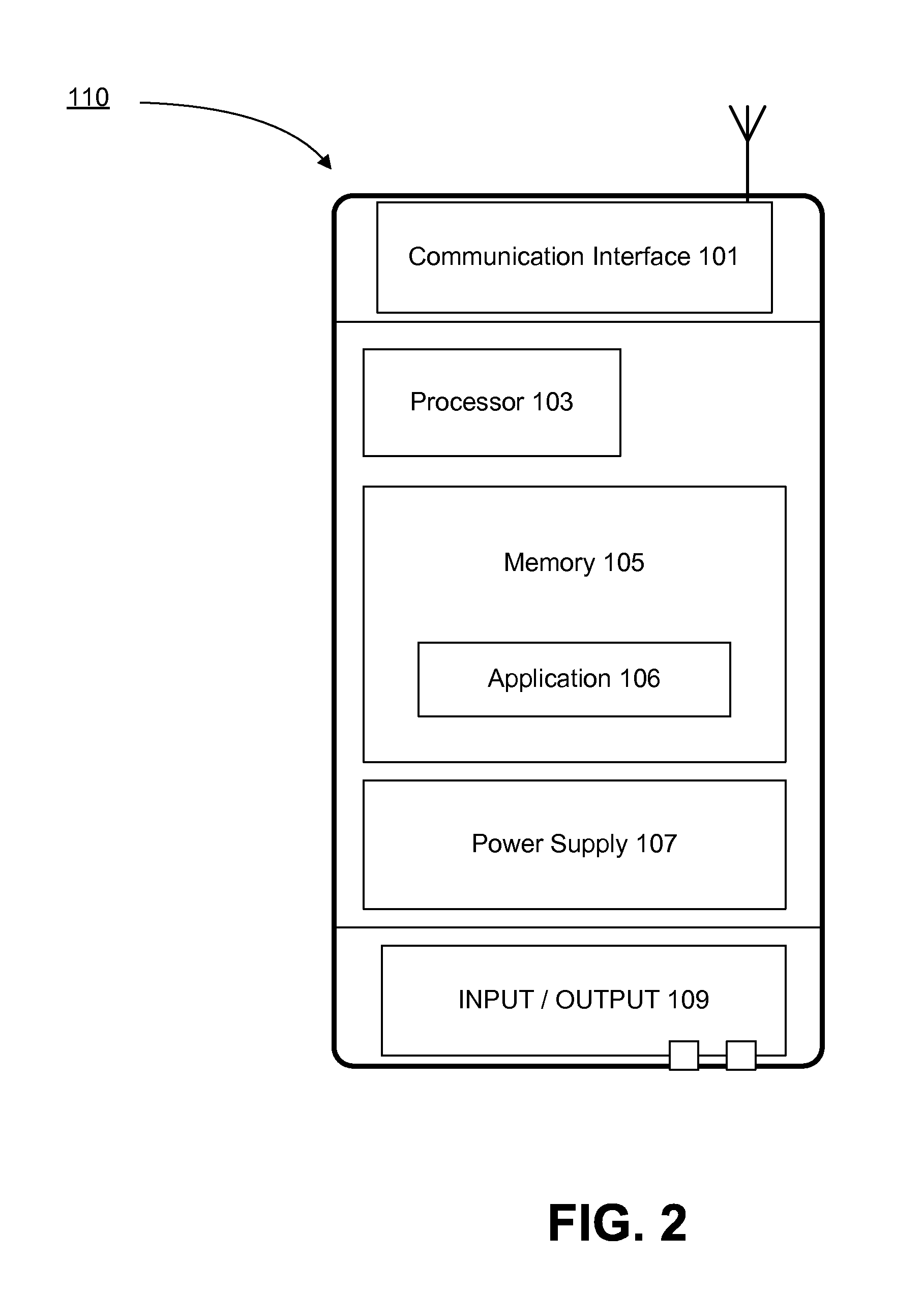
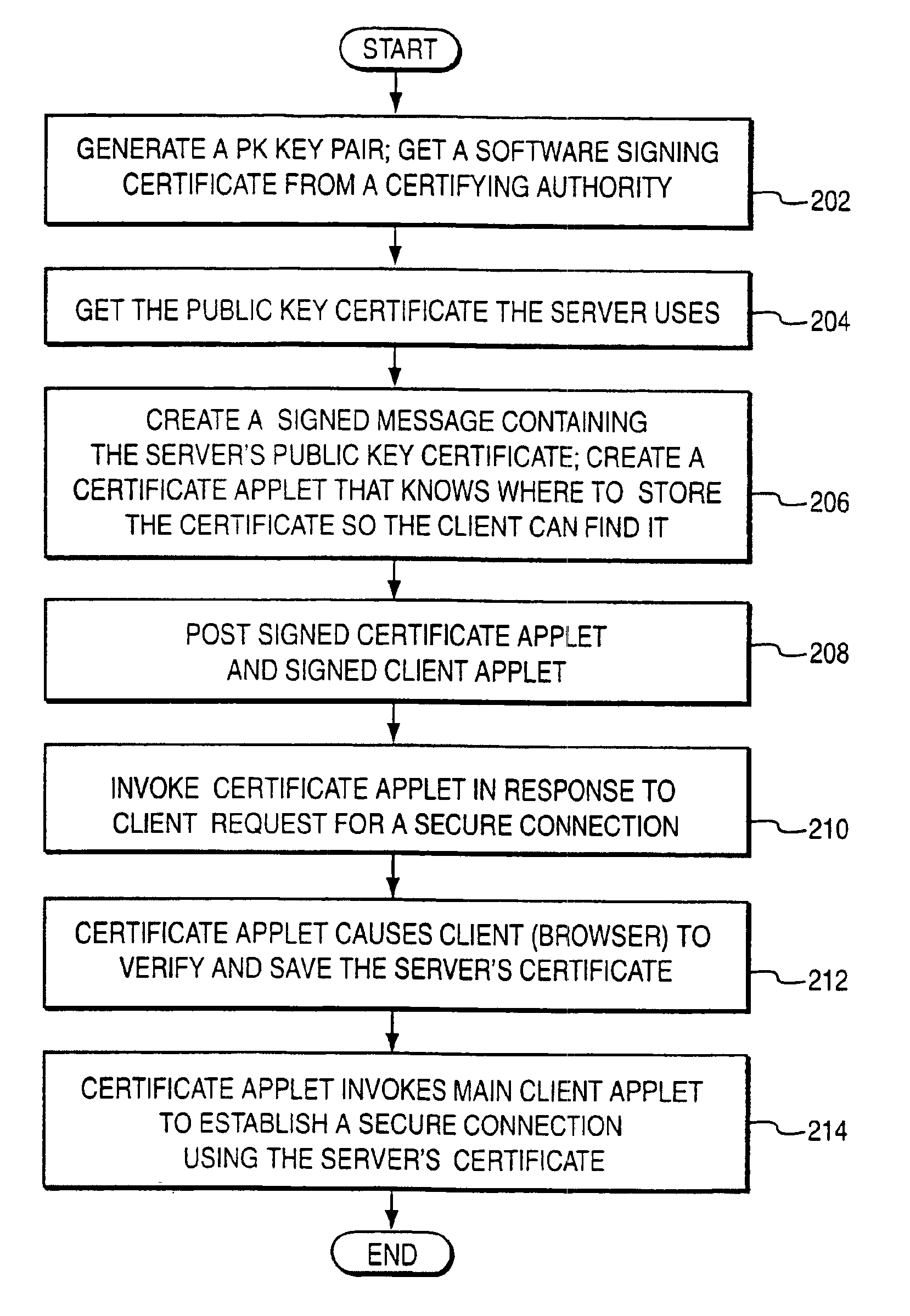
Patents
Literature
222 results about "Chain of trust" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer security, a chain of trust is established by validating each component of hardware and software from the end entity up to the root certificate. It is intended to ensure that only trusted software and hardware can be used while still retaining flexibility.
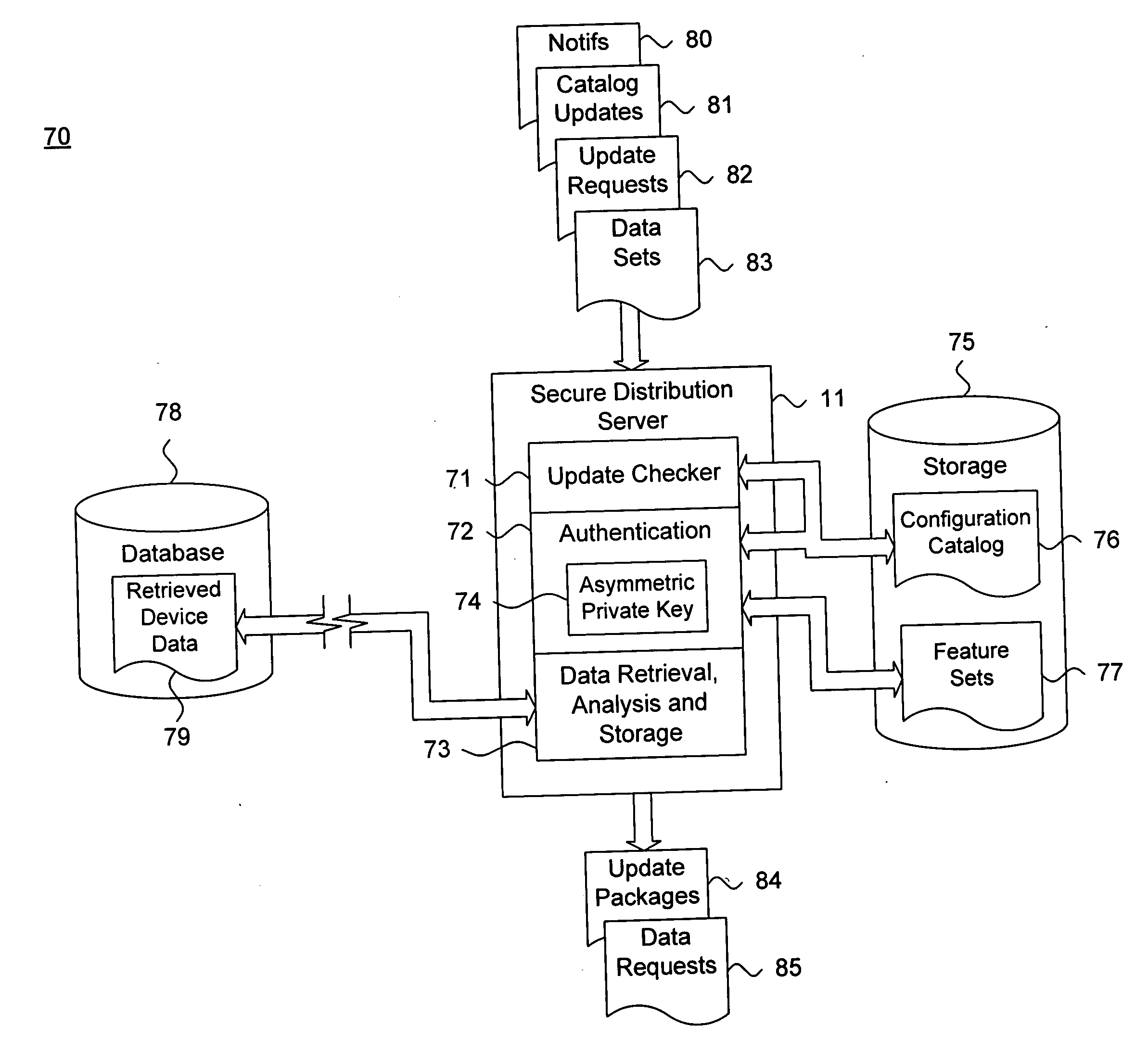
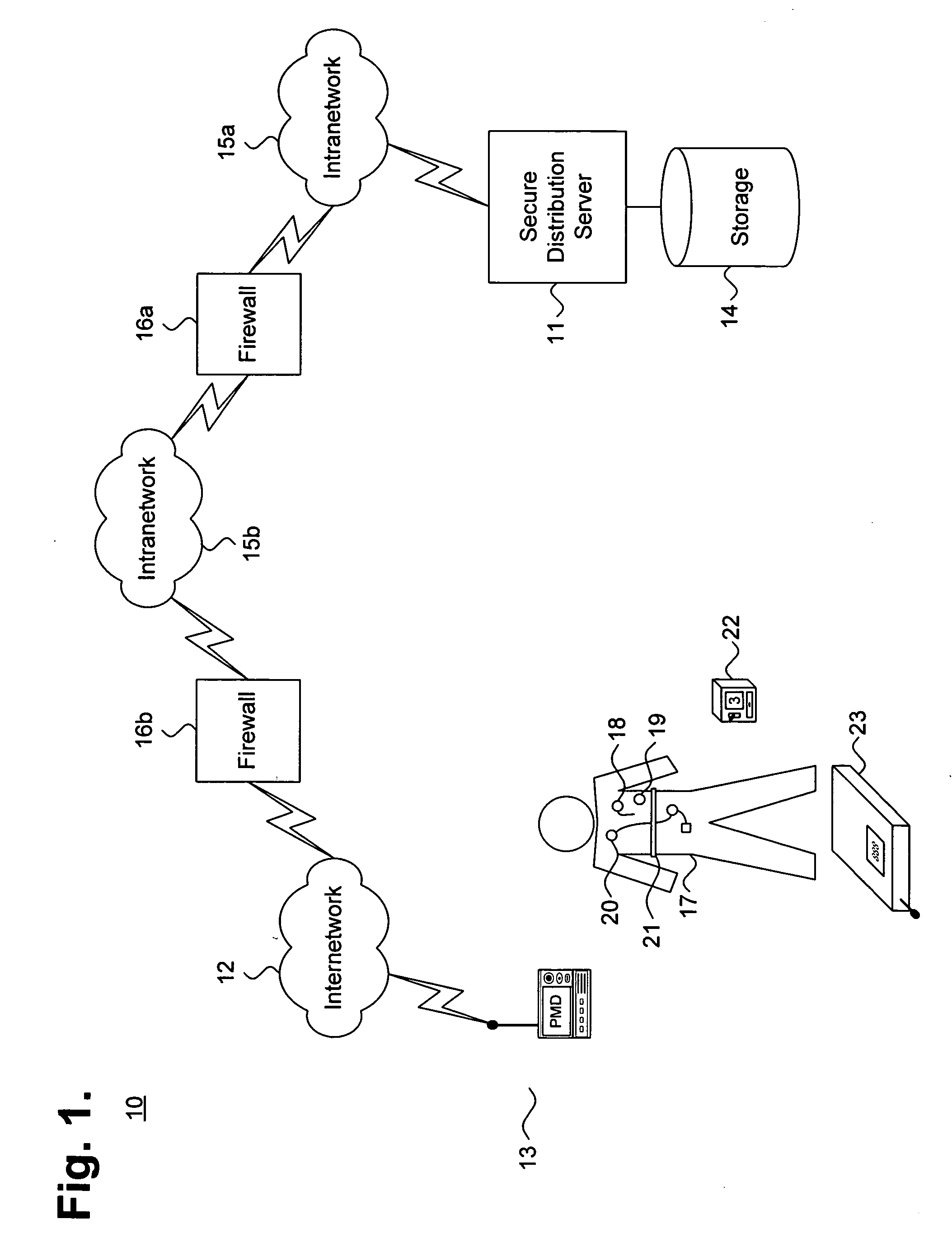
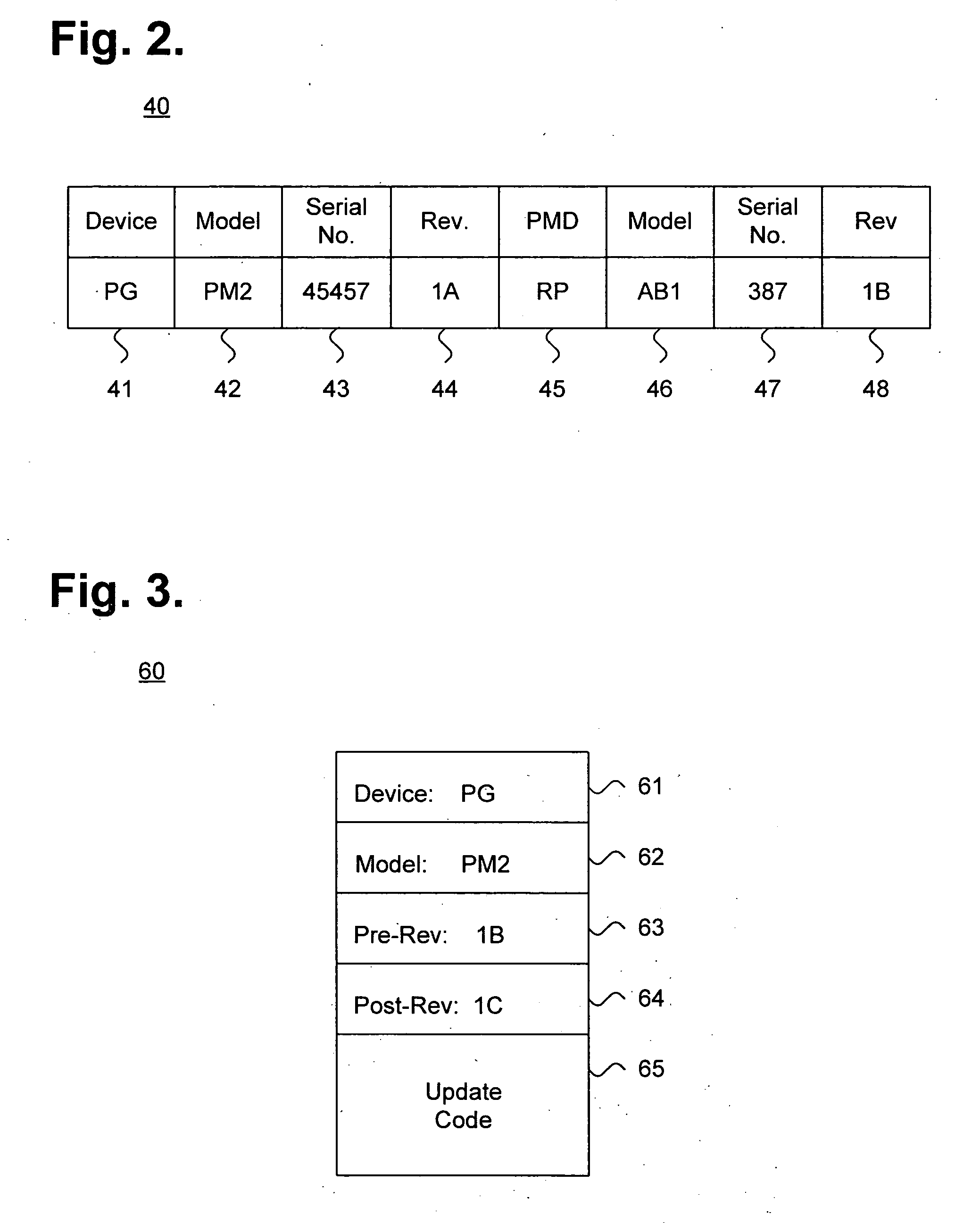
System and method for providing a secure feature set distribution infrastructure for medical device management
InactiveUS20070136098A1ElectrotherapyData processing applicationsFeature setMedical equipment management
A system and method for providing a secure feature set distribution infrastructure for medical device management is presented. A unique association is mapped for data download between a medical device and a communications device transiently coupleable to the medical device. A configuration catalog is maintained, including operational characteristics of at least one of the medical device and the communications device. The operational characteristics as maintained in the configuration catalog are periodically checked against a database storing downloadable sets of features and one or more feature sets including changed operational characteristics are identified for distribution. The one or more feature sets are digitally signed and the one or more feature sets are provided to the communications device over a plurality of networks. The one or more feature sets are authenticated and their integrity is checked over a chain of trust originating with a trusted source and terminating at the communications device.
Owner:CARDIAC PACEMAKERS INC
Trust chain transfer method for trusted computing platform
InactiveCN102332070ANot easy to tamper withNot easy to attackPlatform integrity maintainanceOperational systemTrusted Computing
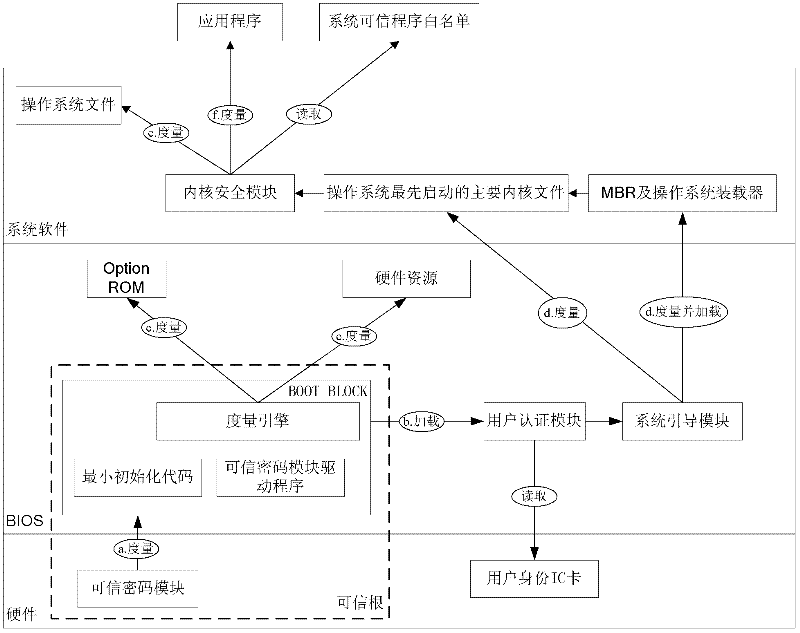
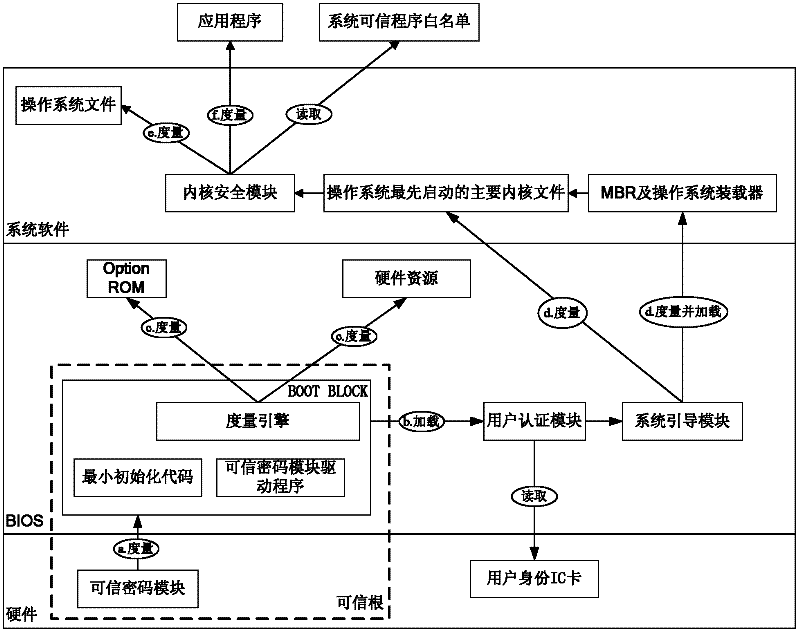
The invention discloses a trust chain transfer method for a trusted computing platform. A trusted computing module (TCM) serving as a starting point of starting a trust chain is started and actively initiated at first to verify the trustiness of a BIOS (basic input output system) chip; after the trusted BIOS chip is started, a MAIN BLOCK of the BIOS chip performs concentrated integrity verification on key files of an MBR (master boot record), an operating system loader and an operating system kernel; in the starting process of an operating system, the starting and running of an unauthorized program are prevented in a way of combining the integrity verification based on a white list and running program control; and hashing operations for the integrity verification are finished by a hardware computing engine. When a user starts any executable program, a security module in the operating system kernel checks the integrity of the program and checks whether the program is in the trusted program white list or not, and only application programs which are in the trusted program white list of the system and have integrity measures consistent with an expected value are permitted to be run. High-efficiency and fine-grained trust chain transfer is realized, the damages of viruses to system files and program files can be prevented, and the execution of the unauthorized program can be prevented.
Owner:中国人民解放军海军计算技术研究所
Hardware-Based Zero-Knowledge Strong Authentication (H0KSA)
InactiveUS20100306531A1Reduce riskUser identity/authority verificationDigital data authenticationHardware security moduleChain of trust
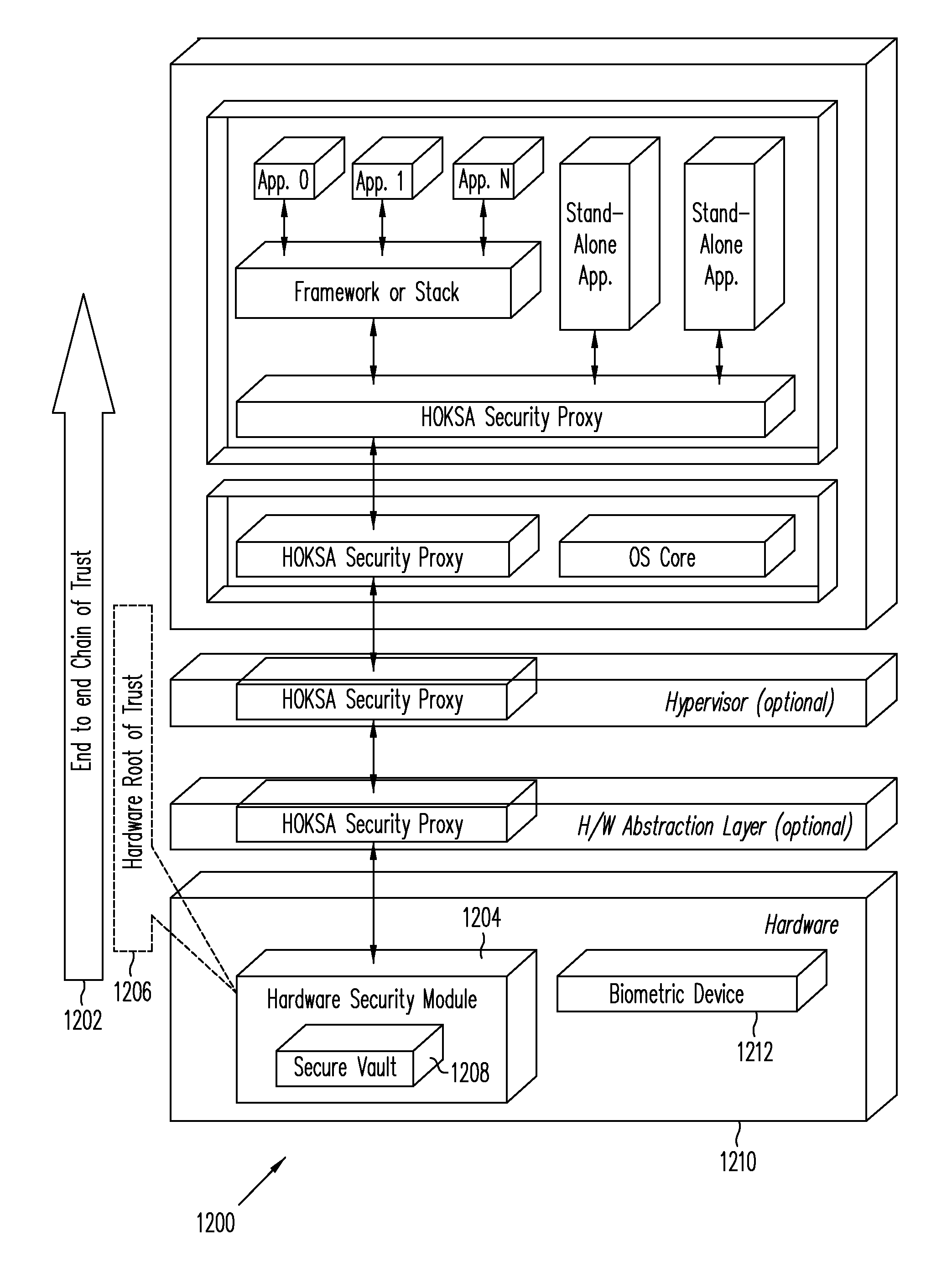
Systems and methods are provided for a device to engage in a zero-knowledge proof with an entity requiring authentication either of secret material or of the device itself. The device may provide protection of the secret material or its private key for device authentication using a hardware security module (HSM) of the device, which may include, for example, a read-only memory (ROM) accessible or programmable only by the device manufacturer. In the case of authenticating the device itself a zero-knowledge proof of knowledge may be used. The zero-knowledge proof or zero-knowledge proof of knowledge may be conducted via a communication channel on which an end-to-end (e.g., the device at one end and entity requiring authentication at the other end) unbroken chain of trust is established, unbroken chain of trust referring to a communication channel for which endpoints of each link in the communication channel mutually authenticate each other prior to conducting the zero-knowledge proof of knowledge and for which each link of the communication channel is protected by at least one of hardware protection and encryption.
