Patents
Literature
226results about How to "Guaranteed not to be tampered with" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
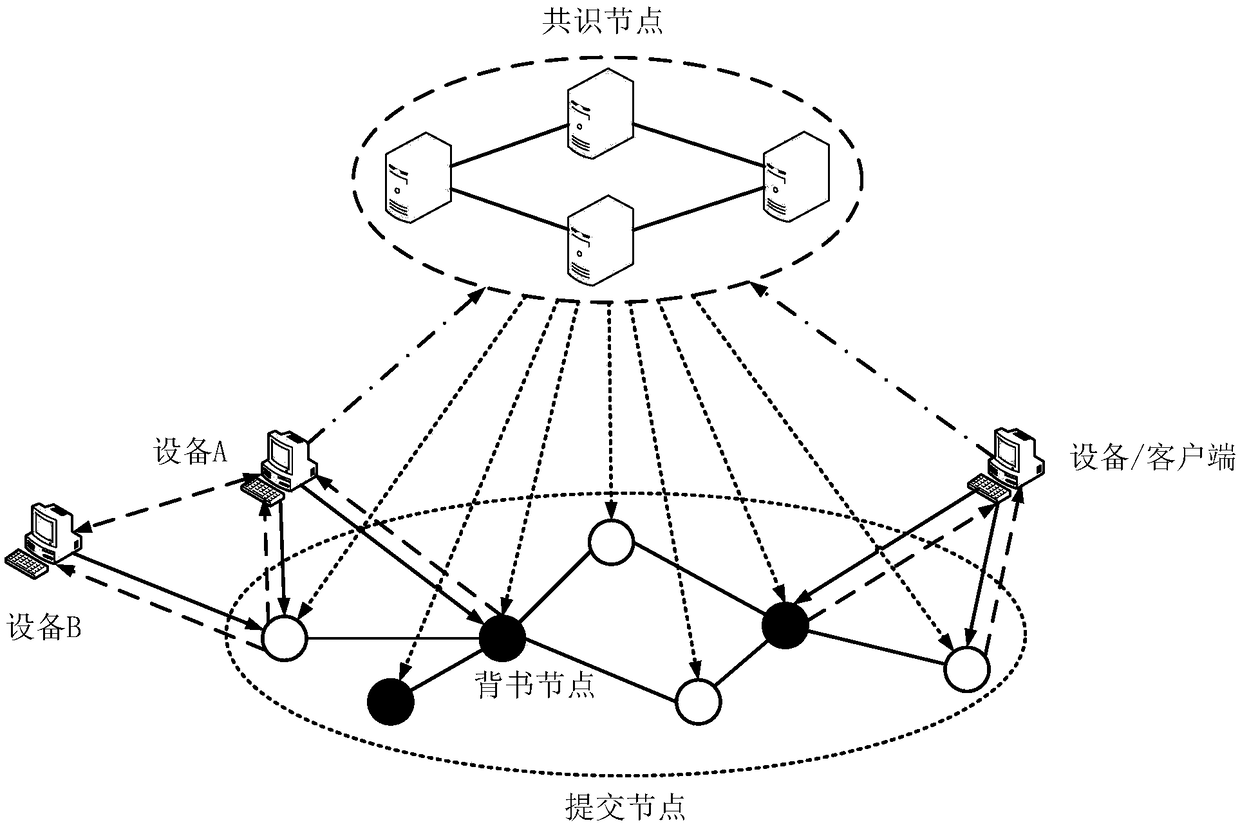
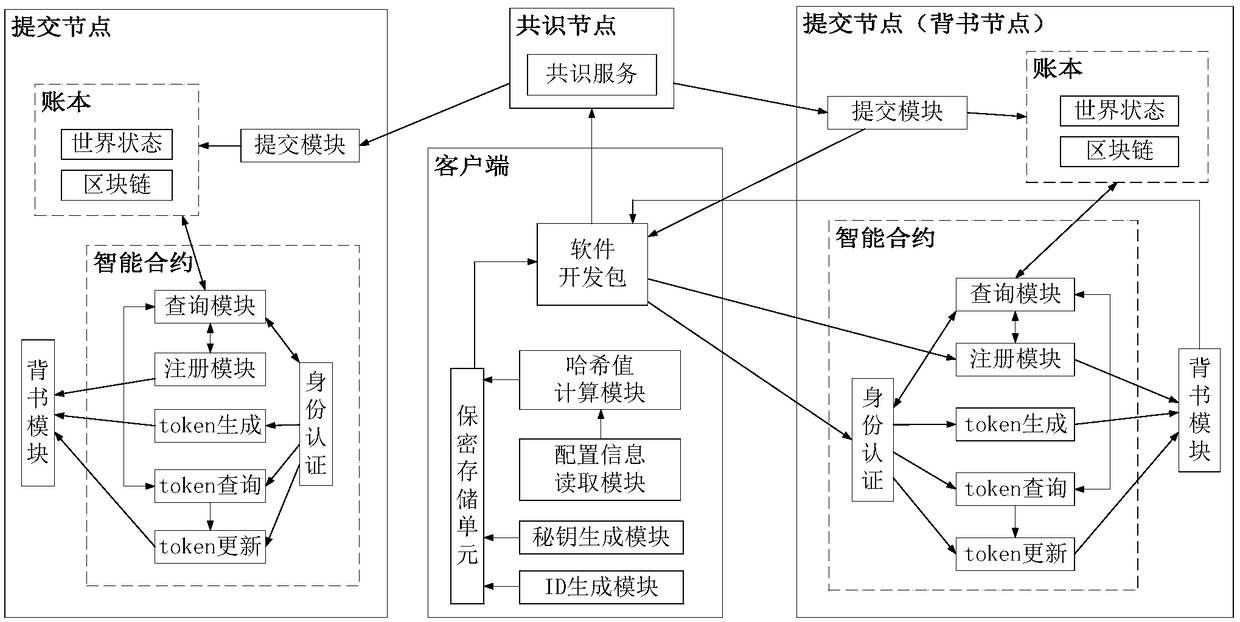
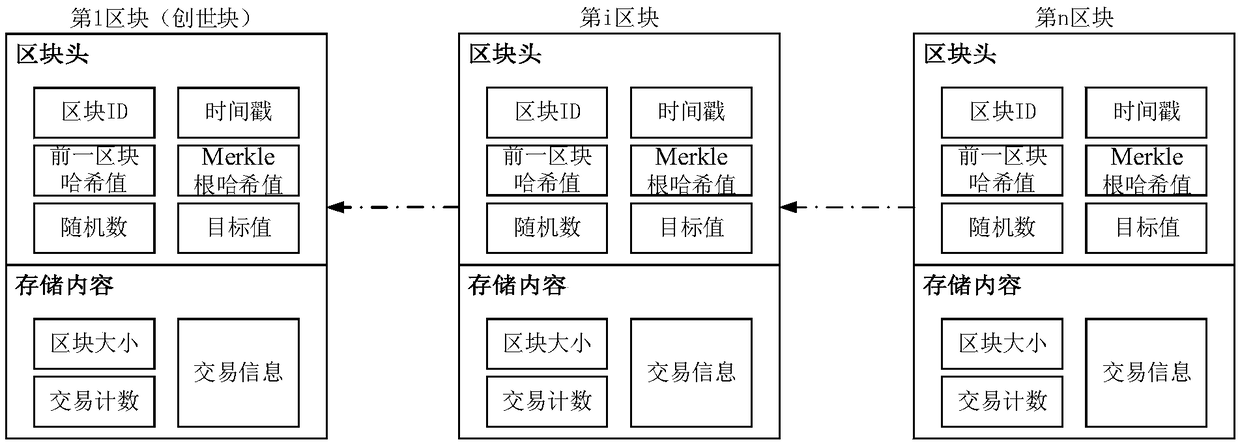
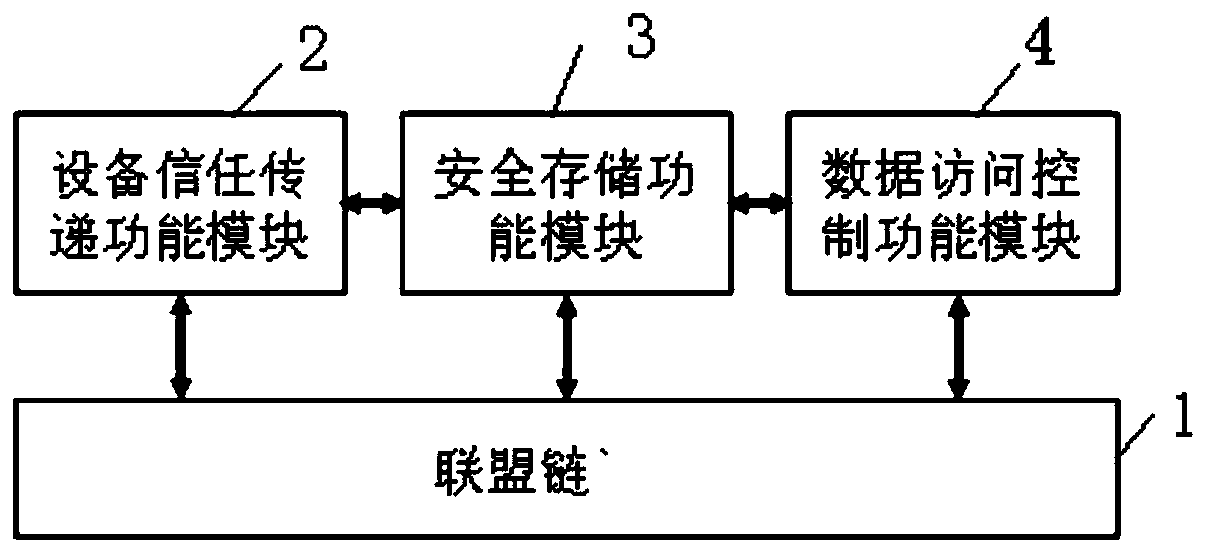
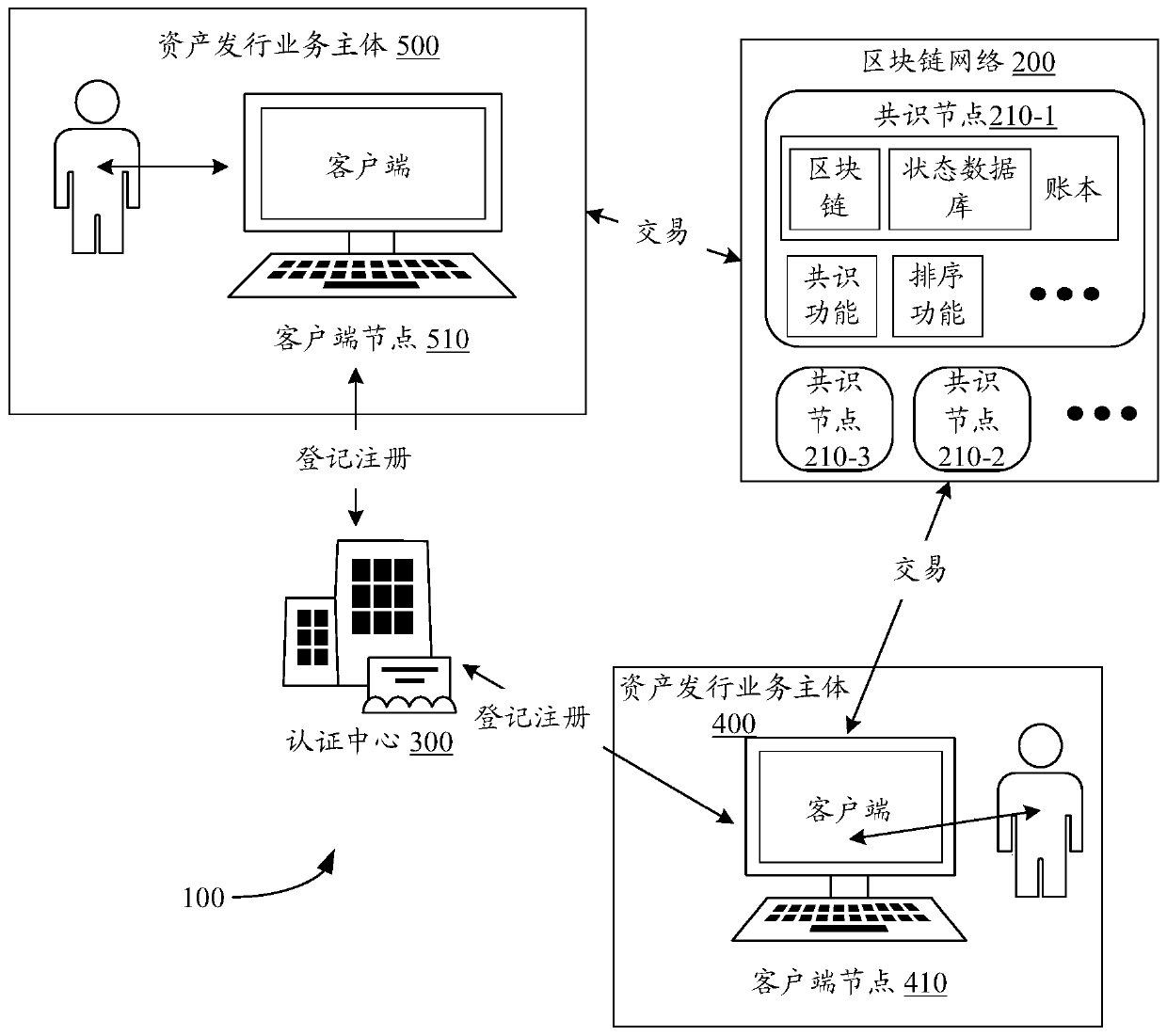
Device networking authentication method based on blockchain
ActiveCN108833081AGuaranteed legalityWill not affect operationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTimestampSmart contract
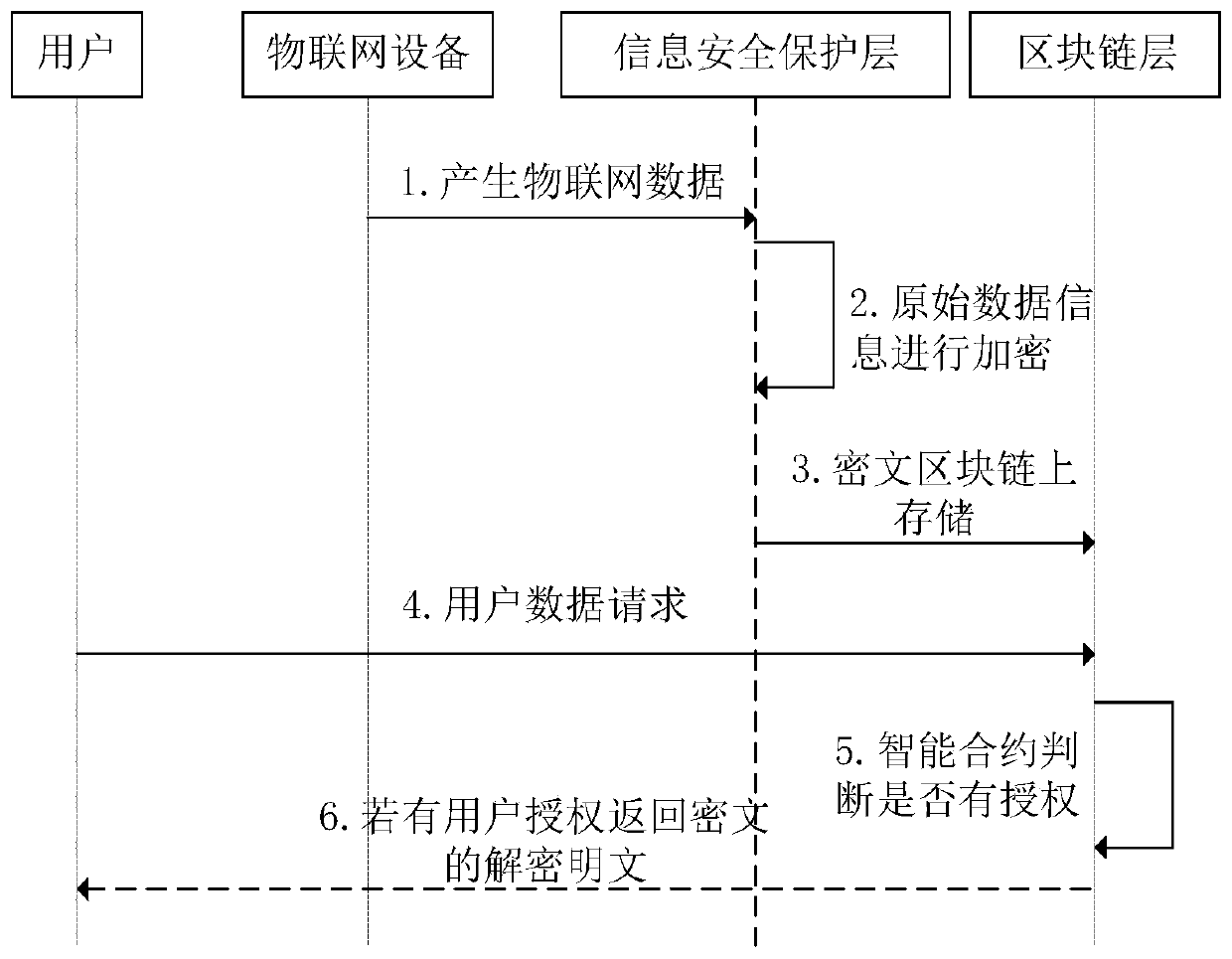
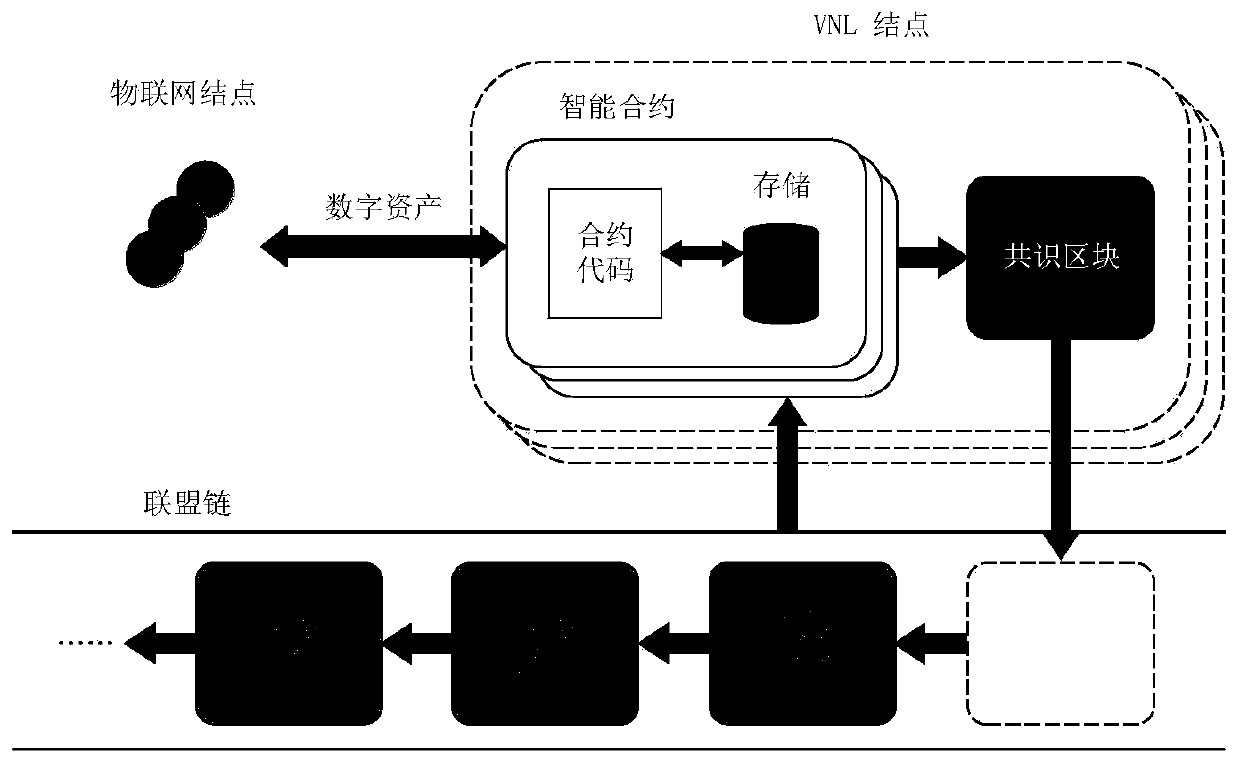
The invention discloses a device networking authentication method based on a blockchain for solving the single point failure problem existing in the current networking authentication method. The technical scheme is to deploy a blockchain network comprising a client, a submission node and a consensus node. By means of the non-tampering property of the blockchain, a device firstly registers on the blockchain before accessing the network, when the device A needs to access the network, the device sends a networking request of a device B that has accessed to the network, the device B compares the information of the device A in the networking request with the information of the device A stored in the blockchain to judge whether the identity of the device A is legal, a smart contract issues a token to the device A, a timestamp in the token ensures that the device A is valid within a certain period of time, and after the token expires, the device A needs to pass the identity authentication toaccess the network again. By adoption of the device networking authentication method disclosed by the invention, the single point failure problem existing in the traditional networking authenticationmethod can be avoided, the legality of the identity of the device is ensured, and the security of the network is improved.
