Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
An identity verification method and digital certificate technology, applied in digital transmission systems, user identity/authority verification, transmission systems, etc., can solve the problems of insecure, unstable, and low-level identity authentication methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0084]An identity verification method based on a TEE digital certificate, comprising a terminal 2 pre-configured digital certificate system 1, a digital certificate signature process and a digital certificate verification process, characterized in that the terminal 2 has a TEE, and the digital certificate signature process , performed on the terminal 2, used to sign the user request using a digital certificate private key, the digital certificate verification process is used to authenticate the identity of the user requesting, and the authentication method includes verifying the legality of the digital certificate and Validity, integrity and correctness of the signature; wherein, the digital certificate signing process is performed under the TEE.
[0085] The user request specifically includes an application request of the client, and the application request needs to be authenticated. The digital certificate system 1 is located in the terminal 2TEE, TEE is the abbreviation of ...
Embodiment 2
[0090] An identity verification method based on a TEE digital certificate, comprising a terminal 2 pre-configured digital certificate system 1, a digital certificate signature process and a digital certificate verification process, characterized in that the terminal 2 has a TEE, and the digital certificate signature process , performed on the terminal 2, used to sign the user request using a digital certificate private key, the digital certificate verification process is used to authenticate the identity of the user requesting, and the authentication method includes verifying the legality of the digital certificate and Validity, integrity and correctness of the signature; wherein, the digital certificate signing process is performed under the TEE.
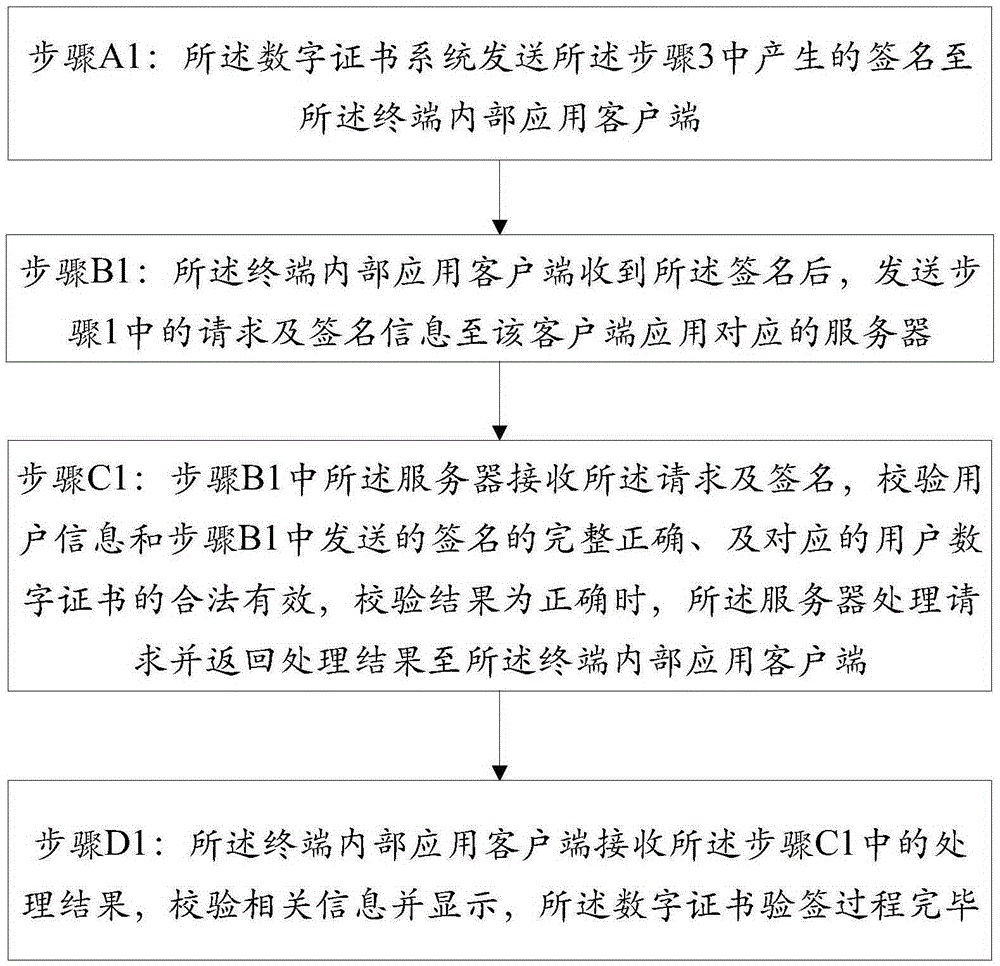
[0091] like figure 1 As shown in the flow chart of the digital certificate signing process in the embodiment of the present application, the client is an internal application client of the terminal 2, and the internal application c...
Embodiment 3
[0101] An identity verification method based on a TEE digital certificate, comprising a terminal 2 pre-configured digital certificate system 1, a digital certificate signature process and a digital certificate verification process, characterized in that the terminal 2 has TEE and REE, and the digital certificate The signature process is performed on the terminal 2, and is used to generate a digital certificate for the user request, and the digital certificate verification process is used to authenticate the identity of the user requesting, and the authentication method includes the digital certificate; wherein the digital certificate The system 1 is located in the terminal 2TEE, and the digital certificate signing process is performed under the TEE.
[0102] The client is an external application client of the terminal 2, and the digital certificate signing process includes:
[0103] Step ①: The digital certificate system 1 securely stores user identity information, root CA cer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com