Patents
Literature
56results about How to "Realize active defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
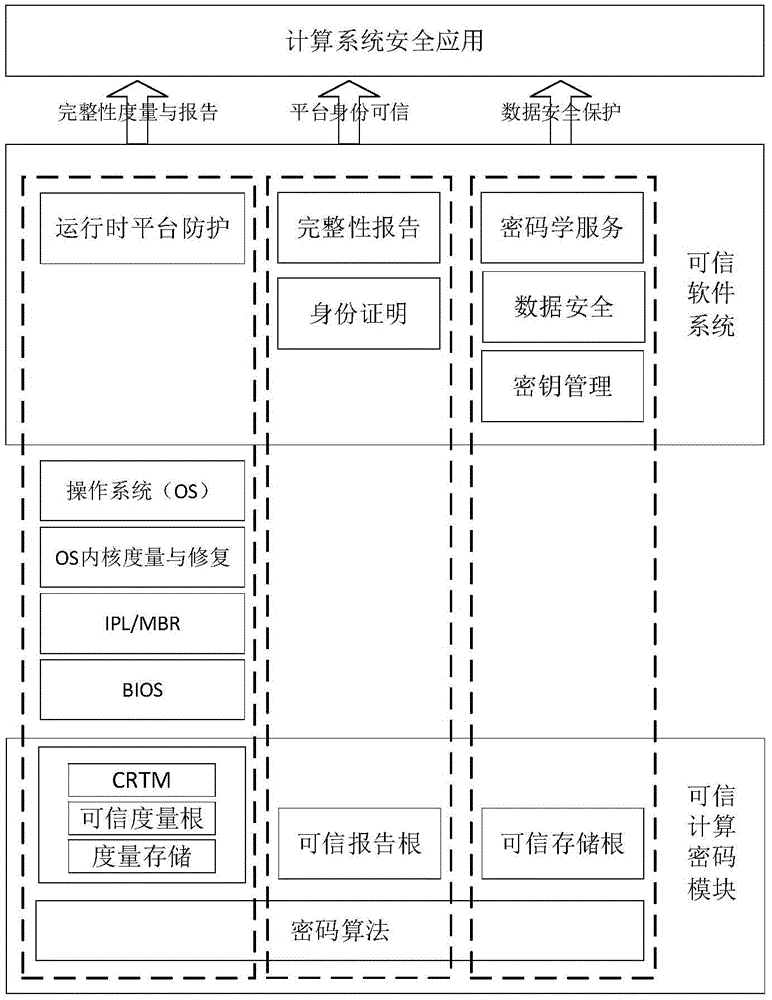
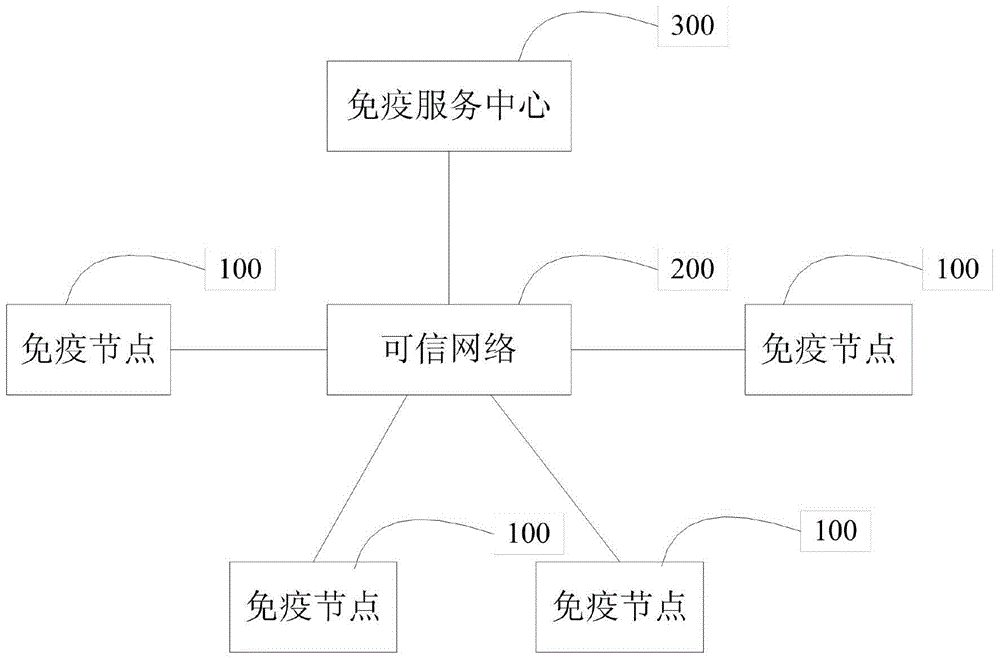
Trusted computing cryptogram platform suitable for general computation platform of electric system
ActiveCN105468978AEnsure credibleGuaranteed recognition effectPlatform integrity maintainanceOperational systemSoftware system
The invention provides a trusted computing cryptogram platform suitable for a general computation platform of an electric system. The cryptogram platform comprises a trusted computing cryptogram module and a trusted software system, wherein the trusted computing cryptogram module comprises a trusted measurement root, a trusted storage root and a trusted report root and is a transferring starting point of a platform trust chain; and the trusted software system comprises a trusted computing cryptogram driving module, a measurement module and an auditing module and provides an interface which uses the trusted computing cryptogram platform for an operating system and application software. The trusted computing cryptogram module is the trusted root which provides trusted environment for the operation of the trusted computing cryptogram platform, and the trusted software system is a core for realizing the functions and the service of the trusted computing cryptogram platform and provides guarantee for the management of the trusted computing cryptogram platform. The trusted computing cryptogram platform can provide functions including static measurement, dynamic measurement, white lists, access control and the like for a business system, and manages the sources and the operation of the system software to guarantee that the software is trusted, recognizable and controllable.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +5
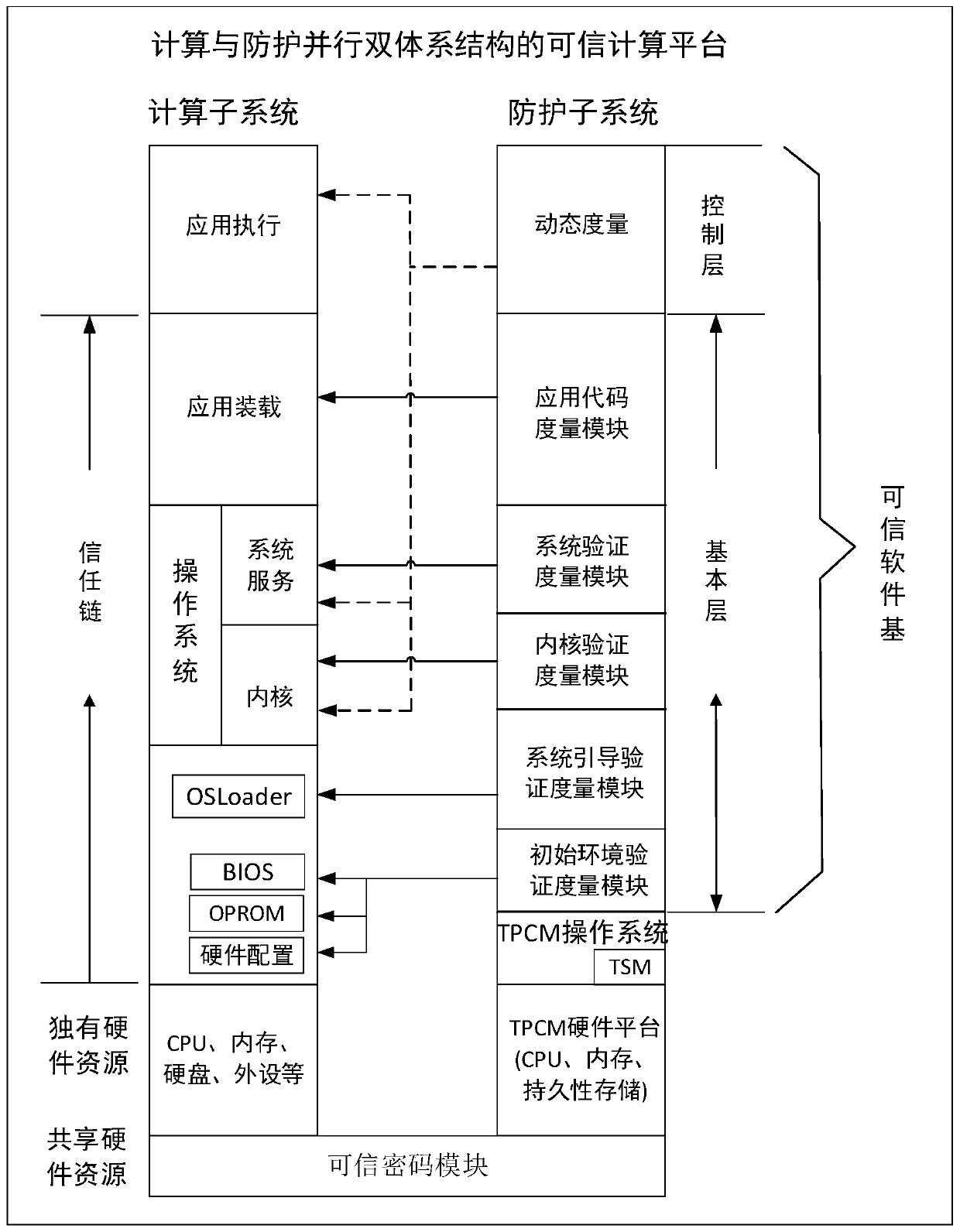
Trusted computing platform of a computing and protection parallel double-system structure
ActiveCN109871695AComputable, measurable and controllableRealize active security protectionPlatform integrity maintainanceActive safetyTrusted Computing
The invention discloses a trusted computing platform of a computing and protection parallel double-system structure. wherein the trusted computing platform comprises a computing subsystem and a protection subsystem which are parallel, the computing subsystem is used for completing a computing task, and the protection subsystem is used for carrying out active measurement and active control on the computing subsystem according to a trusted strategy through a trusted platform control module; And the protection subsystem is specifically used for respectively carrying out static measurement and dynamic measurement on the computing subsystem through the trusted software base. According to the trusted computing platform provided by the invention, active safety protection is realized while computing is realized through the computing subsystem and the protection subsystem which are parallel to each other. In addition to establishing a static trust chain which takes a trusted platform control module as a trust root for step-by-step measurement, a dynamic measurement mechanism based on a security trusted strategy is also designed, and active defense on the whole computer system in the starting and operating processes of the computer is realized.