Owner:PAYPAL INC
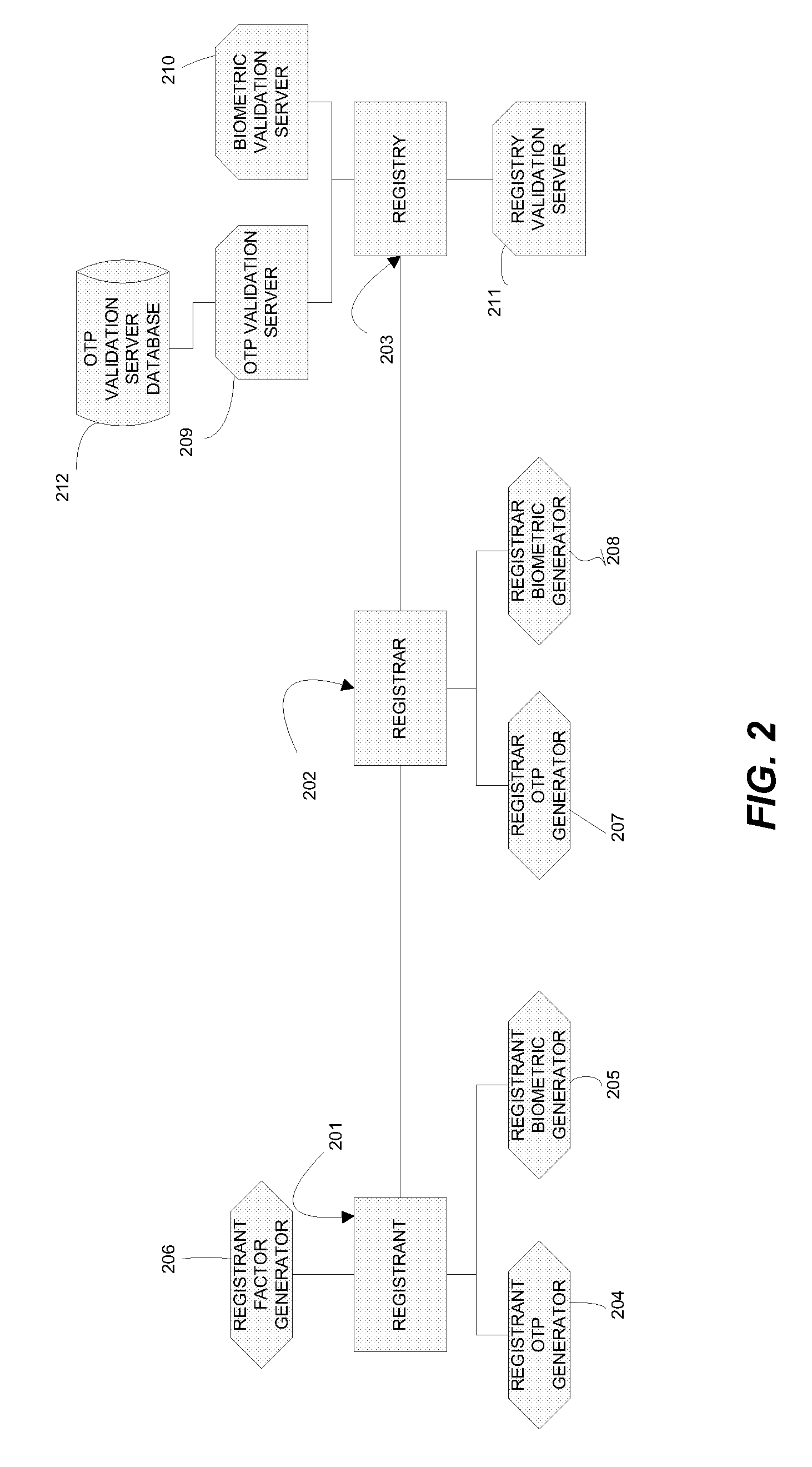
Shared Registration Multi-Factor Authentication Tokens
ActiveUS20120174198A1Avoid changeDigital data processing detailsMultiple digital computer combinationsChain of trustRegistration system
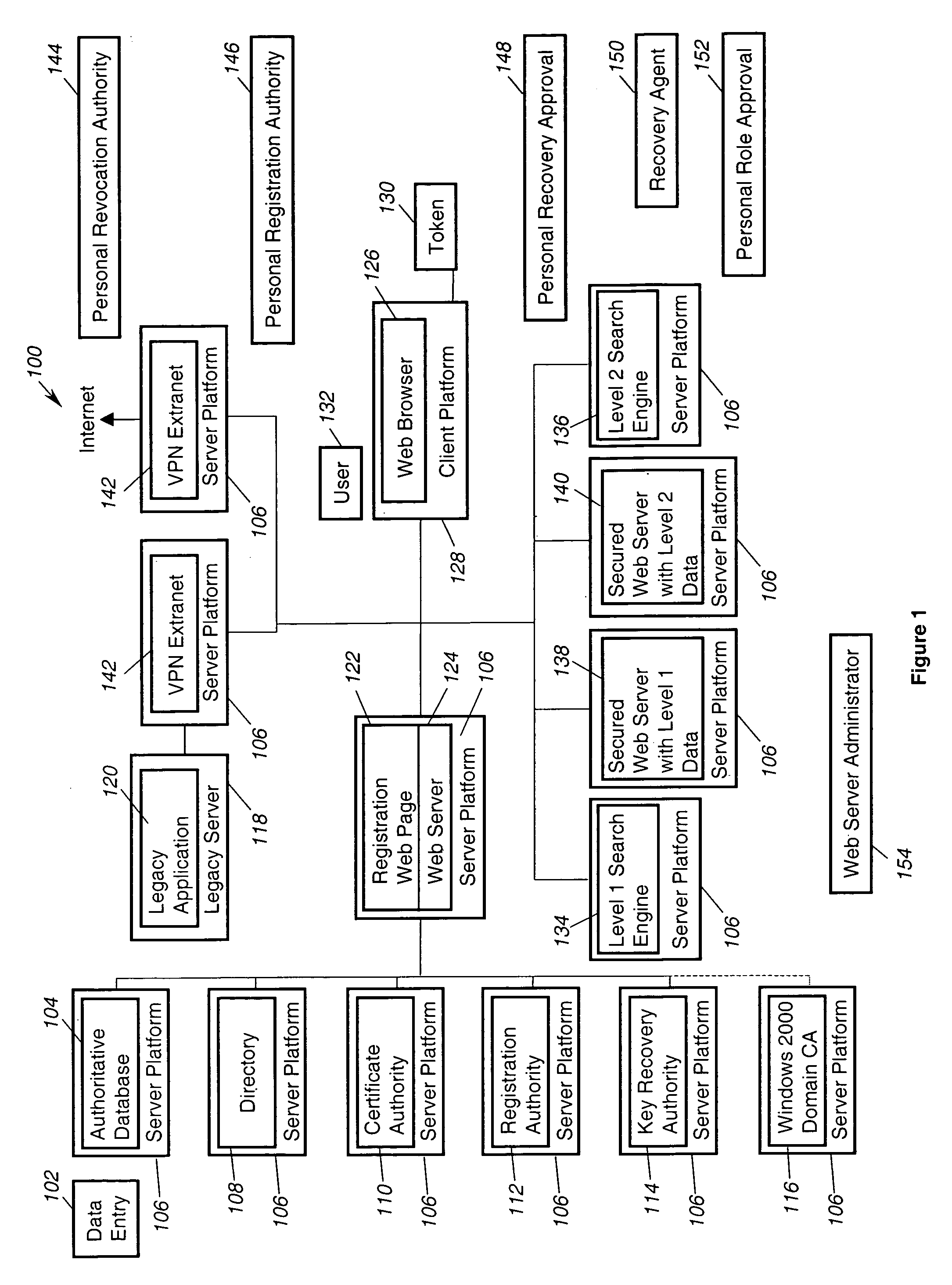
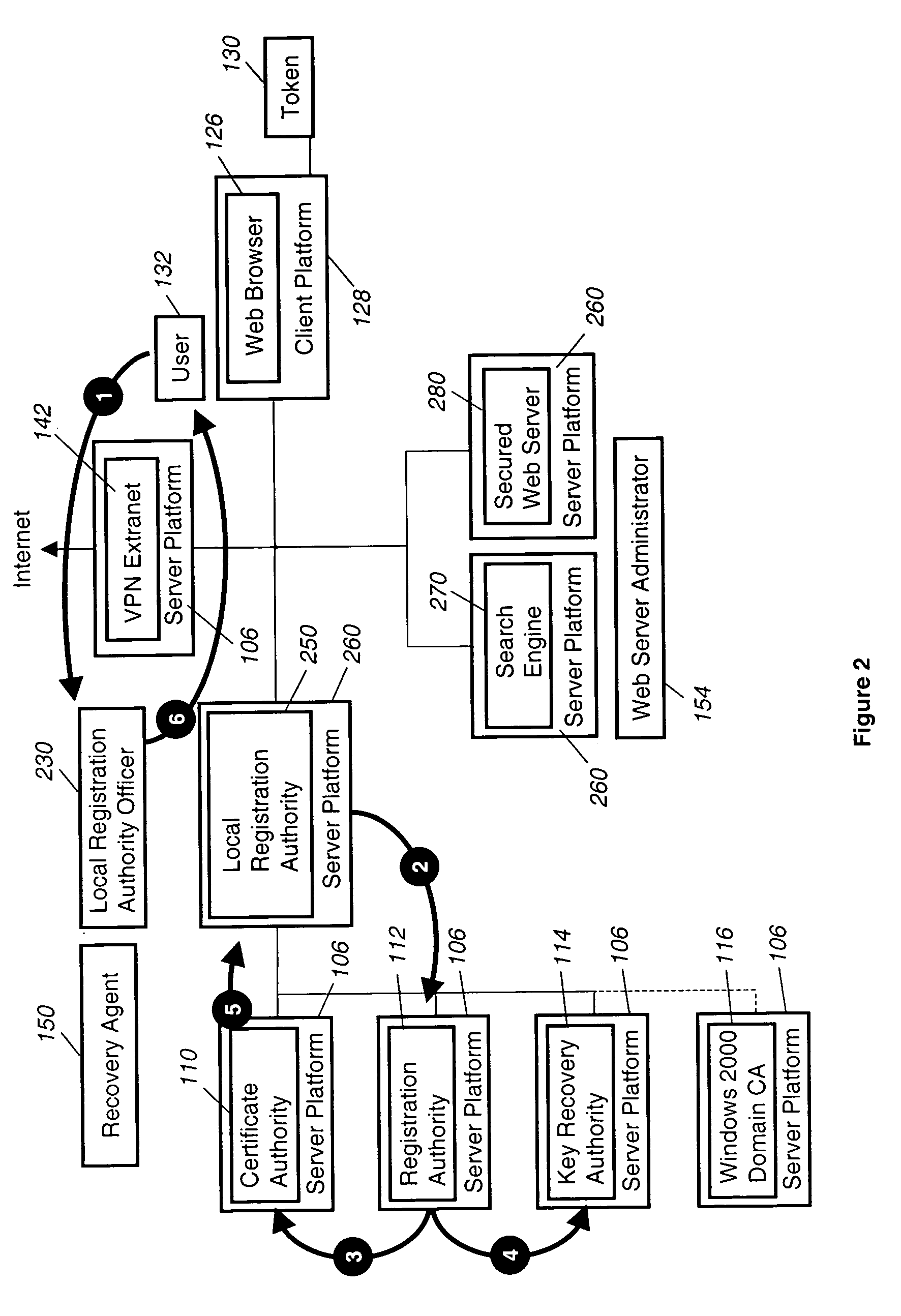
A system and method for more efficiently establishing a chain of trust from a registrant to a registry. A registrant credential is associated with a Shared Registration command and is sent by a registrar to a registry. Upon successful validation, a token is generated and bound to a registrant identifier. The token is included along with the registrant identifier in subsequent discrete Shared Registration commands submitted to the registry on behalf of the registrant. The registrant thus needs to submit its credential only once for changes that require several discrete commands. Also, it is more efficient for the Shared Registration System to validate a token for a set of commands than to validate different registrant credential for each discrete command.
Owner:VERISIGN
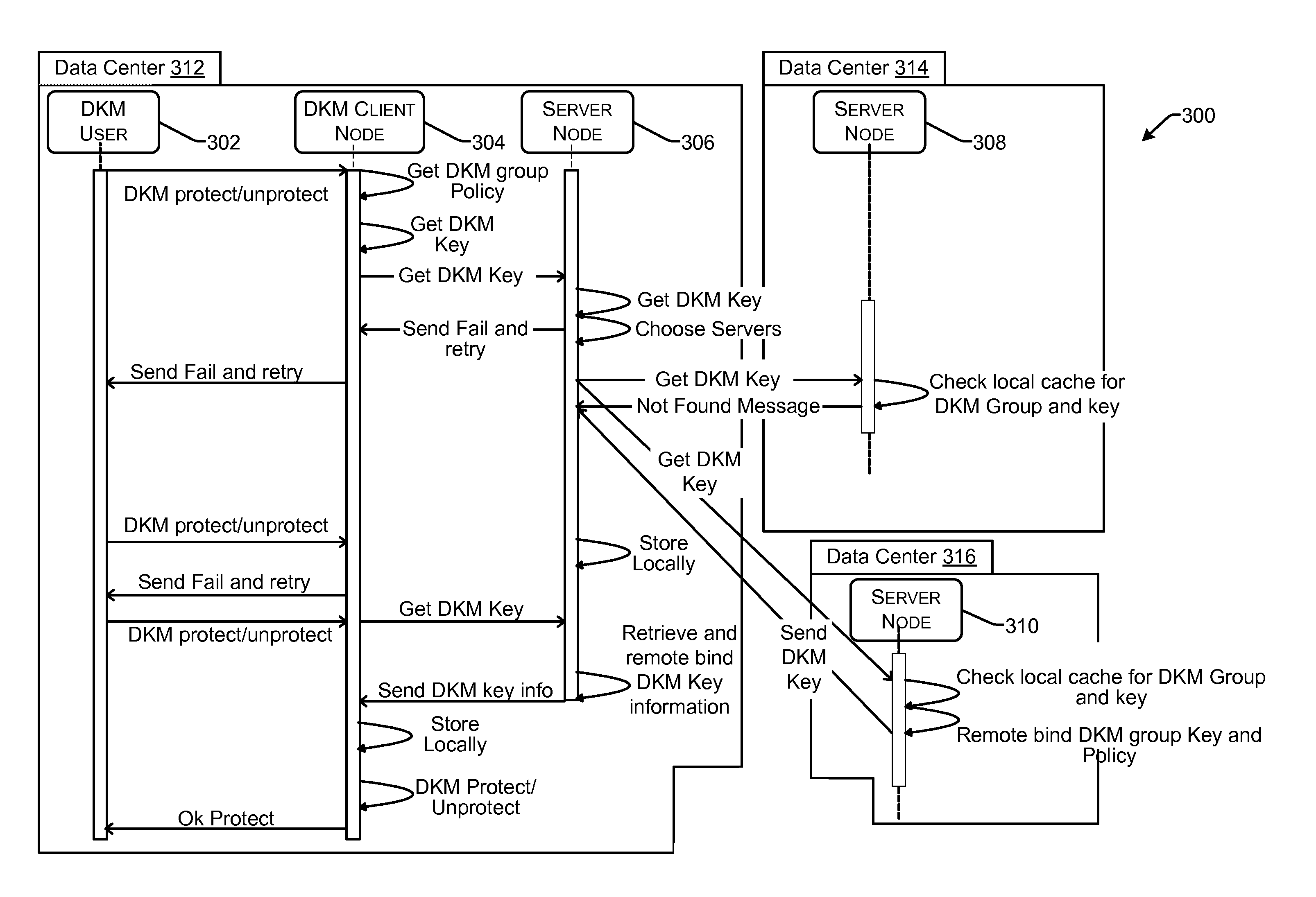
Role-based distributed key management
ActiveUS20130259234A1Key distribution for secure communicationPublic key for secure communicationChain of trustOperating system
Implementations for providing role-based distributed key management (DKM) replication are described. A server node receives a request from a requester node to perform a DKM create or update function. The server node determines the role of the requester node based on a public key of the requester node. The server node determines whether the role of the requester node indicates that the requester node is authorized to request the DKM create or update function. If the requester node's role is authorized to request the DKM create or update function, then the server node performs the requested function. The DKM create or update function may involve a replication function. Public key and trust chains may be derived from physical cryptographic processors, such as TPMs.
Owner:MICROSOFT TECH LICENSING LLC
Digital chain of trust method for electronic commerce
InactiveUS20020065695A1Universally applicableFinancePayment protocolsInternet privacyConfidentiality
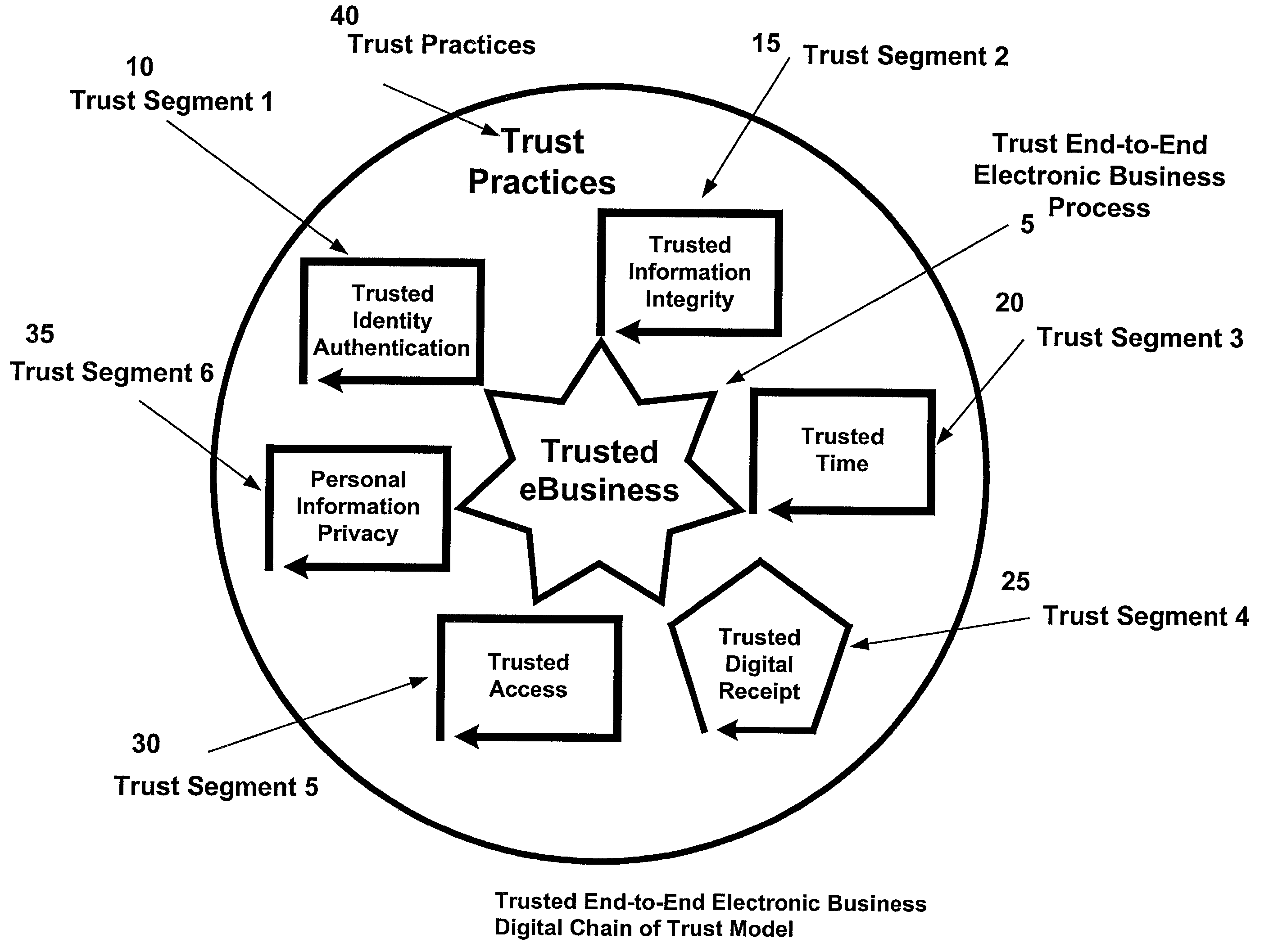
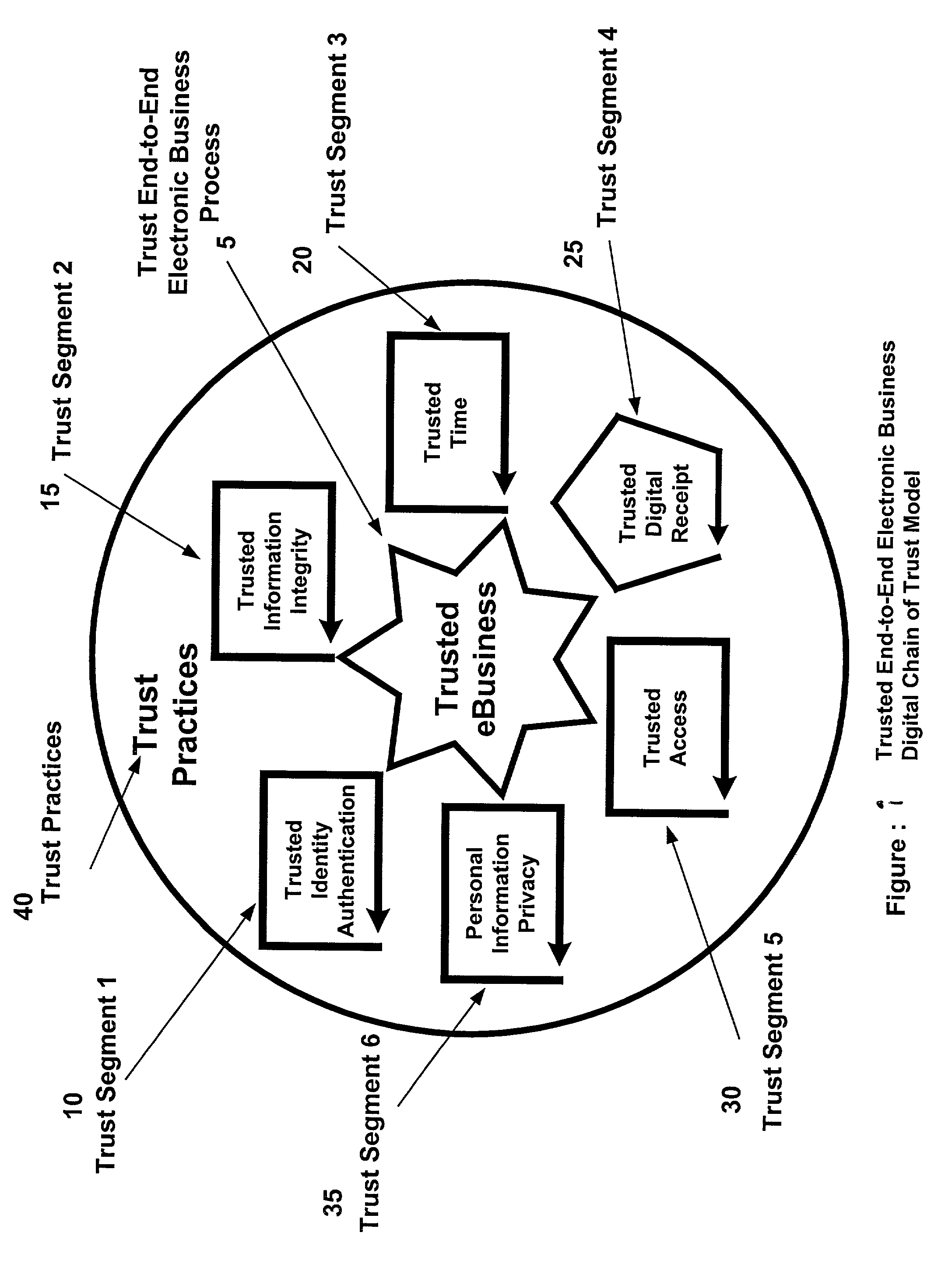
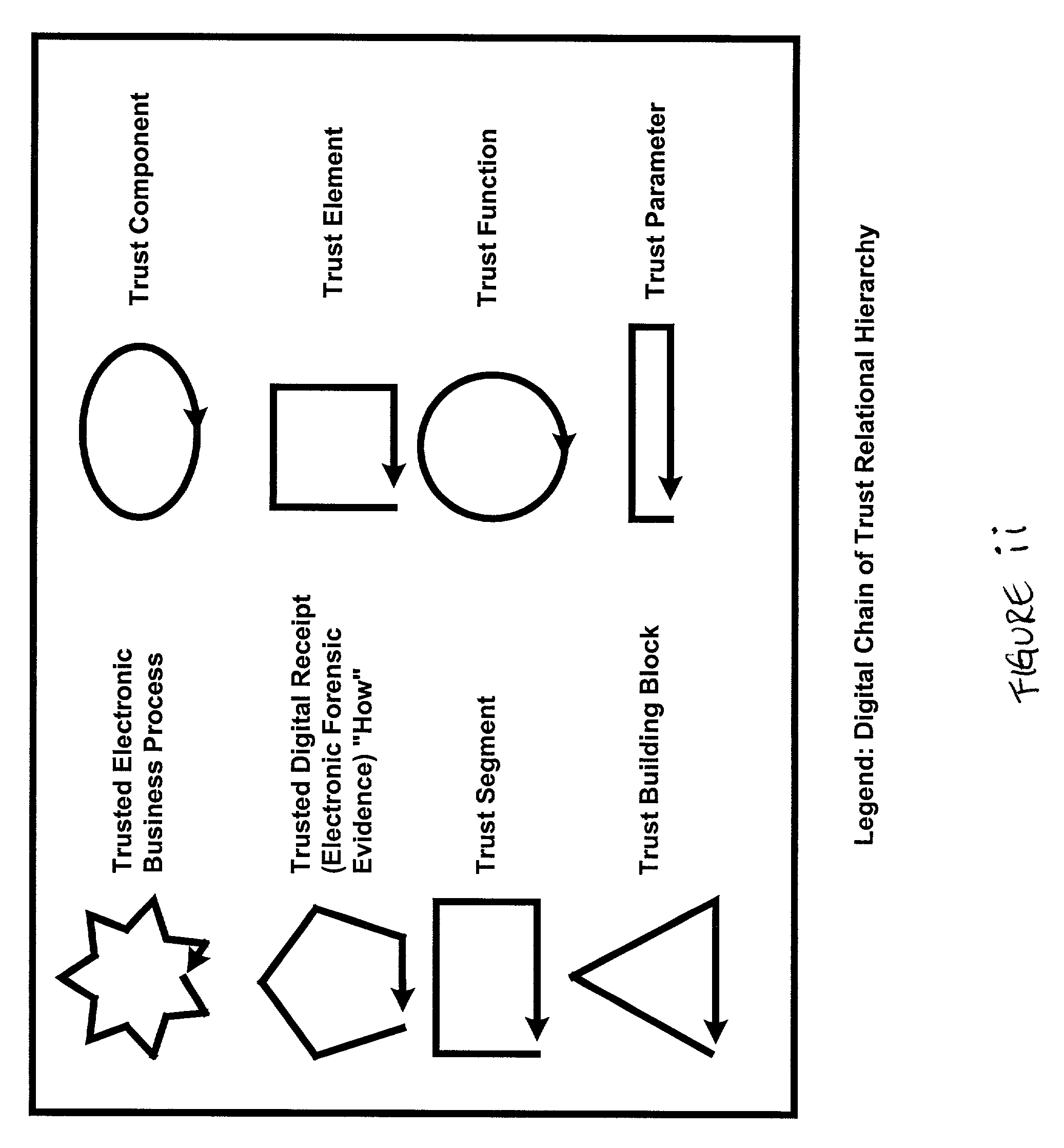
Architecture and method for constructing Digital Chains of Trust for e-commerce comprising integrated, universal modeling, design and evaluation framework for building DCTs for e-Business Processes that provides creation, management, and preservation of legally admissible evidence of electronic events in transactions by employing object-oriented "Trust Building Blocks" having pre-defined functions, inter-connectivity protocols, real-time feedback features, decision support options, and trust standards. It employs an end-to-end design, operation, and audit frame-work: to identify the risk drivers; to establish the necessary trust standards to acceptably mitigate each risk; to ensure the legal enforceability of electronic acts; to generate forensic evidence; and to provide audit metrics for operational compliance. It provides independently verifiable, auditable, legally admissible evidence proving the sequence and nature of electronic events of: identity (who), content (what), time-of-event (when), enforceability (how each event transpired and its compliance to legislative and industry standards), and control of access to assure privacy and confidentiality.
