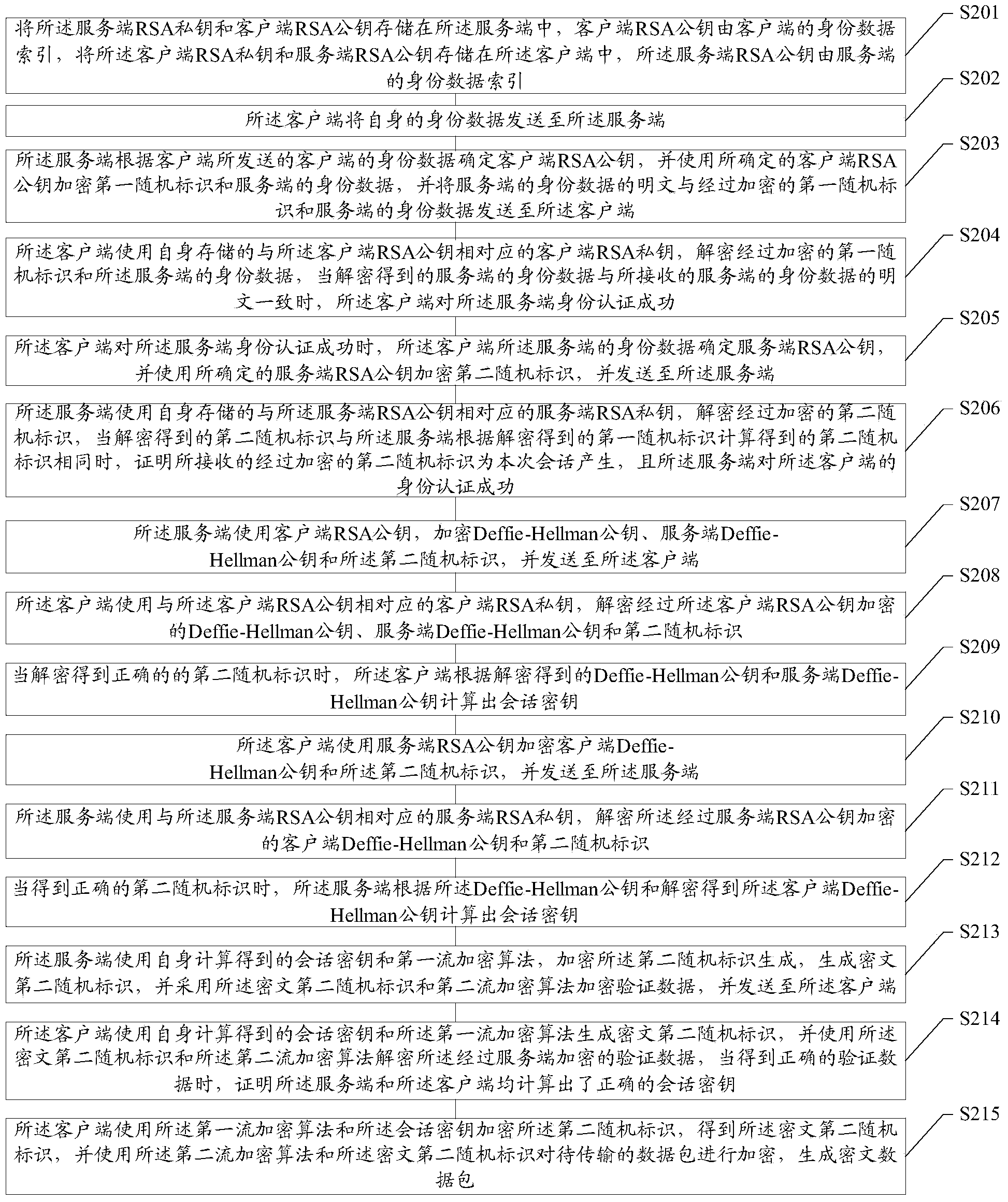Patents
Literature
3172results about How to "Save computing resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
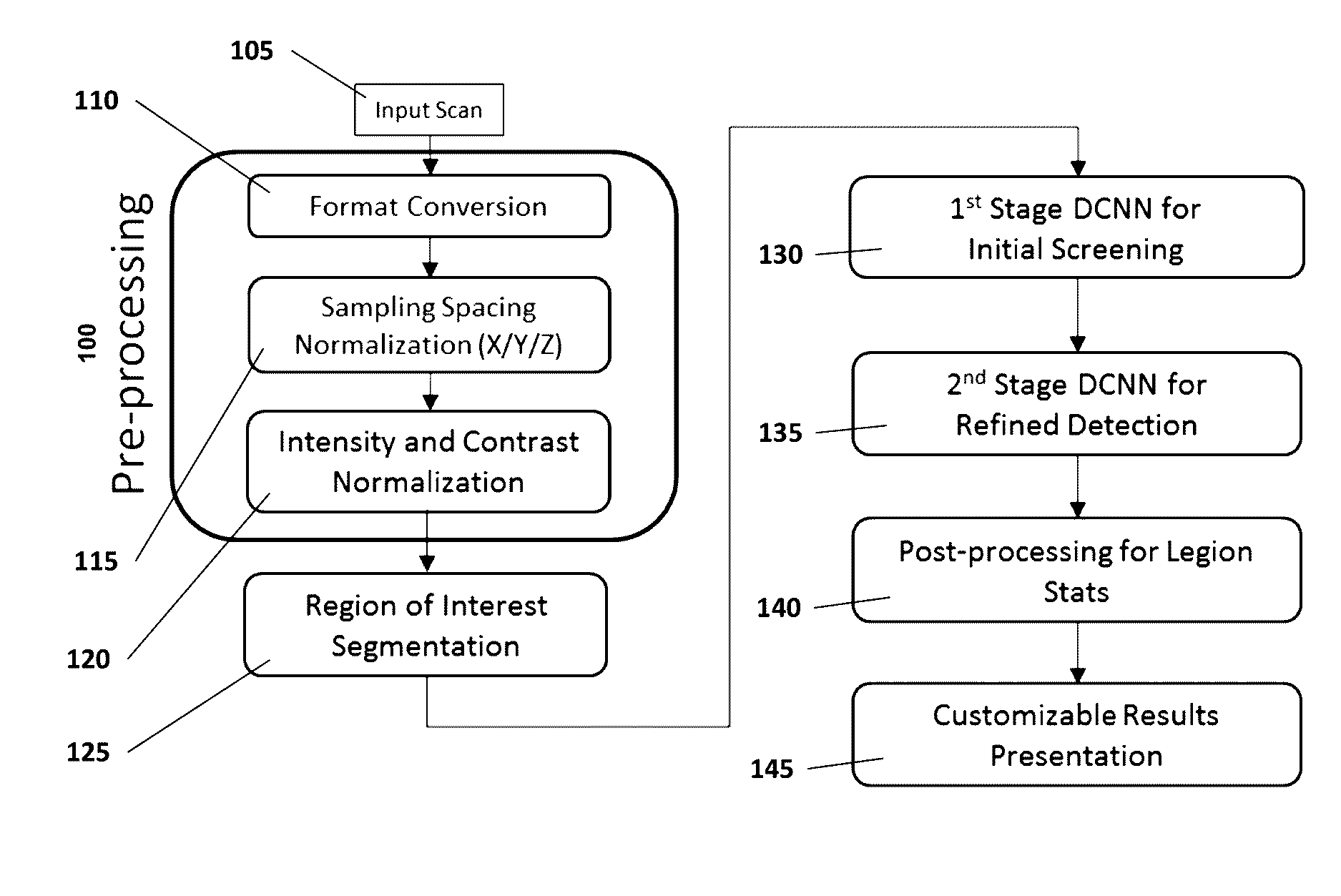
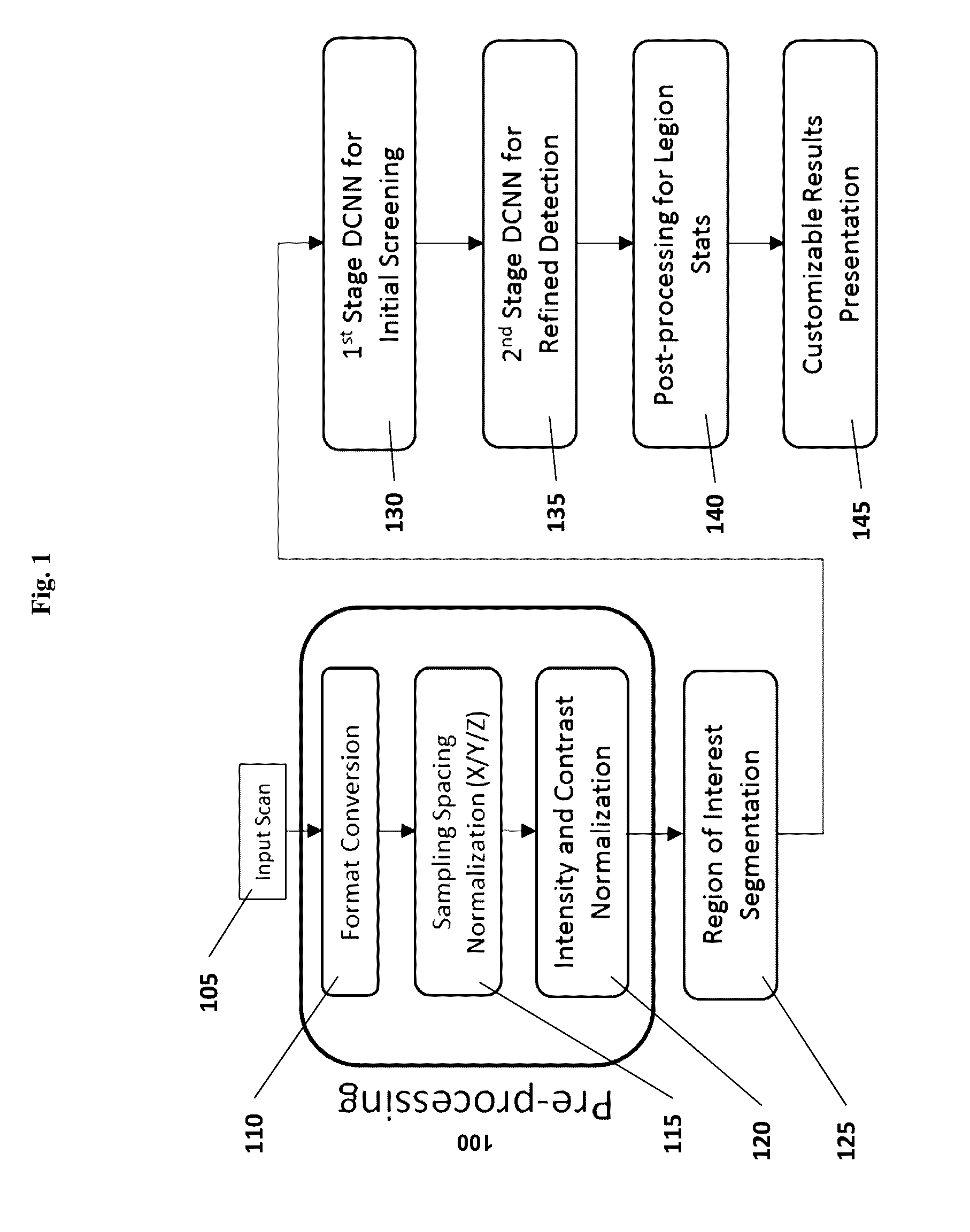
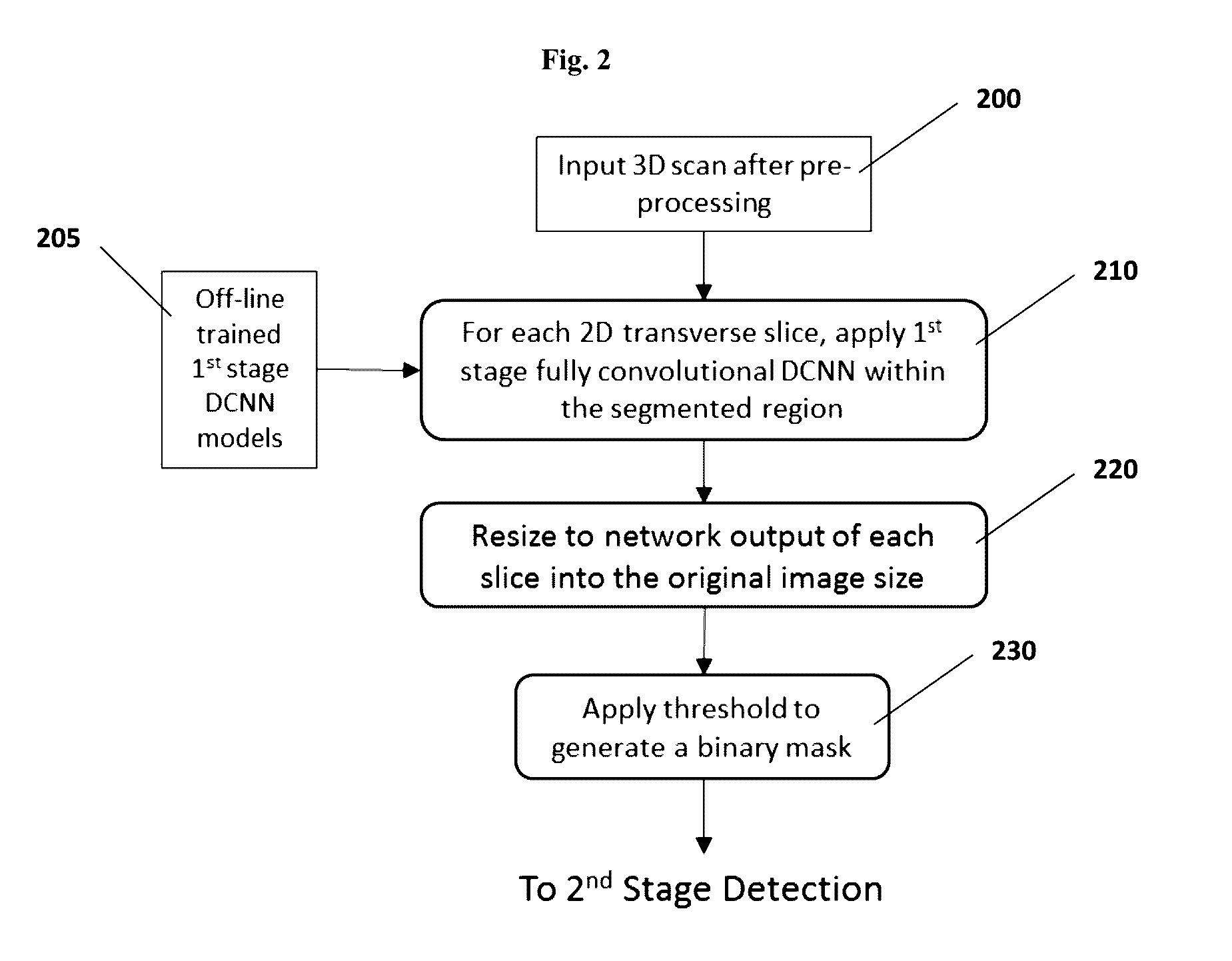
Computer-aided diagnosis system for medical images using deep convolutional neural networks
InactiveUS9589374B1Examination time can be shortenedImprove diagnostic accuracyUltrasonic/sonic/infrasonic diagnosticsImage enhancementComputer visionAided diagnosis
Owner:12 SIGMA TECH
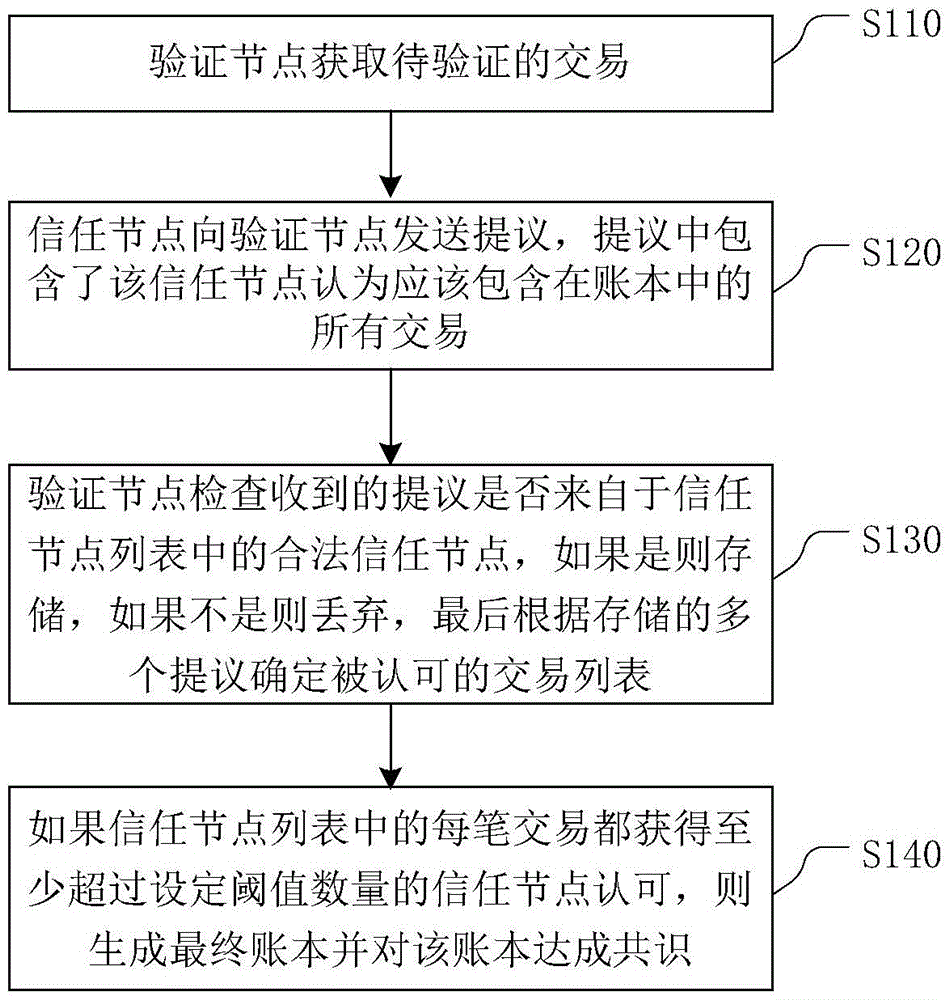
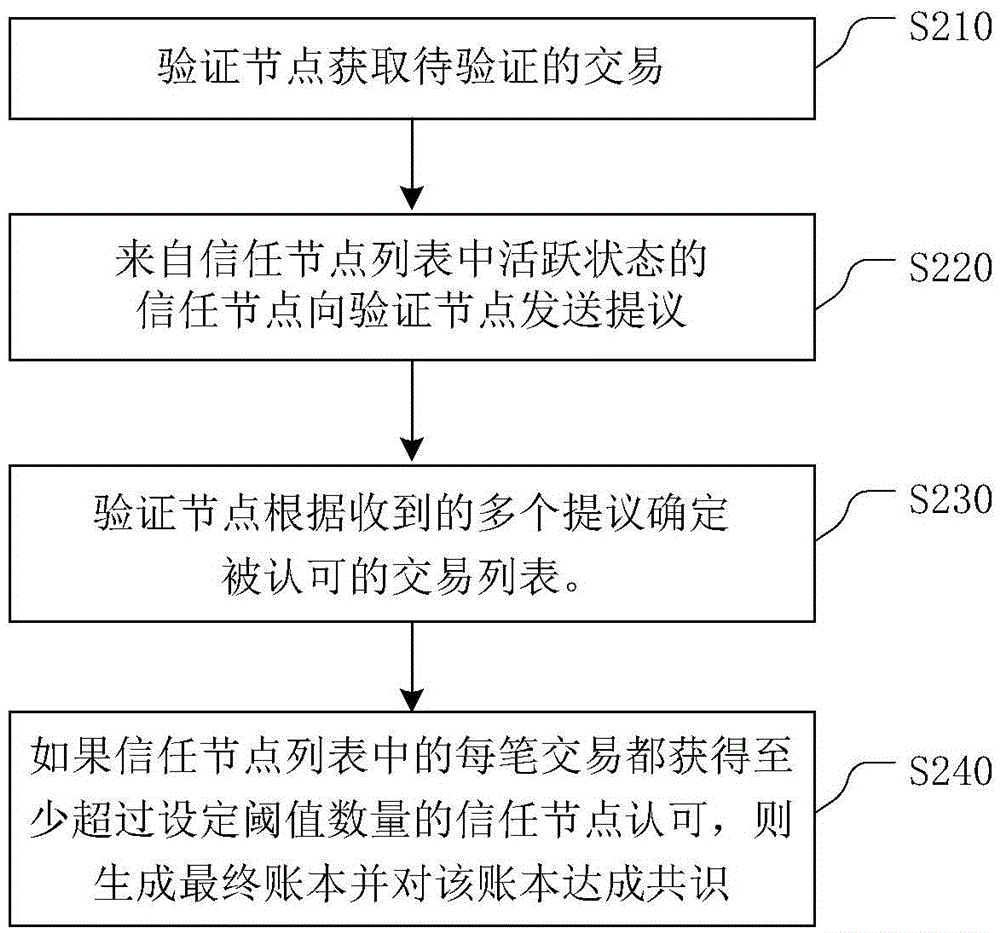
Decentralized transaction method
InactiveCN105488665AShorten transaction confirmation verification timeAvoid exploiting vulnerabilitiesFinancePayment protocolsThe InternetDigital asset
The invention relates to digital asset transactions in the internet and provides a decentralized transaction method. The method comprises the steps that a verification node obtains a to-be-verified transaction; a trusted node sends a proposal to the verification node, wherein the proposal contains all transactions regarded to should be contained in an account book by the trusted node; the verification node checks whether the received proposal is from a legal trusted node in a trusted node list or not, if yes, the proposal is stored, if not, the proposal is discarded, and finally an approved transaction list is determined according to a plurality of stored proposals; and if each transaction in the trusted node list obtains trusted node approvals with a number at least exceeding a set threshold, a final account book is generated and a consensus is reached for the account book. According to the method, the transaction confirmation verification time can be shortened and large amounts of computing resources are saved.
Owner:BUBI BEIJING NETWORK TECH CO LTD
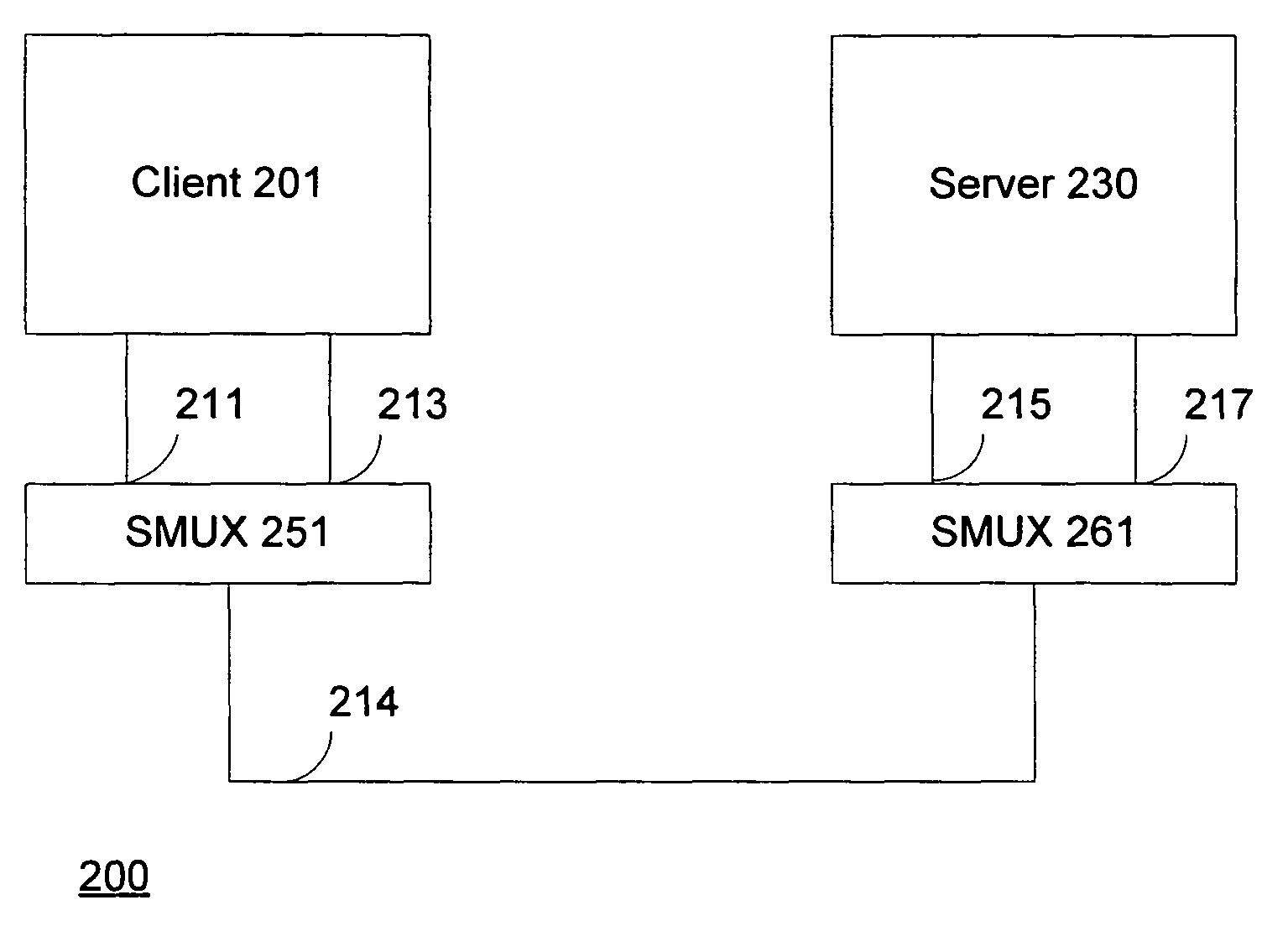
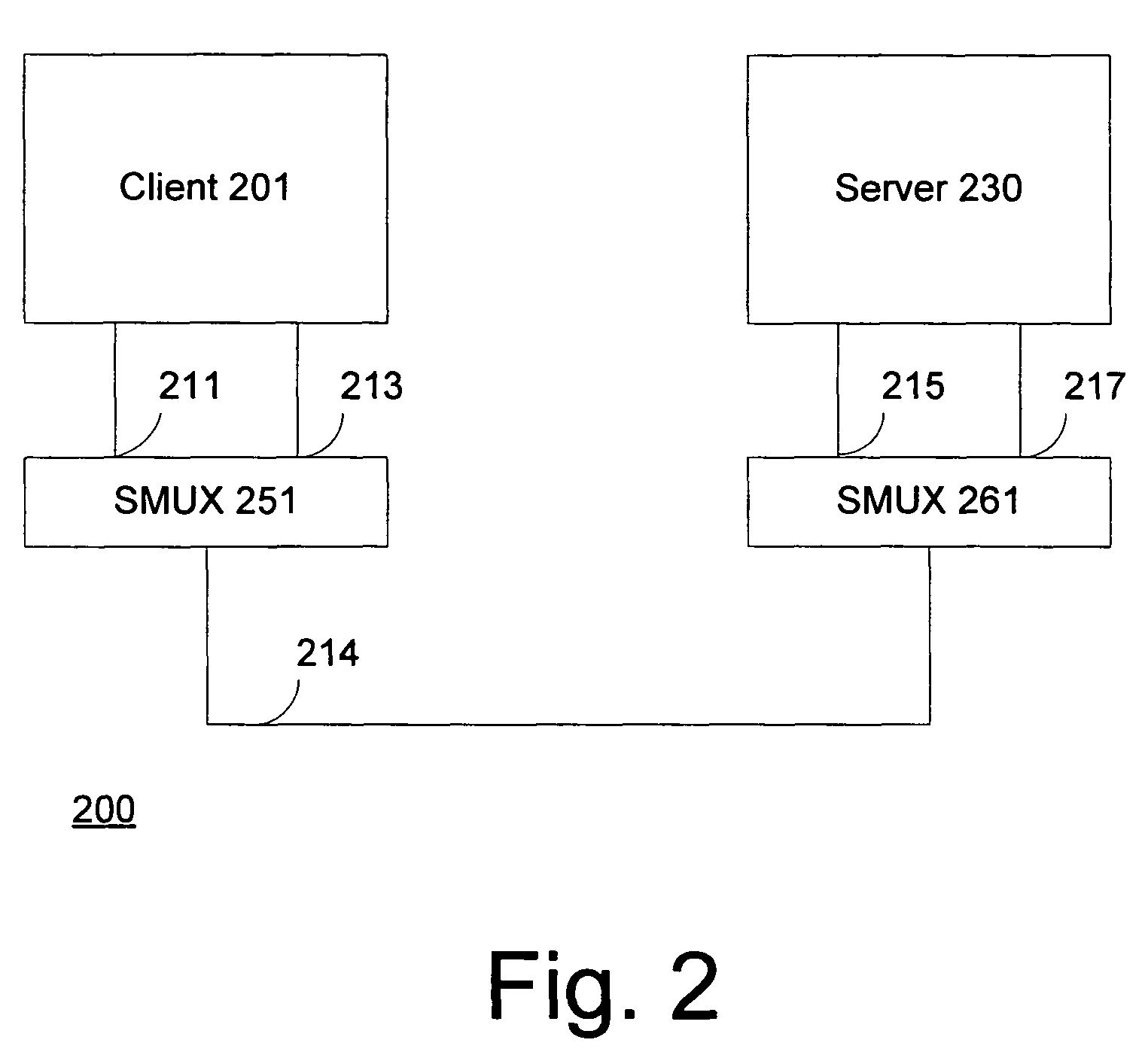
Session multiplex protocol
InactiveUS7966405B2Bandwidth is no longer wastedSave computing resourcesEnergy efficient ICTData switching by path configurationMultiplexingByte
Session multiplex protocol (“SMUX”) is a protocol layered above existing reliable transport mechanisms that can be used to create multiple sessions over a single connection. Data from several different SMUX sessions can be interleaved and message boundaries preserved. Because it sits on top of reliable transport mechanisms, it takes advantage of the underlying protocols to ensure byte-alignment, loss detection / recovery, and reliable delivery. It provides a window based flow control mechanism to ensure suitable fairness among streams of different sessions and prevent deadlocks.
