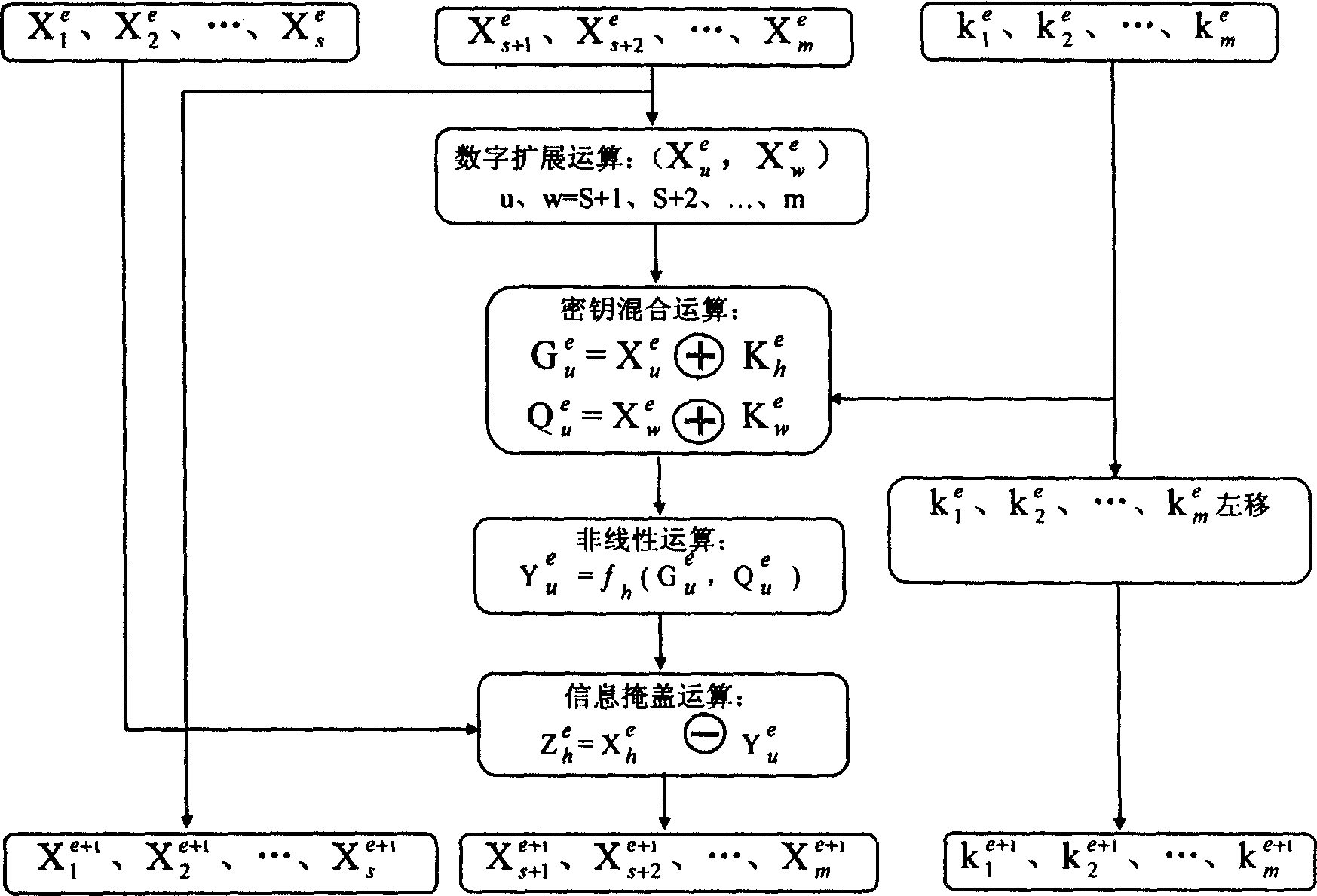
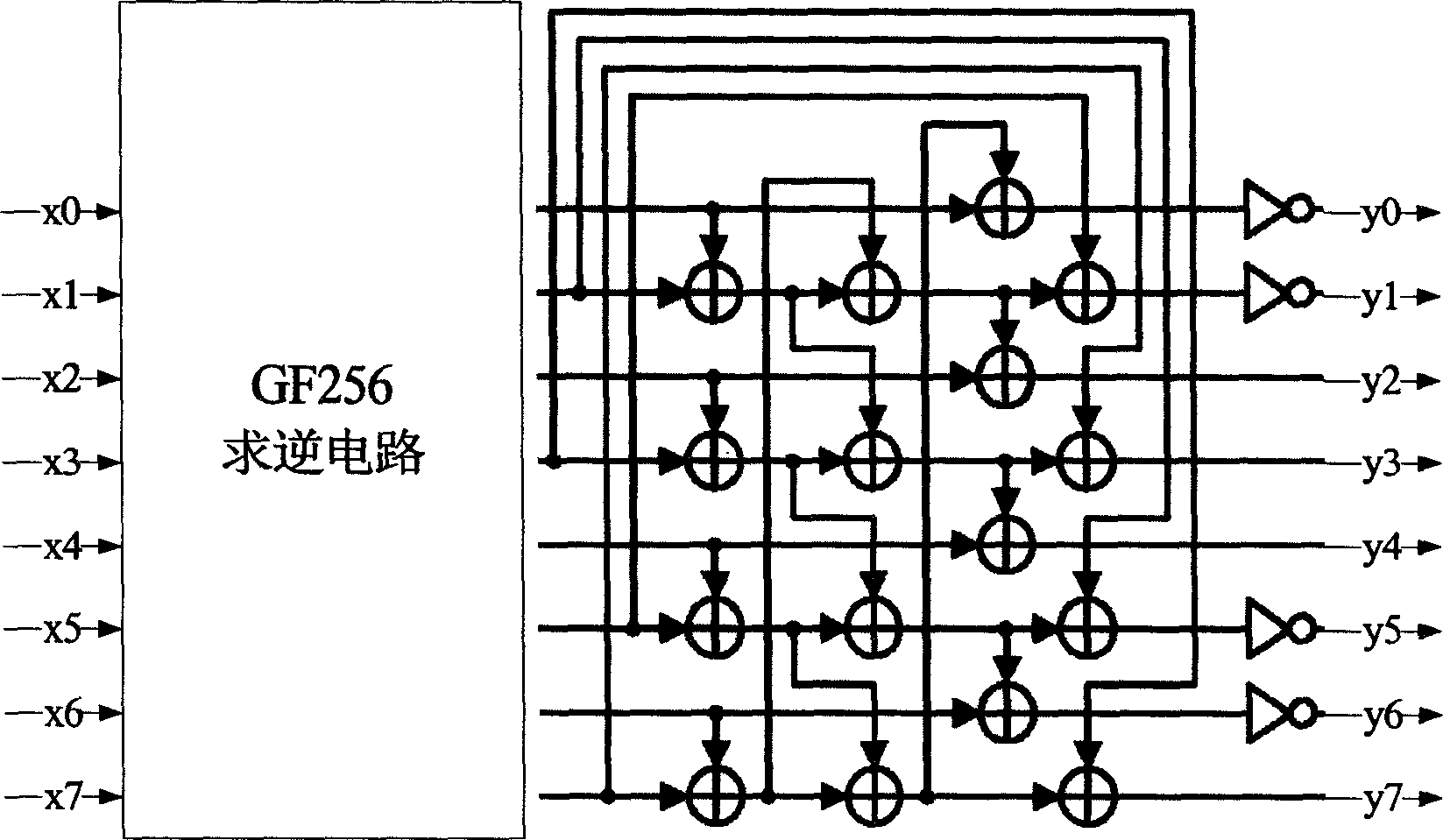
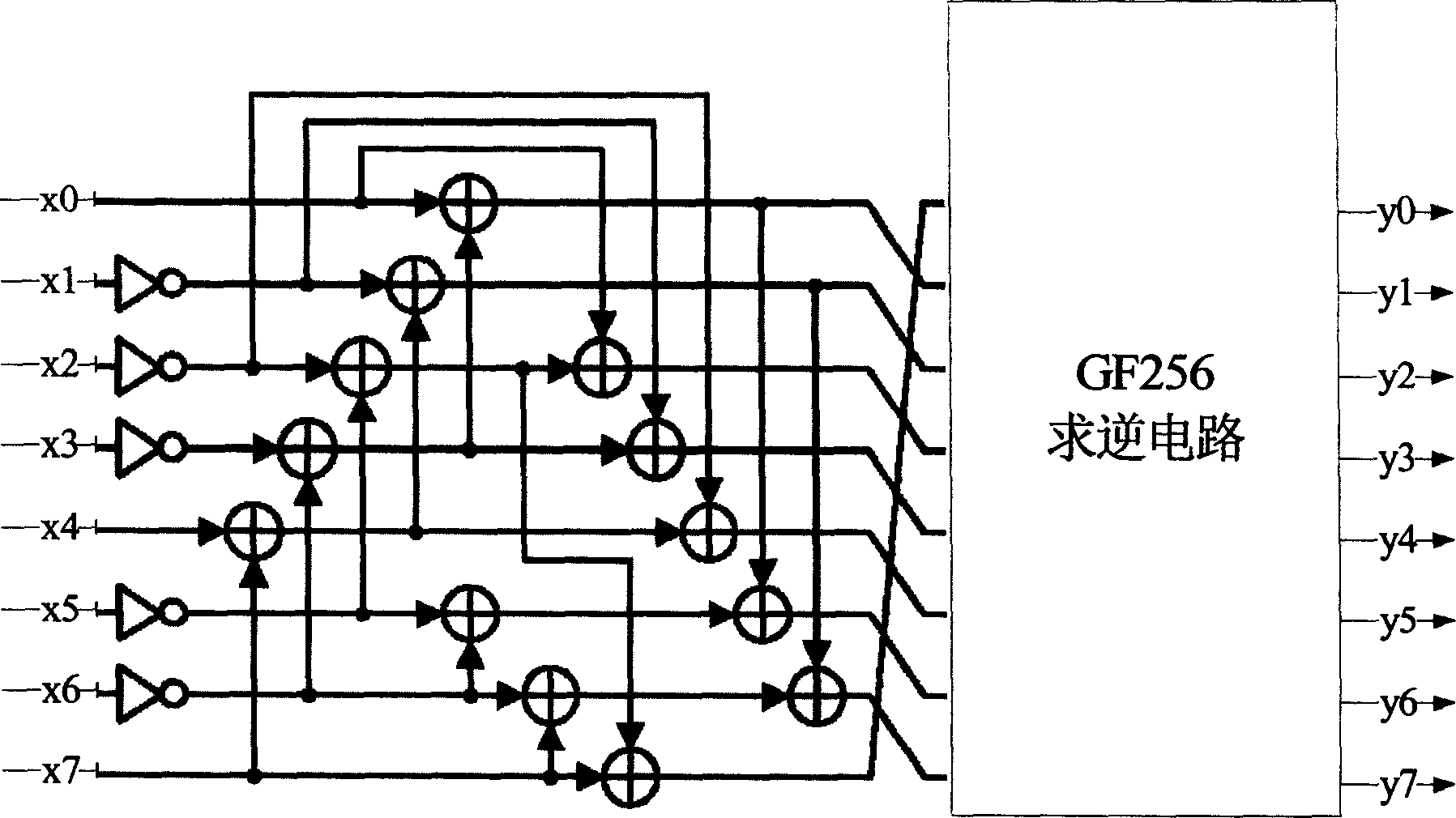
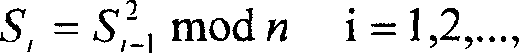Patents
Literature
68 results about "DECIPHER" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
DECIPHER is a web-based resource and database of genomic variation data from analysis of patient DNA. It documents submicroscopic chromosome abnormalities (microdeletions and duplications) and pathogenic sequence variants (single nucleotide variants - SNVs, Insertions, Deletions, InDels), from over 25000 patients and maps them to the human genome using Ensembl or UCSC Genome Browser. In addition it catalogues the clinical characteristics from each patient and maintains a database of microdeletion/duplication syndromes, together with links to relevant scientific reports and support groups.
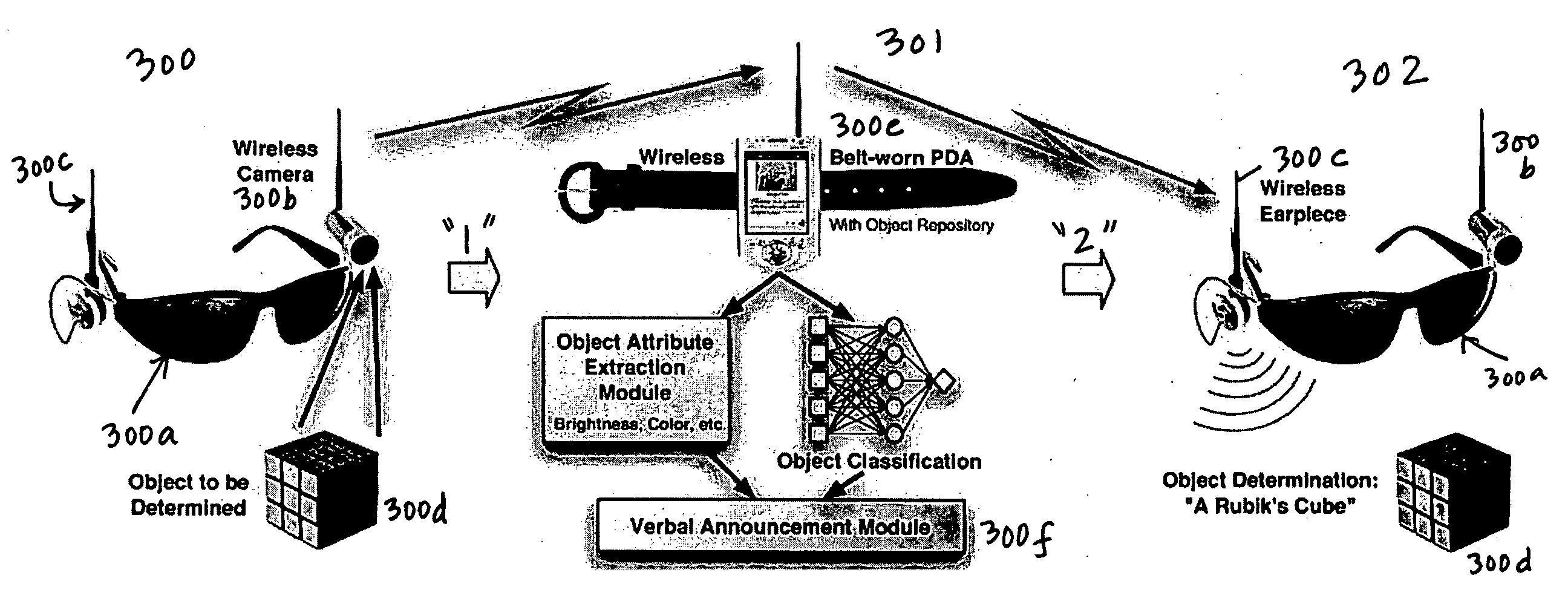
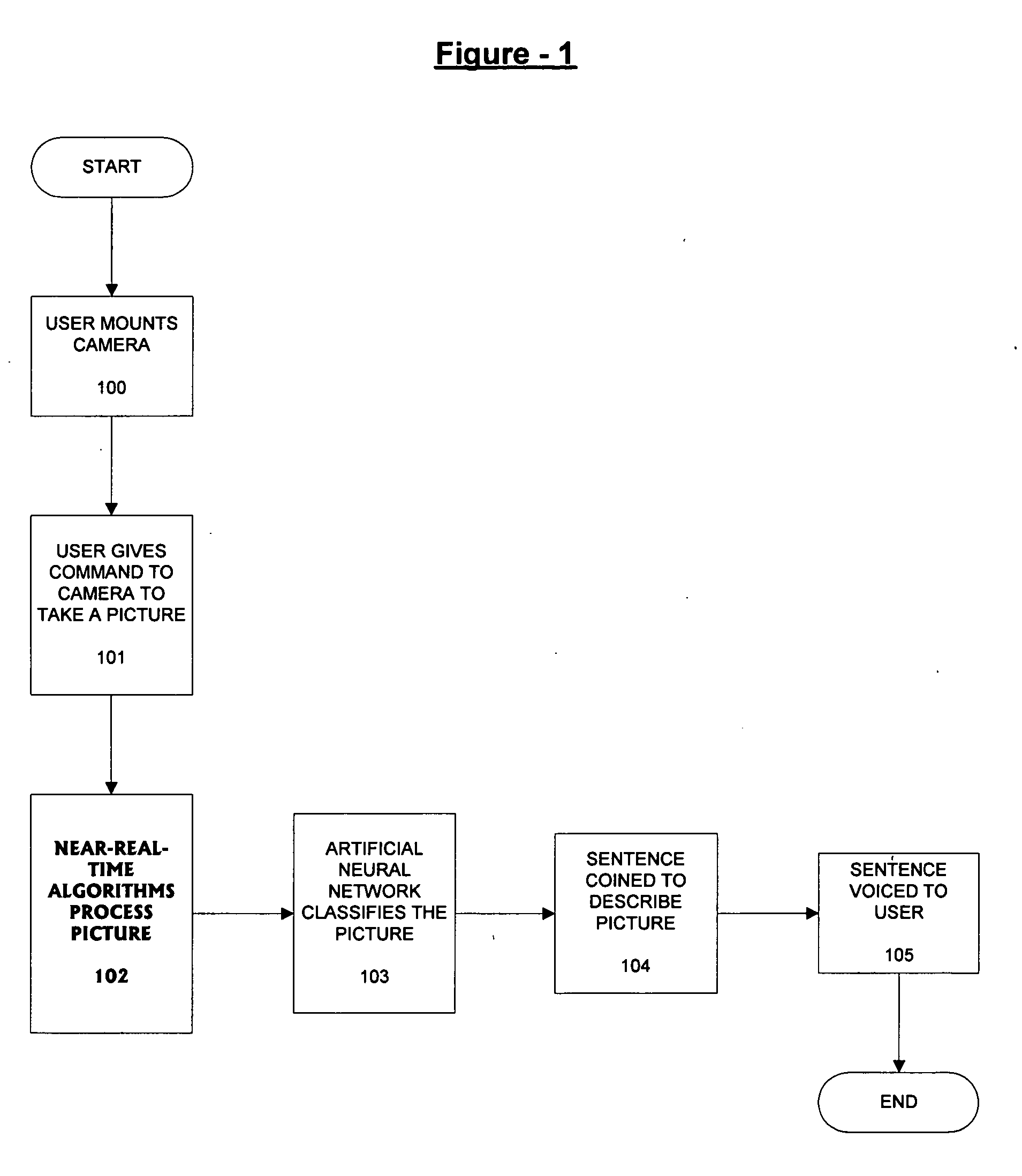
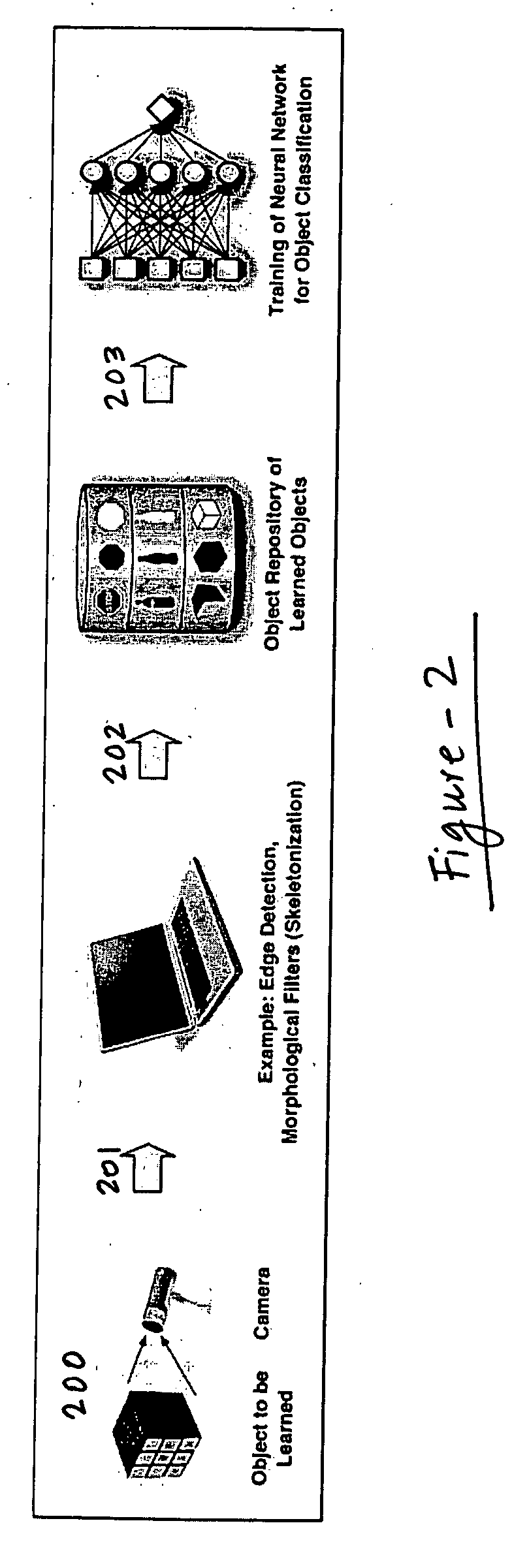
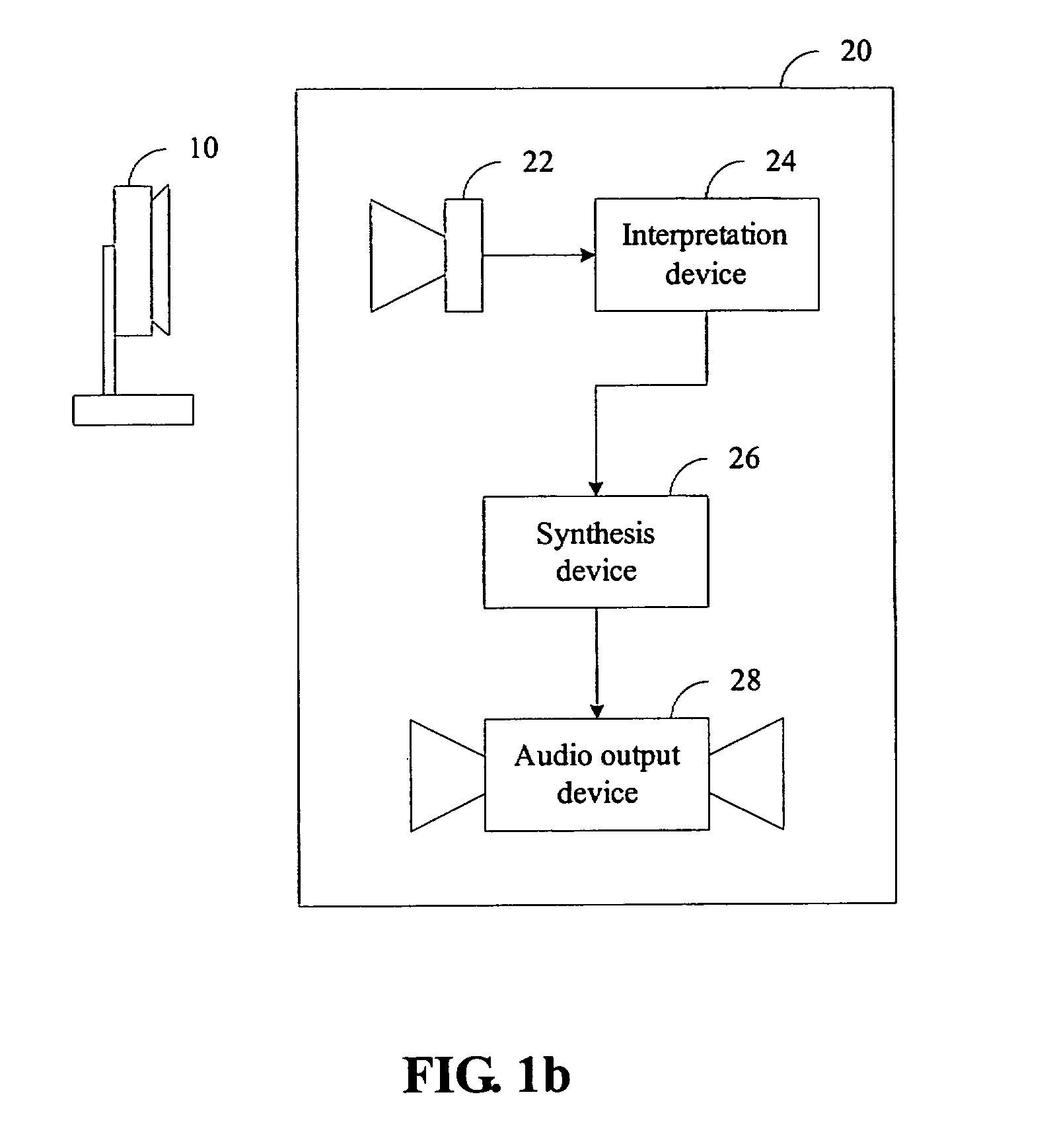
Digital object recognition audio-assistant for the visually impaired
InactiveUS20050208457A1Character and pattern recognitionTeaching apparatusDECIPHERVisually Impaired Persons
A camera-based object detection system for a severely visually impaired or blind person consisting a digital camera mounted on the person's eyeglass or head that takes images on demand. Near-real time image processing algorithms decipher certain attributes of the captured image by processing it for edge pattern detection within a central region of the image. The results are classified by artificial neural networks trained on a list of known objects, in a look up table, or by a threshold. Once the pattern is classified a descriptive sentence is constructed of the object and its certain attributes and a computer-based voice synthesizer is used to verbally announce the descriptive sentence. The invention is used to determine the size of an object, or its distance from another object, and can be used in conjunction with an IR-sensitive camera to provide “sight” in poor visibility conditions, or at night.
Owner:CALIFORNIA INST OF TECH
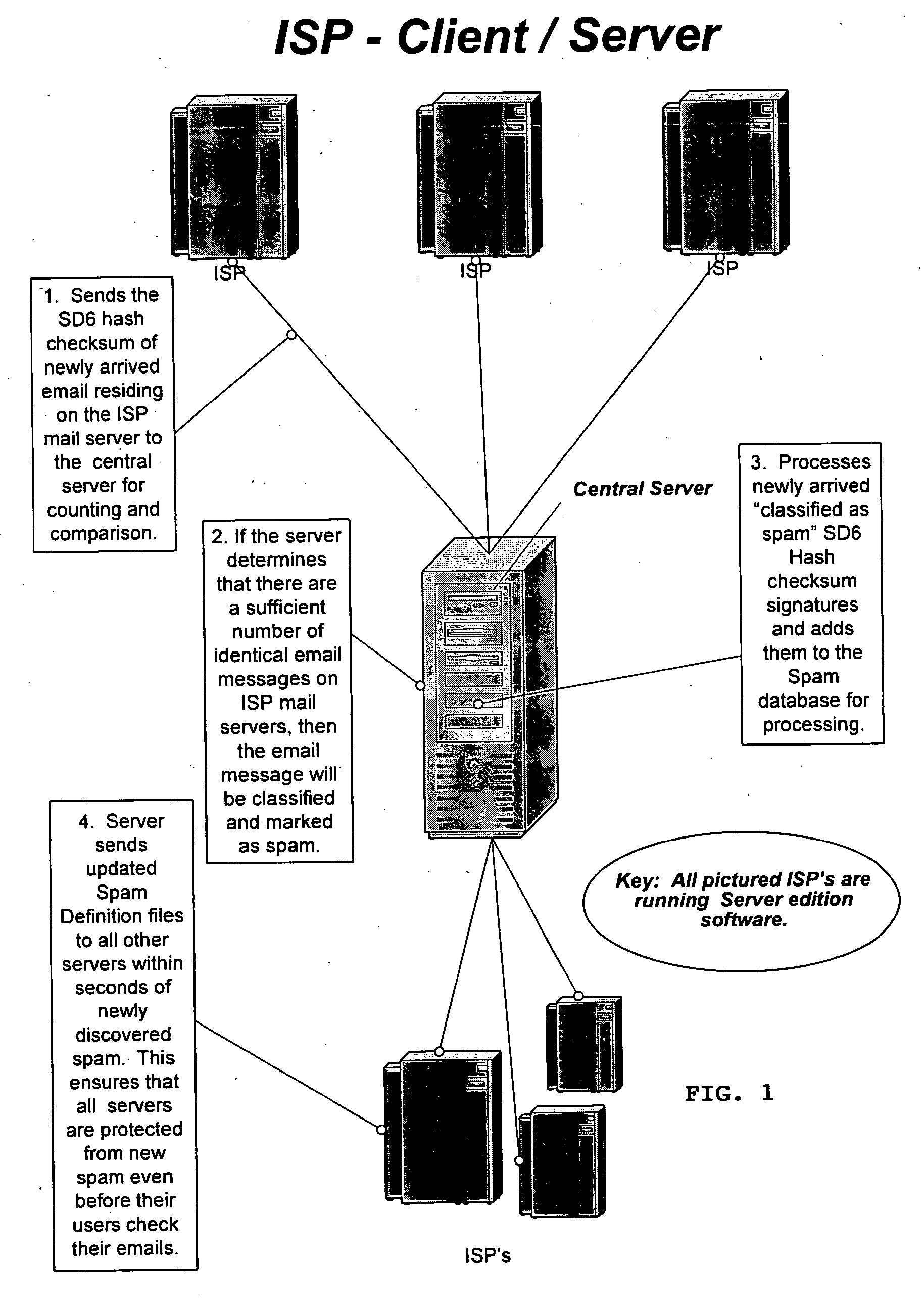
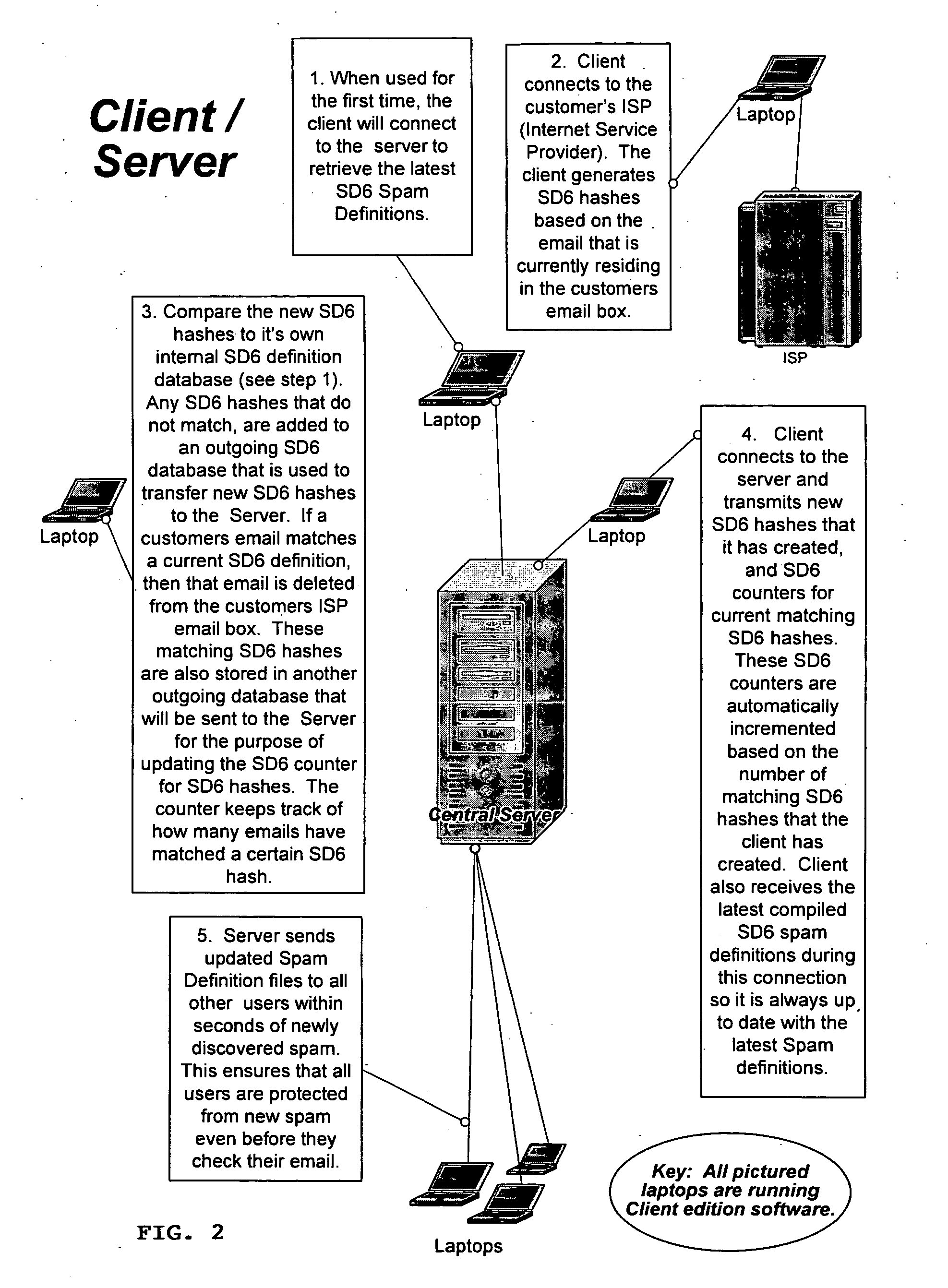
Method of detecting, comparing, blocking, and eliminating spam emails
InactiveUS20060095966A1Avoid detectionIncrease inventoryMemory loss protectionUser identity/authority verificationService provisionDECIPHER
A method of detecting, comparing, blocking, and eliminating spam emails sent through email servers of Internet service providers (ISPs) or to email users' email-boxes. The method includes the steps of generating a spam decipher signature for each email in an ISP's mail server or a user's email-box, comparing newly generated spam decipher signatures to a server or user database containing spam decipher signatures of known spam emails to detect spam emails when there is a probability match at a pre-determined high percentage, and preventing the spam emails from going through the ISP's mail server or to the email user as non-spam emails. The method also includes the steps of updating a master spam decipher signature database by comparing spam decipher signatures in a new signature database with existing spam decipher signatures in the master database, incrementing a counter value of a matching spam decipher signature by the number of matches, and adding all new spam decipher signatures that have counter values reaching or exceeding a pre-set threshold and therefore are considered spam to the master spam decipher signature database. The method further includes the steps of initially loading the master spam decipher signature database to the ISP email server or the user's computer to establish the server or user database, and updating the server or user database with the master spam decipher signature database.
