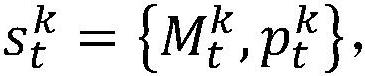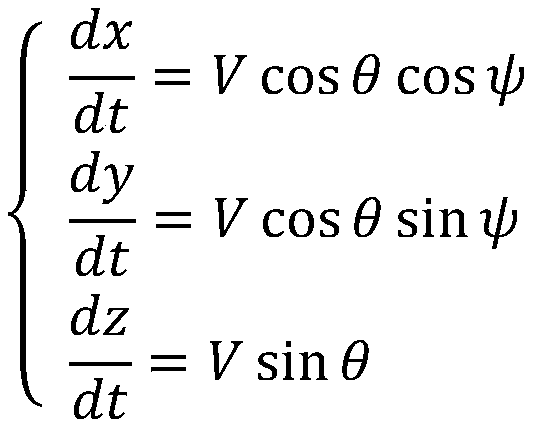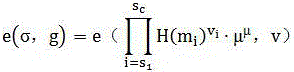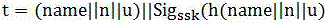Patents
Literature
211results about How to "Reduce storage burden" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
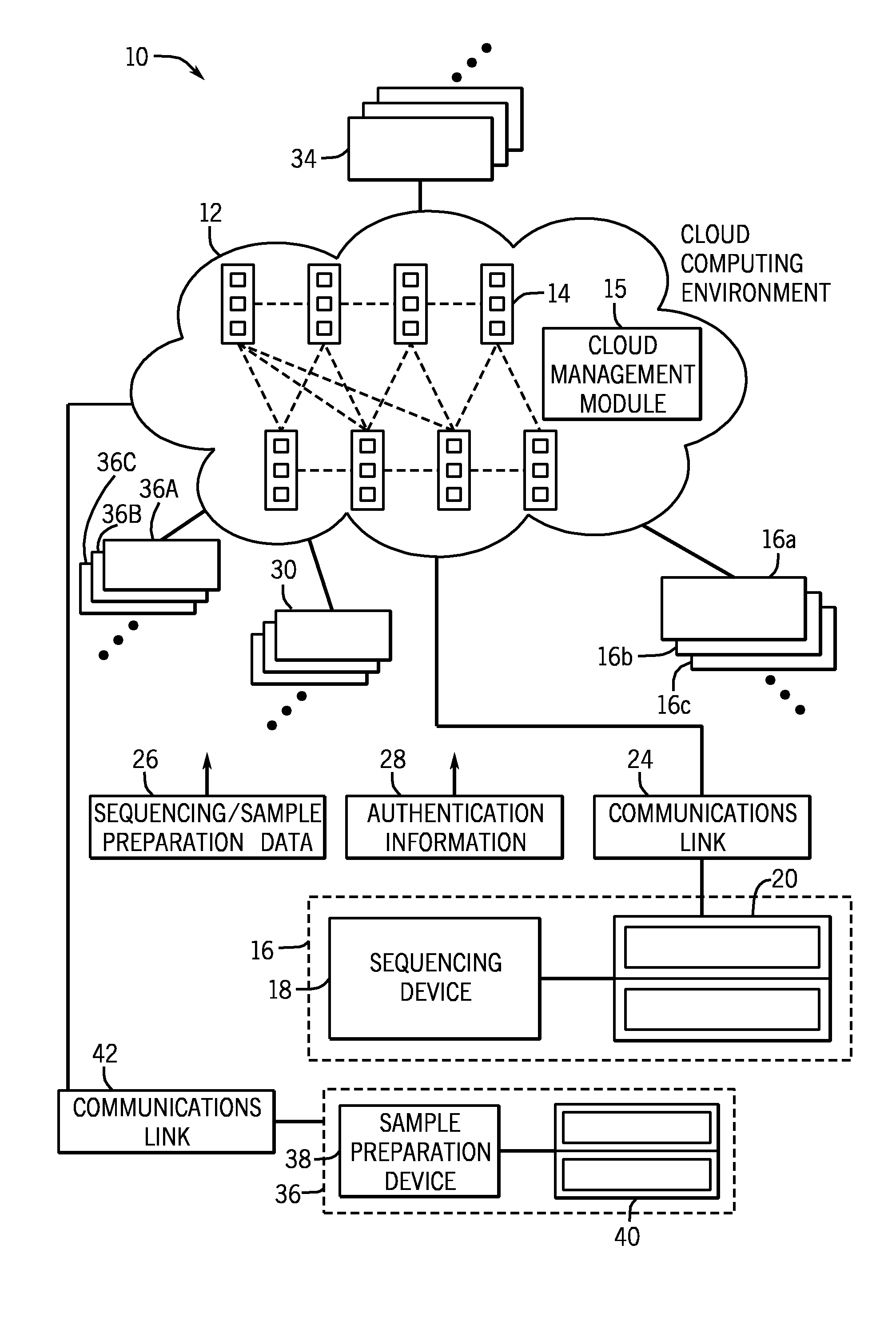
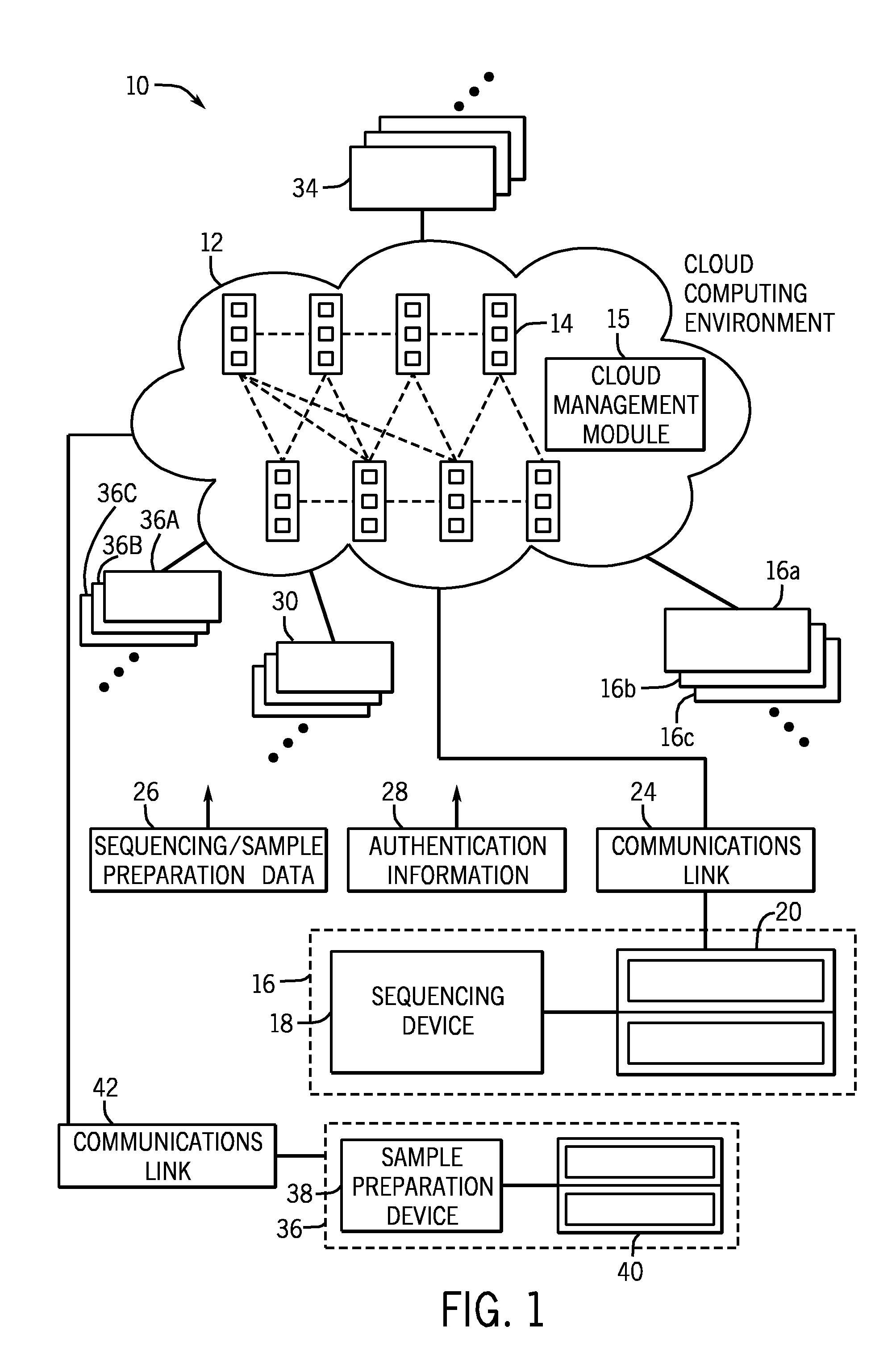
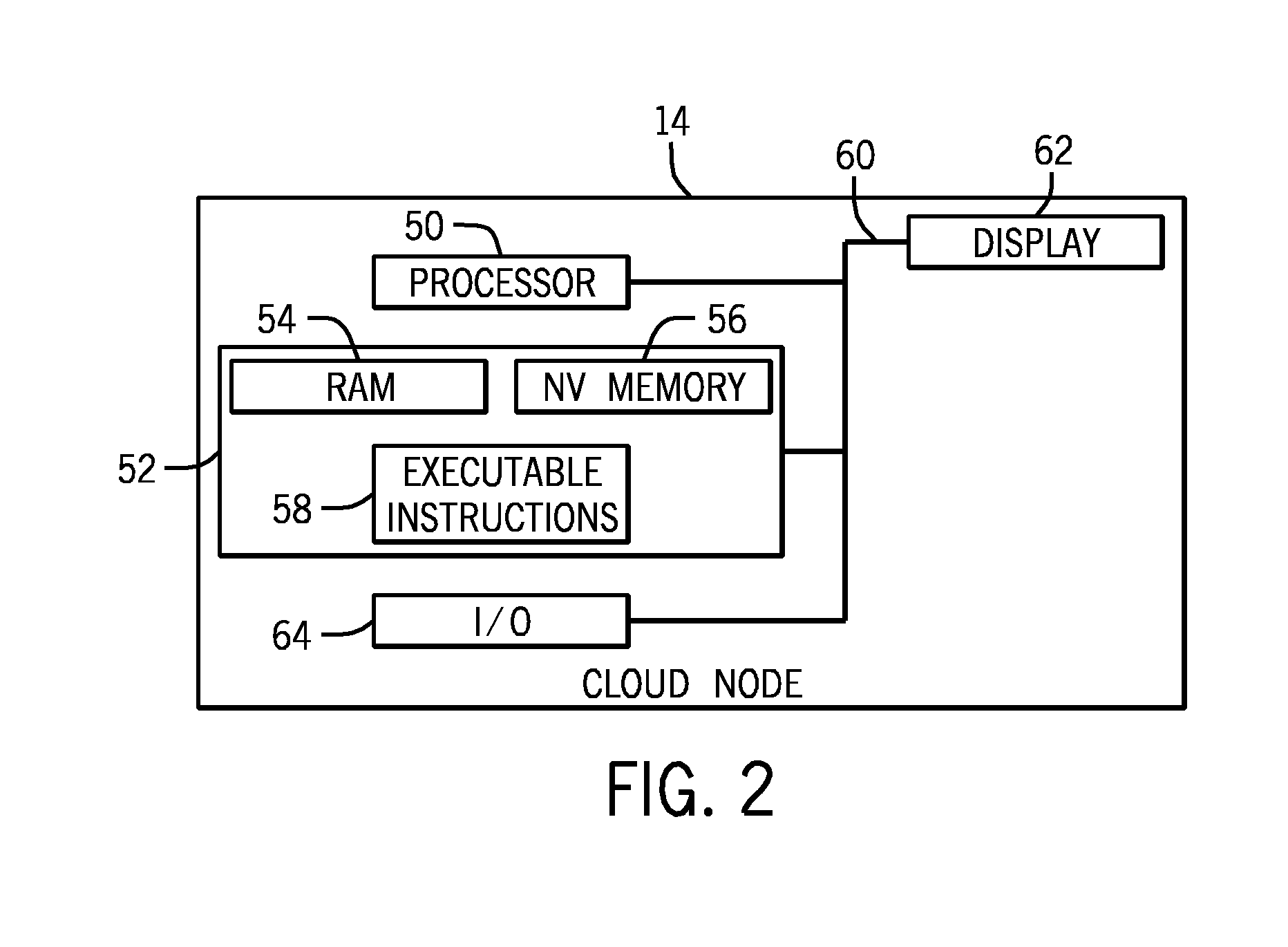
Methods and systems for using a cloud computing environment to share biological related data
ActiveUS20140214579A1Reduce processReduce storage burdenBuying/selling/leasing transactionsSequence analysisCloud baseAnalysis method
The present disclosure provides a novel approach for shifting or distributing various information (e.g., protocols, analysis methods, sample preparation data, sequencing data, etc.) to a cloud-based network. For example, the techniques relate to a cloud computing environment configured to receive this information from one or more individual sample preparation devices, sequencing devices, and / or computing systems. In turn, the cloud computing environment may generate information for use in the cloud computing environment and / or to provide the generated information to the devices to guide a genomic analysis workflow. Further, the cloud computing environment may be used to facilitate the sharing of sample preparation protocols for use with generic sample preparation cartridges and / or monitoring the popularity of the sample preparation protocols.
Owner:ILLUMINA INC
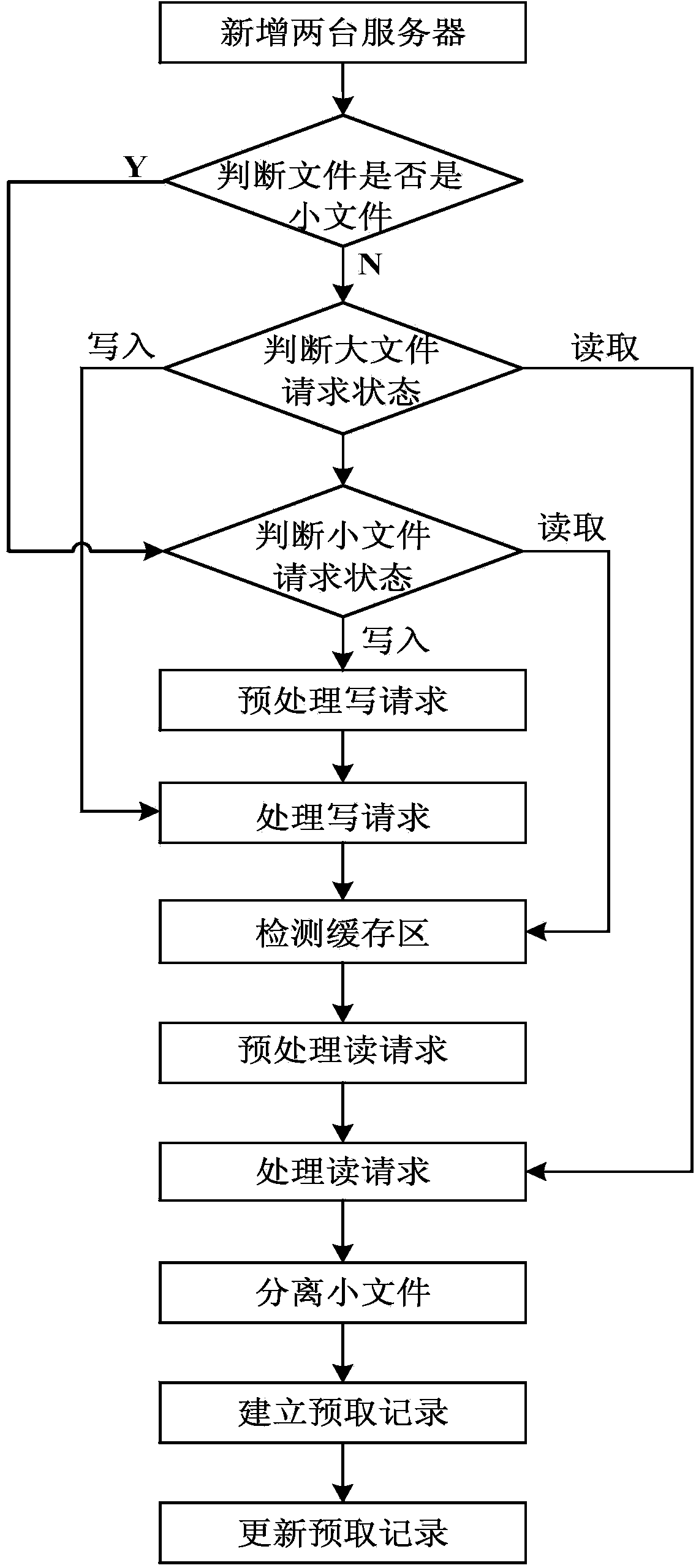
Small file storage method based on Hadoop distributed file system
ActiveCN103856567AImprove work efficiencyReduce storage burdenTransmissionDistributed File SystemFile system
The invention discloses a small file storage method based on a Hadoop distributed file system. The method comprises steps of (1) additionally arranging two servers; (2) judging whether a file is a small file; (3) judging the request state of a large file; (4) judging the request state of the small file; (5) pre-processing a write request; (6) processing the write request; (7) detecting a cache; (8) pre-processing a read request; (9) processing a read request; (10) separating small files; (11) establishing a prefetching record; and (12) updating the prefetching record. Compared with existing methods for storing lots of small files, the small file storage method guarantees universality of the system, and also has advantages of having high reading and writing performance and efficiency, easing NameNode internal storage burden, and solving problems of high NameNode memory usage rate in storing lots of small files, and low storage access efficiency. The small file storage method can be used by the distributed file system for storing and managing lots of small files.
Owner:XIDIAN UNIV
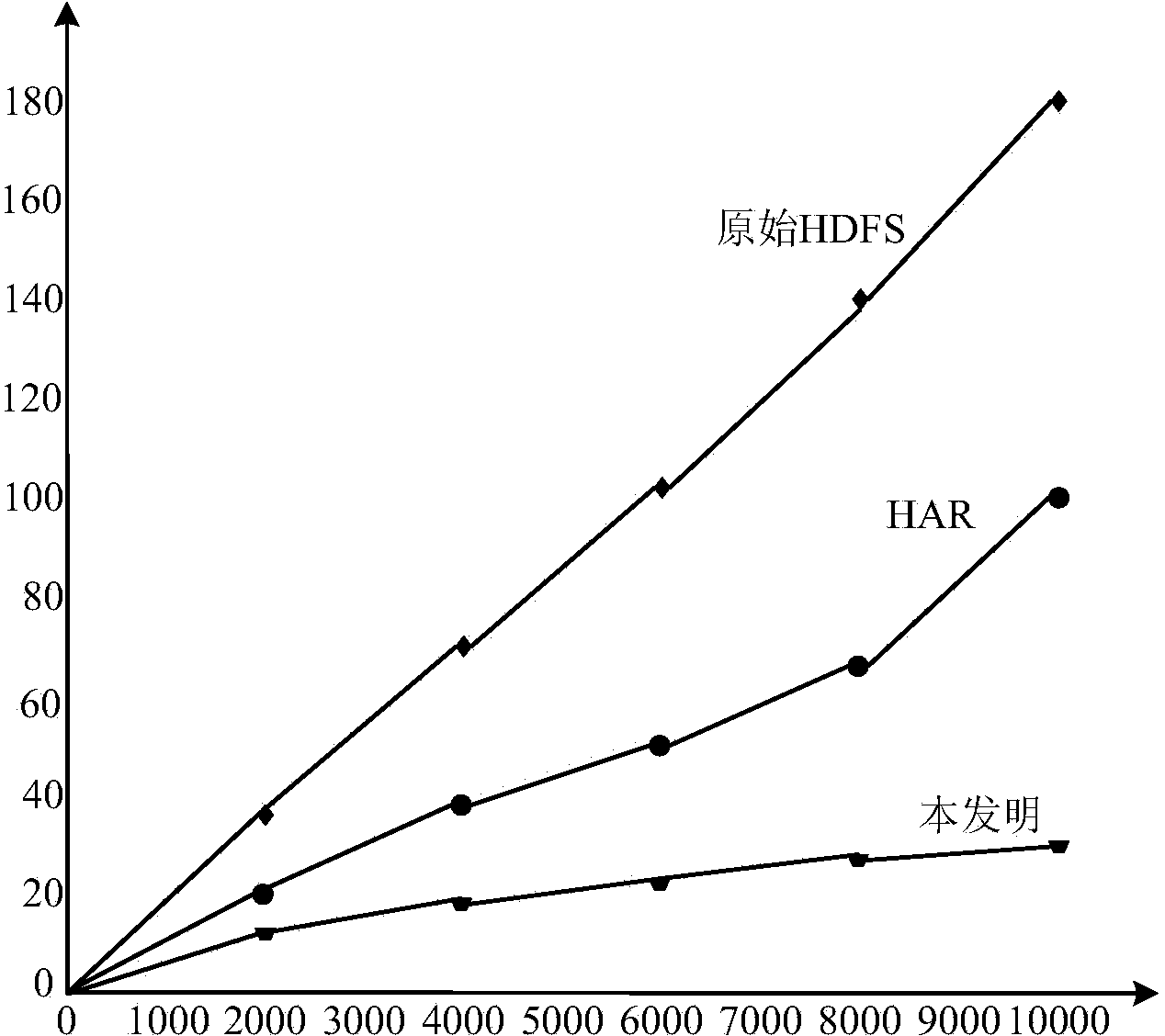
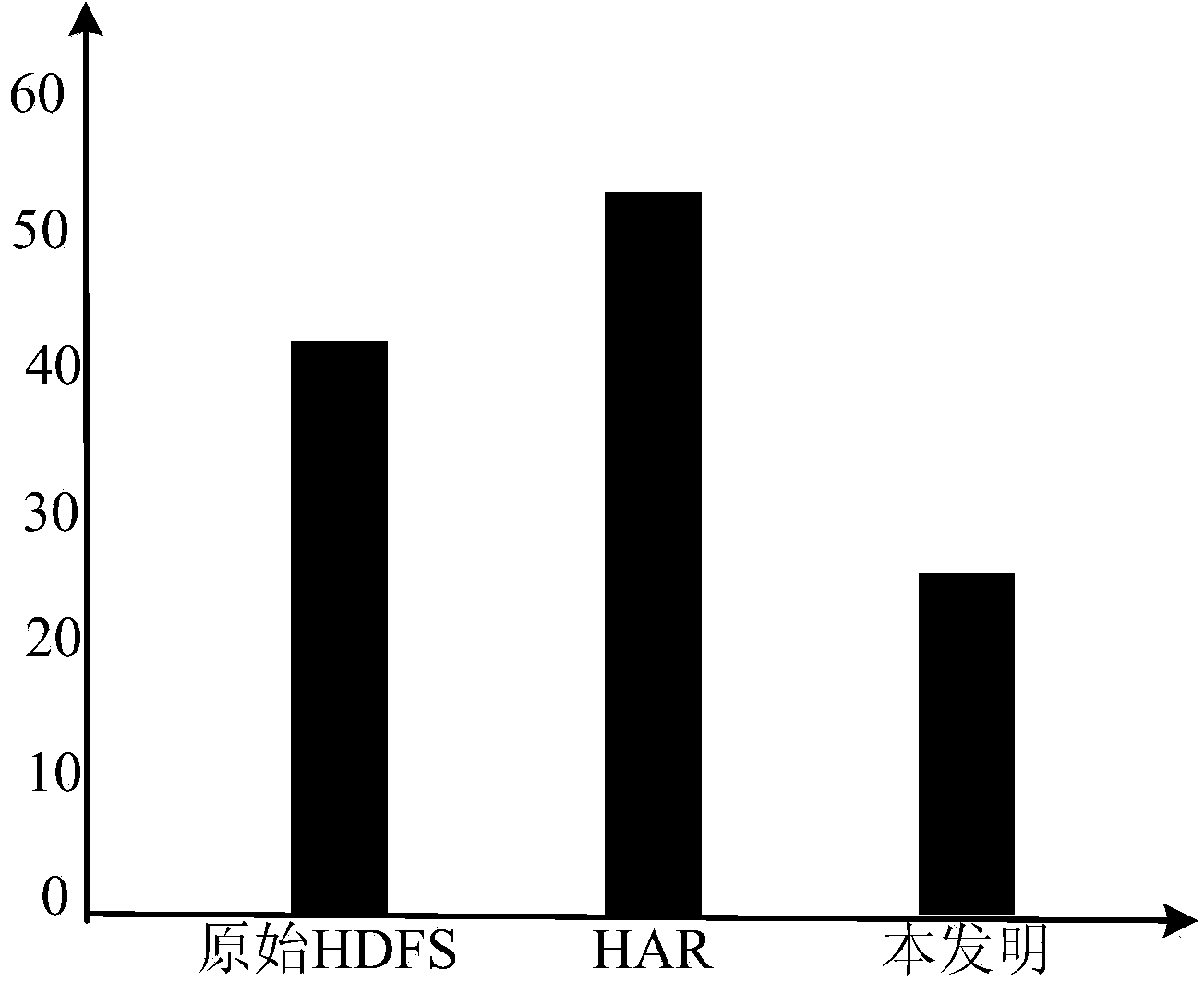
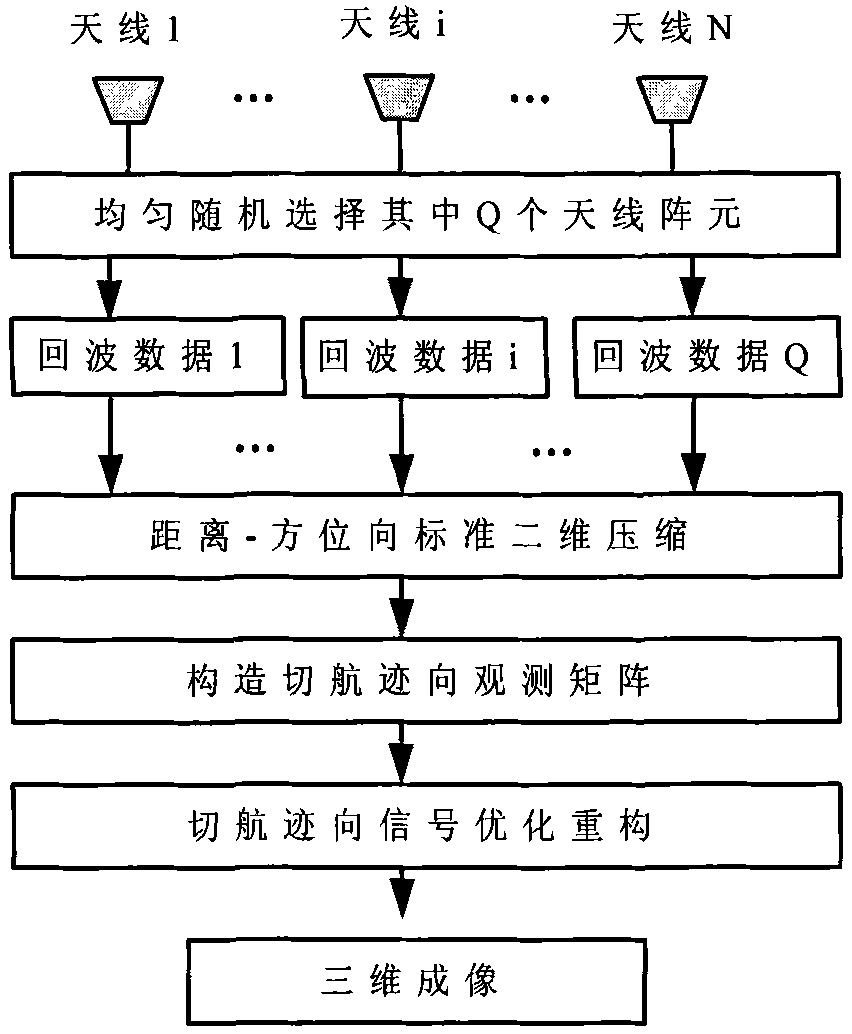
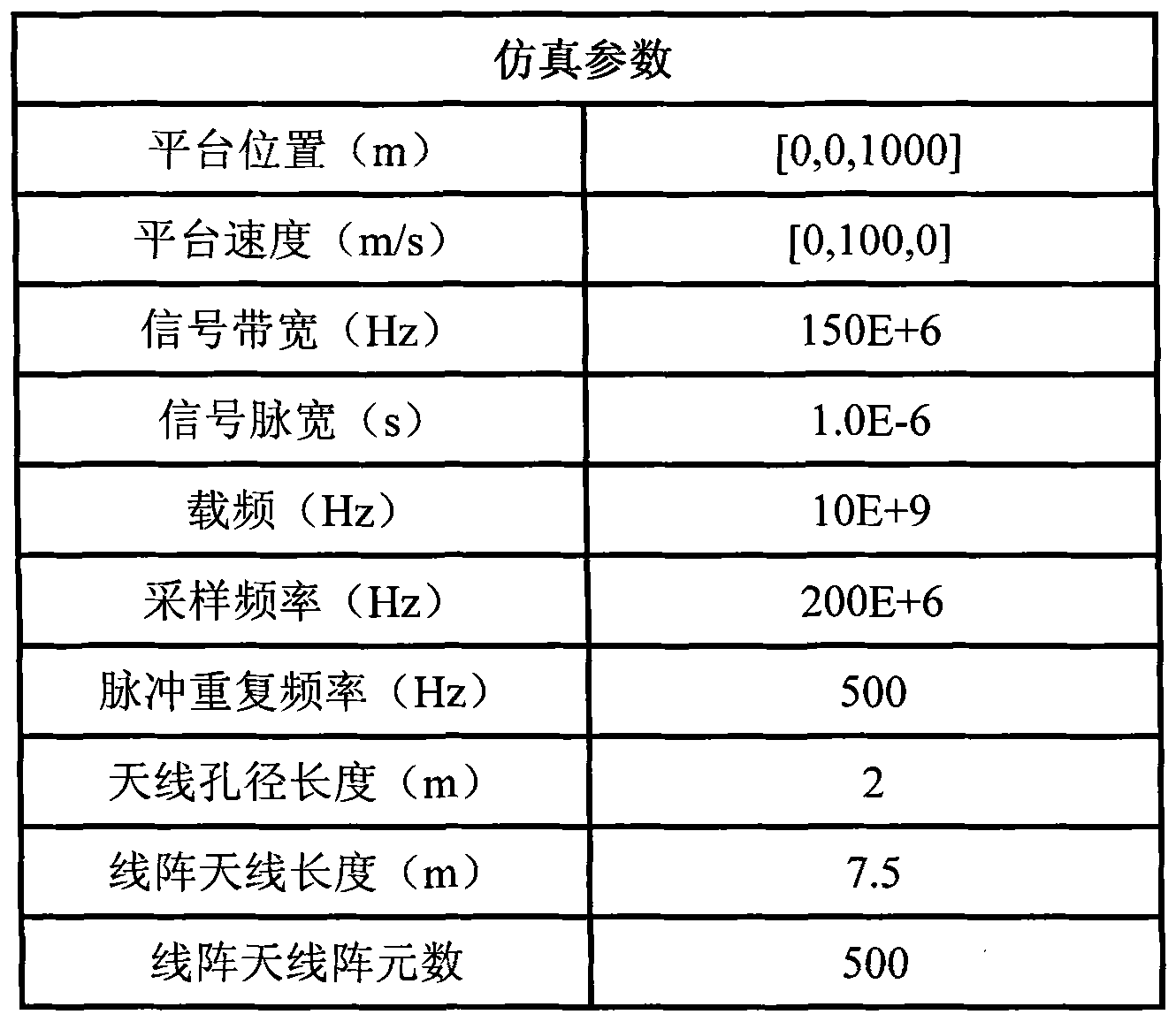
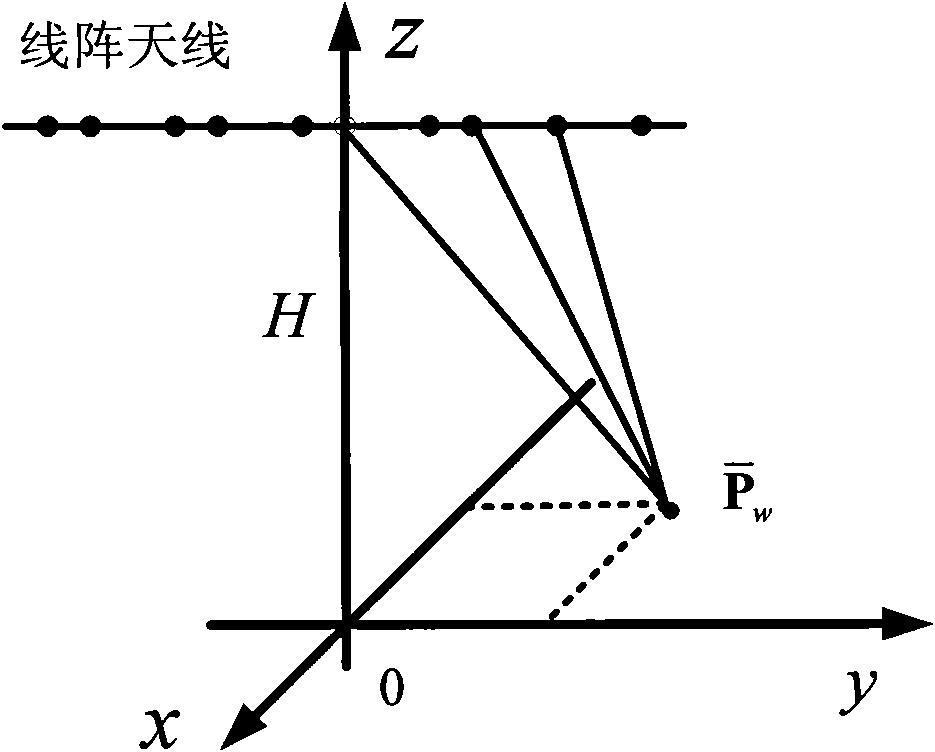
Linear array SAR (synthetic aperture radar) three-dimensional imaging method based on compressed sensing
