Patents
Literature
1167 results about "Object store" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
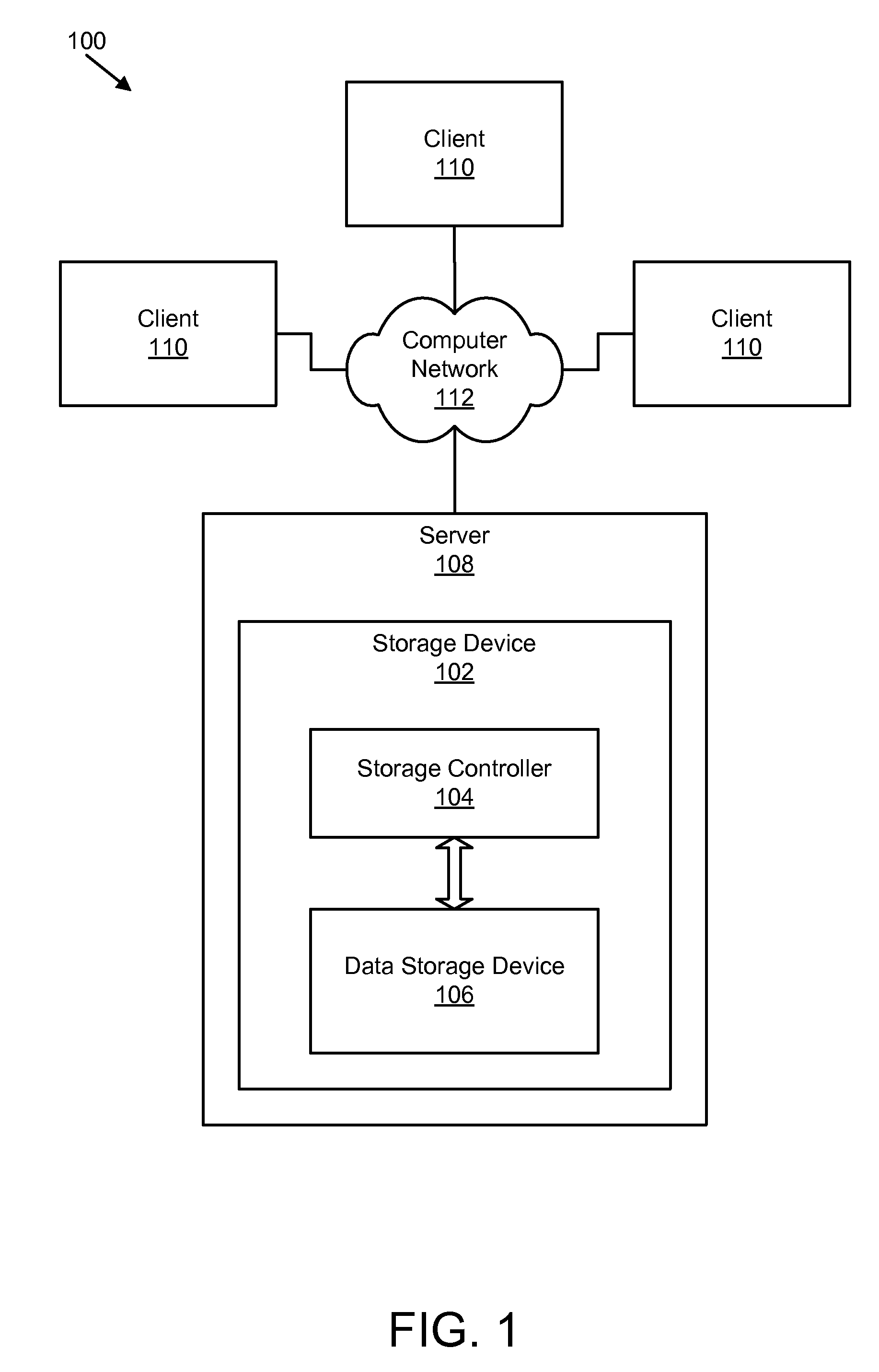
An object store is a repository, or “store”, of objects, as well as a suite of accompanying storage and retrieval services.
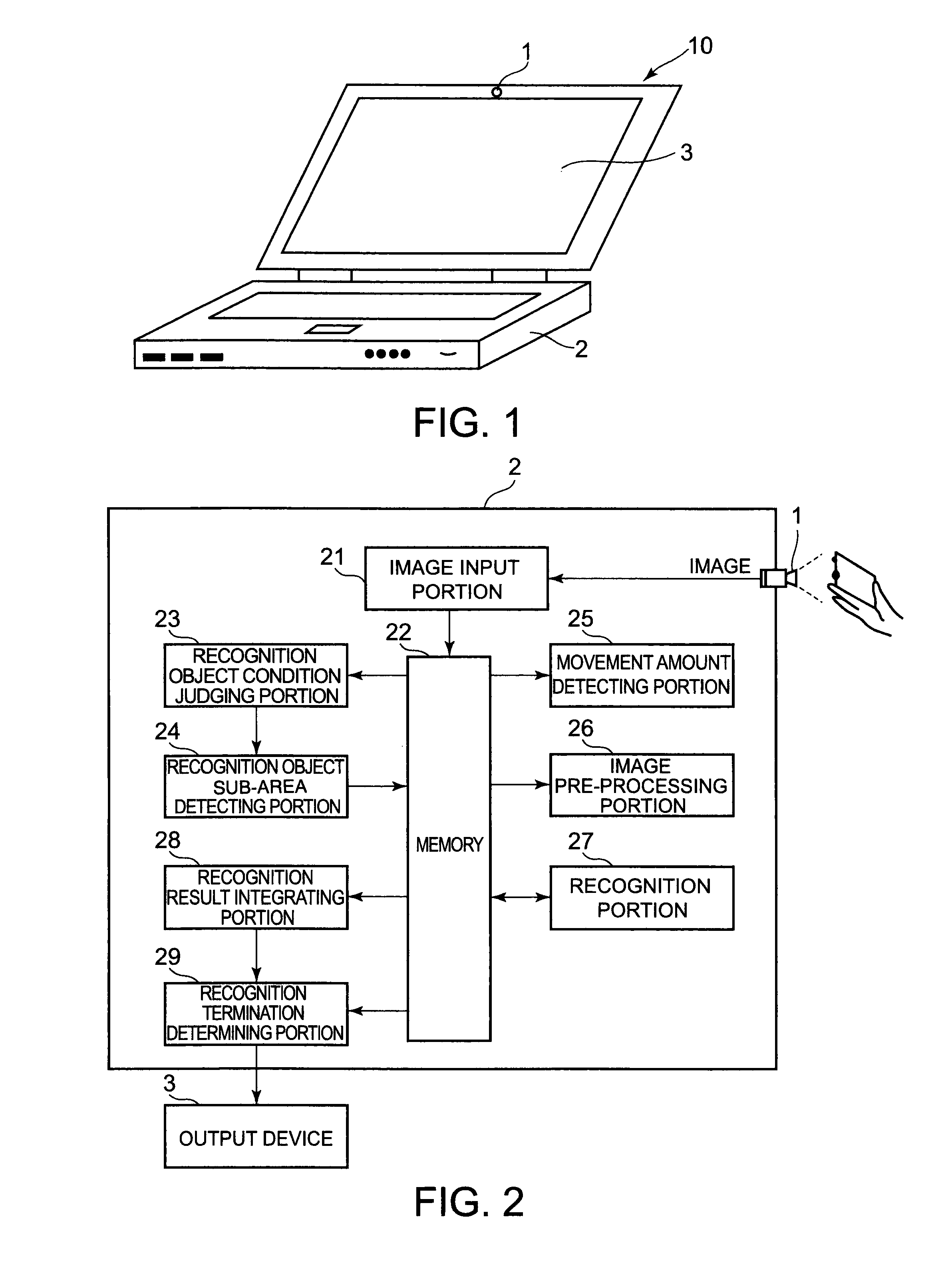
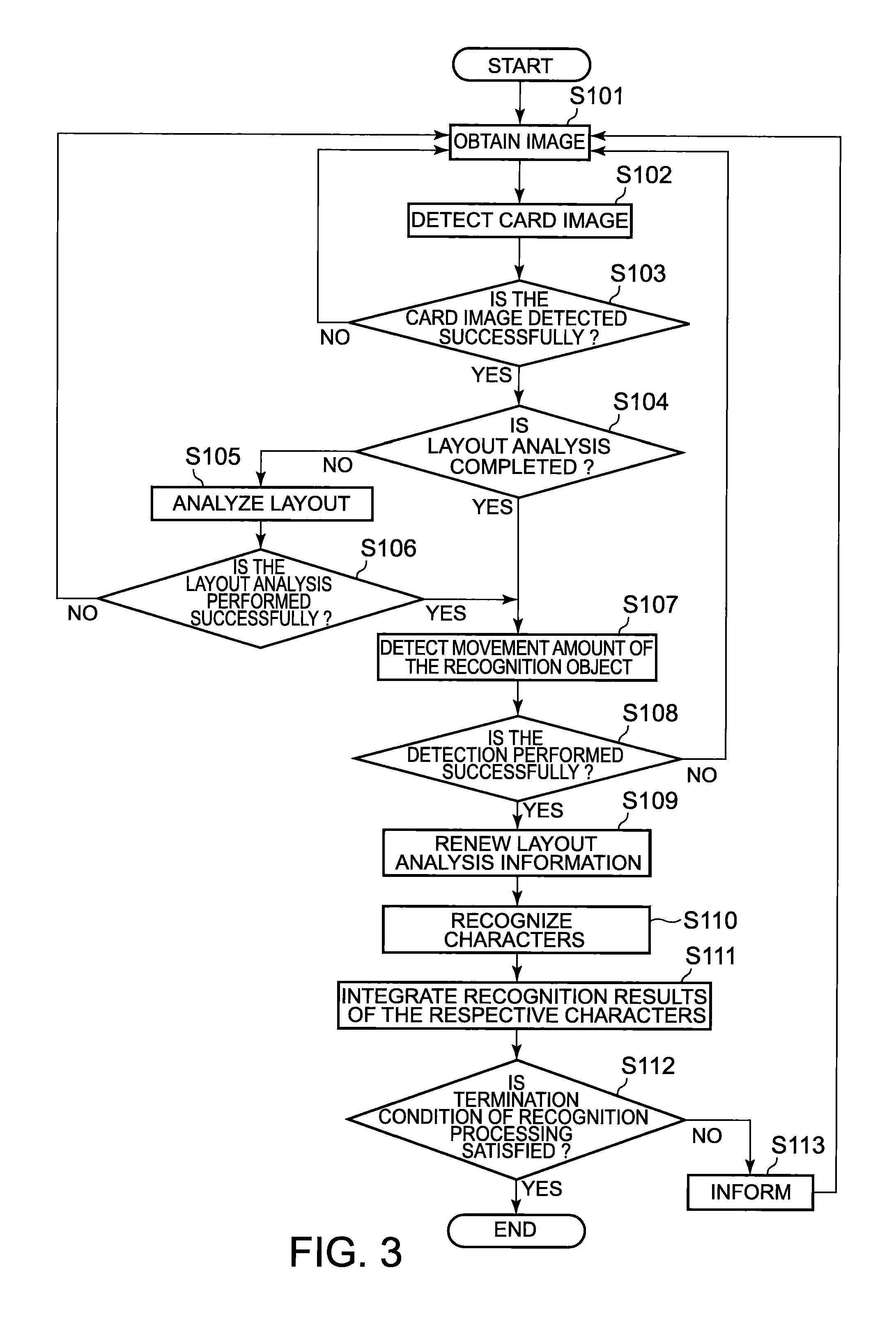
Image processing system
ActiveUS8289403B2Television system detailsColor television detailsPattern recognitionImaging processing
A recognition object detecting portion detects a recognition object existing in each of images which are captured in series at different time points by a camera. Images of the detected recognition object are stored in a memory. A recognition object condition judging portion determines whether image areas of the recognition object are recognizable. A movement amount detecting portion detects a movement amount of the recognition object by using the image areas of the recognition object stored in the memory. A sub-area detecting portion detects a sub-area to be recognized, by using the image areas of the recognition object read out from the memory, in accordance with the movement amount of the recognition object. A recognition portion performs recognition processing on the sub-areas. A recognition result integration portion integrates recognition results of the sub-areas including recognized characters and / or recognized patterns and the corresponding reliabilities, respectively.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
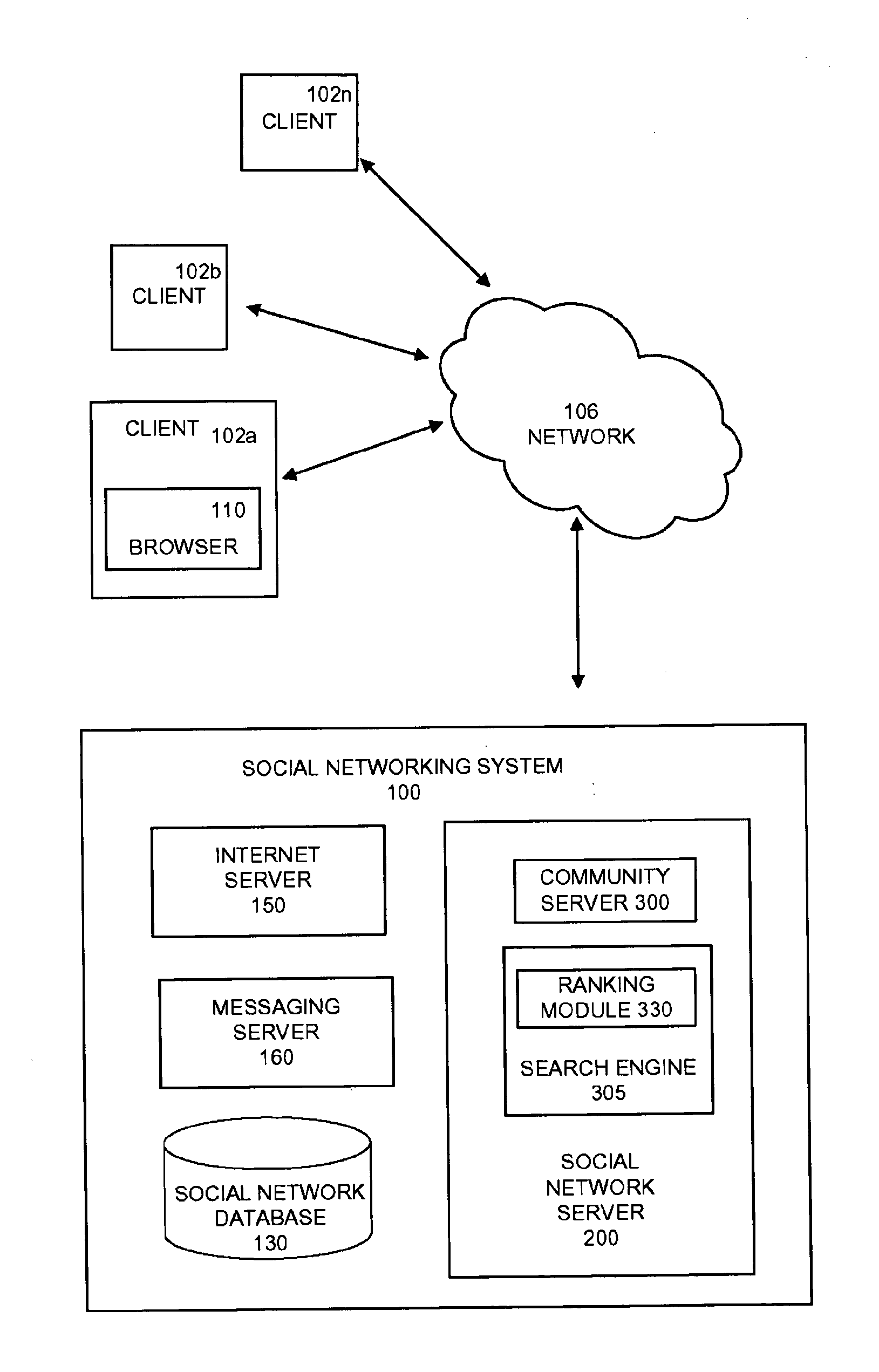
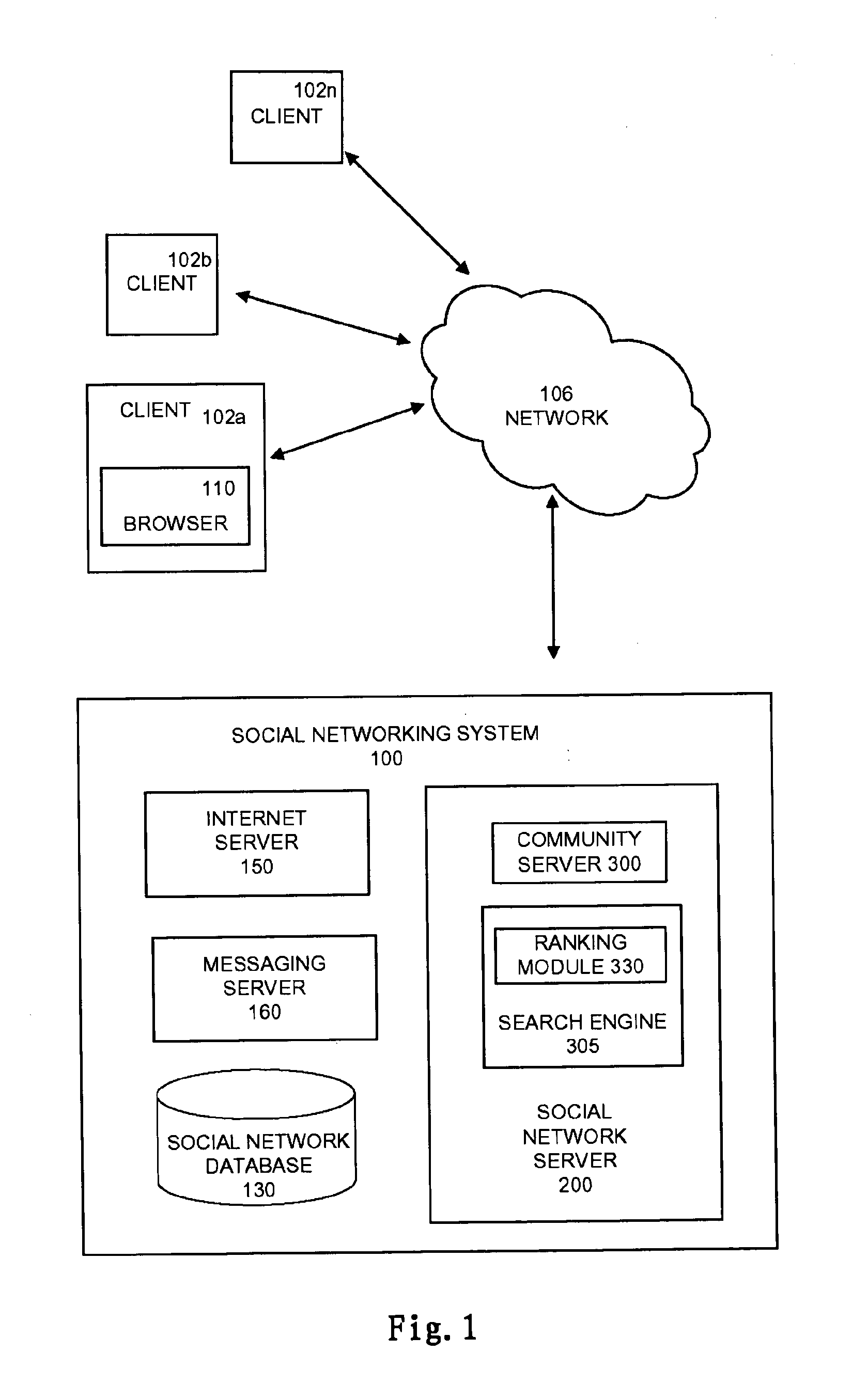
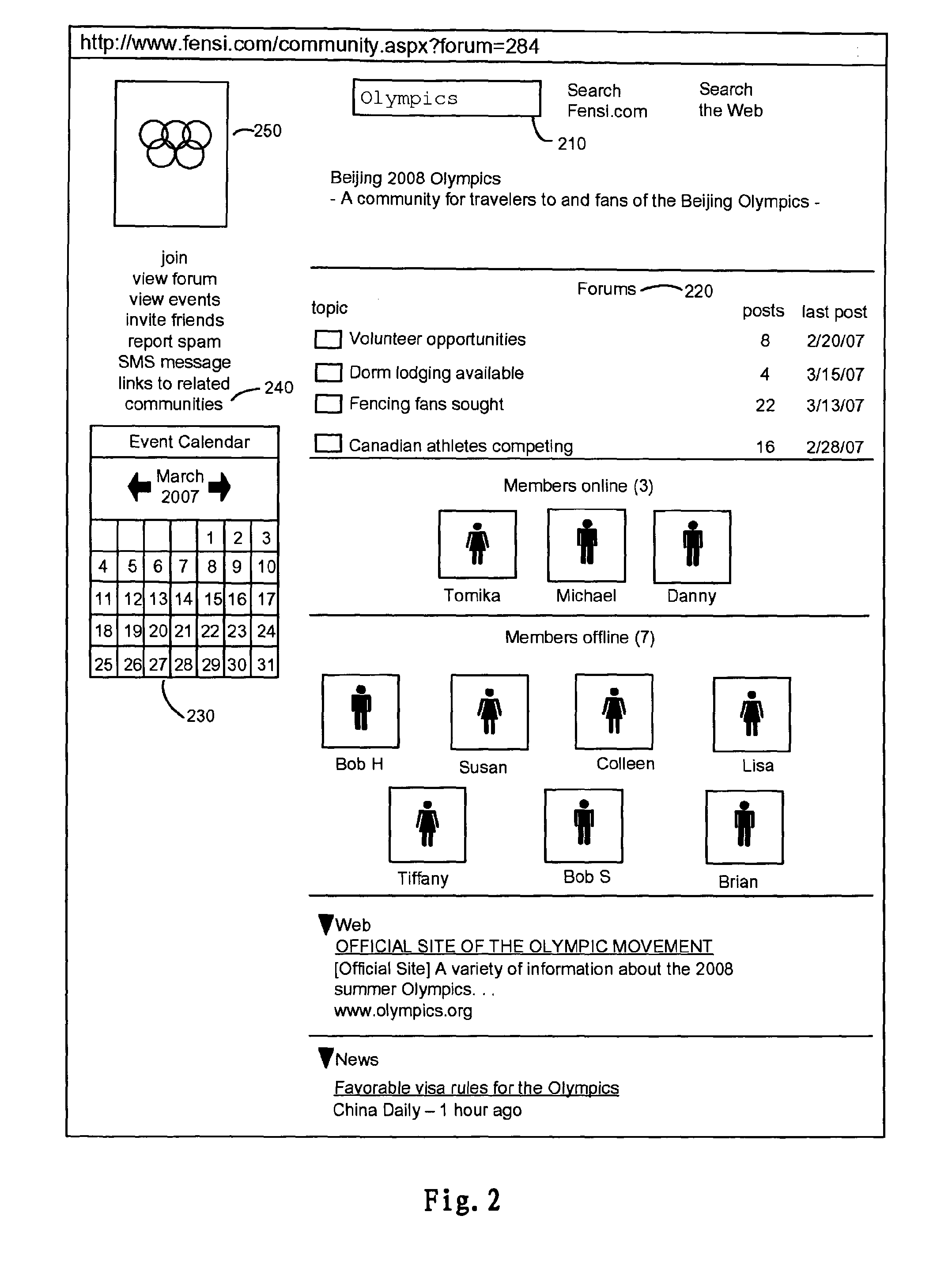
Ranking Social Network Objects
An online social networking system can be used to rank social network objects of various different object types, each according to its type. The objects may comprise types such as users, communities, blogs, blog entries, events, forums, forum topics, postings, photographs, and / or images. The product comprises code for carrying out a method that begins with receiving ranking data about social network objects that comprises data about events performed on the social network. For each social network object, a ranking function is applied to ranking data about the social network object based on its type. In addition, the recency of an event on the social network related to the social network object is evaluated, in order to calculate the score for the social network object. A relative ranking for each of the plurality of social network objects based on its score is determined, and the score and relative ranking of each of the social network objects stored.
Owner:GOOGLE LLC
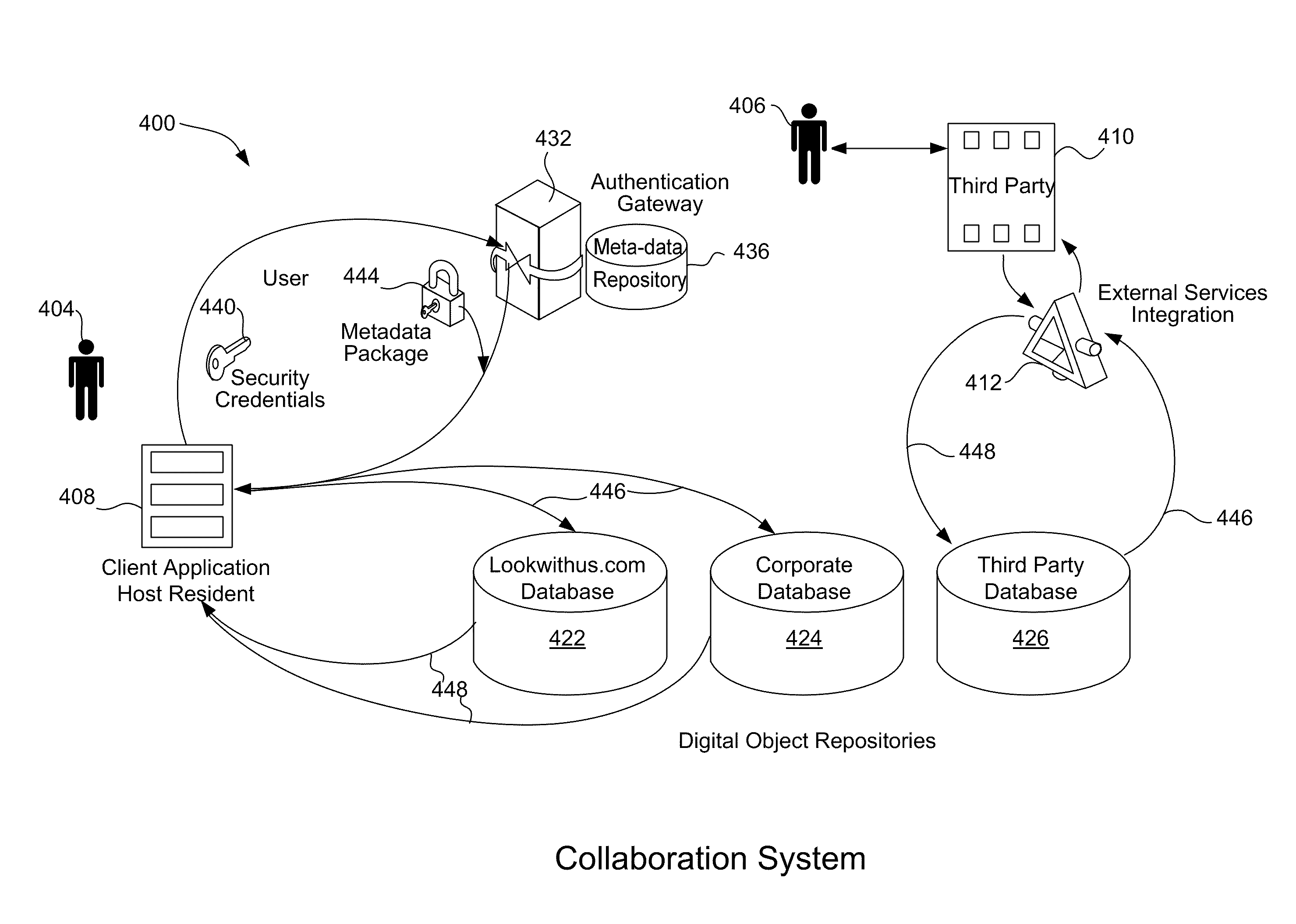
Rich media collaboration system
ActiveUS20090260060A1Unlimited scalabilityUnlimited scalable storageDigital data processing detailsComputer security arrangementsDisintermediationPaper document
A user annotates a shared document with text, sound, images, video, an e-mail message, graphics, screen snapshots, web site snapshots to share with others. The document and its annotations are stored in a digital object repository to which other users have access. Within the closed collaboration system, only users who are authenticated may upload digital objects, annotate digital objects and view objects and their annotations. The user sends a message to other users to invite them to view the object and its annotations and to add their own annotations. An annotated object generates an alert for all of the invited users. A remote authentication gateway authenticates users and has a repository for user metadata. Digital object repositories are separate from the authentication gateway, thus providing for disintermediation of the user metadata from the digital object data. The collaboration system may be hosted by a third party on a server computer available over the Internet that displays a web site. A user is not required to have collaboration system software on his or her computer and may annotate any image on the web site for later viewing by other users of the web site.
