Patents
Literature
686results about How to "Avoid deadlock" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
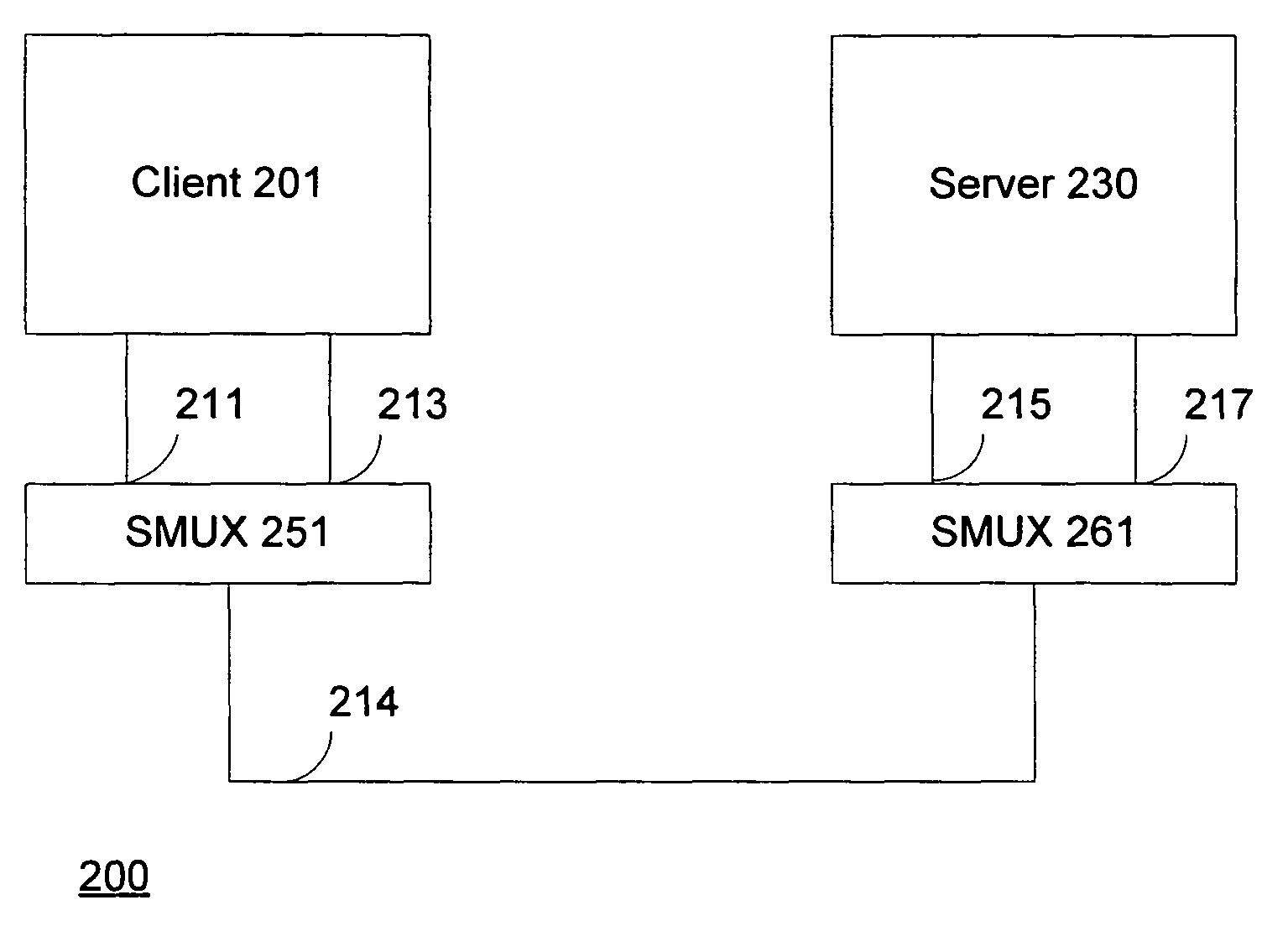
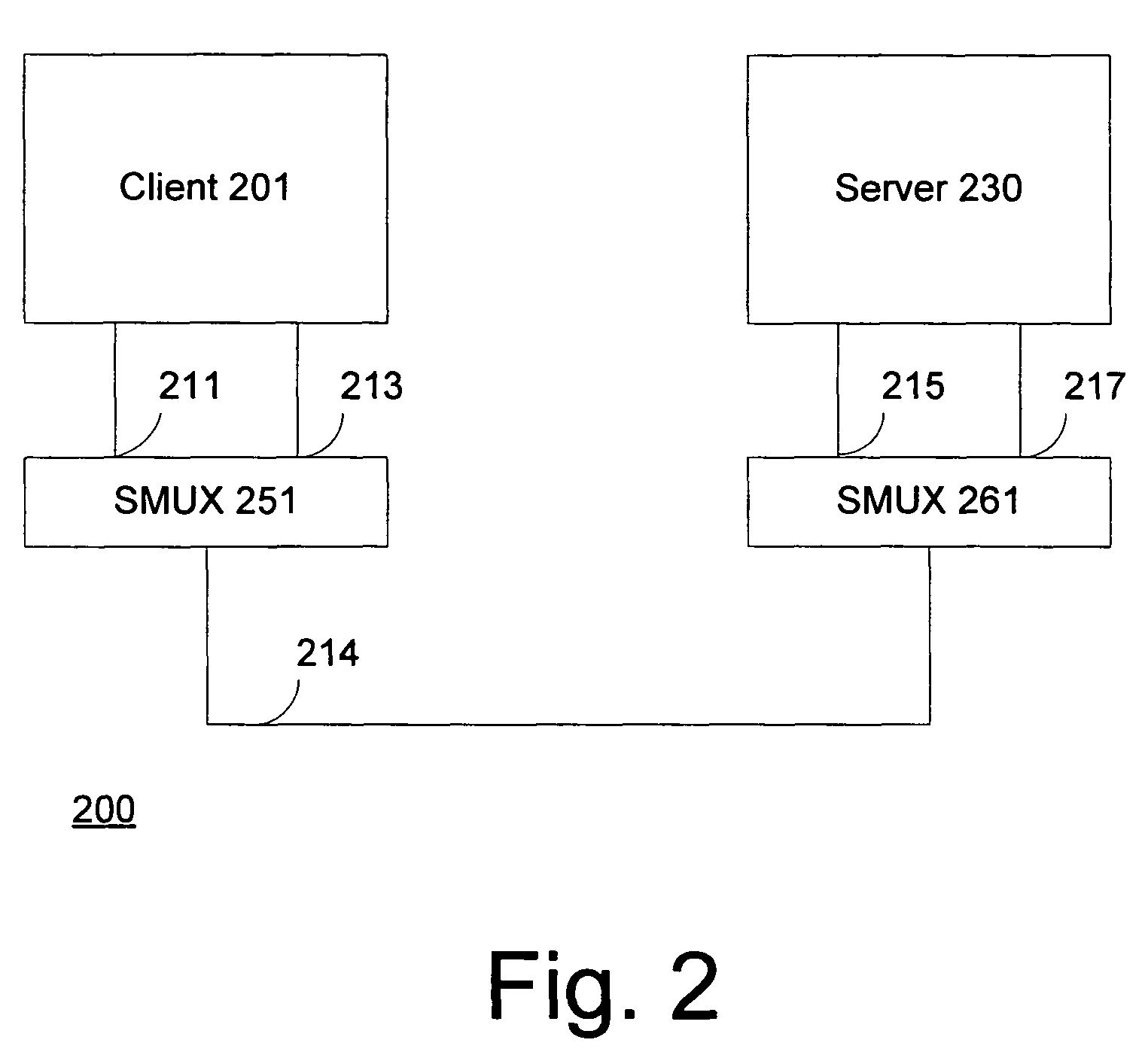
Session multiplex protocol
InactiveUS7966405B2Bandwidth is no longer wastedSave computing resourcesEnergy efficient ICTData switching by path configurationMultiplexingByte
Session multiplex protocol (“SMUX”) is a protocol layered above existing reliable transport mechanisms that can be used to create multiple sessions over a single connection. Data from several different SMUX sessions can be interleaved and message boundaries preserved. Because it sits on top of reliable transport mechanisms, it takes advantage of the underlying protocols to ensure byte-alignment, loss detection / recovery, and reliable delivery. It provides a window based flow control mechanism to ensure suitable fairness among streams of different sessions and prevent deadlocks.
Owner:MICROSOFT TECH LICENSING LLC
Method for processing data
ActiveUS7657877B2Simple programmabilityEasy and efficient connectionDetecting faulty computer hardwareRead-only memoriesParallel computingProgram transformation
A method and device for translating a program to a system including at least one first processor and a reconfigurable unit. Code portions of the program which are suitable for the reconfigurable unit are determined. The remaining code of the program is extracted and / or separated for processing by the first processor.
Owner:SCIENTIA SOL MENTIS AG
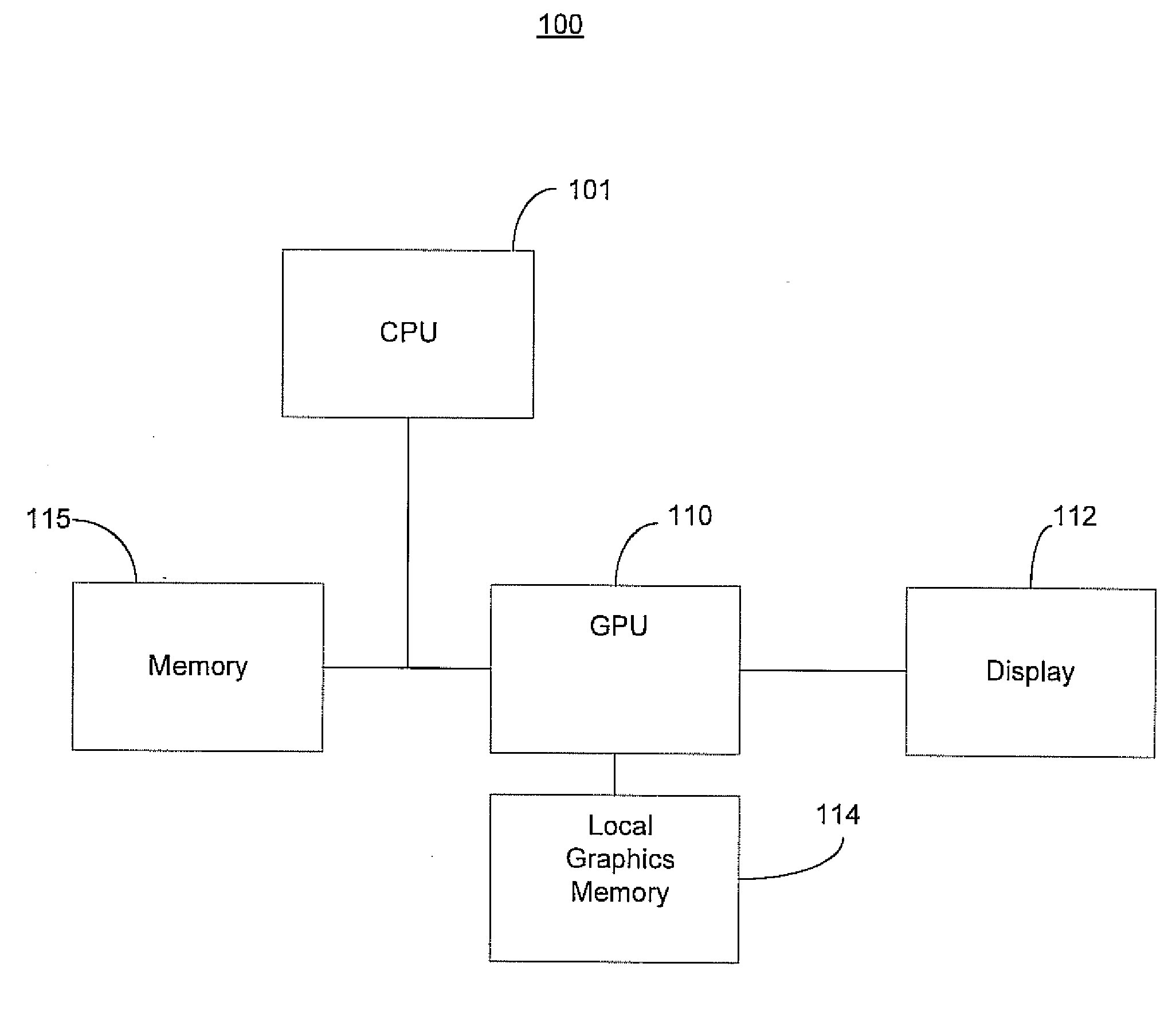
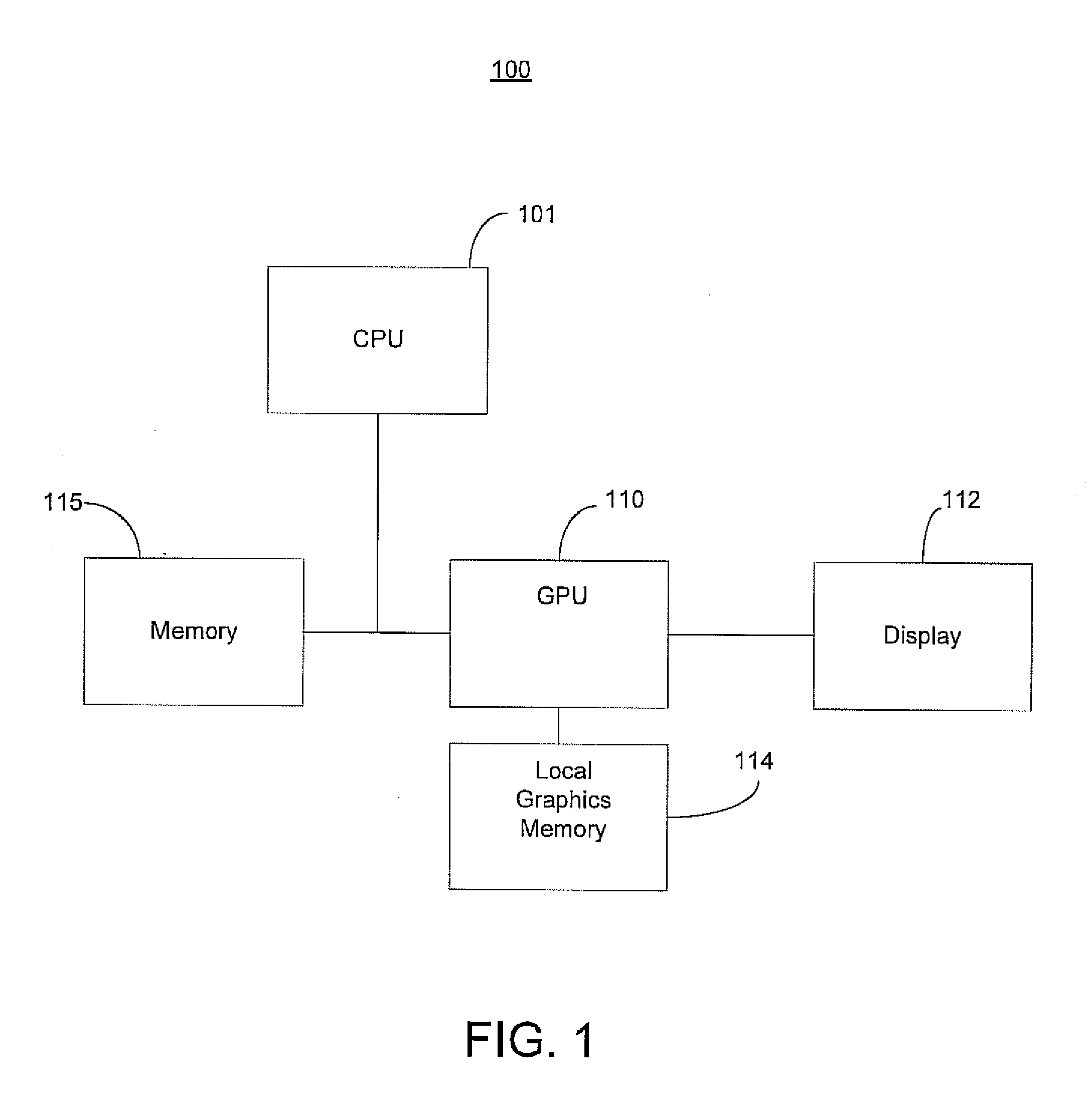
GPU rendering to system memory
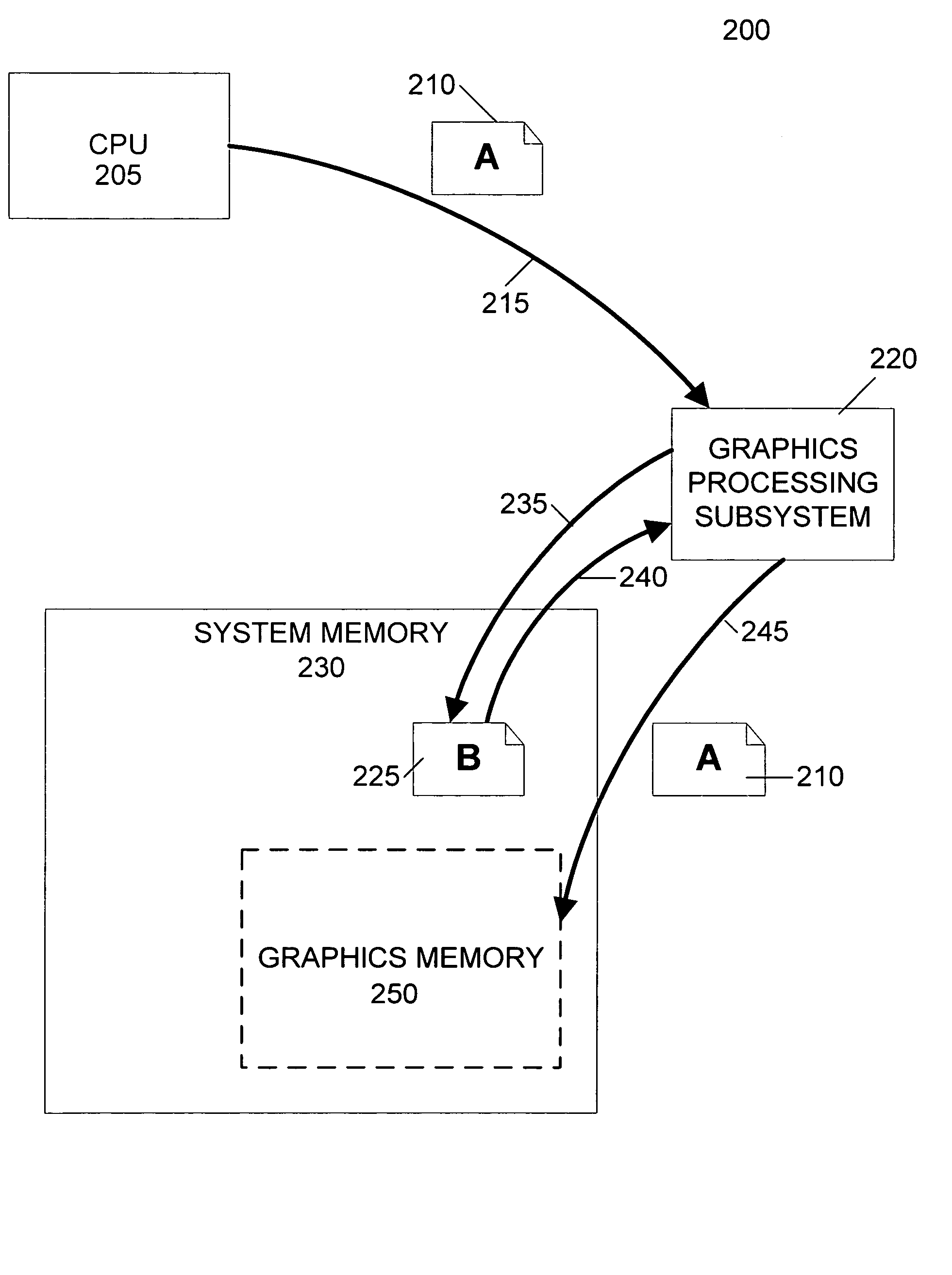
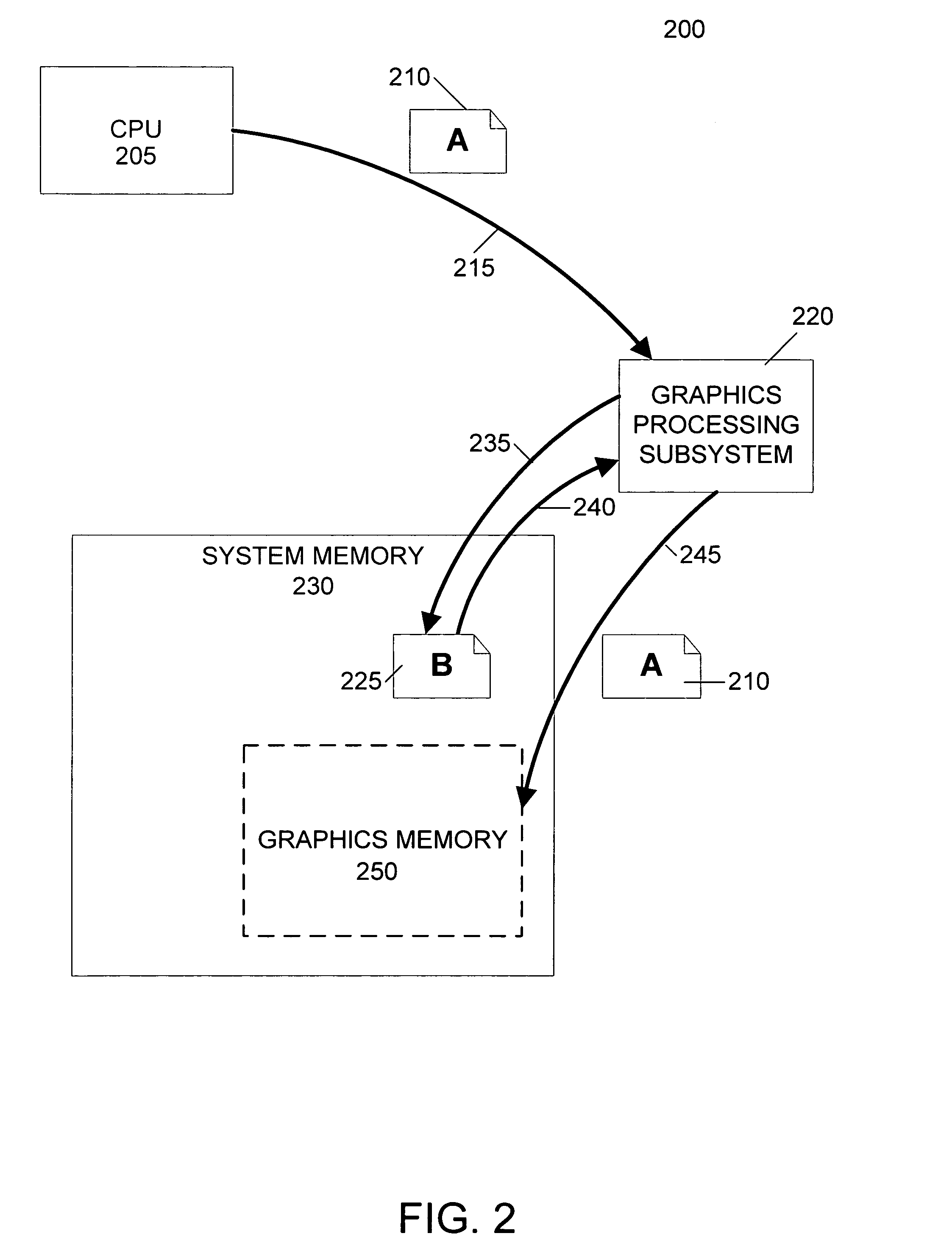
InactiveUS20050237329A1Avoid deadlockHigh degree of two-dimensional localityMemory adressing/allocation/relocationCathode-ray tube indicatorsMemory addressGraphics
A graphics processing subsystem uses system memory as its graphics memory for rendering and scanout of images. To prevent deadlock of the data bus, the graphics processing subsystem may use an alternate virtual channel of the data bus to access additional data from system memory needed to complete a write operation of a first data. In communicating with the system memory, a data packet including extended byte enable information allows the graphics processing subsystem to write large quantities of data with arbitrary byte masking to system memory. To leverage the high degree of two-dimensional locality of rendered image data, the graphics processing subsystem arranges image data in a tiled format in system memory. A tile translation unit converts image data virtual addresses to corresponding system memory addresses. The graphics processing subsystem reads image data from system memory and converts it into a display signal.
