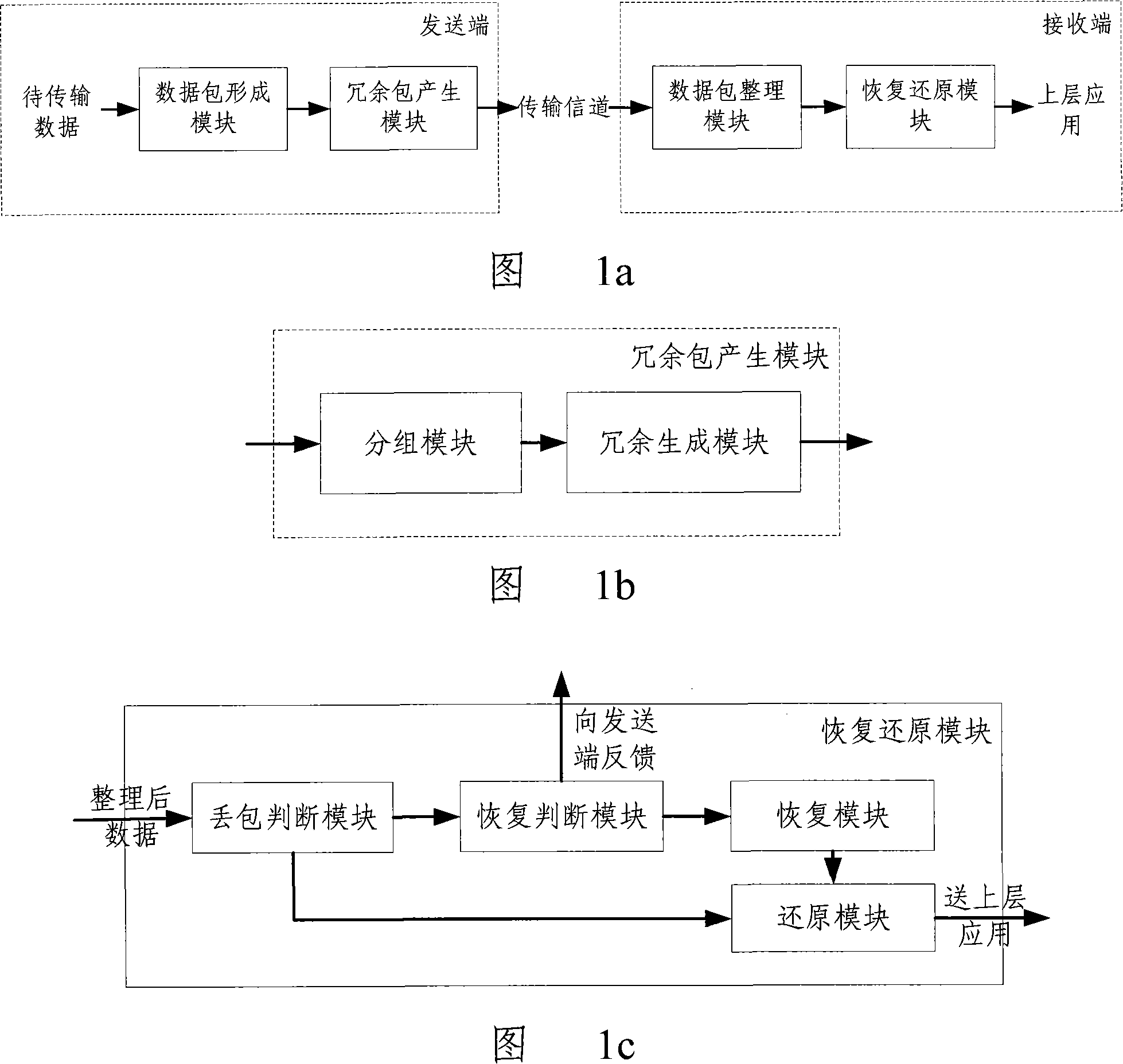
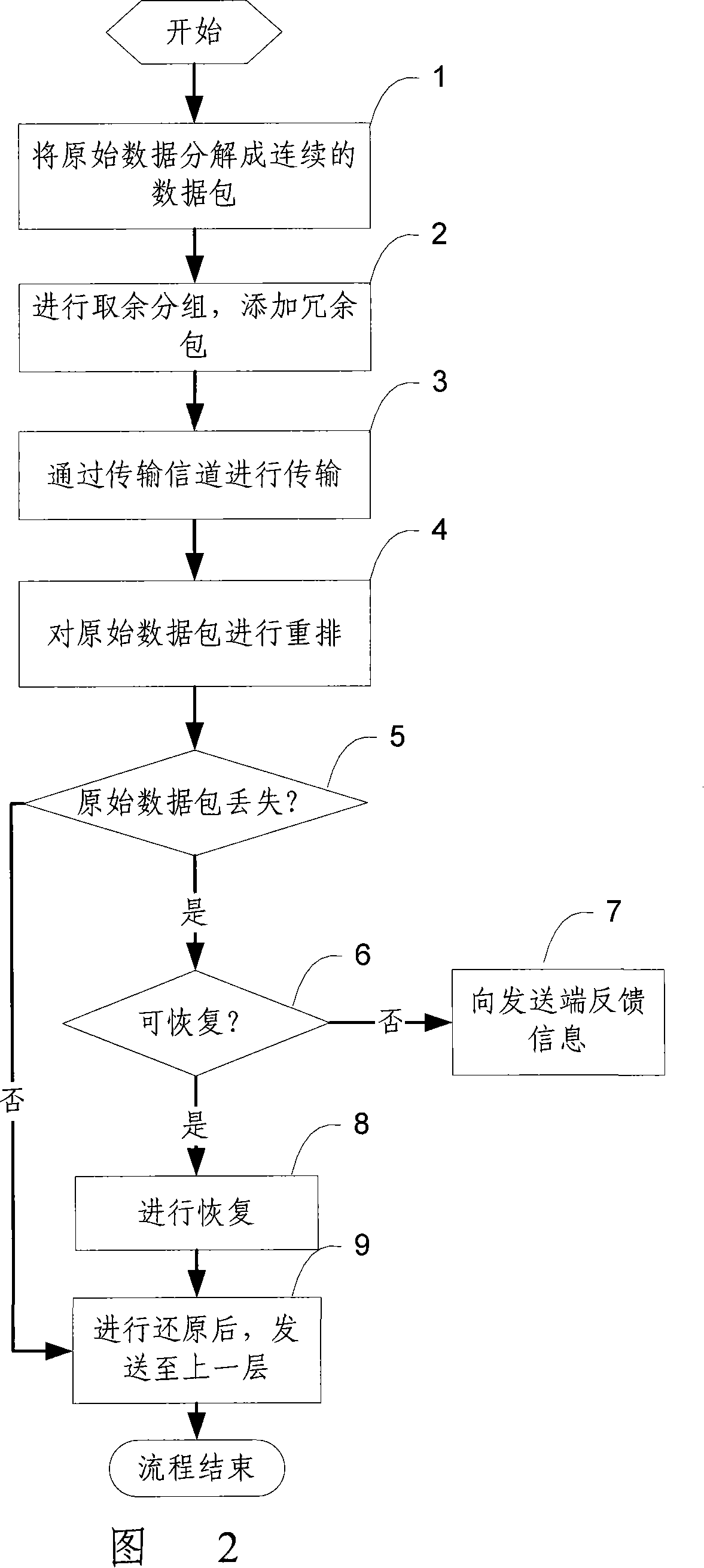
Patents
Literature
3792 results about "Transfer procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
DEFINITION of 'Transfer Procedures'. The procedure by which ownership of a stock moves from one party to another. The transfer agent follows a detailed, documented series of steps governed by the SEC to ensure that a transaction has been completed.
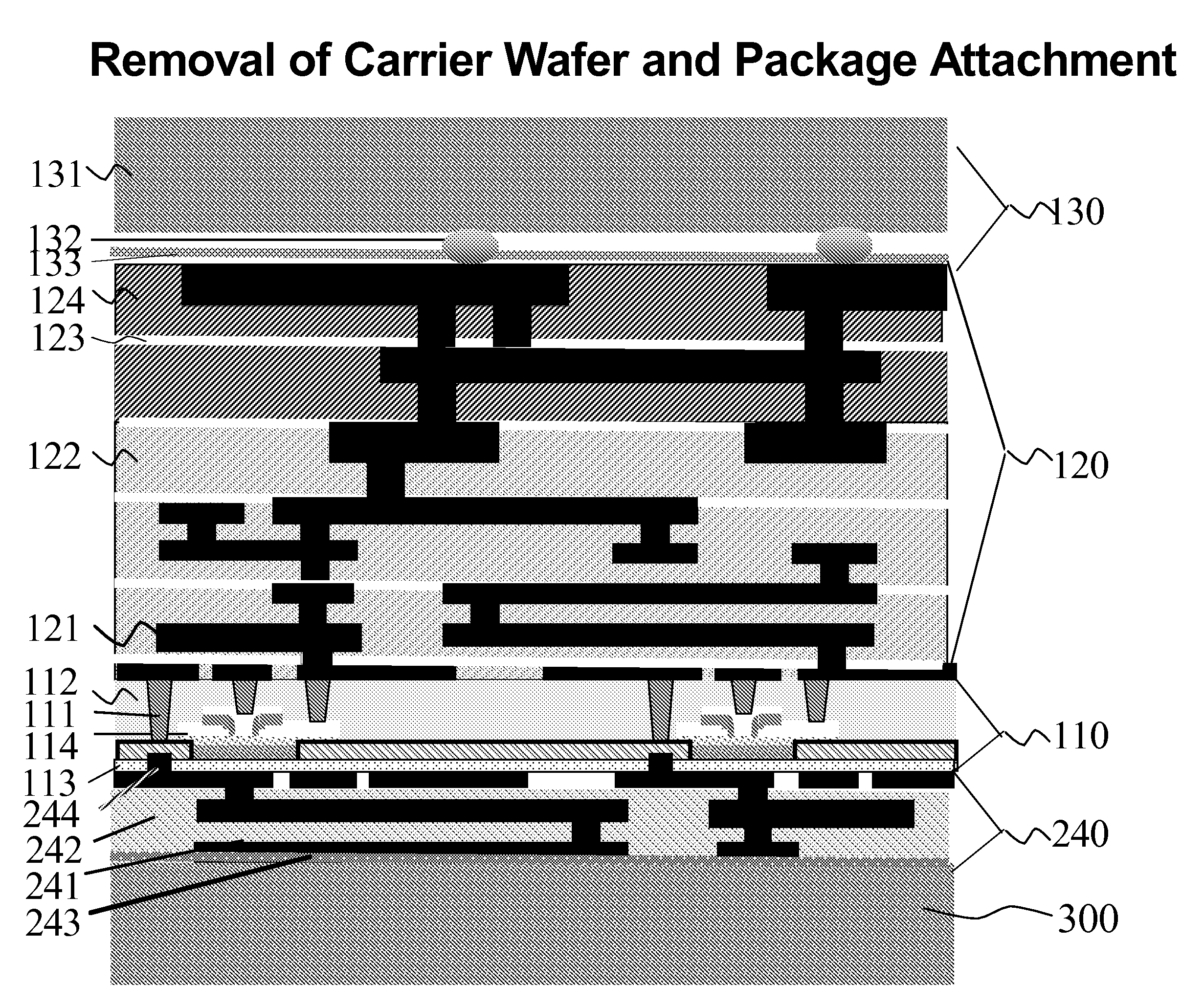
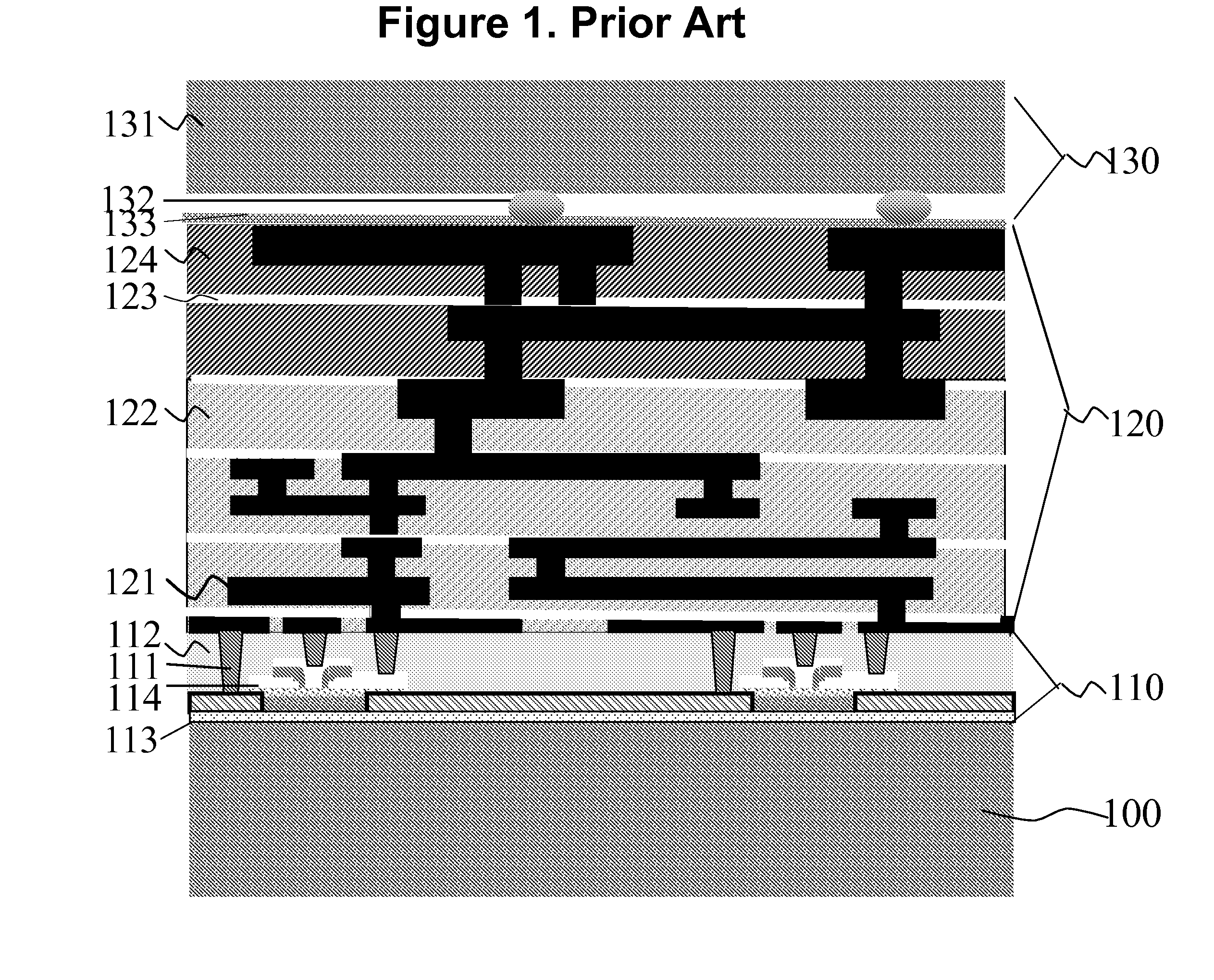
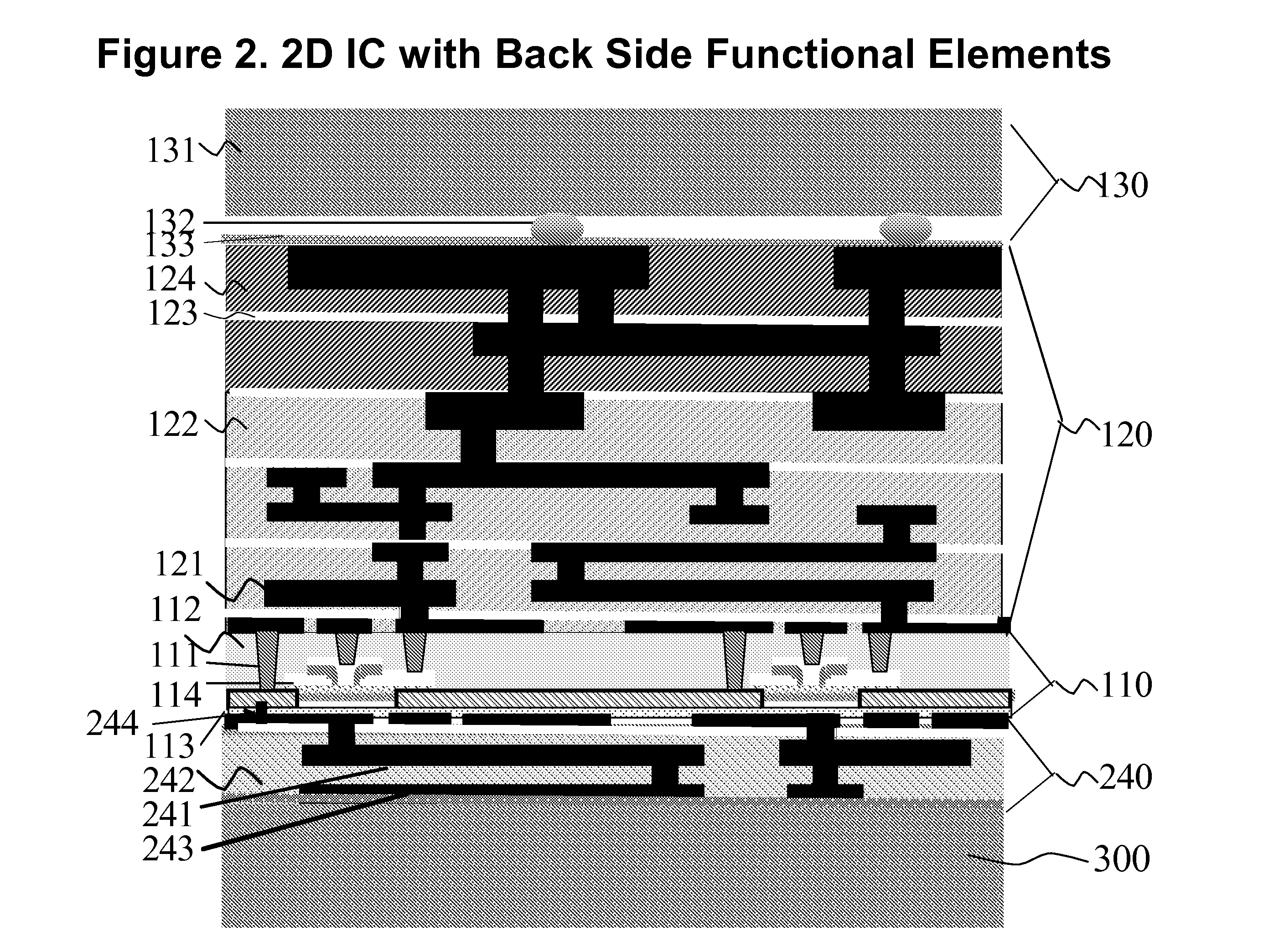
Layer Transfer Process and Functionally Enhanced Integrated Circuits Products Thereby
InactiveUS20080277778A1Low costFunction increaseSemiconductor/solid-state device detailsSolid-state devicesTransfer procedureEngineering
A structure for a semiconductor components is provided having a device layer sandwiched on both sides by other active, passive, and interconnecting components. A wafer-level layer transfer process is used to create this planar (2D) IC structure with added functional enhancements.
Owner:GLOBALFOUNDRIES INC
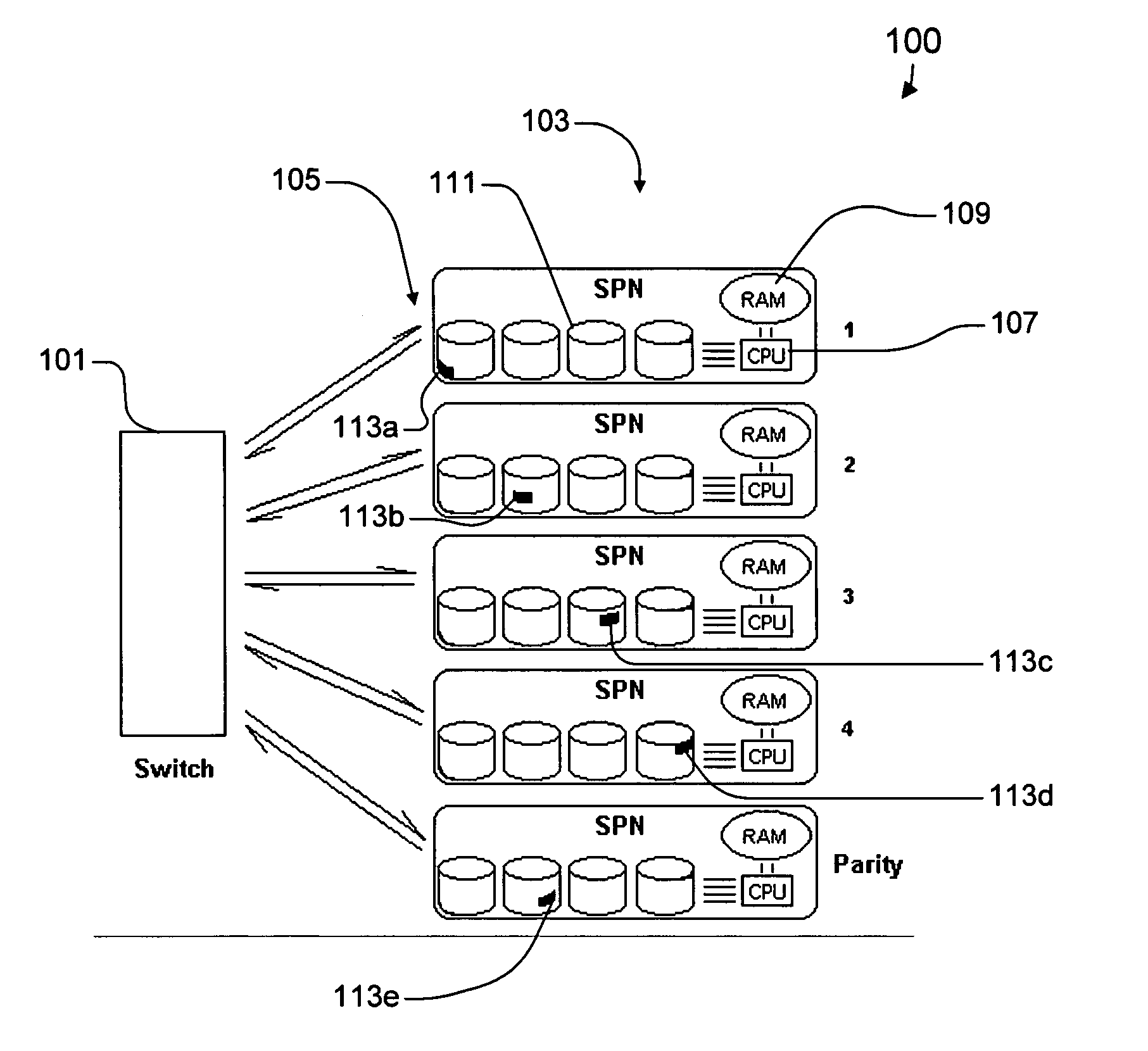
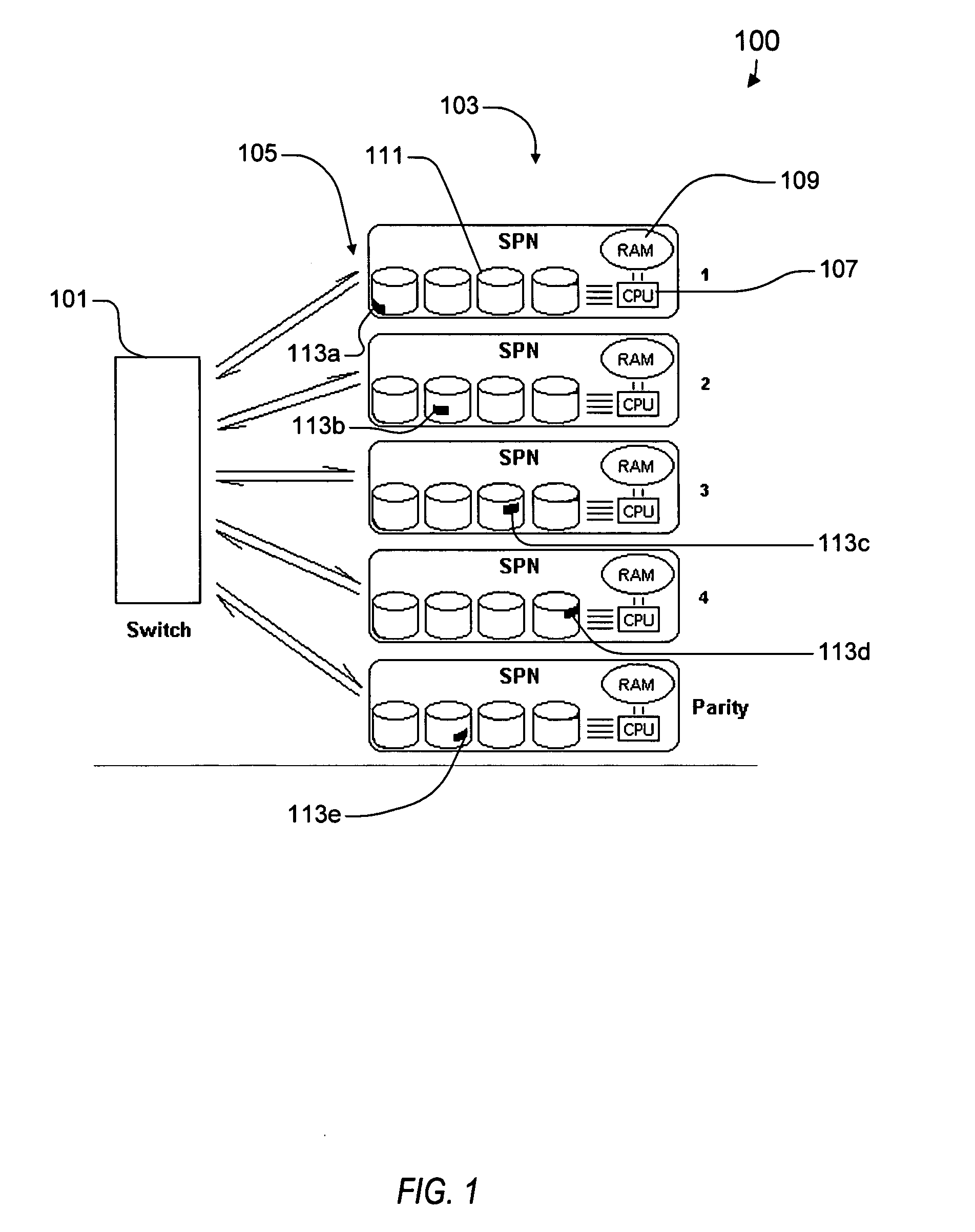
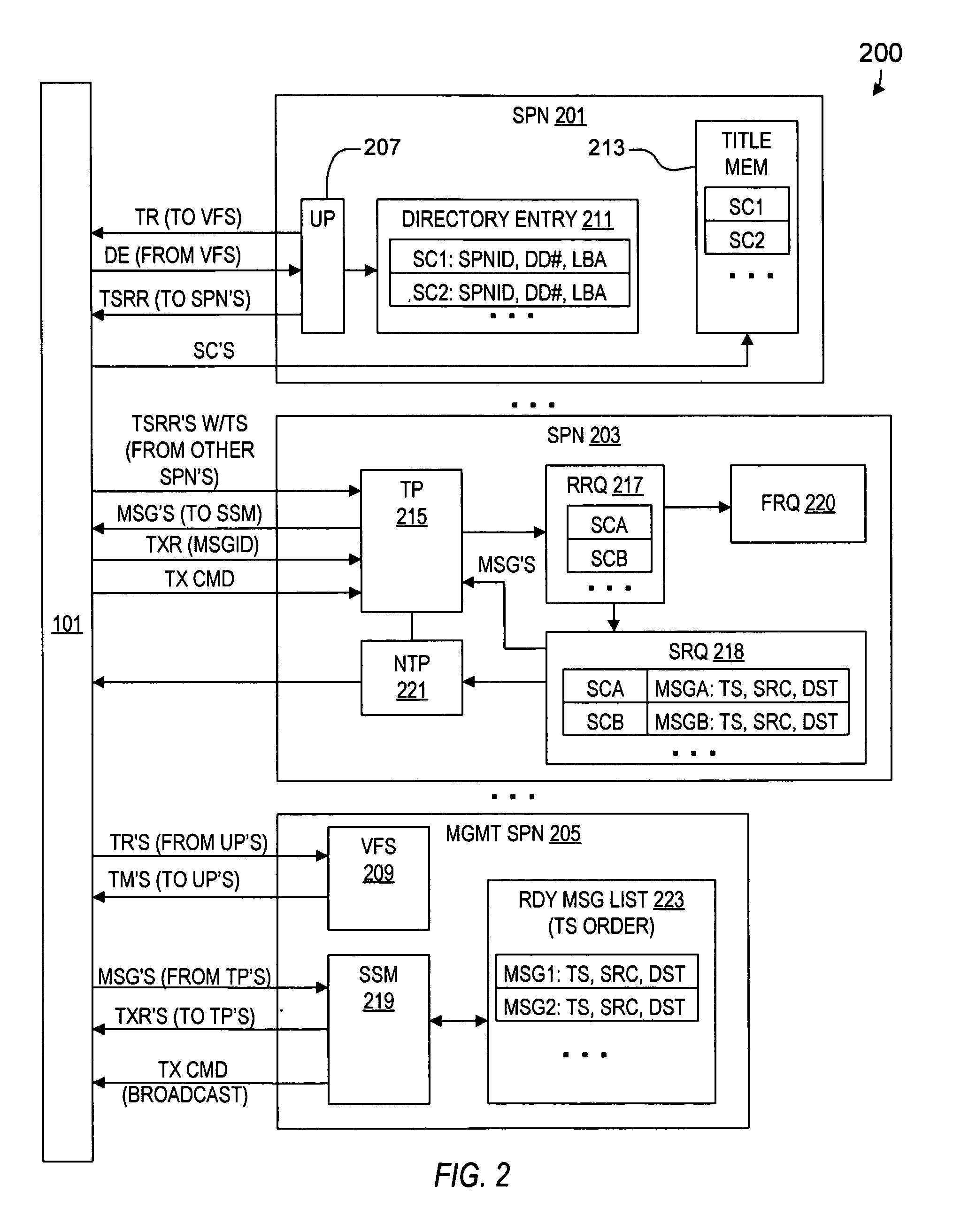
Synchronized data transfer system
ActiveUS20050114538A1Low costTelevision system detailsColor television detailsTransfer systemTransfer procedure
A synchronized data transfer system including storage processor nodes, a backbone communication switch, multiple titles subdivided into subchunks and distributed across the nodes, a user process executed on a first node, a transfer process executed on a second node, and a management process executed on a management node. The user process sends a timestamped read request to request a corresponding subchunk. The transfer process sends a message to the management process for each received read request, where each message identifies source and destination nodes. The management process broadcasts transmit commands to initiate sequential transmit periods, receives the messages, and selects from among the received messages to ensure that each node sends or receives only one subchunk during each transmit period. The management process sends a transmit request for each selected message, and the transfer process sends a subchunk identified by a transmit request in response to the transmit command.
