User identity protection method based on public-key mechanism
A user identity and public key technology, applied in electrical components, wireless communications, security devices, etc., can solve problems such as inability to meet high-end users, imperfect protection of IMSI, ensure validity and legitimacy, increase the difficulty of deciphering, and facilitate maintenance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The specific implementation manners of the present invention will be described below in conjunction with the accompanying drawings.
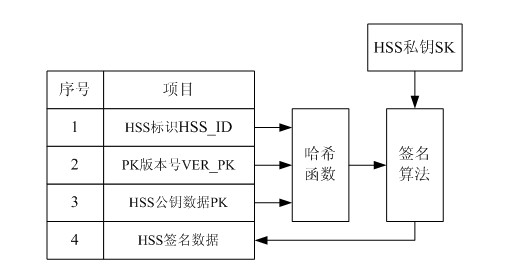
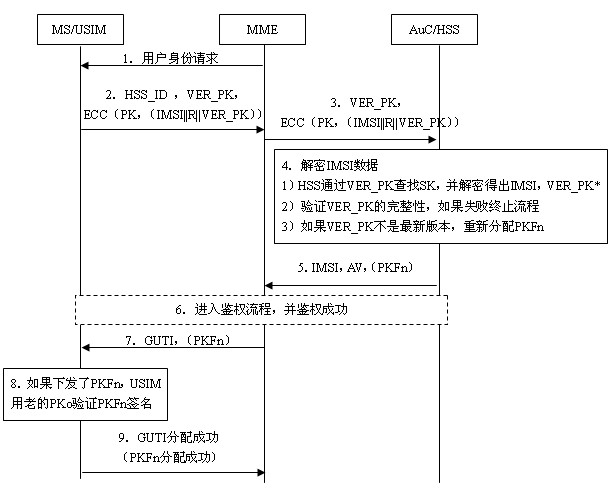
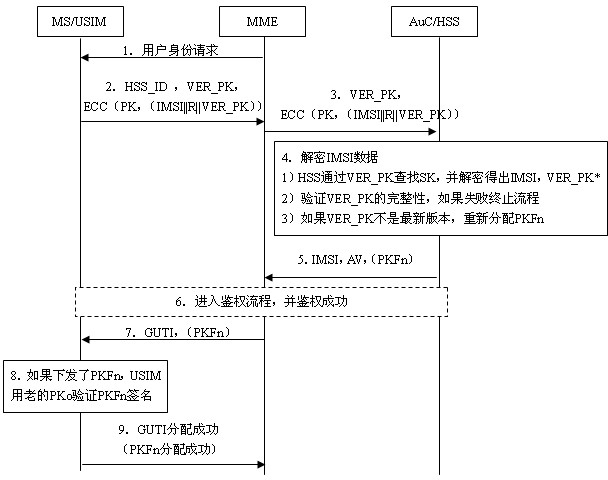
[0036] The present invention provides a user identity protection method based on a public key mechanism, wherein the encryption and decryption and signature verification algorithms use the RSA algorithm, ECC algorithm or other asymmetric encryption algorithms. For the convenience of description, the implementation process in this embodiment uses the ECC algorithm as an example . The above method is the IMSI protection method based on the public key mechanism, such as figure 2 As shown, where: in ECC (PK, (IMSI||R||VER_PK)), ECC represents an asymmetric algorithm, PK represents a public key, and (IMSI||R||VER_PK) represents encrypted data; (PKFn) Indicates that the PKFn will be issued when the public key file needs to be updated, and this parameter will not be used if it is not needed; when the HSS transmits the IMSI to the MME, its ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com