Patents
Literature
584 results about "Check point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Mmw contraband screening system
InactiveUS20050110672A1Geological detection using milimetre wavesMaterial analysis using microwave meansTemperature controlCheck point
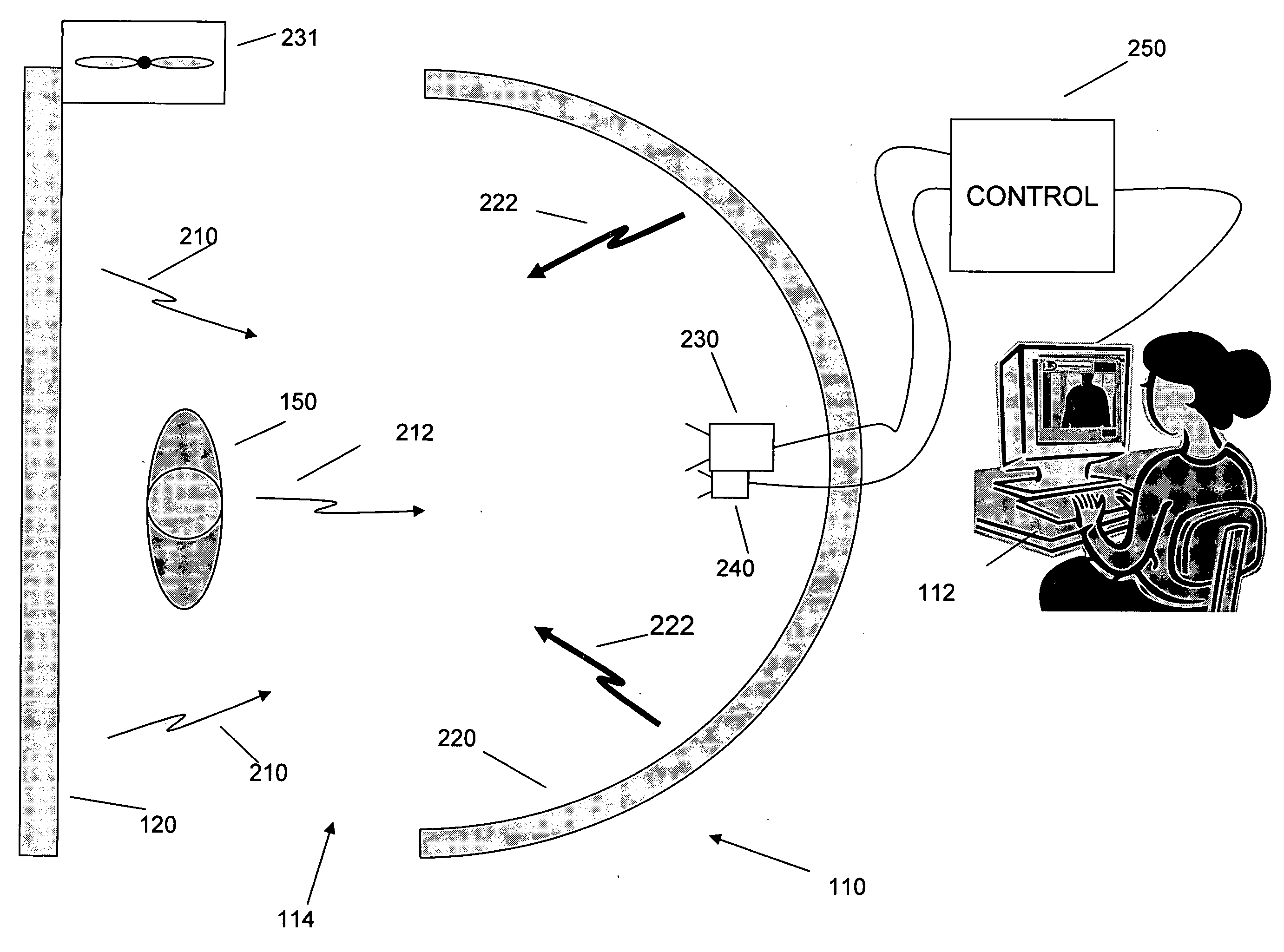
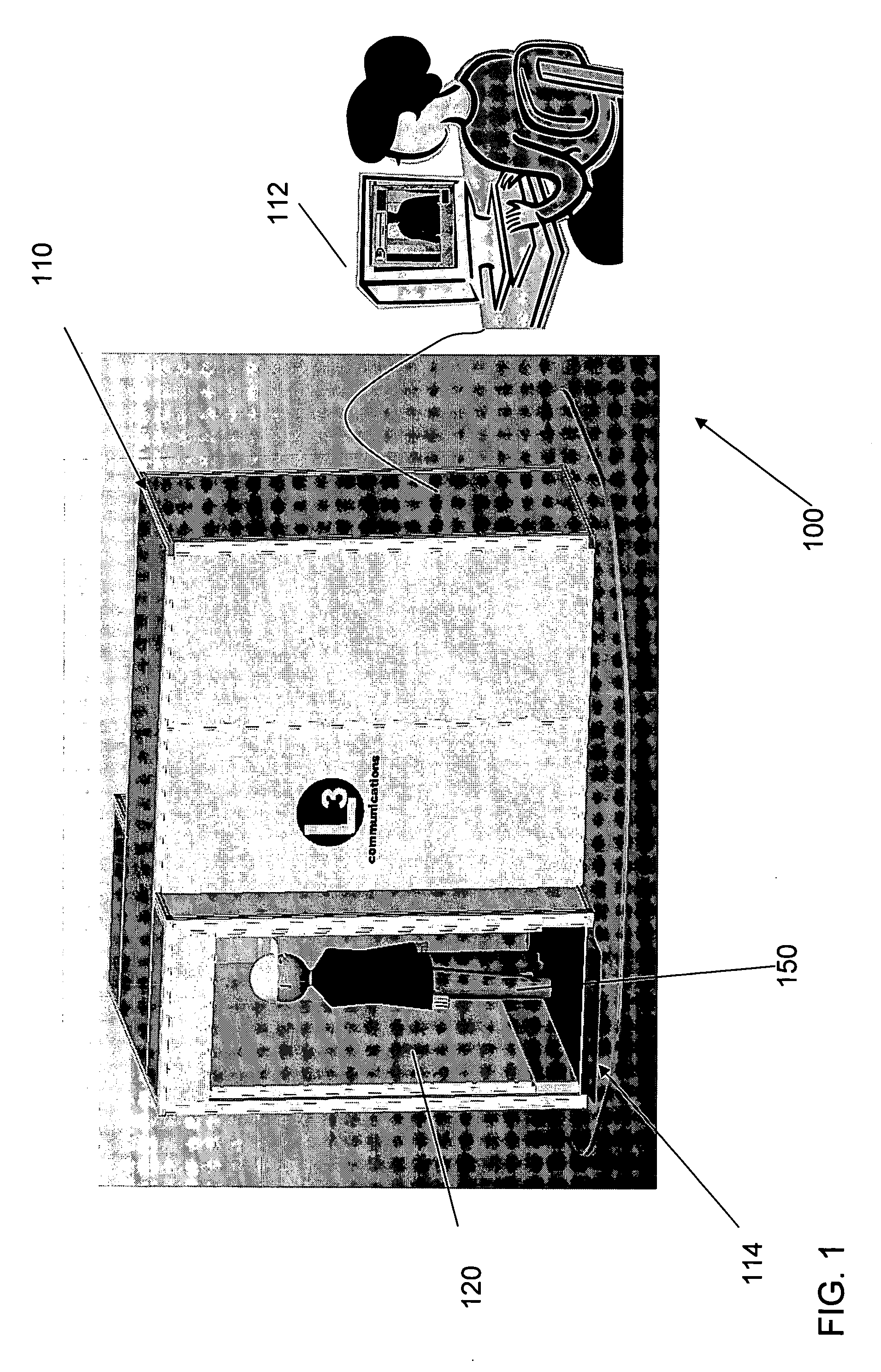
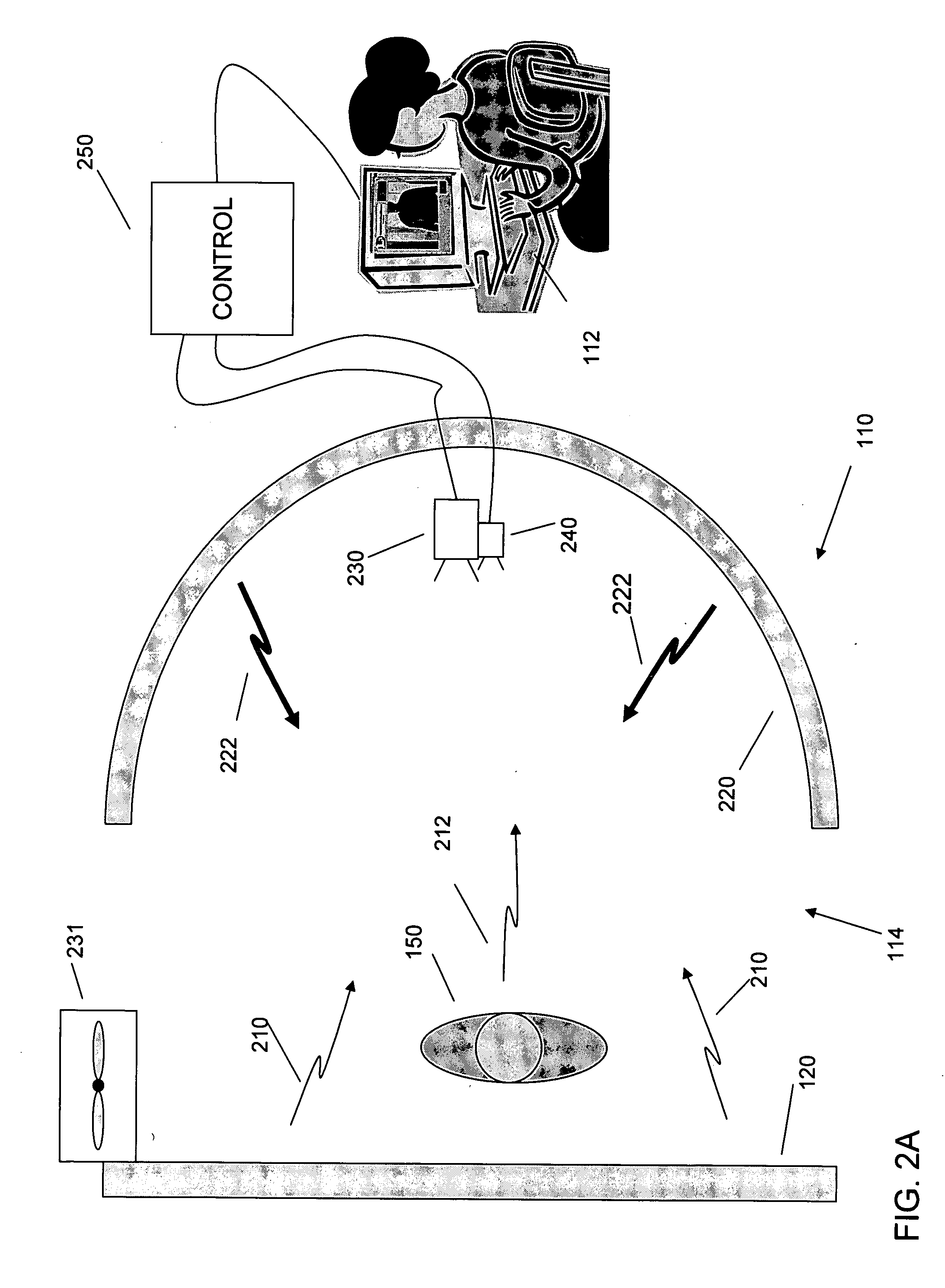
An inspection system that can detect contraband items concealed on, in or beneath an individual's clothing. The system employs mm wave radiation to detect contraband items. The system is described in connection with a check point security system that includes temperature controlled walls to enhance imaging of contraband items. Also, a mm wave camera is used in conjunction with a camera that forms visible images. To address privacy concerns of displaying images of people made with mm wave cameras that effectively “see through” clothes, the mm wave images are not displayed directly. Rather, computer processing produces indications of suspicious items from the underlying raw mm wave images. The indications of suspicious items are overlaid on the visible image.
Owner:L3 COMMUNICATIONS SECURITY & DETECTION SYSTEMS CORPORATION
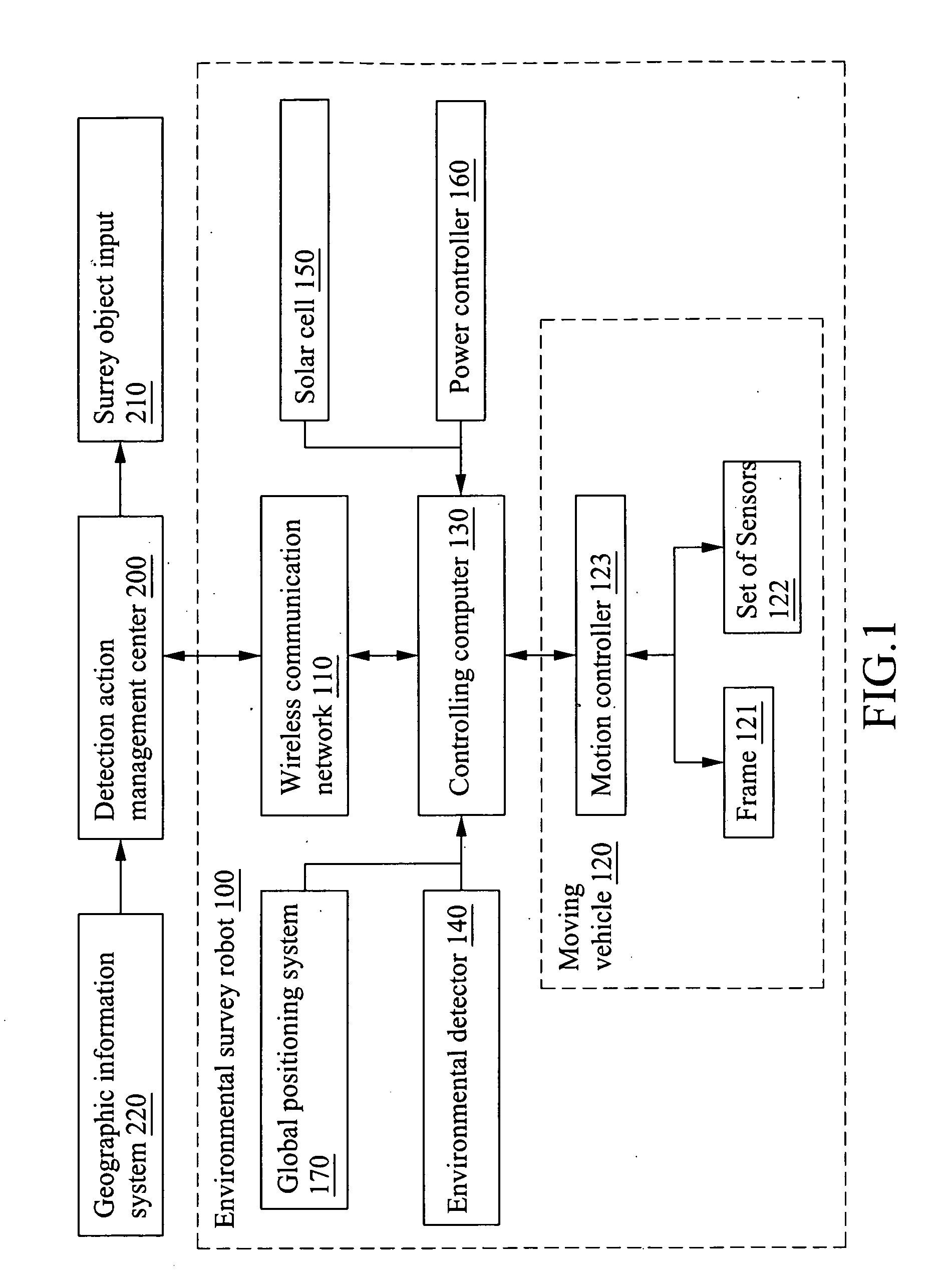
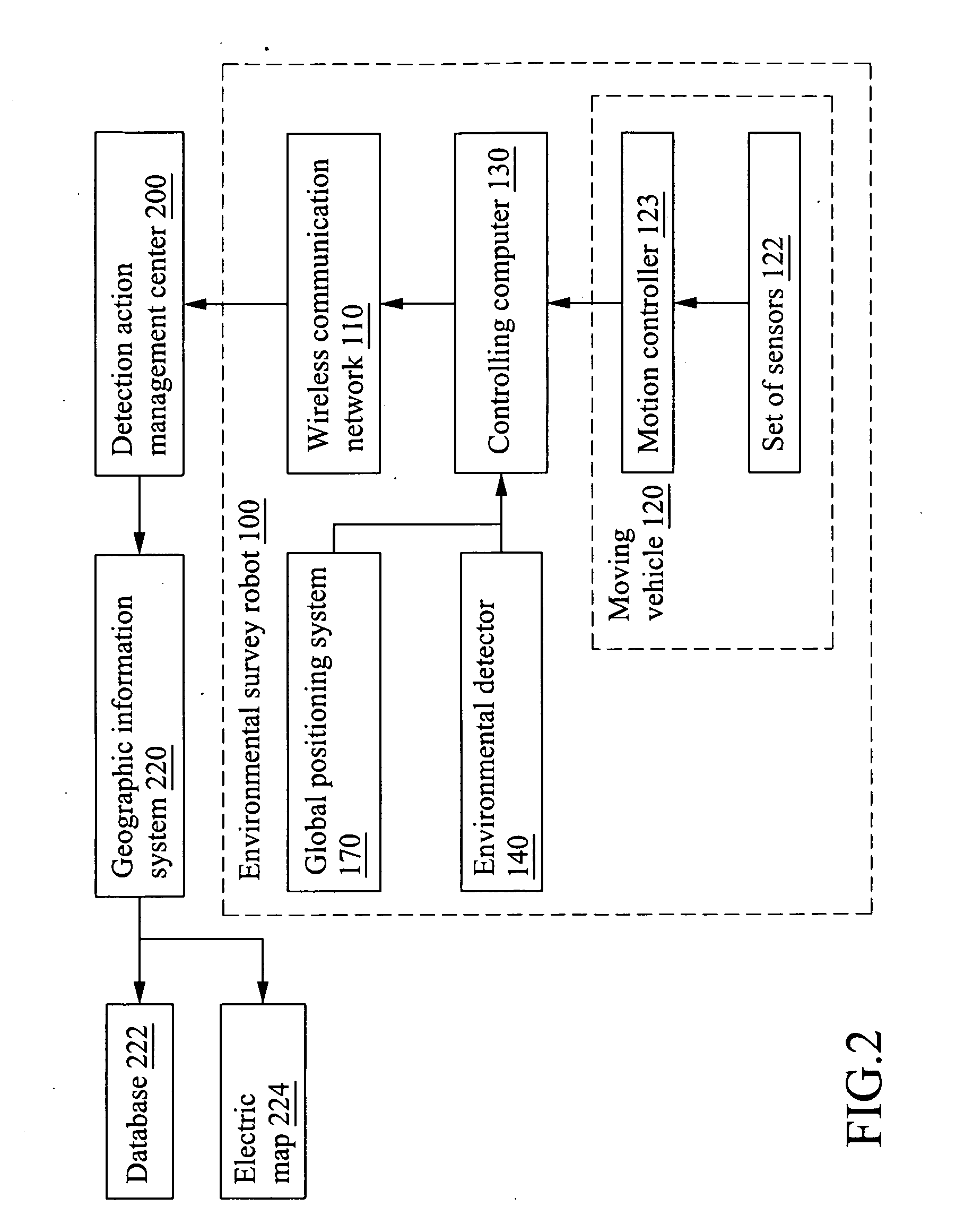
Environmental survey robot
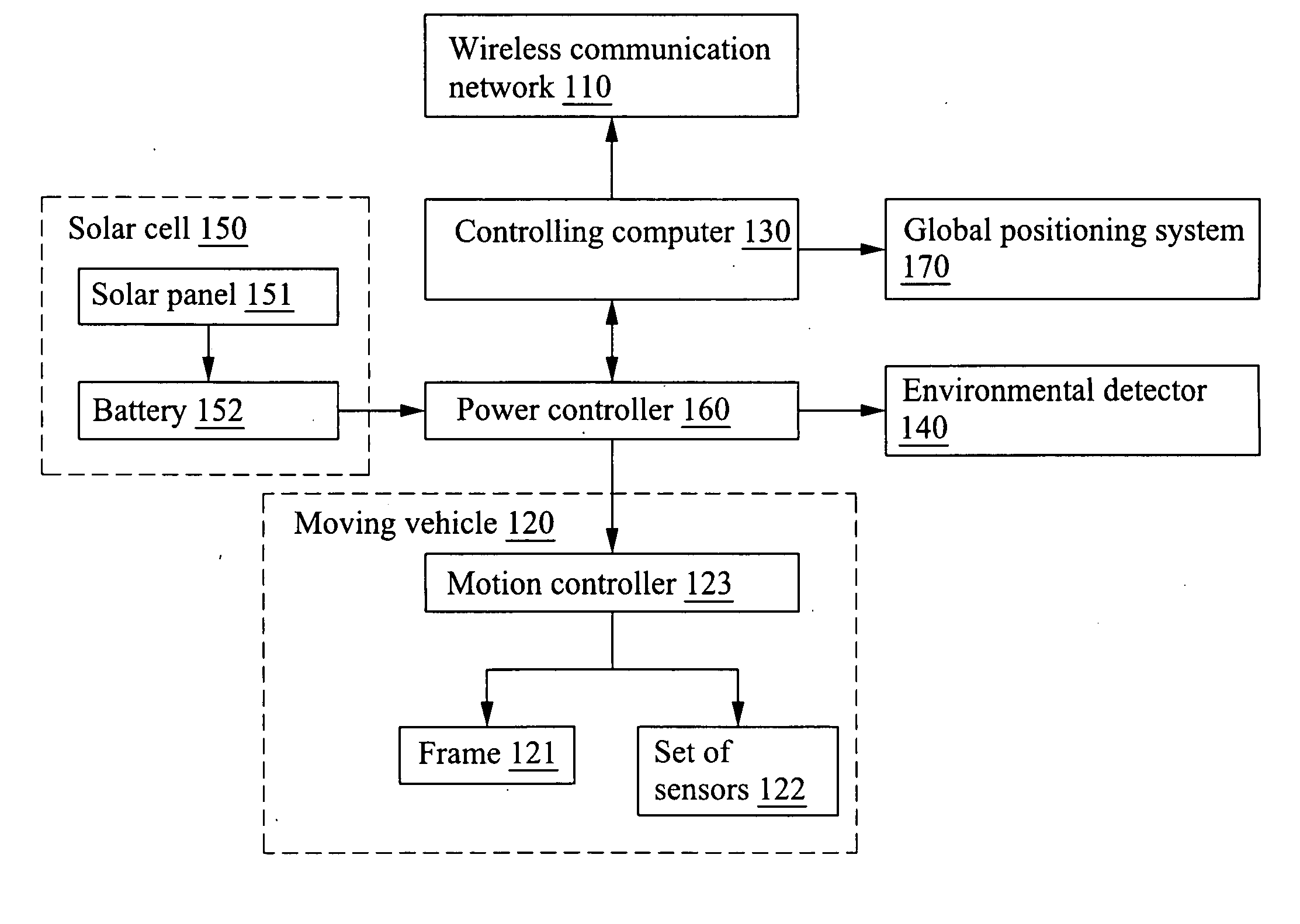
InactiveUS20100030417A1Less obstacleIncrease the areaProgramme controlComputer controlMobile vehiclePower controller
An environmental survey robot suitable for wireless communicating with a survey action management center having a geographic information system to scheme an advance route with multiple check points is provided. The environmental survey robot includes a moving vehicle, a controlling computer, a wireless communication network, a Global positioning system, an environment detector, a solar cell and a power controller. The wireless communication network receives the advance route from the detecting action management center, and the controlling computer autonomously controls the moving vehicle to move in accordance with the advance route. The environmental detector is suitable for detecting the environment information and sending the same to the controlling computer. When the electricity of the solar cell is less than a predetermined value, the power controller will send the signal to the controlling computer such that the action controller will stop the action of the moving vehicle.
