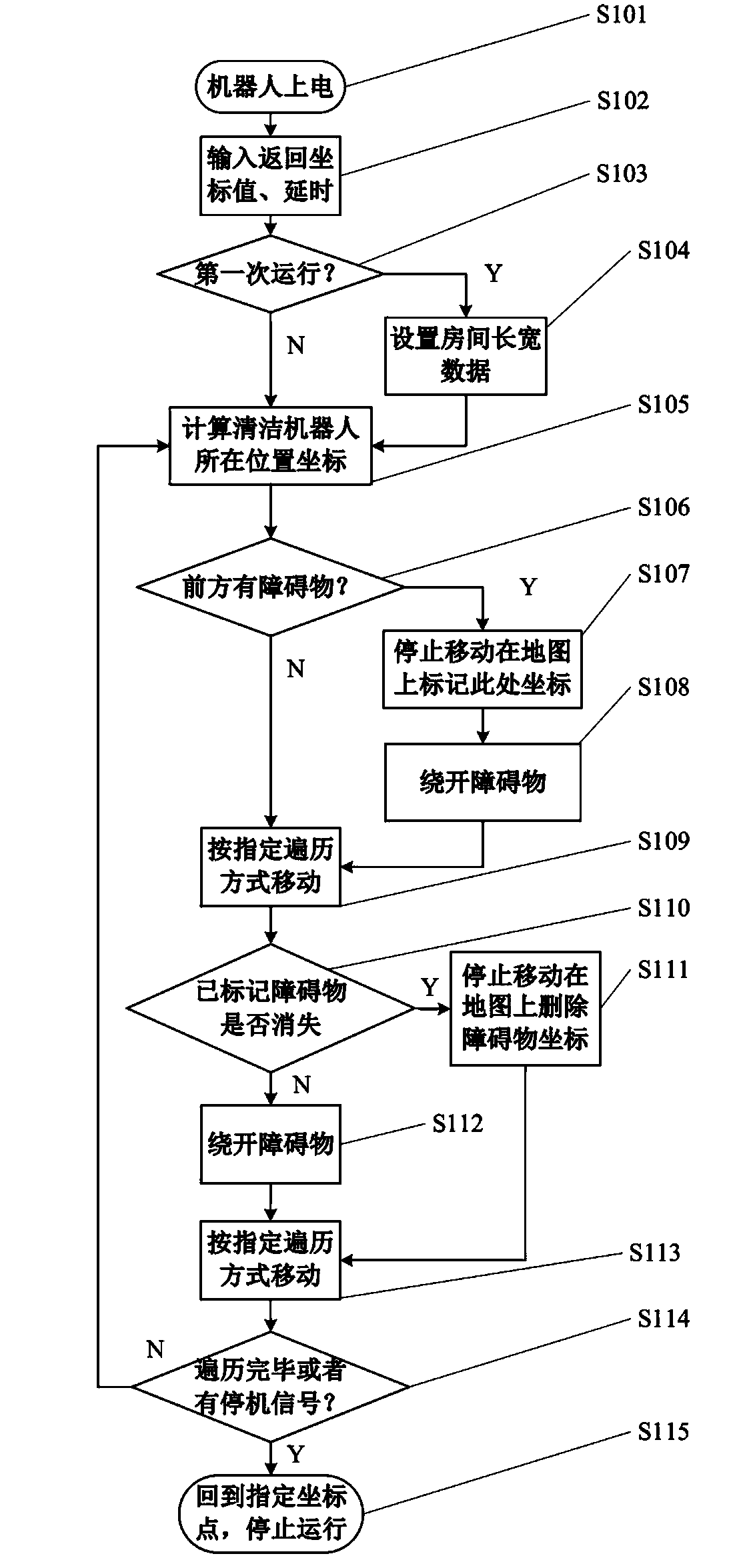
Household cleaning robot capable of establishing map by self and cleaning method
ActiveCN103439973AReduce in quantityQuick fixPosition/course control in two dimensionsControl dataComputer module
The invention discloses a household cleaning robot capable of establishing a map by self and a cleaning method. The household cleaning robot comprises a casing, a control center arranged in the casing, a power supply module, a storage unit, a camera, a lighting alarm device, an ultrasonic wave sensor, an infrared sensor, a photosensitive sensor, a wireless module and an RFID reader-writer, wherein the ultrasonic wave sensor, the infrared sensor and the photosensitive sensor are respectively connected with the control center, and the wireless module and the RFID reader-writer are connected with the control center. The household cleaning robot further comprises a plurality of RFID labels bonded under the periphery of a wall, wherein the RFID labels are used for recording position coordinate information and are active RFID labels. The cleaning robot can establish the indoor two-dimensional map to achieve the indoor location function and acquire the coordinate points in a room. Walking areas and non-walking areas are marked on the two-dimensional map, so that the cleaning robot can quickly determine a cleaning path and accurately reach a target to be cleaned. To hygienic dead angles which cannot be cleaned, the cleaning robot is manually operated and controlled to automatically store operation and control data. When the hygienic dead angles are cleaned again, the stored operation and control data can be called to clean the target.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Analysis of marketing and entertainment effectiveness using central nervous system, autonomic nervous system, and effector data
ActiveUS8484081B2Data acquisition and loggingMarket data gatheringDiagnostic Radiology ModalityCross modality
Central nervous system, autonomic nervous system, and effector data is measured and analyzed to determine the effectiveness of marketing and entertainment stimuli. A data collection mechanism including multiple modalities such as Electroencephalography (EEG), Electrooculography (EOG), Galvanic Skin Response (GSR), etc., collects response data from subjects exposed to marketing and entertainment stimuli. A data cleanser mechanism filters the response data. The response data is enhanced using intra-modality response synthesis and / or a cross-modality response synthesis.
Owner:NIELSEN CONSUMER LLC
Network overload detection and mitigation system and method
ActiveUS20060075491A1Less memoryProcessing speedMemory loss protectionDigital data processing detailsDomain nameName server
A system and method is disclosed for detecting and / or mitigating an overload condition from one or more first computers, such as a distributed denial of service (DDoS) attack, viral attack, or the like, targeting one or more of a plurality of second computers located on a network. While one or more DDoS attacks are mitigated, a meter, detection apparatus, software, or method, detects the condition being mitigated in a data cleaning center, and provides an alert or notification regarding the mitigated attack. Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an overload or attempted overload condition targeting a domain name server. A network connection is provided for receiving one or more DNS requests from one or more client computers located on a network. A preferred embodiment includes a processor for providing a response to the one or more DNS requests to the one or more client computers if more than a threshold number of duplicate DNS requests are received. Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an attempted overload condition targeting a networked computer system that uses a redirection module to divert data until it is deemed to be clean.