Owner:NAT UNIV OF DEFENSE TECH
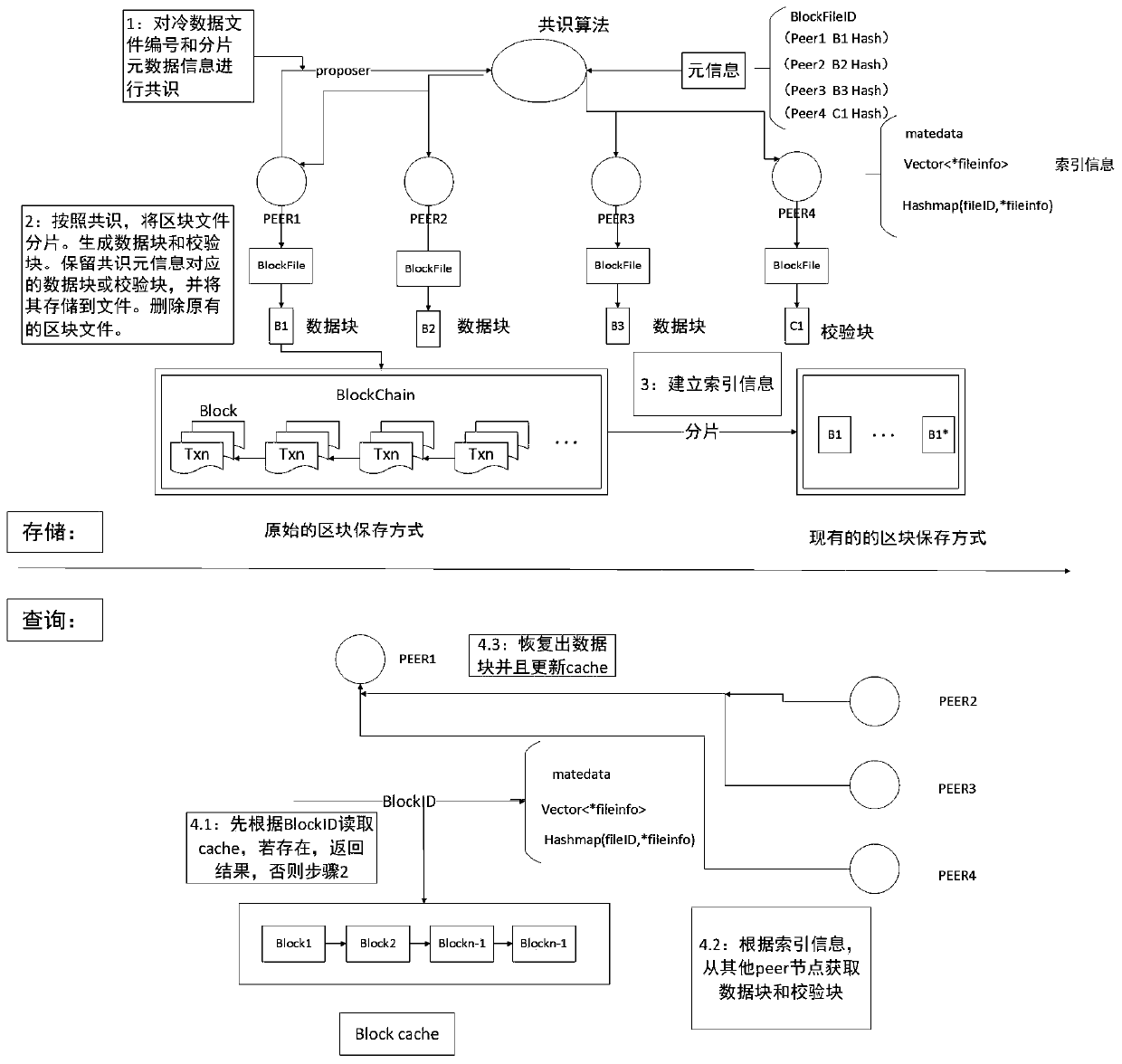
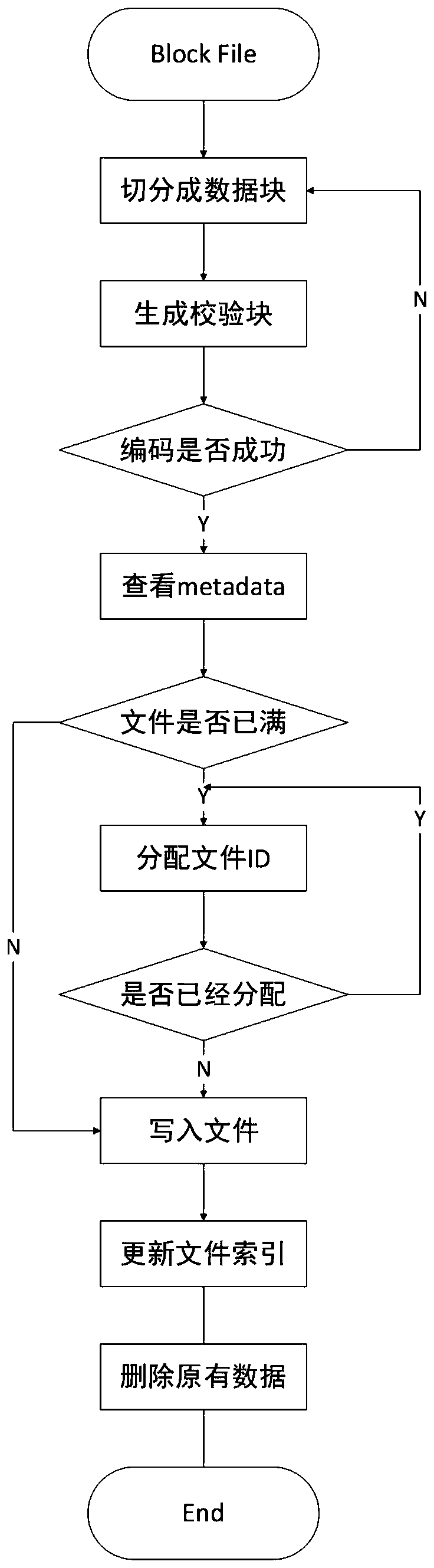
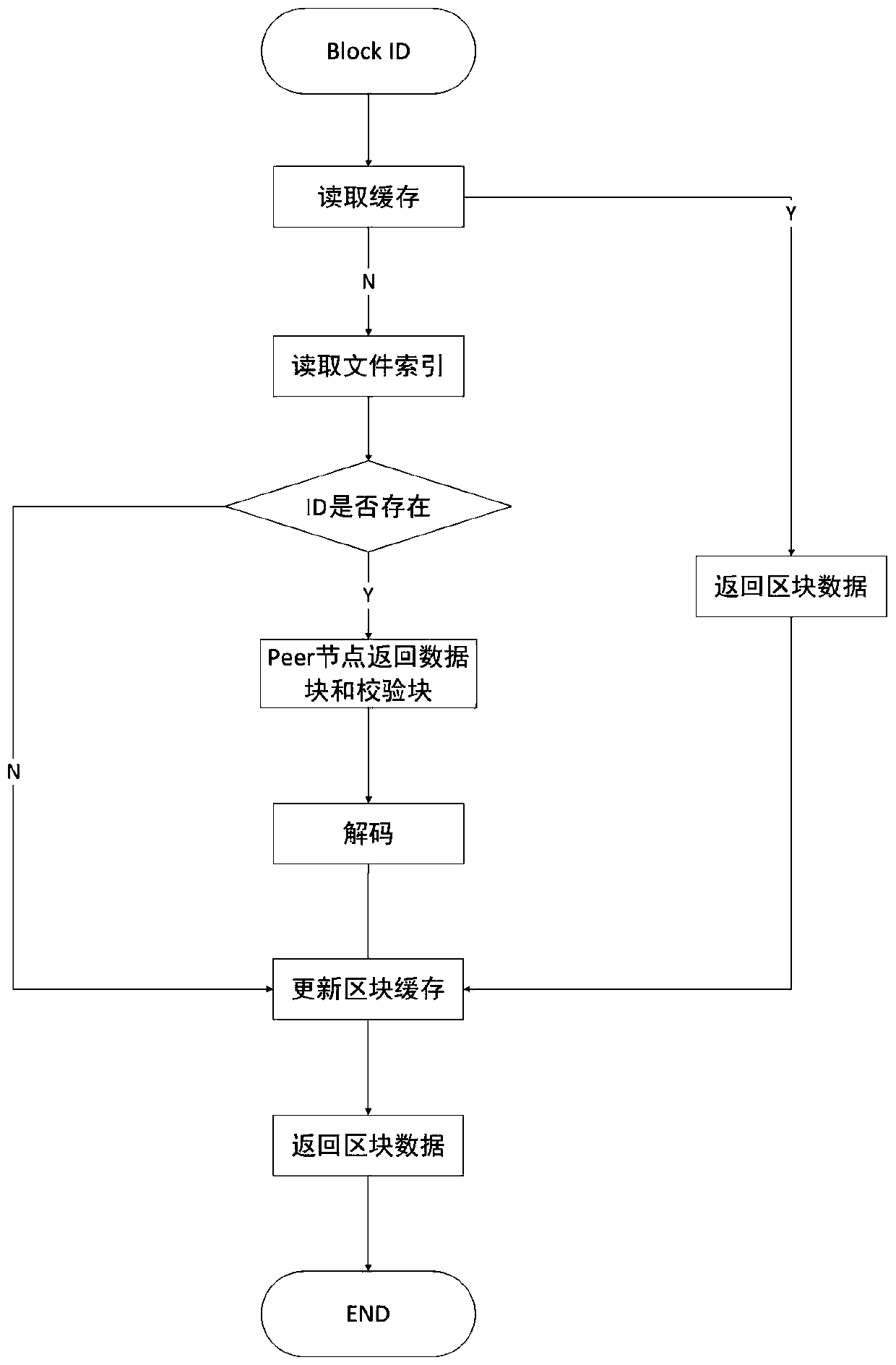
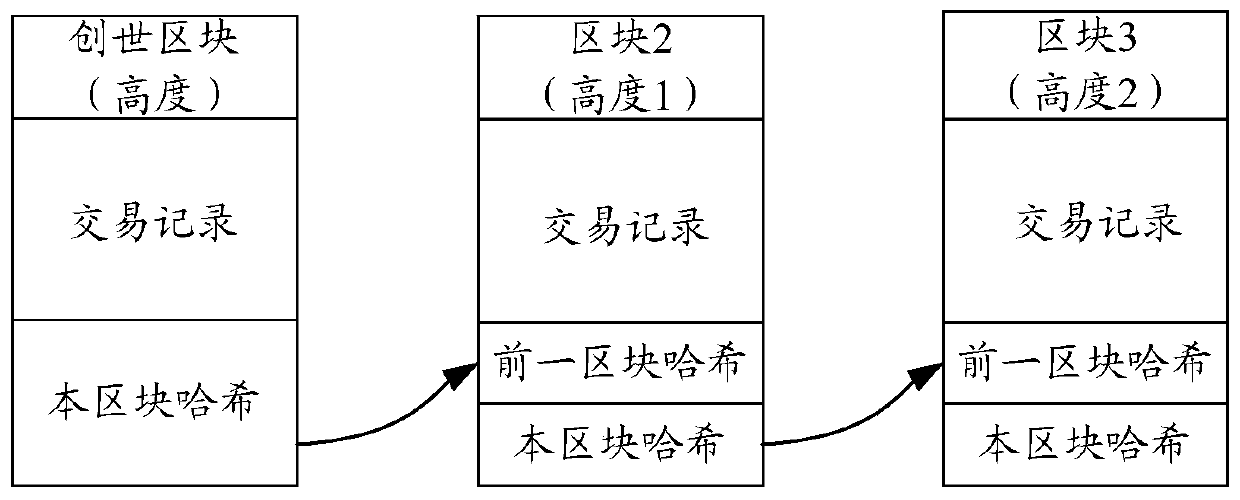
Block chain fragment storage and query method based on erasure codes
ActiveCN109871366AQuick searchEfficient queryFile access structuresSpecial data processing applicationsByzantine fault toleranceErasure code
The invention discloses a block chain fragment storage and query method based on erasure codes. When the block storage reaches a certain threshold, a block is sliced and stored. The method comprises the following steps that firstly, the meta-information of the block file fragments is consented, after the consensus is achieved, the erasure codes are utilized to fragment the block files within thethreshold value into the data blocks and the check blocks, and each node stores one part of the data blocks and the check blocks, so that the storage cost is reduced, and meanwhile, the data fault tolerance under the Bayer fault tolerance is also realized. Besides, when the block files are fragmented, the corresponding index is established, and the corresponding data block or check block can be queried from each node by utilizing the index, so that the block data can be queried efficiently under the condition that the storage space is saved.
Owner:EAST CHINA NORMAL UNIV
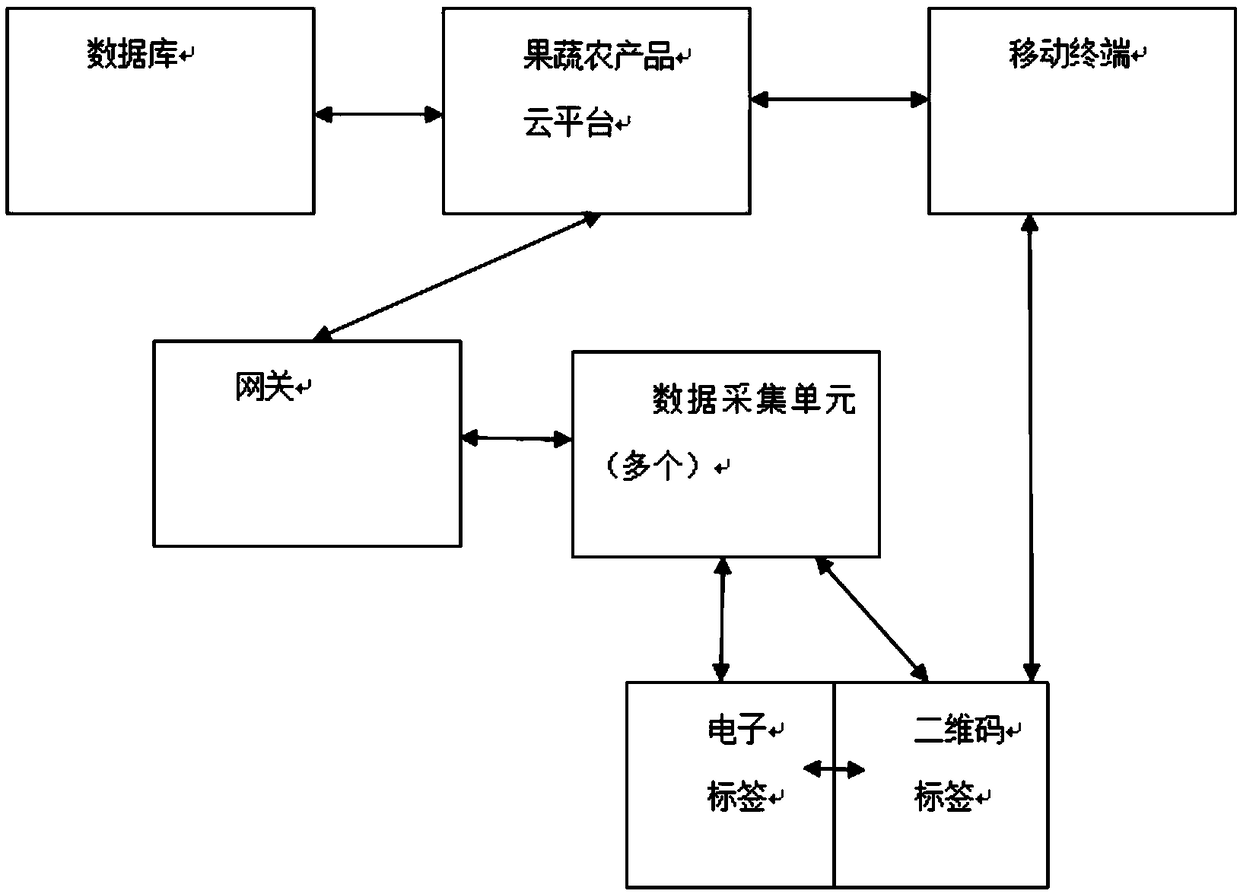
A fruit and vegetable agricultural product quality safety traceability system based on a block chain
InactiveCN109191003AGuaranteed not to be tampered withResolve integrityResourcesCommerceQuality safetyComputer science
The invention provides a fruit and vegetable agricultural product quality safety traceability system based on a block chain, which comprises a fruit and vegetable number generation module, a fruit andvegetable transaction generation recording module, a verification block chain module and a transaction block chain module. The invention utilizes the block chain technology, can ensure that the datain the whole link cannot be tampered with and cannot be replaced, records the whole transaction process through the transaction block chain and verifies the transaction behavior through the verification block chain, thereby solving the integrity and trustworthiness of the quality safety data in the fruit and vegetable agricultural product quality safety traceability system.
Owner:ZHONGKAI UNIV OF AGRI & ENG
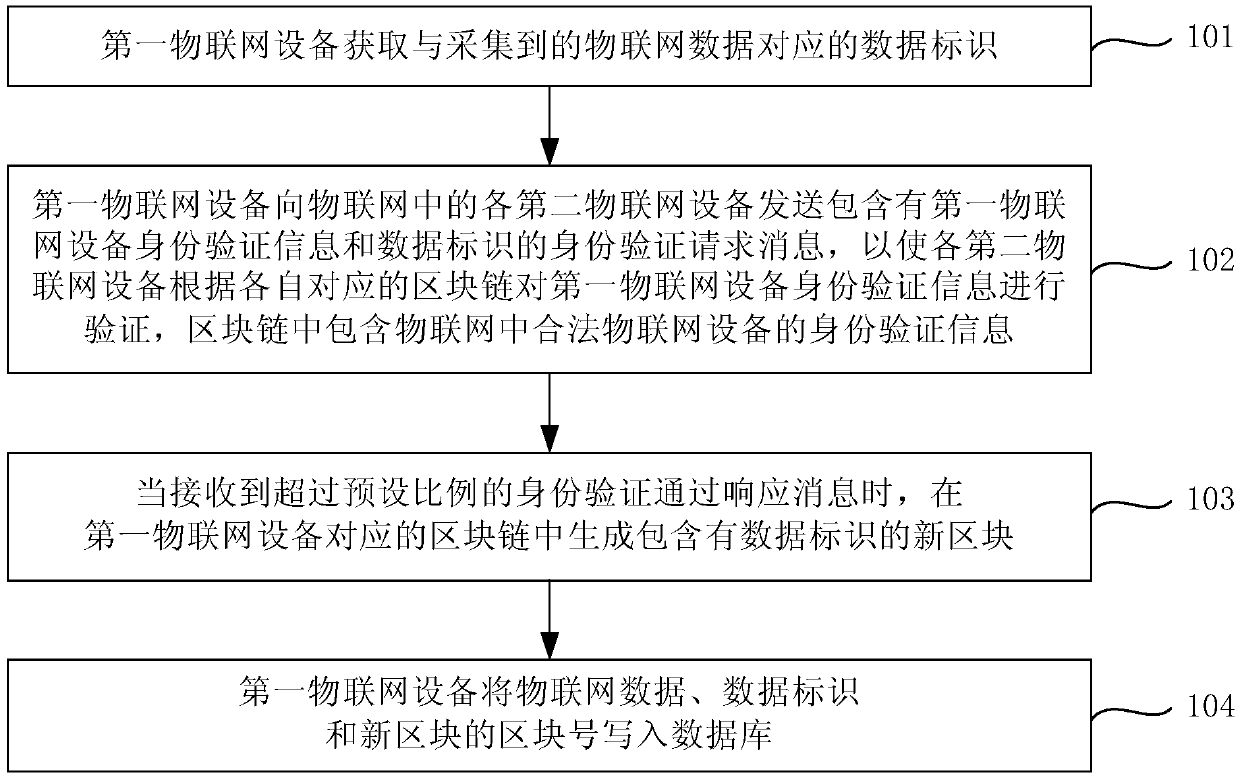
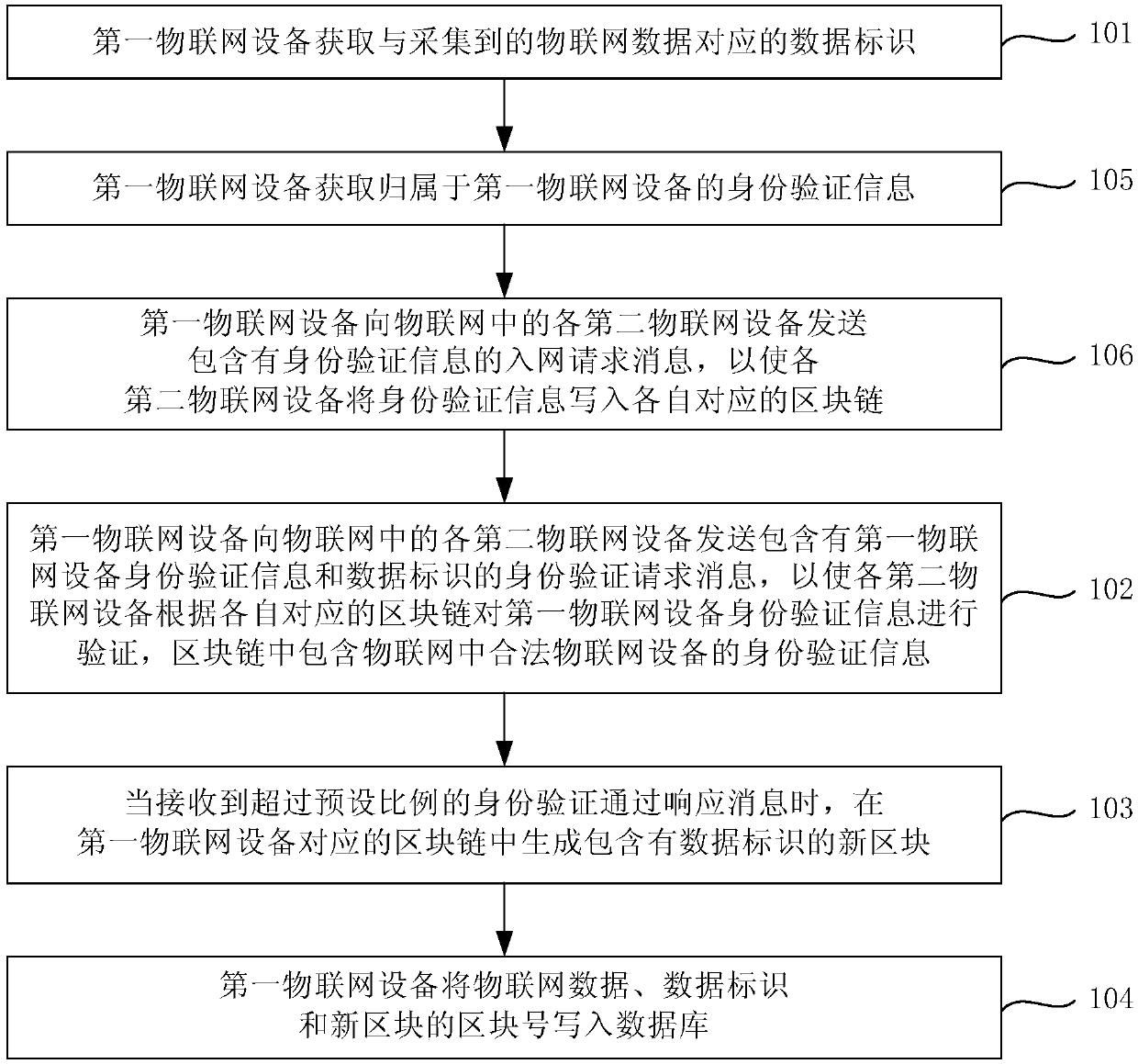
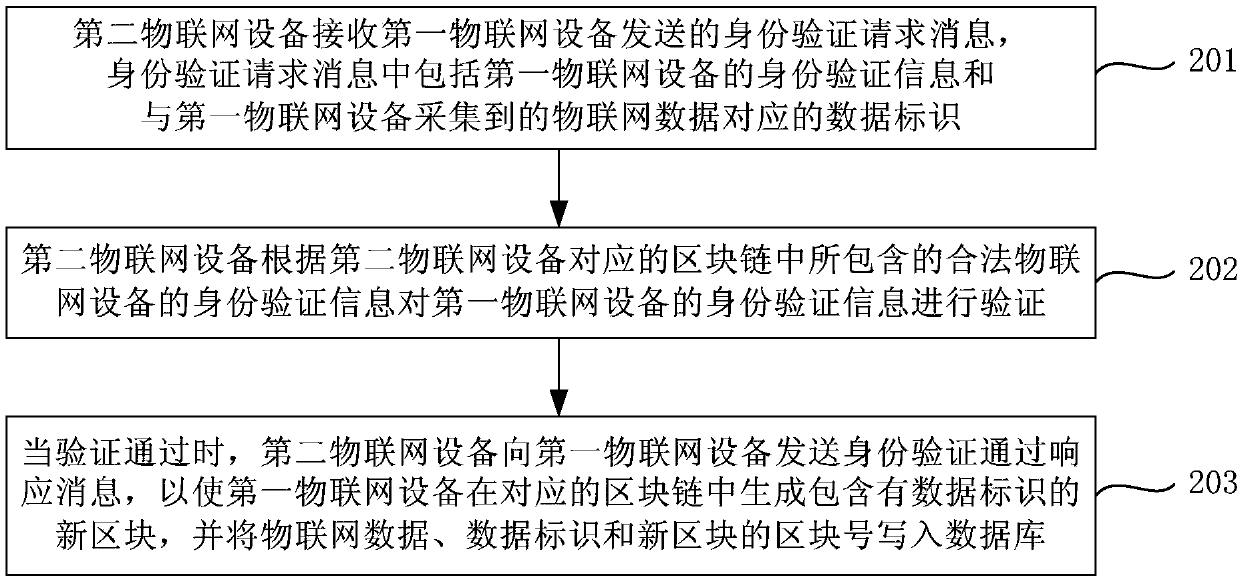
Internet of Things data processing method and device, and Internet of Things system
ActiveCN107749848AGuarantee authenticityGuaranteed not to be tampered withTransmissionThe InternetData library
The invention provides an Internet of Things data processing method and device, and an Internet of Things system the method. The method comprises the following steps of acquiring a data identifier corresponding to collected Internet of Things data, wherein the Internet of Things data is collected by a first Internet of Things device; sending an identity verification request message containing identity verification information of the first Internet of Things device and the data identifier to each second Internet of Things device in the Internet of Things in order to enable each second internetof things device to verify the identity verification information according to the respective corresponding block chain, wherein the block chain comprises identity verification information of the legalInternet of Things devices in the Internet of Things; when identity verification passing response messages exceeding a preset proportion are received, generating a new block comprising the data identifier in the block chain corresponding to the first Internet of Things device; and writing the Internet of Things data, the data identifier and the block number of the new block into a database. According to the Internet of Things data processing method and device, and the Internet of Things system, the authenticity and the reliability of the Internet of Things data can be improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
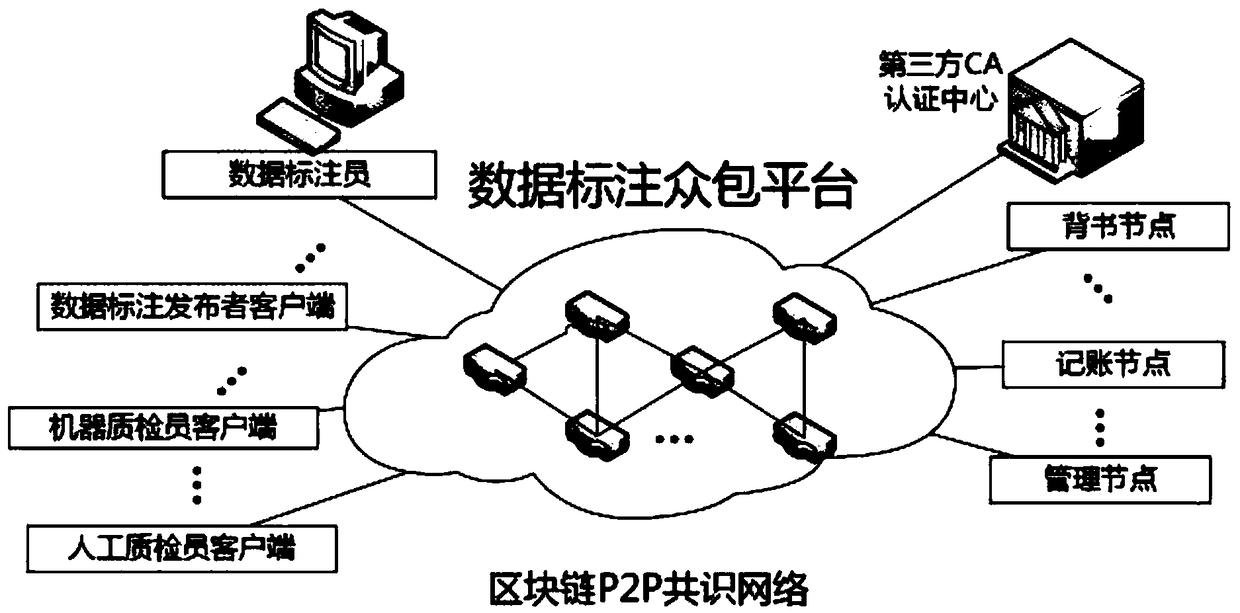
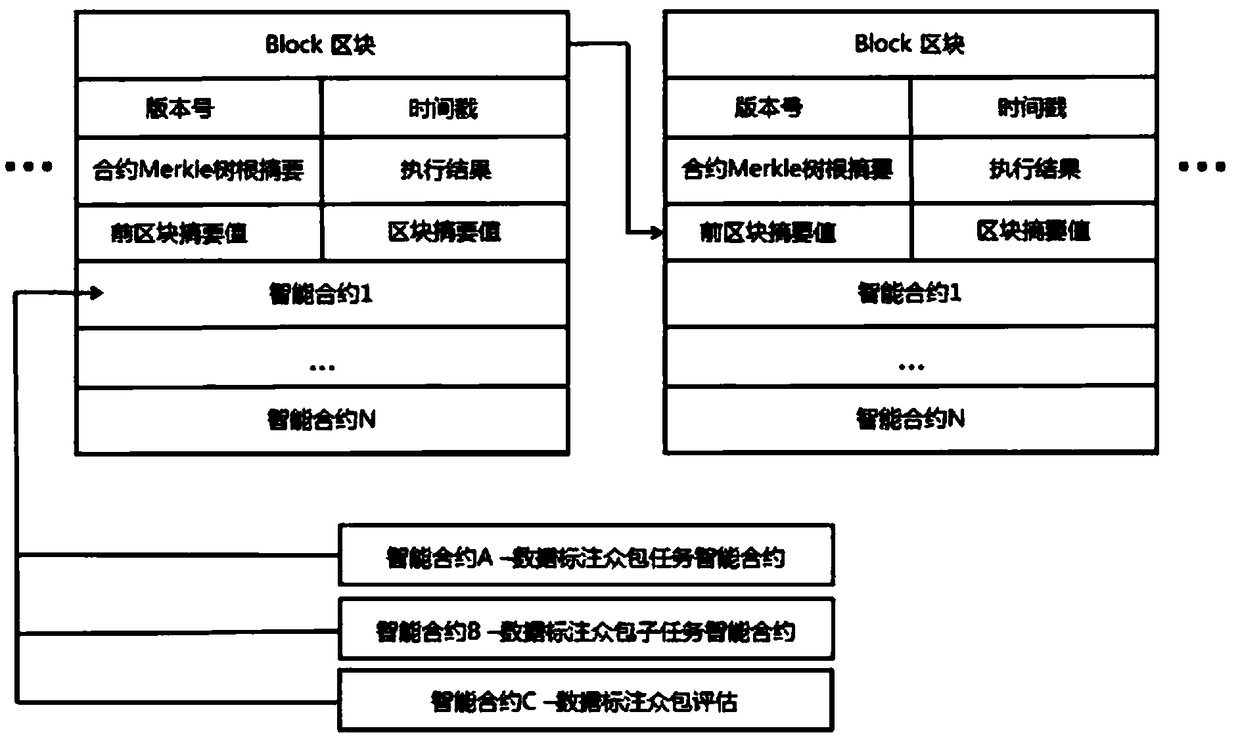
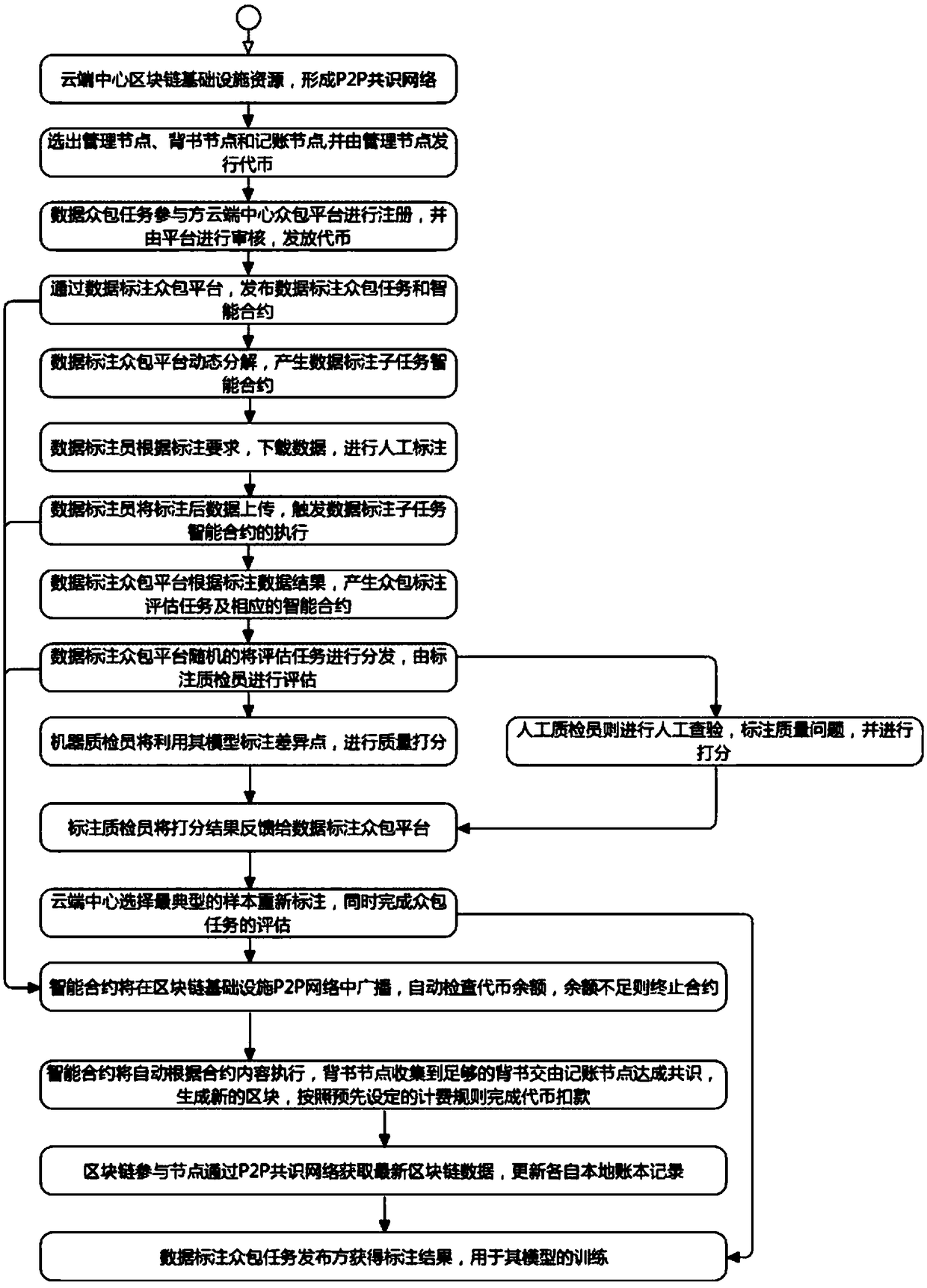
A data annotation crowdsourcing platform system based on an intelligent contract and a crowdsourcing data annotation method
InactiveCN109445948AImprove execution efficiencyImprove accuracyResource allocationDigital data protectionData AnnotationSmart contract
The invention relates to the technical field of block chains, intelligent contracts, data crowdsourcing, machine learning and deep learning, in particular to a data annotation crowdsourcing platform system based on an intelligent contract and a crowdsourcing data annotation method. The crowdsourcing data annotation method comprises the steps of separating the data crowdsourcing annotation task from the annotation result quality evaluation task, evaluating annotation data through the trained model, randomly selecting a plurality of annotation data quality inspectors for crowdsourcing evaluation, and determining the data annotation quality by integrating a plurality of evaluation modes. The whole process of the crowdsourcing task is written into the block chain through the block chain infrastructure, the mutual trust of all parties participating in crowdsourcing is achieved, the integrity and the non-tamper performance of behaviors are guaranteed, the data labeling quality is improved toa certain degree, and then the model training efficiency and the model prediction accuracy are improved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Blockchain technology authentication method based on partial image
