Encipher / decipher method for identity information and recognition system
An identity information and identification system technology, applied in the usage of multiple keys/algorithms, digital marking through data transmission, electromagnetic radiation induction, etc., can solve problems such as inability to encrypt information, inability to exchange terminal equipment information, and easy to be stolen. , to achieve the effect of increasing difficulty, increasing security, and preventing information theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
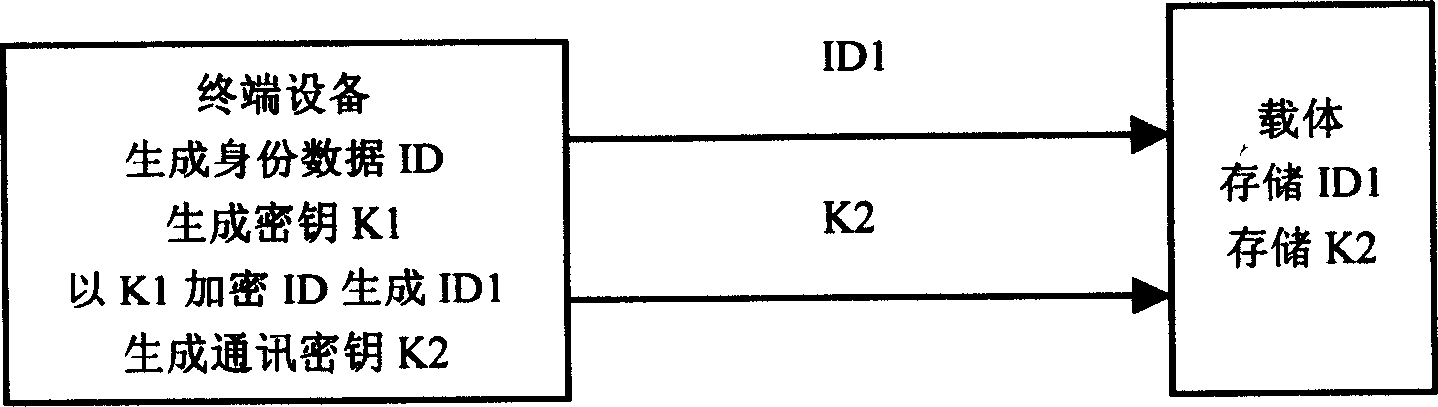
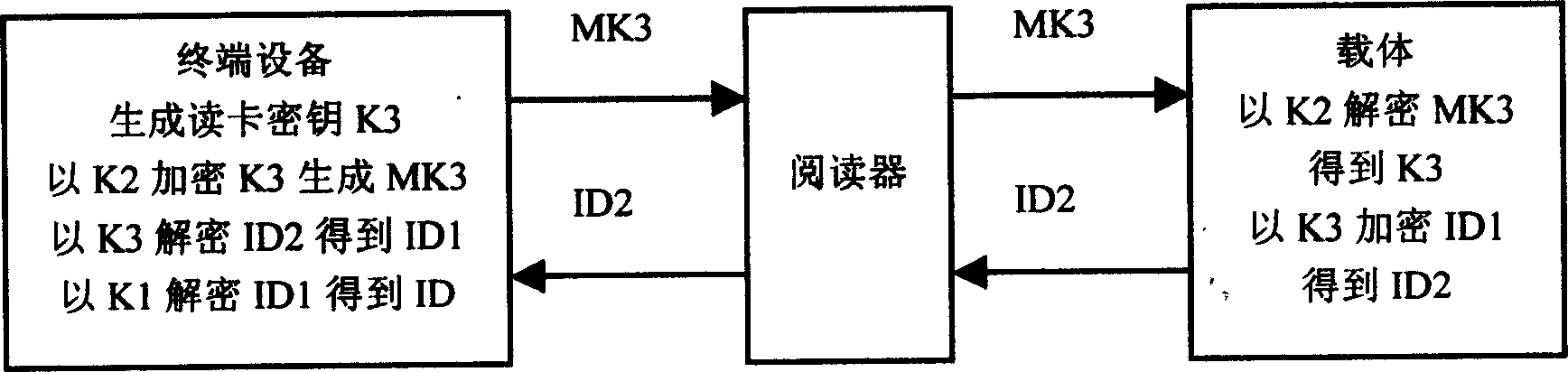
[0032] The identity information identification system in this example is a radio frequency identification system. The system composition includes: radio frequency identification card (or called electronic tag) as carrier, reader and terminal equipment. The reader is connected to the terminal device through the network.
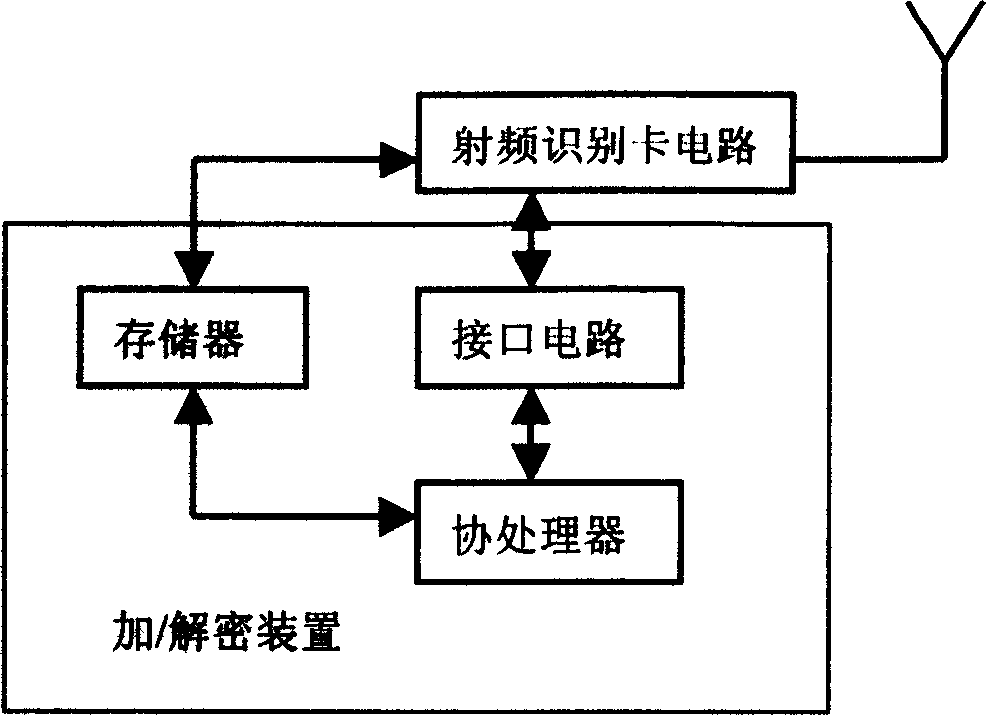
[0033] RFID card for this example. It is formed by adding an encryption / decryption device to the existing radio frequency identification card circuit. The increased hardware structure includes: memory (RAM), used to store encrypted information ID1 and communication key K2; coprocessor, used to complete encryption and decryption processing and system control; interface circuit, used for radio frequency identification card circuit and encryption / decryption device interface. Circuit structure see image 3 . The above-mentioned memory is a non-volatile memory, and the dual-port RAMASIC IP core (unpackaged integrated circuit chip) of D&R Silicon Company is sel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com