Patents
Literature
745 results about "Access stratum" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
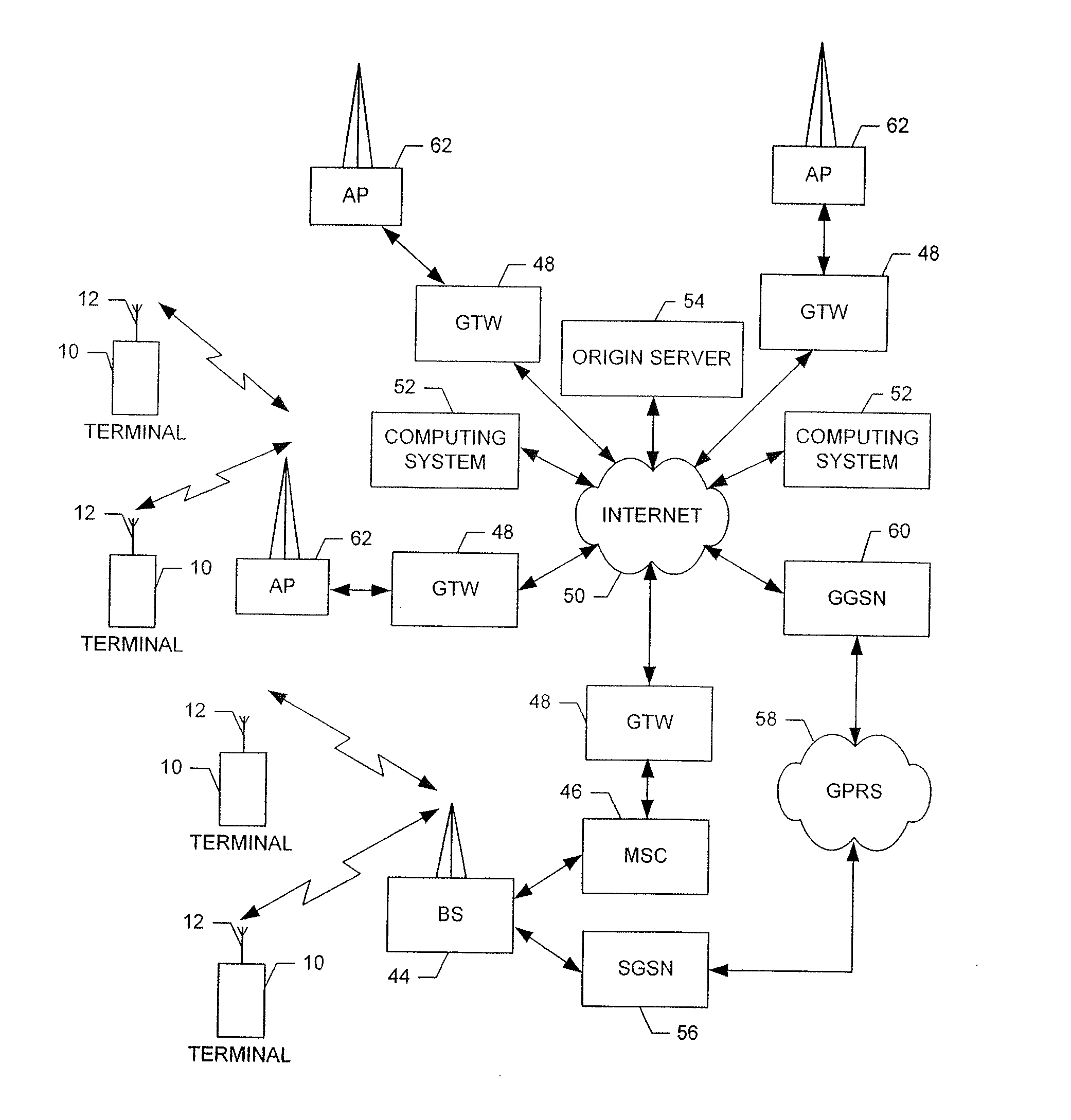
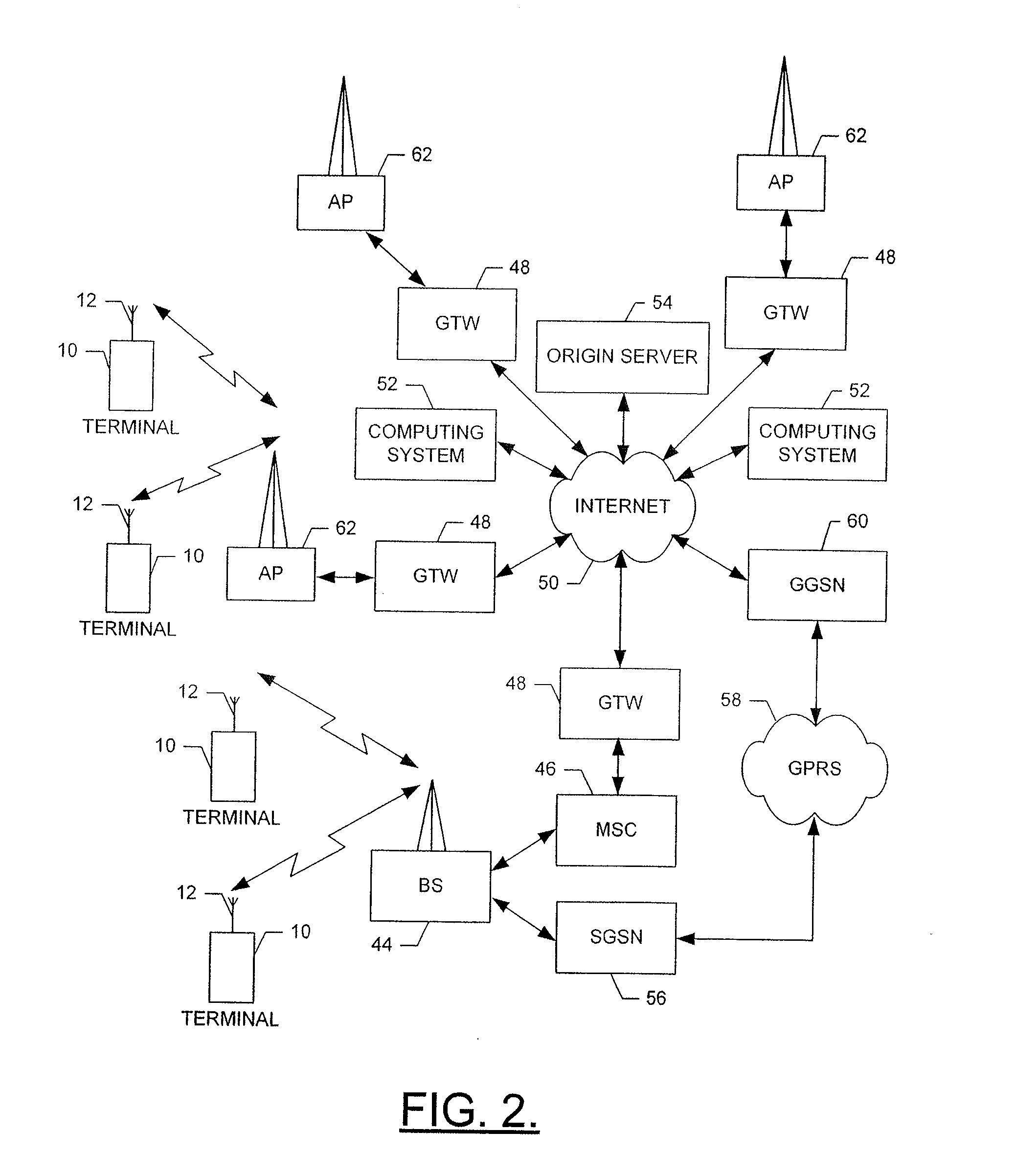
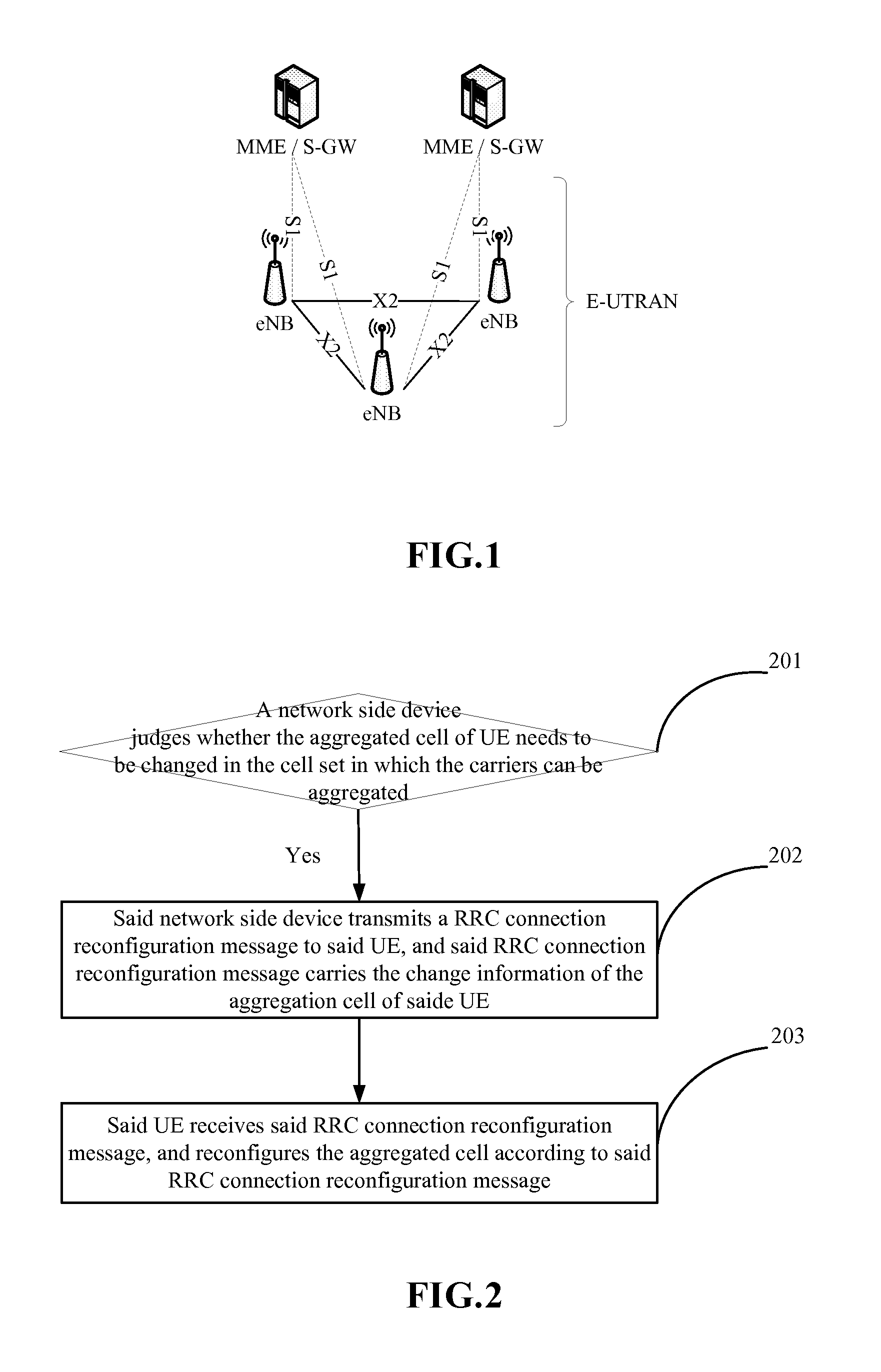
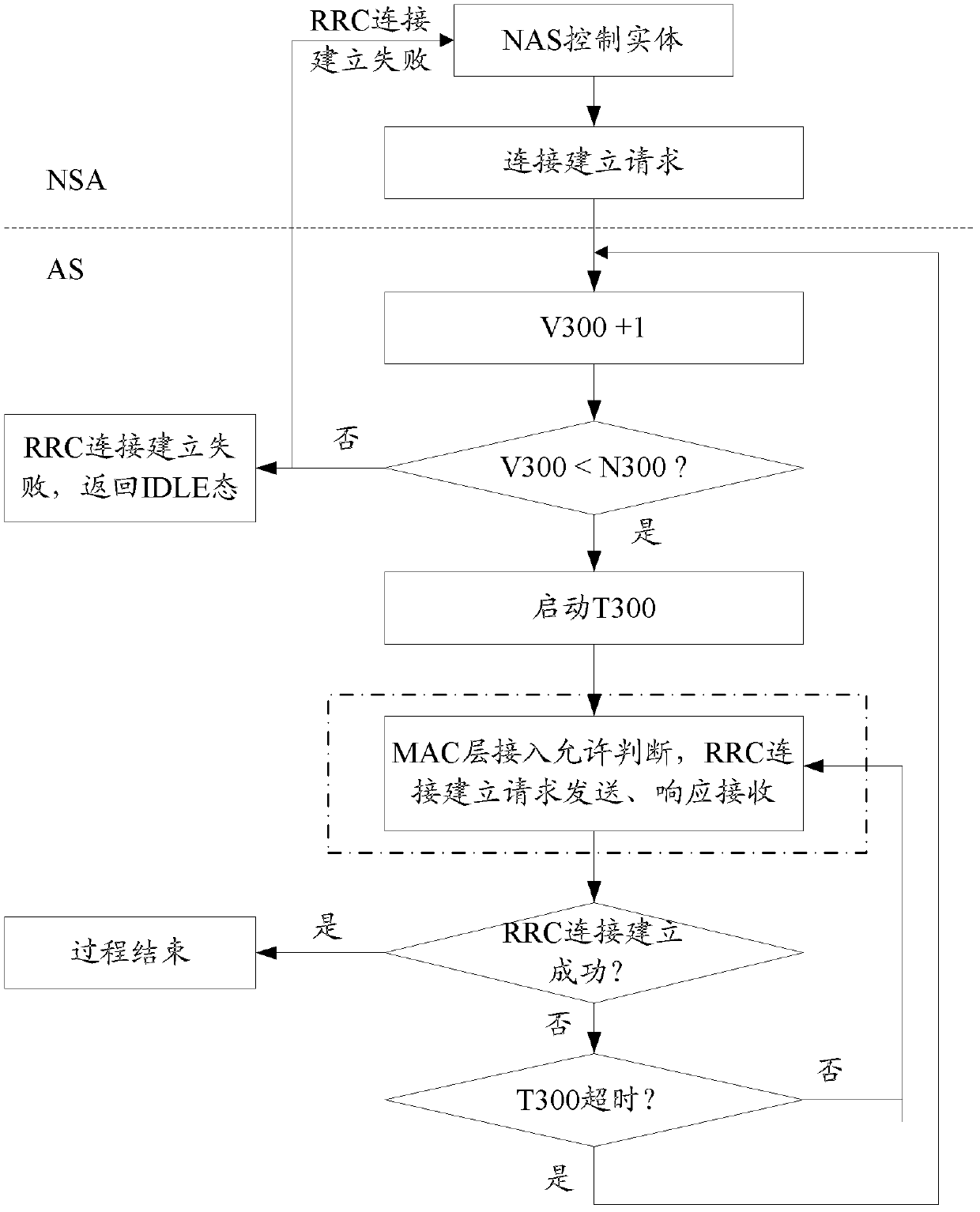
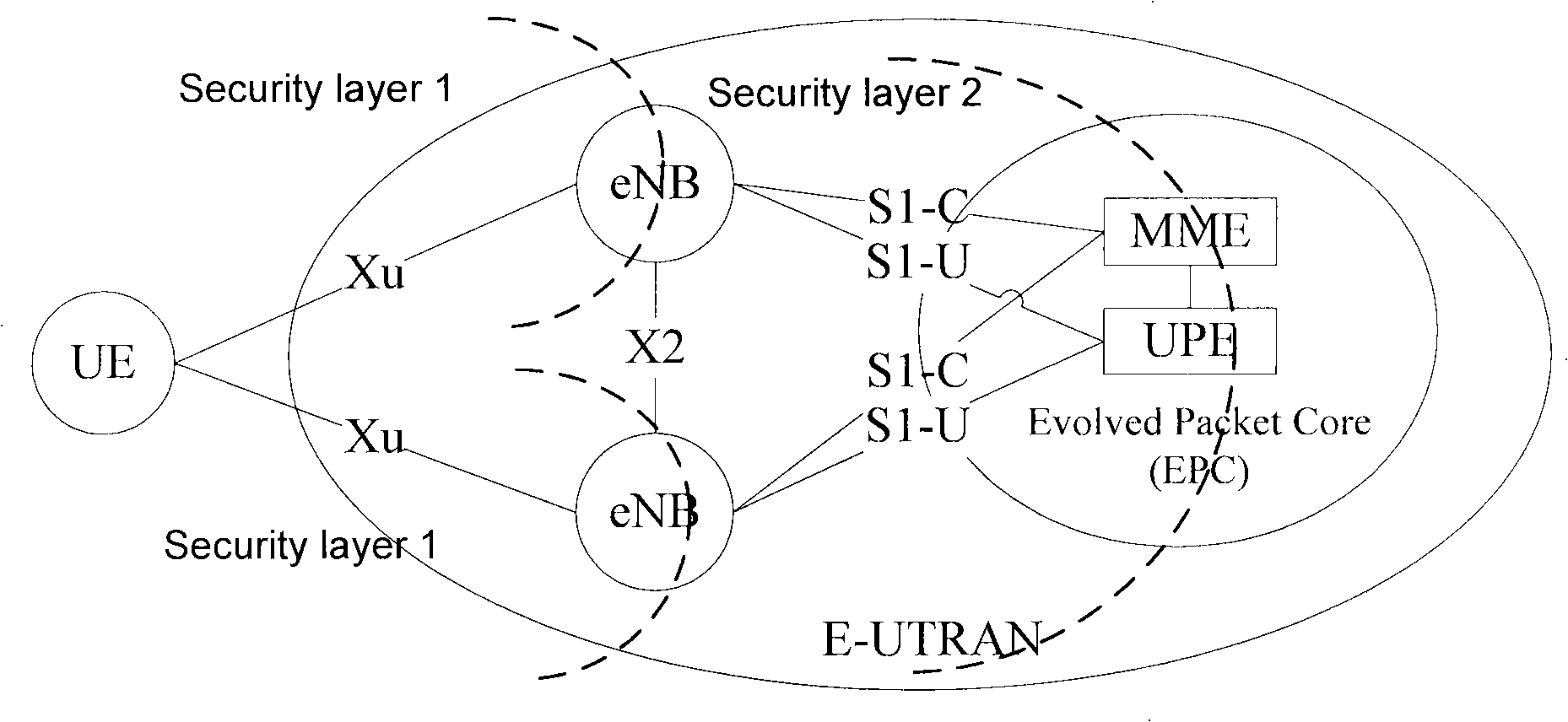
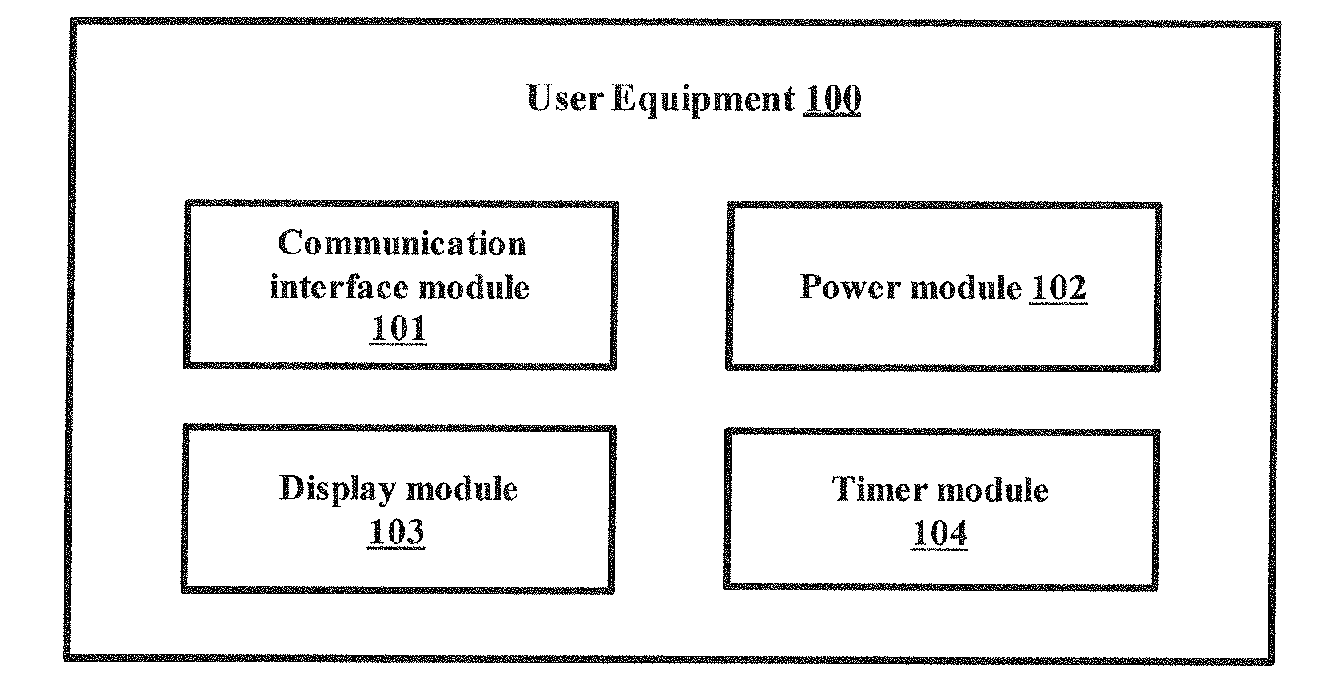
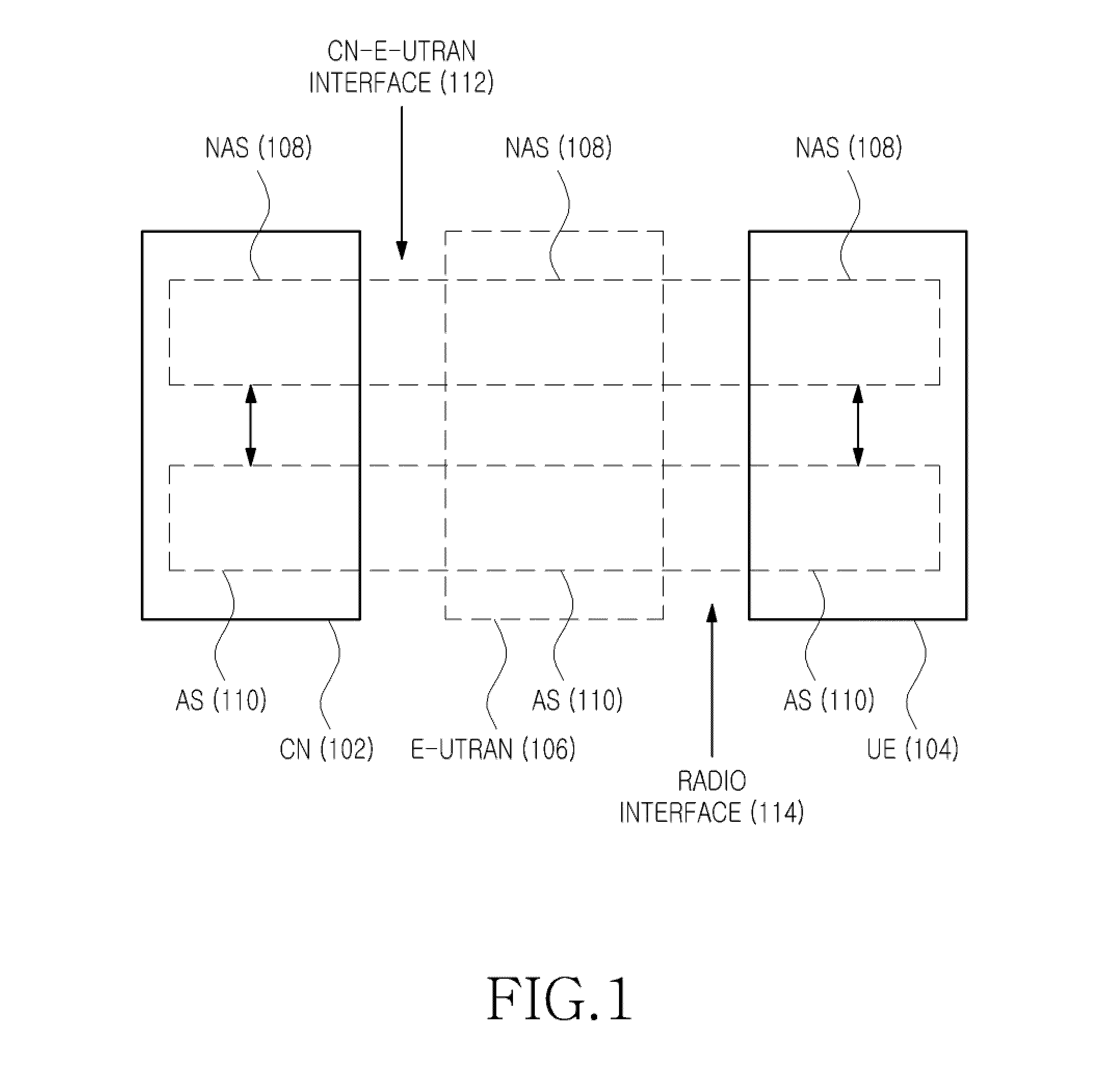
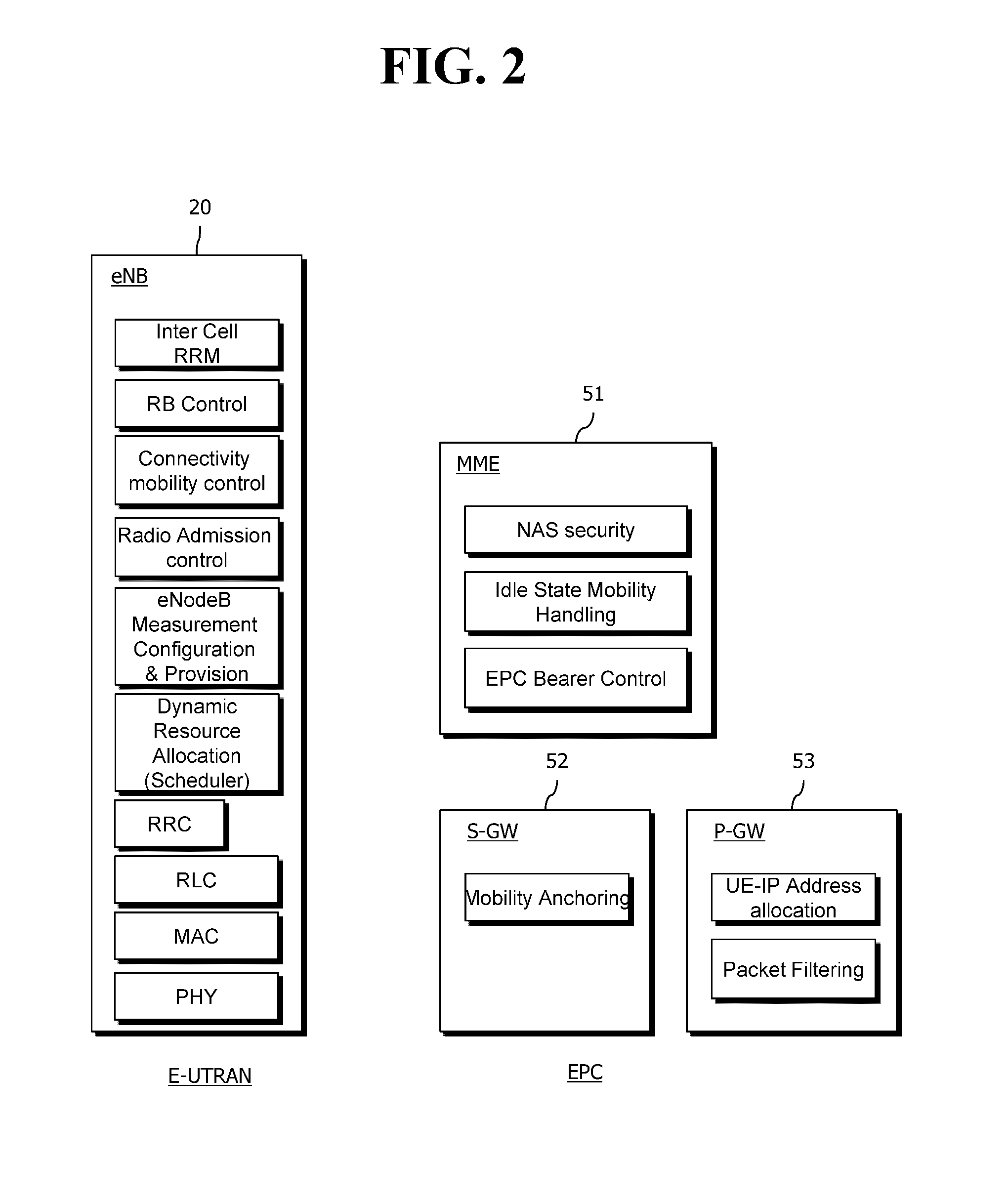
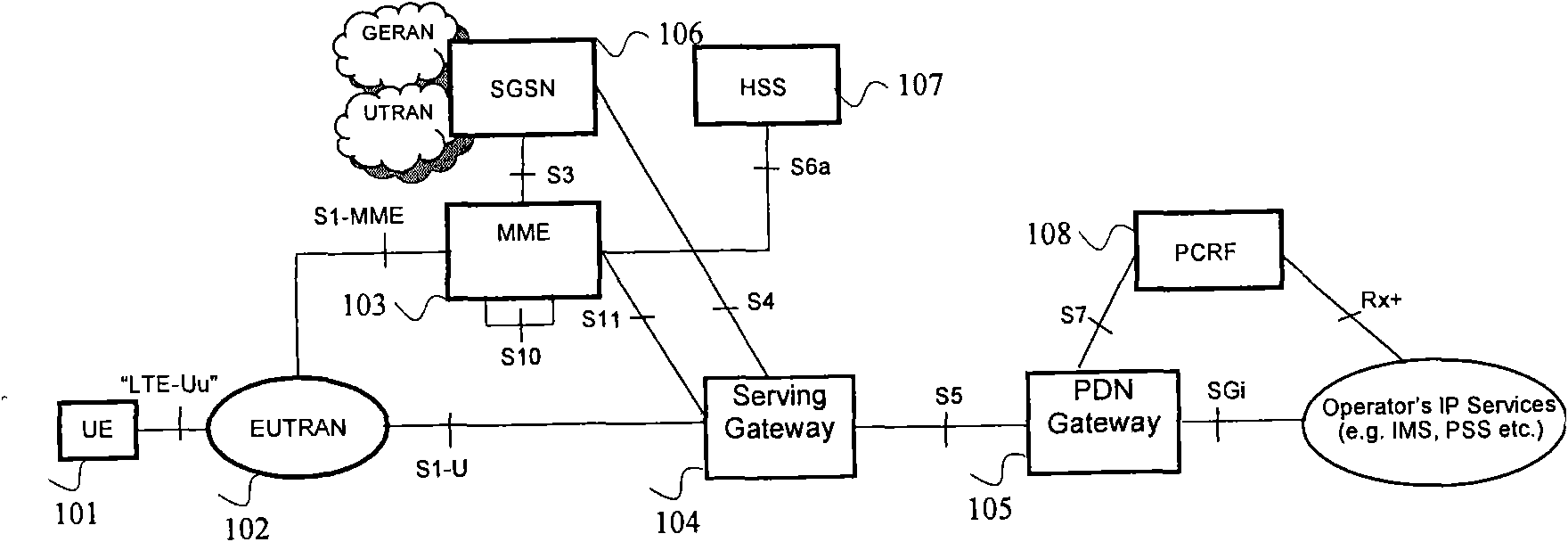
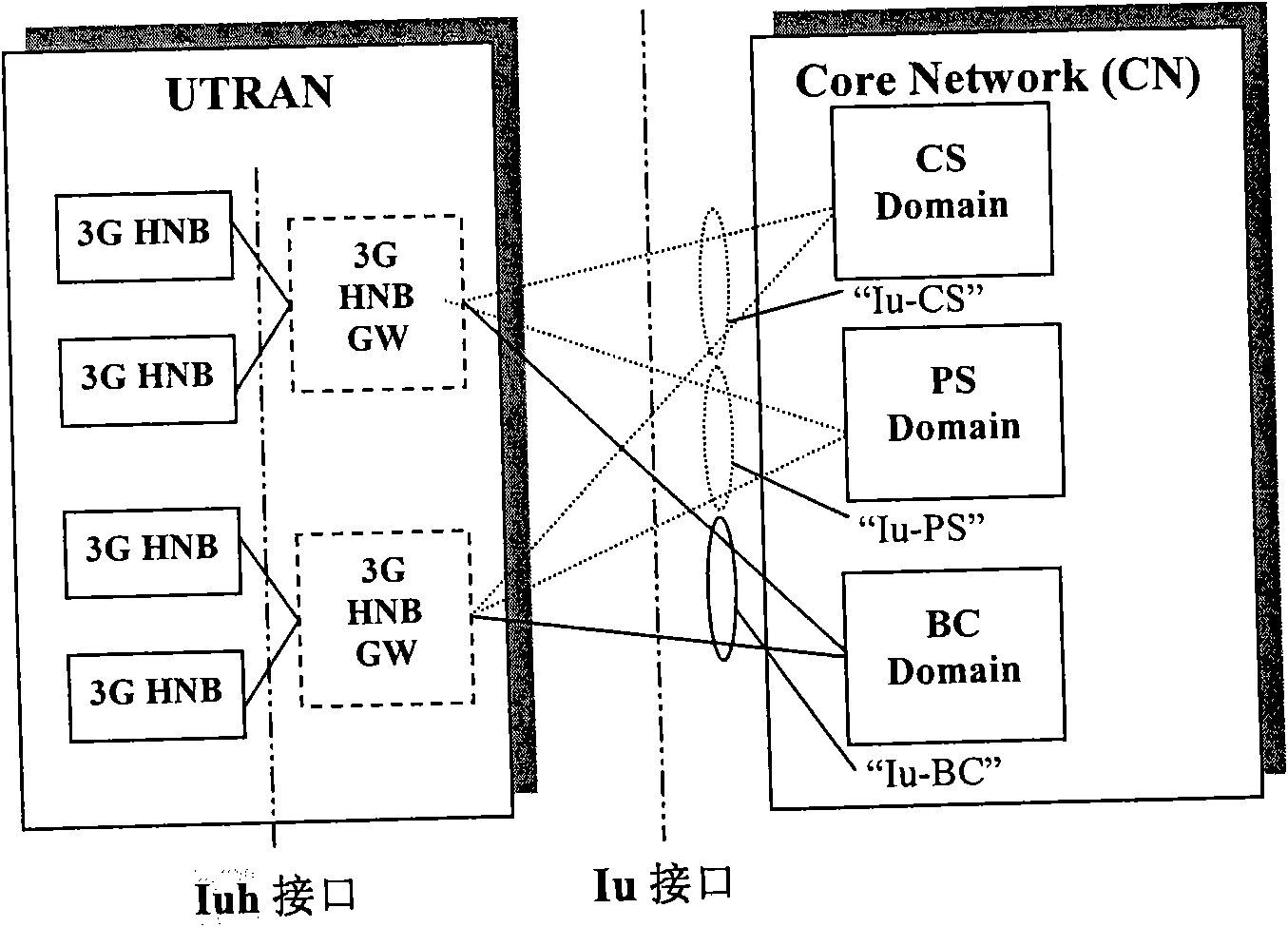
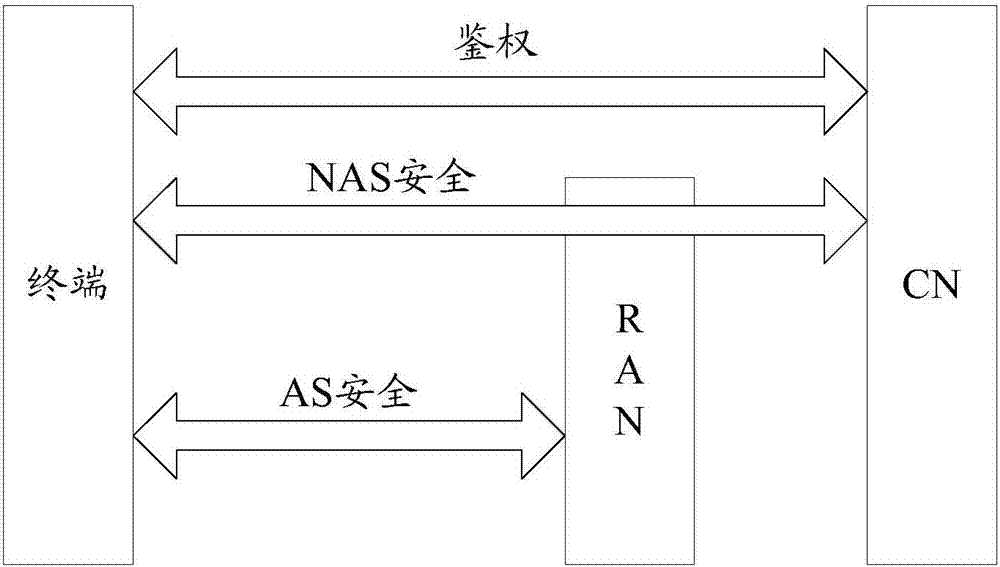
The access stratum (AS) is a functional layer in the UMTS and LTE wireless telecom protocol stacks between radio network and user equipment. While the definition of the access stratum is very different between UMTS and LTE, in both cases the access stratum is responsible for transporting data over the wireless connection and managing radio resources. The radio network is also called access network.
Method, Apparatus and Computer Program Product For Handover Failure Recovery
ActiveUS20100238799A1Fail to recoverImprove handoverError preventionFrequency-division multiplex detailsRadio link failuresComputer science
An apparatus for facilitating handover failure recovery may include a handover management element configured to receive, at a target node, a handover request from a source node regarding the handover of communications with a mobile terminal. The handover request may include identity information indicative of the mobile terminal. The identity information may be the identity information used to identify the mobile terminal to the source node during establishment of the original connection between the source node and the mobile terminal. The handover management element may be further configured to receive a request for a connection from the mobile terminal subsequent to a radio link failure and prior to handover completion. Based on matching the identity information from the request for connection and the identity information received from the source node, the target node may establish communication with the mobile terminal based on access stratum configuration information used by the source node.
Owner:NOKIA TECHNOLOGLES OY
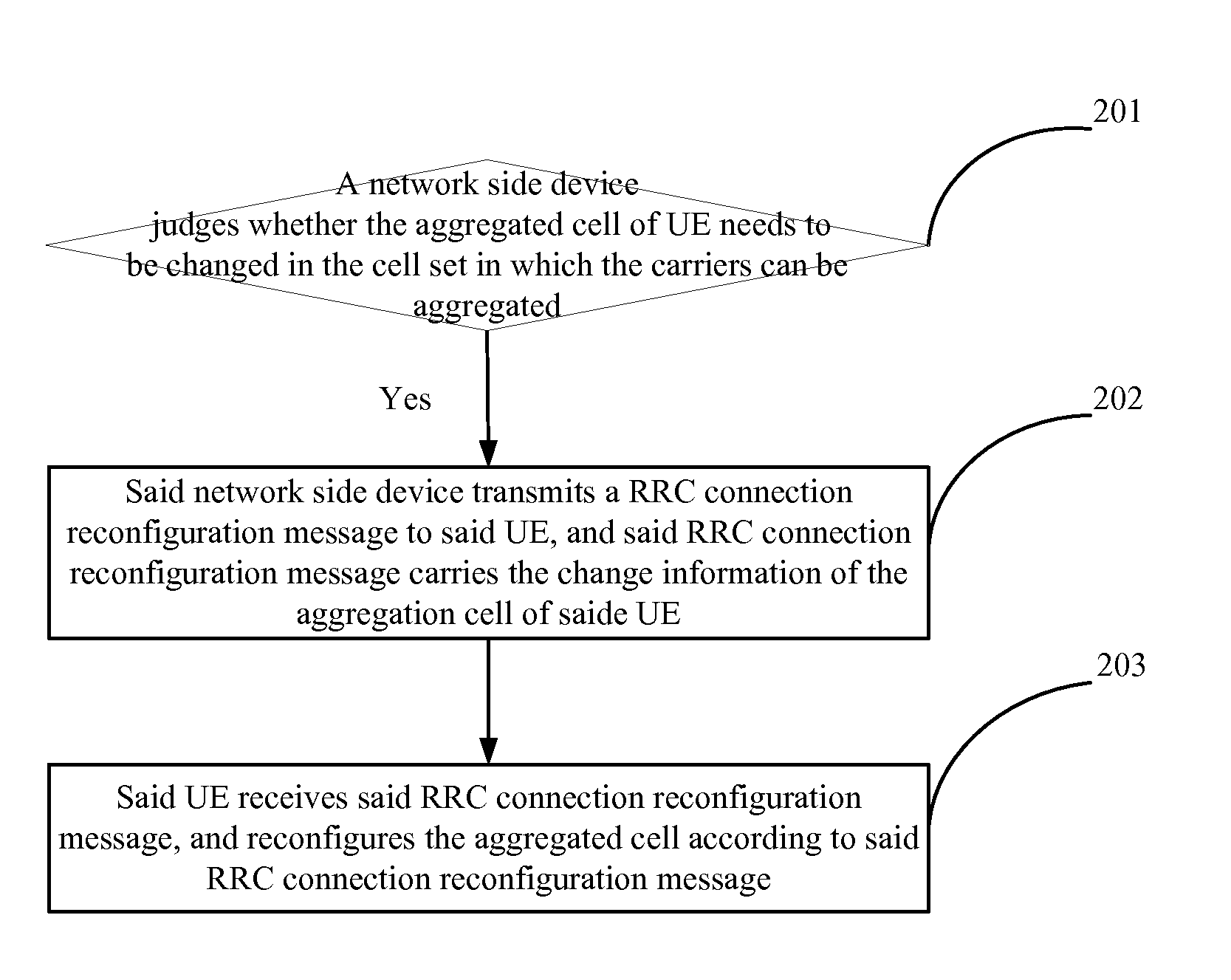
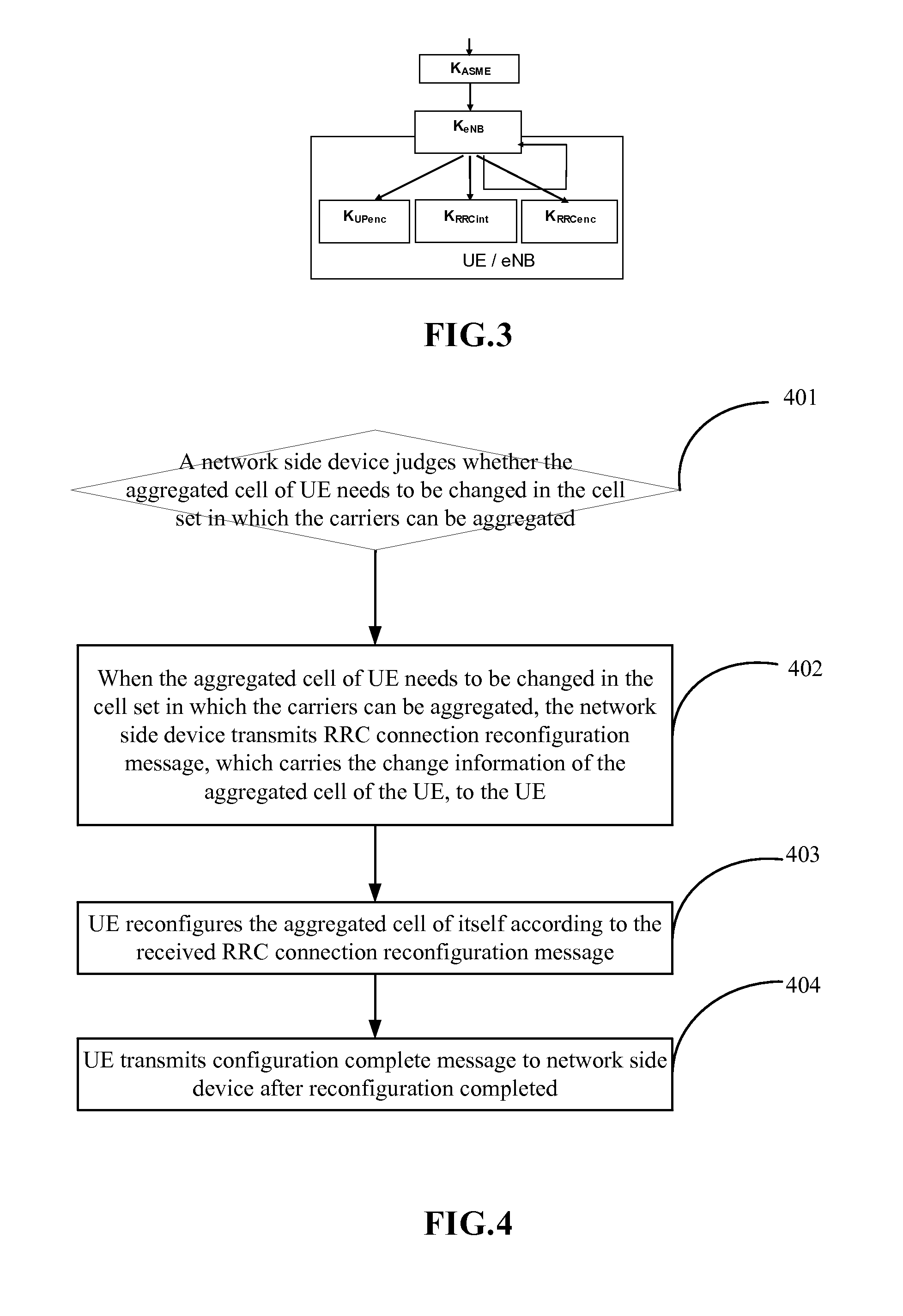
Method, Device and System for Reconfiguring Aggregation Cell
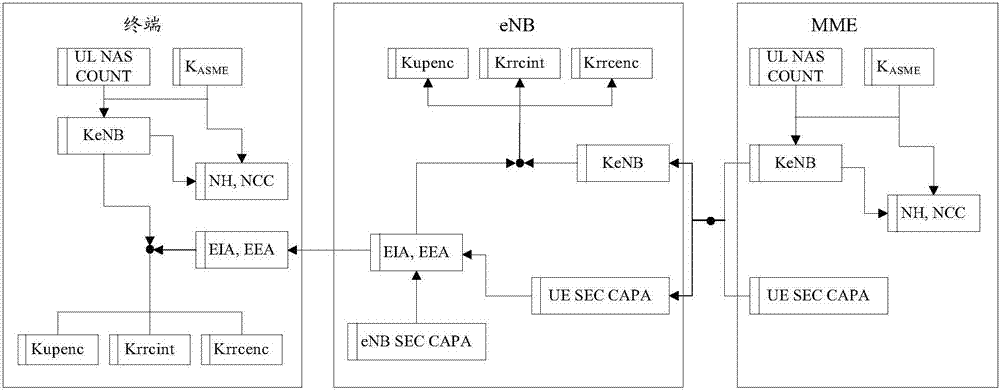