InactiveCN102313888AReduce the number of line array elementsReduce data collectionRadio wave reradiation/reflectionOptimization problemSynthetic aperture sonar
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
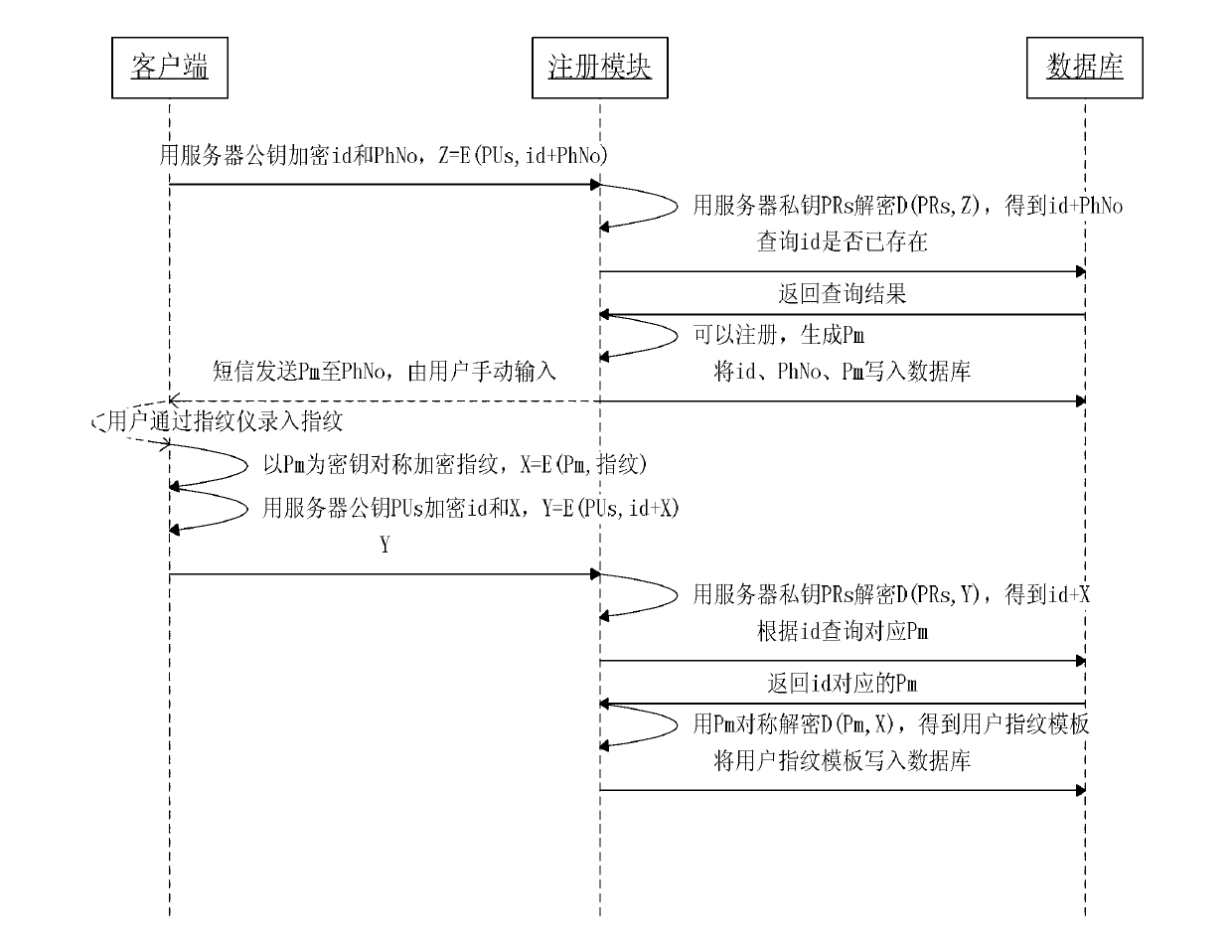
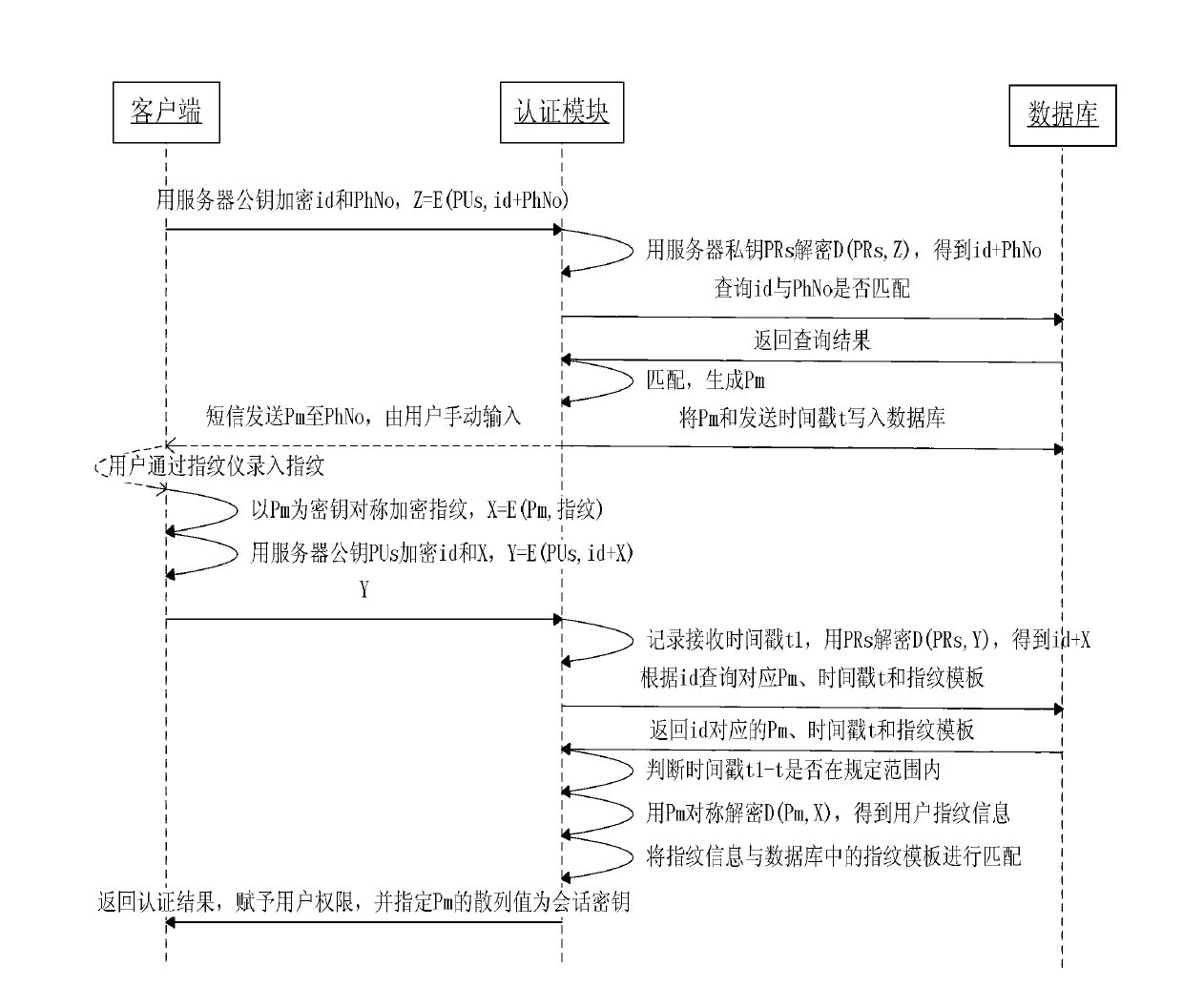
Bidirectional identity authentication method based on dynamic password and biologic features under cloud environment
ActiveCN103124269AImprove securityImprove stabilityUser identity/authority verificationPasswordDependability
The invention discloses a bidirectional identity authentication method based on dynamic password and biologic features under cloud environment, wherein a plurality of authentication methods and encryption technologies are comprehensively used, a one-time random key is obtained by receiving messages, the bidirectional authentication is realized, a user can login anywhere, finish registration process on net, and has no need to register information at designated location. According to the bidirectional identity authentication method based on dynamic password and biologic features under cloud environment, the one-time dynamic password is combined with the biological features, secret key is transmitted to GSM (Global System for Mobile Communication), and accordingly, security and reliability of authentication process are enhanced.
Owner:GUILIN UNIV OF ELECTRONIC TECH
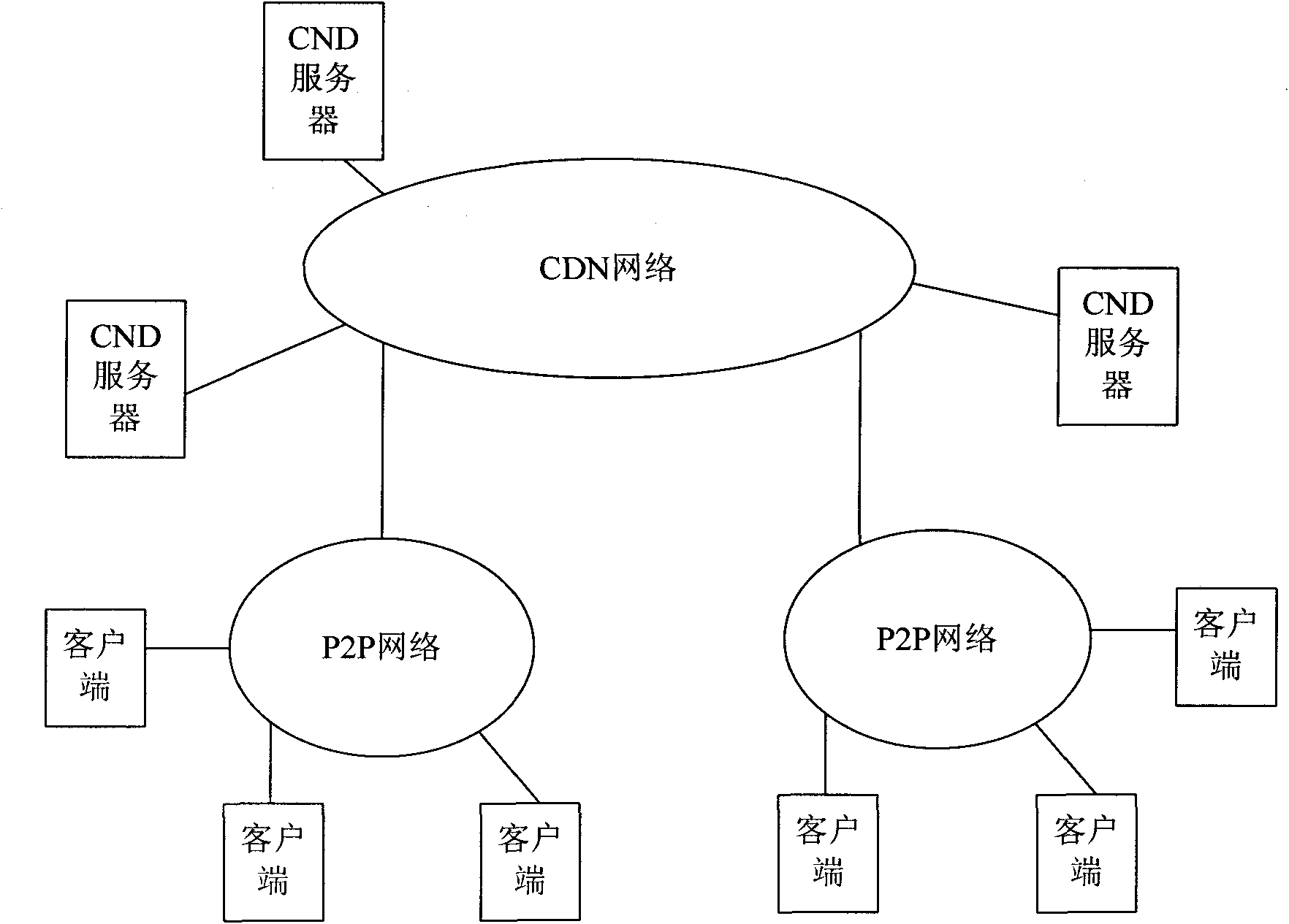
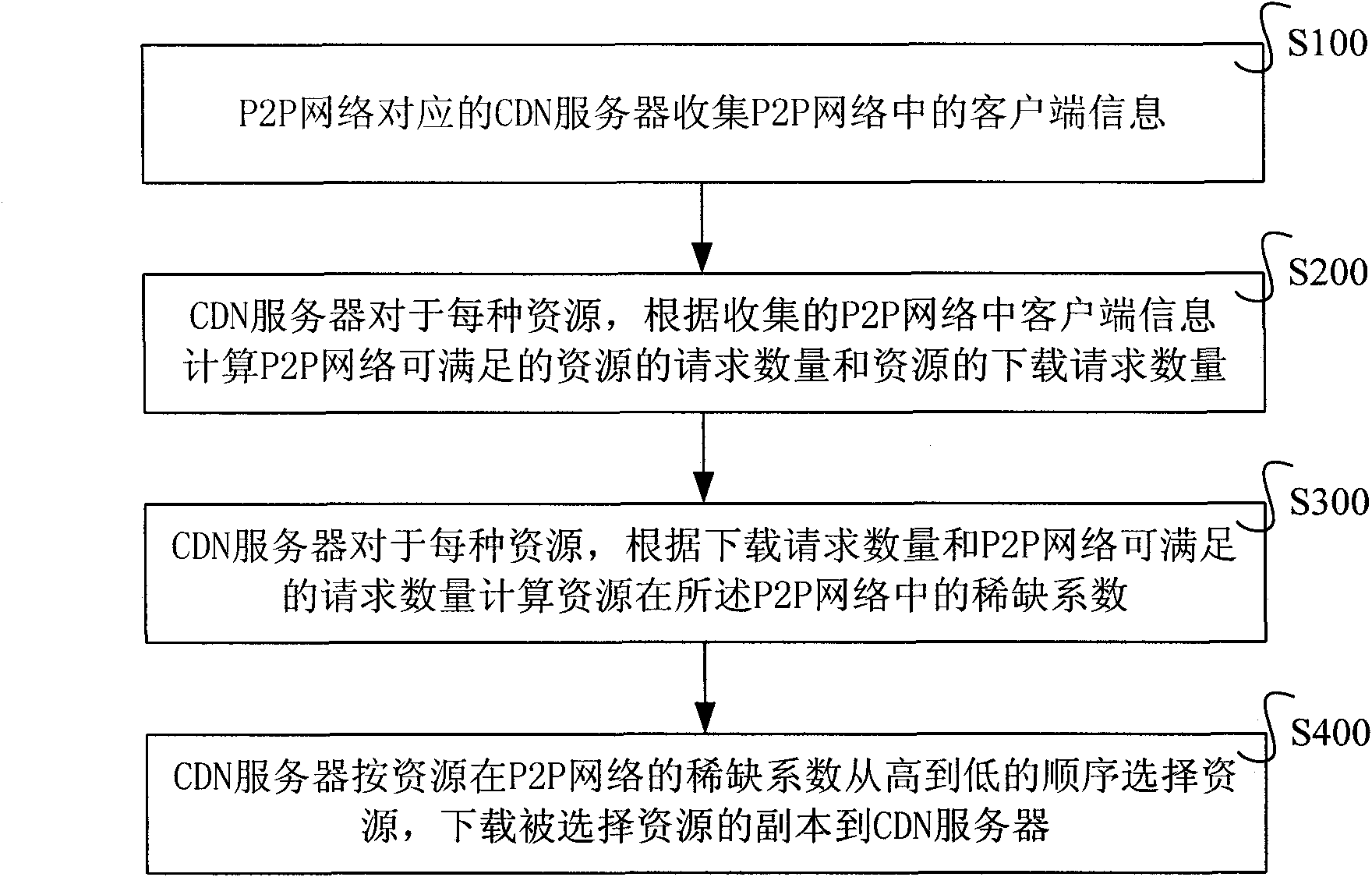
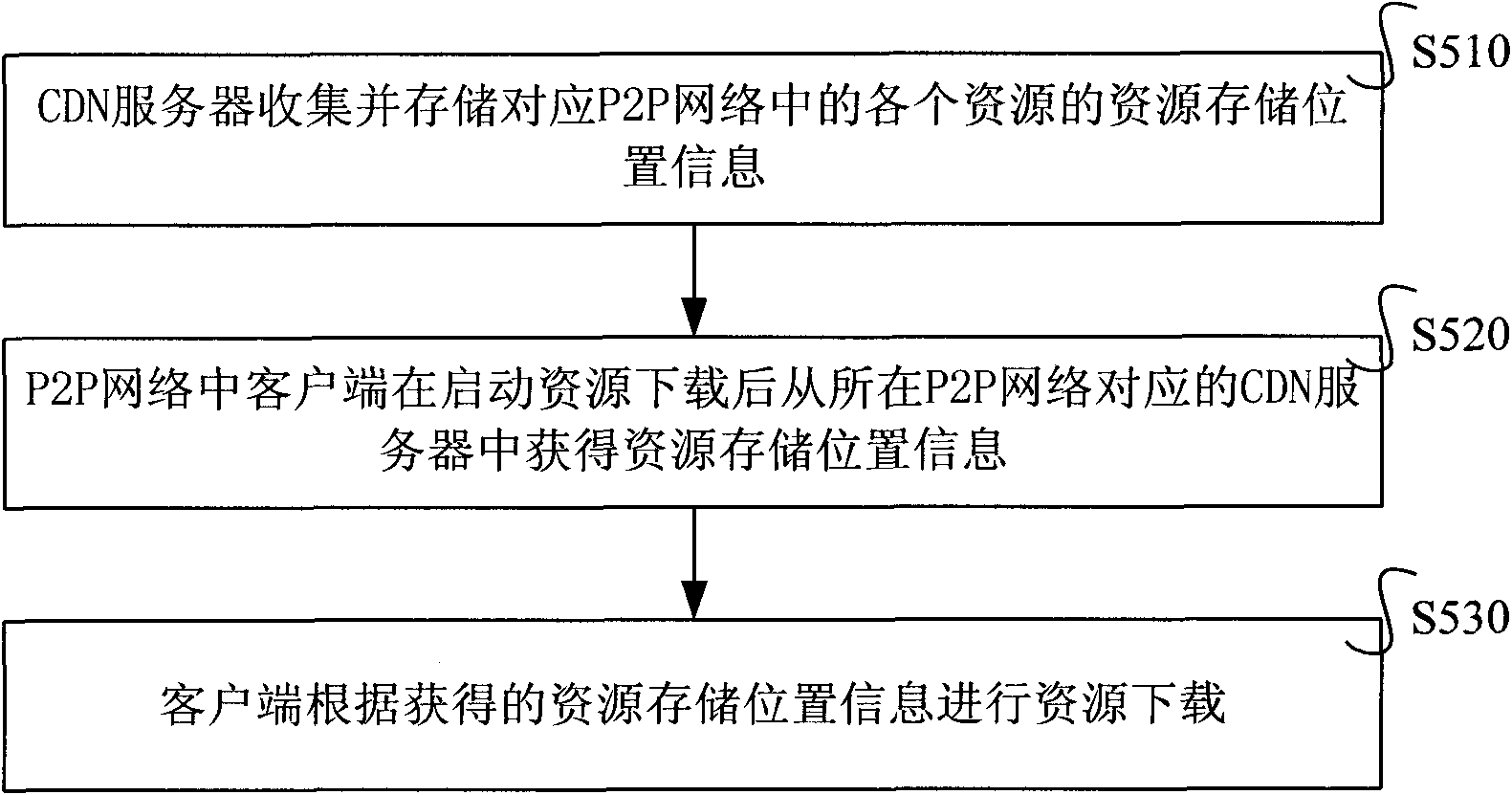
Method and system for placing resources replication in CDN-P2P (Content Distribution Network-Peer-to-Peer) network
ActiveCN101841556AImprove storage space utilization efficiencyImprove distribution efficiencyData switching networksClient-sideContent distribution
The invention relates to a method and a system for placing resources replications in a CDN-P2P(Content Distribution Network-Peer-to-Peer) network. In the method, firstly, a CDN server collects the information of resources downloaded by a client in a corresponding P2P network, the information of resources required to be downloaded by the client and the communication performance index of the clientby the CDN server; secondly, the CDN server calculates the satisfiable number of requests of resources according to the information of resources downloaded and the communication performance index by the CDN server and calculates the number of download requests of resources according to the information of resources required to be downloaded; thirdly, the CDN server calculates the scarcity coefficient according to the number of download requests of resources in the corresponding P2P network and the satisfiable number of requests of resources in the P2P network; and fourthly, the CDN server selects the resources in a hierarchy of the resources from greater to smaller scarcity coefficients in the P2P network by the CDN server and downloads the replications of selected resources to the CDN server. The invention can improve the utilization ratio of the storage space of the CDN server.