Owner:AKAMAI TECH INC
Automatic information sanitizer
ActiveUS7293175B2Quickly and accurately applyOptimize allocationDigital data processing detailsAnalogue secracy/subscription systemsNetwork Communication ProtocolsComputer module
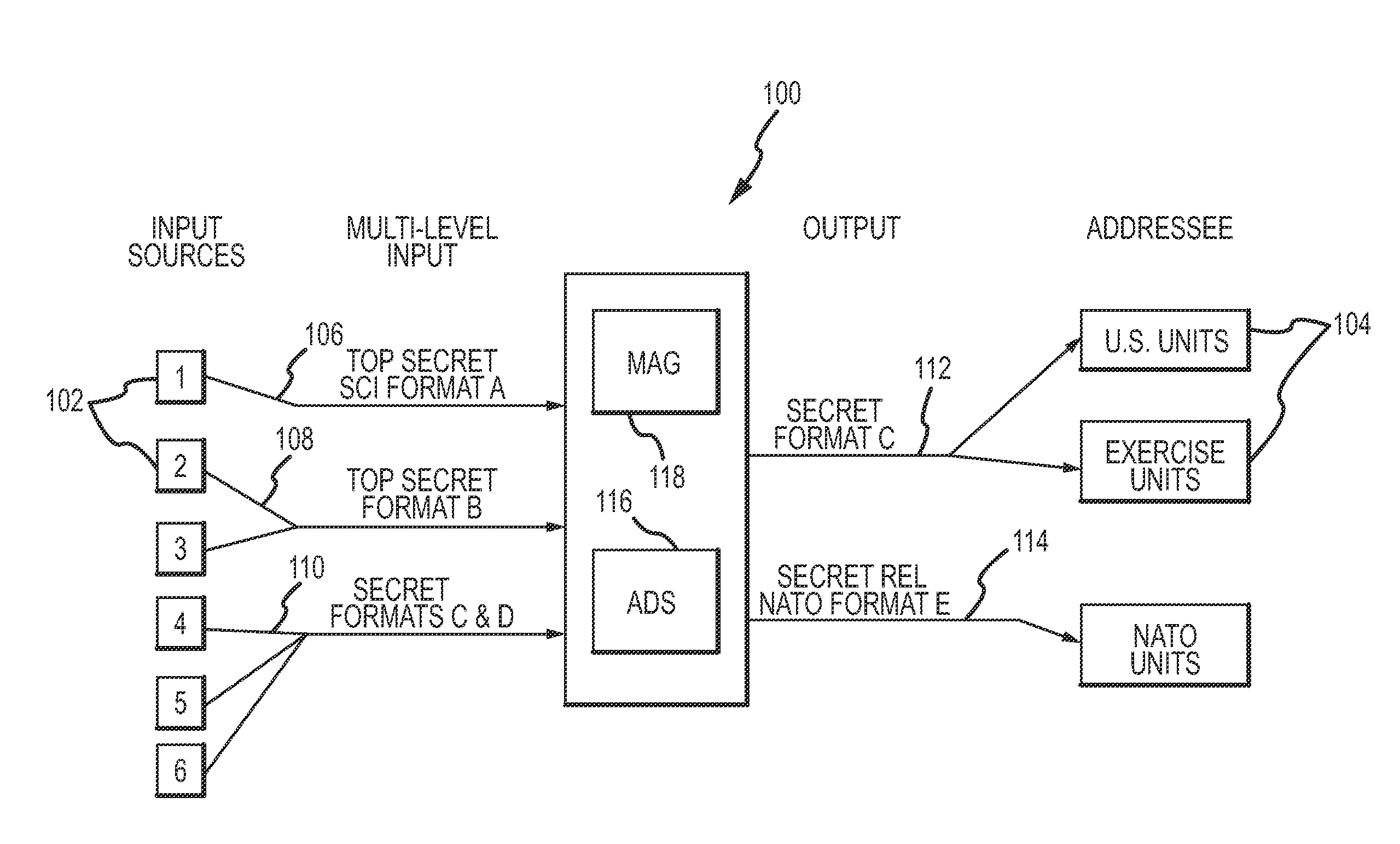
An automatic data sanitizer module sanitizes formatted data from an external source system according to stored sanitization rules for release to an external destination system so that the destination system receives only that data for which it is authorized. The module generally includes an Input Comms module, a Message Processor, an Output Guard a Downgrader and an Output Comms module. The Input Comms module supports the communications protocol dictated by the external source system. The Processor sanitizes the message according to the rules written for the specific external system under consideration. The Guard verifies the modifications performed by the Processor. The Downgrader moves the resulting file to the Output Comms working directory and the Output Comms makes the resulting message available to the destination system. The system supports a variety of different formats and greatly facilitates the timely dissemination of information within a multi-level secure environment while protecting security interests.
Owner:LOCKHEED MARTIN CORP
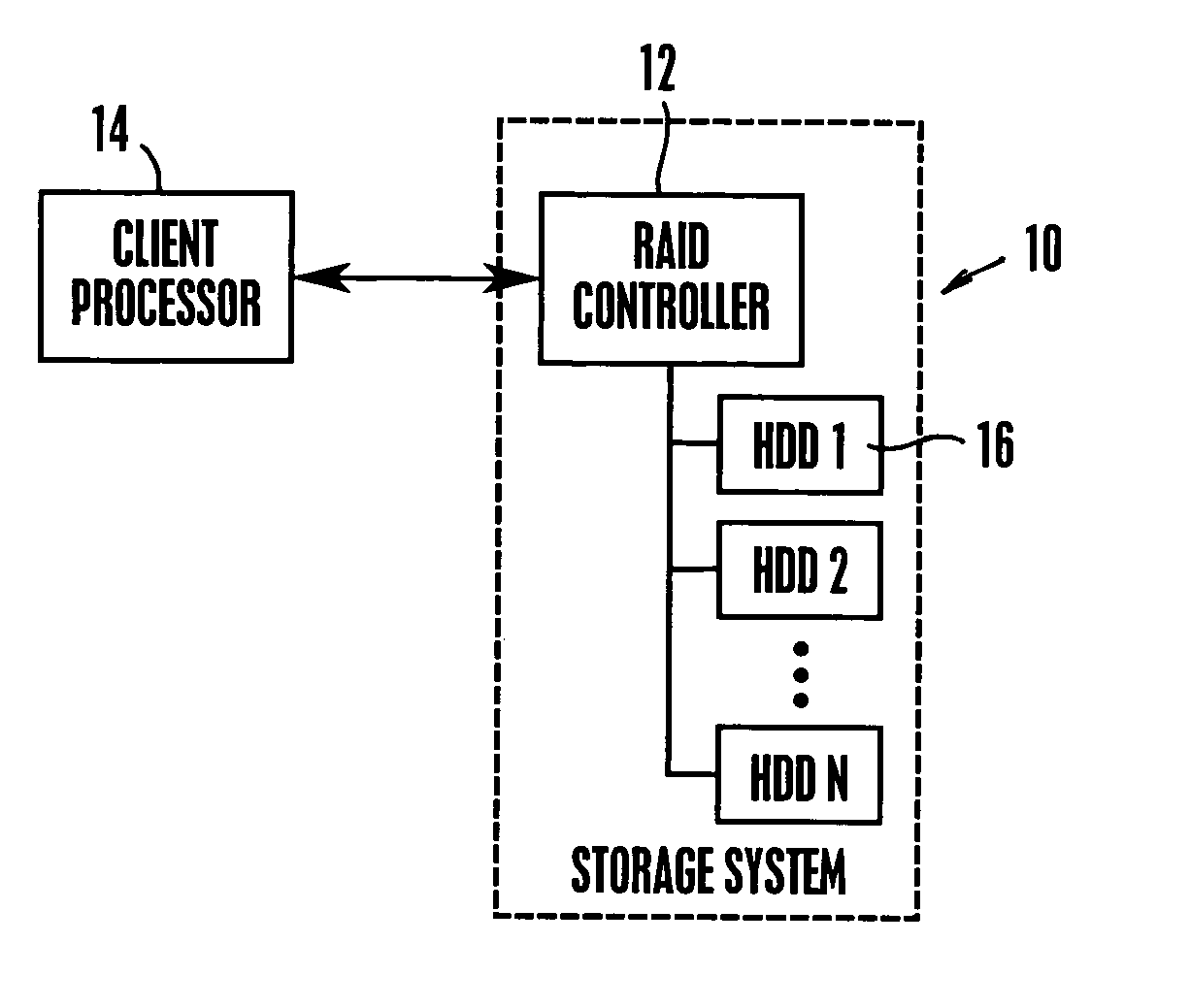
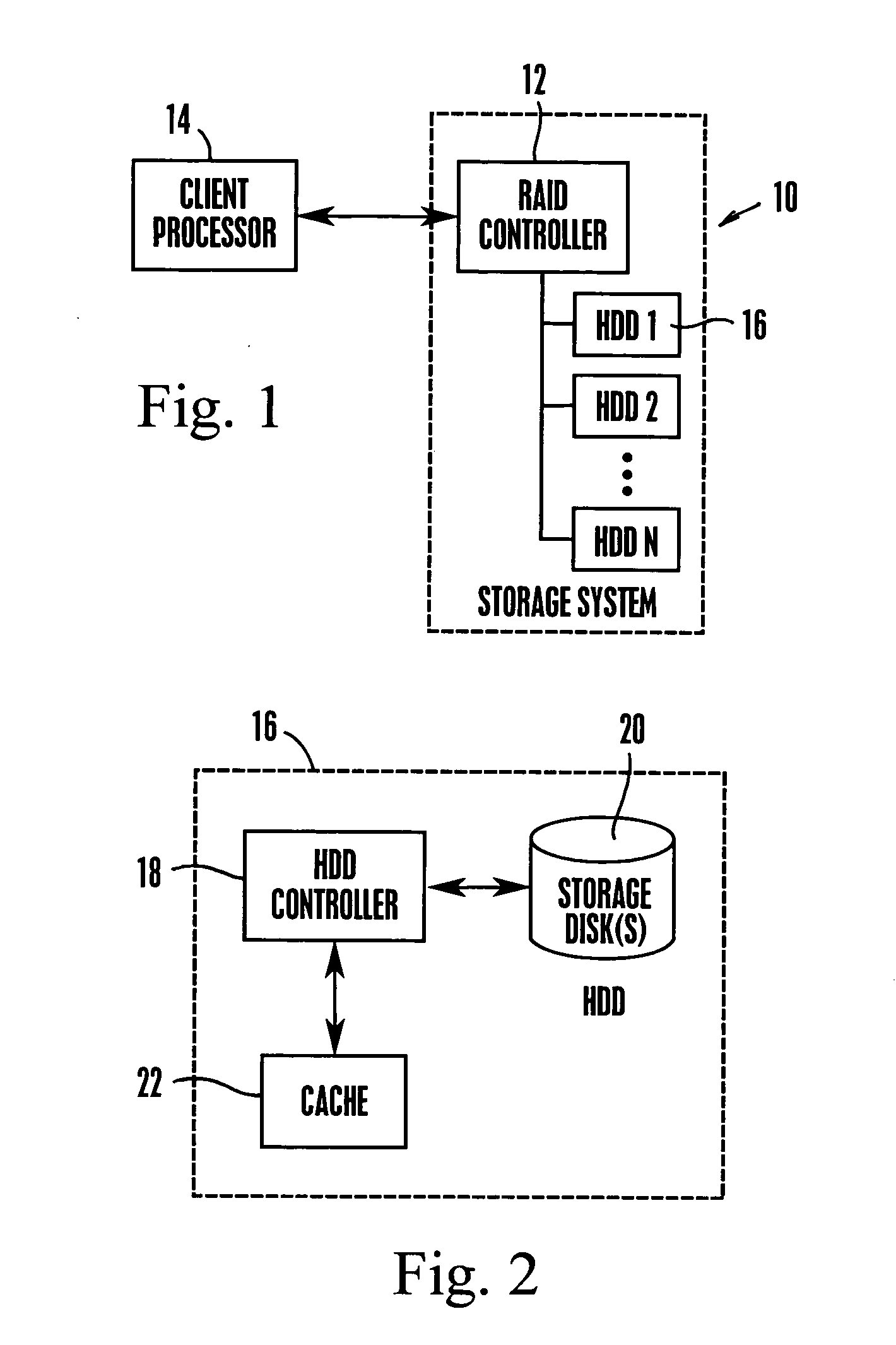
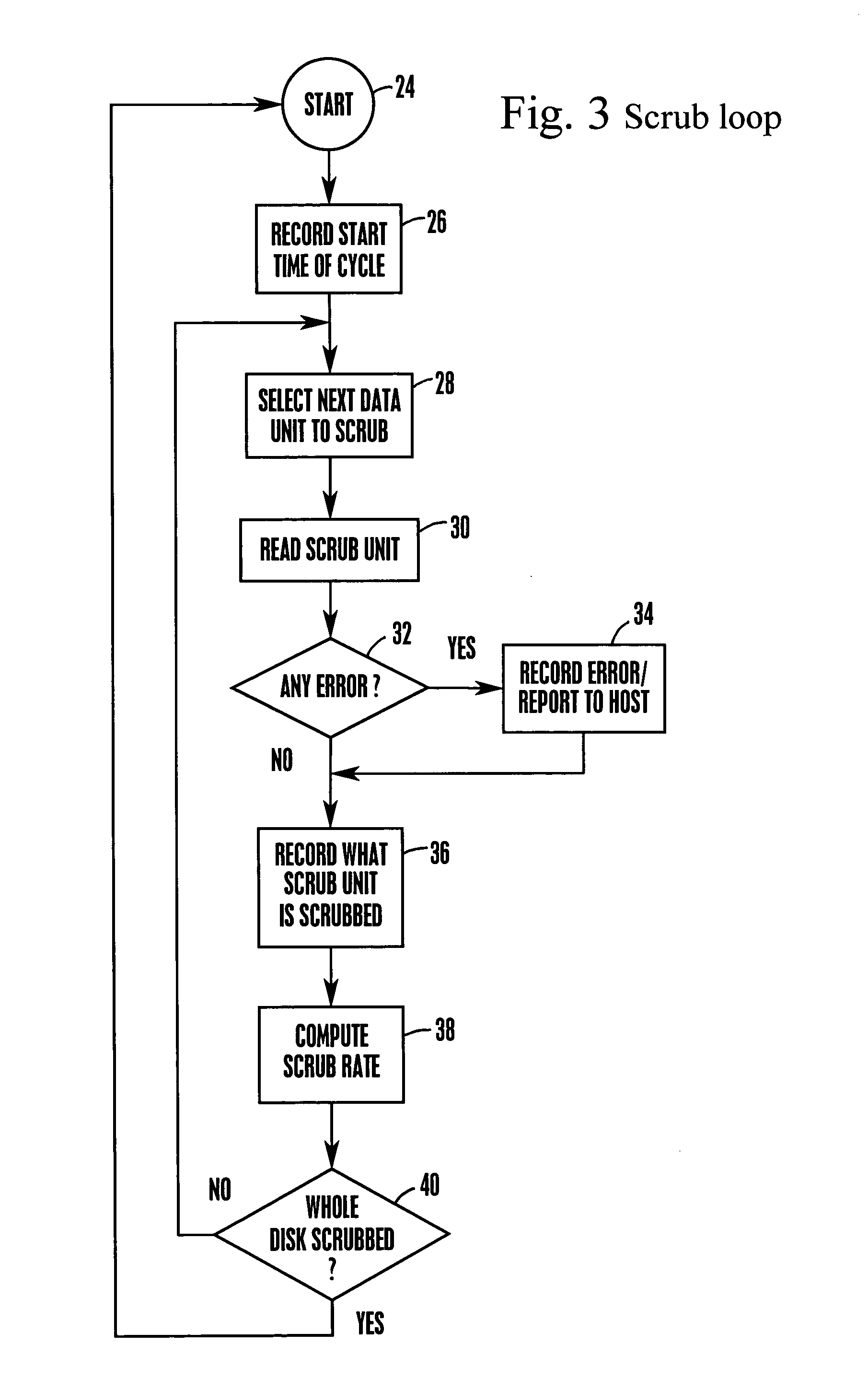
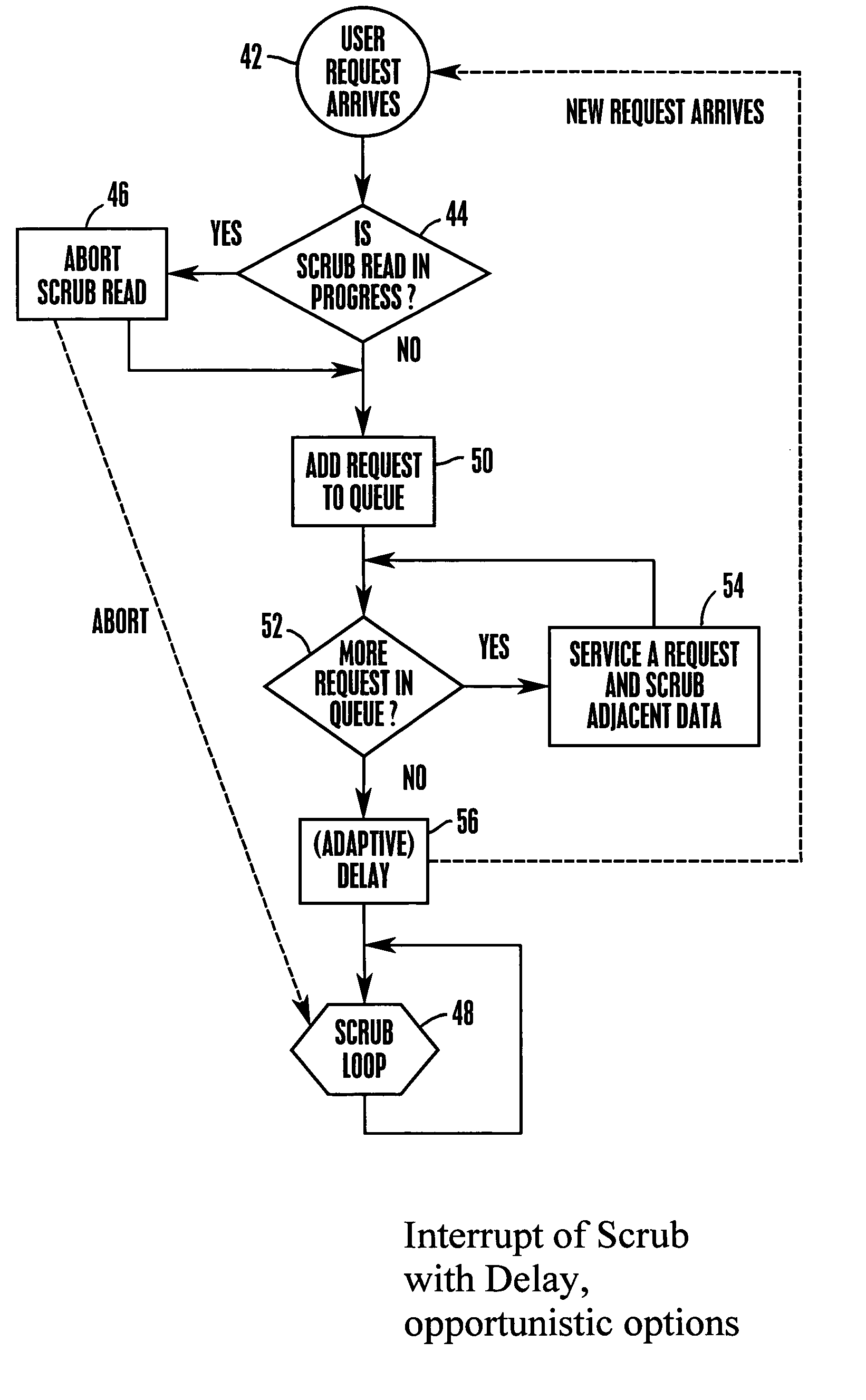
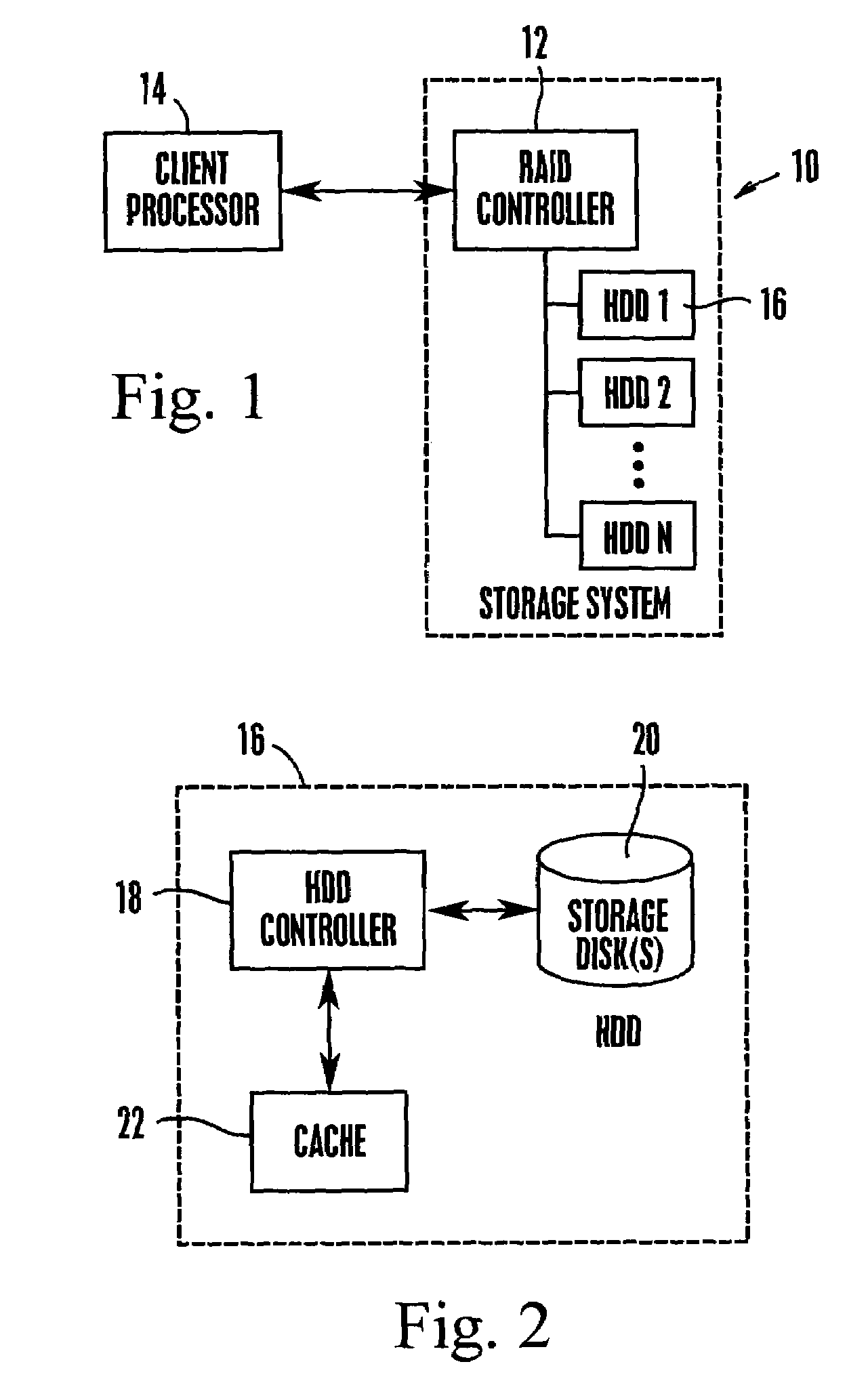
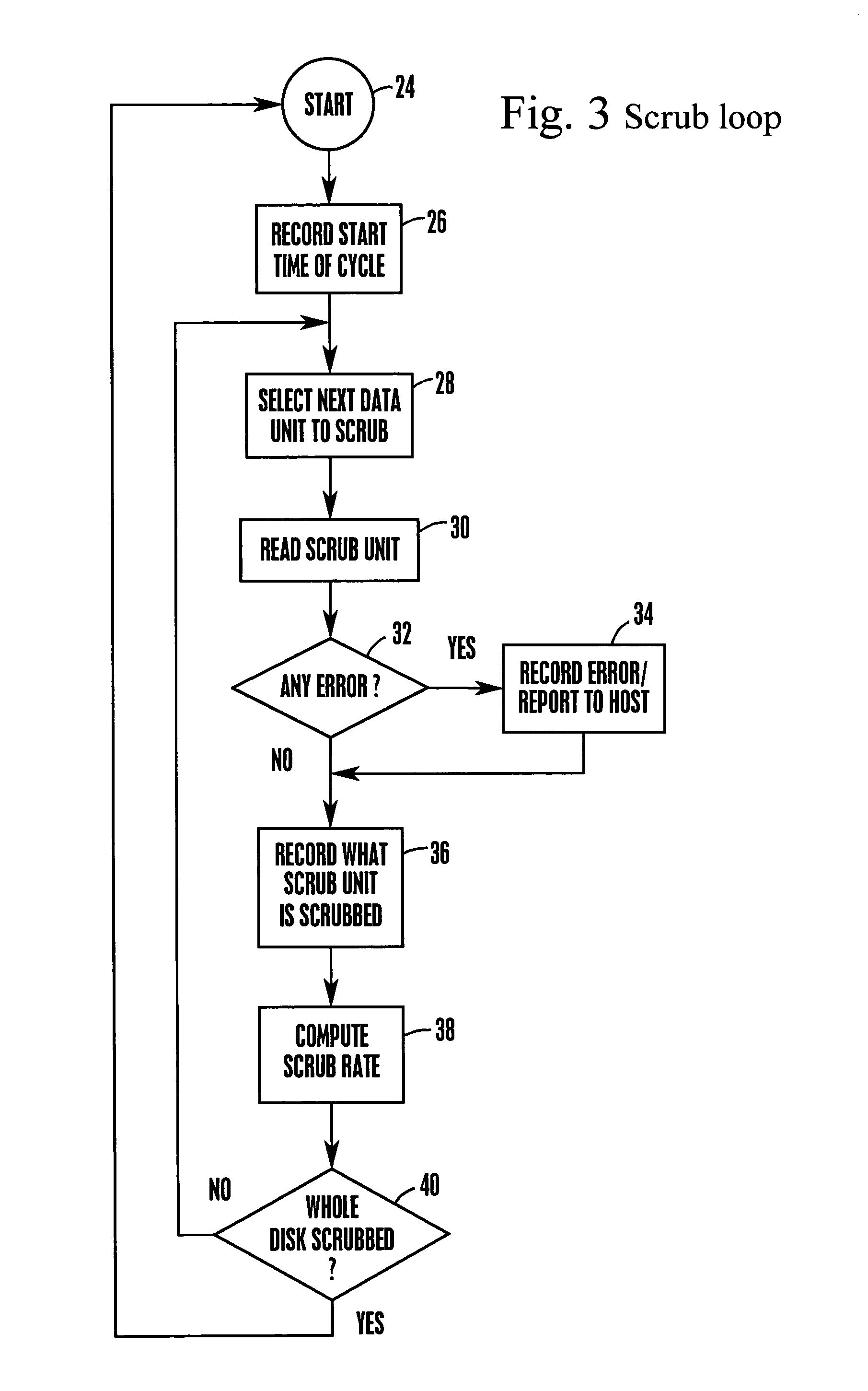
System and method for autonomous data scrubbing in a hard disk drive
A RAID subsystem with a plurality of hard disk drives has each disk controller autonomously executing data scrubbing on its disks instead of requiring the RAID controller to execute data scrubbing. The data scrubbing may be interrupted upon an I / O request from the RAID controller, or it may continue if a guaranteed scrub rate is not being achieved. Data is stored in large bands of concentric data tracks, and a band may be preferentially selected for scrubbing based on frequency of reading the band, or recency of writing to the band.
Owner:WESTERN DIGITAL TECH INC
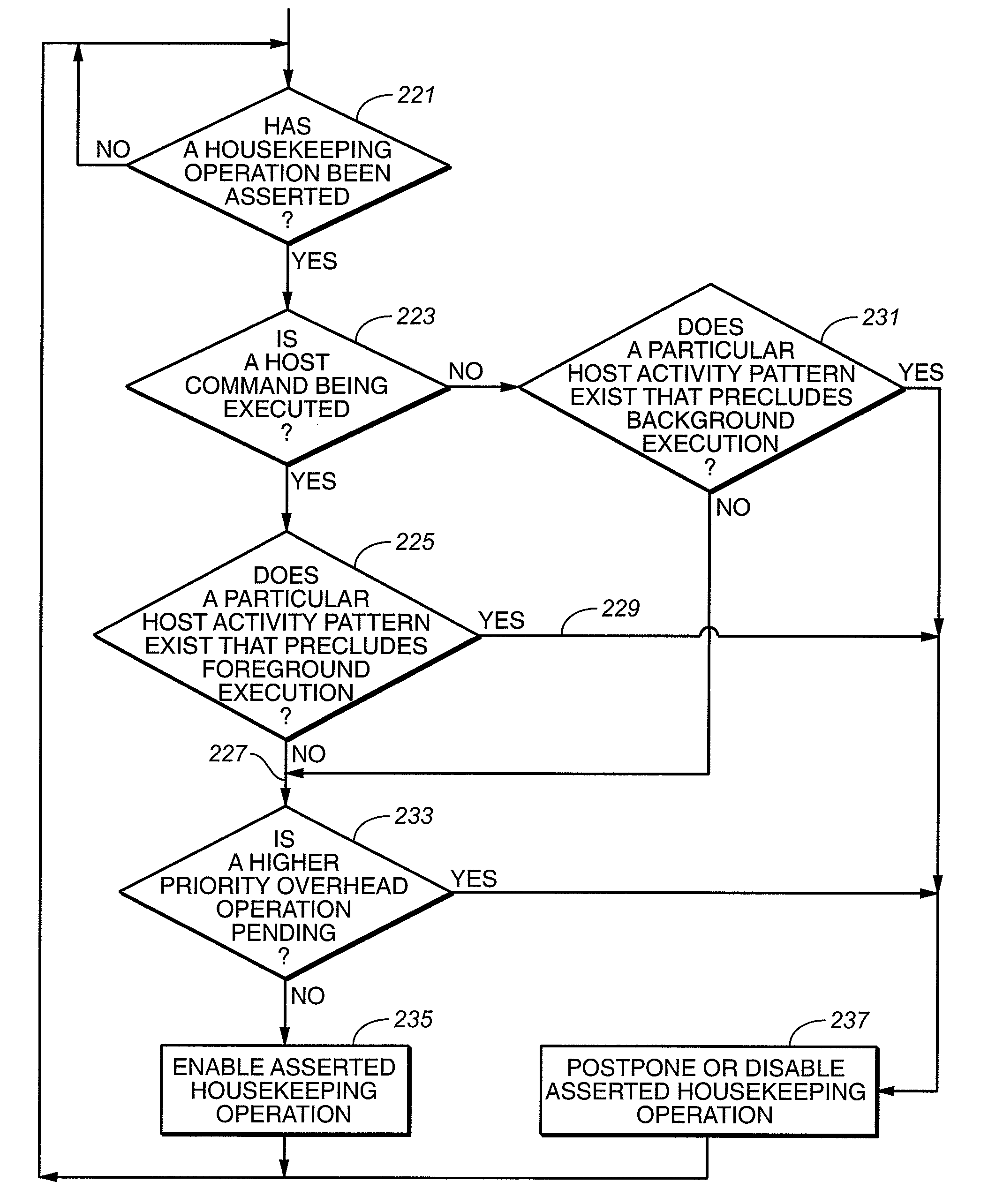
Managing Housekeeping Operations in Flash Memory
InactiveUS20080294813A1Reduce transfer speedImpact performanceMemory architecture accessing/allocationMemory systemsWear levelingVolatile memory
A flash re-programmable, non-volatile memory system is operated to disable foreground execution of housekeeping operations, such as wear leveling and data scrub, in the when operation of the host would be excessively slowed as a result. One or more characteristics of patterns of activity of the host are monitored by the memory system in order to determine when housekeeping operations may be performed without significantly degrading the performance of the memory system, particularly during writing of data from the host into the memory.