Owner:MICROSOFT TECH LICENSING LLC
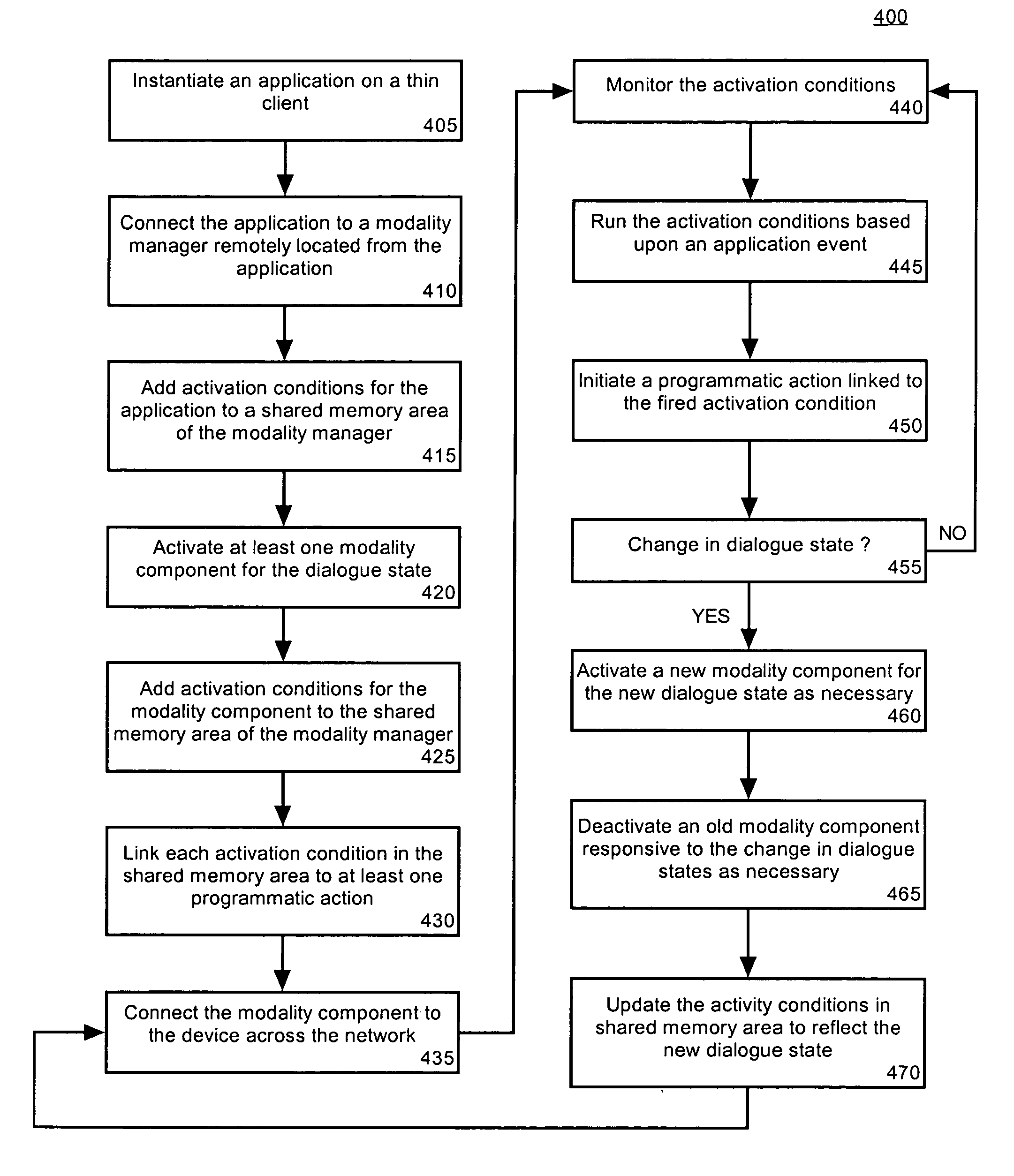
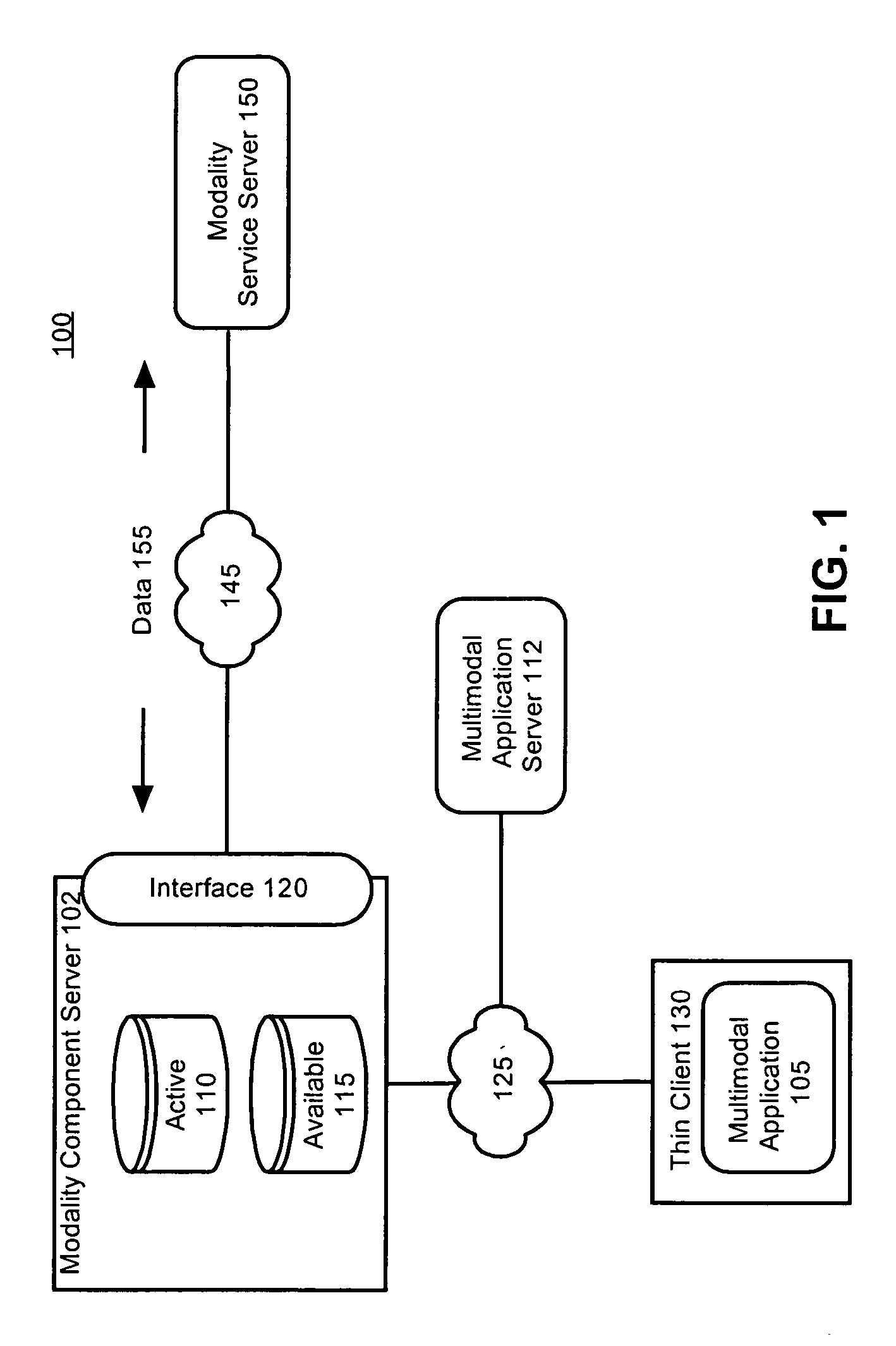
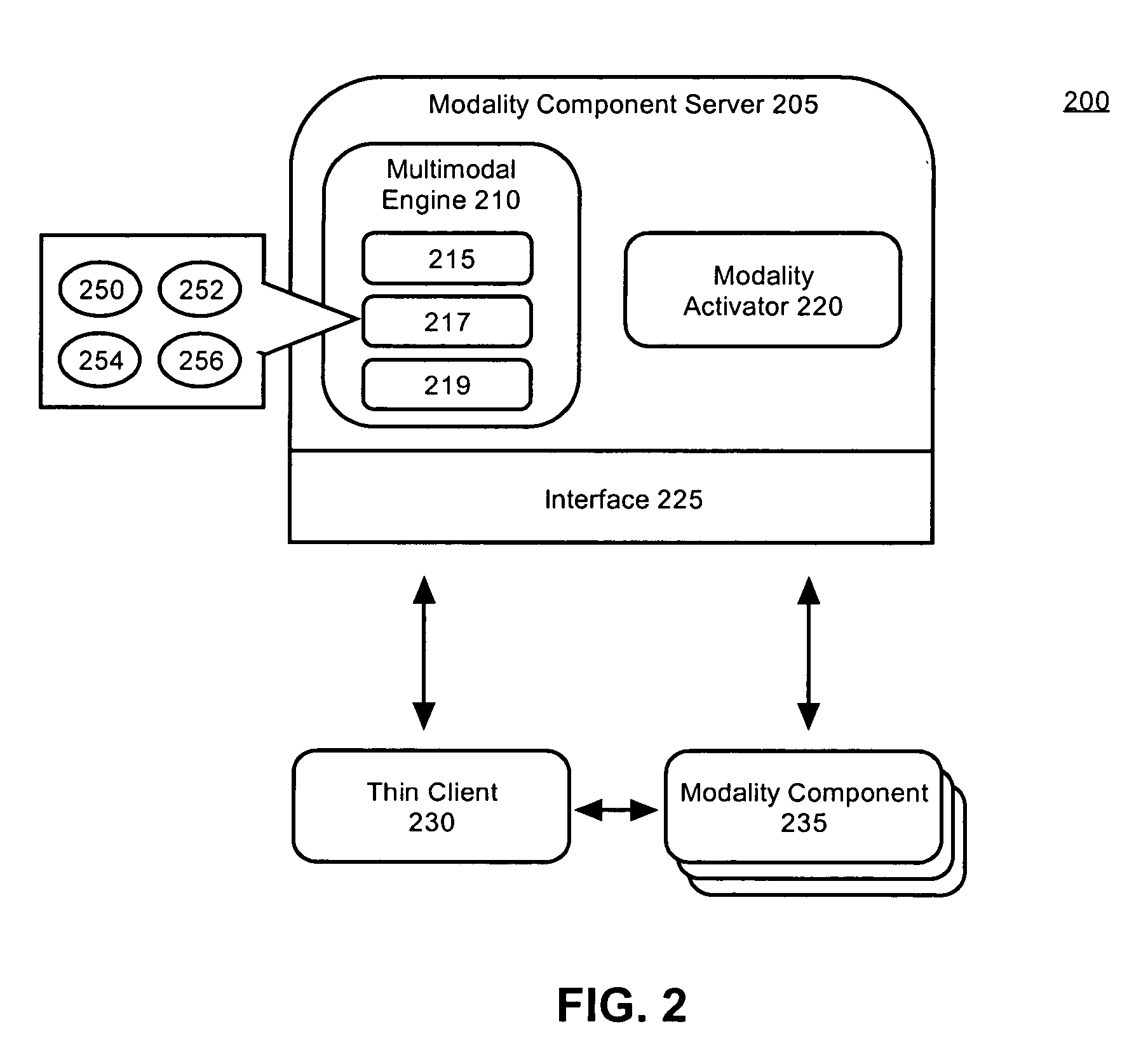
Application module for managing interactions of distributed modality components
ActiveUS20050138647A1Save computing resourcesMultiprogramming arrangementsExecution for user interfacesDiagnostic Radiology ModalityState dependent
Owner:NUANCE COMM INC
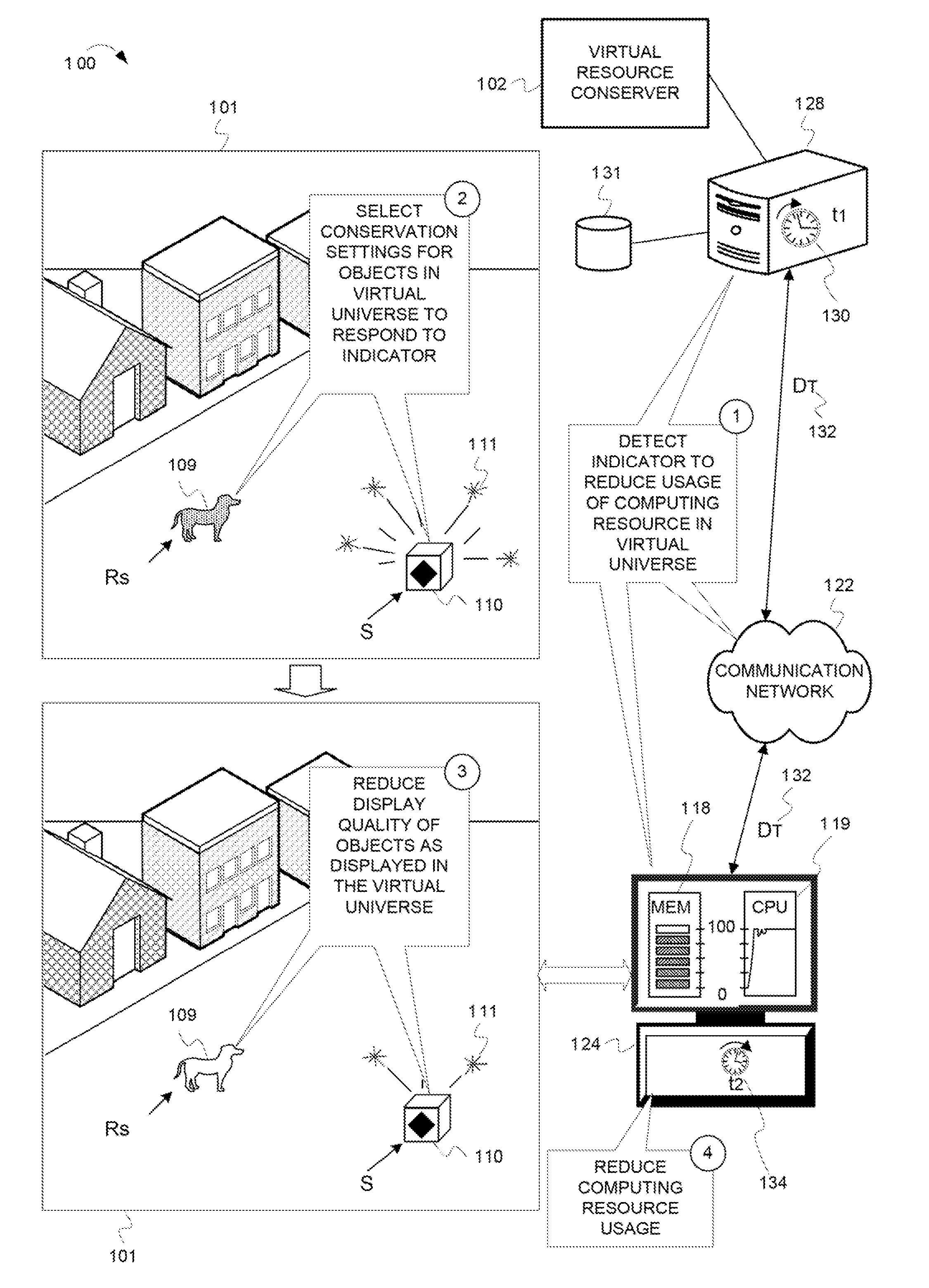
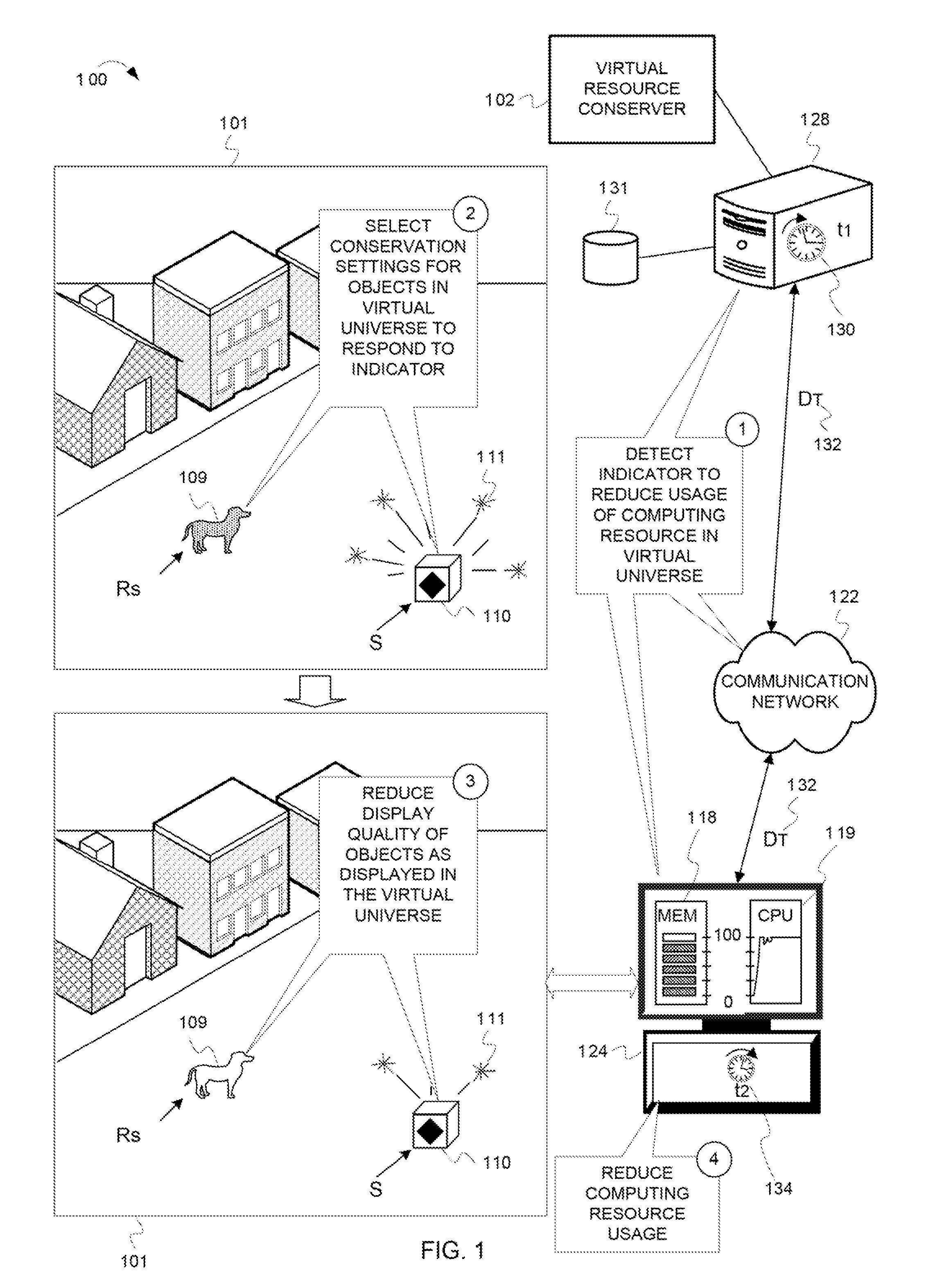
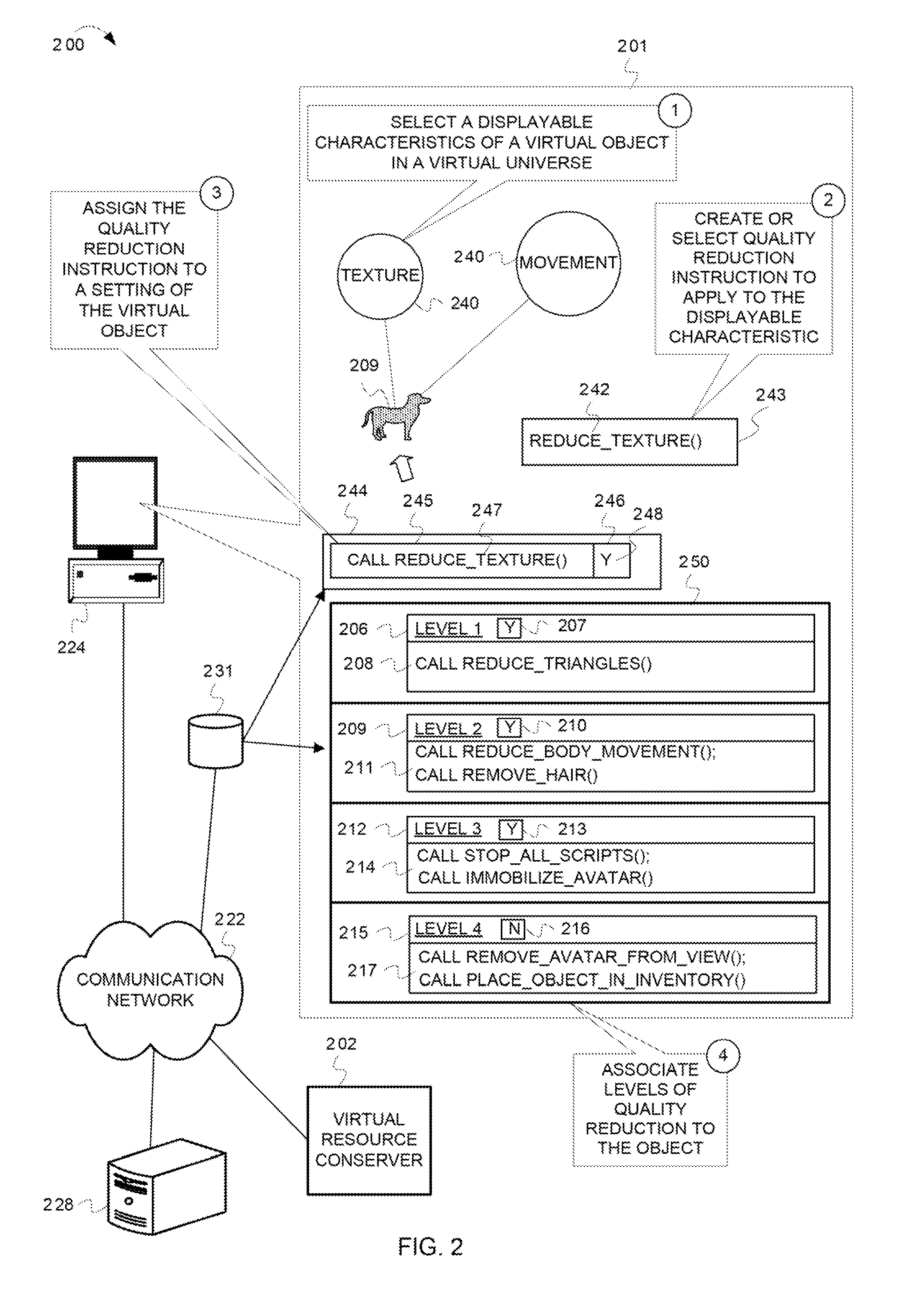
Reducing a display quality of an area in a virtual universe to conserve computing resources
ActiveUS8013861B2Quality improvementReduce displayAnimationVideo gamesHuman–computer interactionVirtual universe
Described herein are processes and devices that reduce a display quality of an area of a virtual universe to conserve computing resources. One of the devices described is a virtual resource conserver. The virtual resource conserver determines, or selects, an area in the virtual universe. A computing resource processes data for presenting the area in the virtual universe. The virtual resource conserver evaluates significance factors about the area to determine a significance of how the area is being used, or an extent to which an area is being viewed by an avatar. The virtual resource conserver reduces a display quality of the area based on the significance of how the area is being used or viewed. The virtual resource conserver thus reduces usage of the computing resource.