Owner:INST NUCLEAR ENERGY RES ROCAEC
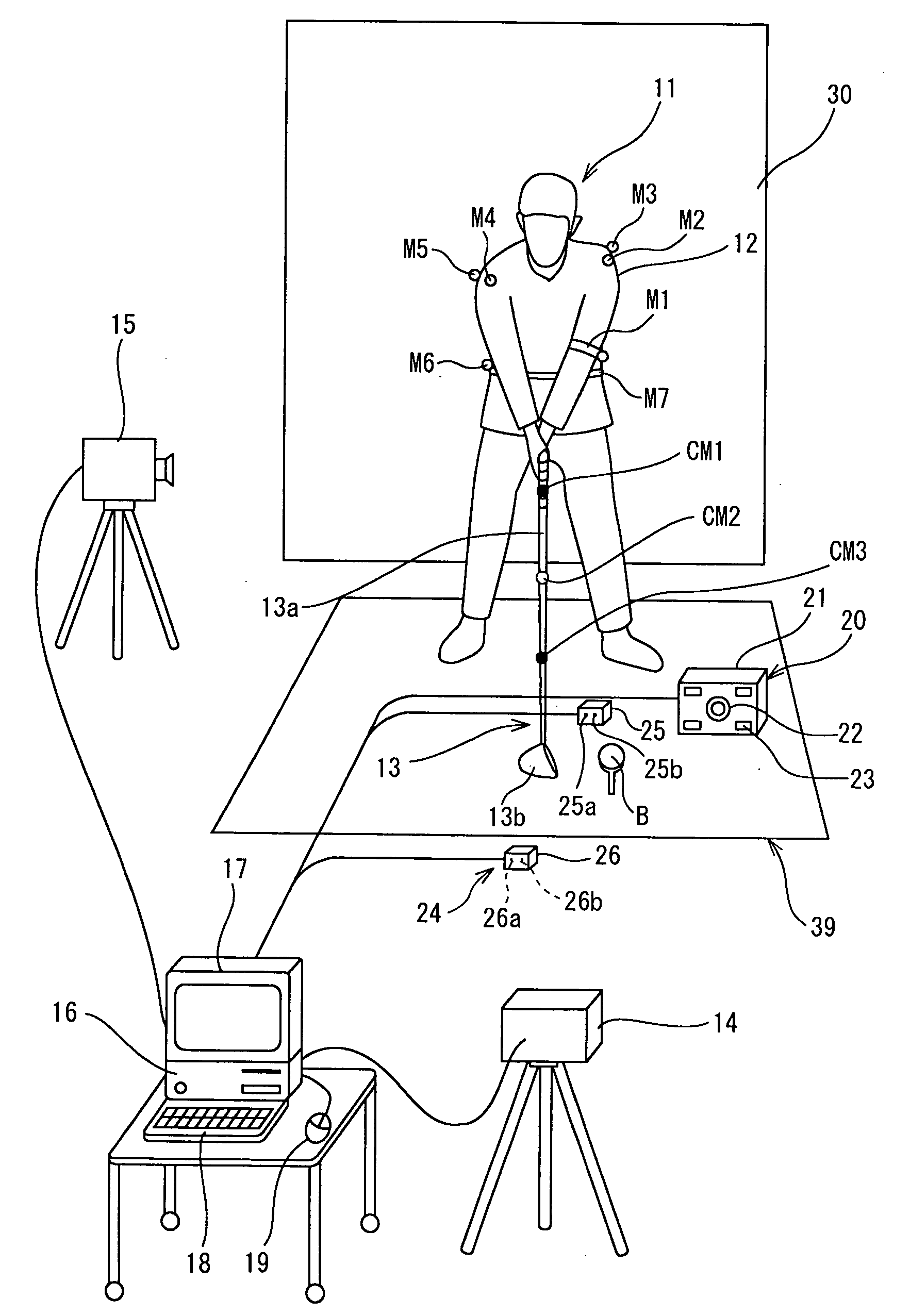
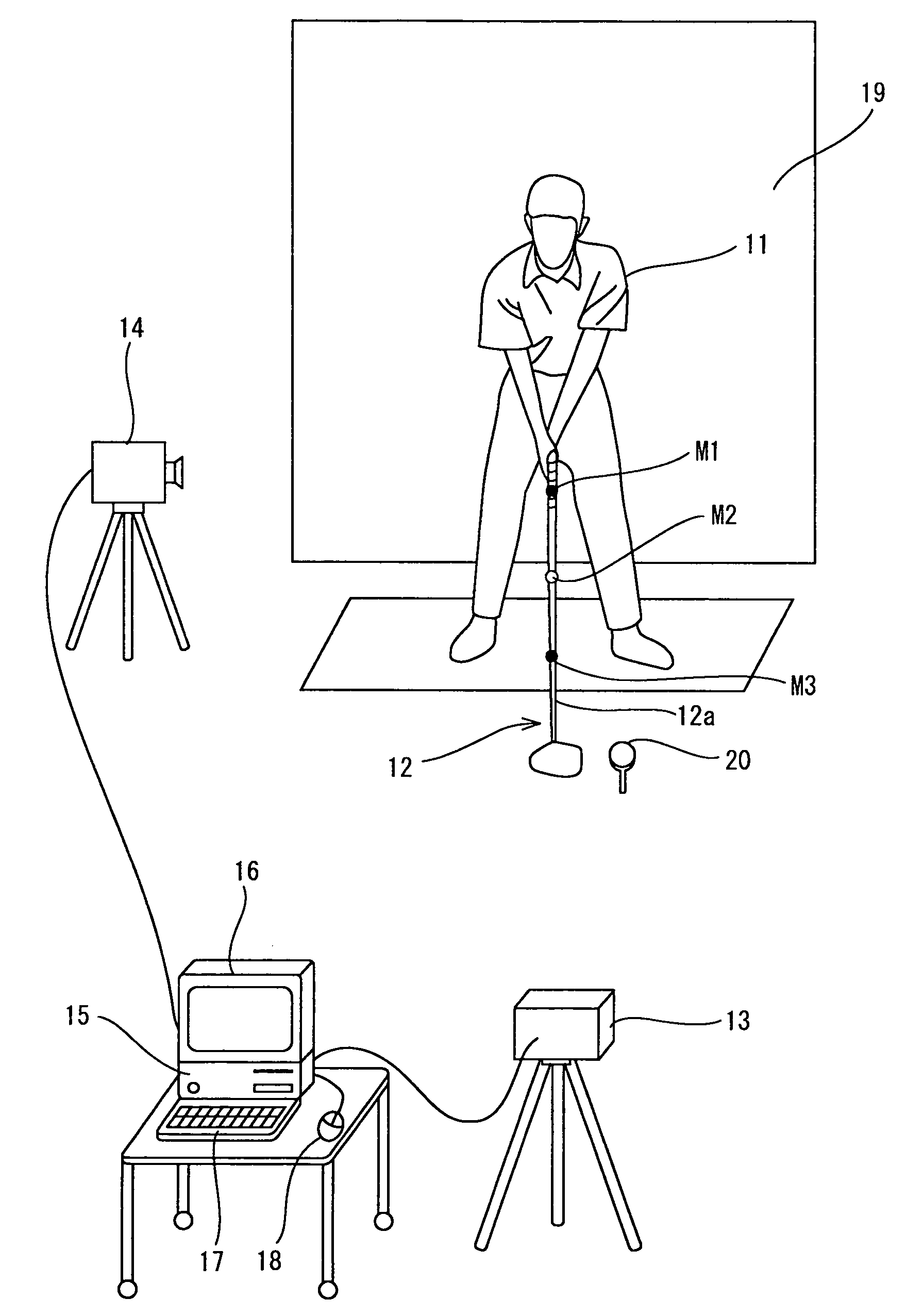
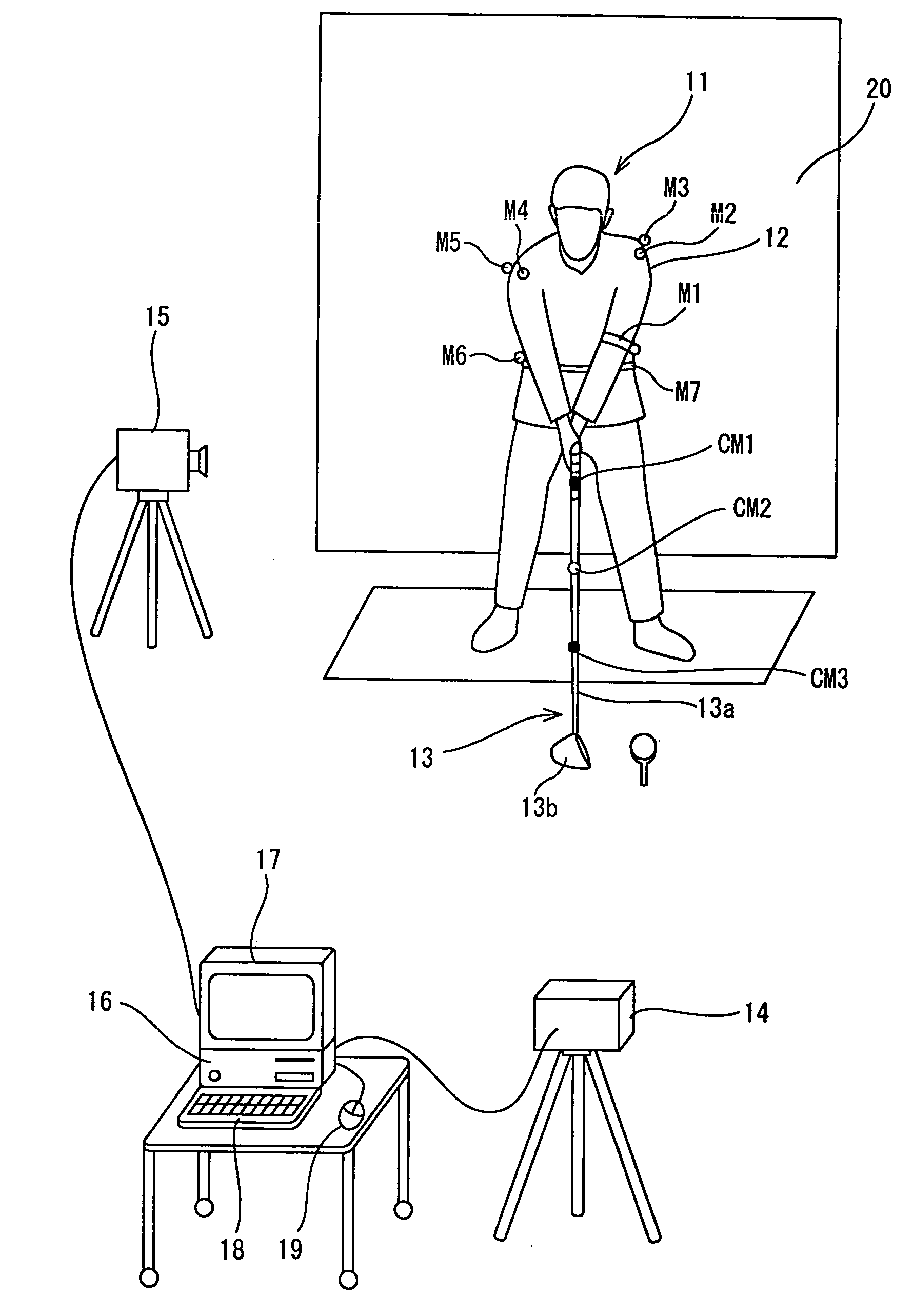
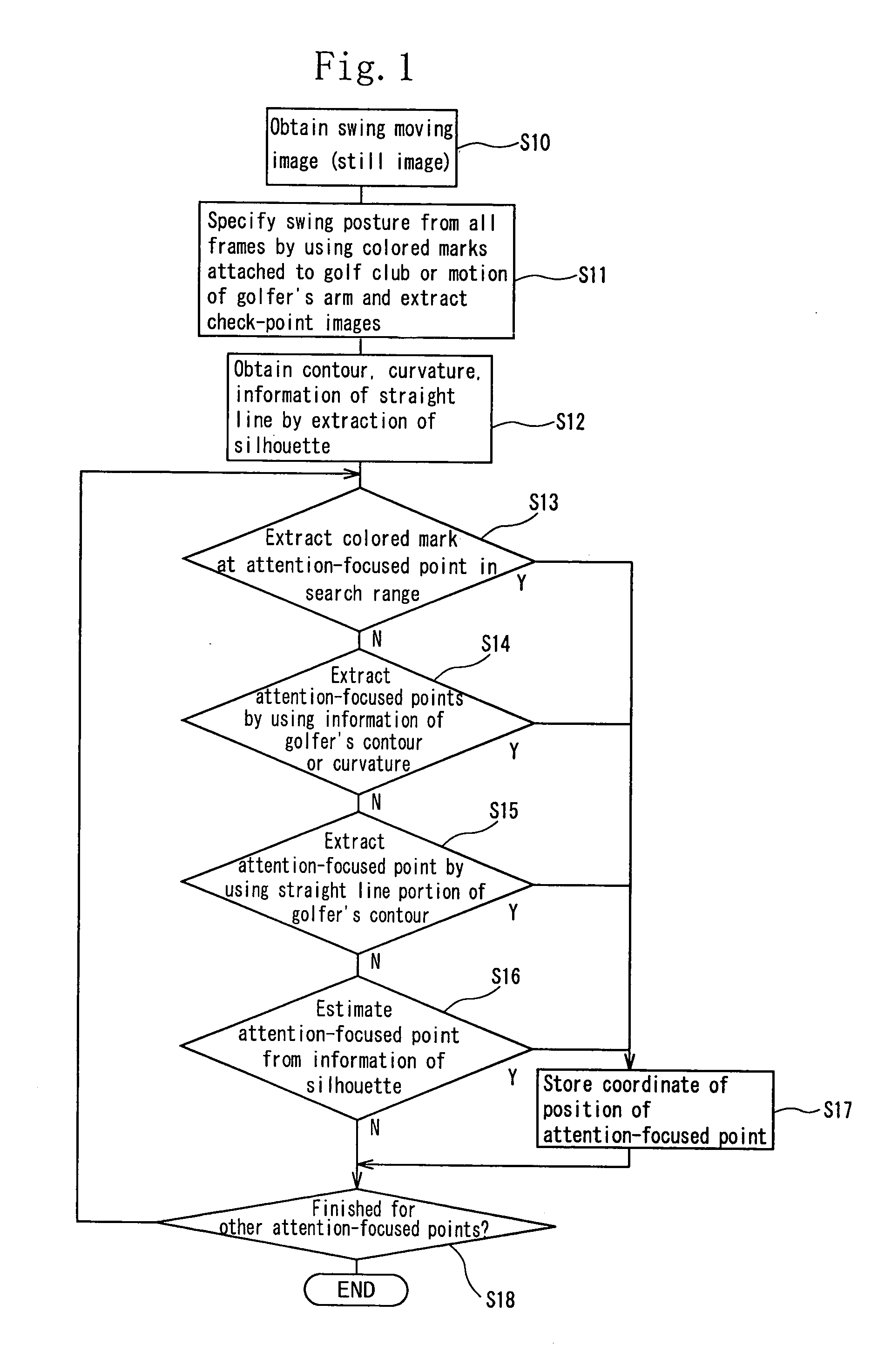
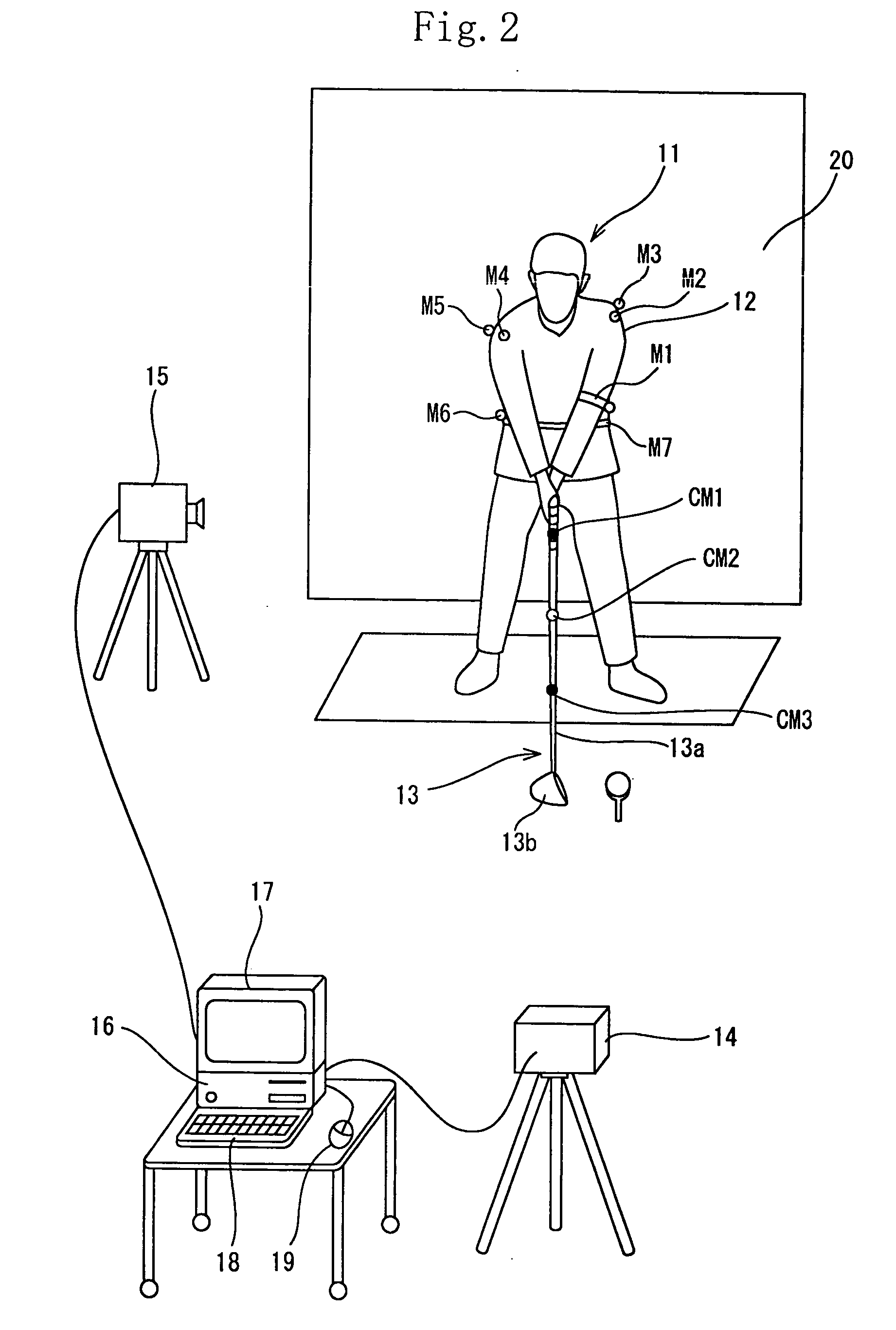
Golf swing-diagnosing system
InactiveUS20050215336A1Improve rigidityEffective diagnosisCosmonautic condition simulationsGymnastic exercisingValue setCheck point
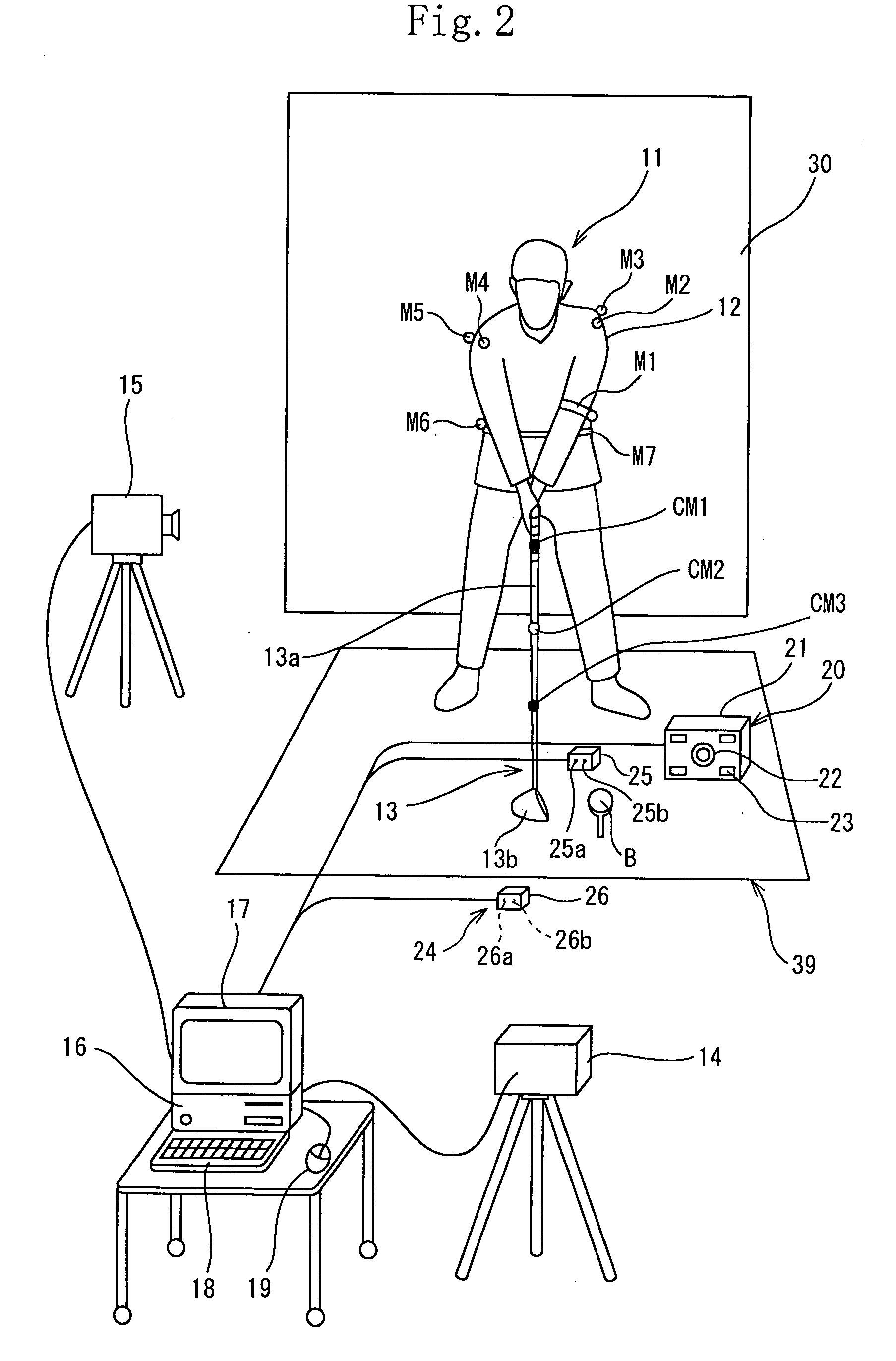
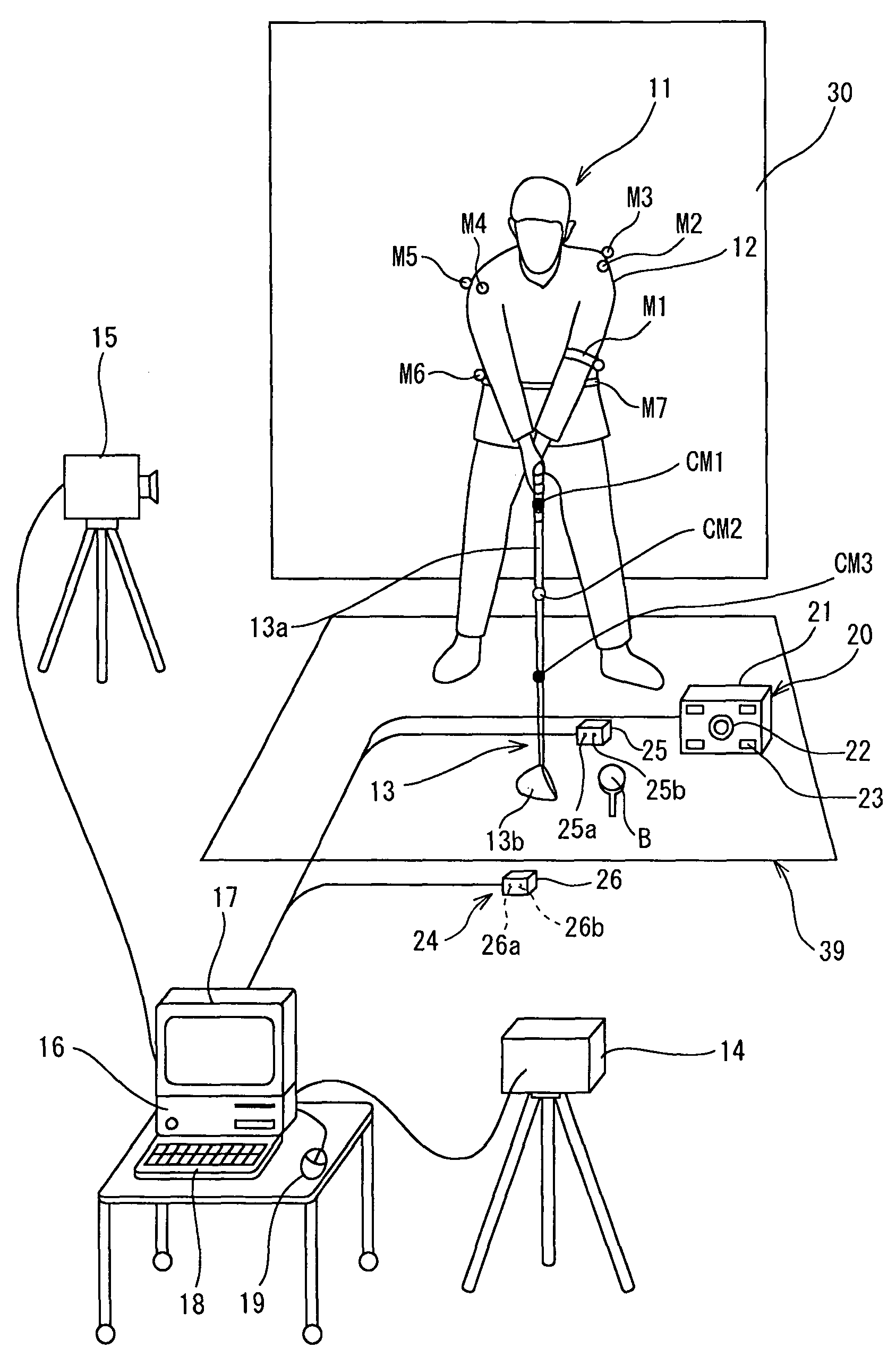
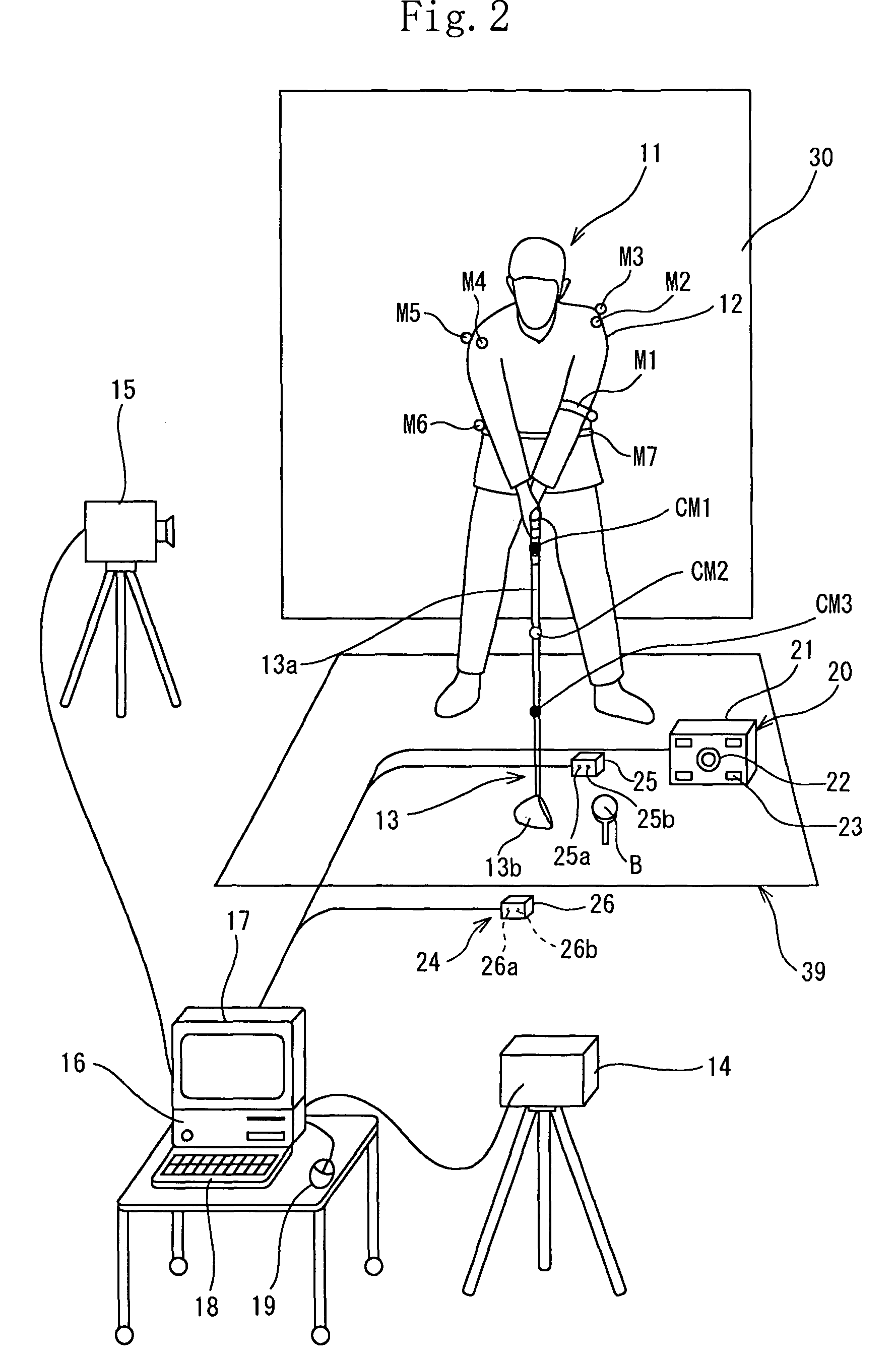
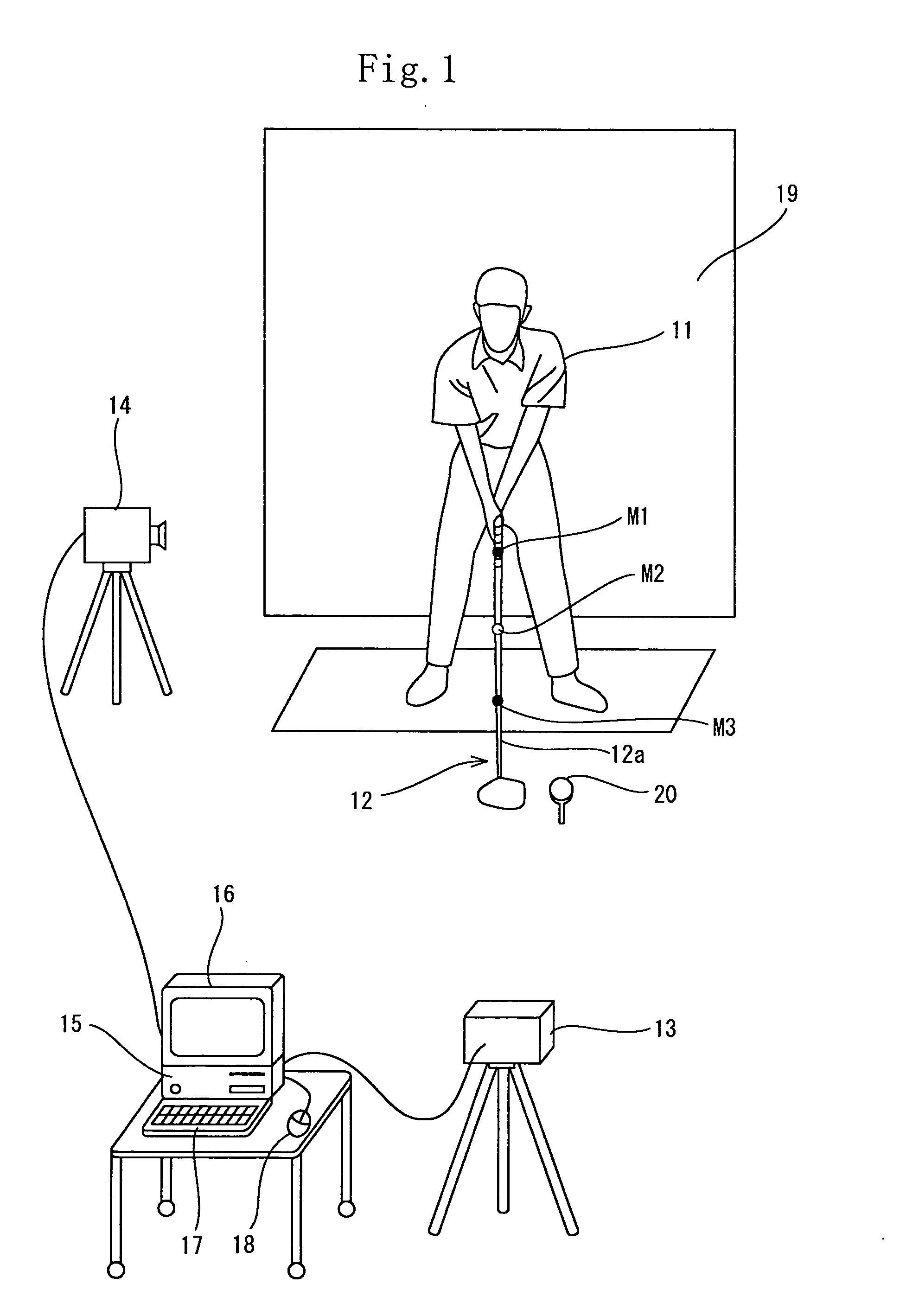
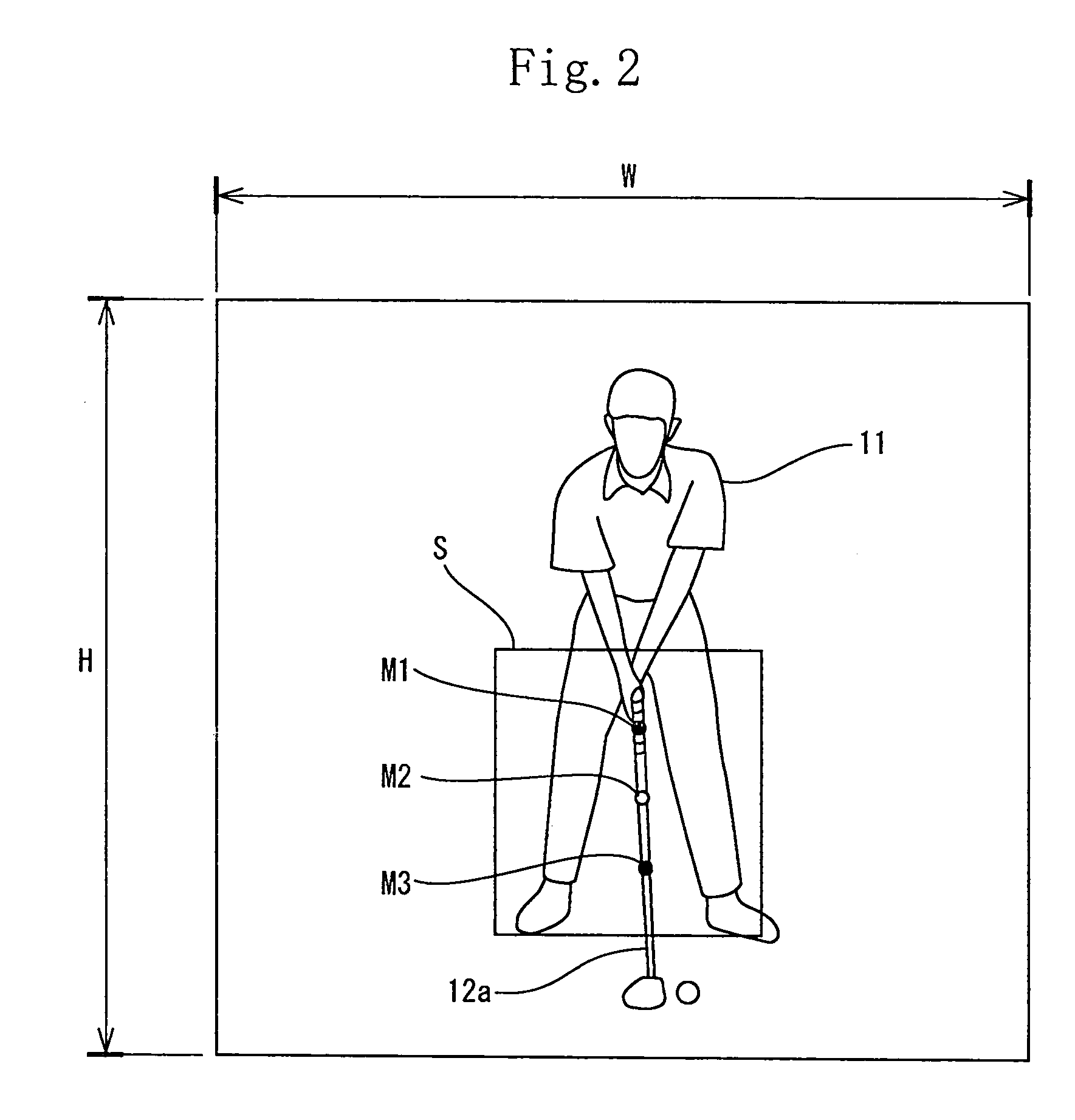
A computer (16) for capturing a colored moving image photographed by photographing means (14, 15) has an extraction means for extracting images having necessary swing postures as check-point images from a large number of still images constituting the color moving image; a means for obtaining a coordinate of a position of each of attention-focused points, which operate, in each of the check-point images, while a golfer (11) is swinging; a means for diagnosing a golfer's swing form by setting a plurality of diagnosis items for each trajectory pattern obtained by a ball motion measuring apparatus (20) to classify behavior of a golf ball and by comparing numerical data generated from data of the coordinate of the position of each of the attention-focused points with a judgement value set in each of a plurality of diagnosis items; and a means for outputting an advice drill corresponding to a result of a diagnosis.
