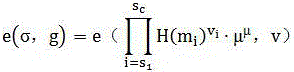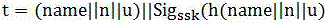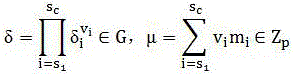Data security verification and updating method supporting third-party administrator (TPA) in mobile cloud computing
An update method and data verification technology, applied in the field of mobile cloud computing, can solve problems such as inappropriateness, and achieve the effect of reducing the burden of computing and storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Mobile cloud computing supports third-party data security verification and update methods. In this method, mobile cloud computing verification is divided into data holders, trusted third parties, cloud service providers, and storage service providers. We will cloud The service provider and the storage service provider are regarded as a whole, which is called the service provider. The trusted third party is an organization that provides data outsourcing verification services. Users can outsource data integrity verification to a trusted third party to reduce their own computing and storage burden. The scheme in this paper relies on the file integrity inspection method based on the Merkle hash tree, and the hash values of the file block tags correspond to the leaf nodes of the hash tree in order from left to right, and then cascade the hashes in pairs, Finally, the hash value of the root node is calculated. For a file with n blocks (n is an integer power of 2), 2n-1 ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com