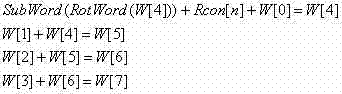AES (Advanced Encryption Standard) key expansion method
A key expansion and key technology, applied in the field of AES key expansion, can solve the problems of long time required, unfavorable parallel implementation, etc., and achieve the effects of reducing correlation, reducing correlation, and increasing the difficulty of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Without showing the corresponding principle more clearly, an existing AES key expansion method is described first.
[0024] It should be noted that there are three kinds of password lengths currently supported by AES, which are 128, 192 and 256 bits (bits). Therefore, the key is 4Byte, which is 32 bits, so 128 corresponds to 4 keys, and 192 corresponds to 6 keys, and 256 corresponds to 8 keys.
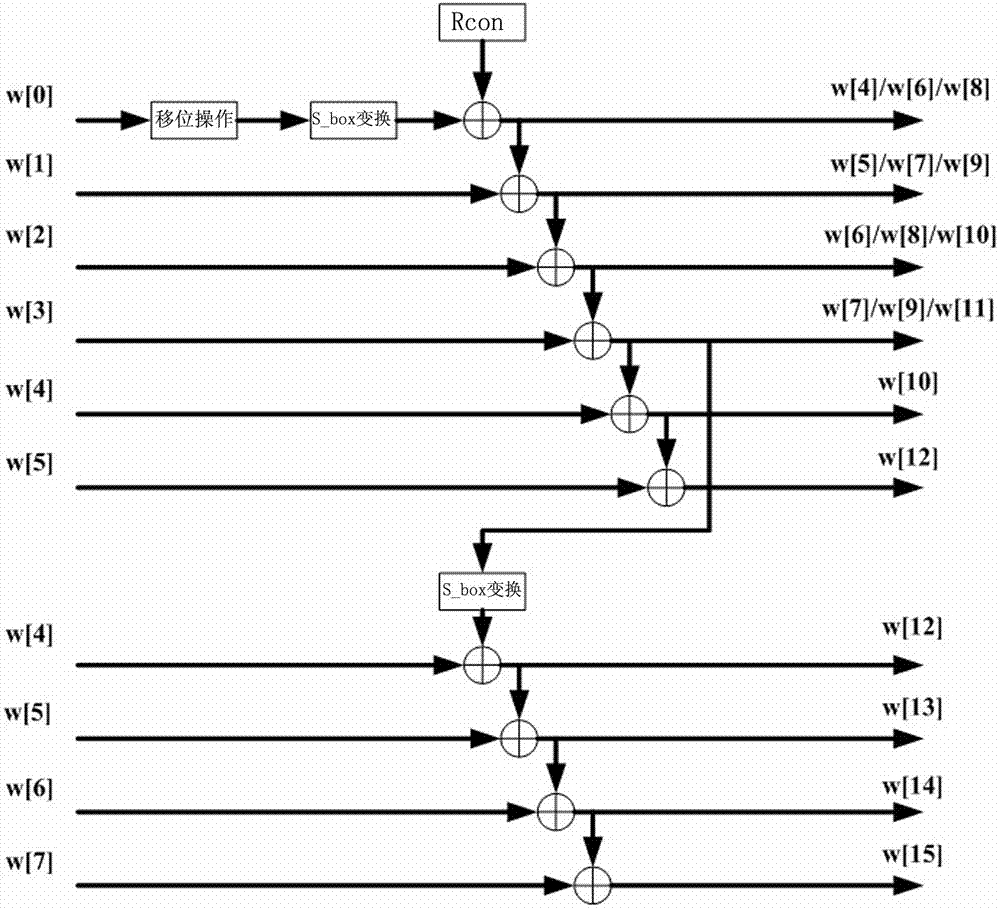
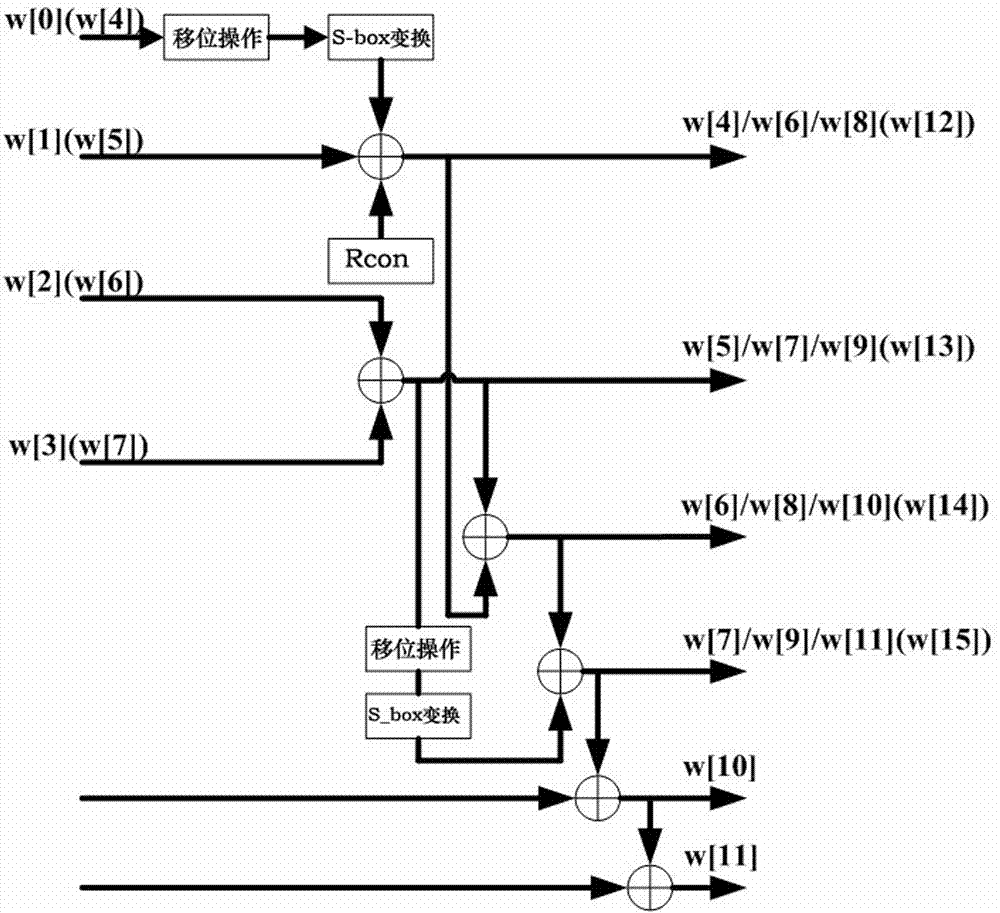
[0025] Refer to the attached figure 1 In the circuit structure shown, there are at most 8 keys in each round, corresponding to W[0] to W[7] respectively, in figure 1 In the structure shown, 10 inputs need to be configured, that is, each round needs to correspond to 10 keys, and the circuit is relatively complicated and the circuit area is relatively large.
[0026] Further, see the attached figure 1 , the existing AES password extension method has the following characteristics:
[0027] Existing AES128 key extension method
[0028]
[0029] Existing AES192 key extension ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com