Owner:INTERACTIVE CONTENT ENGINES LLC
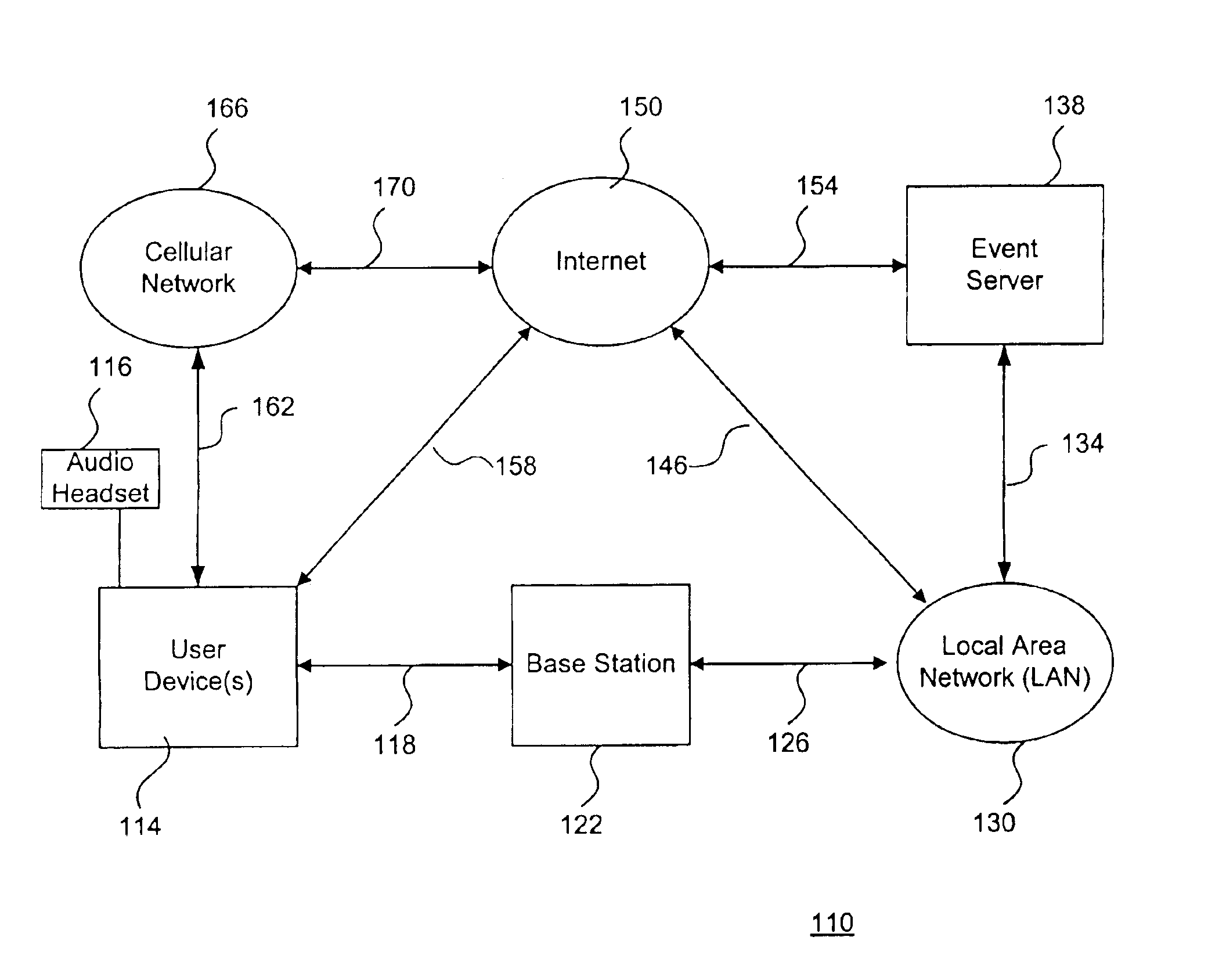
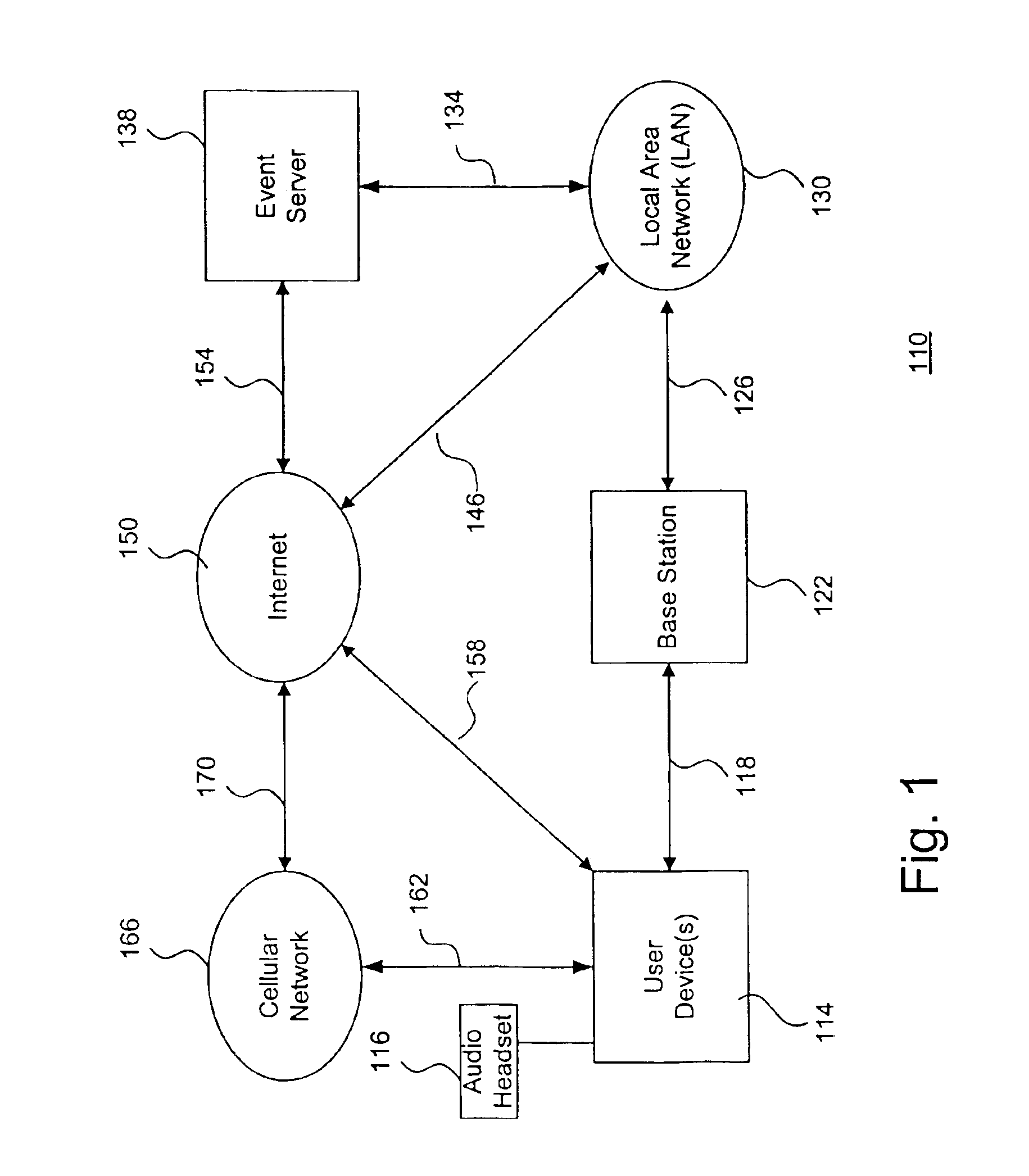
System and method to support gaming in an electronic network
InactiveUS6884162B2Apparatus for meter-controlled dispensingVideo gamesUser deviceRelevant information
A system and method to support electronic gaming in an electronic network includes an event server that provides restricted access to various types of game services. One or more system users may utilize corresponding wireless portable user devices for connecting to the event server to thereby gain access to the foregoing game services as game participants. The system users may thereby utilize the user devices to access the event server for accessing appropriate gaming services and related information. In addition, a source system user may utilize a source user device to perform a transfer procedure for transferring ownership rights of an electronic certificate related to the electronic gaming to a target system user through a target user device. The foregoing transfer procedure may be conducted through the event server, or may occur directly from the source user device to the target user device.
Owner:SONY CORP +1
Method and apparatus for transferring a communication session
ActiveUS7042879B2Network traffic/resource managementSpecial service for subscribersTransfer procedureIp address
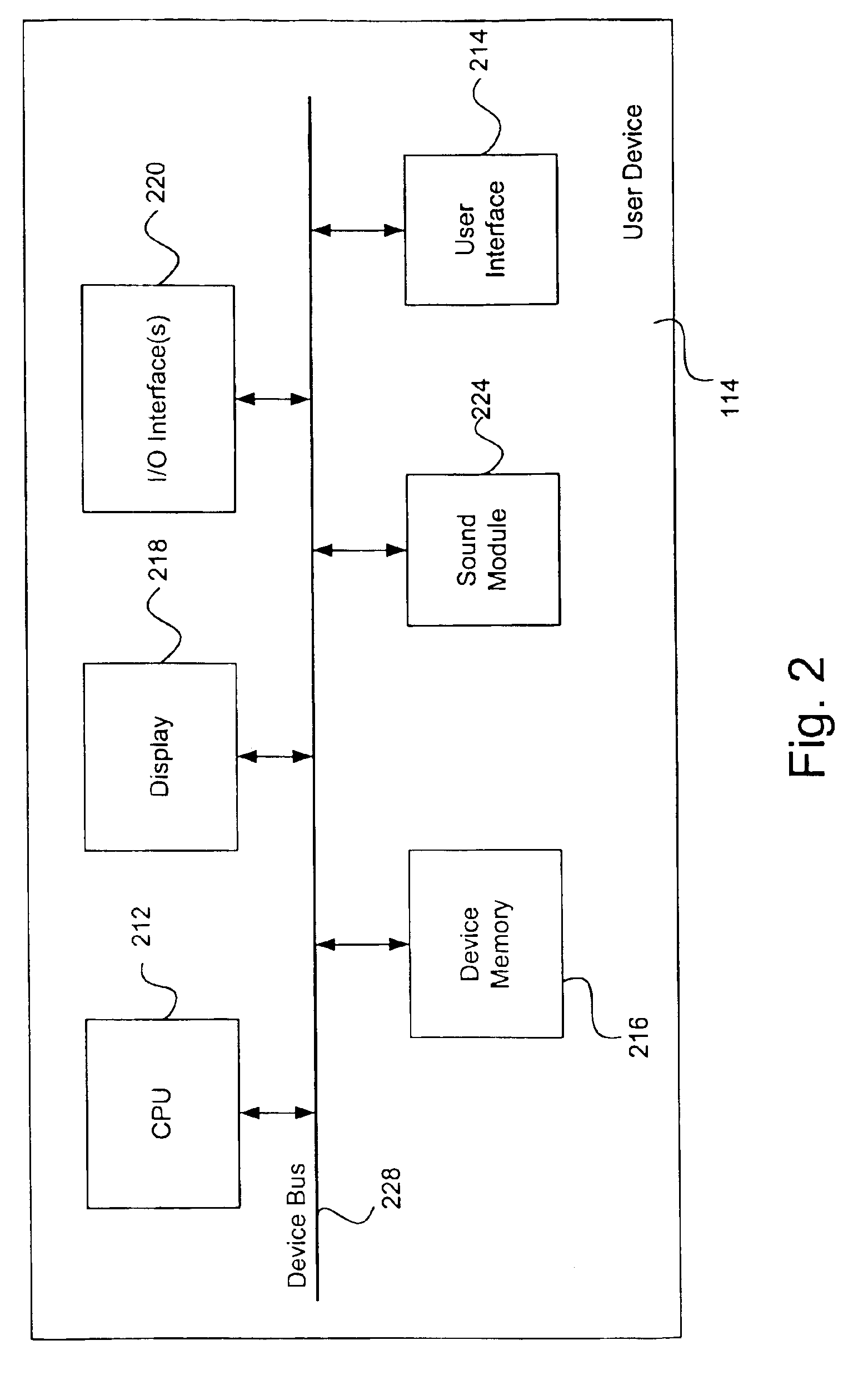
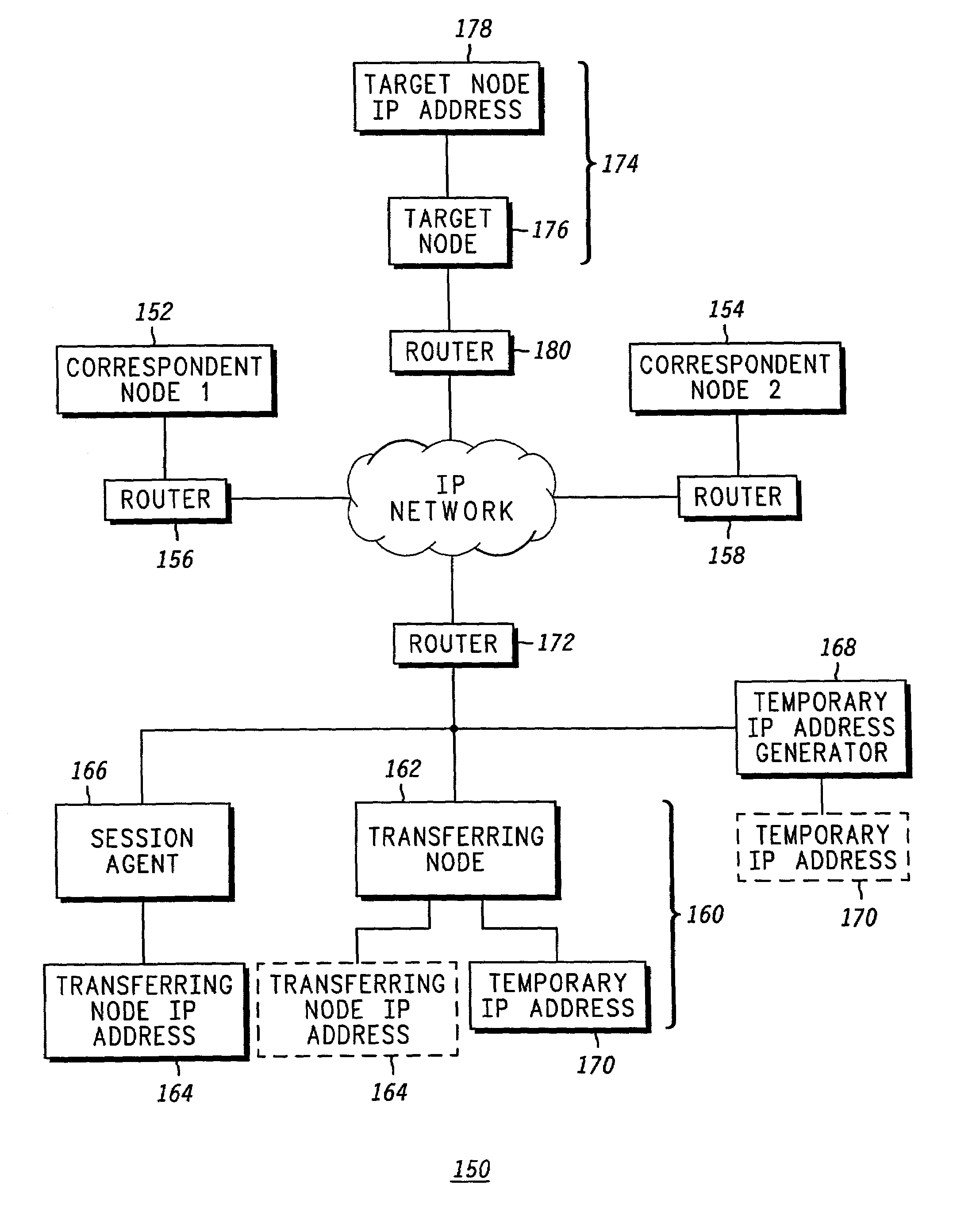
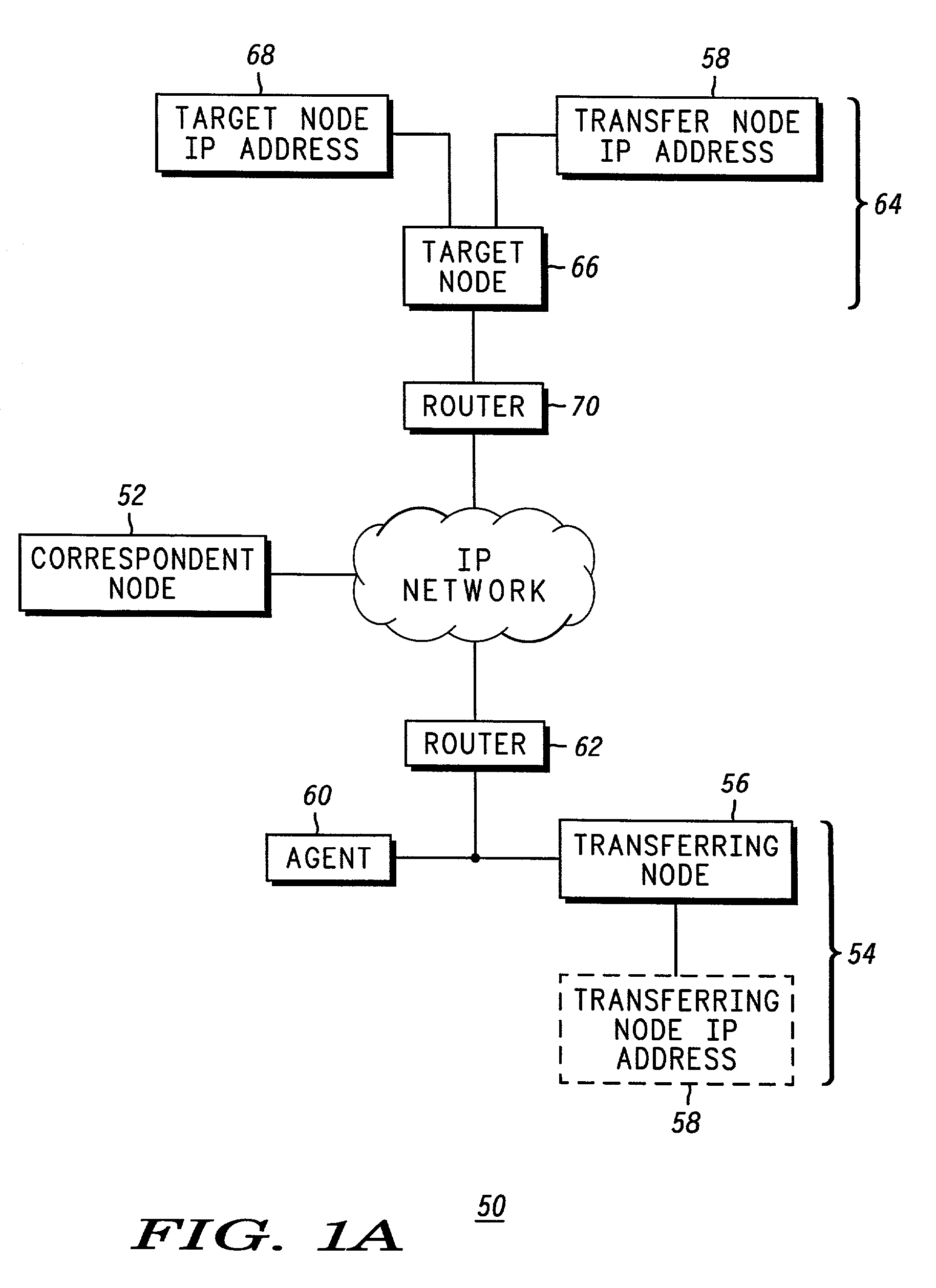
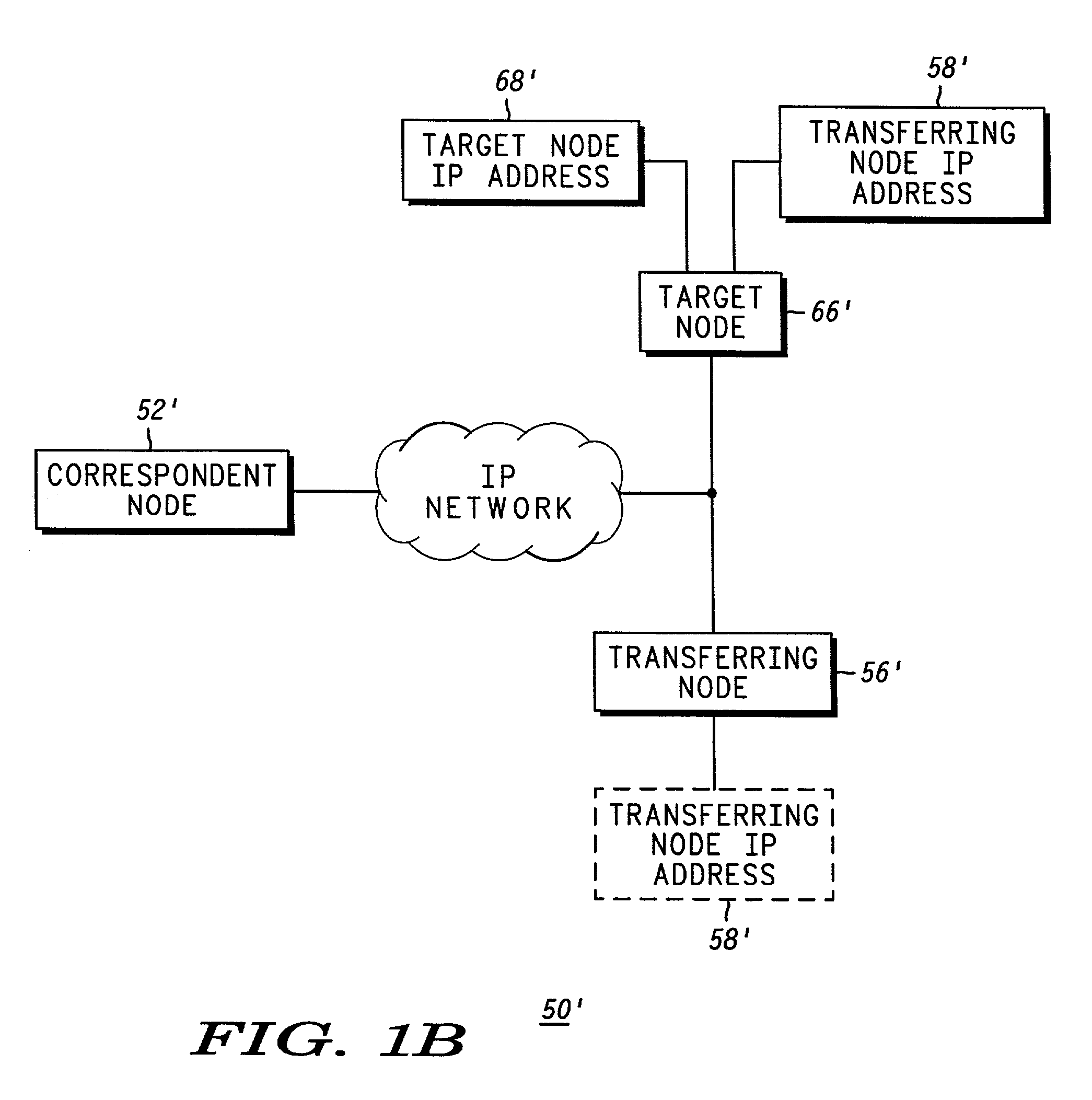
Session Inter-Device (SID) mobility networks (50, 100, 150) are described in which a seamless transfer of a communication session from a first device (56. 106, 116) to a second device (66, 116, 166) can be achieved without interrupting the active session. According to the SID mobility network (50), the transfer can be accomplished by transferring away from the Transferring Node or first device (56) the IP address associated with the active session (58) so that the network (50) will route the session to the desired Target Node or second device (66). The Transferring Node (56) transfers its IP address (58) to the Agent (60) and stops requesting data packets addressed to its IP address (58). The Agent (60) then begins to request and eventually receive the packets addressed to the Transferring Node's IP address (58). The Agent (60) then transfers the packets to the Target Node (66). In an alternate SID mobility network (100), the Transferring Node (106) transfers a session specific IP address (114) to the Agent (110). The Agent (110) then transfers packets sent to the session specific IP address (114) to the Target Node (120). In another SID mobility network (150), the Transferring Node (162) obtains a temporary IP address (170) and transfers its IP address (164) to a Session Agent (166). The Session Agent (166) begins to request and eventually receive the packets addressed to the Transferring Node's IP address (164), and for each received packet determines if it belongs to the session the Transferring Node (162) requested to transfer to the Target Node (176). If it does, the Session Agent (166) will transfer the packet to the Target Node (176) at the Target Node's IP address (178). If it does not, the Session Agent (166) will transfer the packet to the Transferring Node (162) at its temporary IP address (170). In each SID mobility network, the session with respect to the Correspondent Node continues without interruption throughout the transfer, thereby providing a seamless transfer of the session from a first device to a second device.
Owner:GOOGLE TECH HLDG LLC
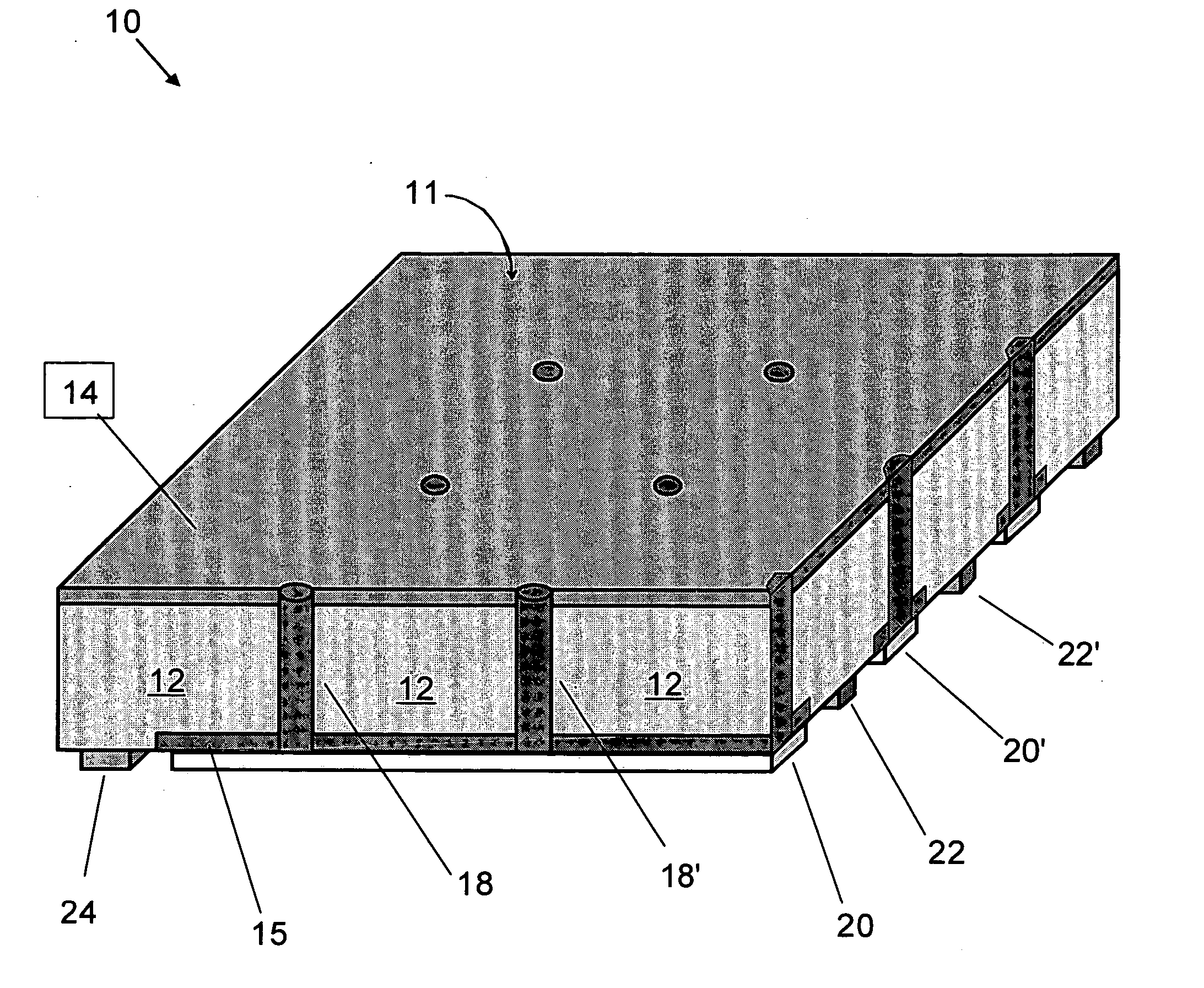
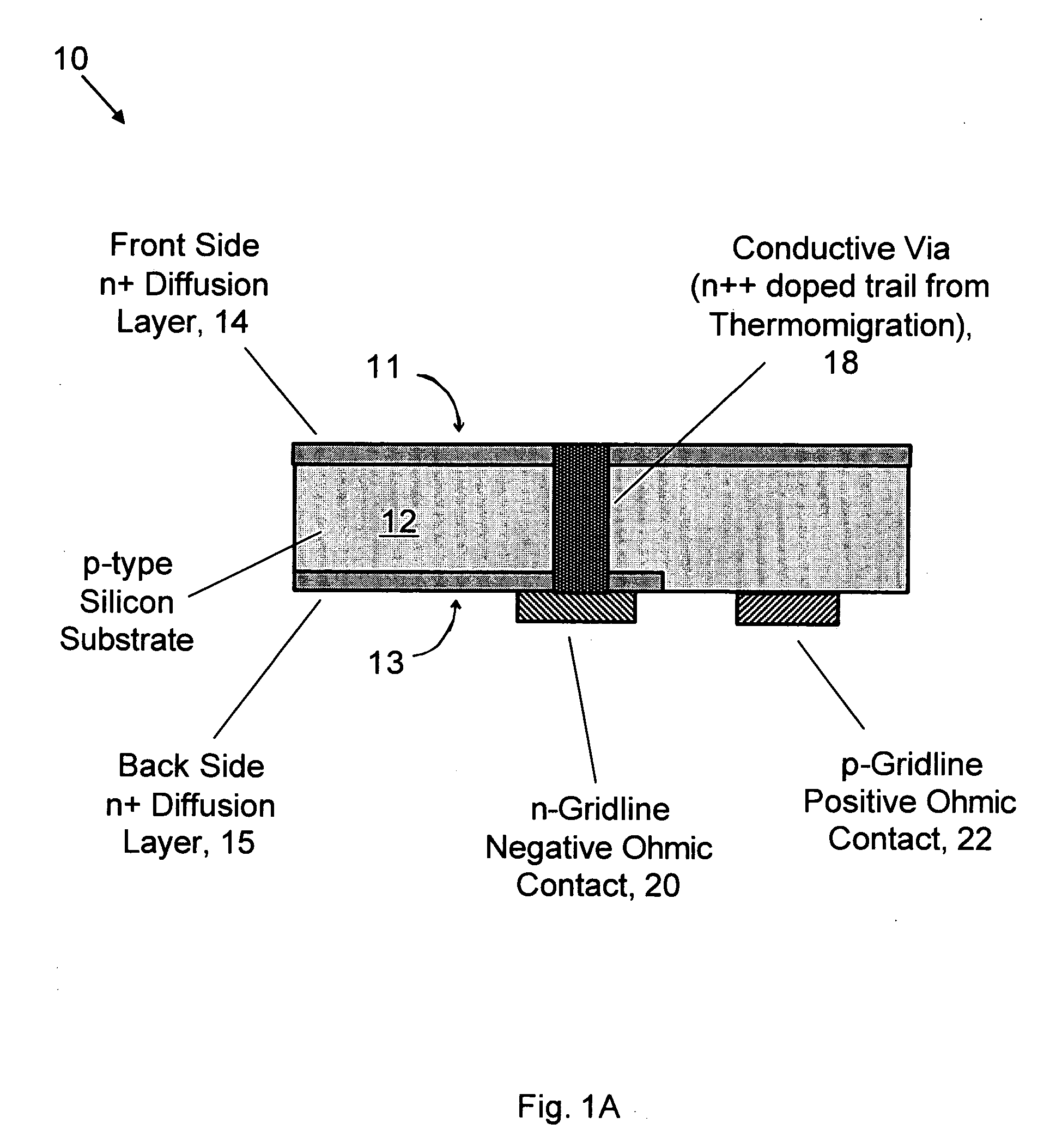
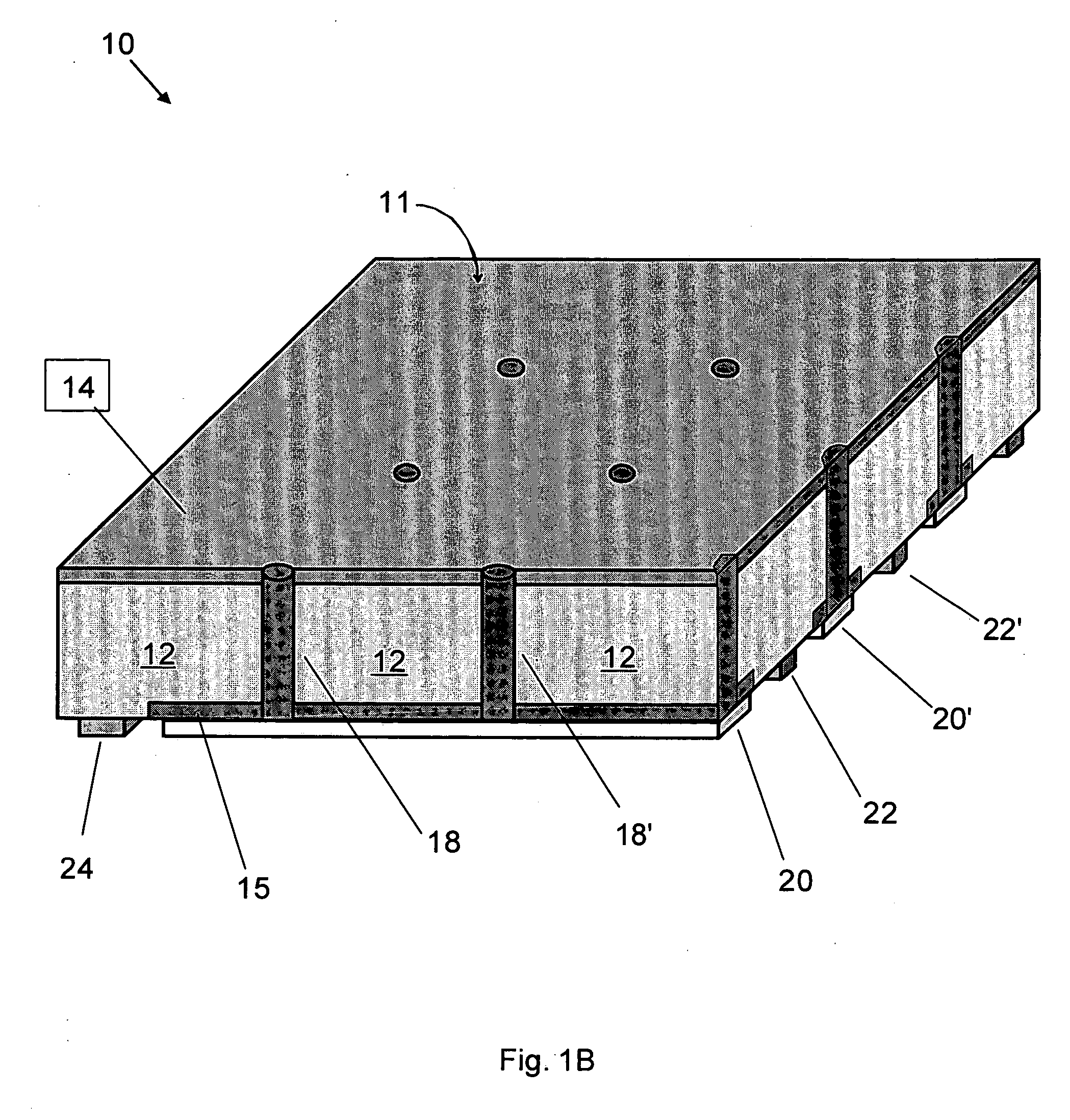
Back-contacted solar cells with integral conductive vias and method of making
Methods of manufacturing back-contacted p-type semiconductor substrate solar cells fabricated using a gradient-driven solute transport process, such as thermomigration or electromigration, to create n-type conductive vias connecting the n-type emitter layer on the front side to n-type ohmic contacts located on the back side, and back-contacted solar cells with integral n-type conductive vias, such as made by a gradient-driven solute transport process.