InactiveCN108416590AGuaranteed not to be tampered withGuaranteed non-replaceableCo-operative working arrangementsPayment protocolsDaily livingSoftware engineering
The invention discloses a blockchain technology authentication method based on a partial image. A partial image of the physical surface of a product at a production end is photographed, a blockchain registration transaction is created by using the partial image and product authentication information as transaction data of the blockchain, and at the time of authentication, a consumer photographs the partial image and an authentication information label at the same position on the physical surface and uses the image recognition technology and blockchain technology to realize the fidelity and traceability of the physical product. The method of the invention uplinks the image of the surface of the physical product as transaction information to the underlying blockchain, ensures that the physical object is not falsified or replaced by identifying whether the physical surface image captured by the authenticator is consistent with the image in the block, and establishes a first link of the Blockchain technology in the fidelity, anti-counterfeiting and traceability of physical products, thereby enabling the blockchain technology to serve the daily lives of the broad masses of the people.
Owner:程昔恩
Distributed account book technology-based sensor network safety management method and safety system
ActiveCN110445827ASolve centralized management problemsAddress shared access controlDigital data protectionTransmissionData setUniform resource locator
The invention provides a distributed account book technology-based sensor network safety management method. The method comprises the following steps of selecting a top layer and a regional server as alliance chain nodes to establish an alliance chain, and storing a distributed account book; generating an asymmetric key for a sensing and aggregation node at the lower layer of the regional server, solidifying a private key in a memory, and writing a public key into an alliance chain; uploading the data collected by the sensing nodes to a regional server through the aggregation node, storing thedata set in an off-chain database of the regional server and encrypting the data set after the verification is passed, calculating a hash value of the data set and writing the hash value into an alliance chain to serve as an evidence; and S3, decrypting the data set, calculating a hash value of the data set, comparing the hash value with the evidence in the step S3 to verify the correctness of thedata set, and returning a uniform resource locator. The invention further provides a safety system. According to the safety management method, a centralized and effective equipment management mechanism and data safety verification are provided for a large-scale sensor network. The problem of data sharing access control is solved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
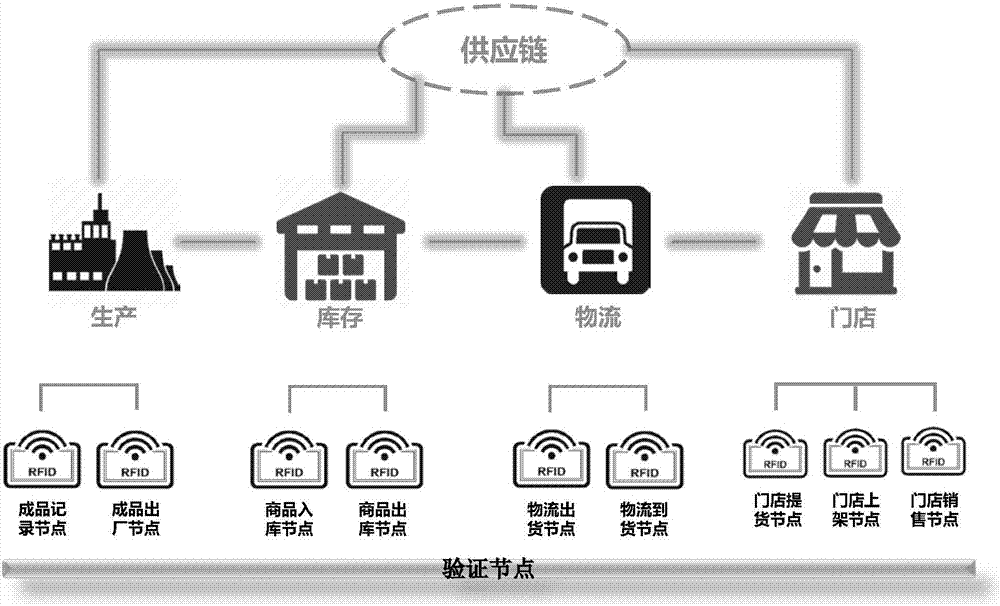
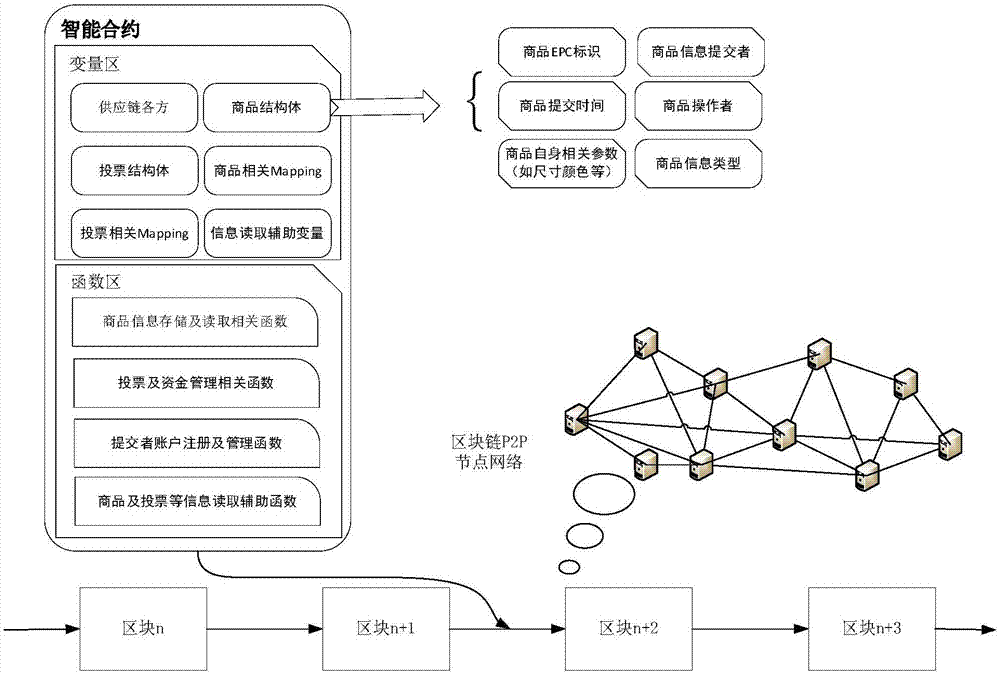
Supply chain management method
ActiveCN108009778ARealize on-chain storageGuaranteed not to be tampered withCo-operative working arrangementsLogisticsMulti linkMulti aspect
The invention relates to a supply chain management method. RFID (Radio Frequency IDentification) and a smart contract technology in a blockchain are mainly used for realizing multi-link fund and information flow management to which practical supply chain management relates; one commodity finishes a quick upper-chain operation in information including production, transportation, warehousing, selling and the like in a supply chain link on the basis of the RFID technology; and the blockchain is taken as a bottom layer distributed account book, the safe upper-chain storage of commodity data is realized through the characteristics of no tampering and integral and accurate data, a consumer can conveniently, quickly and accurately trace all information to which the commodity relates in the supplychain when disputes happen or commodity information needs to be checked, and the traceability, the verification and multi-aspect unification and transparency of the data of each link of the commoditycan be realized.
Owner:南京思利华信息科技有限公司
Crowdsourcing resource distributed anonymous allocation method based on block chain and allocation system thereof
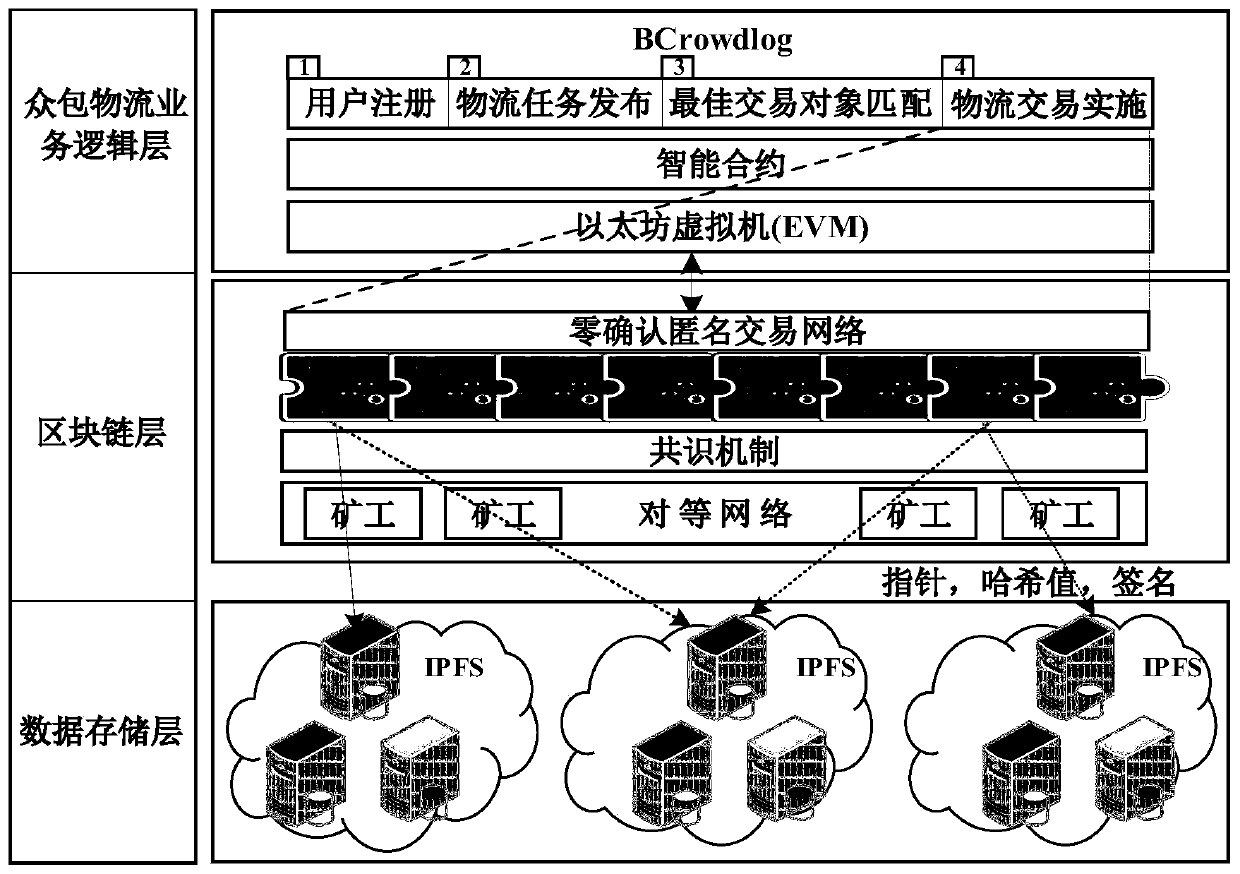
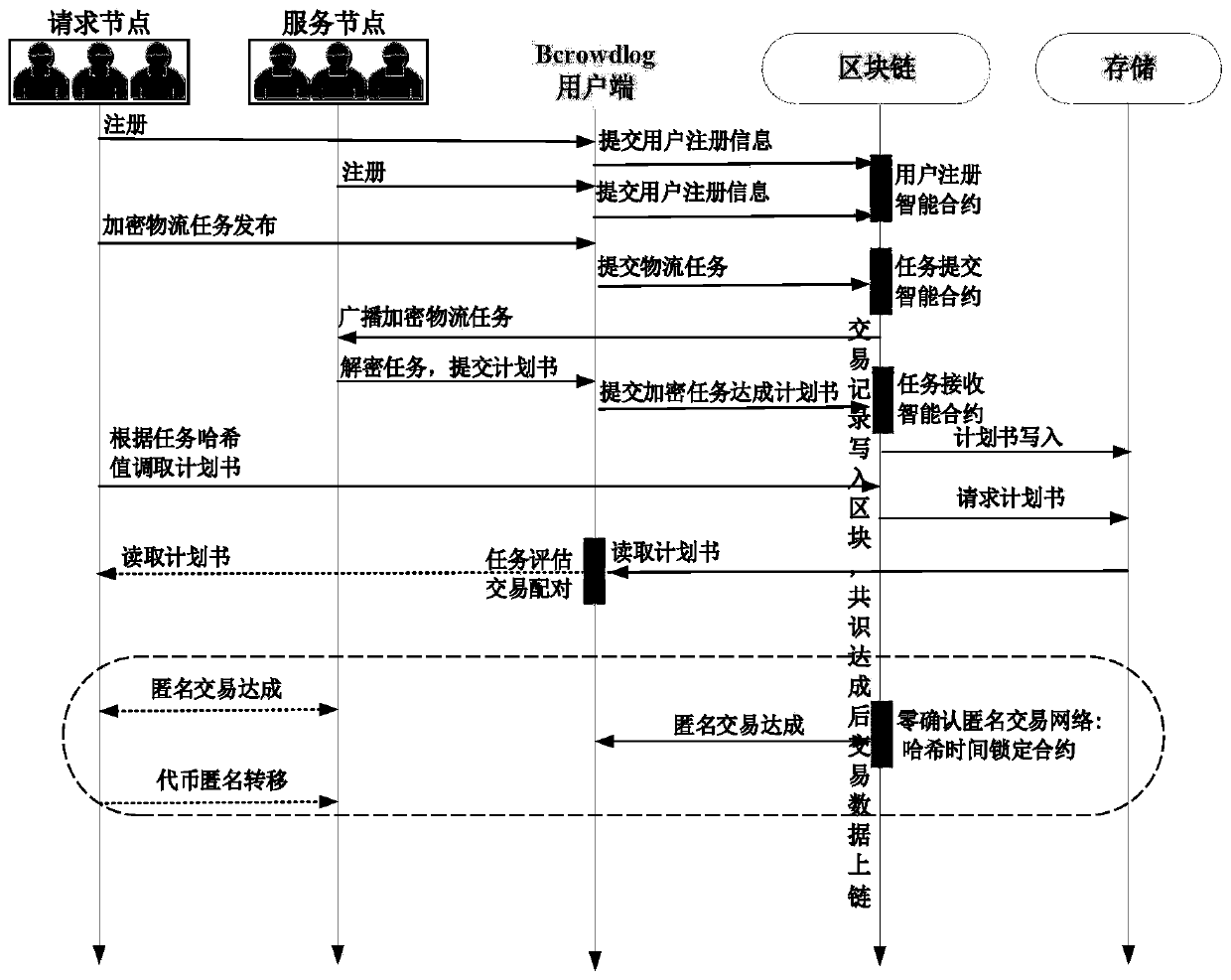
PendingCN110069345AAvoid single point of failureAvoid serious problems with failureKey distribution for secure communicationFinanceChain networkDistributed computing
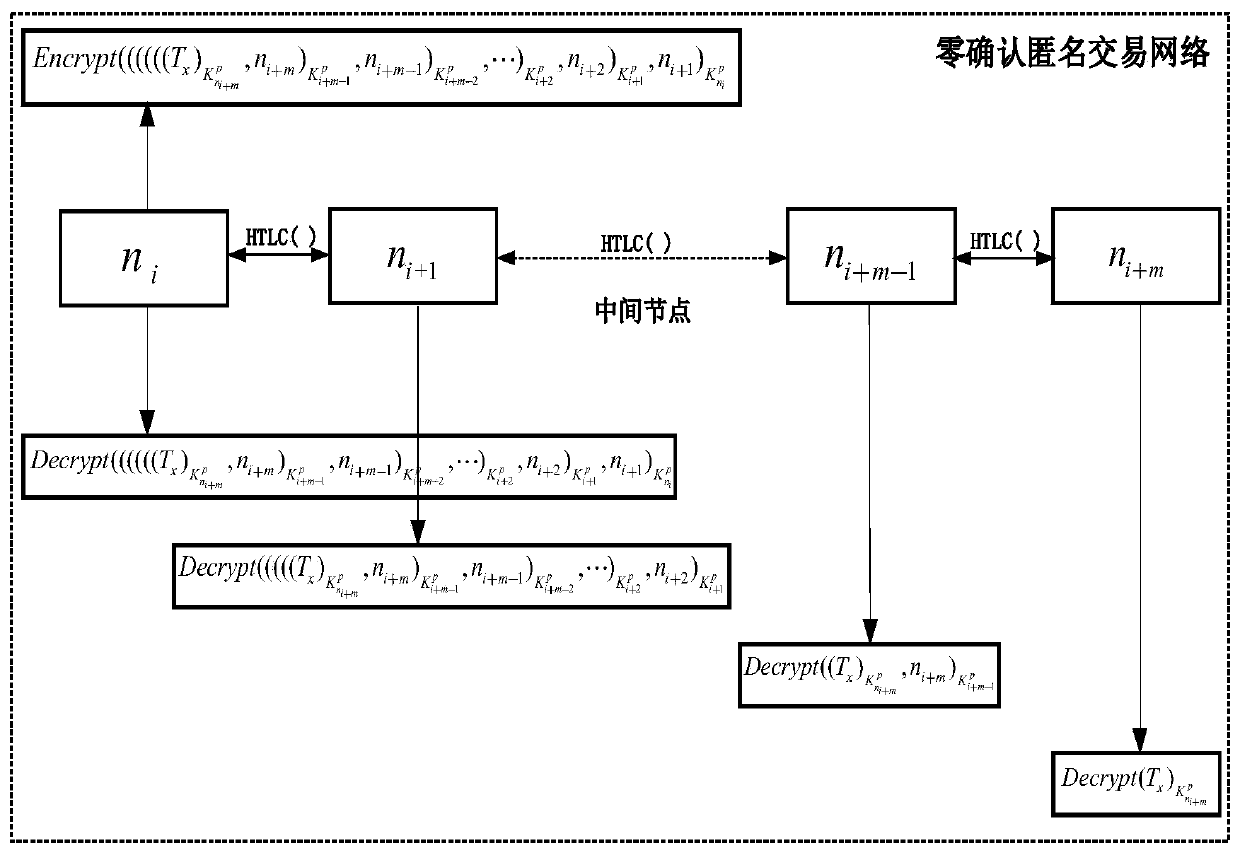
The invention discloses a crowdsourcing resource distributed anonymous allocation method based on a block chain and an allocation system thereof, hereinafter referred to as a crowdsourcing resource anonymous allocation system, comprising the following steps: user registration; linking the user registration information; creating a task release intelligent contract on the block and recording task release information; making a plan on the premise of the service node; enabling the request node to select the most excellent service node from the achievement of the plan; and creating a Hash time locking contract on the block and establishing an onion route to realize anonymous communication of the two parties of the transaction. According to the invention, the Hash time locked smart contract is introduced into the block chain network, zero confirmation transaction chaining is realized, and the transaction amount in unit time is greatly improved. In addition, an onion route from the request node to the service node can be constructed through a payment channel established by the Hash time locking contract, so that anonymous transactions of the request node and the service node are realized.