Owner:ACTIVISION PUBLISHING
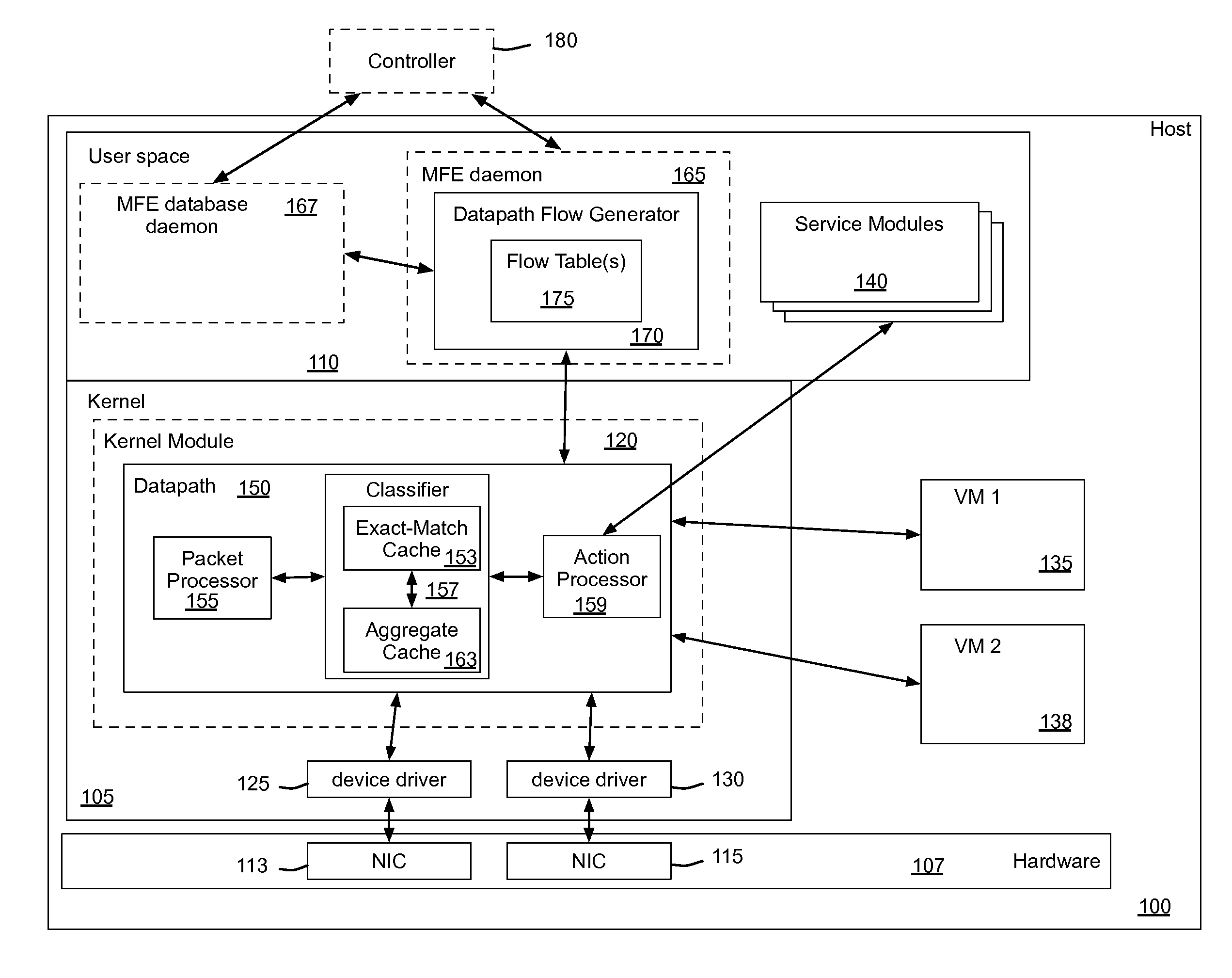
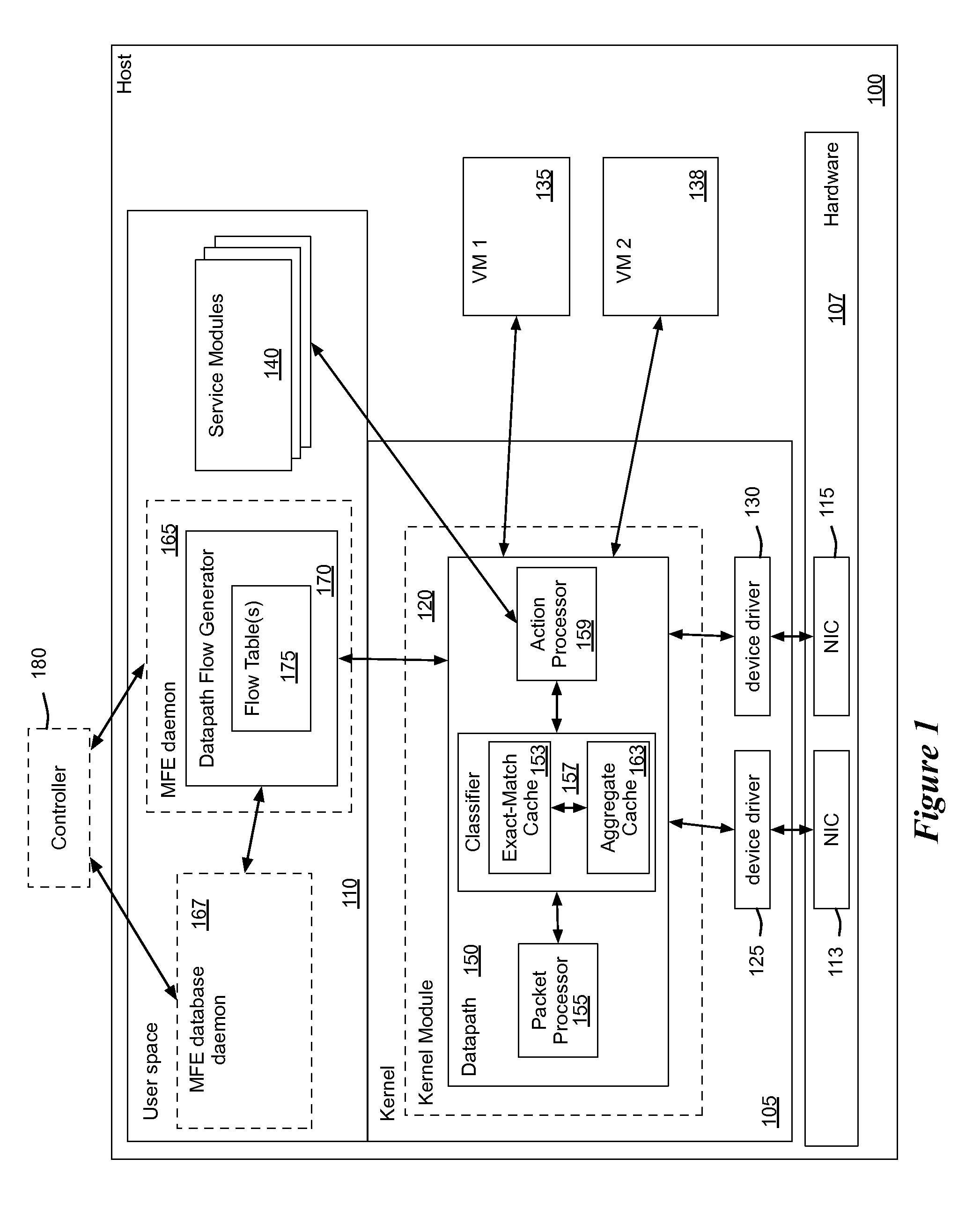
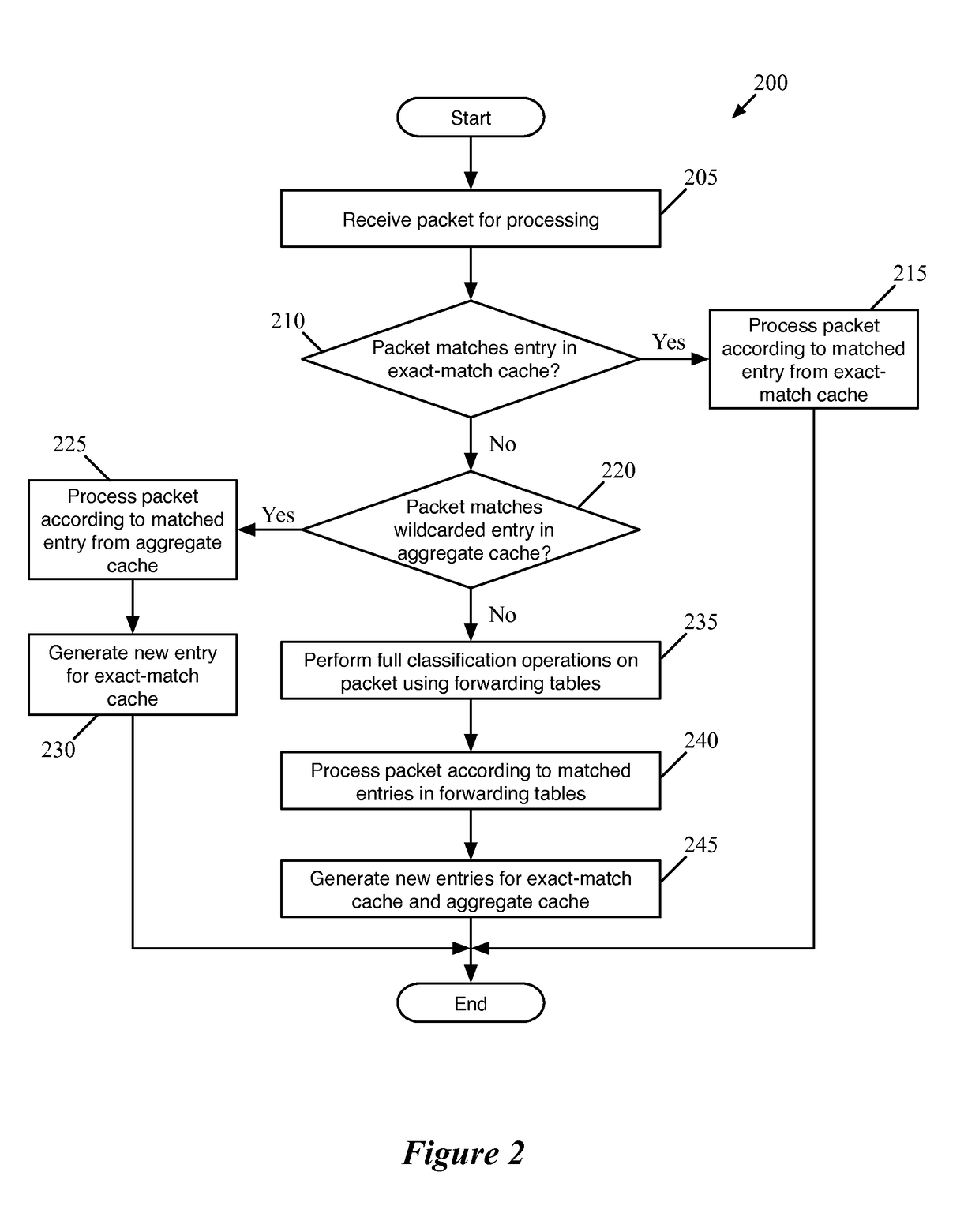
Flow Cache Hierarchy
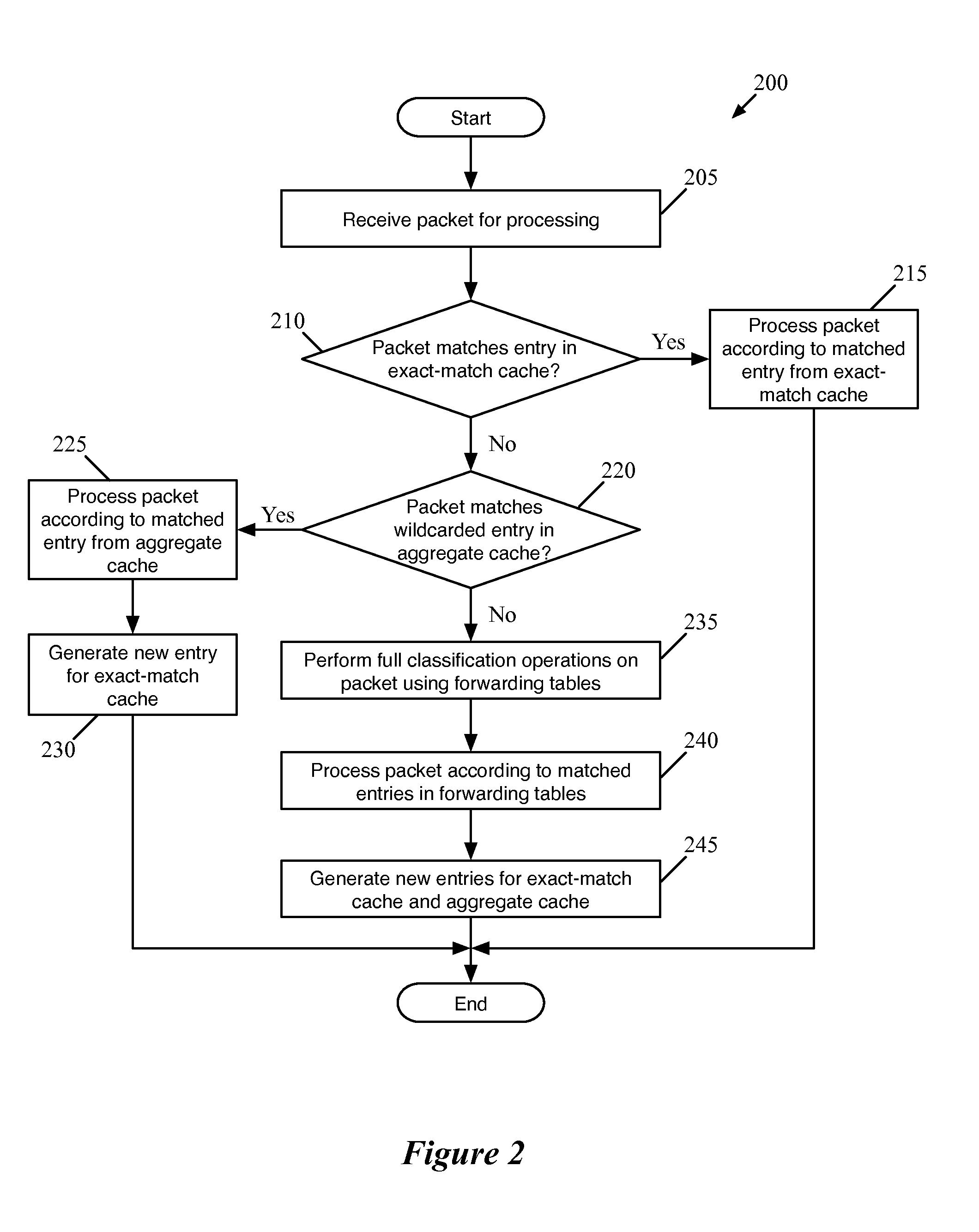
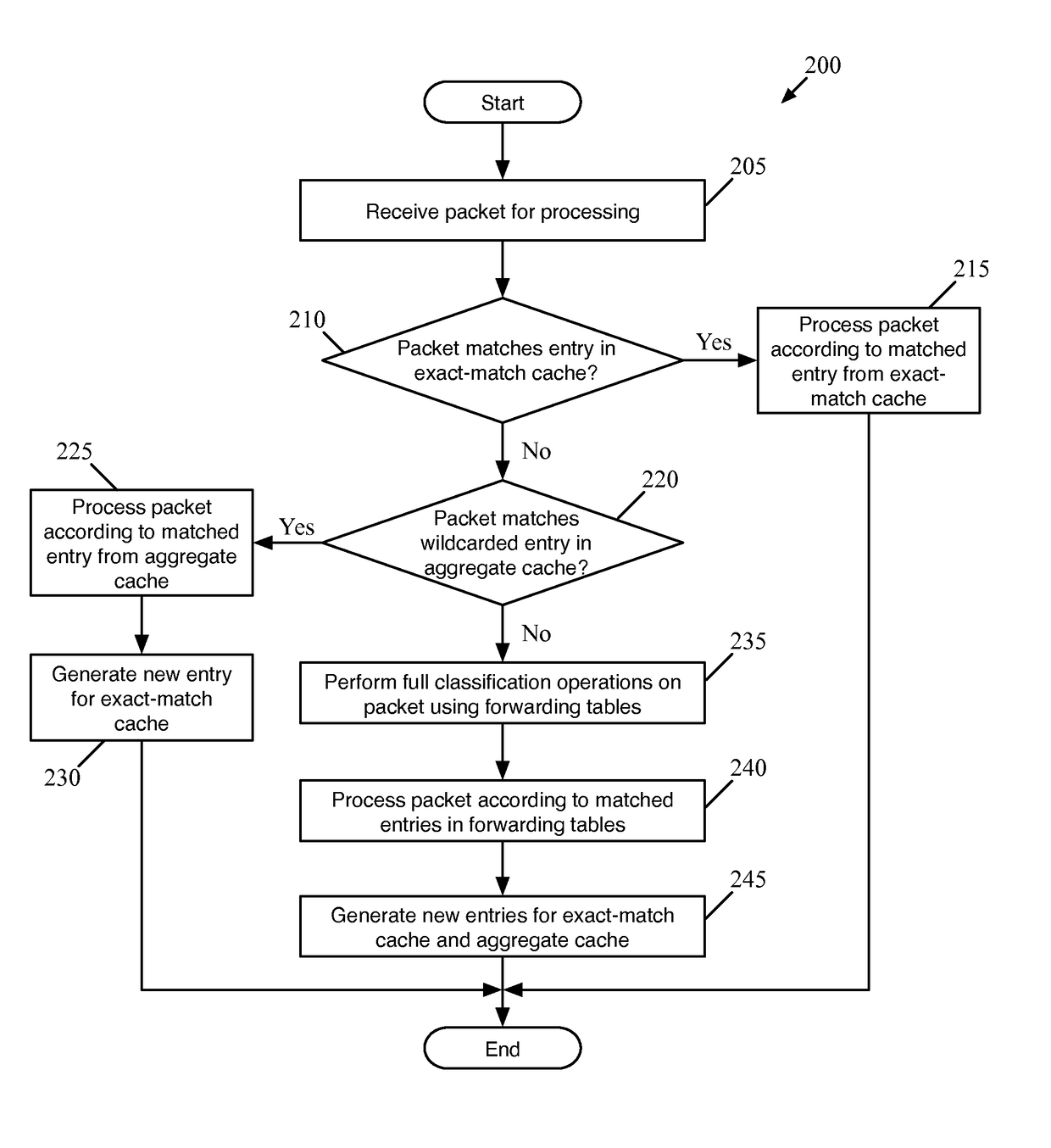
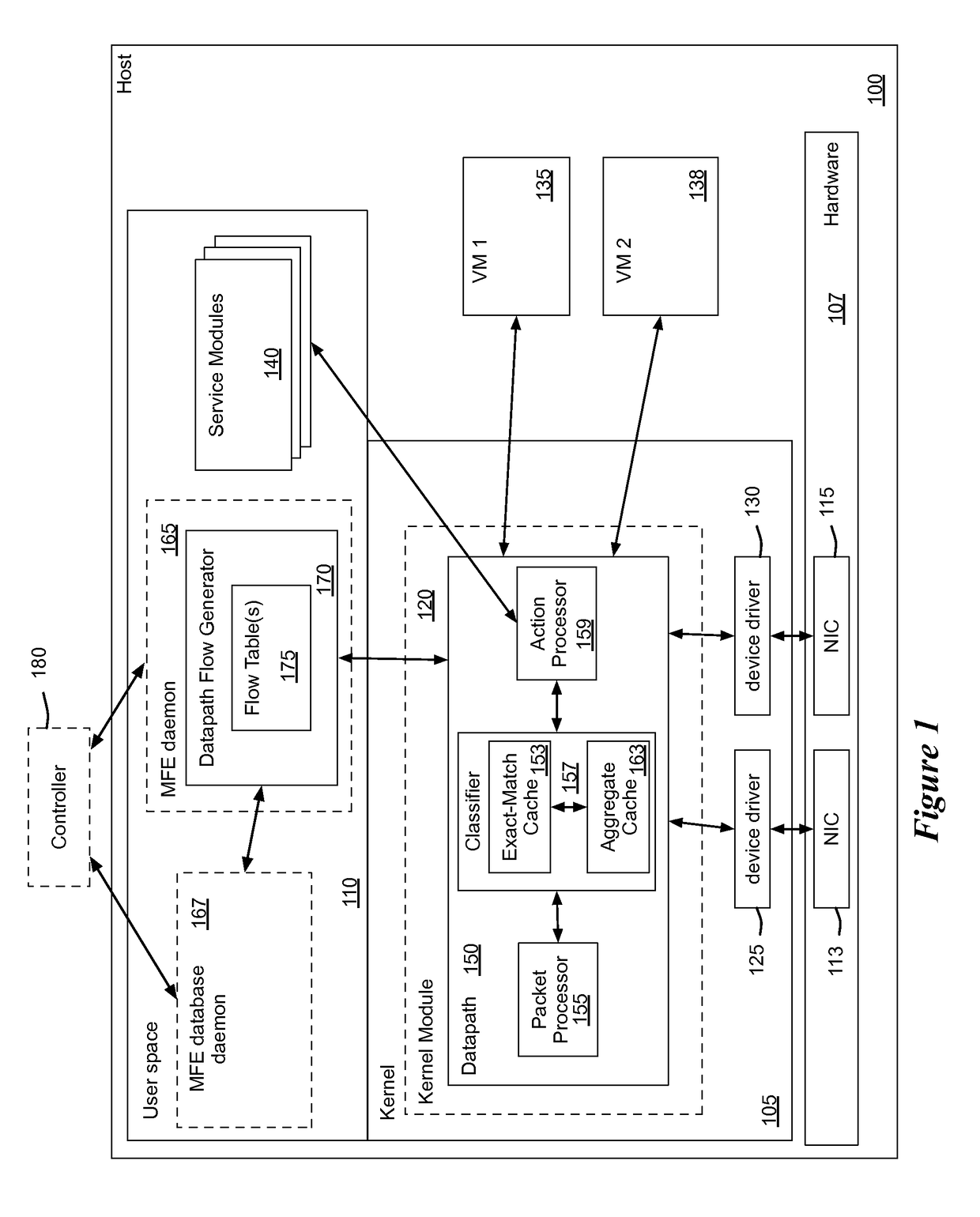
ActiveUS20150281098A1Save computing resourcesSave a lot of timeMemory architecture accessing/allocationError preventionExact matchCache hierarchy
Some embodiments provide a managed forwarding element (MFE that includes a set of flow tables including a first set of flow entries for processing packets received by the MFE. The MFE includes an aggregate cache including a second set of flow entries for processing packets received by the MFE. Each of the flow entries of the second set is for processing packets of multiple data flows. At least a subset of packet header fields of the packets of the multiple data flows have a same set of packet header field values, and a same set of operations is applied to said packets. The MFE includes an exact-match cache including a third set of flow entries for processing packets received by the MFE. Each of the flow entries of the third set is for processing packets for a single data flow having a unique set of packet header field values.
Owner:NICIRA
Target detection method based on a dense connection characteristic pyramid network
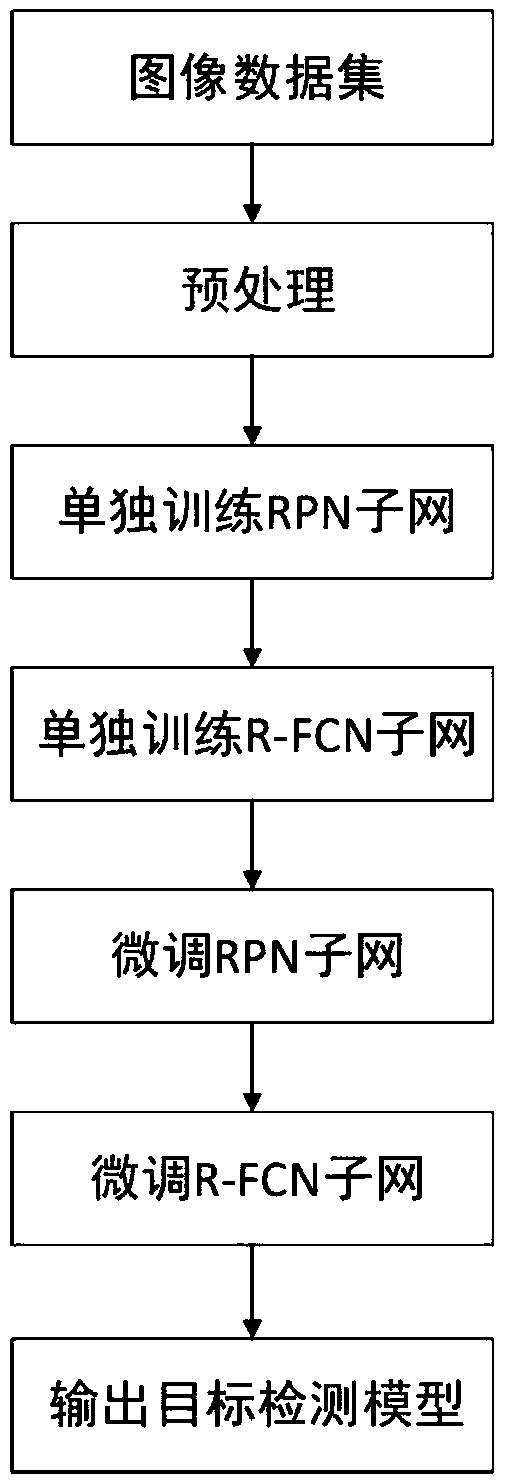
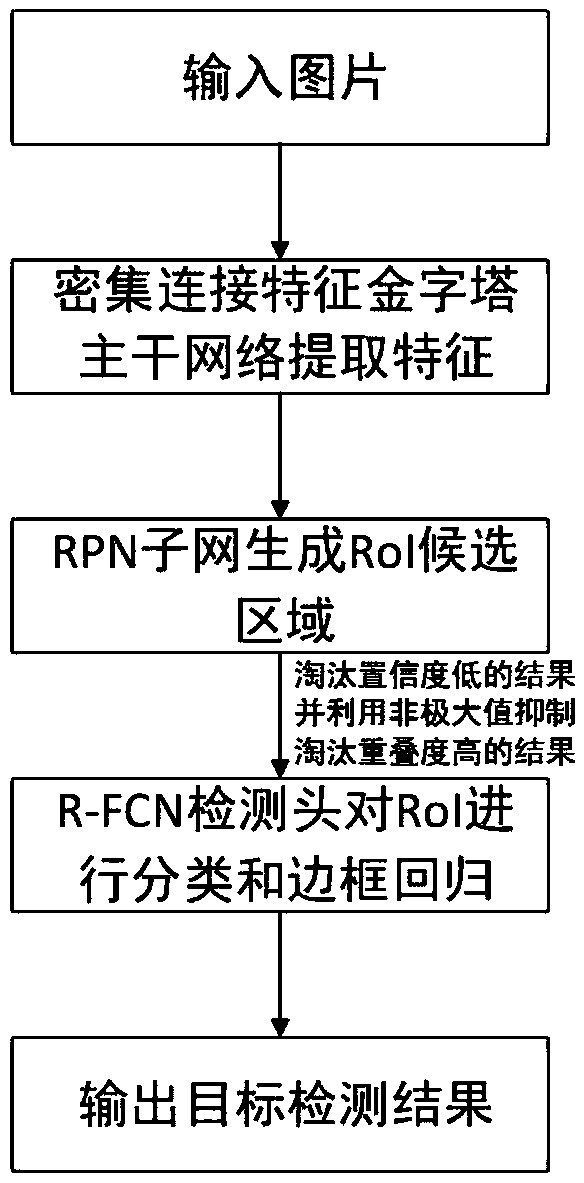
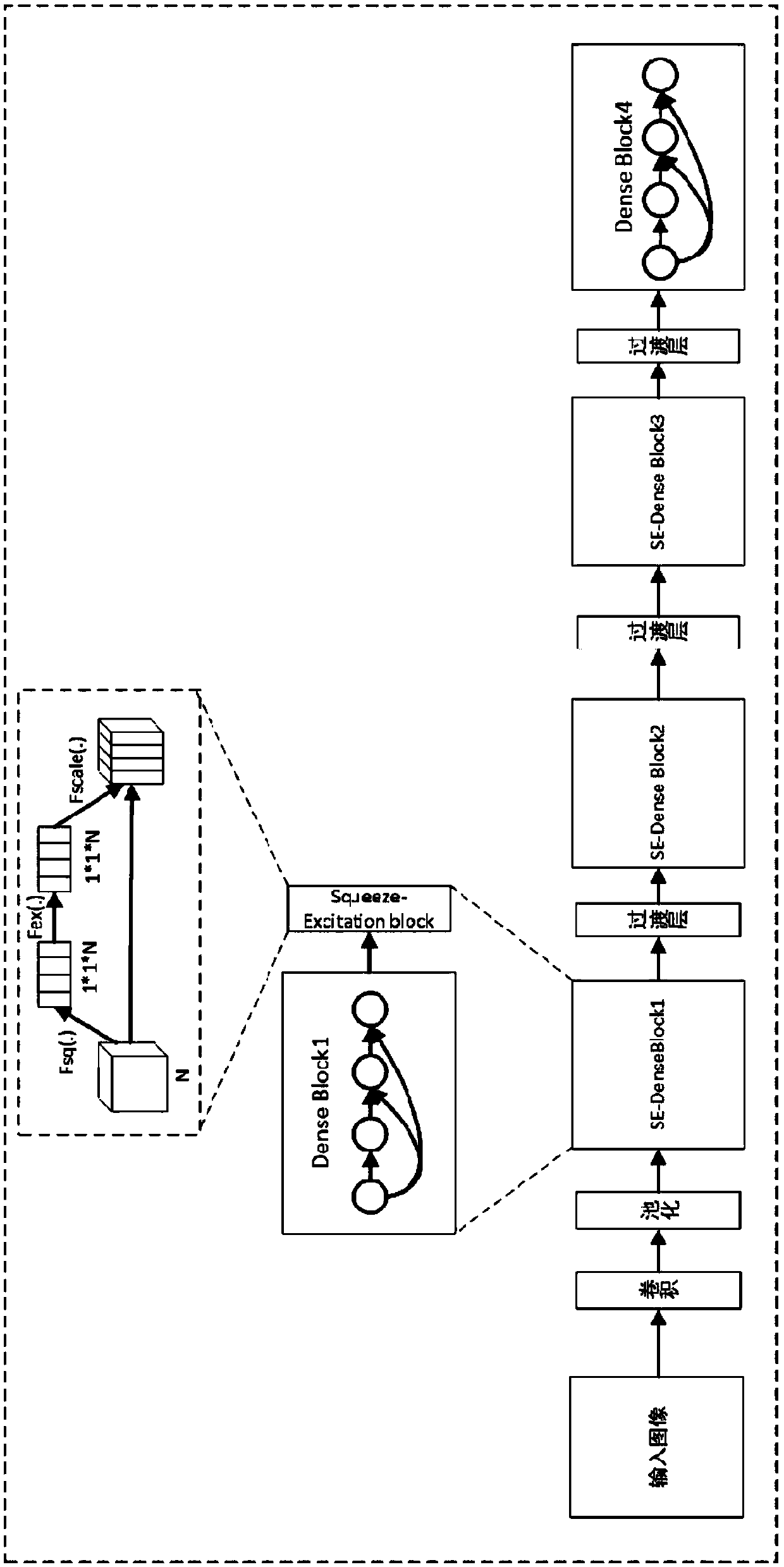
ActiveCN109614985AEnhanced Representational CapabilitiesImprove adaptabilityCharacter and pattern recognitionNeural architecturesData setImaging processing
The invention discloses a target detection method based on a dense connection characteristic pyramid network, and relates to the image processing and computer vision technology. The method comprises the steps of collecting an image data set labeled with a target bounding box and category information; constructing a dense connection feature pyramid network containing a Squeeze-Exciton structure capable of learning a dependency relationship between feature channels as a feature extraction backbone network; alternately training the RPN subnet and the R-FCN subnet to obtain a target detection model; and detecting a specific target in the image by using the model. The squeeze-Exciton structure and a dense connection structure are introduced into a feature extraction trunk network, characterization capability of the model is enhanced, adaptability of the model to targets of different sizes is enhanced through the feature pyramid structure, calculation sharing of the whole network model is achieved to the maximum degree through the R-FCN detection head, calculation resources are saved, and performance of the whole target detection model is improved. .