Owner:ADVENT SOLAR INC
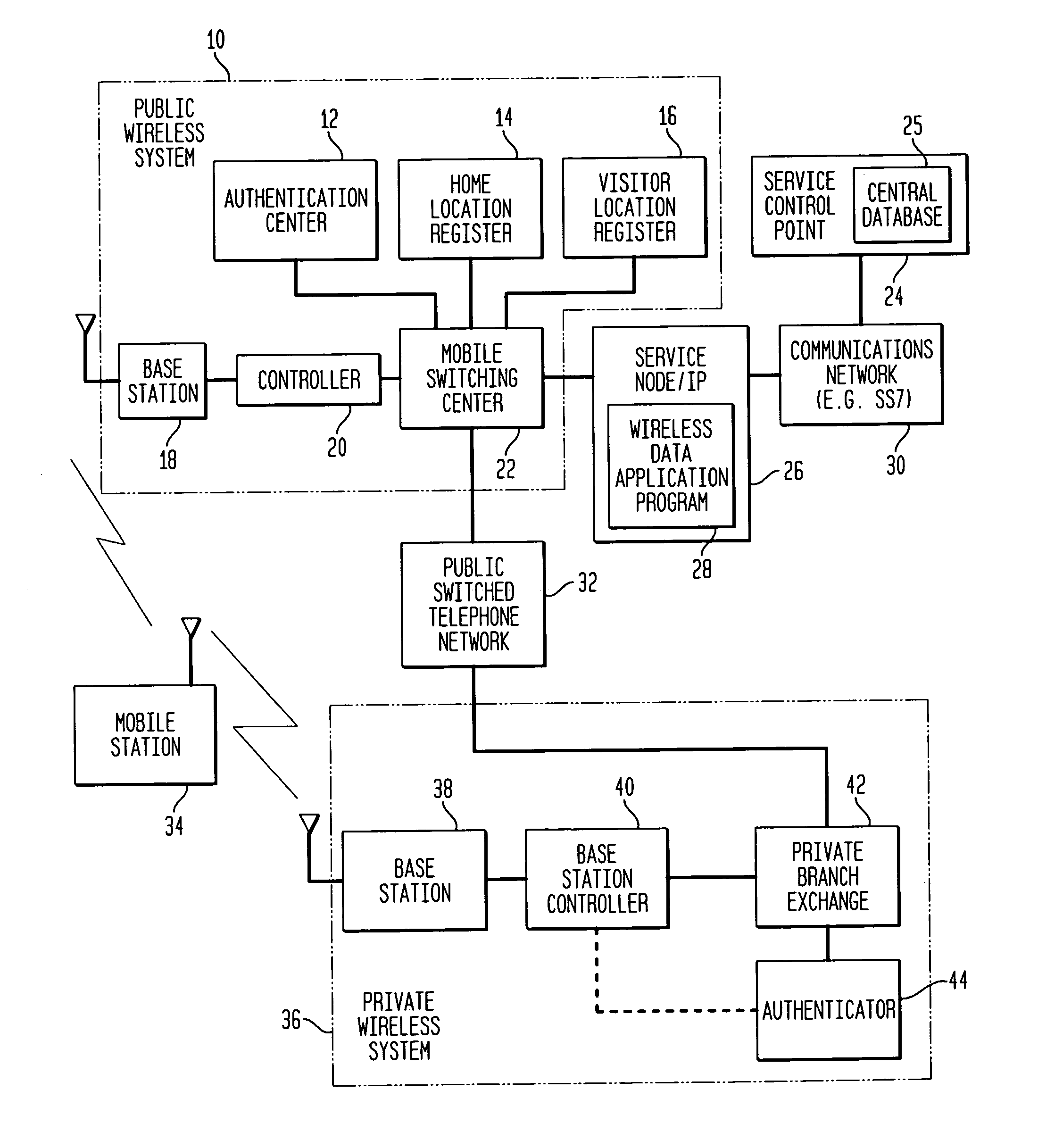
Method and system for directing a data message in a wireless communications network including multiple wireless systems
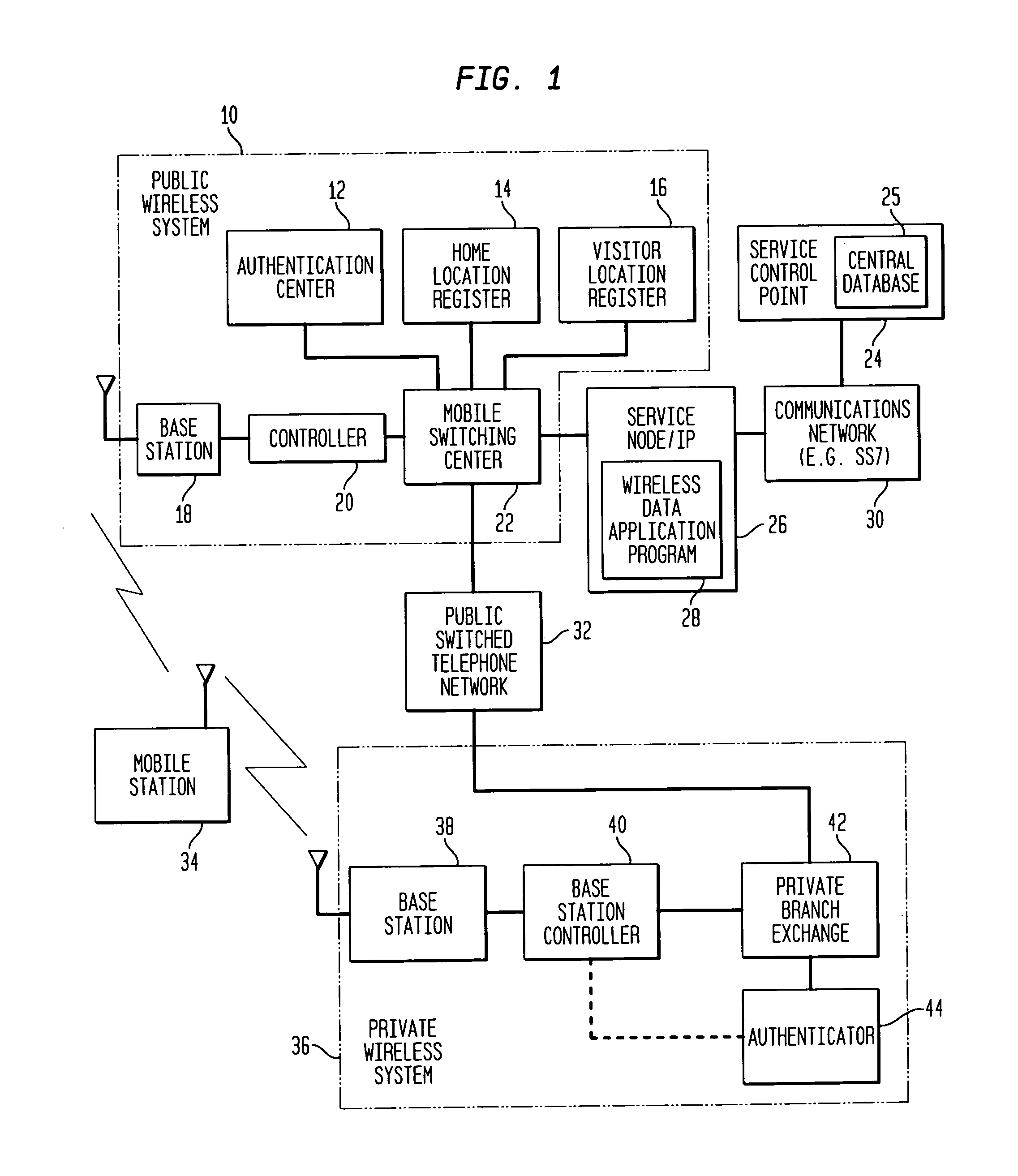
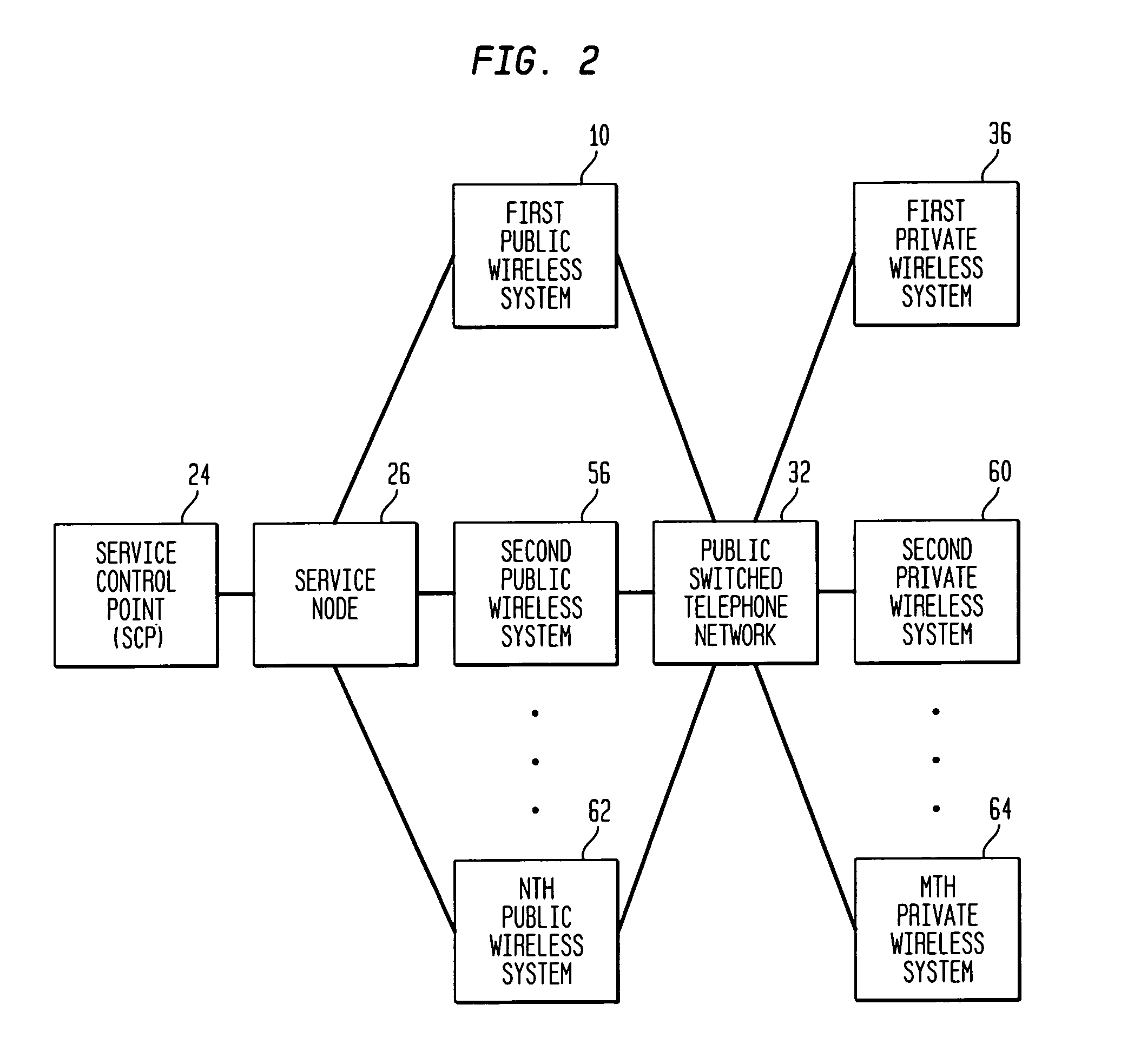
InactiveUS7171199B1Reduces inter-system signaling trafficUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemTransfer procedure
A mobile station scans for electromagnetic signals representing control channels of the public wireless system and the private wireless system. The mobile station measures a received signal parameter of at least one of the scanned control channels. The hybrid communications network may transfer the mobile station's service from the public wireless system to the private wireless system, if the measured signal parameter meets or exceeds a private target. Alternately, the hybrid communications system may transfer service from the private wireless system to the public wireless system, if the measured signal parameter meets or exceeds a public target. A service control point maintains a central database of user profiles updated in response to the transferring procedure. A service node redirects a data message for the mobile station through the public wireless system or through the private wireless system, as facilitated by the central database, to deliver the data message to the mobile station during its operation on an active one of the wireless systems.
Owner:ALCATEL-LUCENT USA INC +1
Article transfer and placement apparatus with active puck
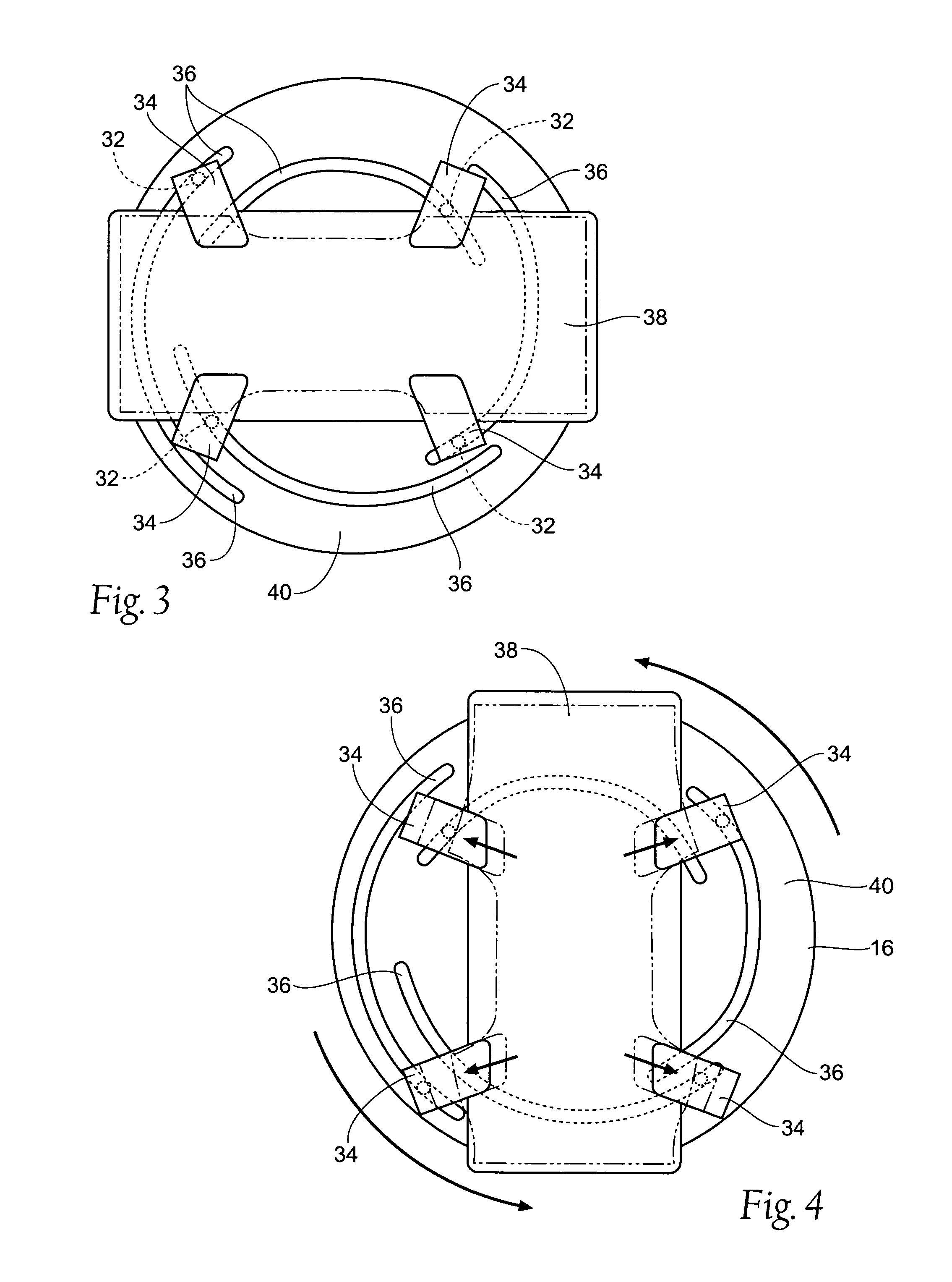
An apparatus for transferring articles such as absorbent cores or disposable diaper chassis components from a rotary mechanism, such as a pad turner, to a linear mechanism, such as a conveyor, for further processing. A puck on the apparatus is capable of manipulating the article during this transfer procedure.
Owner:CURT G JOA
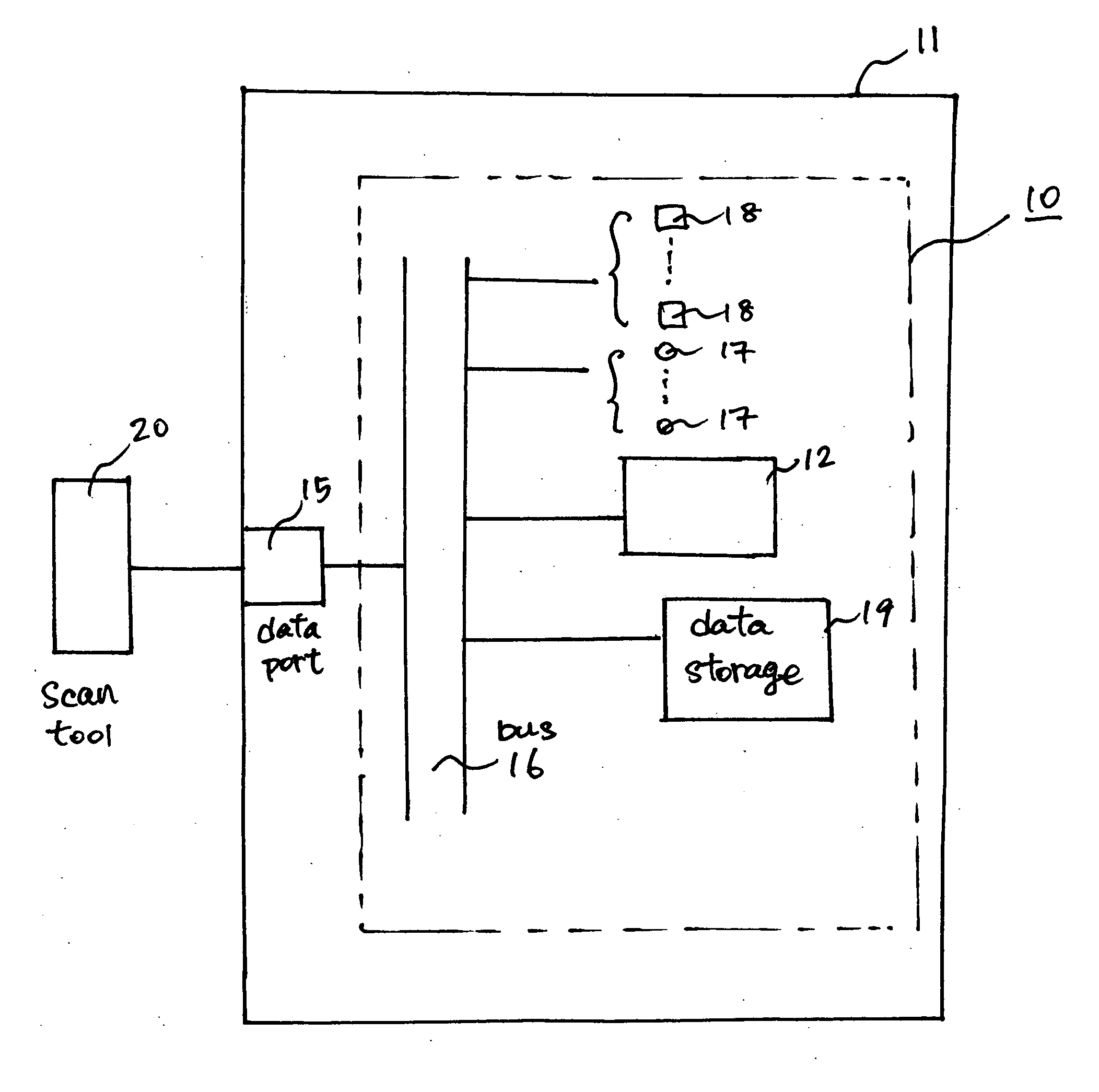
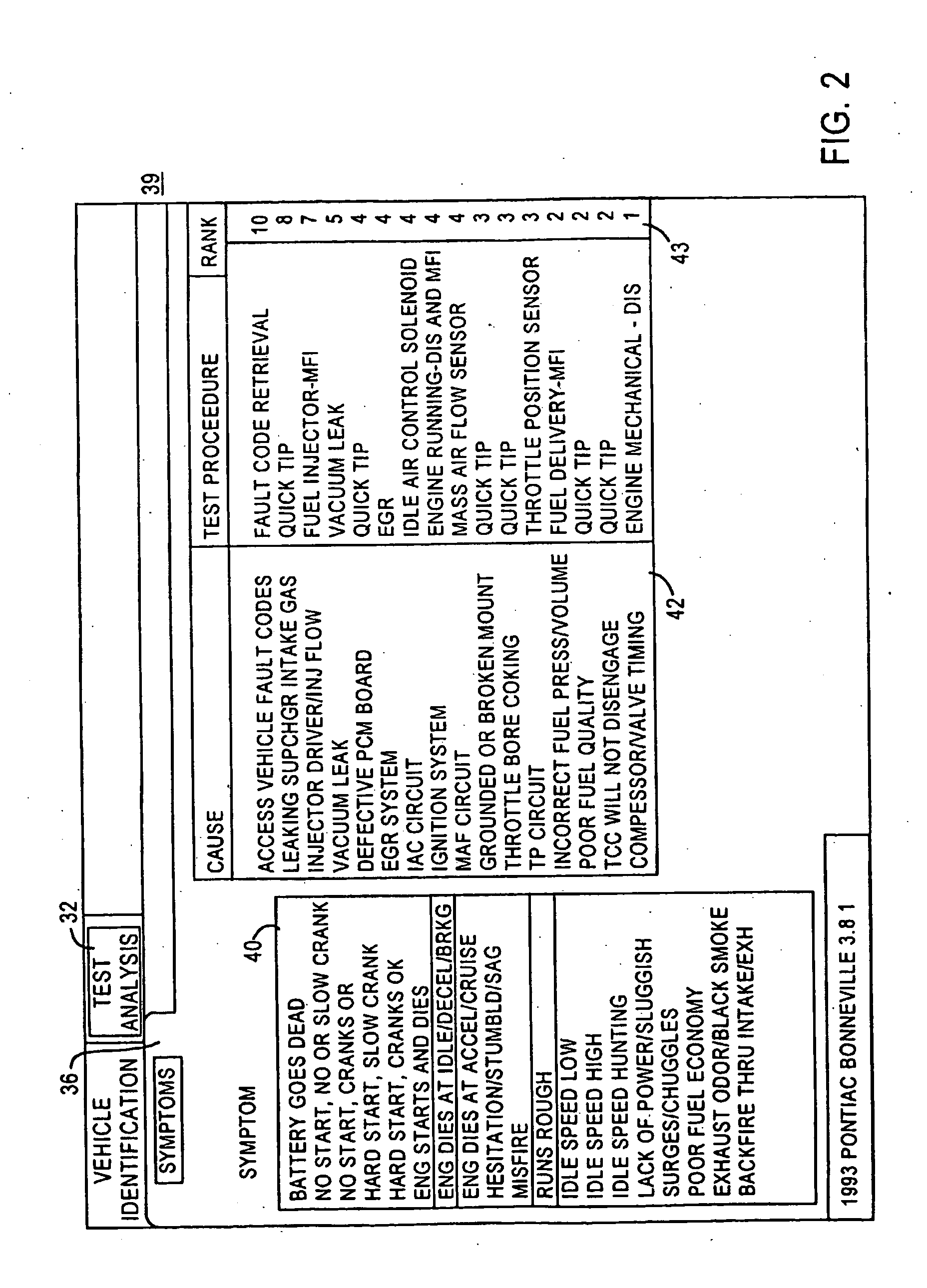
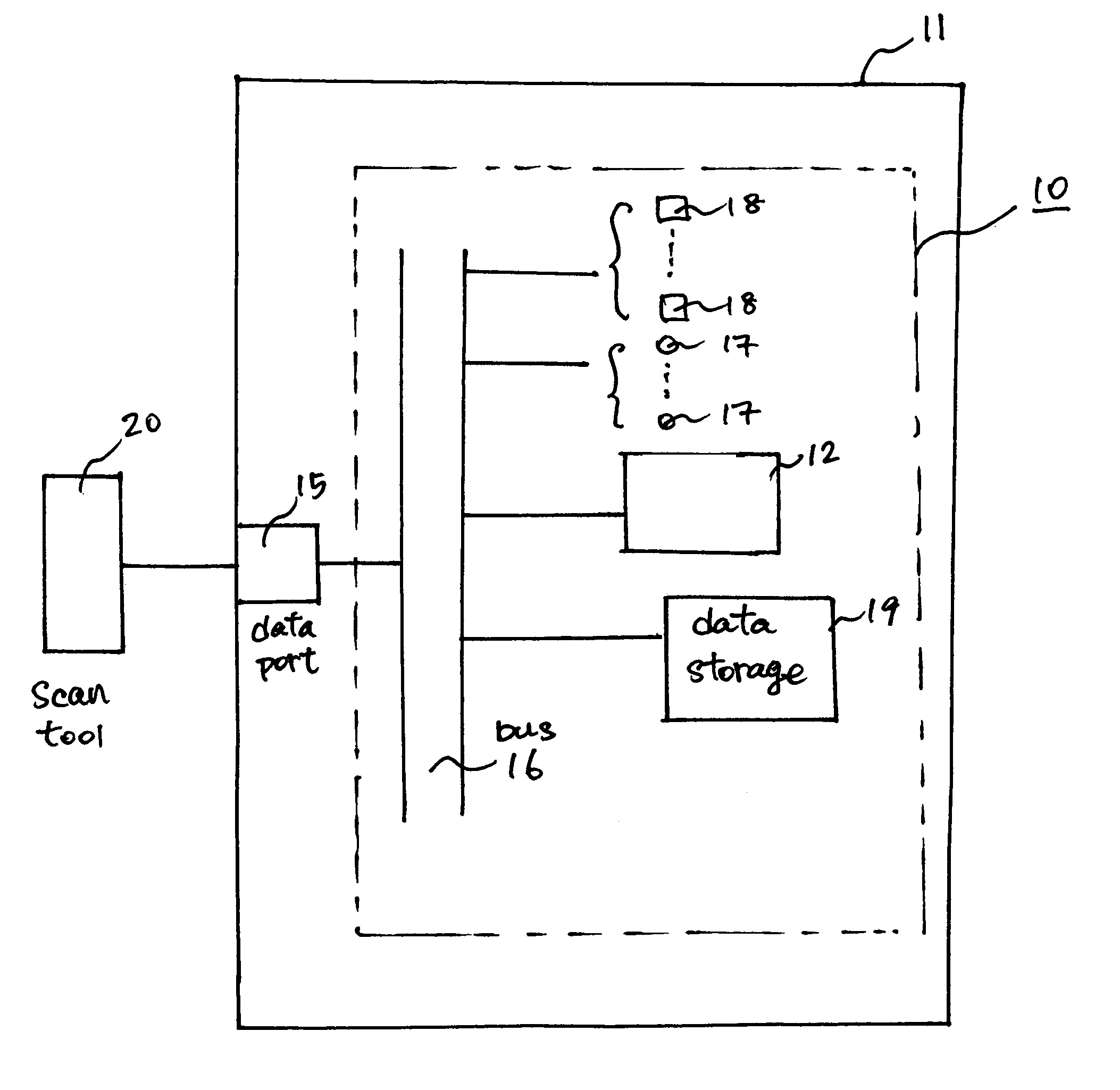
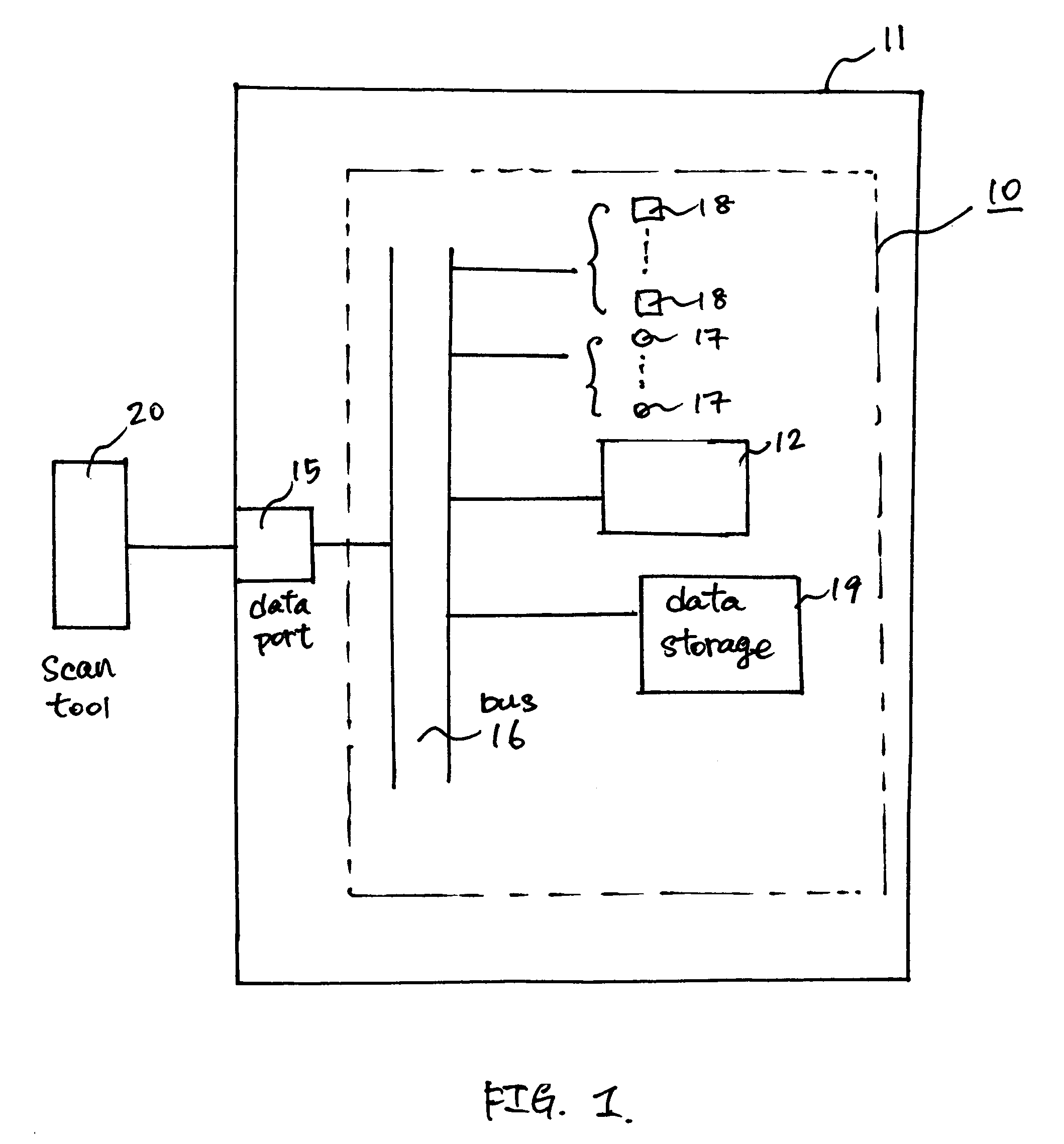
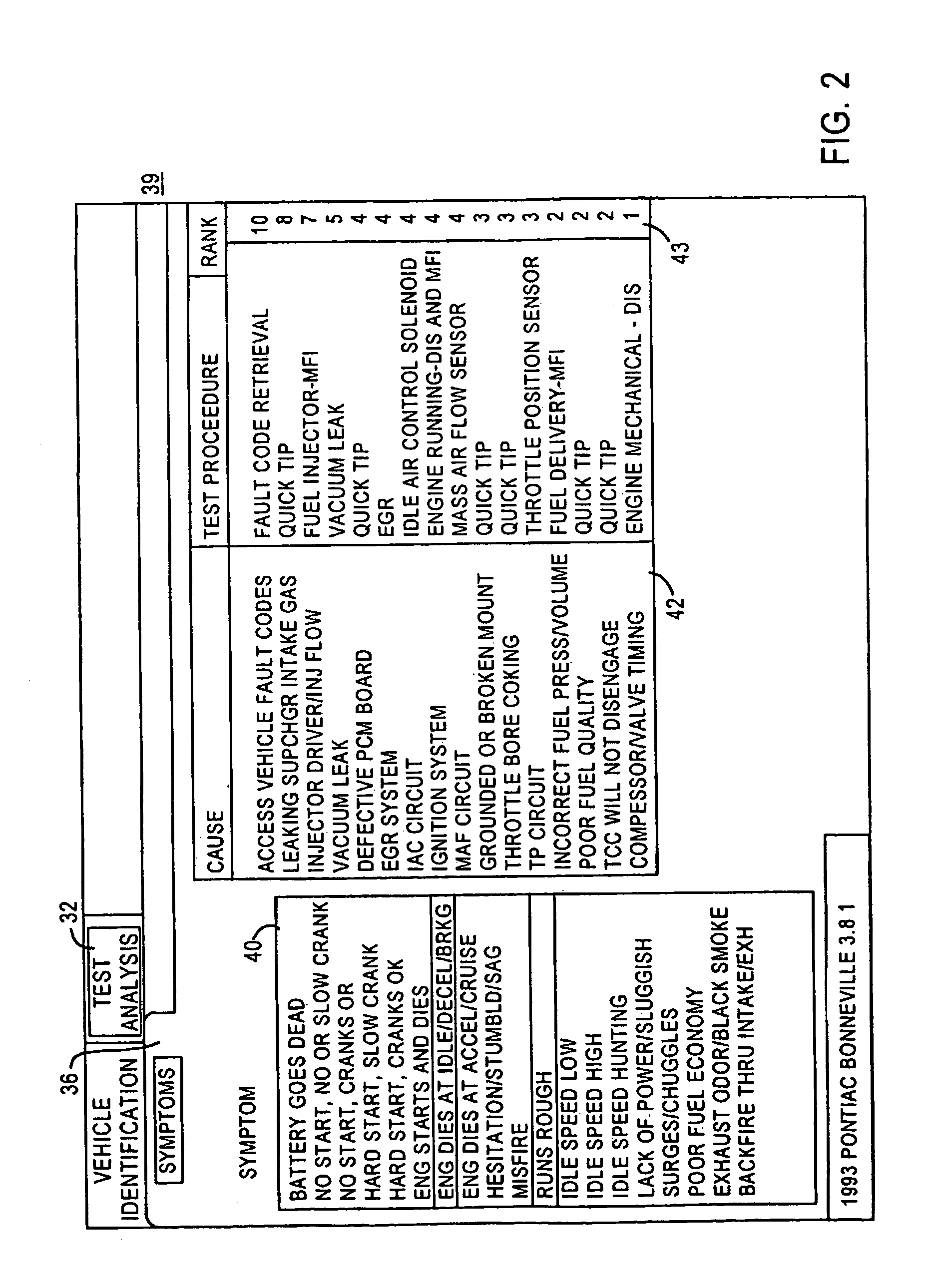
Vehicle diagnostic method and system with intelligent data collection
InactiveUS20070233341A1Vehicle testingRegistering/indicating working of vehiclesTransfer procedureData transmission
Vehicle diagnostic devices and methods that detect the occurrence of a maintenance process performed on a vehicle, and responsive to the detected occurrence of the maintenance process, initiate a data collection process to collect data related to the performed maintenance process, and a data transmission process to provide the collected data to a remote data depository.