Owner:INST OF COMPUTING TECHNOLOGY - CHINESE ACAD OF SCI
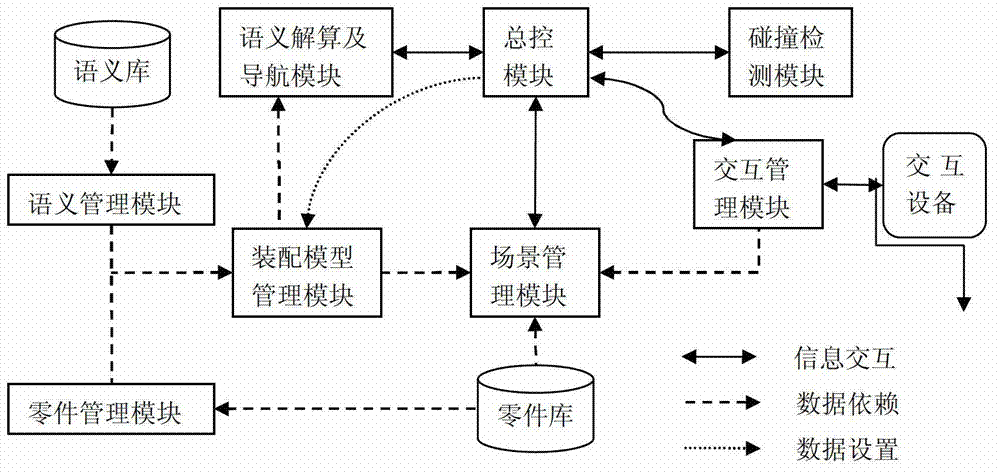
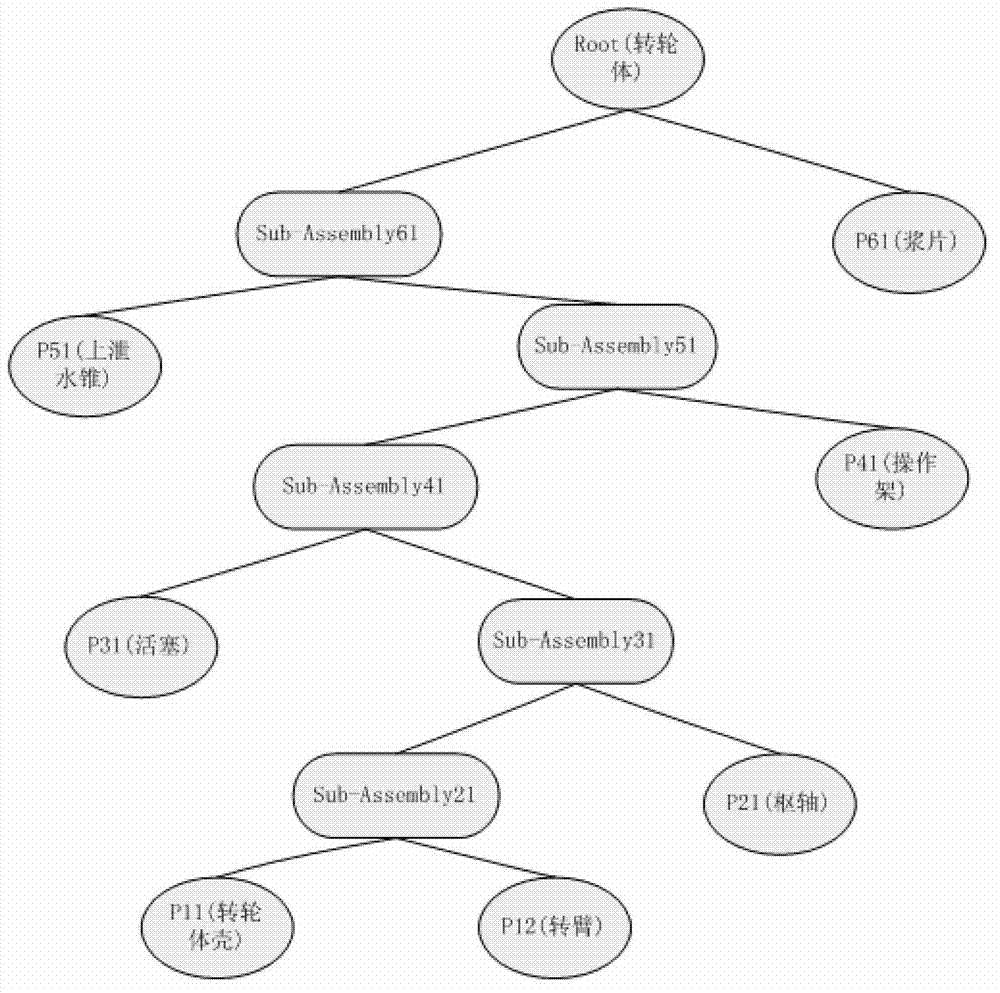
Water-turbine generator set virtual assembly modeling method and system based on tree graph model
InactiveCN102768703ASimple structureReduce storage burdenSpecial data processing applicationsRelational graphBinary tree
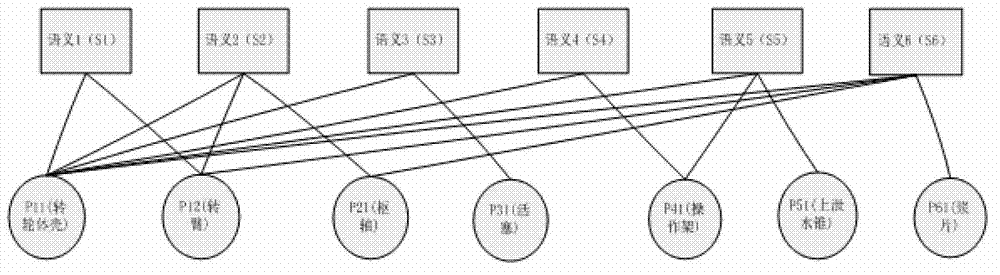
The invention discloses a water-turbine generator set virtual assembly modeling method based on a tree graph model, and is used for simulation of water-turbine generator set virtual assembly. According to the method, the hierarchical structure of a water-turbine generator set and a semantic relation among parts are represented by adopting a mode that an assembly tree and a semantic relational graph are independent; a hierarchical assembly tree is constructed according to a designed structure of the water-turbine generator set in the form of a binary tree, so that structure hierarchicalization for the parts is realized; and a semantic relational graph is constructed according to a semantic constraint relation of the parts in the form of the binary tree. The invention also discloses a semantic identification and calculation method for guiding user interaction based on the molding method and a final water-turbine generator set virtual assembly simulation system. Compared with the prior art, the method and the system have the advantages of lightweight of an assembly model, interaction intellectualization and high interaction efficiency and are applicable to implementation of simulation of virtual assembly of various types of water-turbine generator sets.
Owner:HOHAI UNIV
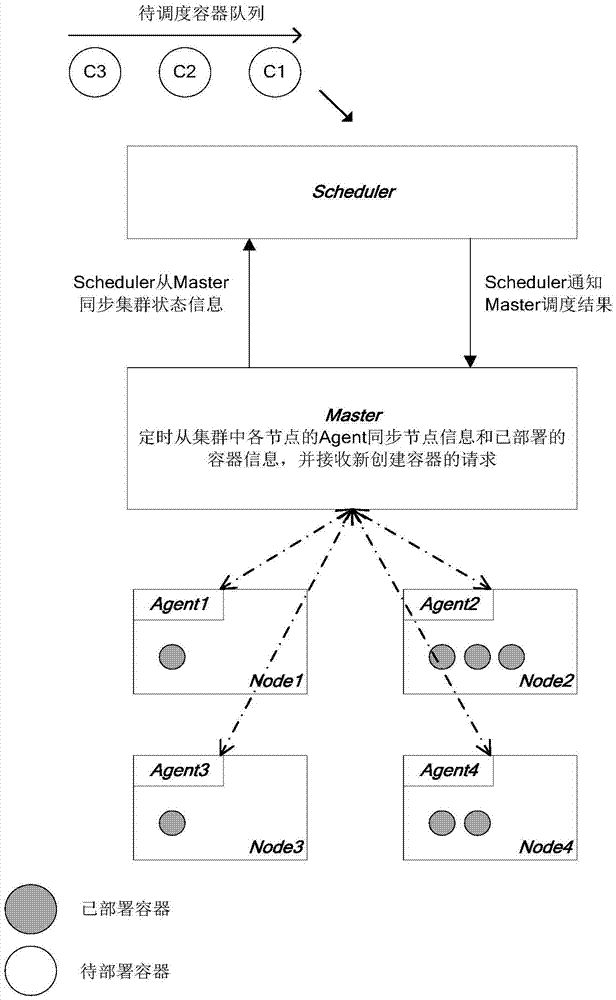
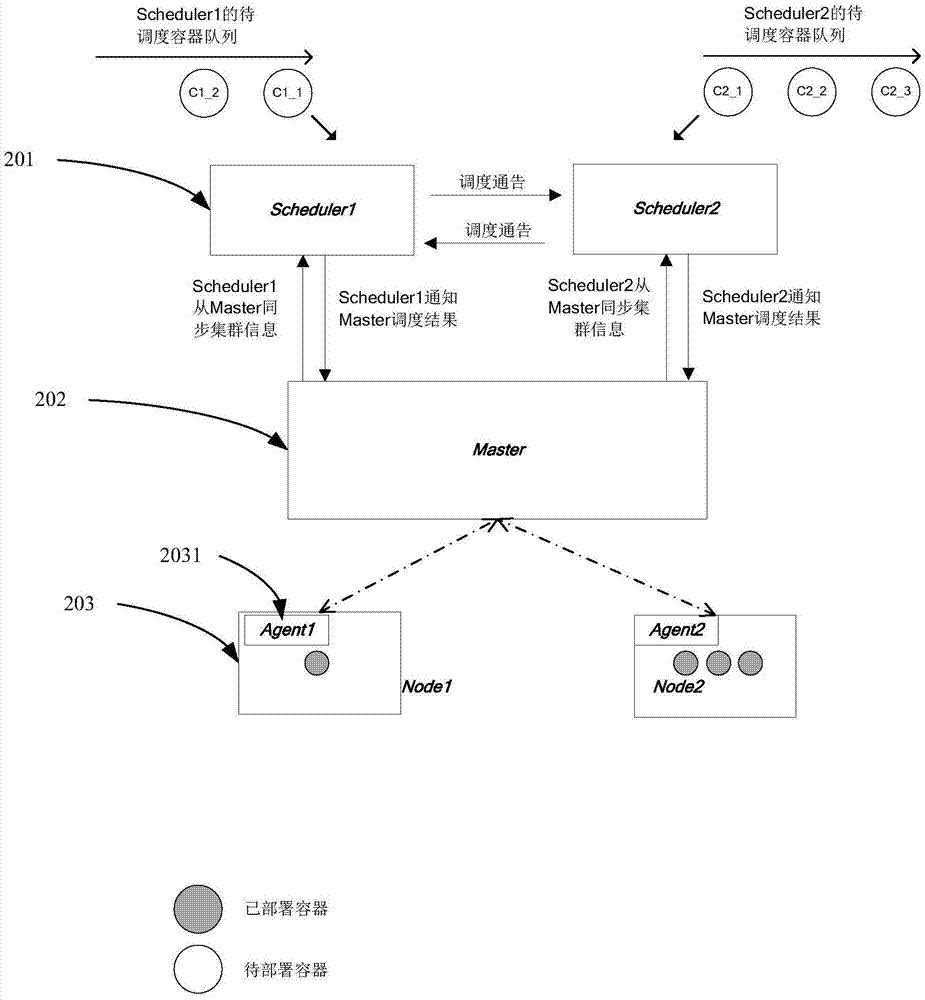
Method and apparatus for scheduling containers in parallel in cluster
ActiveCN106919445AAvoid resource conflictsReduce storage burdenProgram initiation/switchingResource informationCluster state
The invention relates to the technical field of cluster resource scheduling, and provides a method for scheduling containers in parallel in a cluster. The method comprises the steps of periodically obtaining cluster state information by a scheduler, wherein the cluster state information comprises resource information of all nodes in the cluster and description information of all containers in the cluster, the description information of the containers comprises container IDs of the containers, resource demands of the containers and deployment node IDs of the containers, and the resource information of the nodes comprises IDs of the nodes and resource quantities of the nodes; and according to the cluster state information, the container information of the containers scheduled by the scheduler and the container information of the containers scheduled by other schedulers, scheduling to-be-deployed containers to the nodes in the cluster, wherein the scheduled container information comprises container IDs and deployment node IDs of the scheduled containers. Through the scheme, the problem of resource conflicts in parallel scheduling is effectively reduced.
Owner:HUAWEI TECH CO LTD
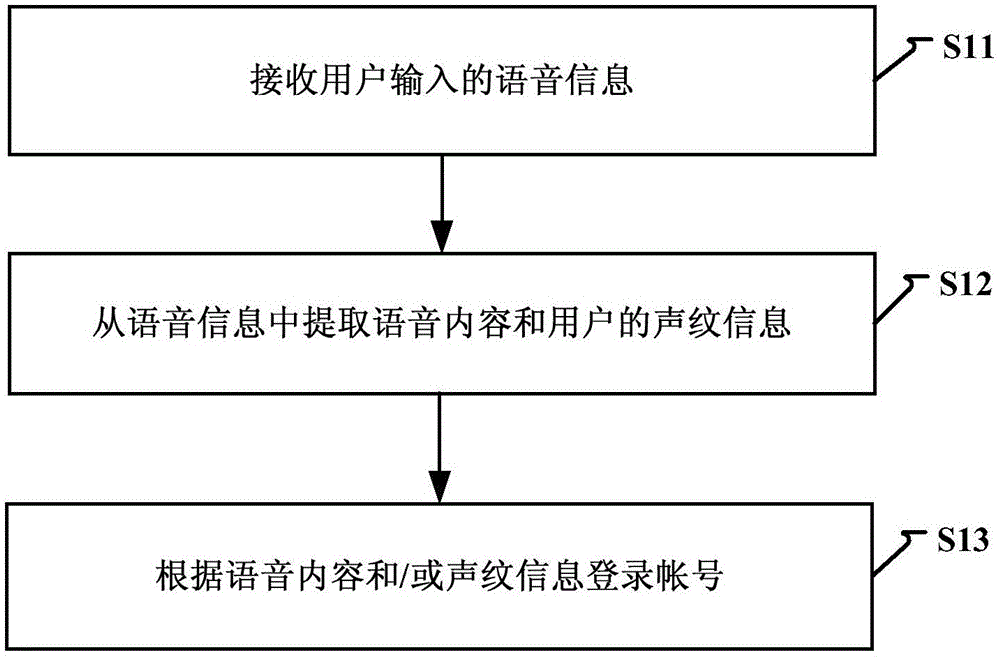
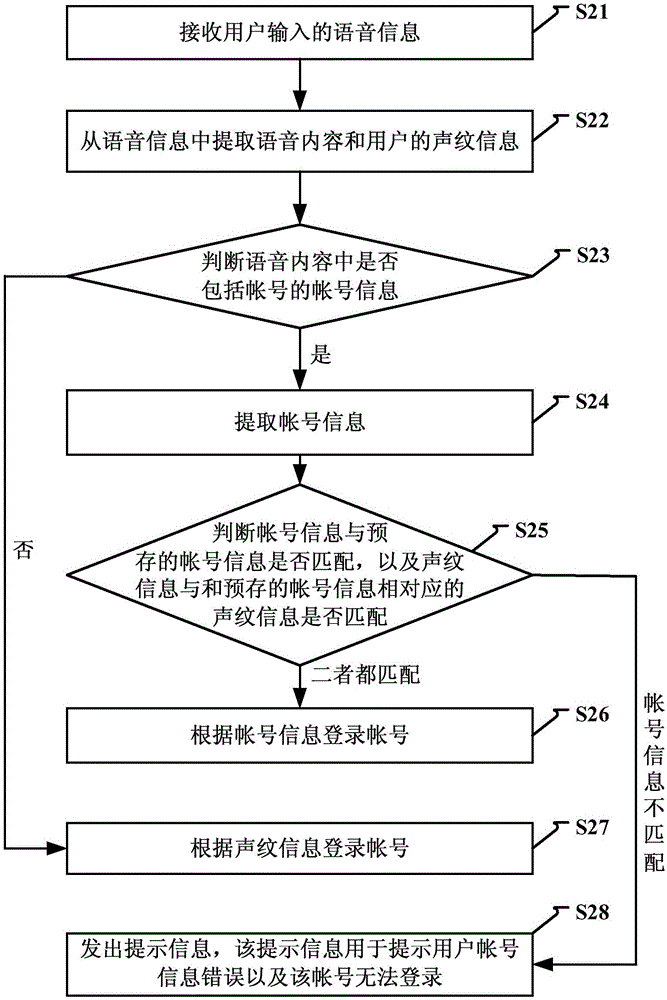
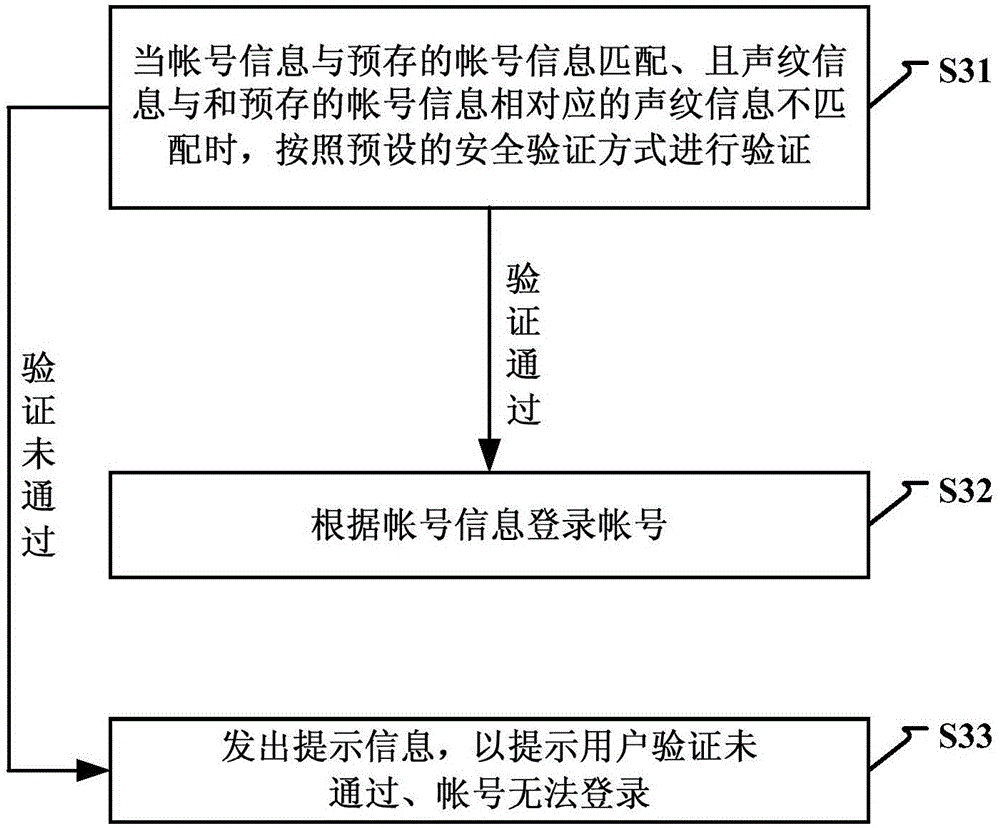
Account login method and device
Owner:BEIJING UNISOUND INFORMATION TECH
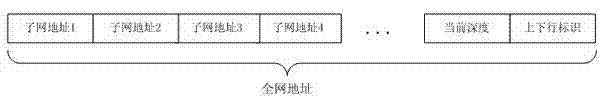
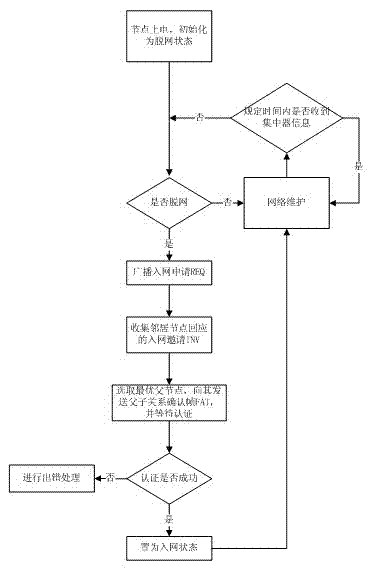
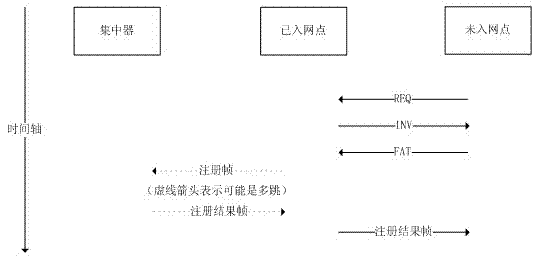
Internetworking method for wireless intelligent meter reading system
InactiveCN103051741AReduce the burden of routing information storageReduce hardware costsStar/tree networksNetwork addressAddress mapping
The invention discloses an internetworking method for a wireless intelligent meter reading system. The internetworking method is applicable to field of wireless intelligent meter reading and provides internetworking, namely communication support for the wireless intelligent meter reading system. The internetworking method totally comprises the following three steps: internetworking, communication and maintenance. In the internetworking stage, the internetworking method adopts a dual-address management algorithm (subnet address and entire network address), a concentrator maintains an entire network address mapping table, besides, the concentrator and a collector all maintain a subnet address mapping table, and accordingly, the storage space of a communication module of the collector is greatly saved. In the communication stage, the entire network address can be resolved as the route of a node, and the uplink and downlink data communication is realized through the operation on the entire network address. In the maintenance stage, the concentrator adopts the naming mechanism for the network nodes, the nodes in the network can be periodically inquired, and the network is enabled to be stable and reliable.