Owner:PARK SHAWN
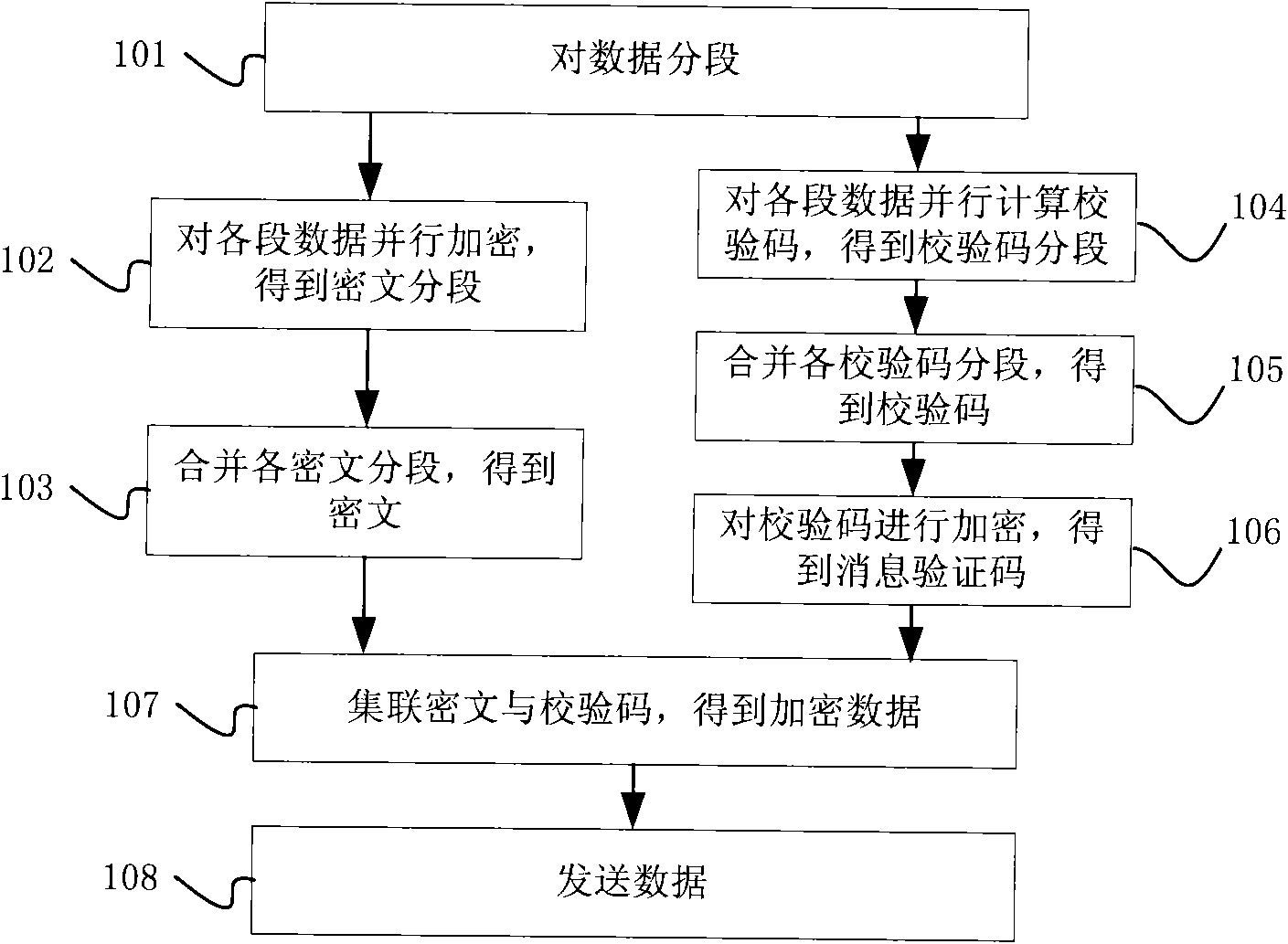
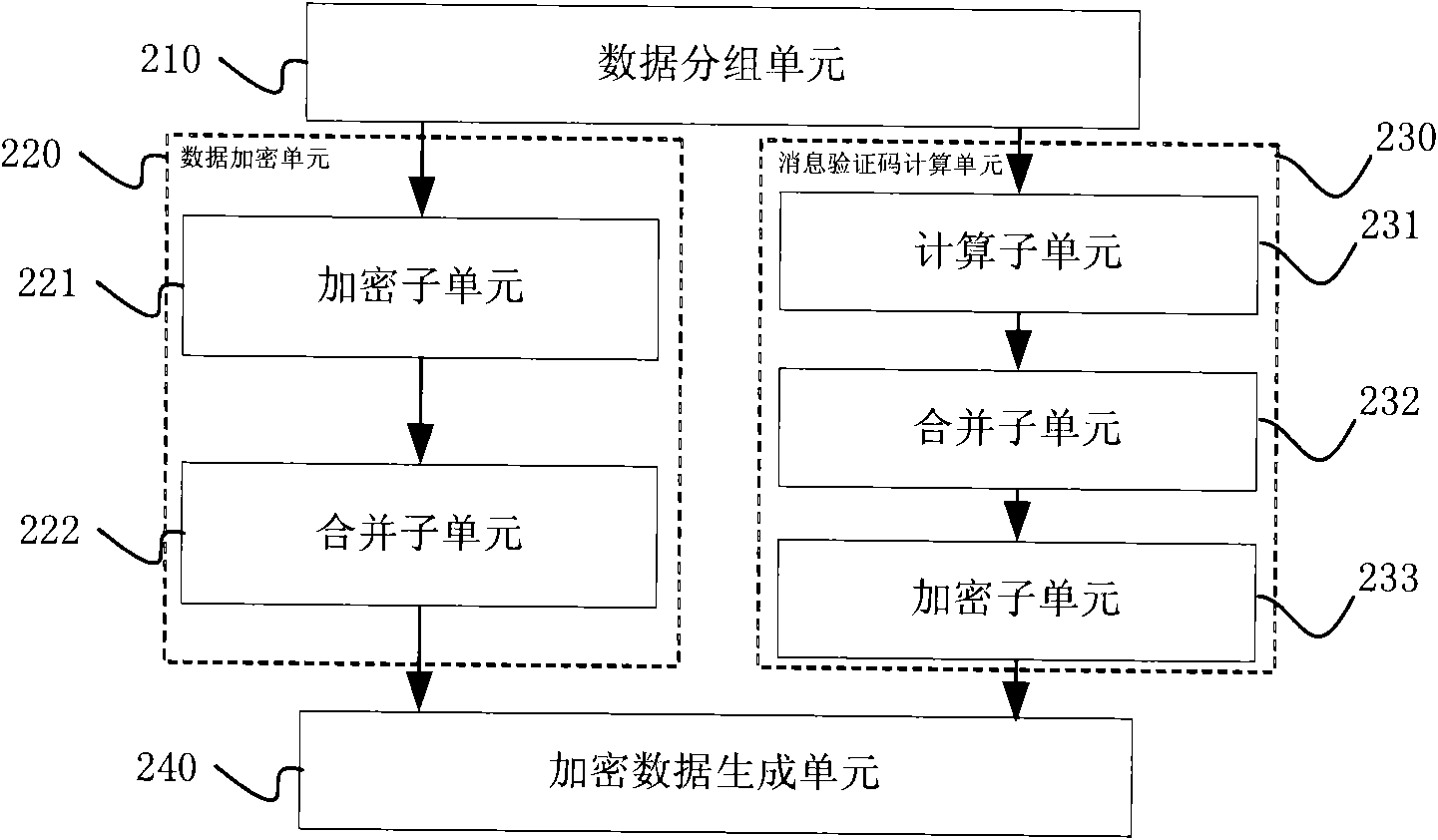
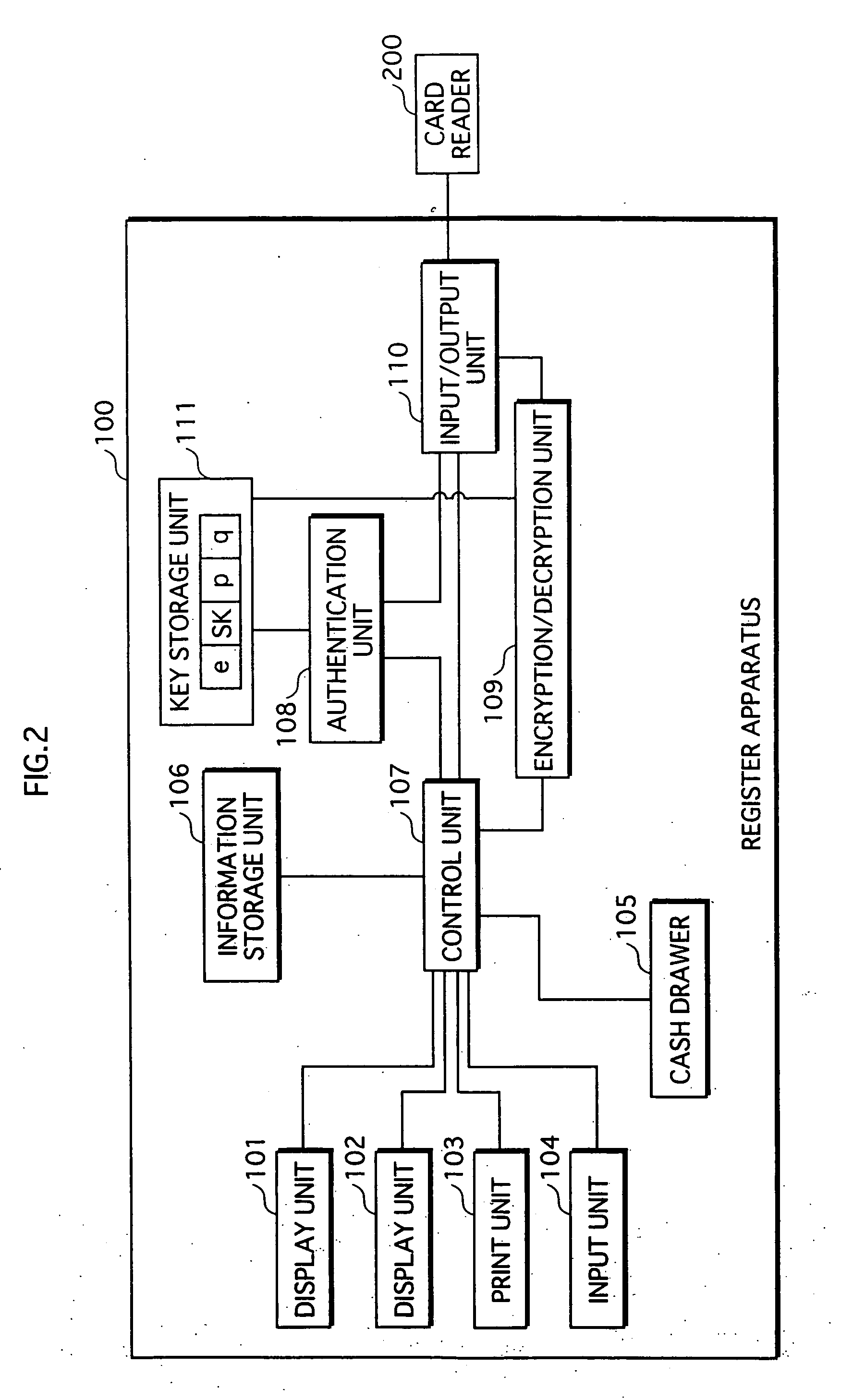
Methods and devices for data encrypting and decrypting and communication system
InactiveCN101594227ATo achieve parallel operationImprove computing efficiencyMultiple keys/algorithms usageComputer hardwareCommunications system
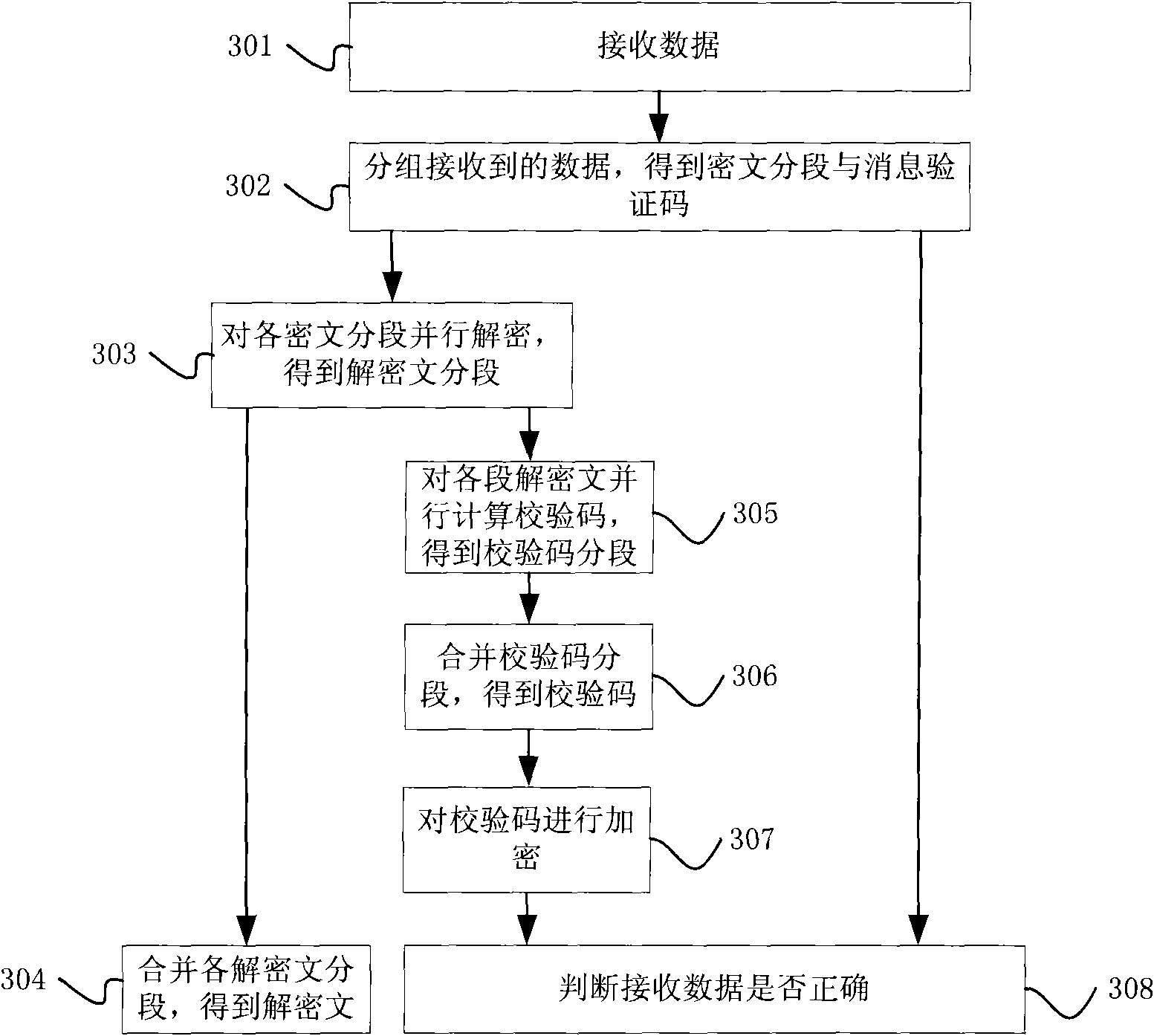
The invention discloses methods and devices for data encrypting and decrypting and a communication system. The method for data encrypting comprises the following steps: segmenting data into segment data comprising at least two segments; encrypting the segment data in parallel to obtain the ciphertext of the segment data; adopting a linear algorithm to calculate all the segment data in parallel to obtain a message authentication code; and obtaining encrypted data according to the ciphertext and the message authentication code. The method for data decrypting comprises the following steps: segmenting data to be verified to obtain ciphertext segments and a message authentication code; decrypting all segment ciphertext to obtain decipher text and decipher text segments; adopting the linear algorithm to calculate all the decipher text in parallel to obtain a check code; and judging whether the data to be verified is right or not according to the check code and the message authentication code.
Owner:HUAWEI TECH CO LTD
Method for Transmitting SyncML Synchronization Data
ActiveUS20070162518A1Synchronising transmission/receiving encryption devicesDigital data processing detailsThird partyTransport layer
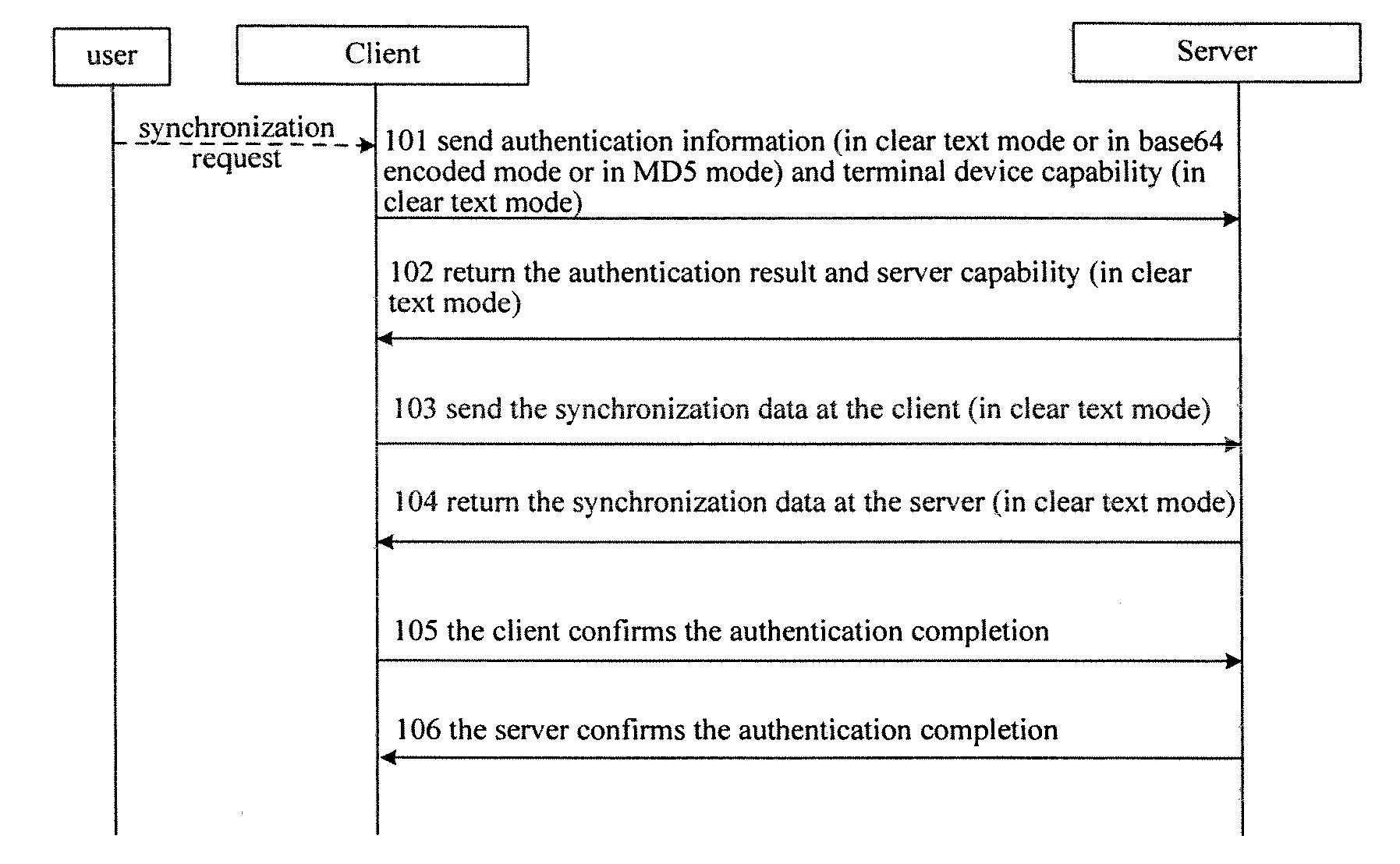
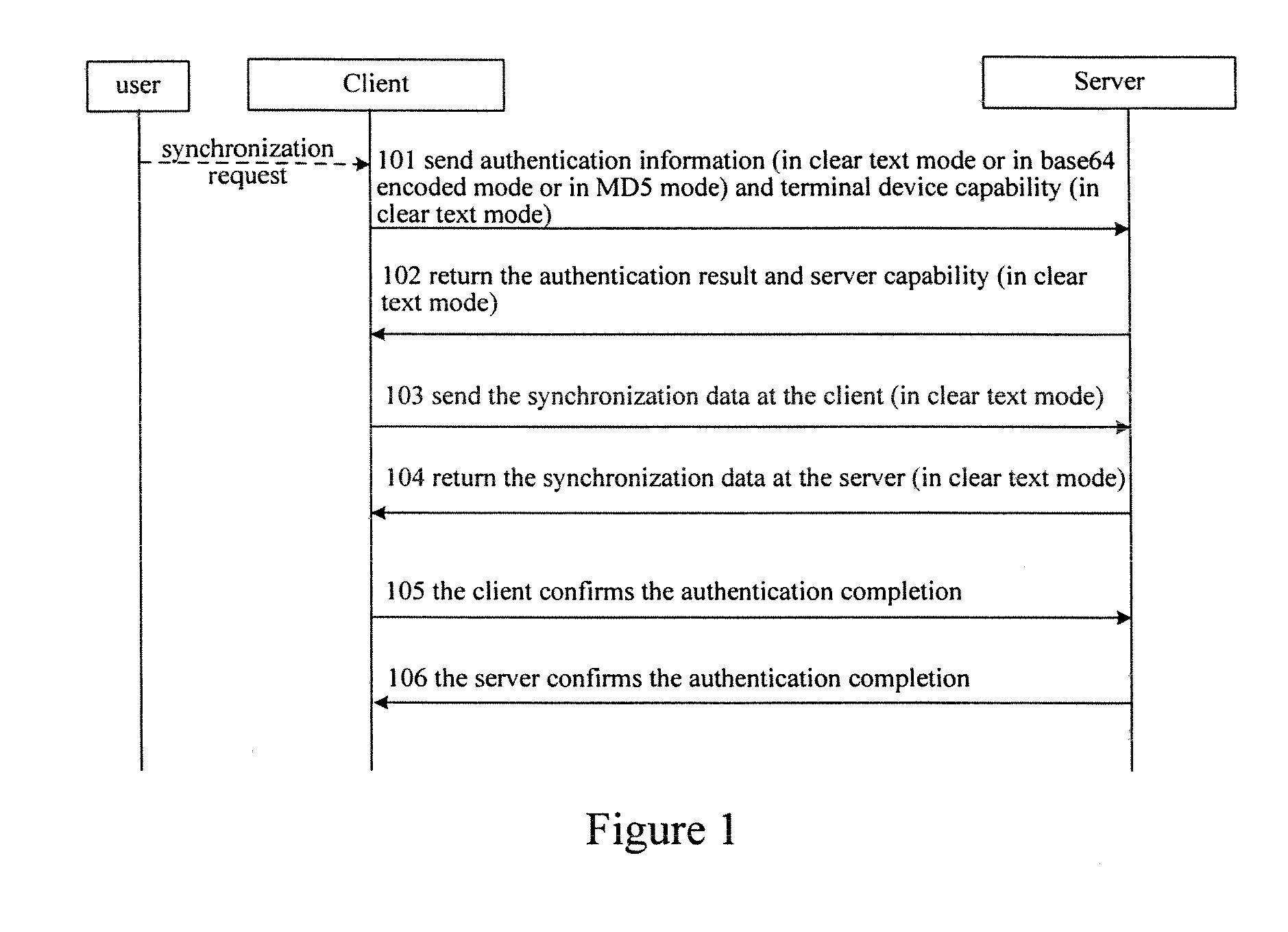
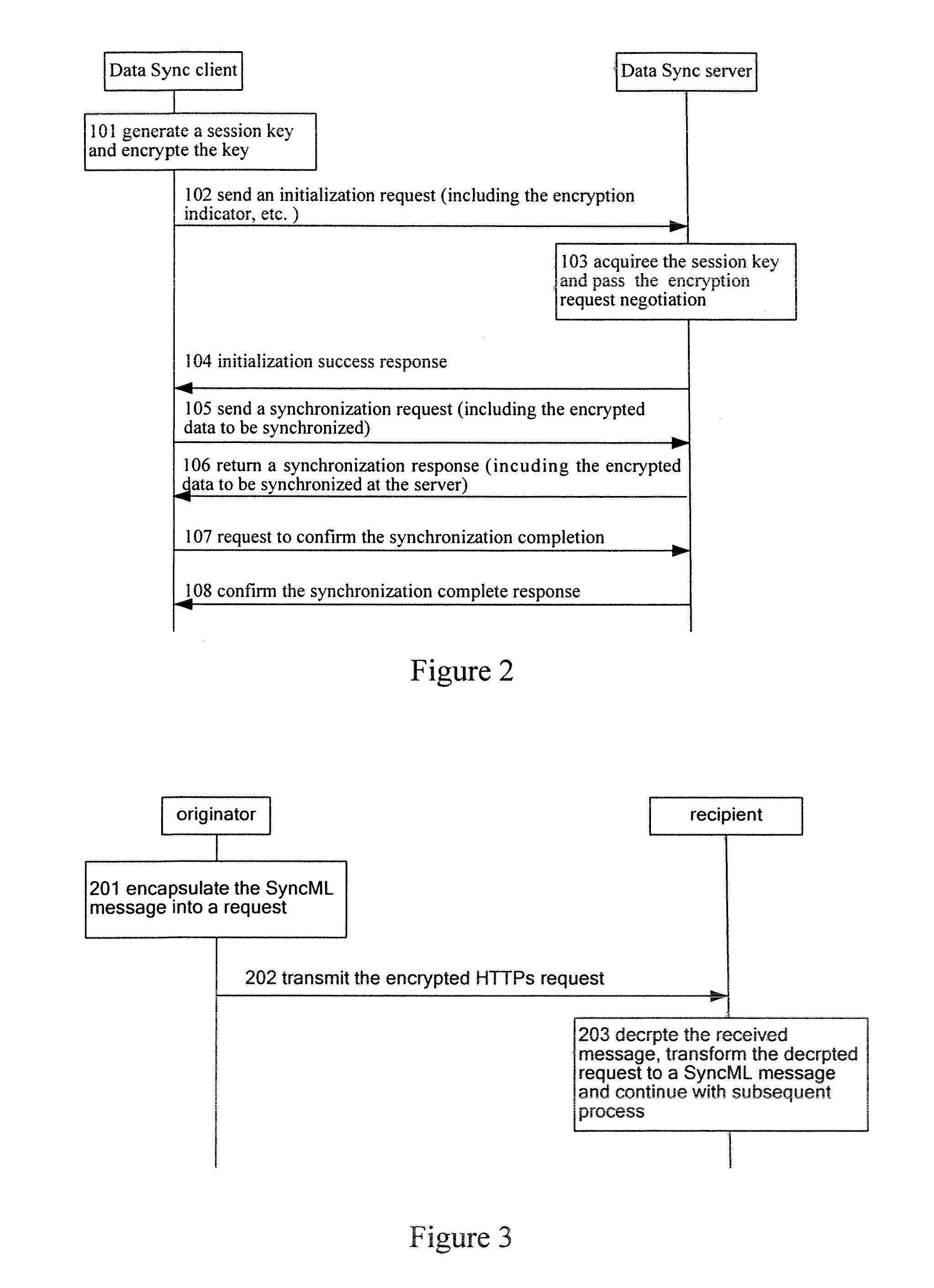
The present invention provides methods for transmitting SyncML synchronization data. One is that the originator constructs a SyncML message after encrypting the user data to be transmitted and then transmits the data in an existing transmission way; the user data includes, but is not confined to, authentication information, terminal capability information and the data to be synchronized; the other method is that the originator encrypts the SyncML message in the transport layer before transmitting the message, and the recipient deciphers the received SyncML message from transport layer and processes the message subsequently. The two methods can be used either separately or together. If they are used together, the transmission of SyncML synchronization data is provided with double safety insurance. By using the present invention, user data can be transmitted safely without being intercepted by the third party.
