Patents
Literature
809results about How to "Guaranteed legality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Firmware upgrading and encapsulating method and device based on digital signing
InactiveCN101436141AIntegrity guaranteedPrevent tamperingProgram loading/initiatingProgram/content distribution protectionDigital signatureXML
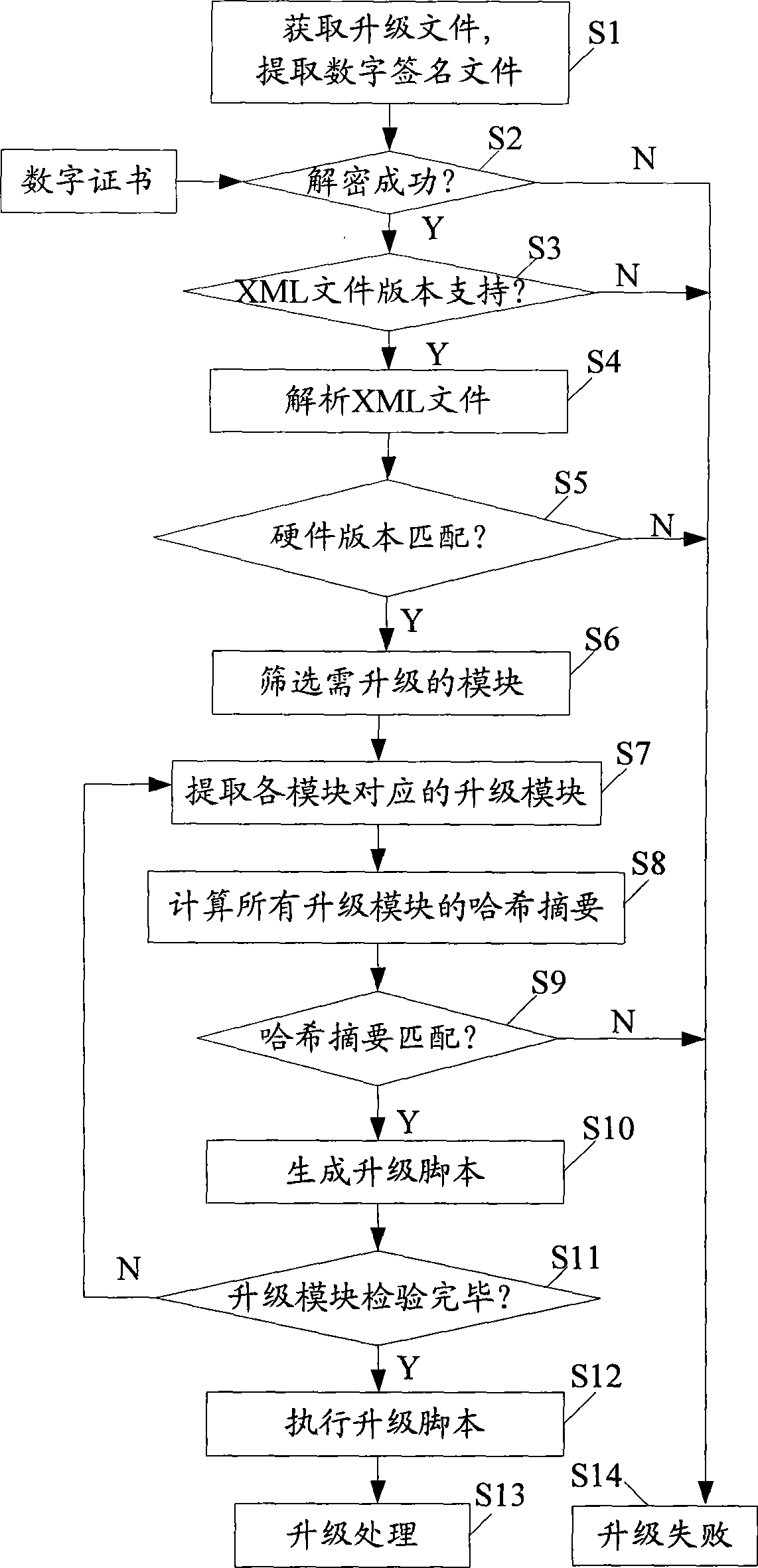
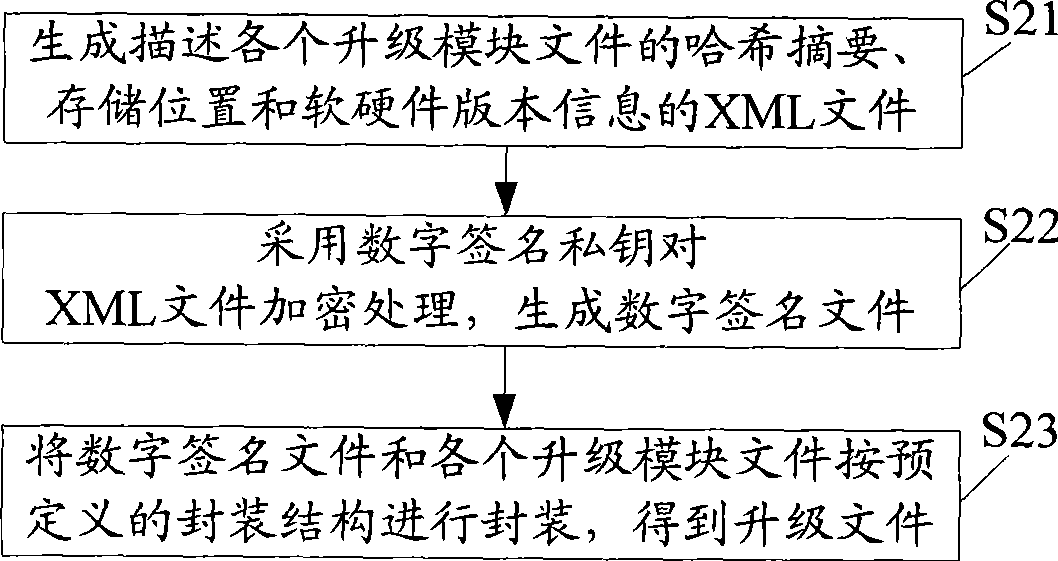
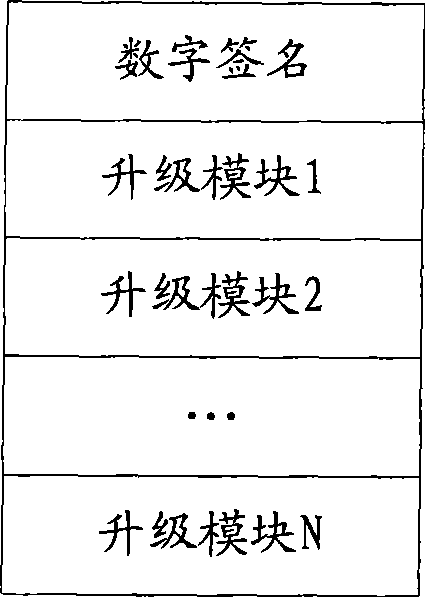
The invention discloses a firmware upgrading method based on digital signatures, and a device thereof, wherein the upgrading method comprises the following steps: encapsulation is performed according to a predefined encapsulation structure so as to generate an upgrading file based on a digital signature; a product needing firmware upgrading obtains the upgrading file; a digital signature file is extracted from the upgrading file and decrypted, so as to obtain an XML file; the XML file is analyzed so as to screen out upgrading module files needing to be upgraded; the legitimacy and integrity of every upgrading module file needing to be upgraded are verified respectively, so as to generate an upgrading script for upgrading all the upgrading module files which pass verification; and the upgrading script is executed so as to upgrade the firmware. The invention discloses a firmware encapsulating method based on digital signatures, and a device thereof. The invention verifies the integrity and legitimacy of every upgrading module file in the upgrading file through the digital signature file, and generates the upgrading script to finish upgrading firmware, thereby improving the security and convenience of firmware upgrading.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
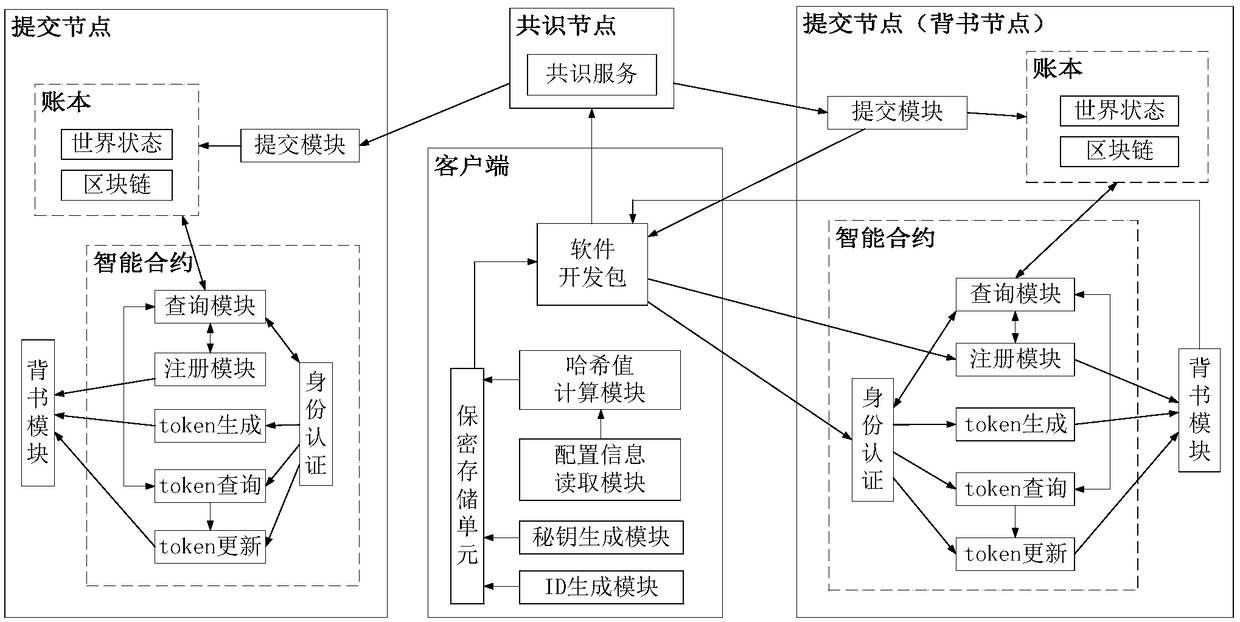
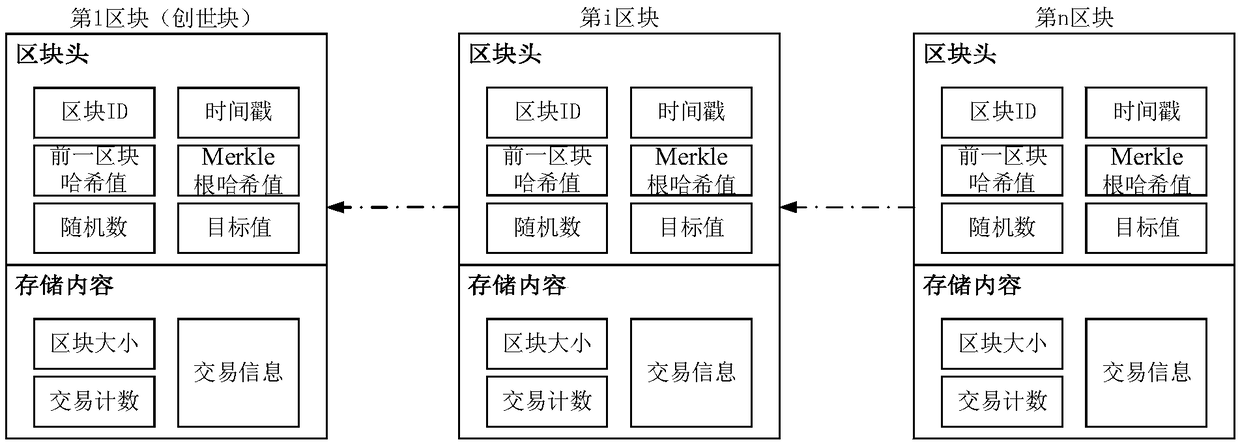
Device networking authentication method based on blockchain
ActiveCN108833081AGuaranteed legalityWill not affect operationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTimestampSmart contract
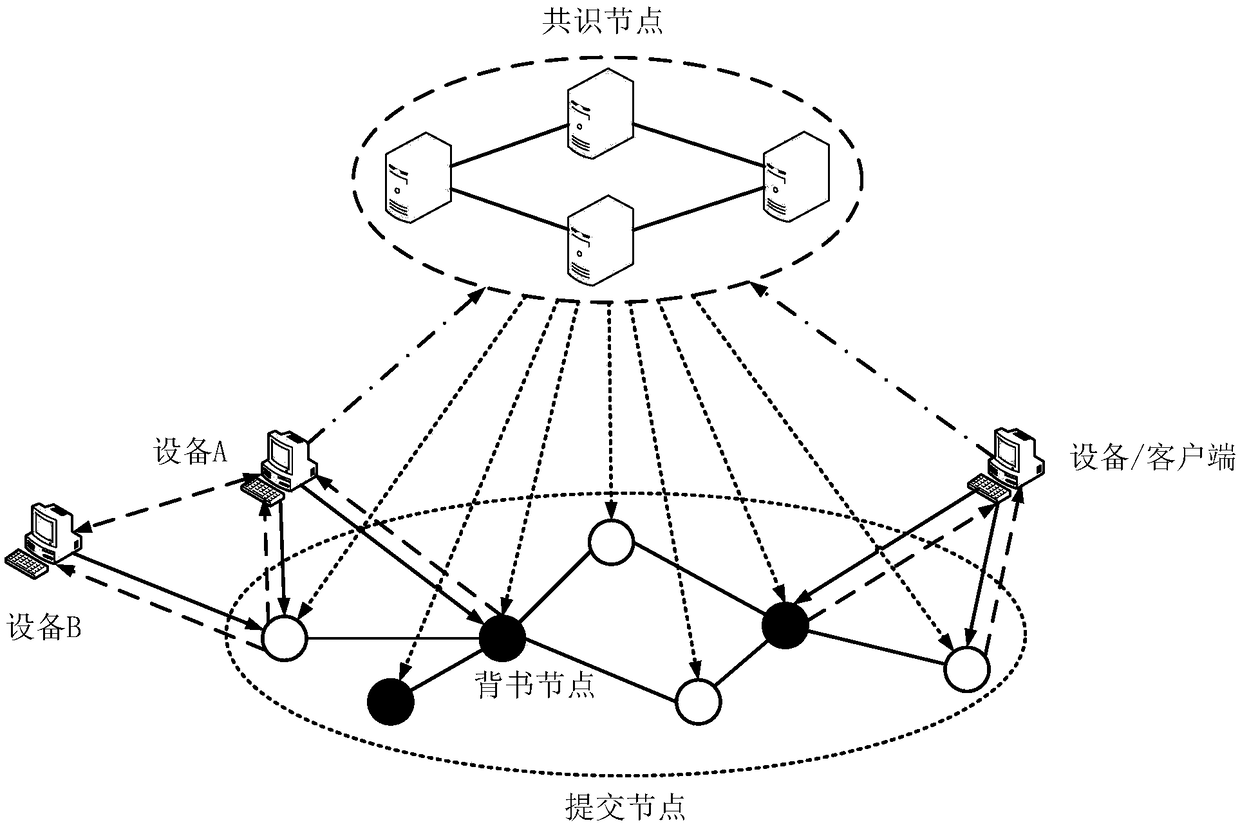
The invention discloses a device networking authentication method based on a blockchain for solving the single point failure problem existing in the current networking authentication method. The technical scheme is to deploy a blockchain network comprising a client, a submission node and a consensus node. By means of the non-tampering property of the blockchain, a device firstly registers on the blockchain before accessing the network, when the device A needs to access the network, the device sends a networking request of a device B that has accessed to the network, the device B compares the information of the device A in the networking request with the information of the device A stored in the blockchain to judge whether the identity of the device A is legal, a smart contract issues a token to the device A, a timestamp in the token ensures that the device A is valid within a certain period of time, and after the token expires, the device A needs to pass the identity authentication toaccess the network again. By adoption of the device networking authentication method disclosed by the invention, the single point failure problem existing in the traditional networking authenticationmethod can be avoided, the legality of the identity of the device is ensured, and the security of the network is improved.
Owner:NAT UNIV OF DEFENSE TECH
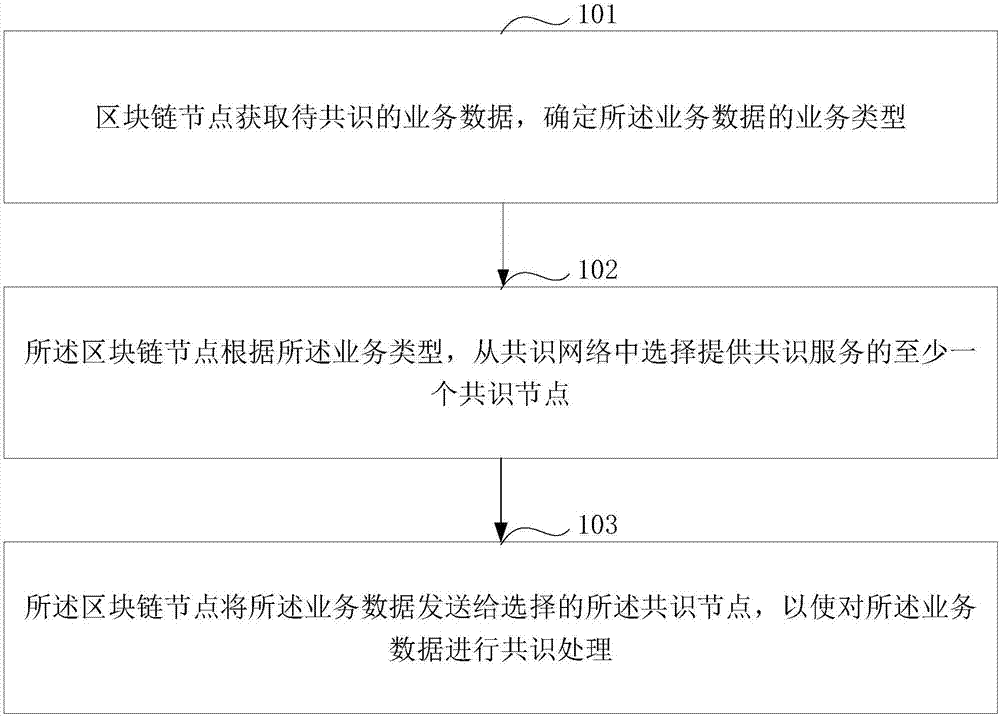
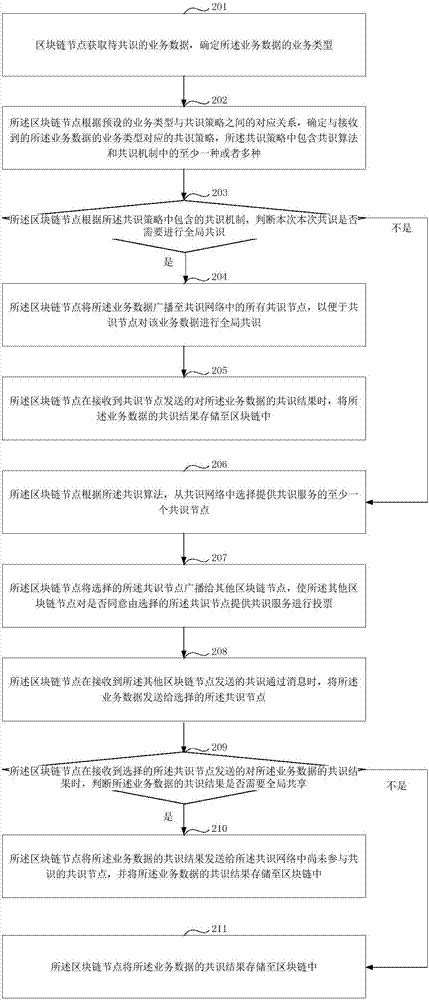
Block chain consensus method and device
ActiveCN107450981AImprove processing efficiencyGuaranteed legalityFinanceResource allocationProcess efficiencyBusiness data
The invention discloses a block chain consensus method and device. The method comprises the steps of obtaining business data to be subjected to consensus processing by a block chain node and determining a business type of the business data; according to the business type, selecting at least one consensus node which provides a consensus service from a consensus network; and sending the business data to the selected consensus node, thereby performing the consensus processing on the business data. For the data to be subjected to the consensus processing, the consensus node providing the consensus service can be selected according to the business type of the business data, and the business data is subjected to the consensus processing, so that for different businesses, part of the consensus nodes are selected from the consensus network to perform the consensus processing on the businesses; and therefore, the problem of excessively long consensus processing time caused by excessive nodes participating in the consensus processing can be avoided, the consensus processing time can be shortened, the legality of a consensus processing result can be ensured, and the business data processing efficiency of a block chain network is effectively improved.