The present invention provides a method for reconfiguring an aggregated cell, which includes that: a network side device judges whether the aggregated cell of a user equipment (UE) needs to be changed in the cell set in which the carriers can be aggregated; when the judgment result is that the change is needed, the network side device transmits a radio resource control (RRC) connection reconfiguration message to the UE, and the RRC connection reconfiguration message carries the change information of the aggregated cell of the UE; the UE receives the RRC connection reconfiguration message, and reconfigures the aggregated cell according to the RRC connection reconfiguration message. In the present invention, for the LTE-A system, when the aggregated cell of UE which supports the carrier aggregation changes within the same cell set in which the carriers can be aggregated, the aggregated cell of the UE can be reconfigured; and the same access stratum (AS) key is used to perform the security processing procedure for the data, which enables the uninterrupted transmission for the data.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Granular network access control and methods thereof
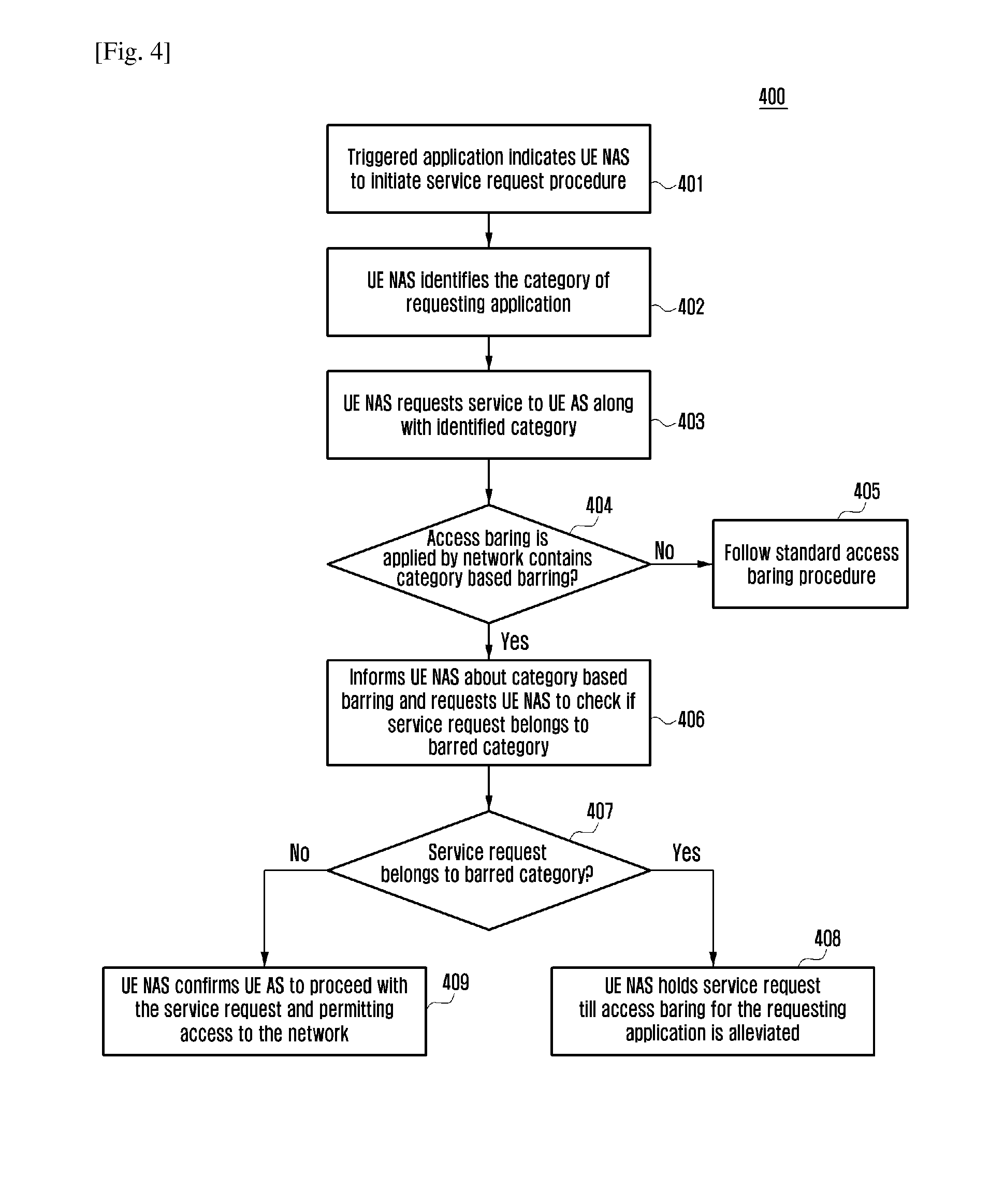
A method and system that enhances the existing access barring mechanism as specified in the current 3GPP specification is disclosed. The method disclosed provides enhancing the access barring mechanism to accommodate application level barring between the User equipment (UE) and the network. The method disclosed individually restricts or permits access of network to every requesting application on the UE, based on granular category of the application and priority levels of the application within the granular category. The method disclosed also specifies handling of back-off timers; reject cause values and Access Point Name (APN) configuration by Access Stratum (AS) and Non Access Stratum (NAS) layer to support application level barring of UEs using the enhanced access barring mechanism. The enhanced access barring mechanism enables providing service to applications independent of other barred applications or priorities. The method disclosed provides a mechanism for access control for connected mode UEs.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for supporting multiple frequency bands efficiently in mobile communication system
ActiveUS20130044708A1Reduce signaling overheadNetwork traffic/resource managementConnection managementData radio bearerTransfer procedure
A method and an apparatus for transmitting a small size data packet efficiently while reducing signaling overhead in a mobile communication system are provided. The method includes determining to apply a low security transfer procedure, transmitting, to a base station, a Radio Resource Control (RRC) connection request message including a temporary Data Radio Bearer (DRB) request to which Access Stratum (AS) security is not applied, receiving an RRC connection setup message, including a temporary DRB configuration, from the base station, and transmitting an Internet Protocol (IP) packet over the temporary DRB.