Owner:SOUTHEAST UNIV
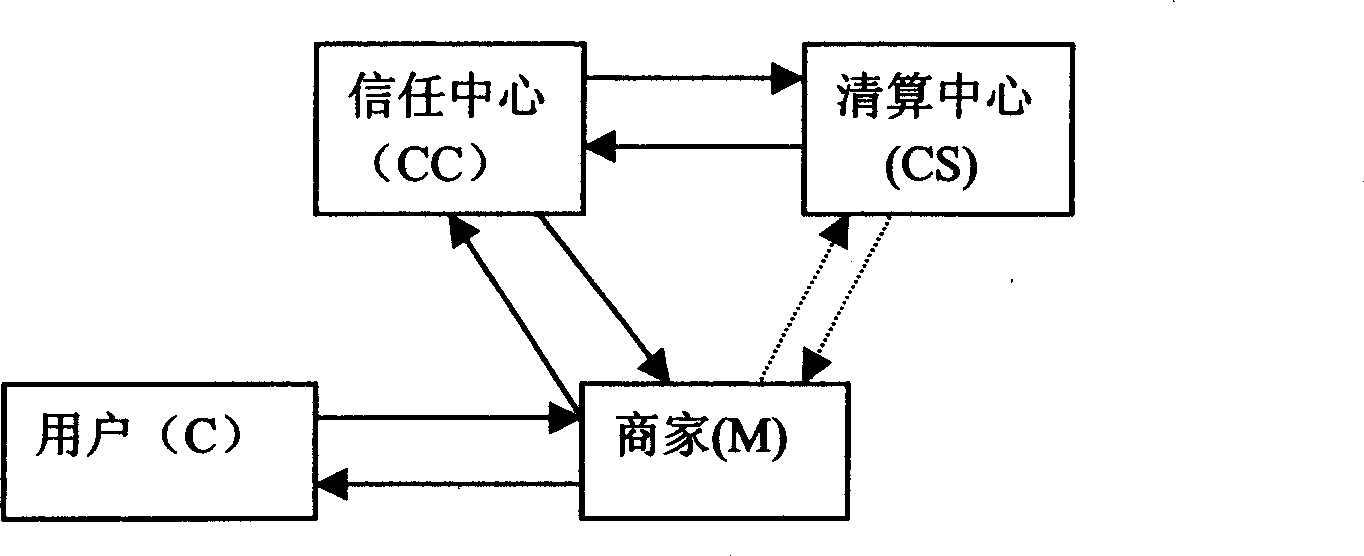
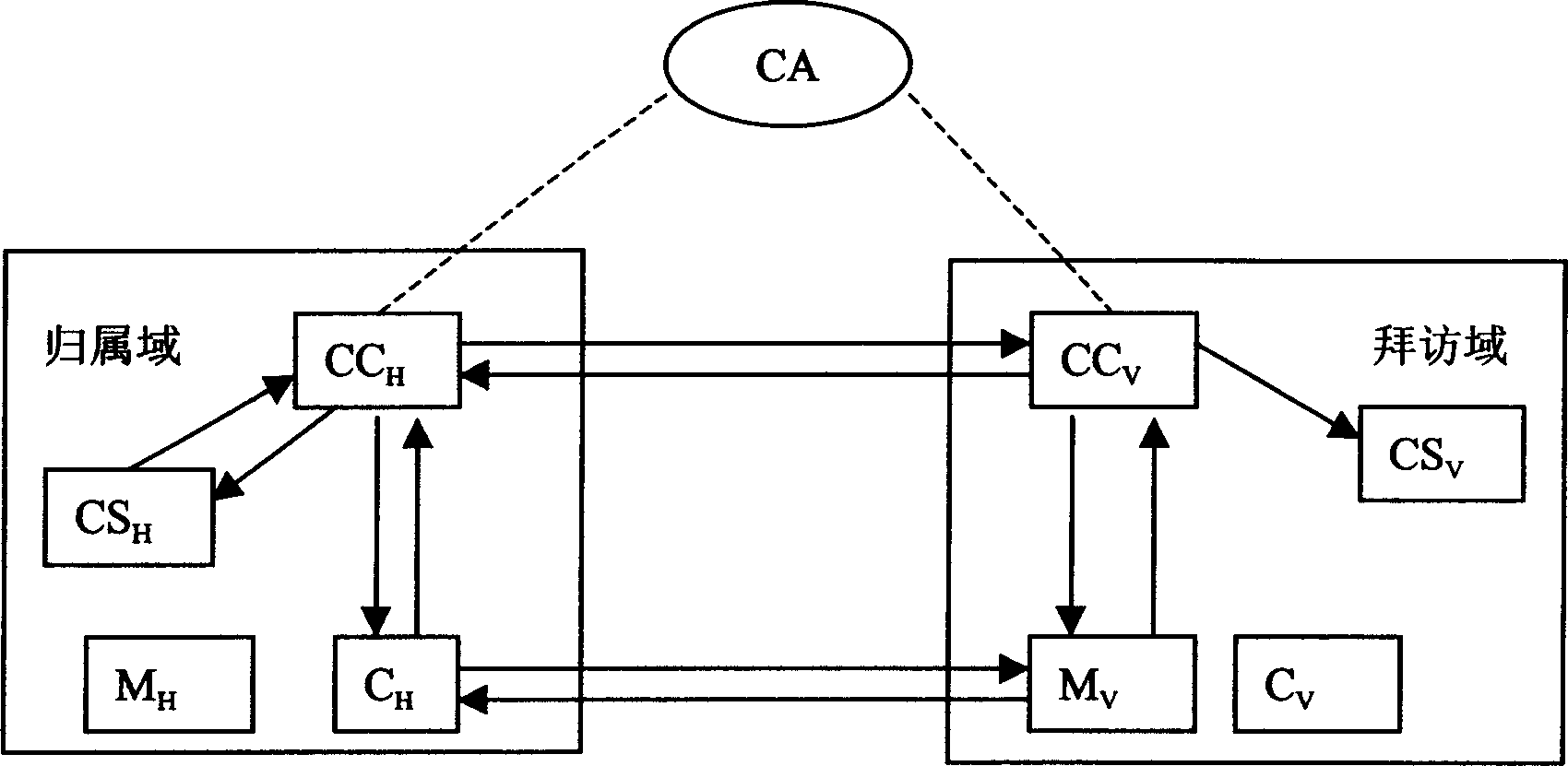
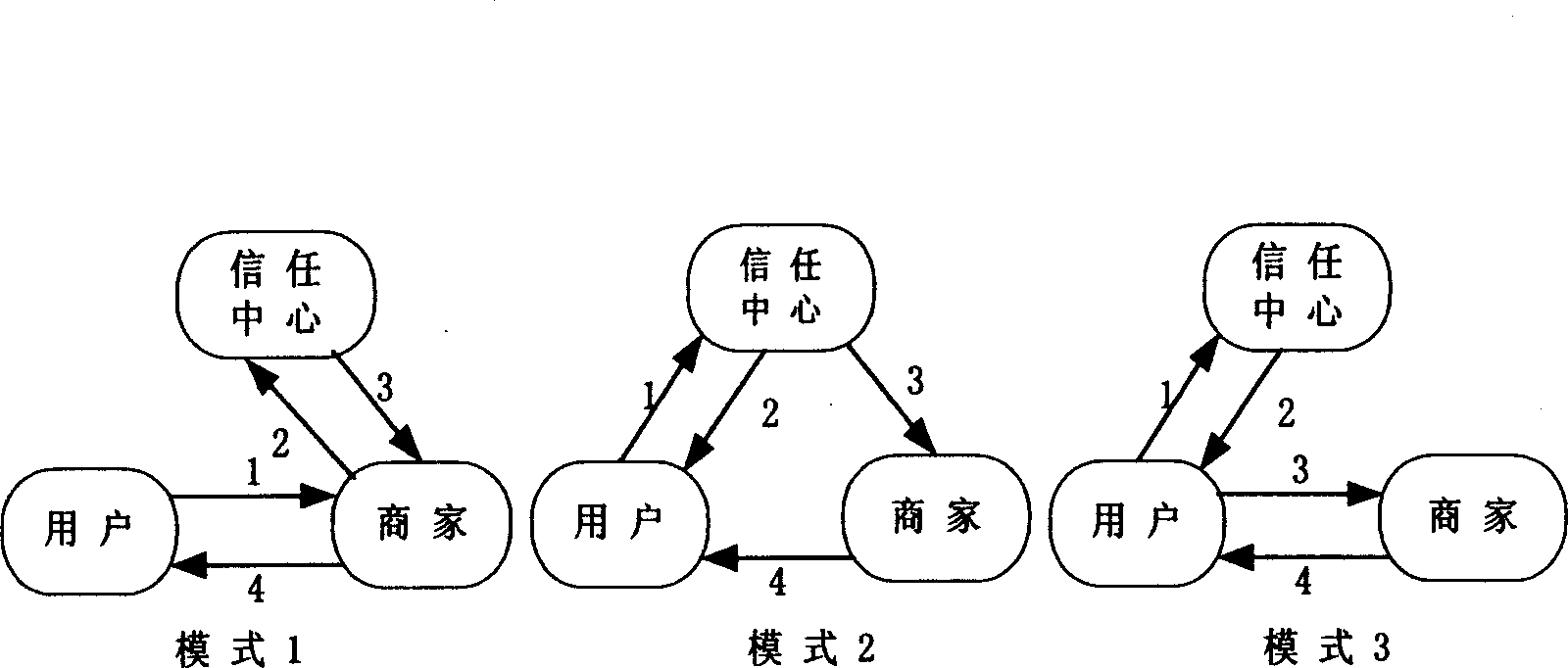
Anonymous payment and its identification method in mobile environment
InactiveCN1581183ALighten the computational burdenReduce storage burdenAccounting/billing servicesPayment architectureInternet privacyEngineering
The present invention provides a method for making anonymous micropayment in mobile environment and its authentication. It is characterized by that in the mobile micropayment the order message and quoted price message can be enciphered, then transferred into credit centre respectively by user and business unit, then the order message and the quoted price message can be deciphered by credit centre, and the identity of user and identity of business unit can be verified, so that the user and business unit can indirectly authenticate their mutual identities, and the business unit cannot know the true identity of the user. After that the user has enough funds to make payment is confirmed by liquidation centre, the confirmation message can be transferred into the credit centre, then the goods can be delivered to user by business unit, and the user can implement payment.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
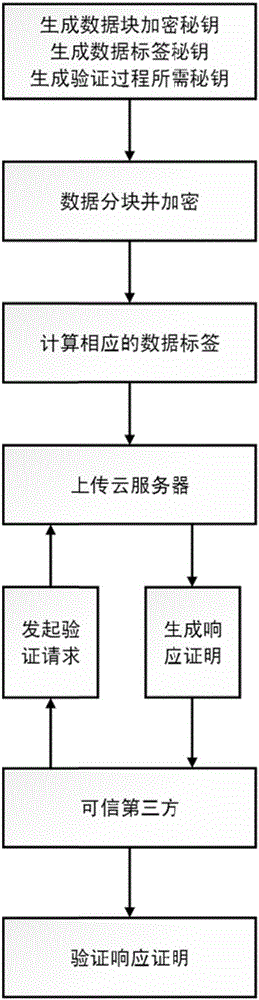
Integrity verification method for data in cloud storage
ActiveCN106357701AEnsure safetyPrevent Forgery AttacksUser identity/authority verificationThird partyData integrity
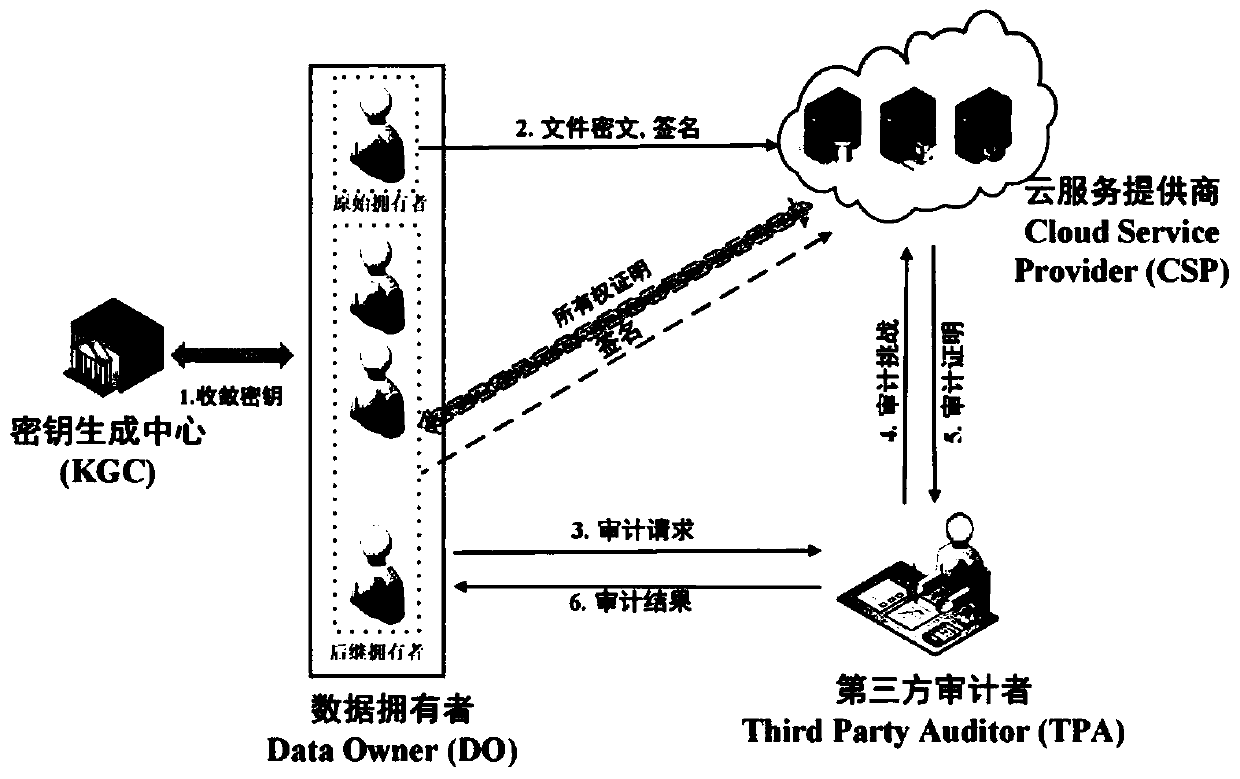
The invention discloses an integrity verification method for data in cloud storage. The method is mainly used for solving problems in the prior art that data privacy is leaked and the storage load of trusty third parties is too high. The technical scheme of the invention is as follows: the method comprises the steps: (1) a user generates secret keys for data encryption, secret keys for data labeling and secret keys for a verification process; (2) data to be uploaded to a cloud server are subjected to blocking processing and encryption, a data label corresponding to each encrypted data block is calculated, and the encrypted data blocks and the data labels are uploaded to the cloud server; (3) a trusty third-party cloud server requests a data integrity verification request; (4) the cloud server generates a corresponding response certification by using user uploaded encrypted data and data labels according to the verification request; (5) a trusty third party verifies the received response certification. According to the method, the privacy safety of the data uploaded to the cloud server by users is ensured, the storage load of the trusty third parties is reduced, the utilization ratio of the cloud server is increased, and thus the method can be applied to the safe outsourcing storage of the data.
Owner:XIDIAN UNIV
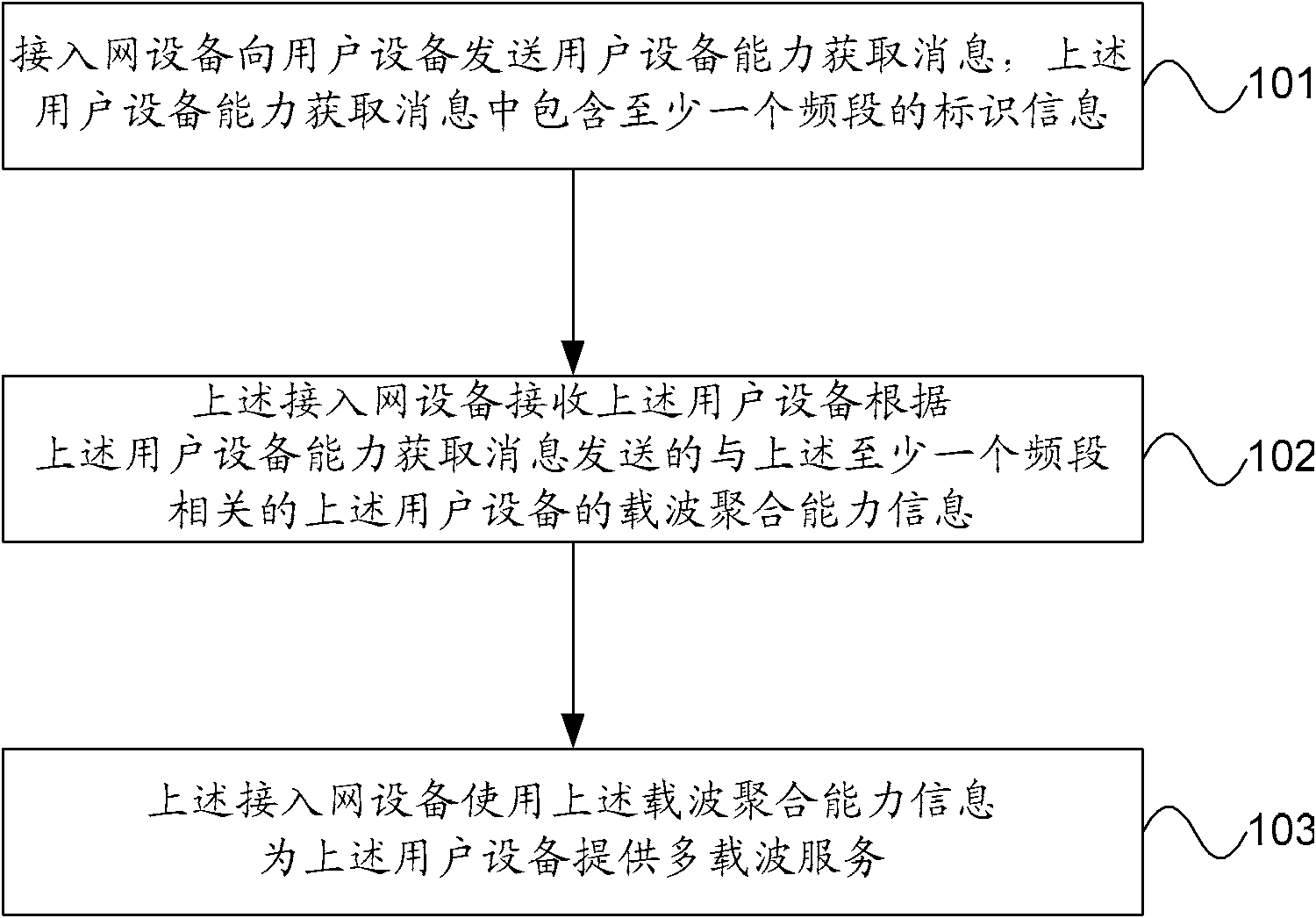
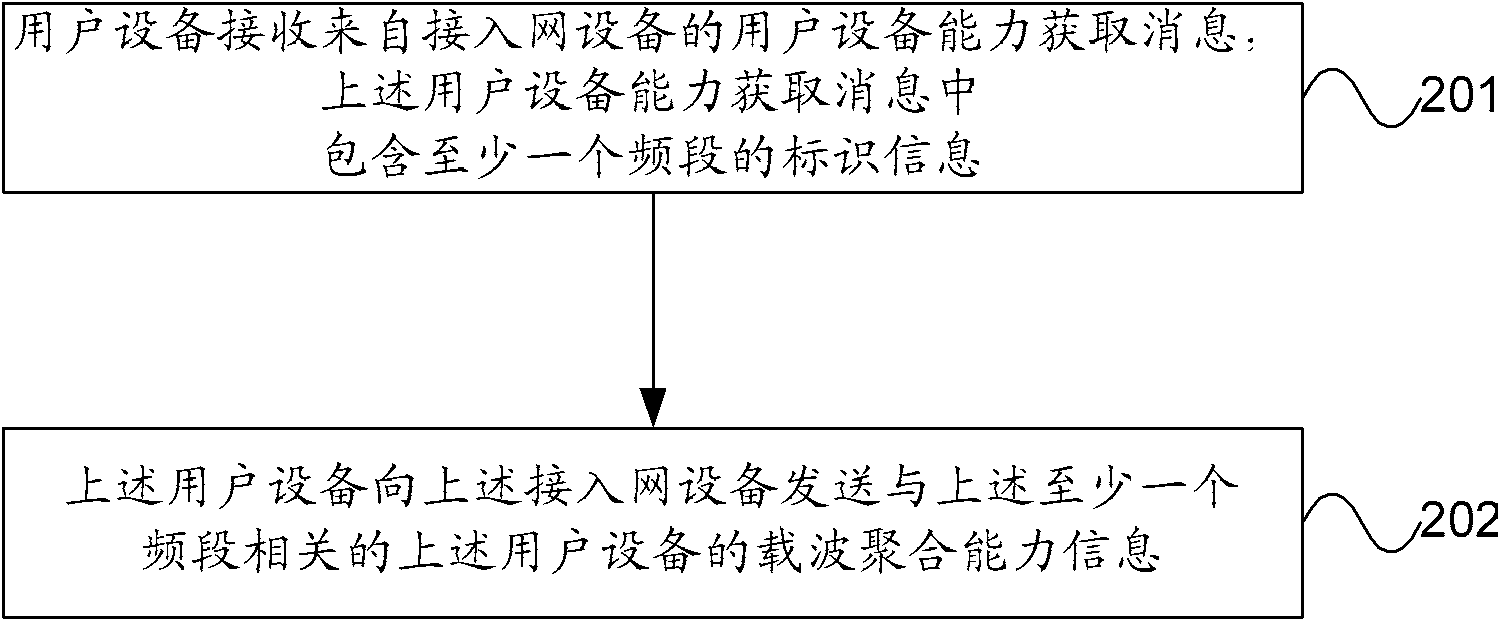
Processing method and device of carrier polymerization capability information of user equipment
ActiveCN102595597AReduce overheadReduce storage burdenNetwork traffic/resource managementTransmission path divisionAccess networkCarrier signal
The embodiment of the invention provides a processing method and a device of the carrier polymerization capability information of user equipment. The method comprises the following steps that: access network equipment sends a user equipment capability obtaining message to user equipment; the user equipment capability obtaining message contains the identification information of at least one frequency band; the access network equipment receives the carrier polymerization capability information of the user equipment, wherein the carrier polymerization capability information is sent according to the user equipment capability obtaining message and is related to at least one frequency band; and the access network equipment uses the carrier polymerization capability information to provide multi-carrier service for the user equipment. According to the embodiment of the invention, the expenditure of interface signaling can be saved, and the storage burden of the access network equipment can be reduced.
Owner:HUAWEI TECH CO LTD
Image loading display method, equipment and system
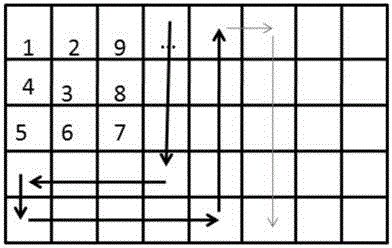
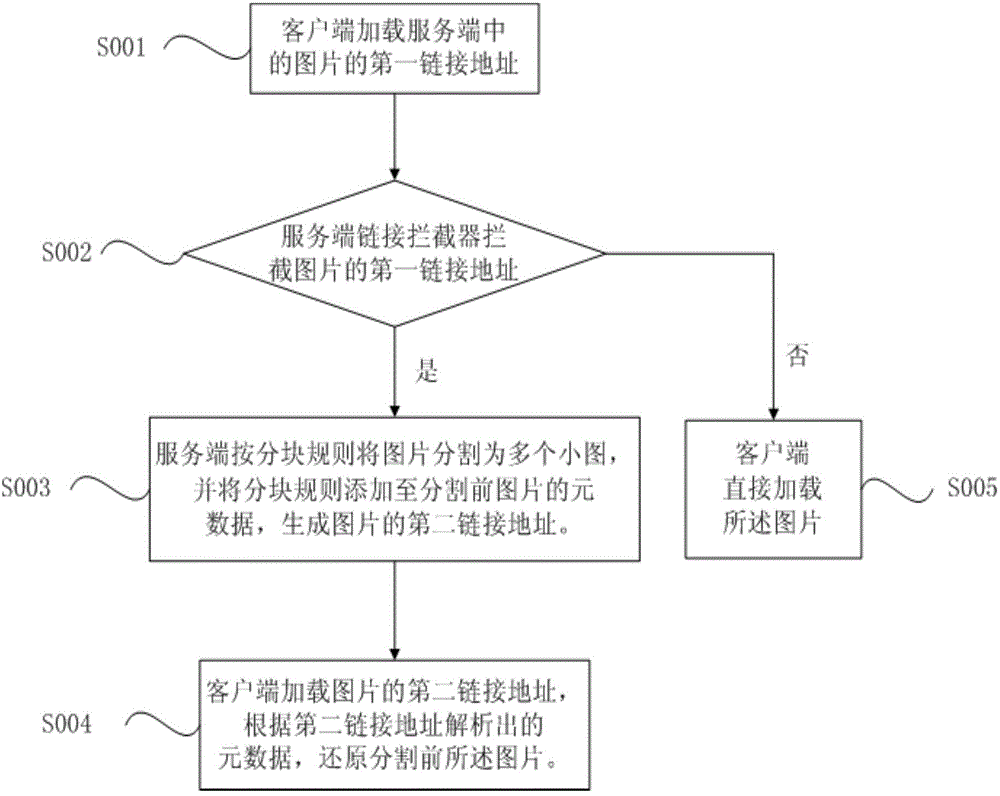
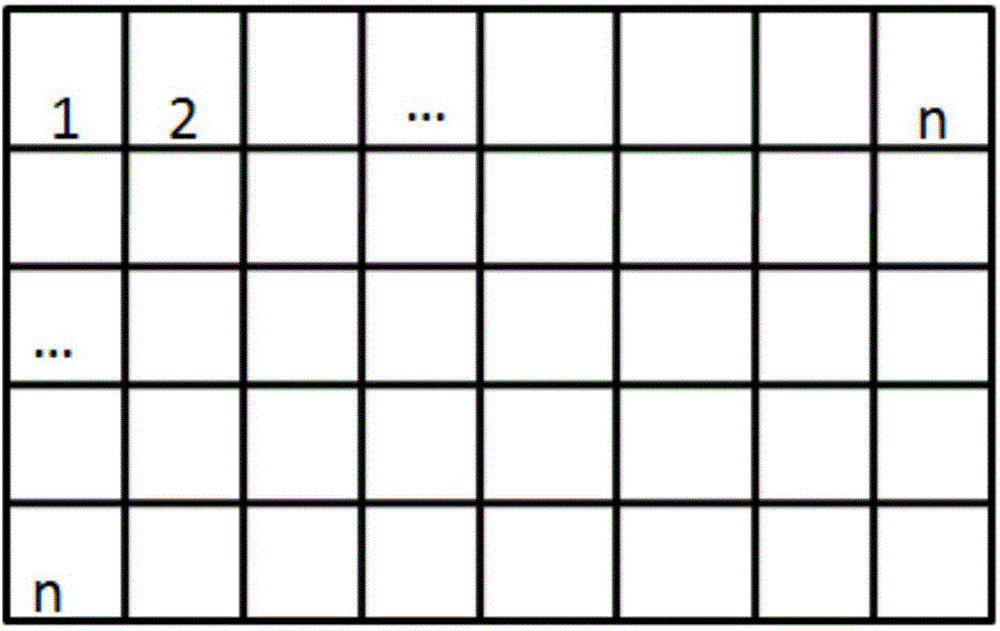
InactiveCN104679570AHigh resolutionGood effectCathode-ray tube indicatorsAnimationValue setAnimation
The invention discloses an image loading display method, which comprises the following steps of loading a first link address of an upload image; judging whether bytes of the image exceed a threshold value set by loading equipment or not according to metadata of the image analyzed by the first link address of the image; if the bytes do not exceeds the threshold value, directly loading the image; if the bytes exceed the threshold value, dividing the image into a plurality of small images according to a set partitioning rule; adding the partitioning rule into the metadata of the image before division to generate a second link address of the image; assembling image data of the small images according to the partitioning rule described by the metadata analyzed by loading the second link address, and restoring the image before division. According to the image loading display method, the image is loaded by an animation way, so that the calculation and storage burdens of a server end is reduced, and better experience can be provided for users.
Owner:XINYU XINGBANG INFORMATION IND
Outsourcing data deduplication cloud storage method supporting privacy and integrity protection
ActiveCN110677487AResolve duplicationSolve protection problemsKey distribution for secure communicationUser identity/authority verificationCiphertextData file
The invention discloses an outsourcing data deduplication cloud storage method supporting privacy and integrity protection. Firstly, client deduplication and security authentication label deduplication of a data file are realized, so that the communication overhead and the storage burden of a cloud server are greatly reduced; and secondly, by adopting the extractor technology, the ciphertext of the outsourcing storage data does not depend on an encipher and an encryption algorithm, but depends on the data, so that ciphertext data deduplication is realized, and the privacy of the data is ensured in the deduplication process and the integrity auditing process. And finally, the RS erasure code technology is adopted to improve the fault-tolerant capability of deduplication cloud storage; a cloud service provider is also supported to spontaneously and regularly delegate a third-party auditor to carry out batch public cloud auditing on the data stored in the cloud server so as to ensure theintegrity of the data; meanwhile, a data owner is also supported to initiate public cloud auditing on the integrity of the file anytime and anywhere, so that the privacy of the data can be always protected in auditing and deduplication processes. The method provided by the invention is effective in the aspect of deduplication and efficient in the aspect of integrity cloud auditing.
