A point-to-point data transmission method based on nfc
A data transmission method and point-to-point technology, which is applied in the field of point-to-point data transmission, can solve problems such as weak security and serious plaintext transmission, and achieve the effects of good security, improved security, and elimination of eavesdropping
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
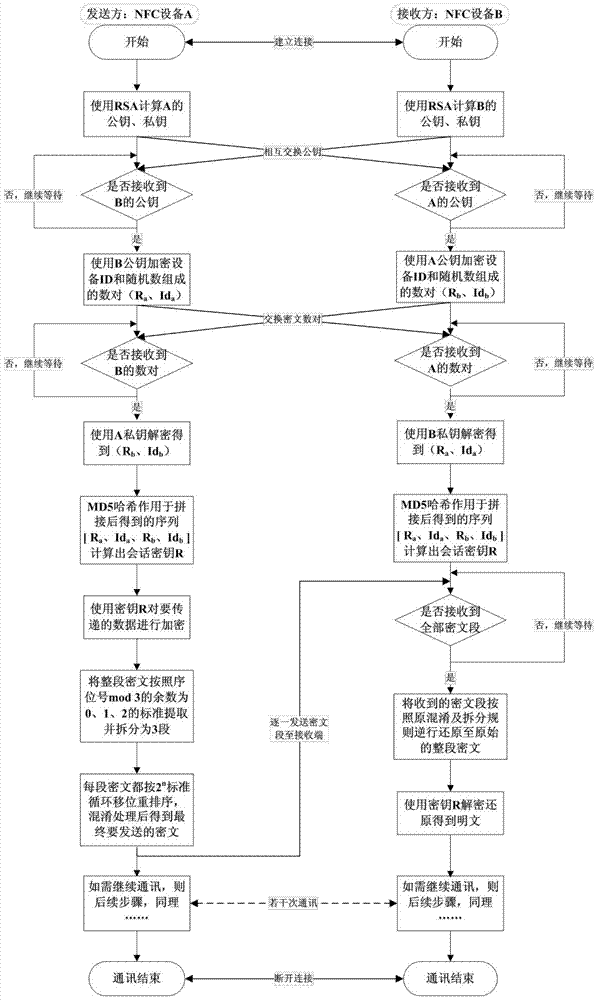
[0019] In order to make the purpose of the present invention, implementation scheme and advantages clearer, the specific implementation of the present invention will be described in further detail below, and the specific illustrations of the present invention can be found in figure 1 and figure 2 shown.
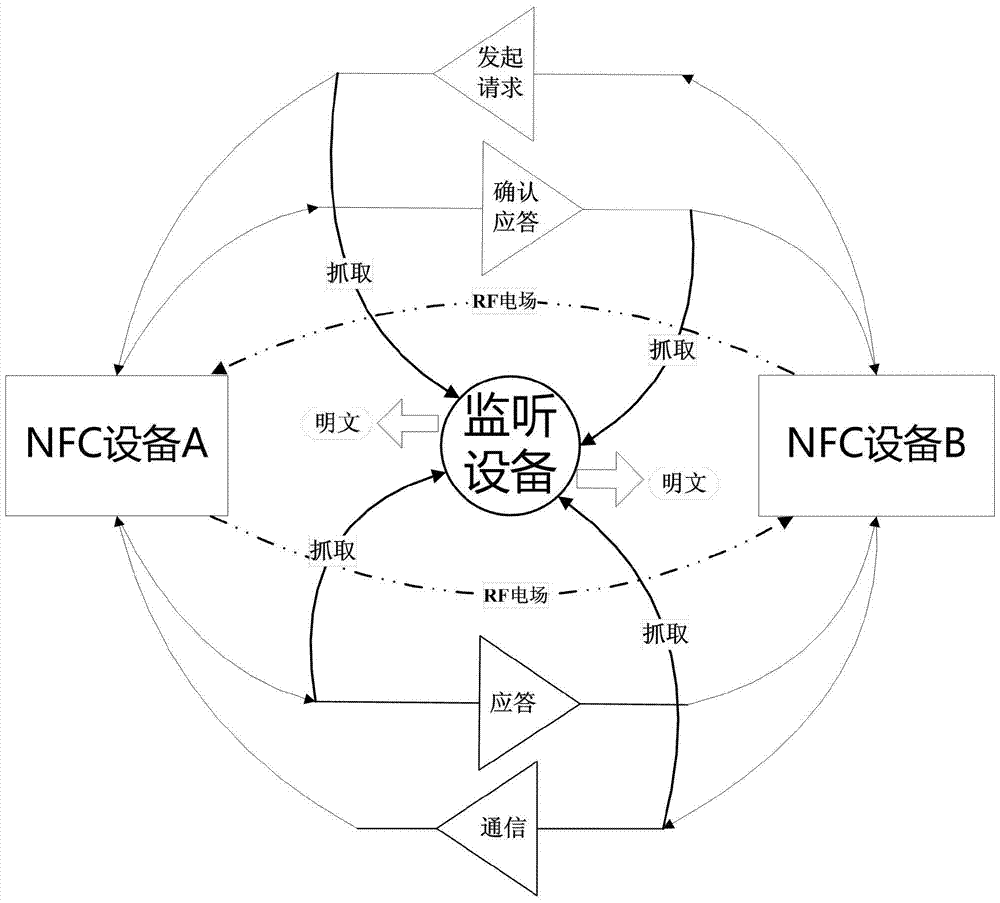
[0020] (1) When two NFC devices are used to directly sense each other to transmit data, the relevant eavesdropping devices are used to intercept and capture midway. The analysis and test results show that the captured data is either from the handshake response phase or the actual transmission after the connection is established. clear text. the following figure 1 It is a schematic diagram for analyzing the working principle of NFC point-to-point transmission mode and discovering test loopholes. Therefore, it is necessary to add an additional NFC encryption method on top of the current NFC protocol stack to protect data transmitted in point-to-point mode.
[0021] (2) In ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com