Owner:FRANCOEUR JACQUES R +1
Method and system for implementing a secure chain of trust
InactiveUS20090259854A1Improve data securityImproved safety mechanismEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionComputer hardwareChain of trust
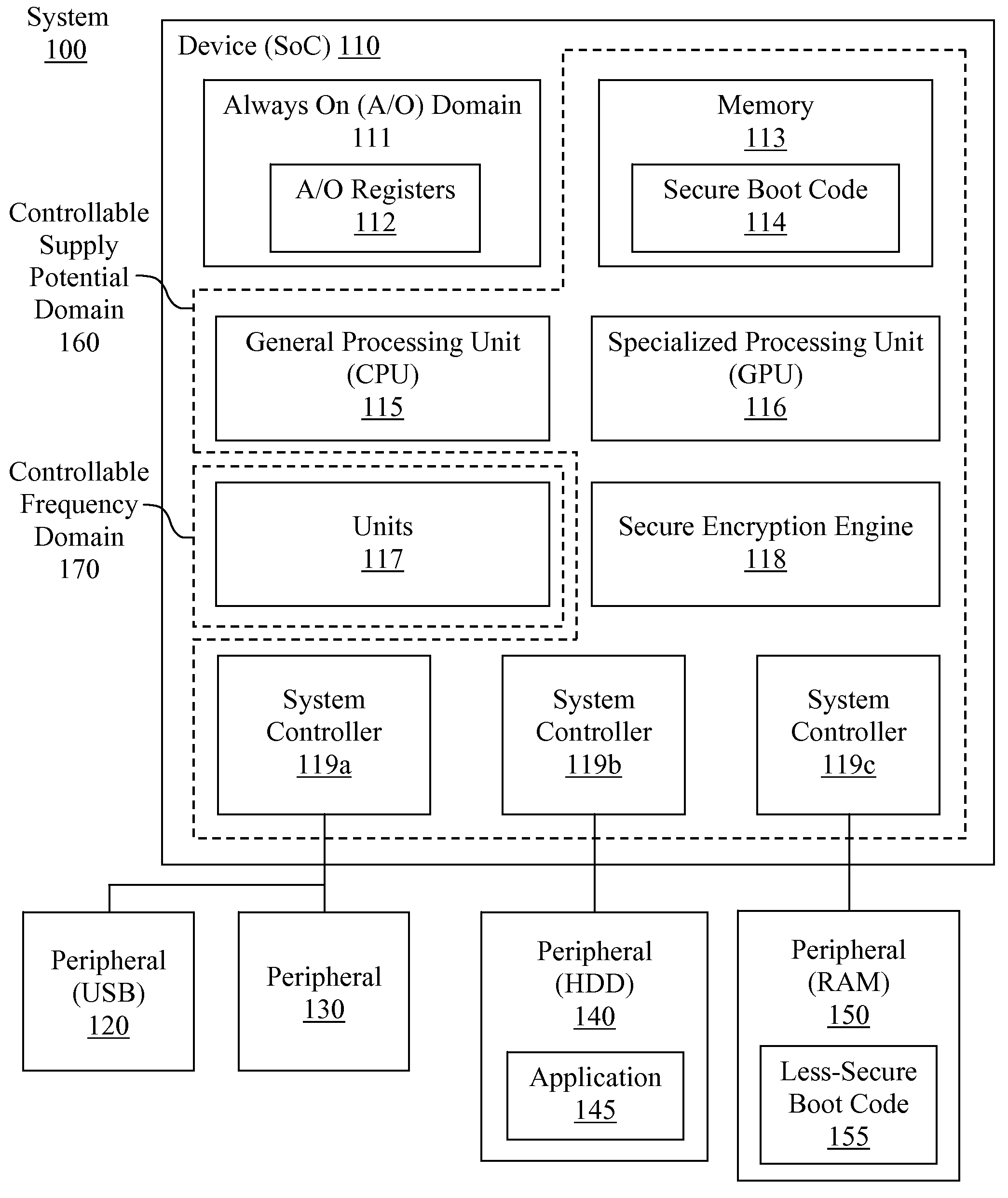
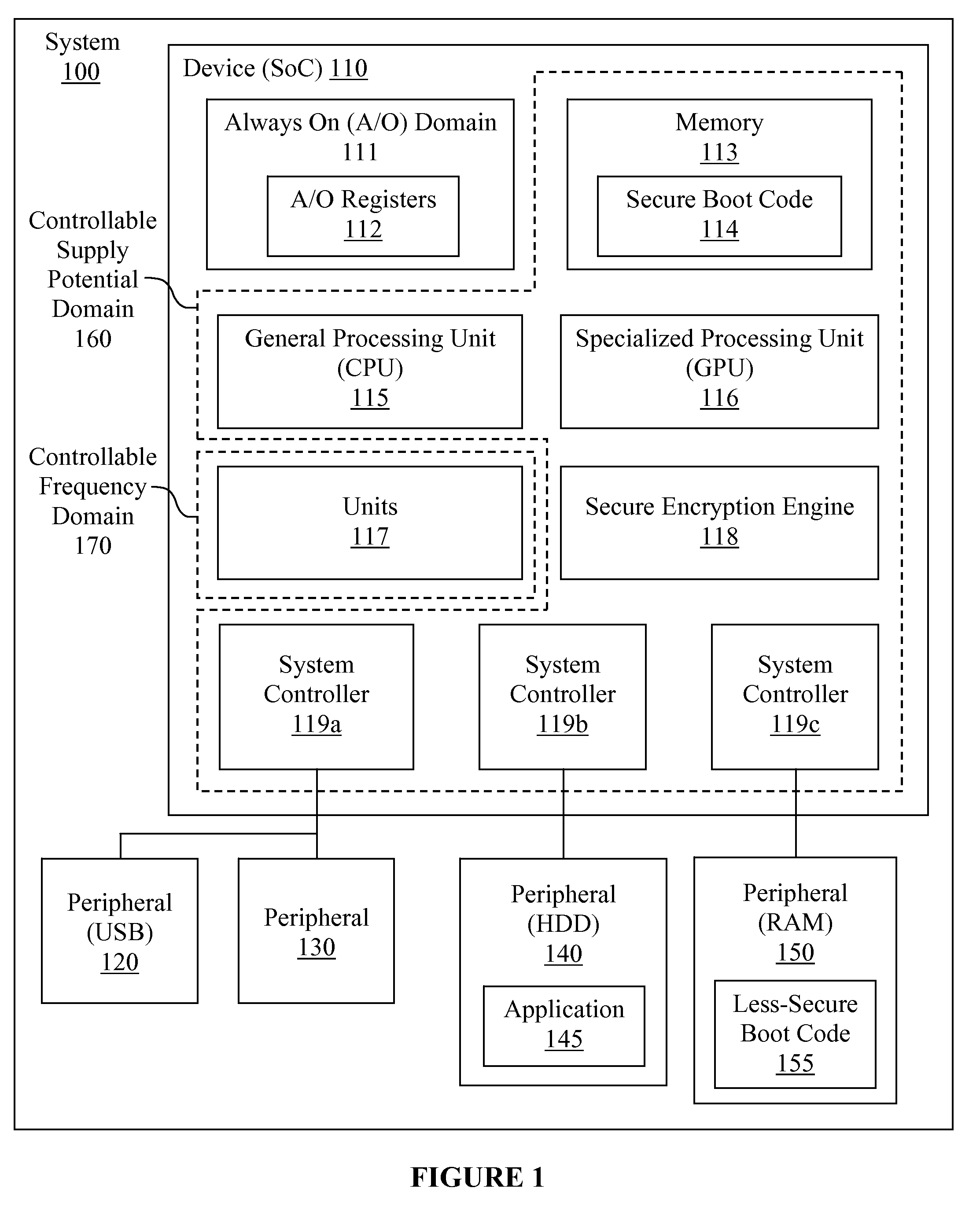
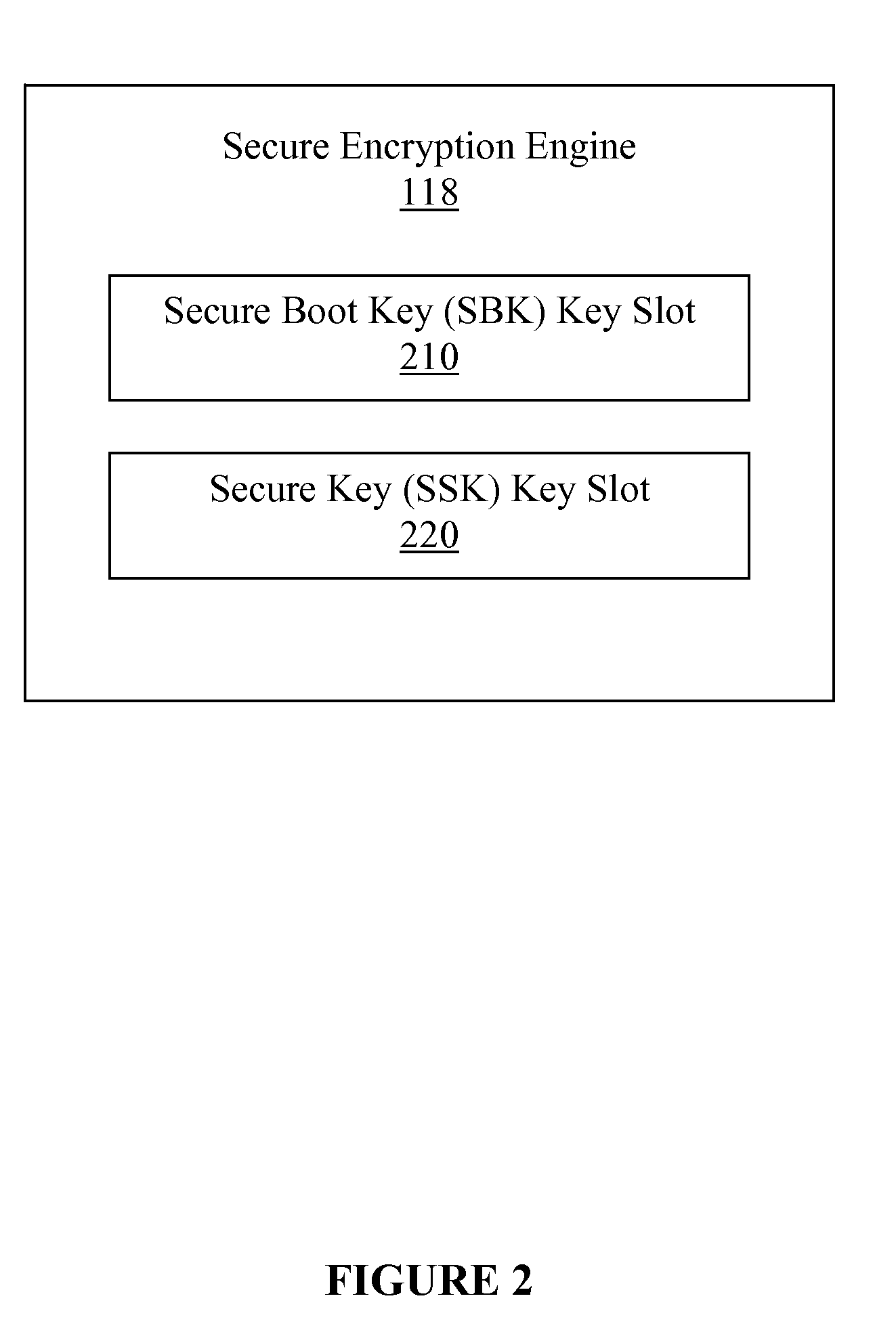
A method, an integrated circuit and a system for implementing a secure chain of trust is disclosed. While executing secure boot code in a secure boot mode, less-secure boot code may be authenticated using a secret key. A secure key may also be calculated or generated during the secure boot mode. After control is turned over to the authenticated less-secure boot code, at least one application may be authenticated using the secure key. Once authenticated in the less-secure boot mode, the application may be executed by the programmable integrated circuit. In this manner, a secure chain of trust may be implemented for the programmable integrated circuit.
Owner:NVIDIA CORP
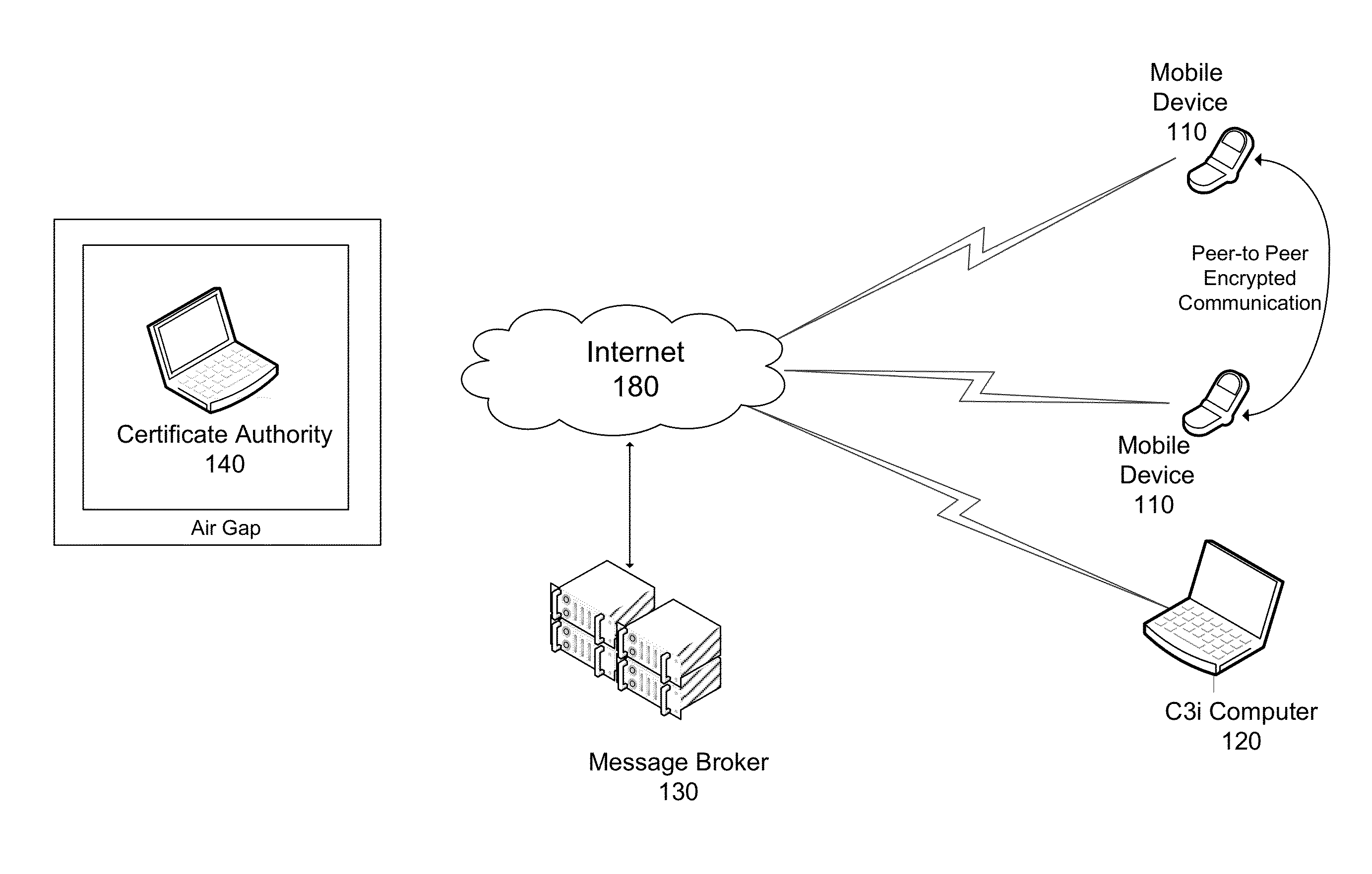
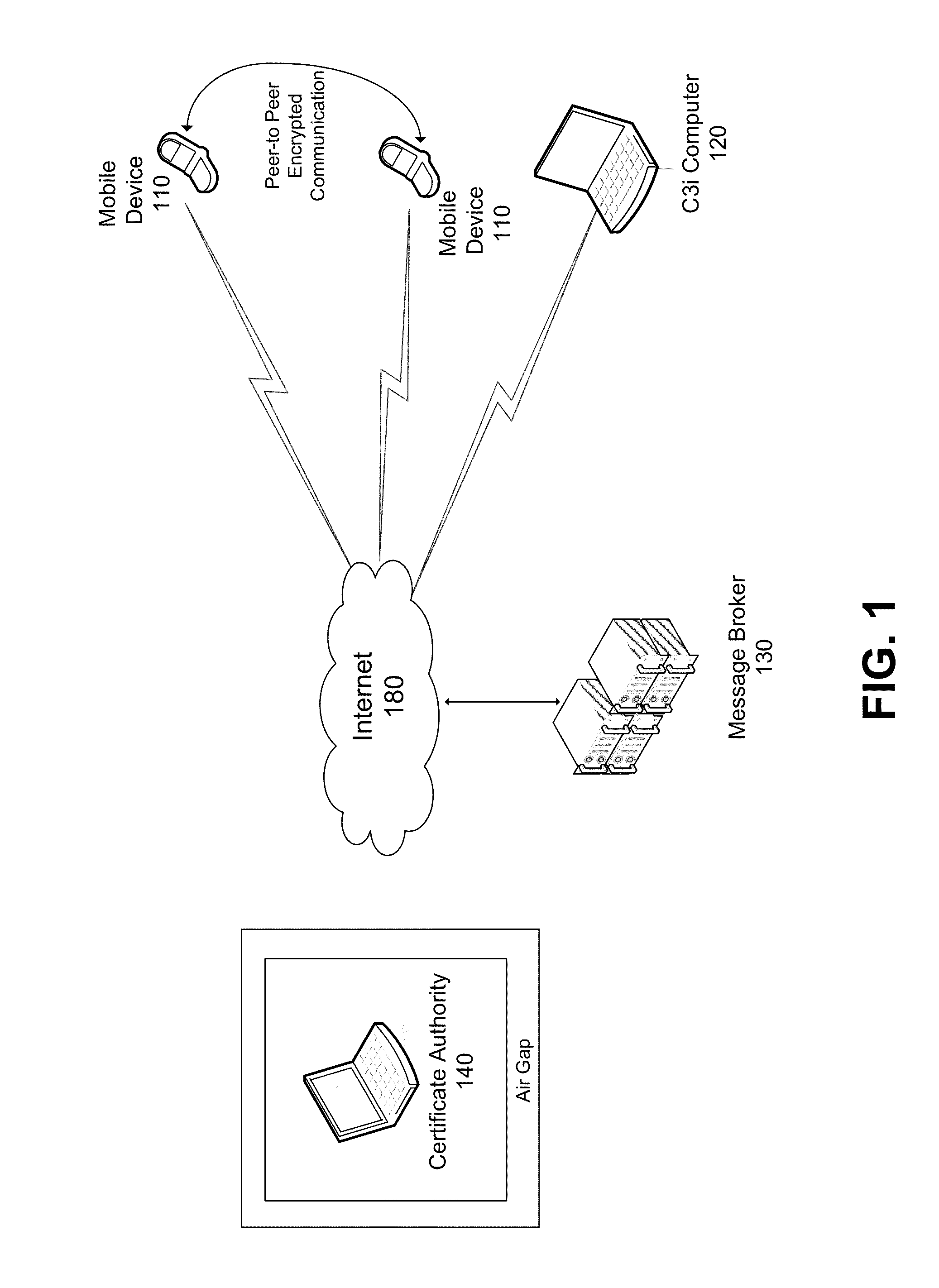
Secure Communication System For Mobile Devices
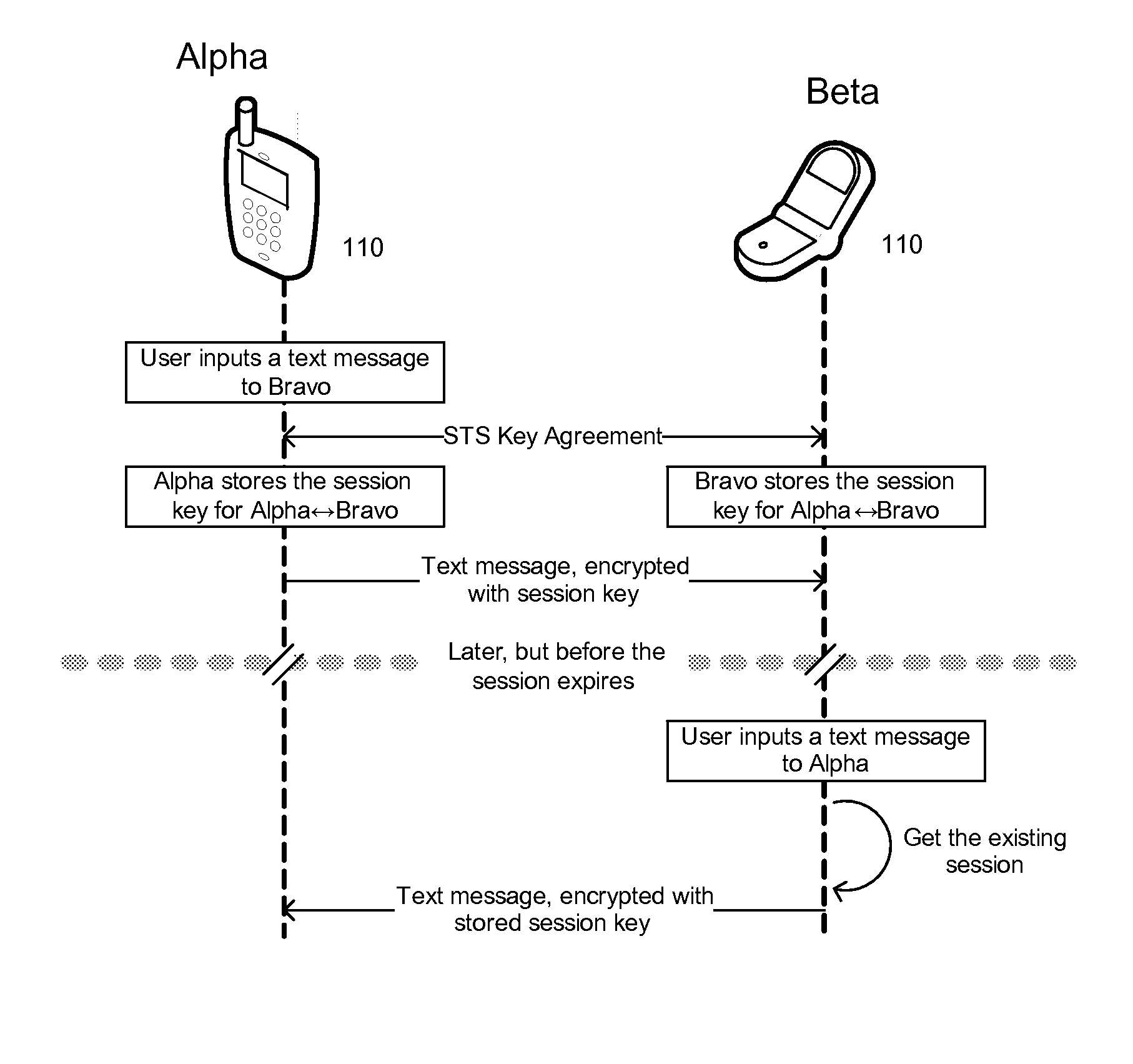
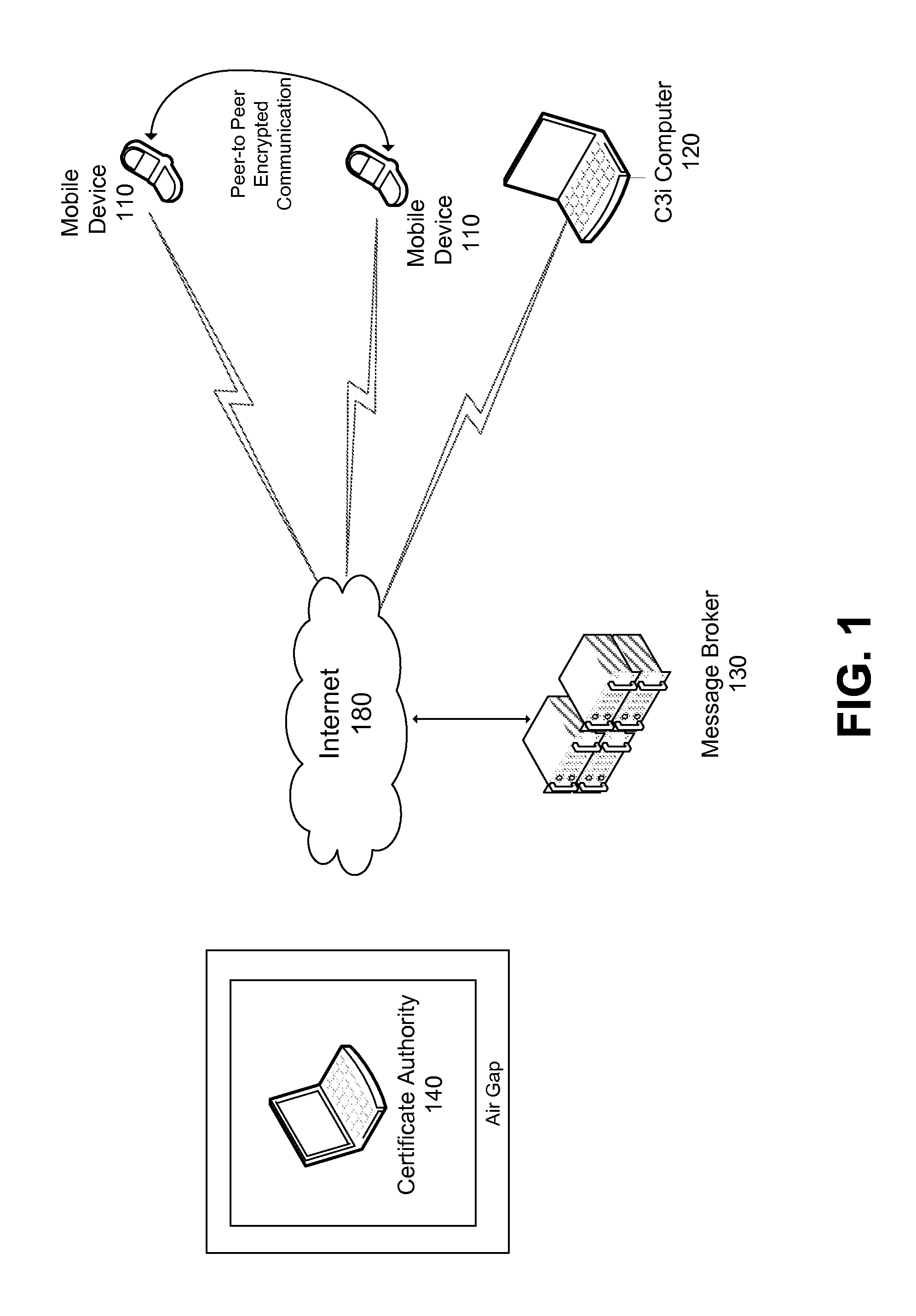
ActiveUS20110131406A1Multiple keys/algorithms usageSecret communicationControl communicationsChain of trust
A comprehensive solution for providing secure mobile communication is provided. The system includes techniques for authentication and control of communication end-points; chain of trust to ensure devices are certified as authentic; contact list management; peer-to-peer encrypted voice, email, and texting communication; and a technique for bypassing an IP PBX to ensure high levels of security. The system is able to support use of commodity mobile communication devices (e.g., smart phones, laptops) over public carrier networks.
