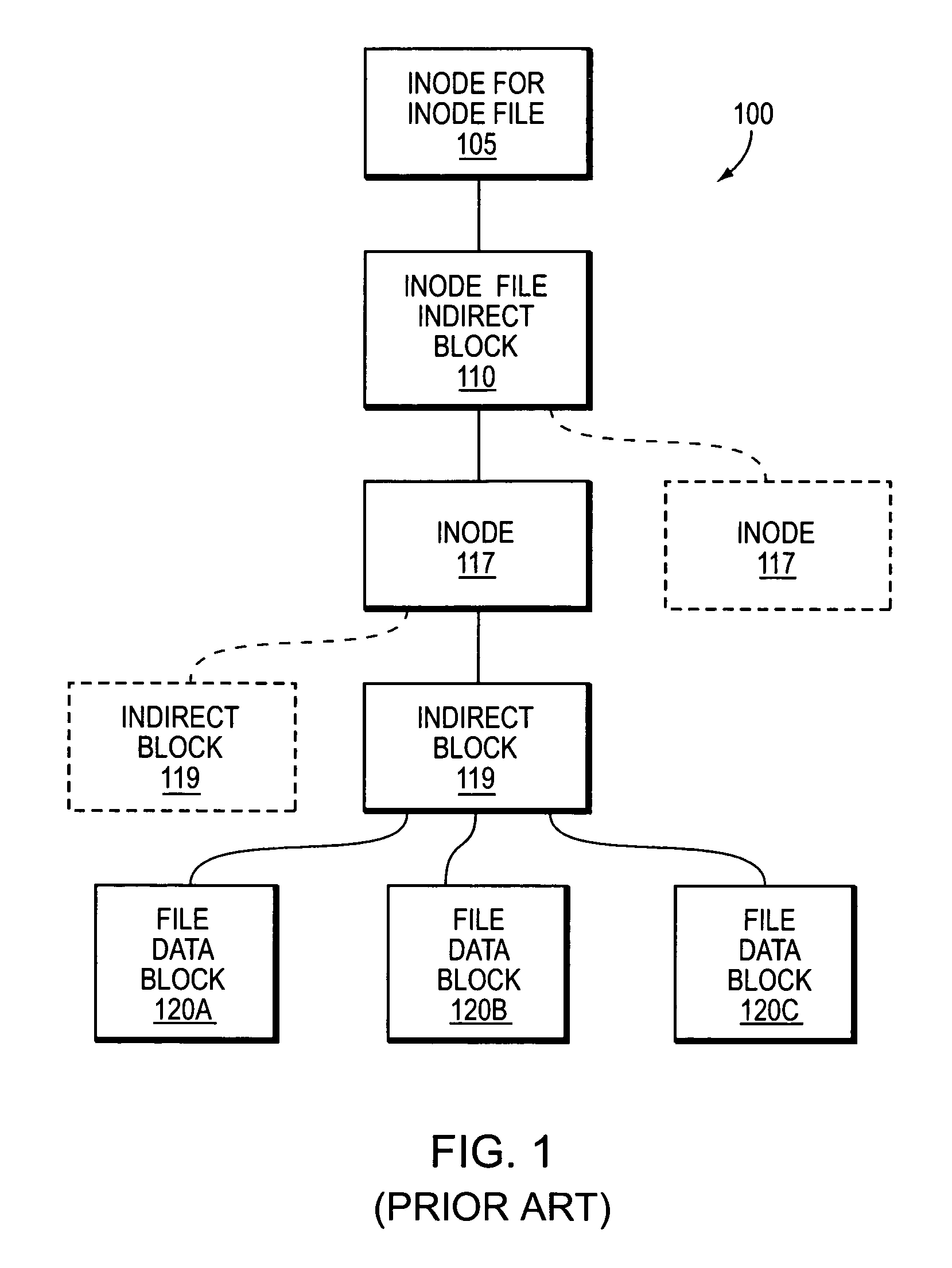
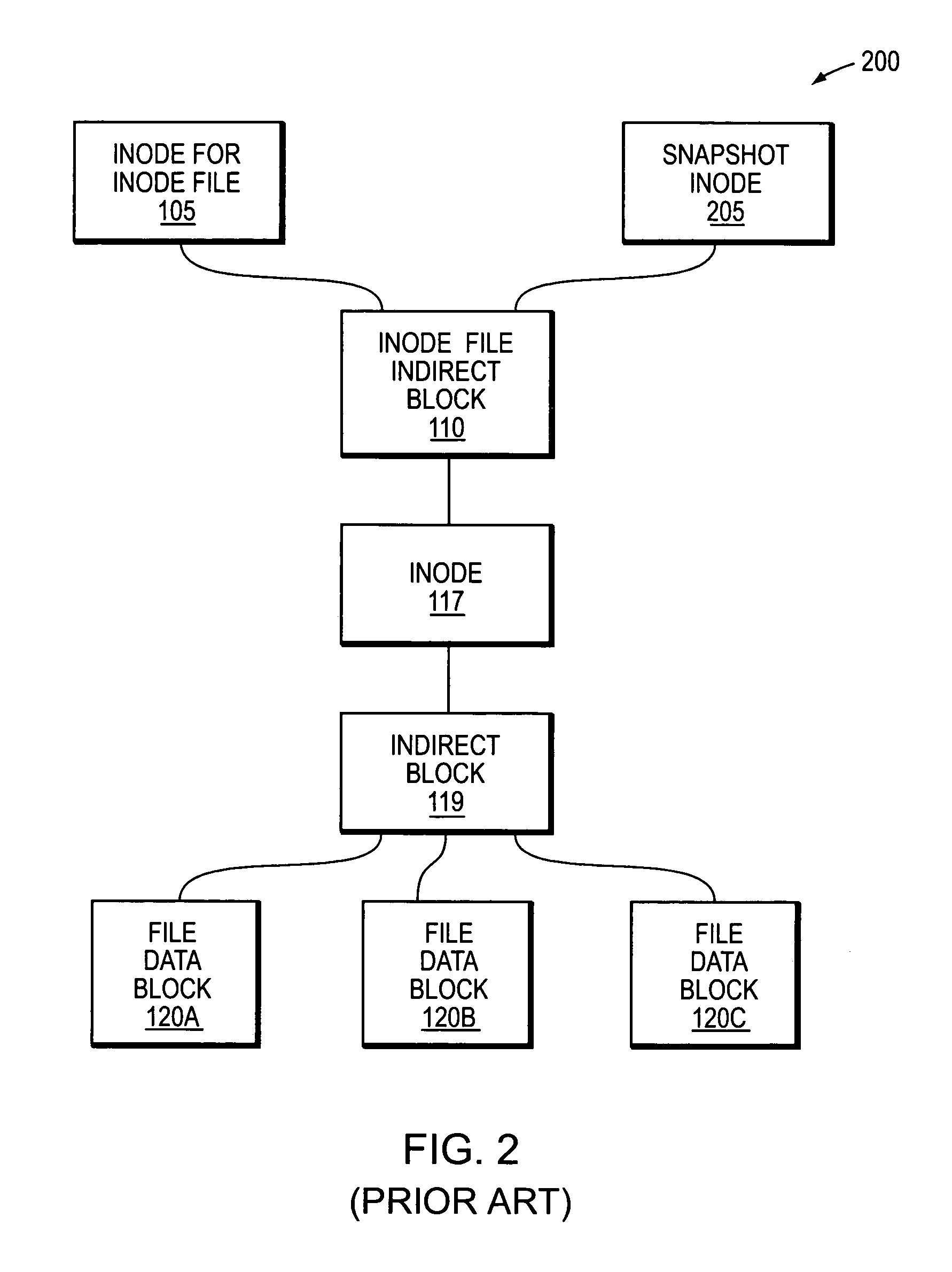
Patents
Literature
1295results about How to "Save storage resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
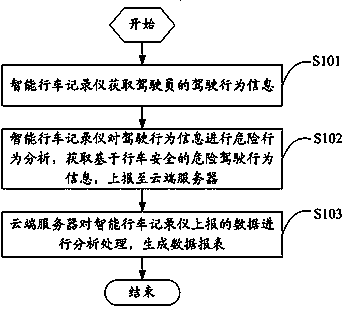
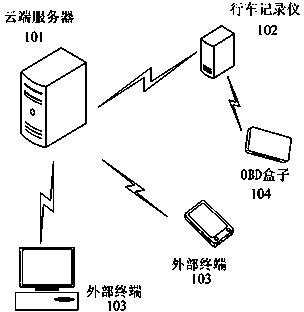
Remote monitoring method and system based on driving safety
ActiveCN104077819AImprove management flexibilitySave storage resourcesRegistering/indicating working of vehiclesDetection of traffic movementWireless transmissionMonitoring system
The invention discloses a remote monitoring method and a remote monitoring system based on driving safety. The method comprises the steps that an intelligent automobile data recorder acquires driving behavior information of a driver; the intelligent automobile data recorder performs dangerous behavior analysis on the driving behavior information to acquire dangerous driving behavior information based on the driving safety and submits the dangerous driving behavior information to a cloud server; the cloud server analyzes data on the intelligent automobile data recorder to generate a data report. According to the method, the information such as the driving behavior and an automobile is submitted to the cloud server, so that the whole driving habit of the driver can be marked or graded, monitored and proofed due to logic analysis of the cloud, and the information of the driving behavior and the automobile is effectively monitored and managed; therefore, not only is the driving safety improved, but also the automobile management flexibility is improved. Compared with the prior art, the remote monitoring method and the remote monitoring system have the advantages that only a process of a bad driving behavior which is detected by a vehicle-mounted terminal system is monitored and stored, so that a wireless transmission bandwidth and storage resources of a server are saved.
Owner:珠海大轩信息科技有限公司
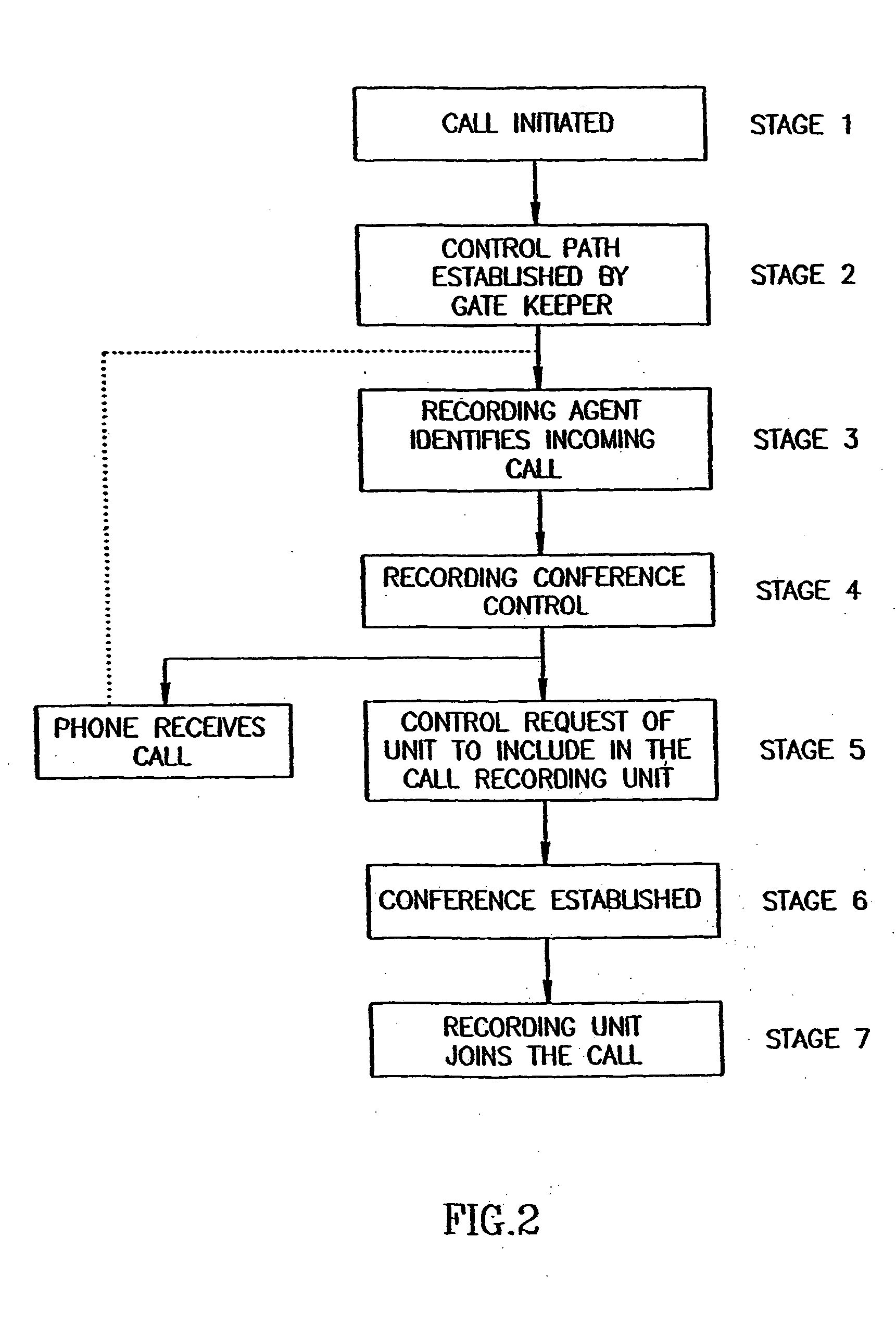
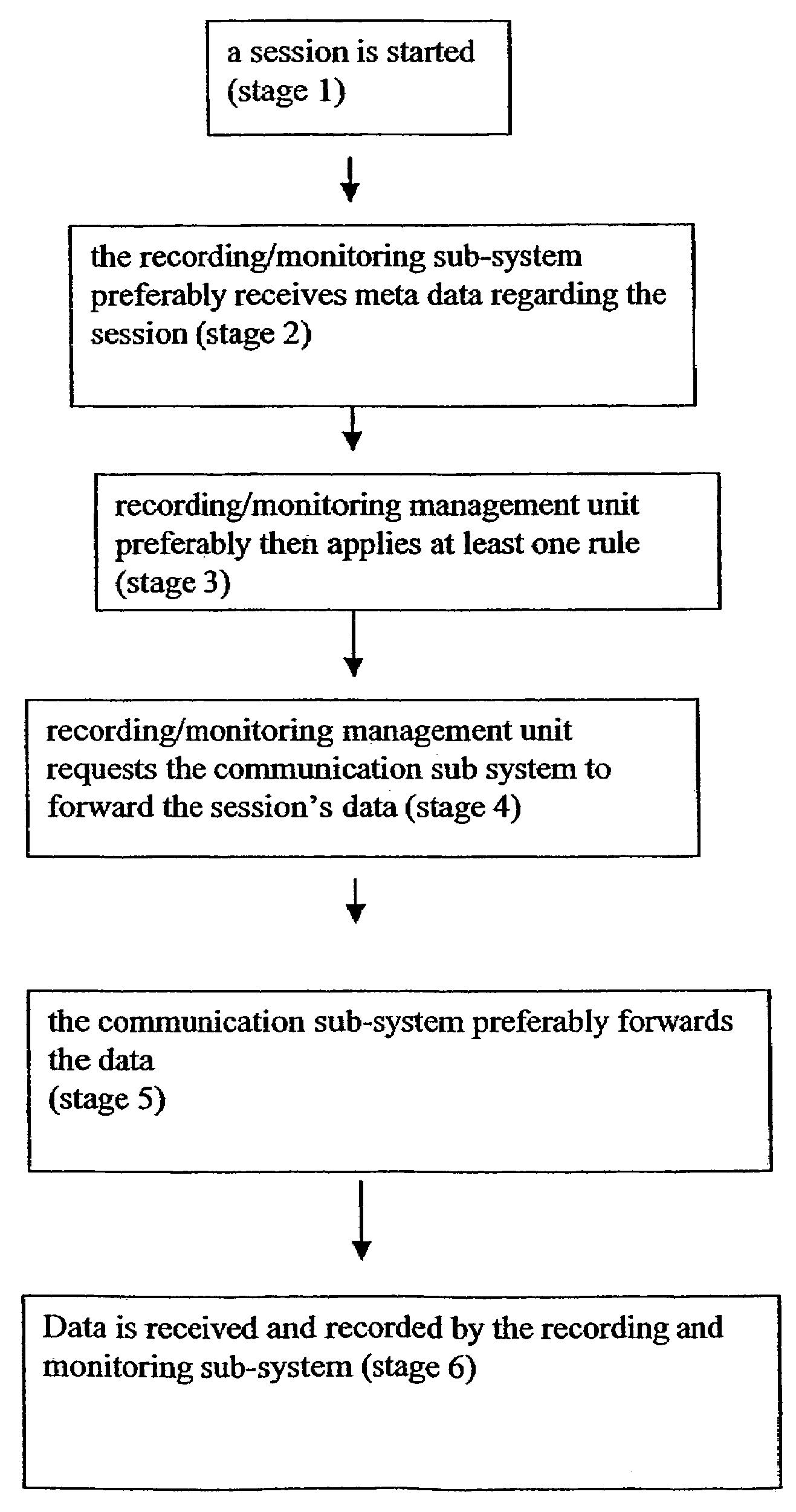
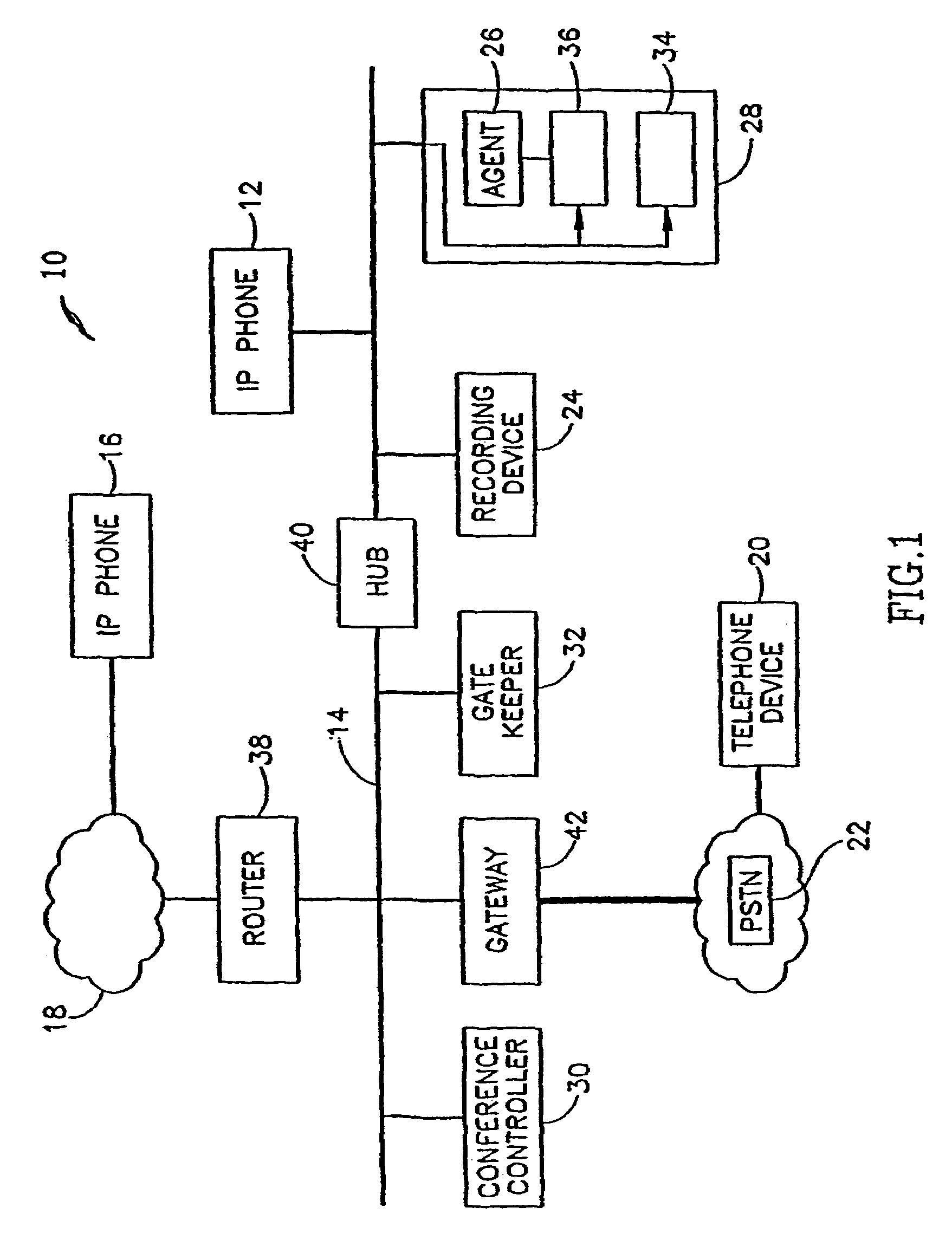
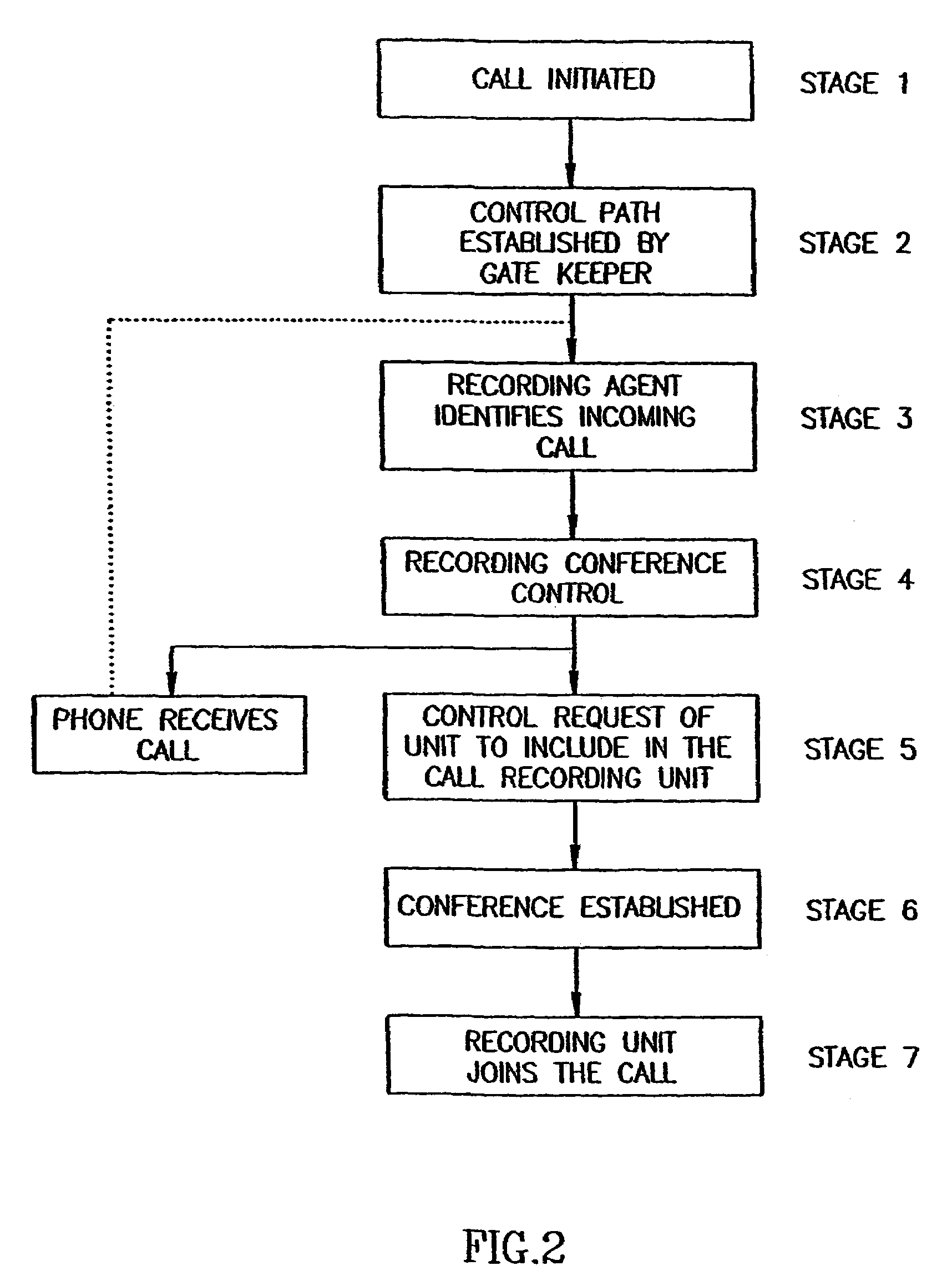
Method for forwarding and storing session packets according to preset and /or dynamic rules
ActiveUS20050018622A1Reduce network bandwidth utilizationSave storage resourcesMultiplex system selection arrangementsSpecial service provision for substationData miningPreprocessing algorithm
A system and method for recording and / or monitoring data by forwarding it, with or without analyzing or otherwise filtering the data itself. According to preferred embodiments of the present invention, the system and method are operative over IP networks. According to a preferred embodiment of the present invention, there is provided a system and method for forwarding data according to at least one characteristic of the data, such as the session's metadata for example, without analyzing or otherwise filtering the data itself. According to another preferred embodiment of the present invention, before the data is forwarded to the recording device, pre-processing algorithms are performed according to a system preset or according to one or more rules.
