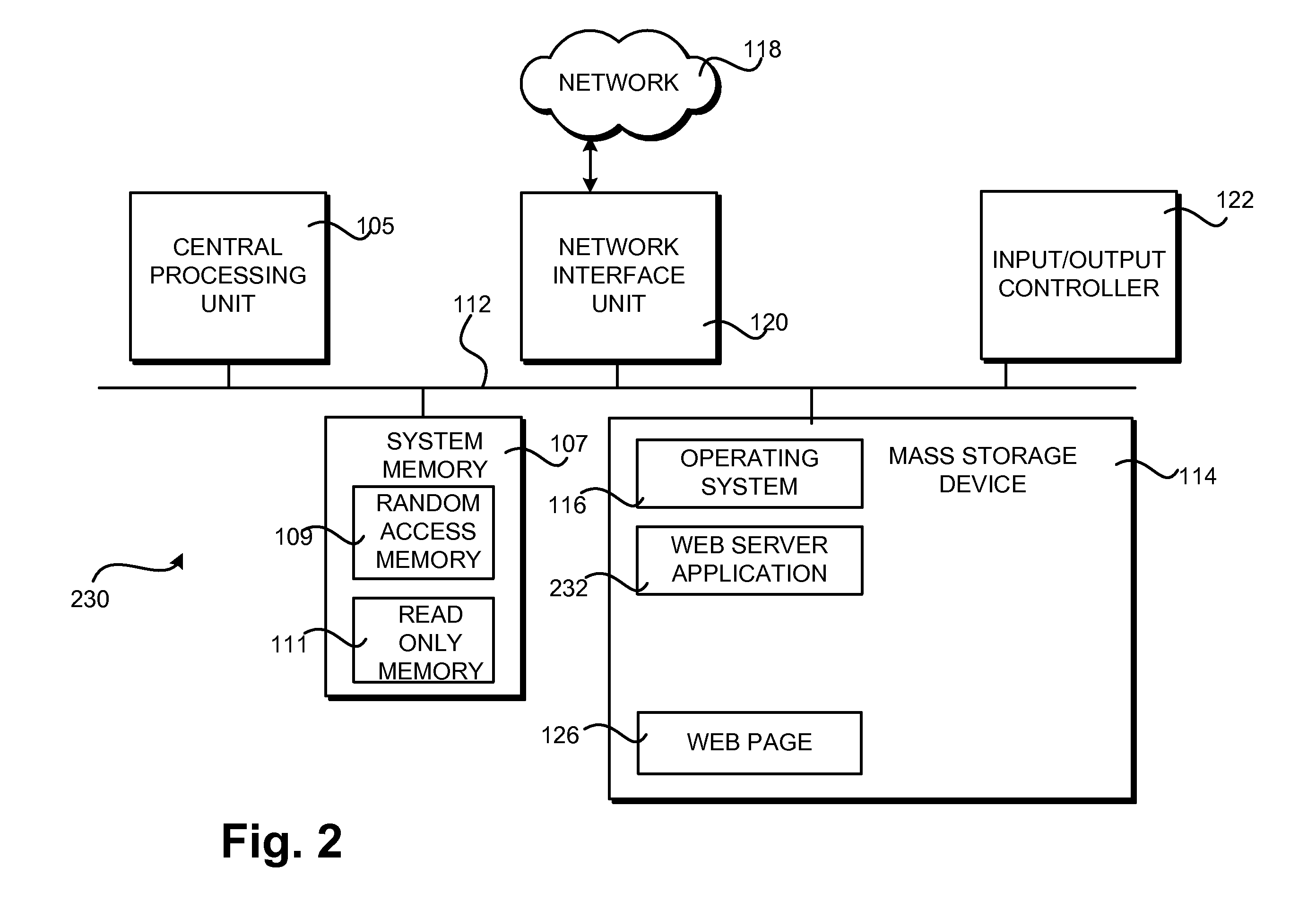
Patents
Literature
180 results about "Personal identity verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Personal Identity Verification (PIV) is a common credentialing and standard background investigation process required by Homeland Security Presidential Directive 12 (HSPD-12).
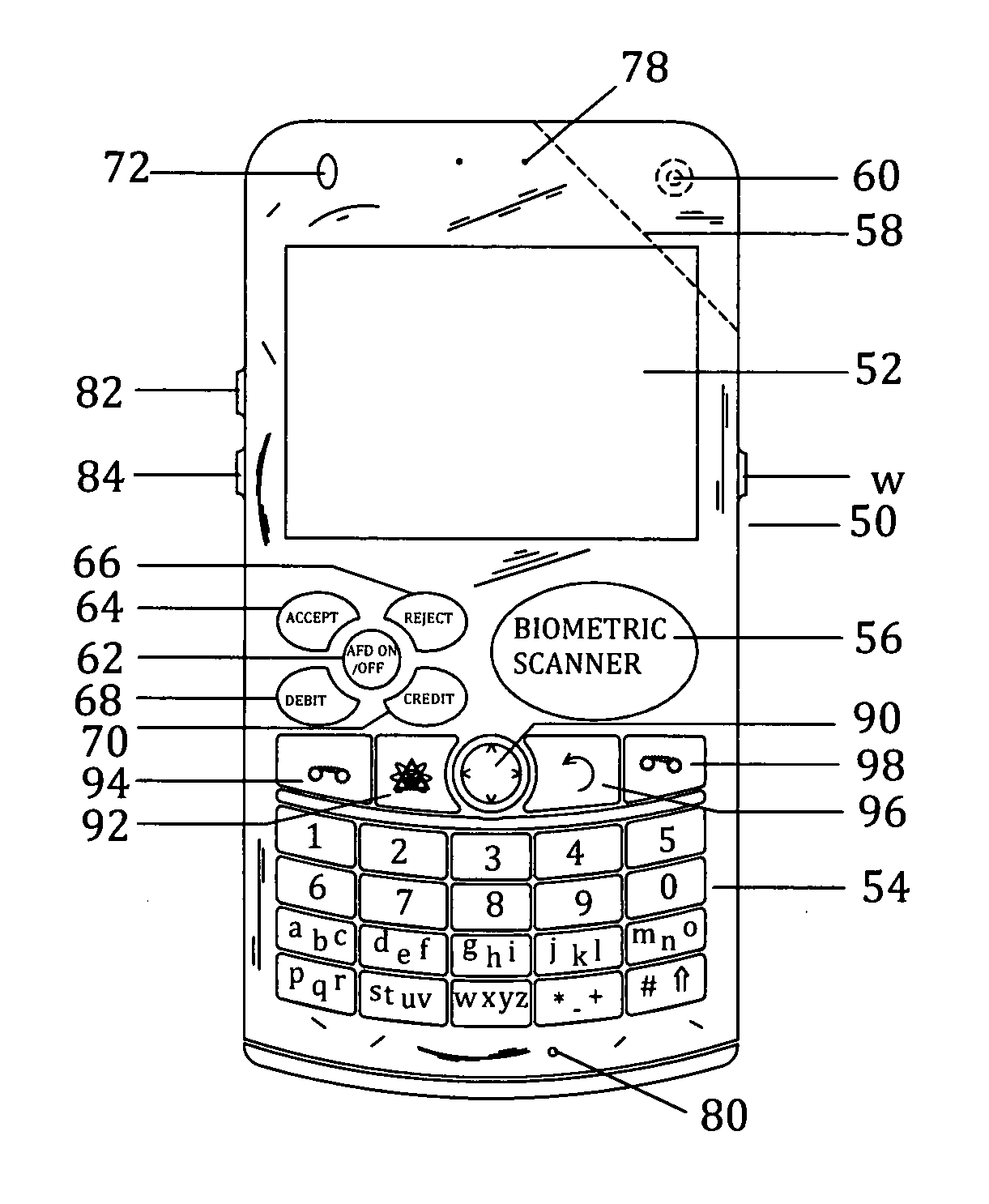
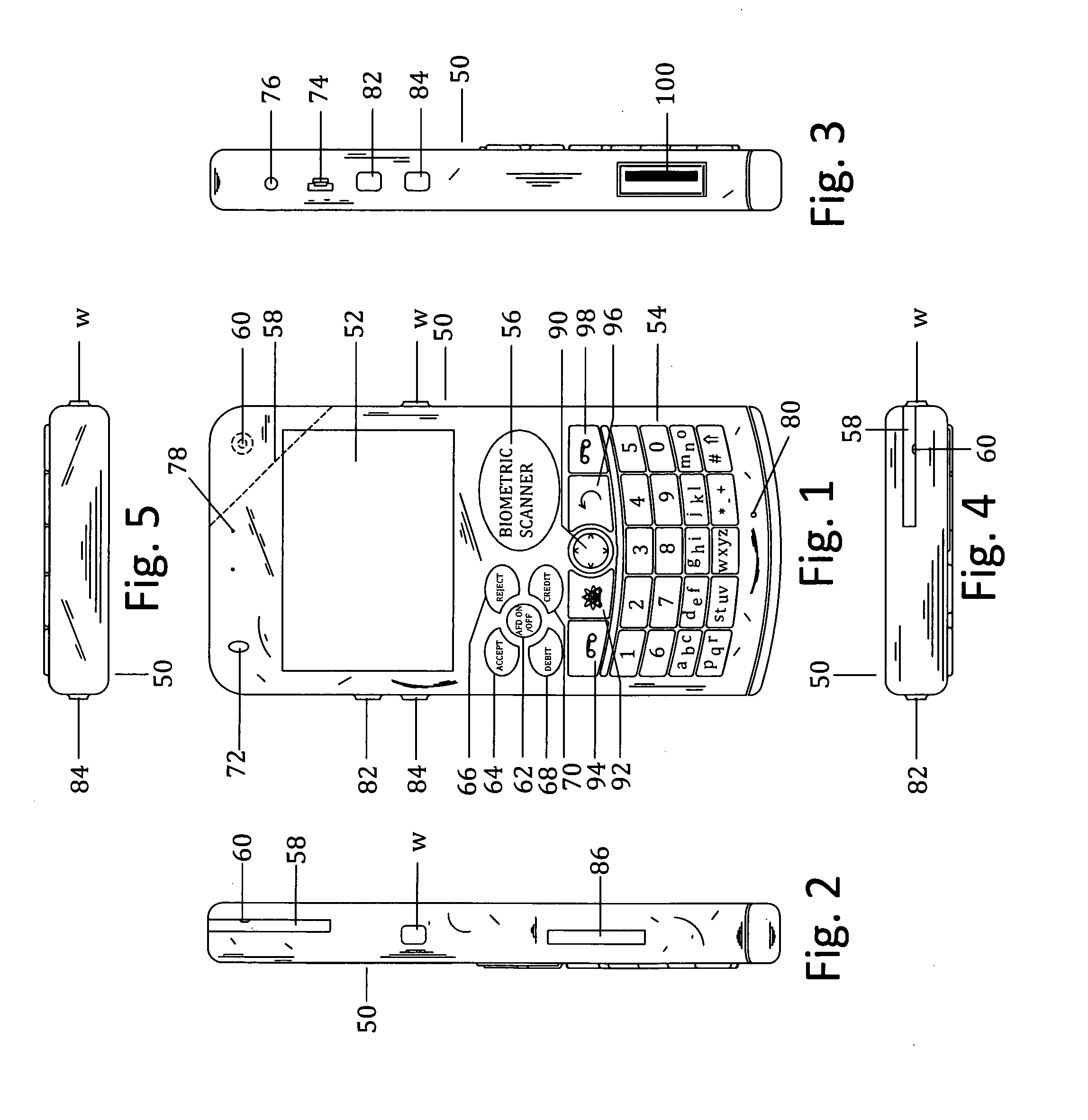
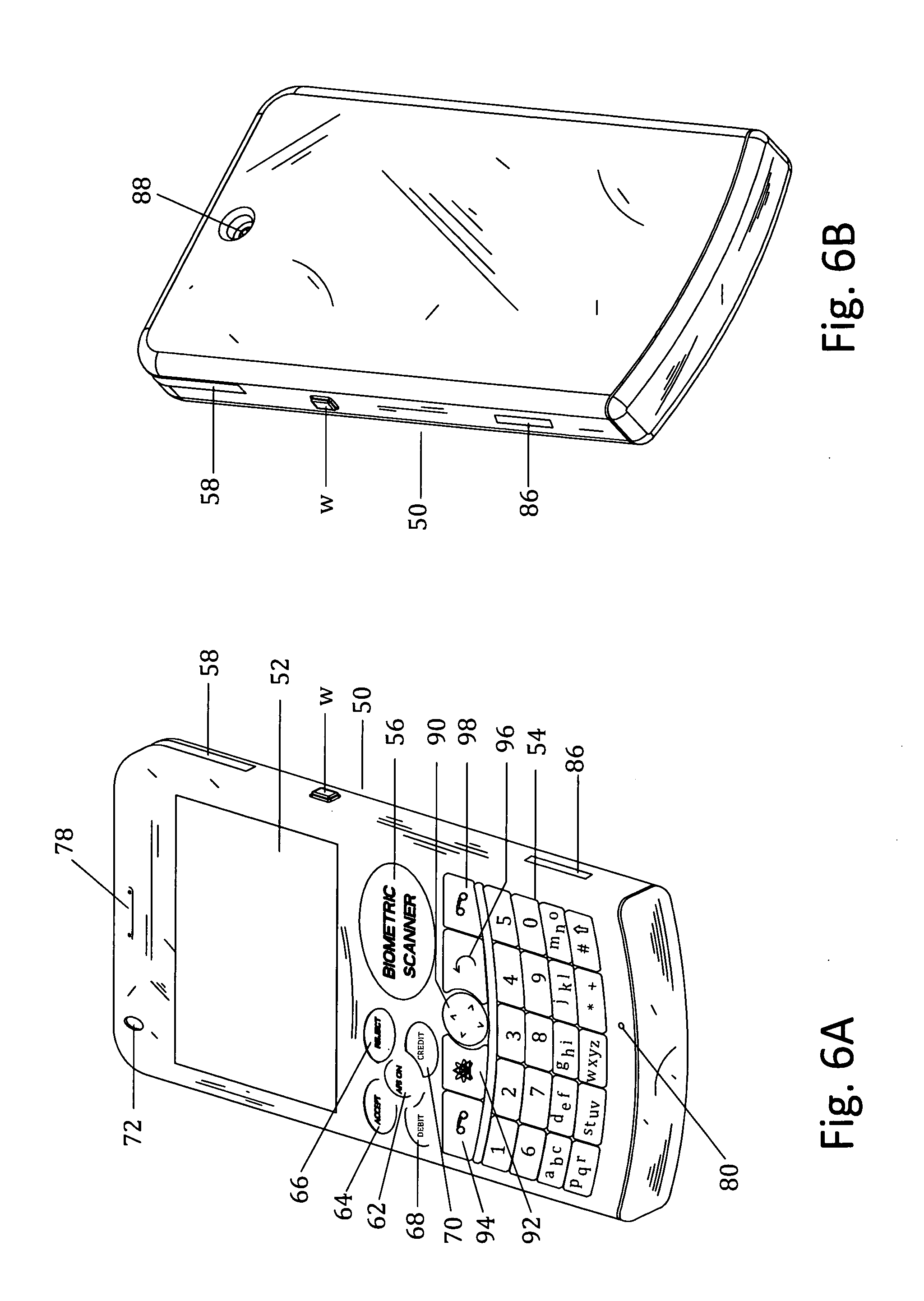
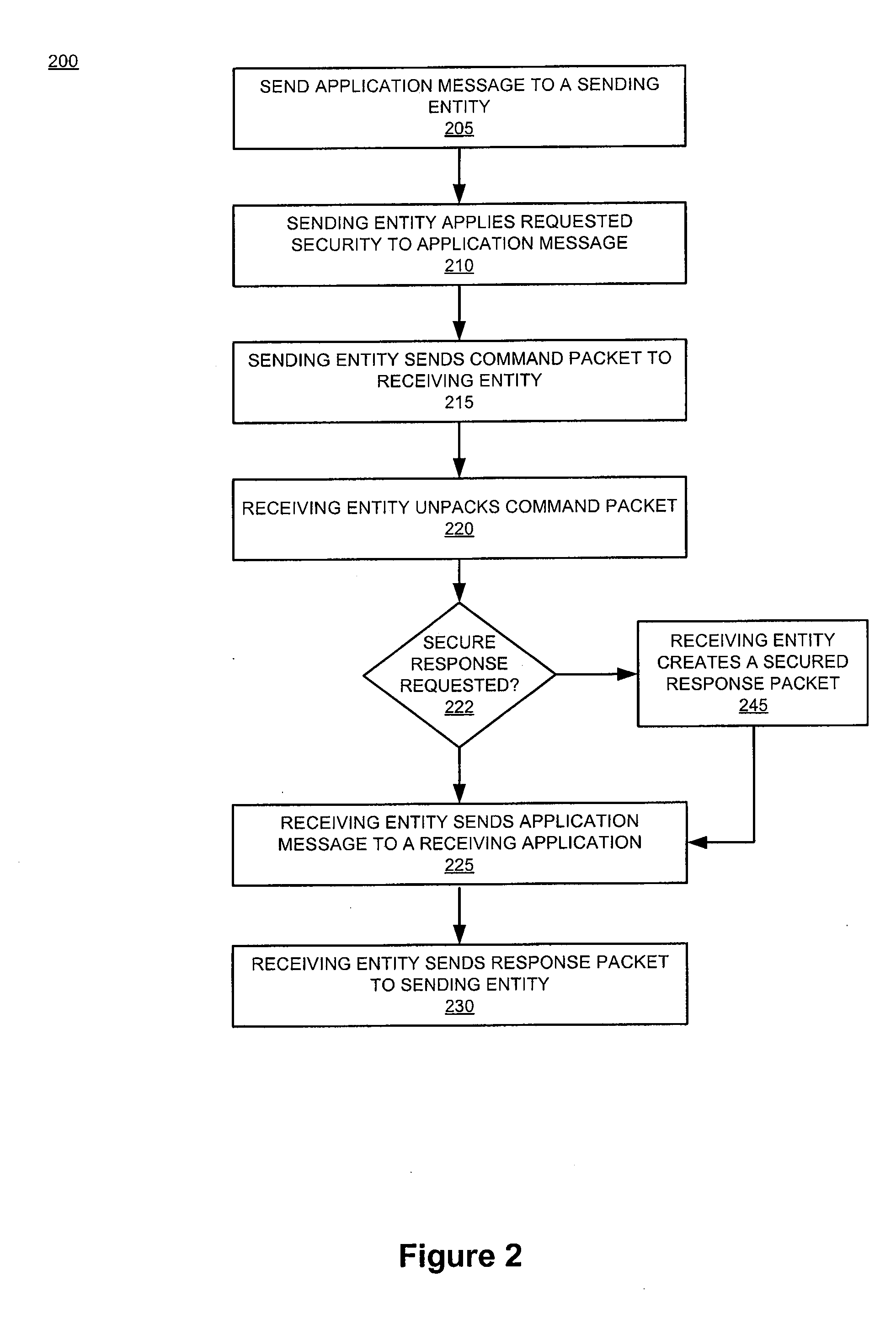
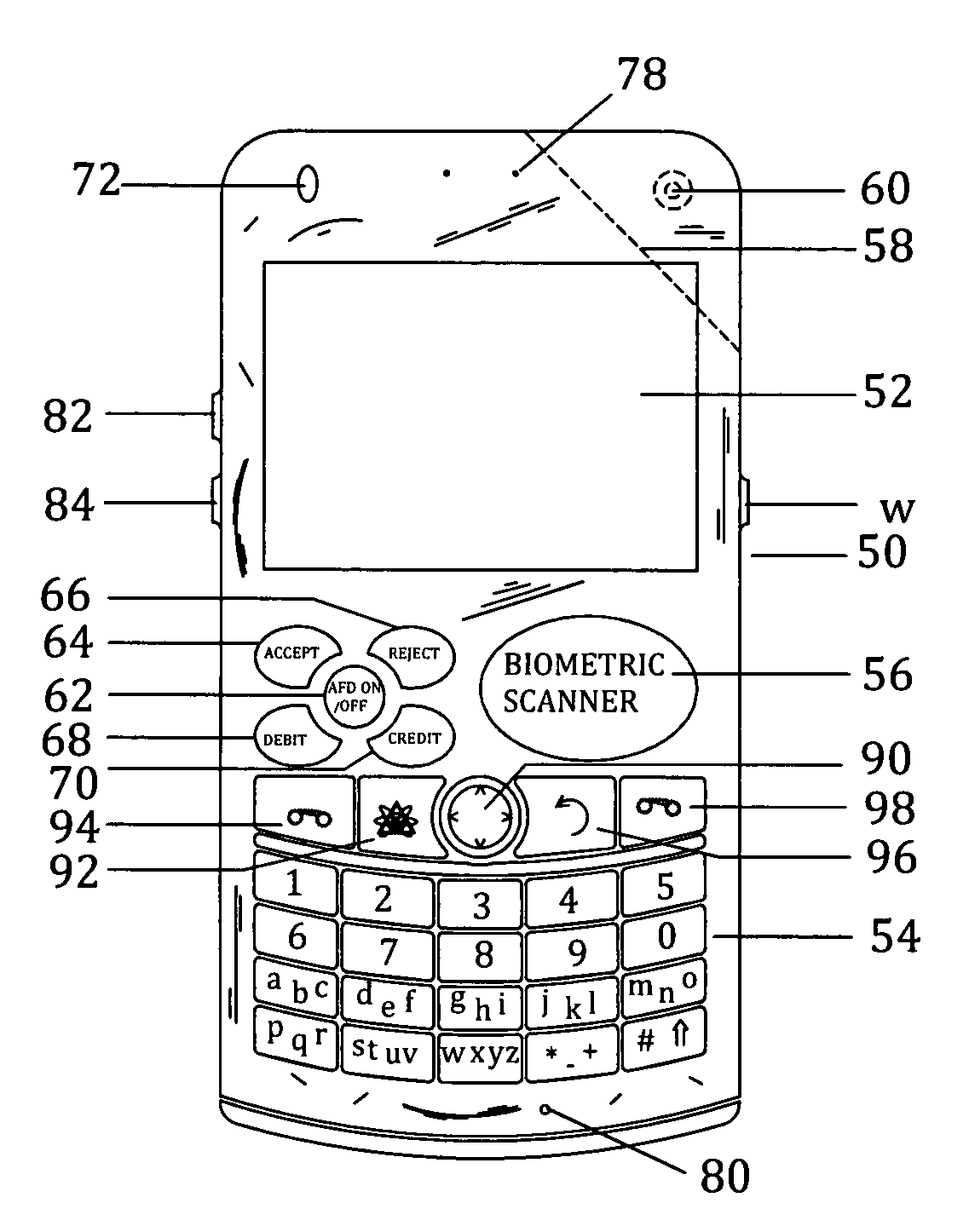
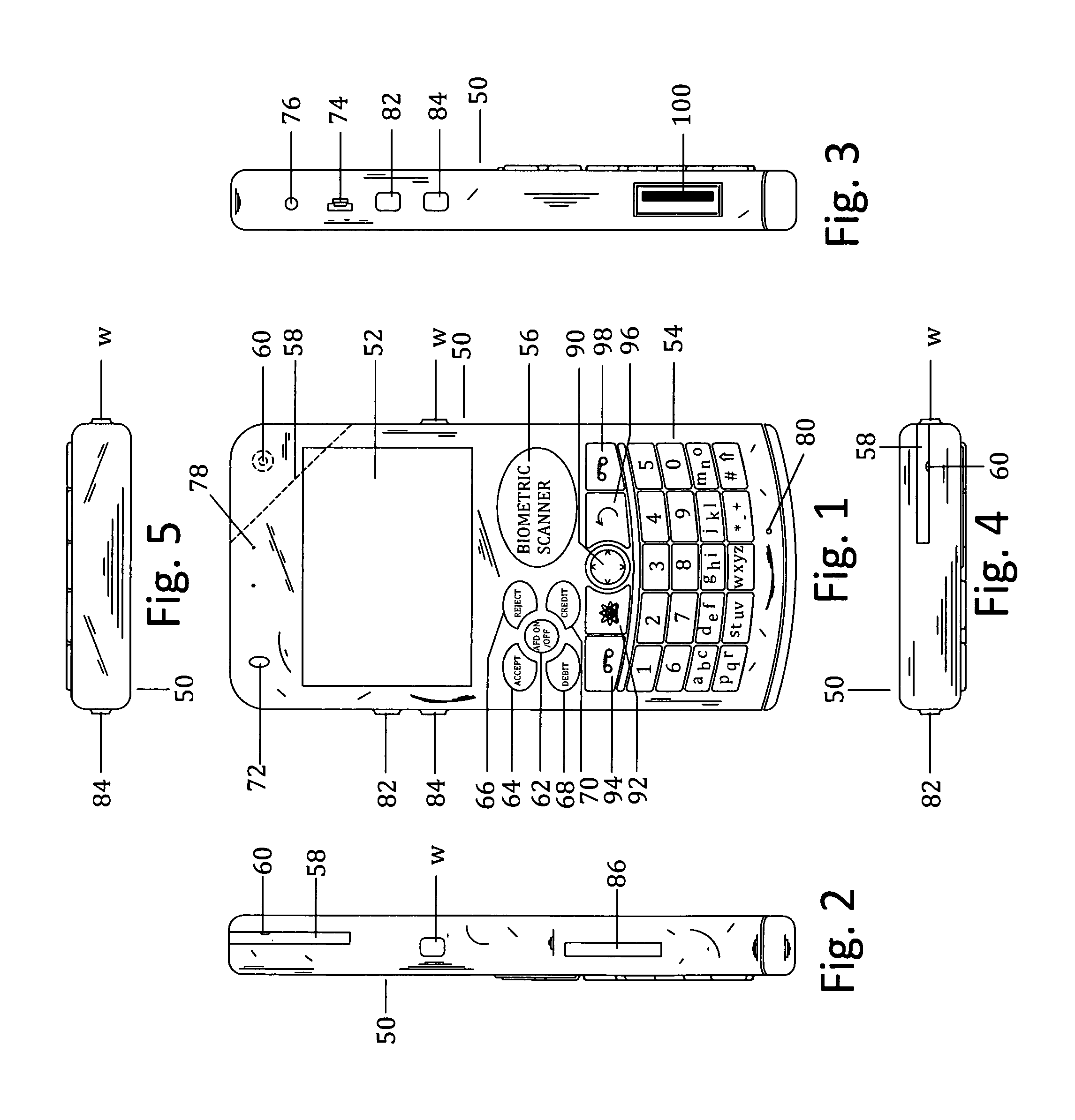
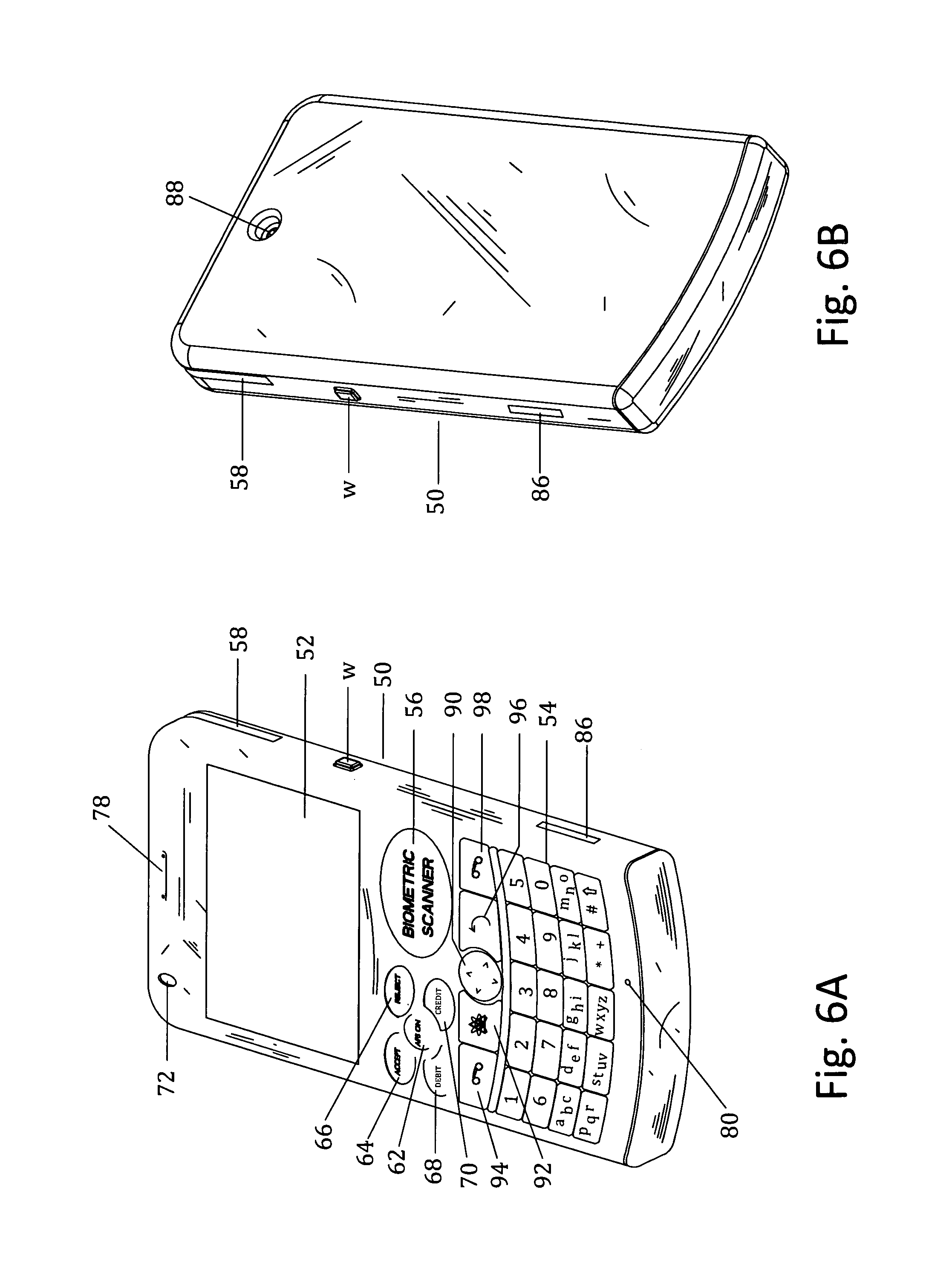
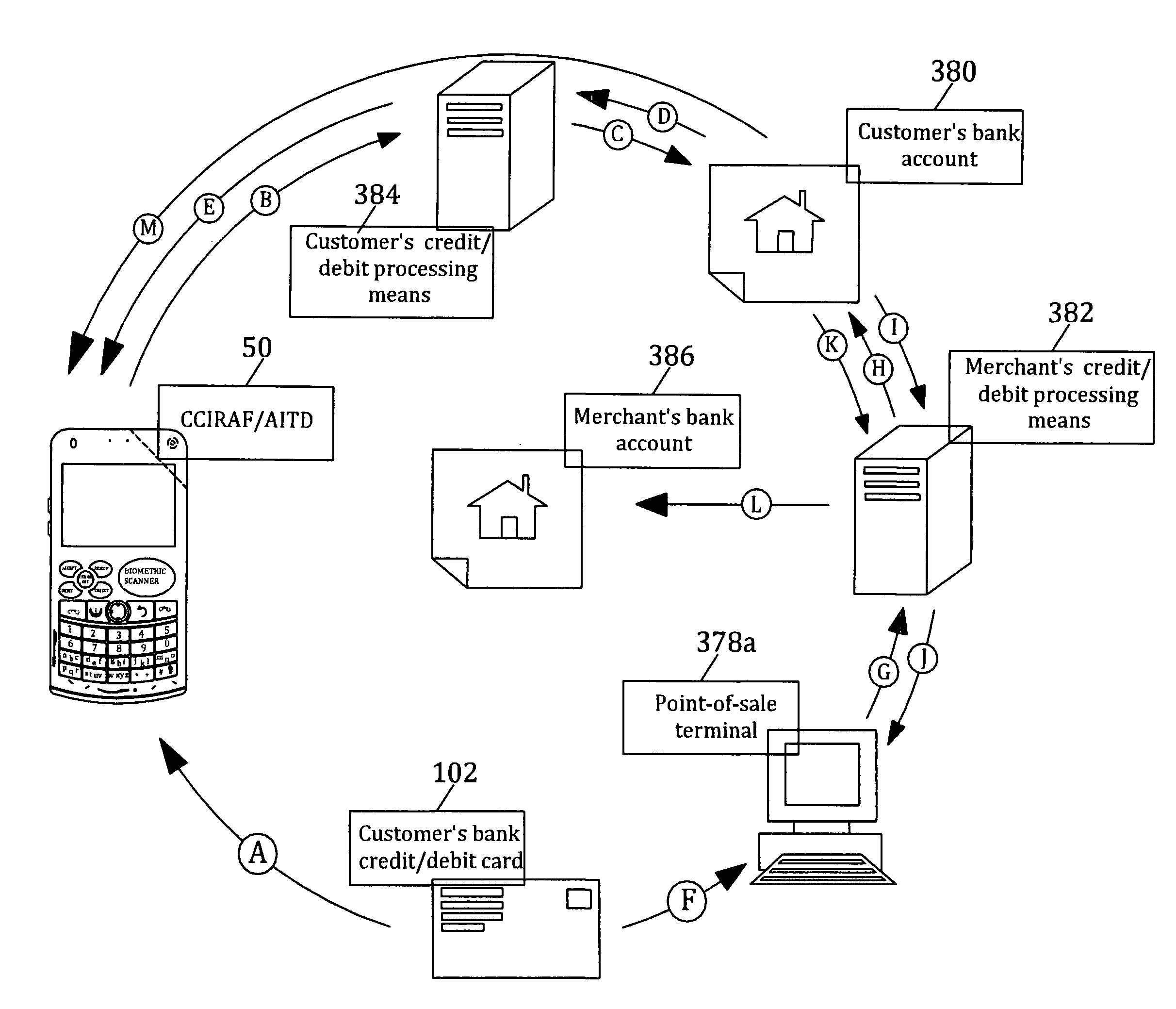
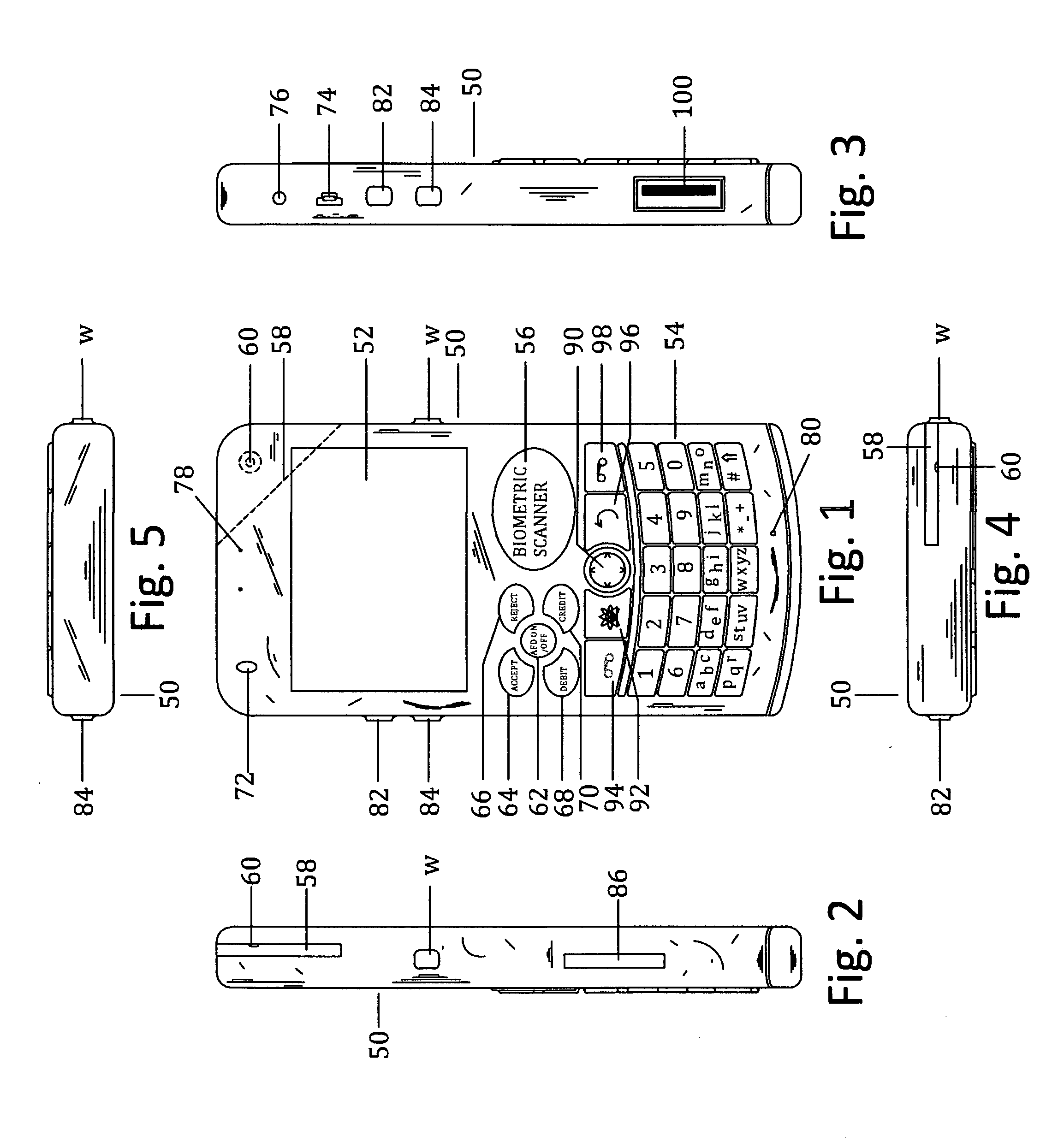
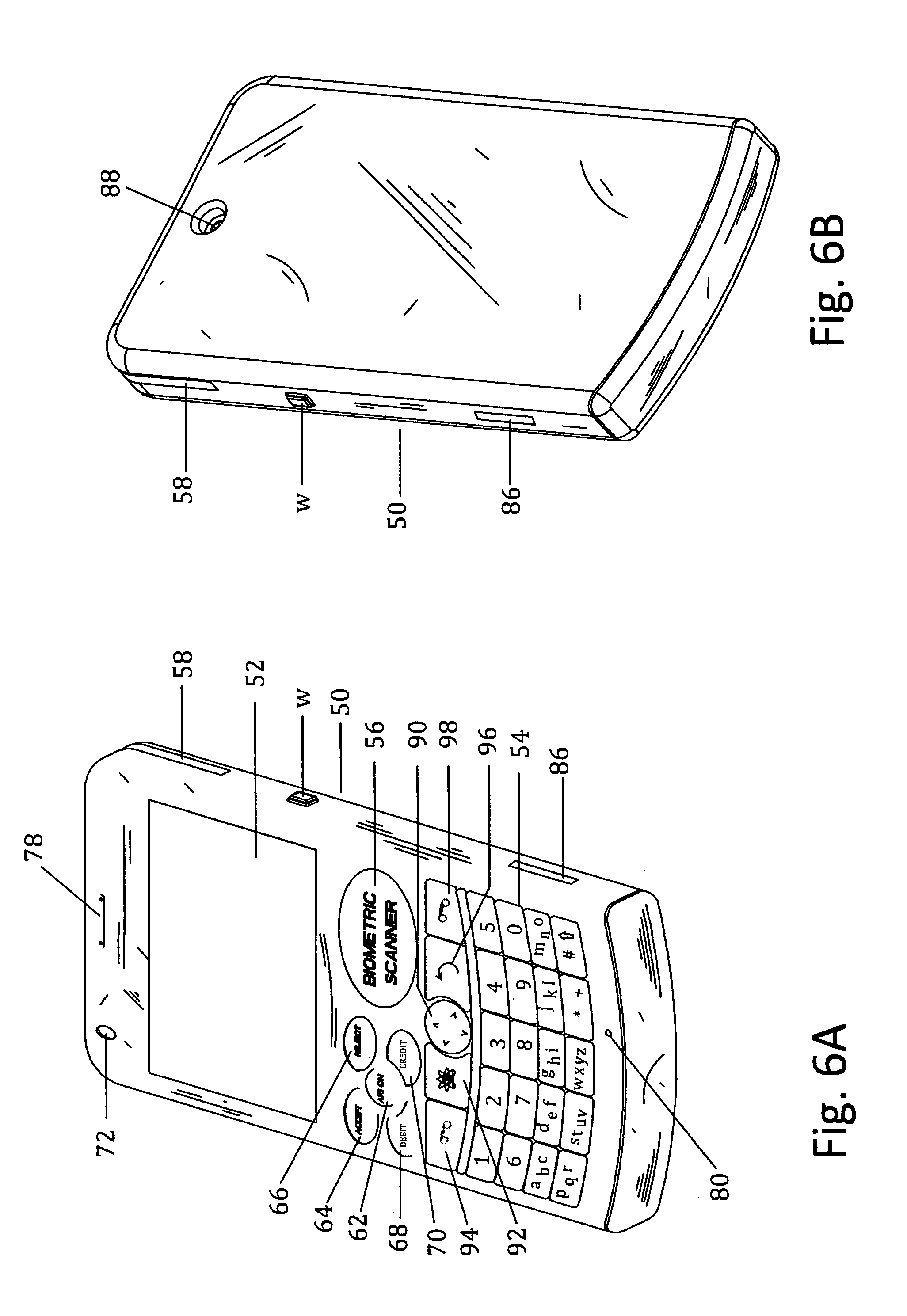
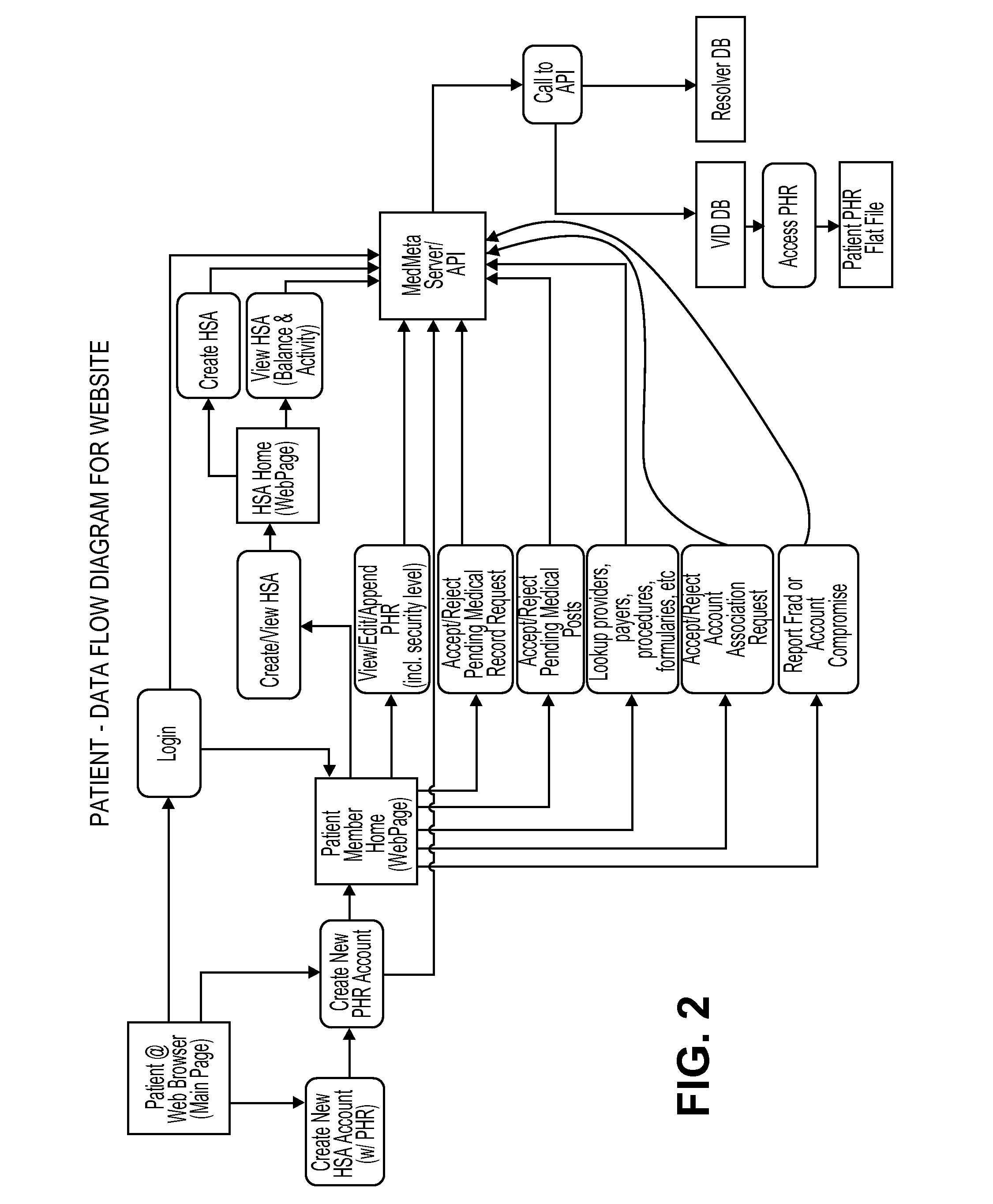
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
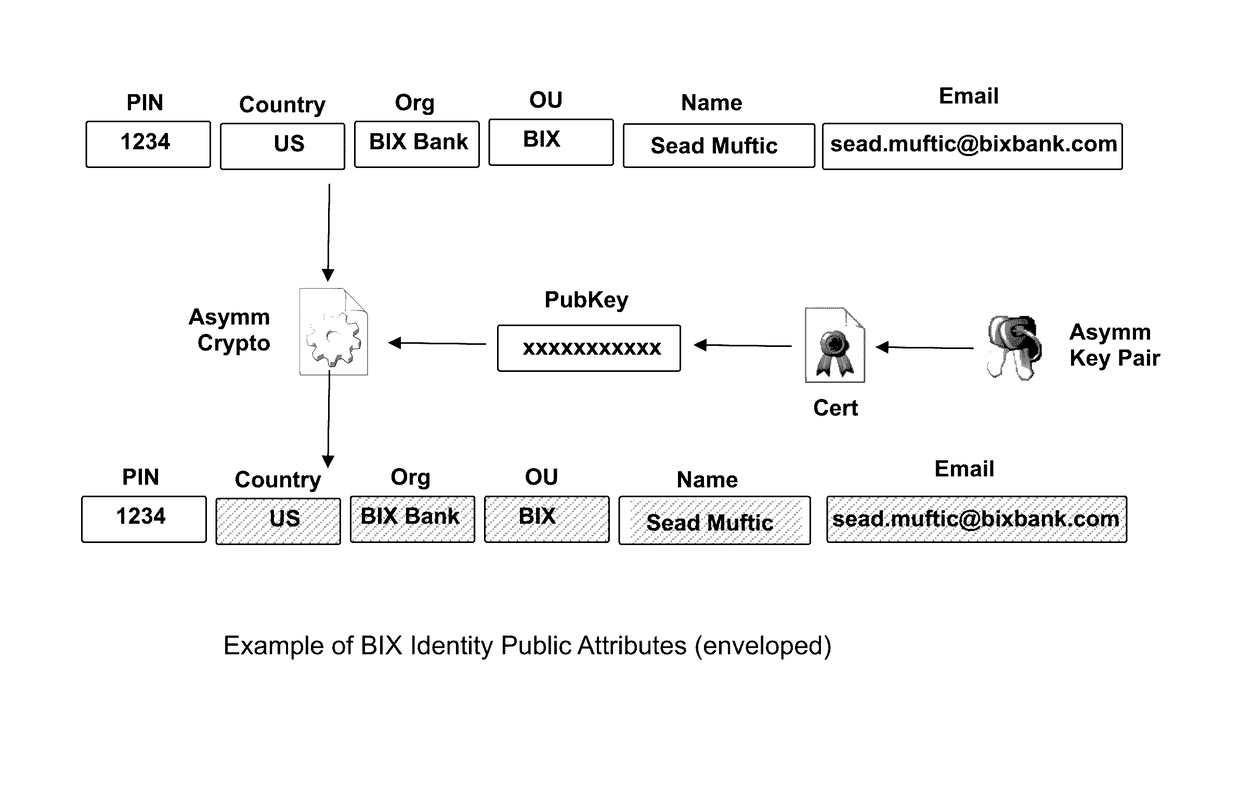
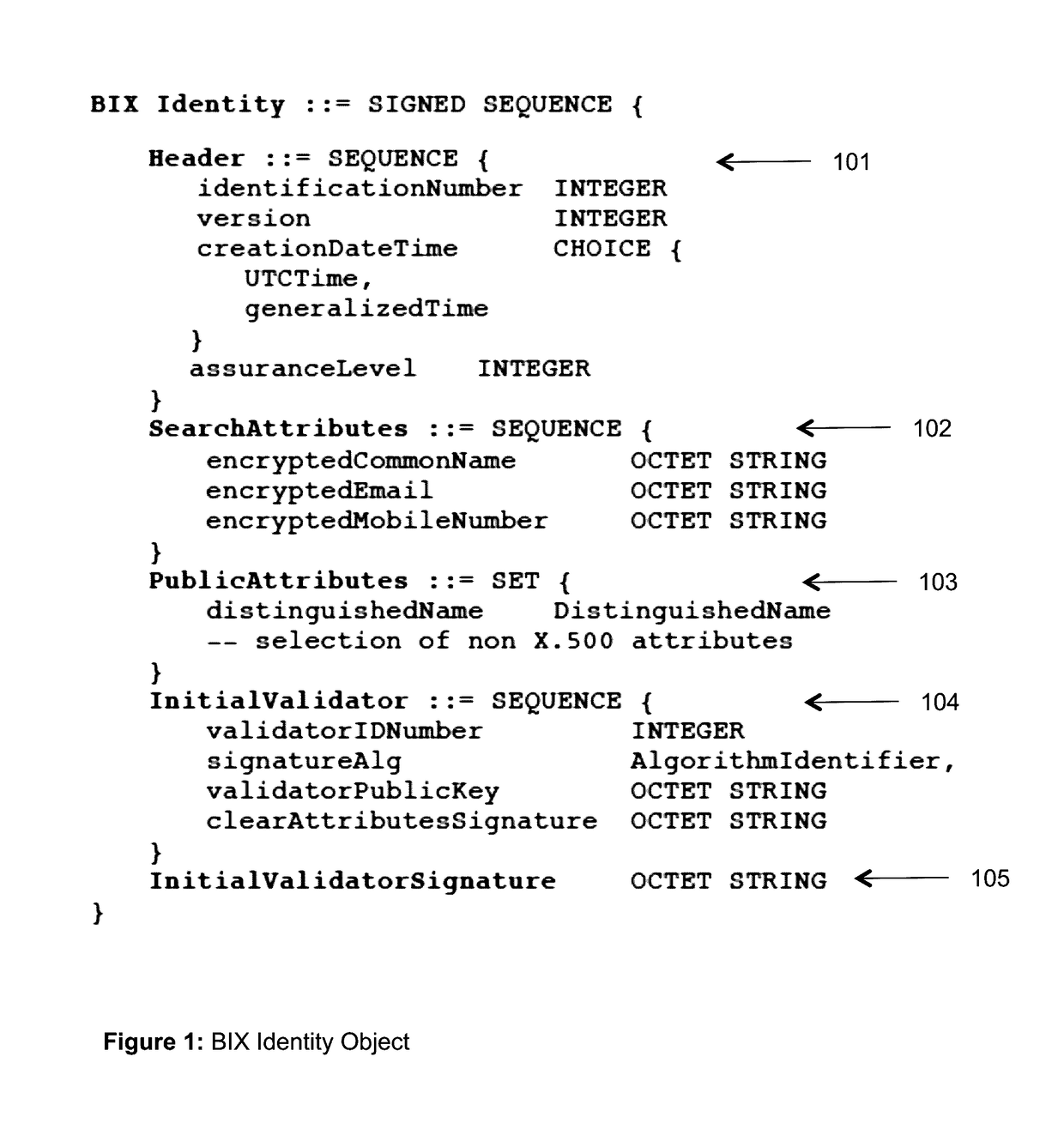
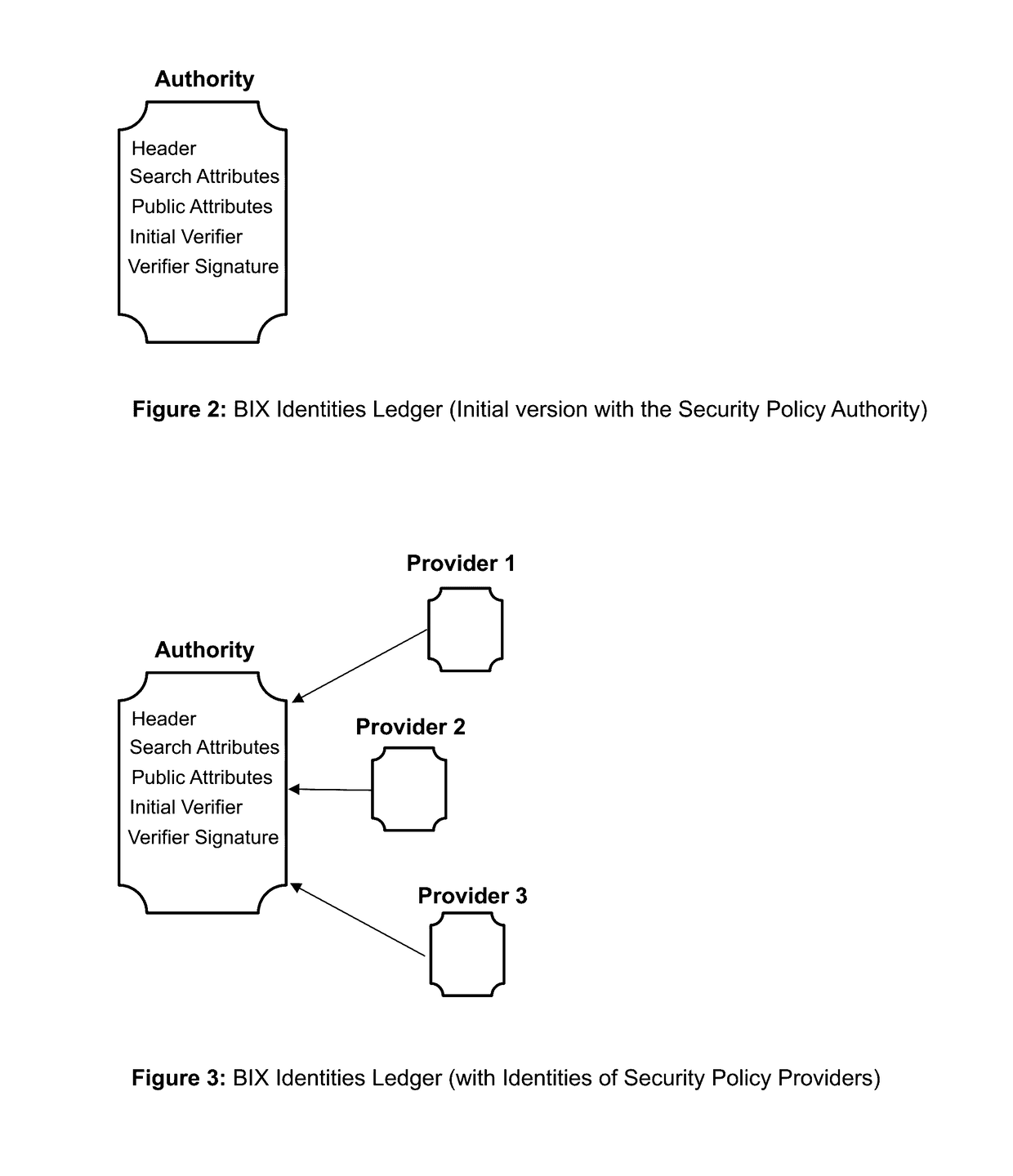
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
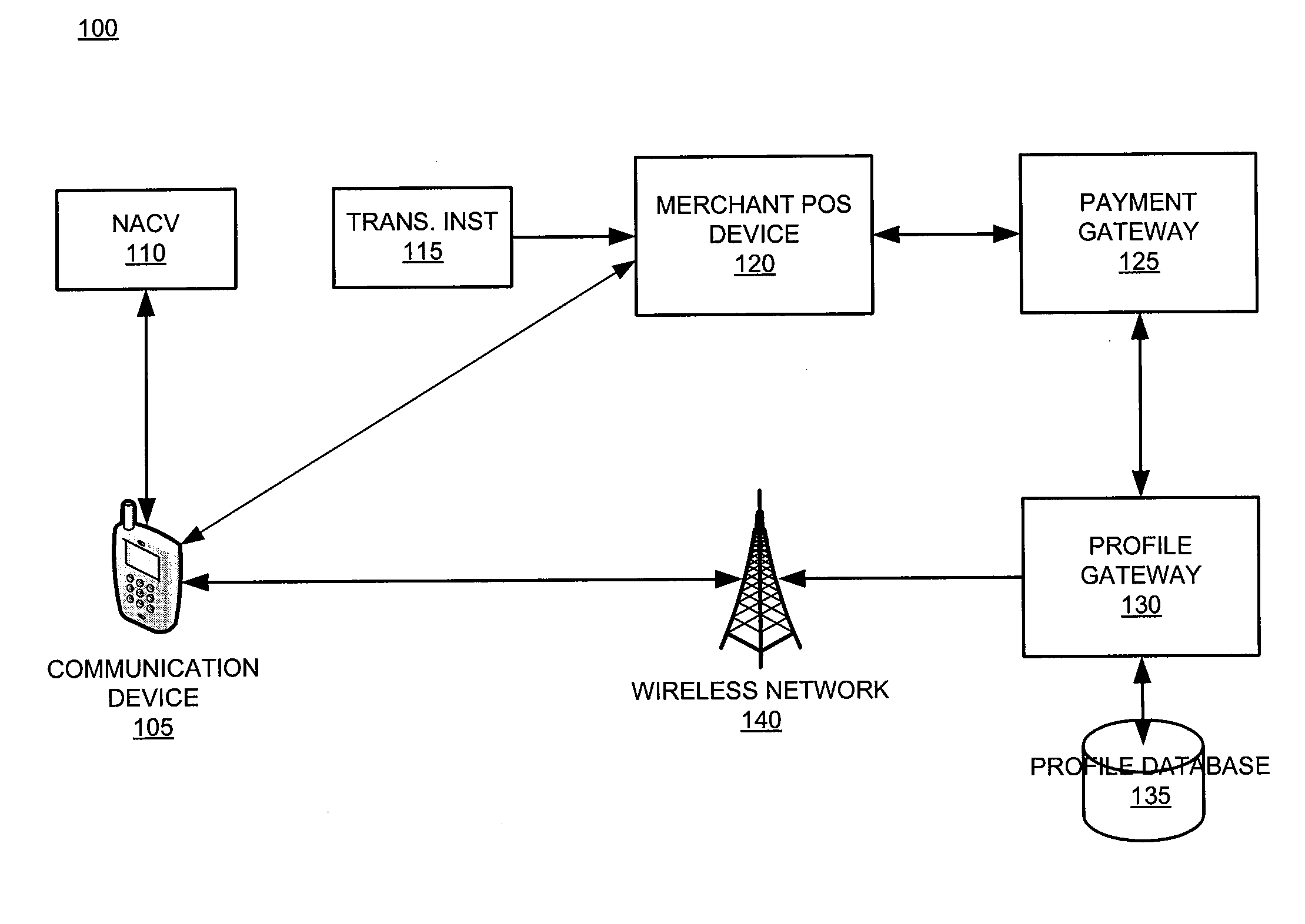
System and device for facilitating a transaction by consolidating sim, personal token, and associated applications for electronic wallet transactions