Owner:SAMSUNG ELECTRONICS CO LTD
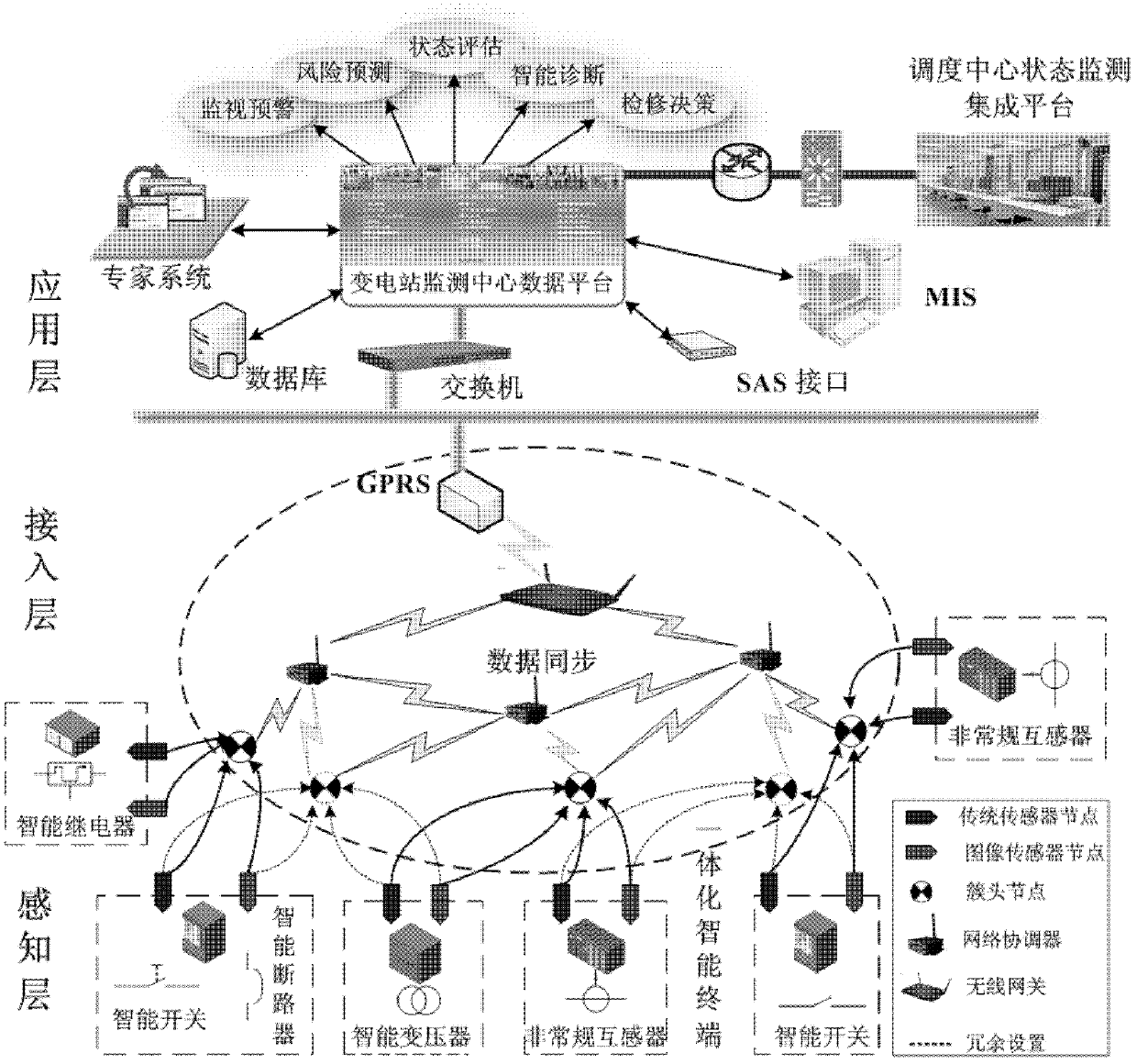
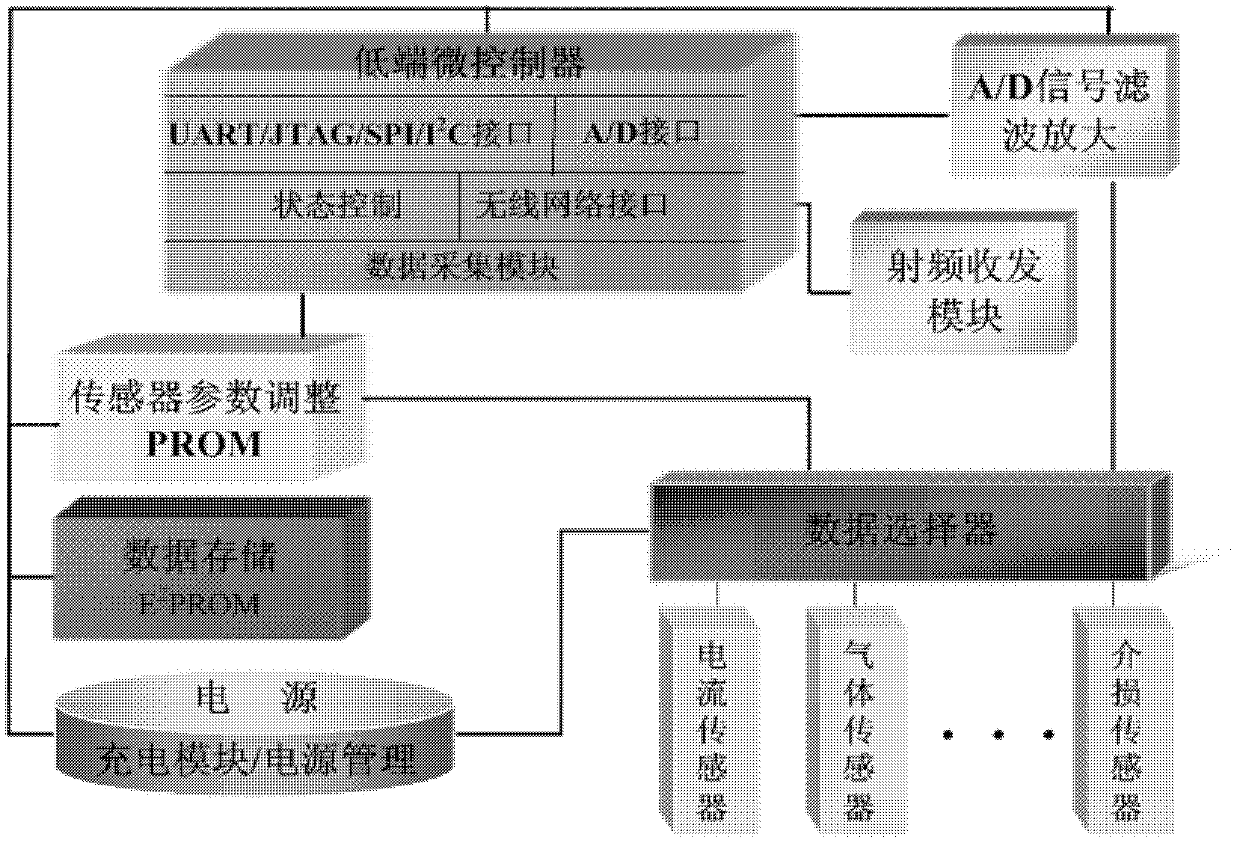
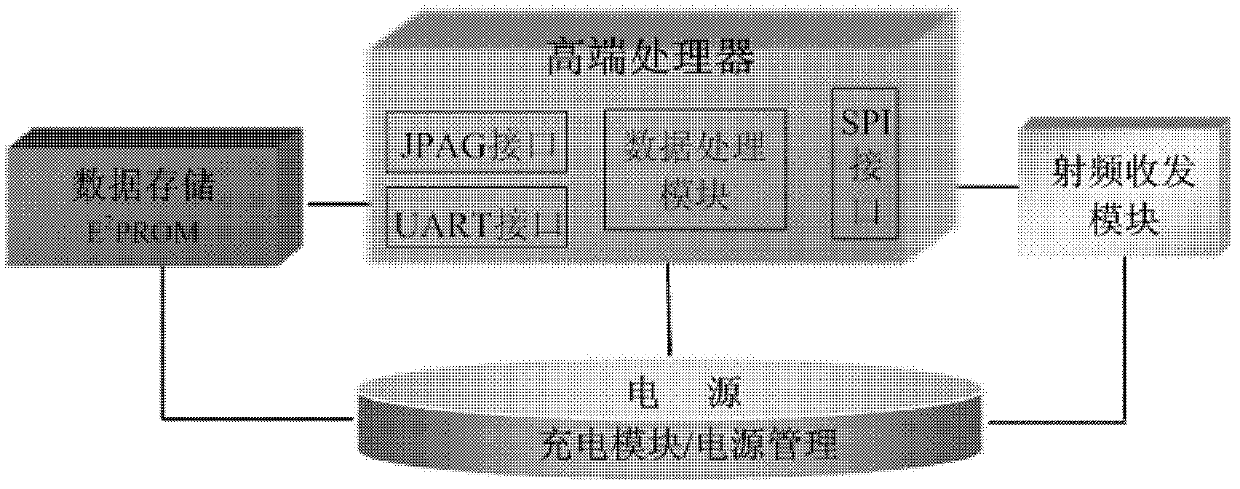
Wireless intelligent sensor network system for monitoring states of intelligent substation devices
InactiveCN103124105AEasy to integrateEasy to analyzeCircuit arrangementsInformation technology support systemSmart substationNetworked system
The invention relates to a wireless intelligent sensor network system for monitoring states of intelligent substation devices. The system is overall divided into a transformer substation level state monitoring system and a dispatching center level state monitoring system, the transformer substation level state monitoring system is divided into a sensing layer, an accessing layer and an application layer, an intelligent sensor on the sensing layer is responsible for collecting image and scalar data, and transmitting information to a monitoring center platform on the application layer through the accessing layer, and key information is transmitted to a dispatching center monitor integration platform through an electric power data communication network. A self-organization and self-recovery wireless substation device monitoring network is established to replace traditional wired ways, so that hierarchical distribution co-processing of data is achieved, communication load balancing capacity of the monitoring network is improved, wiring difficulties of installation are reduced, installation costs of transformation and upgrade of the substation devices are reduced, flexibility and use ratio of the monitoring network system are enhanced, overall assessment of operation conditions of the substation devices is enhanced, and fault hidden dangers of the devices can be timely found and eliminated.
Owner:HUNAN UNIV
Terminal access control processing method and device
InactiveCN102892177AEasy to handleSimplify configuration parametersAssess restrictionTelecommunicationsAccess time
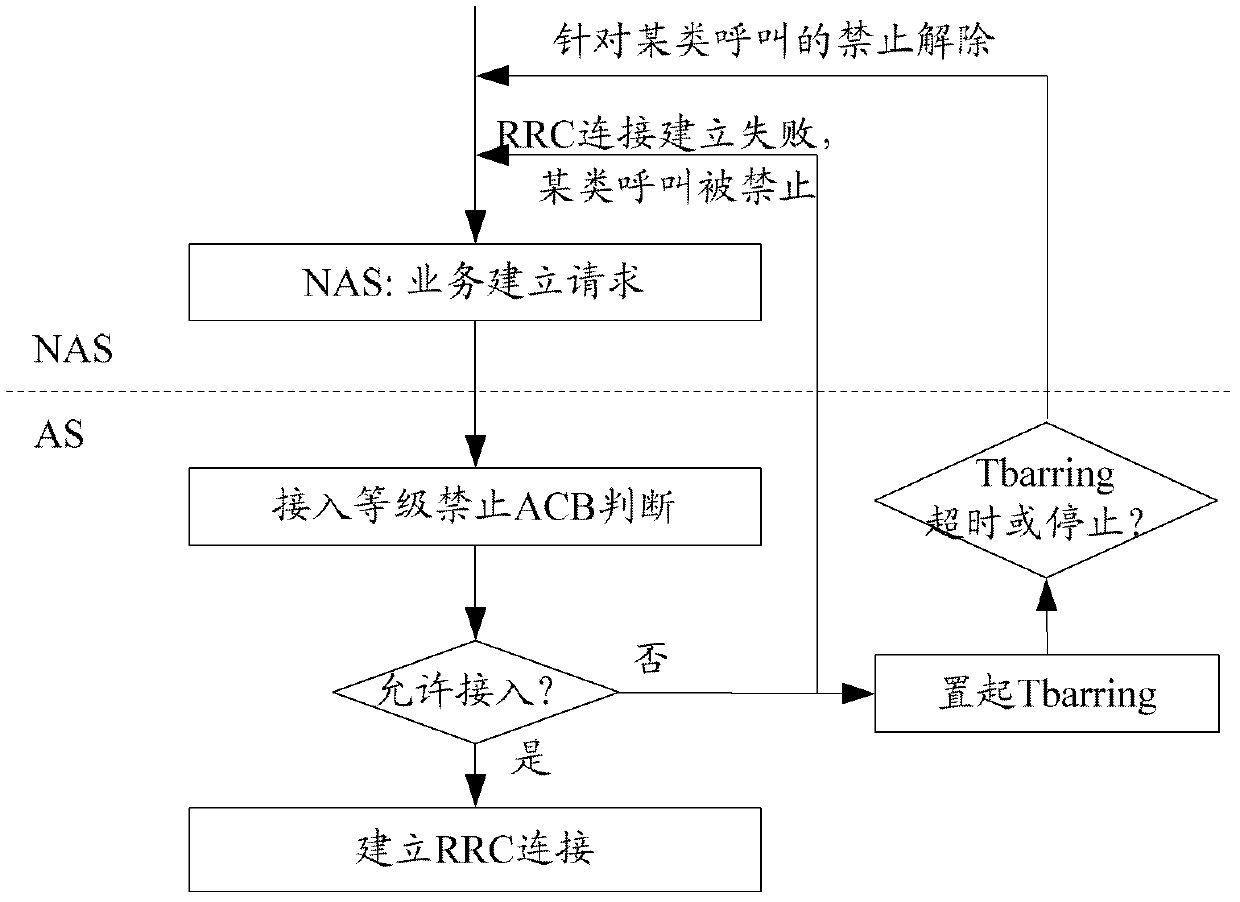
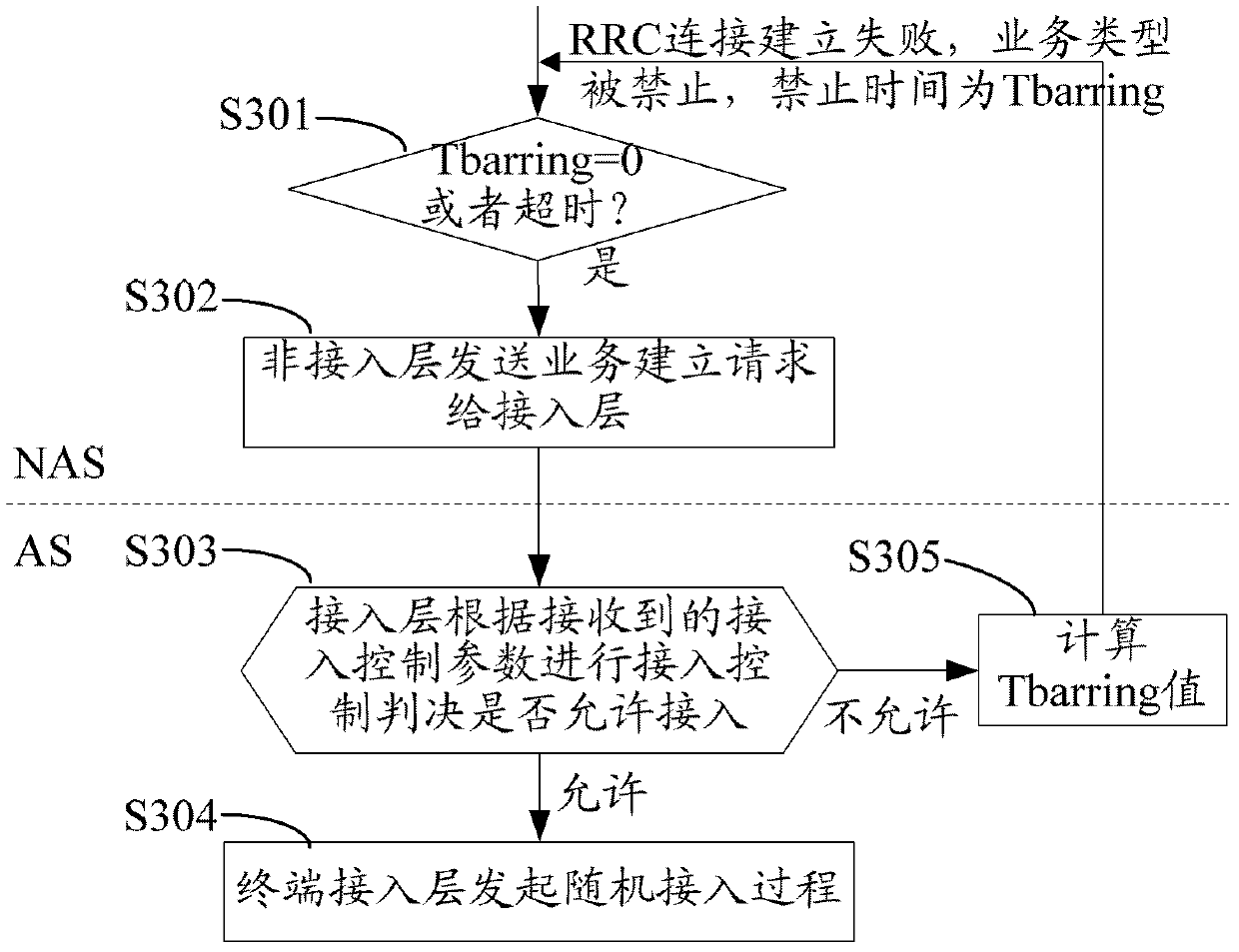
The invention discloses a terminal access control processing method and device, solving the problem of causing a terminal to initiate connection establishment for similar other services owing to the fact a barred access timer stops due to other reasons of an access stratum when the barred access timer is maintained by the access stratum. According to the terminal access control processing method and the terminal access control processing device, an access decision is executed by a terminal access stratum; when the access decision is to bar access, barred access time is further calculated, and an non-access stratum is informed with the unsuccessful establishment of an RRC (radio resource control) connection and the size of the barred access time; another barred access timer is maintained by the non-access stratum of the terminal; and before the barred access timer is time-out, the non-access stratum of the terminal no longer initiates establishment requests of similar other services. According to the terminal access control processing method and the terminal access control processing device, the terminal processing process and the network configuration parameters can be simplified.