Owner:SNAP ON INC
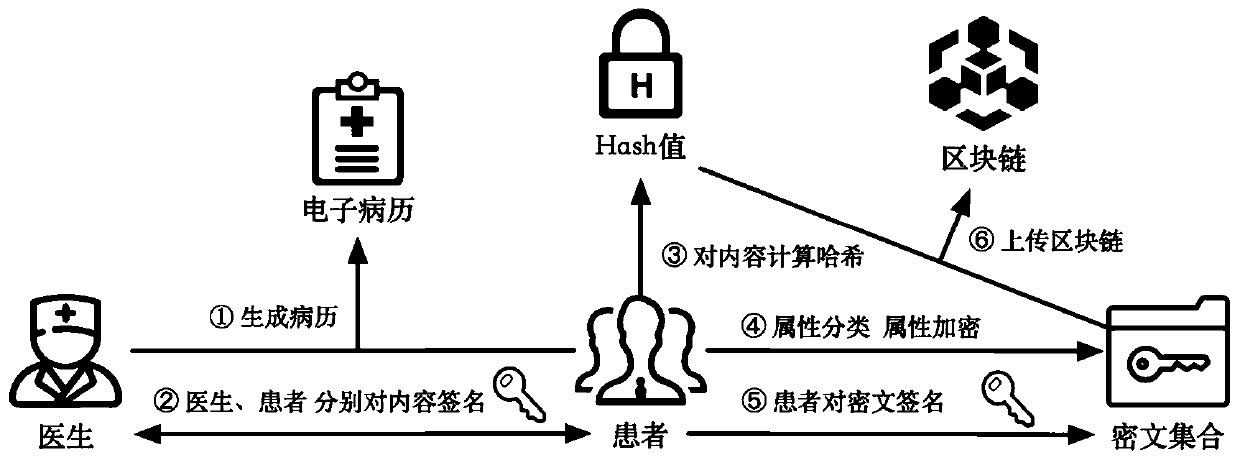
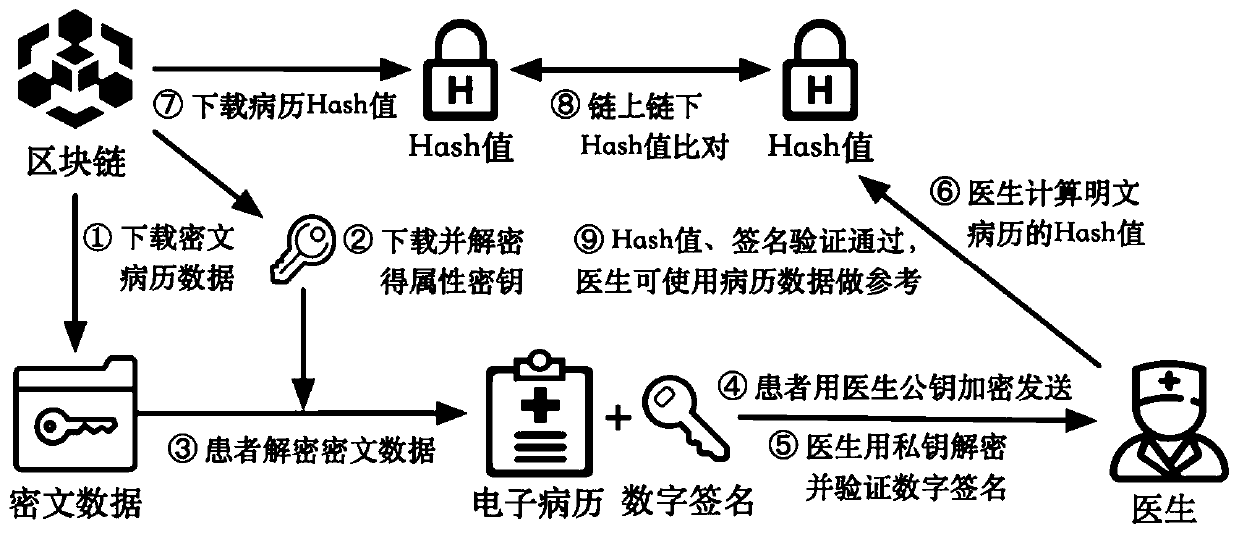
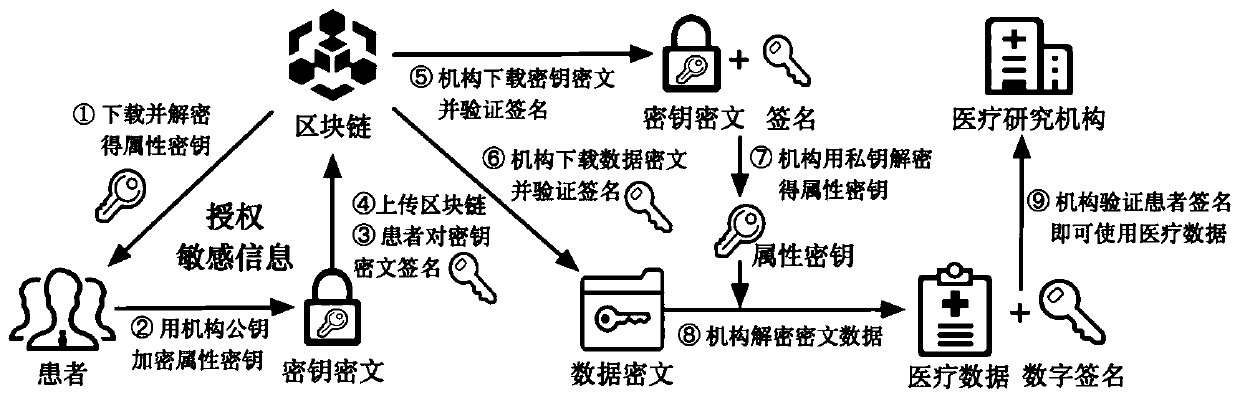
Medical data security cooperation system based on block chain
The invention discloses a medical data security cooperation system based on a block chain, which realizes unified management of medical big data and solves the problem of medical data islands. According to the system, a set of stable, authentic and decentralized medical record data storage system is designed by combining a block chain technology and a cryptography technology; reliable storage of personal electronic health records is ensured by using the decentralized, traceable and tamper-proof core application capability of the block chain; a ciphertext access control strategy for sensitive data is designed by applying cryptography hybrid encryption, attribute encryption and other technologies while reliable storage of personal electronic health records is guaranteed, and personal privacyand data security are fully protected through data desensitization and encryption in the processes of information authentication, broadcasting and transmission. An effective excitation mechanism is also designed, and interconnection and intercommunication and security cooperation of medical big data are realized under the action of the excitation mechanism.
Owner:NANJING UNIV
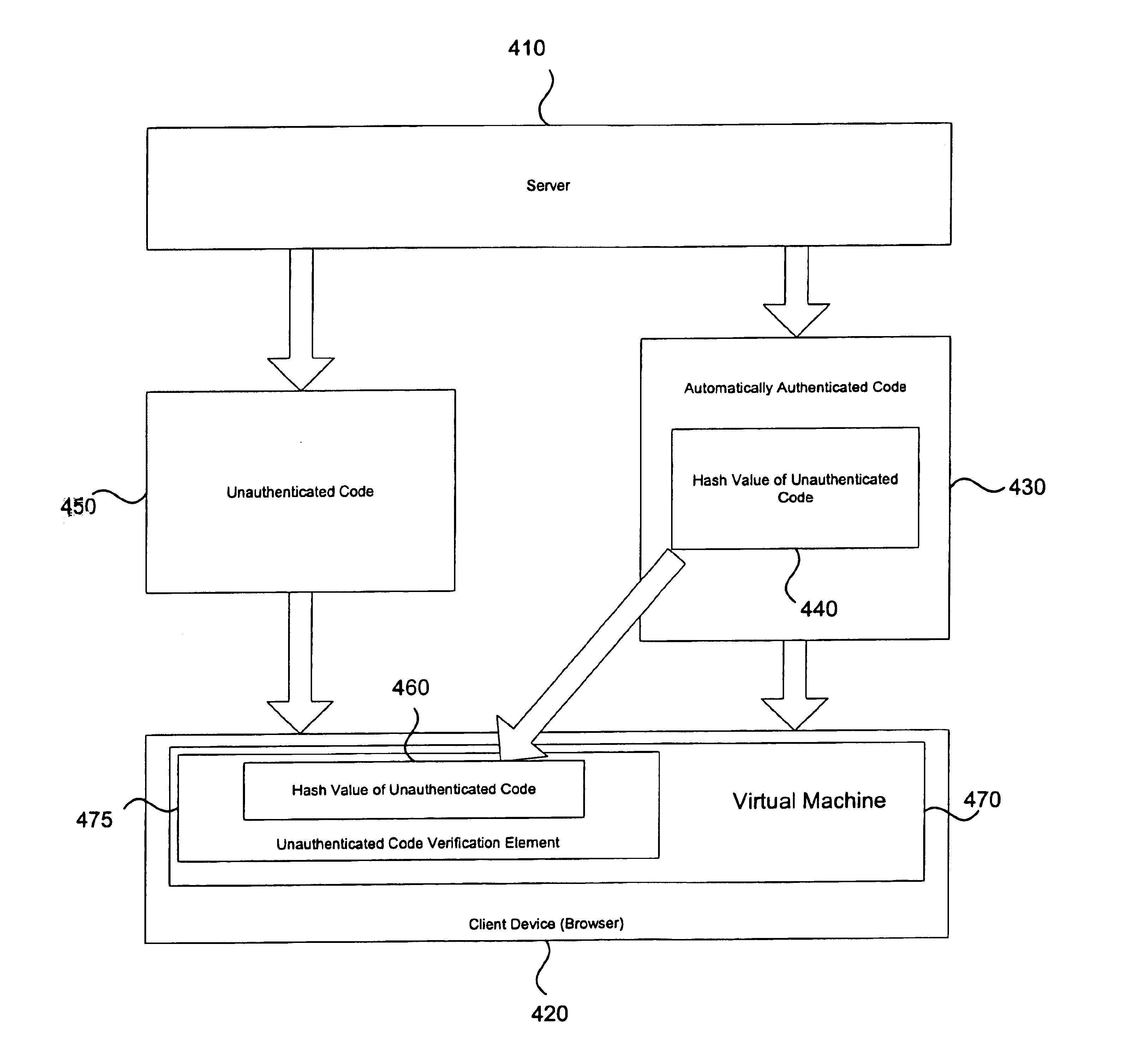
Apparatus and method for ensuring data integrity of unauthenticated code
InactiveUS6922782B1Easy to useUser identity/authority verificationUnauthorized memory use protectionComputer hardwareData integrity
An apparatus and method for ensuring data integrity of unauthenticated code is provided. With the apparatus and method, a hash value of unauthenticated code is embedded in associated automatically authenticated code. When the automatically authenticated code is downloaded and executed, the automatically authenticated code may require that the unauthenticated code also be downloaded for proper execution of the automatically authenticated code on a particular client device. The unauthenticated code can be downloaded and its integrity verified by generating a hash value of the unauthenticated code and comparing the generated hash value to a hash value embedded in the automatically authenticated code. If there is a match, the unauthenticated code is verified. If there is not a match, the unauthenticated code has been corrupted during transmission and is not verified. As a result, the unauthenticated code is not used by the client device. The download of the unauthenticated code can then be attempted again and the verification process repeated.
Owner:IBM CORP
Method for constructing data quanta space in network and distributed file storage system
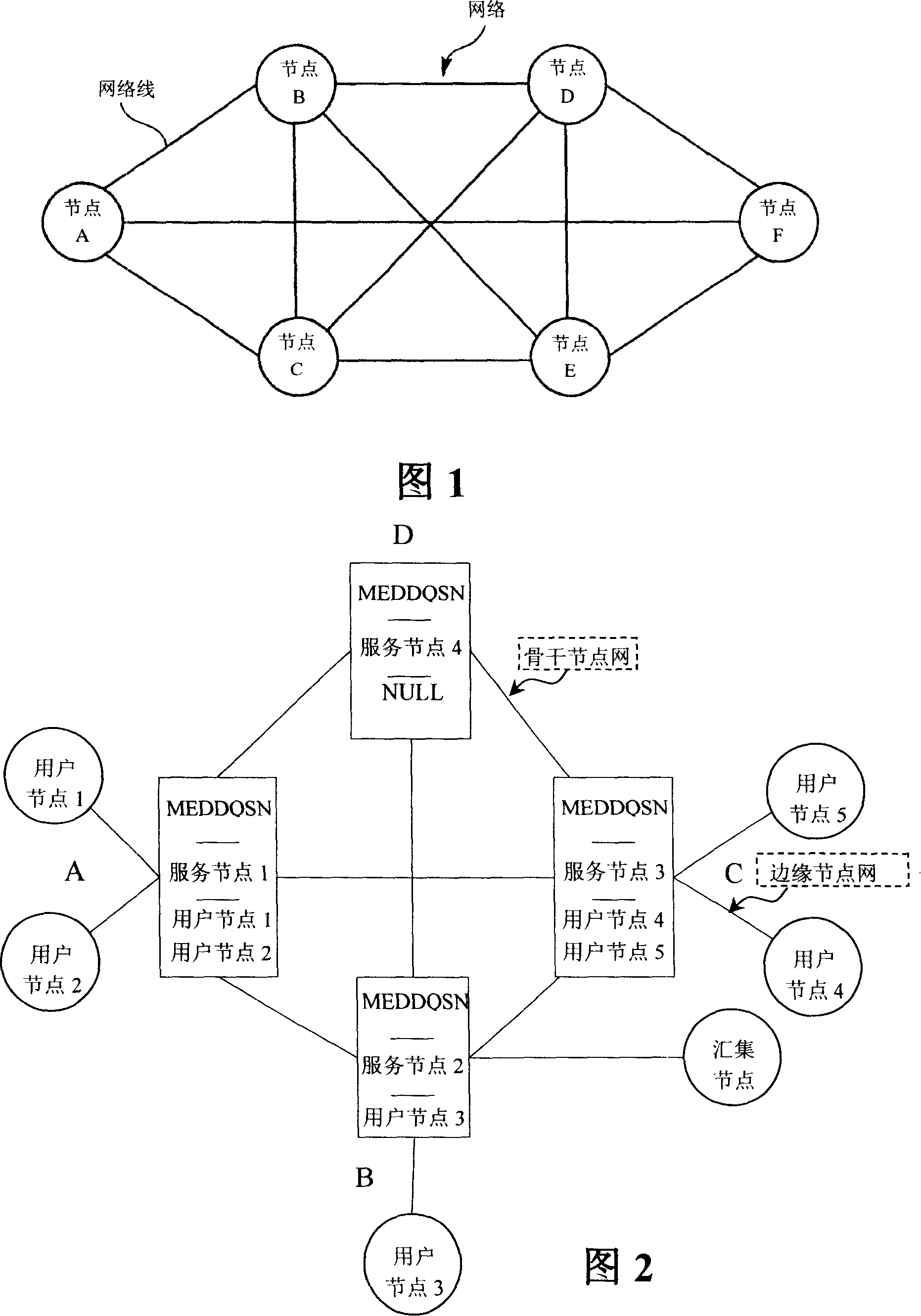
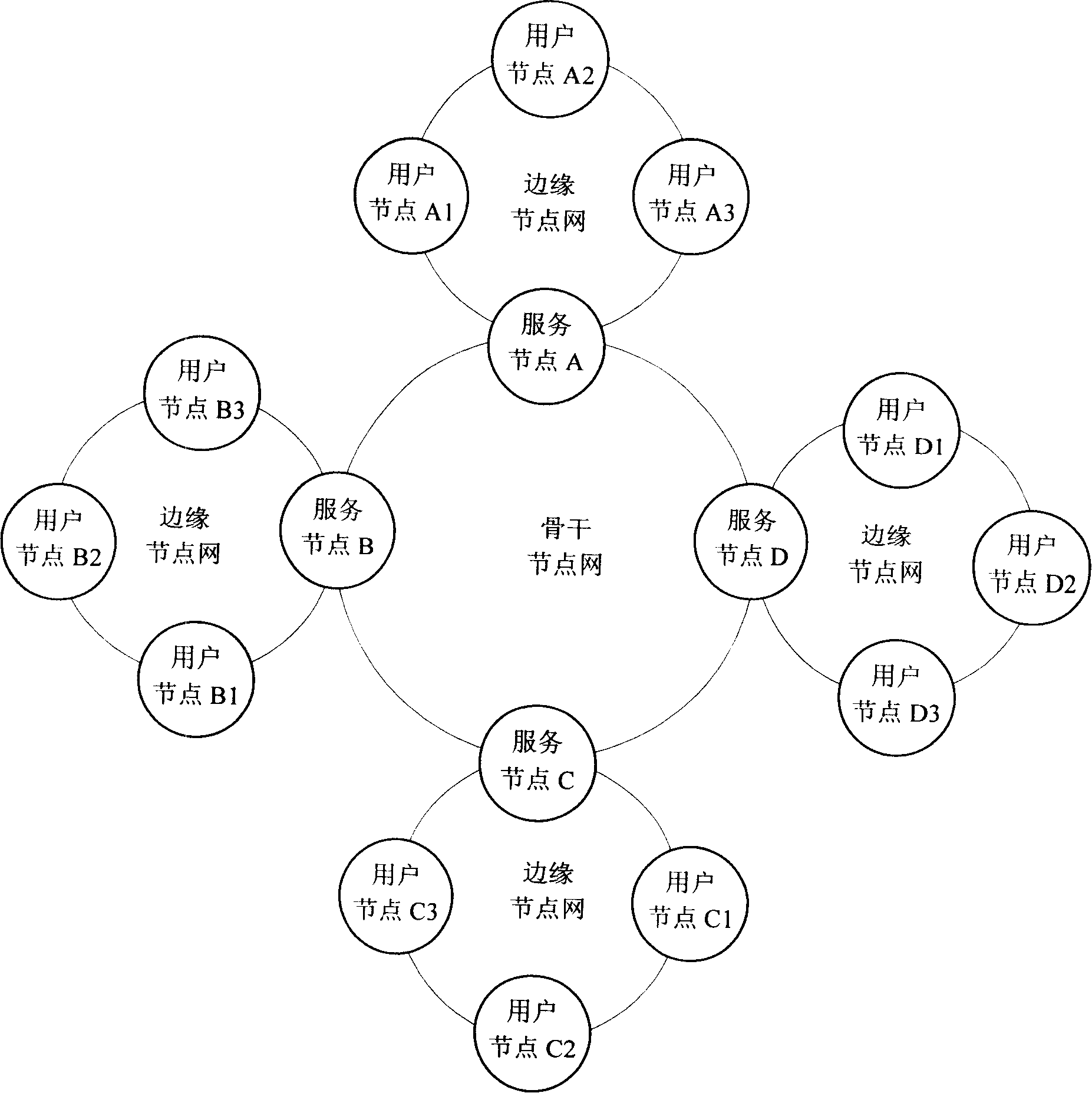
ActiveCN101188569AEasy to monitorGuaranteed monitoringData switching networksElectric digital data processingTransfer procedureData file
The invention relates to a method for data quantity subspace construction on the network and a distributed document storage system. Through the distributed document storage system, user nodes use service nodes to choose and upload data documents onto usable user nodes in the network, and the distributed nodes are formed; after the user nodes upload the data documents or during the transmission of the data documents, the service nodes adjust the usable nodes in the whole backbone nodes network automatically to distribute tasks which are undertaken, the data documents that the user requests to upload or transmit are distributed and stored in the sharing space of a plurality of user nodes through copying the data documents, a plurality of sharing nodes are formed to be used by the user nodes to download or transmit the documents, so a data storage and transmit quantity subspace is formed in the network. The invention can realize stable, high efficient and opened enterprise-level distributed storage application.