Owner:NVIDIA CORP
Method, system and protocol that enable unrestricted user-level access to a network interface adapter
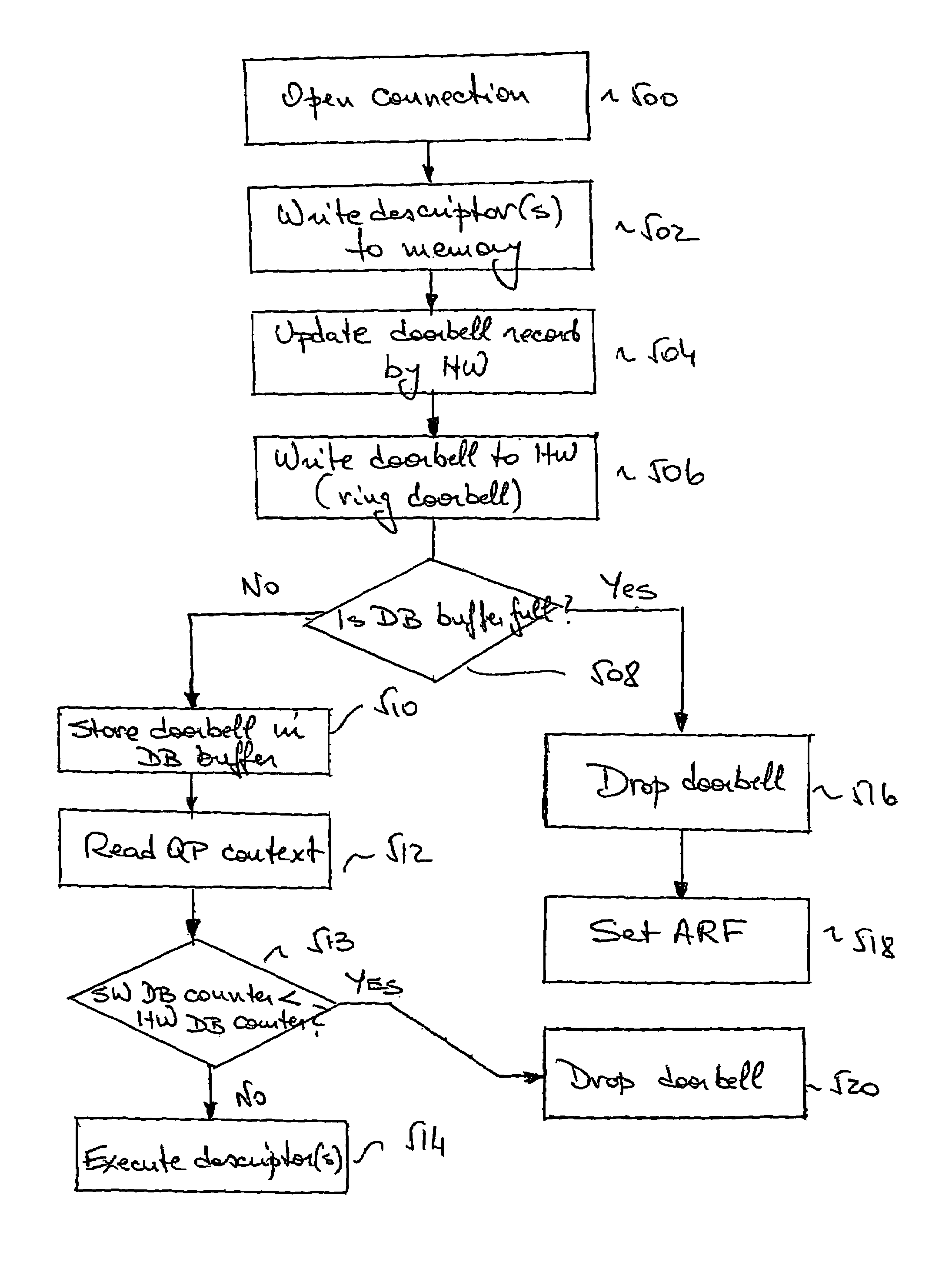
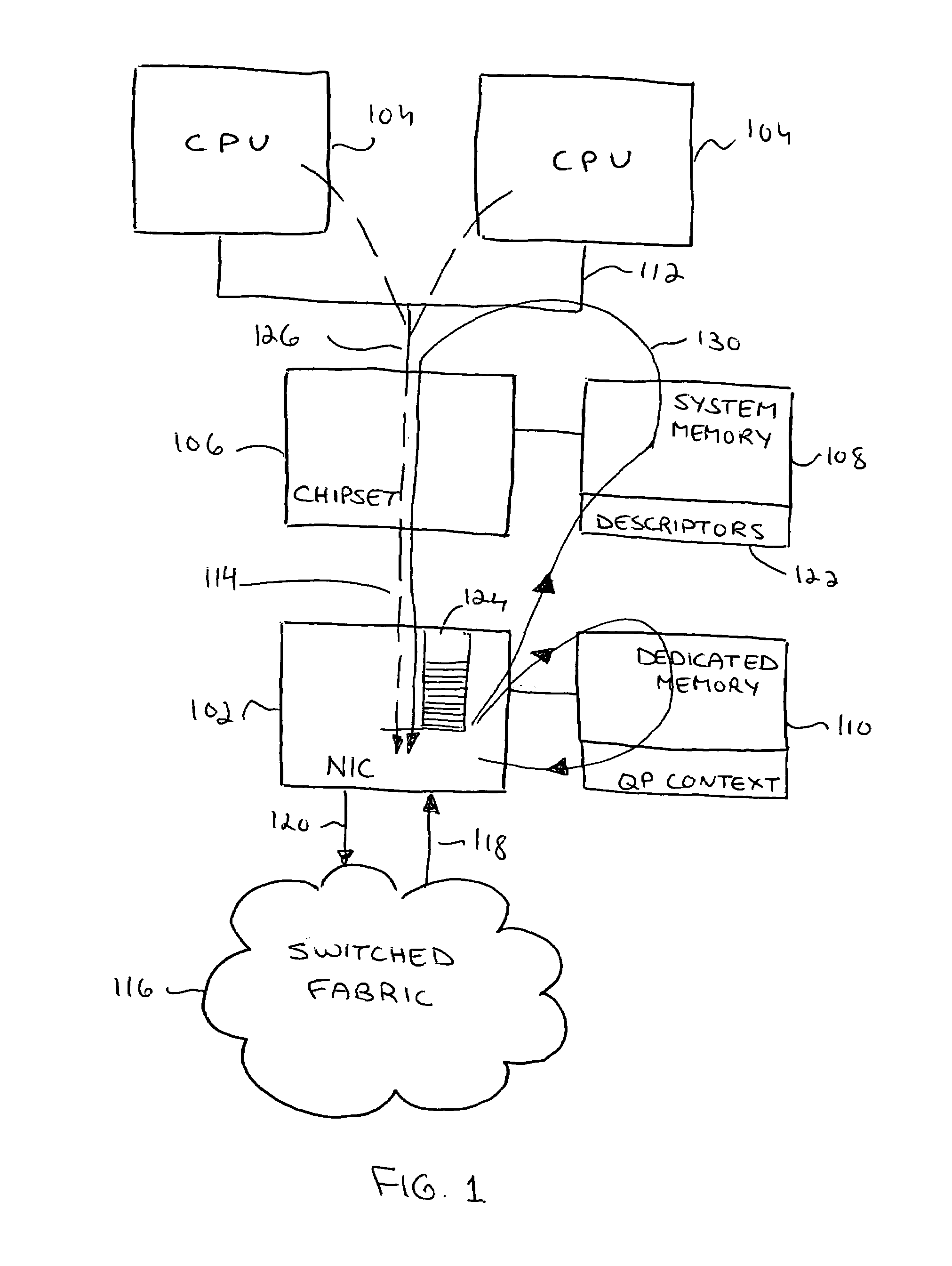
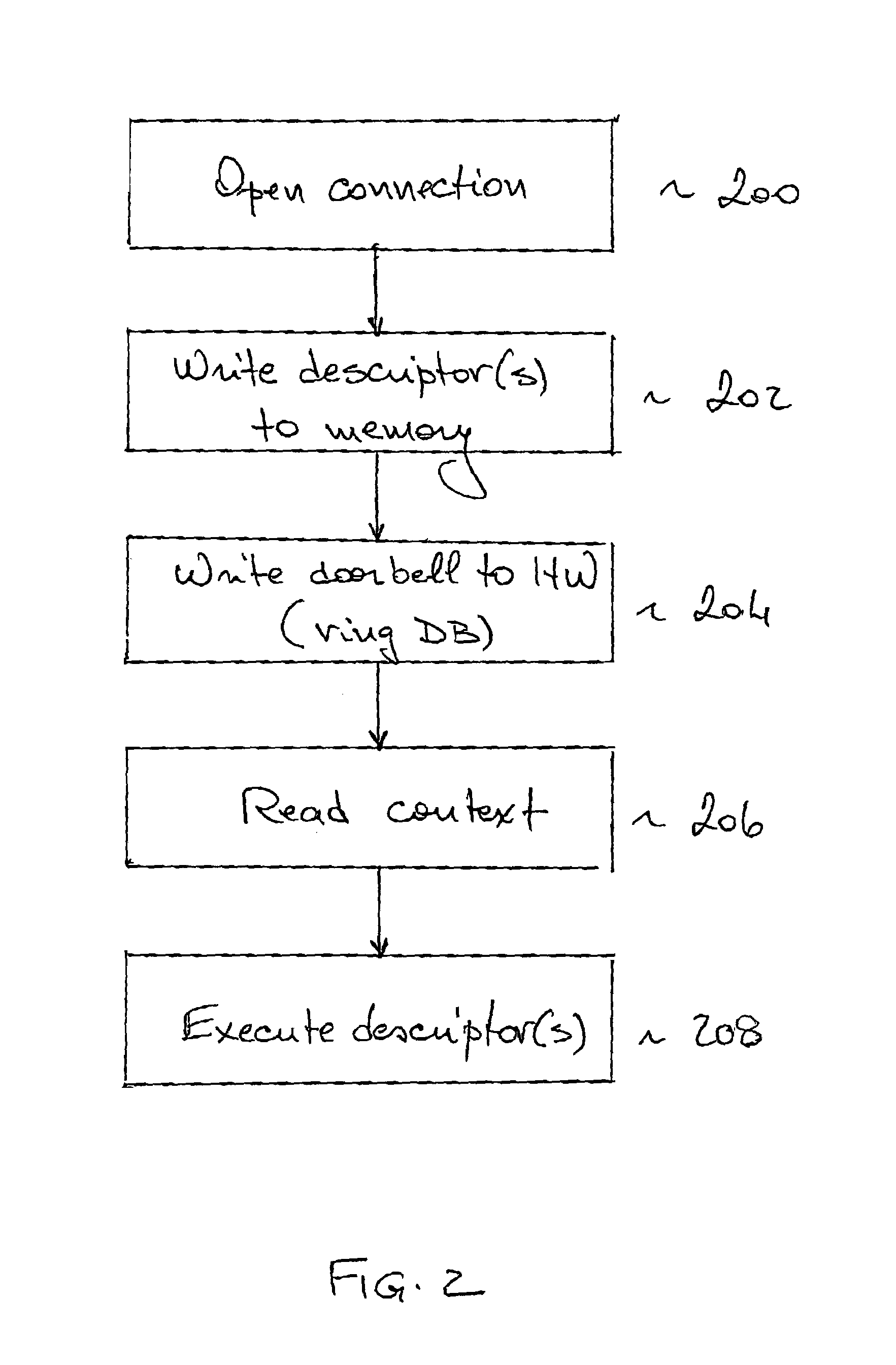
ActiveUS7653754B2Avoid deadlockUnrestricted user-level access to the NICConveying record carriersMultiple digital computer combinationsDoorbellApplication software
A method for preventing deadlock in communication between a host software application and a network interface card (NIC), comprises writing a doorbell associated with at least one descriptor having a descriptor context to a buffer in the NIC, dropping at least one doorbell from the buffer if the buffer is full, thereby allowing a write of a new doorbell to the buffer, and recovering each dropped doorbell for further execution of descriptors associated with this doorbell. The descriptor execution is in order of posting by the application to the NIC. A system implementing the method comprises a doorbell drop mechanism and a doorbell recovery mechanism.
Owner:MELLANOX TECHNOLOGIES LTD
Double-machine redundant tolerant system and redundant switching method thereof
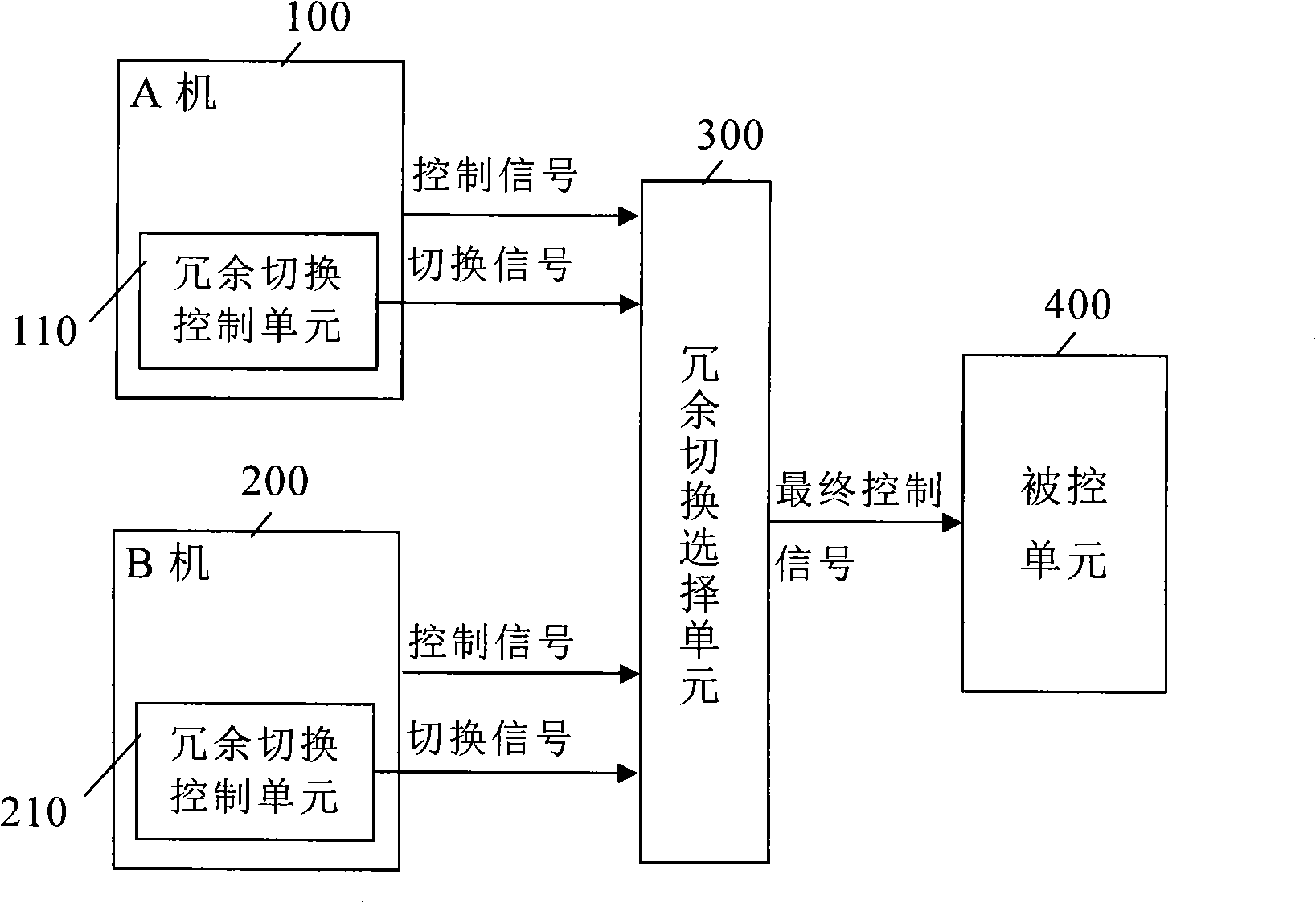
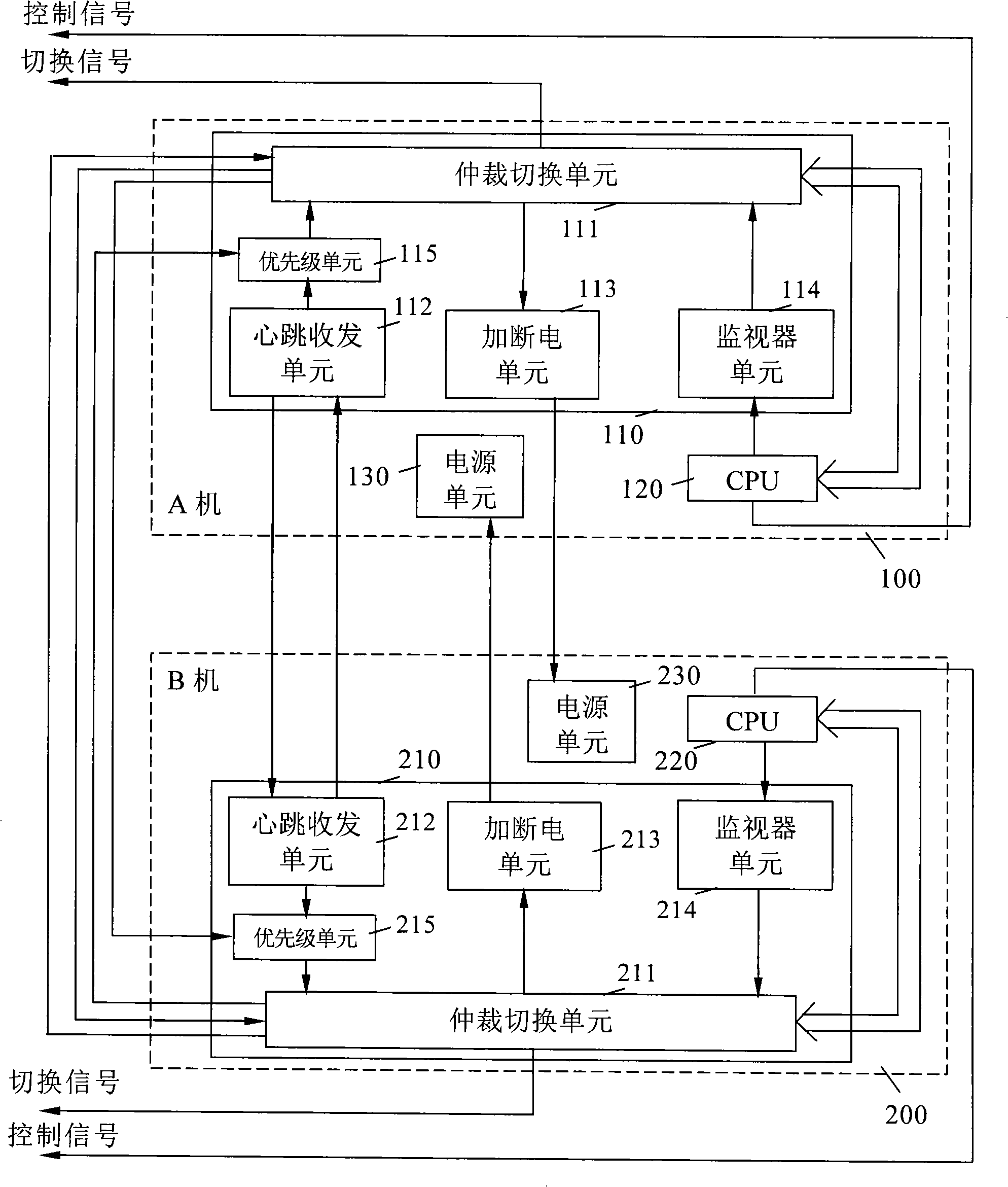
InactiveCN101281483AGuaranteed to workPrevent catastrophic failureRedundant hardware error correctionElectricityControl signal
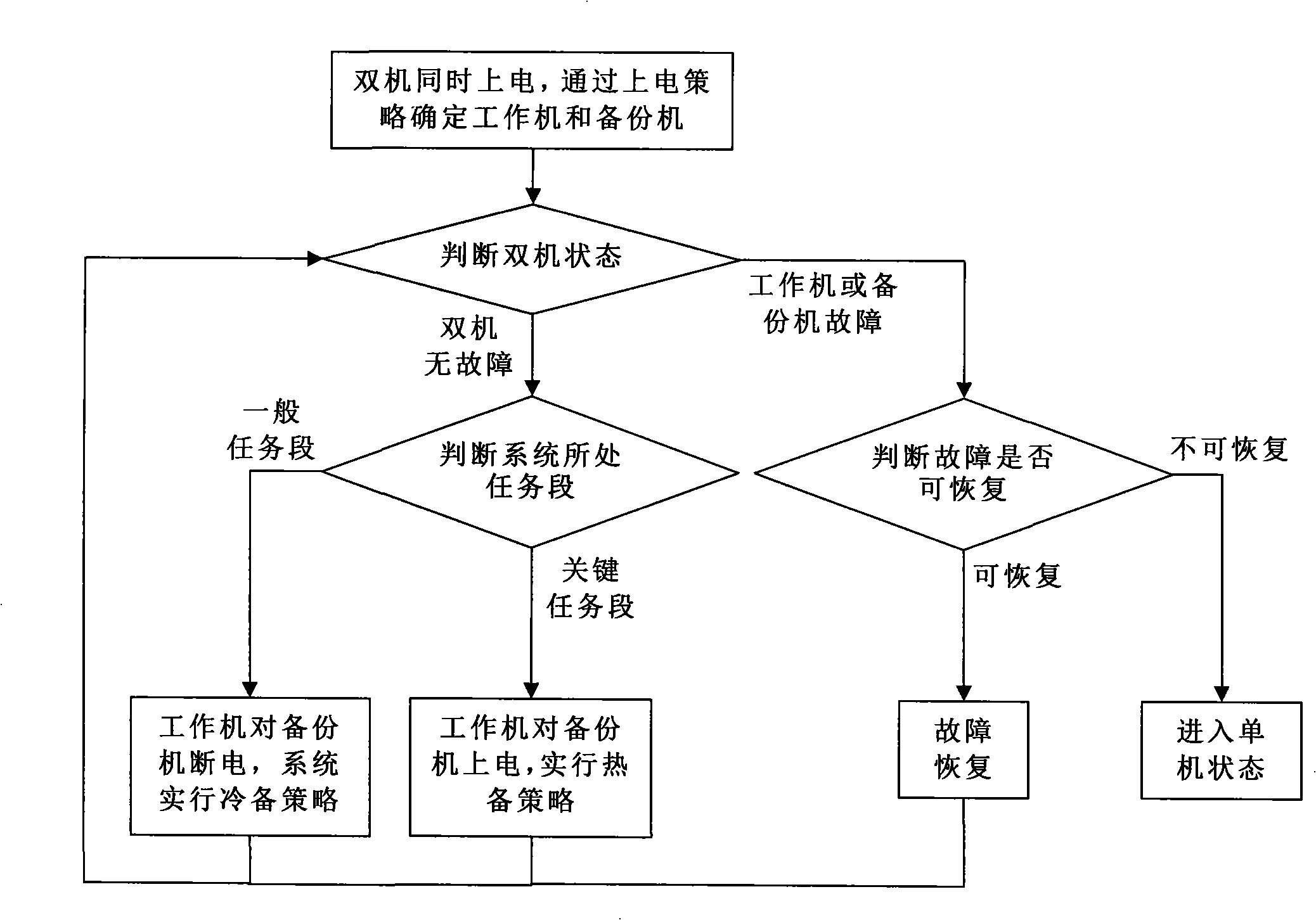
The invention discloses a dual-computer redundancy fault-tolerant system and the redundancy switching method. The system comprises an A computer, a B computer, redundancy switch control units in the A and B computers transmit respective switch signals to a redundancy switch selecting unit, and the final control signal generated by the redundancy switch selecting unit is transmitted to a controlled unit. The redundancy switch control unit includes an arbitrary switch unit, a heartbeat receiving unit, a power on-off unit and a monitoring unit. The method comprises the following steps: the two computers are powered up, a master computer and a slavery computer are decided by power up strategy; the states of the two computers are judged; if the two computers have no fault, the task segment of a system is judged: if the system is in normal task segment, a working computer powers up a backup computer, and executes cold backup strategy; if the system is in key task segment, the working computer powers down the backup computer, and executes hot backup strategy; if a single computer has fault which is restorable, the fault is restored, or else, the system enters into single computer state. The system has simple structure and reliable signal transmission; the method is easy to control, the system fault rate is greatly reduced, thus having good fault-tolerant effect.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Deadlock avoidance mechanism in multi-threaded applications
InactiveUS20080209422A1Avoid deadlockResource allocationMemory systemsComputerized systemApplication software
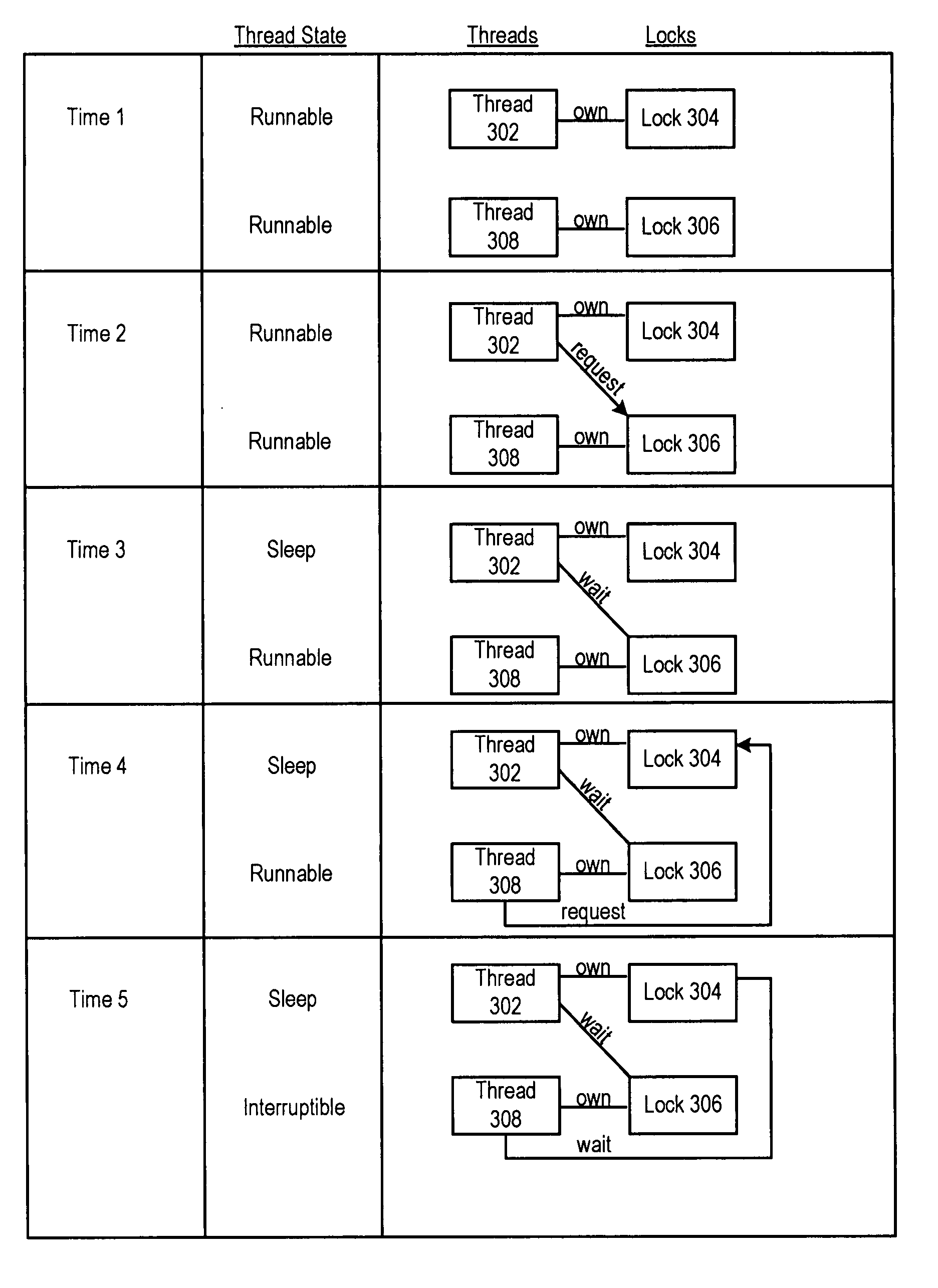
A computer-implemented method for implementing a deadlock avoidance mechanism to prevent a plurality of threads from deadlocking in a computer system wherein a first thread of the plurality of threads request for a first resource is provided. The computer-implemented method includes employing the deadlock avoidance mechanism to intercept the request. The computer-implemented method also includes examining a status of the first resource. The computer-implemented method further includes, if the first resource is owned, identifying an owner of the first resource, analyzing the owner of the first resource to determine if the owner of the first resource is requesting a second resource, and analyzing the second resource to determine if the second resource is owned by the first thread. The computer-implemented method yet also includes, if the first thread owns the second resource, preventing deadlocking by handling a potential deadlock situation.