Owner:CUMMINGS ENG CONSULTANTS
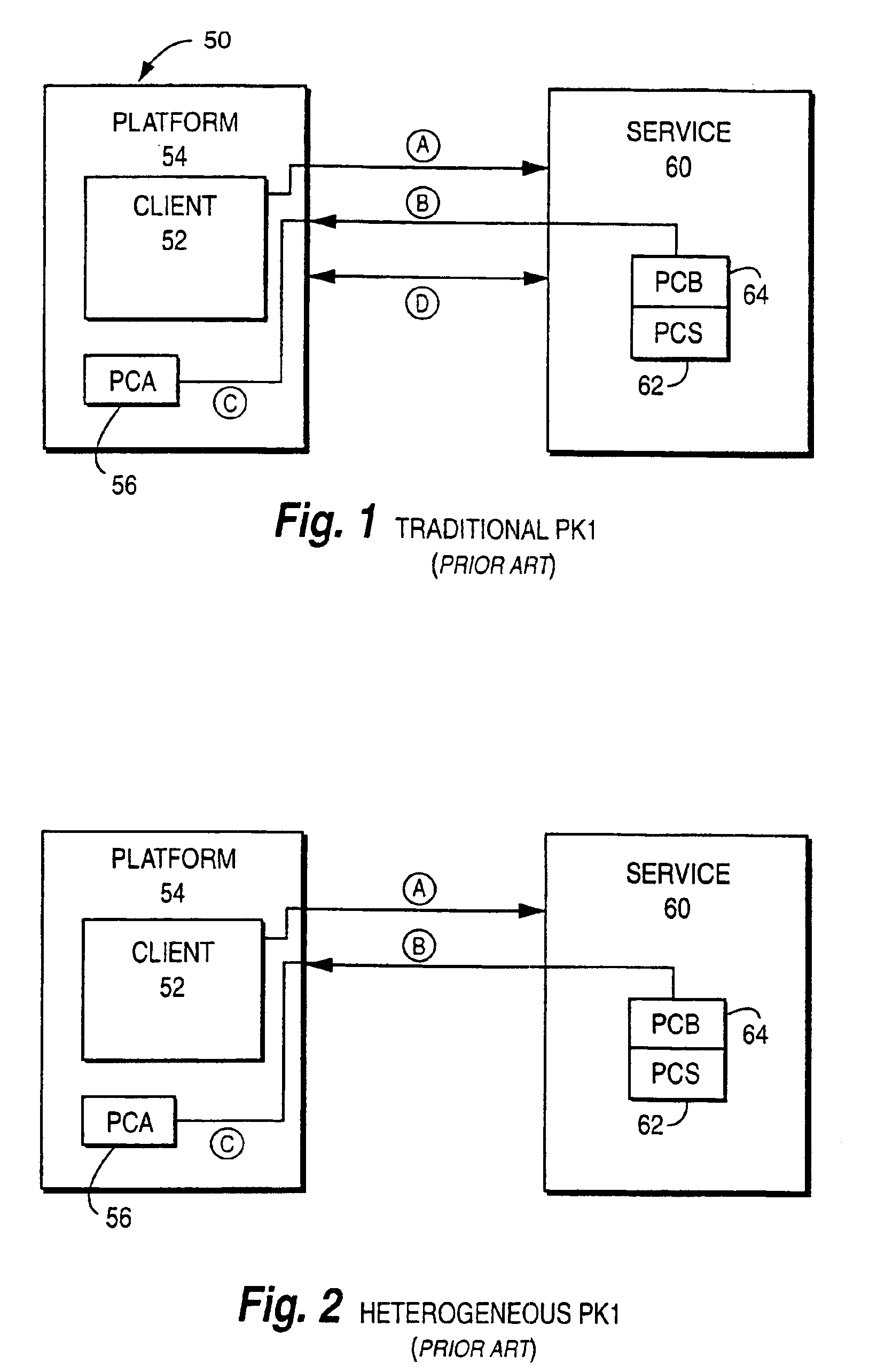
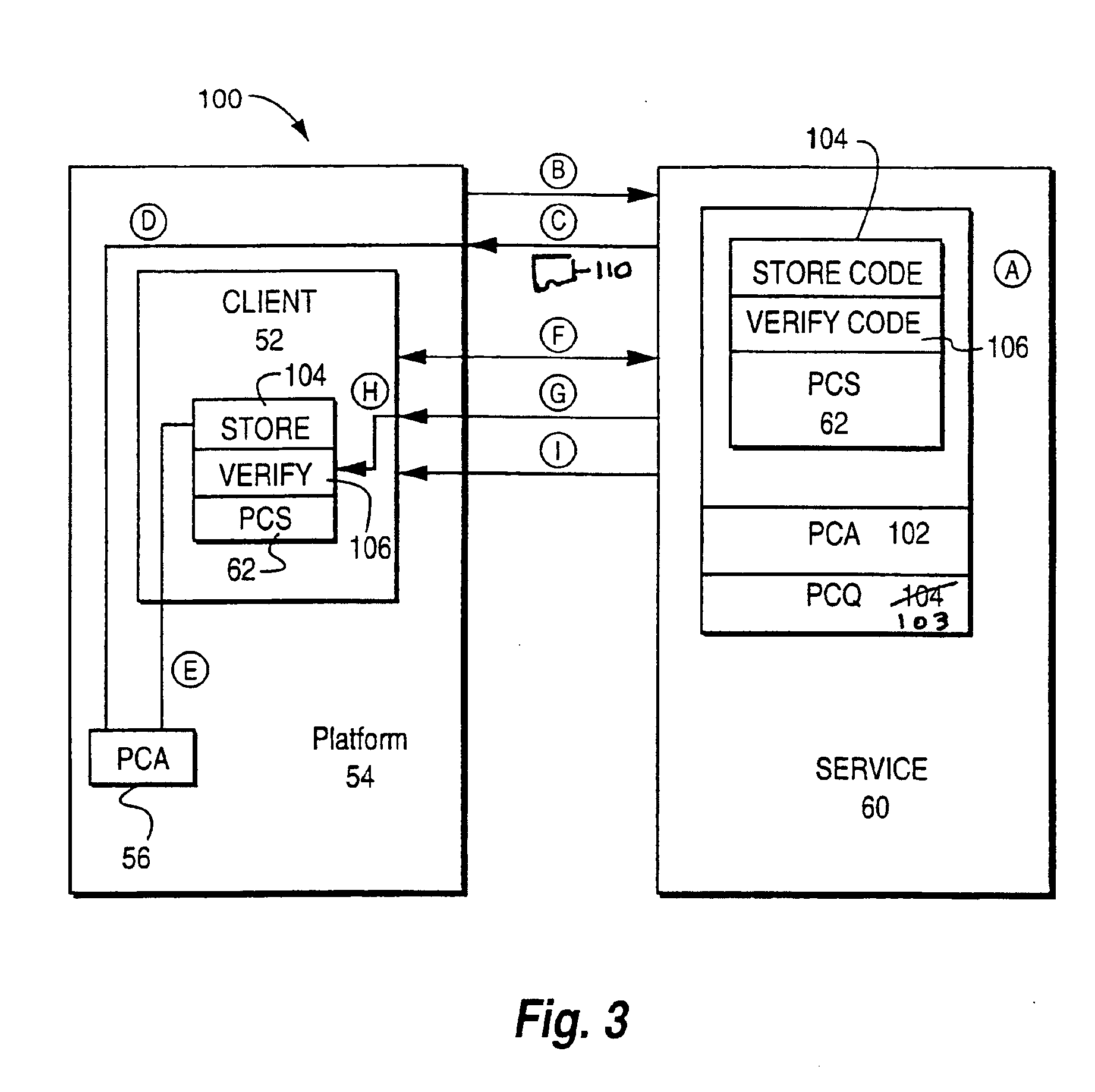
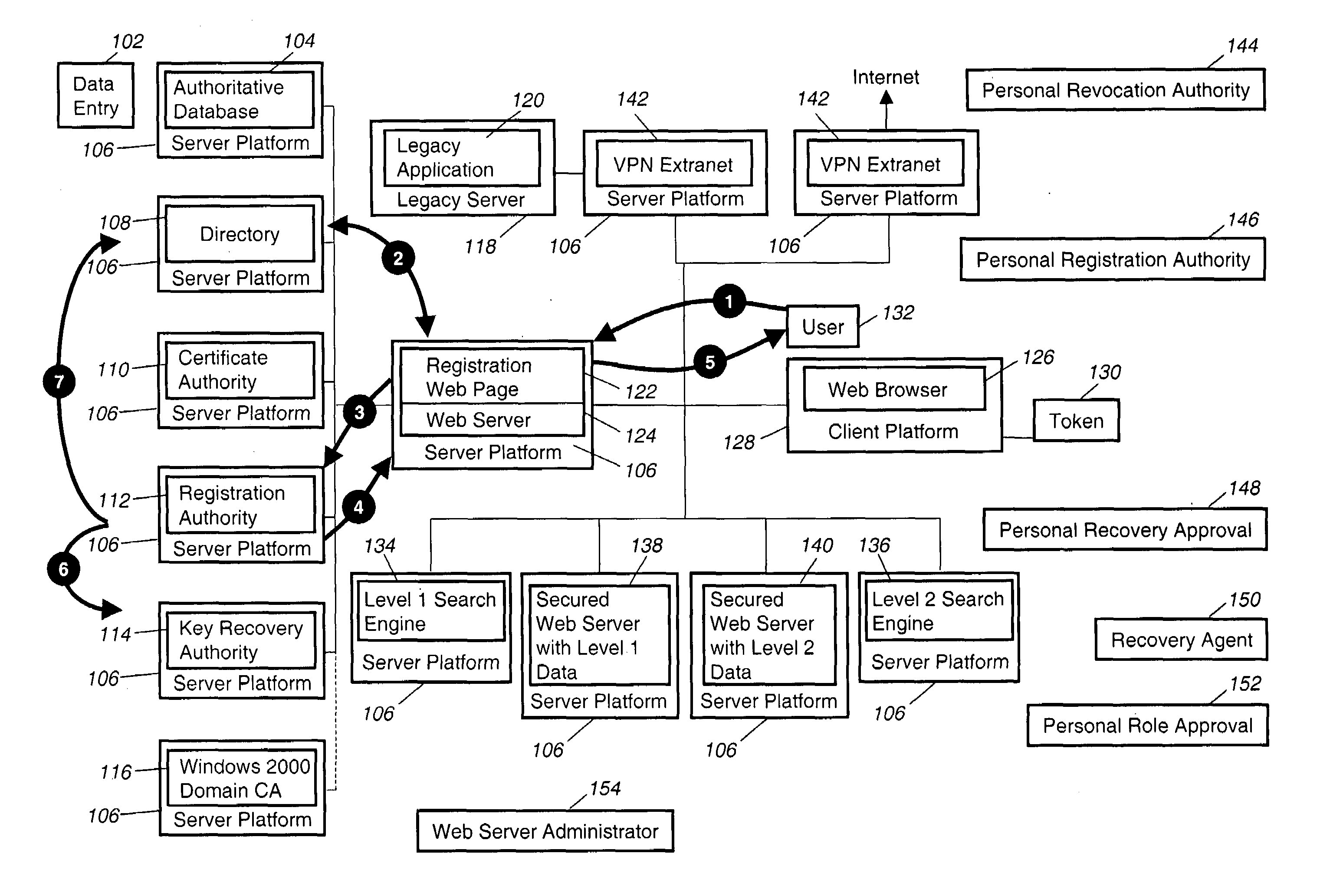
Method and apparatus for distributing, interpreting, and storing heterogeneous certificates in a homogenous public key infrastructure
InactiveUS6895501B1Avoid less flexibilityUser identity/authority verificationWeb browserDigital signature
A connection is established between a server and a web browser having access to a first, trusted public key. The server downloads a digitally signed archive to the browser, the archive including a second public key. The browser verifies the digitally signed archive using the first public key, and stores the second public key in response to the verification. The browser then uses the stored second public key to authenticate the server and establish a secure connection with the server. The second public key and its chain of trust need not be known by the browser beforehand, and the archive may include program fragments that store the key in an area where the browser (or an applet running under the browser) can access and use it. The archive may also include a program fragment that performs certificate validation for the client—enabling the client to handle certificate types it does not know about. Advantages include allowing the archive to be transmitted over any insecure connection since it is integrity protected and authenticated; and allowing the client to make a direct connection to the server without having to access certificate stores on the platform.
Owner:ATTACHMATE
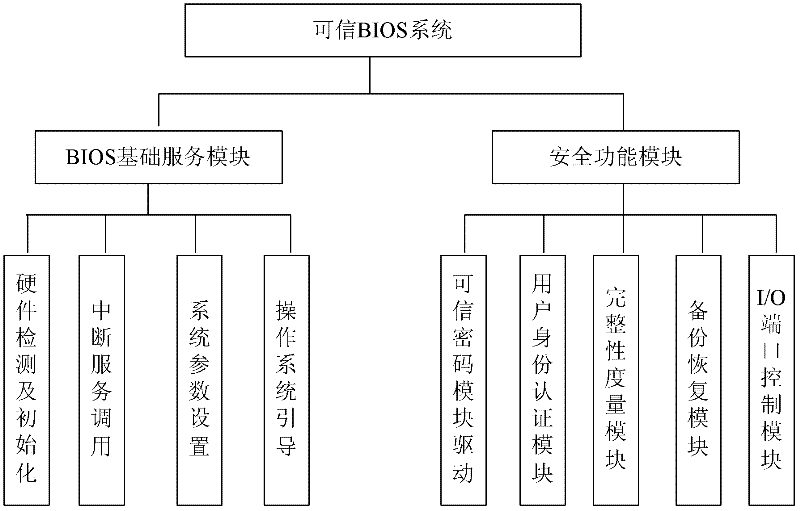
Dynamic trusted measurement method and safe embedded system
InactiveCN102436566AEnsure safetyEffective defenseInternal/peripheral component protectionAttackTrusted Platform Module
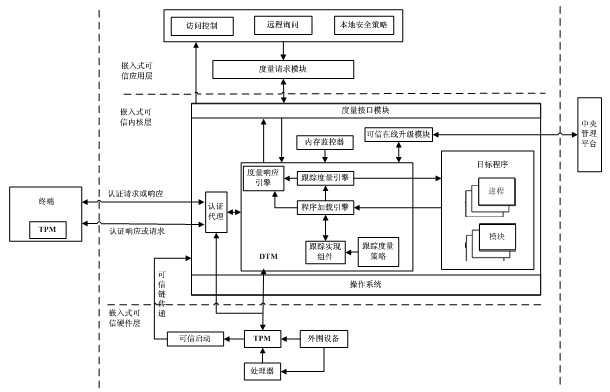
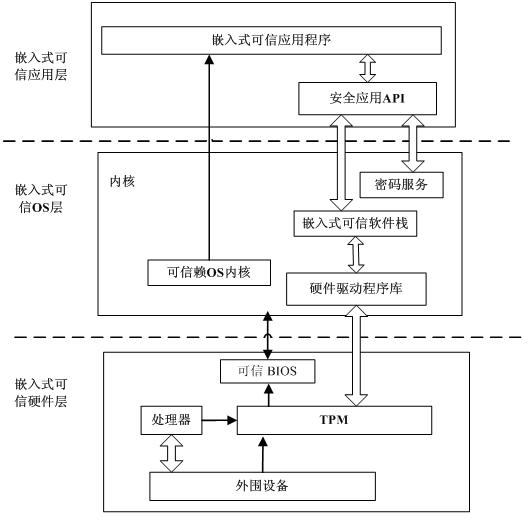
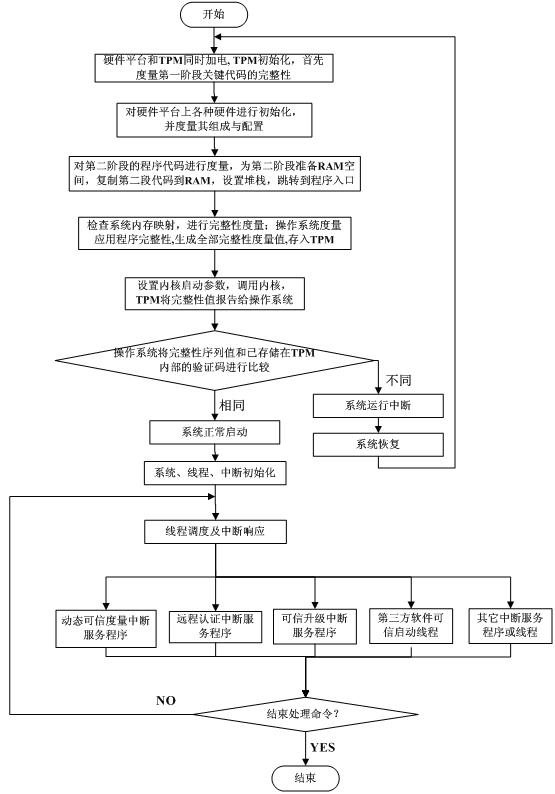
The invention discloses a dynamic trusted measurement method and a safe embedded system. The method comprises the following steps that: S1. a hardware layer redesigns a trusted BIOS (Basic Input Output System) by a TPM (Trusted Platform Module) chip and traditional hardware, a trust chain is transferred to an application program from the TPM security chip, trusted BISO, a trusted OS (Operating System) kernel and an embedded software stack to realize the trusted starting of a dynamic trusted measurement module (DTM); S2. an application layer measurement request module generates measurement request information according to a suspicious event from safety equipment and a local security strategy requirement, the measurement request information is formatted, and the measurement request is sent to the DTM of a kernel layer to activate the DTM; and S3. the DTM carries out trusted measurement to a system progress or module and responds. According to the dynamic trusted measurement method, the complex real-time attack can be effectively detected and defended, the attack on an internal physical layer can be actively detected and defended, and a safe embedded system platform can be realized.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
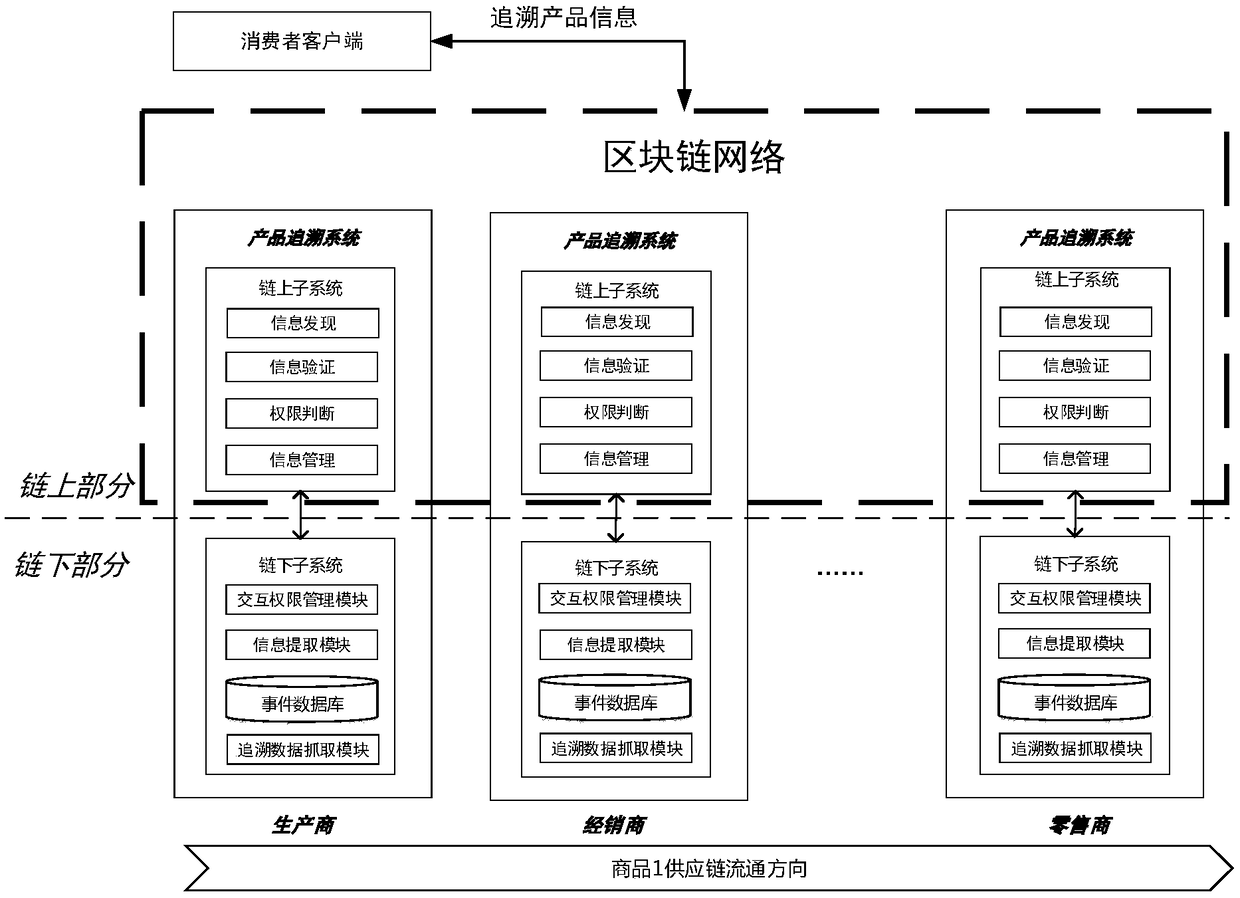
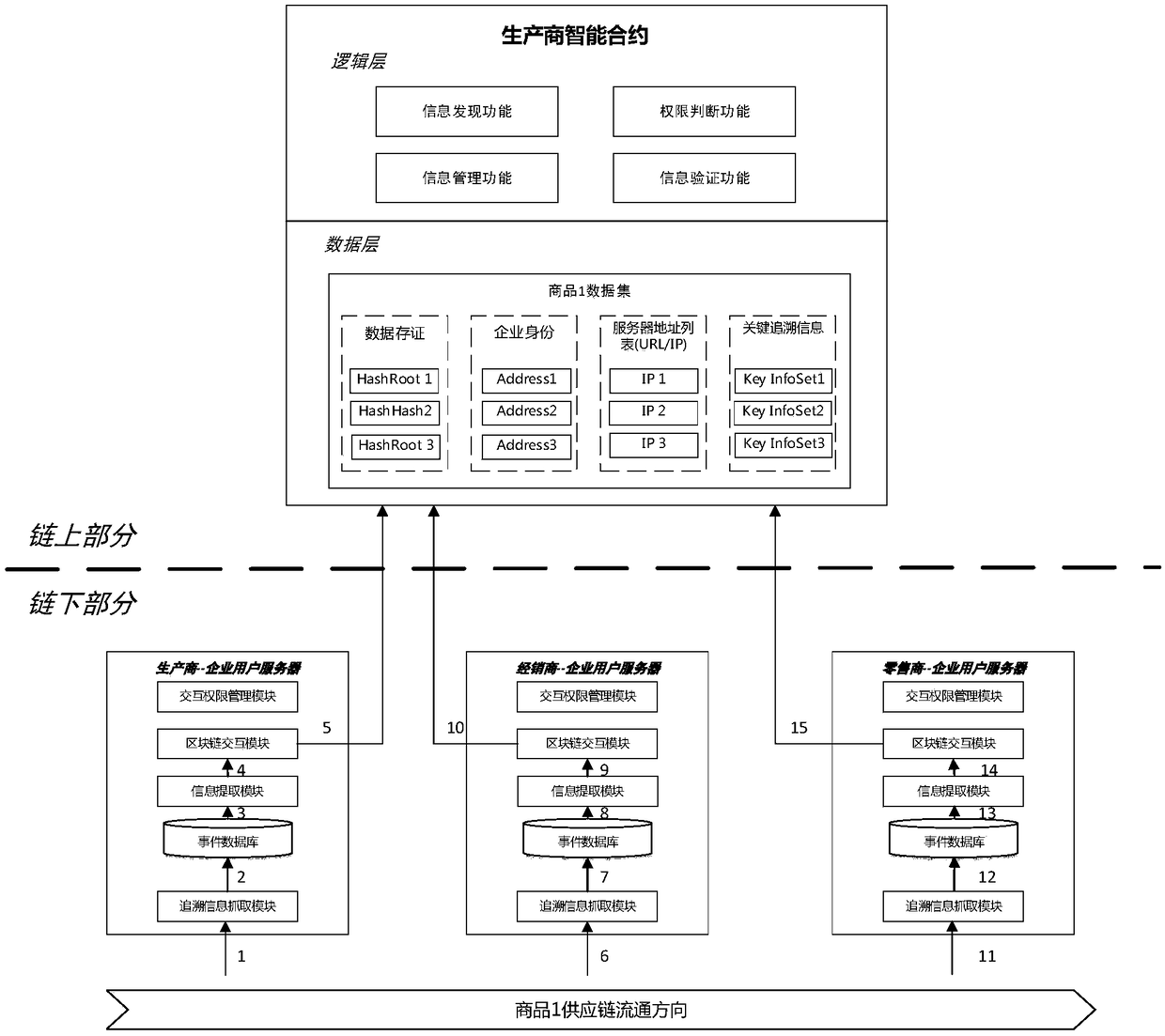
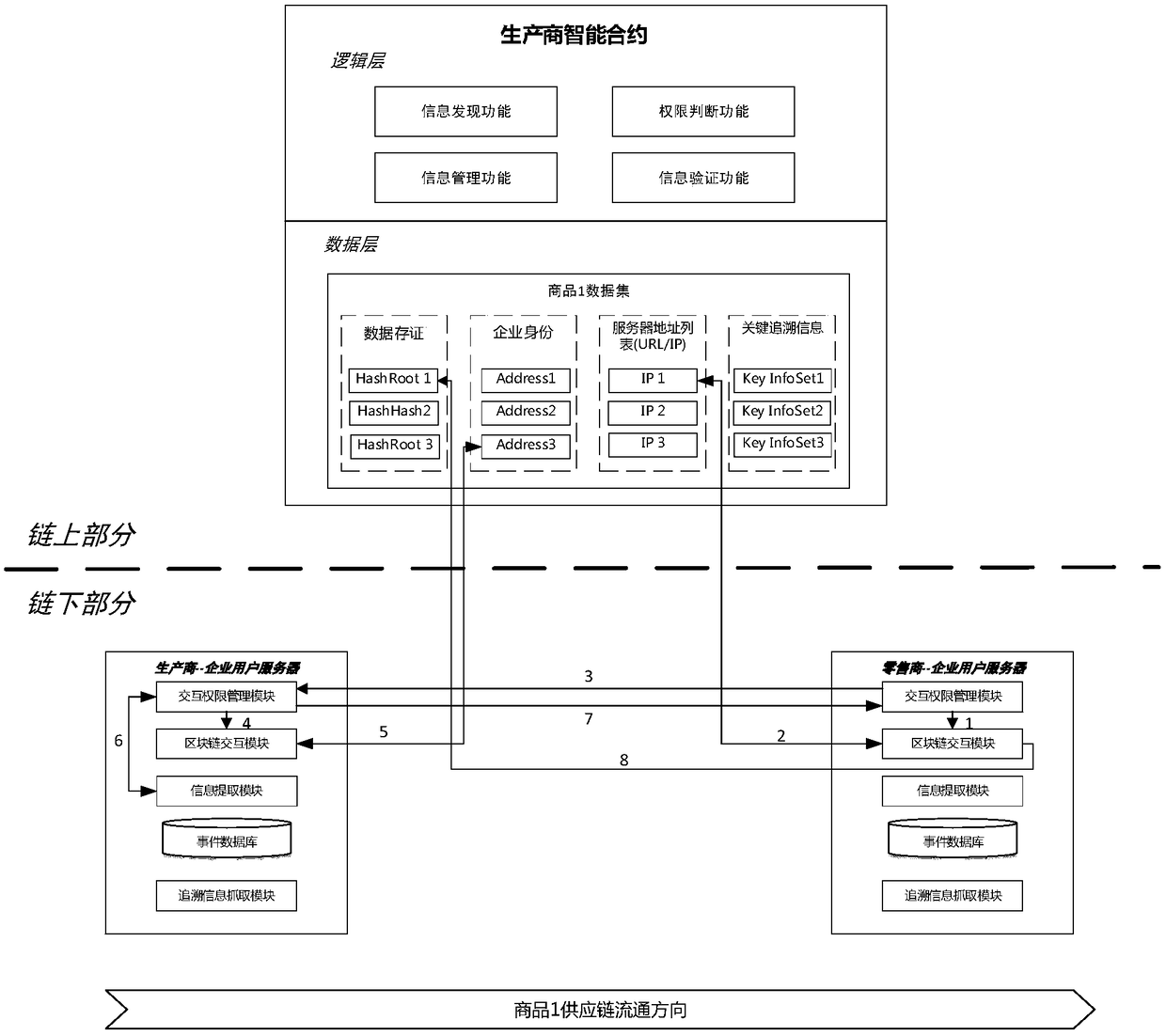
A product traceability information management system and method based on a block chain
ActiveCN109034833AParticipate in operationalParticipate in maintenanceTransmissionCommerceChain of trustProduct traceability
The invention belongs to the technical field of Internet of things, in particular to a product traceability information management system and method. The system adopts an up-chain and down-chain coordination mechanism to manage supply chain information: the manufacturer of a product supply chain collects, stores and manages the product information or the event information produced in the process of supply chain through the sub-system under the chain, and uploads the key traceability information with anti-tamper requirements, such as information storage certificate, information location, identity authentication evidence, etc. to the sub-system on the chain based on the block chain for storage and management; each link in the same supply chain is found through the functional modules of the subsystems on the chain to verify and share the data of the subsystems under each link in the supply chain to ensure the safety of the whole process. The invention solves the unauthorized tampering problem and the trust chain transmission problem faced by the traditional tracing system, improves the credibility of the product tracing system, and ensures the flexibility and scalability of the system.
