Patents
Literature
287 results about "Exclusive access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
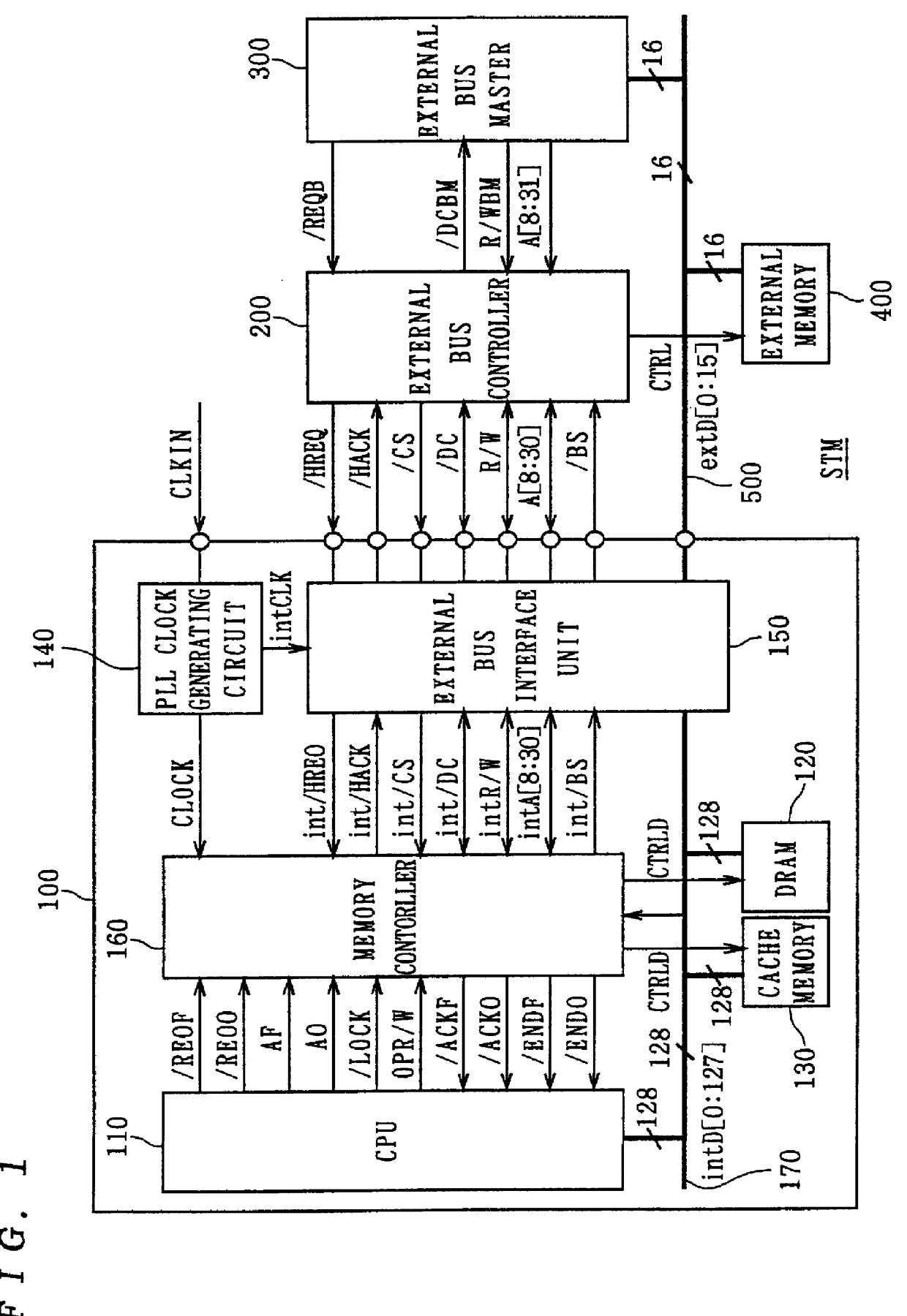
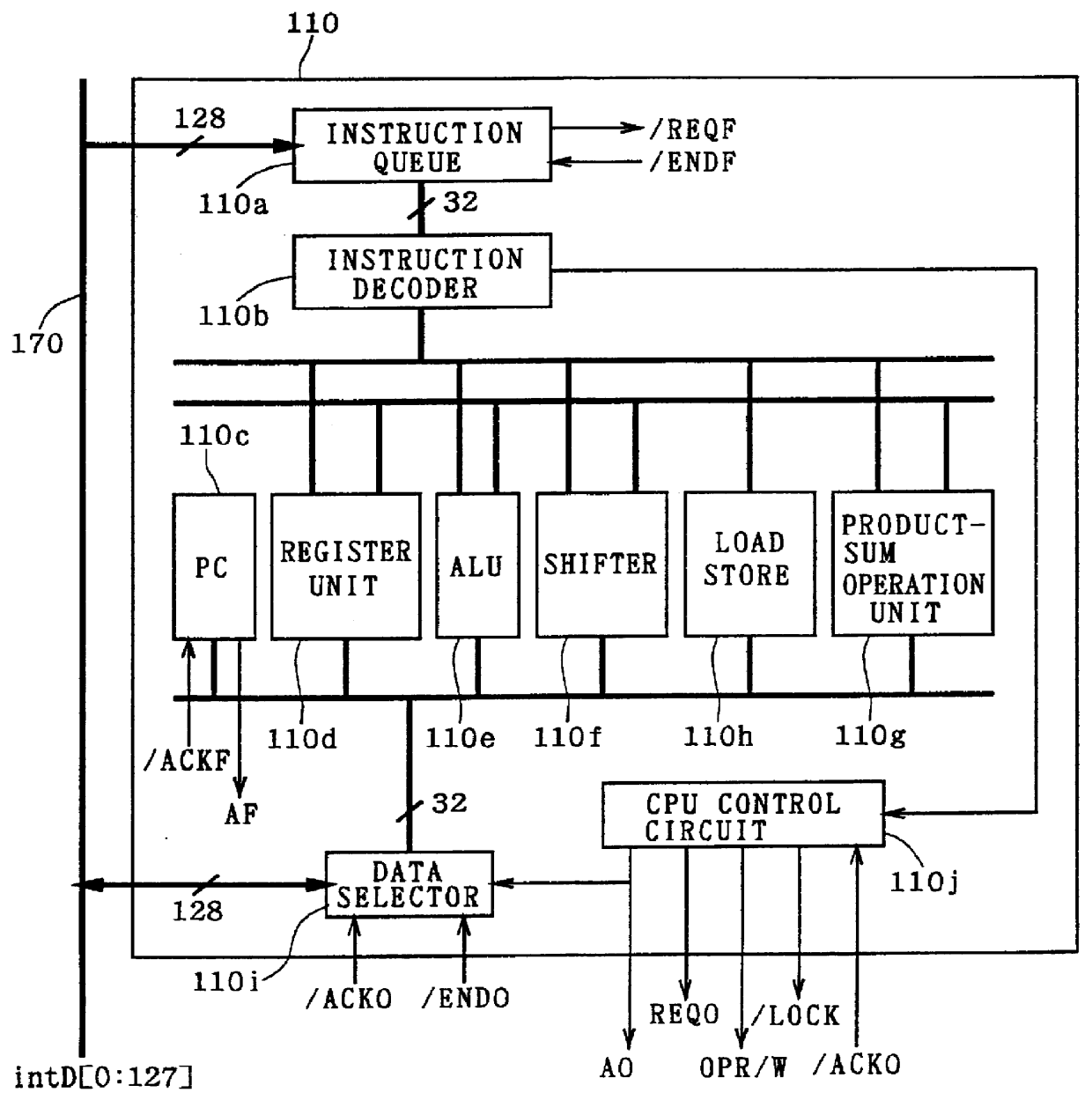
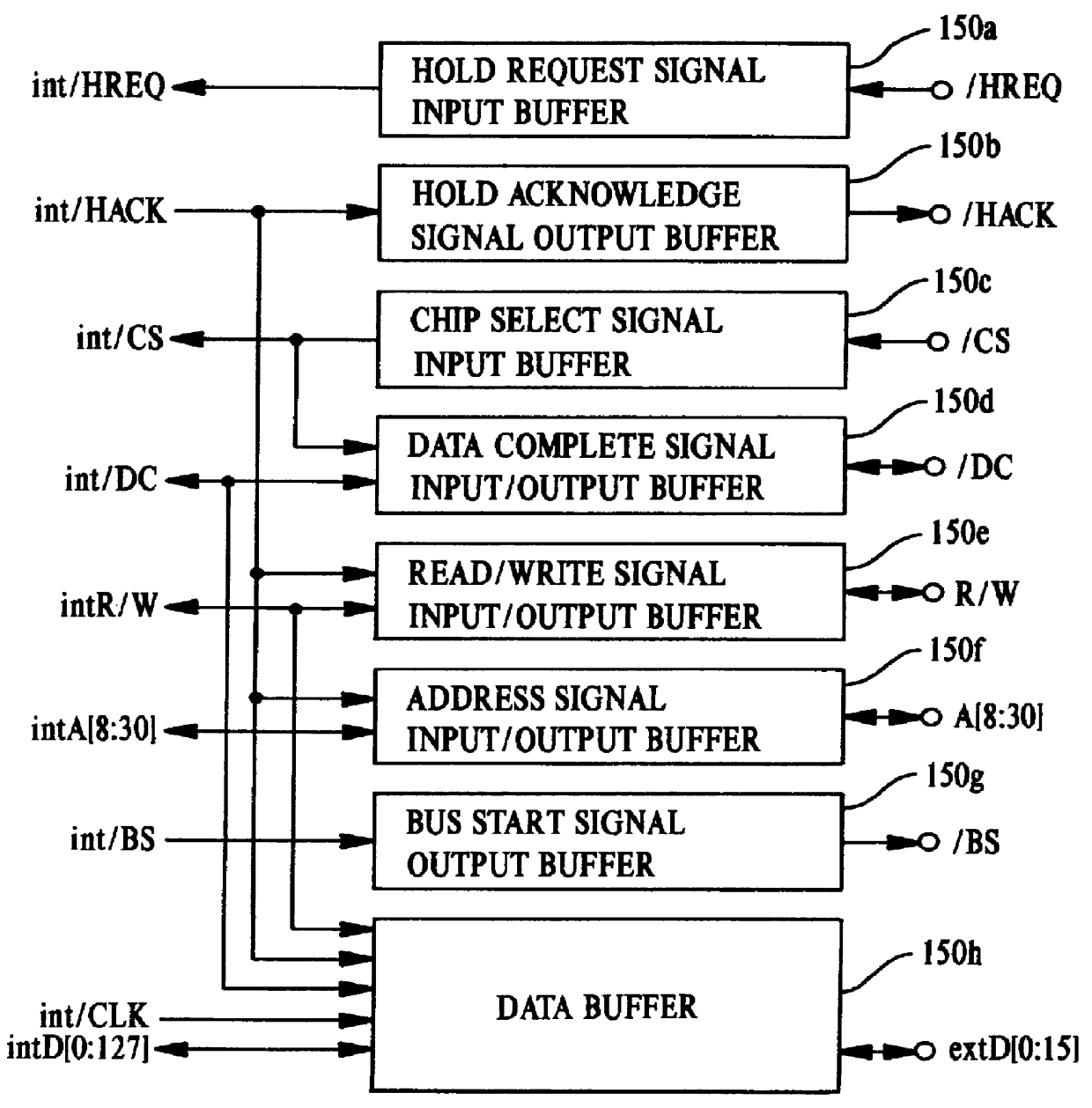
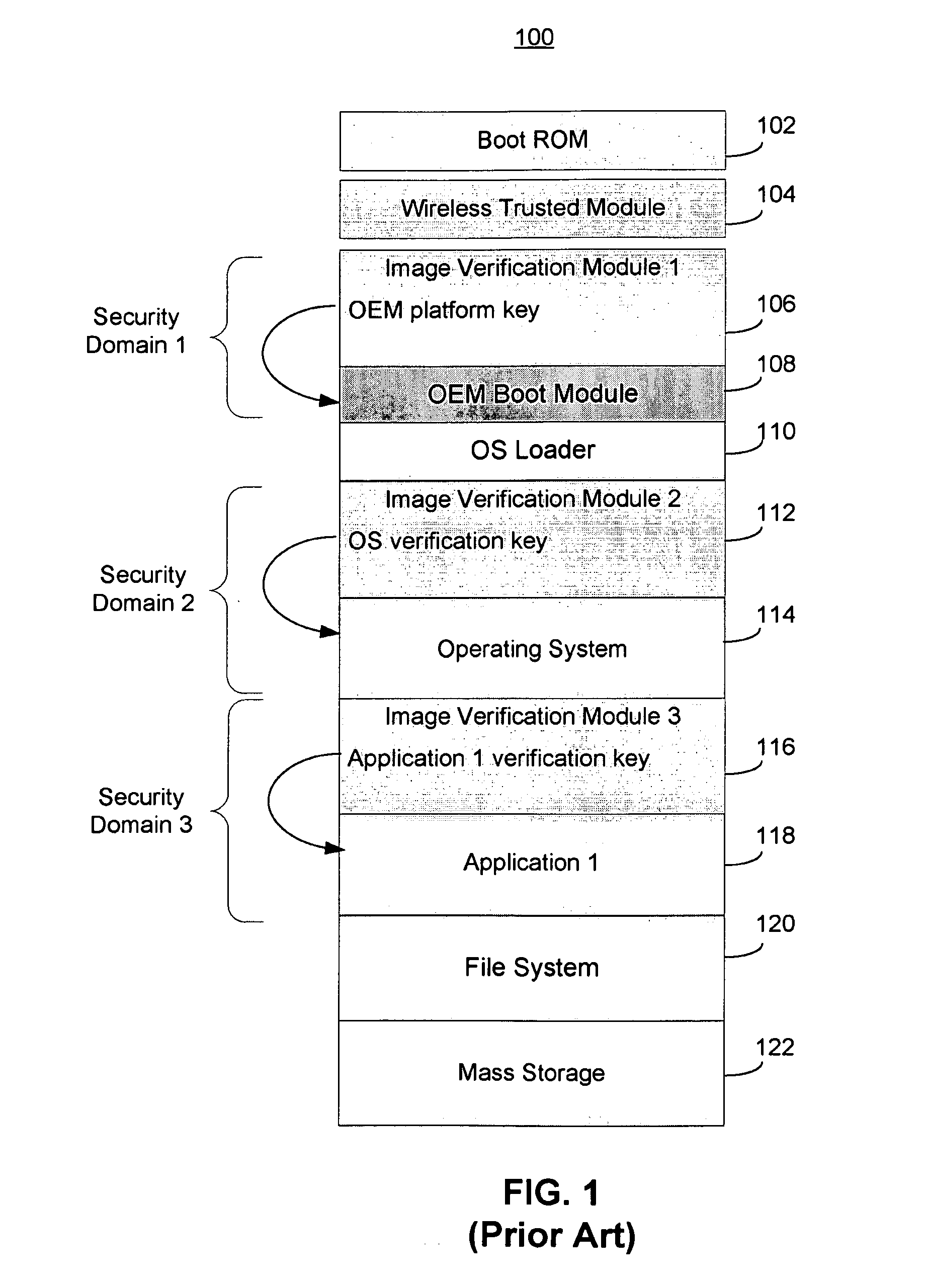
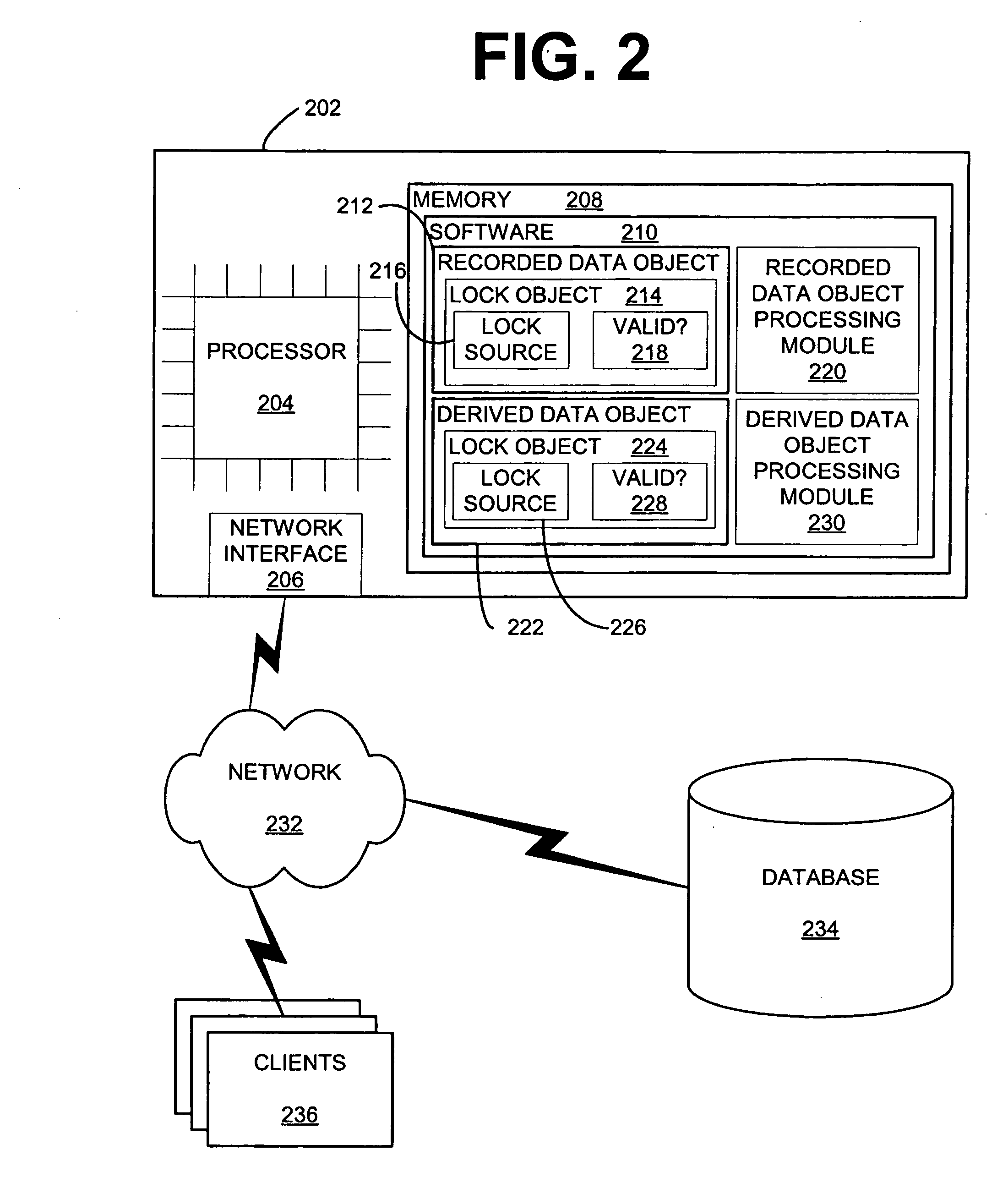
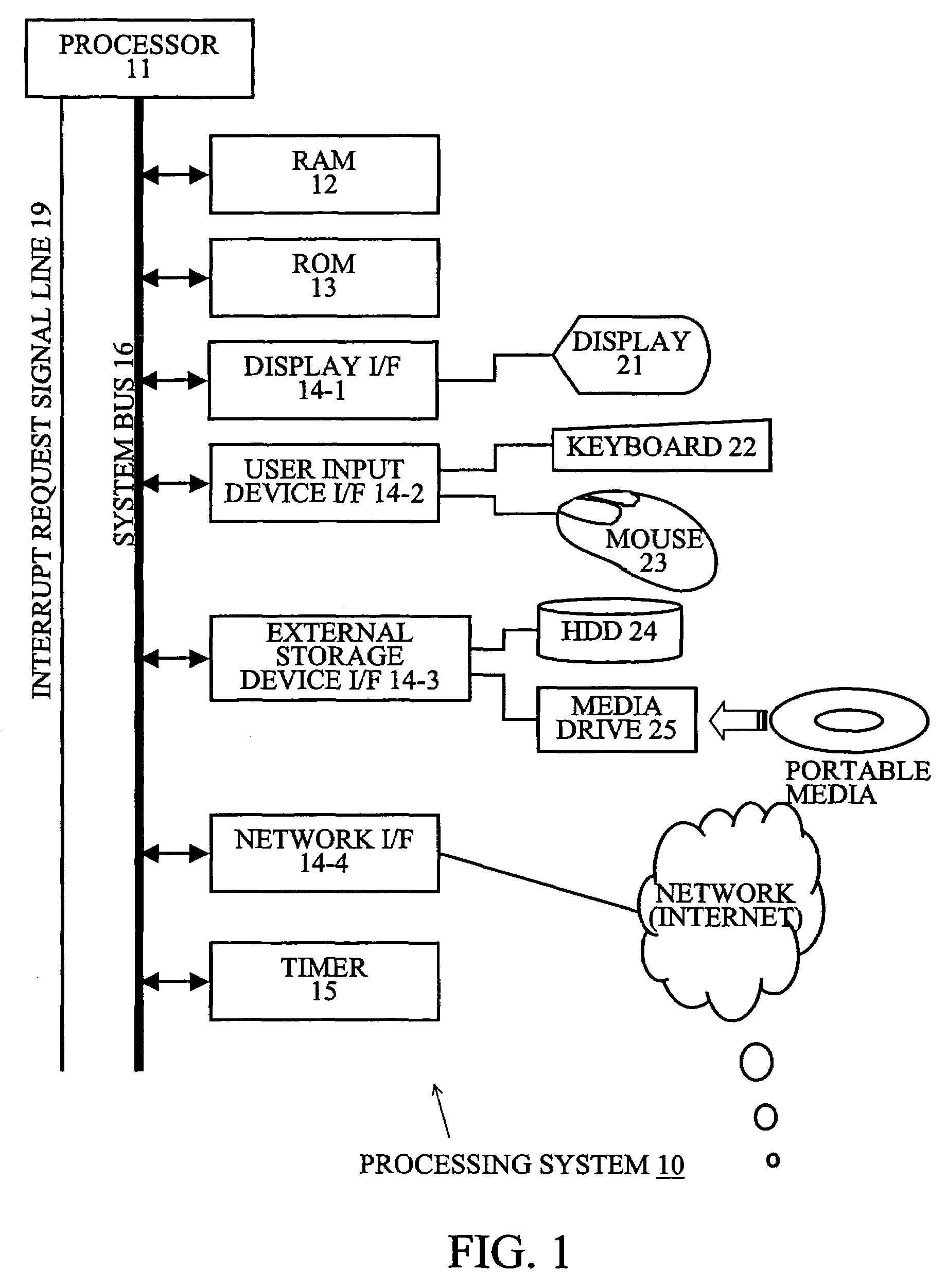
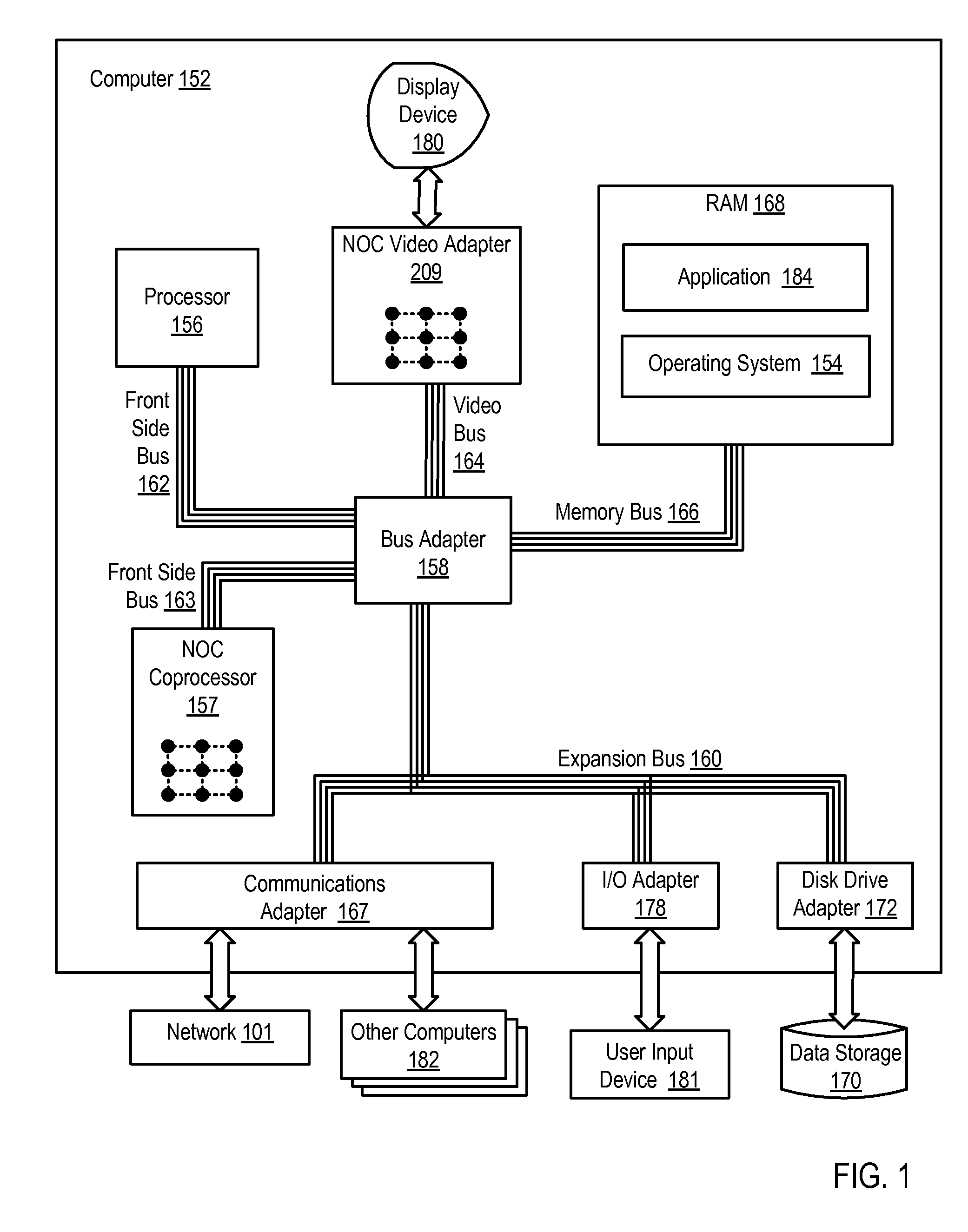
Computer system and semiconductor device on one chip including a memory and central processing unit for making interlock access to the memory
InactiveUS6101584AUnauthorized memory use protectionMultiple digital computer combinationsChip selectComputerized system
A central processing unit (CPU) having a built-in dynamic random-access memory (DRAM) with exclusive access to the DRAM when the CPU performs an interlock access to the DRAM. A memory controller prevents the DRAM from being externally accessed while the CPU is performing the interlock access. When the memory controller receives an external request for accessing the DRAM during a time when the CPU is performing an interlock access to the DRAM, the memory controller outputs a response signal indicating that external access to the DRAM is excluded or inhibited. The request signal can be a hold request signal for requesting a bus right or can be a chip select signal. The response signal can be a hold acknowledge signal or a data complete signal. The memory controller can be switched to and from first and second lock modes, where hold request and hold acknowledge signals are used during the first lock mode and chip select and data complete signals are used in the second lock mode.
Owner:MITSUBISHI ELECTRIC CORP
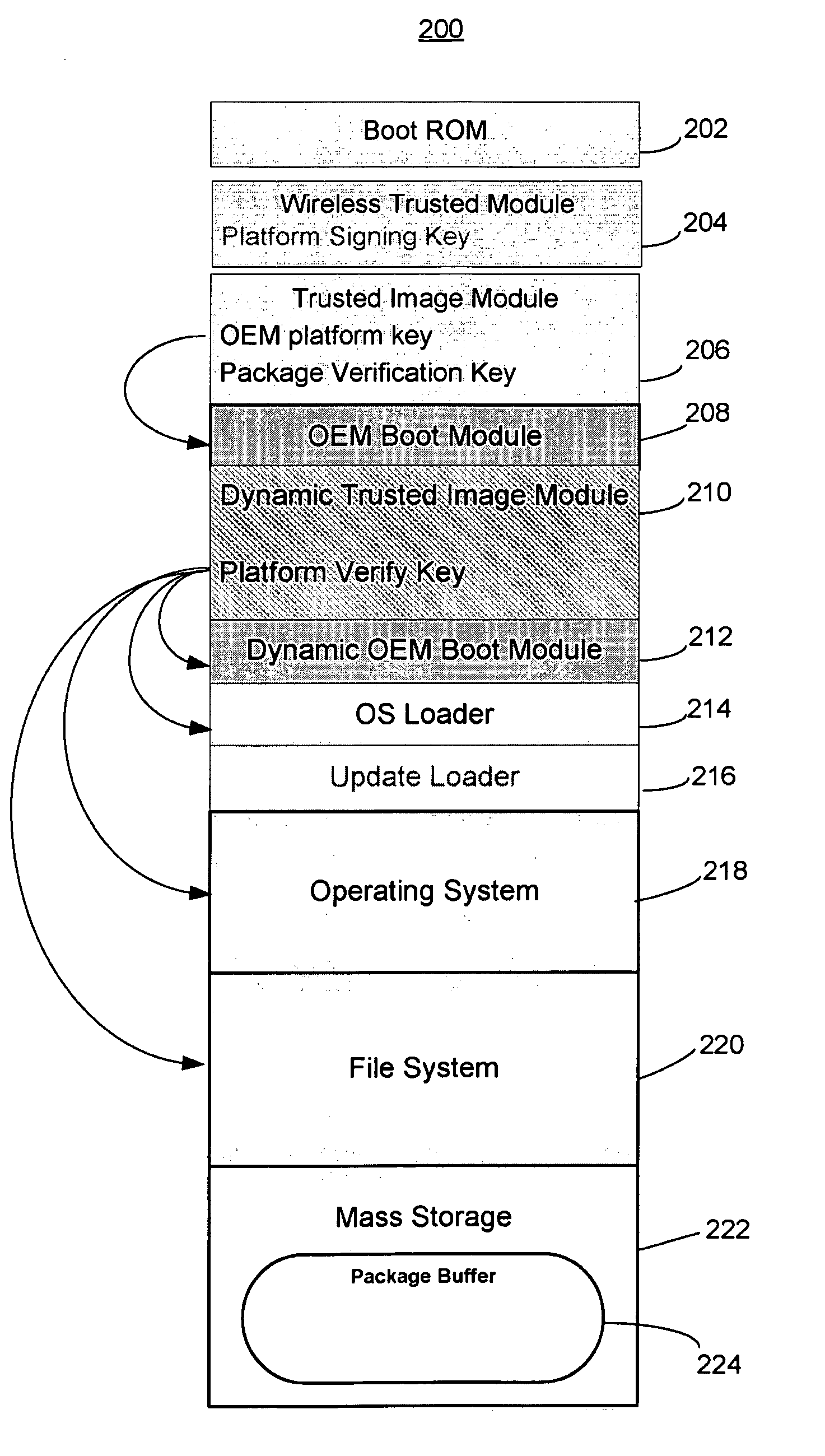
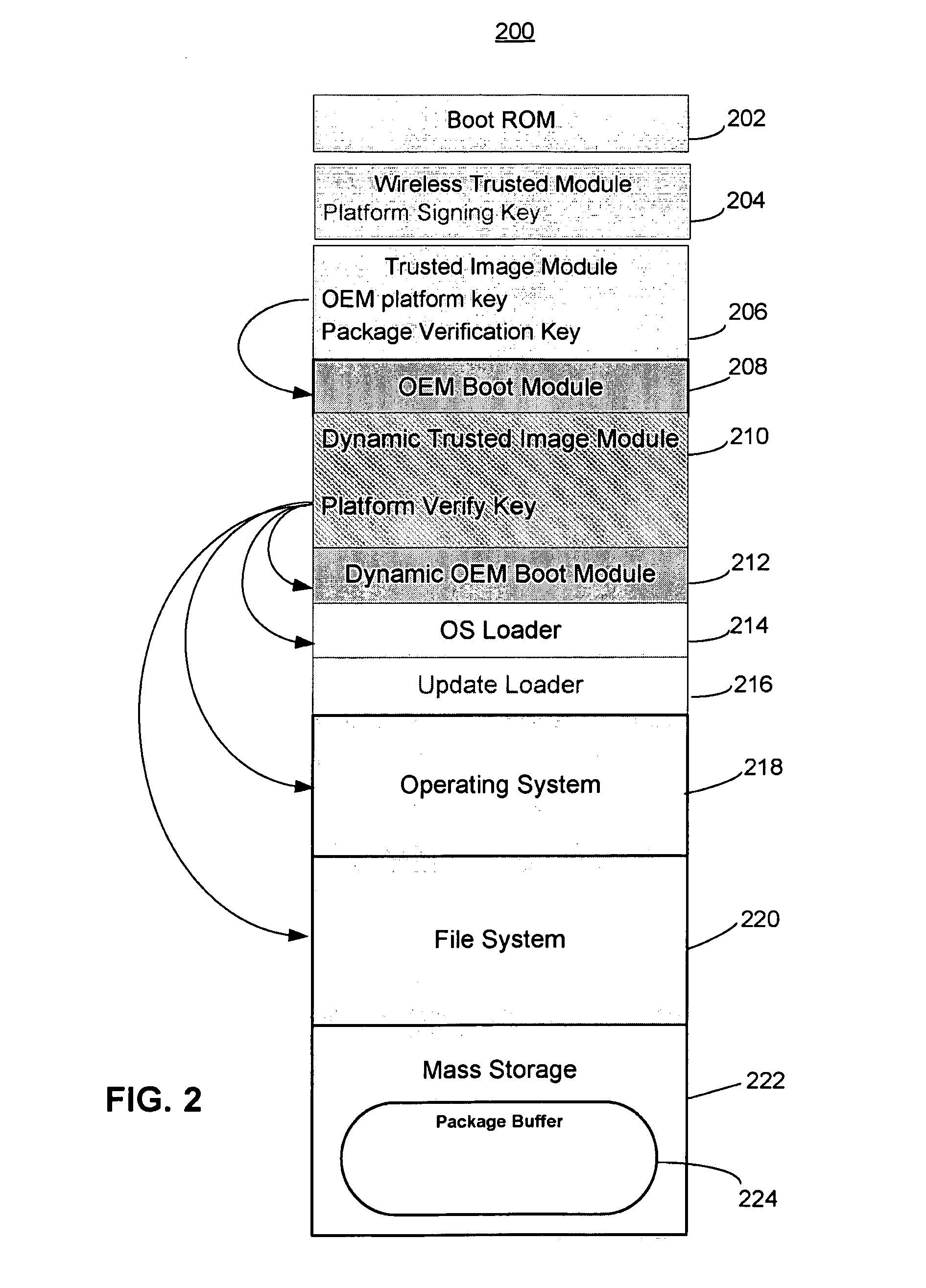
Trusted modular firmware update using digital certificate
An over-the-air firmware update is accomplished in a secure manner using a two-step process. The first step uses an initial boot using a fixed boot program and an authenticated and verified secondary environment to complete starting of only authenticated code. After verifying a pending update, the second step is started with the electronic device being booted into an update mode with an update loader that has exclusive access to a signing key. A dummy update image is loaded into a temporary memory location and a hash is taken. A digital certificate is created corresponding to the update image and signed using the signing key. The update and digital certificate are atomically installed and the signing key is deactivated. Upon reboot, the new image is used for operation and is verified by the hash data and public key in the digital certificate.