Owner:HUAWEI TECH CO LTD
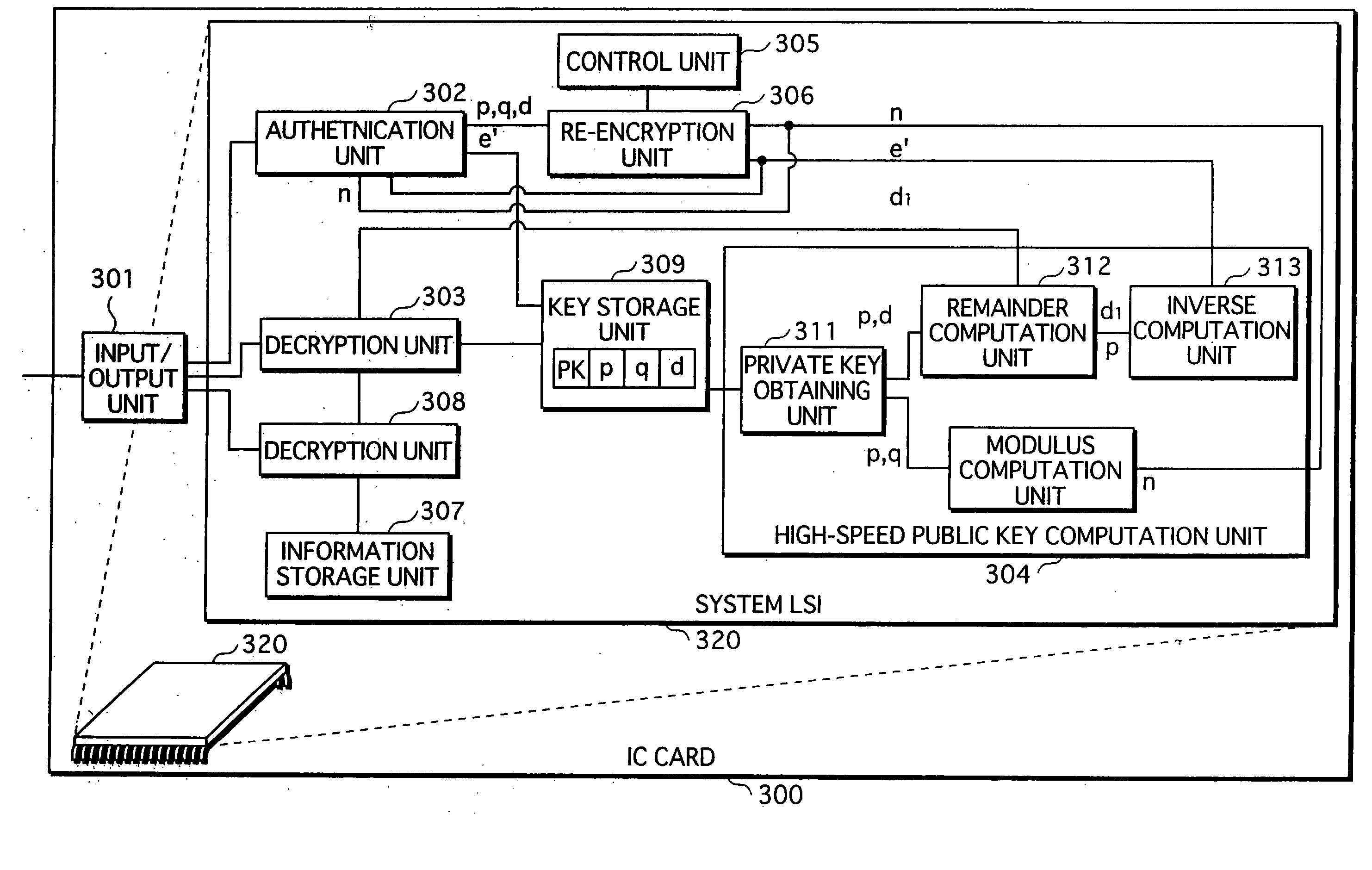
RSA public key generation apparatus, RSA decryption apparatus, and RSA signature apparatus
InactiveUS20050157872A1Increase speedPublic key for secure communicationUser identity/authority verificationComputer hardwareSource Data Verification
An RSA decryption apparatus that is used in an IC card or the like counters a differential fault attack. The RSA decryption apparatus computes at high speed a public key used in data verification, without having to obtain the public key from an external source. The RSA decryption apparatus includes a remainder computation unit 412 that calculates dp=d mod (p−1), and an inverse computation unit 414 that finds an inverse of dp over a residue field with p−1 as a modulus. The RSA decryption apparatus verifies a decipher text with use of the inverse of dp as the public key. The reduced bit count in inverse computation compared to if the inverse of d is found as the public key increases computing speed.
Owner:PANASONIC CORP
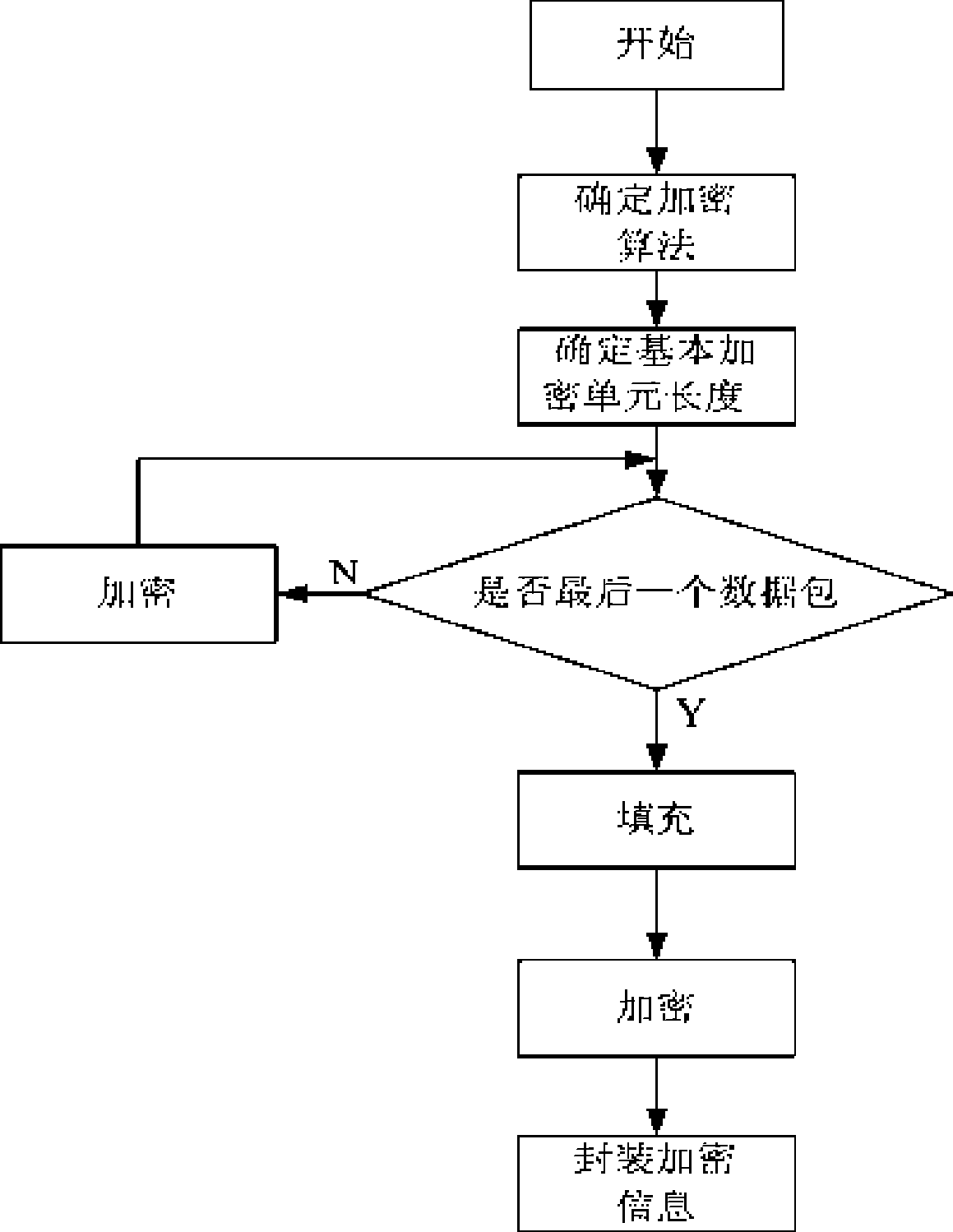
File ciphering, deciphering method
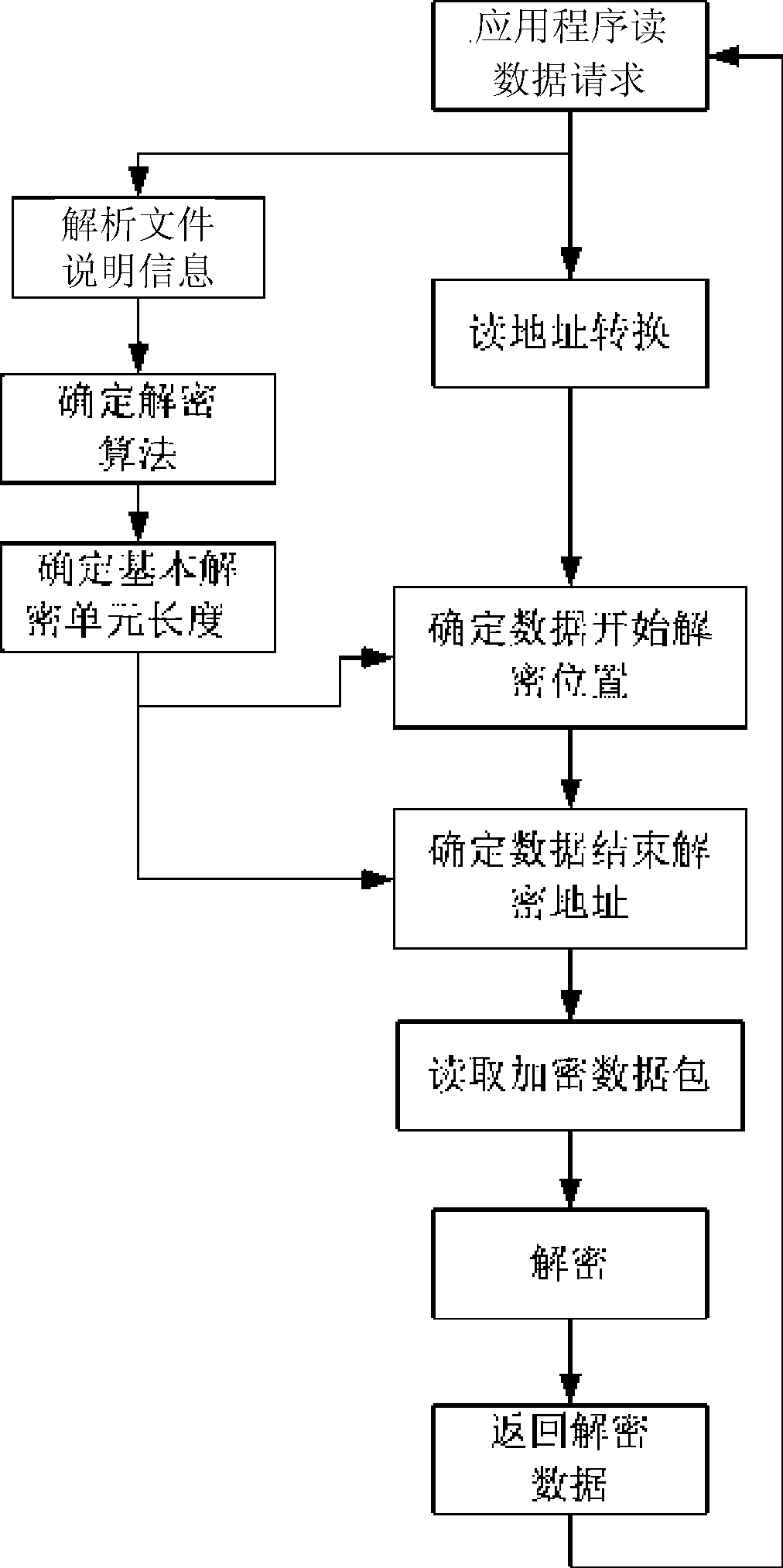
InactiveCN101488860ADoes not affect normal useCutting costsError preventionEncryption apparatus with shift registers/memoriesComputer hardwareDECIPHER
The invention relates to a file ciphering technology. The invention provides a ciphering and decipher method based on a basic ciphering unit. The file ciphering comprises the following steps: the ciphering part divides the files into a plurality of data packets with the length of the basic ciphering unit; the data packets are ciphered; the data is filled until ciphering to the last one data packet, and the filled data is ciphered. The file deciphering method comprises the following steps: a. the deciphering part determines the deciphering algorithm and the length of the basic deciphering unit according to the ciphering algorithm and the length of the basic ciphering unit; b. the deciphering part determines the data length read for every time according to the basic deciphering unit, the ciphering data packets are deciphered and the deciphered data packets are returned; the filled data can be deleted after the last one data packet is deciphered. The invention can implement the ciphering for file of arbitrary format, can implement the simultaneous deciphering and using of the file, the invention can be applied to the content protection of the office system and the digital medium.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Deciphering encapsulated and enciphered UDP datagrams
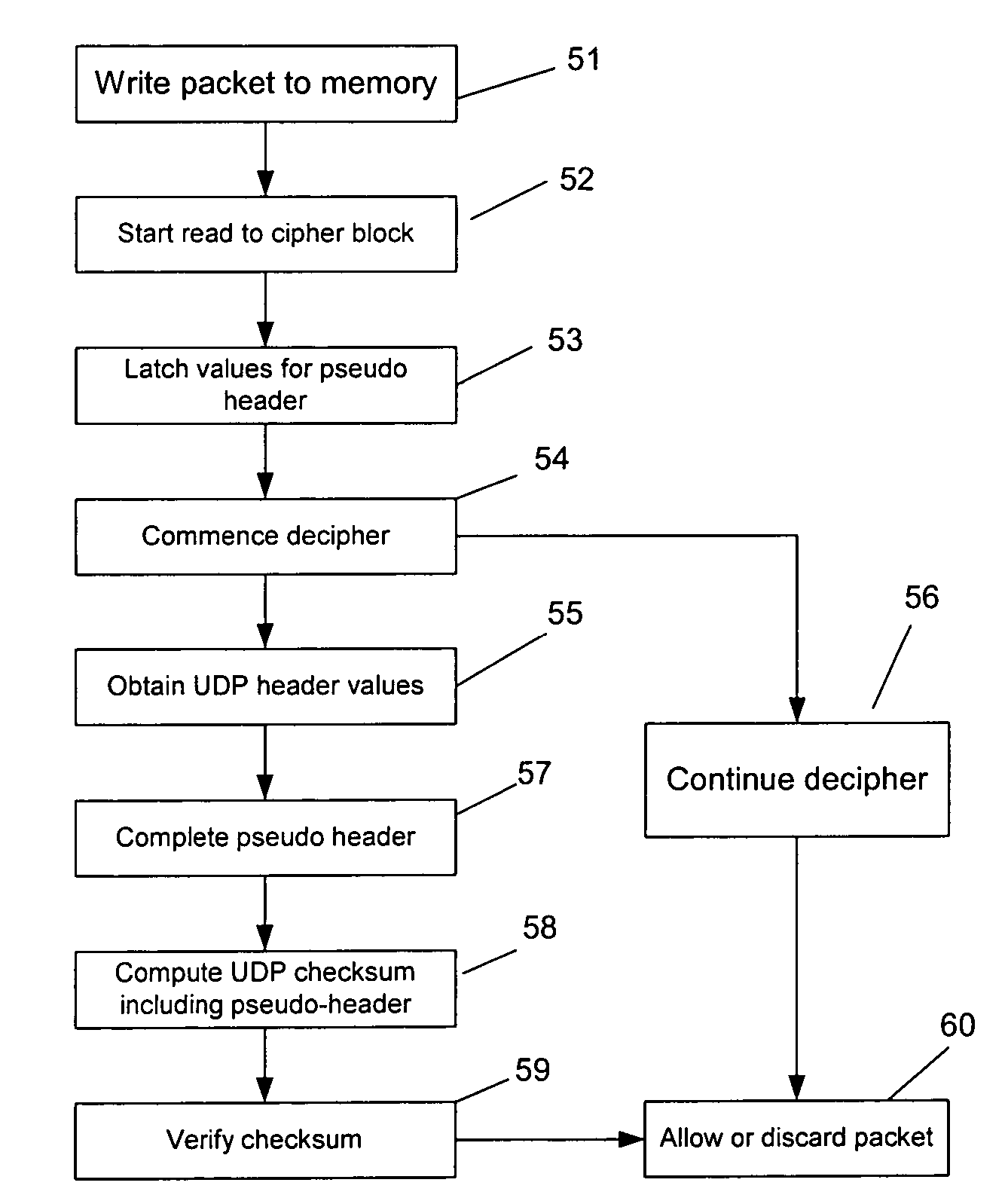
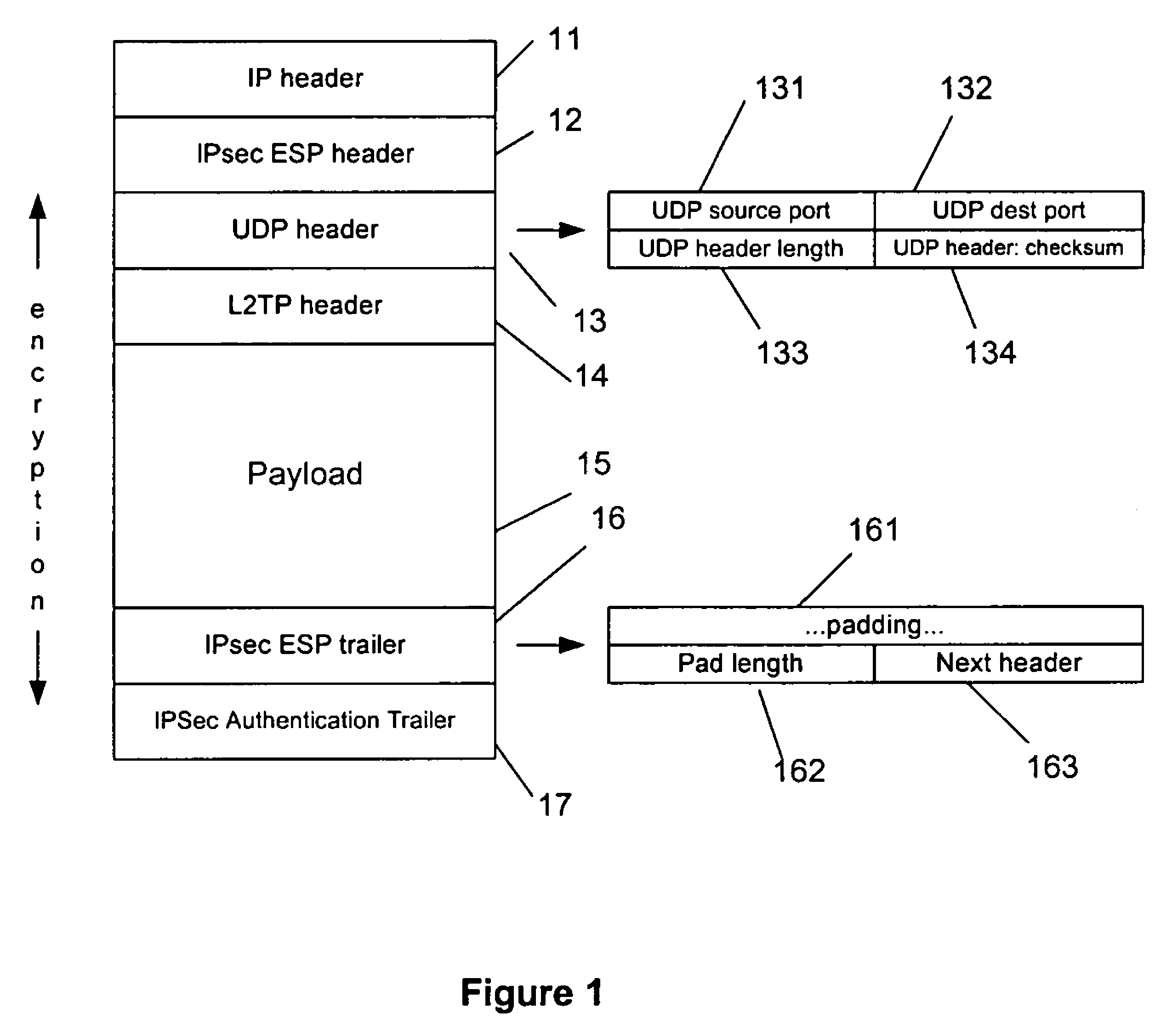
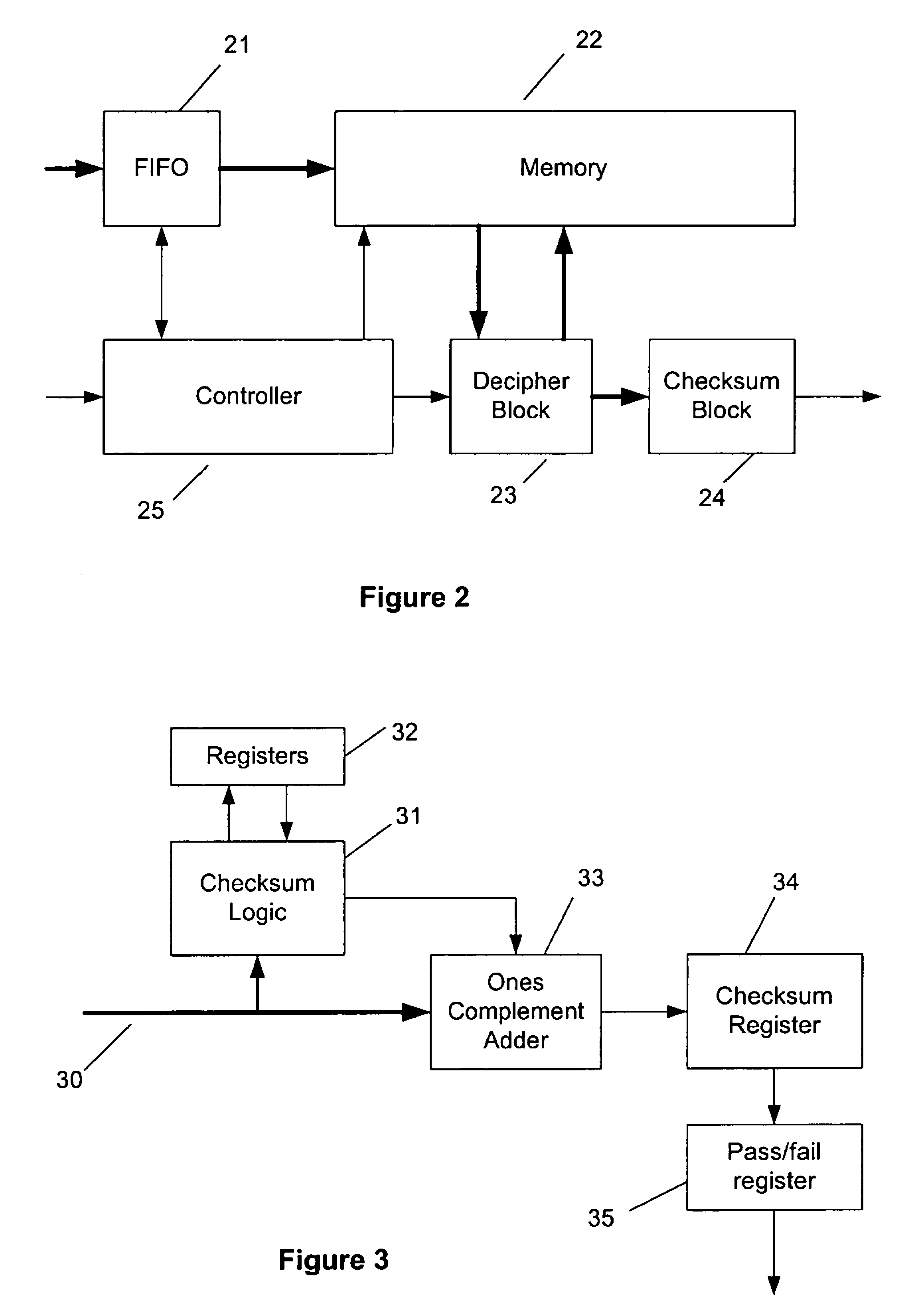
InactiveUS7843910B2Improve deciphering and verificationTime-division multiplexData switching by path configurationComputer hardwareProcessor register
Deciphering and verification of the checksum of enciphered and encapsulated UDP datagrams, particularly those which enclose a tunneling protocol such as L2TP, are achieved by the provision of a checksum verifier in parallel with a decipher block. Checksum logic creates a pseudo UDP header needed for checksum verification using fields that would occur at the start of the packet that encapsulates the UDP datagram. The first part of the packet to be deciphered is the UDP header; checksum logic can latch the checksum field into a local register. As the rest of the packet is deciphered the checksum verifier processes the data at the same time. Eventually the checksum logic will acquire a complete checksum which can be compared with the checksum that had been previously latched, so as to verify the checksum.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
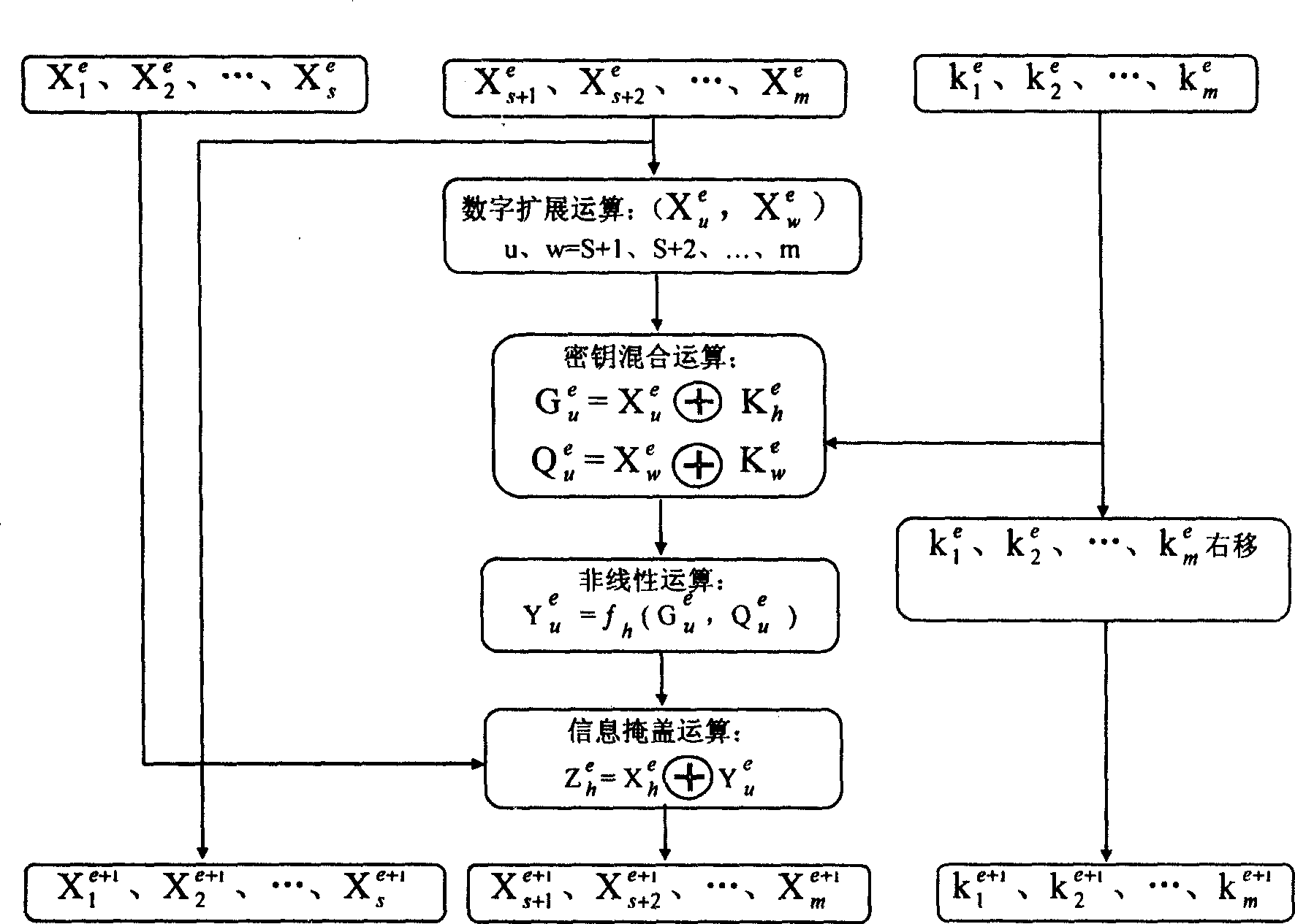
A data encryption/decryption method and encryption/decryption apparatus
InactiveCN1633070AConfidentiality is not compromised by unauthorizedSimple thinkingMultiple keys/algorithms usagePlaintextCiphertext
This invention discloses a data ciphering and deciphering method which randomly selects a random cryptographic key to replace positions to clear-text data, then dispatches a user cryptographic key to cipher the random cryptographic keys and the data layer by layer and outputs the cipher-text. Deciphering method: the random cryptographic key is recovered first, then the clear-text data position replaced vector is got and clear-text data are recovered by dispatching suitable user cryptographic key to output the clear-text finally. A device includes a cipher / decipher processor, clear-text cipher-text buffer memory for storing the clear-text cipher-text input data and inputting them to a processor, a memory for staring various data and inputting them to a processor, an output device for outputting the cipher-text.
Owner:徐子杰
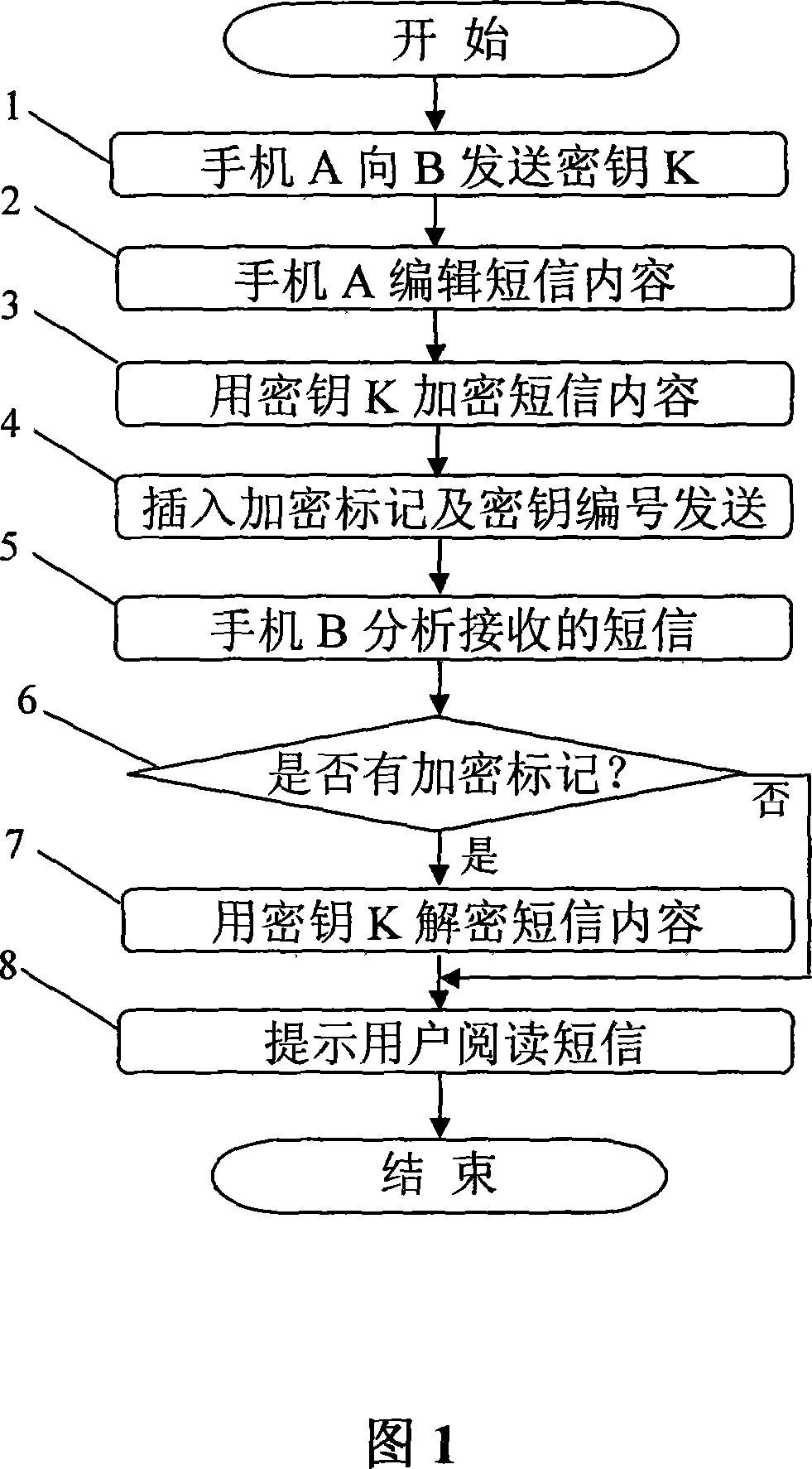
A mobile phone message encrypting and decrypting method
InactiveCN101060670AReduce operational burdenDon't change habitsMultiple keys/algorithms usageRadio/inductive link selection arrangementsComputer hardwareDECIPHER
The disclosed enciphering and deciphering method for mobile phone SMS comprises: phone A random generates key K and sends to phone B, and following enciphers SMS with key K; phone B checks all SMS to find out the enciphered SMS, deciphers and indicates user read. This invention brings no extra load to user, and improves SMS security.