Owner:FUDAN UNIV
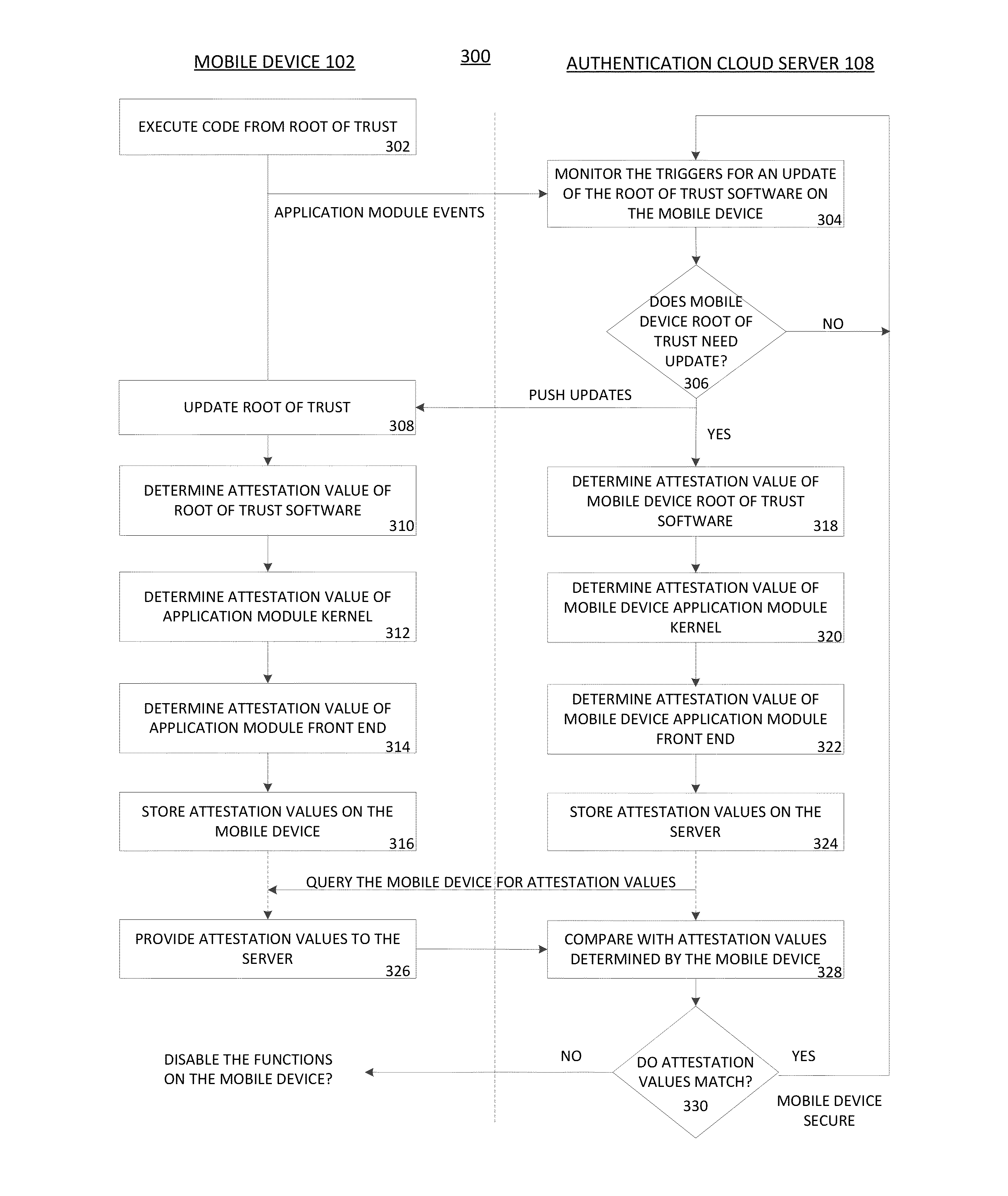
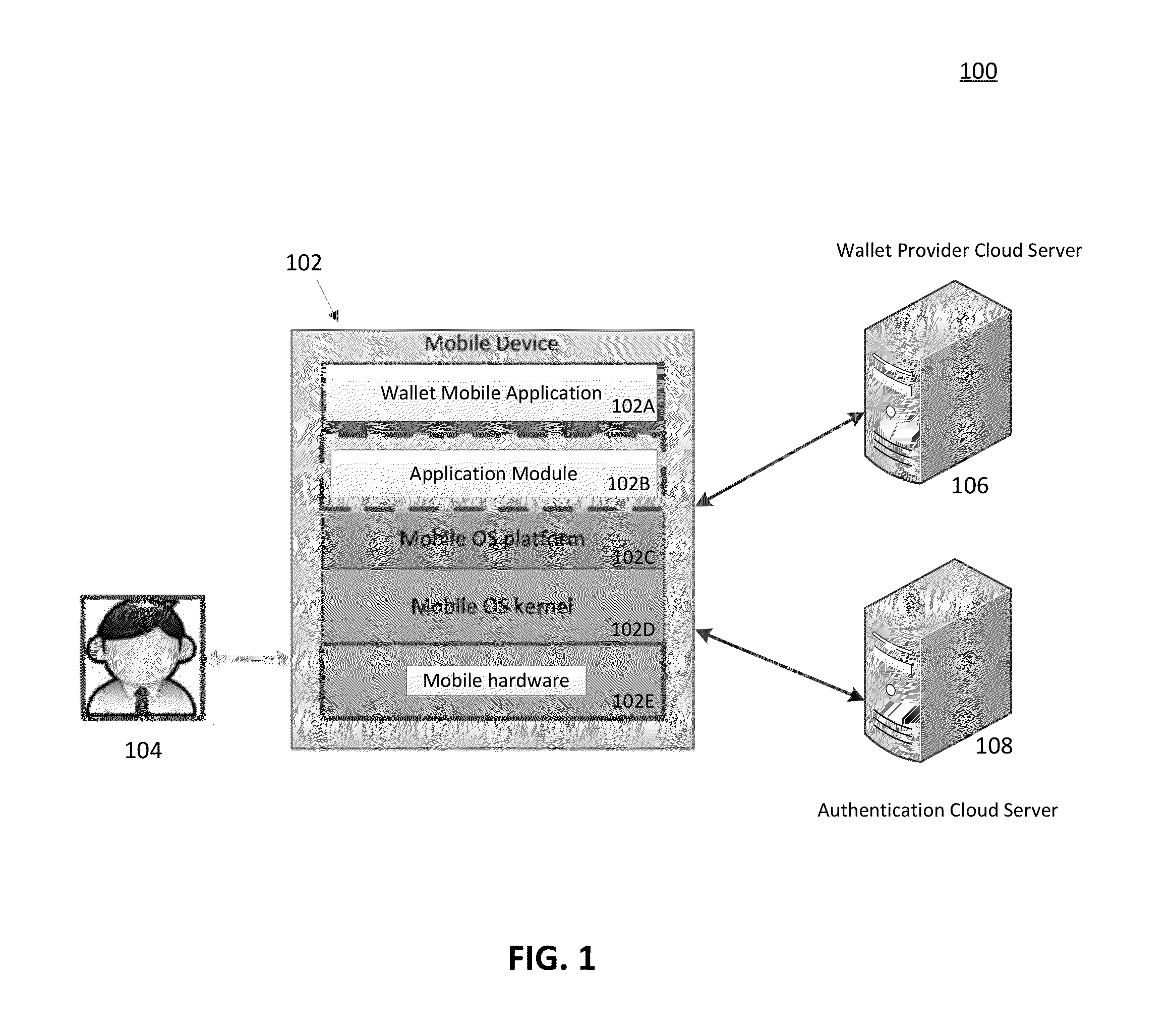
Secure execution and update of application module code
ActiveUS20150007262A1Frequent updateRandom number generatorsDigital data protectionConfidentialityLoad time
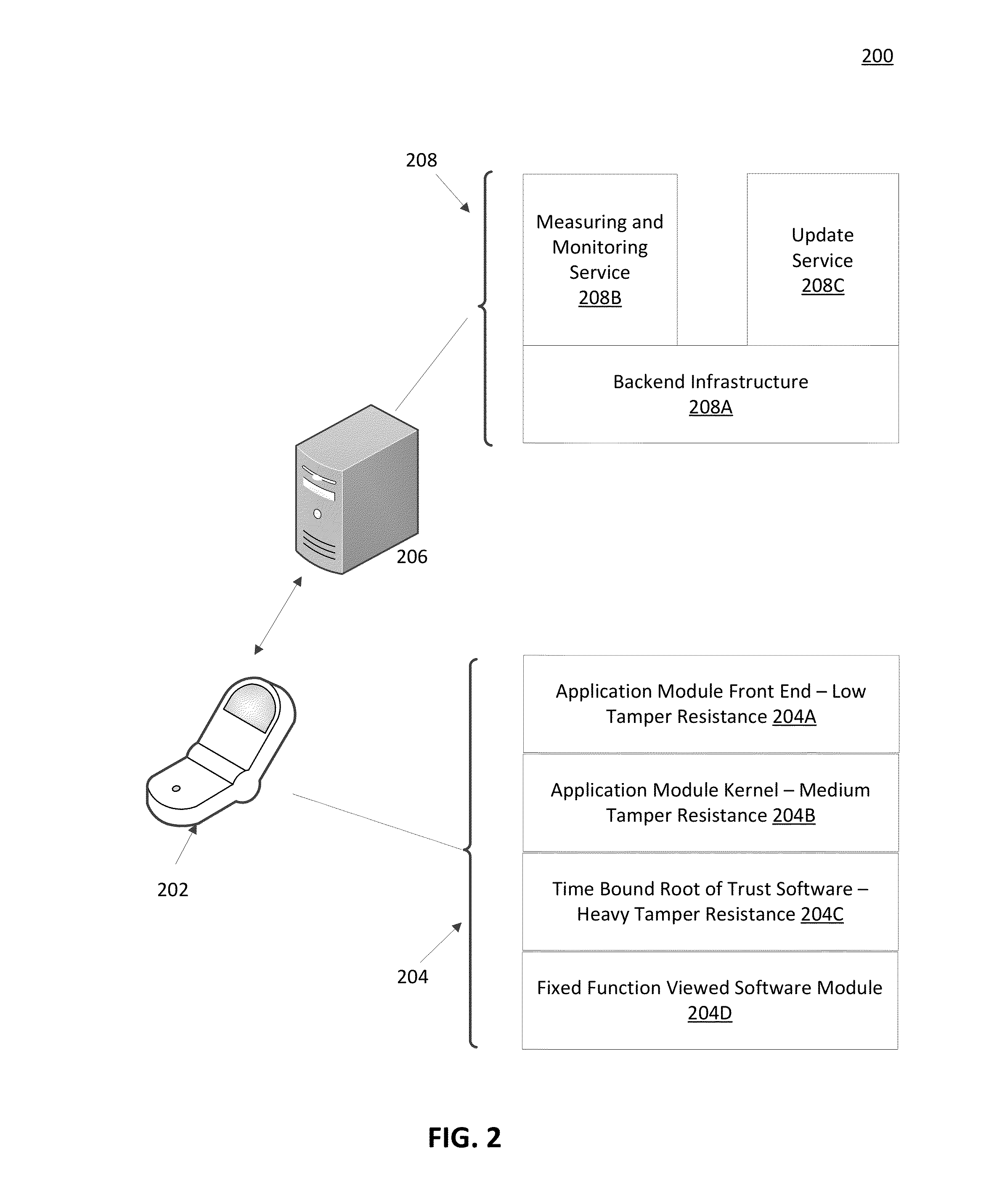
A dynamic root of trust can be injected in an application module on a client device using a backend server and can be continuously monitored to ensure authenticity, integrity and confidentiality at load time, run time and update time of the application module. The dynamic root of trust can be updated directly from the backend server and can be used to establish a time bound trust chain for the other software modules loaded and executed as part of the application module.
Owner:VISA INT SERVICE ASSOC
Embed type platform guiding of credible mechanism
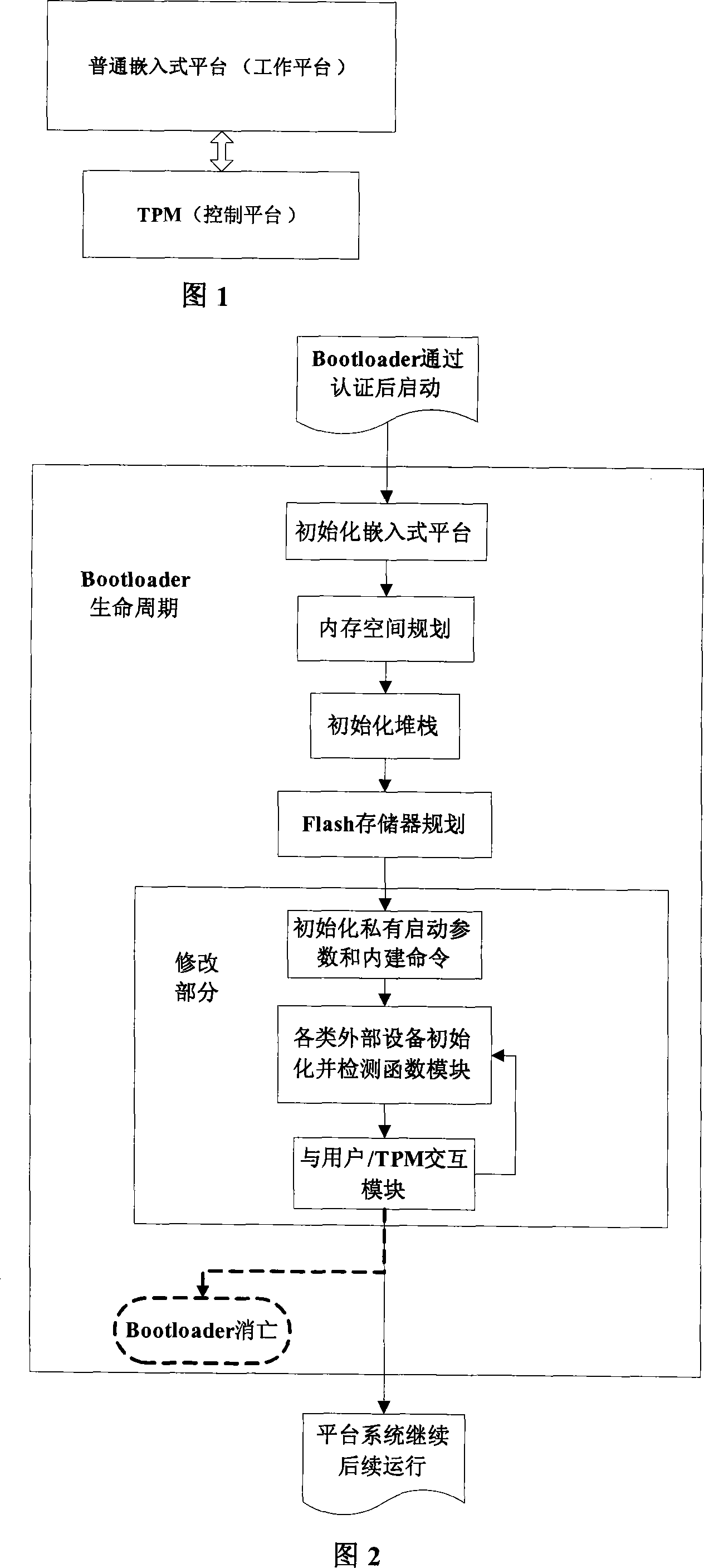
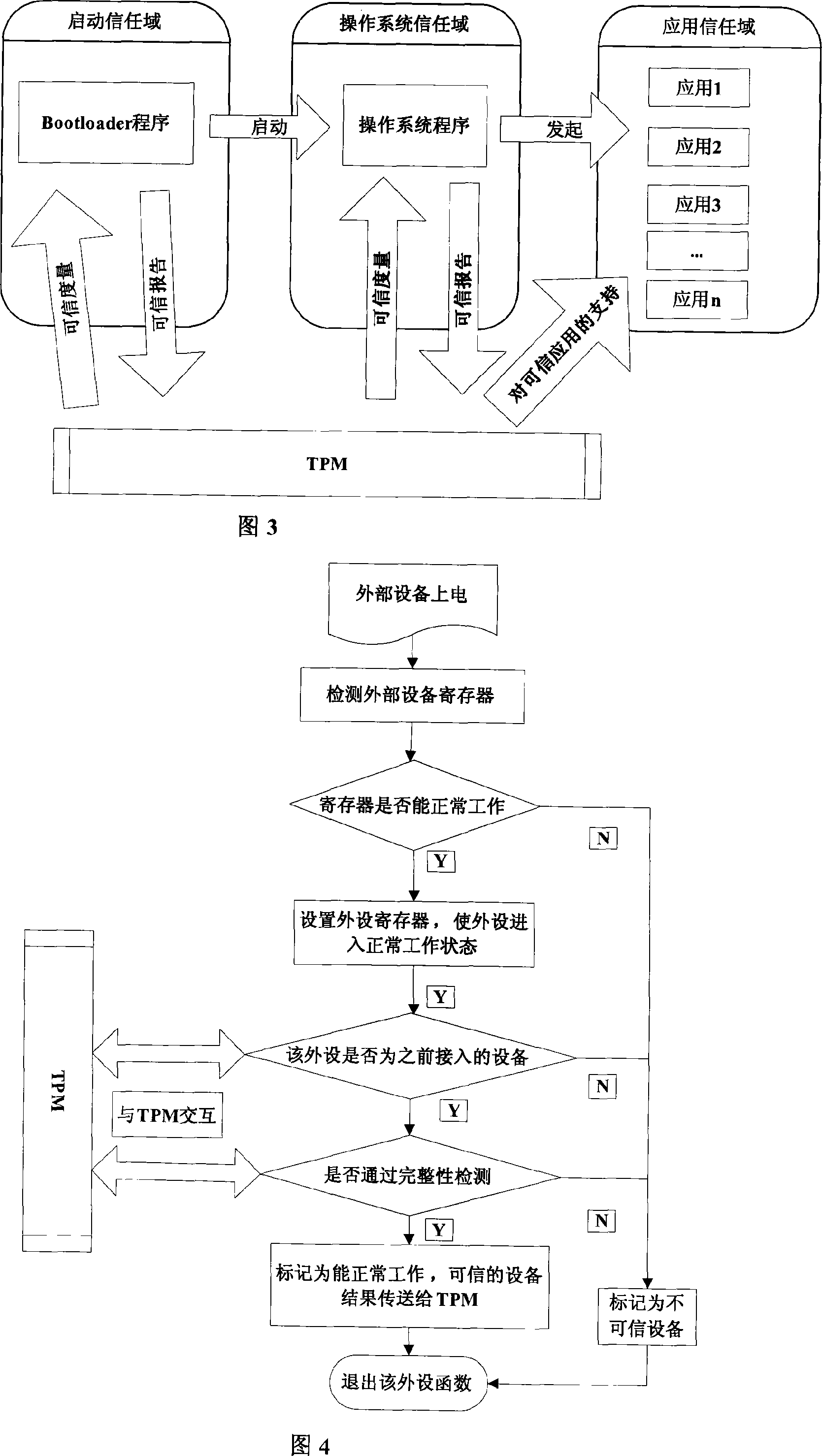
InactiveCN101122936AImprove integrityAchieving Trusted MeasurementsDigital data protectionProgram loading/initiatingOperational systemChain structure
The invention discloses an embedded platform guide on a creditable mechanism, i. e.: placing the embedded platform and a TPM together, and using the TPM to support safety and creditability of the embedded platform; In accordance with the creditability completeness measuring roots and prior to running of the CPU of the embedded platform, the TPM carries out completeness verification for the Bootloader and the operation system which are stored in the embedded platform to ensure that the software executable codes in the platform startup chain is not modified, and then permits the CPU of the embedded platform to read the Bootloader for startup; and the TPM controls the startup process and measures completeness and reliability of the appointed external devices as well as initializes the external devices. The invention is used for completeness measuring of the Bootloader executed at the platform in accordance with the creditability chain structure, ensuring good completeness of the Bootloader, and realizing a reporting mechanism in a creditable environment with a TPM monitoring.
Owner:WUHAN UNIV
Chain of trust processing
InactiveUS7275155B1User identity/authority verificationPublic key infrastructure trust modelsChain of trustEncryption
A technique for automatically obtaining a second certificate for a user using a first certificate includes accessing a server platform using a user's server and the first certificate of the user to create a connection that authenticates both the user's server identity via a server certificate of the user server and the user's identity via the user's first certificate. A secure data channel is then created between the server platform and the user platform. A request for the second certificate is forwarded by the user from the user server to the server platform and the server platform then generates the second certificate. The first certificate may be a signature certificate and the second certificate may be an encryption certificate. The first certificate may be an expiring signature certificate and the second certificate may be a replacement signature certificate. The first certificate may be a signature certificate and the second certificate may be a replacement encryption certificate to replace an expiring encryption certificate. The first certificate may be a signature certificate and the second certificate may be one of either the user's current encryption certificate or an expired encryption certificate of the user. Thus, the first certificate may be used as a mechanism for establishing a “chain of trust” that can be used to obtain all other certificates without requiring the manual intervention of an enterprise officer, thereby considerably reducing the time and expense of obtaining additional certificates for a user.
Owner:NORTHROP GRUMMAN SYST CORP
Shared registration system multi-factor authentication
ActiveUS20100325723A1Digital data processing detailsUser identity/authority verificationDomain nameChain of trust
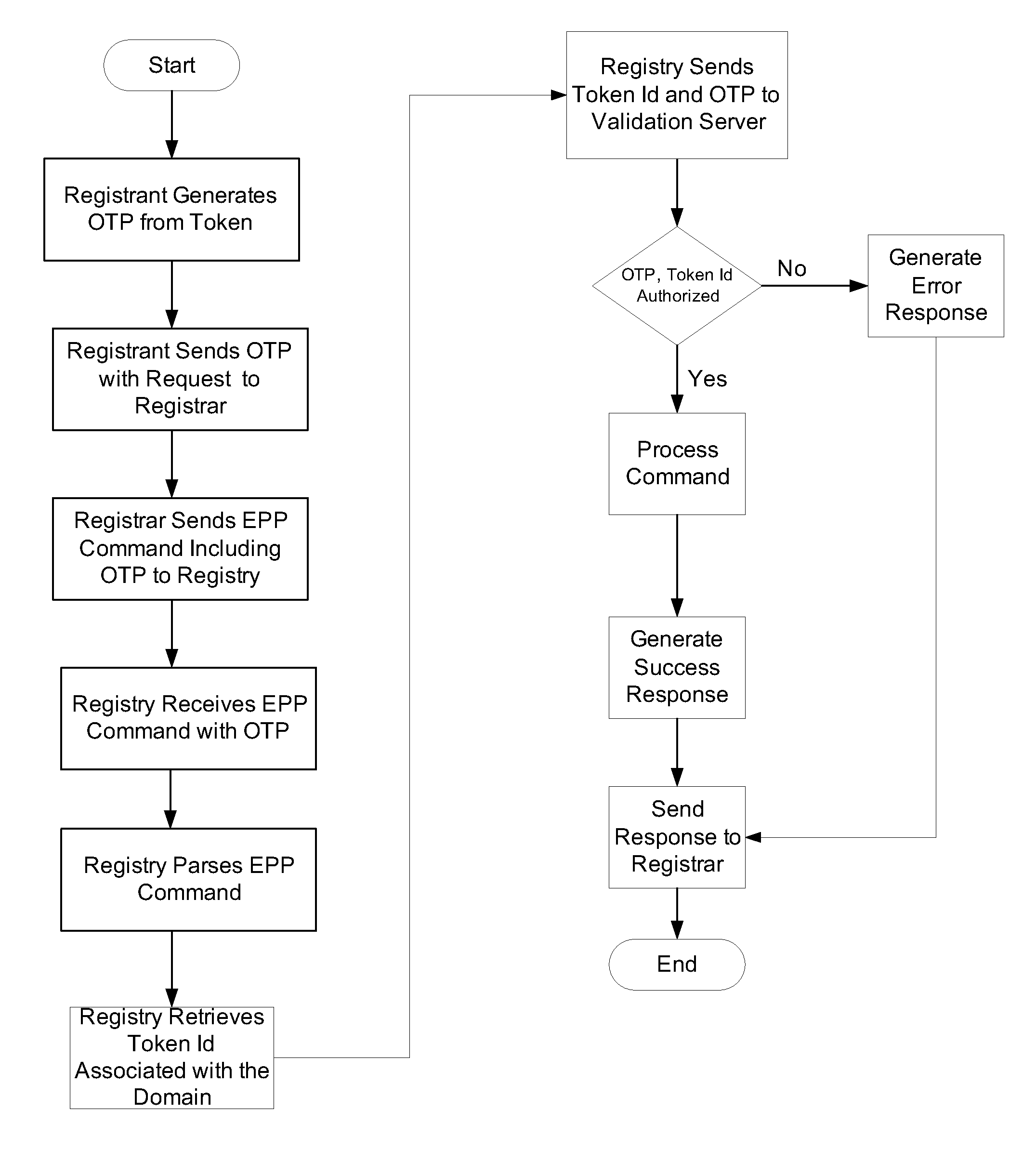
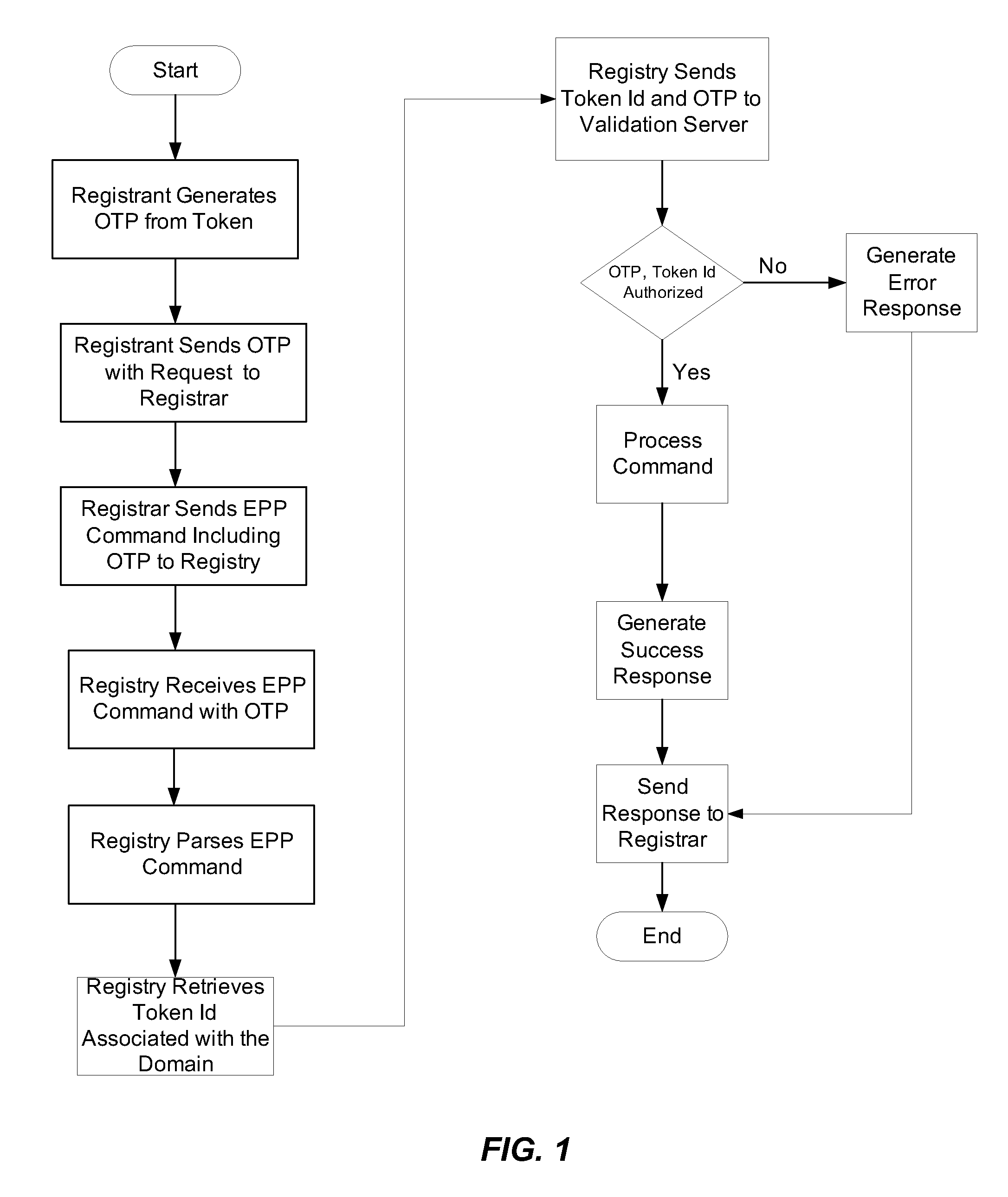
A system and method for establishing a chain of trust from a registrant to a registry. A registrant request to a registrar to change a domain name record includes at least one registrant factor, such as a one time password. The registrar can formulate an extended EPP command that includes the factor to effectuate the change and send it to a registry. The registry can verify the at least one factor using at least one validation server. If the factor is successfully verified, the EPP can be processed by the registry. If the factor is not verified, the EPP command may not be processed and an error message may be generated and sent to the registrar.