Owner:ADVANCED NEW TECH CO LTD
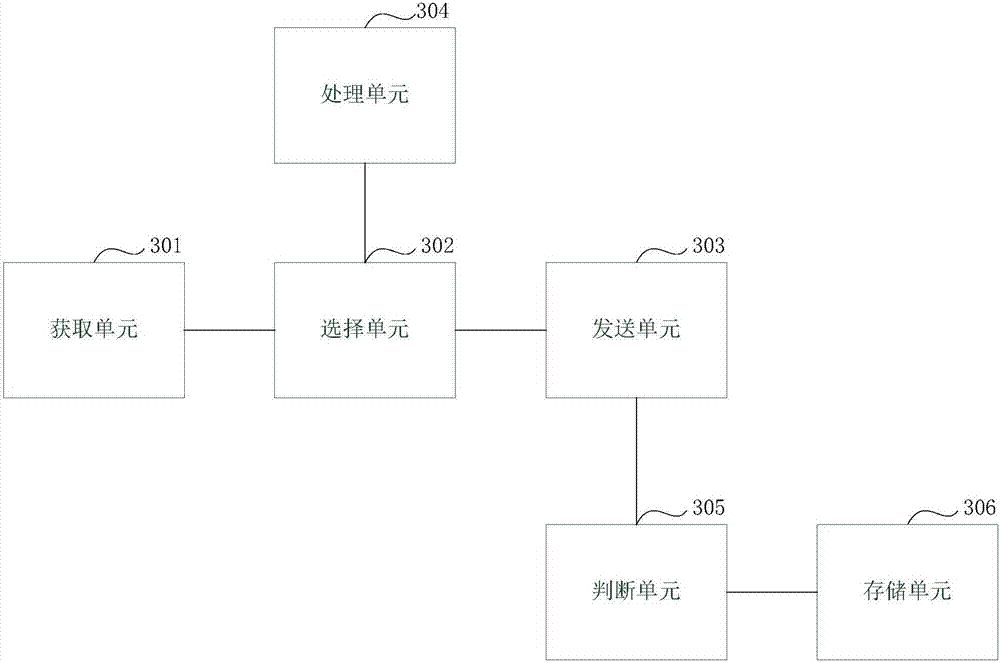
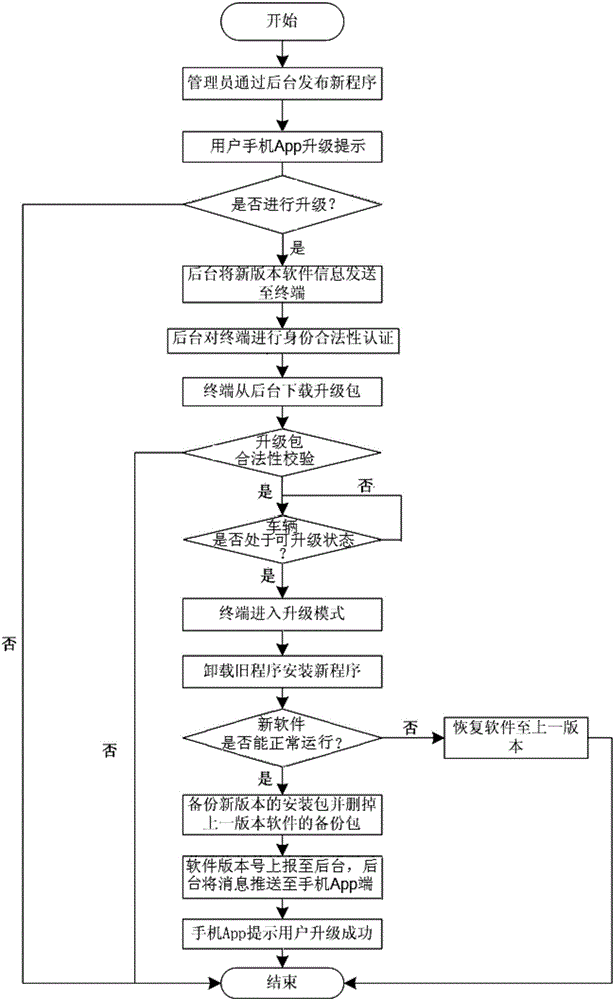
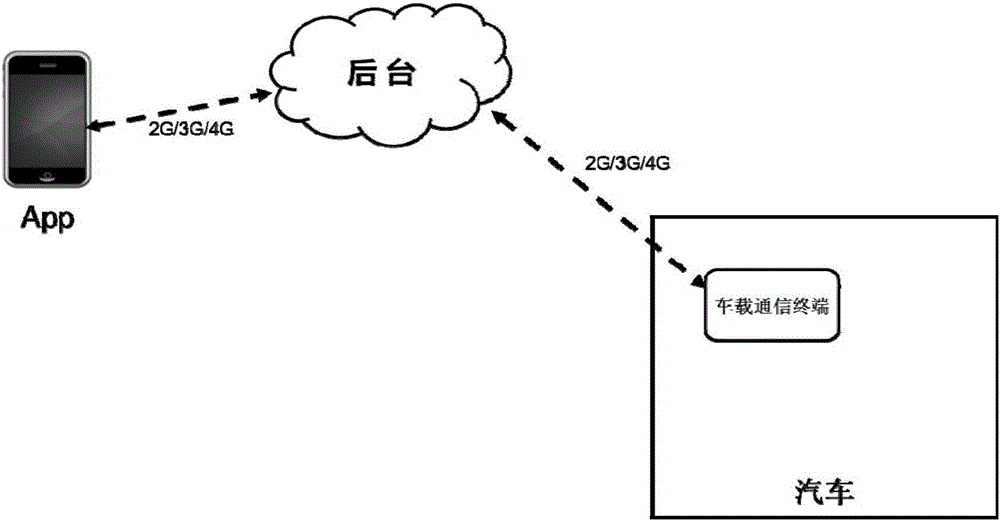
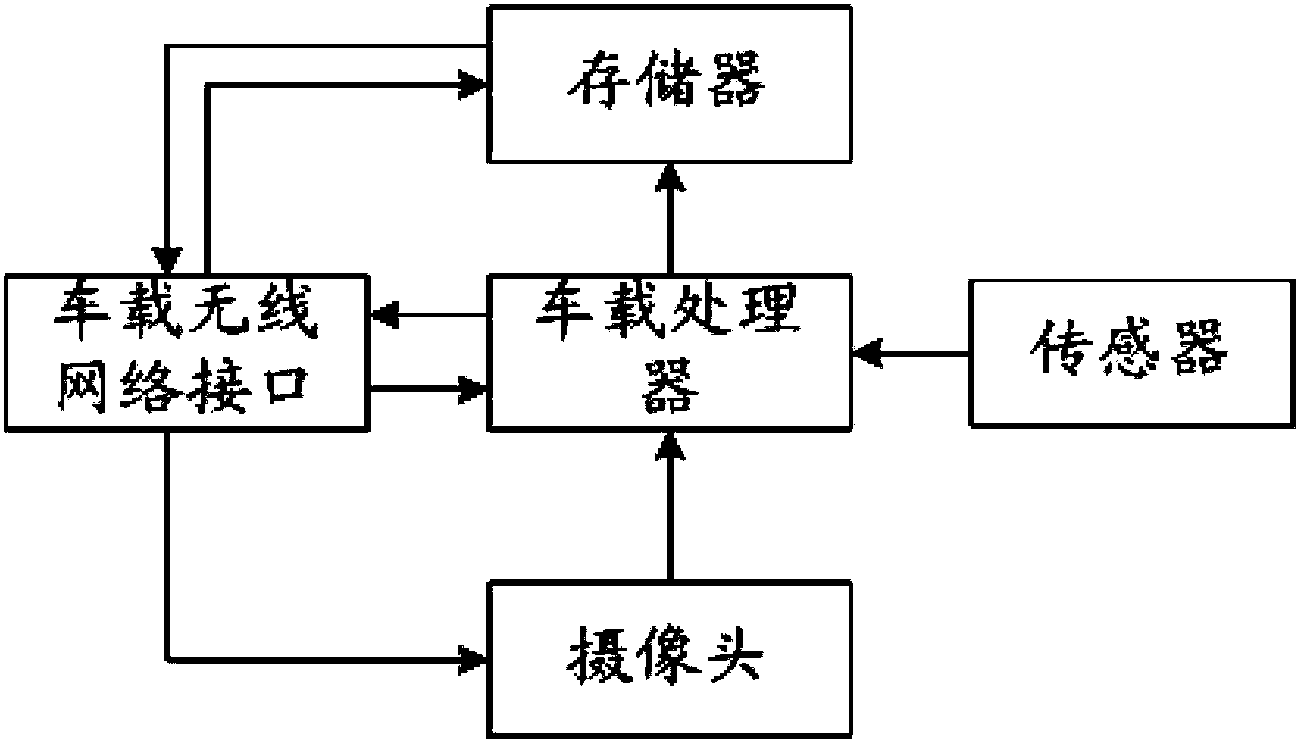
Remote upgrading method for vehicle-mounted communication terminal
InactiveCN105978921AImprove safety and reliabilityInformation transparencySoftware maintainance/managementTransmissionMobile phoneSoftware
The invention relates to a remote upgrading method for a vehicle-mounted communication terminal. The method comprises the following steps that 1, a background server issues a new version of a terminal; 2, the background server sends an upgrading inform to a mobile phone App end; 3, the mobile phone App end receives an upgrading selection sent by a user; 4, the background server sends new version software information to the terminal; 5 the background server authenticates the identity legality of the terminal; 6, the terminal downloads an upgrading patch; 7,upgrading patch legality and integrity are checked; 8, whether a vehicle has the upgrading condition or not is judged; 9, the terminal is remotely upgraded; 10, a new version program is installed for the terminal; 11, the terminal judges whether operation of new version software is normal or not is judged; 12, an original version program back-up patch is deleted, and the new version program is backed up; 13, the number of the new version software is reported to the background server; 14, the mobile phone App end prompts the user to upgrade information. The safety problems in the upgrading process in the prior art are solved.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
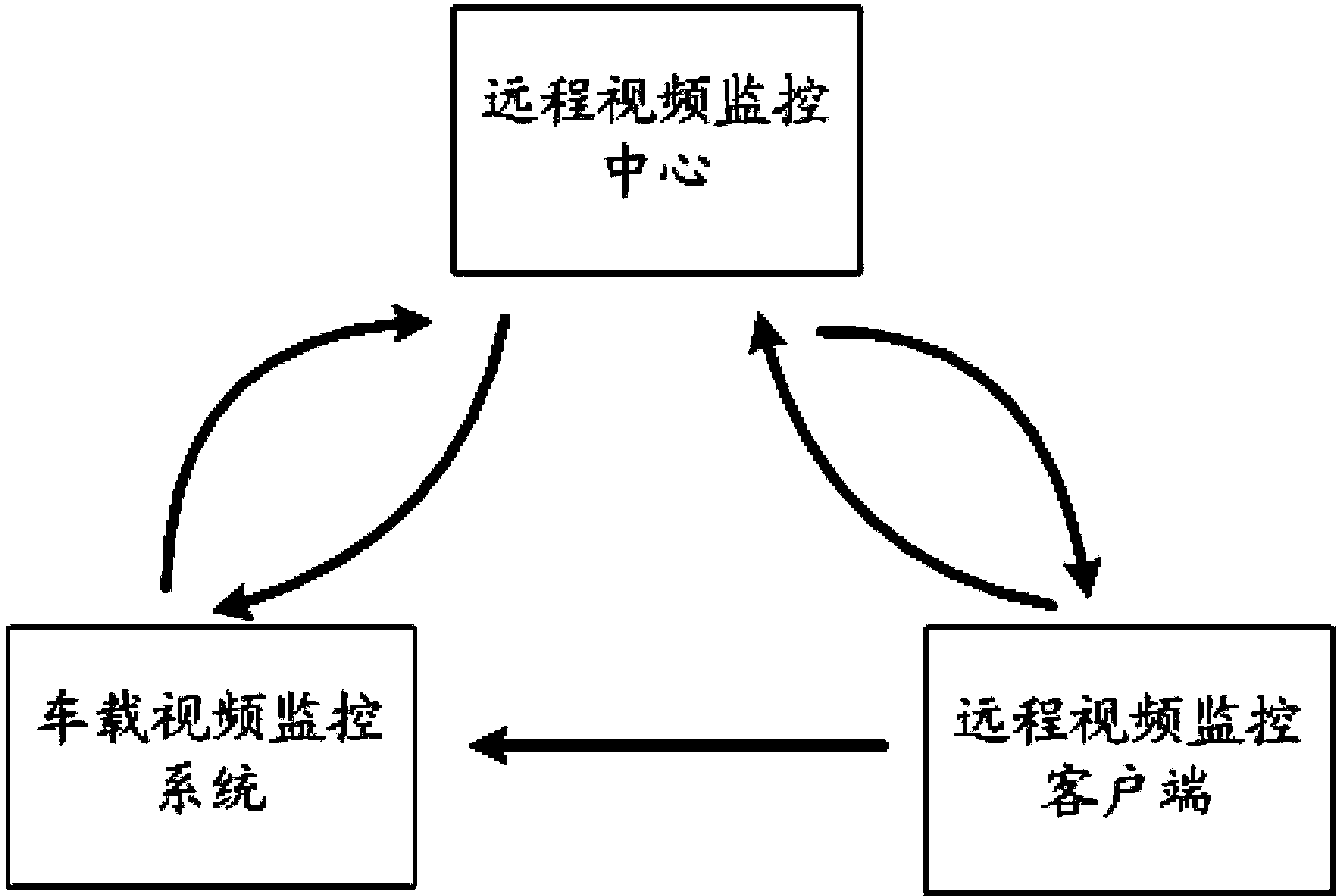
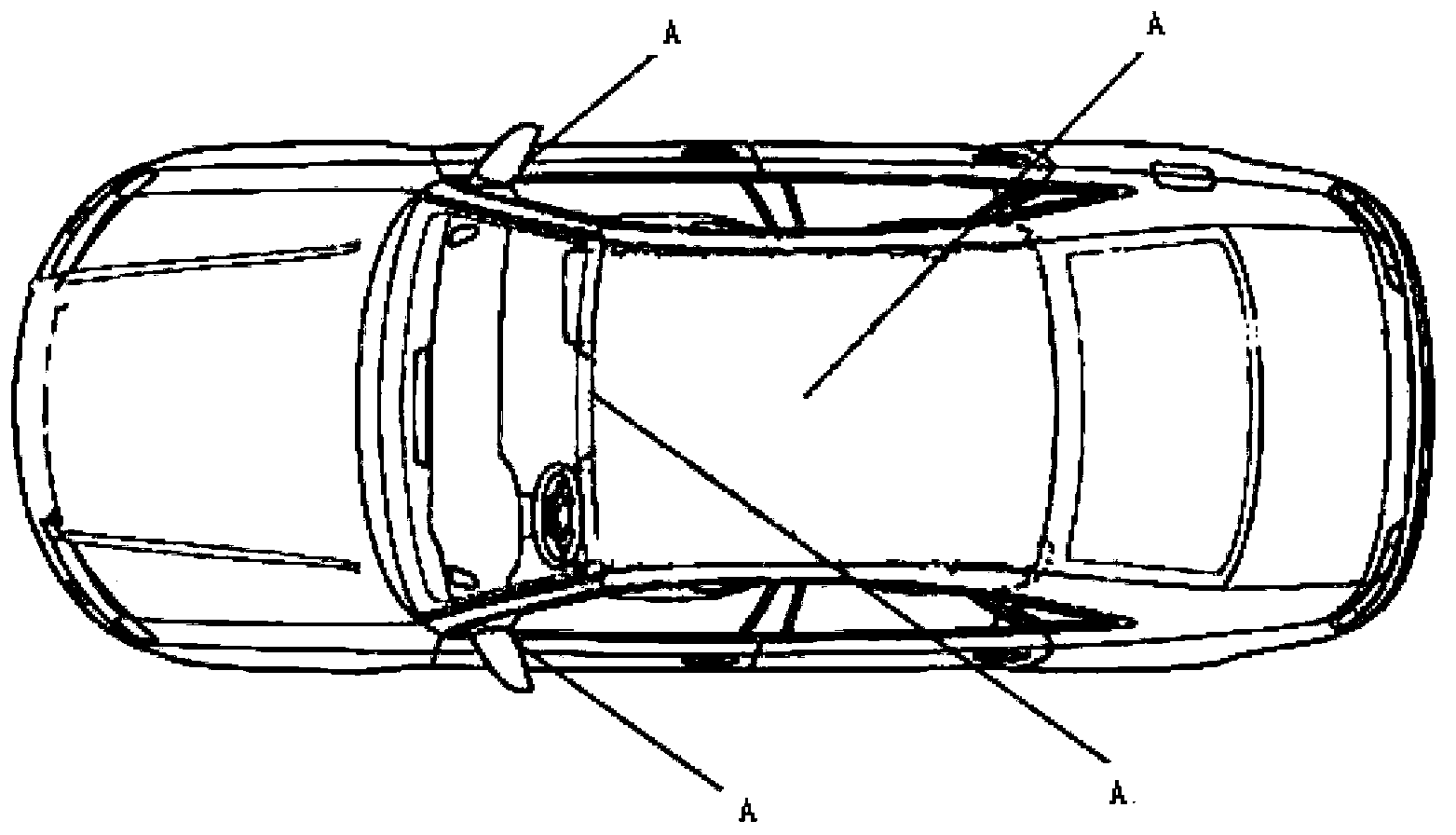
Remote video monitoring system for vehicle and vehicle remote video monitoring method
InactiveCN103395404AGuaranteed legalityAnti-theft devicesClosed circuit television systemsVideo monitoringClient-side
The invention discloses a remote video monitoring system for a vehicle. The remote video monitoring system for the vehicle comprises a vehicle-mounted video monitoring system, a remote video monitoring client side and a remote video monitoring center for the vehicle-mounted video monitoring system and the remote video monitoring client side to conduct data interaction. The vehicle-mounted video monitoring system receives environmental images inside and outside the vehicle, sends access addresses of the images to the remote video monitoring client side through the remote video monitoring center, and achieves real-time monitoring. In addition, under the situation of sensing the unusual conditions, the environmental images are stored, and the storage addresses of the environmental images are sent to the remote video monitoring center so as to achieve the alarm function. In addition, the remote video monitoring client side can send an angle adjustment command of a camera, and the angle of the camera is adjusted as needed. The invention further discloses a vehicle remote video monitoring method by utilizing the remote video monitoring system for the vehicle, under the situation that the sight of a user is far from the vehicle, the functions of real-time monitoring and alarm are achieved, and safety of the vehicle is improved.
Owner:ZHEJIANG UNIV
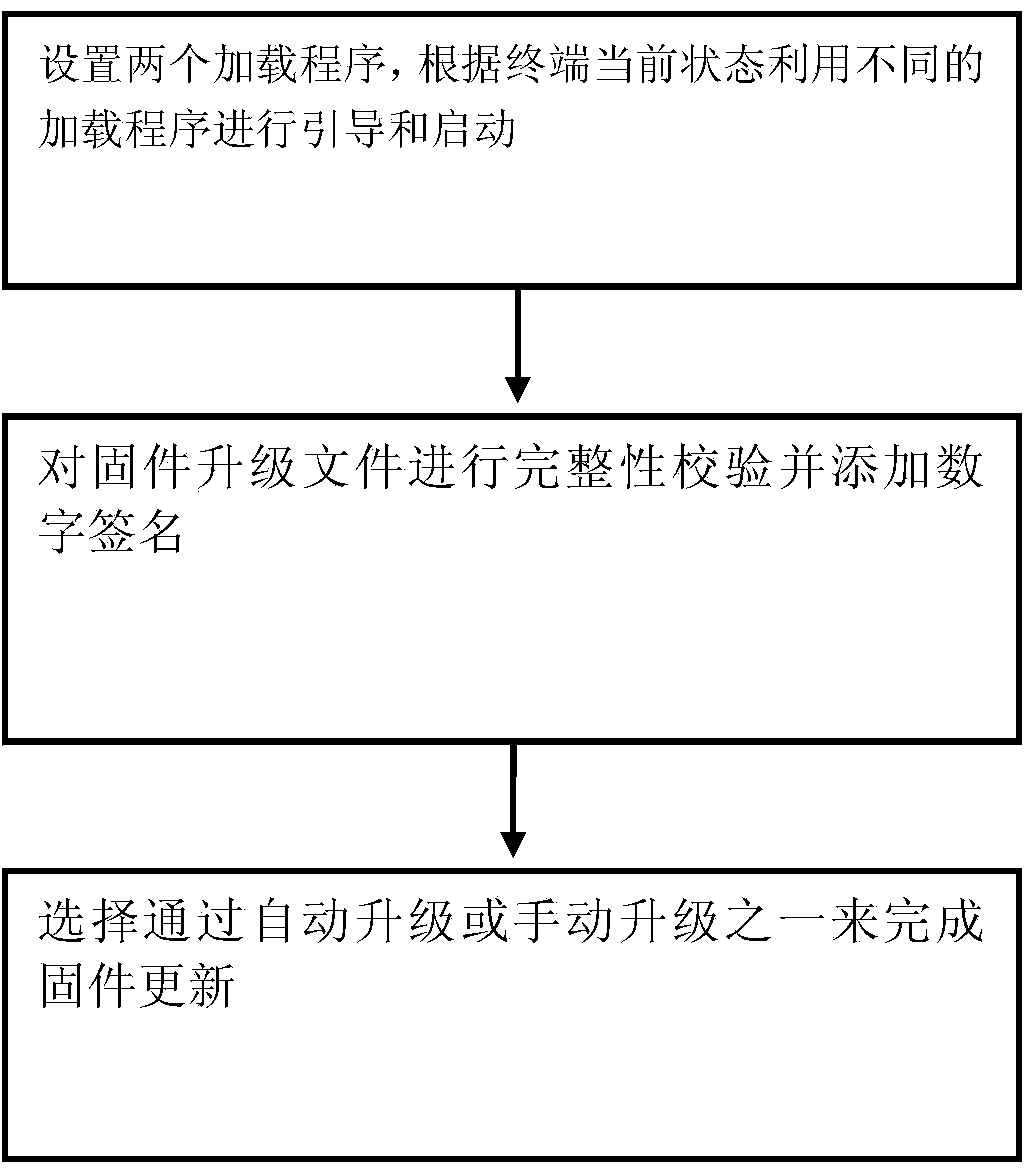
Intelligent display terminal firmware updating method
ActiveCN104166565ALow failure rateGuaranteed correctnessUser identity/authority verificationComputer security arrangementsFailure rateDigital signature
The invention provides an intelligent display terminal firmware updating method. The firmware updating method includes the steps that two loading programs are set, and a terminal is guided and started through the different loading programs according to the current state of the terminal; the integrity of updating files is checked; the updating files are added with digital signatures; automatic updating and manual updating are selected alternatively to finish updating. According to the intelligent display terminal firmware updating method, the failure rate of the intelligent display terminal is reduced, and correctness of the updating files and security of updating are ensured.