Owner:中科柏诚科技(北京)股份有限公司
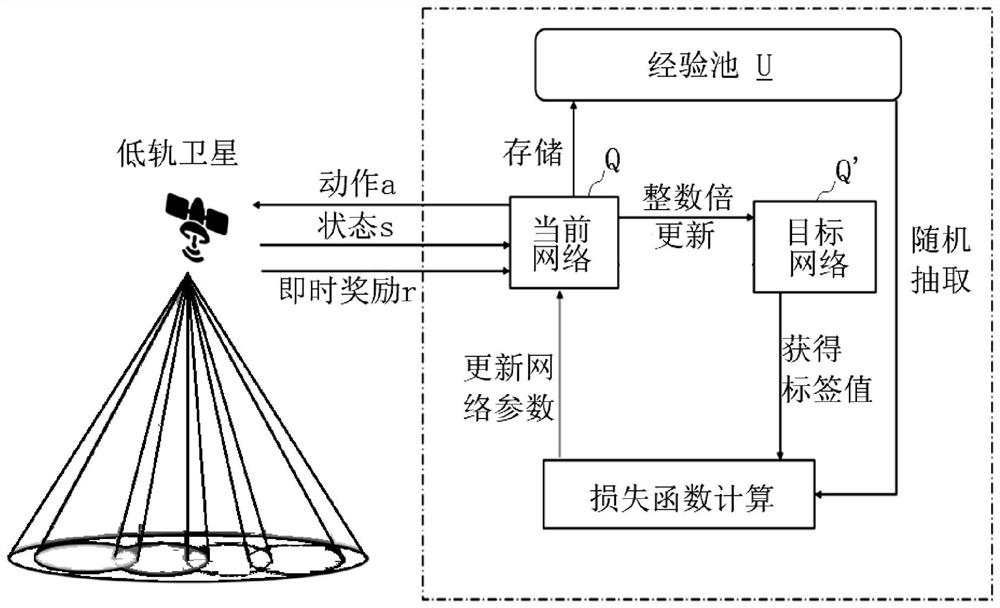
Power distribution method and power distribution device for downlink of low-earth-orbit satellite
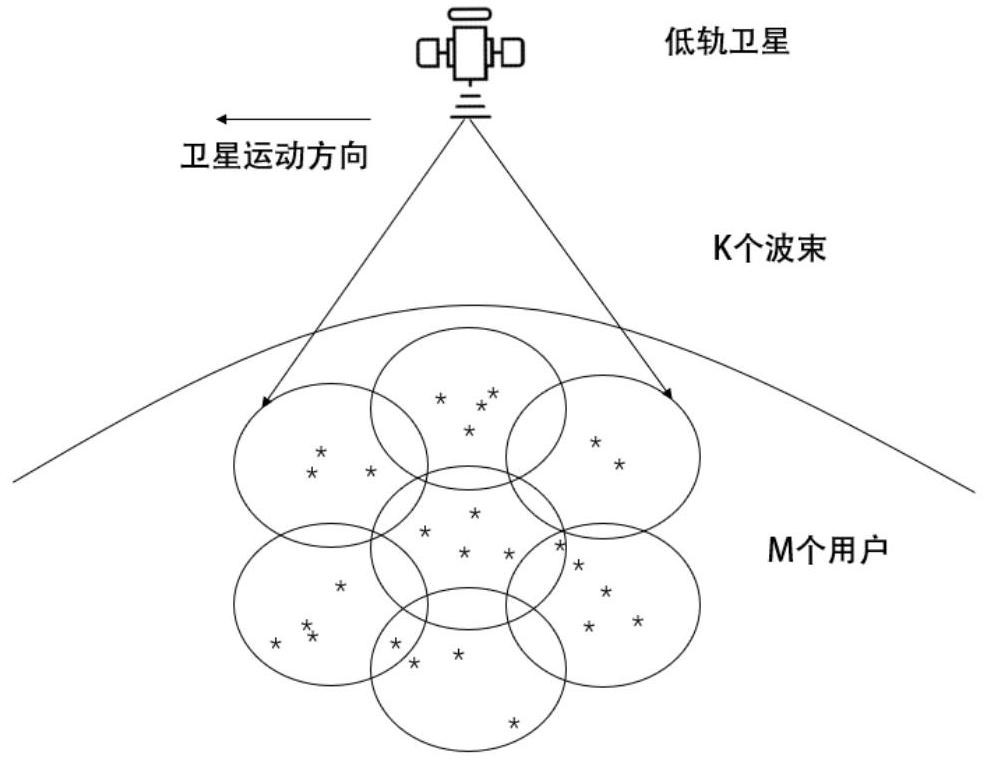
ActiveCN111867104ASolve the problem of low capacityAccelerating the Convergence Speed of Reinforcement LearningTransmission path divisionCriteria allocationFrequency spectrumSpectral efficiency
The invention provides a power distribution method for the downlink of a low-orbit satellite. The method comprises the steps of: initializing the low-orbit satellite, and building a Markov decision process; observing the current state St; randomly selecting an action or selecting an optimal action according to the probability of an exploration factor; obtaining a new state St+1 and the instant reward rt of the current state St according to an action at, and storing the (st, at, rt, st+1) tetrad into an experience pool; under the condition that a cycle period is greater than a training number,training a current network; under the condition that the current time slot is integer multiples of the updating frequency of a target network, updating parameters of the target network; adding 1 to the current time slot; repeating the above steps until the current time slot is greater than a time slot counter, setting the current time slot to be 1 and adding 1 to the count of the cycle period; andrepeating the steps until the cycle period is greater than the training network period number. According to the distribution method, a deep reinforcement learning algorithm is adopted to dynamicallydistribute the subcarrier power of the multi-beam low-orbit satellite, so that the capacity of the low-orbit satellite is maximized, and the spectral efficiency is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
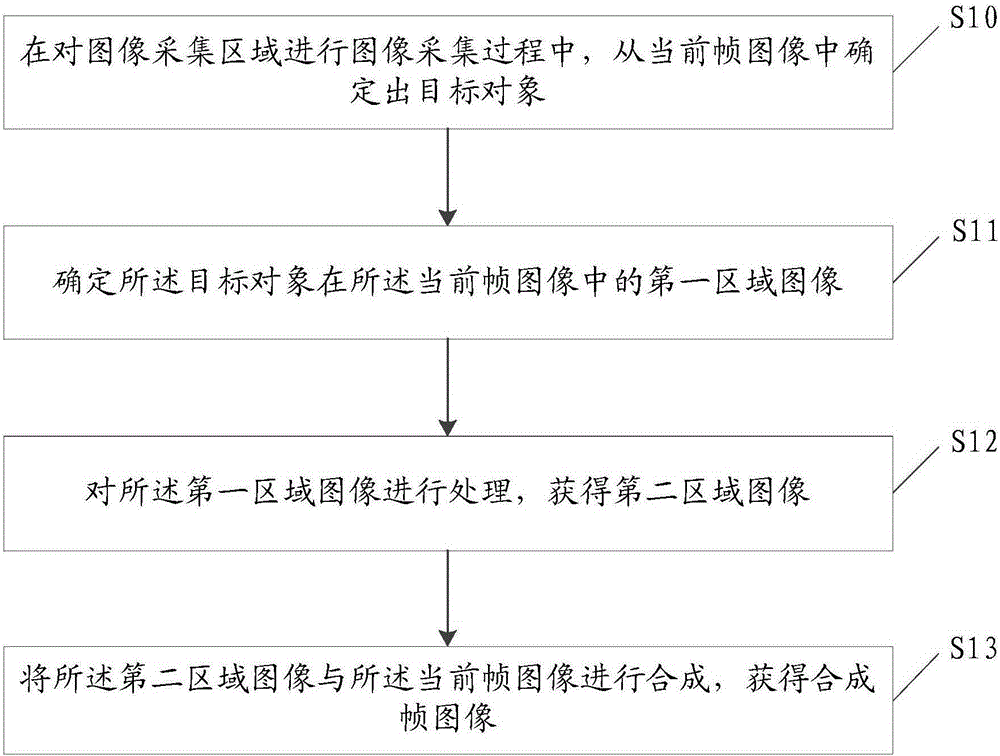
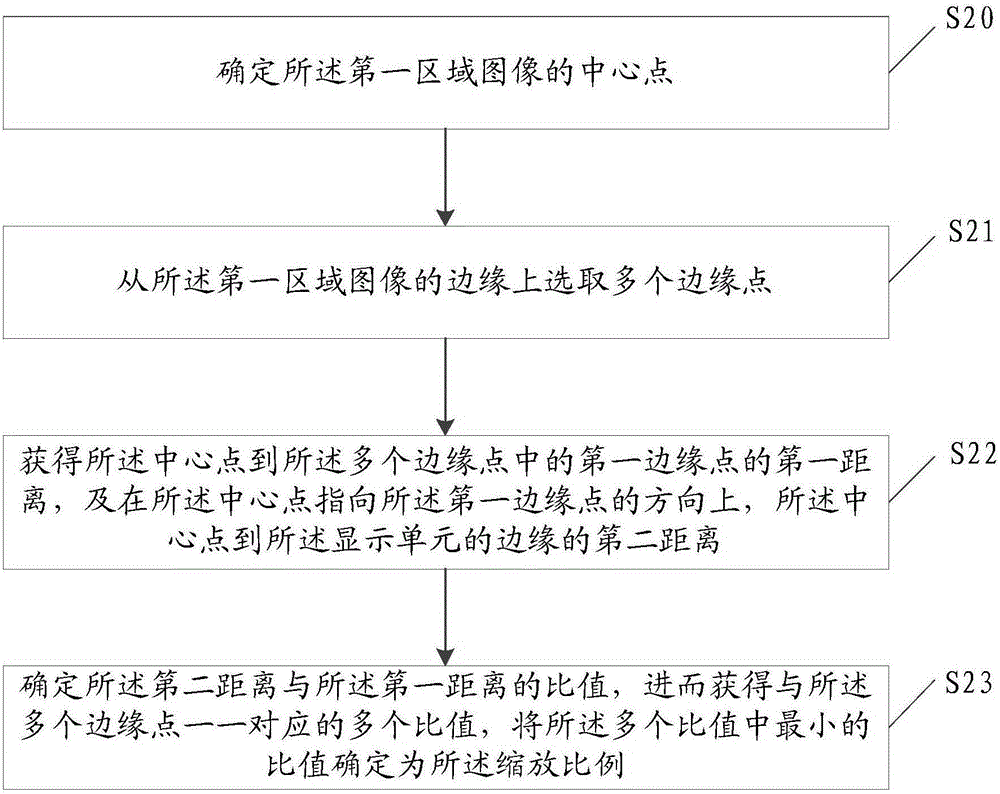
Image processing method and electronic device
InactiveCN105227867AReduce the burden onReduce storage burdenImage enhancementTelevision system detailsImaging processingImage acquisition
The invention discloses an image processing method and an electronic device. The image processing method comprises the steps of determining a target object from a current frame image in a process of acquiring an image in an image acquisition region; determining a first regional image of the target object in the current frame image; processing the first regional image to obtain a second regional image; and compounding the second regional image and the current frame image to obtain a composite frame image. The image processing method provided by the invention is used for solving the technical problem of relatively heavy burden of a processor of the electronic device in the image shooting and processing processes in the prior art; and the technical effect of lightening the burden of the processor of the electronic device in the image shooting and processing processes is realized.
Owner:LENOVO (BEIJING) CO LTD
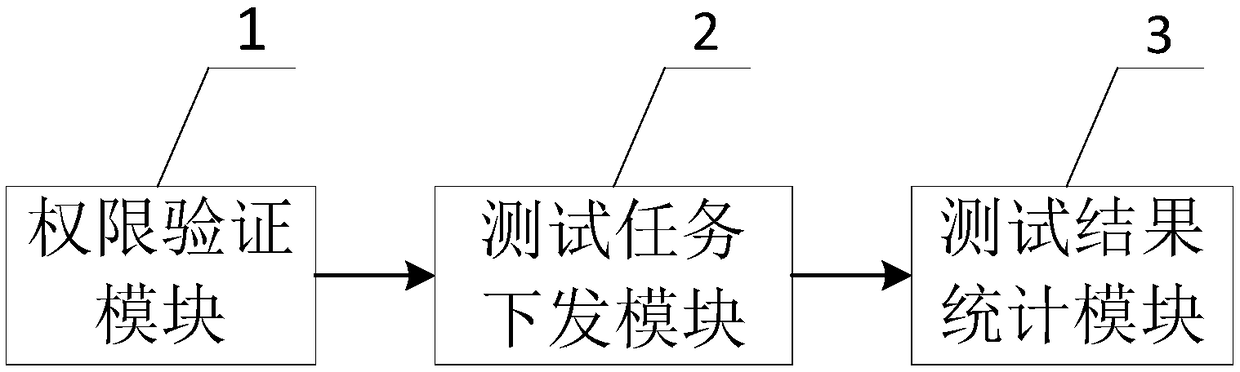
Cross-platform algorithm testing method and system
InactiveCN109144857AReduce computing burdenReduce storage burdenSoftware testing/debuggingWeb serviceStatistical analysis
The invention provides a cross-platform algorithm testing method and a system thereof. The method comprises steps: after a user logs on a testing client, if the testing authority is verified to be passed, the testing client obtaining a testing task corresponding to the user ID from a Web server, a test case and test data for the user to select; obtaining the test task selected by the user, as a target test task, the target test data and the target test platform corresponding to the target test task being obtained for any target test task, the target test instructions corresponding to the target test task being generated, and the target test data and the target test instructions being sent to the target test platform for testing; receiving the test results reported by each target test platform, and making statistical analysis on all the test results. The method and the system can support a plurality of platforms and a plurality of algorithms, and can dynamically expand and adapt to newrequirements. To a certain extent, it reduces the burden of operation and storage of the test platform, and is conducive to the sharing of resources among the test platforms.
Owner:武汉普利商用机器有限公司 +1
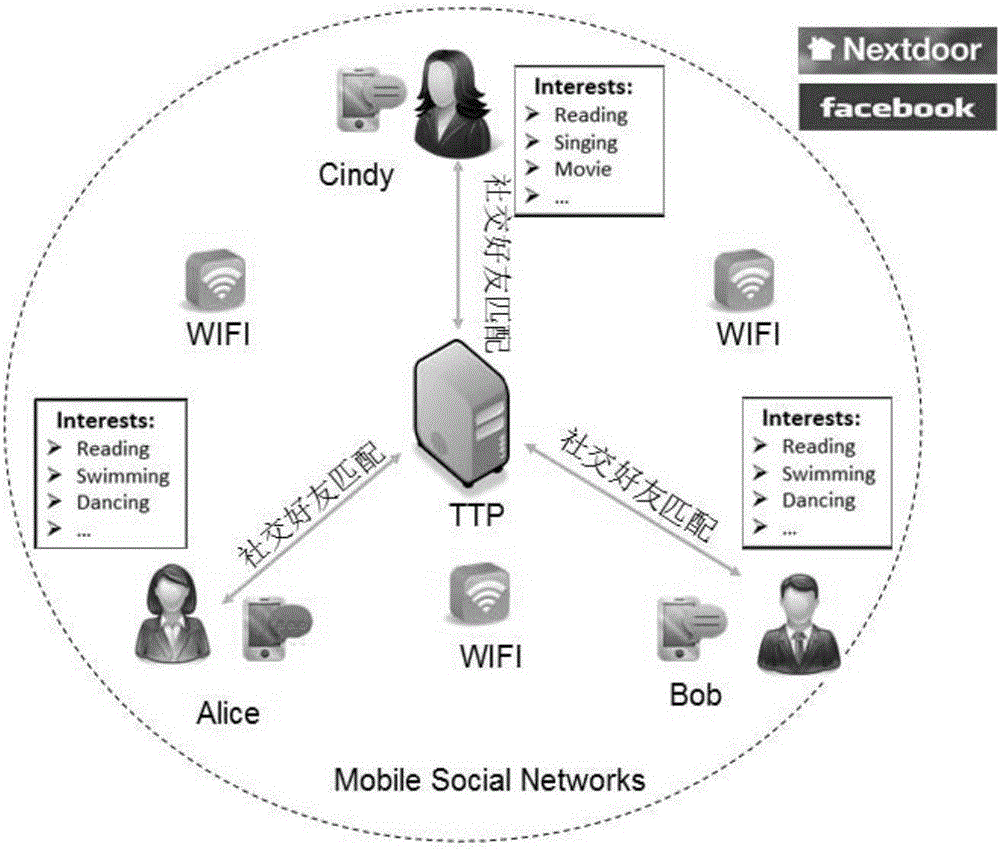
Anonymous bidirectional authentication method in mobile social network based on single hash function and false identity
InactiveCN105871869AAvoid non-repudiation authenticationPrevent Forgery AttacksUser identity/authority verificationHash functionDual identity
The invention discloses an anonymous bidirectional authentication method in a mobile social network based on the single hash function and the false identity. The self characteristic attributes of users are subjected to hash through the function characteristic of the single hash function, the hash result and the identifiers of the users are encrypted and sent to a TTP through a public key. After the TTP authenticates the permission of the users, the hash results of different users are compared, and therefore the similarity of the attributes of the users is obtained. In the process, the TTP sends the respective identifiers to the matched users to help the user to establish an identical shared key, then the TTP encrypts the matched attribute set through the key negotiated by the users and sends the matched attribute set to the users participating in friend making. The access permission of the users is controlled through an identity authentication and key negotiation dual-authentication mechanism, and the calculating and storage loads of an intelligent user terminal are relieved through the strong calculating and storage capacity of the TTP.
Owner:HUNAN UNIV OF SCI & ENG
Double-layer path planning method for overcoming limitations ofcalculation and storage capacity of UAV (unmanned aerial vehicle)
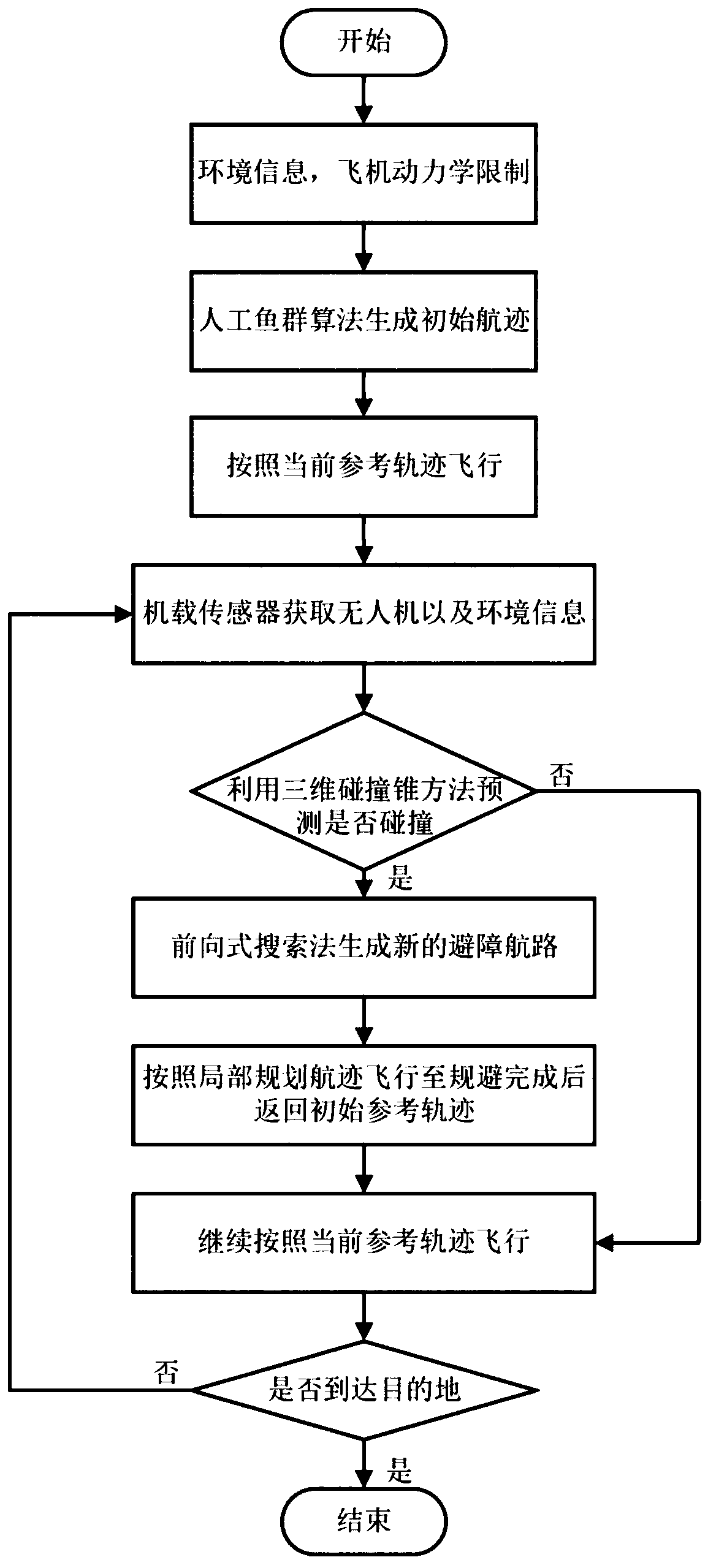
ActiveCN110456823AQuick responseReduce storage burdenNavigational calculation instrumentsPosition/course control in three dimensionsUncrewed vehicleObstacle avoidance
The invention relates to a double-layer path planning method for overcoming limitations ofcalculation and storage capacity of a UAV (unmanned aerial vehicle). For overcoming limitations of the calculation and storage capacity of the UAV, the method comprises the following steps: firstly, an initial reference track isgenerated on the basis of existing map information and limitations of dynamic performance of the UAV; secondly, environmental information of theUAV and surrounding obstaclesis acquired by an airborne sensor, and whether obstacles pose a threat to the UAVis judged with a three-dimensional collision cone technology; thirdly, a local obstacle avoidance path is generated with a forward search method based on Markov process in case of the threat, and the UAV flies in accordance withthe local planned path, otherwise, theUAVcontinues to fly along the reference path; fourthly,the UAV continues to fly untilthe desired point of the reference track is reached after obstacle avoidance. The method has the advantages of high convergence speed, low data storage burden, high safety and the like, can be used by the UAV for avoiding obstacles safely and rapidly, and can also be popularized to autonomous obstacle avoidance of unmanned vehicles and the UAV.
Owner:BEIHANG UNIV
Web of Things micro energy self-collecting micro electro mechanical systems (MEMS) sensing pre-storage system
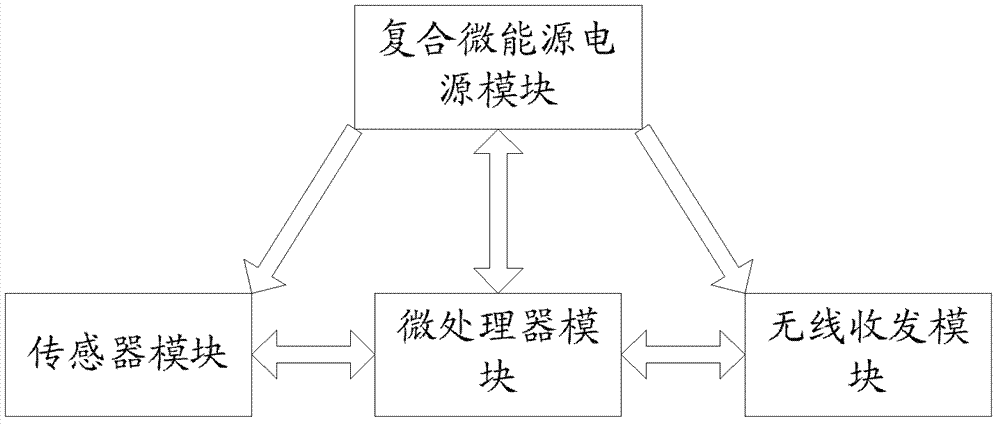
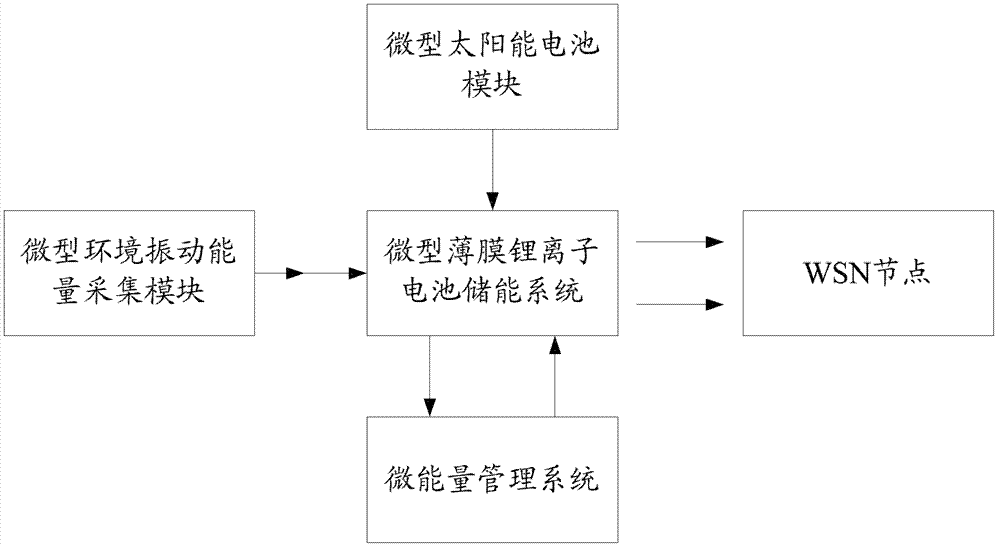
ActiveCN103096437AEnsure safetyGuaranteed long-term usePower managementBatteries circuit arrangementsWireless transmissionComputer module
The invention discloses a Web of Things micro energy self-collecting micro electro mechanical systems (MEMS) sensing pre-storage system. The Web of Things micro energy self-collecting MEMS sensing pre-storage system comprises a composite micro energy power module, a sensor module, a micro processor module and a wireless transmission module, wherein the micro processor module is used for coordinating working of a wireless sensor network (WSN) node, processing data sent by the sensor module and controlling working of the wireless transmission module; the wireless transmission module is used for data communication between the WSN node and other WSN nodes, the WSN node and a gateway, and the WSN node and cloud. By optimizing a plurality of main modules, power consumption of the whole system is reduced from multi-angle, meanwhile the composite micro energy power module which is capable of effectively supplying power for the whole system is further provided, and therefore long-term use of WSN node power supply is guaranteed, and working performance and stability of the WSN node is improved.