Owner:北京自主可信科技有限公司
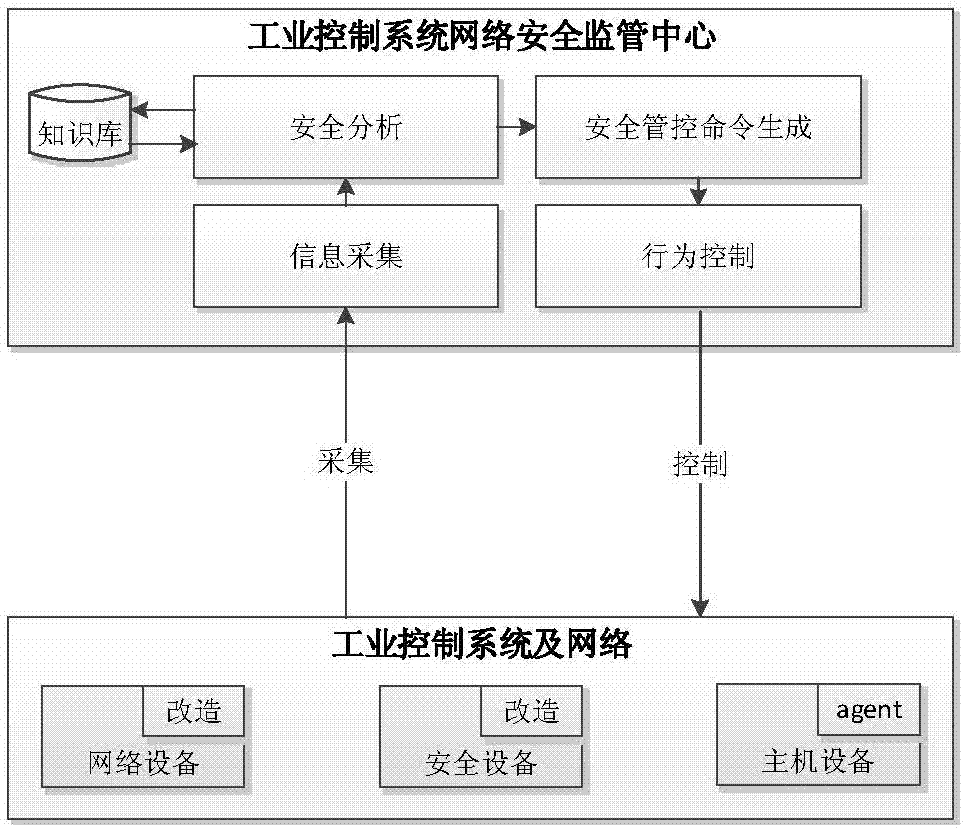
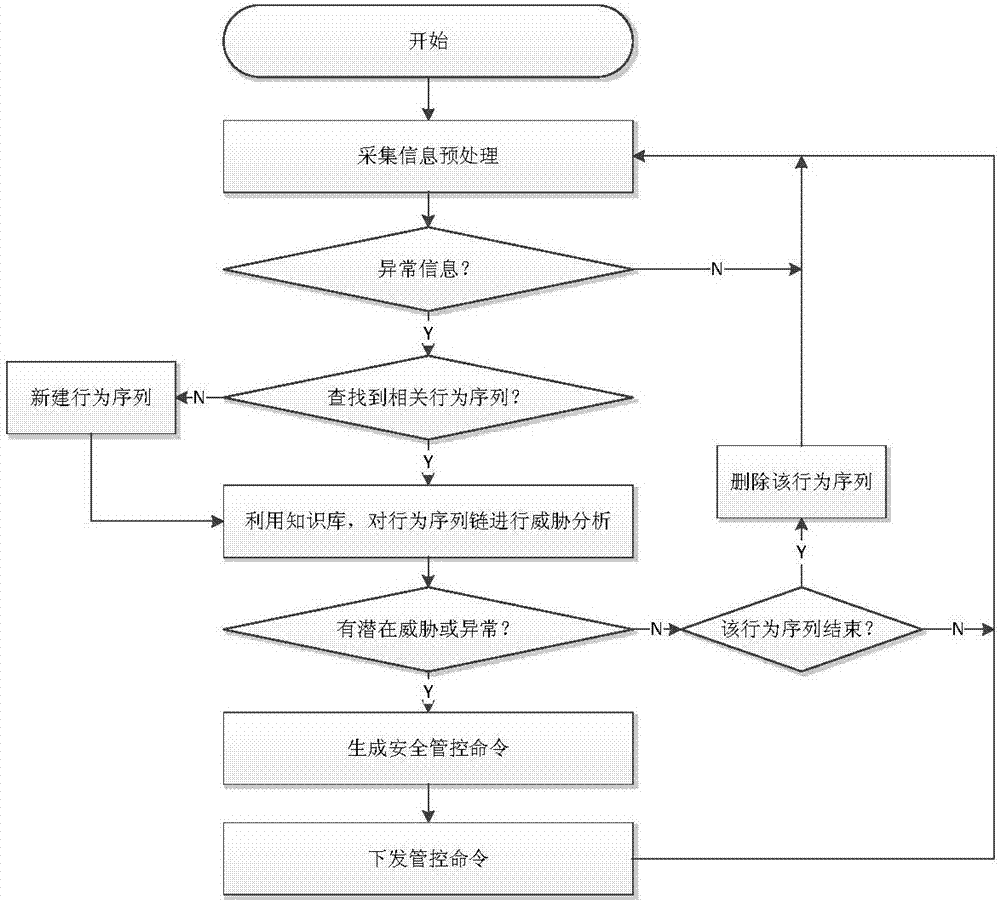
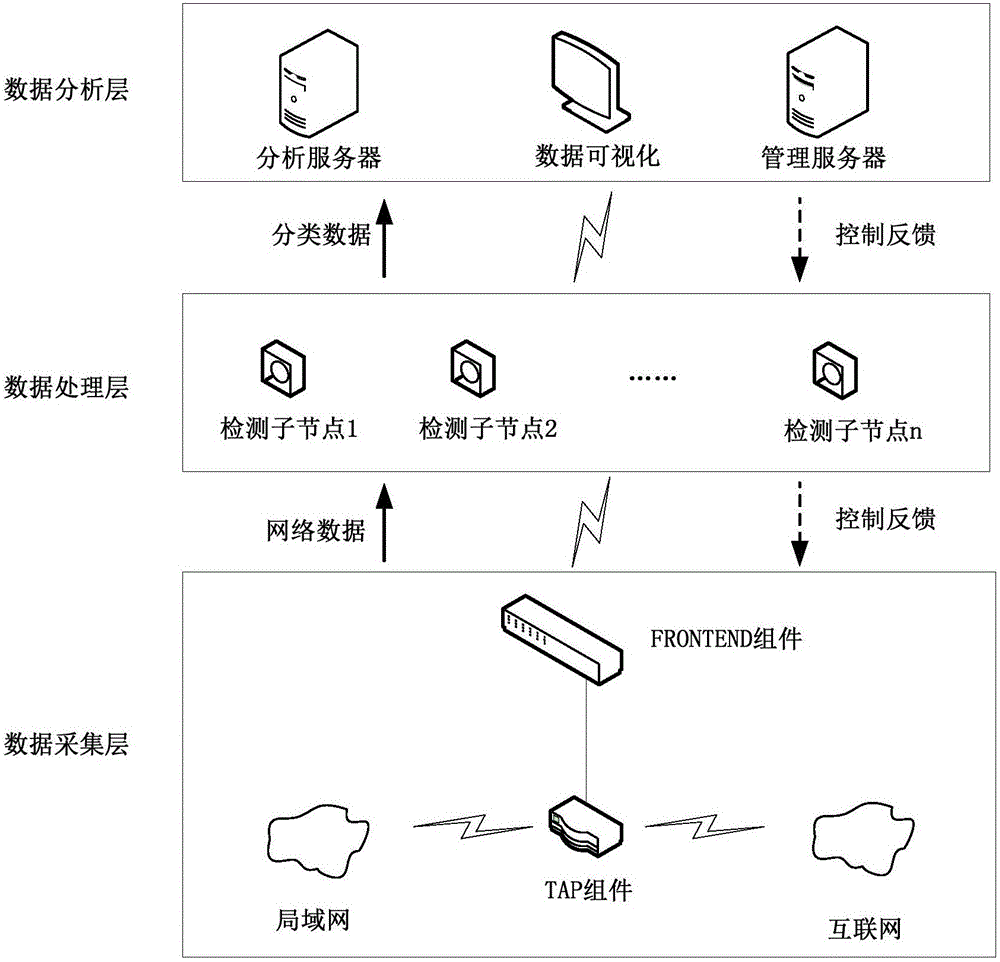
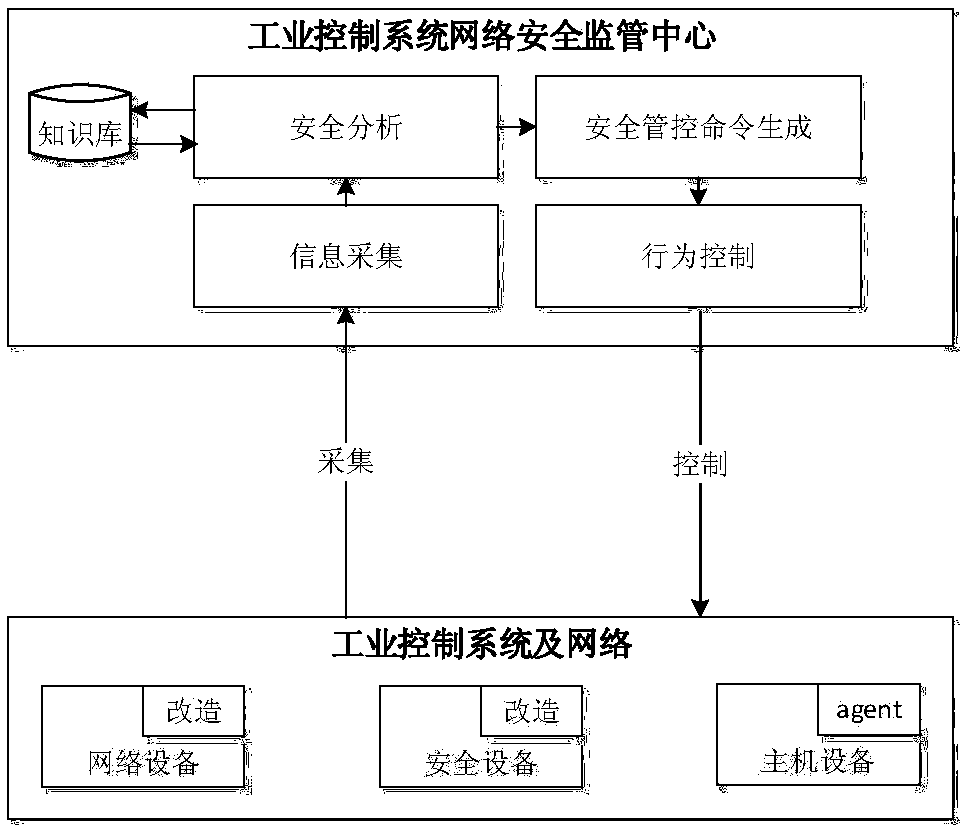
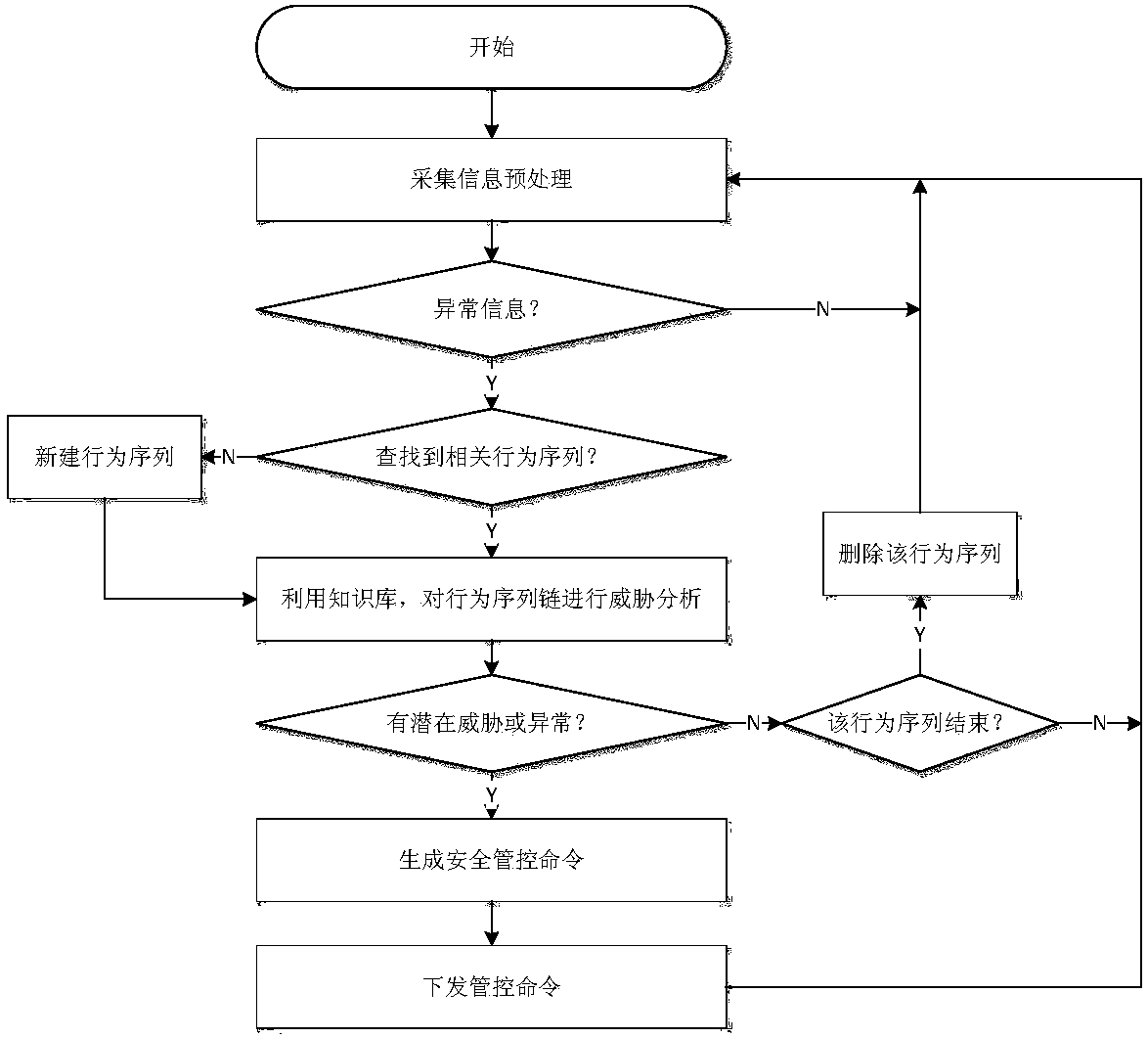
Network security monitoring method for industrial control system
ActiveCN107493265ARealize real-time monitoringRealize active defenseData switching networksRelevant informationIndustrial systems
The invention discloses a network security monitoring method for an industrial control system. The method comprises the following steps: collecting relevant information of an internal monitoring object of the industrial control system; performing security analysis on the collected relevant information; and when potential abnormal behavior is found through analysis, generating a relevant safety control order, and issuing the order to the relevant monitoring object for execution so as to block the abnormal behavior. According to the invention, real-time monitoring on major hidden security dangers of the industrial control system such as peripheral access, personnel operation, network external connection and the like is realized through abundant data acquisition of core networking equipment of the industrial control system. At the same time, through analysis processing on various behavior, the abnormal behavior is found and blocked timely, and thus real active defense of the industrial system is realized. For the current difficulty of effectively applying traditional security protection measures to the industrial control system, the major security threats to the industrial control system at present are well solved from the perspective of monitoring early warning.
Owner:NANJING NARI GROUP CORP +2
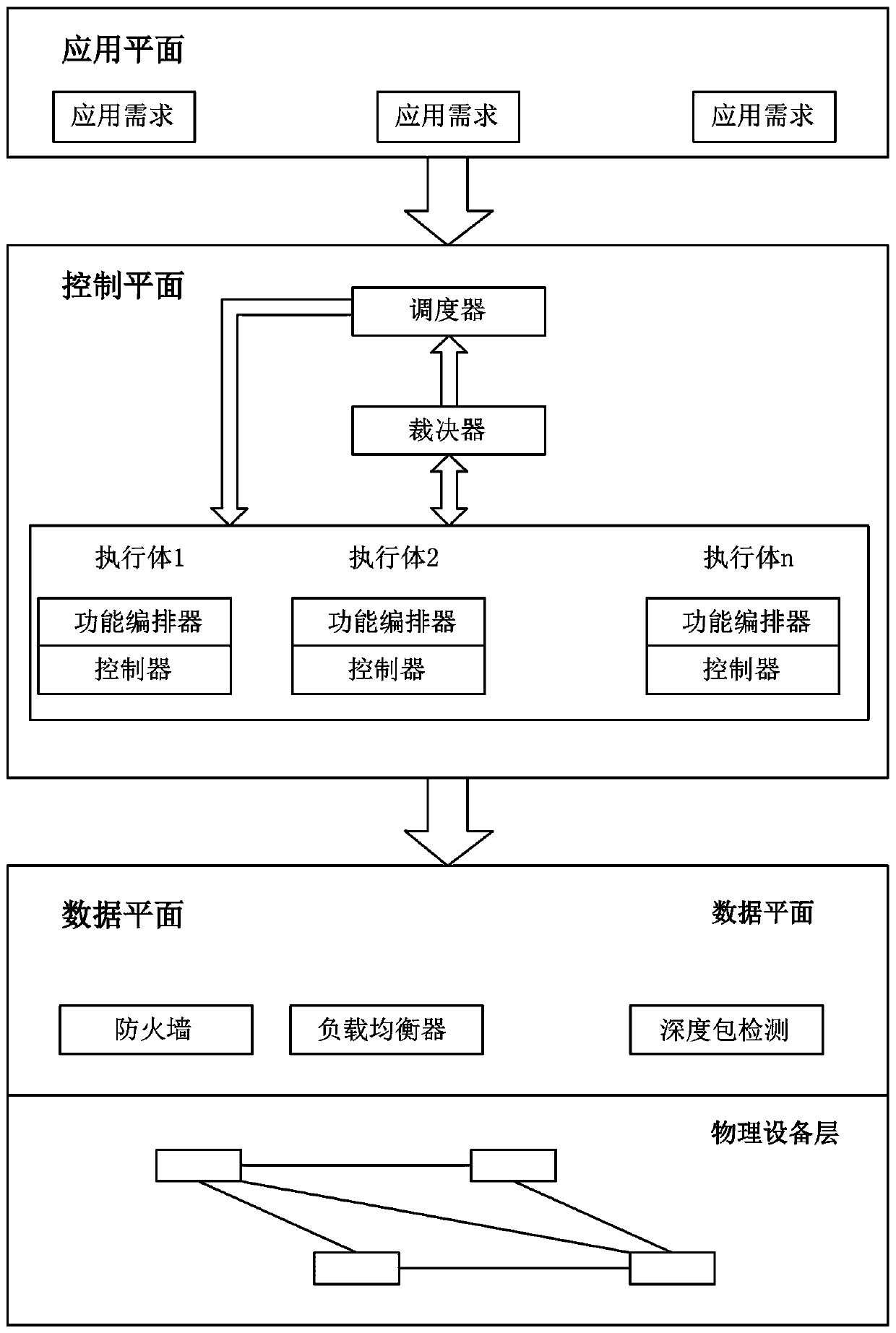
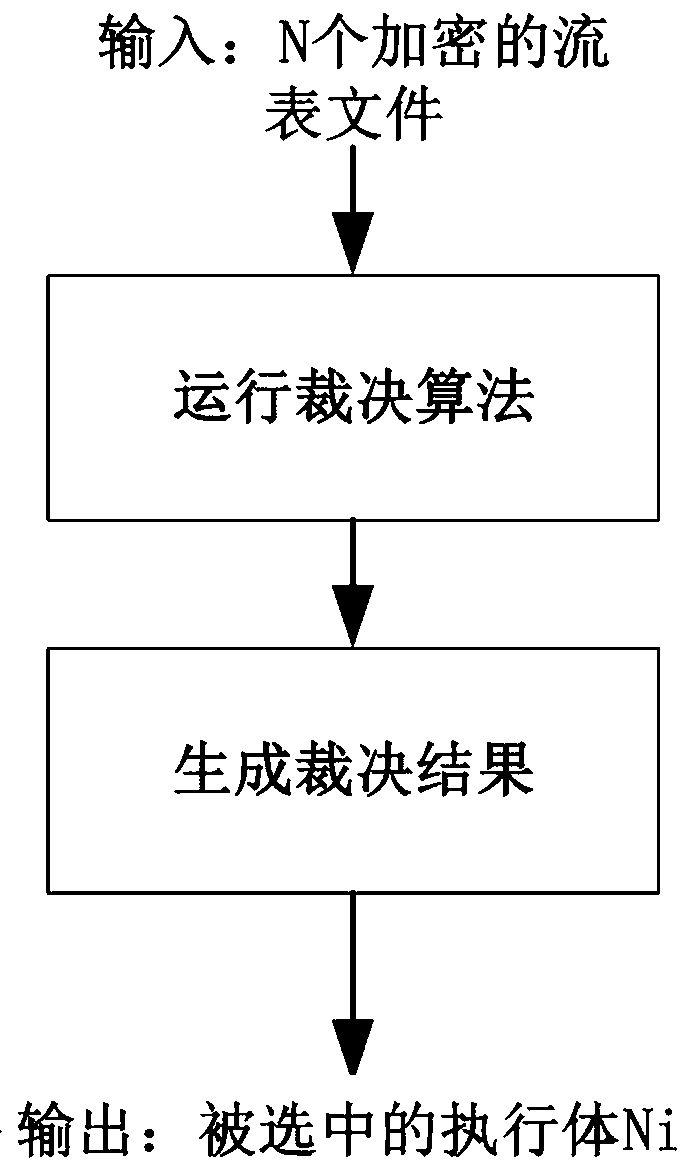
Mimetic defense-based network function deploying method in software defined network
ActiveCN109587168AIncrease attack difficulty and attack costImprove securityData switching networksVirtualizationSoftware-defined networking
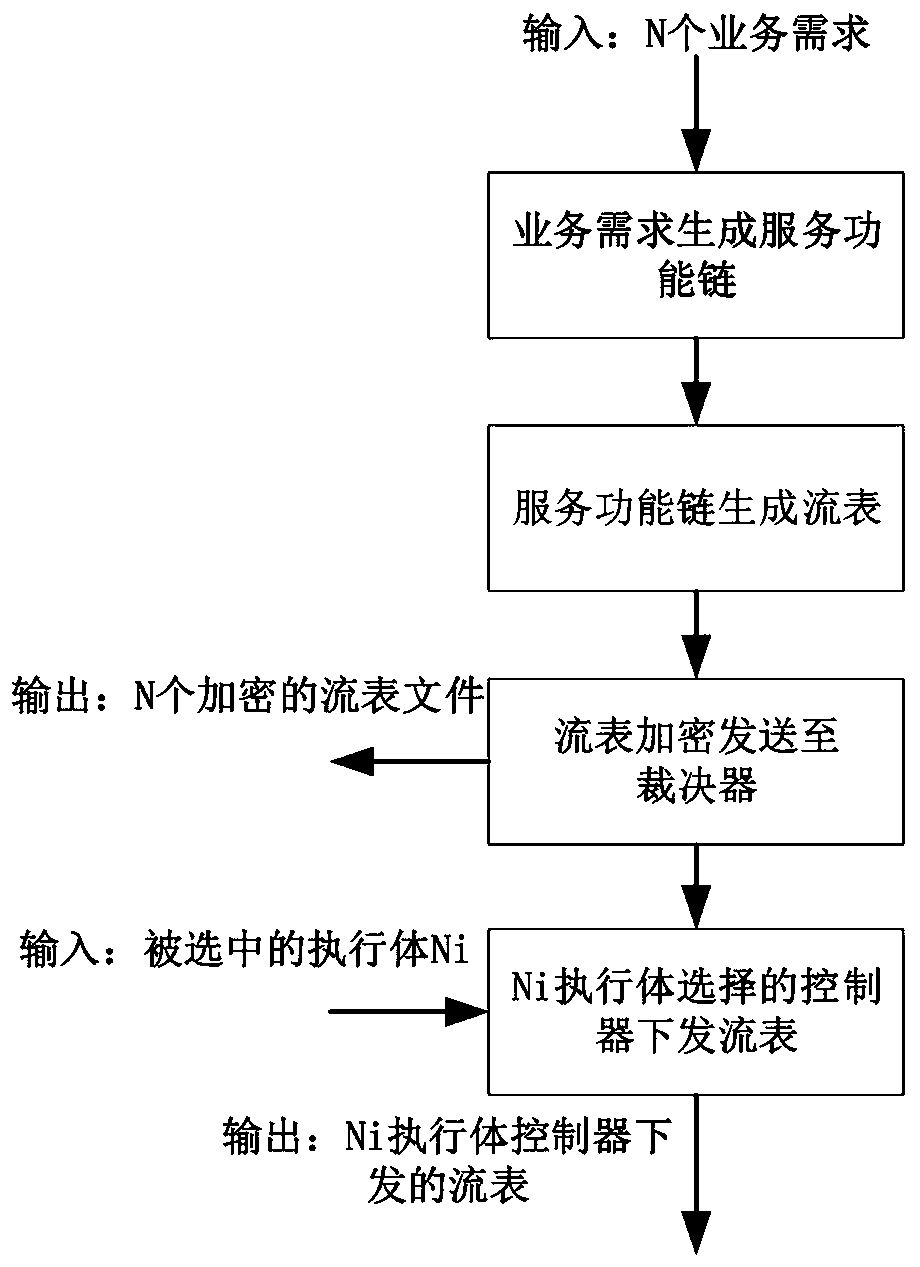
The invention provides a mimetic defense-based network function deploying method in a software defined network. The method comprises the following steps: 1, virtual network functions are deployed on adata plane through a virtualization technology; 2, based on a mimetic architecture, a heterogeneous executor pool, a dispatcher and an adjudicator part are constructed on a control plane; 3, the dispatcher performs dynamic dispatching on heterogeneous executors in the heterogeneous executor pool based on business requirements of an application plane, and a business deployment strategy flow tablefile is generated; 4, the adjudicator adjudicates the business deployment strategy flow table file and outputs the number of the selected heterogeneous executor to the heterogeneous executor pool; and5, the heterogeneous executor pool controls the selected heterogeneous executor to issue the business deployment strategy flow table file to the data plane according to the number of the selected heterogeneous executor, and the business deployment strategy flow table file is guided to complete deployment of the network functions through the virtual network functions.