Owner:李明 +1
Data processing system
InactiveUS7328373B2Promote recoverySolve the lack of balanceData processing applicationsMemory systemsData processing systemTransfer procedure
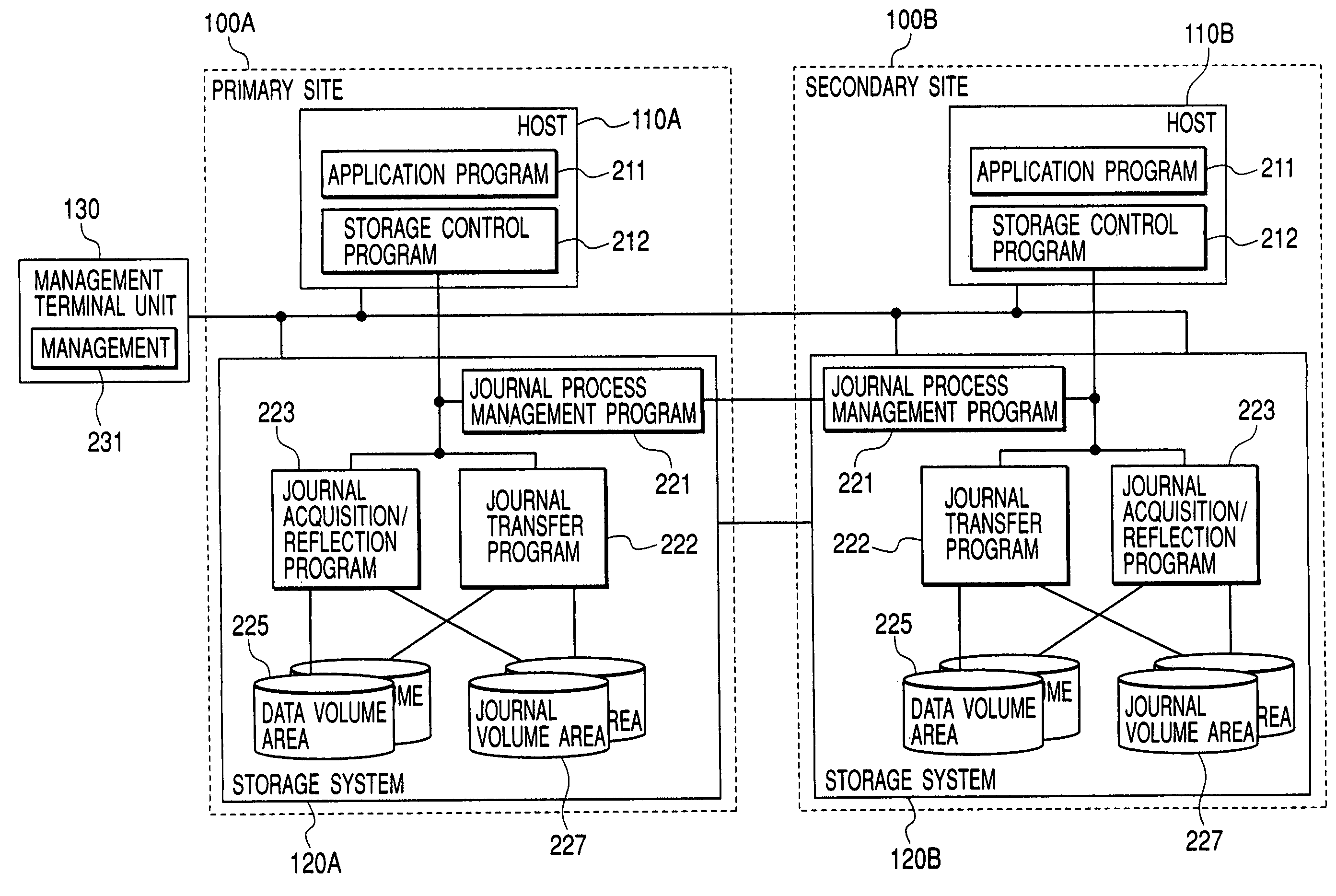
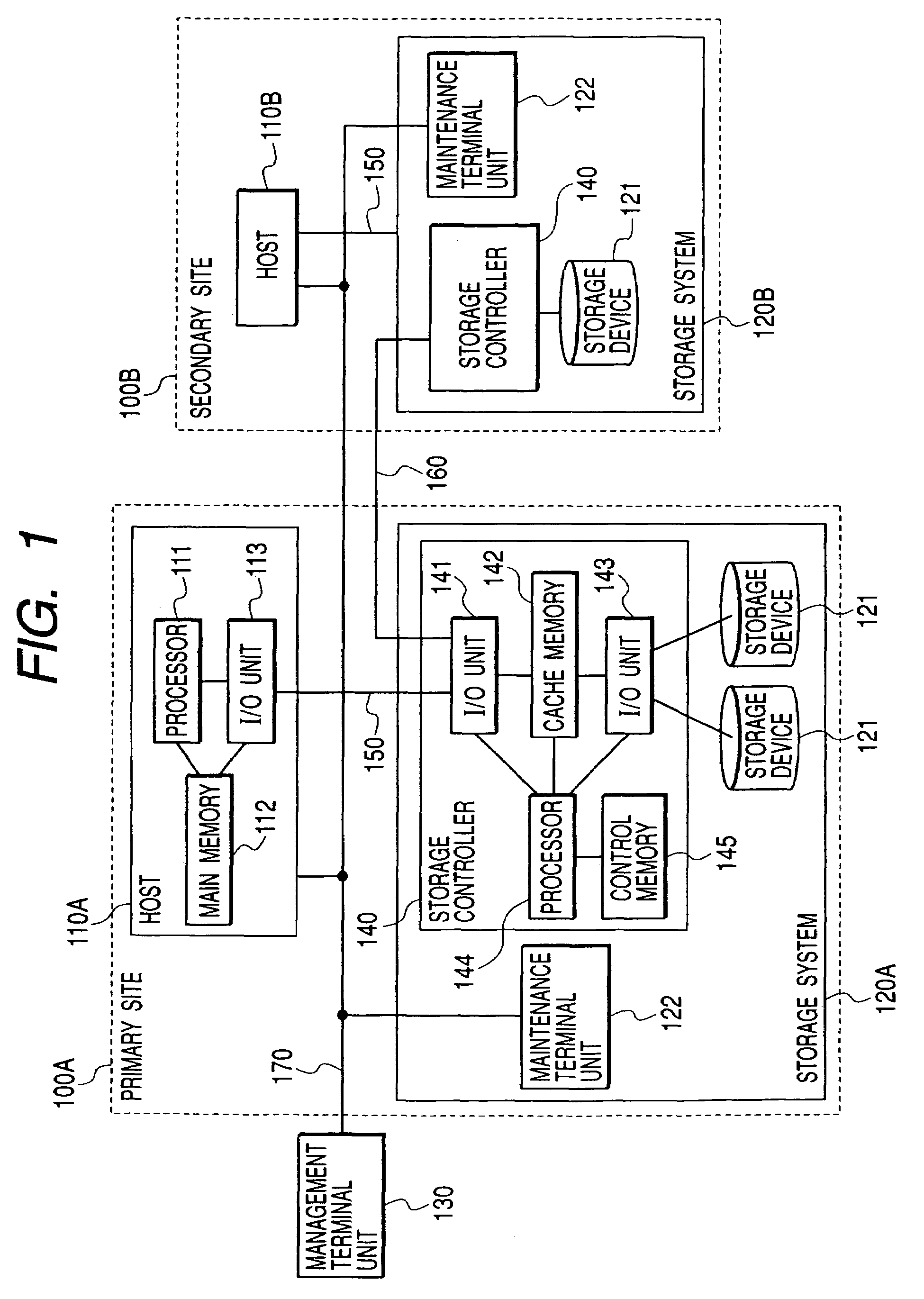
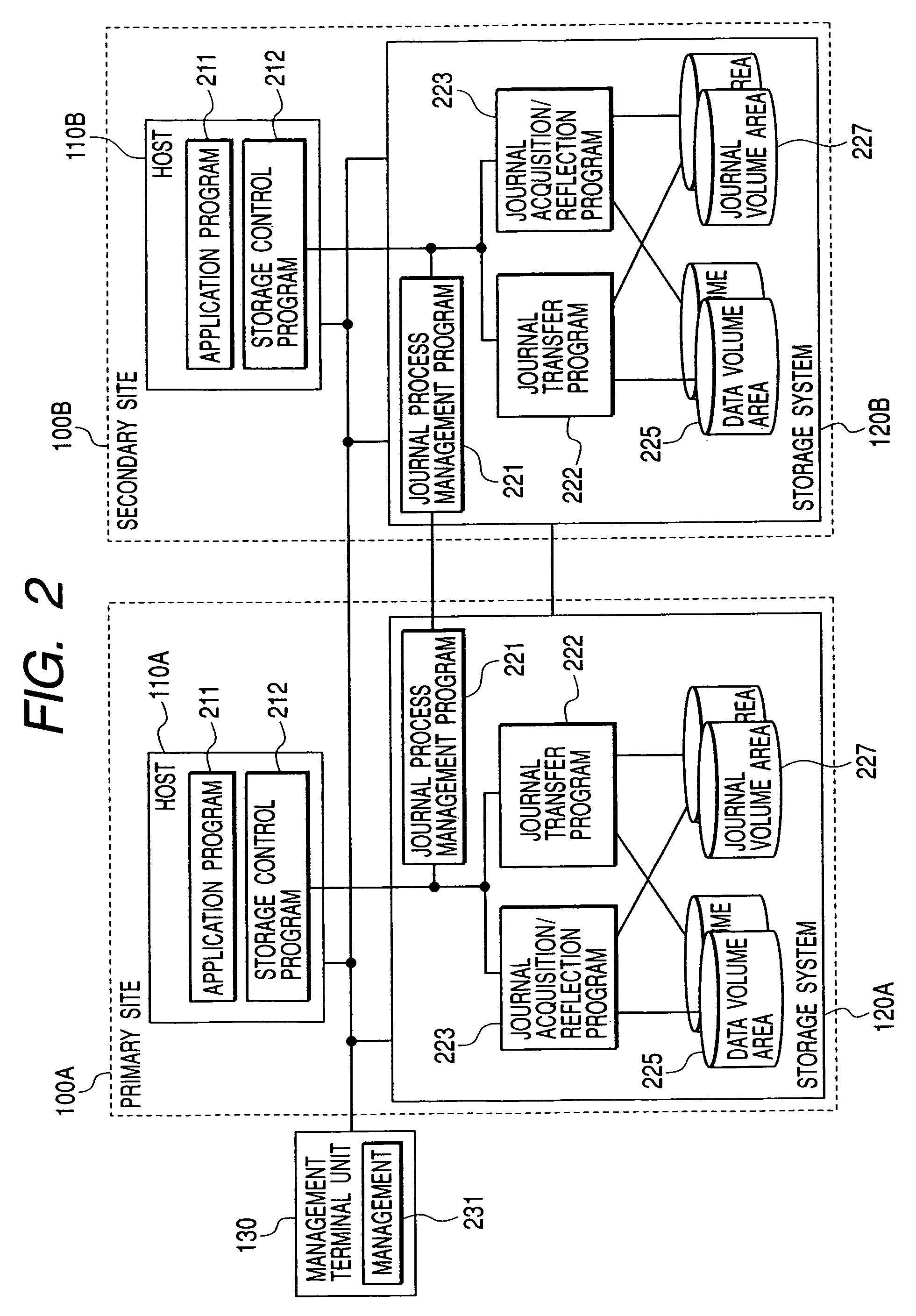
In a data processing system Saving a primary site and a secondary site, storage systems are connected to each other via a communication line, data update history is recorded in a storage device as a journal in the primary site, and the journal is transferred to the secondary site via the communication line. During such transfer, loads will not concentrate to a specific volume, by switching the volume that stores the journal in the primary site, while, by switching the transfer-destination volume of the journal in the secondary site.With such arrangement, in a data processing system, it is possible to ensure data consistency in a plurality of sites and prevent the system throughput capacity from being deteriorated without applying loads to a host and a network, and without causing load concentration on a specific storage device that is caused as a result of data update or recovery operations.
Owner:GOOGLE LLC
Vehicle diagnostic method and system with intelligent data collection
InactiveUS7739007B2Vehicle testingRegistering/indicating working of vehiclesTransfer procedureSmart data
Owner:SNAP ON INC
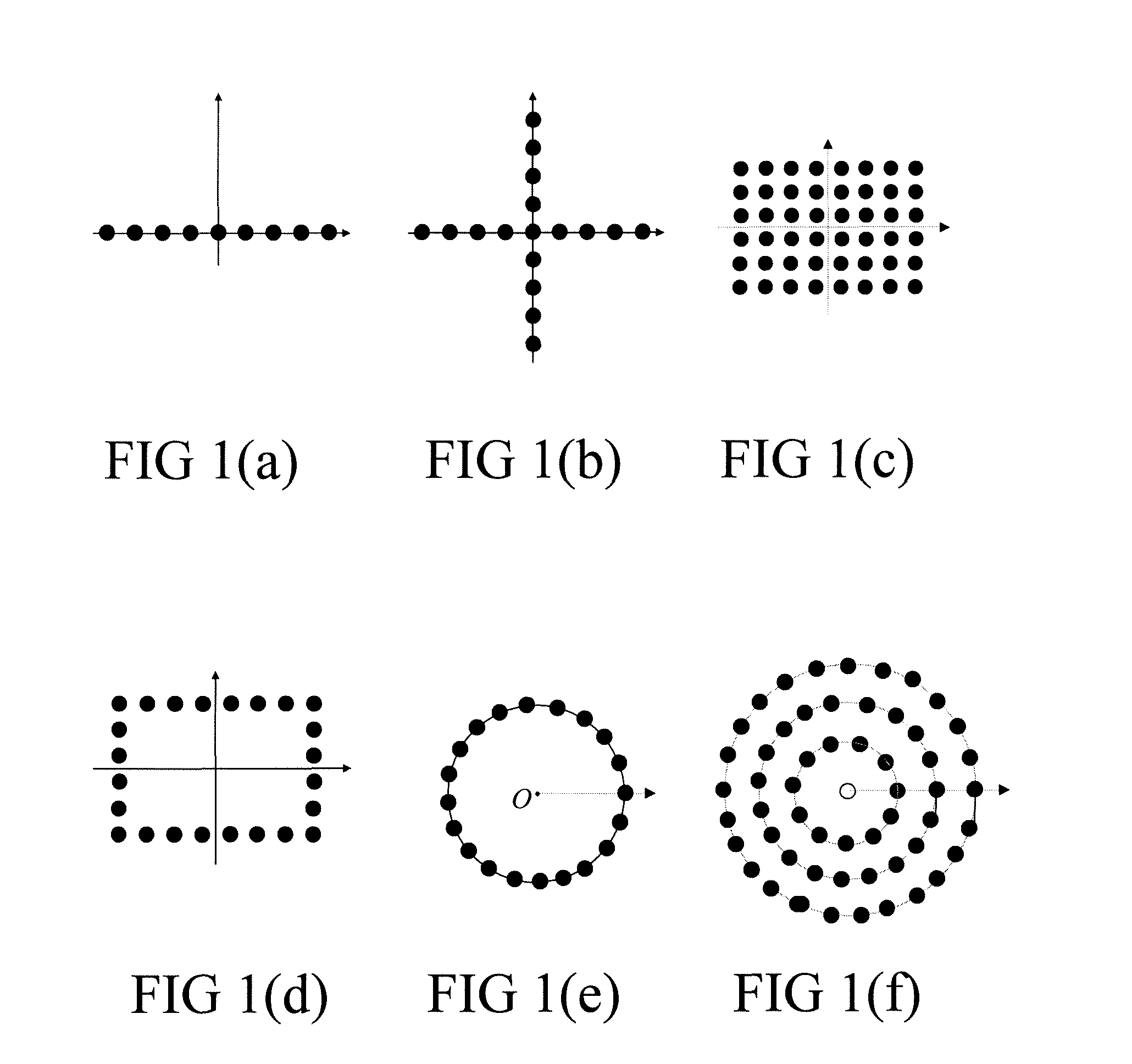
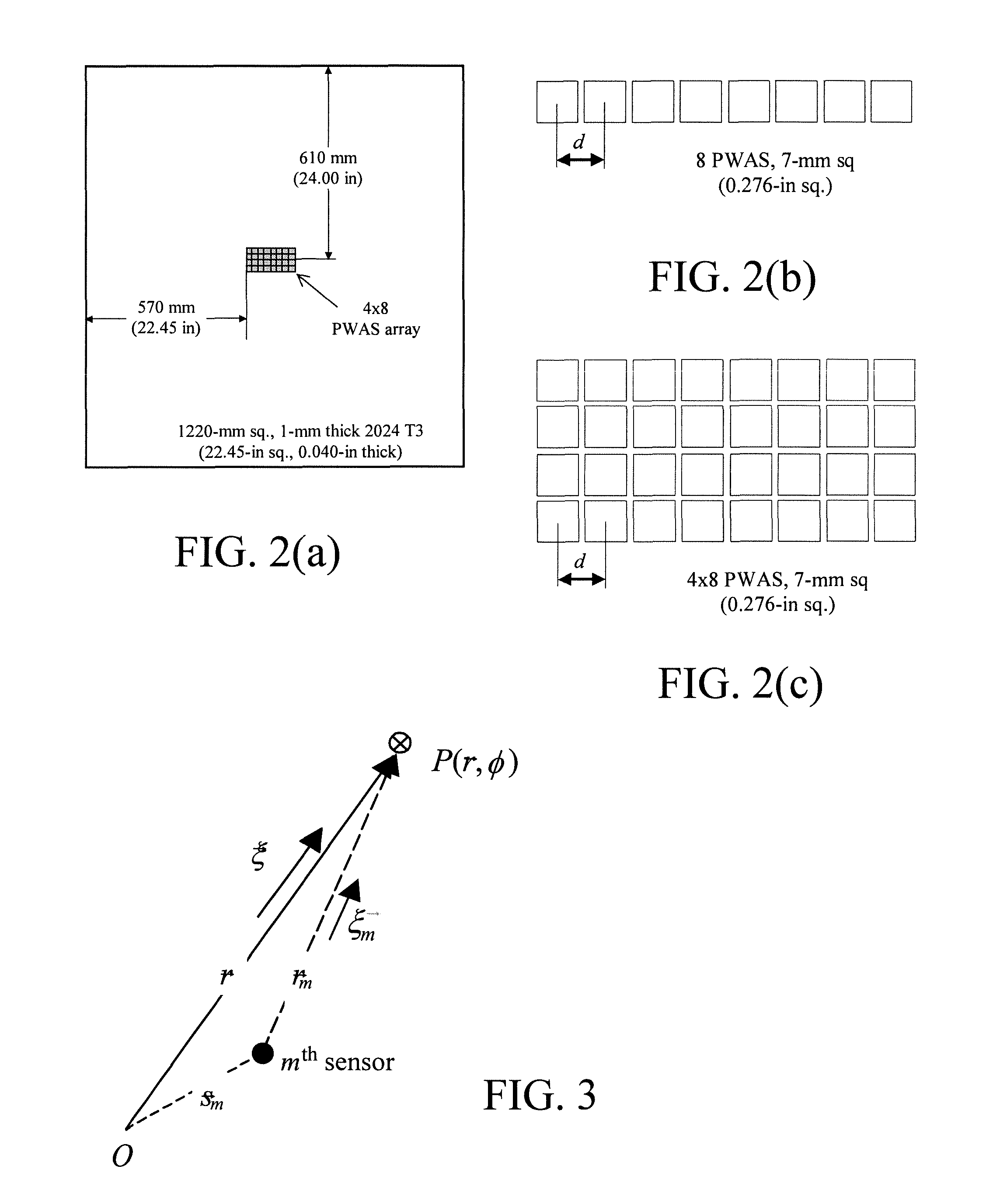
Optimized Embedded Ultrasonics Structural Radar System With Piezoelectric Wafer Active Sensor Phased Arrays For In-Situ Wide-Area Damage Detection
InactiveUS20090048789A1Improve accuracyEasy to getAnalysing solids using sonic/ultrasonic/infrasonic wavesSpecial data processing applicationsRadar systemsTransfer procedure
The present subject matter is direct to apparatus and methodologies for performing omnidirectional (360°) damage detection in a thin-wall structure using a planar embedded piezoelectric wafer active sensors (PWAS) phased array. Virtual beamforming for the array is implemented through either a transmission process by selective energizing selected sensors or by a signal post-processing procedure. Sensors may be embedded in a thin-walled structure as planar or circular arrays to achieve omnidirectional damage detection.
Owner:UNIVERSITY OF SOUTH CAROLINA
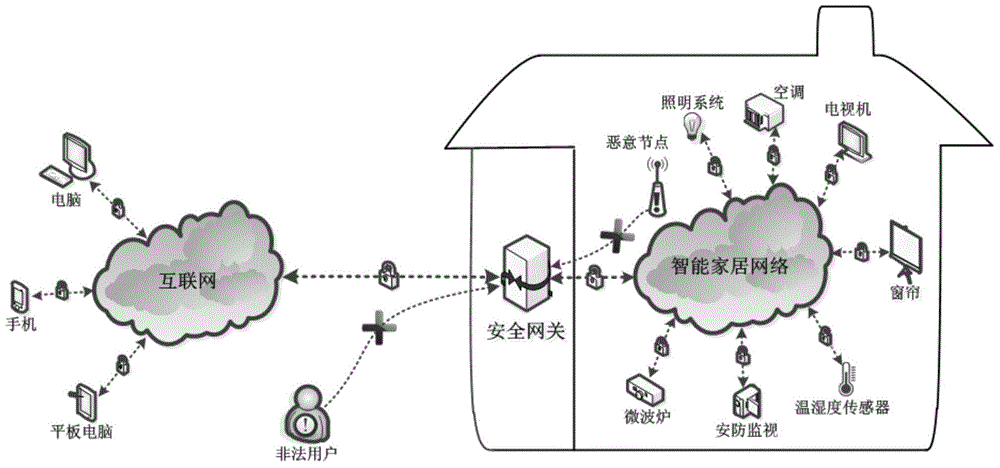
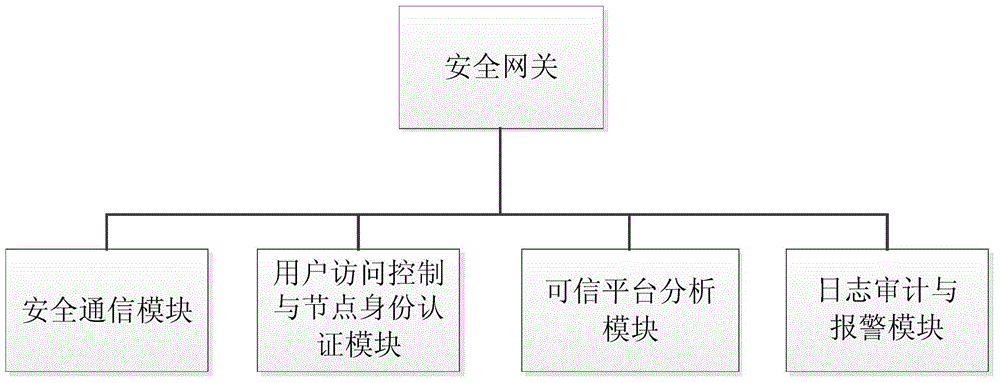
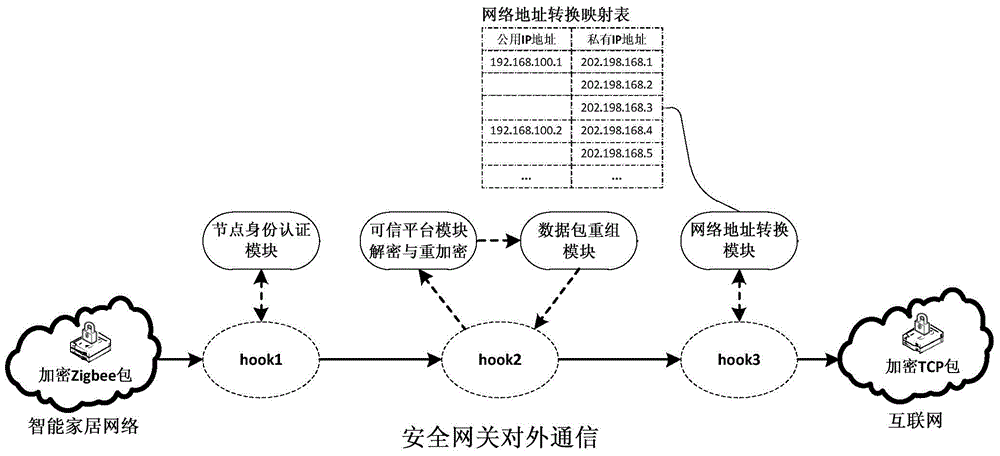
Internet of Things smart home security gateway system
ActiveCN104580233AEnhanced defense against attacksRealize free decouplingUser identity/authority verificationNetwork connectionsThe InternetSecure authentication
The invention relates to an Internet of Things smart home security gateway system. The system comprises a user side, a security gateway and a terminal node. The user side and the terminal node each comprise a data encrypting / decrypting module used for encrypting / decrypting a sent control order and received data through a preset encrypting program on a remote client side or the terminal node; the security gateway comprises a safety communication module, a user access control and node identity authentication module, a credible platform module and a log audit and alarm module; the safety communication module achieves data safety filtering, reconstructing and forwarding and guarantees safety of the bi-direction transmission; the credible platform module is used for achieving system safety authentication, user behavior credibility analysis, data sealing storage and free decoupling and can be independently maintained and upgraded; the log audit and alarm module is used for recording user access and node authentication behaviors, carrying out safety audit on the operation of viewing logs and giving a timely alarm for an abnormal phenomenon found in the gateway system safety monitoring process. By means of the Internet of Things smart home security gateway system, the safety performance of a smart home system and the running efficiency of a gateway can be improved, and a safety guarantee is provided for Internet of Things smart home.
Owner:重庆中邮信科集团股份有限公司
Method and apparatus for supporting multiple frequency bands efficiently in mobile communication system
ActiveUS20130044708A1Reduce signaling overheadNetwork traffic/resource managementConnection managementData radio bearerTransfer procedure
A method and an apparatus for transmitting a small size data packet efficiently while reducing signaling overhead in a mobile communication system are provided. The method includes determining to apply a low security transfer procedure, transmitting, to a base station, a Radio Resource Control (RRC) connection request message including a temporary Data Radio Bearer (DRB) request to which Access Stratum (AS) security is not applied, receiving an RRC connection setup message, including a temporary DRB configuration, from the base station, and transmitting an Internet Protocol (IP) packet over the temporary DRB.
Owner:SAMSUNG ELECTRONICS CO LTD
Mixing automatic re-transmission method and apparatus for TDD system
ActiveCN101414900AReduce complexityError prevention/detection by using return channelDuplex signal operationSystems designTransfer procedure
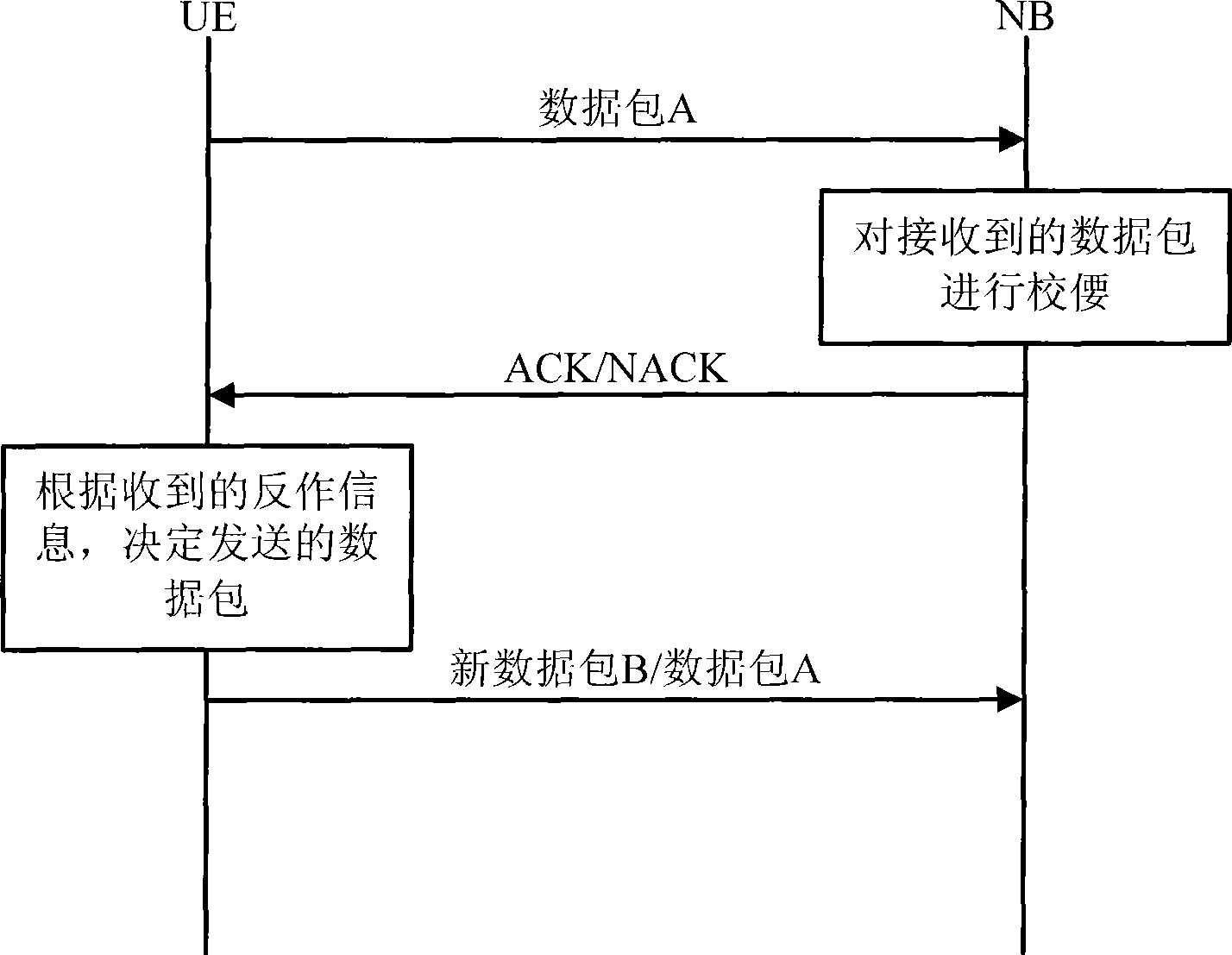
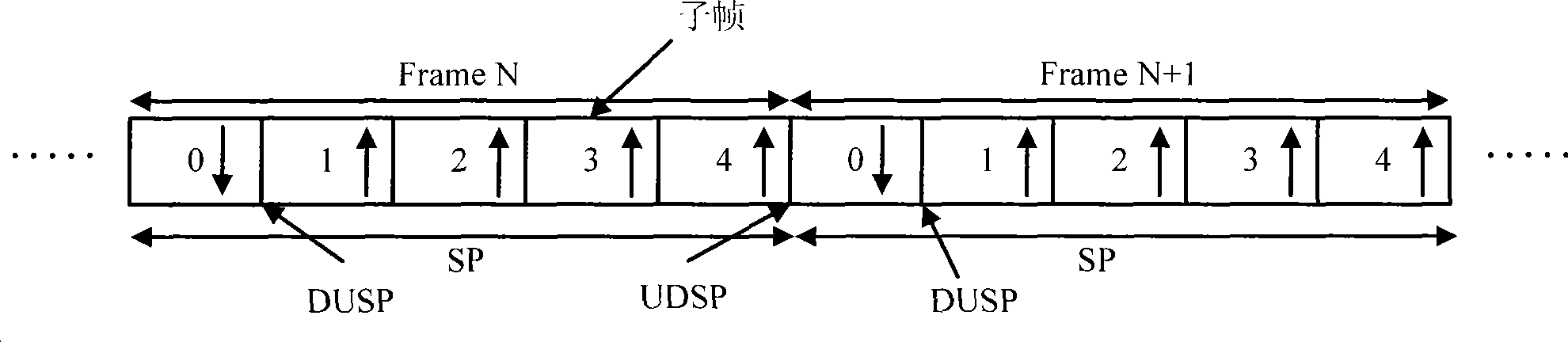
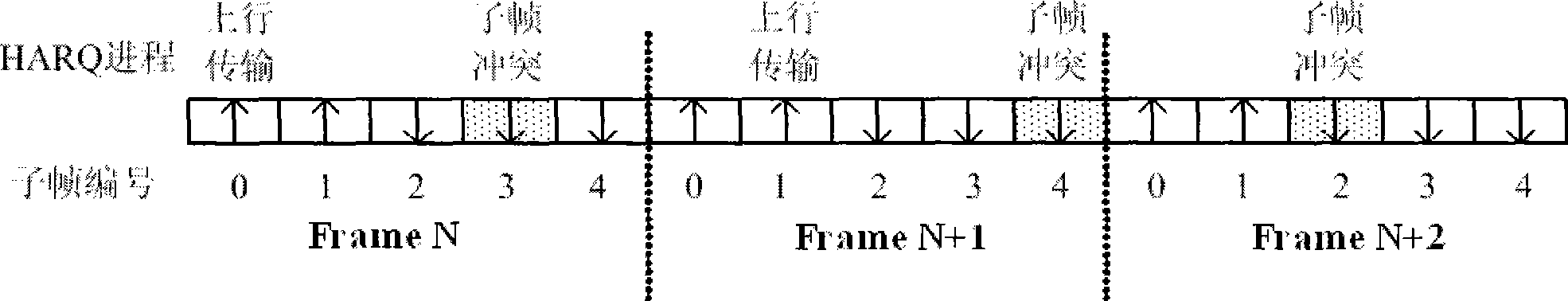
The invention discloses a hybrid automatic repeat method for a time division duplex system. The method ensures that the TTI numbers of an uplink and a downlink are the same by setting the length and the number of TTI in a frame structure, thus establishing the one-to-one corresponding relationship between TTI of the uplink and the downlink, so that in the HARQ transmission process, fixed relationship can exist among the feedback of ACK / NACK, HARQ process id and TTI. The feedback of ACK / NACK and HARQ process id can be easily determined by TTI, thus reducing the complexity of realizing the TDD system design of HARQ effectively.