Owner:JIANGSU UNIV
Information prediction method and apparatus based on blockchain, medium, and electronic equipment
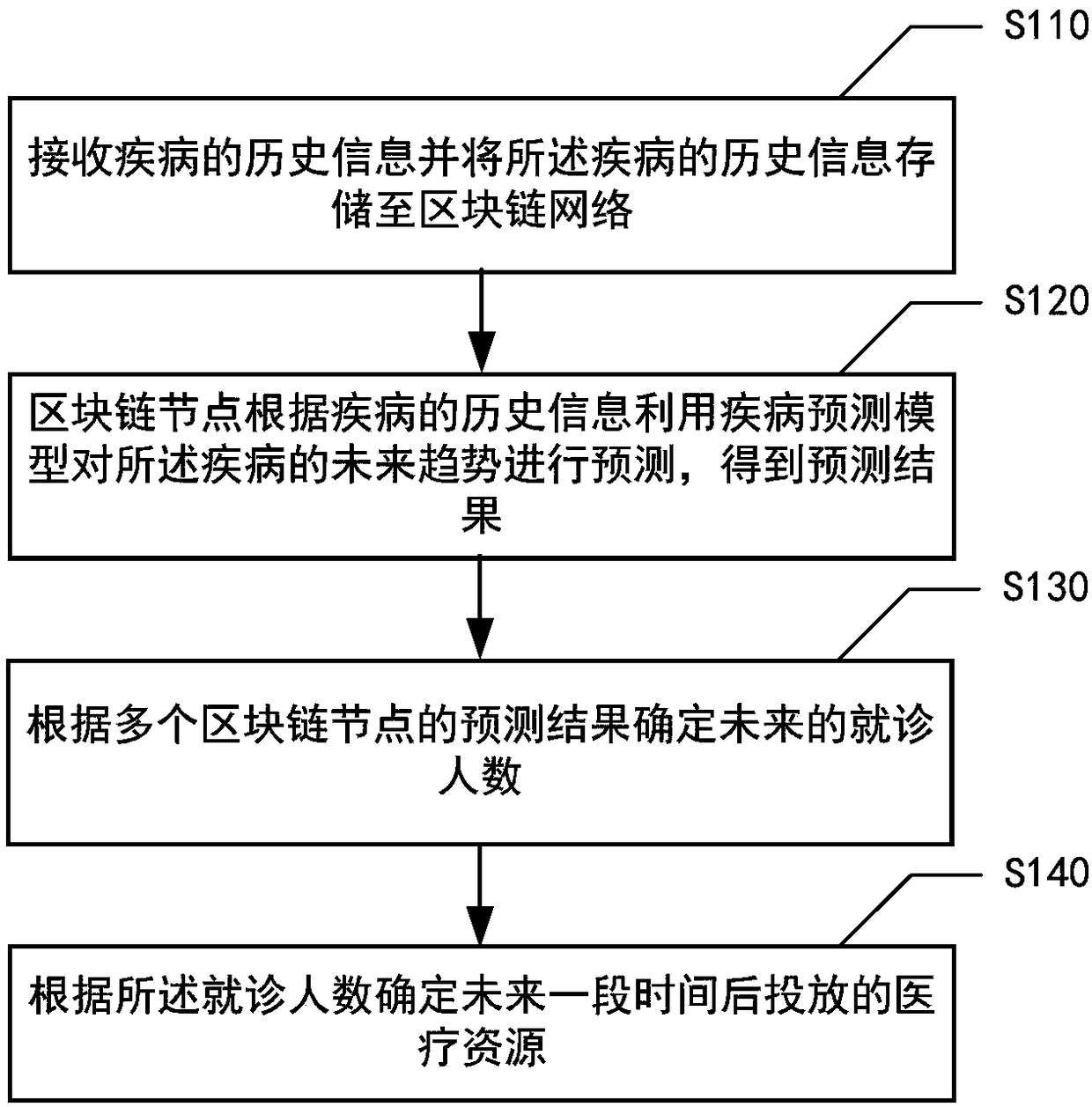
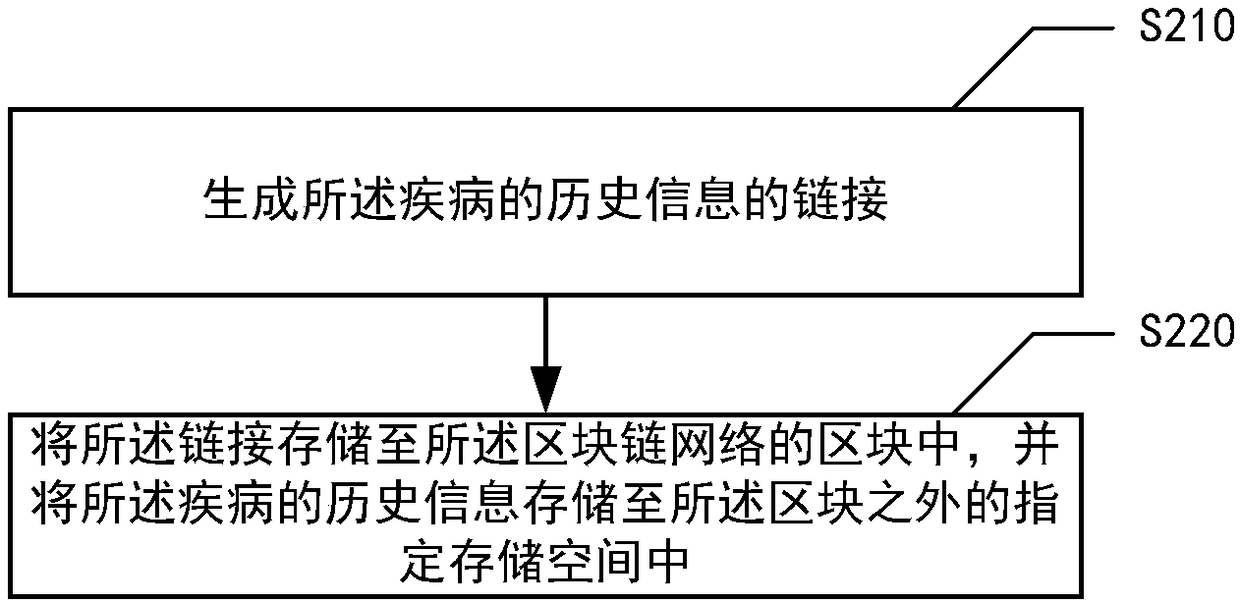
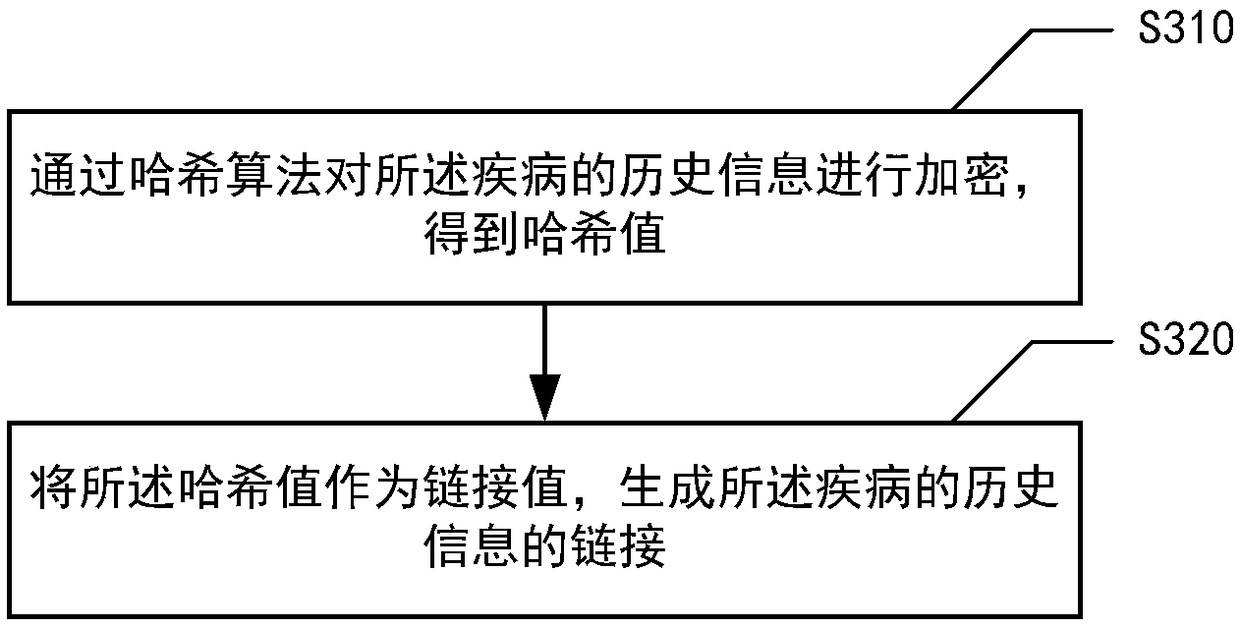
ActiveCN109036579AAutomatically predict outbreaksTimely reminder of preparationsEpidemiological alert systemsSpecial data processing applicationsOutbreakMachine learning
The embodiment of the invention provides an information prediction method based on a blockchain. The information prediction method is characterized in that the method includes steps: receiving historical information of a disease and storing the historical information of the disease in a blockchain network; predicting the future trend of the disease according to the historical information of the disease through a disease prediction model and obtaining prediction results by blockchain nodes, wherein the type of the disease prediction model corresponds to the type of the disease; determining thedoctor-seeing people number according to the prediction results of multiple blockchain nodes; and determining medical resources after a future period according to the doctor-seeing people number. According to the technical scheme of the method, the outbreak condition of the disease in the future period can be effectively and automatically predicted, the preparation condition of required drug materials and medical personnel for dealing with the outbreak condition can be reminded in time, and the problem of high manpower cost caused by manual prediction of the outbreak condition of the disease is solved.
Owner:TAIKANG LIFE INSURANCE CO LTD
Anti-tampering private fund electronic contract signing system and method based on block chain
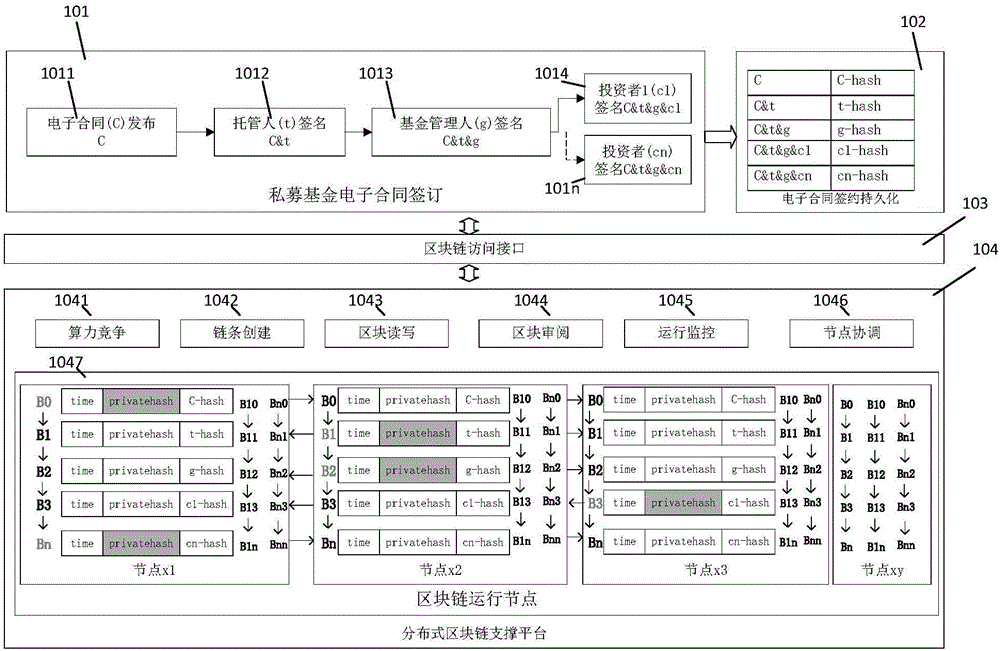
InactiveCN106570681AMake sure not to disappearGuaranteed not to be tampered withFinanceUser identity/authority verificationElectronic contractsData bank
The invention discloses an anti-tampering private fund electronic contract signing system and method based on a block chain. A private fund electronic contract signing unit is used for issuing electronic contracts, receiving trustee signatures, receiving fund manager signatures, and receiving investor signatures. The original electronic contract, the custody-signed electronic contract, the fund manager-signed electronic contract and the investor-signed contract are sent to the distributed block chain support platform for storage through the distributed block chain access interface. At the same time, the signature hash codes of contracts fed back by the distributed block chain support platform in different signature stages are received. An electronic contract signing database stores electronic contract summaries, signature information and signature hash codes of electronic contracts in different signature stages. The distributed block chain access interface accesses the distributed block chain support platform. The private fund tripartite contract whole-course electronic supervision and management is achieved, and the security, repudiation resistance, zero loss and traceability of private fund tripartite contract management can be achieved.
Owner:山东明和软件有限公司
Internet of Things information security protection method based on block chain
ActiveCN109889522AGuaranteed not to be tampered withProtection securityTransmissionData informationCiphertext
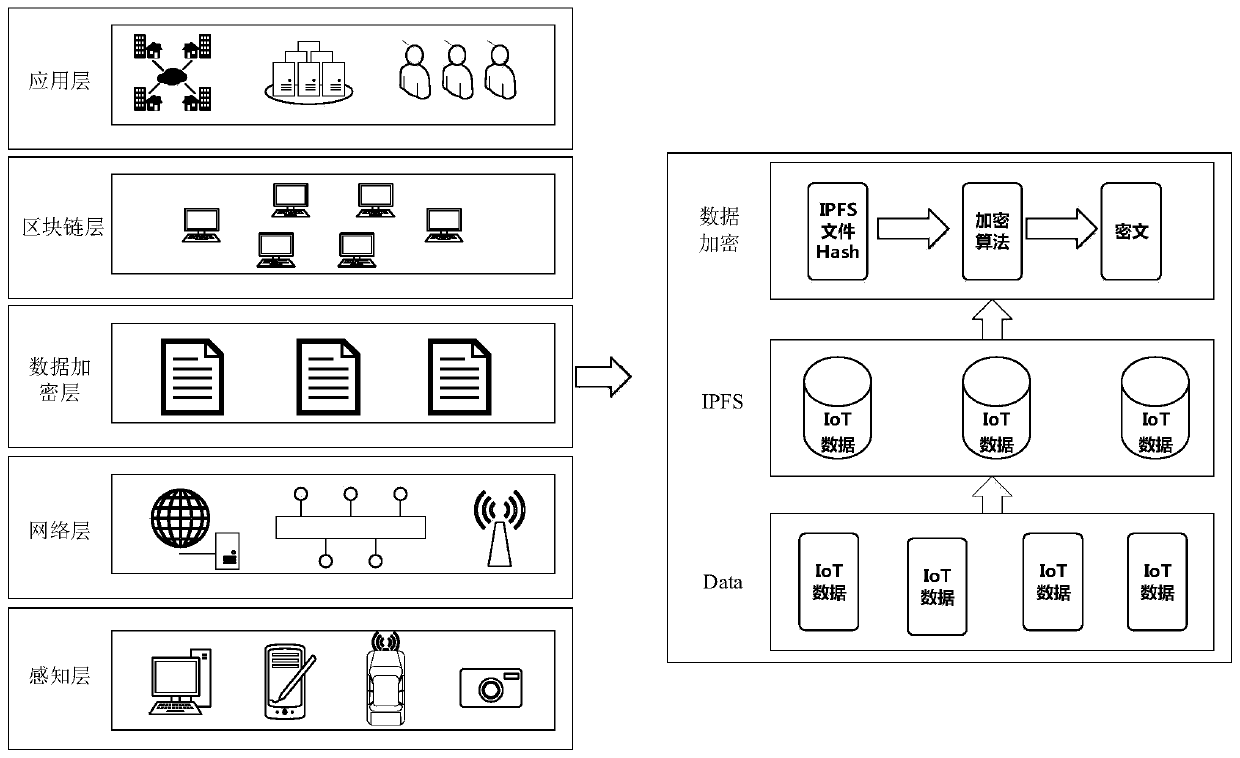
The invention requests to an Internet of Things information security protection method based on a block chain. The method comprises the following steps: a, dividing an Internet of Things information security protection system; b, carrying out data segmentation on the received data information of the Internet of Things; c, establishing an index of a data block for the segmented data; and d, storingthe data in a Hash value returned by the IPFS system for encryption, and storing the encrypted ciphertext in a block chain. According to the invention, massive Internet of Things data information canbe effectively stored, illegal users can be tracked illegally, and the data privacy of the Internet of Things can be protected.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
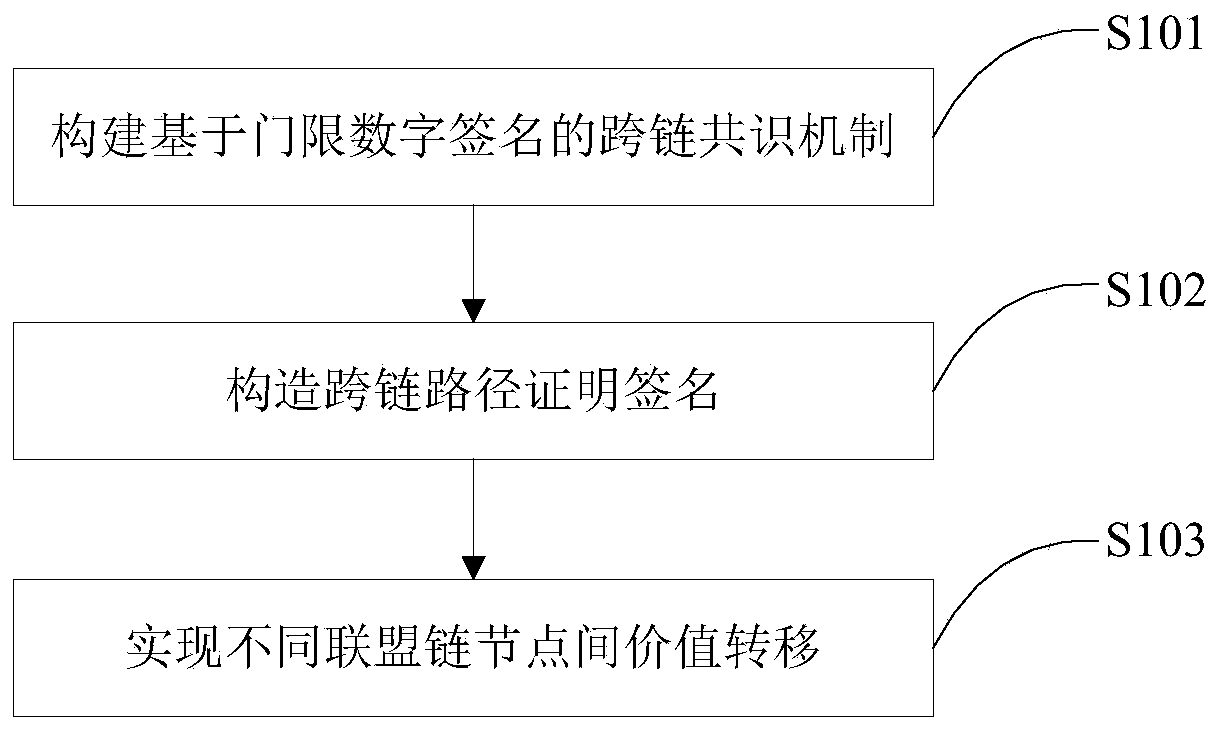
Medical alliance chain lightweight dynamic autonomous cross-chain interaction method
ActiveCN110993044AGuaranteed Data IntegrityGuarantee data reliabilityDigital data protectionPatient-specific dataDigital signatureSmart contract
The invention belongs to the technical field of medical alliance chains, and discloses a medical alliance chain lightweight dynamic autonomous cross-chain interaction method. The method comprises thesteps: constructing a cross-chain consensus mechanism based on a threshold digital signature; constructing a cross-chain path certification signature, including group key generation and sharing, threshold subgroup signature generation and path certification updating; and realizing the value transfer among different alliance chain nodes. According to the method, the inter-node communication topology of a medical alliance chain is simplified, a node cross-chain communication model based on an intelligent contract state period and a node cross-chain communication identity credibility path provingconstruction rule are given, and dynamic construction and verification of inter-chain transaction interactive credible path proving are carried out; the consensus process of cross-chain transactionsby a plurality of alliance chain verification node lists is modeled into a threshold digital signature process with a plurality of privilege subgroups, so the alliance chain internal consensus based on the verification node lists is expanded into the inter-alliance chain cross-chain consensus on the premise of not increasing the computational complexity.
Owner:ZHOUKOU NORMAL UNIV
Two-dimensional code identification method based on digital signatures and timestamps
InactiveCN105095728ALarge information capacityImprove reliabilityDigital data authenticationPaymentElectronic identification
The invention discloses a two-dimensional code identification method based on digital signatures and timestamps. The two-dimensional code identification method comprises the steps of performing the digital signatures and stamping the timestamps. Because the timestamps are adopted in electronic identification of the two-dimensional code identification method disclosed by the invention, the signature time can be fixed; the integrity and the authenticity of a time stamp are ensured through the digital signatures; the backdating behaviour can be effectively prevented; the security protection to electronic identity information is enhanced; strong evidences can also be provided for related disputes; and the two-dimensional code identification method disclosed by the invention can be applicable to occasions, such as meeting signatures, entrance guards and payments.