Owner:SOUTH CHINA UNIV OF TECH
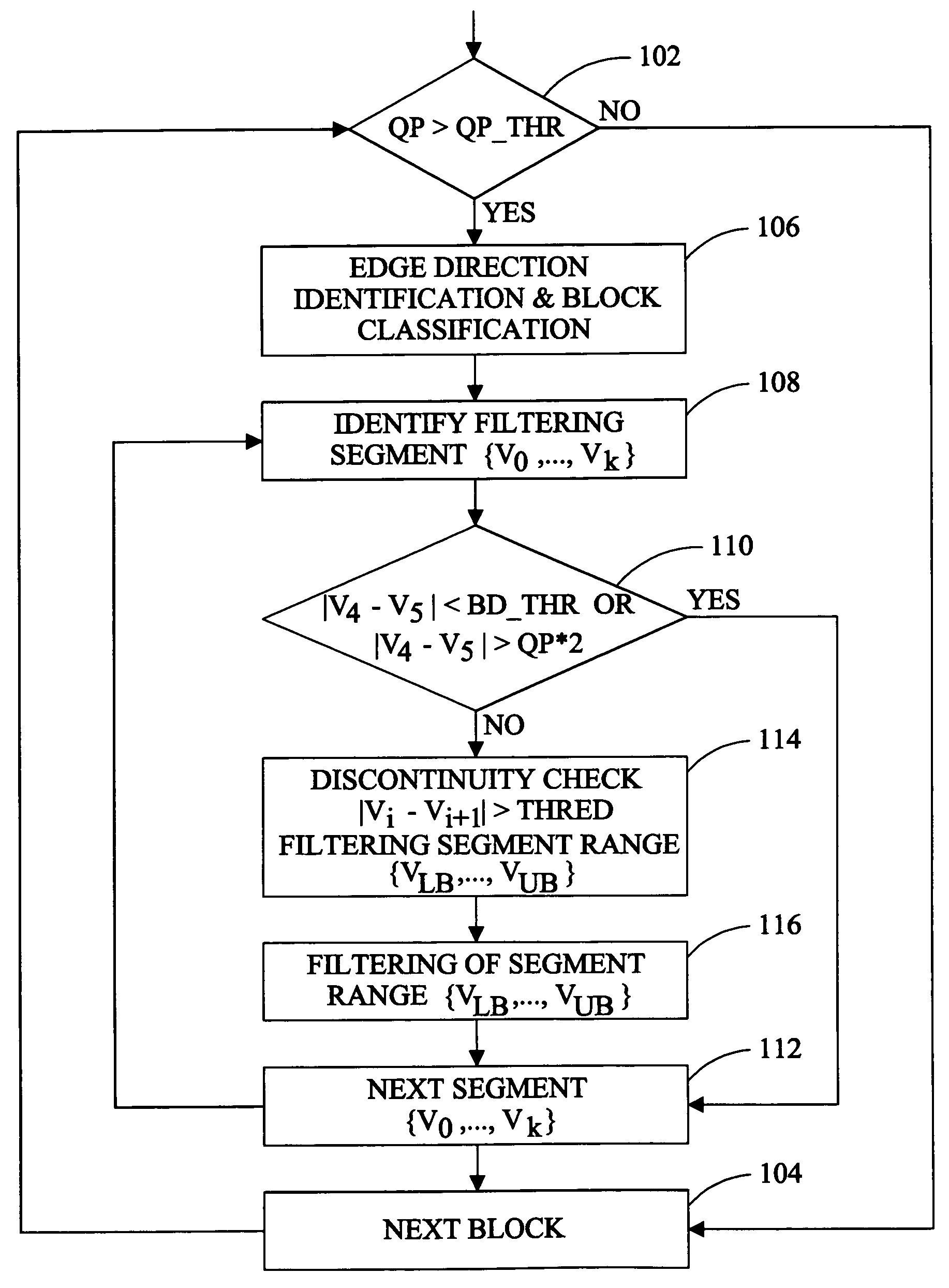
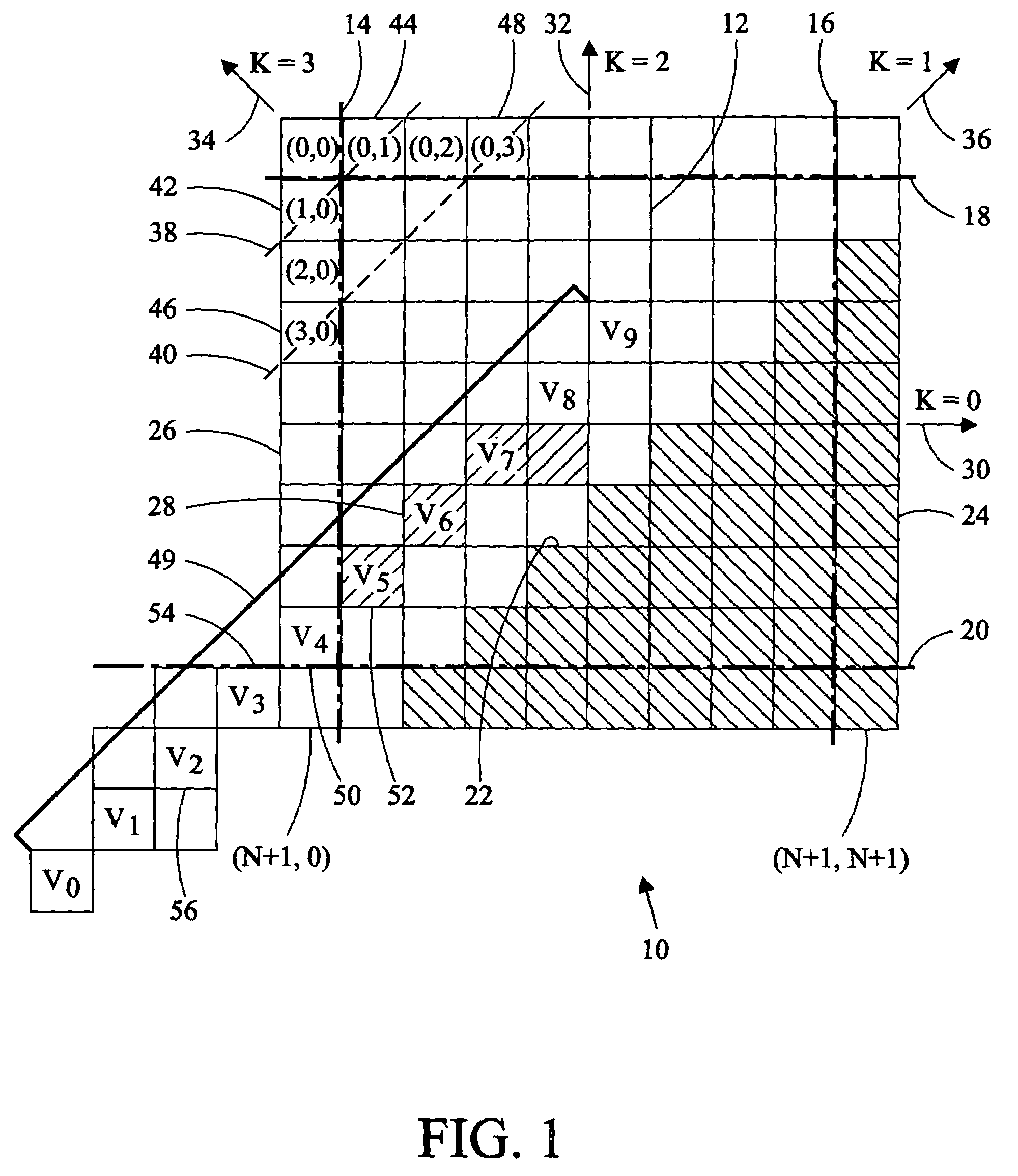
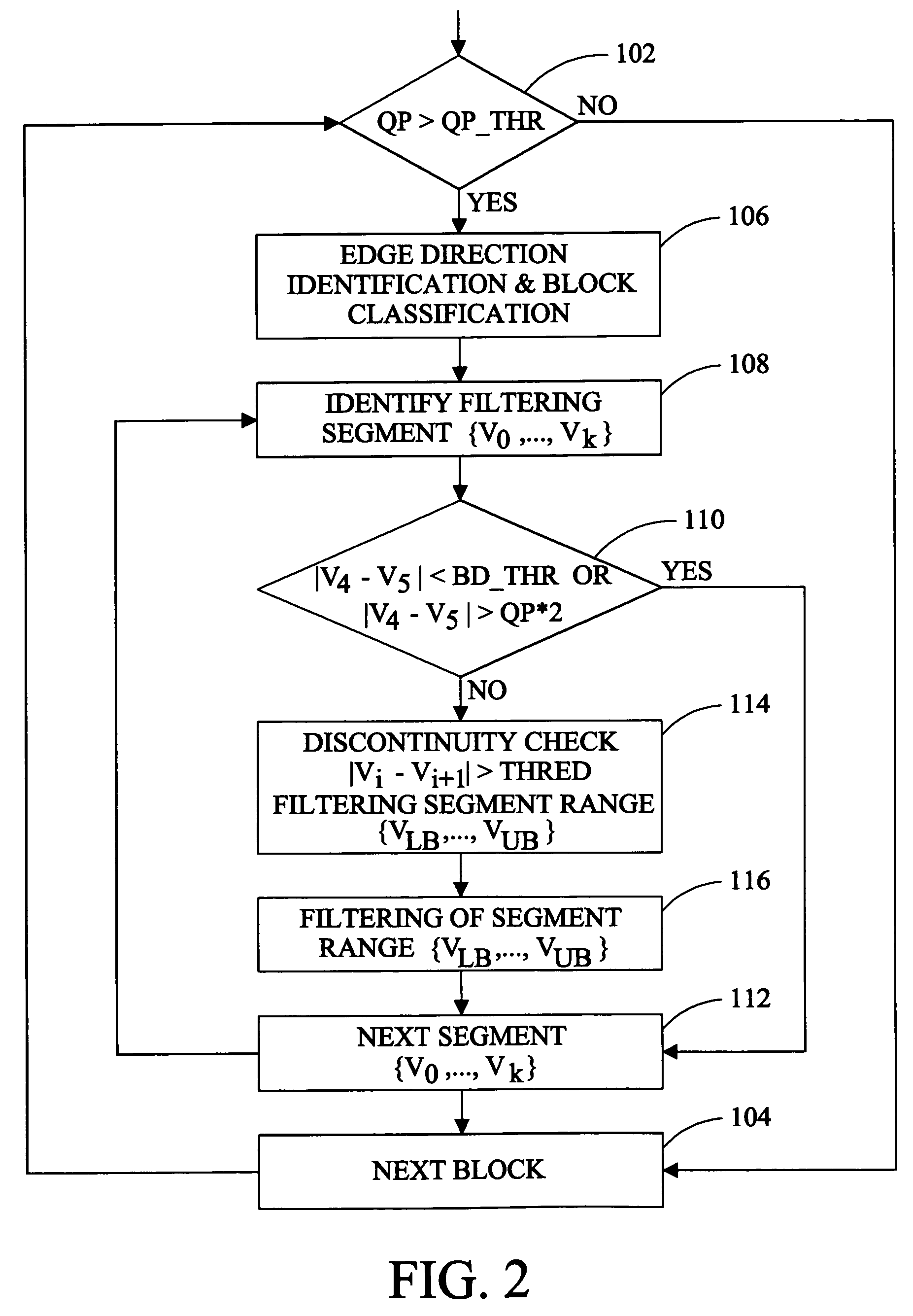
Method of directional filtering for post-processing compressed video
InactiveUS7203234B1Minimize impactSave computing resourcesImage enhancementTelevision system detailsInterlaced videoRinging artifacts
A method of post-processing decompressed images includes identification of the direction of an image edge in a pixel block of the image and filtering applied along the boundary of the block in a direction substantially parallel to the detected image edge. Pixels are selected for filtering on the basis of the quantization parameter of the block of which they are members, the relative difference between pixels adjacent to the block boundary, and significant changes value of pixels in a filtering segment. Filtering is applied parallel to the detected edge to protect the sharpness of the edge while reducing or eliminating blocking and ringing artifacts. A method of separately post-processing fields of interlaced video eliminating complications arising from separate compression of the fields is also disclosed.
Owner:SHARP KK
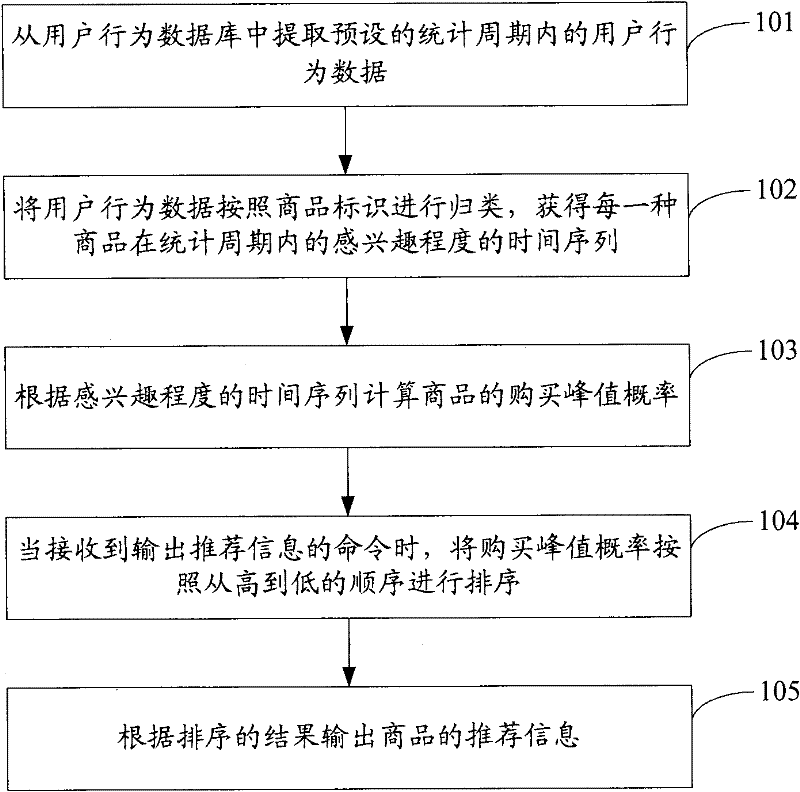
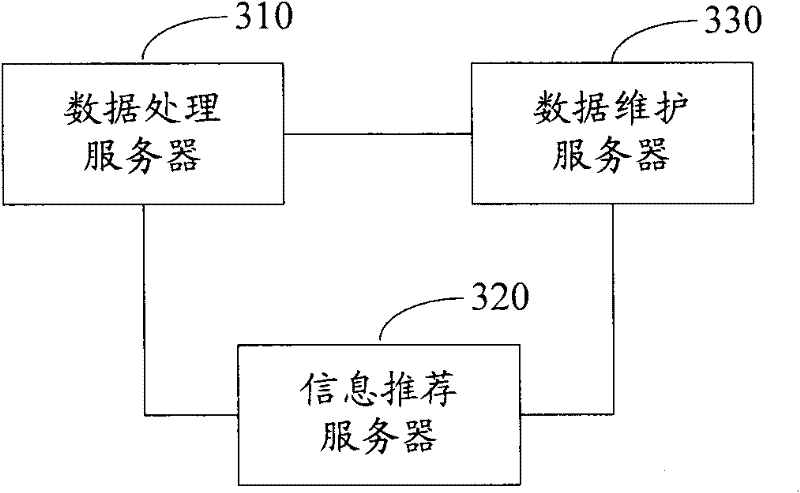
Output method, system and server of recommendation information
ActiveCN102346894AImprove experienceImprove recommendation accuracyTransmissionCommerceData miningOperations research
The invention discloses an output method, system and server of recommendation information. The method comprises the following steps of: extracting user action data in a predetermined statistic period from a user action database; classifying the user action data according to commodity identifications to obtain a time sequence about interestingness of each commodity in the statistic period; computing a purchase peak probability of the commodity according to the time sequence about interestingness; when receiving a command of outputting the recommendation information, sorting the purchase peak probability according to an order from high to low, and outputting the recommendation information of the commodity according to a sorting result. The method provided by the invention automatically computes the purchase peak probability of the commodity on time dimension according to the user action data, thereby improving the recommendation accuracy of a recommendation system and reducing the transmission quantity of unnecessary data in the network; since the recommendation information is automatically modified and output by a server, and the computation capability of the server is sufficiently used, the information input quantity and computation resource of the recommendation system can be reduced when the recommendation information is adjusted according to the purchase peak probability.
Owner:ALIBABA GRP HLDG LTD
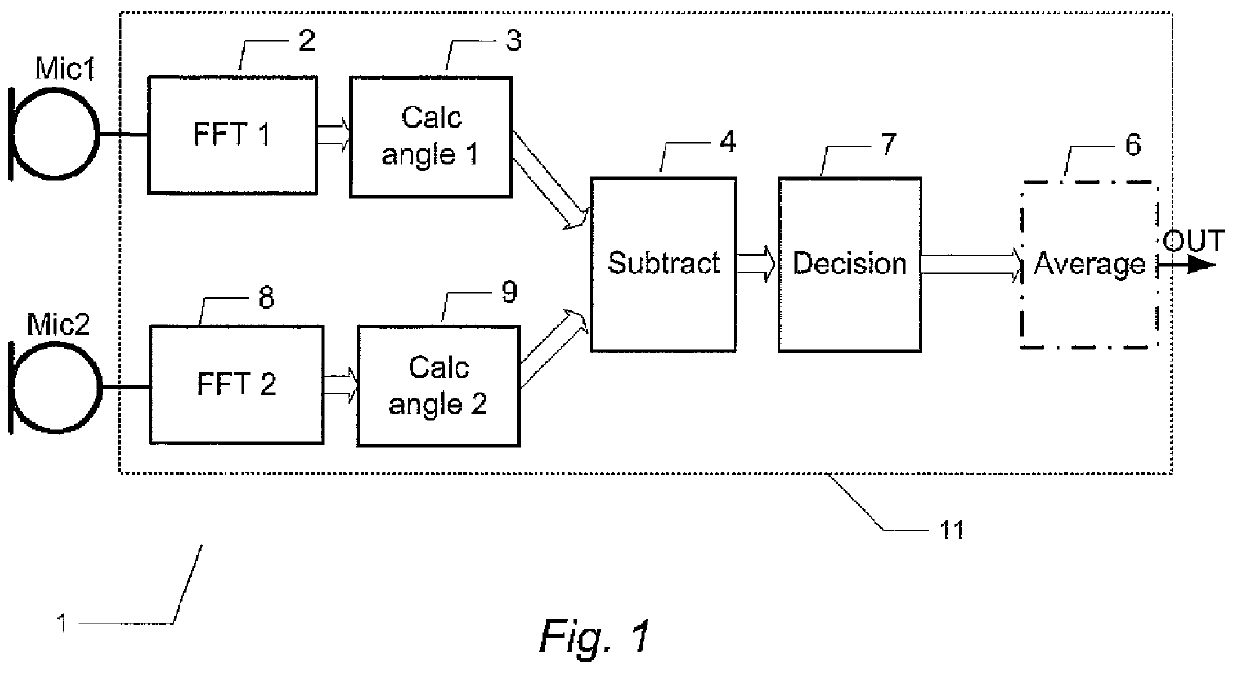
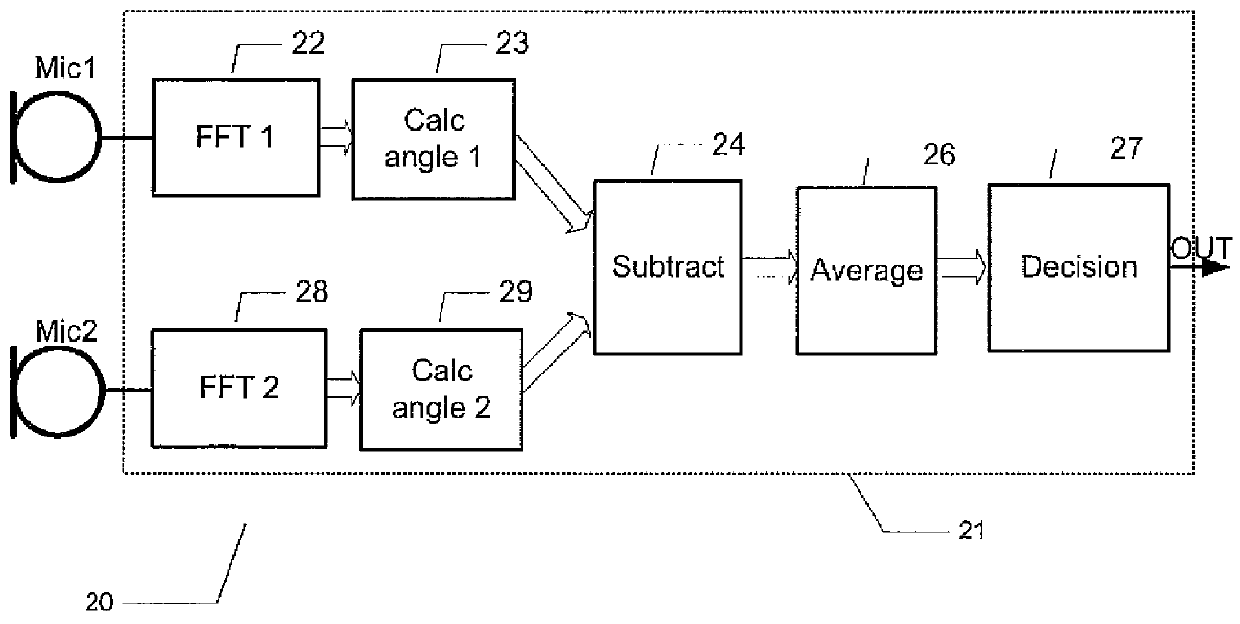
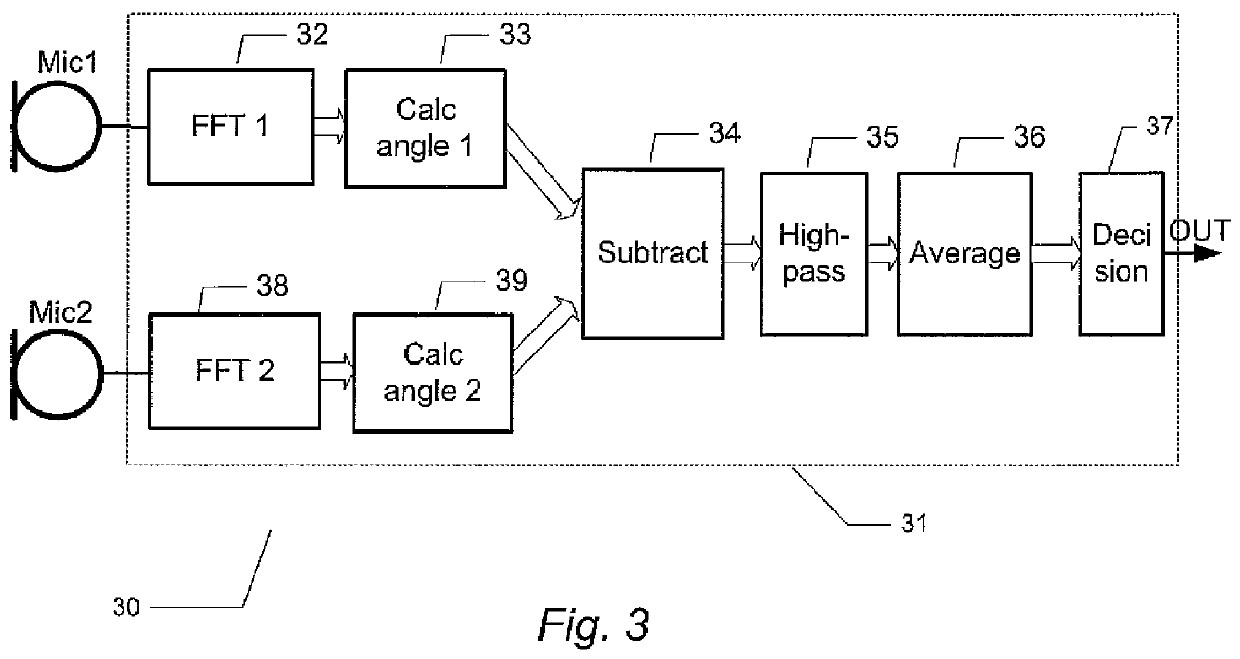
Wind noise detection method and system
ActiveUS20120148067A1Save computing resourcesReduce power consumptionMicrophonesMicrophones signal combinationPhase differencePhase angle difference
The present invention relates to a multi-microphone system and method adapted to determine phase angle differences between a first microphone and a second microphone signal to detect presence of wind noise.