Owner:江苏电无忧电气技术服务有限公司
Efficient statistical timing analysis of circuits
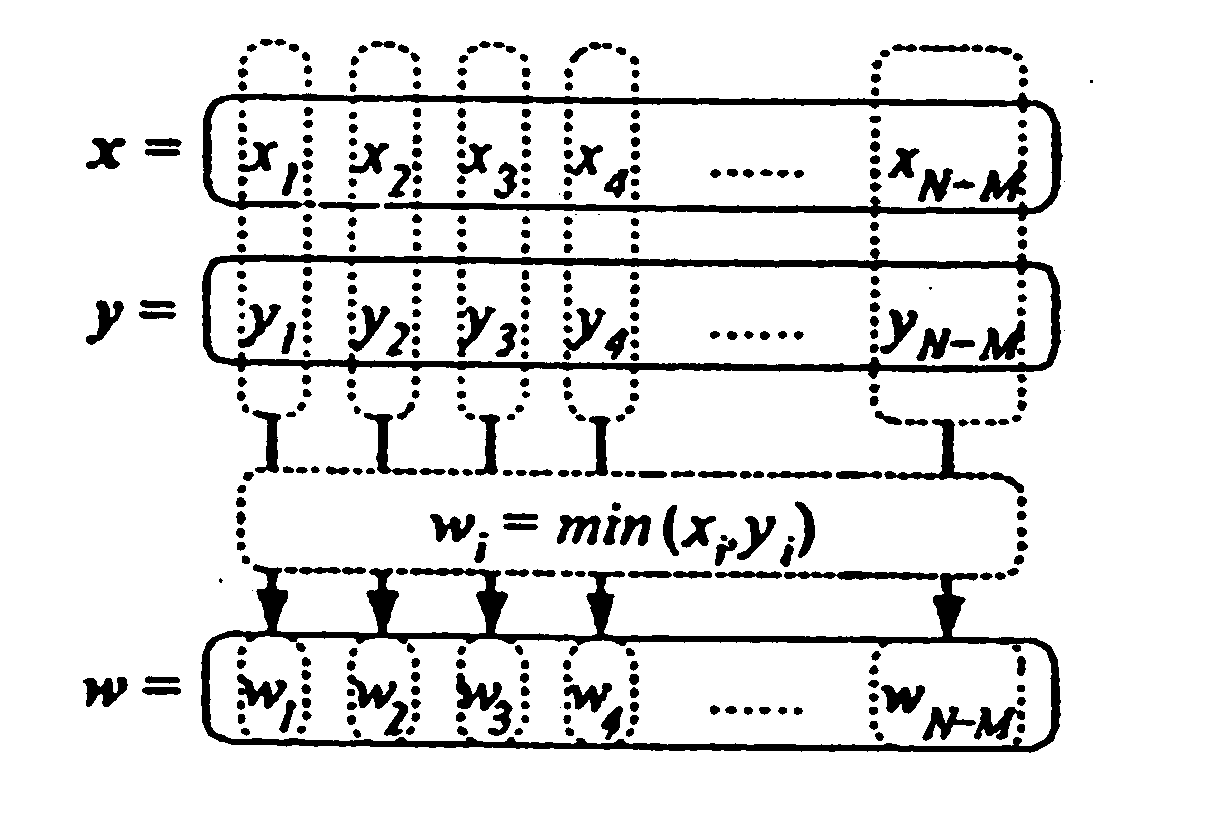
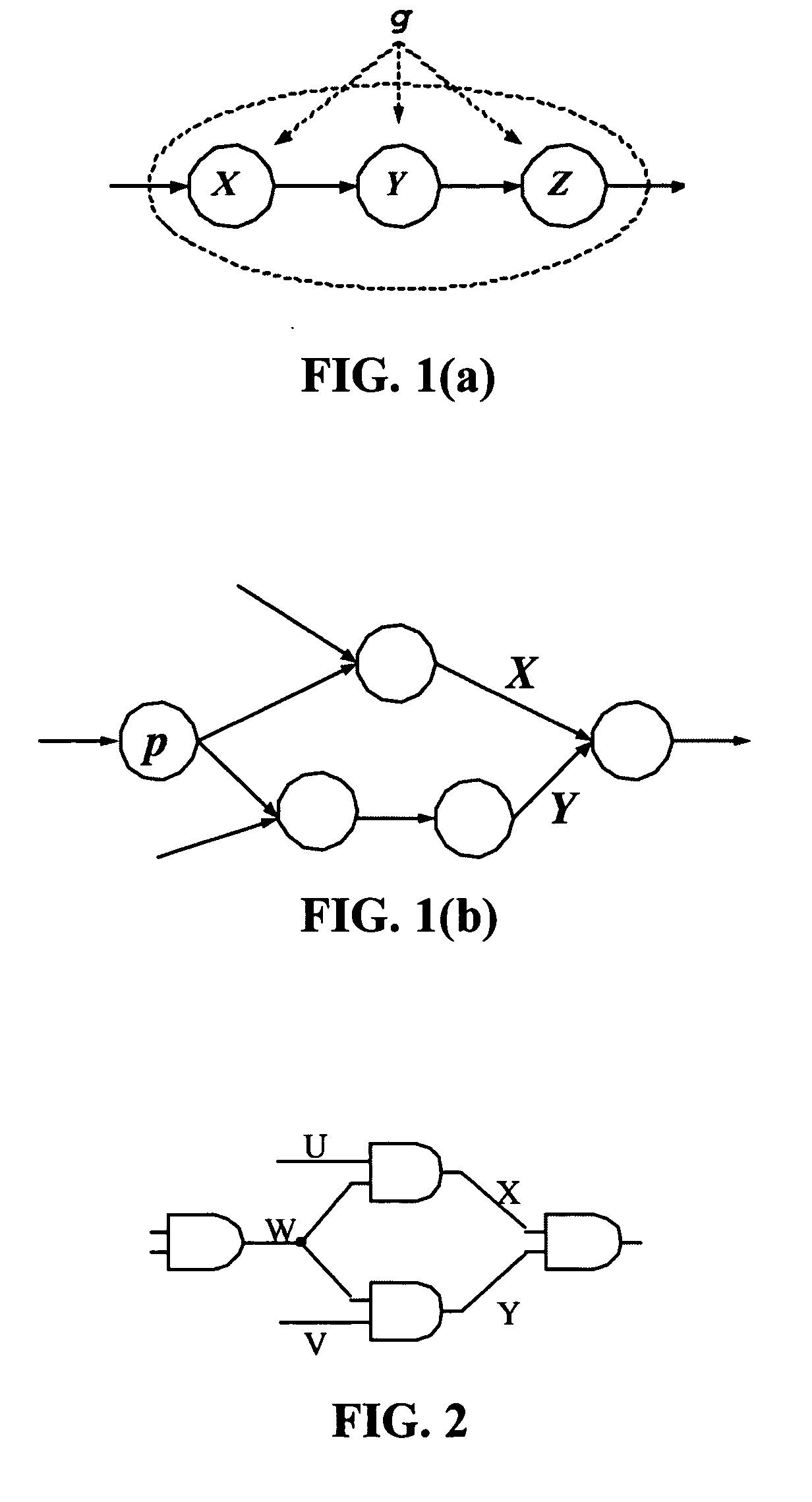
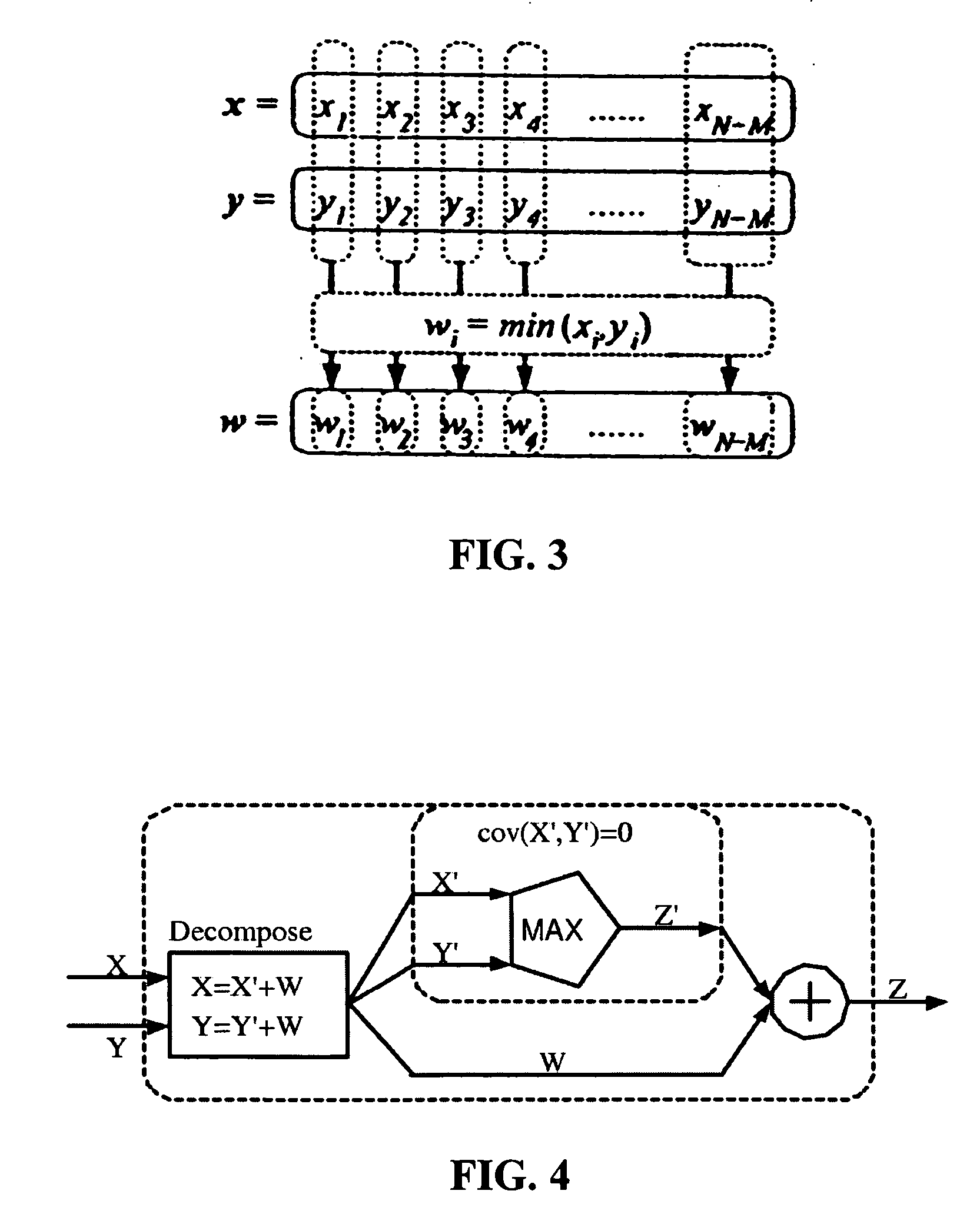
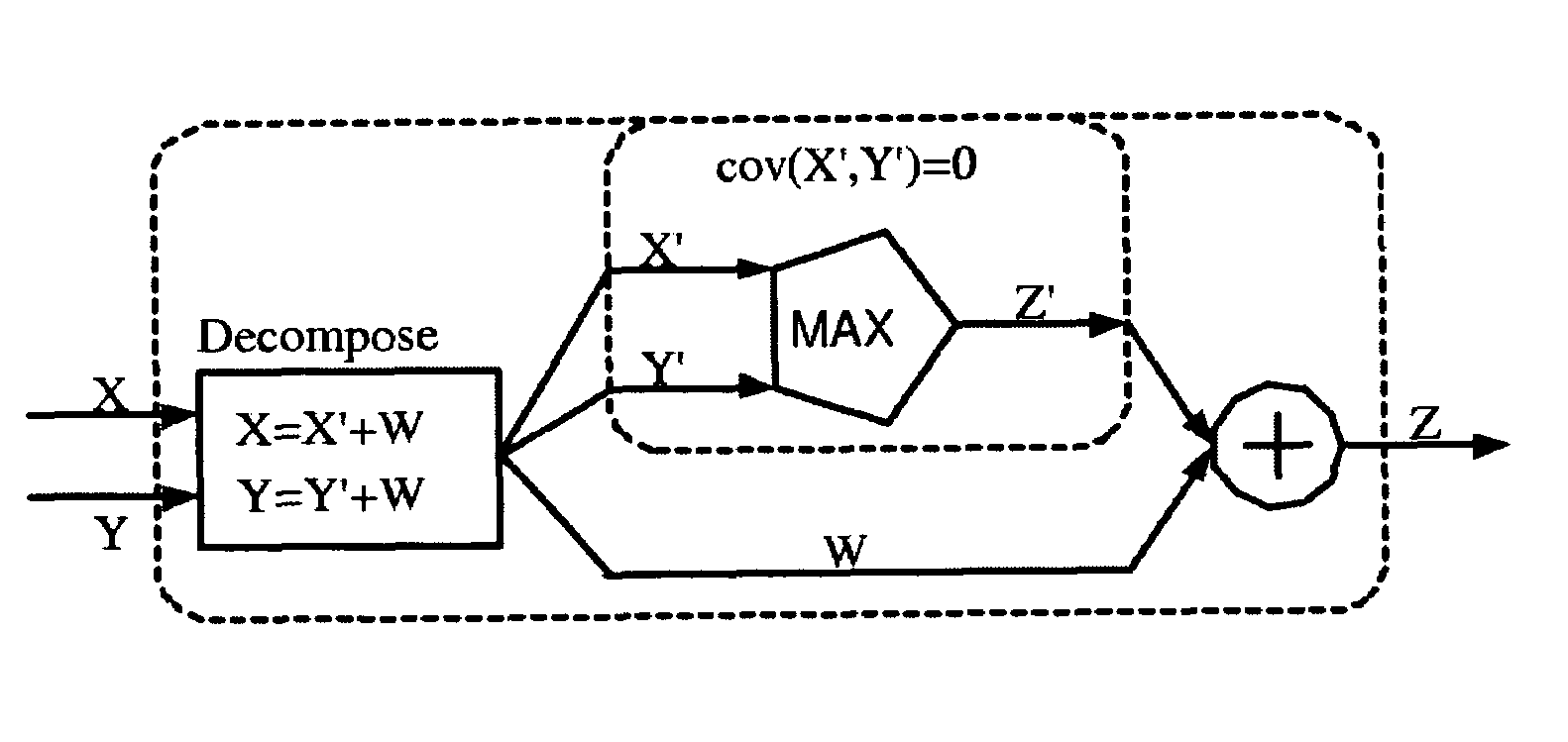
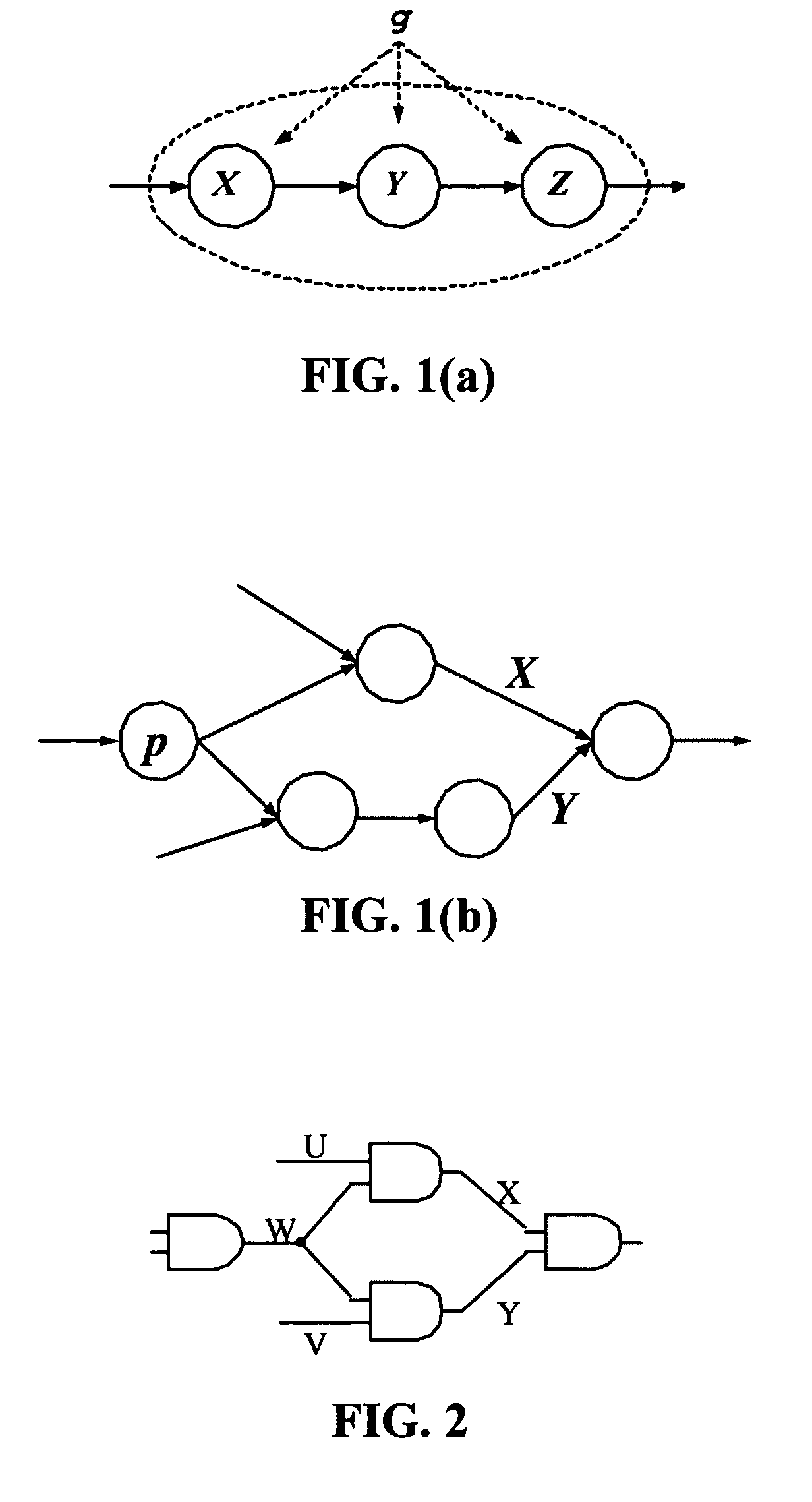
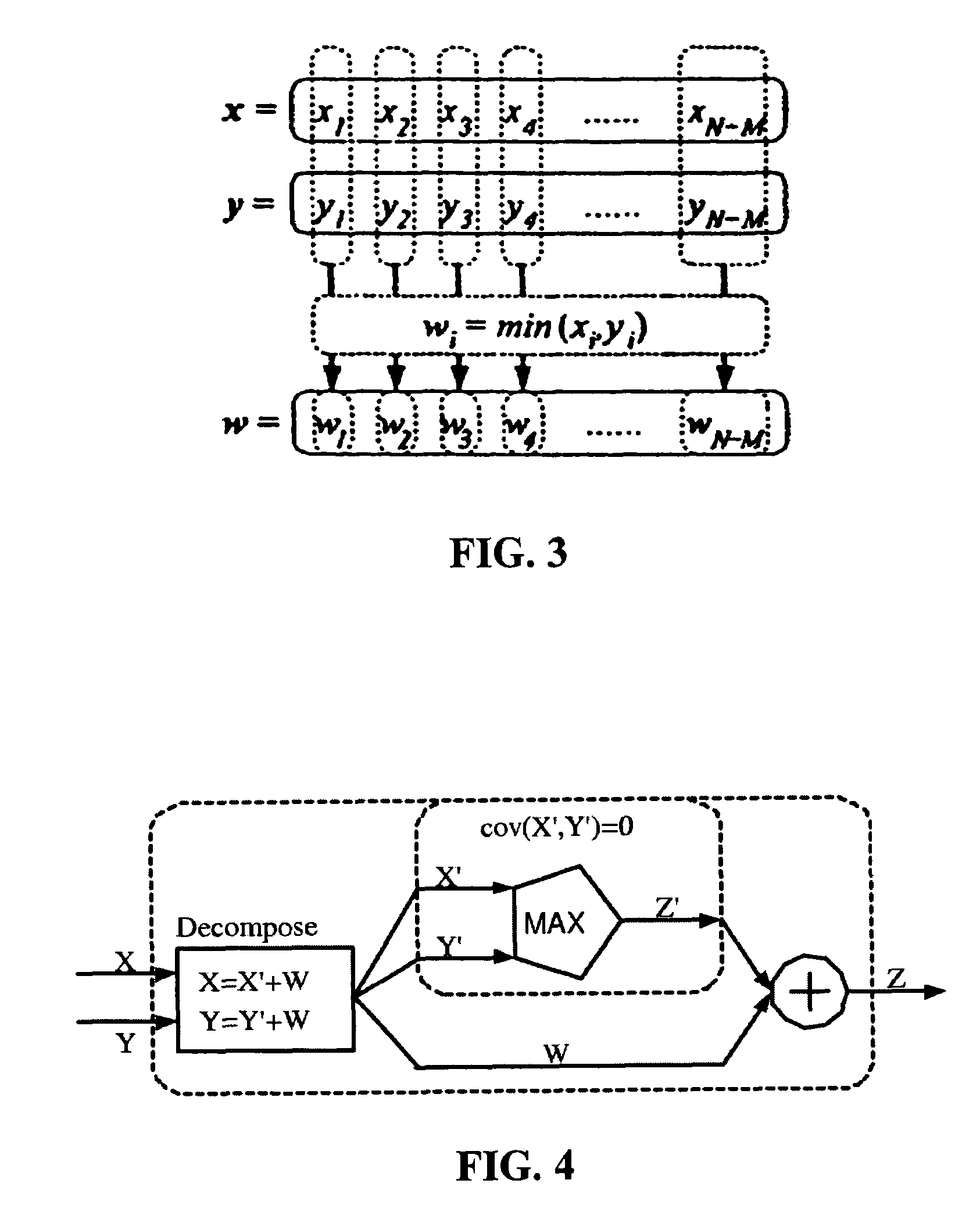
ActiveUS20070113211A1Increase computing speedReduce storage burdenComputation using non-denominational number representationComputer aided designDecompositionGlobal temperature
Statistical timing analysis methods for circuits are described which compensate for circuit elements having correlated timing delays with a high degree of computational efficiency. An extended canonical timing model is used to represent each delay element along a circuit path, wherein the model bears information regarding any correlations that each element has to any other elements in the circuit (and / or to any external global factors, e.g., global temperature variations over the circuit, etc.). The model can be represented in a vectorized format which allows enhancement of computational efficiency, wherein the coefficients of the vectors allow an objective measure of element correlation (and wherein the vectors can be “pruned” by dropping insignificant coefficients to further enhance computational efficiency). A decomposition procedure can be used to decompose correlated elements into uncorrelated elements to allow delays to me more easily propagated through the timing diagram representing the circuit. Finally, a bounded approximation for the output of the MAX operator is described which provides a safely conservative approximation regardless of the linearity of the MAX output.