Owner:深圳市杰特电信控股有限公司
Smart find
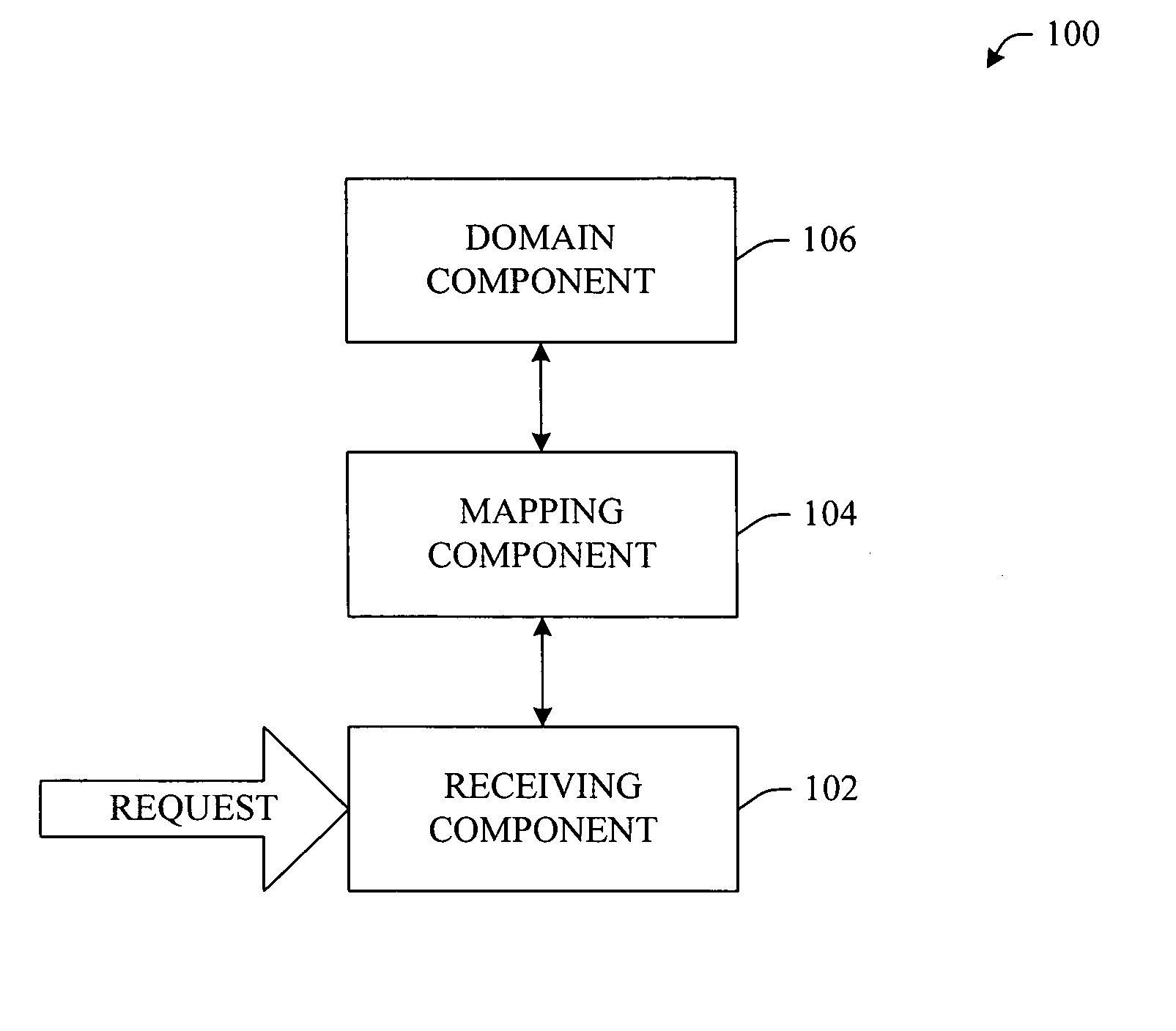
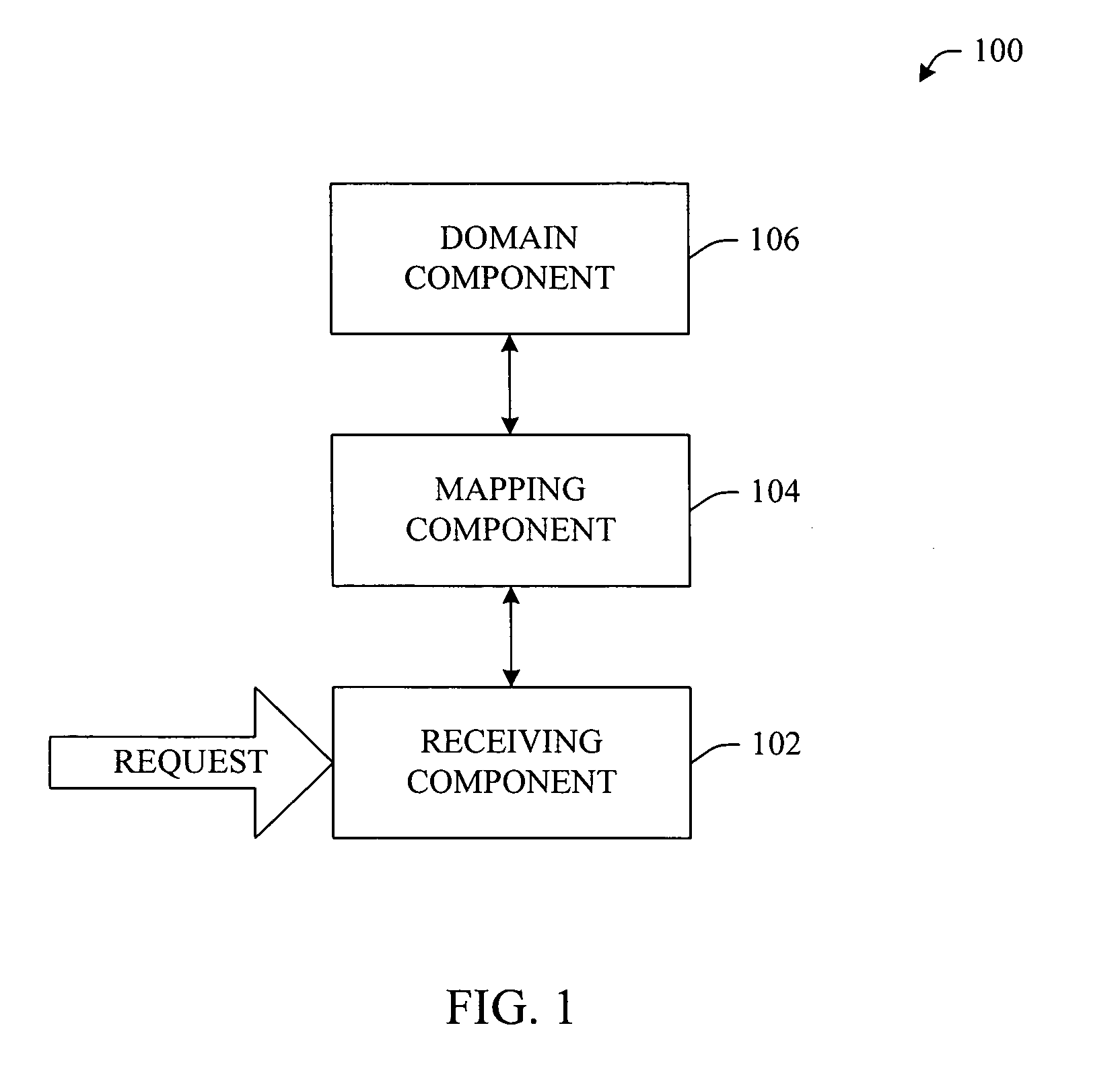
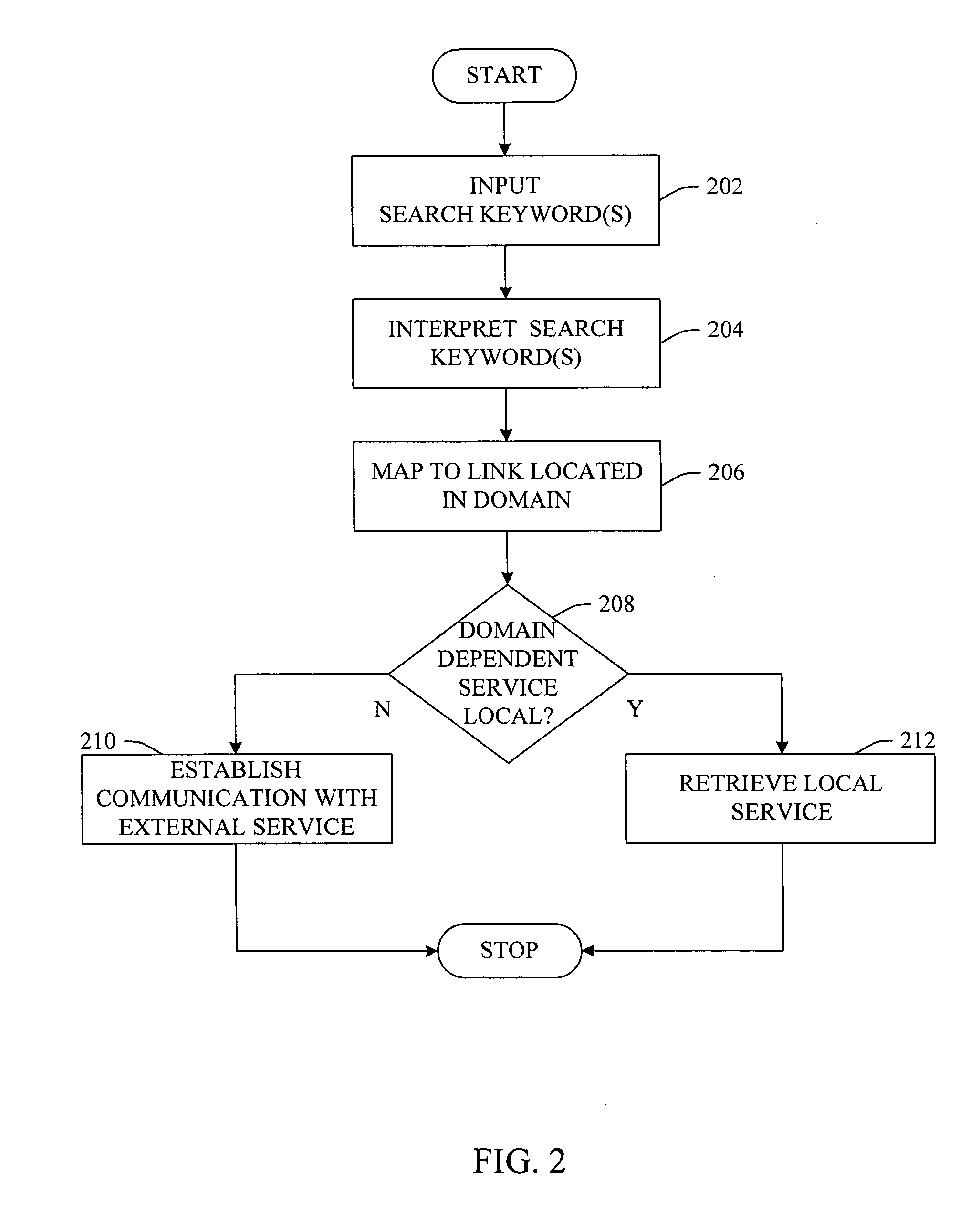
InactiveUS20070043736A1Facilitates intelligently locatingPromote associationWeb data indexingSpecial data processing applicationsDECIPHERLookup table
A domain specific search mechanism having “smart find” functionality of locating a webpage dependent service is provided. In other words, the mechanism facilitates intelligent location of web page dependent links / services via a versatile mechanism that looks-up, deciphers, and / or interprets search criteria. Once an intended target is identified, a mechanism can be employed to locate an appropriate link or group of links resident on a web page. The domain specific search mechanism can employ a local (or remote) dictionary and / or lookup table to associate a search input to a domain specific link / service. Additionally, the described “smart find” mechanism(s) can employ embedded metadata to effect the association of a search input to a domain specific link or group of link(s).
Owner:MICROSOFT TECH LICENSING LLC
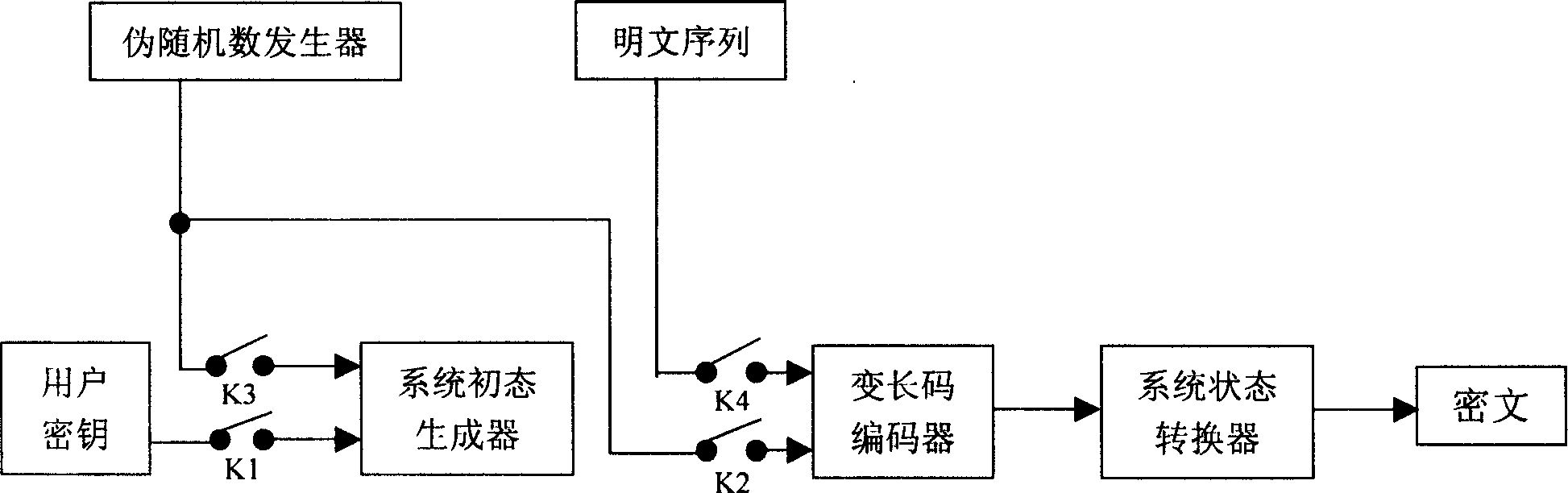
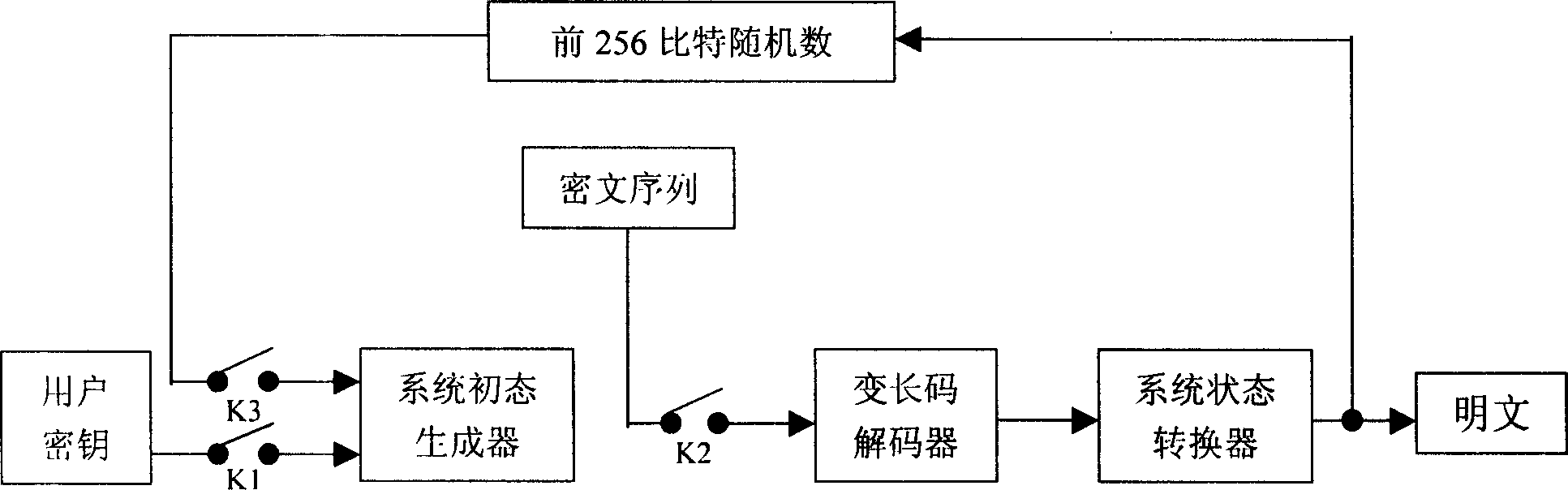
Data encipher and decipher system based on dynamic variable-length code
The invention relates to an information security technology in information technology field, which concretely relates to binary code and decode of data. The invention belongs to sequence coding system; the essence is periodless multi-table code substituting method. It uses dynamic length variable code technology, a group of input data with fixed length (8 bits), the length of the output code is between 1 and 255, the size of the encrypted text is determined according to the state of the coding system. The state of the system will change after coding a group of plain text, and the initial state of the system is determined by the user key, the code analyzer is hard to determine the relation between the encrypted text and the plain text, thus the attacking method to each kind of system can be resisted effectively.
Owner:北京唐桓科技发展有限公司
Autonomous robot for music playing and related method
InactiveUS20080167739A1Improve dynamic performanceHighly flexible performanceElectrophonic musical instrumentsComputer controlGraphicsDECIPHER
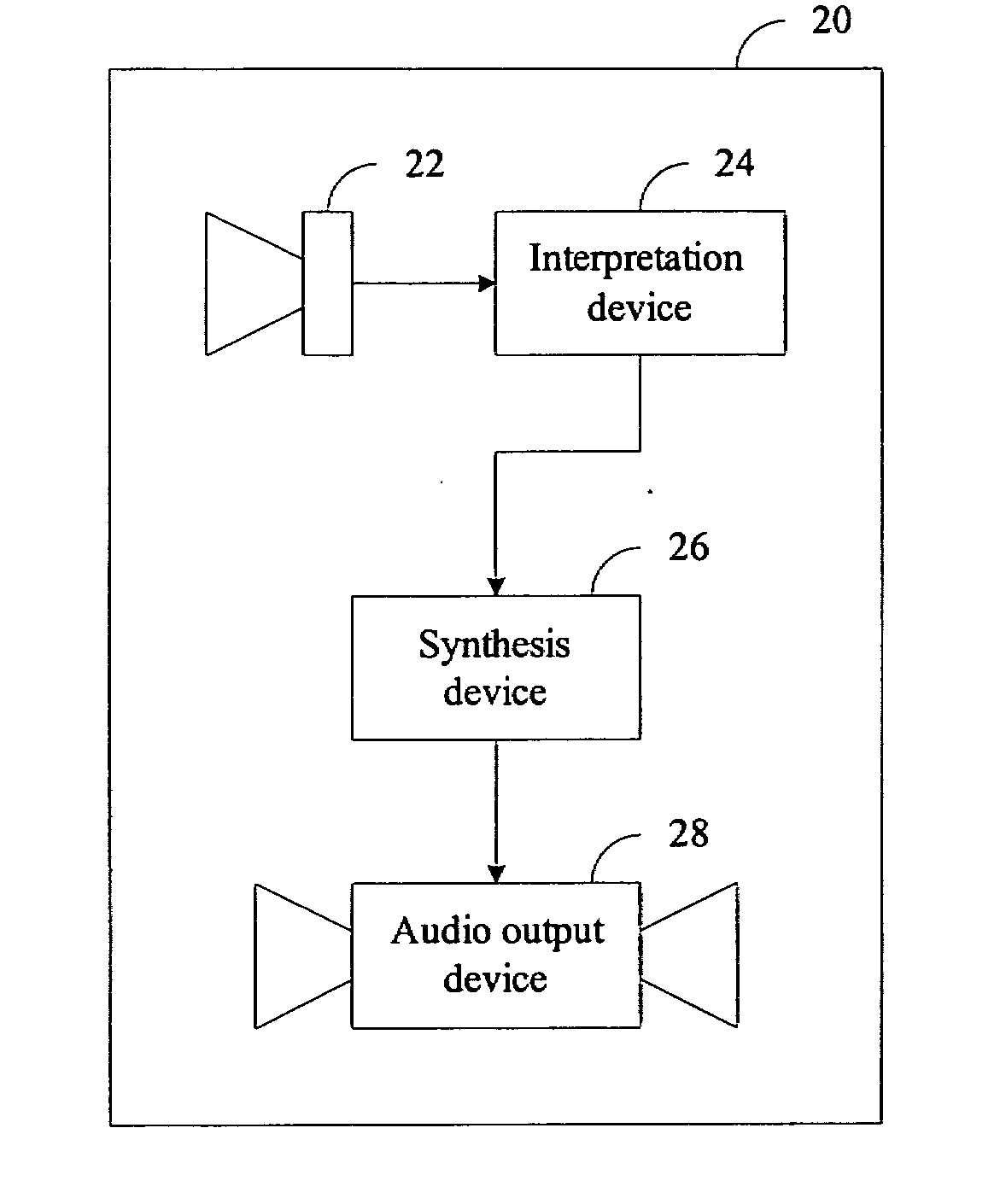
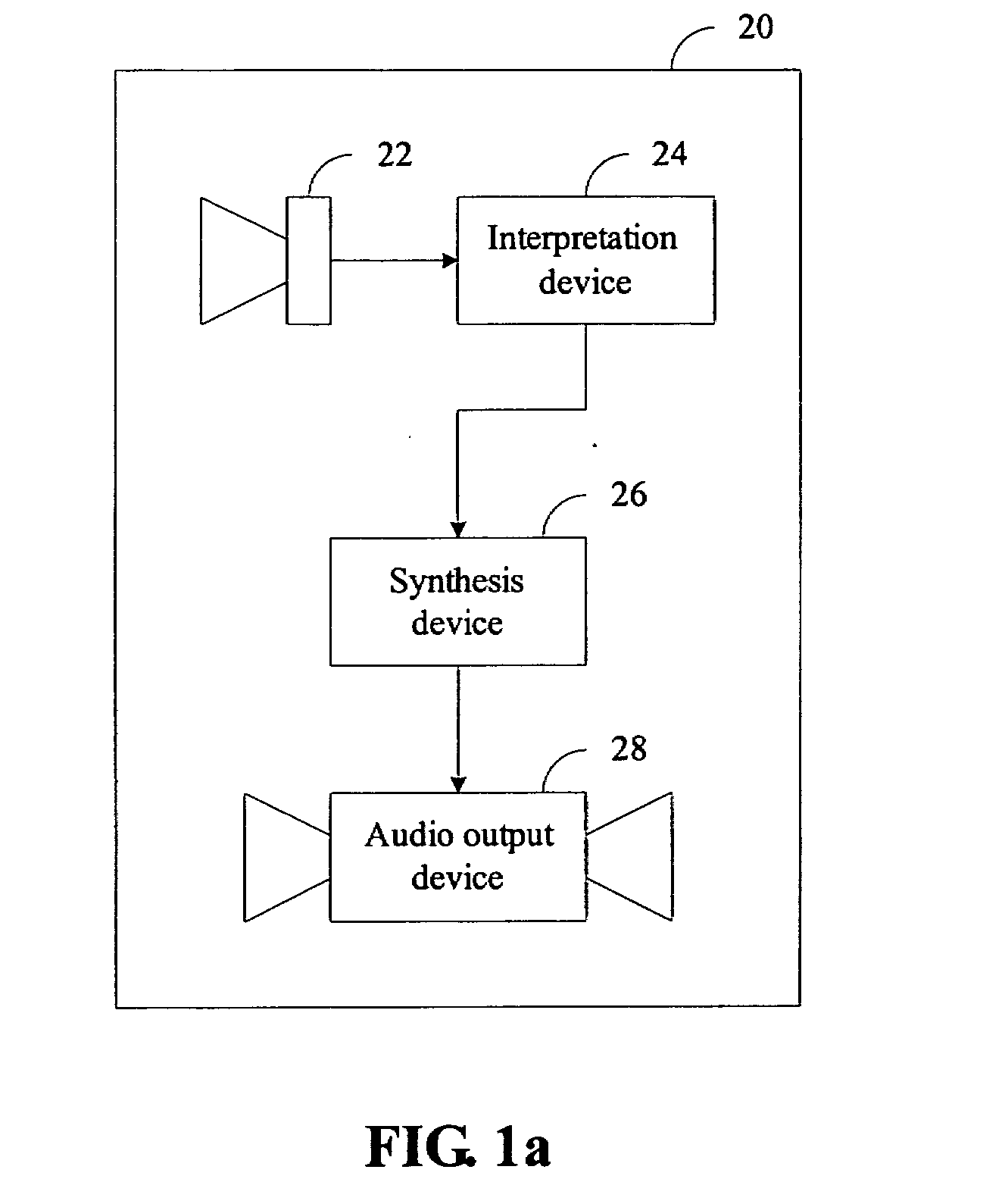
An autonomous robot mainly contains an image capturing device, an interpretation device, a synthesis device, and an audio output device. The image capturing device captures pages of graphical images in which appropriate musical information is embedded, and the interpretation device deciphers and recognizes the musical information contained in the captured graphical image. The synthesis device simulates the sound effects of a type of instrument or a human singer by synthesis techniques in accordance with the recognized musical information. The audio output device turns the output of the synthesis device into human audible sounds. The graphical image of appropriate musical information is prepared in a visually recognizable form. The graphical image can also contain special symbols to give instructions to the autonomous robot such as specifying an instrument.
Owner:NAT TAIWAN UNIV OF SCI & TECH
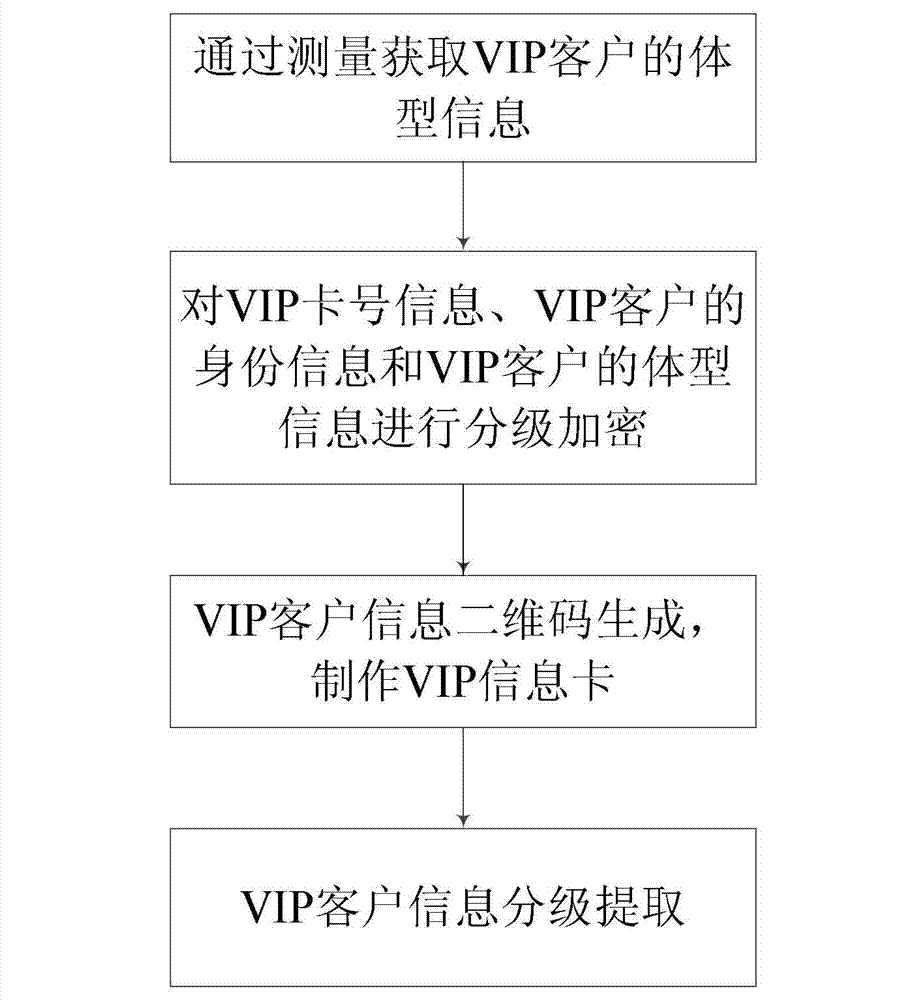
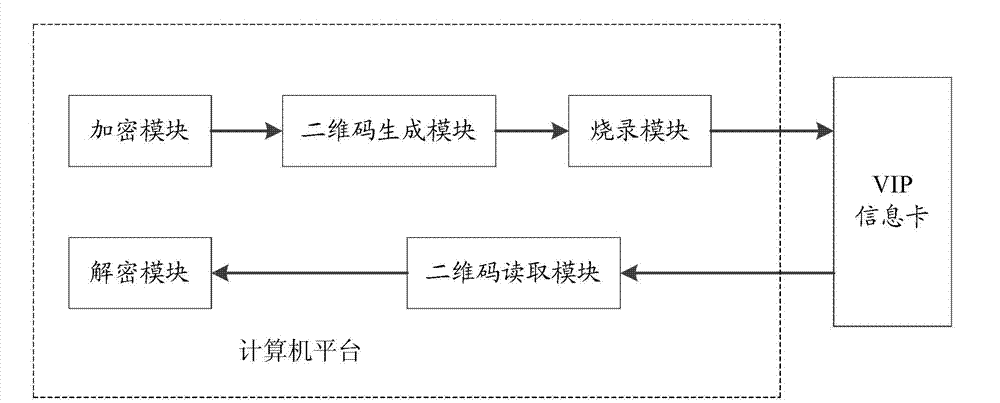
Two-dimensional code based clothing industry client information management method
InactiveCN103049869AImprove efficiencyImprove securityRecord carriers used with machinesMarketingInformation CardDECIPHER
The invention discloses a two-dimensional code based clothing industry client information management method. The card number information, the identity information and the body type information of a client are encrypted so as to code the encrypted information to generate a two-dimensional code; the two-dimensional code is typed into the VIP (very important person) information card of the client; and when the VIP information card of the client is used, the two-dimensional code is read to decode and decipher to obtain the client information. According to the two-dimensional code based clothing industry client information management method disclosed by the invention, data for describing the client identity information and measurement data for describing the client body type information are packaged into the two-dimensional code to make the VIP information card of the client; when the client customizes or purchase clothes, the client only needs to input the two-dimensional code in the VIP information card into the reading terminal of a clothes manufacturer or a store; and the system can automatically read the user body type data to customize. The method disclosed by the invention has the advantages of low cost, big information storage content and convenience in popularization, and the efficiency and the safety of the clothes industry service system can be greatly improved.