Owner:SANDISK TECH LLC
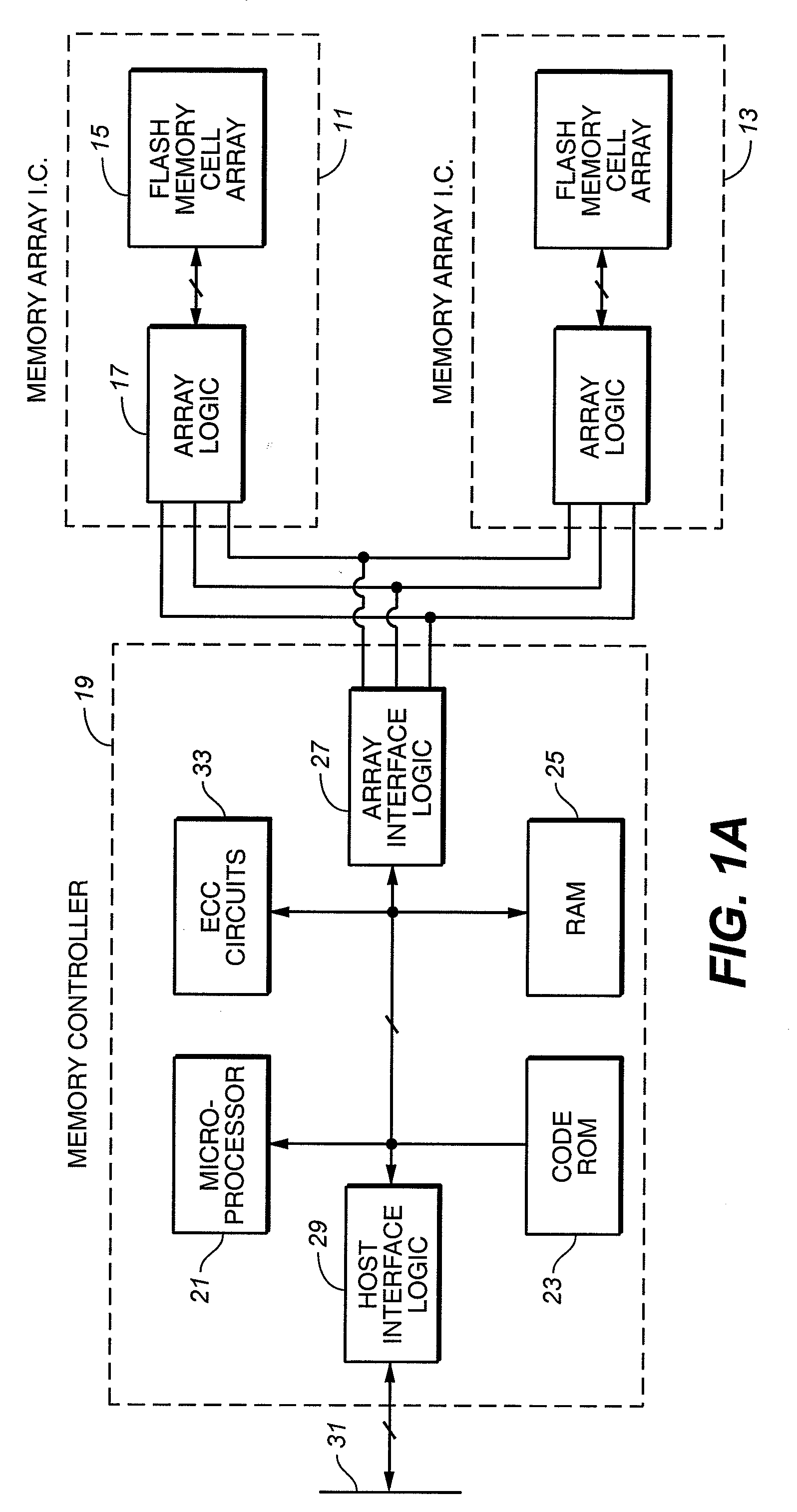
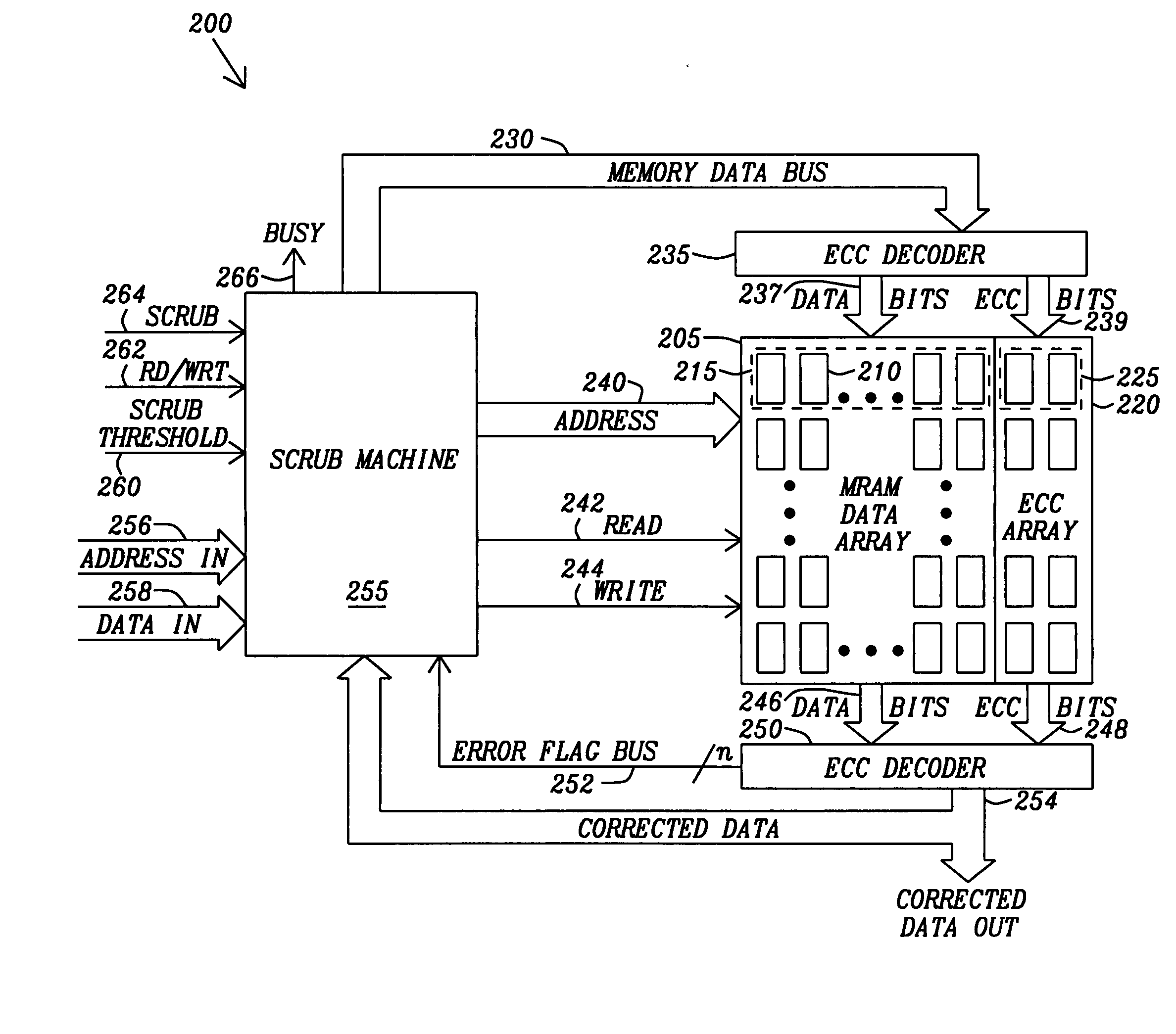
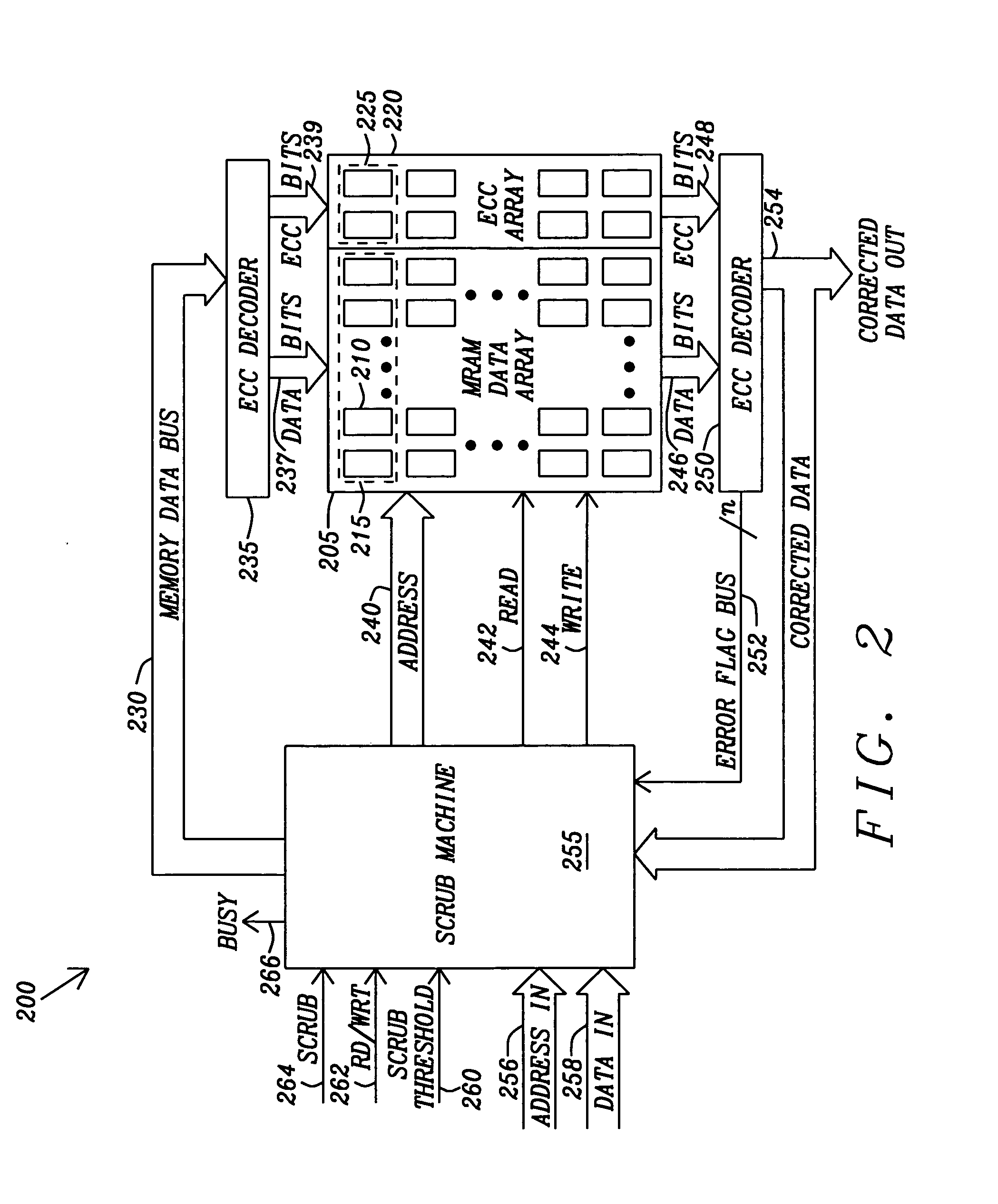
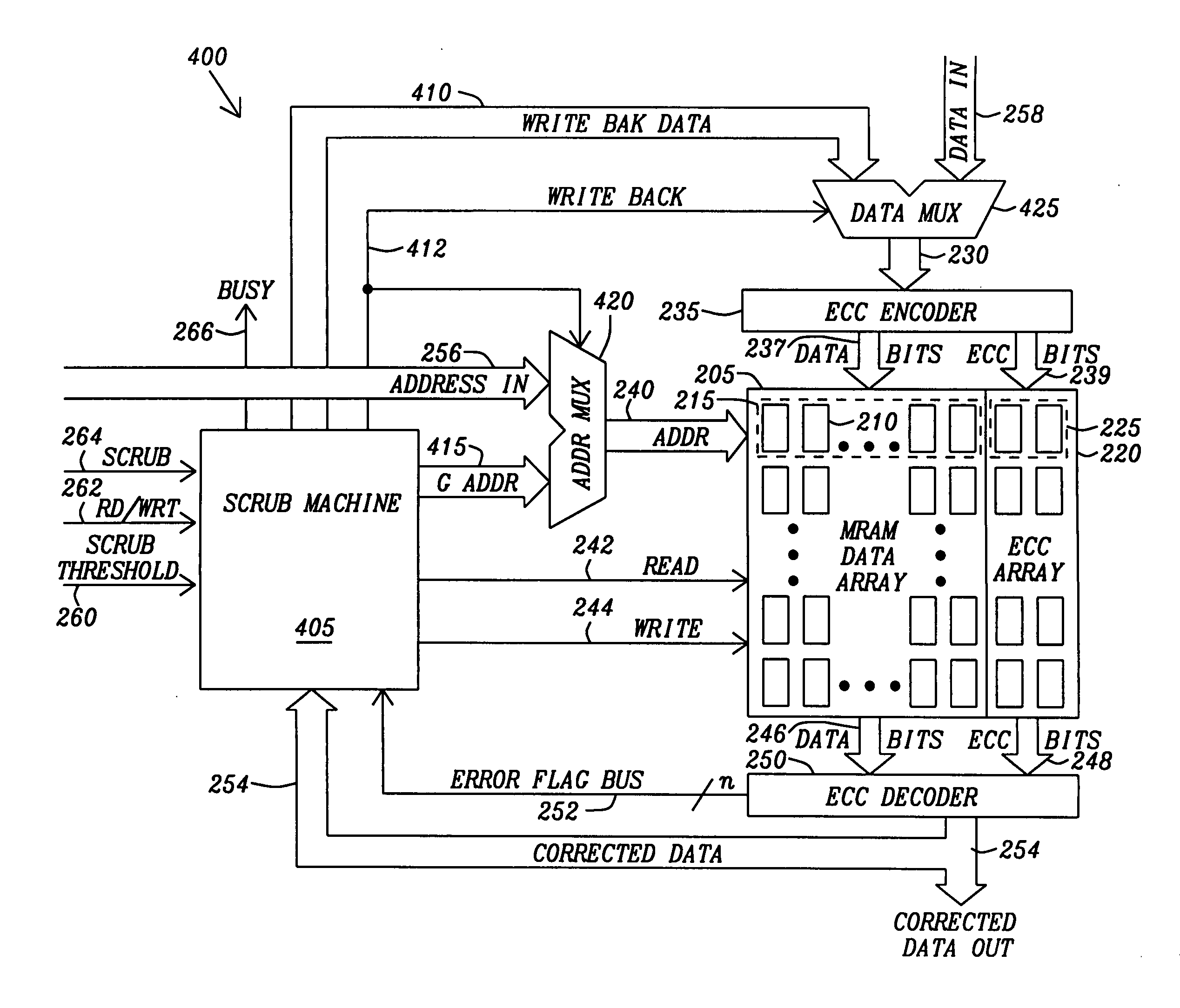
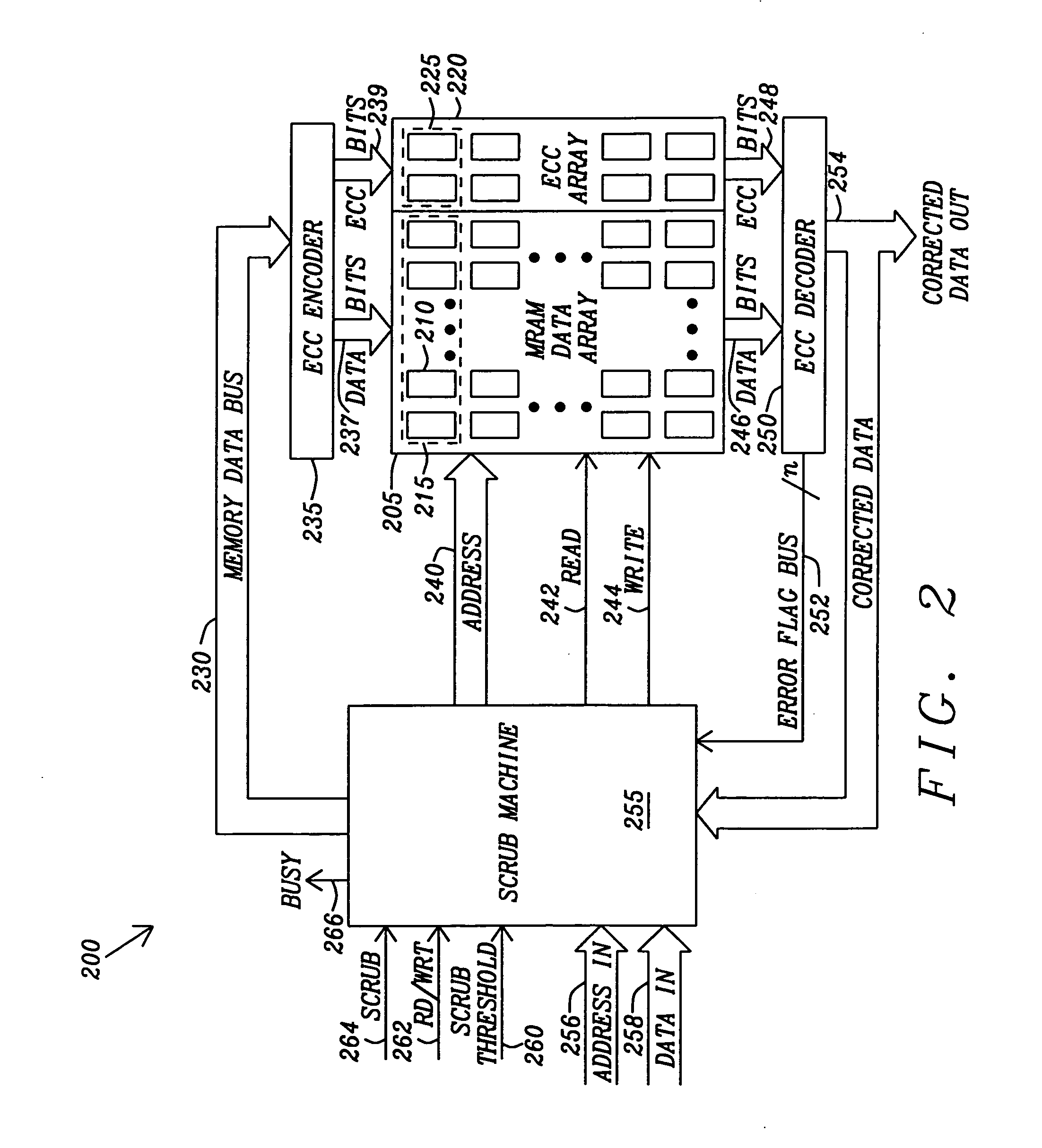
Method and apparatus for scrubbing accumulated data errors from a memory system
ActiveUS20100332900A1Disturb errorMemory adressing/allocation/relocationRedundant operation error correctionParallel computingData error
A data scrubbing apparatus corrects disturb data errors occurring in an array of memory cells such as SMT MRAM cells. The data scrubbing apparatus receives an error indication that an error has occurred during a read operation of a grouping of memory cells within the array of memory cells. The data scrubbing apparatus may generate an address describing the location of the memory cells to be scrubbed. The data scrubbing apparatus then commands the array of memory cells to write back the corrected data. Based on a scrub threshold value, the data scrubbing apparatus writes the corrected data back after a specific number of errors. The data scrubbing apparatus may further suspend writing back during a writing of data. The data scrubbing apparatus provides a busy indicator externally during a write back of corrected data.