Owner:DISPLAY SOCIAL INC
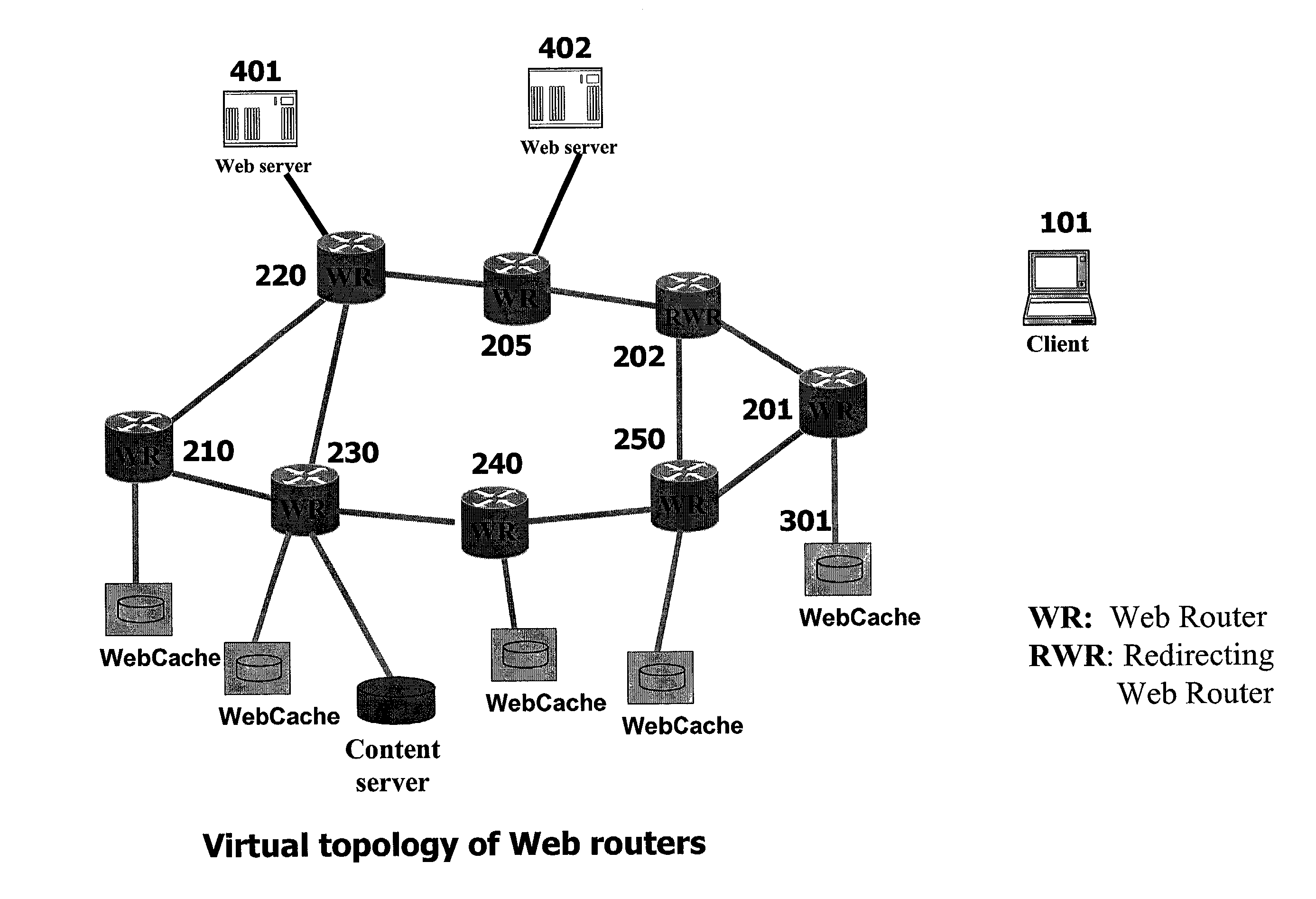
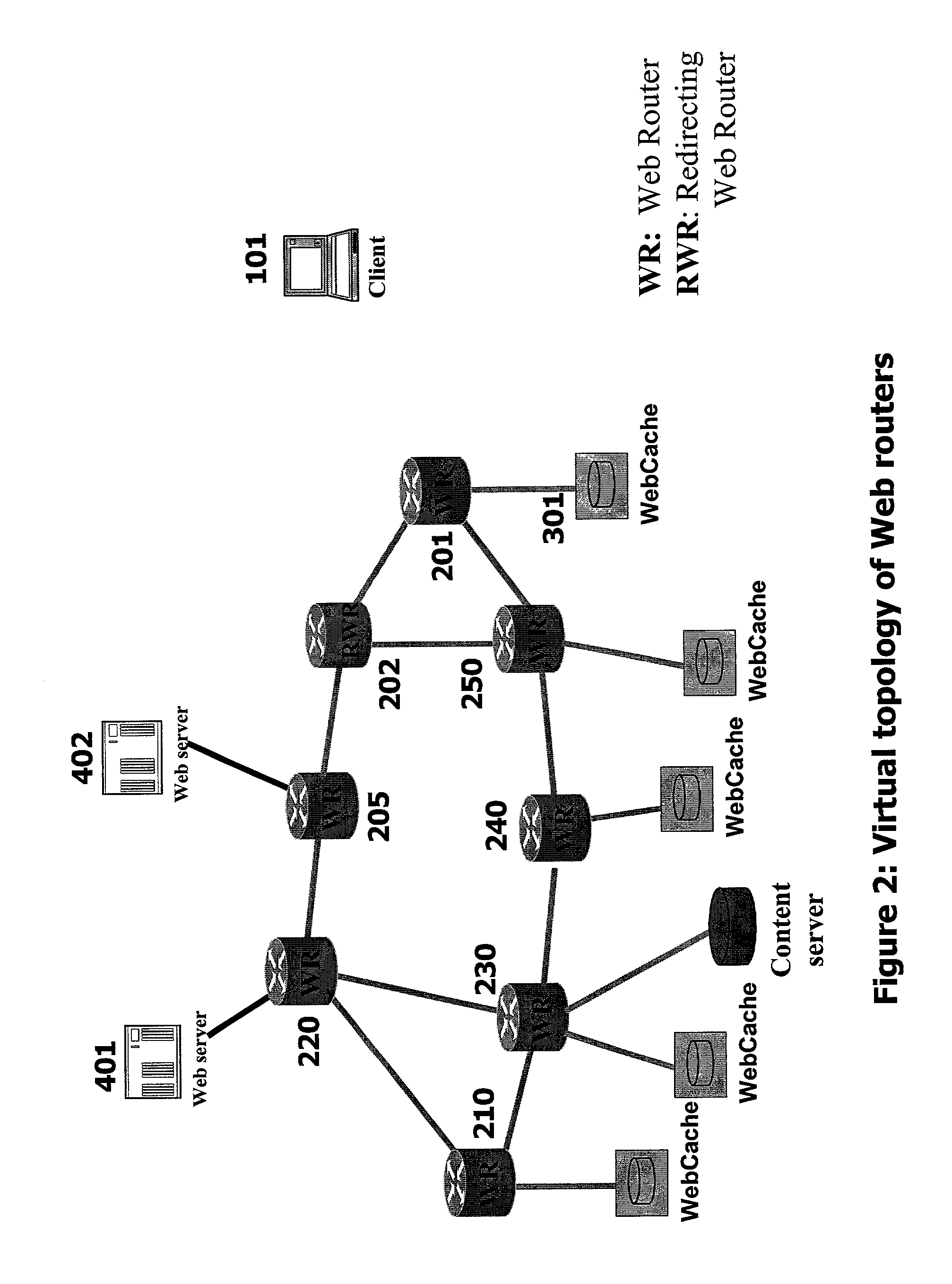
System and method for discovering information objects and information object repositories in computer networks
InactiveUS7162539B2Special service provision for substationDigital data information retrievalInformation repositoryInformation object
An address of an information object repository that should service a client request for an information object is returned in response to a request therefor. The address of the information object repository which is returned is selected according to specified performance metrics regardless of whether or not the information object repository maintains a local copy of the information object that is the client request. In some cases, the address of the information object repository is further selected according to an address of a client making the client request. Further, the address of the information object repository is selected from a number of addresses of information object repositories. The specified performance metrics may include one or more of an average delay from the information object repository to the client, average processing delays at the information object repository, reliability of a path from the information object repository to the client, available bandwidth in said path, and loads on the information object repository. In some cases, the information object repository may be instructed to obtain a copy of the information object after the address of the information object repository is returned in response to the request therefore.
Owner:ADARA NETWORKS
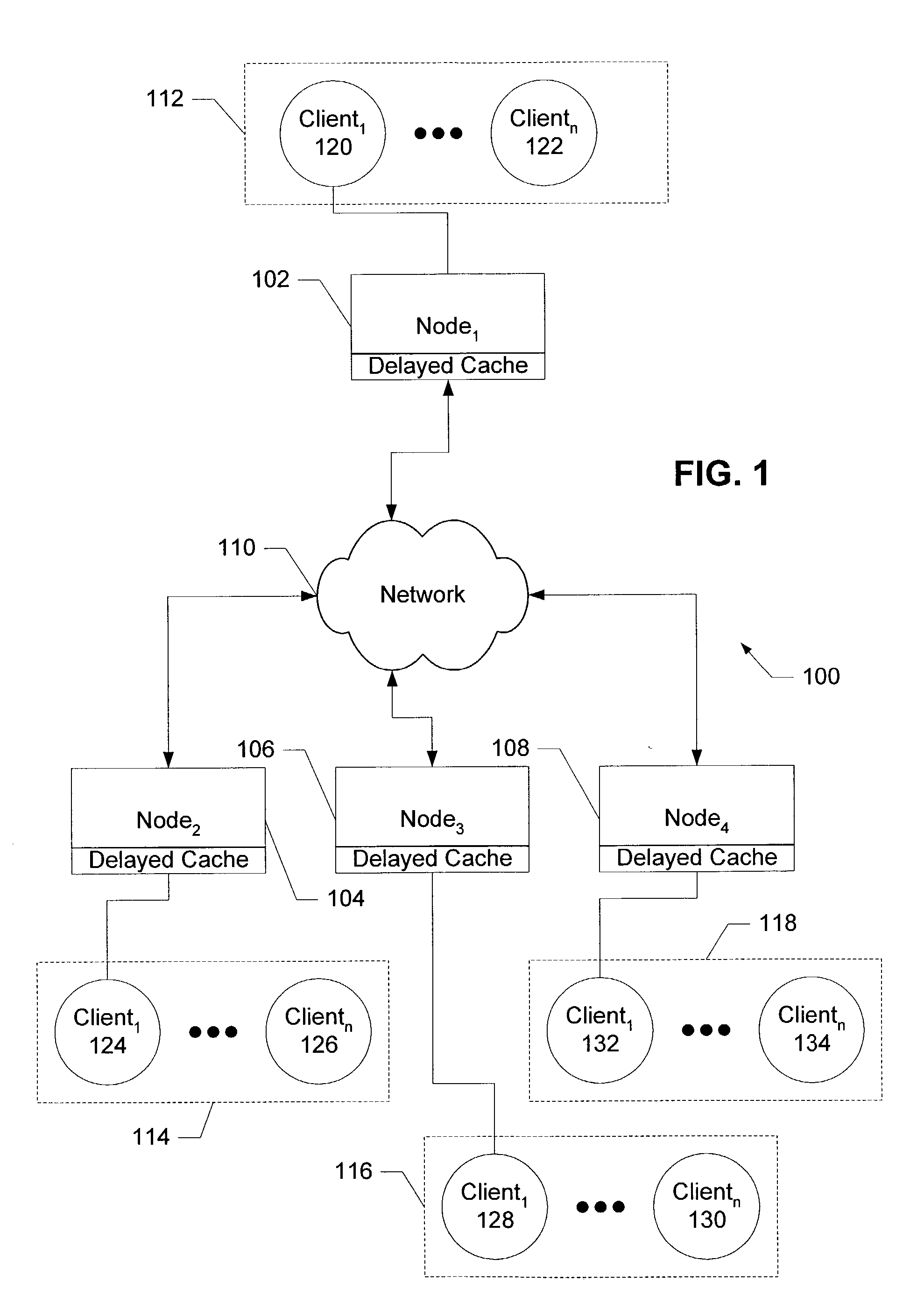
Delay cache method and apparatus
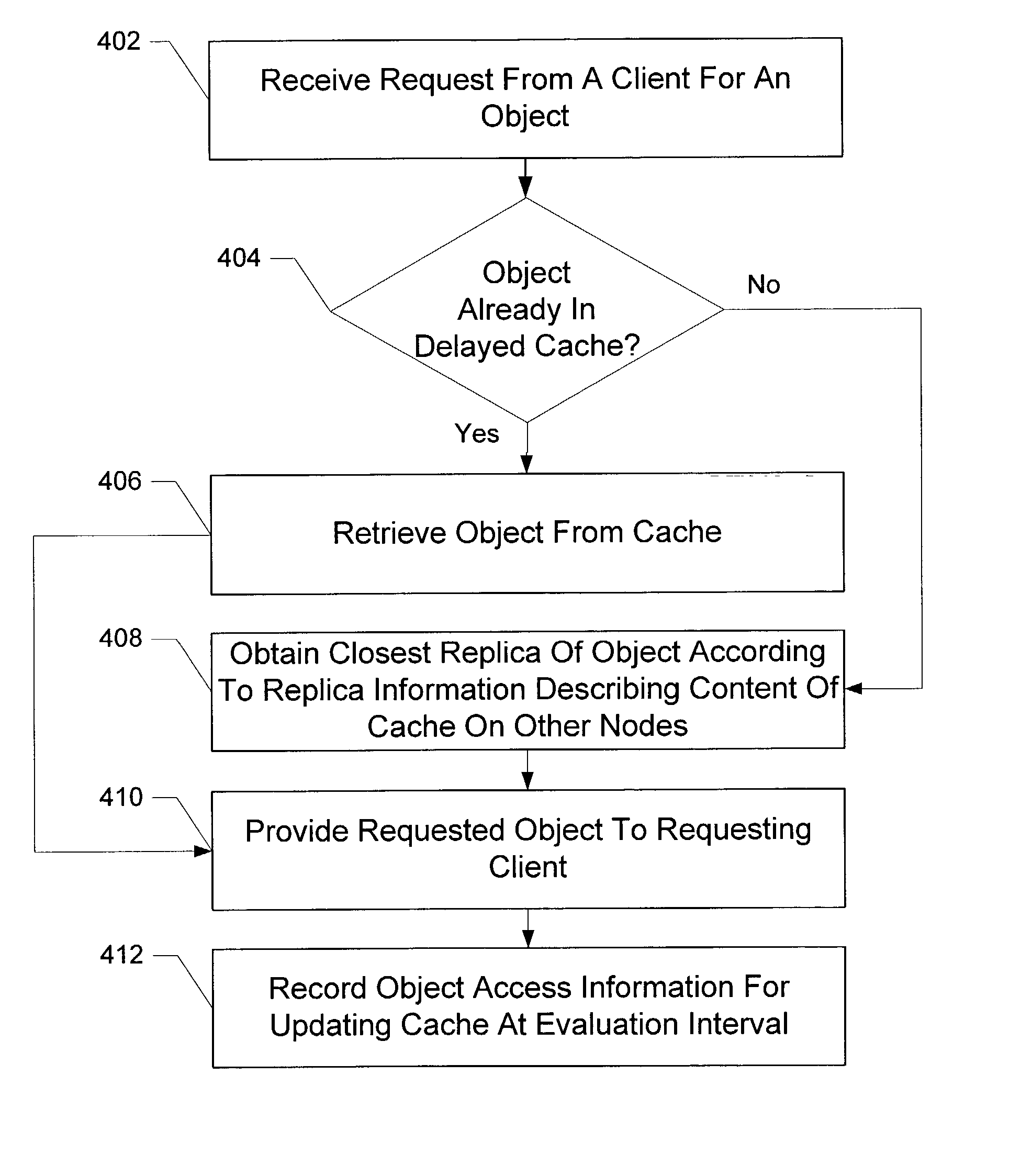
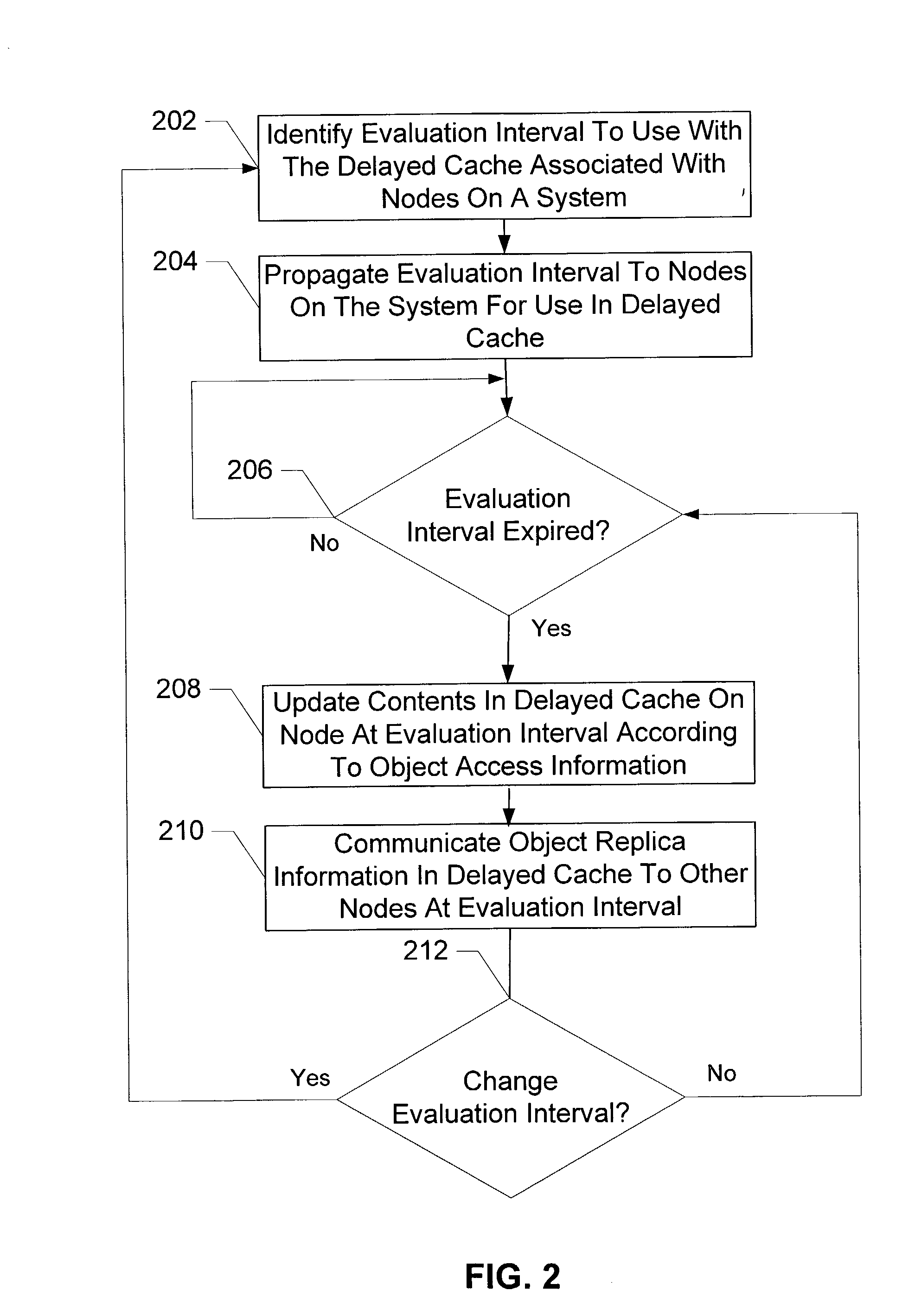
InactiveUS20040034744A1Promote disseminationReduce the amount of processingDigital data information retrievalMemory adressing/allocation/relocationEvaluation IntervalTime segment
Delayed caching receives an evaluation interval to delay updating the objects stored in a delayed cache, delays a time period corresponding to the evaluation interval, and updates the objects stored in the contents of the delayed cache when the time period delay has completed. The configuration operation for the delayed cache selects a time interval to sample a trace having object access frequencies for objects stored in a cache, creates a first working set of objects accessed during the time interval and a second working set of objects accessed during a subsequent time interval based on the historical trace, determines that the difference between the objects contained in the first and second working sets does not exceed a maximum threshold with the selected time interval, and sets a evaluation interval for evaluating the contents of the cache to the selected time interval.