Owner:ZHEJIANG SCI-TECH UNIV
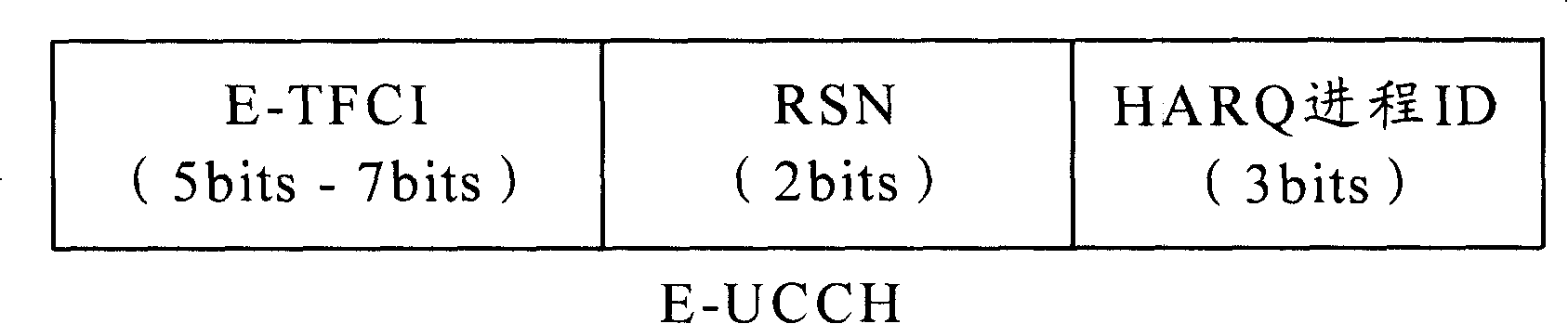
Method for enhancing decipher of uplink physical channel
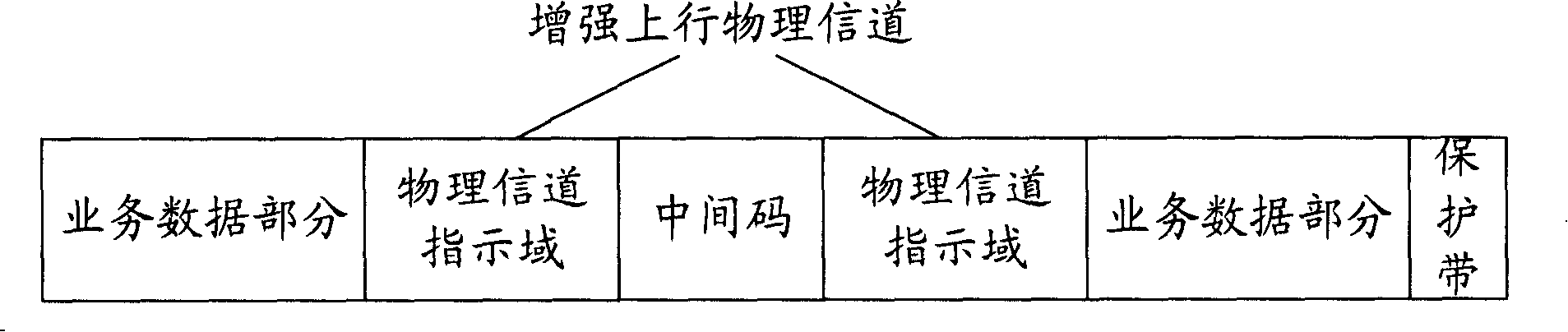
InactiveCN101207843AImprove receiving efficiencyAvoid cachingError preventionRadio/inductive link selection arrangementsCode division multiple accessDECIPHER
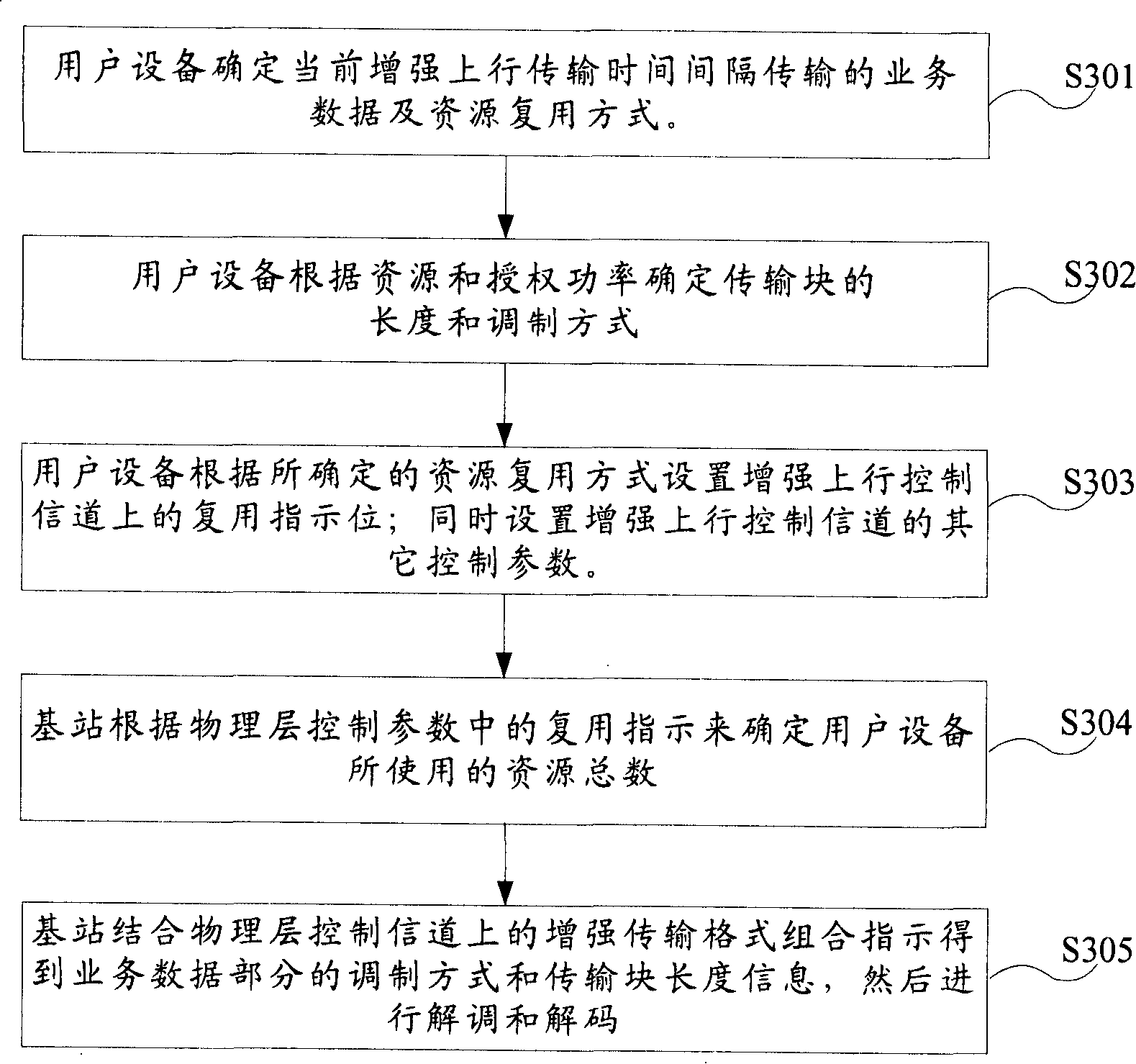
The invention provides a decoding method of enhancing an uplink physical channel by a time division synchronous code division multiple access system. The decoding method includes the following steps: step S301, when an enhanced uplink transmission time interval comes, user equipment determines a data type and a resource multiplexing mode transmitted in the current transmission time interval; step S302, the user equipment determines the length of a transmission block and the modulation type of the enhanced uplink service data; step S303, the user equipment determines the physical layer control channel parameters of the current transmission; step S304, a base station determines the total number of resources used by the user equipment; and step S305, the base station combines enhanced transmission format combined indication to obtain part of the length of a transmission block and the modulation type of service data and then carries out demodulation and decoding; wherein, the data type includes a dispatching service data type and a non-dispatching service data type. In this way, under the condition of no increment of channel load, the invention can avoid the caching of channel data, realize the synchronous demodulation of the channel and improve the receiving efficiency of the channel.
Owner:ZTE CORP
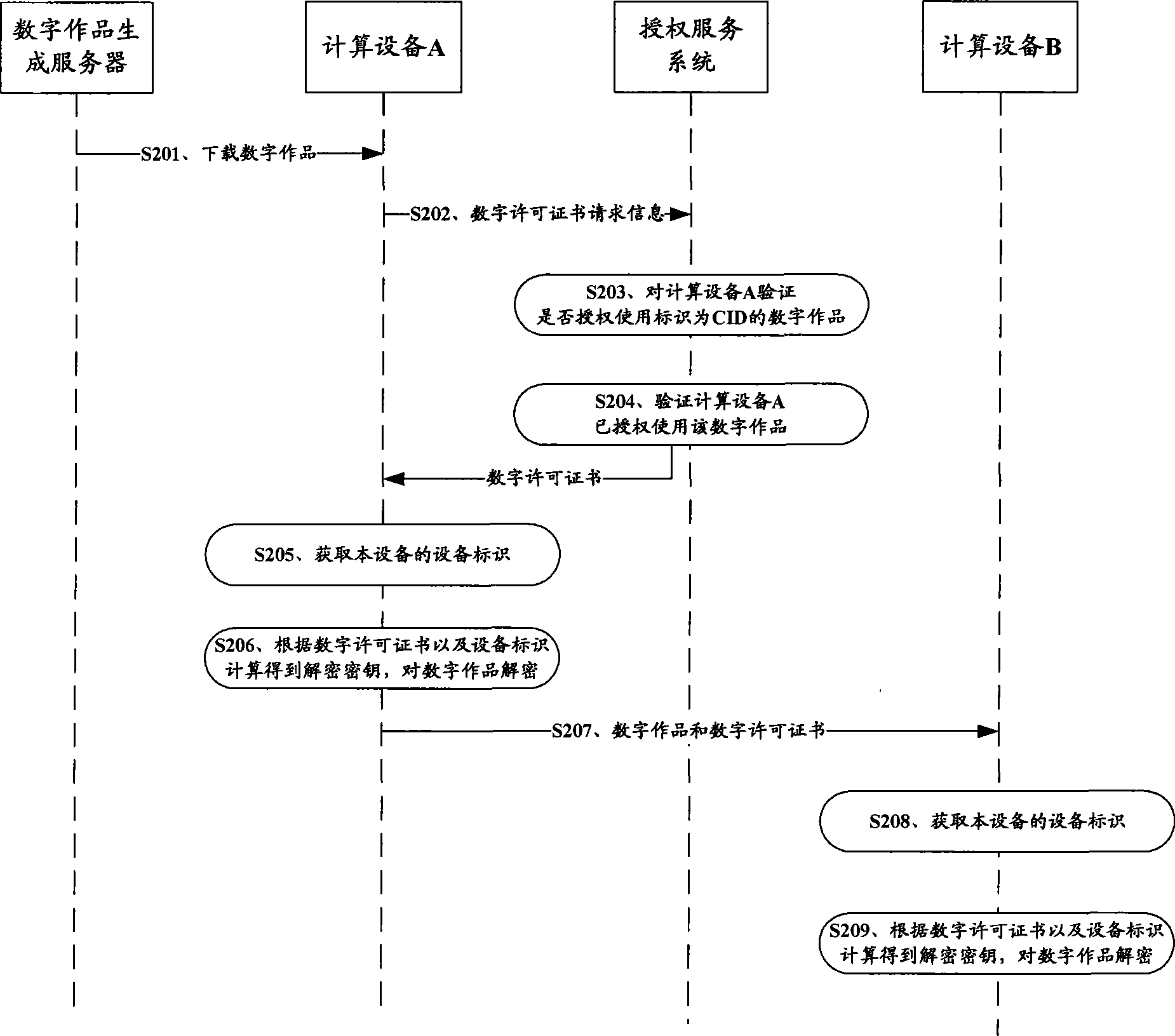
Digital exequatur sending system and digital work decipher operation method
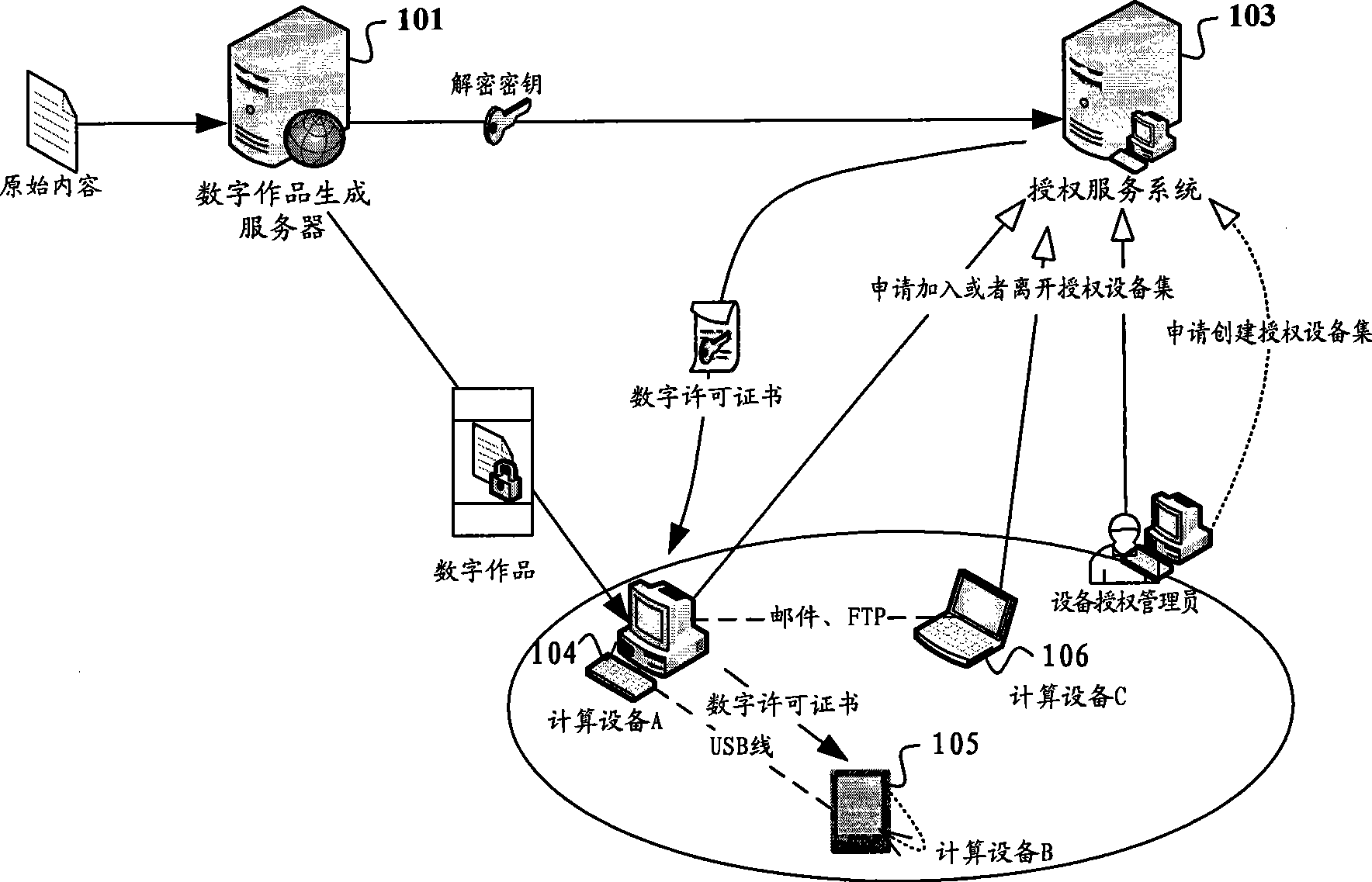
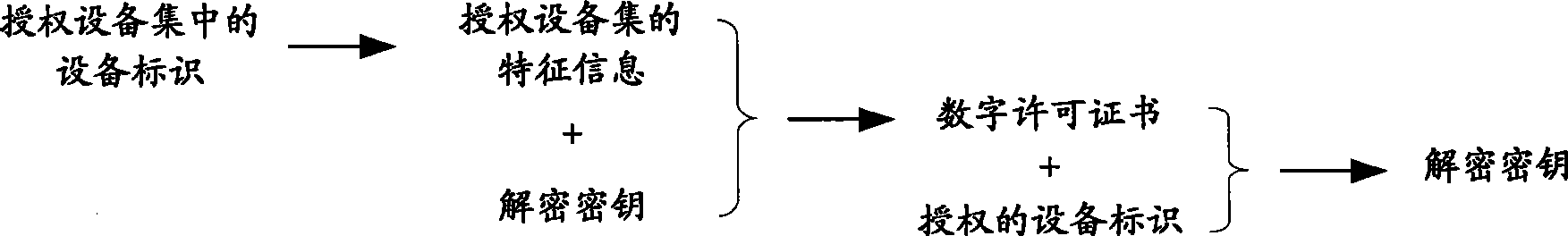
ActiveCN101425112AGood replicationEasy to getDigital data authenticationProgram/content distribution protectionDECIPHERAuthorization
The invention relates to the field of digital work copyright protection, in particular to a technique in which a multi-computing apparatus uses a digital work upon authorization, and more particular to a digital permit transmitting system, a computing apparatus and a digital work decryption operating method. The method comprises the following steps: the computing apparatus obtains a digital permit of the digital work; the digital permit is generated according to characteristic information of an authorization apparatus set and a decryption key of the digital work; and the computing apparatus obtains an apparatus identifier of the present computing apparatus, restores the decryption key according to the digital permit and the apparatus identifier of the present computing apparatus, and operates the digital work after decrypting the digital work by using the decryption key. Due to the convenient reduplication of the digital permit, the authorized computing apparatus can conveniently obtain the digital permit and conveniently utilizing the apparatus identifier of the present computing apparatus and the digital permit to obtain the decryption key so as to decrypt and operate the digital work.
Owner:PEKING UNIV +2
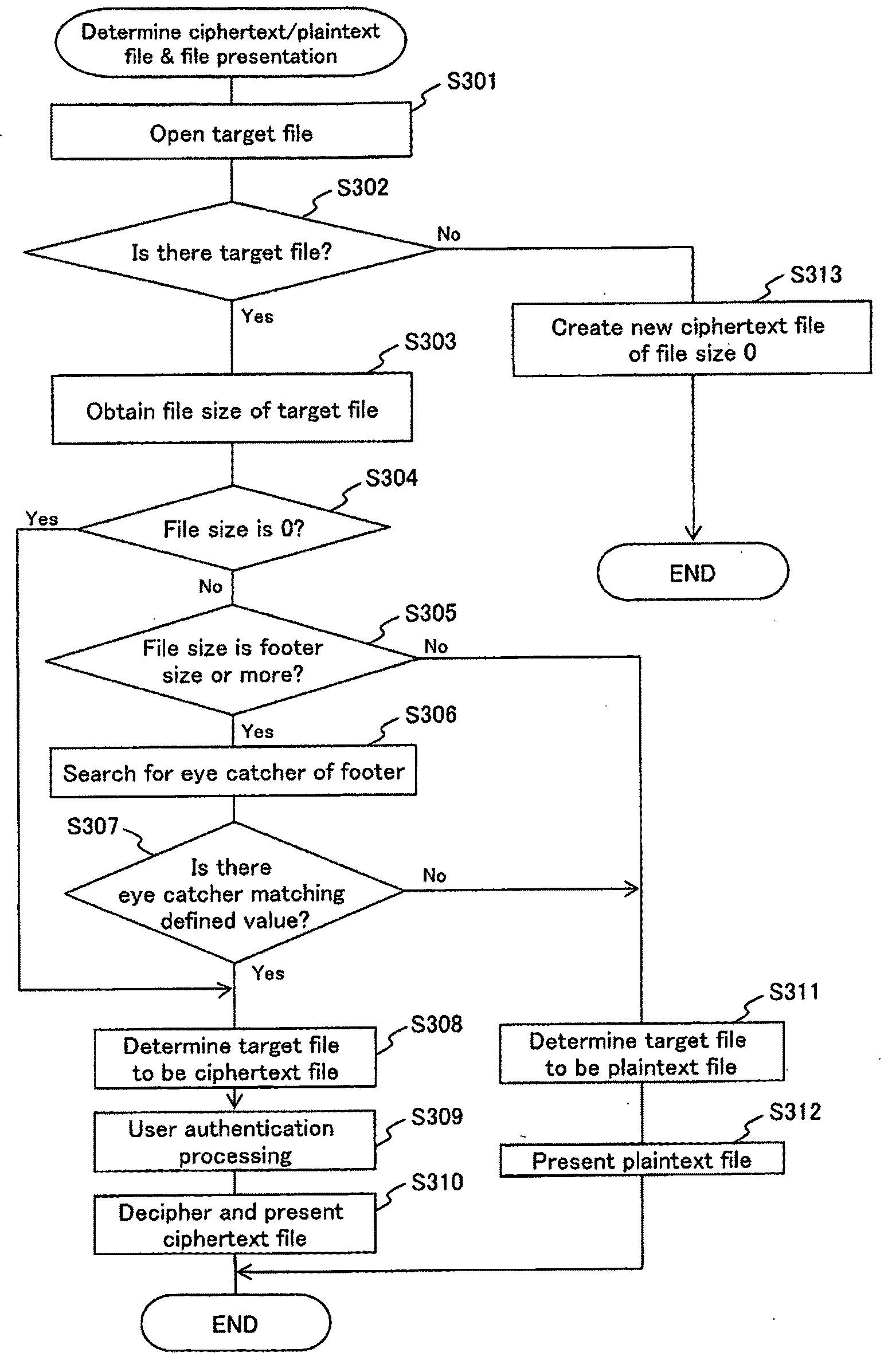
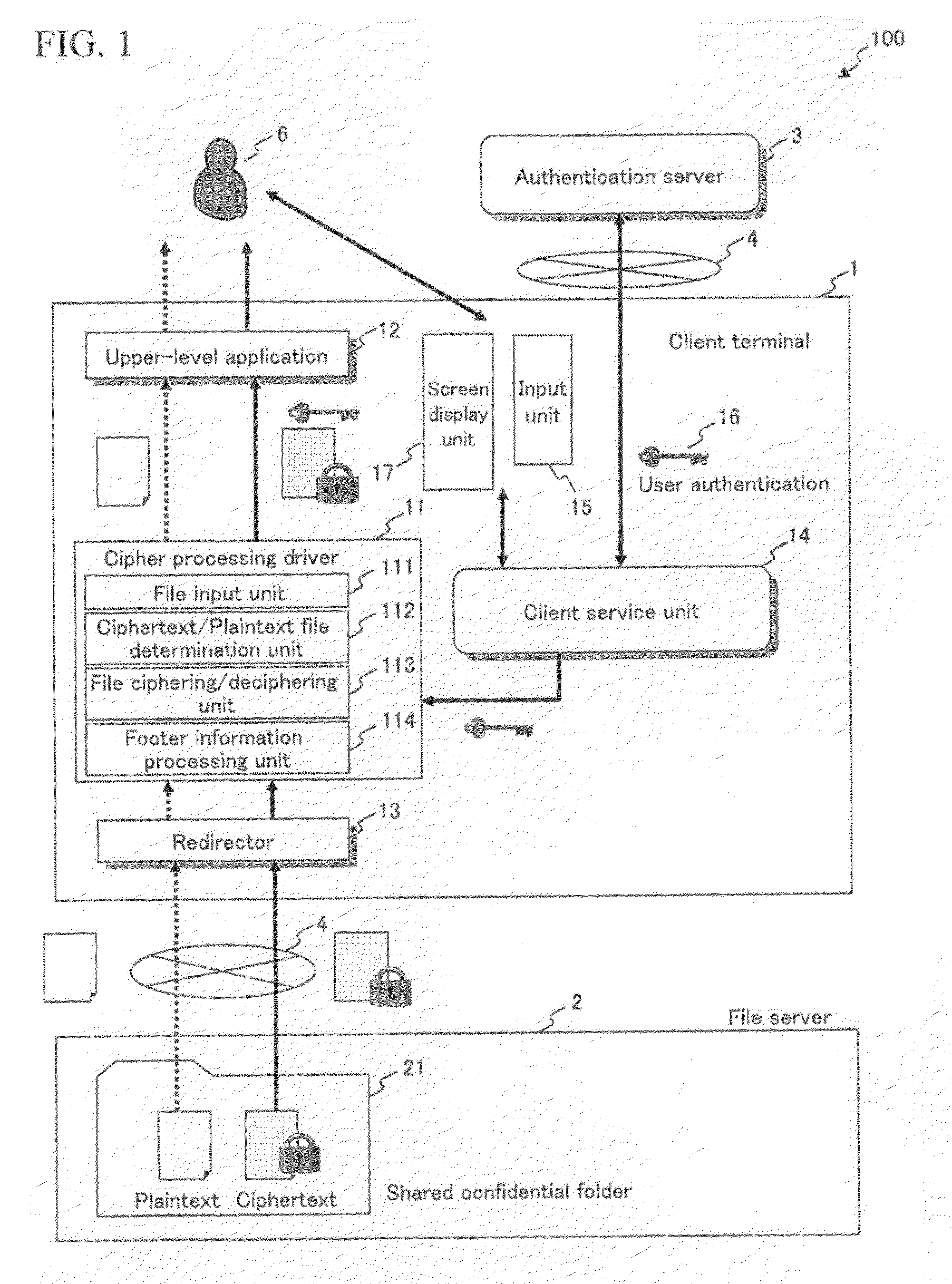
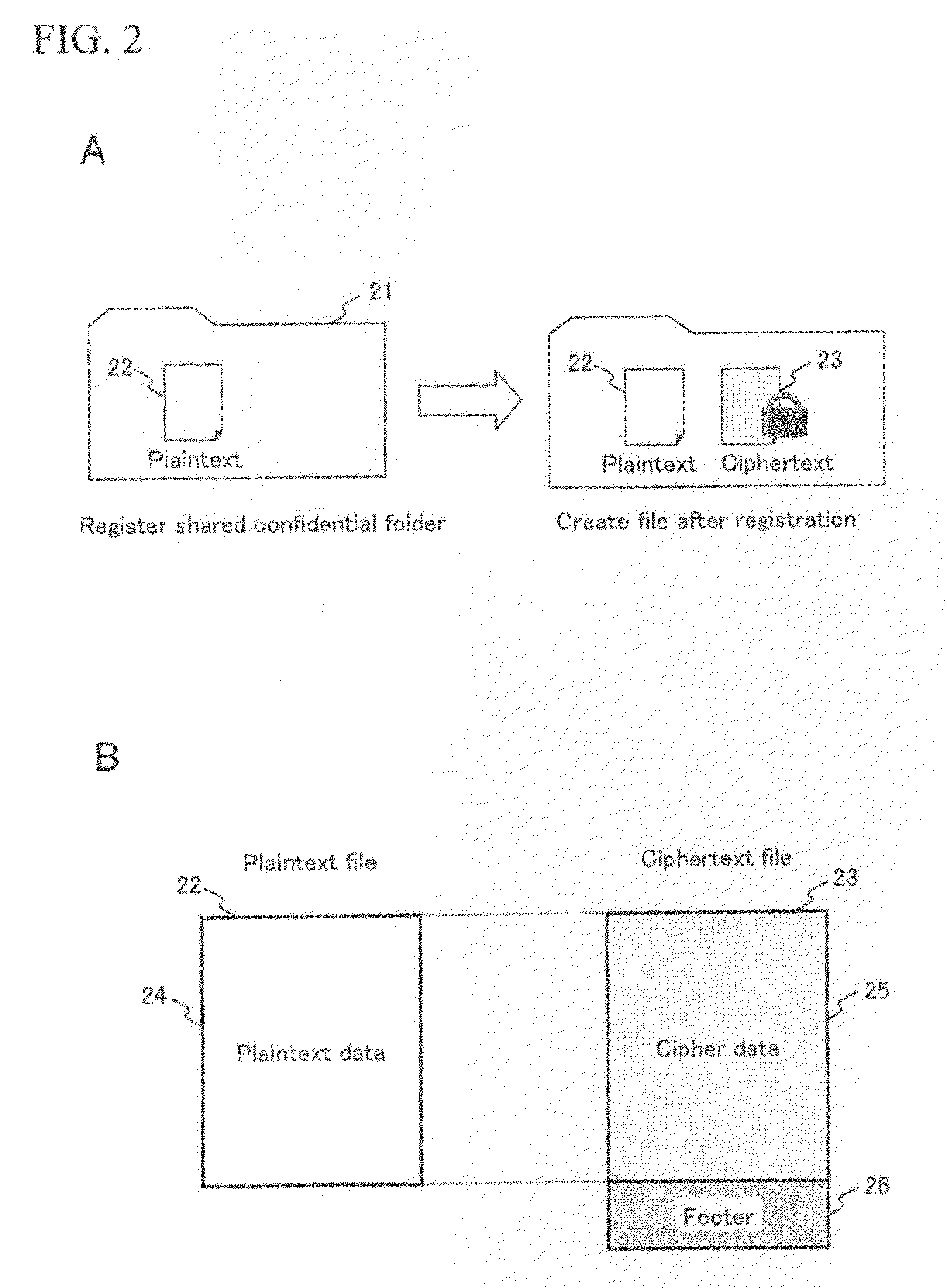
System and method for file processing and file processing program
ActiveUS20100185873A1Maintain integrityUnauthorized memory use protectionHardware monitoringPlaintextDECIPHER
A cipher processing system is provided for allowing file access while maintaining the integrity without a user being conscious of the difference between files when the user accesses a file in a folder containing both a ciphertext file and a plaintext file. Thus, according to the present invention, if a folder stores both a ciphertext file and a plaintext file, the ciphertext file is attached with identification information (preferably, footer information) indicating that the file is a ciphertext file, so that the plaintext file and the ciphertext file can be differentiated from each other when the files are read. A deciphered file gained by removing identification information from a ciphertext file and deciphering the file is delivered to an upper-level application. If the read file is a plaintext file, decipher processing is not executed on the plaintext file but the plaintext file is passed to the upper-level application program.