Owner:INVENSENSE
Neural network model compression method and device
ActiveCN106485316AReduce sizeReduce occupancyAnalogue/digital conversionElectric signal transmission systemsCompression deviceModel parameters
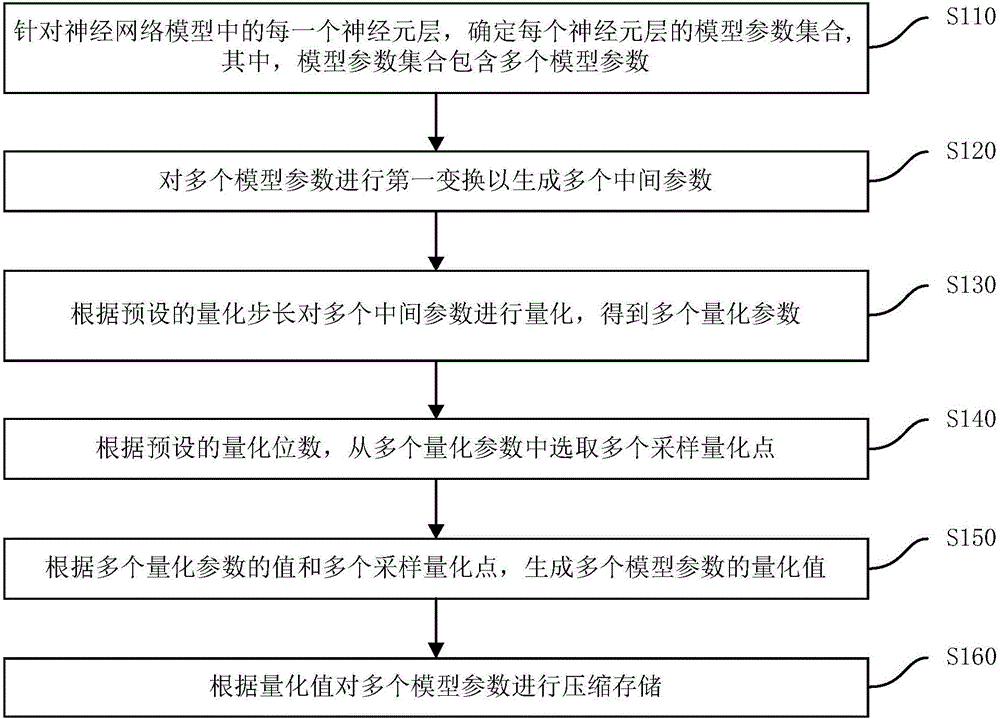
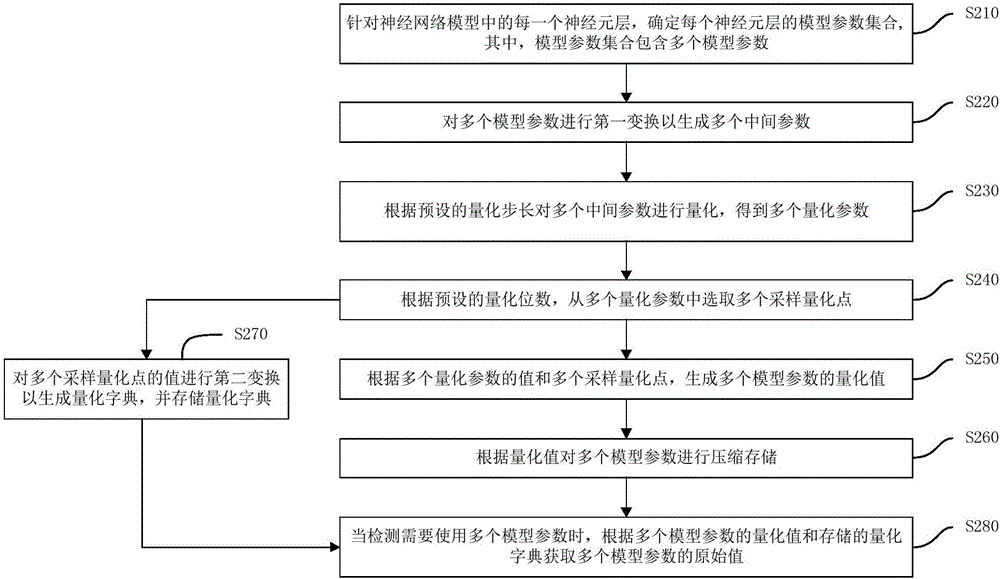
The invention discloses a neural network model compression method and a neural network model compression device. The neural network model compression method comprises the steps of: determining a model parameter set of each neuron layer for each neuron layer in a neural network model, wherein the model parameter set includes a plurality of model parameters; carrying out first transformation on the plurality of model parameters to generate a plurality of intermediate parameters; quantizing the plurality of intermediate parameters according to a preset quantization step size to obtain a plurality of quantization parameters; selecting a plurality of sampling quantization points from the plurality of quantization parameters according to a preset quantization bit number; generating quantized values of the plurality of model parameters according to values of the plurality of quantization parameters and the plurality of sampling quantization points; and compressing and storing the plurality of model parameters according to the quantized values. The neural network model compression method can better maintain the effect of the model, greatly reduces the size of the neural network model, and reduces the occupation of computing resources, especially memory resources.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Pedestrian detection method based on end-to-end convolutional neural network
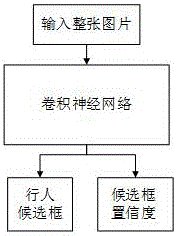
InactiveCN106022237AEasy to train and testImprove recallCharacter and pattern recognitionAlgorithmConfidence measures
The invention discloses a pedestrian detection method based on an end-to-end convolutional neural network in order to solve the problem that the existing pedestrian detection algorithm has the disadvantages of low detection precision, complex algorithm and difficult multi-module fusion. A novel end-to-end convolutional neural network is adopted, a training sample set with marks is constructed, and end-to-end training is performed to get a convolutional neural network model capable of predicting a pedestrian candidate box and the confidence of the corresponding box. During test, a test picture is input into a trained model, and a corresponding pedestrian detection box and the confidence thereof can be obtained. Finally, non-maximum suppression and threshold screening are performed to get an optimal pedestrian area. The invention has two advantages compared with previous inventions. First, through end-to-end training and testing, the whole model is very easy to train and test. Second, pedestrian scale and proportion problems are solved by constructing a candidate box regression network, the pyramid technology adopted in previous inventions is not needed, and a lot of computing resources are saved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
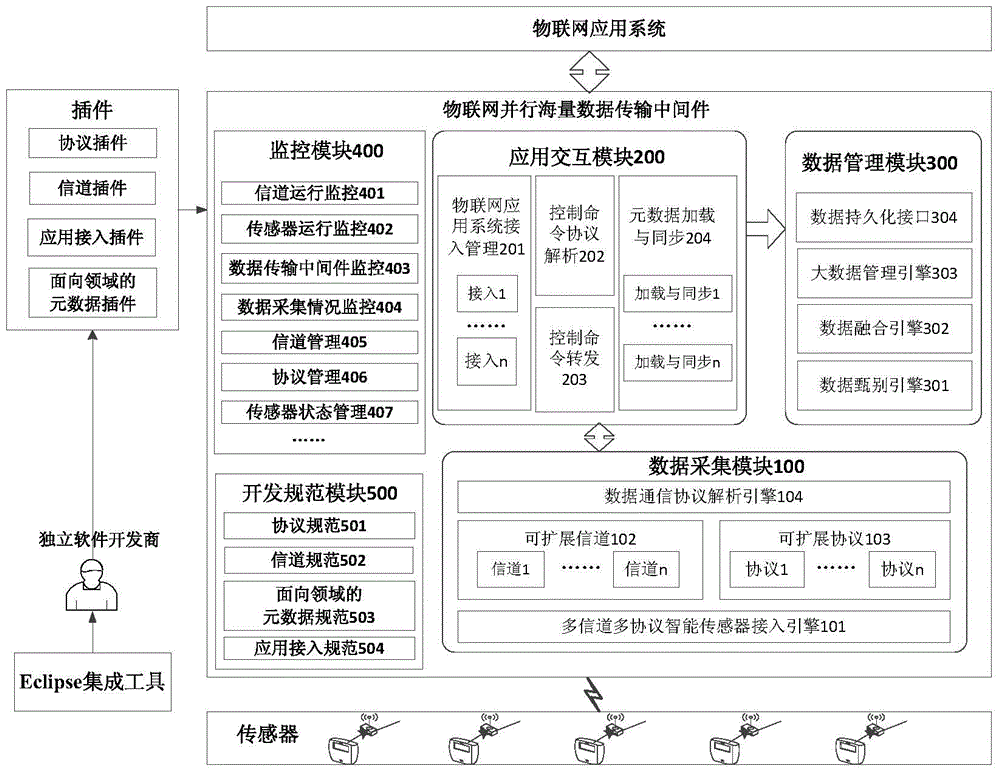
Parallel mass data transmitting middleware of Internet of things and working method thereof
The present invention discloses parallel mass data transmitting middleware of Internet of things and a working method thereof. The invention includes: a data collection module, for forwarding data collected from different types of sensors to an application interaction module after analysis; the application interaction module, for achieving communication between the parallel mass data transmitting middleware of the Internet of things and an application system of the Internet of things, analyzing a control command of the application system of the Internet of things, transmitting to the data collection module, and further transmitting the analyzed sensor data to a data management module; the data management module, for performing data screening, fusion, conversion on the mass data analyzed by the application interaction module, and finally storing the calculated data into the application system of the Internet of things; and a developing regulation module, for setting out a protocol plug-in regulation, a communication channel plug-in regulation, a service field metadata plug-in regulation, etc. The present invention can meet high concurrency access and management of the large scale sensing apparatus of different application fields, various communication channels and various communication protocols.
Owner:SHANDONG UNIV +1
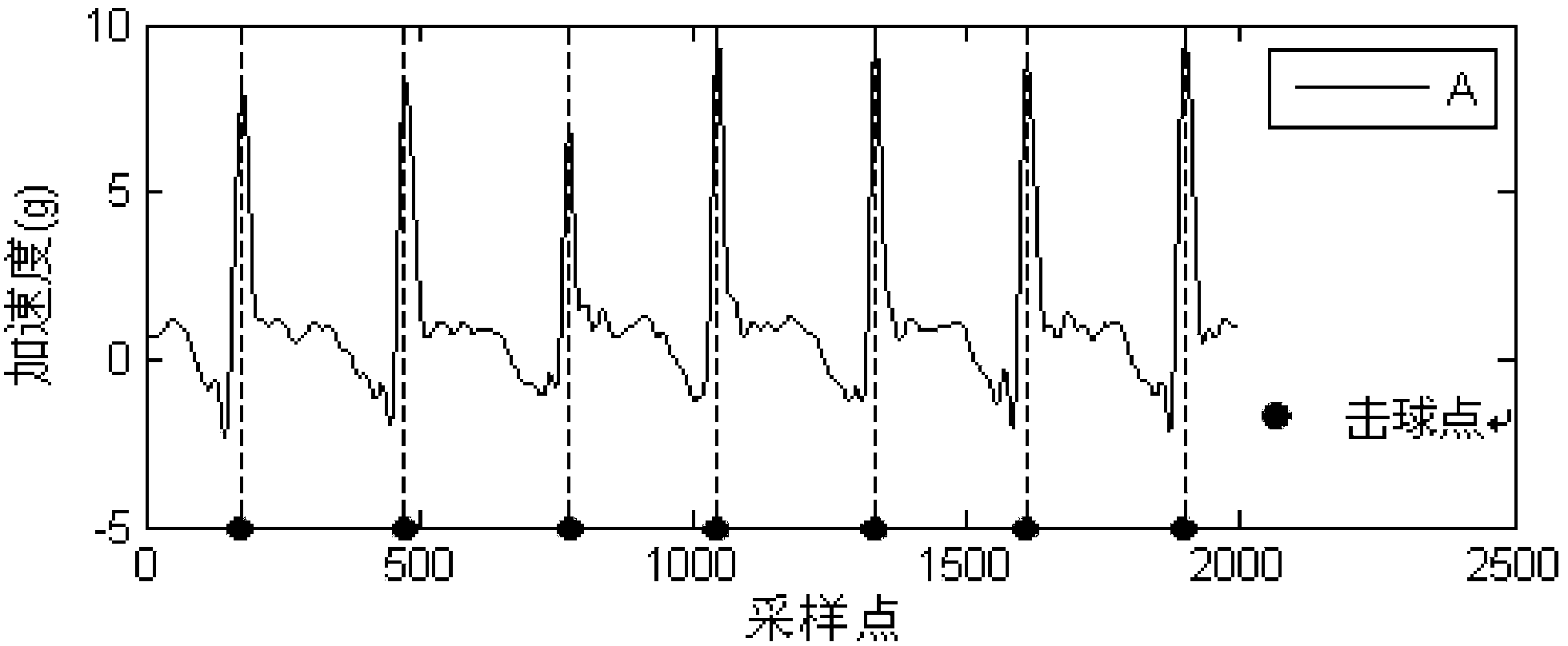
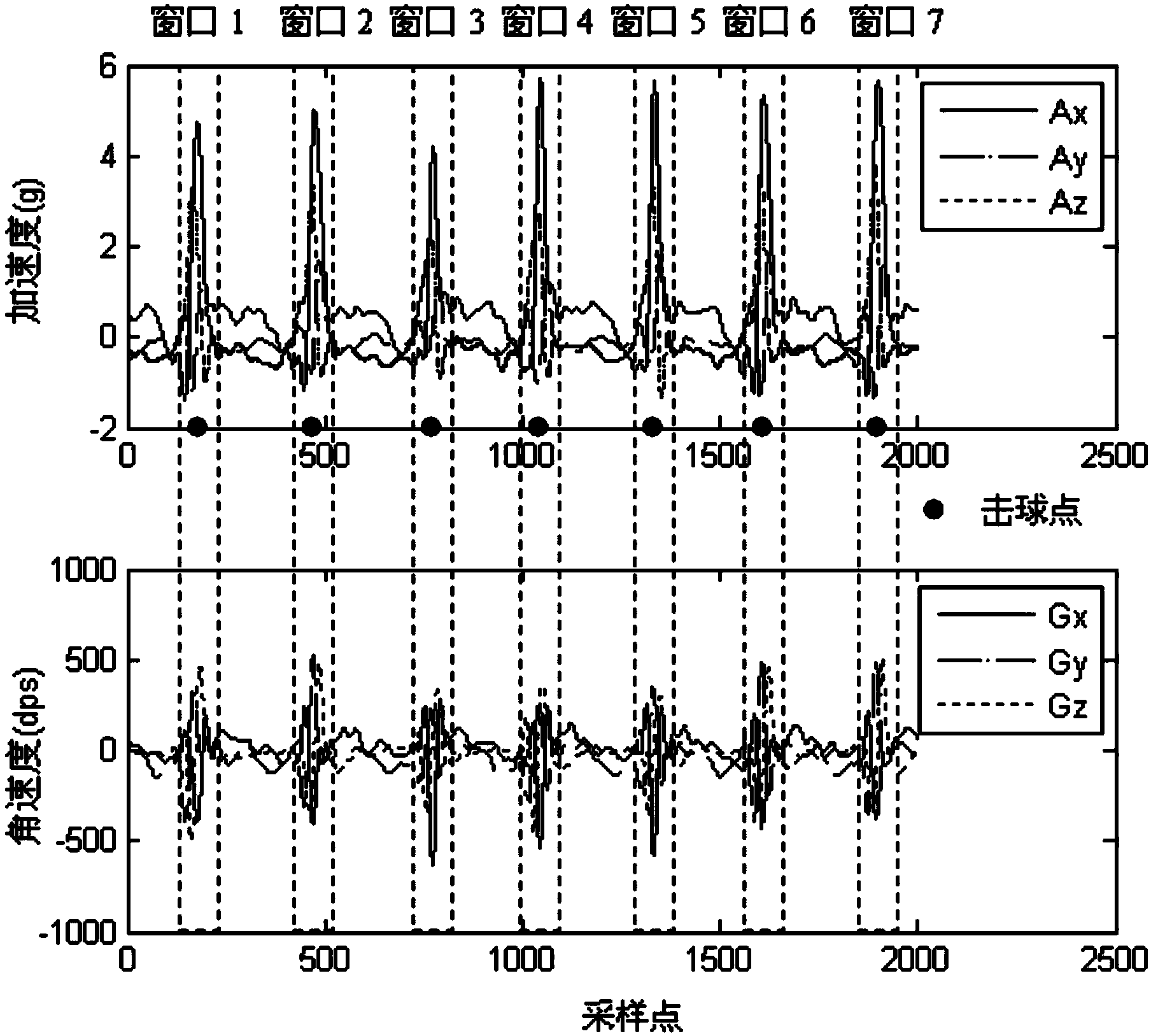
Human body behavior identification method based on inertial sensor
The invention provides a human body behavior identification method based on an inertial sensor. The method comprises the steps of acquiring human body behavior data of testees by means of the inertial sensor, conducting sliding window segmentation on the acquired human body behavior data, conducting feature extraction on a triaxial accelerated speed subsequence and a triaxial angular speed subsequence which are obtained after sliding window segmentation, conducting feature fusion on a feature vector to form a sample set of the human body behaviors of the testees, conducting feature selection on the sample set by means of the least correlated maximum redundant algorithm and the Bayes regularization sparse polynomial logistic regression algorithm, obtaining the classification feature vectors of all human body behaviors of all the testees, obtaining a classifier model of each human body behavior by means of a fuzzy least square support vector machine, and obtaining a human body behavior identification result after the human body behavior data are tested by means of the fuzzy least square support vector machine. By means of the human body behavior identification method, self-adaptation and identification efficiency can be improved.
Owner:DALIAN UNIV OF TECH
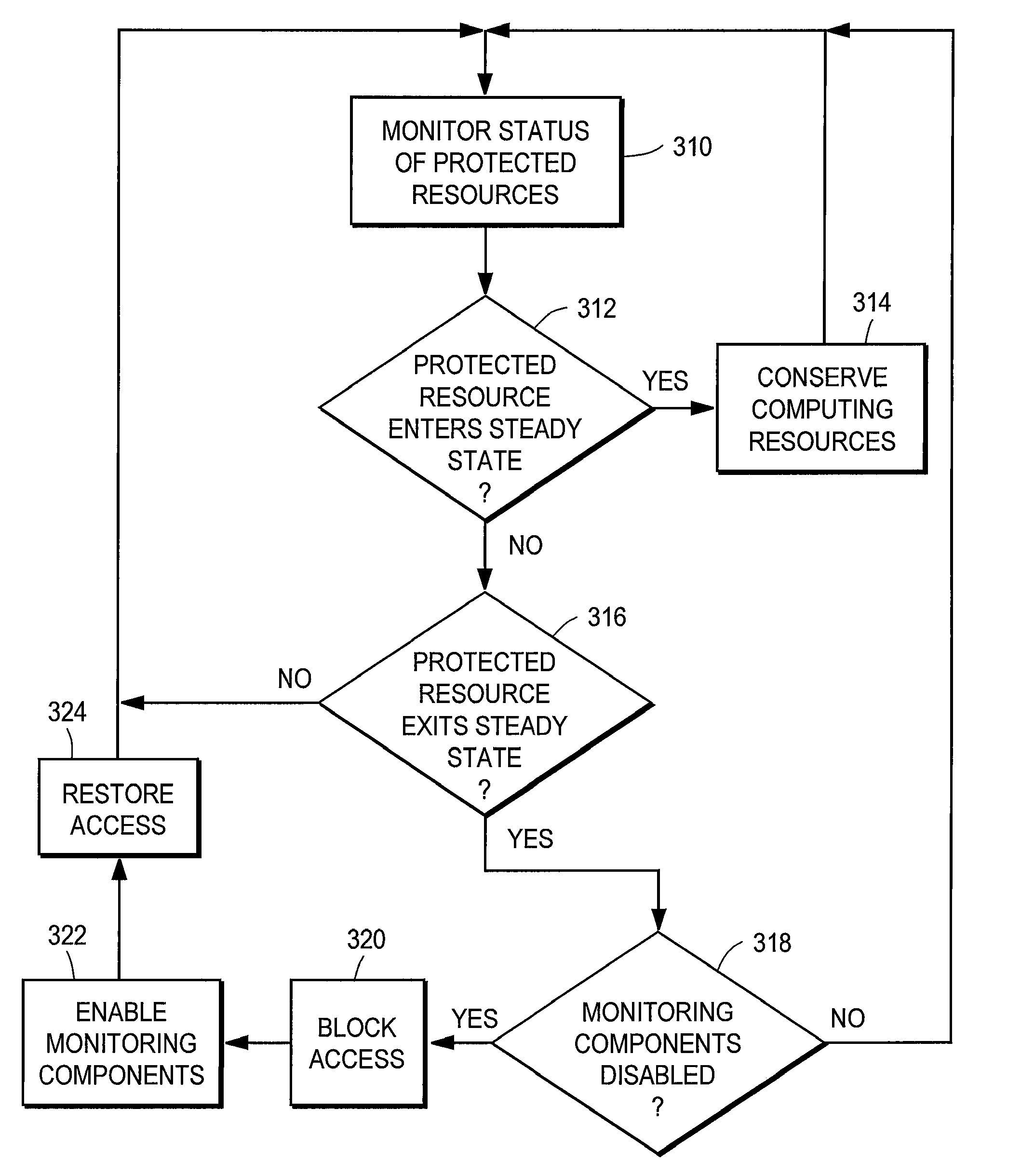
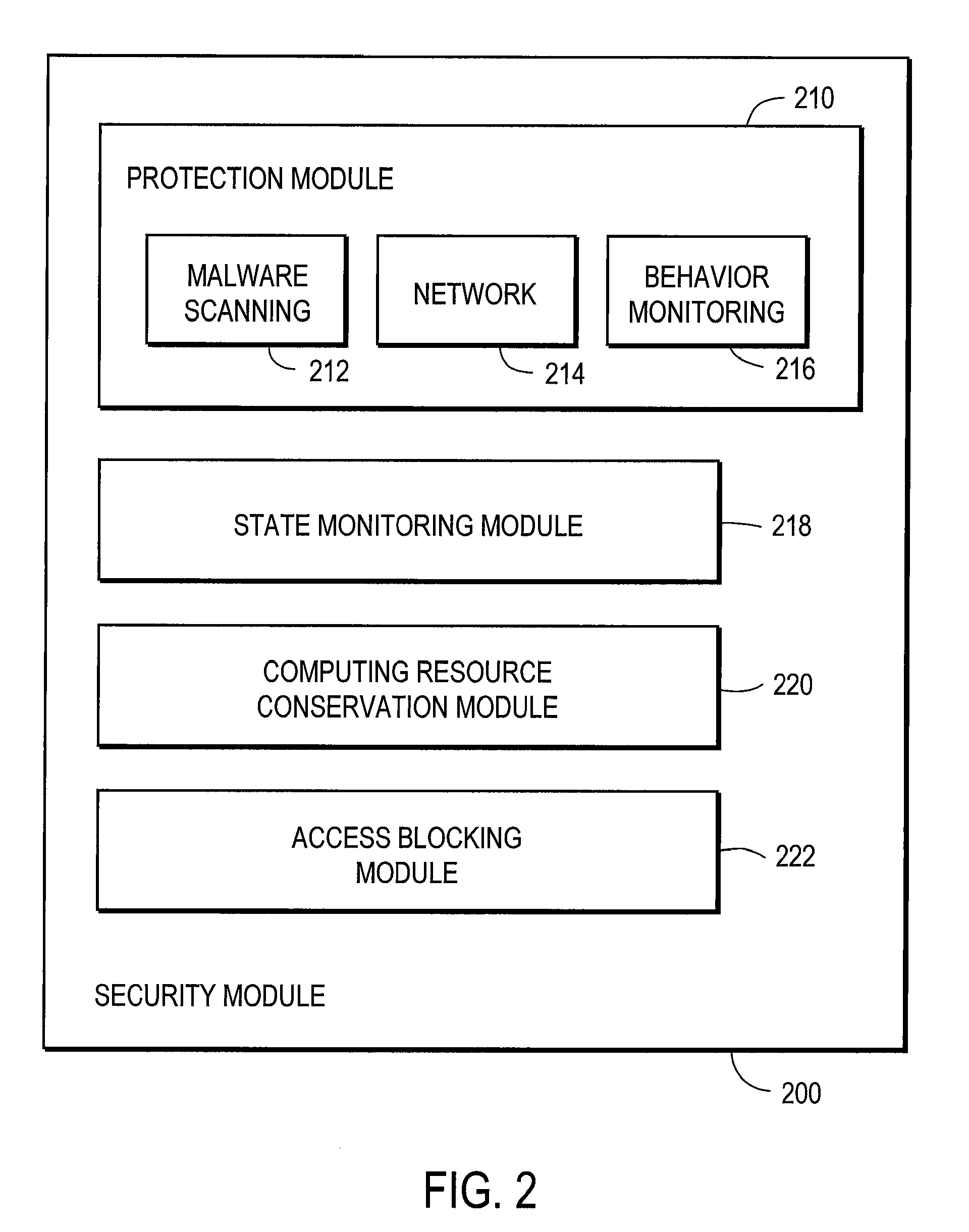
Conserving computing resources while providing security
ActiveUS7823205B1ConserveFree computational resourceMemory loss protectionError detection/correctionStable stateSecure state
A computer has protected resources presenting threat vectors that malicious software can use to attack the computer. A security module has monitoring components that monitor the protected resources to detect malicious software. The security module detects if a protected resource enters a steady security state. In response to a protected resource entering a steady state, the security module selectively disables the components that monitor the protected resource, thereby conserving the computing resources utilized by the security module and freeing the computing resources for other tasks. If the resource exits the steady security state, the security module temporarily blocks access to the resource while it enables the monitoring components for that resource.