Owner:TAIWAN SEMICON MFG CO LTD
Anti-cheating method and anti-cheating system of application program
ActiveCN104424433AEasy to cleanReduce the risk of miscalculationPlatform integrity maintainanceApplication softwareDatabase
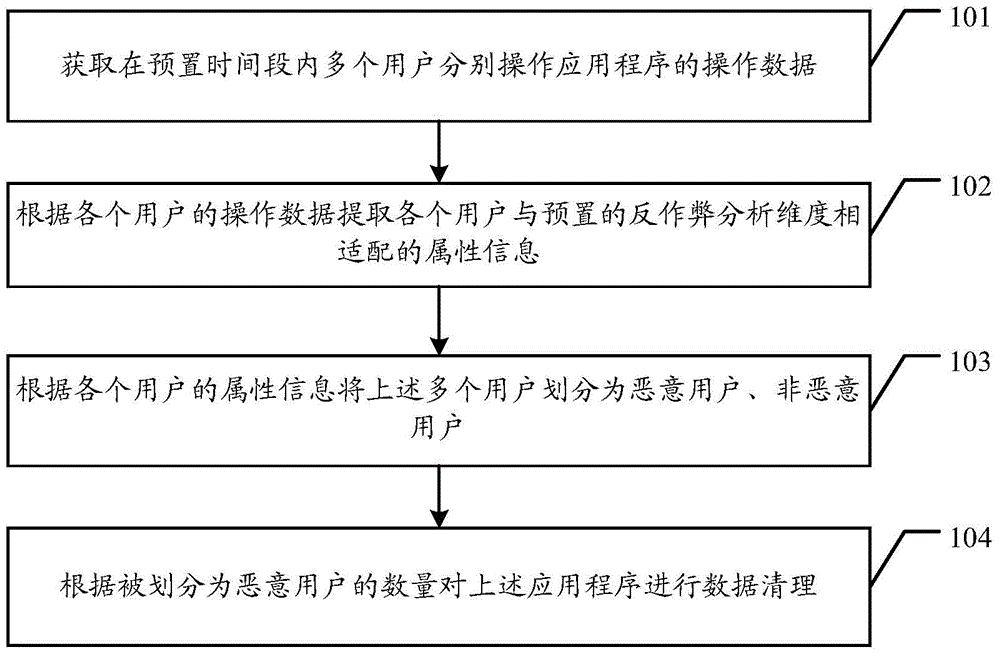
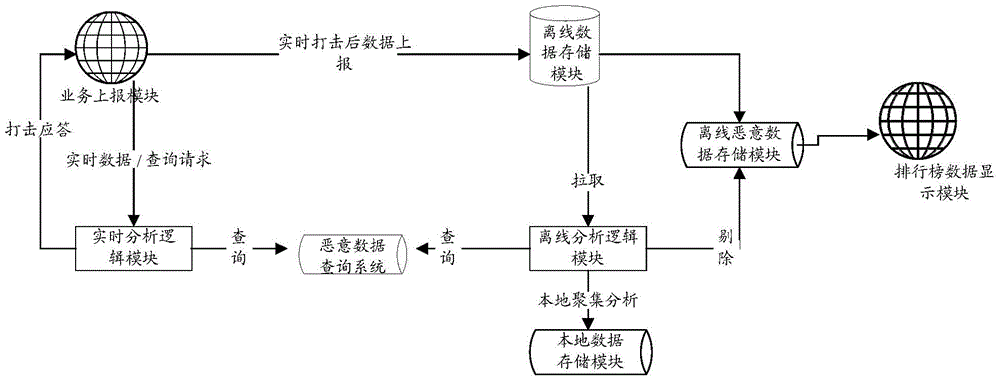
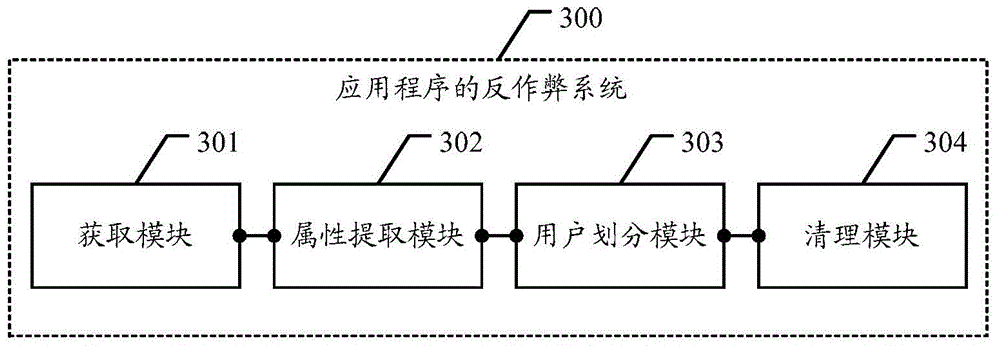
The embodiment of the invention discloses an anti-cheating method and anti-cheating system of an application program. The anti-cheating method and the anti-cheating system are used for against the cheating behavior targeting the application program with low misjudgment risk. According to the embodiment of the invention, the method comprises the following steps of: obtaining the operation data of the operation program operated by a plurality of users within a preset time quantum; extracting the attribute information adaptive to the preset anti-cheating analysis dimension of each user according to the operation data of each user; dividing the plurality of the users into malicious users and un-malicious users according to the attribute information of each user; and clearing the data of the application program according to the quantity of the divided malicious users.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Alert flags for data cleaning and data analysis
InactiveUS20050028046A1Made preciselyMoreError detection/correctionData miningData profilingData structure
A data structure and methods for generating and using the data structure which contains cleaning attribute flags for each field of a database record which has been modified by a data cleaning operation. The flags may are used to determine if a pattern, cluster or trend identified during data mining of the cleaned data is likely to have been influenced by the data cleaning process, especially to a degree which leads to identification of false trends, patterns, or clusters.
Owner:IBM CORP
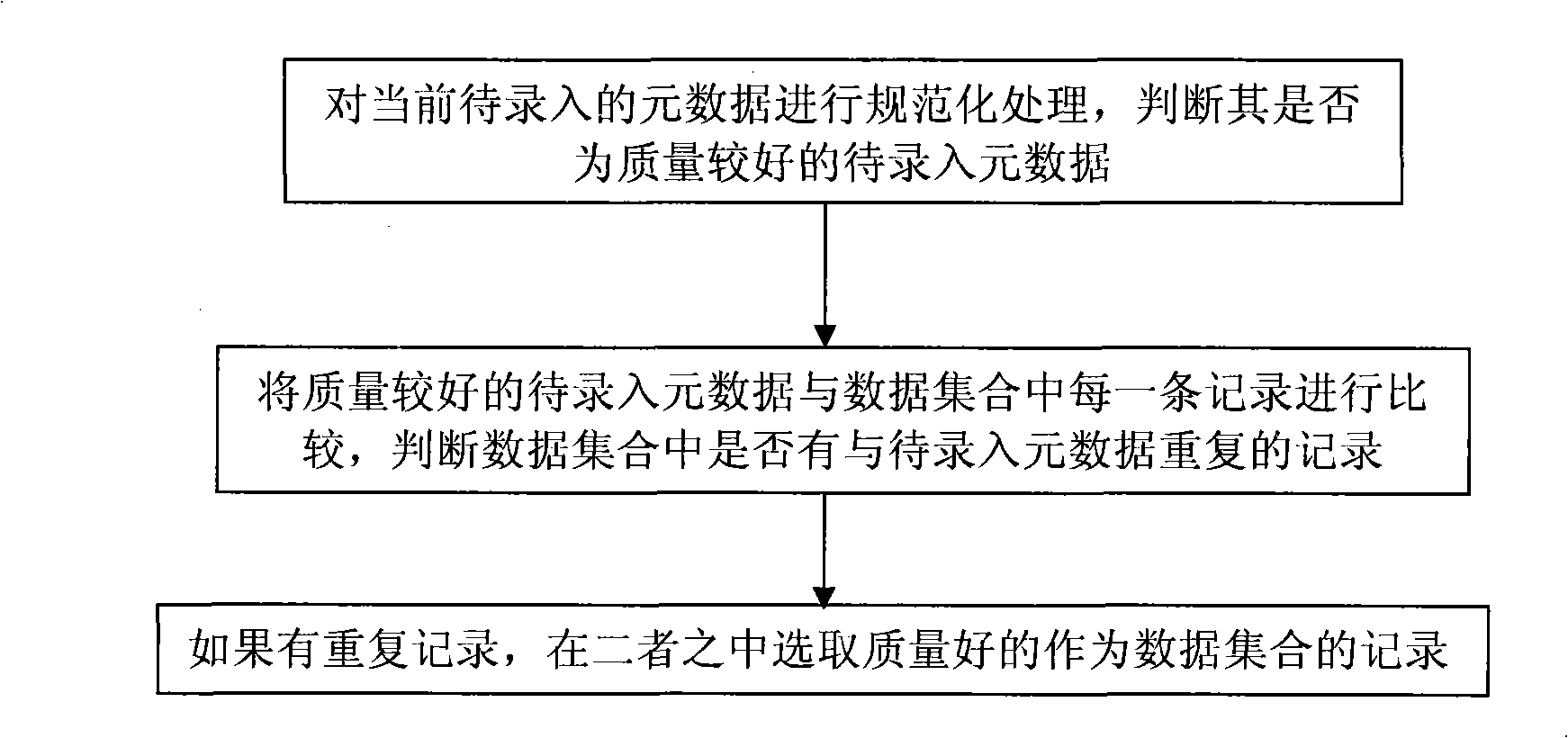
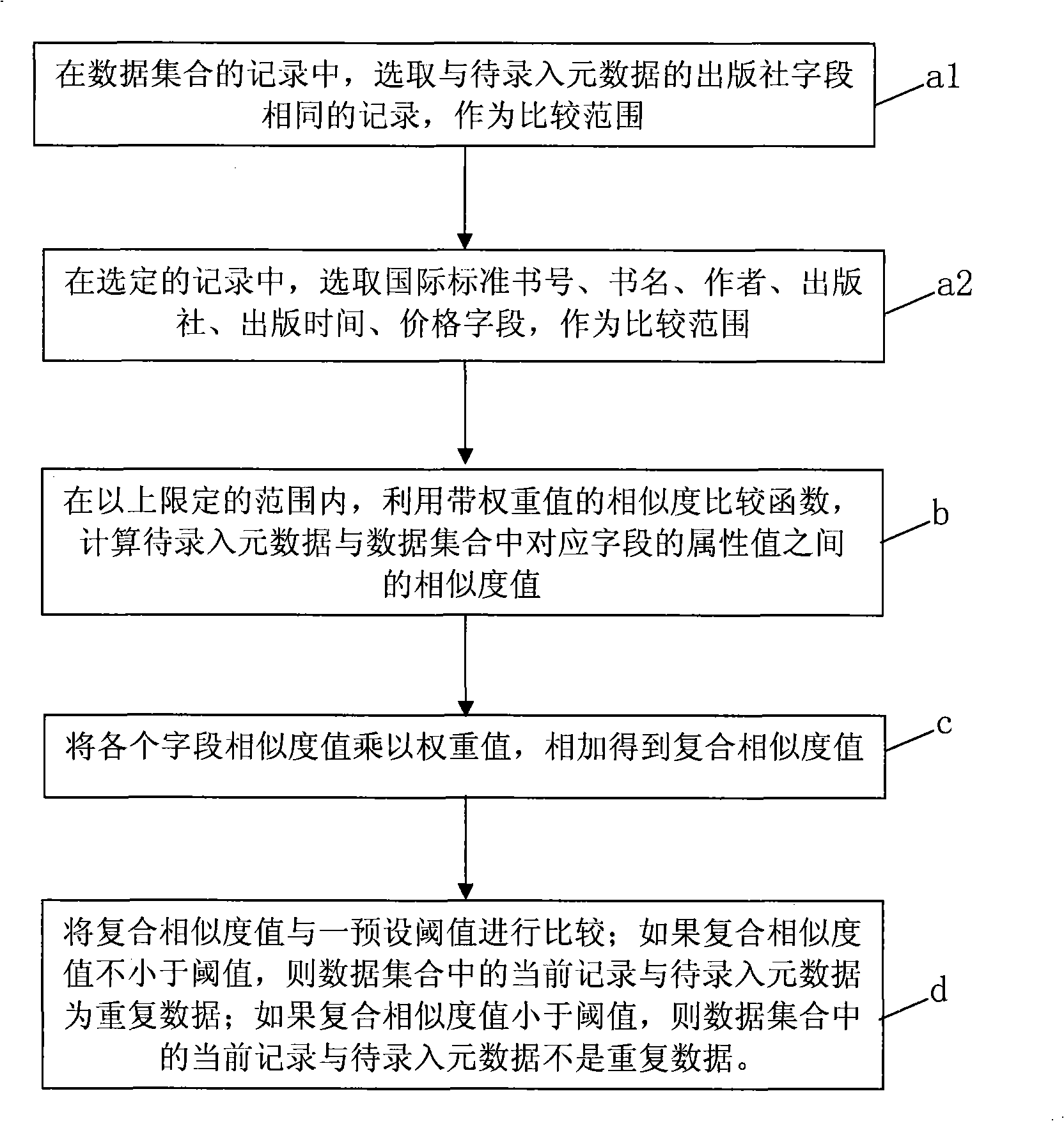
Method for removing repeated object based on metadata
ActiveCN101286156AReduce workloadImprove work efficiencySpecial data processing applicationsData setObject based
The invention discloses a method for removing repeated objects on the basis of meta data, relating to meta data removal field, solving the problem that the working quantity of the repeated data removal is large. The method firstly carries out standardized processing to the meta data to be recorded. During the comparison, by reducing the comparison range, the working quantity is reduced and the working efficiency is improved. In the date set record, records which have the same press fields with the meta data to be recorded are selected; in the selected record, isbn, book name, author, press, publishing time and price character are selected as the comparison range. A similarity comparison function with weighing values is used to calculate the similarity value between the meta data to be recorded and the attribute value of the corresponding fields in the data set; the weighing value is multiplied by the similarity value of each field and then added by the gained complex similarity value; the complex similarity value is compared with the prearranged threshold value; if the complex similarity value is not less than the threshold value, the current record in the data set and the meta data to be recorded are repeated data.
Owner:利德科技发展有限公司 +1
System and method for autonomous data scrubbing in a hard disk drive
A RAID subsystem with a plurality of hard disk drives has each disk controller autonomously executing data scrubbing on its disks instead of requiring the RAID controller to execute data scrubbing. The data scrubbing may be interrupted upon an I / O request from the RAID controller, or it may continue if a guaranteed scrub rate is not being achieved. Data is stored in large bands of concentric data tracks, and a band may be preferentially selected for scrubbing based on frequency of reading the band, or recency of writing to the band.
Owner:WESTERN DIGITAL TECH INC
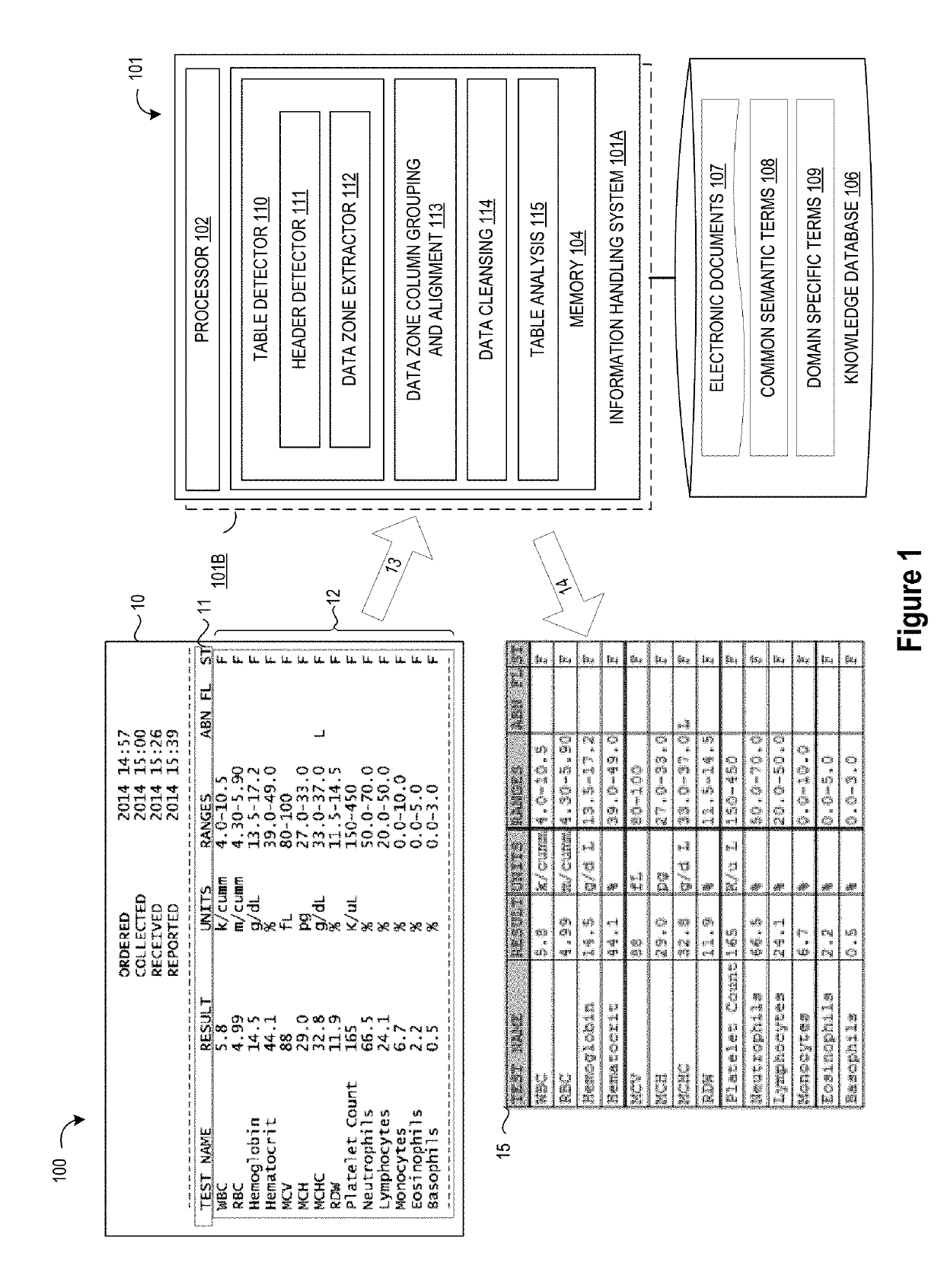
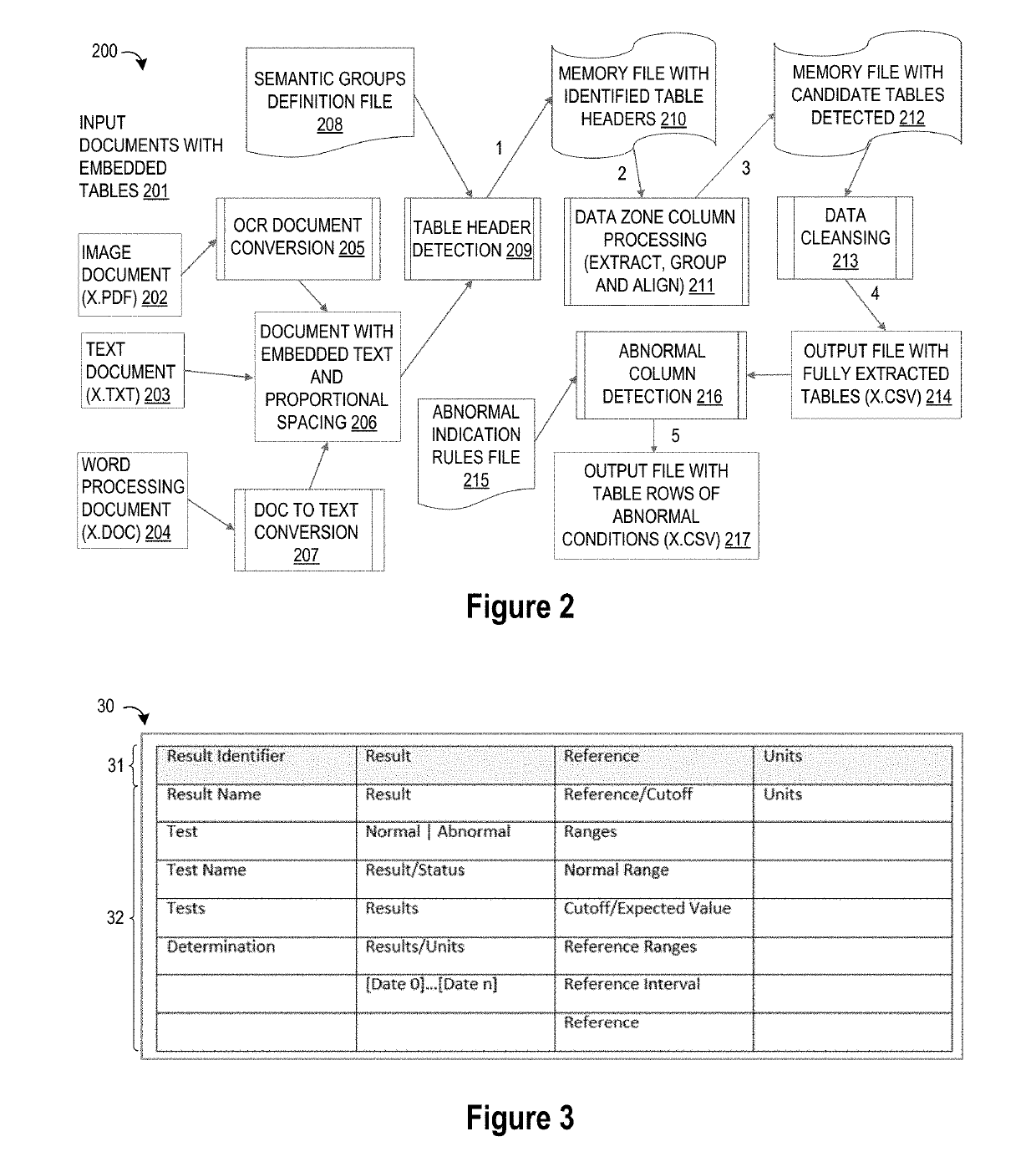
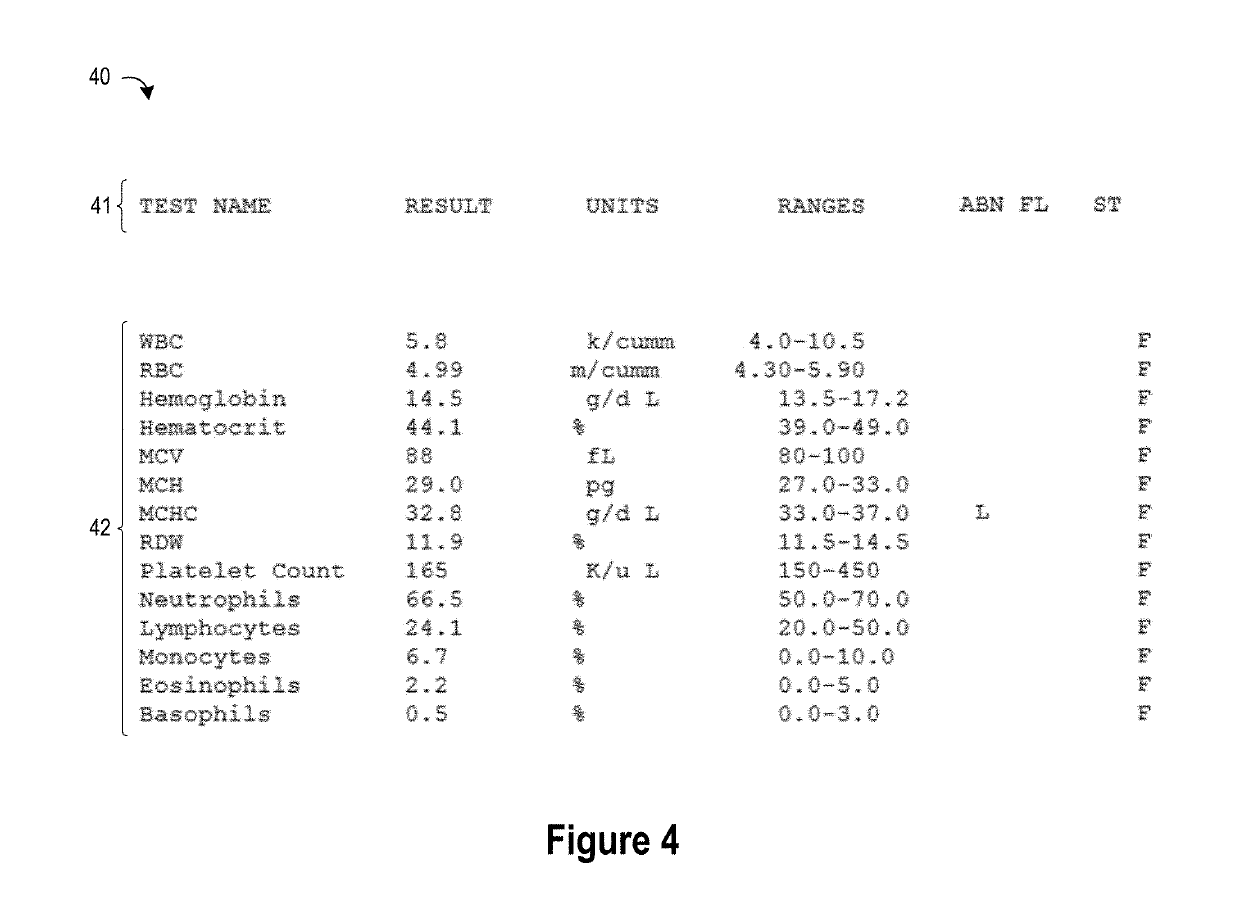
Heuristic Domain Targeted Table Detection and Extraction Technique
ActiveUS20190171704A1Improve accuracyHighly accurate targeted table type detection capabilityNatural language data processingSpecial data processing applicationsScan lineCorrelation analysis
A method, system, and apparatus are provided for processing tables embedded within documents wherein a first table header is detected by using semantic groupings of table header terms to identify a minimum number of table header terms in a scanned line of an text document; a potential data zone is extracted by applying white space correlation analysis to a portion of the text document that is adjacent to the first table header; one or more data zone columns from the potential data zone are grouped and aligned with a corresponding header column in the first table header to form a candidate table; data cleansing is performed on the candidate table; and then one or more columns of the candidate table are evaluated using natural language processing to apply a specified table analysis.