Owner:成都瑞博慧窗信息技术有限公司
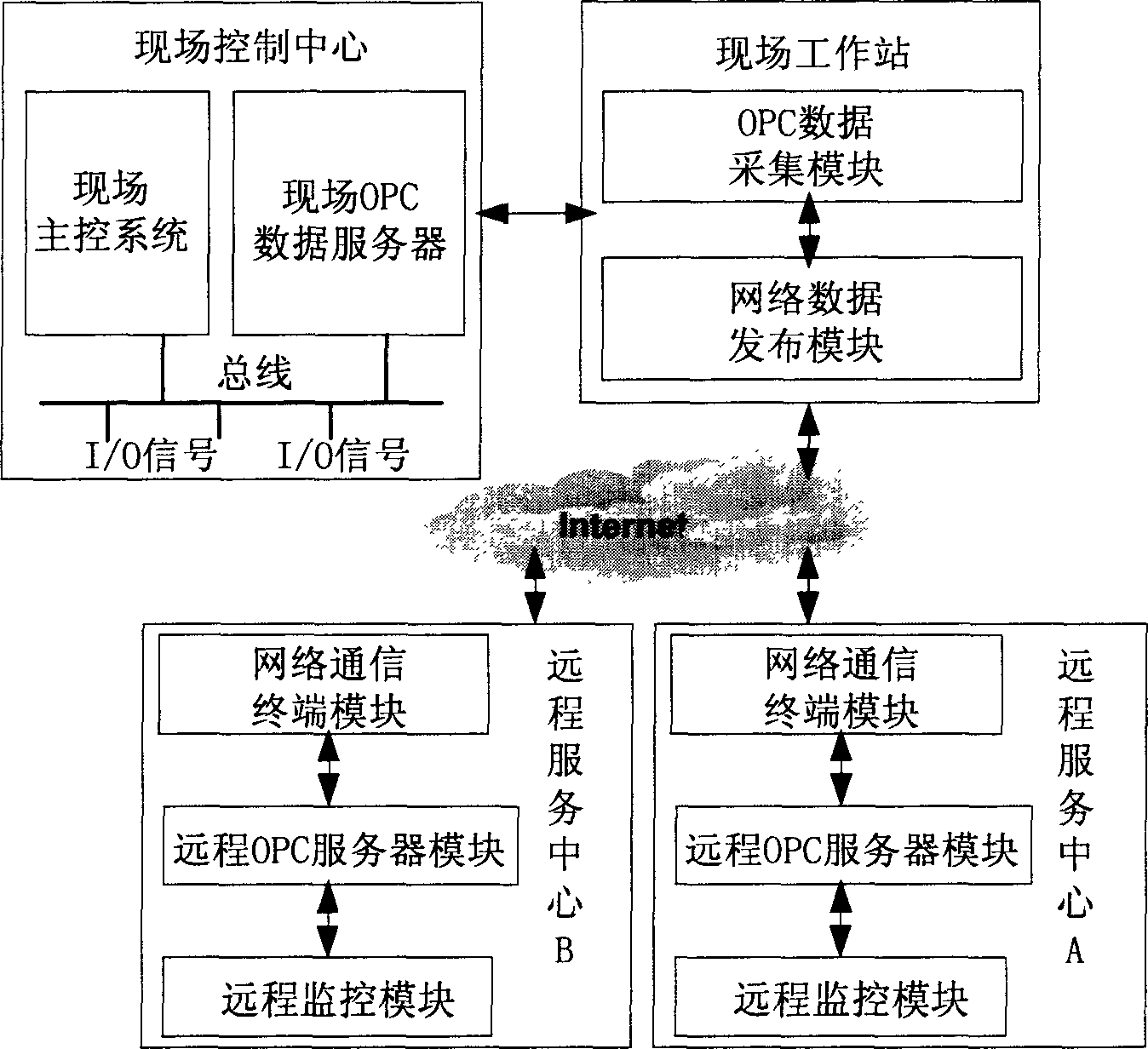
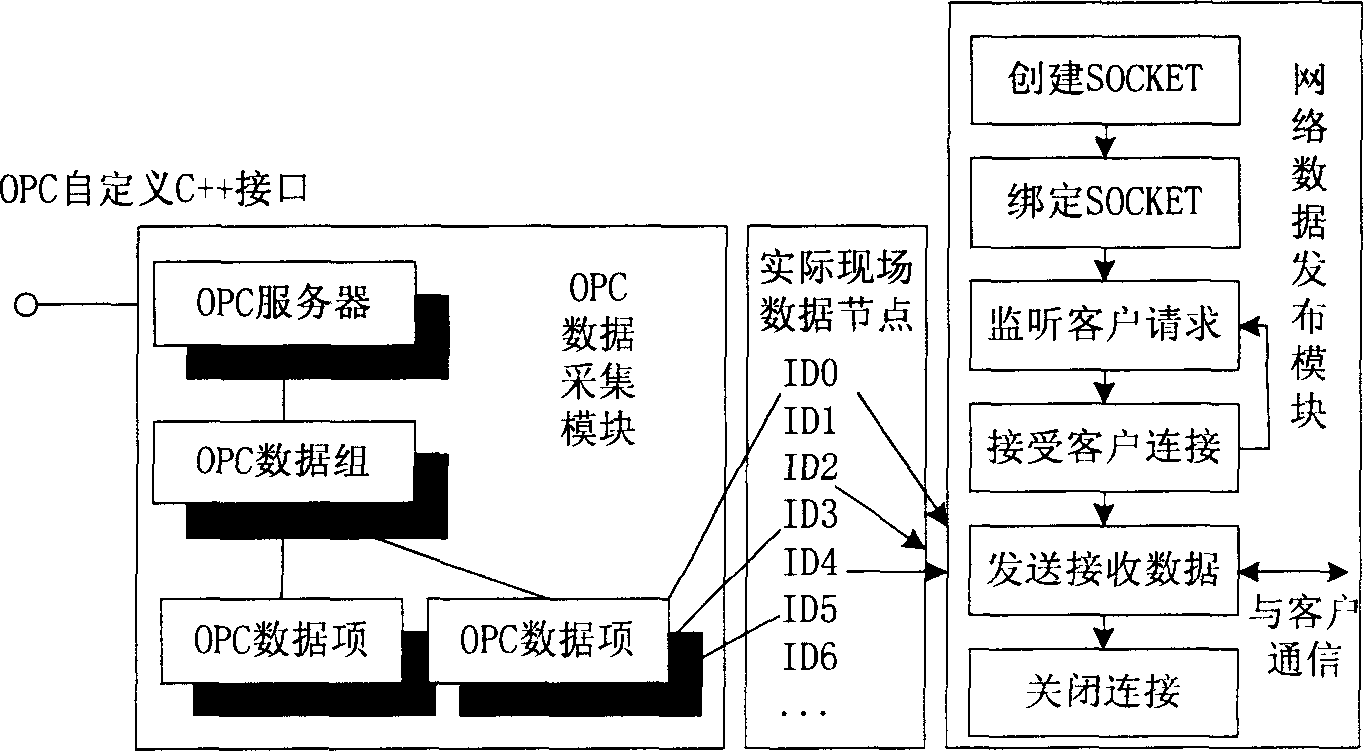
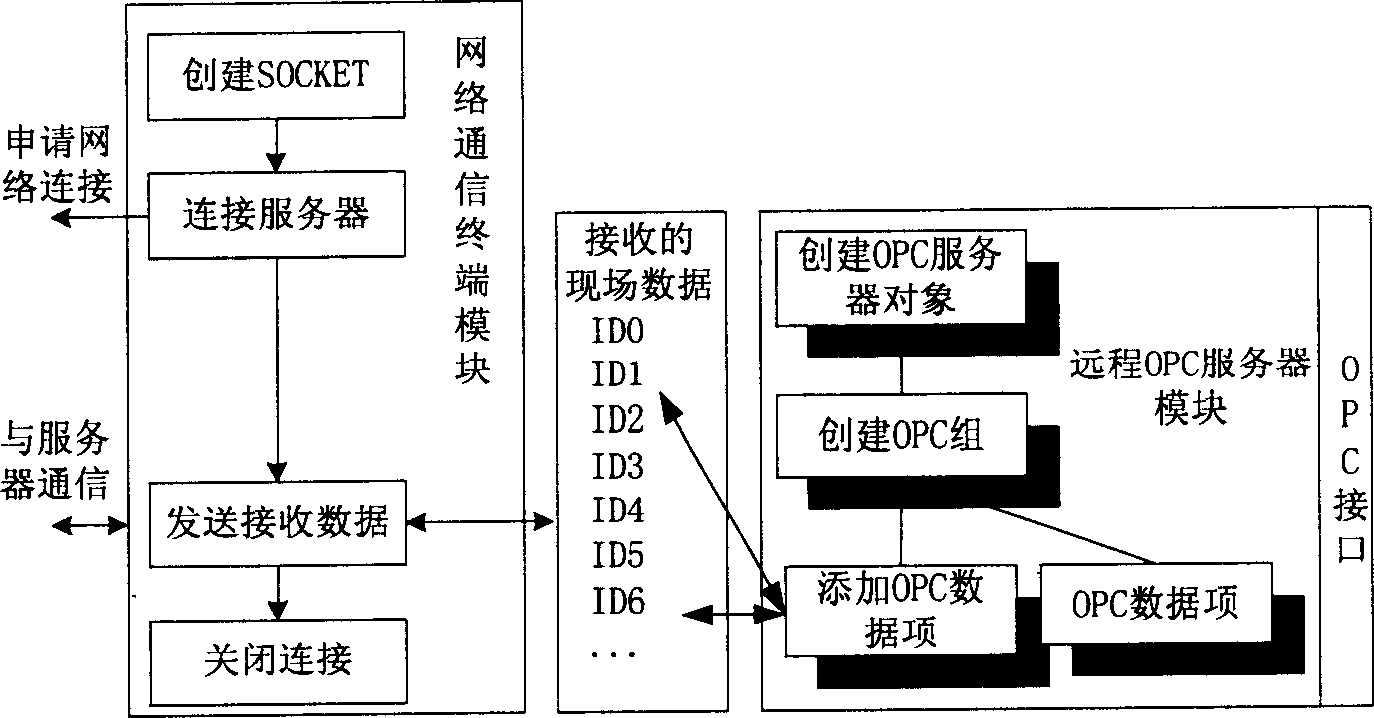
System accorded with OPC standard for monitoring remote configuration
InactiveCN1798141ATroubleshoot Remote TroubleshootingSolve problemsData switching networksTotal factory controlRemote controlData acquisition
The system includes a field working station and a remote service center. The field working station runs the OPC data collection module and the network data releasing module conforming to TCP / IP protocol by using the OPC data collection and network data releasing application program, and is connected to the field control center through OPC interface. The remote service center runs the network terminal module conforming to TCP / IP protocol, the remote OPC server module and the remote control module supporting OPC interface by using network terminal application program and the remote OPC service application program. The network communication terminal module receives the field data released by the network data releasing module, and then releases the received data to the remote OPC service module by which the data is transmitted to the remote monitoring module.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
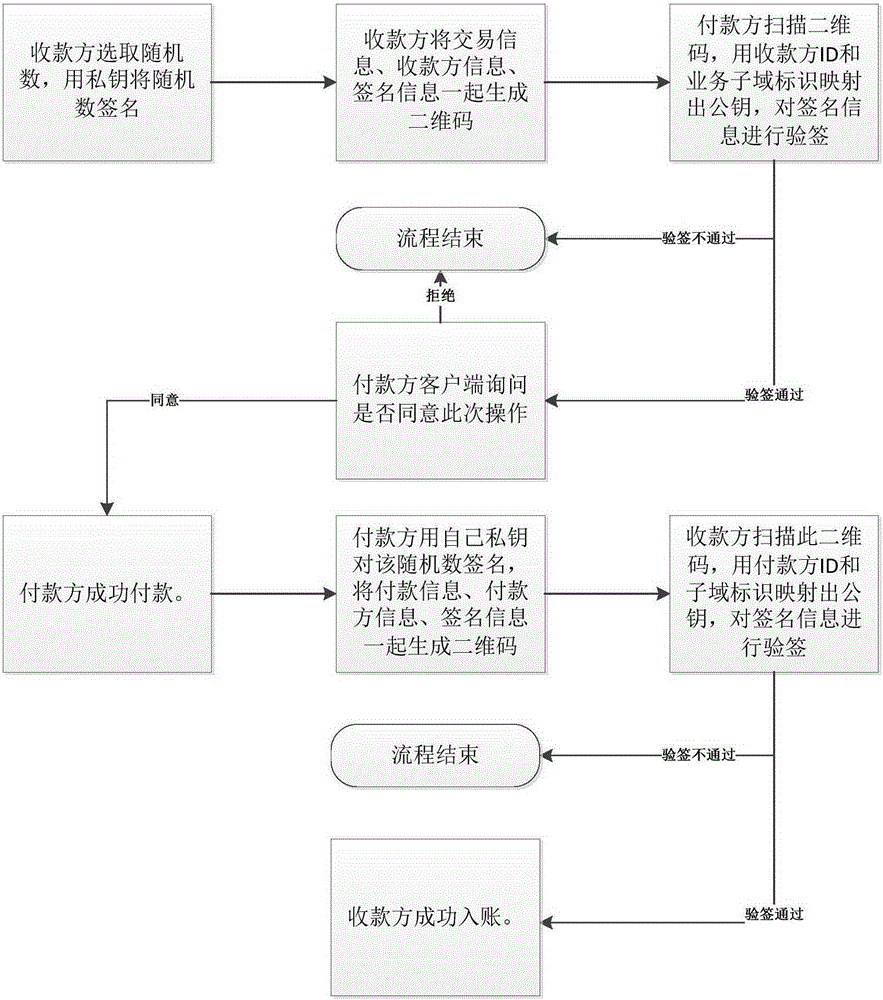
Novel offline payment method
InactiveCN105205664AConvenient paymentPrevent illegal tamperingPayment architecturePaymentMobile device
The invention discloses a novel offline payment method. The method comprises the steps that account numbers of an accountee party and a receiving party serve as IDs, and a corresponding public key and private key are mapped according to business sub-domain identifications; a random number is selected from the receiving party, signature is conducted on the random number through the private key, and a two-dimension code is generated; the two-dimension code is scanned through the accountee party, the public key is mapped by means of the receiving party ID and the service sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, the accountee party successfully pays according to transaction information; signature is conducted on the random number by the accountee party through the private key after payment to generate a two-dimension code; the receiving party scans the two-dimension code, the public key is mapped through the accountee party ID and the business sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, posting is successfully conducted on the receiving party. According to the novel offline payment method, payment does not rely on the support of a network any more, payment is achieved on various mobile equipment, and the payment process is greatly facilitated. The two-way authentication process based on the identifications is adopted by the two payment parties, the legality of transactions is fully guaranteed, and illegal manipulation of information and information disguising are prevented.
Owner:CHINA SMARTCITY TECH
Method of controlling network access and its system
ActiveCN1753364AEasy to useNot threatenedData taking preventionUser identity/authority verificationSystem maintenanceClient-side
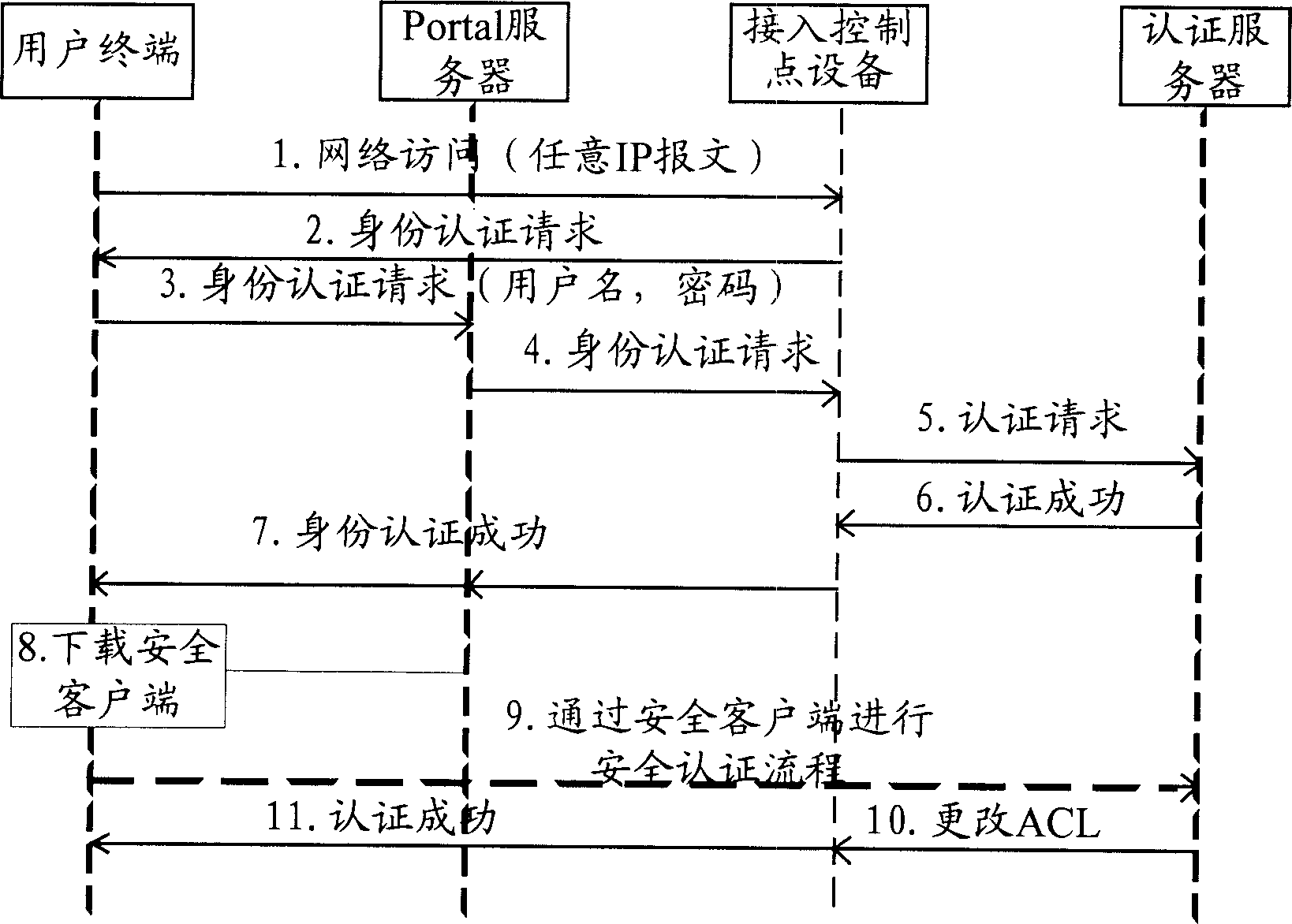
This invention discloses a network access control method and a system including: limiting the access extent of authority to users on-line by the web certification of a portal server to limit it to access the limited network resources only, a user downloads the safety UE by the Web, when the user accesses the protected network resources, the safety UE is used to certificate the safety of the UE and users passing through the safety certification access the protected network resources freely. The system includes: network access devices connected by network, a portal server and an AAA server.
Owner:NEW H3C TECH CO LTD
Identity verification method and system
InactiveCN104021472AProtection against record theftEnsure safetyUser identity/authority verificationProtocol authorisationPaymentElectronic identification
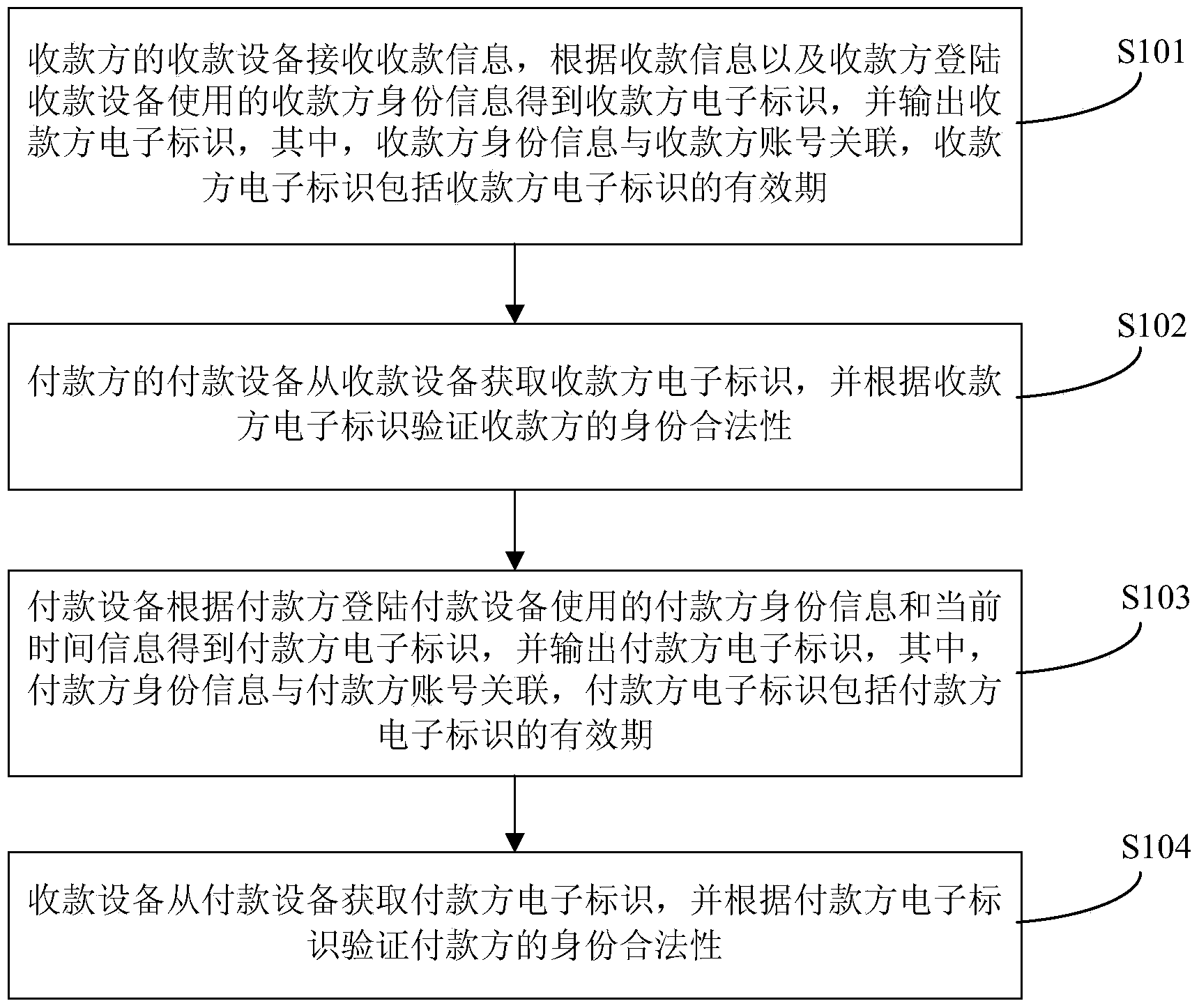
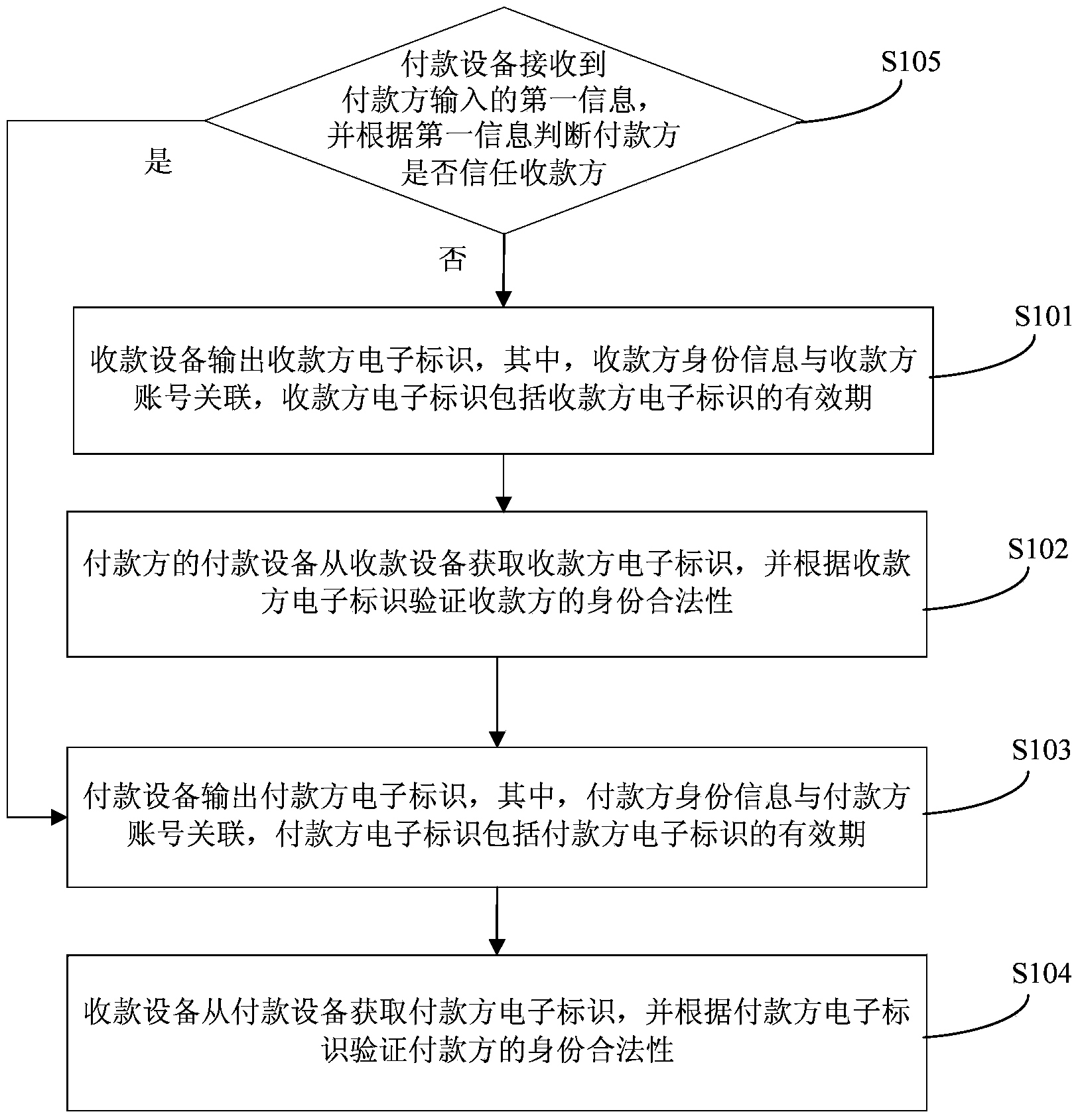
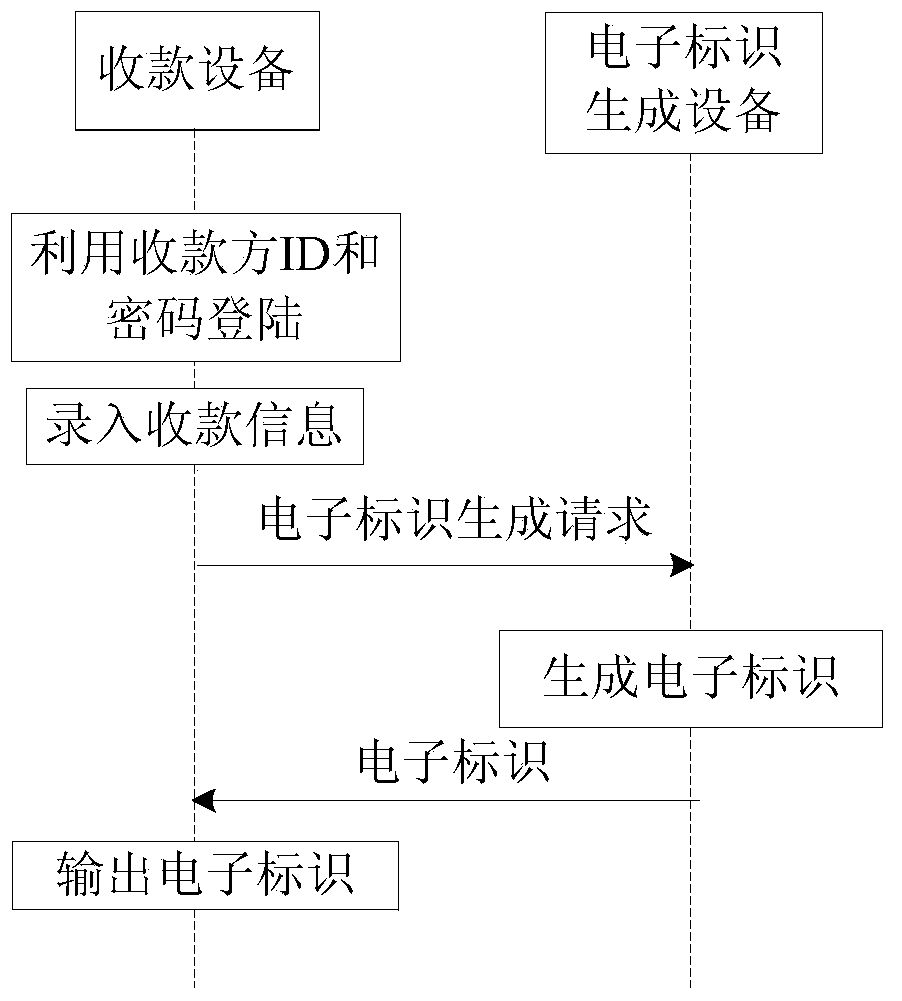
The invention discloses an identity verification method and system. The method comprises: a cash collecting device receiving cash collecting information, according to the cash collecting information and payee identity information, obtaining payee electronic identification for outputting, and associating the payee identity information with a payee account, the payee electronic identification comprising an electronic identification expiration date; a payment device obtaining payee electronic identification, and verifying payee identity validity according to the payee electronic identification; the payment device, according to the payer identity information and current time information, obtaining a payer electronic identification for outputting, and associating the payer identity information with a payment account, the payer electronic identification comprising an electronic identification expiration date; and the cash collecting device obtaining the payer electronic identification, and verifying payer identity validity and according to the payer electronic identification. According to the invention, payee and / or payer identity validity are verified by use of a dynamic electronic identification, such that cheating of a phishing website is prevented; and each identity is bound with an account, and payment can be carried out without inputting a password and exposing an account medium, such that the security of the password and the account medium is ensured.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Distributed remote vibration monitoring and fault diagnosis system of large steam turbine-generator
InactiveCN102086784AQuick installation and layoutImprove accuracyMachines/enginesSafety/regulatory devicesSelf organizing map neural networkWeb service
The invention discloses a distributed remote vibration monitoring and fault diagnosis system of a large steam turbine-generator, comprising a database subsystem in which steam turbine-generator vibration data is stored, a workstation subsystem capable of providing real-time status monitoring, historical data analysis and fault symptom analysis, and a Web server subsystem provided with remote monitoring and fault diagnosing software, wherein, the subsystems are connected with one another by the Ethernet, and are integrated by a Web services technique. A method combining a traditional fault diagnosing technique based on Fourier analysis, a novel independent component analysis feature extraction technique, a Hilbert-yellow time frequency analysis technique, an empirical decomposition algorithm trend analysis technique and a self-organizing map neural network is adopted for monitoring and diagnosing in the system, thus improving the monitoring real time and the accuracy of diagnosis. The system has strong universality and reliability; and the system configuration can be adjusted, thus conveniently realizing distributed remote monitoring and diagnosis based on the internet as a medium.