Owner:SUMITOMO RUBBER IND LTD
Method for Determining the Horizontal Profile of a Flight Plan Complying with a Prescribed Vertical Flight Profile
ActiveUS20080306680A1Reduce computing costReduce calculationInstruments for road network navigationRoad vehicles traffic controlCheck pointStraight segment
The present invention relates to the definition, in a flight plan, of the horizontal profile of an air route with vertical flight and speed profile prescribed on departure and / or on arrival, by a stringing together of check-points and / or turn points associated with local flight constraints and called “D-Fix” because they are not listed in a published navigation database like those called “Waypoints”. It consists in charting, on curvilinear distance maps, a direct curvilinear path joining the departure point to the destination point of the air route while complying with vertical flight and speed profiles prescribed on departure and / or on arrival and while guaranteeing a circumnavigation of the surrounding reliefs and compliance with regulated overfly zones, then in approximating the series of points of the direct curvilinear path by a sequence of straight segments complying with an arbitrary maximum deviation threshold relative to the points of the series and an arbitrary minimum lateral deviation threshold relative to the set of obstacles to be circumnavigated and in adopting as “D-Fix” points the points of the intermediate intersections of the rectilinear segments.
Owner:THALES SA
Multi-row database data loading for enterprise workflow application
ActiveUS20140222768A1Faster loading and updatingReduce processDigital data information retrievalDigital data processing detailsCheck pointDatabase
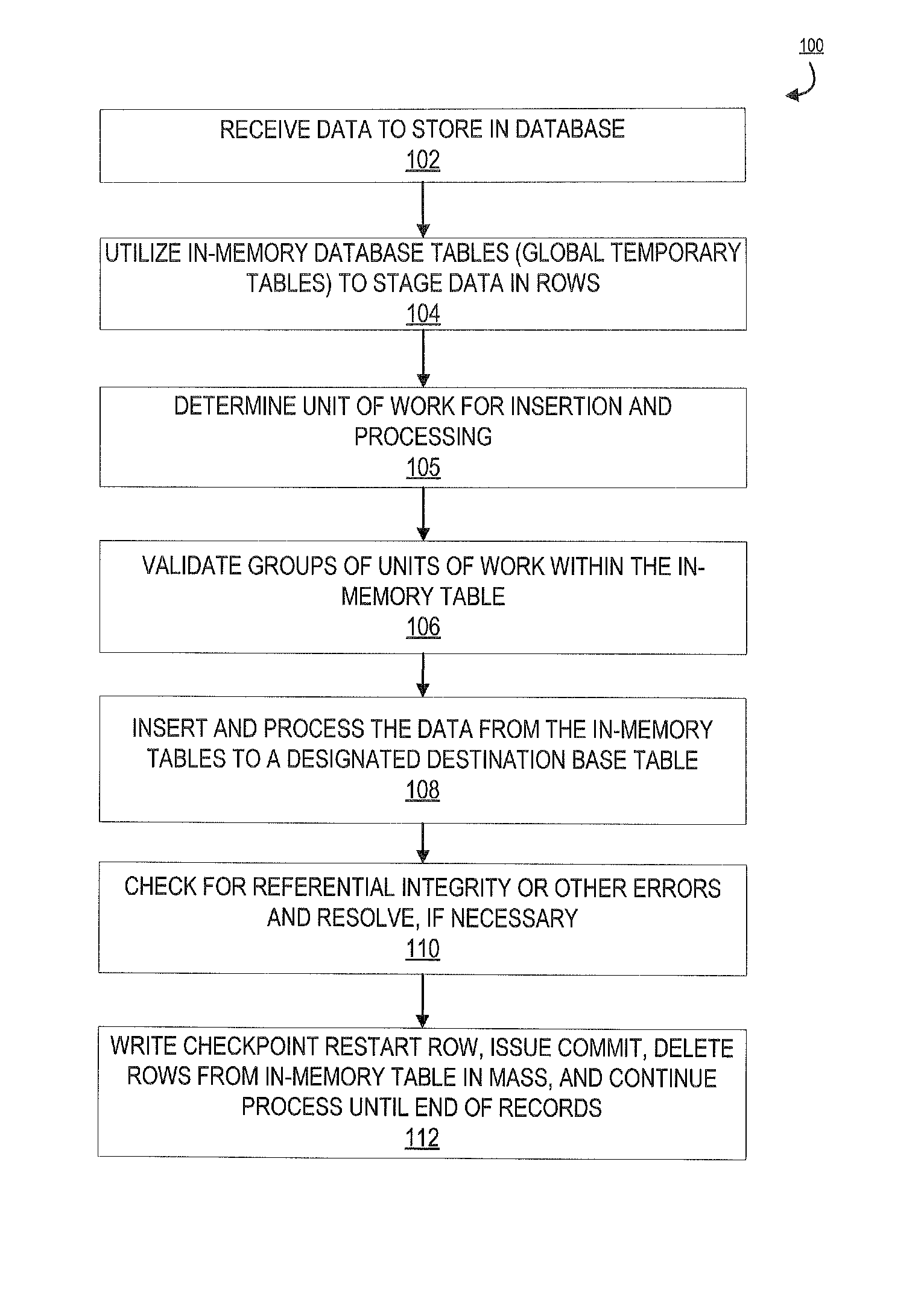
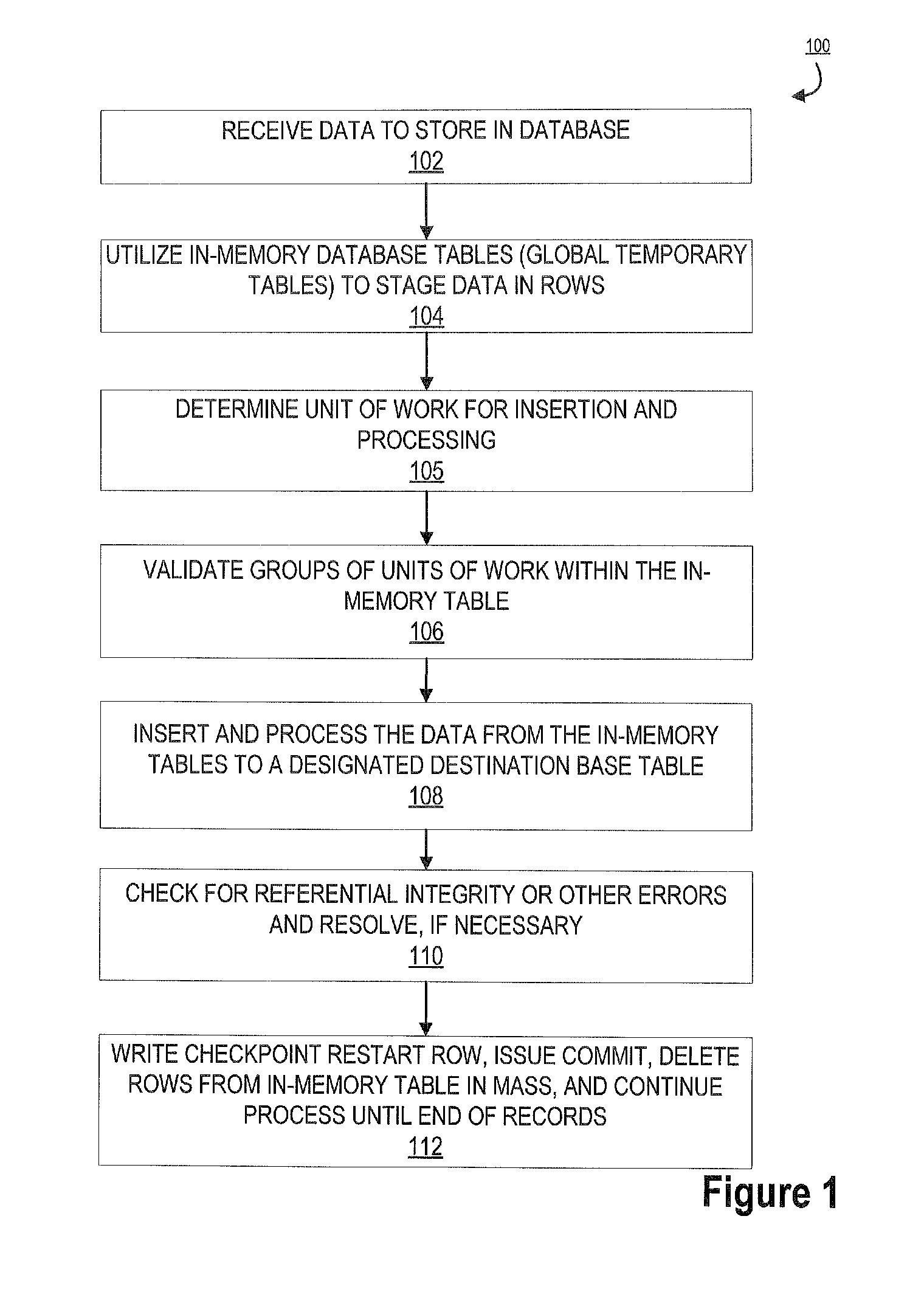
Embodiments of the invention are directed to a system, method, or computer program product for providing expedited loading / inserting of data by an entity. Specifically, the invention expedites the loading / inserting of large quantities of data to database tables. Initially received data for loading is processed, via multi-row insert, onto in-memory or temporary tables. The data is staged on a temporary table while the appropriate base table is determined. Once determined, data from the temporary table is pointed to the base table. In this way, a massive amount of data loading from the temporary table to a base table may occur. This prevents logging and locking associated with adding individual data points or row to a base table independently. Errors are check and processed accordingly. Once updated, the data on the temporary table is deleted in mass and a check point restart is issued.
Owner:BANK OF AMERICA CORP
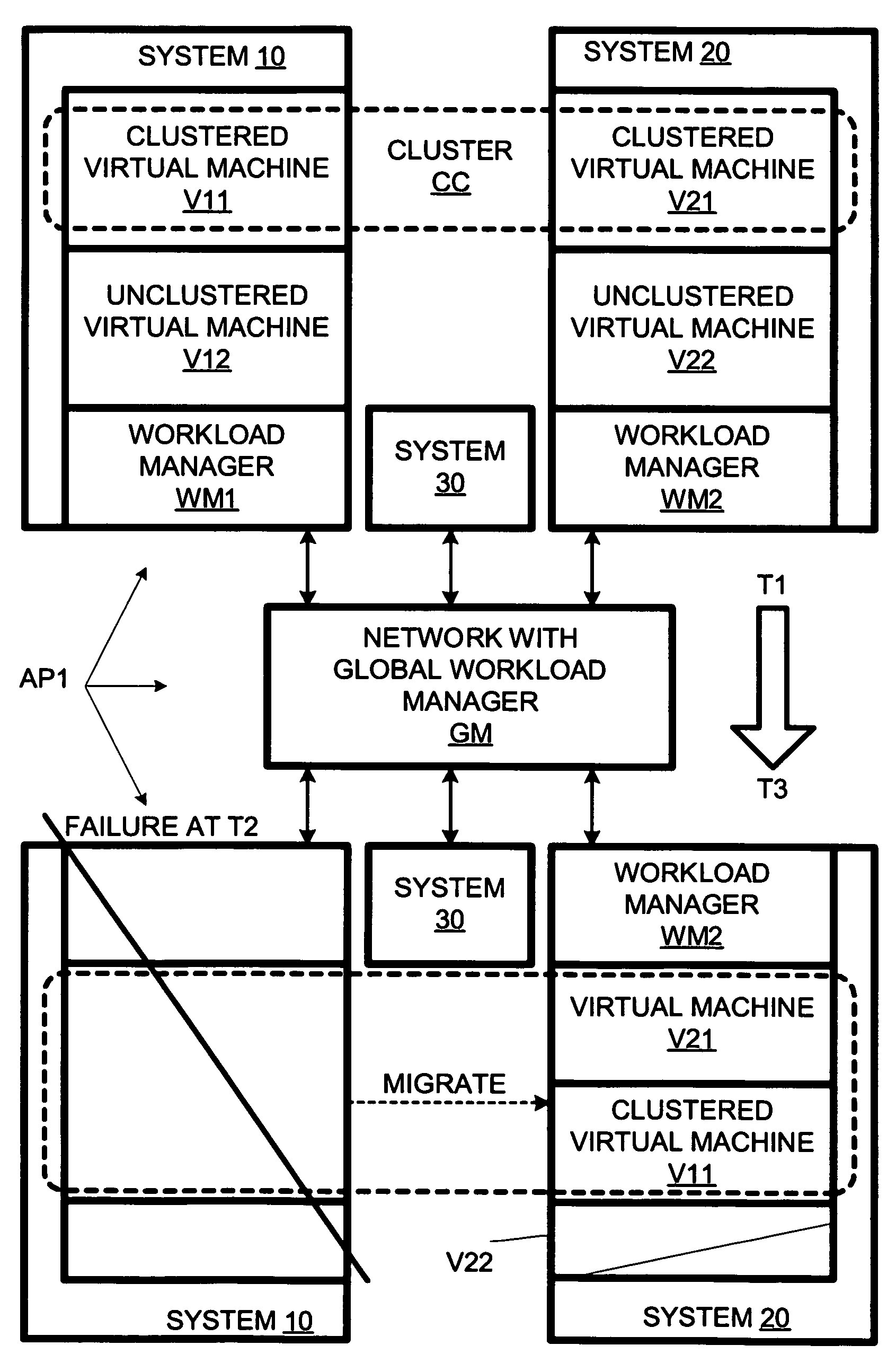
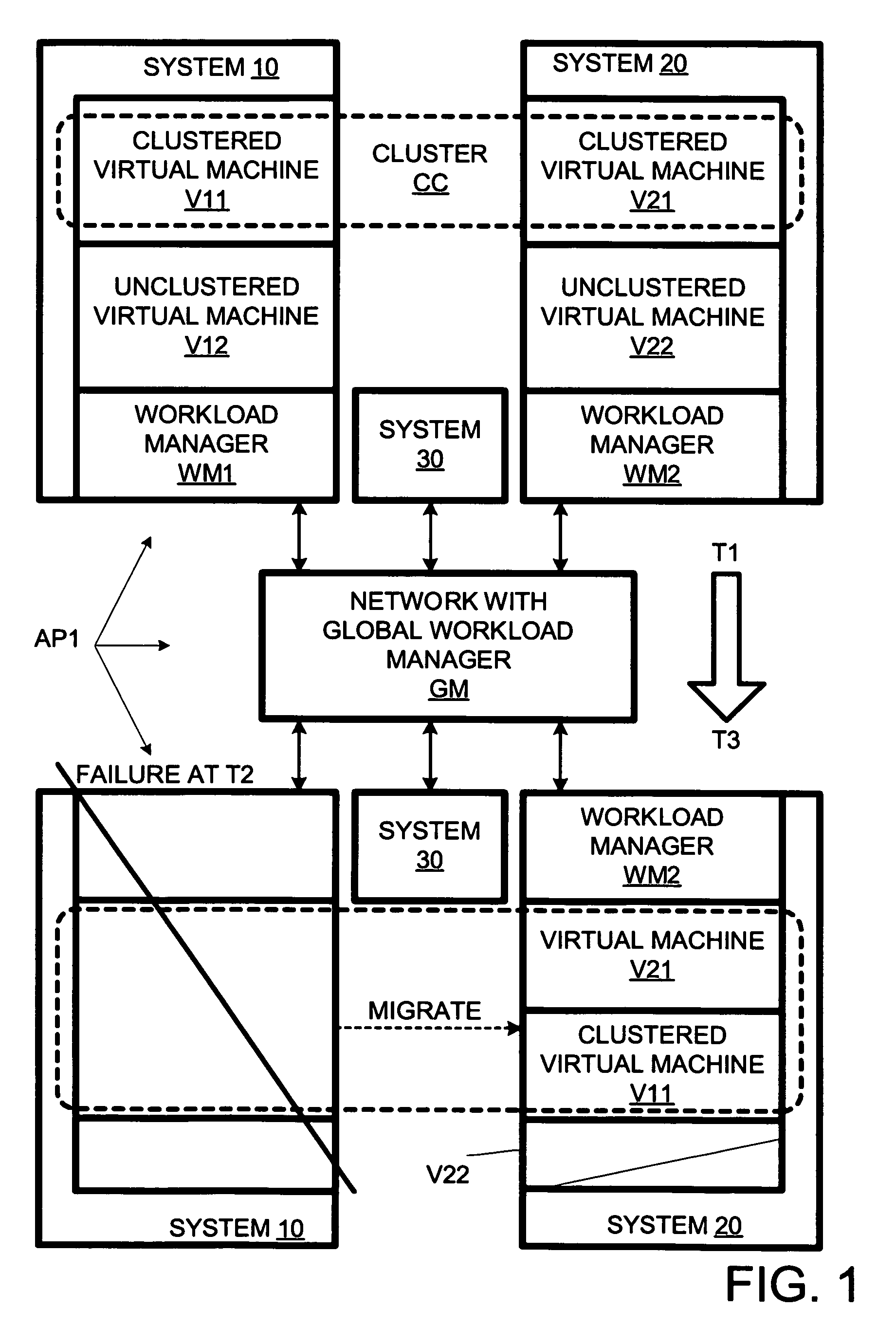
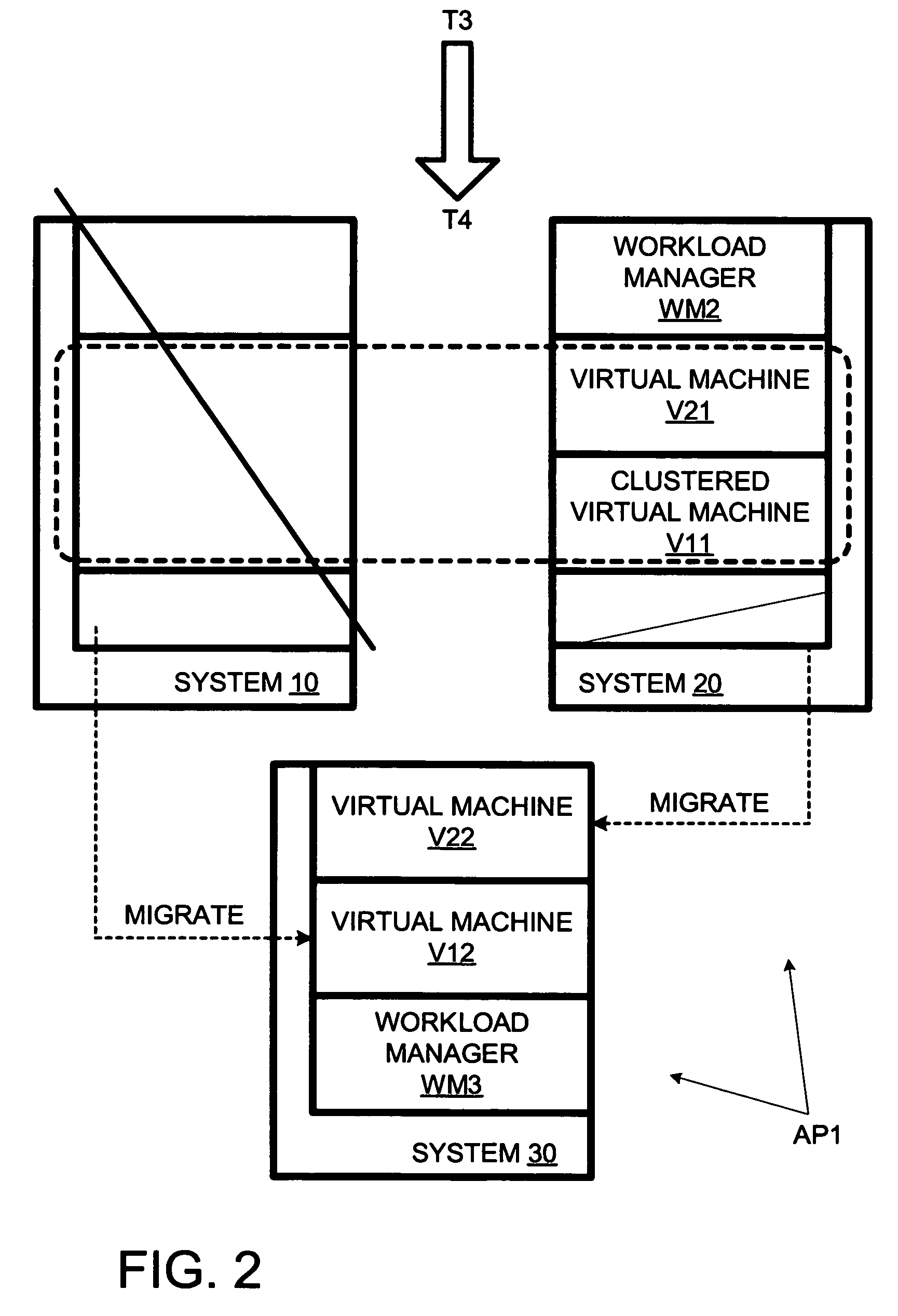
Terminating a non-clustered workload in response to a failure of a system with a clustered workload
ActiveUS7653833B1Error detection/correctionSoftware simulation/interpretation/emulationCheck pointComputerized system
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Golf swing-diagnosing system
InactiveUS7857708B2Shorten the maintenance periodReduce recognitionCosmonautic condition simulationsGymnastic exercisingValue setCheck point
Owner:SUMITOMO RUBBER IND LTD
Method for automatically testing recording playback mode of terminal system
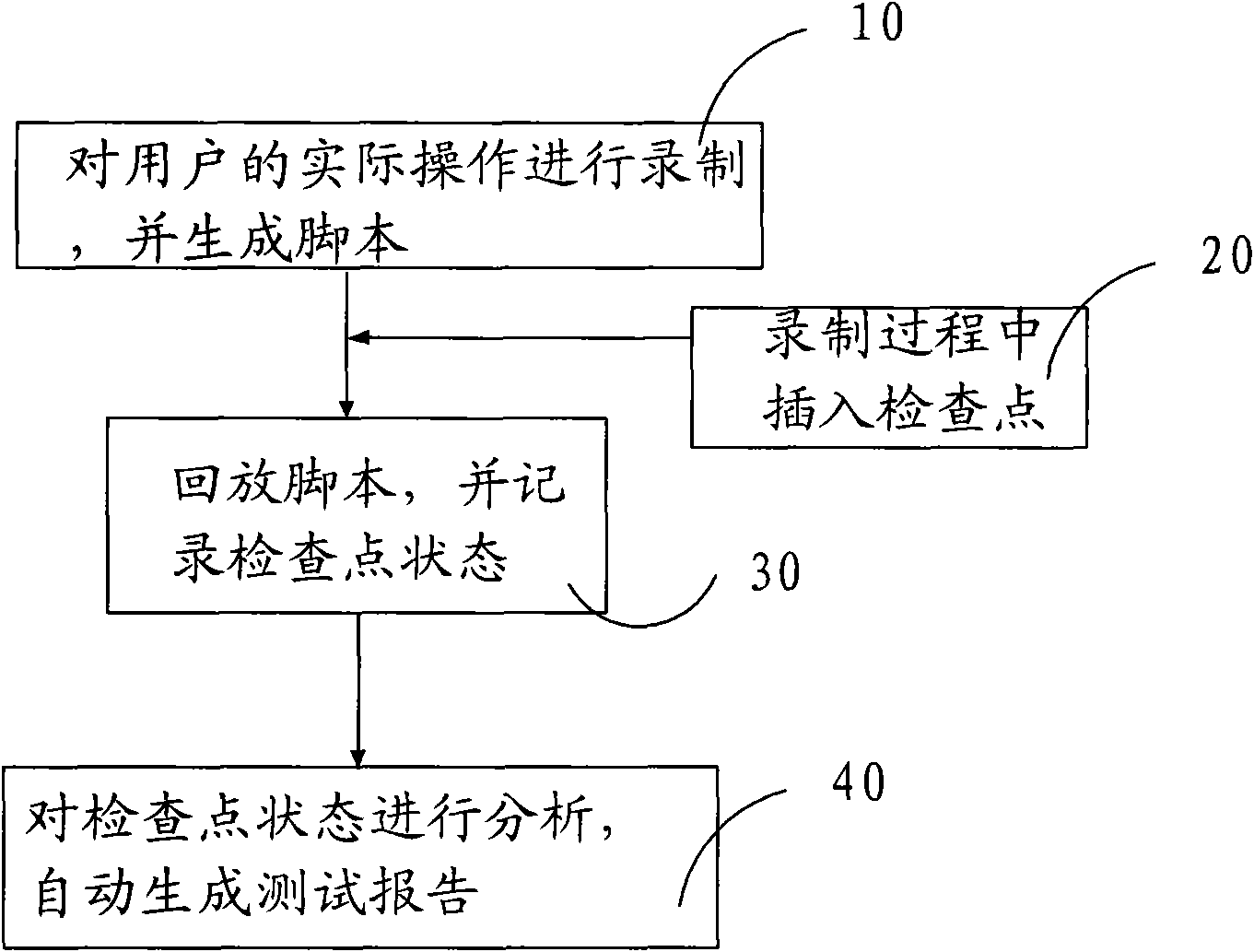
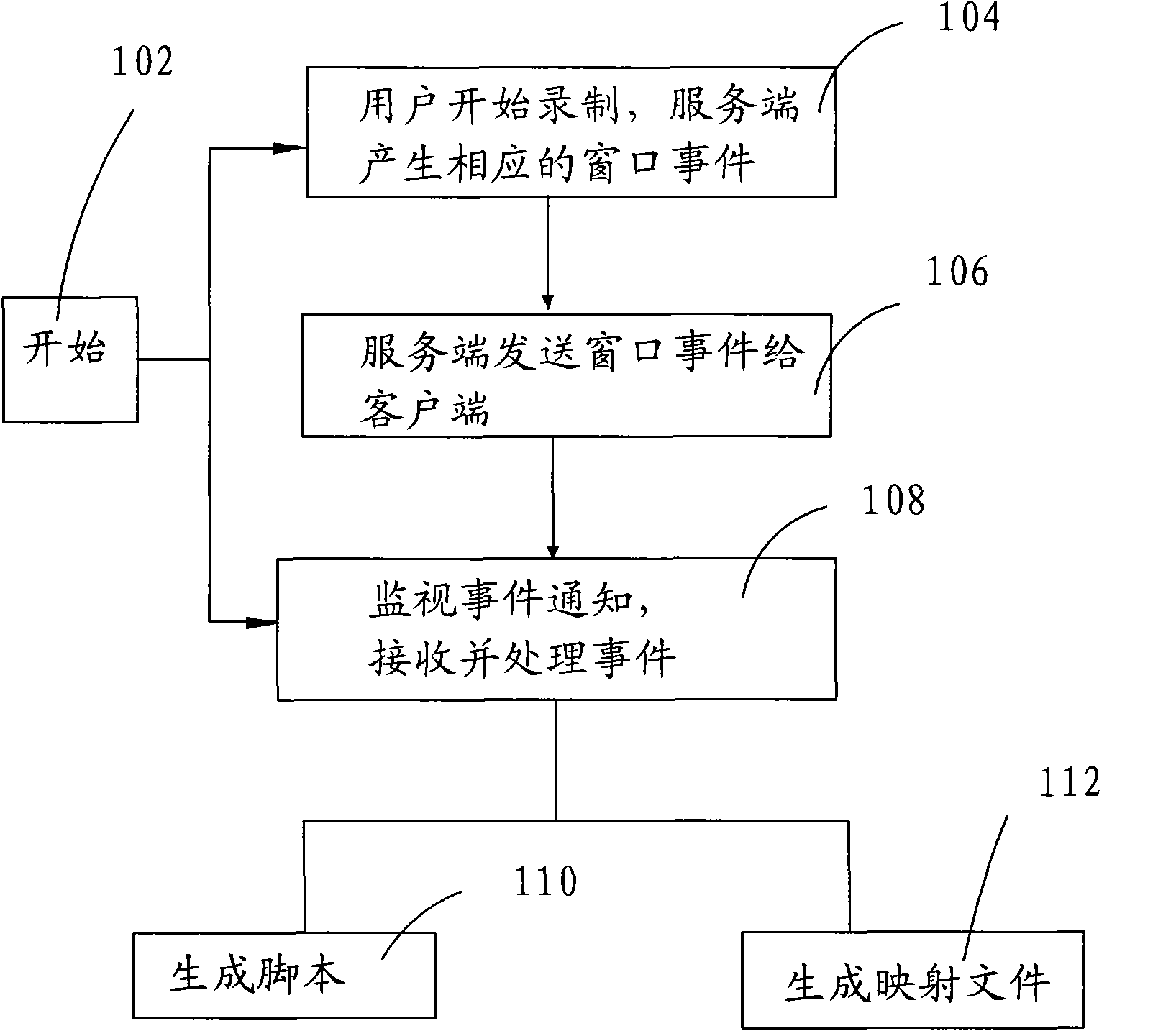
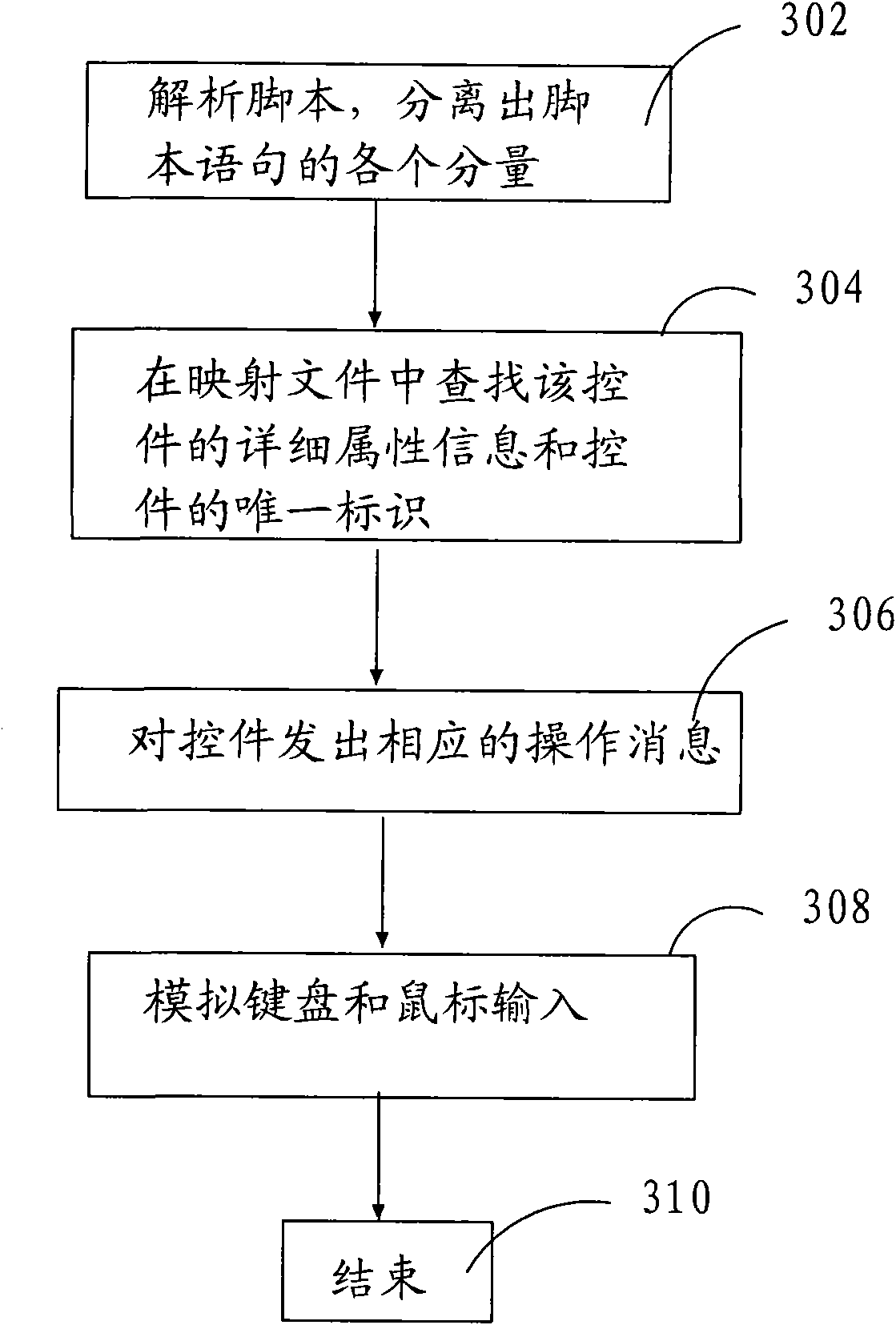
InactiveCN101620564ACheckpoints are reliableShorten test timeSoftware testing/debuggingCheck pointTerminal system
The invention relates to a method for automatically testing a recording playback mode of a terminal system, which comprises the following steps: 10, recording actual operation of a user, which comprises mouse operation and keyboard operation, and automatically generating a script which is easily understood by the user and can be edited manually; 20, in the recording process in the step 10, inserting a check point of which the state is required to be checked in an automatic test; 30, playing the script generated in the step 10 back, automatically executing the test, and recording the state of the check point; and 40, finishing the playback of the script, analyzing the recorded state of the check point, summarizing test results, and automatically generating a test report. The method has the advantages of being suitable for automatic functional tests of terminal embedded systems and non-embedded systems, supporting tests for functions of protocols such as ICA, RDP and the like, providing reliable check points for testing GUI functions, and saving testing time.