Owner:VERISIGN
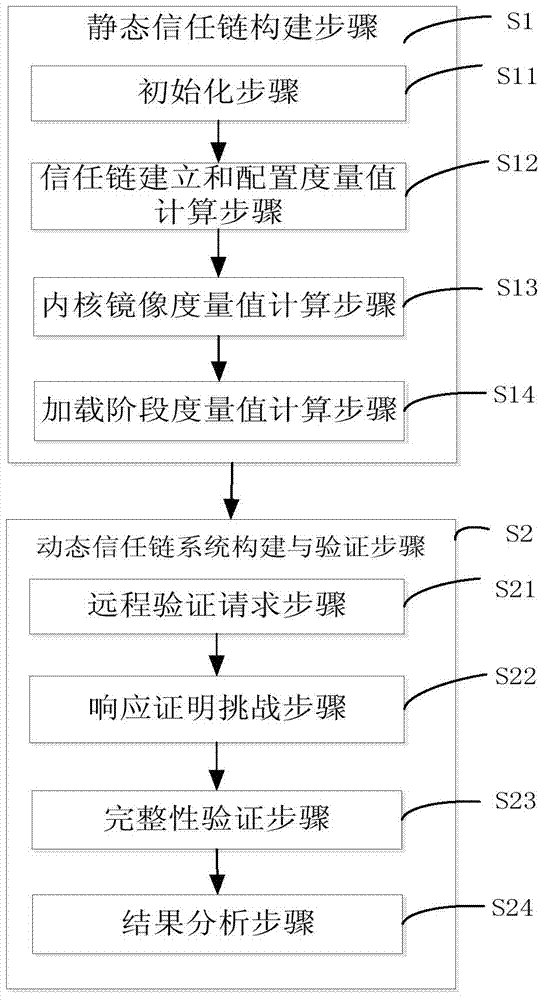
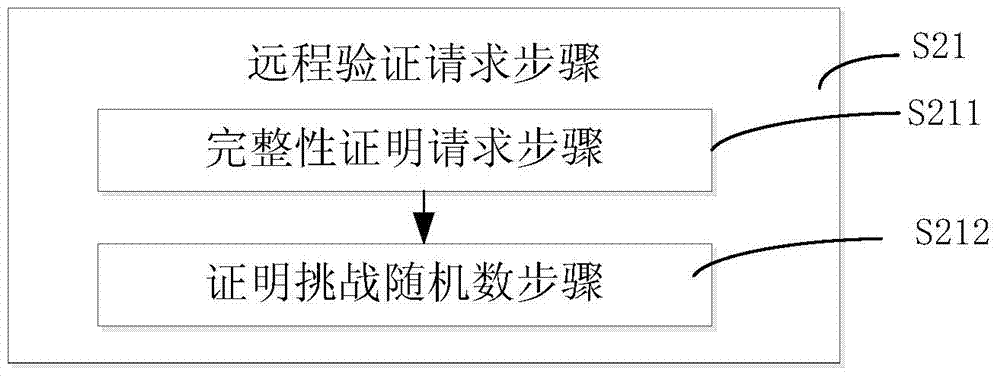
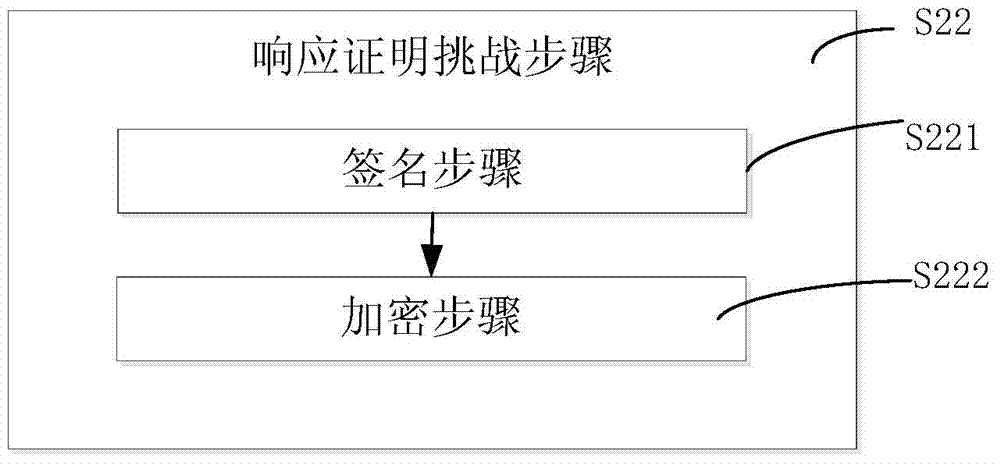
Method and system for proving integrity of cloud computing platform
The invention discloses a method and system for proving the integrity of a cloud computing platform. The method is used for proving the integrity of the platform based on a composite trust chain, wherein the composite trust chain comprises a static trust chain provided by a cloud end virtual machine and a dynamic trust chain system constructed by a remote verification party. The method comprises the steps of static trust chain construction and dynamic trust chain system construction and verification, wherein in the static trust chain construction step, the static trust chain is constructed through a virtualized trusted platform module provided by the cloud end virtual machine; in the dynamic trust chain system construction and verification step, the dynamic trust chain system is constructed by the remote verification party, platform integrity verification is conducted in a trusted executing environment, and the operation evidence of the trusted executing environment is generated by the remote verification party, so that the virtual machine can trust a received verification result more safely.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
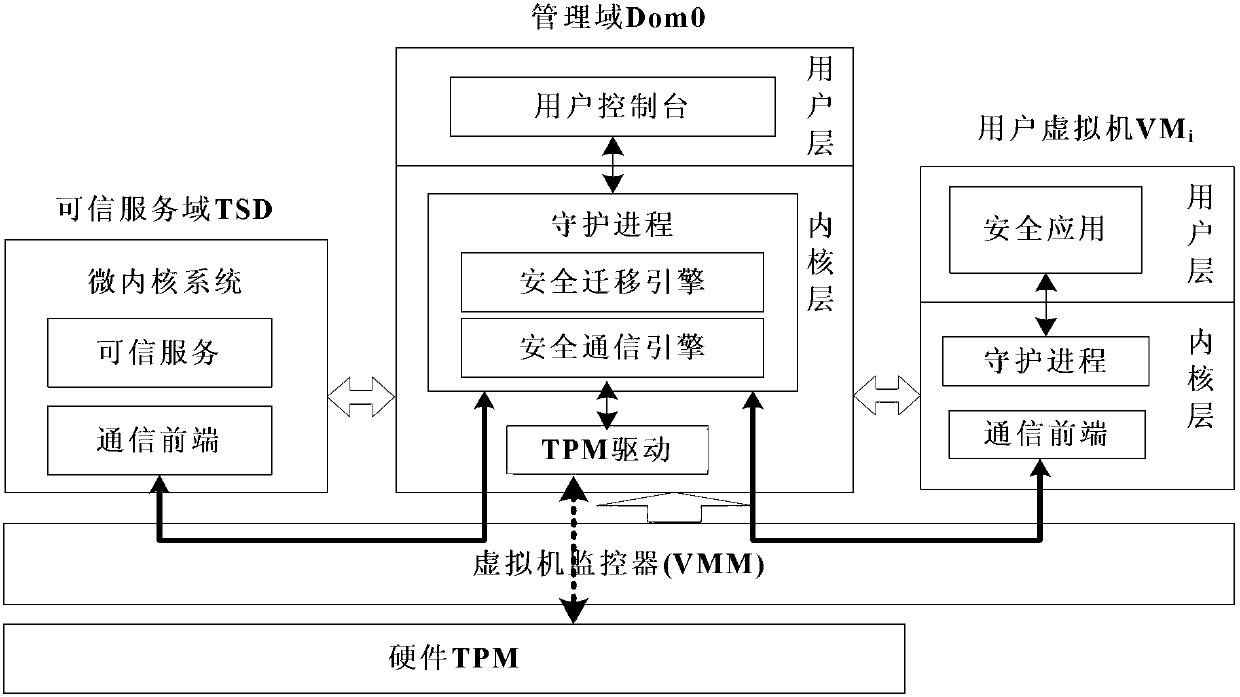
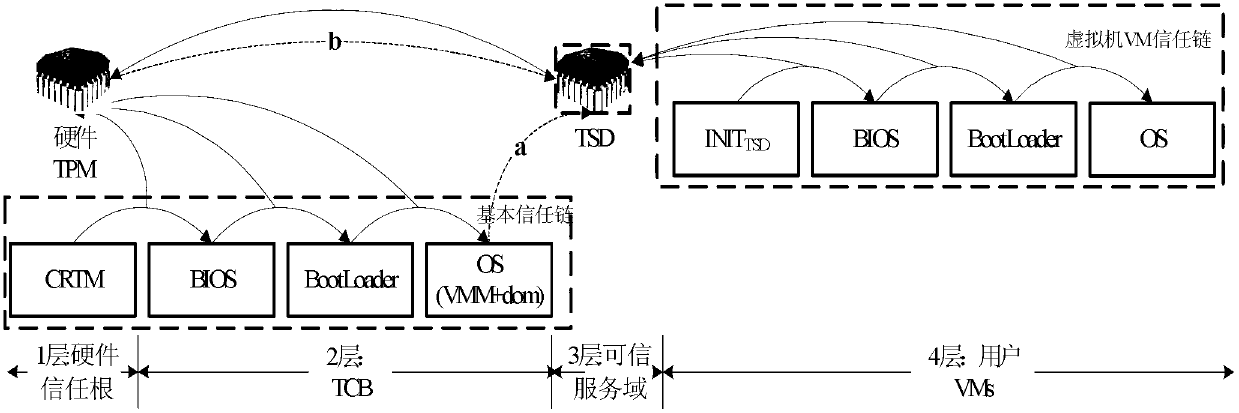
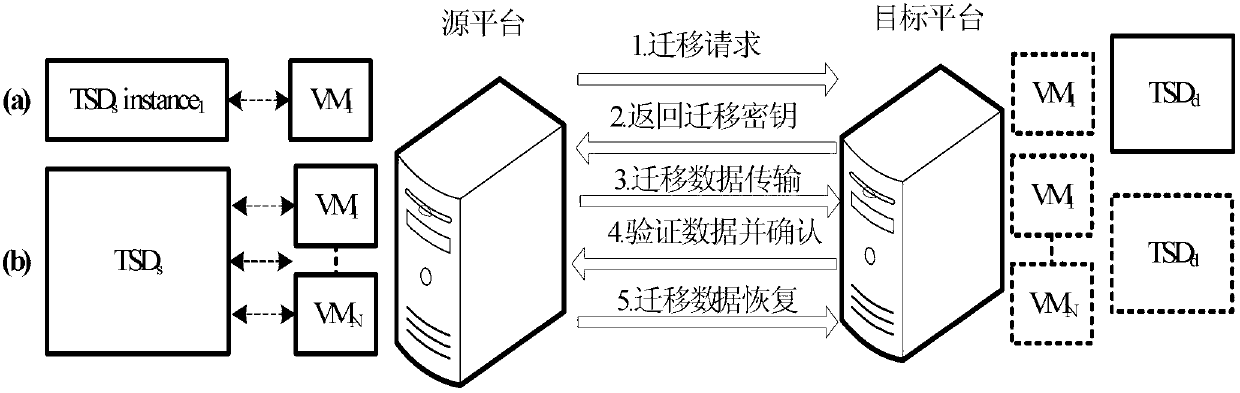
Dependable virtual platform and construction method thereof, data migration method among platforms
InactiveCN103139221AFlexible migrationQuick migrationTransmissionSecure communicationAdministrative domain
The invention discloses a dependable virtual platform and a construction method thereof, a data migration method among platforms. The dependable virtual platform comprises a hardware security chip, a virtual machine monitor (VMM), an administrative domain, a user domain and a dependable serving domain (TSD), wherein an expanded trust chain is used by the TSD for users to establish dependable operating environment. The construction method includes: building the TSD; then establishing secure communication mechanisms between the managing domain and the TSD and between the managing domain and a domestic user domain; accomplishing calls of security application of the user domain to a dependable function by the user domain through interaction with the managing domain, accomplishing transmission and treatments of dependable orders by the managing domain through the interaction of the TSD; interacting a source platform migration engine and a goal platform migration engine; migrating migration data which is produced and based on the hardware security chip and the TSD to a goal platform, and recovering data on the goal platform, accomplishing quick migration of the TSD and a virtual machine. The dependable virtual platform and the construction method thereof, the data migration method among platforms are capable of improving safety of dependable service and providing flexible operation and deployment mechanisms for the platforms.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
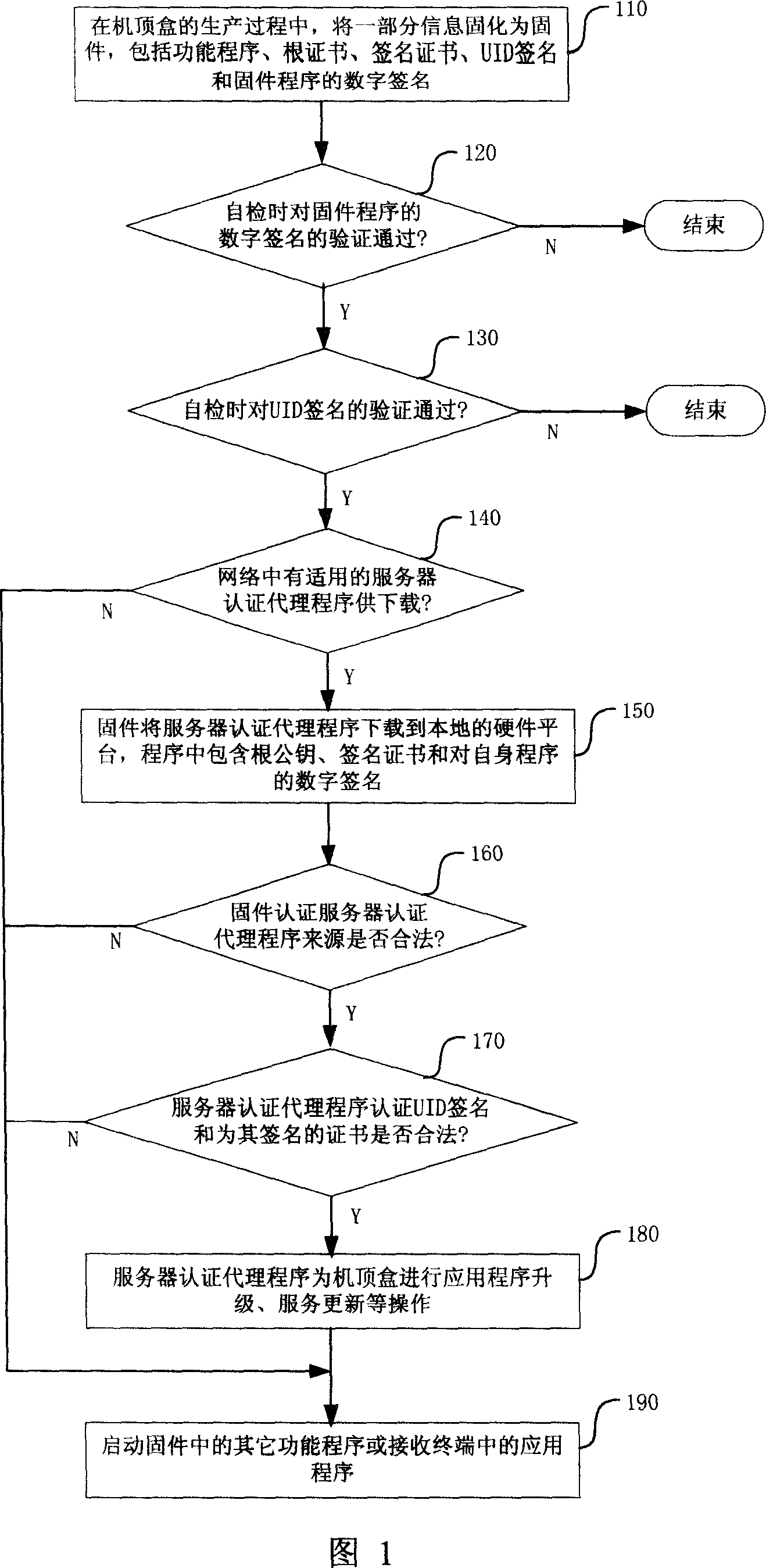
Method and system for authenticating legality of receiving terminal in unidirectional network
ActiveCN101145906ARealize the identification of legitimacyPrevent imitationUser identity/authority verificationDigital signatureTerminal equipment
The invention relates to a method and system for legality authentication of receiving terminals in a unidirectional network. The digital signature of UID of chips is written in terminal equipment, terminal firmware downloads a server authentication agent program from the network, the program runs on the hardware platform of the terminal, and UID signature is decrypted by using a built-in public key or the public key of the signature certificate acquired from the network; if the decrypted value and the abstract value of UID read out from the chips are determined to be identical and the signature certificate is in a trust chain established by the rood certificate, the terminal is legal, or the terminal is illegal. Also, in the process of self-test of the firmware, the decrypted value can be obtained by using the public key in the signature certificate to decrypt UID signature, then UID of the chips is read out and the abstract value thereof is calculated, and if the two values are identical, the self-test passes, or the work state ends. By using the self-test of the terminal firmware or the mutual authentication between the server authentication agent program and the firmware, the invention makes clone and copied set-top boxs not work normally in the network.
Owner:北京邦天信息技术有限公司
Transparent trust chain constructing system based on virtual machine architecture
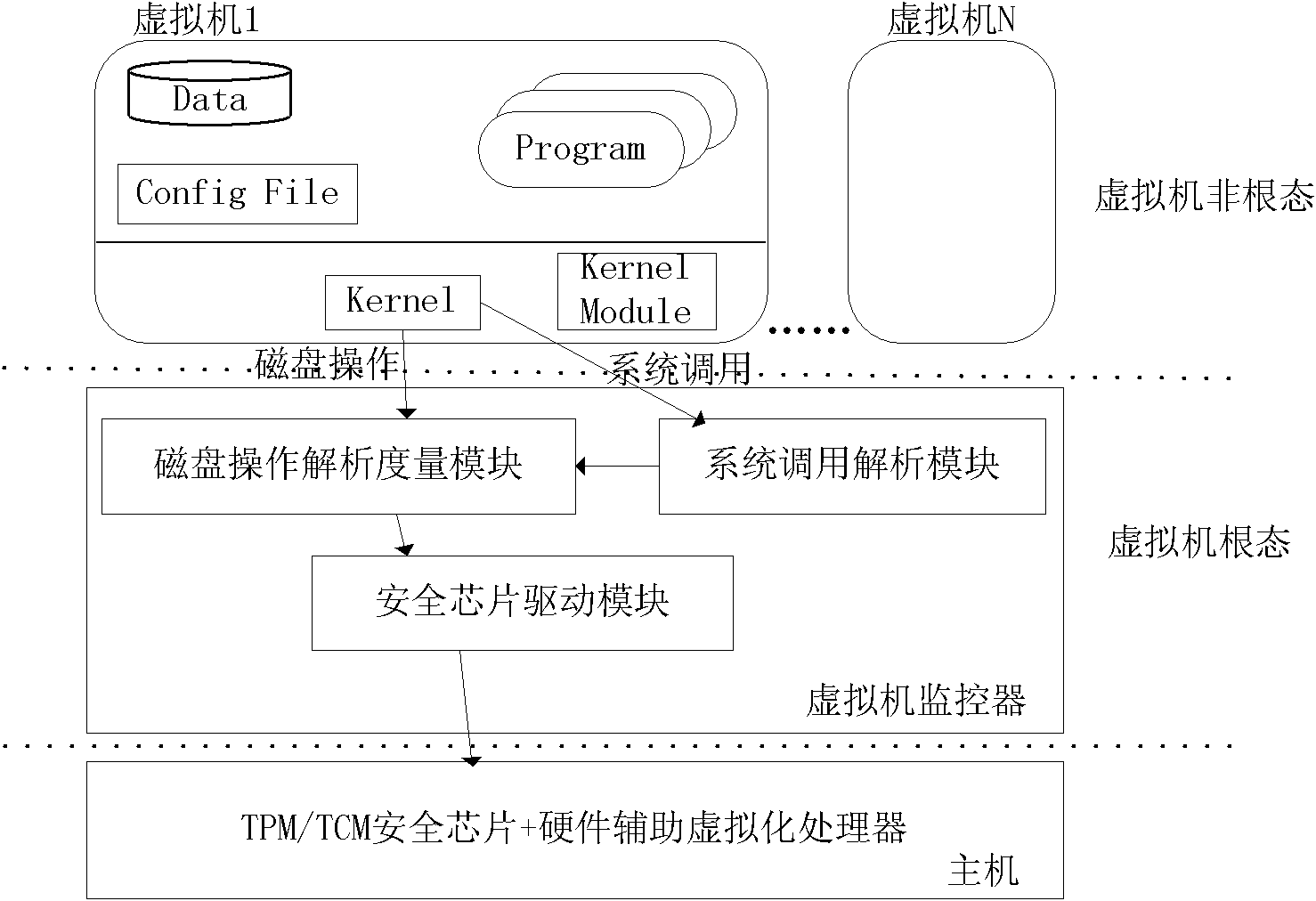
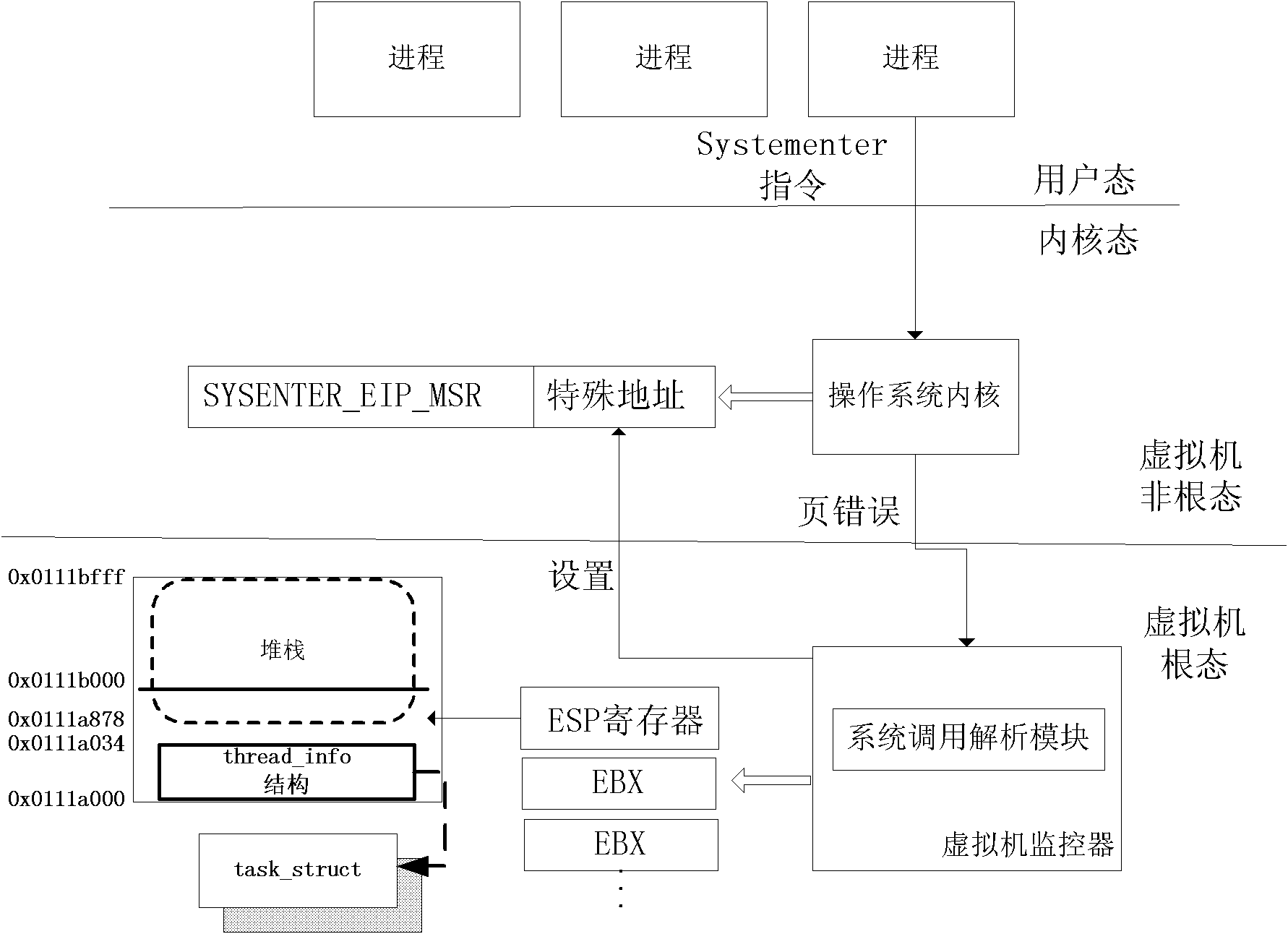
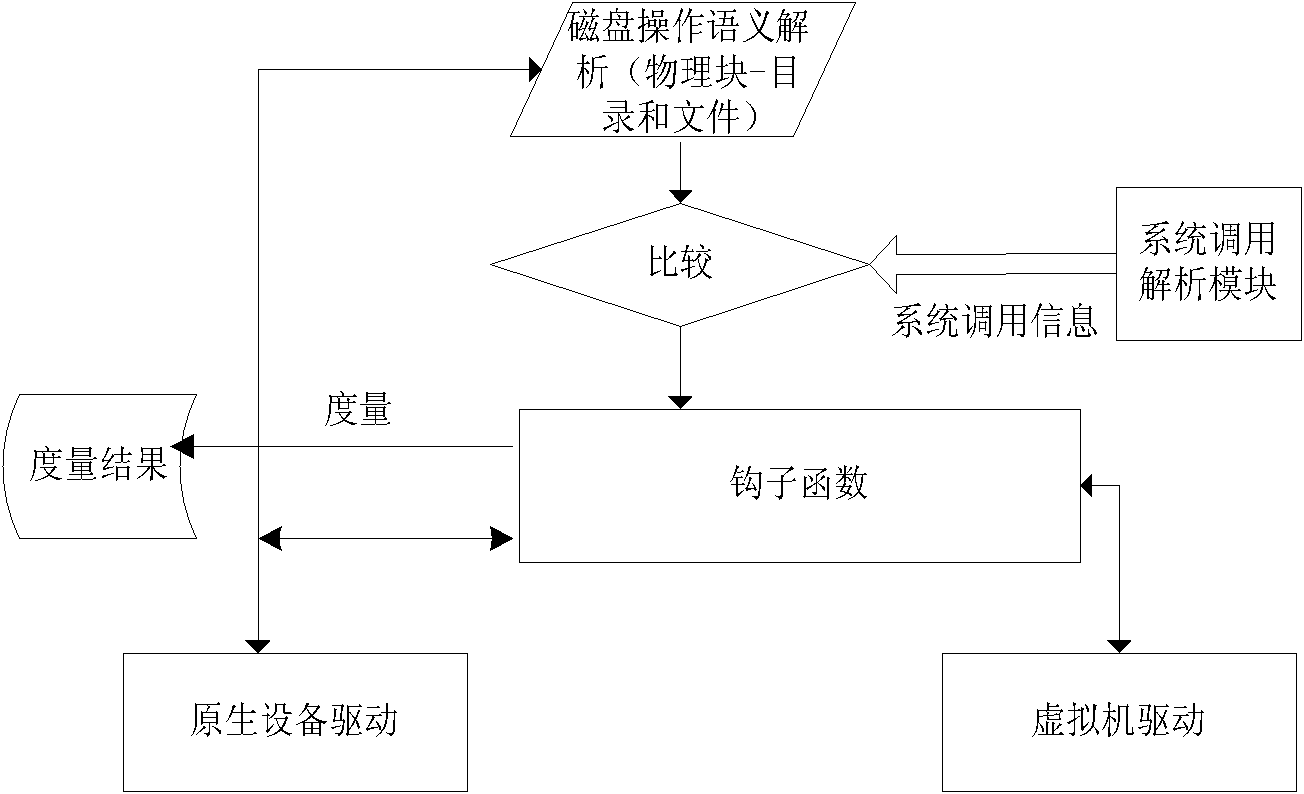
InactiveCN101866408AReduce the amount of codeReduce vulnerabilityPlatform integrity maintainanceSoftware simulation/interpretation/emulationOperational systemSemantics
The invention discloses a transparent trust chain constructing system based on virtual machine architecture. The system is provided with a virtual machine monitor on the mainframe, the virtual machine monitor comprises a safety chip drive module, a system call analysis module and a disk analysis measurement module. The invention measures the operation system and the executable code loaded after the operation system is started in the virtual machine monitor, without any modification of the existing operation system and the application program. The invention can obtain low-level operation semantic information, such as the system call and the disk access, of the operation system in the client machine, analyzes the operation semantics of the client machine operation system, and controls the operation of the client operation system on the disk to realize the transparent measurement. The technology can be used in the distributed cooperation environment, and provide transparent trust chain and integrity certification for the operation system. The invention can protect the existing property of the user and enable the existing operation system to support the process level TCG trust chain without any modification.