Owner:ZTE CORP
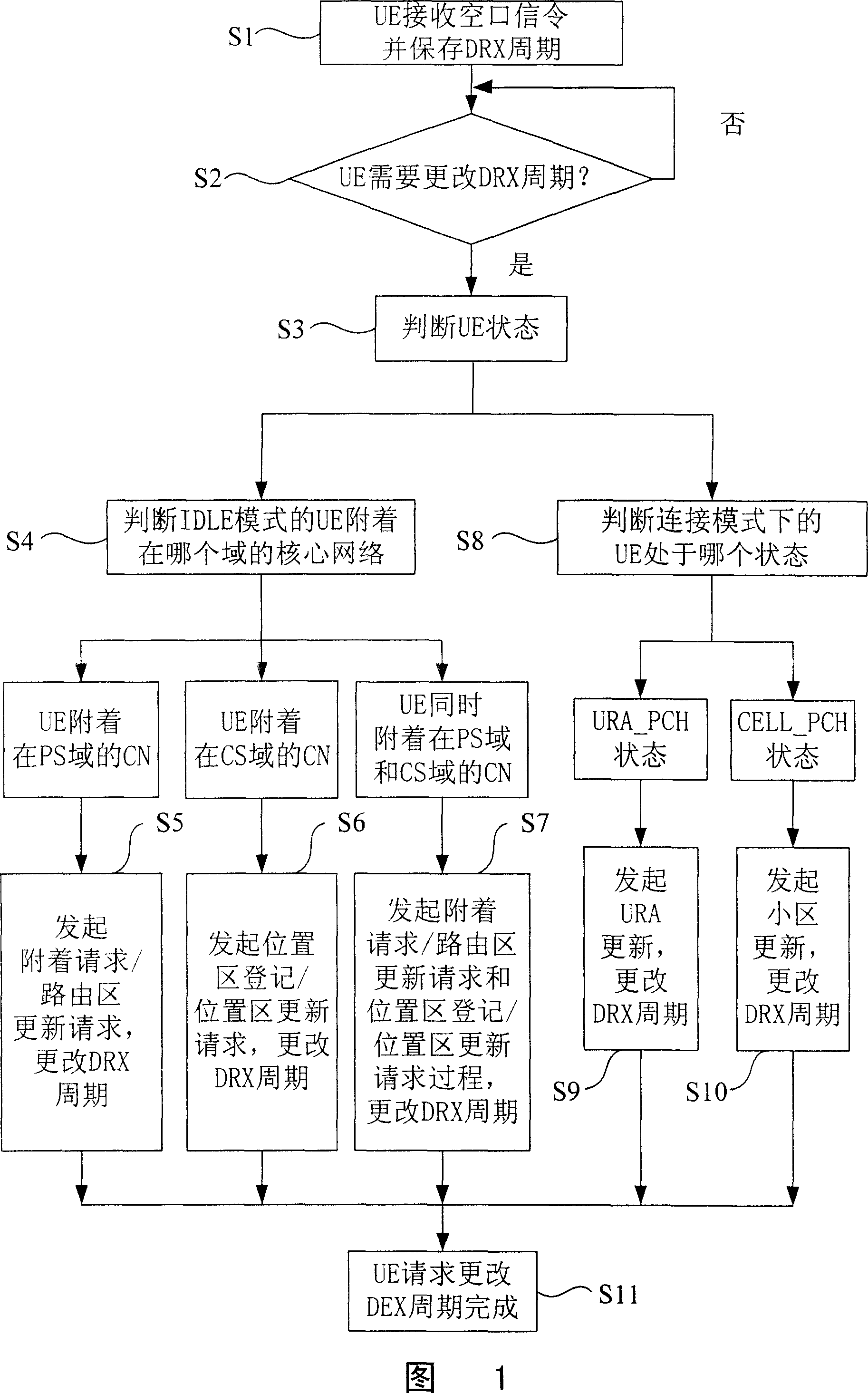
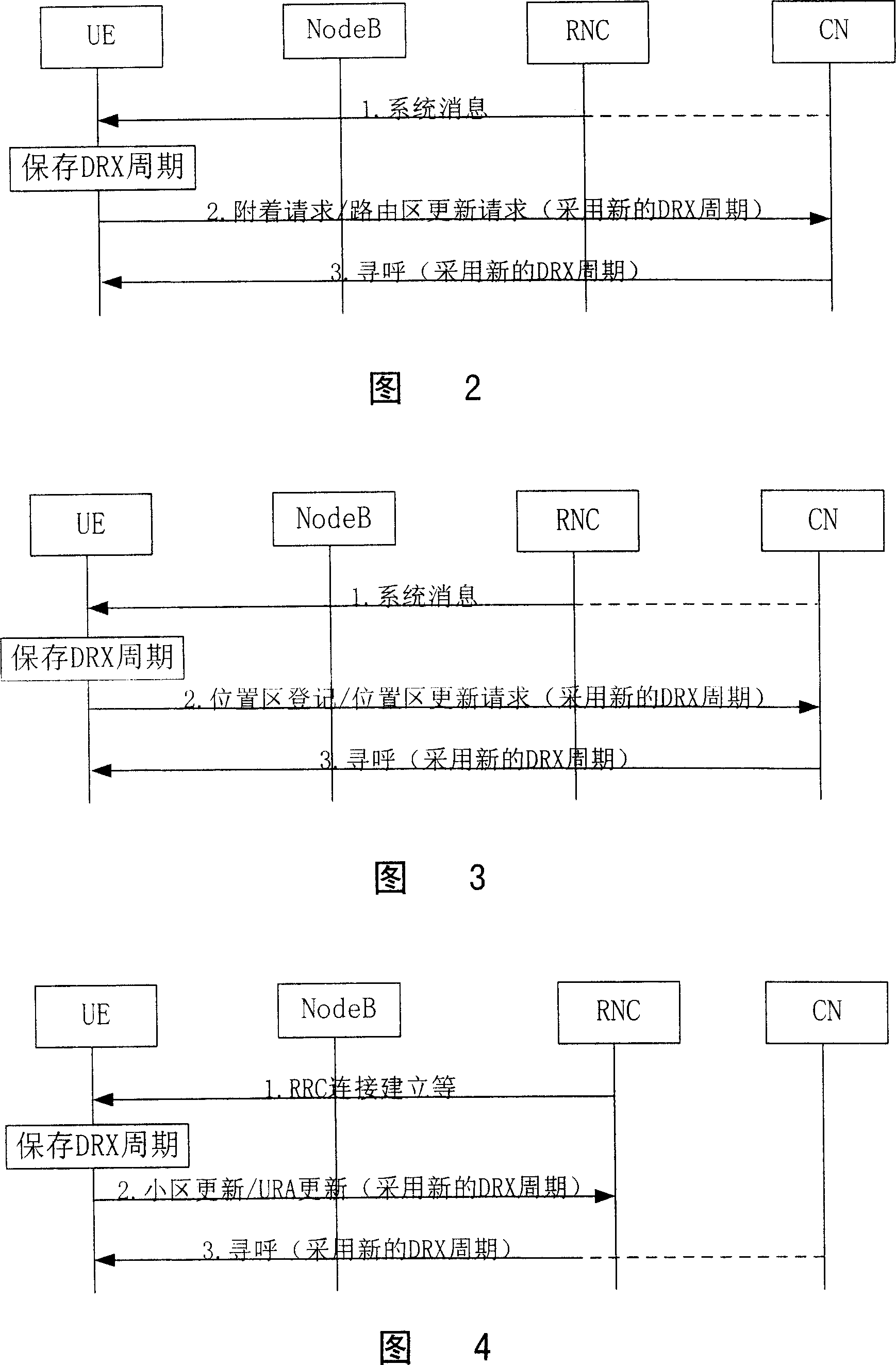
Method for negotiating DRX period in mobile communication system
ActiveCN101111051ANetwork traffic/resource managementConnection managementMobile communication systemsAccess stratum
The present invention discloses a method for negotiating a DRX cycle in a mobile communication system, which enables a user terminal to perform the negotiation of the DRX cycle with a core network and a UTRAN within the max. scope. The technical proposal is that the present invention adds a cell in an update message of a signaling through modifying the signaling in a Non Access Stratum or the signaling in an Access Stratum according to the condition located by the user terminal, to indicate the utilized DRX cycle expected by the user terminal. And, the expansion can be performed to the periodic scope of the DRX. The present invention applies to the paging mechanism realization of a mobile communication system.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
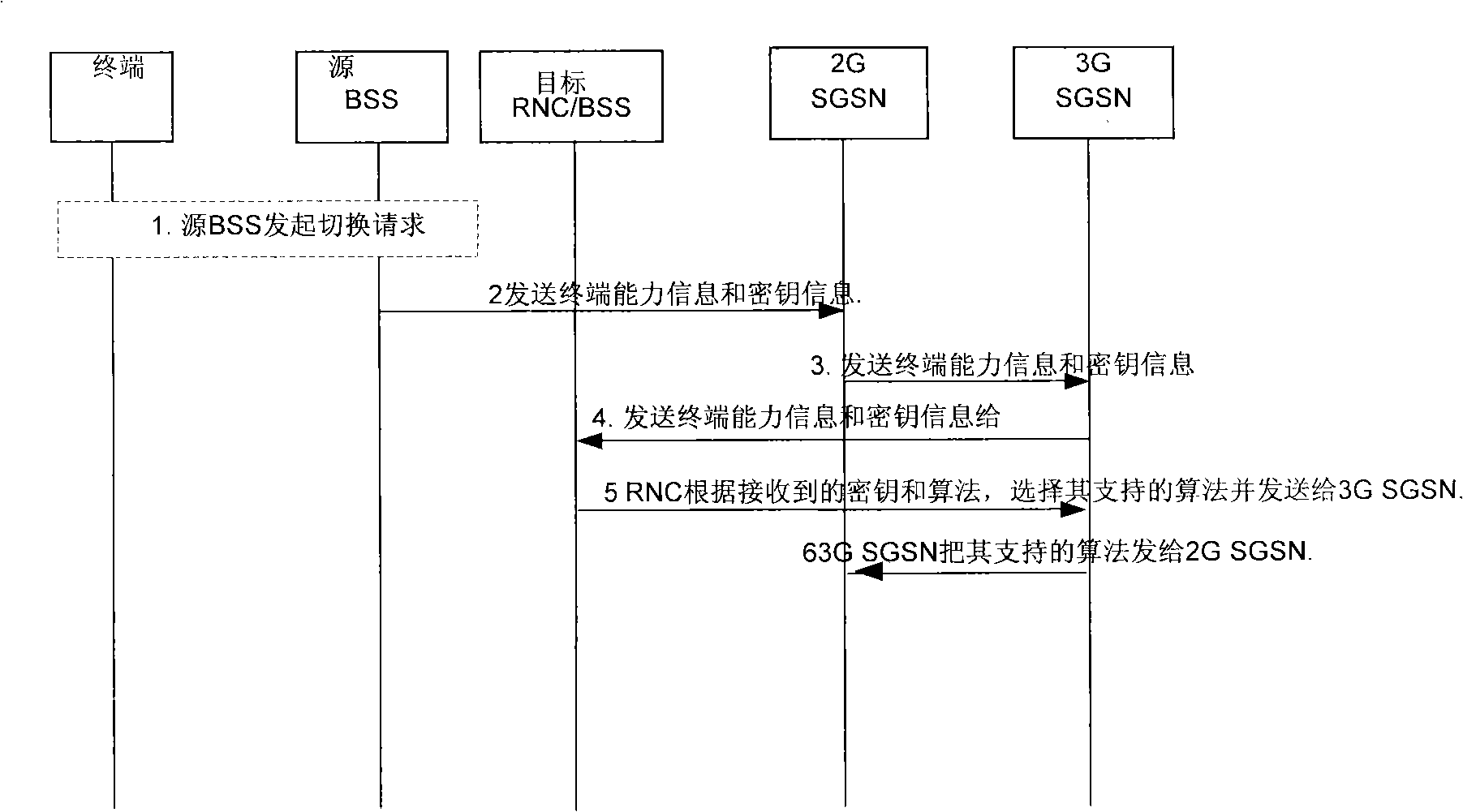
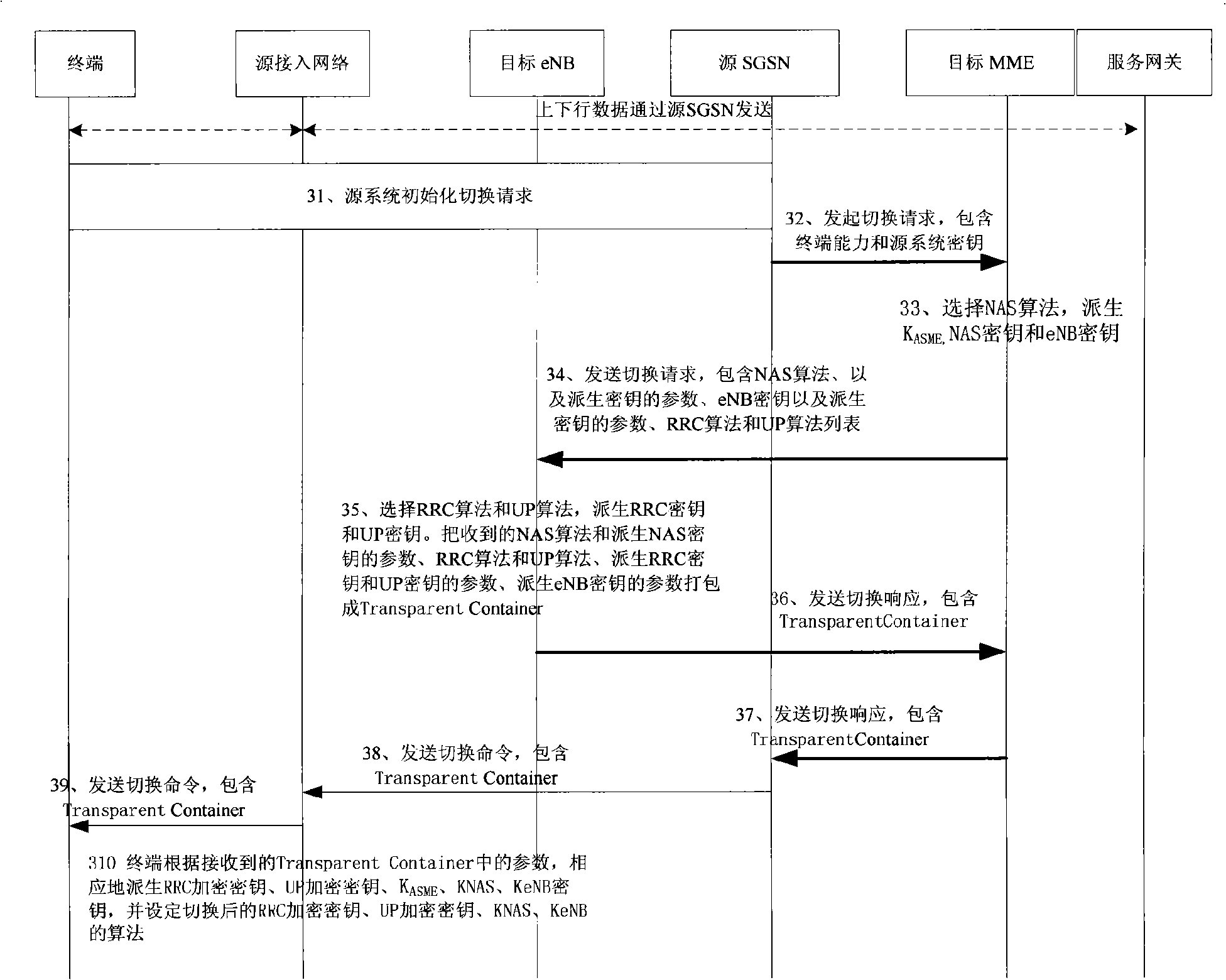
Security negotiation method and apparatus when switching between different wireless access technologies
ActiveCN101309500AEstablish Security AssociationKey distribution for secure communicationMultiple keys/algorithms usageAccess networkAccess technology
The embodiment of the invention provides a method for security negotiation when switching is performed among different wireless access technologies, and the device thereof. The method mainly comprises that the security information of an NAS (non access stratum) and an AS (access stratum) which are selected by a target system is included in a transparent container when the terminal performs switching among different wireless access technologies; the content in the transparent container is transmitted to the terminal, and the terminal performs security negotiation according to the content in the transparent container and the target system. The device mainly comprises an eNB (eNB) equipment and a resource access network equipment. Through the invention, when the foreign system is switched to the LTE (long term evolution) system at the terminal, the terminal can obtain the parameter information of the cryptographic keys of the NAS and the AS selected by the LTE system, and performs security negotiation with LTE system.
Owner:HUAWEI TECH CO LTD
Synchronization, scheduling, network management and frequency assignment method of a layered wireless access system
InactiveUS20110122769A1Improve synchronicitySmooth upgradeError preventionFrequency-division multiplex detailsManagement unitNetwork management
The present invention discloses as synchronization method of a layered wireless access system, which is applied to the layered wireless access system including an access point management unit located in an access layer and its linked access points. The access point management unit has a timing server, each access point having a timing client. The timing server generates timing information and distributes it to the timing client of each linked access point, and the timing client recovers the timing information as a local timing reference signal. The method may implement clock synchronization between the access point management unit and the access points to ensure the normal operation of the system. The present invention also provides network management, scheduling, frequency assignment and flow control methods based on the layered wireless access system.
Owner:ZTE CORP
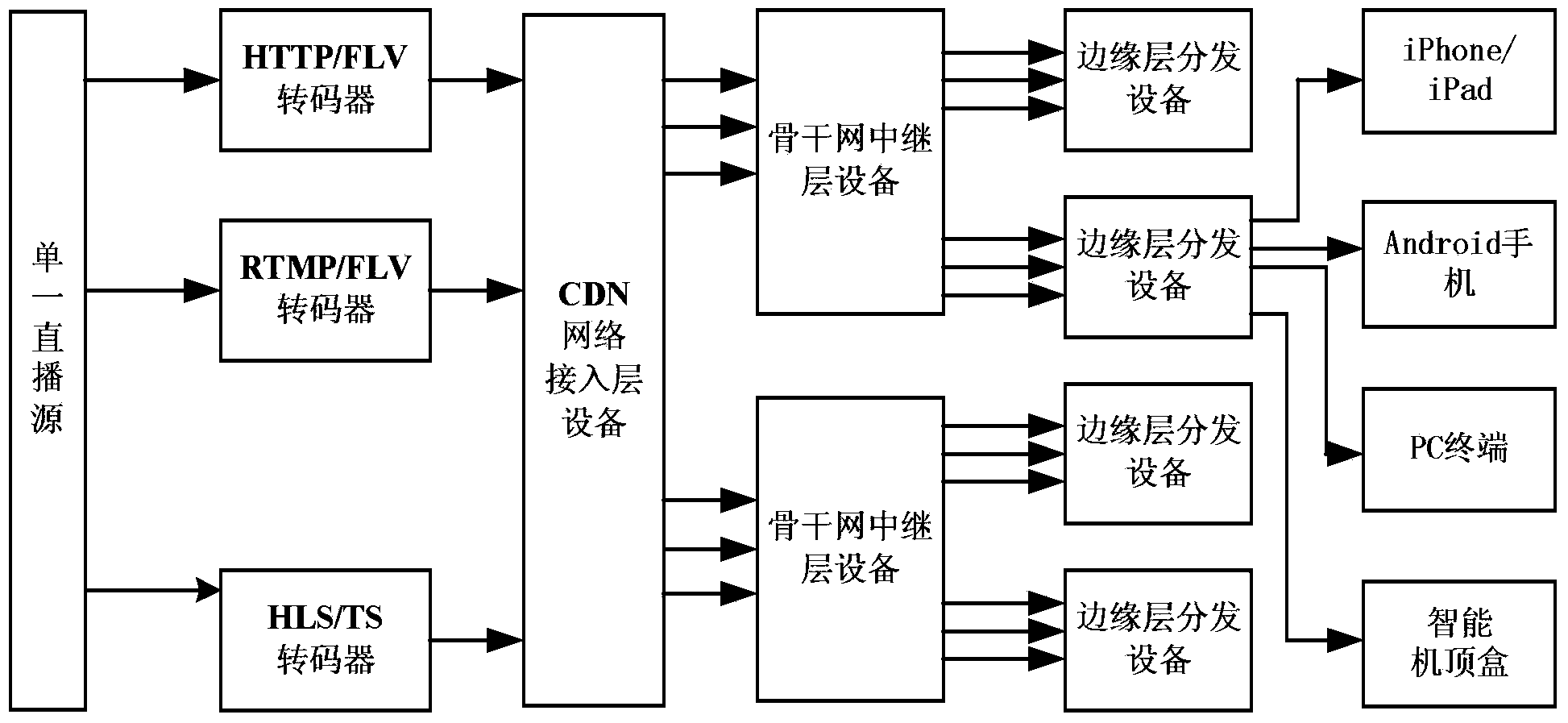
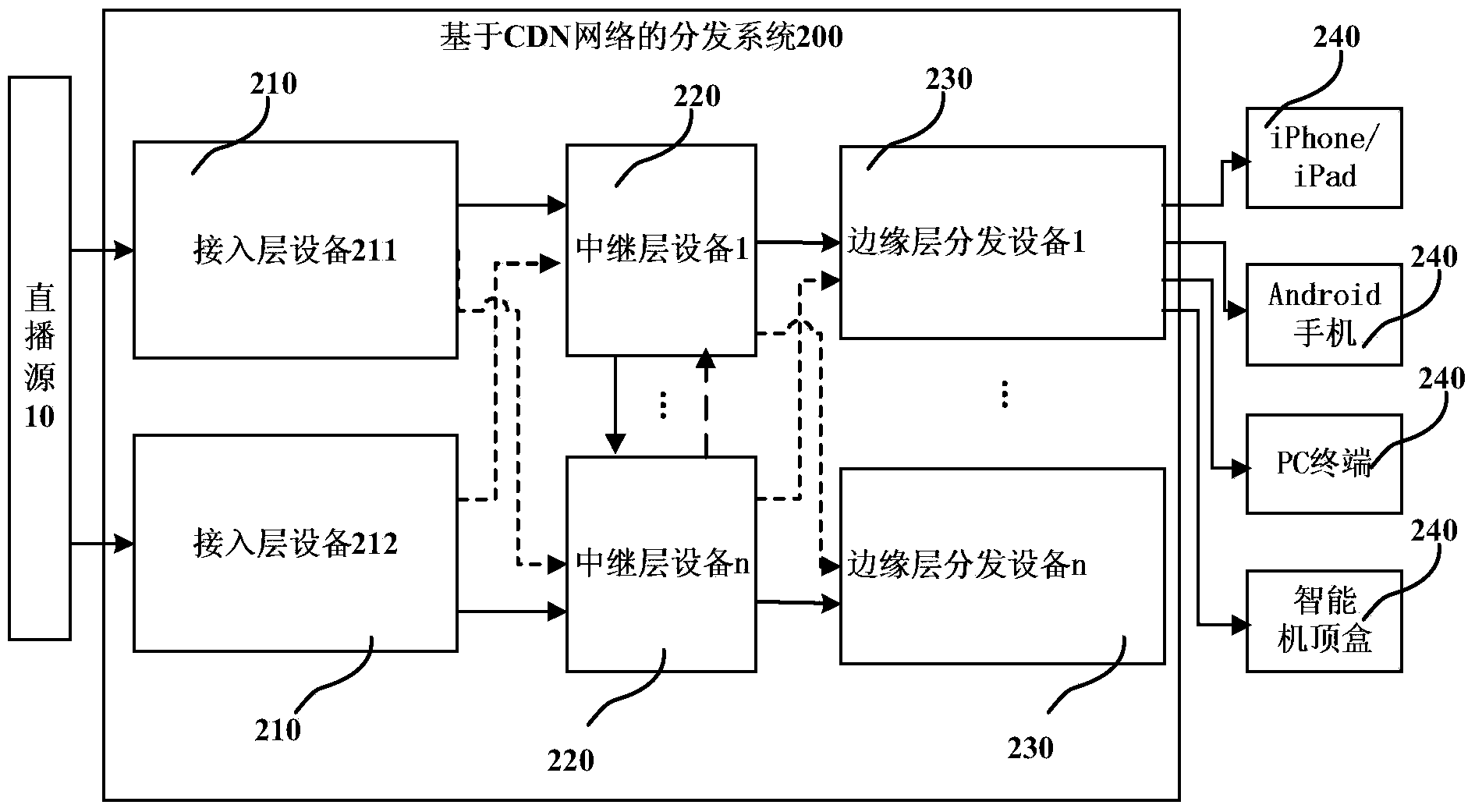
Data distribution system and method based on CDN (content distribution network)
InactiveCN103986942AReduce bandwidthReduce trafficSelective content distributionTransmission protocolContent distribution
The invention discloses a data distribution system based on a CDN (content distribution network). The data distribution system comprises an access layer device, one or more relay layer devices and one or more margin layer distribution devices, wherein the access layer device is suitable for receiving a broadcasting data packet from a broadcasting source and converting the broadcasting data packet to a transmission data packet of a predetermined format; each relay layer device is suitable for performing relay transmission on the transmission data packet of the predetermined format converted by the access layer device through a uniform transmission protocol; each margin layer distribution device is suitable for receiving the transmission data packet of the predetermined format after relay transmission performed by each relay layer device and converting the transmission data packet of the predetermined format to a data packet of a terminal broadcasting protocol according to a terminal request and distributing the data packet to the terminal. The invention also provides a data distribution method based on the CDN. By utilizing the data distribution system and the data distribution method, the reliability of live stream can be greatly improved, and the transmission efficiency among backbone networks also can be greatly improved.
Owner:BEIJING SOOONER TECH DEV
Indicating radio capability changes in an inactive state
Apparatuses, methods, and systems are disclosed for indicating radio capability changes in an inactive state. One method includes detecting a trigger to change radio capabilities of a UE in an inactive state; transmitting a first message comprising information indicating to change the radio capabilities of the UE, wherein the first message comprises a first access stratum message; receiving a second message, wherein the second message comprises information corresponding to an action, and the second message comprises a second access stratum message; receiving a third message comprising information requesting the radio capabilities of the UE; transmitting a fourth message comprising the radio capabilities of the UE; and receiving a fifth message comprising information for configuring a radio resource control of the UE and activating data radio bearers of the UE, wherein the fifth message is determined based on the radio capabilities of the UE.
Owner:LENOVO (SINGAPORE) PTE LTD
Method and system for selective access control with ensured service continuity guarantees
ActiveUS20150055447A1Error preventionFrequency-division multiplex detailsTelecommunicationsAccess stratum
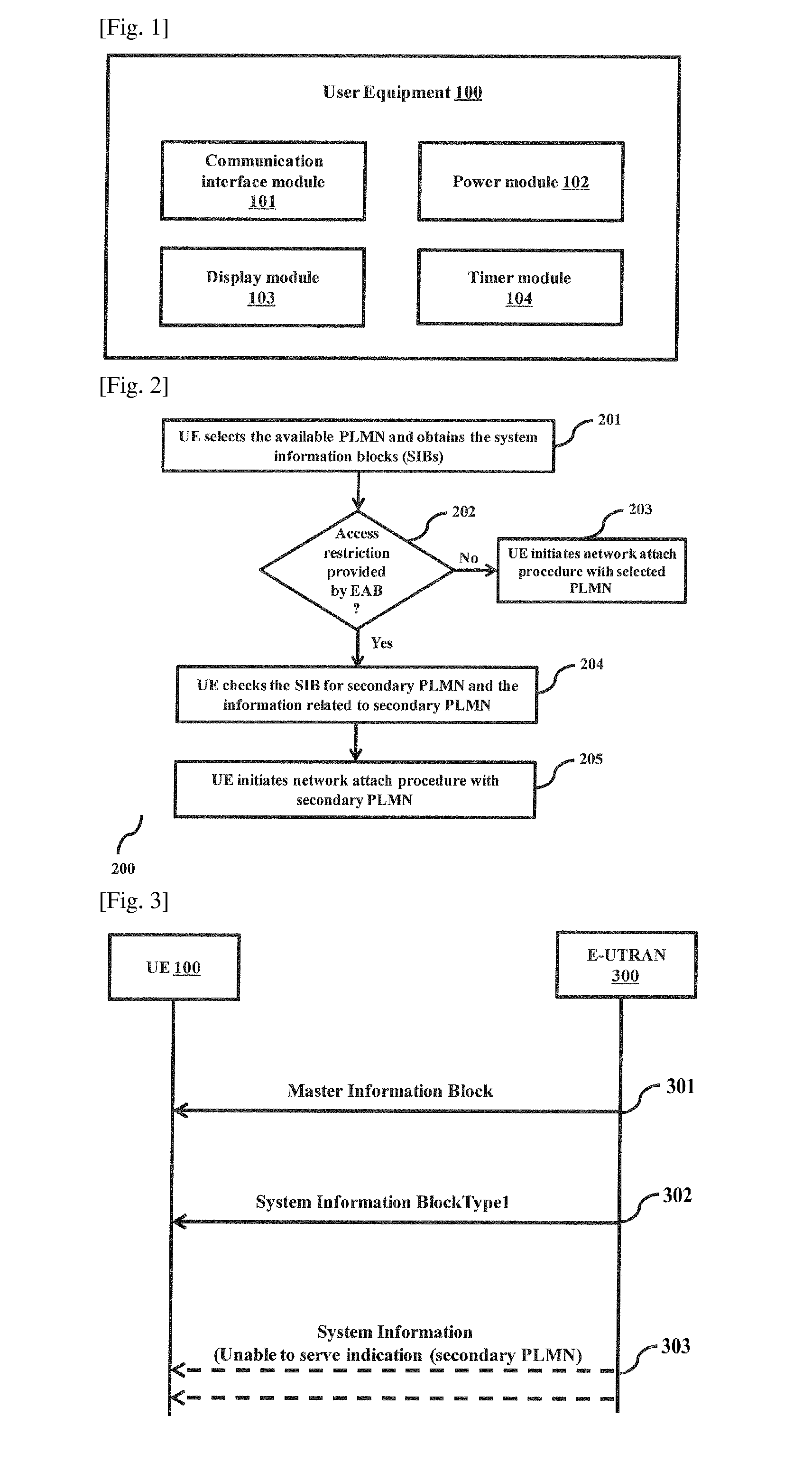
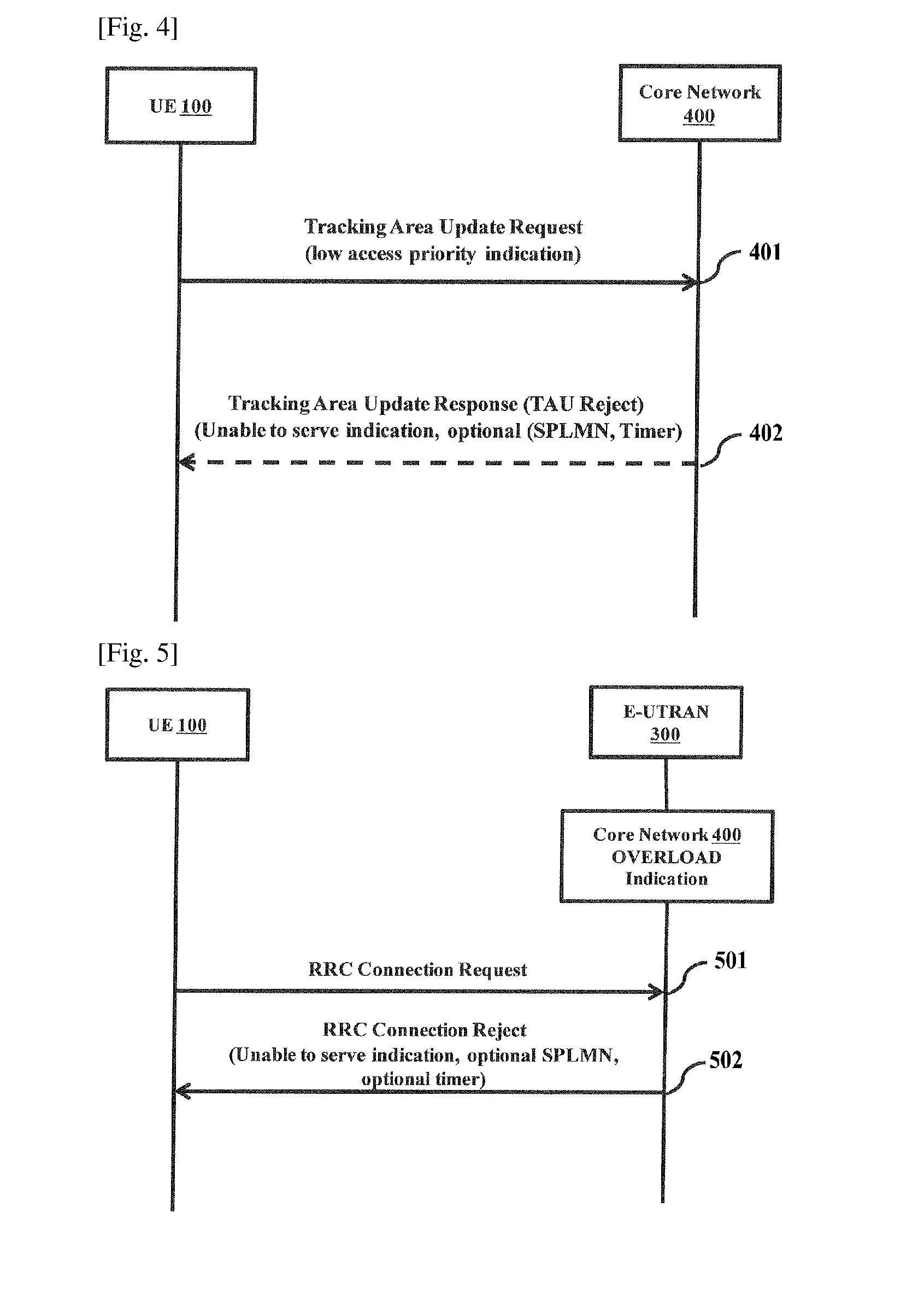
A method and system for providing a continued service to user equipment (UE) under overload conditions is disclosed. A primary network undertakes a protective measure under unable to serve conditions by commanding a change in the UE network access behavior so that the UE can move to the secondary PLMN. After receiving the indication from the primary network, the UE connects to the secondary network and continues to obtain the services from the secondary network. The secondary PLMN ID can be sent to the UE in system information. Further, the information like overload indication, secondary PLMN ID and the time for which the UE can obtain the services from the secondary PLMN ID can be sent to individual UEs over dedicated messages either on an Access Stratum (AS) message or over a Non Access Stratum (NAS) message.