Owner:FUJIAN CENTM INFORMATION
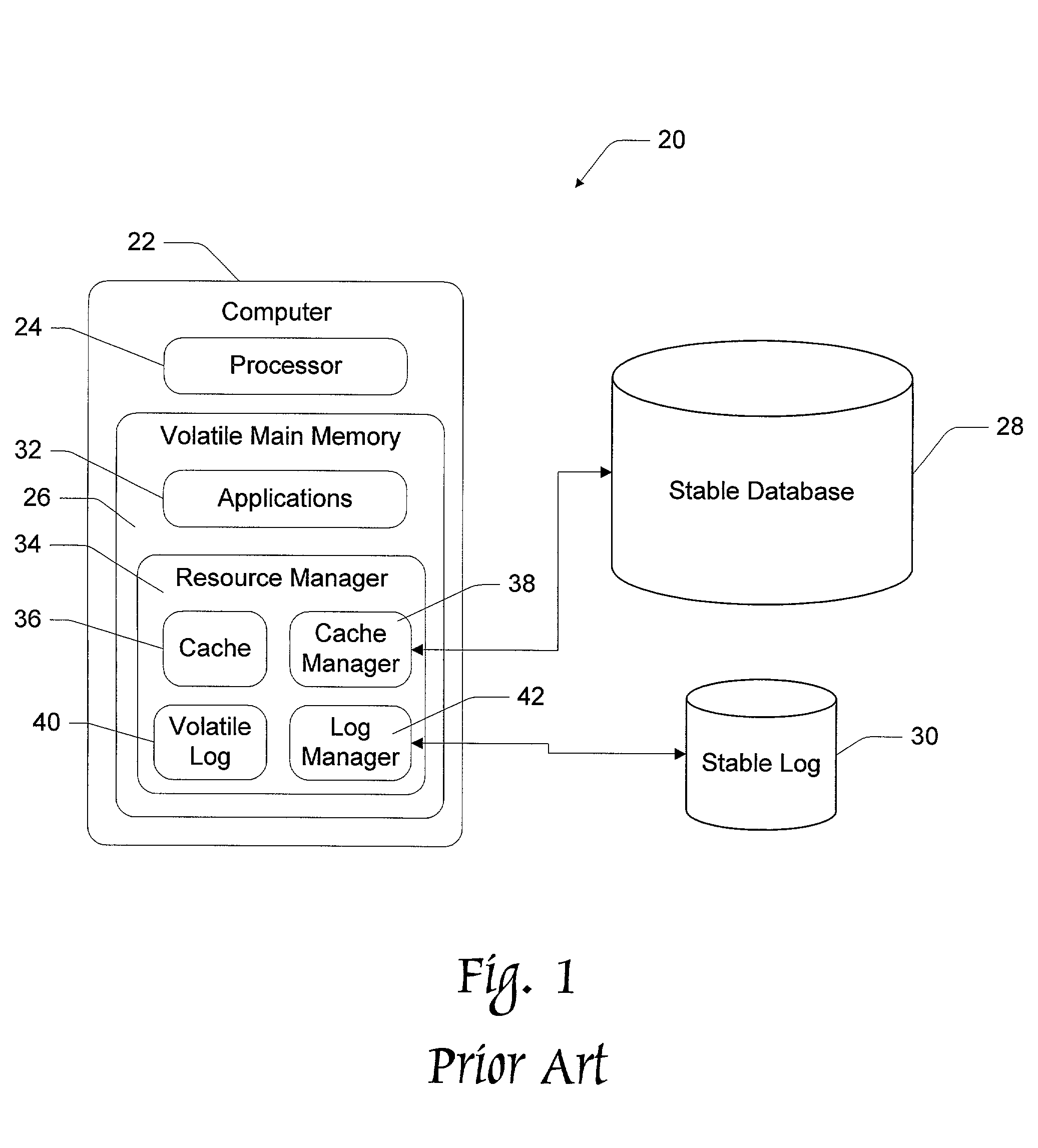
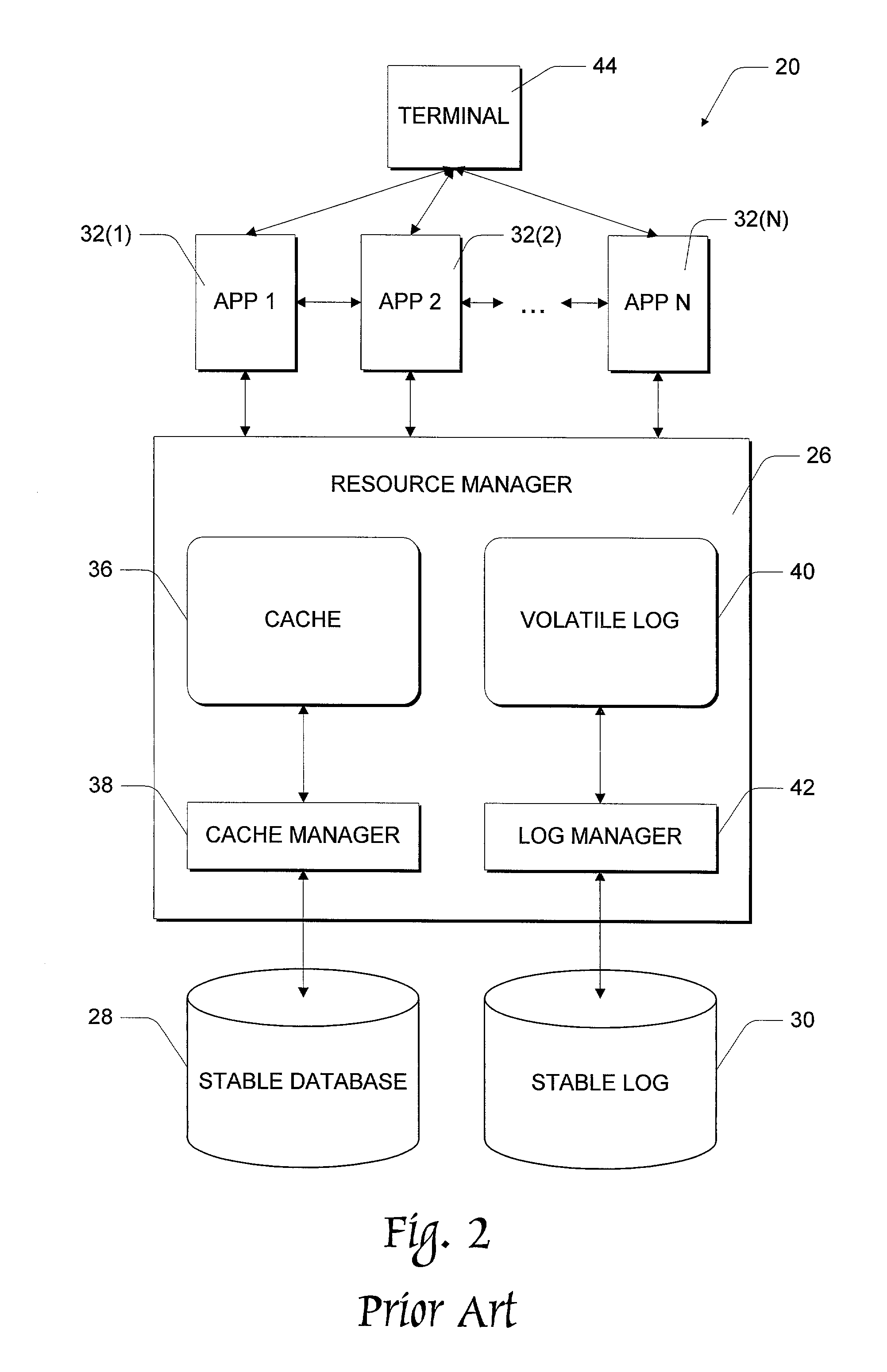
Database computer system using logical logging to extend recovery
InactiveUS6978279B1Reduce data volumeData processing applicationsError detection/correctionCheck pointDatabase machine
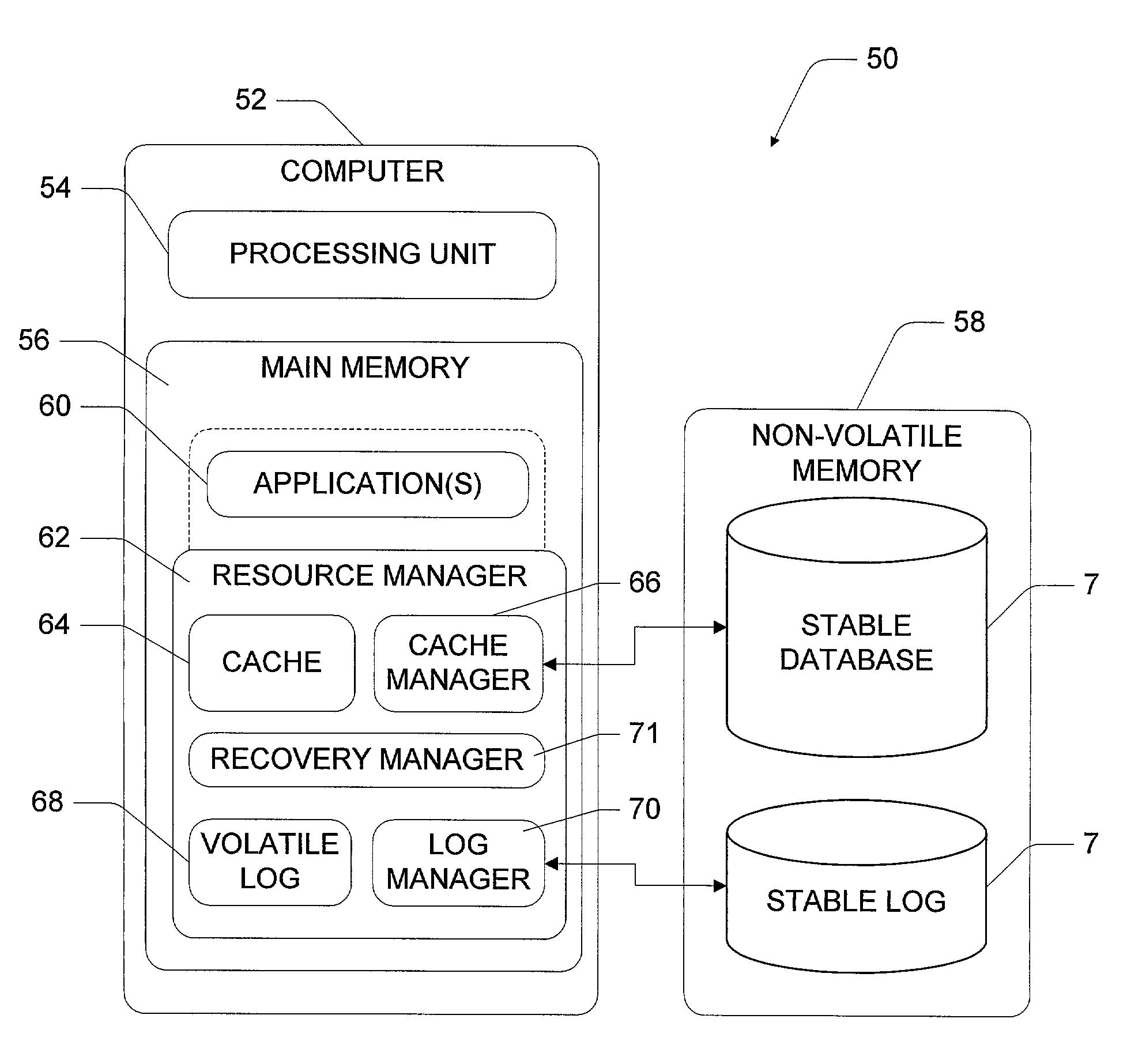
This invention concerns a database computer system and method for making applications recoverable from system crashes. The application state (i.e., address space) is treated as a single object which can be atomically flushed in a manner akin to flushing individual pages in database recovery techniques. To enable this monolithic treatment of the application, executions performed by the application are mapped to logical loggable operations that can be posted to the stable log. Any modifications to the application state are accumulated and the application state is periodically flushed to stable storage using an atomic procedure. The application recovery integrates with database recovery, and effectively eliminates or at least substantially reduces the need for check pointing applications. In addition, optimization techniques are described to make the read, write, and recovery phases more efficient. Atomic flush sets, whether generated from cyclic flush dependencies or otherwise, can be broken apart. This enables an ordered flushing sequence of first flushing a first object and then flushing a second object, rather than having to flush both the first and second objects simultaneously and atomically.
Owner:MICROSOFT TECH LICENSING LLC +1
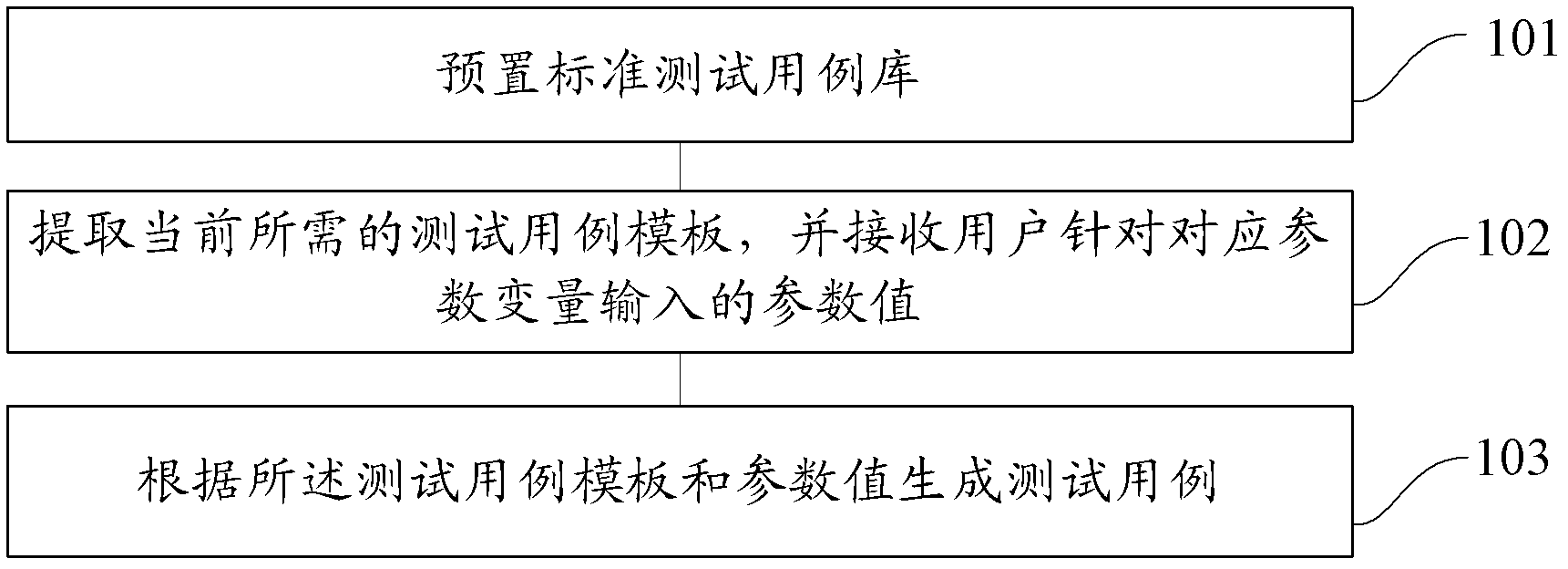
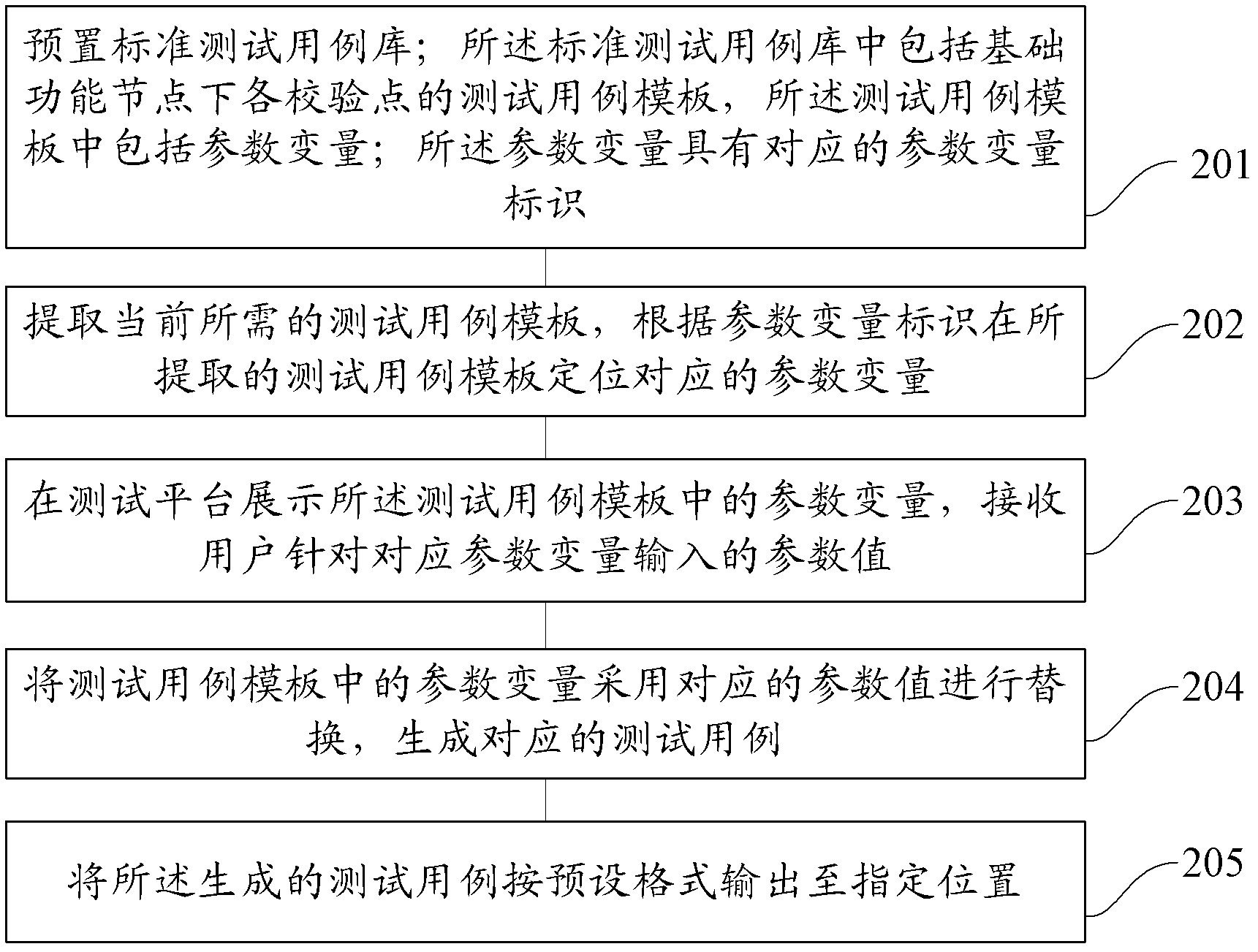
Method and device for automatically generating test case
InactiveCN103186457AImprove design efficiencyImprove writing efficiencySoftware testing/debuggingProgramming languageCheck point
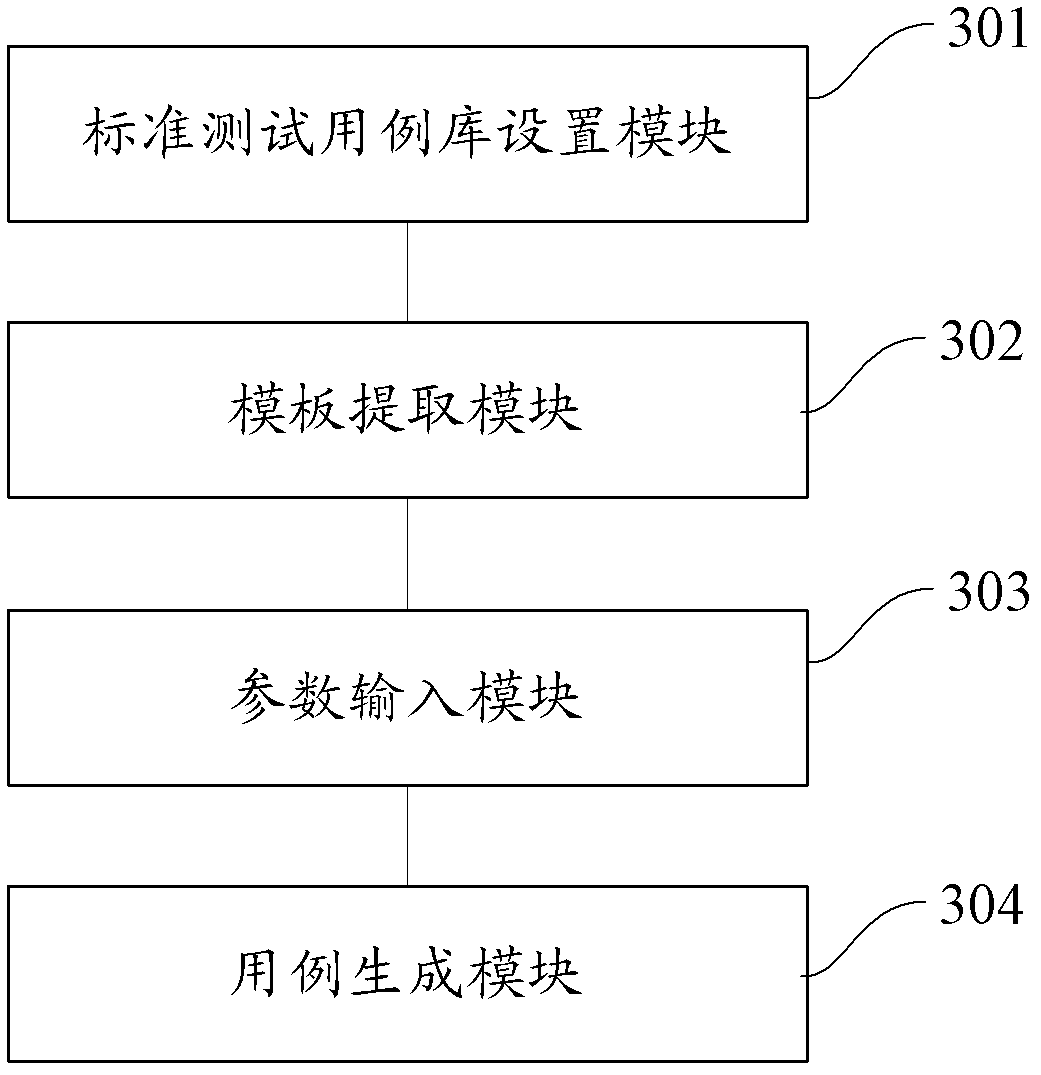
The invention provides a method and a device for automatically generating a test case. The method comprises the following steps of presetting a standard test case library, wherein the standard test case library comprises test case templates of all check points under a basic functional node and the test case templates comprise parameter variables; extracting a currently required test case template and receiving parameter values input for the corresponding parameter variables by a user; and according to the test case template and the parameter values, generating the test case. According to the invention, the test case can be rapidly and automatically generated and the compiling efficiency of the test case is promoted.