Owner:HEWLETT PACKARD DEV CO LP
Decoupling parallel scheduling method for rely tasks in cloud computing
InactiveCN102591712AStrong parallelismLoad balancingMultiprogramming arrangementsTransmissionParallel computingPerformance index
The invention belongs to the field of cloud computing application, and relates to method for task rely relation description, decoupling, parallel scheduling and the like in cloud service. Rely task relations are provided, and a decoupling parallel scheduling method of rely tasks are constructed. The method comprises first decoupling the task rely relations with incoming degree being zero to construct a set of ready tasks and dynamically describing tasks capable of being scheduled parallelly at a moment; then scheduling the set of the ready tasks in distribution type and multi-target mode according to real time resource access so as to effectively improve schedule parallelism; and during the distribution of the tasks, further considering task execution and expenditure of communication (E / C) between the tasks to determine whether task copy is used to replace rely data transmission so as to reduce the expenditure of communication. The whole scheduling method can schedule a plurality of tasks in the set of the ready tasks in dynamic parallel mode, well considers performance indexes including real time performance, parallelism, expenditure of communication, loading balance performance and the like, and effectively improves integral performance of the system through the dynamic scheduling strategy.
Owner:DALIAN UNIV OF TECH
Data processing method and system
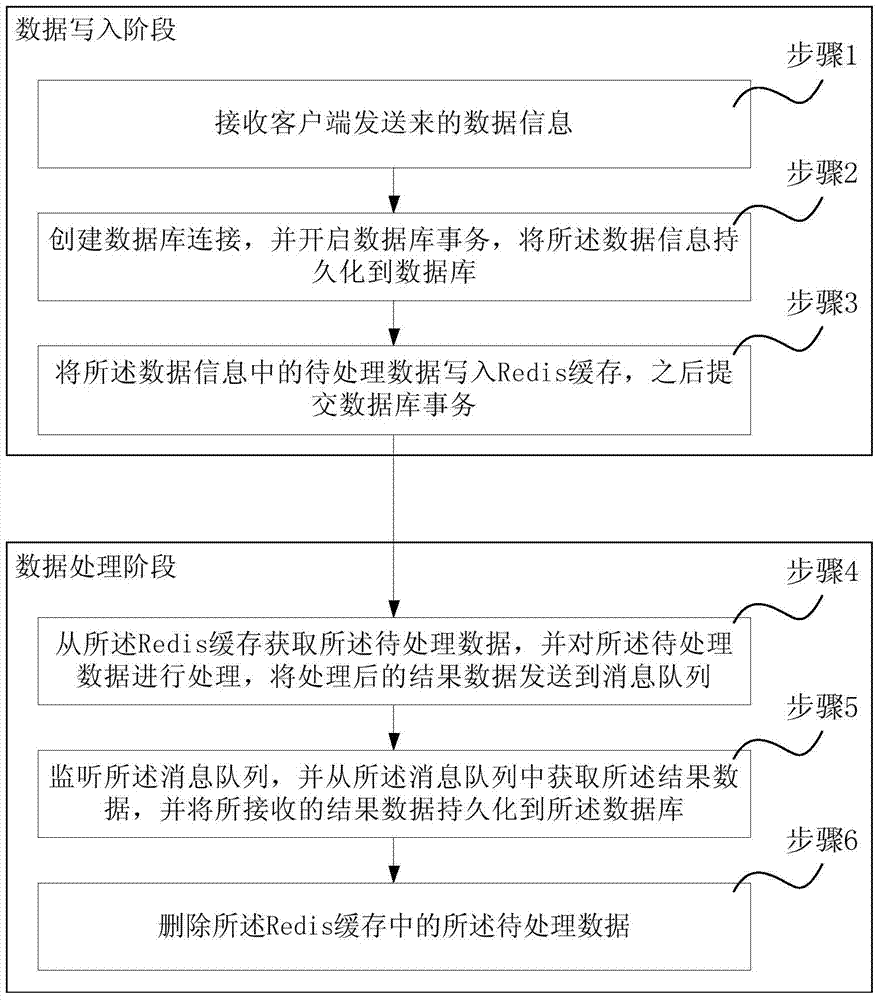
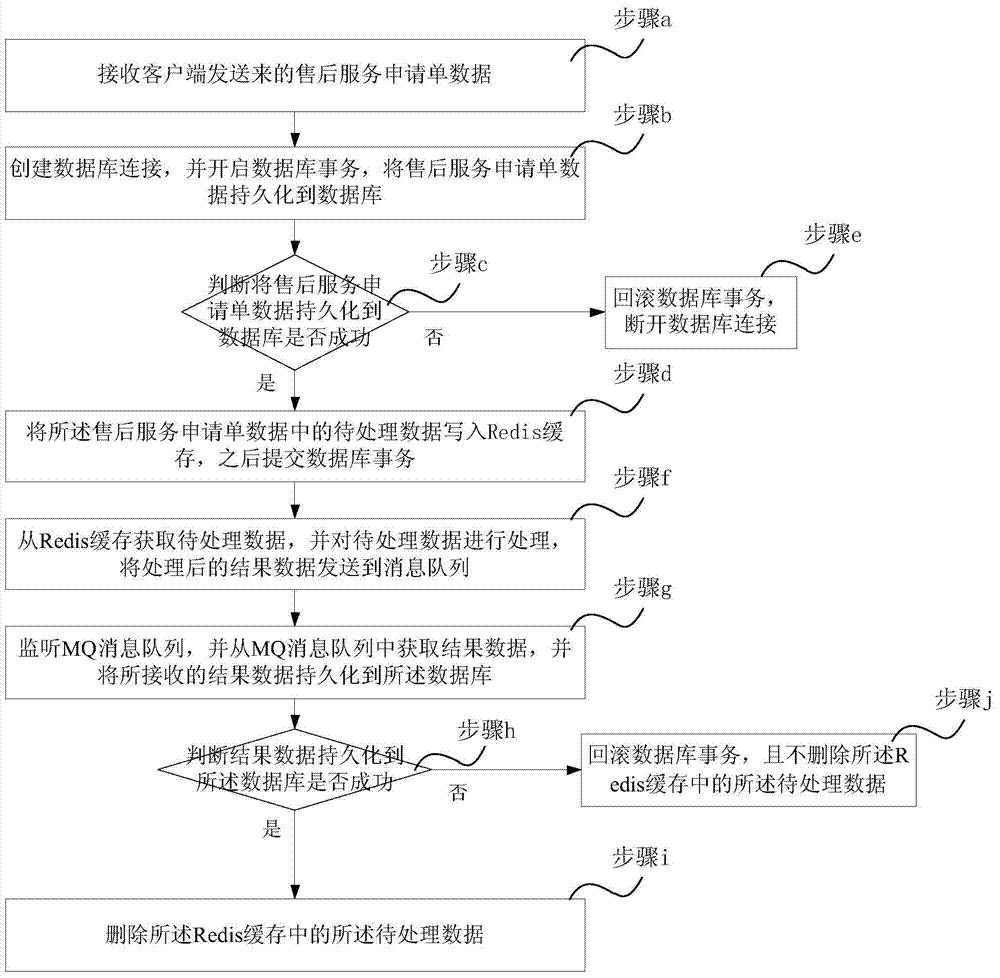
ActiveCN103886079AEnhanced Concurrency ProcessingSolve bottlenecksCommerceSpecial data processing applicationsMessage queueData information
The invention discloses a data processing method and system. The data processing method comprises the first stage of data writing, wherein data information sent by a client-side is received, persistence is carried out on the data information into a database, and to-be-processed data in the data information are written into a Redis cache; the second state of data processing, wherein the to-be-processed data are obtained from the Redis cache and are processed, processed result data are sent to an information queue, the result data are obtained from the information queue, and persistence is carried out the result data into the database. As the Redis cache stores the to-be-processed data, concurrent preemption and processing of the to-be-processed data in the Redis cache are achieved, and persistence on the processed result data into the database is achieved in a serialization mode through the information queue. According to the data processing method and system, concurrency processing of the data is enhanced, good experience is brought to clients, the bottleneck problem brought to the database under the condition of high concurrency is avoided, the deadlock problem of the database is avoided, and consistency and completeness of the data are ensured.
Owner:西安京迅递供应链科技有限公司
Mobile robot path planning method based on ant colony algorithm under dynamic environment
The invention discloses a mobile robot path planning method based on an ant colony algorithm under a dynamic environment. The method comprises the following steps of 1, modeling the environment by using a grating method; 2, building local diffusion information pheromone tau''rs; 4, computing a transition probability; 5, adding a feasible node S into a tabu table; 6, completing paths; 7, acquiringthe shortest path via path information recorded in the tabu table; 8, updating pheromone matrix elements; and 9, finding the optimal path via iteration, that is to say an algorithm ending condition ismet, and outputting a final result. According to the ant colony algorithm based on a potential field method provided by the invention, the faster convergence speed and optimizing ability are provided, the local diffusion information pheromone has relative good smoothness, the collaboration ability of individual ants is further enhanced, the local cross paths are reduced, the quantity of lost antsis reduced, and thus the ant colony algorithm is converged to the global optimum with the faster speed, and meanwhile also achieves the diversity of learning, and the defect that an artificial potential field method is easy to trap in the local optimum is overcome.
Owner:TIANJIN XIQING RUIBO BIOLOGICAL TECH CO LTD
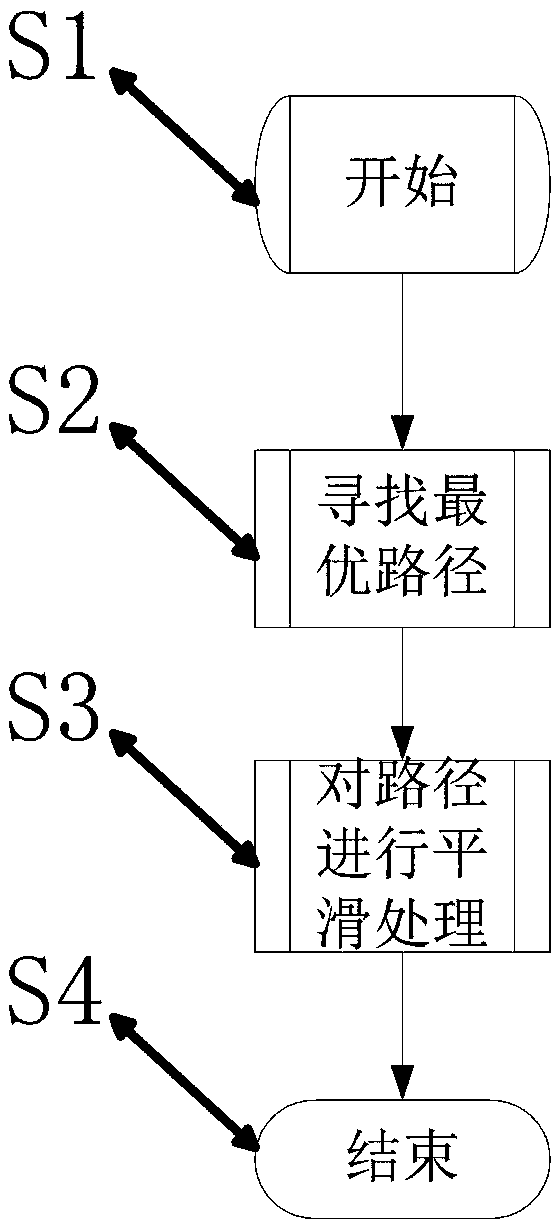
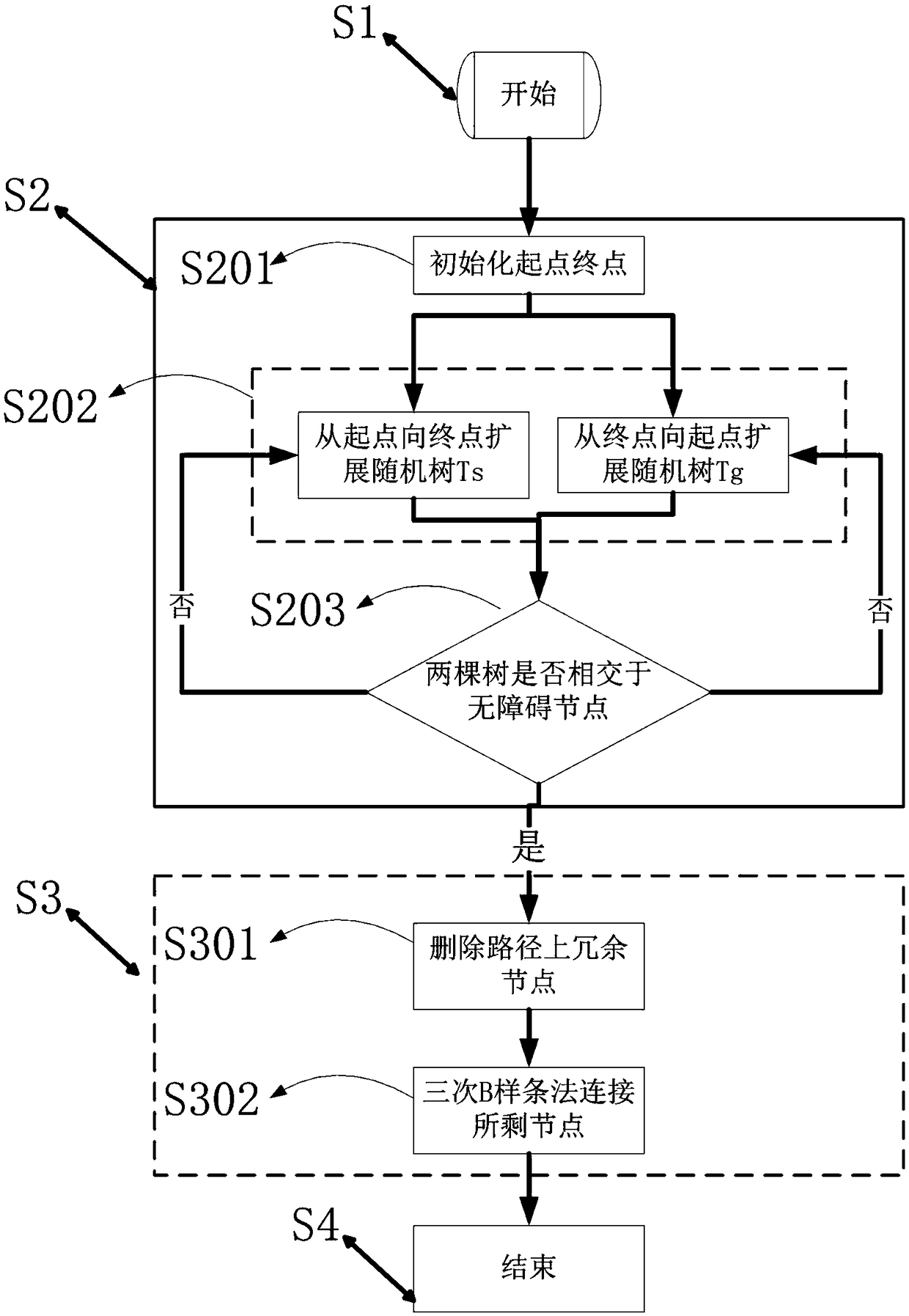
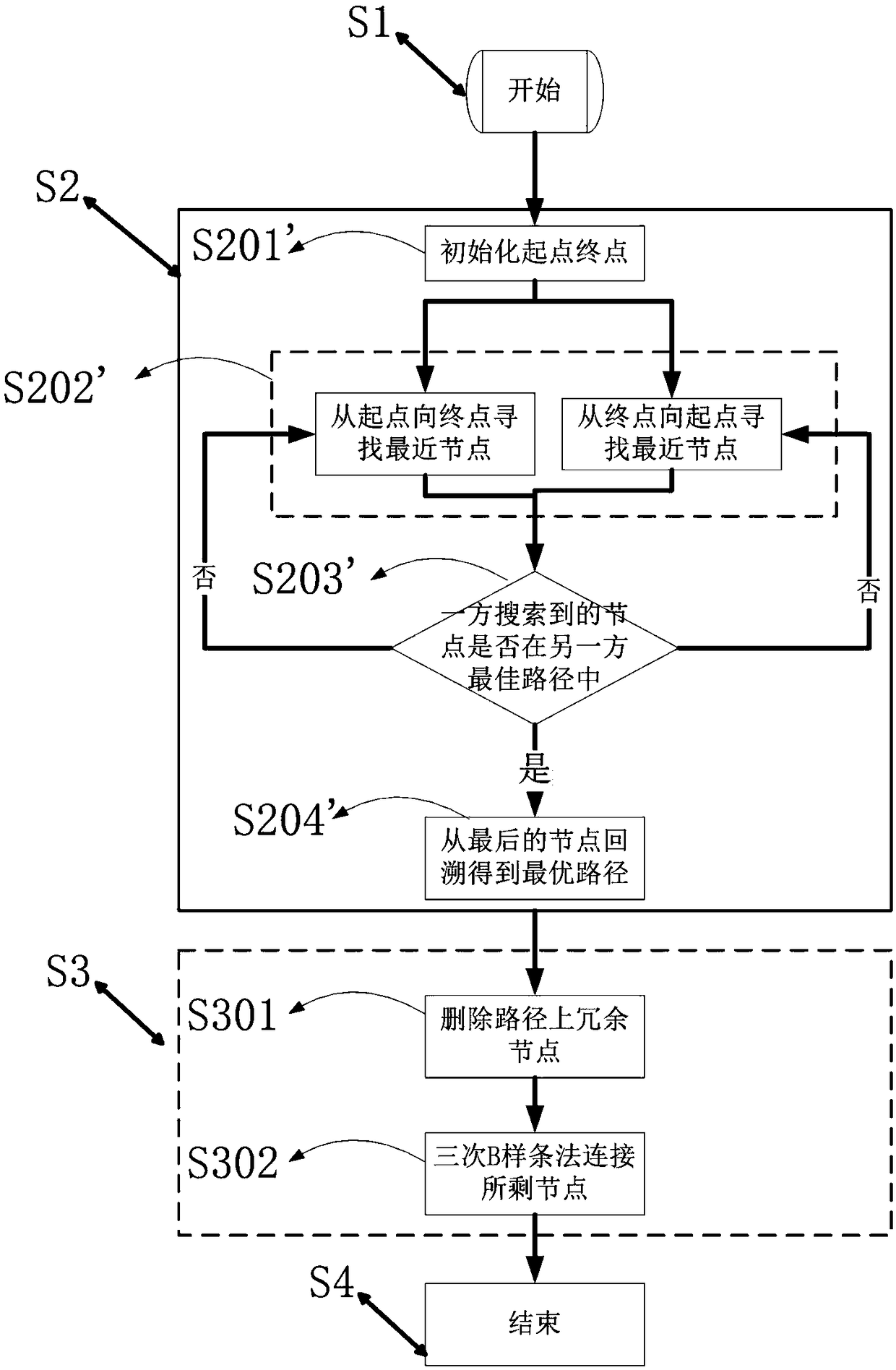
Smooth path planning method for mobile robots based on dynamic complex environment
PendingCN108896052AAvoid deadlockSolve the problem of path shock and collisionNavigational calculation instrumentsPosition/course control in two dimensionsFactor baseNODAL
The invention relates to a smooth path planning method for mobile robots based on a dynamic complex environment, and belongs to the field of robot path planning. The method comprises the steps of starting; searching for an optimal path; conducting smooth treatment on the optimal path; ending. The step of searching for the optimal path uses a two-way RRT algorithm with the idea of gravity of an artificial potential field to perform path searching, that is, the artificial potential field gravity guides a random tree to grow toward a target direction, and the RRT algorithm is prevented from randomly sampling the global; a two-way A* algorithm after a heuristic function is improved is adopted to add angle factors based on distance factors, the units of distances and angles are normalized, thepath planning time is greatly reduced, and the convergence speed of paths is improved; smoothing treatment is conducted on the optimal path, a Freudian smoothing algorithm is adopted to remove redundant nodes, a B-spline method is used three times for smoothly connecting remaining nodes, and the smooth optimal path is finally obtained.