Owner:SAMSUNG ELECTRONICS CO LTD
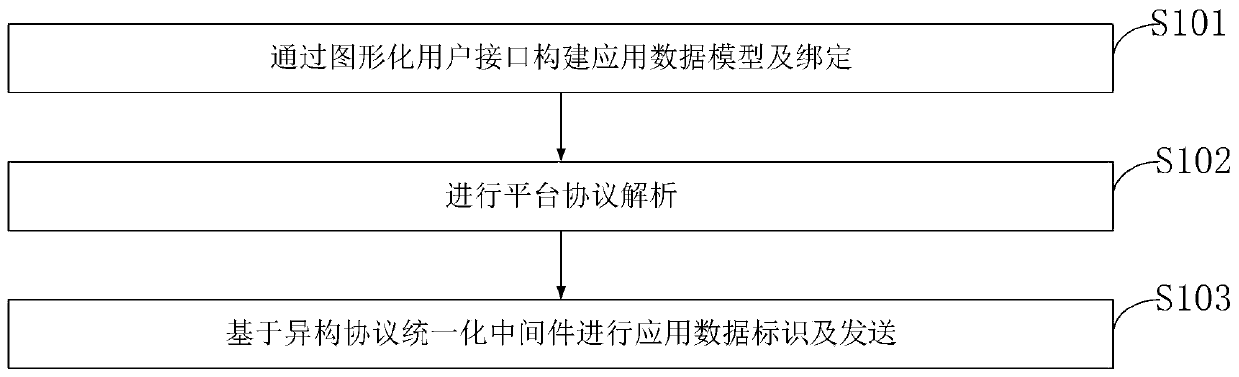
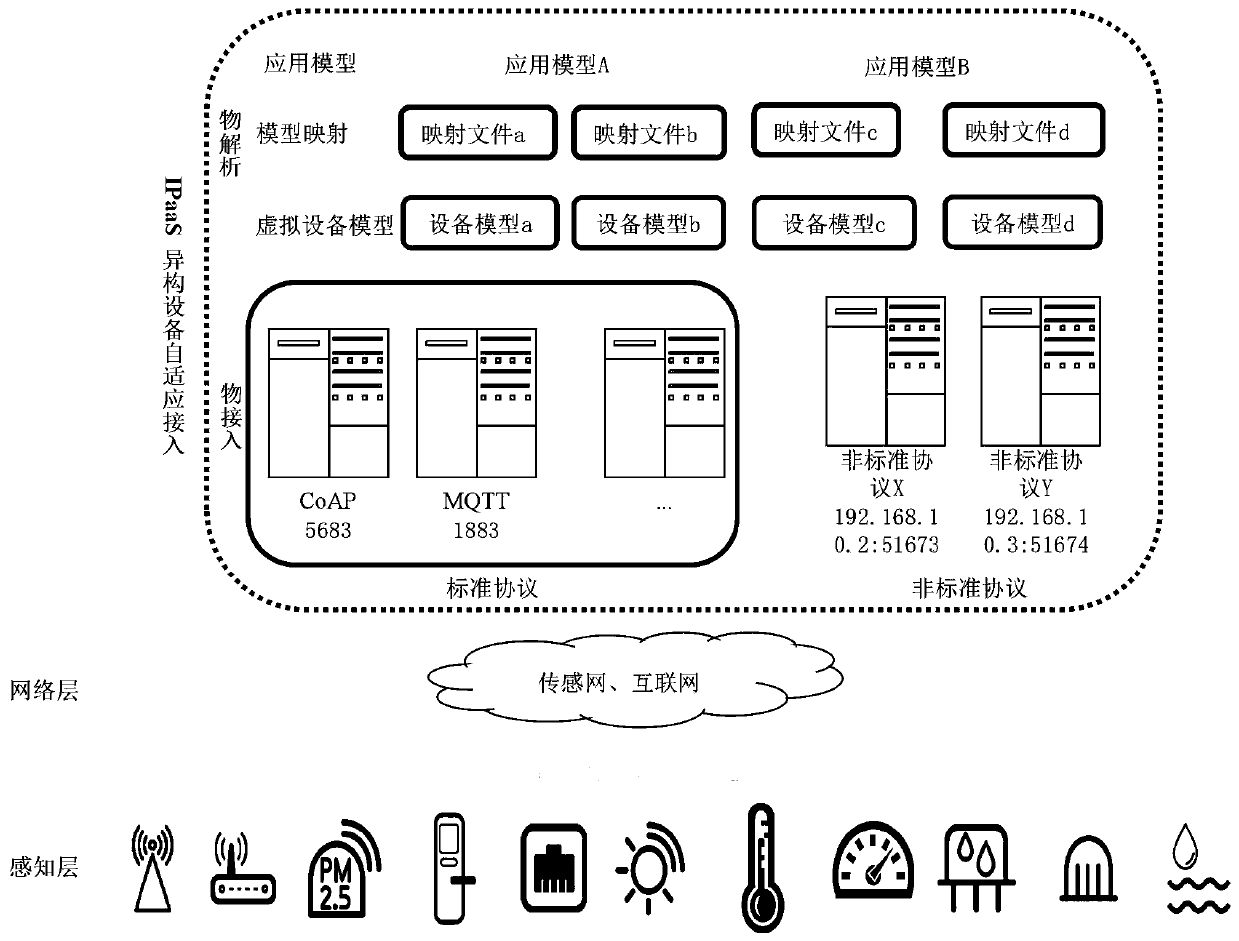
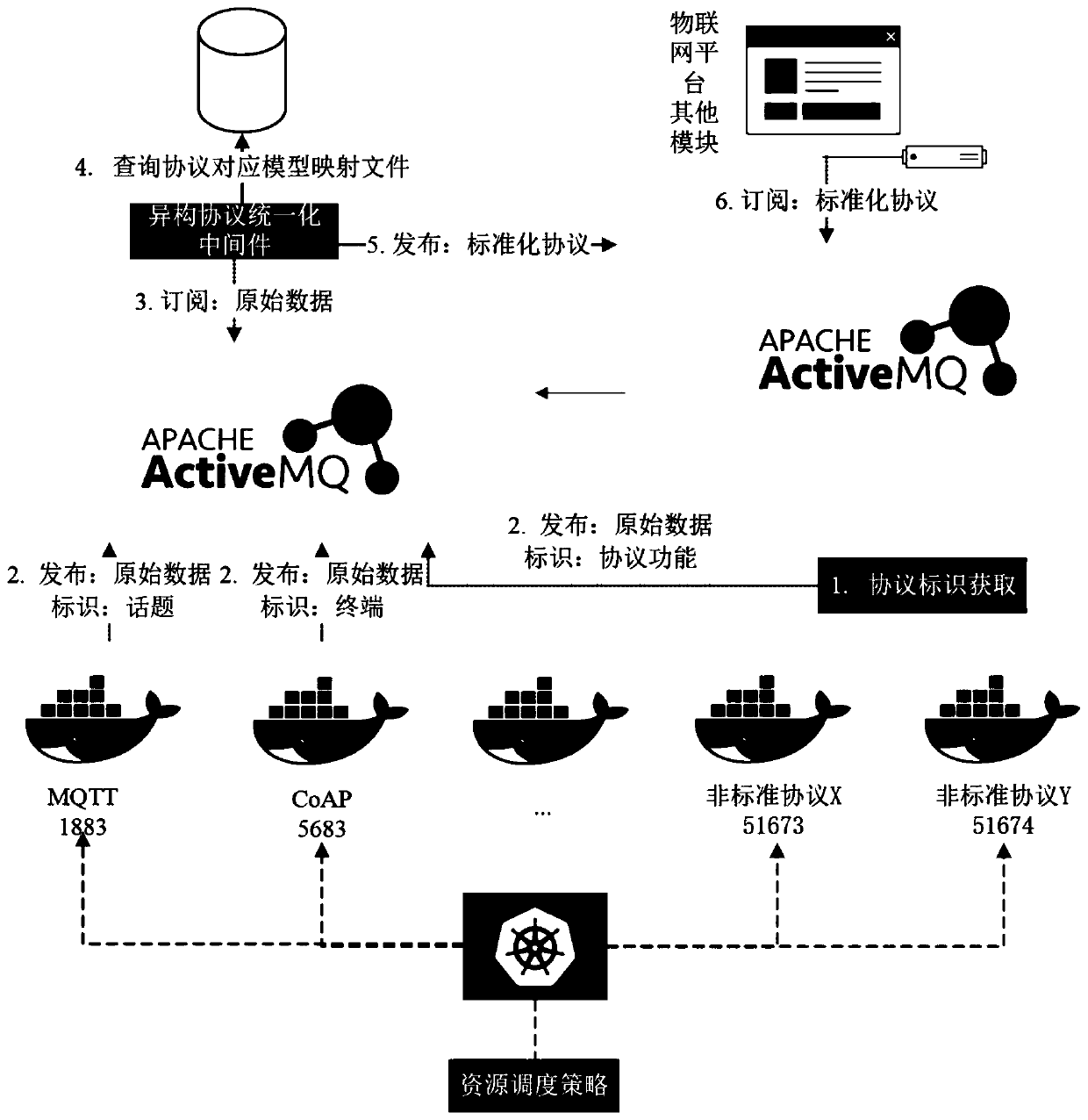
Self-adaptive access method and system for heterogeneous equipment of Internet of Things platform
ActiveCN111585958AIncrease flexibilityEfficient use ofTransmissionInstrumentsAccess methodSoftware engineering
The invention belongs to the technical field of Internet of Things, and discloses a self-adaptive access method and system for heterogeneous equipment of an Internet of Things platform. The system comprises a protocol identification obtaining module which is used for obtaining the identification of an equipment access layer non-standard Internet of Things protocol in an overall architecture; and aheterogeneous protocol unification middleware which comprises a virtual device model layer, a model mapping layer and an application data model layer. According to the method, the Internet of Thingsplatform with application development as the center is constructed, existing software development companies and personnel are better utilized, and the flexibility, user experience and software qualityof constructing the Internet of Things application are improved. According to the invention, a stable virtual device data model mapping mechanism is developed for an application program, and a virtual device data model sharing co-construction method suitable for software developers is constructed.
Owner:XIDIAN UNIV
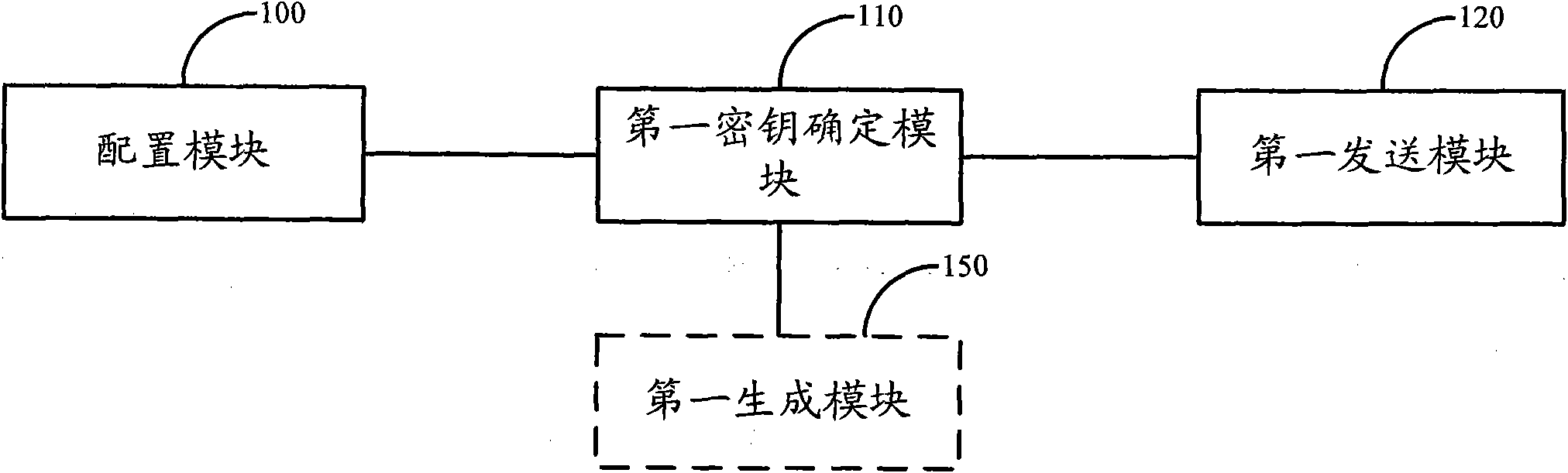
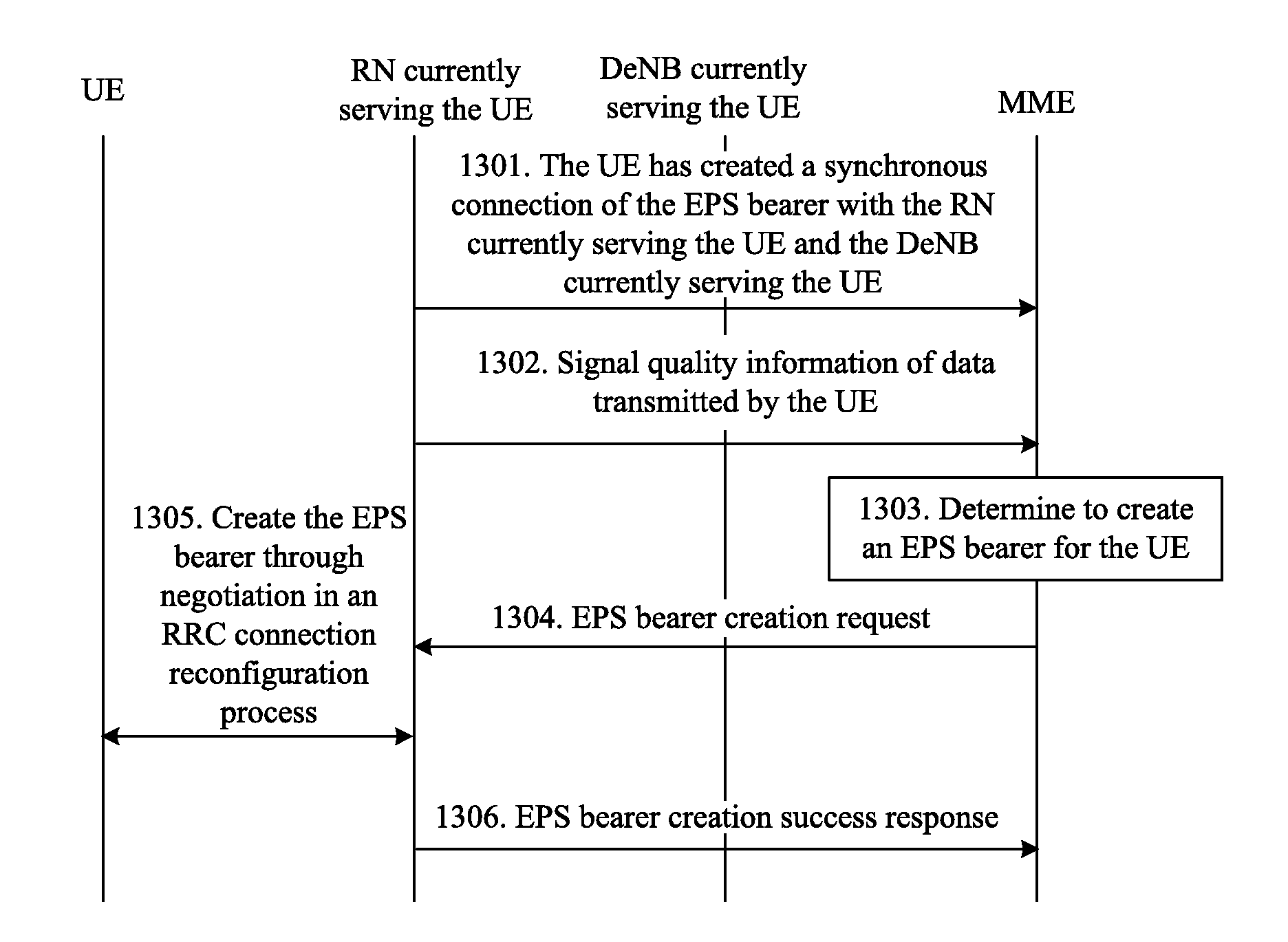
Method, system and device for determining keys and ciphertexts
The embodiment of the invention relates to radio communication technology, in particular to a method, a system and a device for determining keys and ciphertexts, which are used for increasing the number of keys so as to improve the security of an Un port when a plurality of pieces of user equipment (UE) access relay node (RN) equipment and a plurality of relay node (RN) radio bearers are requiredto be established in a long term evolution-advanced (LTE-A) system. The method for determining the key comprises that: after a user terminal initiates an attachment request, first network equipment configures a key parameter for the user terminal; and the first network equipment and second network equipment respectively determine a pair of access stratum (AS) keys corresponding to the user terminal according to the key parameter configured by the first network equipment and a preset encryption parameter. Through the embodiment of the invention, according to accessed user terminals, a different pair of AS keys is allocated to each user terminal, so that the security of the Un port is improved when the plurality of pieces of user equipment (UE) access relay node (RN) equipment and the plurality of relay node (RN) radio bearers are required to be established in the long term evolution-advanced (LTE-A) system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
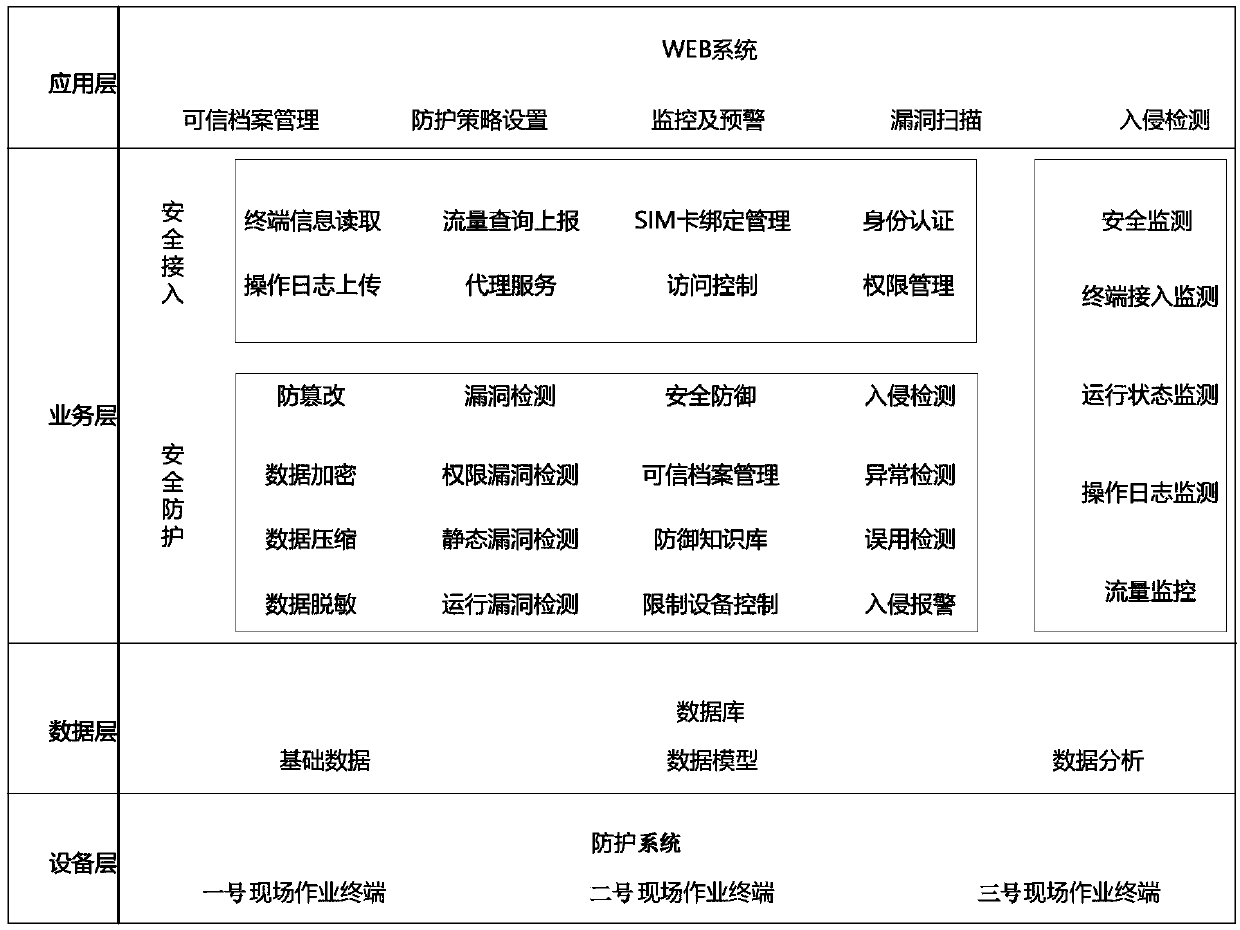
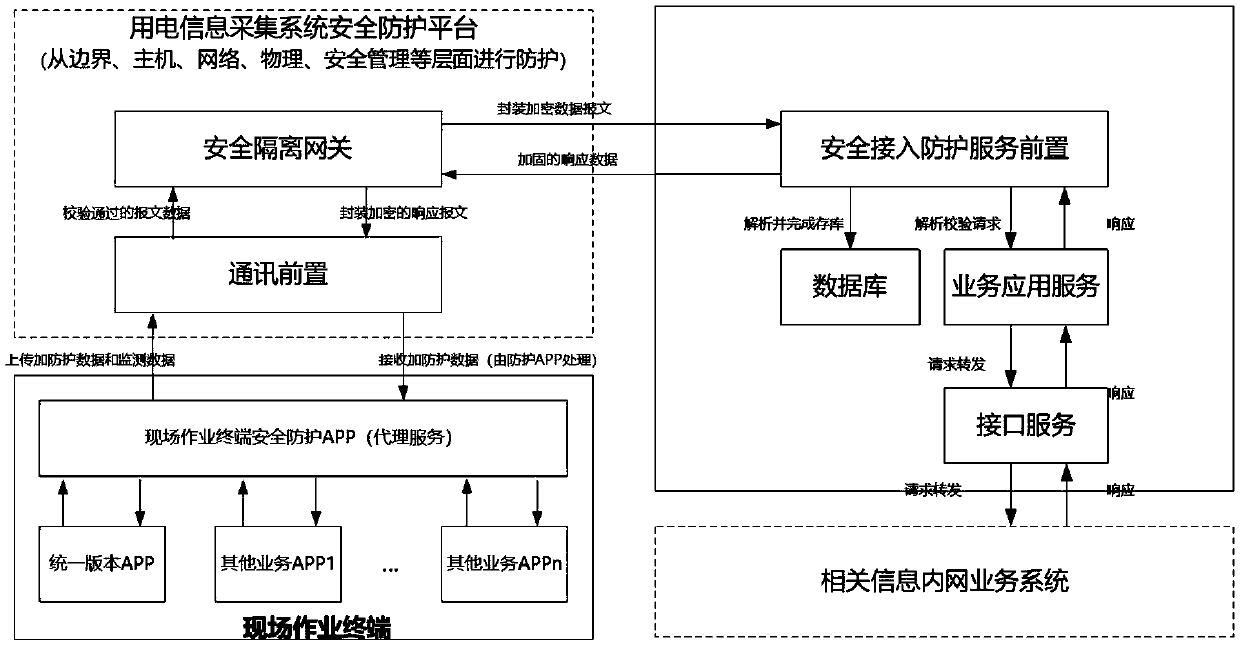
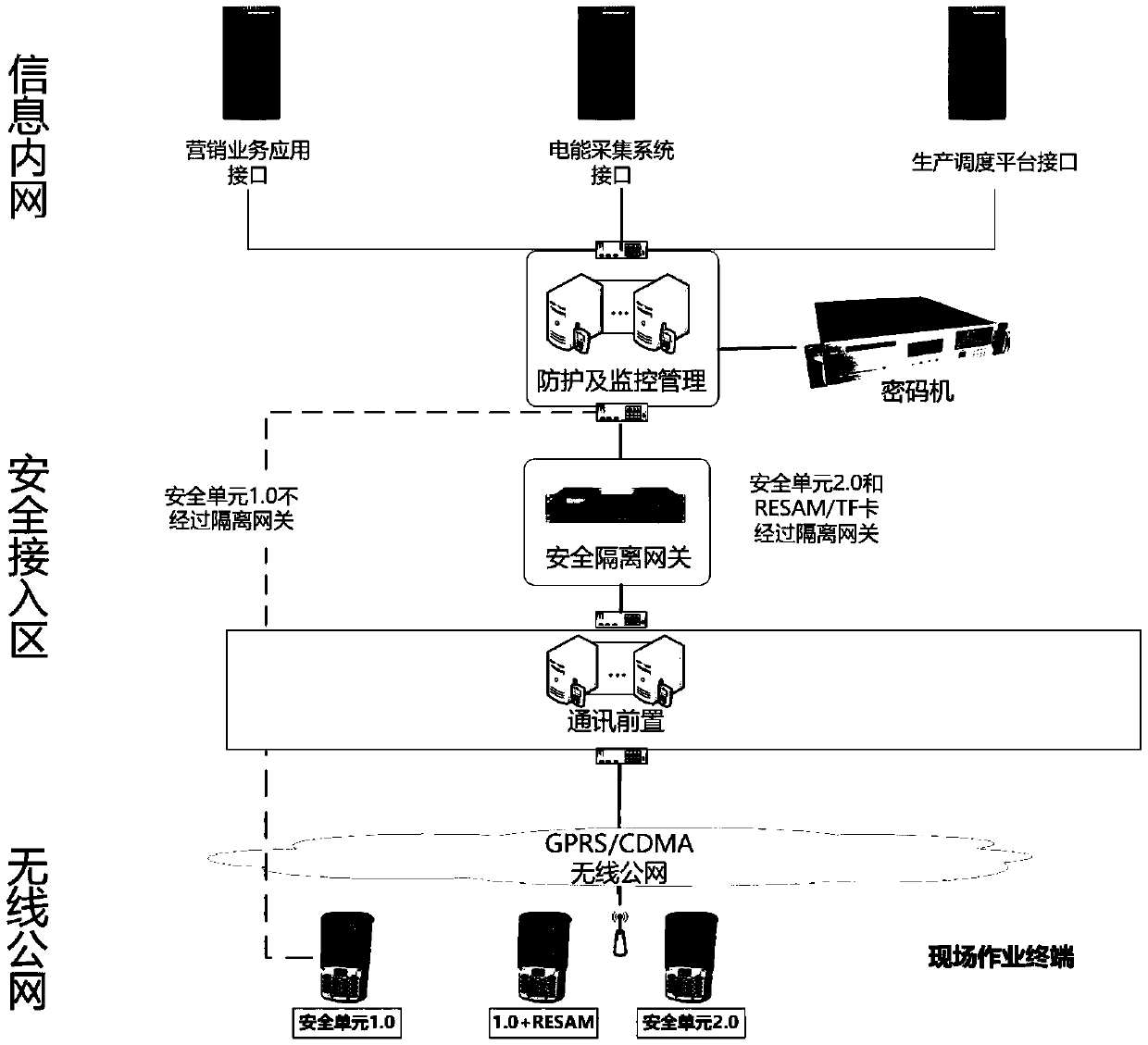
Field operation terminal security access protection and detection system
ActiveCN110691064AAchieving the goal of comprehensive protectionImprove security levelTransmissionCollection systemInformation security
The invention discloses a field operation terminal security access protection and detection system, which comprises an equipment layer, a data layer, a service layer and an application layer; the access layer is used for the field operation terminal to access the protection system; the data layer is used for storing basic data, constructing a data model and analyzing real-time data; the service layer is composed of a security access part, a security protection part and a security monitoring part; the application layer is composed of a unified management platform of a WEB terminal with trustedarchive management, protection strategy setting, monitoring and early warning, vulnerability scanning and intrusion detection service functions; safety protection is carried out from the aspects of field operation terminals, terminal applications, data and the like, and the comprehensive protection target of information safety of the collection system is achieved; through omnibearing safety management of equipment access, access protection, access monitoring and early warning, multi-dimensional analysis and processing are carried out on a protection main body, a protection strategy, a monitoring mechanism and the like, and the information safety level of the acquisition system is improved.