Owner:NICE LTD
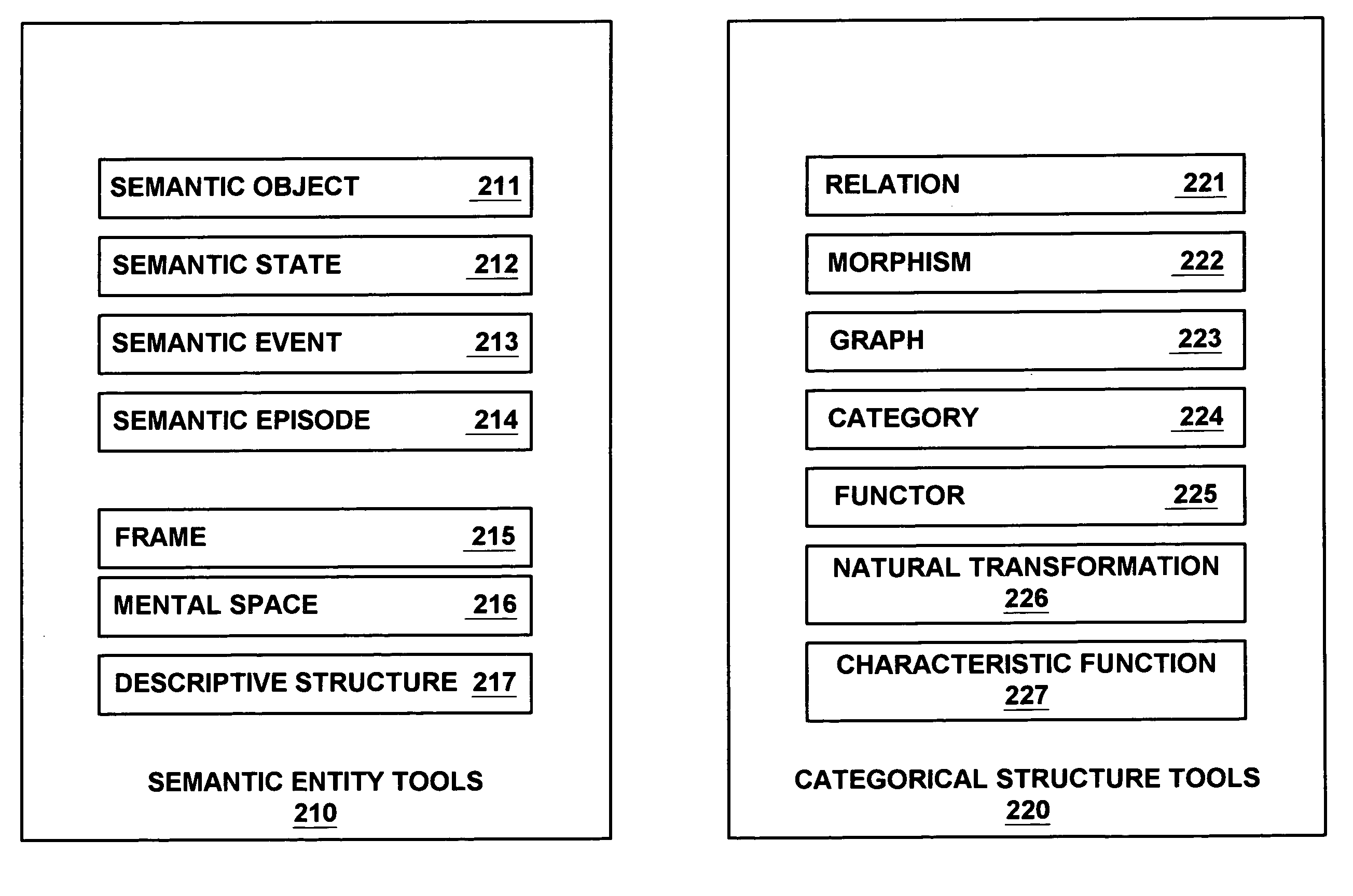
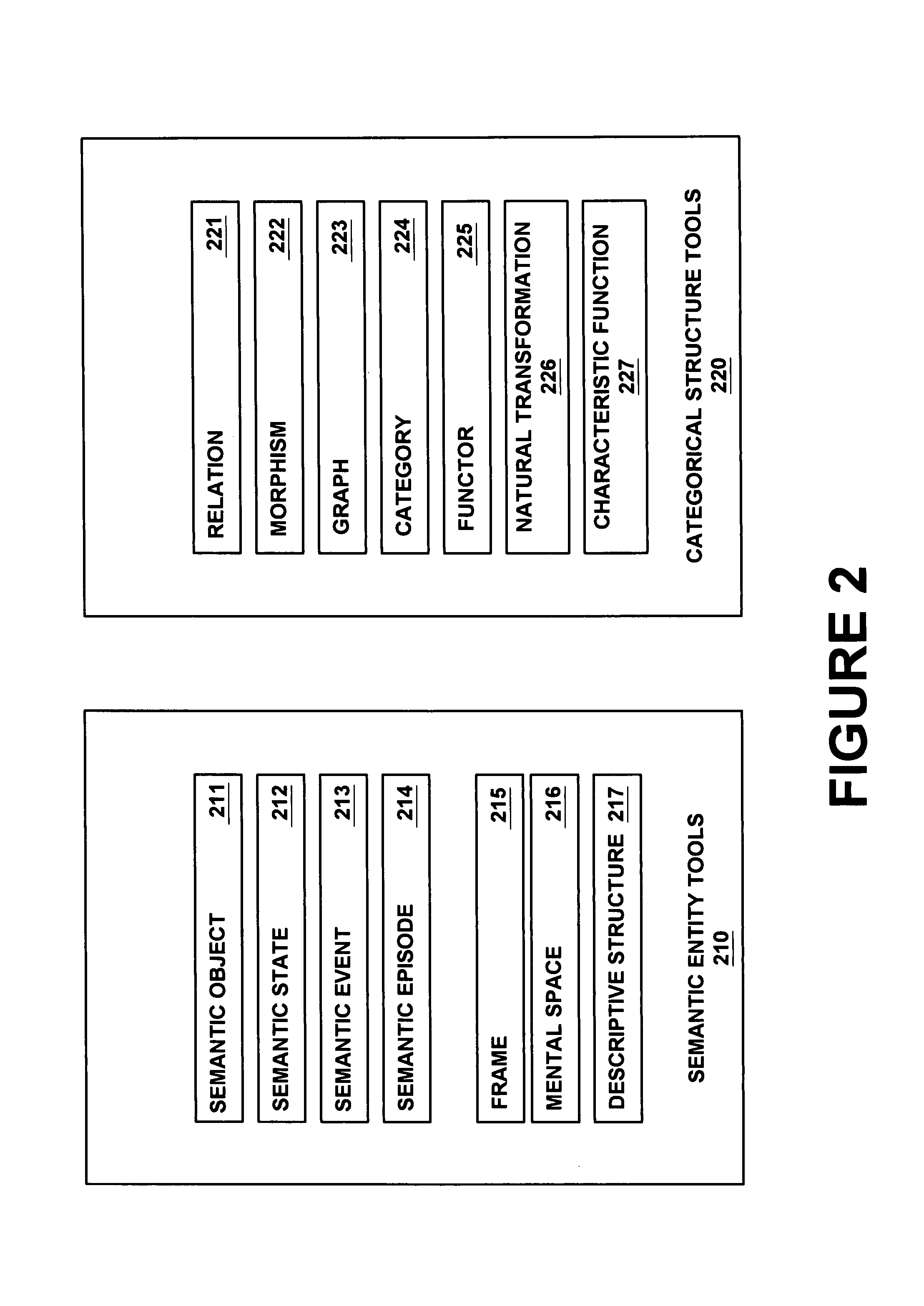
Application of category theory and cognitive science to design of semantic descriptions for content data
InactiveUS7319951B2Easy to createFacilitates navigation and browsingMultimedia data retrievalMultiple digital computer combinationsDescription schemeData semantics
Owner:SONY ELECTRONICS INC
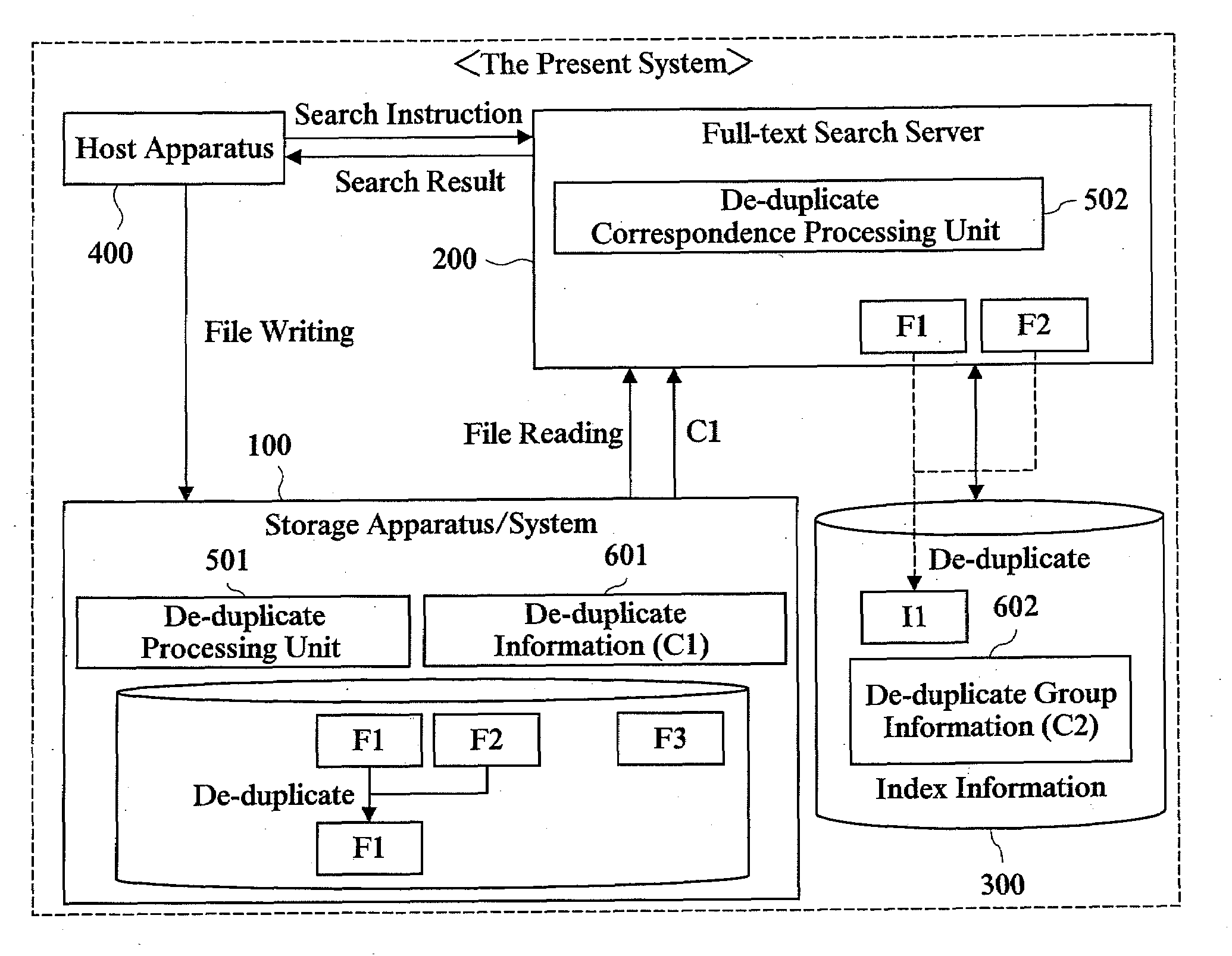
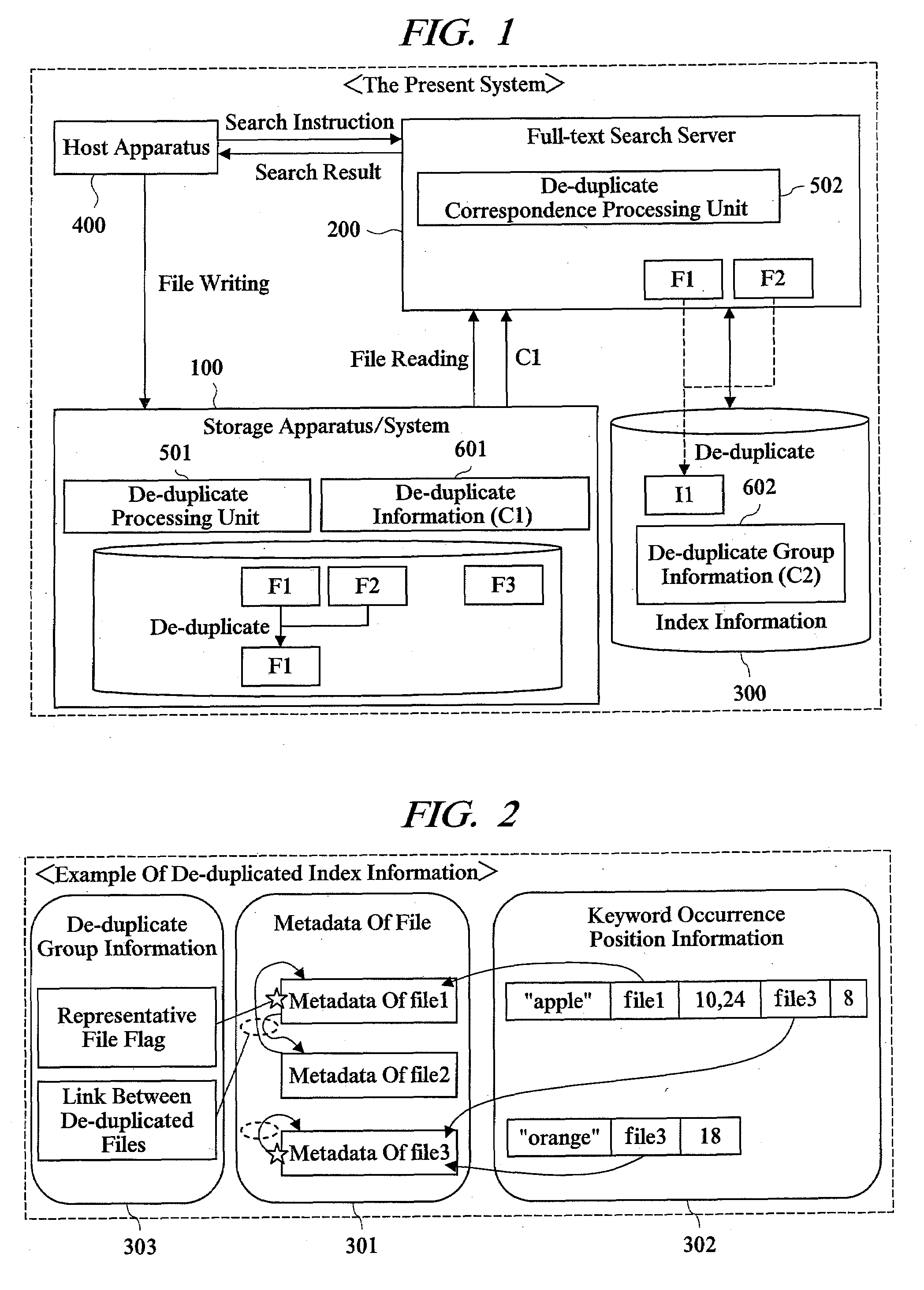
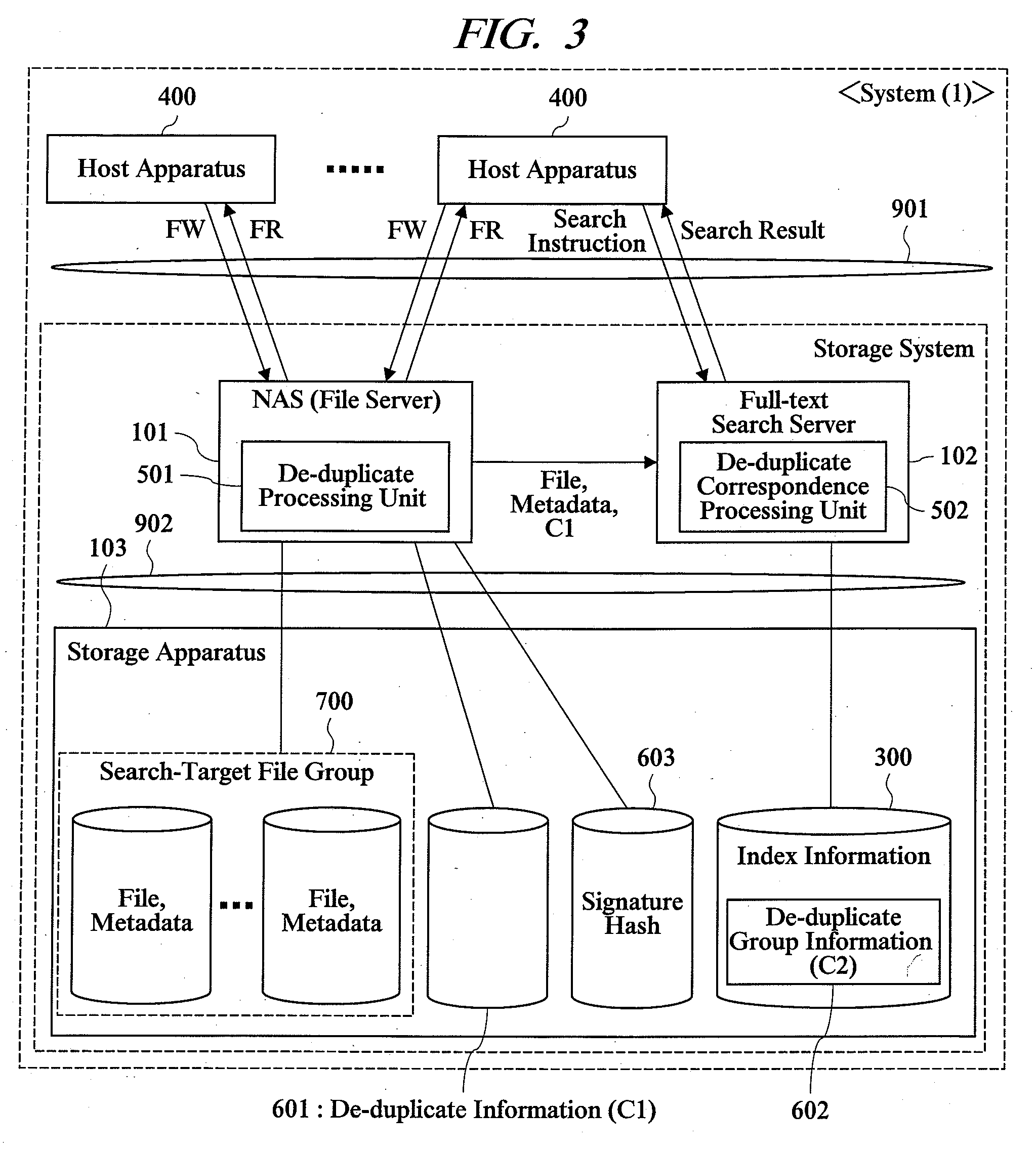
Storage system
InactiveUS20080155192A1Reduce storageReduce the amount requiredDigital data information retrievalDigital data processing detailsFull text searchDatabase
The present invention relates to a storage system including a de-duplicate function and a full-text search function or the like, and reduces an amount of index information about full-test search to save storage resource. In this system, a storage apparatus includes a processing unit for de-duplicating a plurality of files having the same content regarding a file group of data inputted / outputted through a host apparatus. A full-text search processing server performs a full-text search processing to the file group and includes a processing unit for causing the full-text search processing to correspond to de-duplicate. An index information creation processing performed to a plurality of target files having the same content by the full-text search processing unit is inhibited according to a status of de-duplicate to the file group by the processing unit. Thereby, the amount of index information can be reduced.
Owner:HITACHI LTD
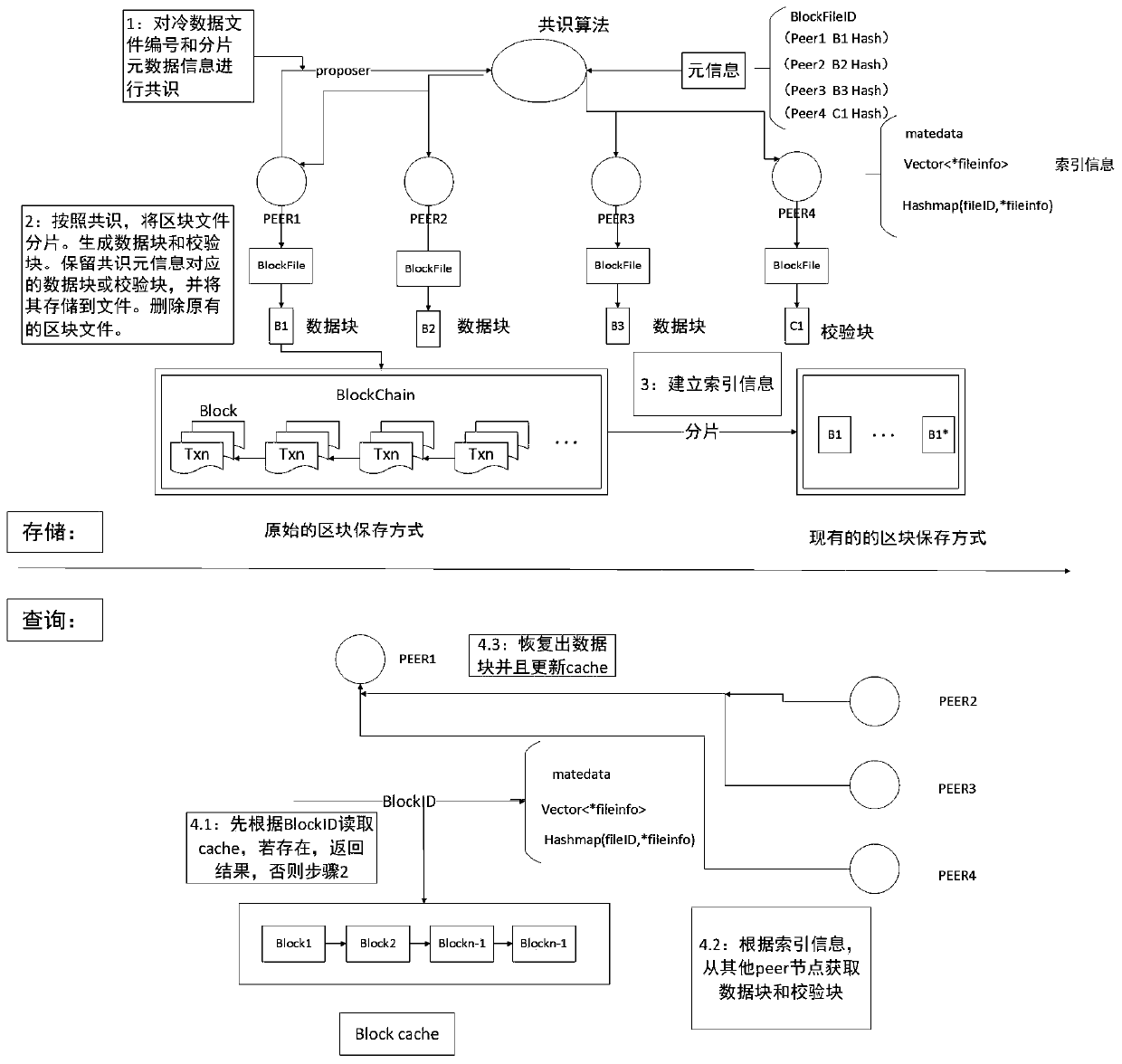
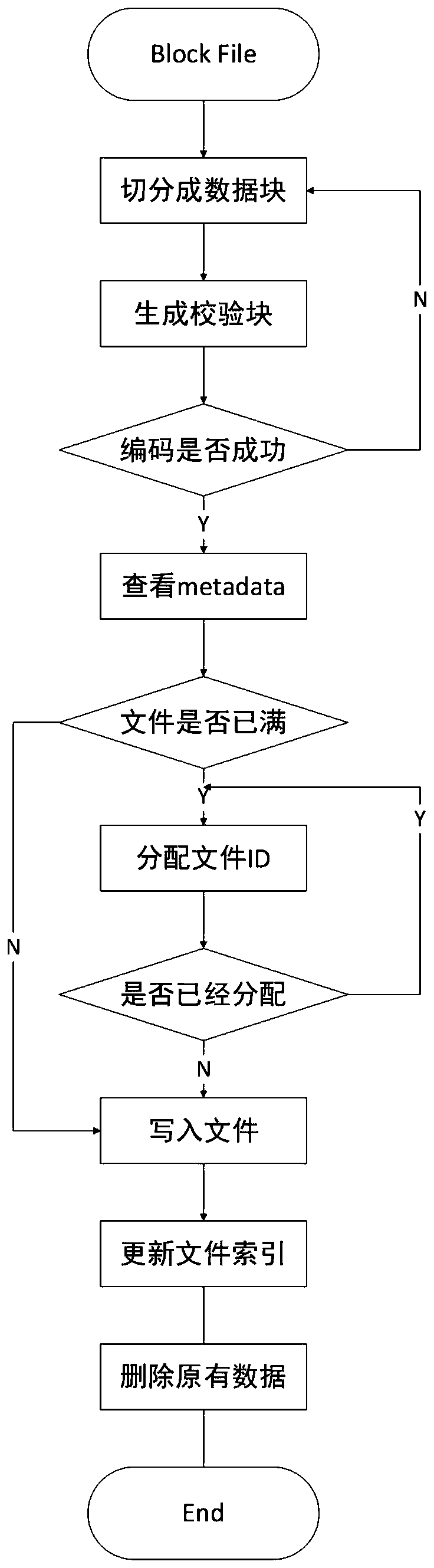
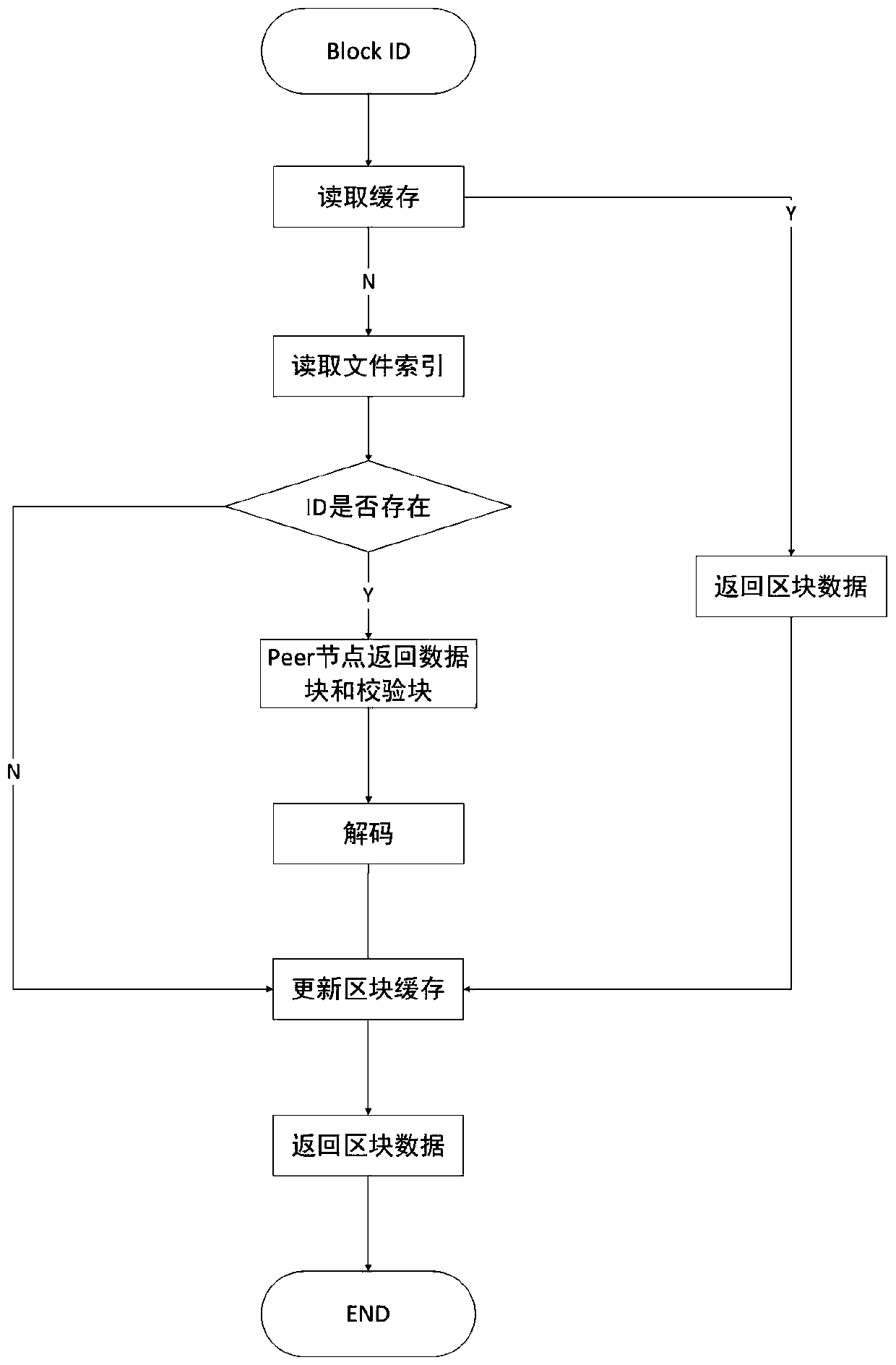
Block chain fragment storage and query method based on erasure codes
ActiveCN109871366AQuick searchEfficient queryFile access structuresSpecial data processing applicationsByzantine fault toleranceErasure code
The invention discloses a block chain fragment storage and query method based on erasure codes. When the block storage reaches a certain threshold, a block is sliced and stored. The method comprises the following steps that firstly, the meta-information of the block file fragments is consented, after the consensus is achieved, the erasure codes are utilized to fragment the block files within thethreshold value into the data blocks and the check blocks, and each node stores one part of the data blocks and the check blocks, so that the storage cost is reduced, and meanwhile, the data fault tolerance under the Bayer fault tolerance is also realized. Besides, when the block files are fragmented, the corresponding index is established, and the corresponding data block or check block can be queried from each node by utilizing the index, so that the block data can be queried efficiently under the condition that the storage space is saved.