Owner:ZHEJIANG UNIV
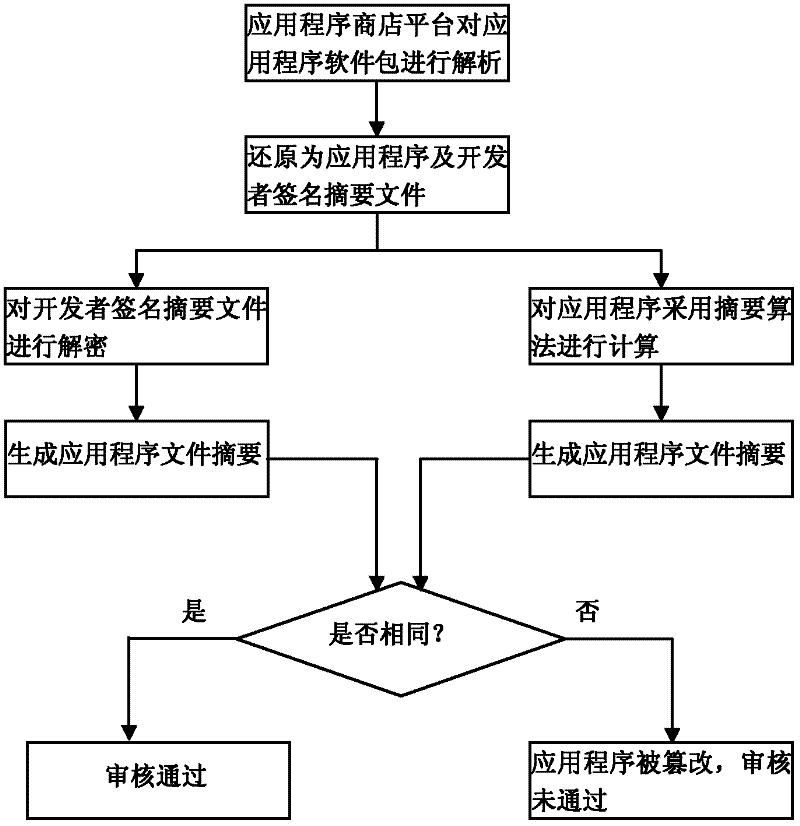
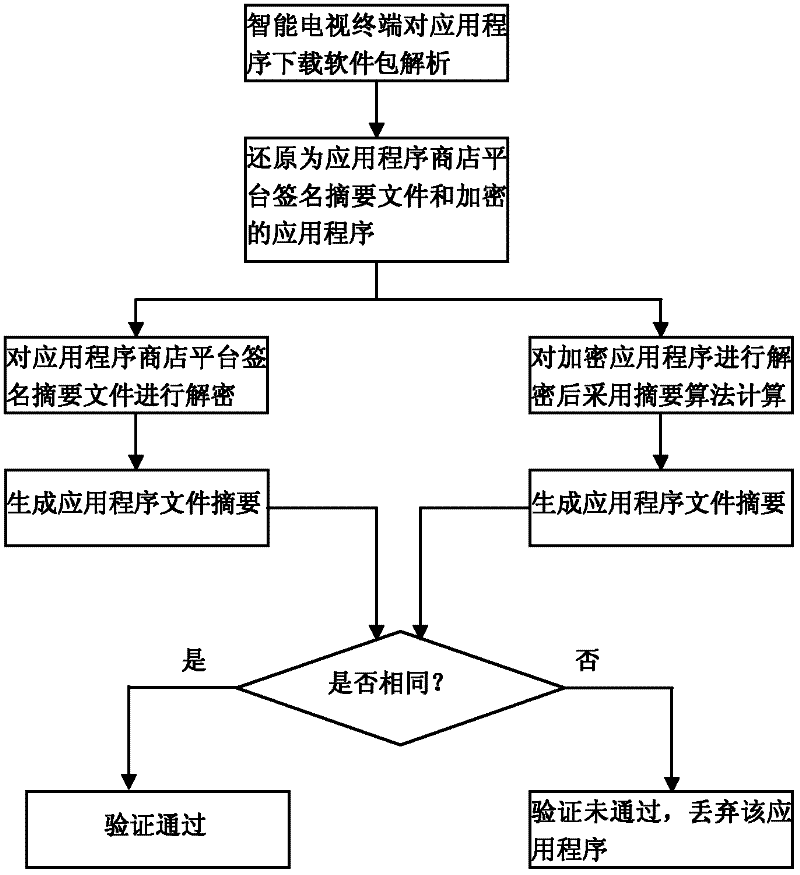
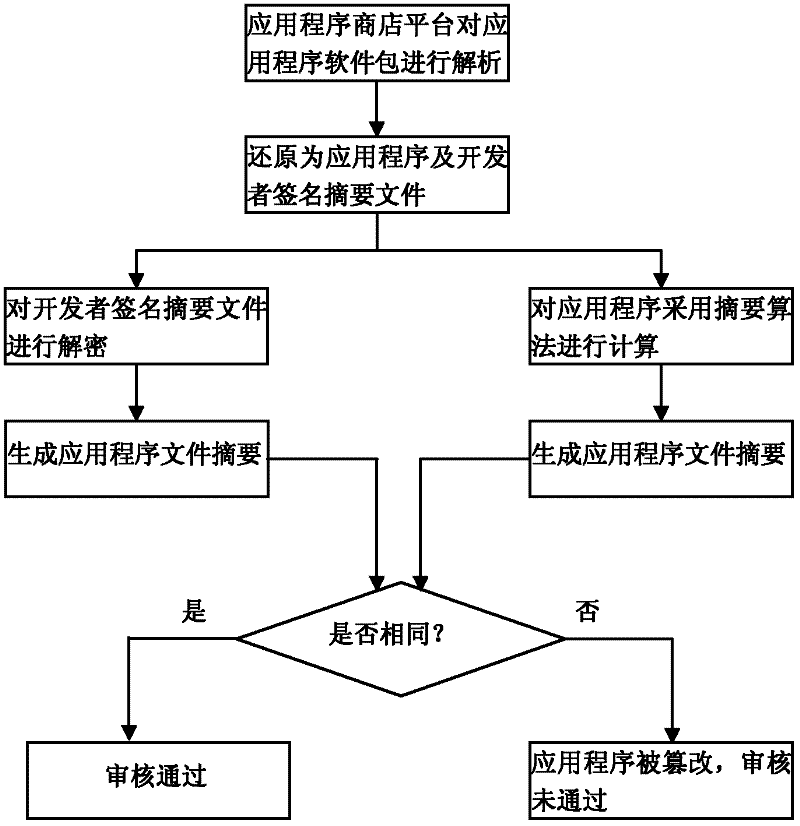
Security control method of intelligent television application program
ActiveCN102546604AGuaranteed legalityEnsure safetyUser identity/authority verificationSelective content distributionNetwork connectionApp store
The invention relates to software security control technology and discloses a security control method of intelligent television application programs, wherein the security of application software is monitored from a plurality of levels, thereby ensuring the security of application software downloaded and installed in an intelligent television terminal. The key points of the technical scheme are summarized as that an application program developer signs for the first time when packing and uploading the application program to an application program store platform; signature of the second time is performed after the application program store platform verifies the application program; the intelligent television terminal hands over a public key of the intelligent television terminal to the platform through a network connection platform, the software is encrypted using the public key at the platform and transmitted to the intelligent television terminal, the intelligent television terminal performs security verification to the application program, and the application program is installed after the verification is accepted. Legitimacy and security of application of the application program is ensured with such method, and such method is applicable for security control of the application software.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
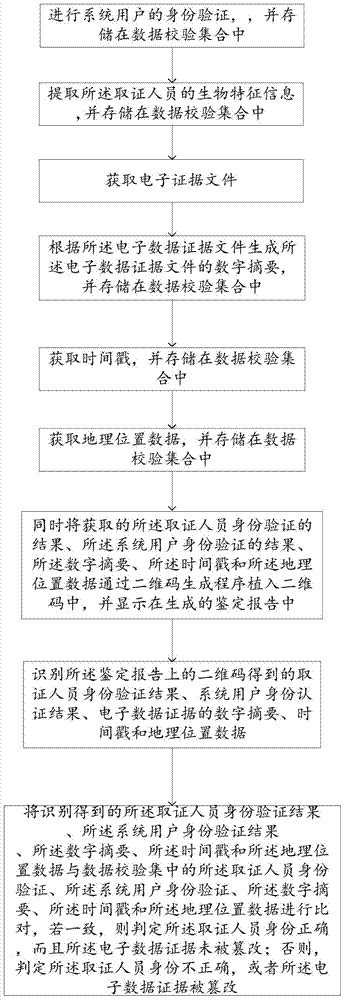
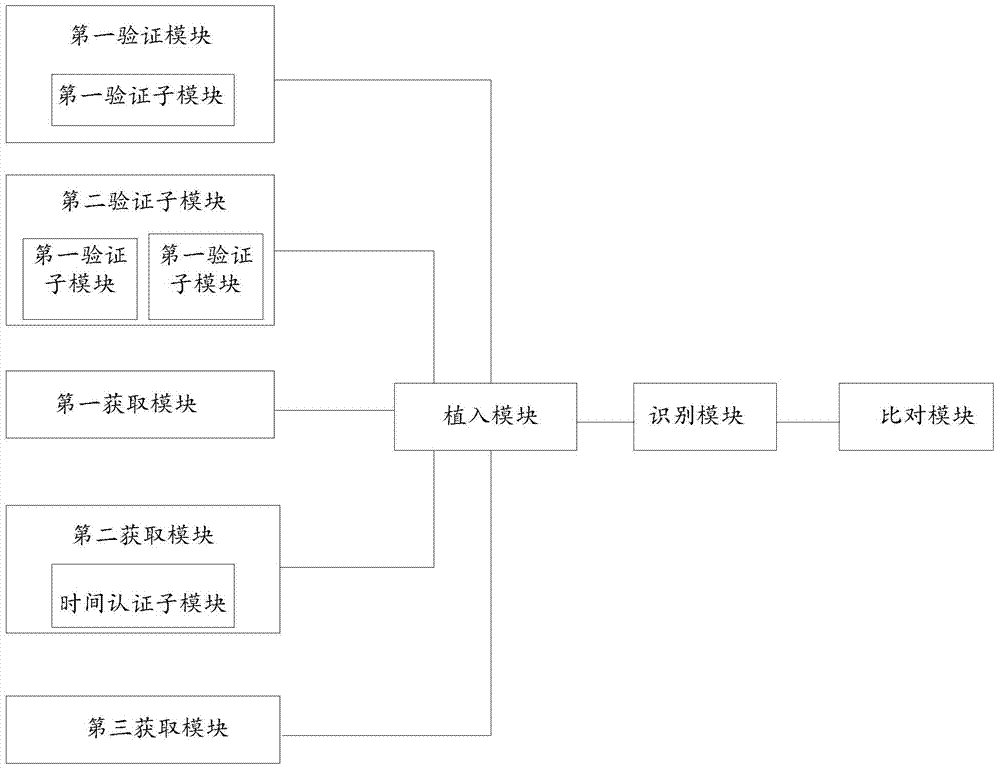
Verification method and system for adoptability of electronic data evidence
InactiveCN103593618AGuaranteed availabilityProof of integrityDigital data protectionDigital data authenticationGeographic siteTimestamp
The invention relates to a verification method and system for adoptability of electronic data evidence. The method includes: authenticating a forensics subject and a system user, embedding authentication results and data such as digital digest, timestamp and geographic location into a QR code through a QR code generating program, displaying the results and data in a generated authentication report, comparing the information recognized through the QR code to corresponding information collected by data verification during authentication to determine whether the information is consistent to the corresponding information or not; if yes, determining that identity of the forensics subject is correct and that the electronic data evidence remains not tampered; if not, determining that identity of the forensics subject is not correct or that the electronic data evidence remains tampered. The completeness of the electronic data evidence is proved by extracting the digital digest from the electronic data evidence; legality of the forensics subject is guaranteed through authentication and verification over the forensics subject; adoptability of the electronic data evidence is guaranteed in terms of both time and space by adding the timestamp and geographic location data information.