Owner:LUDONG UNIVERSITY
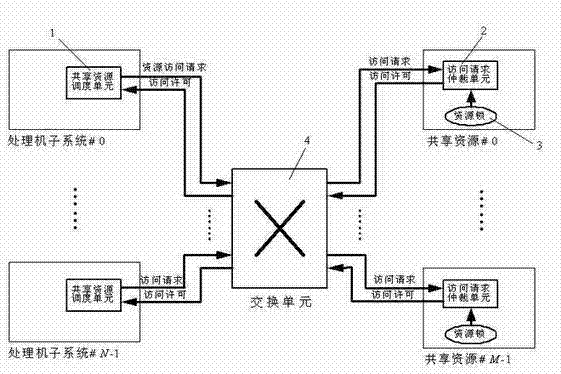
A shared resource scheduling method and system for distributed parallel processing
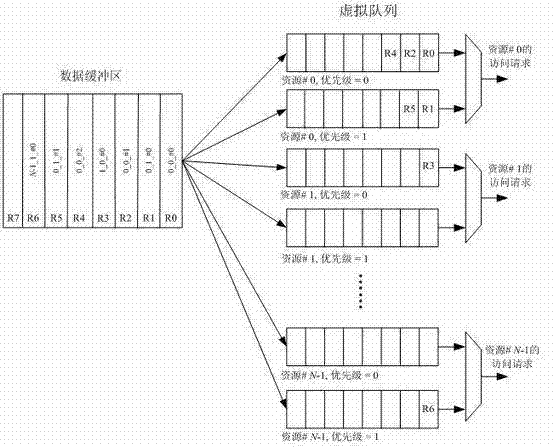
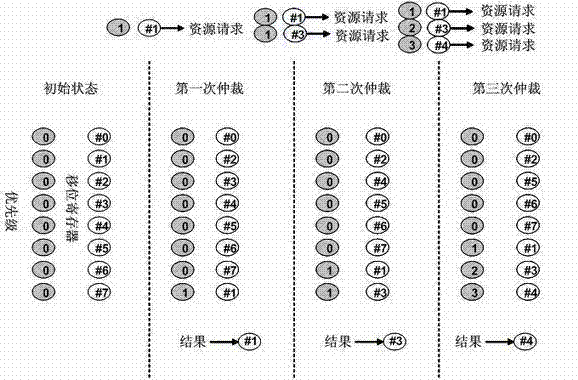
InactiveCN102298539ASolve the access contention problemAvoid deadlockProgram initiation/switchingParallel processingShared resource
The invention discloses a shared resource scheduling method and system used in distributed parallel processing. The method and system are based on a distributed operation mechanism. The shared resource scheduling units distributed in each processor subsystem are distributed in each shared Resource locks and resource request arbitration units are implemented. These distributed processing units communicate by sending messages (resource access requests / permissions) to each other through the switching unit. The shared resource scheduling unit in the processor subsystem uses virtual queue technology to manage all resource access requests in the data cache, that is, a special queue is specially opened for each accessible shared resource. Resource locks in shared resources are used to ensure the uniqueness of access to shared resources at any time. Resource locks have two states: lock occupation and lock release. The request arbitration unit in the shared resource uses a priority-based fair polling algorithm to arbitrate resource access requests from different processing nodes. The invention can effectively avoid the competition problem when each processing node accesses the shared resource, can also avoid the deadlock of the shared resource and the starvation problem of the processing node, and provides high-efficiency mutually exclusive access to the shared resource.
Owner:EAST CHINA NORMAL UNIV
Class-based deterministic packet routing
InactiveUS8306042B1Avoid deadlockMultiplex system selection arrangementsSpecial service provision for substationAnalysis dataMulti processor
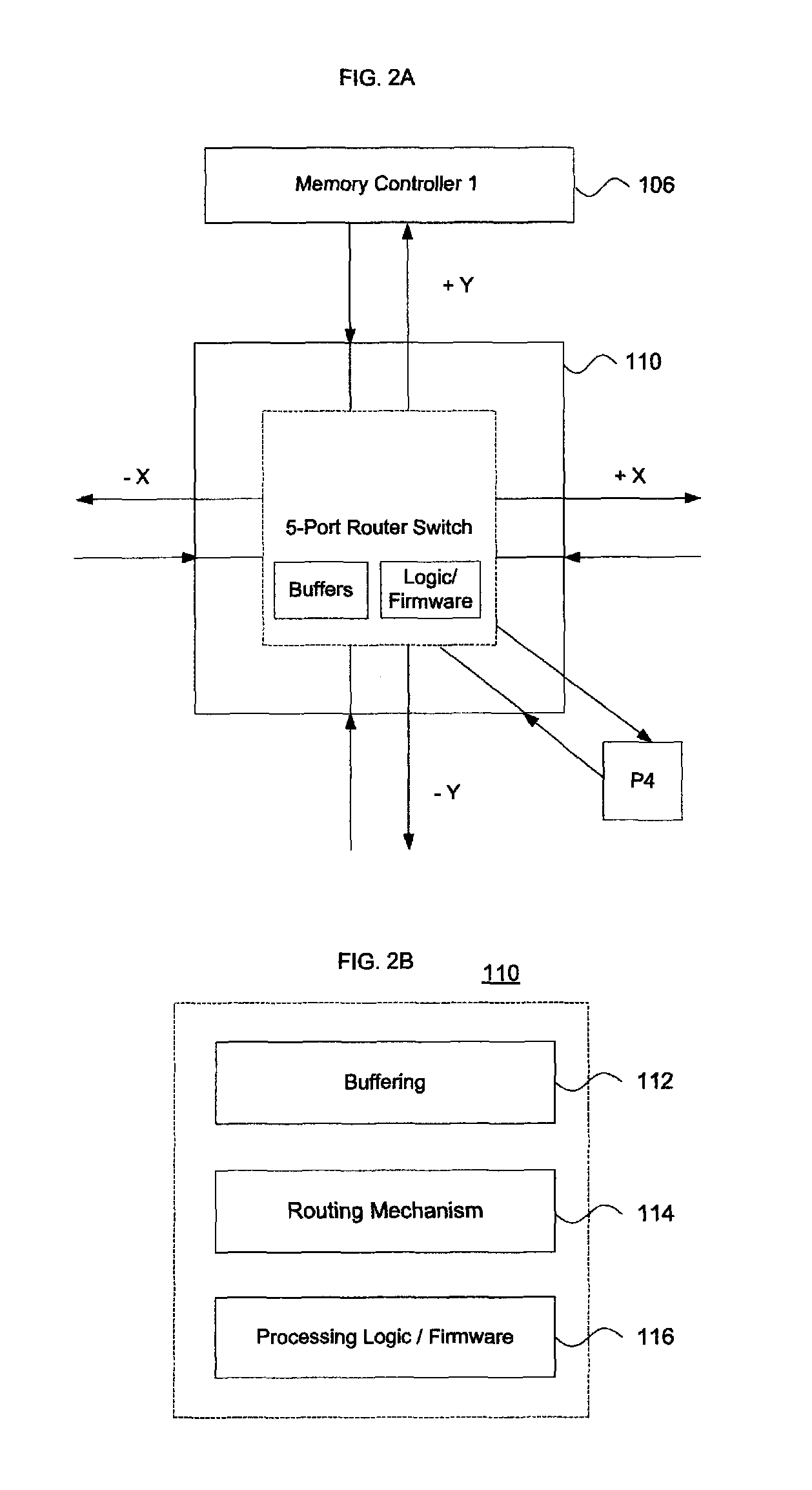
Aspects of the invention pertain to deterministic packet routing systems and methods in multiprocessor computing architectures. Packets are analyzed to determine whether they are memory request packets or memory reply packets. Depending upon the packet, it is routed through nodes in the multiprocessor computer architecture in either an XY or YX path. Request and reply packets are sent in opposing routes according to a deterministic routing scheme. Multiport routers are placed at nodes in the architecture to pass the packets, using independent request and response virtual channels to avoid deadlock conditions.
Owner:GOOGLE LLC
Method and system for automatically preventing deadlock in multi-robot systems
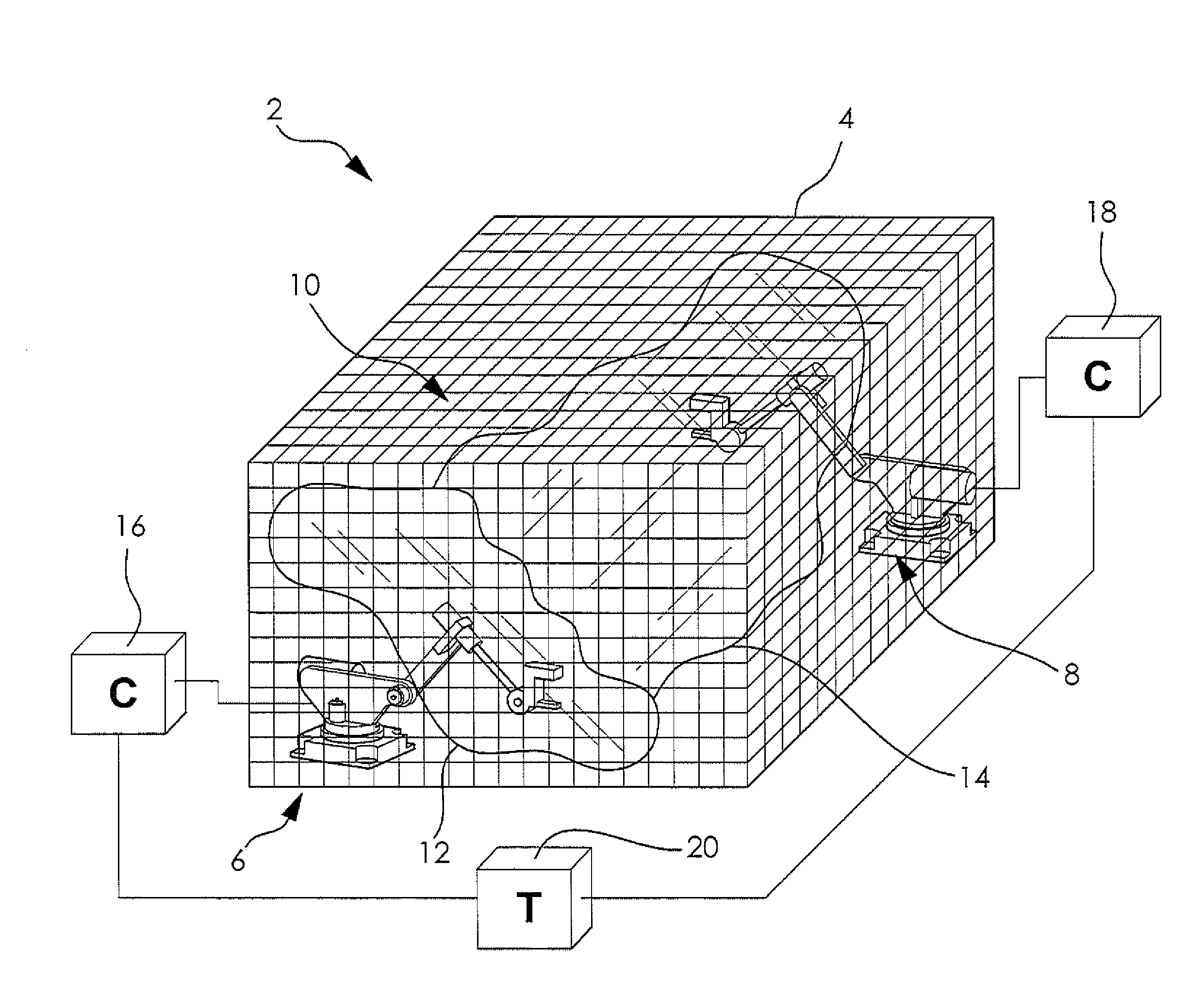
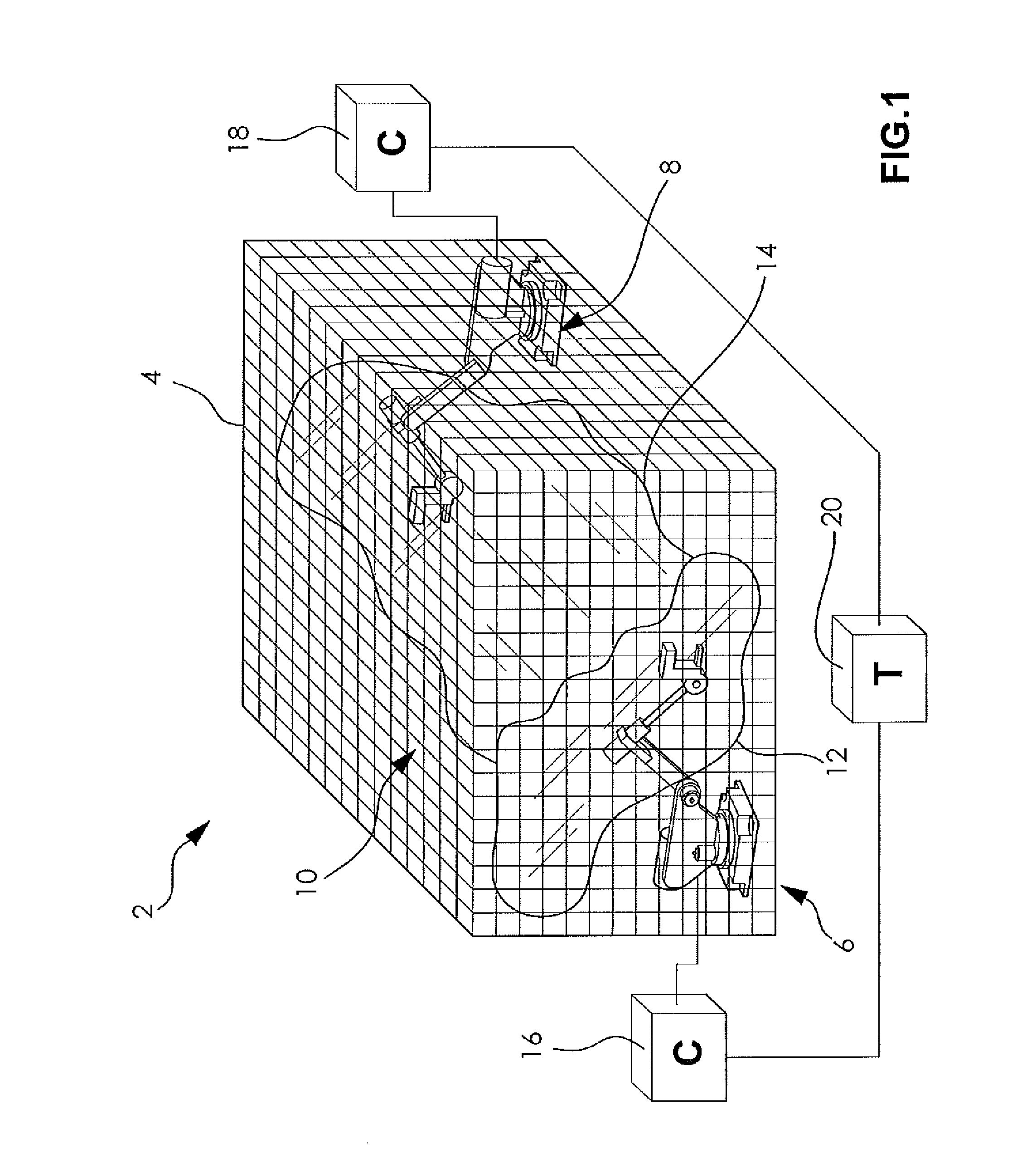
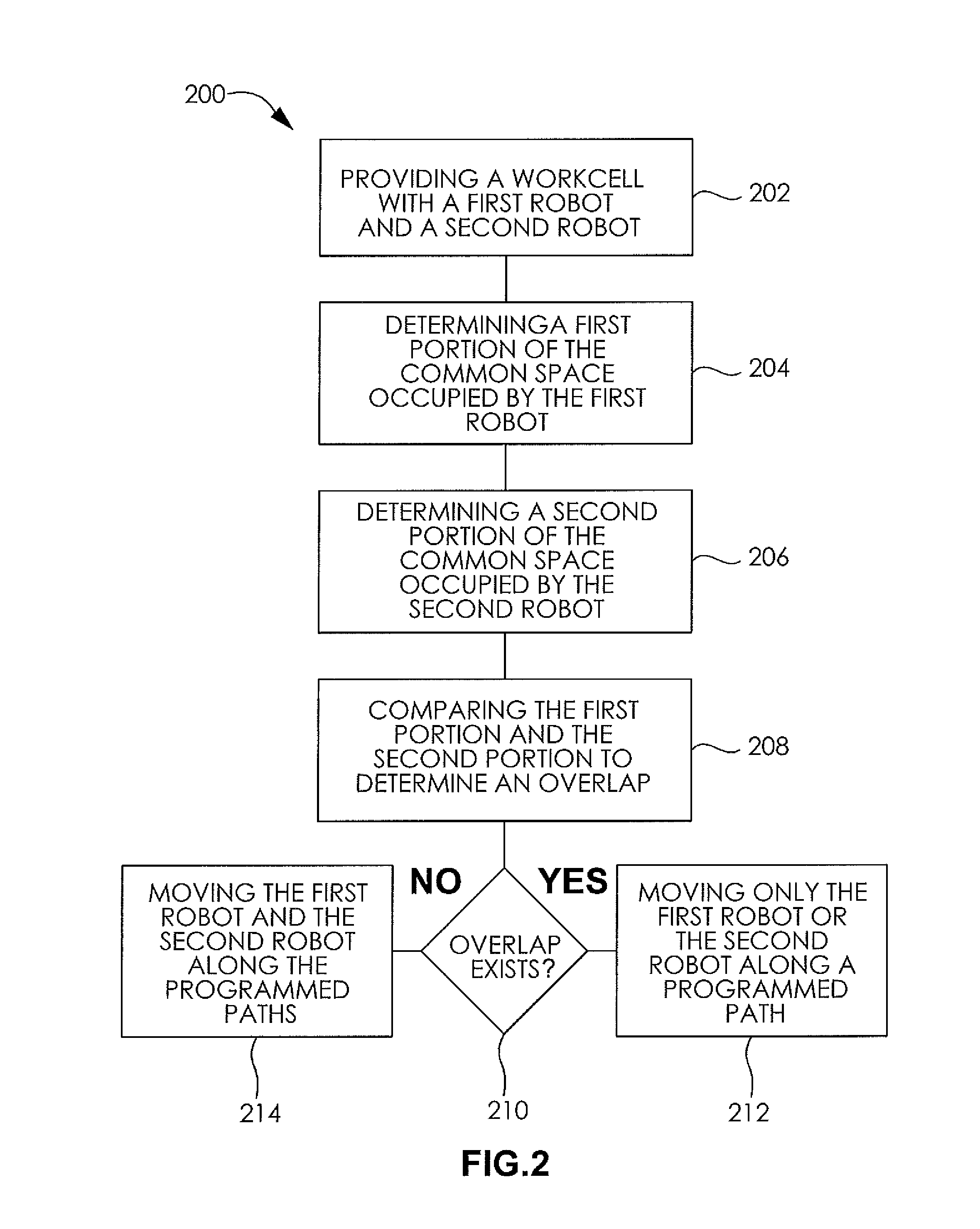
ActiveUS20120215351A1Avoid deadlockAvoid adjustmentProgramme-controlled manipulatorComputer controlWorkcellMultirobot systems
A system and method for controlling avoiding collisions and deadlocks in a workcell containing multiple robots automatically determines the potential deadlock conditions and identifies a way to avoid these conditions. Deadlock conditions are eliminated by determining the deadlock-free motion statements prior to execution of the motions that have potential deadlock conditions. This determination of deadlock-free motion statements can be done offline, outside normal execution, or it can be done during normal production execution. If there is sufficient CPU processing time available, the determination during normal production execution provides the most flexibility to respond to dynamic conditions such as changes in I / O timing or the timing of external events or sequences. For minimal CPU impact the determination is done offline where many permutations of programming sequences can be analyzed and an optimized sequence of execution may be found.
