Authorization method and system
An authentication method and an authentication system technology, which are applied in the field of authorization authentication methods and systems, and can solve the problems of USBKey being easily transferred and signed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
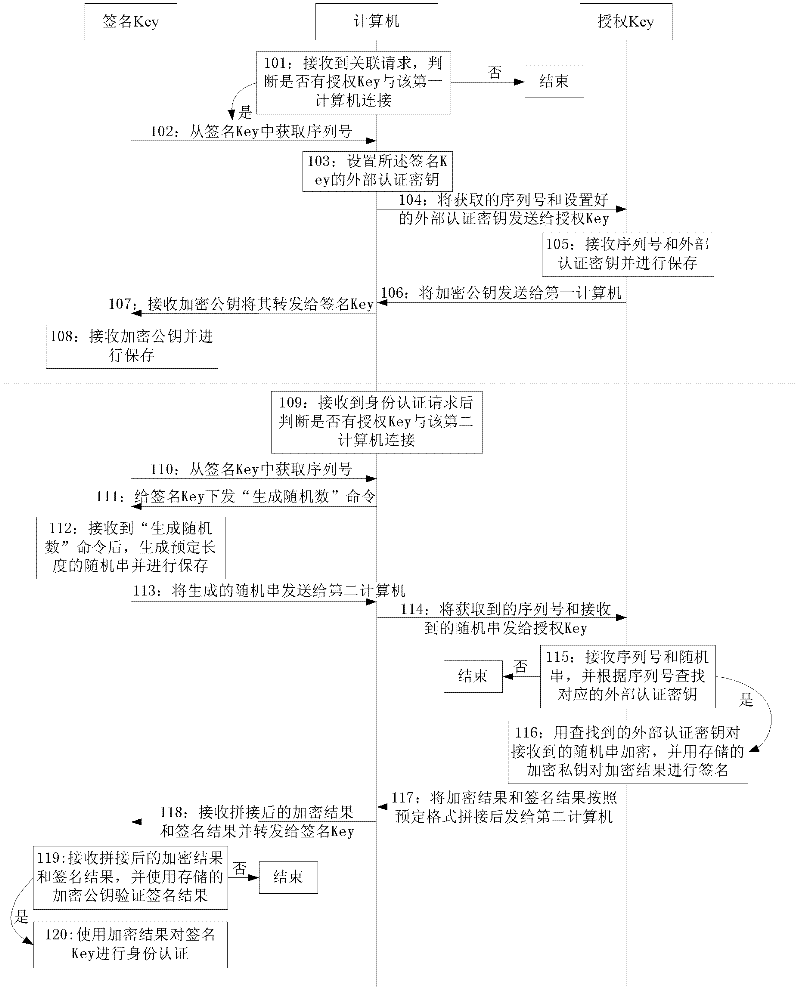
[0101] This embodiment provides a method of authorization authentication, which is performed when the signature Key is inserted into the computer, and the signature Key is associated with the signature Key one-to-many, such as figure 1 As shown, the process of establishing an association between the authorization Key and the signature Key in the method includes S101-S107;
[0102] S101: The first computer receives the association request, and judges whether there is an authorization key connected to the first computer, if yes, execute S102, otherwise end;
[0103] S102: the first computer obtains the serial number from the signature Key;
[0104] Specifically, in this embodiment, the length of the serial number is 12 bits agreed in advance, and the serial number is used as the ID of the external authentication key;
[0105] S103: The first computer sets the external authentication key of the signature key, if the setting is successful, execute step 104, otherwise end;
[010...
Embodiment 2
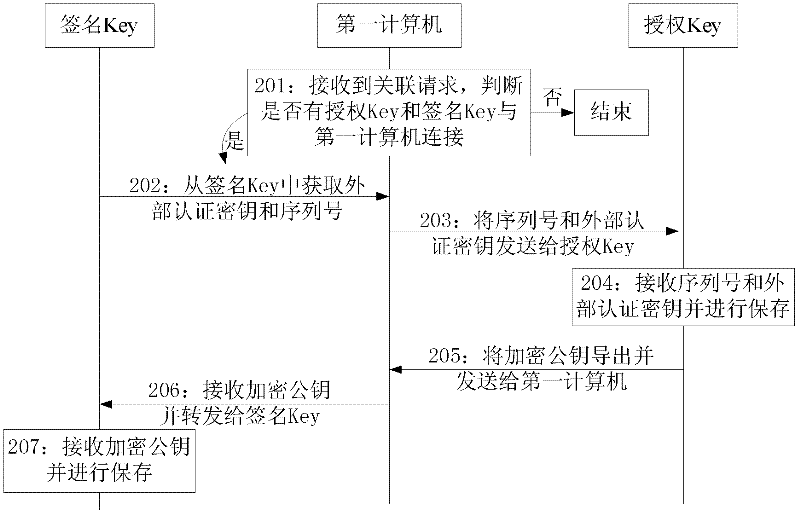
[0147] An authorization authentication method provided by Embodiment 2 of the present invention includes an association process and an authentication process. The specific implementation technical solution is: the authorization key and the signature key are transmitted through the computer, and after the PIN verification of the authorization key is passed, the authorization key and the signature key Perform one-to-many association. After association, when using the signature key to operate, the signature key needs to be authenticated by the authorization key in advance. After the authentication is passed, the signature key can be used for operation.