Owner:EAST CHINA NORMAL UNIV
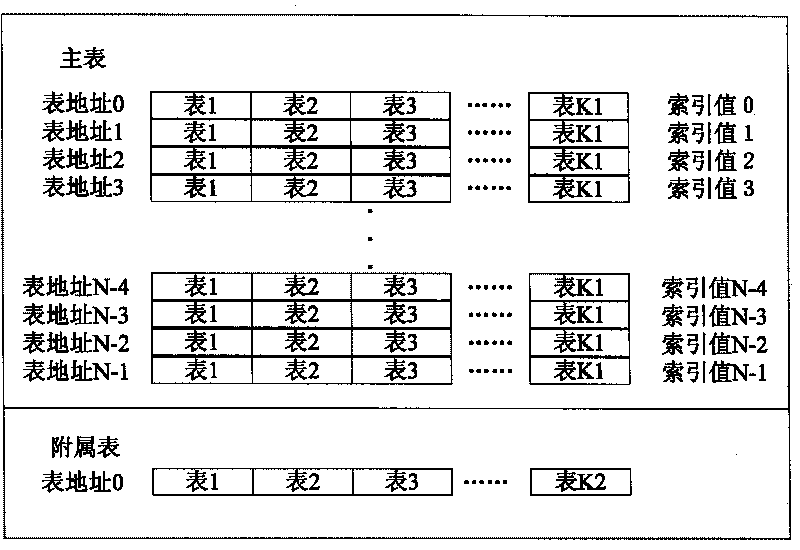
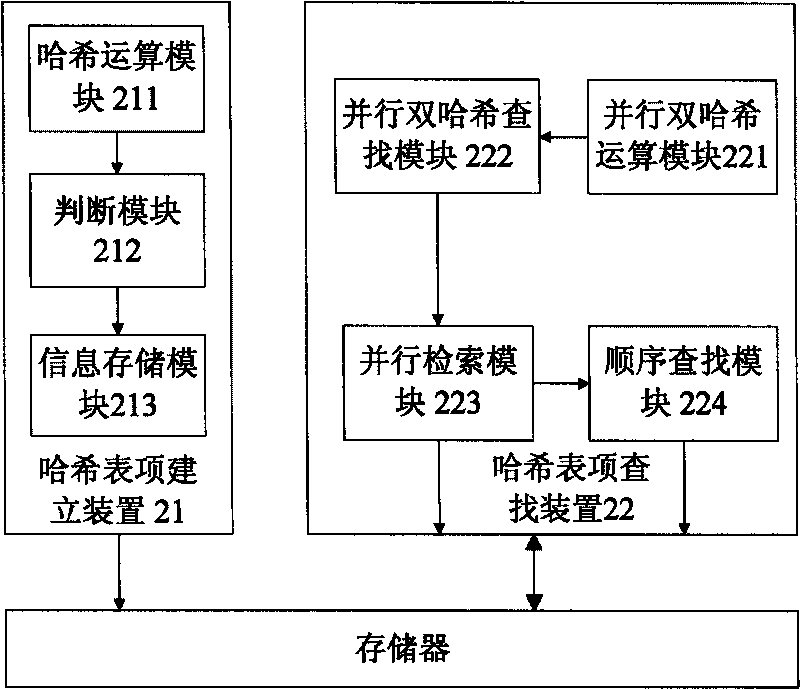
Method and device for Hash lookup table
ActiveCN101692651AReduce incidenceIncrease profitDigital data information retrievalData switching networksLookup tableData mining
The invention discloses a method and a device for a Hash lookup table. When storing a table, the method comprises the following steps of: planning a main table storage space which is divided into a plurality of address spaces; establishing a plurality of Hash functions and performing Hash calculation on a keyword of a piece of information to be stored by using the plurality of Hash functions to obtain a plurality of index values; and comparing the empty / full degrees of the address spaces corresponding to the plurality of index values and storing the information to be stored in the address space with the least stored information. When looking up the table, the method comprises the following steps of: using the plurality of different established Hash functions to perform Hash calculation on the keyword to be looked up so as to obtain a plurality of index values and performing match search on the keyword of a table entry of an address space position corresponding to the plurality of index values and the key word to be looked up. The method and the device for the Hash lookup table can save storage resource for the Hash table and improve the efficiency of Hash lookup.
Owner:ZTE CORP
Data cross-platform migration method and device
InactiveCN103440273AEasy to expandSave storage resourcesSpecial data processing applicationsData migrationSource data
The invention discloses a data cross-platform migration method and a data cross-platform migration device, which are used for data migration between different database systems. The device comprises a source data information module, a target data information module, a conversion module, an SQL (Structured Query Language) Engine, a data packet encapsulation, transmission and analysis module and an SQL statement execution module. The information on a source data platform and the information on a target data platform are described through the source data information module and the target data information module, a table is acquired from the source database to generate a Table object, the Table object is subjected to format conversion by the conversion module according to an XML (Extensible Markup Language) file for describing the mapping relation of fields between the databases, the converted information is constructed into an SQL statement by the SQL Engine, the SQL statement is encapsulated and transmitted to the platform where the target database is positioned, and the SQL statement is executed on the target platform to finish data migration. The method and the device realize smooth and lossless migration of the data between different databases of a heterogeneous platform.
Owner:BEIHANG UNIV
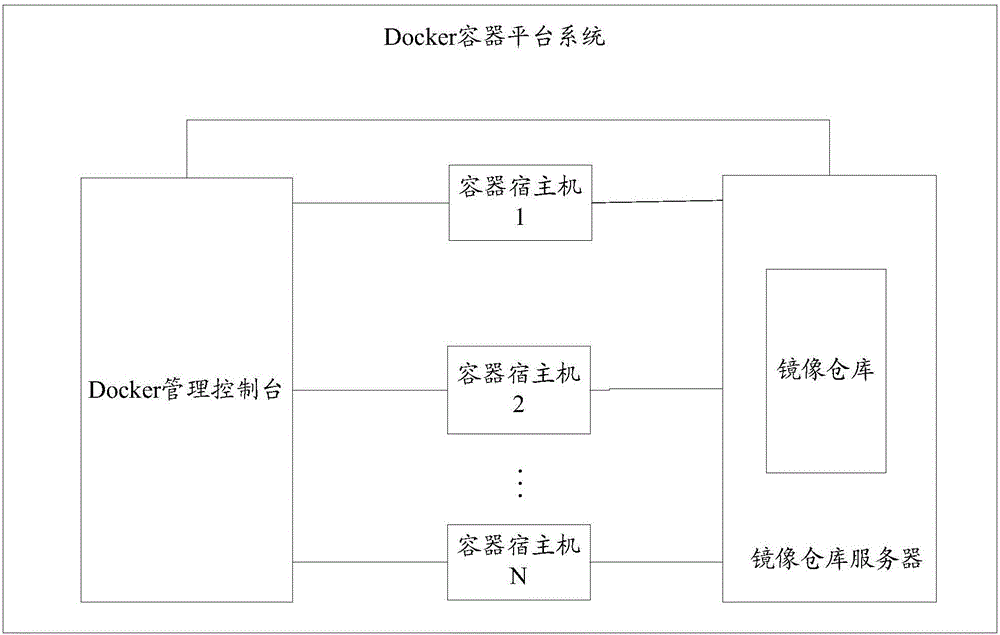
Docker container building method and Docker management console
ActiveCN106227579AReduce data volumeReduce in quantitySoftware simulation/interpretation/emulationComputer graphics (images)Computer science
The invention discloses a Docker container building method and a Docker management console. By adding a layer combining instruction into an image building script, combining of multiple image layers can be realized according to the layer combining instruction in the process of Docker image building, so that number of Docker image levels and data size of an image file are reduced, working efficiency is improved, and storage resources are saved. The method includes: acquiring a related application file and an image building script of an application, wherein the image building script contains a layer combining instruction; performing image compiling on the related application file according to the image building script to acquire a Docker image layer; if a current instruction is the layer combining instruction, acquiring an image file of a current image layer in the Docker image layer, and acquiring an image file of a target image layer corresponding to a target image layer identity; acquiring a difference file according to the image file of the current image layer and the image file of the target image layer, and building a layer-combined image layer according to the difference file; submitting the layer-combined image layer to an image repository.
Owner:深圳市中润四方信息技术有限公司
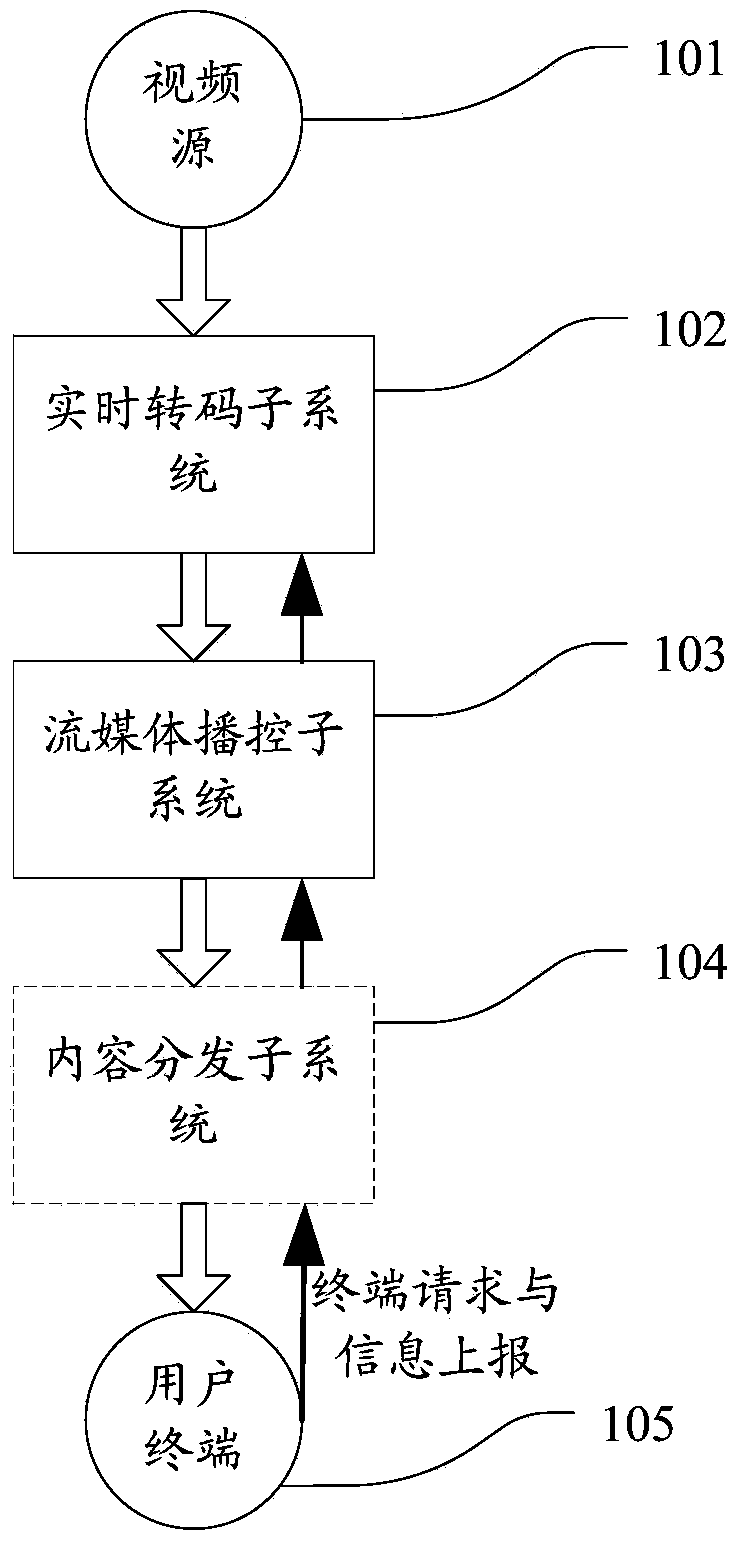
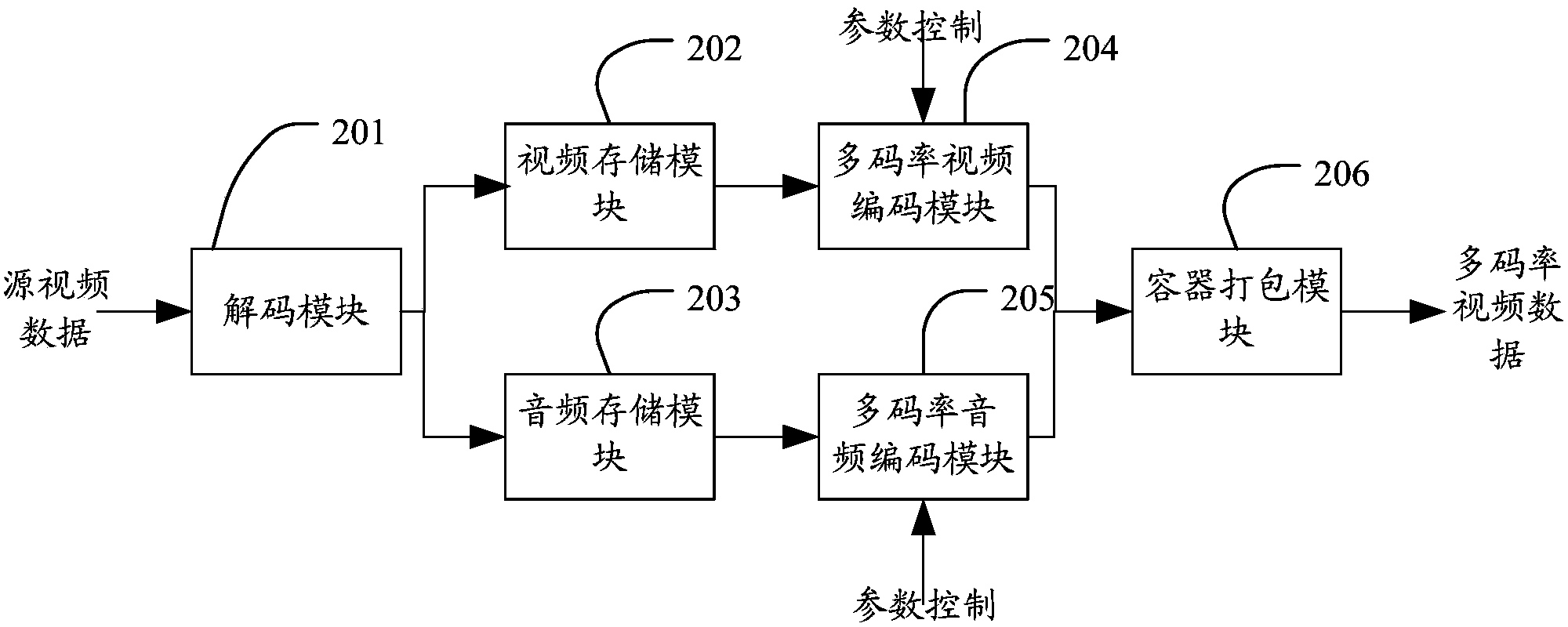
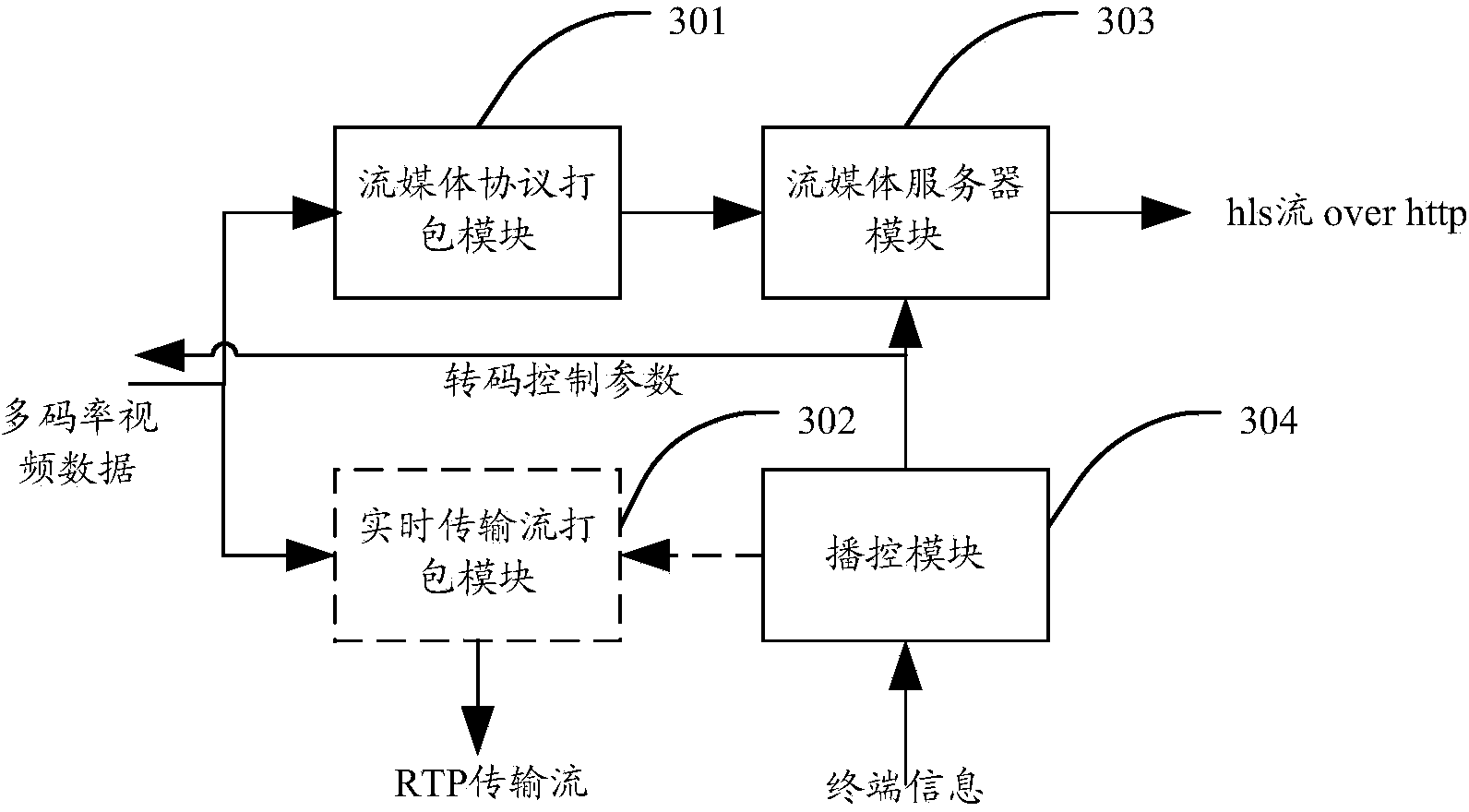
System and method for required real-time transcoding and self-adaptive code rate stream media playing
ActiveCN104349178ASave computing resources and network resourcesSave storage resourcesSelective content distributionSelf adaptiveContent distribution
The invention relates to a system and a method for required real-time transcoding and self-adaptive code rate stream media playing. The system comprises a real-time transcoding subsystem, a stream media playing subsystem, a content distribution subsystem and a user terminal module, wherein the real-time transcoding subsystem is used for transcoding the original videos of a video source into video encoding data which is suitable for a user terminal to play, the stream media playing subsystem is used for packaging the video encoding data outputted by the real-time transcoding subsystem into video steams which are suitable for the stream media to transmit, and providing the stream media service for the user terminal, and the user terminal module is used for sending a request to the real-time transcoding subsystem or the stream media playing subsystem, and dynamically switching and transcoding in real time according to the network state information, so as to obtain the video streams with different code rates for playing. By adopting the structure, the system and the method for the required real-time transcoding and the self-adaptive code rate stream media playing have the advantages that the required real-time transcoding of the stream media is realized, the playing code rate is dynamically selected according to the change of the band width of the terminal network, different user terminals can be flexibly matched, and the application range is wider.