Owner:DATANG MOBILE COMM EQUIP CO LTD
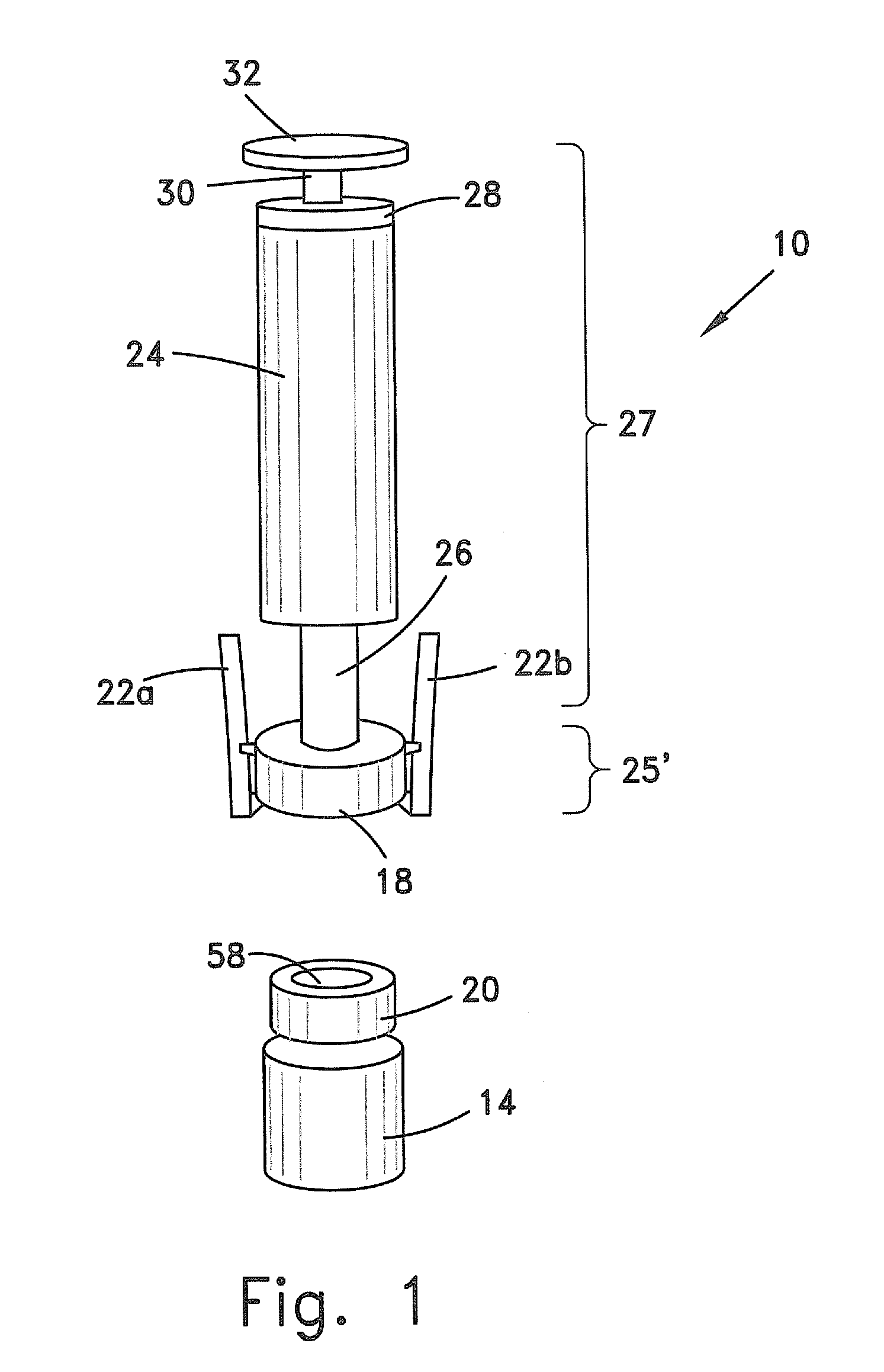
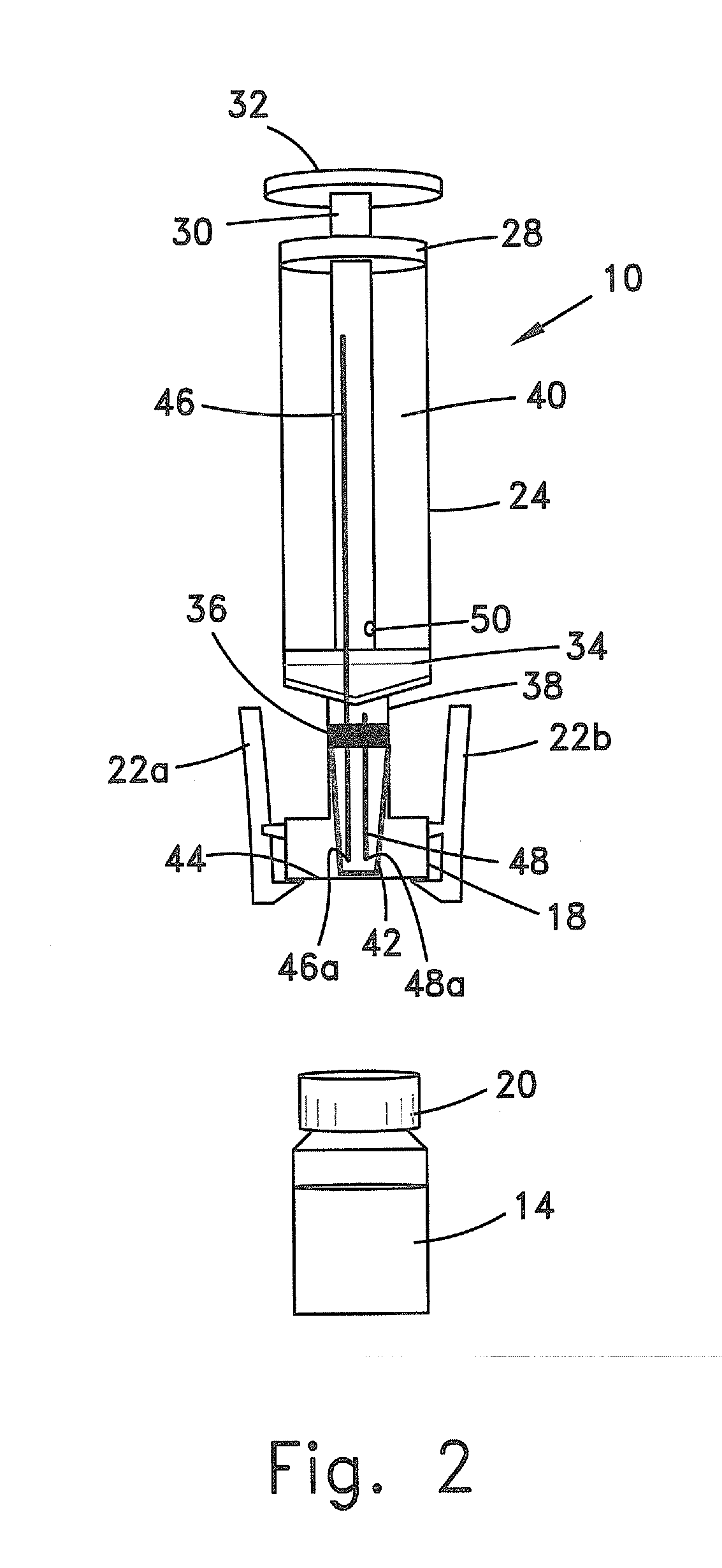
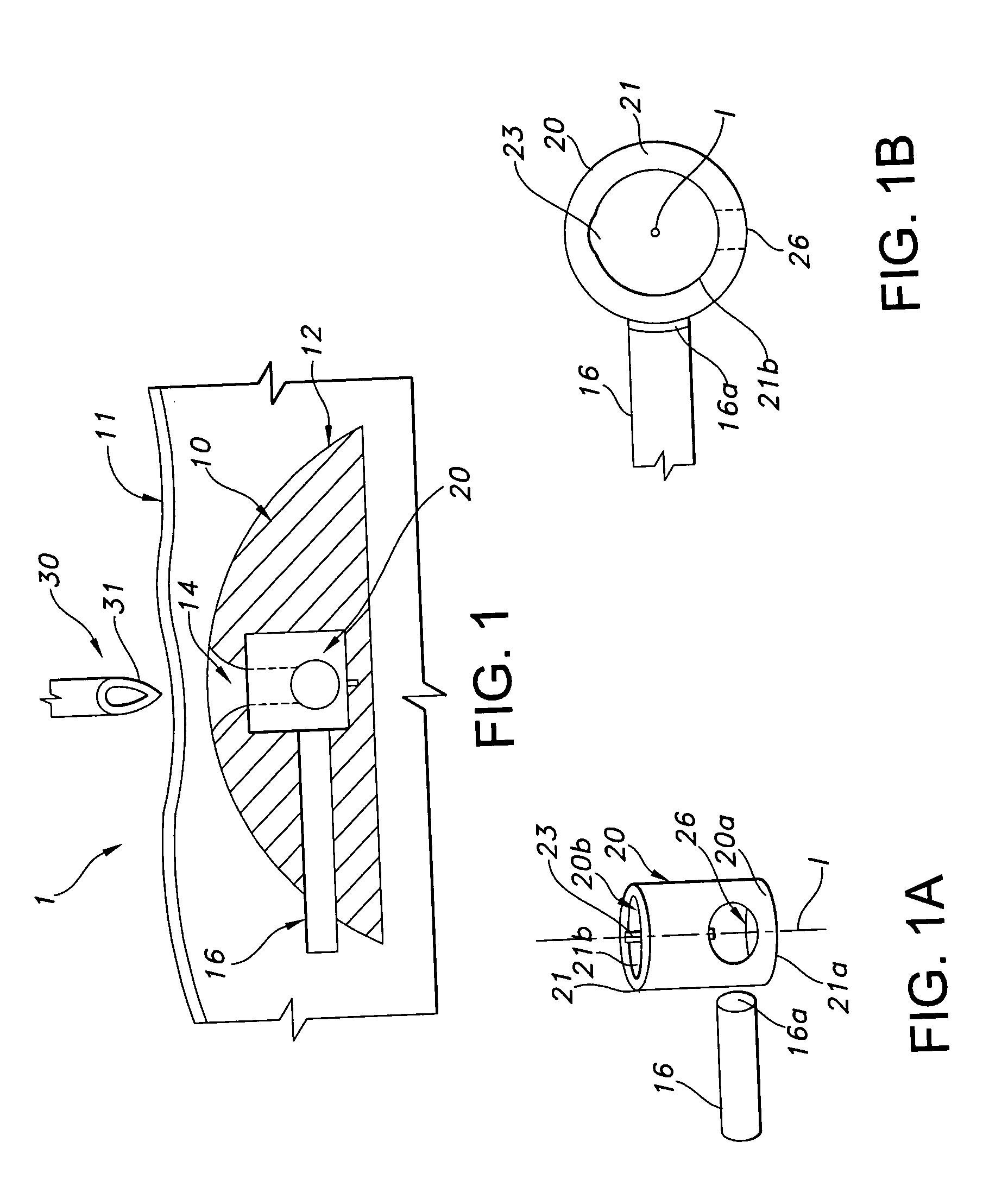
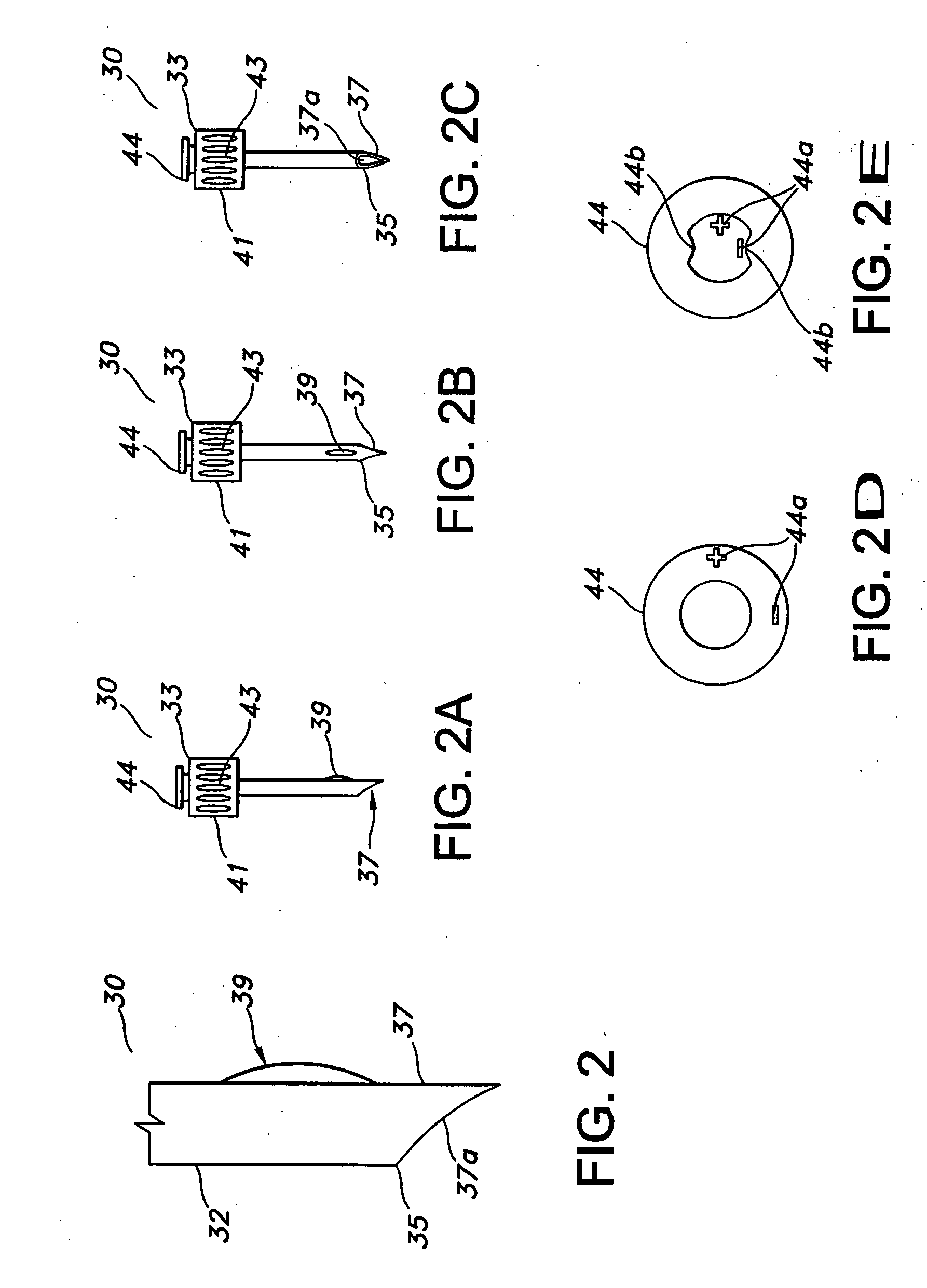
Method and apparatus for contamination-free transfer of a hazardous drug
The invention is a method that allows contamination-free transfer of a liquid from one container to another and devices including embodiments of a transfer apparatus and adaptors that are used to carry out the method. By contamination-free transfer of liquid it is meant that during the transfer process there is no leakage of the liquid or air contaminated by the liquid or vapors of the liquid to the surroundings and also that no contaminants from the surroundings come into contact with the liquid. The main advantages of the method, in addition to its simplicity, is that at no stage of the transfer procedure is there leakage of the liquid or air contaminated by the liquid or vapors of the liquid to the surroundings and also that no contaminants from the surroundings come into contact with the liquid. The present invention is particularly directed towards providing an apparatus that is adapted to effect contamination-free transfer of a hazardous drug to and from any container equipped with a standard connector port.
Owner:EQUASHIELD MEDICAL
Data transmission method and device for multi-data channel
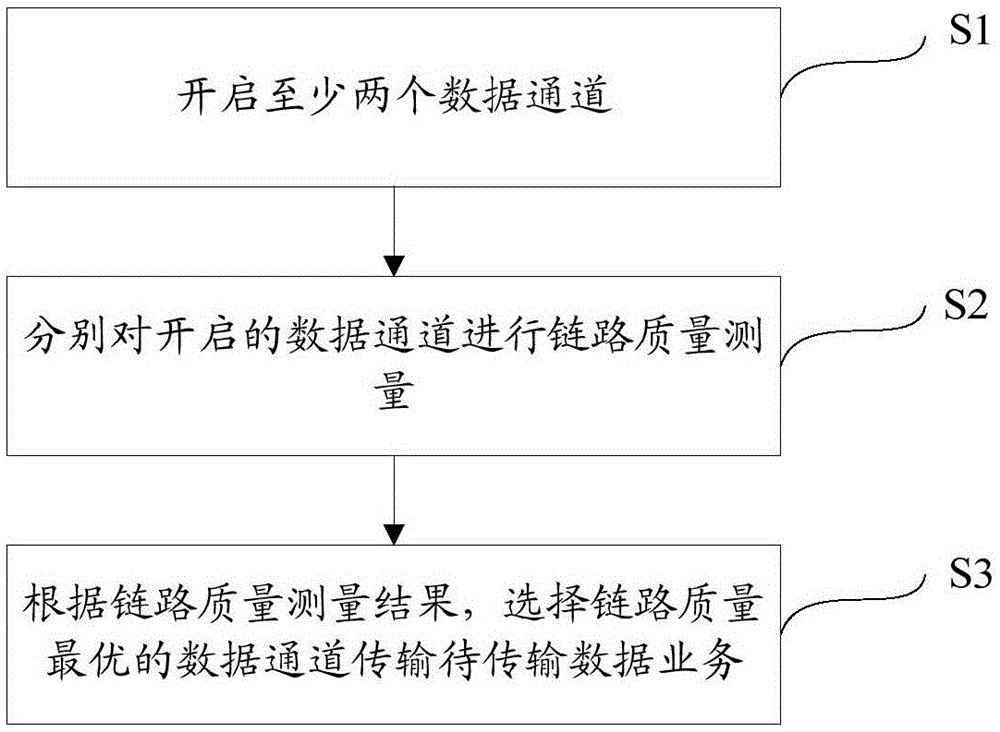
ActiveCN105101316AMaximize UtilizationMeasuring mechanism is simpleWireless communicationOpen dataTransfer procedure
The invention discloses a data transmission method and device for a multi-data channel. The method comprises the following steps of opening at least two data channels; performing link quality measurement on the opened data channels respectively; selecting a data channel with optimal link quality to transmit data traffics to be transmitted according to a link quality measuring result. The beneficial effects of implementing the invention are as follows: a transmission rate is improved through selecting and switching, and using the data channel with optimal link quality to transmit the data traffics; besides, in the transmission process of the data traffics, the optimal data channel can be always kept to be used, thus, the utilization ratio of data channels can be optimized to the maximum, and the network interaction rate and user experience can be improved.
Owner:山东聚盛联创信息科技有限公司
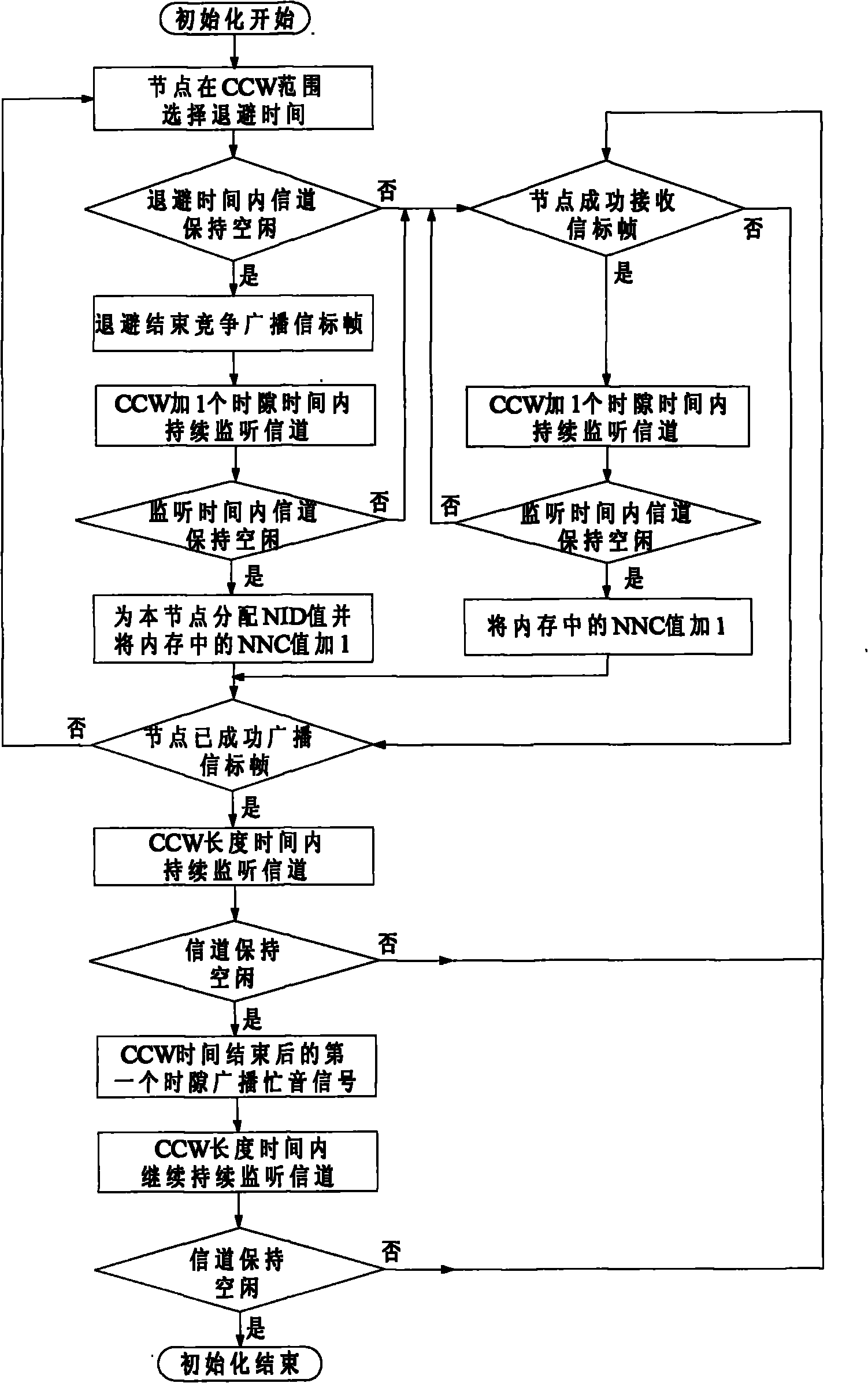
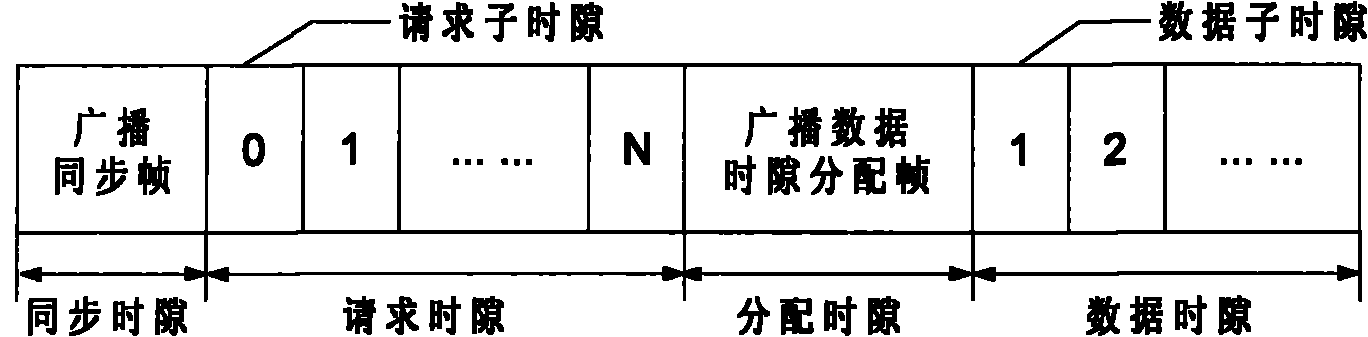
DSAM (Dynamic Slot-time Allocation Method) of scale-extensible single-jump ad hoc network supporting QoS (Quality of Service)
InactiveCN101977385ANetwork traffic/resource managementNetwork planningQuality of serviceTransfer procedure
The invention discloses a DSAM (Dynamic Slot-time Allocation Method) of scale-extensible single-jump ad hoc network supporting QoS (Quality of Service), comprising the following steps of: requiring total network nodes to complete broadcasting beacon frame in the process of networking initialization, judging whether each node in the network successfully receives the broadcasting beacon frame of remainder nodes or not by adopting a distributed manner, thereby obtaining sequentially ordered unique identifiers and the total quantity of the network nodes at networking initialization time. In the running process of the network, the time axis of the total network nodes are synchronously divided into a series of continuous network frames without fixed lengths, each node invokes data transmission within each network time frame, and the transmission process comprises four stages of node synchronization, time-slot requirement, time-slot allocation and data transmission; meanwhile, the method can effectively support a new node to access the network and a node to quit so as to meet the requirement of network scale dynamic extension. And the simulation experiment data in a wireless network simulation environment Qua1Net proves the validity of the method.
Owner:WUXI JUWEI TECH CO LTD
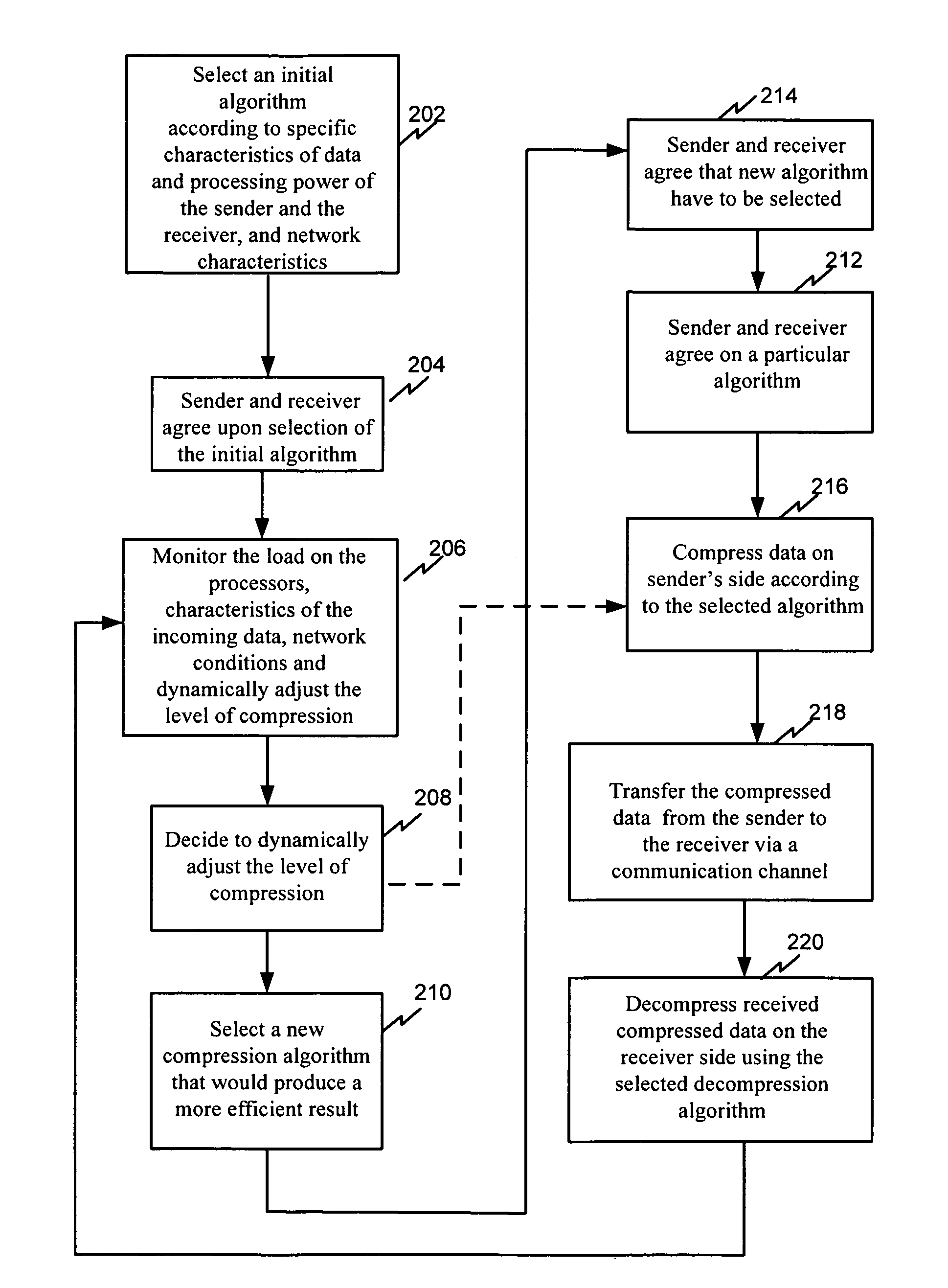
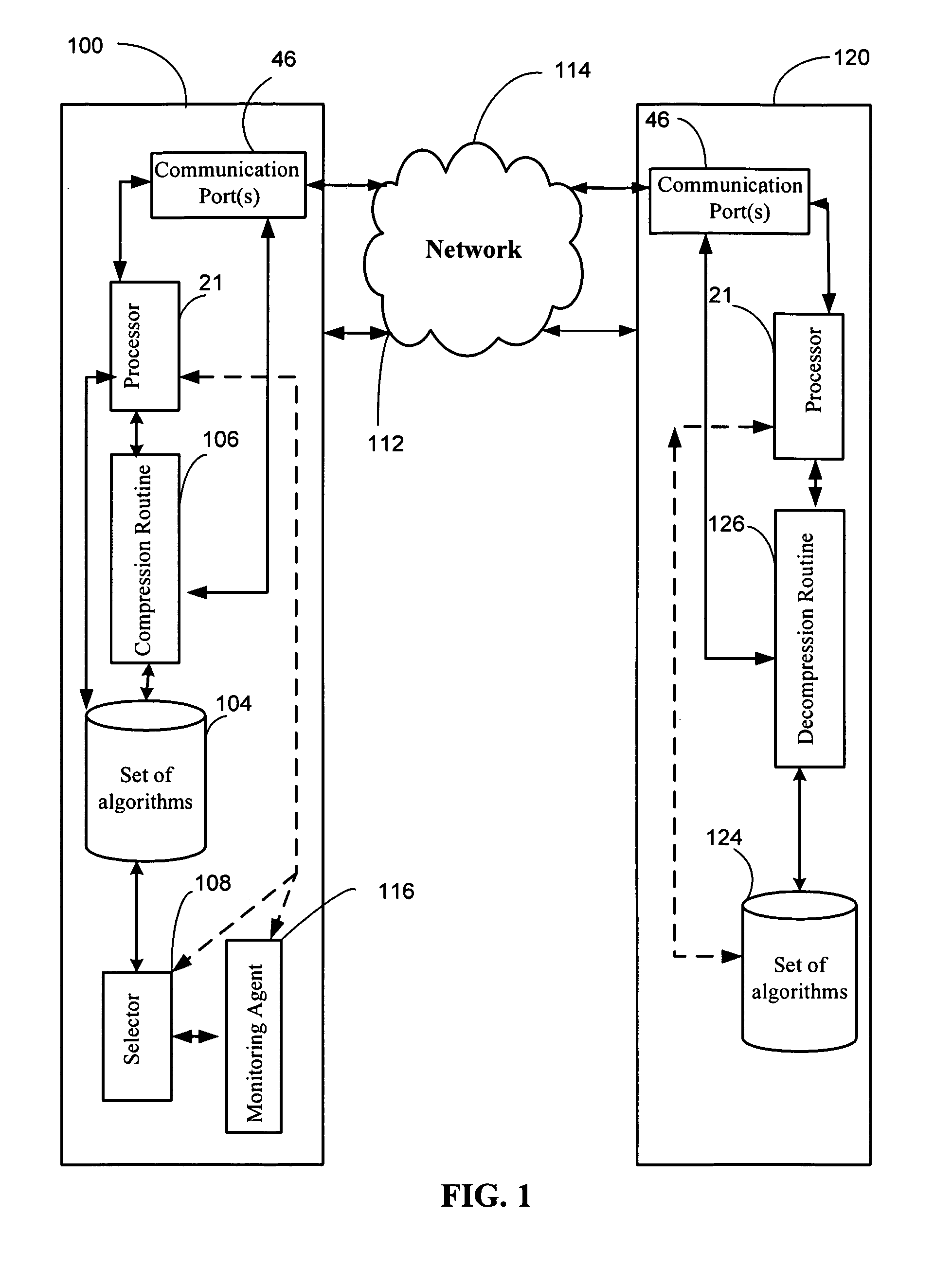
System and method for dynamically adjusting data compression parameters
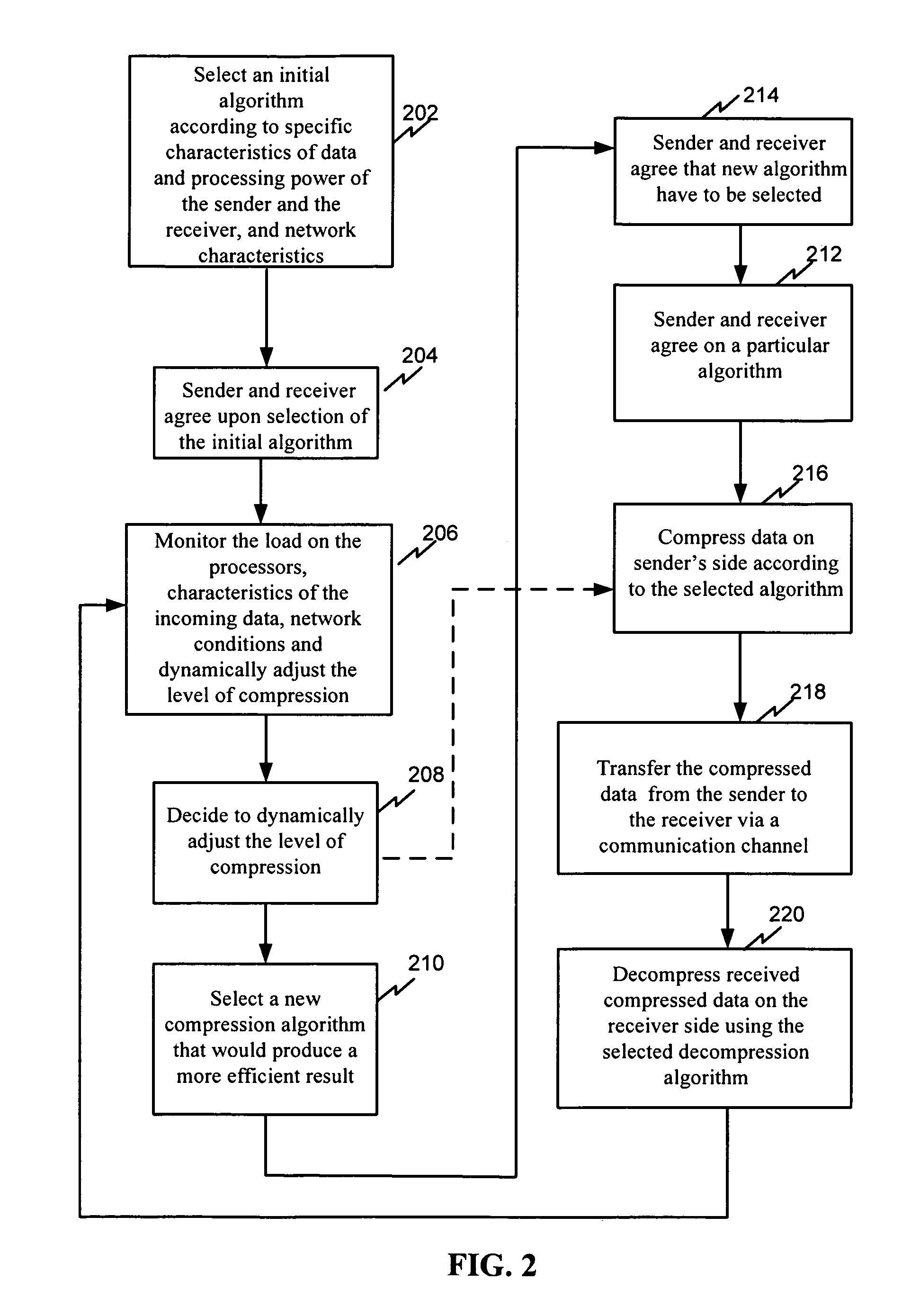
InactiveUS7930436B1Time-division multiplexMultiple digital computer combinationsTransfer procedureNetwork conditions
The present invention relates generally to a system and a method for dynamically adjusting data compression parameters. The process of dynamic transfer of data parameters from the sender to the receiver has four steps: determining optimal compression parameters, compressing data that are on a sender side using the selected algorithm, transferring compressed data from the sender to the receiver and decompressing received data on the receiver's side. On the sender side, the transmitting computer stores multiple compression algorithms, and one of these algorithms is used to compress the data. A monitoring agent monitors the available processor resources, data type, and network conditions. The monitoring agent also determines when to dynamically adjust the level of compression and / or compression algorithm and sends a signal when it decides dynamically adjust the level of compression. A selector dynamically changes the compression algorithm.