Owner:FANUC ROBOTICS NORTH AMERICA
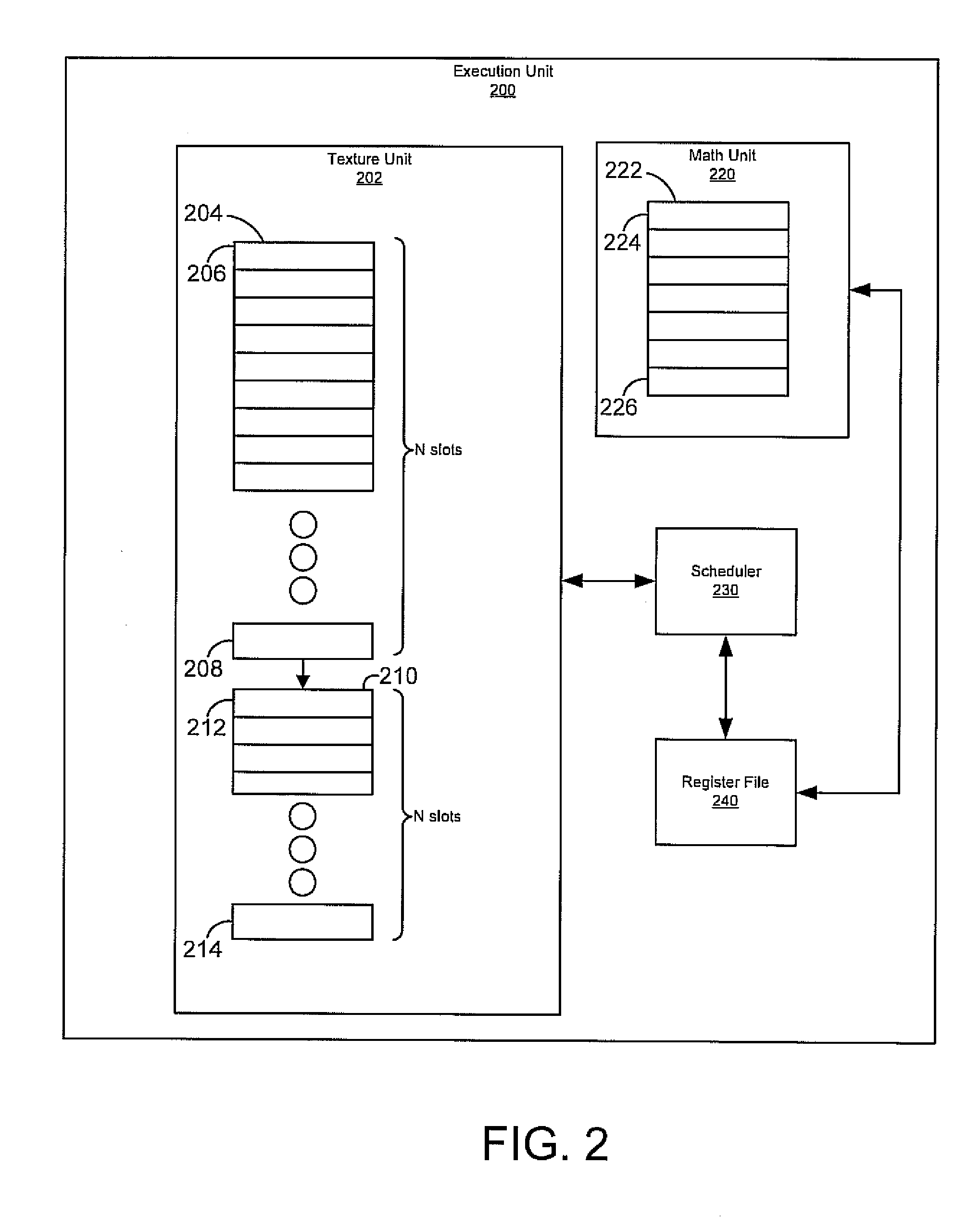
System and method for deadlock-free pipelining
ActiveUS20100259536A1Increase performanceReduce requirementCathode-ray tube indicatorsProcessor architectures/configurationDeadlock freeRegister file
A system and method for facilitating increased graphics processing without deadlock. Embodiments of the present invention provide storage for execution unit pipeline results (e.g., texture pipeline results). The storage allows increased processing of multiple threads as a texture unit may be used to store information while corresponding locations of the register file are available for reallocation to other threads. Embodiments further provide for preventing deadlock by limiting the number of requests and ensuring that a set of requests is not issued unless there are resources available to complete each request of the set of requests. Embodiments of the present invention thus provide for deadlock free increased performance.
Owner:NVIDIA CORP
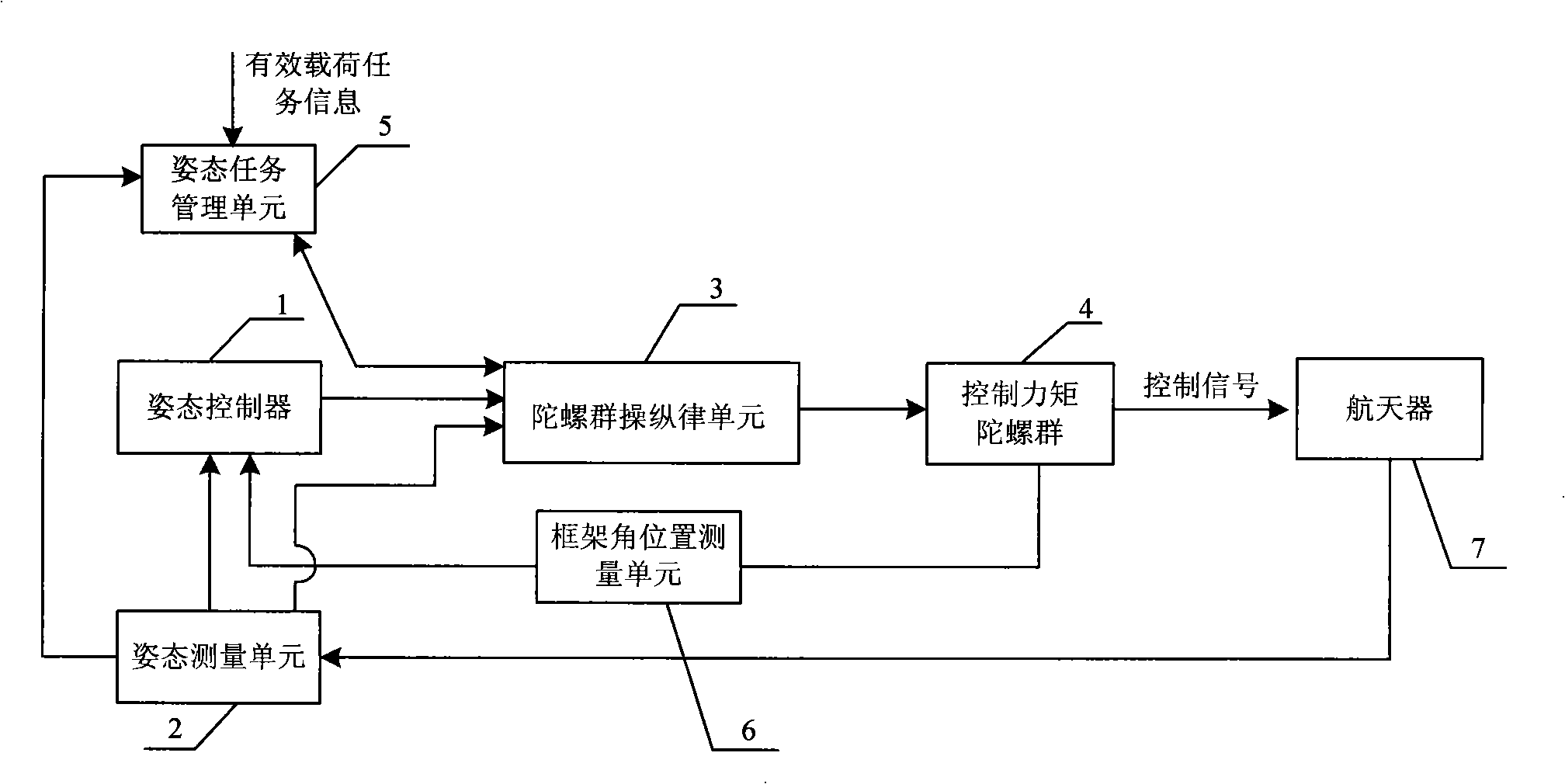
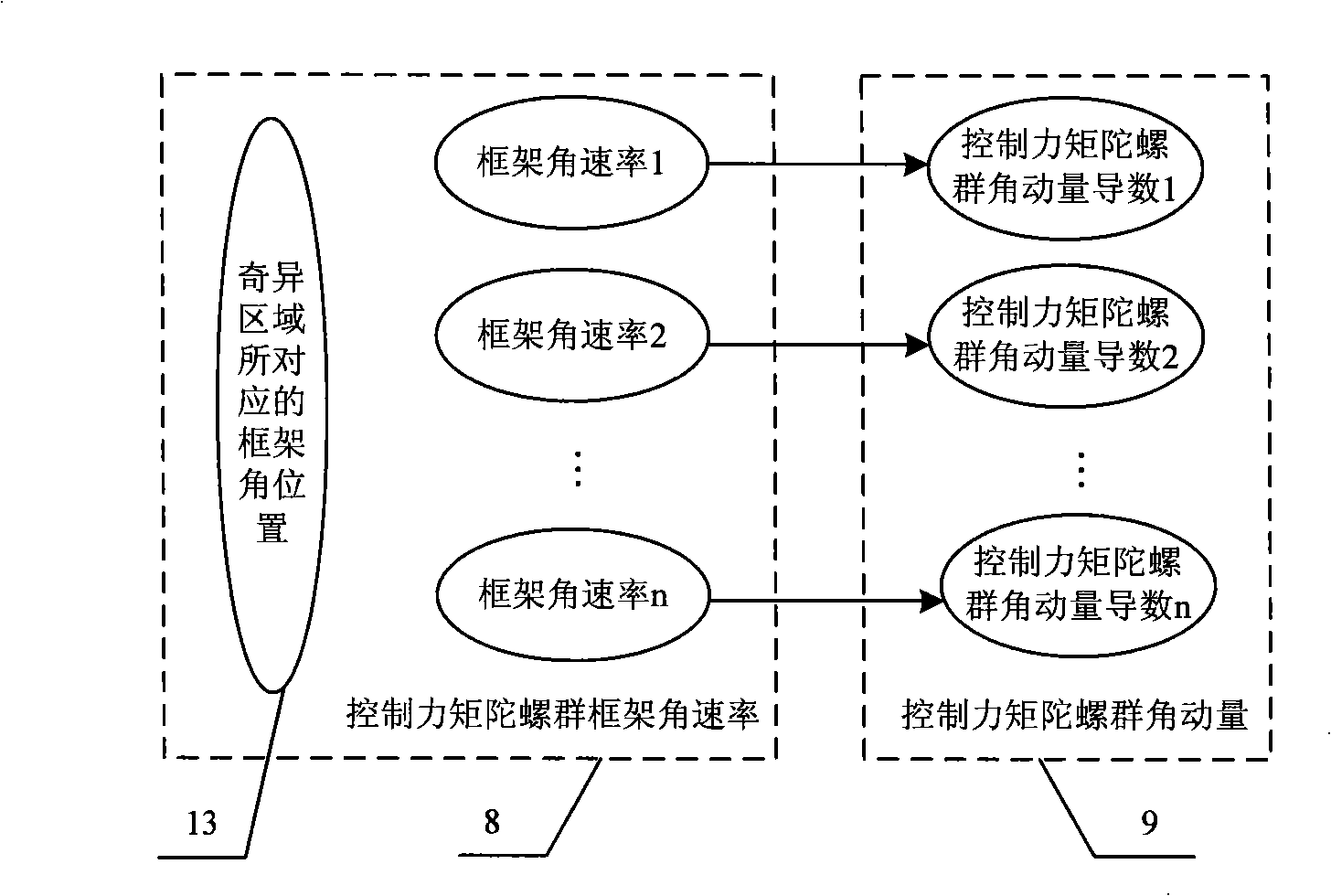
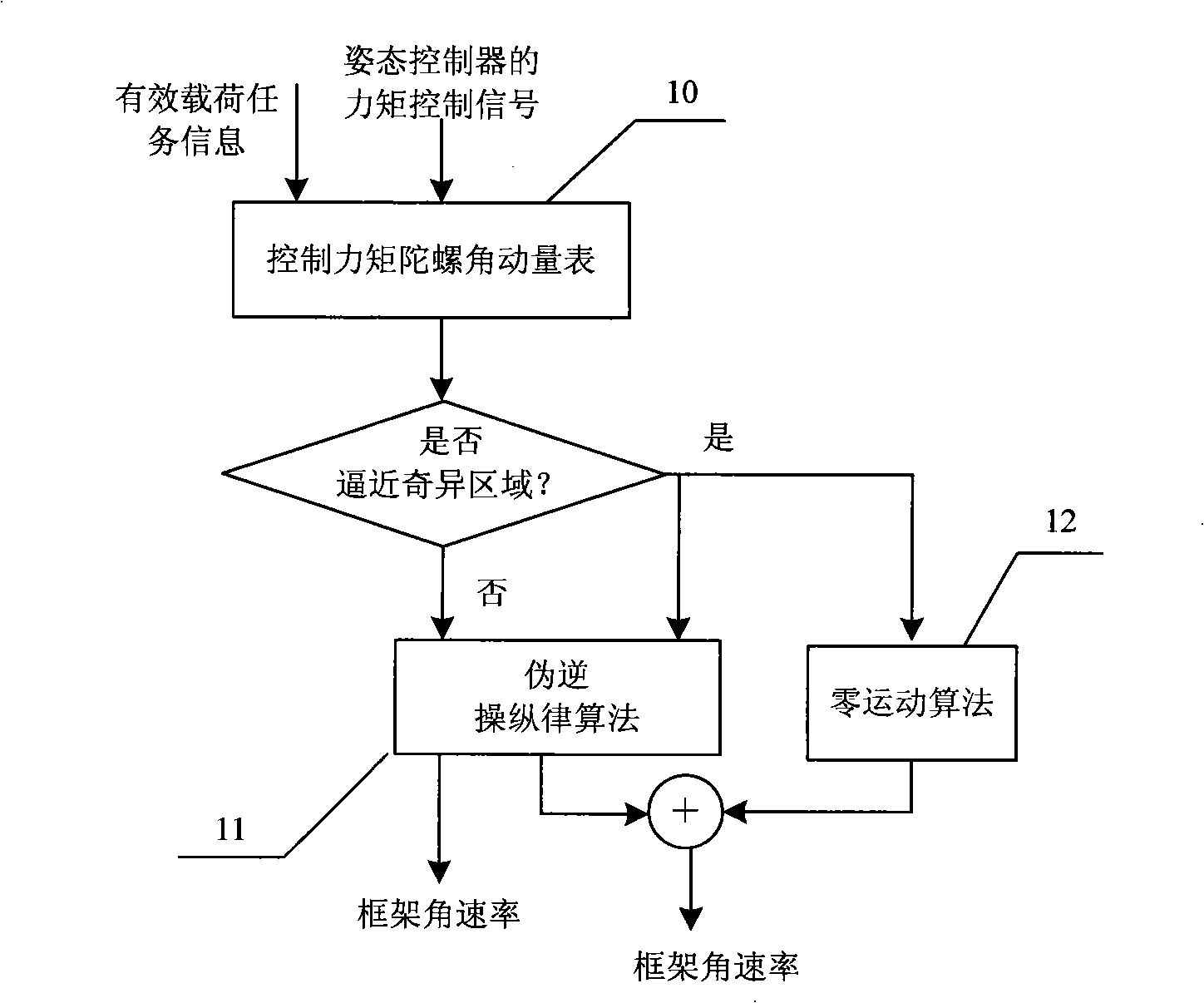
Steering law singularity avoidant spacecraft attitude control system
ActiveCN101353086AChange the output torqueAchieve high precision controlSpacecraft guiding apparatusAttitude control systemSpacecraft
The invention relates to a steering-law singularity avoiding aircraft attitude control system, comprising an attitude task managing unit, an attitude controller, an attitude measuring unit, a gyro group steering-law unit, a frame angle position measuring unit, a control moment gyro group and an aircraft. The gyro group steering-law unit calculates the frame angle rate of the control moment gyro group by cooperating control moment gyro angle momentum table, zero motion algorithm and pseudoinverse steering-law algorithm, and adopts the angle rate value as the set signal of the control moment gyro group to improve the control precision of the aircraft attitude. The steering-law singularity avoiding aircraft attitude control system introduces the steering-law design method that chooses frame angle rate and the initial value of frame angle position based on look-up table, realizes accurate moment output of the control moment gyro group, avoids the singularity problem produced in the process of calculating frame angle rate of the control moment gyro group by the pseudoinverse steering-law algorithm as well as avoids the deadlock problem caused by the control moment gyro steering law when adopting zero motion algorithm and robust pseudoinverse steering-law iterative computations.
Owner:AEROSPACE DONGFANGHONG SATELLITE
Online learning method for optimizing signalized intersection queuing length
InactiveCN103077615AAble to learnHave memoryControlling traffic signalsOffline learningStudy methods
The invention discloses an online learning method for optimizing a signalized intersection queuing length. The online learning method comprises the following steps of: 1, selecting states, behaviors and rewards; 2, reinforcing a learning matrix updating formula; 3, establishing a simulation optimizing platform; and 4, carrying out online operation. The online learning method is a signal timing dial optimizing technology which is capable of calculating a globally optimal solution and has the memorability. Compared with the risk neutral reinforcing learning technology, the online learning method has the advantages of no need of advanced offline learning, and better instantaneity and adaptability.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Method for realizing cache coherence protocol of chip multiprocessor (CMP) system
ActiveCN102103568AImprove performanceImprove stabilityDigital computer detailsElectric digital data processingData informationData provider
The invention discloses a method for realizing a cache coherence protocol of a chip multiprocessor (CMP) system, and the method comprises the following steps: 1, cache is divided into a primary Cache and a secondary Cache, wherein the primary Cache is a private Cache of each processor in the processor system, and the secondary Cache is shared by the processors in the processor system; 2, each processor accesses the private primary Cache, and when the access fails, a failure request information slot is generated, sent to a request information ring, then transmitted to other processors by the request information ring to carry out intercepting; and 3, after a data provider intercepts the failure request, a data information slot is generated and sent to a data information ring, then transmitted to a requestor by the data information ring, finally, the requestor receives data blocks and then completes corresponding access operations. The method disclosed by the invention has the advantages of effectively improving the performance of the system, reducing the power consumption and bandwidth utilization, avoiding the occurrence of starvation, deadlock and livelock, and improving the stability of the system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method, system and terminal device capable of calling asynchronous procedure
InactiveCN102567111AAvoid deadlockSimple calling logicProgram initiation/switchingTerminal equipmentDeadlock
The invention discloses a method, a system and a terminal device capable of calling an asynchronous procedure. The method disclosed by the invention comprises the following steps: returning and continuing executing a follow-up command after a first thread sends a service request; receiving and processing the service request by a second thread, generating a first processing result, and feeding back the first processing result to a third thread through a callback function; and generating a second processing result by the third thread according to the first processing result. According to the method disclosed by the invention, after the first thread sends the service request, and the waiting for a feedback result is not required, so that thread deadlock can be avoided and call logic is simple. When initialization is performed, the first thread is used for creating the third thread, the priority of the third thread is higher than that of the first thread, after the first processing result is received, the resources of a CPU (central processing unit) of the first thread are occupied, the second processing result is finally generated, and access exception can be avoided even callback frequency is higher.
Owner:融创天下(上海)科技发展有限公司
Method for managing thread group of process
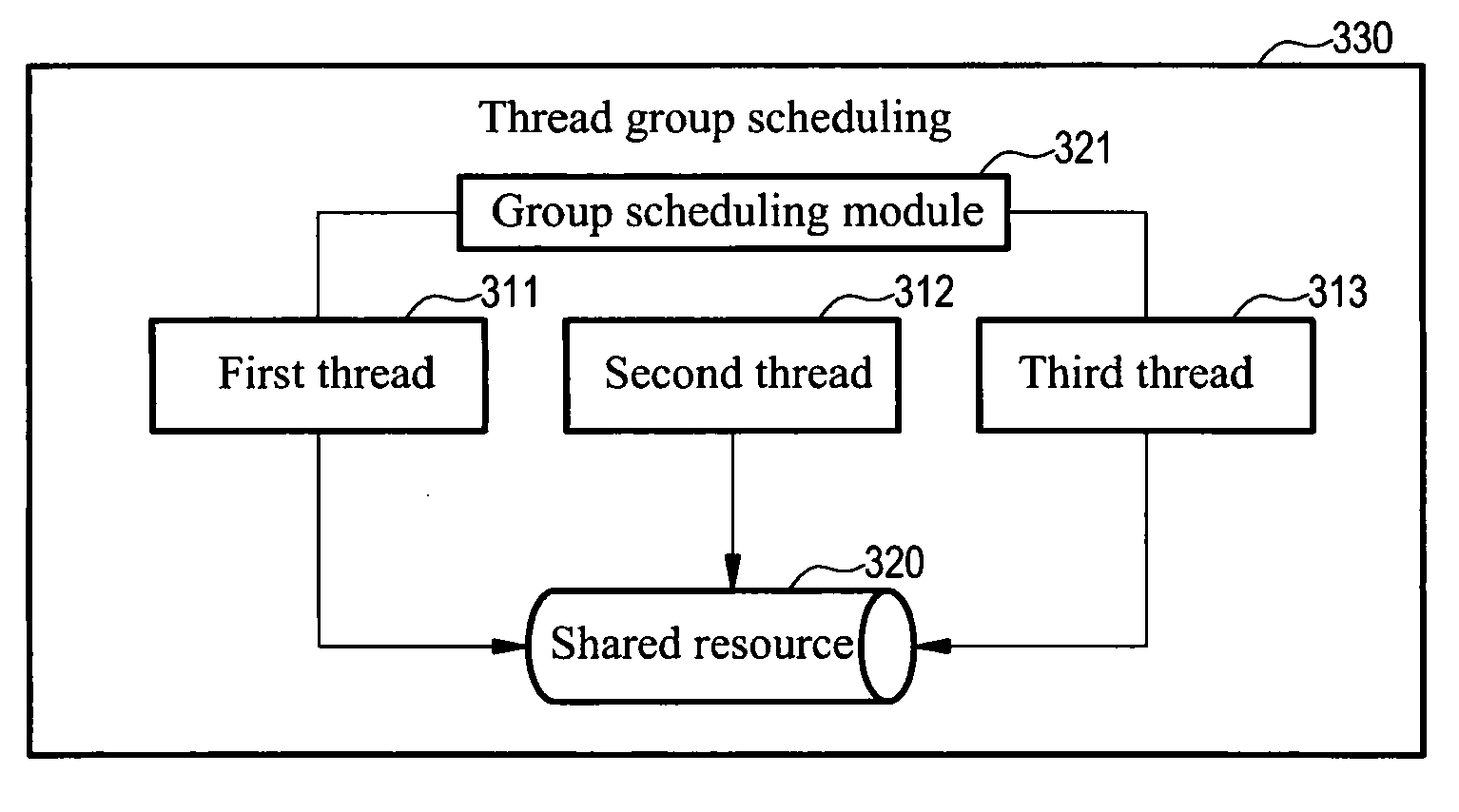
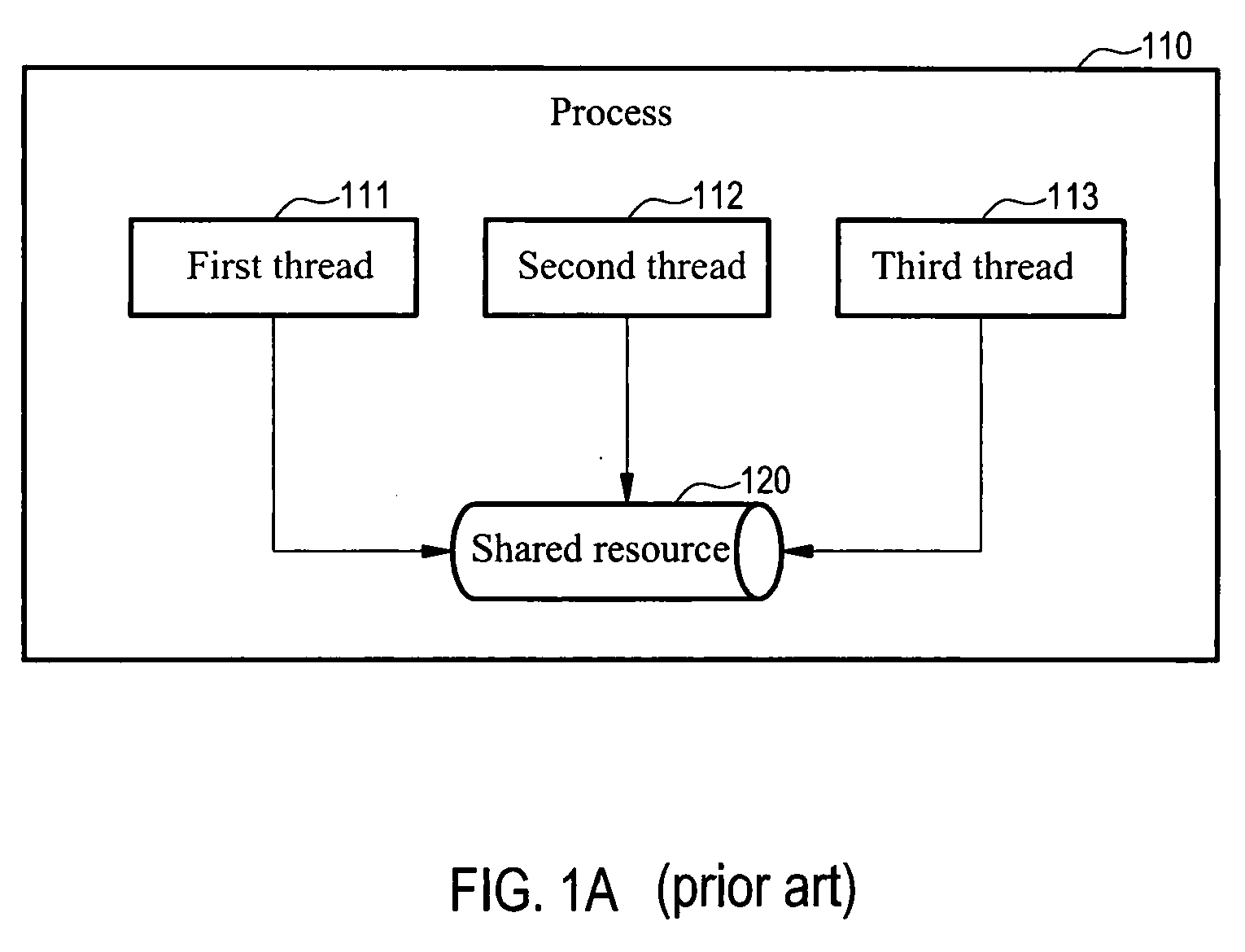
InactiveUS20090172686A1Avoid retrievingPrevent incorrect computation dataMultiprogramming arrangementsMemory systemsGroup schedulingShared resource
A method for managing a thread group of a process is provided. First, a group scheduling module is used to receive an execution permission request from a first thread. When detecting that a second thread in the thread group is under execution, the group scheduling module stops the first thread, and does not assign the execution permission to the first thread until the second thread is completed, and till then, the first thread retrieves a required shared resource and executes the computations. Then, the first thread releases the shared resource when completing the computations. Then, the group scheduling module retrieves a third thread with the highest priority in a waiting queue and repeats the above process until all the threads are completed. Through this method, when one thread executes a call back function, the other threads are prevented from taking this chance to use the resource required by the thread.
