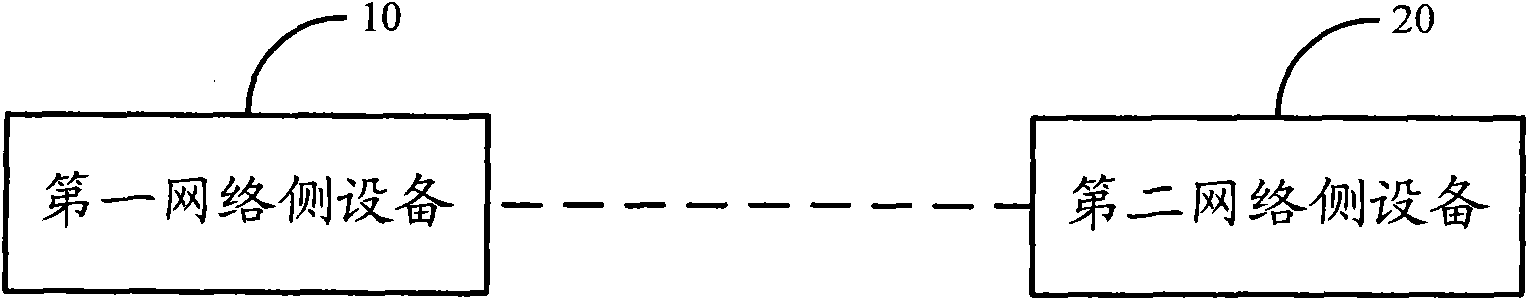Method, system and device for determining keys and ciphertexts
A key and key parameter technology, applied in security devices, electrical components, wireless communication, etc., can solve problems such as insufficient use of RNBearerID, insufficient number of RNBearerIDs, and reduce the security of the Un port, so as to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] Aiming at the problem that the number of RN Bearer IDs in candidate architecture 4 may not be sufficient, the embodiment of the present invention proposes two solutions.
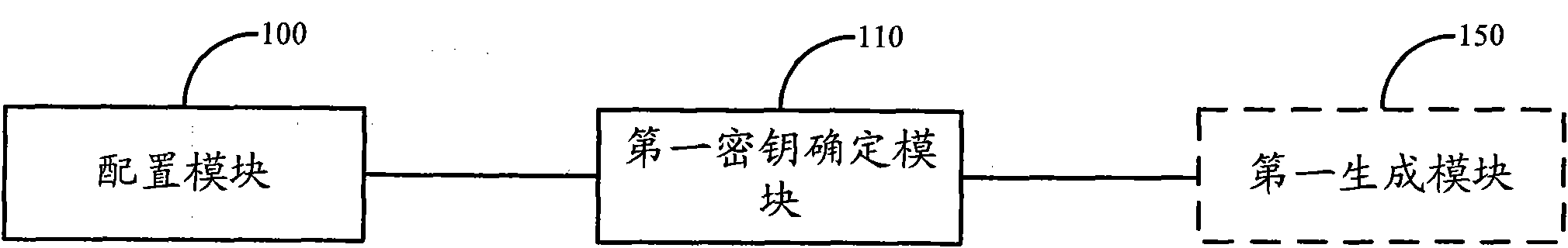
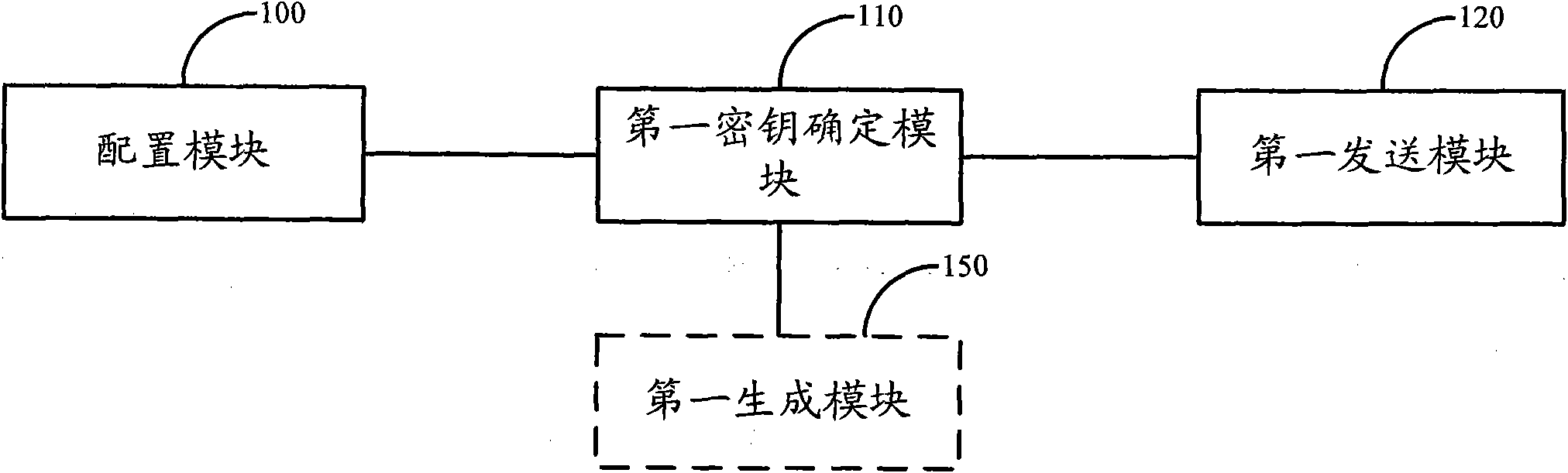
[0047] Solution 1: In the embodiment of the present invention, after the user terminal initiates an attach request, the first network-side device configures a key parameter for the user terminal, and the first network-side device and the second network-side device connected to the first network-side device respectively according to The key parameters configured by the first network side device and the preset encryption parameters determine a pair of access layer AS keys corresponding to the user terminal. Since a different key can be assigned to each user terminal according to the accessed user terminal, in the LTE-A system, when a large number of UEs access the RN equipment in candidate architecture 4, multiple RN radio bearers need to be established In this case, the security of the Un port is impro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com