Owner:CERTUS NETWORK TECHNANJING
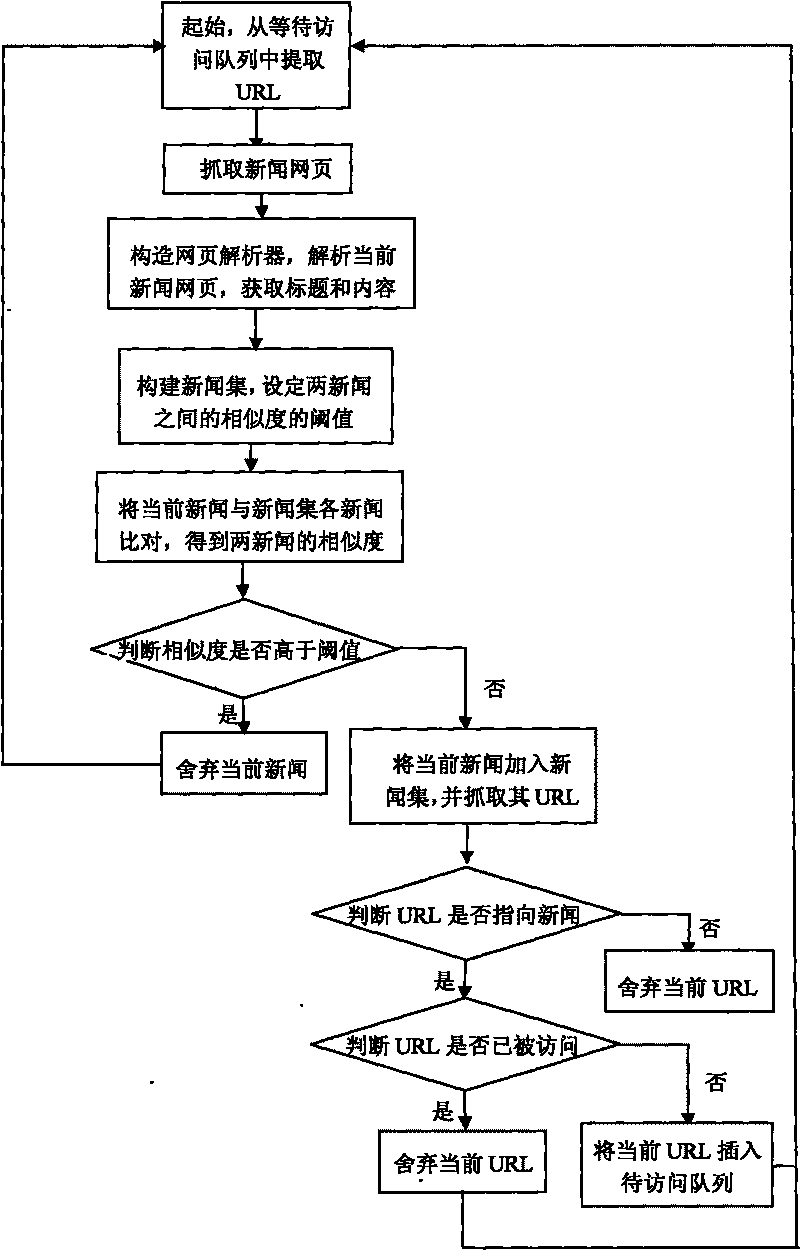
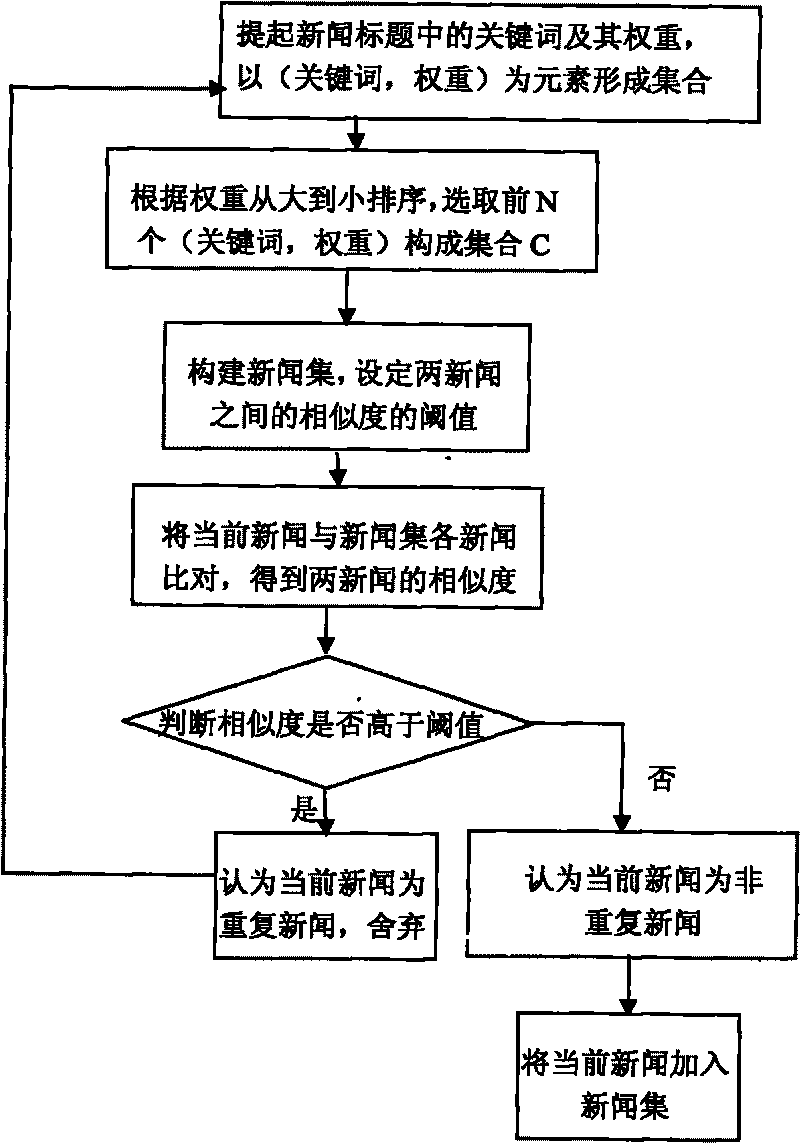
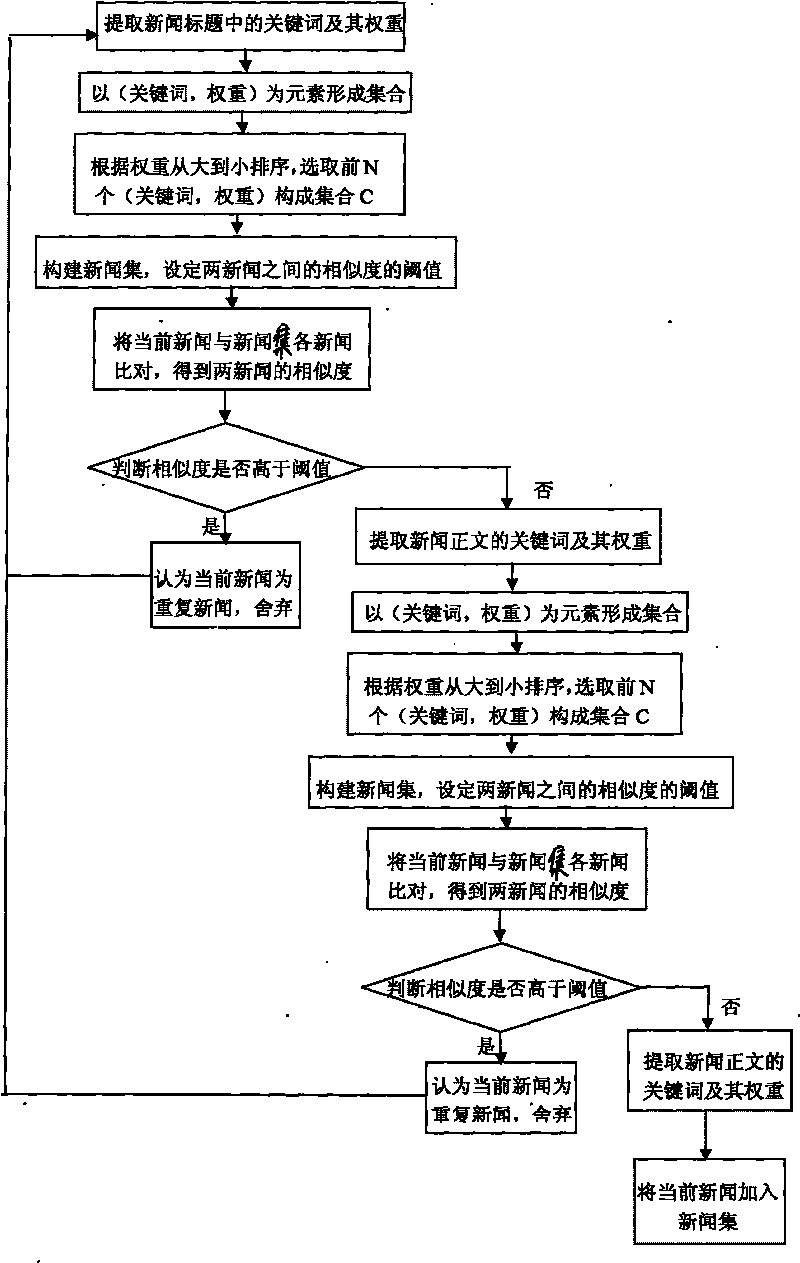
Method for constructing webpage crawler based on repeated removal of news
ActiveCN101694658AAvoid downloadingReduce consumptionSpecial data processing applicationsUniform resource locatorWeb page
The invention relates to a method for constructing a webpage crawler based on the repeated removal of news, which comprises the following steps: constructing an analyzer for analyzing news webpages; constructing a news set; setting a threshold value of the similarity among the webpages; comparing the currently grabbed news webpage with the news set and judging whether the similarity is higher than the threshold value or not; if the similarity is lower than the threshold value, adding the current webpage into the news set; if the similarity is higher than the threshold value, discarding the news and grabbing the next webpage; grabbing a URL of the current webpage and judging whether the URL points at the news webpage or not, if so, judging whether the URL is accessed or not; otherwise, discarding; if the URL is accessed, discarding the URL; if the URL is not accessed, storing the URL into a queue to be accessed; sequentially extracting the URL from the queue to be accessed to access; and repeatedly executing the steps. The invention has the advantages of high algorithm efficiency, less resource waste and convenient data maintenance and prevents from grabbing the webpage with repeated content.
Owner:ZHEJIANG UNIV
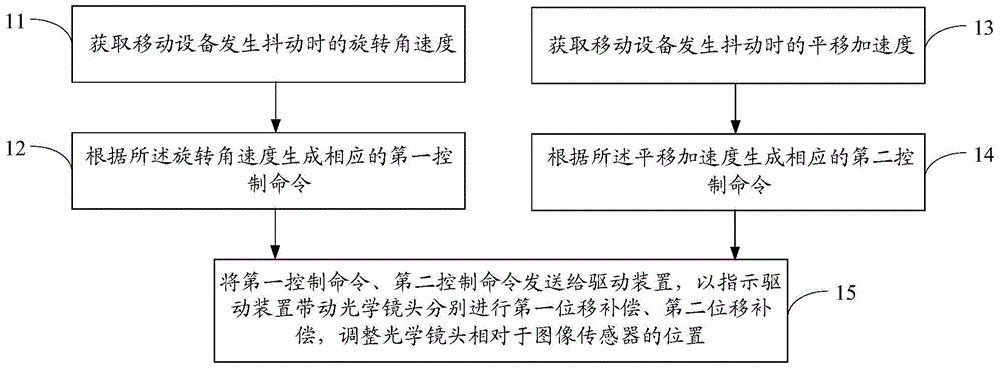
Method and apparatus for controlling optical image stabilization
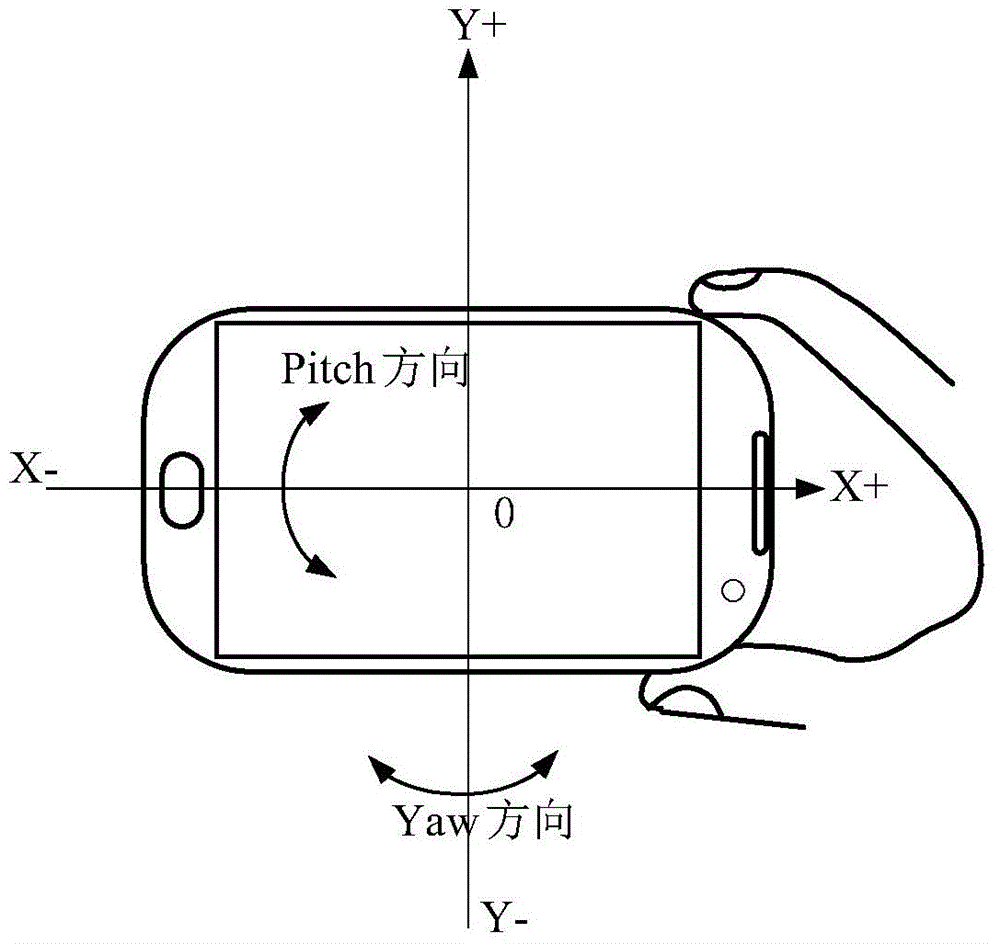
ActiveCN104967785AImprove performanceAvoid blurTelevision system detailsPrintersHorizontal axisAngular velocity
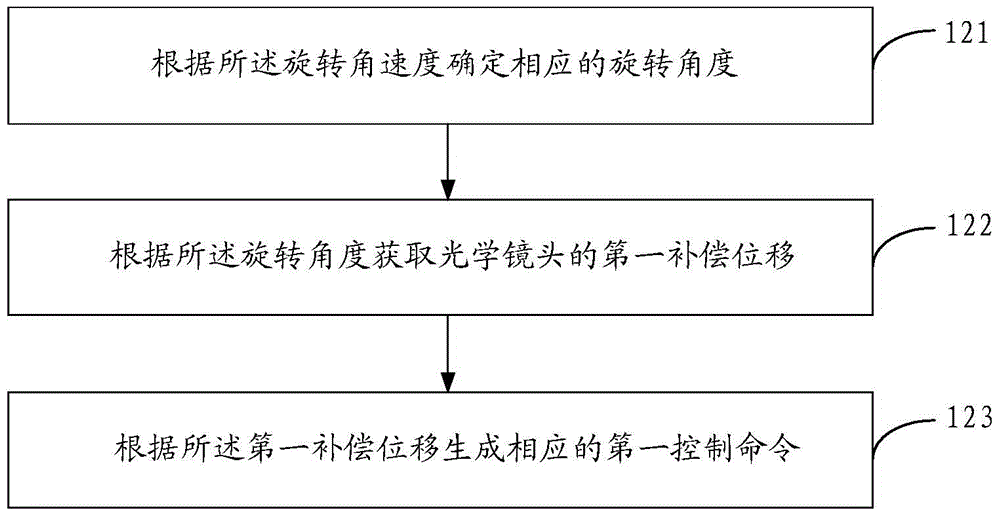
The invention provides a method and apparatus for controlling optical image stabilization, and an image acquisition device of a mobile device. The method includes the following steps that: a rotational angular velocity when the mobile device jitters is acquired; a corresponding first control command is generated according to the rotational angular velocity; translational acceleration when the mobile device jitters is acquired; a second control command is generated according to the translational acceleration; and the first control command and the second control command are transmitted to a driving device so as to command the driving device to drive an optical lens to move, so that first displacement compensation and second displacement compensation can be performed. According to the method for controlling optical image stabilization provided by the invention, 4-axis optical image stabilization (OIS) is adopted, and effective light compensation can be performed on rotation and translation jigger in horizontal-axis and vertical-axis directions quickly and accurately in the close shot photographing process of the mobile device.
Owner:XIAOMI INC
Construction method of multi-code rate compatible LDPC code and its decoder
InactiveCN101047387AChange the maximum read and write depthSave storage resourcesError correction/detection using multiple parity bitsCode conversionH matrixTheoretical computer science
A method for structuring multi-code rate compatible LDPC code includes carrying out sequencing from high to low as per code rate, distributing dimensionality in following to constraint conditions, using block-PEG algorithm to structure out H matrix of LDPC code with highest code rate, utilizing said matrix as reference to restructure H matrix with different code rate as per code rate order from high to low, making said restructuring obey on constraint conditions and setting zero element position in H matrix of high code rate LDPC code still to be zero element in H matrix of low code rate.
Owner:PEKING UNIV
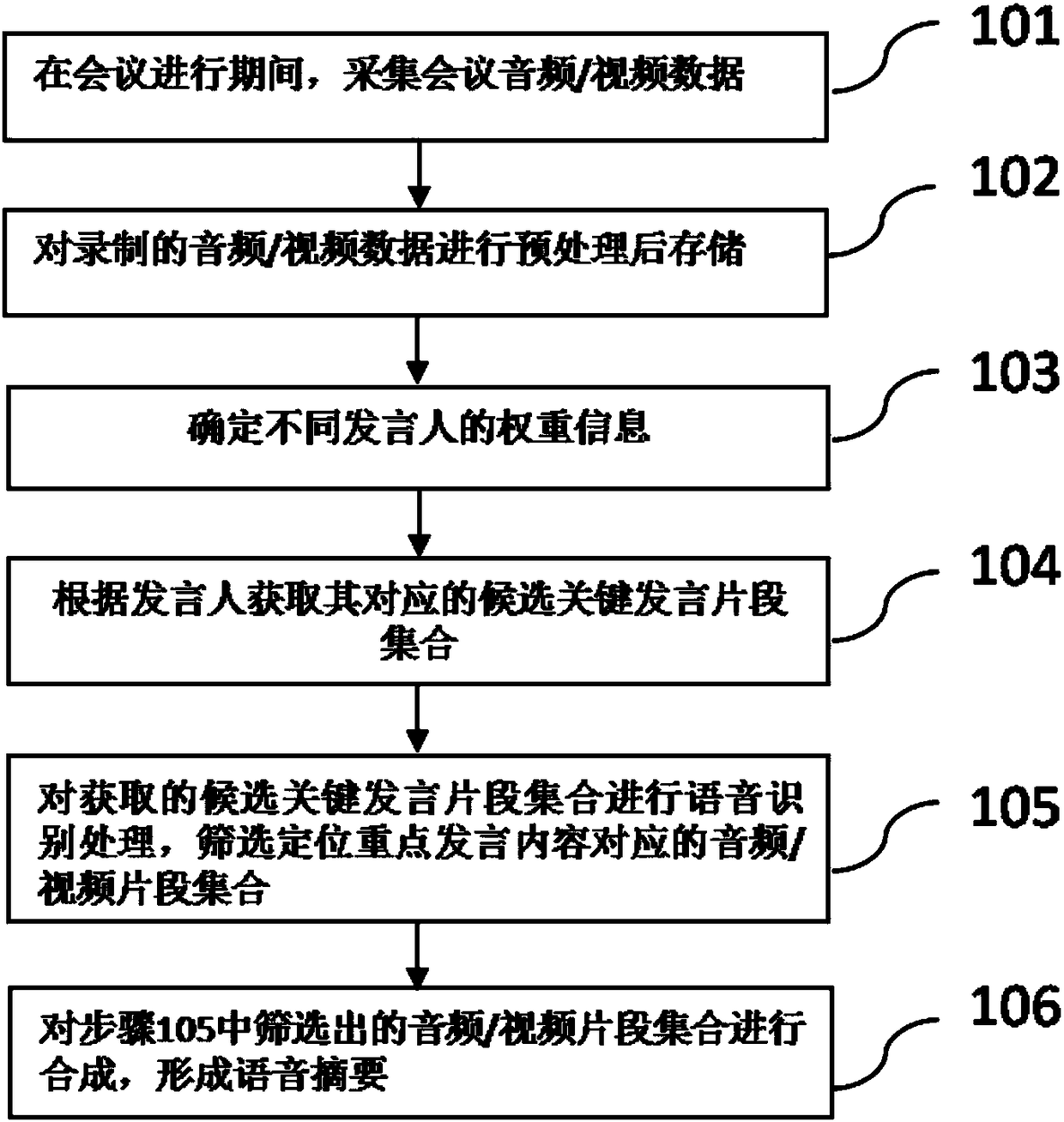
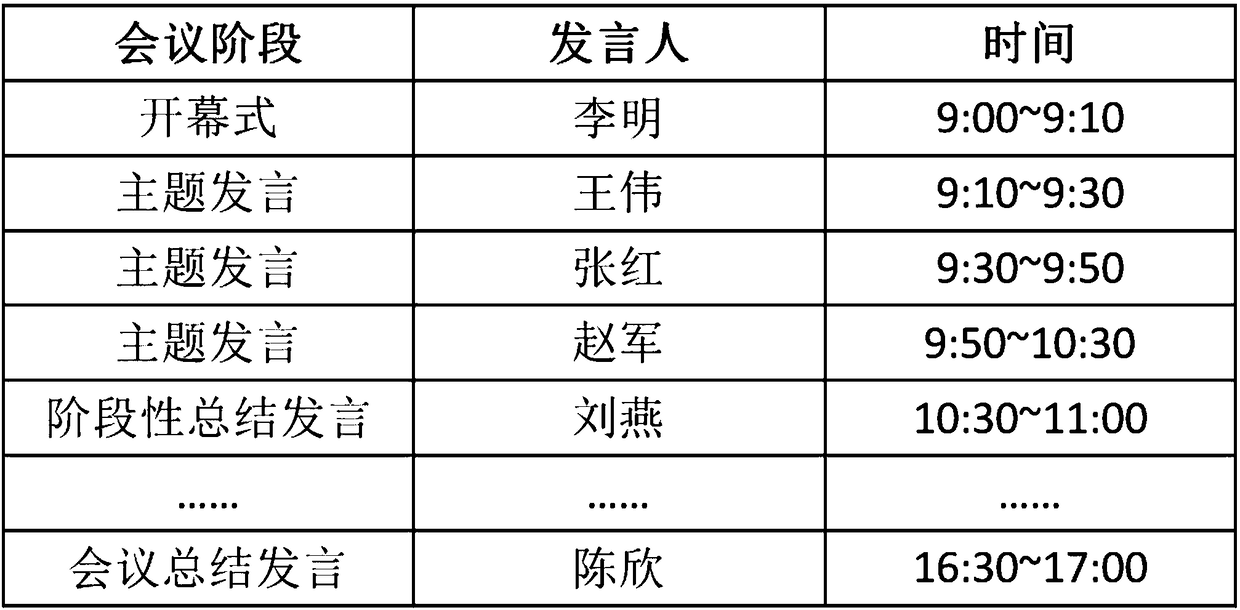
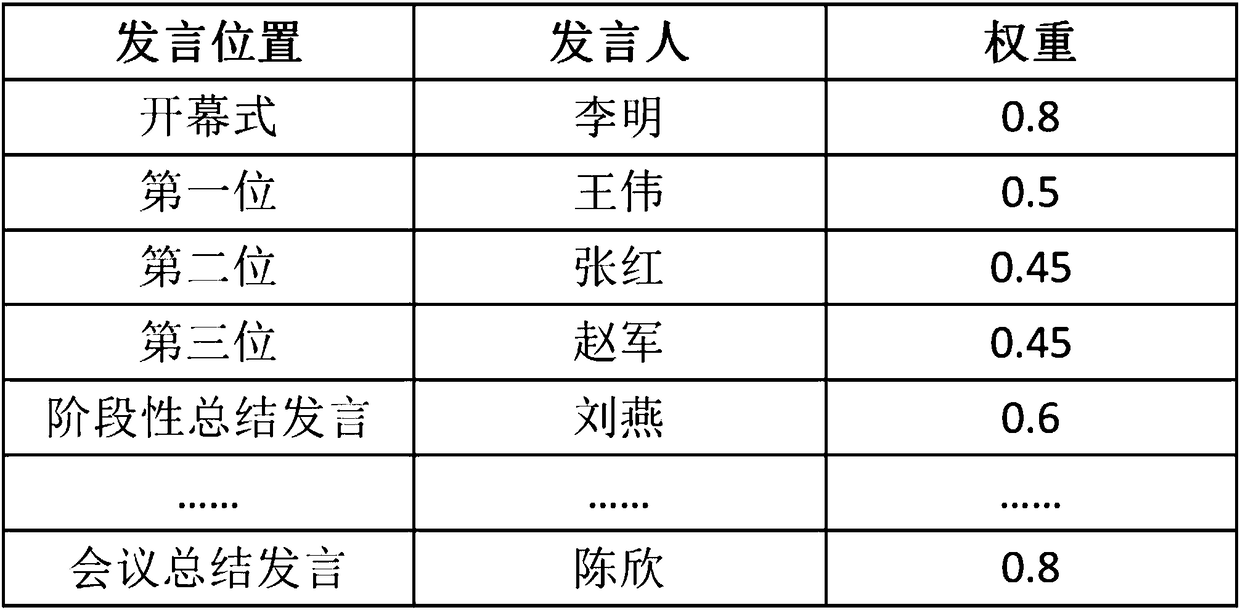
Voice abstract forming method and voice abstract forming system for conference
ActiveCN108305632AImprove effectivenessReduce recordsTelevision system detailsTelevision conference systemsWeight coefficientSpeech sound
The invention discloses a voice abstract forming method and a voice abstract forming system for a conference, and relates to the field of voice recognition. According to the invention, the speaking position, the identity information, the personnel data and other information of a speaker in a conference are analyzed, and then the weight coefficient of the speaker is determined. As a result, candidate key speaking segments corresponding to different speakers can be obtained by using different preset strategies according to the weight coefficients of speakers. Furthermore, according to the characteristics of the speaking content, for example, the large-probability interval of the important content of the utterance on a speaking time axis, key transitional words and key connection words in theimportant content of statements, and the like, a set of candidate key speaking segments is intercepted. The intercepted set of candidate key speaking segments is processed and then a set of audio / video segments for forming a voice abstract is obtained. As a result, more content is extracted from important statements, while less content is extracted from non-important statements. The content of afinally formed abstract is more reasonable. The more effective help is provided for users.