Owner:ACCTON TECHNOLOGY CORPORATION
Apparatus and method for avoiding deadlocks in a multithreaded environment
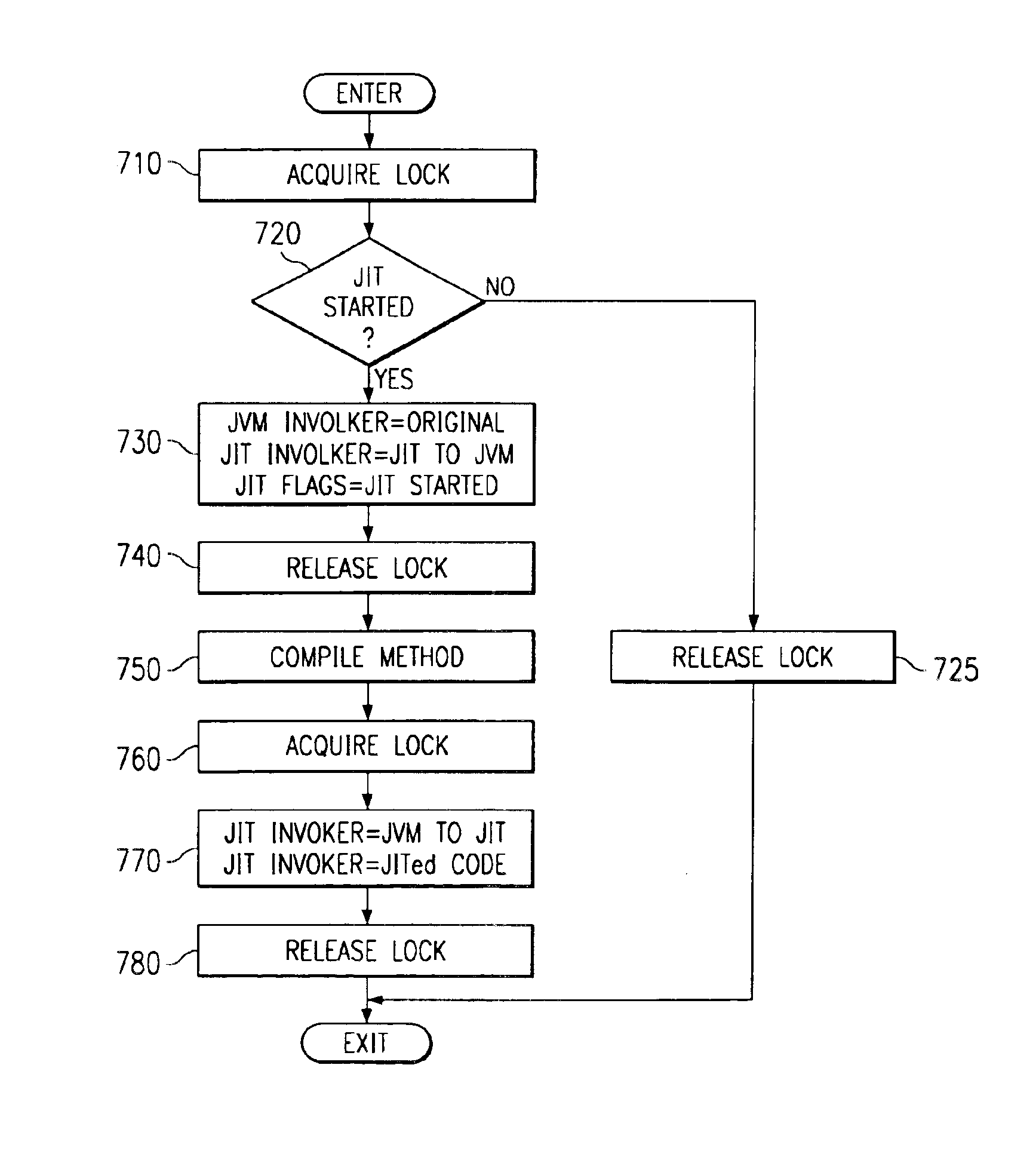
InactiveUS6883165B1Avoid deadlockPrevent deadlock situationMultiprogramming arrangementsExecution paradigmsDeadlock
An apparatus and method for avoiding deadlocks in a multithreaded environment is provided. The apparatus and method provide a mechanism by which multiple threads are allowed to call a method virtually simultaneously without experiencing the problems regarding multiple compilations of the same method or a lock being held by one thread while other threads wait on the lock. With the apparatus and method, the first thread to call a method is the thread that causes the method to be compiled. Subsequent calls to the method, during a period of time in which the method is being compiled, are redirected to the JVM interpreter, thereby avoiding any deadlock situation.
Owner:IBM CORP
System and method for avoiding deadlock in multi-node network
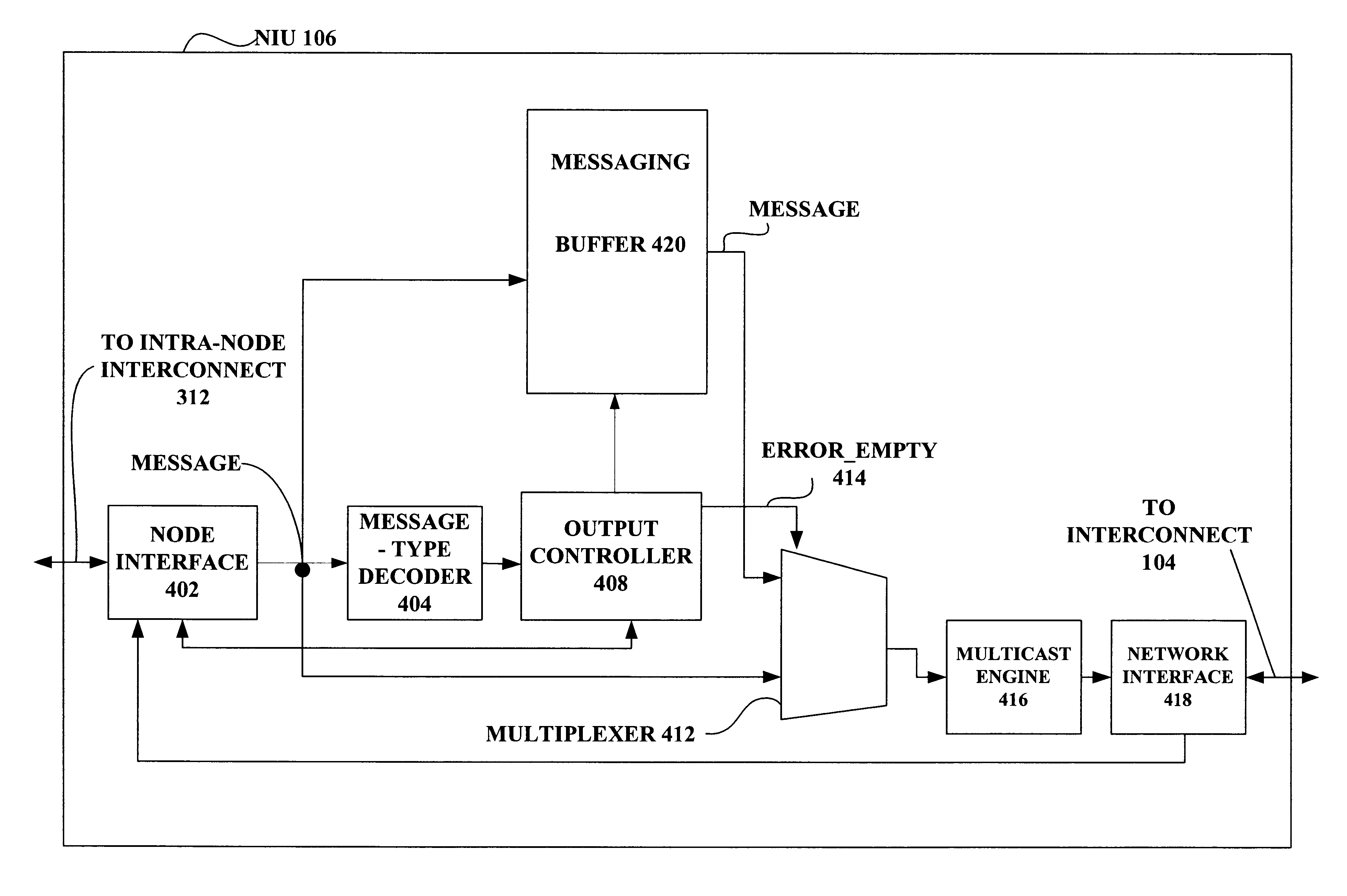
InactiveUS6490630B1Avoid overheadAvoid deadlockError preventionTransmission systemsMulticastDense packing
A computer architecture for avoiding a deadlock condition in an interconnection network comprises a messaging buffer having a size pre-calculated to temporarily store outgoing messages from a node. Messages are classified according to their service requirements and messaging protocols, and reserved quotas in the messaging buffer are allocated for different types of messages. The allocations of the reserved quotas are controlled by a mechanism that, to prevent overflow, limits the maximum number of messages that can be outstanding at any time. The messaging buffer is sized large enough to guarantee that a node is always able to service incoming messages, thereby avoiding deadlock and facilitating forward progress in communications. The buffer may be bypassed to improve system performance when the buffer is empty or when data in the buffer is corrupted. In addition, a multicast engine facilitates dense packing of the buffer and derives information from a message header to determine whether there is a multicast to perform and to permit passage of messages. Other considerations to reduce the buffer size are incorporated.
Owner:FUJITSU LTD
System controlling exclusive access by control programs to system resources
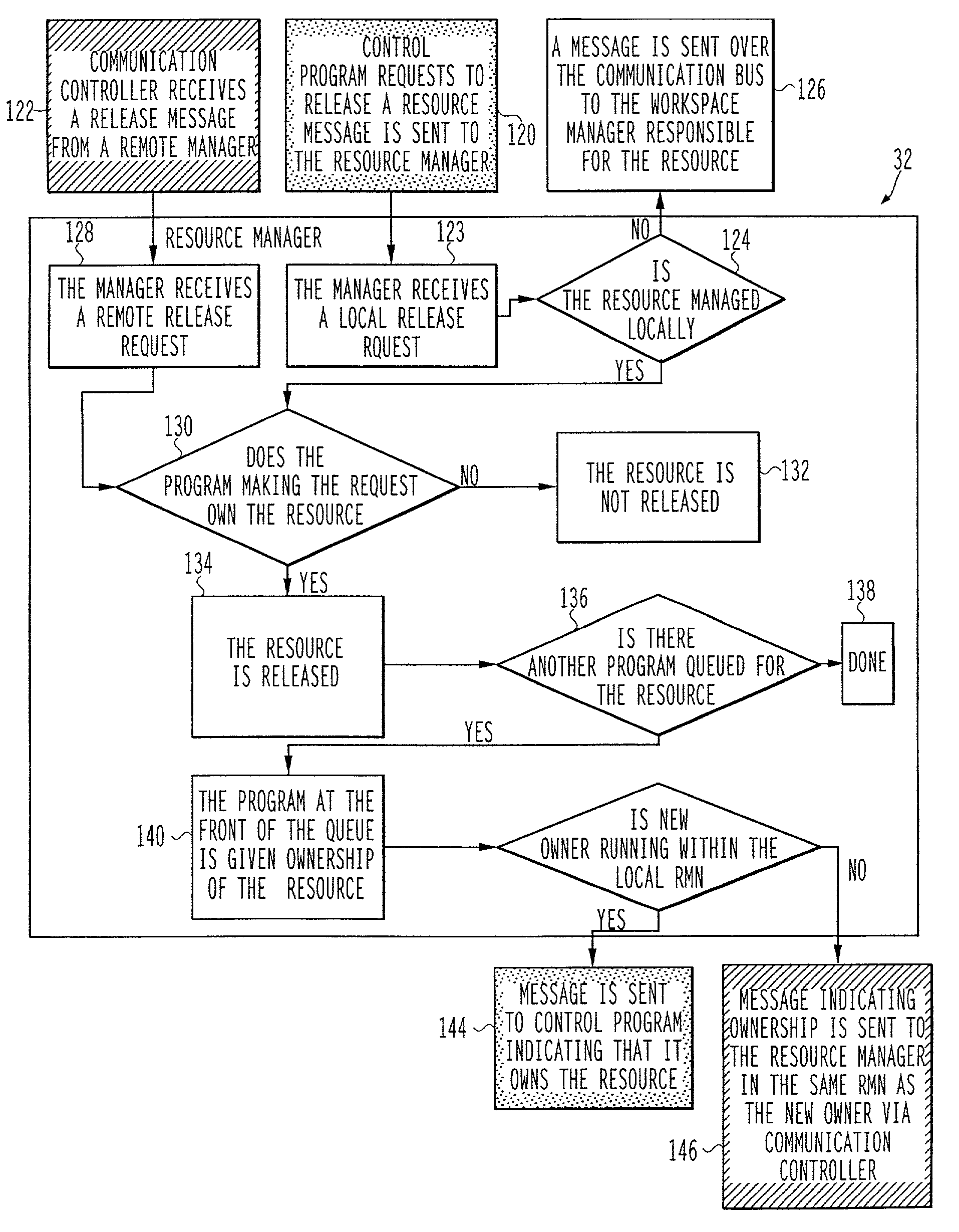
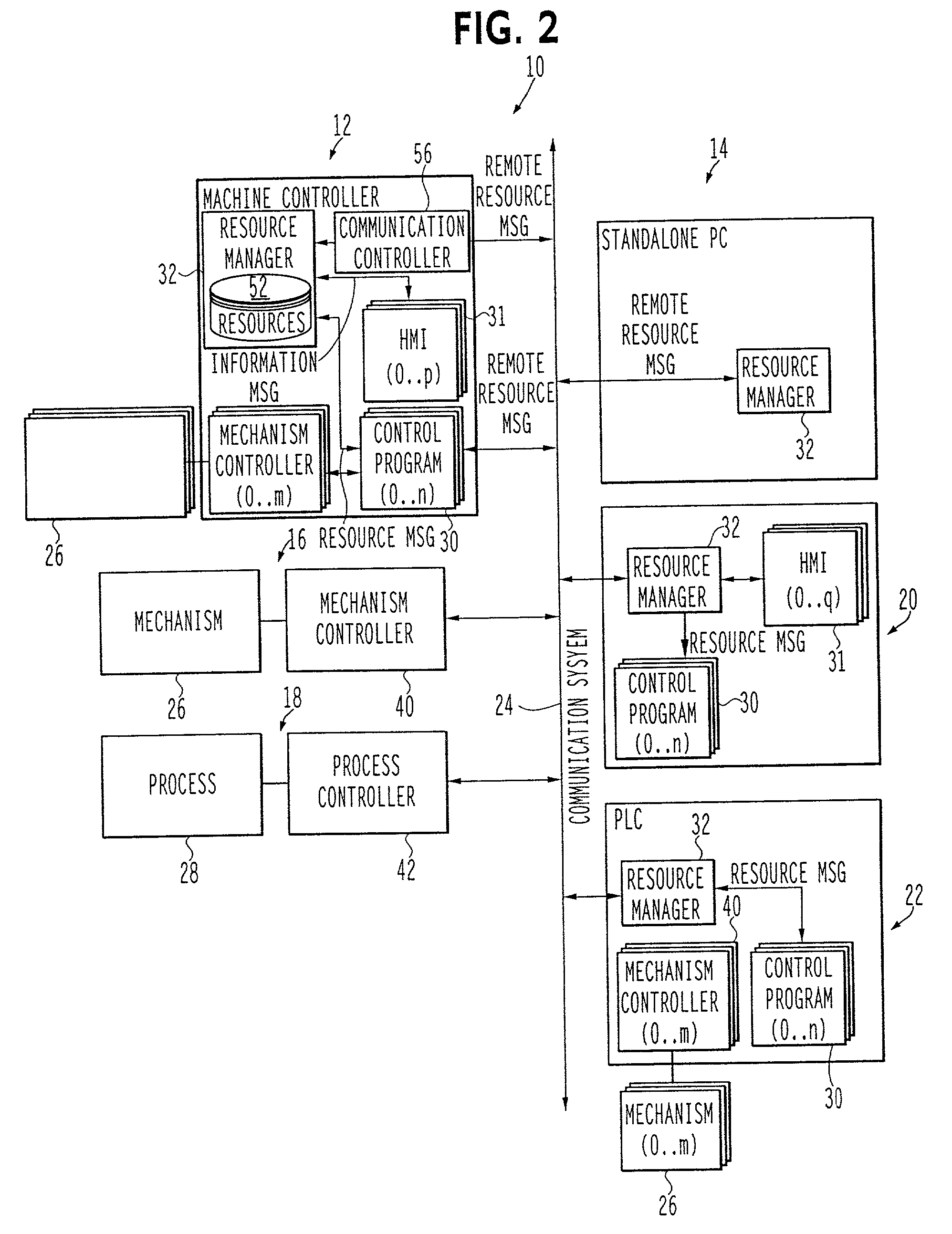
ActiveUS7114157B2Avoid deadlockProgramme-controlled manipulatorMultiprogramming arrangementsMachine controlCommunications system
The present invention is a system for controlling exclusive access by control programs (30) to system resources (52). A system in accordance with the invention includes a plurality of addressable locations (12, 14, 16, 18, 20 and 22) in the system; a communication system (24) connecting the addressable locations which transmits communications between the addressable locations; a plurality of machines (26), the machines being located at at least one of the addressable locations; a plurality of control programs which use resources including a plurality of machine control programs, each machine control program controlling at least one machine; and a plurality of resource managers (32), the resource managers being located at a plurality of the addressable locations, each resource manager communicating over the communication system with at least one other resource manager, and the plurality of resource managers arbitrating which control program of the plurality of control programs is given exclusive use of at least one resource during execution of the control program.