Owner:MARVELL ASIA PTE LTD
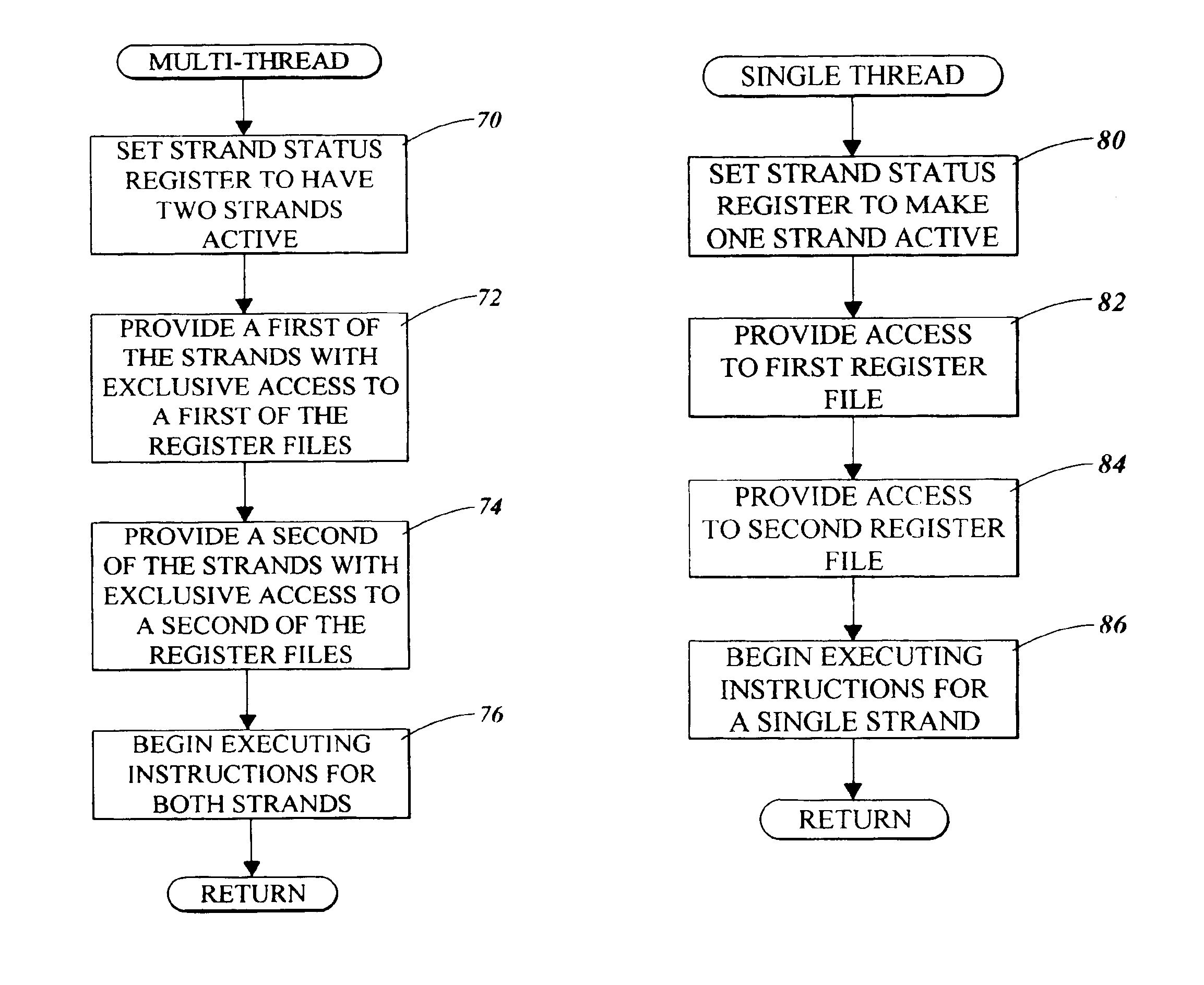
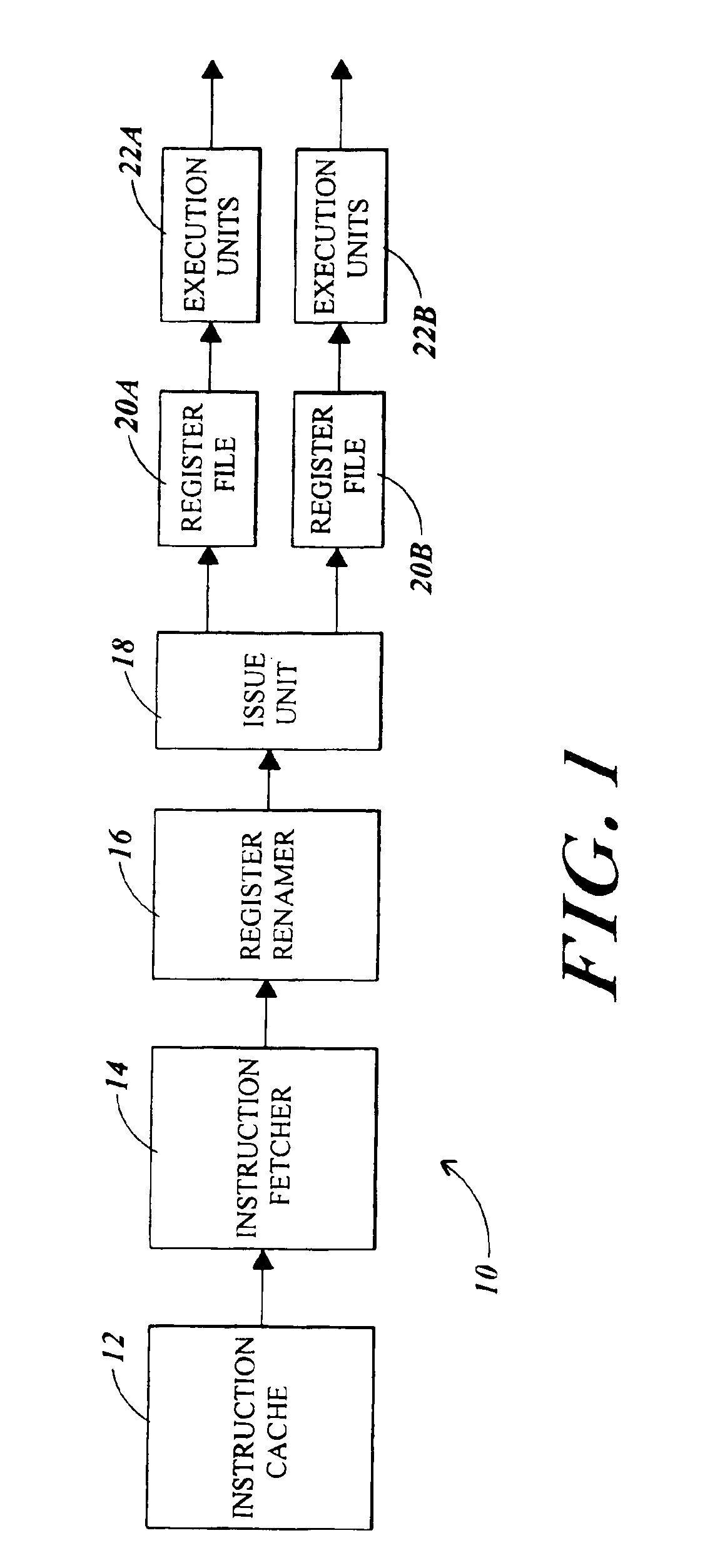
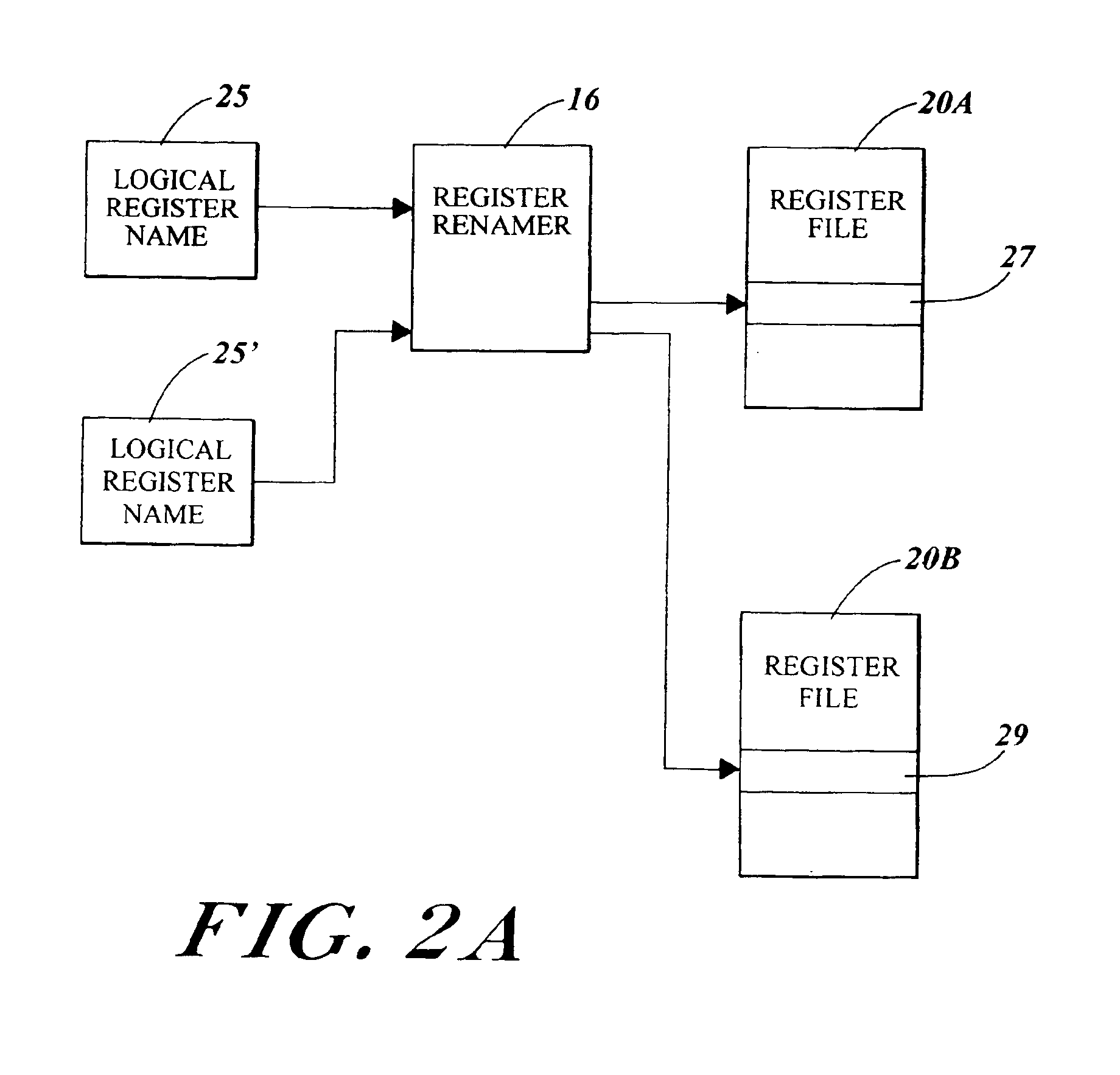
Microprocessor and method for giving each thread exclusive access to one register file in a multi-threading mode and for giving an active thread access to multiple register files in a single thread mode
InactiveUS6954846B2Maximize issue rateRegister arrangementsUnauthorized memory use protectionMicroprocessorExclusive access
A microprocessor includes multiple register files. In a single thread mode, the microprocessor allows a single thread to have access to multiple ones of the register files. In a multi-thread mode, each thread has access to respective ones of the register files. In the multi-thread mode, multiple threads are simultaneously executing. Circuitry and hardware are provided to facilitate the respective modes and to facilitate transitions between the modes.
Owner:ORACLE INT CORP
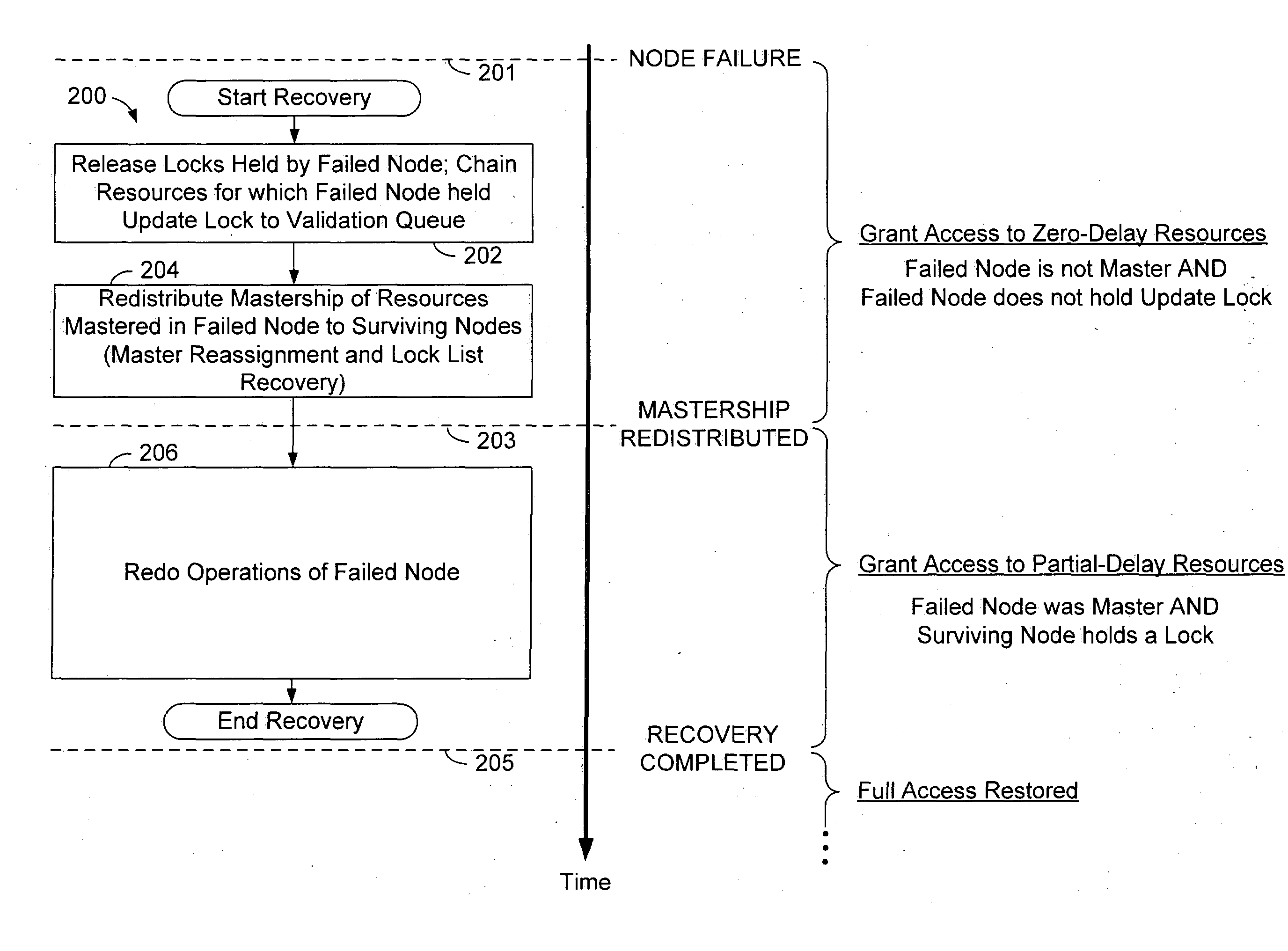
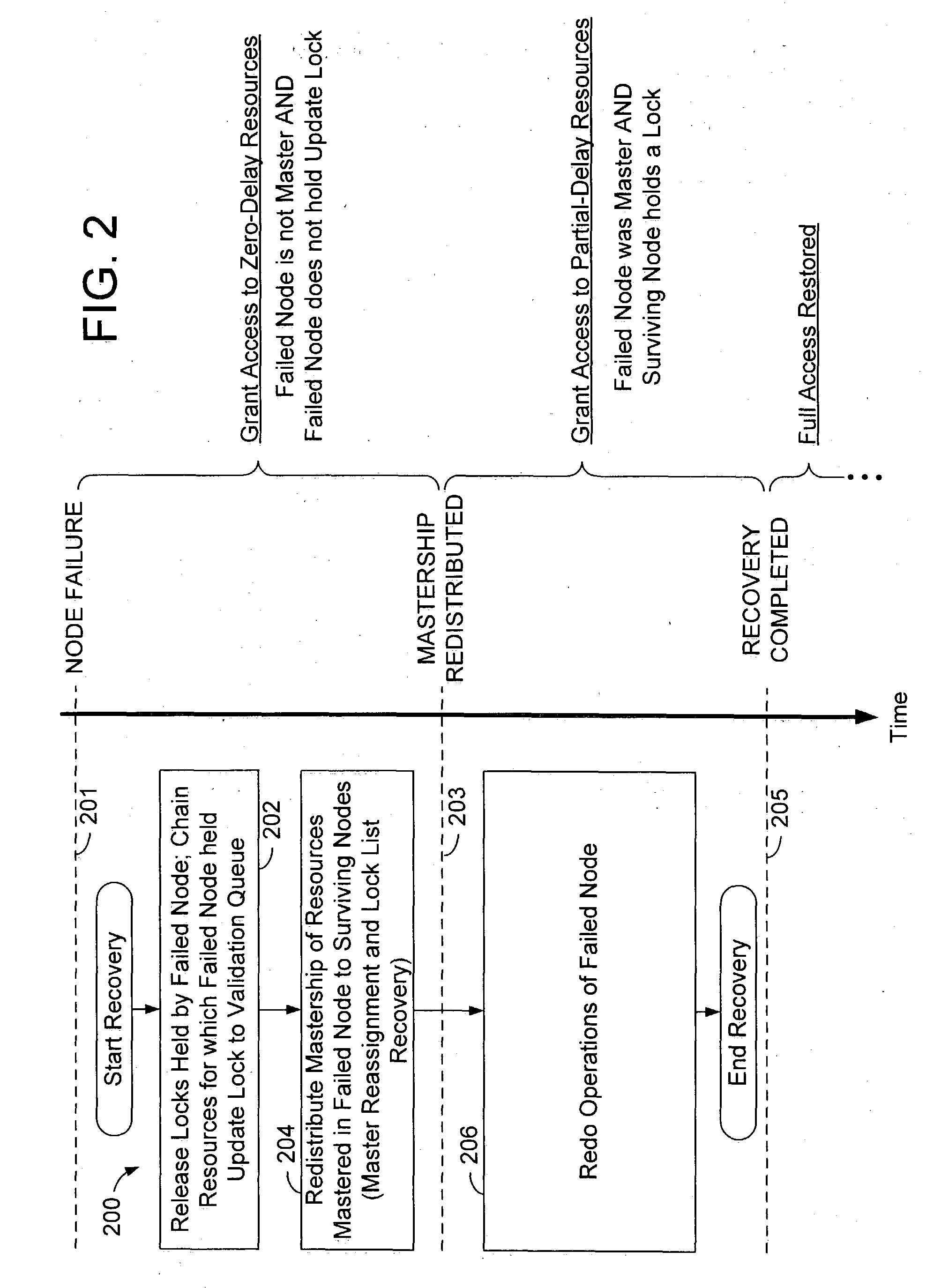
Conditional data access after database system failure
ActiveUS20050022047A1Digital data information retrievalRedundant operation error correctionData processing systemData access
A method of operation within a data processing system that includes a plurality of processing nodes each having access to a set of shared resources. Failure of one of the processing nodes is detected, followed by receipt of a request to access a first resource of the set of shared resources. Access to the first resource is granted if the failed node was not responsible for controlling access to the first resource and did not have exclusive access to the first resource when the failure was detected.
Owner:ORACLE INT CORP
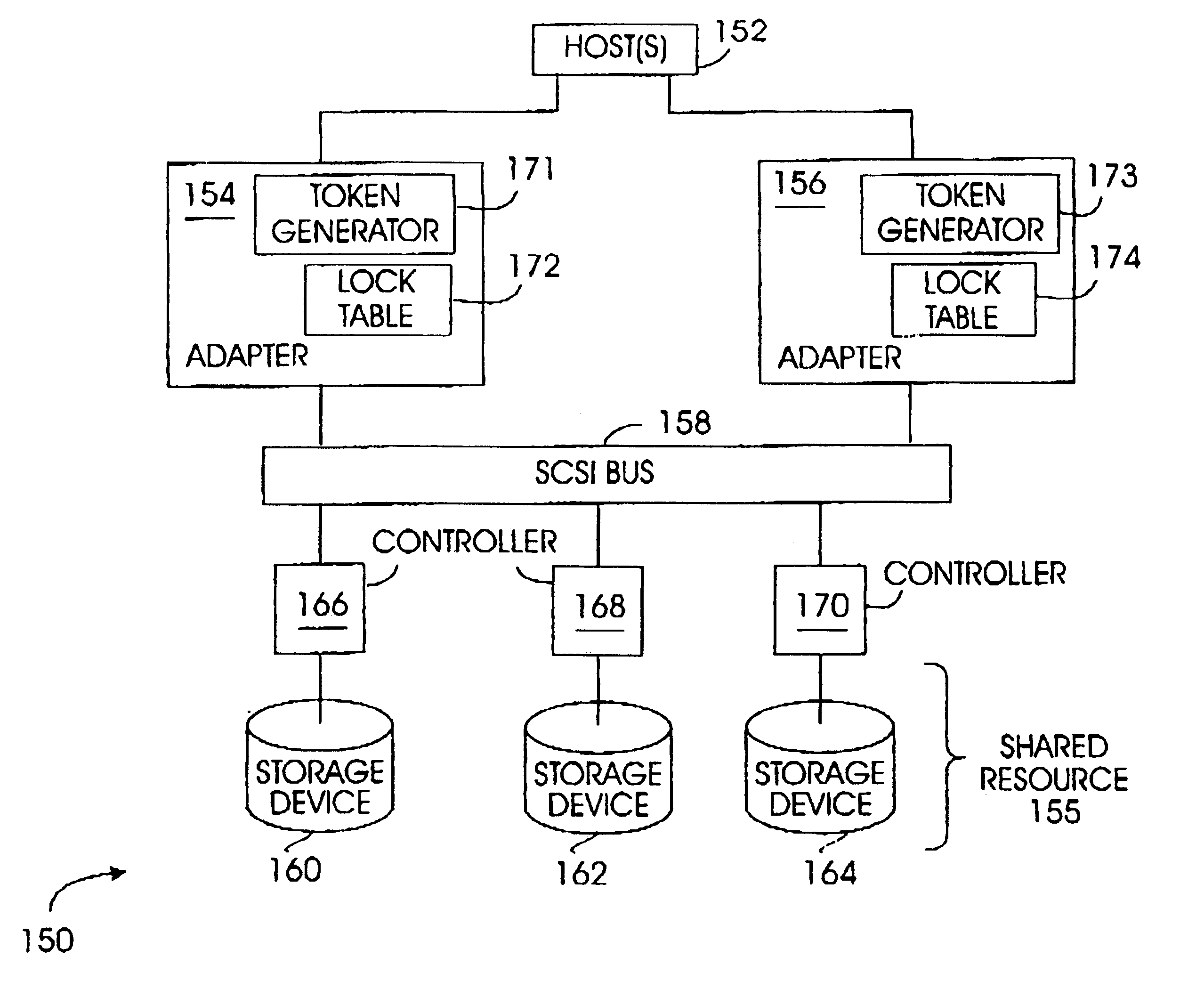
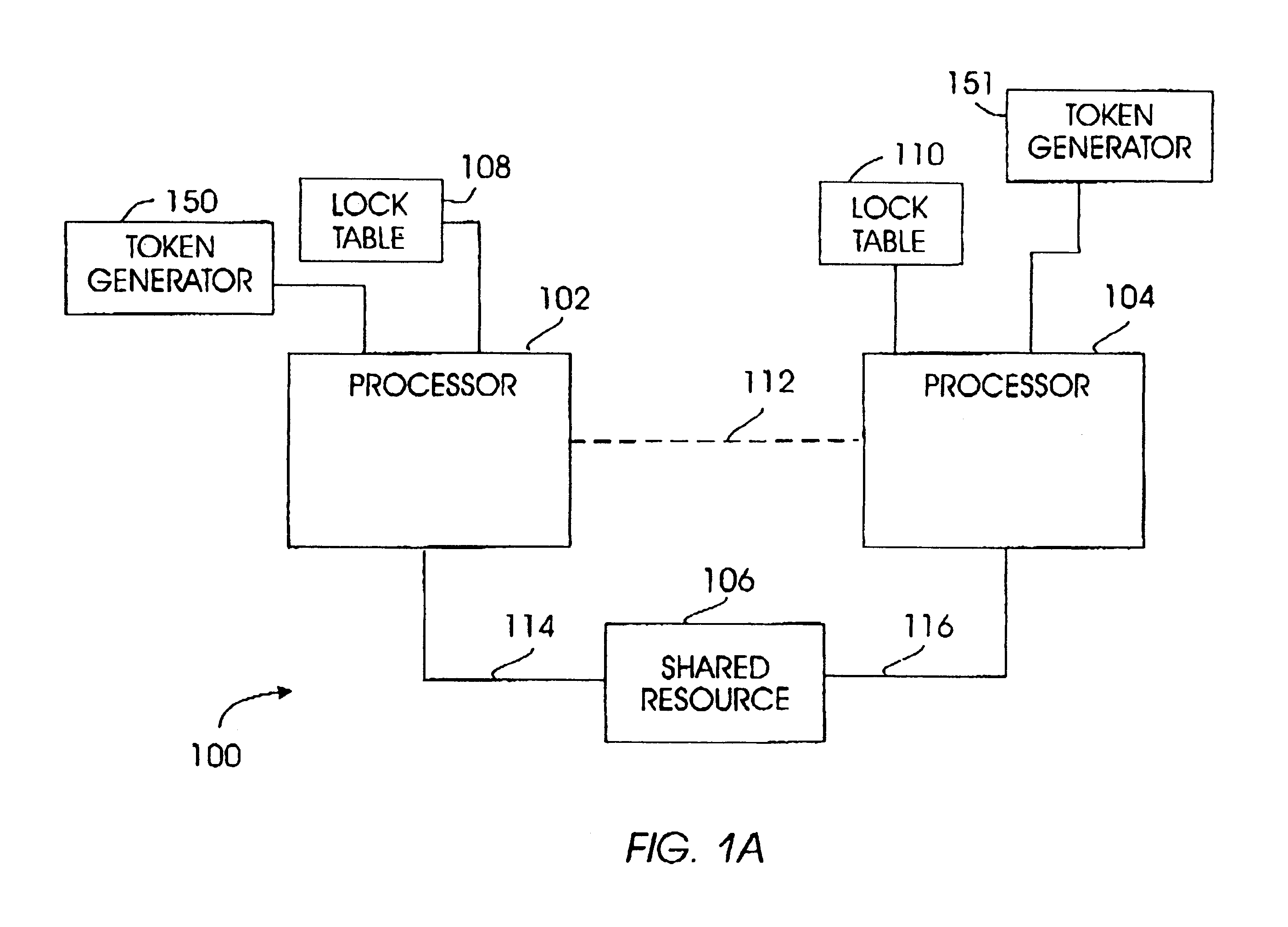
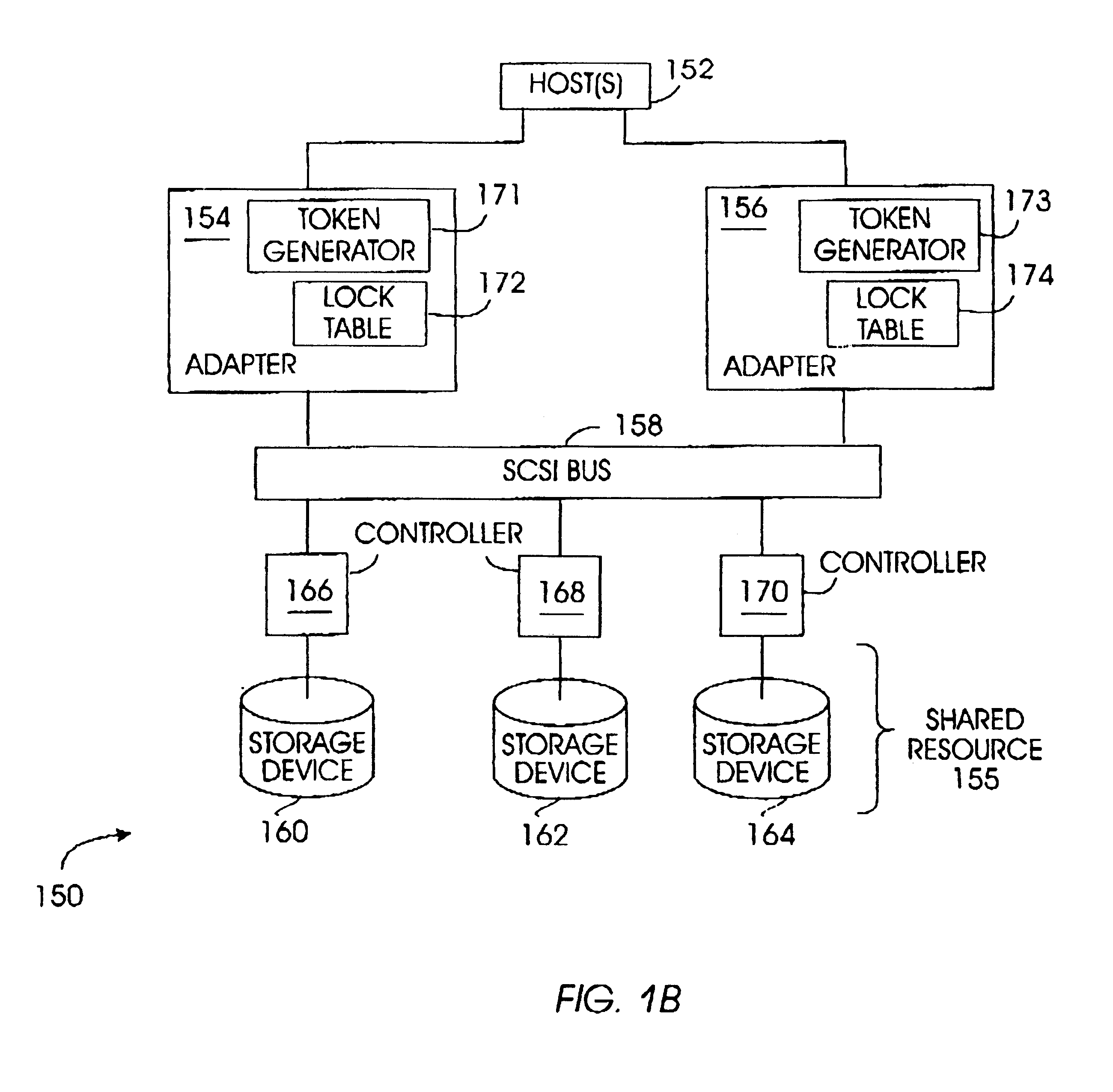
Method and apparatus for controlling exclusive access to a shared resource in a data storage system
InactiveUS7246187B1Unauthorized memory use protectionProgram controlParallel computingShared resource
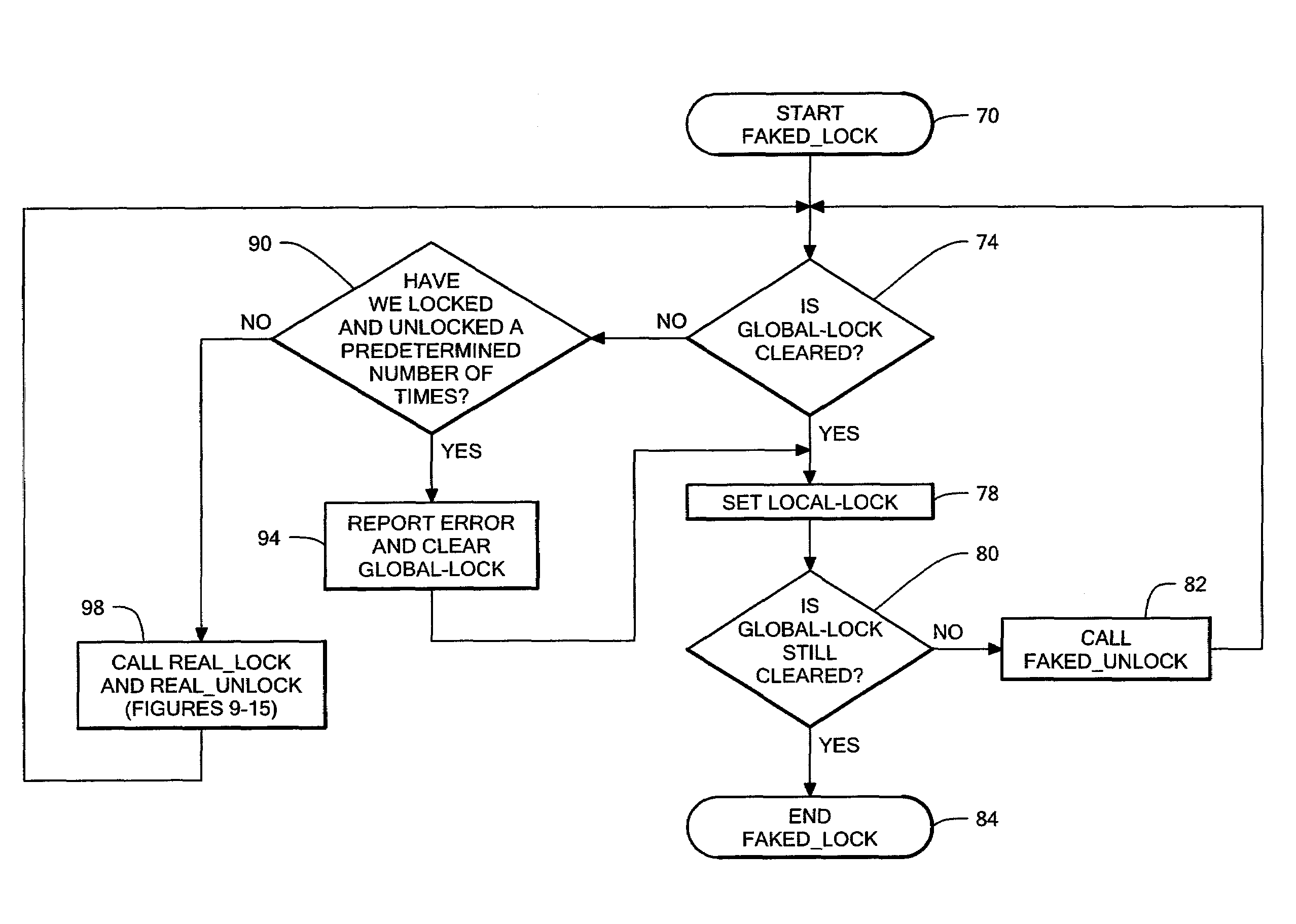
A method for controlling exclusive access to a resource shared by multiple processors in a data storage system includes providing a system lock procedure to permit a processor to obtain a lock on the shared resource preventing other processors from accessing the shared resource and providing a faked lock procedure to indicate to the system lock procedure that a processor has a lock on the shared resource where such a lock does not exist, and wherein the faked lock procedure prevents another processor from obtaining the lock on the shared resource, but does not prevent other processors from accessing the shared resource. A data storage system according to the invention includes a shared resource, a plurality of processors coupled to the shared resource through a communication channel, and a lock services procedure providing the system lock procedure and the faked lock procedure. In one embodiment, the shared resource is a cache and the system lock procedure permits a processor to lock the entire cache whereas the faked lock procedure is implemented by a processor seeking exclusive access of a cache slot.