Owner:SHENZHEN EAGLESOUL TECH CO LTD
Point-variable assembly line FFT processor
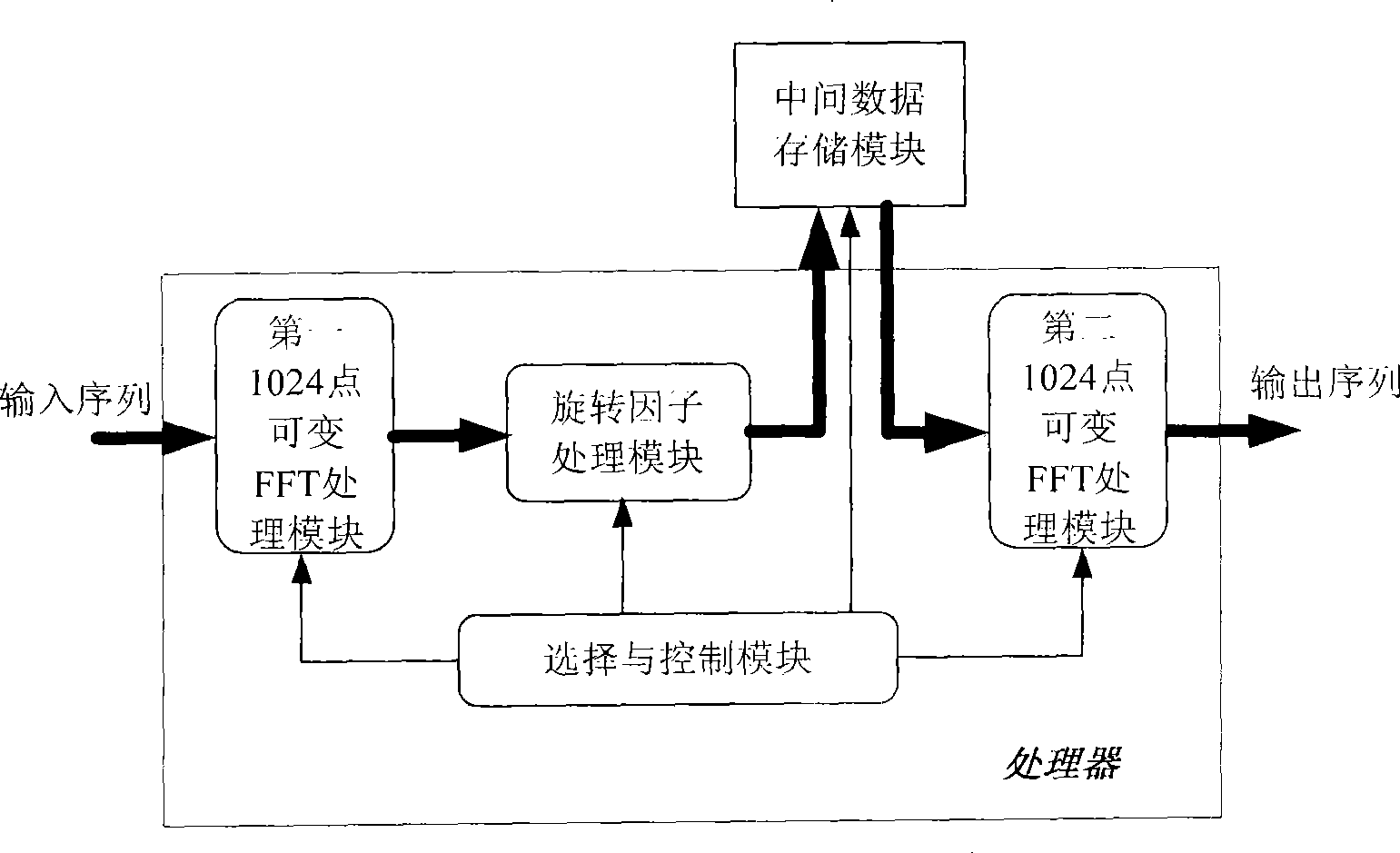
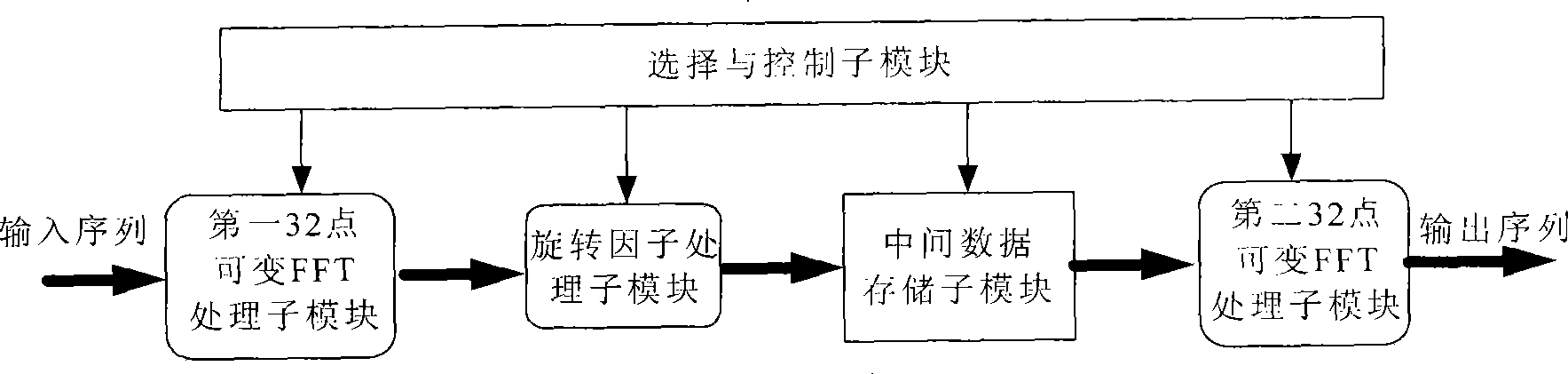
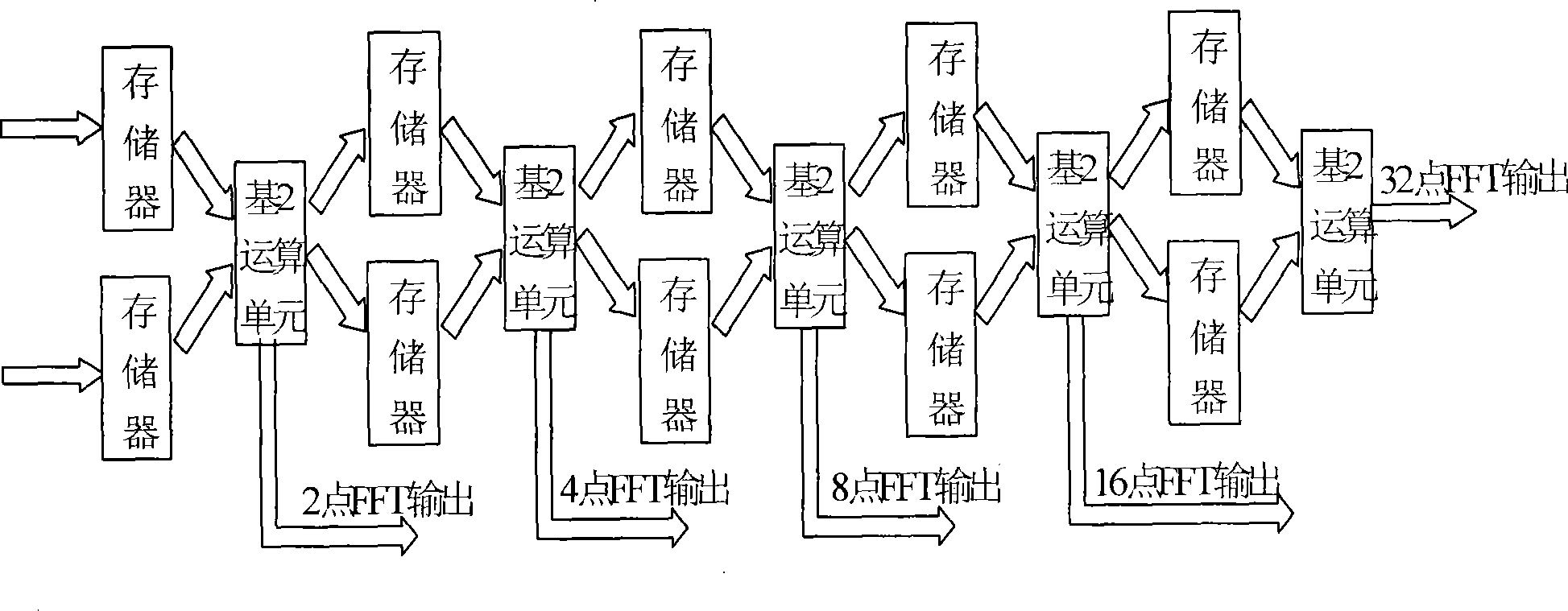
InactiveCN101504638AReal-time processingUpdate output data in real timeComplex mathematical operationsFft processorParallel computing
The invention provides a pipeline FFT processor variable in the number of points, which comprises a first 1024-point variable FFT processing module, a twiddle-factor processing module, a second 1024-point variable FFT processing module and a selection-control module, wherein the four modules and an intermediate data storage module outside the processor jointly complete FFT two-dimensional processing large in the number of points; each 1024-point variable FFT processing module comprises a first 32-point variable FFT processing sub-module, a second 32-point variable FFT processing sub-module, a twiddle-factor processing sub-module, an intermediate data storage sub-module and a selection-control sub-module; variable-point FFT operation is implemented through the 32-point variable FFT processing sub-modules; the twiddle-factor processing module generates and multiplies intermediate twiddle factors by the result of FFT operation; and the selection-control module realizes control over a whole chip. The processor is suitable to be realized in single-chip FPGA or ASIC, and can simultaneously obtain high speed, low power consumption, high precision and other characteristics.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Hierarchical memory system and logical volume management method thereof
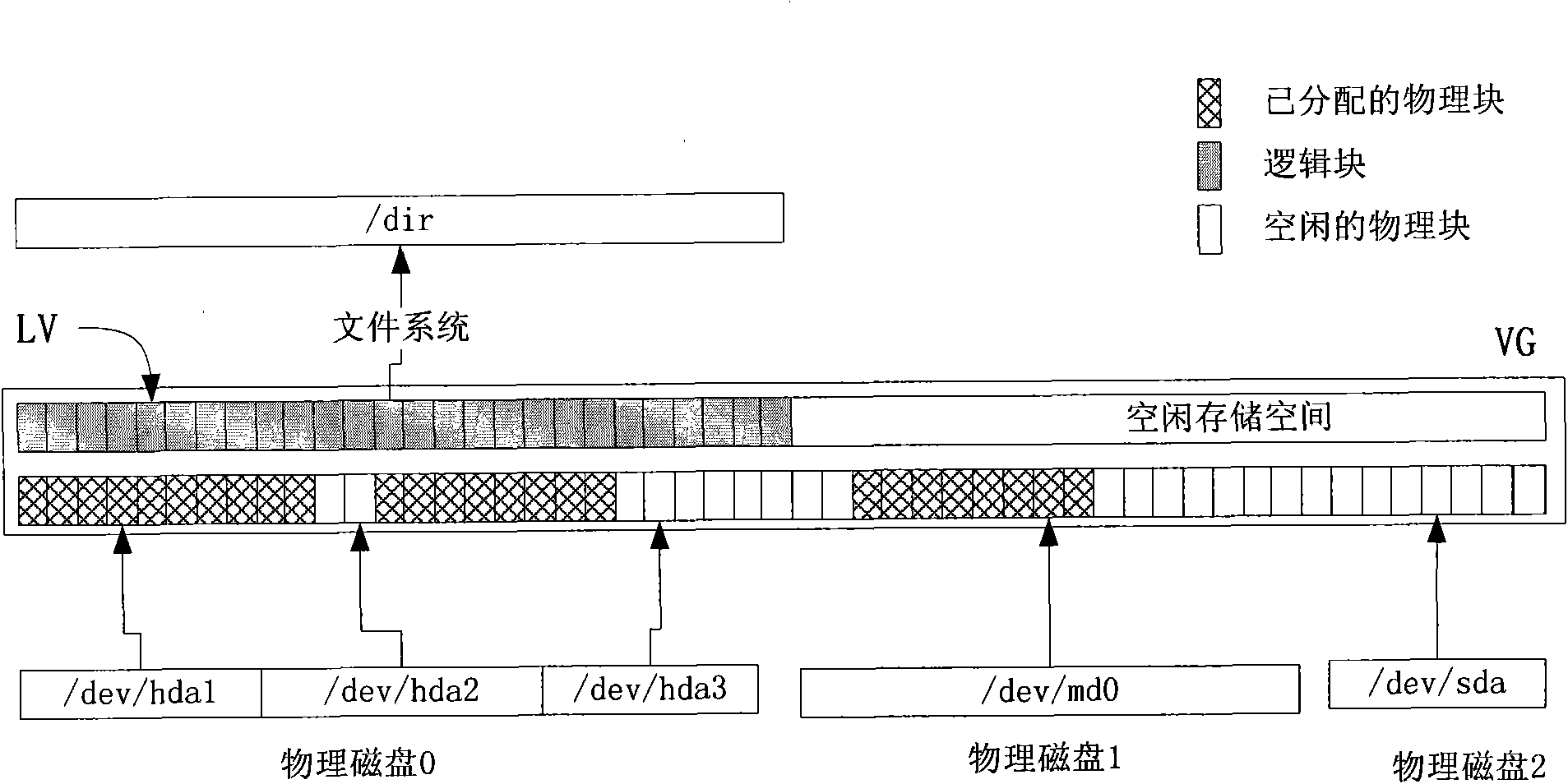
ActiveCN101840308ASave storage resourcesInput/output to record carriersArray data structureComputer architecture
The invention discloses a logical volume management method applied for a hierarchical memory system. A volume group bit chart is arranged, and the bits of the volume group bit chart correspond to the physical zones of a physical volume one to one; and the bits in the volume group bit chart indicate whether the corresponding physical zone is occupied or not. The method comprises the following steps: A. initializing a mapping array, wherein each element in the mapping array corresponds to one bit in the volume group bit chart, and the element value shows the position of the corresponding bit in the volume group bit chart; B. seeking a bit set to be invalid in the volume group bit chart and setting the value of the bit to be valid; C. recording the position of the sought bit in the volume group bit chart into the element corresponding to the mapping array of the logical volume; and D. creating a new logical volume which is mapped to the physical zone corresponding to the sought bit. The invention also discloses a memory system adopting the logical volume management method. With the scheme, the invention does not need to distribute a large number of physical zones in initialization, achieves the dynamic use of the physical zones, and greatly saves the memory resources.
Owner:UNITED INFORMATION TECH +1
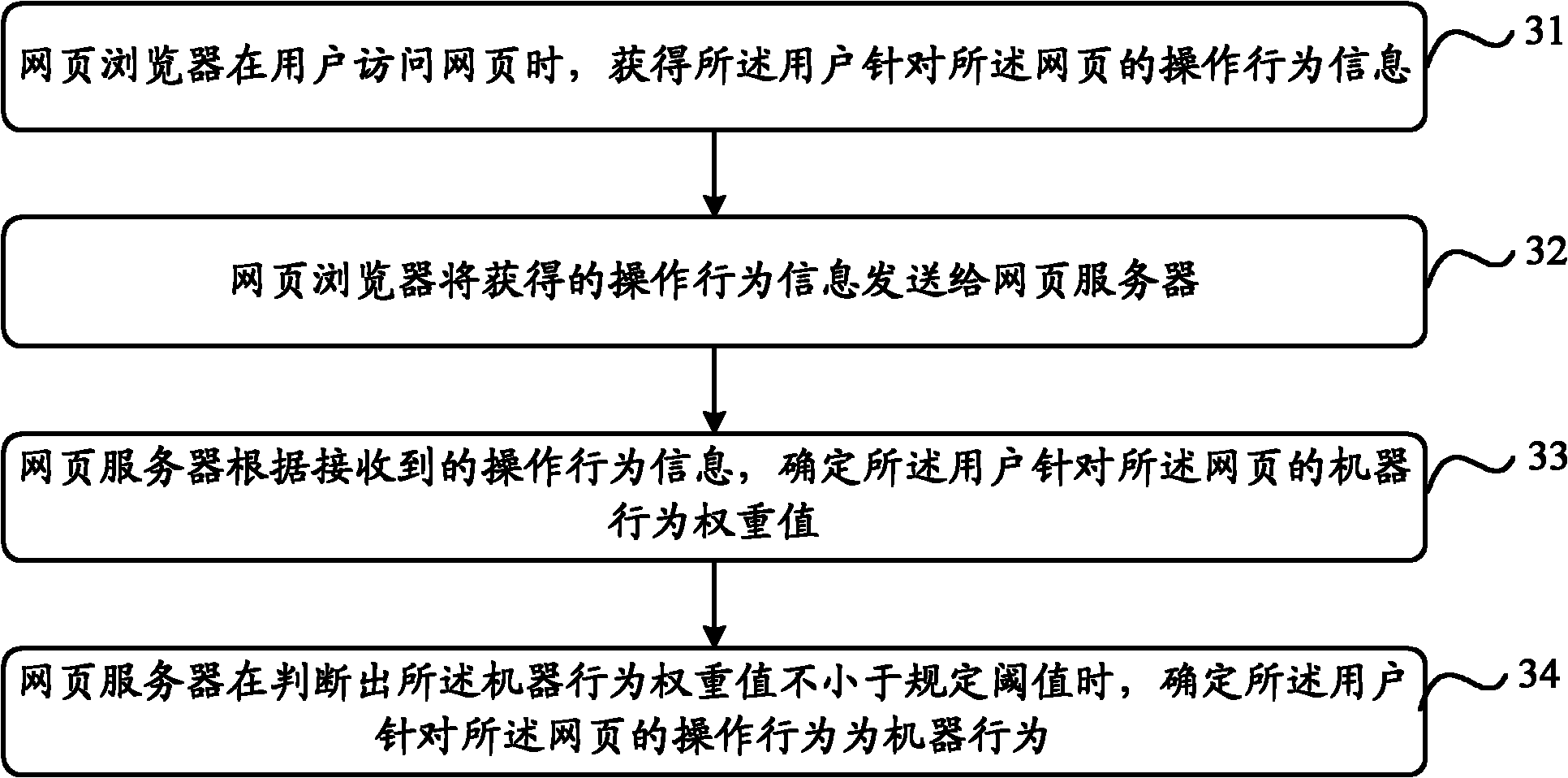
Machine behavior determining method, webpage browser and webpage server
ActiveCN102737019ASave processing resourcesSave more processing resources of the web serverComputer security arrangementsWebsite content managementWeb browserOperational behavior
The invention discloses a machine behavior determining method, a webpage browser and a webpage server, wherein the method includes the following steps that: when a user accesses a webpage, the webpage browser acquires operating behavior information of the user for the webpage; the webpage browser sends the acquired operating behavior information to the webpage server; according to the received operating behavior information, the webpage server determines a weight value of a machine behavior of the user for the webpage; and when determining the weight value of the machine behavior is not less than a predetermined threshold value, the webpage server determines the operating behavior of the user for the webpage is a machine behavior. By adopting the method according to the above technical schemes, the problem of low accuracy in determining a machine behavior in the prior art can be solved.