Owner:HUAZHONG UNIV OF SCI & TECH
Secure communication system for mobile devices
ActiveUS8392699B2Multiple keys/algorithms usageSecret communicationControl communicationsChain of trust
Owner:CUMMINGS ENG CONSULTANTS
Trusted computing cryptogram platform suitable for general computation platform of electric system
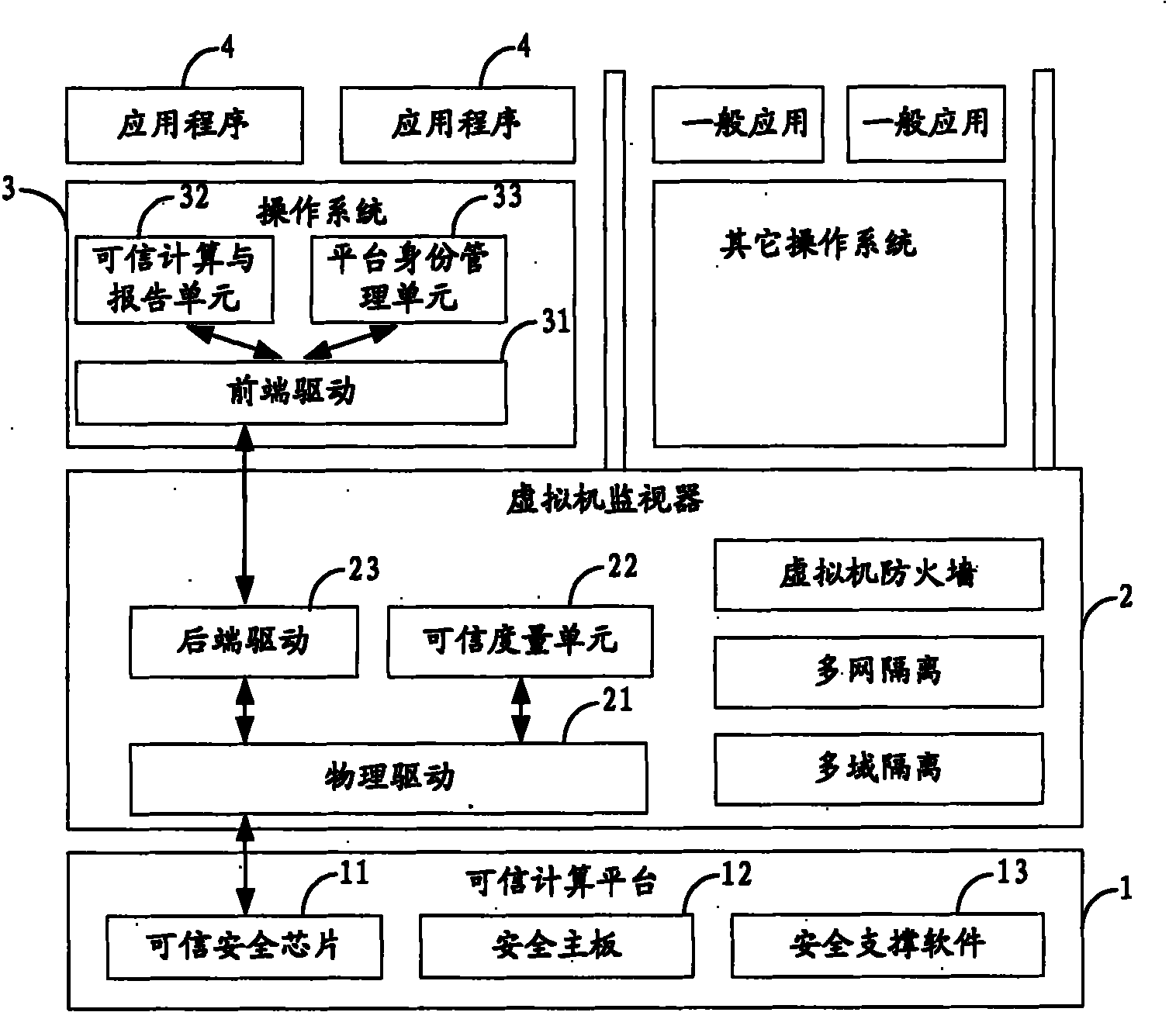
ActiveCN105468978AEnsure credibleGuaranteed recognition effectPlatform integrity maintainanceOperational systemSoftware system
The invention provides a trusted computing cryptogram platform suitable for a general computation platform of an electric system. The cryptogram platform comprises a trusted computing cryptogram module and a trusted software system, wherein the trusted computing cryptogram module comprises a trusted measurement root, a trusted storage root and a trusted report root and is a transferring starting point of a platform trust chain; and the trusted software system comprises a trusted computing cryptogram driving module, a measurement module and an auditing module and provides an interface which uses the trusted computing cryptogram platform for an operating system and application software. The trusted computing cryptogram module is the trusted root which provides trusted environment for the operation of the trusted computing cryptogram platform, and the trusted software system is a core for realizing the functions and the service of the trusted computing cryptogram platform and provides guarantee for the management of the trusted computing cryptogram platform. The trusted computing cryptogram platform can provide functions including static measurement, dynamic measurement, white lists, access control and the like for a business system, and manages the sources and the operation of the system software to guarantee that the software is trusted, recognizable and controllable.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +5
Firmware-licensing system for binding terminal software to a specific terminal unit
InactiveUS20070078957A1Effective and secureSoftware engineeringDigital computer detailsChain of trustTerminal unit
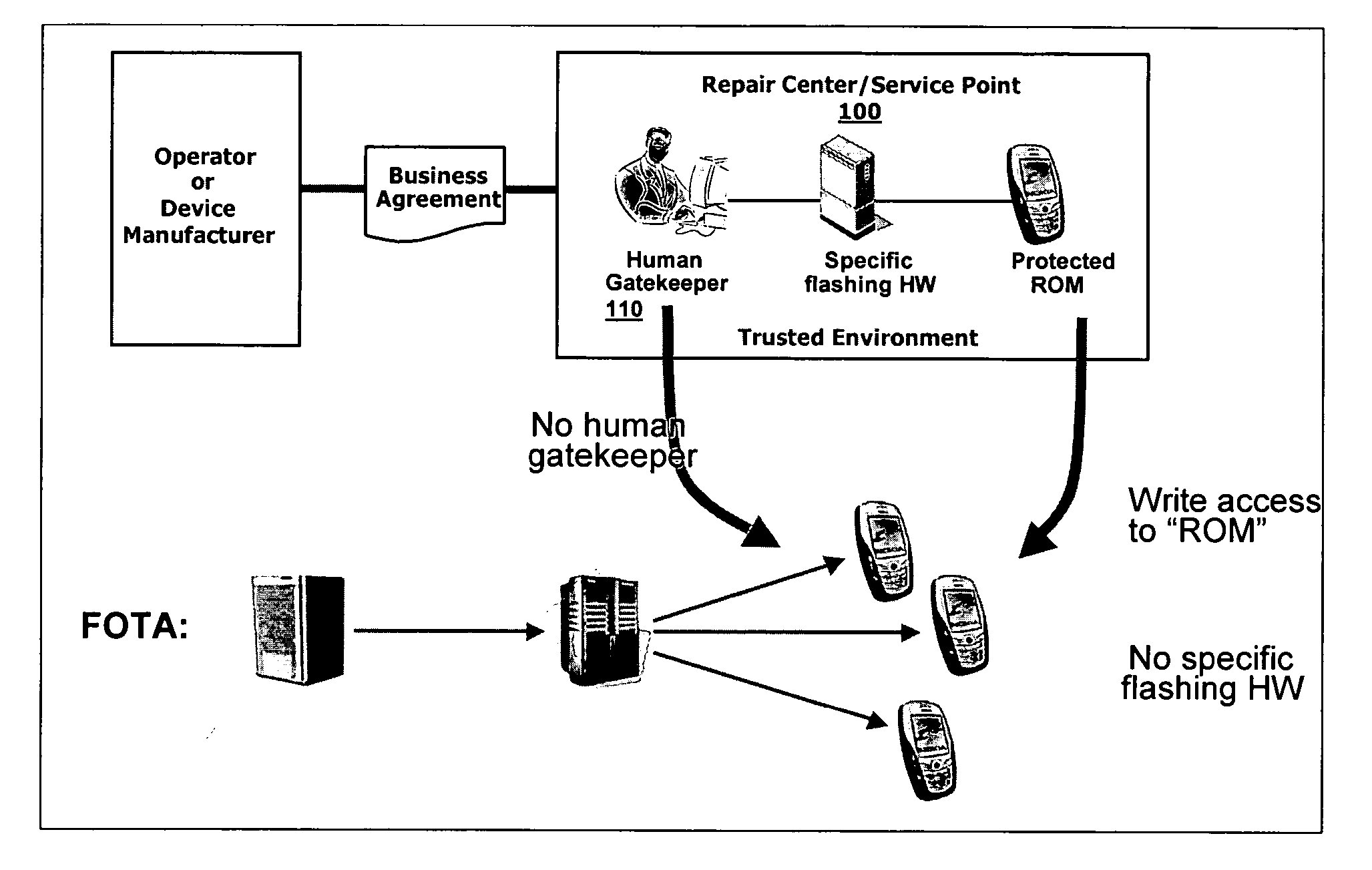
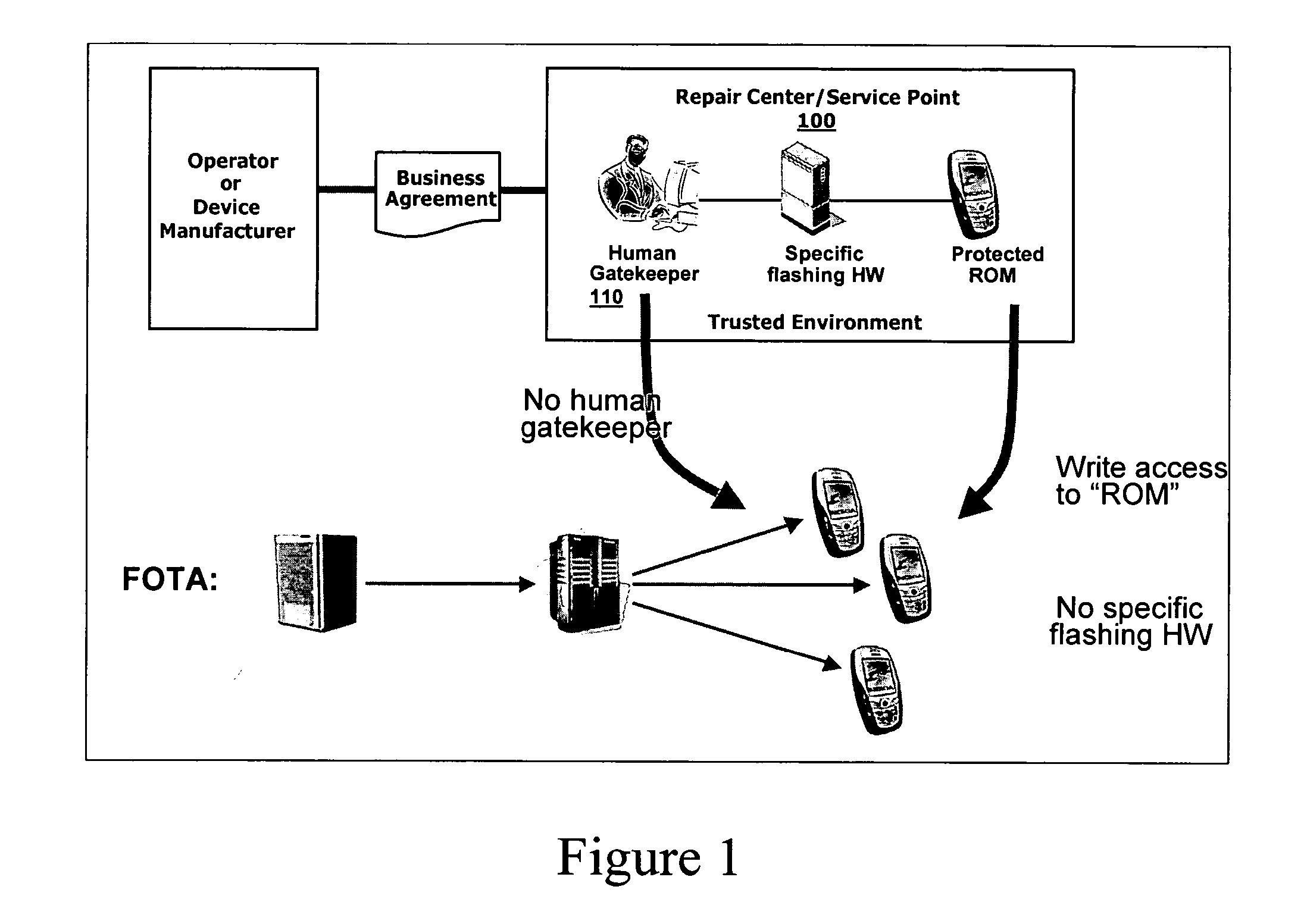
An improved system and method for providing firmware upgrades and similar information to mobile electronic devices while protecting the firmware from impermissible copying and other undesirable activities. The delivery of a firmware upgrade to a terminal is divided into two parts. A firmware upgrade package contains the payload and the real binary content for the firmware reflashing process in the terminal. A license package binds the firmware package to a specific terminal and enables its use. The binding forms a chain of trusted elements: the firmware, a firmware identifier, a license identifier, a hardware identifier, and hardware.
Owner:NOKIA CORP
PKI (Public Key Infrastructure) implementation method based on safety certificate
InactiveCN102664739AKeep storage safeEnsure credibleUser identity/authority verificationCiphertextCryptographic protocol
The invention discloses a PKI (Public Key Infrastructure) implementation method based on a safety certificate. The method comprises the following steps of: deploying an encryption card or encryption equipment hardware equipment on the end part of a CA (Certificate Authority); encrypting all final entity CA certificates in the CA into a cipher text for storing; storing each middle-class CA certificate and root CA certificate in a CA encryption card or a chip of the encryption equipment; generating a key in a safety protocol of the PKI and calling the key to encrypt or decrypt the certificate in the chip; establishing a 'chip-class' PKI safety protocol between a user terminal and a CA terminal; establishing a certificate safety detection protocol in the CA; and detecting the CA certificate in a full trusted link in the CA timely to prevent an attacker from tampering the CA certificate to establish a PKI system based on the safety certificate.
Owner:杜丽萍 +1
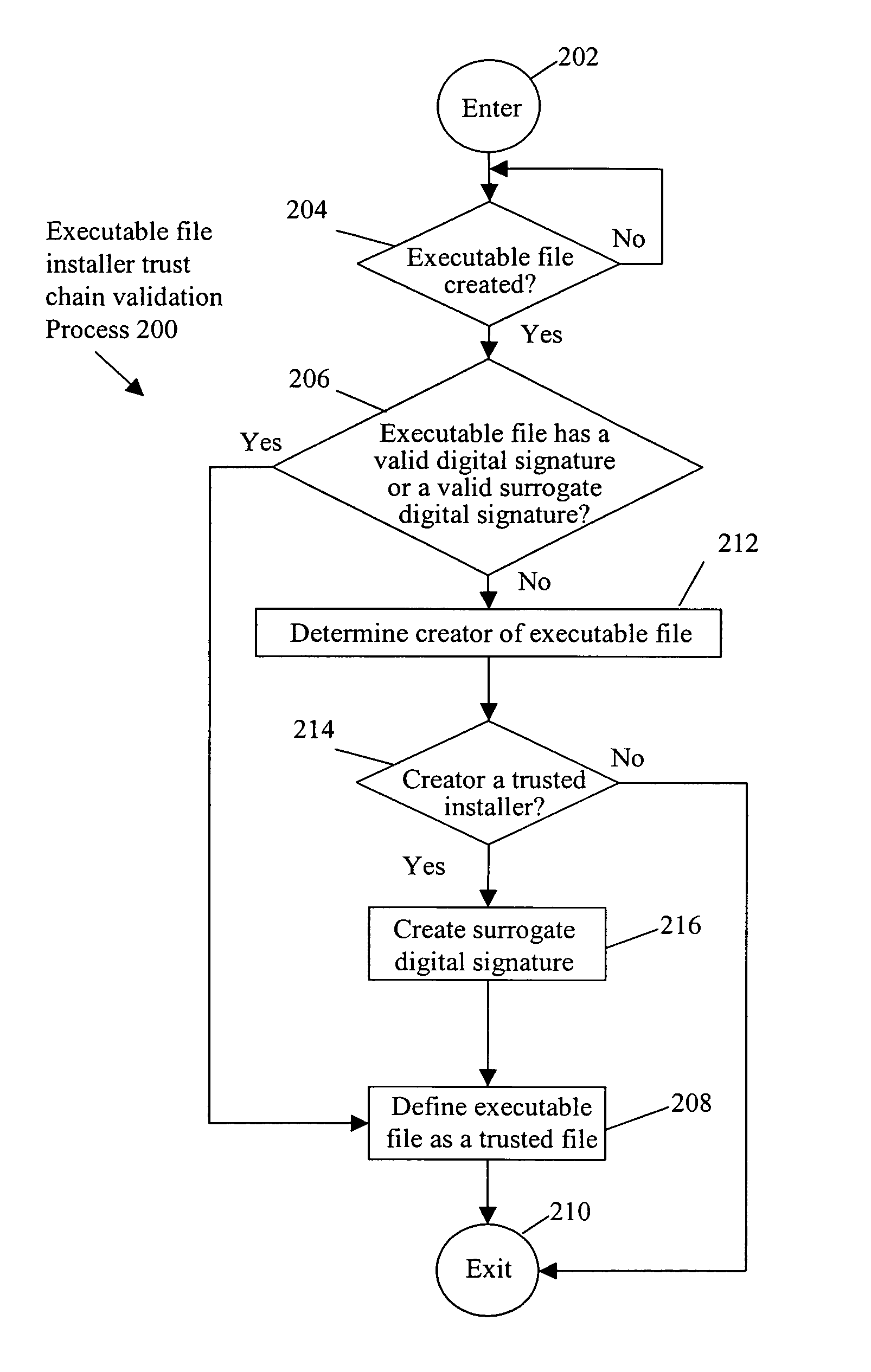
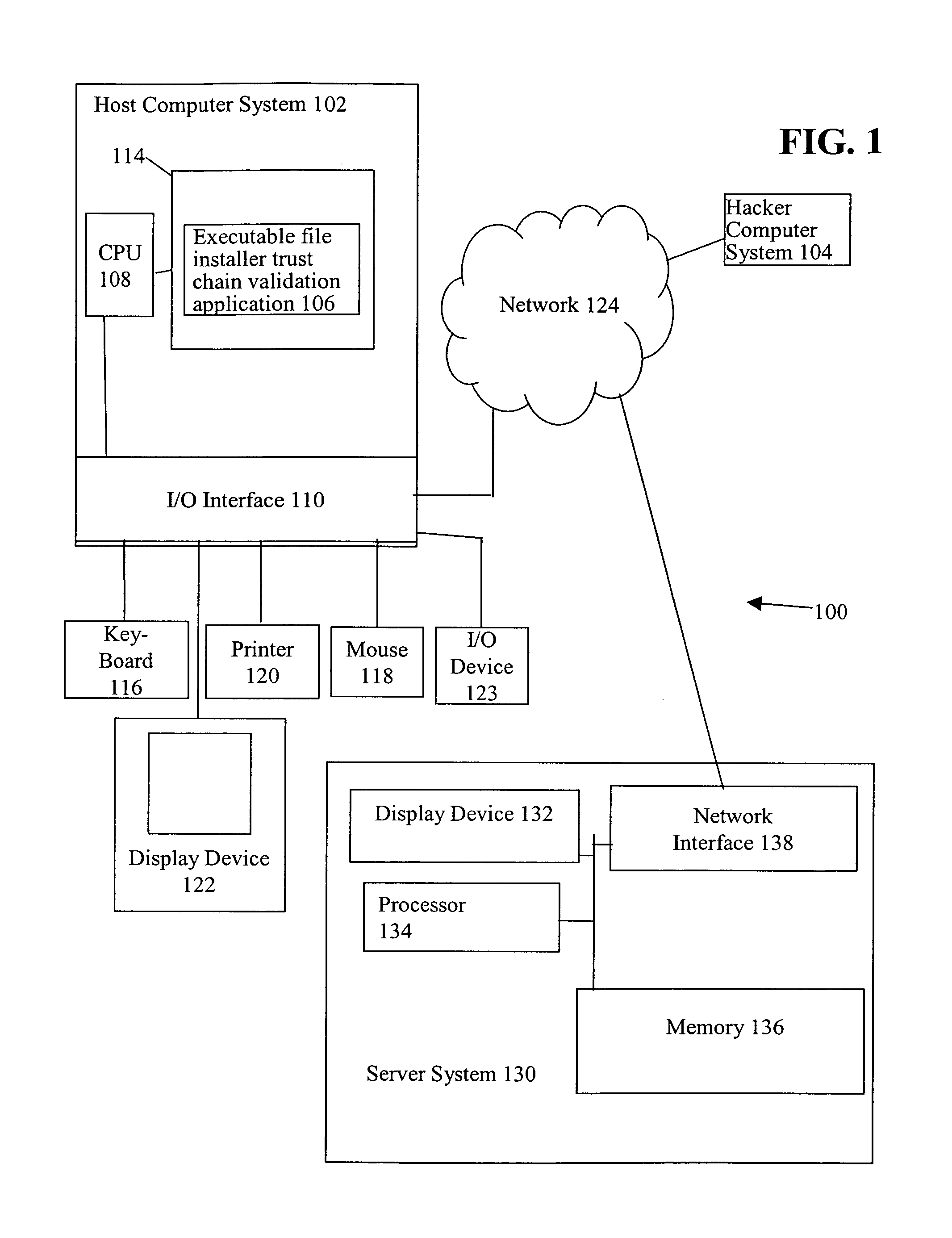
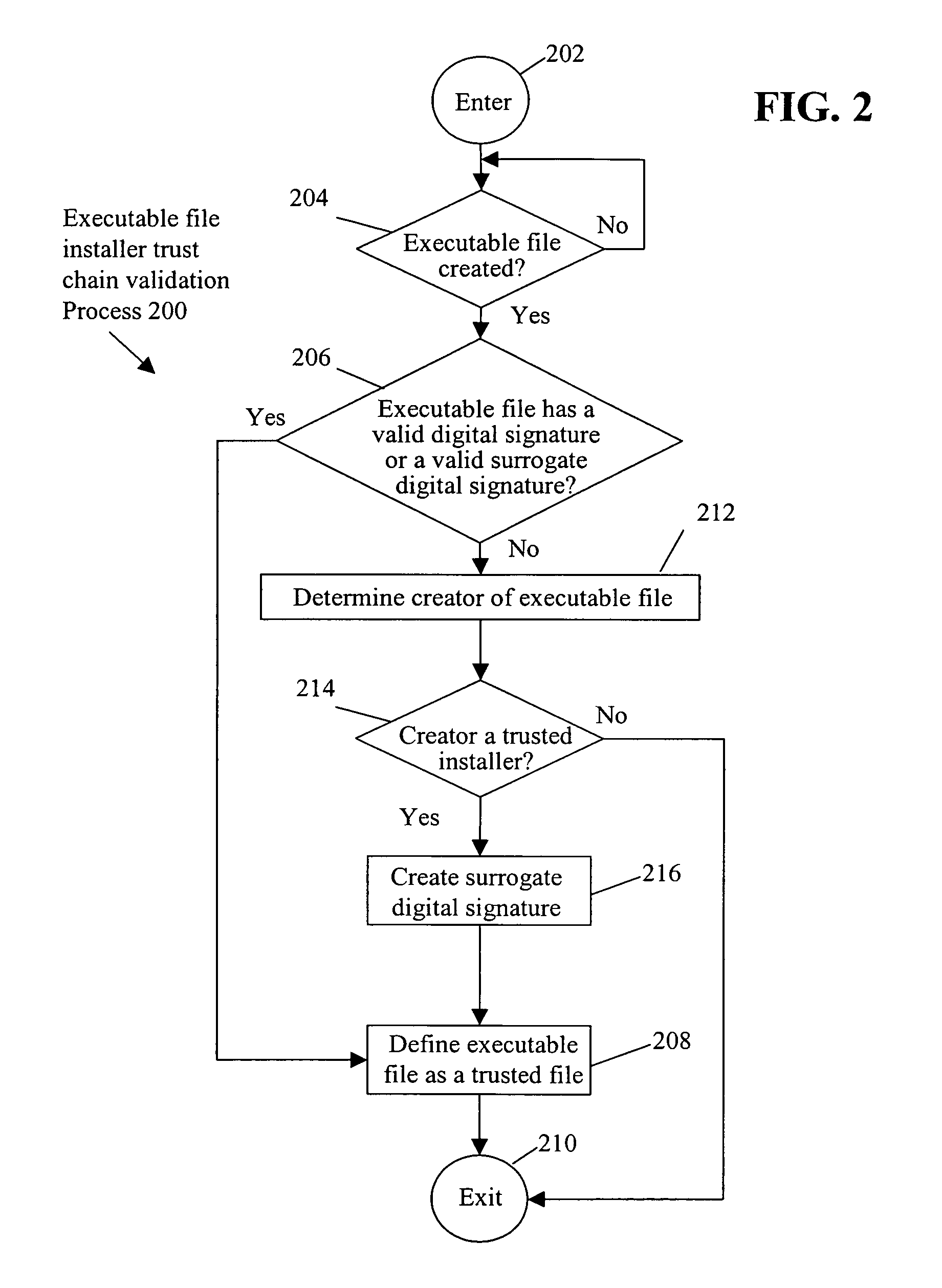
Installer trust chain validation
InactiveUS9098706B1Memory loss protectionError detection/correctionComputer hardwareDigital signature
A determination is made as to whether a creator of a created executable file is a trusted installer, e.g., a digitally signed installer. Upon a determination that the creator is a trusted installer, the created executable file is defined as a trusted file. By bestowing the trust of a trusted installer to the executable files that the installer creates, suspicious behavior by the created executable files and associated processes, which otherwise would be blocked, is allowed. In this manner, false positives, e.g., blocking of legitimate behavior by the created executable file and associated process(es), are avoided.