Owner:南京市信息中心 +1
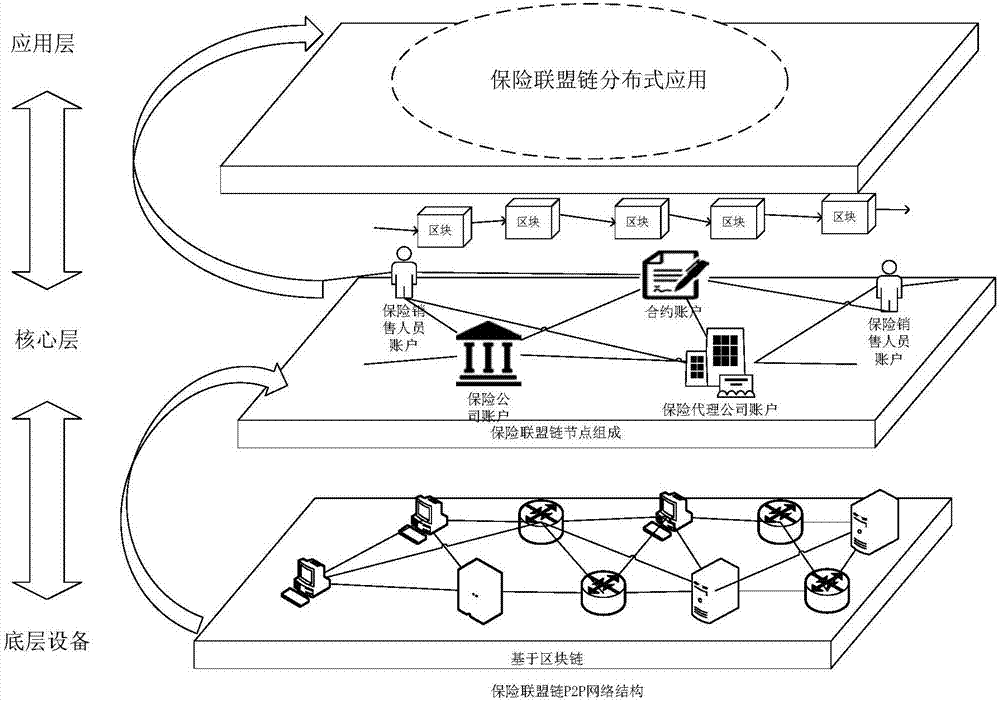
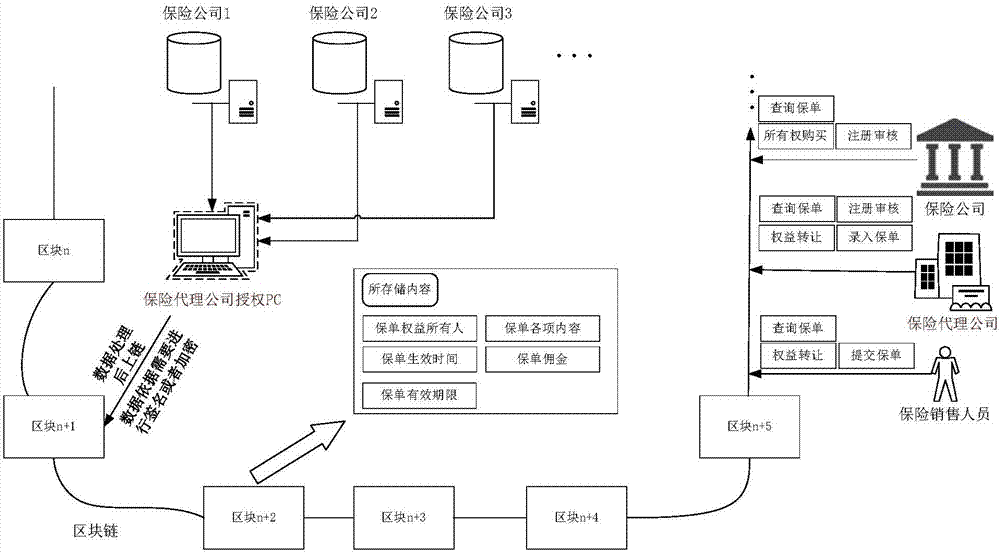
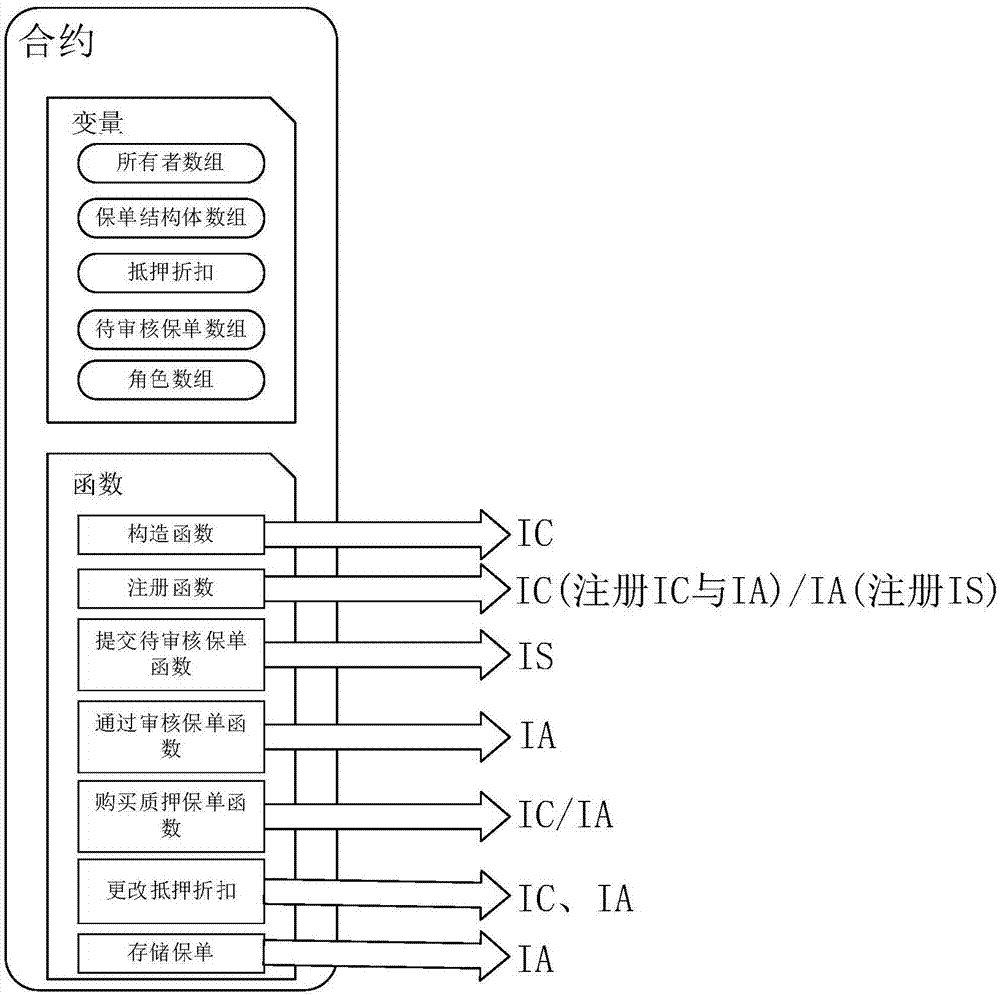
Method for managing insurance policy sales commission rights and interests on basis of block chains
ActiveCN107993047AGuaranteed not to be tampered withGuaranteed robustnessFinanceDatabase distribution/replicationAmbiguitySmart contract
The invention relates to a method for managing insurance policy sales commission rights and interests on the basis of block chains. The method mainly includes carrying out a series of standard management on the insurance policy sales commission rights and interests by the aid of intelligent contracts in the block chains, and insurance sales personnel and insurance agencies are related to the insurance policy sales commission rights and interests when the rights and interests are acquired by the insurance sales personnel and the insurance agencies from sold insurance policies. The method has the advantages that the block chains are a distributed de-centralization ledger technology and can be free of dependency on trust of optional trusted third parties, and data stored in the block chains can be guaranteed against being illegally stolen or forged or tampered; the method is benefited by the deficiency of ambiguity of programs and the safety characteristics of the block chains, established business logics can be conveniently completed among various characters in systems by the aid of intelligent contract technologies, and business can be processed in a transactional manner.
Owner:焦文华
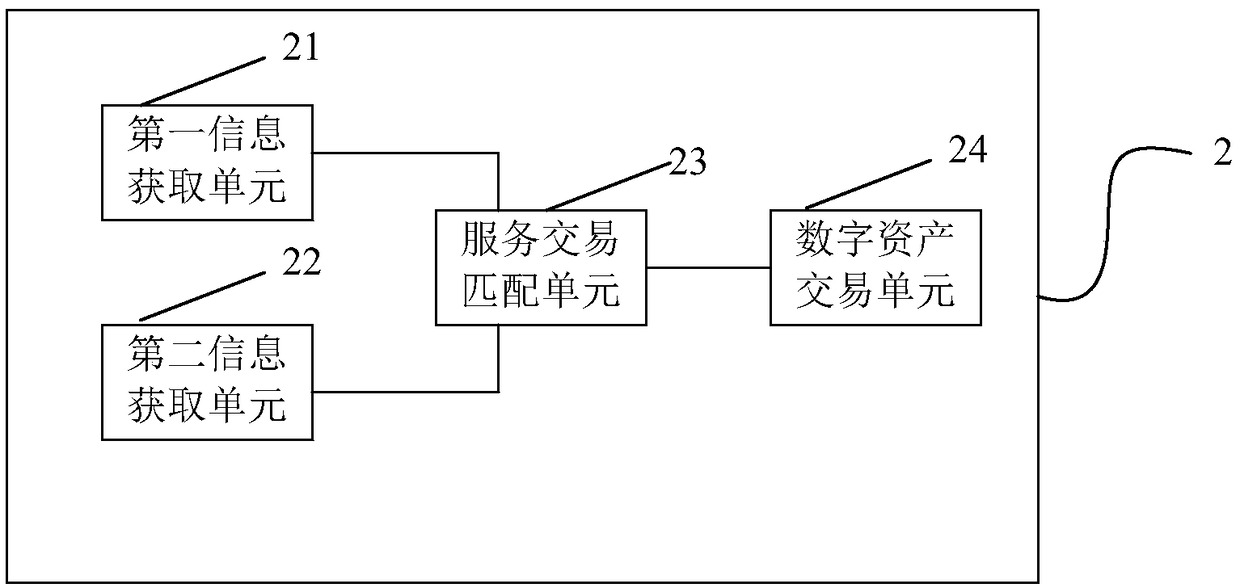
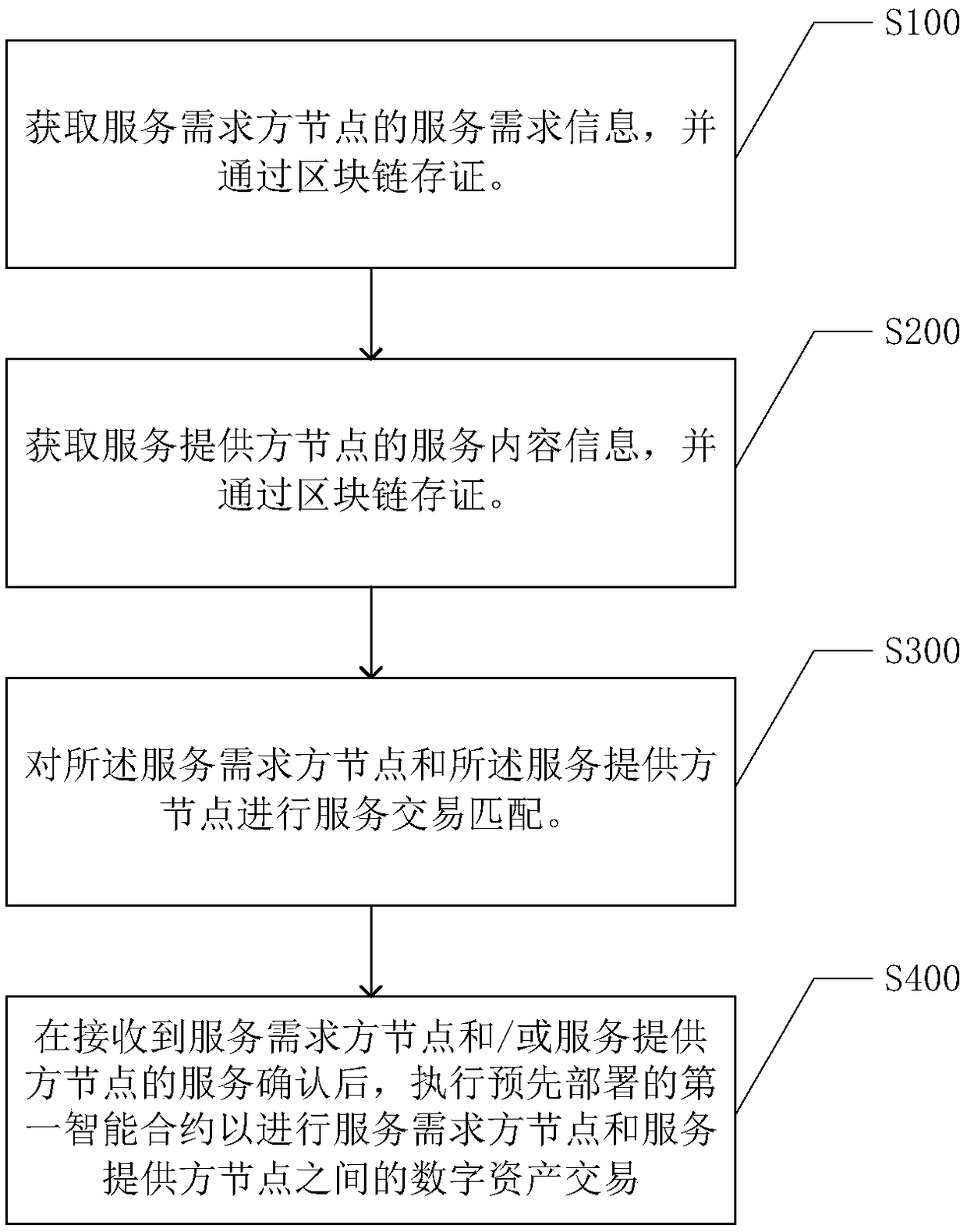
Service transaction processing method, system and device based on federated block chain
InactiveCN109064330AGuaranteed not to be tampered withIncrease credibilityFinanceTransmissionDigital assetService provider
The present application discloses a service transaction processing method based on federated block chain, system, device, Electronics and computer readable storage media, by acquiring service contentinformation and service demand information and matching based on the service content information and service demand information to match a service provider node and a service demander node to therebyconclude a service transaction, A pre-deployed smart contract is executed after completion of the service to perform a digital asset transaction between the service demander node and the service provider node, thereby completing the service transaction. As a result, the service transaction mode fully mobilizes the social resources and records the service transaction process based on the block chain technology to ensure that the service transaction information can not be tampered with and improve the credibility of the service transaction.
Owner:苏州朗润创新知识产权运营有限公司
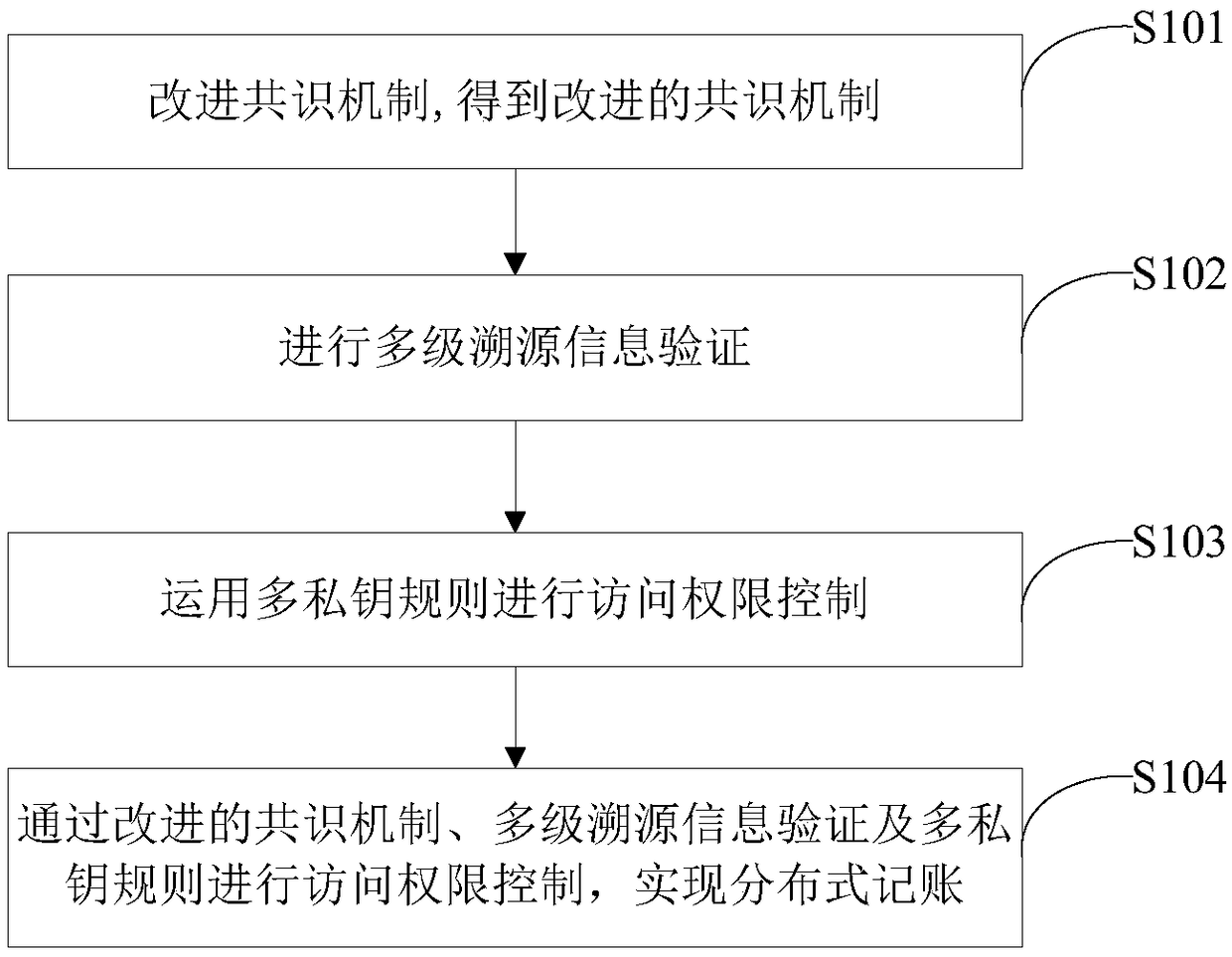
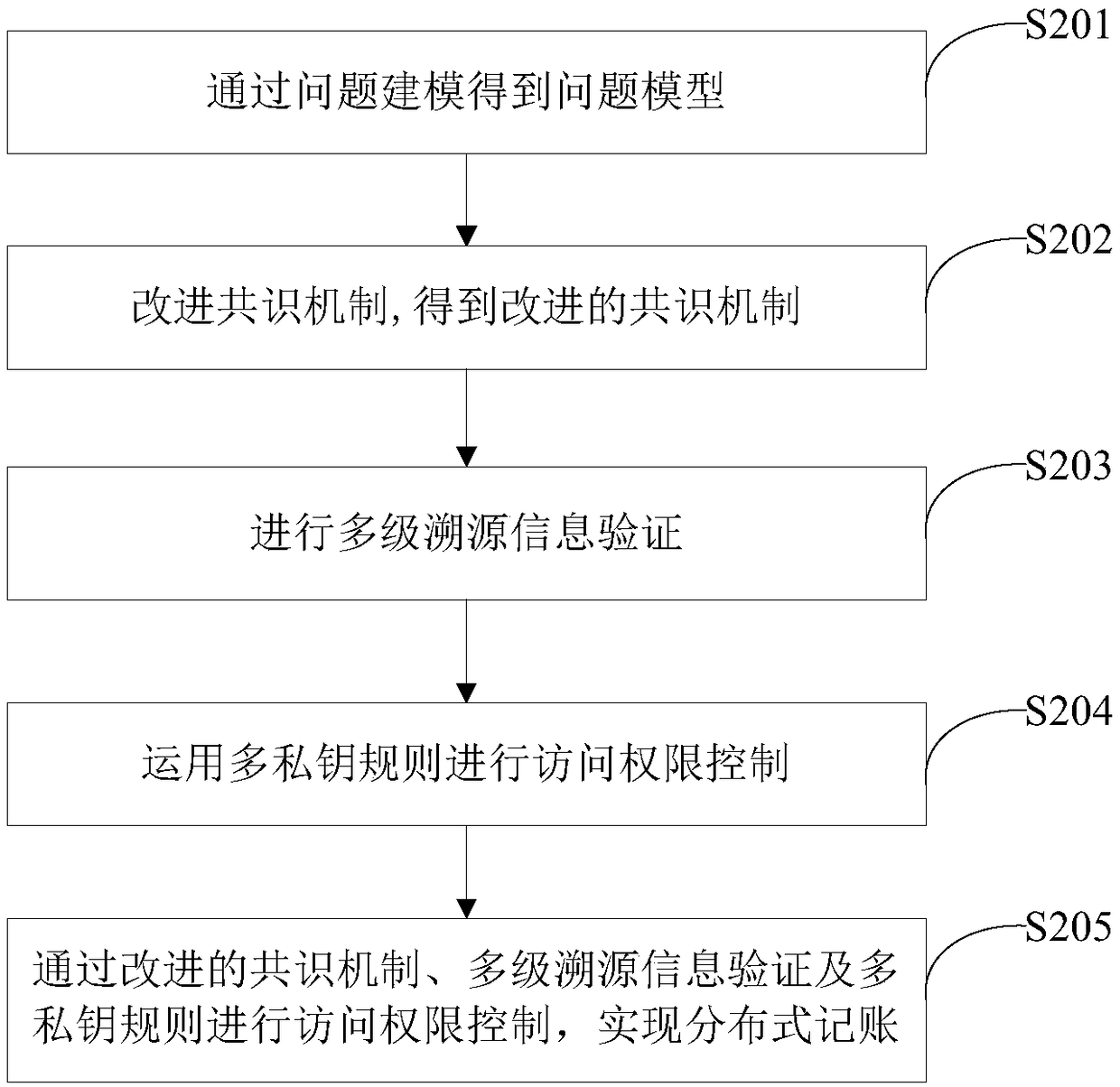
A method of traceability information security of agricultural products based on block chain technology
InactiveCN109146524ARealize distributed accountingGuaranteed Data IntegrityFinanceUser identity/authority verificationProduct traceabilityProduct base
The invention relates to the technical field of traceability information security of agricultural products, in particular to a traceability information security solution of agricultural products adopting block chain technology. The method comprises the following steps: an improved consensus mechanism being obtained, wherein the improved consensus mechanism is that when all entity terminals hold blocks to be submitted for verification, in order to maximize their own benefits, no entity terminal can change the verification result of blocks generated by packaging other entity terminals; conducting multi-level traceability information verification; using multi-private-key rules to control access rights; through the improved consensus mechanism, multi-level traceability information verificationand multi-private key rules for access control, distributed bookkeeping being realized. The invention solves the data storage safety problem existing in the agricultural product traceability system.