Owner:河南信大网御科技有限公司
Network attack data analysis and intelligent processing method
The invention relates to a network attack data analysis and intelligent processing method which comprises the steps that: S1, various network safety devices are connected to one or more SDN switches to form a safety resource pool; S2, a safety controller sends out a safety control instruction to operate the SDN switches, and according to different user safety demands, pulling network traffic to designated network safety devices to carry out processing; and S3, the safety controller carries out strategy centralized management and state real-time monitoring on the network safety devices, and when the network safety devices are abnormal, the safety controller sends out a safety strategy instruction to carry out balanced load or traffic migration so as to ensure no influence on normal network communication. The network attack data analysis and intelligent processing method is characterized by further comprising the steps of: by a Telent protocol, actively collecting real-time state information, local flash memory information and collection log center information of a network device, a safety device and a server; carrying out big data real-time comprehensive analysis; updating and synchronizing a third-party IDS feature library; carrying out whole network attack modeling; generating a defense instruction; and carrying out combination defense.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
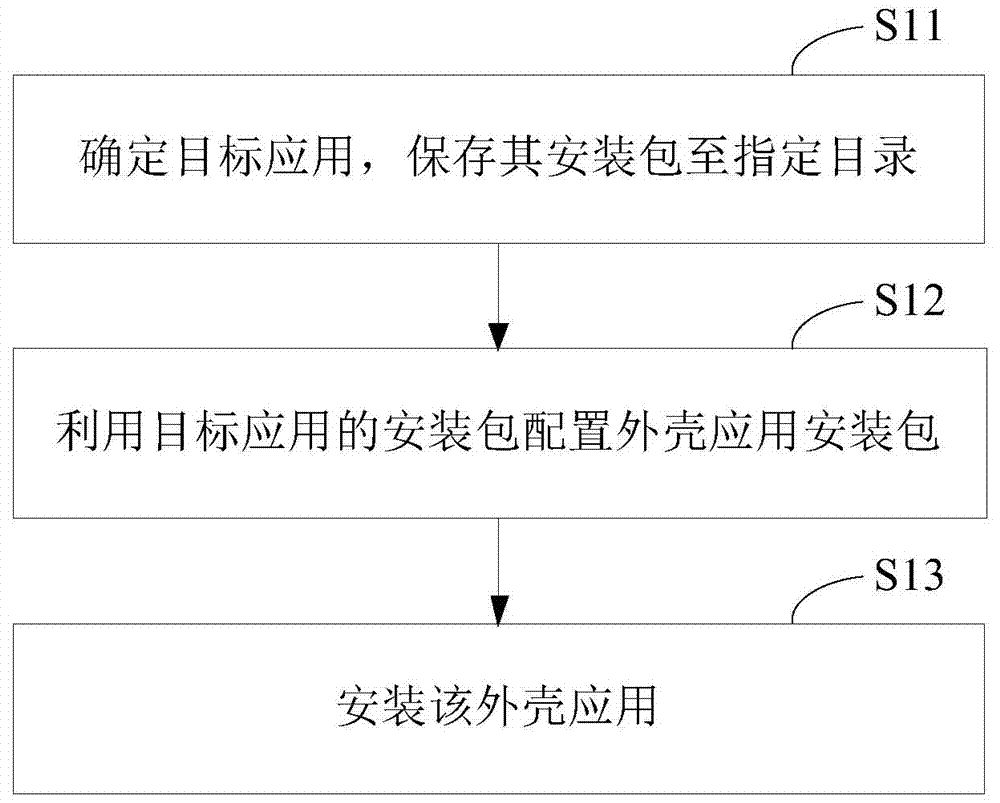
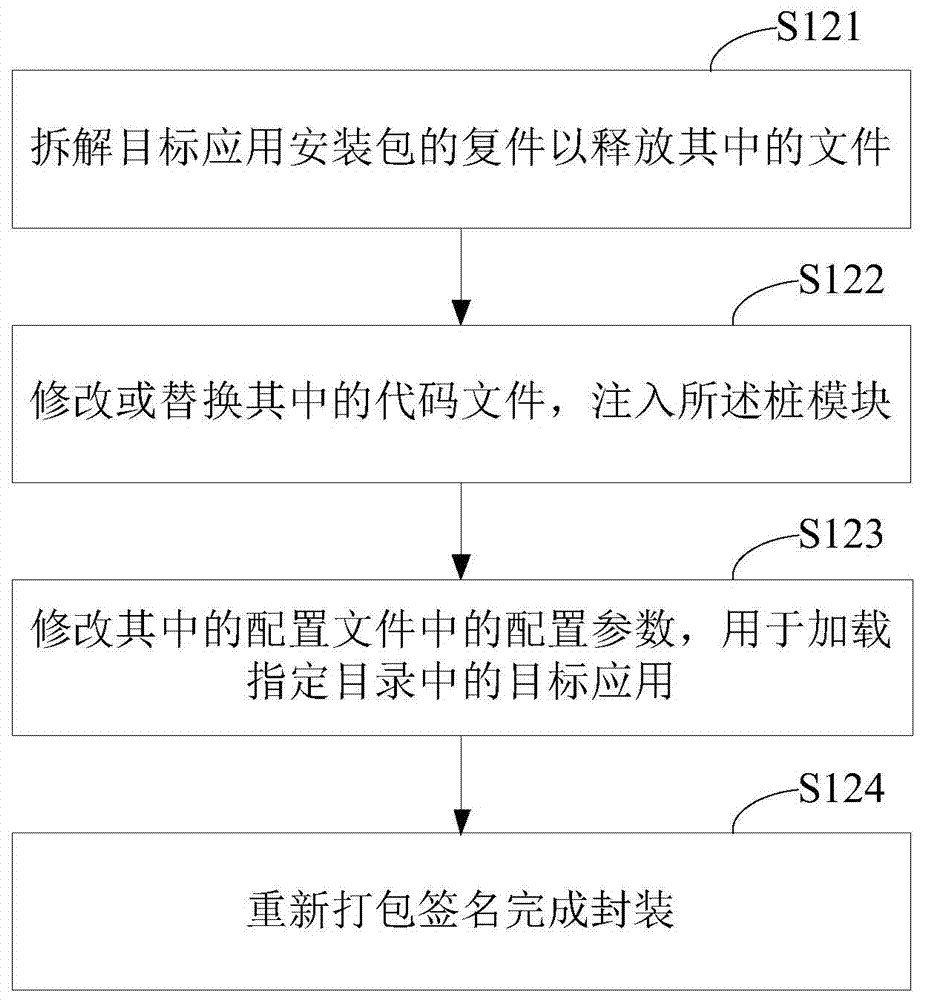
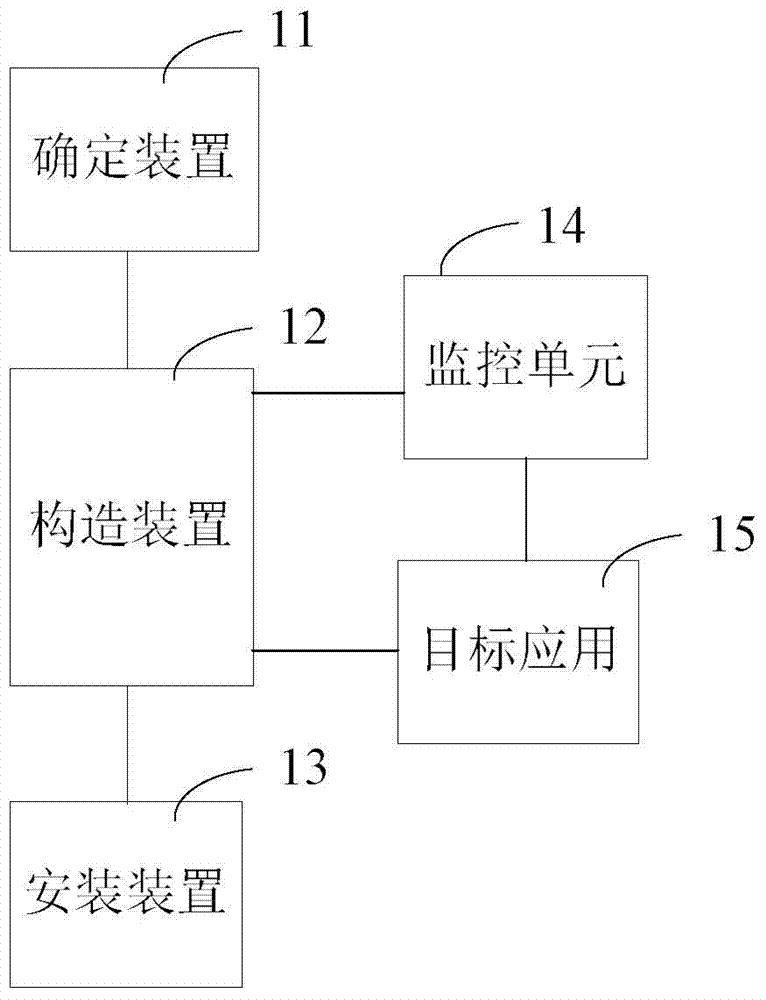
ROOT-free active defense configuration method and device
ActiveCN104239786ARealize active defenseRealize dynamic active defensePlatform integrity maintainanceEngineeringActive Defense
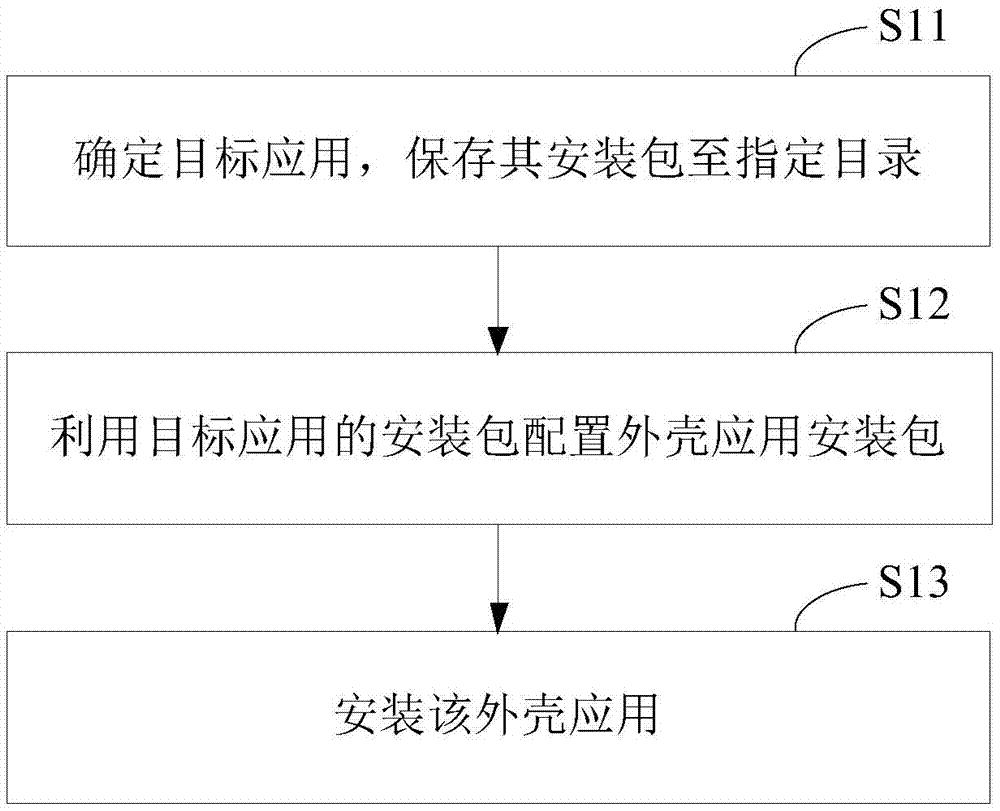
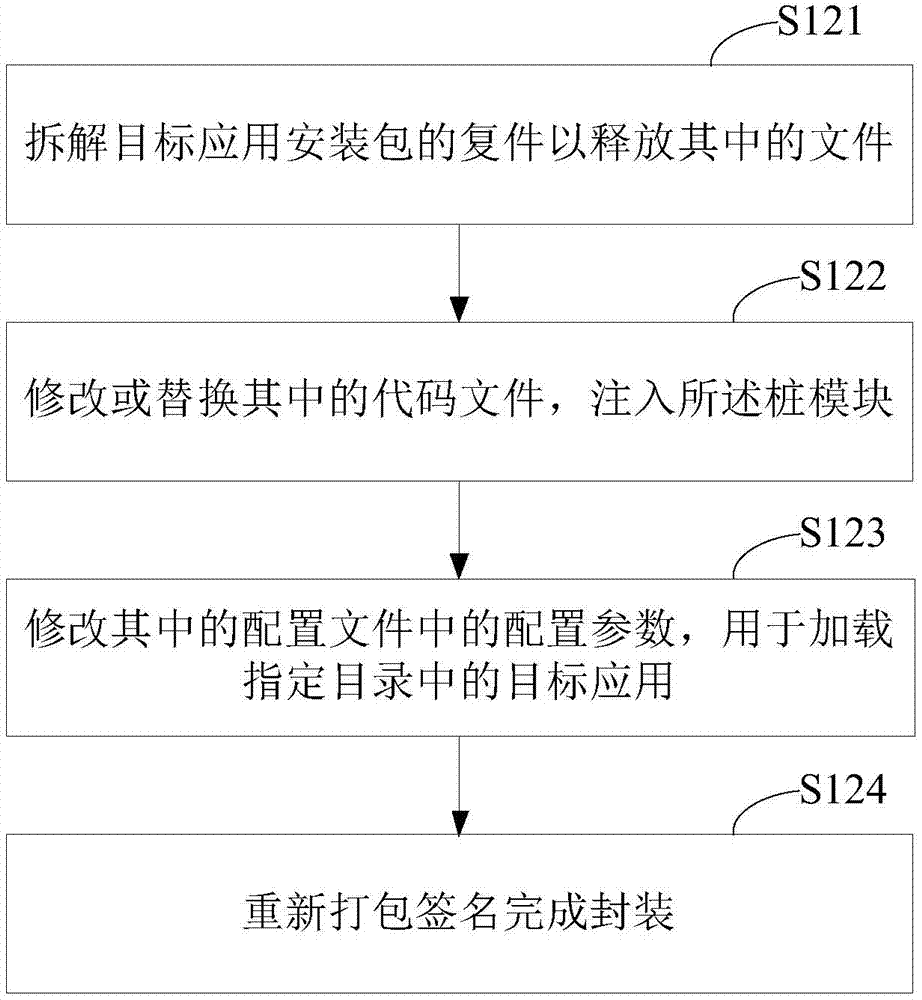
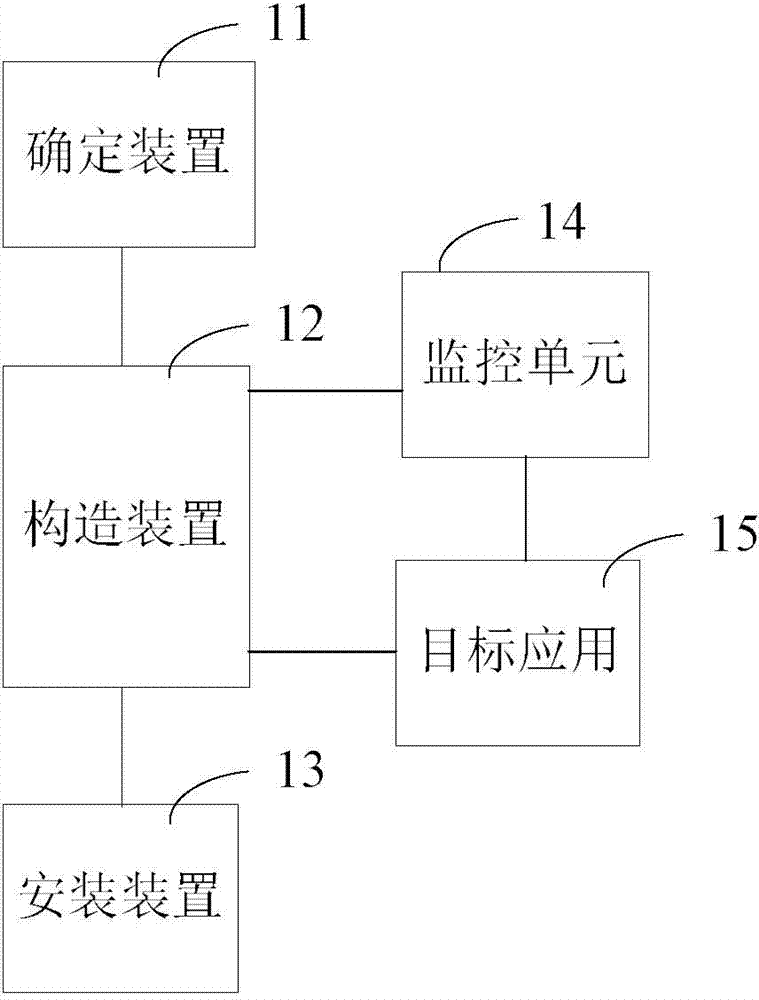
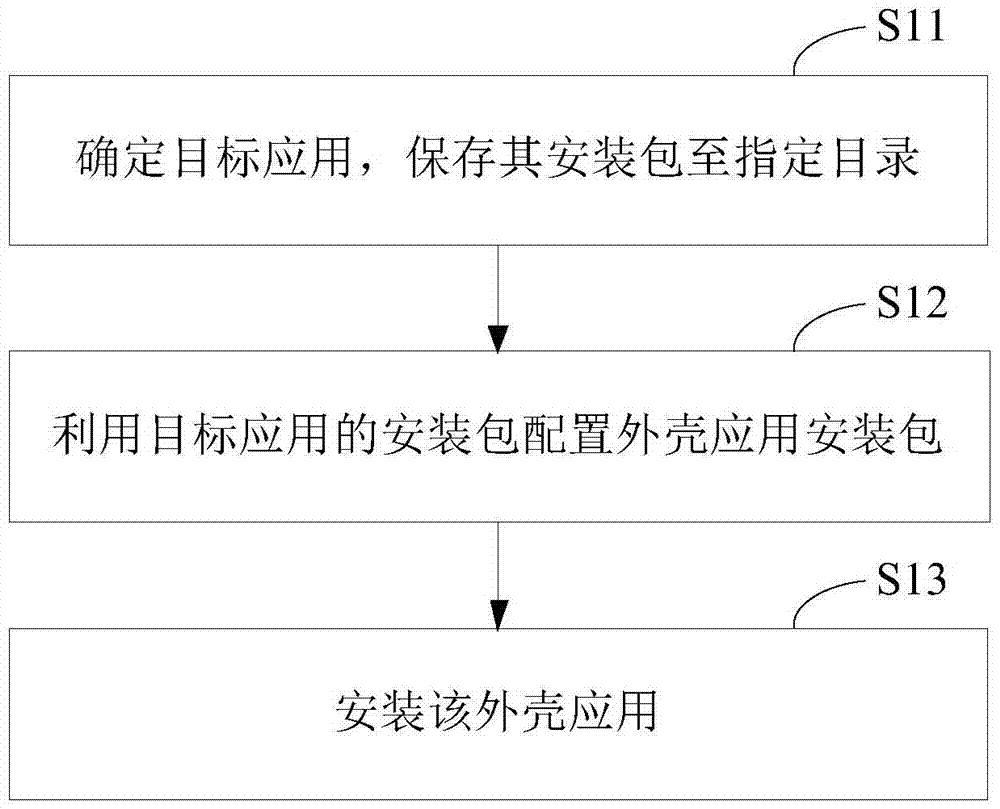
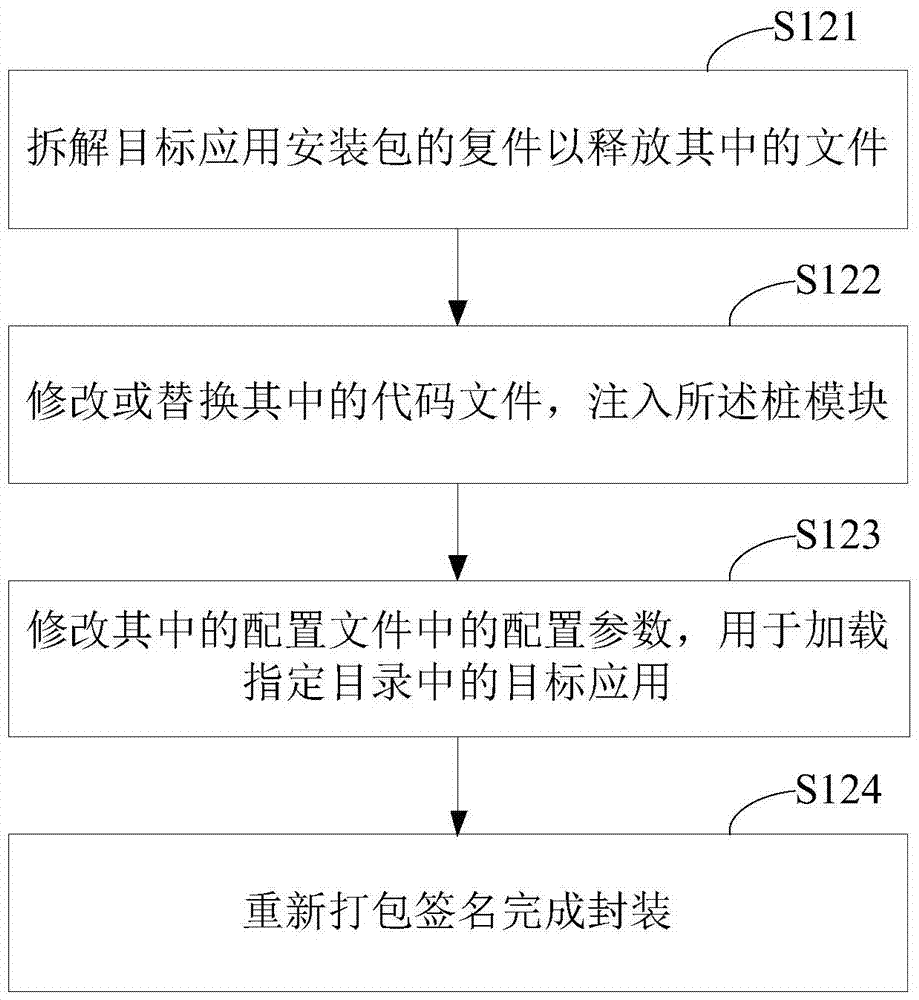
The invention provides a ROOT-free active defense configuration method and a corresponding device. The method comprises the following steps that a target application is determined, and an installation package of the target application is stored to a specified catalogue; an outer shell application installation package is configured through the installation package of the target application, a stub module for calling a monitoring unit is injected into the outer shell application installation package, configuration parameters in the pier module are modified to load the target application, and the monitoring unit is used for carrying out hooking monitoring on event behaviors from the target application; the outer shell application is installed. According to the active defense scheme, an existing system is modified a little, system compatibility cannot be influenced, and method and the device are easy to implement and efficient.
