Device networking authentication method based on blockchain
A technology of blockchain and equipment, applied in the field of computer networks, can solve the problems of authentication system damage, system paralysis, and the inability of both communication parties to know that information has been tampered with.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
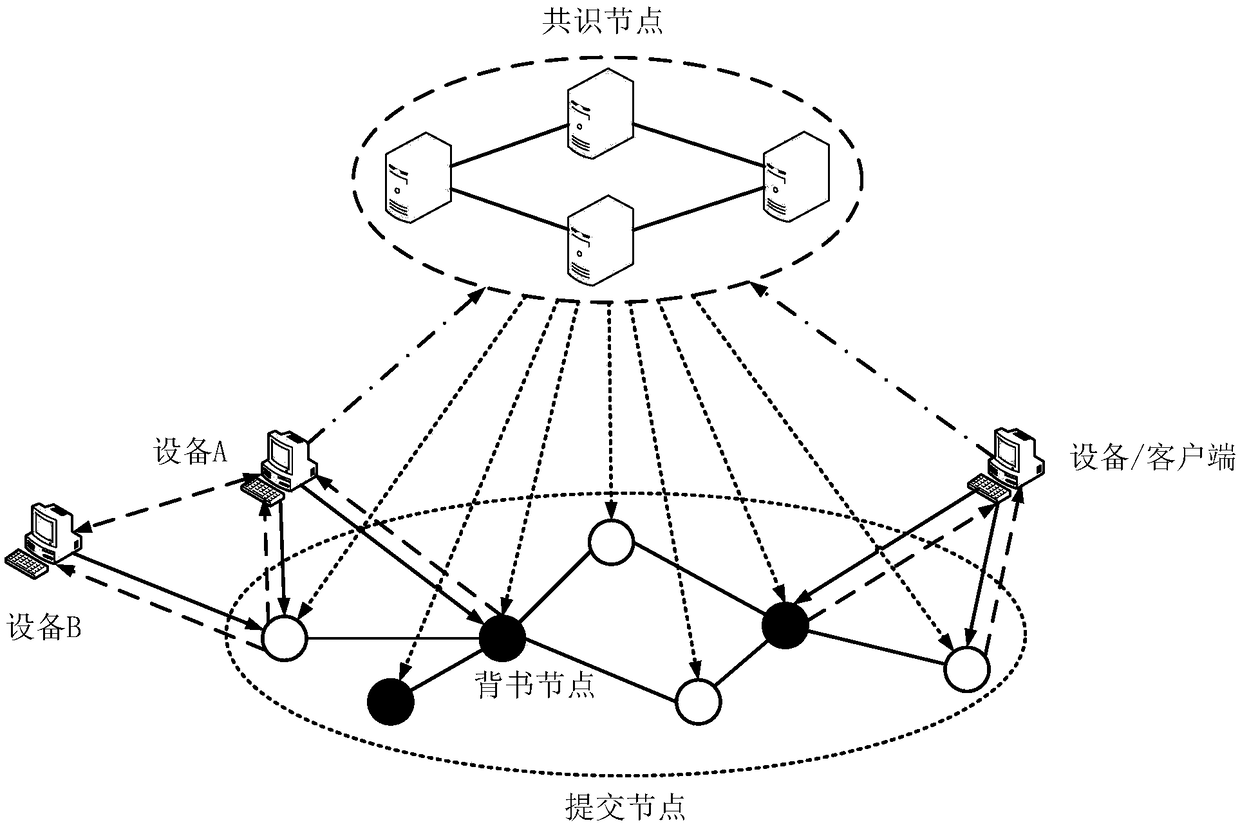
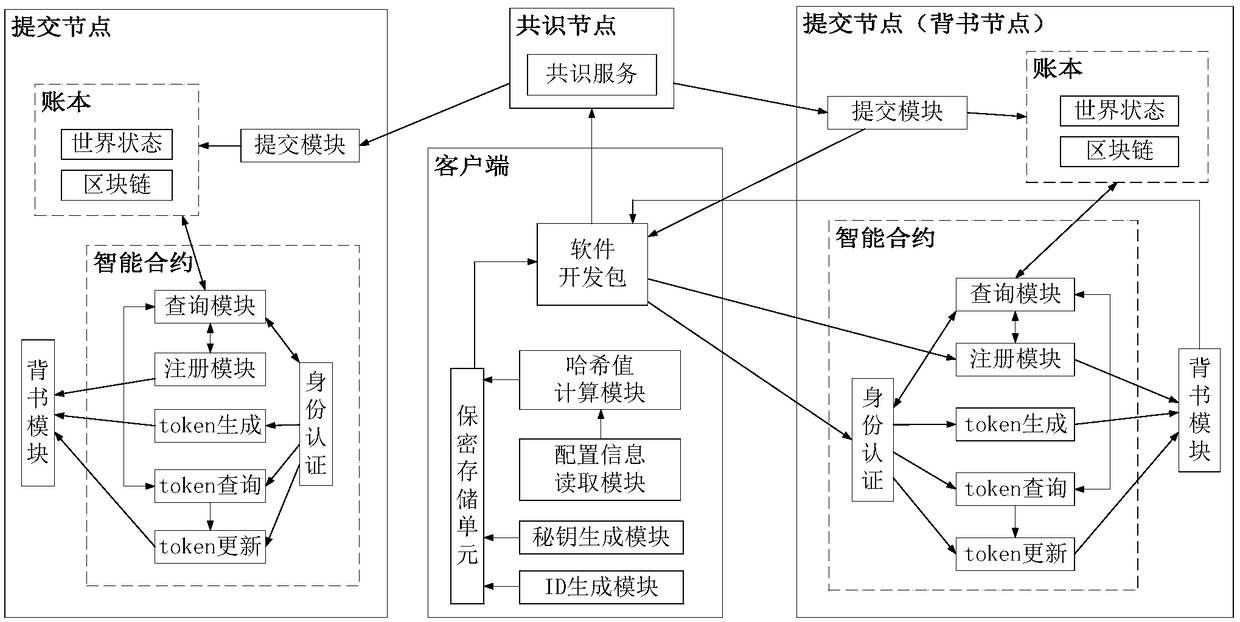
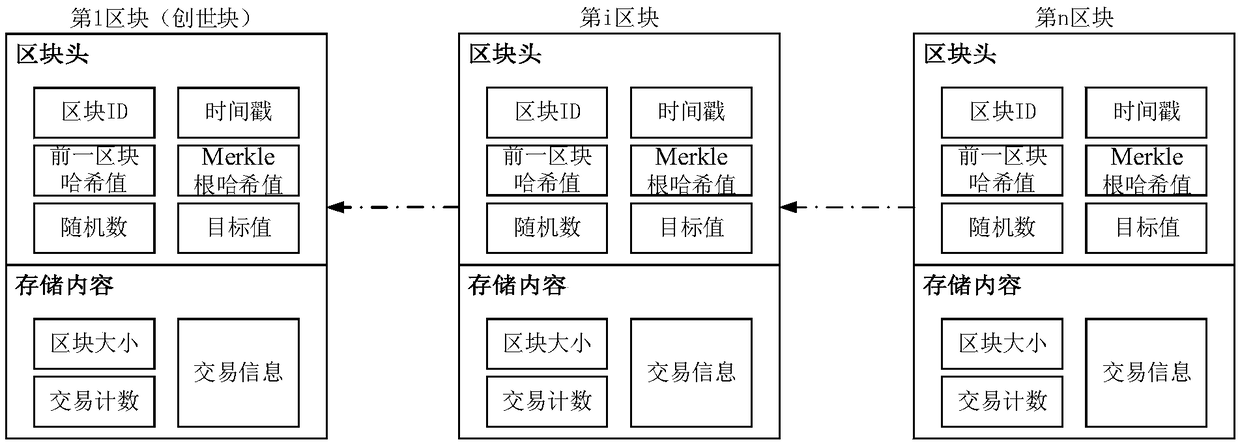
[0132] figure 1 It is the blockchain network structure diagram constructed in the first step of the present invention. Such as figure 1 As shown, the blockchain network includes multiple clients, multiple submission nodes and multiple consensus nodes, the submission nodes are connected to each other, and the consensus nodes are connected to each other. Among them, the lines without arrows indicate that the nodes are connected through the network, and the lines with arrows indicate the input and output of information. The client is connected to the endorsement node and the consensus node. The client initiates a transaction proposal to the endorsement node, receives and verifies the endorsement result returned by the endorsement node, and sends the transaction proposal and the verified endorsement result to the consensus node. The consensus node is connected to the client and the submission node. The consensus node generates a block based on the transaction proposal sent by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com