[0148] The first computer in this embodiment includes a terminal and associated programs installed inside it. see figure 2 , the association process specifically includes:
[0149] S201: The first computer receives the association request, and judges whether there is an authorization key and a signature key connected to the fir...
Embodiment 3
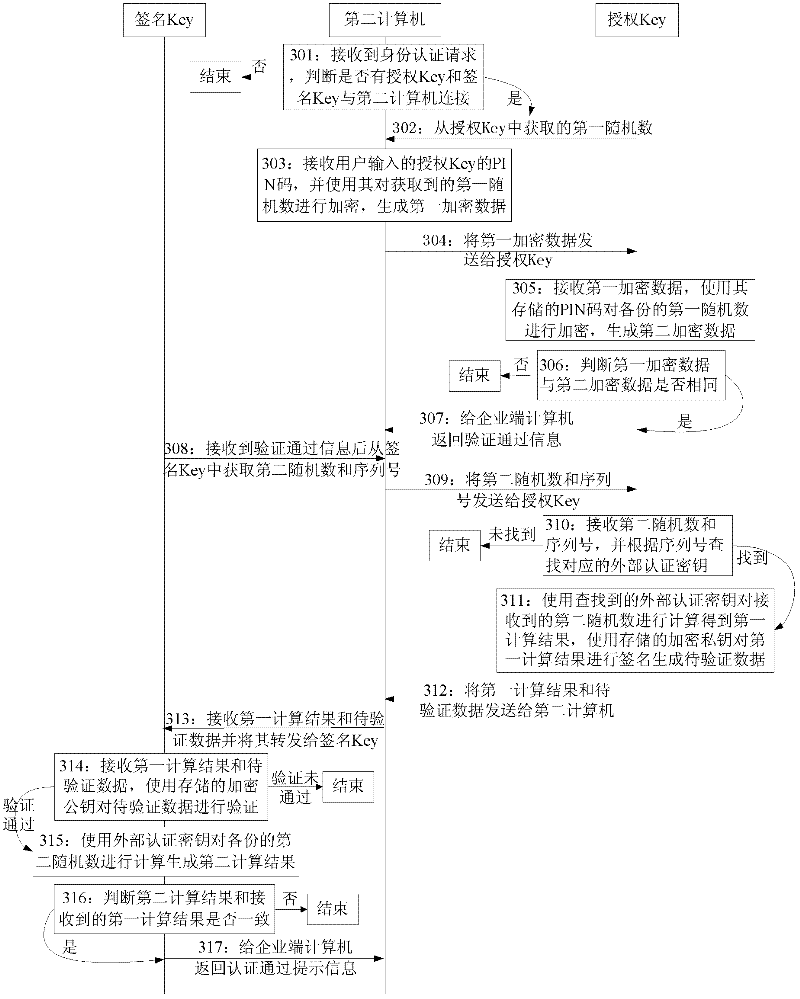
[0210] Embodiment 3 of the present invention provides an authorization authentication system, such as Figure 5 As shown, including: authorization Key3, computer 2 and signature Key1;
[0211] Authorization Key1 specifically includes:
[0212] The first receiving module 11 is used to receive the serial number and the external authentication key of the signature Key sent by the computer during association, and receive the first encrypted data, the serial number and the second random number of the signature Key sent by the computer during authentication;
[0213] The first generating module 12 is used to generate an encrypted public key and an encrypted private key according to the RSA encryption algorithm (), and is also used to generate the first random number and / or random string;
[0214] The first storage module 13 is used to store the encrypted public key and the encrypted private key, the serial number of the signature Key received during association, the external authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com