Owner:BEIJING REALDATA SCI & TECH
Multi-party authorized APK signature method and system
ActiveCN103944903AIntegrity guaranteedGuaranteed legalityComputer security arrangementsCash registersSignature fileTerminal equipment
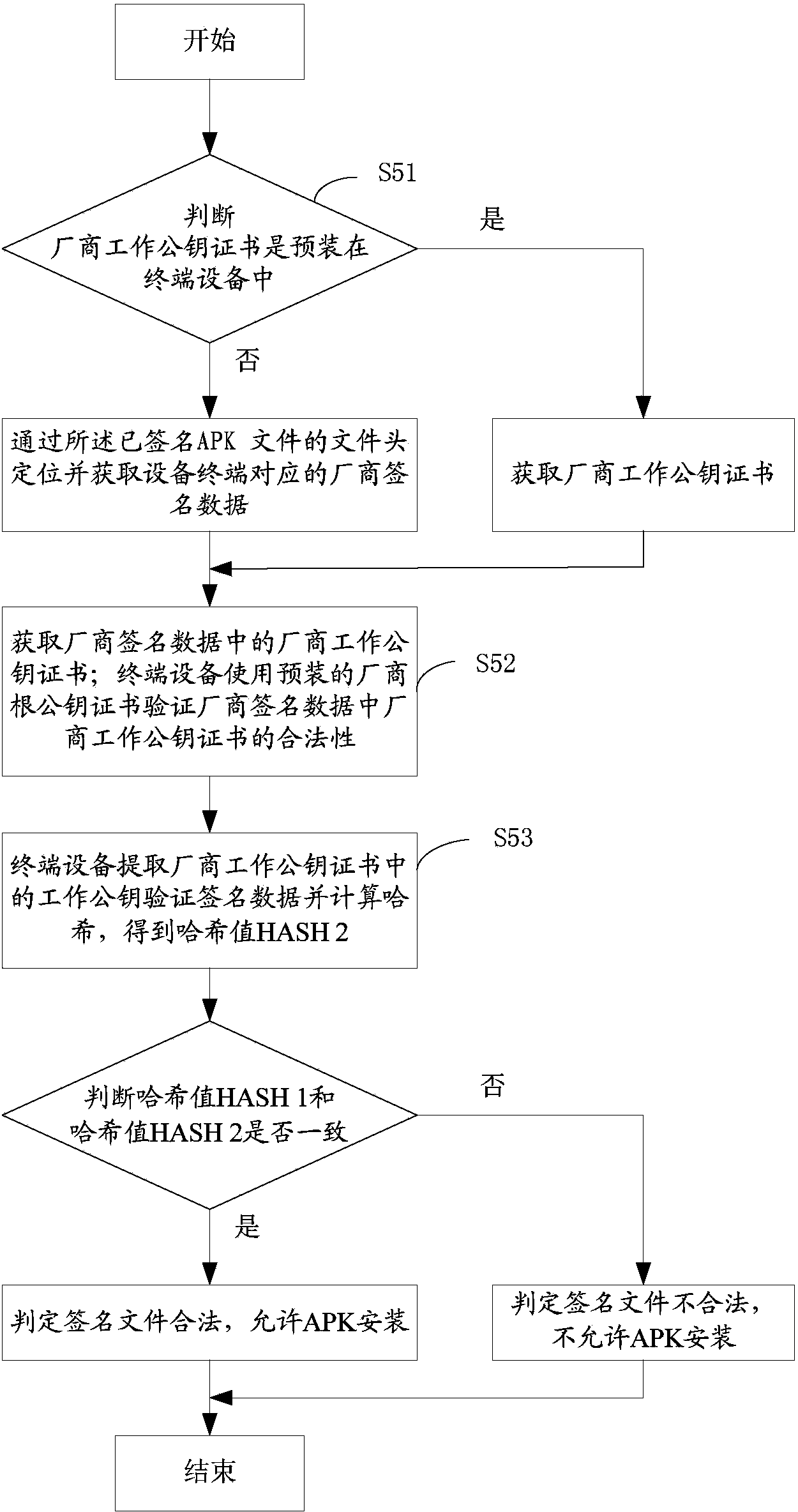
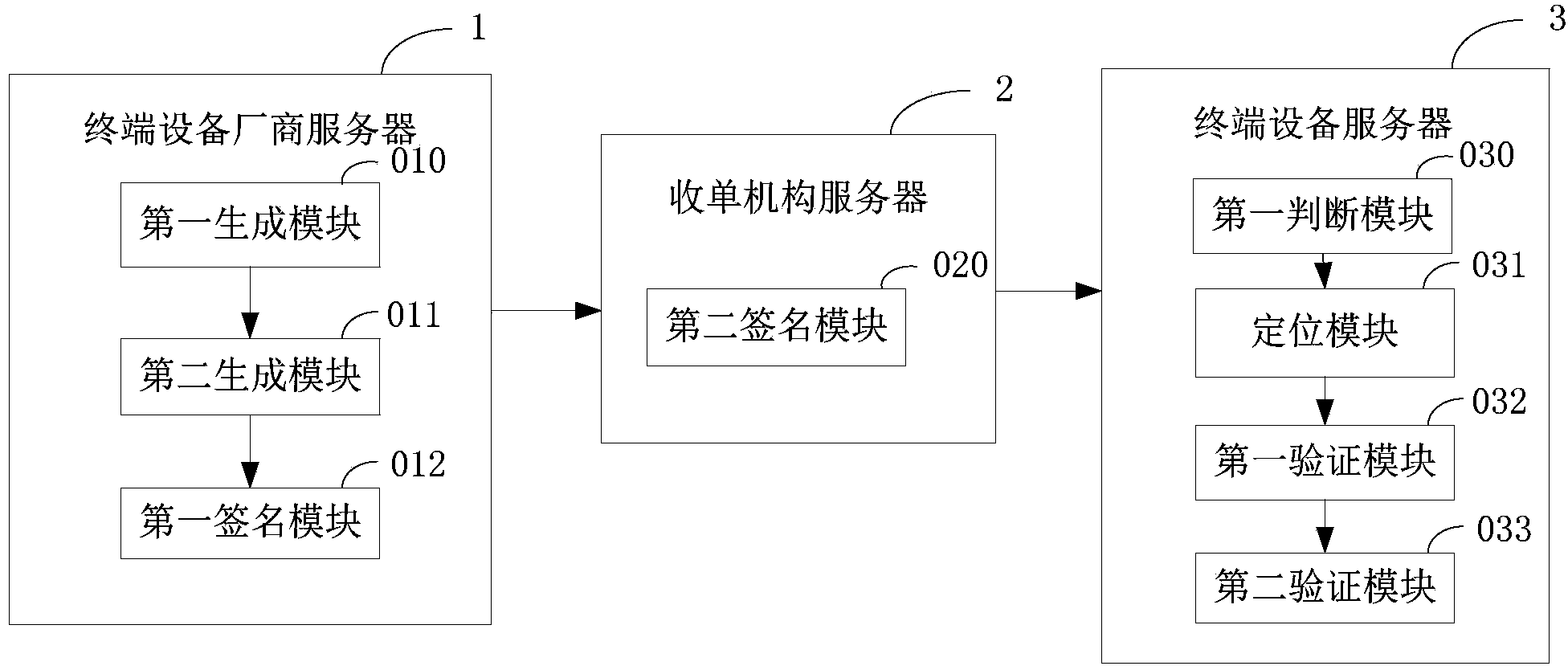
The invention provides a multi-party authorized APK signature method and system. The multi-party authorized APK signature method includes the steps that different terminal device manufacturer signature servers conduct signature on signed data containing an original ARK file through respective work key pairs to generate different terminal device manufacturer signature data, and manufacturer work public key certificates are put into the terminal device manufacturer signature data or are preinstalled in terminal devices; an acquirer signature server combines the different terminal device manufacturer signature data in the form of DER according to the sequence of signature time to form a signed APK file; the signed APK file comprises the original APK file and a signature file header, the signature file header comprises a file for marking the files subjected to signature operation and a file for marking the numbers of the corresponding manufacturer signature data of the different terminals and marking the specific positions of the corresponding manufacturer signature data of the different terminals in the signed APK file; the terminal devices acquire the signed APK file and conduct verification after judging that the manufacturer signature data generated by the corresponding terminal device manufacturers of the terminal devices exist in the signed APK file, and after the verification is successful, installation and operation are allowed.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Right information management method and right information management device
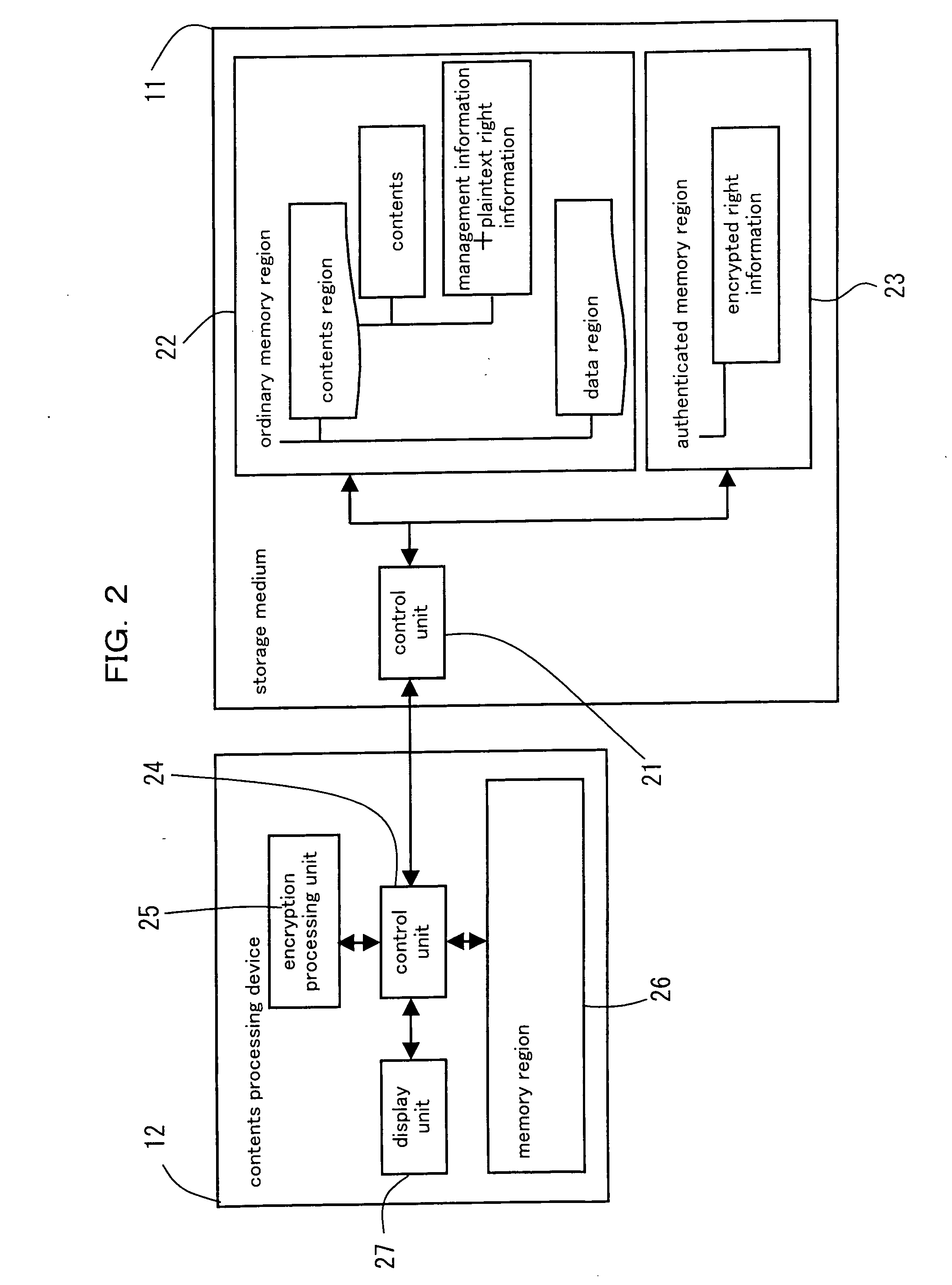
ActiveUS20060117013A1Prevent forgeryGuaranteed legalityKey distribution for secure communicationDigital data protectionPlaintextWorld Wide Web
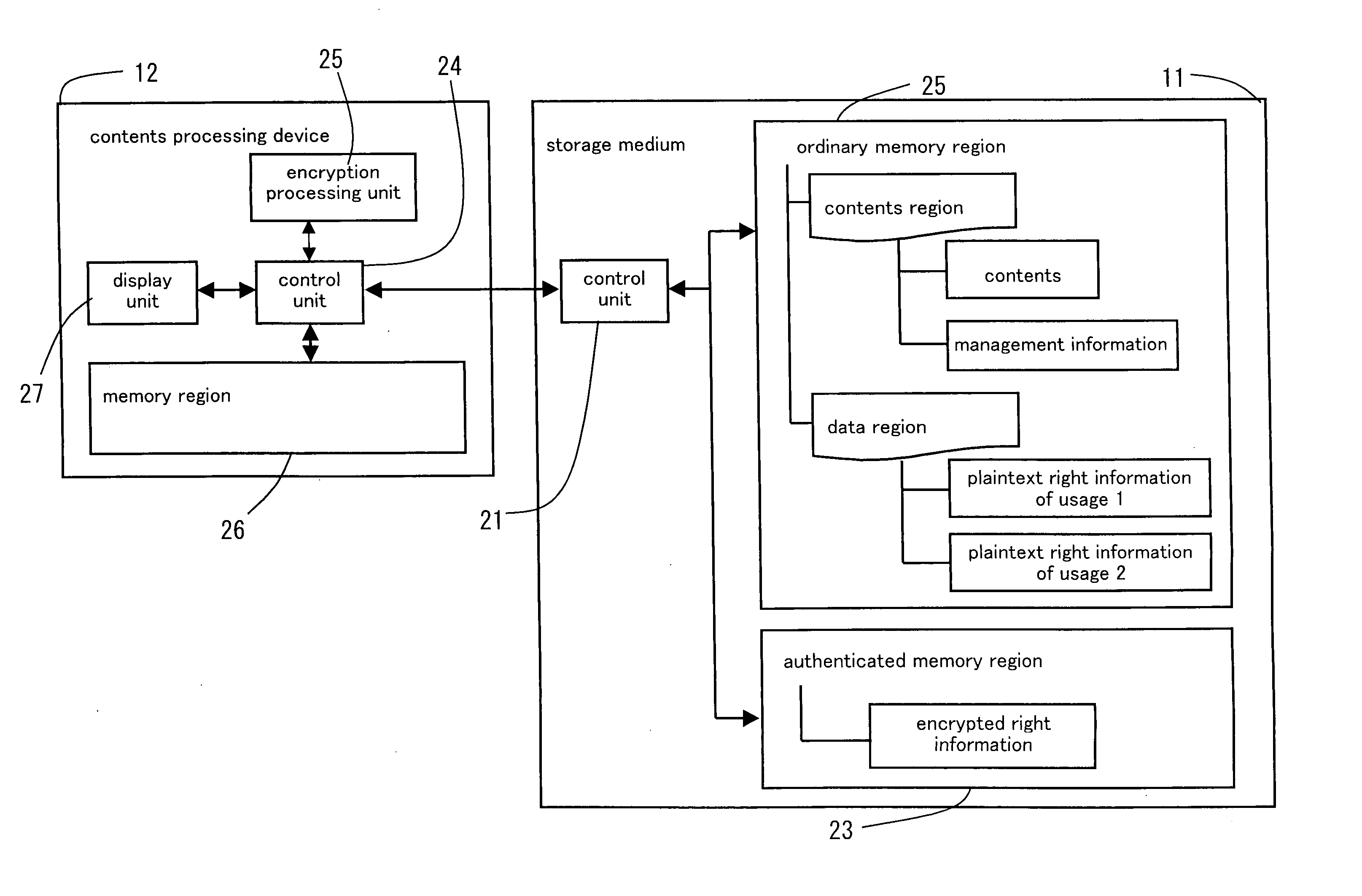
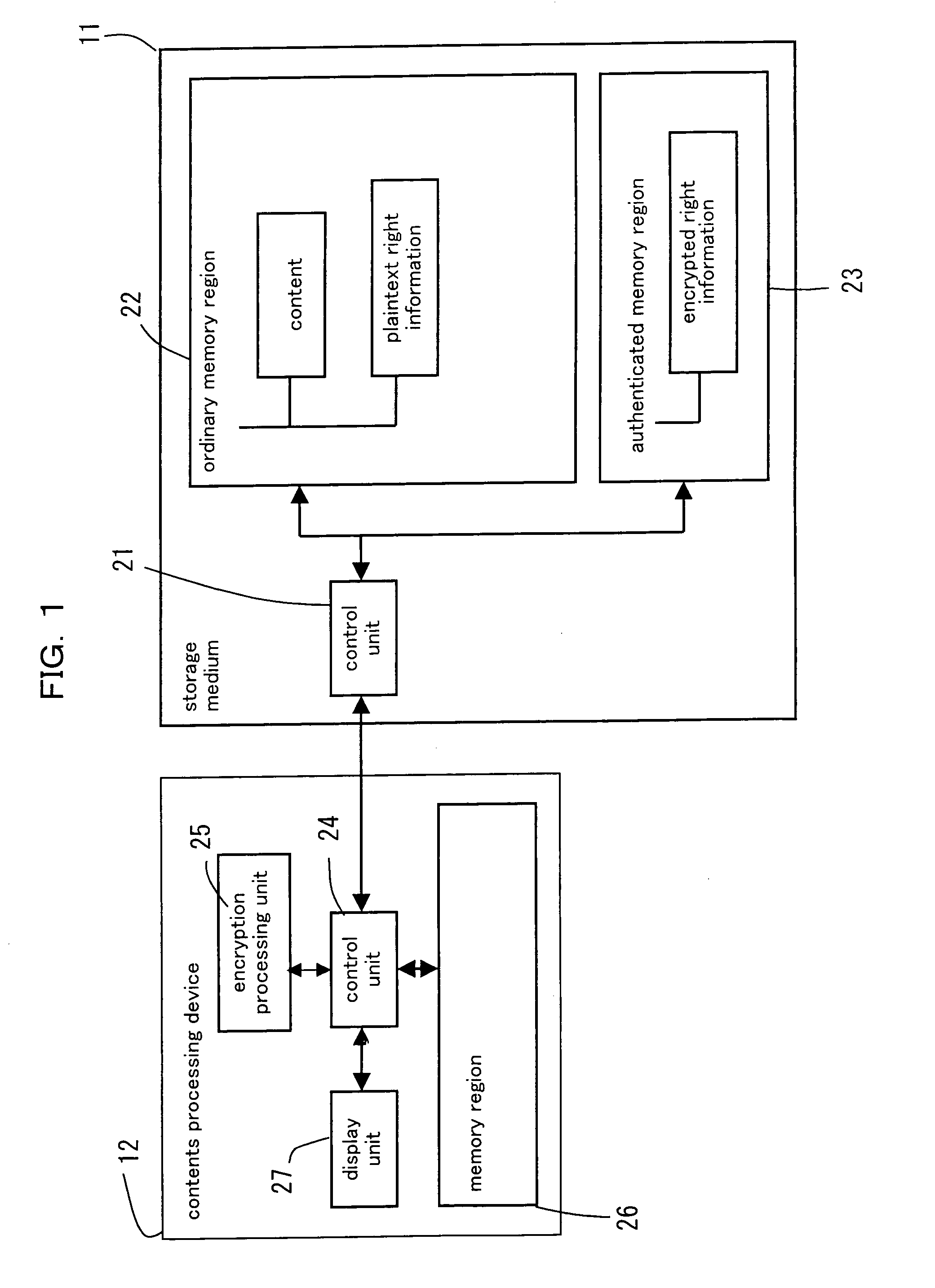
A right information management method for managing a right information of contents retained in a storage medium comprising an authenticated memory region accessible after a mutual authentication is obtained relative to a contents processing device and an ordinary memory region accessible without obtaining the mutual authentication, comprising a step of reading an encrypted right information retained in the authenticated memory region, a step of decoding the read encrypted right information and retrieving a plaintext right information, and a step of retaining the plaintext right information in the ordinary memory region. According to the right information management method, a user can be notified of the contents and the right information of the contents managed in the storage medium in a speedy manner via the contents processing device.
Owner:SOCIONEXT INC
Dynamic password authentication method based on digital certificate implement
InactiveCN1477810AGuarantee the legitimacy of identityAchieve convenienceRandom number generatorsMultiple keys/algorithms usagePasswordDigital signature
The present invention relates to a method for implementing dynamic password authentication based on digital certificate, belonging to the field of computer and information safety technology. On the basis of certificate authentication. It adopts the dynamic generation mechanism of password and utilizes the certificate authentication mechanism to acknowledge the user's identity, then utilizes the dynamic password mechanism to implement safe logging of various application systems.
Owner:KOAL SOFTWARE CO LTD
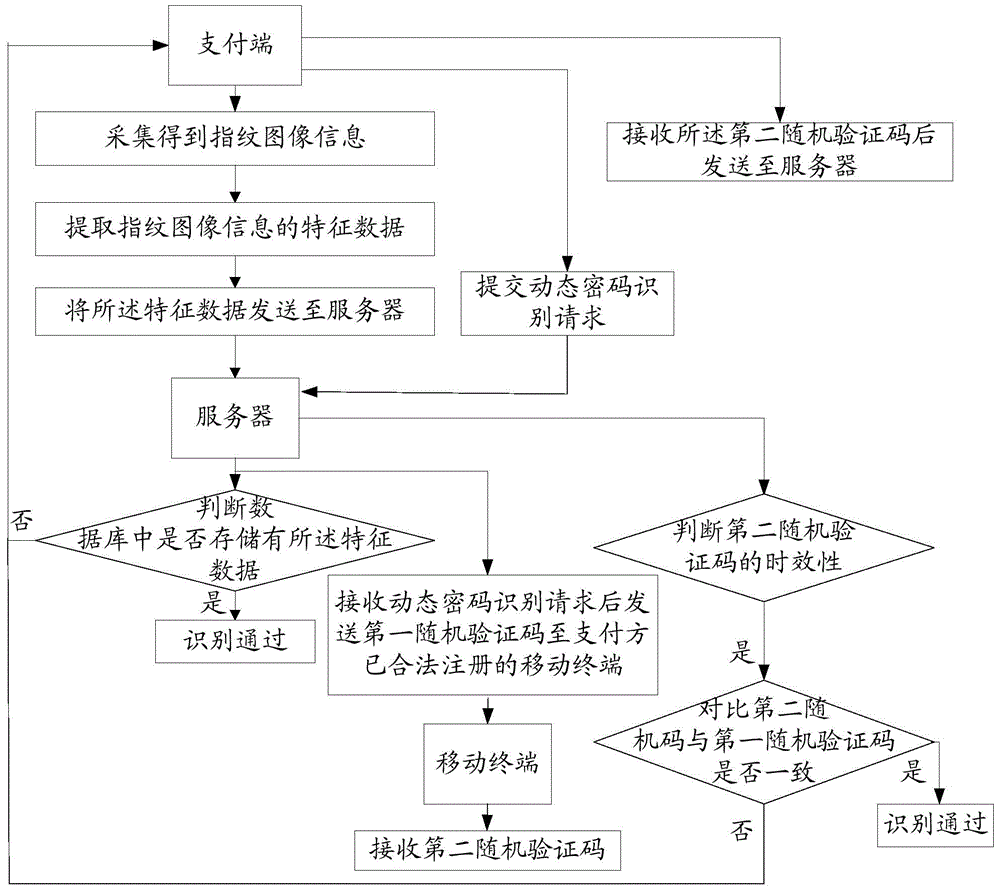
Secure fingerprint transaction paying method and system
InactiveCN104484804AGuaranteed safety and legalityImprove security levelProtocol authorisationFingerprintWireless
The invention provides a secure fingerprint transaction paying method and system. The system comprises a paying terminal, a server and a mobile terminal which are in wireless communication connection. The method comprises the following steps: the paying terminal collects and obtains fingerprint image information; characteristic data of the fingerprint image information are extracted and sent to the server; the server judges whether the characteristic data are stored in a database, and if yes, identification is passed; the paying terminal submits a dynamic password identification request to the server, and the server sends a first random verification code to the mobile terminal legally registered by a paying party; the mobile terminal receives a second random verification code and inputs the code, if the server determines that the second random verification code has timeliness, and whether the second random code and the first random verification code are consistent is compared; and if the second random code and the first random verification code are consistent, verification is passed. At least double identification and verification are adopted to ensure that the paying party is a legal user, the characteristic of concise and convenient transaction flow is considered, and the security level of a financial transaction process is increased.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Blockchain-based micro node B communication management method and system and equipment
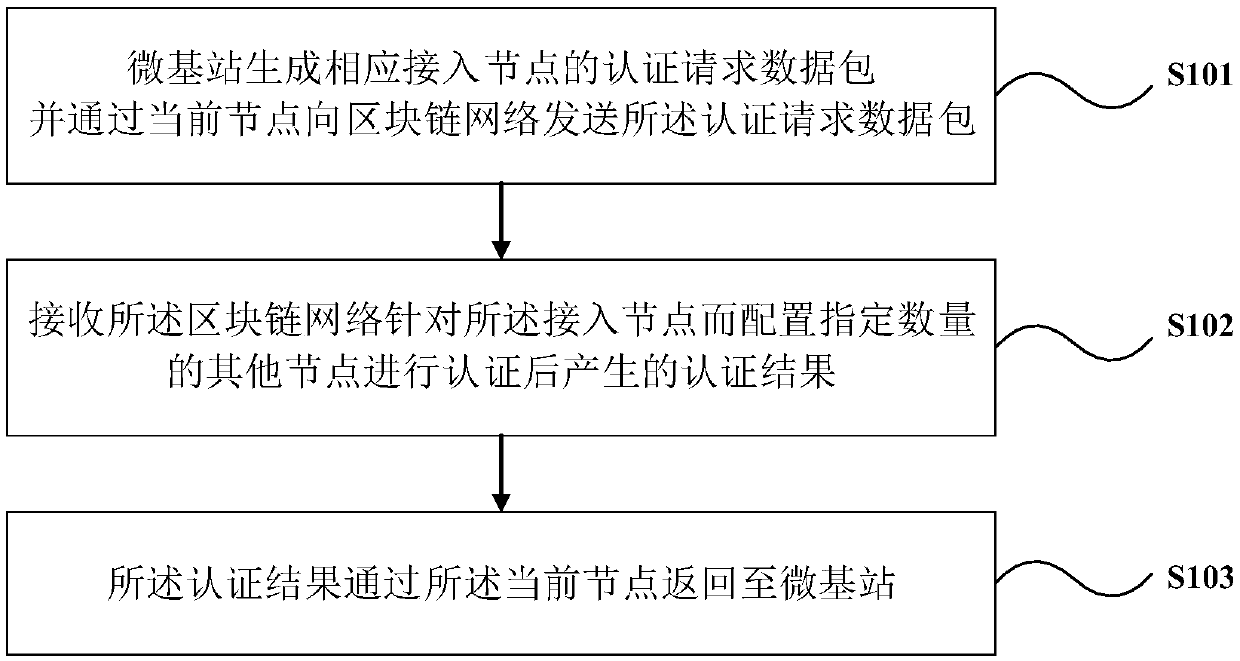
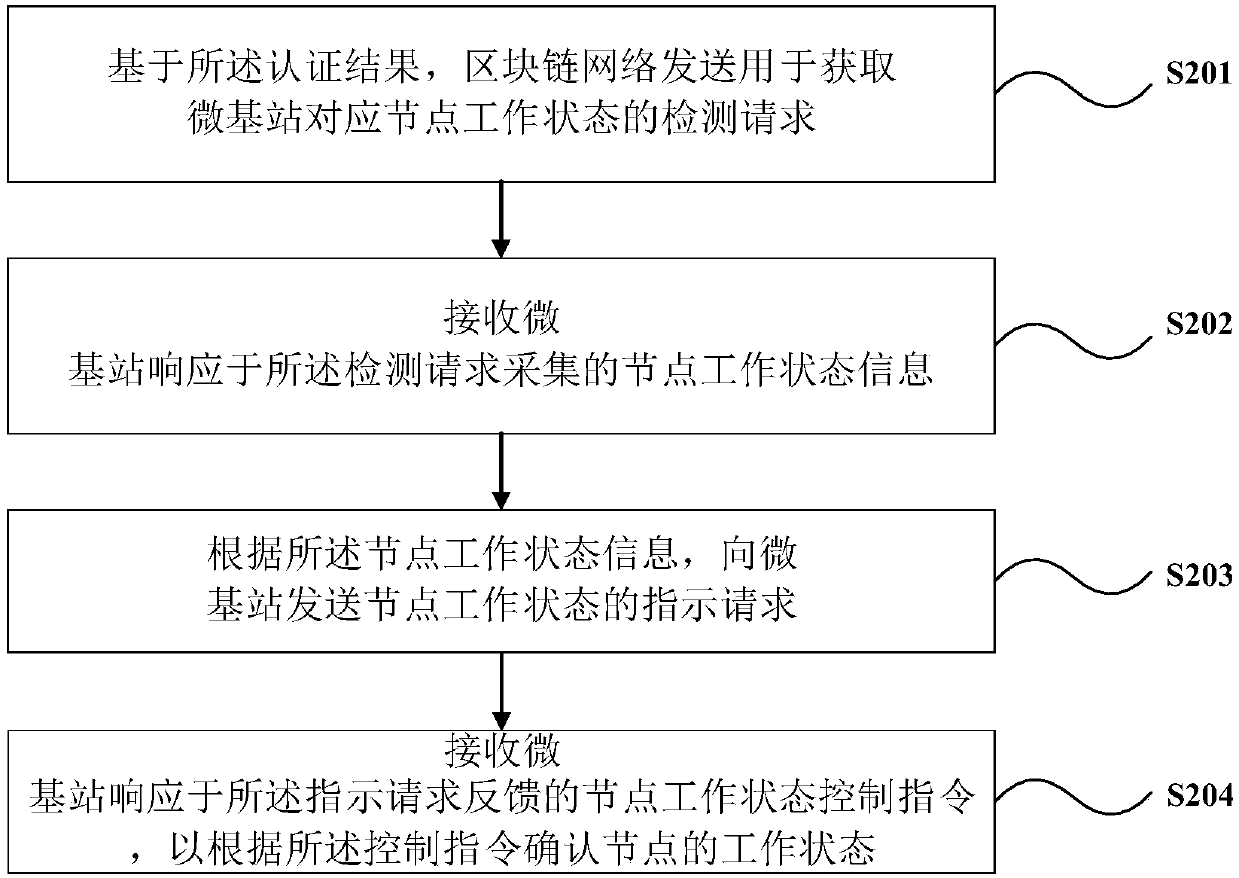
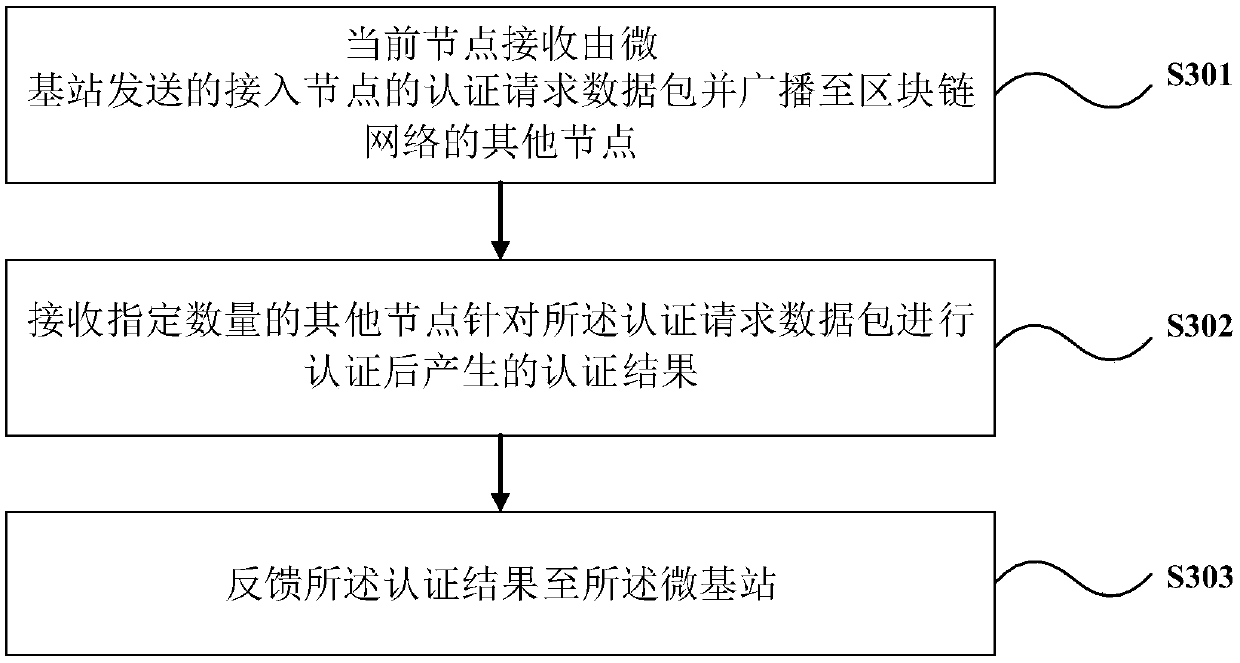
ActiveCN107734502AGuaranteed legalityGuaranteed validityAssess restrictionTransmissionBlockchainDistributed management
The invention discloses a blockchain-based micro node B cell communication management method and system and equipment. The method comprises the following steps: generating an authentication request data packet of a corresponding access node by a micro node B, and transmitting the authentication request data packet to a blockchain network through a current node; receiving an authentication result of the blockchain network generated after authentication by configuring a specified number of other nodes for the access node; and returning the authentication result to the micro node B through a current node. Through a blockchain technology, the validity and effectiveness of the access node are ensured; normal and effective transmission of data are ensured; the access node is enabled to effectively provide a service; distributed management of an access node communication system is realized; and the integrity of the whole blockchain network is maintained.