Owner:NORTONLIFELOCK INC
Track planning method of redundant space mechanical arm for on-track catching
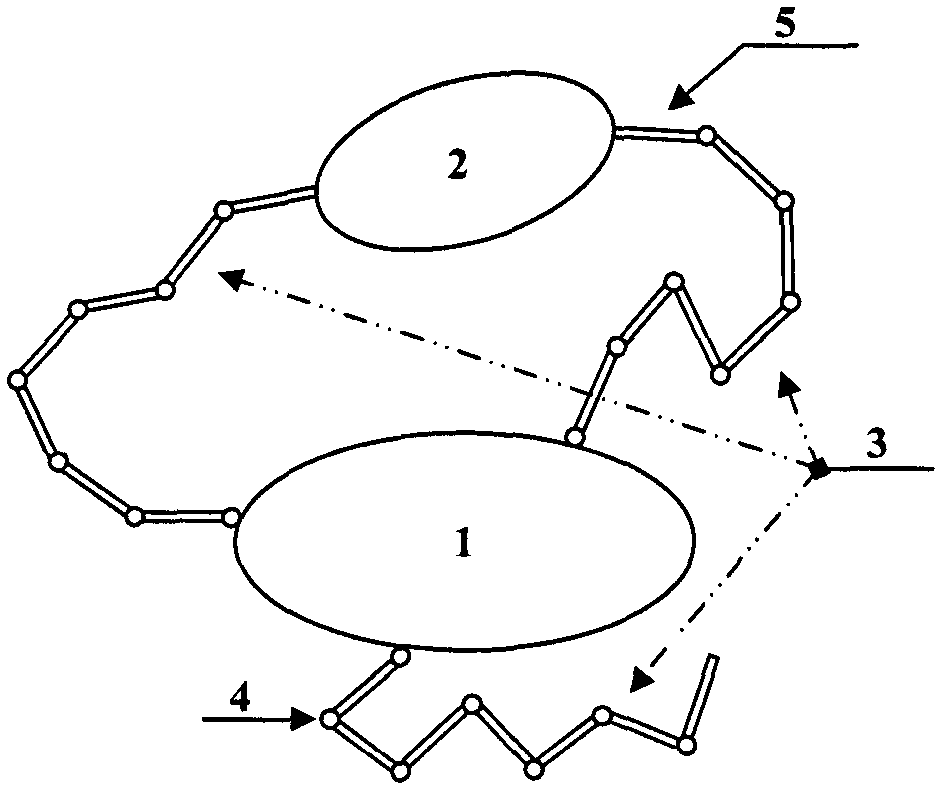
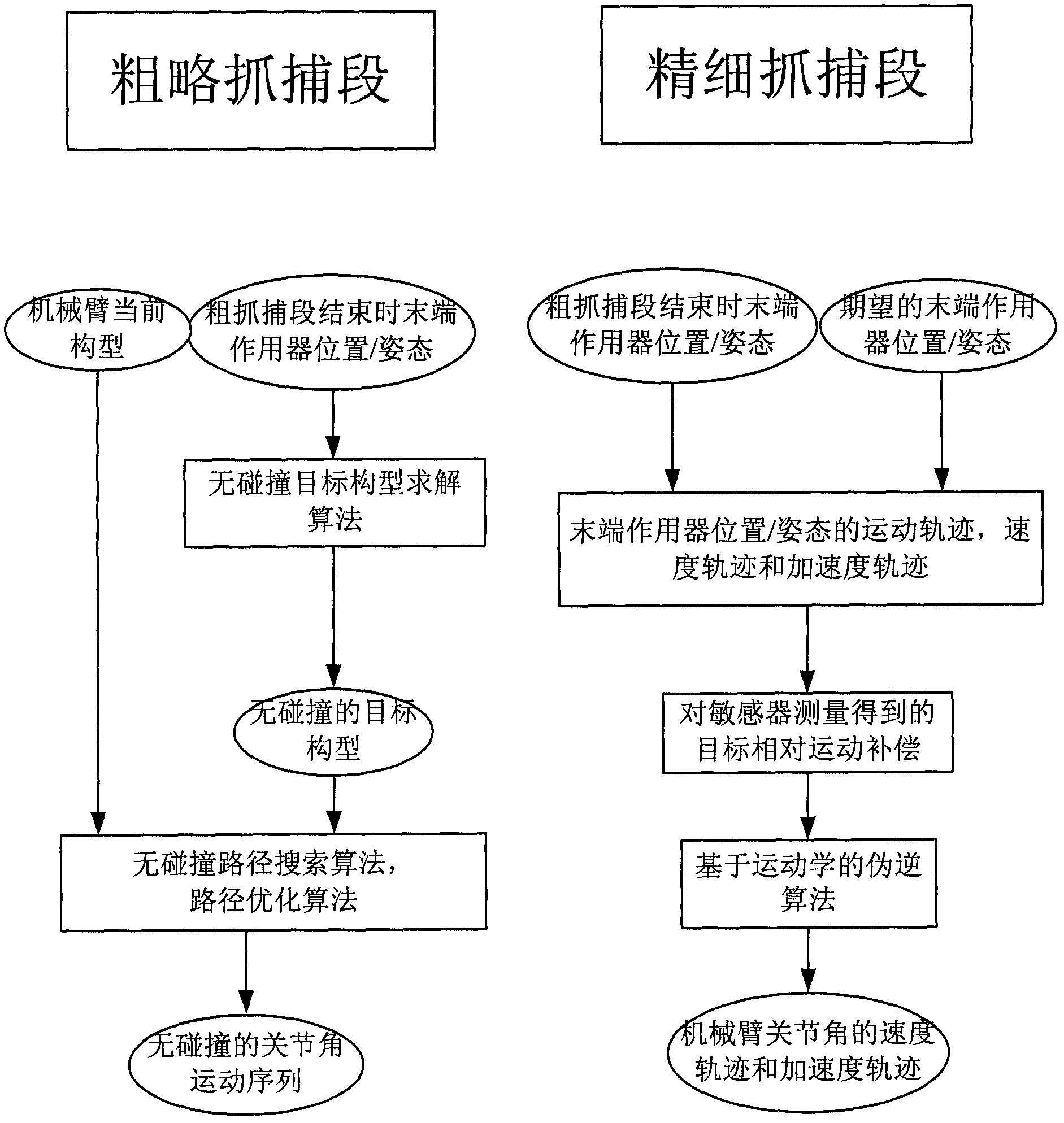
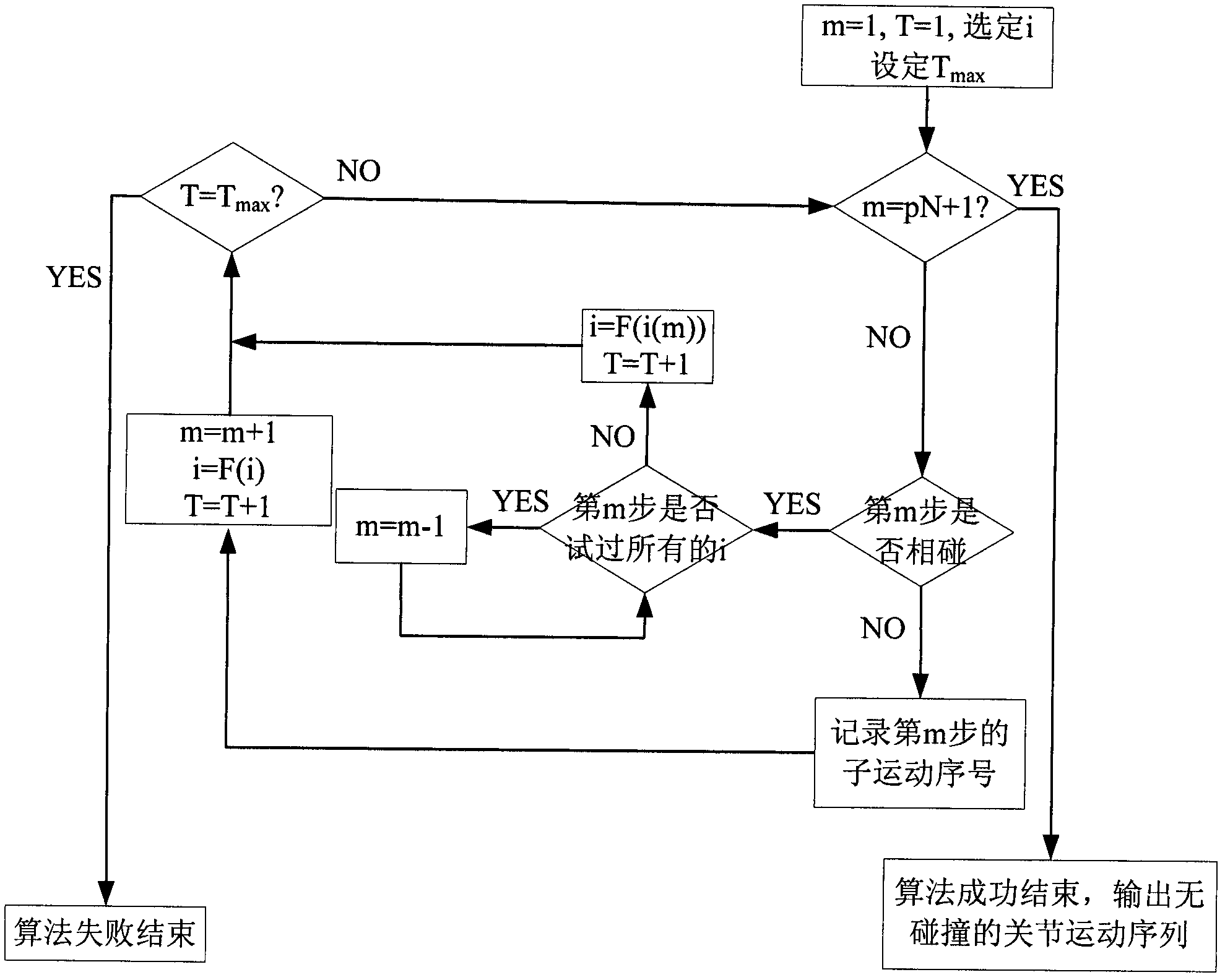
ActiveCN103009389AGuaranteed accurate captureAchieve circumventionProgramme-controlled manipulatorKinematicsEngineering
The invention relates to a track planning method of a redundant space mechanical arm for on-track catching. The catching operation of the space mechanical arm is divided into a rough catching stage and a fine catching stage, so that problems are simplified. By aiming at outstanding problems of different stages, different planning algorithms are adopted. In the rough catching stage, a track searching algorithm based on configuration space is adopted, and the algorithm is based on the test in the configuration space; and in the fine catching stage, a pseudo-inverse algorithm based on kinematics is adopted, and the final precise catching is guaranteed by compensating the relative movement of a target.
Owner:BEIJING INST OF CONTROL ENG
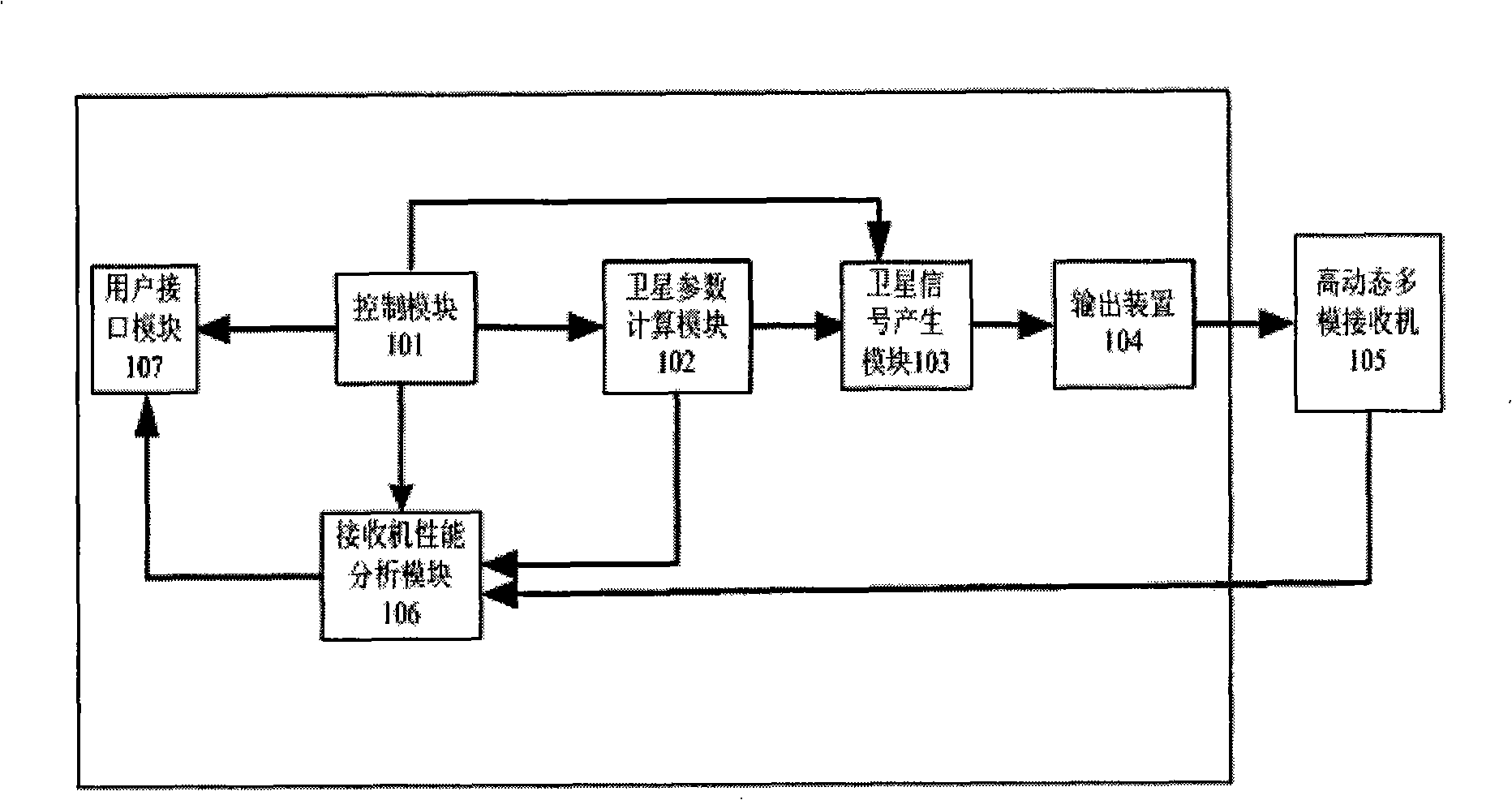
High dynamic state multi- mode satellite navigation signal source analogue method and its device
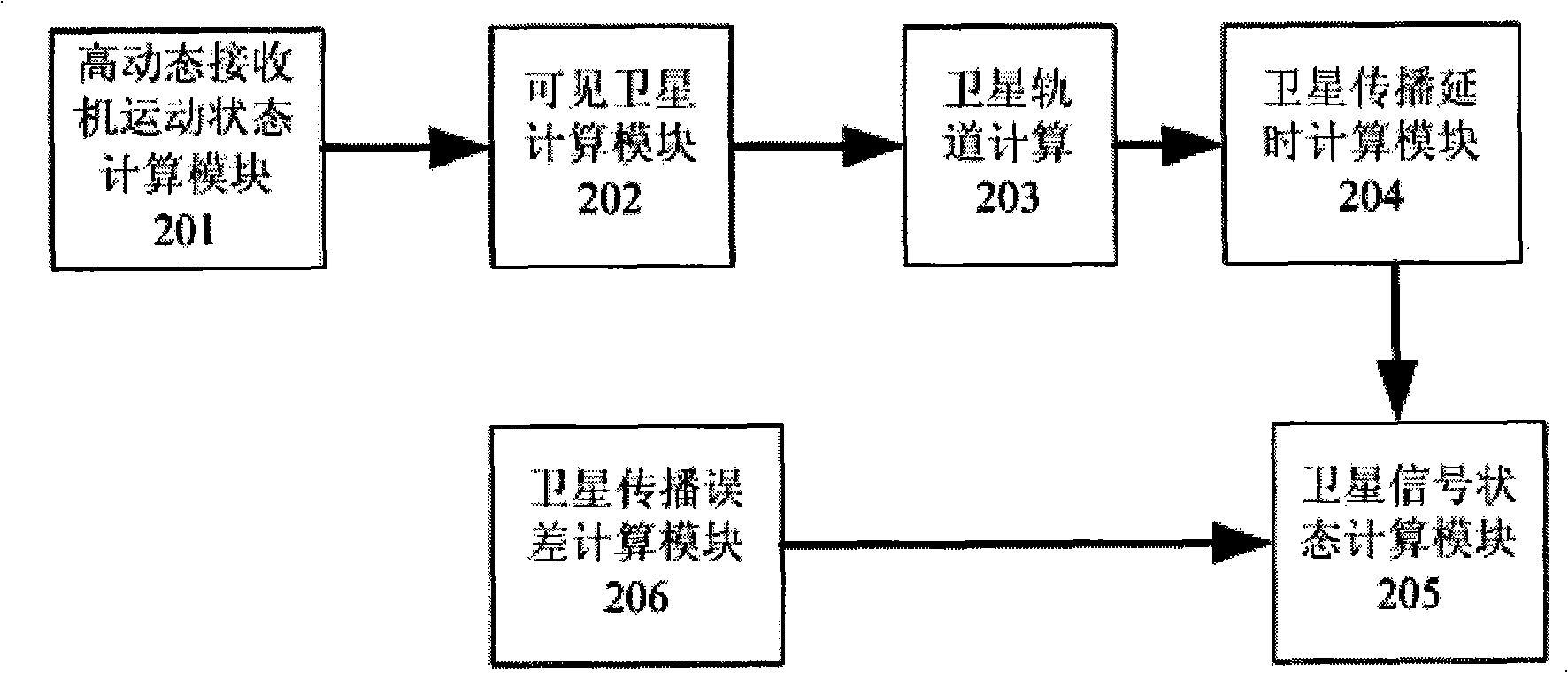
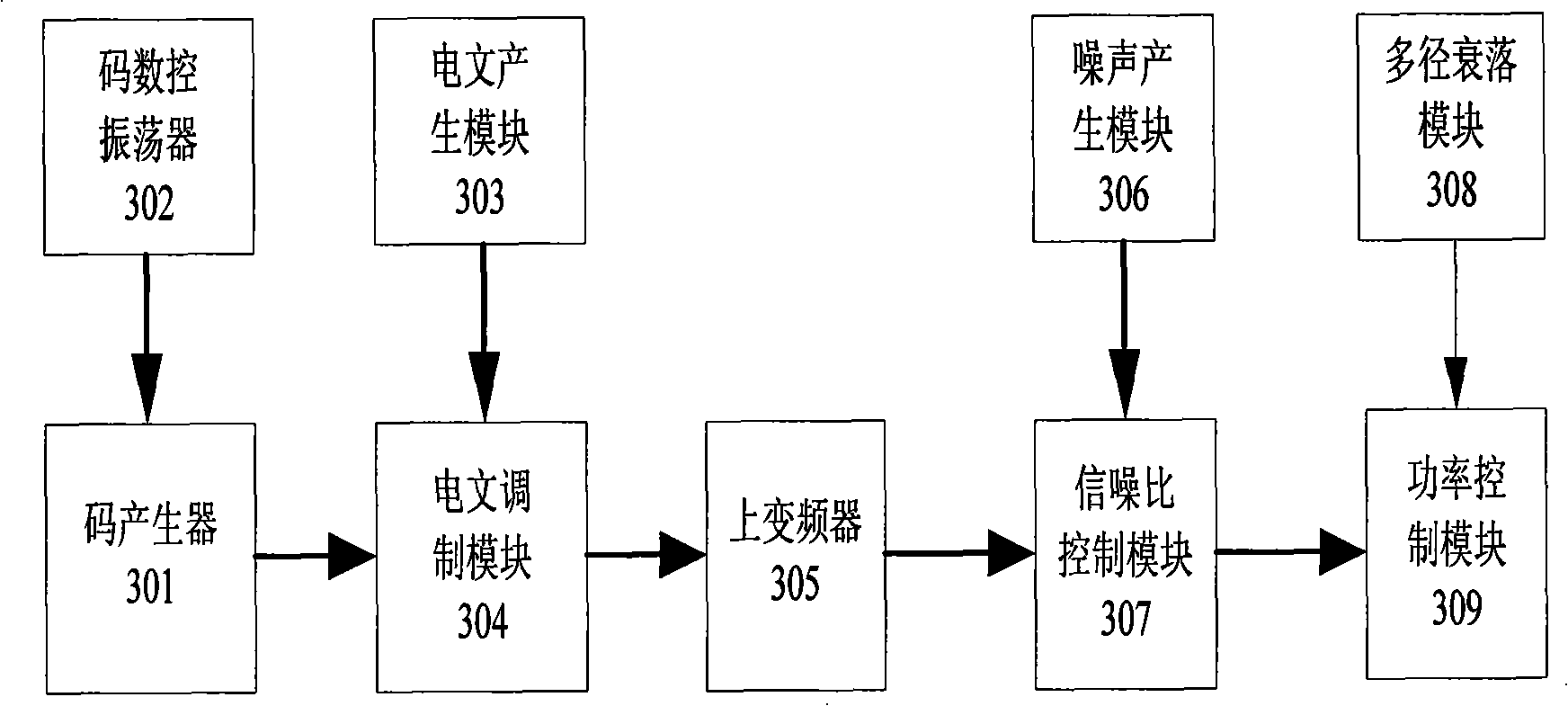
InactiveCN101261317ASave computing resourcesImprove interpolation accuracyBeacon systems using radio wavesPosition fixationEnvironmental geologyMarine navigation
The invention discloses a simulation method for high dynamic multi-mode satellite navigation signal source and a device thereof, wherein, the high dynamic multi-modal satellite navigation signal source can simulate satellite signals of the following three systems: Global Position Satellite system, global navigation satellite system and second-generation Beidou satellite navigation system in space, and the satellite signals are received by a dynamic navigation receiver; the signal resource can simulate the moving state of a user receiver, imitate the error of satellite signals caused in the course of transmission and produce three-mode satellite signals in real time. In the embodiment, the device consists of a user interface module, a control module, a satellite parameter calculation module, a satellite signal producing module, an output device and a data receiving and analysis module. The device simulates simultaneously three-mode satellite signals to accelerate the research of multi-mode navigation receiver. By using an inner fumitoshi interpolation method, the device saves calculation resources and improves interpolation accuracy. By using a parametric design, the device can improve the reusable ability of modules and aim at different satellite navigation systems to implement convenient transformation.
Owner:ZHEJIANG UNIV
Flow cache hierarchy
ActiveUS9686200B2Save a lot of timeOperation is necessaryMemory architecture accessing/allocationMemory adressing/allocation/relocationCache hierarchyExact match
Some embodiments provide a managed forwarding element (MFE that includes a set of flow tables including a first set of flow entries for processing packets received by the MFE. The MFE includes an aggregate cache including a second set of flow entries for processing packets received by the MFE. Each of the flow entries of the second set is for processing packets of multiple data flows. At least a subset of packet header fields of the packets of the multiple data flows have a same set of packet header field values, and a same set of operations is applied to said packets. The MFE includes an exact-match cache including a third set of flow entries for processing packets received by the MFE. Each of the flow entries of the third set is for processing packets for a single data flow having a unique set of packet header field values.
Owner:NICIRA
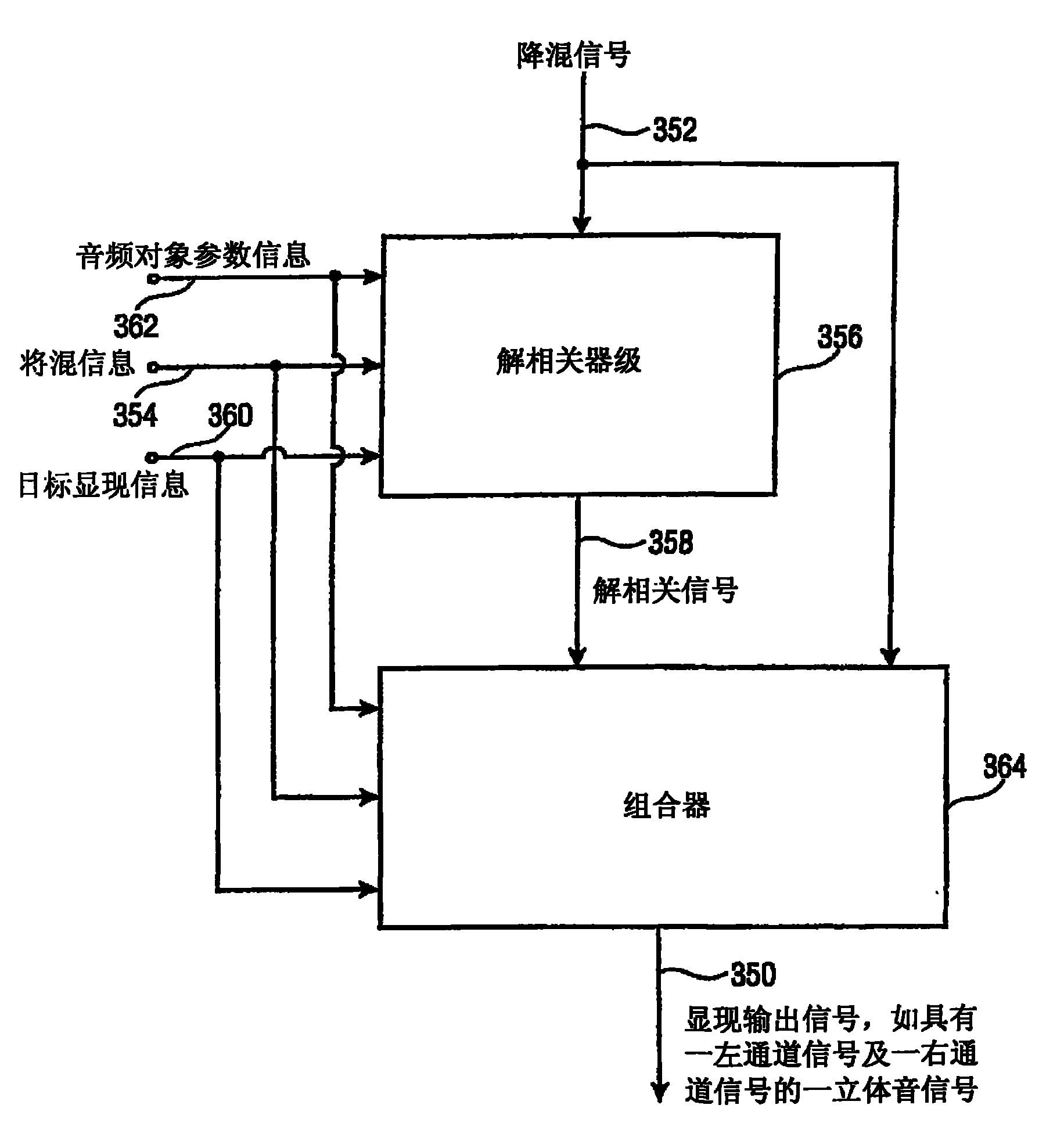
Apparatus and method for synthesizing an output signal
ActiveCN101809654AReduce complexitySave memory resourcesSpeech analysisTwo-channel systemsDecorrelationAudio frequency
An apparatus for synthesizing a rendered output signal having a first audio channel and a second audio channel includes a decorrelator stage (356) for generating a decorrelator signal based on a downmix signal, and a combiner (364) for performing a weighted combination of the downmix signal and a decorrelated signal based on parametric audio object information (362), downmix information (354) andtarget rendering information (360). The combiner solves the problem of optimally combining matrixing with decorrelation for a high quality stereo scene reproduction of a number of individual audio objects using a multichannel downmix.