Owner:STATE GRID CORP OF CHINA +3
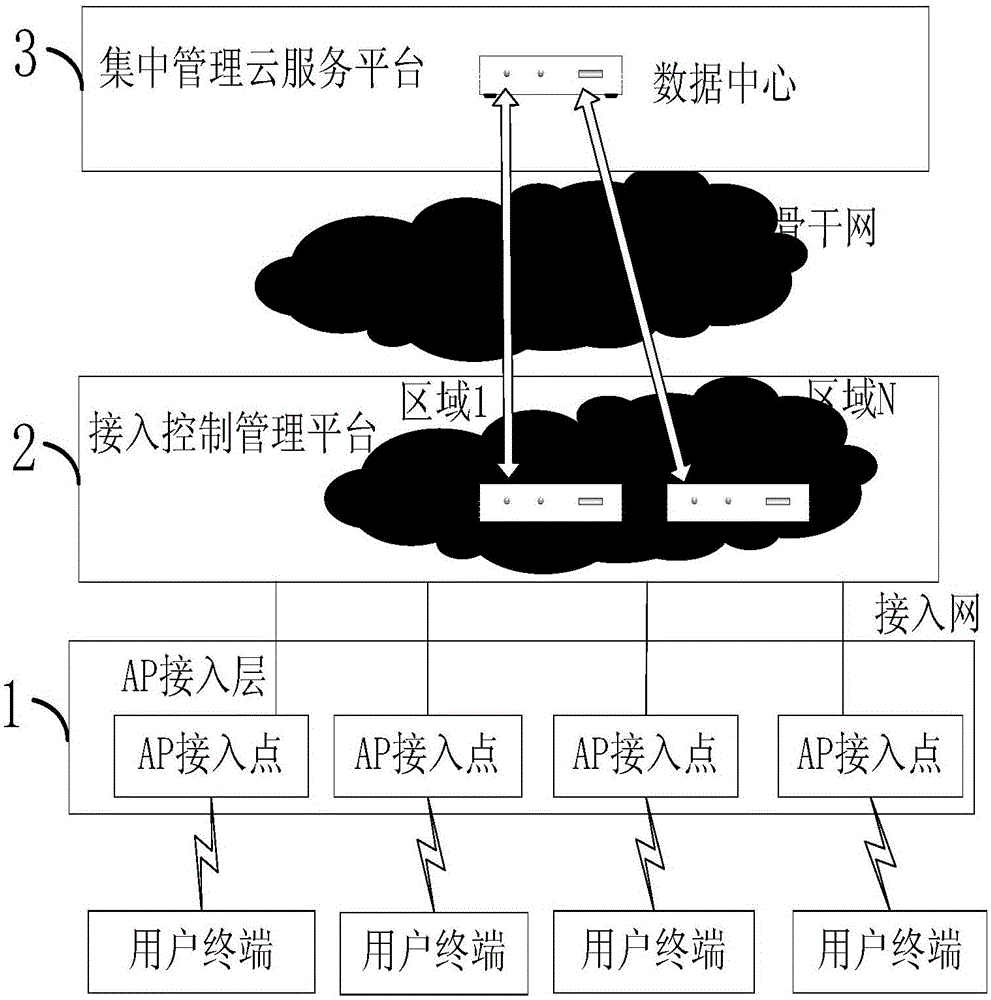
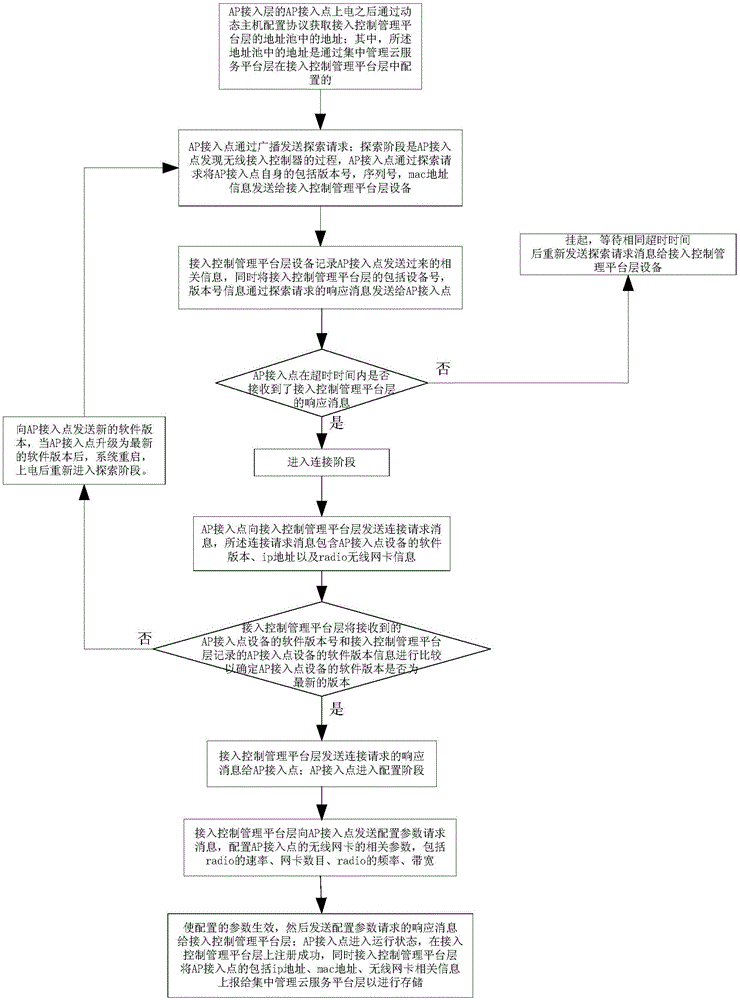
Cloud platform distributed system and method based on Internet and wifi mode
InactiveCN105049457AAchieve the role of advertisingRealize plug and playNetwork topologiesNetworks interconnectionNetwork sizeThe Internet
The invention discloses a cloud platform distributed system and method based on Internet and a wifi (Wireless Fidelity) mode. The system comprises an AP (Access Point) access layer, an access control management platform layer and a centralized management cloud service platform layer from top to bottom in sequence. Through adopting a layered management technology based on the cloud service, a wlan (Wireless Local Area Network) is taken as a wireless access technology and the Internet is taken as a carrier to implement a new cloud management system of the wlan. After a user terminal is connected to an AP access point, the centralized management cloud service platform layer pushes a webpage which is customized by a merchant so as to achieve an advertising effect. According to the distributed three-layer cloud structure, the flexibility of a wlan application is implemented, and plug and play of the AP access point can be implemented, so that the expansion capability and the flexibility of the system can be greatly improved, and the system can accomplish with ease under the modes of public cloud, private cloud and mixed cloud; owing to virtual sharing of a storage of a controller, the system can support a larger network scale as a representative of a latest generation of wireless networking technology.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
Method for processing nas message in wireless communication system and apparatus for same
InactiveUS20200015311A1Reduce signaling loadReduce storage burdenError preventionNetwork traffic/resource managementCommunications systemUplink transmission
Disclosed are a method for processing a NAS message in a wireless communication system and an apparatus for the same. Specifically, a method for processing a non-access stratum (NAS) message by an access and mobility management function (AMF) in a wireless communication system may include: receiving, from a user equipment (UE), an uplink (UL) NAS transport message including an uplink message; and when the uplink message is not successfully transported to a network function (NF), transmitting, to the UE, a first downlink (DL) NAS transport message indicating that the uplink message is not transported.
Owner:LG ELECTRONICS INC
PLMN (Public Land Mobile Network) network selecting method of multimode terminal
The invention provides a PLMN (Public Land Mobile Network) network selecting method of a multimode terminal, comprising the steps: when an access mode is LTE (Long Term Evolution) and an access stratum (AS) is in PLMN searching, searched cells with signals are stored in the AS layer; the AS of the terminal leads PLMN_IdentityList of all the cells and signal intensity to form a PossiblePLMN(maxPlmnNum) list; all the lists are reported to a non-access stratum (NAS) together; the PLMN network selecting process of the LTE access technology is fused to the PLMN network selecting method of a GSM (Global System for Mobile Communication) and TD-SCDMA (Division-Synchronization Code Division Multiple Access) dual-mode terminal. In the PLMN network selecting method provided by the invention, the problems that in the GSM or TD-SCDMA system, one cell only has one PLMN identification and one cell of the LTE can affiliate to different PLMN networks possibly are effectively solved, the characteristics of the existing GSM-TD-SCDMA system are fully utilized, the terminal design is simplified and the hardware cost is reduced.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems
ActiveUS20150004924A1Facilitating congestion controlPossible changeEmergency connection handlingNetwork traffic/resource managementCommunications systemMobile communication systems
The present invention relates to a method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems. In a wireless communication system according to one embodiment, the method for transmitting and receiving data by a terminal including a user equipment (UE) non access stratum (NAS) and a UE access stratum (AS) includes the steps of: receiving by the UE AE, information including emergency call-related information which includes barring information by type for the emergency call, from a base station; transmitting, by the UE NAS, a service request for the emergency call to the UE AS; and determining, by the UE AS, whether to bar the service request on the basis of emergency call-related information. According to one embodiment, during the emergency call transmission, network congestion can be easily controlled by enabling various types of emergency calls to be transmitted, and enabling access to be barred information according to the situation of a communication network and types of emergency calls. Also, even when a specific type of emergency call is barred from access, the terminal can change to another type of emergency call and try for access. Therefore, it is effective in that an emergency call can be transmitted in various schemes even in a state where the network is congested.
Owner:SAMSUNG ELECTRONICS CO LTD
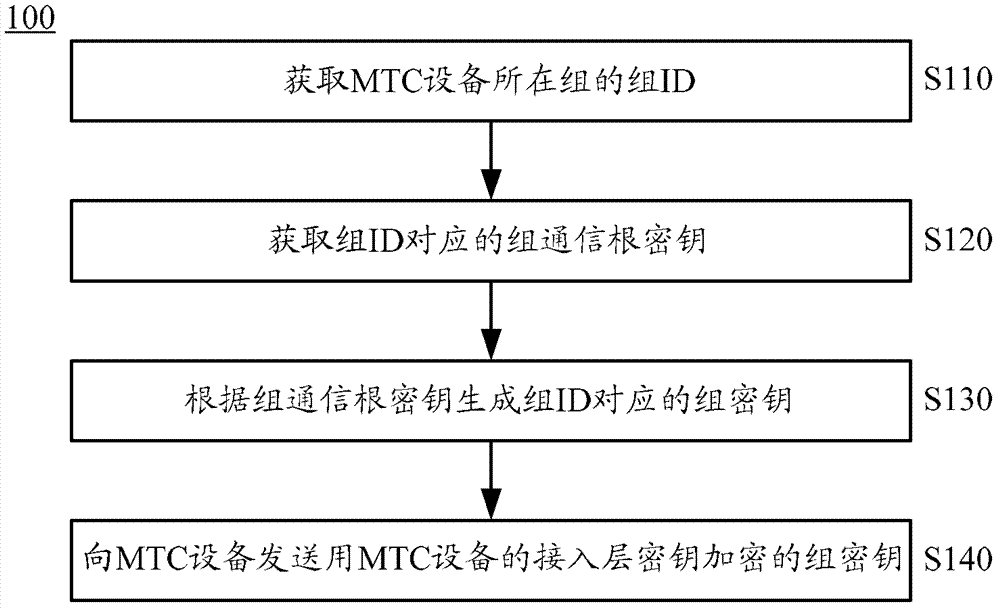
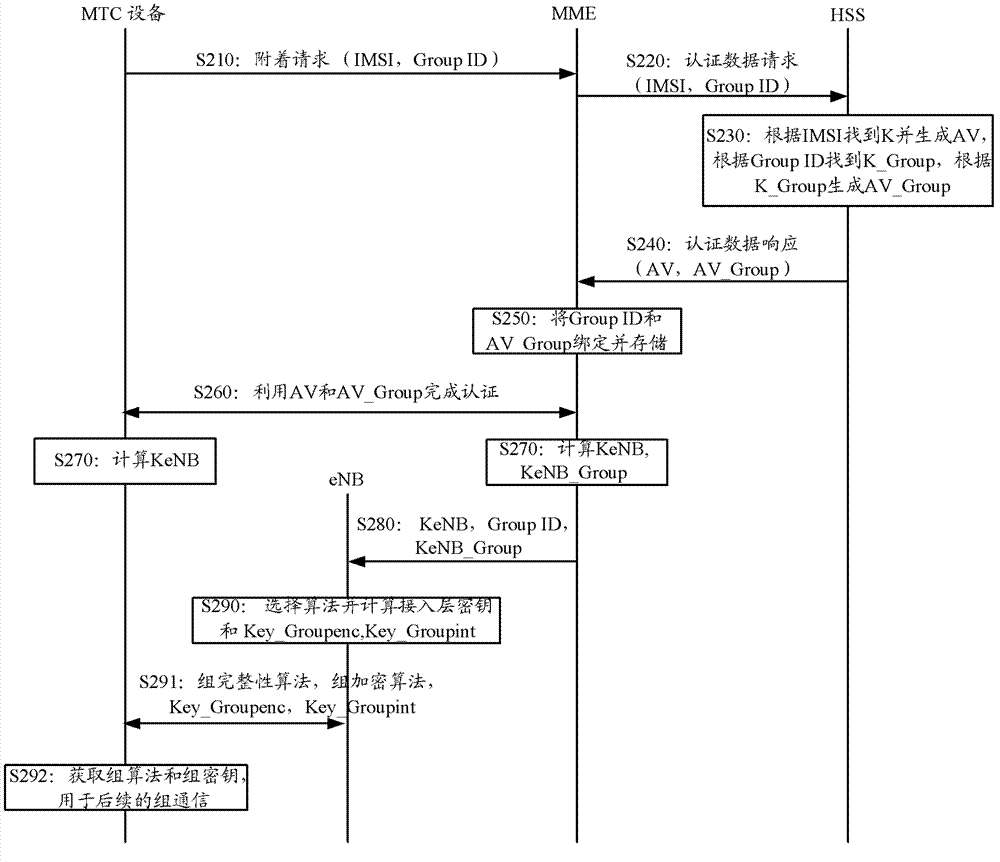
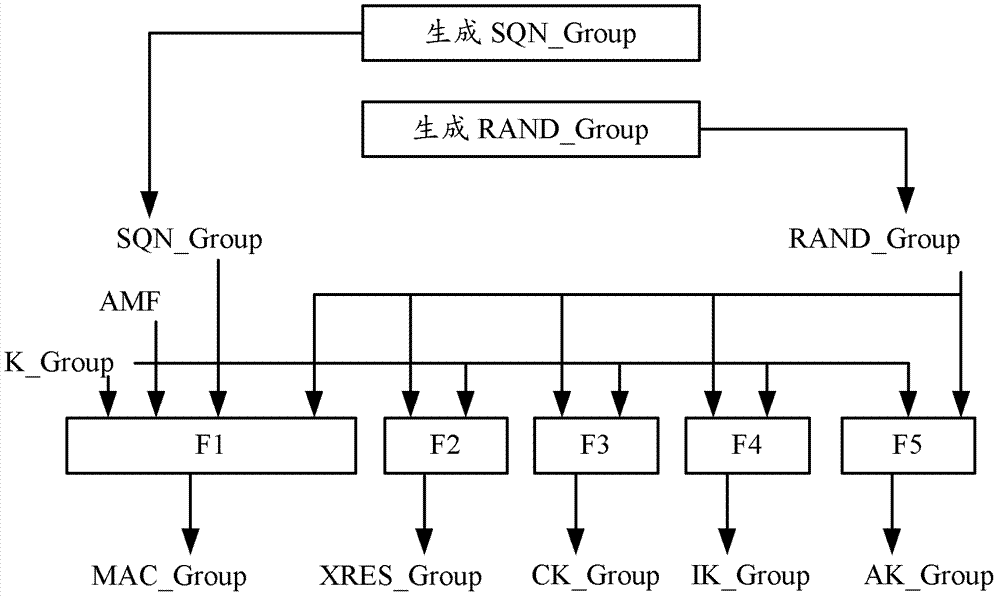
Method for generating group key and associated device
ActiveCN103096309AReduce complexityReduce the number of keysBroadcast service distributionTransmissionAccess stratumBase station
The invention provides a method for generating a group key and an associated device. The method comprises obtaining the group identification (ID) of the group which a machine-type communication (MTC) device is in, obtaining a group communication root key corresponding to the group ID, generating a group key corresponding to the group ID according to the group communication root key, sending the group key encrypted by an access stratum of the MTC device to the MTC device, so that the MTC device can obtain the group key by deciphering according to the key of the access stratum of the MTC device. According to the technical scheme, a base station can distribute the group key corresponding to the group which the MTC device is in to the MTC device, so that the MTC devices in the same group can conduct a group communication normally by means of the same group key, and the same group key is only needed keeping for the same group in the base station. Thus the complexity of the base station operation is reduced, the number of the keys for base station maintenance and management is reduced and performance of the base station is improved.
Owner:HUAWEI TECH CO LTD
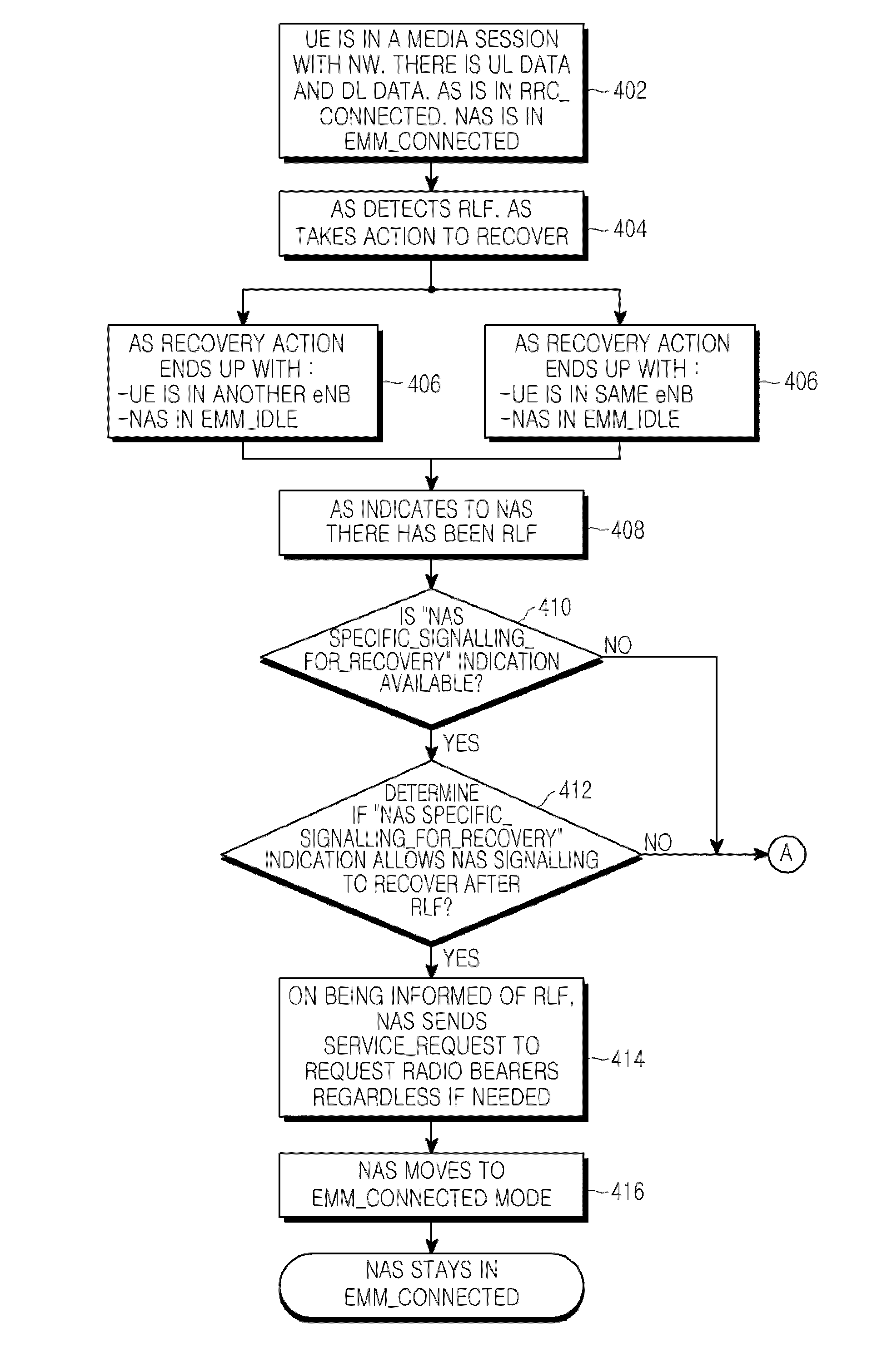
Method of operating a communication system
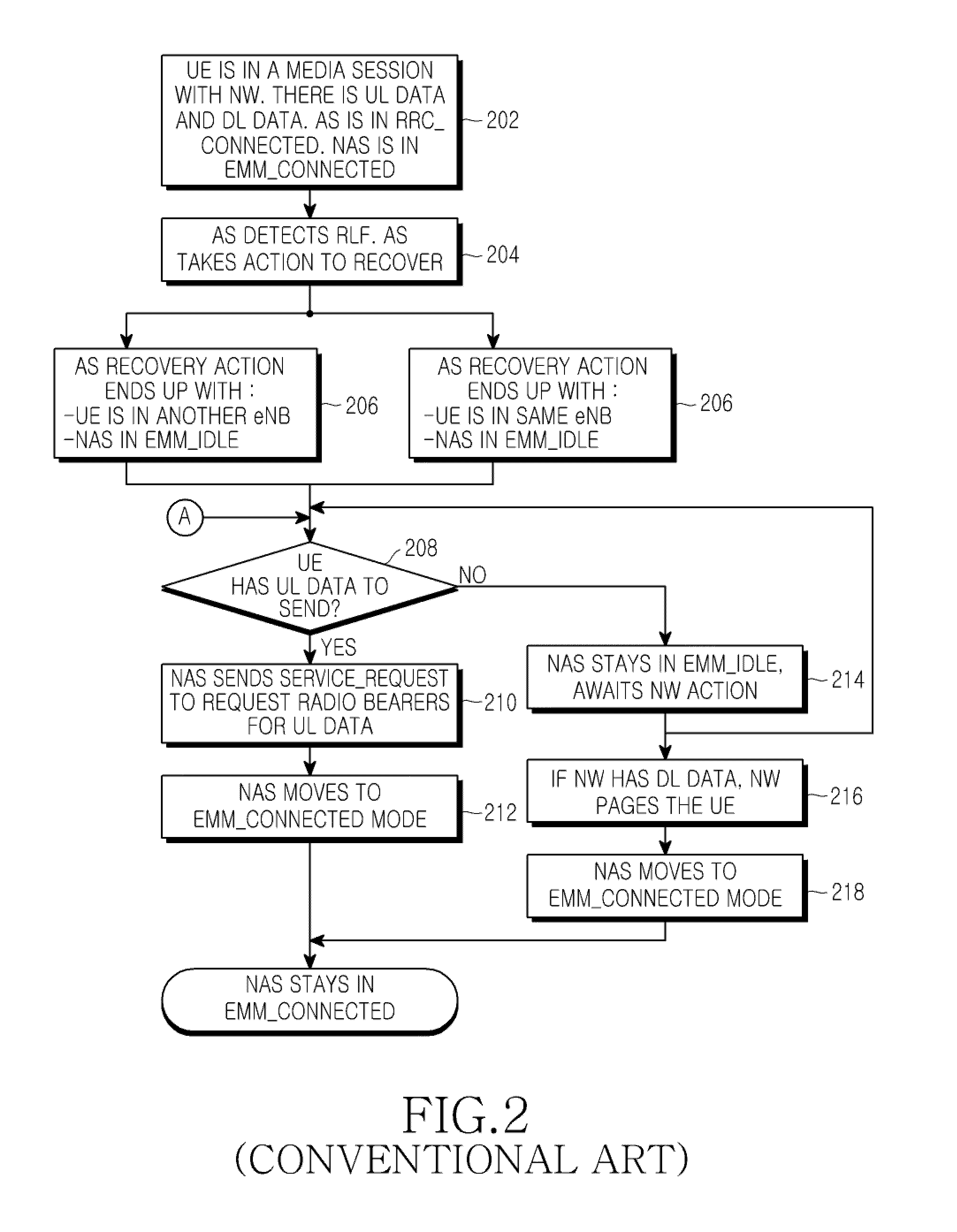
ActiveUS20100087193A1Promote recoveryConnection managementWireless commuication servicesCommunications systemRadio link failures
A method of operating a communication system is provided. The communication system comprises a NetWork (NW) and User Equipment (UE), a Non Access Stratum (NAS) via which the NW and UE communicate with each other, and an Access Stratum (AS) providing a physical connection to enable the NAS communication between the NW and UE to be achieved, the physical connection including a wireless radio link to the UE. The method includes sending information from the NW to the UE to determine at least one action of the UE in response to a failure of a radio link to the UE, detecting a Radio Link Failure (RLF), in response to the detecting of the RLF, deciding on an action to be performed by the UE according to the received information, and performing, by the UE, the decided action.