Owner:BEIJING QIHOO TECH CO LTD
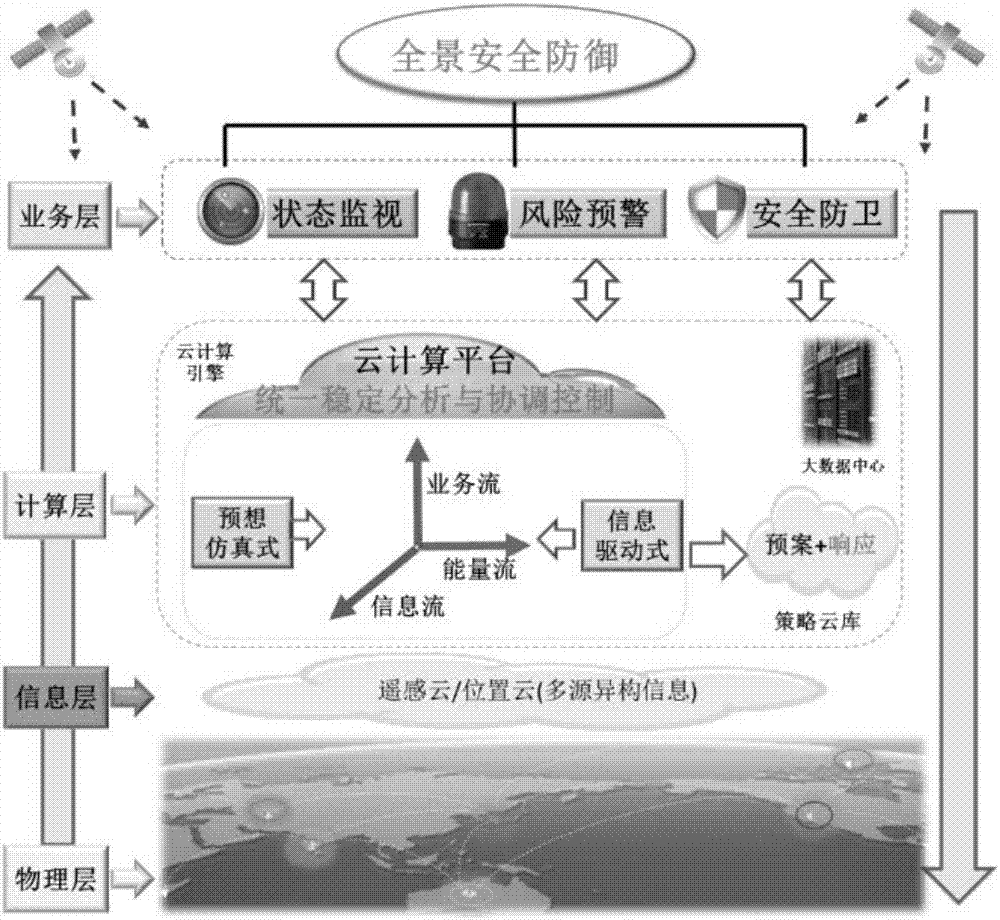
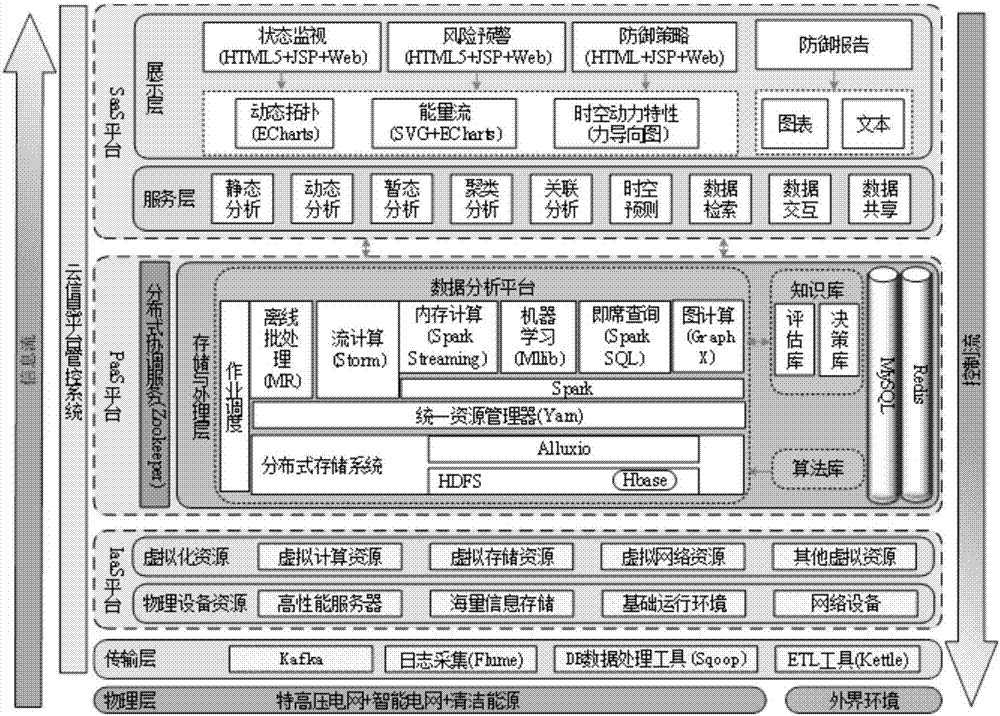
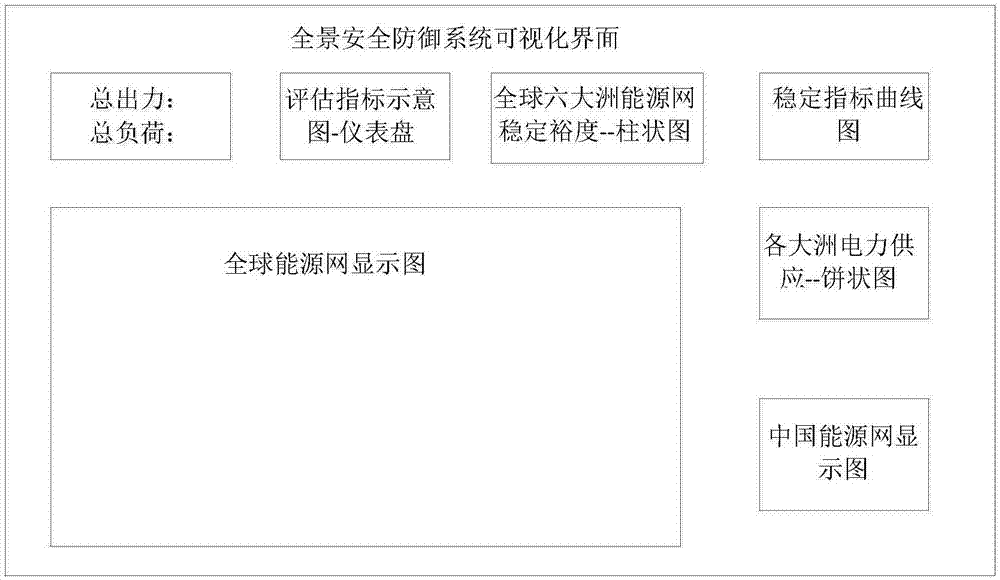
Large power grid panoramic security defense method and system
ActiveCN107133255AImprove depth and breadth of useApplication value and pre-promotion of large projectsResourcesOther databases browsing/visualisationTechnical supportPower grid
The invention provides a large power grid panoramic security defense method and system. The system comprises a physical layer, a transmission layer, a calculation layer and a presenting layer; the defense system fuses and transmits acquired periodical power grid data, and analyzes and stores transmission data to conduct data mining on power grid data; according to data mining of the power grid data, the power grid data after being processed is calculated through a big data technology, and a calculation result is presented. According to the large power grid panoramic security defend method and system, electrical space-time big data intelligent mining depth and utilization breadth are effectively expanded, and solid technical support is provided to achieve global energy Internet active defense.
Owner:CHINA ELECTRIC POWER RES INST +2
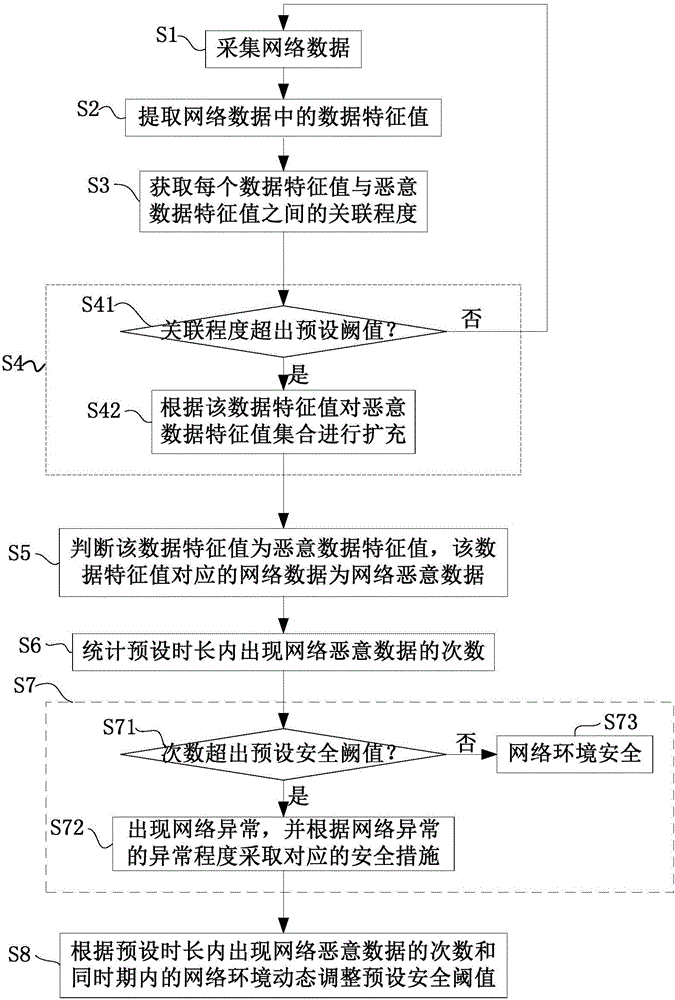
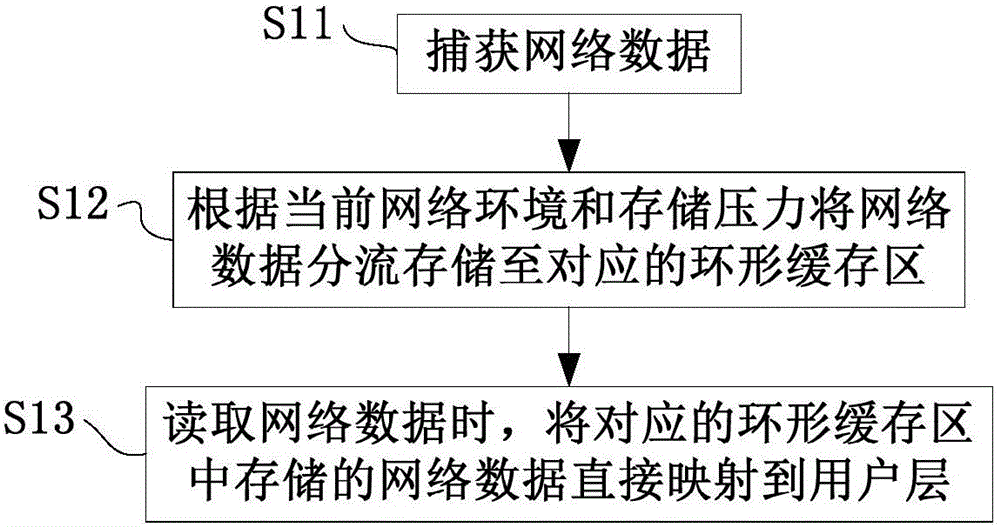
Network malicious data detection method, device and system
ActiveCN106101130AReduce false positivesRealize predictive judgmentTransmissionLeakage rateFalse alarm
The invention provides a network malicious data detection method, device and system, and the method comprises the steps: firstly collecting network data, and extracting a data characteristic value in the network data; secondly obtaining the correlation between the data characteristic value and a malicious data characteristic value in a pre-stored malicious characteristic set; and finally carrying out the expansion of the malicious data characteristic set according to the data characteristic value when the correlation between one data characteristic value and the malicious data characteristic value exceeds a preset correlation threshold value. The method can continuously correct and optimize the malicious data characteristic set, achieves the prediction judgment of unknown network threats and the active defense of the network safety, and reduces the false alarm and alarm leakage rates of intrusion detection of network malicious data.