Owner:ALIBABA GRP HLDG LTD
Cluster fault-tolerance system, apparatus and method
InactiveCN101369241AGuaranteed to recover correctlyQuick checkError detection/correctionExtensibilityFault tolerance
The invention discloses a cluster fault tolerance system, a device and a method. The system includes: a remote checkpoint server which is used to respond the remote checkpoint request from a faulty node and execute the checkpoint operation; a node faulty checking module which is used to monitor the operating system of a local node and the running state of an assigned process and to trigger a remote checkpoint; and a communication system checkpoint module which is used to realize the checkpoint of the communication device and support the recovery function of communication breakpoint. The invention provides localized fast fault restoration for the parallel processing cluster, has a lower overhead and good expansibility, and makes ideal availability for the cluster system with ten billions and hundred billions calculation scale.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
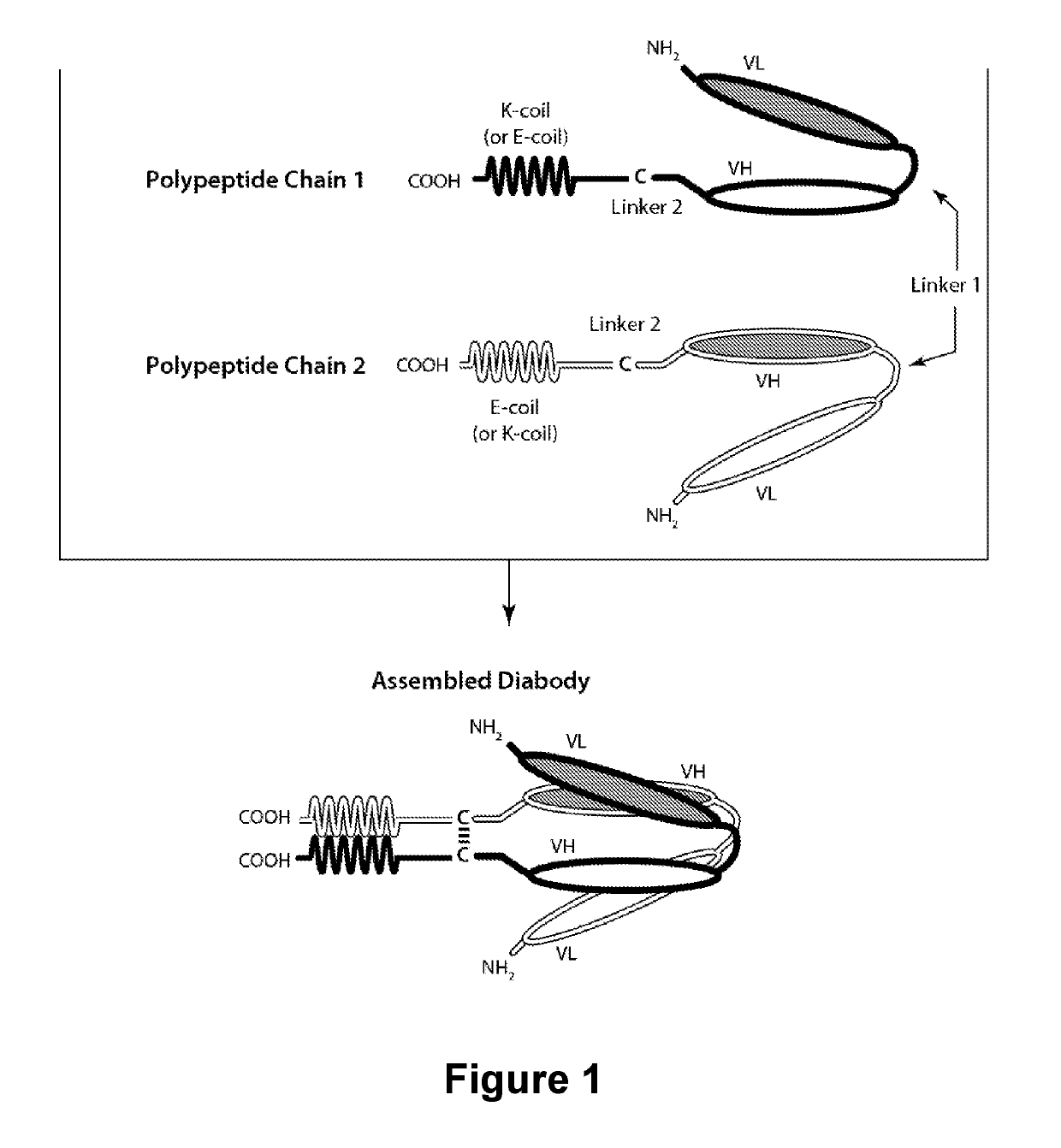
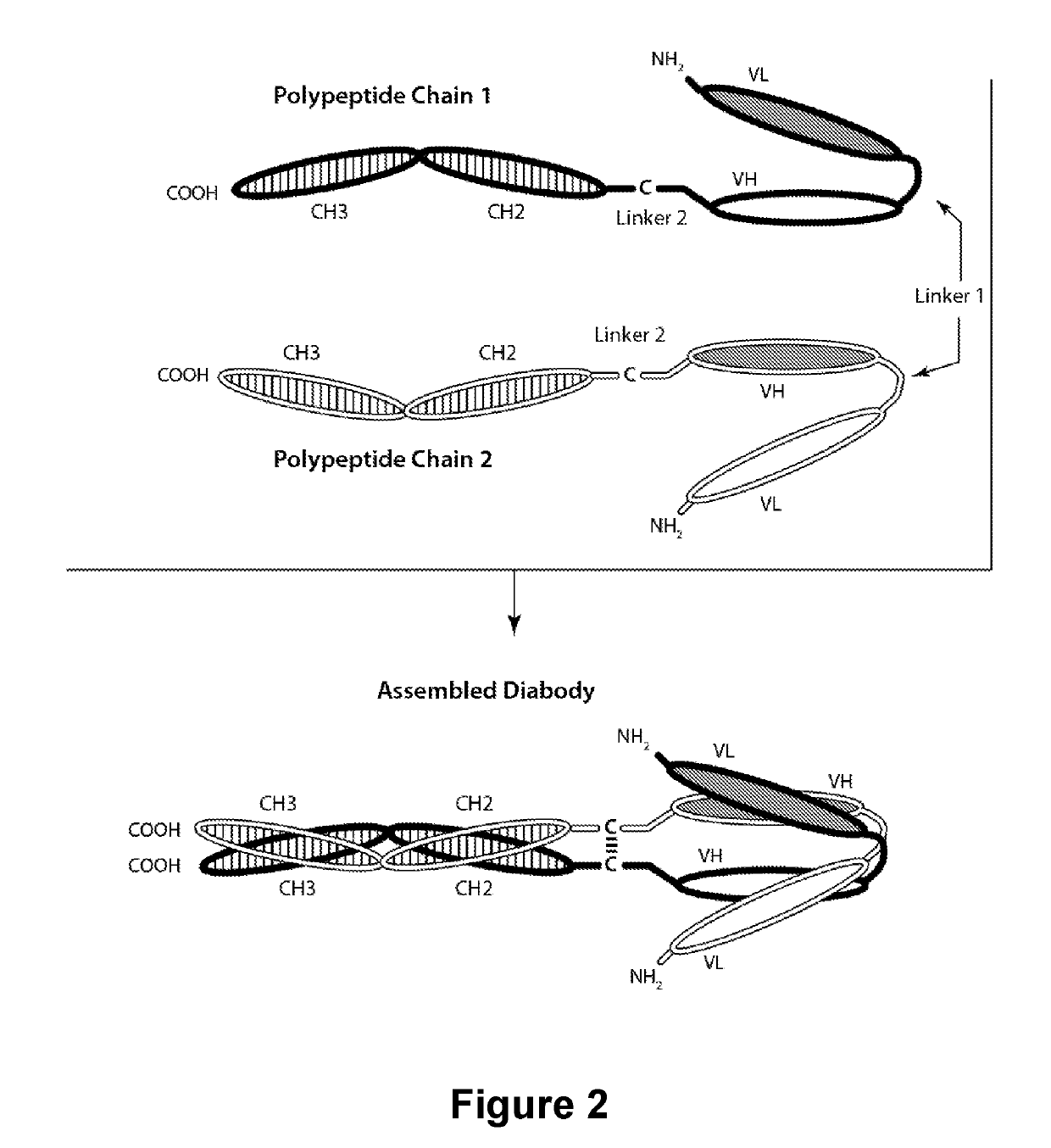
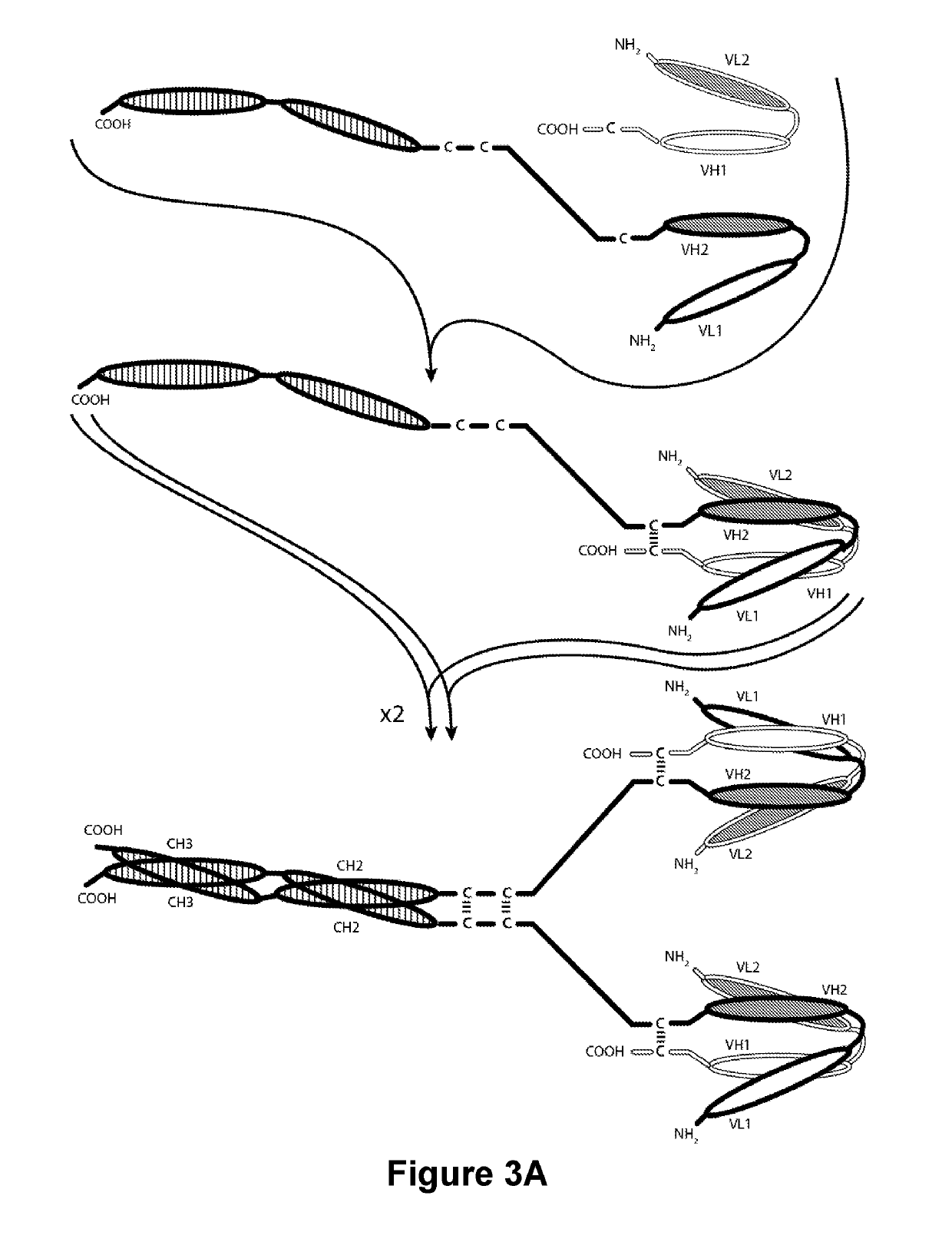
PD-1-Binding Molecules and Methods of Use Thereof
ActiveUS20190127467A1Low affinityIncreased serum half-lifeAntibacterial agentsNervous disorderEpitopeCheck point
The present invention is directed to selected anti-PD-1 antibodies capable of binding to both cynomolgus monkey PD-1 and to human PD-1: PD-1 mAb 1, PD-1 mAb 2, PD-1 mAb 3, PD-1 mAb 4, PD-1 mAb 5, PD-1 mAb 6, PD-1 mAb 7, PD-1 mAb 8, PD-1 mAb 9, PD-1 mAb 10, PD-1 mAb 11, PD-1 mAb 12, PD-1 mAb 13, PD-1 mAb 14, or PD-1 mAb 15, and to humanized and chimeric versions of such antibodies. The invention additionally pertains to PD-1-binding molecules that comprise PD-1 binding fragments of such anti-PD-1 antibodies, immunocongugates, and to bispecific molecules, including diabodies, BiTEs, bispecific antibodies, etc., that comprise (i) such PD-1-binding fragments, and (ii) a domain capable of binding an epitope of a molecule involved in regulating an immune check point present on the surface of an immune cells. The present invention also pertains to methods of using molecules that bind PD-1 for stimulating immune responses, as well as methods of detecting PD-1.
Owner:MACROGENICS INC
Golf swing diagnosis system
InactiveUS20050143183A1Accurate extractionRemove colorGymnastic exercisingCharacter and pattern recognitionCheck pointEngineering
A computer (15) captures the colored moving image of the golfer (11) who swings by gripping a golf club (12) having colored marks (M1 through M3) attached to a shaft (12a) thereof. The computer (15) converts the colored moving image into a plurality of still images; executes binarization for each pixel of a plurality of the still images by using a specific threshold of color information and recognizes pixels, of the still images, which satisfy the threshold as positions of the colored marks (M1 through M3) and extracts a movement of the shaft (12a) by using a movement vector amount of one of the colored marks (M1 through M3 ) or by using a vector angle between two of the colored marks (M1 through M3). In this manner, the computer (15) automatically extracts check-point images.
Owner:SHIRAI YOSHIAKI +2
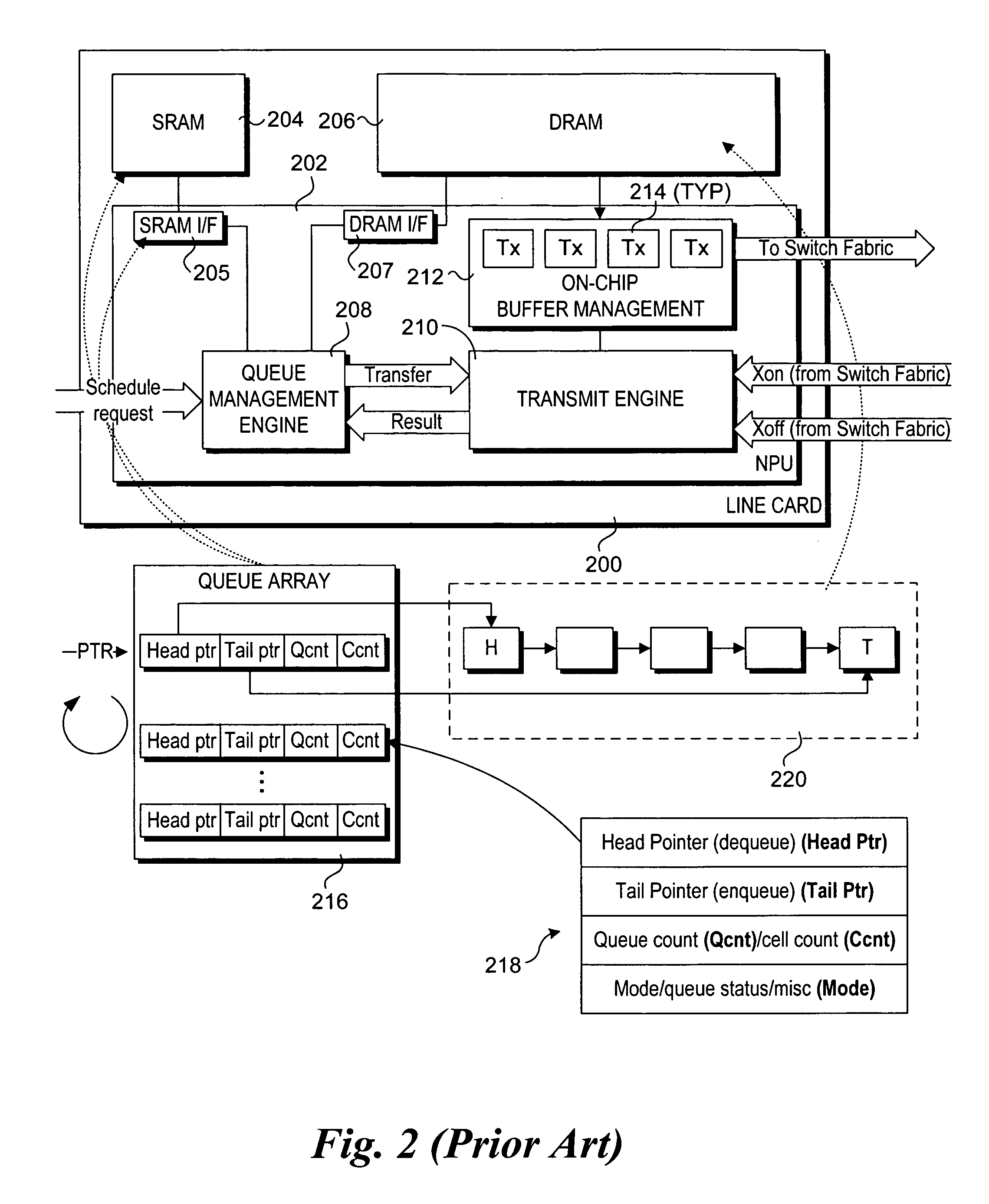
Method and apparatus to support efficient check-point and role-back operations for flow-controlled queues in network devices
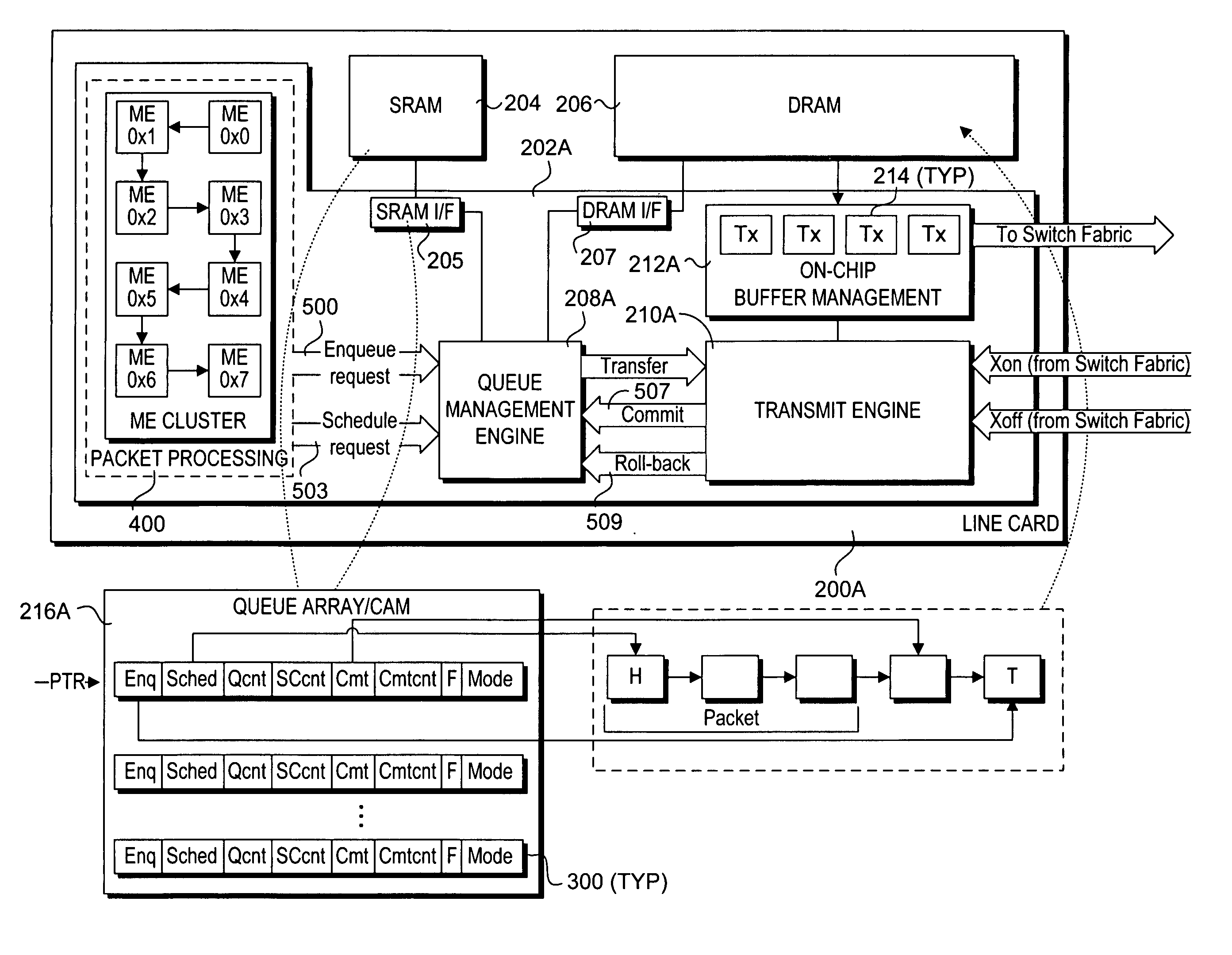
Method and apparatus to support efficient check-point and role-back operations for flow-controlled queues in network devices. The method and apparatus employ queue descriptors to manage transfer of data from corresponding queues in memory into a switch fabric. In one embodiment, each queue descriptor includes an enqueue pointer identifying a tail cell of a segment of data scheduled to be transferred from the queue, a schedule pointer identifying a head cell of the segment of data, and a commit pointer identifying a most recent cell in the segment of data to be successfully transmitted into the switch fabric. In another embodiment, the queue descriptor further includes a scheduler sequence number; and a committed sequence number that are employed in connection with transfers of data from queues containing multiple segments. The various pointers and sequence numbers are employed to facilitate efficient check-point and roll-back operations relating to unsuccessful transmissions into the switch fabric.
Owner:INTEL CORP
Golf swing-measuring system
InactiveUS20050215337A1Low costReduce false recognition rateImage enhancementImage analysisCheck pointGolf Ball
A golf swing-measuring system including a computer (16) for capturing a colored moving image obtained by photographing a golfer (11) who swings by gripping a golf club (13). The computer (16) selects and extracts one or more images each showing a swing posture as check-point images such as an address image, a take-back shaft 8 o'clock image, a take-back shaft 9 o'clock image, a take-back unskillful arm horizontal image, a top image, a downswing unskillful arm horizontal image, a downswing shaft 9 o'clock image, an impact image, a follow-through shaft 3 o'clock image, and a finish image and extracts from a large number of still images constituting said color moving image. Thereafter the computer (16) obtains coordinates of positions of attention-focused points that operate in said check-point images when said golfer swings.
Owner:SUMITOMO RUBBER IND LTD +2
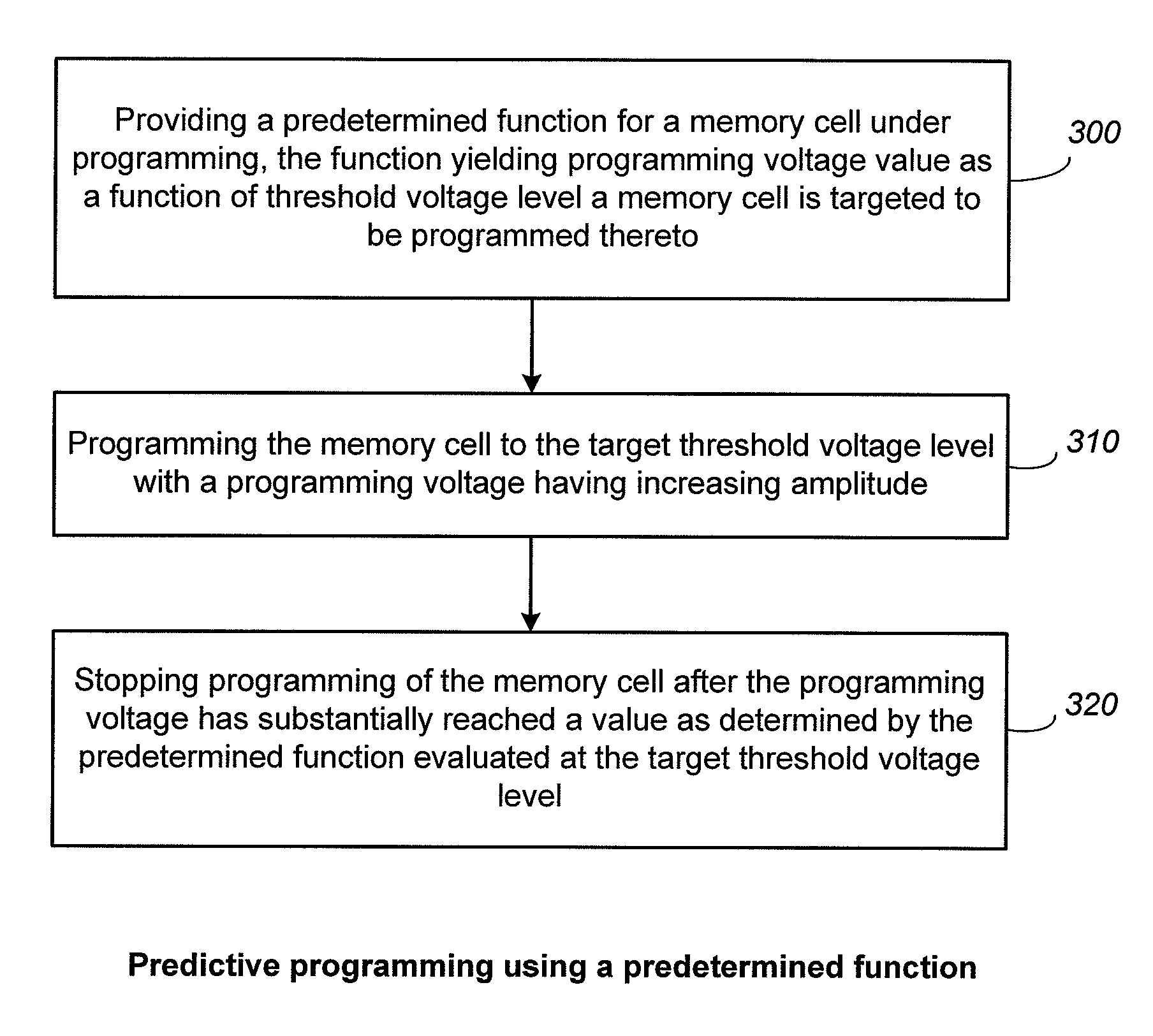
Non-Volatile Memory with Predictive Programming
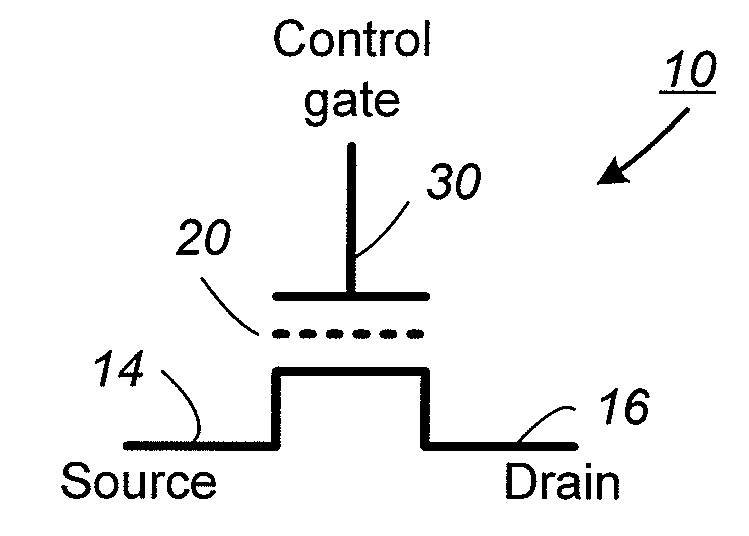
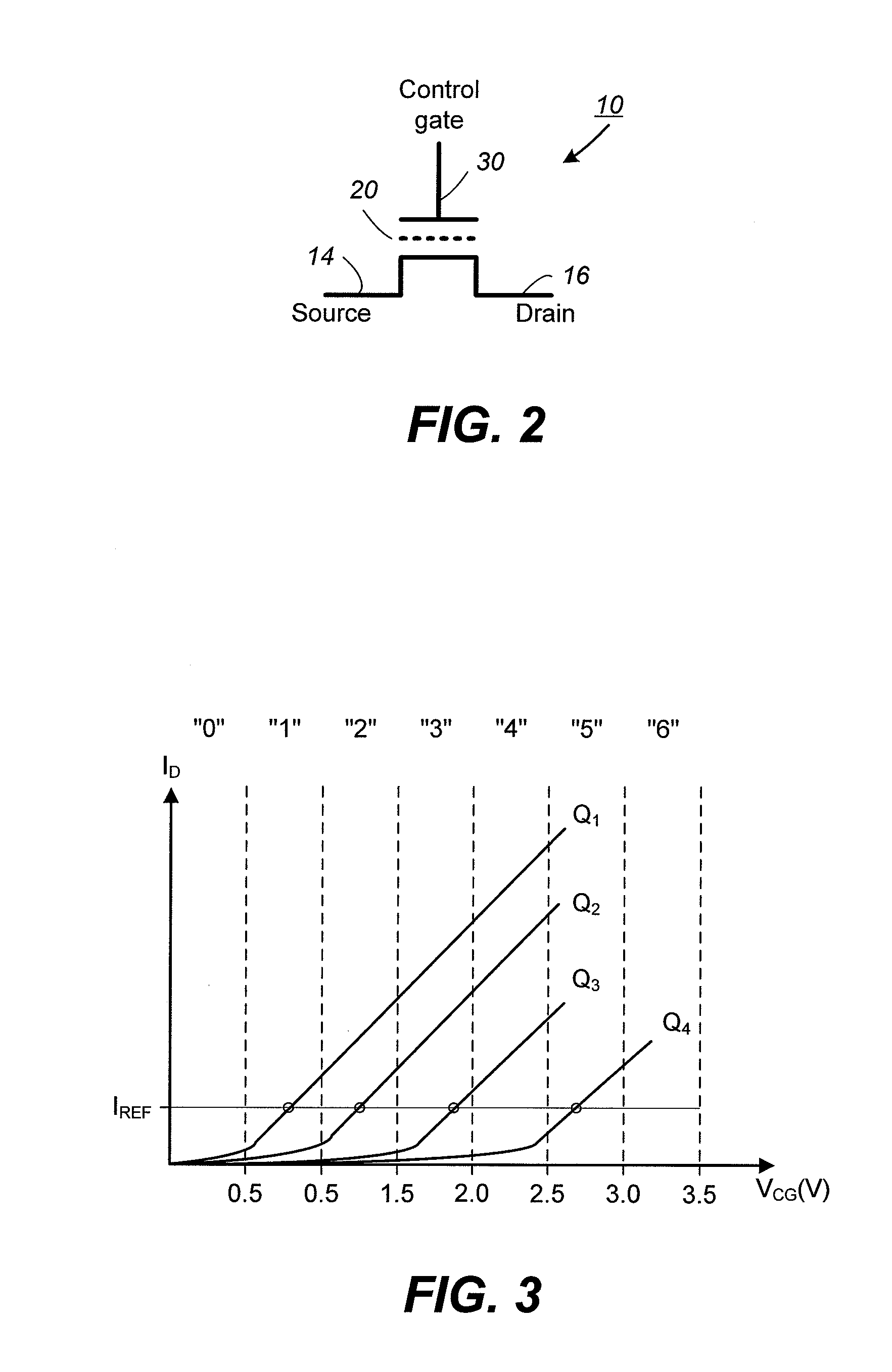
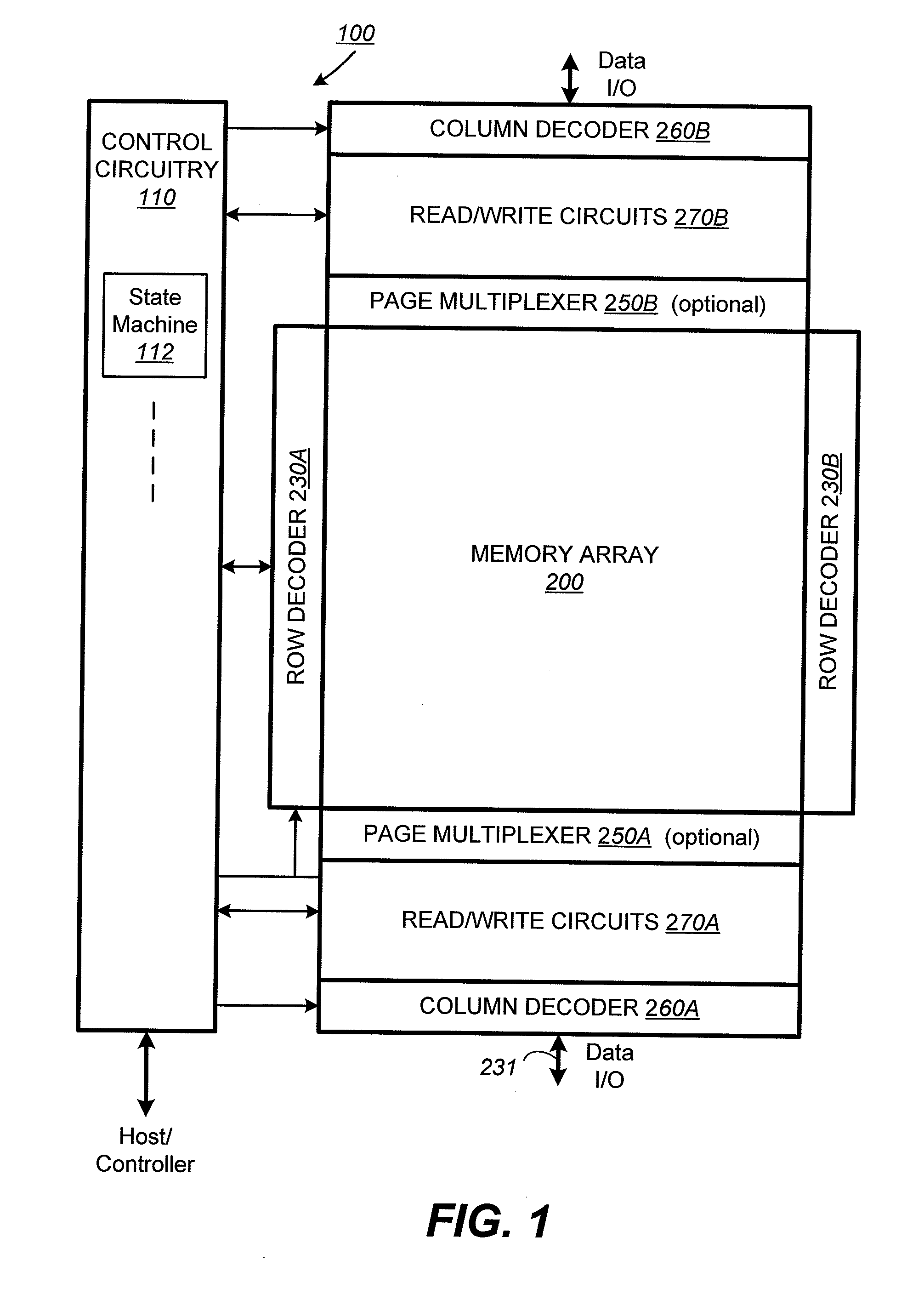
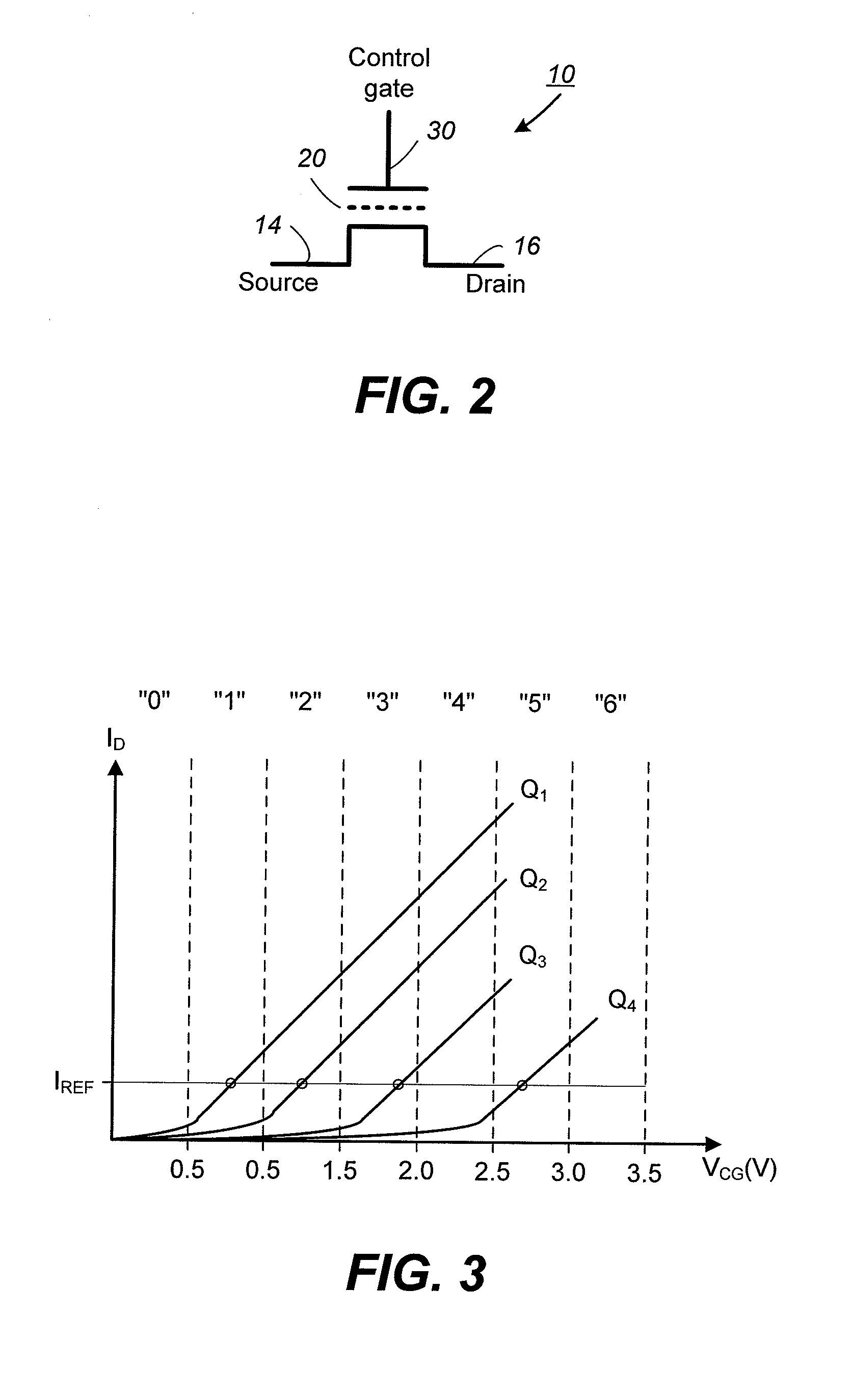
ActiveUS20080253193A1Improve performanceRead-only memoriesDigital storageCheck pointComputer science
In a nonvolatile memory having an array of memory cells, wherein the memory cells are individually programmable to one of a range of threshold voltage levels, there is provided a predictive programming mode in which a predetermined function predicts what programming voltage level needs to be applied in order to program a given memory cell to a given target threshold voltage level. In this way, no verify operation needs to be performed, thereby greatly improving the performance of the programming operation. In a preferred embodiment, the predetermined function is linear and is calibrated for each memory cell under programming by one or more checkpoints. A checkpoint is a set of coordinates on the predetermined function determined by a conventional programming mode employing alternating program and verify operations.