Owner:HITACHI SOFTWARE ENG
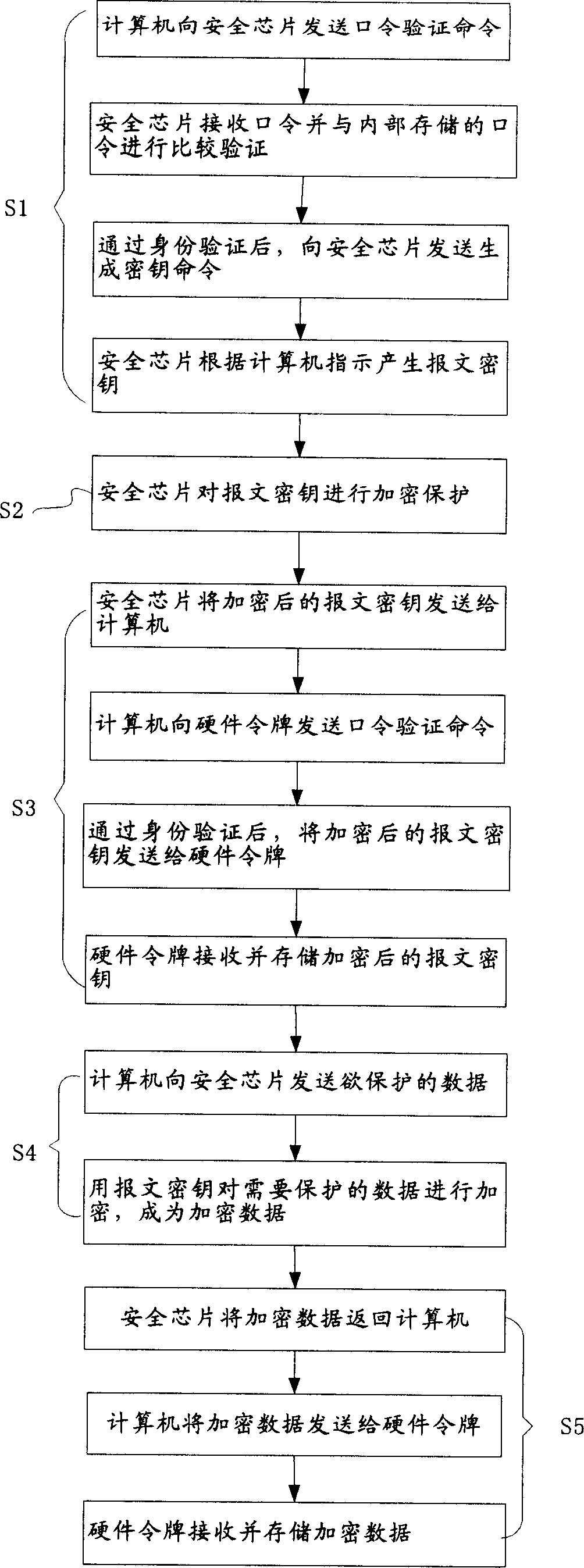
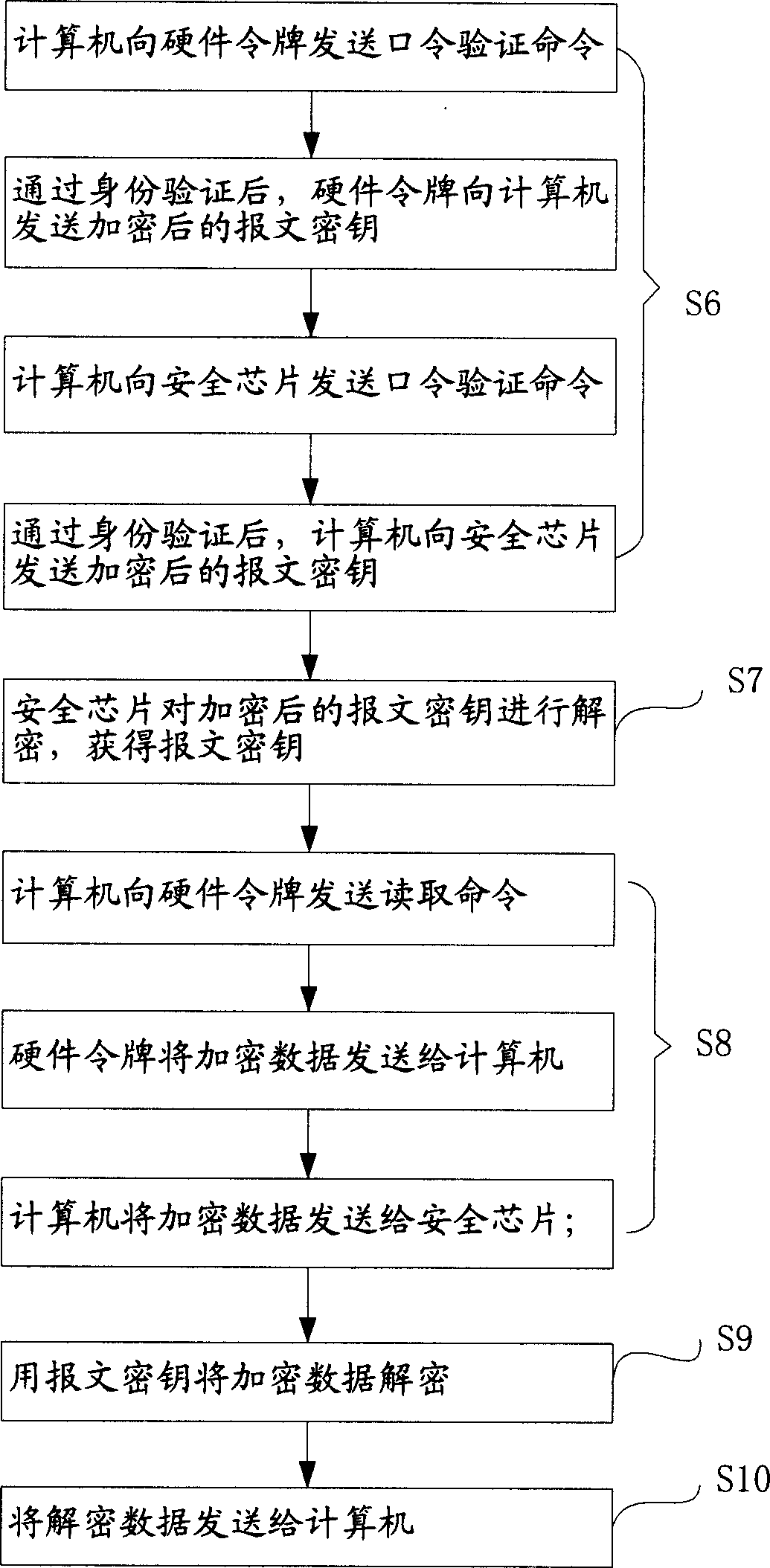
Data protection method and system
InactiveCN1607511APrevent illegal theftAvoid lossMemory loss protectionUnauthorized memory use protectionDECIPHERKey storage
This invention relates to a data protection method and a protection system. The method includes a cipher flow and a decipher flow, in which, the cipher flow includes the following steps: a safety chip generates a report cryptographic key and ciphers it to store it in hardware token. The data is ciphered with the report cryptographic key to be stored in the hardware token. The deciphering flow includes the following steps: The safety chip gets the ciphered report cryptographic key from the token and deciphers it to get the report key, the safety chip gets ciphered data from a hardware token and deciphers the data with the report cryptographic key. The data protection system includes a safety chip, a hardware token and a computer.
Owner:LENOVO (BEIJING) LTD
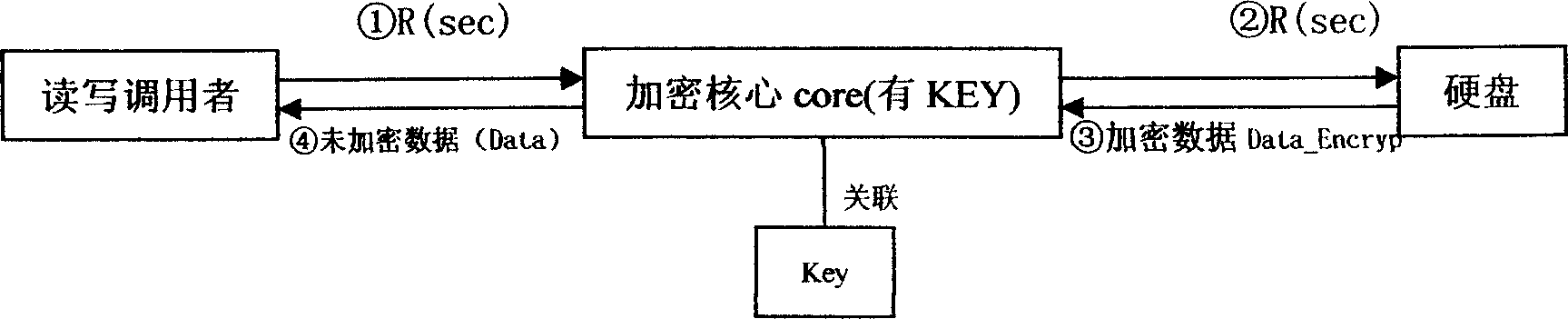
Enciphered protection and read write control method for computer data
InactiveCN1725196APrevent leakageAvoid destructionDigital data processing detailsUnauthorized memory use protectionDECIPHERBus encryption
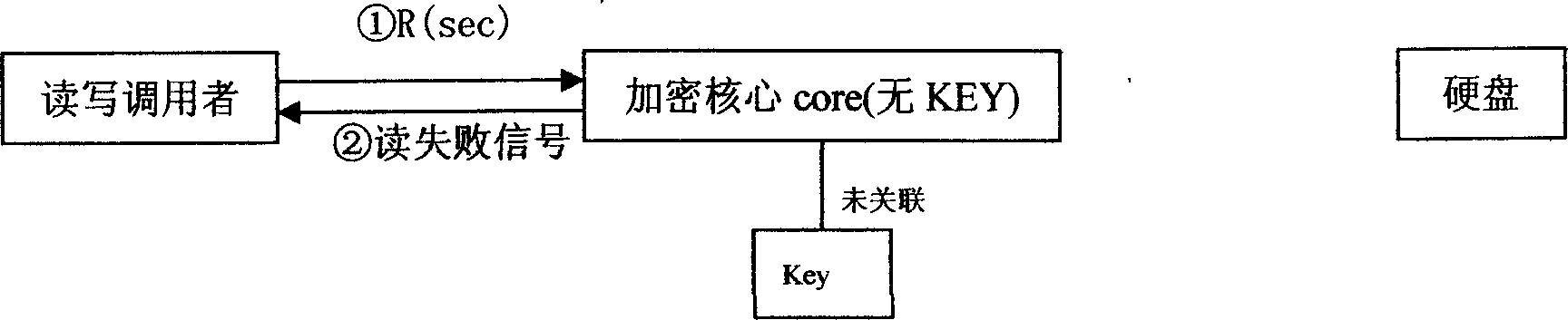
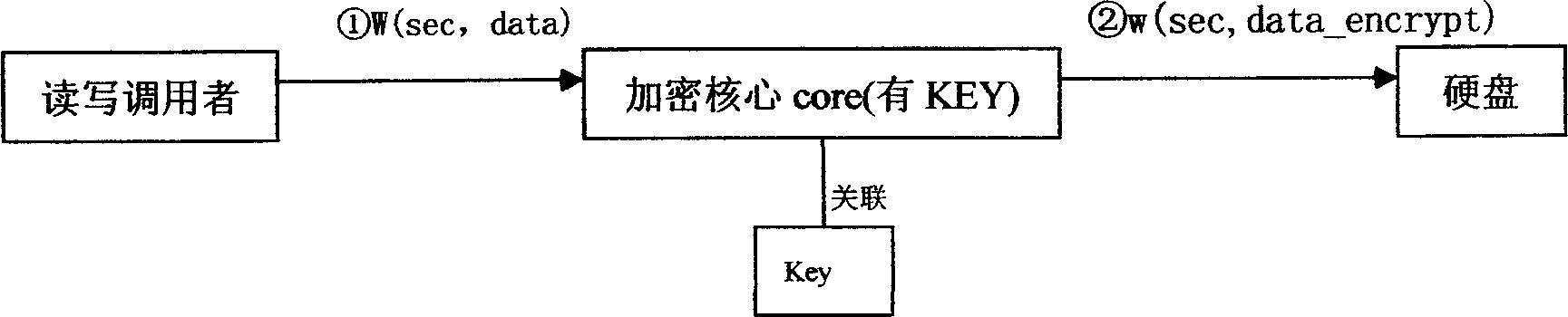
This invention relates to a computer data cipher protection and a read / write control method, which applies a generate method combining a serial bus ciphering dog or software identity certification with the sector stage read / write interception to realize cipher to hard disk data, which utilizes the sector stage read / write interception method to intercept all read / write operations, carries out cipher / decipher conversion in the cipher core under the condition of existing related identity certification to realize the cipher to disk data and read / write control.
Owner:陆峰
Decipher processing method for digital content format
InactiveCN101466020AMeet technical needsMake up for the limitations of not being able to handle data streamsAnalogue secracy/subscription systemsComputer security arrangementsNetwork packetDigital content
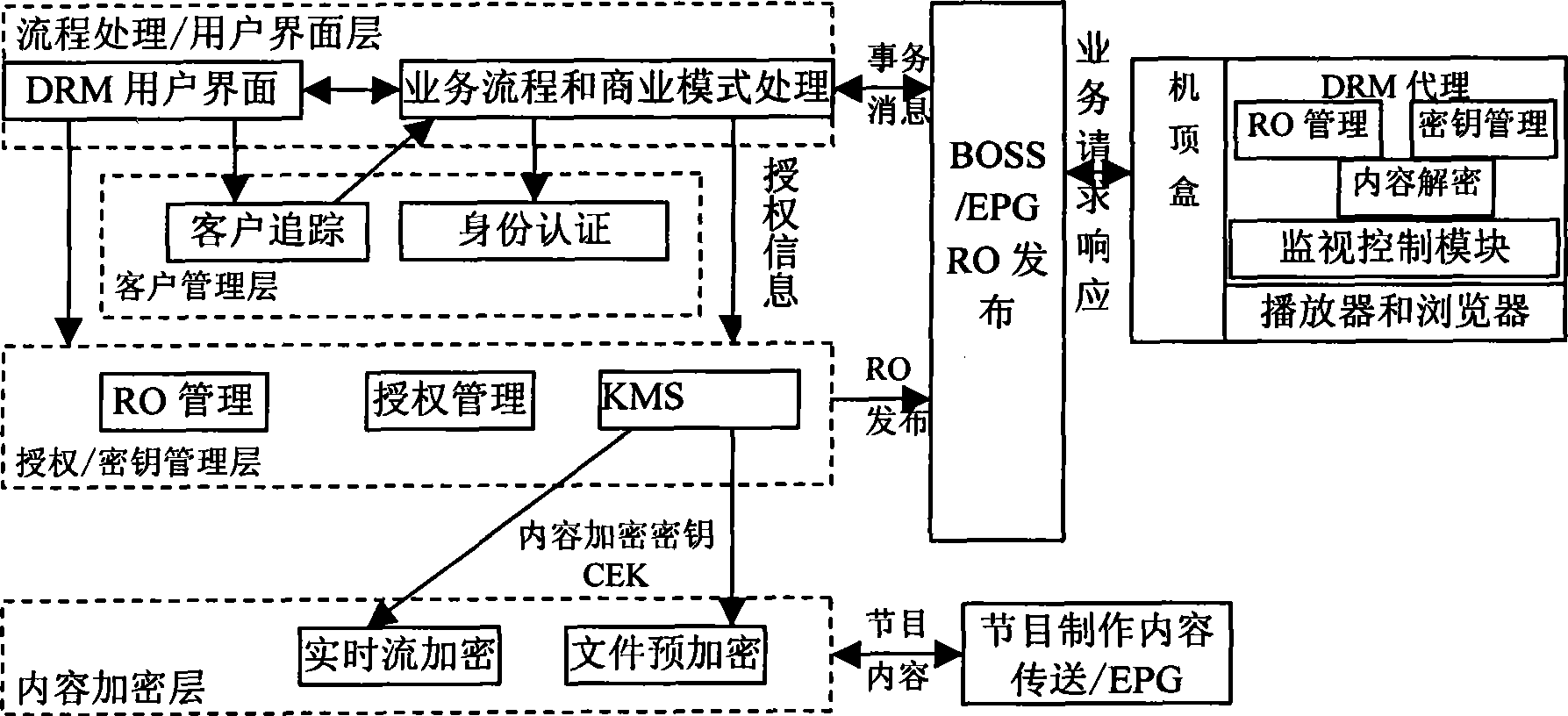
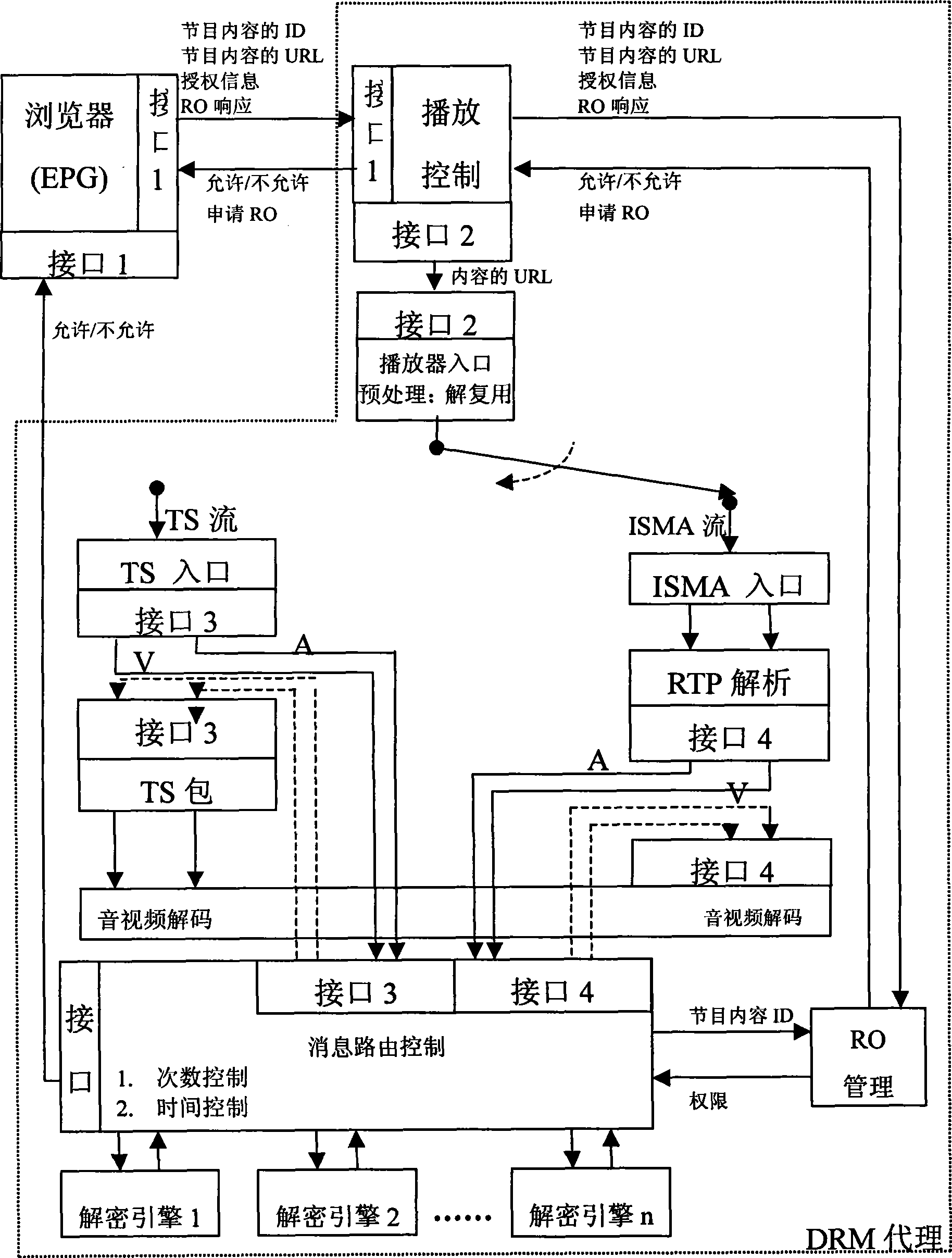
The invention discloses a decryption processing method of SDCF and relates to the technical field of digital copyright protection, aiming at solving the technical problem of SDCF decryption processing. The decryption processing method relates to the following platforms: a DRM agent of a set-top box, a DRM copyright releasing system and a middleware; wherein, the DRM agent comprises an RO management module, a key management module, a content decryption module, a monitoring control module with a playing-before control submodule, a player, a browser and the like. The decryption processing method comprises the following steps: 1) users select programs by a user interface and acquire a global unique program logo and the URL of the program contents; 2) according to the program logo, the playing-before control submodule locally searches the corresponding RO and checks the limits to rights; 3) according to the URL in a data packet for transmitting digital contents, the content decryption module acquires the corresponding RO, a decryption mode and a content key to finish the decryption. The decryption processing method has the characteristics that: the network load can be reduced; the operation is simple and convenient; and the technical requirements can be satisfied.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Issued software storing and enciphering method
InactiveCN1344995AImprove reliabilityImprove portabilityMemory loss protectionUnauthorized memory use protectionDECIPHERRemovable media
Owner:BEIJING BROADMAKING TECH DEV
Cipher
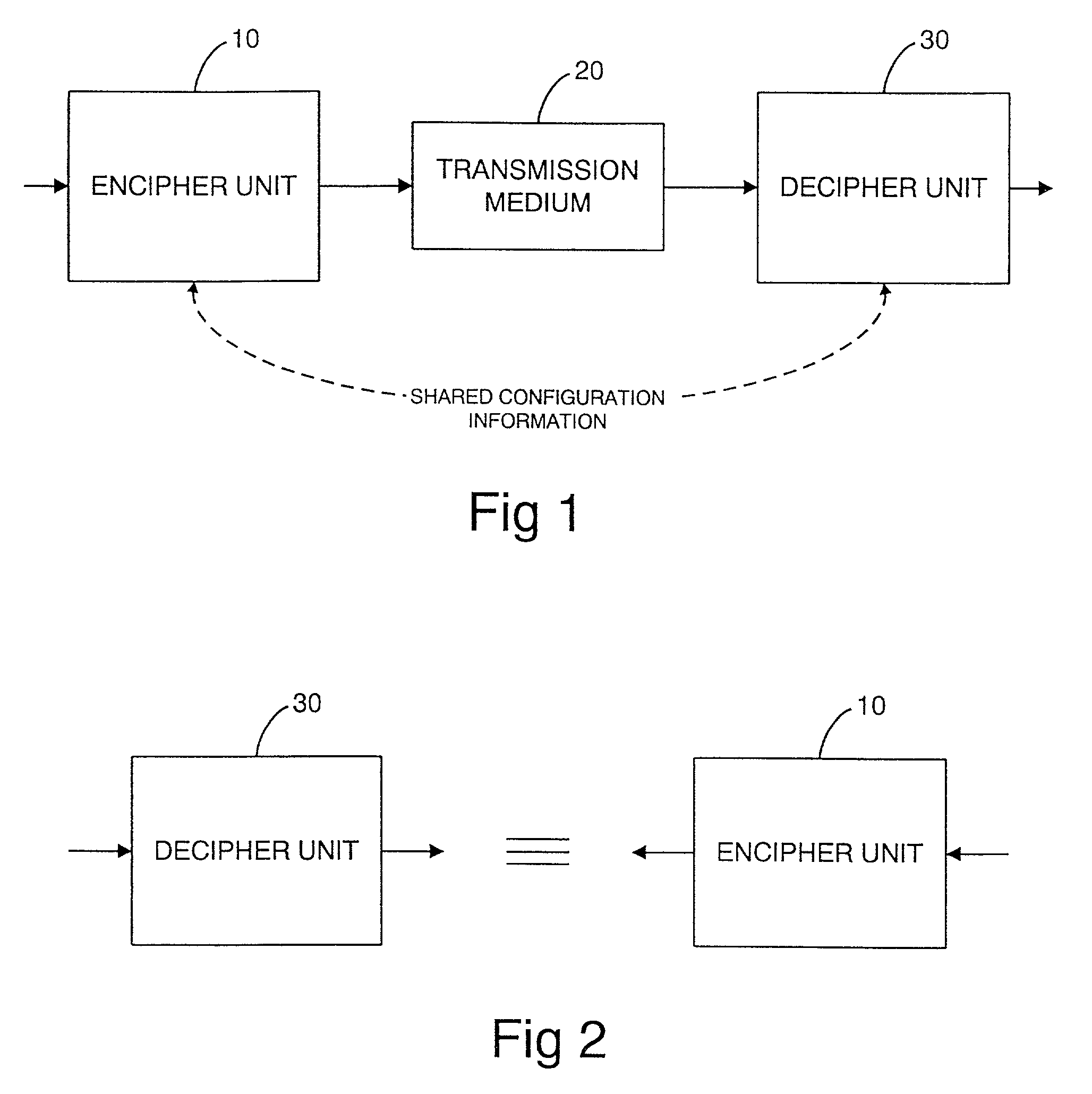
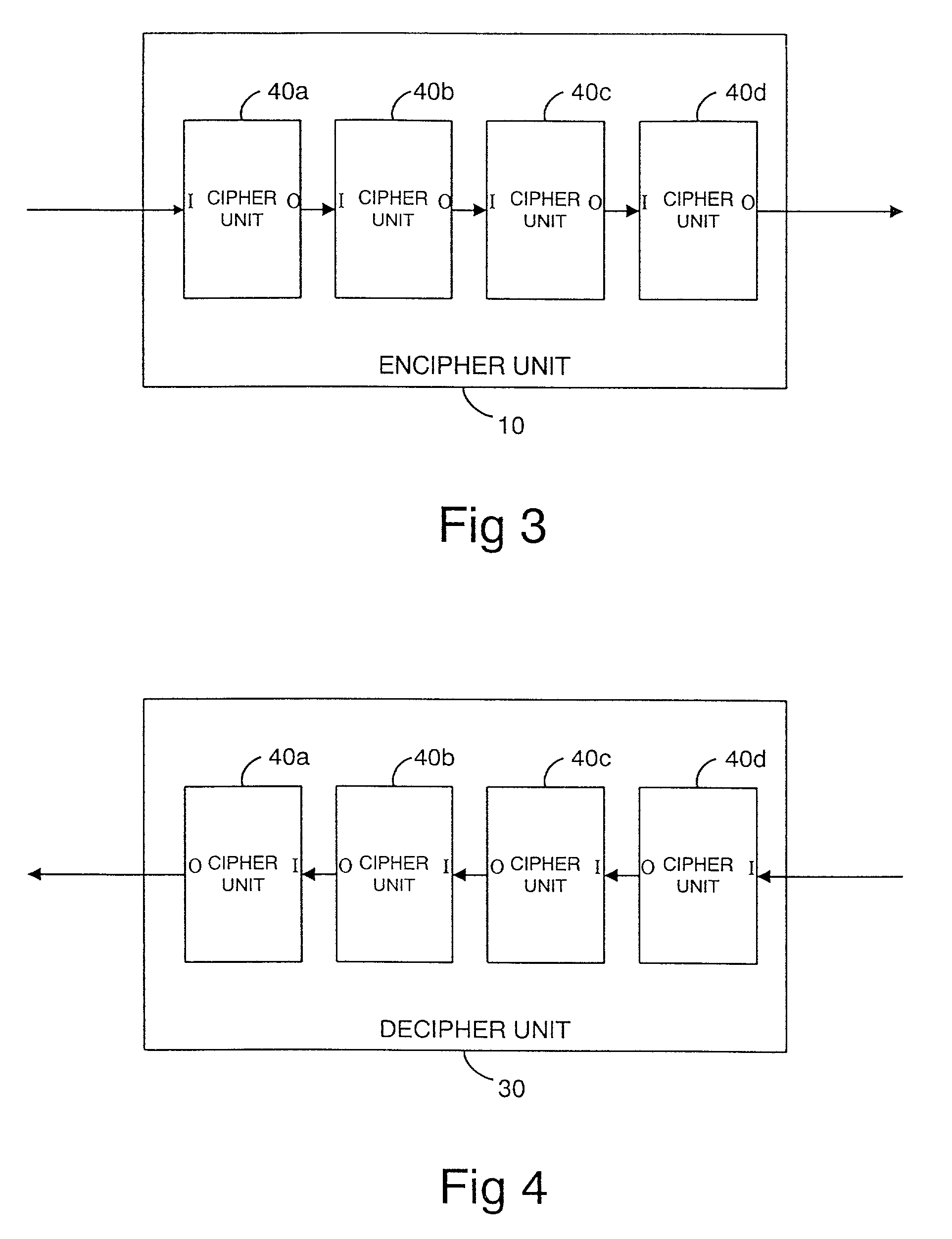
InactiveUS7076060B1Encryption apparatus with shift registers/memoriesDigital data processing detailsComputer hardwareDECIPHER
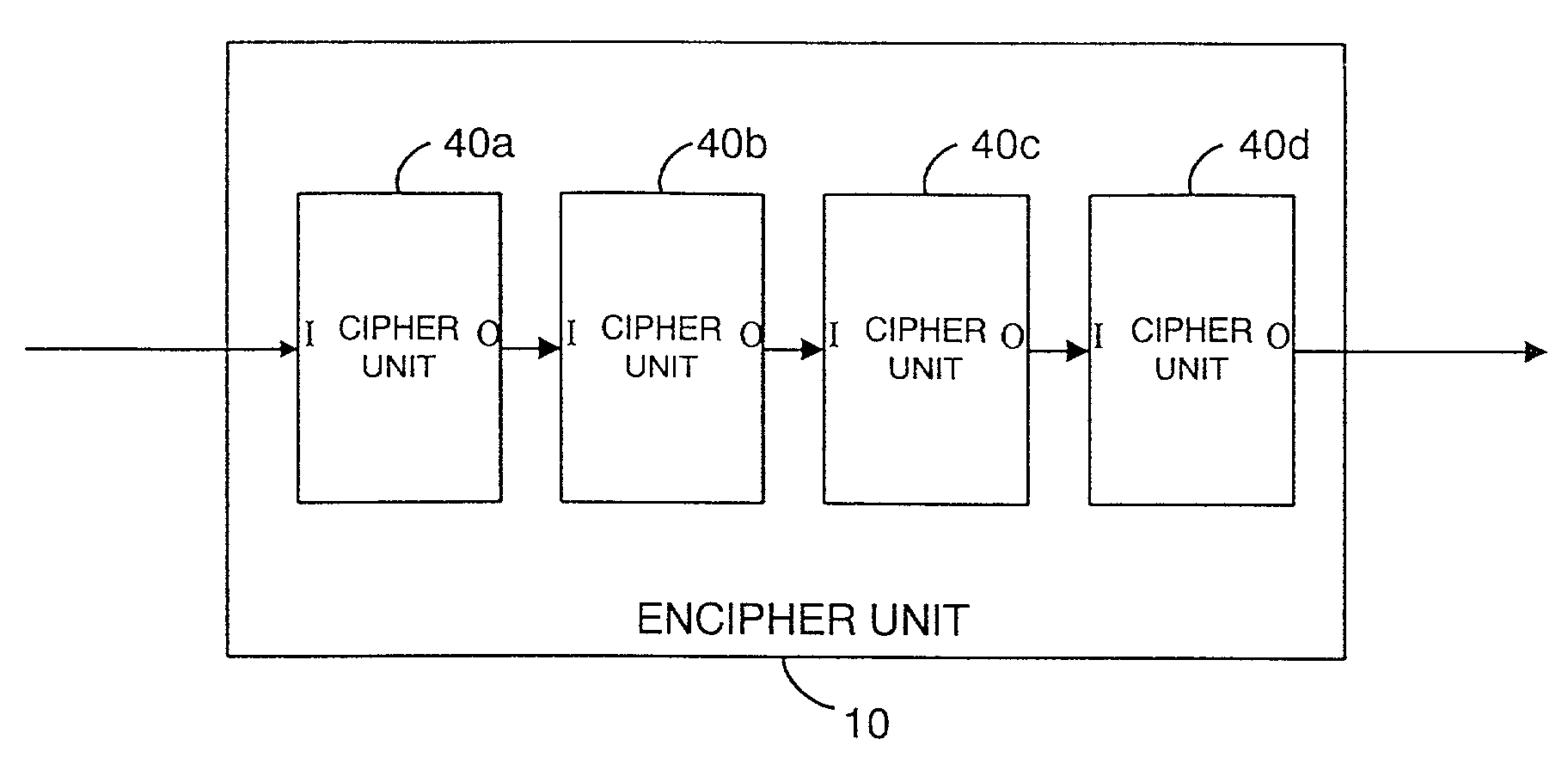
A cipher for enciphering and deciphering a signal includes a plurality of sequentially coupled cipher units, each cipher unit being operable to carry out a reversible operation on the signal. The couplings between cipher units can be randomly configured using a cipher code. The cipher code can be secretly shared between the encipher and decipher. A signal which is enciphered using this technique is thus deciphered using a randomly selected cipher circuit as described by the cipher code.