Owner:国富瑞数据系统有限公司 +1
Active defense method and device
ActiveCN104239797ARealize monitoringMonitor Event BehaviorPlatform integrity maintainanceComputer compatibilityActive Defense
The invention provides an active defense method and device. The method includes the following steps of responding to an instruction used for running a target application and running a corresponding shell application; sequentially loading a monitoring unit and the target application by means of the shell application, monitoring and capturing event behaviors of the target application through the monitoring unit; obtaining an event behavior processing strategy after specific event behaviors are captured, and processing the specific event behaviors according to the processing strategy. According to the active defense scheme, an existing system is modified a little, compatibility of the system is not influenced, and the method is easy and efficient to implement.
Owner:BEIJING QIHOO TECH CO LTD
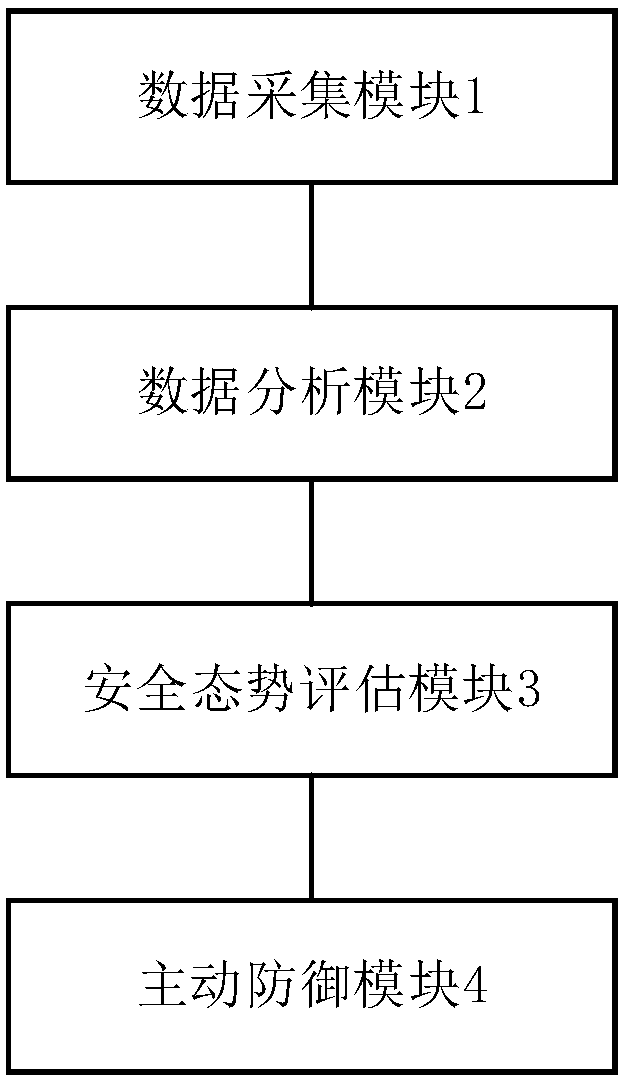
Active defense system for security threats to key information infrastructure based on artificial intelligence
InactiveCN108494802ARealize monitoringImprove securityTransmissionCritical information infrastructureSecure state
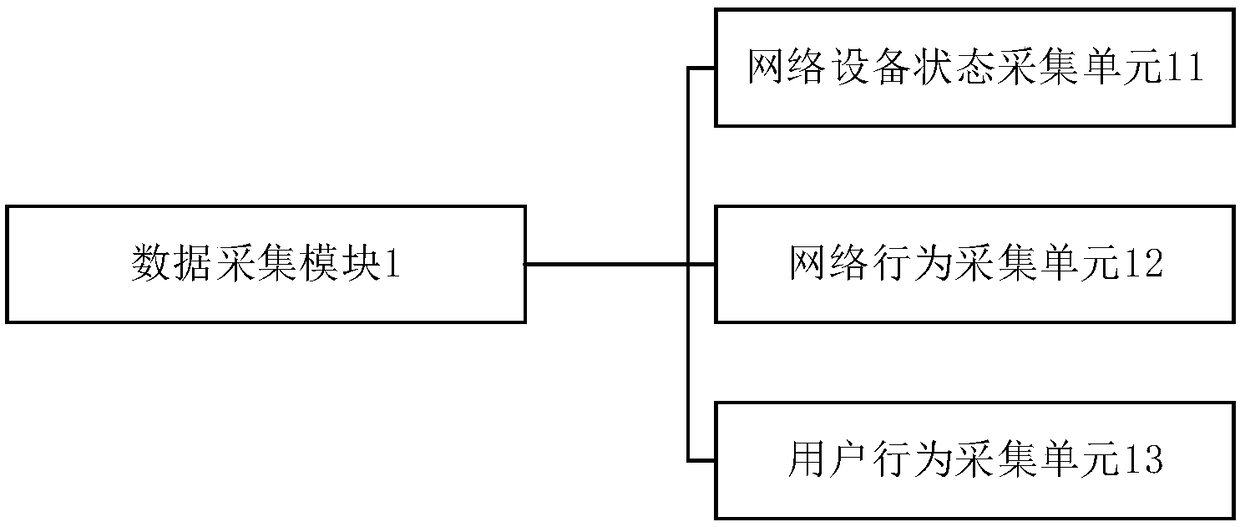
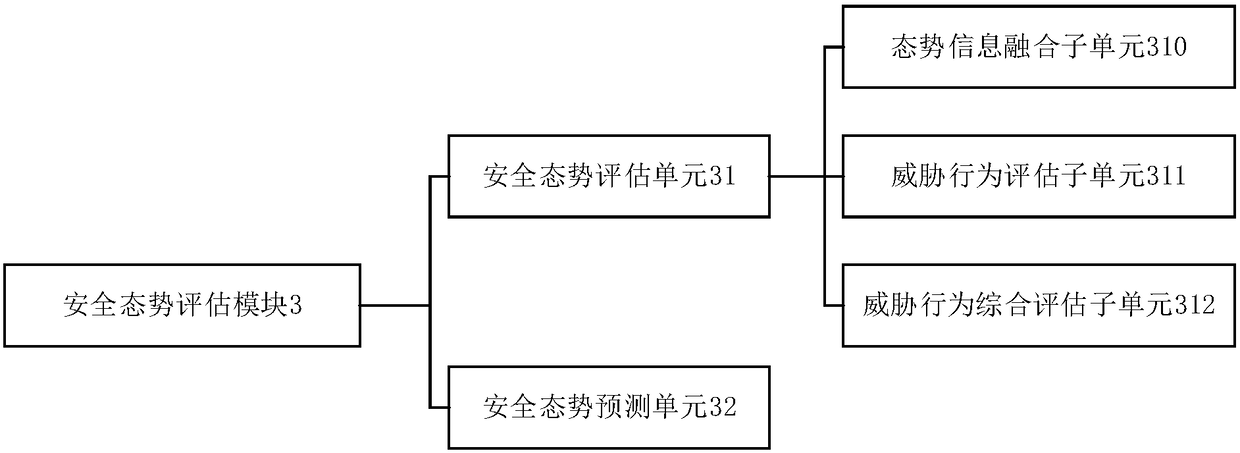
The invention provides an active defense system for security threats to a key information infrastructure based on artificial intelligence. The system comprises a data acquisition module, a data analysis module, a security situation assessment module and an active defense module, wherein the data acquisition module is used for acquiring network detection data in a network system; the data analysismodule is used for analyzing and processing the acquired network detection data, and generating situation information used for describing a security state of network equipment; the security situationassessment module is used for assessing a secure state of the current network equipment according to an analysis result of the data analysis module; and the active defense module is used for determining a defense grade according to an assessment result of the security situation assessment module, and adopting a corresponding defense strategy according to the defense grade. According to the system,the threat behavior in the network system can be effectively detected, and different defense grades are determined according to a security situation value of the network equipment, so that the activedefense of the threat behavior is achieved, and the security and the stability of the network system are improved.
Owner:GUANGXI POWER GRID CORP
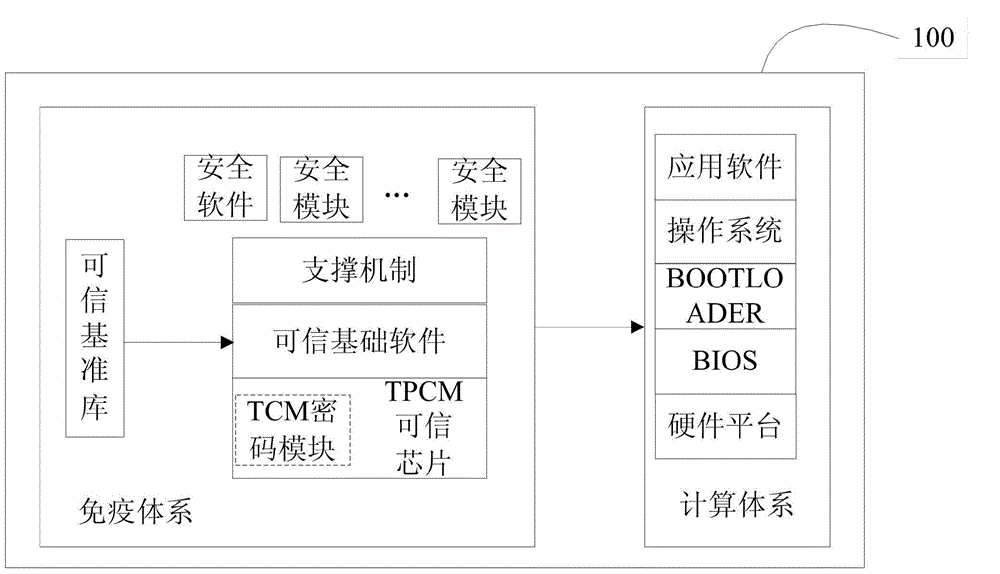
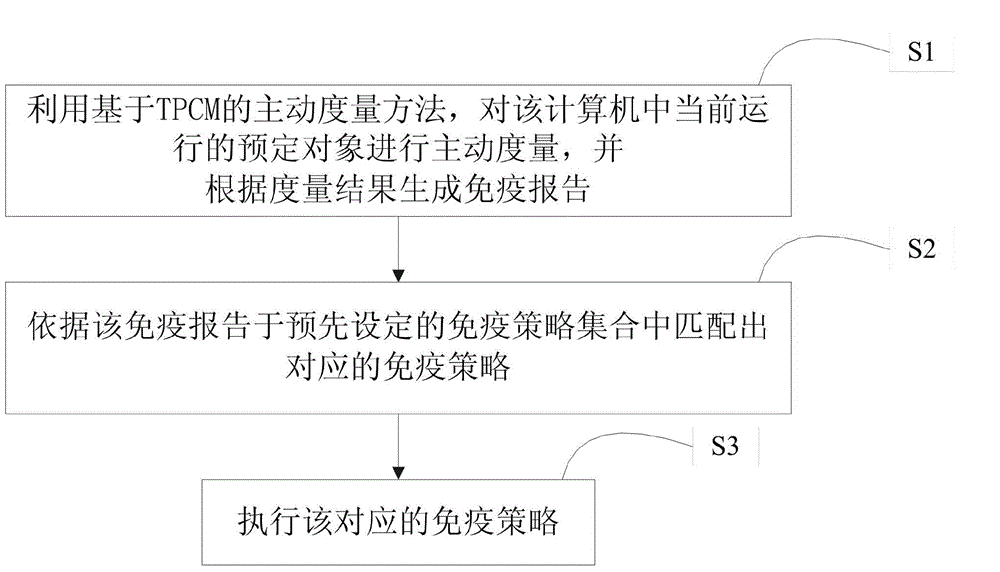
Computer immune system design method and realization
InactiveCN104933358AImprove securityRealize active defensePlatform integrity maintainanceImmune controlDesign methods
The invention discloses a computer immune system design method and realization. The method includes the steps that 1, an active measuring method based on a TPCM is used for actively measuring a preset object currently operating in a computer and generating an immune report according to the measuring result; 2, according to the immune report, a corresponding immune strategy is matched in a preset immune strategy set; 3, the corresponding immune strategy is executed. By executing the active measuring method based on the TPCM, active defense of a computer system is achieved, immune recognition is achieved before the preset object completely operates, immune control is carried out on any suspicious program according to the set immune strategy, and therefore the safety of the computer is improved.
Owner:沈军
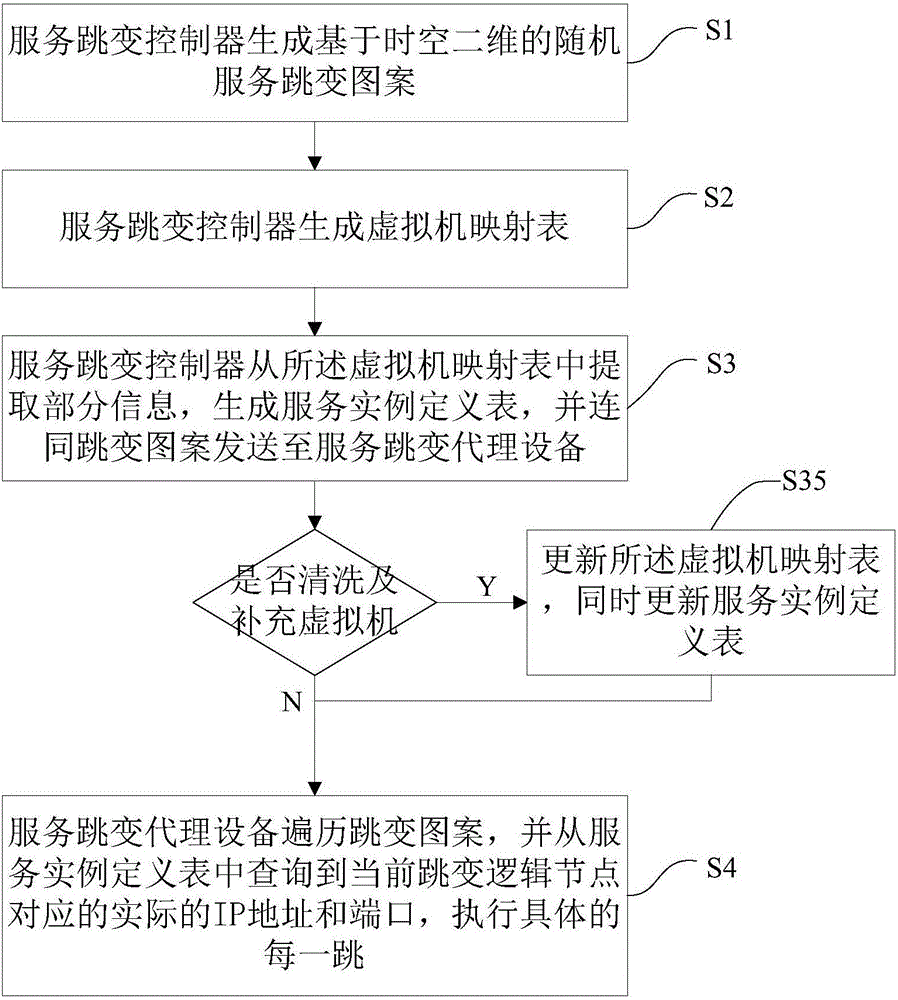
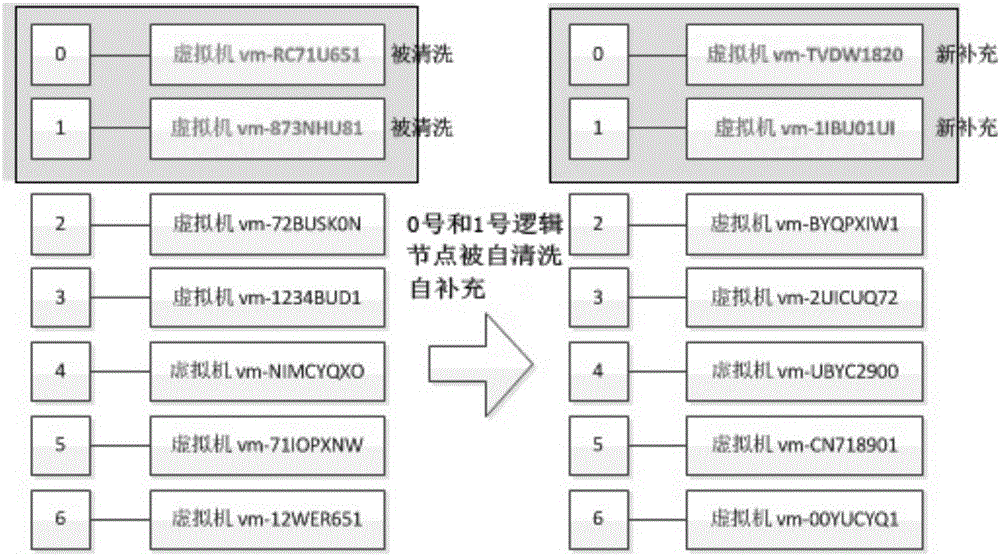
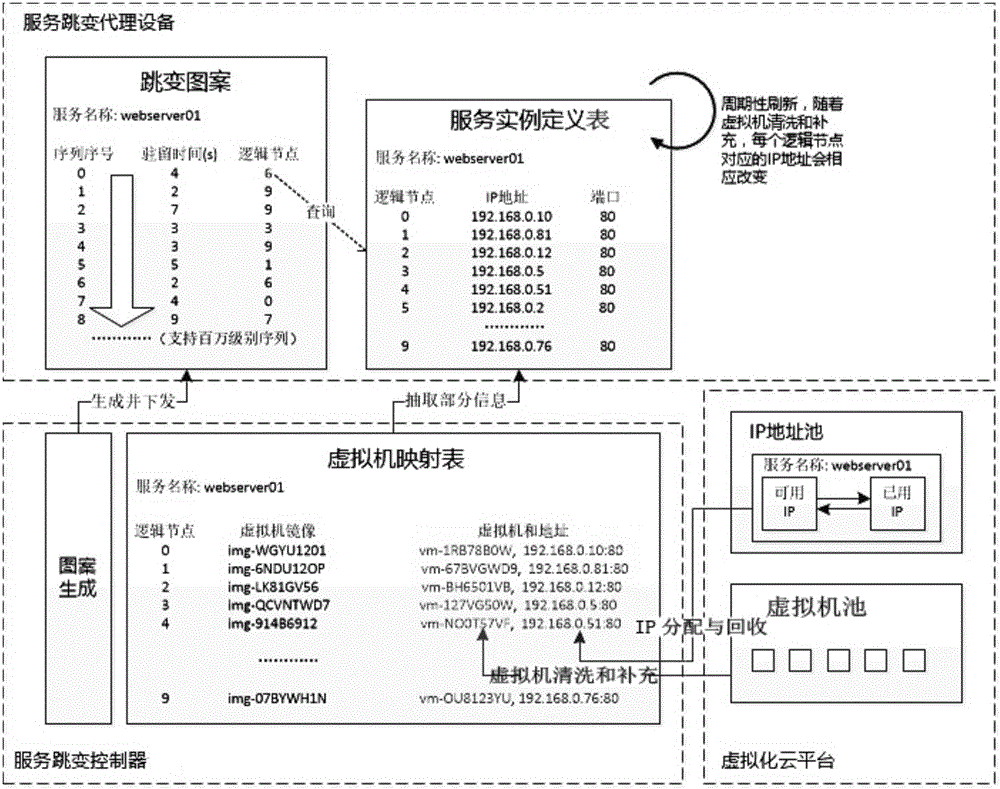
Dynamic service realization method and system base on service hopping and intelligent cleaning
ActiveCN105978875AIncrease variabilityAvoid frequent update issuesProgram controlTransmissionVirtualizationIp address
The invention provides a dynamic service realization method and system base on service hopping and intelligent cleaning suitable for the field of network information safety. The method comprises the following steps that a service hopping controller generates a time-space 2D based hopping pattern; the service hopping controller generates a virtual machine mapping table; the service hopping controller extracts part of information from the virtual machine mapping table to generate a service instance definition table, and the service instance definition table together with the hopping pattern is sent to a service hopping agent device; and the service hopping agent device traverses the hopping pattern, and inquires the service hopping agent device to obtain practical IP addresses and ports corresponding to present hopping logic nodes, and each hop is executed. According to schemes of the invention, virtual service hopping is combined with intelligent cleaning, and attacks of known and unknown Trojan and virus on network services can be defended actively.