Owner:HEWLETT PACKARD DEV CO LP
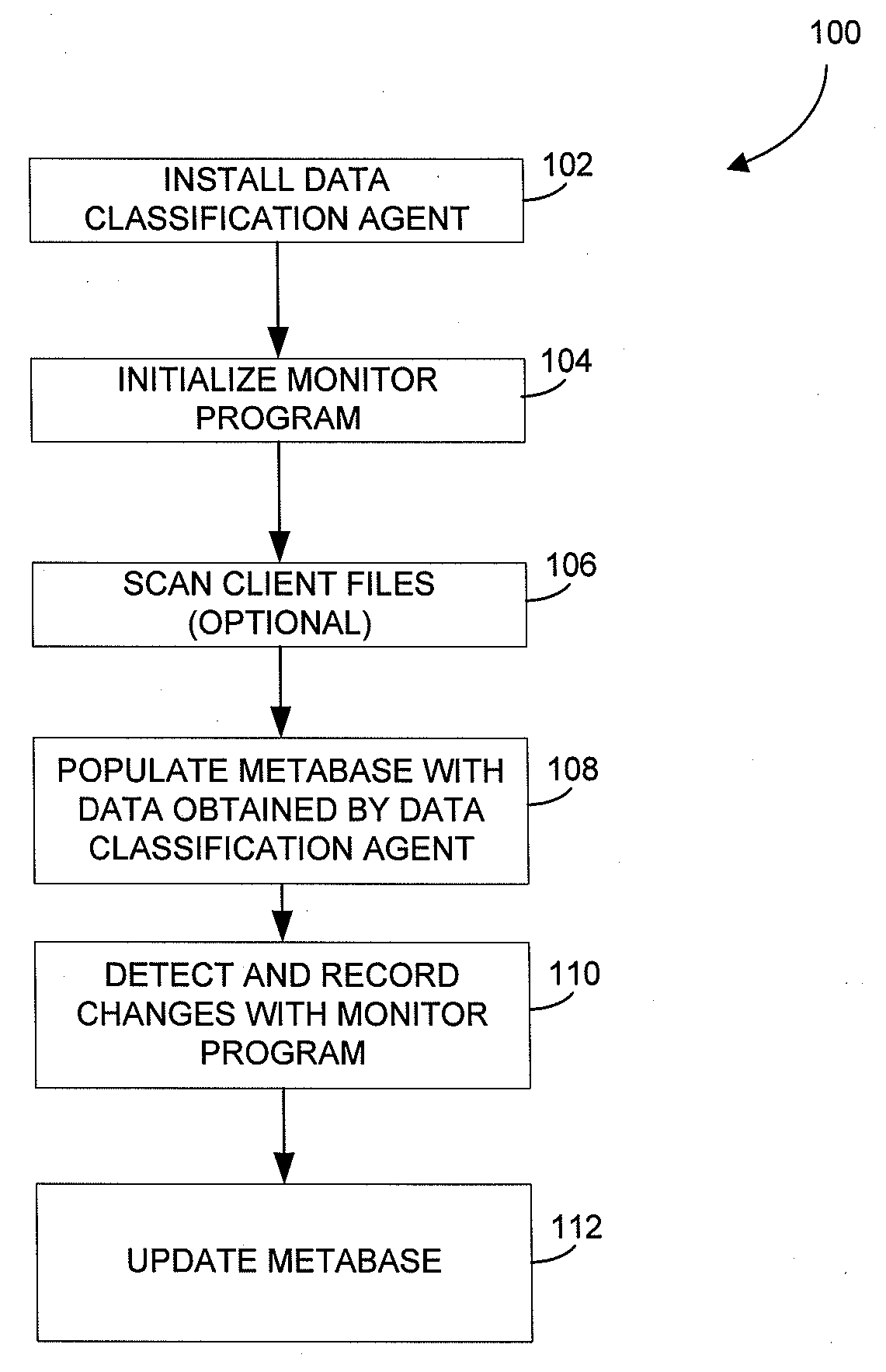
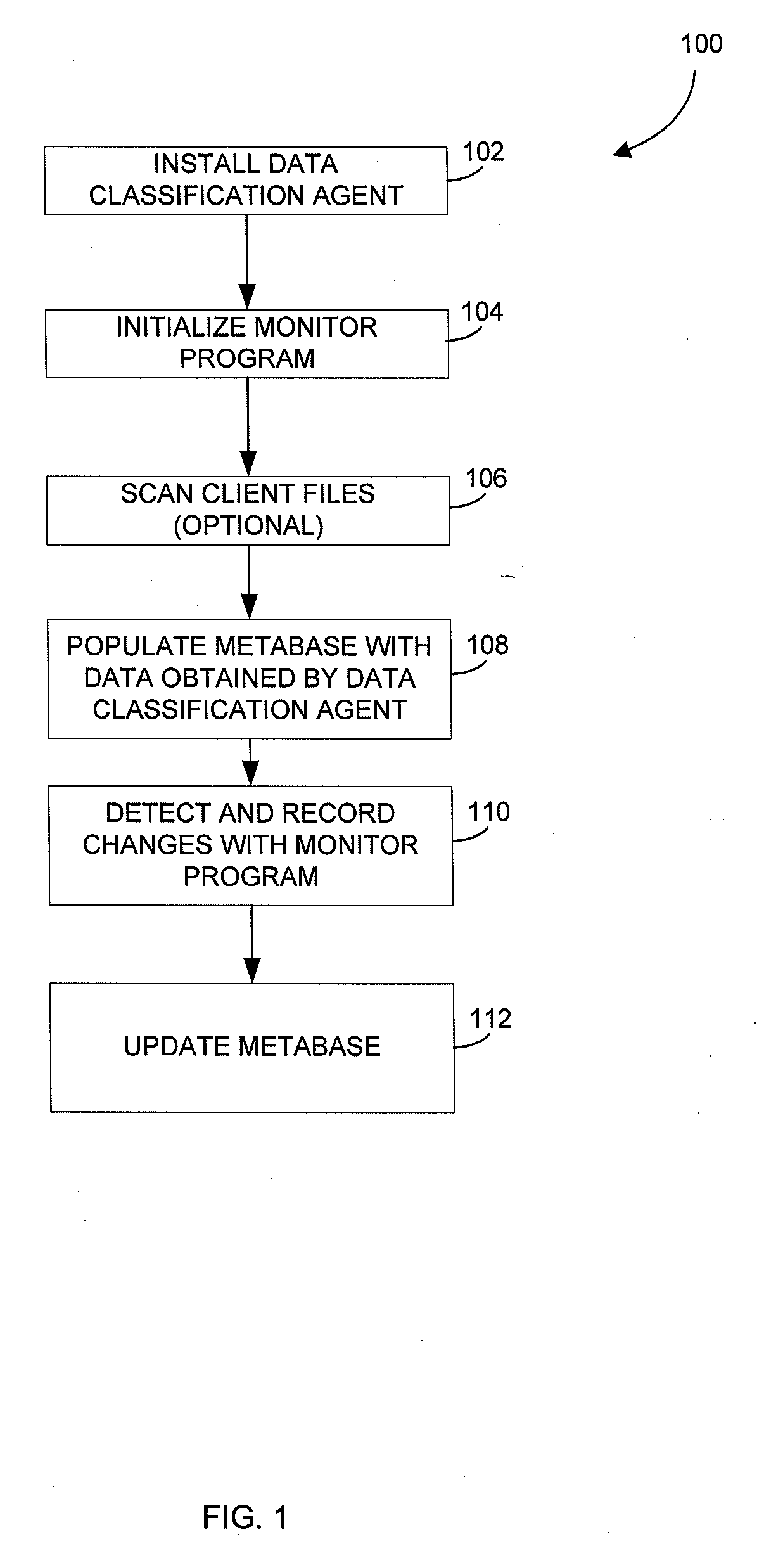
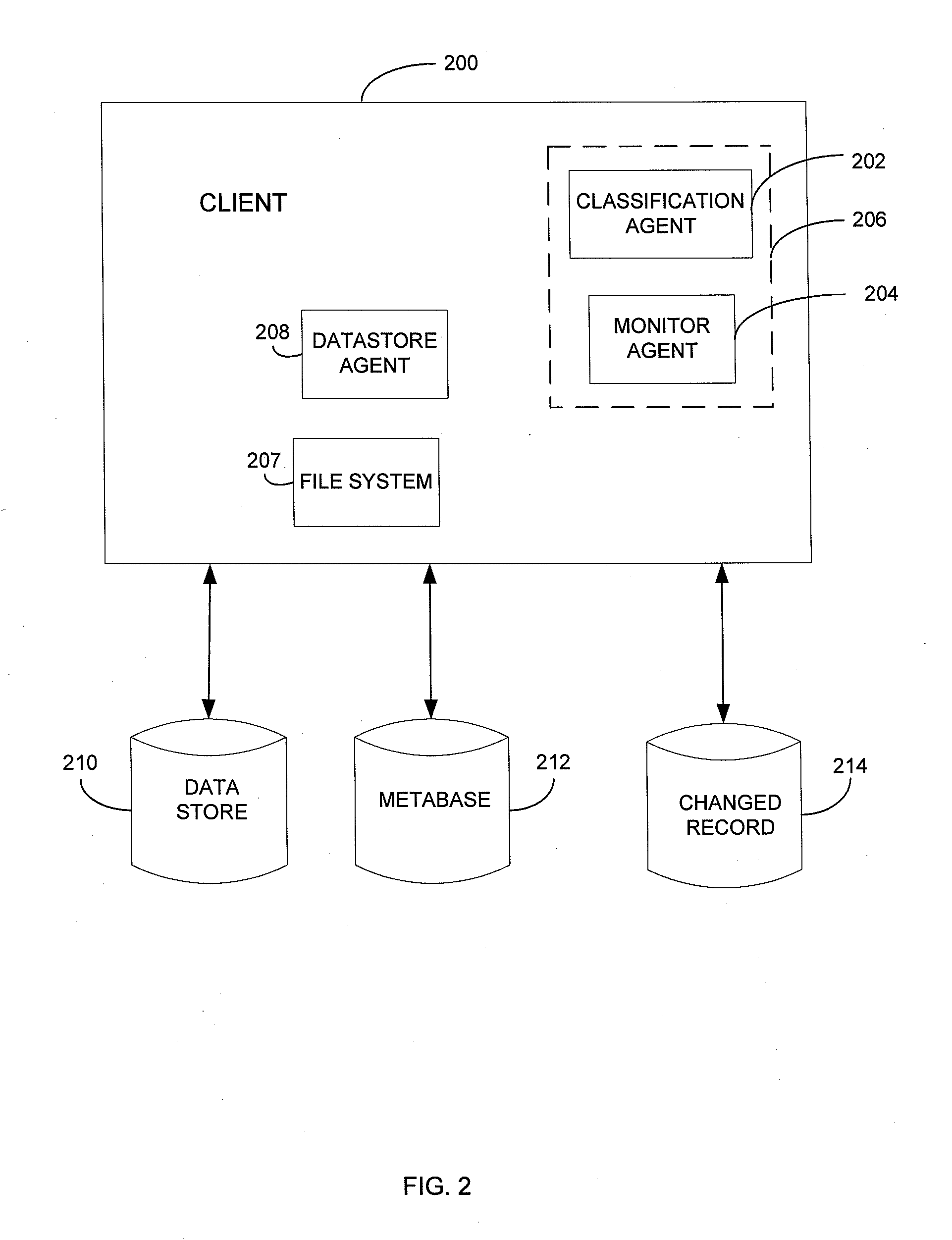
Metabase for facilitating data classification
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
Recovering a file system to any point-in-time in the past with guaranteed structure, content consistency and integrity
InactiveUS20080256138A1Improve integrityDigital data information retrievalDigital data processing detailsFile systemData management
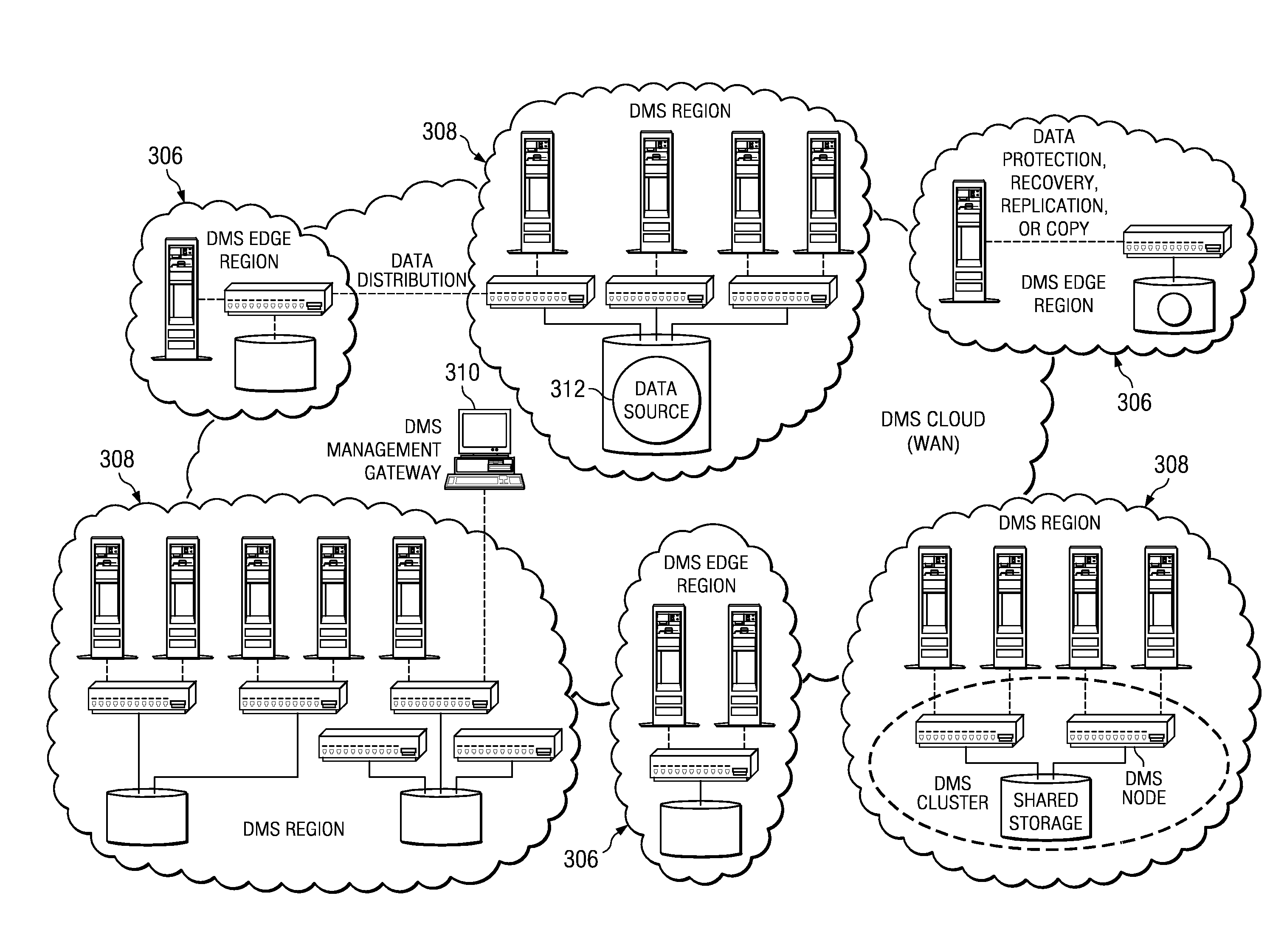
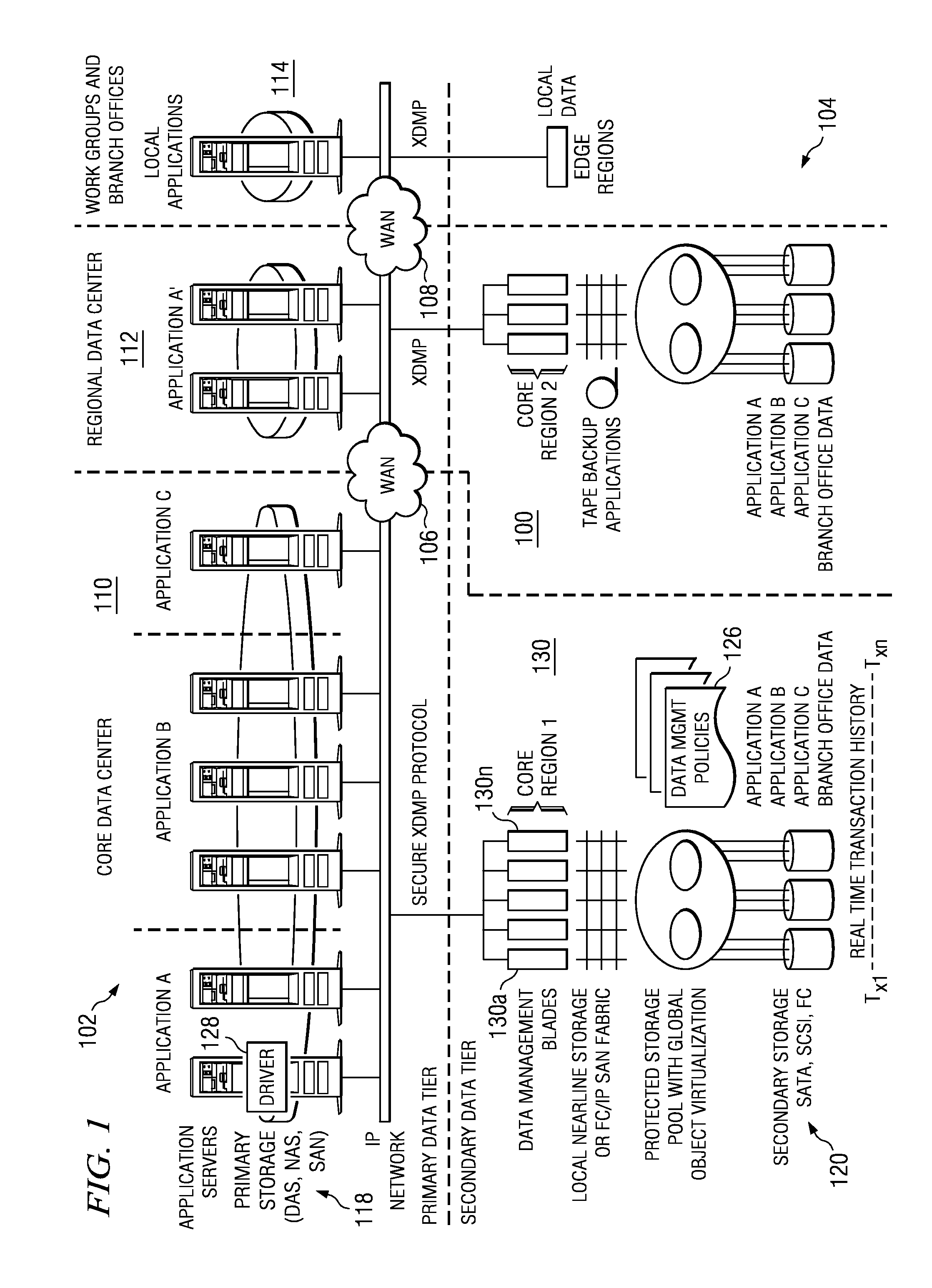
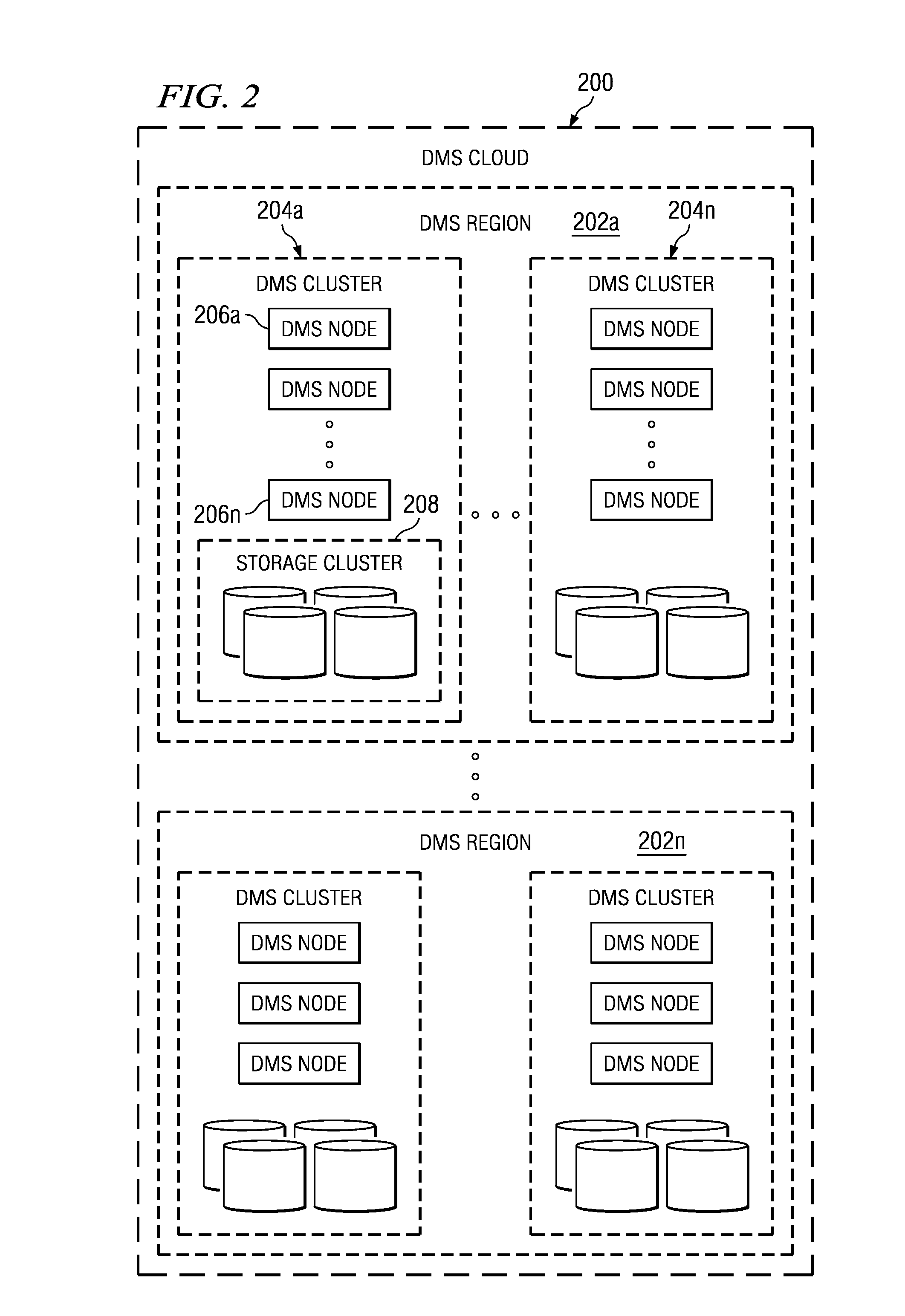
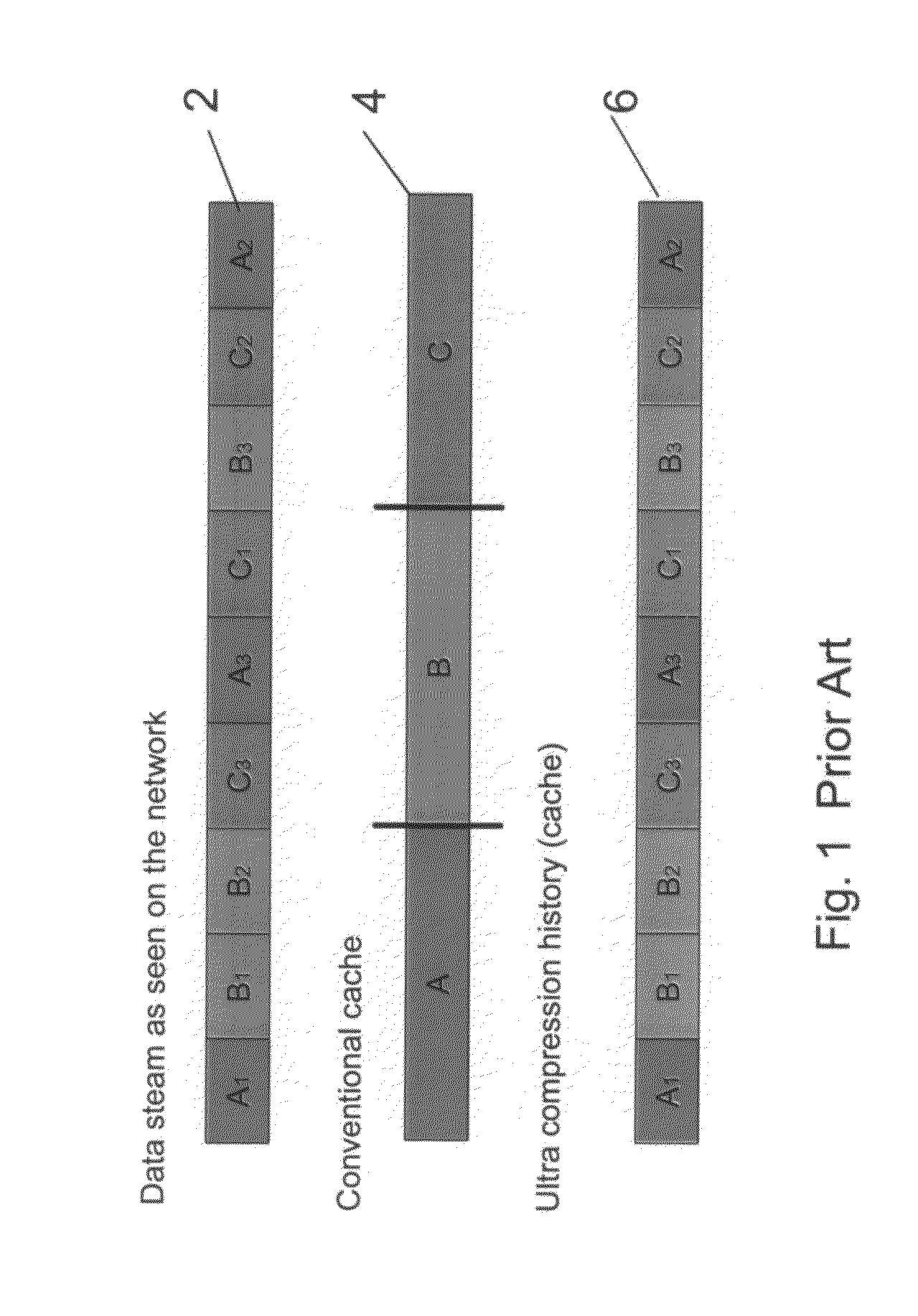
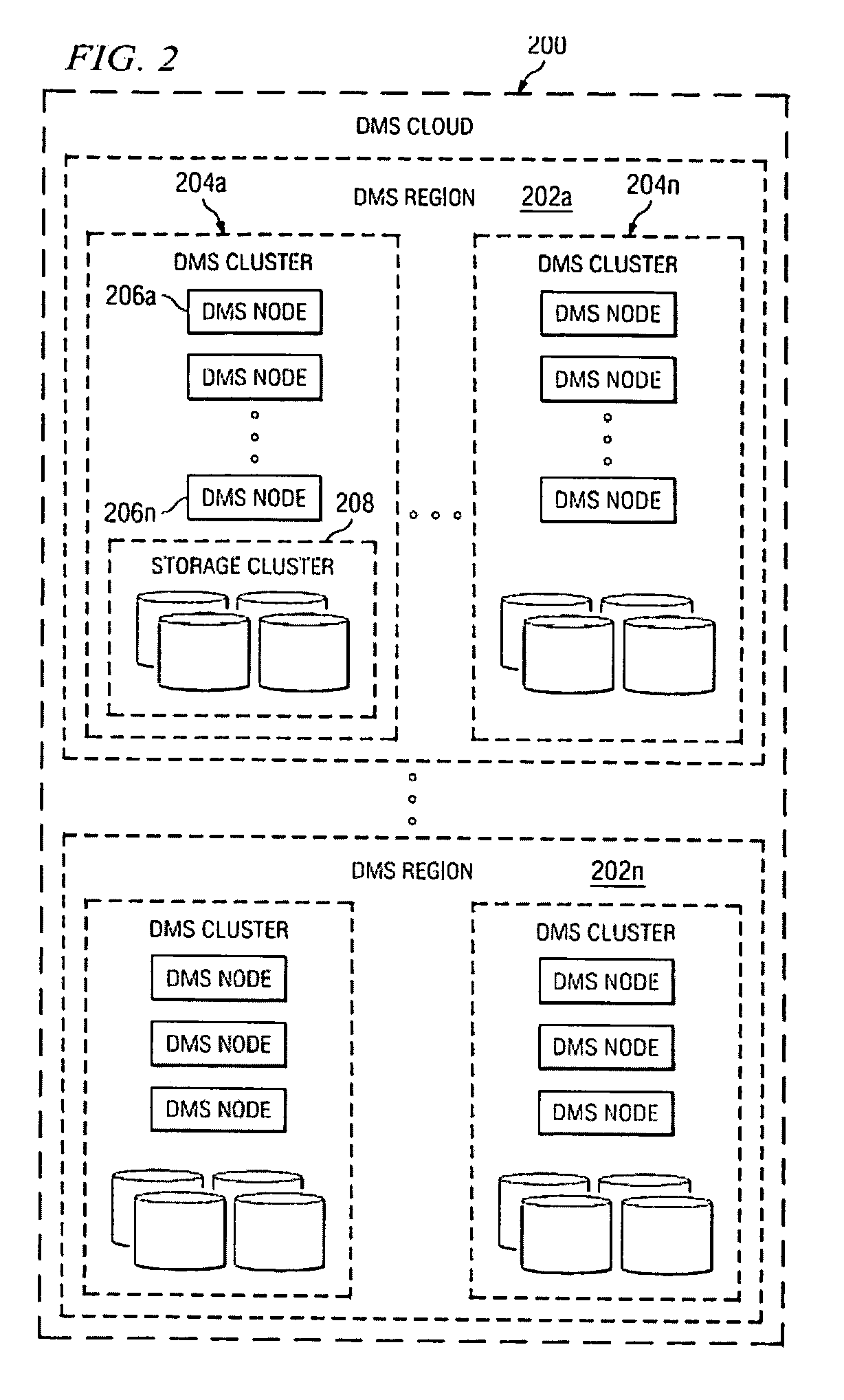
A data management system (DMS) includes a continuous real-time object store that captures all real-time activities, with associated object metadata information. The DMS is capable of reintroducing any point-in-time view of data ranging from a granular object to an entire file system. A set of algorithms (for creation of a file or directory, modification of a file or directory, deletion of a file or directory, and relocation / renaming of a file or directory) are used to generate and maintain a file system history in the DMS and to ensure that a latest version of a directory always refers to a latest version of its children until the directory changed. Any point-in-time recovery is implemented using the file system history in one of various ways to provide strong individual file integrity, exact point-in-time crash consistency, and / or recovery of last version of all files in the file system.
Owner:QUEST SOFTWARE INC
Enhanced method and system for assuring integrity of deduplicated data
ActiveUS20090271454A1Access latencyDigital data information retrievalDigital data processing detailsHash functionDigital signature
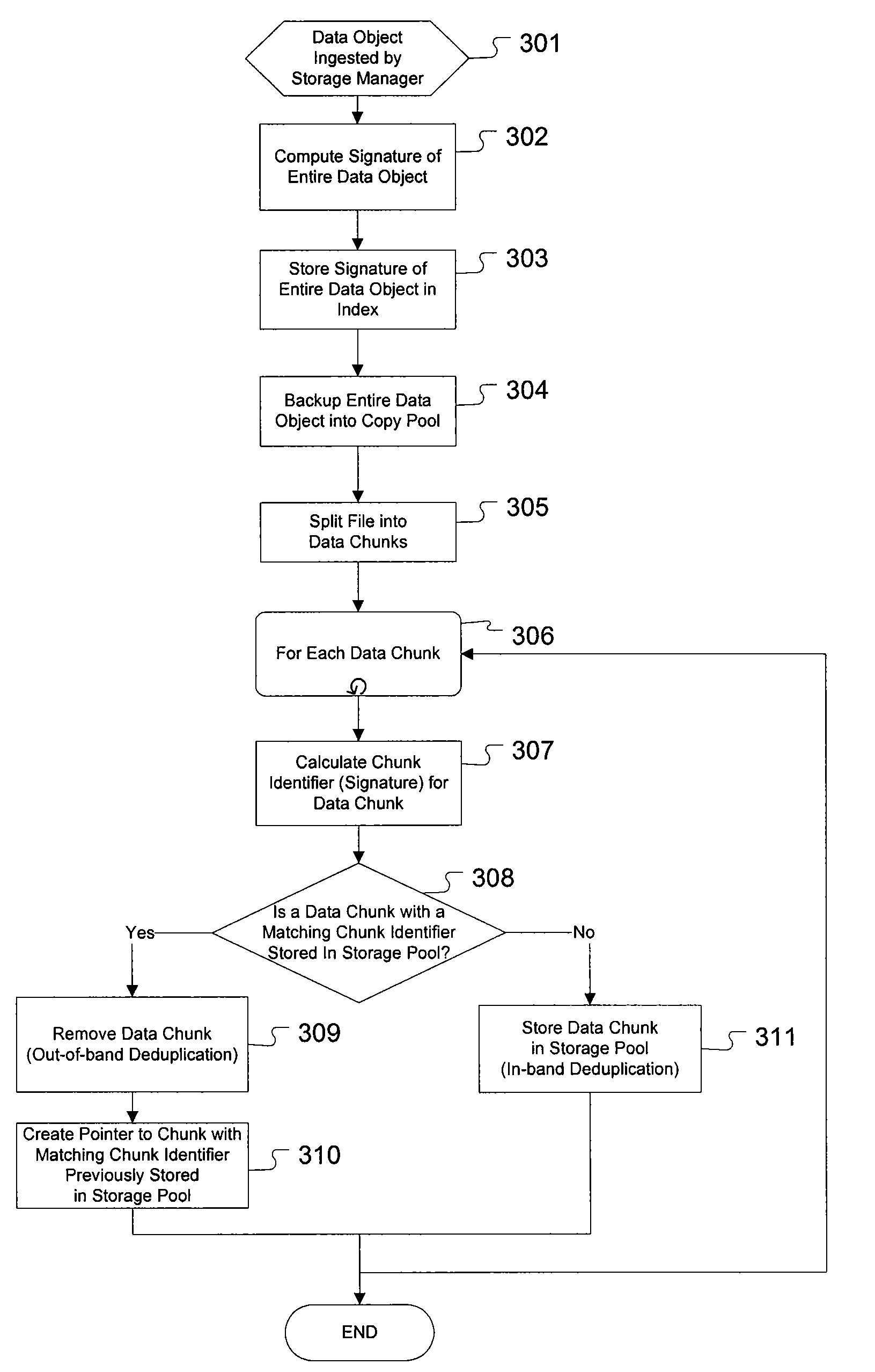
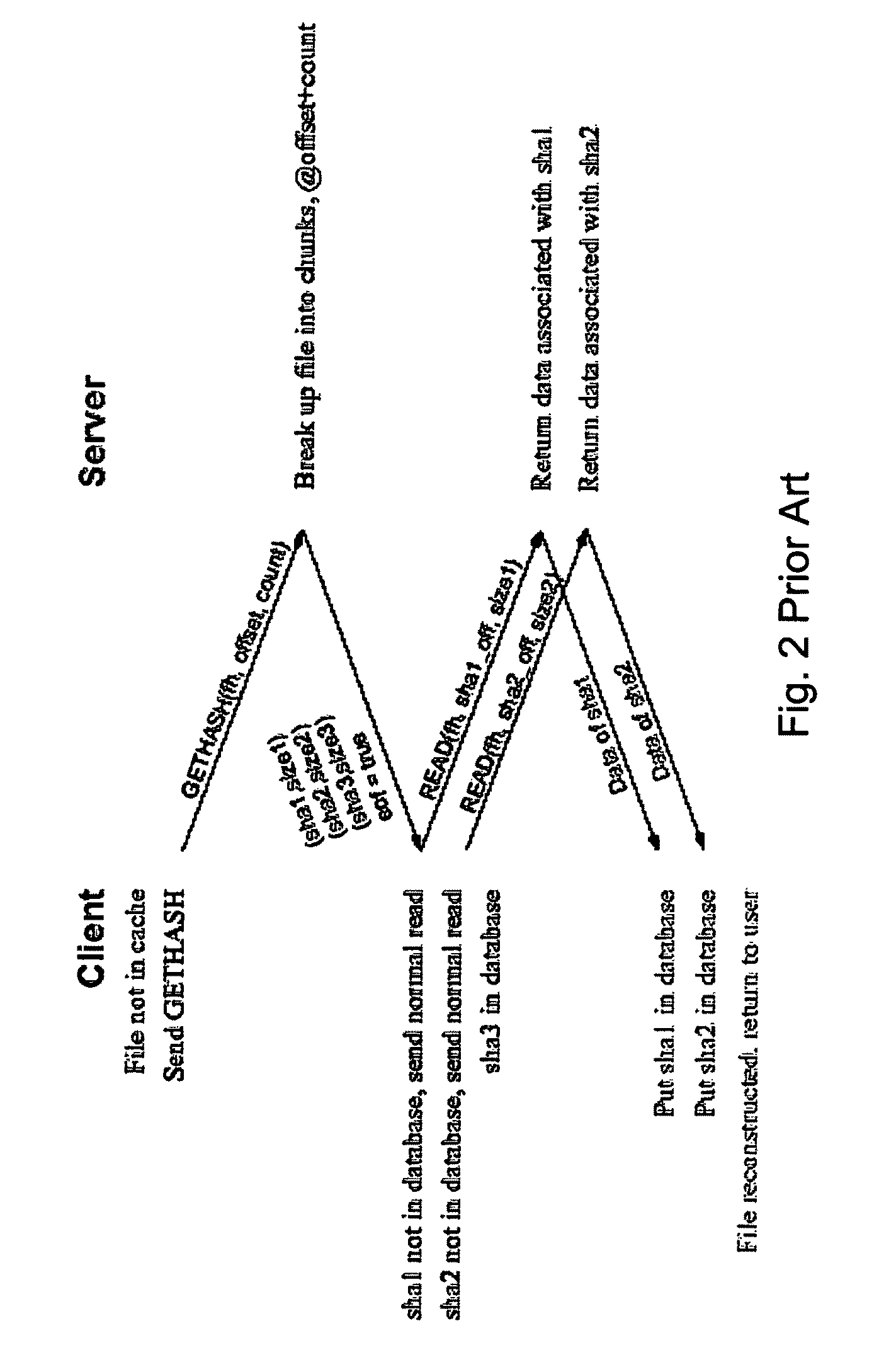
The present invention provides for an enhanced method and system for assuring integrity of deduplicated data objects stored within a storage system. A digital signature of the data object is generated to determine if the data object reassembled from a deduplicated state is identical to its pre-deduplication state. In one embodiment, generating the object signature of a data object before deduplication comprises generating an object signature from intermediate hash values computed from a hash function operating on each data chunk within the data object, the hash function also used to determine duplicate data chunks. In an alternative embodiment, generating the object signature of a data object before deduplication comprises generating an object signature on a portion of each data chunk of the data object.