InactiveUS20120231844A1Increase dependenceFacilitating secure and convenient electronic transactionsPayment architectureSubstation equipmentPayment transactionSmart card
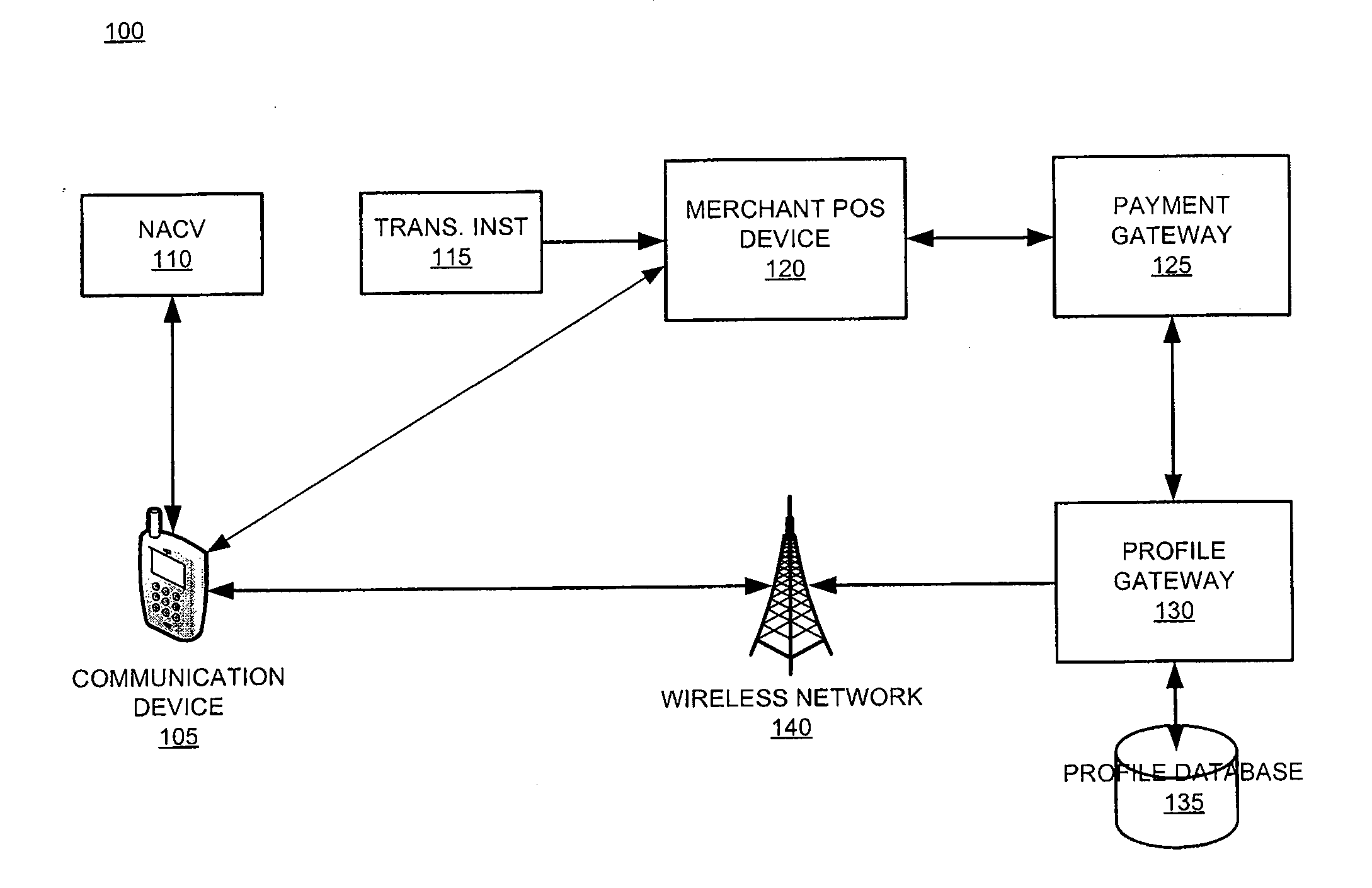
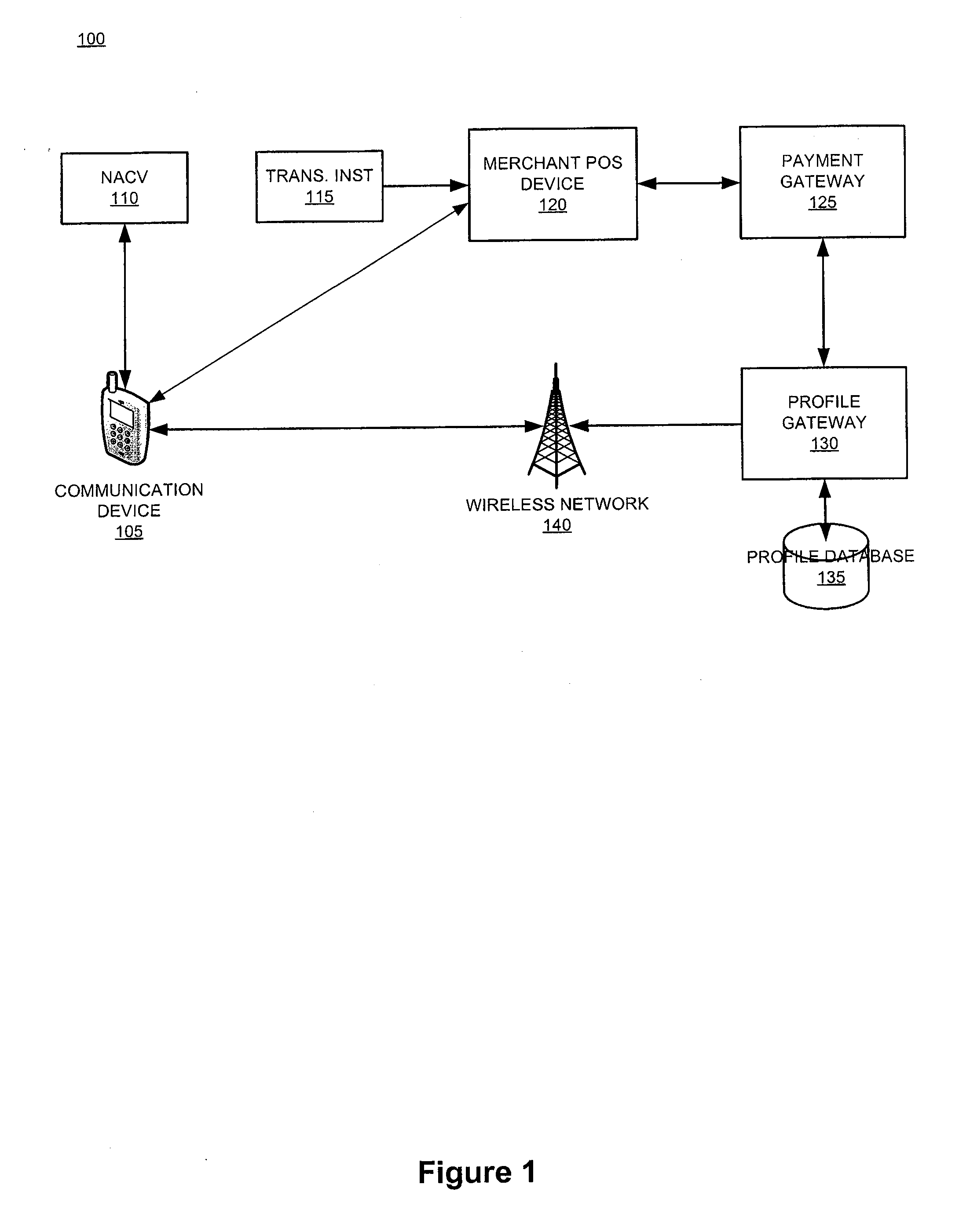
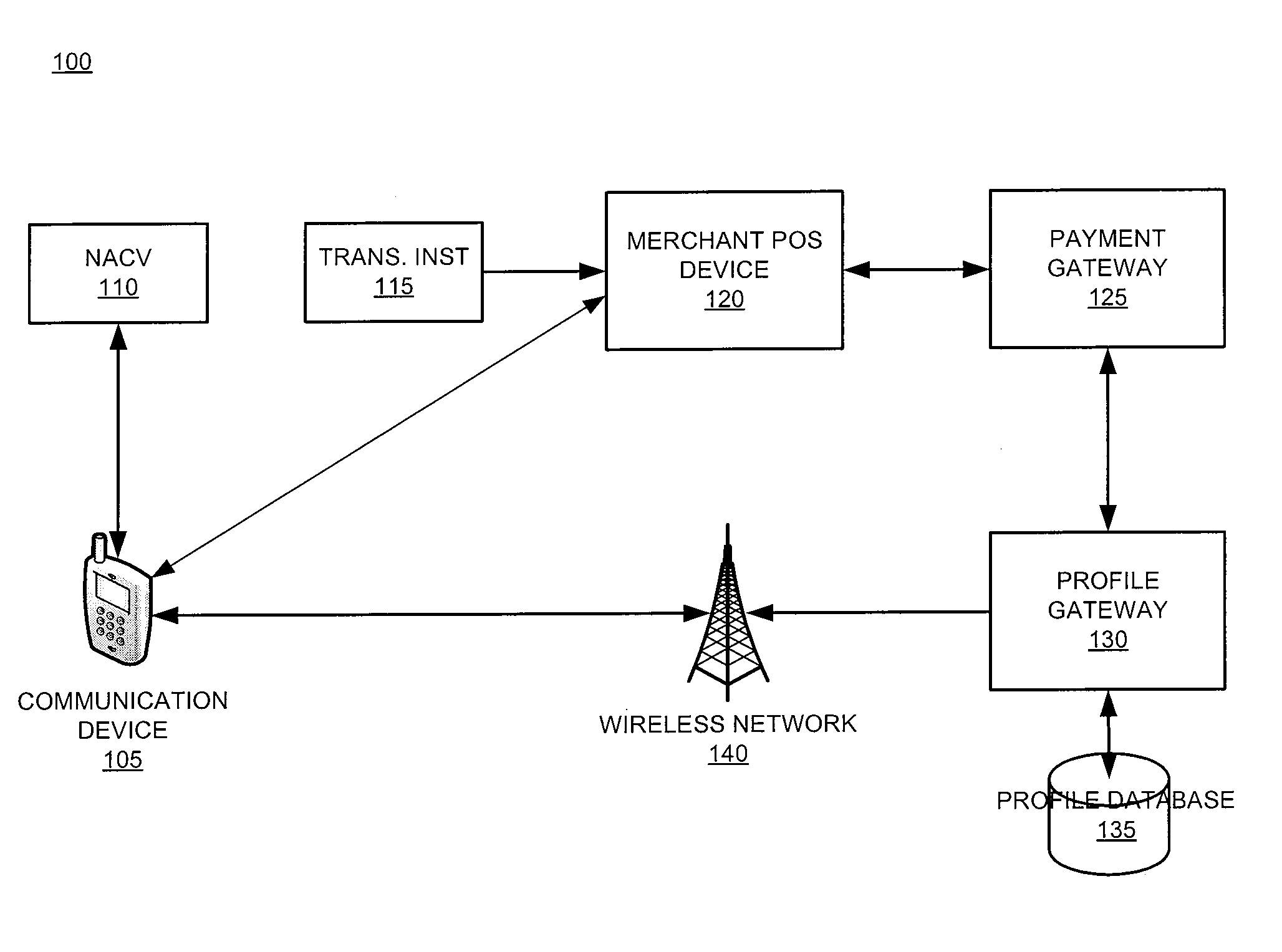
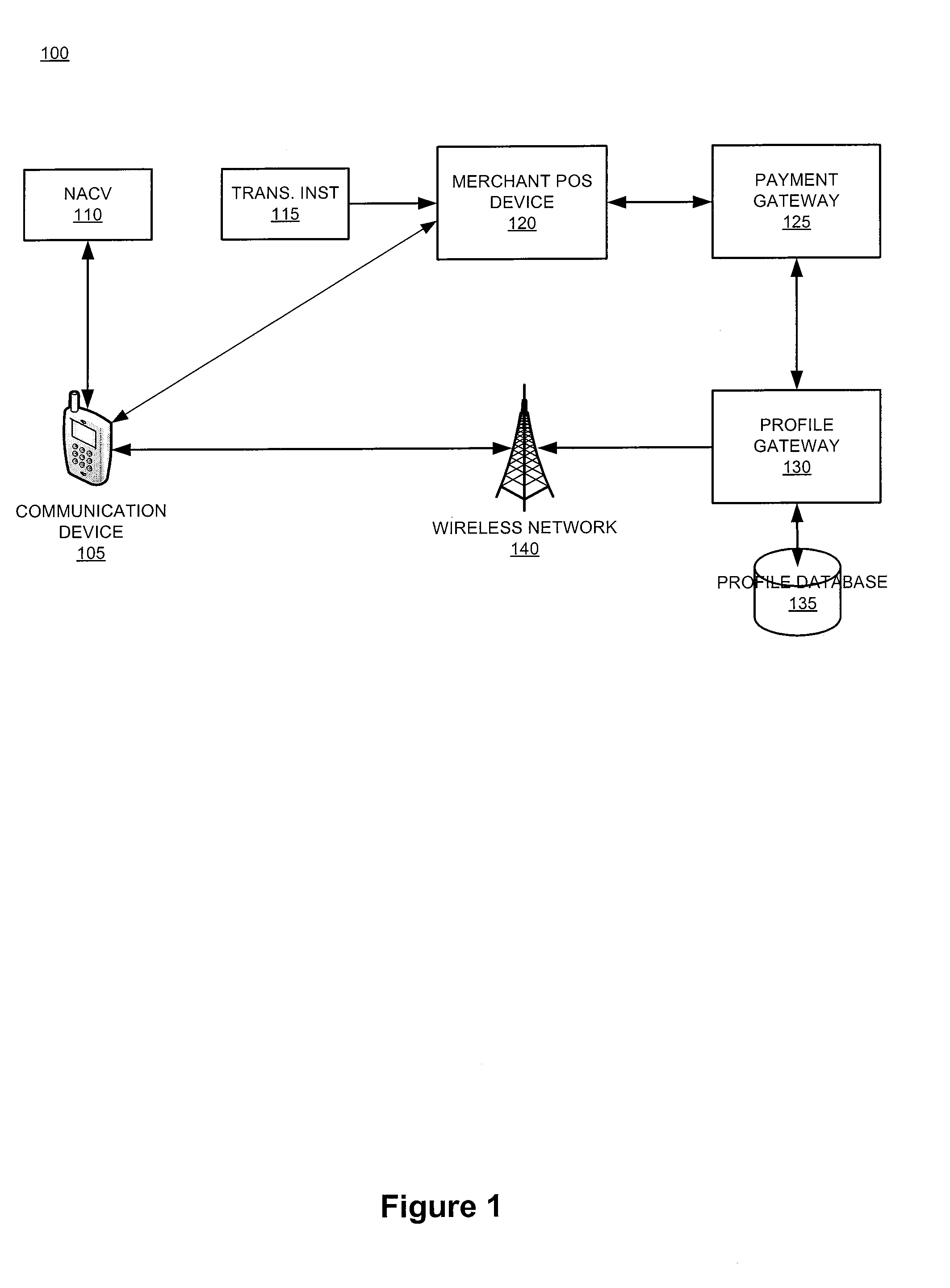
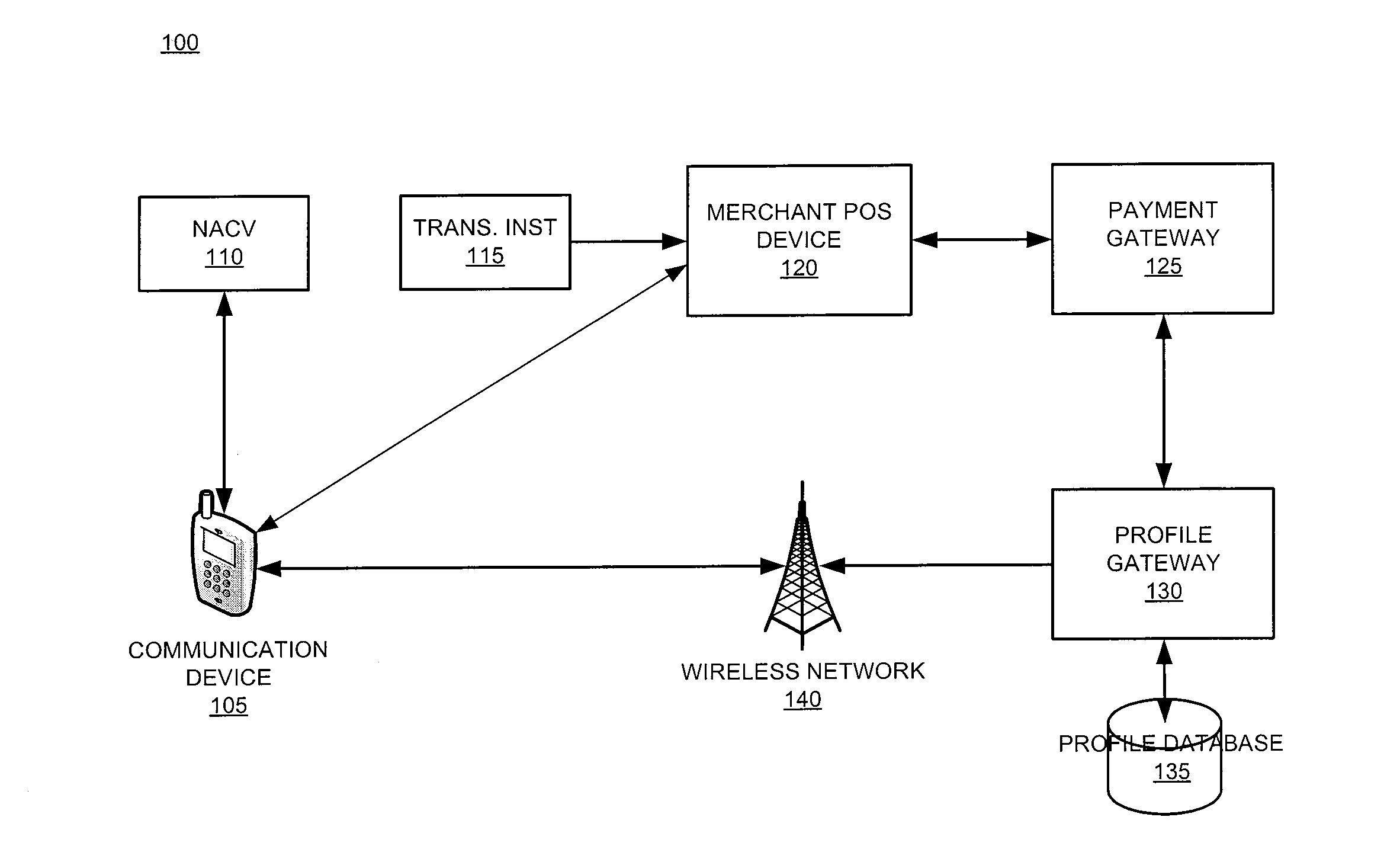
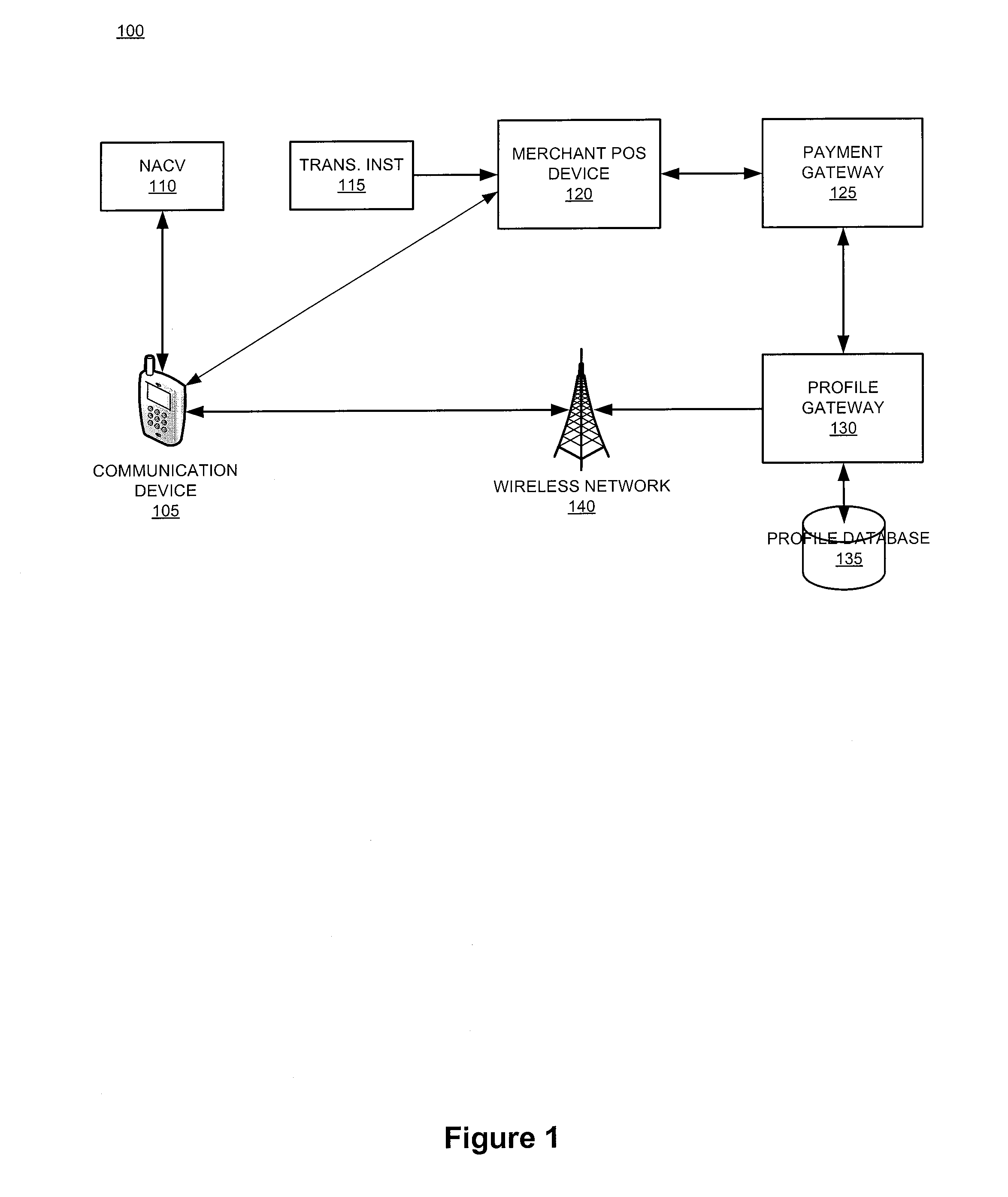
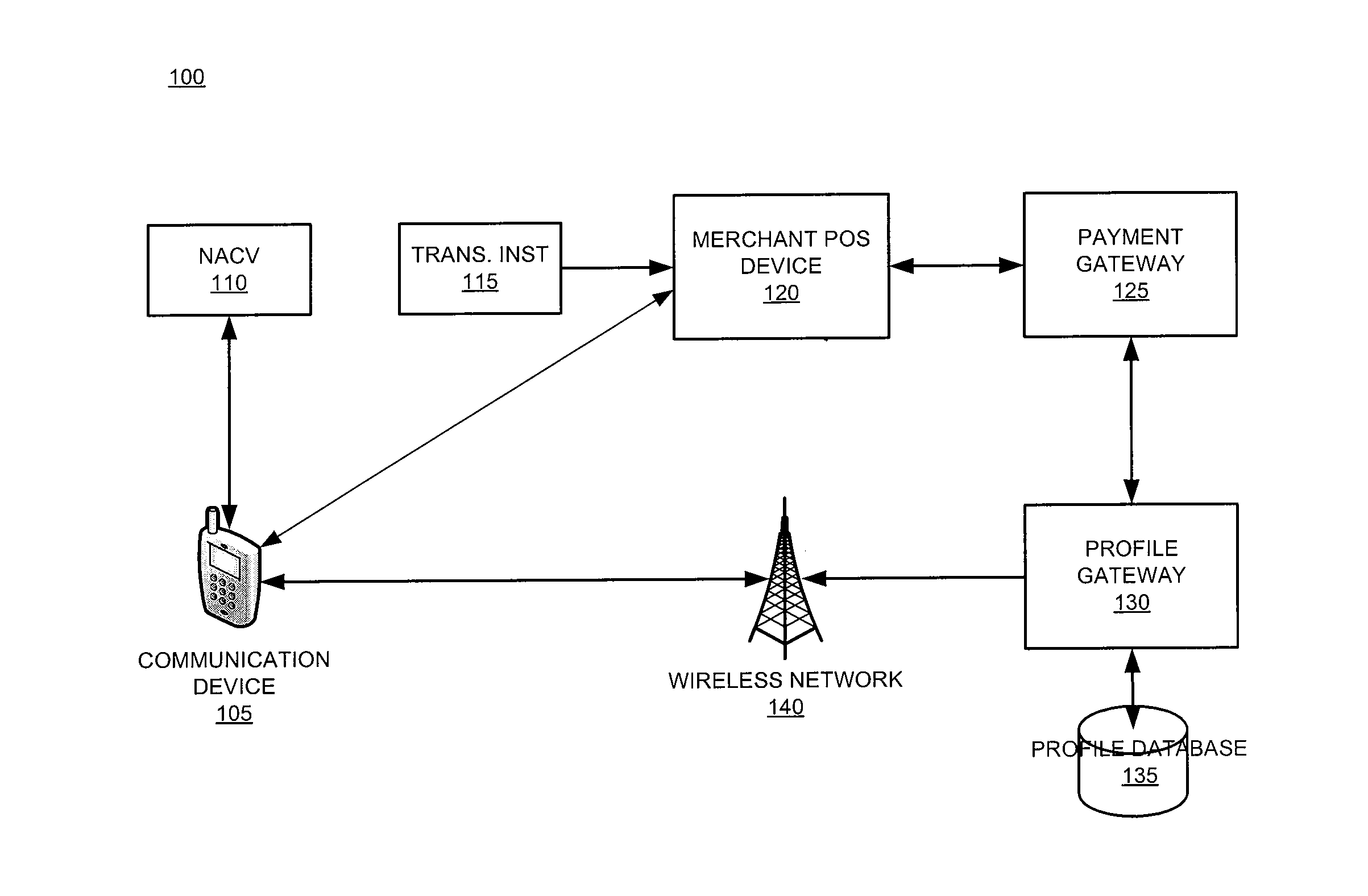
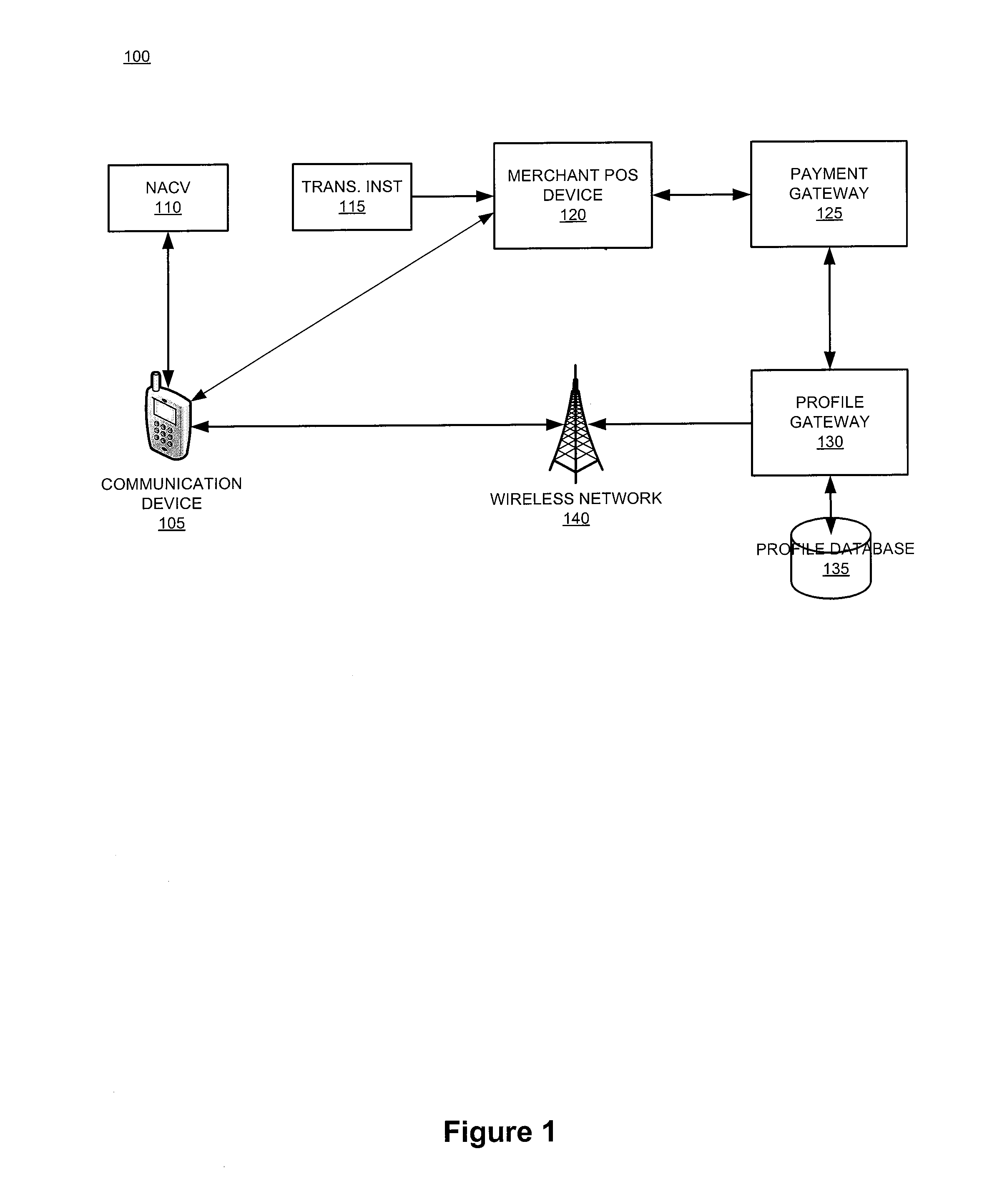
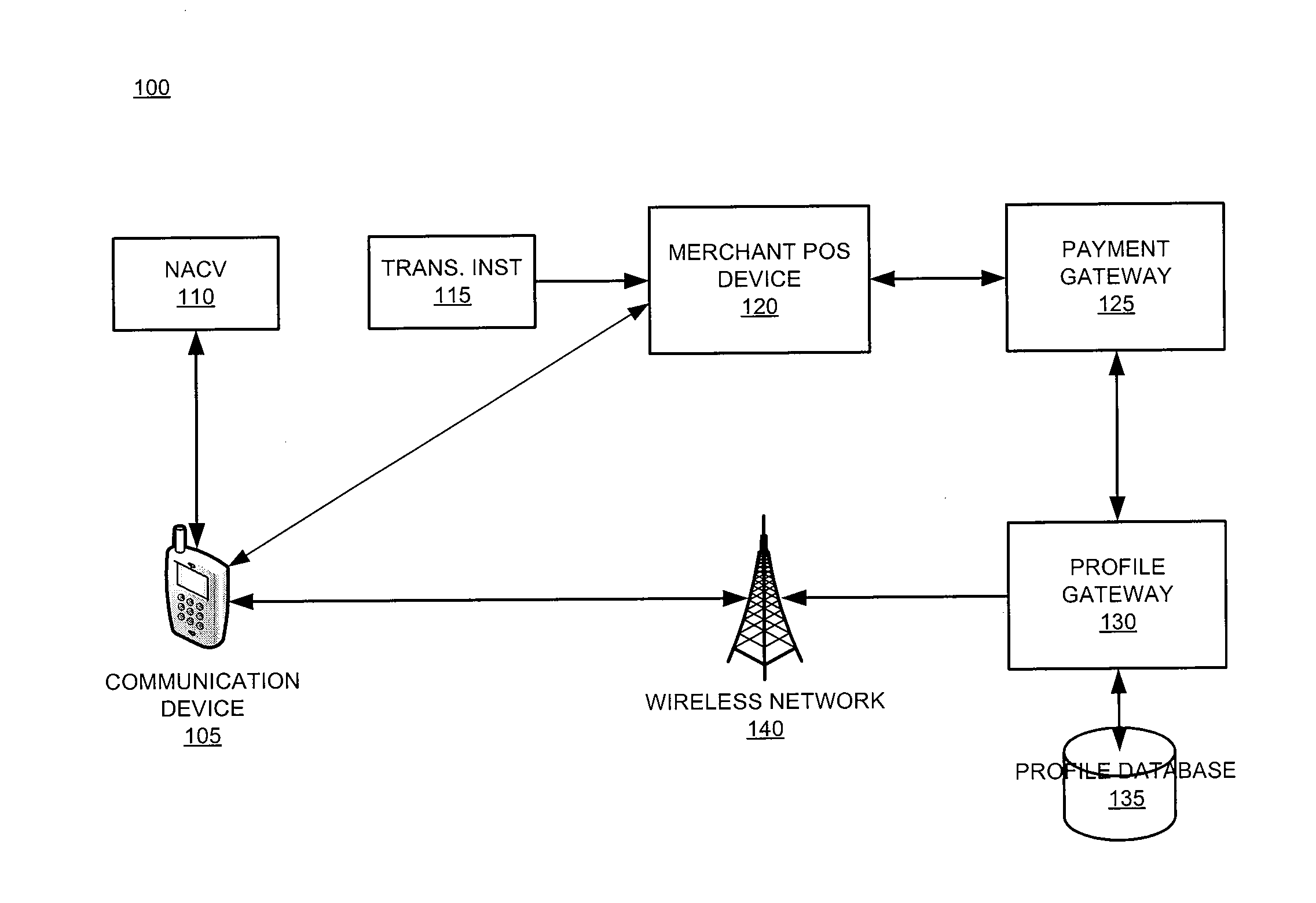
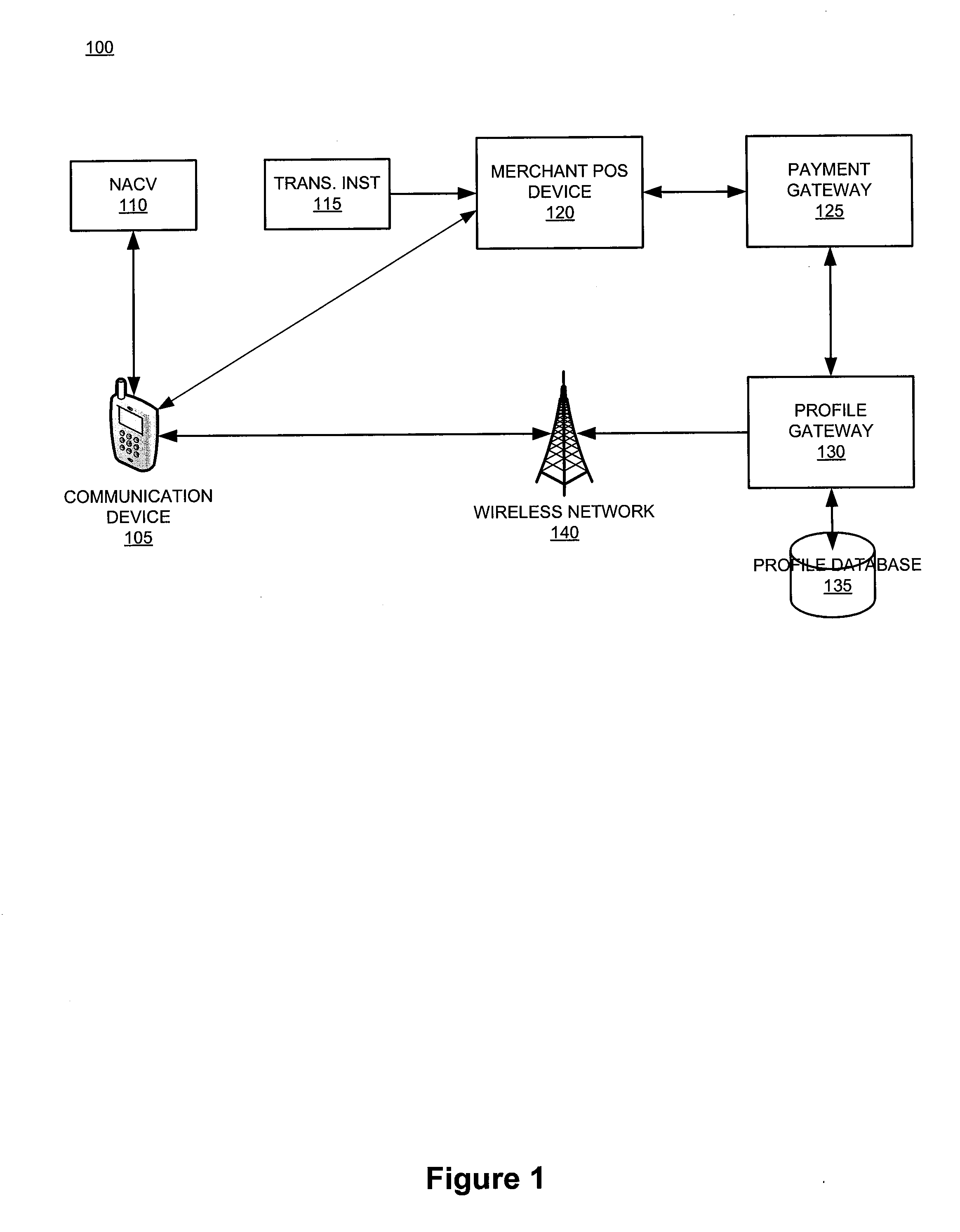
The invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true-personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with checks anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
System and device for facilitating a transaction through use of a proxy account code
InactiveUS20110246317A1Increase dependenceFacilitating secure and convenient electronic transactionsFinancePoint-of-sale network systemsPayment transactionSmart card
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
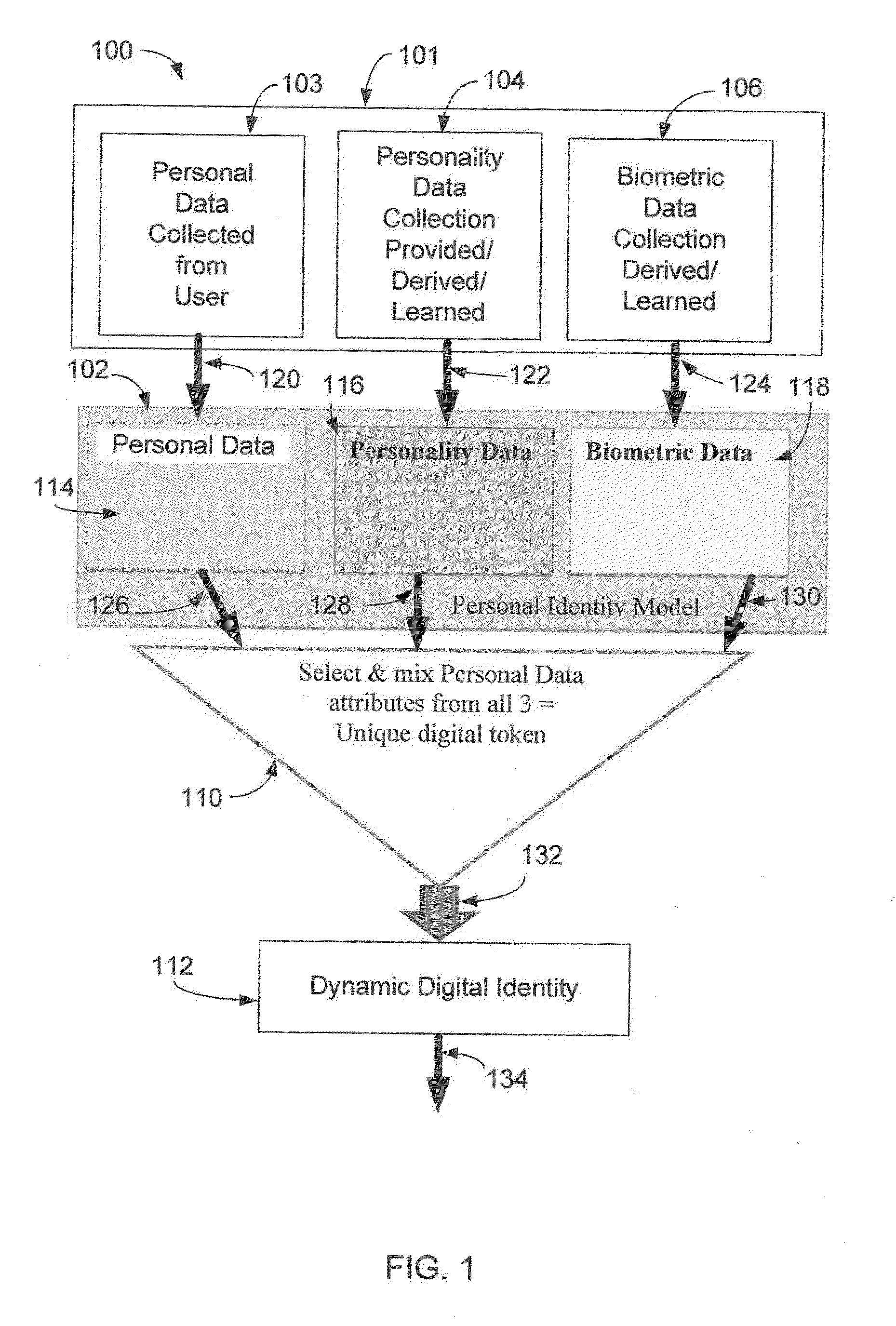
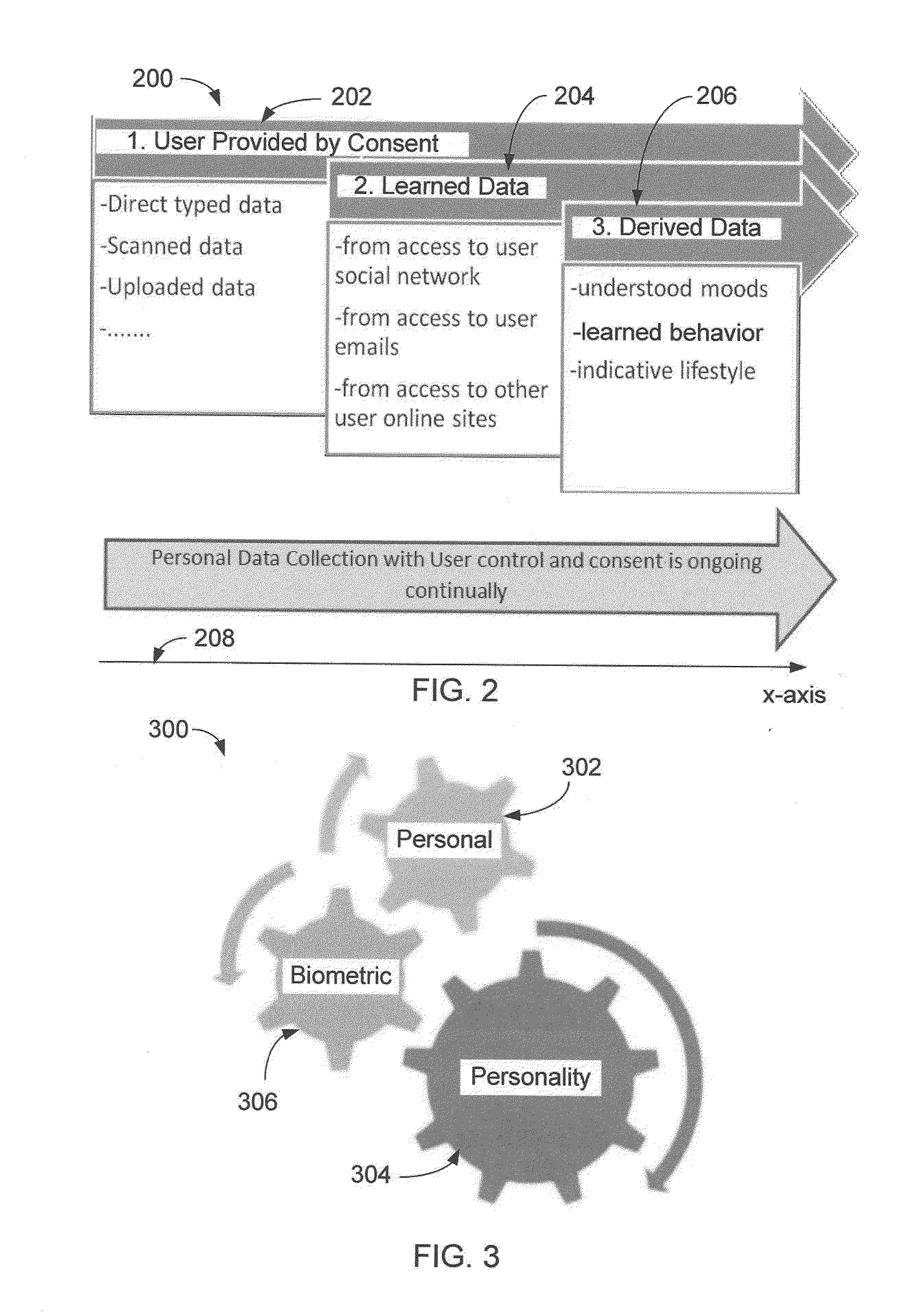