Owner:DOLBY INT AB +1
Convenient information search method, system and an input method system
ActiveCN101231636AImprove search efficiencyReduce stepsSpecial data processing applicationsInternet searchingInternet search engines
The invention provides a method and a system for searching information, as well as an input method system, wherein, the method for searching the information comprises the following steps that: a searching keyword required by a user is determined; according to the searching keyword, the input method system generates a searching command, which is sent out to a searching engine; the searching enginereturns the searching result to the input method system; the searching result is displayed. The invention can greatly improve the searching efficiency, reduce the operation steps of the user, and avoid the invalid data exchange and the invalid data processing. For some simple searching results, the invention can also directly call the display of an affiliated window or candidate word window, thereby a browse is avoided to be called, thus saving the resources of the system and calculating the sources. The invention is applicable to various internet searching engines as well as various local searching engines, and is also applicable to various searching tools or searching websites.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
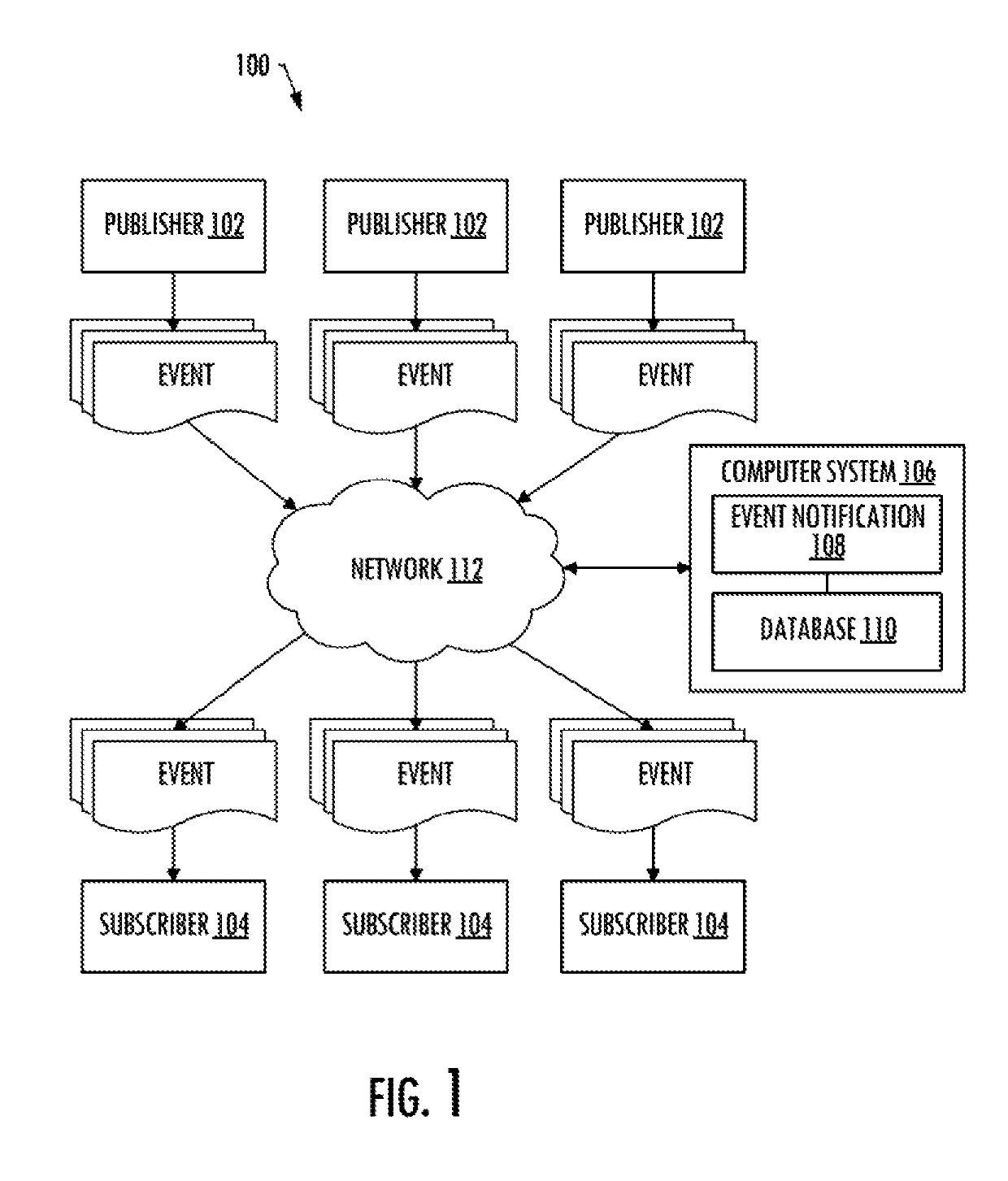
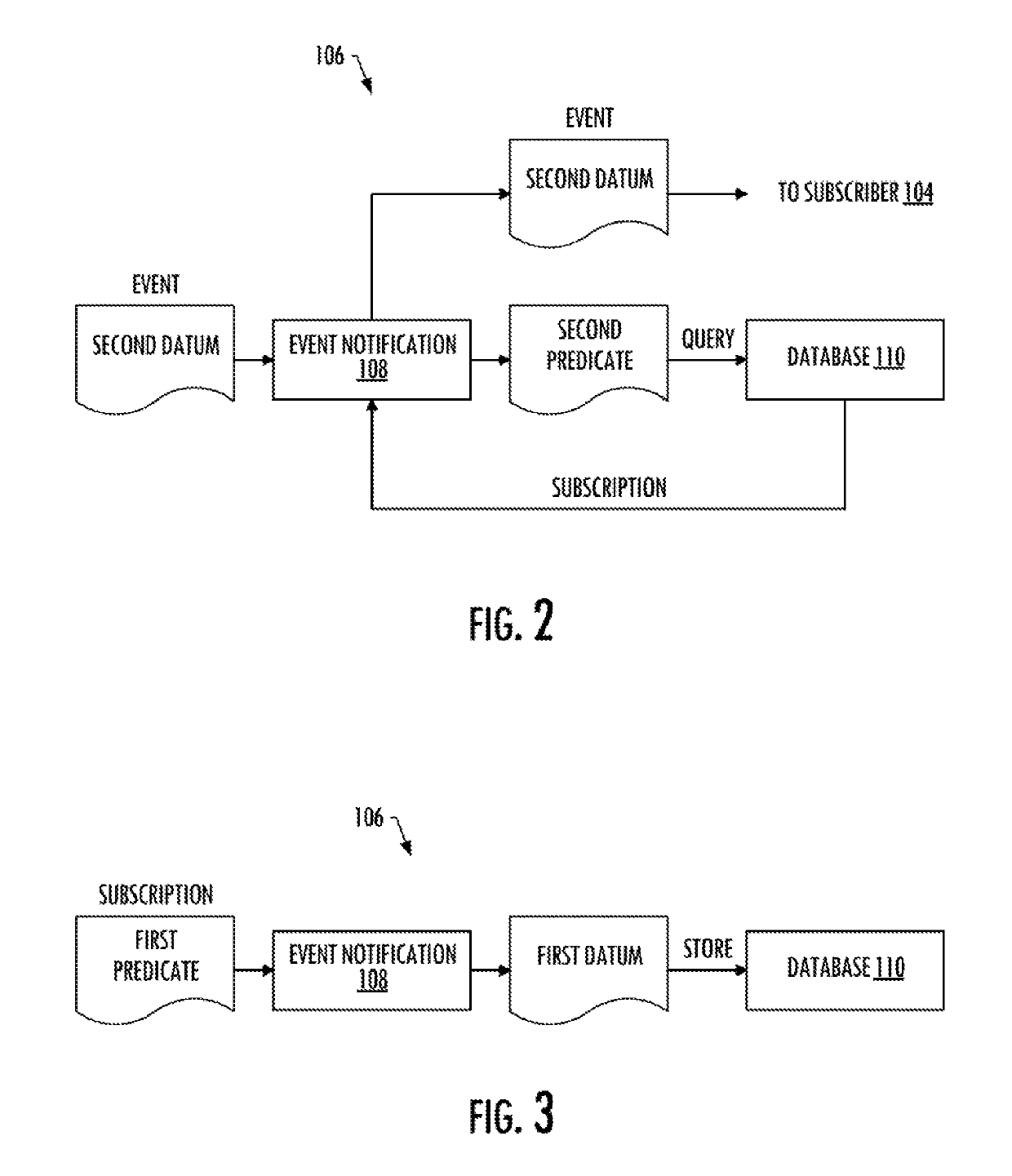
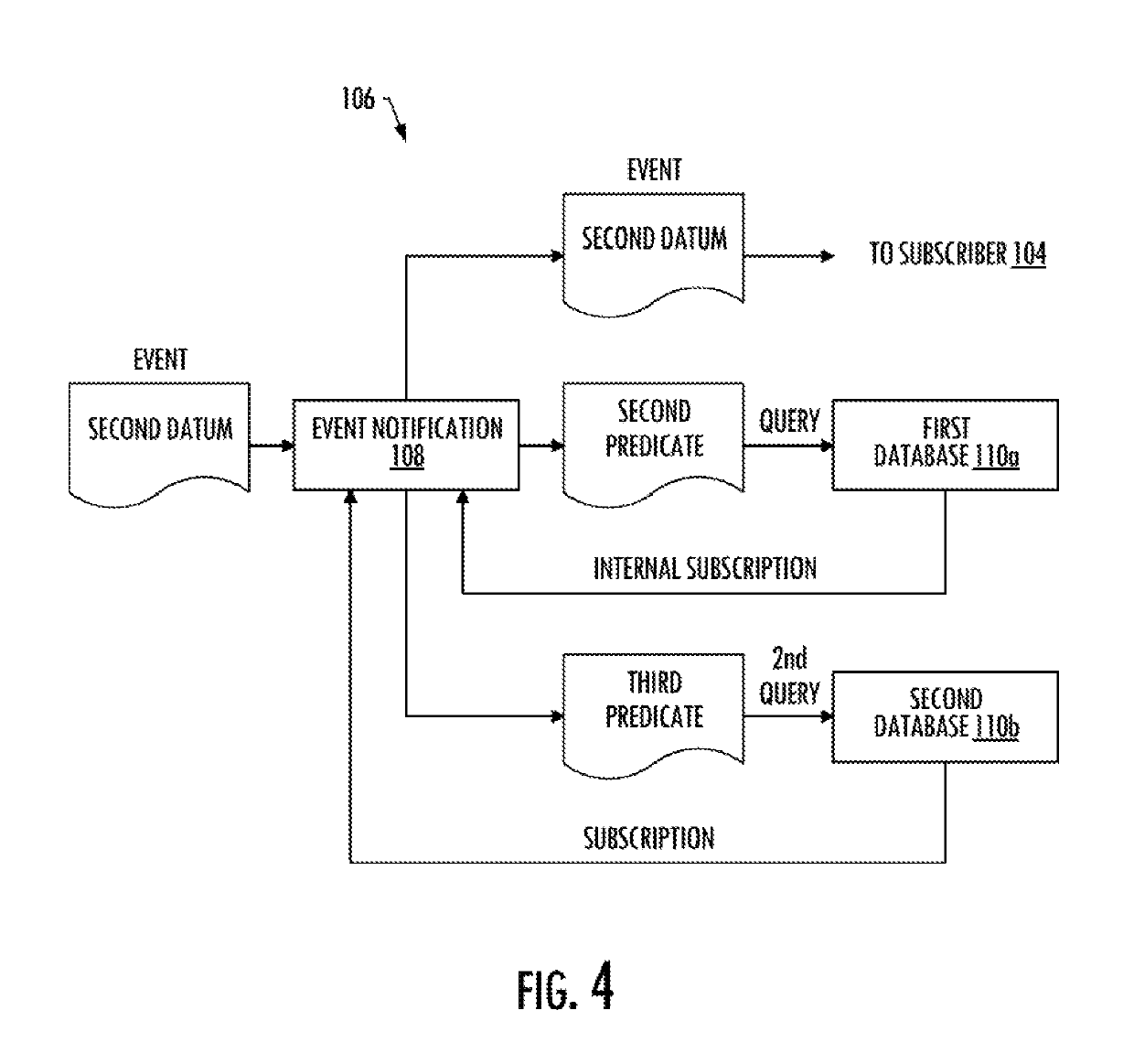
Efficient event notification
ActiveUS10437653B2Save computing resourcesKeep paceWeb data indexingInterprogram communicationQuery languageComputer science
Owner:THE BOEING CO
Method and system for optimizing data access in a database using multi-class objects
ActiveUS20090210445A1Save computing resourcesEasy to classifyDigital data information retrievalSpecial data processing applicationsData setRelational database
Methods for optimizing data access in a row-oriented relational database containing data sets having attributes using a computer are presented the method including: causing a computer to analyze a database workload to determine an access frequency for each of the attributes; causing the computer to assign each of the attributes to a priority classes corresponding with the access frequency, where the priority classes include a higher priority class and a lower priority class, and where a higher priority class corresponds with a higher access frequency and a lower priority class corresponds with a lower access frequency; causing the computer to store the attributes in accordance with the classes, where the attributes assigned to the higher priority class are stored in a high priority storage medium, and where the attributes assigned to a lower priority class are stored in a low priority storage medium.
Owner:IBM CORP
Proxy server using a statistical model
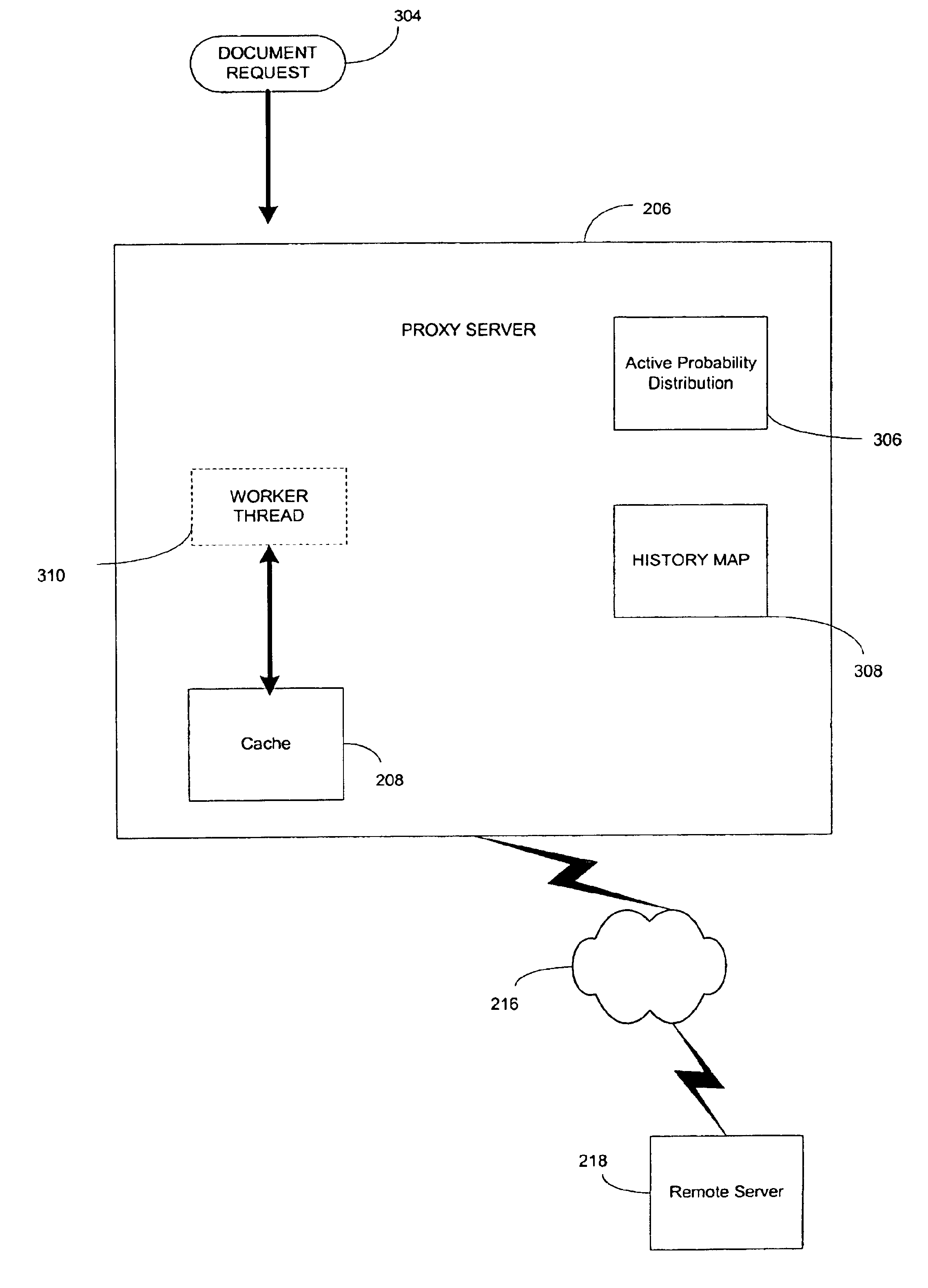
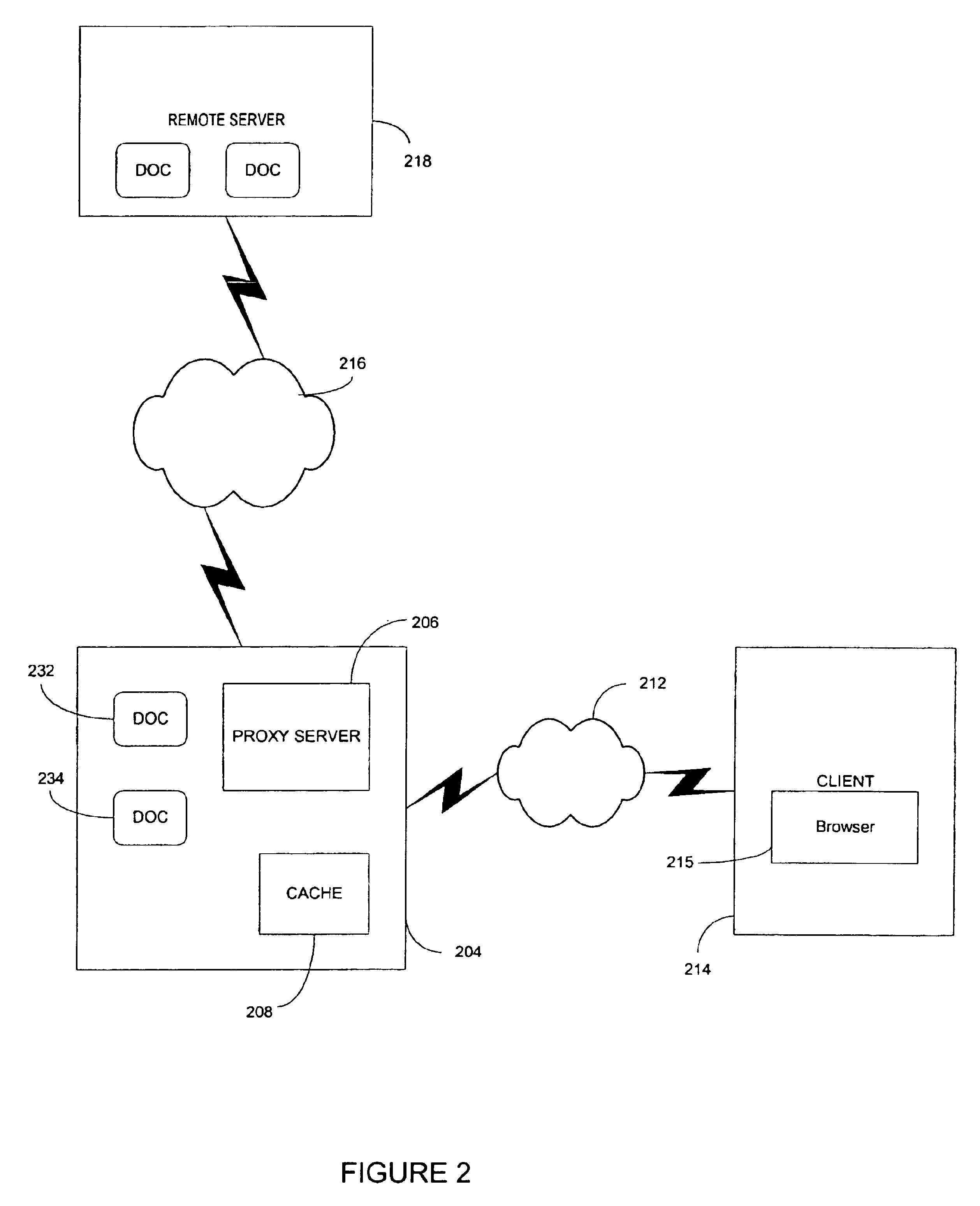
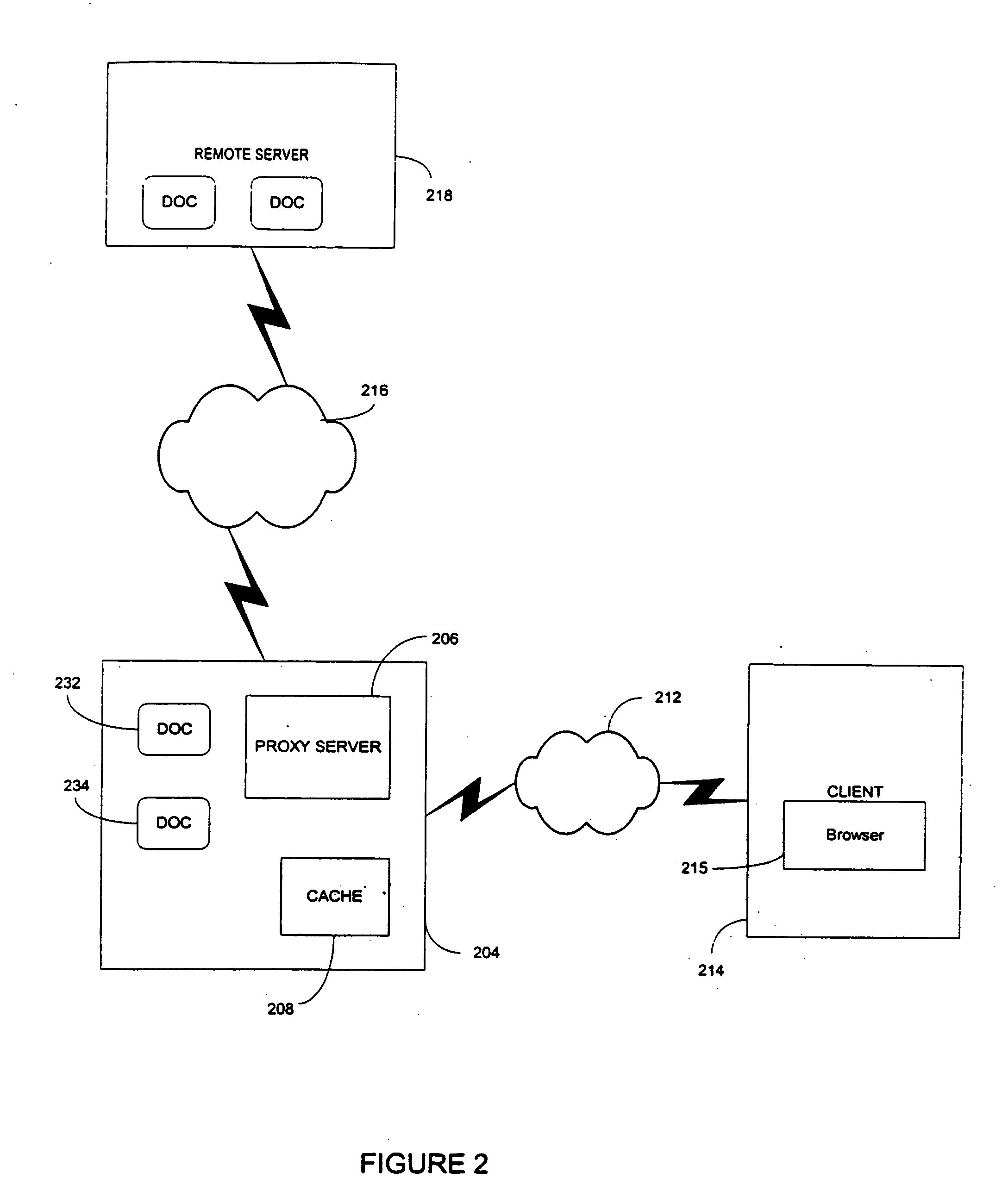
InactiveUS6883135B1Minimizes re-fetchingLess timeData processing applicationsWeb data indexingDocument preparationProxy server
A computer based system and method of determining whether to re-fetch a previously retrieved document across a computer network is disclosed. The method utilizes a statistical model to determine whether the previously retrieved document likely changed since last accessed. The statistical model is continuously improving its accuracy by training internal probability distributions to reflect the actual experience with change rate patterns of the documents accessed. The decision of whether to access the document is based on the probability of change compared against a desired synchronization level, random selections, maximum limits on the amount of time since the document was last accessed, and other criterion. Once the decision to access is made, the document is checked for changes and this information is used to train the statistical model.
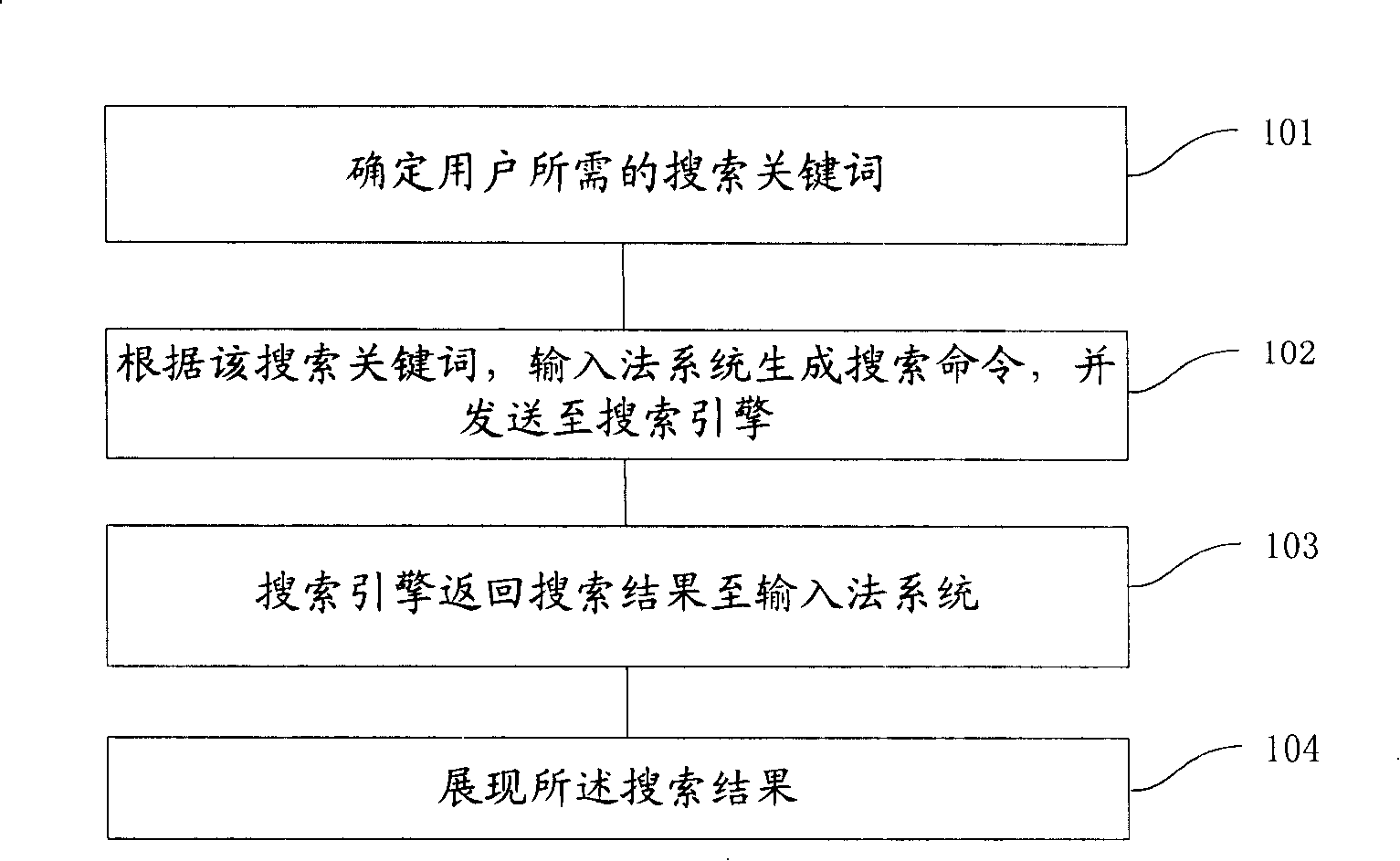
Owner:ZHIGU HLDG
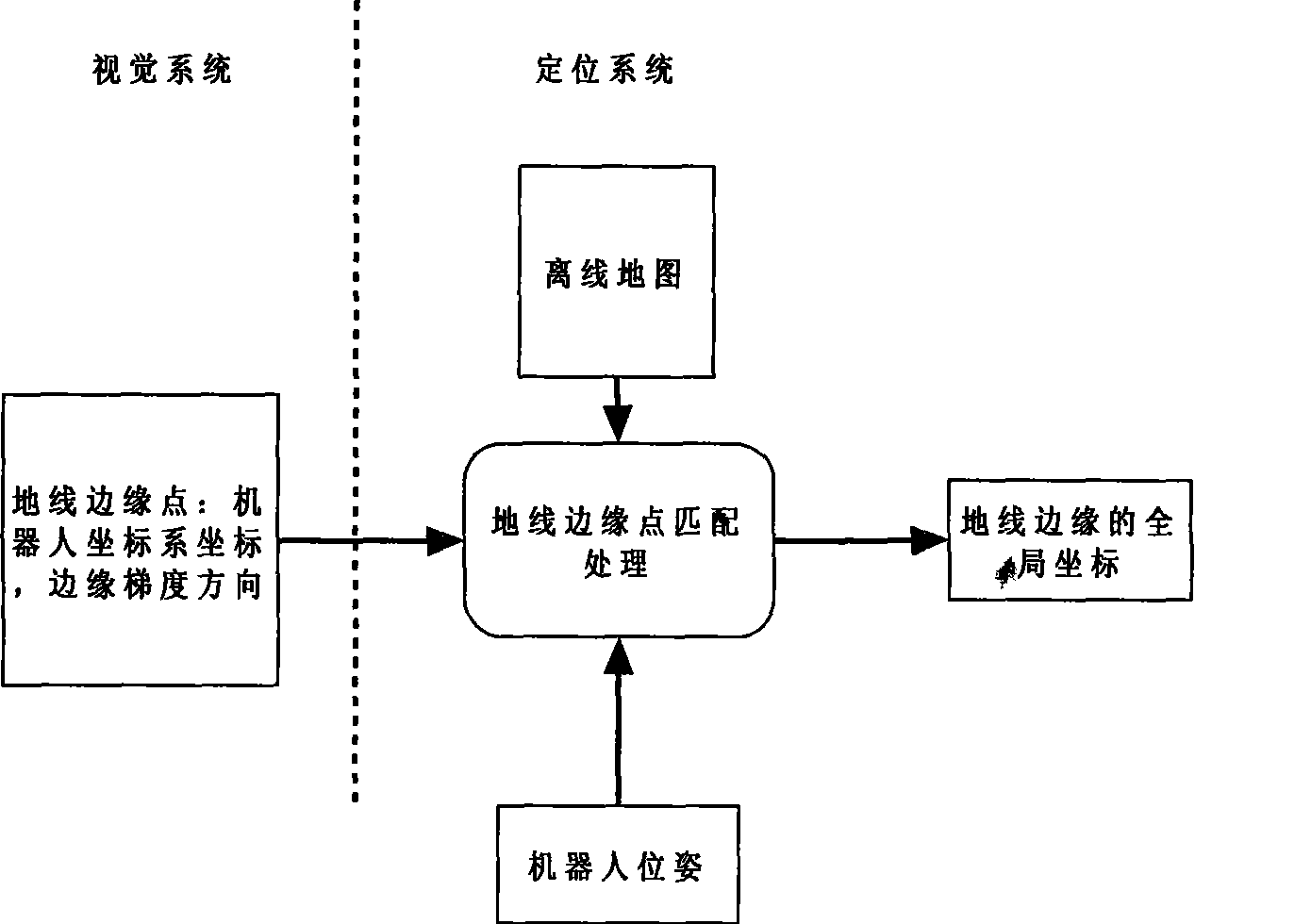
Walking robot positioning system based on monocular cam
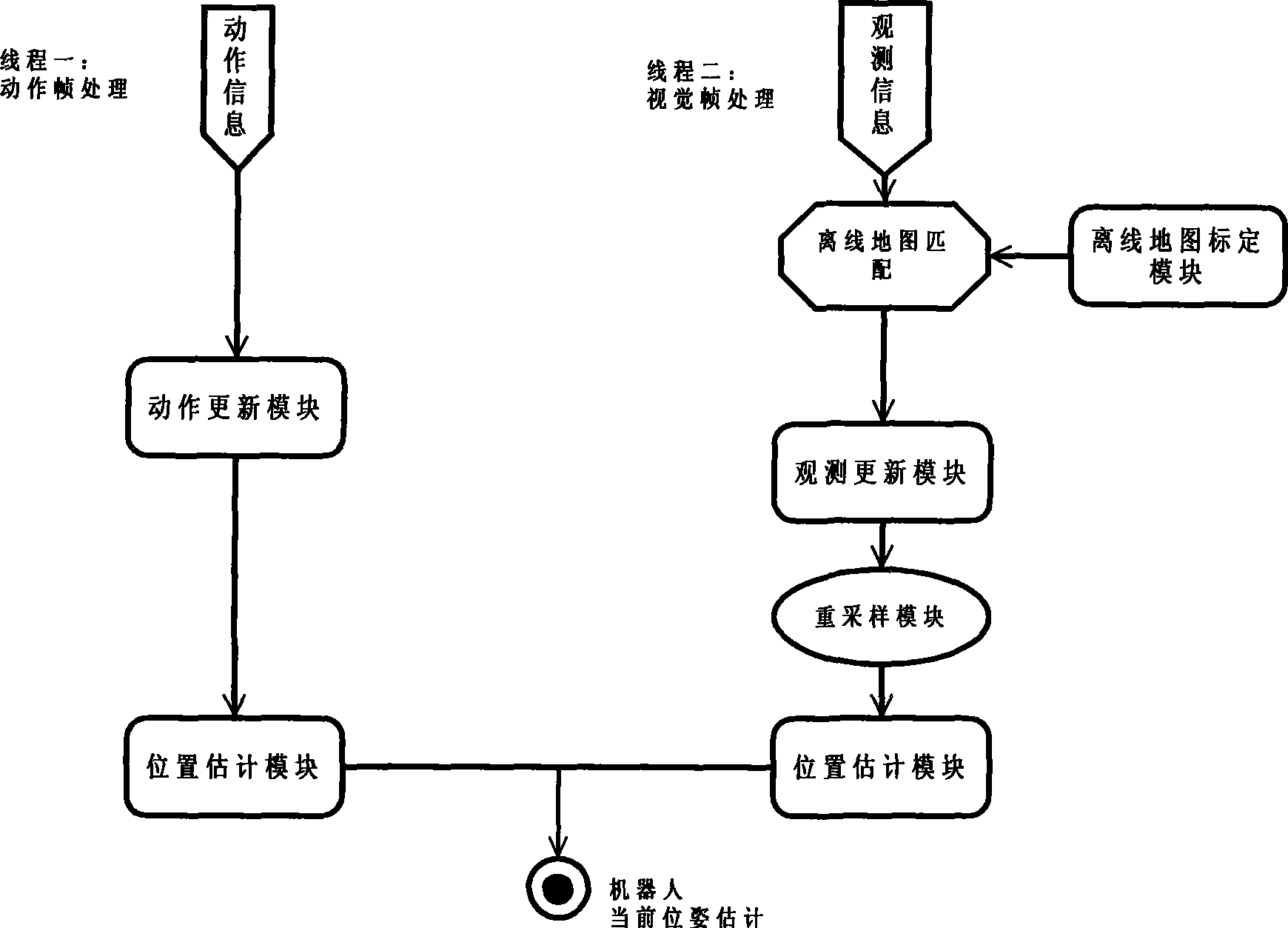
ActiveCN101509781ASmall amount of calculationImprove real-time positioningInstruments for road network navigationNavigational calculation instrumentsParticle densityEngineering
The invention discloses a travelling robot positioning system based on a single camera. In the system, a point model is adopted for representing an environmental model, an off-line map is calibrated, an action model and an observation model are established for carrying out position updating and road sign calibration, Monte Carto particle filter technology is adopted, particle swarm distribution with weights is adopted for representing robot pose estimation, the weights and the distribution of particles are updated through road sign matching processing, field particle distribution is rasterized, and a sub-region with maximal particle density is selected for positioning the robot. As an independent platform, the system greatly improves the map calibration technology on the environmental model, has great flexibility on the identification of ground line sections, and just needs re-calibration but not needs model re-establishment after environment change. The model reduces the matching complexity in visual processing and improves calculation efficiency. The Monte Carlo localization algorithm is expanded on the information integration processing technology, thus ensuring the real-time property and robustness of the system.