Owner:ZHANG LIZHENG +2
Ship electronic chart data multi-platform shared service device and construction method thereof
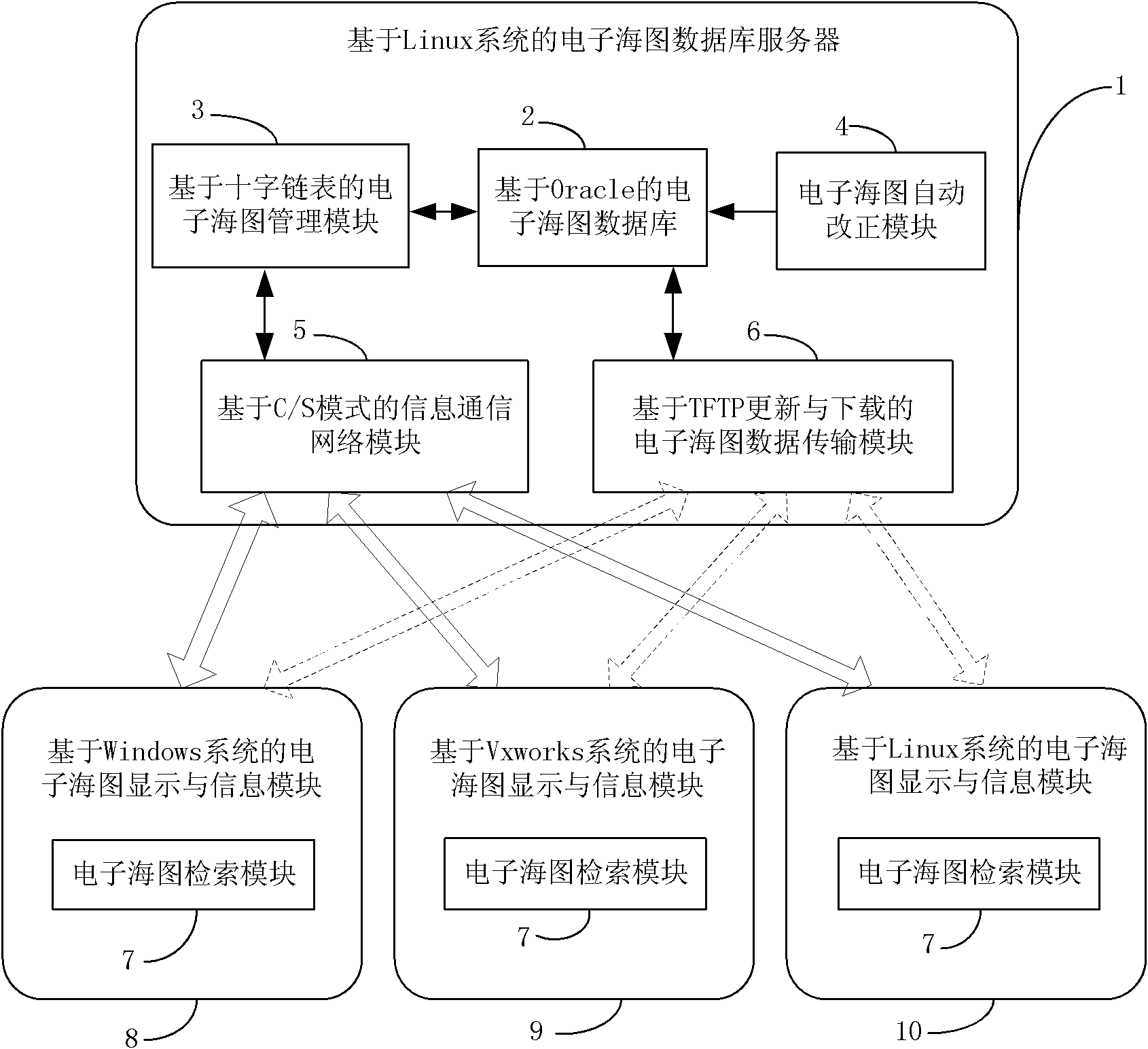
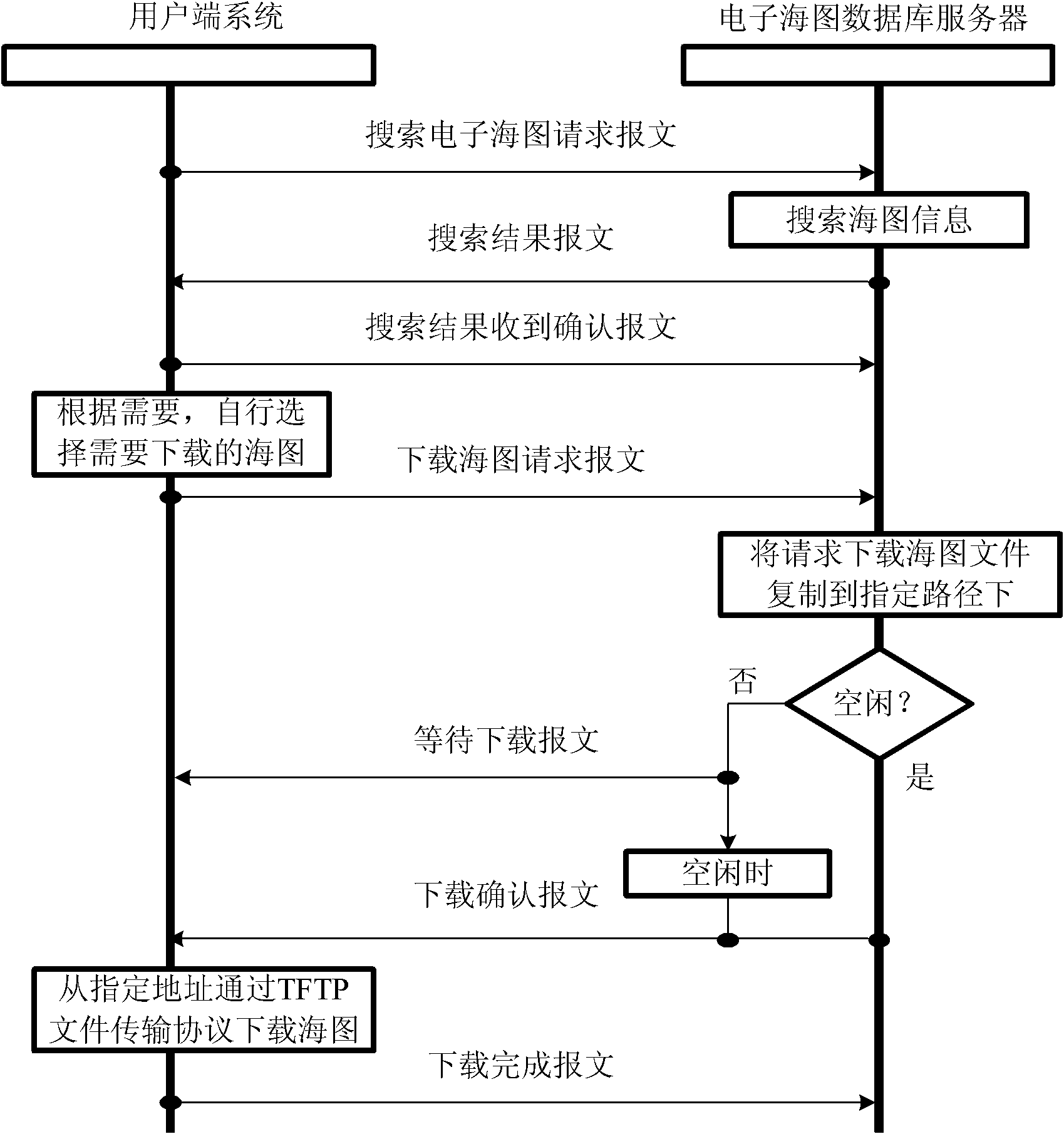
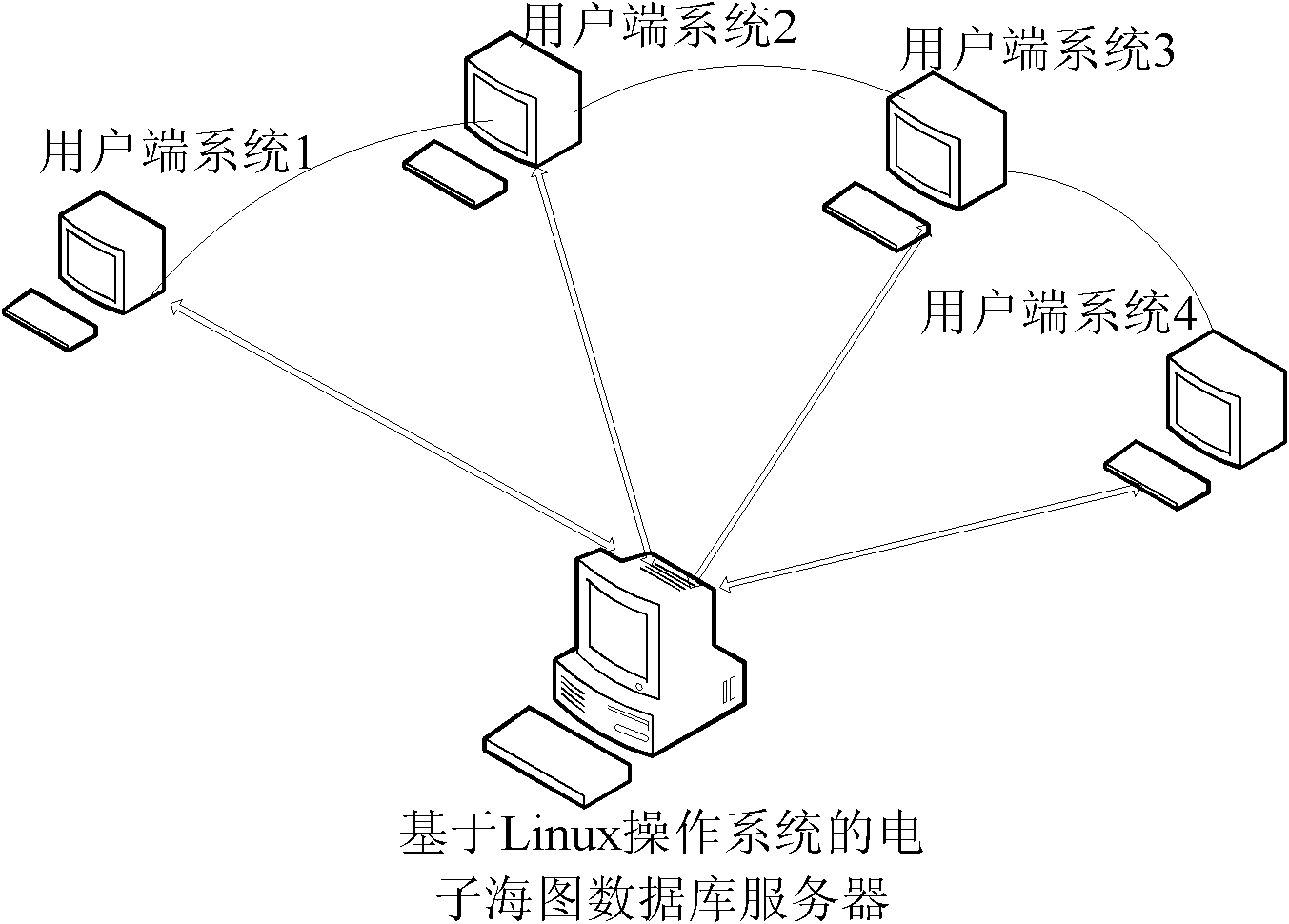
InactiveCN102306165AFacilitate centralized and unified managementGuaranteed correctnessTransmissionSpecial data processing applicationsData transmissionDatabase
The invention discloses a ship electronic chart data multi-platform shared service device and a construction method thereof. A server of the device is based on a Linux system and comprises a database for storing an electronic chart, an orthogonal-list-based electronic chart management module, an automatic electronic chart correction module, an information communication module and a data transmission module; and a display and information client is realized on the basis of a Windows system, a Vxworks system and the Linux system, and an electronic chart search module is embedded into the client. The method comprises the following steps of: configuring the server in the Linux system, establishing a display and information client system for different operating systems, inputting the search condition by using the electronic chart search module embedded into the client, searching the chart from the server and downloading to the client. The device is favorable for the centralized and unified management of electronic chart data, and a client system can quickly and accurately download and update the electronic chart data.
Owner:HARBIN ENG UNIV
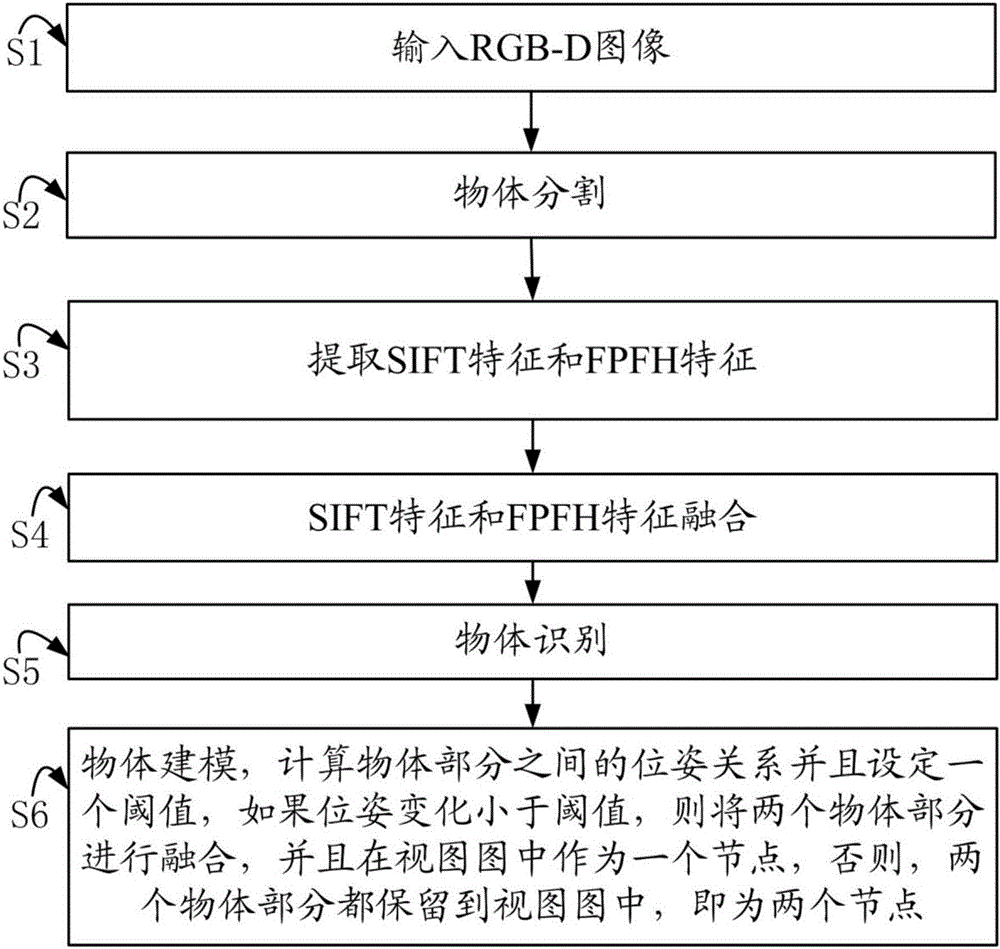
Indoor scene and object simultaneous recognition and modeling method
ActiveCN106529394AAchieving identifiabilityRealize modelingThree-dimensional object recognition3D modellingNODALObject detection
Owner:GUANGDONG UNIV OF TECH
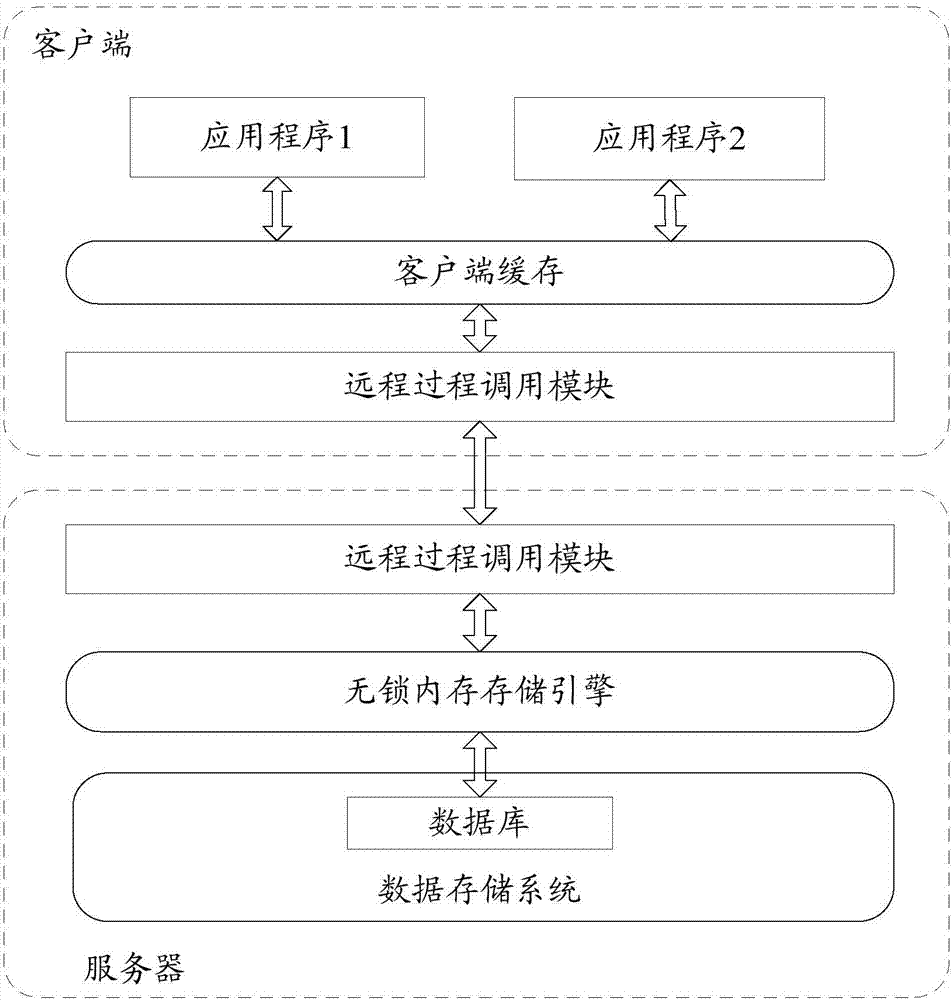
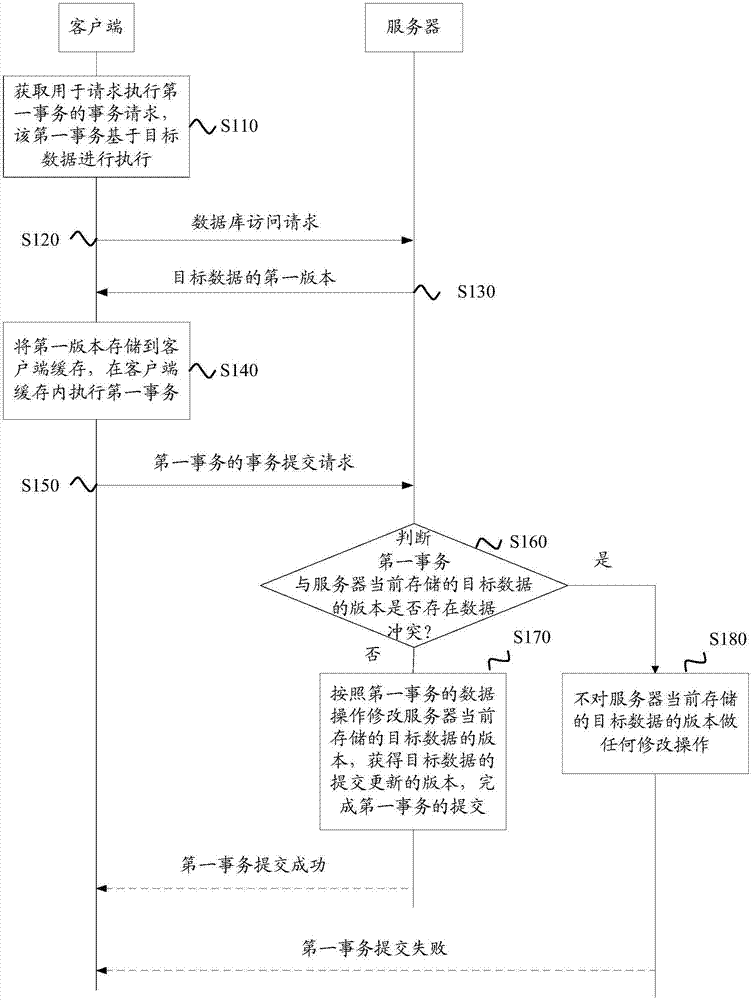
Method for processing database affair, client, and server
ActiveCN107577678AGuaranteed isolation effectEnsure consistencyMemory adressing/allocation/relocationSpecial data processing applicationsData operationsStorage management
The invention provides a method for processing a database affair, a client and a server. The method includes: allowing the server to receive a database access request for requesting target data and sent by the client; sending a first version of the target data to the client, wherein the first version is a version of the target data which is currently stored in the server, and the server only savesthe last submitted updated version of the target data; receiving an affair submitting request sent by the client who executes a first affair on the basis of the first version, wherein the affair submitting request includes a log for recording data operation of the first affair; modifying the version of the target data stored in the server currently according to the data operation of the first affair if the data operation of the first affair and the version of the target data stored in the server currently do not have data conflicts according to the log, and acquiring a submitted updated version of the target data. The method for processing the database affair can achieve an unlocked affair mechanism, and can lower the complexity of storage management of the database.
Owner:HUAWEI TECH CO LTD
Efficient statistical timing analysis of circuits
ActiveUS7350171B2Reduce calculationHigh expressionComputation using non-denominational number representationComputer aided designDecompositionGlobal temperature
Statistical timing analysis methods for circuits are described which compensate for circuit elements having correlated timing delays with a high degree of computational efficiency. An extended canonical timing model is used to represent each delay element along a circuit path, wherein the model bears information regarding any correlations that each element has to any other elements in the circuit (and / or to any external global factors, e.g., global temperature variations over the circuit, etc.). The model can be represented in a vectorized format which allows enhancement of computational efficiency, wherein the coefficients of the vectors allow an objective measure of element correlation (and wherein the vectors can be “pruned” by dropping insignificant coefficients to further enhance computational efficiency). A decomposition procedure can be used to decompose correlated elements into uncorrelated elements to allow delays to me more easily propagated through the timing diagram representing the circuit. Finally, a bounded approximation for the output of the MAX operator is described which provides a safely conservative approximation regardless of the linearity of the MAX output.
Owner:ZHANG LIZHENG +2
Verifying method and system based on general weight discrimination framework
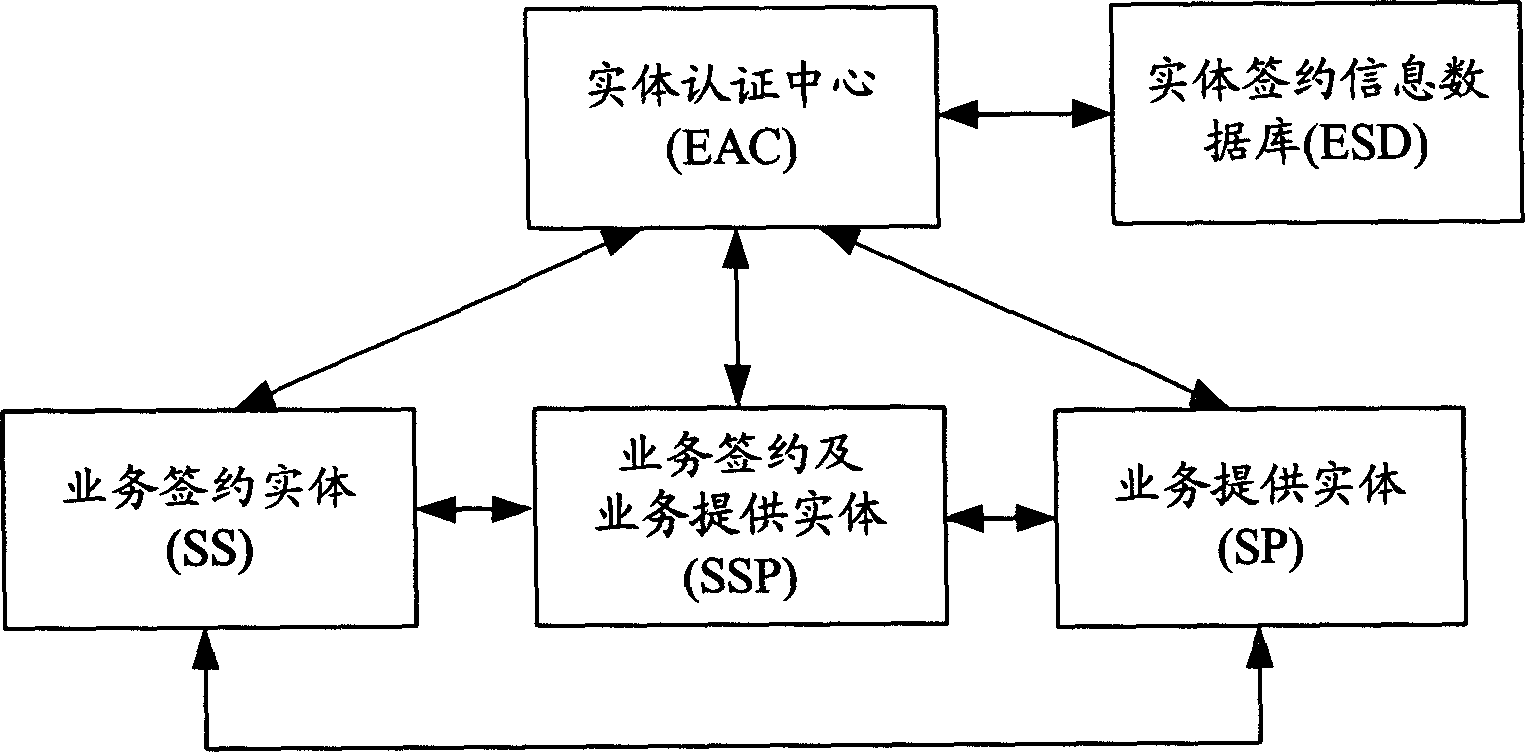
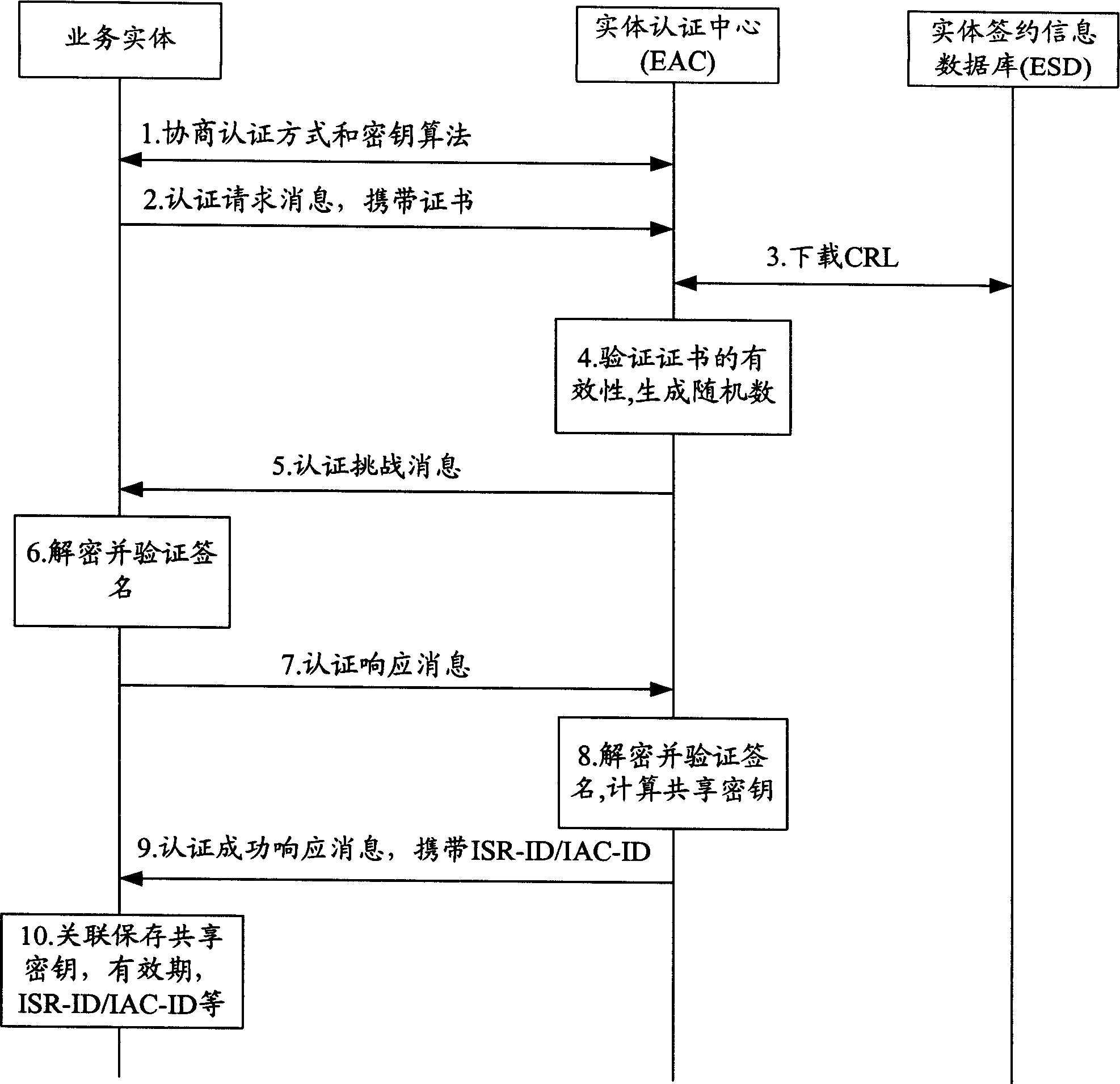
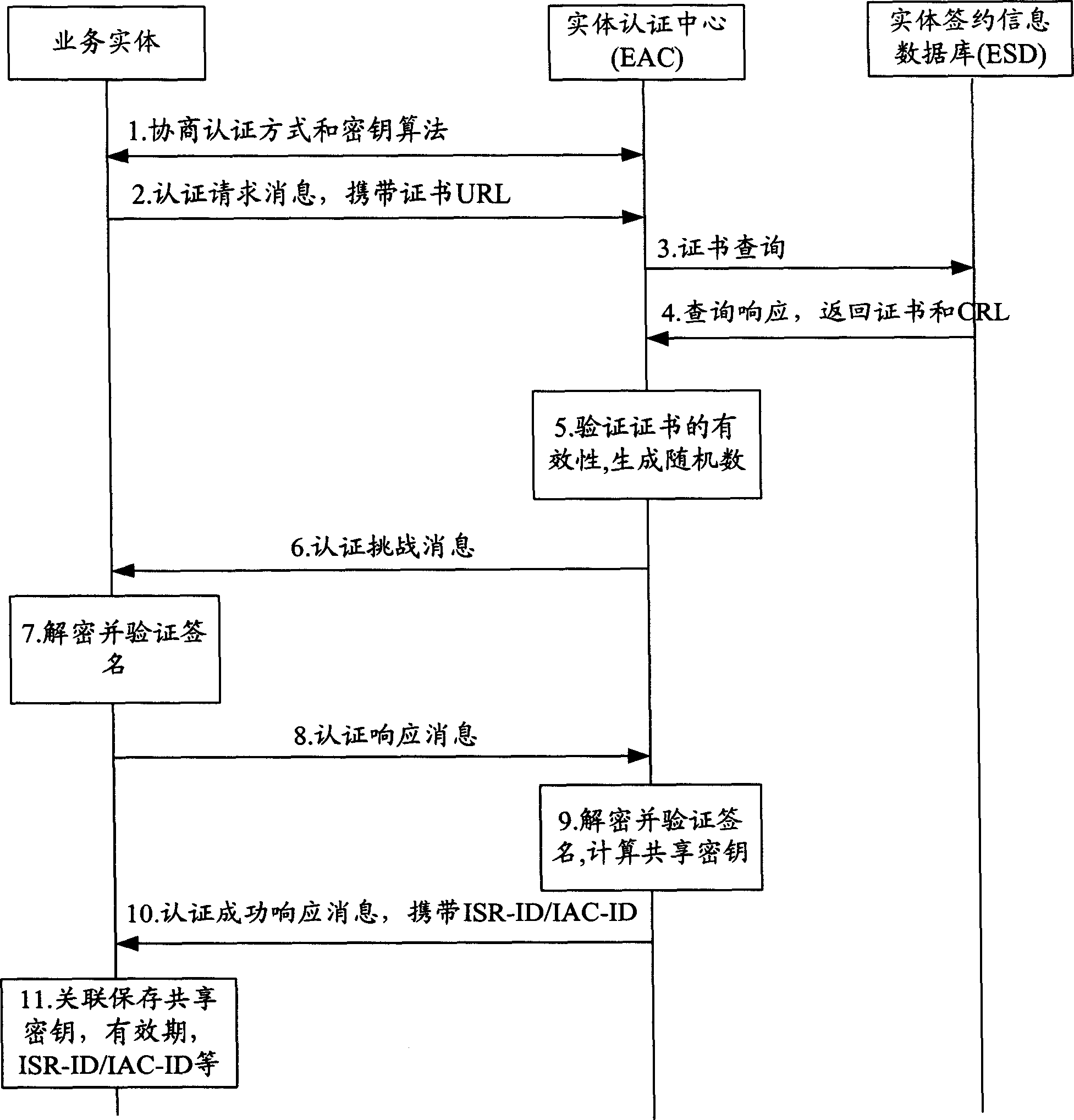
ActiveCN1859097AImprove versatilityReduce storage burdenUser identity/authority verificationRadio/inductive link selection arrangementsInformation dataAuthentication
This invention provides a certification method and a system based on a general authority authentication frame including an entity certification center connected with the service entity and a database storing the service entity agreement information, in which, the method includes: A, the entity certification center negotiates with the service entity about the certification mode and a cipher algorithm to determine applying a mode of public key to mutually certificate, B, the entity certification center verifies the certificate of the service entity to get its public key, C, the center and the service entity certify each other by the public key of the opposite to generate a share cryptographic key.