Owner:IBM CORP
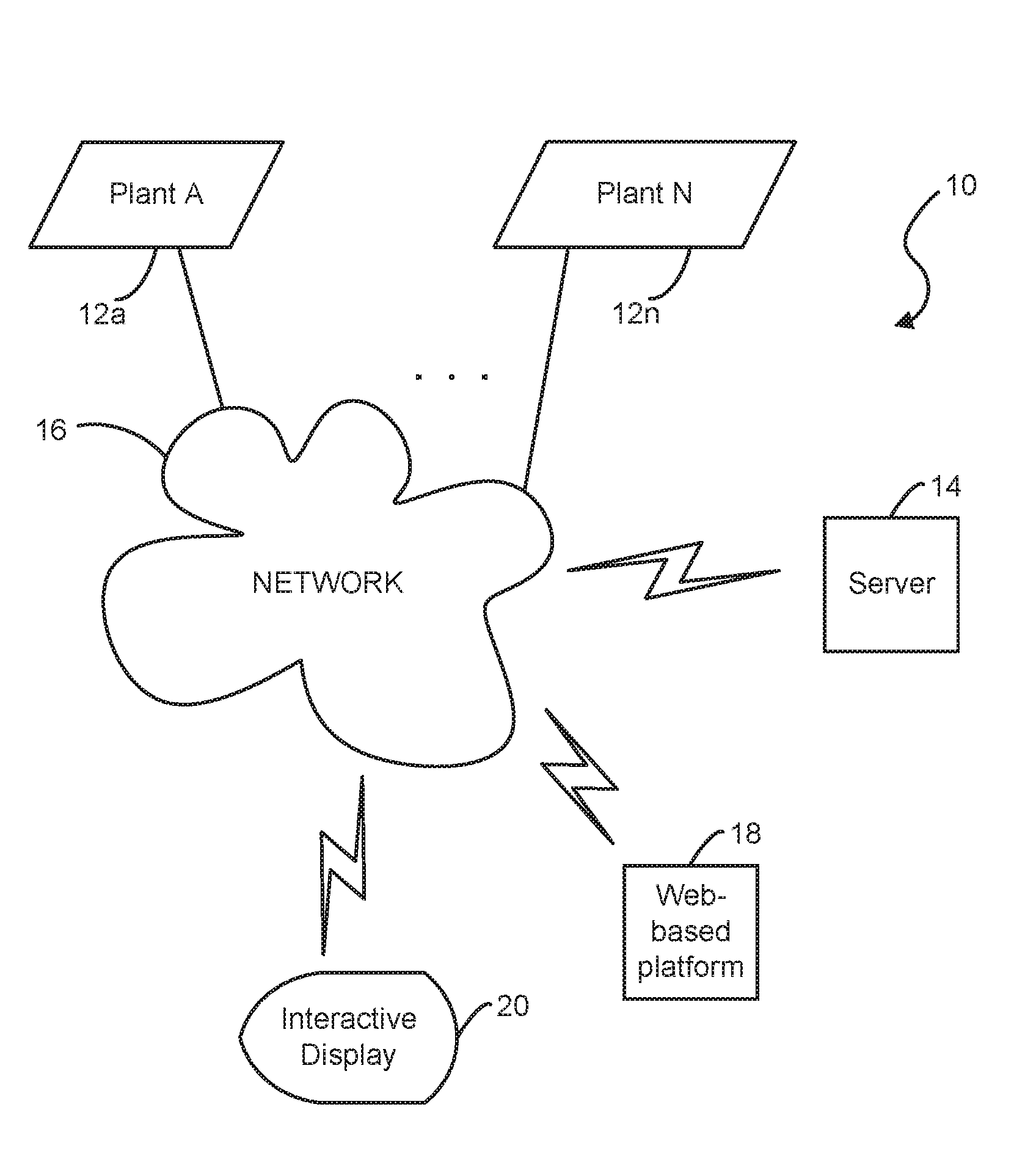
Advanced data cleansing system and method
InactiveUS20160292325A1Improving measurement error estimationEasy to detectTesting/monitoring control systemsVolume variation compensation/correction apparatusObservational errorComputerized system
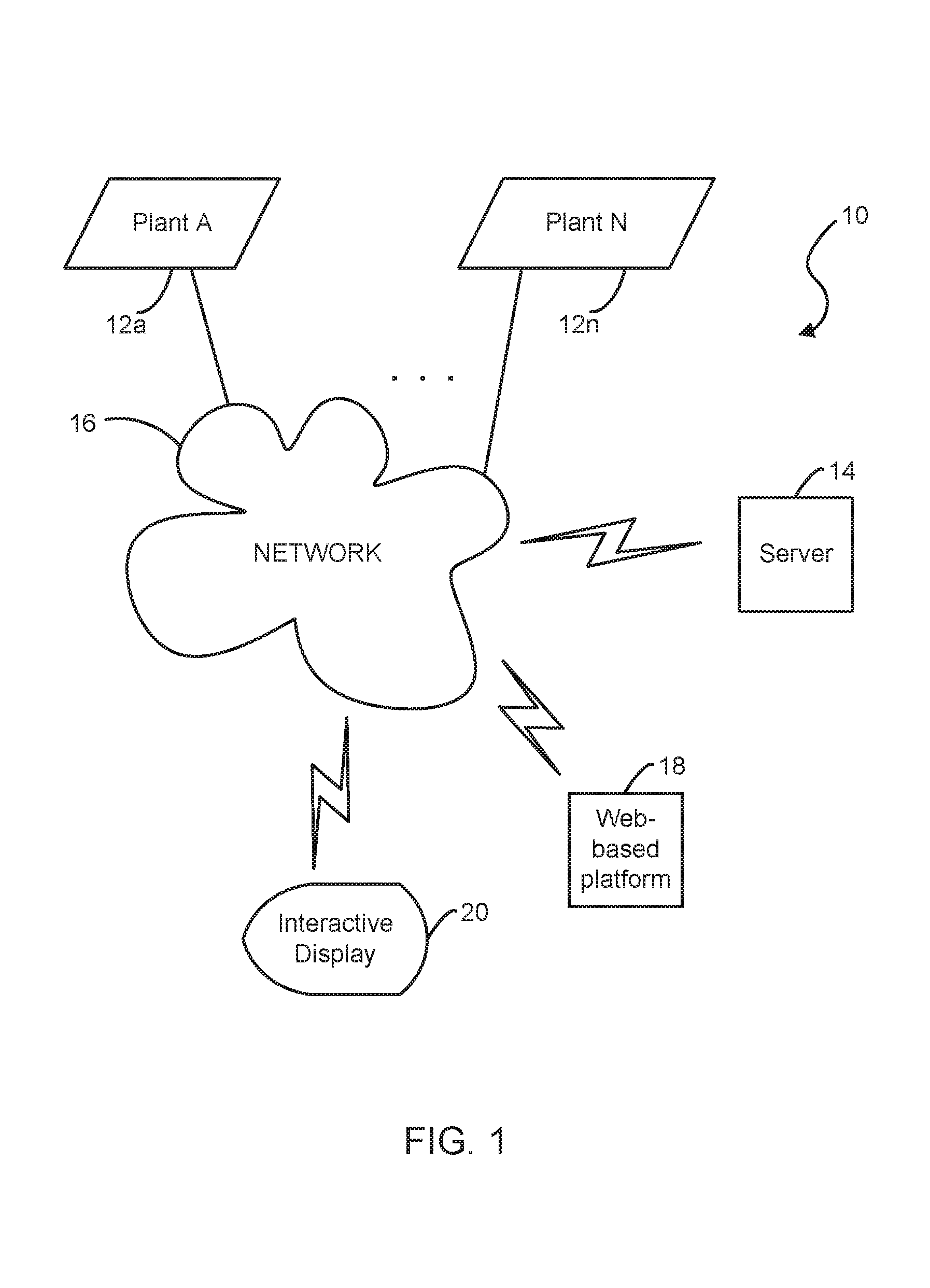
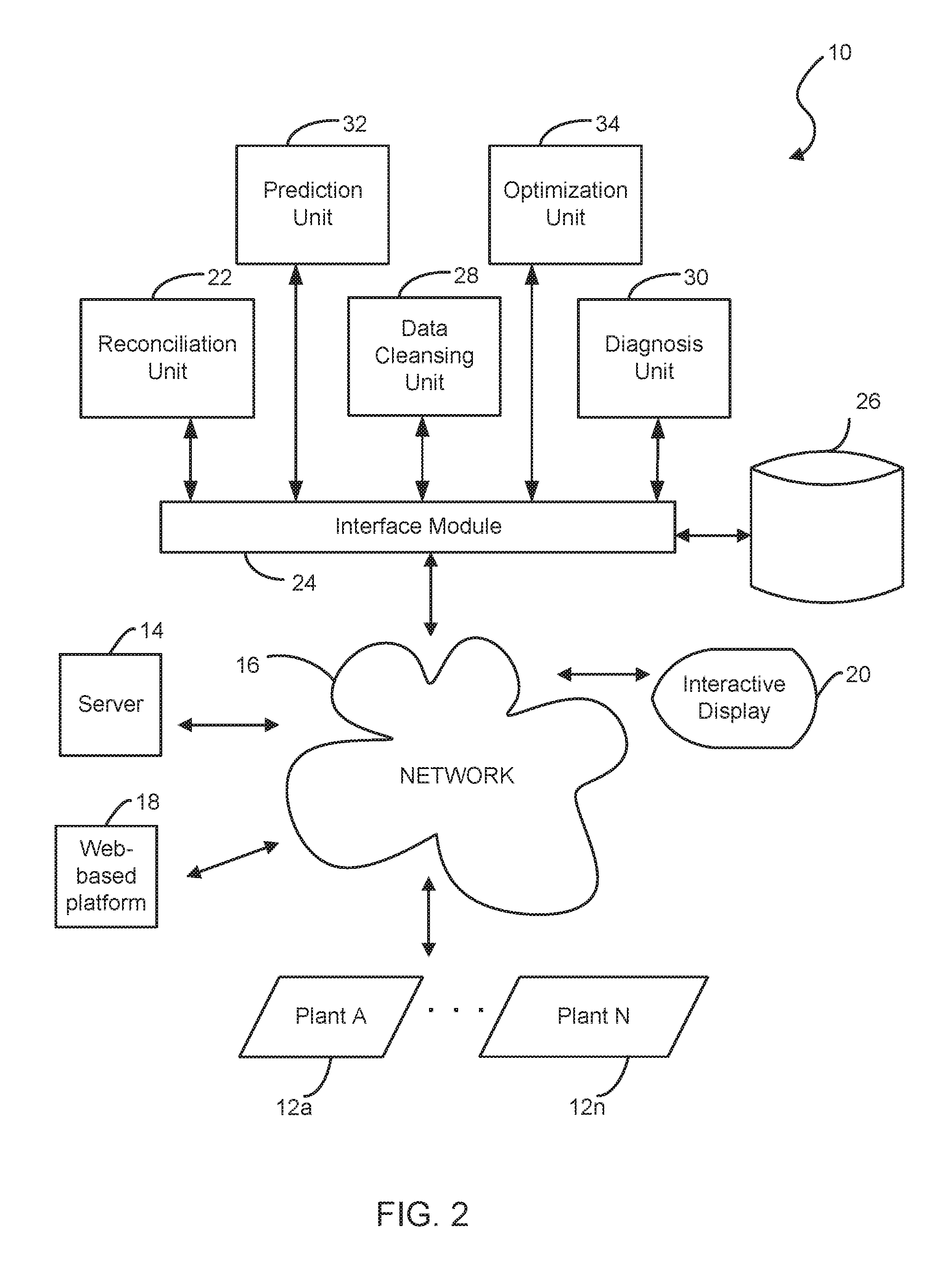
A cleansing system for improving operation of a plant. A server is coupled to the cleansing system for communicating with the plant via a communication network. A computer system has a web-based platform for receiving and sending plant data related to the operation of the plant over the network. A display device interactively displays the plant data. A data cleansing unit is configured for performing an enhanced data cleansing process for allowing an early detection and diagnosis of the operation of the plant based on at least one environmental factor. The data cleansing unit calculates and evaluates an offset amount representing a difference between a measurement and a simulation for detecting an error of measurement during the operation of the plant based on the plant data.