Owner:DROPBOX
Elimination of duplicate objects in storage clusters
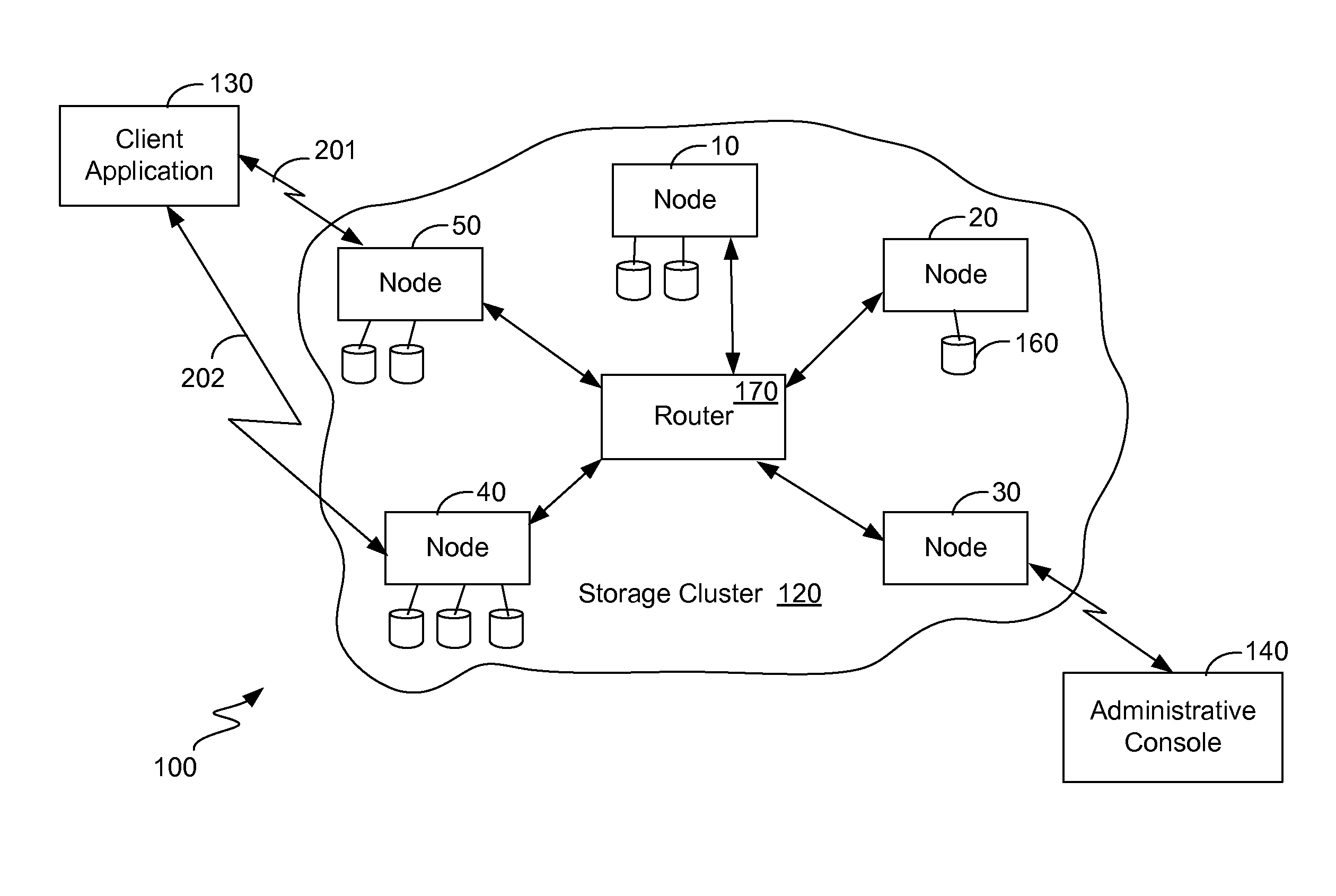
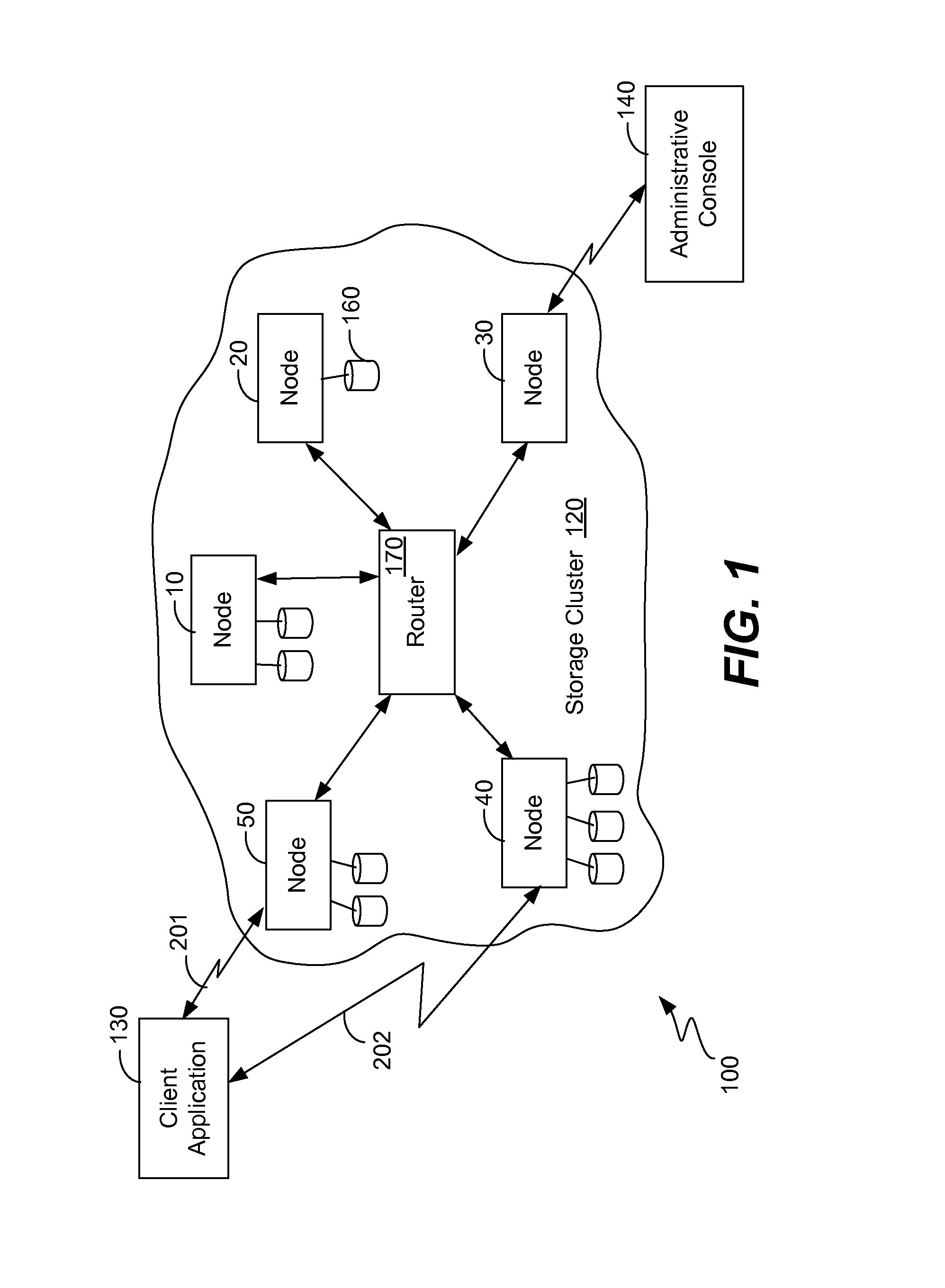
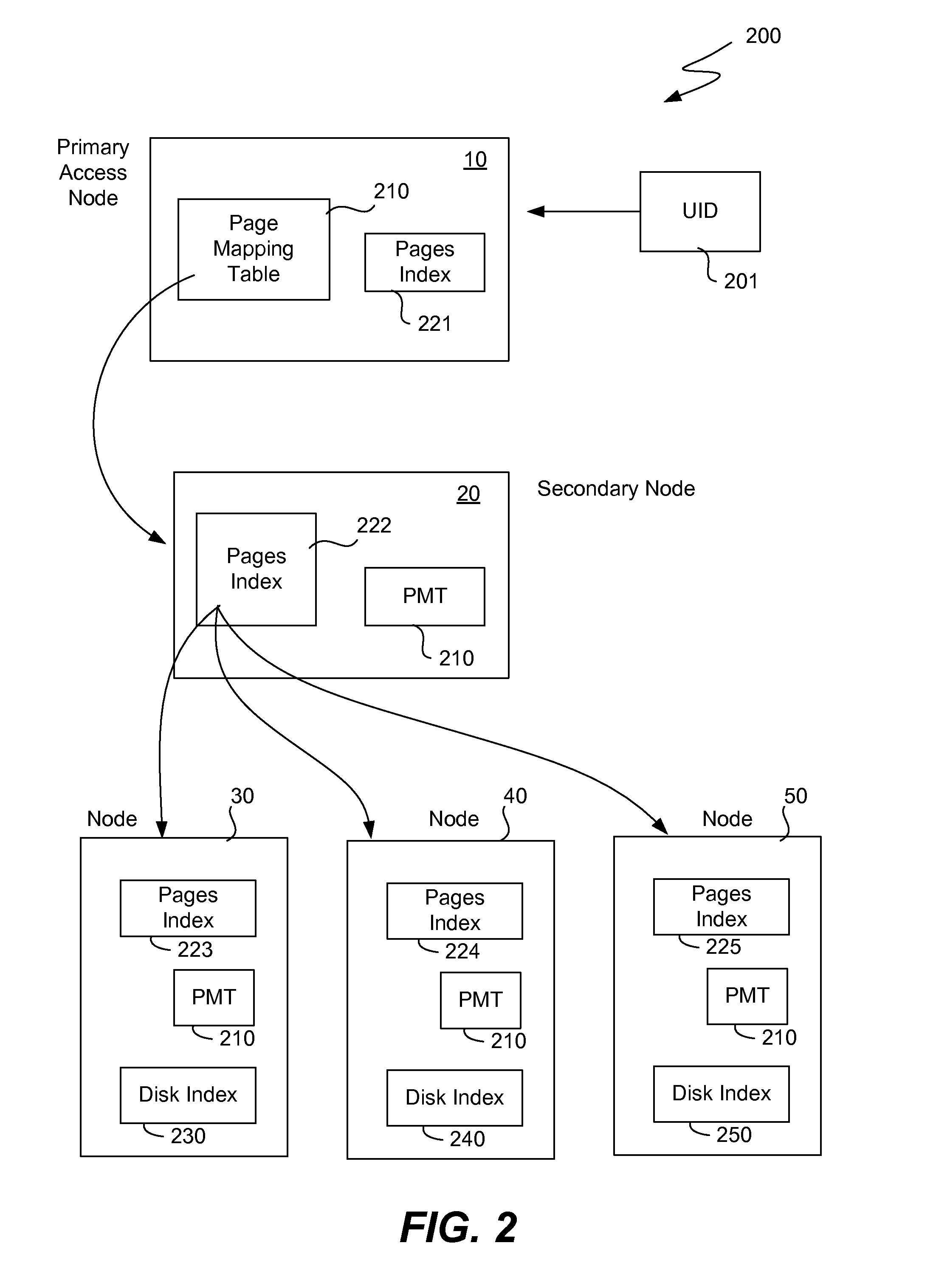
ActiveUS20130339314A1Digital data processing detailsSpecial data processing applicationsUnique identifierObject store
Digital objects within a fixed-content storage cluster use a page mapping table and a hash-to-UID table to store a representation of each object. For each object stored within the cluster, a record in the hash-to-UID table stores the object's hash value and its unique identifier (or portions thereof). To detect a duplicate of an object, a portion of its hash value is used as a key into the page mapping table. The page mapping table indicates a node holding a hash-to-UID table indicating currently stored objects in a particular page range. Finding the same hash value but with a different unique identifier in the table indicates that a duplicate of an object exists. Portions of the hash value and unique identifier may be used in the hash-to-UID table. Unneeded duplicate objects are deleted by copying their metadata to a manifest and then redirecting their unique identifiers to point at the manifest.
Owner:DATACORE SOFTWARE
System and method for performing granular invalidation of cached dynamically generated objects in a data communication network
ActiveUS20070156966A1Great time intervalMemory architecture accessing/allocationMemory systemsExpiration TimeGranularity
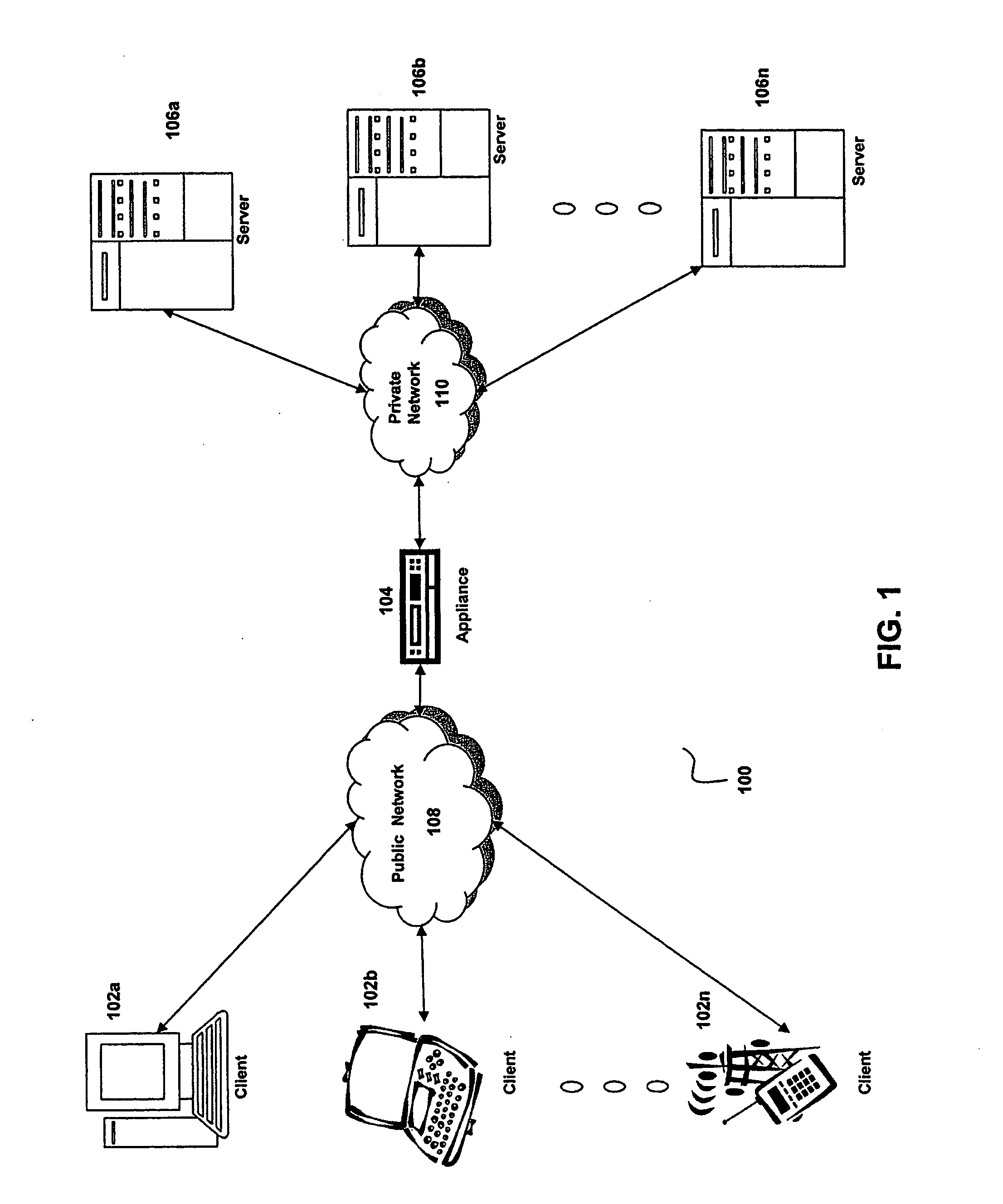
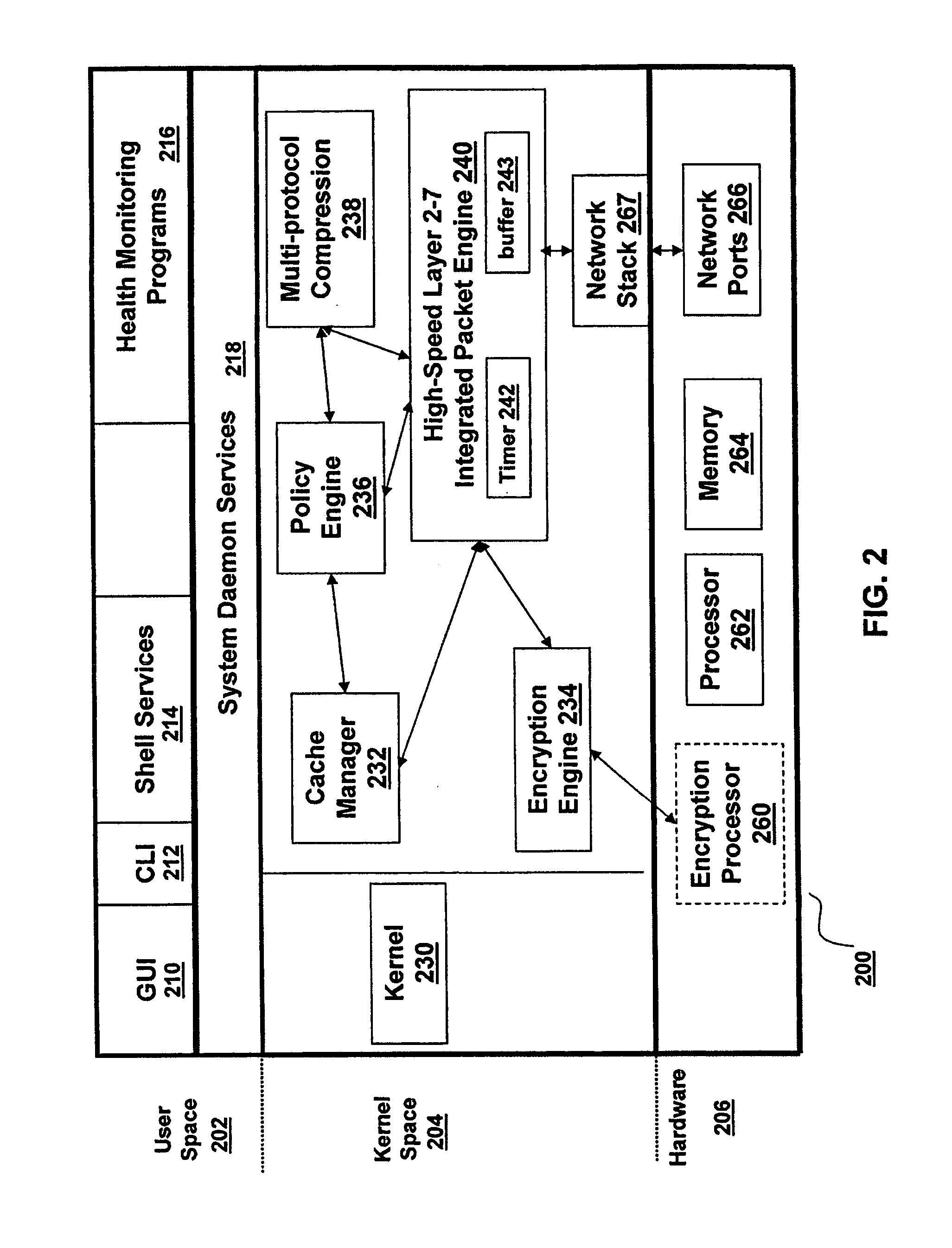
The present invention is directed towards a method and system for providing granular timed invalidation of dynamically generated objects stored in a cache. The techniques of the present invention incorporates the ability to configure the expiration time of objects stored by the cache to fine granular time intervals, such as the granularity of time intervals provided by a packet processing timer of a packet processing engine. As such, the present invention can cache objects with expiry times down to very small intervals of time. This characteristic is referred to as “invalidation granularity.” By providing this fine granularity in expiry time, the cache of the present invention can cache and serve objects that frequently change, sometimes even many times within a second. One technique is to leverage the packet processing timers used by the device of the present invention that are able operate at time increments on the order of milliseconds to permit invalidation or expiry granularity down to 10 ms or less.
Owner:CITRIX SYST INC
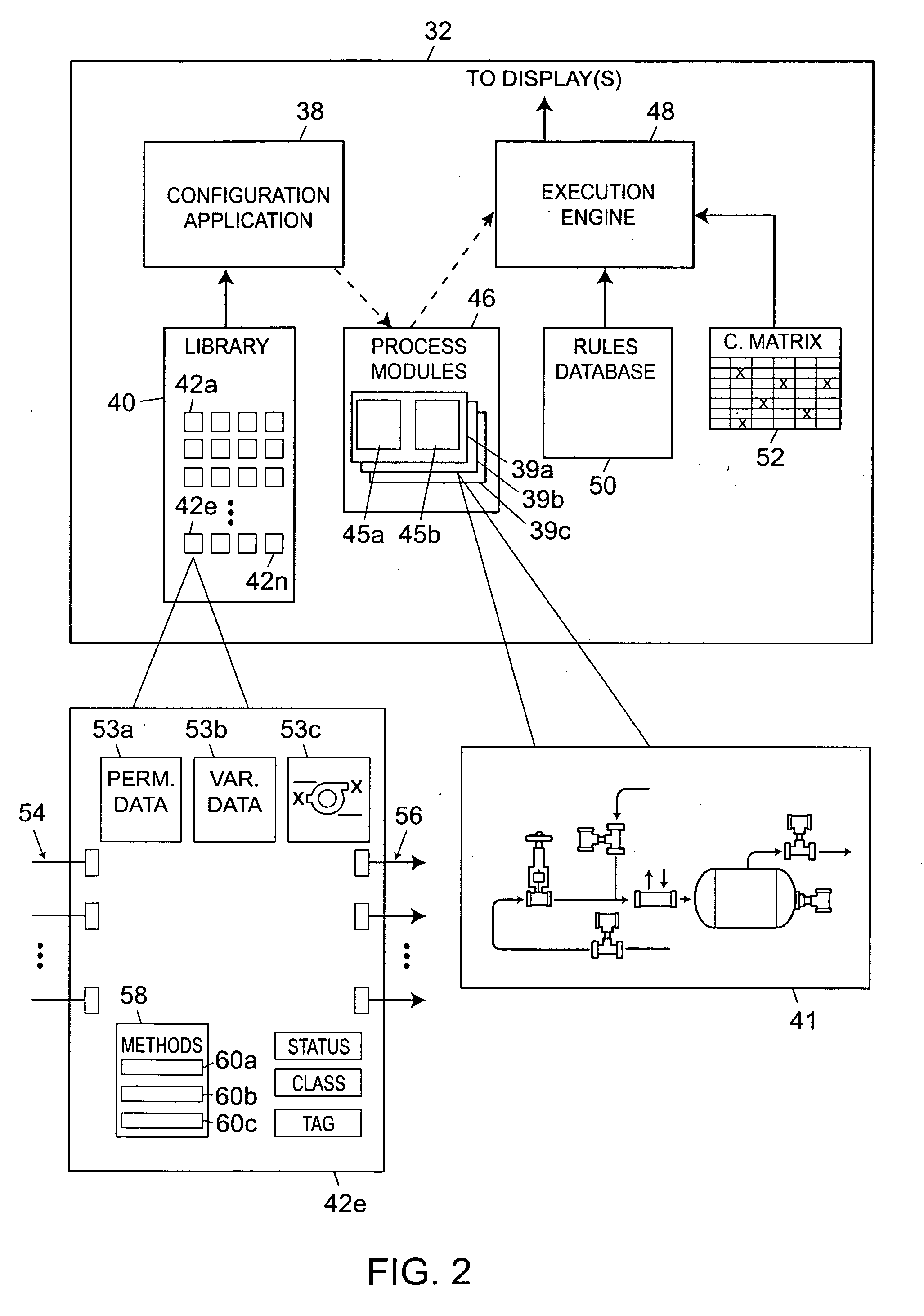
Integrated configuration system for use in a process plant
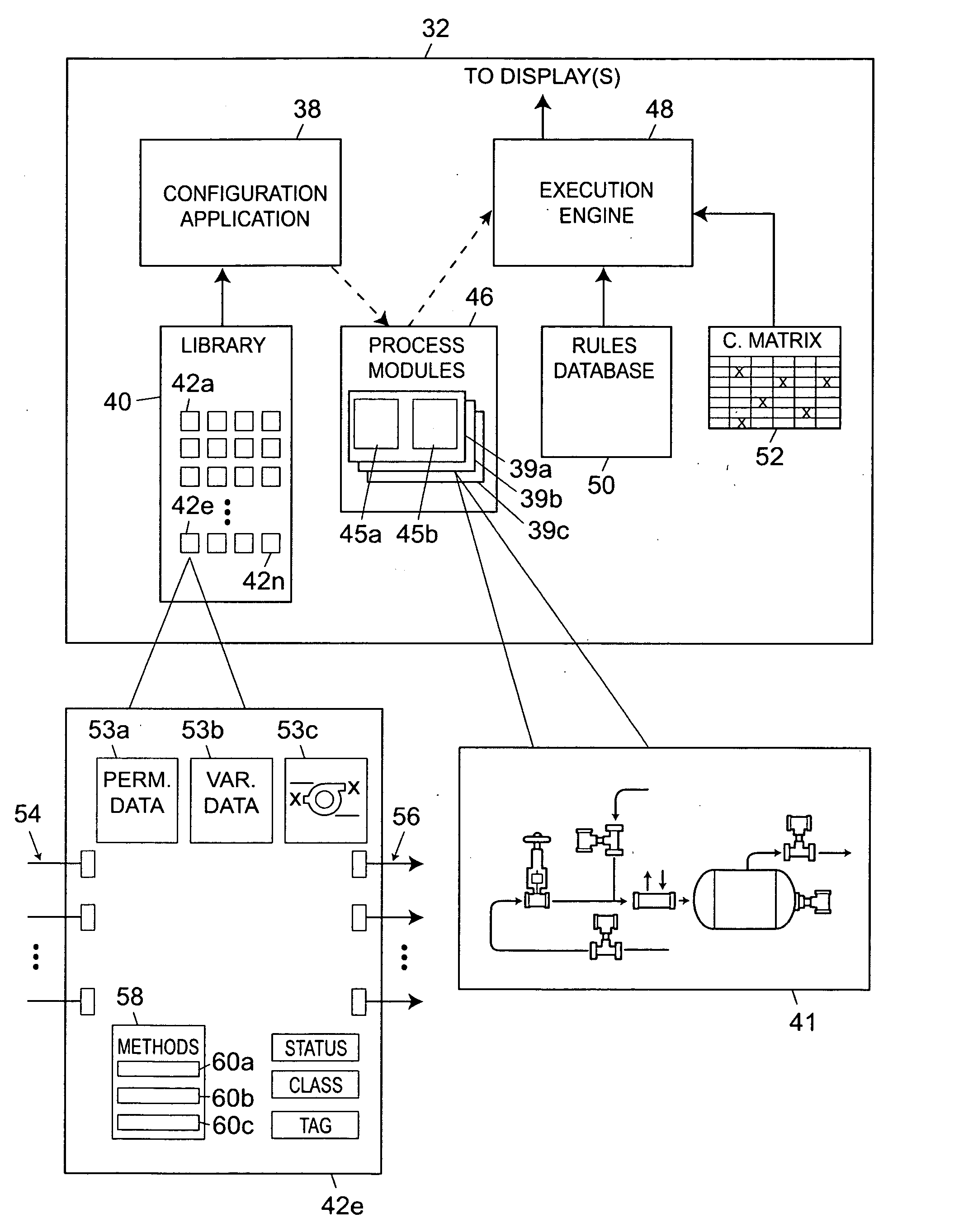
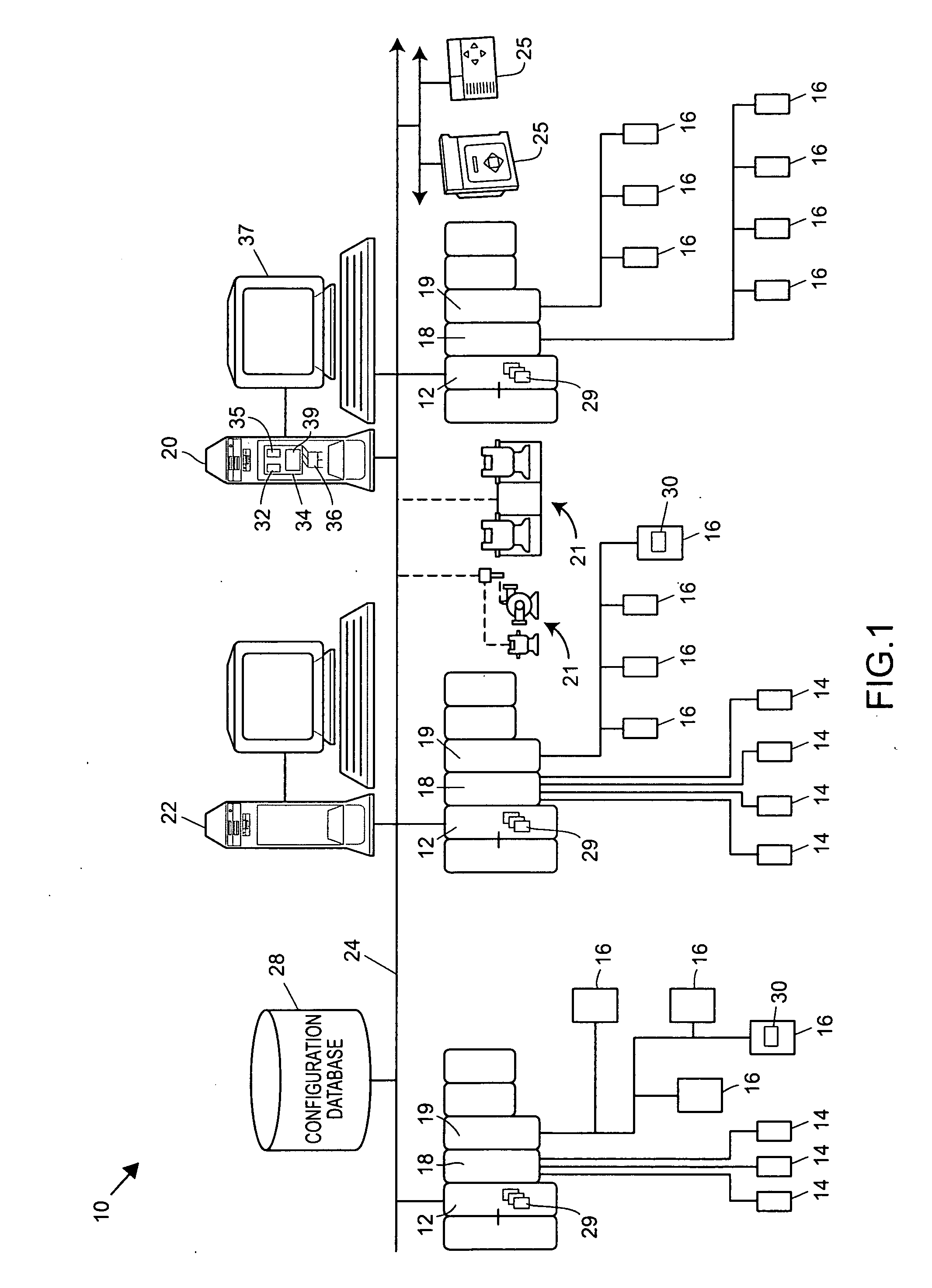
An integrated configuration viewing system for use in a process plant includes a computer readable memory and a plurality of template configuration objects stored on the computer readable memory. Each of the plurality of template configuration objects includes a graphical representation of a physical entity within the process plant, a parameter storage adapted to communicate with the process plant to obtain and store device parameter information associated with the physical entity within the process plant, and a configuration storage adapted to store configuration parameters associated with the physical entity within the process plant. A first routine is stored on the computer readable memory and adapted to be executed on the processor to present a library section on a user interface. The library section is adapted to present depictions of the plurality of template configuration objects to a user via the user interface. A second routine is stored on the computer readable memory and adapted to be executed on the processor to present a configuration area on the user interface. And a third routine is stored on the computer readable memory and adapted to be executed on the processor to enable a user to select one of the plurality of template configuration objects from the library section and to place the selected template configuration object within the configuration area to create a process configuration module within the configuration area.