Owner:中国人民解放军国防信息学院
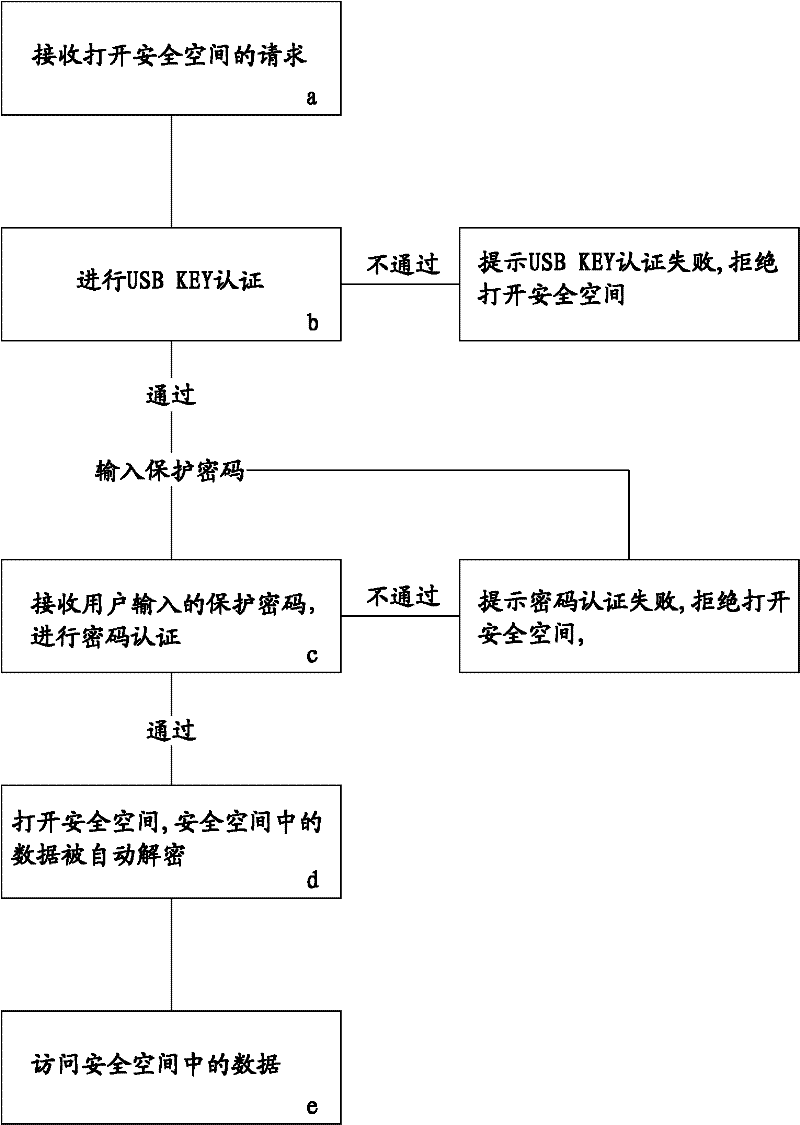
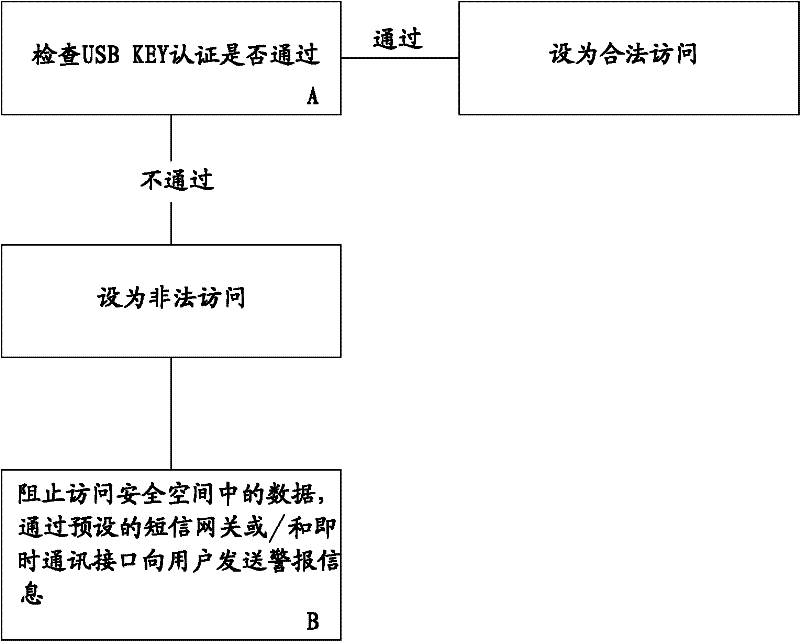
Method for realizing secure access of data in hard disk
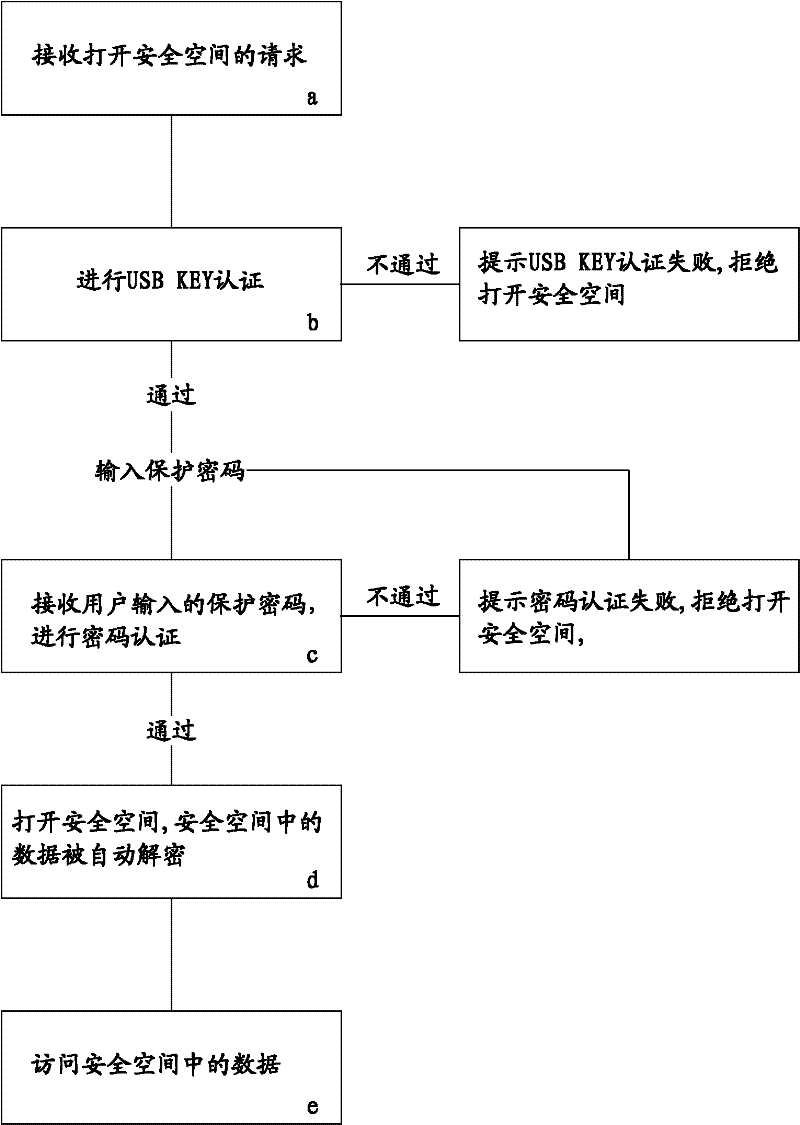
ActiveCN102508792ARealize active defenseImplement proactive alertsUnauthorized memory use protectionDigital data protectionPasswordSecret code
The invention discloses a method for realizing secure access of data in a hard disk. The method is realized by the following steps: establishing a secure space on the hard disk and monitoring the secure space; automatically encrypting the data written in the secure space; associating the secure space with a USBKEY; and setting protection passwords required for opening the secure space. When the data in the secure space is accessed, USBKEY authentication and passwords authentication are carried out in sequence, the secure space can be opened only after the double authentication; and when the situation that the data in the secure space is accessed but the secure space is not opened is monitored, whether the USBKEY authentication passes or not is checked, if not, the accessing is blocked, and a preset ISMG (internet short message gateway) or / and an instant communication port is / are used for sending an alarm information to a user. In the invention, by virtue of the double authentication and the monitoring on the secure space, the secret-divulging risk is reduced, the effects of safety, rapidness and easiness in use are achieved, and the active defense and active alarming are also realized, therefore, the safety is improved to the maximum extent.
Owner:GUANGZHOU SHINE TECH
Industrial control system function safety verification method based on immune learning
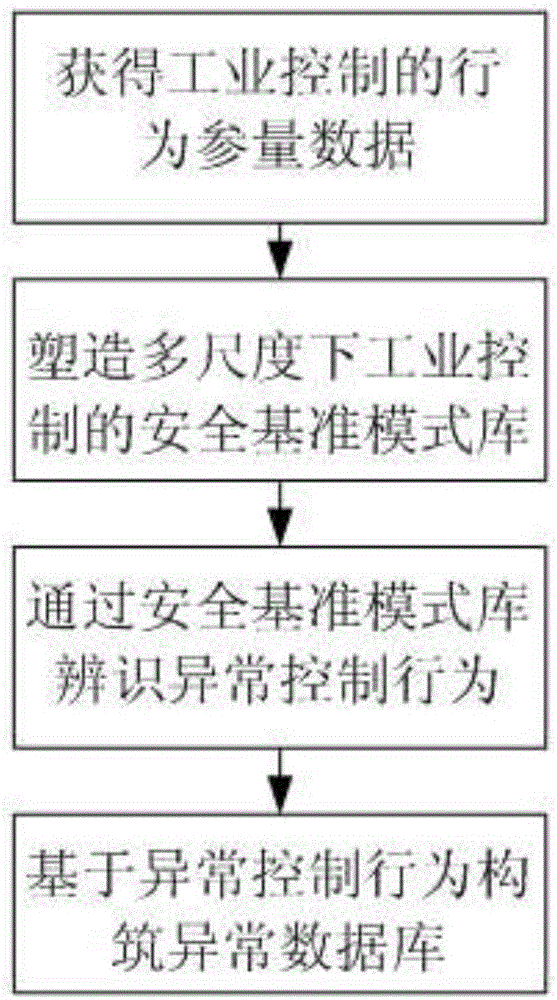
ActiveCN106778210AImprove securityPrecise lock failureDigital data authenticationPlatform integrity maintainancePrior informationIndustrial control system
The invention discloses an industrial control system function safety verification method based on immune learning. The verification method includes the steps: A, acquiring behavior parameter data of industrial control by testing an industrial control component in an offline in-loop manner; B, constructing safety standard mode bases of industrial control under multiple scales according to the behavior parameter data; C, identifying abnormal control behaviors through the safety standard mode bases; D constructing abnormal behavior mode databases based on the abnormal control behaviors. The verification method does not depend on prior information such as normal analysis rules and abnormal black features, lose efficacy and hidden danger are accurately determined from a behavioral expression level without knowing reasons, characteristics and use details of specific defects, function safety risks are remarkably reduced.
Owner:成都巧班科技有限公司
Explosion-proof shock-proof protecting system of cable-girder anchorage zone and manufacturing method of explosion-proof shock-proof protecting system
InactiveCN106192750ABuffer direct damage effectPlay a fixed roleBridge structural detailsBridge erection/assemblyBridge engineeringSheet steel
The invention relates to an explosion-proof shock-proof protecting system of a cable-girder anchorage zone and a manufacturing method of the explosion-proof shock-proof protecting system, belongs to the technical fields of highway, railway and municipal engineering traffics and bridge engineering protection, and aims to provide a protecting system of the cable-girder anchorage zone, which can actively defend explosion shock, of a wide-span cable beam bridge structure, and the manufacturing method of the protecting system. The protecting system is characterized in that an alpha type semi-hydrated gypsum mold wraps the outer part of the cable-girder anchorage zone; at least three PTFE film material layers wind and wrap the outer side of the alpha type semi-hydrated gypsum mold; an inner steel plate, a foam aluminum layer and an outer steel plate are sequentially arranged on the outer part of the PTFE film material layer in a sleeving manner; sand blasting is firstly performed on the cable-girder anchorage zone for rust cleaning before the alpha type semi-hydrated gypsum mold is wrapped; after being harden and demouded, the alpha type semi-hydrated gypsum mold needs to be dried and roasted; the cable beam anchoring region is wrapped once again; and then the PTFE film material layers, the inner steel plate, the foam aluminum layer and the outer steel plate are sequentially arranged on the outer part of the alpha type semi-hydrated gypsum mold to form the protecting system. The explosion-proof shock-proof protecting system and the manufacturing method thereof disclosed by the invention are applied to the traffic and the bridge engineering protection.
Owner:ZHONGBEI UNIV
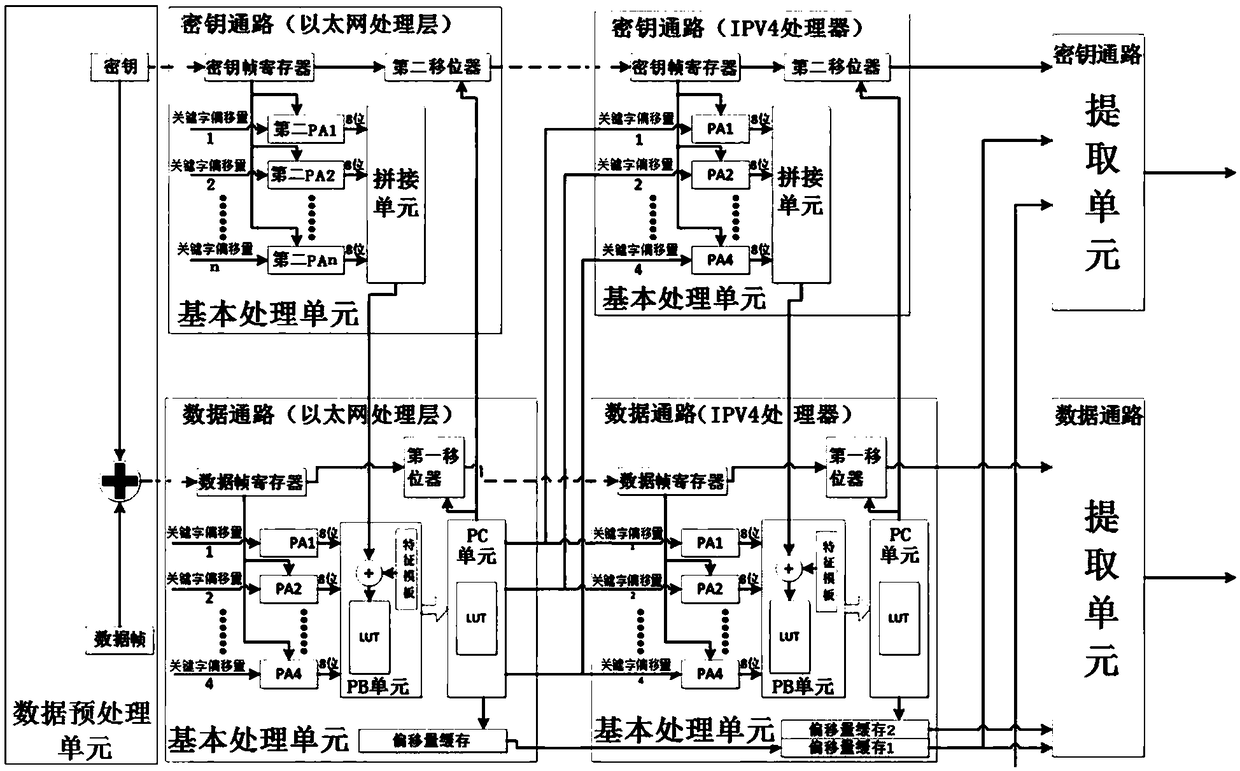
Reconfigurable switch forwarding engine analyzer capable of destroying hardware Trojan
ActiveCN109474641AIncrease flexibilityImprove securityData switching networksKeyword extractionPacket processing
The invention relates to a reconfigurable switch forwarding engine analyzer capable of destroying hardware Trojan. The analyzer comprises a data preprocessing unit, a plurality of cascaded basic processing units and an extraction unit; a key path of the basic processing unit of the first stage is used for extracting and shifting key bit keywords of a key, and sending a result to a data path of thecurrent stage and a key path of the next stage; the data path of the basic processing unit is used for extracting and shifting key fields of data frames, generating extracted field offsets of the basic processing unit of the next stage and field offsets of the current stage, and sending the field offsets, field identifiers and the shifted data frames to the basic processing unit of the next stageor the current stage; the basic processing units of other stages carry out key word extraction and shifting on key frames and the data frames in sequence; and the extraction unit carries out key frame and data frame extraction from the basic processing unit of the last stage and forwards the extracted key and data frames to a subsequent packet processing part. The analyzer can be widely applied to the design of the switch forwarding engine analyzer.