Owner:SAMSUNG ELECTRONICS CO LTD
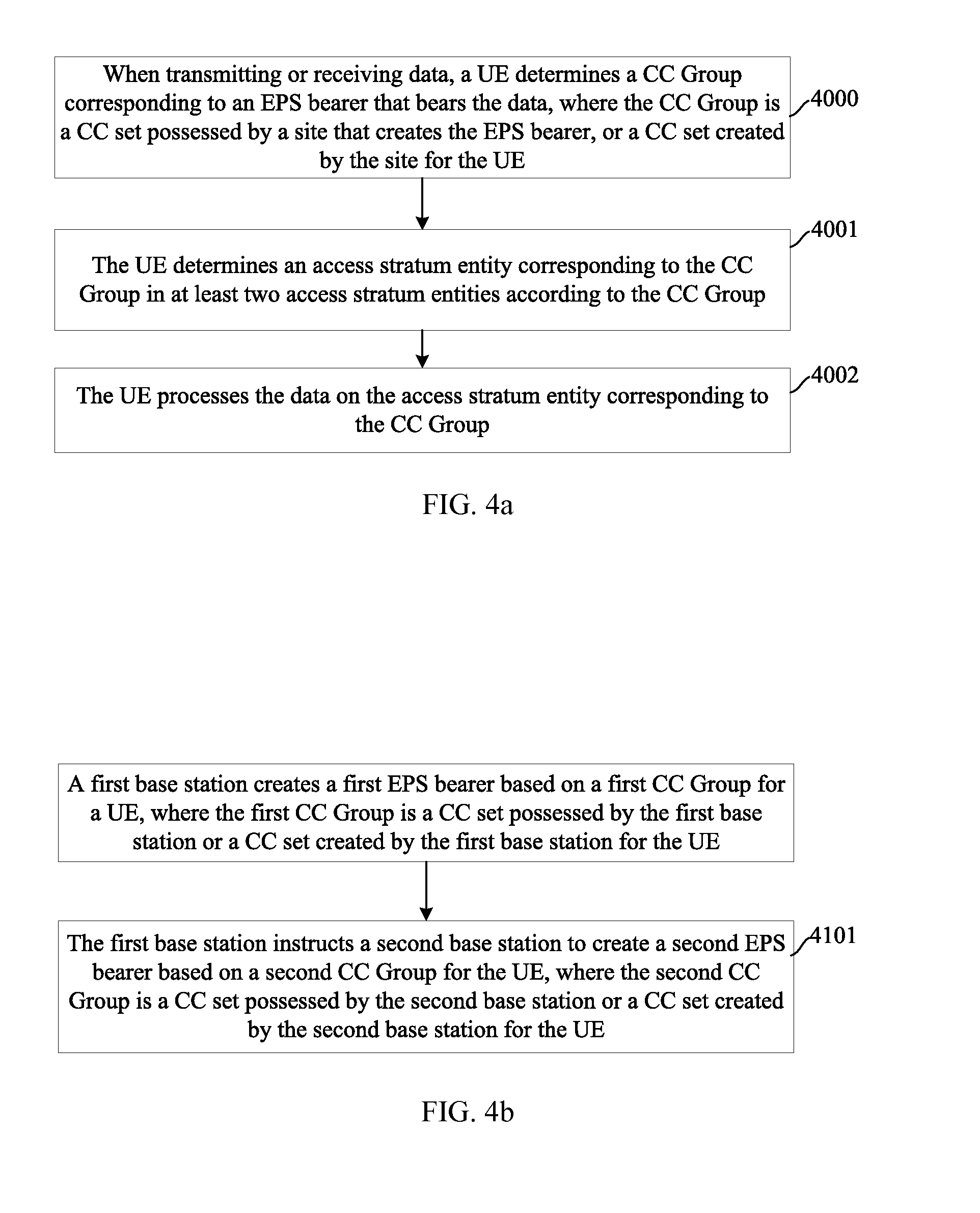
Method, System and Apparatus for Transmitting Data in Carrier Aggregation Manner
ActiveUS20140010192A1Improve throughputImproving throughput of data transmittedSite diversityTransmission path divisionCarrier signalAccess stratum
A method, a system and an apparatus can be used for transmitting data in a CA manner. A first base station currently serving a user equipment (UE), creates EPS bearers under different component carriers CC Groups for the UE. The UE sets different access stratum entities corresponding to the CC Groups to process data in the process of creating the EPS bearers. The UE determines, when transmitting or receiving data, a corresponding CC Group according to an EPS bearer that bears the data. An access stratum entity corresponding to the CC Group processes the data that needs to be transmitted or received, a site is a first base station currently serving the UE or a second base station currently serving the UE.
Owner:HUAWEI TECH CO LTD
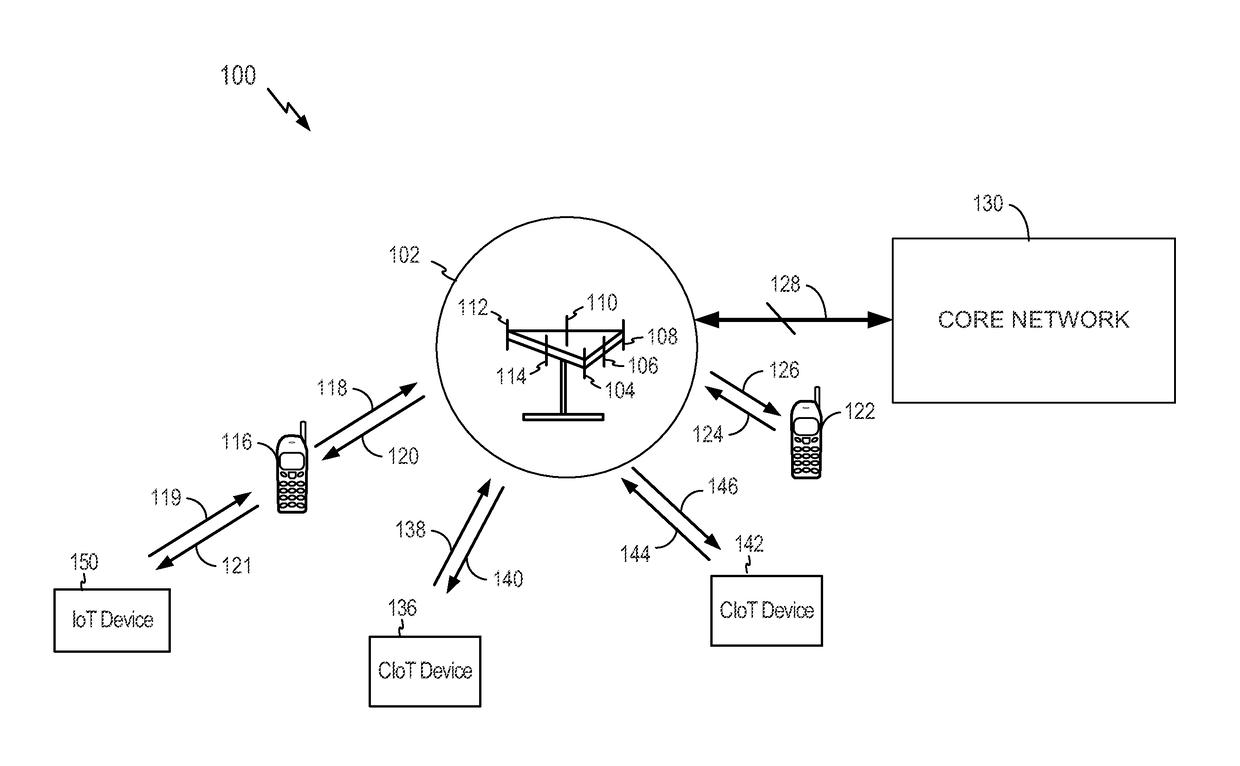
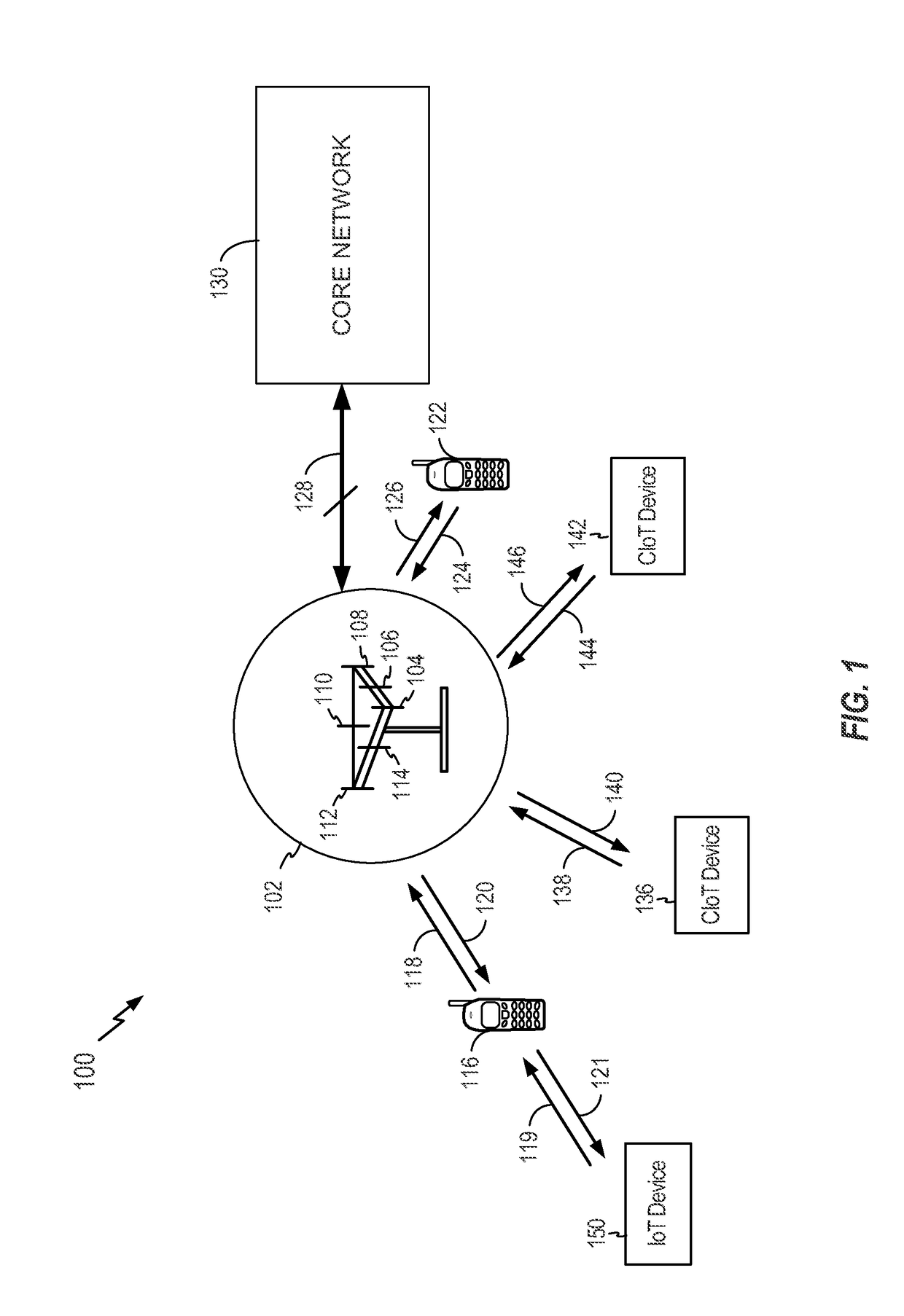
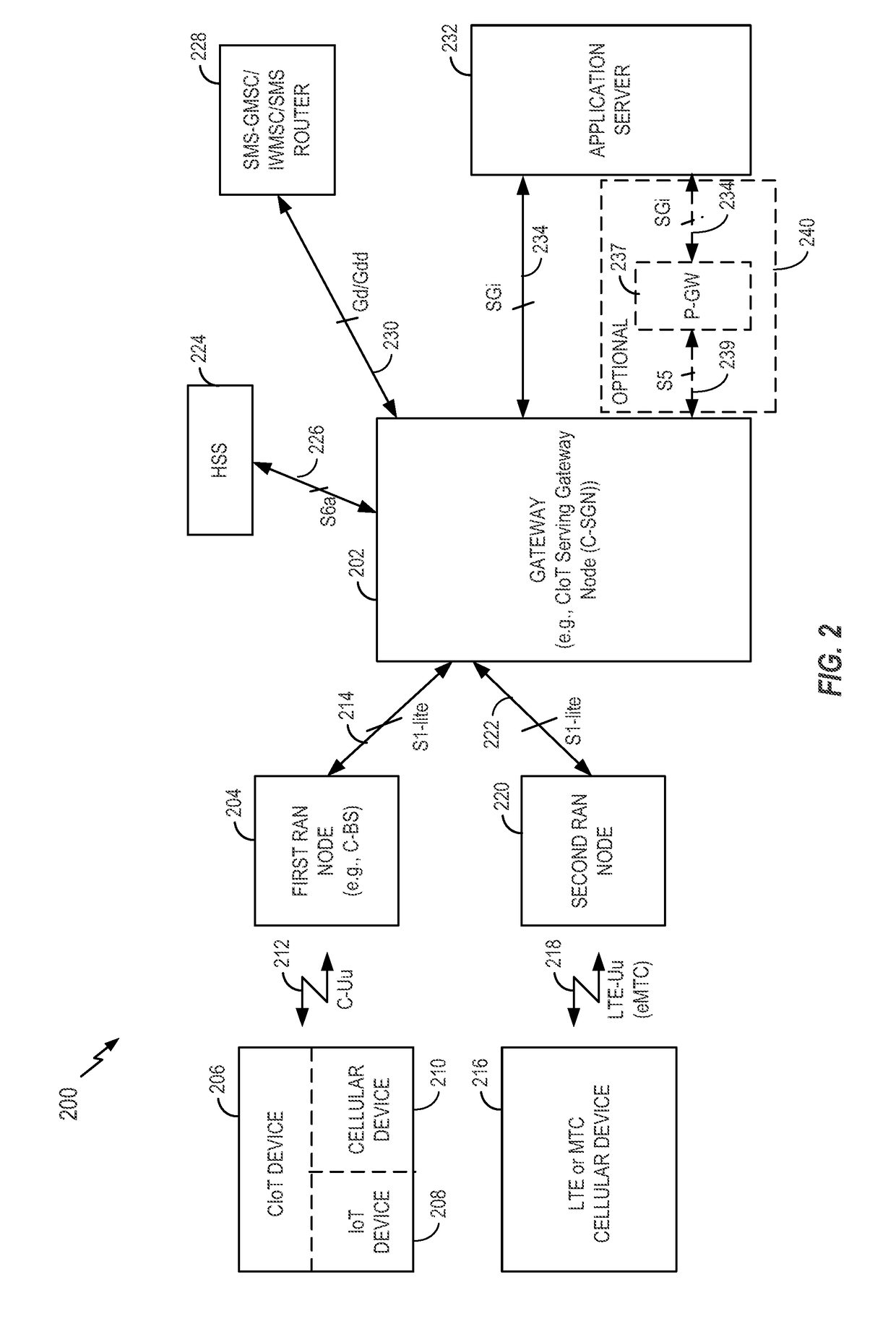
Stateless access stratum security for cellular internet of things
ActiveUS20170187691A1Little dataReduce latencyKey distribution for secure communicationMultiple keys/algorithms usageInternet in the United StatesAccess stratum
Aspects of security schemes (e.g., integrity protection, encryption, or both) are described. A measure of access stratum security can be realized without overhead associated with establishing and / or maintaining the per-cellular-device access stratum security context at a Cellular Internet of Things (CIoT) base station (C-BS). A gateway (e.g., a CIoT Serving Gateway Node (C-SGN)) may derive a first key. The first key may be only known to the C-SGN. The C-SGN may derive a second key from the first key and a parameter unique to the C-BS. The C-SGN may also derive a third key from the second key and an identity of a cellular device. The C-SGN may send the second and third keys to the C-BS and cellular device, respectively. Small data messages encrypted and / or integrity protected by the cellular device may be decrypted and / or verified by the C-BS.
Owner:QUALCOMM INC
Unicast Sidelink Access Stratum Level Connection Maintenance
PendingUS20200252989A1Stable supportParticular environment based servicesCriteria allocationPhysical layerAccess stratum
Embodiments are presented herein of apparatuses, systems, and methods for performing unicast sidelink access stratum level connection maintenance. A first wireless device and a second wireless device may establish a unicast sidelink wireless connection. One or both of the first wireless device and the second wireless device may perform access stratum level connection maintenance on the unicast sidelink wireless connection. This may include performing any or all of radio link monitoring, radio resource management, or physical layer based link quality detection. The access stratum and the non-access stratum of each device may also communicate with each other regarding either or both of link quality or link status of the unicast sidelink wireless connection.
Owner:APPLE INC
Method for reselecting network node in charge of control plane
InactiveUS20160219503A1Avoid wastingNetwork load can be preventedAssess restrictionNetwork data managementTelecommunicationsAccess stratum
One embodiment of the present specification provides a method by which a user equipment (UE) reselects a network node in charge of a control plane. The method can comprise the steps of: retransmitting, by the UE, a non-access stratum (NAS) request message if the UE transmitted the NAS request message to a network node in charge of the control plane through a base station but has not received a response message; transmitting, by the UE, an access stratum (AS) message, which includes an indication showing no response from the network node, to the base station if the retransmission of the NAS request message has repeated by a preset value or more; and reselecting another network node in charge of the control plane instead of the network node in a disabled state if information indicating that the network node is in the disabled state is received from the base station.
Owner:LG ELECTRONICS INC
User access control method
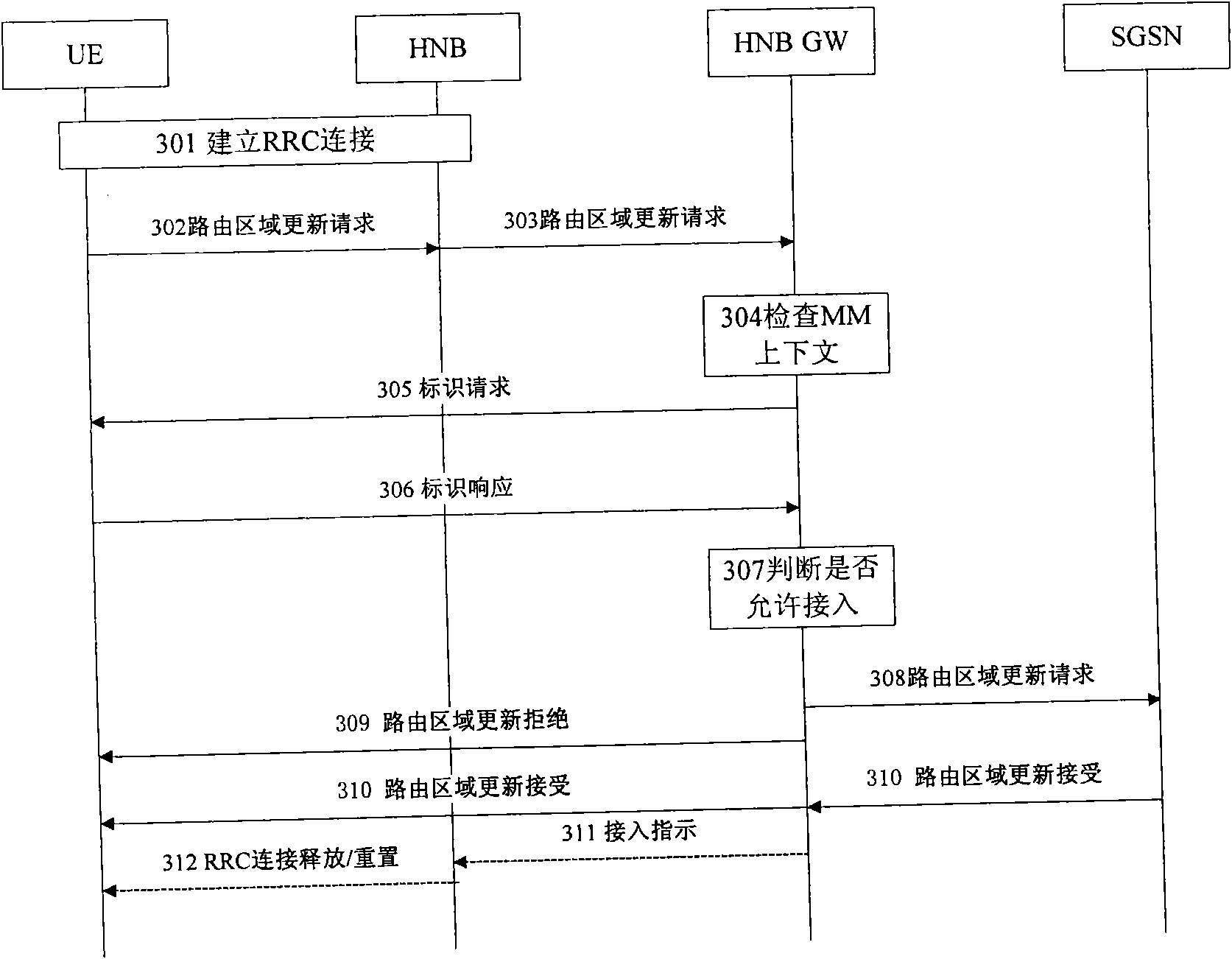
The invention relates to a user access control method comprising the following steps: a home base station sends information to a home base station gateway, wherein the information includes the information on the measurement of surrounding cells by user equipment (UE) and the non-access stratum (NAS) information which is sent to a core network node by the UE; the home base station gateway analyzes the NAS information so as to obtain the user identification contained in the NAS information; the home base station gateway compares the user identification and a user group list and decides if the UE is allowed to be accessed; and the home base station gateway sends the response of NAS information to the home base station and informs the home base station of the UE access indication. The invention simplifies the complexity of a home node B (HNB), improves the safety performance of the HNB and enables the user to reside in the HNB under the condition of the coverage of a micro cell nearby or reside in the micro cell.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Environmental-friendly accessing method and environmental-friendly accessing network
InactiveCN101800774AAvoid oscillationFast convergenceData switching networksAddress Resolution ProtocolComputer network
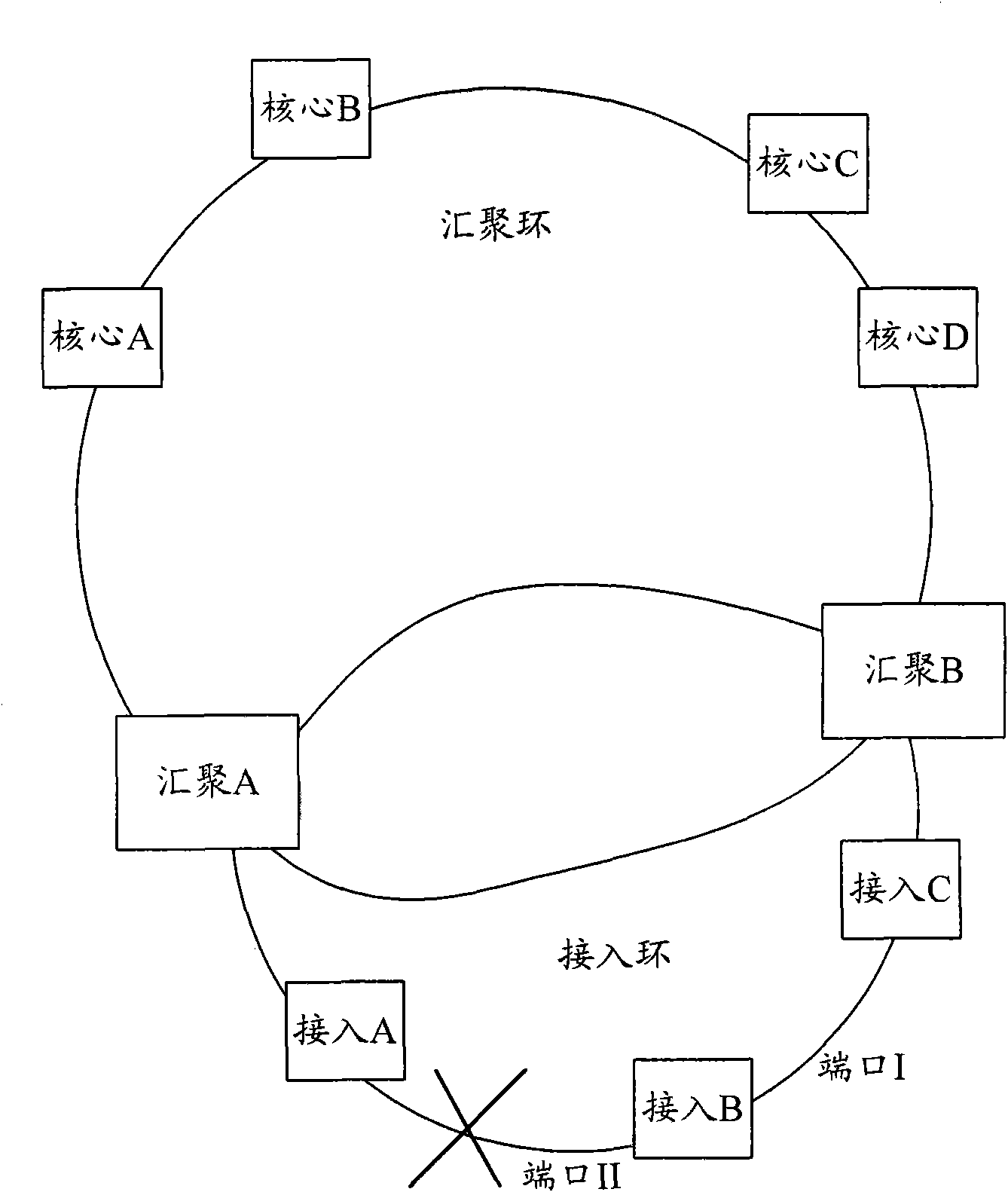
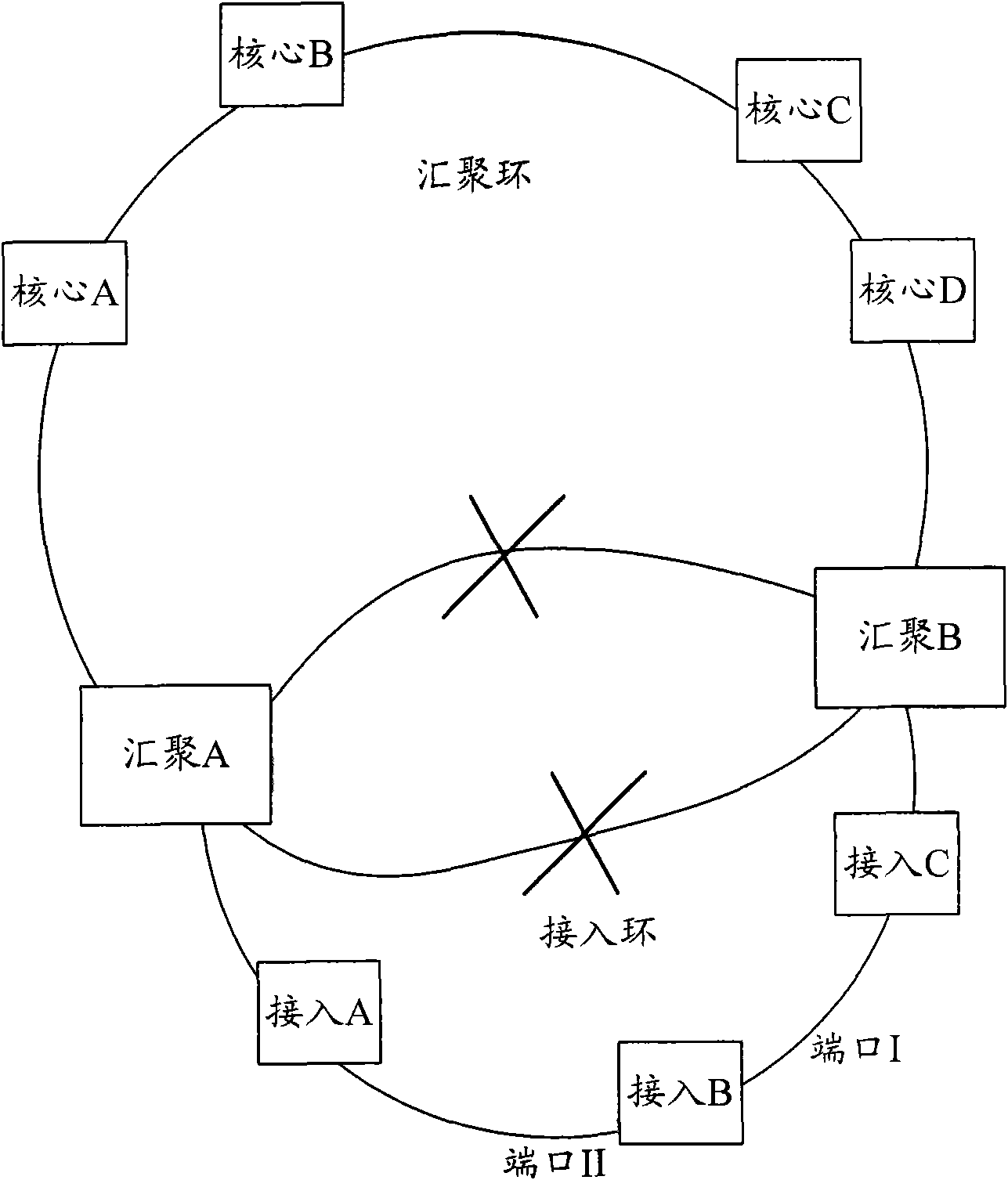
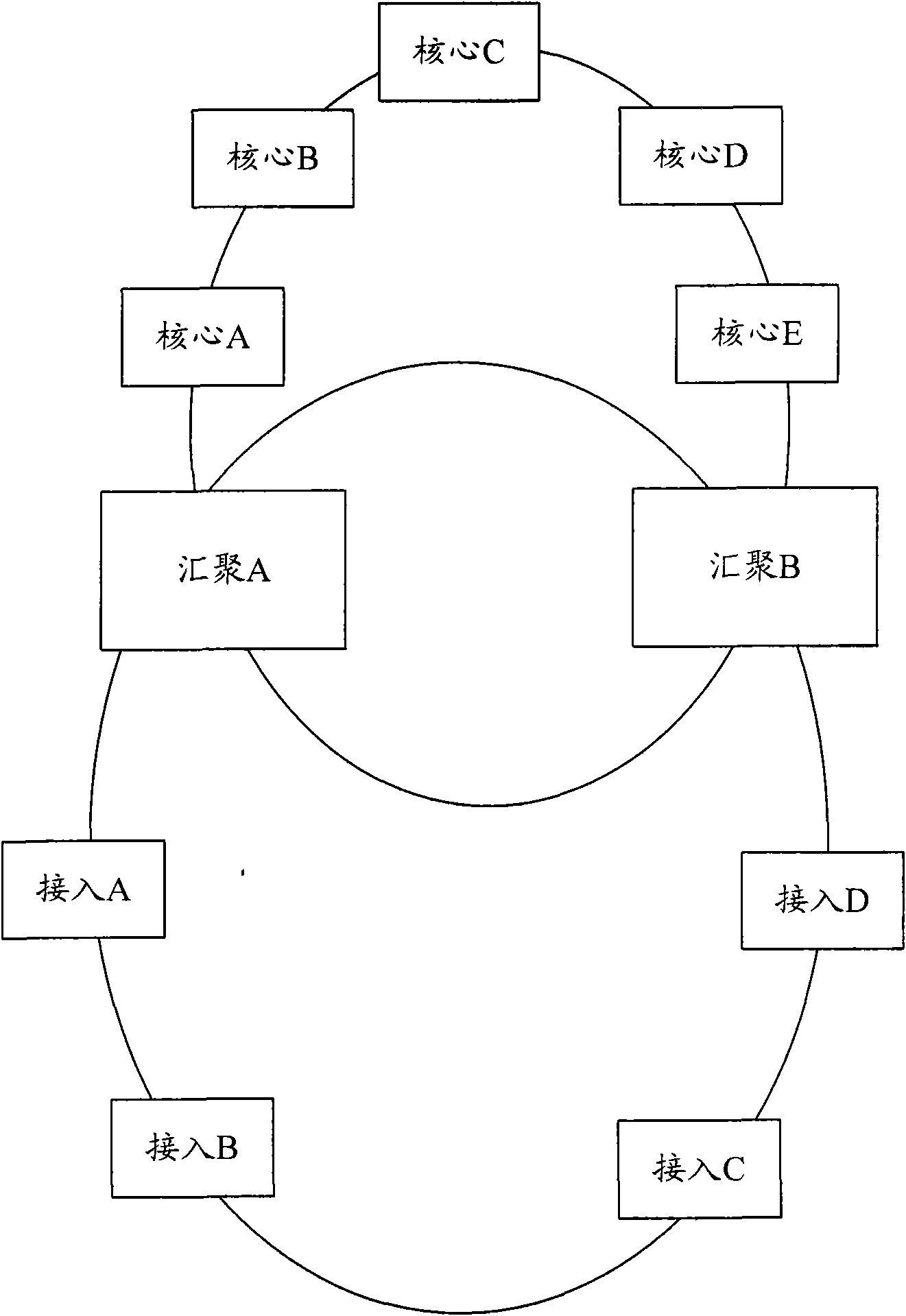
The invention discloses an environmental-friendly accessing method which comprises the following steps: forwarding only the message on the third layer by a convergence ring, forwarding only the message on the second layer by an access ring, and configuring dual gateways uplinked to a core node, wherein each access node of the access ring takes two convergence nodes as primary and standby gateways. The invention also discloses an environmental-friendly accessing network. Because the hardware in the access layer forwards the message on the second layer, no software needs to be started for learning routing. In addition, because the static primary and standby routing technology is used, the convergence time can be shortened, the fault-tolerant ability can be improved, the defect that virtual router redundancy protocol (VRRP) is used for backing up the primary gateway on two sides can be avoided. The invention can avoid the oscillation of the address resolution protocol (ARP) of the gateway, improve the stability of the system and save the resource of the central processing unit (CPU).