Owner:FISHER-ROSEMOUNT SYST INC
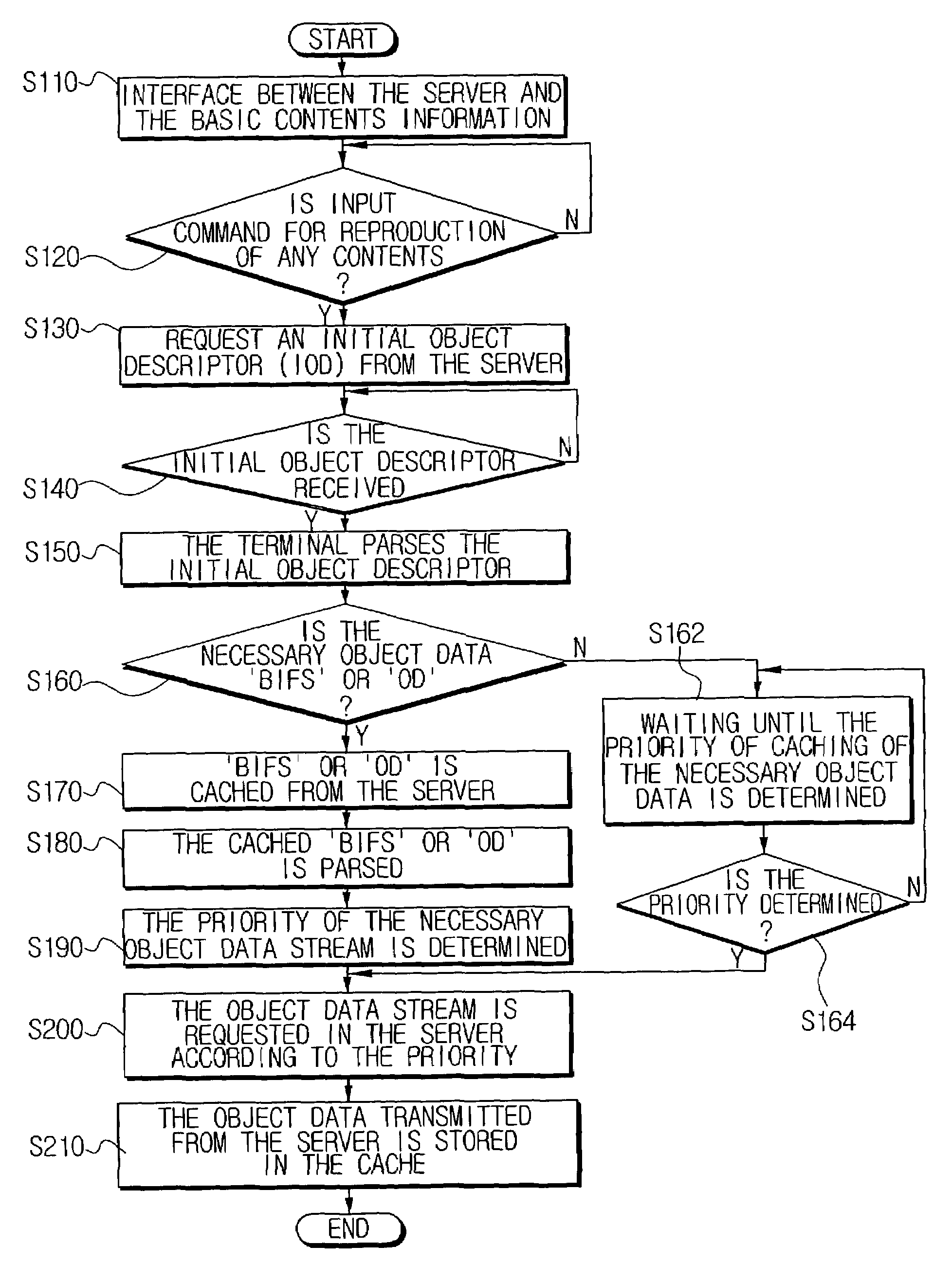
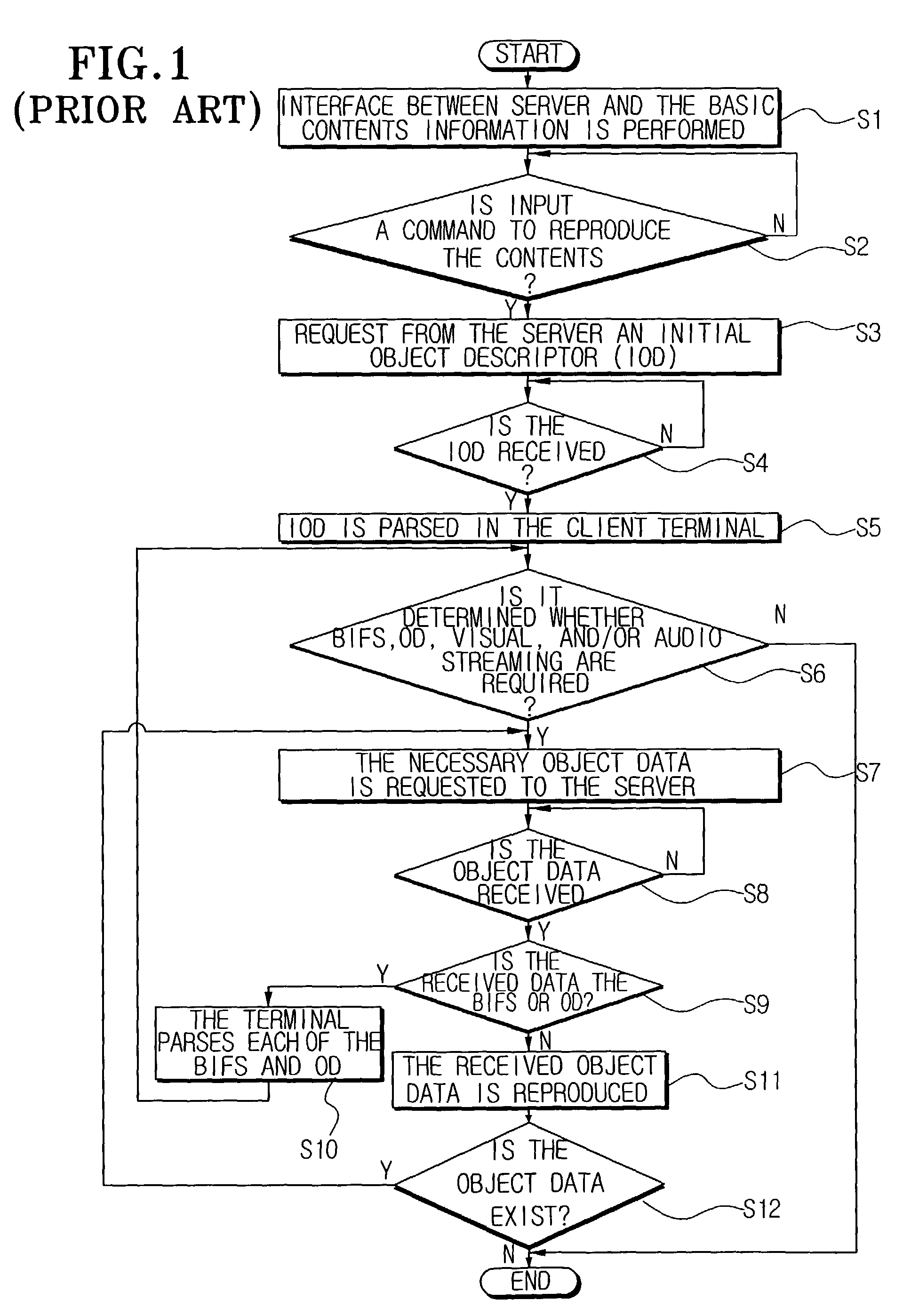
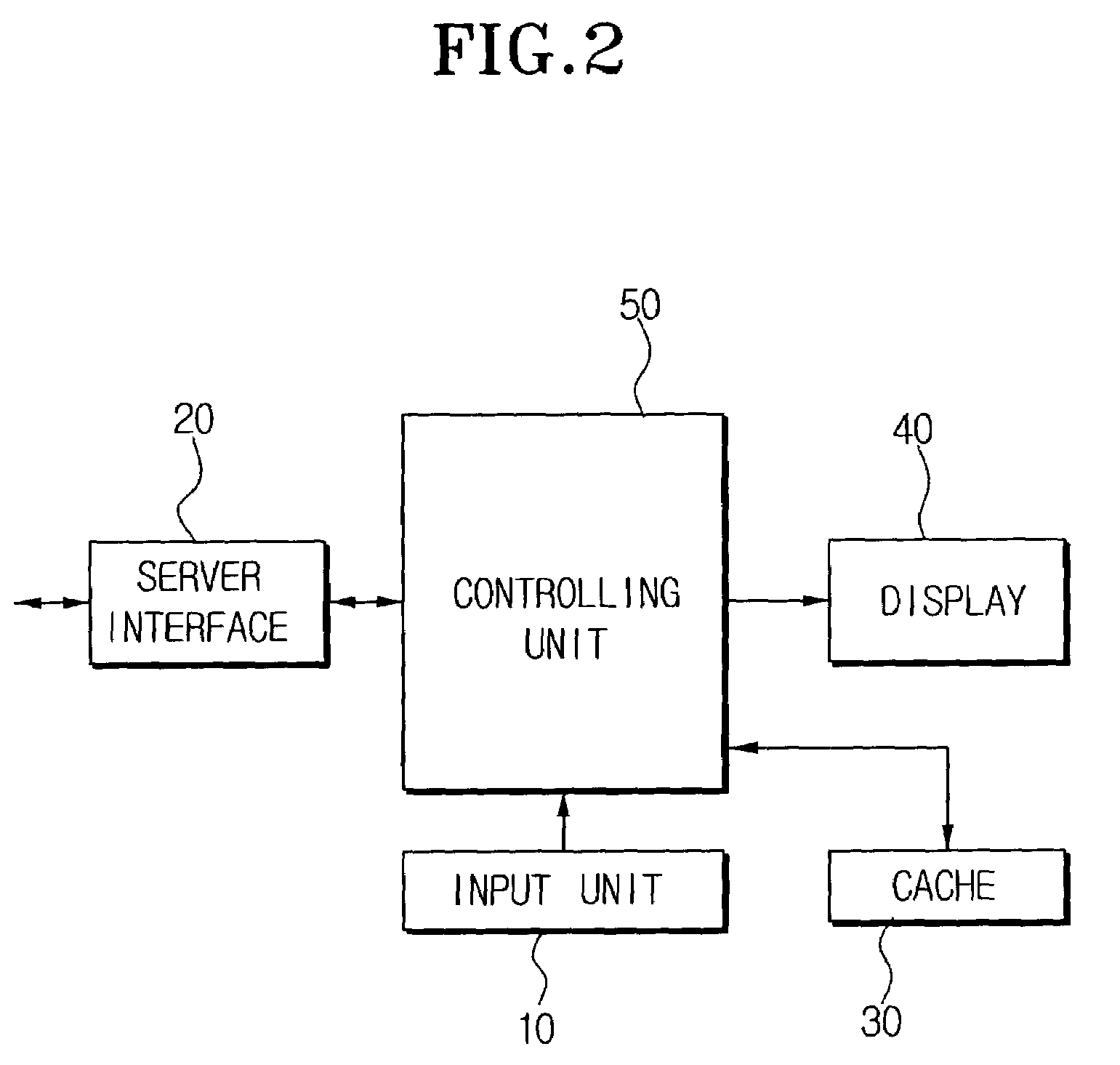
Method of controlling terminal of MPEG-4 system using caching mechanism
InactiveUS7370115B2Breed fastStable contentPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningParallel computingObject store
Owner:SAMSUNG ELECTRONICS CO LTD
Efficient large-scale access control for internet/intranet information systems
InactiveUS6219667B1Data processing applicationsDigital data processing detailsDecompositionInformation object
An efficient method and apparatus for regulating access to information objects stored in a database in which there are a large number of users and access groups. The invention uses a representation of a hierarchical access group structure in terms of intervals over a set of integers and a decomposition scheme that reduces any group structure to ones that have interval representation. This representation allows the problem for checking access rights to be reduced to an interval containment problem. An interval tree, a popular data structure in computational geometry, may be implemented to efficiently execute the access-right checking method.
Owner:IBM CORP
Apparatus, system, and method for validating that a correct data segment is read from a data storage device
ActiveUS20100031000A1Digital data information retrievalMemory adressing/allocation/relocationData segmentNetwork packet
An apparatus, system, and method are disclosed for validating that correct data is read from a storage device. A read request receiver module receives a read storage request to read a data segment of a file or object stored on a data storage device. The storage request includes one or more source parameters for the data segment. The source parameters include one or more virtual addresses that identify the data segment. A hash generation module generates one or more hash values from the virtual addresses. A read data module reads the requested data segment and returns one or more data packets and corresponding stored hash values stored with the data packets. The stored hash values were generated from a data segment written to the data storage device that contains data of the data packets. A hash check module verifies that the generated hash values match the respective stored hash values.
Owner:UNIFICATION TECH LLC
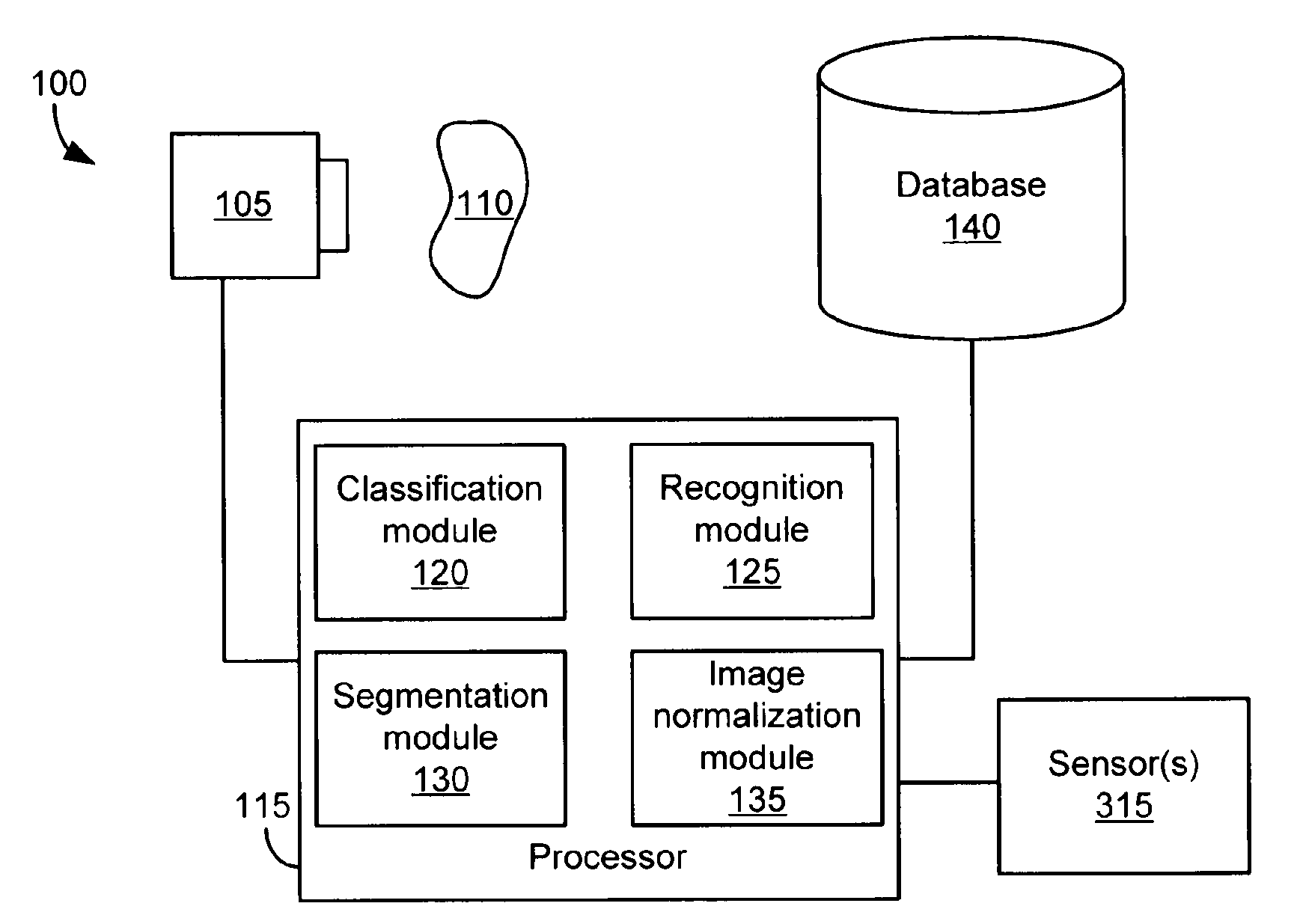
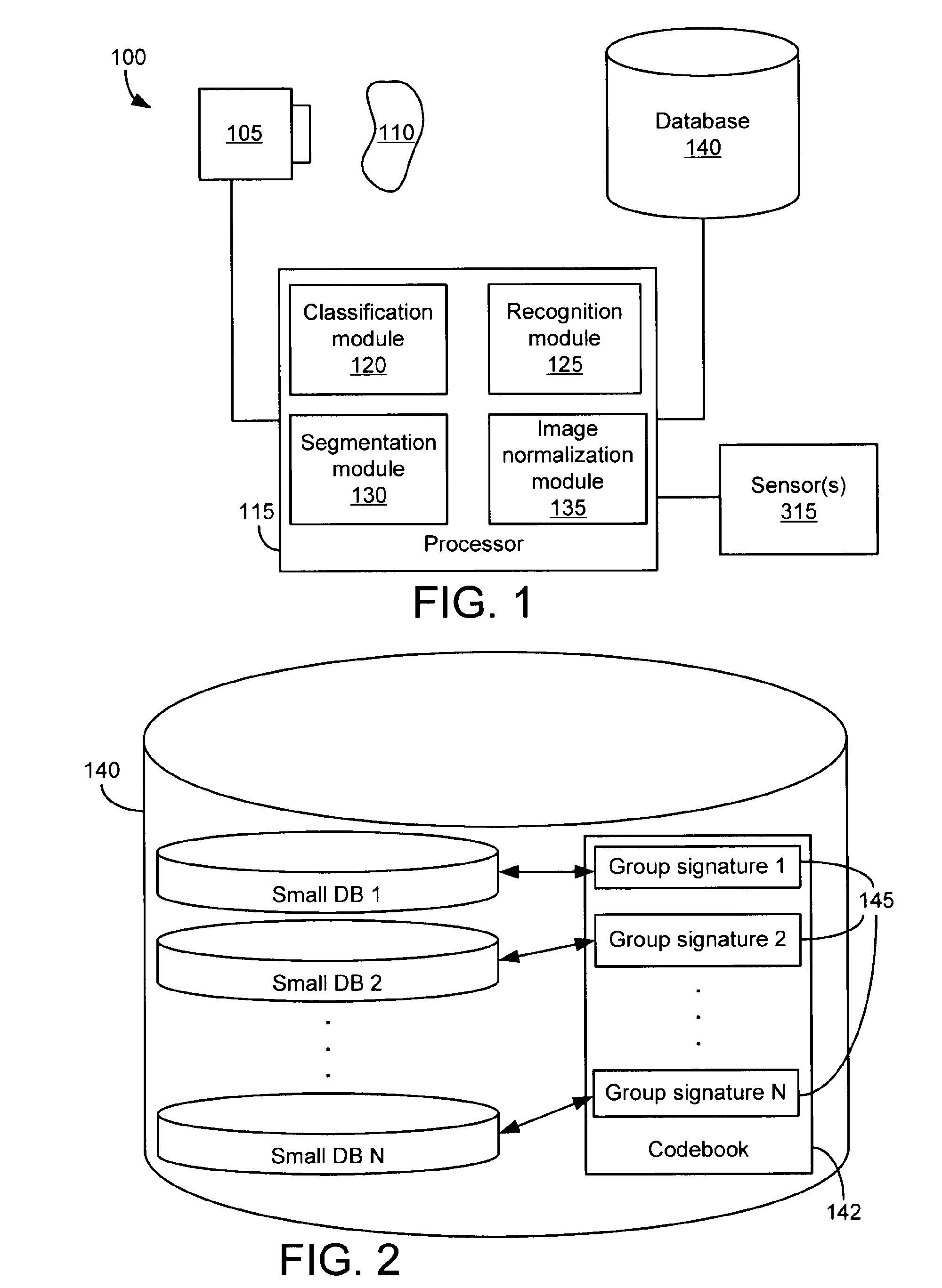
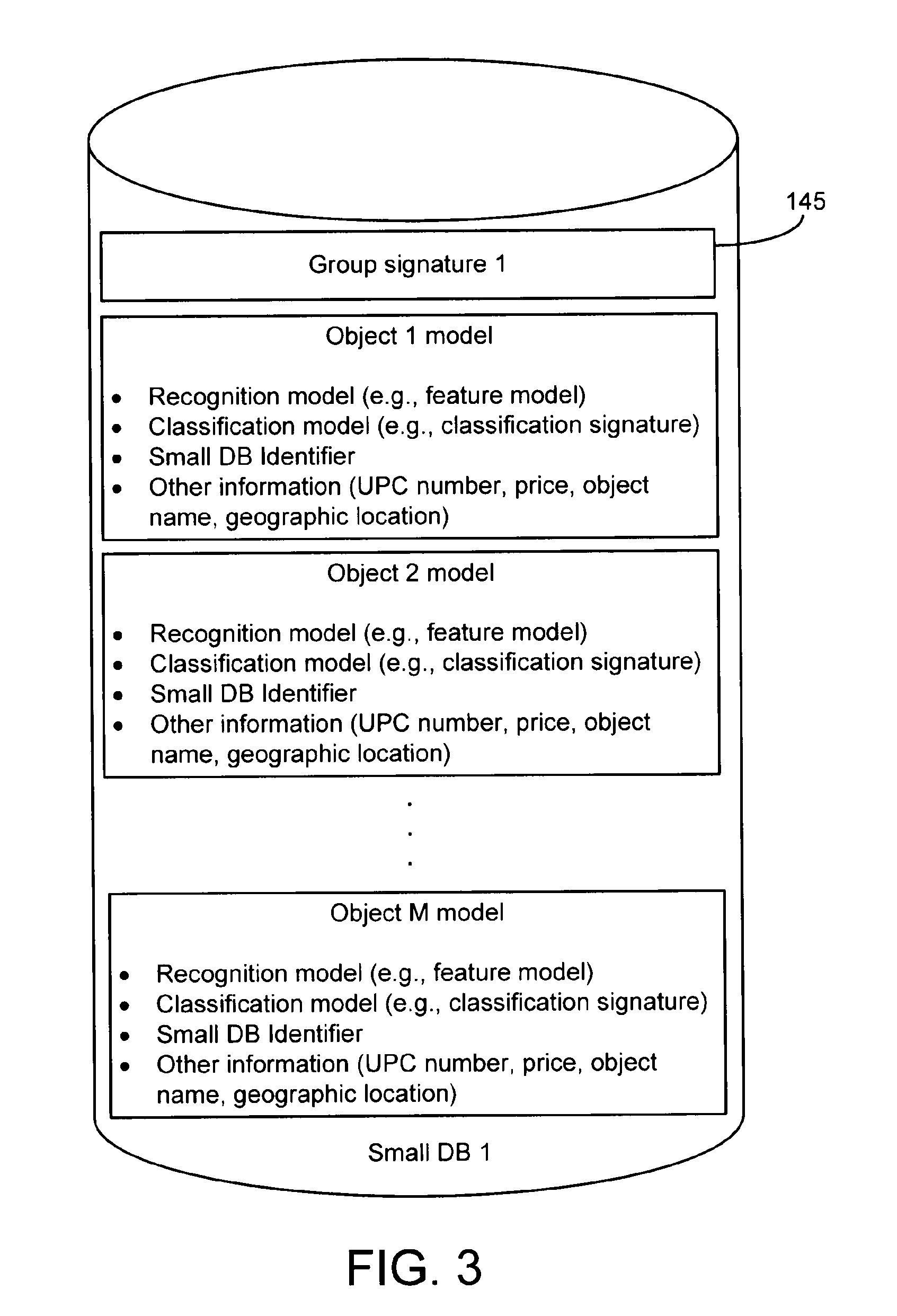
Systems and methods for object recognition using a large database
InactiveUS20110286628A1Digital data information retrievalCharacter and pattern recognitionObject storeVery large database
A method of organizing a set of recognition models of known objects stored in a database of an object recognition system includes determining a classification model for each known object and grouping the classification models into multiple classification model groups. Each classification model group identifies a portion of the database that contains the recognition models of the known objects having classification models that are members of the classification model group. The method also includes computing a representative classification model for each classification model group. Each representative classification model is derived from the classification models that are members of the classification model group. When a target object is to be recognized, the representative classification models are compared to a classification model of the target object to enable selection of a subset of the recognition models of the known objects for comparison to a recognition model of the target object.
Owner:DATALOGIC ADC
Method for Configuring an Optical Network
InactiveUS20090296719A1Huge complexityHuge timeData switching by path configurationOptical multiplexObject definitionNetwork model
A network model for the planning and / or the provisioning of traffic flows in a communication network includes nodes interconnected with each other by links according to a given network topology. The network model uses a graph defined by arc objects storing information related to both the links and adjacent nodes thereof.
Owner:TELECOM ITALIA SPA
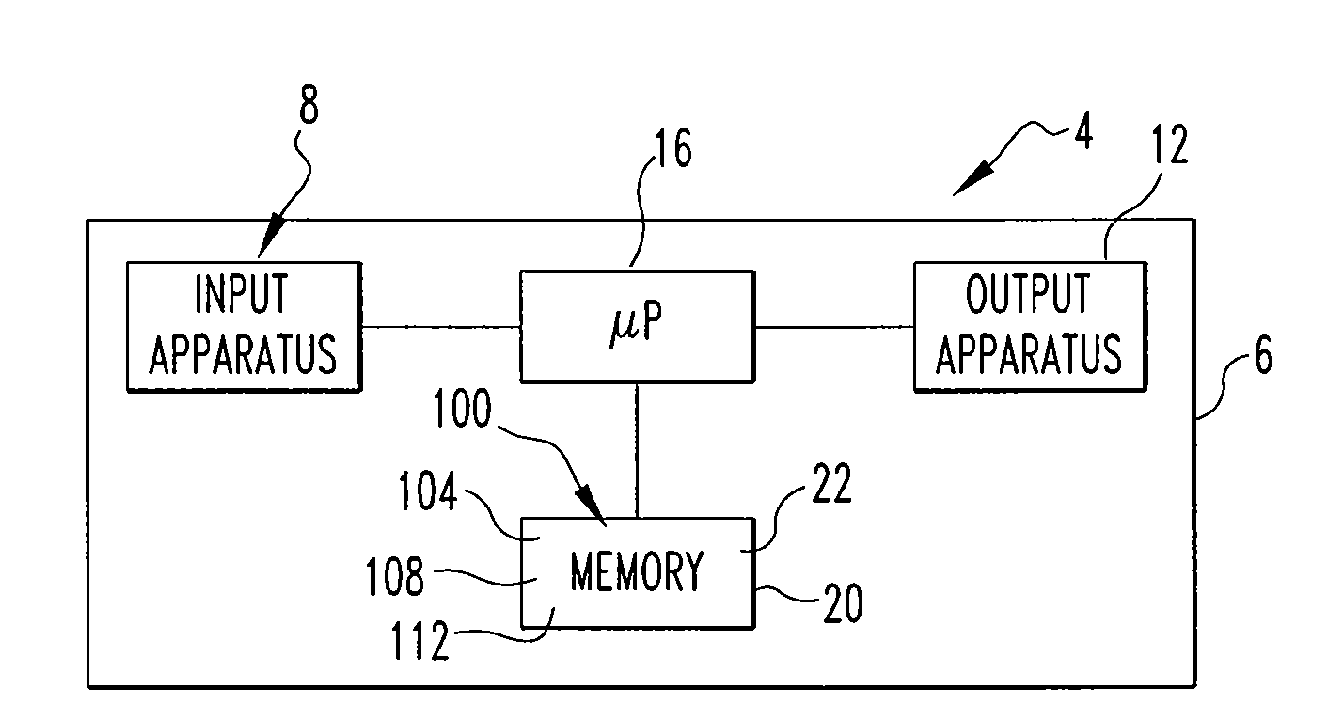
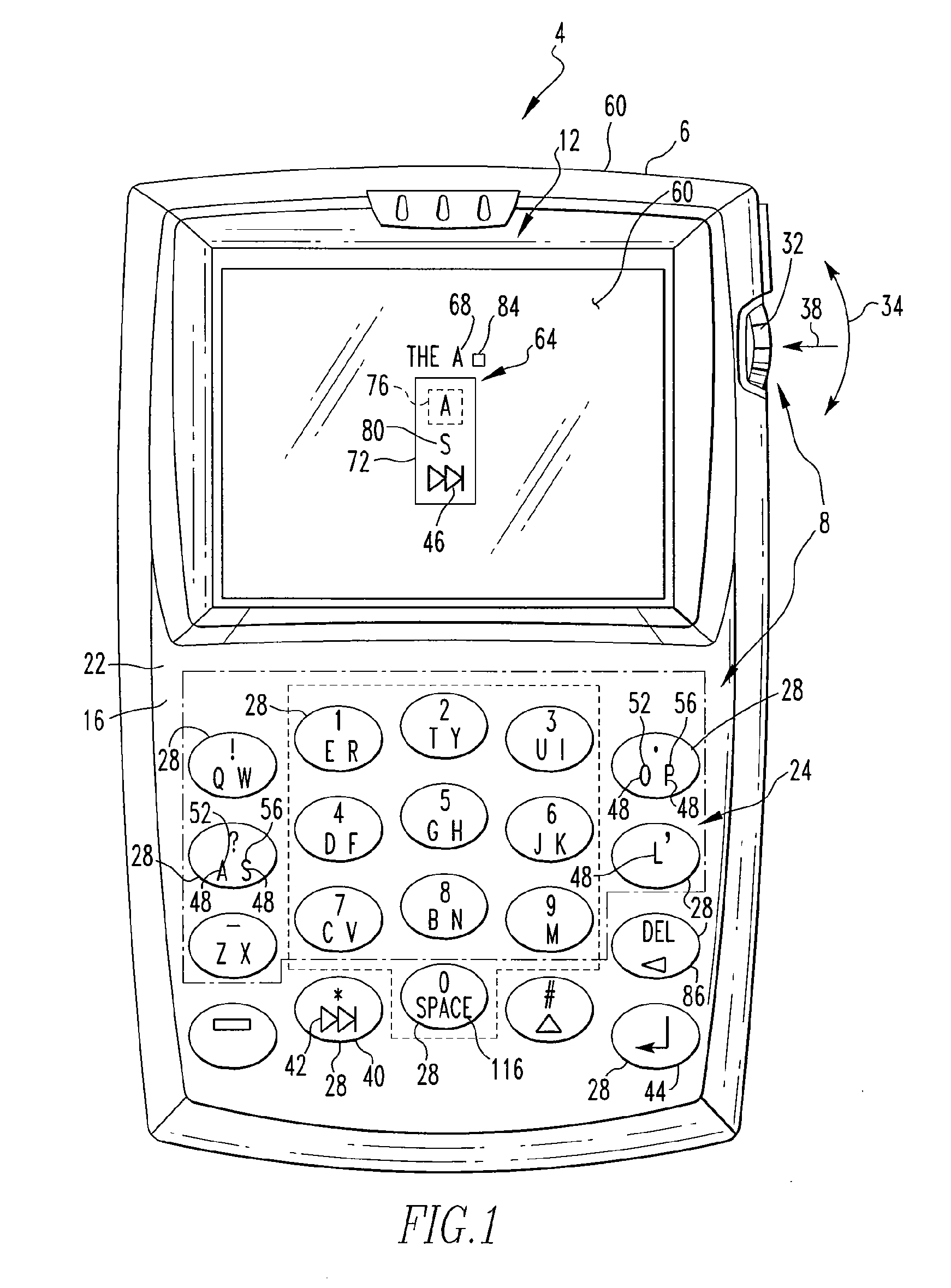
Disambiguated text message retype function
ActiveUS20090112576A1Input/output for user-computer interactionCathode-ray tube indicatorsAmbiguityObject store
Owner:MALIKIE INNOVATIONS LTD
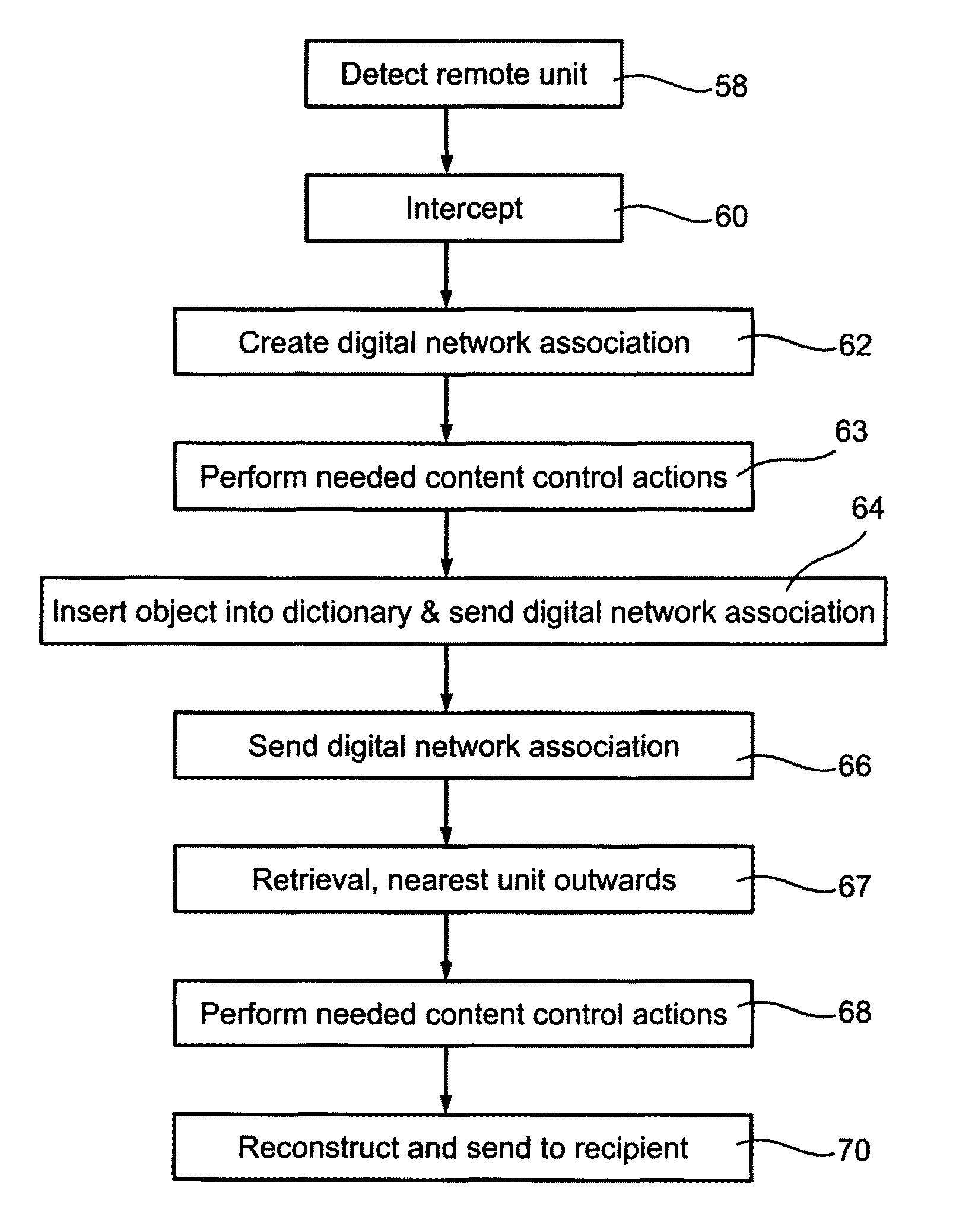
Bidirectional data transfer optimization and content control for networks
A method of transferring data objects over a network comprises intercepting a network transfer message with a passing object, creating a unique identifier for the object using a predetermined function, the same function having been used to provide identifiers for objects stored at predetermined nodes of said network, removing the object and sending on the network transfer message with the unique identifier in place of the object. Then, at the recipient end it is possible to obtain the unique identifier and use it as a key to search for a corresponding object in the local nodes. The search starts with a node closest to the recipient and steadily spreads outwards. The object when found is reattached for the benefit of the recipient and network bandwidth has been saved by the avoidance of redundant transfer since the object is brought to the recipient from the node which is the closest to him.