Owner:KUKA ROBOTER
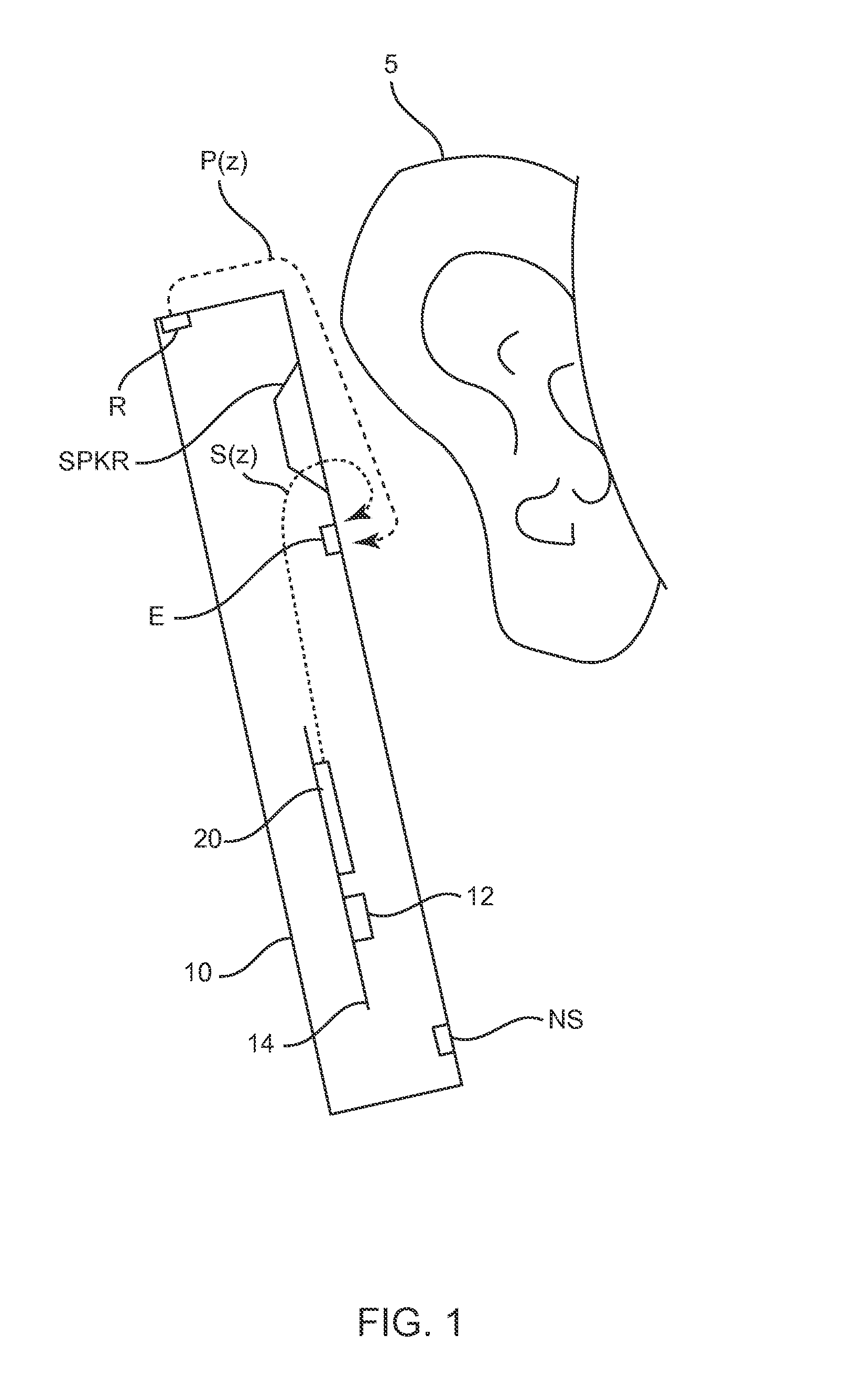
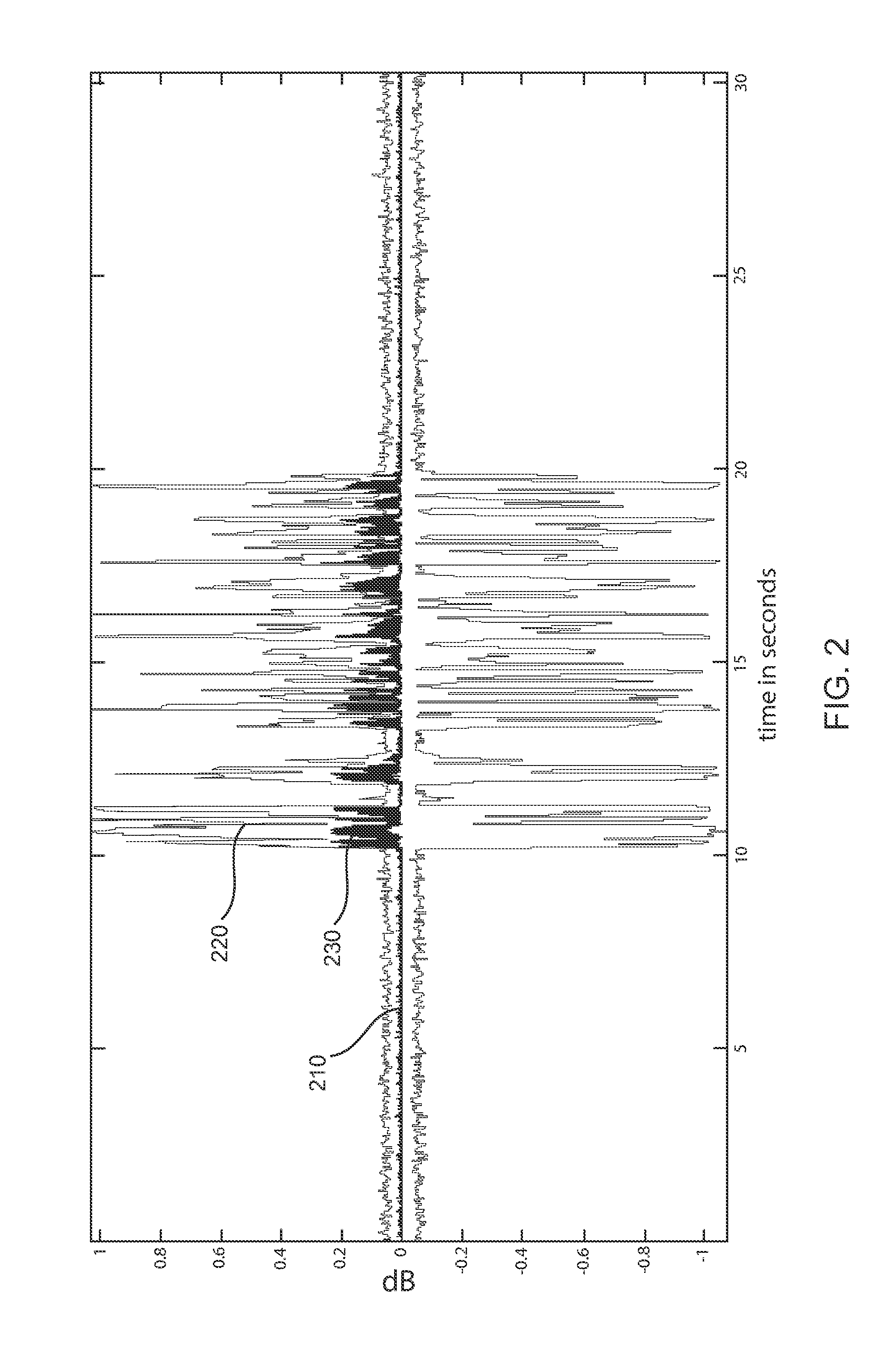
Ambient noise root mean square (RMS) detector
An RMS detector uses the concept of the k-NN (classifying using nearest neighbors)-algorithm in order to obtain RMS values. A rms detector using first-order regressor with a variable smoothing factor is modified to penalize samples from center of data in order to obtain RMS values. Samples which vary greatly from the background noise levels, such as speech, scratch, wind and other noise spikes, are dampened in the RMS calculation. When background noise changes, the system will track the changes in background noise and include the changes in the calculation of the corrected RMS value. A minimum tracker runs more often (e.g. two or three times) than the rate as in prior art detectors and methods, tracks the minimum rms value, which is to compute a normalized distance value, which in turn is used to normalize the smoothing factor. From this data, a corrected or revised RMS value is determined as the function of the previous RMS value multiplied by one minus the smoothing factor plus the smooth factor times the minimum rms value to output the corrected RMS for the present invention. The rms value is used to generate a reset signal for the minimum tracker and is used to avoid deadlock in the tracker, for example, when the background signal increases / decreases over time.
Owner:CIRRUS LOGIC INC
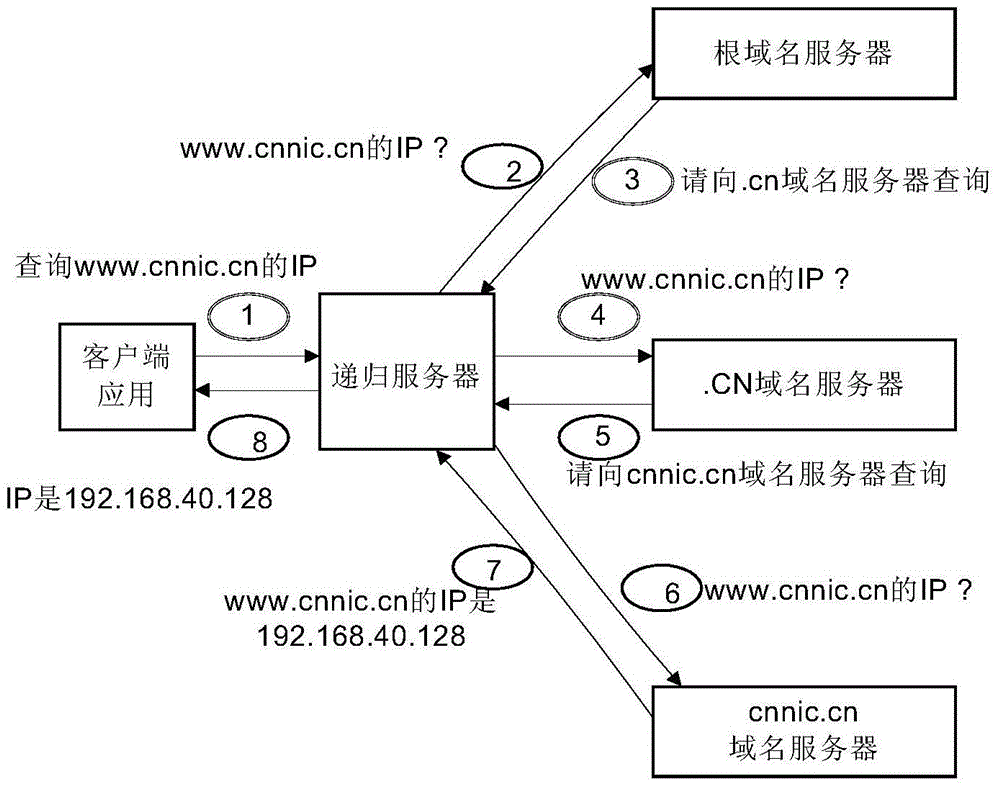
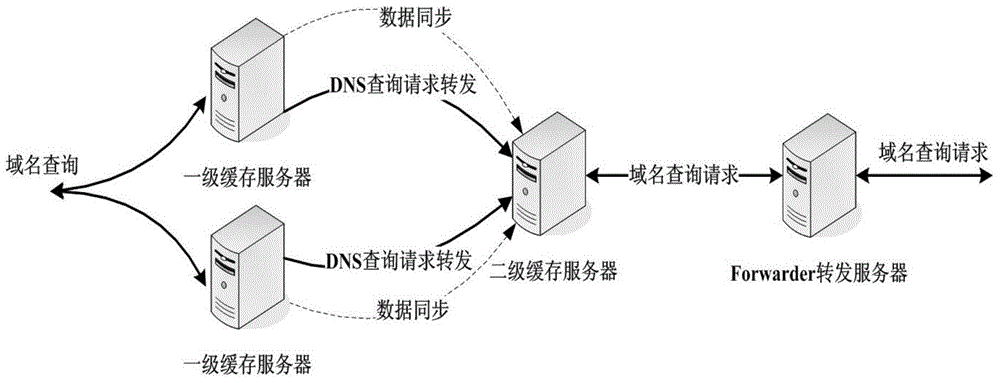
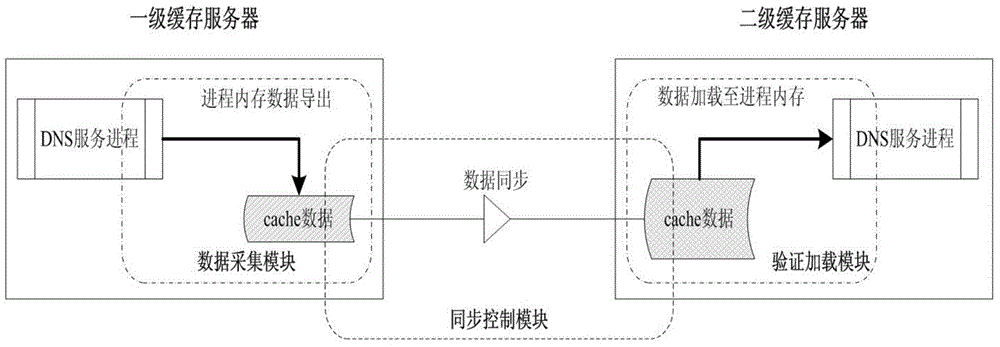
Recursive domain name service system and method of multi-level shared cache
The invention relates to a recursive domain name service system and method of multi-level shared cache. The system comprises first-level cache servers, a second-level cache server and a forward server. The second-level cache server is used for collecting cache records of all first-level cache servers at a front end through a consistency cache sharing mechanism, and establishing a relatively large cache region; and checking a local server cache region after receiving a domain name query request forwarded by the first-level cache server; and directly returning data to the first-level cache server if a requested resource record exists in the local cache region, or forwarding the domain name query name to the forward server; and then the forward server is used for iteratively querying to obtain a query result. Furthermore, the system comprises a data acquisition module, a synchronous control module and a verification loading module. The sharing of cache resource records between different cache servers can be realized, the domain name cache hit ratio is obviously improved, and the domain name analysis time delay is shortened.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Proactive transfer ready resource management in storage area networks
InactiveUS20050262309A1Avoid deadlockAlleviating deadlock situationInput/output to record carriersUnauthorized memory use protectionStorage area networkNetsniff-ng
Systems and methods in accordance with various embodiments can manage transfer ready resources of one or more physical targets to avoid deadlock of a storage switch or storage area network when attempting to write data to a mirrored virtual target. When writing data to a mirrored virtual target, a storage switch simultaneously or synchronously routes data from an initiator to multiple physical locations, such as multiple physical targets. A switch or network can become deadlocked while waiting to receive a transfer ready resource from each of the physical targets involved in the operation. In accordance with an embodiment, a storage switch determines the availability of a transfer ready resource from a physical target prior to issuing a write command to the target. In this manner, the switch can ensure that the target will be available to issue a transfer ready signal when a write command is issued, thus alleviating potential deadlock situations. In accordance with one embodiment, a resource table can be used to store an indication of the availability of transfer ready resources from one or more targets. The resource table can be updated as transfer ready resources are allocated to incoming commands. In one embodiment, a circular first in / first out buffer can be used to queue information relating to write commands for mirrored virtual targets.
Owner:EMC CORP
Trasmitting/receiving apparatus and method in a mobile communication system
InactiveUS20070249351A1Avoid deadlockError preventionNetwork traffic/resource managementBandwidth allocationHandover