Owner:UOP LLC
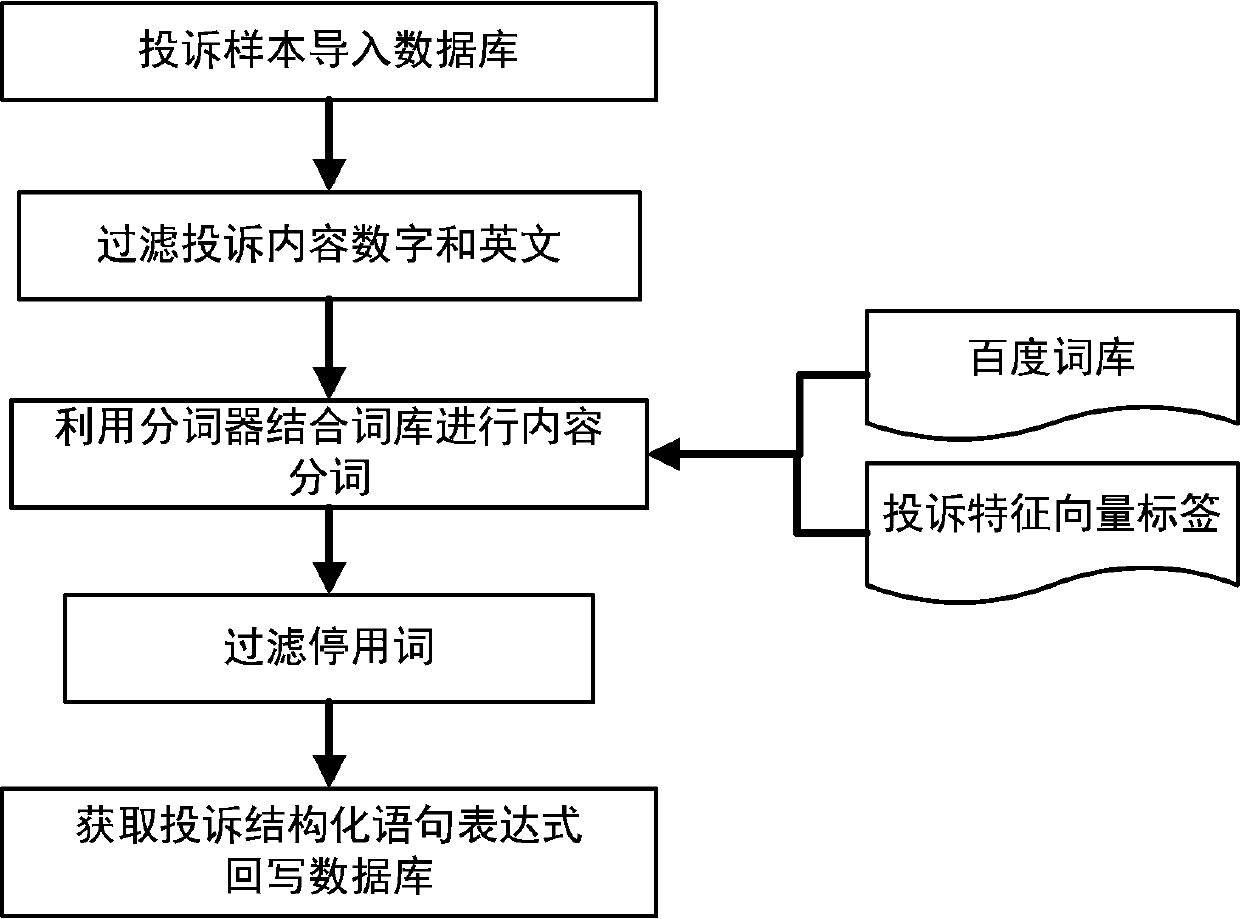
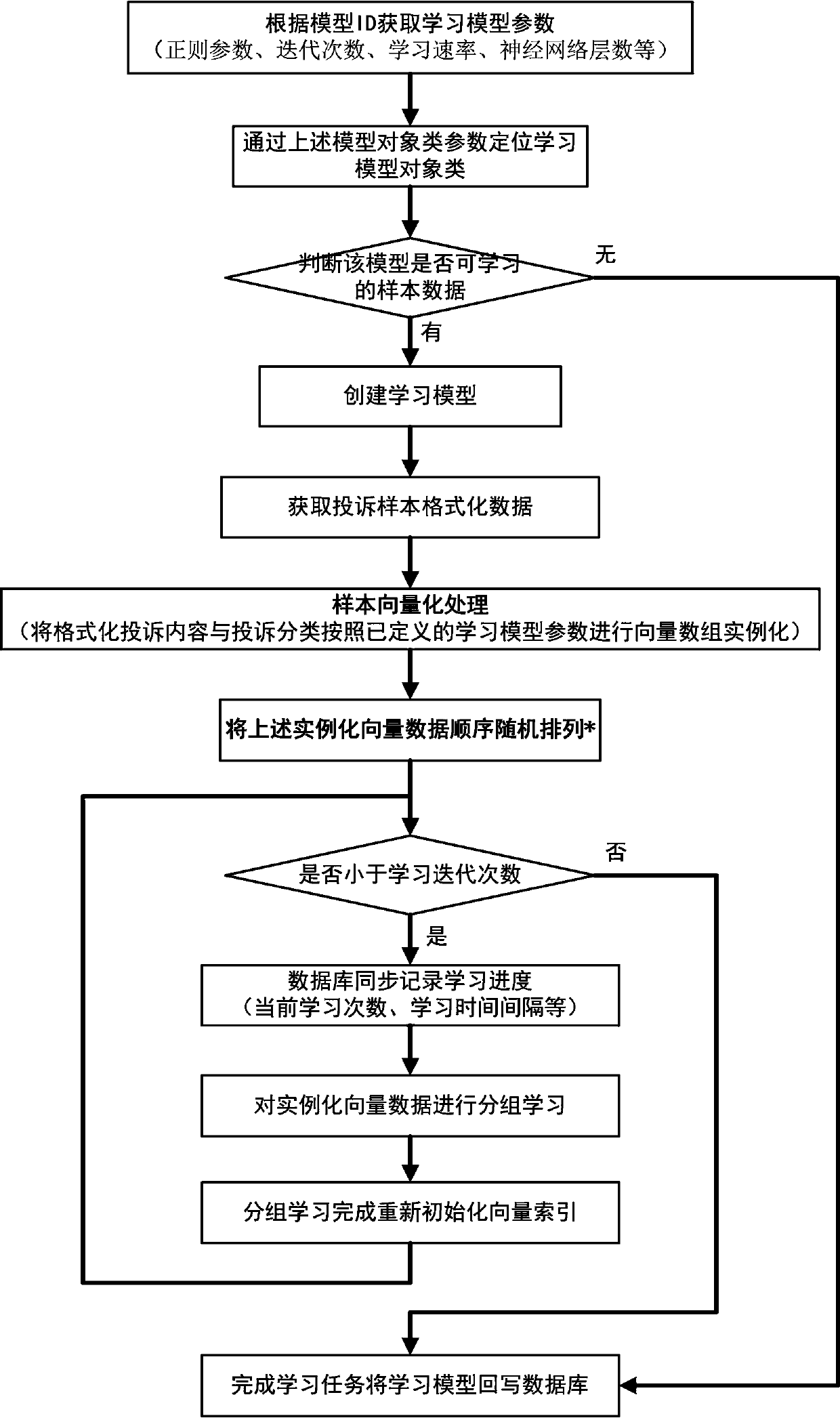
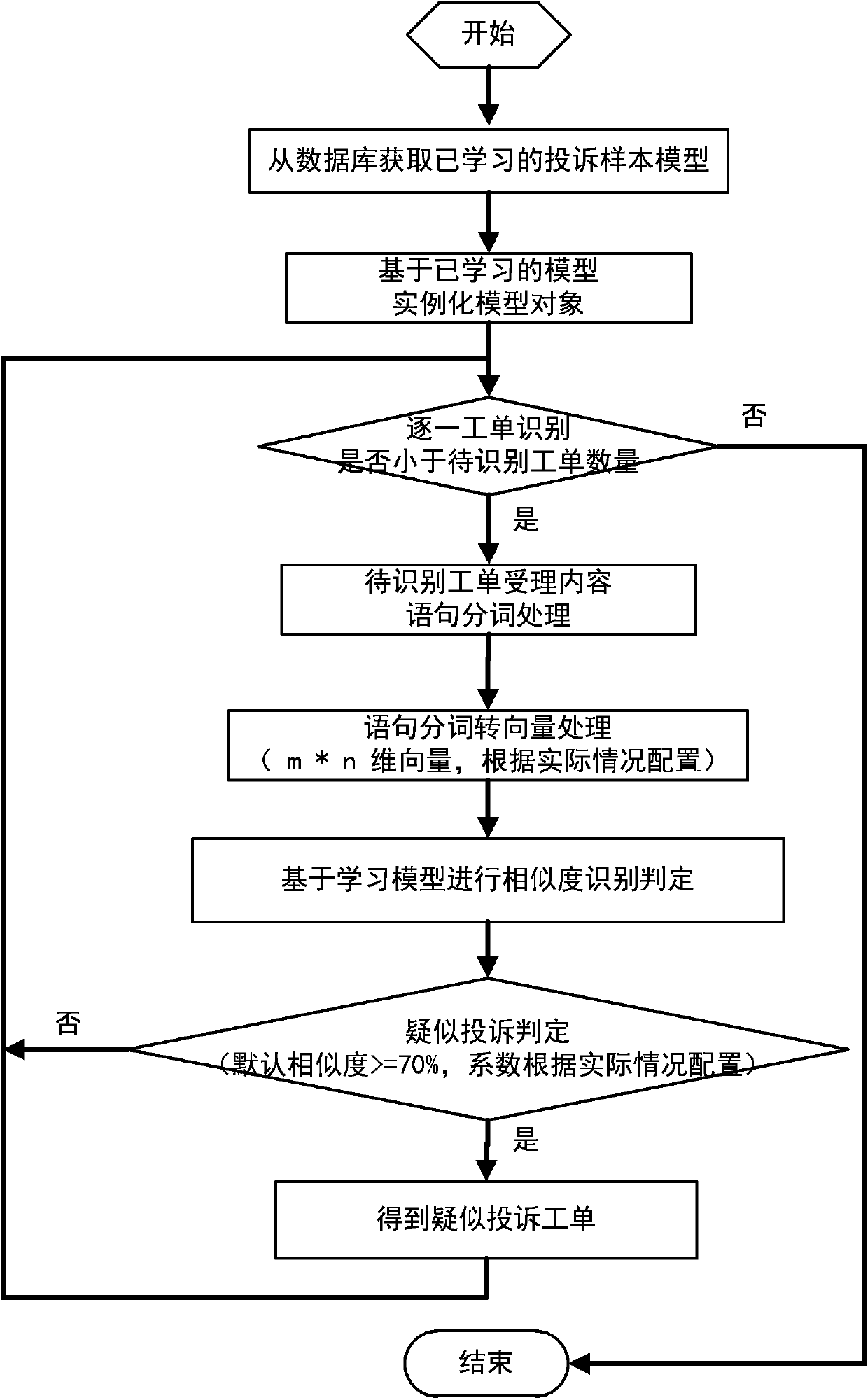
Deep learning-based electric power suspected complaint work order recognition method
ActiveCN107861942ARelieve pressureImprove scalabilityNatural language data processingCommerceData modelingElectric power system
The invention discloses a deep learning-based electric power suspected complaint work order recognition method, and relates to complaint recognition method for electric power customer services. At present, electric power suspected complaint work orders are artificially recognized, so that the efficiency is low, the timeliness is bad and human resources are wasted. The method comprises the following steps of: 1) deep learning model configuration; 2) complaint feature label extraction; 3) complaint sample formatting; 4) model learning and training; 5) suspected complaint recognition; and 6) suspected complaint classification. According to the method, a series of work such as data cleaning and sorting, complaint tendency word extraction, data modeling and optimization, sample iterative learning and training, machine learning and prediction and the like can be carried out on complaint lists through a deep learning technology, so that deep learning-based intelligent recognition and classification of suspected complaint work orders are realized, the intelligent work experience is enhanced and the service quality control work efficiency is improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO MARKETING SERVICE CENT +1
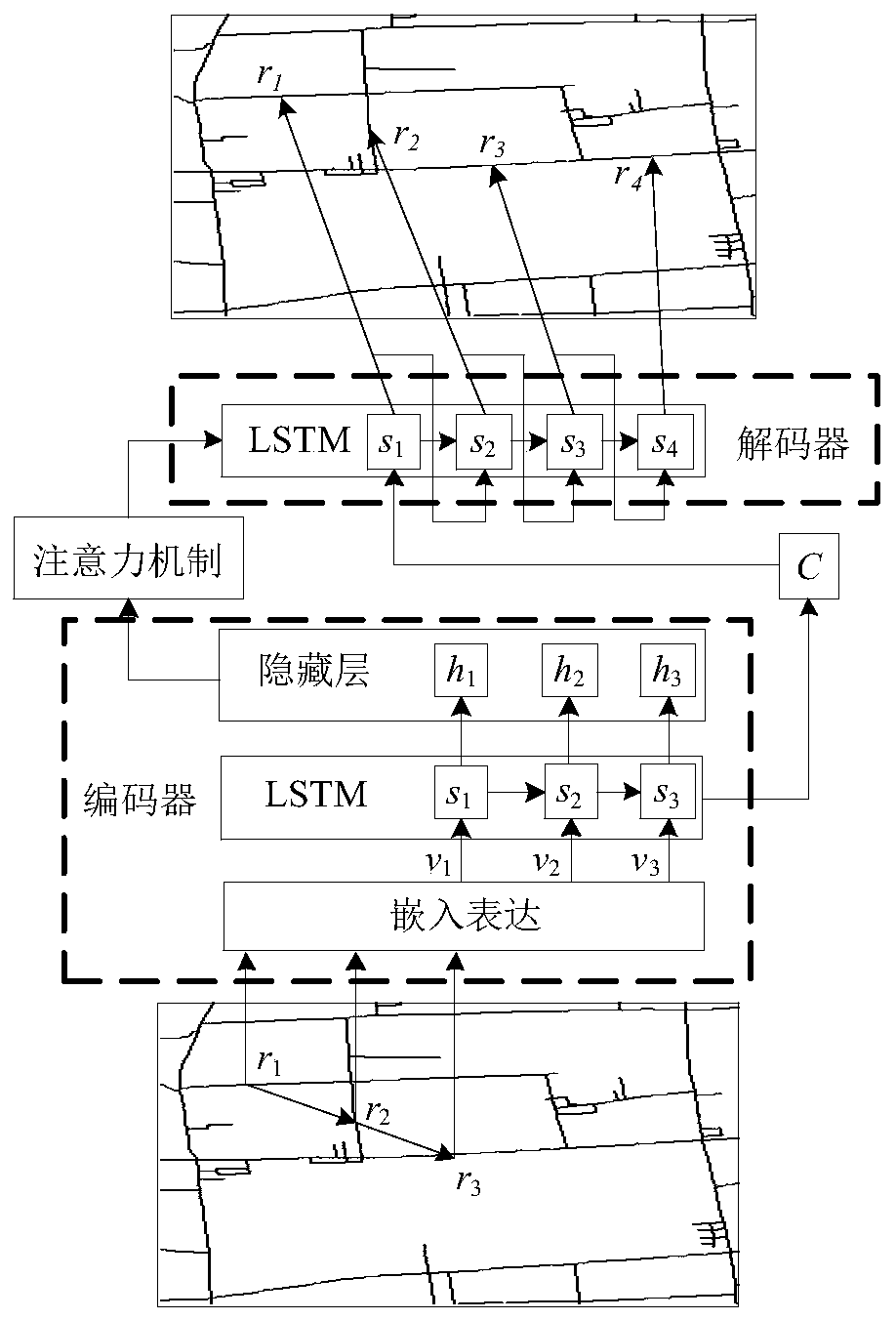
Urban scale taxi track prediction method based on attention mechanism
PendingCN110163439AAvoid vanishing gradientsImprove accuracyForecastingGeographical information databasesHidden layerSimulation
An urban scale taxi track prediction method based on an attention mechanism comprises the following steps that 1, GPS data are collected, and noise appearing in the GPS data collection process is subjected to data cleaning; step 2, map matching is carried out on the cleaned GPS data to obtain experimental data required by the model; step 3, model training; an LSTM network is adopted at an encodingend of the encoder, an encoding vector C is used as the LSTM network of the decoding end at a decoding end, an attention mechanism is applied to a hidden layer vector of the encoder, and a predictedvalue at the previous moment is used as an input value at the current moment each time and is sent into the decoder. According to the method, the embedded vector is adopted to represent the road section information in the urban area, the encoder is used for encoding the track of the taxi, the decoder containing the attention mechanism is used for predicting the track, the correlation in the tracksequence is fully mined, and the track prediction accuracy can be effectively improved.
Owner:CHANGAN UNIV
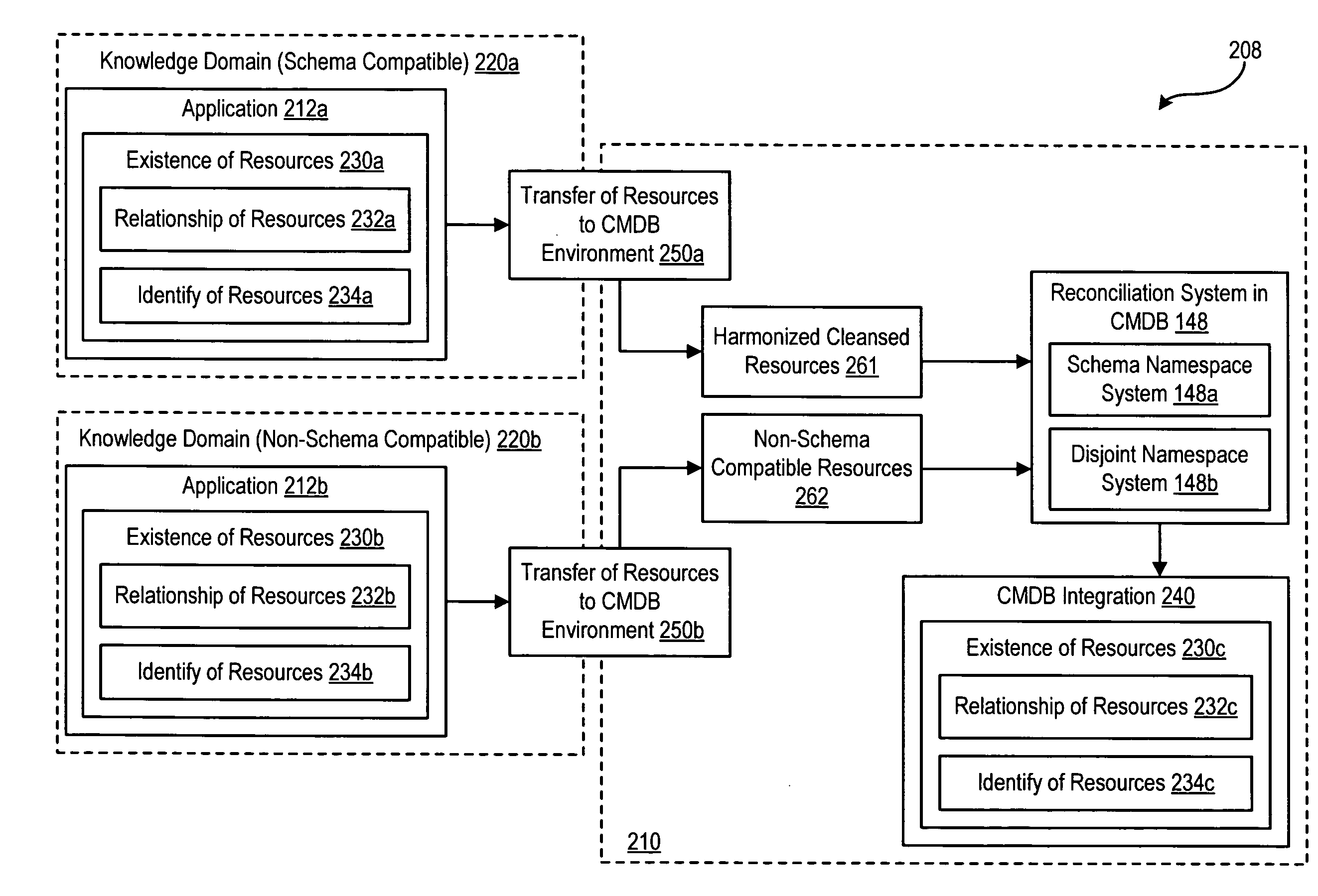
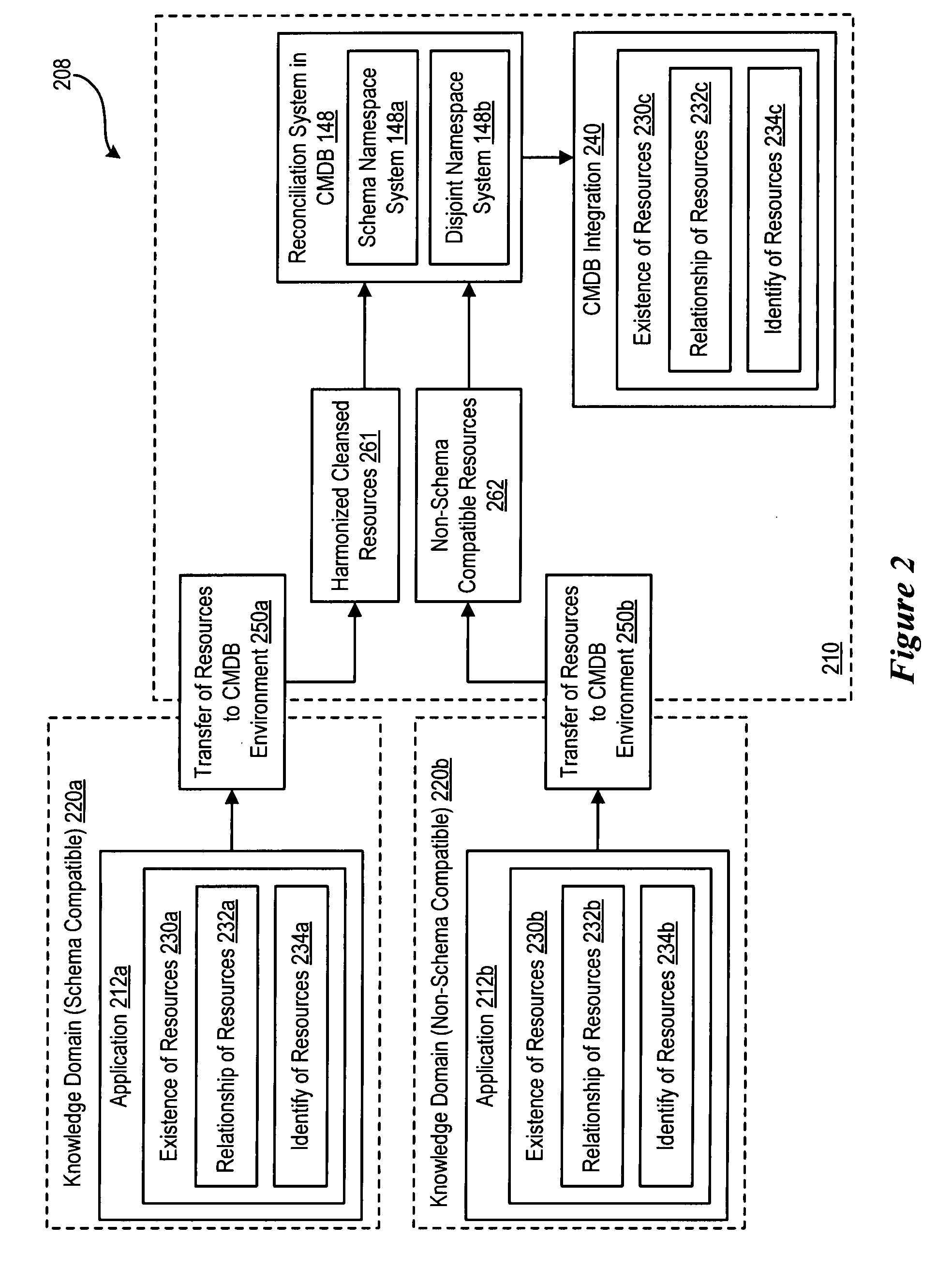
Importing and Reconciling Resources From Disjoint Name Spaces to a Common Namespace
InactiveUS20090063562A1Database management systemsDigital data processing detailsHarmonizationApplication software
A namespace exploits individual resource identity attributes of an application to allow the integration of resource instances from applications into a configuration management database (CMDB), prior to any data cleansing or namespace harmonization activities. An approach for incremental reconciliation of resource instances within the CMDB is defined.