Owner:ZNOSKO DMITRY Y
Method of controlling a channel between a radio terminal and a cellular radiocommunication infrastructure, and access network implementing such a method
InactiveUS6909887B2Simple procedureMinimizing duration of transmissionKey distribution for secure communicationUnauthorised/fraudulent call preventionAccess networkCellular radio
The infrastructure has a core network, radio network controllers linked to the core network and base stations provided with radio interfaces and each linked to one of the controllers. Ciphered information is transmitted over a first communication path in circuit mode between the core network and the terminal, passing through a first master controller, then over a second communication path in circuit mode between the core network and the terminal, passing through a second master controller. The second path is established in a transfer procedure comprising the transmission of adjustment data from the first to the second master controller and the suppression of the first path. These data are representative of a current value of a sequence number used to encipher the information and incremented at regular intervals, and of an offset between this sequence number and a time reference available to the second controller.
Owner:ALCATEL LUCENT SAS
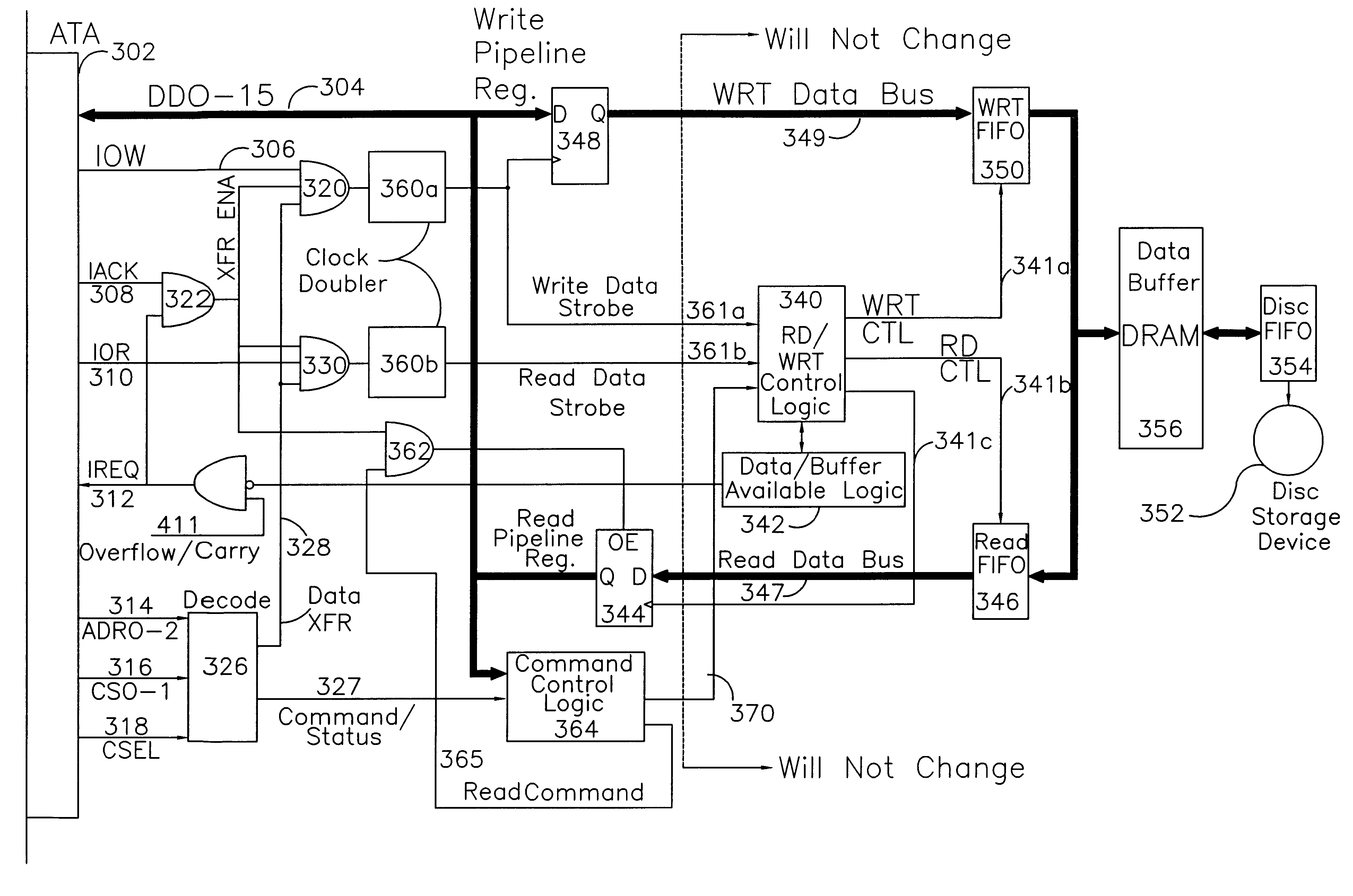
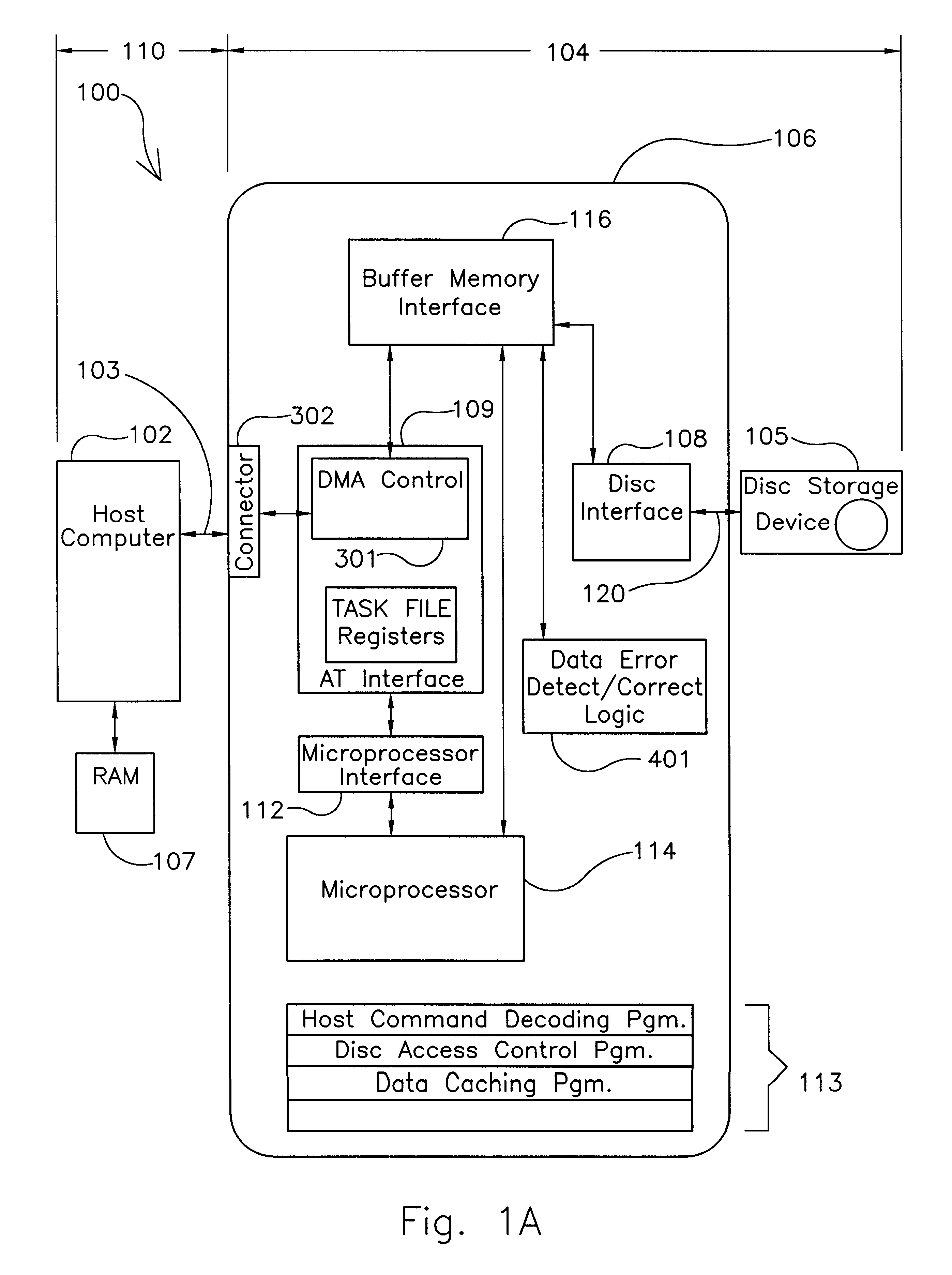
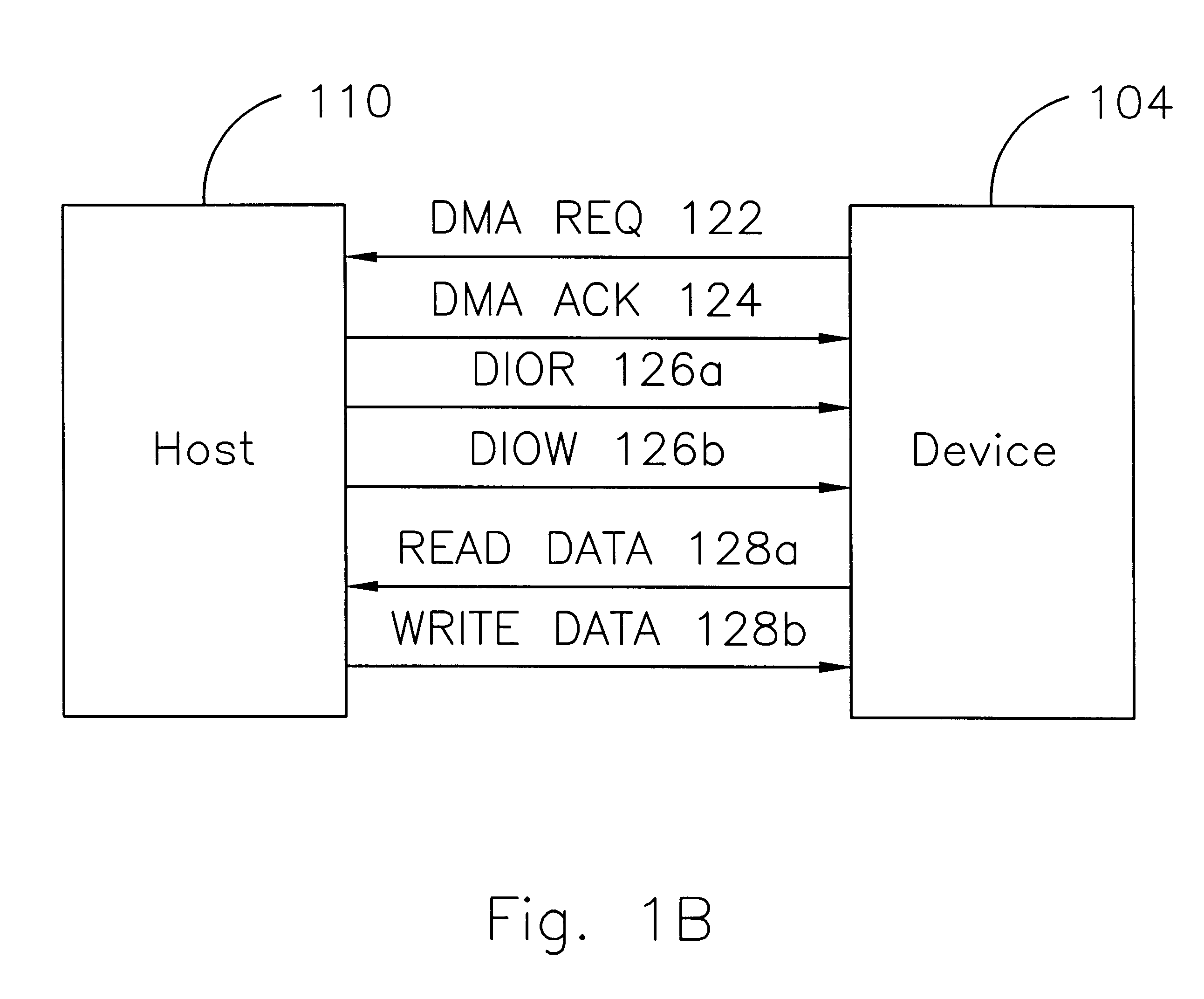
Fast ATA-compatible drive interface with error detection and/or error correction
InactiveUS6192492B1Emergency protective arrangements for automatic disconnectionStatic storageHard disc driveData integrity
An ATA-compatible drive interface with error correction and detection capabilities is disclosed. Being fully ATA backward compatible, this interface functions with the same physical cable and connectors as current ATA systems, employs bus drivers that are the same as or backward compatible with those provided by earlier versions of the ATA standard and uses signals with cable signal transitions no faster than those presently seen by current ATA devices. The error detection feature indicates when a data block is erroneously transferred between the device and host; the error correction feature identifies the words transmitted in error and corrects those words on the receiving side of the interface. So that ATA backward compatibility is maintained, the data integrity checking feature does not require additional words in a data transfer, and the data correction feature does not require new data transfer protocols or additional data transfer overhead. Also disclosed are interface circuitry and a new ATA-compatible transfer mode capable of transferring data at 40 MB / sec, the rate supported by local bus adapters for disk drives. Given the physical limits of the ATA cables and connectors, the error correction and detection features are especially useful for correcting data words corrupted during high-speed transmission; however, error correction and detection can also operate independently of the fast transfer mode. Consistent with full backward compatibility, a hard drive configured with the new, fast, error-correcting interface is transparently functional when plugged into a current ATA adapter provided by a legacy computer system.
Owner:SEAGATE TECH LLC
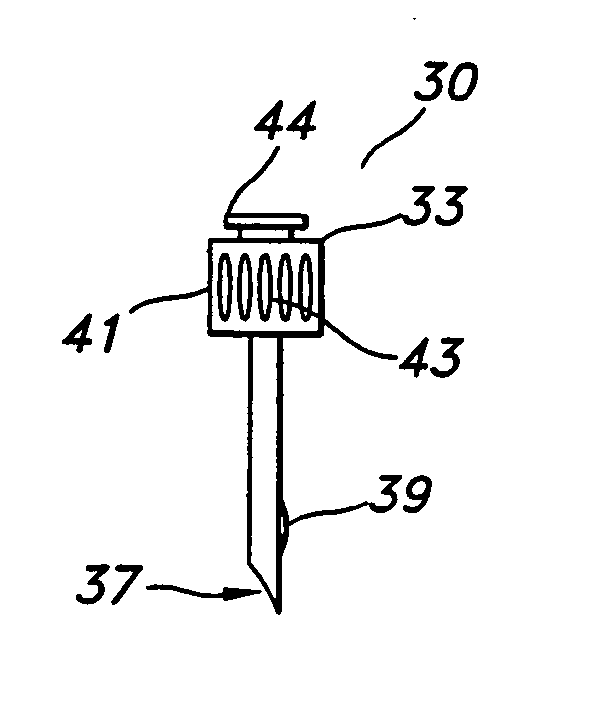
Valve port assembly with coincident engagement member for fluid transfer procedures
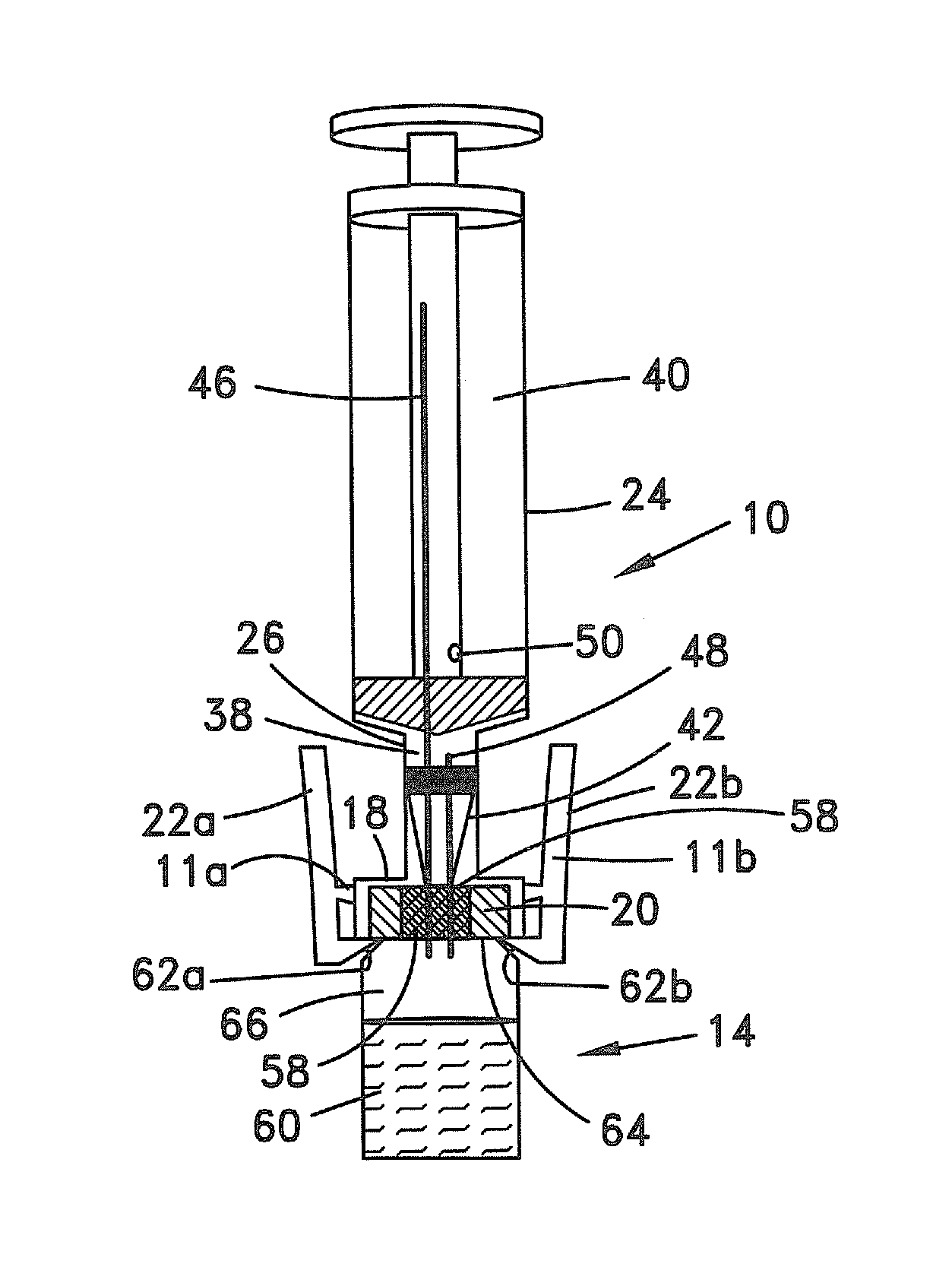
InactiveUS20050080401A1Prevent exitLow profilePharmaceutical delivery mechanismIntravenous devicesProximateTransfer procedure
An improved valve port system provides blood access in a patient through a subcutaneous fluid flow conduit during a dialysis procedure. The system includes several elements, including a engagement member defined by a tubular body having a proximal end, a distal end and a tubular lumen therebetween. The distal end has a tapered bevel defined thereat and a tapered protrusion proximate thereto defined upon an exterior surface of the tubular body. In addition, the system provides a dialysis port member having a housing with a generally cylindrical valve rotatably positioned therein. The valve includes an open end, a closed end and an orifice near the closed end. The valve further includes a longitudinal groove defined along an interior surface thereof. The groove, which is capable of being in registry with the protrusion, is coincident with the protrusion so as to intussuscept the protrusion therein. In this manner, rotation of the engagement member effects rotation of the valve between an open position wherein the orifice is in fluid communication with the fluid flow conduit and a closed position wherein fluid communication between the orifice and the conduit is precluded.
Owner:NAVILYST MEDICAL
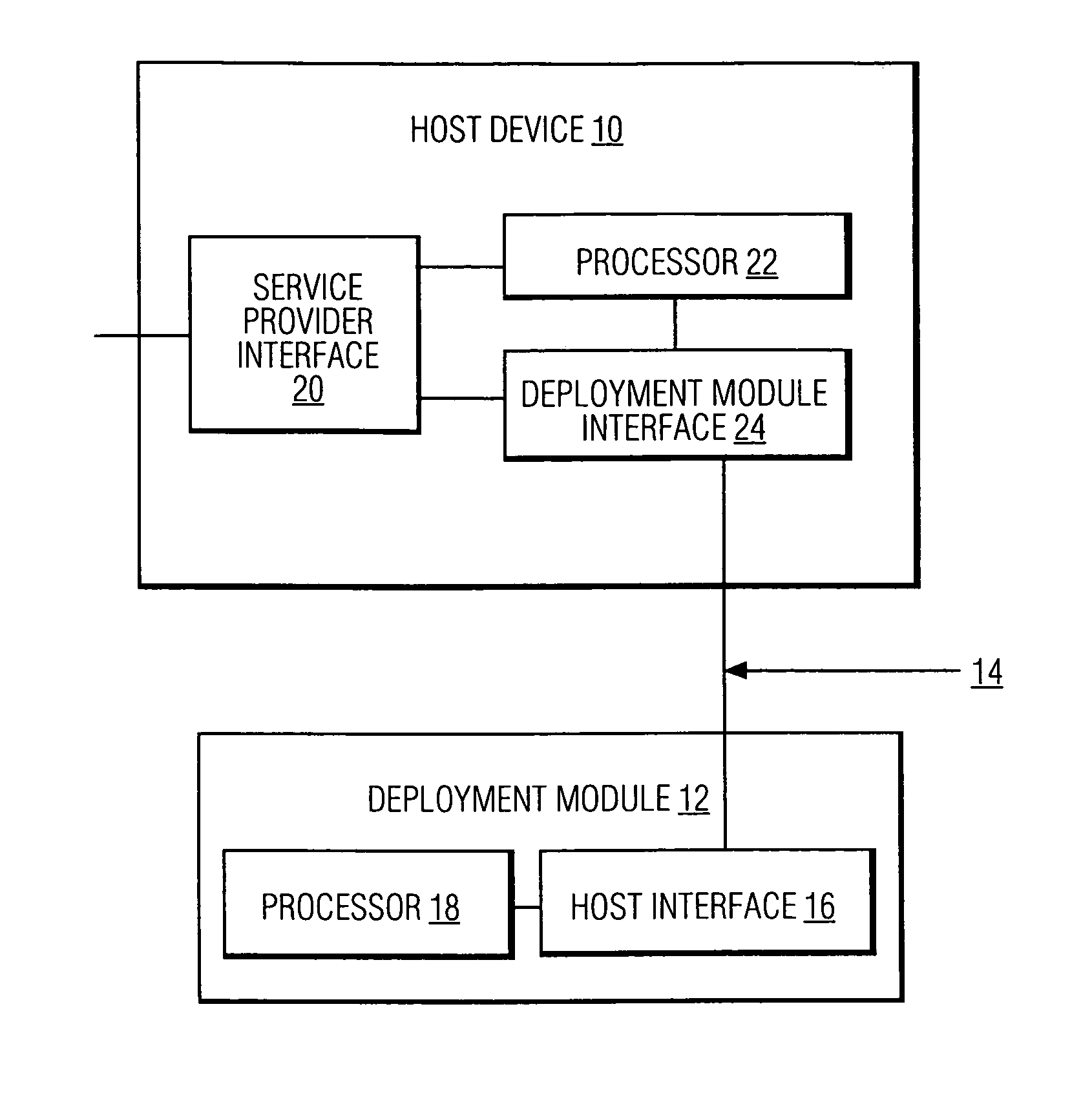
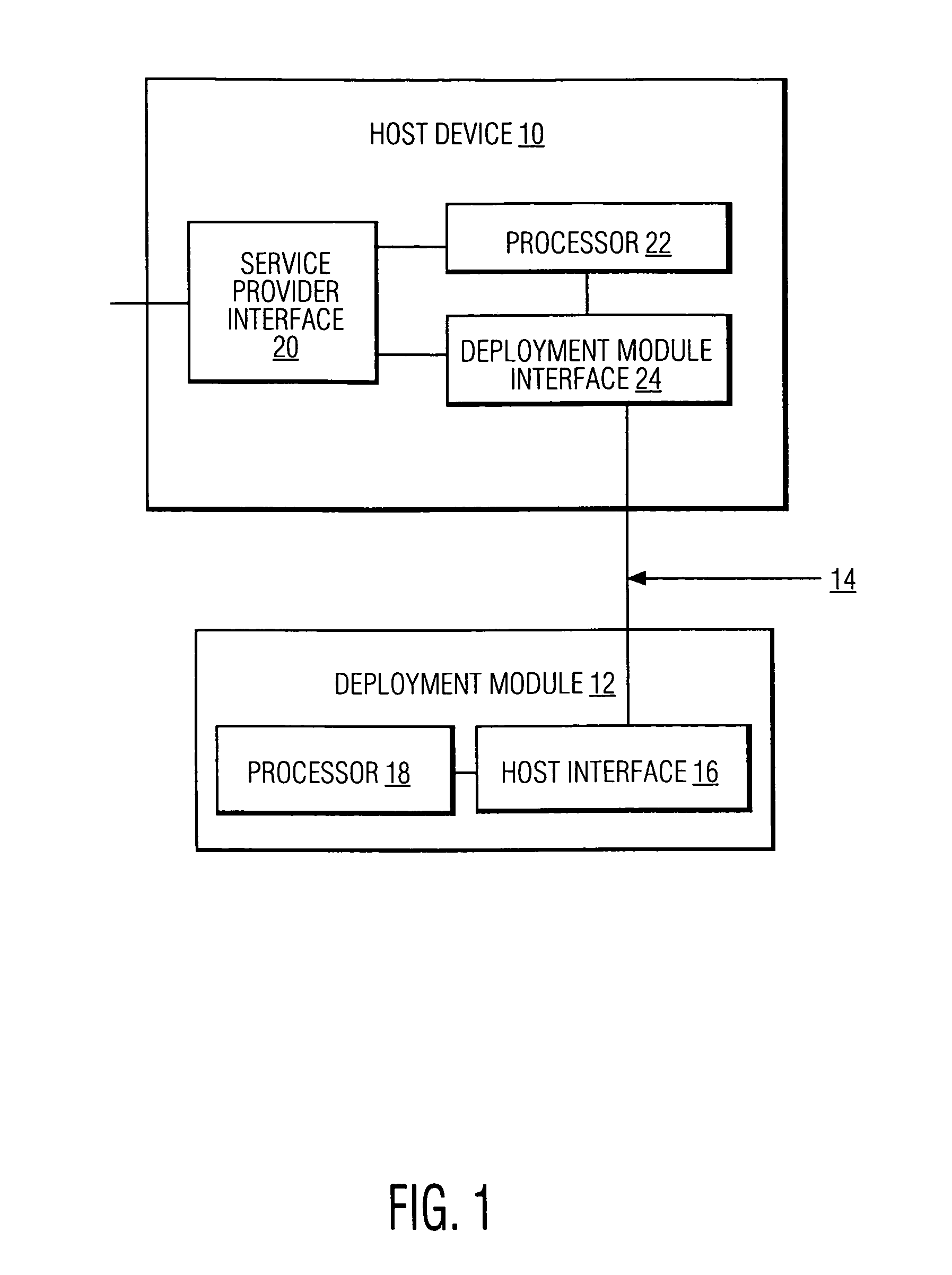
System and method for copy protecting transmitted information
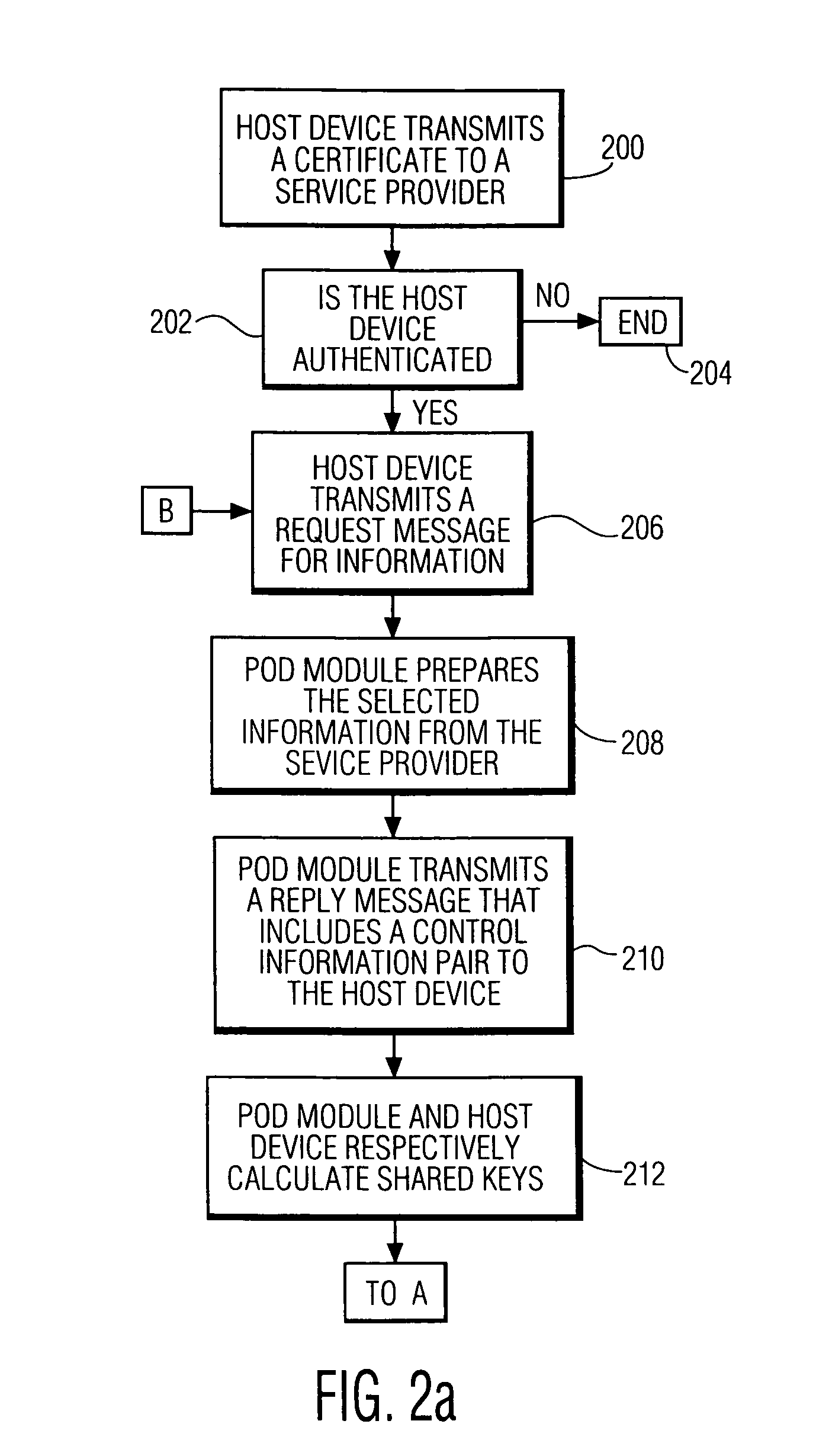
InactiveUS7336785B1Protect informationEliminate useTelevision system detailsKey distribution for secure communicationTransfer procedureService provision
To afford copy protection for information, e.g. elementary streams, from a service provider while in transit between a point of deployment (POD) module and a set-top box, the information is accompanied by control information pairs. The pairs are respectively associated with the portions of the copy protected information and are incorporated into a shared key calculation in the POD module and set-top box. The shared keys are used by the POD module and set-top box to encrypt and decrypt the information. Tampering with a control information pair, as by an intruder or hacker, prevents keys shared by the set-top box and POD module from matching. A mismatch prevents the set-top box from correctly decrypting information received from the deployment module.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Safety data transmission method and paying method, paying terminal and paying server