Owner:EMC IP HLDG CO LLC
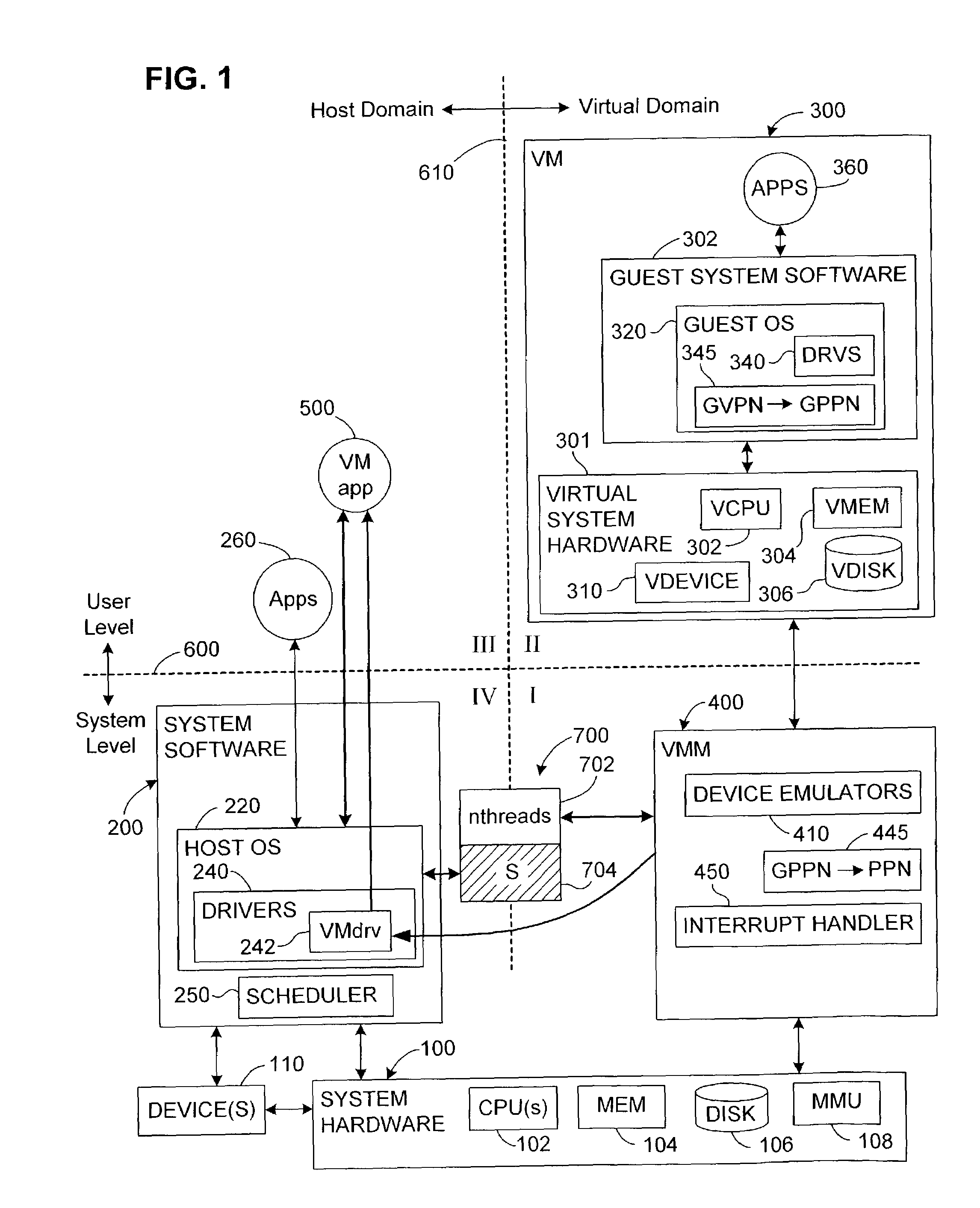
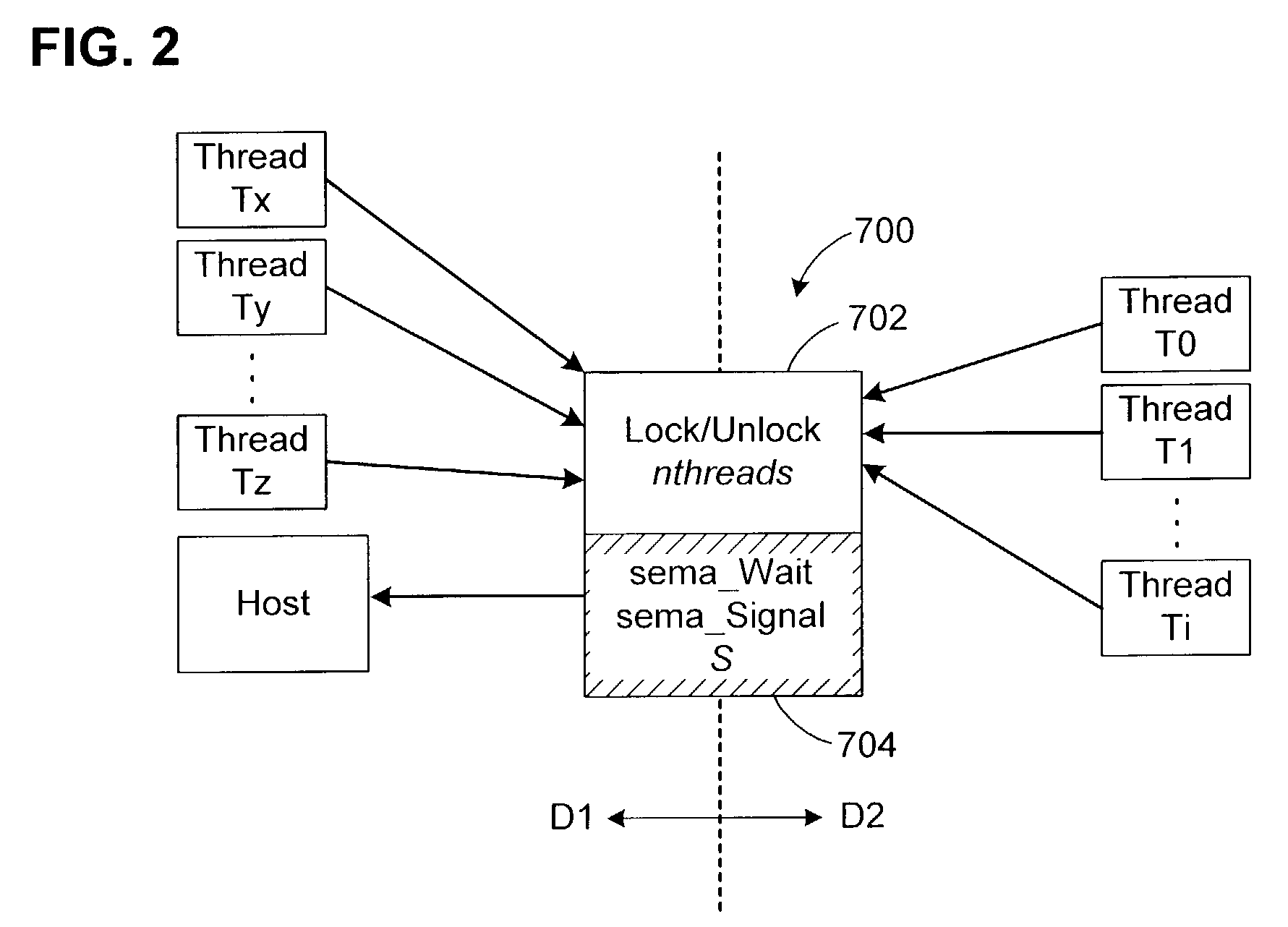
Composite lock for computer systems with multiple domains
ActiveUS7117481B1Increased complexitySpeedSpecific program execution arrangementsMemory systemsComputerized systemA domain
In a multi-domain computer system in which several processes are running, a composite lock provides mutually exclusive access to a resource. The composite lock has a back-end component and a front-end component. The back-end component is platform-dependent and operates as a semaphore, with Wait and Signal functions. The front-end component conditionally calls the Wait and Signal functions depending on whether the lock is currently contested when a new process wishes to acquire the lock, and on whether any process is currently suspended, waiting to acquire the lock. The front-end and back-end components may execute in different domains. In the uncontested case, the invention avoids costly domain crossings. The front-end component may also include a spinning feature to further reduce the need to invoke the back-end component and cause a domain crossing. The composite lock is particularly advantageous in computer systems that include a virtual machine.
Owner:VMWARE INC
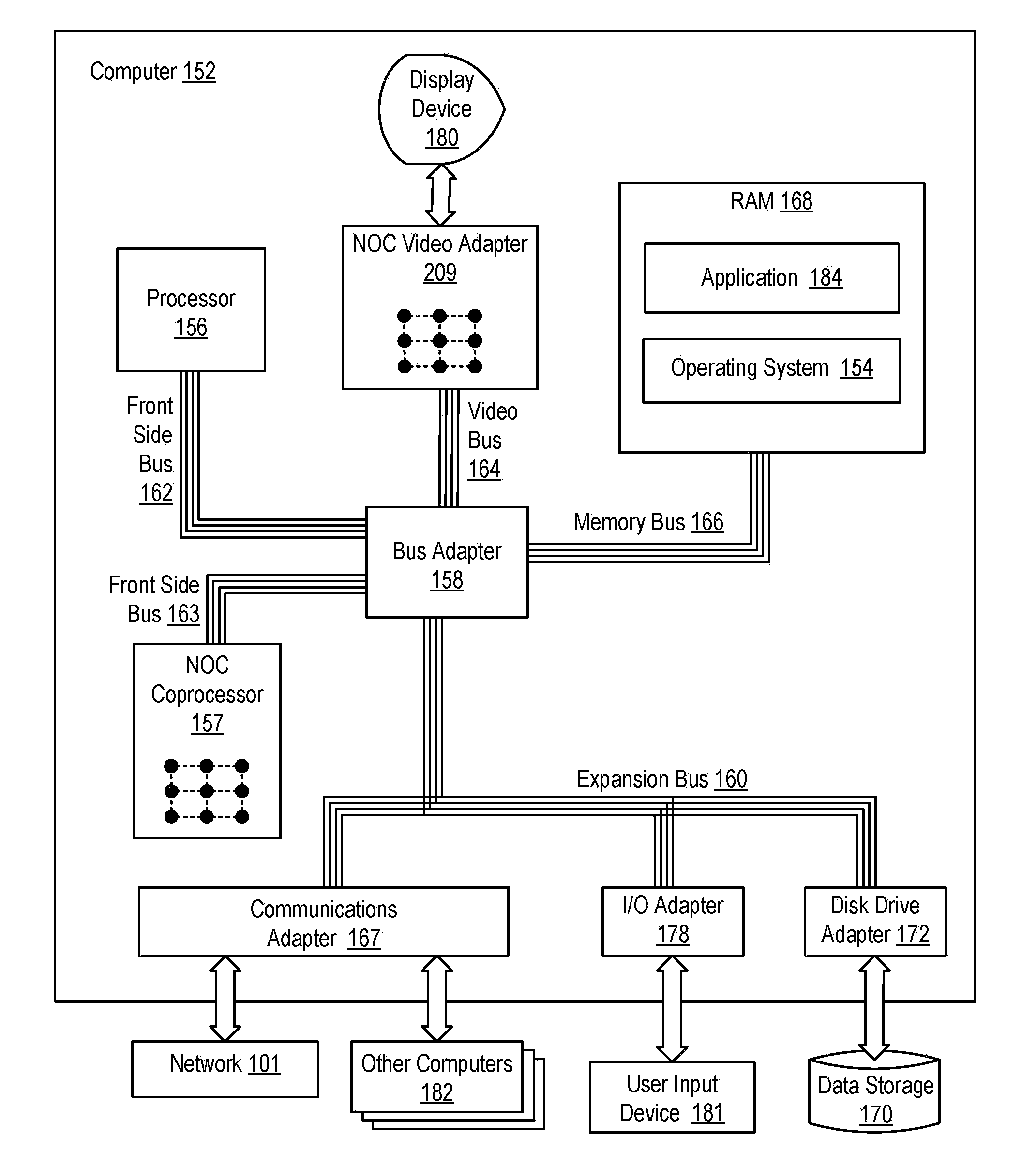
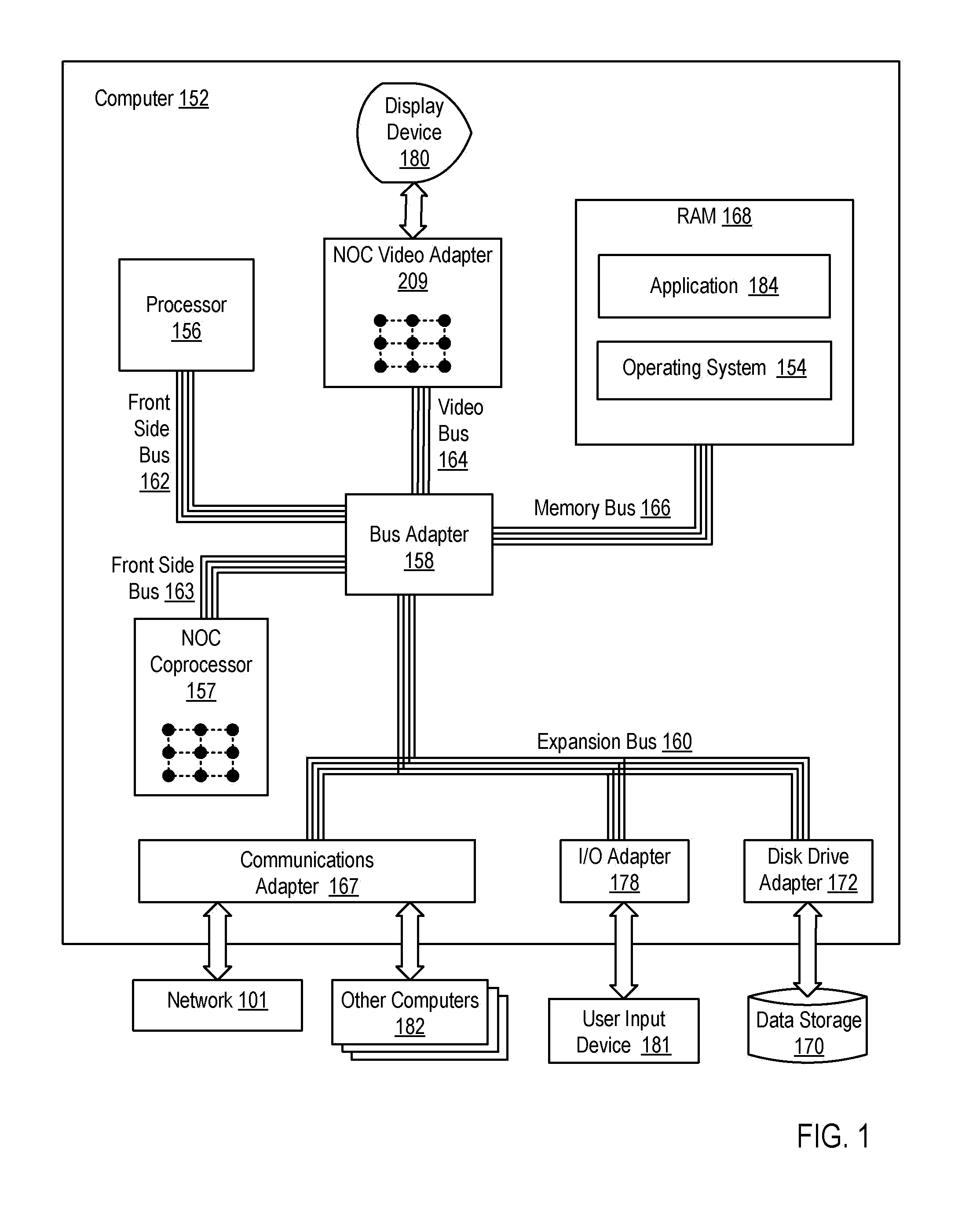
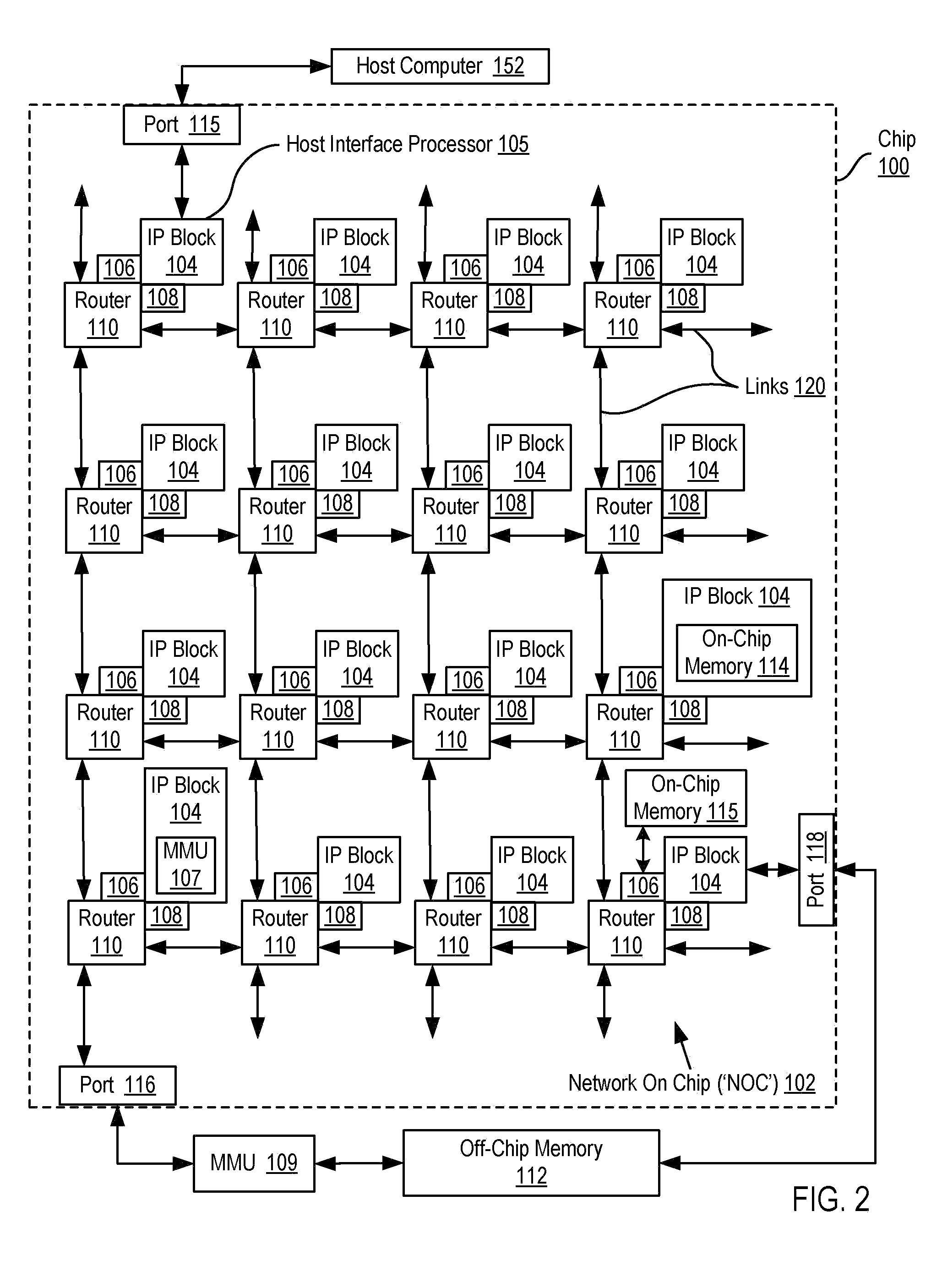
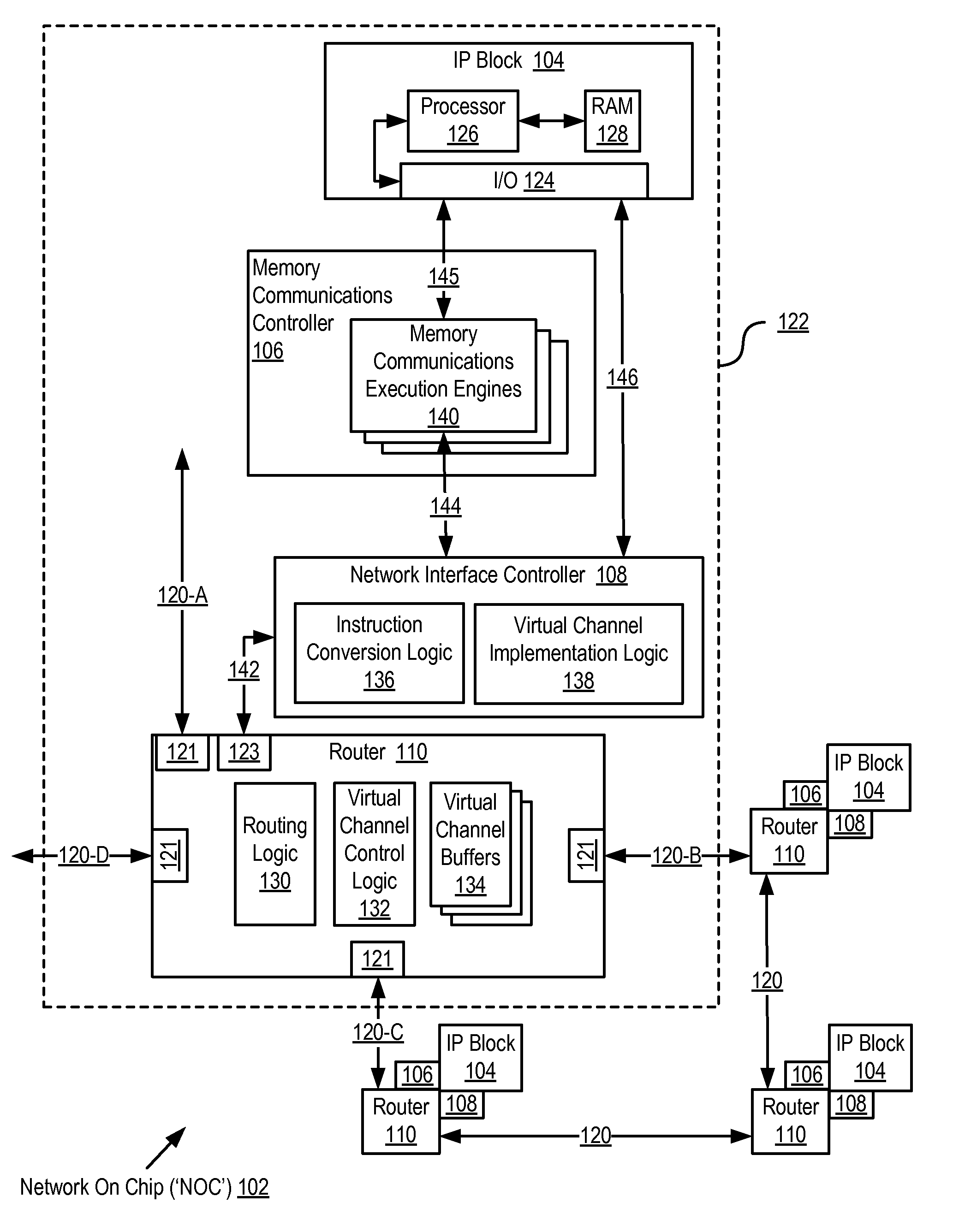
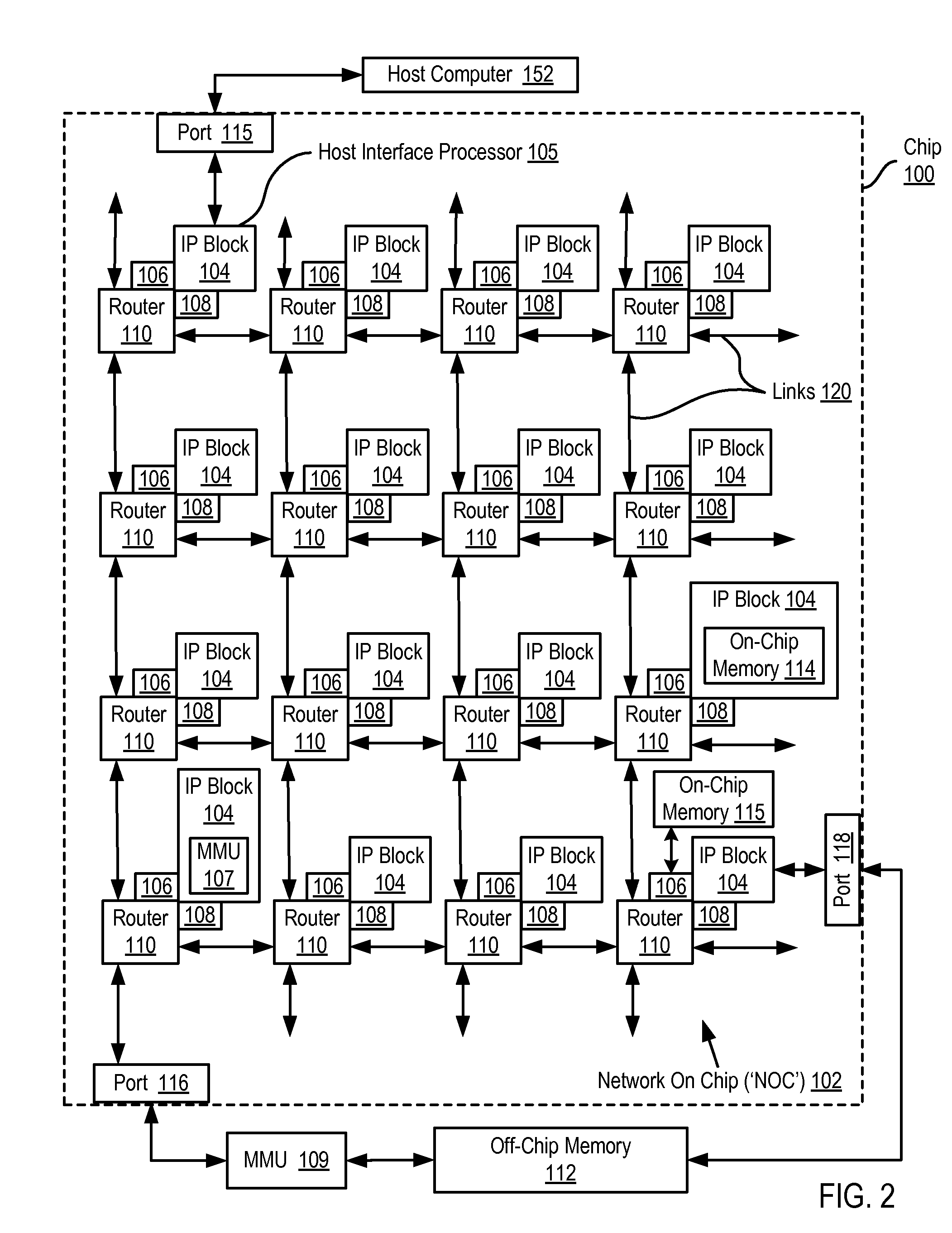
Network On Chip With Partitions
InactiveUS20090135739A1Digital computer detailsData switching by path configurationMemory addressParallel computing
A network on chip (‘NOC’) that includes integrated processor (‘IP’) blocks, routers, memory communications controllers, and network interface controllers, with each IP block adapted to a router through a memory communications controller and a network interface controller, where each memory communications controller controlling communications between an IP block and memory, and each network interface controller controlling inter-IP block communications through routers, with the network organized into partitions, each partition including at least one IP block, each partition assigned exclusive access to a separate physical memory address space and one or more applications executing on one or more of the partitions.