System and Digital Token for Personal Identity Verification
ActiveUS20140032723A1Data processing applicationsDigital computer detailsInternet privacyUser authentication
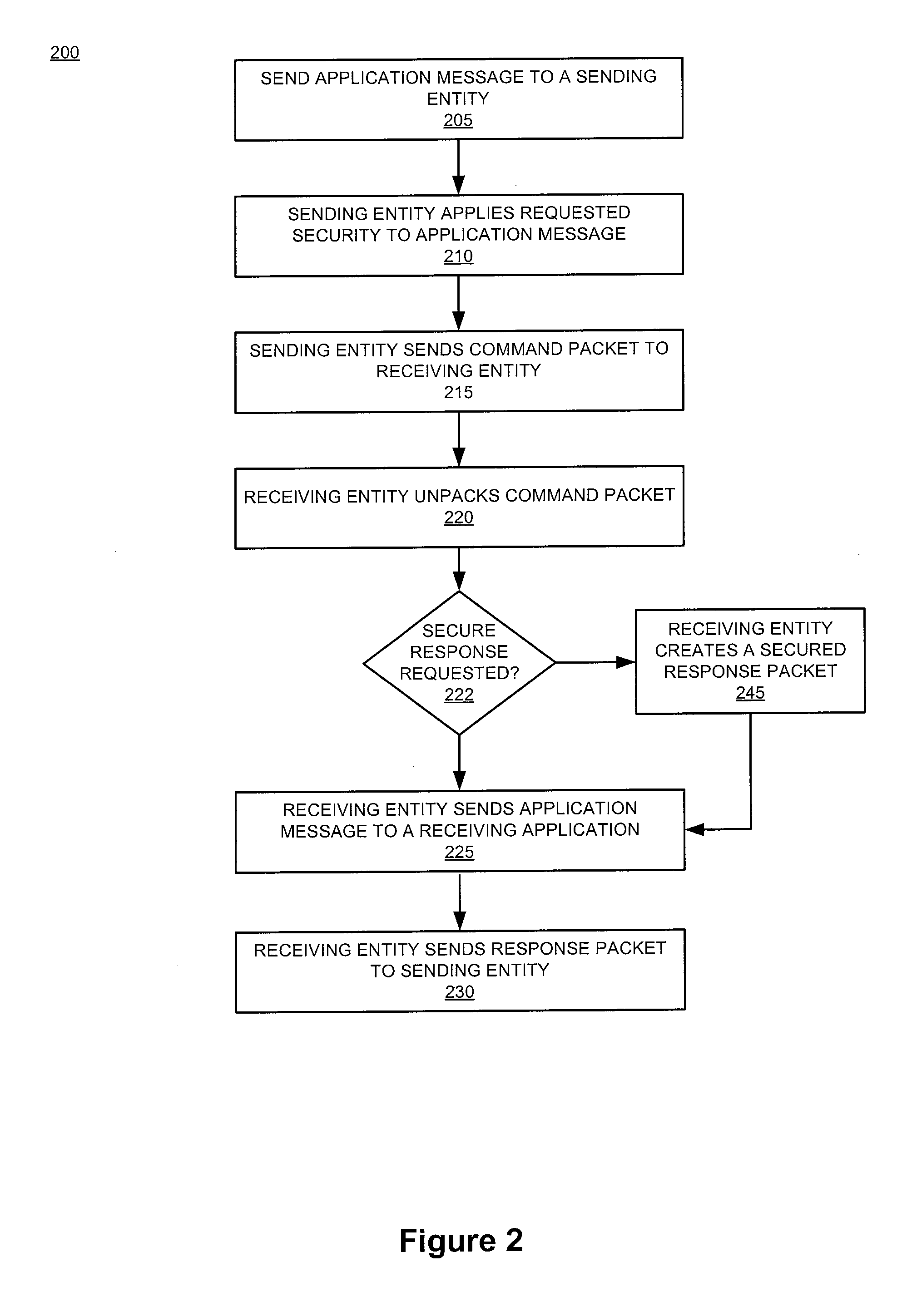
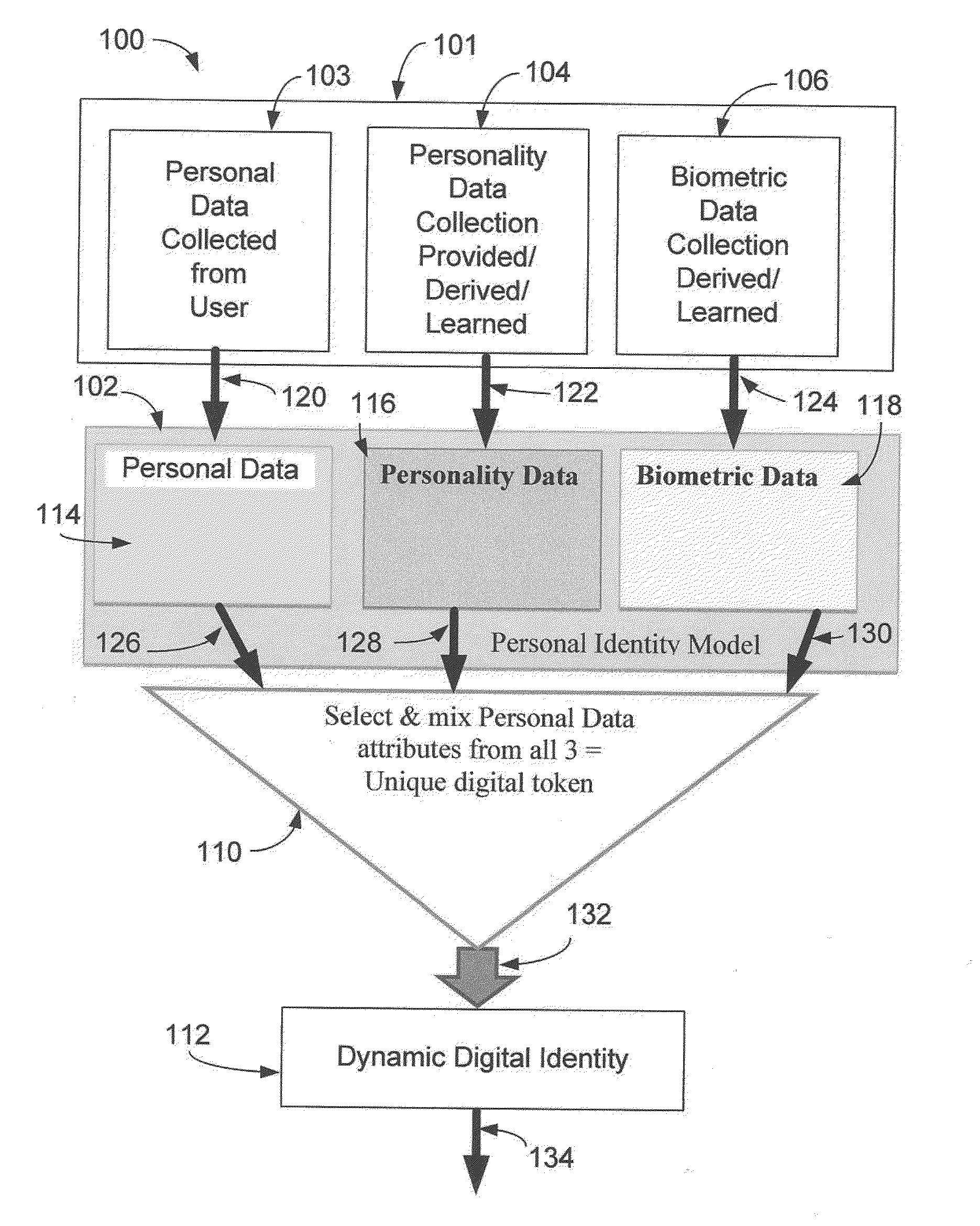
A system and a digital token for user identity verification comprise a control device for communicating over a network. The control device executes program applications and displays outputs to a user. A server communicates over the network to the control device and to other devices. The server comprises a personal identity model, a personal identity engine and a personal identity controller. The personal identity model collects and stores user information comprising personal information, personality, and biometric information. The personal identity engine processes the stored user information to produce the digital token. The personal identity controller manages exchange of the digital token in a user identity verification process. A claim point exchanges the digital token with the server in the user identity verification process in which upon verification the user's identity, the claim point provides a service to the user.