A handover method and apparatus in a communication system are provided. The method includes an MS sending to a serving BS a bandwidth allocating request message for sending a MOB_MSHO-REQ message requesting a handover; activating a timer set to a bandwidth allocation waiting time in relation to the bandwidth allocating request message; stopping the timer upon receipt of a bandwidth allocation message from the serving BS before the timer expires; and determining to perform a handover to a target BS if the MS does not receive the bandwidth allocation message from the serving BS before the timer expires.
Owner:SAMSUNG ELECTRONICS CO LTD
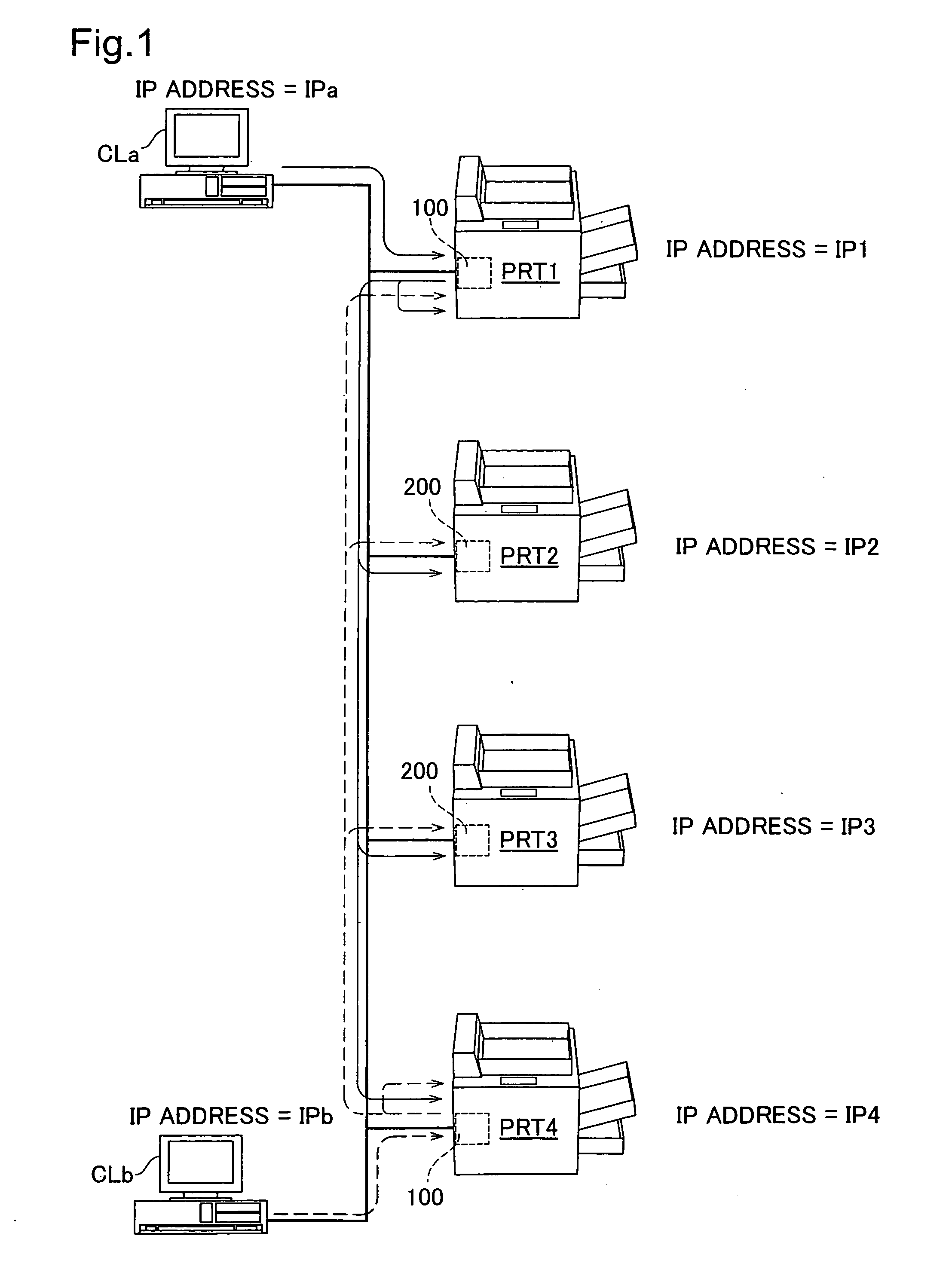
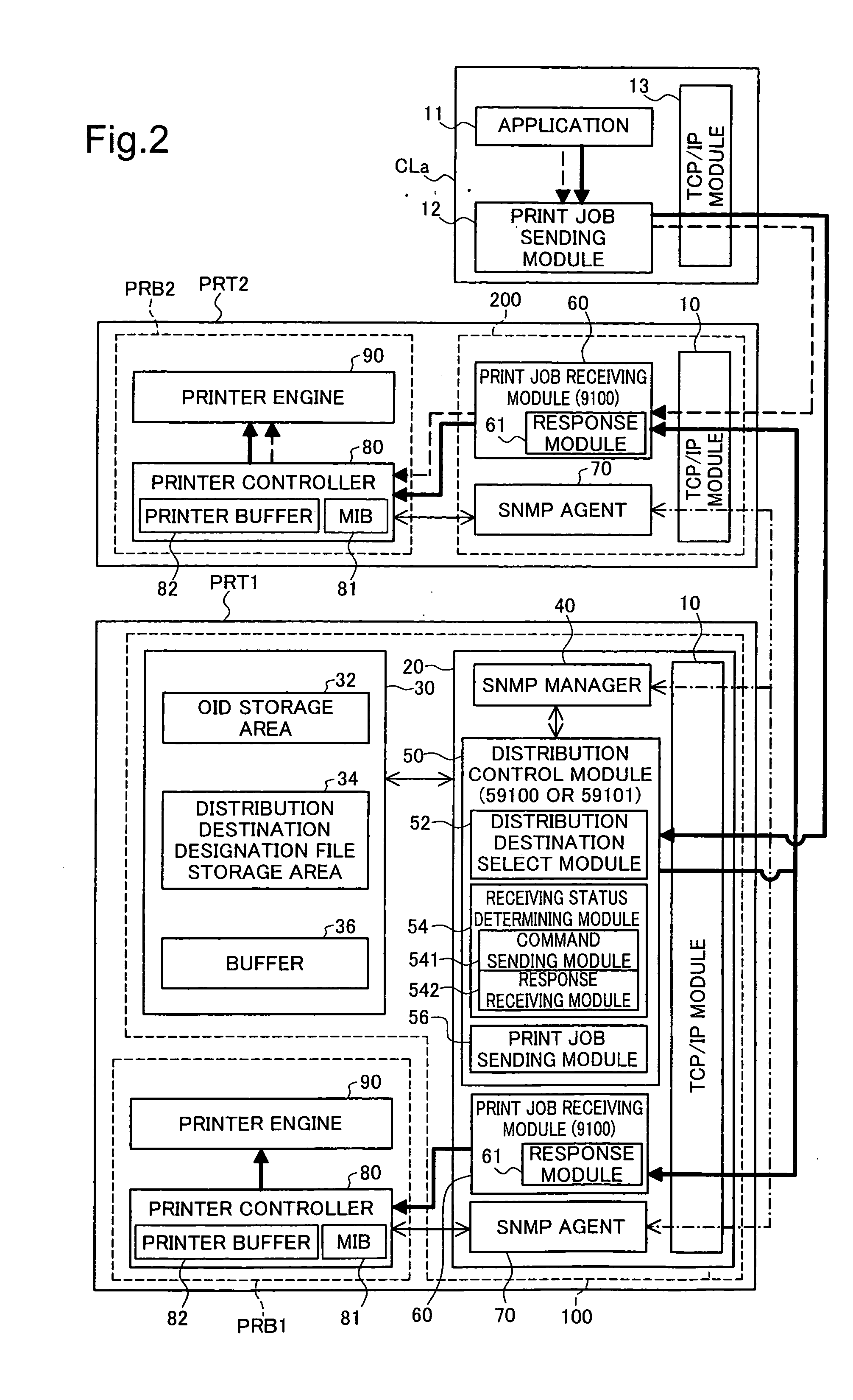
Control technology used in distributed printing for printing control device and printer
InactiveUS20060274370A1Smooth distributed printing processThe printing process is smoothVisual presentation using printersDigital output to print unitsConnection typeComputer science
Owner:SEIKO EPSON CORP
Method, system and apparatus for the operation of reordering and repeated elimination
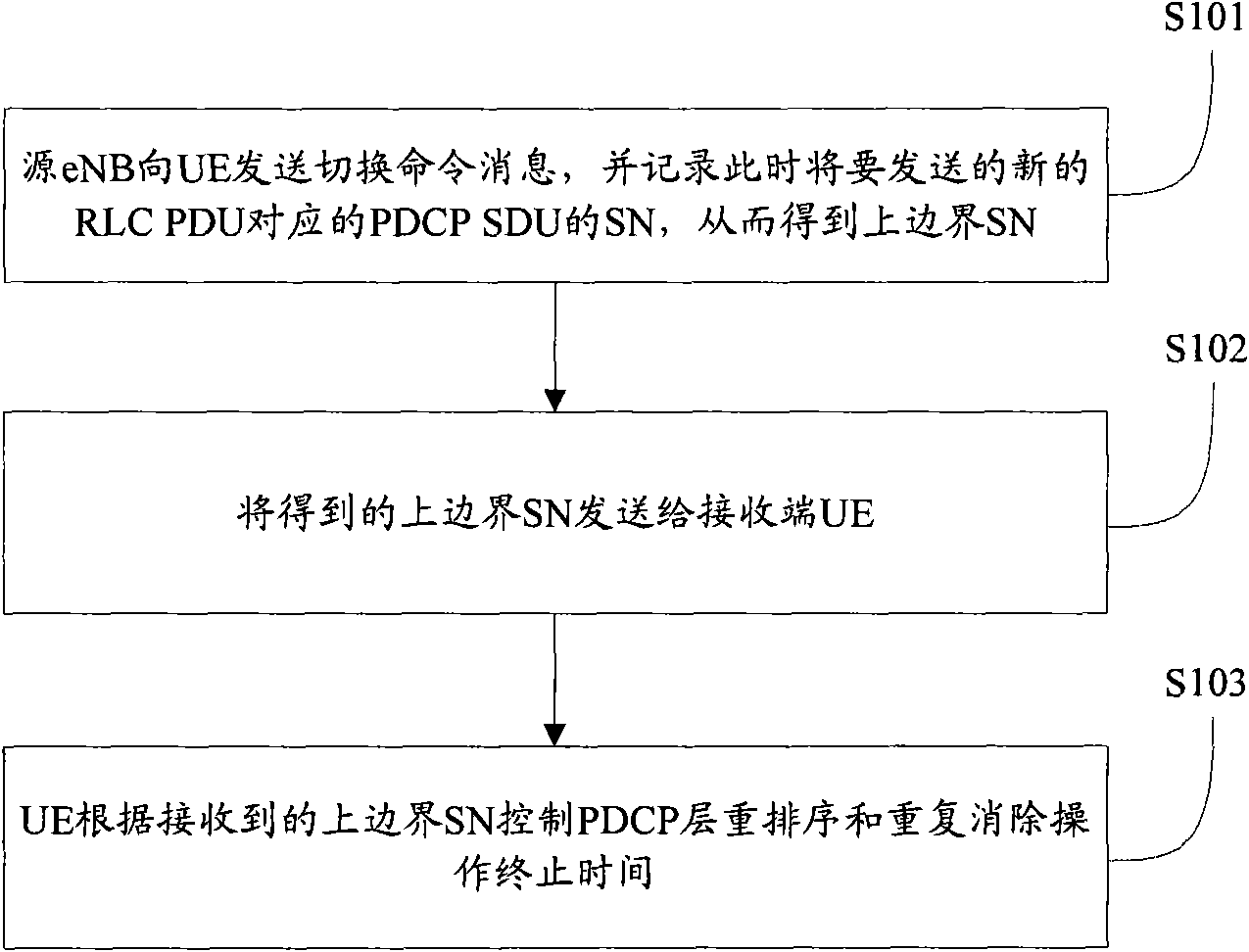
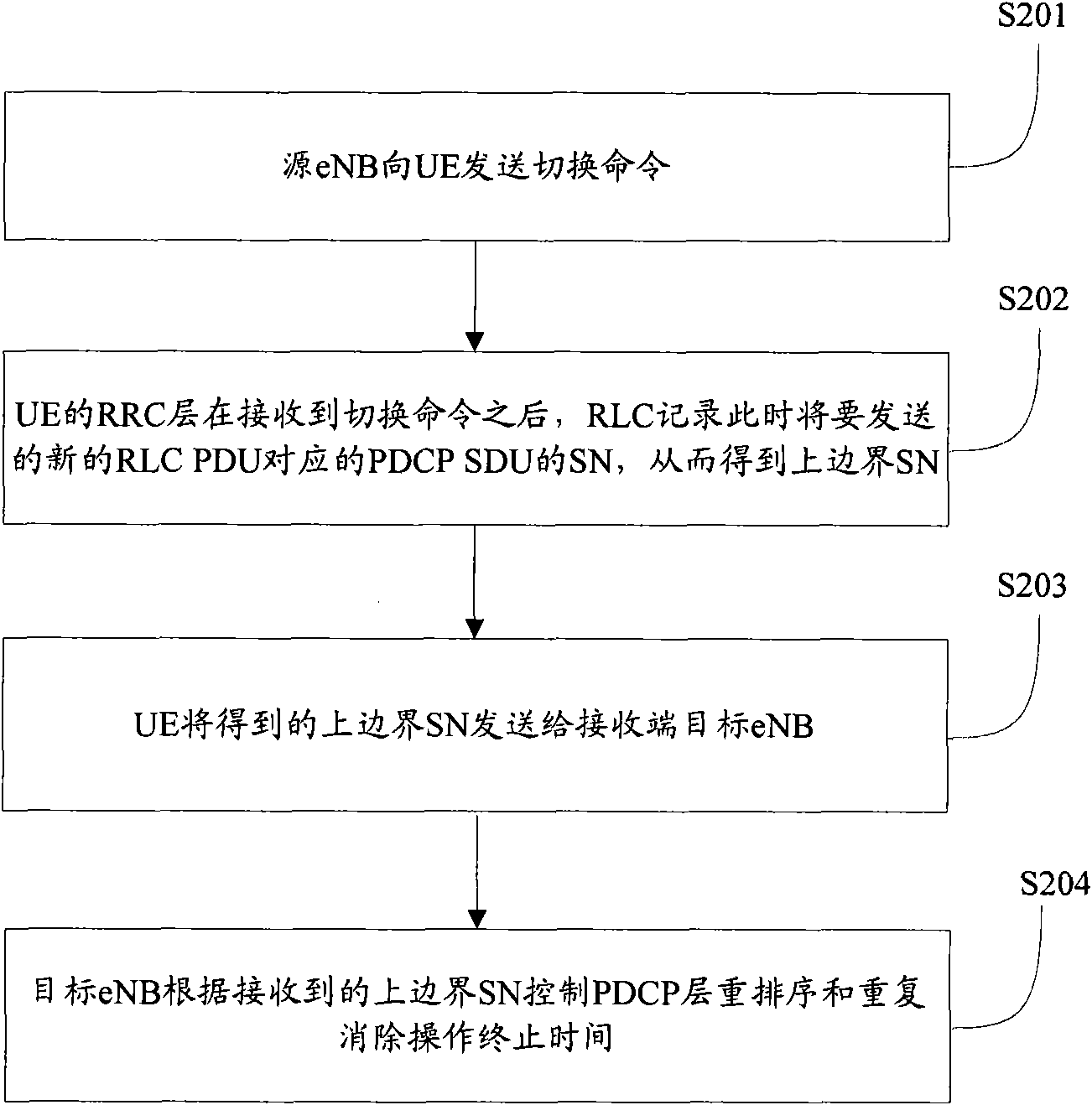
ActiveCN101677266AAvoid technical defects caused by inaccurate time settingOvercoming technical deficienciesError prevention/detection by using return channelData switching networksComputer scienceTimer
The invention provides a method for controlling the operation of reordering and repeated elimination, includes the following steps: a receiving end receiving the sequence number SN of the upper boundary after receiving, wherein, the upper boundary SN is the upper boundary of SN of Packet Data Convergence Protocol Service Data Unit PDCP SDU where disorder may occur; the receiving end determining the termination time of the operation of reordering and repeated elimination based on the received upper boundary SN. By the transmission of the upper boundary SN, the receiving end determines the termination time of the operations of reordering and repeated elimination based on the upper boundary SN, so that the Flush-timer timer in the prior art is not needed, thereby avoiding the technology defect caused by inaccurate timing length setting of the Flush-timer timer.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Fan impellor locking device and wind-driven power generator set
ActiveCN102226445AAvoid many problems such as damageGood repeatabilityWind motor controlMachines/enginesWind drivenImpeller
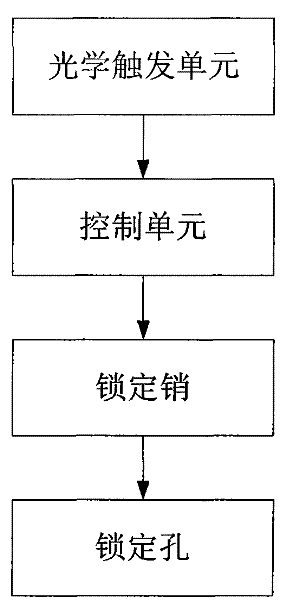
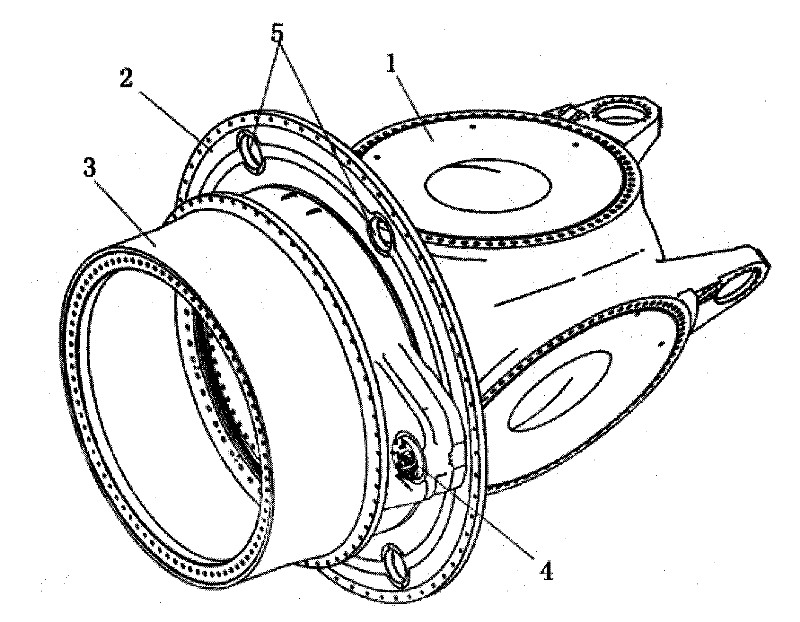
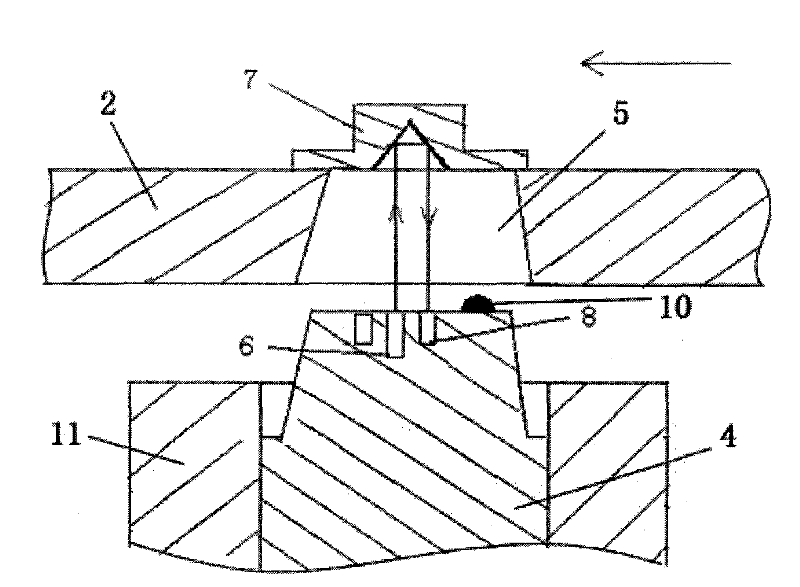
The invention provides a fan impellor locking device which comprises a locking pin, a locking hole, an optical triggering unit and a control unit which are respectively arranged on a stator main shaft and a rotating shaft, wherein the optical triggering unit is used for sending triggering units to the control unit when the locking pin and the locking hole are aimed or to be aimed; and the control unit is used for driving the locking pin to execute corresponding locking motions according to triggering signals. The invention also provides a wind-driven power generator set with the fan impellor locking device. The automatic, efficient and accurate locking operations to the fan impellor can be realized through the fan impellor locking device and the wind-driven power generator set provided by the invention, and simultaneously the deadlock between the locking pin and the locking hole can be avoided effectively.
Owner:JIANGSU GOLDWIND SCI & TECH CO LTD
Dynamic avoidance method for multiple robots in collaborative operation
ActiveCN110209485AReduce the avoidance areaReliable designProgram initiation/switchingResource allocationSimulationPlant automation
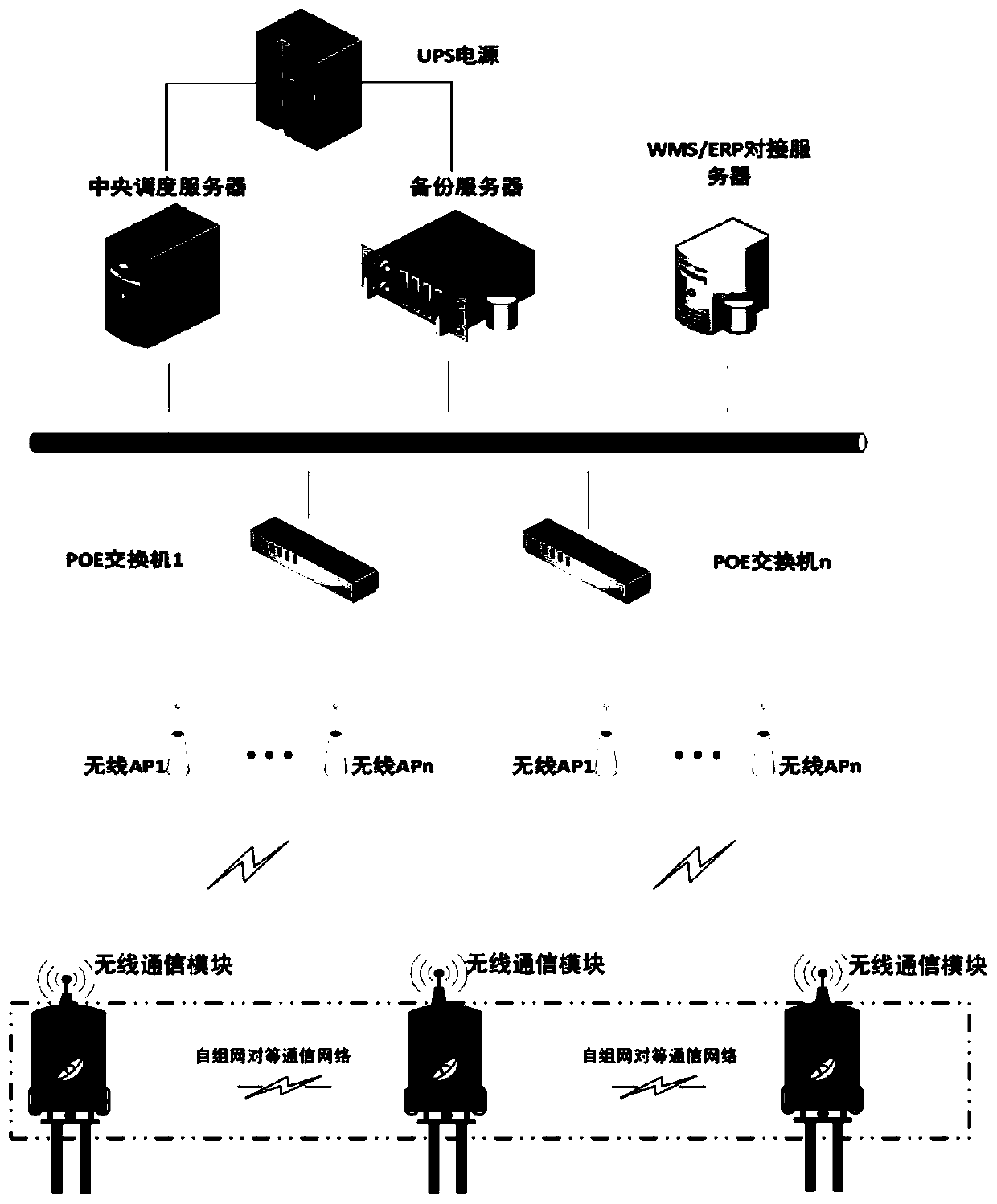
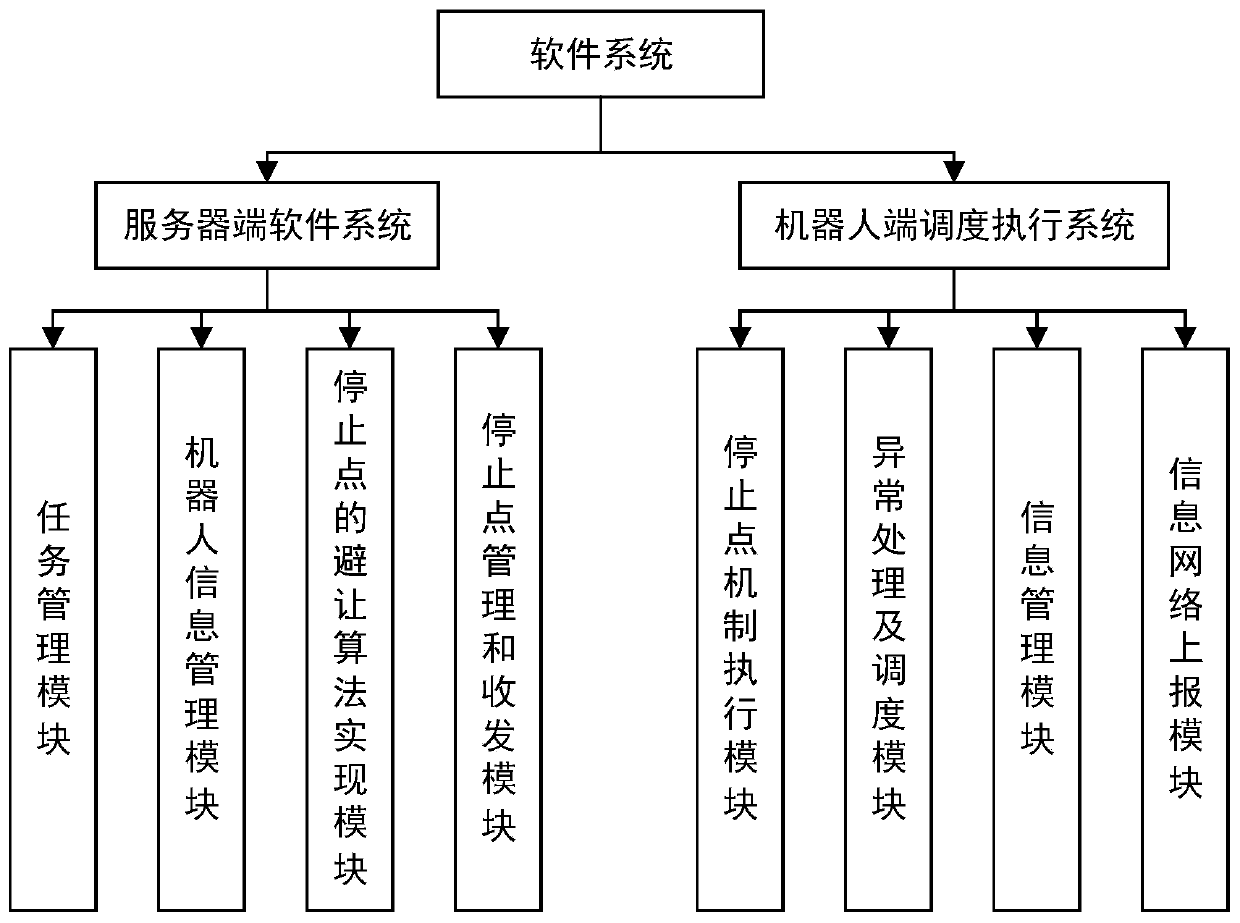
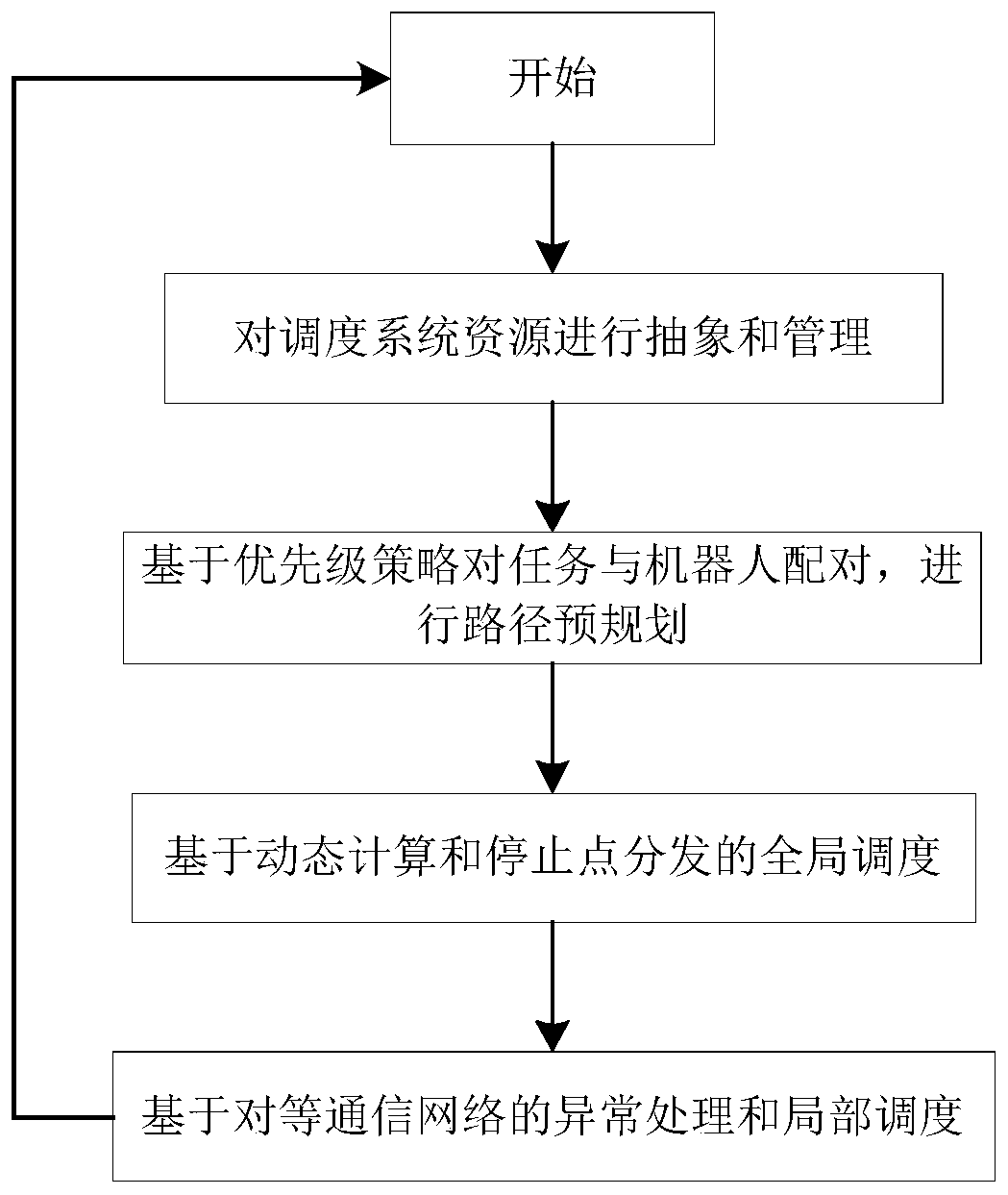
The invention discloses a dynamic avoidance method for multiple robots in collaborative operation. The method comprises the steps: carrying out the path pre-planning of all tasks in a task pool according to the priorities, and reducing the conflict intervention between robots from a planning layer; monitoring the current operation states of all the robots, dynamically pre-judging the safety distance, generating different types of stop points, coordinating the operation of the robots, and solving the technical problems of collision, delay, interlocking and the like during the cooperative operation of the robots. Overall scheduling is carried out to optimize resource distribution, traffic control and coordinated avoidance are achieved, local peer-to-peer communication solves the overall operation problem after the robot individual is abnormal, and therefore the robustness of the whole scheduling system is guaranteed. The method is suitable for multi-robot scheduling avoidance scenes suchas factory automation and storage commodity transfer.
Owner:青岛海通胜行智能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com