Owner:IBM CORP
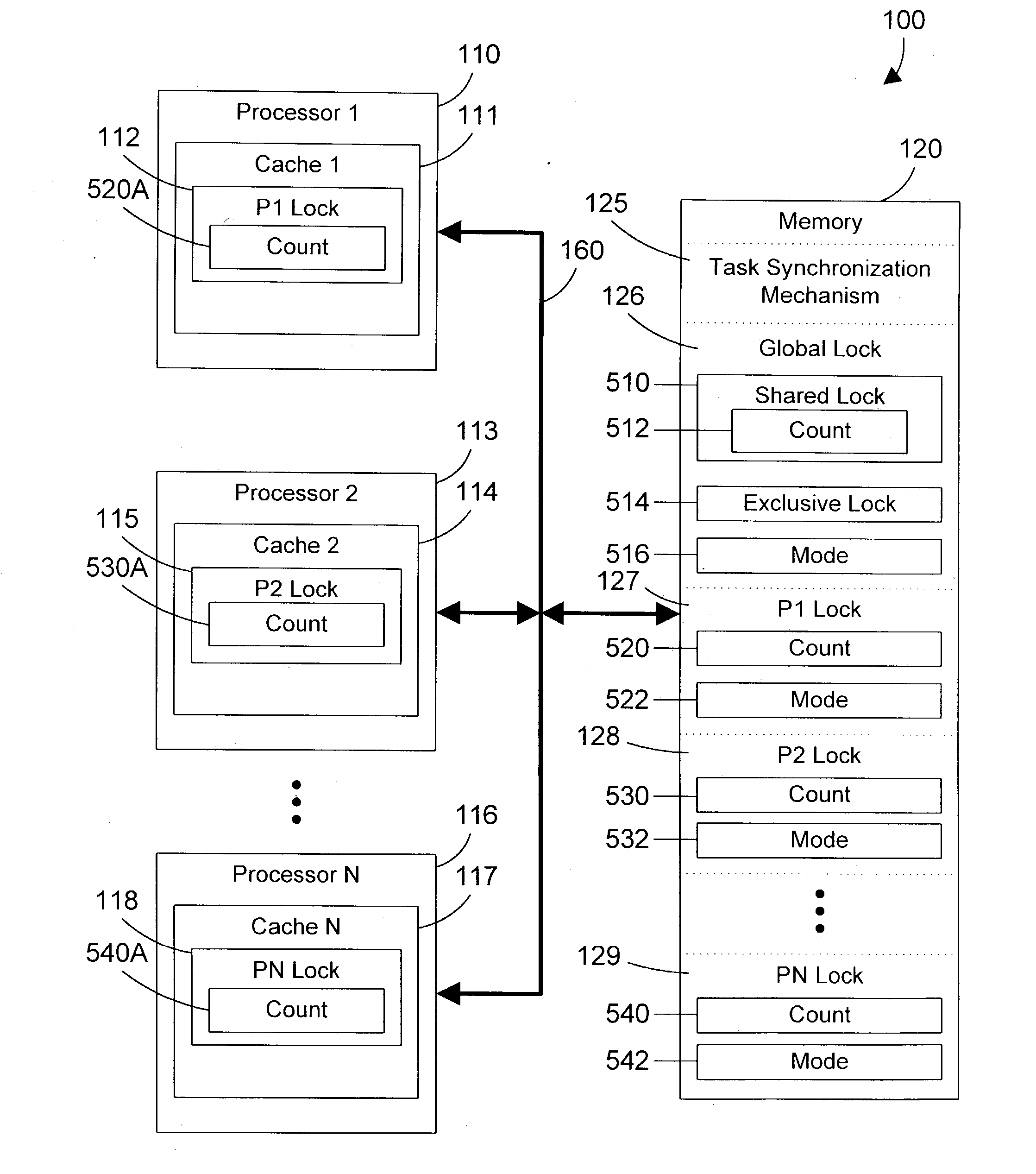
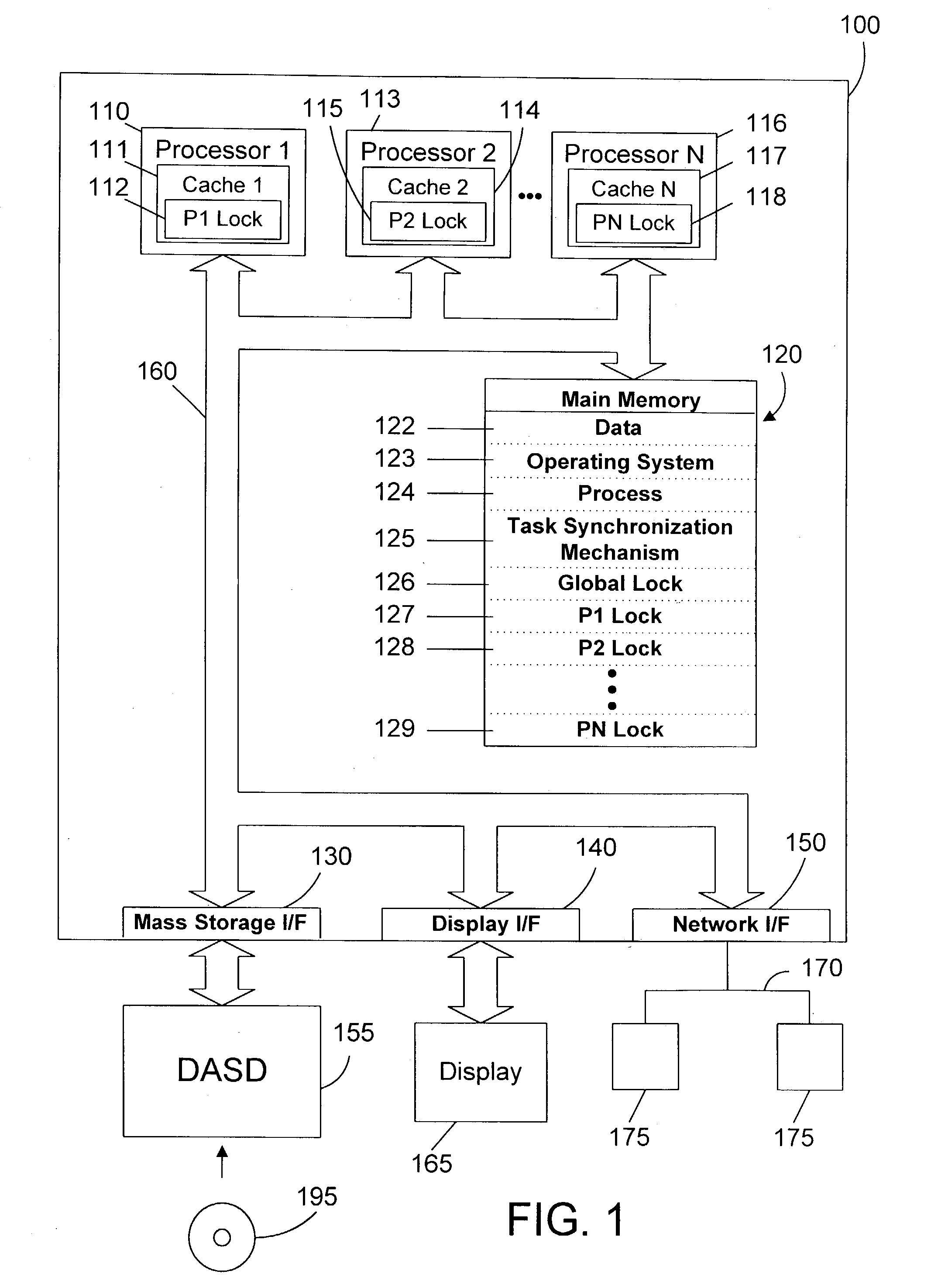
Task synchronization mechanism and method
ActiveUS20040143712A1Significant overheadSignificant performanceUnauthorized memory use protectionMultiprogramming arrangementsComputer architectureMemory bus
A task synchronization mechanism operates on a global lock that is shared between processors an on local locks that are not shared between processors. The local locks are processor-specific locks. Each processor-specific lock is dedicated to a particular processor in the system. When shared access to a resource is required, a processor updates its processor-specific lock to indicate the processor is sharing the resource. Because each processor-specific lock is dedicated to a particular processor, this eliminates a significant portion of the memory bus traffic associated with all processors reading and updating the same lock. When exclusive access to a resource is required, the requesting processor waits until the count of all processor-specific locks indicate that none of these processors have a lock on the resource. Once no processor has a lock on the resource, exclusive access to the resource may be granted. By changing from a single lock to multiple processor-specific locks, significant performance benefits are achieved by eliminating the memory bus traffic associated with caching a single lock to multiple processors.
Owner:IBM CORP
Data integrity for data storage devices shared by multiple hosts via a network
InactiveUS20090043971A1Digital data information retrievalMemory adressing/allocation/relocationData integrityNetworked system
Owner:LEE HEON SU
Storage system and control method
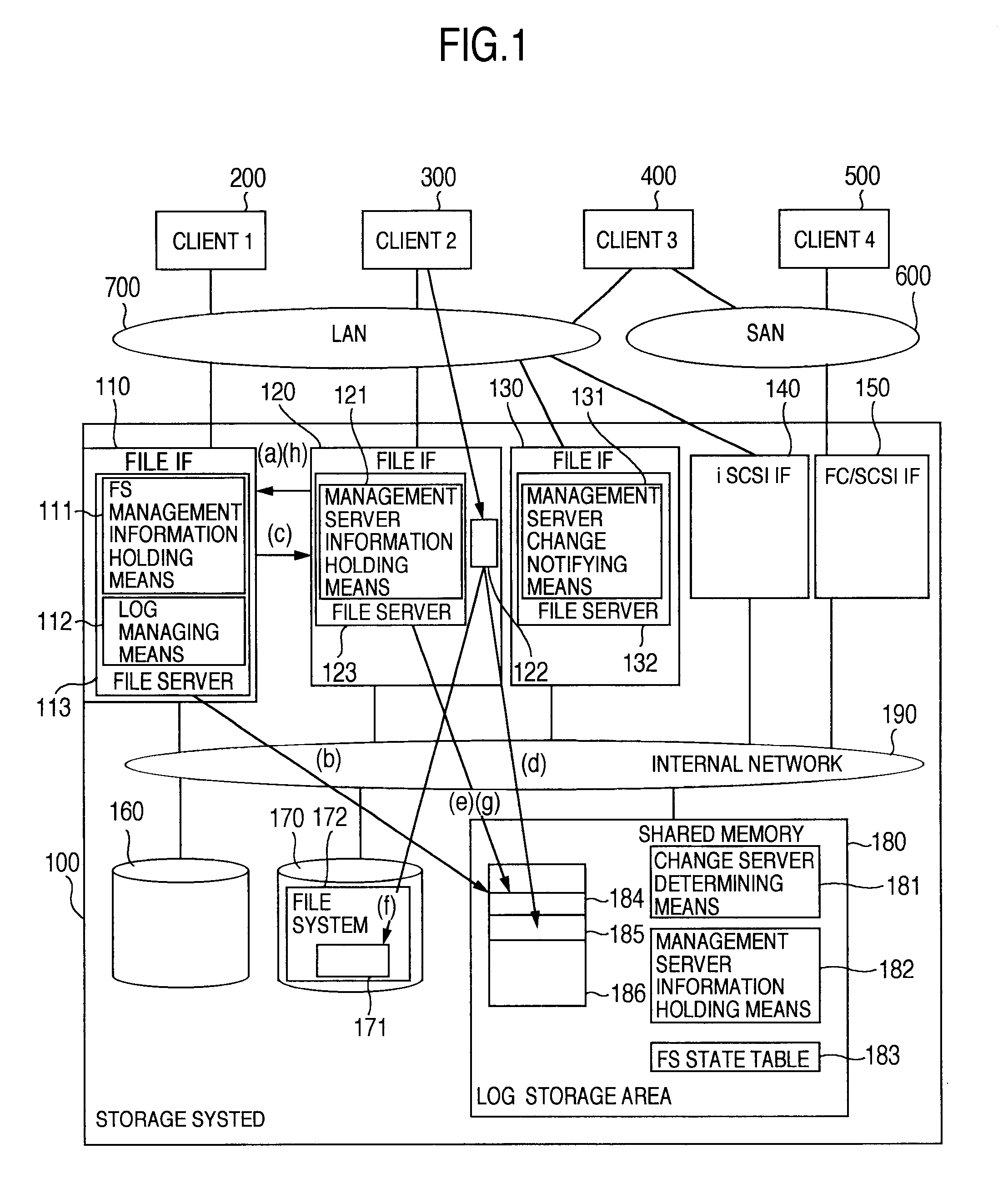
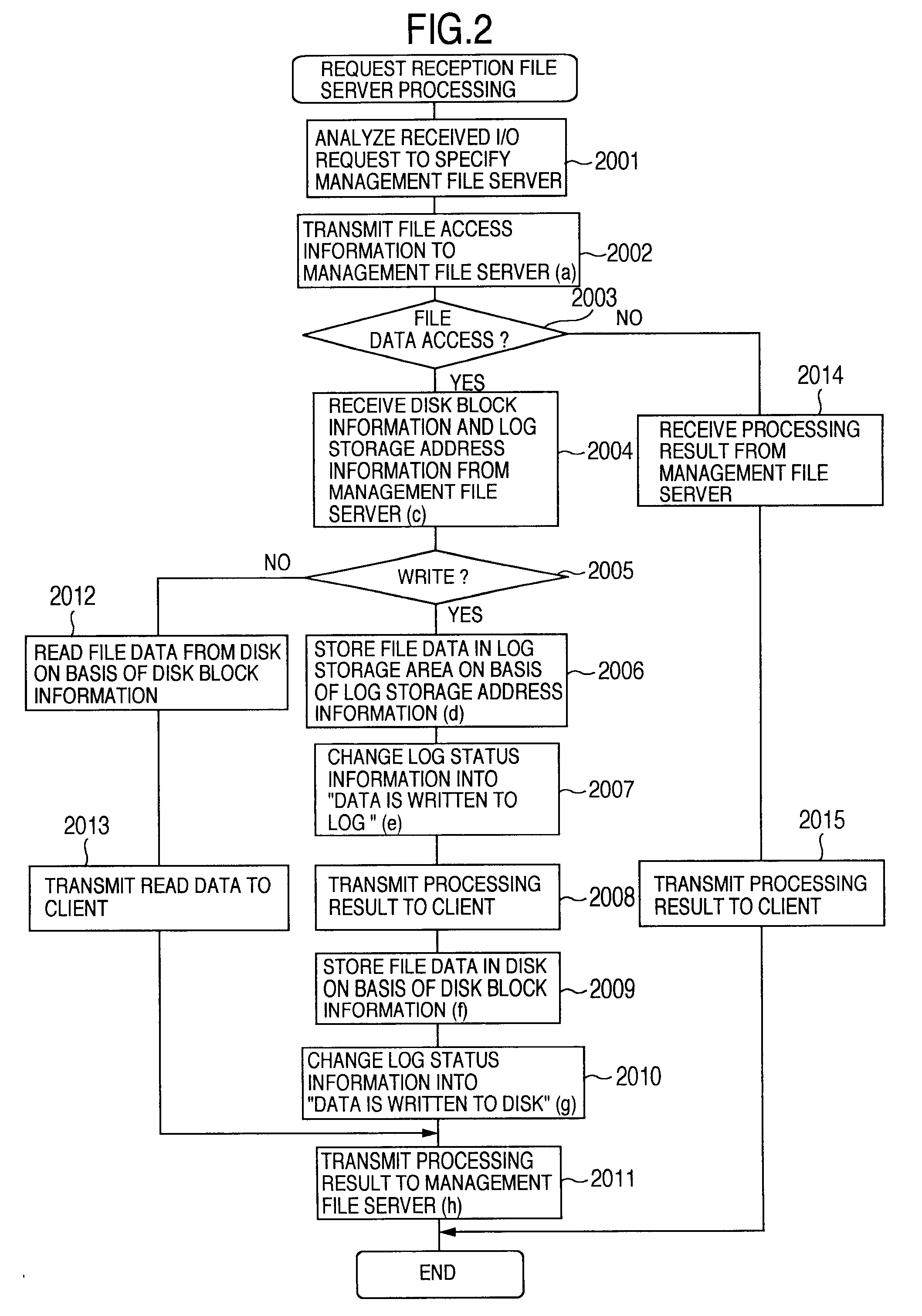
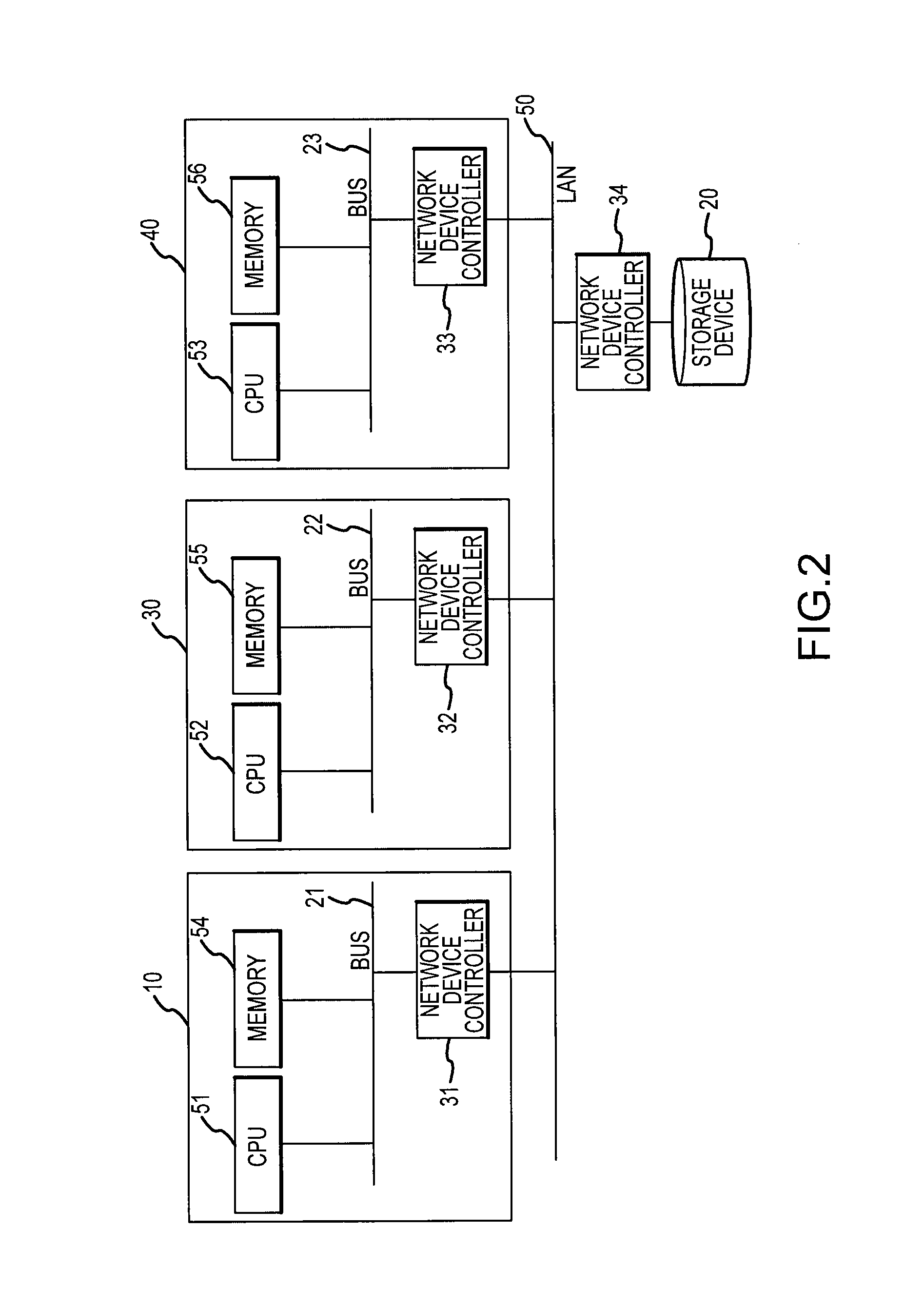
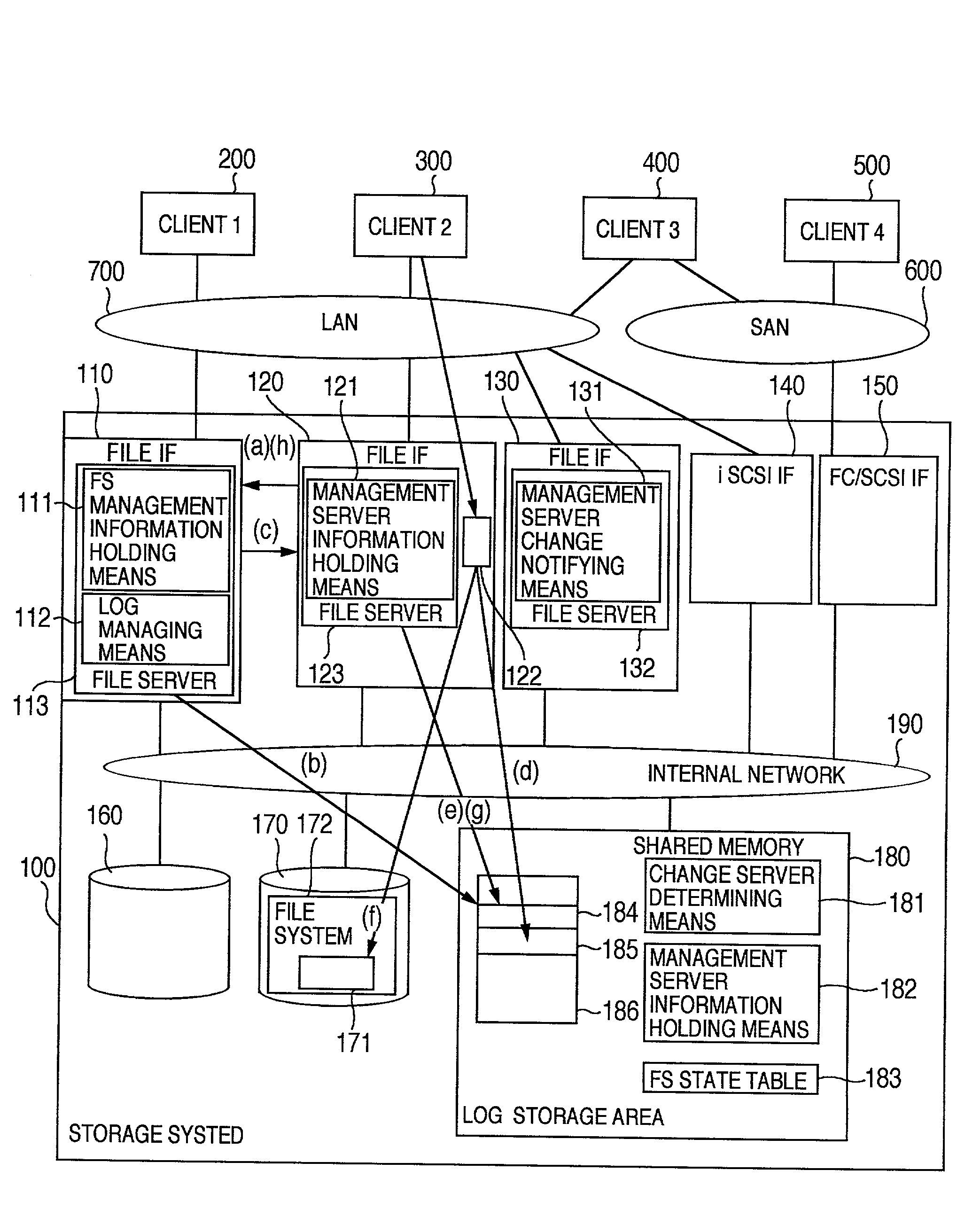
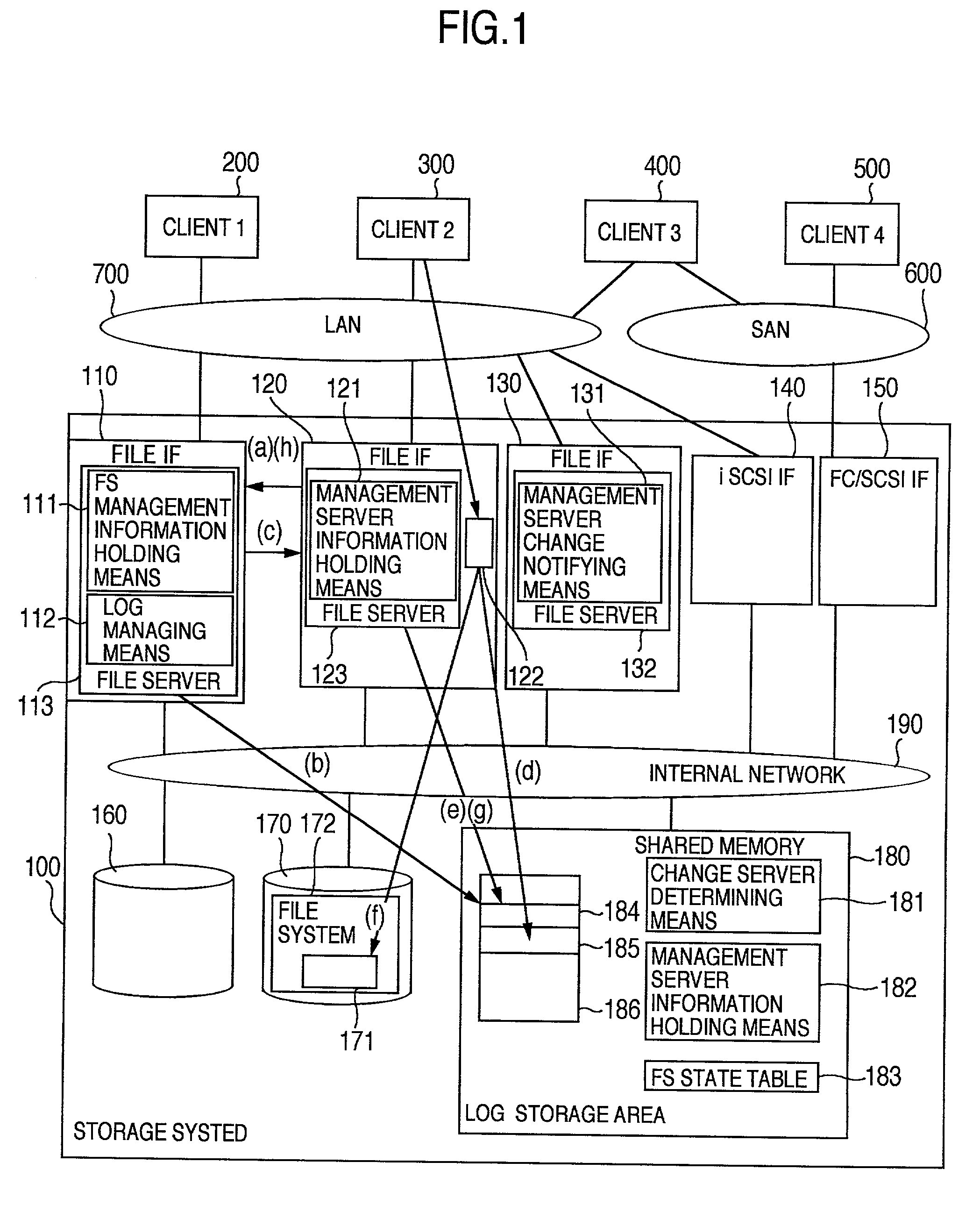
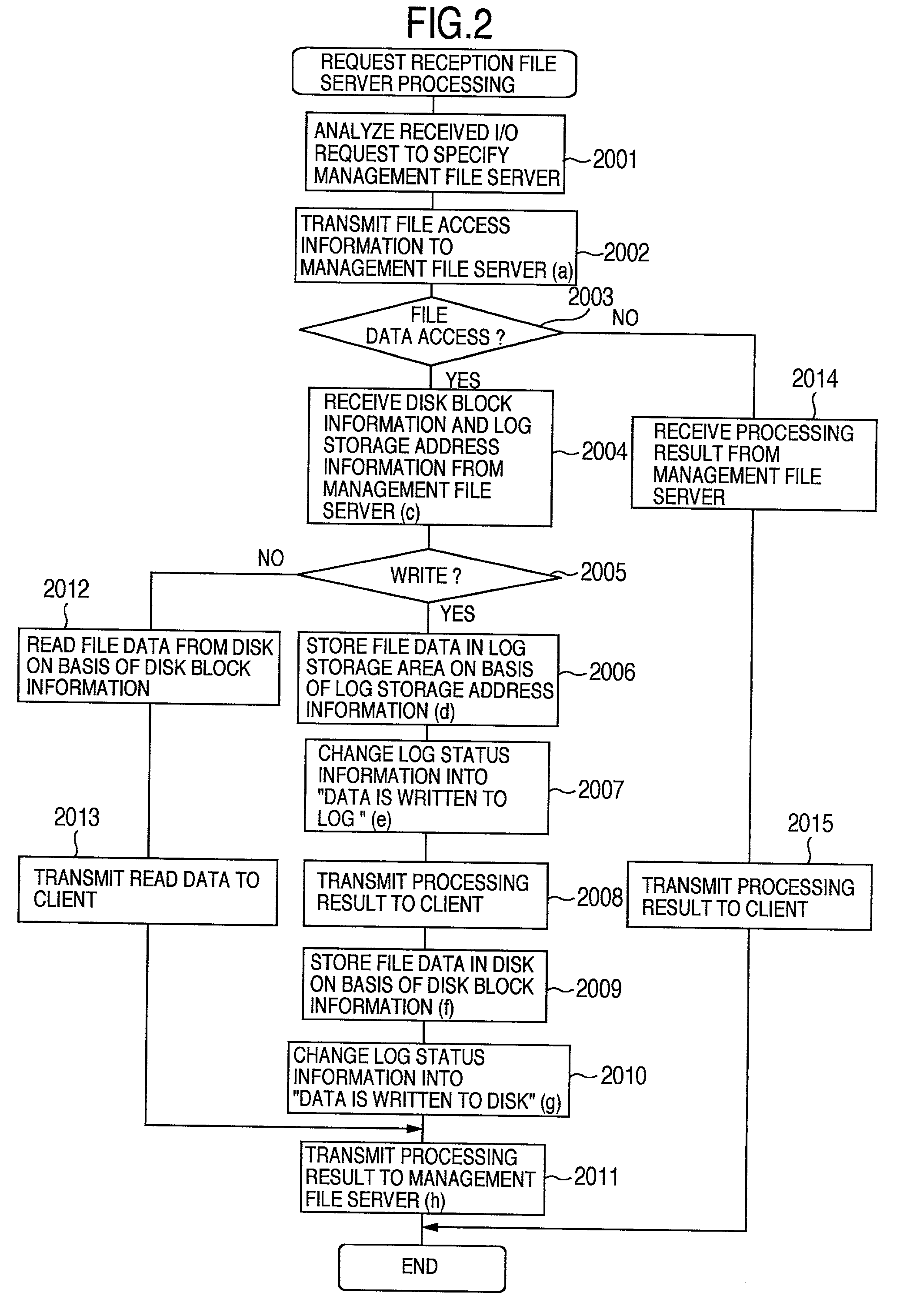
InactiveUS6850955B2Reduce management costsIncrease management costsInput/output to record carriersData processing applicationsFile systemFile server
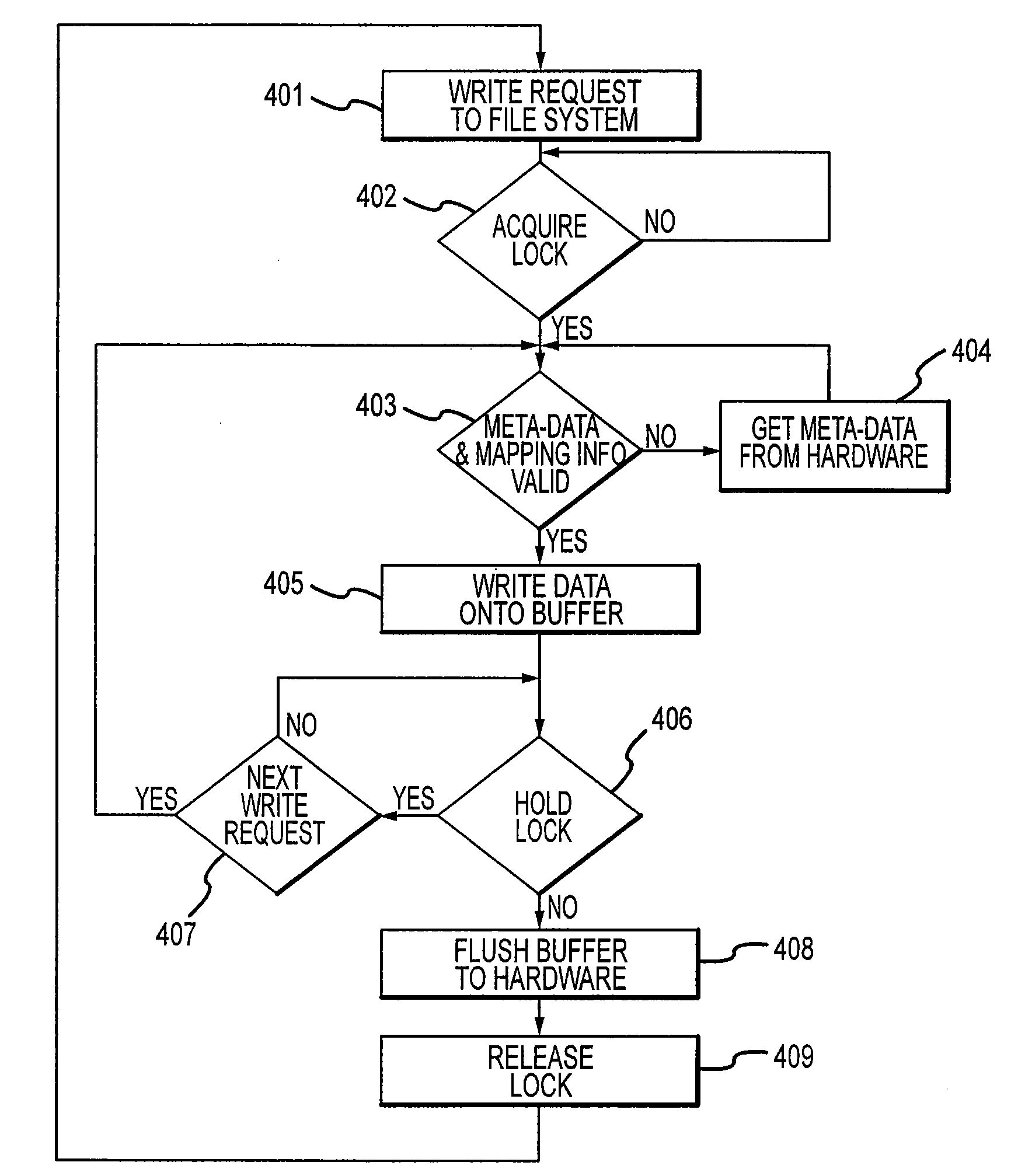
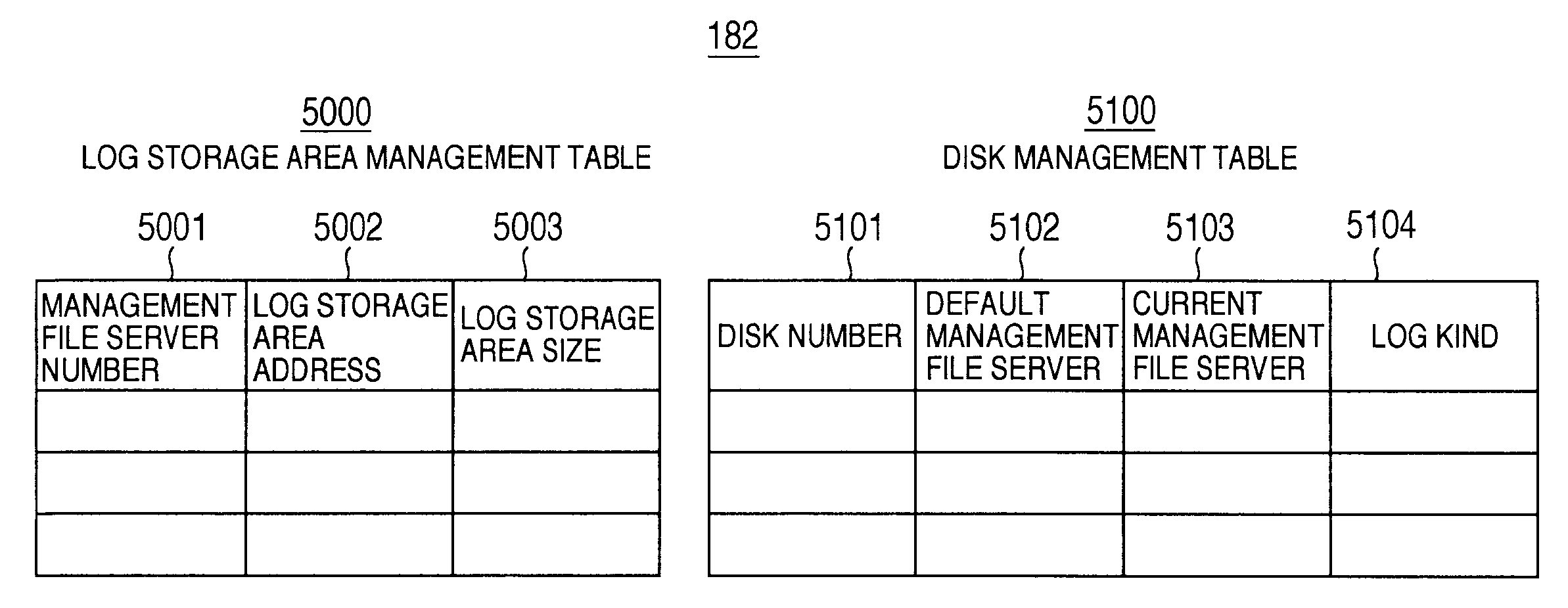
The invention provides both interfaces of SAN and NAS, prevents data miss even when a trouble occurs and makes it possible that an arbitrary number of NAS interfaces access the same file system with high performance. A storage system includes multiple interfaces for external connection, multiple disks accessed from multiple interfaces, and a shared memory accessed from multiple interfaces. The multiple interfaces are block interfaces executing disk block I / O request, and file interfaces of file servers executing file I / O request. A file system in the file servers is constructed in a part of the disks, and a log storage area holding change log of the file system, and a management file server information storage area holding information of managing file server performing exclusive access control of file system and management of log storage area are formed in the shared memory.