Owner:B OBVIOUS LTD
Management interface for a system that provides automated, real-time, continuous data protection
ActiveUS20060101384A1Digital data information retrievalError detection/correctionDisplay deviceContent Time
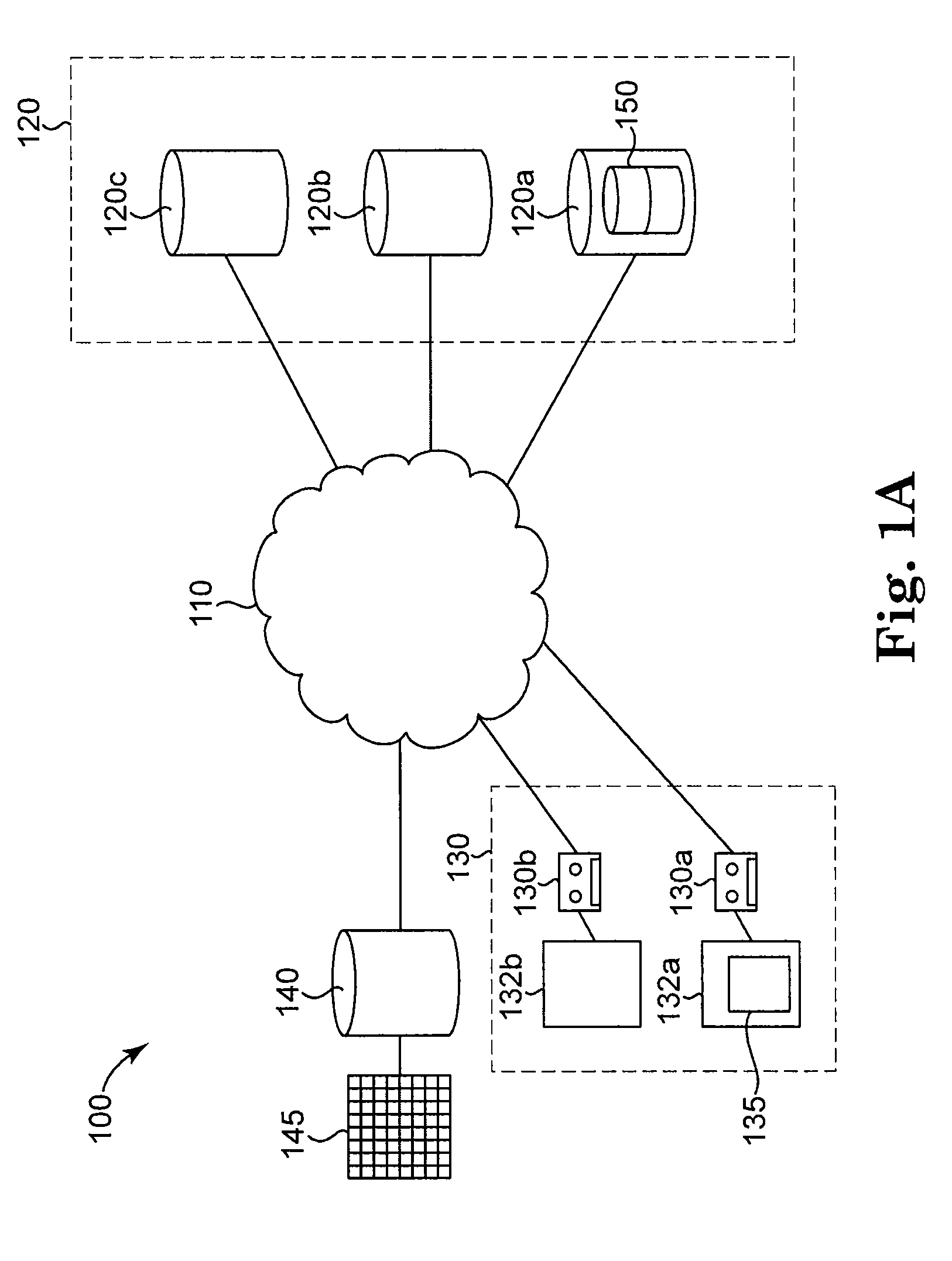
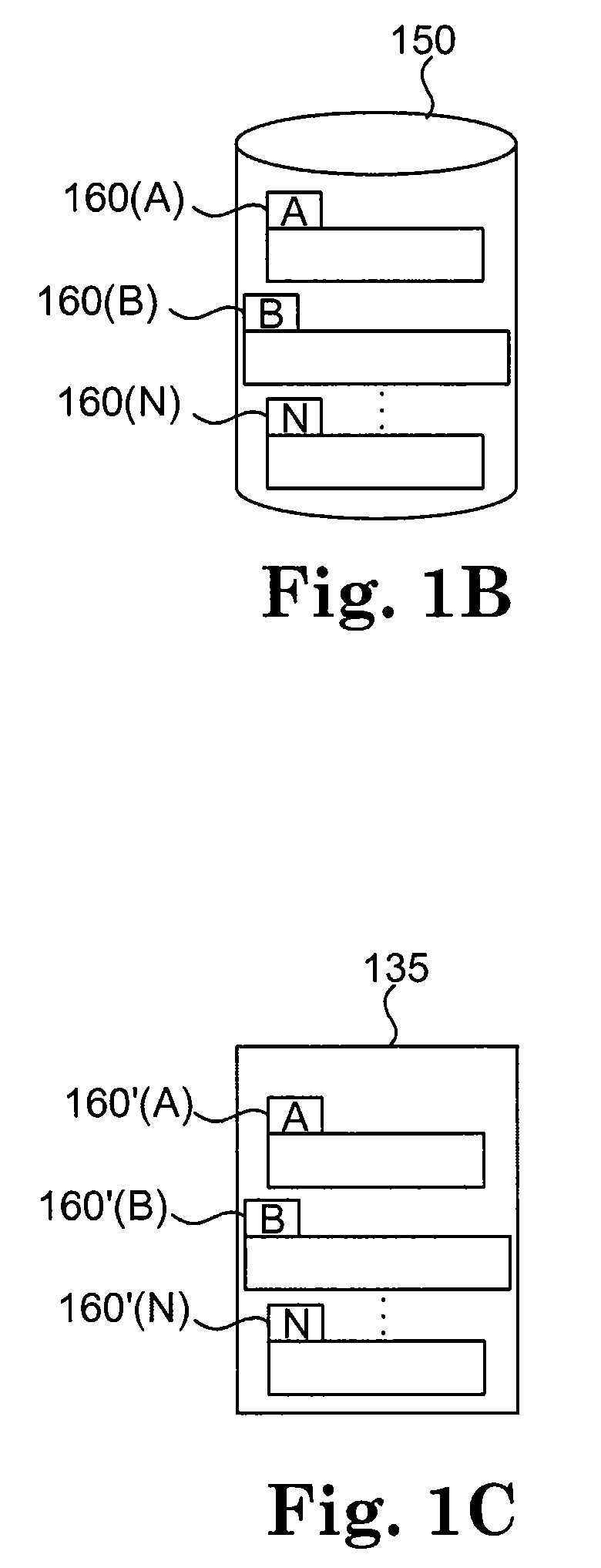
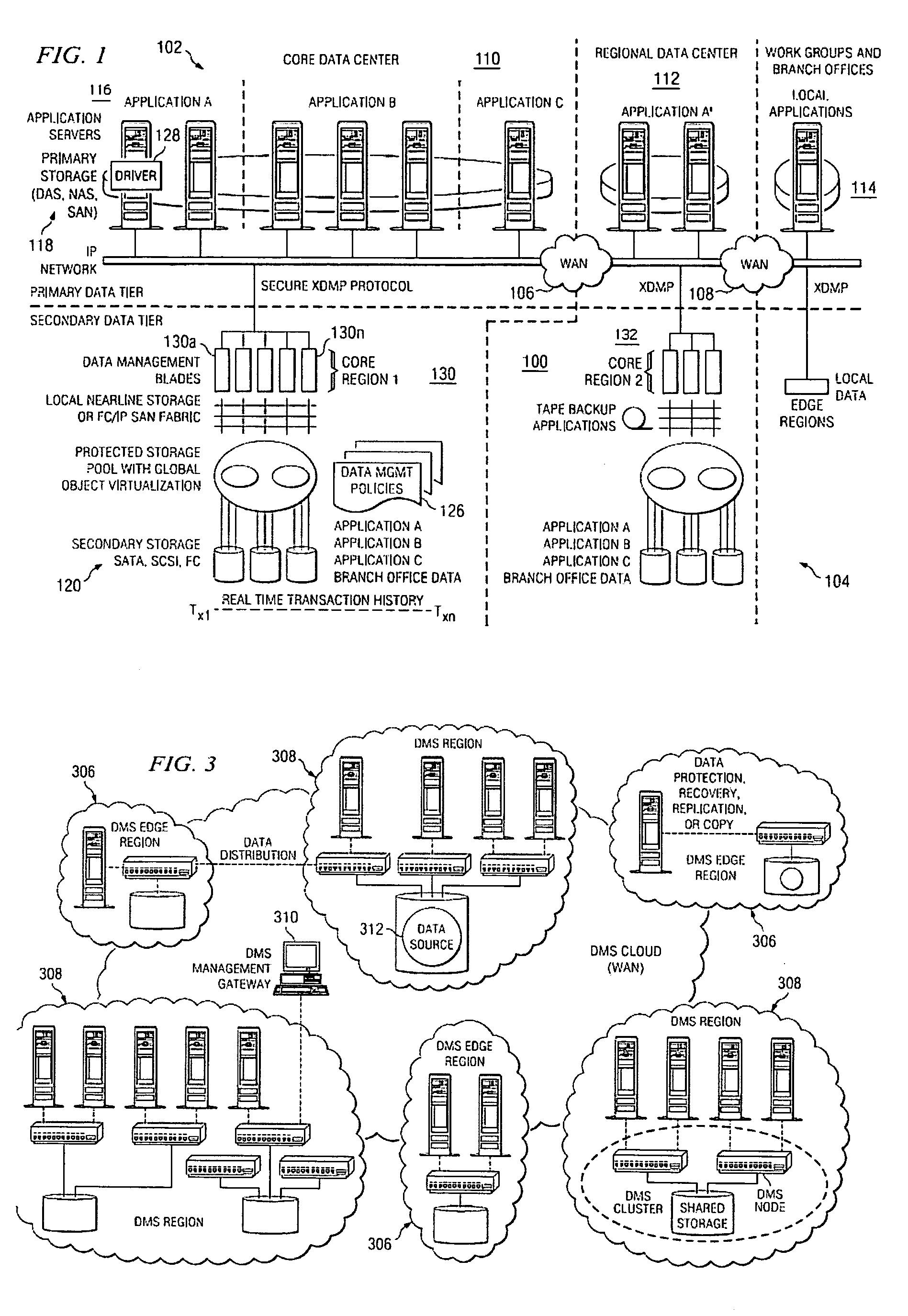
A data management system that protects data into a continuous object store includes a management interface having a time control. The time control allows an administrator to specify a “past” time, such as a single point or range. When the time control is set to a single point, a hierarchical display of data appears on a display exactly as the data existed in the system at that moment in the past. Preferably, the visualization includes both the structure of the hierarchy (e.g., the identity of the directories, their files, databases, and the like) and also the contents of the data objects themselves (i.e., what was in the files and databases). The time control enables the management interface to operate within a history mode in which the display provides a visual representation of a “virtual” point in time in the past during which the data management system has been operative to provide the data protection service. In addition, the management interface can be toggled to operate in a real-time mode, which provides an active view of the system data as it changes in real-time, typically driven by changes to primary storage. This real-time mode provides the user with the ability to view changes that occur to a set of data currently visible on the display screen. The interface also allows an administrator to specify and manage policy including, without limitation, how long data is retained in the management system. A policy engine enables the user to assert “temporal-based” policy over data objects.
Owner:QUEST SOFTWARE INC
Automated application discovery and analysis system and method
ActiveUS20060123022A1Digital data processing detailsObject oriented databasesSystems designMonitoring system
Owner:GLOBAL SAAS SOLUTIONS PTE LTD
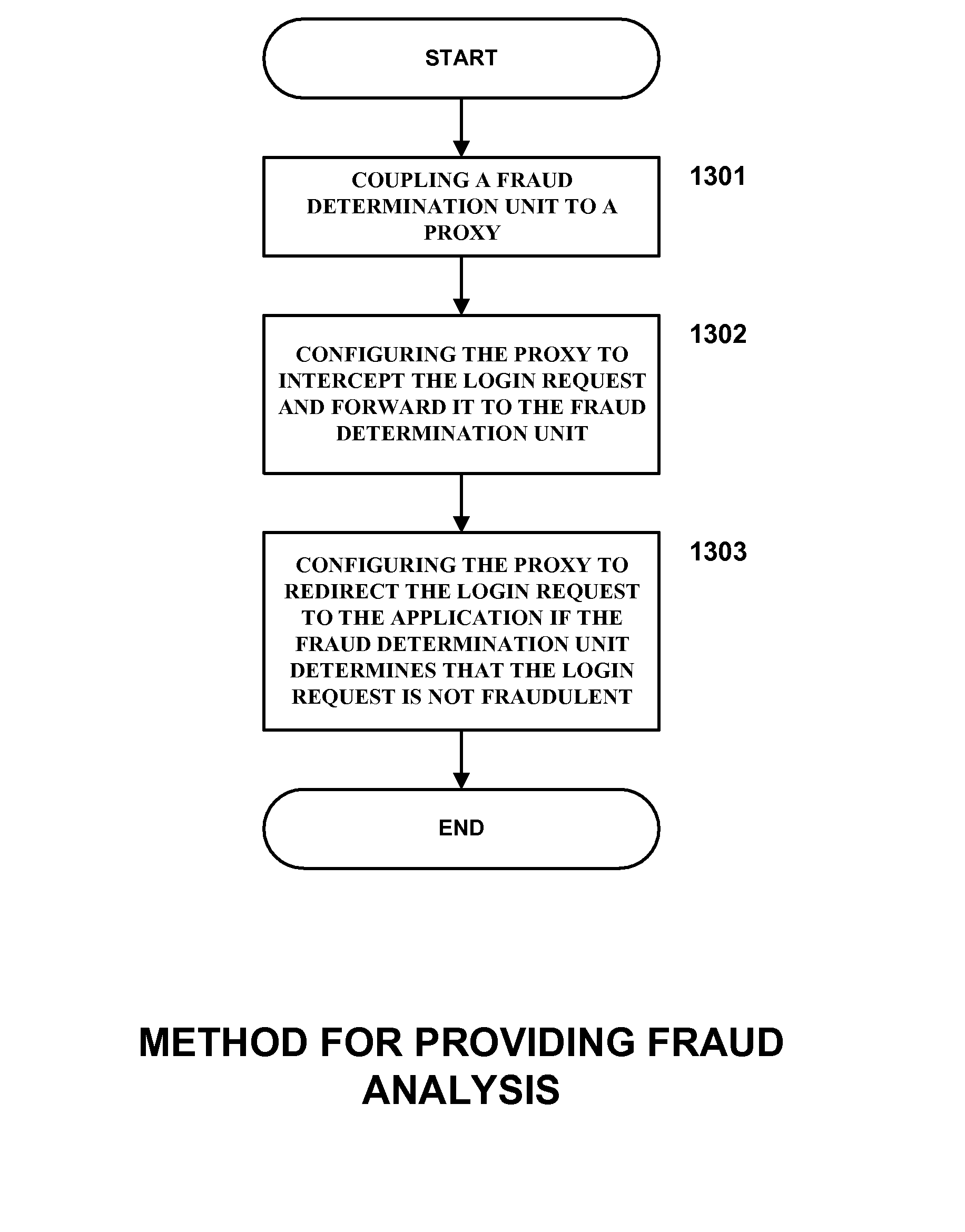
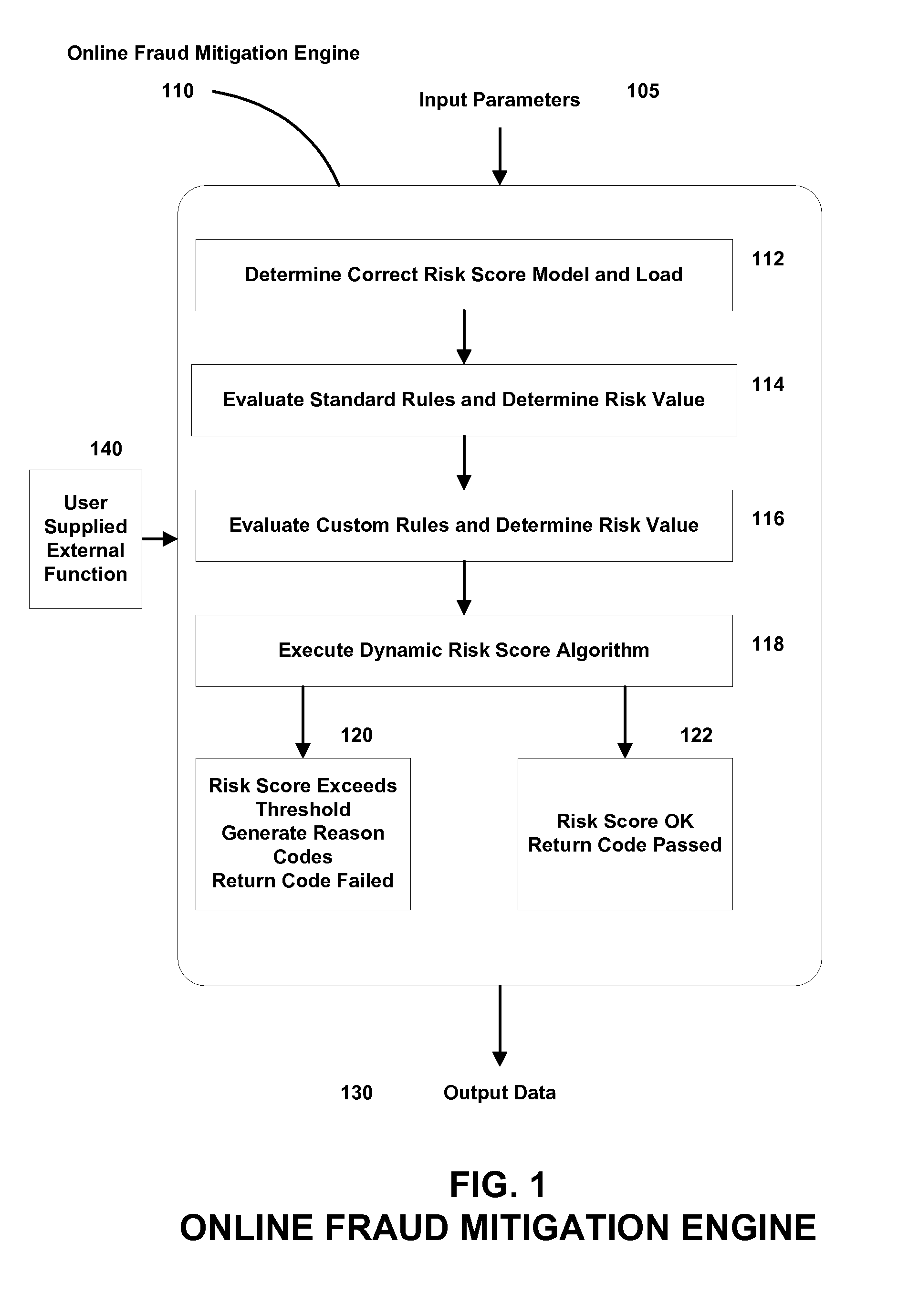
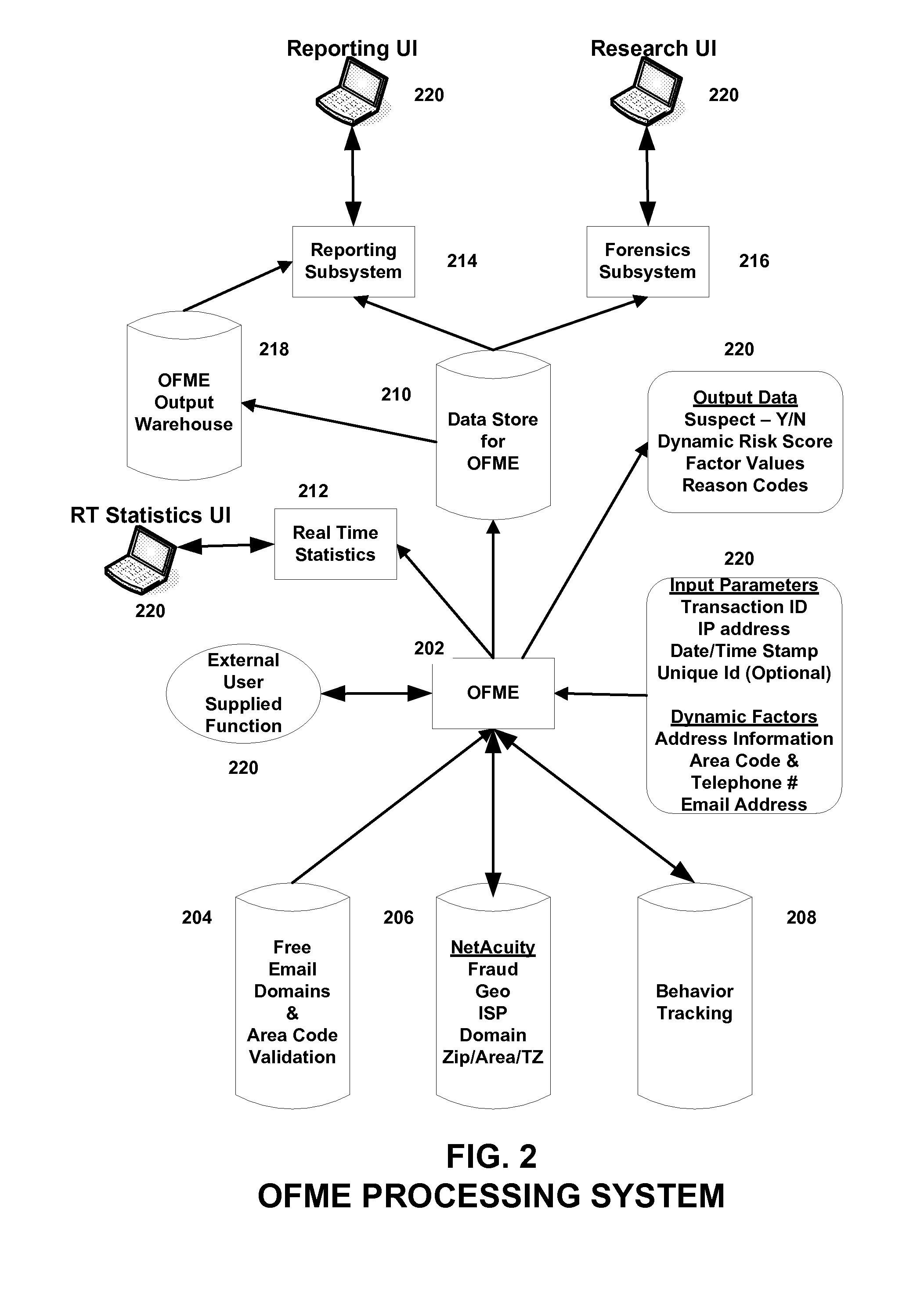
Authentication Proxy
InactiveUS20080010678A1Multiple digital computer combinationsProgram controlInternet privacyObject store
Systems, methods, and computer program products for providing fraud analysis to an application using a proxy and a fraud determination unit are provided. An Online Fraud Mitigation Engine is also provided in embodiments of the present invention for determining fraudulent transactions. Embodiments are also provided for calculating travel velocity and transaction frequency, which are useful for determining a fraudulent transaction. Further embodiments are provided for authenticating a transaction using an object stored on a client device and a behavior profile stored on a server.
Owner:DIGITAL ENVOY
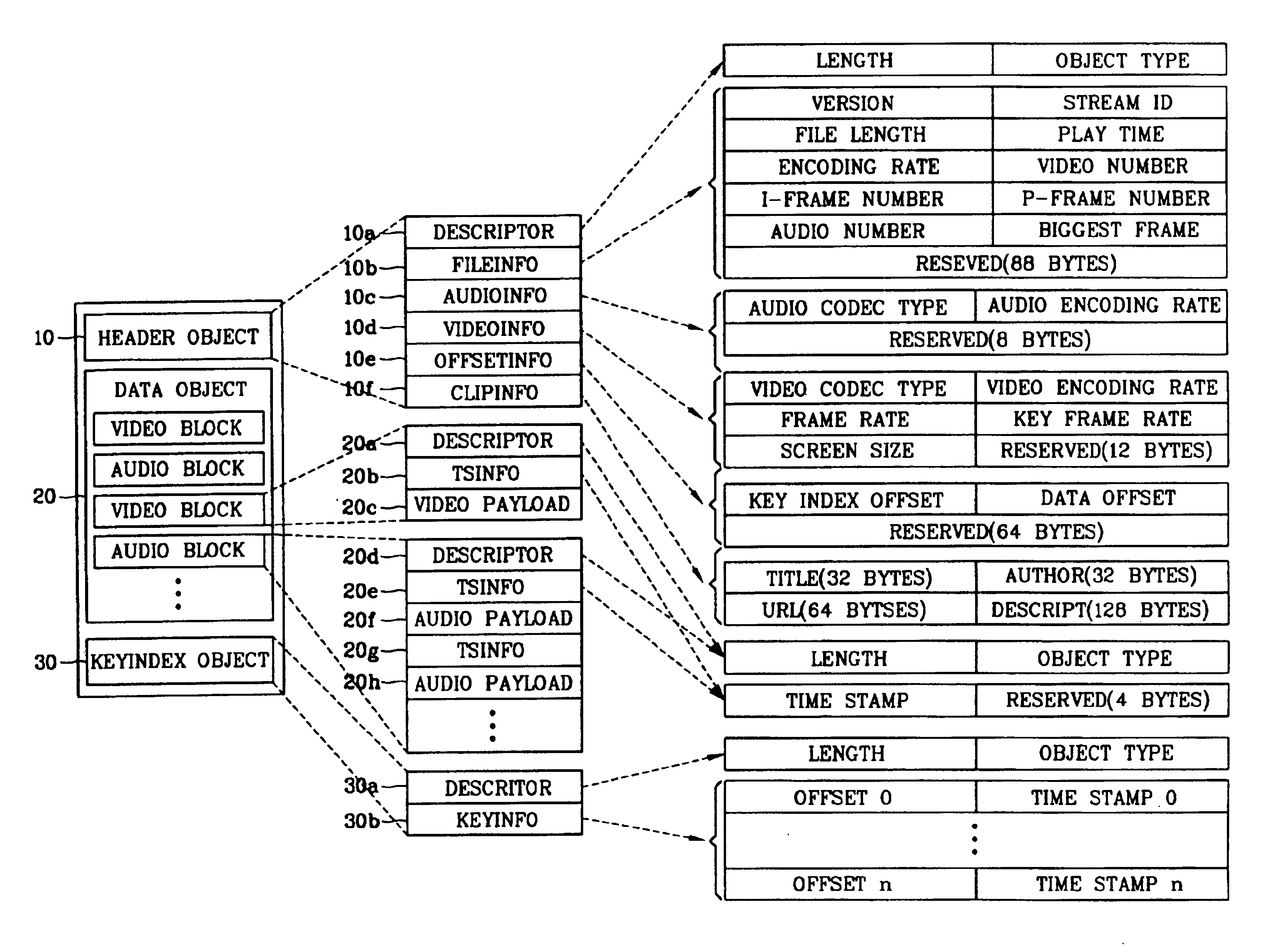
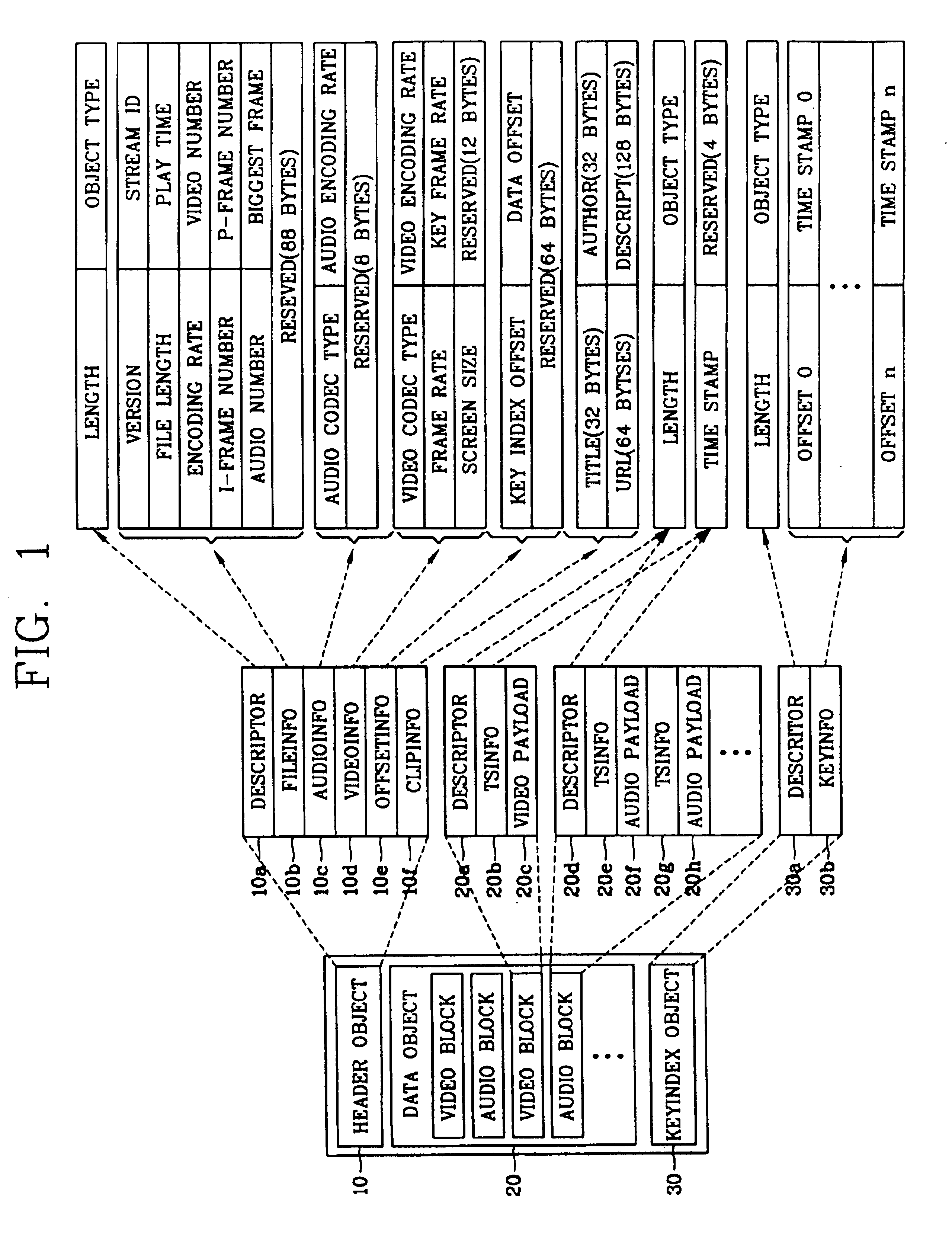
Apparatus and method for providing file structure for multimedia streaming service
InactiveUS6856997B2Reduce bandwidth wasteFast data transferData processing applicationsPulse modulation television signal transmissionData synchronizationTemporal information
In a file structure for a streaming service and a method for providing a streaming service, a file structure includes a header object having basic information about a file and information for an application service, a data object synchronizing multimedia data with temporal information and storing it, and a key index object storing an offset and temporal information of a video block having a key frame in video blocks as a basis on a time axis for random access and reproduction. Accordingly, data can be transmitted quickly by not including unnecessary additional data, an application region can be expanded by including other media file besides a video and an audio files, because a random access and random reproduction by key index information are possible, it is possible to support various reproduction functions such as a fast play, a reverse play and random reproduction, etc.