Owner:DHANA SYST
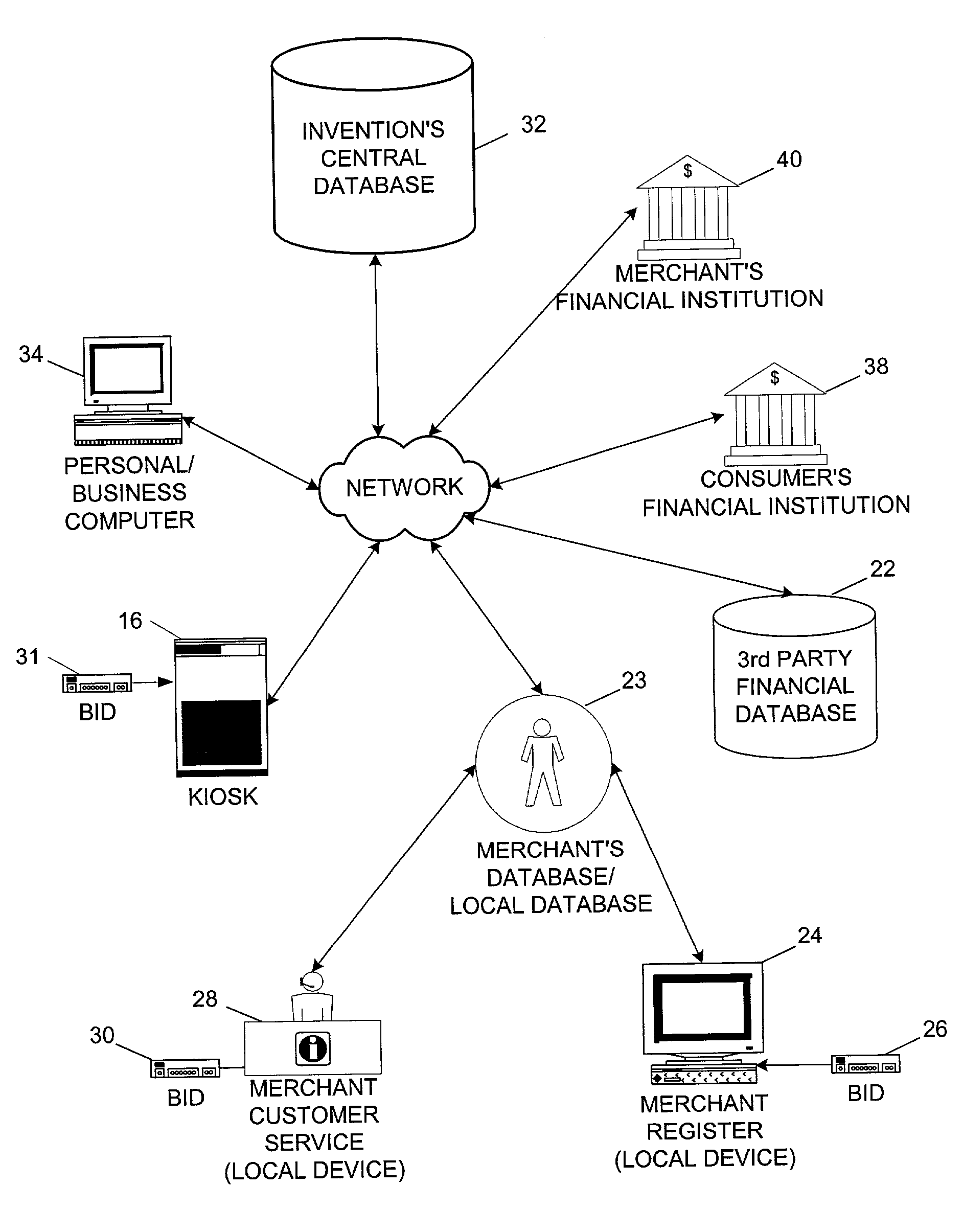
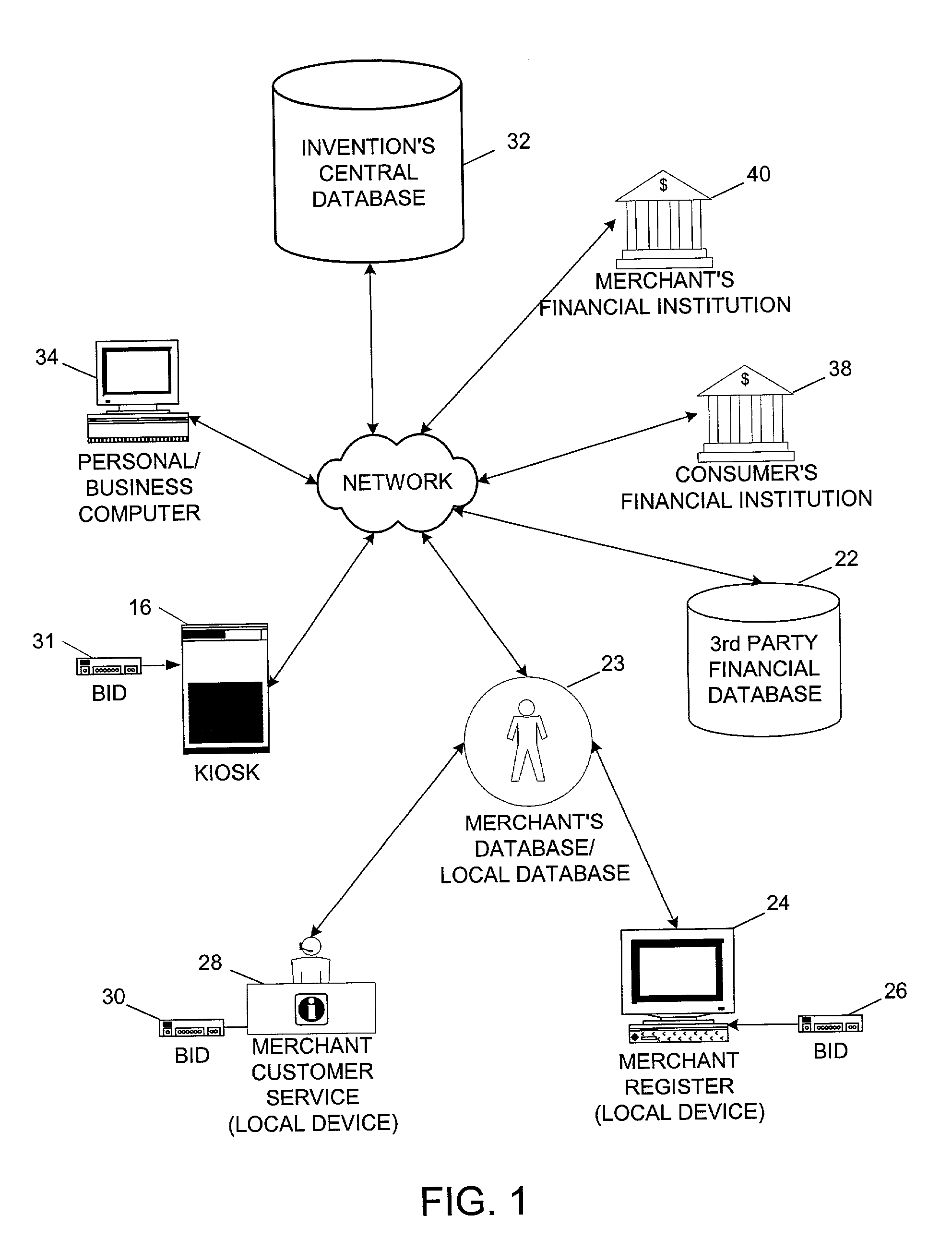
System and method for biometric authorization for check cashing
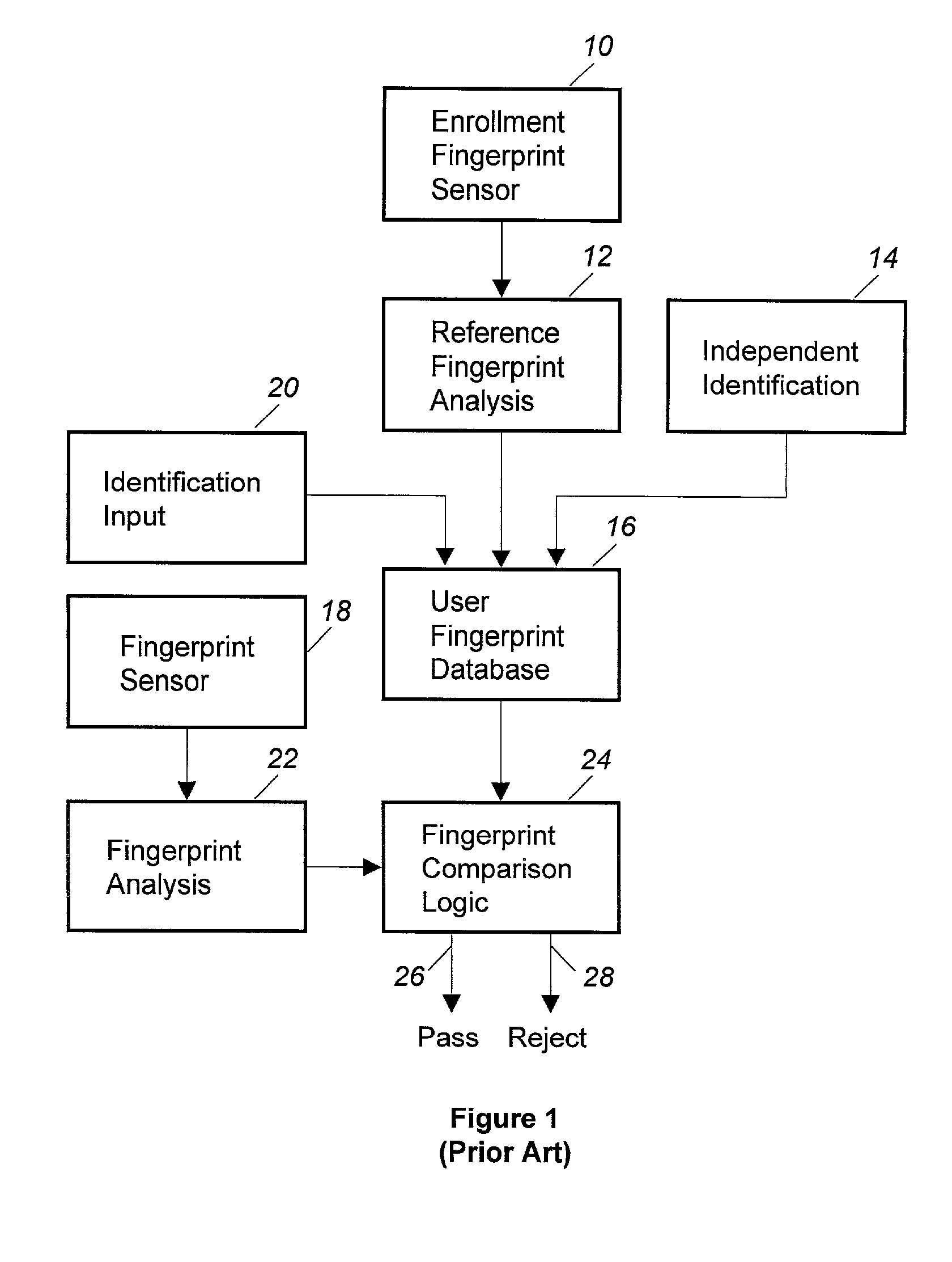
A system for authorizing a check cashing transaction between a consumer and a merchant using identity verification based on biometric information. A system comprises a central biometric information database containing biometric and personal identity-verifying data registered therein by a consumer and containing merchant identity-verifying data registered therein by a merchant. The system further comprises a merchant local device having a biometric reader and linked via a network to the central biometric information database. Using the biometric reader, a consumer desiring to cash a check presents biometric data to the central biometric information database via the biometric reader. The central biometric information database provides an electronic comparison of the present biometric data with the biometric data registered by the consumer. If the presented data and the registered data match, an approval signal is transmitted to the merchant local device.
Owner:VALSOFT CORP INC
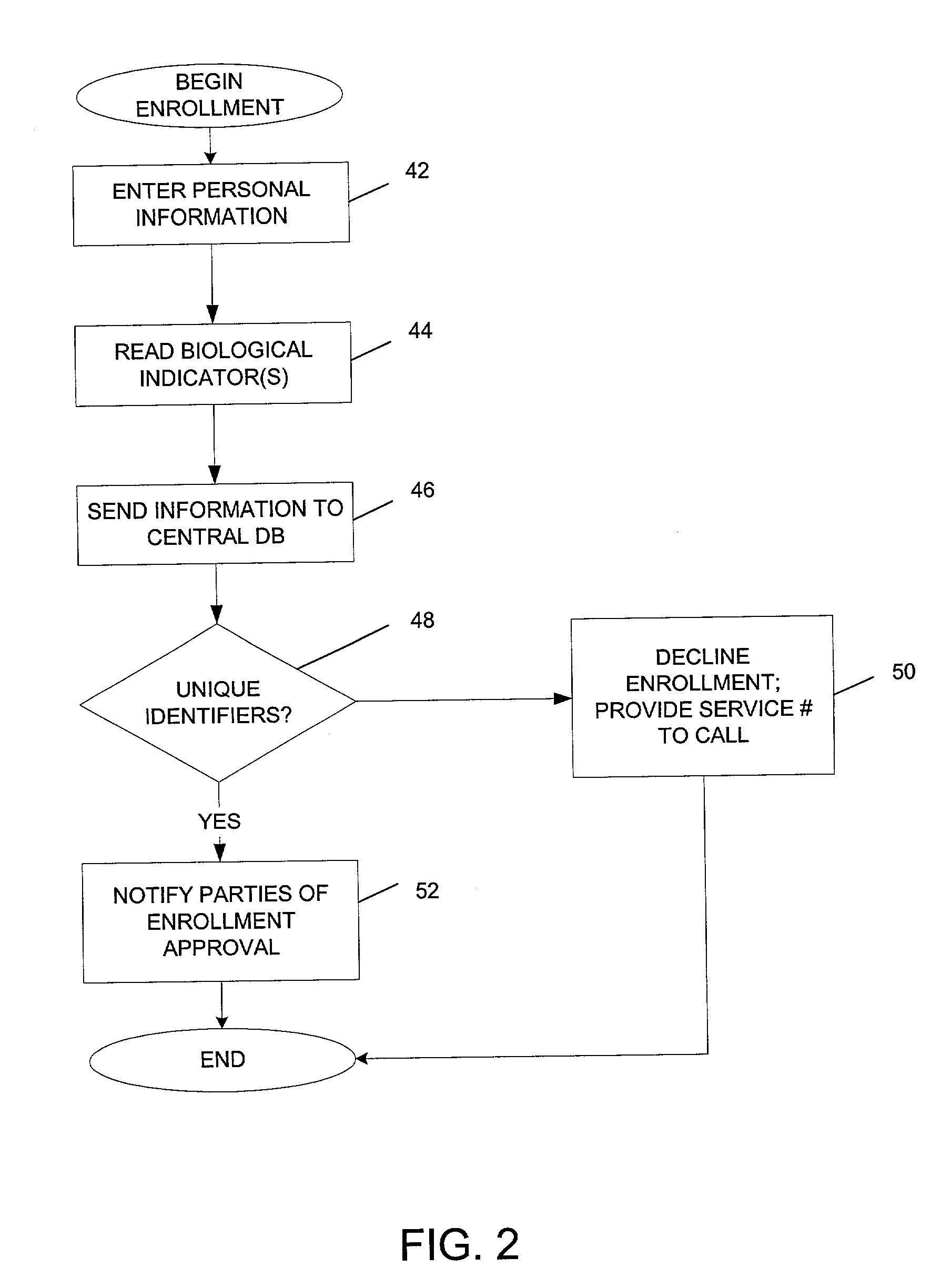
Anti-identity theft system and method
InactiveUS20060239512A1Reduce and eliminate identity theftEliminate needElectric signal transmission systemsDigital data processing detailsIdentity theftData bank
A method of entering information for identity validation of an individual is provided, where an individual enters their personal information and biometric information that is compared to one or more databases to verify the identity of the individual. Once the identity is verified, the individual selects one or more random biometrics that are stored as random biometric information on a database for later identity verification purposes. When the individual later wants to review or change his personal information, or when the individual wants to perform or consummate a transaction, the individual simply submits his / her one or more random biometrics that were previously selected and stored in the database. The biometrics are compared with the random biometric information in the database, and if the one or more random biometrics match the random biometric information in the database, then the identity is verified.
Owner:IMME
Identity verification system
InactiveUS20080066188A1Digital data processing detailsUser identity/authority verificationVerification systemAuthentication system
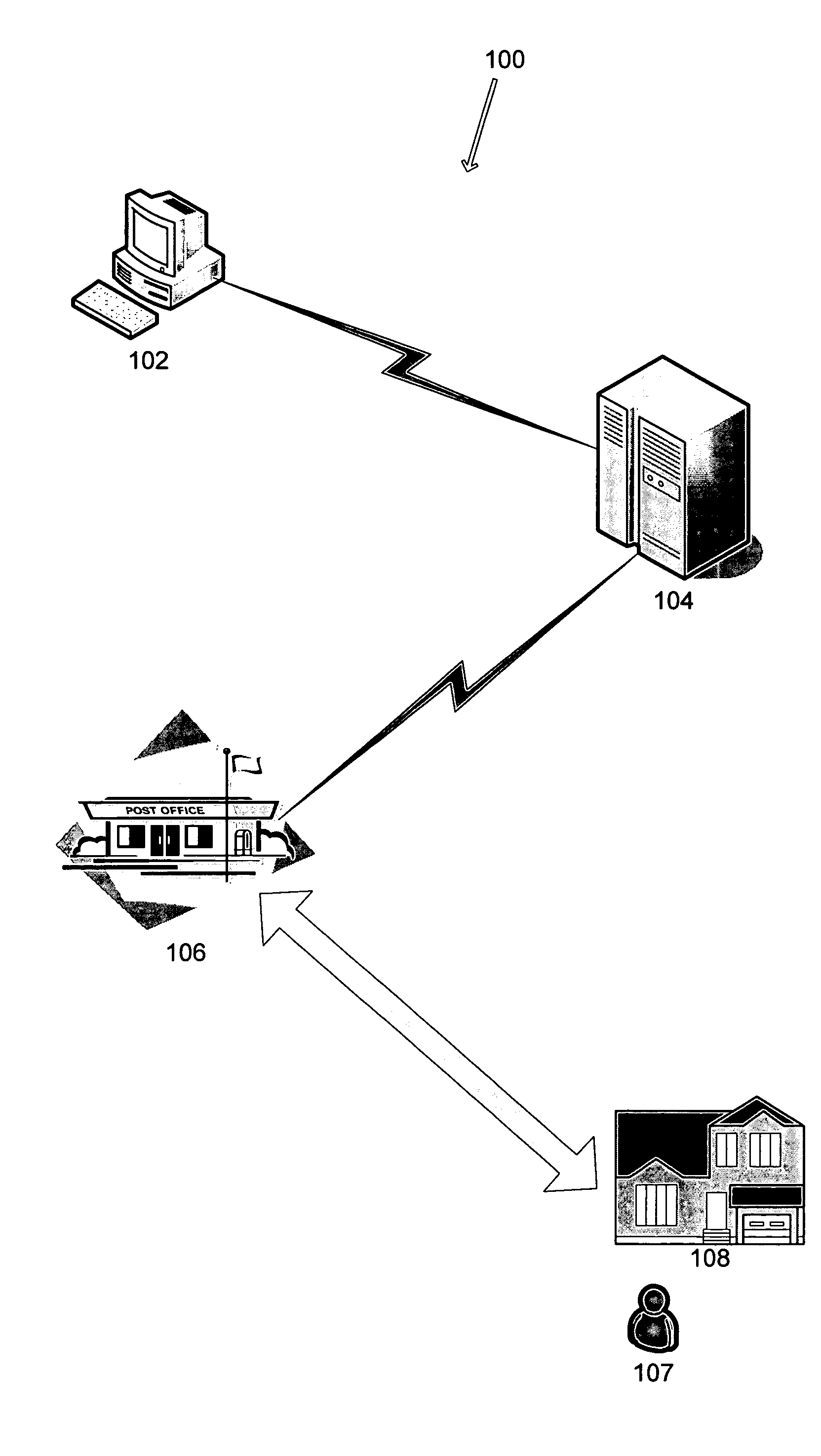
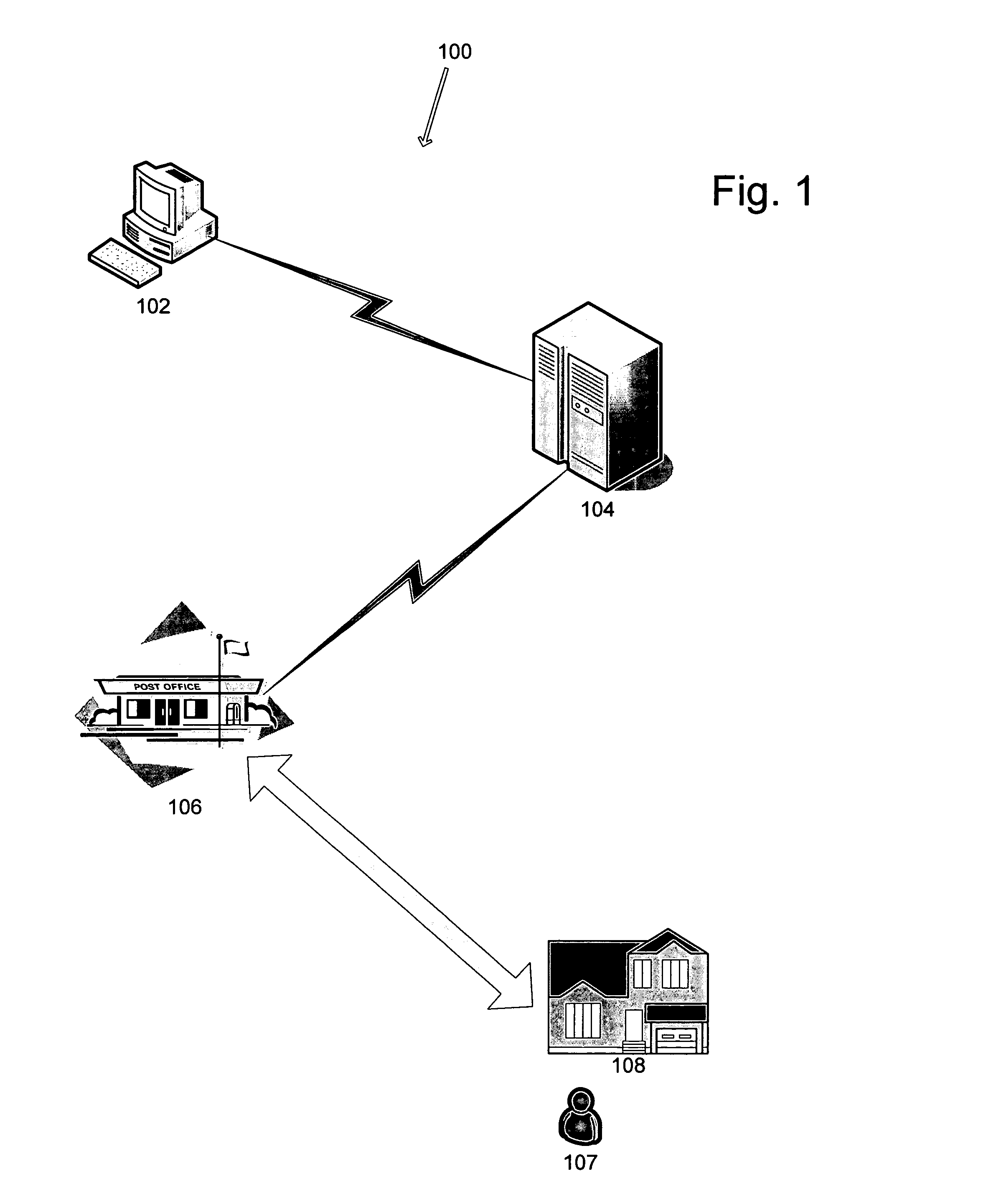
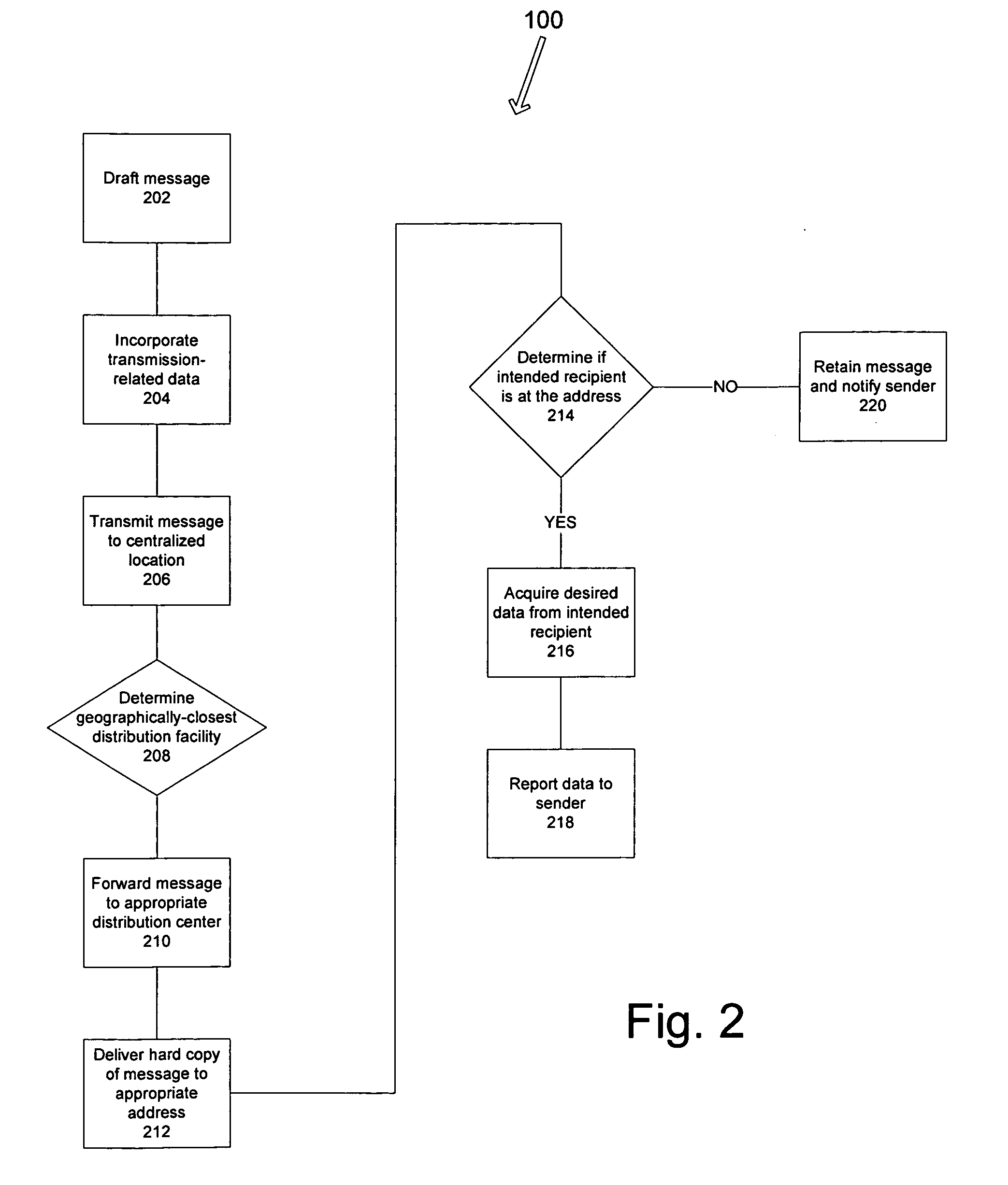
A method and system for certifying the identity of a party. The method and system may include a first party transmitting an electronic message that is ultimately intended for a second party to an identity verifying party. The identity verifying body may use data contained in the electronic message to transmit the message to a distribution center geographically proximately located to the second party. A delivery person associated with the distribution center may then deliver the message to the second party and obtain identification data, which may be relayed back to the first party. Additionally, the method and system may be used to disseminate mass mailings through both electronic and traditional mail.