Owner:ZHOUKOU NORMAL UNIV
Cloud storage fine grit access control method and data uploading and data accessing method
ActiveCN108900483ATo achieve the purpose of fine-grained access controlGuaranteed safe storageTransmissionAttribute-based encryptionData access control
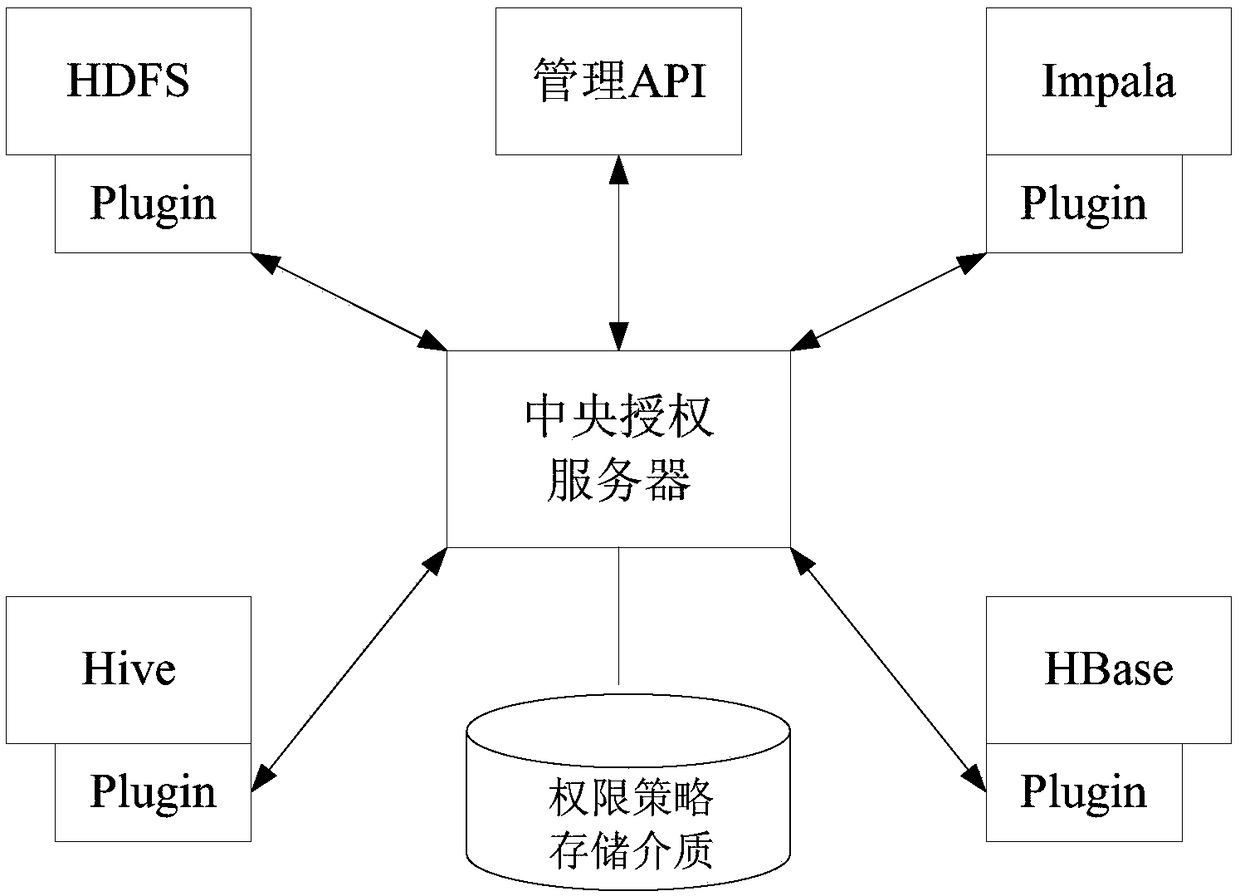
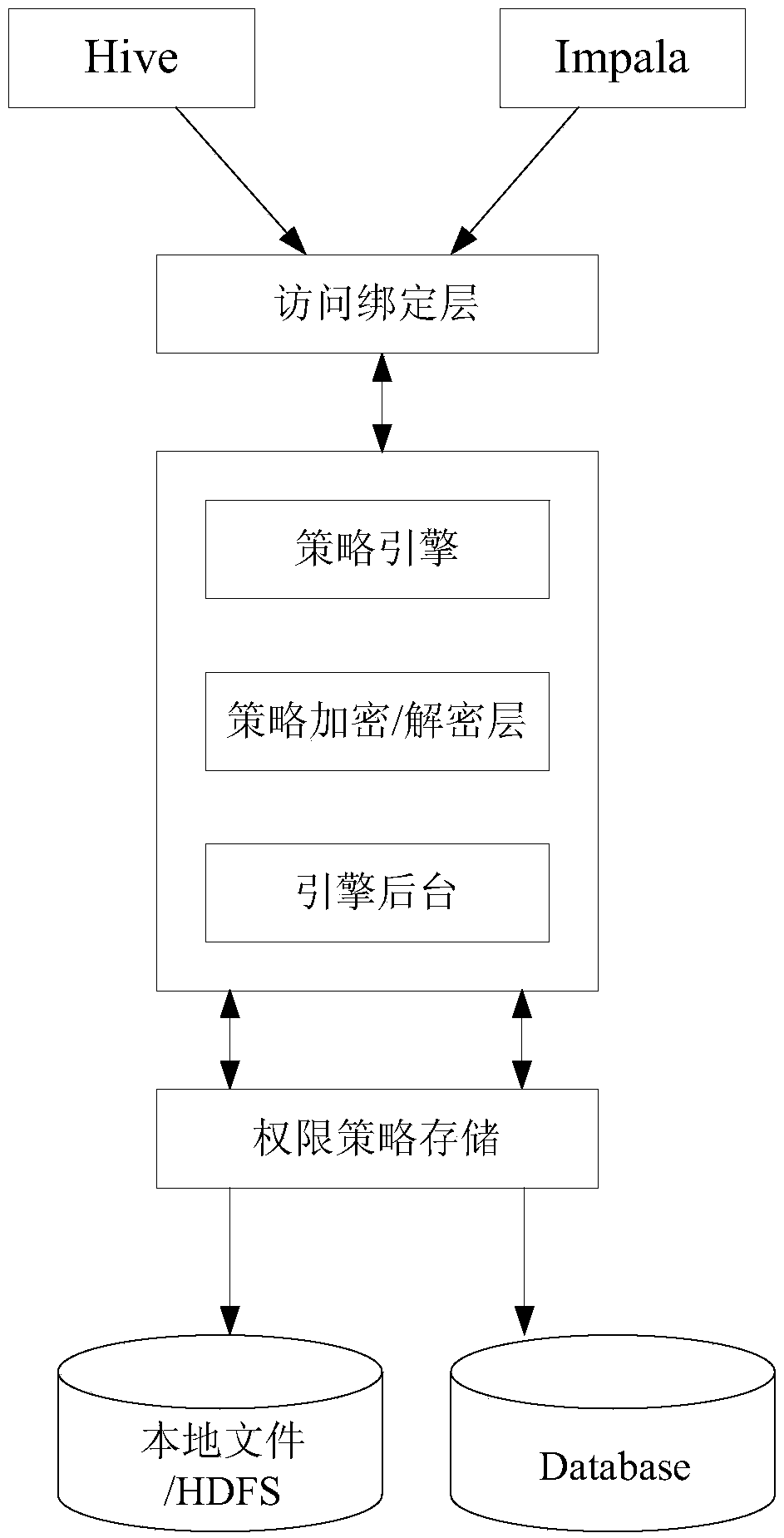
The invention provides a cloud storage fine grit access control method. The method is compatible to access control of a Hadoop assembly in a Plugin way and access control is performed through a central authorization server. Requests intercepted and sent to the central authorization server from the Plugins are accessed to a strategy engine by accessing a binding layer. Authority strategies are encrypted / decrypted through a strategy encryption / decryption layer, finally, through an engine background, storage and reading of the authority strategies are finished, and the storage form is authority encryption ciphers. The decrypted authority strategies are analyzed by the strategy engine, and authorities which can be identified by each Plugin are obtained through the analysis and returned to thecorresponding Plugins. Verification of the authorities is finished by the Plugins and whether user requests of this time are permitted is judged through the Plugins. According to the invention, by introducing autonomous access control, access control authorization of data by a data uploader is achieved; and by introducing a method based on attribute-based encryption, self-description of an accesscontrol structure is performed through attribute labels of data.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
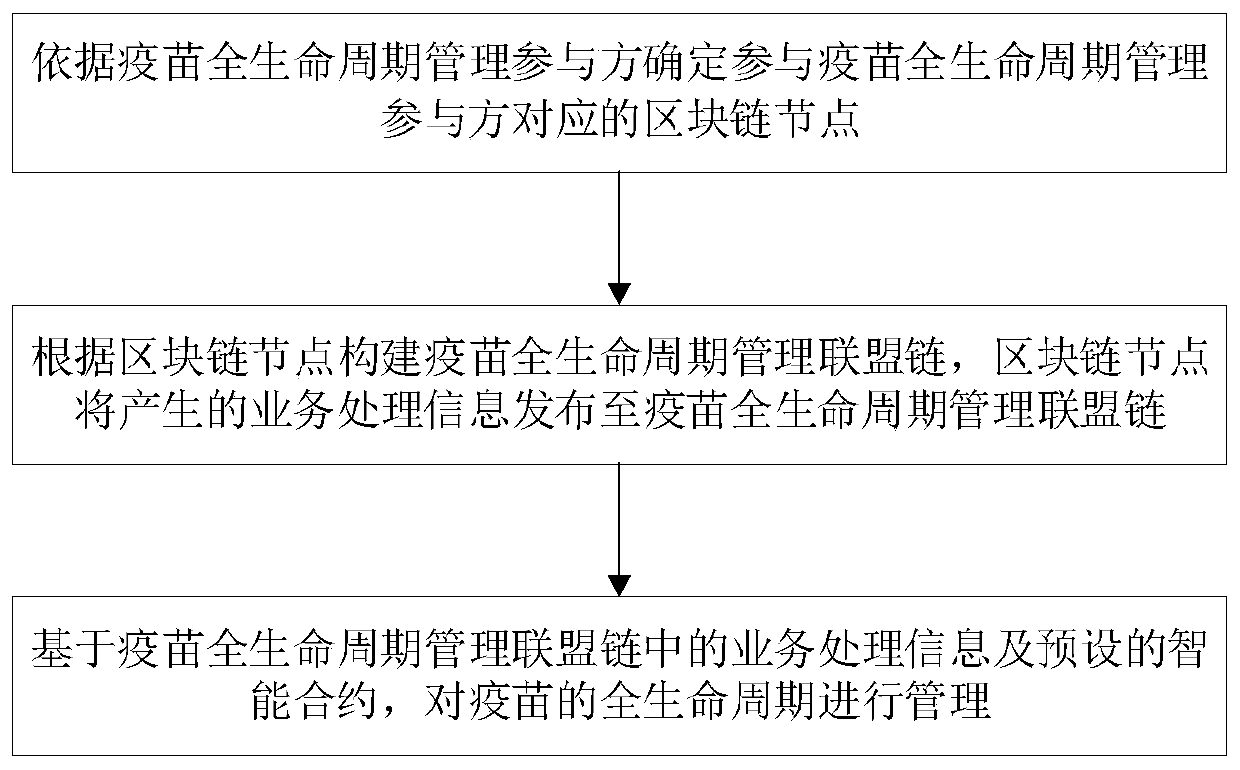
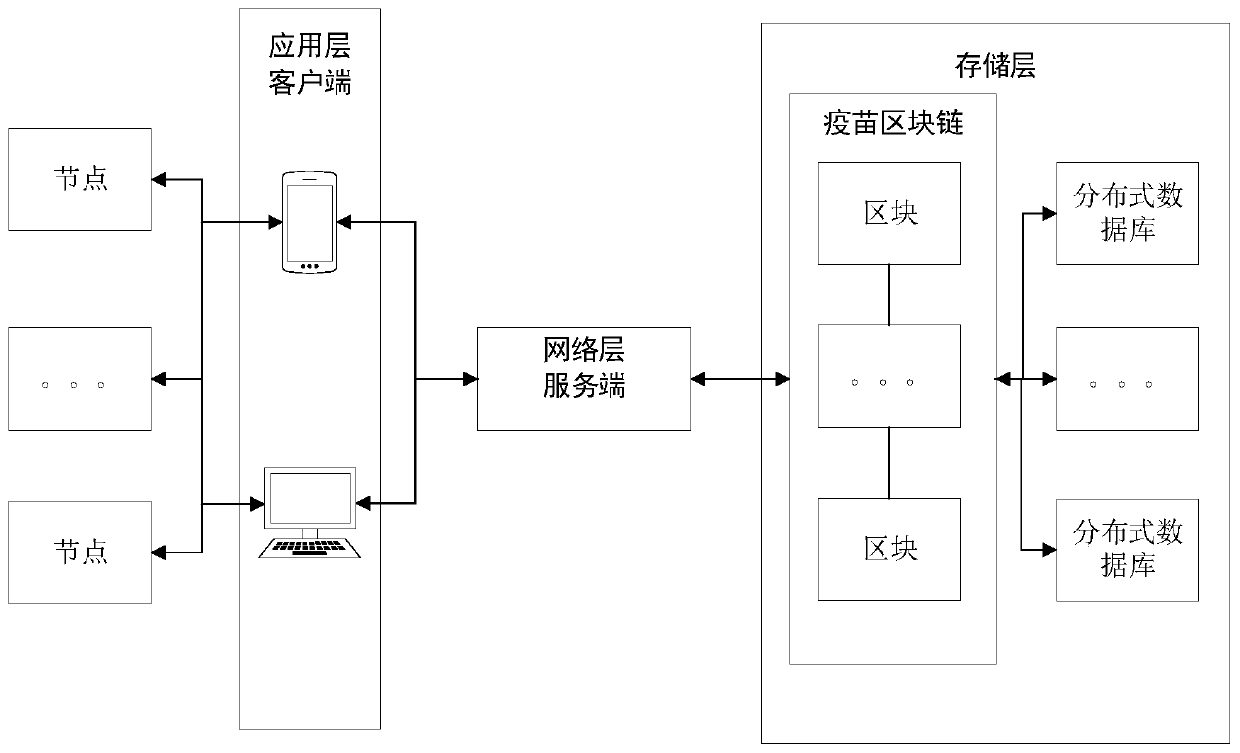
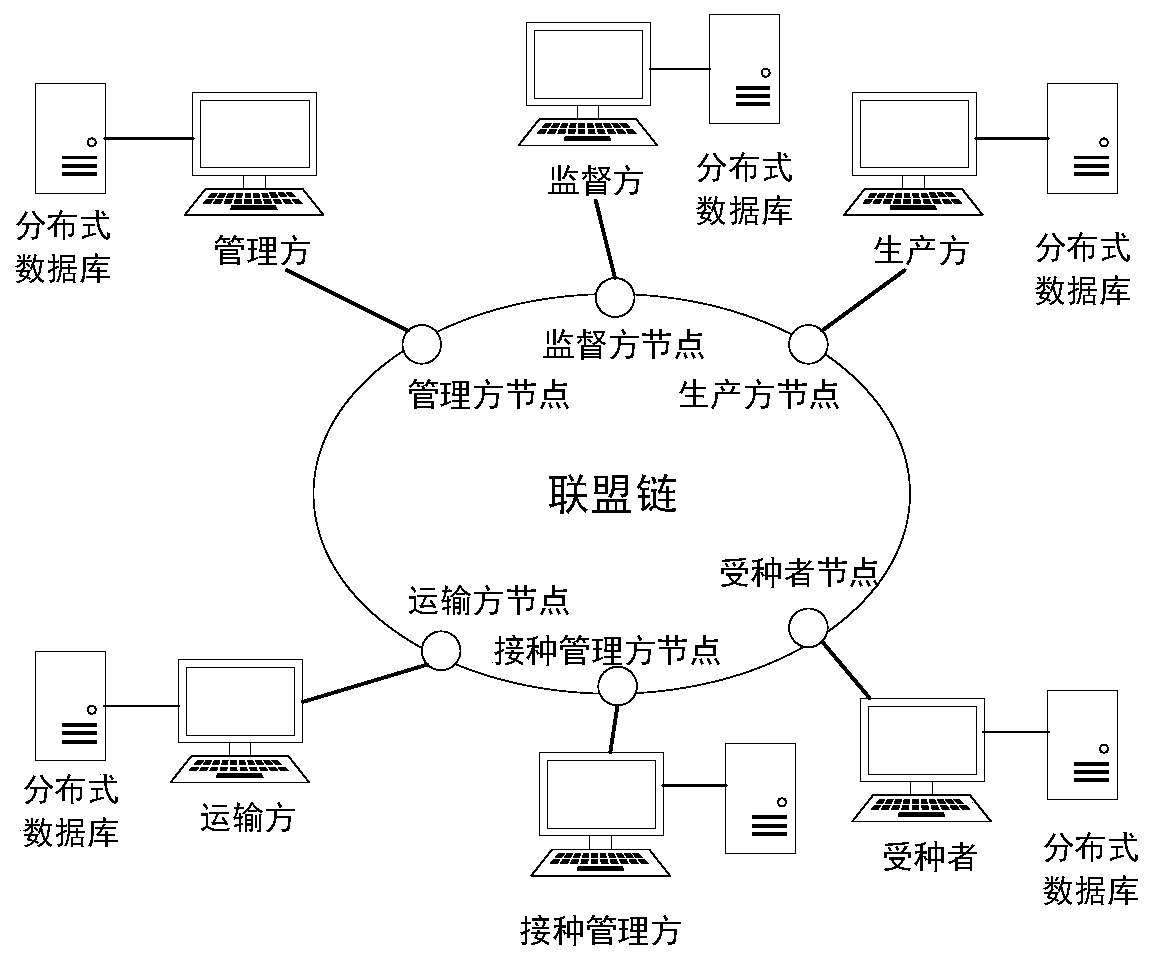
Vaccine full-life-cycle management method and system based on block chain
ActiveCN110992068APrevent counterfeitingGuaranteed not to be tampered withCommerceICT adaptationTGE VACCINEOperating system
The embodiment of the invention provides a vaccine full-life-cycle management method and system based on a block chain and belongs to the technical field of block chains. The method comprises the steps: determining a block chain node corresponding to a vaccine full-life-cycle management participant according to a vaccine full-life-cycle management participant; constructing a vaccine full-life-cycle management alliance chain according to the block chain node, and publishing generated business processing information to the vaccine full-life-cycle management alliance chain by a block chain node;and managing the full life cycle of a vaccine based on the service processing information in the vaccine full life cycle management alliance chain and a preset intelligent contract. By establishing the block alliance chain disclosed by the vaccine full-life-cycle information, participation nodes of all links of the vaccine life cycle are published through the alliance chain and information and record data related to the vaccine are obtained, it can be effectively guaranteed that all the information and records cannot be tampered, and meanwhile vaccine information can be traced back.
Owner:ZHEJIANG UNIV
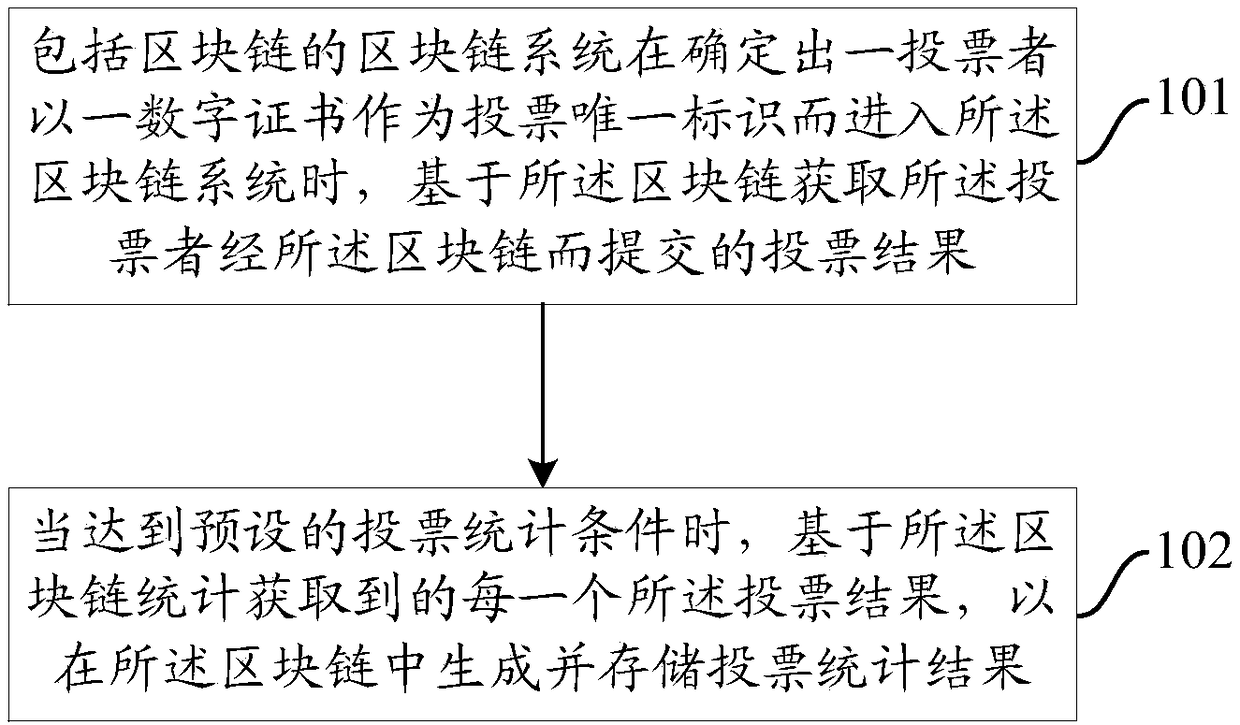
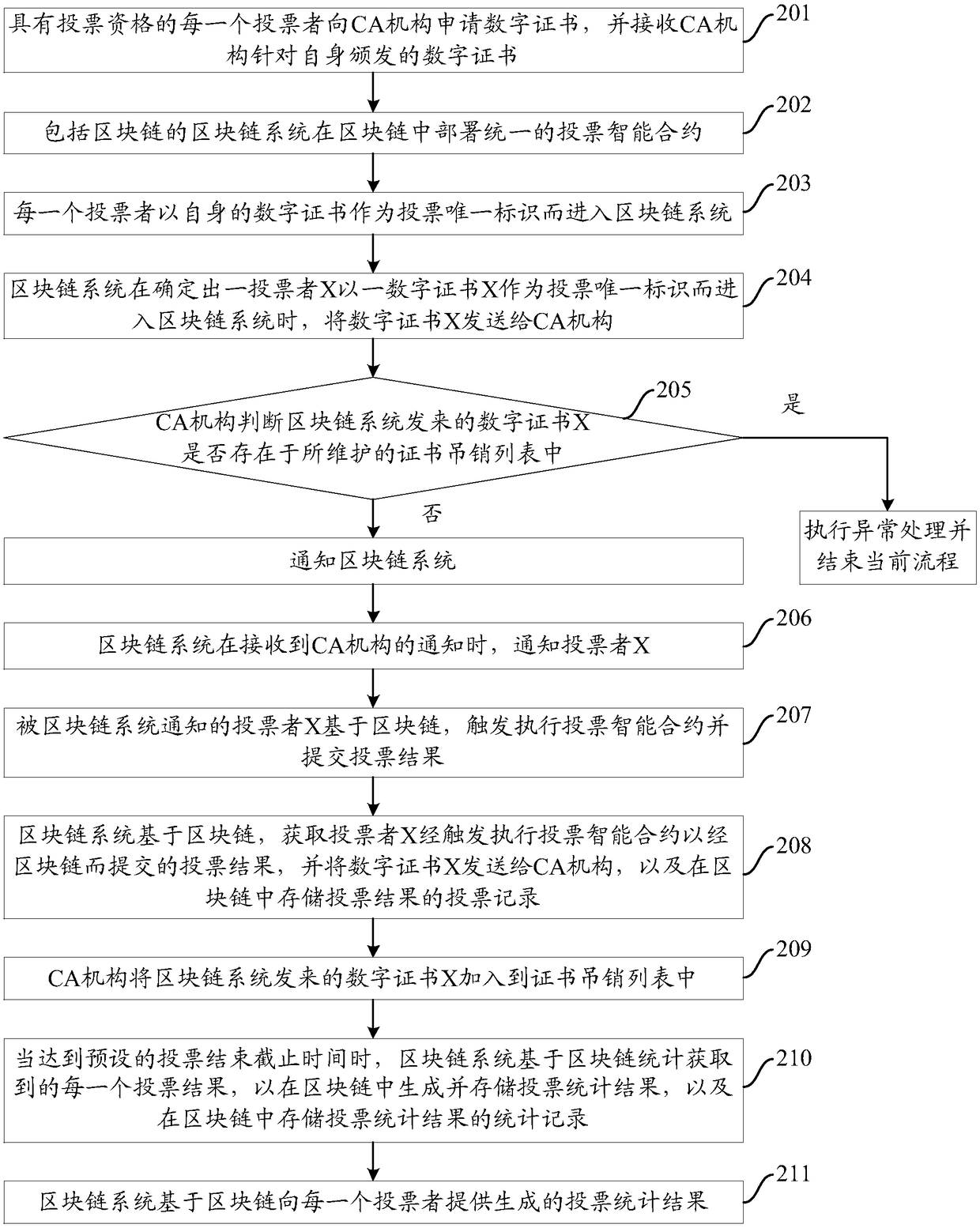
Blockchain-based voting method, and device and system thereof
InactiveCN108597090AGuaranteed not to be tampered withPrevent tamperingVoting apparatusDigital data protectionComputer scienceData structure
The invention provides a blockchain-based voting method, and a device and a system thereof. The method comprises the following steps: the blockchain system of a blockchain acquires a voting result submitted by a voter through the blockchain while determining that the voter enters the blockchain system with a digital certificate as the unique voting identifier; and when preset voting statistical conditions are achieved, a vote statistical result is generated and stored in the blockchain based on the every voting result obtained through the statistics of the blockchain. The blockchain combines data blocks in a time sequence to form a chained data structure in order to ensure that the data blocks cannot be tampered or forged. The voting behavior in the blockchain, so the result is prevented from being tampered.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
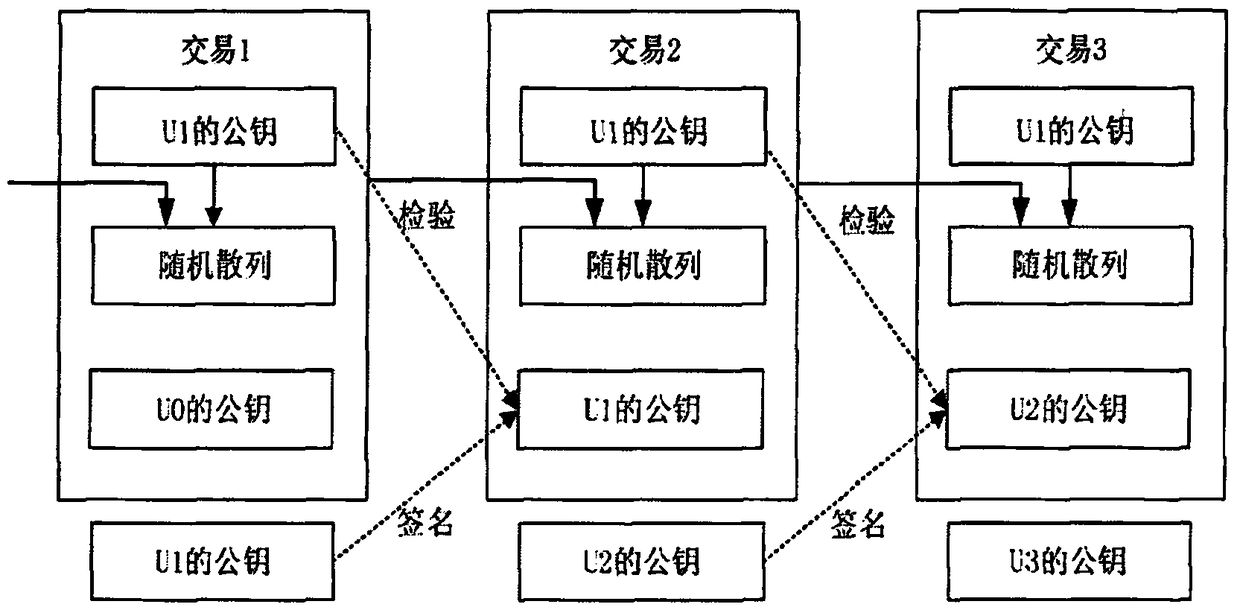
Networked transaction certification system and method
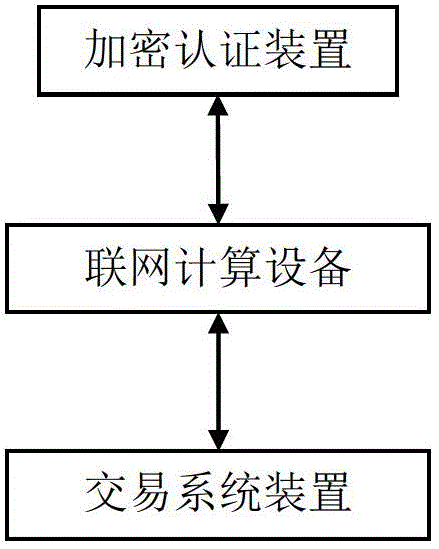
ActiveCN102868531AImprove security strengthAvoid transaction hijackingUser identity/authority verificationPayment architectureCiphertextPassword
The invention discloses a networked transaction certification system which comprises an encryption authentication device, a networked computing device and a transaction system device, wherein the encryption authentication device is connected with the transaction system device through the networked computing device, the networked computing device is used for receiving request transaction information submitted by a user, and transmitting the request transaction information to a transaction system device; the transaction system device is used for generating a random code according to the request transaction information, and searching an elliptic curve password public key corresponding to the user in a user database, and the transaction system device is also used for encrypting request transaction information and a random code by using the elliptic curve password public key, transmitting the encrypted ciphertext to the networked computing device, and storing the request transaction information and the random code into a transaction information database. The invention can realize confidentiality and integrity of a message, authenticity of a transaction entity and non-repudiation of transaction, and has the characteristics of high safety, capability of avoiding transaction hijacking, transaction falsification and remote control.
