Trusted computing platform and method for verifying trusted chain transfer
A technology of trusted computing and trust chain, applied in the field of information security, can solve the problem of transmission trust decay and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be described in detail below in conjunction with the accompanying drawings and examples of implementation.
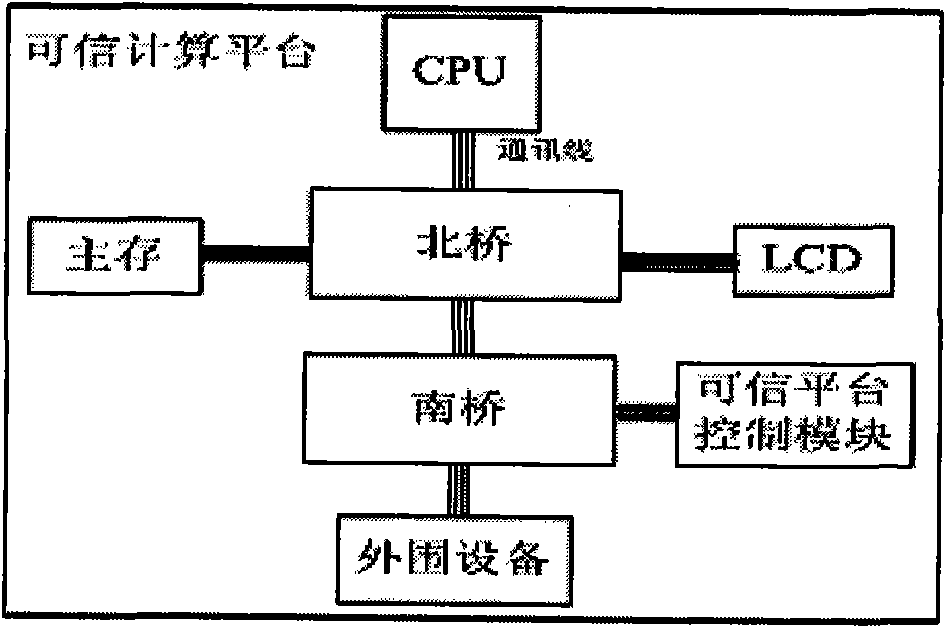
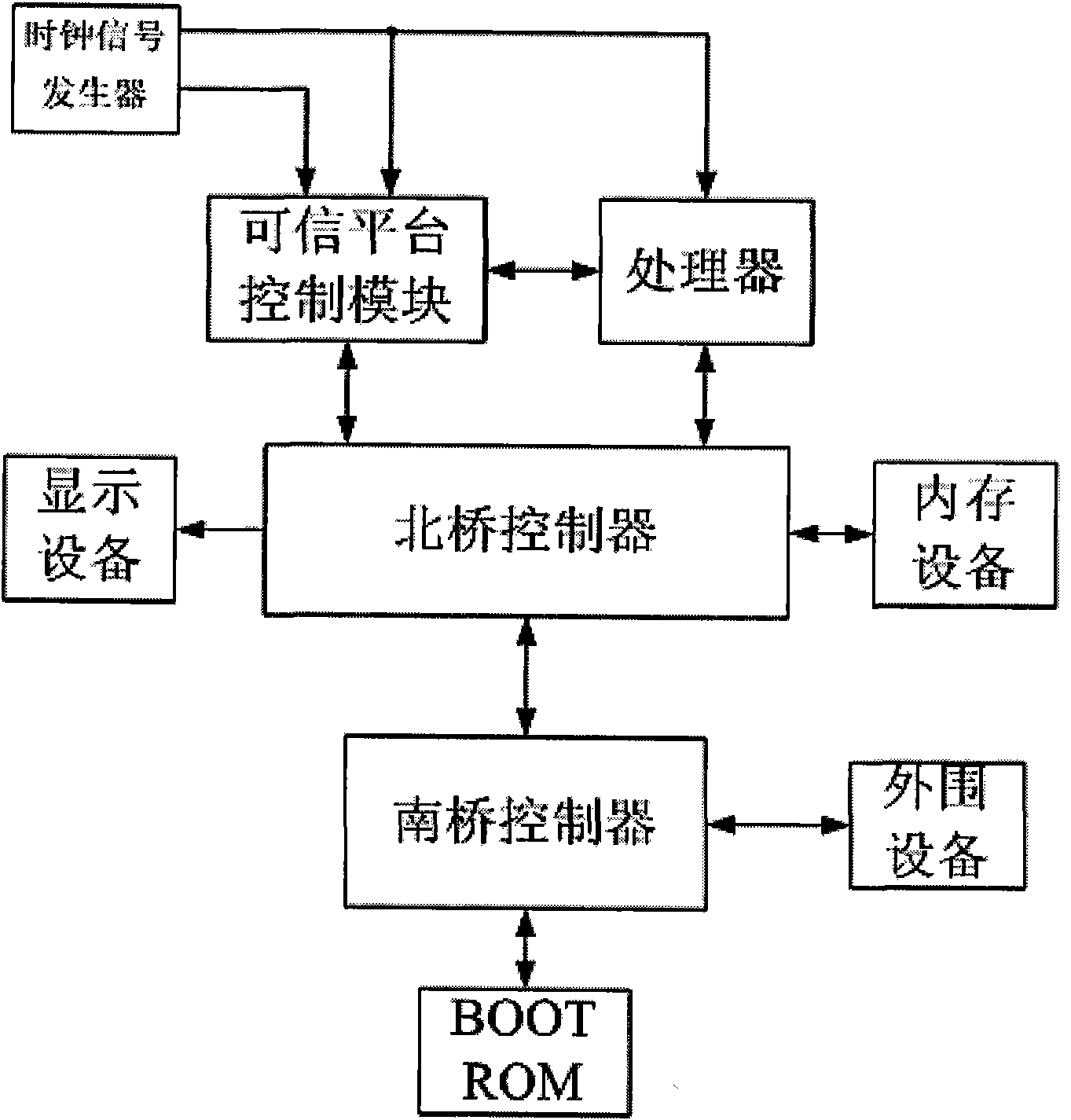
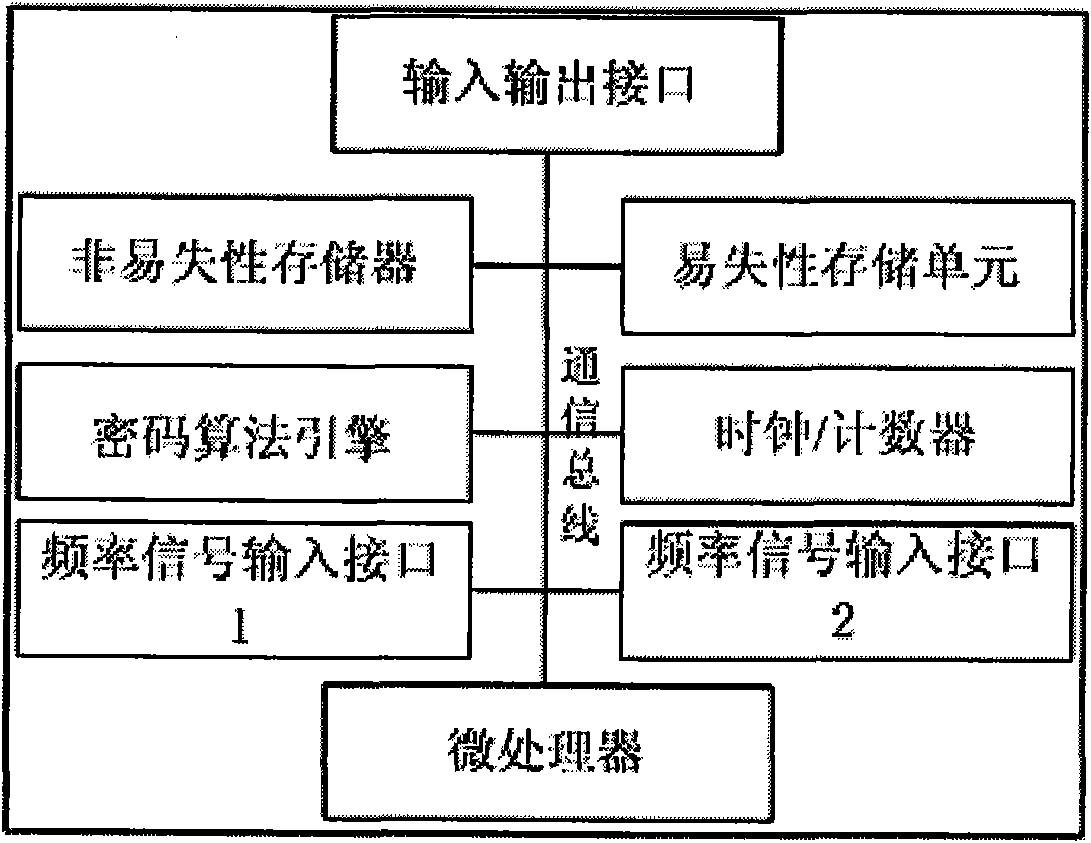
[0069] 1. Hardware Composition of Trusted Computing Platform
[0070] A kind of trusted computing platform, it is characterized in that, hardware composition comprises: processor, trusted platform control module, clock frequency generator, display device controller, memory device, north bridge controller, south bridge controller, peripheral equipment and BOOT ROM;
[0071] In actual application, the specific configuration is as follows:
[0072] 1) Asustek P5K-VM, an Intel G33 motherboard, is selected as the motherboard of the Trusted Computing Platform;
[0073] 2) The processor uses Intel's Core 2 processor, and a control switch needs to be set on the clock input signal interface and reset interface of the processor, which is used for the trusted platform control module to control the stop, continue, and reset of the processor;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com