Voice encryption method and device and voice decryption method and device
A voice encryption and voice technology, applied in the field of information security, can solve the problems of reduced information security and easily deciphered information, and achieve the effect of improving security and increasing the difficulty of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
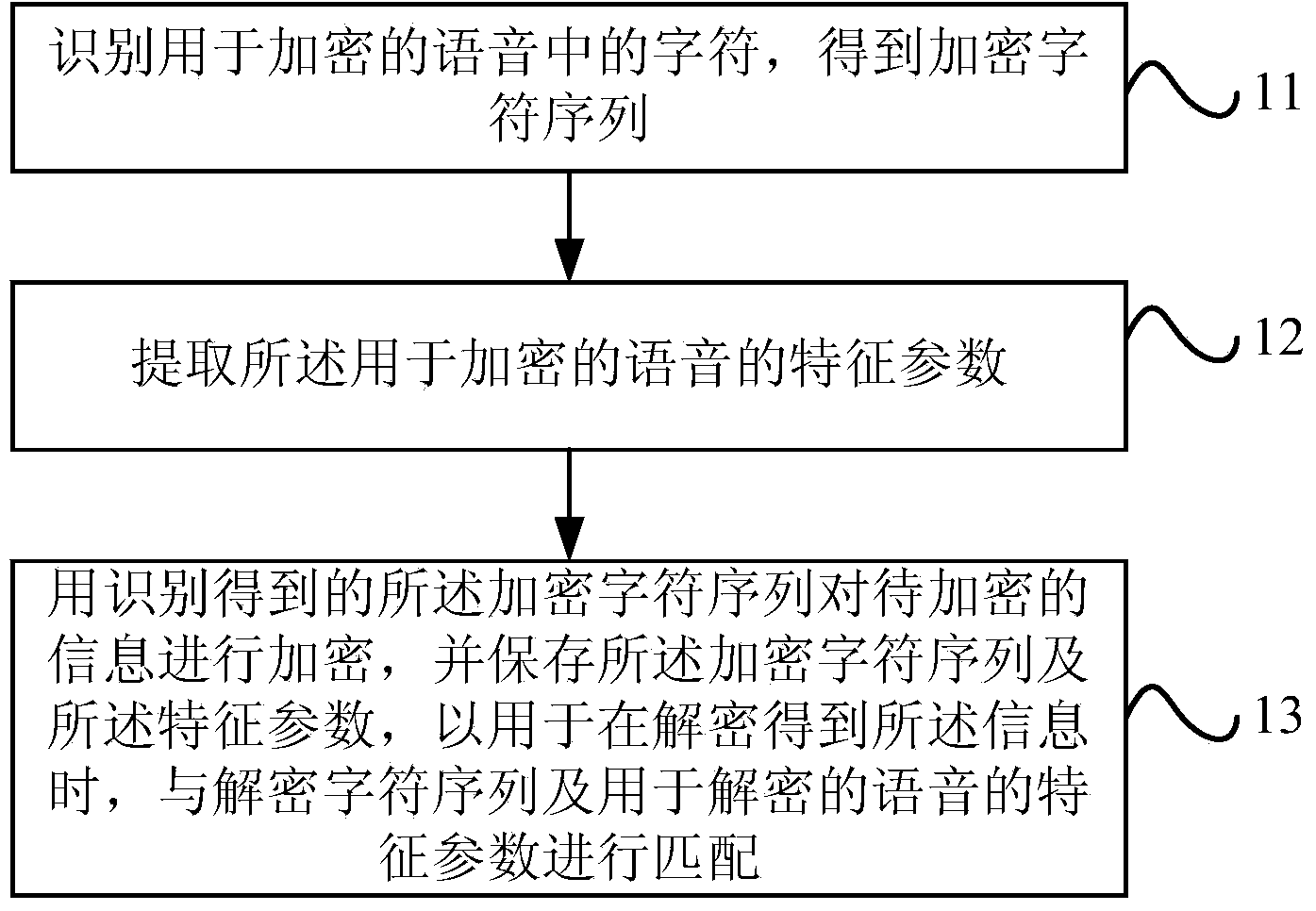
[0033] see Figure 1a , is a flow chart of a speech encryption method provided in Embodiment 1 of the present invention. The method of the embodiment of the present invention can be executed by a voice encryption device implemented in hardware and / or software. The implementation device is typically configured in a terminal capable of providing voice encryption services, such as a smart phone, a tablet computer, etc. various mobile terminals.
[0034] The method includes: operation 11-operation 13.