Owner:HONOR DEVICE CO LTD
kNN (k-nearest neighbor) fault detection method for online upgrading master sample model
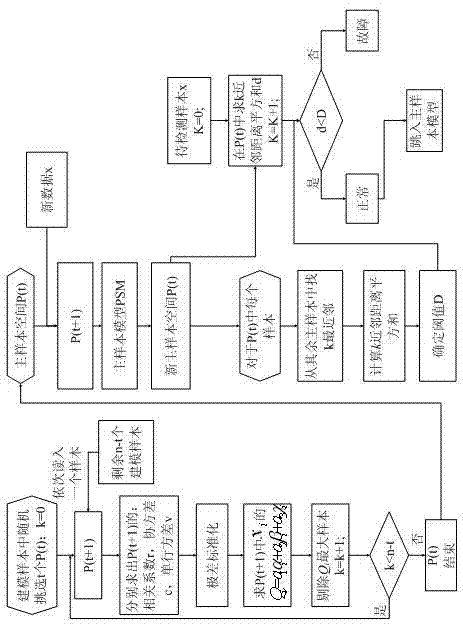
InactiveCN103488561AReduce storage burdenEfficient use ofSoftware testing/debuggingProgram loading/initiatingNear neighborAlgorithm
The invention discloses a kNN (k-nearest neighbor) fault detection method for an online upgrading master sample model and relates to a fault detection method for a batch process. The kNN fault detection method for the online upgrading master sample model comprises the following steps of performing modeling and fault detection by utilizing the kNN fault detection method by taking data of a master sample space as a training set of modeling data, finding out k nearest neighbors of each sample from the master sample space, calculating the quadratic sum of distances of the k nearest neighbors on each sample, permuting the quadratic sums of the k nearest neighbors of all samples in sequence to determine a threshold value of fault detection; finding out k nearest neighbors of a sample x from the master sample space for the new to-be-detected sample x, calculating the quadratic sum of the distances of the k nearest neighbors of the sample x and comparing the quadratic sum of the distances of the k nearest neighbors of the sample x with the threshold value, judging that the sample x is normal if the quadratic sum of the distances of the k nearest neighbors of the sample x is smaller than the threshold value, otherwise, judging that the sample x is faulted. By the selection of the master sample model, data structures of all working conditions are optimized, and the accuracy of a fault detection model is improved.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
Adjustable light filter type hyperspectral imager and method based on compressed sensing
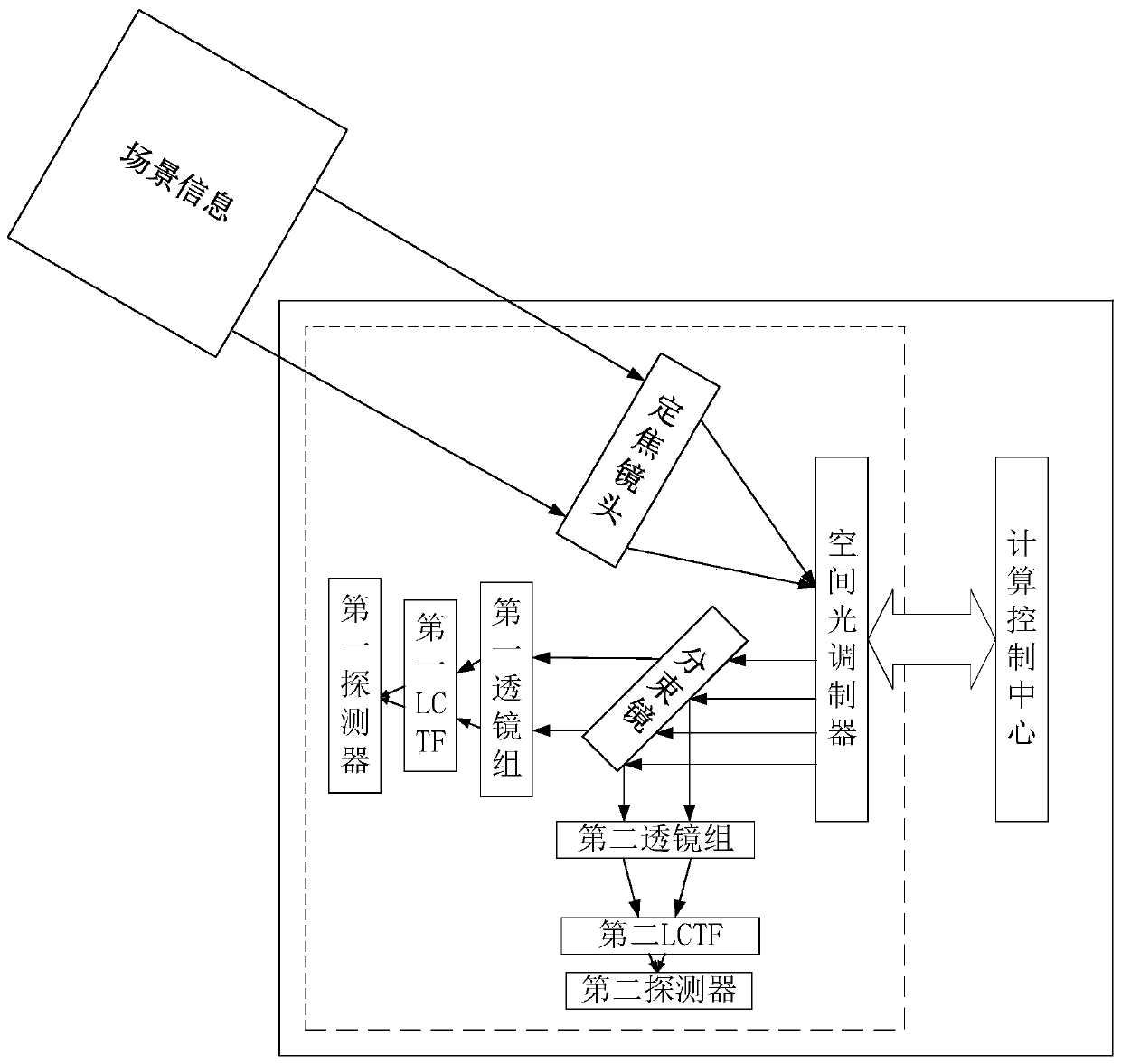
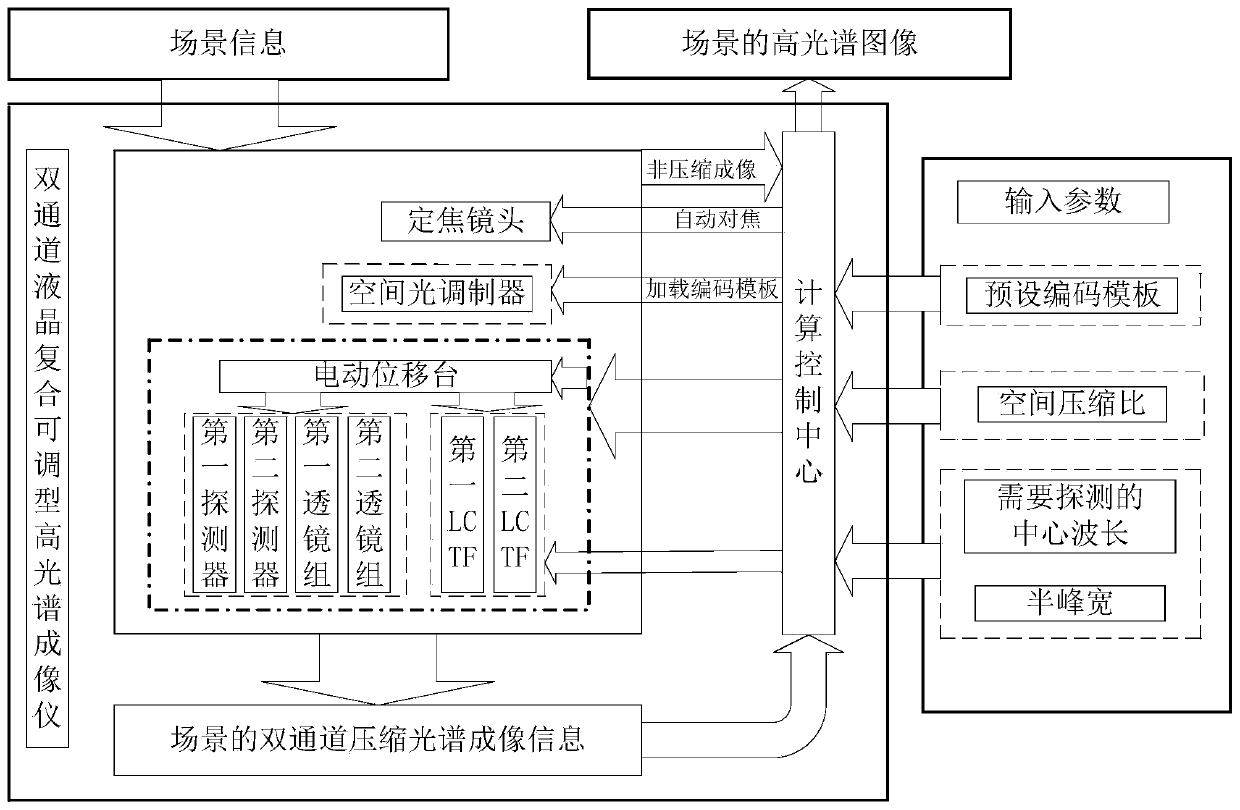
ActiveCN110081977ASolve the problem that the space compression ratio is fixed and cannot be adjustedRealize automatic focusSpectrum investigationBeam splitterCompressed sensing
The invention discloses an adjustable light filter type hyperspectral imager and method based on compressed sensing. An imaging device is provided with an electric translation platform. A calculationcontrol module adjusts an object distance and an image distance of the imaging device to realize automatic focusing, which solves a problem that a space compression ratio of a traditional compressed sensing hyperspectral imaging system is fixed and can not be adjusted. A beam splitter is used to divide a scene spectrum into two parts which are collected by two LCTFs with different spectrum segments via two different optical paths, and the problem that the LCTF has a single imaging spectrum segment range in a hyperspectral compressed sensing imaging field is solved. According to an input compression ratio, basic parameters of the optical paths are automatically calculated, and the optical paths are automatically adjusted under the coordination of an electric displacement platform. A compressed sensing theory is combined with the LCTF so as to solve the problem that a spatial resolution is limited by the detector in traditional LCTF hyperspectral imaging.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Data acquisition system, data analysis system and monitoring analysis system based on intelligent terminal
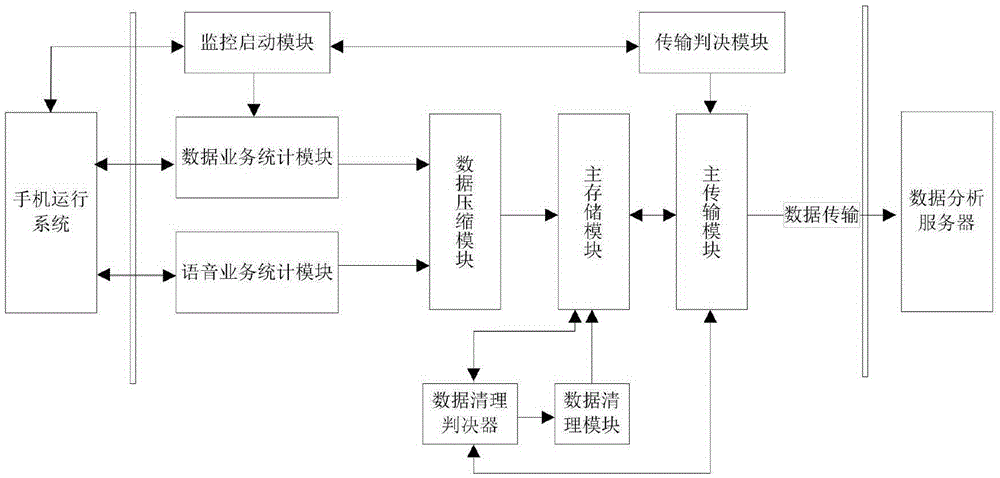
ActiveCN105391573ASurveillance awarenessIncrease awarenessData switching networksData acquisitionData analysis system
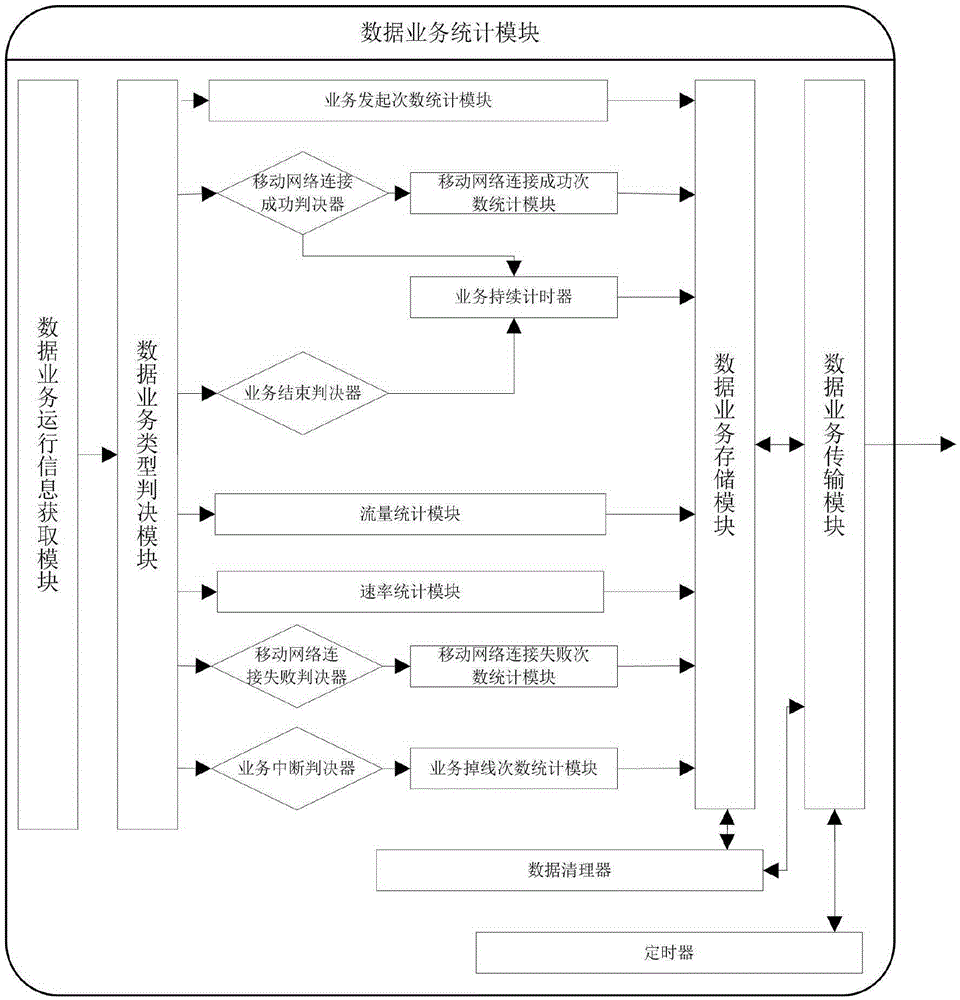
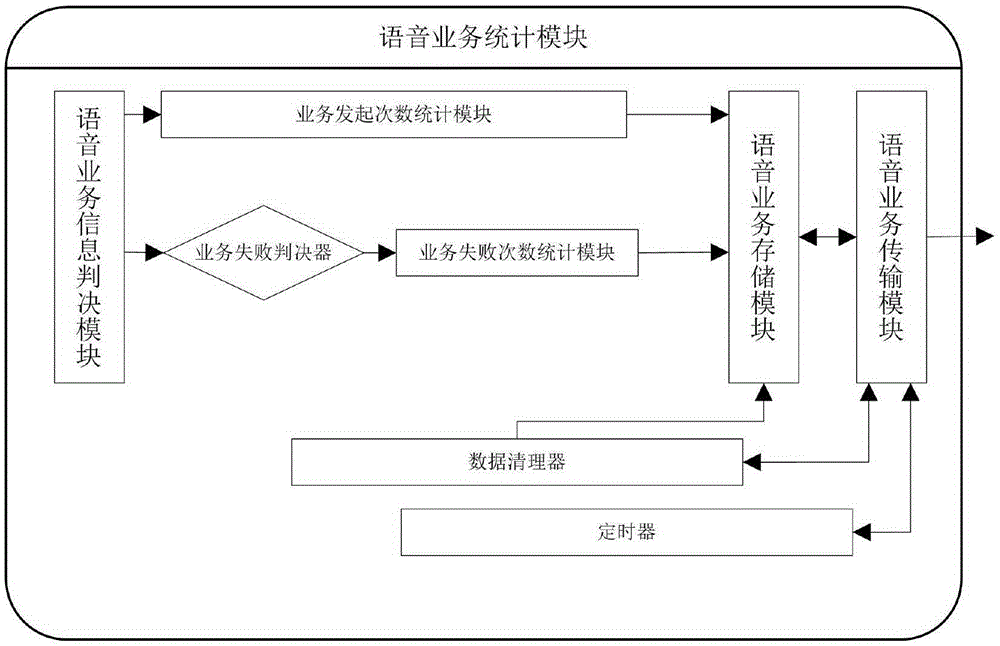
The invention discloses a data acquisition system based on an intelligent terminal, a data analysis system based on an intelligent terminal, and a monitoring analysis system comprising the data acquisition system and the data analysis system. The data acquisition system is installed on a terminal, and is used for monitoring an operation system of the terminal, acquiring data of service execution condition of the terminal and transmitting the data to a data server. The data analysis system comprises a data server and a client, wherein the client is used for receiving operation commands and displaying graphs. The data acquisition system, the data analysis system and the monitoring analysis system aim to monitor user's perception condition of a mobile network, and have the advantages of judging event occurrence situation based on user behavior and recording data, being capable of acquiring and analyzing networks of various systems, being suitable for various kinds of terminals, being capable of distinguishing actual operation service types of the user, effectively monitoring user's perceptibility of the mobile network, providing data basis for improving perceptibility, judging whether to acquire data according to a wireless environment where the terminal is positioned and data service opening situation, and being capable of reducing data volume acquired by the terminal without consuming flow of the user.
Owner:POTEVIO INFORMATION ENG DESIGN SERVICE CO LTD
Data security verification and updating method supporting third-party administrator (TPA) in mobile cloud computing
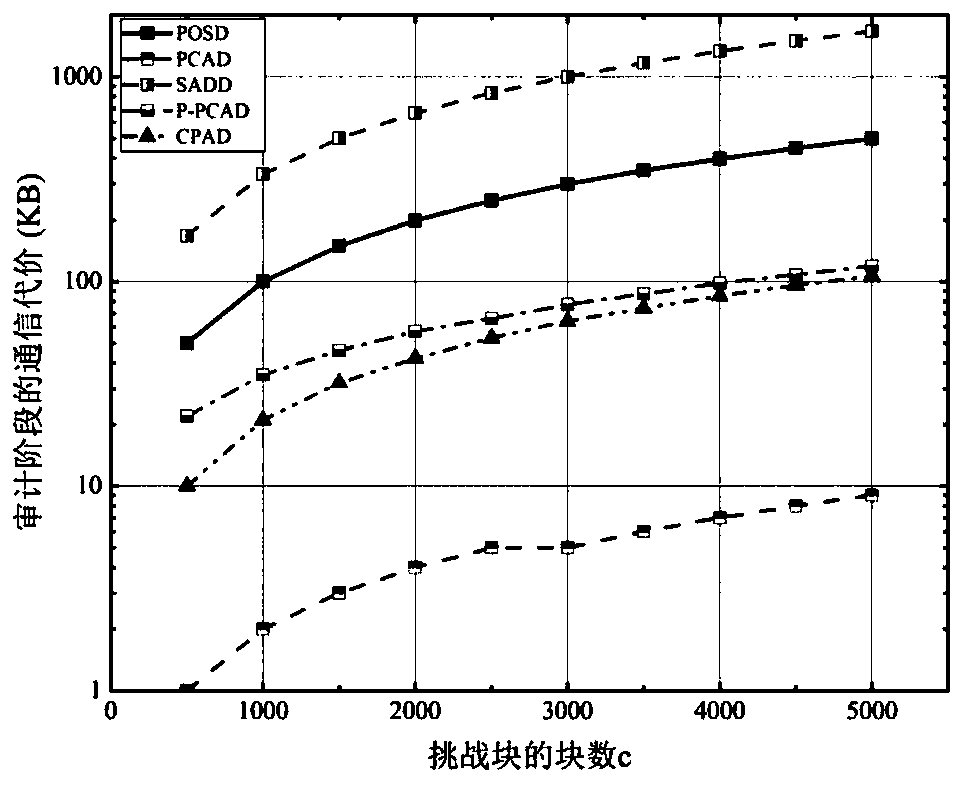
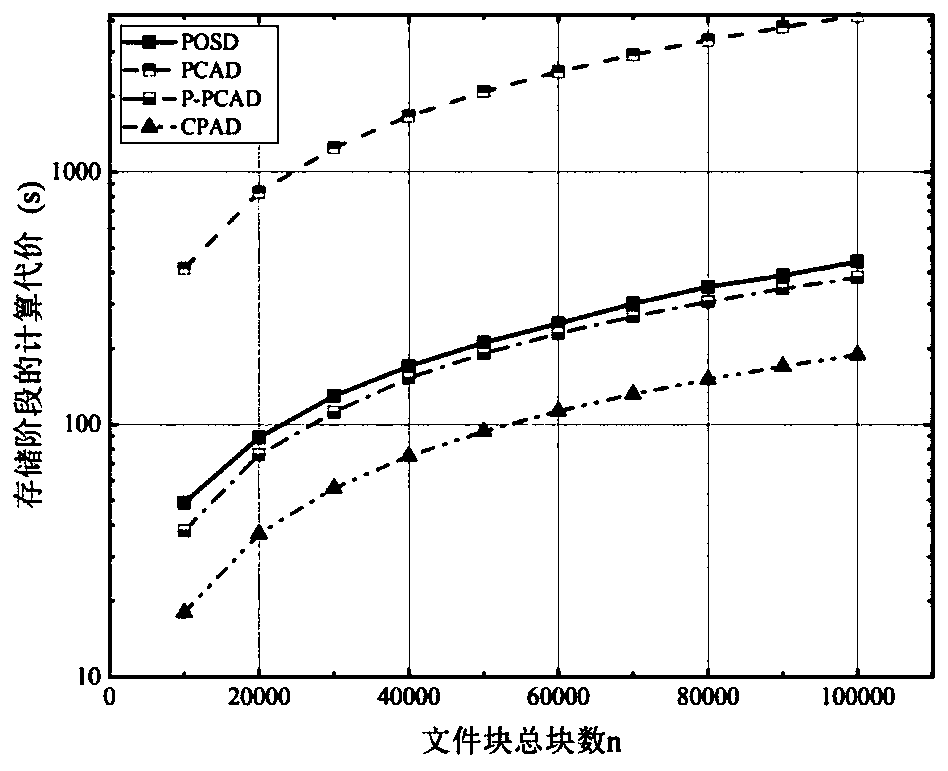
InactiveCN106612174AReduce calculationReduce storage burdenKey distribution for secure communicationData verificationCloud service provider
The invention provides a data security verification and updating method supporting a third-party administrator (TPA) in mobile cloud computing. The method adopts the technical scheme that based on the BLS short signature algorithm and the hash tree algorithm, a key is generated through the key generation algorithm in mobile cloud, and a signature is generated through the signature generation algorithm in mobile cloud, so that challenge information is created, verification information is generated, and data verification is finally carried out. The method provided by the invention has the advantages that a verification process can be outsourced, so that computing and storage burdens on a mobile terminal are reduced; no status information is saved during the verification process, and a cloud service provider only needs to construct corresponding verification data according to a challenge request sent by a verifier and returns the verification data; and the verification does not involve source file blocks, and a verification terminal operates file blocks which have been processed through mapping functions during the whole verification process, so that file information can be prevented from being disclosed to the TPA.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com