Owner:KWAK DUSIC
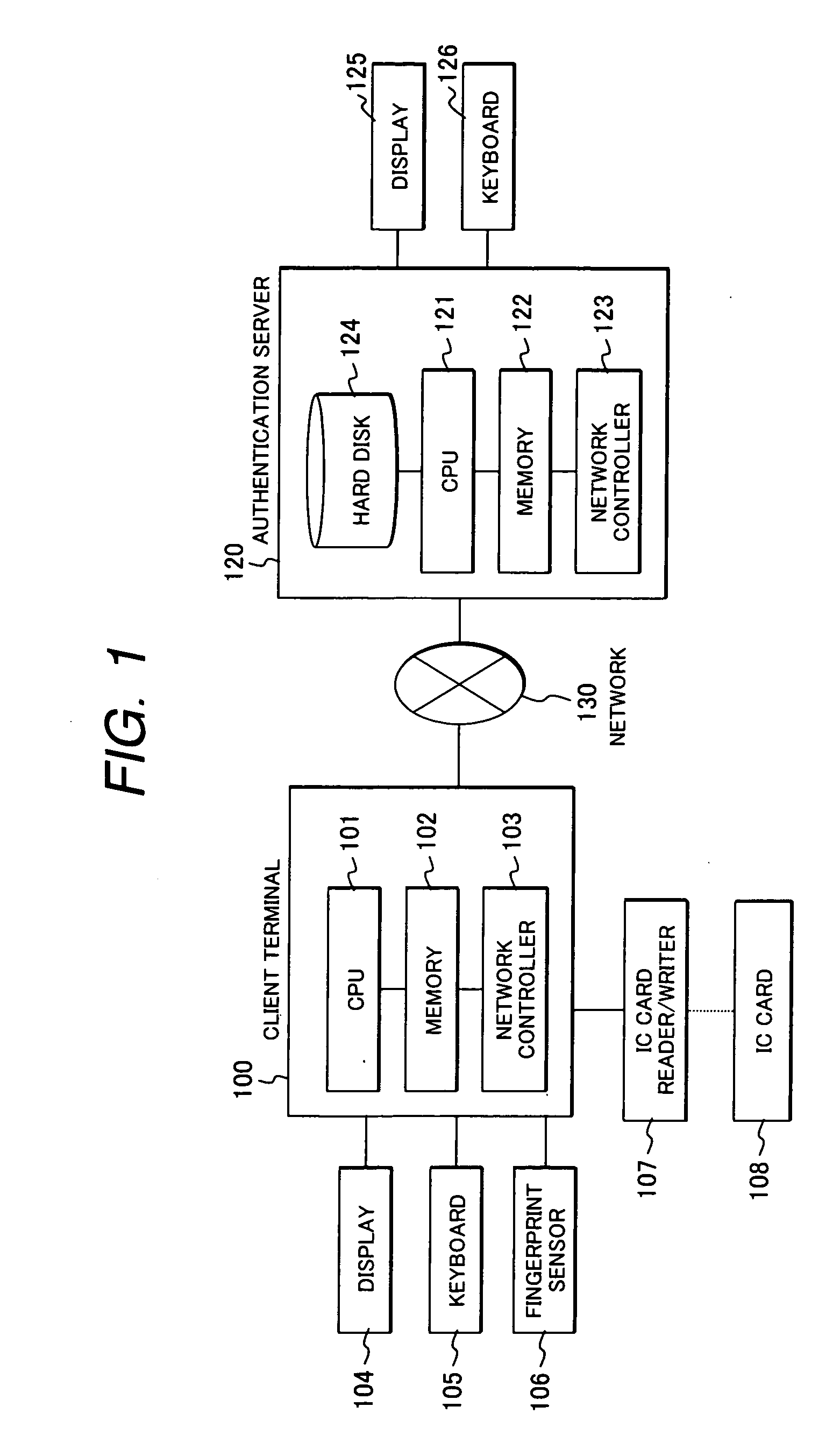
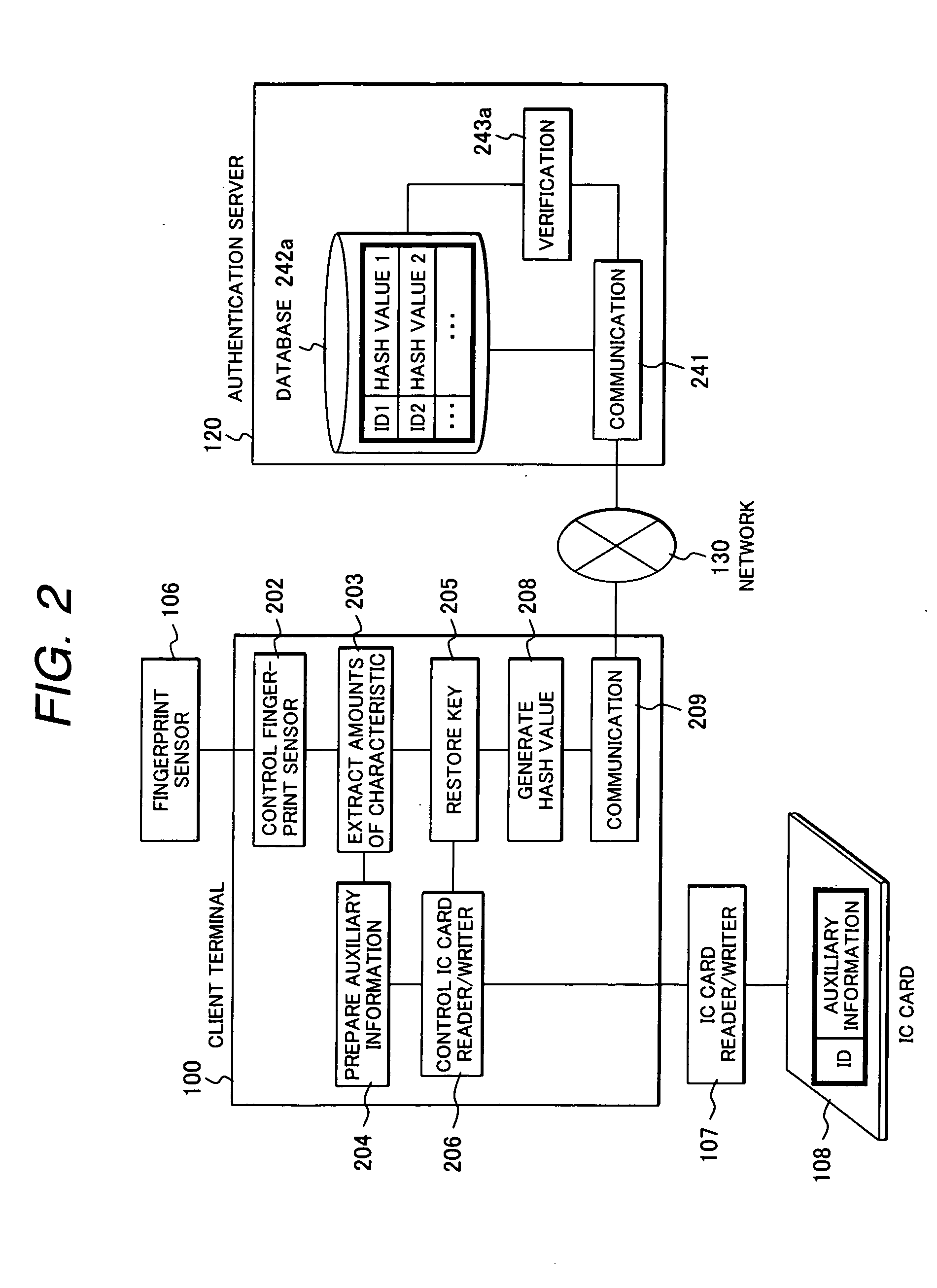
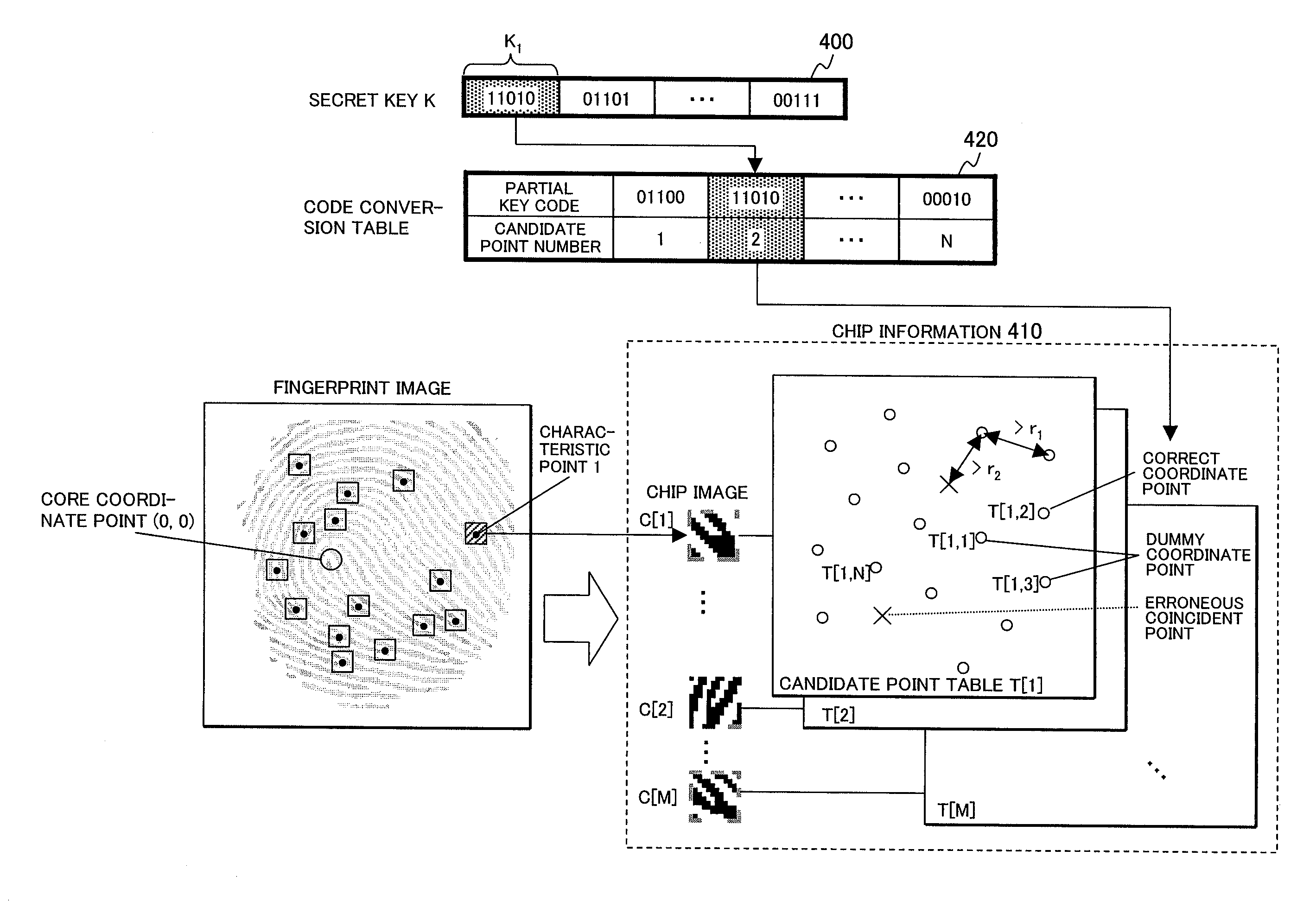
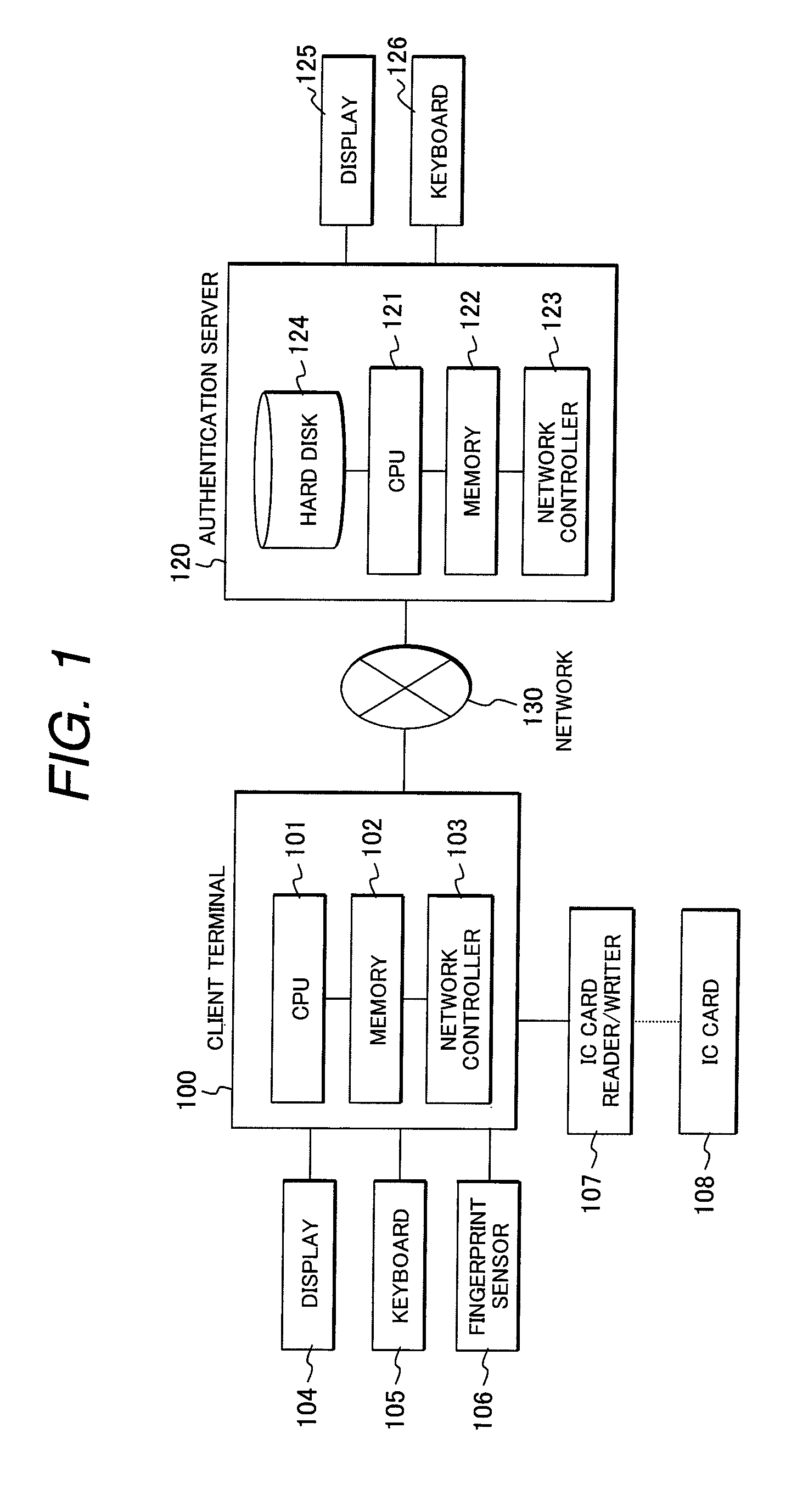
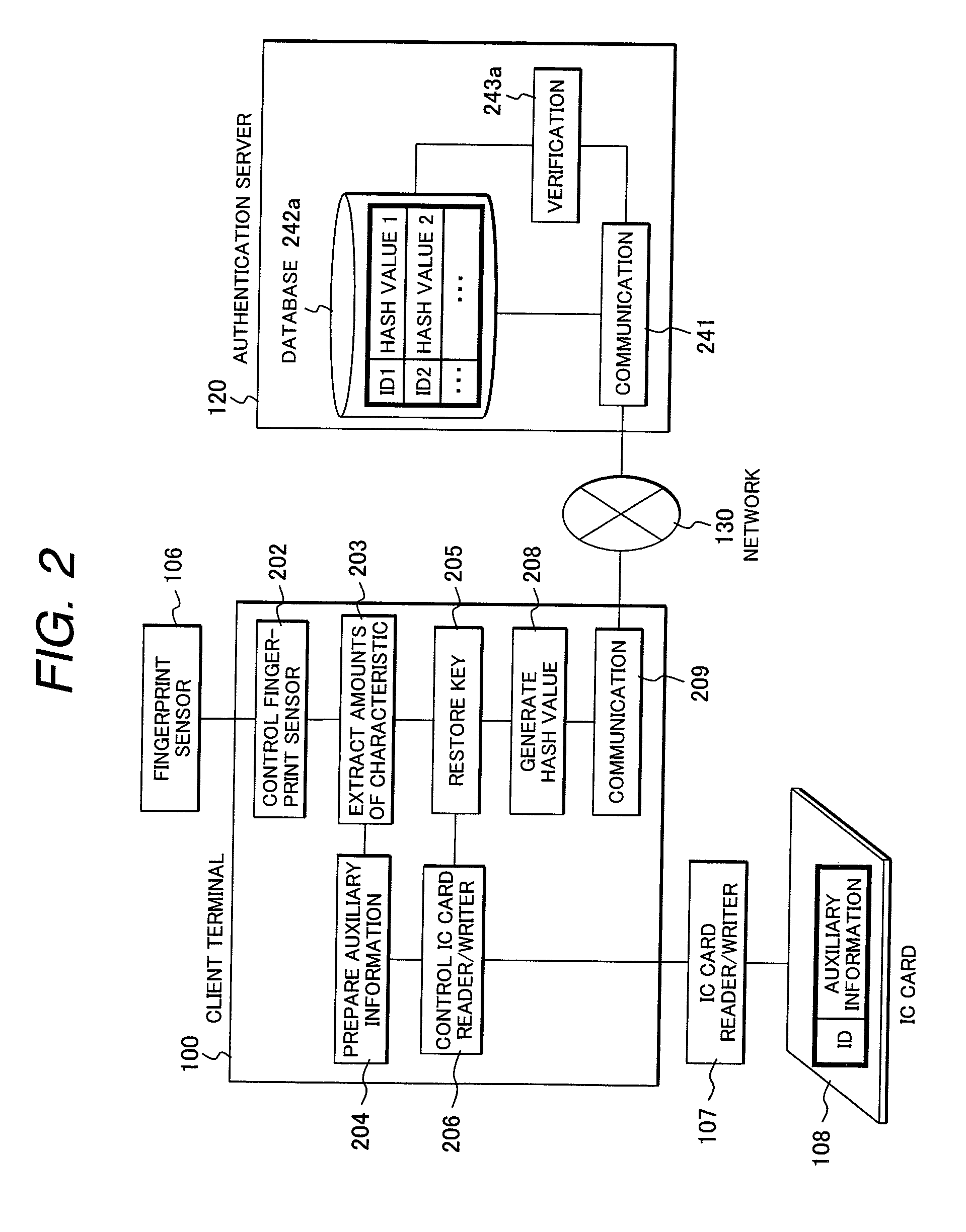
Method for generating an encryption key using biometrics authentication and restoring the encryption key and personal authentication system
InactiveUS20080072063A1Electric signal transmission systemsDigital data processing detailsComputer hardwareAuthentication system
A personal authentication system using biometrics information. The system orders, when an characteristic element in the biometrics information (such as a characteristic point in a fingerprint) can be expressed with two types of information (such as, for instance, a coordinate values for a characteristic point in a fingerprint and a local partial image), the characteristic points using one type of information (for instance, local partial image) as label information, and outputs other type of information (such as coordinate values) as key information according to the order.
Owner:HITACHI LTD
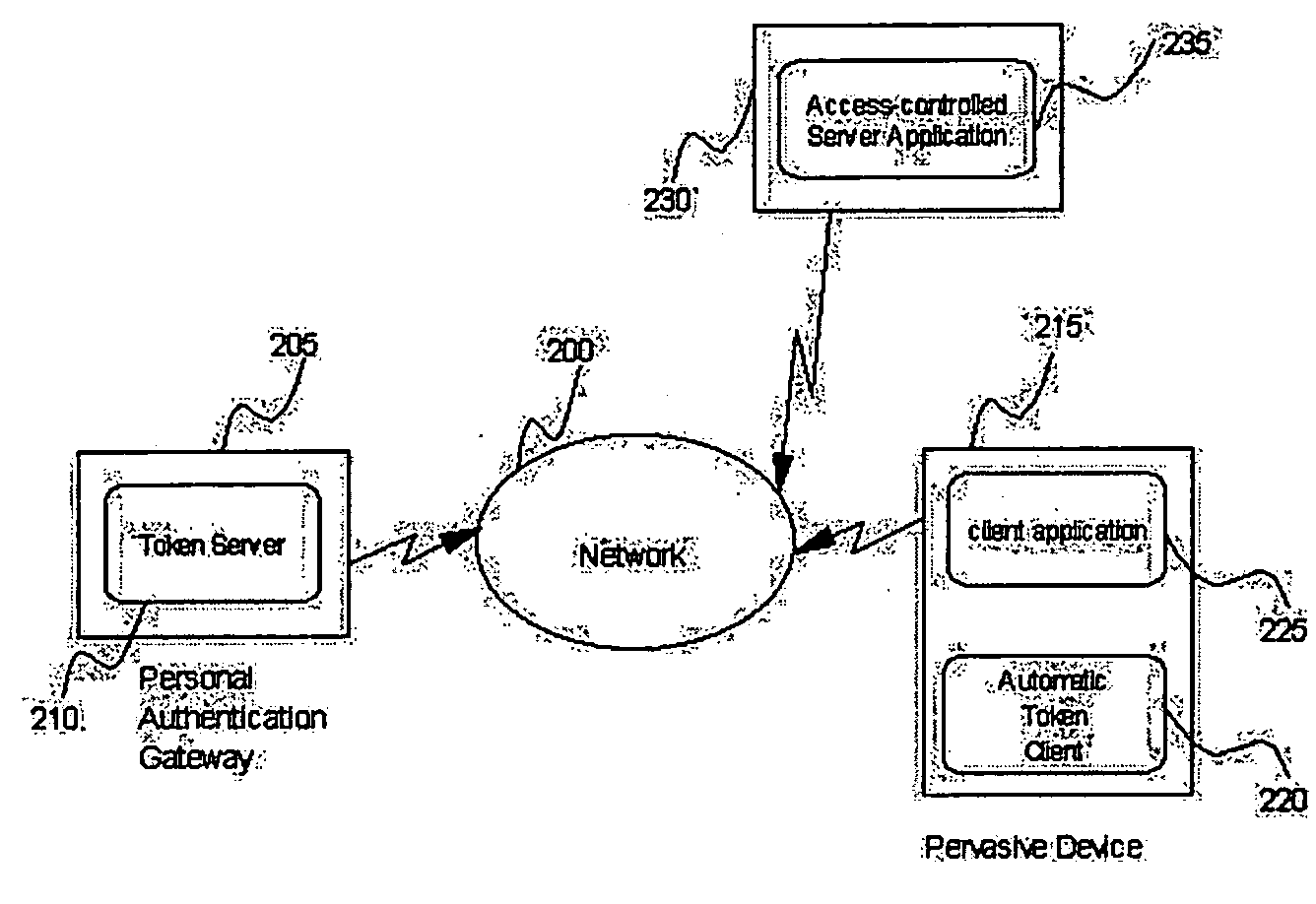
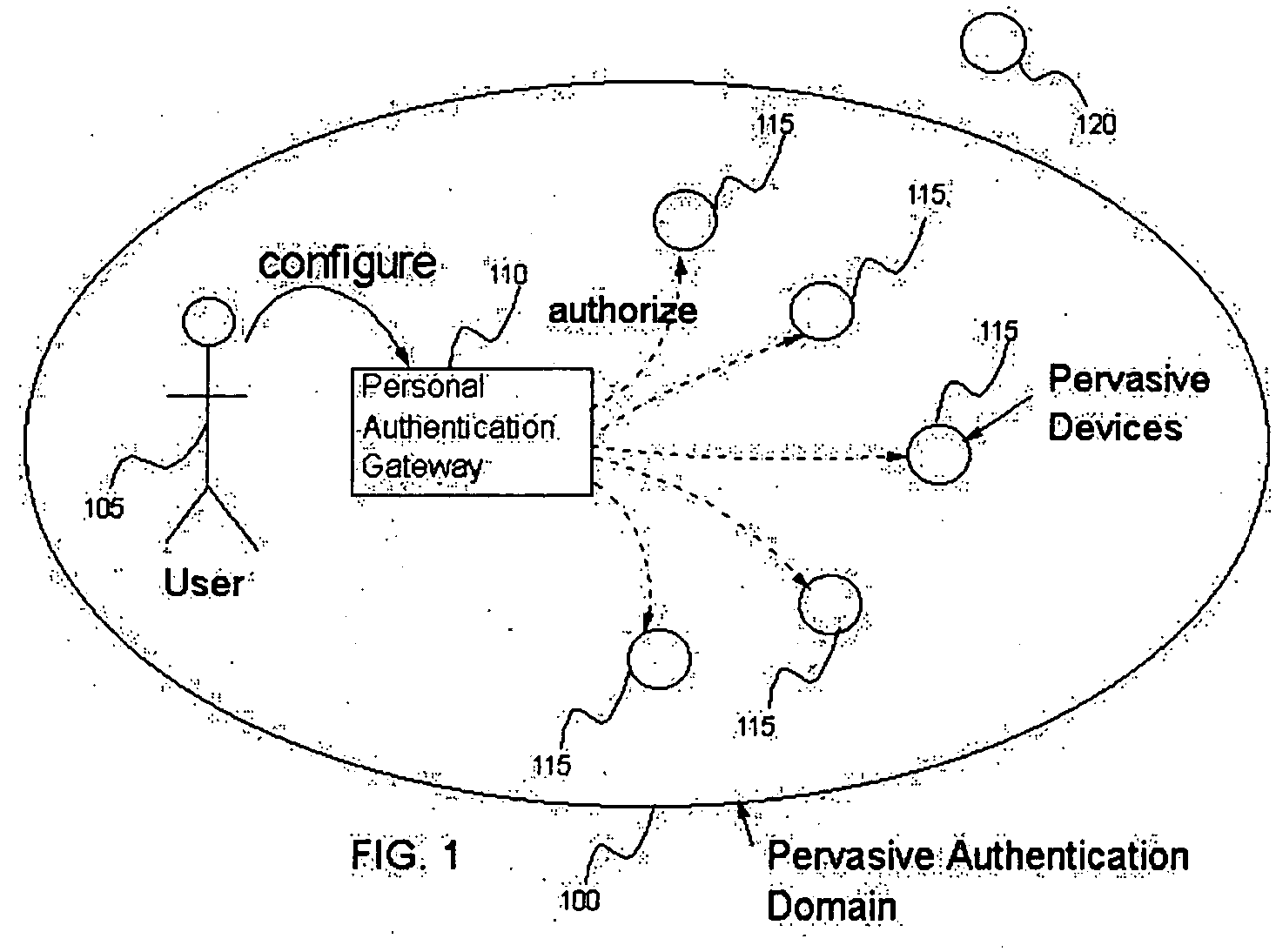
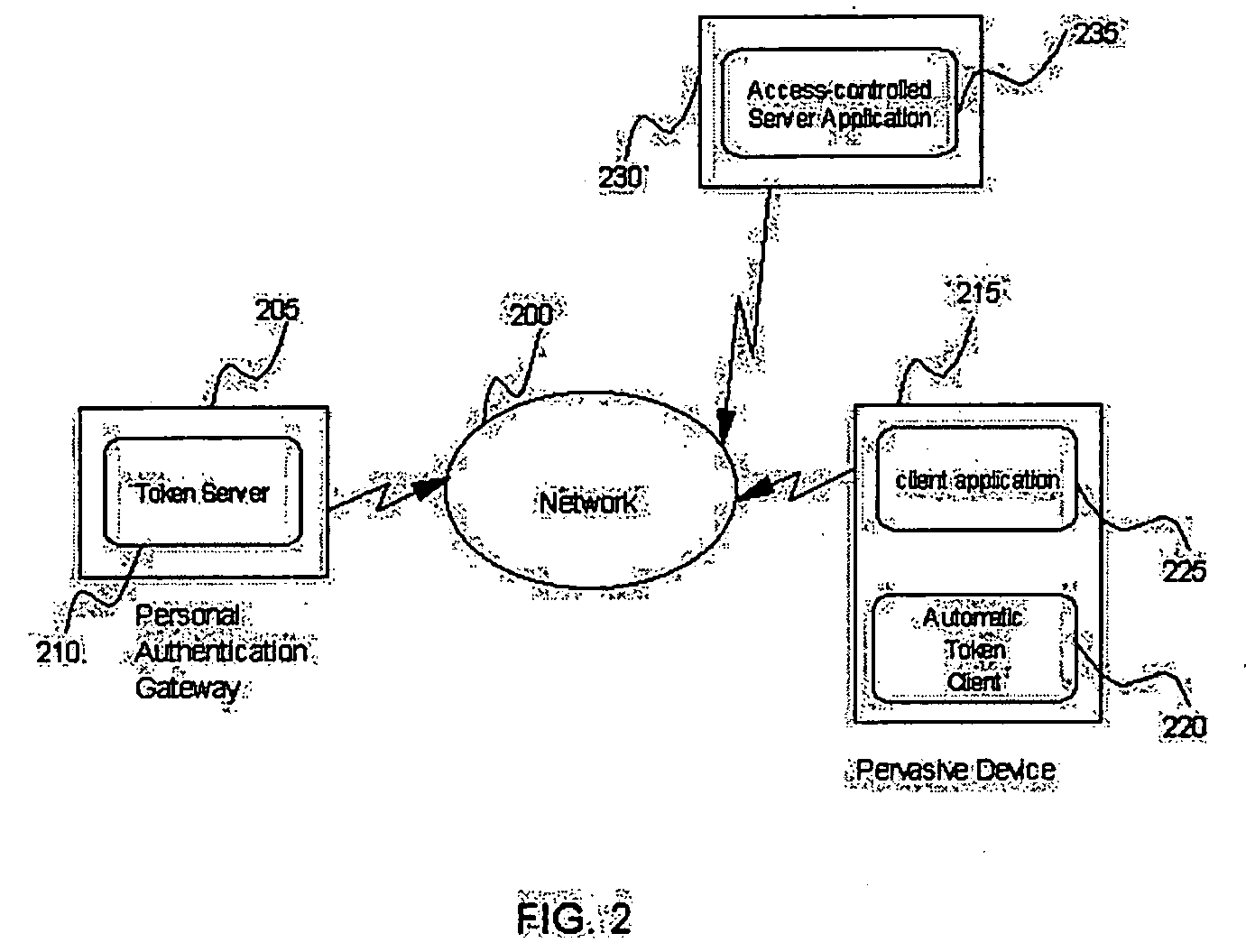
Method and apparatus for pervasive authentication domains
InactiveUS20050081044A1Reduce the burden onImprove protectionDigital data processing detailsUser identity/authority verificationSignal strengthPersonal identity verification
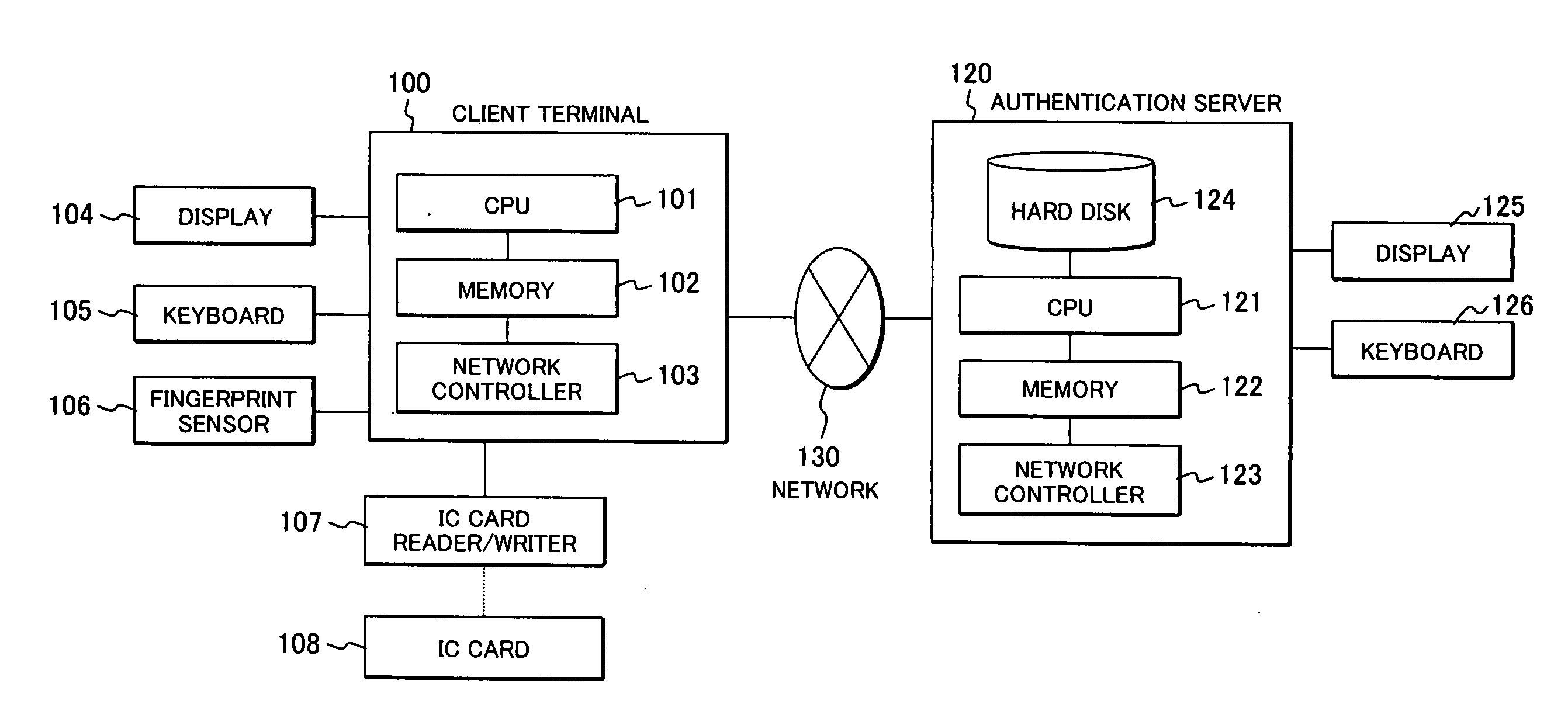
Methods and apparatus for enabling a Pervasive Authentication Domain. A Pervasive Authentication Domain allows many registered Pervasive Devices to obtain authentication credentials from a single Personal Authentication Gateway and to use these credentials on behalf of users to enable additional capabilities for the devices. It provides an arrangement for a user to store credentials in one device (the Personal Authentication Gateway), and then make use of those credentials from many authorized Pervasive Devices without re-entering the credentials. It provides a convenient way for a user to share credentials among many devices, particularly when it is not convenient to enter credentials as in a smart wristwatch environment. It further provides an arrangement for disabling access to credentials to devices that appear to be far from the Personal Authentication Gateway as measured by metrics such as communications signal strengths.