Owner:SANDISK TECH LLC
Checking device and recording medium for checking the identification of an operator
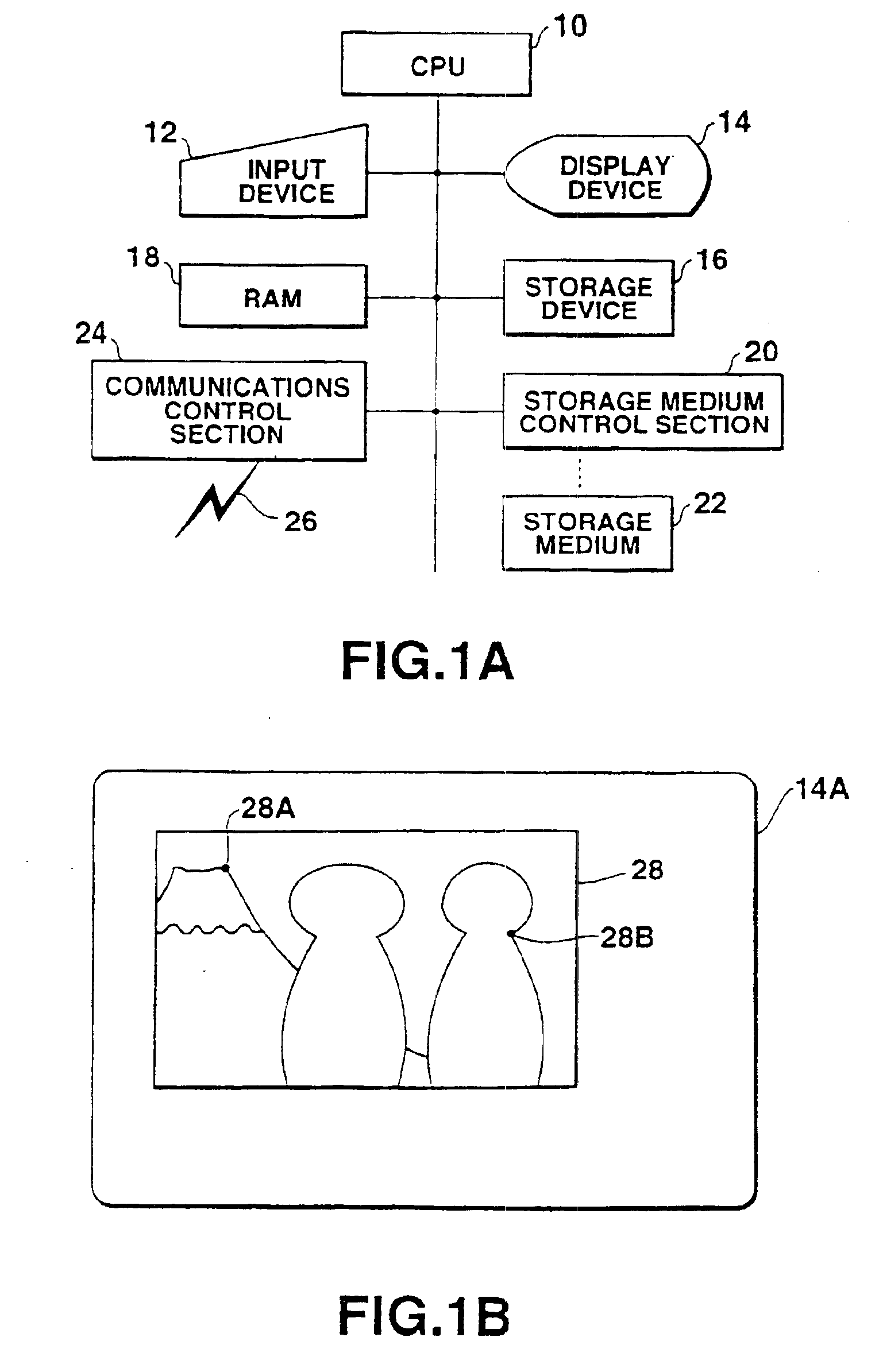
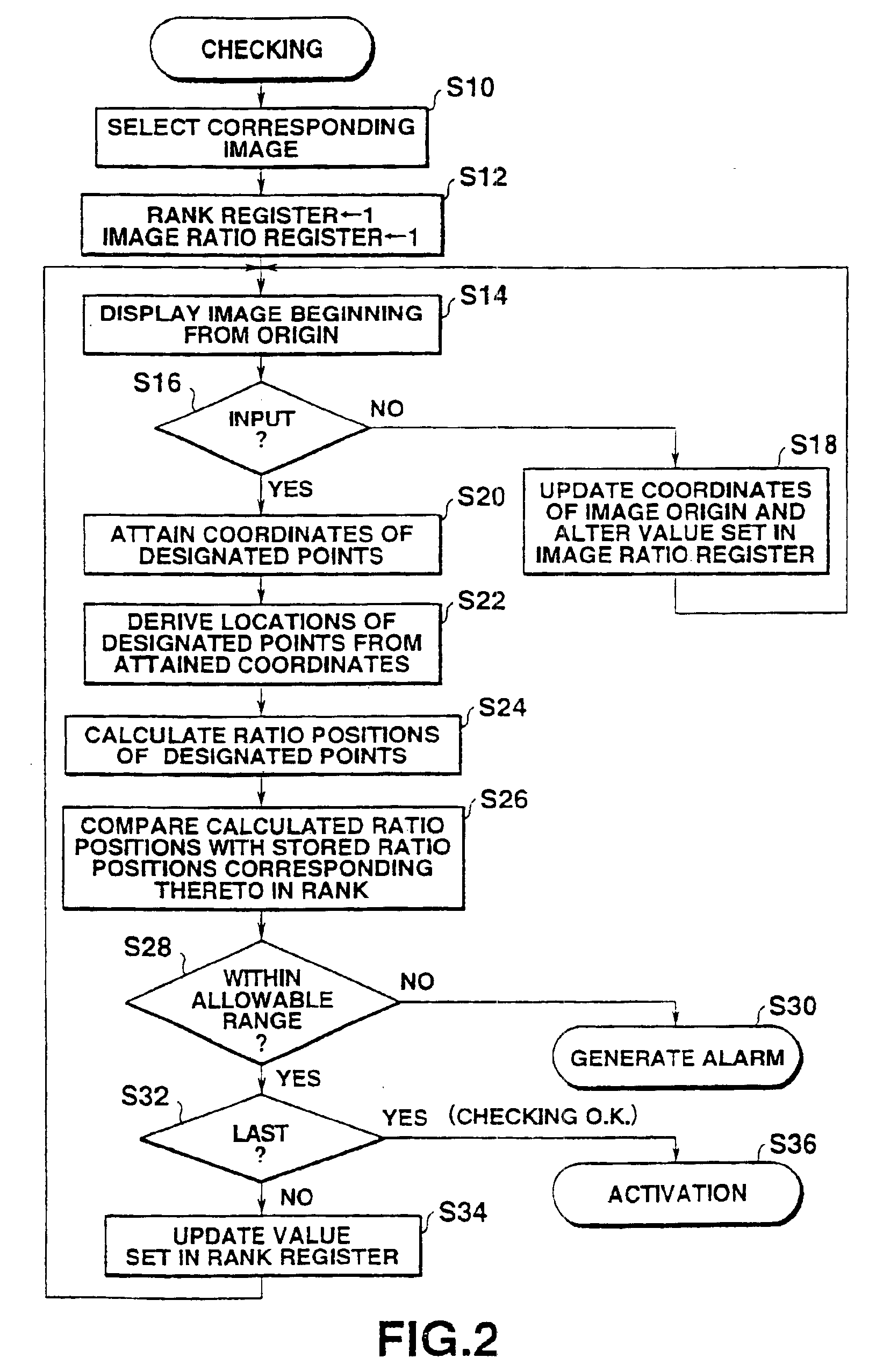
InactiveUS6862687B1Easy to rememberEasy to specifyDigital data processing detailsUnauthorized memory use protectionCheck pointDisplay device
A CPU displays an image on a display device with reference to an image location table stored in advance in a RAM. When coordinates on the image are sequentially designated by an input device, the CPU sequentially compares the locations specified by the designated coordinates with those of checking points stored in the image location table. The CPU determines that the operator is authorized when errors or differences between the locations compared with each other are within an allowable range and when the order of designation of the coordinates is appropriate.
Owner:CASIO COMPUTER CO LTD
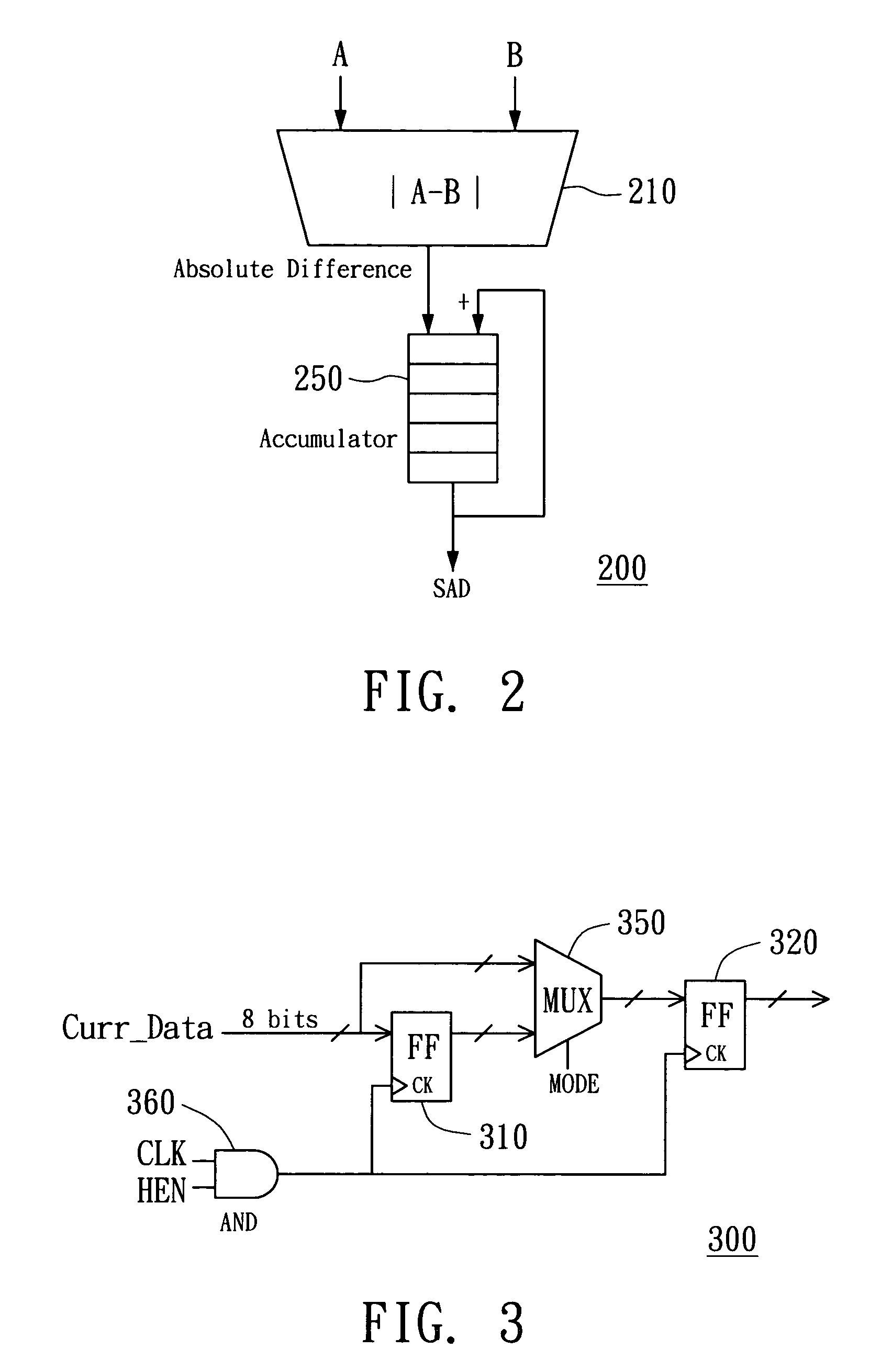
Apparatus for motion estimation using a two-dimensional processing element array and method therefor
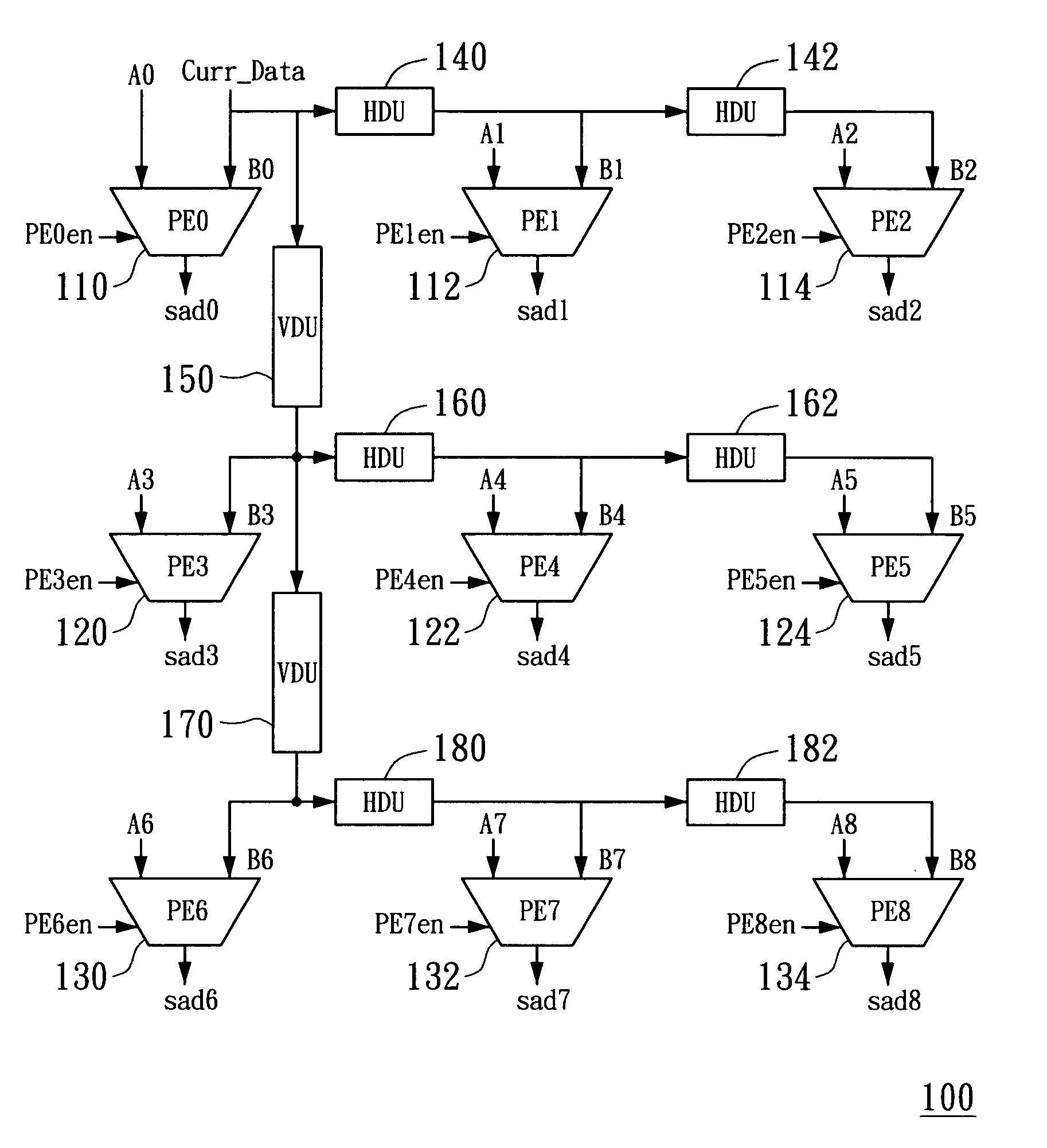
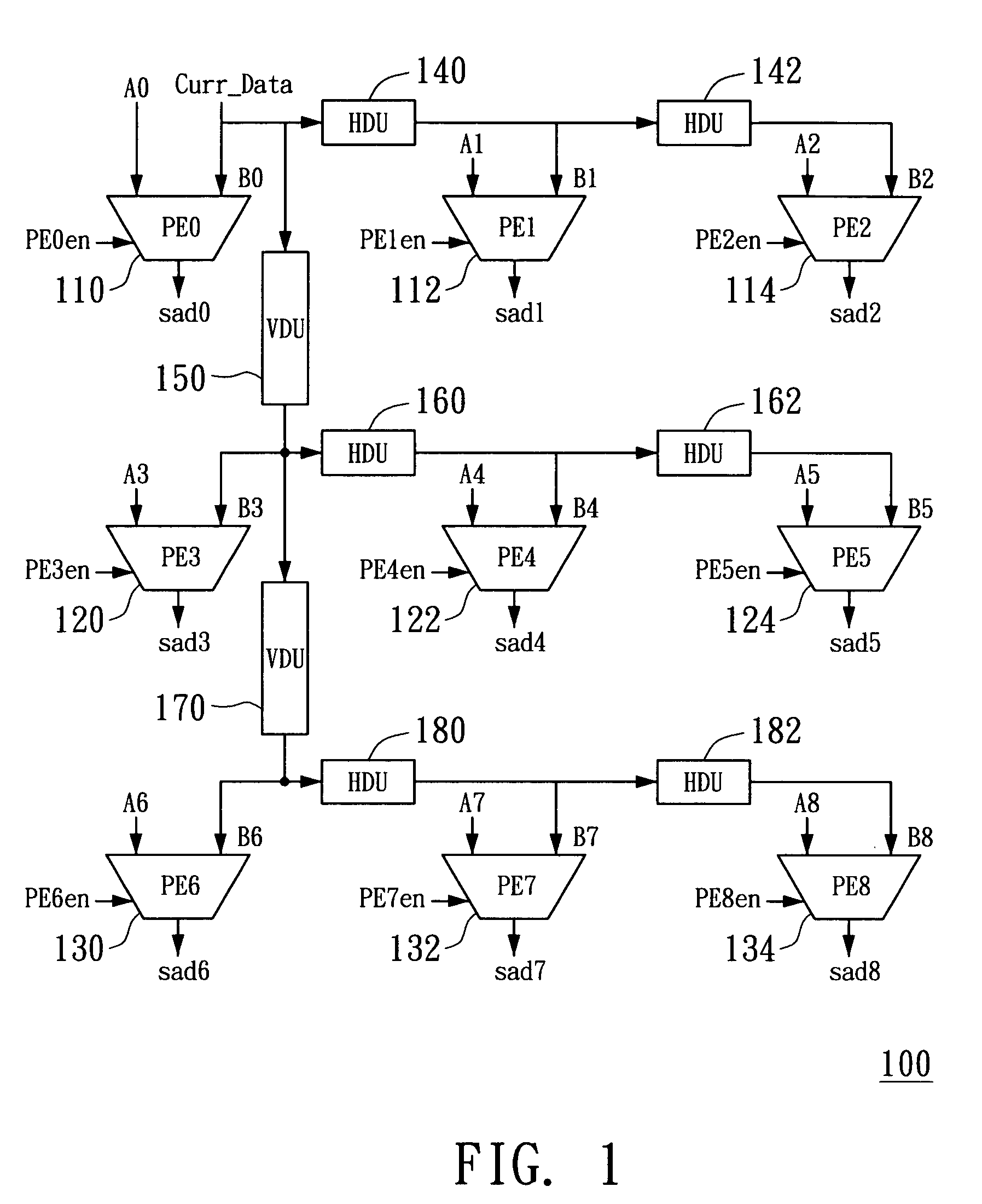
InactiveUS20060098735A1Reduce hardware complexityLess power consumptionTelevision system detailsImage analysisData streamCheck point
An apparatus for motion estimation and method therefor are provided. The apparatus includes a processing element (PE) array unit that includes a delay unit array and a PE array. The delay unit array outputs different data flows of current data to the PE array with respect to checking points in one step of an N-step seach algorithm, while a regular data flow of reference data is fed into the PE array. One search step of the N-step search algorithm for motion estimation can be performed while the pixel data of a search area is read in a regular pixel scan order. When the search area is read completely, the search step is completed. In this way, the PE array unit achieves the N-step search algorithm. Further, the PE array unit can be configured to perform half-pel motion estimation with respect to a best point found in a full-pel search.
Owner:MEDIATEK INC
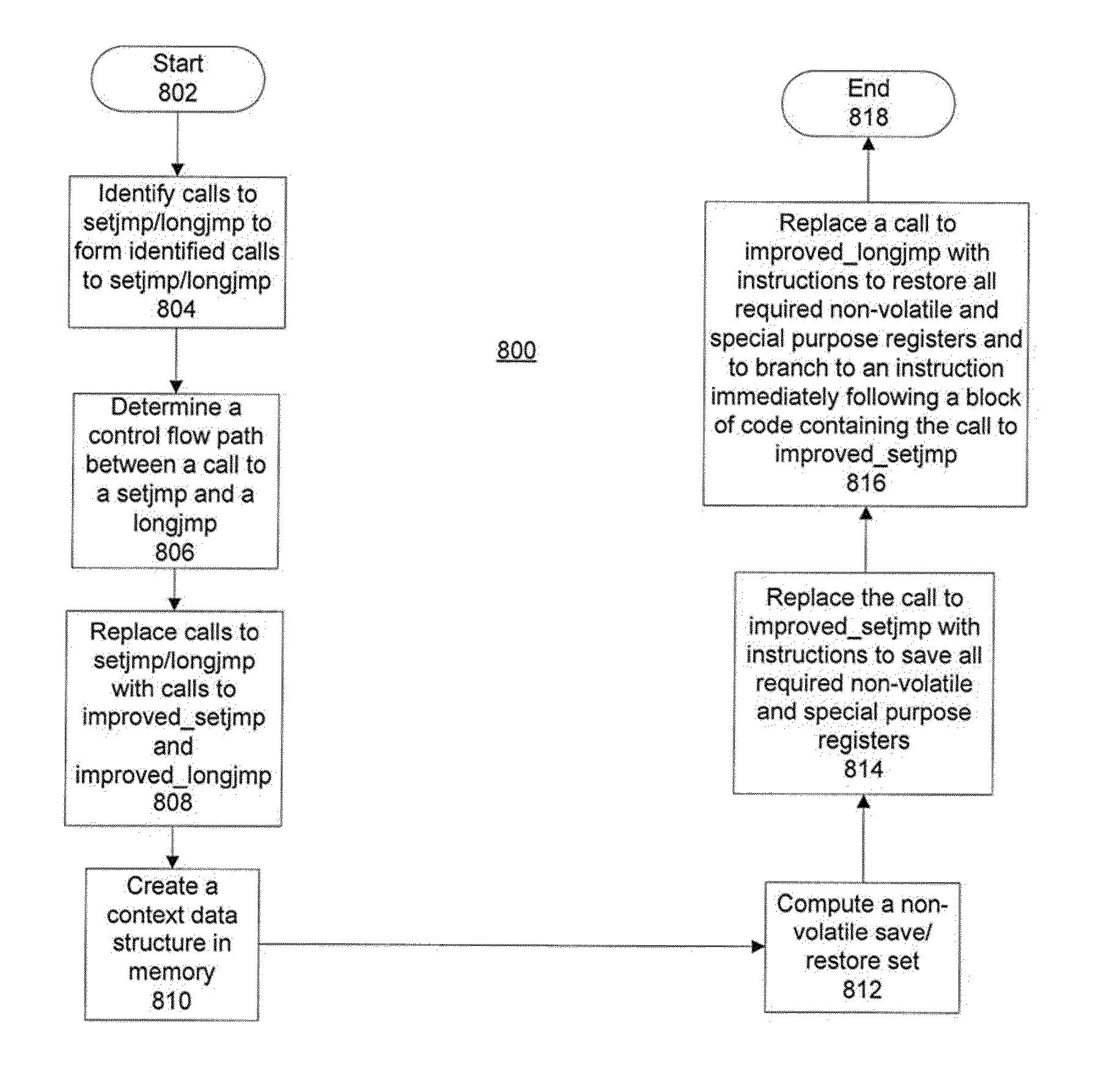
Setjmp/longjmp for speculative execution frameworks
InactiveUS20110289303A1Digital computer detailsSpecific program execution arrangementsSpeculative executionControl flow
A process for check pointing in speculative execution frameworks, identifies calls to a set of setjmp / longjmp instructions to form identified calls to setjmp / longjmp, determines a control flow path between a call to a setjmp and a longjmp pair of instructions in the identified calls to setjmp / longjmp and replaces calls to the setjmp / longjmp pair of instructions with calls to an improved_setjmp and improved_longjmp instruction pair. The process creates a context data structure in memory, computes a non-volatile save / restore set and replaces the call to improved_setjmp of the setjmp / longjmp pair of instructions with instructions to save all required non-volatile and special purpose registers and replaces a call to improved_longjmp of the setjmp / longjmp pair of instructions with instructions to restore all required non-volatile and special purpose registers and to branch to an instruction immediately following a block of code containing the call to improved_setjmp.