Owner:LG ELECTRONICS INC
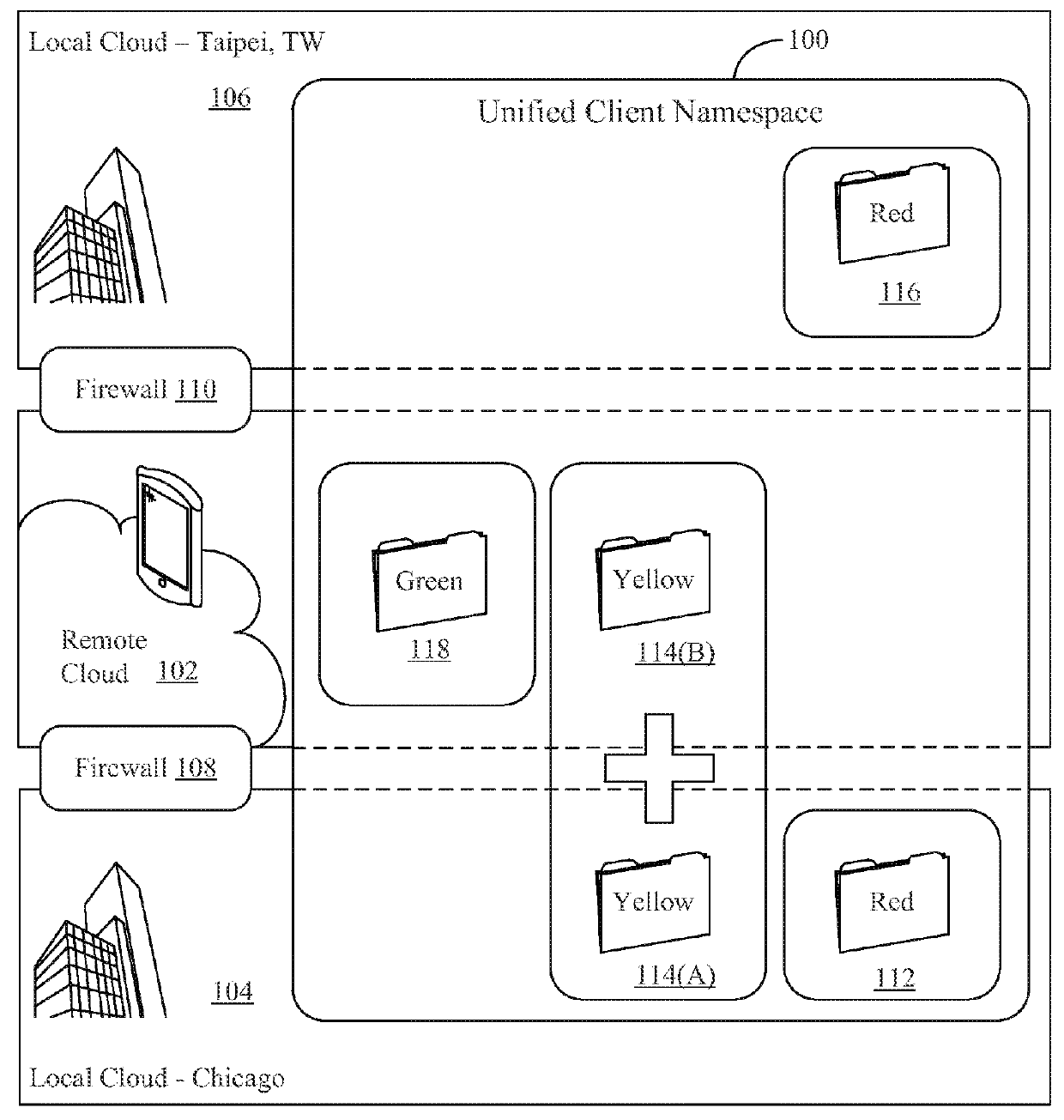
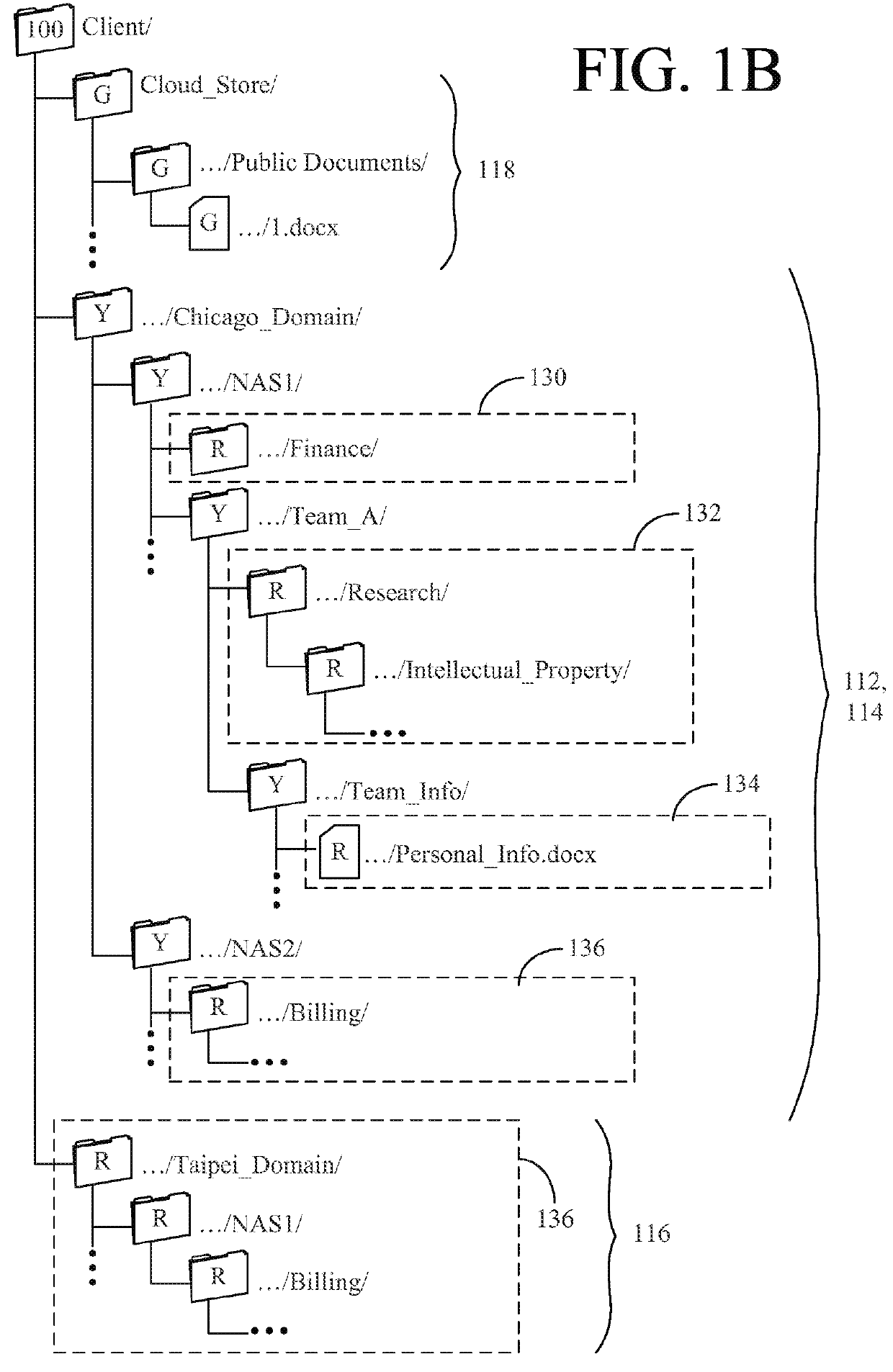
Systems and methods for facilitating access to private files using a cloud storage system
ActiveUS9251114B1Facilitates accessing fileOvercome problemsDatabase distribution/replicationDigital data protectionFile systemObject store
A method for providing access to objects associated with a particular client in a cloud storage system is disclosed. The method includes the steps of establishing a connection with a user, providing a client namespace associated with the client to the user, where the client namespace represents objects stored on the cloud storage system and objects stored on a private storage system apart from the cloud storage system, receiving a request from the user to access an object stored on the private storage system, and providing information to the user to facilitate access to the object stored on the private storage system by said user. Other systems and methods are also disclosed. Important advantages of the present invention are facilitated by separating the logic for user access (control plane) from the actual storage (Storage plane). Private file system access can still be managed from the cloud, while keeping the client data private.
Owner:EGNYTE
System and method for aggregating query results in a fault-tolerant database management system
ActiveUS20120078881A1More burdensomeDigital data information retrievalDigital data processing detailsEngineeringObject store
A redundant array of independent nodes are networked together. Each node executes an instance of an application that provides object-based storage. Metadata objects are stored in a set of regions distributed among the nodes across the array. A given region is identified by hashing a metadata object attribute and extracting a given set of bits of a resulting hash value. A method of managing query results comprises: receiving, by a first node of the plurality of independent nodes from a client application, a request for a list of objects with a criterion; issuing by the first node a query to all the nodes based on the received request; processing the query by each node over the regions in the node using the metadata objects stored in the regions; aggregating and filtering by the first node results of the query from all the nodes; and returning by the first node the aggregated and filtered results to the client application.
Owner:HITACHI VANTARA LLC
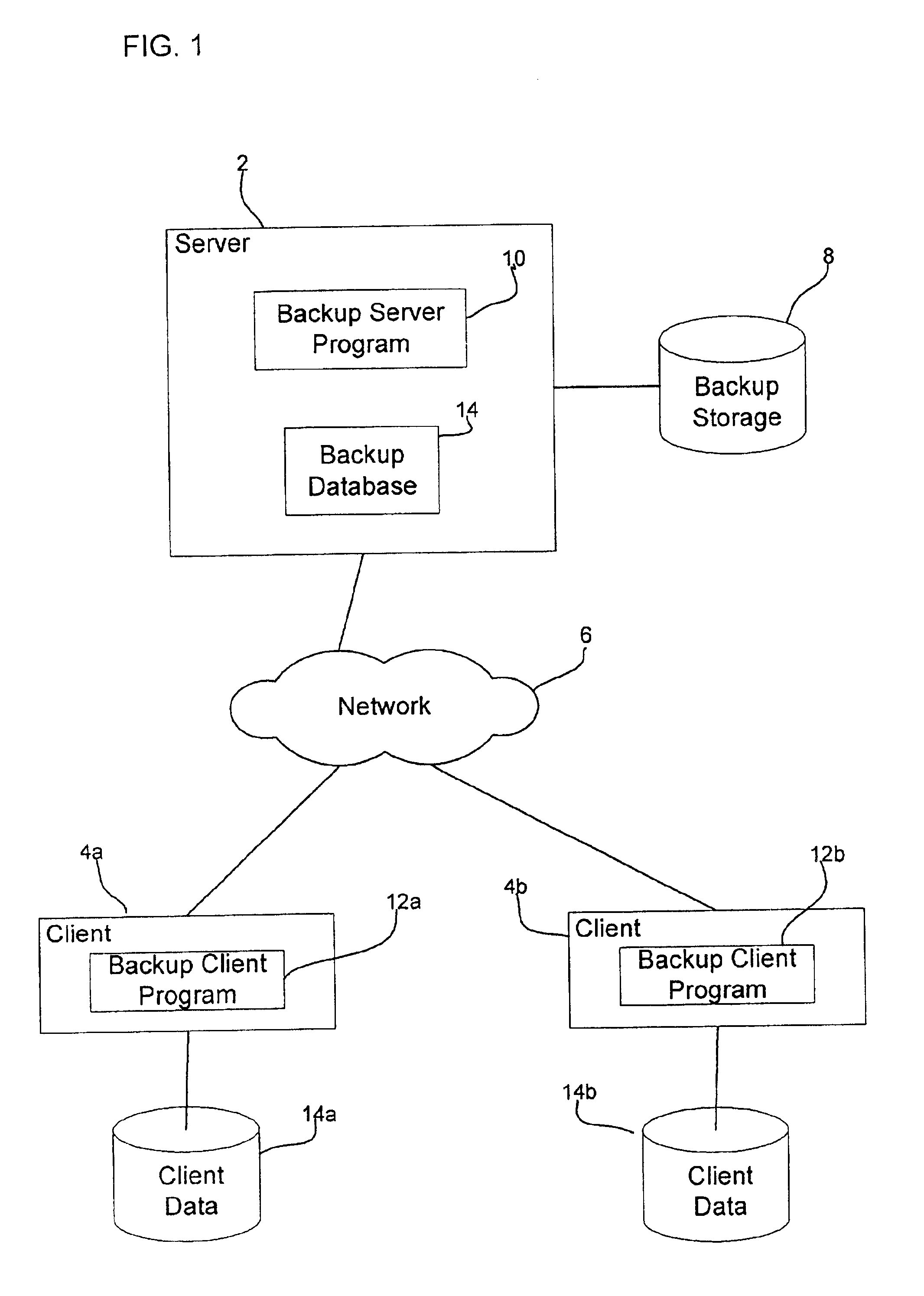
Method and system for scaleable, distributed, differential electronic-data backup and archiving
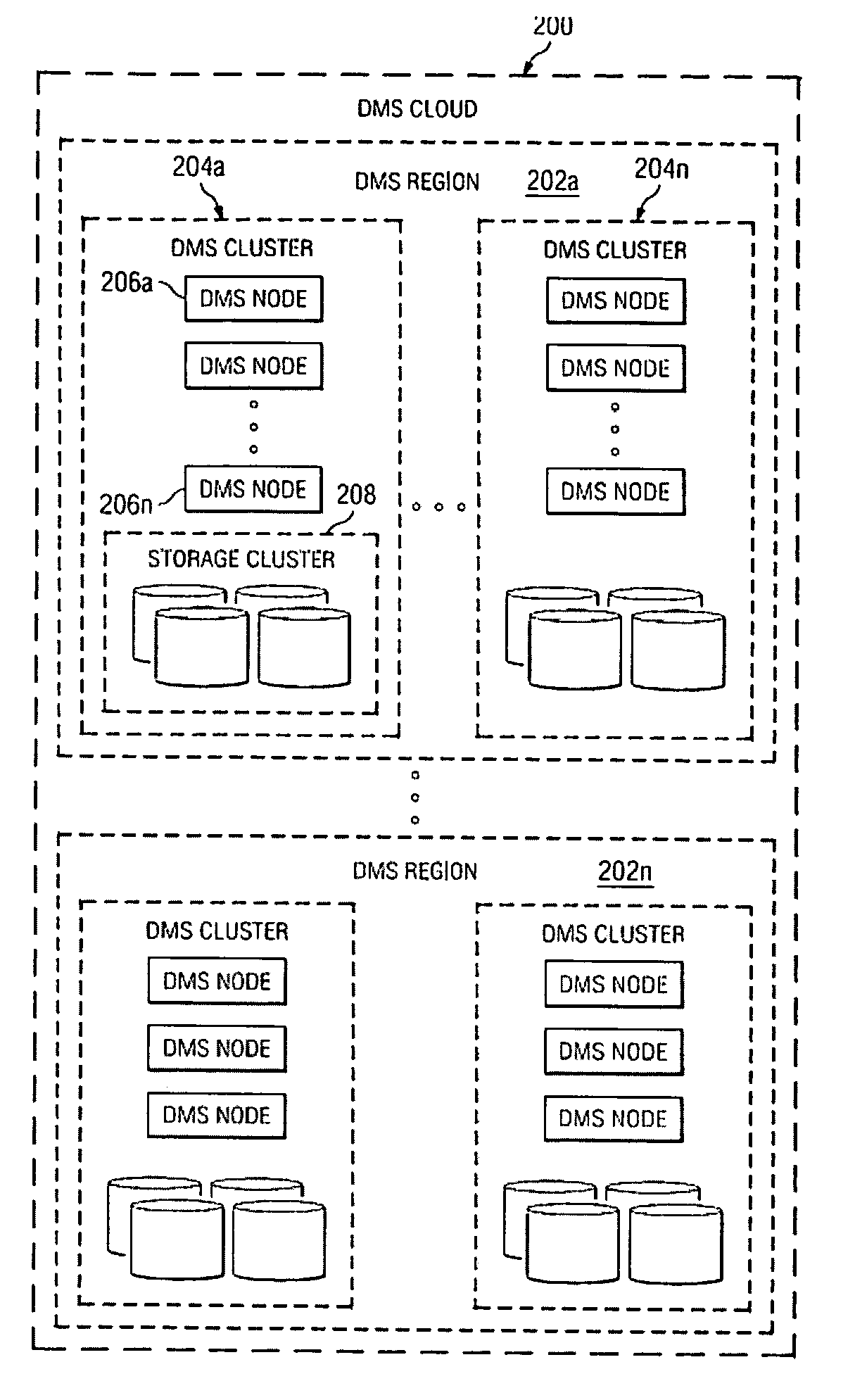
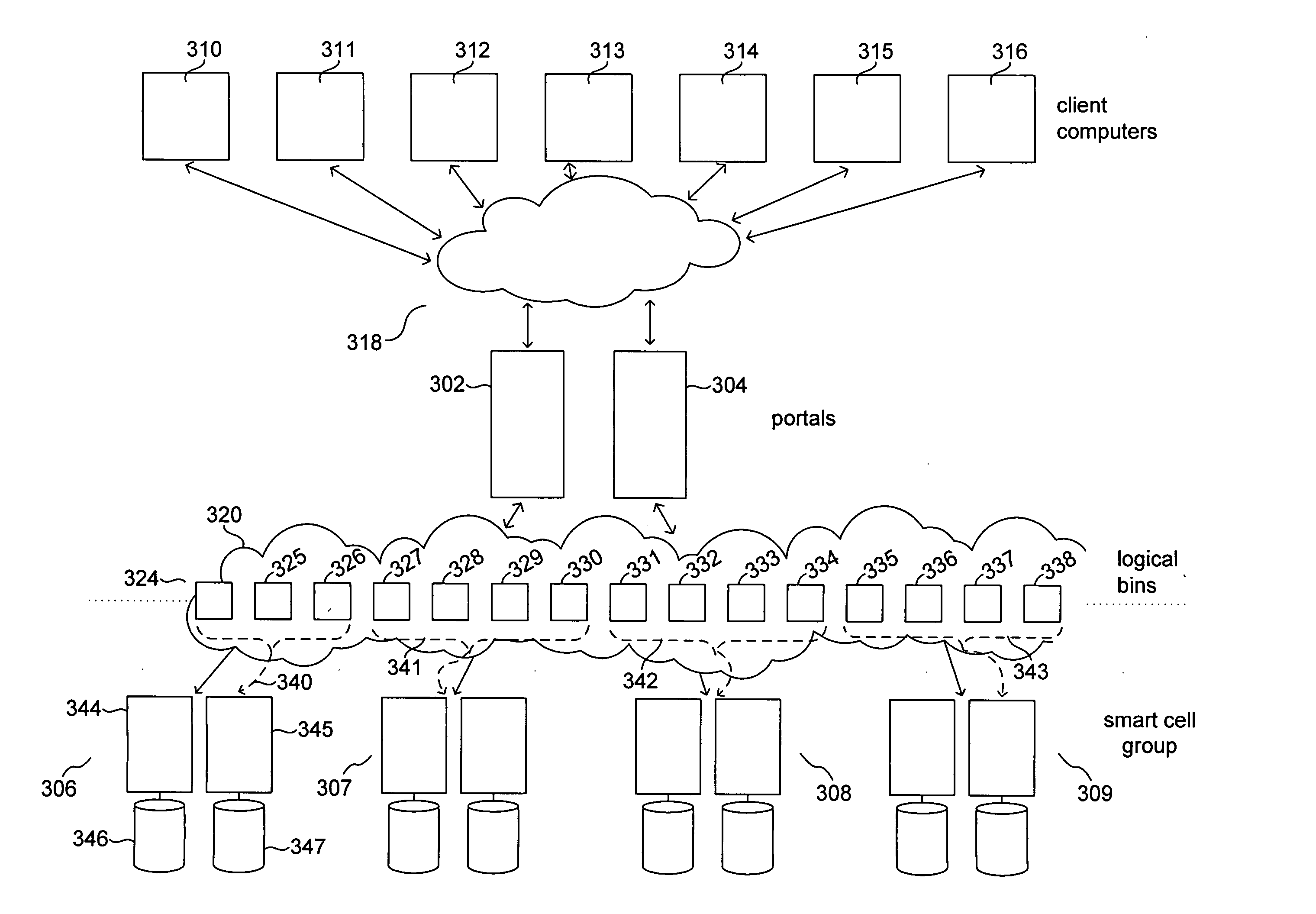
One embodiment of the present invention provides a distributed, differential electronic-data backup and archiving system that includes client computers and cells. Client computers execute front-end-application components of the distributed, differential electronic-data backup and archiving system, the front-end application components receiving data objects from client computers and sending the received data objects to cells of the distributed, differential electronic-data backup and archiving system for storage. Cells within the distributed, differential electronic-data backup and archiving system store the data objects, each cell comprising at least one computer system with attached mass-storage and each cell storing entire data objects as lists that reference stored, unique data chunks within the cell, a cell storing all of the unique data chunks for all data objects stored in the cell.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
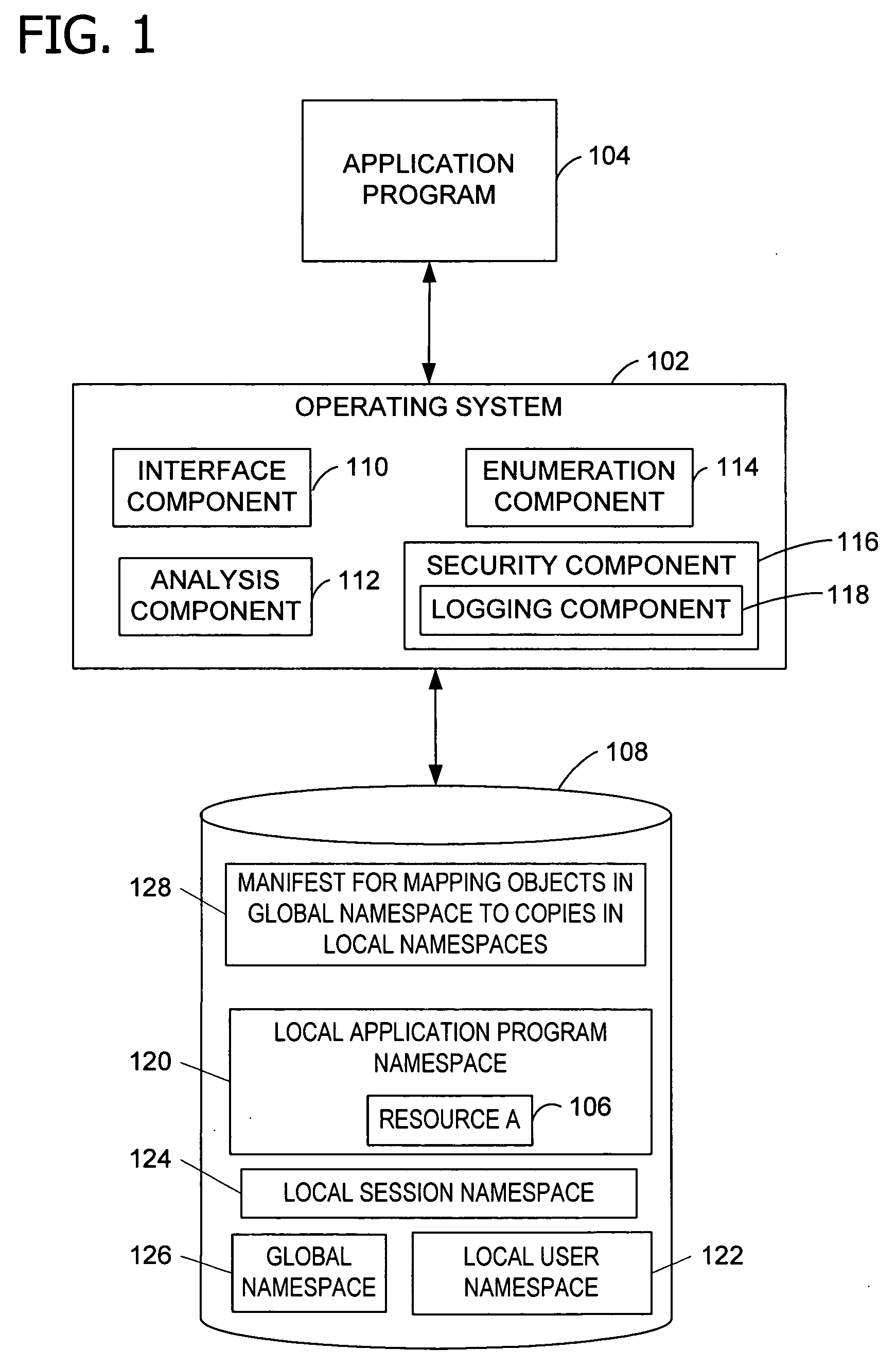
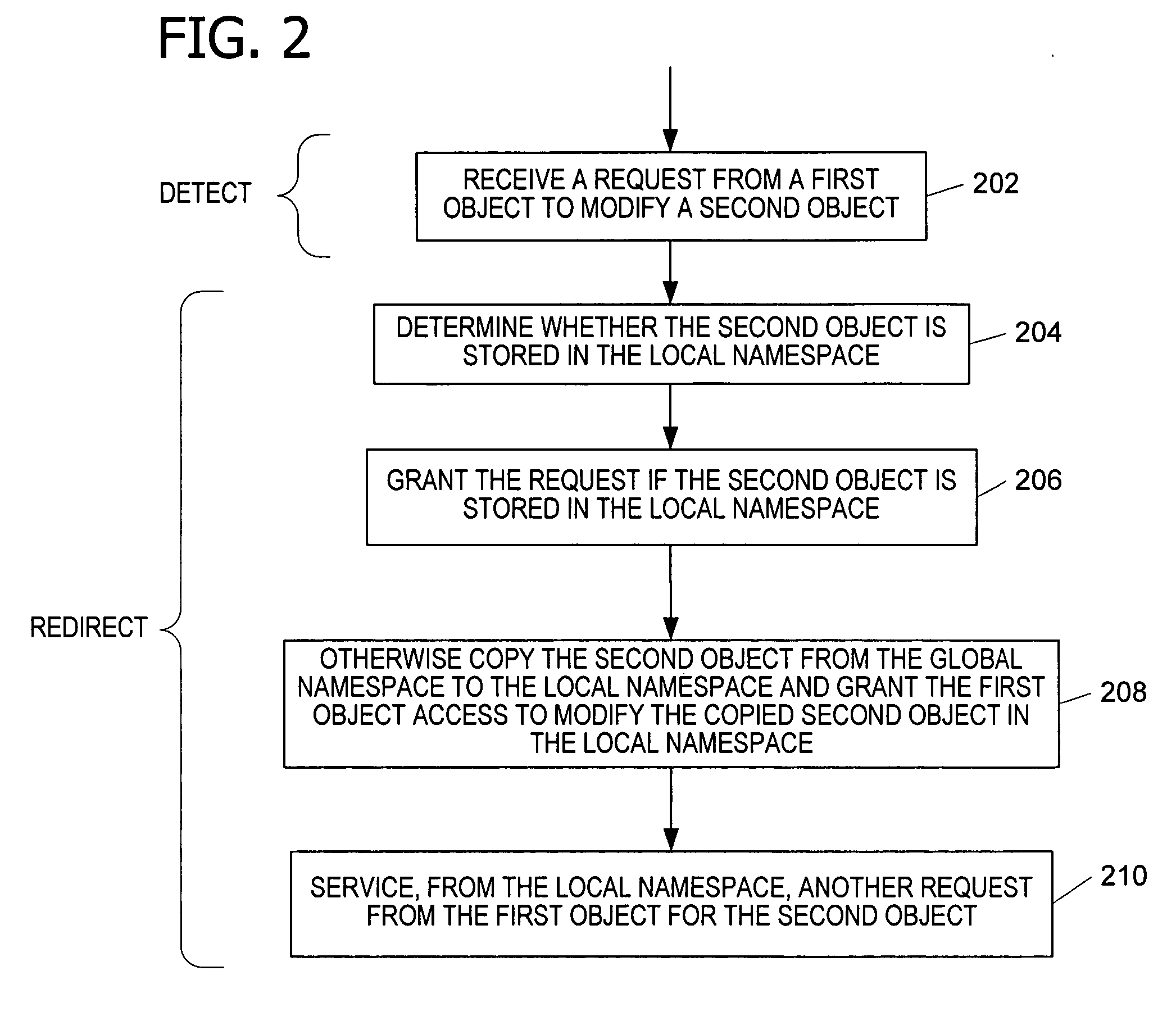
Internal object protection from application programs
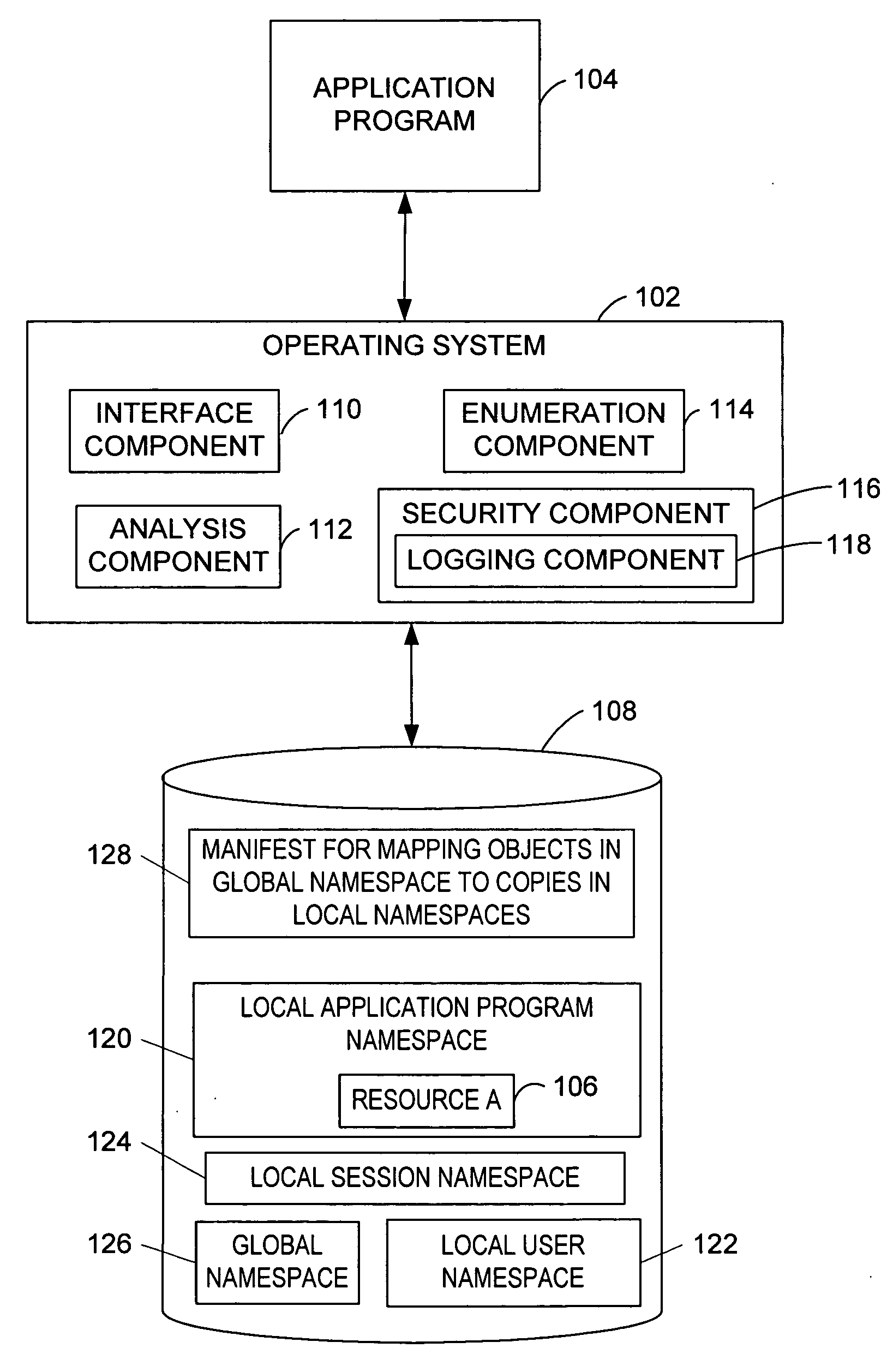
InactiveUS20050091214A1Reduce the possibilityResource allocationDigital data processing detailsOperational systemObject store
Granting an executable object (e.g., an application program, thread, or process) access to a namespace object (e.g., a named object, resource, file, or folder). A request by the executable object for the namespace object is intercepted and processed to determine whether a local namespace associated with the executable object, user, or session stores a copy of the requested namespace object. If the copy exists in one of the local namespaces, the request is granted and allowed to operate on that local namespace. If the requested namespace object exists only in a global namespace, the namespace object is copied to a local namespace. The request is then granted and allowed to operate on the copy of the namespace object in the local namespace. Protecting the namespace objects stored in the global namespace from modification improves the stability of the application program and operating system.