Owner:IBM CORP
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true-personal identity verification), methods and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without nfc component and system, with cellular/satellite phone/internet/multi-media functions
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
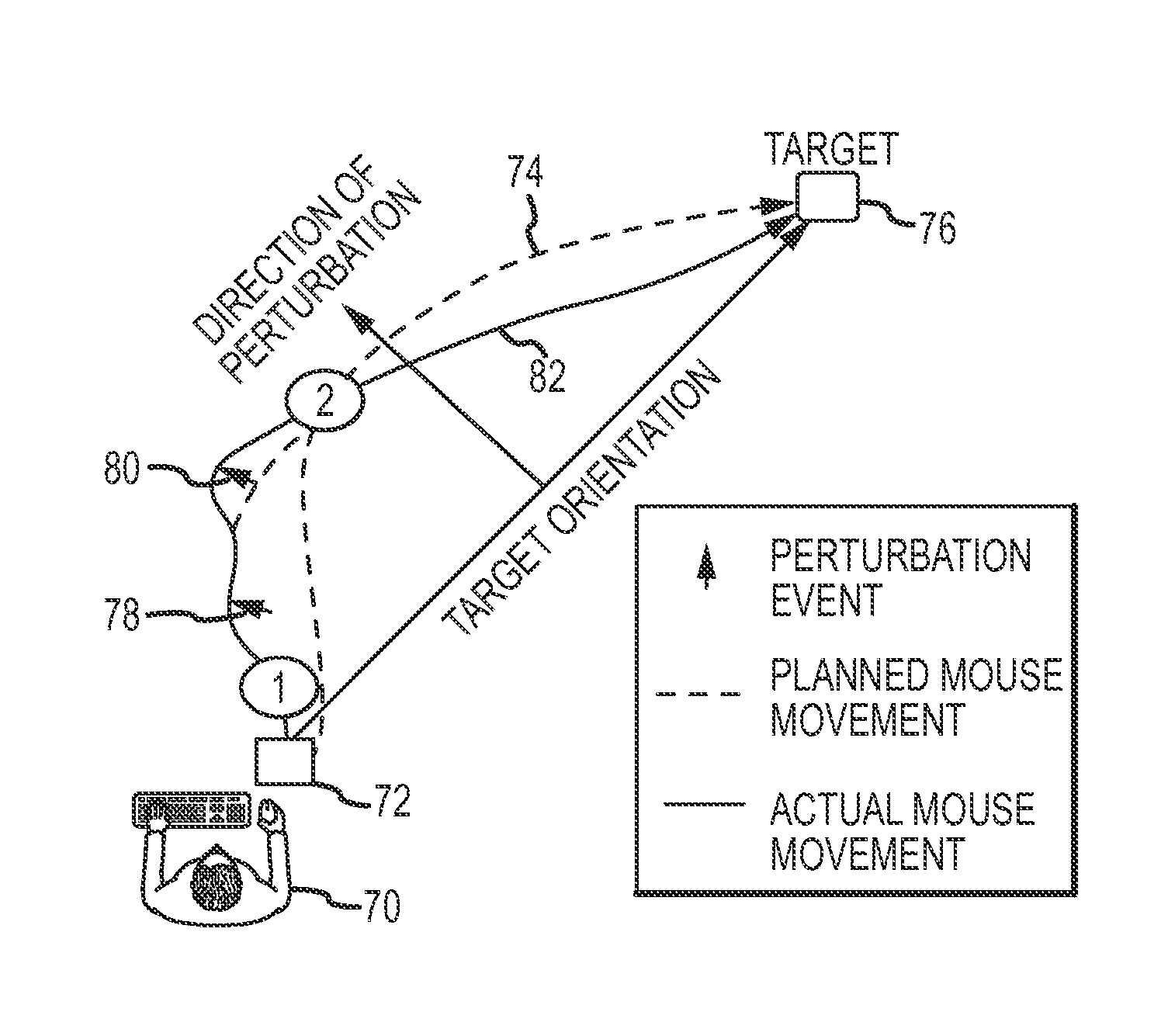
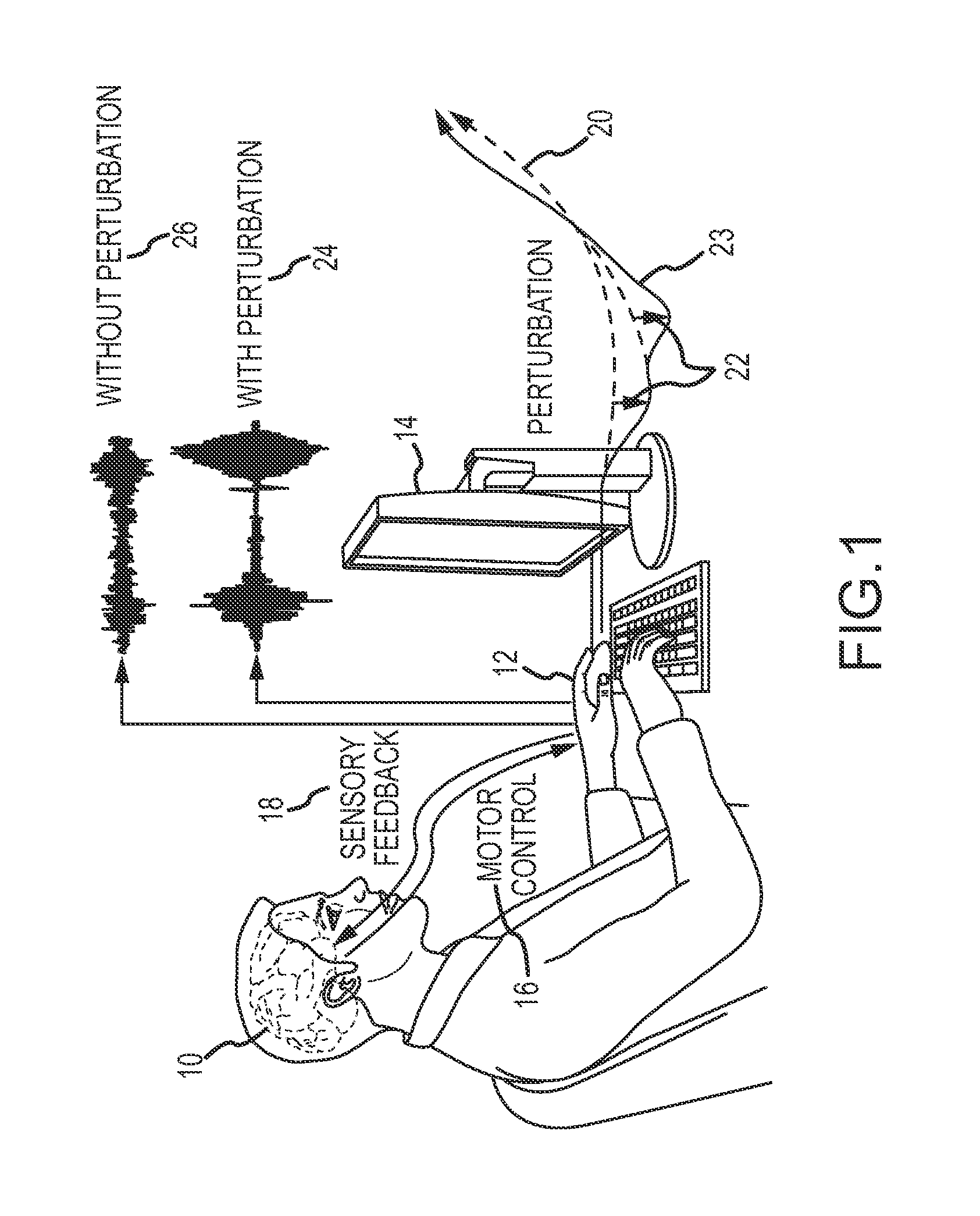
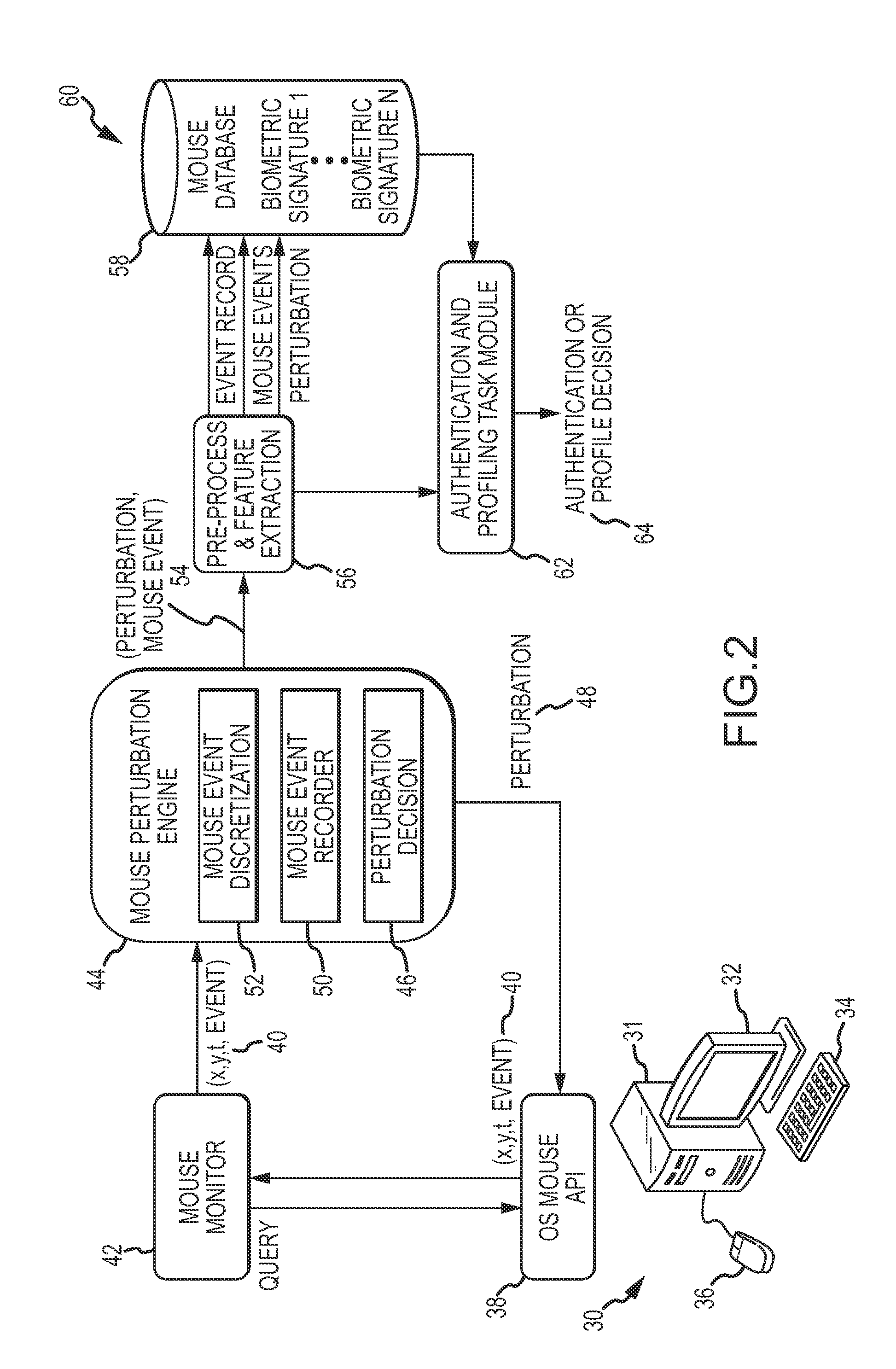
Cognitive biometrics using mouse perturbation
InactiveUS20140078061A1Increase richnessCathode-ray tube indicatorsDigital data authenticationCognitive strategyOrganism
Cognitive biometrics comprises augmenting the richness of biometric signatures that can be extracted from mouse dynamics by introducing perturbations in the response of the computer mouse and measuring the motor responses of the individual user. User responses to unexpected and subtle perturbations (e.g., small changes in mouse velocity, position and / or acceleration) reveal new unique sources of information in the mouse movement signal that reflect the user's cognitive strategies and are inaccessible via existing mouse biometric technologies. A user's response to these perturbations contains information about intrinsic cognitive qualities that can be used as a robust biometric for personal authentication and to support profiling of the individual (e.g., gender, cultural background, cognitive or emotional state, cognitive quality etc.).
Owner:TELEDYNE SCI & IMAGING
Method for generating an encryption key using biometrics authentication and restoring the encryption key and personal authentication system
InactiveUS8417960B2Programme controlElectric signal transmission systemsComputer hardwareAuthentication system
A personal authentication system using biometrics information. The system orders, when an characteristic element in the biometrics information (such as a characteristic point in a fingerprint) can be expressed with two types of information (such as, for instance, a coordinate values for a characteristic point in a fingerprint and a local partial image), the characteristic points using one type of information (for instance, local partial image) as label information, and outputs other type of information (such as coordinate values) as key information according to the order.
Owner:HITACHI LTD
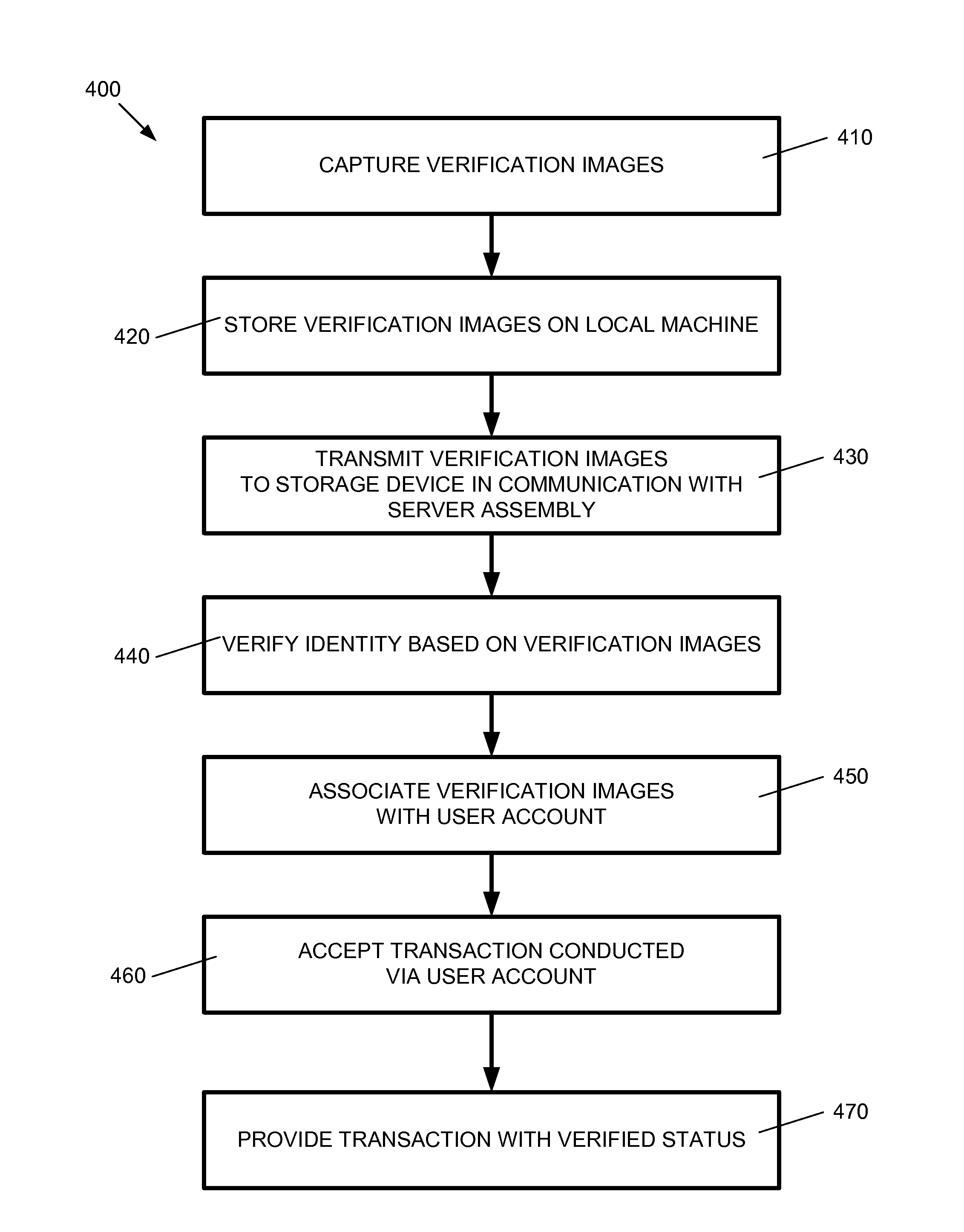
Identity verification systems
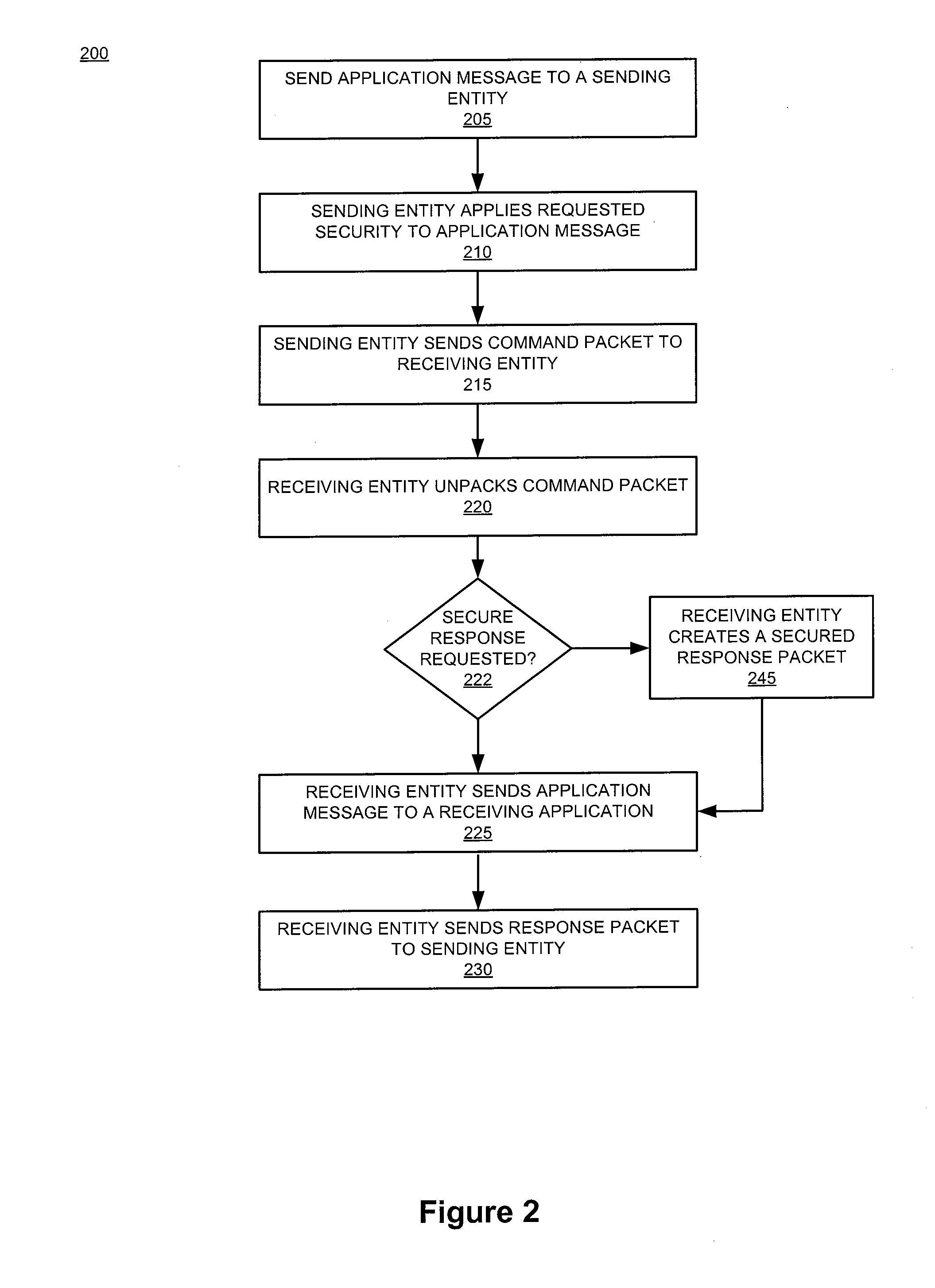
Identity verification systems and methods for remotely verifying a user's identity are disclosed. In some exemplary embodiments, the identity verification systems and methods may be used to verify an identity for a remote transaction. An exemplary embodiment of the system may comprise a capture unit, a delivery unit, a verification unit, a transaction unit, and a user account associated with the user. The capture unit may capture one or more verification images of the user, an identification document, and one or more other financial or identification documents. The delivery unit may transmit the verification documents to a server assembly. The verification unit may provide verification of the user's identity based on the verification images. The transaction unit may determined whether a transaction requested via the user's user account qualifies for verified status based on identity verification and, accordingly, whether the transaction should be afforded predetermined privileges of verified status.
Owner:GREGORY A PEARSON
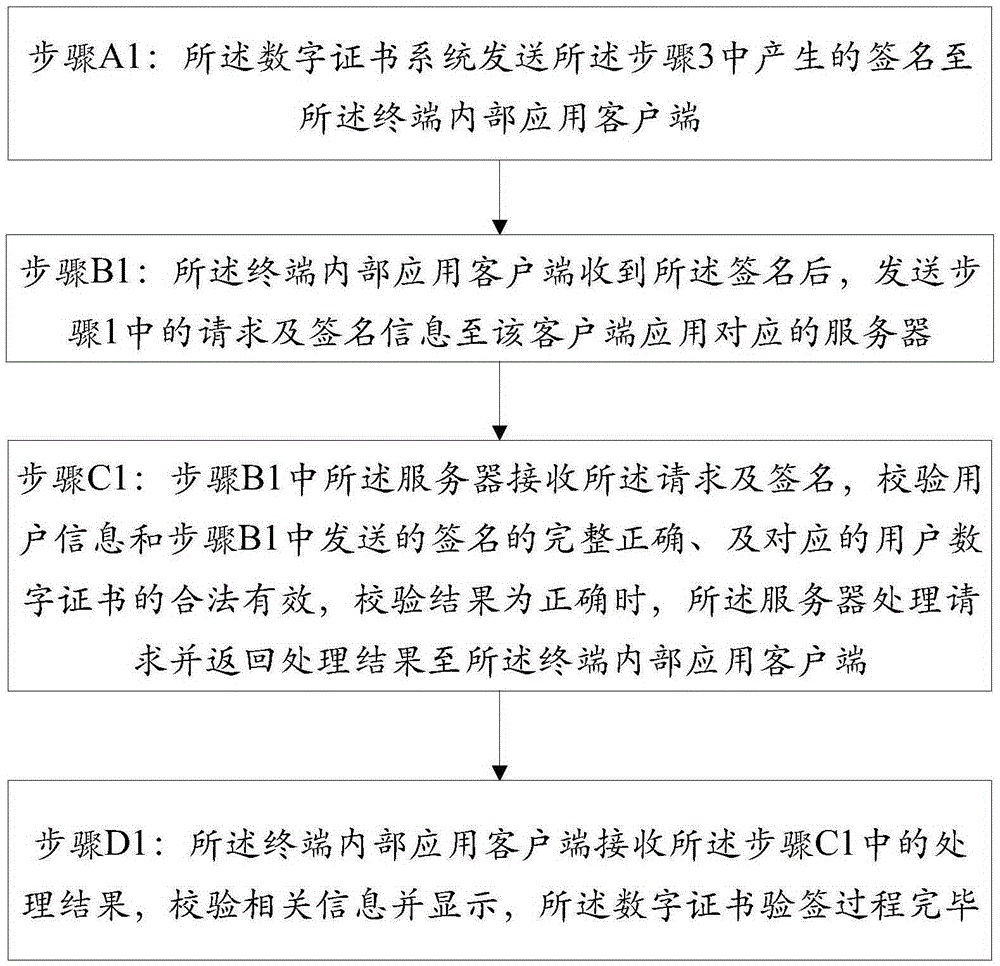
Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
ActiveCN105429760AEnsure true willEnsure that the identity verification process can reflect the true willUser identity/authority verificationPasswordPersonal identity verification
The invention discloses a method for identity verification of a digital certificate based on a TEE (Trusted Execution Environment). The method comprises pre-configuration of a digital certificate system through a terminal, a digital certificate signature process and a digital certificate signature verification process. The method is characterized in that the terminal is provided with the TEE; the digital certificate signature process is carried out on the terminal and is used for utilizing a private key of the digital certificate to sign for a user request; the digital certificate signature verification process is used for authenticating identity of a requested user, and the authentication method comprises verification of validity and effectiveness of the digital certificate and integrity and correctness of the signature, wherein the digital certificate signature process is carried out under the TEE; the sensitive information, such as a user key, identity information, biological characteristic information and password information, is stored through a secure storage module, so that the problems that the signature process is carried out in REE and the sensitive information of the user is stored under the REE environment to cause privacy disclosure and stolen hidden danger of property in the prior art are avoided.
Owner:神州融安数字科技(北京)有限公司
Vision detection system for vehicles not yielding to pedestrians at zebra crossing
InactiveCN107730906AEnsure safetyImprove detection accuracyRoad vehicles traffic controlCharacter and pattern recognitionPedestrian behaviorVideo image
The invention provides a vision detection system for vehicles not yielding to pedestrians at zebra crossing, comprising a monitoring camera covering the whole zebra crossing area, a HD (high definition) snapshot camera for taking snapshots of vehicles, a traffic cloud server, and a vision detection subsystem. The vision detection subsystem comprises a zebra crossing area detection module, a not-yielding-to-pedestrians behavior detection module, a not-yielding-to-pedestrians behavior vehicle image snapshot module, a vehicle type identification module, a license plate positioning and identifyingmodule, and a violation detection report generating module. The traffic cloud server is used for receiving video data of the whole zebra crossing area obtained by the monitoring camera, and submitting the video data to the vision detection subsystem to conduct not-yielding-to-pedestrians behavior detection and personal identity verification of violation vehicles. A violation detection report canbe automatically generated and stored with the detection and identification result, three snapshots of not-yielding-to-pedestrians vehicle images, and the process video images. The invention is quitehigh in detection precision and robustness.
Owner:ENJOYOR COMPANY LIMITED
System and device for facilitating a secure transaction with a validated token
InactiveUS20110238579A1Increase dependenceFacilitating secure and convenient electronic transactionsPoint-of-sale network systemsTransmissionPayment transactionData memory
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network by way of a transaction account token. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Method and system for identity verification using multiple simultaneously scanned biometric images
InactiveUS6970582B2Improve accuracyLow costElectric signal transmission systemsImage analysisBiometric dataComputer vision
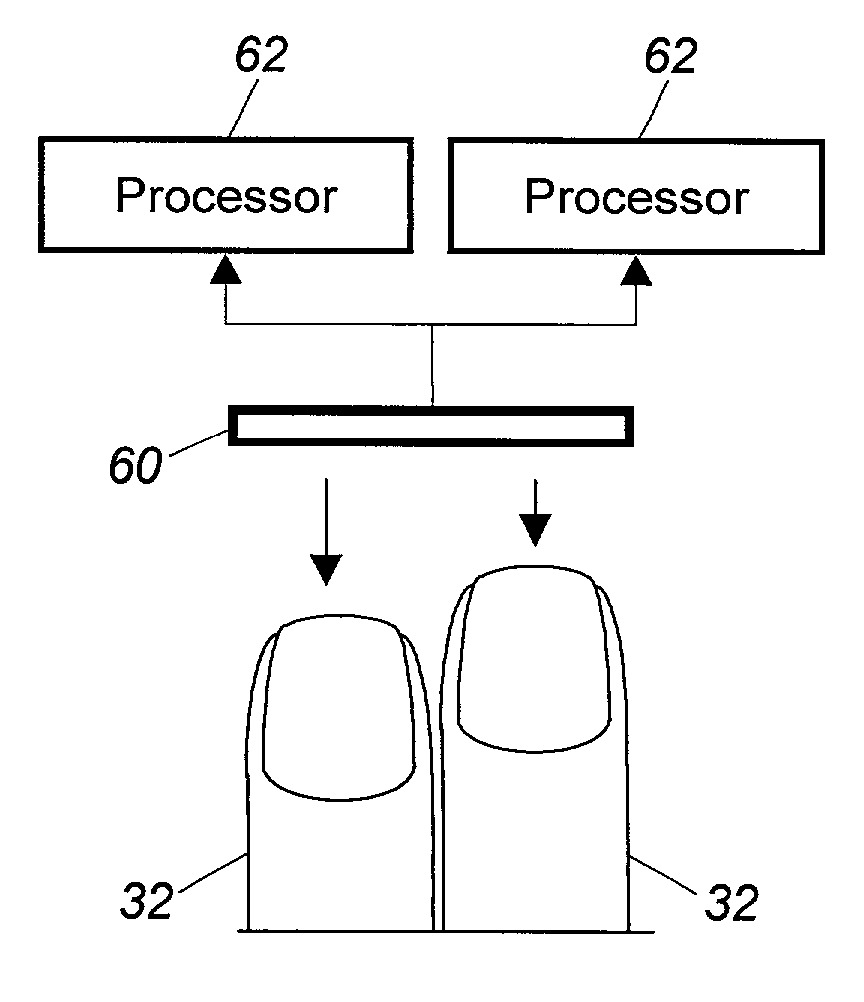
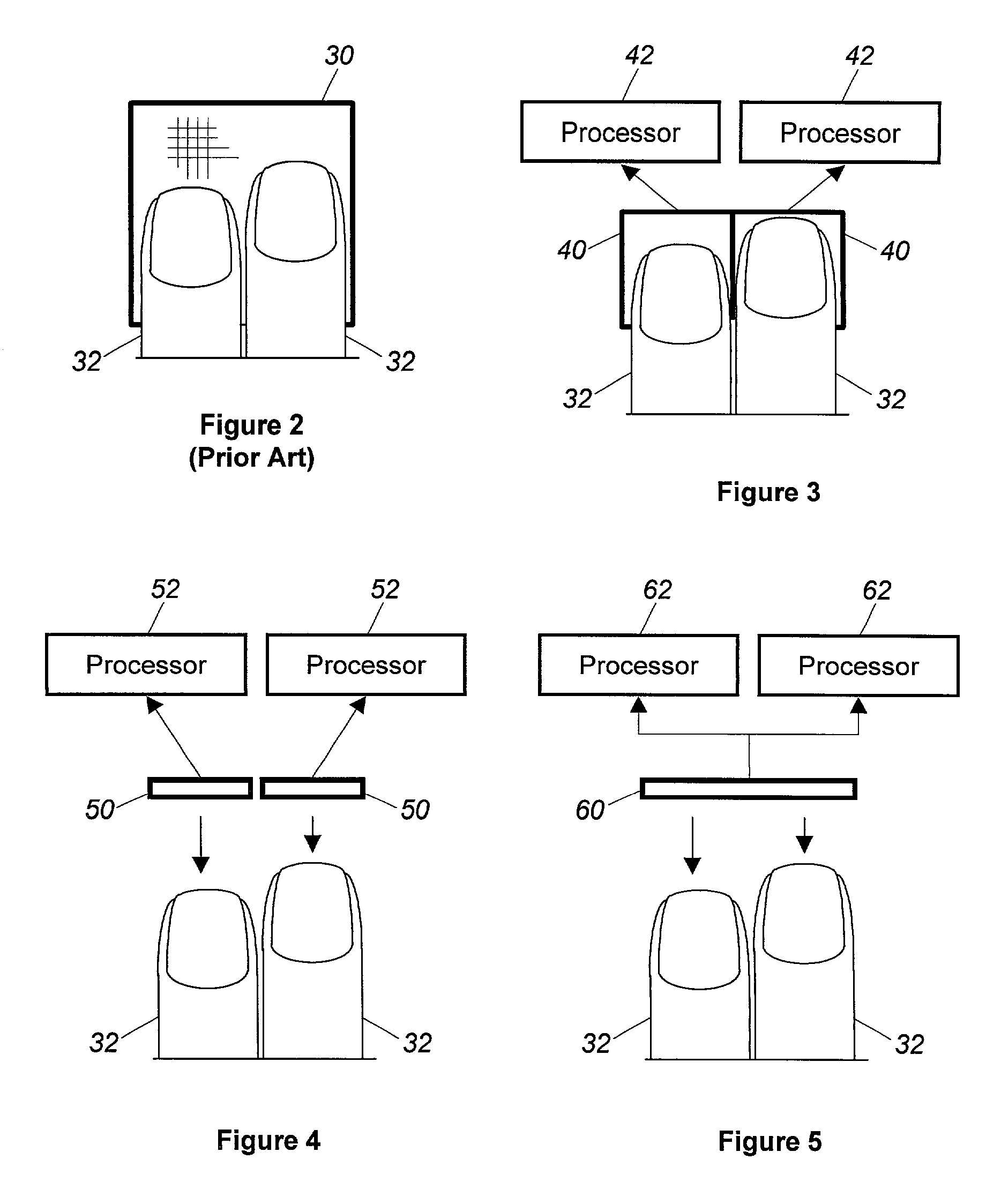
Accuracy and speed of biometric identity verification are significantly improved by use of multiple simultaneous scans of biometric features of a user, such as multiple fingerprints, using multiple scanners (40, 50) of smaller size than would be needed to accommodate all of the fingerprints in a single scanner (30), and using multiple parallel processors (42, 52), or a single higher speed processor, to process the fingerprint data more efficiently. Obtaining biometric data from multiple user features by use of multiple scanners increases verification accuracy, but without the higher cost and slower processing speed that would be incurred if a single large scanner were to be used for improved accuracy.