Owner:IBM CORP
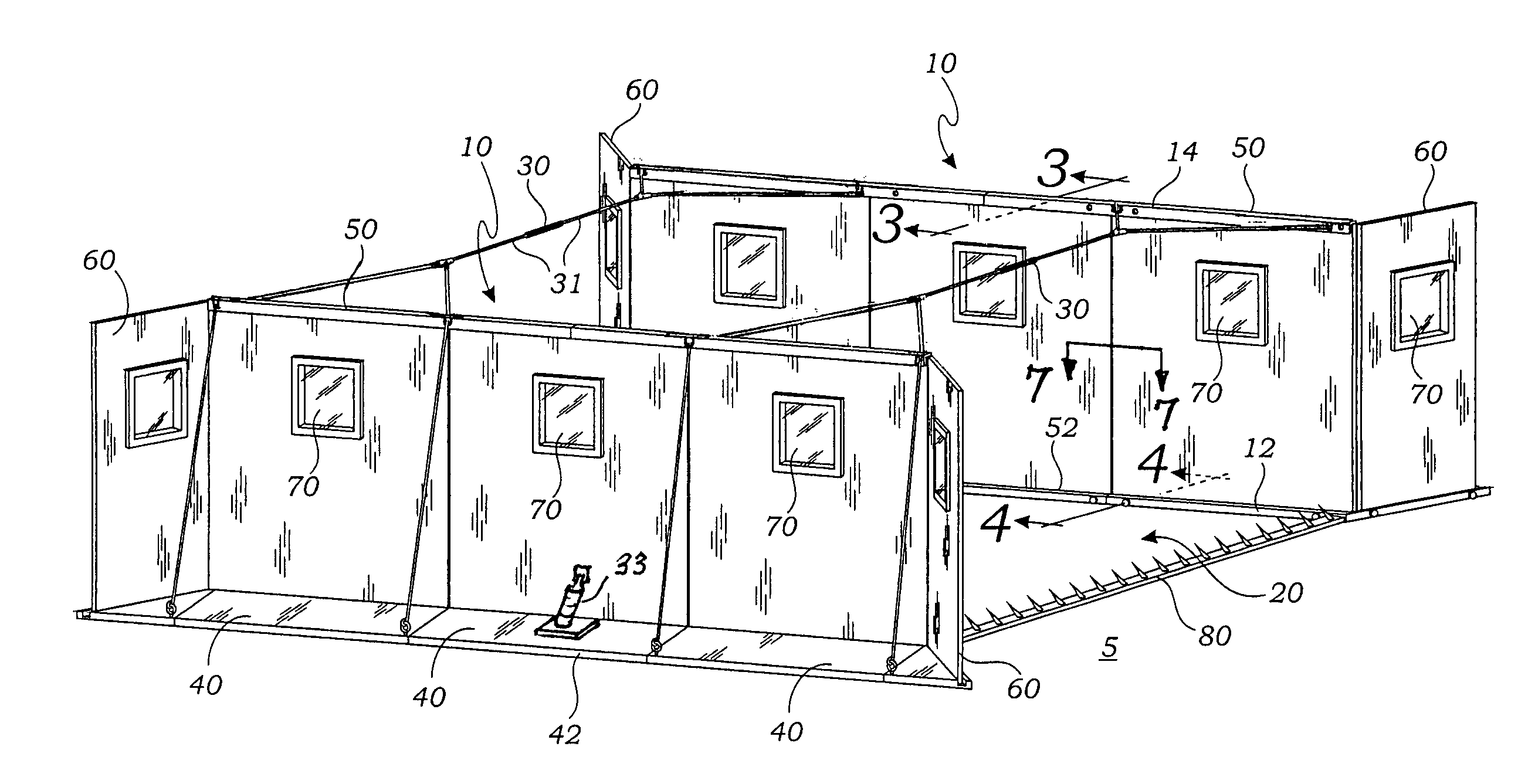
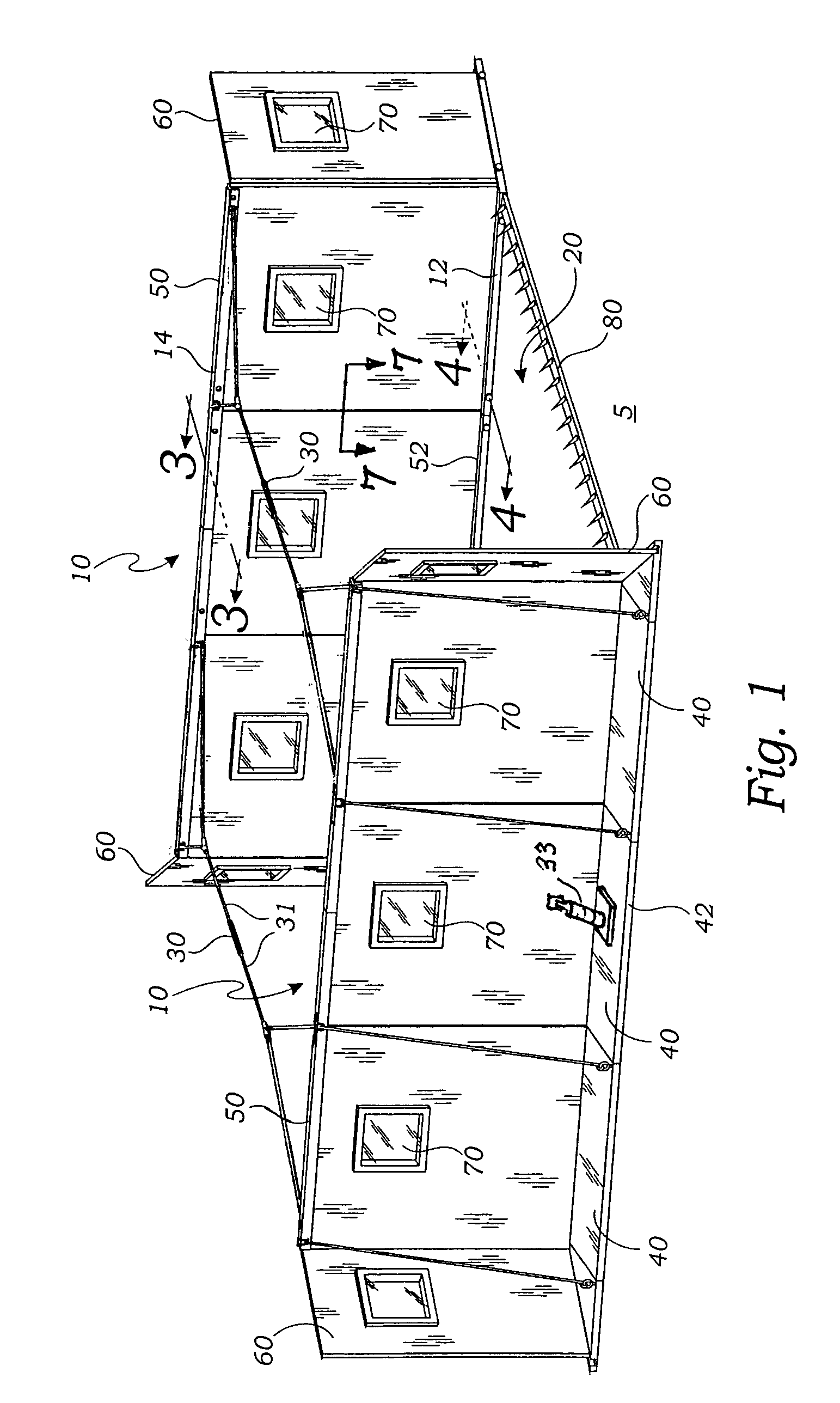
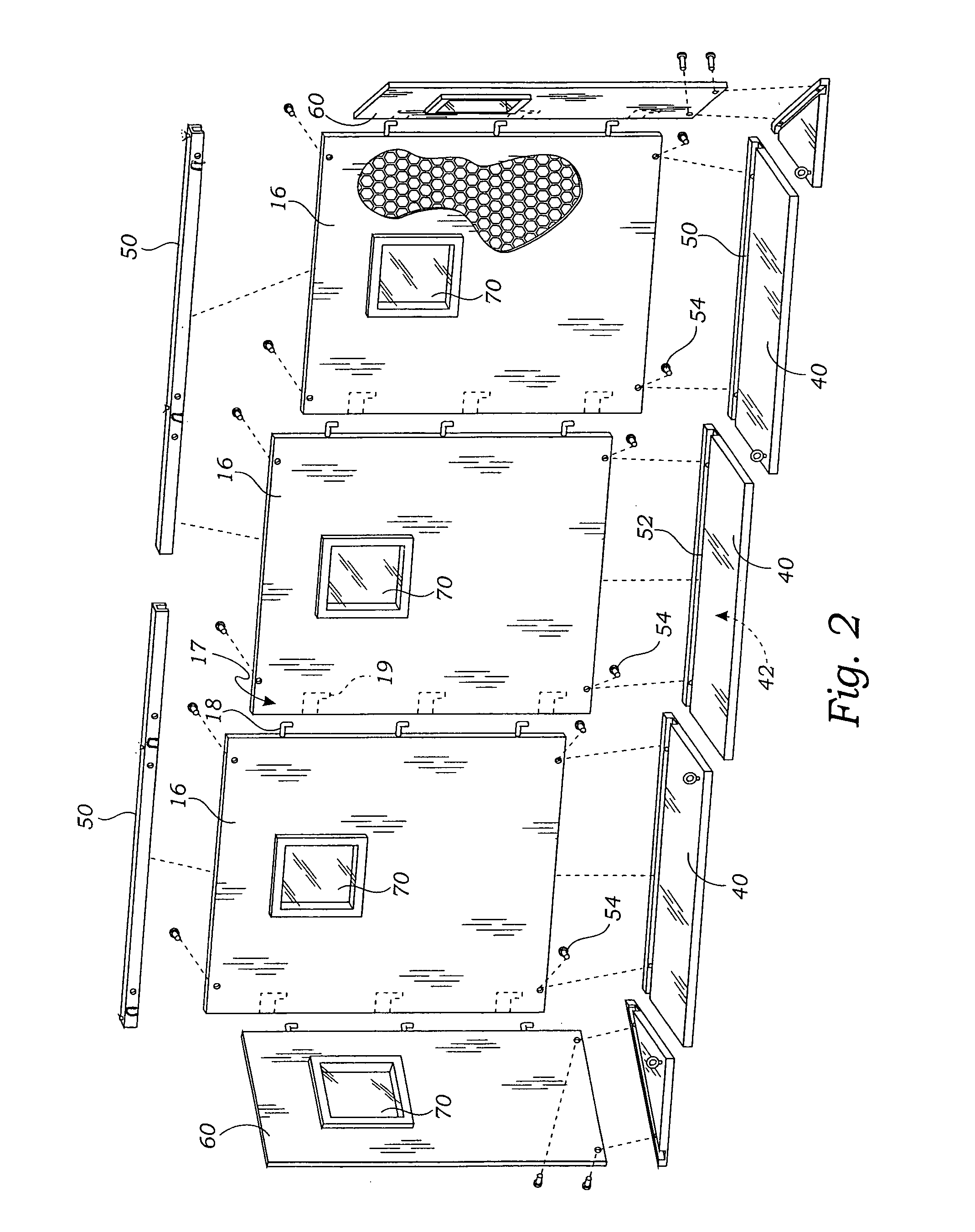
Modular, light weight, blast protective, check point structure
An explosion protective shelter apparatus comprises a pair of spaced apart upright parallel walls without rigid structural interconnection. The walls supported by the ground surface so as to define a vehicular space between them. The walls are joined by elastic members or secured against shock absorbers. The walls are easily erected on site and placed in service where personnel may be sheltered from an exploding vehicle that is being inspected between the walls.
Owner:WEATHERWAX JOHN
Vehicular operation processing system
InactiveUS6104980AAccurately determineAccurate detectionInstruments for road network navigationAnalogue computers for trafficCheck pointHandling system
A vehicular operation processing system has a memory card for storing coordinates of a plurality of check point sets, each of which is composed of a set of check points, and an ECU for, when determining that a vehicle has approached to any one of the check point sets based on the coordinate of a current vehicle position and the coordinate of the check point set, detecting a next check point based on a relation between each of check points contained in that check point set and a check point detected in the last time and performing associated processes such as a voice guidance and automatic sampling of operation record for that check point.
Owner:DENSO CORP
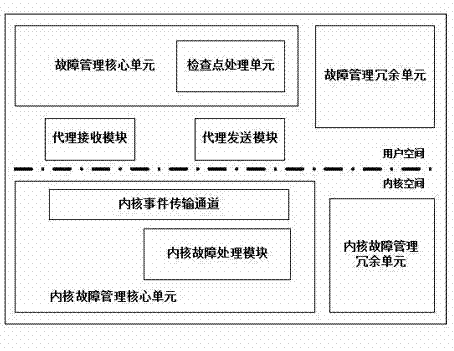
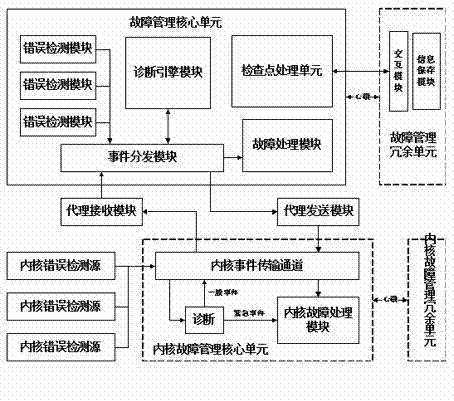
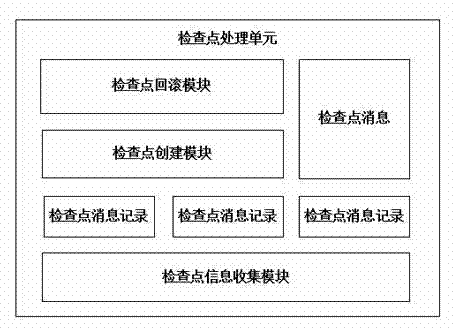
Fault-tolerant method for computer fault management system
The invention provides a fault-tolerant framework for a computer fault management system. The fault-tolerant framework is divided into two parts, namely a user space and a kernel space and comprises a fault management core unit 1), a checking point processing module 2), a fault management redundancy unit 3), an agent receiving module 4), an agent sending module 5), a kernel fault management core unit 6), a kernel event transmission channel 7), a kernel fault processing module 8) and a kernel fault management redundancy unit 9).
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Trusted computing platform and method for verifying trusted chain transfer
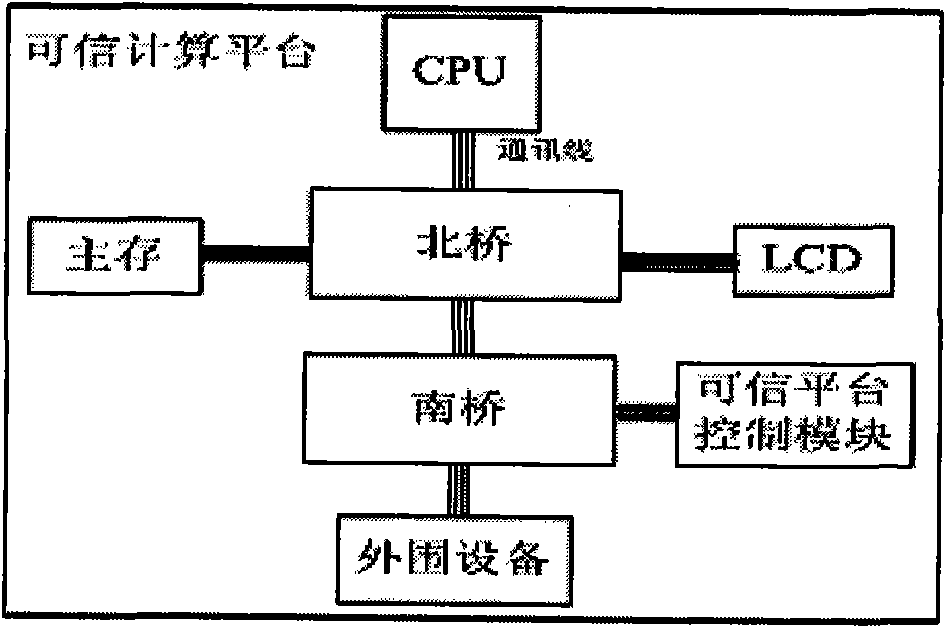
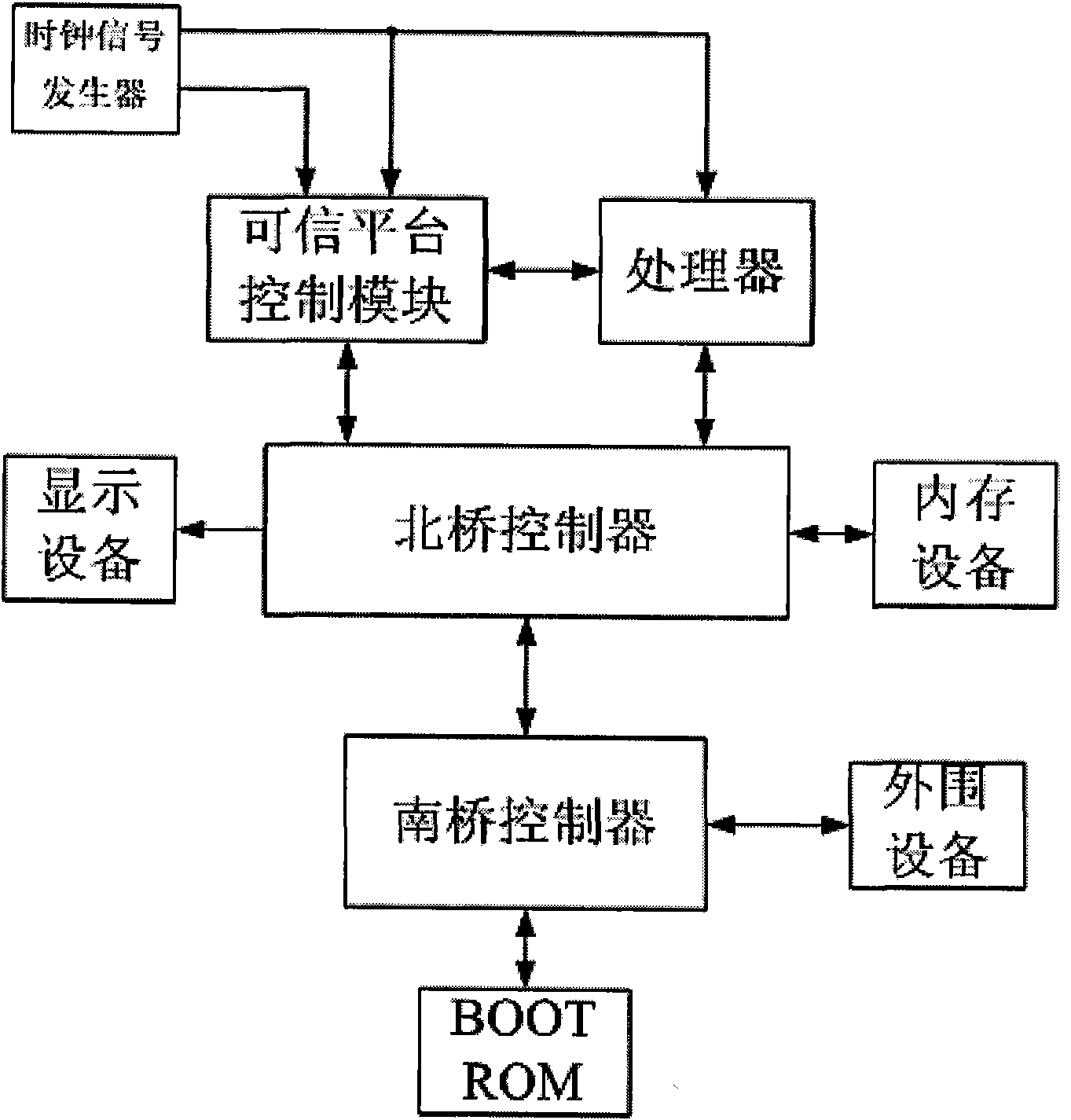
InactiveCN101901319ASolve the trust decay problemGuaranteed Metric Efficiency IssuesPlatform integrity maintainanceCheck pointValidation methods
The invention relates to a trusted computer platform and a method for verifying trusted chain transfer. A trusted chain is a key component of a trusted computer system, and ensures the safety and credibility of the computer system in the integral process from a trusted source to system starting, but the conventional trusted transfer mode is a chained transfer mode, and due to the problem of layer-by-layer attenuation of the trust level of chained transfer, potential safety hazards exist in the process of establishing the trusted chain of the trusted computer platform. A CPU is authorized by a trusted platform control module (TPCM) to perform chained measurement on the trusted computer platform, and simultaneously, the TPCM follows the CPU to perform the real-time, random and partitioned measurement on the trusted chain, and check points are embedded into codes of each part of the platform trusted chain to perform statistics and comparison on total operating time and total expected time and the operating time and expected time of each partition so as to judge whether each trusted node is distorted or not. The trusted computer platform and the method for verifying the trusted chain transfer improve the real-time of establishment and checking of the trusted chain, and particularly can protect against TOUTOC attack.