Owner:北京信安世纪科技股份有限公司 +1
Block chain asset issuing method and platform, service node and storage medium
ActiveCN110769035AHigh transparencyAchieve synchronizationFinanceUser identity/authority verificationComputer networkEngineering
The invention provides a block chain asset issuing method and platform, a service node and a storage medium. The method comprises the steps of obtaining at least one service node, wherein the at leastone service node is a node corresponding to a service main body of each asset issuing mechanism; receiving asset data sent by any one service node in the at least one service node; generating a corresponding new block according to the asset data; adding the new block to the tail of the current block, and completing the uplink of asset data corresponding to any business node; when the at least onepiece of asset data corresponding to the at least one service node is completely uploaded, taking the at least one piece of asset data stored in the obtained block chain as account book data; and responding to a synchronization request initiated by at least one service node for the account book data to realize synchronization of the account book data. According to the invention, the transparencyand safety of asset issuing data can be improved.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD
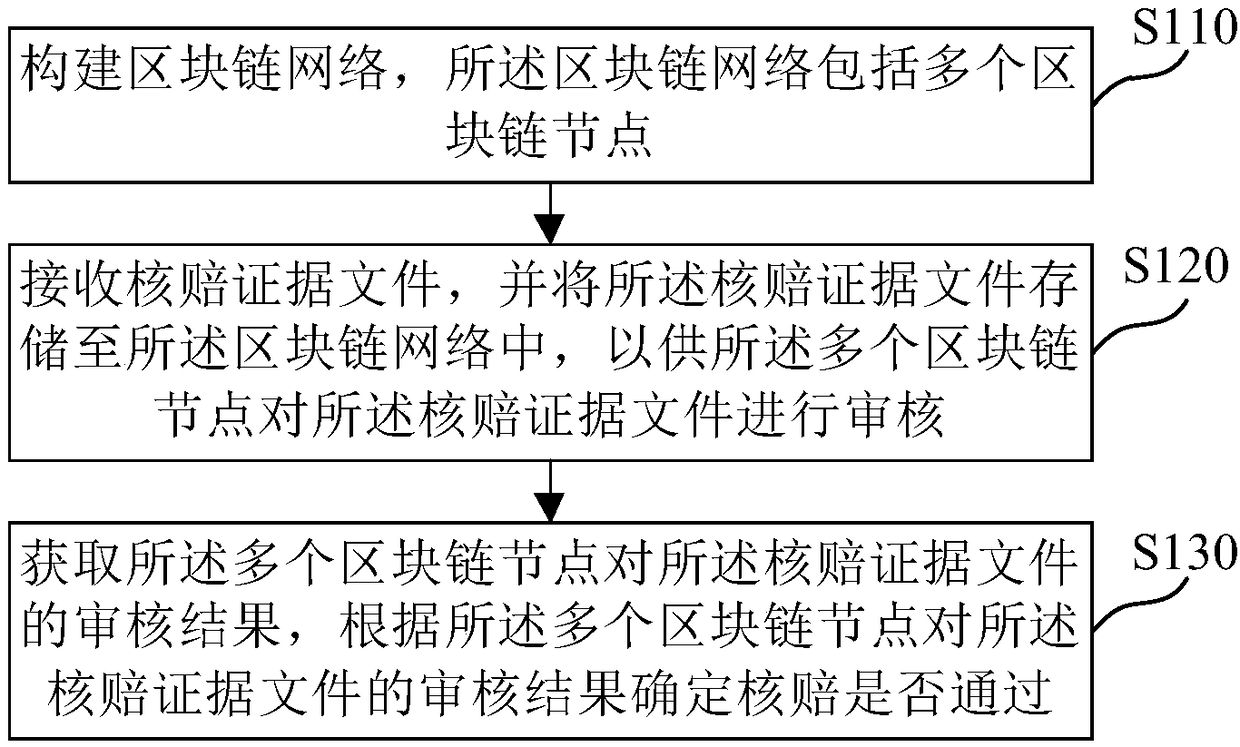
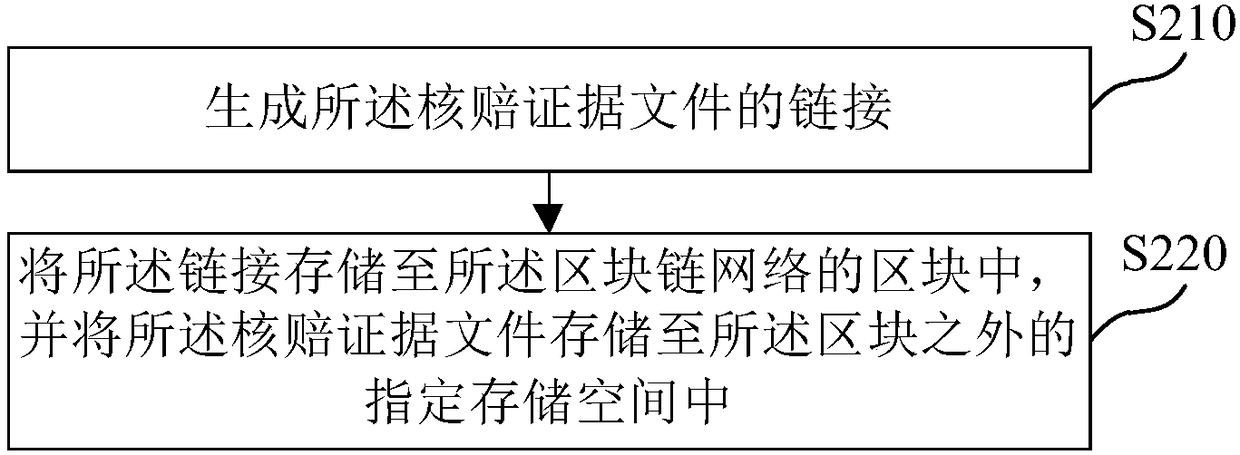
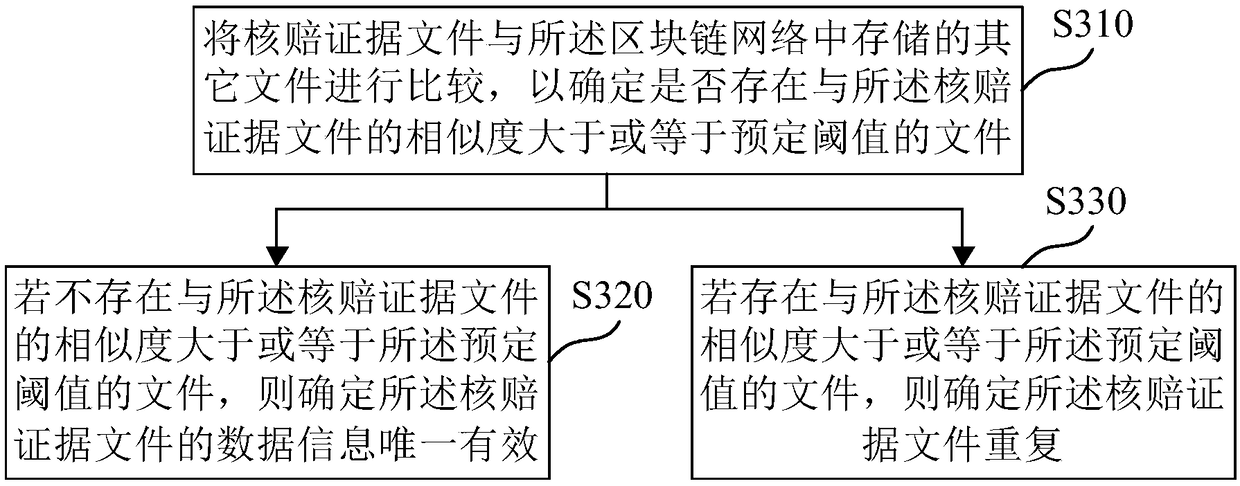
Claim checking method and claim checking device on basis of block chain technologies, medium and electronic equipment
InactiveCN108280628AGuaranteed accuracyPrevent Duplicate ClaimsFinanceOffice automationChain networkBlockchain
An embodiment of the invention provides a claim checking method and a claim checking device on the basis of block chain technologies, a medium and electronic equipment. The claim checking method includes constructing block chain networks comprising a plurality of block chain nodes; receiving claim checking evidence files and storing the claim checking evidence files in the block chain networks toallow the claim checking evidence files to be checked by the multiple block chain nodes; acquiring claim checking evidence file checking results of the multiple block chain nodes and determining whether to pass claim checking or not according to the claim checking evidence file checking results of the multiple block chain nodes. According to the technical scheme, the claim checking method, the claim checking device, the medium and the electronic equipment in the embodiment of the invention have the advantages that the problem of repeated claim can be effectively prevented, and the problem of high labor cost due to manual comparison and re-checking modes can be solved.
Owner:TAIKANG LIFE INSURANCE CO LTD
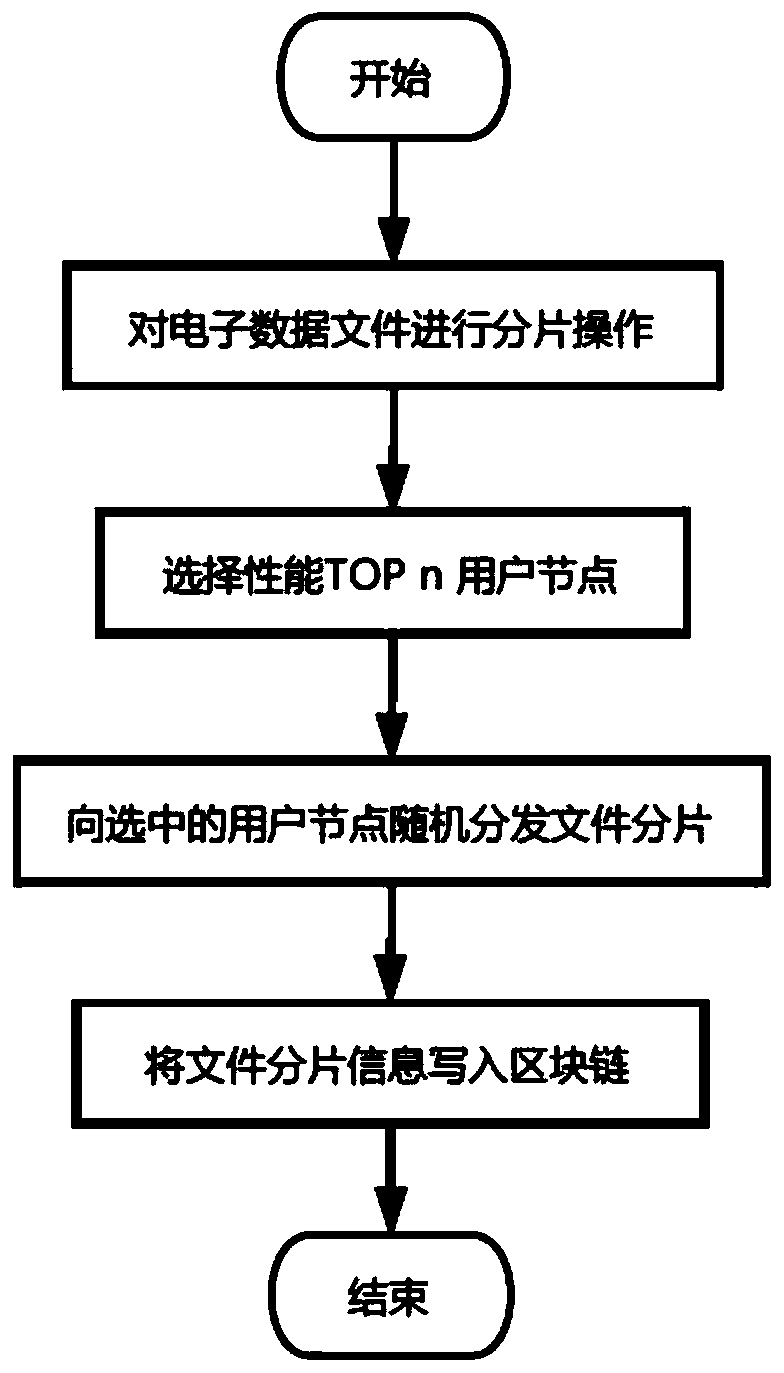
Data storage data processing method based on block chain
PendingCN110334053AGuaranteed not to be tampered withEnsure safetyDigital data protectionPayment protocolsSmart contractElectronic data
The invention discloses a data storage data processing method based on a block chain, and relates to a data processing technology. While ensuring authenticity, integrity and security of stored certificate data, privacy information of user can be protected to certain extent, the Web3j interaction function is utilized, the intelligent contract is compiled, the packaged key information is anchored tothe main chain of the block chain in a structural body mode, and it is guaranteed that the electronic data cannot be tampered. Meanwhile, an index thought is introduced in the compiling process of the intelligent contract to constrain access permissions of different users to the electronic data, multi-point fragmentation storage of the electronic data is completed by using a distributed storage fault-tolerant technology, and the safety of data fragmentation storage of each node is ensured with relatively low redundancy cost. According to the method, a scheme for evaluating the performance ofthe user nodes is provided for the network and storage, and a basis is provided for selection of the storage user nodes.
Owner:HARBIN UNIV OF SCI & TECH
Blockchain-based network security auditing system and network security auditing method
ActiveCN108833440AGuaranteed not to be tampered withGuaranteed confidentialityUser identity/authority verificationData bufferBlockchain
The invention relates to a blockchain-based network security auditing system and a blockchain-based network security auditing method. The network security auditing method comprises the steps that: anauditing server applies for a signature public / private key pair and a secret key to a secret key management server, a block generation server of the blockchain applies for a signature public key to the secret key management server, the auditing server acquires data to be audited and encrypts the data to be audited to generate C1, re-encrypts an encryption secret key to generate a C2, and performing digital signature on the C1 and the C2 by means of the private key to generate sigma; and the auditing server transmits the C1, the C2 and the sigma to the block generation server, the data to be audited is placed in a data buffer region after the C1, the C2 and the sigma are verified to be valid by using the public key, generates a new block and broadcasts the new block when a block generationcondition is met, and a display terminal can request the block generation server to view the audit data. The blockchain-based network security auditing system and the blockchain-based network securityauditing method utilize the blockchain technology, and adds the blockchain into the auditing system, thus the audit data cannot be tampered, the data security is improved, the audit data in the blockchain is encrypted to ensure that the audit data can only be accessed by authorized users, and the confidentiality of the audit data is protected.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Implementing method of dynamic electric stamp
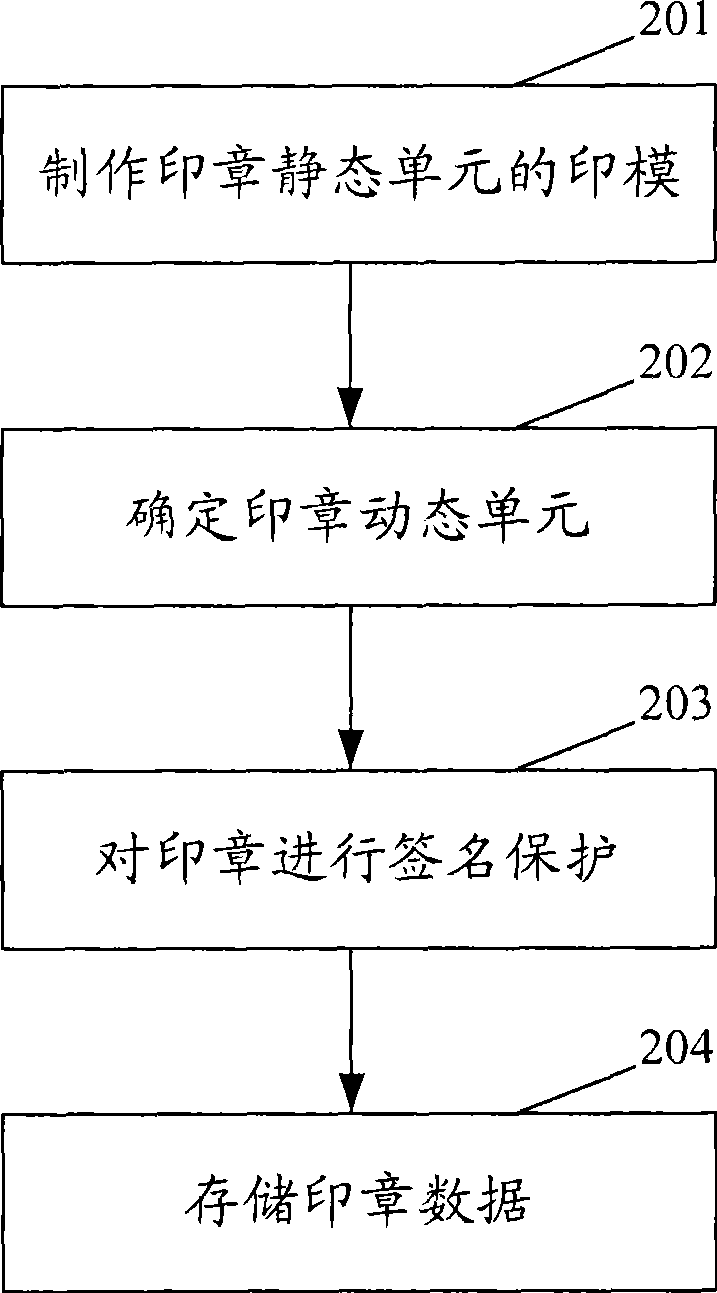
InactiveCN101436270AEasy to manufactureGuaranteed not to be tampered withOffice automationSpecial data processing applicationsComputer science
The invention discloses a realizing method for a dynamic electronic stamp. The method comprises the following steps: manufacturing a stamping mold of a static unit of the stamp; and determining that a dynamic unit of the stamp is formed by which parameters and determining attribute of each parameter. Through respectively manufacturing an unchanged part which is the static unit and a changeable part which is the dynamic unit in the stamp and then combining the two parts, the method can conveniently manufacture the electronic stamp containing dynamic information.
Owner:北京书生电子技术有限公司 +1
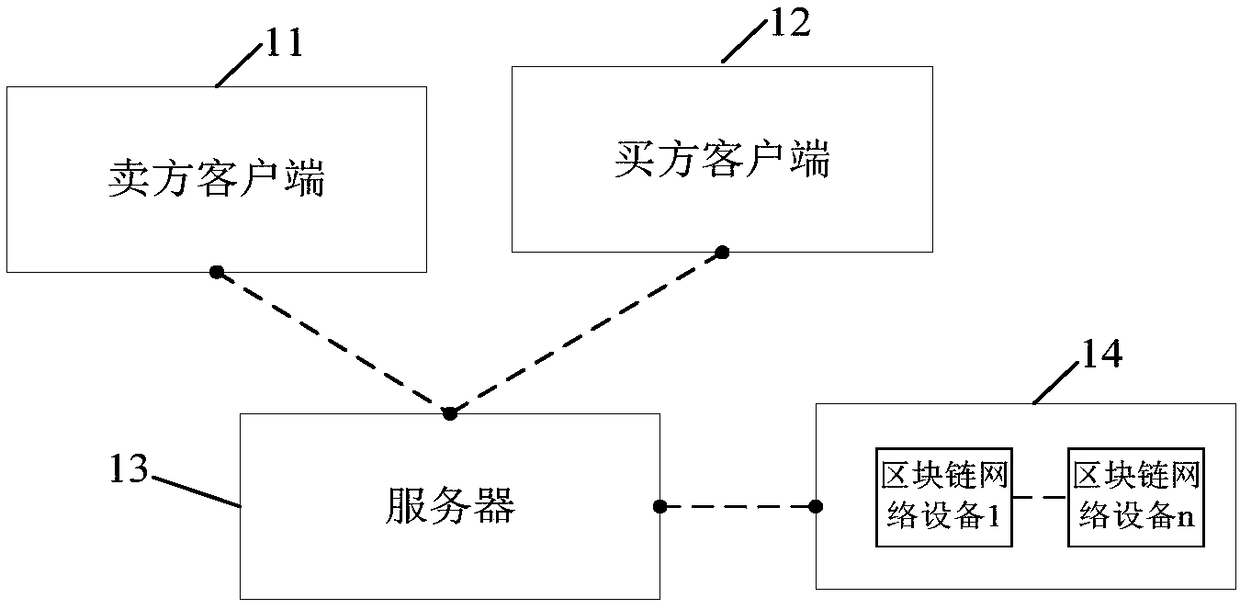
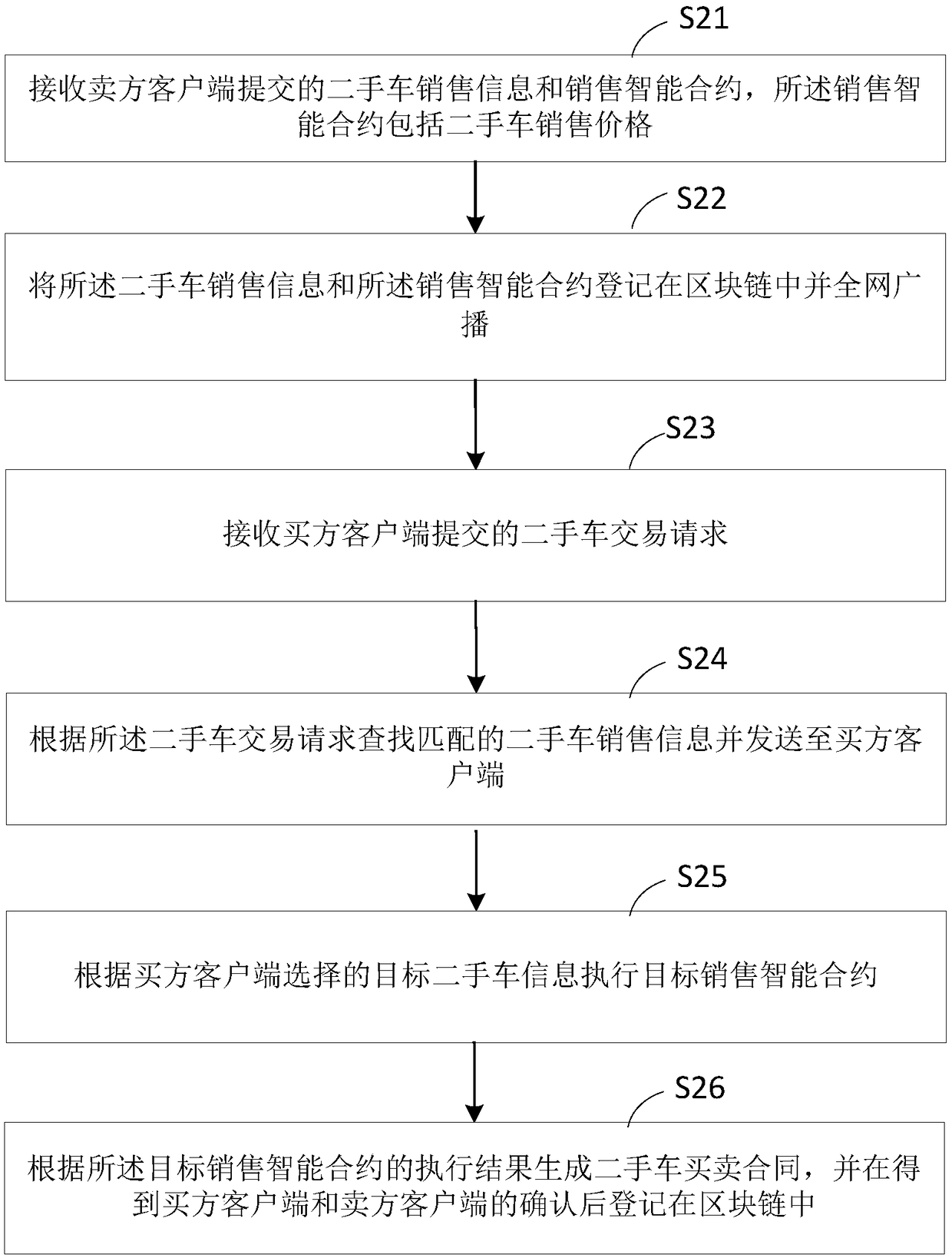
Second-hand car transaction method and server
InactiveCN109074602AEnsure safetyGuaranteed not to be tampered withProduct appraisalCryptography processingSales intelligenceTransaction data
The application provides a second-hand car transaction method and server, and the method comprises the following steps: receiving second-hand car sales information and a sales intelligent contract submitted by a seller client, registering the second-hand car sales information and sales intelligent contract in a block chain and broadcasting in the whole network; receiving a second-hand car transaction request submitted by a buyer client; searching matched second-hand car sales information according to the second-hand car transaction request and sending the matched second-hand car sales information to the buyer client; executing a target sales intelligence contract according to target second-hand car information selected by the buyer client; generating a second-hand car sales contract according to an execution result of the target sales intelligent contract, and registering in the block chain after obtaining confirmation by the buyer client and the seller client. In the process, the server registers the sales information of a second-hand car seller and the information of second-hand car purchase of a second-hand buyer in the block chain, so as to ensure that the second-hand car transaction data are secure and cannot be tampered, and ensure the security of the transaction data and the transparency of the transaction.