Owner:NORTHROP GRUMMAN SYST CORP
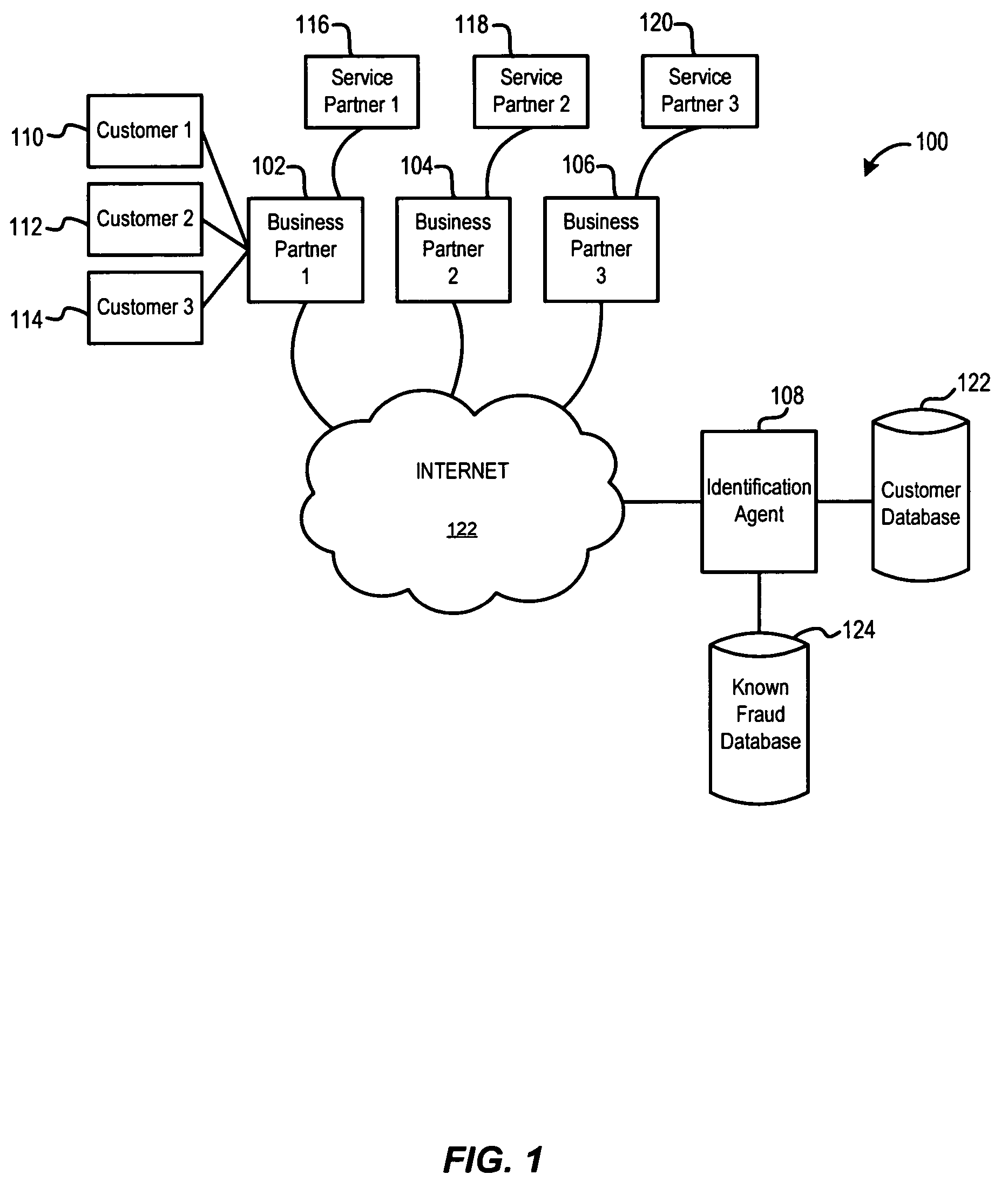
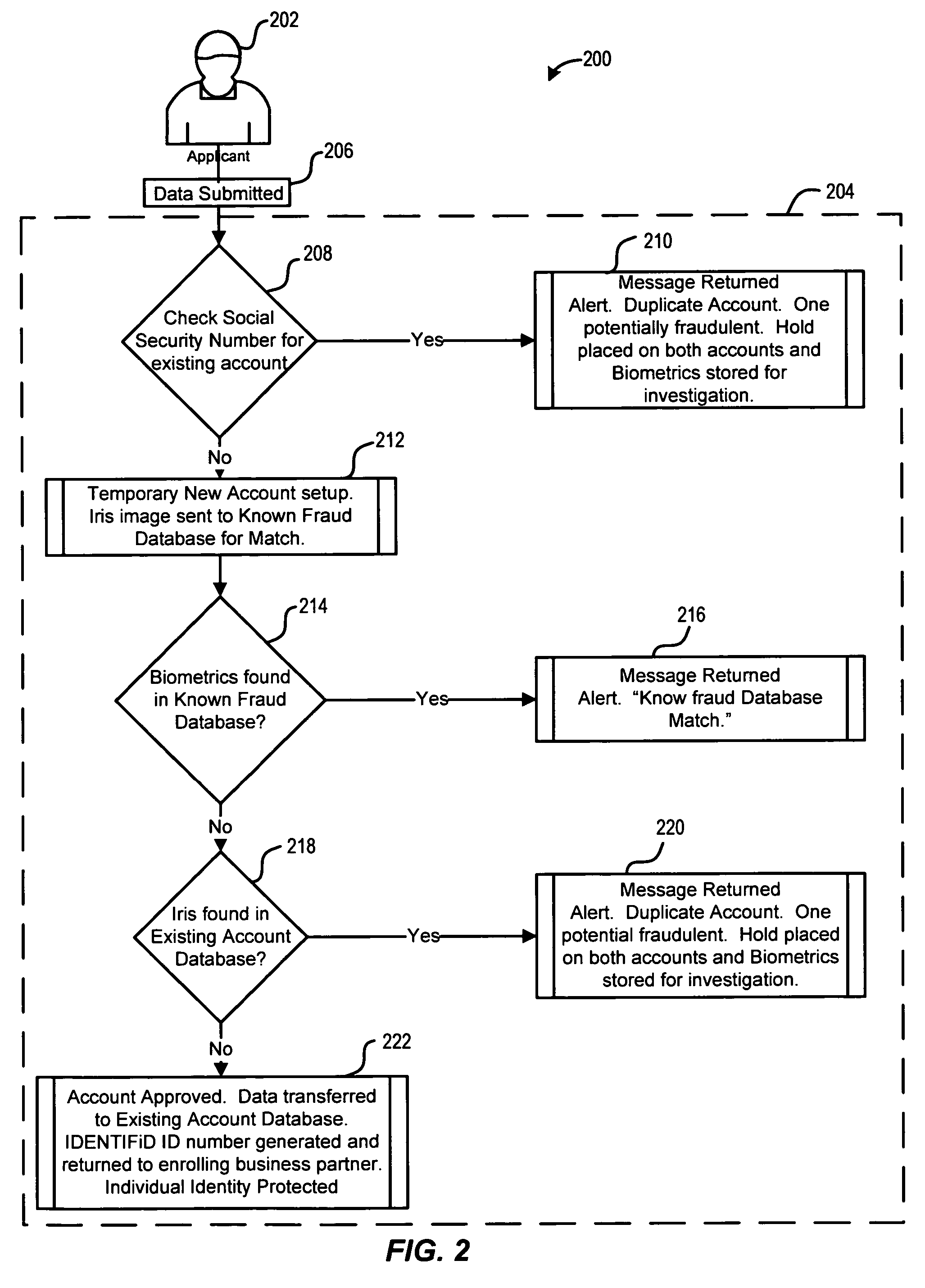
Identity verification system
ActiveUS7779457B2Easy access to dataElectric signal transmission systemsDigital data processing detailsElectronic systemsBiometric data
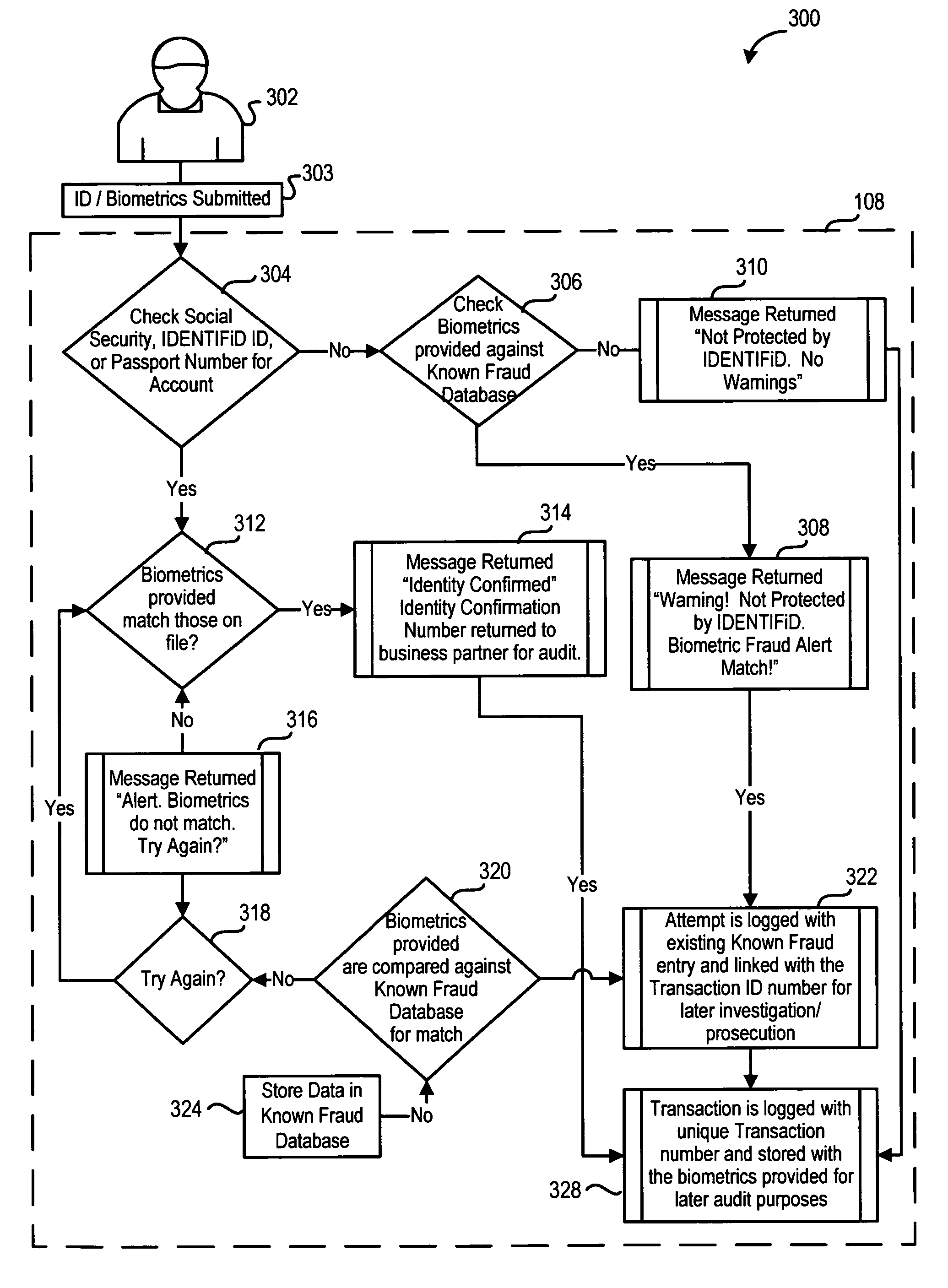
An electronic system is provided to confirm the identity of an individual or customer. The confirmation process permits businesses and other entities to access a preapproved list of authorize customers for purposes of preventing identity theft or fraud. Biometric data obtained from the person of the customer is compared against an authorized version of customer biometric data for this purpose. Even if an individual customer is not an authorized customer, the biometric data may be compared to a known fraud database to see if this individual has perpetrated past instances of fraud.
Owner:IDENTIFID LLC
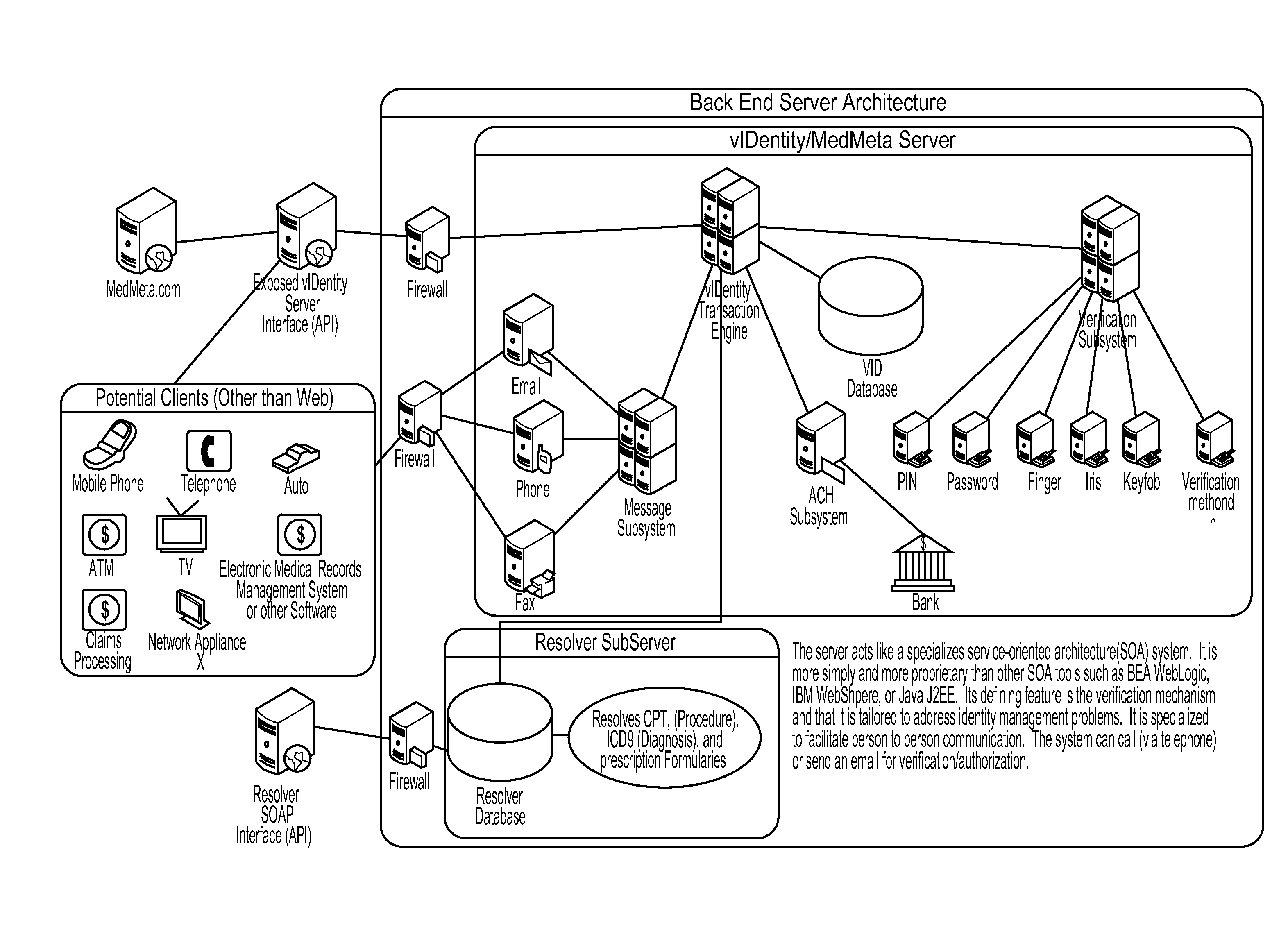
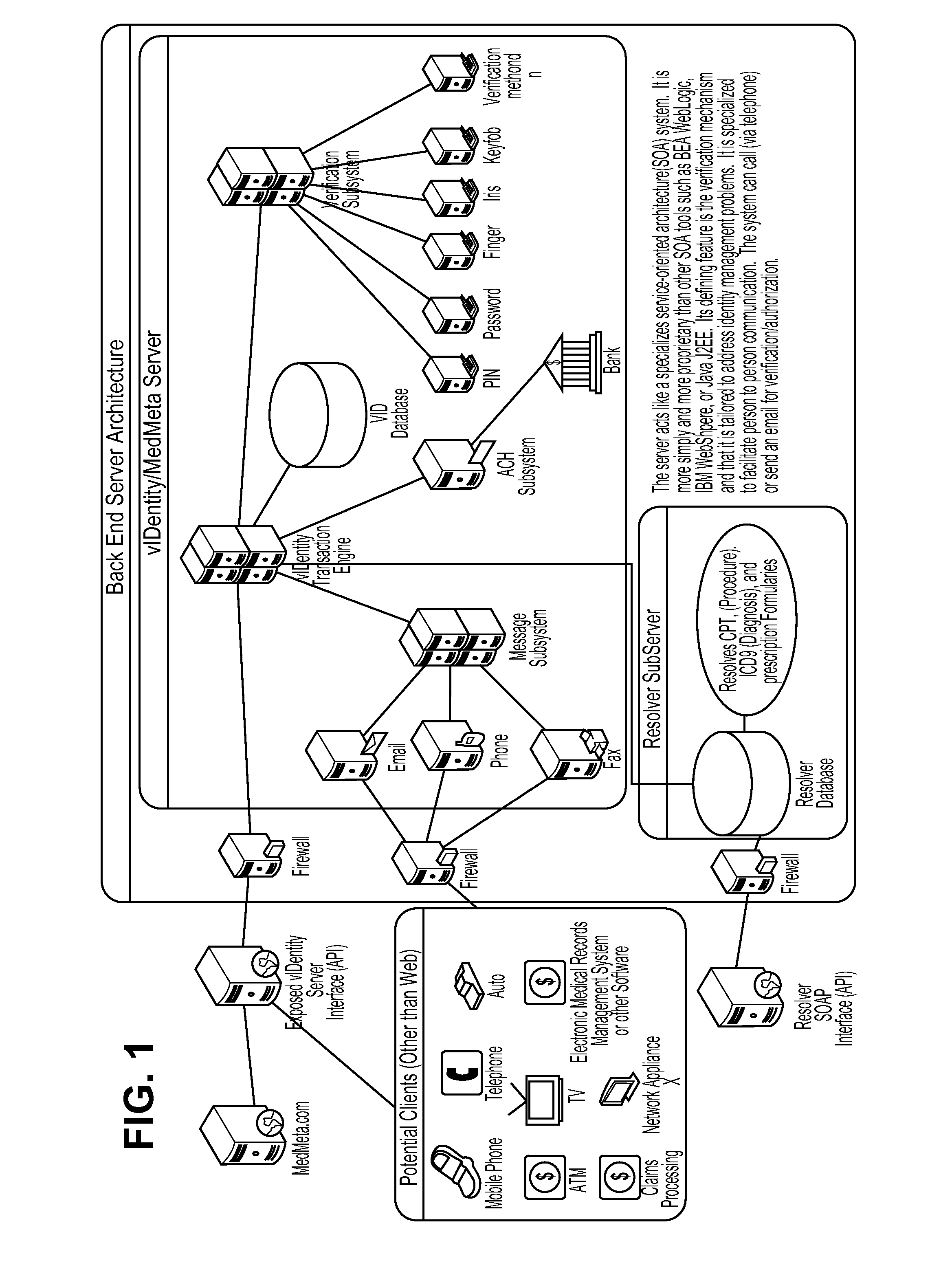
Identity verification and information management
InactiveUS20110047628A1Efficient and secure and verified information exchangeEfficient, secure and verified information exchangeDigital data processing detailsAnalogue secracy/subscription systemsClient-sideData format
The present invention provides an efficient, secure and verified information exchange using an identity verification platform and common interface data formats, whereby an individual can set different levels of access for different clients and further set different levels of access for different files. Therefore, the present invention provides a multi-layer access to records particular to an individual.
Owner:VIDENTITY SYST
Biometrics authentication method, media for individual authentication, and biometrics authentication device
ActiveUS20080065901A1Prevent illegal usePrevent illicit acquisition and mergingUser identity/authority verificationPerson identificationBiometric dataConfidentiality
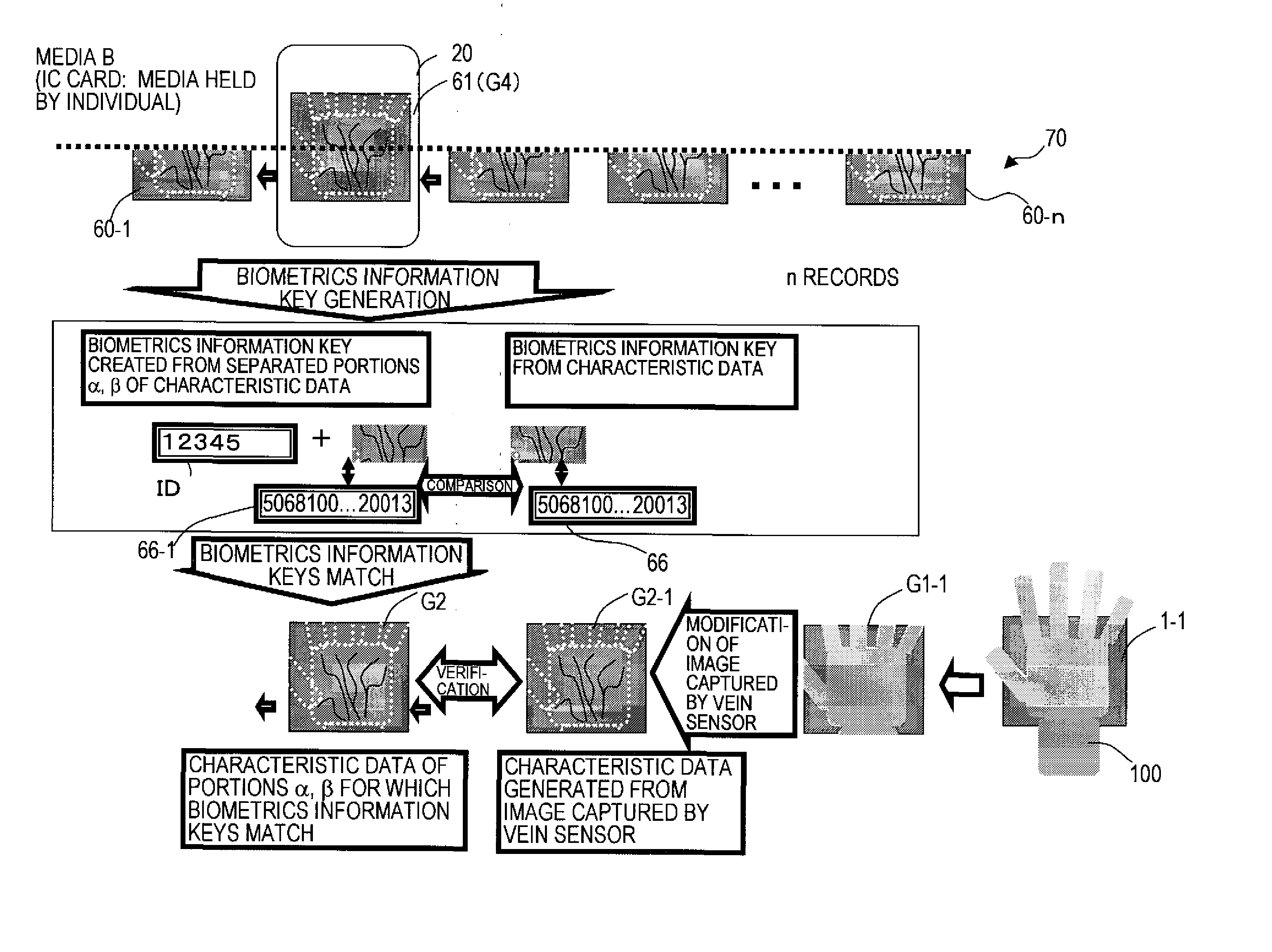
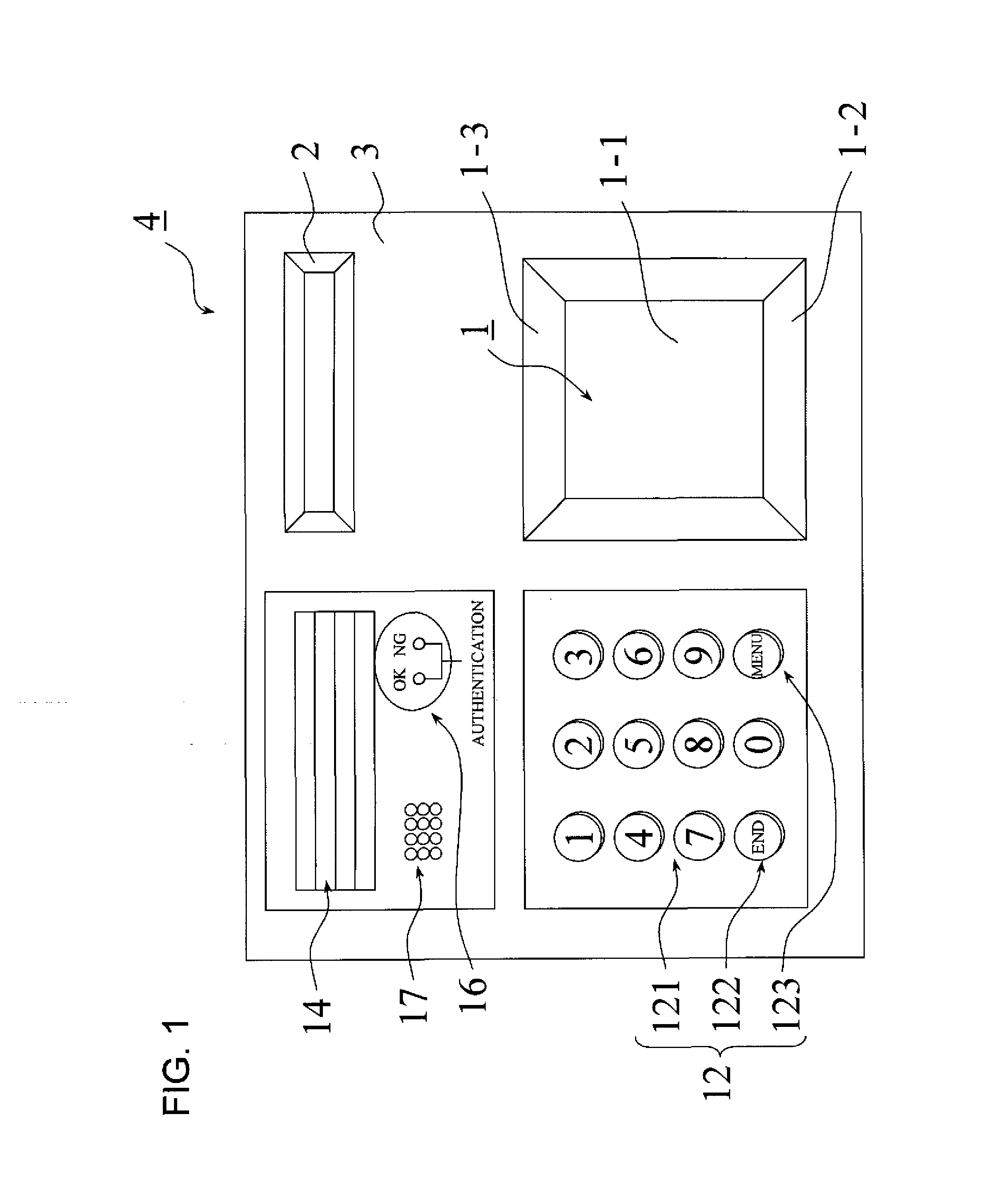
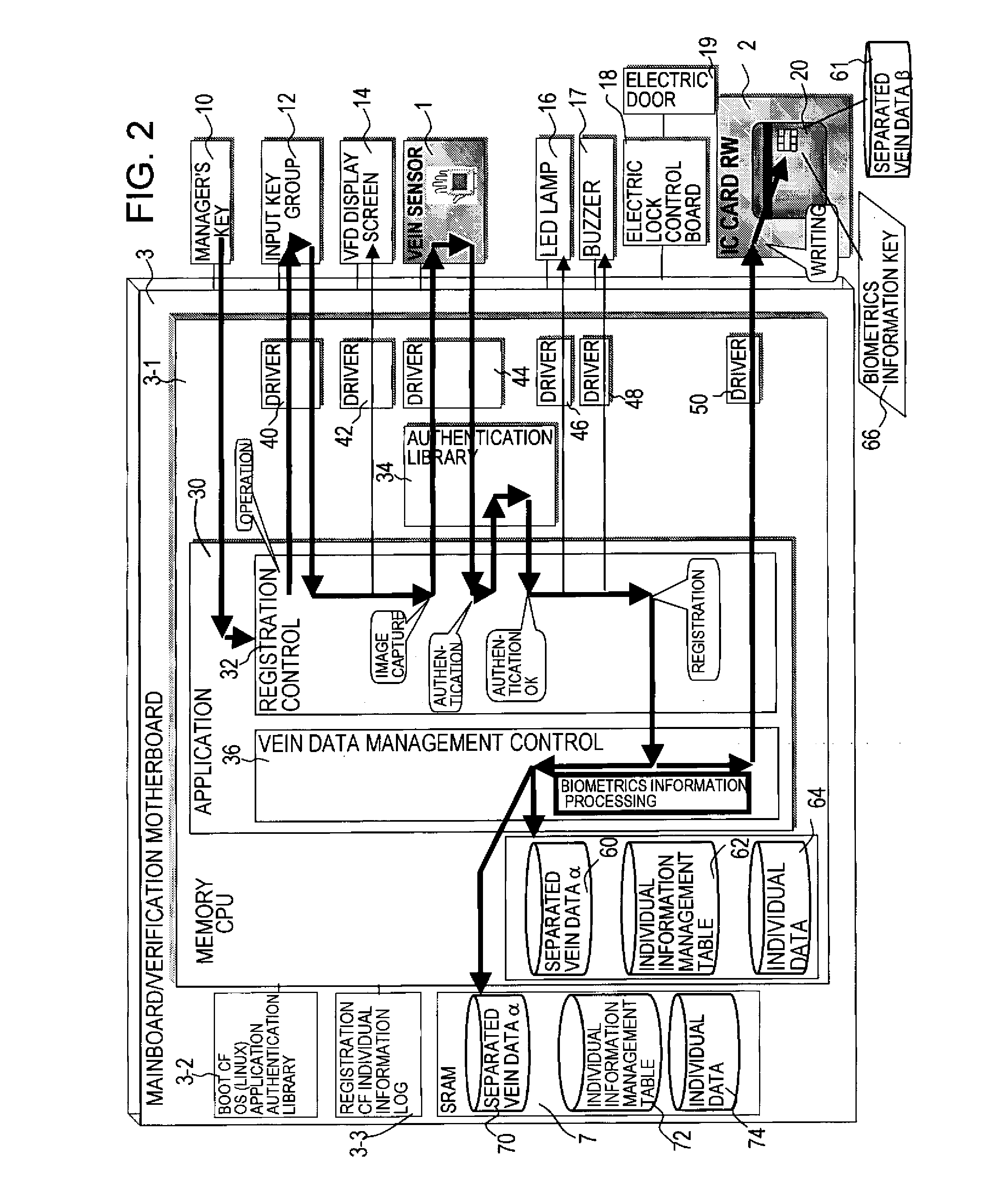
A biometrics authentication device which detects body characteristics, performs verification against registered biometrics data, and performs individual authentication, by which confidentiality is improved even when biometrics data is separated, distributed and stored. A biometrics information key is created from biometrics data detected by a detection device, the biometrics data is divided into a plurality of portions, and the portions are stored on different media. The biometrics information key is stored on one media, and at the time of authentication, the separated biometrics data portions are combined and a biometrics information key is created and is compared with the biometrics information key, to judge the linked relationship. Hence confidentiality of the association of the individual separated data portions can be improved even when the biometrics data is separated, distributed and stored, contributing to prevent illicit use resulting from leakage or theft of biometrics data.
Owner:FUJITSU LTD +1
System and device for facilitating remote invocation of personal token capabilities
InactiveUS20110237224A1Increase dependenceFacilitating secure and convenient electronic transactionsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPayment transactionSmart card
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Individual authentication method, individual authentication device, and program for same
InactiveUS20060080254A1Smooth transitionAcutation objectsImage analysisComputer hardwareRecording media
An individual authentication device, which verifies individual data of recording media against input individual data and performs individual authentication, is enabled to make a smooth transition to biometrics authentication. The device judges whether a biometrics unit is installed, and by judging whether the biometrics unit is installed, selects between individual authentication by the biometrics unit and individual authentication by verifying individual data of storage media against input individual data. An individual authentication device onto which biometrics authentication functions are not loaded can make a smooth transition to an individual authentication device onto which the biometrics authentication functions are loaded.
Owner:FUJITSU LTD +1
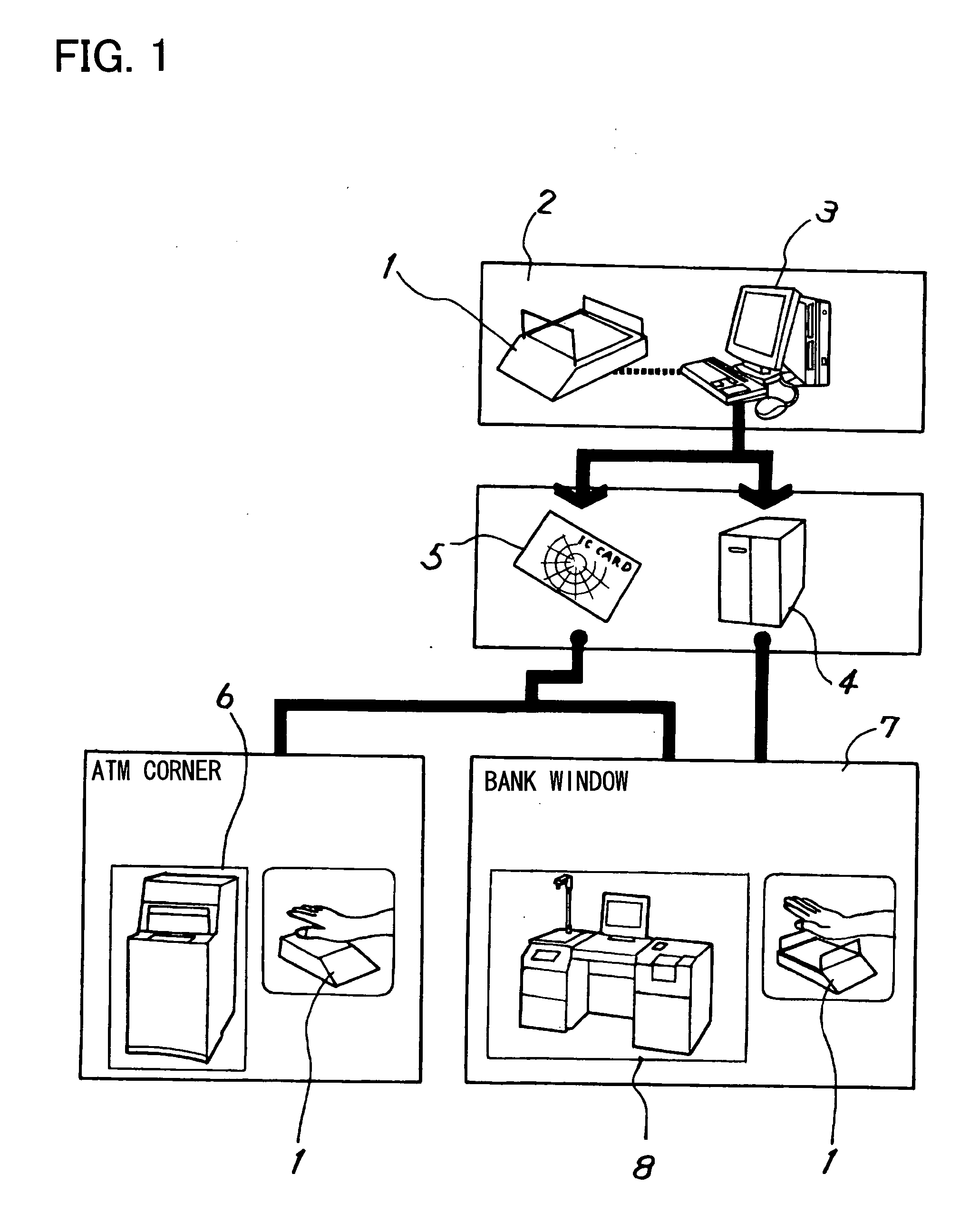
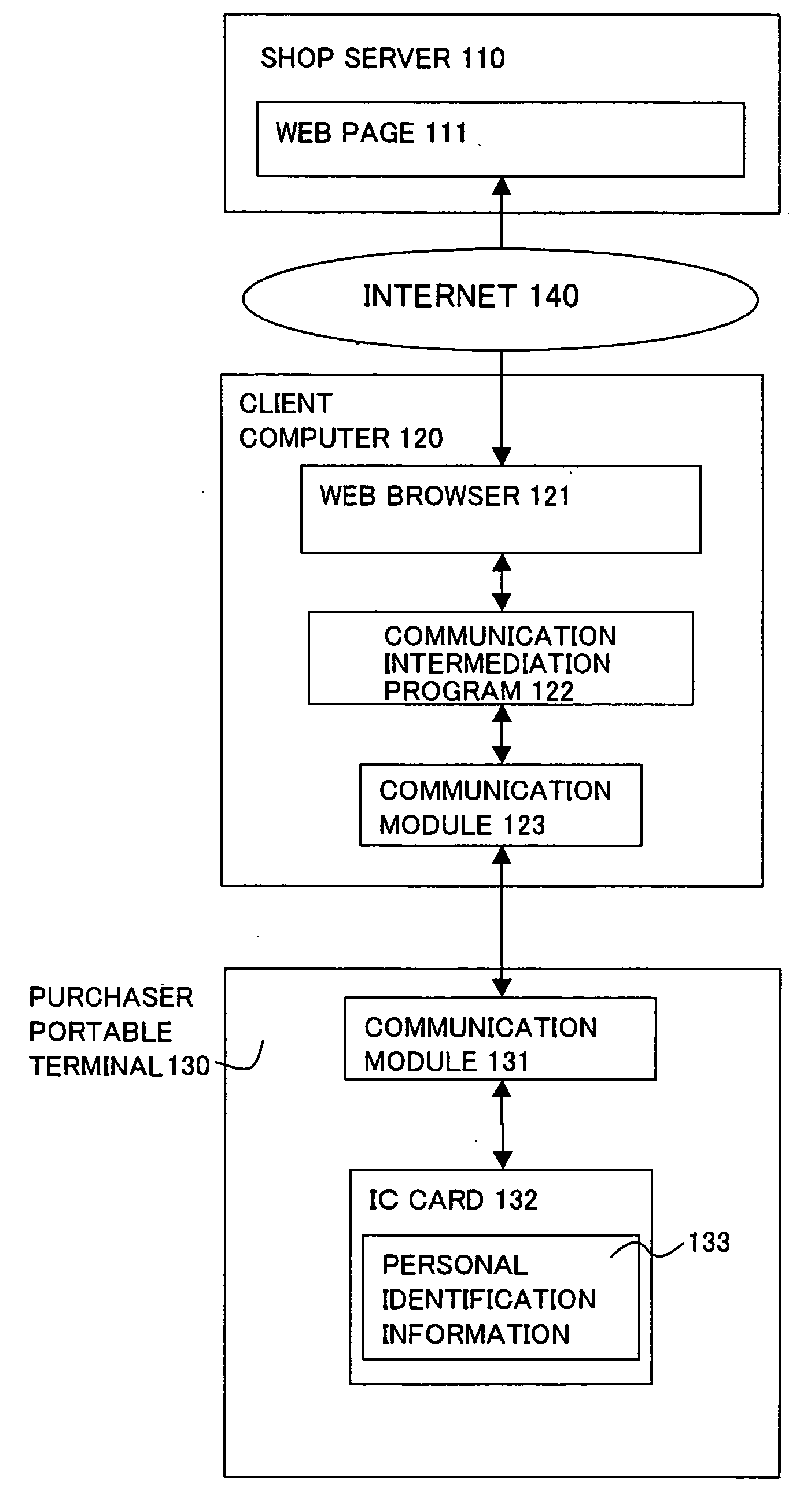
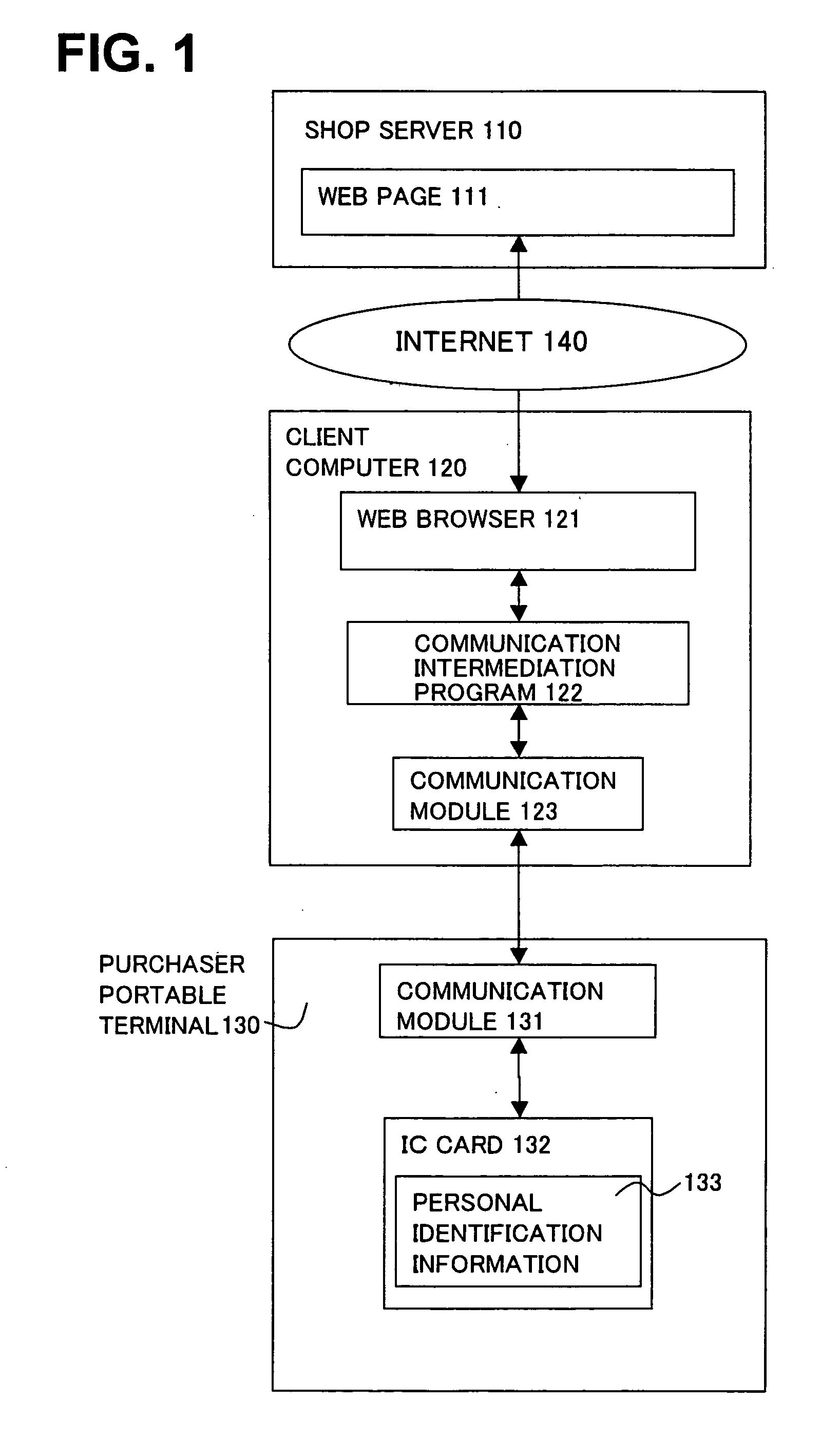
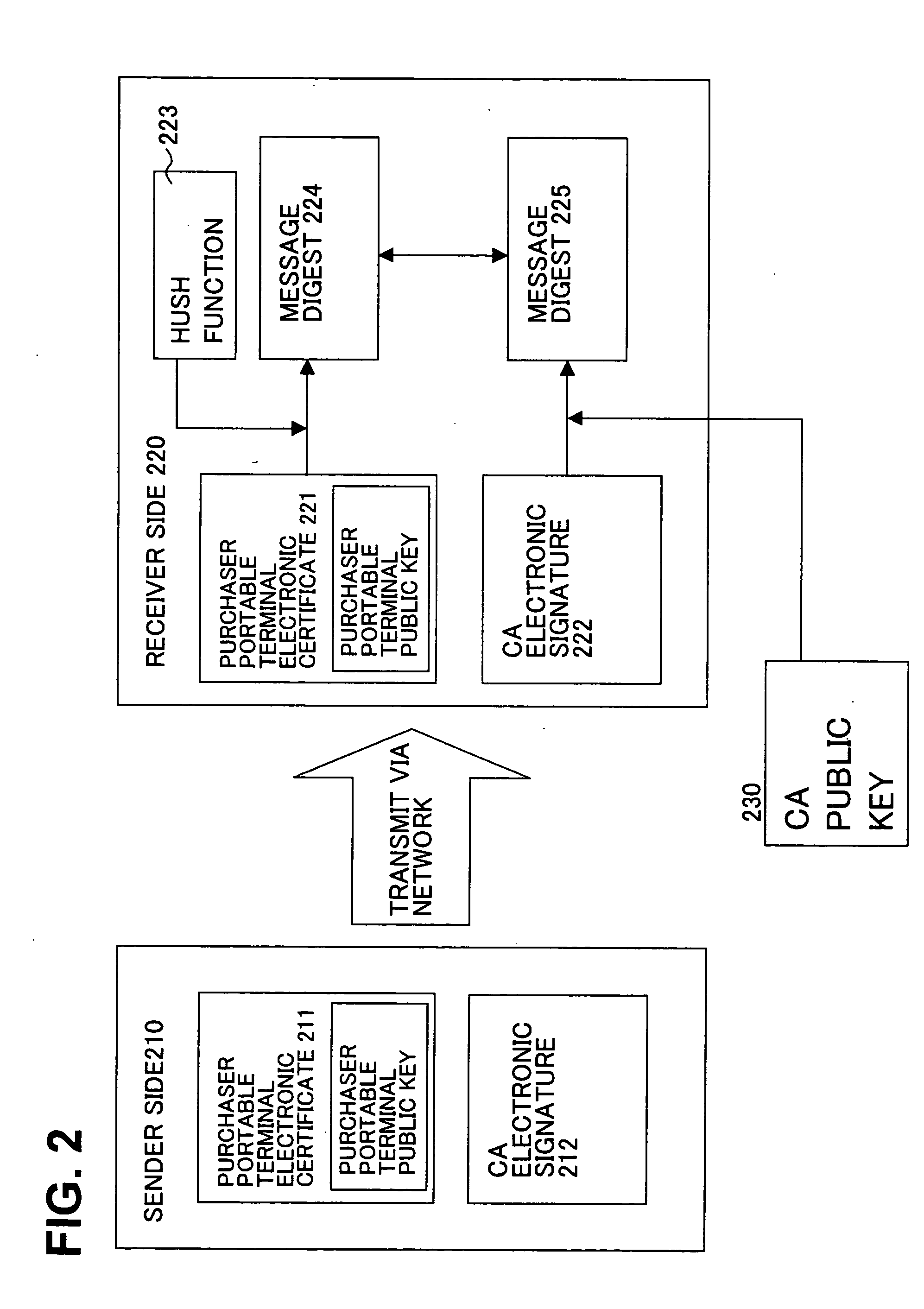
Data communication intermediation program and apparatus for promoting authentication processing in cooperation with purchaser portable terminal having personal identification information and communication function
InactiveUS20050138429A1Easy to operate“spoofing” can be preventedDigital data processing detailsMultiple digital computer combinationsComputer hardwareThird party
In a personal authentication and a settlement authentication required for the Internet shopping, in order to make above authentication processing executed between a server and a client computer be executed between the server and a purchaser portable terminal equipped with personal identification information and a communication function, a program of the present invention has functions for transferring to the purchaser portable terminal a personal identification information request sent from the server and data associated with the authentication processing and for transferring to the server the data associated with the authentication processing sent from the purchaser portable terminal. Due to the program, while products are selected with a client computer such as a personal computer with a large screen and good operability, personal identification information required for the personal authentication and a settlement authentication is transmitted from the purchaser portable terminal and will not be stored in a hard disk of the client computer. Also, by encrypting communication, leakage of the personal identification information to a third party can be prevented and, as a result, the “spoofing” can be prevented.