Owner:IBM CORP
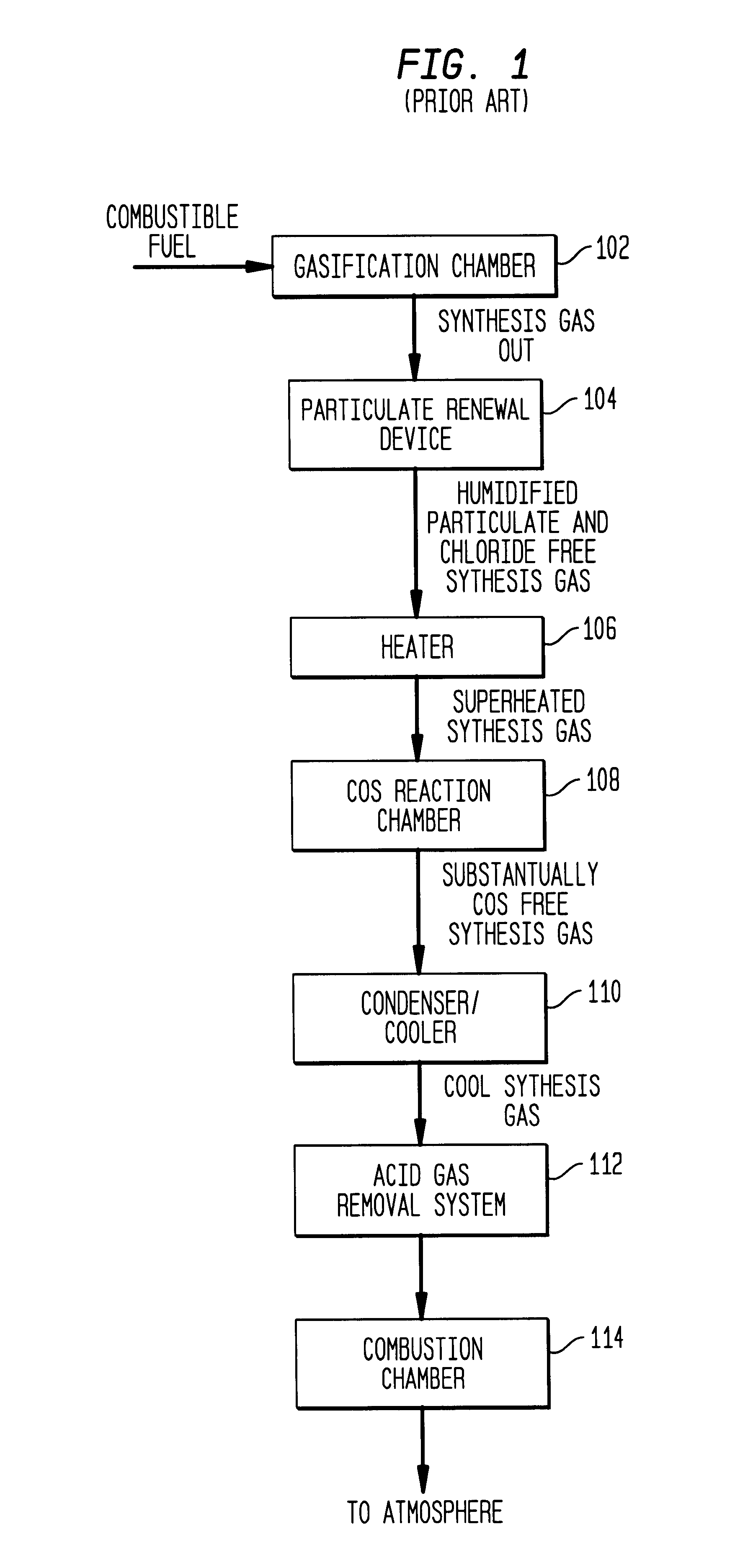
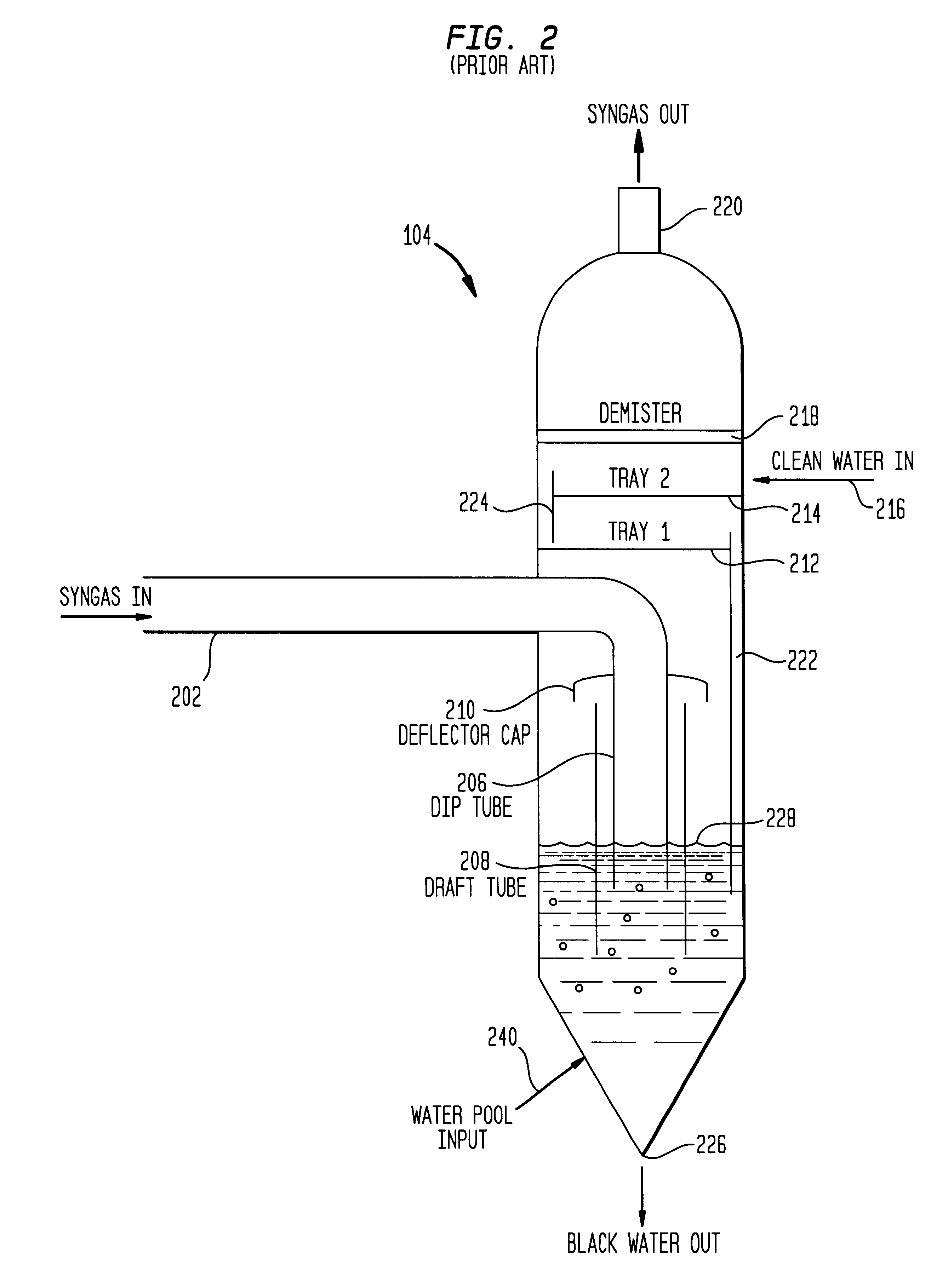
Method and apparatus for removing carbonyl sulfide from a gas stream via wet scrubbing
InactiveUS6322763B1Weaken energyLower Level RequirementsGas treatmentUsing liquid separation agentCarbonyl sulfideWater flow
Methods for removing carbonyl sulfide (COS) from a synthesis gas stream are disclosed. The method entails raising the water level of a wet scrubber so that hydrolysis of the COS may occur in the scrubber itself instead of a COS reduction chamber and no additional catalysts other than those naturally occurring in the production of the synthesis gas need be introduced into the scrubber. The water is raised, in one example, to a level such that water within an inner tube of the wet scrubber flows over an upper end of the inner tube. Raising the water level in the scrubber ensures intimate and vigorous interaction between the water, the COS, and the naturally occurring catalyst, and promotes the hydrolysis of the COS. In one example, the naturally occurring catalyst (e.g., alumina oxide) is present in the coal ash produced when coal is the fuel gasified that creates the synthesis gas stream.
Owner:MTI INSULATED PROD
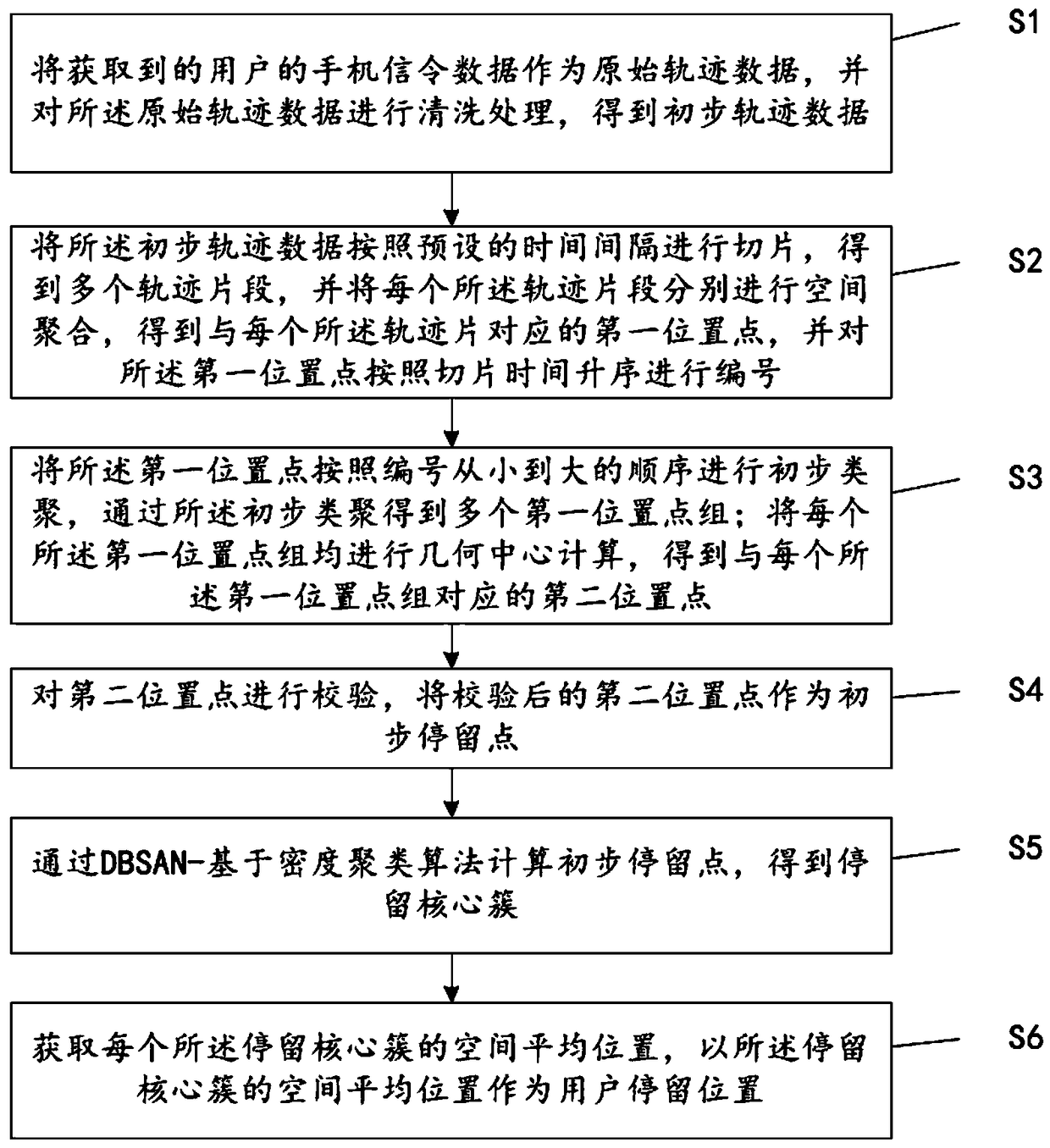
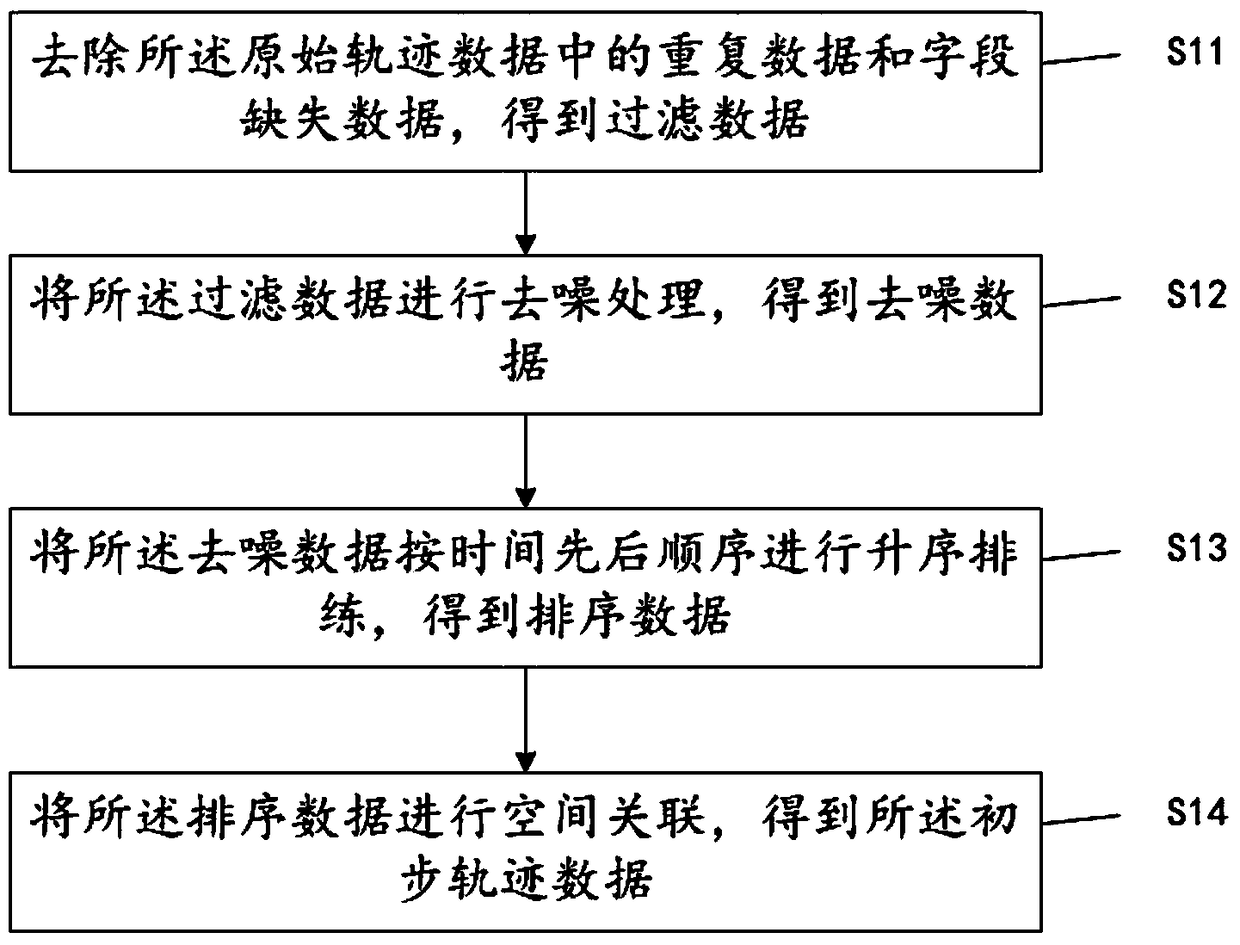
A method and a system for discovering a user stay position based on mobile phone signaling
ActiveCN109104694ASolve the shortcomings of being unable to adapt to processing spatio-temporal dataLow resolution accuracyLocation information based serviceSpecial data processing applicationsCluster algorithmPoint density
The invention relates to a method and a system for discovering a user residence position based on mobile phone signaling. The method comprises the following steps: the obtained mobile phone signalingdata of the user is taken as the original trajectory data, and the original trajectory data is sequentially processed by data cleaning, data slicing, preliminary clustering, data verification and corecluster calculation, and finally the user staying position is obtained. Adopting a series of algorithms such as track slice aggregation, hierarchical clustering algorithm, kernel density clustering algorithm and machine learning algorithm, etc., considering mobile phone track point density, signaling time interval, track point moving direction and moving distance, etc., we can judge user 's staying position, staying time, entering and leaving staying point time. The algorithm can effectively eliminate the interference of base station drift on user location judgment, improve the identificationaccuracy of user dwell point position and dwell time, and objectively restore the user dwell position.
Owner:重庆市交通规划研究院
Method and apparatus for scrubbing accumulated data errors from a memory system
ActiveUS20110289386A1Disturb errorData representation error detection/correctionStatic storageElectricityData error
A data scrubbing apparatus corrects disturb errors occurring in a memory cell array, such as SMT MRAM cells. The data scrubbing apparatus activates scrubbing of the data and associated error correction bits based on a number of errors corrected, at a power up of the memory cell array, or a programmed time interval. The data scrubbing apparatus may generate an address describing the location of the memory cells to be scrubbed. The data scrubbing apparatus then commands the array of memory cells to write back the corrected data, the associated error correction bits, and reference bits. The data scrubbing apparatus provides a busy indicator externally during a write back of corrected data.