Owner:COMBA TELECOM SYST CHINA LTD
Non-contact CPU (Central Processing Unit) card entrance guard reader
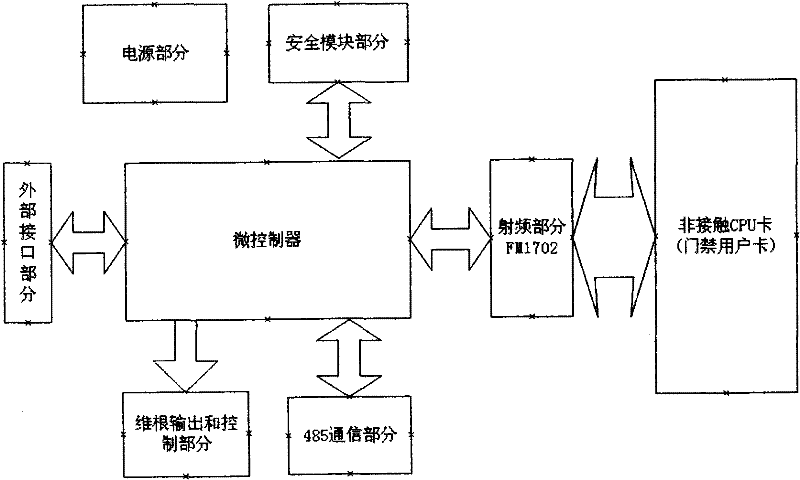
InactiveCN102129730AMake the most of security featuresImprove security levelSensing record carriersIndividual entry/exit registersMicrocontrollerComputer module
The invention discloses a non-contact CPU (Central Processing Unit) card entrance guard reader comprising a radio frequency part, a 485 communication part, a security module part, a Wigan output and external control part, a power supply part, an external connection part, a microcontroller part and other parts. The non-contact CPU card entrance guard reader is internally provided with a PSAM (Pilot Symbol Assisted Modulation) card and applies security certification read-write mechanisms of the PSAM card and a CPU card. The CPU card entrance guard reader builds an integral and strict key management system by adopting the security certification of the PSAM card and the CPU card, sufficiently uses the security characteristics of the CPU card and comprises key systems of the CPU card and the PSAM card; after a key is input into the PSAM card, the key cannot be externally read, the PSAM card is inserted into card reading equipment, two-way validation is carried out through the PSAM card and the CPU card, a verified message is calculated through the participation of random data, and a same card is different every time when swiped on one equipment, therefore a counterfeit card is thoroughly prevented.
Owner:SHANGHAI ZTRON ELECTRONICS
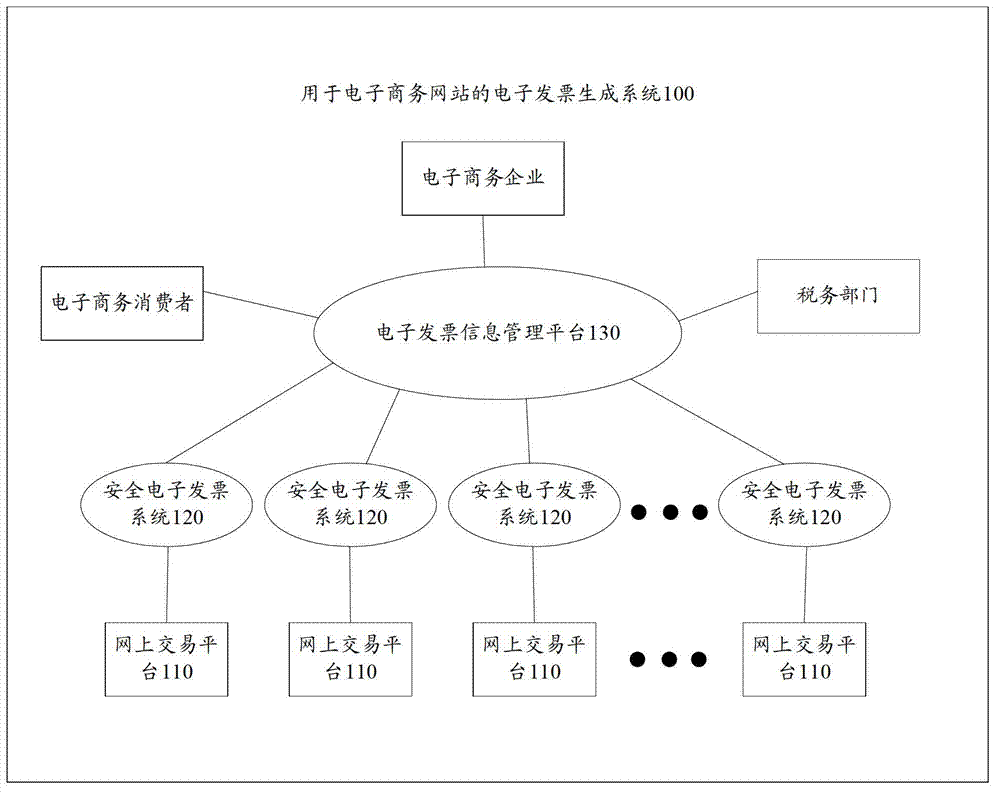
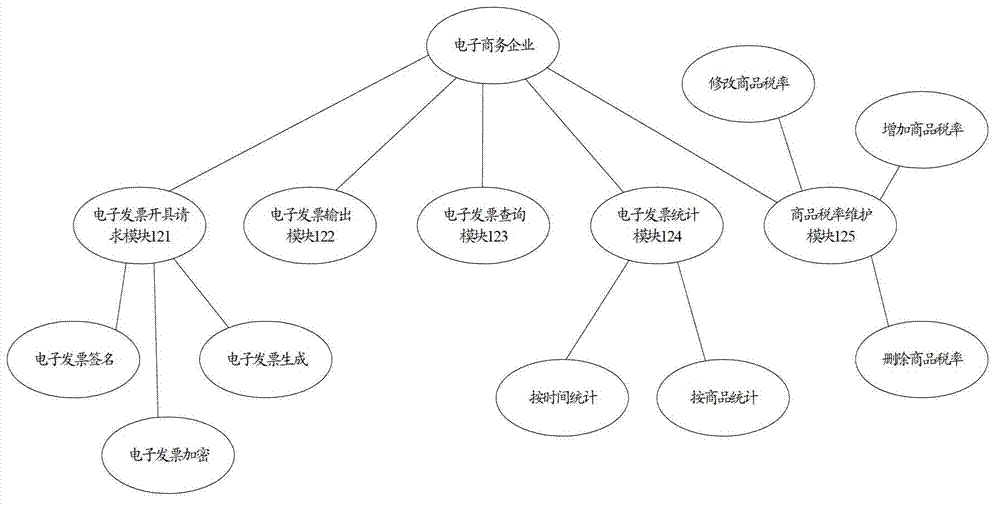
Electronic invoice generating system for electronic commerce website
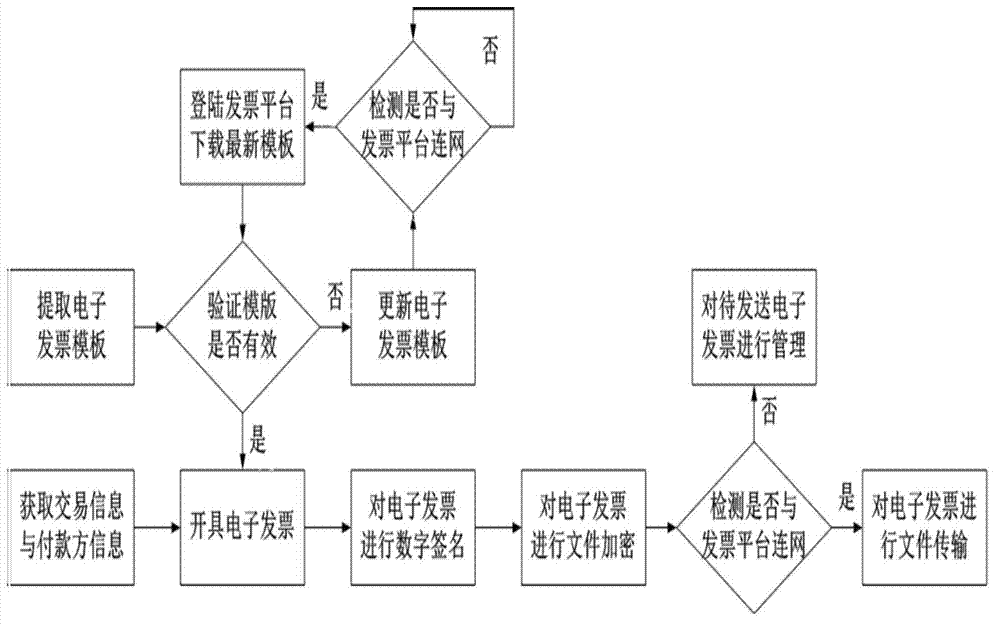
InactiveCN102855587AGuarantee authenticityGuaranteed legalityPayment architectureBilling/invoicingDigital signatureInvoice
The invention provides an electronic invoice generating system for an electronic commerce website. The electronic invoice generating system comprises an online transaction platform, a safety electronic invoice system and an electronic invoice information management platform, wherein the safety electronic invoice system is pre-stored with a goods and service code table, an electronic invoice template and digital certificates of electronic commerce enterprises and is used for receiving the payer information and transaction information from the online transaction platform, adding the payer information and transaction information into the electronic invoice template to generate a corresponding electronic invoice according to the goods and service code table and performing digital signature on the electronic invoice through the digital certificates of electronic commerce enterprises; and the electronic invoice information management platform comprises an access interface and is used for acquiring the electronic invoice from the safety electronic invoice system so as to put on records of the electronic invoice and providing the record information to a preset user through the access interface. According to the embodiment, the problems of fake invoice, no invoice and virtual invoice are effectively solved, the tax erosion is reduced, the whole process is paper-free, and the system has the advantages of high speed and energy conservation.
Owner:TSINGHUA UNIV
Smart grid information transmission safety protection device and safety protection method
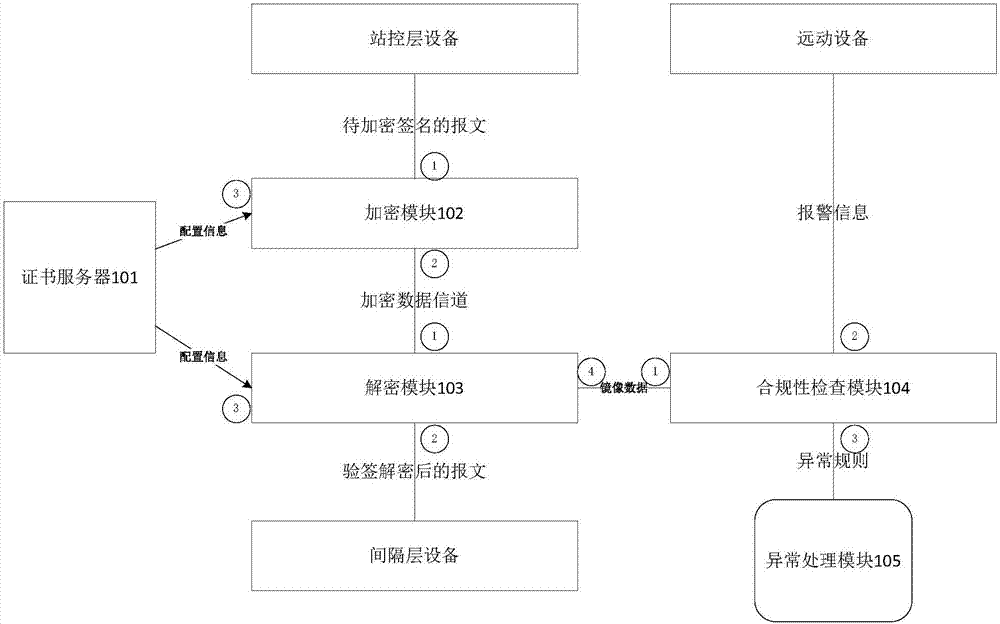
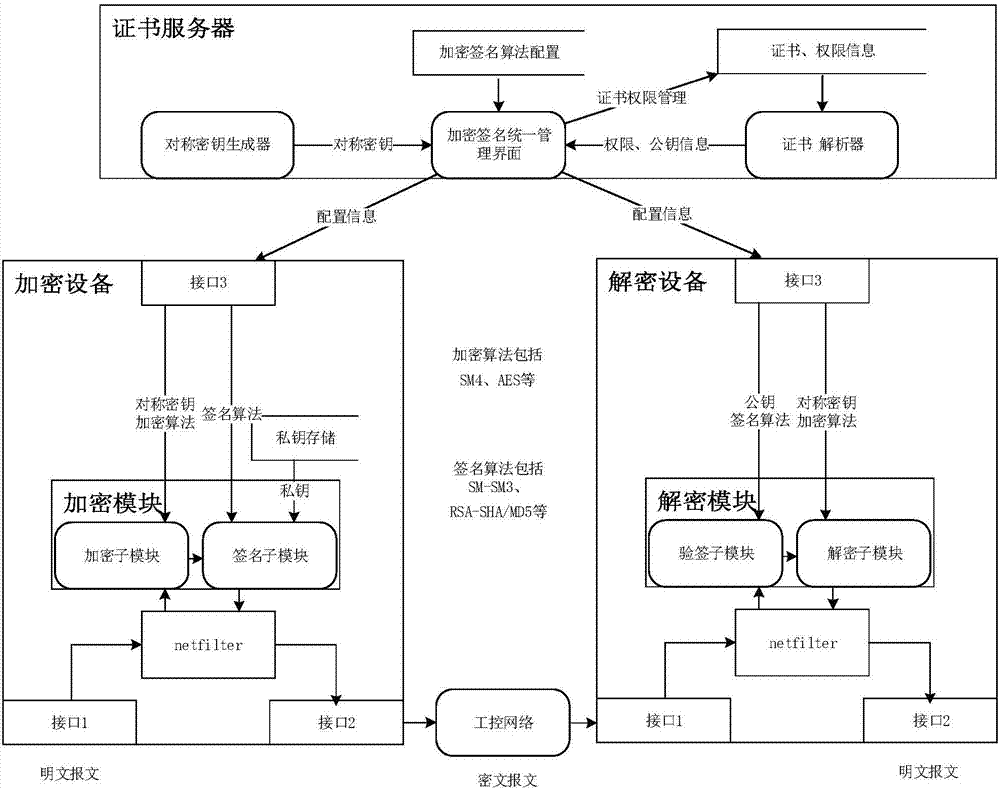
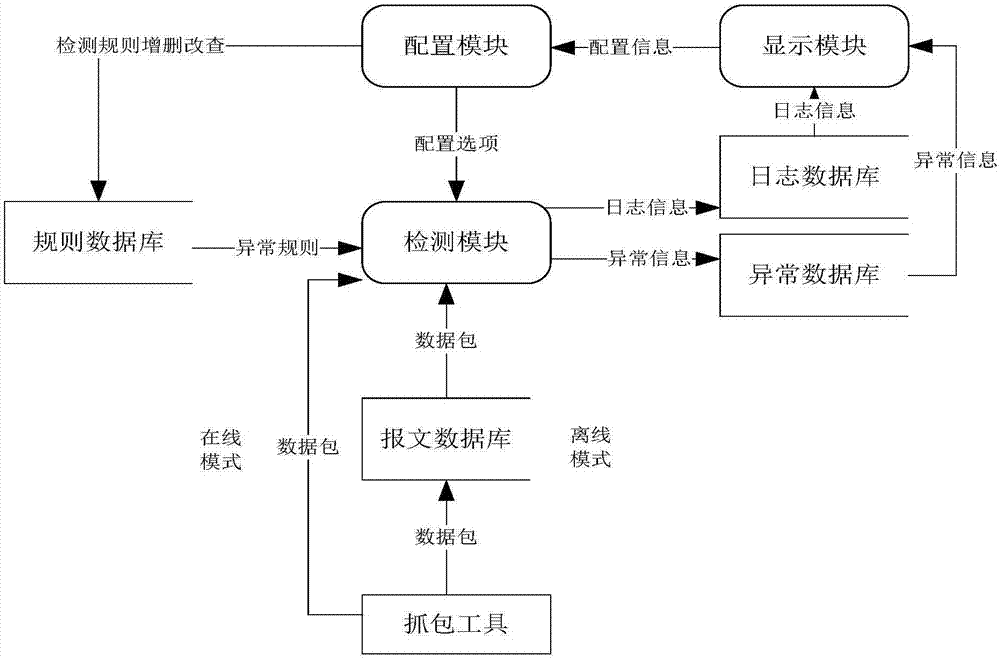
ActiveCN107483444AEasy to deployReduce maintenance costsUser identity/authority verificationPlaintextInformation transmission
The invention discloses a smart grid information transmission safety protection device and a safety protection method, which relate to the technical field of smart grid information transmission safety. The device comprises a certificate server, an encryption and decryption module, a compliance check module and an exception handling module, wherein the encryption and decryption module is wholly serially connected between a station level and a bay level for carrying out encryption signature and signature verification decryption functions on original transparently-transmitted data; the compliance check module grabs a plaintext data packet in an offline or online mode and submits the plaintext data packet to the detection module for compliance check, and as for a compliance message, an analysis result is stored to a log database in a log format; and exception information is independently stored in an exception database through the exception handling module, and an administrator is notified. In the case of permissible delay in the smart grid, the encryption and decryption module together protects the internal information of the smart grid, behaviors that the internal data are tampered and destructed in the case of transmission are resisted, and the safety of the grid is further improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
Transmission method of multichannel video streams and system thereof
ActiveCN102231863AGuaranteed legalityEffective filteringSelective content distributionNetwork packetVideo processing
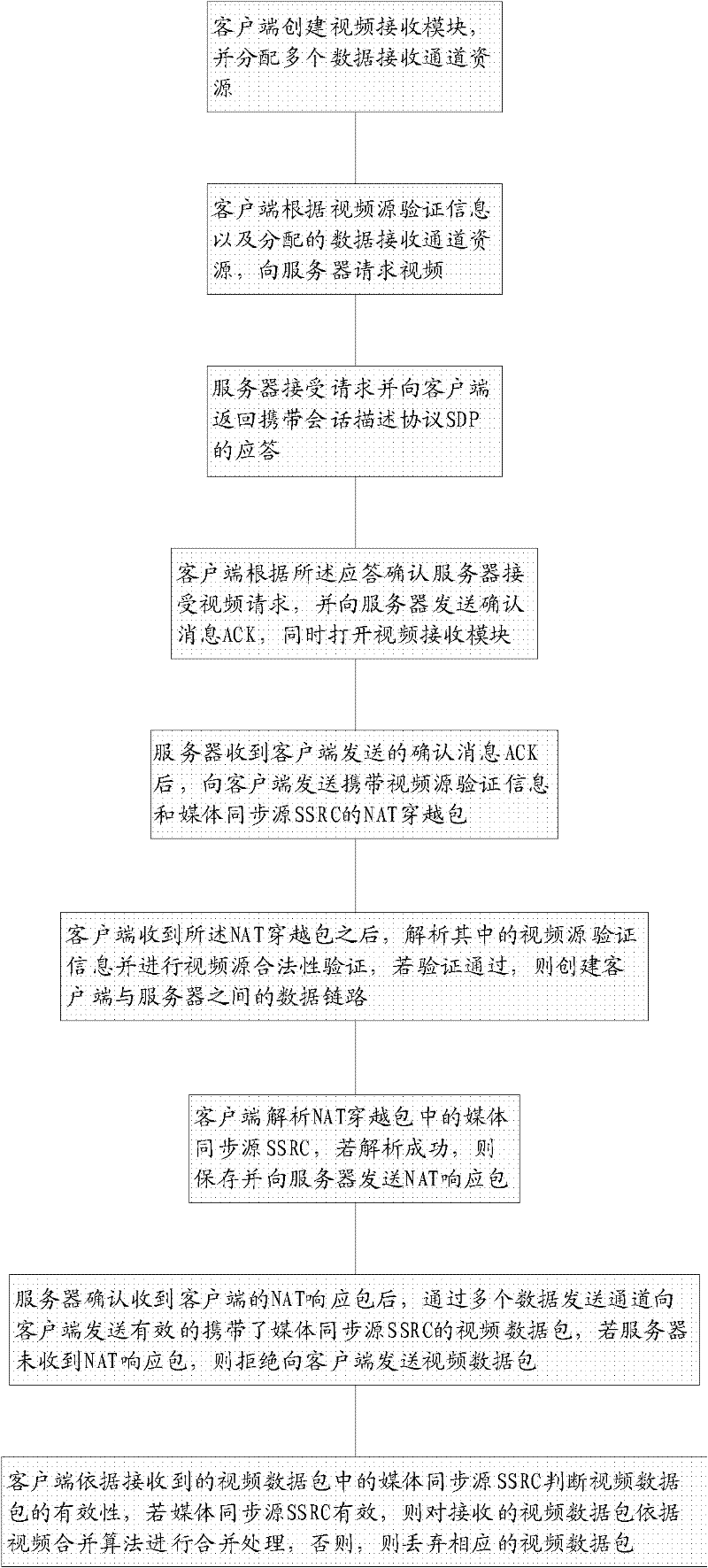
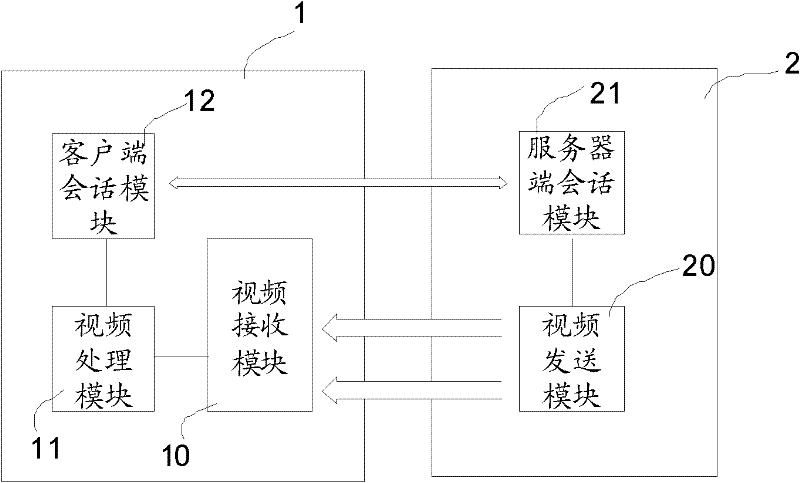
The invention discloses a transmission method of multichannel video streams and a system thereof. The system comprises a client and a server. The client comprises a video receiving module, a video processing module and a client session module. The server comprises: a plurality of video sending modules, which are matched with the video receiving module, and a server session module. The client session module is used to complete signaling interaction with the server session module and control the video receiving module to receive video data packets transmitted by the server. The video processingmodule is used to process the video data packets received by the video receiving module. The server session module controls the video sending modules to send the video data packets to the client. In the invention, video source validity verification and video data packet validity verification are added during a video request negotiation process by the client so that correctness and reliability of the video stream transmission can be raised.