Owner:FUJITSU LTD
System and device for consolidating sim, personal token, and associated applications for electronic wallet transactions
ActiveUS20110244920A1Increase dependenceFacilitating secure and convenient electronic transactionsSubstation equipmentPoint-of-sale network systemsPayment transactionFinancial transaction
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Mobile phone all-in-one card intelligent medical service system
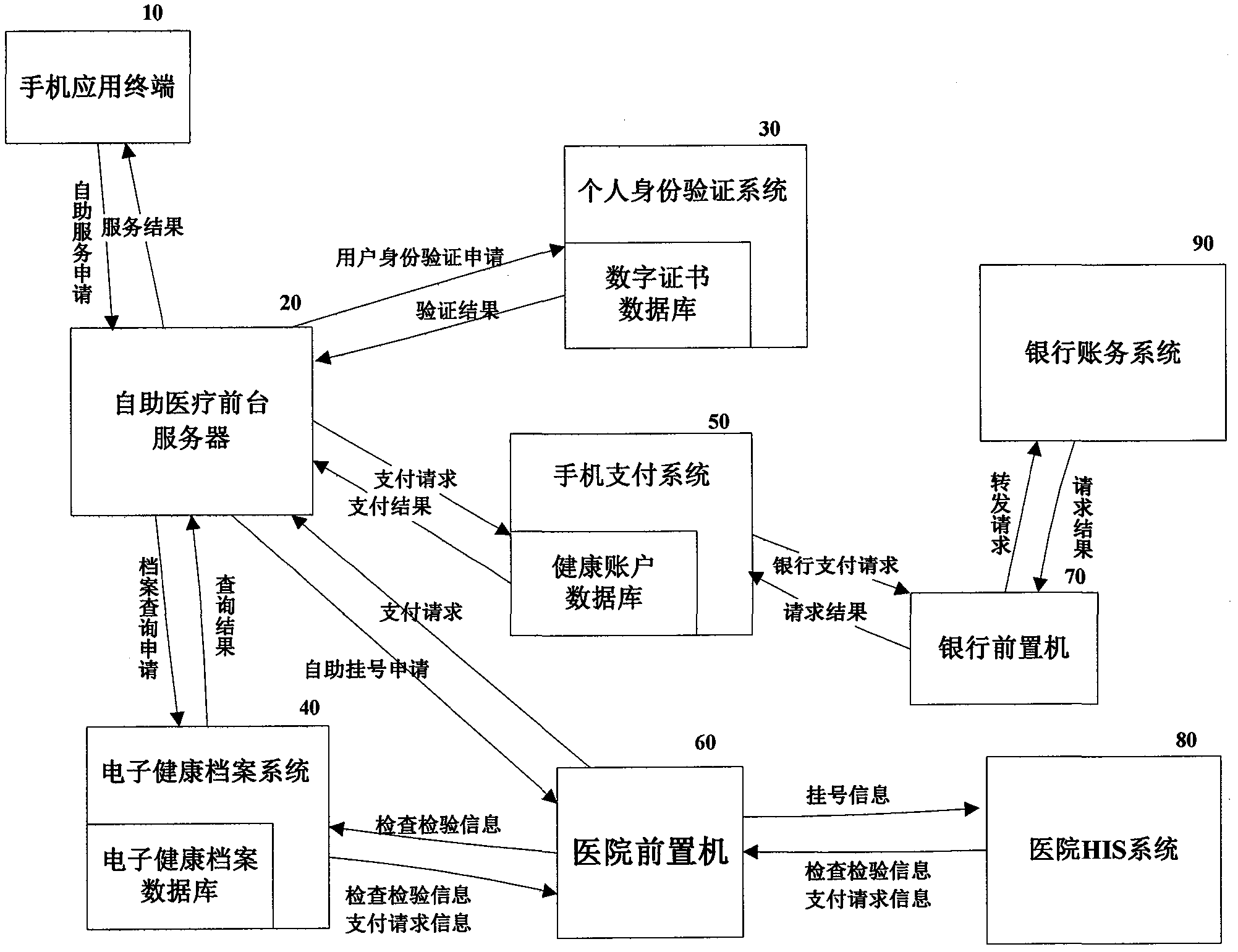
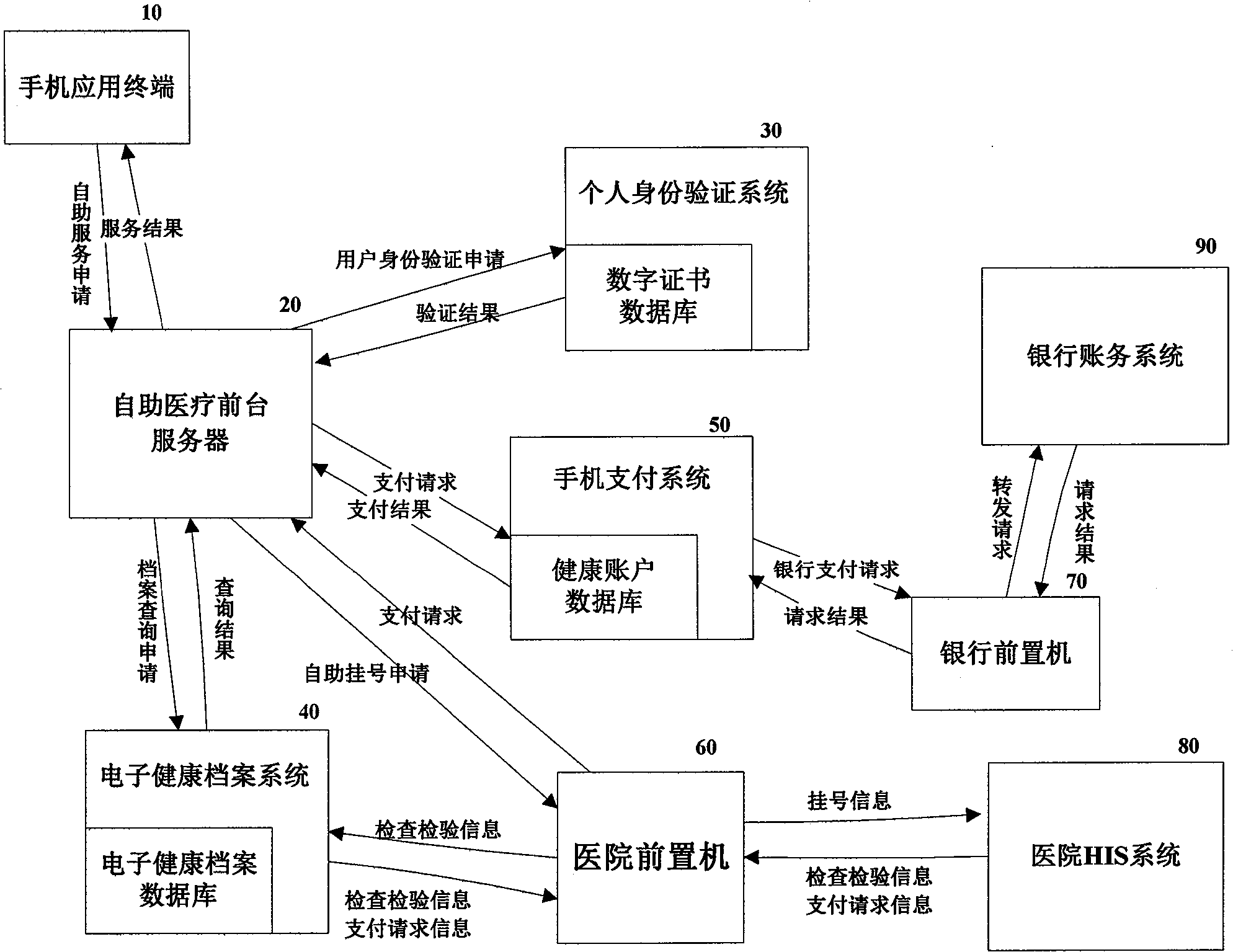
InactiveCN101957887AImprove the quality of medical servicesDifficulty in improving registrationSpecial data processing applicationsHospital information systemMedical treatment
The invention discloses a mobile phone all-in-one card intelligent medical service system. The system comprises a mobile phone application terminal, a self-help medical foreground server, a personal identity authentication system, a payment system and a bank front-end processor. The system is formed by the linkage of a mobile phone and a hospital information system (HIS) of a hospital. A patient can finish self-help registration, payment, medical service appointment, health service consultation and various self-help inquiry services through the mobile phone, and the mobile phone is endowed with the functions of a hospital service window, which effectively reduces the pressure of a hospital outpatient window, effectively improves work efficiency, enhances the medical service quality of the hospital, solves the problems of registration difficulty and medical treatment difficulty of the hospital, and simultaneously better protects the privacy of the patient.
Owner:SUZHOU SUCHENG WIRELESS APPL CENT
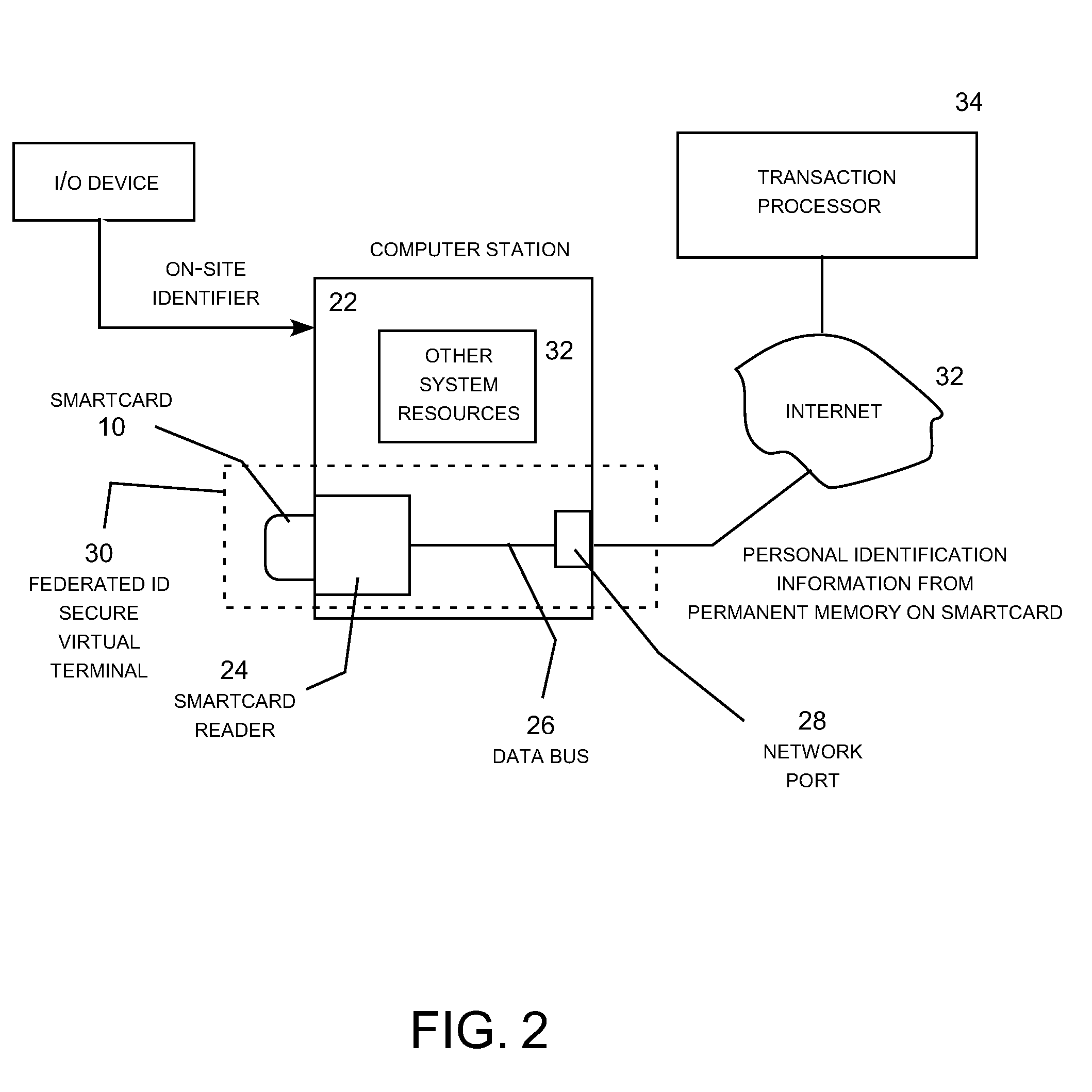
Federated ID Secure Virtual Terminal Emulation Smartcard
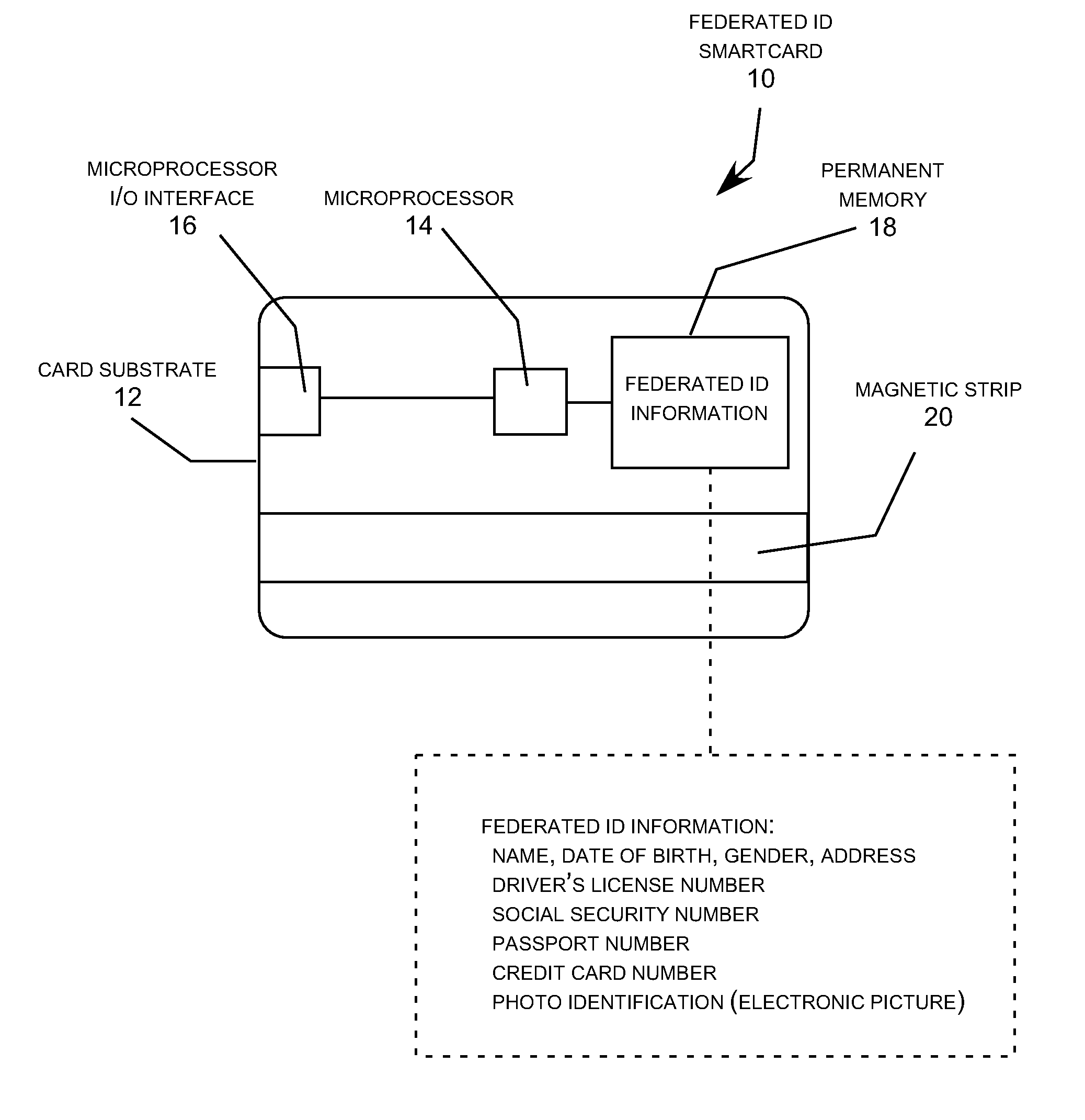
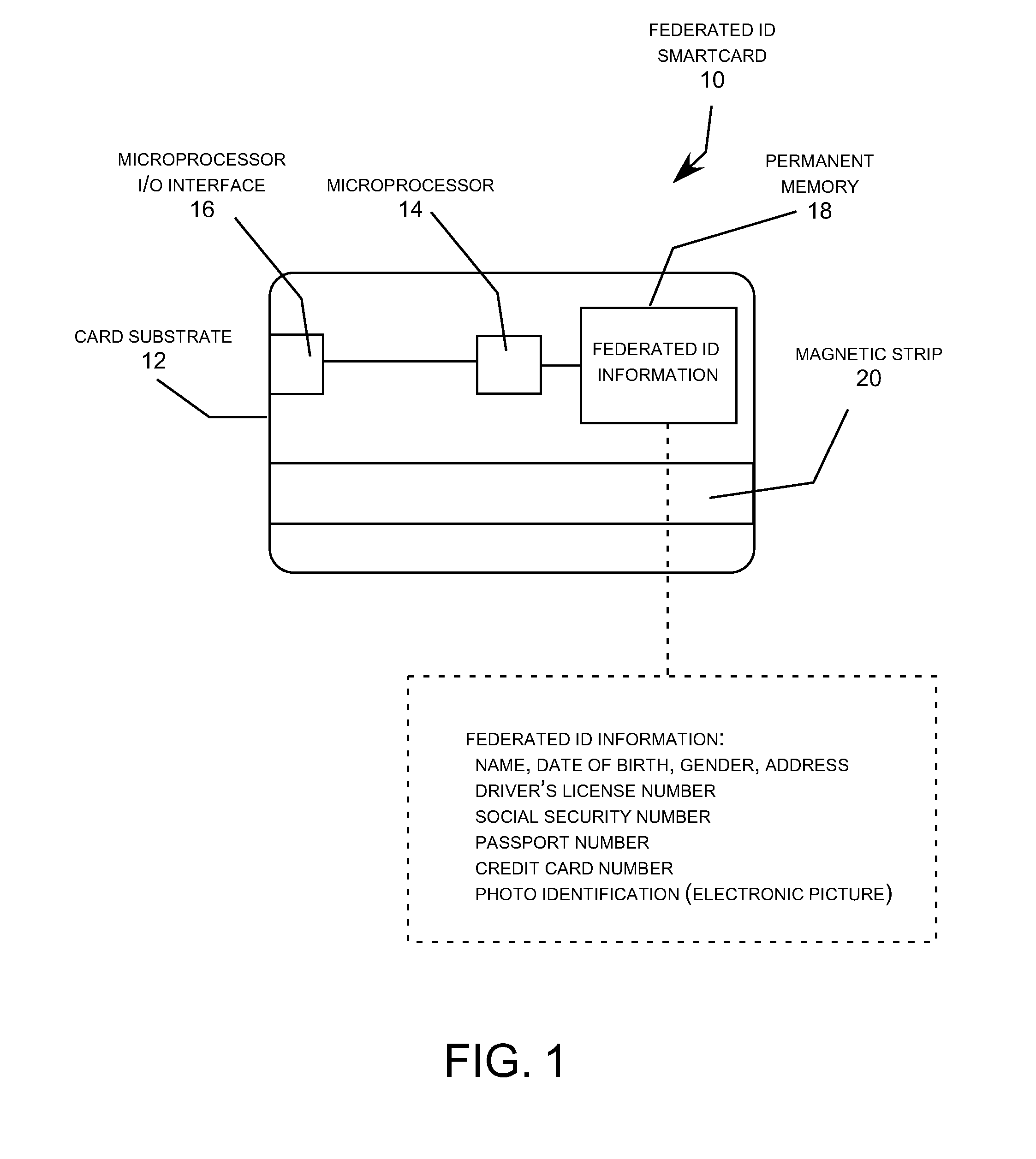
InactiveUS20090045257A1High degreePrevent theftRecord carriers used with machinesVerifying markings correctnessVirtual terminalSmart card
A smartcard using a combination of secure virtual terminal emulation implemented by the smartcard and Federated ID information stored on the smartcard (and optionally on a transaction processor server) to provide secure verification of the personal identity of the cardholder. The Federated ID information provides a high level personal identity verification for the cardholder while secure virtual terminal emulation by the smartcard prevents the Federated ID information from being exposed to the microprocessor and memory resources of a host computer station when the smartcard is used with the host computer station to engage in transactions. The Federated ID smartcard provides a flexible, dynamically adjustable, highly efficient and secure system for personal identity verification for online commerce and a wide range of other application involving personal identity verification.
Owner:LIFENEXUS
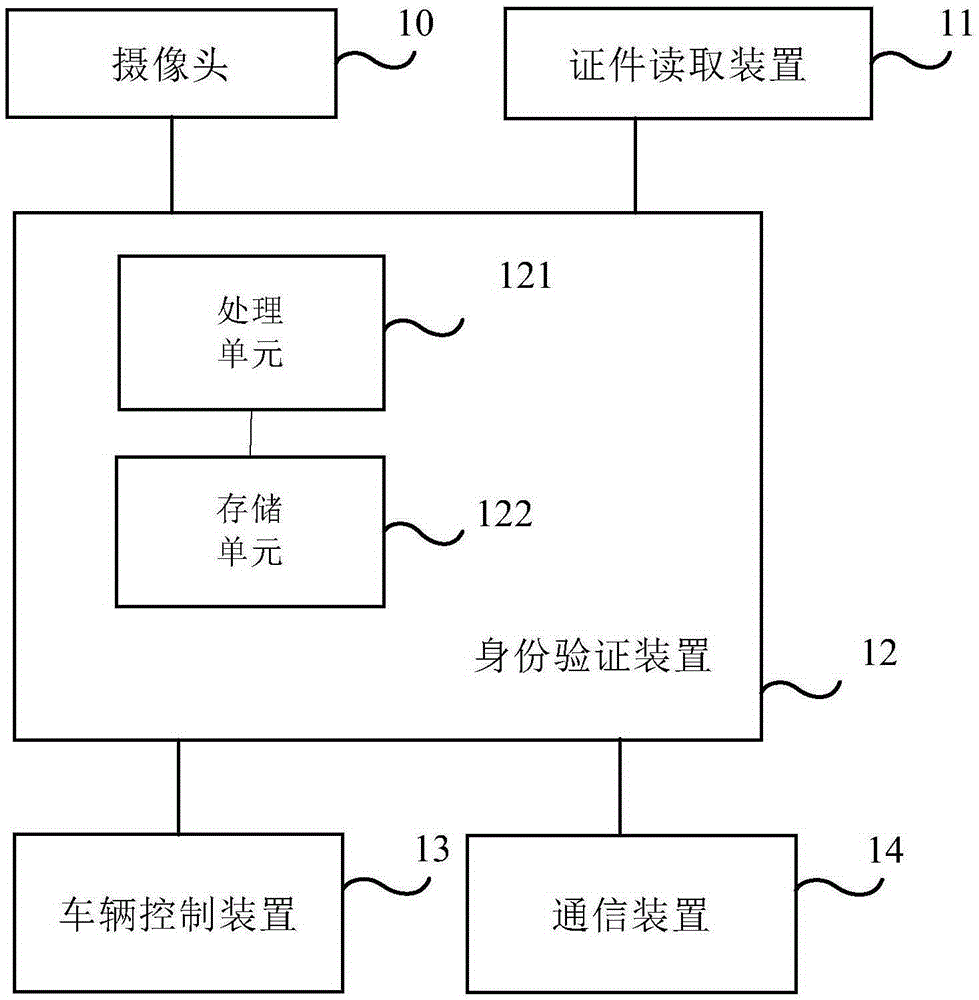
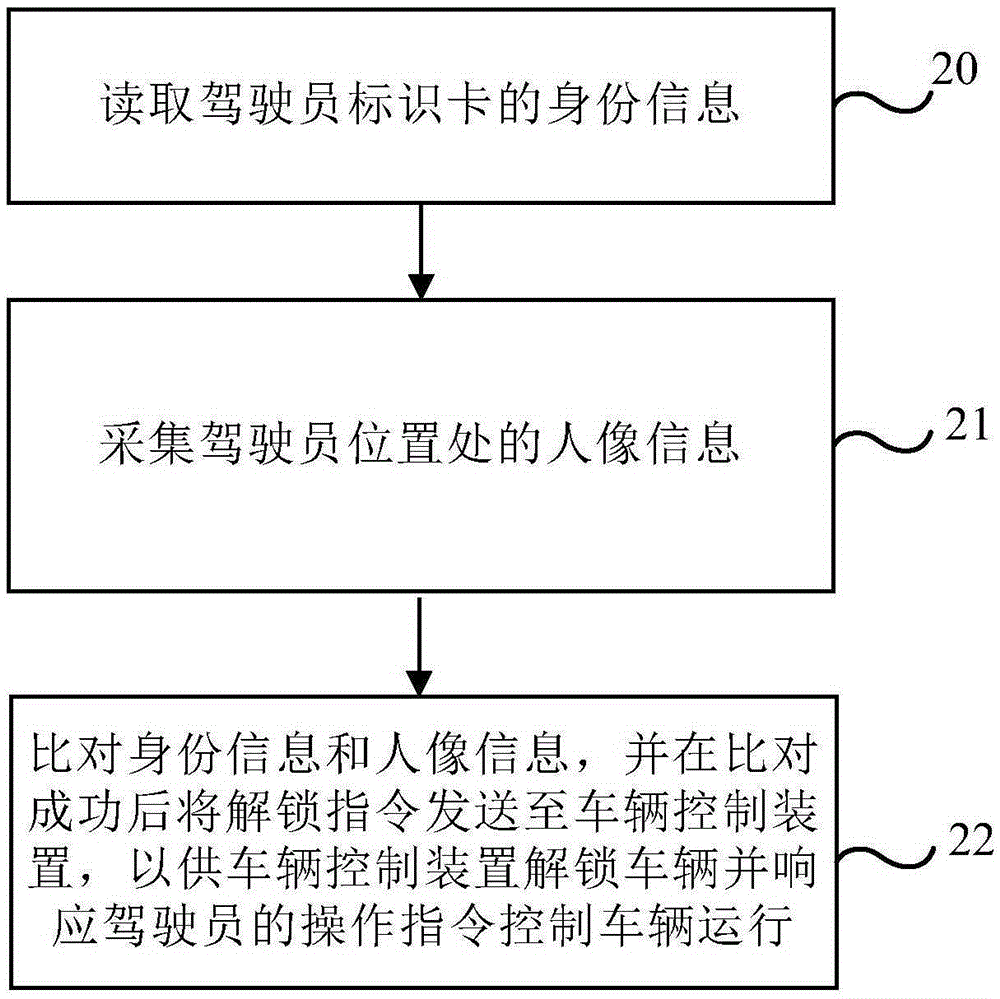
Driver identity verification system and method
InactiveCN105320863AAccurate verificationEnsure safetyDigital data authenticationElectricityVerification system
Embodiments of the present invention disclose a driver identity verification system and method, and can overcome the defect that an existing vehicle management technology cannot accurately and timely verify the identity of a driver and determine whether the driver is the vehicle owner or a legally authorizer. The system comprises: a document reading apparatus which is electrically connected to an identity verification apparatus and is used for reading identity information of a driver by a driver identification card inserted into the document reading apparatus and transmitting the identity information to the identity verification apparatus; a camera which is arranged in a cockpit of a vehicle, is electrically connected to the identity verification apparatus and is used for acquiring personal image information at the position of the driver according to an instruction of the identity verification apparatus and transmitting the personal image information to the identity verification apparatus; and the identity verification apparatus which is electrically connected to a vehicle control apparatus and is used for comparing the identity information with the personal image information and sending an unlocking instruction to the vehicle control apparatus when the comparison is successful, so that the vehicle control apparatus unlocks the vehicle and responds to an operation instruction of the driver to control the vehicle operation.
Owner:宝鸡市公安局交通警察支队
System and Device for Consolidating SIM, Personal Token, and Associated Applications
InactiveUS20110117966A1Increase dependenceFacilitating secure and convenient electronic transactionsPayment architectureSubstation equipmentPayment transactionFinancial transaction
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com