Owner:ALIBABA GRP HLDG LTD
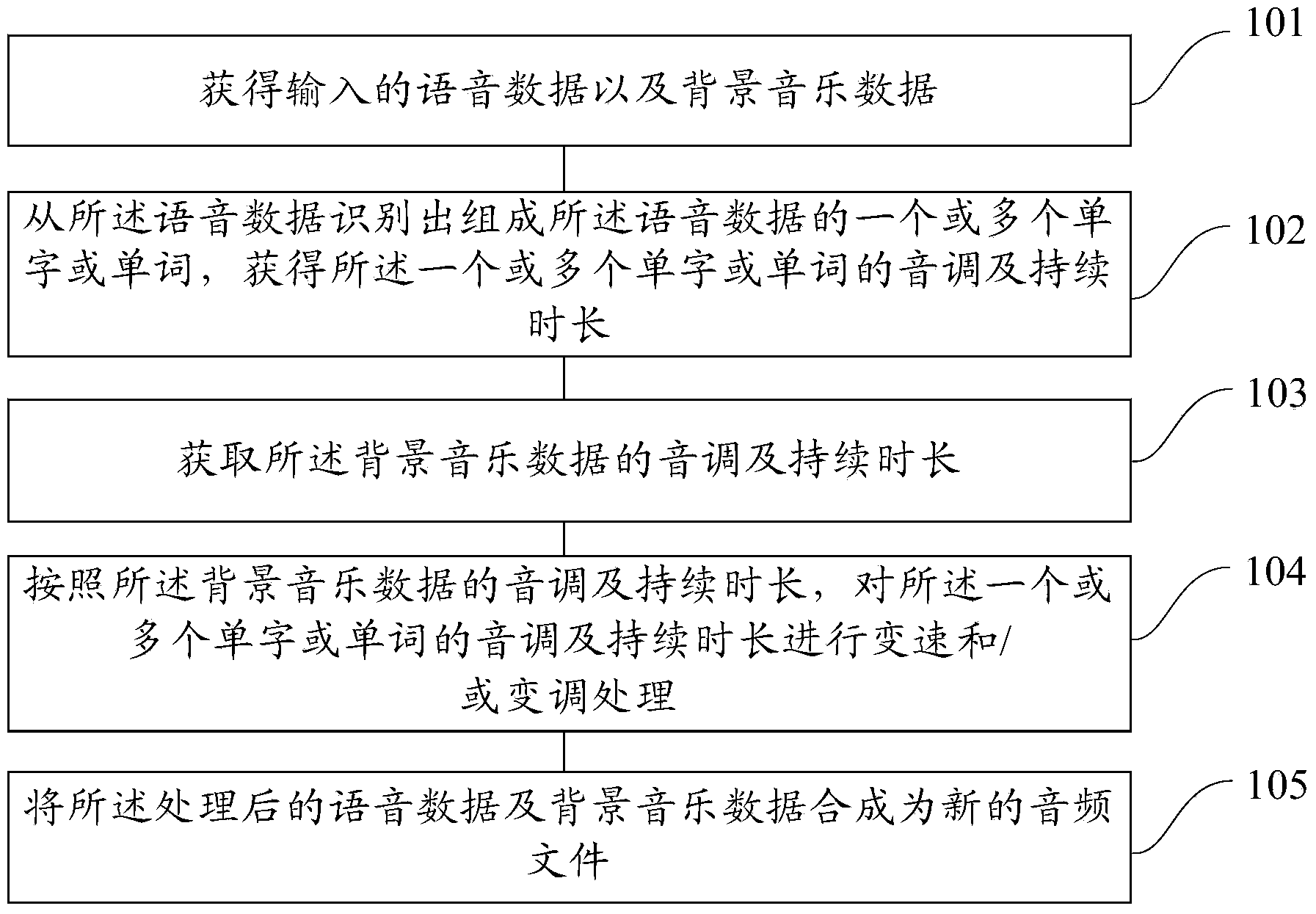
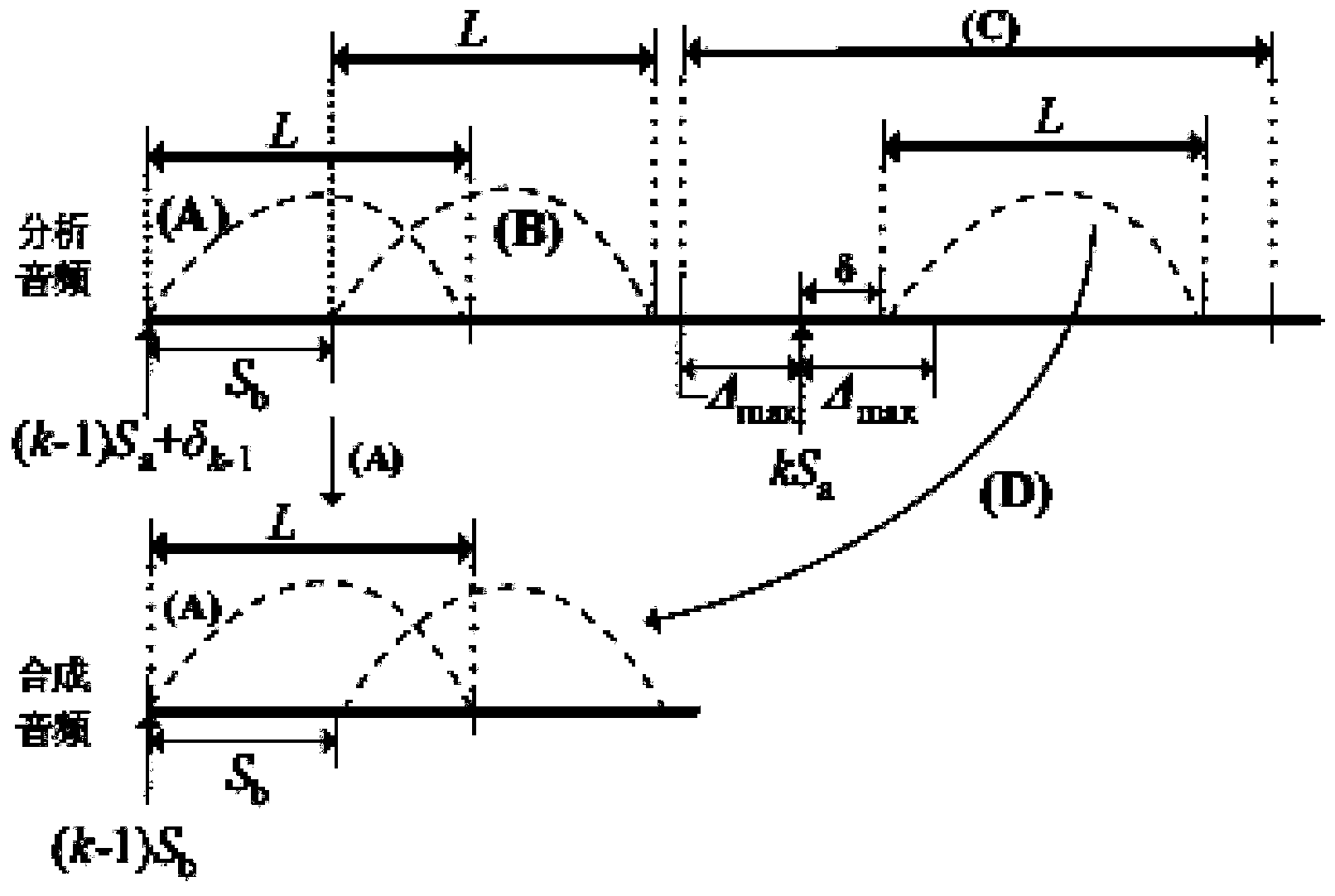
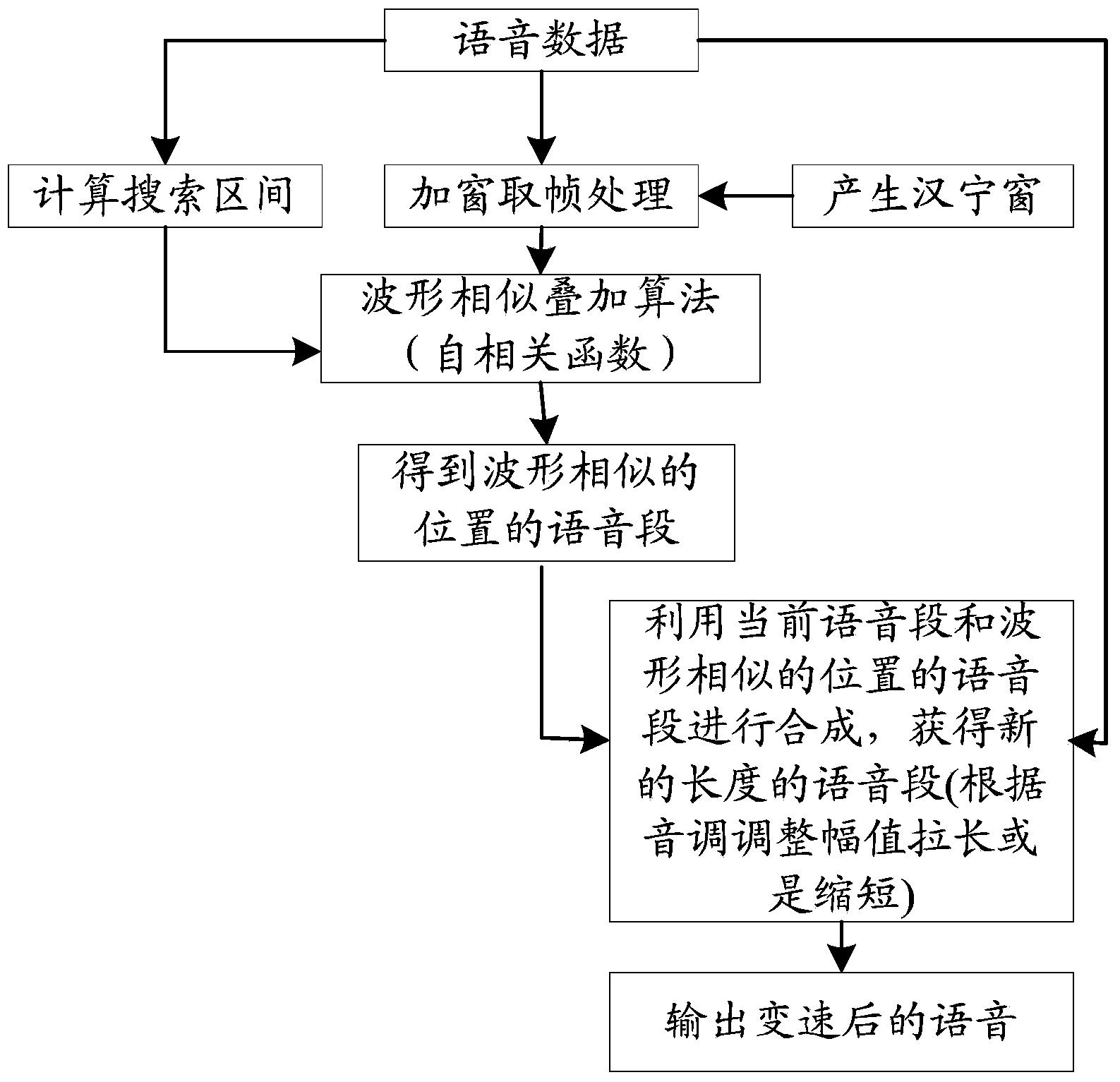
Method, device and equipment for synthesizing voice and music
InactiveCN103440862AImprove user experienceQuality improvementSpeech synthesisAudio frequencySpeech sound
The embodiment of the invention provides a method, device and equipment for synthesizing voice and music. The method comprises the steps that input voice data and background music data are obtained; one or more words or phrases are identified in the voice data and tones and lasting time of the words or the phrases are obtained, wherein the voice data are composed of the words or the phrases; tone and lasting time of the background music data are obtained; according to the tone and the lasting time of the background music data, speed change processing and / or tone modification processing are / is conducted on the tones and the lasting time of the words or the phrases; the processed voice data and the background music data are synthesized so that a new audio file can be formed. According to the method, device and equipment for synthesizing voice and music, independent voice data and music data can be perfectly combined together, a music attribute is offered to the monotonous voice data, so that the quality of an whole voice stream is improved, and the gradually improved and changed requirements for voice and music synthesis of users are satisfied.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Self-adaptive method for mobile terminal to display or download pictures through network
InactiveCN101668255AEasy to operateShorten the timeWireless network protocolsMessaging/mailboxes/announcementsComputer programmingModel Number
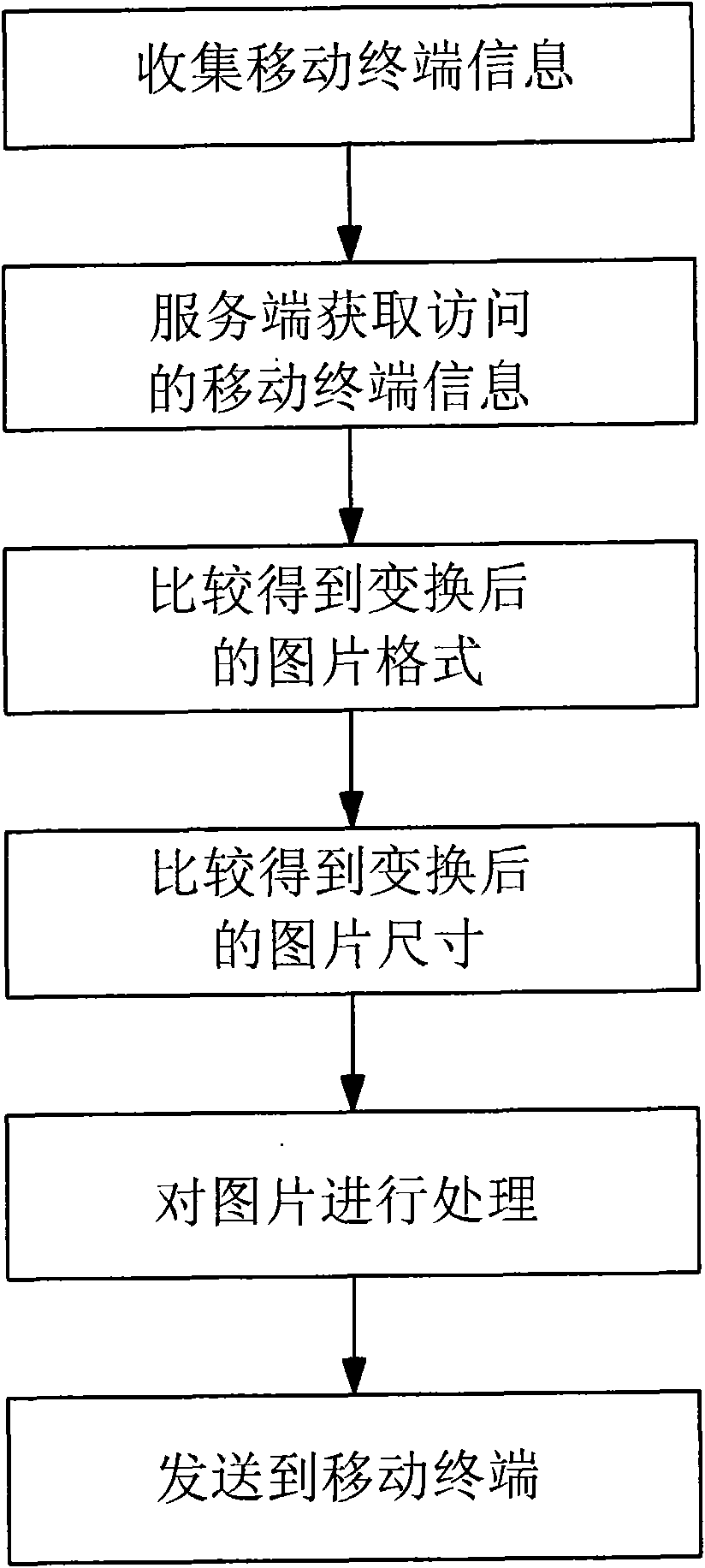
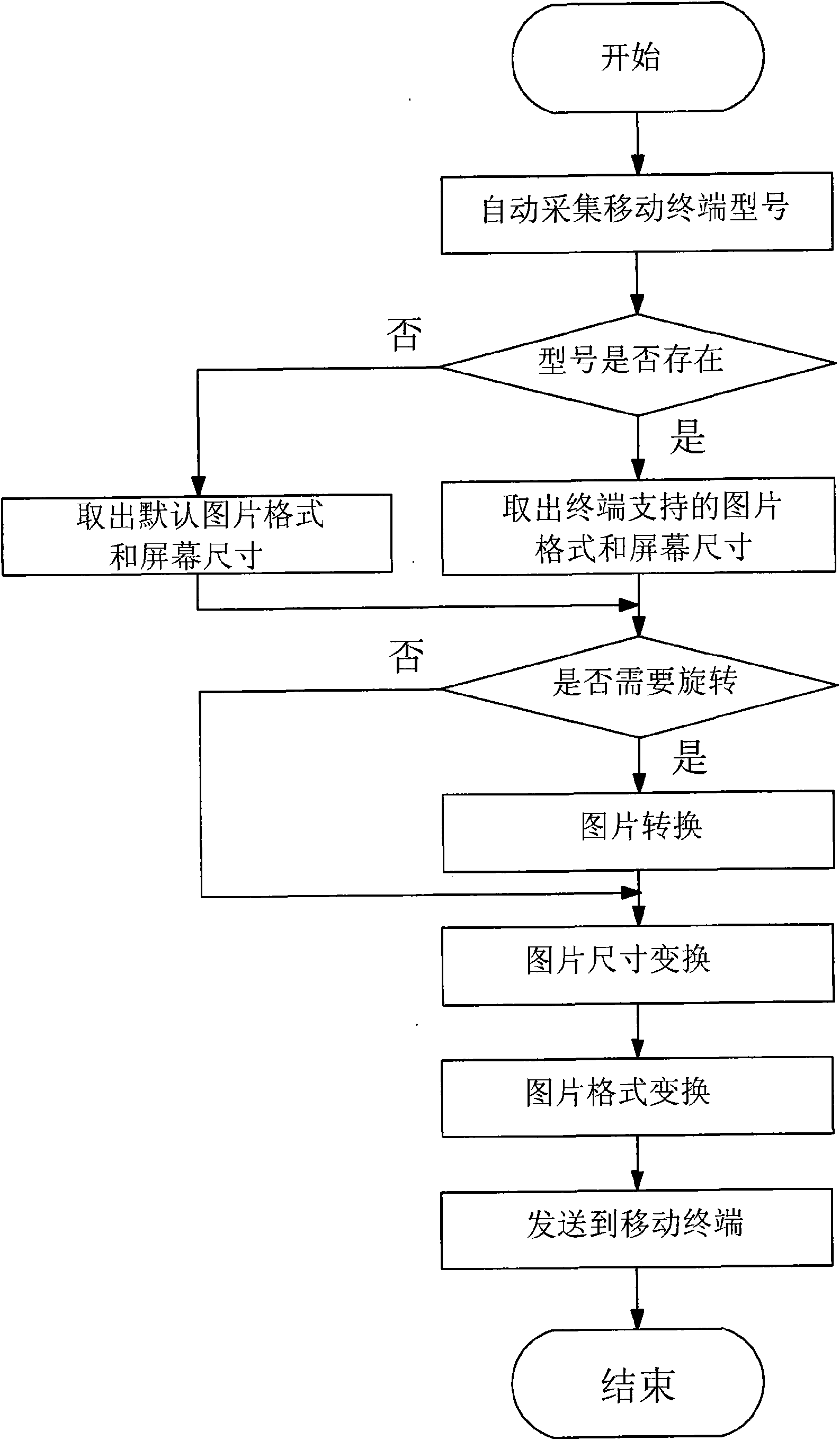
The invention discloses a self-adaptive method for a mobile terminal to display or download pictures through a network. The prior scheme cannot meet the requirements of modern information developmenton high speed, humanization and intellectualization. The self-adaptive method for the mobile terminal to display or download the pictures through the network comprises that a content server acquires agroup of mobile terminal information and picture information, wherein the content server automatically extracts the type of the mobile terminal through program design and compares the extracted typewith the type of the mobile terminal acquired by the content server to acquire the size of a display screen of the mobile terminal and a supported picture format, automatically converts picture formats, changes the sizes or rotates the pictures at the background to realize match between the pictures and the mobile terminal, and sends the pictures to the mobile terminal. The method is used for themobile terminal to automatically browse the pictures on the network.
Owner:杨明极
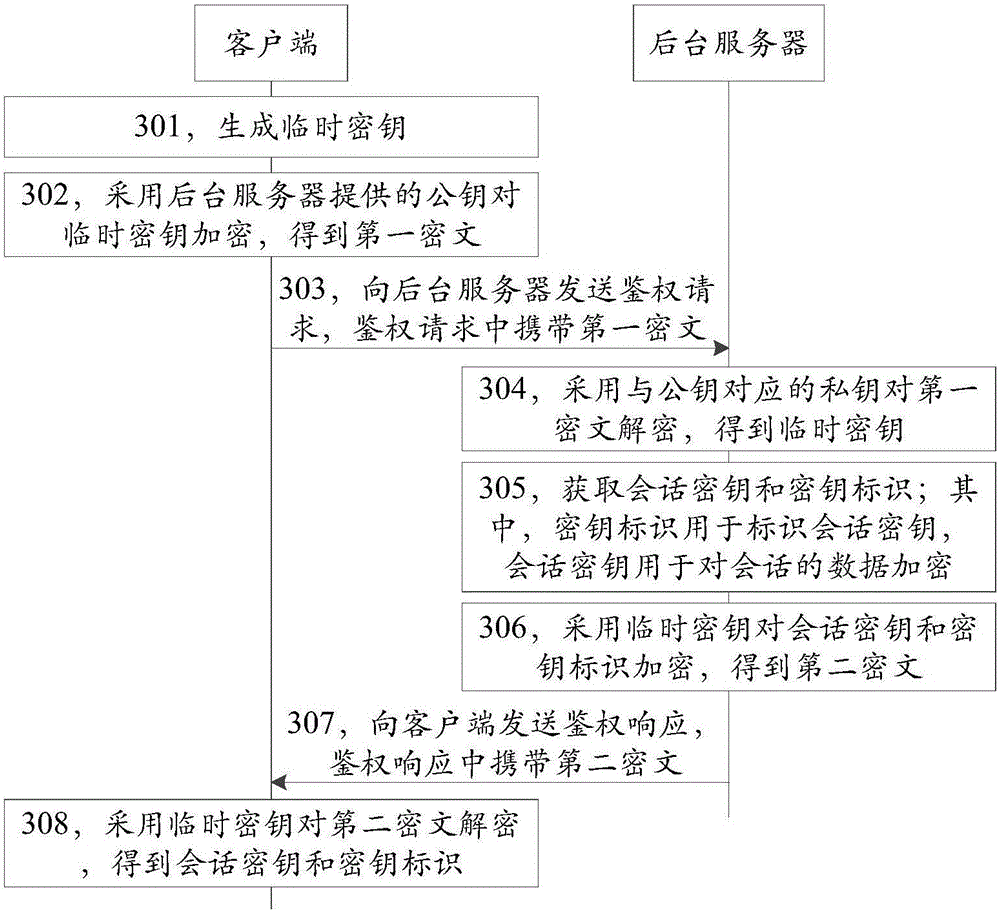
Secret key management method, device and system
ActiveCN106712932ASolve the problem of requiring a lot of resources to manage symmetric keysSimplify complexityKey distribution for secure communicationCiphertextClient-side
The invention discloses a secret key management method, device and system, and belongs to the technical field of information security. The method comprises the steps that a client side generates a temporary secret key, and the temporary secret key is encrypted by using a public key provided by a background server so that a first cryptograph is obtained and transmitted to the background server; the background server applies a private key corresponding to the public key to decrypt the first cryptograph so as to obtain the temporary secret key, a session key and a key identifier are acquired, and the session key and the key identifier are encrypted by using the temporary secret key so that a second cryptograph is obtained and transmitted to the client side; and the client side applies the temporary secret key to decrypt the second cryptograph so as to obtain the session key and the key identifier, wherein the key identifier is used for identifying the session key, and the session key is used for encrypting the session data. The management complexity of the background server for the secret key can be simplified under the premise of considering the security of the secret key and the efficiency of encryption and decryption so that the processing and storage resources of the background server can be saved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
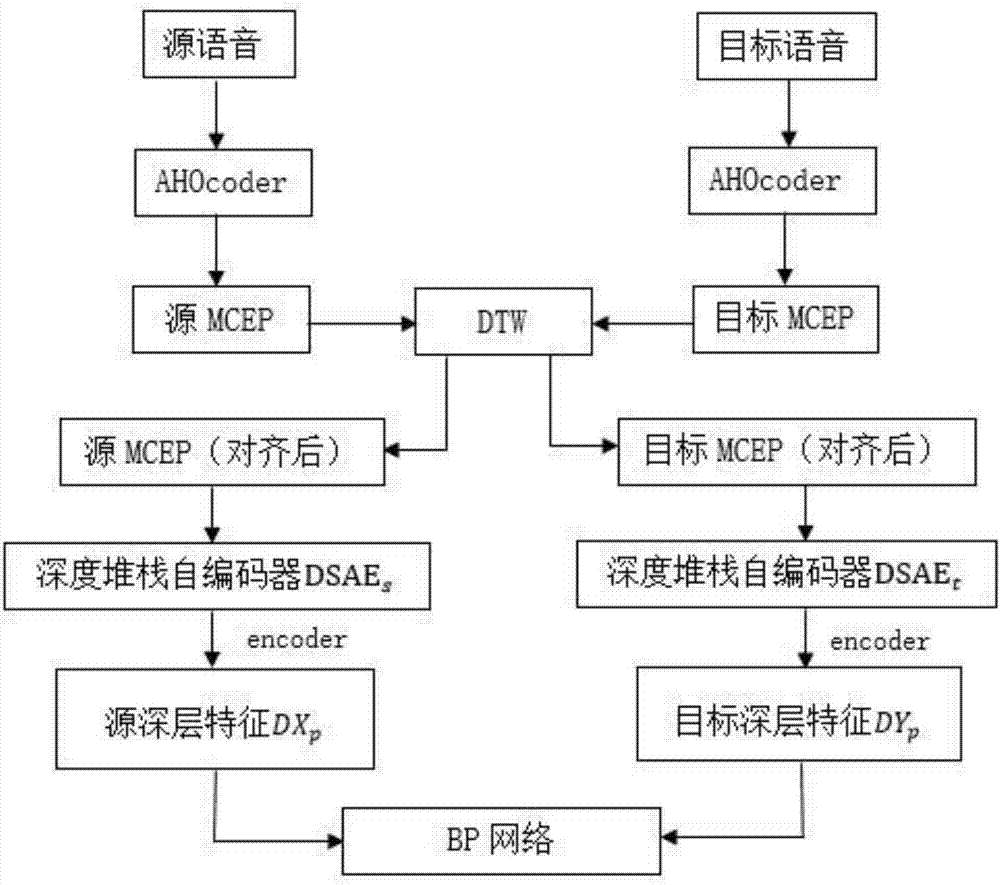
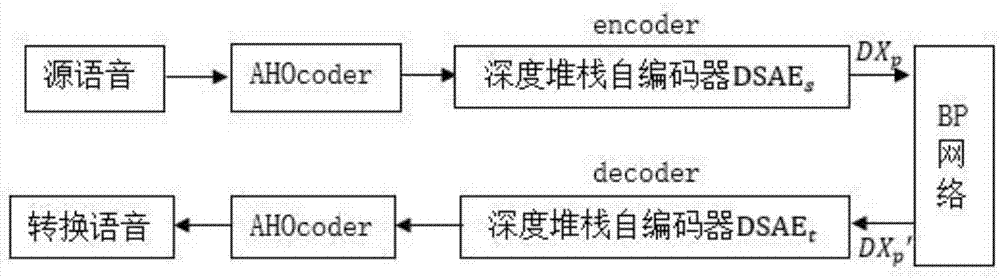
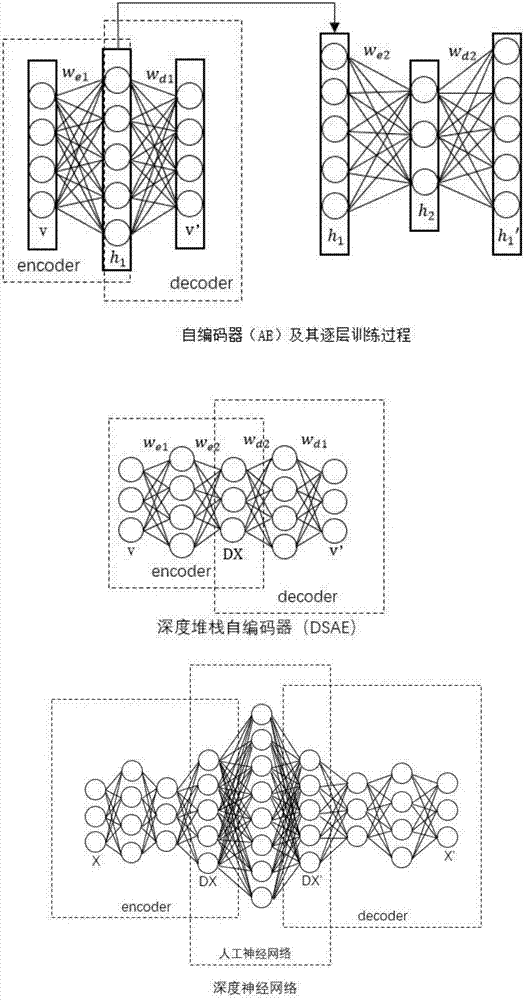
Voice converting method based on deep learning
ActiveCN107545903AImprove the voice conversion effectSave computing resourcesSpeech analysisOffline learningFeature extraction
The invention discloses a voice converting method based on deep learning, and belongs to the technical field of voice signal processing. According to the invention, the method includes the following steps: configuring a voice encoding and decoding device AHOcoder as a feature extraction terminal and a voice synthesis terminal, training voice features by using the deep leaning method to separatelyobtain deep features of a source speaker and a target speaker, also obtaining the capability of decoding the deep features to original features, mapping the source speaker and the target speaker by using a BP neural network, thus realizing voice conversion. According to the invention, the method stitches the original features of voice, the combined feature parameters obtained from stitching are deemed to include the dynamic features of the voice features of the speaker, the training of the deep neural network is accelerated by pre-training the deep autoencoders, and by converting the deep features, the method herein obtains quality converted voice even when less voice materials are trained. The method also supports offline learning, and saves computing resources and memory of terminal devices.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and device for LSP intermediate node label distribution in MPLS ordered mode
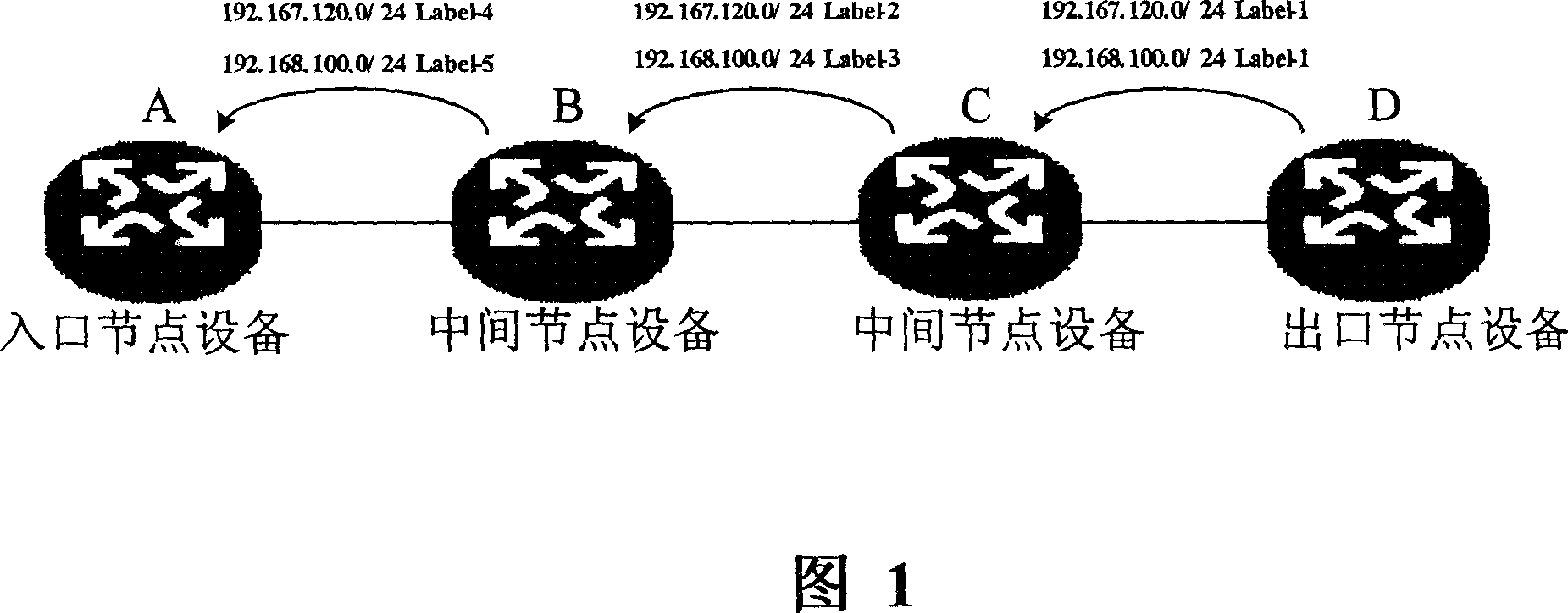
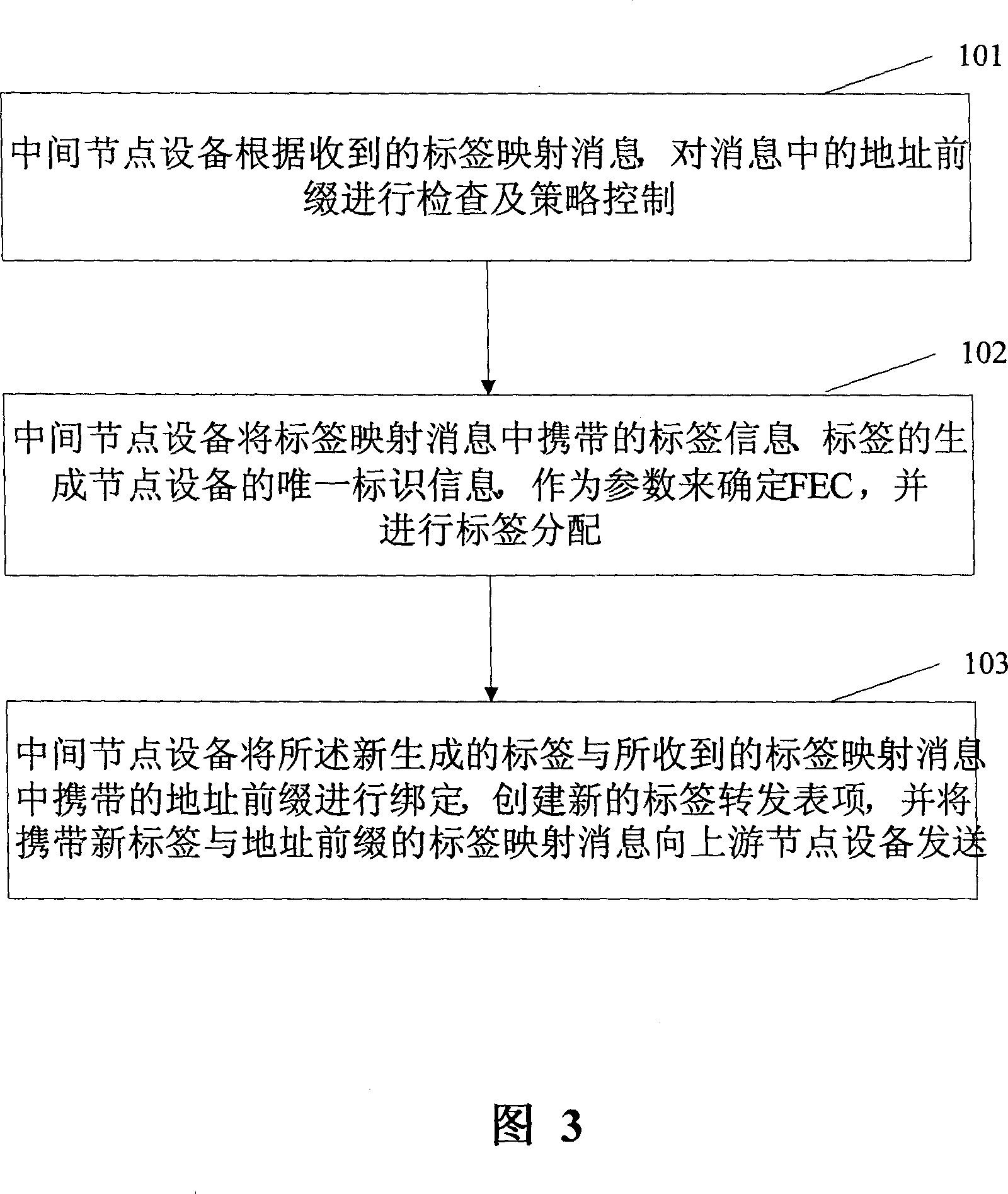
ActiveCN1921453AReduce usageImprove forwarding efficiencyData switching networksComputer scienceAllocation method
The invention relates to a label distributing method of LSP middle node at serial type in MPLS system, and a relative device. Wherein, when the middle node device receives the label projection message, the middle node device based on the label information carried in said message, to generate the unique label information of node device and fix the transfer equivalent kind; the middle node device via fixed transfer equivalent kind distributes label. The invention can reduce the label consumption, save memory and improve the transfer efficiency.