Owner:TSINGHUA UNIV
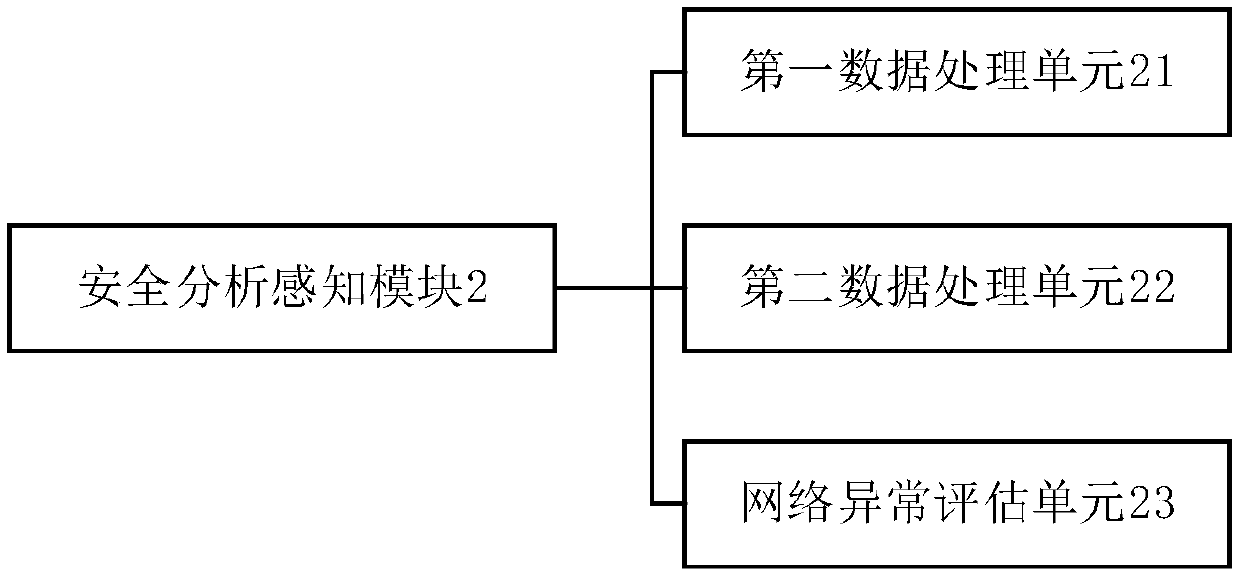
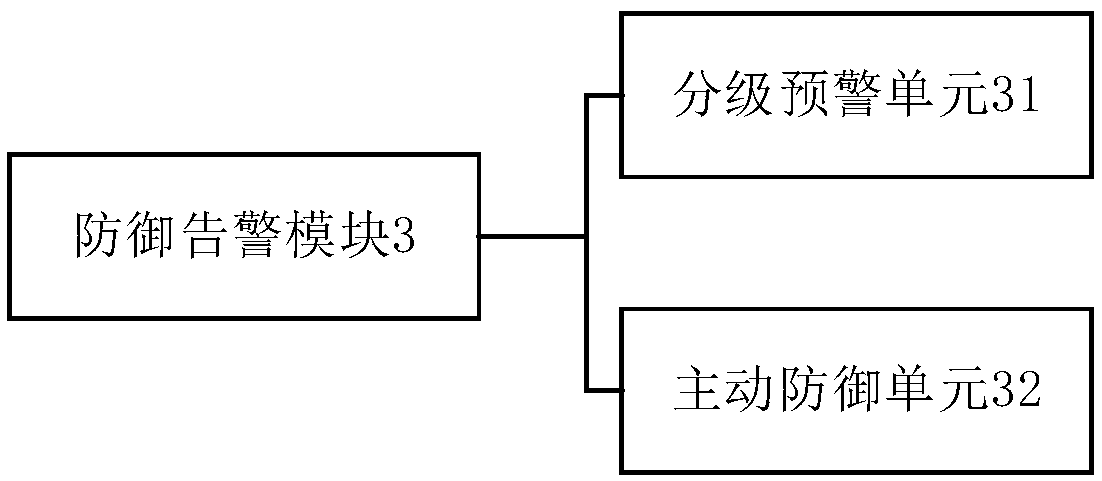
Network risk monitoring system of transformer substation
ActiveCN108809706AAnalyze Threat LevelRealize graded early warningData switching networksTransformerSecurity analysis
The invention provides a network risk monitoring system of a transformer substation. The system comprises a collection monitoring module used for collecting monitoring data in real time, a security analysis perception module used for performing transformer substation network security risk perception and comprehensive analysis on the collected monitoring data and further evaluating threat degrees of different network security events which the transformer substation network is faced with, a defending and alarming module used for realizing graded early warning and active defense for different network security risks based on the evaluation result of the security analysis perception module. The network risk monitoring system of the transformer substation is used for monitoring the transformer substation network in real time, analyzing threat degrees of different network security events to the transformer substation network rapidly and making out a response rapidly, realizes graded early warning and active defense for different network security events in the transformer substation network, removes security hazards in time and guarantees that the transformer substation has a secure and clean network environment.
Owner:GUIZHOU POWER GRID CO LTD
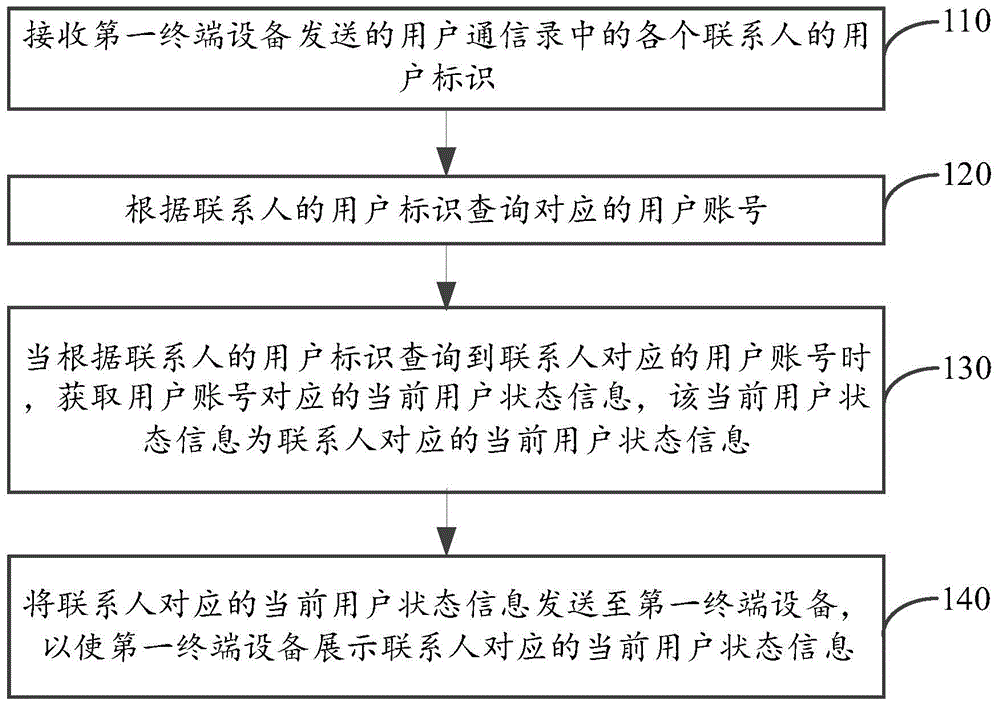
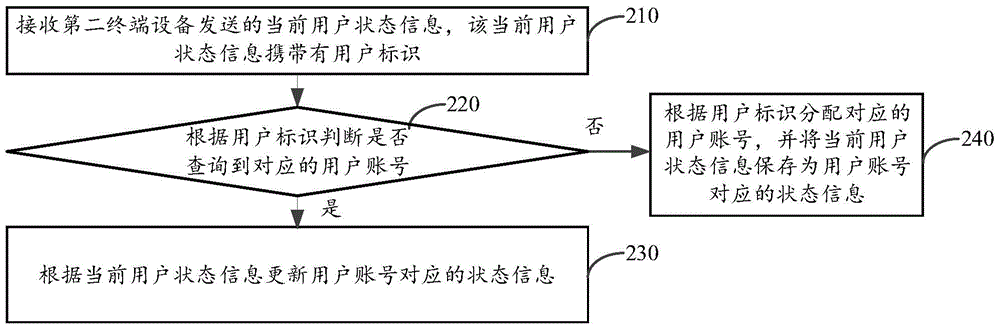
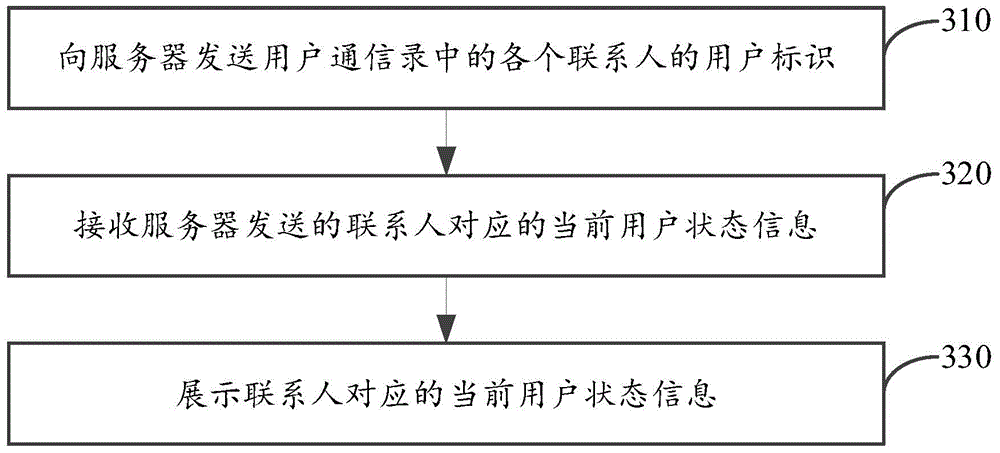
User status information sharing method and device
InactiveCN104902105AImprove experienceReduce distractionsSpecial service for subscribersCommmunication supplementary servicesUser stateUser identifier
The invention discloses a user status information sharing method and device. The method is applied to a server and includes the following steps that: user identifiers of contacts in a user contact list which are transmitted by a first terminal device are received; corresponding user accounts are searched according to the user identifiers of the contacts; current user status information corresponding to the user accounts is obtained when the user accounts corresponding to the contacts are found according to the user identifiers of the contacts, wherein the current user status information is current user status information corresponding to the contacts; and the current user status information corresponding to the contacts is transmitted to the first terminal device, so that the first terminal device can display the current user status information corresponding to the contacts. With the user status information sharing method and device of the invention adopted, interference on the contacts can be decreased, and user experience can be improved.
Owner:XIAOMI INC
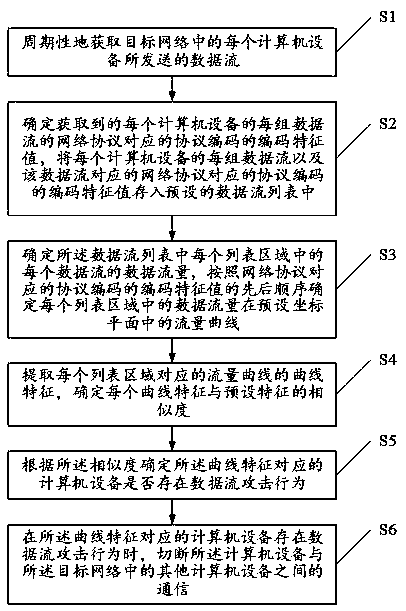
Active defense method and device for data flow attacks
ActiveCN111343206ARealize active defenseAvoid internet delaysTransmissionNetworking protocolData stream
The invention provides an active defense method and device for data flow attacks. The method includes: correspondingly storing the obtained data stream and the coding characteristic value of the network protocol code corresponding to the data stream into a preset data stream list; determining a flow curve of the data flow in a preset coordinate plane according to the flow of the data flow in eachlist area of the data flow list and the coding characteristic value of the protocol code corresponding to the network protocol; determining the similarity between the preset characteristic and the curve characteristic of the extracted flow curve in the list area. When it is determined that the computer equipment corresponding to the curve characteristics has the data flow attack behavior accordingto the similarity, communication between the computer equipment and the target network can be actively cut off before the computer equipment starts the data flow attack behavior, and active defense of data flow attacks is achieved.
Owner:上海飞旗网络技术股份有限公司
Power grid CPS prevention control method based on anticipated accident scenes
ActiveCN108832630AReduce the numberRealize active defenseContigency dealing ac circuit arrangementsPrevention controlHeavy load
The invention provides a power grid CPS prevention control method based on anticipated accident scenes. The power grid CPS prevention control method relates to the technical field of power system automation. The power grid CPS prevention control method comprises the steps of: firstly, constructing an initial accident scene model, and acquiring an optimized anticipated accident scene set based on feature similarity; secondly, comprehensively analyzing and calculating a benefit function according to an economic loss index, a heavy-load consequence severity index, a voltage offset severity index,a frequency offset severity index and a communication interruption severity index of loads of a power grid respectively; thirdly, acquiring a power flow transfer control strategy, a voltage instability adjustment strategy, a node removal strategy and a communication reliable adjustment strategy based on sensitivity; and further constructing a solution model, and adopting a relaxation method to perform a finite number of iterations to obtain a hybrid prevention control measure. The power grid CPS prevention control method based on the anticipated accident scene provided by the invention obtains the power grid hybrid prevention control method for different anticipated accident scenes, realizes active defense of the power grid, and ensures the safe operation of the power system.
Owner:NORTHEASTERN UNIV
A network security monitoring method for industrial control systems
ActiveCN107493265BRealize real-time monitoringRealize active defenseData switching networksRelevant informationIndustrial systems
The invention discloses a network security monitoring method for an industrial control system. The method comprises the following steps: collecting relevant information of an internal monitoring object of the industrial control system; performing security analysis on the collected relevant information; and when potential abnormal behavior is found through analysis, generating a relevant safety control order, and issuing the order to the relevant monitoring object for execution so as to block the abnormal behavior. According to the invention, real-time monitoring on major hidden security dangers of the industrial control system such as peripheral access, personnel operation, network external connection and the like is realized through abundant data acquisition of core networking equipment of the industrial control system. At the same time, through analysis processing on various behavior, the abnormal behavior is found and blocked timely, and thus real active defense of the industrial system is realized. For the current difficulty of effectively applying traditional security protection measures to the industrial control system, the major security threats to the industrial control system at present are well solved from the perspective of monitoring early warning.
