Trusted computing cryptogram platform suitable for general computation platform of electric system
A technology of trusted computing and general computing, applied in the field of trusted computing, can solve problems such as inability to actively defend, actively defend, and insecure information systems, so as to reduce the risk of being destroyed and tampered, and ensure safe and stable operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The specific embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
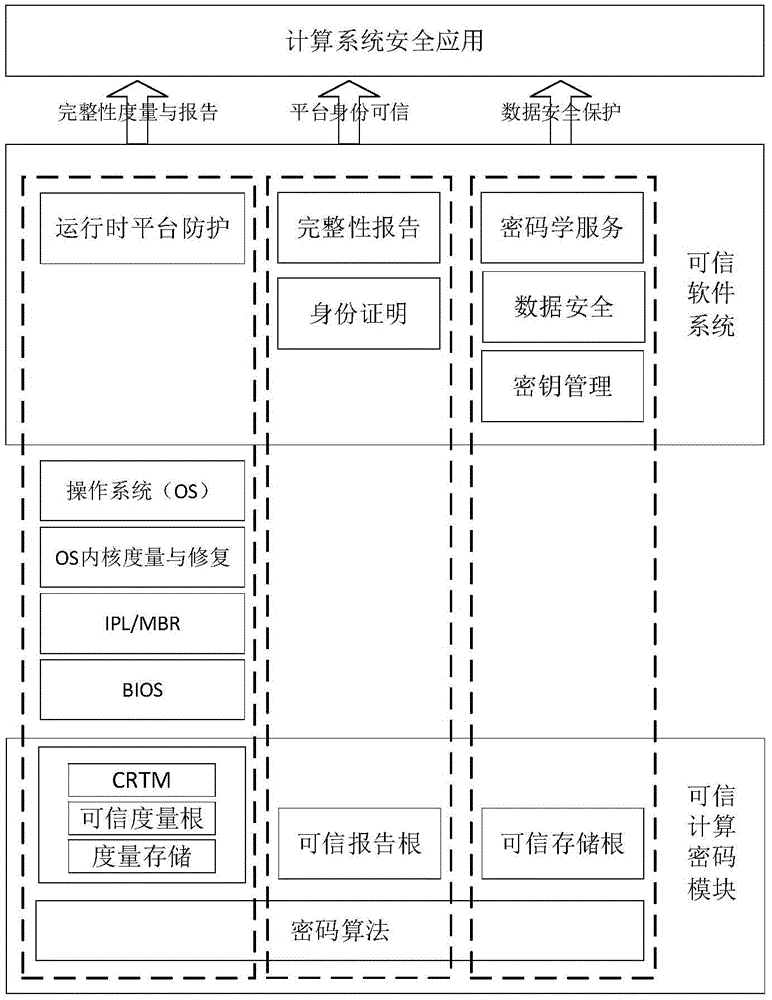
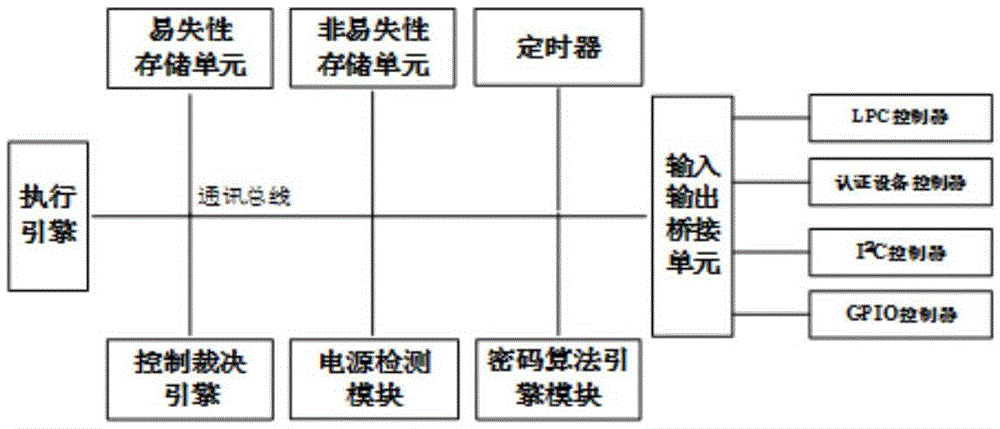
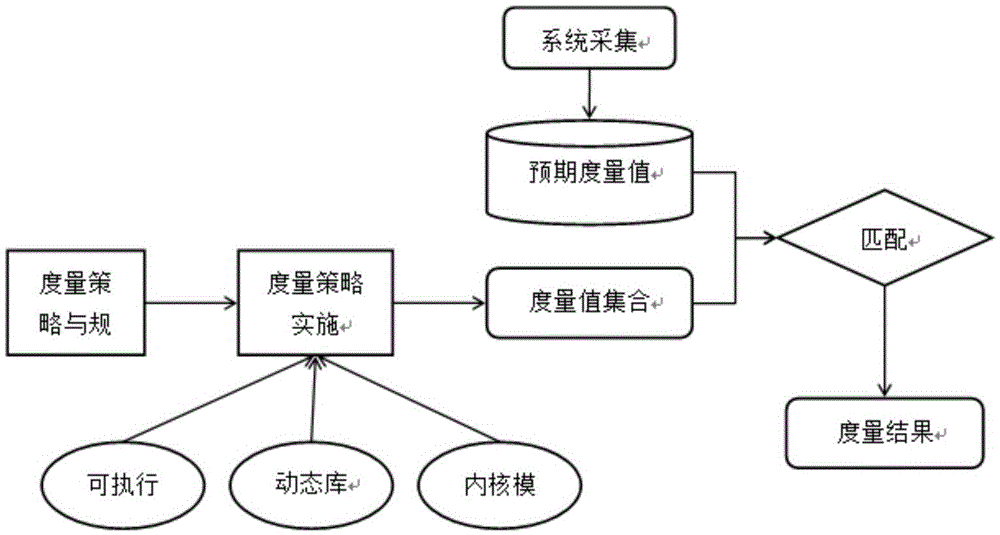
[0045] When the system starts, the trusted chip first measures the integrity of the BIOS, and compares the measurement result with the expected value collected during the initial operation of the system and stored in the trusted chip. If the results are consistent, it shows that the BIOS has not been tampered with and is credible. The measurement code in the BIOS will measure the OSLoader (including the master boot sector MBR, the operating system boot sector, etc.), when it is determined that the OSLoader is credible Next, execute the loader of the operating system. Before loading the operating system, OSLoader first measures the operating system and trusted computing cryptographic platform, and when it is judged to be credible, loads and executes the operating system and trusted computing cryptographic platform. After the operat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com