Owner:NEW H3C TECH CO LTD
Image processing method and system
ActiveCN107391505AImprove accuracyImprove efficiencyCharacter and pattern recognitionSpecial data processing applicationsImaging processingSpatial structure
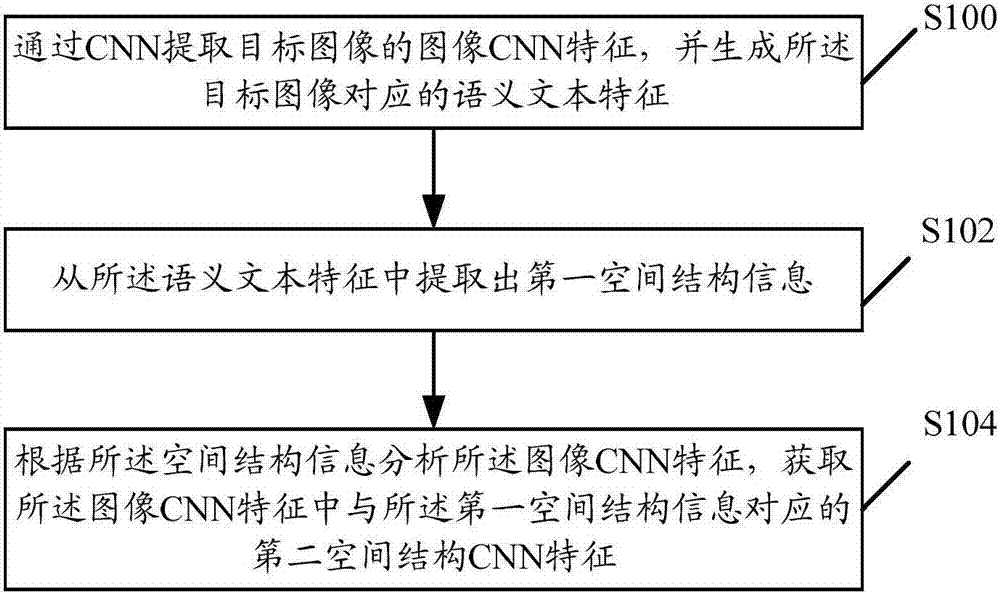
The embodiment of the invention discloses an image processing method. The method comprises: extracting image CNN (convolutional neural network) features of a target image through a CNN, and generating semantic text features corresponding to the target image; extracting first spatial structure information from the semantic text features; and analyzing the image CNN features according to the spatial structure information to acquire second spatial structure CNN features which is in the image CNN features and corresponds to the first spatial structure information. The invention also discloses an image processing system. By adopting the method and the system, the spatial structure information can be obtained directly from the image CNN features, thus people are helped to further understand the CNN features, and applications such as image and text cross-retrieval, image annotation, object detection, zero-shot learning and visual Q&A systems can be enabled to be benefited.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
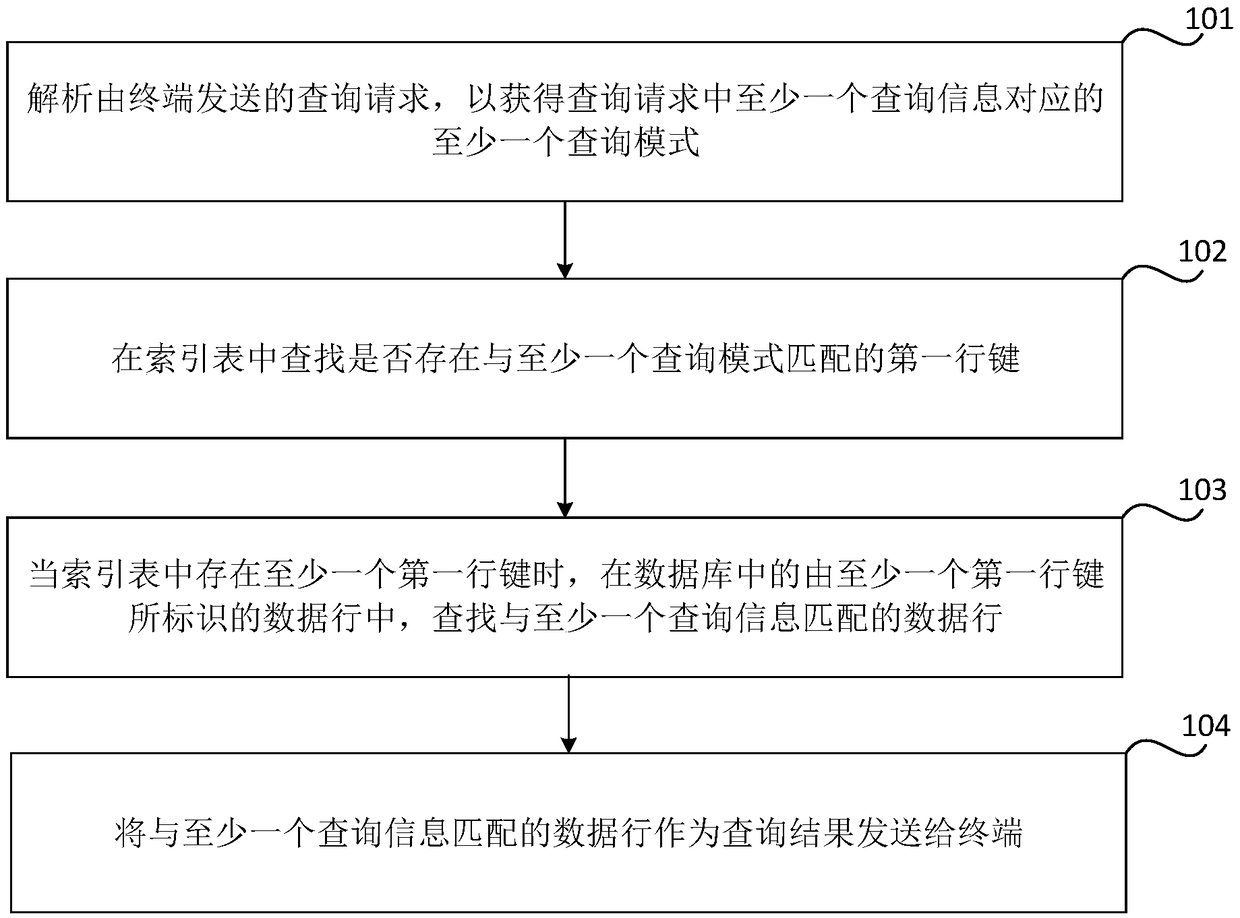
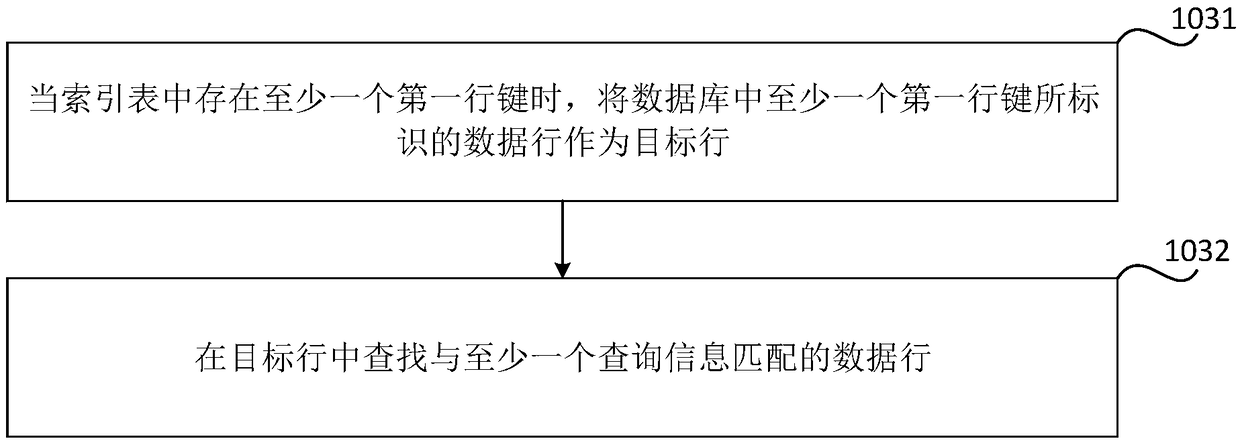
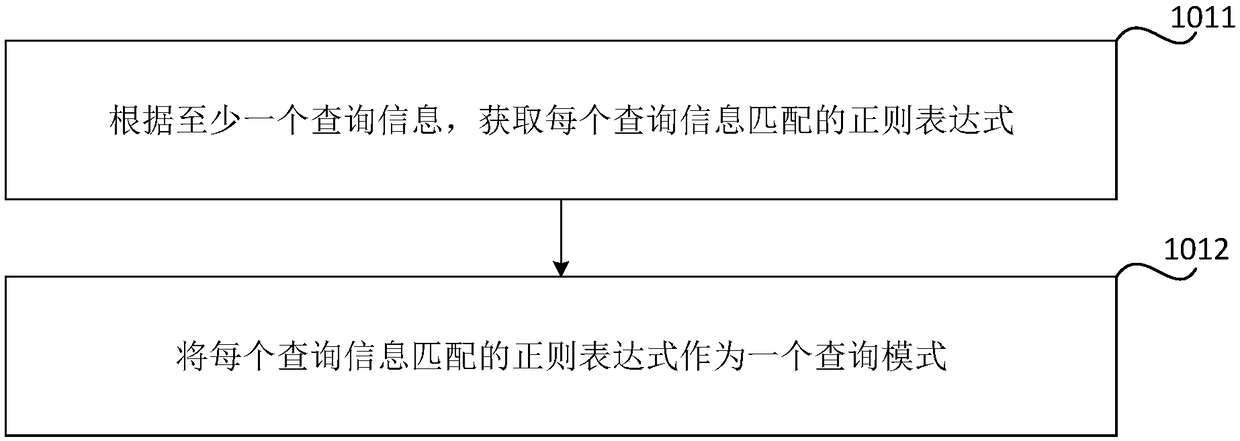
Data inquiry method, device, storage medium and electronic device
ActiveCN109299110AImplement queryImprove query efficiencySpecial data processing applicationsDatabase indexingPattern matchingComputer terminal
The invention relates to a data inquiry method, device, storage medium and electronic device, in the field of information technology, applied to Server, The method comprises: parsing the query requestsent by the terminal, At least one query pattern correspond to at least one query information in that query request is obtain, looking in the index table for the existence of a first row key that matches at least one query pattern, When at least one first row key exists in the index table, the data row matching the at least one query information is searched in the data row identified by the at least one first row key in the database, and the data row matching the at least one query information is sent to the terminal as a query result. The invention realizes the query of the distributed database, improves the query efficiency of the distributed database, and saves the storage resources.
Owner:NEUSOFT CORP
Method for forwarding and storing session packets according to preset and/or dynamic rules
ActiveUS7474633B2Reduce utilizationSave storage resourcesMultiplex system selection arrangementsSpecial service provision for substationDistributed computingMetadata
Owner:NICE LTD
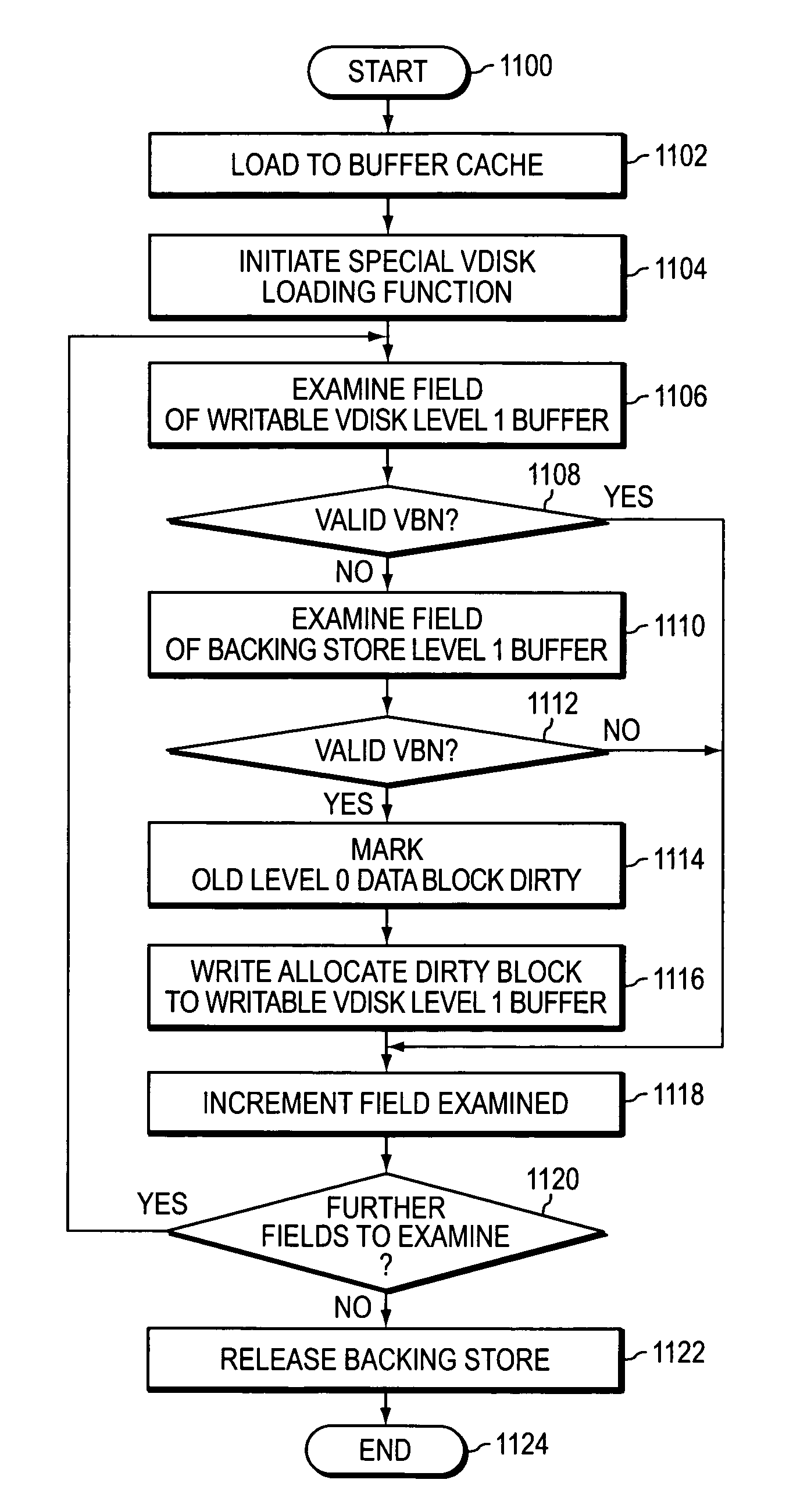
System and method for LUN cloning
ActiveUS8041888B2Save storage resourcesReduced activityInput/output to record carriersDigital data processing detailsOperating systemLogical unit number
A logical unit number (LUN) cloning technique separates data blocks referenced by a writable virtual disk (vdisk) from data blocks referenced only by a backing store to conserve storage resources of a storage system. The LUN cloning technique separates the writable vdisk data blocks from the backing store during periods of reduced processing activity and in a manner that does not interfere with storage service provided by the system.
Owner:NETWORK APPLIANCE INC
Intelligent monitoring pick-up head device using acoustic location
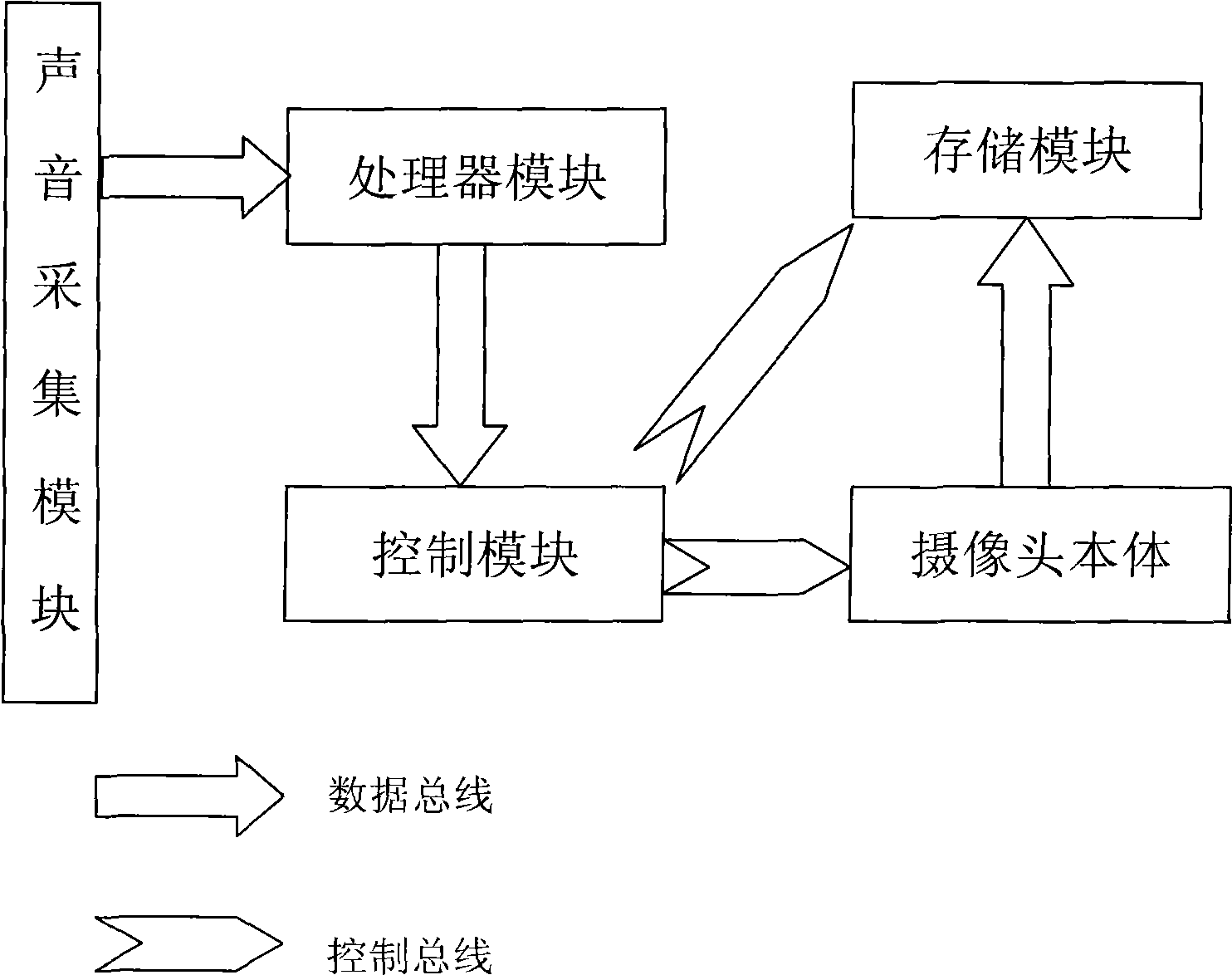
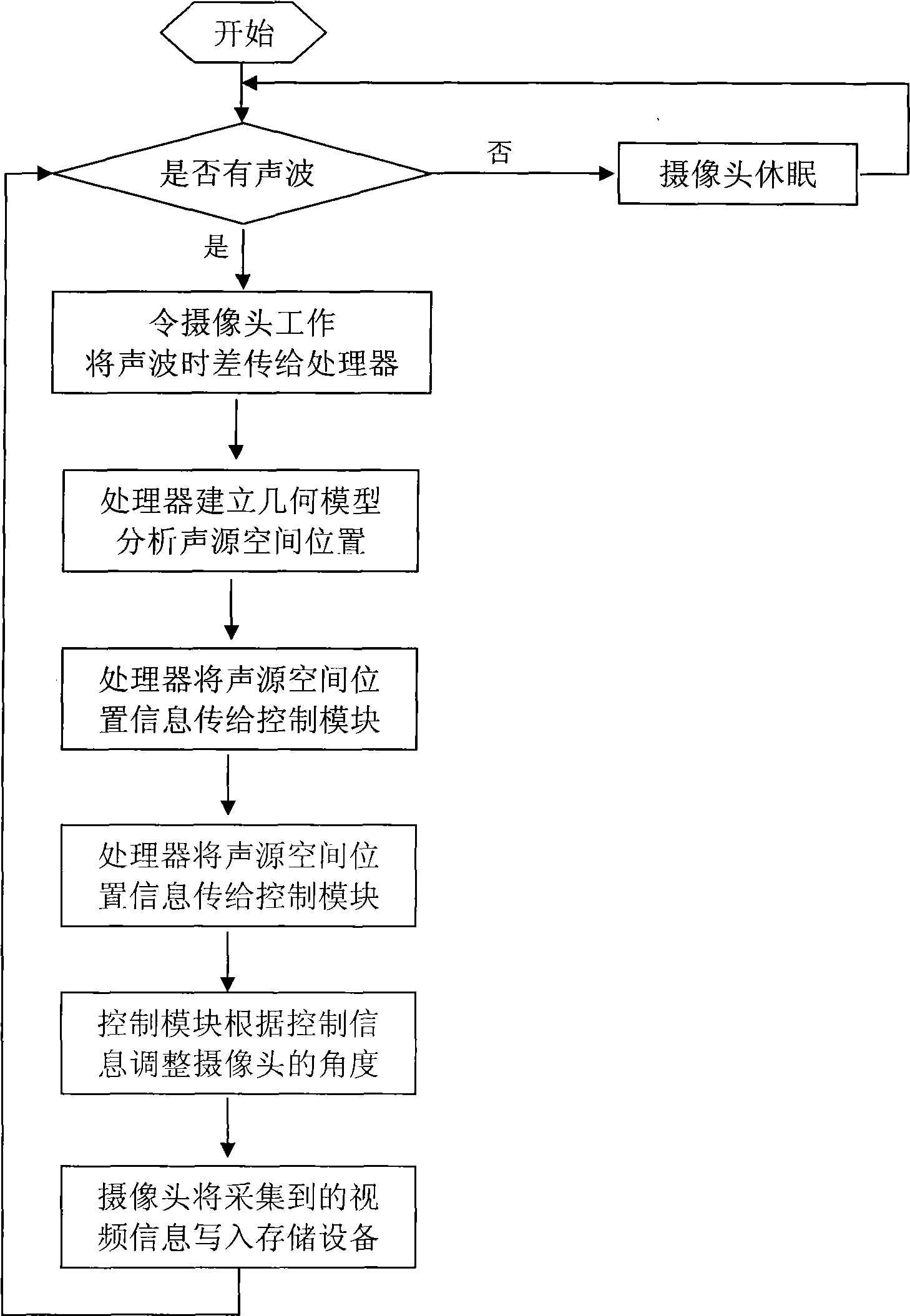
InactiveCN101511000ASave time at workExtend your lifePosition fixationClosed circuit television systemsWork periodVideo monitoring
The invention relates to an intelligent monitoring camera device which locates by means of acoustic waves, comprising a sound collection module, a processor module, a control module, a camera body and a storage module. The utilization of the device saves expensive storage resources, improves the effectiveness of collected video information and can also reduce the working time of a video monitoring device. At the same time, when target objects appear at monitoring places, a monitoring screen can automatically open, which is convenient and greatly improves the working efficiency.