Owner:HITACHI LTD
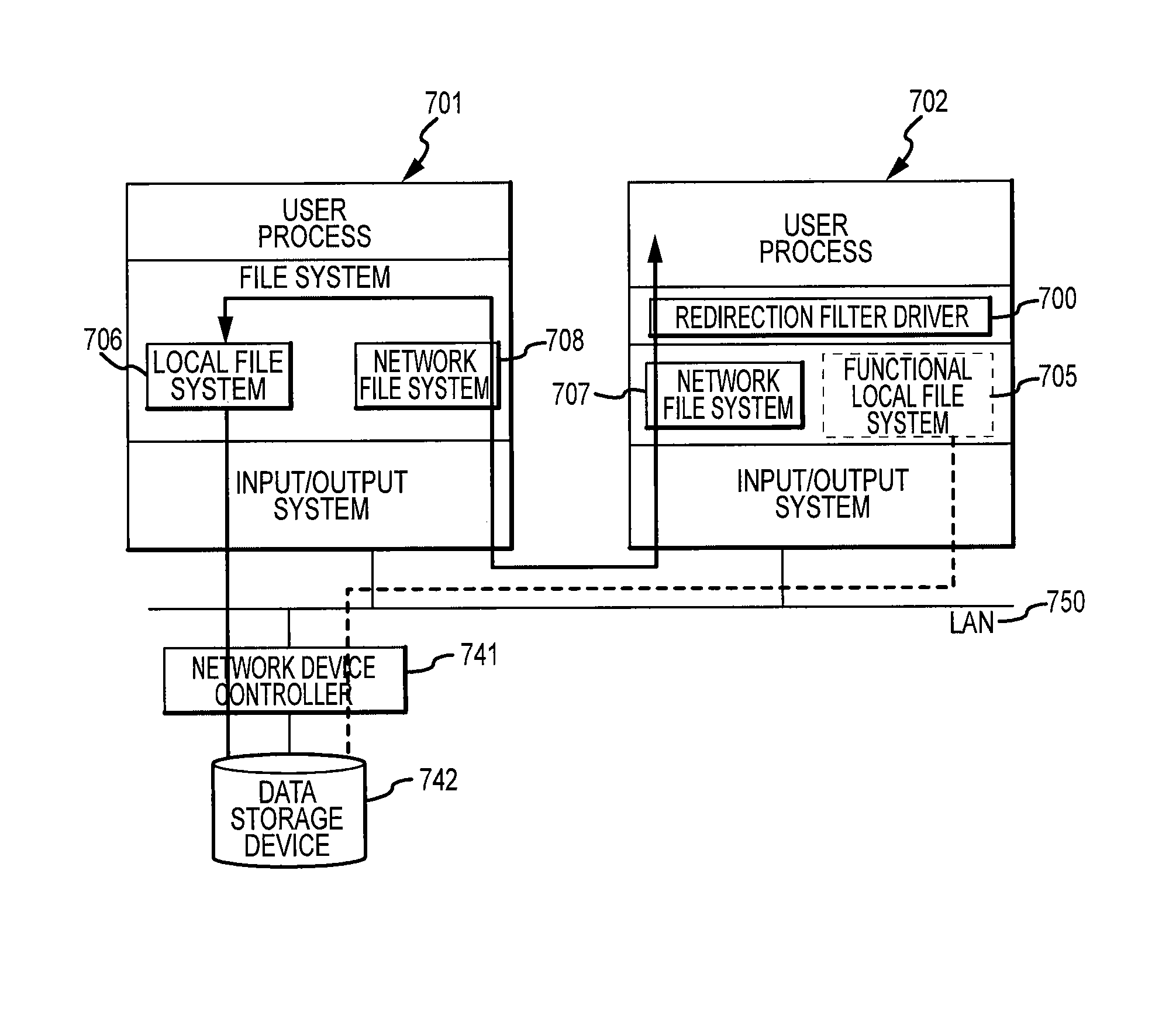
System using a single host to receive and redirect all file access commands for shared data storage device from other hosts on a network
ActiveUS7457880B1Maintain data integrityDigital data information retrievalMultiple digital computer combinationsData integrityNetworked system
Access by multiple hosts, such as computers, to a data storage device by way of a network while maintaining data integrity. In one embodiment, a method for accessing the storage device includes acquiring a resource “lock” that provides exclusive access to one of the hosts at a time. In another embodiment, the file systems of a first and second host provide file system attributes stored in a storage device to provide mutually exclusive access for each host to free blocks of the device. In another embodiment, a networked system contains a first host having exclusive direct access to a storage device over a digital network. A second host requiring access to the storage device communicates with the first host by way of the digital network. File access requests generated by the second host are transferred by a redirection filter driver within the second host to the first host.
Owner:SYNKLOUD TECH LLC
Storage system and control method
InactiveUS20030105767A1Input/output to record carriersData processing applicationsFile systemFile server
The invention provides both interfaces of SAN and NAS, prevents data miss even when a trouble occurs and makes it possible that an arbitrary number of NAS interfaces access the same file system with high performance. A storage system includes multiple interfaces for external connection, multiple disks accessed from multiple interfaces, and a shared memory accessed from multiple interfaces. The multiple interfaces are block interfaces executing disk block I / O request, and file interfaces of file servers executing file I / O request. A file system in the file servers is constructed in a part of the disks, and a log storage area holding change log of the file system, and a management file server information storage area holding information of managing file server performing exclusive access control of file system and management of log storage area are formed in the shared memory.
Owner:HITACHI LTD
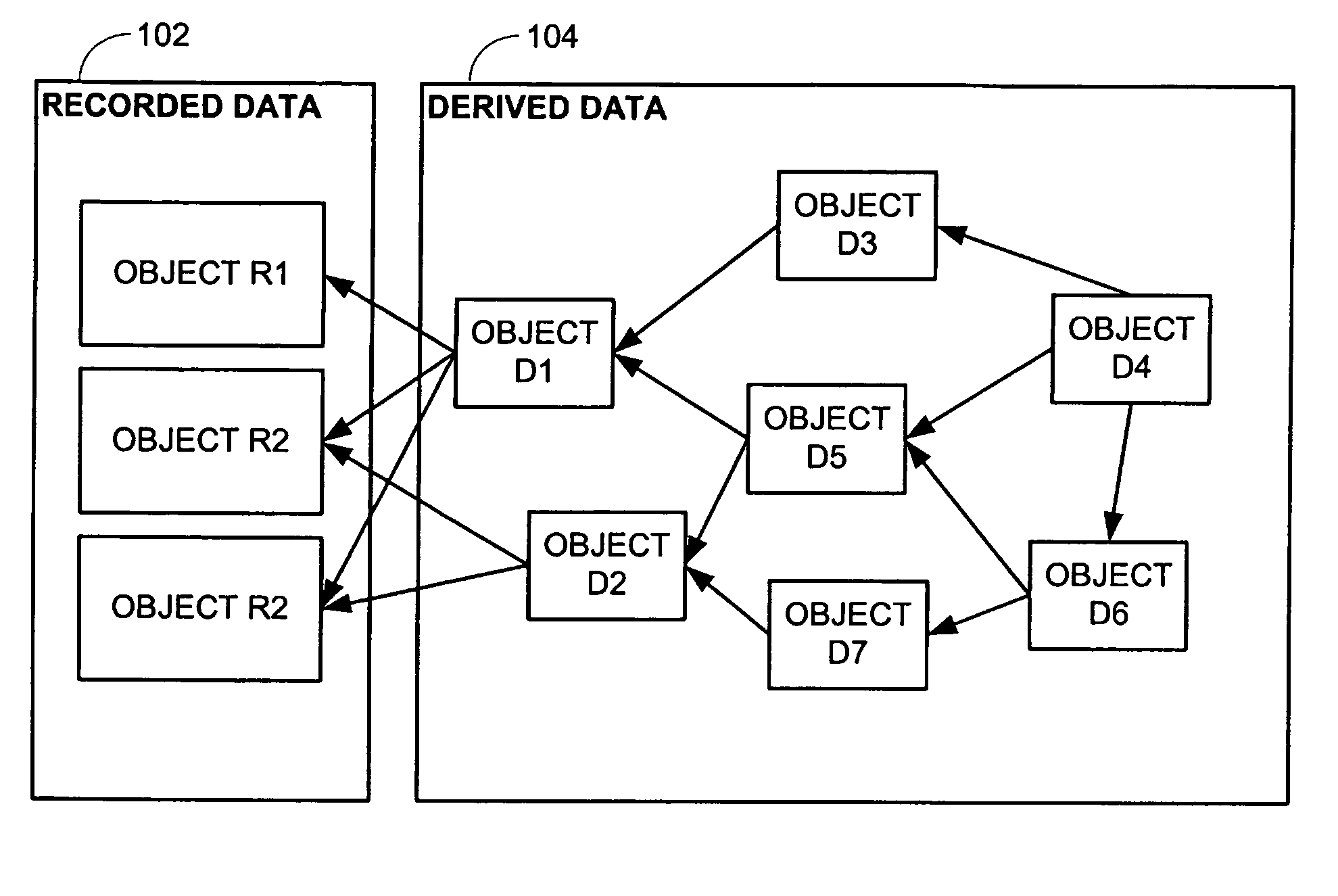
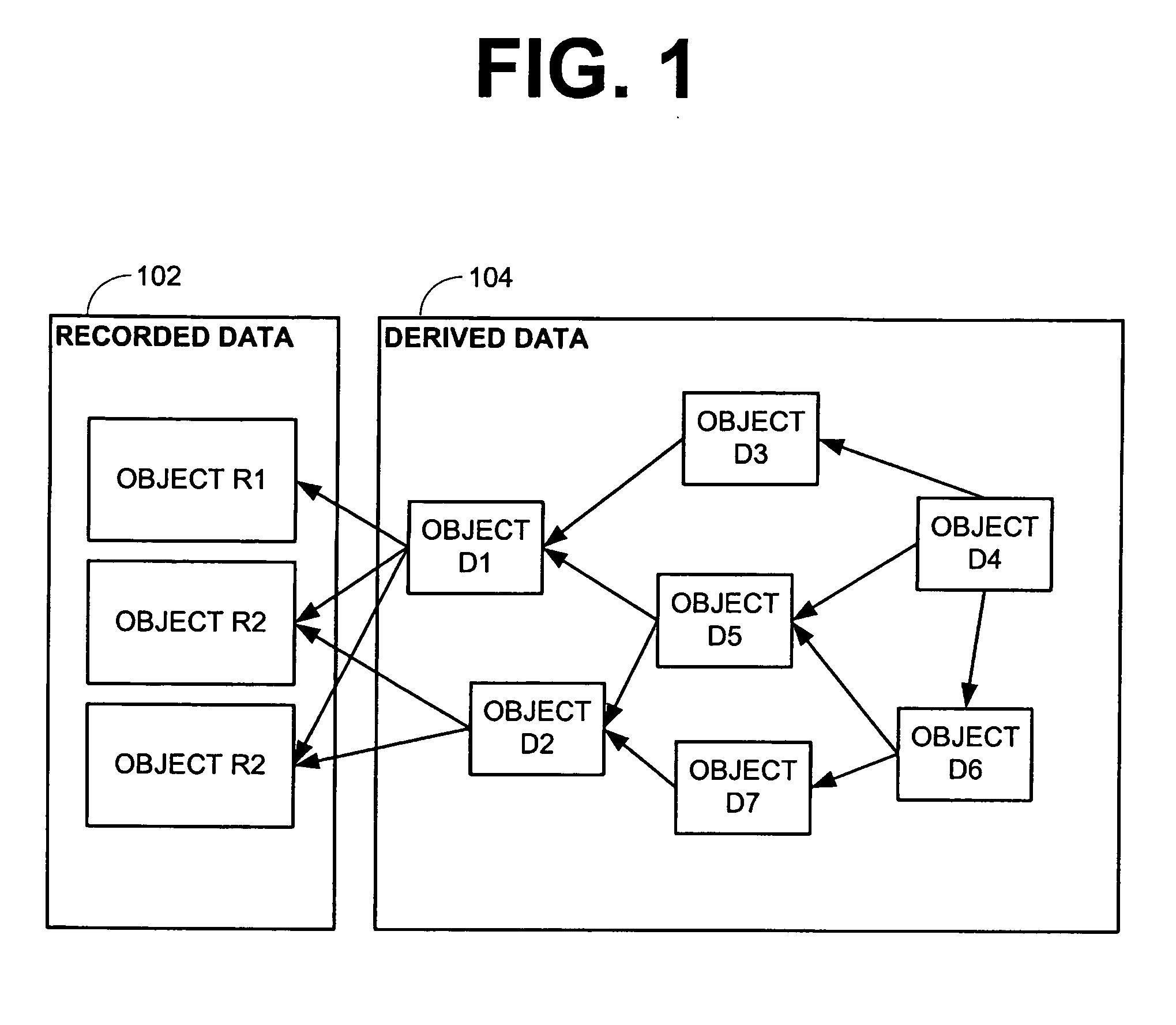
Systems and methods of accessing and updating recorded data via an inter-object proxy
ActiveUS20070156690A1Data processing applicationsDigital data information retrievalData accessData access object
Some embodiments provide a system including a database, two or more data access objects, and a proxy object. In some such embodiments, each data access object has exclusive access privileges to a subset of data within the database. Further each object includes one or more of a read method that provides access to data and a write method that causes data to be stored. In such embodiments, the proxy object accesses data via data access object methods and includes a valuate method, the execution of which causes data to be passed from a data access object to the proxy object.
Owner:SAP AG
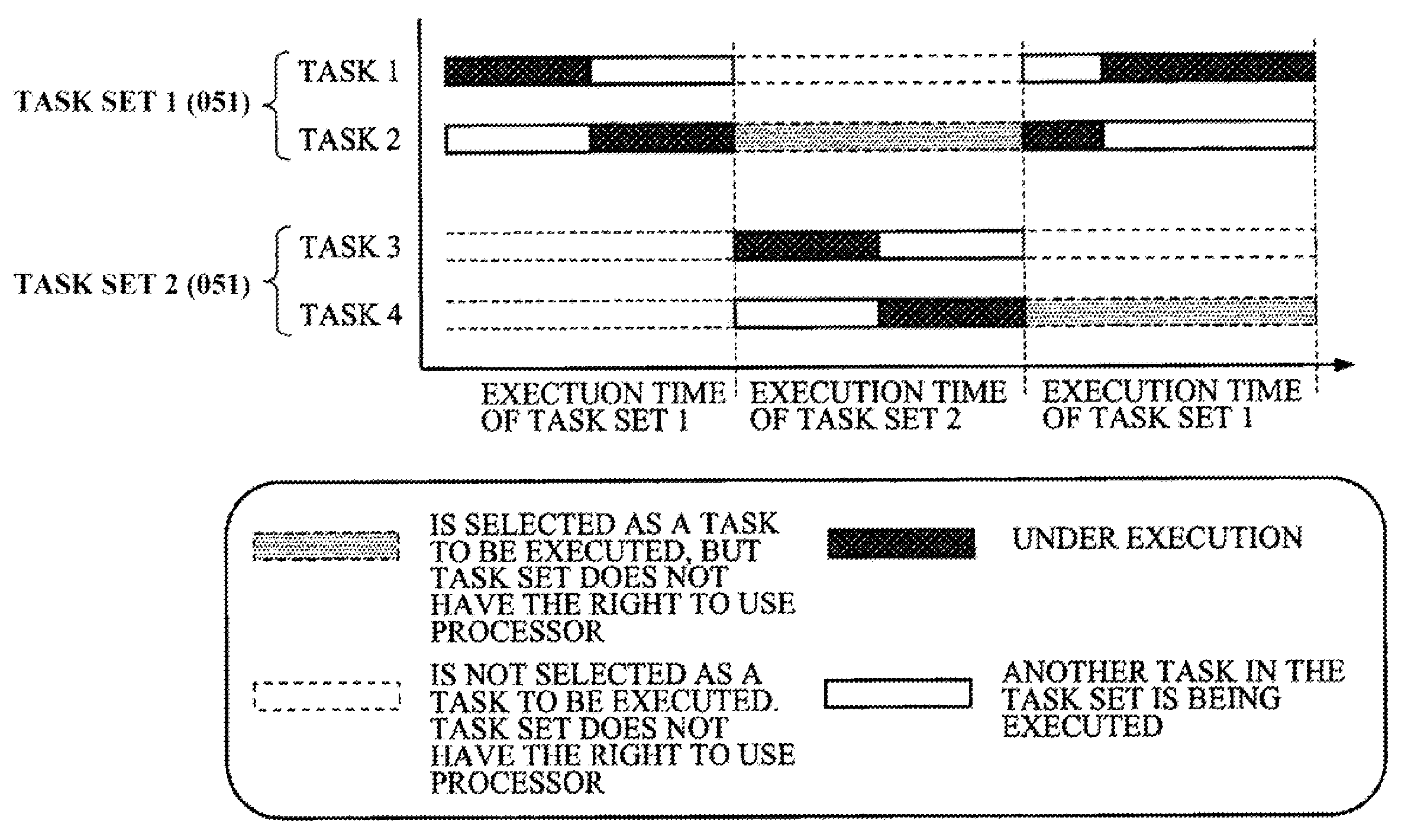
Processor system, task control method on computer system, computer program
InactiveUS7647594B2Simple methodProgram initiation/switchingResource allocationEmergency procedureComputer architecture
A mechanism for recording a timing in which a high urgency process is started is provided, and upon entry to a critical section in the middle of a low urgency process, by referencing the record, it is inspected whether a high urgency process will be started during execution of the critical section. If it will not be started, the critical section is entered, and if it will be started, control is exerted so that entry to the critical section is postponed until the high urgency process is completed. Exclusive access control in a critical section can be performed suitably under conditions where a plurality of task execution environments exist.
Owner:SONY CORP
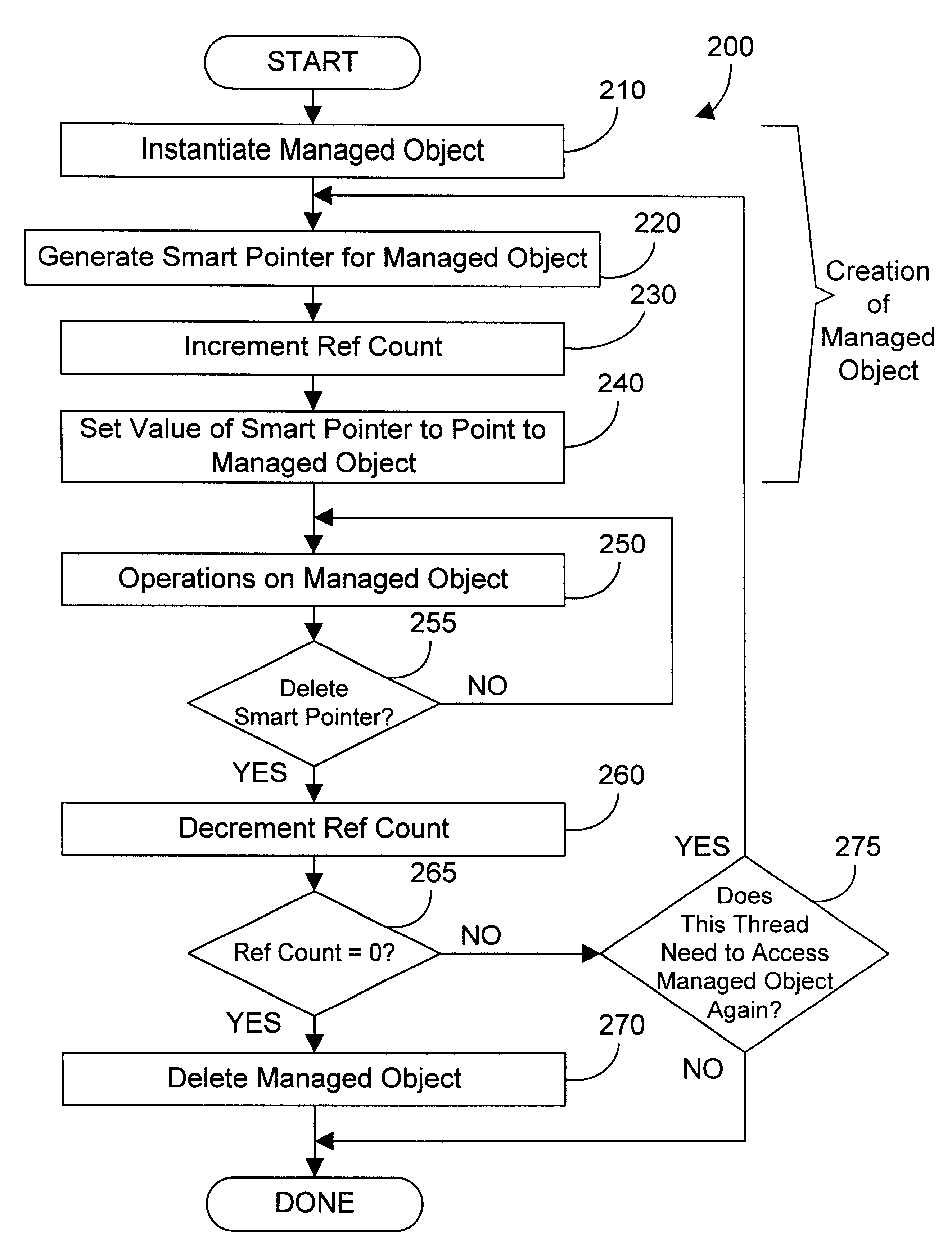
Apparatus and method for accessing an object oriented object using a smart passive reference
InactiveUS6366932B1Improve reusabilityEasy to useData processing applicationsMemory adressing/allocation/relocationComputer hardwareEngineering
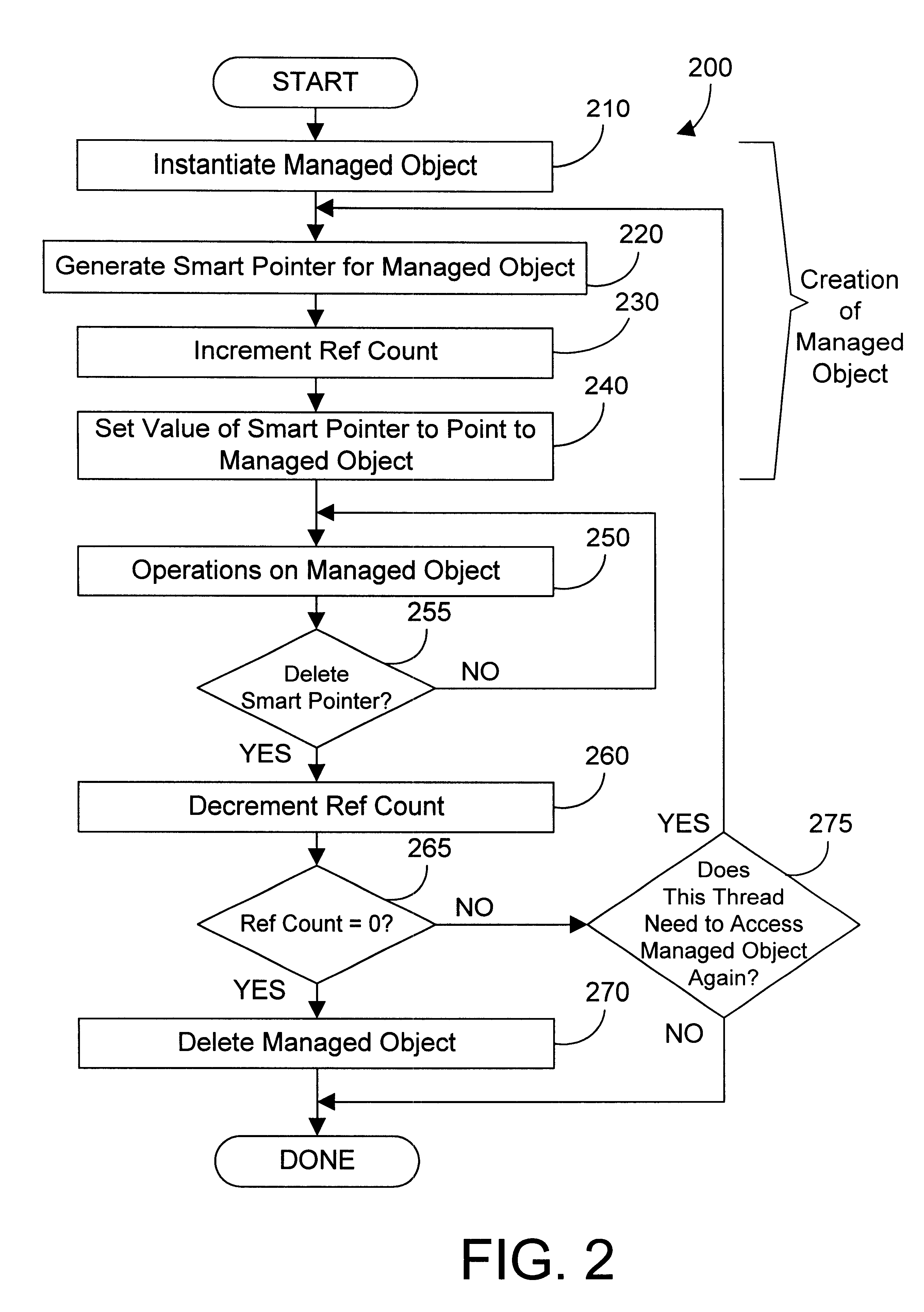
A smart passive reference to an object oriented object provides control over creation and deletion of the object it references. A reference count is incremented when an active reference to an object is created, and is decremented when an active reference to the object is deleted. The smart passive reference allows suspending the activity of a thread until no threads have active references to the object. In addition, the smart passive reference can be used to invalidate the smart passive references in other threads, thereby allowing a thread to obtain exclusive access to an object. The smart passive reference also provides an interface to cause the managed object to be deleted when the reference count goes to zero.
Owner:IBM CORP
Mechanism to accelerate removal of store operations from a queue
ActiveUS20090138659A1Memory adressing/allocation/relocationProgram controlProcessing coreParallel computing
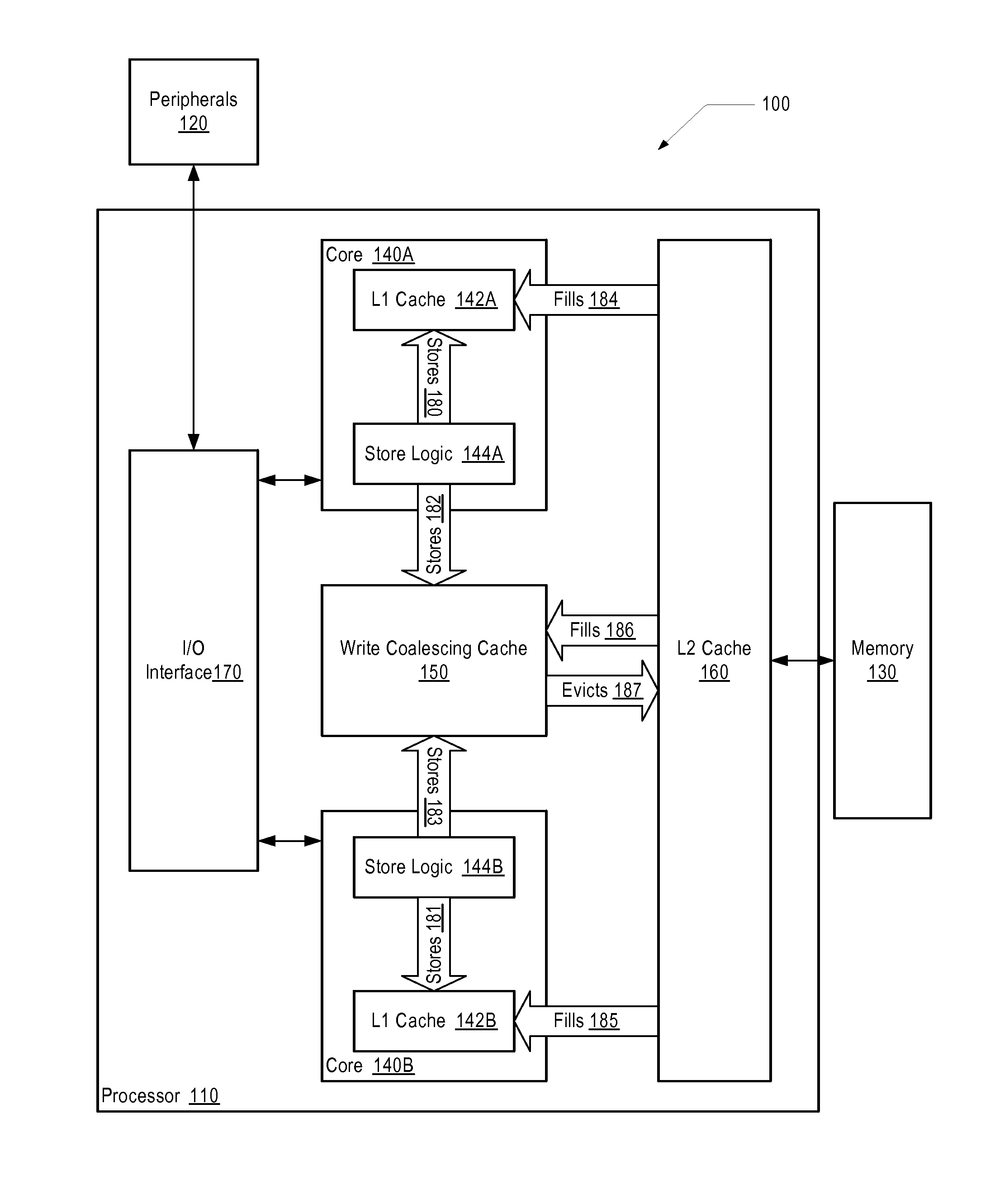
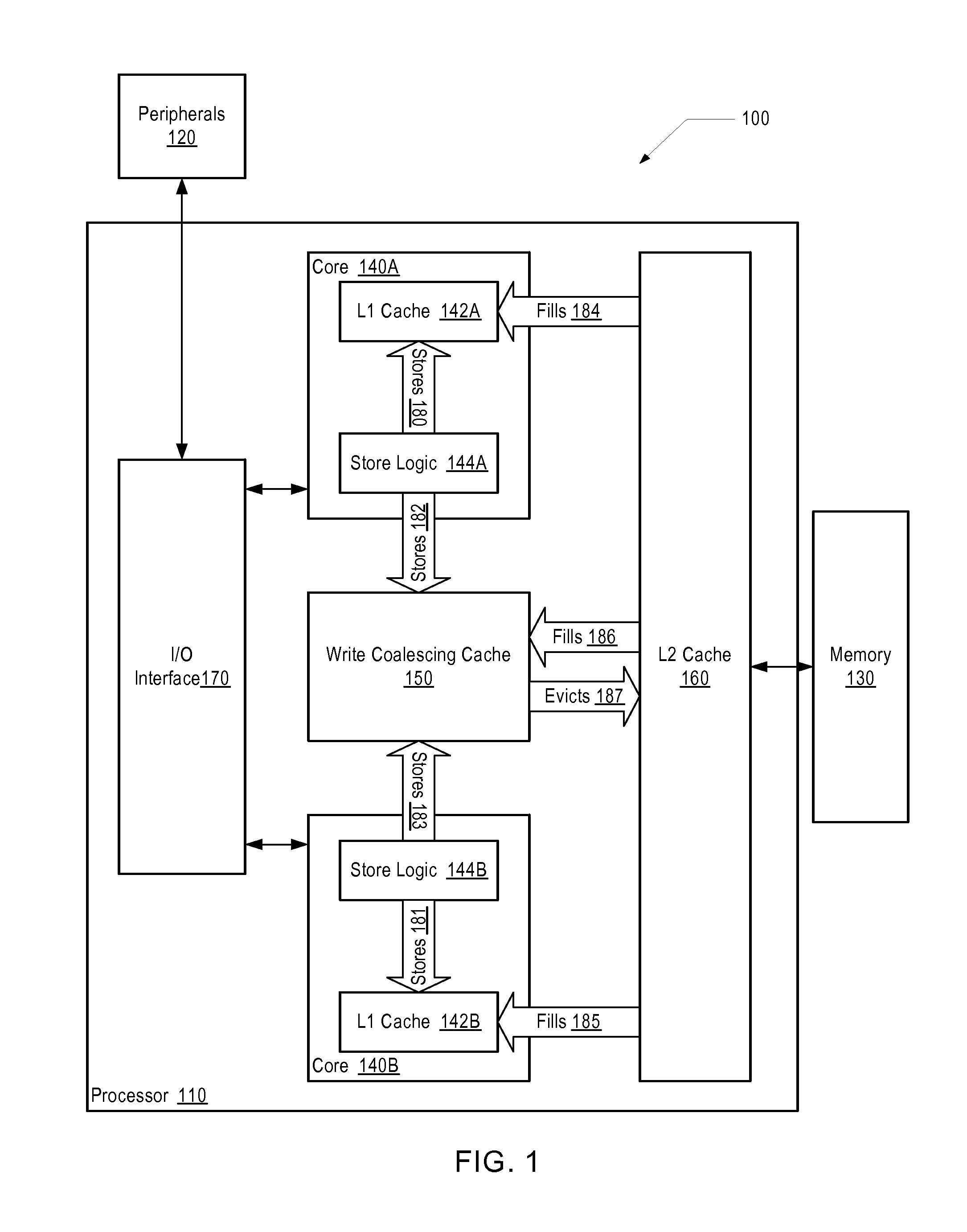
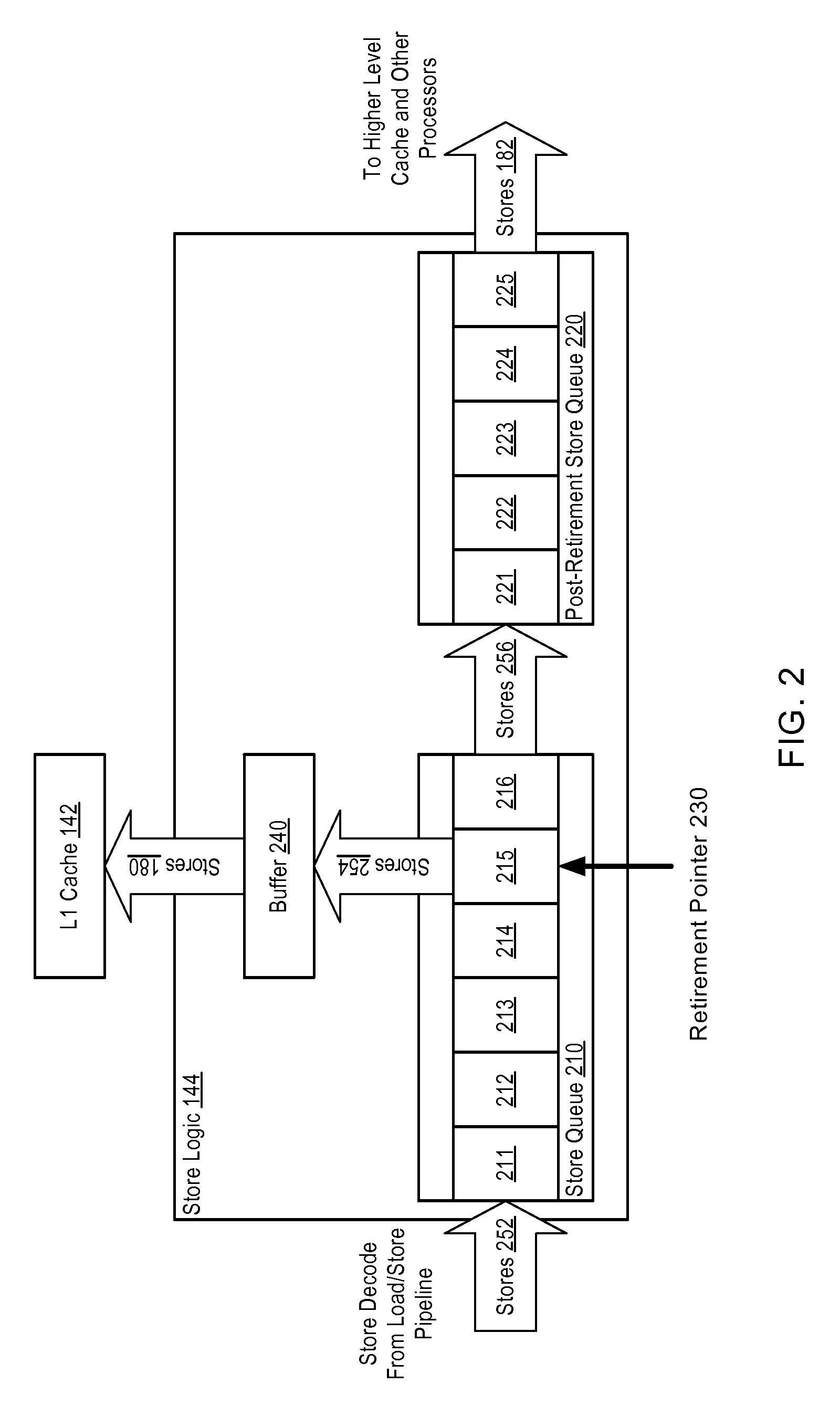
A processor includes at least one processing core. The processing core includes a memory cache, a store queue, and a post-retirement store queue. The processing core retires a store in the store queue and conveys the store to the memory cache and the post-retirement store queue, in response to retiring the store. In one embodiment, the store queue and / or the post-retirement store queue is a first-in, first-out queue. In a further embodiment, to convey the store to the memory cache, the processing core obtains exclusive access to a portion of the memory cache targeted by the store. The processing core buffers the store in a coalescing buffer and merges with the store, one or more additional stores and / or loads targeted to the portion of the memory cache targeted by the store prior to writing the store to the memory cache.