Owner:ZTE CORP
Communication security processing method, device and system
ActiveCN107371155AReduce overheadNetwork topologiesSecurity arrangementCommunications securityComputer terminal
The invention relates to a communication security processing method which is applied to AS (Access Stratum) security processing when a terminal switches from a source cell to a target cell. The communication security processing method comprises the steps of acquiring a derivation parameter, deriving a target AS root key according to a source AS root key and the derivation parameter, calculating an AS security key used in the target cell according to the target AS root key, wherein the source AS root key is an AS root key used in the source cell, the target AS root key is an AS root key used in the target cell, the derivation parameter is used for deriving the AS root key and corresponds to an RAN node, an RAN node group or a region where the target cell is located, and cells in the same RAN node, the same RAN node group or the same region have the same derivation parameter. Therefore, a terminal does not need to update an AS security key when switching in the same RAN node, the same ARN node group or the same region, and the overhead required for updating the AS security key is saved.
Owner:HUAWEI TECH CO LTD
Cipher key replacing method, system and device
ActiveCN101478752AGuaranteed synchronizationImprove communication qualitySecurity arrangementCommunication qualityNetwork key
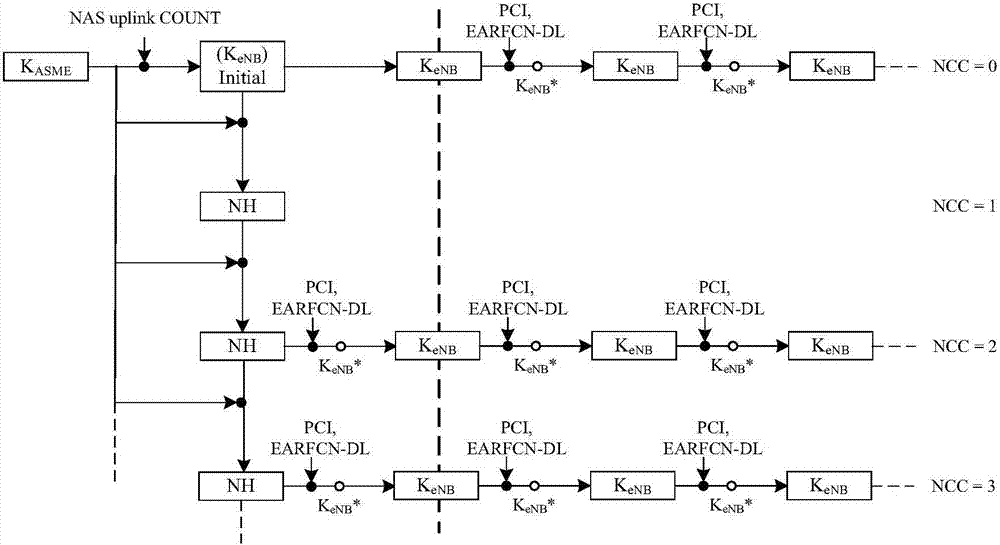
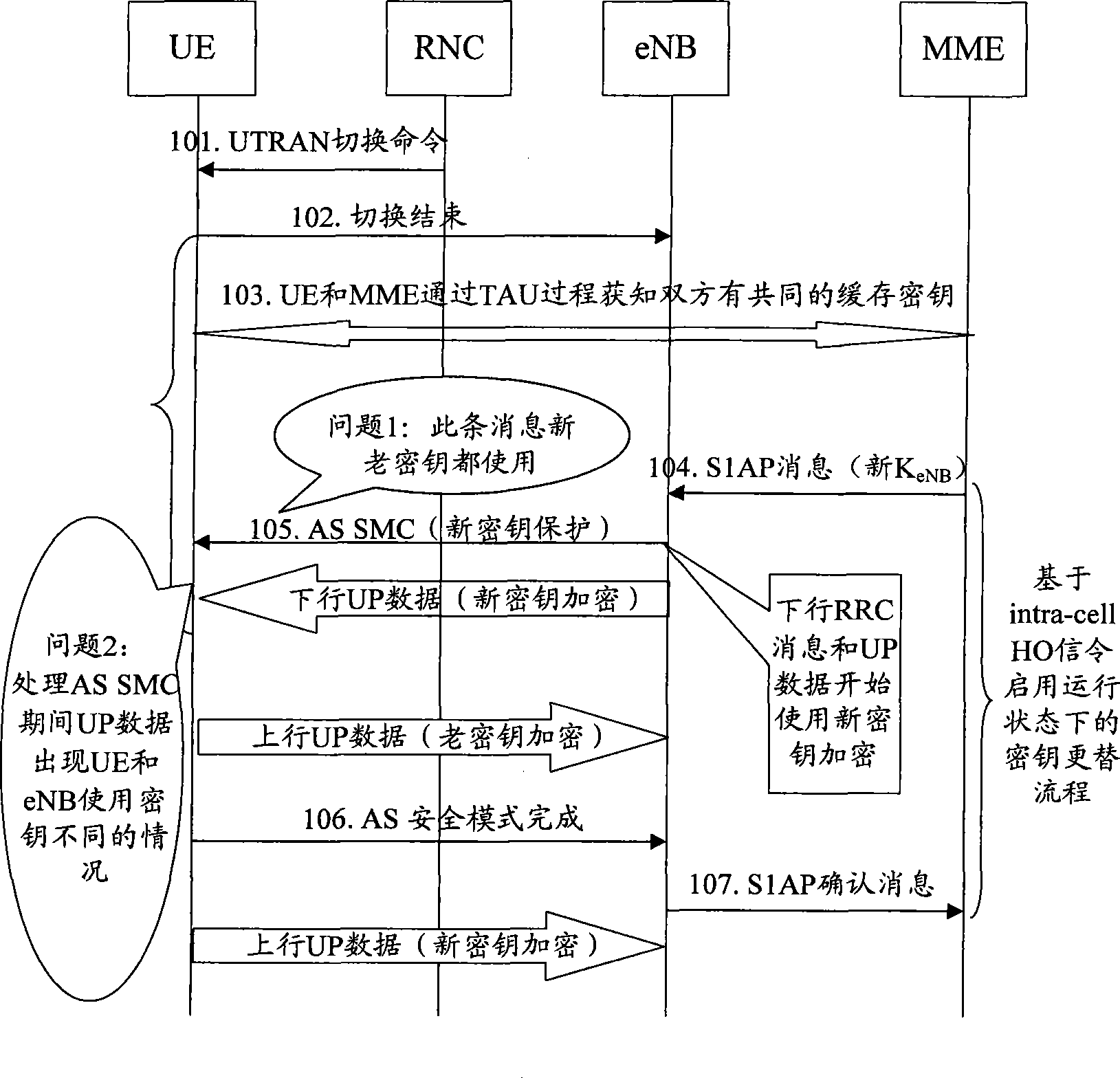
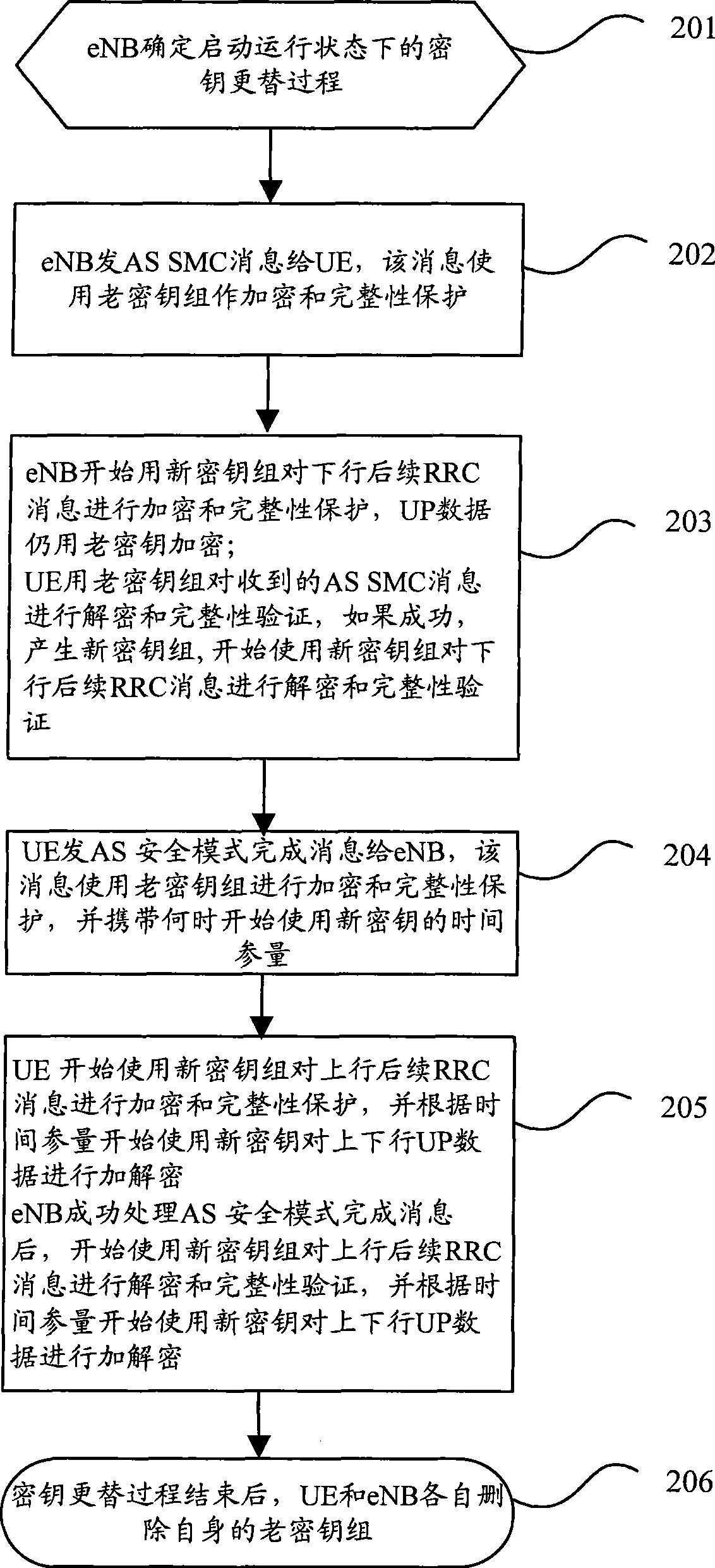
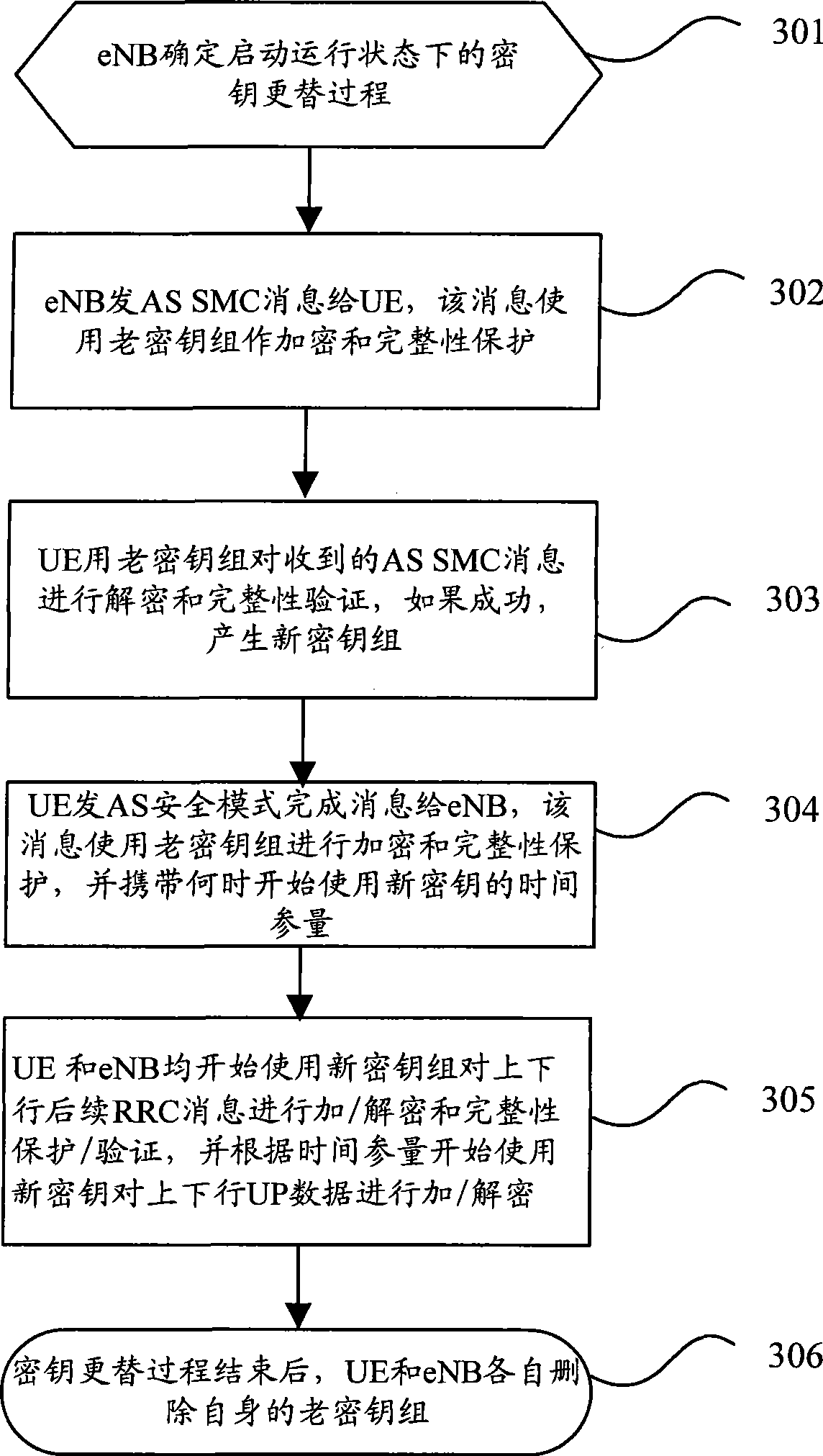
The invention discloses a key alternation method which comprises the following procedures: evolution nodes send access stratum safe mode command information which is encrypted and wholly protected through an old key set to user equipment; after successfully processing the access stratum safe mode information with the old key set, the user equipment sends the finished access stratum safe mode information which is encrypted and wholly protected through an old key set to the evolution nodes, and next, the user equipment begins encrypting or decrypting user plane data with a new key; after processing the finished access stratum safe mode information with the old key set, the evolution nodes begins encrypting or decrypting user plane data with a new key. The invention also discloses a key alternation system and the composition equipment. The invention can be used for ensuring that the key used by the user equipment is synchronous with the key used by the network user information when keys are alternated, thus avoiding user communication data from losing lead by the de-synchrony between the key used by the user equipment and the network key, and fatherly raising the communication quality of users.
Owner:ZTE CORP
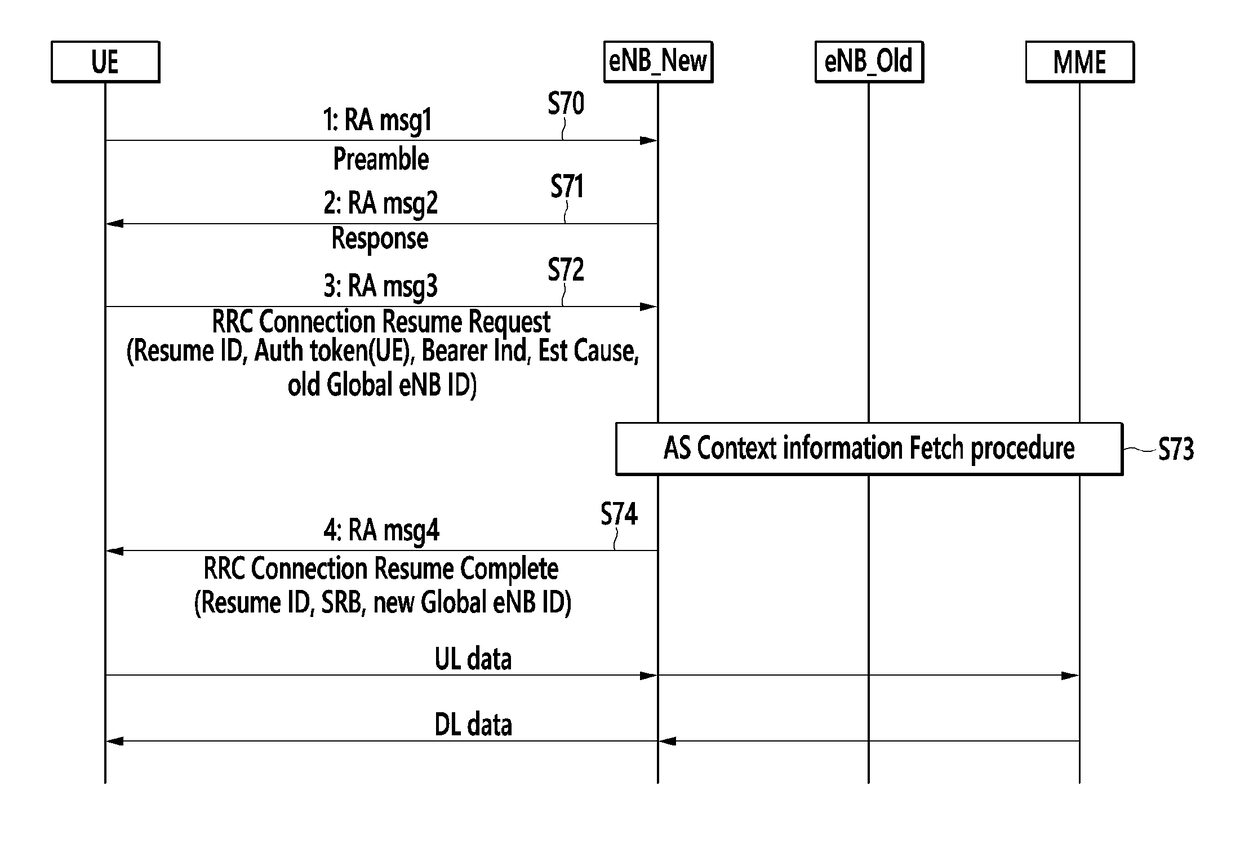
Method and apparatus for reusing access stratum context through unique base station identifier, and method and apparatus for resuming radio resource control (RRC) connection by using the same
InactiveUS20170202051A1Reduce signaling overheadReduce battery consumptionConnection managementTelecommunicationsAccess stratum
Provided is a method for resuming, by a first base station, a radio resource control (RRC) connection suspended by a second base station. The first base station receives an RRC connection resume request message including a first identifier and a resume identifier for identifying the second base station from a terminal. The first base station identifies the second base station using the first identifier. Further, the first base station acquires access stratum (AS) context information matching the resume identifier from the second base station, using the resume identifier.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com