Owner:BRITISH TELECOMM PLC
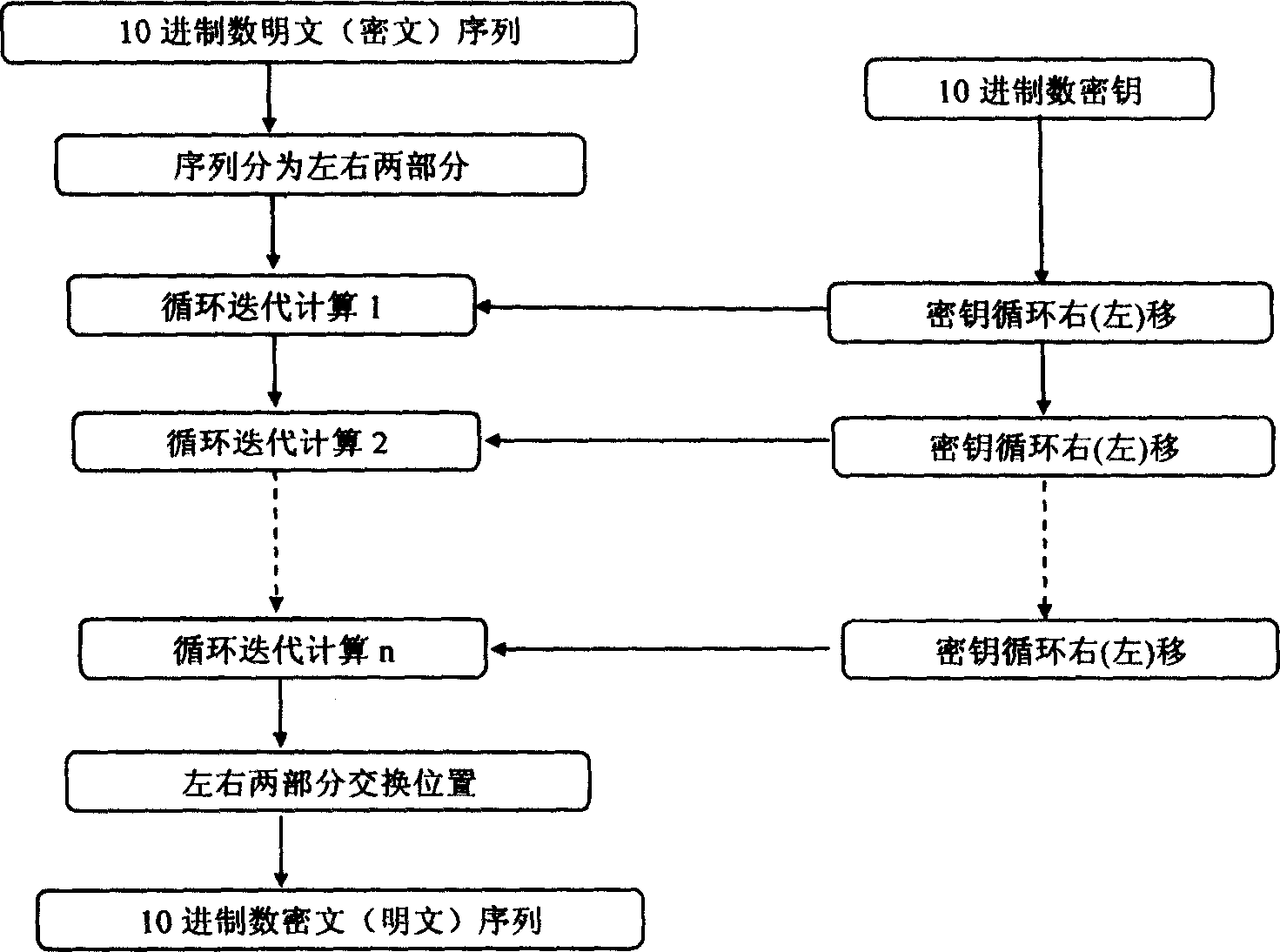
Grouping encryption and decryption algorithm
The invention discloses sectionalization encipher-decipher algorithm, which is characterized by the following: adopting 10-bit number for clear text and secret text as basic arithmetic unit; adopting 10-subtraction method for deciphering course; making the digital sequence length of obtained 10-bit secret text; reducing the problem of secret text inputting time and operating quantity.
Owner:BEIJING FORTUNE INVESTMENT
AES add decipher circuit optimization method and multiplex sbox module
InactiveCN1688121ASmall scaleReduce power consumptionEncryption apparatus with shift registers/memoriesDECIPHERControl unit
This invention relates to an AES cipher / decipher circuit multiplex Sbox module including a negating circuit, a first gating switch, a second gating switch, a ciphered affine transformation circuit, a deciphered affine transformation circuit and a control unit, in which, the first gating switch is connected with the input of the negating circuit, the deciphered affine transformation circuit is connected with high order end 1, the second gating switch is connected with the output of the negating circuit. The ciphered affine transformation circuit is connected with low order end o of the second gating switch and the control unit controls the two switches to gate high order end 1 or low order end o simultaneously. Besides, this invention also provides an optimizing method for AES cipher / decipher circuits.
Owner:VIMICRO CORP
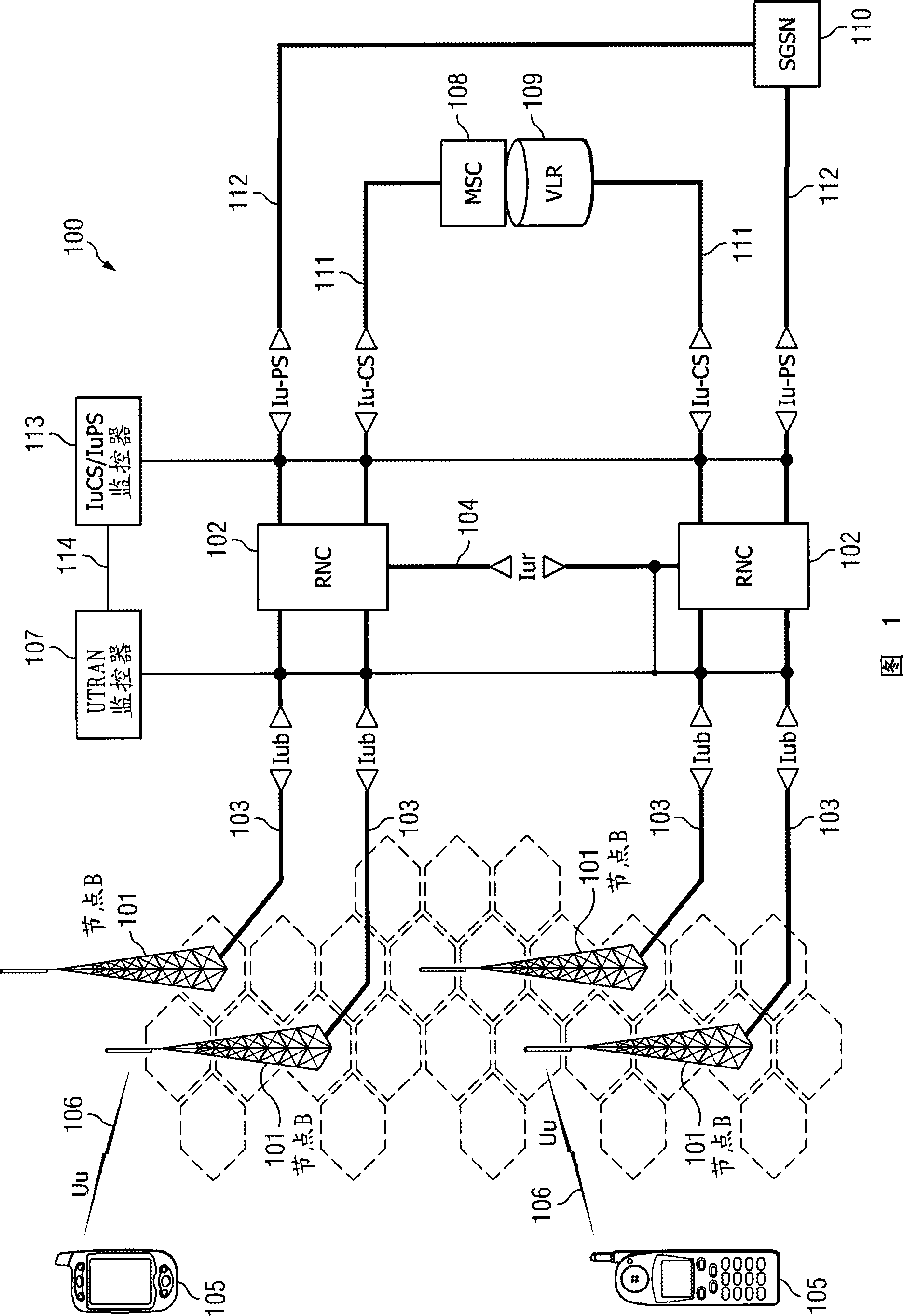
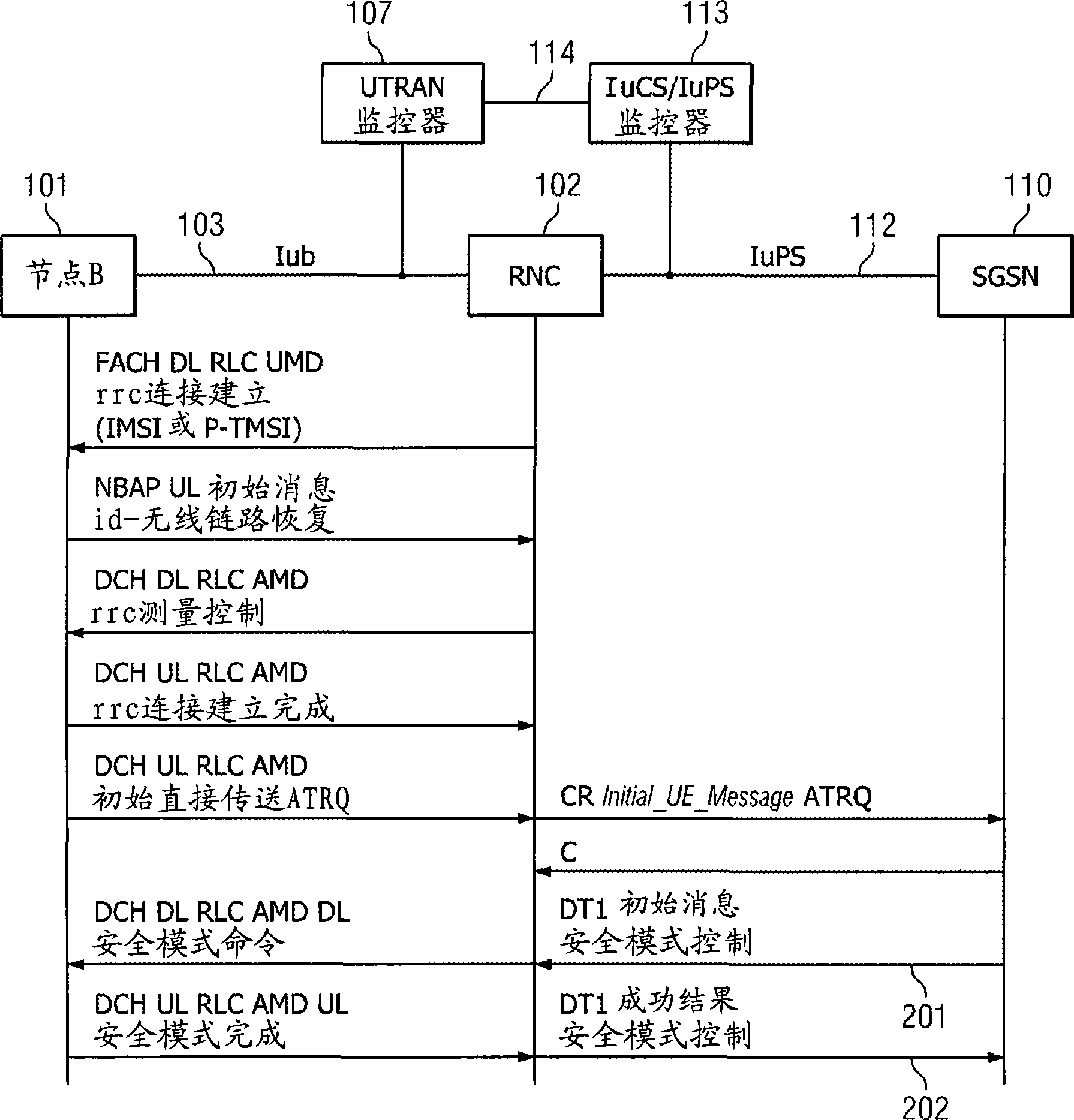
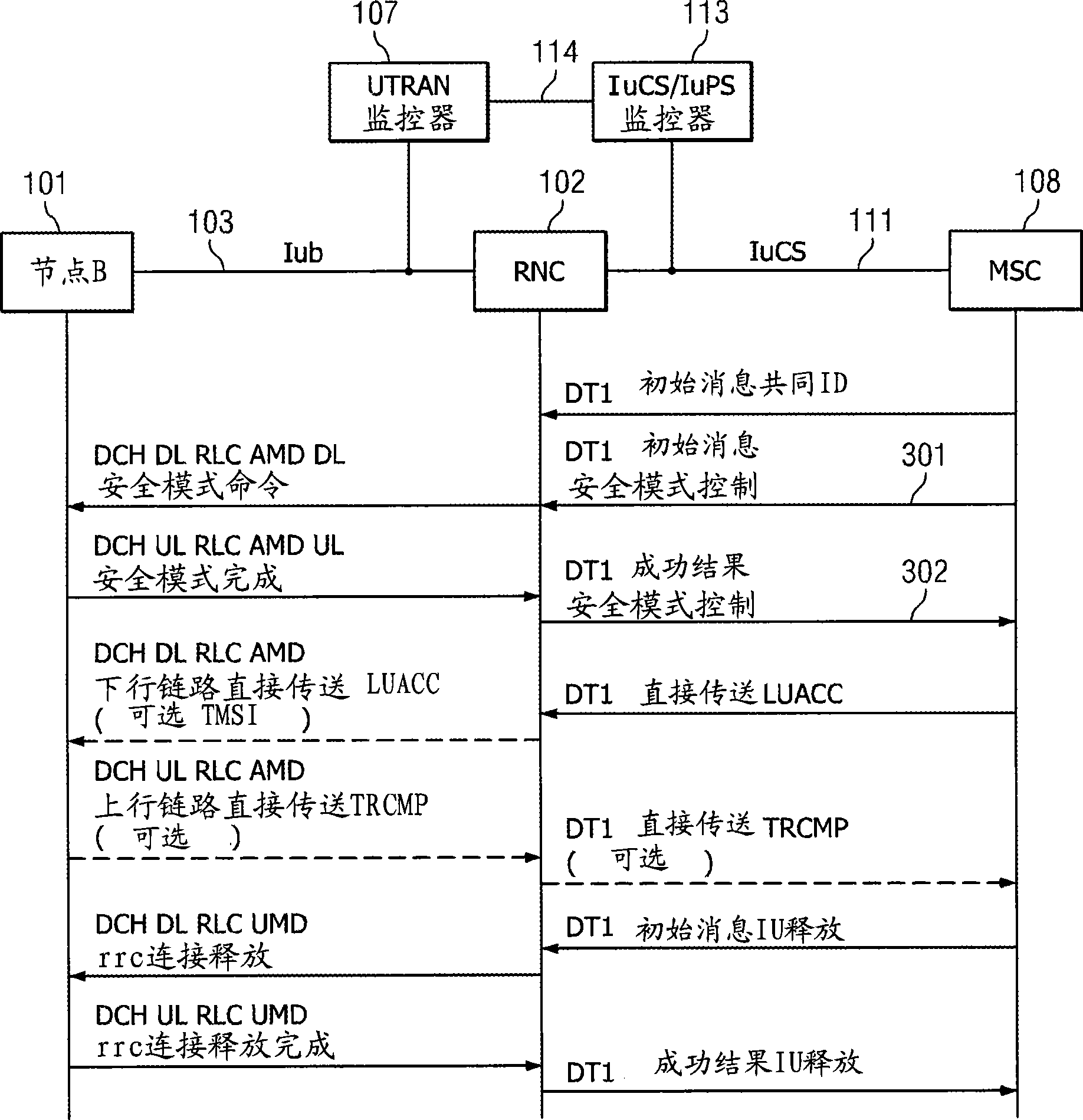
System and method for ciphering key forwarding and RRC packet deciphering in a UMTS monitoring system
System and method for forwarding a ciphering key to a decipher application comprising capturing a first message carrying the ciphering key from a first network interface, identifying a network node associated with the first network interface, identifying a monitor responsible for processing messages captured from interfaces coupled to the network node, and forwarding the ciphering key to the monitor. In an alternative embodiment, the method may further comprise capturing second messages carrying encrypted messages from a second network interface, and deciphering the second messages using the ciphering key. The method may also comprise identifying user equipment associated with the first messages, and selecting a deciphering application running on the monitor using a user equipment identity.
Owner:TEKTRONIX INC
Separating and replaying method for video frequency image
InactiveCN1649412ARealize the operationProtect intellectual propertyPulse modulation television signal transmissionSelective content distributionDECIPHERComputer graphics (images)
This invention provides a method for the splitting and reproduction of video images including: the video image forms several reference frames and non-reference frames by encoding, among which, the splitting refers to extract a part or total compressed video image data in the above total or part reference frames, the extracted video compressed data are key contents, others are basic contents, which are stored or transmitted separately, a user decoder can split-join the key and basic contents to a complete original video image to play it if getting them the same time, if it cannot get the key content, then the decoded recovered image is wrong, which can protect the copyright of video images effectively not needing extra cipher / decipher algorithms.
Owner:BEIDA QINGNIAO INTEGRATED CIRCUIT BEIJING
Image picture encipher and decipher method
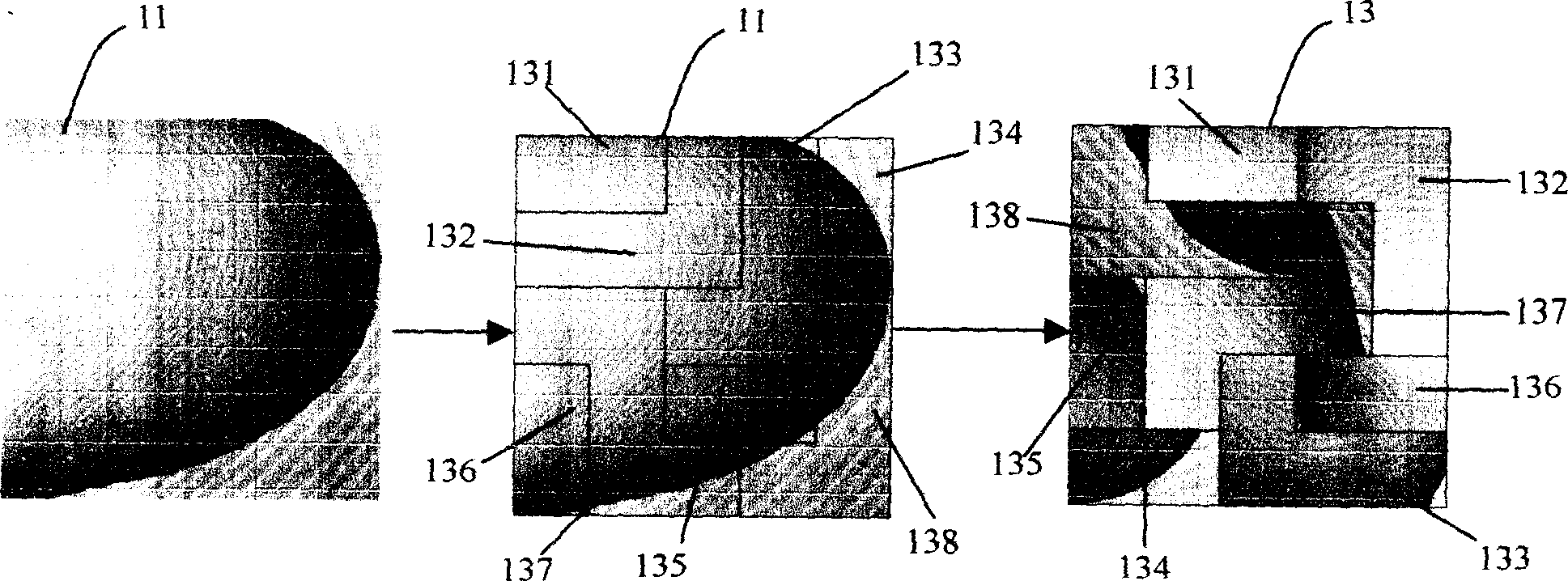
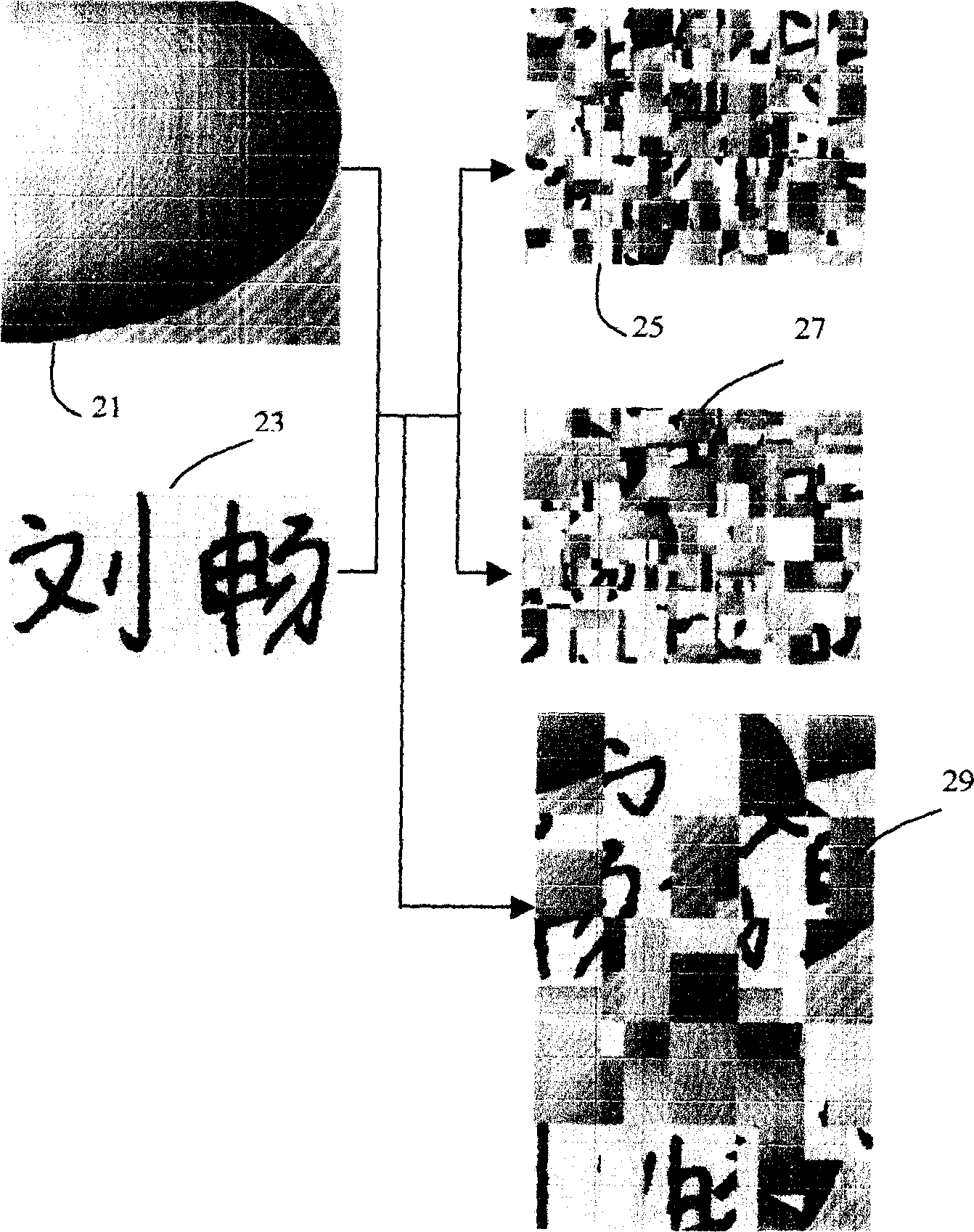
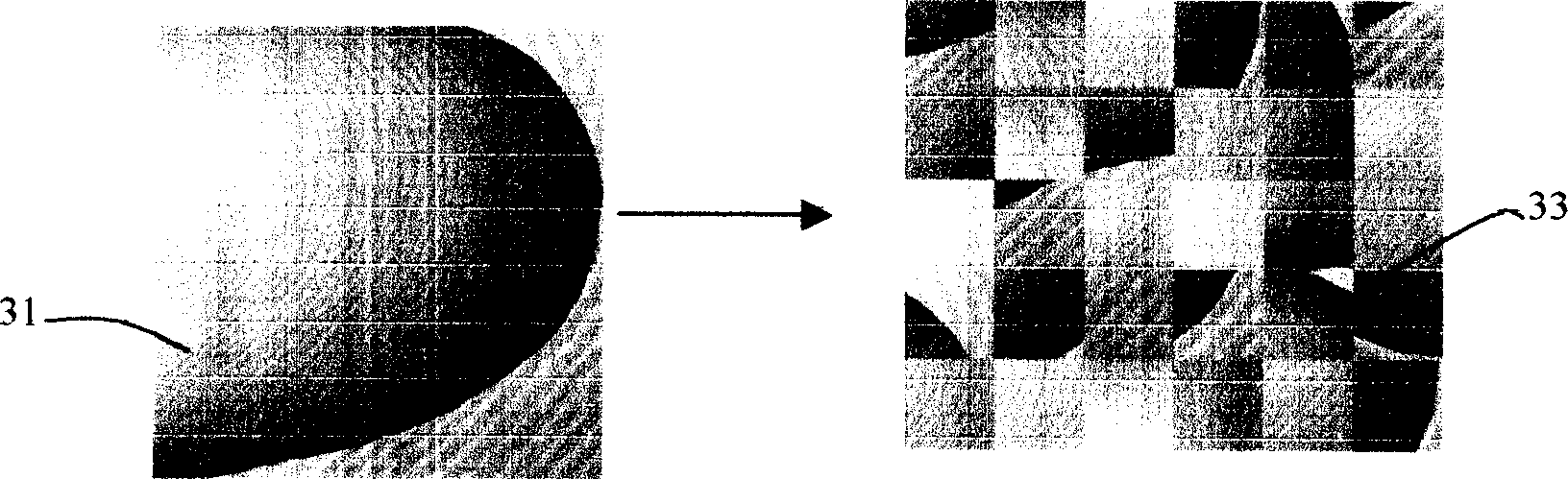
A method for enciphering and deciphering image pattern includes dividing a frame of original image pattern to be a numbers of region randomly and rearranging said divided regions to form a frame of enciphered image pattern, enabling to do said process cyclically to let enciphered image pattern be changed essentially, restoring original image pattern by carrying out retrace course of rearrangement for realizing deciphering when it is required.
Owner:刘畅
Enciphering method for combining accidental enciphering and exhaust algorithm decipher
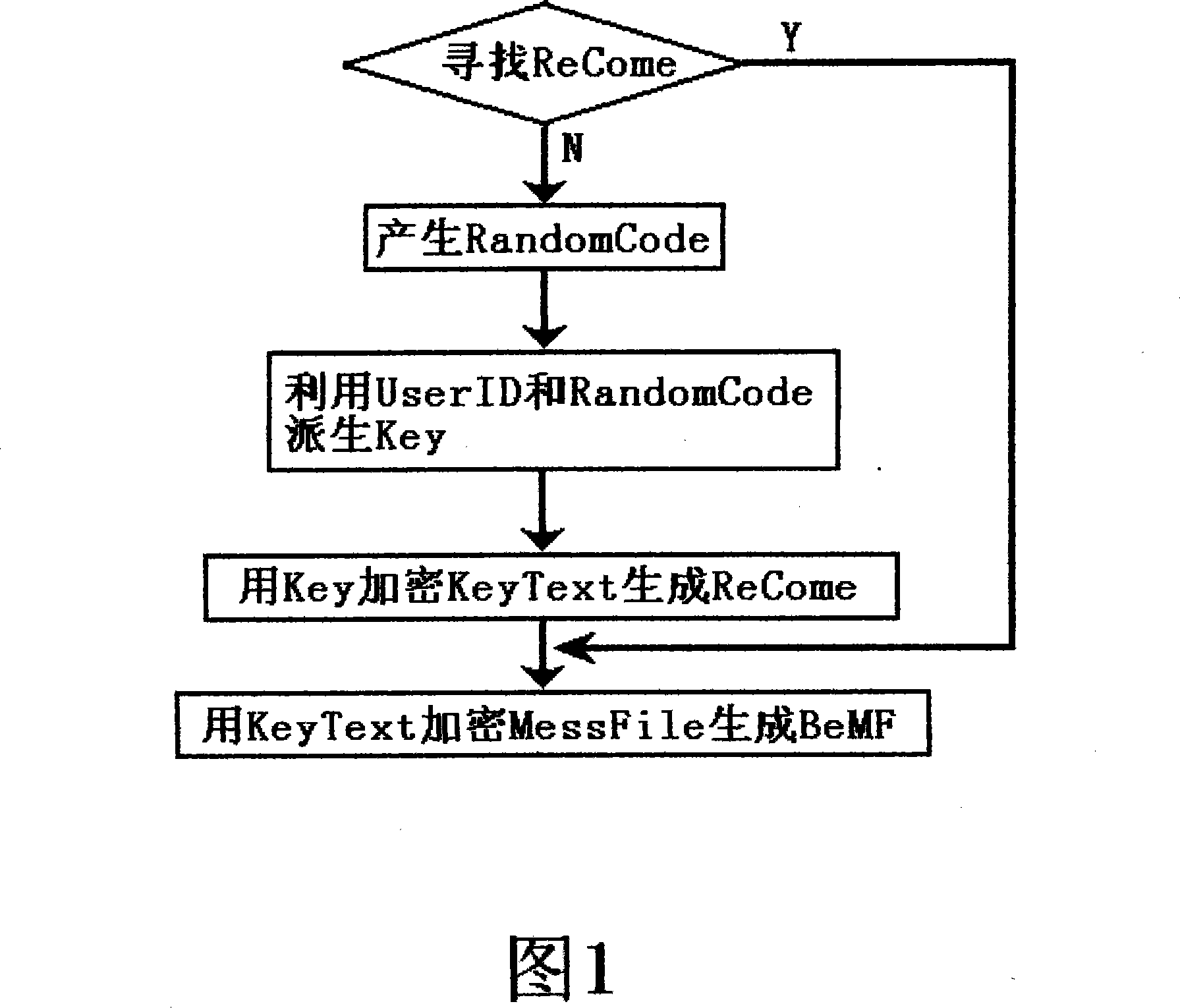
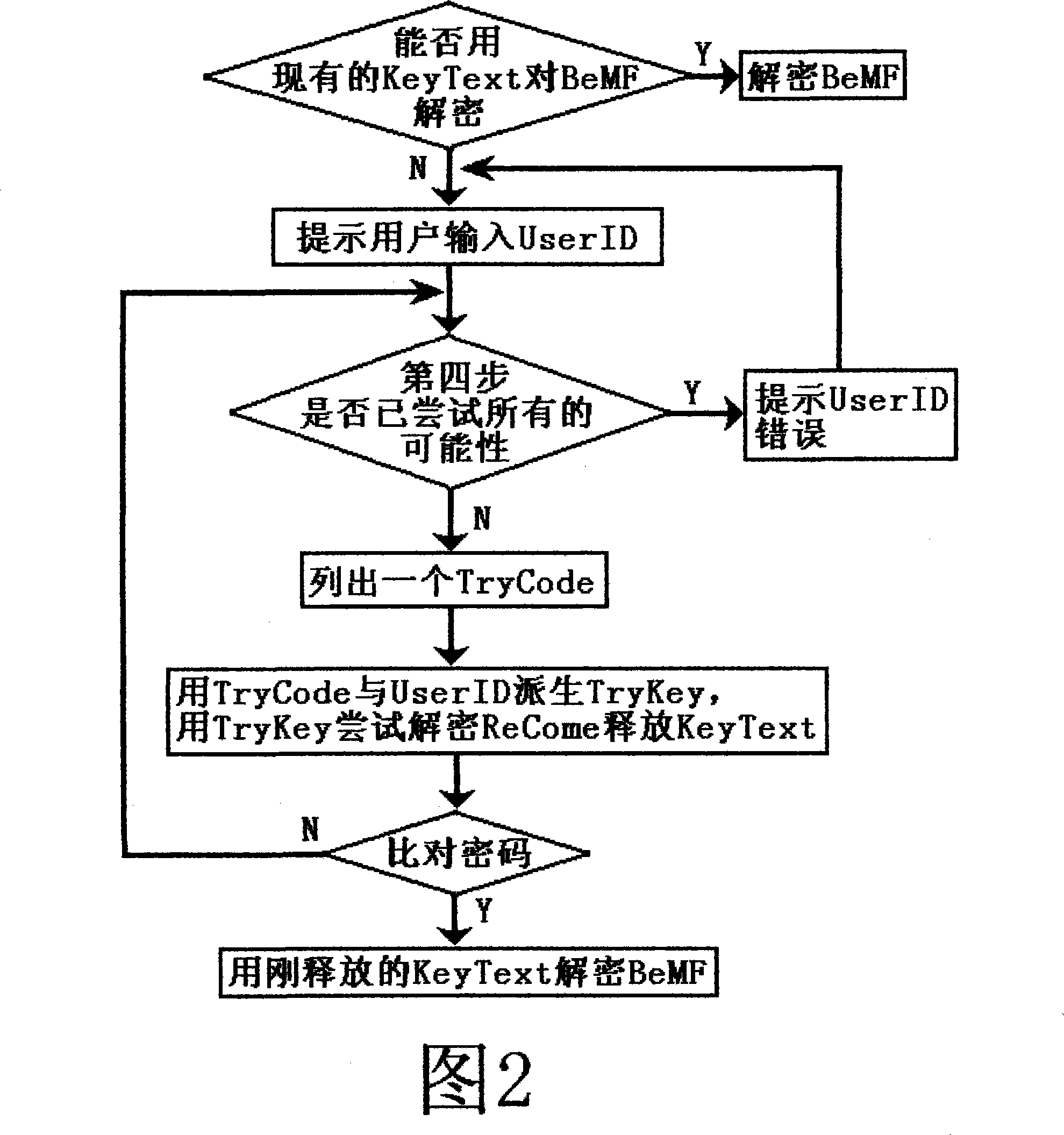
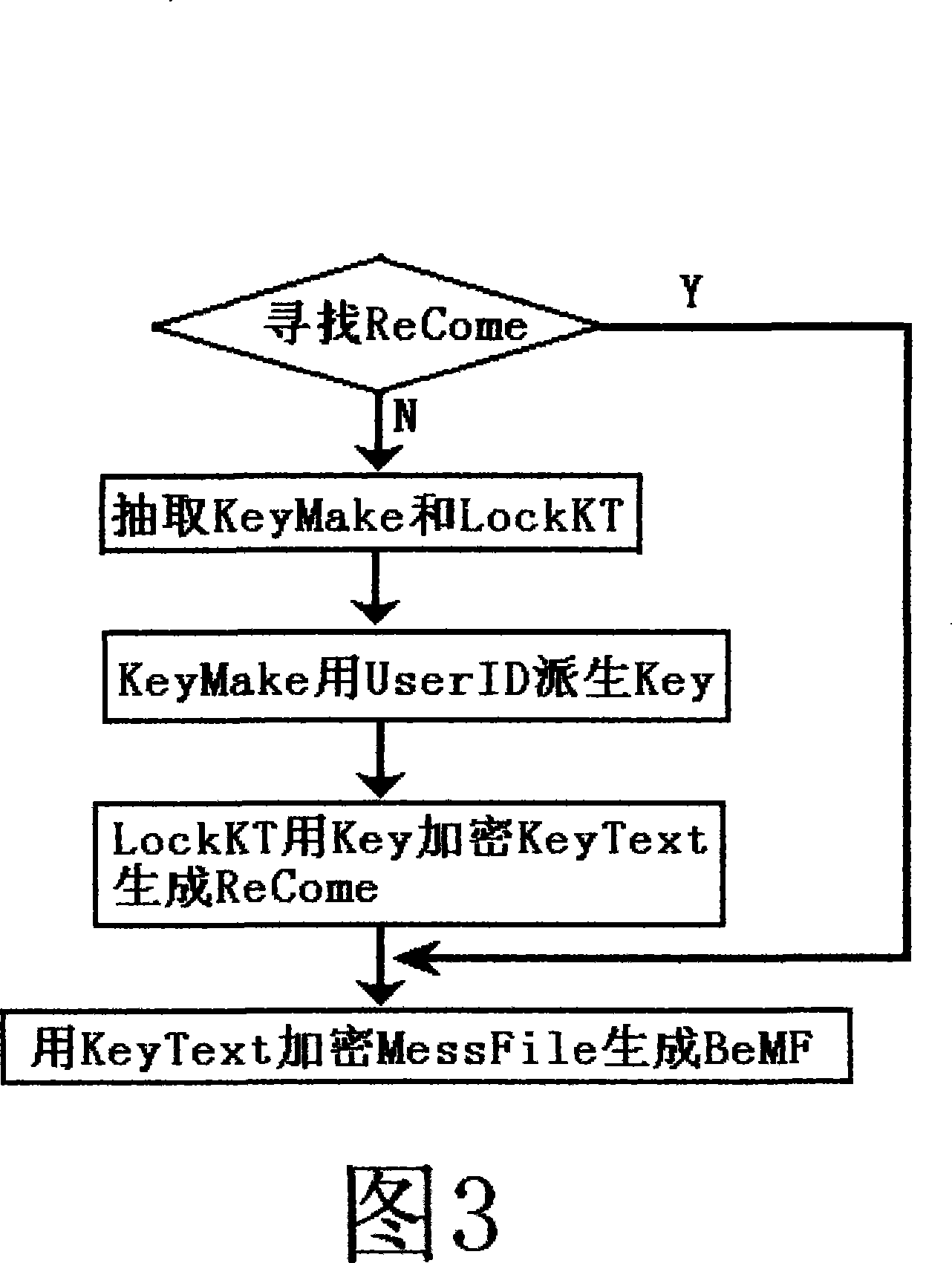
The invention discloses a method for encrypting, which combines random encryption and exhaustive method decryption. When the invention is used in encryption, a random password or a randomized algorithm are utilized to encrypt information, when the invention is used in decryption, decrypted programs can not guarantee that reduced secret keys or decryption algorithms can be correctly found out in one time, the decrypted programs need adopting an exhaustive method to try to decrypt for many times and to compare with password recognition information for many times, correct reduced secret keys or decryption algorithms can be found out, and the even decryption computational complexity when the information which is decrypted by the invention is decrypted is bigger for many times than that when the information is encrypted. The invention mainly encrypts backups of important information such as internal passwords, certifications and the like and certainly can encrypt information such as common files and the like.