Owner:TAIWAN SEMICON MFG CO LTD
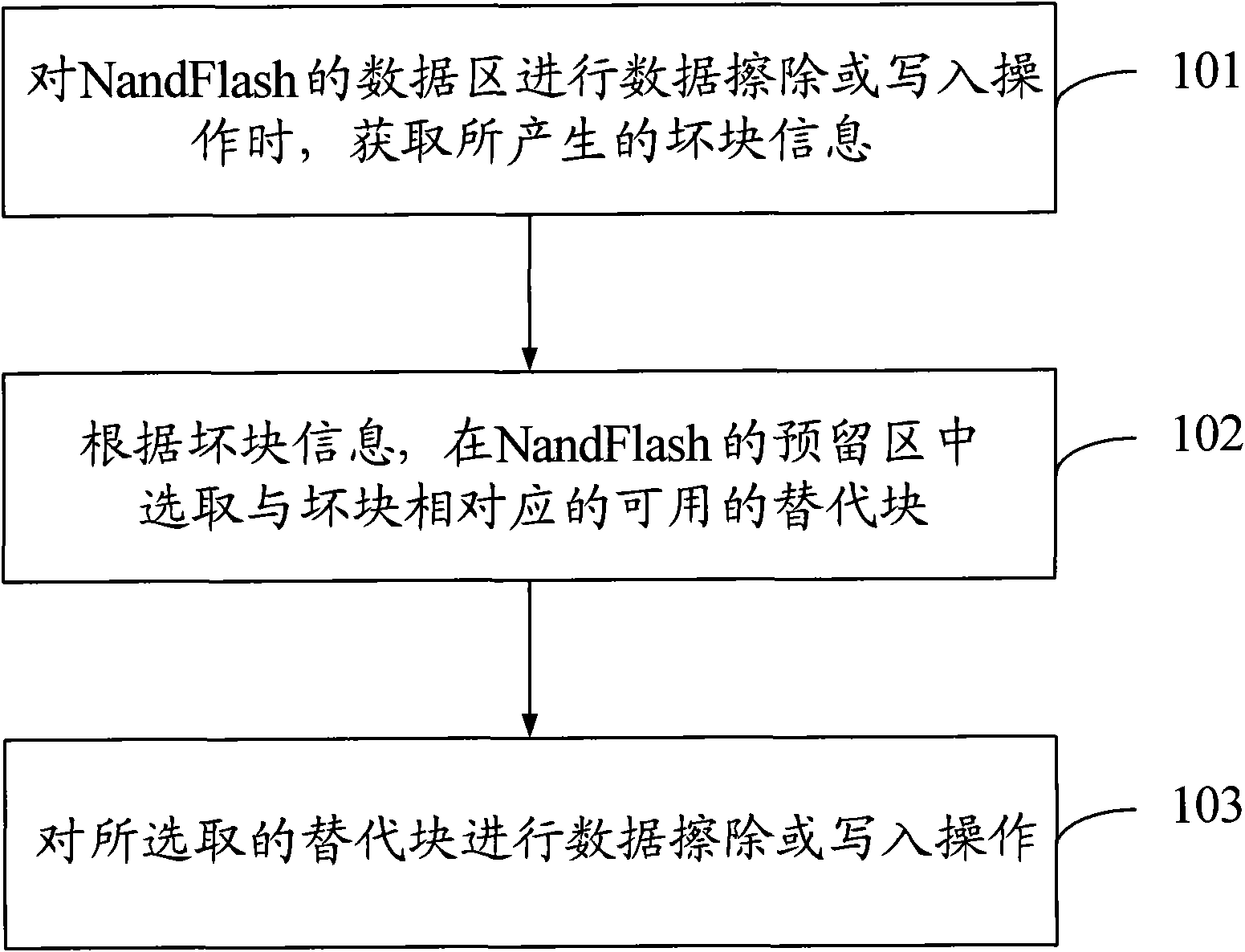
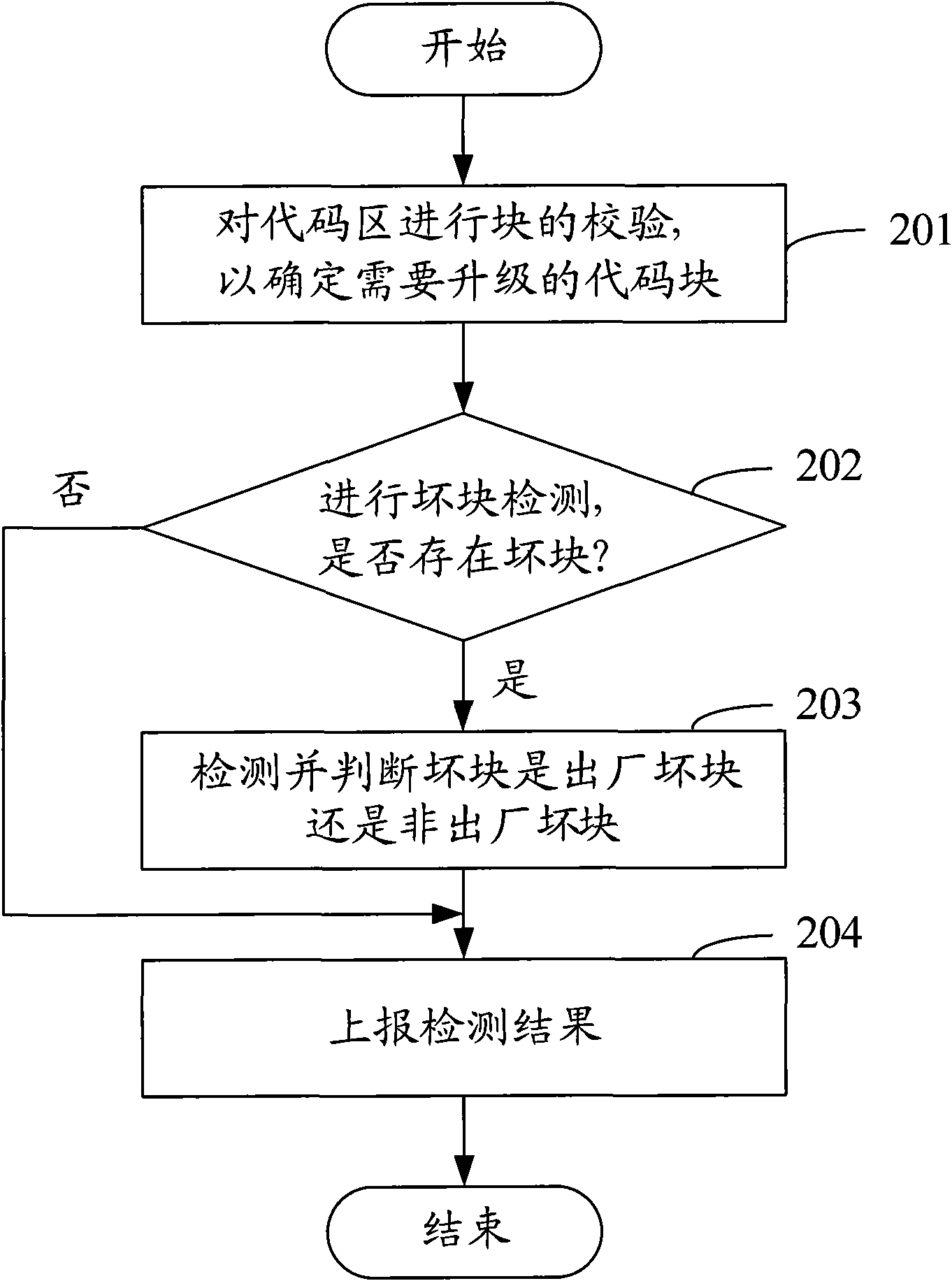
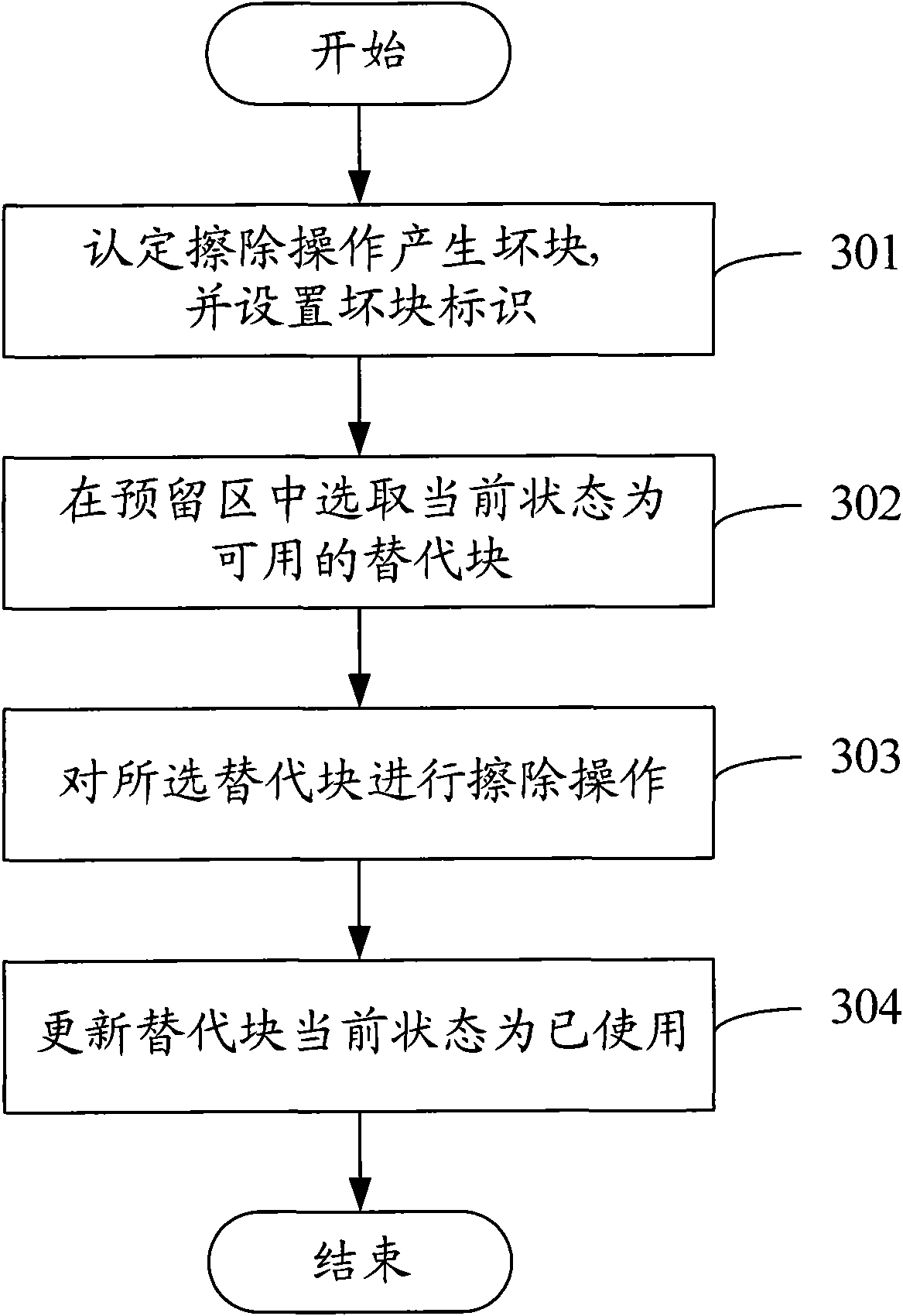
Bad block management (BBM) method and device for Nand Flash
InactiveCN101593157AFast searchImprove upgrade efficiencyMemory adressing/allocation/relocationSpatial partitionComputer science
The invention discloses a bad block management method and a device for a Nand Flash, in which the memory space of the Nand Flash is divided into data areas and reserve areas. The bad block management method comprises the following steps: generated bad block information is obtained when data scrubbing or writing is operated in the data areas of the Nand Flash; available substitute blocks which correspond to the bad blocks are chosen in the reserve areas of the Nand Flash; data scrubbing or writing is carried out on the substitute blocks. The invention also discloses a bad block management device for Nand Flash, the substitute blocks are used for realizing scrubbing, writing and other operations of the bad blocks, the mapping relationship between the bad blocks and the substitute blocks is only needed to be established, and the substitute blocks can be found quickly on the premise of establishing; the substitute operation has no effect on other normal blocks. In addition, the invention can be applied into the firware upgrading of terminals, thus avoiding effects on firware upgrading caused by bad blocks and improving the efficiency of firware upgrading.
Owner:ZTE CORP
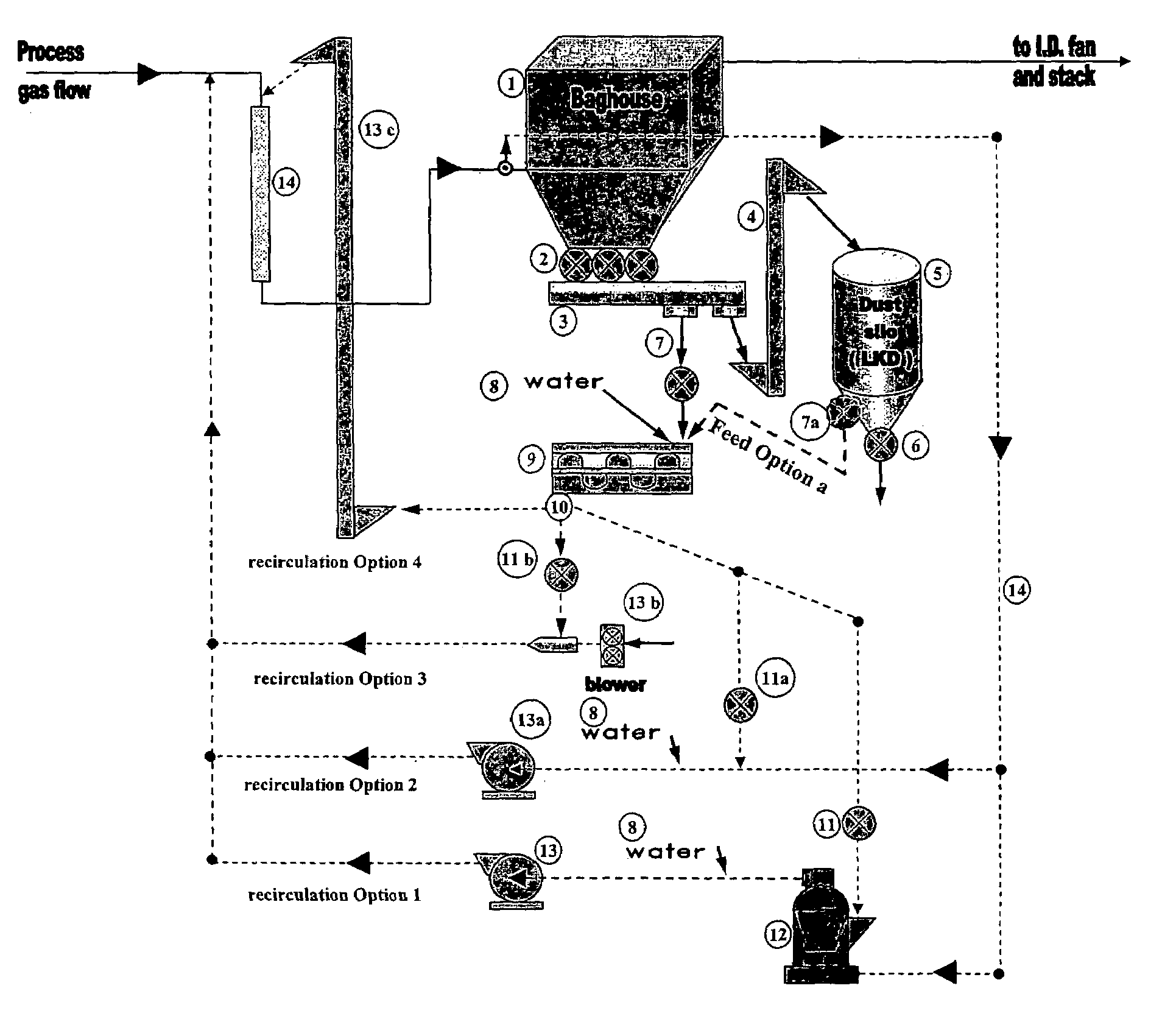
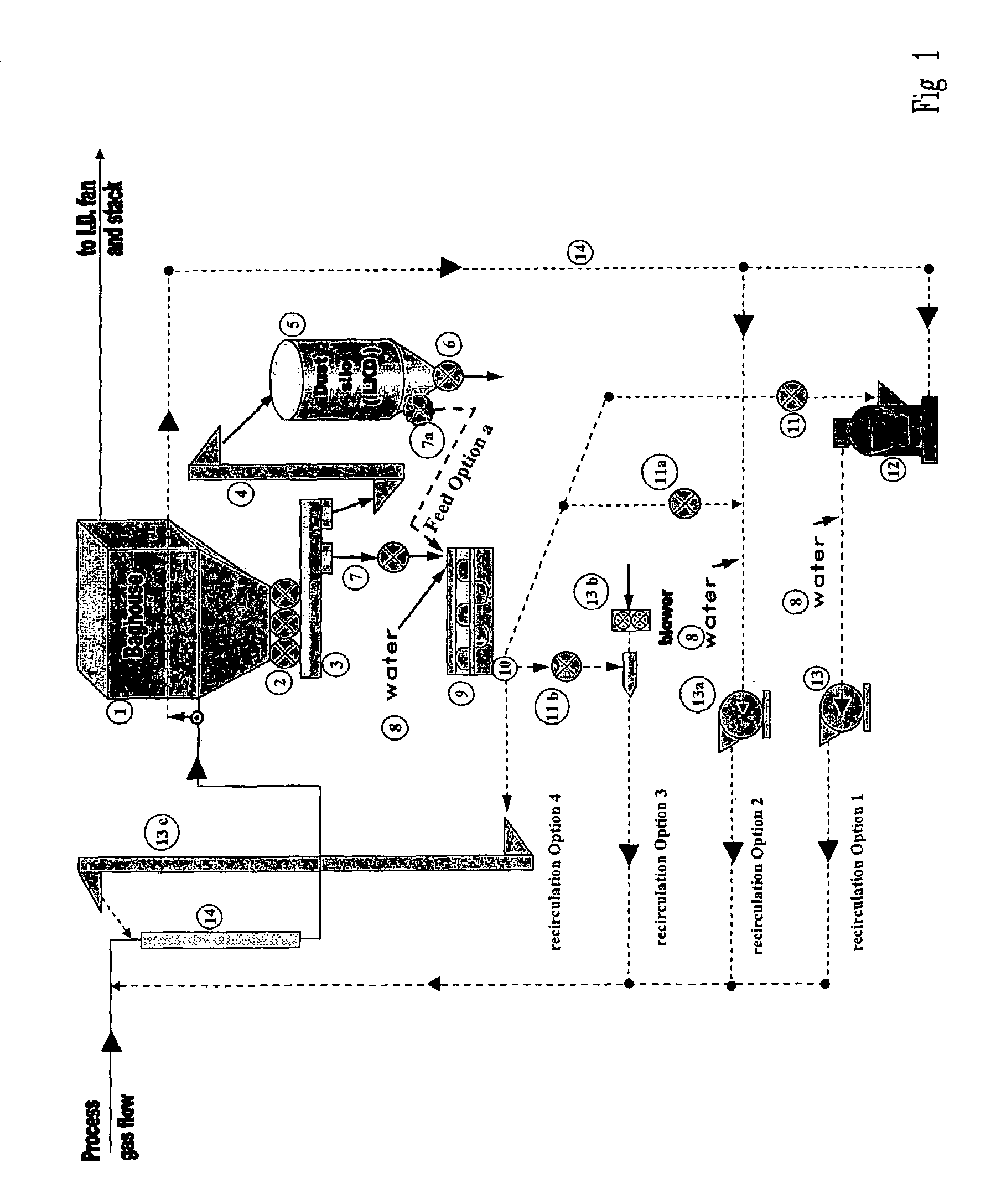
Hydrated lime kiln dust recirculation method for gas scrubbing
ActiveUS7141093B2Effectively self-cleaningEffective sorbentGas treatmentIsotope separationSorbentFlue gas
Owner:GRAYMONT PA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com