Owner:NANJING ZNV SOFTWARE CO LTD
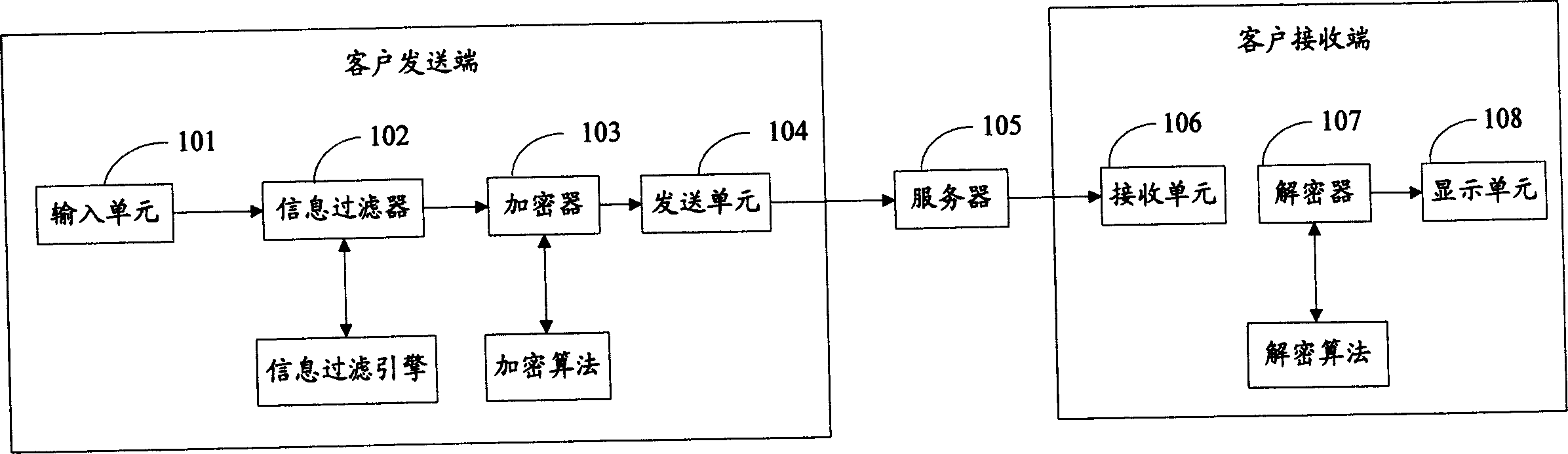
Information filtering and secret-keeping method and apparatus in instantaneous communication
ActiveCN1885836AGuaranteed legalityGuaranteed healthData switching networksEncryption systemComputer science
The disclosed filter and secret method for information in immediate communication comprises: using a filter engine to filter target information to send the healthy and inhibit the unhealthy; using a system to encipher the information. This invention adds a enciphering / deciphering machine on transmission / receiving end respectively.
Owner:HUAWEI TECH CO LTD
User identity protection method based on public-key mechanism
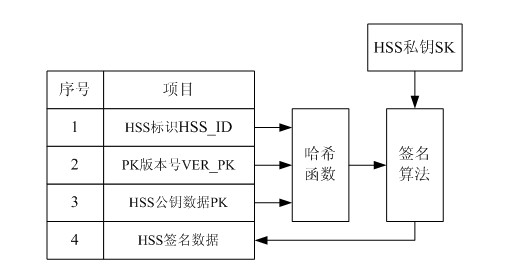
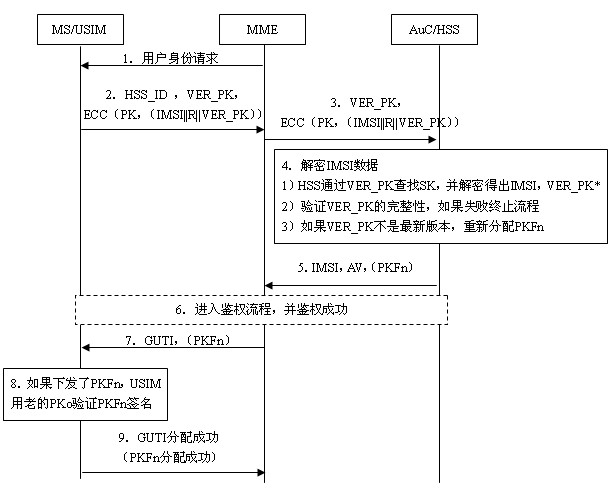
ActiveCN102026178AIncrease the difficulty of decipheringIntegrity guaranteedSecurity arrangementInternet privacyEngineering
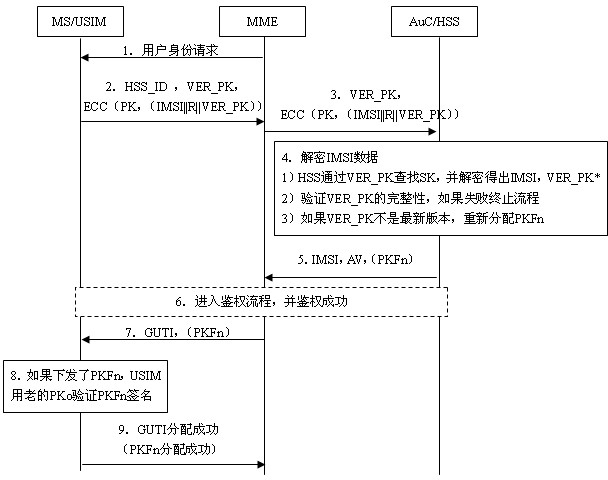
The invention relates to the secret communication field of mobile communication technologies, and discloses a user identity protection method based on a public-key mechanism. The method comprises the following steps: an HSS (hierarchical service system) produces a pair of keys, namely, a public key PK and a secret key SK, then the public key PK is preset to a USIM (universal subscriber identity module) card of UE (user equipment) belonging to the public key PK in the form of a public key file PKF, and the secret key SK is stored in the HSS; a mobile phone sends the following information to anMME (mobility management entity), including HSS identification: HSS_ID, public-key PK version number: VER_PK; and data (IMSI || R|| VER_PK) encrypted by using an asymmetric encryption algorithm; after receiving the information, the MME sends the VER_PK and the (IMSI || R|| VER_PK) to the HSS according to the HSS_ID; and the HSS decrypts the VER_PK and the (IMSI || R|| VER_PK) by using the secret key SK. Because attackers do not know the secret key SK of the HSS, the attackers can not decrypt the (IMSI || R|| VER_PK).
Owner:成都三零瑞通移动通信有限公司
Intelligent entrance guard control system with wireless ad hoc network function and control method thereof
InactiveCN102496199AEasy to installSolve wiring difficultiesNetwork topologiesIndividual entry/exit registersSystems managementControl system
The invention discloses an intelligent entrance guard control system with a wireless ad hoc network function and a control method thereof, which achieve the wireless ad hoc network function and remove difficulty in project wire arrangement. A safety identification module is added in a card reader to improve system safety. An entrance guard system management terminal applies an embedded gateway to manage every entrance guard controller on one hand and exchange information with an entrance guard management server on the other hand. The system adopts the mode of combination of the B / S structure and the C / S structure and is formed by a center server, branch center servers and an intelligent entrance guard controller. A center server database is interlinked with each branch center server database, and the branch center servers start ZigBee protocol stack and conduct data communication with the intelligent entrance guard controller through a ZigBee and / or transmission control protocol (TCP) / Internet protocol (IP) interface. The entrance guard controller is connected with a card reader connected with an encryption module. The swiping card record is uploaded by the intelligent entrance guard controller to corresponding branch center servers and then to the center server.
Owner:SHANDONG UNIV
Authorization method and system
ActiveCN102510333AGuarantee authenticityGuaranteed legalityPublic key for secure communicationUser identity/authority verificationAuthorizationSerial code
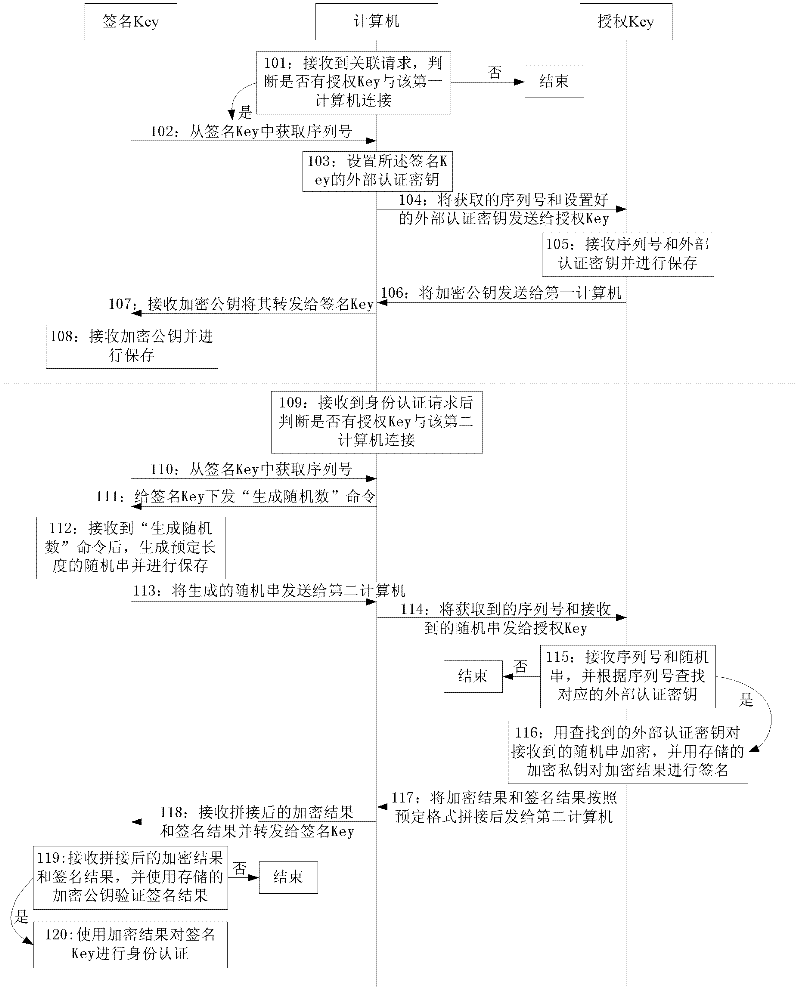
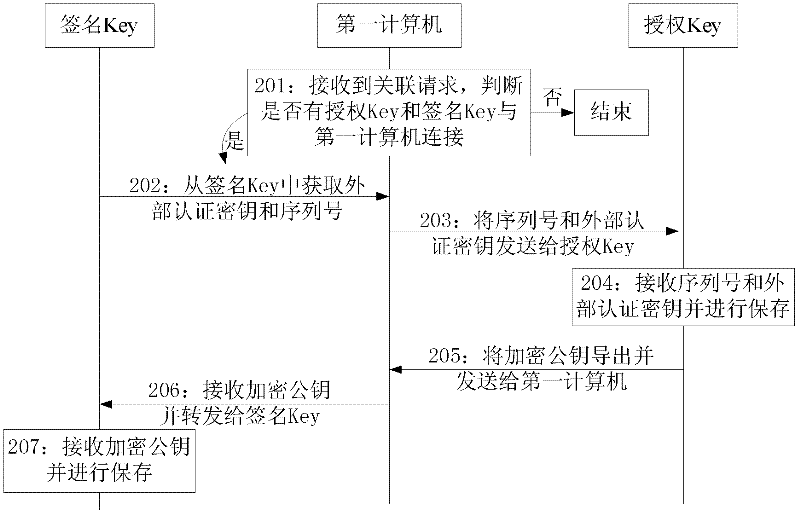
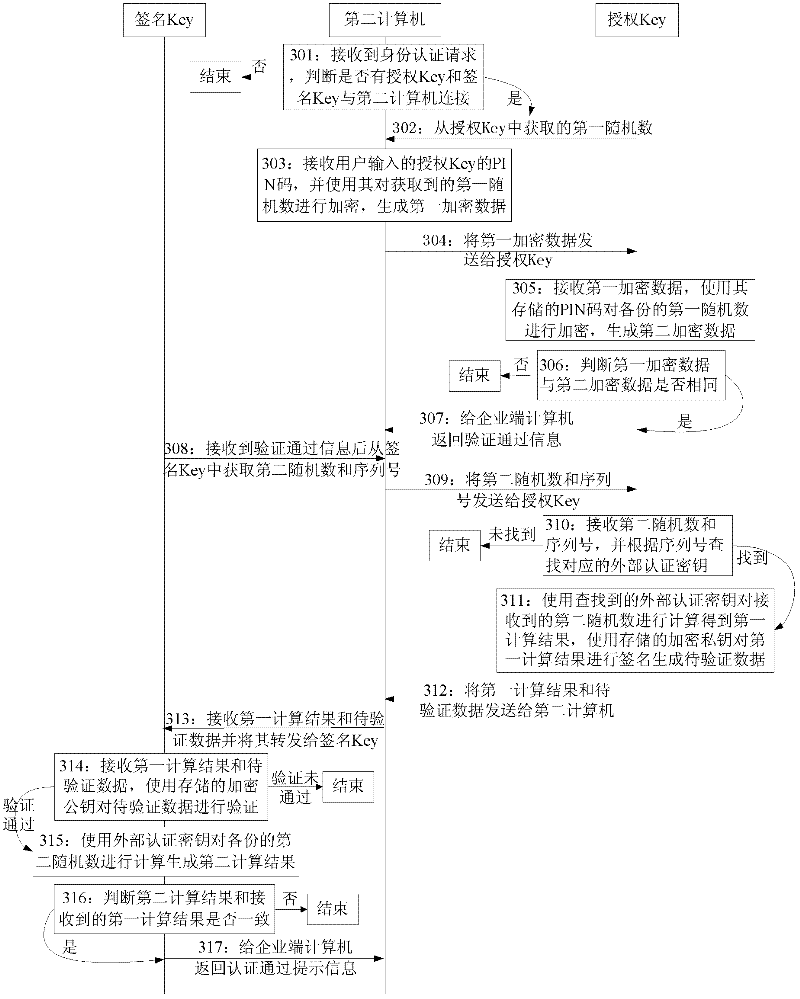
The invention discloses an authorization method and system. The method comprises the following steps: setting an external authentication secret key in a signature Key and an authorization Key, wherein the external authentication secret key is in one-to-one relationship with a serial number of the signature Key; the authorization Key sends an encrypted public key to the signature Key through a first computer to save; after receiving an identity authentication request, a second computer obtains a second random number and the serial number from the signature Key and sends the same to the authorization Key; the authorization Key searches the external authentication secret key by using the serial number, and uses the external authentication secret key and an encrypted private key to sign the second random number to generate to-be-verified data to send to the signature Key through the second computer; and the signature Key verifies the received to-be-verified data by using the encrypted public key and the external authentication secret key. The method provided by the invention realize the one-to-one or one-to-many relevance of the authorization Key and the signature Key, after the identity is authenticated, the signature Key and the authorization Key can sign the data of each transaction so as to guarantee the authenticity and validity of the transaction between bank and enterprise.