Owner:MICROSOFT TECH LICENSING LLC
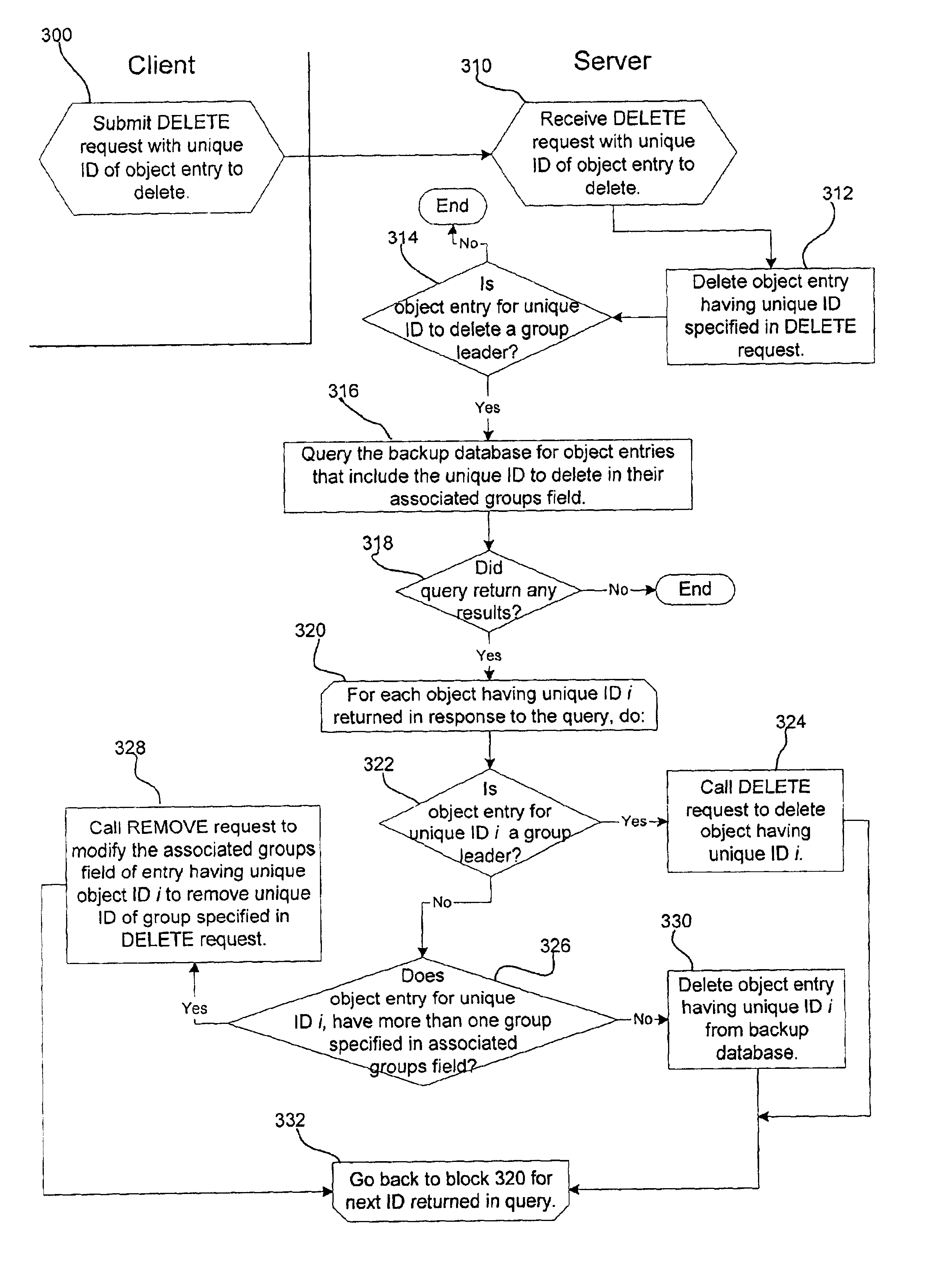
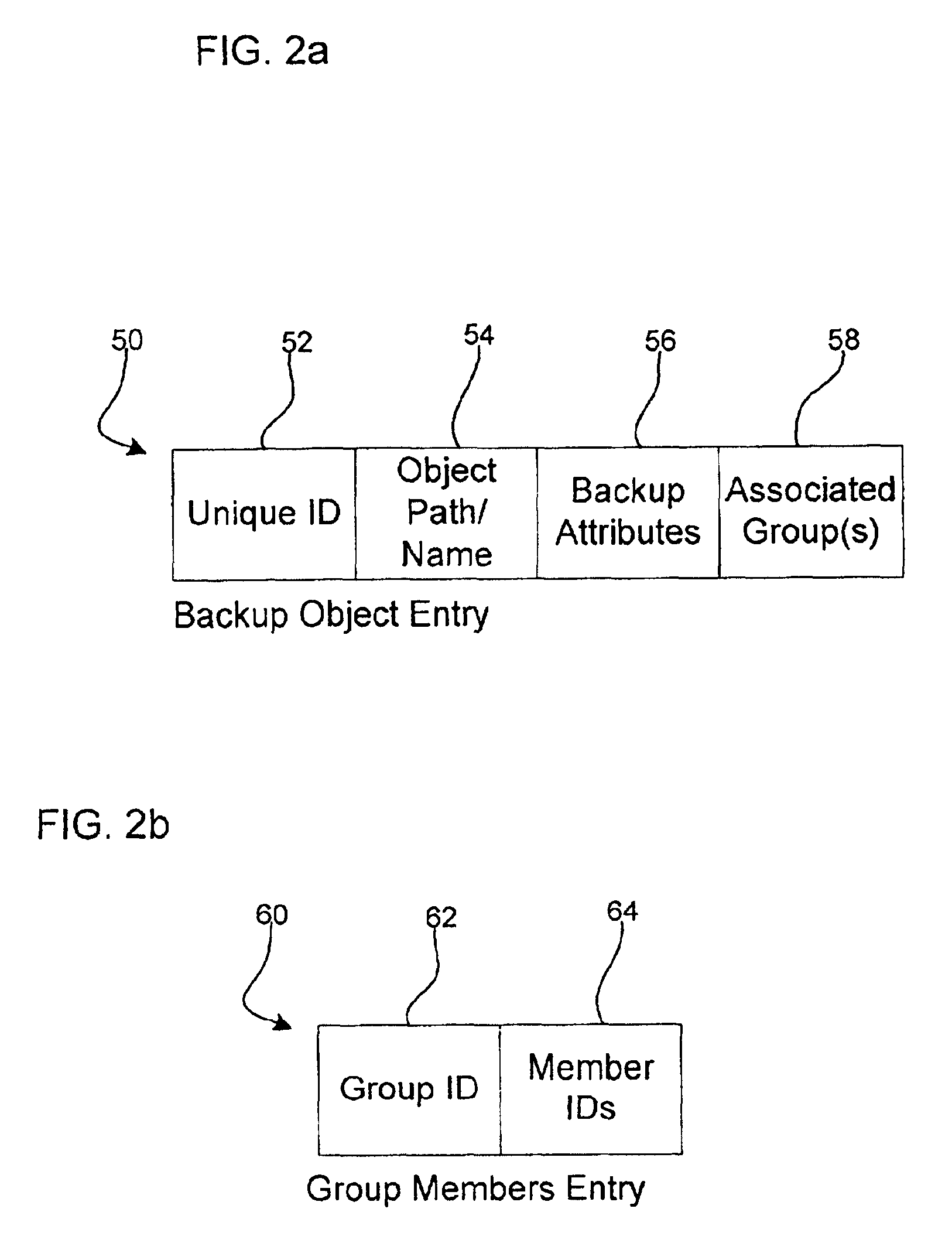
Method, system, and program for backing up objects by creating groups of objects
Provided are a system, method, and program for grouping backup objects stored in backup storage. A backup group is created and a plurality of backup objects are added as members of the backup group in separate backup transactions. The backup objects added to the backup group are stored to backup storage.
Owner:INT BUSINESS MASCH CORP
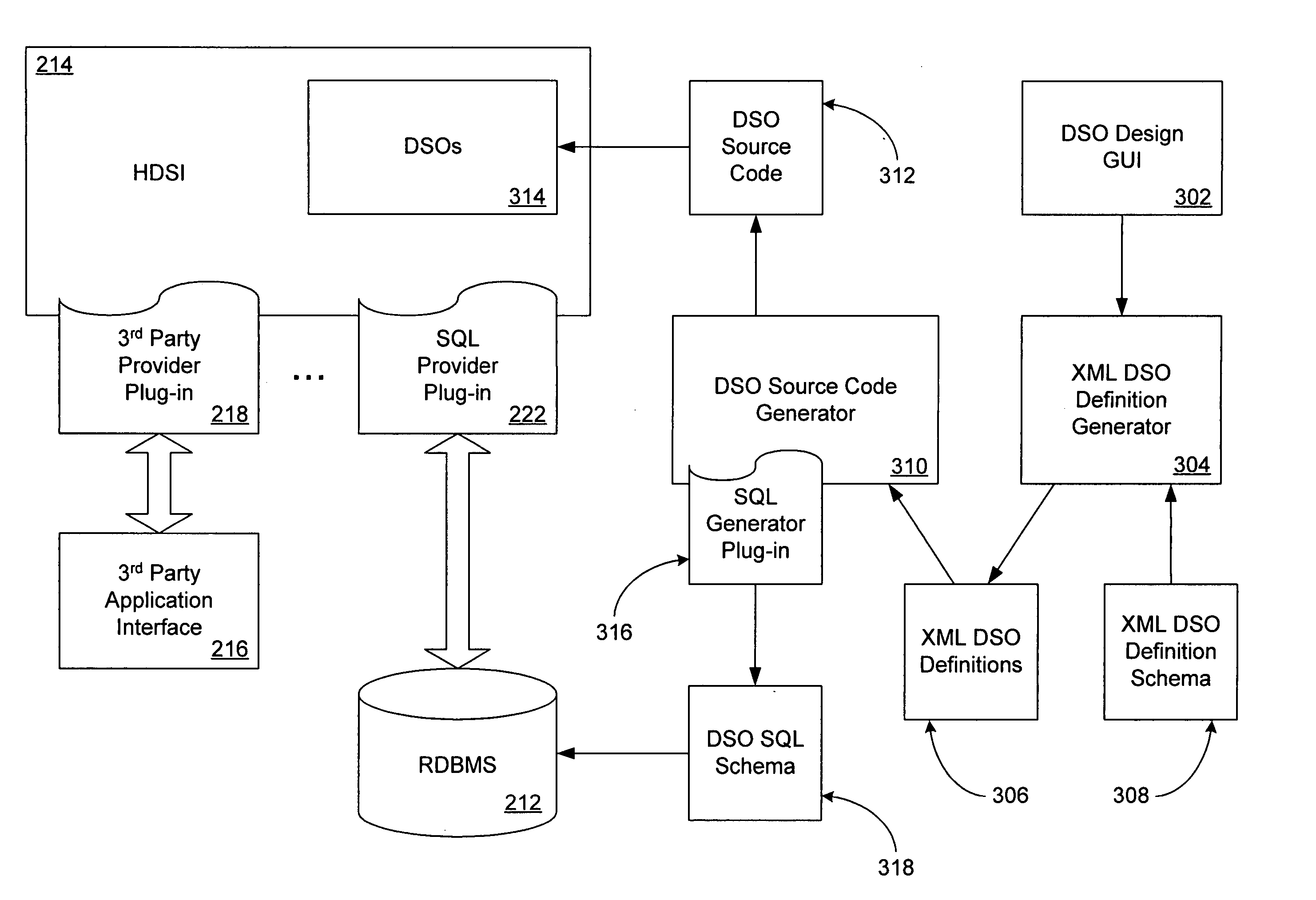
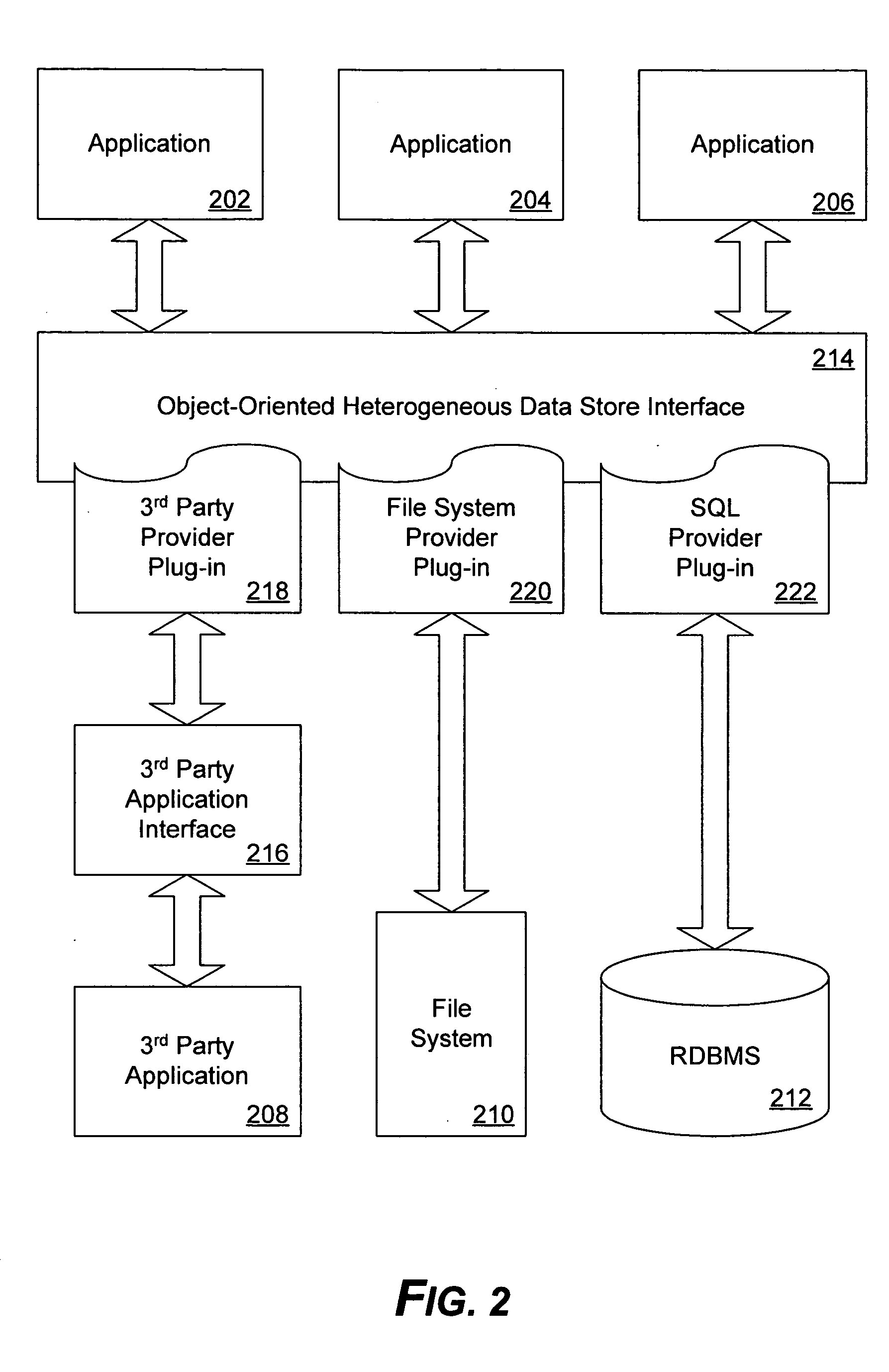
System and method for object-oriented interaction with heterogeneous data stores
InactiveUS20050108206A1Object oriented databasesSpecial data processing applicationsGraphicsObject store
Modern enterprises have multiple dissimilar data stores. Collectively, the enterprise data stores store a set of enterprise data objects, typically in multiple dissimilar formats. An object-oriented heterogeneous data store interface (HDSI) for interacting with such enterprise data stores and data objects is described. The HDSI may include a query component, a data store component and a provider interface that specifies a query behavior with a query component parameter. For each type of data store, there may be a provider plug-in to the HDSI. Each provider plug-in may include provider components that conform to the provider interface. The HDSI may further include data store object components corresponding to data objects stored in the data stores. A data store object design GUI may be utilized to build graphical representations of data objects. A data store object source code generator may generate object-oriented programming language source code for each data store object component.
Owner:MICROSOFT TECH LICENSING LLC
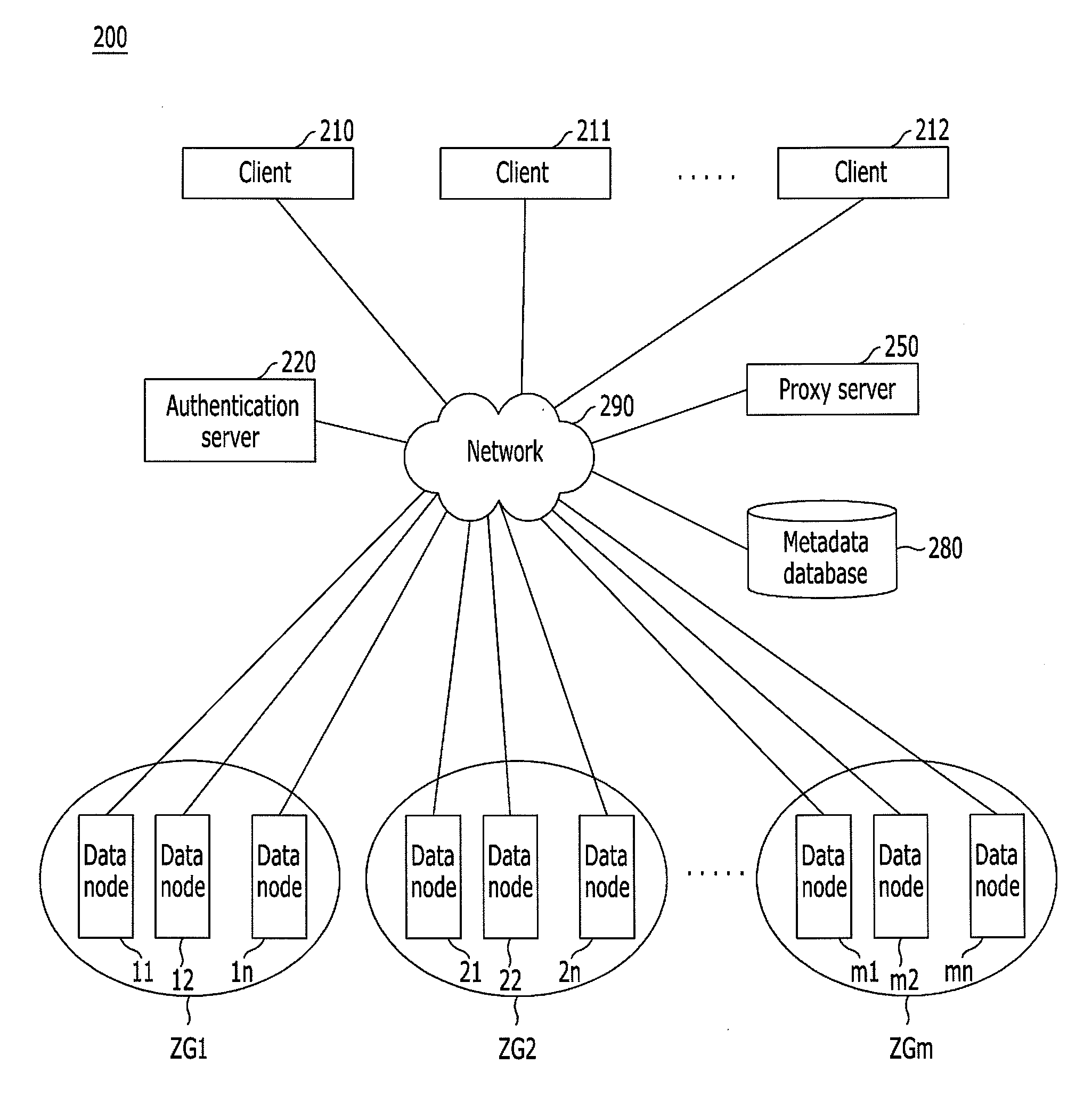
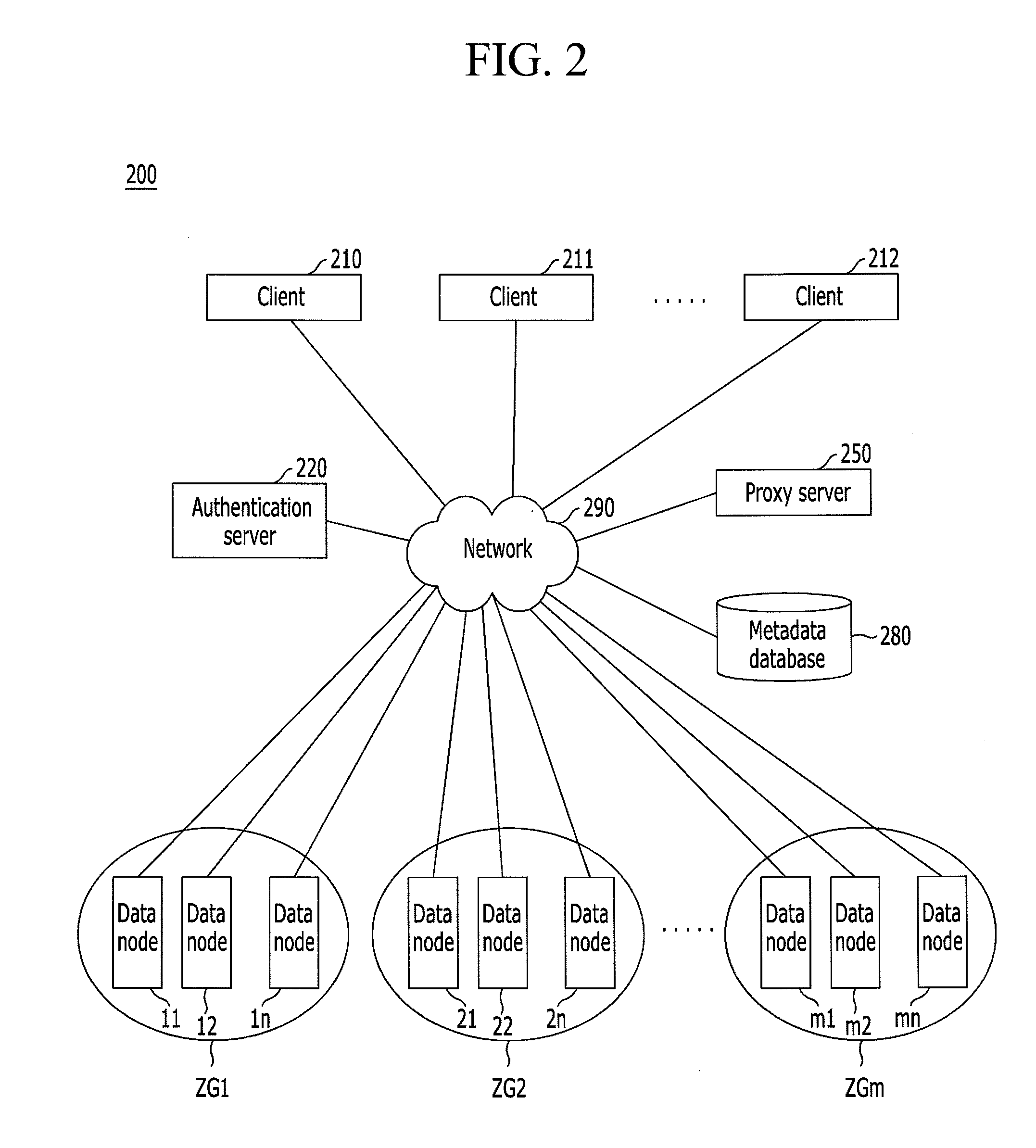
Distributed storage system having content-based deduplication function and object storing method
InactiveUS20120166403A1Eliminate redundancyEfficient executionDigital data information retrievalDigital data processing detailsObject storeObject storage
Distributed storage system having content-based deduplication function and object storing method. The distributed storage system may include a plurality of data nodes and a server coupled with the plurality of data nodes. Each one of the plurality of data nodes may be configured to store at least one object. The server may be configured to perform a deduplication function based on a content-specific index of a target object and content-specific indexes of objects stored in the plurality of data nodes in response to an object storage request from a client, and configured to store the target object in one of the plurality of data nodes based on a result of the deduplication function performed by the server.
Owner:KT CORP
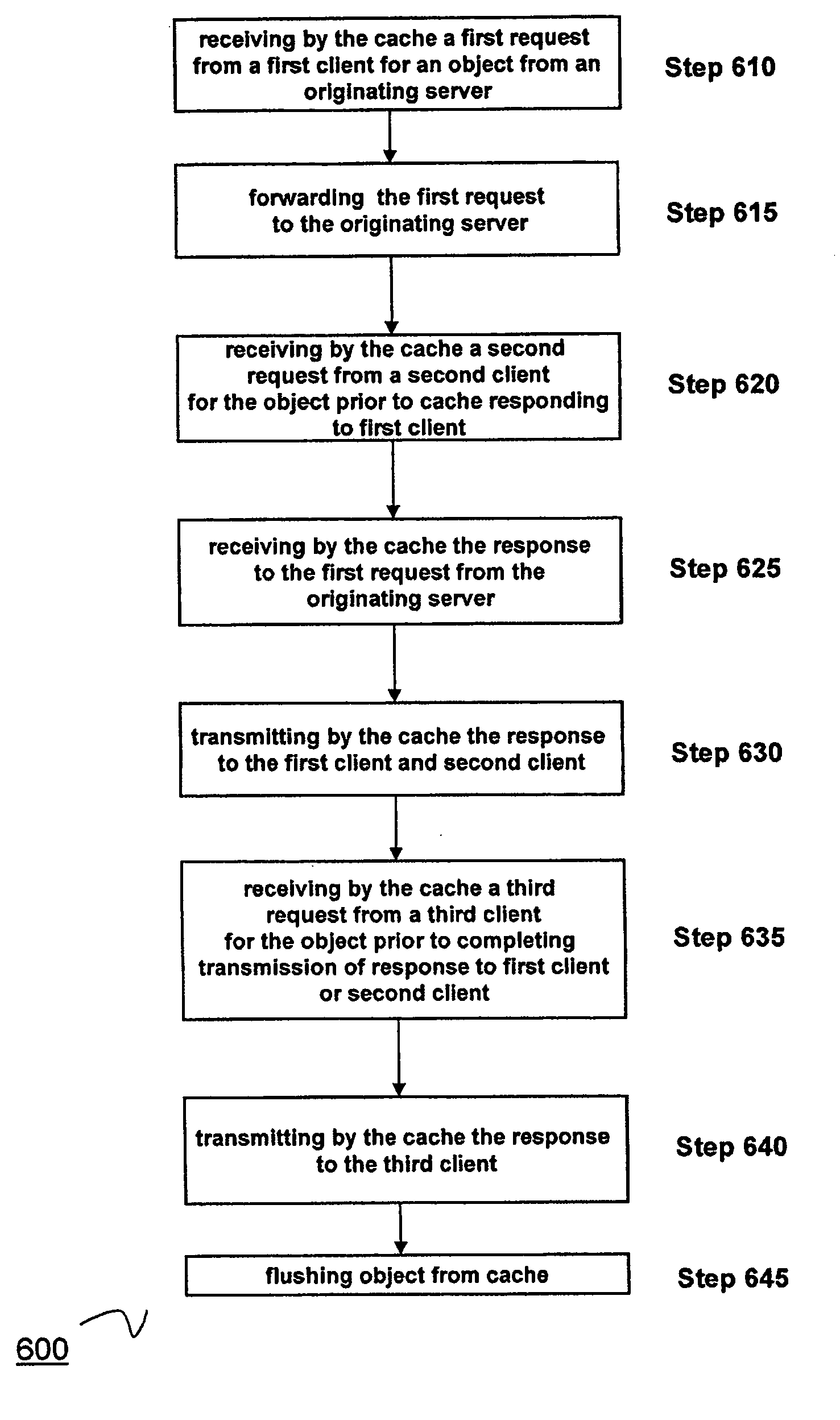
System and method for performing flash caching of dynamically generated objects in a data communication network
ActiveUS20070156876A1Improve cache hit ratioQuick changeMultiprogramming arrangementsMultiple digital computer combinationsObject storeClient-side
The present invention is directed towards a method and system for providing a technique referred to as flash caching to respond to requests for an object, such as a dynamically generated object, from multiple clients. This technique of the present invention uses a dynamically generated object stored in a buffer for transmission to a client, for example in response to a request from the client, to also respond to additional requests for the dynamically generated object from other clients while the object is stored in the buffer. Using this technique, the present invention is able to increase cache hit rates for extremely fast changing dynamically generated objects that may not otherwise be cacheable.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com