Owner:MEDIATEK INC
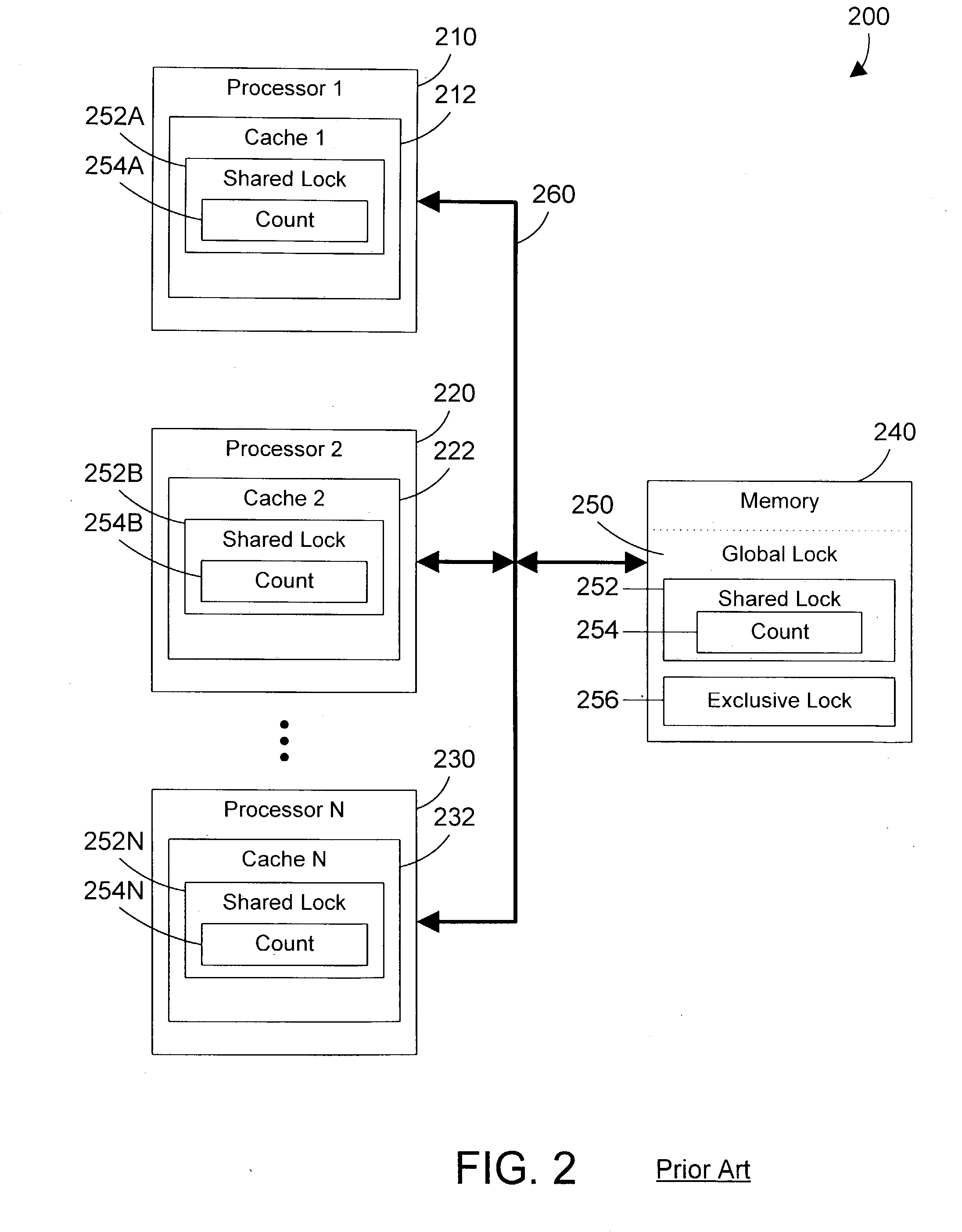
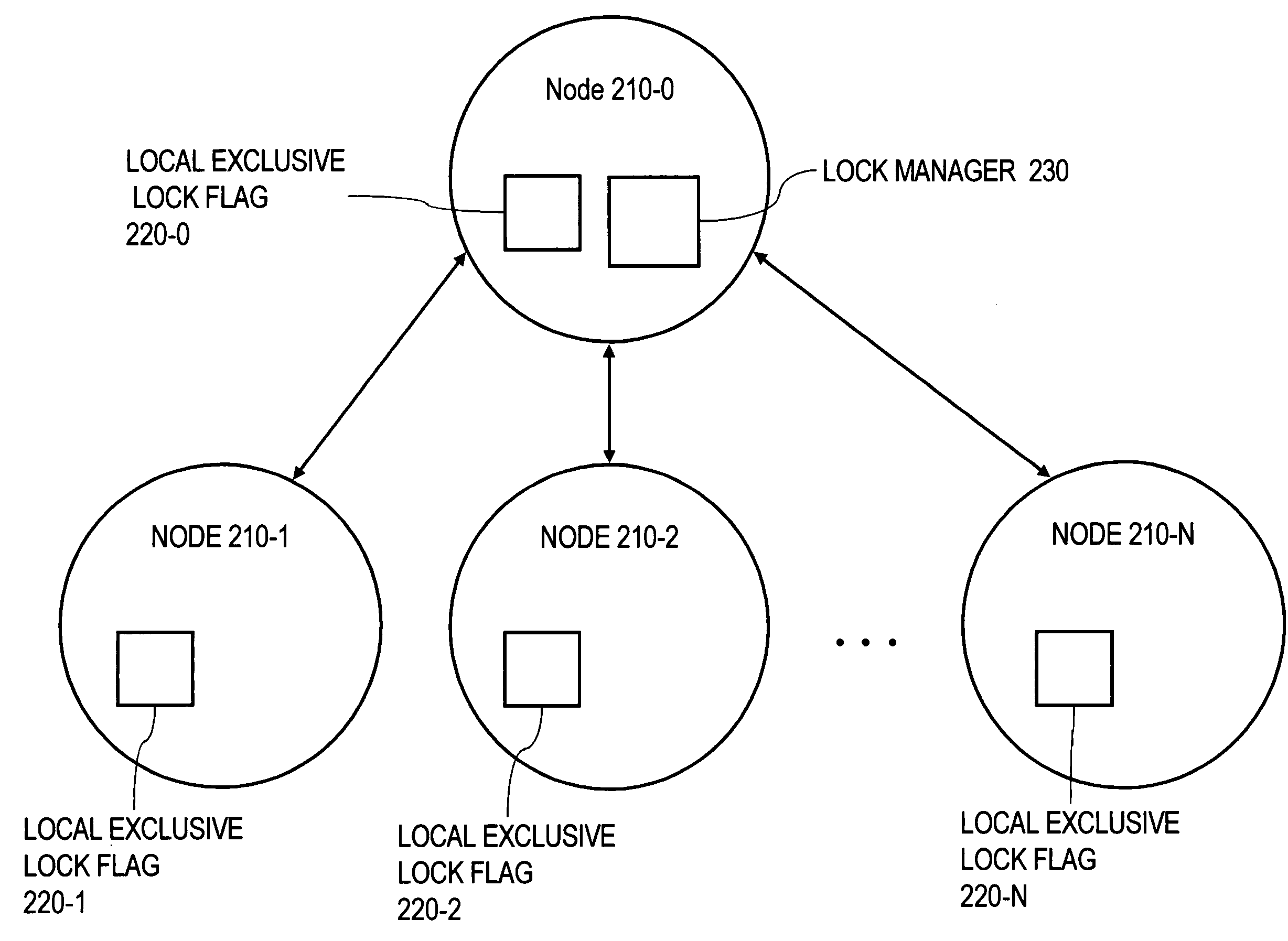
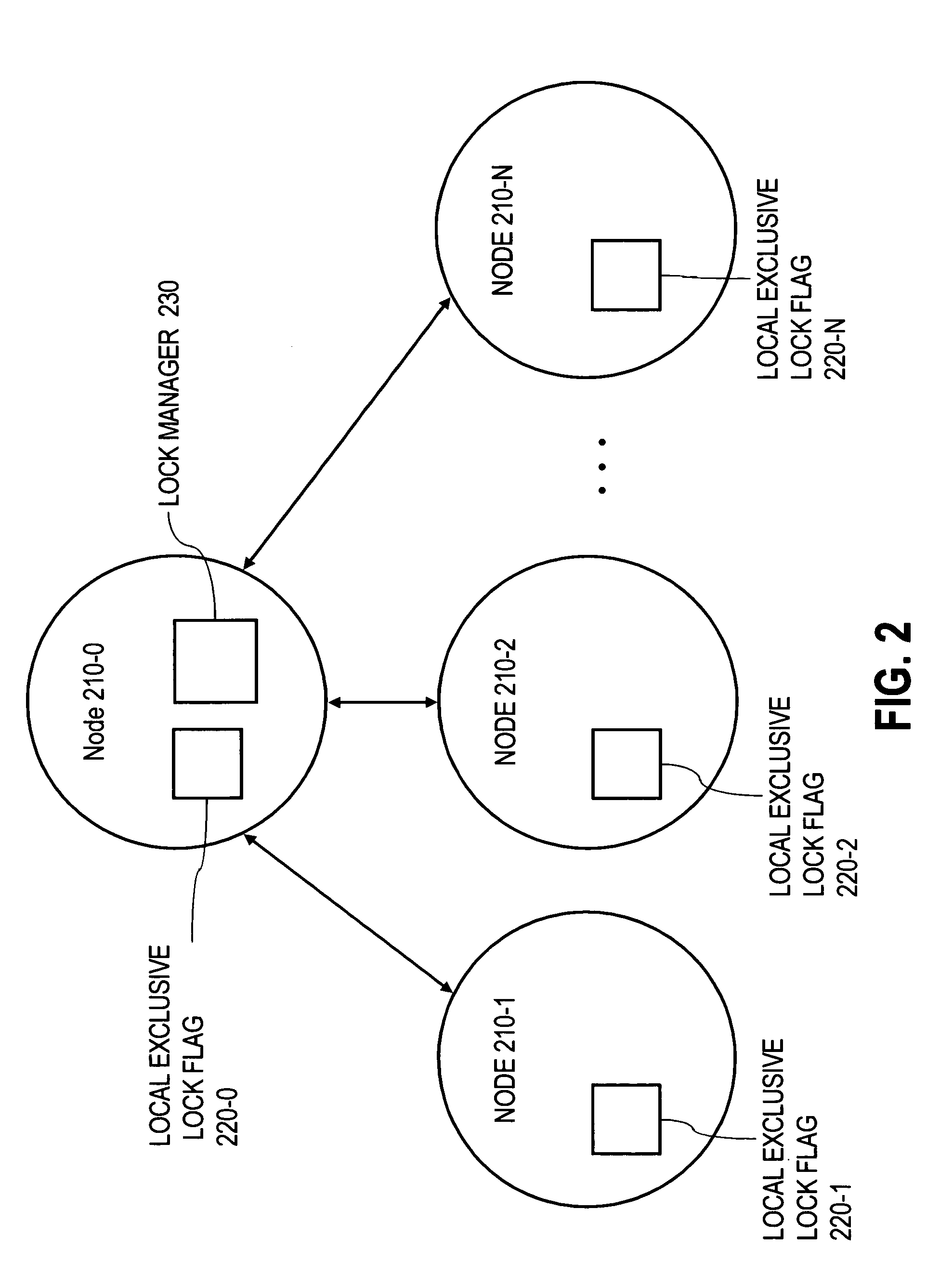
Techniques for granting shared locks more efficiently
ActiveUS6965893B1Effective resourcesImprove efficiencyData processing applicationsDigital data information retrievalResource managementOperating system
Techniques are disclosed for managing resources that are accessible to a plurality of entities. In one embodiment, shared locks on a resource are granted more efficiently by maintaining data that is local to (e.g. on the same node as) each entity to indicate whether an exclusive lock has been granted on the resource to any entity of the plurality of entities. Data that (15) is maintained local to an entity, and that (16) indicates whether any entity has an exclusive lock on a particular resource is referred to herein as a “local exclusive lock flag” for that particular resource. When an entity of the plurality of entities seeks to acquire a shared lock for a particular resource, that entity checks the local exclusive lock flag for that particular resource. If the local exclusive lock flag indicates that no entity holds an exclusive lock on the resource, then the entity seeking the shared lock acquires the shared lock without first receiving a lock grant from the resource manager that manages the resource. In many cases, the resource manager that manages the resource is remotely located relative to the entity that desires the shared lock. Because the local exclusive lock flag is local, the act of checking it does not incur the overhead associated with communicating with a remotely located resource manager. Thus, obtaining a shared lock based on the state of a local exclusive lock flag significantly increases the efficiency of managing access to the resource, particularly for resources for which entities do not frequently require exclusive access.
Owner:ORACLE INT CORP
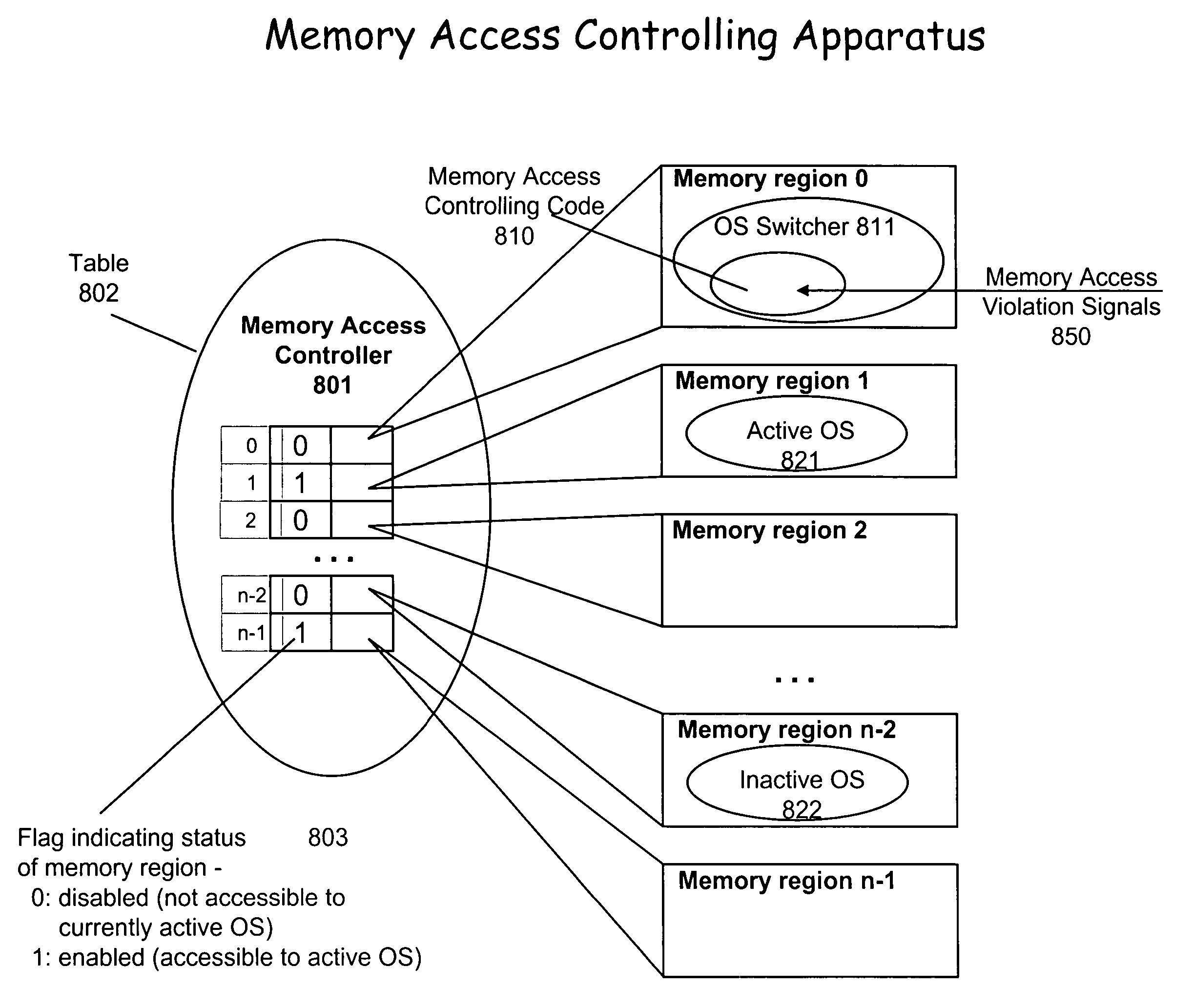
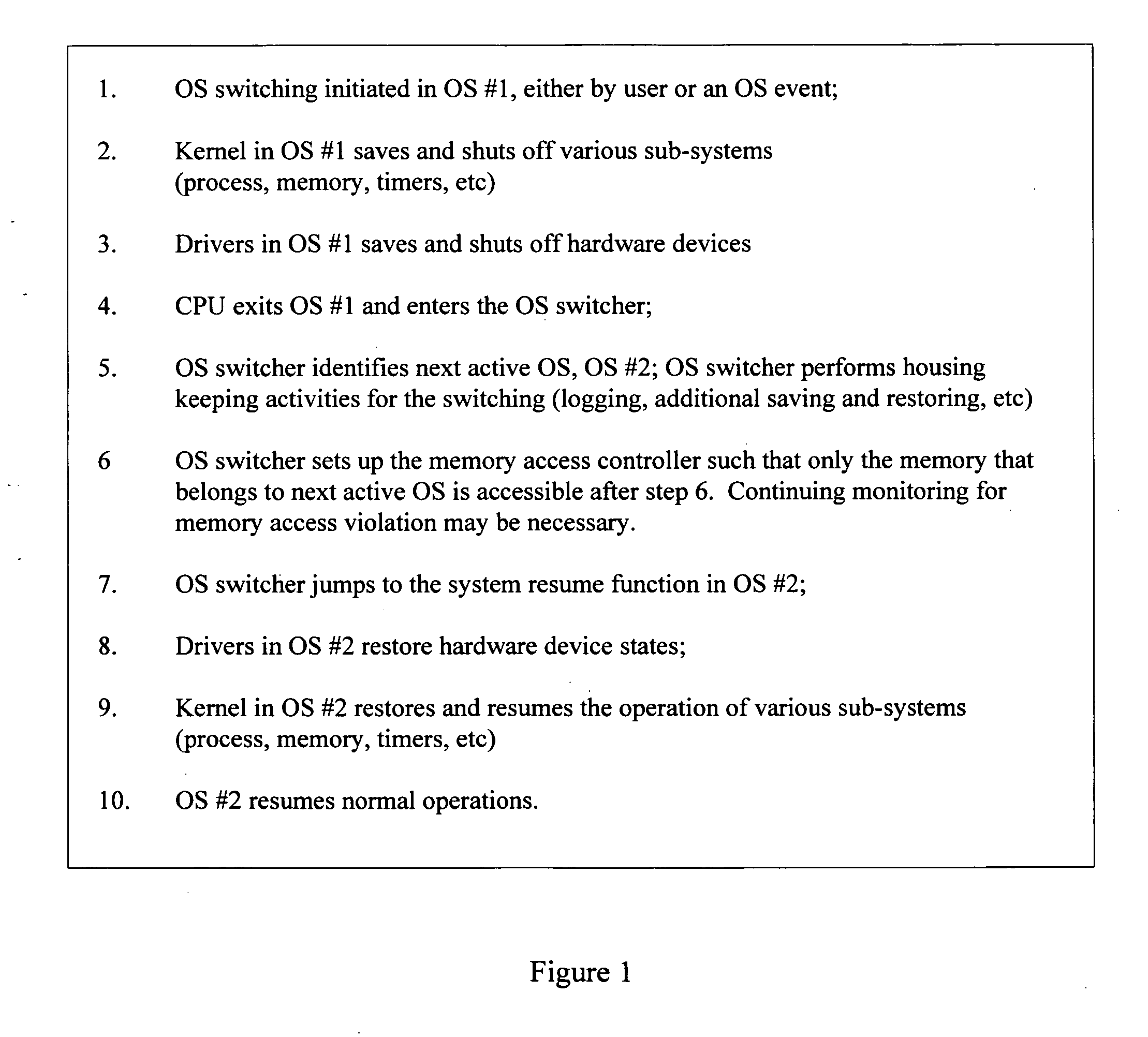
Secure operating system switching
A method and apparatus is disclosed herein for secure operating system switching. In one embodiment, the method comprises identifying a second operating system of a plurality of operating systems that is to be active next; causing a memory access controller to enable exclusive access to a portion of memory for the second operating system once the second operating system becomes active; and causing the second operating system to become active.
Owner:NTT DOCOMO INC
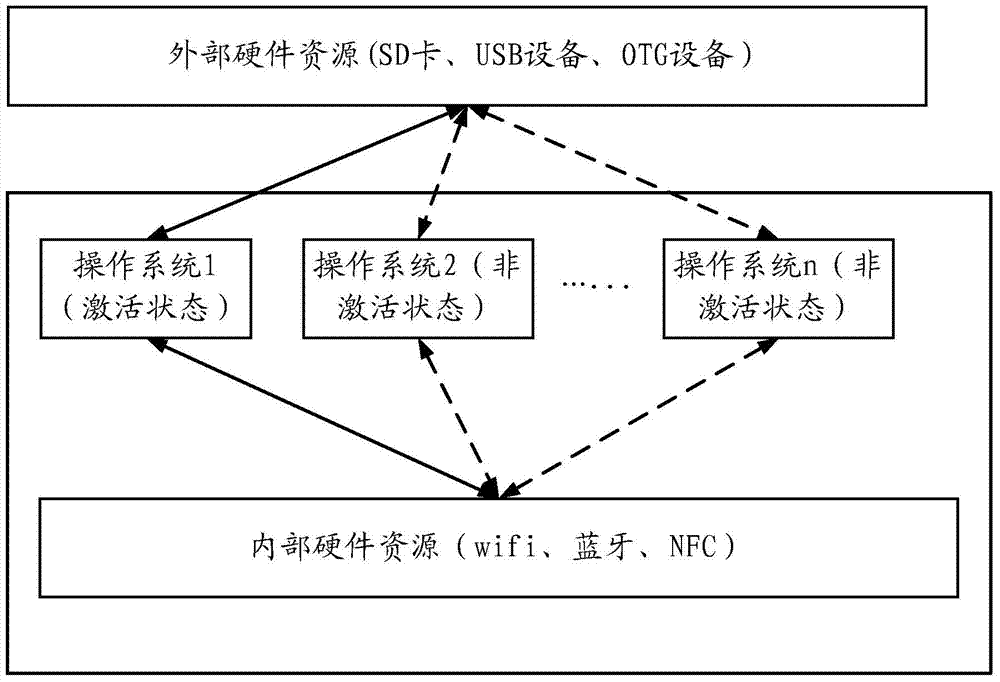
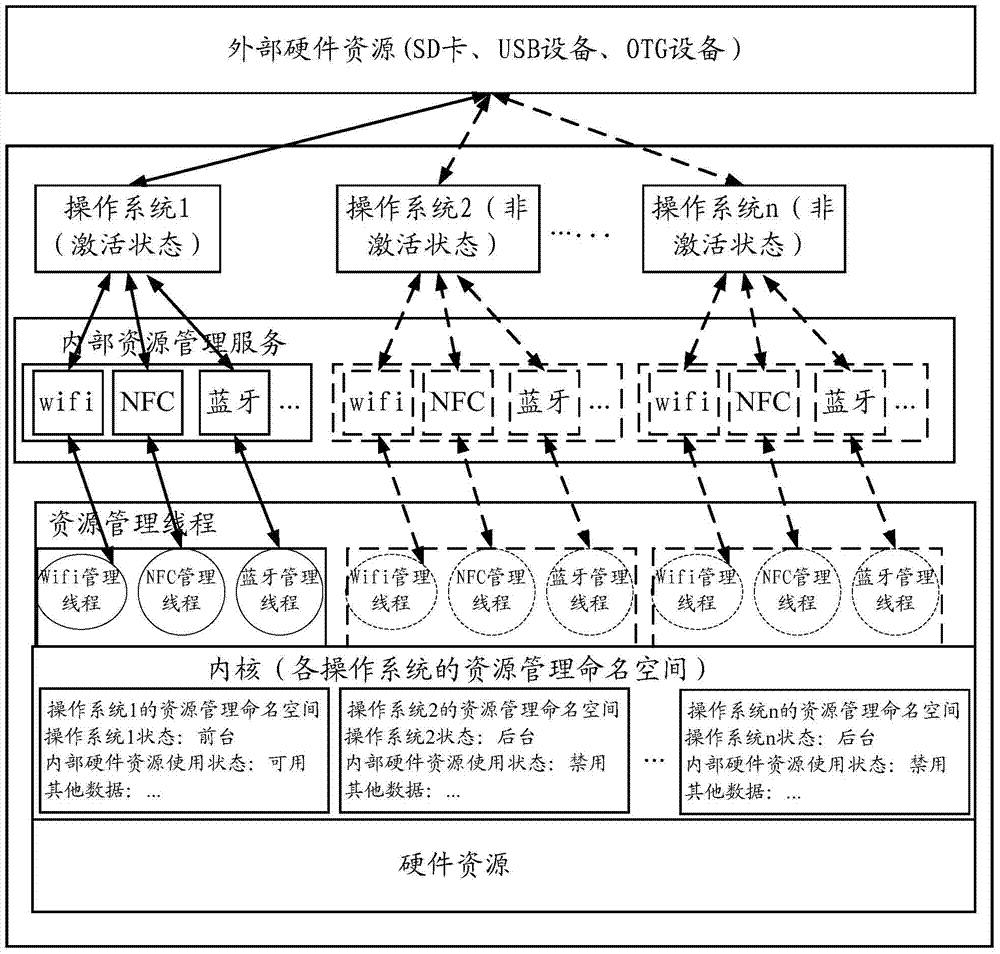
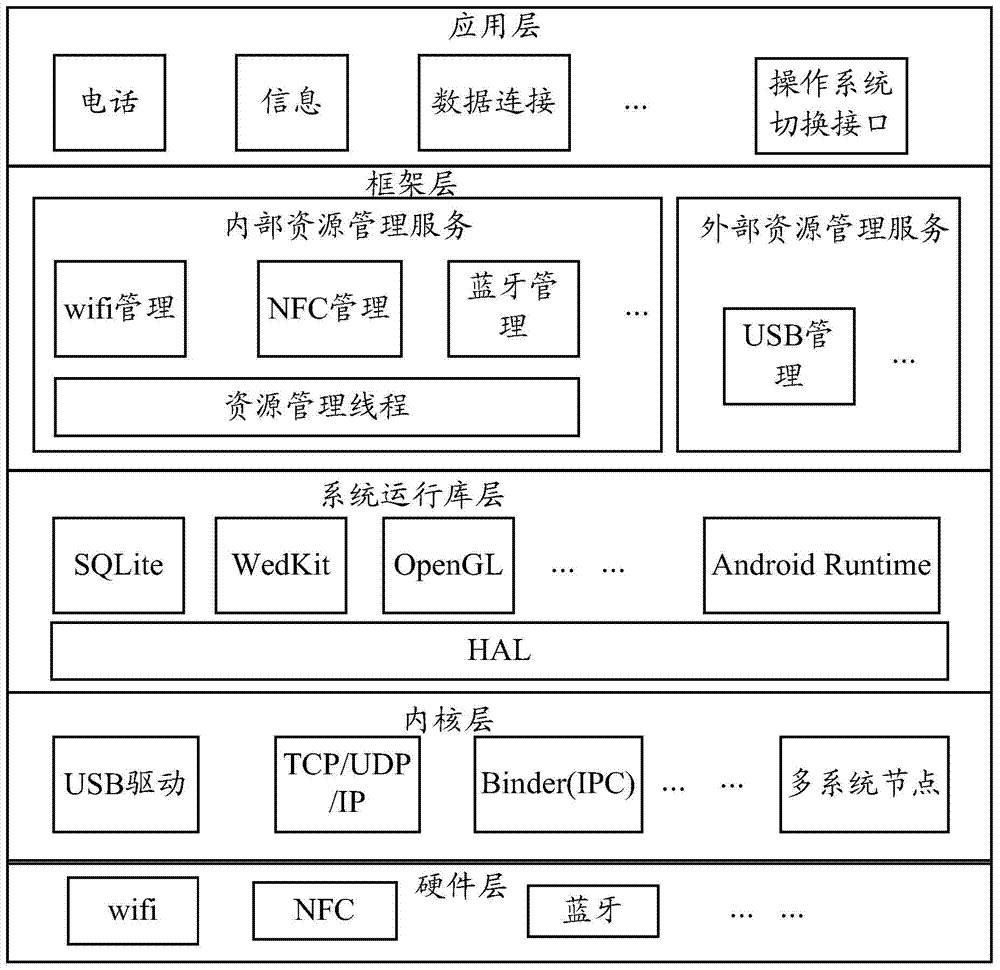
Operating system hot-switching method and device and mobile terminal
ActiveCN104516760AEasy to useGuaranteed reliabilityProgram initiation/switchingBootstrappingOperational systemEmbedded operating system
The invention discloses an operating system hot-switching method applied to a mobile terminal on which multiple operating systems run. The multiple operating systems comprise a front-end operating system and at least one back-end operating system, wherein the current front-end operating system serves as a first operating system, and the at least one back-end operating system comprises a second operating system. The method includes the steps of obtaining an operating system switching instruction, wherein the operating system switching instruction comprises identification and switching identification of the second operating system; according to the switching identification, releasing hardware resources occupied by the first operating system and switching the front-end operating system from the first operating system to the second operating system. The operating system hot-switching method ensures exclusive access to the hardware resources and the coordinate use of the hardware resources of the multiple operating systems to a certain extent and accordingly ensures the reliability of the use of the hardware resources after the operating system is switched.