[0035] In operation 11, characters in the speech for encryption are identified to obtain an encrypted character sequence.
[0036] This operation specifically uses speech recognition technology to recognize and obtain an encrypted character sequence from the speech used for encryption.
[0037] Wherein, the voice used for encryption refers to the voice for encrypting the information to be encrypted, which can be the voice input by the user through the microphone in the terminal c...
Embodiment 2
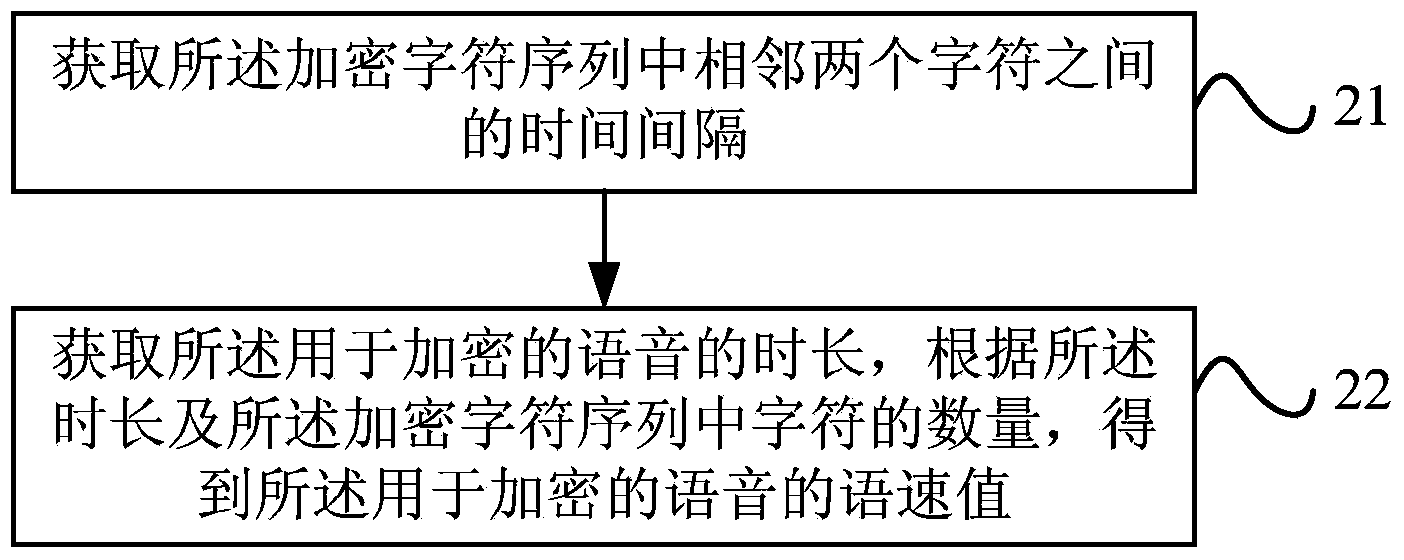
[0053] see figure 2 , is a flow chart of a voice encryption method provided in Embodiment 2 of the present invention. On the basis of the foregoing embodiments, this embodiment provides a preferred solution for the operation of extracting the characteristic parameters of the speech used for encryption, and specifically provides a preferred solution for extracting the speech rate value of the speech used for encryption.
[0054] The preferred method includes: operation 21-operation 22.
[0055] In operation 21, the time interval between two adjacent characters in the encrypted character sequence is acquired.
[0056] In this embodiment, by acquiring the time interval between two adjacent characters in the encrypted character sequence, the obtained time interval is used as the speech rate value of the speech used for encryption. In other words, based on the pause between two adjacent characters in the encrypted character sequence, characterize the speech rate value of the spe...
Embodiment 3
[0068] see image 3 , is a schematic structural diagram of a speech encryption device provided in Embodiment 3 of the present invention. The device includes: a voice recognition module 31 , a feature extraction module 32 and an encryption module 33 .
[0069] Wherein, recognition module 31 is used for identifying the character in the speech that is used for encrypting, obtains encrypted character sequence; Feature extraction module 32 is used for extracting the characteristic parameter of described speech that is used for encrypting; Encryption module 33 is used for using described speech recognition The encrypted character sequence obtained by module identification is used to encrypt the information to be encrypted, and save the encrypted character sequence and the characteristic parameters, so that when the information is obtained by decryption, the decrypted character sequence and the voice used for decryption The characteristic parameters are matched.
[0070] In the tec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com