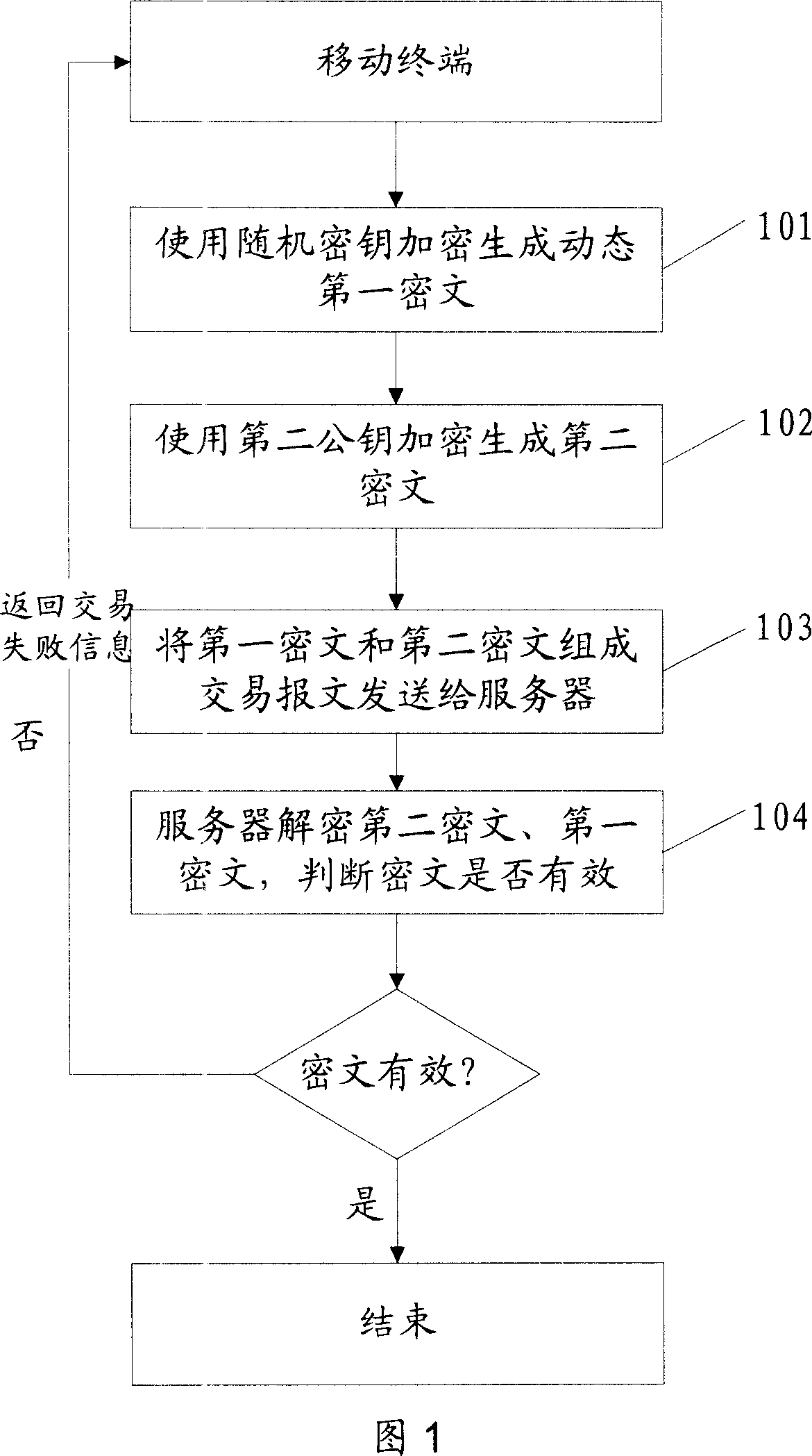
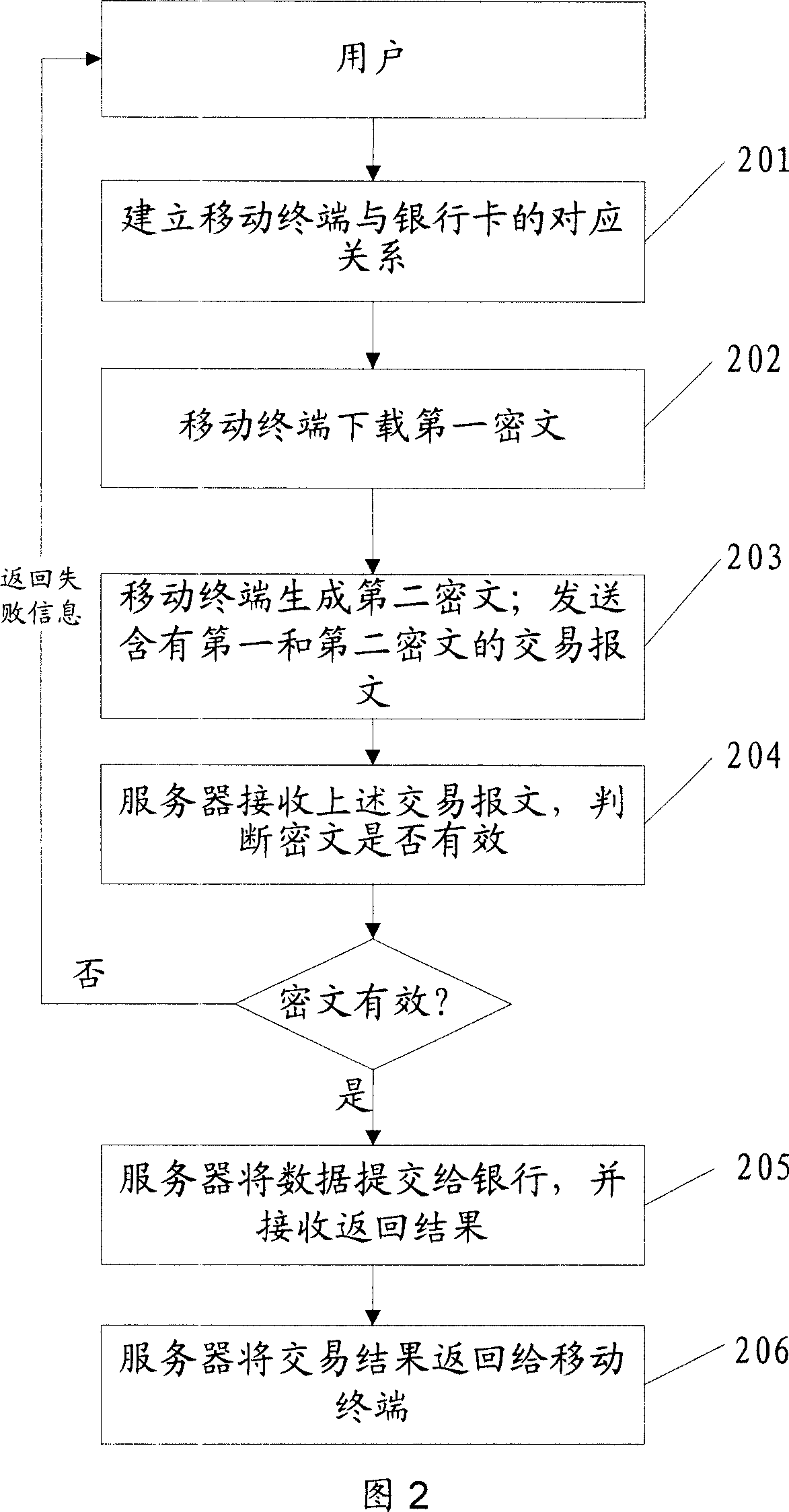
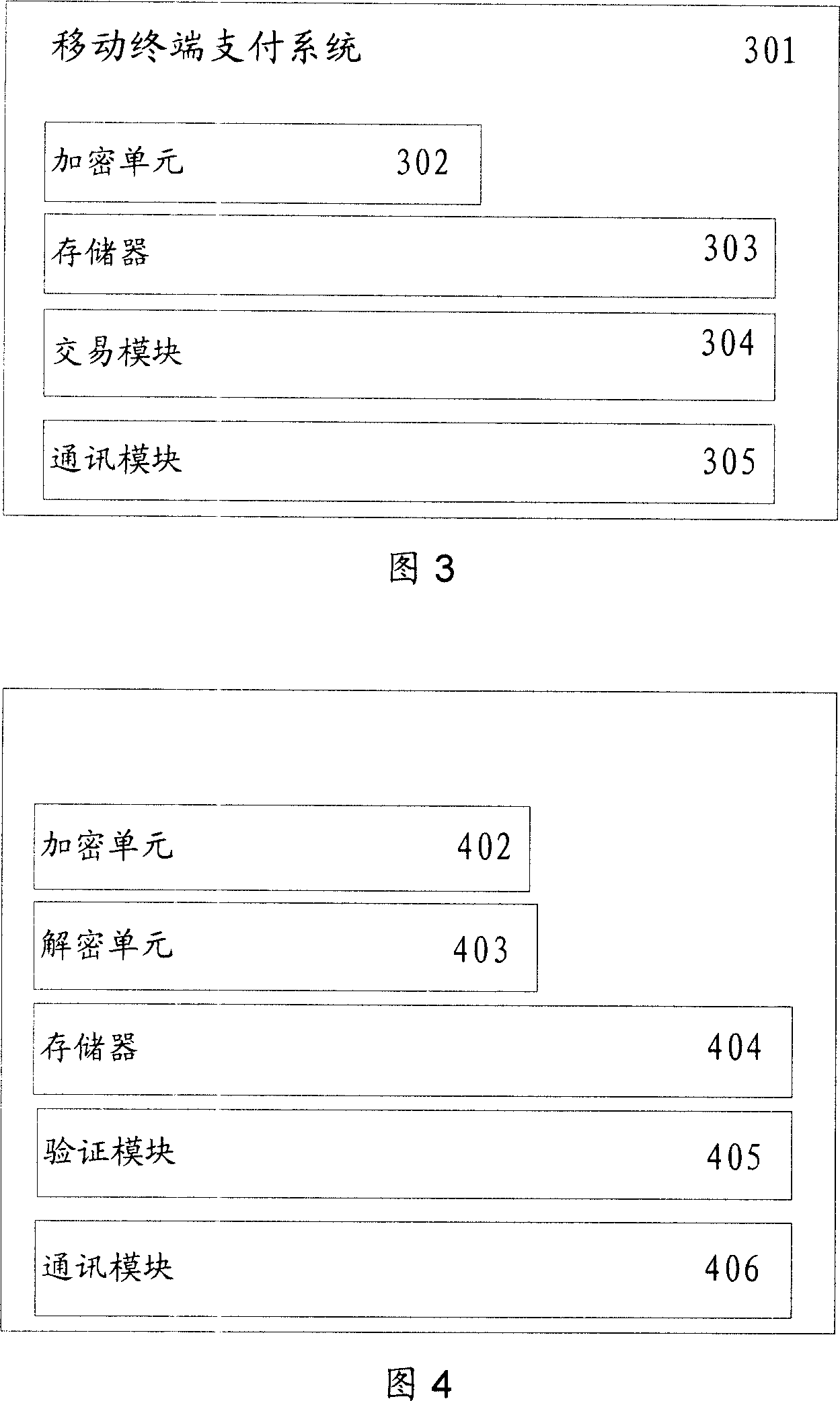
ActiveCN101098225AProtection securityEnsure safetyUser identity/authority verificationPayment architectureTime markPassword
The invention discloses a safe data transmission method, comprising that a mobile terminal uses a second public key to encrypt the personal password of bank card to generate a second cryptogram, the mobile terminal combines the first and second cryptograms into a trade report to be sent to a server, while the first cryptogram contains card track information stored in the mobile terminal, the server decrypts the first and second cryptograms, for best, the mobile terminal can use random password to encrypt the first cryptogram to generate a dynamic first cryptogram, while the random password is generated by relative algorism according to dynamic factor. The invention uses asymmetry encrypt technique to encrypt the data sent by mobile terminal, and uses random password to generate dynamic cryptogram, and generates the cryptogram with living period according to time mark, therefore, the transmission safety of finance data as cark track information or the like is effectively protected via the combined encrypt methods, to realize mobile payment.
Owner:CHINA UNIONPAY
Method, transmitting/receiving device and system against lost packet in data transmission process
ActiveCN101119319AImprove the immunityLow costError preventionData switching networksTransfer procedureNetwork packet
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data transmission method, device and system
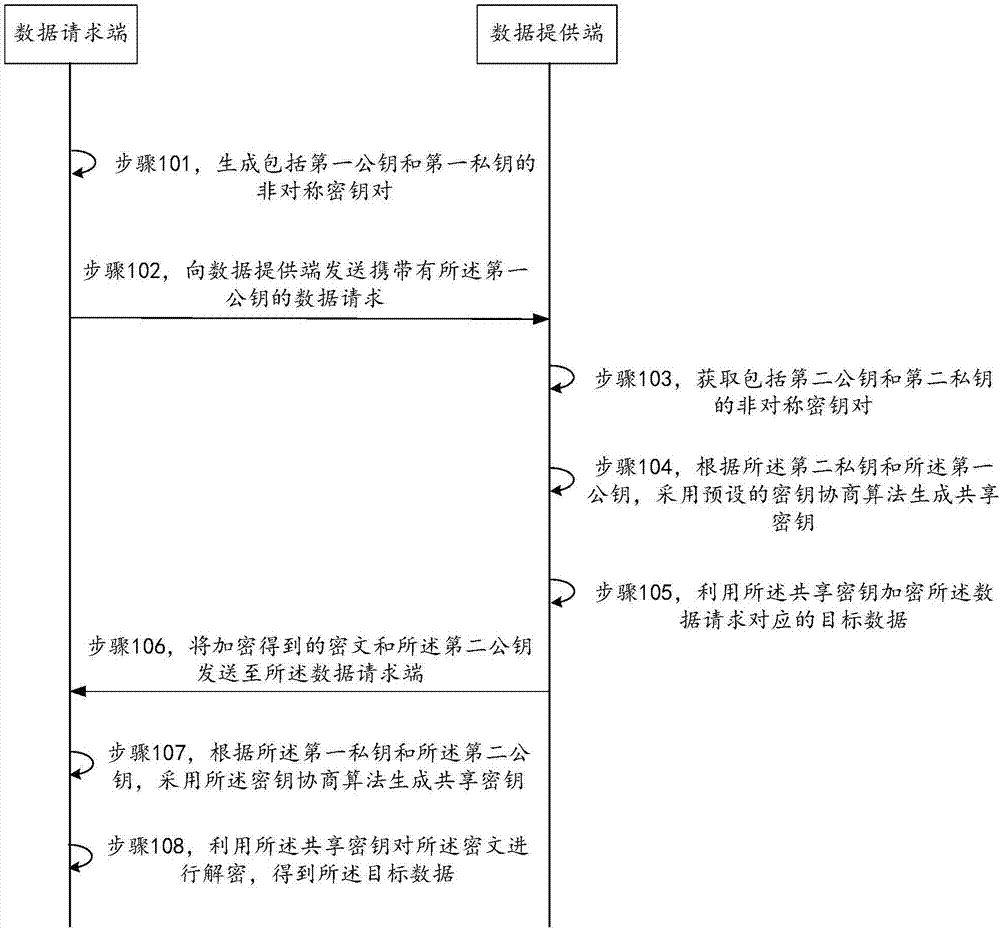
ActiveCN107040369AAvoid the defect of long encryption and decryption timeSimplify the encryption processKey distribution for secure communicationMultiple keys/algorithms usagePaymentCiphertext
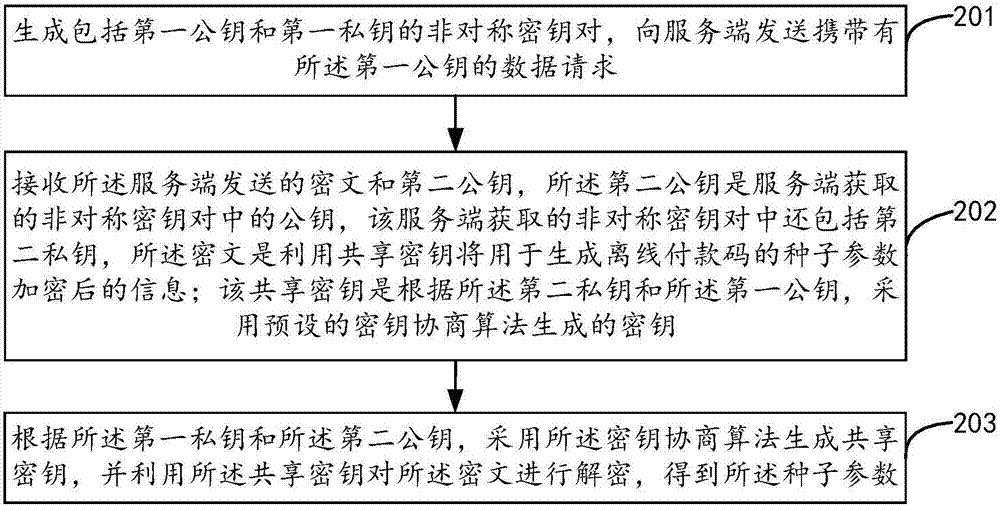
The invention provides a data transmission method, a data transmission device and a data transmission system. The method comprises the steps of generating an asymmetrical secret key pair including a first public key and a first private key, and sending a data request carrying the first public key to a server side; receiving a ciphertext and a second public key sent by the server side, wherein the second public key is the public key in the asymmetrical secret key pair acquired by the server side, the asymmetrical secret key pair acquired by the server side also comprises a second private key, the ciphertext is information generated by encrypting a seed parameter used for generating an offline payment code by using a sharing secret key, and the sharing secret key is the secret key by using a preset secret key negotiation algorithm according to the second private key and the first public key; and generating the sharing secret key by using the secret key negotiation algorithm according to the first private key and the second public key, using the sharing secret key to decrypt the ciphertext, thus acquiring the seed parameter. According to the method, the device and the system provided by the invention, security of the data during a whole transmission process is ensured, and decryption and encryption efficiency is also improved.
Owner:ADVANCED NEW TECH CO LTD
Satellite network simulation system
InactiveCN101404547AComprehensive solutionSolve the characteristicsRadio transmissionTransmission monitoringSoftware systemNetwork topology
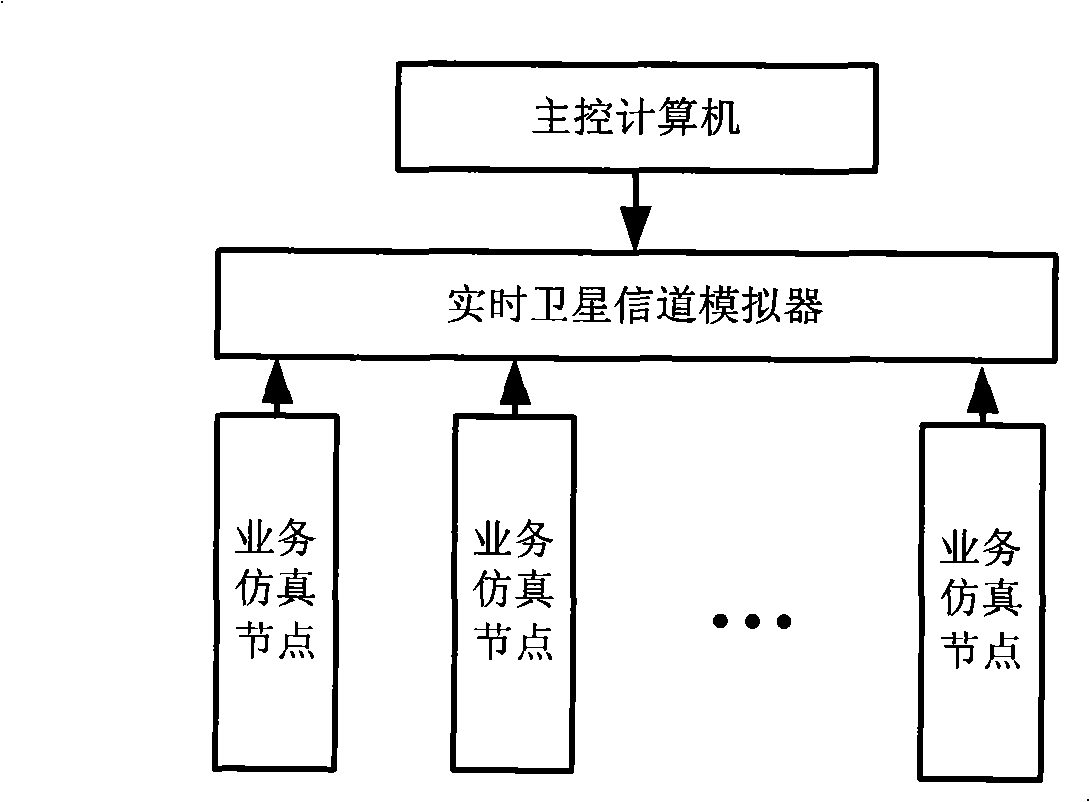
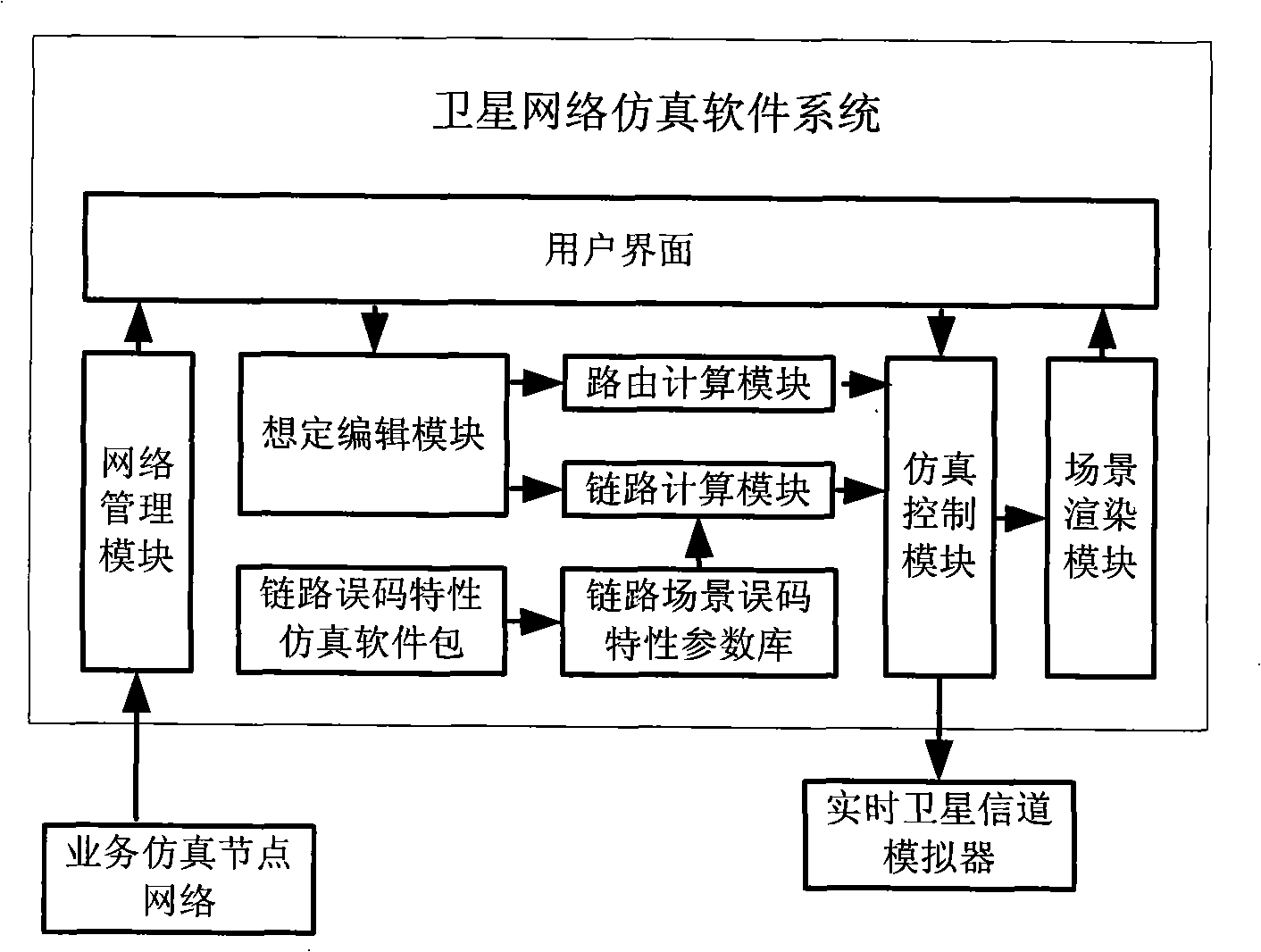
The invention discloses a satellite network simulation system and belongs to the technical field of satellite communication simulation. The system comprises a main control computer, a real-time satellite channel simulator and a plurality of service simulation node computers; the main control computer is provided with a satellite network simulation software system which can achieve establishment of a satellite network simulation scene, can select a routing algorithm, set link parameters and achieve the information management of the simulation satellite network, and is connected with the real-time satellite channel simulator by an RS232 bus; the service simulation node is provided with a service simulation software which achieves simulation of a transmission process of the satellite network service, and is connected with the real-time satellite channel simulator by an Ethernet port. The satellite network simulation system can truly and comprehensively simulate topological changes of the satellite network, channel characteristics of an inter-satellite link and a satellite-to-earth link, and the transmission process of the satellite network service under the laboratory condition.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
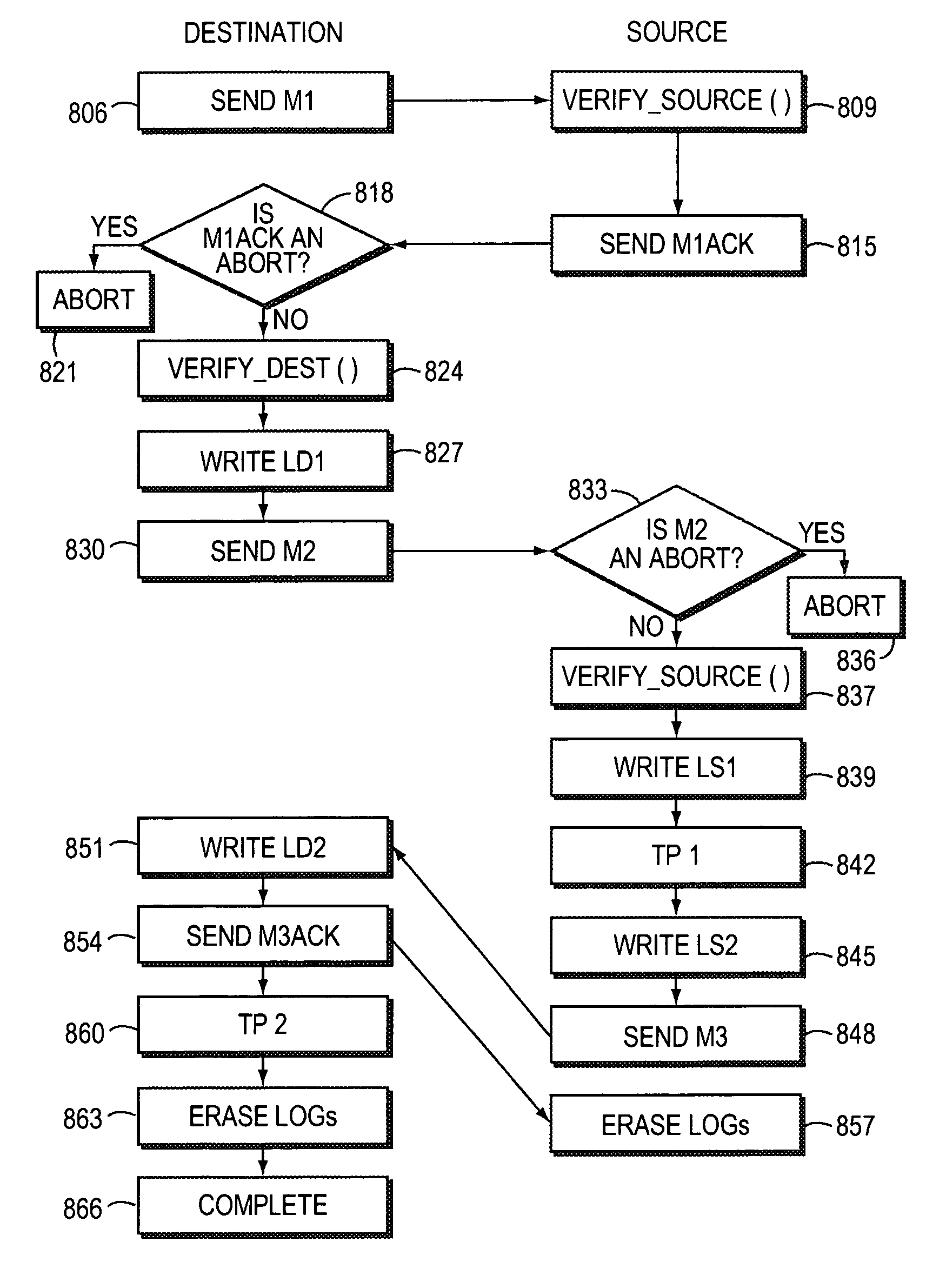
System and method for transfering volume ownership in net-worked storage
A system and method for transferring ownership of a volume in a networked storage environment. The method first moves the disks that comprise the volume being transferred from a source-owned state to an un-owned state. Next the disks are moved to a destination-owned state. Each step of the transfer process completes on all disks before the next step begins to ensure consistency and disks that have conflicting owners. Alternate embodiments include logging by the source and destination nodes to permit a resumption of the transfer if one node becomes inactive during the transfer.
Owner:NETWORK APPLIANCE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com