Owner:TONGJI UNIV
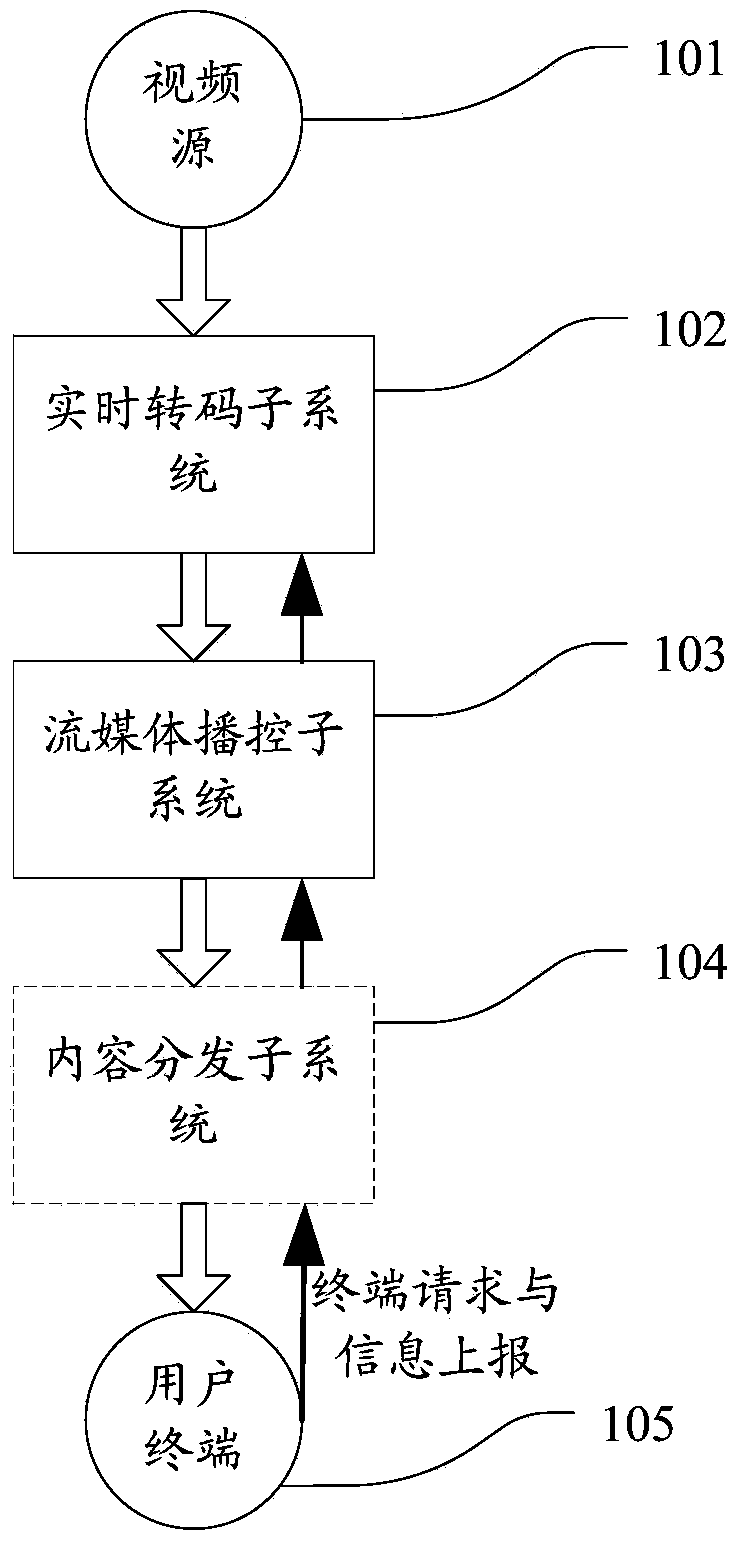
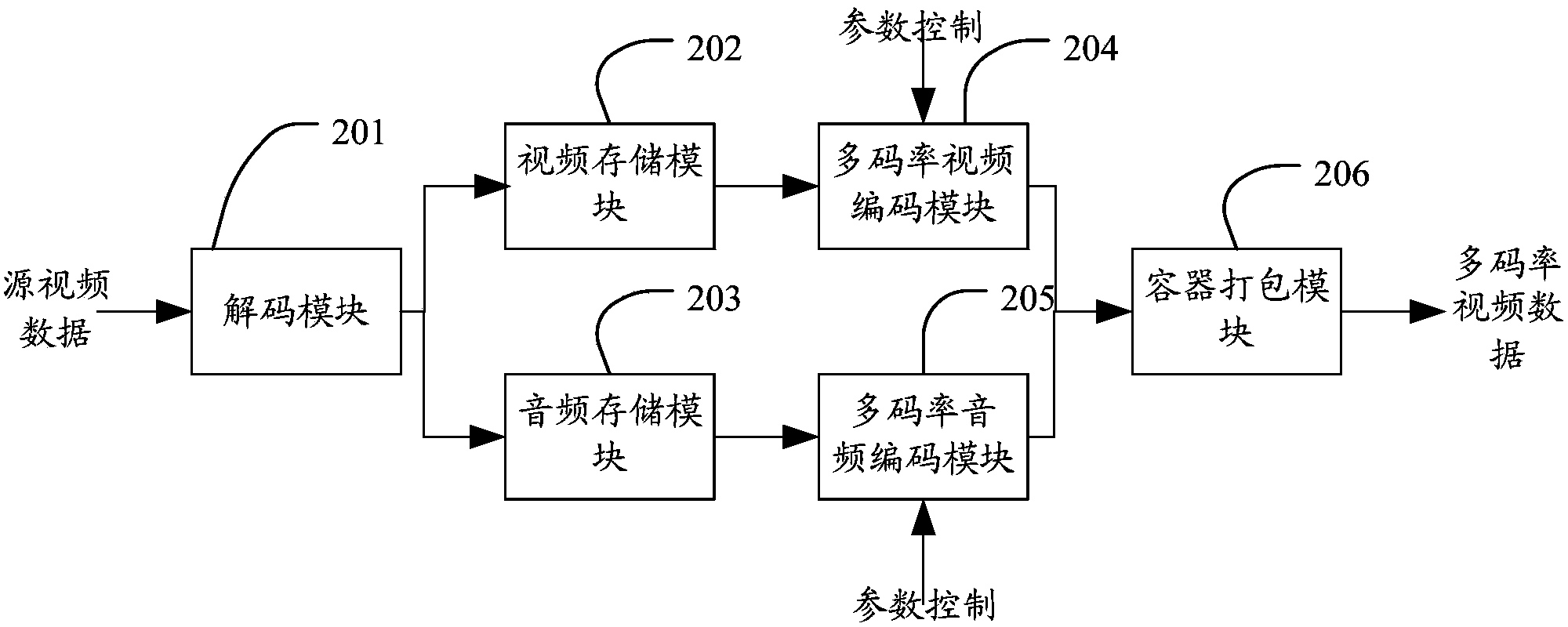
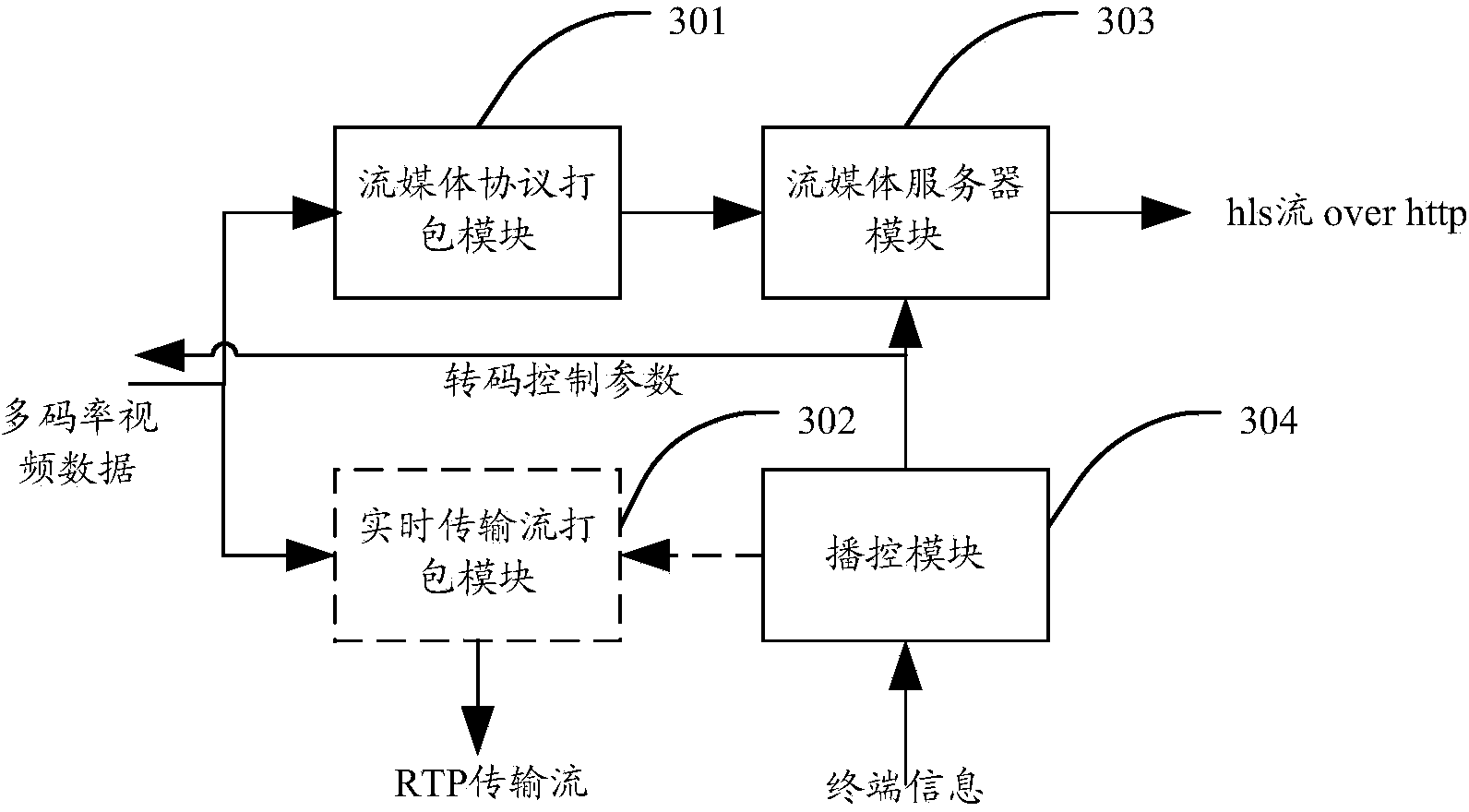
System and method for required real-time transcoding and self-adaptive code rate stream media playing
ActiveCN104349178ASave computing resources and network resourcesSave storage resourcesSelective content distributionSelf adaptiveContent distribution
The invention relates to a system and a method for required real-time transcoding and self-adaptive code rate stream media playing. The system comprises a real-time transcoding subsystem, a stream media playing subsystem, a content distribution subsystem and a user terminal module, wherein the real-time transcoding subsystem is used for transcoding the original videos of a video source into video encoding data which is suitable for a user terminal to play, the stream media playing subsystem is used for packaging the video encoding data outputted by the real-time transcoding subsystem into video steams which are suitable for the stream media to transmit, and providing the stream media service for the user terminal, and the user terminal module is used for sending a request to the real-time transcoding subsystem or the stream media playing subsystem, and dynamically switching and transcoding in real time according to the network state information, so as to obtain the video streams with different code rates for playing. By adopting the structure, the system and the method for the required real-time transcoding and the self-adaptive code rate stream media playing have the advantages that the required real-time transcoding of the stream media is realized, the playing code rate is dynamically selected according to the change of the band width of the terminal network, different user terminals can be flexibly matched, and the application range is wider.
Owner:CERTUS NETWORK TECHNANJING
Data transmission method, server side and client
ActiveCN104023013ASecure transmissionSecure one-way transmissionUser identity/authority verificationKey exchangeClient-side
The invention discloses a data transmission method, a server side and a client. The data transmission method comprises the following steps that: the server side and the client carry out information interaction through an authentication protocol, and perform identity authentication with each other; a session key is generated by the server side and the client through a key exchange protocol; a data packet to be transmitted is encrypted by the client through adopting an encryption algorithm and the session key, and the encrypted data packet is transmitted to the server side; and the received encrypted data packet is decrypted by the server side through utilizing the session key and the encryption algorithm, and the corresponding operation is executed. According to the scheme, unidirectional transmission of the transmitted data packet from the client to the server side can be implemented, establishing process is simple, and the computing resource is effectively saved, so that the data transmission is safer and more reliable.
Owner:SHANGHAI DNION INFORMATION & TECH
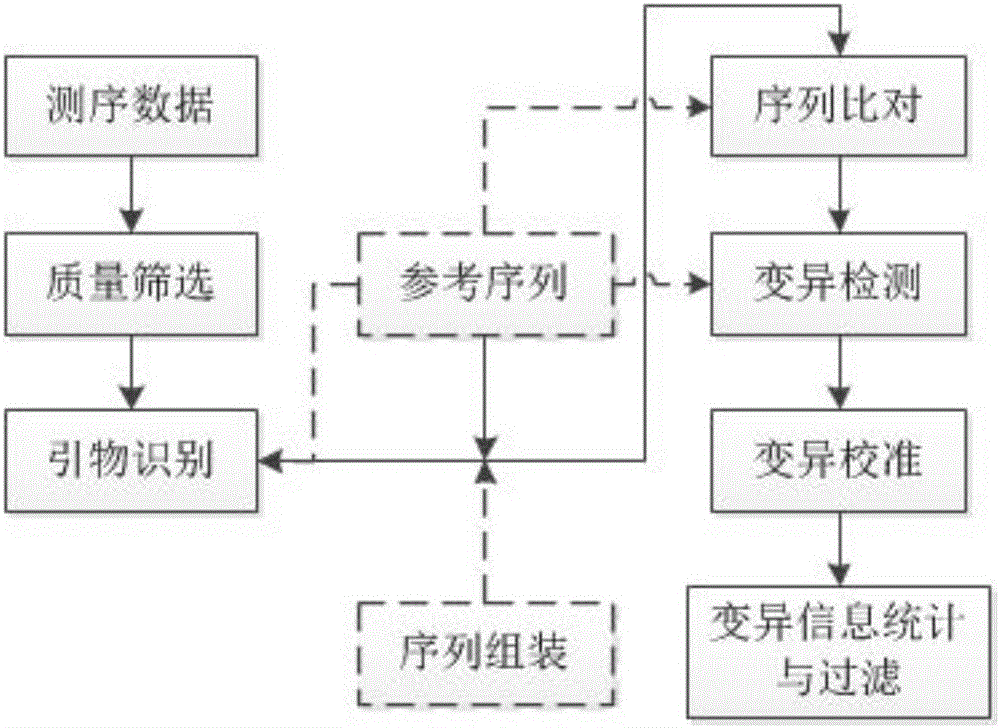
Method for detecting mutation information in multiplex amplification sequencing product of genome
ActiveCN106202991AEfficient identificationQuick identificationHybridisationSpecial data processing applicationsReference genesNatural abundance
The invention discloses a method for detecting mutation information in a multiplex amplification sequencing product of a genome. The method comprises steps as follows: sequencing data are subjected to quality assessment and preprocessing; a recognizable sequencing sequence is selected for sequence assembling; the recognizable sequencing sequence or a sequence obtained through assembling is compared with a reference gene sequence, and preliminary variation information is obtained; fine calibration of sequence variation is performed according to different types of conditions; a calibrated sequencing fragment is obtained; the homozygosis or heterozygosis state of a target fragment is obtained according to the type of the sequencing fragment with the highest abundance; finally, the mutation information in the multiplex amplification sequencing product of the genome is obtained. By means of the method, the amplification product can be rapidly, efficiently and accurately recognized, and the calculation resources are saved; the sequence assembling process is compatible, and the problem of reduction of the quality value of basic groups produced in the sequencing process can be effectively solved; the homozygosis / heterozygosis state of variation information can be more effectively and stably judged, and random errors introduced in the PCR (polymerase chain reaction) process and the sequencing process are eliminated.
Owner:AMOY DIAGNOSTICS CO LTD +1
Two-pass device access management
InactiveUS7167919B2Eliminate needSave computing resourcesMultiple digital computer combinationsInternal/peripheral component protectionAccess managementAuthentication information
Access control to a networked peripheral device by a walk-up user, wherein the networked peripheral device is accessible by both the walk-up user and a remote user, based on centralized access management information. Access control comprises receiving authenticated information for the walk-up user from the networked peripheral device at a centralized location, determining at a server connected to the network a first level of access to the networked peripheral device, determining at the networked peripheral device a second level of access to the networked peripheral device by the walk-up user based on received access management information for the walk-up user, and allowing the walk-up user to access determined user-available features of the networked peripheral device based on the determined first and second levels of access.
Owner:CANON KK
Multi-tenant policy-driven type software-defined networking method for cloud data center
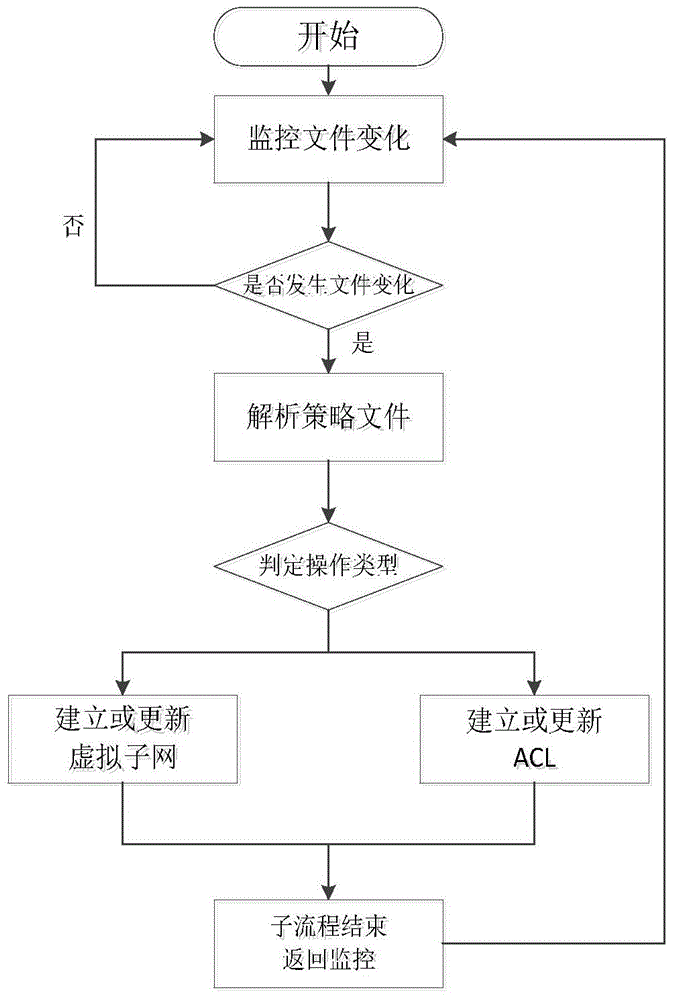
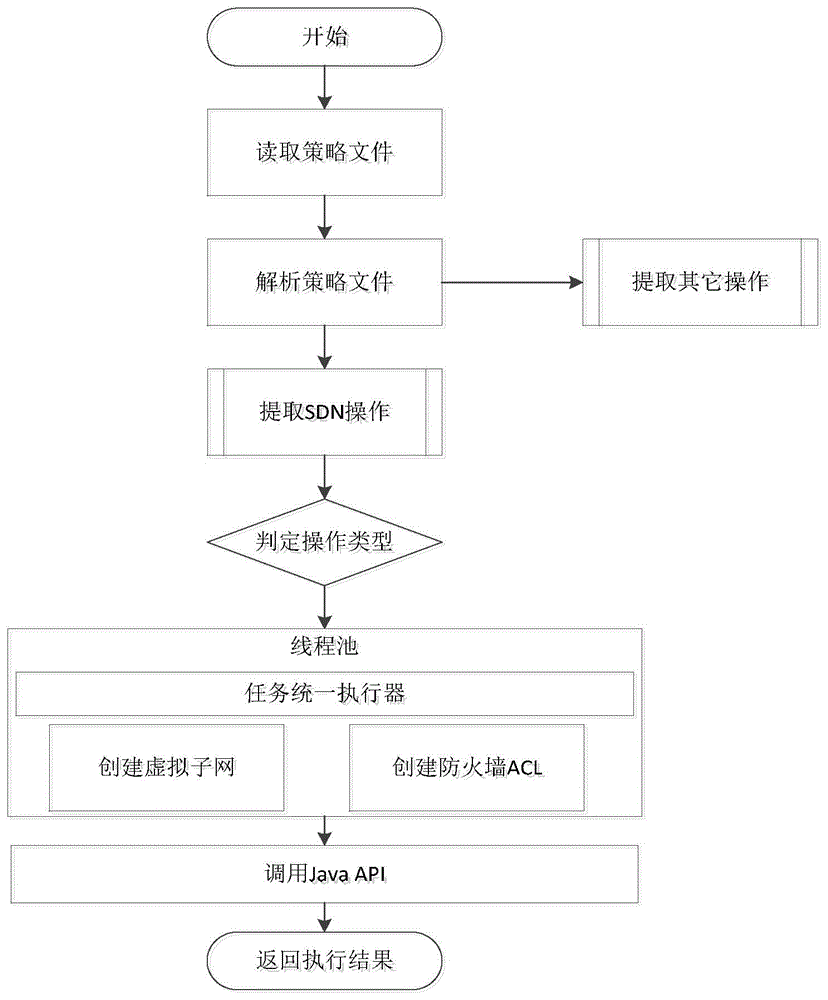
InactiveCN104092565AShorten the timeSave computing resourcesData switching networksVirtual firewallCloud data center
The invention belongs to the technical field of cloud computing and novel networks, and particularly provides a multi-tenant policy-driven type software-defined networking method for a cloud data center. The method includes the specific steps of tenant policy defining, user definition policy authority limiting, policy conflict solving and policy file parsing and executing. According to the method, a network is configured through policy defining, tenants can define virtual networks, virtual firewalls and the like of the tenants in a visual mode without writing programs or using a programming interface provided by a software-defined networking controller; management on a cloud computing platform and management on an SDN controller are unified; the networks are managed through policy parsing, so that higher efficiency can be achieved, computing resources, such as a CPU, of the software-defined networking controller are saved, and the time for processing requests of the tenants through the controller is shortened. On the premise that user friendliness is ensured, the performance can be close to the performance achieved when calling is conducted by a local API, and meanwhile the performance is quite better than the performance achieved when calling is conducted by an RESTAPI.
Owner:FUDAN UNIV
Proxy server using a statistical model
InactiveUS20050086583A1Save computing resourcesMinimal amountData processing applicationsWeb data indexingDocument preparationProxy server
A computer based system and method of determining whether to re-fetch a previously retrieved document across a computer network is disclosed. The method utilizes a statistical model to determine whether the previously retrieved document likely changed since last accessed. The statistical model is continuously improving its accuracy by training internal probability distributions to reflect the actual experience with change rate patterns of the documents accessed. The decision of whether to access the document is based on the probability of change compared against a desired synchronization level, random selections, maximum limits on the amount of time since the document was last accessed, and other criterion. Once the decision to access is made, the document is checked for changes and this information is used to train the statistical model.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com