Owner:HUAWEI TECH CO LTD
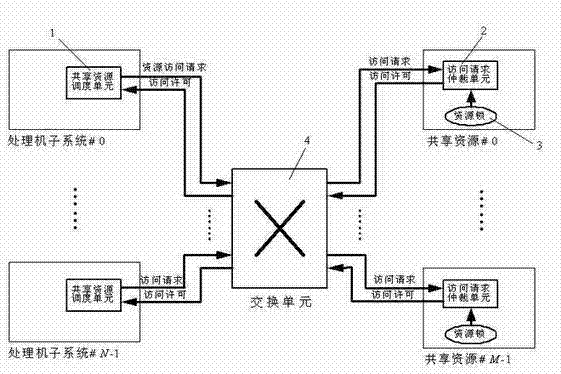
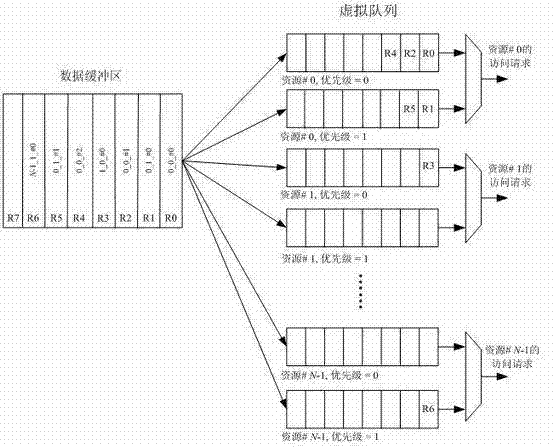
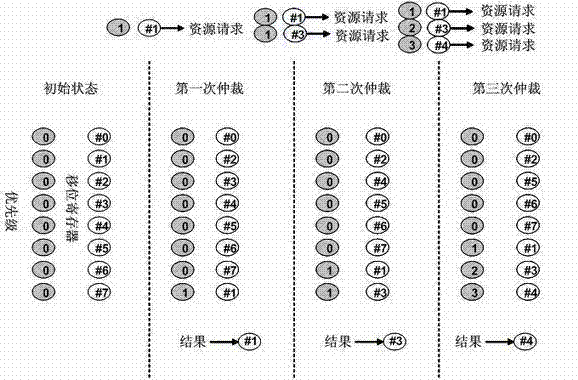
A shared resource scheduling method and system for distributed parallel processing
InactiveCN102298539ASolve the access contention problemAvoid deadlockProgram initiation/switchingParallel processingShared resource
The invention discloses a shared resource scheduling method and system used in distributed parallel processing. The method and system are based on a distributed operation mechanism. The shared resource scheduling units distributed in each processor subsystem are distributed in each shared Resource locks and resource request arbitration units are implemented. These distributed processing units communicate by sending messages (resource access requests / permissions) to each other through the switching unit. The shared resource scheduling unit in the processor subsystem uses virtual queue technology to manage all resource access requests in the data cache, that is, a special queue is specially opened for each accessible shared resource. Resource locks in shared resources are used to ensure the uniqueness of access to shared resources at any time. Resource locks have two states: lock occupation and lock release. The request arbitration unit in the shared resource uses a priority-based fair polling algorithm to arbitrate resource access requests from different processing nodes. The invention can effectively avoid the competition problem when each processing node accesses the shared resource, can also avoid the deadlock of the shared resource and the starvation problem of the processing node, and provides high-efficiency mutually exclusive access to the shared resource.
Owner:EAST CHINA NORMAL UNIV
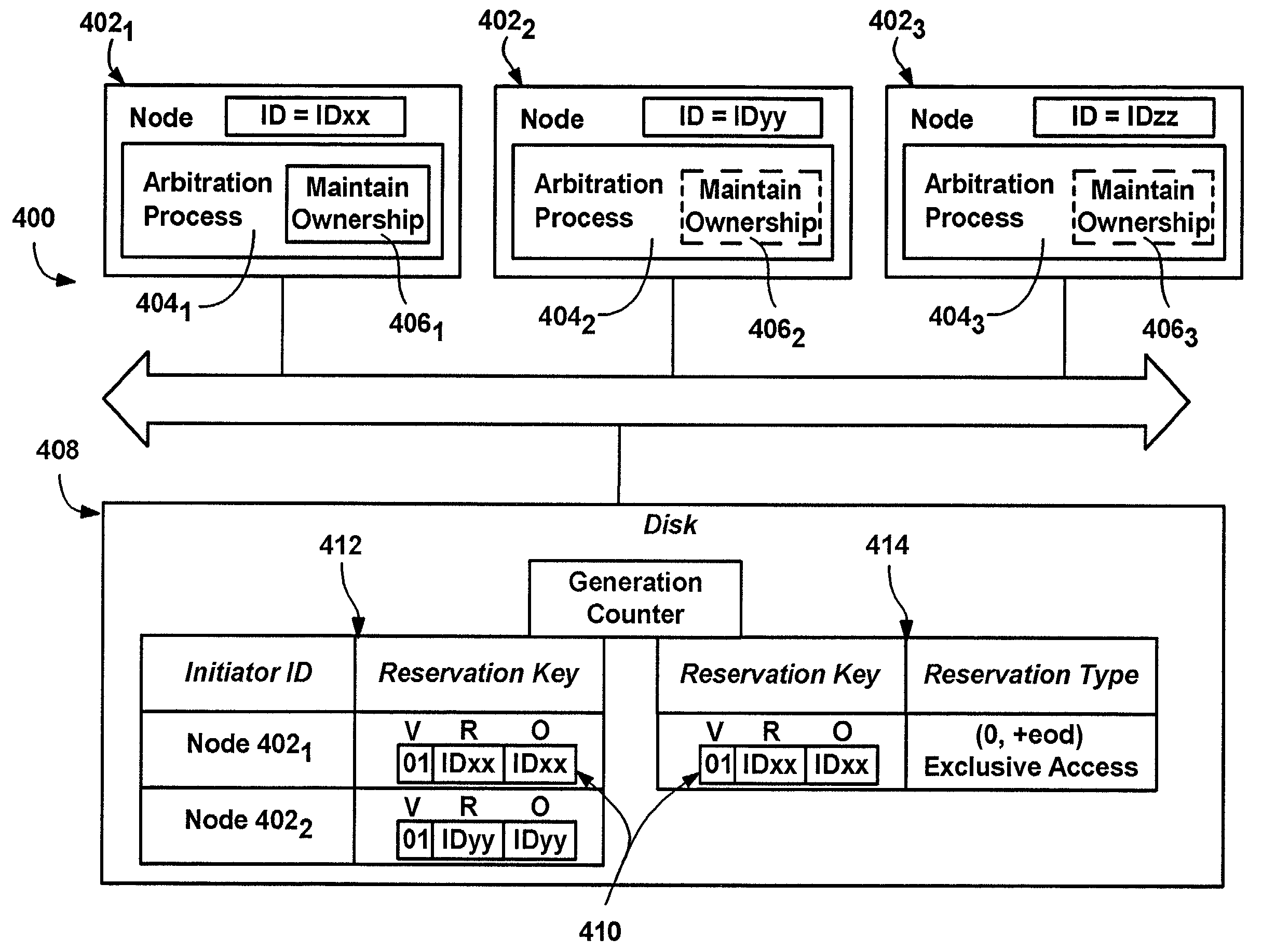
Distributed system resource protection via arbitration and ownership
InactiveUS7277952B2Resource allocationMultiple digital computer combinationsResource protectionExtensibility
In a distributed system, a resource such as a storage device is protected by an owner node's exclusive access to it, wherein exclusive access is established via a persistent reservation on the resource. A persistent reservation is never removed, however the owner node's persistent reservation may be challenged in an arbitration process, to take it away from a failed owner node. A challenger node challenges by changing an owner's access key (that establishes the persistent reservation) to a challenge key, delaying, and determining whether the owner restored the owner's access key during the delay, because a properly operating owner replaces a challenge key with its owner access key. If the owner fails to restore its owner access key, the challenger node becomes the new resource owner by replacing the challenge key with an owner access key of the challenger node. The key may include additional information to provide extensibility.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus to manage independent memory systems as a shared volume
InactiveUS6842829B1Memory architecture accessing/allocationMemory adressing/allocation/relocationLocking mechanismLogical block addressing
A switched architecture is provided to allow controllers to manage physically independent memory systems as a single, large memory system. The switched architecture includes a path between switches of controllers for inter-controller access to memory systems and input / output interfaces in a redundant controller environment. Controller memory systems are physically independent of each other; however, they are logically managed as a single, large memory pool. Cache coherency is concurrently maintained by both controllers through a shared locking mechanism. Volume Logical Block Address extents or individual cache blocks can be locked for either shared or exclusive access by either controller. There is no strict ownership model to determine data access. Access is managed by the controller in the pair that receives the access request. When a controller is removed or fails, a surviving controller may take appropriate action to invalidate all cache data that physically resides in the failed or missing controller's memory systems. Cached write data may be mirrored between redundant controllers to prevent a single point of failure with respect to unwritten cached write data.
Owner:AVAGO TECH INT SALES PTE LTD
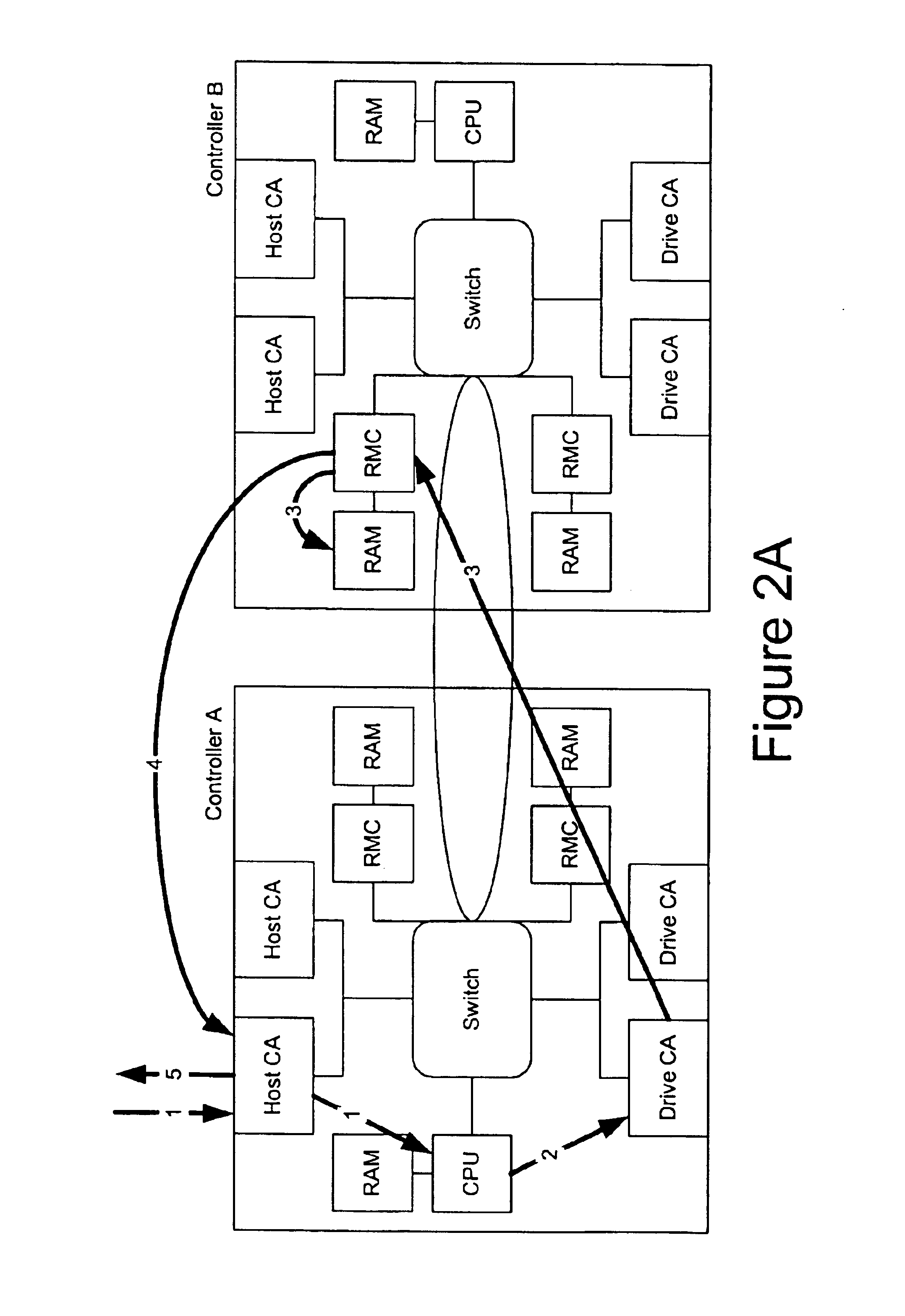
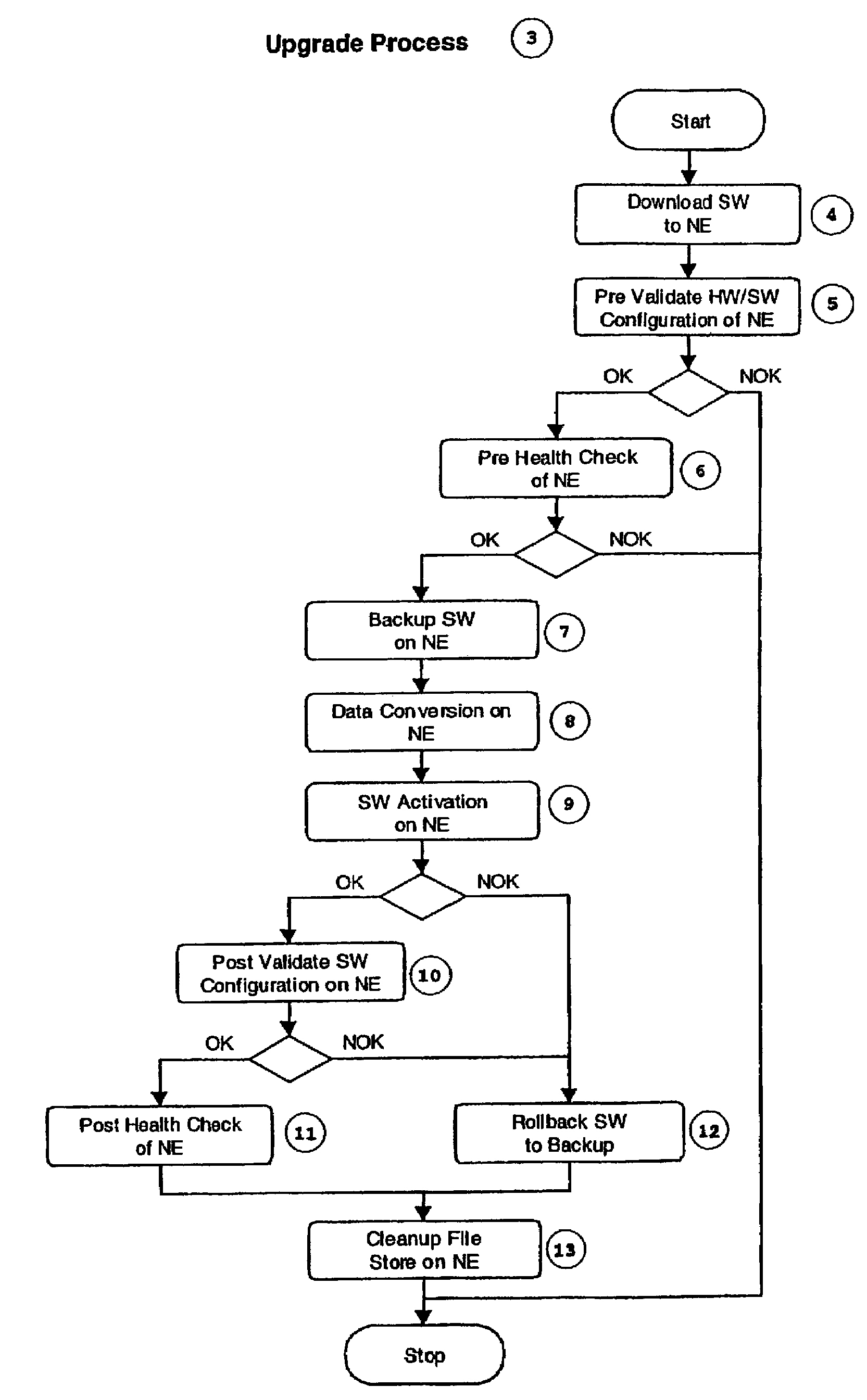
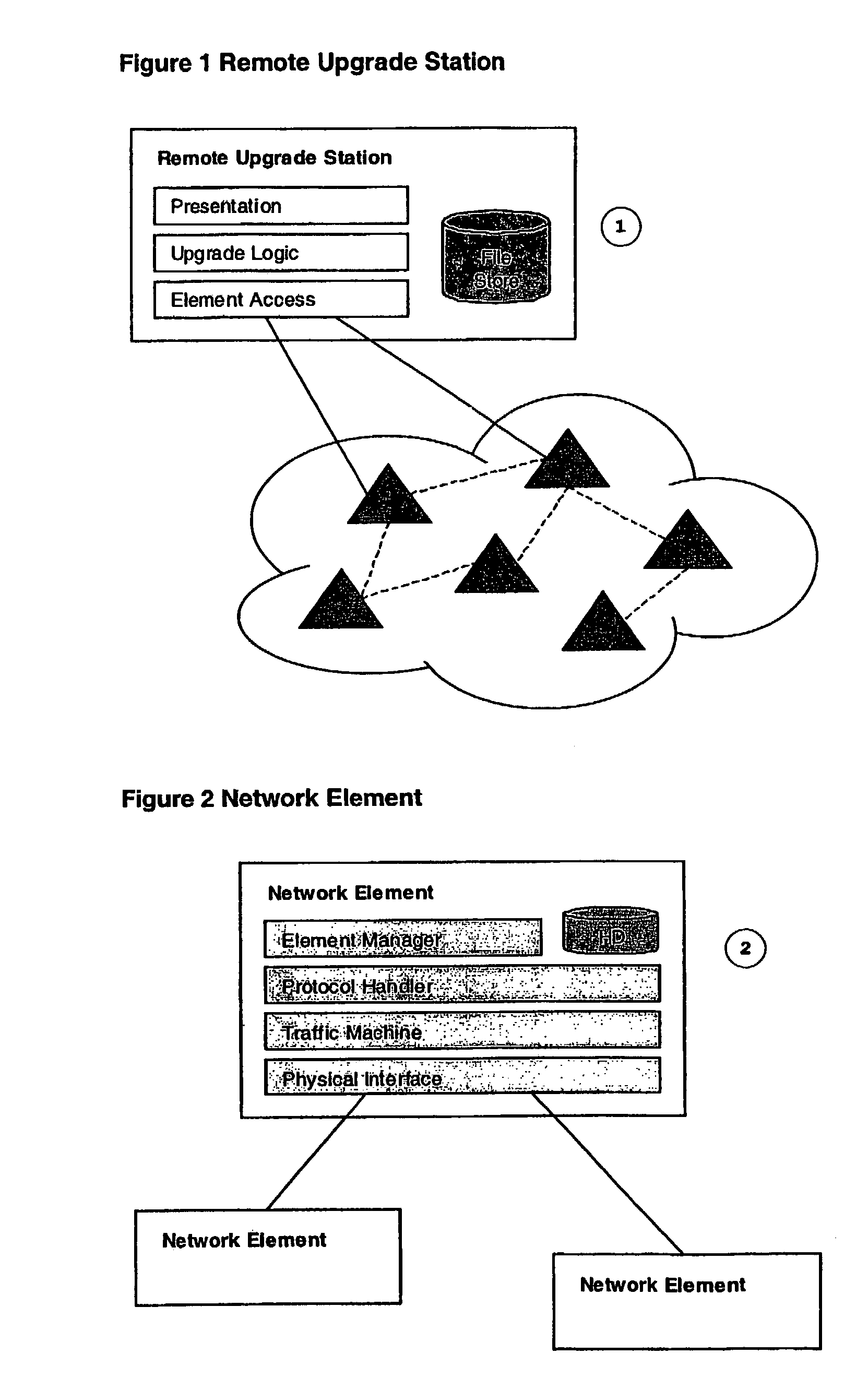
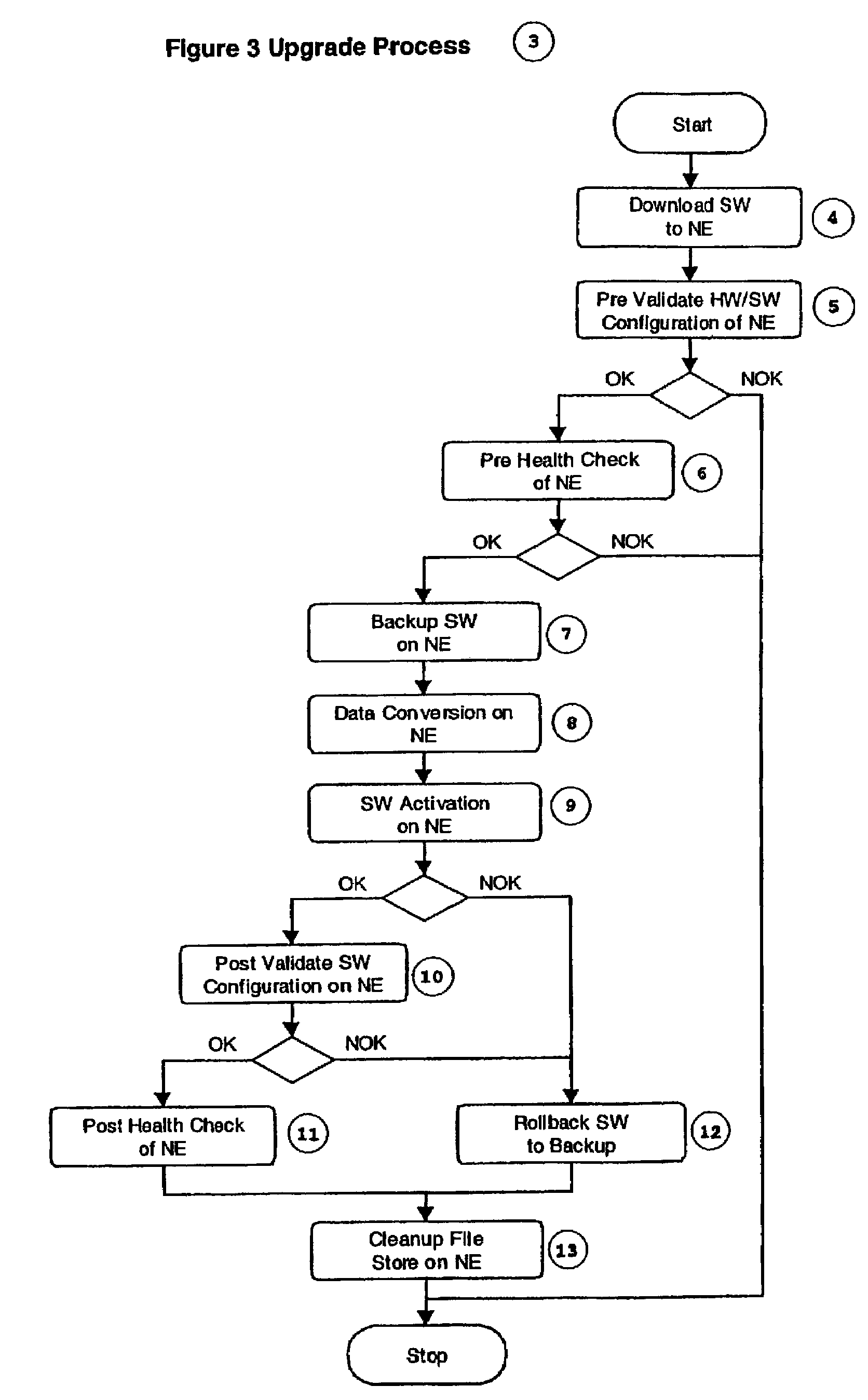
Method for automation of software upgrade
InactiveUS7266819B2Multiplex system selection arrangementsDigital data processing detailsCommunications systemHealth check
The present invention relates to a method for automation of software upgrade of network elements in data and communication networks. In a preferred embodiment of the present invention, an upgrade of network elements in a communication system is controlled from one certain workstation. Before the actual activation of the new software of the network elements takes place, the hardware configuration (5) is validated ensuring that the new software is loadable in the hardware. The software configuration is then also validated ensuring that the new software and the existing software are compatible. A health check is then executed investigating whether the status of the network elements is as required. Then, the certain workstation from which the upgrade is controlled is assigned exclusive network administration access to the network elements. Assuming that the above mentioned is carried through successfully, the actual activation of the new software is executed. Thereafter, the exclusive access which was assigned to the workstation is released, and before cleaning up and terminating, post validation and post health checks are executed.
Owner:TELEFON AB LM ERICSSON (PUBL)
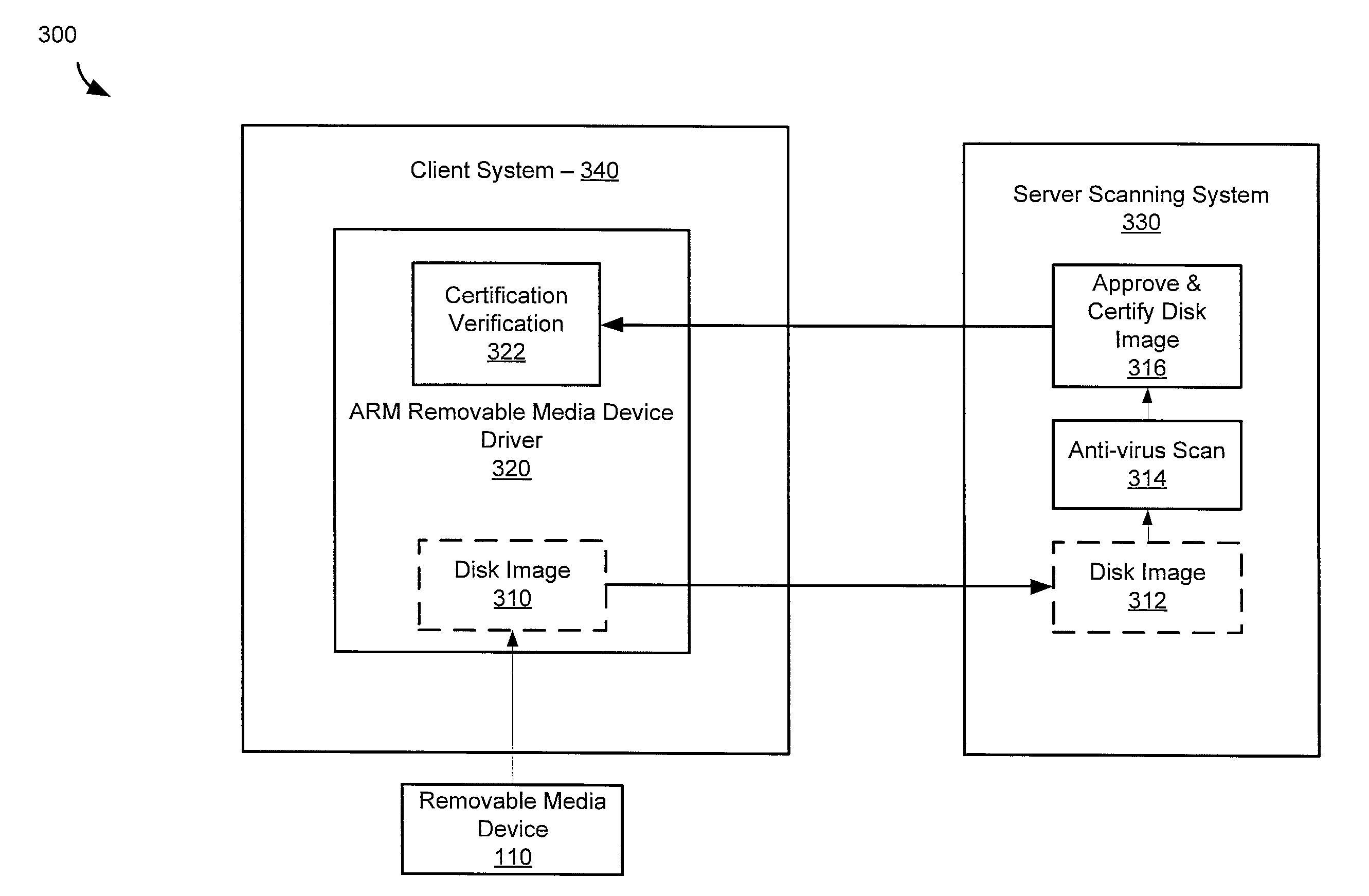
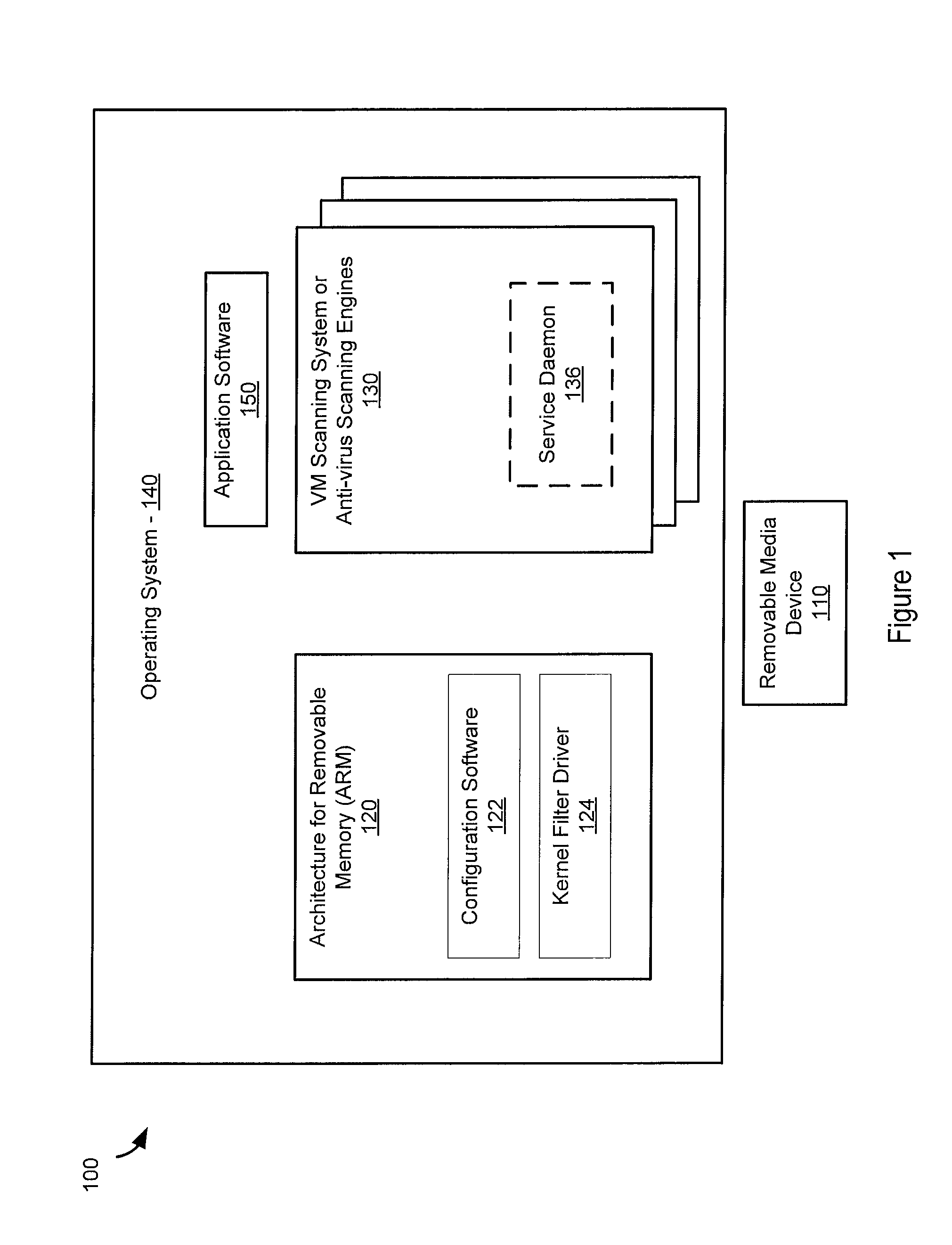
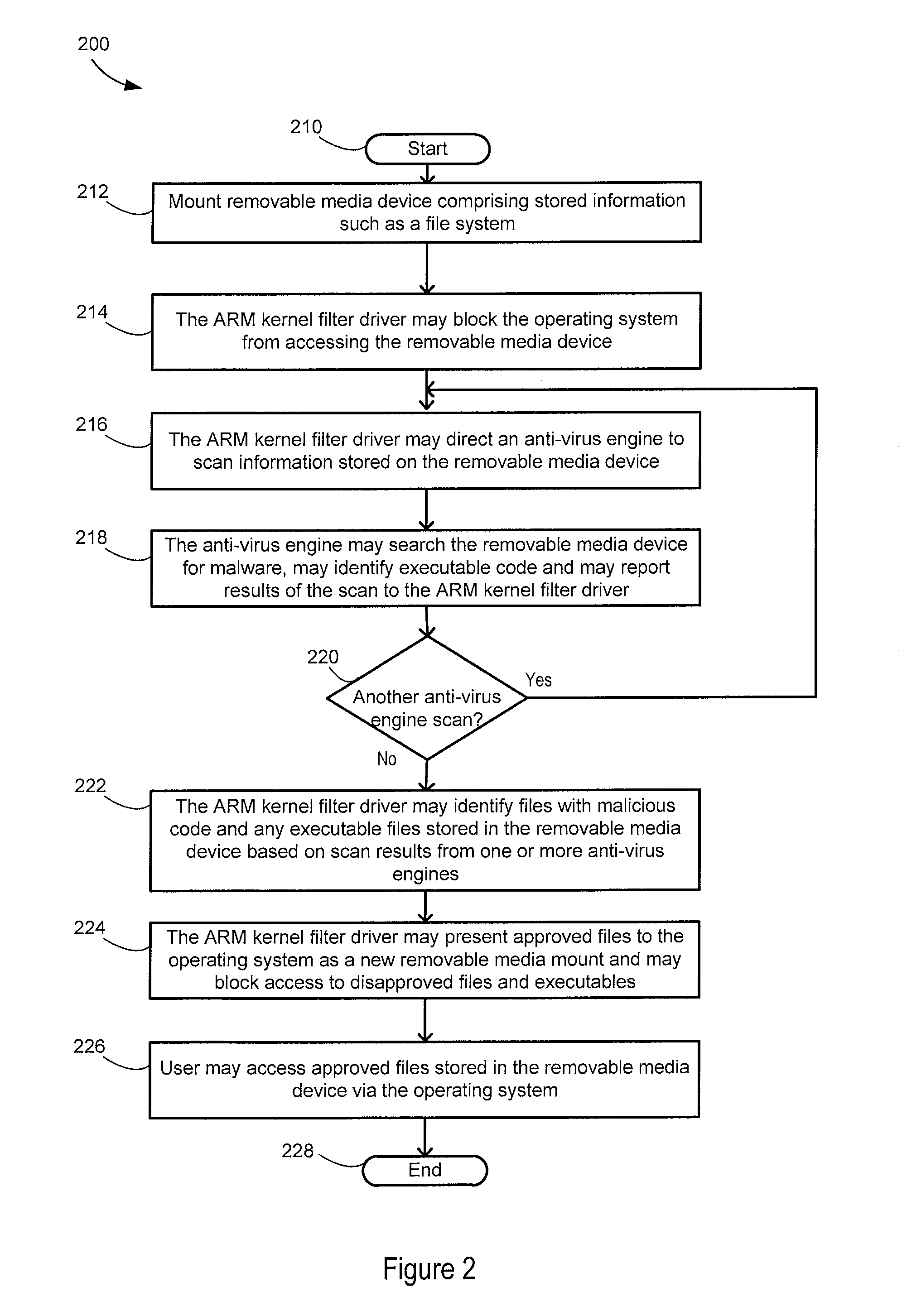
Architecture for removable media usb-arm
A storage device is coupled to a computing system comprising an operating system and application software. Access to the storage device is blocked by a kernel filter driver, except exclusive access is granted to a first anti-virus engine. The first anti-virus engine is directed to scan the storage device for malicious software and report results. Exclusive access may be granted to one or more other anti-virus engines and they may be directed to scan the storage device and report results. Approval of all or a portion of the information on the storage device is based on the results from the first anti-virus engine and the other anti-virus engines. The storage device is presented to the operating system and access is granted to the approved information. The operating system may be a Microsoft Windows operating system. The kernel filter driver and usage of anti-virus engines may be configurable by a user.