Owner:CA TECH INC
Device Security Features Supporting a Distributed Shared Memory System
ActiveUS20120191933A1Memory architecture accessing/allocationEnergy efficient ICTChain of trustProtection system
A memory management and protection system that incorporates device security features that support a distributed, shared memory system. The concept of secure regions of memory and secure code execution is supported, and a mechanism is provided to extend a chain of trust from a known, fixed secure boot ROM to the actual secure code execution. Furthermore, the system keeps a secure address threshold that is only programmable by a secure supervisor, and will only allow secure access requests that are above this threshold.
Owner:TEXAS INSTR INC
Trusted computing platform and method for verifying trusted chain transfer
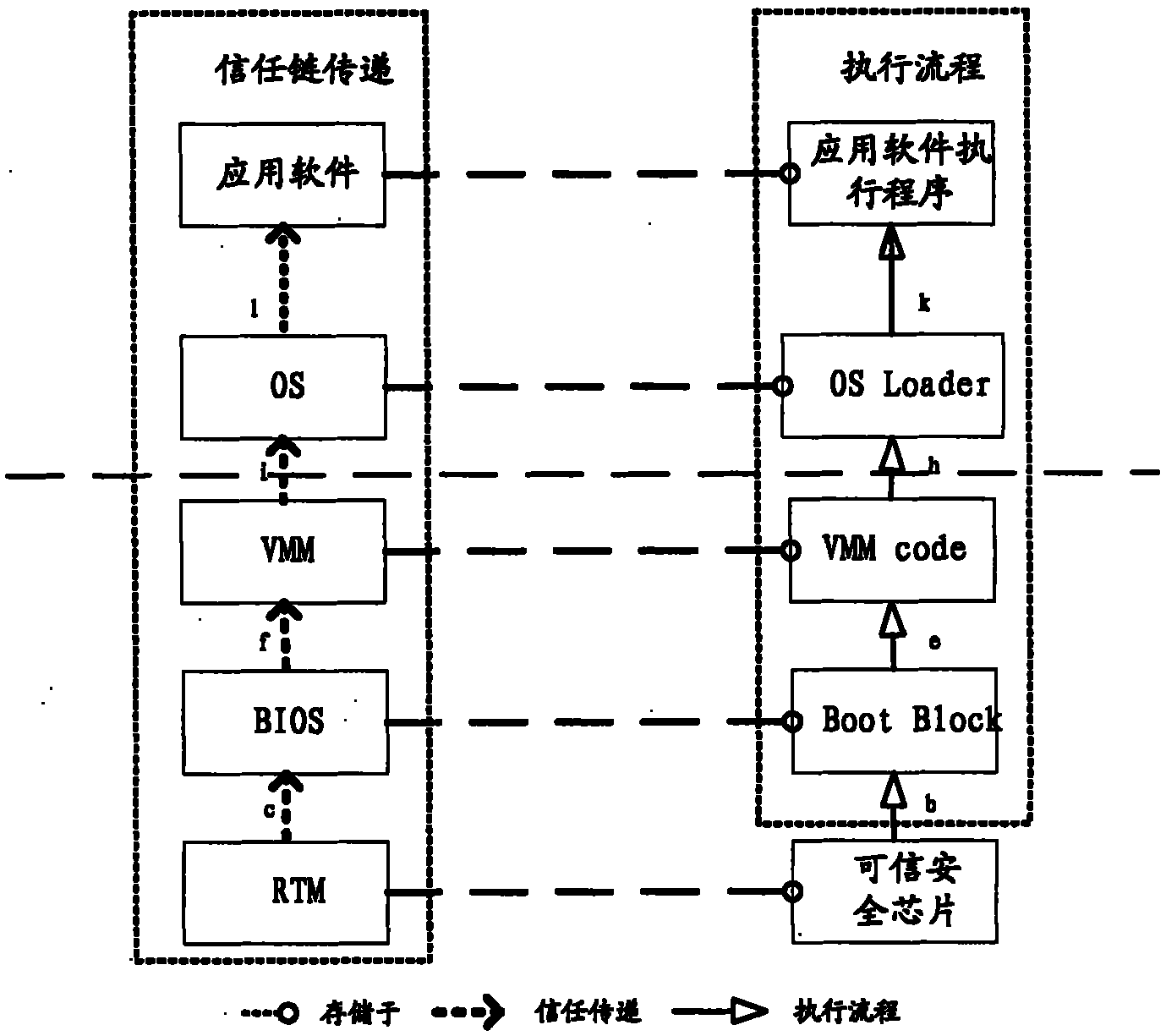
InactiveCN101901319ASolve the trust decay problemGuaranteed Metric Efficiency IssuesPlatform integrity maintainanceCheck pointValidation methods
The invention relates to a trusted computer platform and a method for verifying trusted chain transfer. A trusted chain is a key component of a trusted computer system, and ensures the safety and credibility of the computer system in the integral process from a trusted source to system starting, but the conventional trusted transfer mode is a chained transfer mode, and due to the problem of layer-by-layer attenuation of the trust level of chained transfer, potential safety hazards exist in the process of establishing the trusted chain of the trusted computer platform. A CPU is authorized by a trusted platform control module (TPCM) to perform chained measurement on the trusted computer platform, and simultaneously, the TPCM follows the CPU to perform the real-time, random and partitioned measurement on the trusted chain, and check points are embedded into codes of each part of the platform trusted chain to perform statistics and comparison on total operating time and total expected time and the operating time and expected time of each partition so as to judge whether each trusted node is distorted or not. The trusted computer platform and the method for verifying the trusted chain transfer improve the real-time of establishment and checking of the trusted chain, and particularly can protect against TOUTOC attack.
Owner:BEIJING UNIV OF TECH
Plug and play mobile services
InactiveUS20050153683A1Increase the likelihood of successPromote activationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDomain nameProcessor register
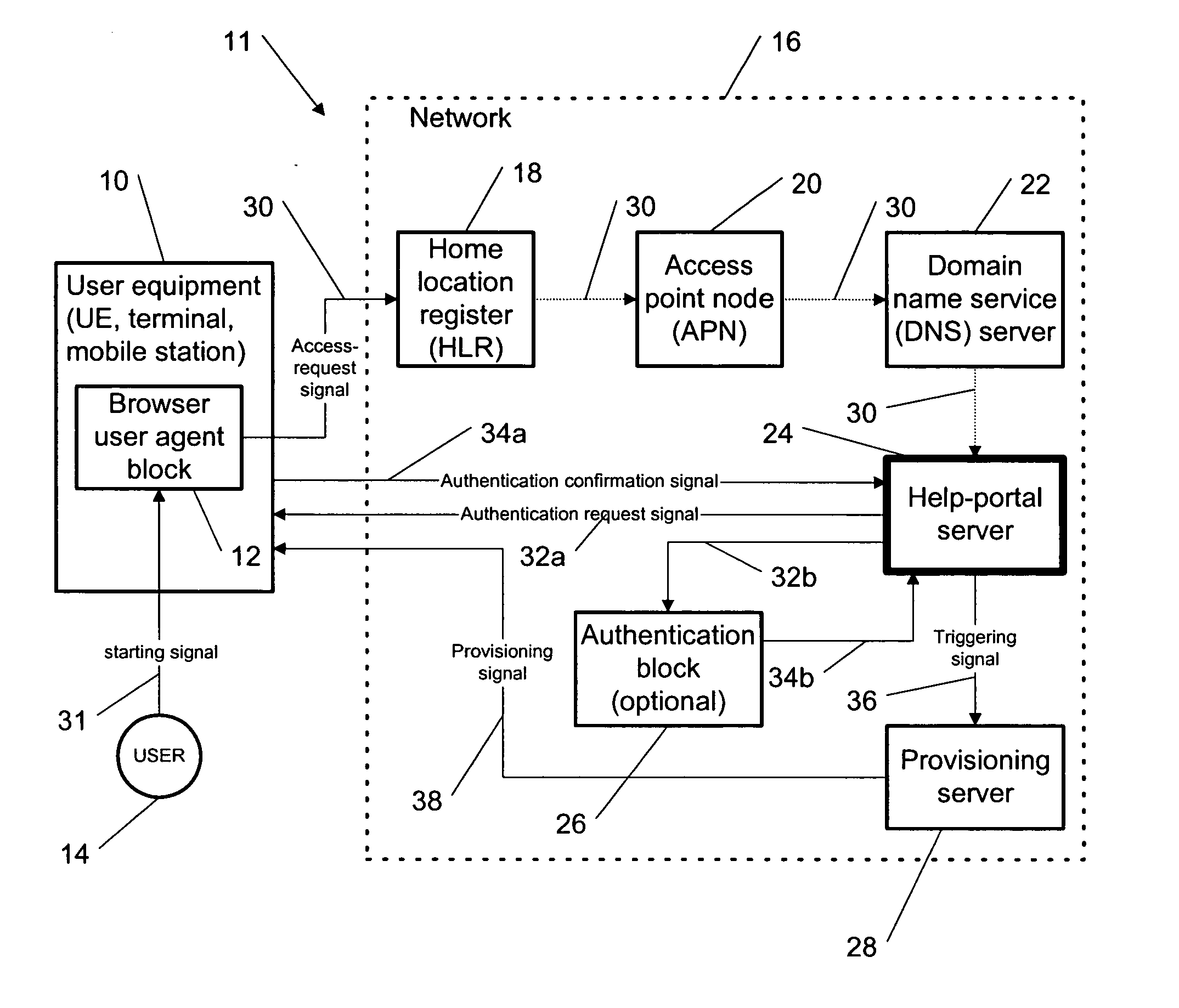
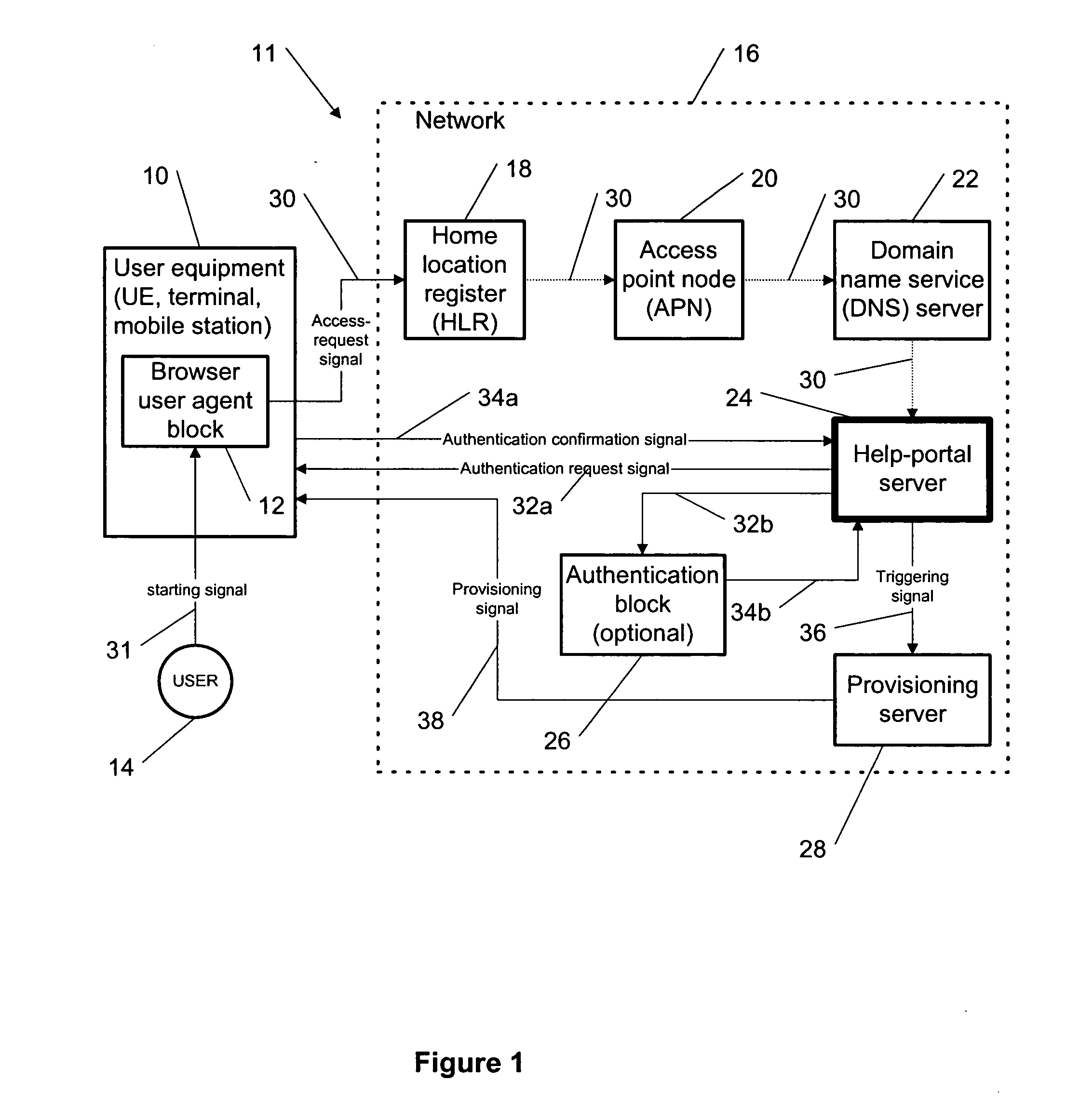
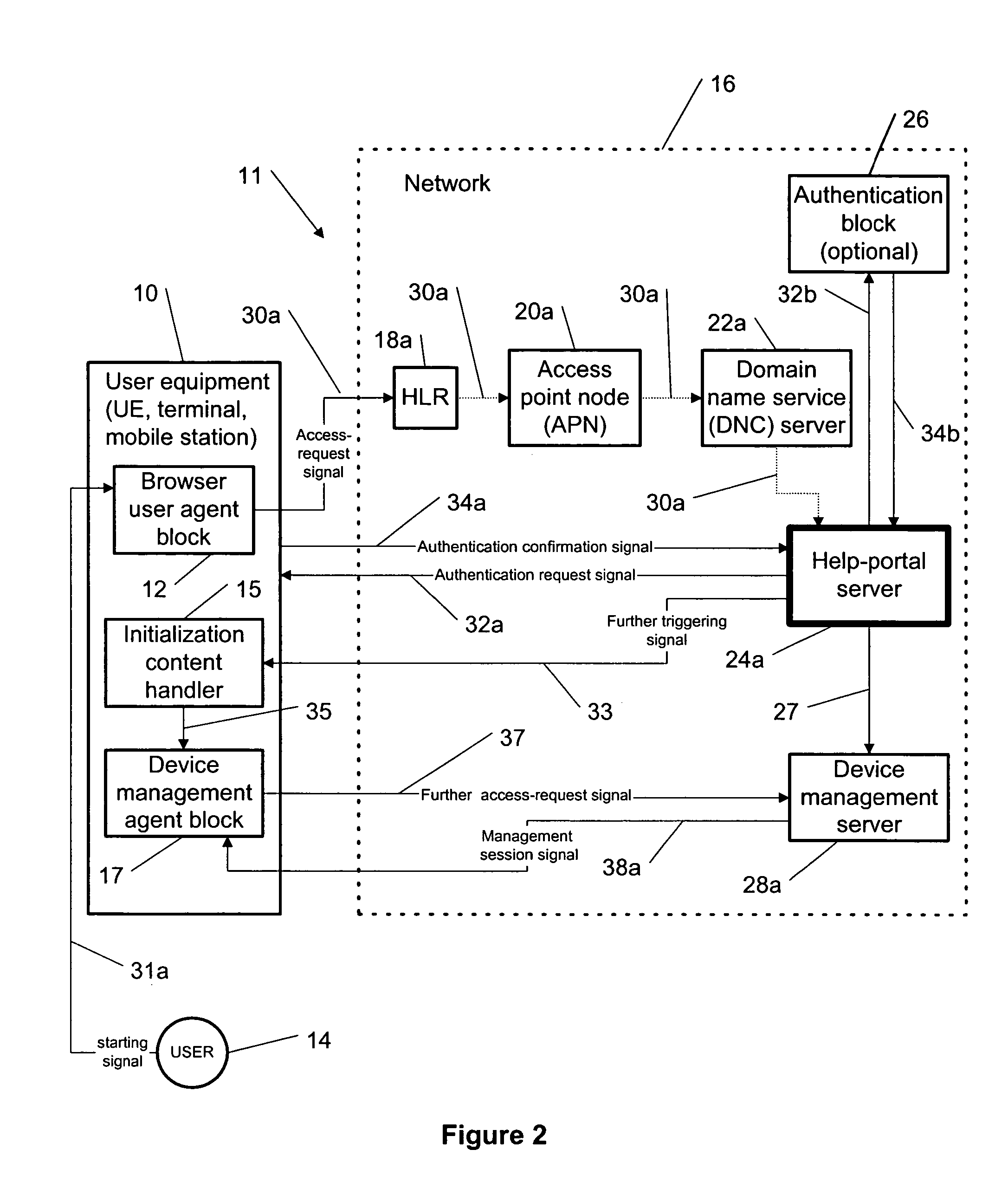
This invention describes “plug and play” methodology for configuring a terminal, enabled for handling data-protocol services (e.g. GRPS), for the data-protocol services specific to a service provider so as to be able to connect said terminal to an IP backbone network via a network, which provides said data-protocol services and which is provided by said service provider. The invention further consists of using a well-known access point node (APN) name, and a well-known uniform resource locator (URL) string to access a service provider specific help-portal server of the network to request information for configuring the terminal. A core part of the invention is the fact that the security of the download is ensured by means of a chain of trust that originates with a trusted home location register or the well-known APN name, and is built using a trusted APN, the well-known URL string and a trusted domain name service.
Owner:NOKIA CORP
Integration of high-assurance features into an application through application factoring
ActiveUS20050091661A1Better at ensuring correct behavior of their hosted environmentsTransformation of program codeDigital data processing detailsChain of trustApplication software
Application factoring or partitioning is used to integrate secure features into a conventional application. An application's functionality is partitioned into two sets according to whether a given action does, or does not, involve the handling of sensitive data. Separate software objects (processors) are created to perform these two sets of actions. A trusted processor handles secure data and runs in a high-assurance environment. When another processor encounters secure data, that data is sent to the trusted processor. The data is wrapped in such a way that allows it to be routed to the trusted processor, and prevents the data from being deciphered by any entity other than the trusted processor. An infrastructure is provided that wraps objects, routes them to the correct processor, and allows their integrity to be attested through a chain of trust leading back to base component that is known to be trustworthy.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and method for providing sealed storage in a data processing device
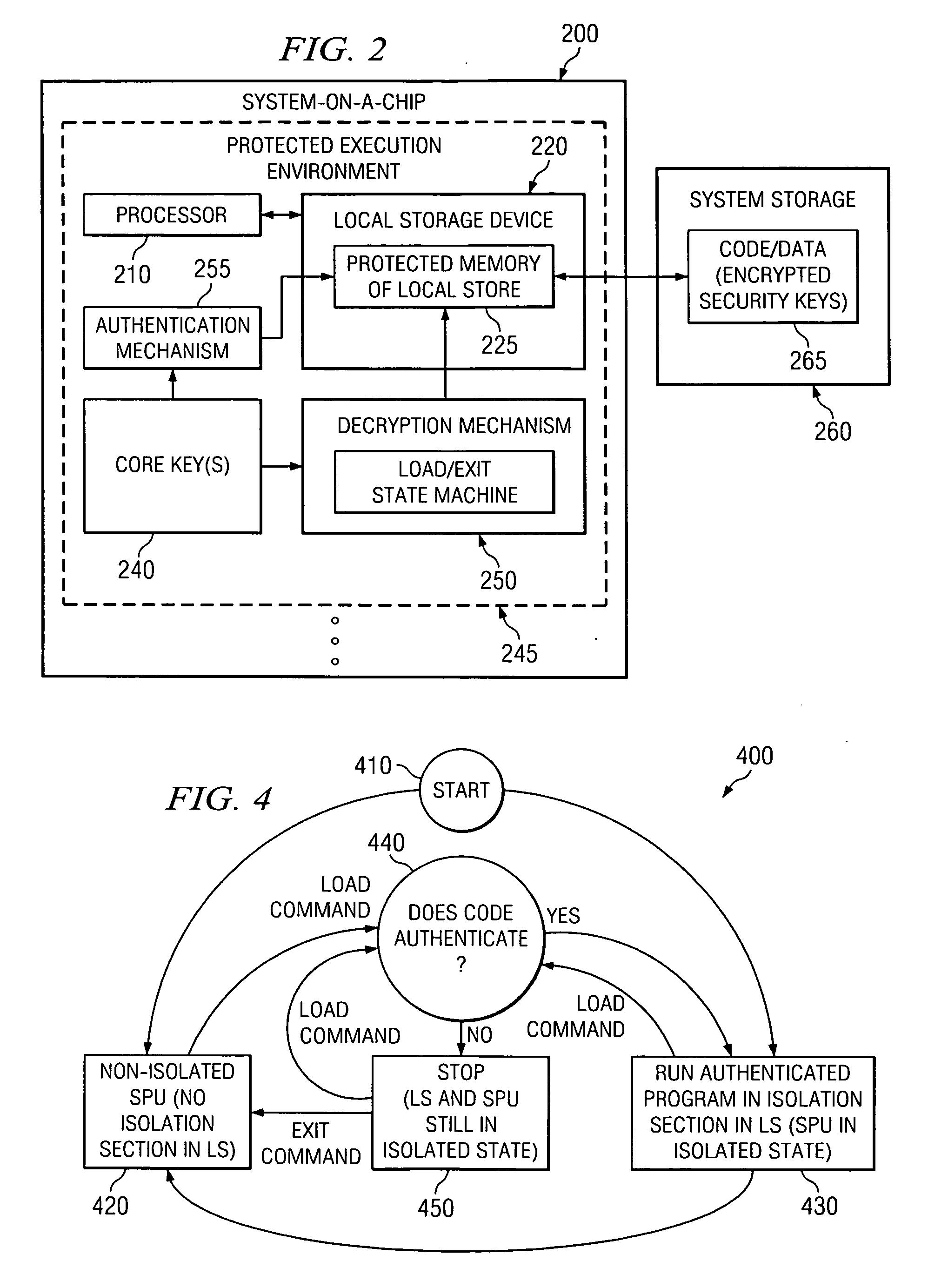
InactiveUS20070179904A1Protection attackGenerate accuratelyDigital data processing detailsUser identity/authority verificationComputer hardwareChain of trust
An apparatus and method for providing a sealed storage in a data processing device are provided. Processors of the data processing device may operate in a hardware isolation mode which allows a process to execute in an isolated environment on a processor and associated memory thereby being protected from access by other elements of the data processing device. In addition, a hardware controlled authentication and decryption mechanism is provided that is based on a hardware core key. These two features are tied together such that authentication occurs every time the isolation mode is entered. Based on the core key, which is only accessible from the hardware when in isolation mode, a chain of trust is generated by providing authentication keys for authenticating a next piece of software in the chain, in each piece of software that must be loaded, starting with the core key.
Owner:IBM CORP
Computer system and measuring method thereof
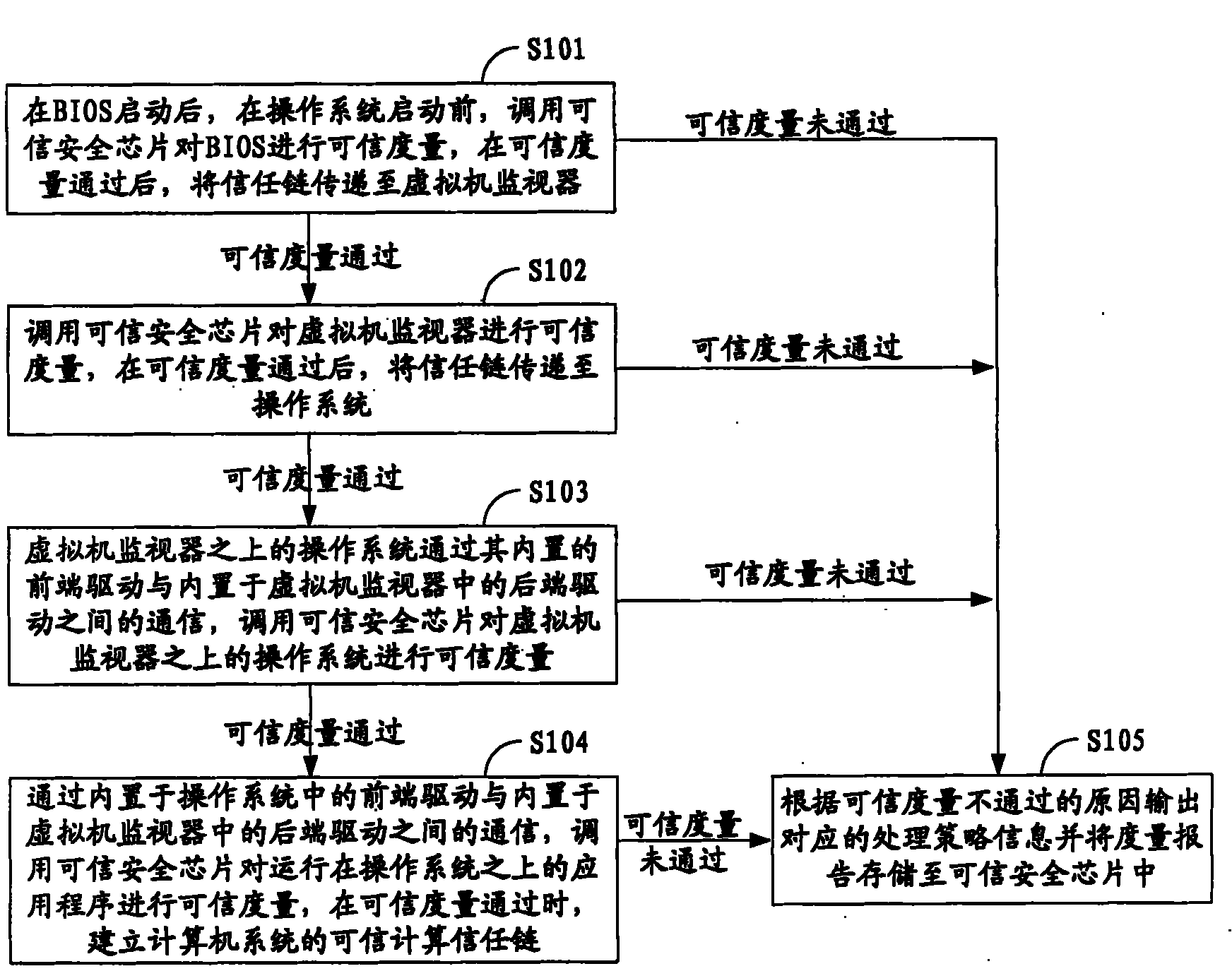
ActiveCN102136043AImprove securityHardware monitoringInternal/peripheral component protectionOperational systemComputerized system
The invention is suitable for the field of computer application and provides a computer system and a measuring method thereof. The method comprises the following steps of: after the startup of a BIOS (Basic Input Output System) and before the startup of an operating system, calling a credible security chip to perform measurement of trust on the BIOS and transmitting a trust chain to a virtual machine monitor after the measurement of trust passes; calling the credible security chip to perform measurement of trust on the virtual machine monitor and transmitting a trust chain to the operating system after the measurement of trust passes; calling the credible security chip to perform measurement of trust on the operating system and transmitting a trust chain to an application program running on the operating system after the measurement of trust passes; and calling the credible security chip to perform measurement of trust on the application program running on the operating system and establishing a dependable computing trust chain of the computer system when the measurement of trust passes. By adopting the embodiment of the invention, the security of the computer system can be greatly enhanced.
Owner:天津长城计算机系统有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com