Owner:FEITIAN TECHNOLOGIES
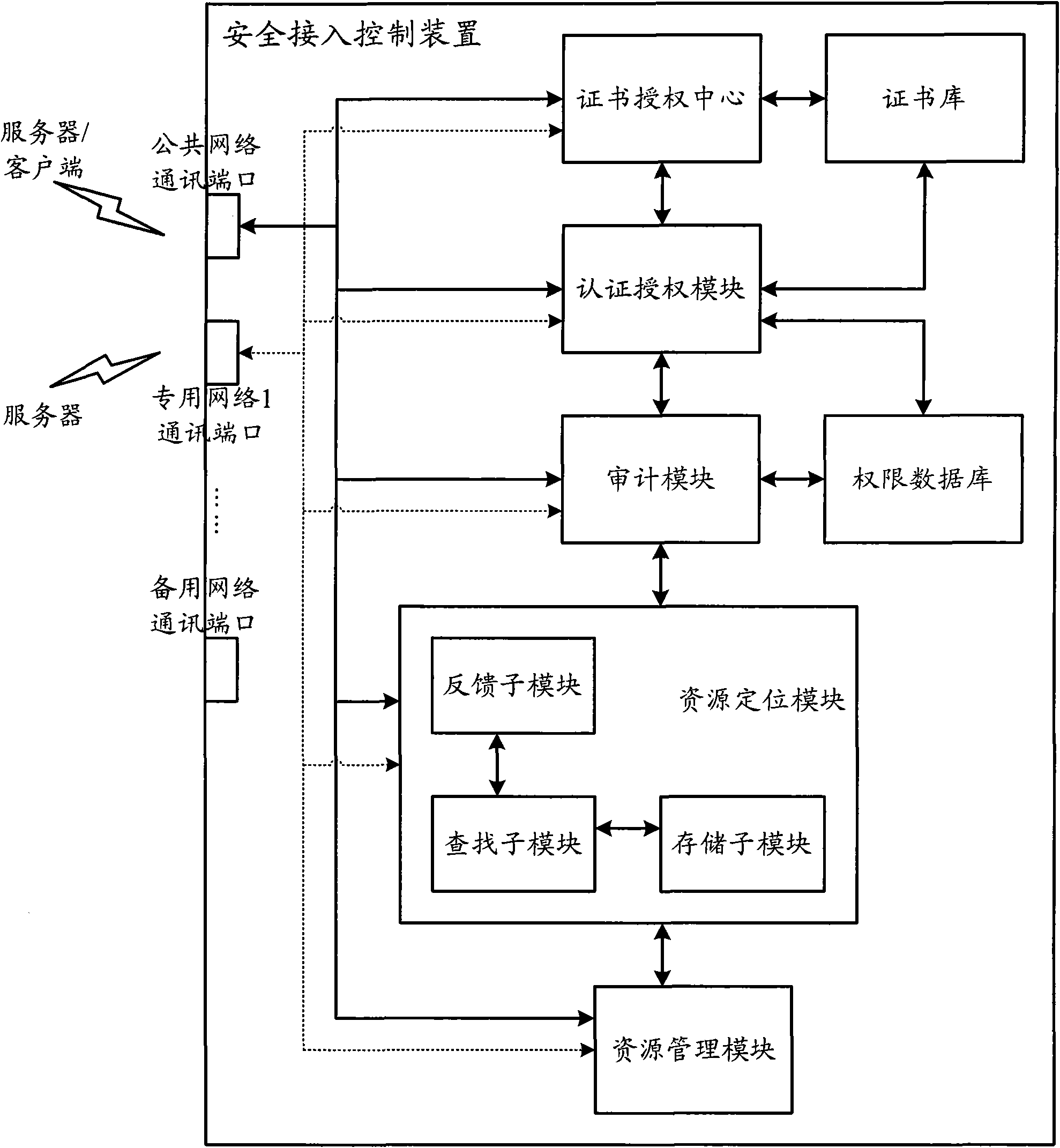
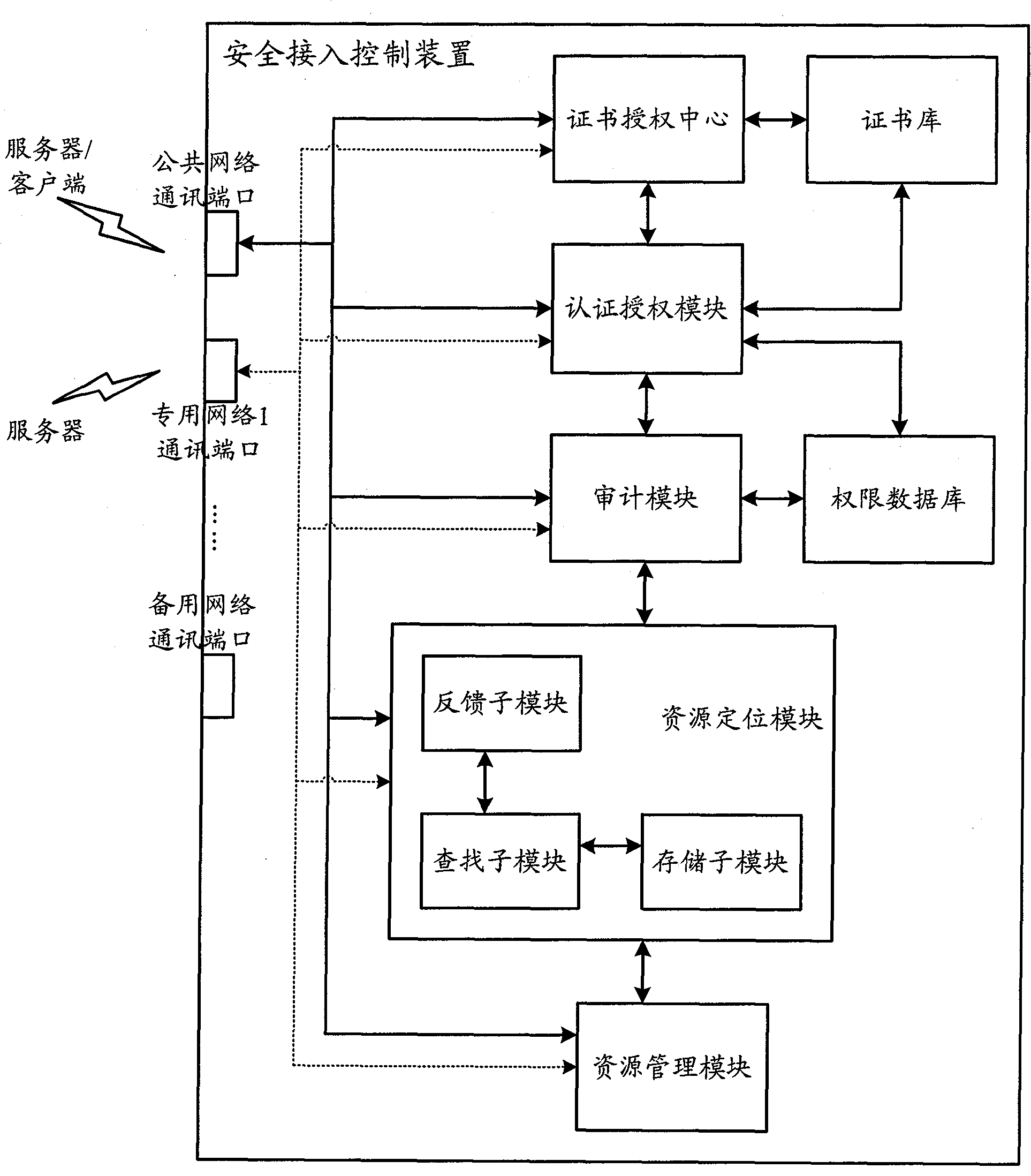
Industrial Internet distributed system safety access control device
ActiveCN102487383AGuaranteed legalityPrevent theftUser identity/authority verificationThe InternetIndustrial Internet
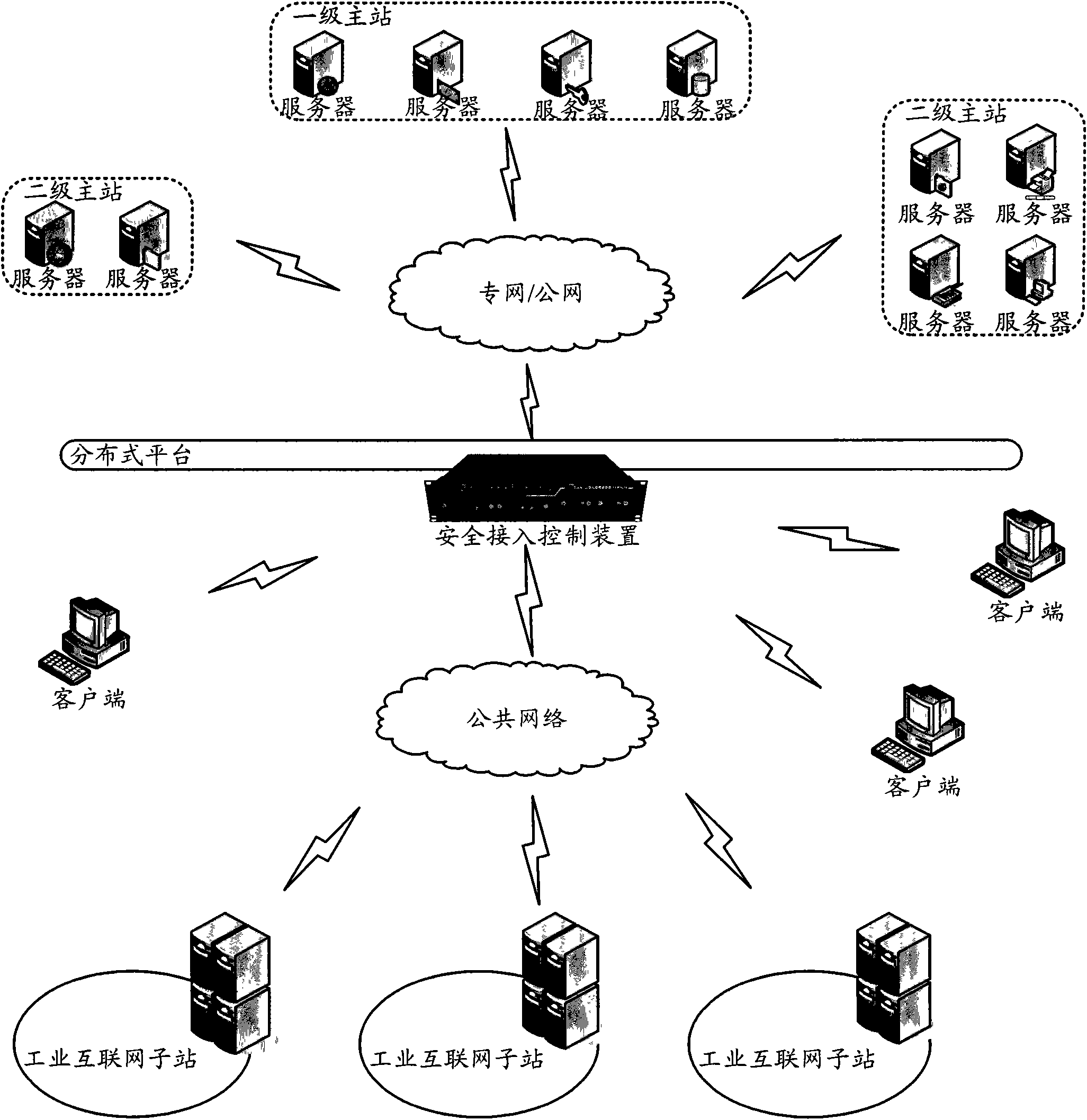
The invention discloses an industrial Internet distributed system safety access control device. The device integrates a module which is used to carry out authentication and authorization to identities and access operations of a user and a server, the module which is used to audit the access operations of the user and the server and the module which is used to carry out uniform resource positioning to object resources accessed by the user and the server. Identity security and authority validity of the user or the server which access to the industrial Internet distributed system and acquire information / service can be effectively ensured. In addition, the user and the server in the industrial Internet do not need to know an actual storage position of the needed object resources. Through a uniform resource positioning platform of the distributed system, the corresponding server can be positioned and the needed object resources can be acquired. A demand in a distributed environment can be rapidly and conveniently satisfied.
Owner:ASAT CHINA TECH
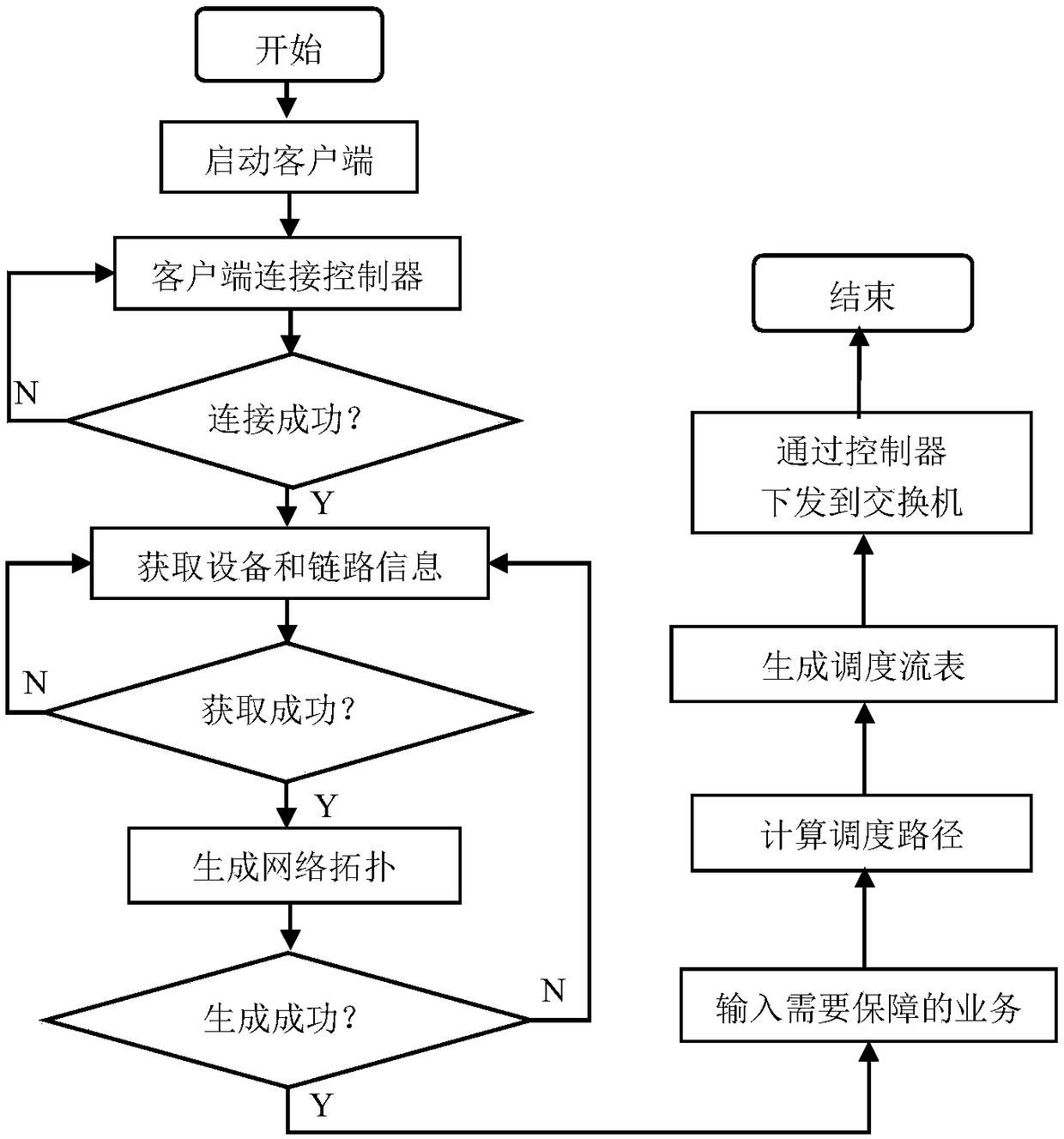
Method for traffic monitoring and business service quality guarantee strategy based on SDN
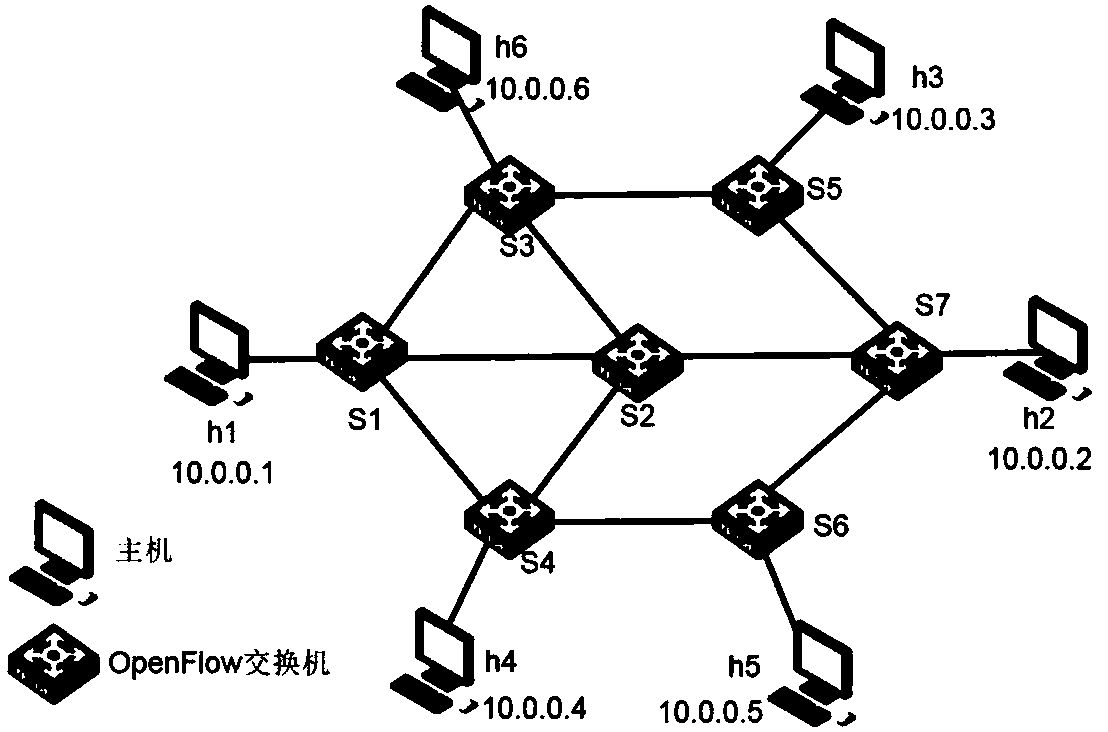
InactiveCN108809857AReduce the impactGuaranteed service qualityData switching networksService flowTraffic capacity
The invention discloses a method for a traffic monitoring and business service quality guarantee strategy based on SDN. The method comprises the following steps: a. creating a network topology under the SDN architecture, configuring an Openflow switch, and establishing a connection between the switch and an SDN controller; b. providing an open northbound API interface on the SDN controller; c, obtaining, by an application system program, complete device information and link information; d, inputting the business to be guaranteed according to the business requirements; e, according to a sourcedestination address of the service flow, transmitting an algorithm class to calculate a scheduling path, and generating the optimal scheduling path of the current network; f. transmitting the scheduling path in e into a strategy generation class, generating a scheduling flow table in combination with the business guarantee strategy in d, and issuing the scheduling flow table into the switch; and g. adding a data transmission queue to a switch port according to the scheduling flow table in f. By adoption of the method disclosed by the invention, the stable operation of the network business, theefficient use of the link bandwidth and the maximum optimization of the whole network performance are maximally guaranteed.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Charging method and charging device based on blockchain
InactiveCN108632480AAvoid the problem that the billing process is not transparent enoughAlleviate the technical problem that the billing process is not transparent enoughAccounting/billing servicesUser identity/authority verificationTraffic capacityUser identifier
The invention provides a charging method and a charging device based on blockchain. The method is applied in a blockchain system, the blockchain system comprises a plurality of communication nodes, the blockchain system respectively communicates with a plurality of telecommunication operator nodes, one supervision organization node and one blockchain operator node, and the method comprises the following steps: acquiring a user identifier uploaded by a communication node and traffic information corresponding to the user identifier; according to the traffic information and a preset first smart contract, obtaining charge information corresponding to the user identifier through calculation; signing the charge information with a digital certificate in the first smart contract, and obtaining signed charge information; acquiring a user public key corresponding to the user identifier, encrypting the signed charge information with the user public key, and obtaining encrypted charge information.With the method and the device provided by the invention, a technical problem of poor transparency of a charging process of network usage charges in the existing technology is eased, and a technicaleffect of making the charging process of the network usage charges become transparent is realized.
Owner:北京阿尔山区块链联盟科技有限公司
Method for uniformly configuring configuration files
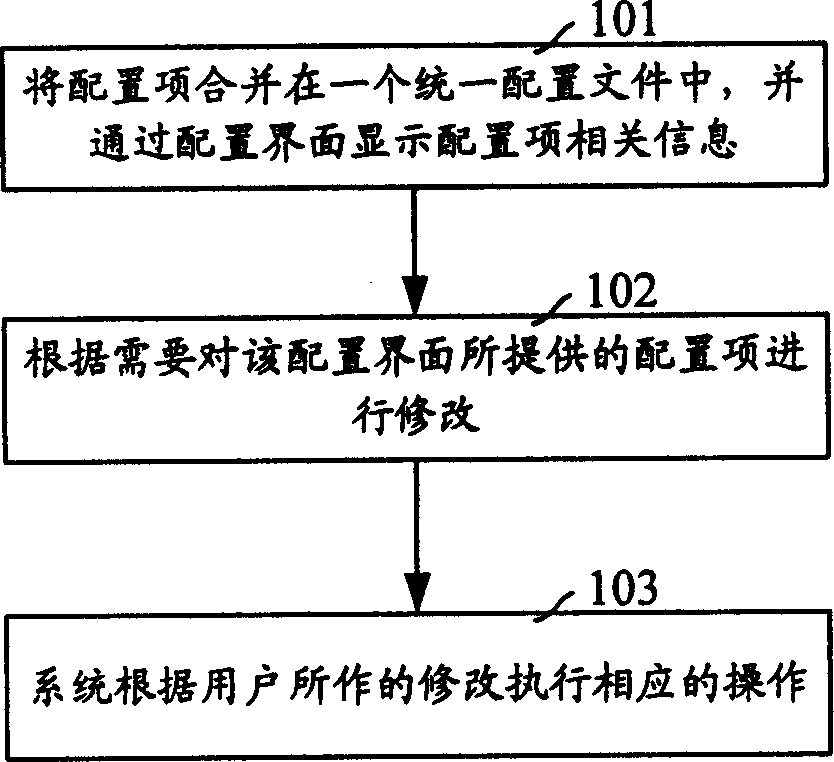
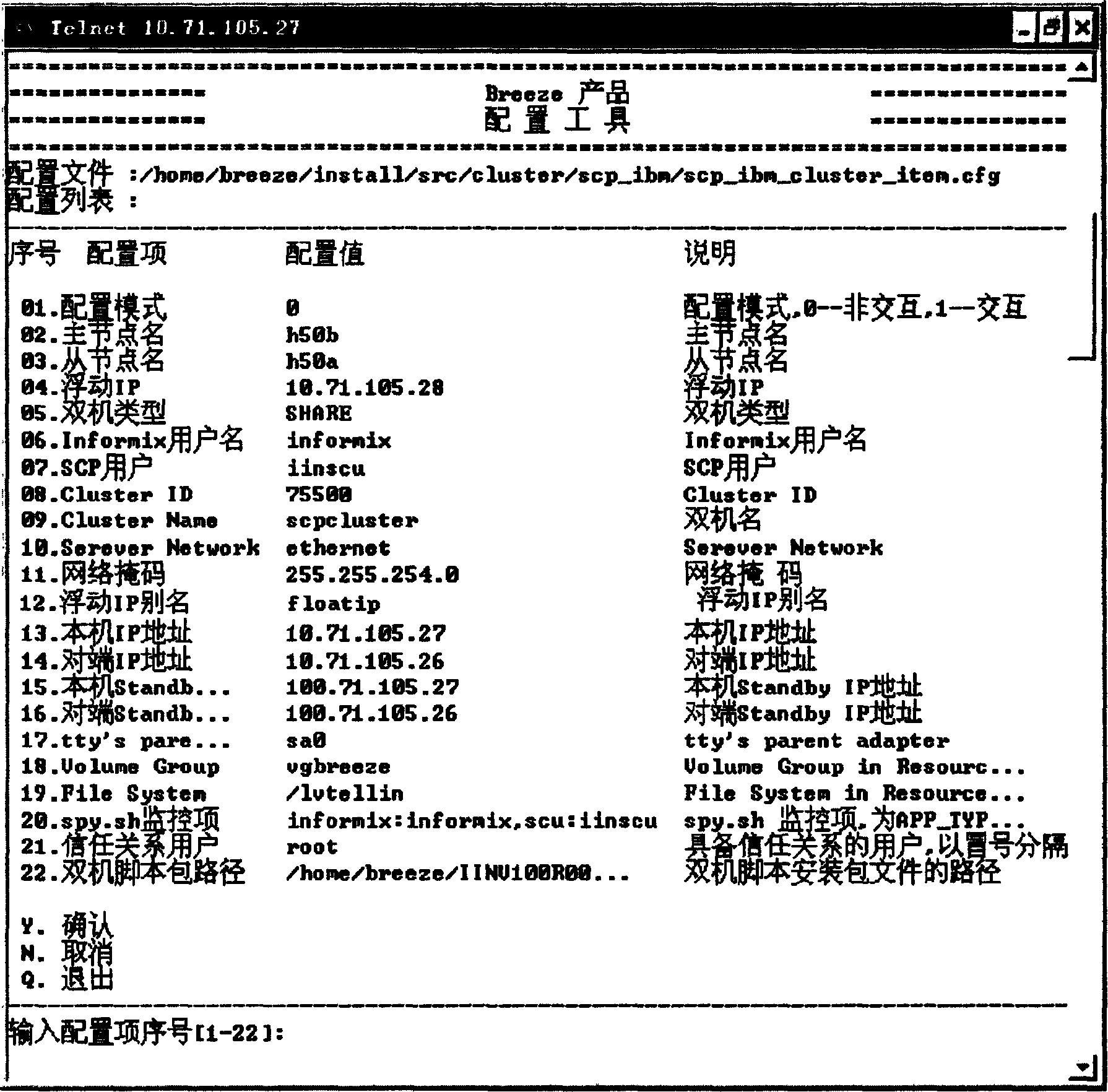
ActiveCN1790257AEasy to operateImprove satisfactionSpecific program execution arrangementsRelevant informationFile allocation
The invention discloses a uniform file allocation method, which comprises the following steps: setting the uniform allocation file with allocation items in the system; displaying the allocation item through the allocation interface; allocating the allocation item on the allocation interface; executing the corresponding operation according to the allocation item. The invention can switch and modify the allocation file at manual pattern, which guarantees the legitimate and improves the precision.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com