Owner:BEIJING UNIV OF TECH
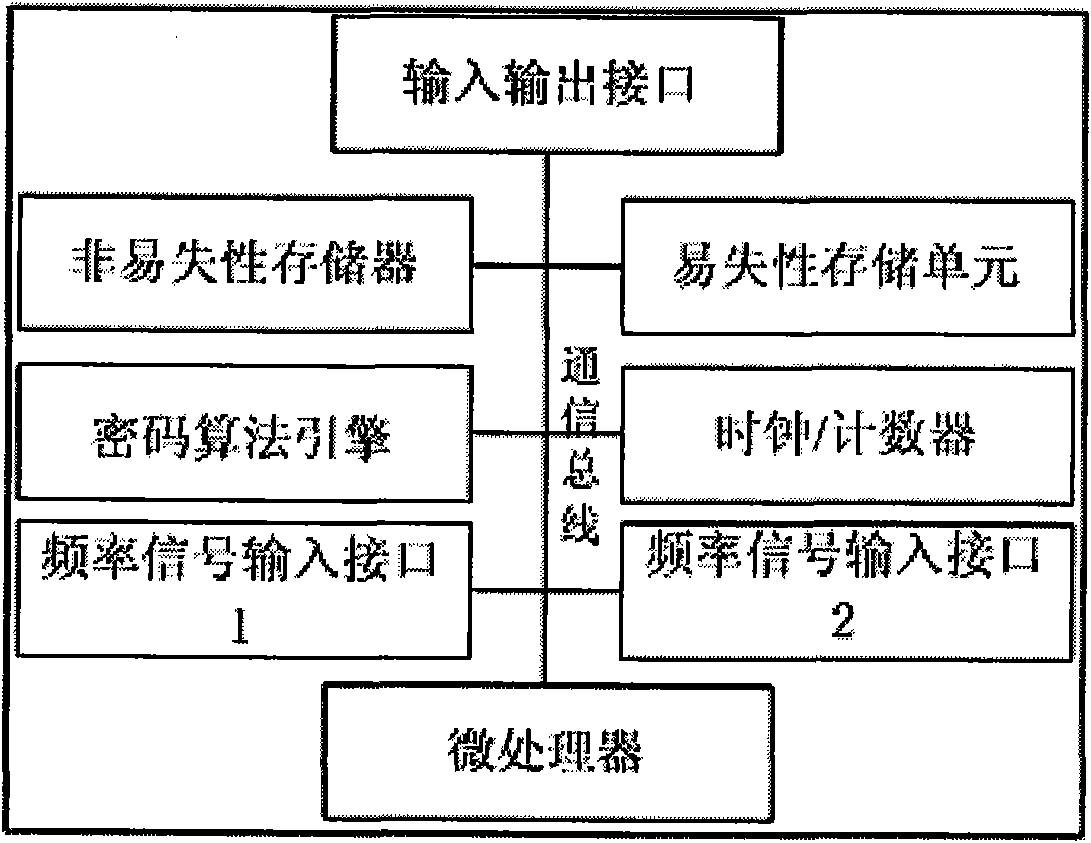
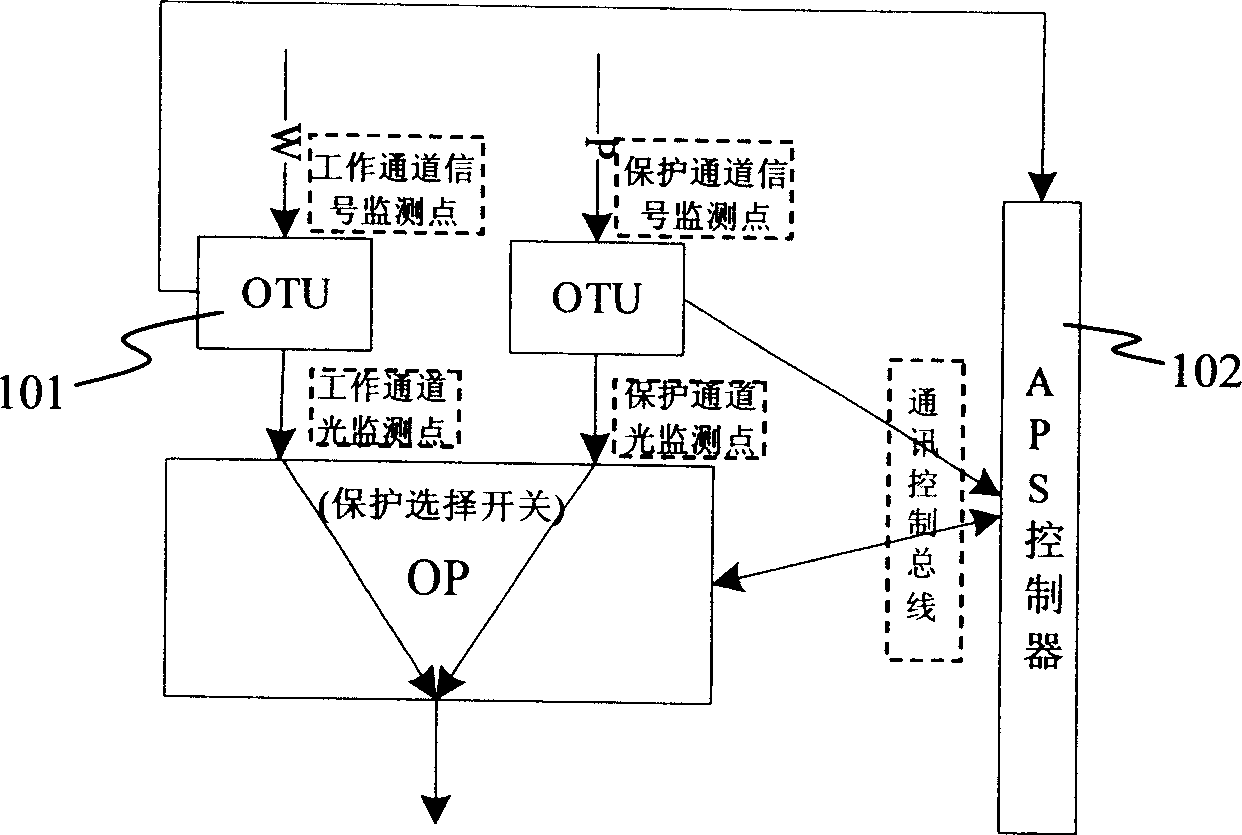
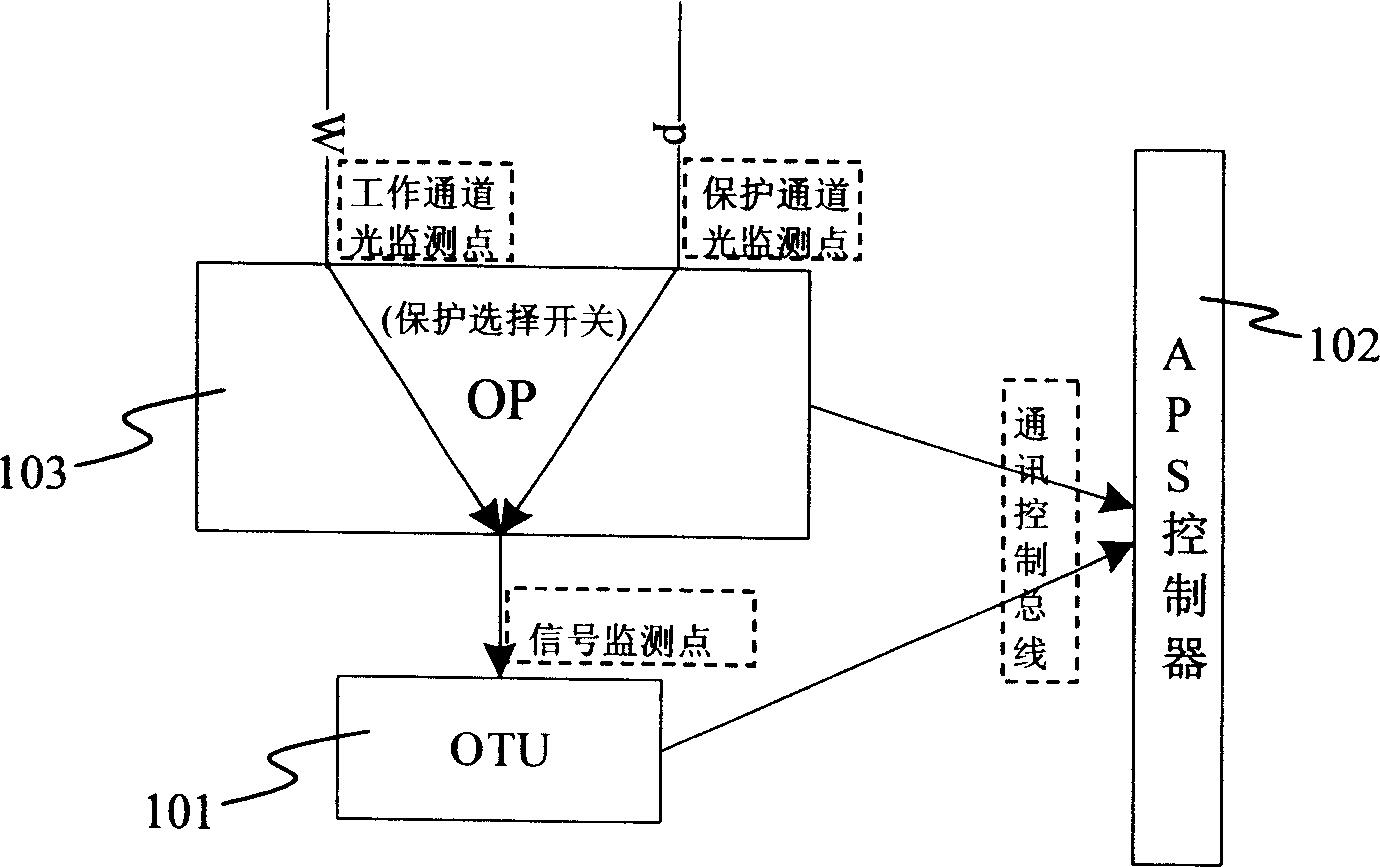
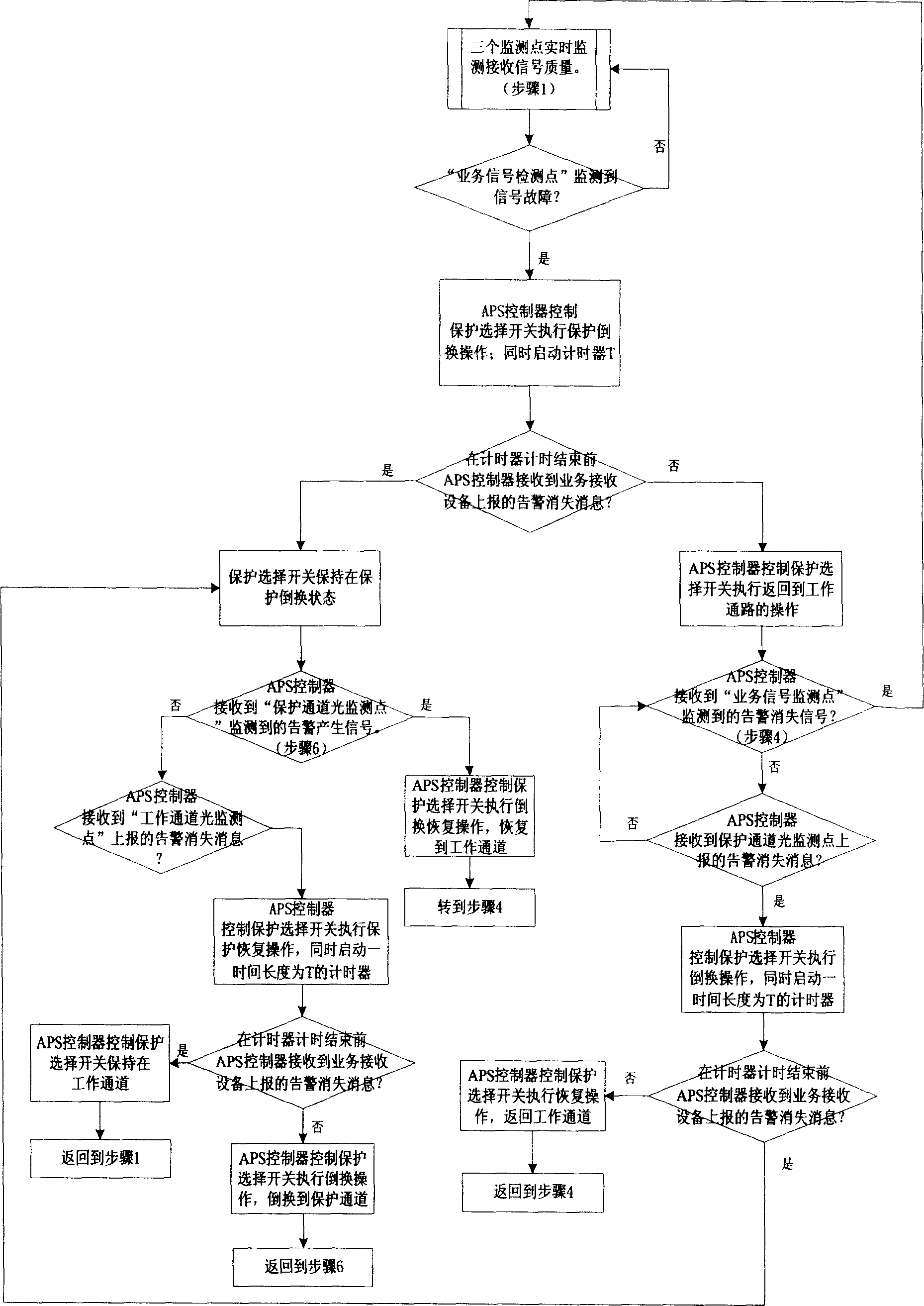
Method and equipment for triggering protection of optical network under shared configuration of receiving devices
ActiveCN1874201AAccurate operationMultiplex system selection arrangementsElectromagnetic transmissionCheck pointTelecommunications
The method includes steps: selecting single board to connect working channel or protected channel to equipment of receiving service; based on detected results from light check point in working channel, light check point in protected channel, and check point of service signal of the receiving equipment, automatic protecting rearrangement controller determines whether fault in working channel and protected channel occurs. Moreover, the controller controls the selected single board to carry out switching according to following modes: if working channel is good, then switch is retained at the working channel; if working channel is in fault, and protected channel is good, then switch is retained at the protected channel; if both of working channel and protected channel are in fault, then switch is retained at working channel. The invention can determine restoring signals caused by rearrangement, and caused by restored working channel effectively so as to avoid error operation of system.
Owner:ZTE CORP
Predictive programming in non-volatile memory
In a nonvolatile memory having an array of memory cells, wherein the memory cells are individually programmable to one of a range of threshold voltage levels, there is provided a predictive programming mode in which a predetermined function predicts what programming voltage level needs to be applied in order to program a given memory cell to a given target threshold voltage level. In this way, no verify operation needs to be performed, thereby greatly improving the performance of the programming operation. In a preferred embodiment, the predetermined function is linear and is calibrated for each memory cell under programming by one or more checkpoints. The checkpoint is an actual programming voltage that programs the memory cell in question to a verified designated threshold voltage level.
Owner:SANDISK TECH LLC
Predictive Programming in Non-Volatile Memory
ActiveUS20080253197A1Improve performanceRead-only memoriesDigital storageCheck pointComputer science
In a nonvolatile memory having an array of memory cells, wherein the memory cells are individually programmable to one of a range of threshold voltage levels, there is provided a predictive programming mode in which a predetermined function predicts what programming voltage level needs to be applied in order to program a given memory cell to a given target threshold voltage level. In this way, no verify operation needs to be performed, thereby greatly improving the performance of the programming operation. In a preferred embodiment, the predetermined function is linear and is calibrated for each memory cell under programming by one or more checkpoints. The checkpoint is an actual programming voltage that programs the memory cell in question to a verified designated threshold voltage level.
Owner:SANDISK TECH LLC
Earthwork measurement and calculation method with combination of oblique photography, RTK and BIM technologies
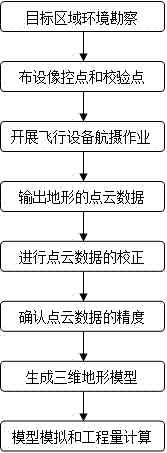
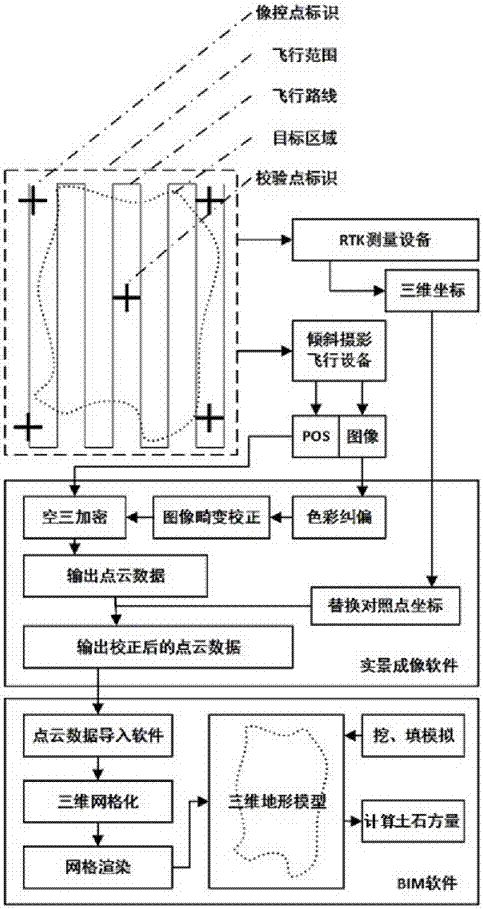
InactiveCN107421501AFinish quicklyEffectively completedPhotogrammetry/videogrammetryTerrainCheck point
The invention provides an earthwork measurement and calculation method with combination of oblique photography, RTK and BIM technologies. The method includes the steps of: S1) environment exploration of a target zone; S2) arrangement of photo control points and check points surrounding the target zone; S3) aerial photography above the target zone with an air vehicle; S4) import of an oblique photography image from the air vehicle into a real scene imaging software, and image processing to output point cloud data of the terrain; S5) correction to the point cloud data; S6) precision determination of the point cloud data; S7) generation of a three-dimensional terrain model; S8) digging / filling simulation to the three-dimensional terrain model and calculation of earthwork project quantity. By means of the earthwork measurement and calculation method with combination of oblique photography, RTK and BIM technologies, a complete route from data collection to model establishment to project quantity calculation is formed. The method can increase the efficiency of measuring and calculating earthwork, wherein acquired original data has higher precision and data in the calculated result is more accurate.
Owner:SUNYOUNG CONSTR GROUP
Automatic recovery method for blockchain consensus node
ActiveCN107423152AImprove usabilityAccelerate the speed of participation in consensusPayment protocolsNon-redundant fault processingByzantine fault toleranceCheck point
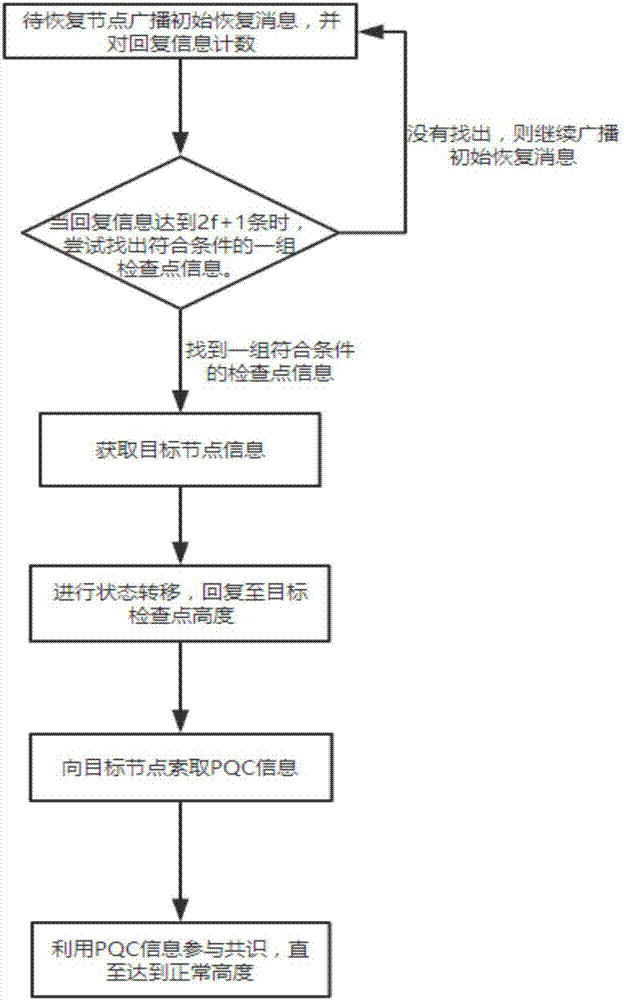
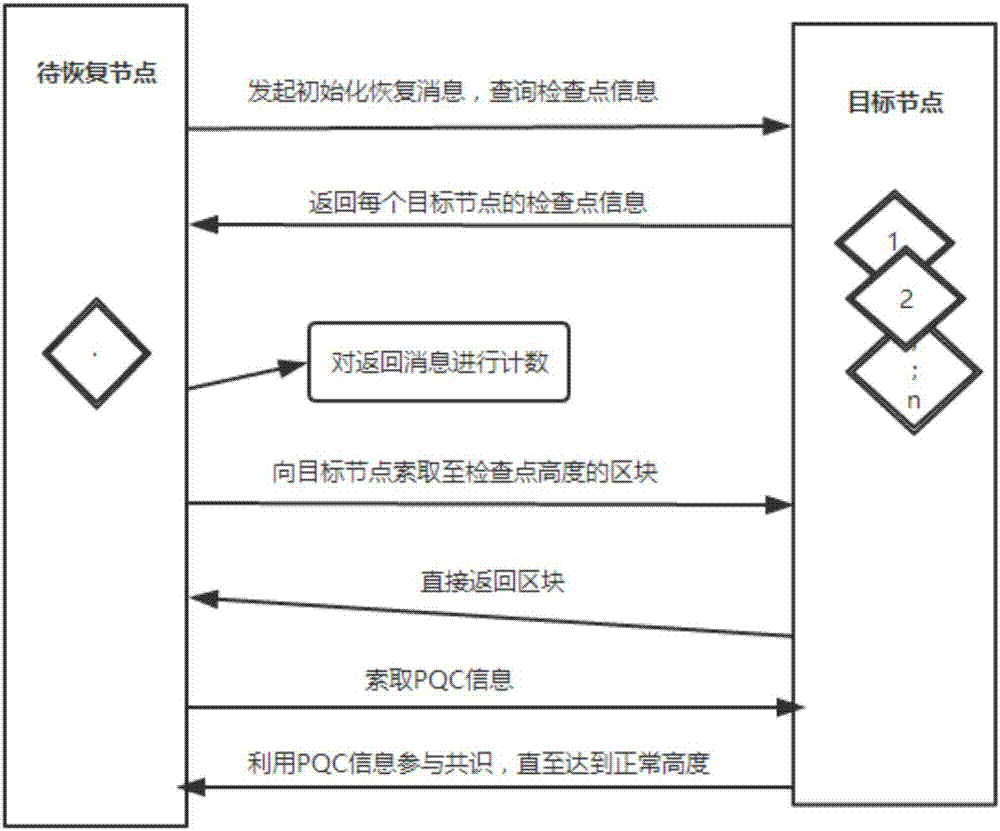
The invention discloses an automatic recovery method for a blockchain consensus node. The method comprises the following steps that: 1) after crash, a reconnection node broadcasts an initial recovery message and obtains the check point information and the block height of other nodes; 2) the reconnection node receives the reply information of other nodes and counts the check point and the block height of a sender; 3) a target node is found, and the check point information, the block height and the block Hash of the target node are obtained; 4) the reconnection node carries out state transition and is recovered to the check point height of the target node; 5) the reconnection node asks for the message of PQC (Process Quality Control) from the target node; and 6) the reconnection node receives the PQC information returned from the target node, carries out normal consensus processing and repeatedly executes S5) and 6) until the height of the reconnection node block is recovered to normal node height. By use of the method, the problem that crash node reconnection is slow in a traditional PDFT (Practical Byzantine Fault Tolerance) consensus process is solved, and a quick reconnection method for the crash reconnection node on the blockchain is put forward.
Owner:HANGZHOU QULIAN TECH CO LTD
Compact integrated redundancy controller and control method thereof
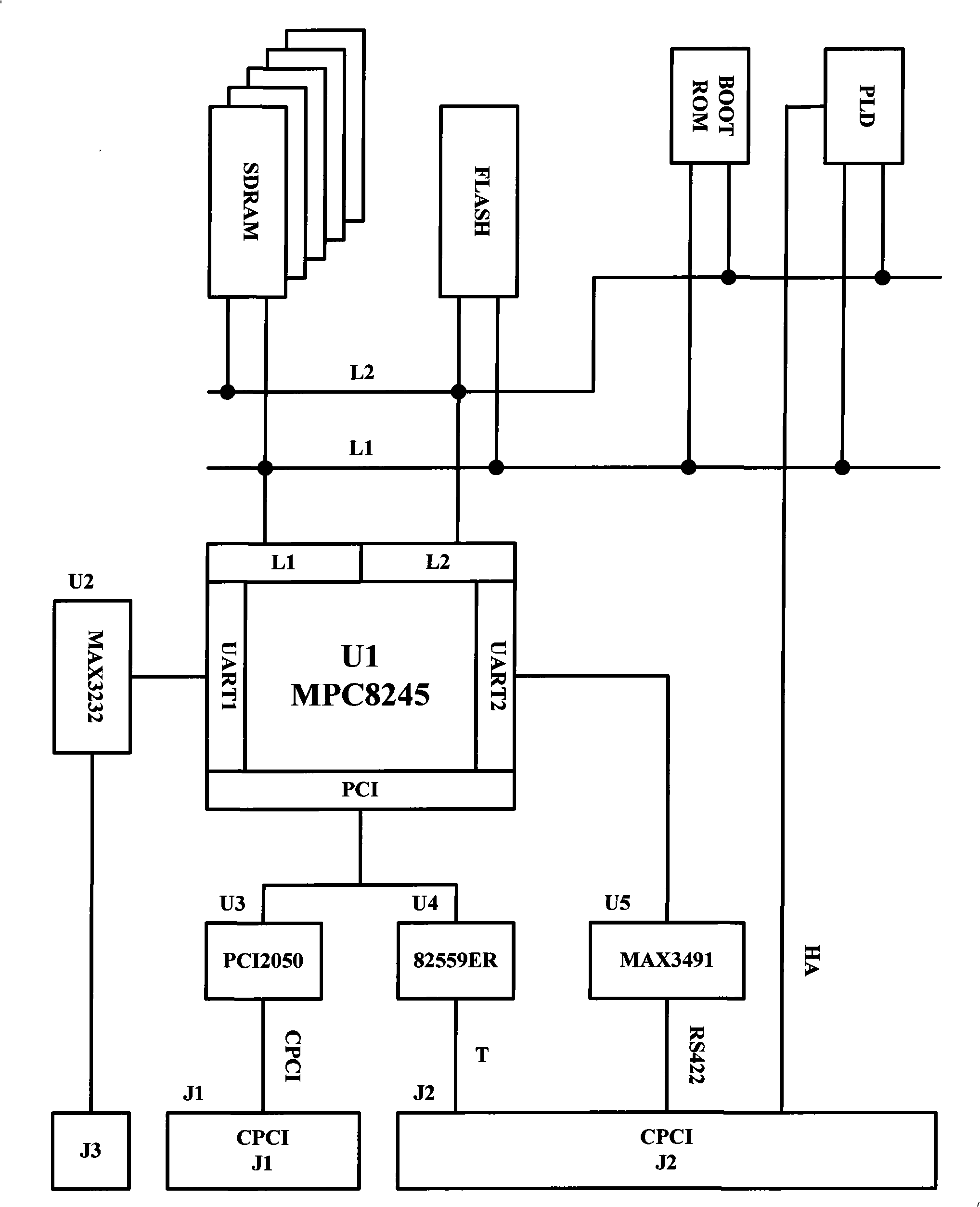
ActiveCN101271332ASolve the hidden dangers that are prone to single point failureSolve the hidden danger of single point of failureSafety arrangmentsTotal factory controlCheck pointTransceiver
The invention provides a compact integrated redundancy controller and a controlling method thereof. The controller is provided with two controllers which have identical structure and can be used alternatively by displacing. Each controller is provided with a storage chip, a flash memory chip, a firmware chip and a programmable apparatus which are respectively connected with a main control chip; the controller is also provided with a first serial port transceiver, a second serial port transceiver, a PCI bridge piece and a network card controller. The serial port transceivers are connected with a CPCI connector by a RS422 serial port; the network card controller is connected with the CPCI connector by an Ethernet port; the PCI bridge piece is connected with the CPCI connector by a CPCI bus; the serial port transceivers are also connected with a maintenance serial port; a programmable apparatus PLD is also connected with the CPCI connector by a HA control signal. The methods comprise the starting method of main / standby controllers, the method that a standby controller is upgraded into a main controller automatically and a check point protocol control method when the main controller and the standby controller are switched in a system. The controller and the method can upgrade the system controller of a traditional CPCI system into a double-redundancy standby system, which solves the hidden trouble that single-point failure can easily occur in a CPCI system controller.
Owner:BEIJING FOUNTAIN MICROSYST
Signature creation for malicious network traffic
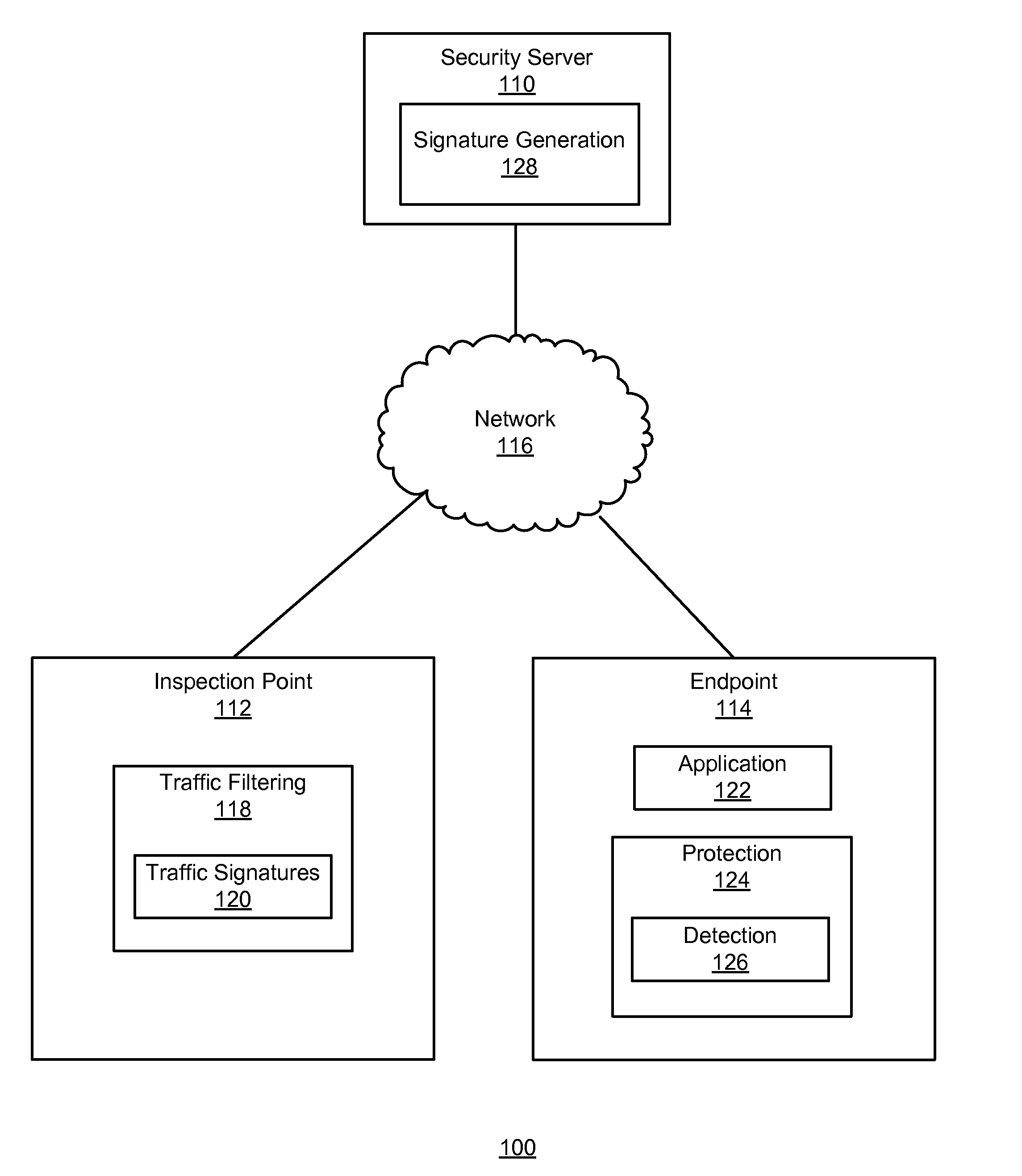
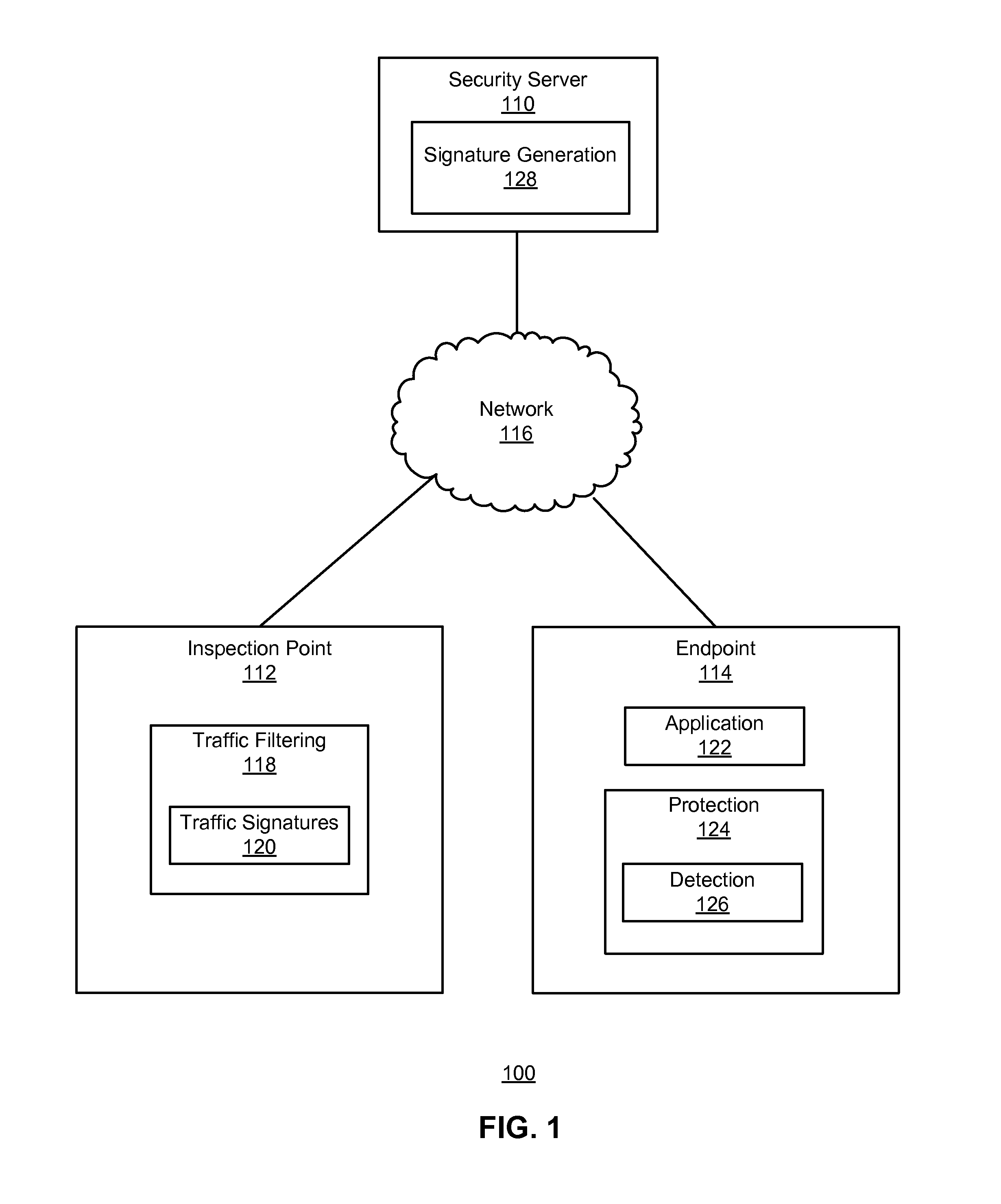
An endpoint on a network uses detection data to detect a malicious software attack. The endpoint identifies content associated with the attack, such as a component of a web page, and generates a description of the content. The endpoint sends the description to a security server. The security server analyzes the content and identifies characteristics of the content that are present when the content is carried by network traffic. The security server generates a traffic signature that specifies the identified characteristics and provides the traffic signature to inspection points. The inspection points, in turn, use the traffic signature to examine network traffic passing through the inspection points to detect network traffic carrying the content. The attack detection at the endpoint thus informs the traffic signature-based detection at the inspection points and reduces the spread of malicious software.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com