Owner:UT BATTELLE LLC
Network on chip with partitions
InactiveUS20090138567A1Multiple digital computer combinationsMemory systemsMemory addressApplication software
A design structure embodied in a machine readable medium is provided. Embodiments of the design structure include a network on chip (‘NOC’), the NOC comprising: integrated processor (‘IP’) blocks, routers, memory communications controllers, and network interface controller, each IP block adapted to a router through a memory communications controller and a network interface controller, each memory communications controller controlling communication between an IP block and memory, and each network interface controller controlling inter-IP block communications through routers; the network organized into partitions, each partition including at least one IP block, each partition assigned exclusive access to a separate physical memory address space; and one or more applications executing on one or more of the partitions.
Owner:IBM CORP
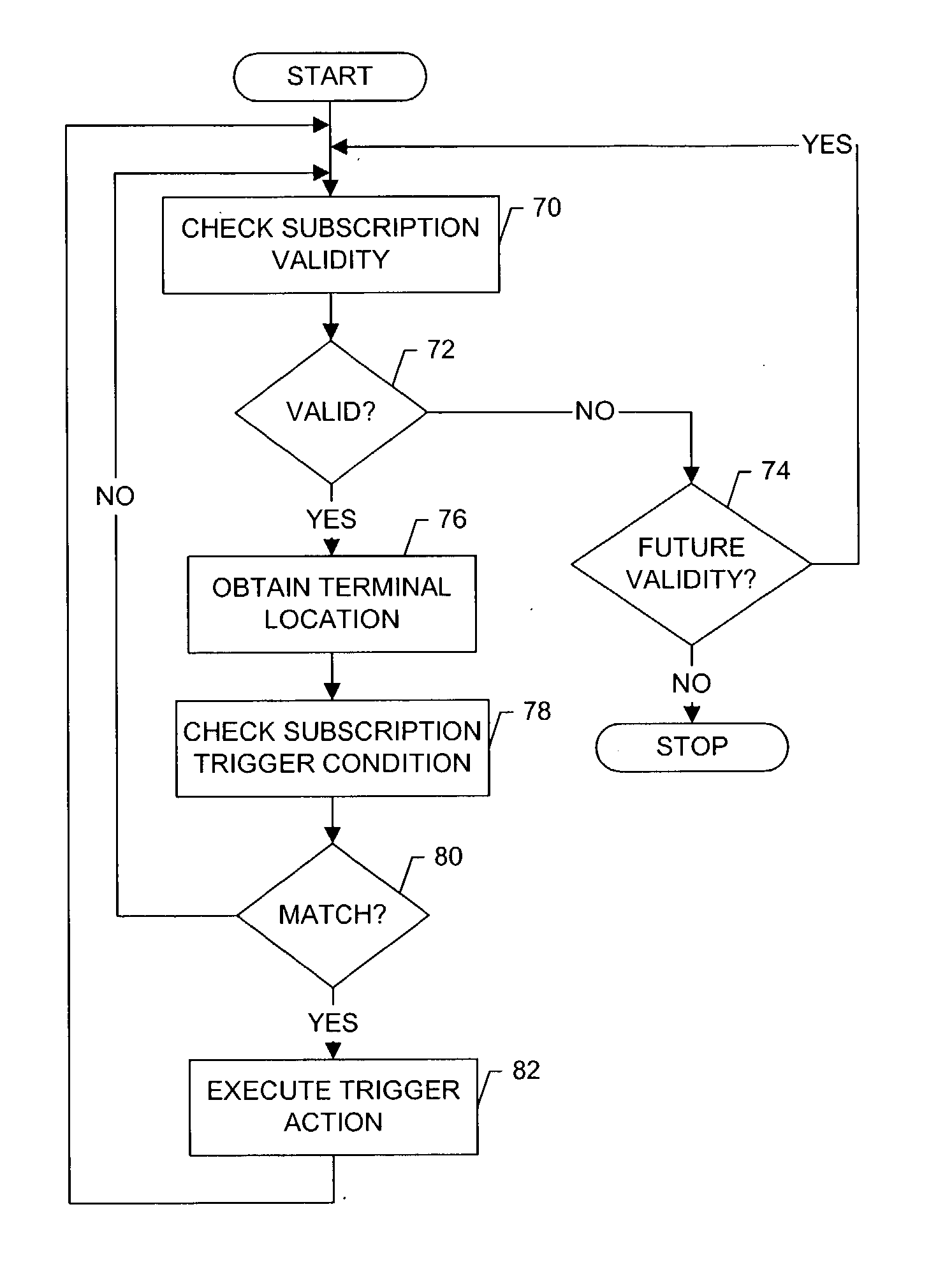
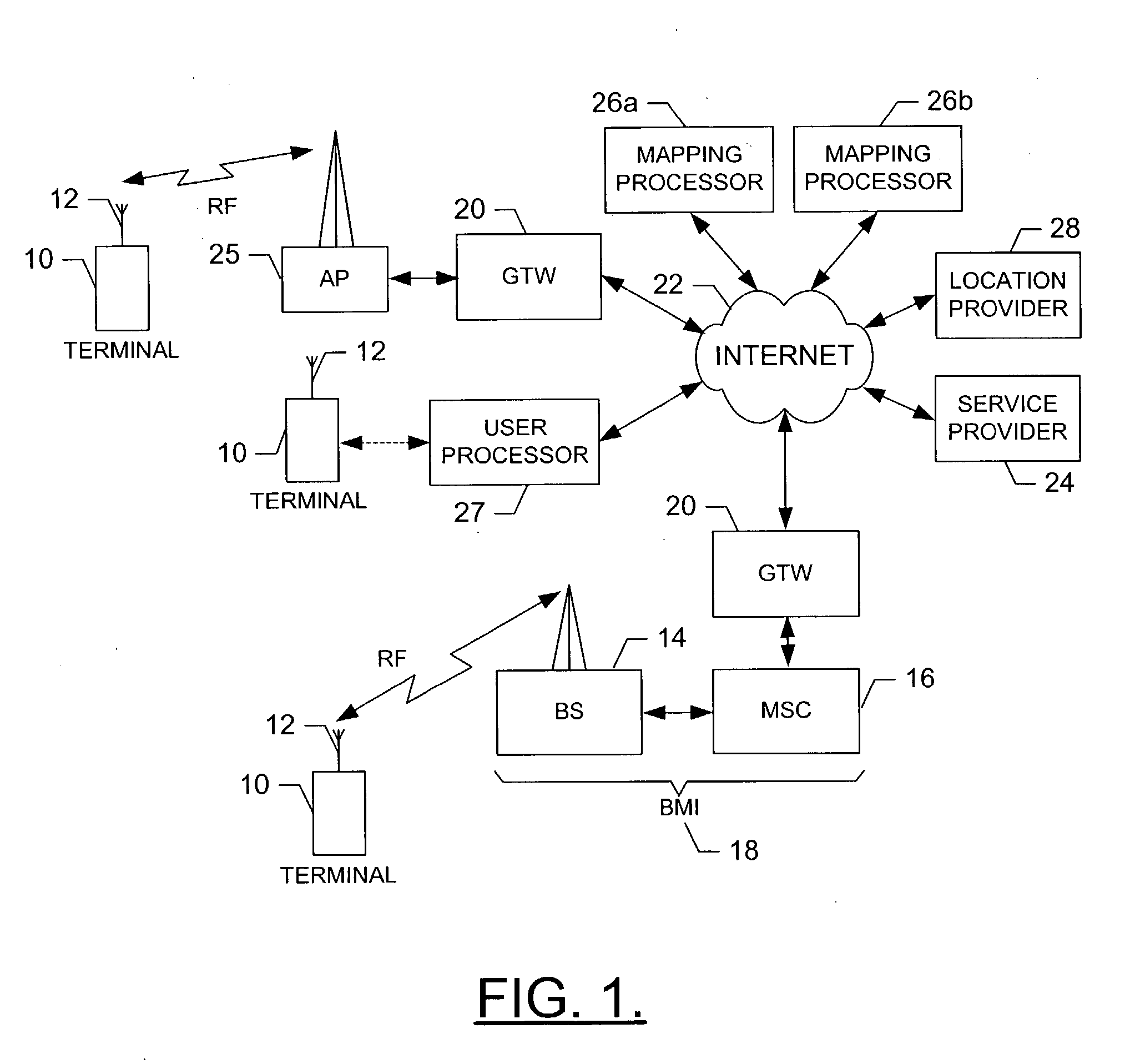
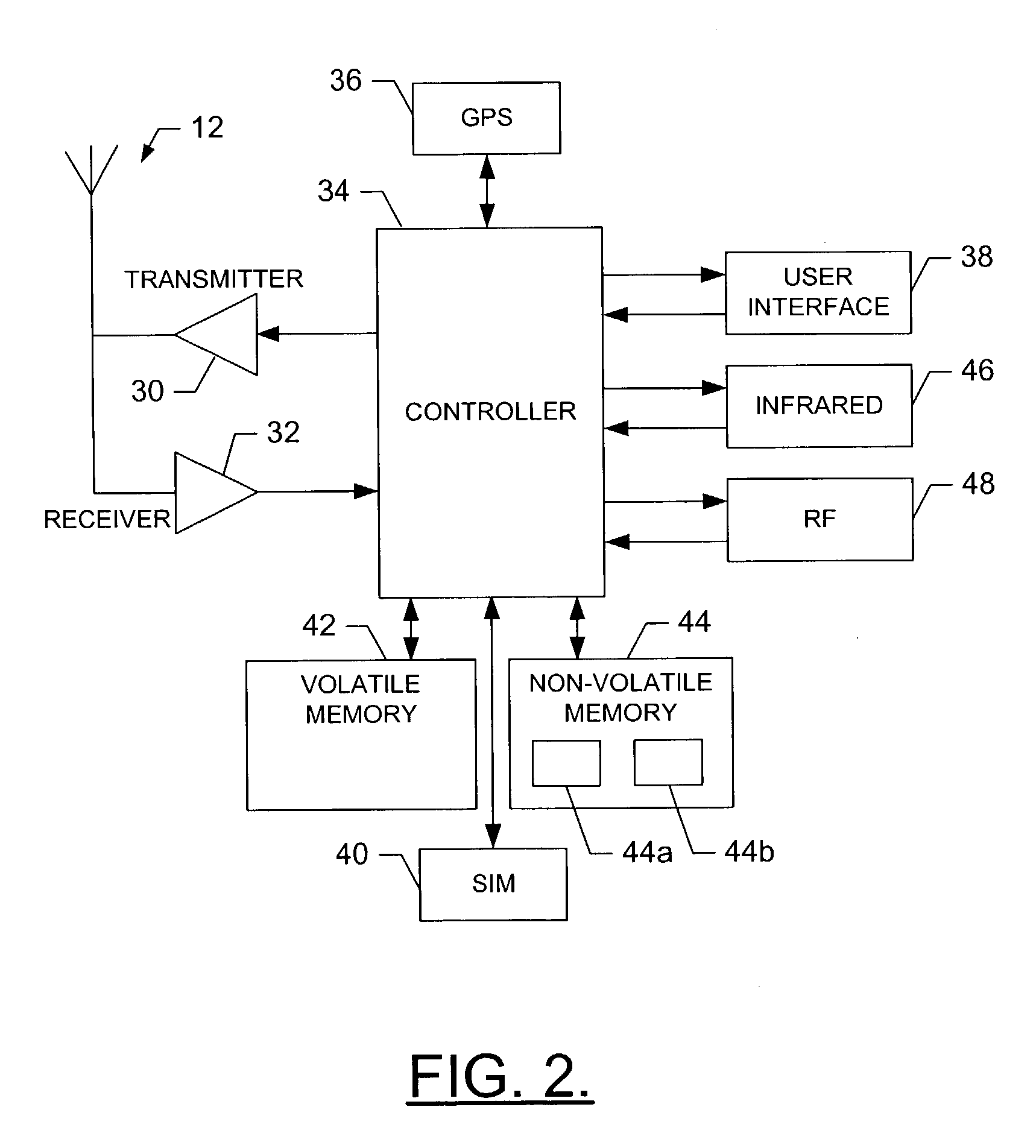
System, method and computer program product for providing differential location services with mobile-based location tracking
InactiveUS20050136946A1Reduce the burden onReduce resource requirementsTelephonic communicationRadio/inductive link selection arrangementsLocation trackingSystems approaches
A system for providing differential location service includes a service provider capable of receiving a request for a differential location service that includes a geographic area defined independent of a specific format. The service provider is capable of receiving the request such that the geographic area can be transformed to thereby define the geographic area in a predetermined manner. The system can include a tracking entity capable of sending the request. The system can additionally, or alternatively, include a network entity (e.g., service provider or a tracked entity) capable of entering a subscription including the geographic area defined in the predetermined manner such that the tracking entity has exclusive access rights to modify the subscription. The network entity can also determine whether to provide the requested differential location service based upon a current location of the tracked entity located remote from the tracking entity, and upon the subscription.
Owner:NOKIA CORP
Method for managing concurrent processes using dual locking
InactiveUS6401110B1Multiprogramming arrangementsMultiple digital computer combinationsMemory addressParallel computing
Multiple competing processors cooperatively manage access to a shared resource. Each processor separately stores a lock table, listing shared resource subparts, such as memory addresses of a data storage device, for example. The lock tables are stored in nonvolatile storage. In each lock table, each subpart is associated with a "state," such as; LOCAL or REMOTE. In response to access requests from the hosts, the processors exchange various messages to cooperatively elect a single processor to have exclusive access to the subparts involved in the access requests. After one processor is elected, the lock-holding processor configures its lock table to show the identified subpart in the LOCAL state, and all non-lock-holding processors configure their lock tables to show the identified subpart in the REMOTE state. Thus, rather than replicating one lock table for all processors, the processors separately maintain lock tables that are coordinated with each other. Importantly, each processor honors its lock table by refraining from accessing a subpart of the shared resource unless the processor's lock table indicates a LOCAL state for that subpart. In one embodiment, optimized for the two processor environment, the messages exchanged by the processors include lock request, lock release, and lock grant messages.
Owner:INT BUSINESS MASCH CORP
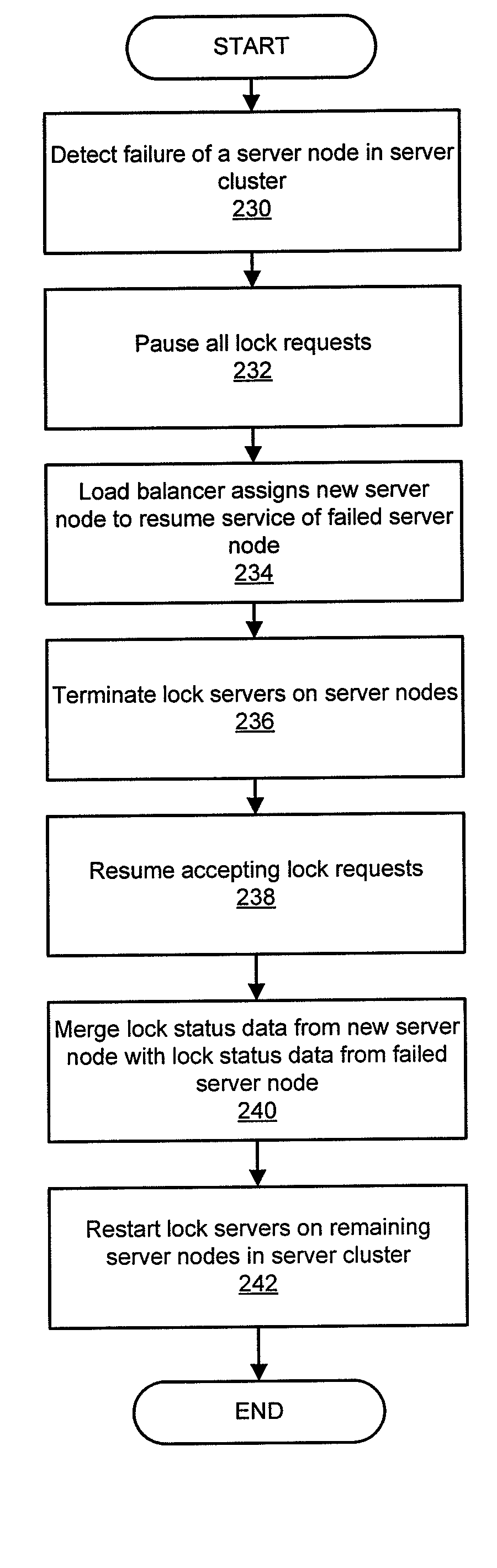
System and method for implementing clustered network file system lock management
A system and method for implementing clustered network file system lock management is provided. A failure of a first server node among a collection of nodes is detected. The first server node includes lock status data. The lock status data grants a first client exclusive access to data stored on a server storage device. The server storage device is coupled to the collection of server nodes. The lock status data is transferred to a second server node among the collection of server nodes. The first client is granted exclusive access to data stored on the server storage device, based on the lock status data transferred to the second server node from the first server node, in response to the transferring. Lock requests from the collection of clients are accepted, in response to the transferring.
Owner:VERITAS TECH
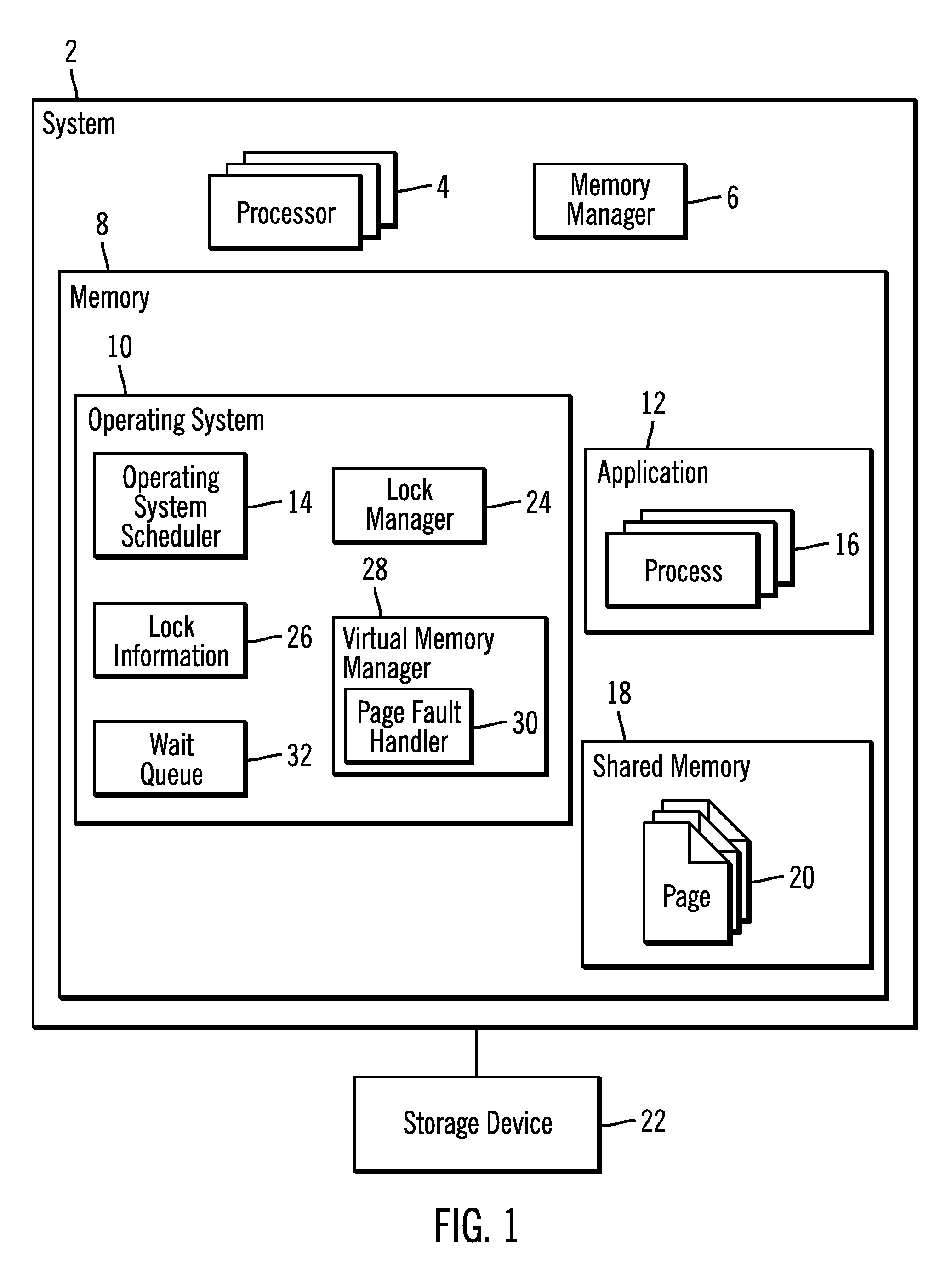
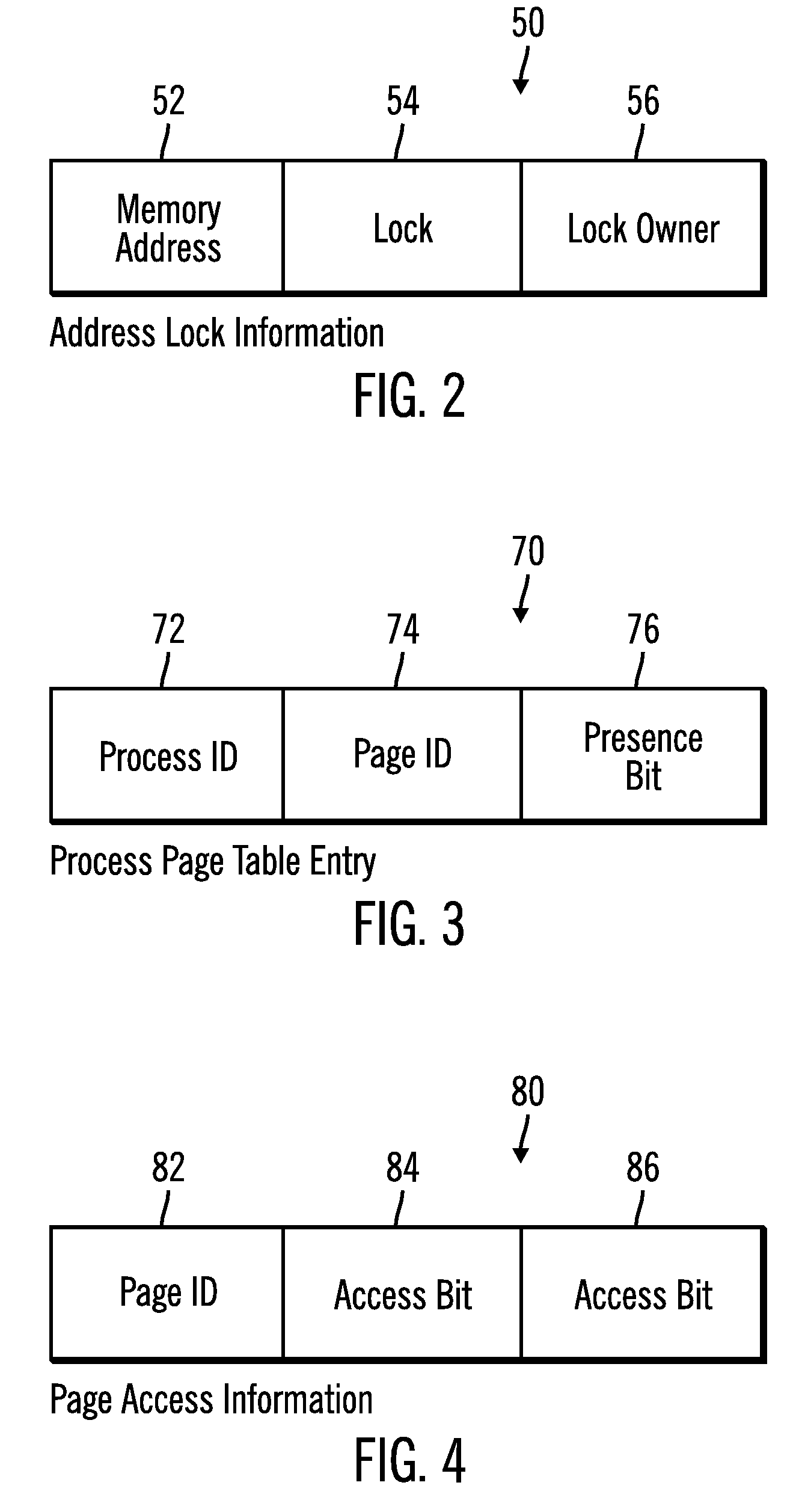
Providing a process exclusive access to a page including a memory address to which a lock is granted to the process
Provided are a method, system, and article of manufacture for providing a process exclusive access to a page including a memory address to which a lock is granted to the process. A request is received for a memory address in a memory device from a requesting process. A lock is granted to the requested memory address to the requesting process. The requesting process is provided exclusive access to a page including the requested memory address for a page access time period. The exclusive access to the page provided to the requesting process is released in response to an expiration of the page access time period.
Owner:LINKEDIN
Architecture for a read/write thread lock
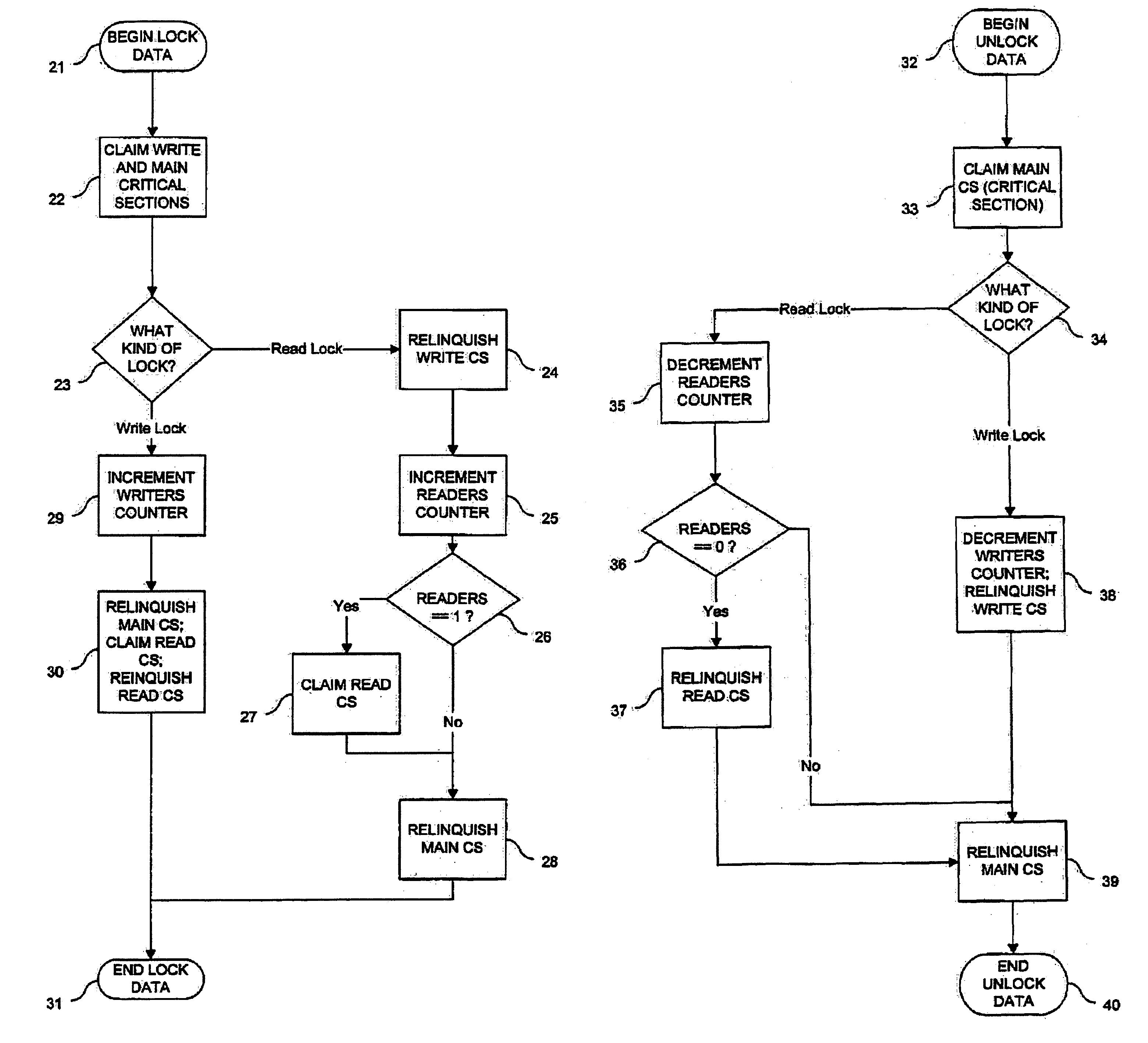
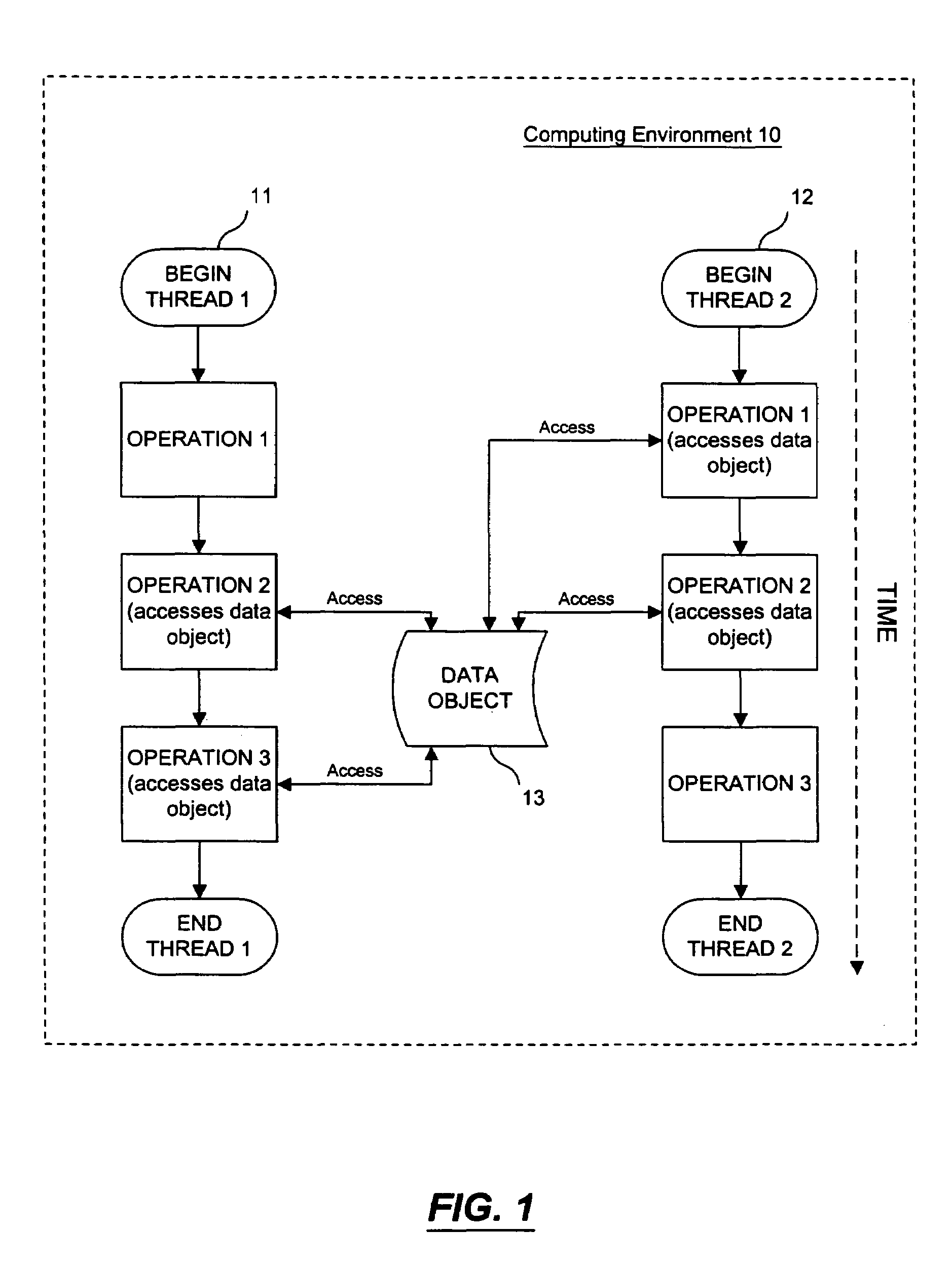
InactiveUS7188344B1Minimizing chanceMultiprogramming arrangementsMemory systemsComputer architectureCritical section
An architecture for a read / write thread lock is provided for use in a computing environment where several sets of computer instructions, or “threads,” can execute concurrently. The disclosed thread lock allows concurrently-executing threads to share access to a resource, such as a data object. The thread lock allows a plurality of threads to read from a resource at the same time, while providing a thread exclusive access to the resource when that thread is writing to the resource. The thread lock uses critical sections to suspend execution of other threads when one thread needs exclusive access to the resource. Additionally, a technique is provided whereby the invention can be deployed as constructors and destructors in a programming language, such as C++, where constructors and destructors are available. When the invention is deployed in such a manner, it is possible for a programmer to issue an instruction to lock a resource, without having to issue a corresponding unlock instruction.
Owner:UNISYS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com