Non-contact CPU (Central Processing Unit) card entrance guard reader
A card reader, non-contact technology, applied in the field of non-contact CPU card access control card reader, can solve the problems of M1 card attack, low security, weak security, etc., to ensure legality, enhance security, and improve security level effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention is further described below in conjunction with embodiment;
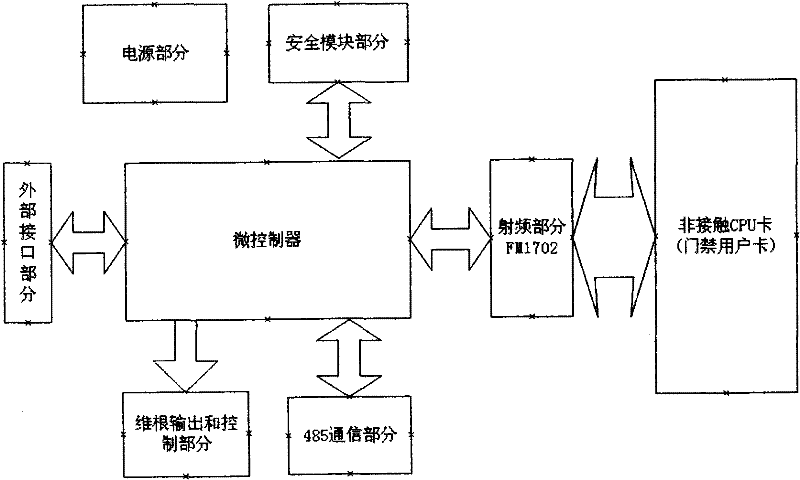
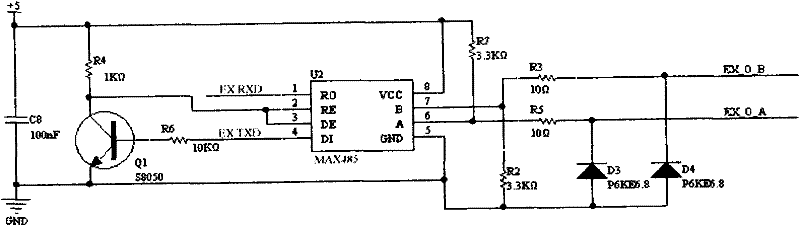
[0054] See figure 1 , non-contact CPU card access control card reader, composed of radio frequency part, 485 communication part, security module part, Wiegand output and external control part, power supply part, external connection part, microcontroller part, radio frequency part, security module part, The external interface part, the 485 communication part and the microcontroller communicate with each other, the microcontroller signal is output and controlled through the Wiegand output and the external control part, and the power supply part is used to provide electric energy.
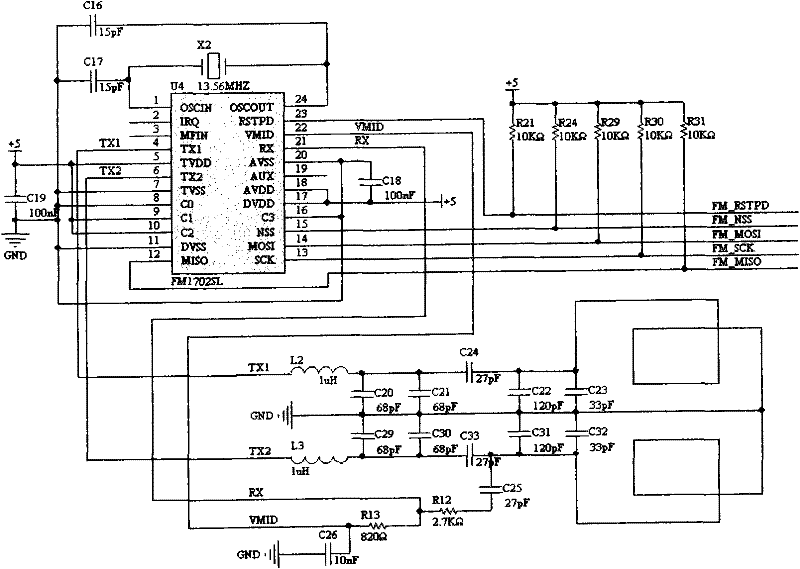
[0055] See figure 2 , the radio frequency part consists of coupling elements and circuits, including a radio frequency card reader chip U4, DC bias resistors R12, R13, R21, R24, R29~31, capacitors C16~C26, C29~C32, inductors L2, L3, preferably U4 adopts the FM1702s1 card reader chip of Fudan Microelectronics C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com