Owner:LAUNCH TECH CO LTD
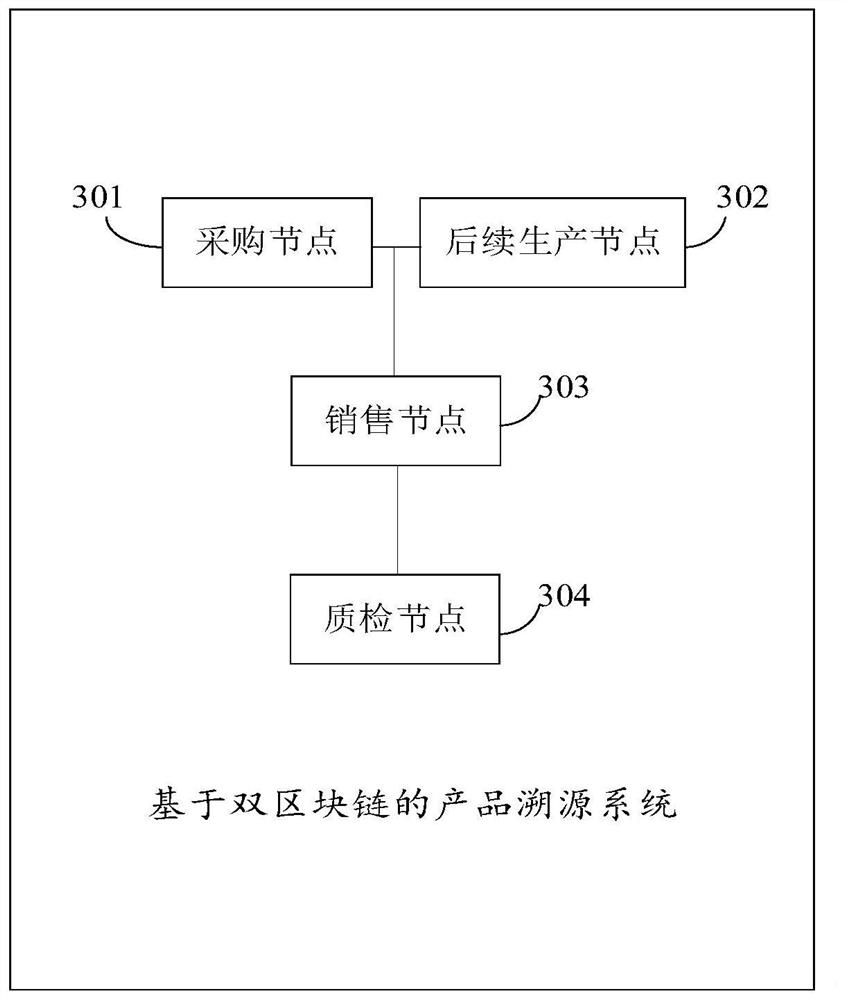
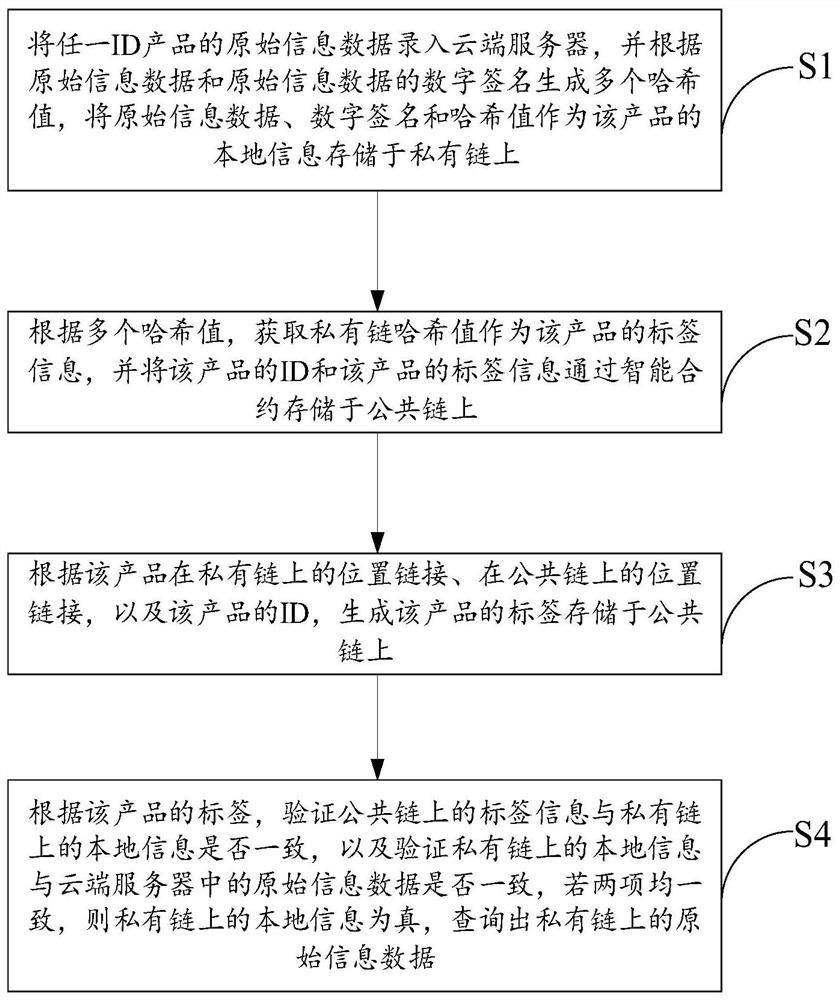
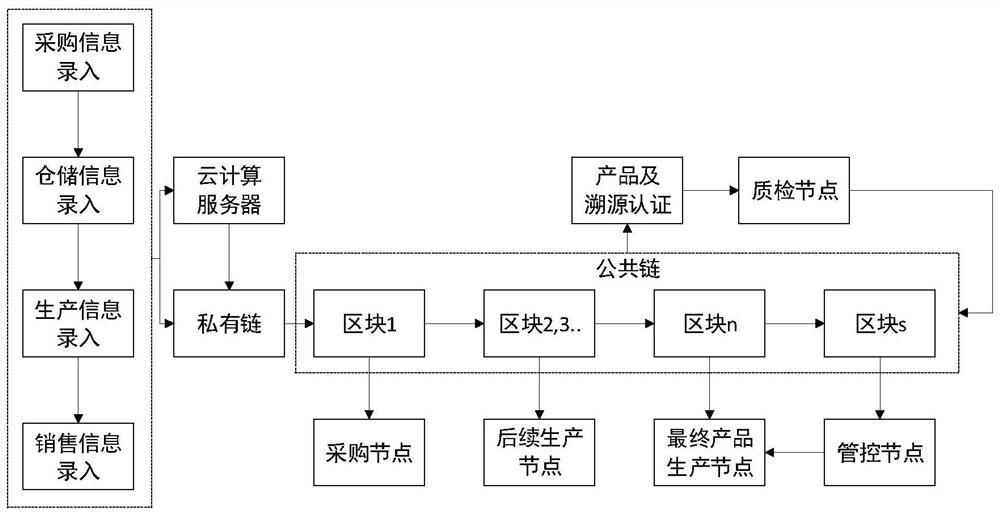
Product traceability method and system based on double block chains
PendingCN111667279AGuaranteed not to be tampered withGuaranteed follow-up verificationDatabase distribution/replicationDigital data protectionBusiness enterpriseProduct traceability
The embodiment of the invention provides a product traceability method and system based on double block chains, being characterized by processing existing cloud computing data and server resources ofan enterprise, constructing a double-blockchain fusion model based on a private chain and a public chain by combining a high-efficiency private chain mode and a cross-chain technology, effectively fusing the cloud computing data and the block chain, and extracting cloud computing data and recording hash values of the cloud computing data into a private chain, and the private chain traceability necessary data is uploaded to the public chain, so as to ensure data tampering prevention and subsequent verification, thus realizing high-efficiency interaction between cloud computing data and on-chaindata, reducing the difficulty of deploying a blockchain system by an enterprise, finally realizing intelligent generation of product traceability information, and meanwhile, eliminating human factorsof information circulation among main bodies of a supply chain, so that traceability information authentication which is more accurate, and more complete and more reliable than traditional product traceability is generated.
Owner:WUHAN UNIV OF TECH
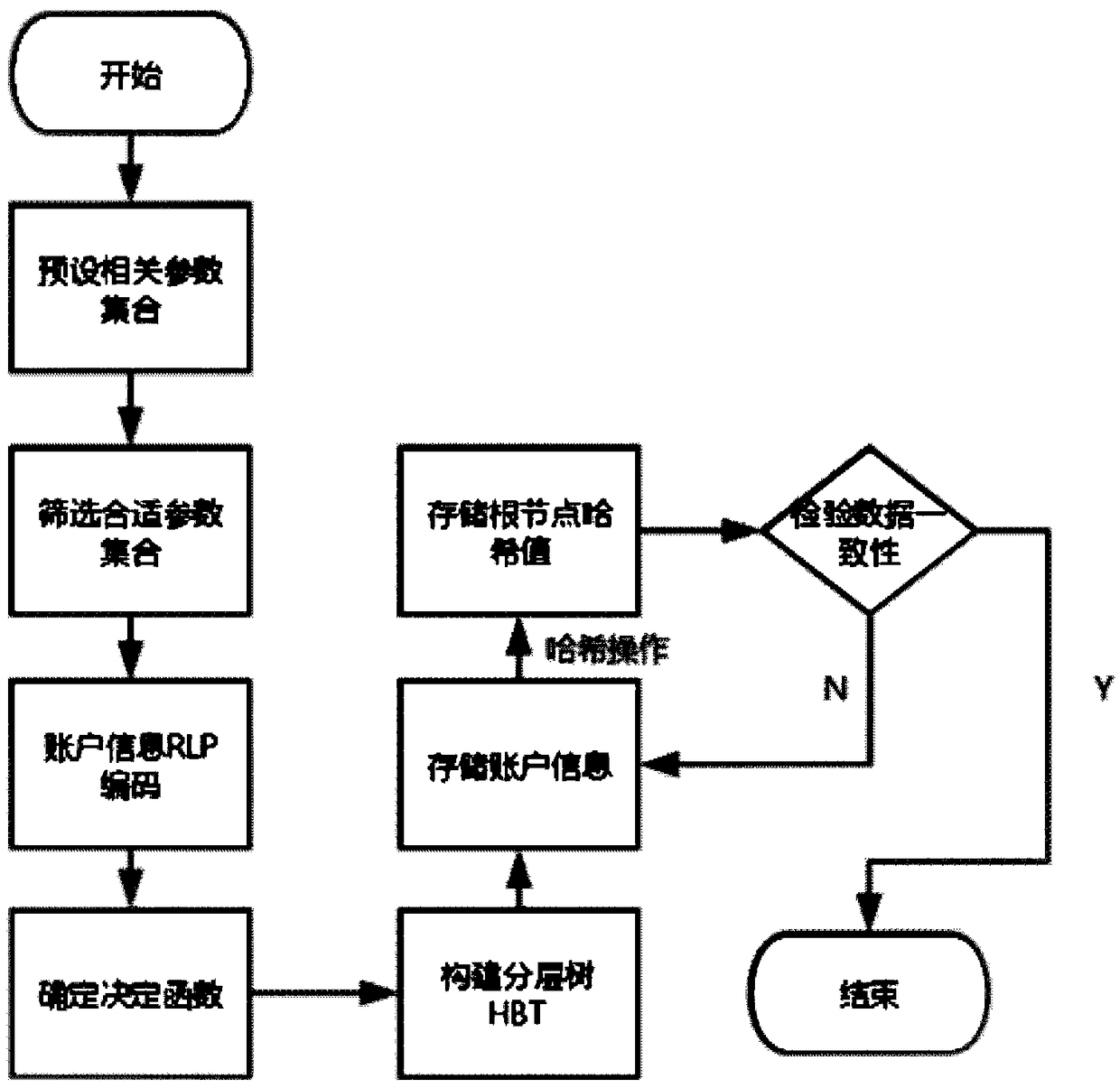
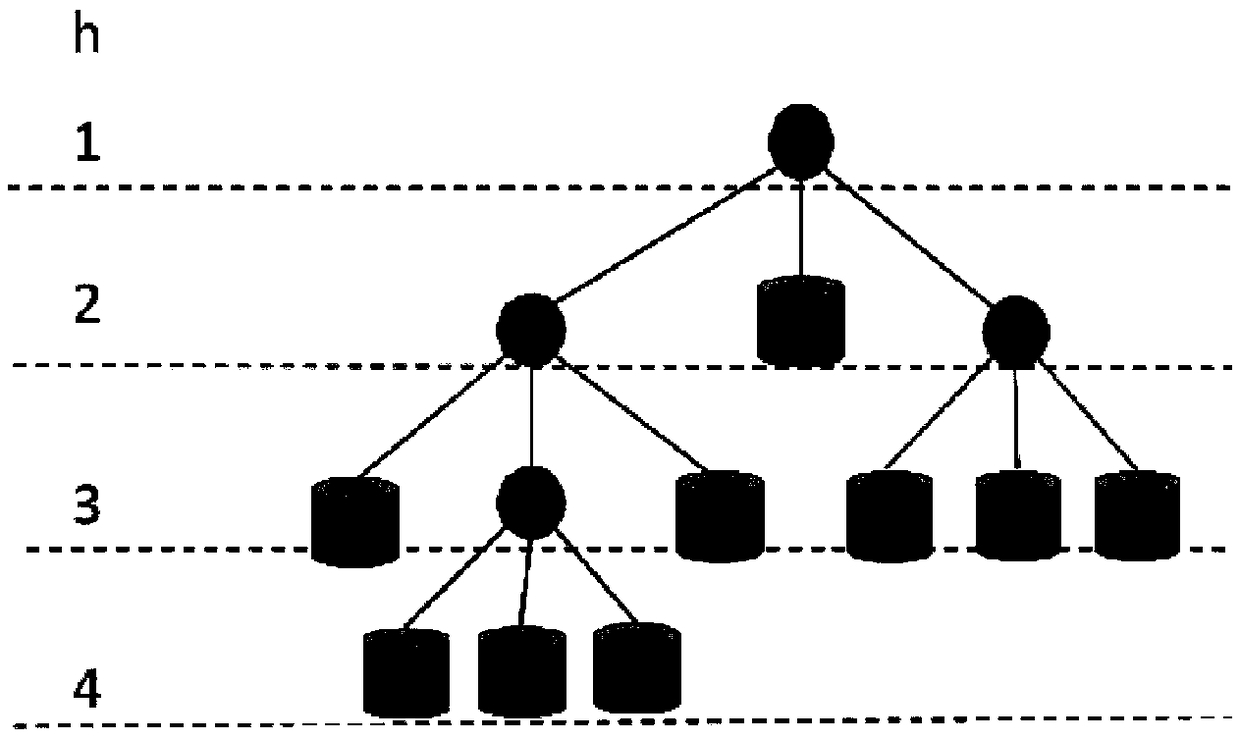
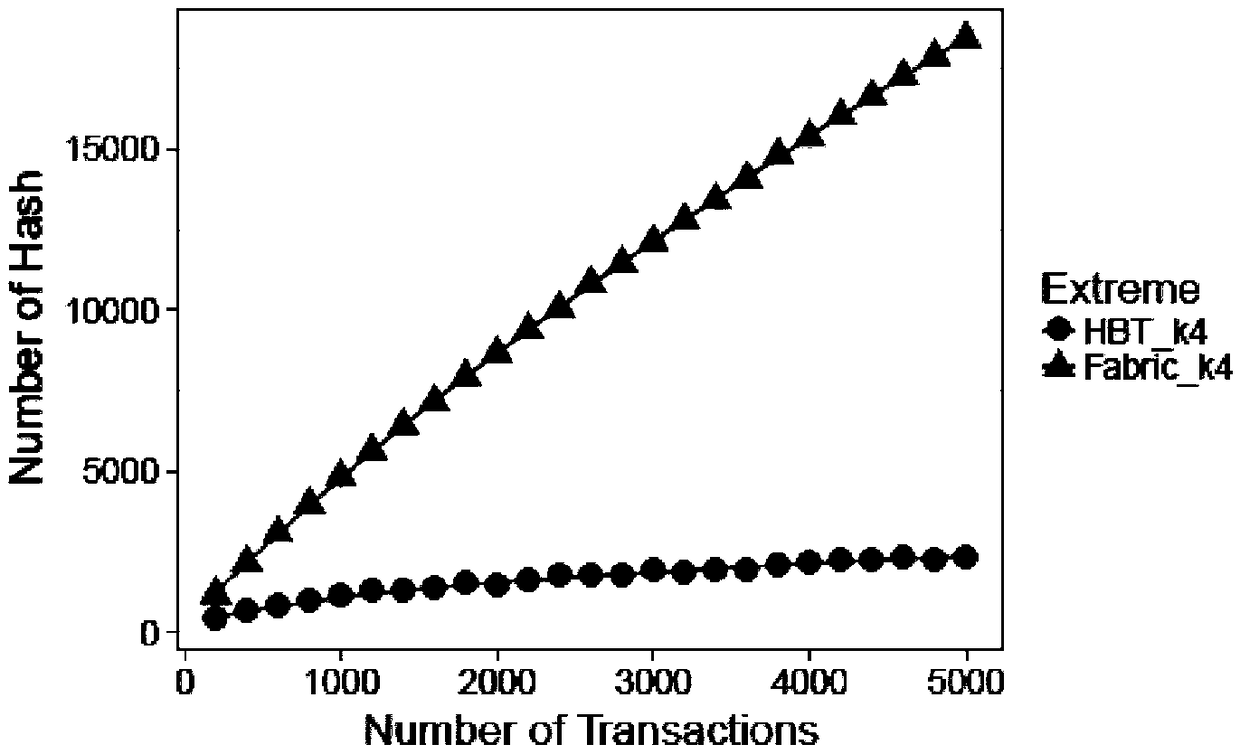
A method and apparatus for efficiently storing block chain information based on hierarchical tree structure
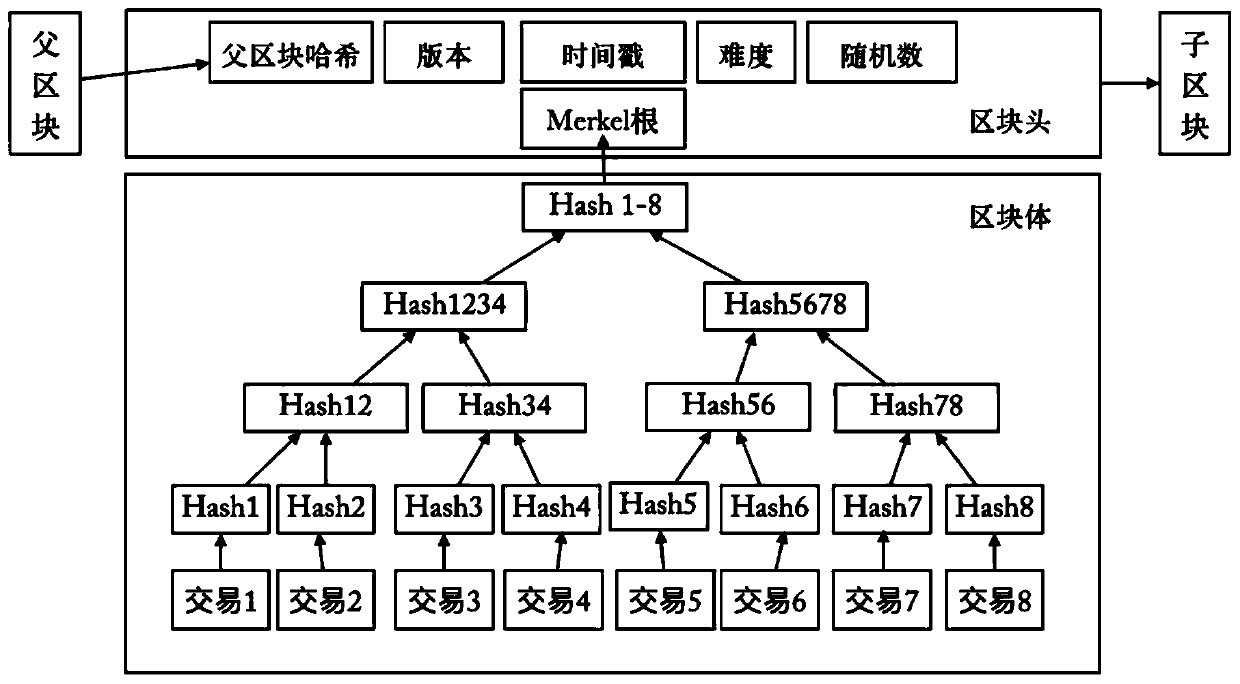
ActiveCN109410043AReduce the number of hashesHash times decreaseFinanceTheoretical computer scienceStructure of Management Information
The invention discloses a method for efficiently storing block chain information based on a hierarchical tree structure, which comprises the following steps: preset classification of block chain accounts; division of barrel storage; construction of hierarchical tree structure; input of account information; verification of account information consistency. An innovative block chain account storage structure is proposed, which ensures that the block chain information can not be tampered with, and the accounts are stored hierarchically according to the transaction frequency. Generally speaking, the accounts with higher transaction frequency will be stored in the node closer to the root node, so as to reduce the overall number of hash.
Owner:SUN YAT SEN UNIV
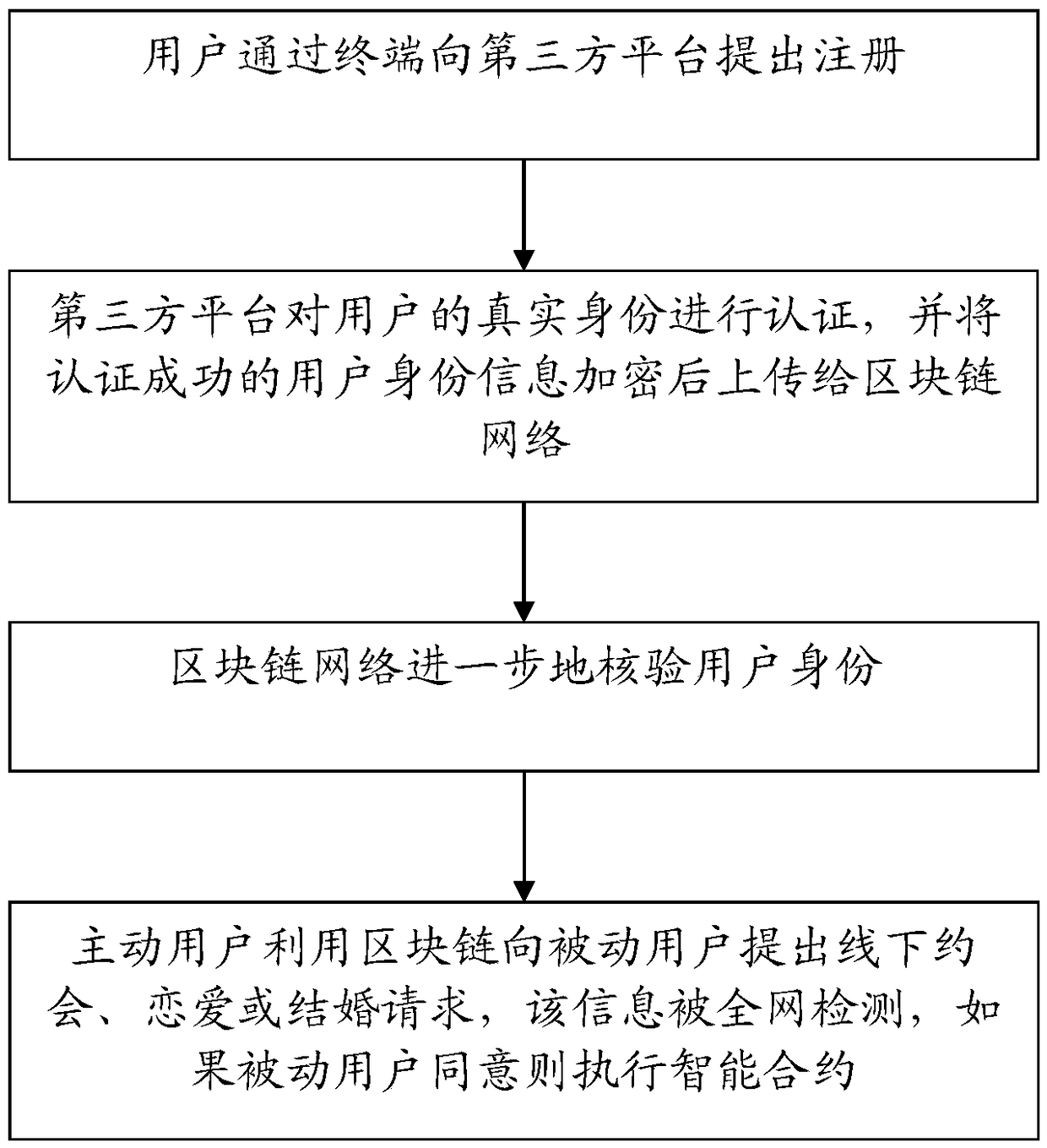
Method and system for comprehensive management of dating and making friends based on block chain
InactiveCN109146699AGuaranteed not to be tampered withStrong shapingData processing applicationsTransmissionThird partyChain network
The invention discloses a method and a system for comprehensive management of dating and making friends based on a block chain. The method comprises the following steps: a user applies for registration to a third party platform through a terminal; the third-party platform authenticates the user's real identity and encrypts the authenticated user's identity information and then uploads it to the block chain network; the block chain network further verifies the identity of the user; the active user makes an off-line appointment, love or marriage request to the passive user by using the block chain, the information is detected by the whole network, and an intelligent contract is executed if the passive user agrees. On the basis of a third party platform of a marriage brokering website, the technical scheme provides fourth-party chunk chain technical support, ensures the privacy of users and user evaluation information not to be tampered with, but also has a very powerful role in shaping the people, so that any link to the node must always standardize all their words and deeds, and constantly improve their quality, because the block chain cross-industry data will record all your behavior.
Owner:SUZHOU KUWAI CULTURAL MEDIA CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com