Owner:SUN YAT SEN UNIV
Standing wave detecting device and method thereof
InactiveCN101132240ASuppress measurement effectsImprove anti-interference abilityRadio/inductive link selection arrangementsPropogation channels monitoringMicrocontrollerInterference resistance
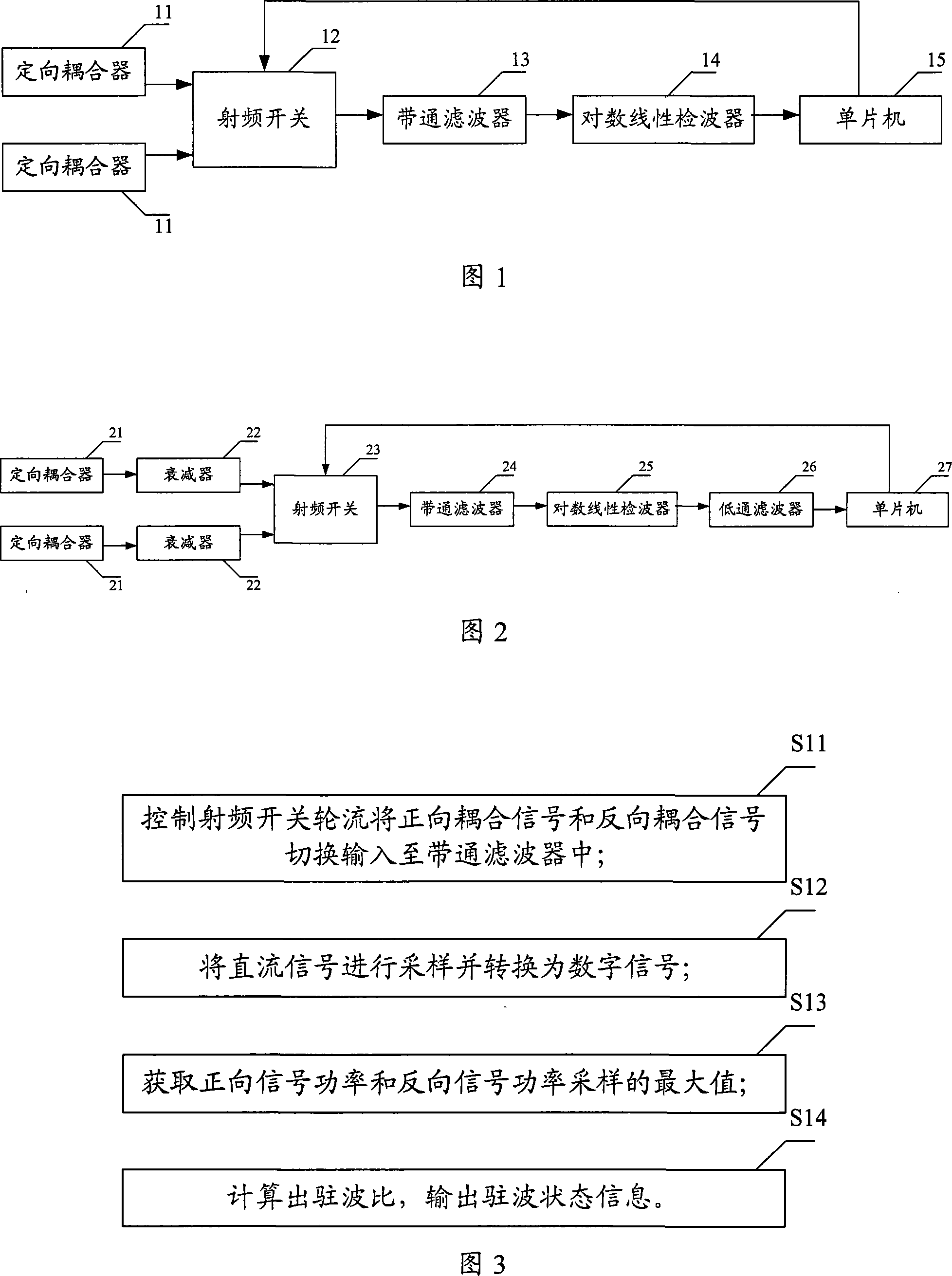
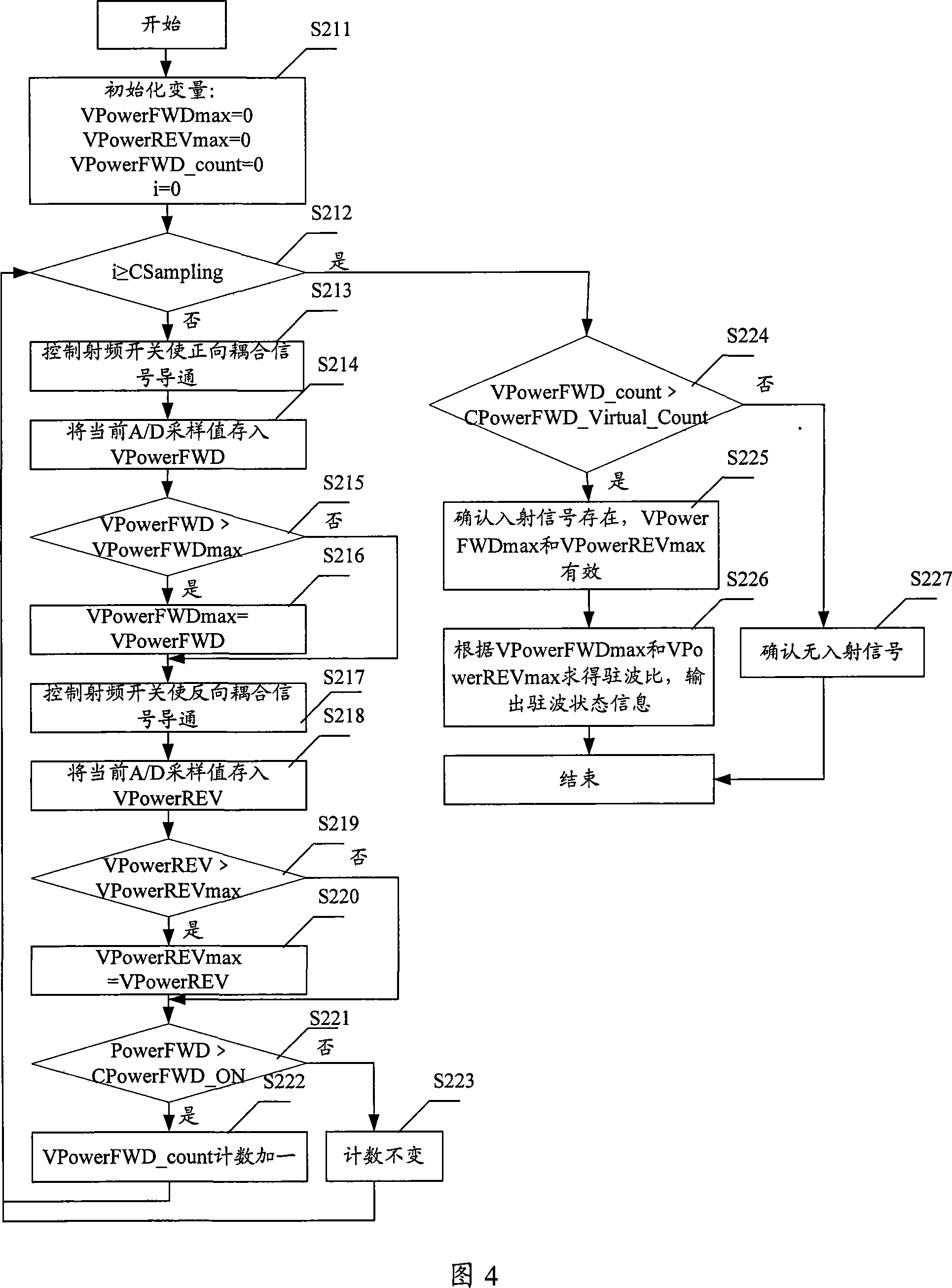
This invention discloses a standing-wave test device and a method, in which, the device includes two directional couplers, a radio switch, a band-pass filter, a logarithm linear detector and a SCM used in controlling said radio switch to switch and input positive and negative coupled signals to the band-pass filter in turn and receiving the DC signals output by the logarithm linear detector to sample and convert them to digital signals and get the sampled maximum values of positive and negative signal power, compute the SWR and output information of the standing-wave state.
Owner:MOBILE ANTENNA TECH SHENZHEN
An intelligent camera device
ActiveCN105323488ASimple structureEasy to installTelevision system detailsColor television detailsComputer hardwareEngineering
Owner:ZHANGZHOU CITY MICROINJECT ELECTRONICS TECH +5
A network transfer method for audio/video data
ActiveCN101009824AReal-time transmissionReduce the amount of data transferredPulse modulation television signal transmissionDigital video signal modificationComputer hardwareTransfer procedure
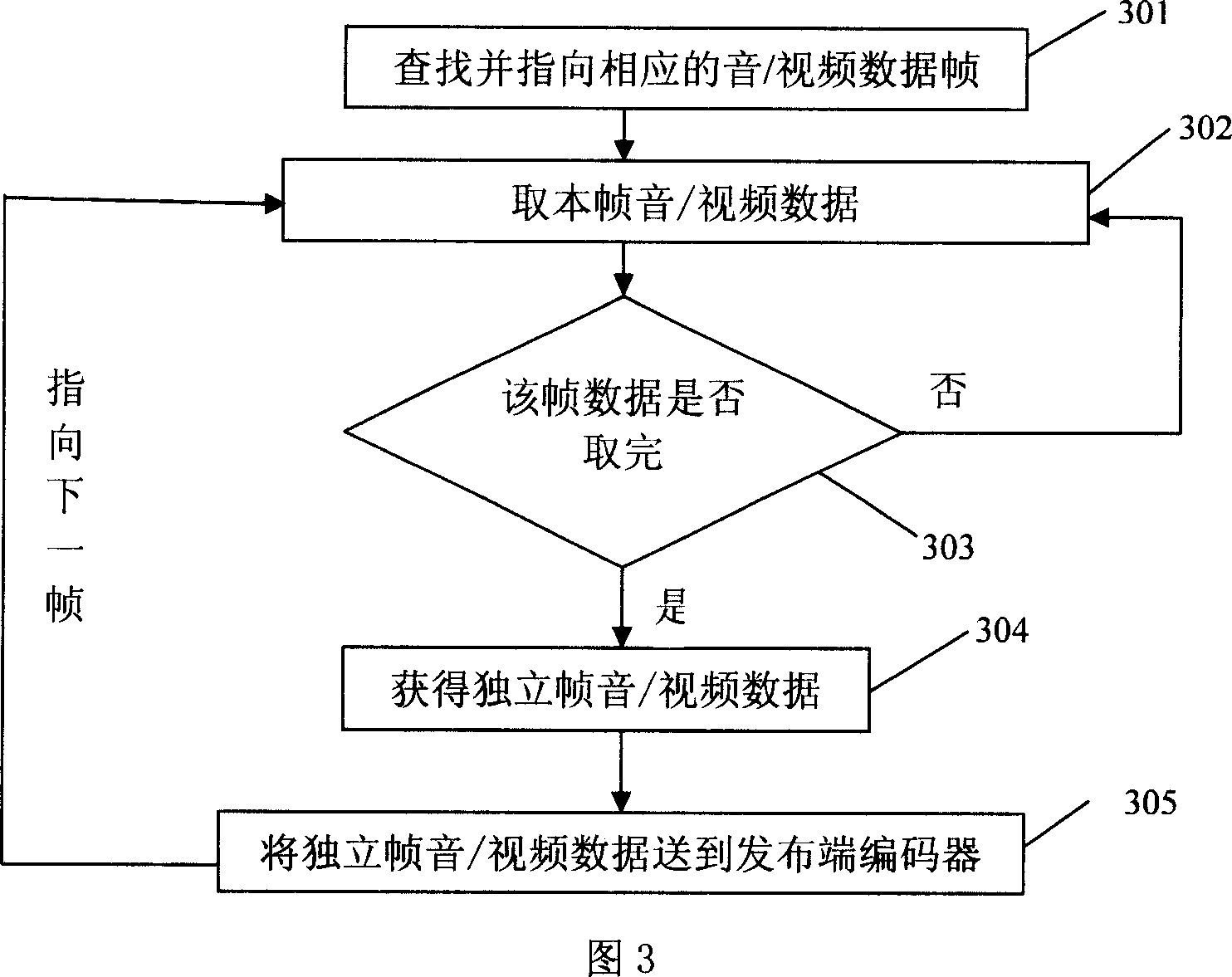
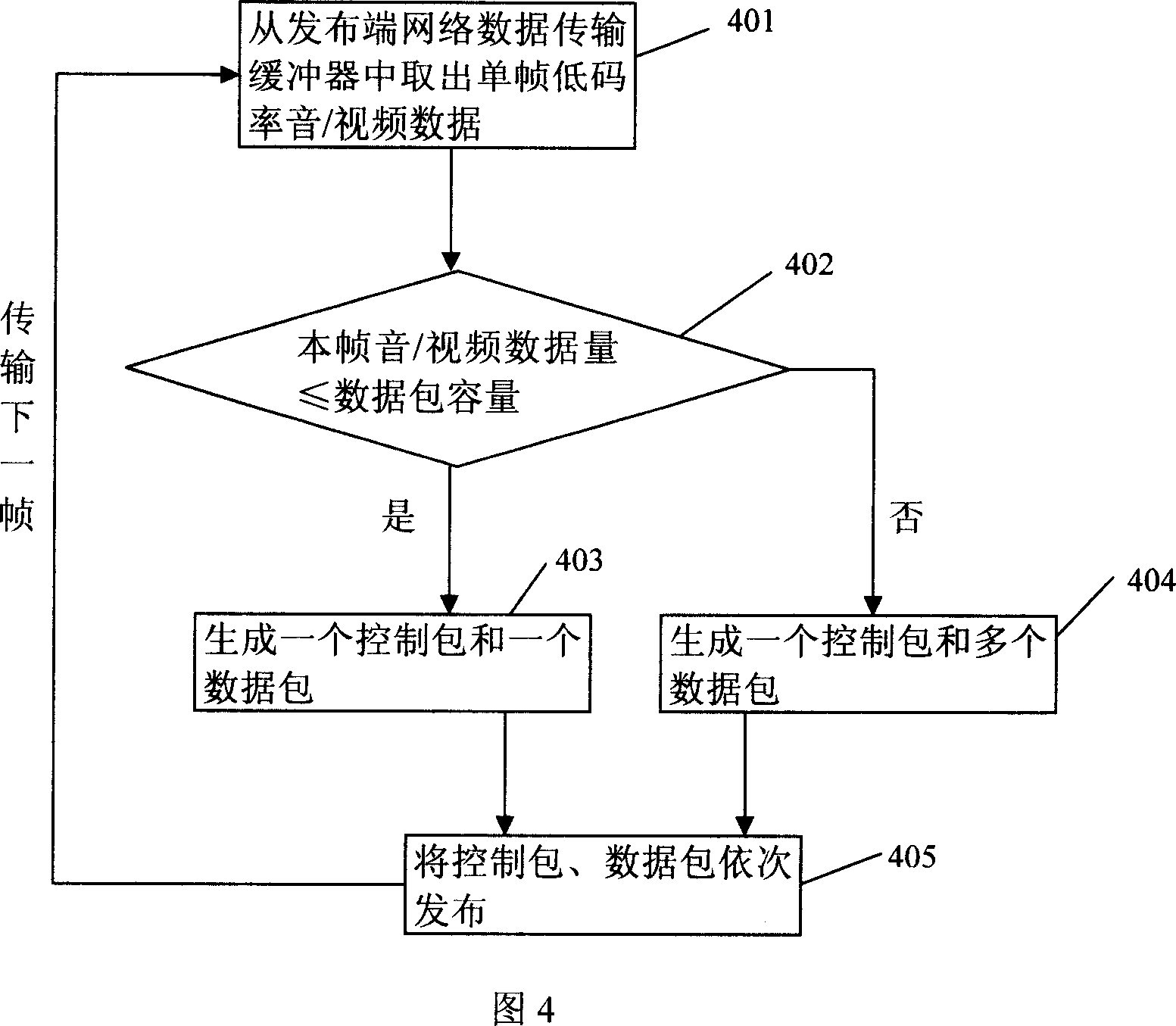
The disclosed network transmission method for audio / video data comprises: with real-time frame-to-code technology, coding the being-transmitted high code rate data with audio / video frame as unit, compressing and packing to send to the receive end; on the receive end, also with independent audio / video frame as unit, decoding to form audio / video flow for display or storing as file. This invention can transmit any high code rate data in bandwidth-limited network, and displays audio / video content real-time while stores file as requested format.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
Parameter quantization method of spiking neural network (SNN)
InactiveCN108717570ARealize parameter quantizationPerformance is not affectedPhysical realisationNeural learning methodsPattern recognitionNerve network
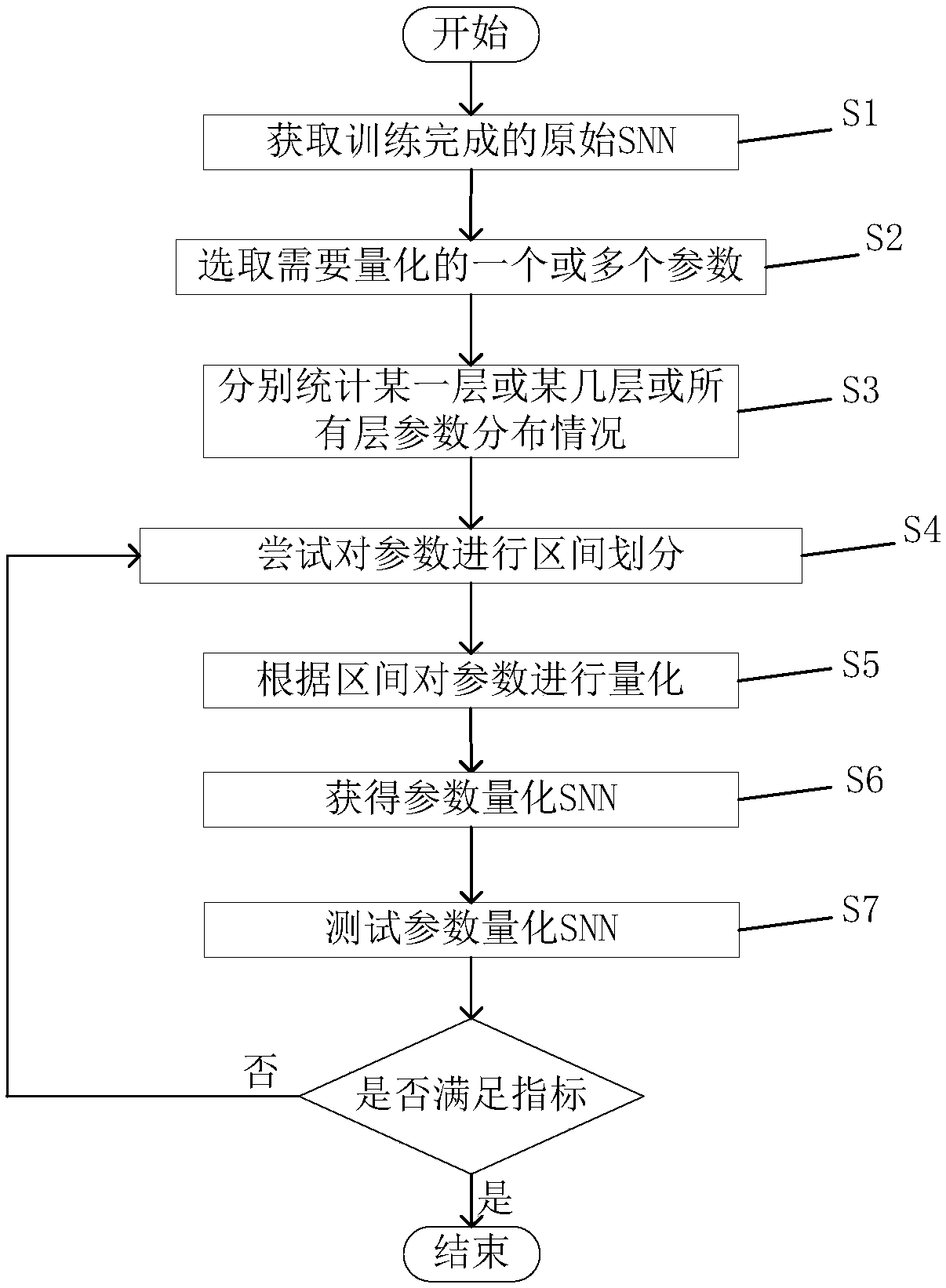
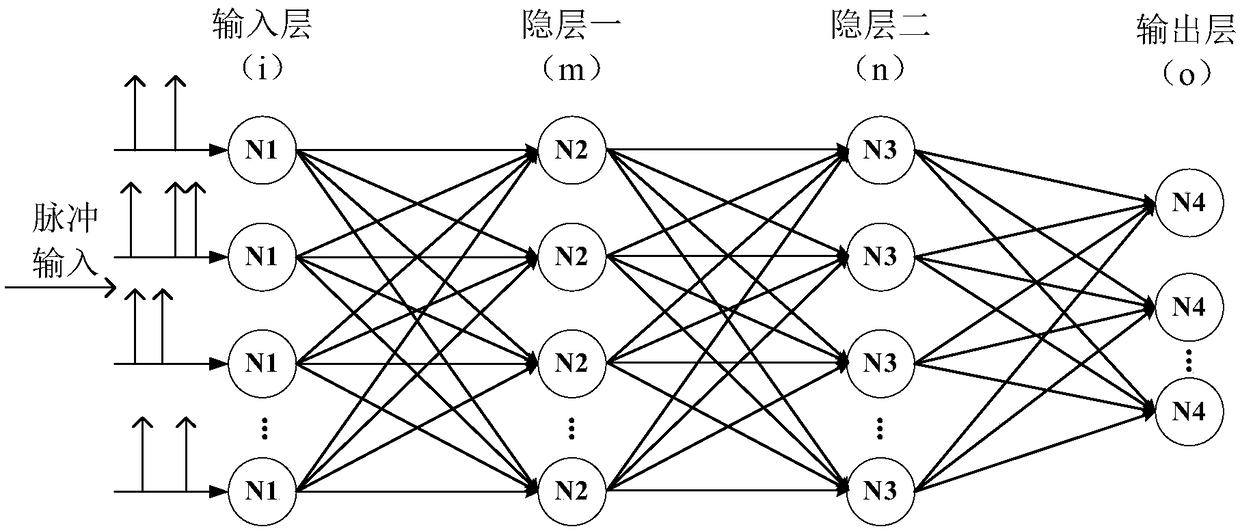
The invention relates to the field of neural network technology, and particularly to a parameter quantization method of a spiking neural network (SNN). According to the method of the invention, the original spiking neural network of which training is completed is obtained through offline mapping or online training, parameters of weights, thresholds, leakage constants, set voltage, refractory periods, synaptic delay and the like of the spiking neural network of which training is completed are quantified, and all layers of the neural network can share the same set of quantified parameters or each layer respectively has one set of quantified parameters. The spiking neural network after parameter quantization requires only a small number of parameters for realizing high-precision spiking-neural-network functions. According to the method, parameter storage space of the spiking neural network is effectively saved while high precision is maintained, operation speed is improved, and operationpower consumption is lowered.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com