Security negotiation method and apparatus when switching between different wireless access technologies
A wireless access technology and security technology, which can be used in security devices, radio/induction link selection arrangements, access restrictions, etc., and can solve problems such as switching to LTE systems for unsuitable terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Embodiments of the present invention provide a method and device for security negotiation when switching between different wireless access technologies.
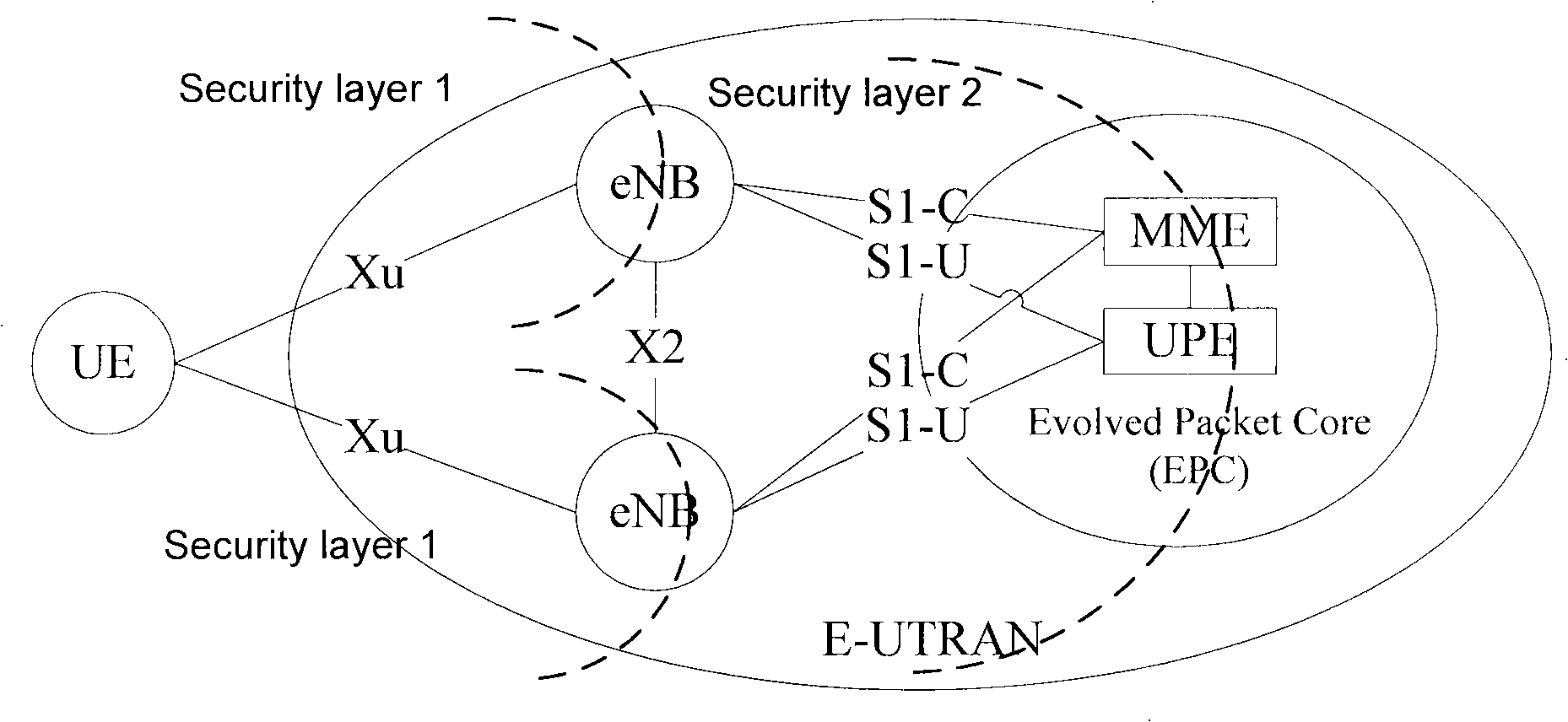
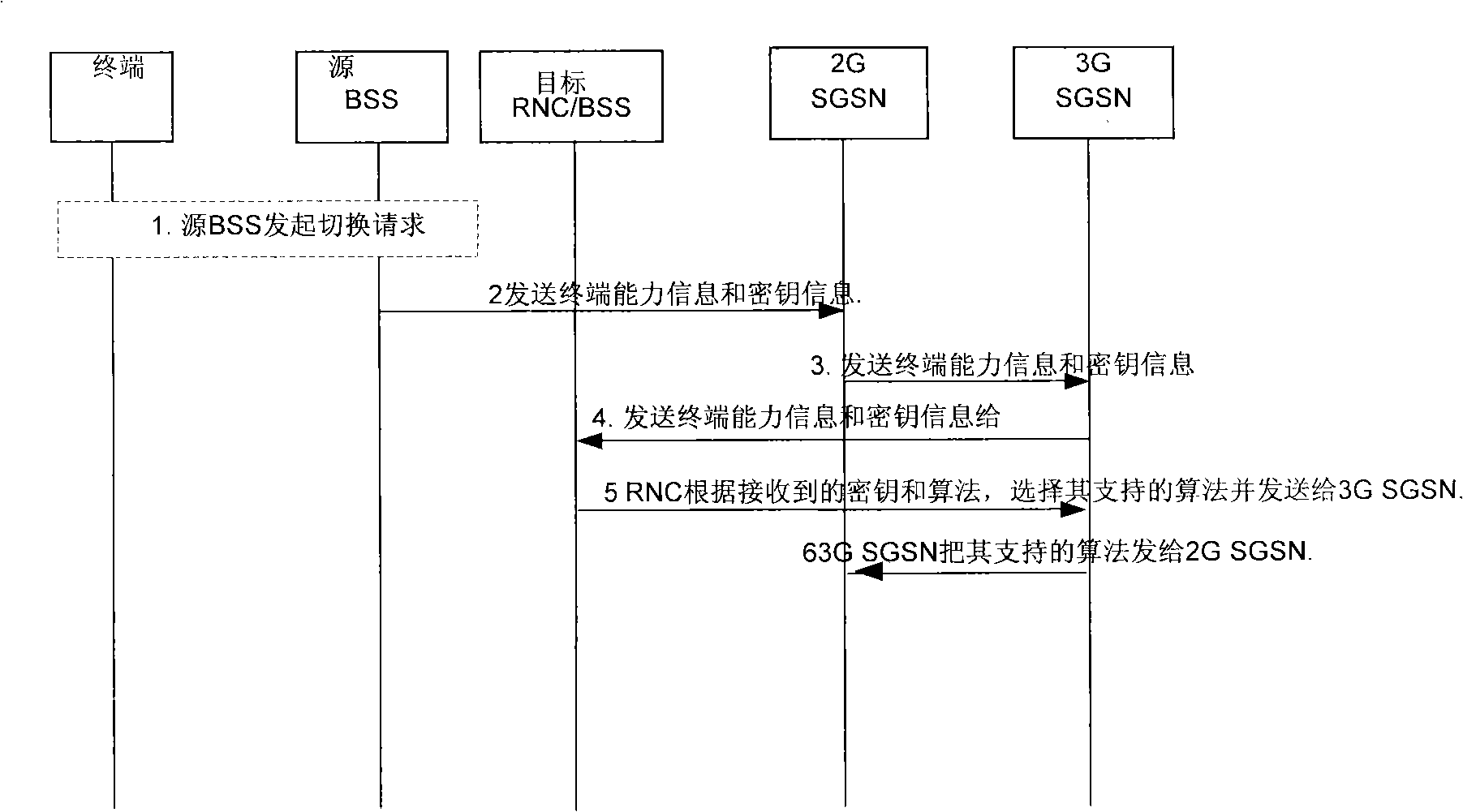
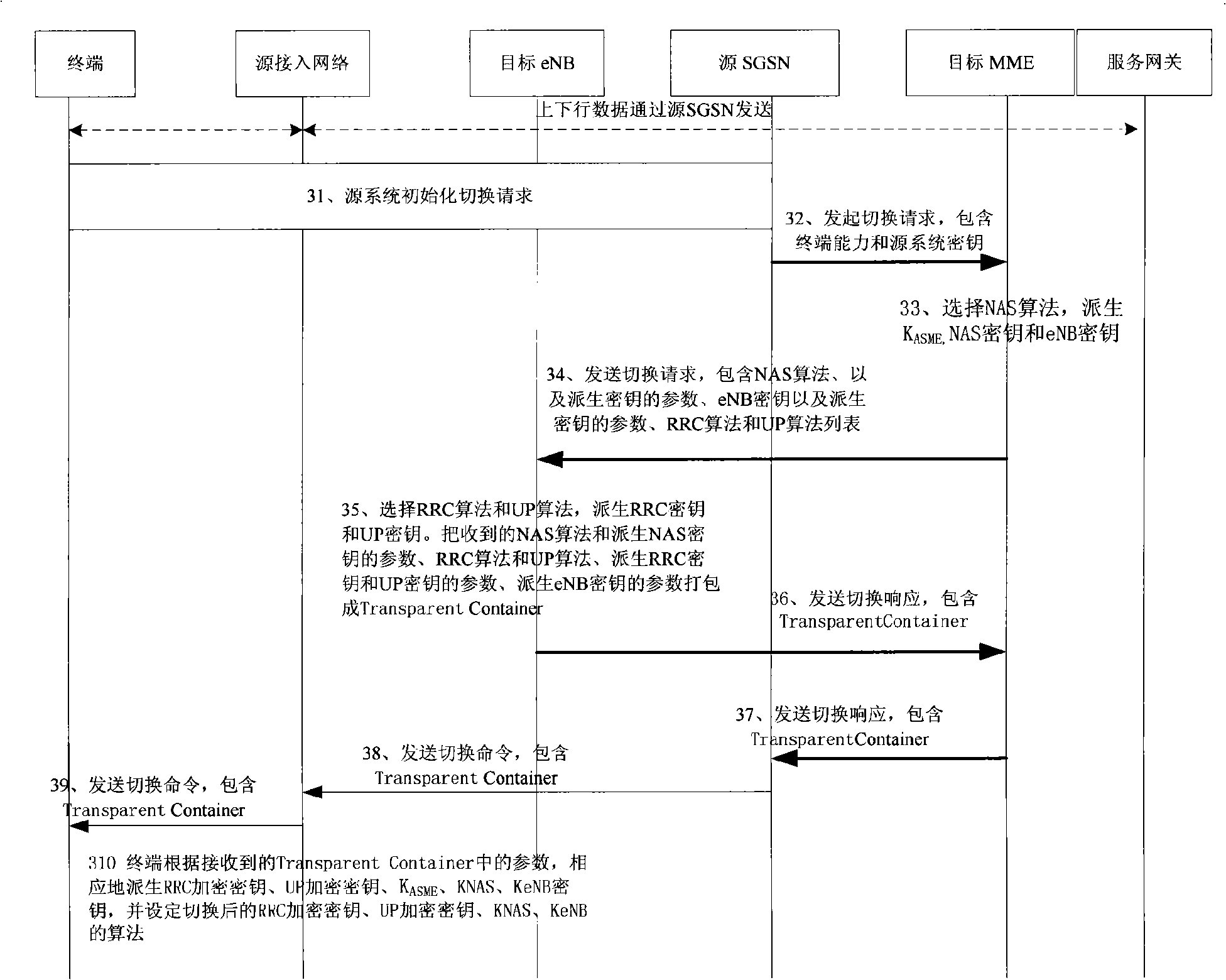
[0041]The handover of the terminal between different radio access technologies in the embodiment of the present invention includes the handover of the terminal from a different system to the LTE system. The following uses the handover of the terminal from the UTRAN system to the LTE system as an example to illustrate the method and device in the embodiment of the present invention.
[0042] In the embodiment of the present invention, when the terminal switches from the UTRAN system to the LTE system, the TargetMME (Mobile Management Entity, target mobile management entity) generates information related to NAS security and sends it to the Target eNB (target evolved base station), and the Target eNB also Generate information related to AS security, and form a TransparentContainer according to the security information of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com