Owner:刘海云
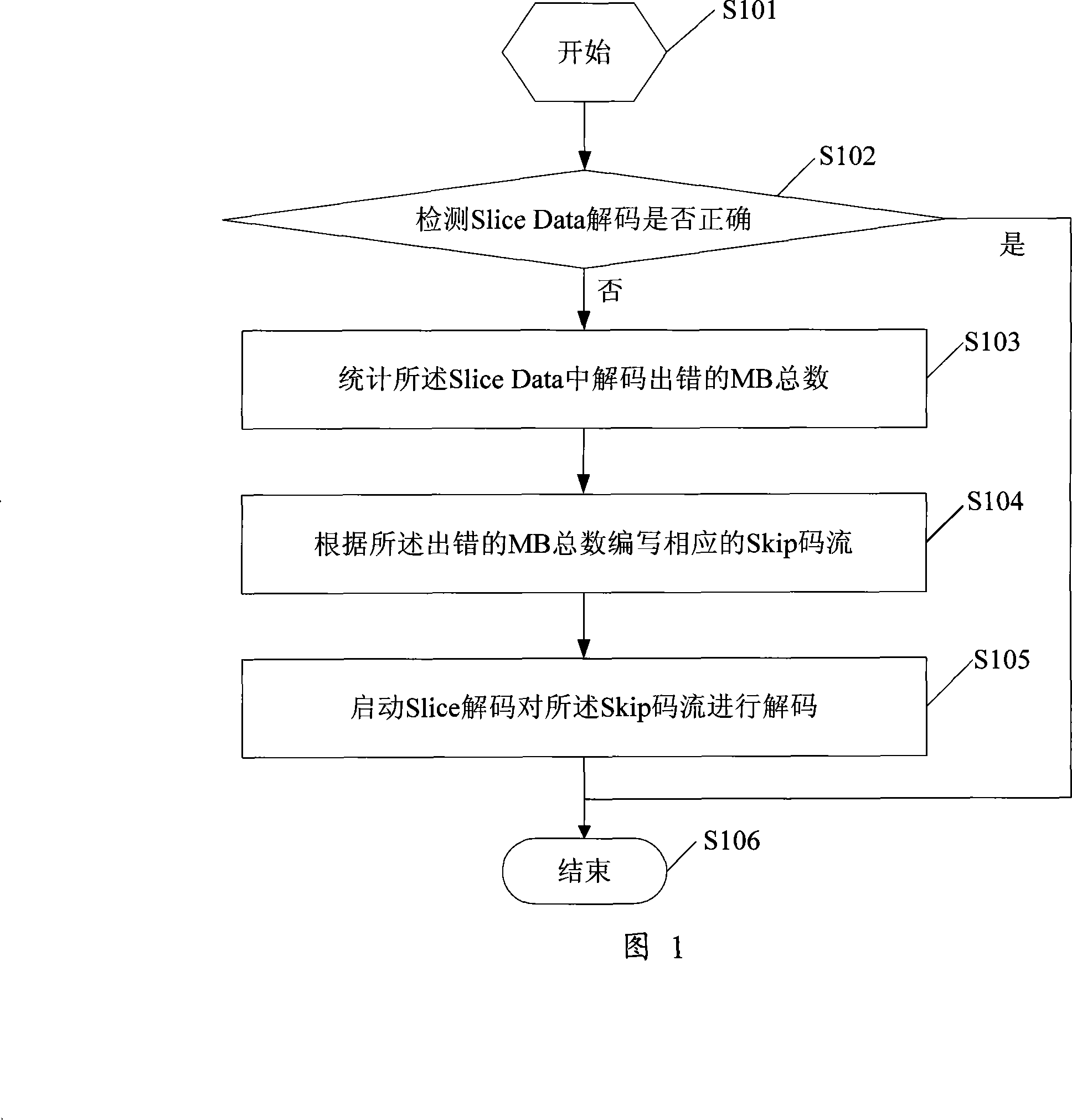
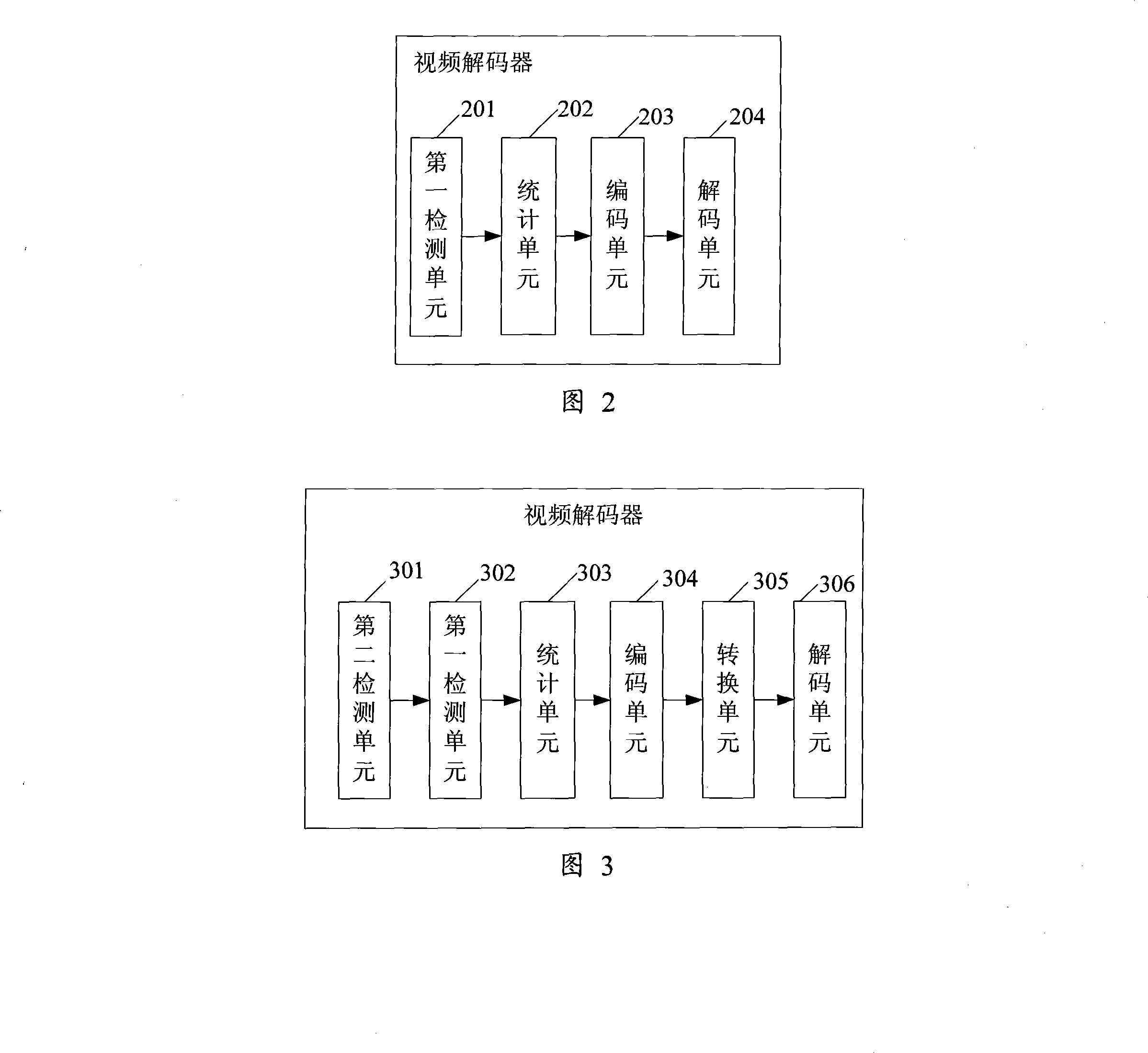
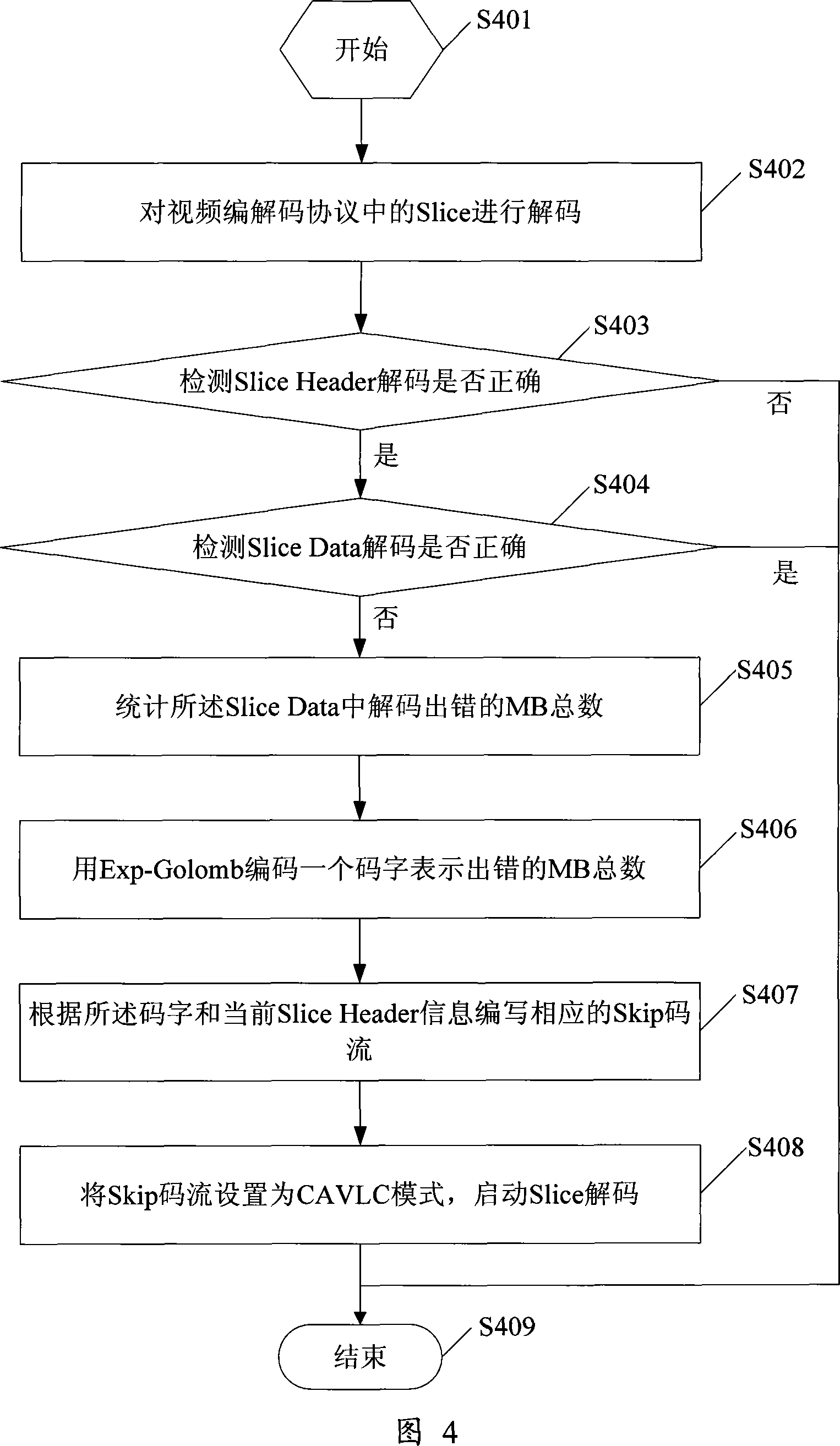
Method for realizing image error covering in video decipher and video decoder
ActiveCN101227619AGood error concealmentTelevision systemsDigital video signal modificationDECIPHERData information
The example of the invention discloses a method for concealing image error in a realization of video decoding, which comprises the following steps detecting whether encoding errors are occurred on a slice compressing data information, calculating the total number of the error macro module in the slice compressing data information if the encoding error is detected on the slice compressing the data information, generating a coding flow of a corresponding jumping-macro module according to the total number of the macro module, and encoding a coding flow of a corresponding jumping-macro module. The example of the invention further discloses a video decoder, a segment of a whole Skip code flow are coded by the coder to allocate into a sub-layer encoding to the Slice through the method for concealing image errors in the realization of video decoding and the video decoder which are provided by the invention, under the error condition of the slice compressing data information (Slice Date), thereby realizing the function of repairing error images.
Owner:HUAWEI TECH CO LTD
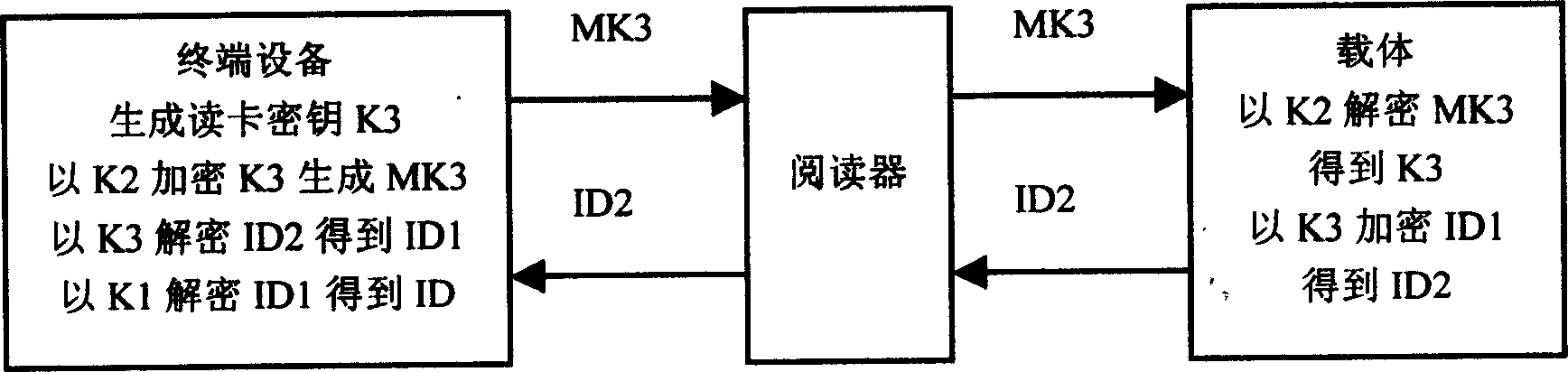
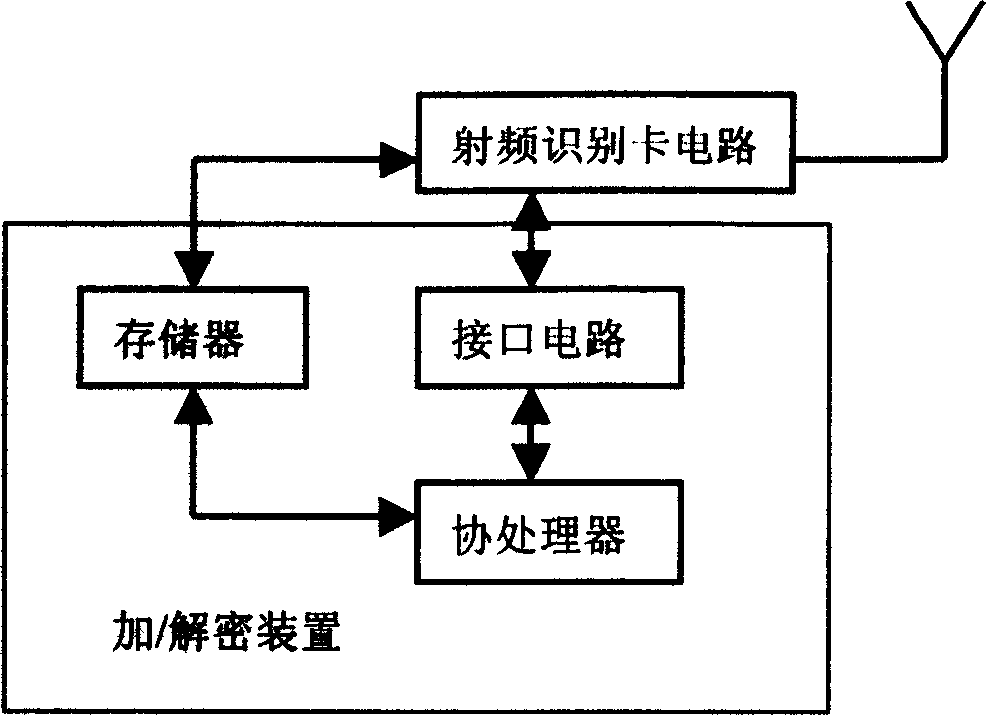
Encipher / decipher method for identity information and recognition system
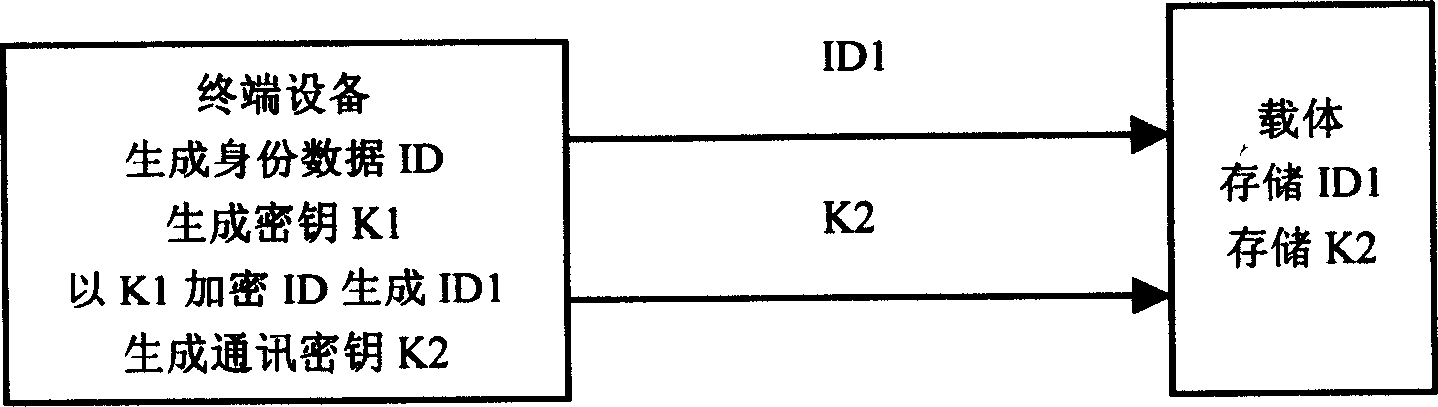
InactiveCN1598862AImplement multiple encryptionIncrease the difficultyMultiple keys/algorithms usageDigital marking by data transferDECIPHERIdentity recognition
The invention relates to information encryption technology. It provides an identity information encryption and decryption method and an identification system to overcome shortcoming of low security, easy embezzlement, duplication and malversation. Its steps are memorize encrypted identify information into carrier; ulteriorly, encryption and decryption devices are set in carrier to encrypt and decrypt input and output information; especially, random time key is adopted to encrypt transferred information. With a very powerful function of anti-false and anti-pilfer, the system especially adapts to commodity anti-false, identify identification and other field.
Owner:ZHONGNAN RONGHAI TECH
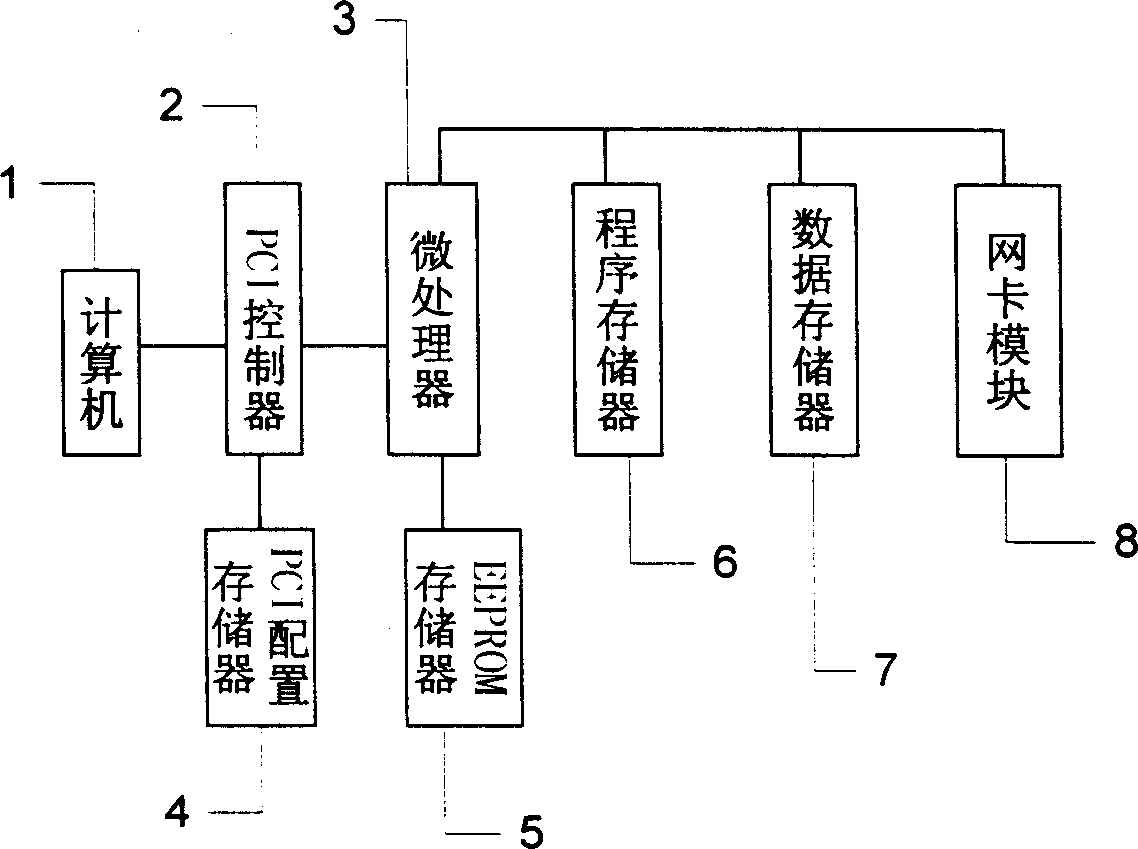
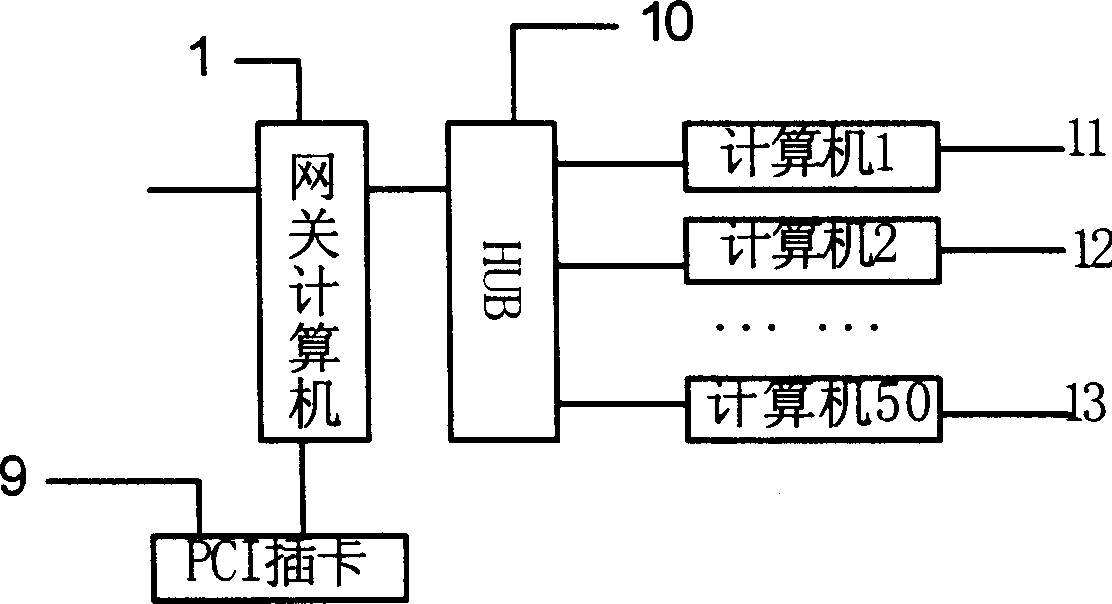
Virtual private network applying hardware encipher/decipher
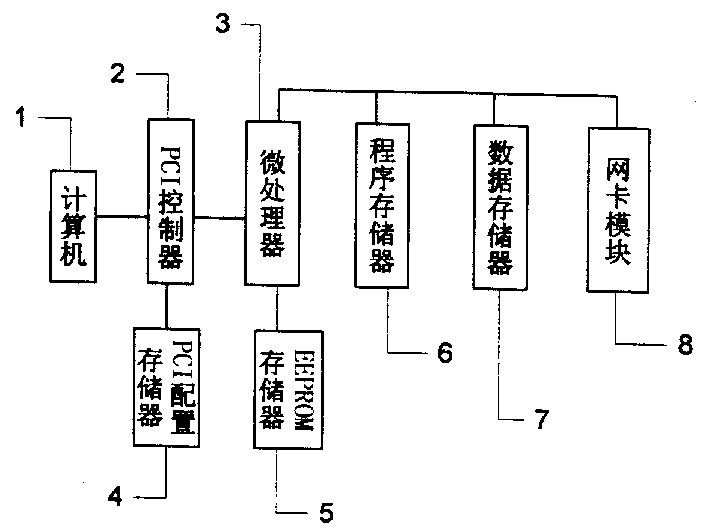
The hardware enciphering and deciphering virtual private network belongs to the field of information safety. Built-in PCI card is inserted into computer used as gateway to realize enciphering algorithm, deciphering algorithm, digital signature, identity confirmation, etc. During the mutual access among users in different subnetwork in virtual private network, the data passing through PCI controller, in which some available data flow enciphering algorithm cured in the card memory is adopted, is received by microprocessor and stored temporarily in memory, and the enciphered data are output via network card to reach safe and efficient communication among computers under VPN environment. The present invention is even safer than software realized VPN function.
Owner:SHANGHAI JIAO TONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com