Owner:NANJING NARI GROUP CORP +2
Endogenous security implementation device and method for forwarding flow table
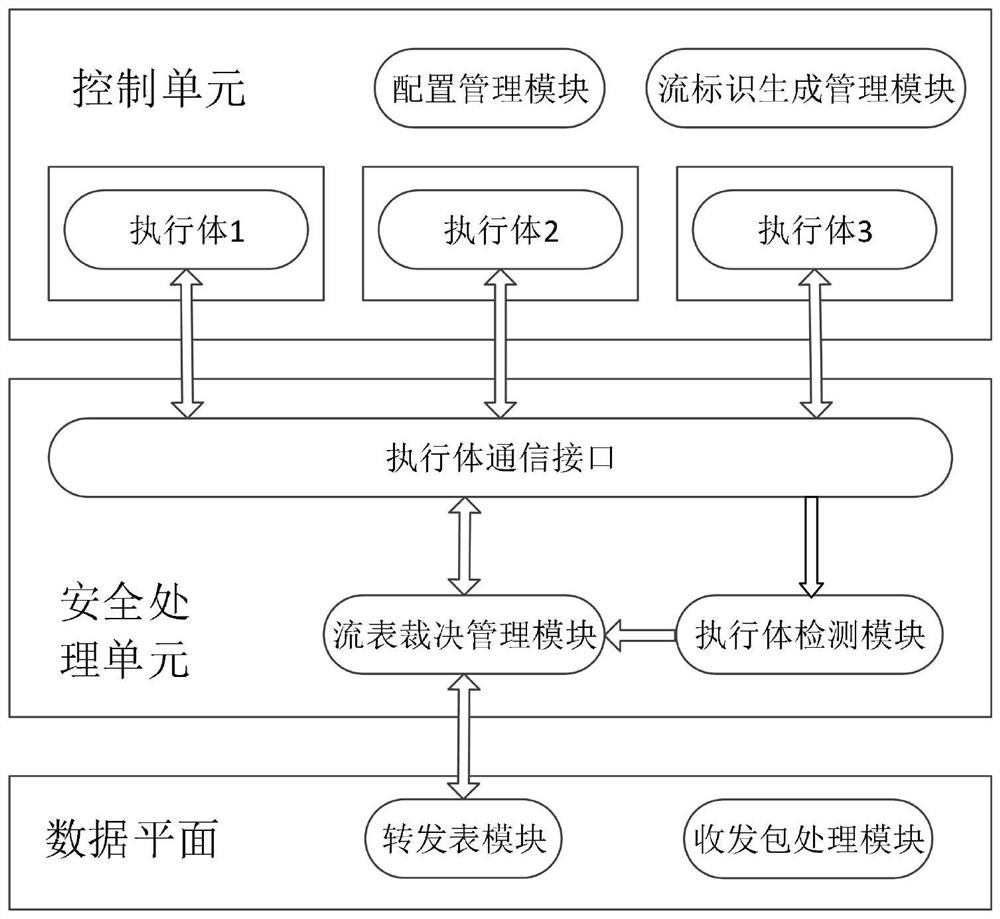
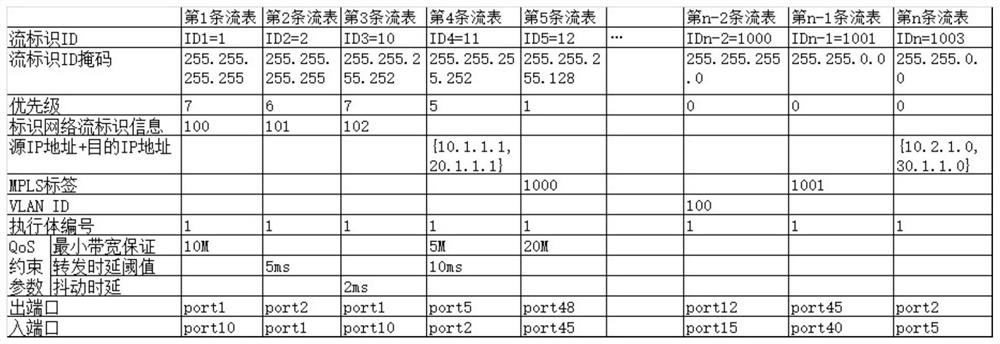
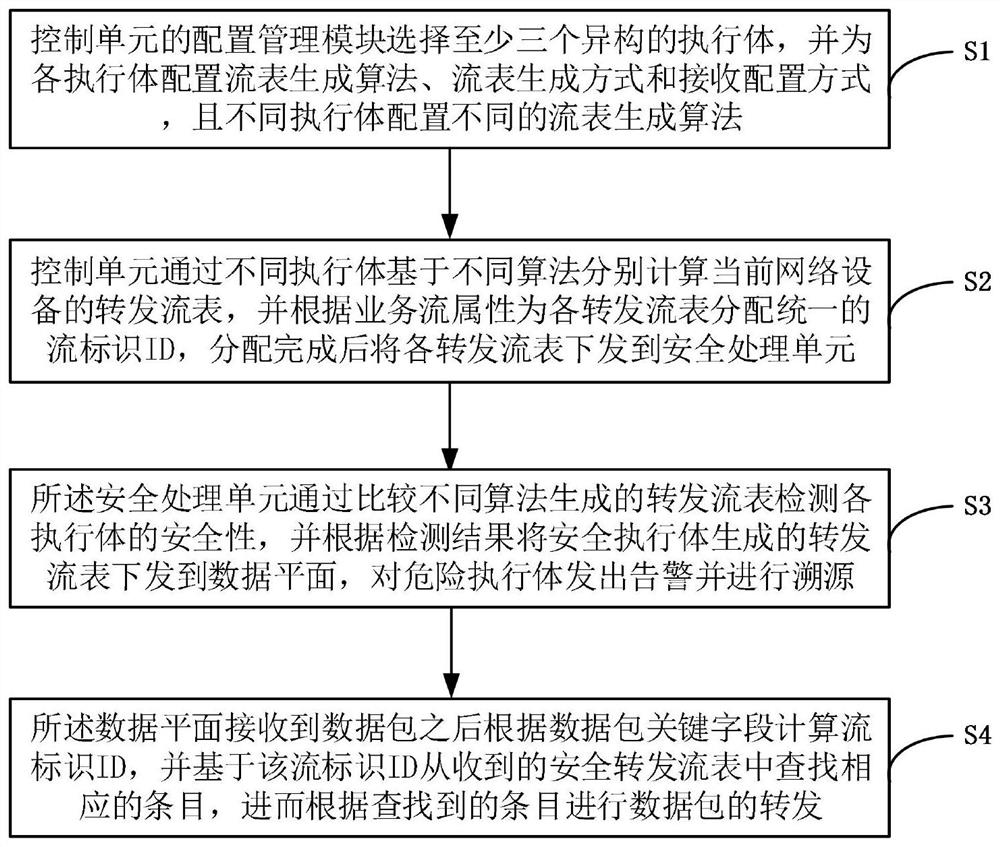
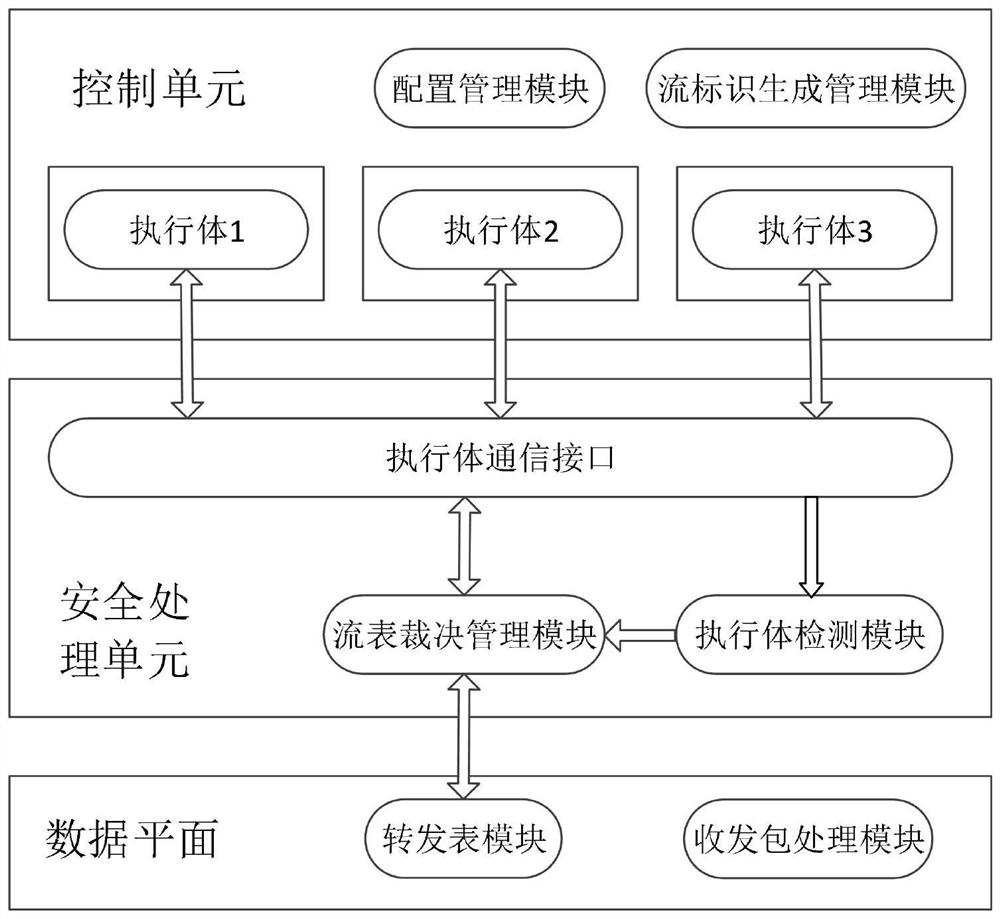
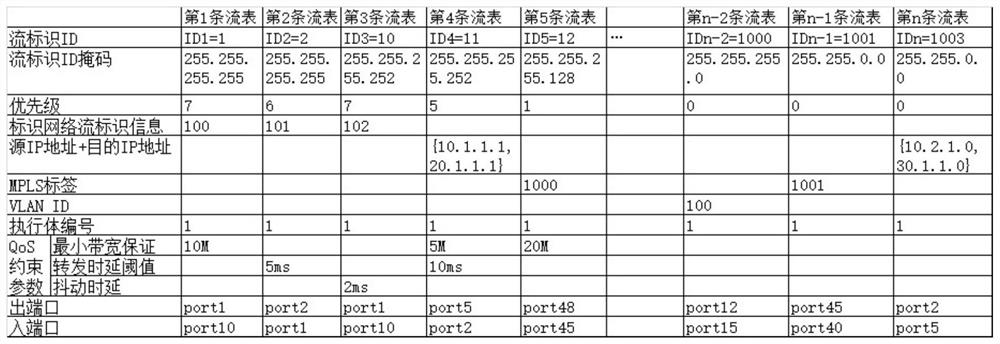
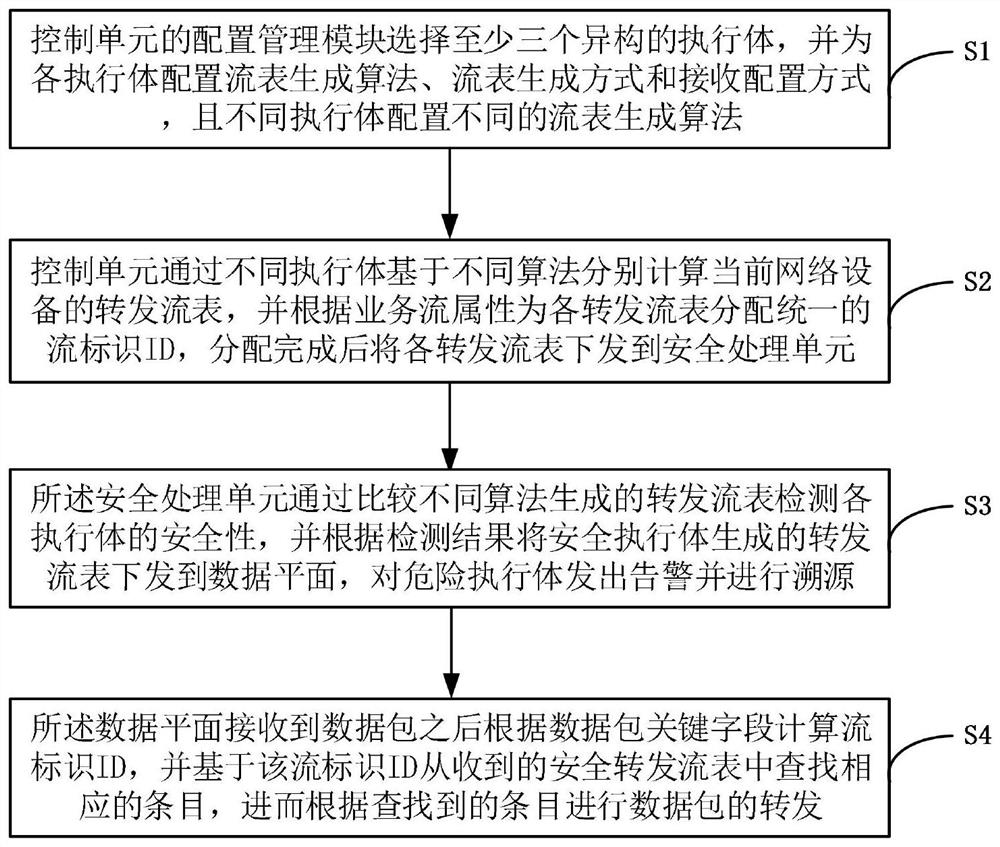
ActiveCN113079096AAchieving endogenous securityRealize active defenseData switching networksData packService flow
The invention discloses an endogenous security implementation device and method for a forwarding flow table, and the method comprises the steps: a control unit separately calculates the forwarding flow table of current network equipment through different execution bodies based on different algorithms, allocates a uniform flow identifiers ID to each forwarding flow table according to a service flow attribute, and transmits each forwarding flow table to a security processing unit after the allocation is completed; a security processing unit detects the security of each execution body by comparing different forwarding flow tables, and issues the forwarding flow tables generated by the security execution bodies to a data plane according to a detection result; and after receiving the data packet, the data plane calculates the flow identifiers ID according to a key field, searches for a corresponding entry from the received secure forwarding flow tables based on the flow identifiers ID, and forwards the data packet. According to the method, the dynamic heterogeneous redundancy of the forwarding flow table is generated based on different algorithms, the problem that a single algorithm is easily attacked and is untrusted is avoided, and the endogenous security of the network equipment is realized in a better heterogeneous mode.
Owner:FENGHUO COMM SCI & TECH CO LTD
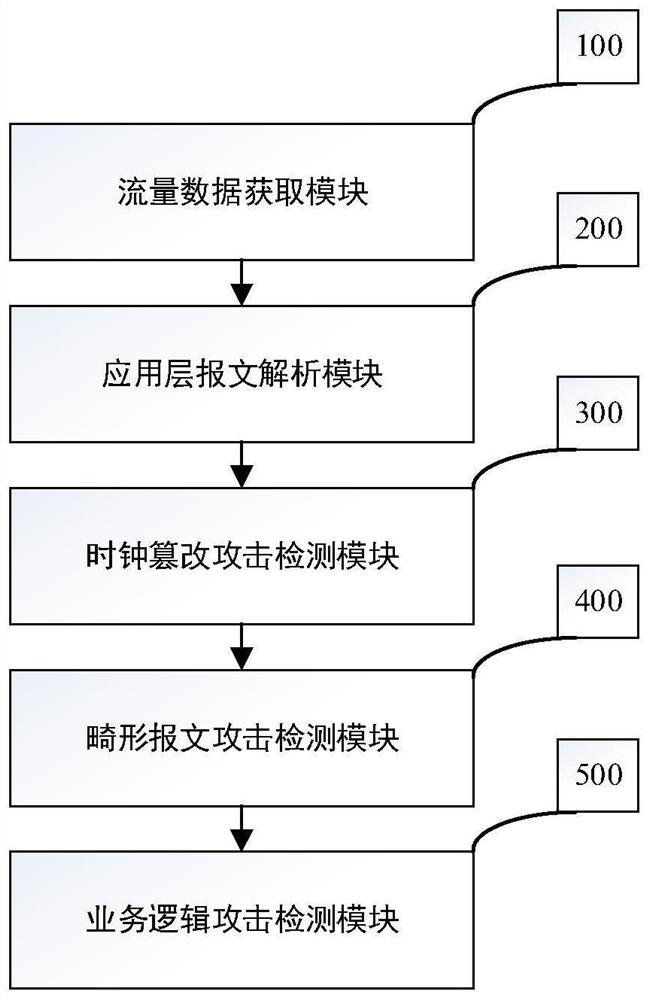
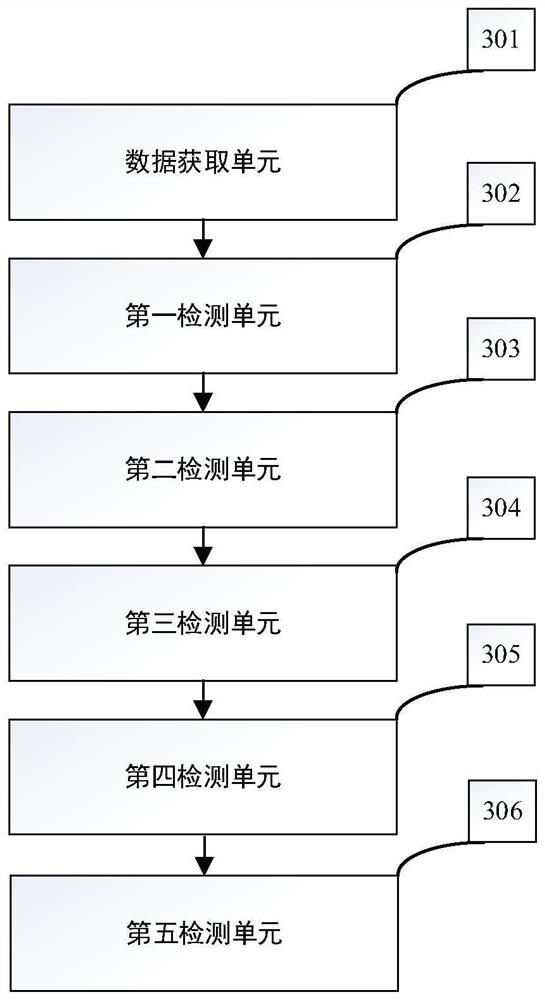
Relay protection information processing system attack behavior monitoring method and device
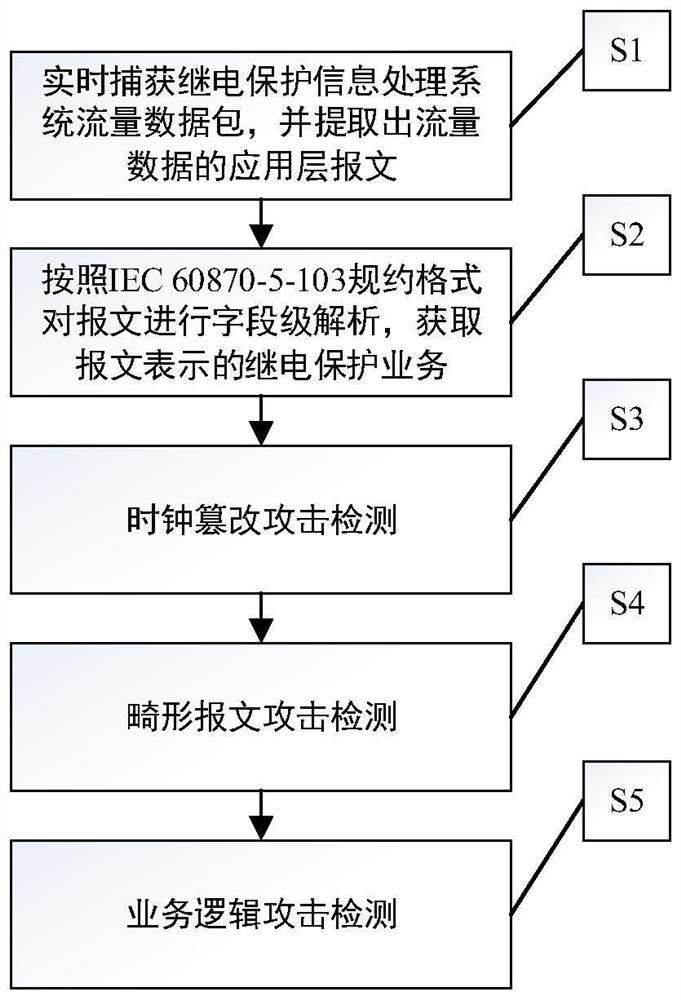
PendingCN114825607AOvercome limitationsImprove securityCircuit arrangementsSecuring communicationInformation processingAttack
The invention discloses a relay protection information processing system attack behavior monitoring method and device, and the method comprises the steps: carrying out the application layer message extraction of the traffic data of a relay protection information processing system captured in real time, and carrying out the analysis according to an IEC 60870-5-103 protocol. And secondly, carrying out clock tampering attack detection on the message. And then abnormal message attack detection is carried out on the message format according to protocol requirements. And finally, establishing a normal behavior model of various system services, and carrying out application layer attack behavior detection on the system flow data according to the normal behavior model. According to the method, the defects that an existing relay protection information processing system attack behavior detection method focuses on data analysis of a relay protection device measurement point and lacks attack behavior detection for a flow data application layer message are overcome, and the accuracy of relay protection information processing system attack behavior detection is improved.
Owner:HUNAN UNIV
Gene similarity intrusion detection method based on electric power network IEC protocol
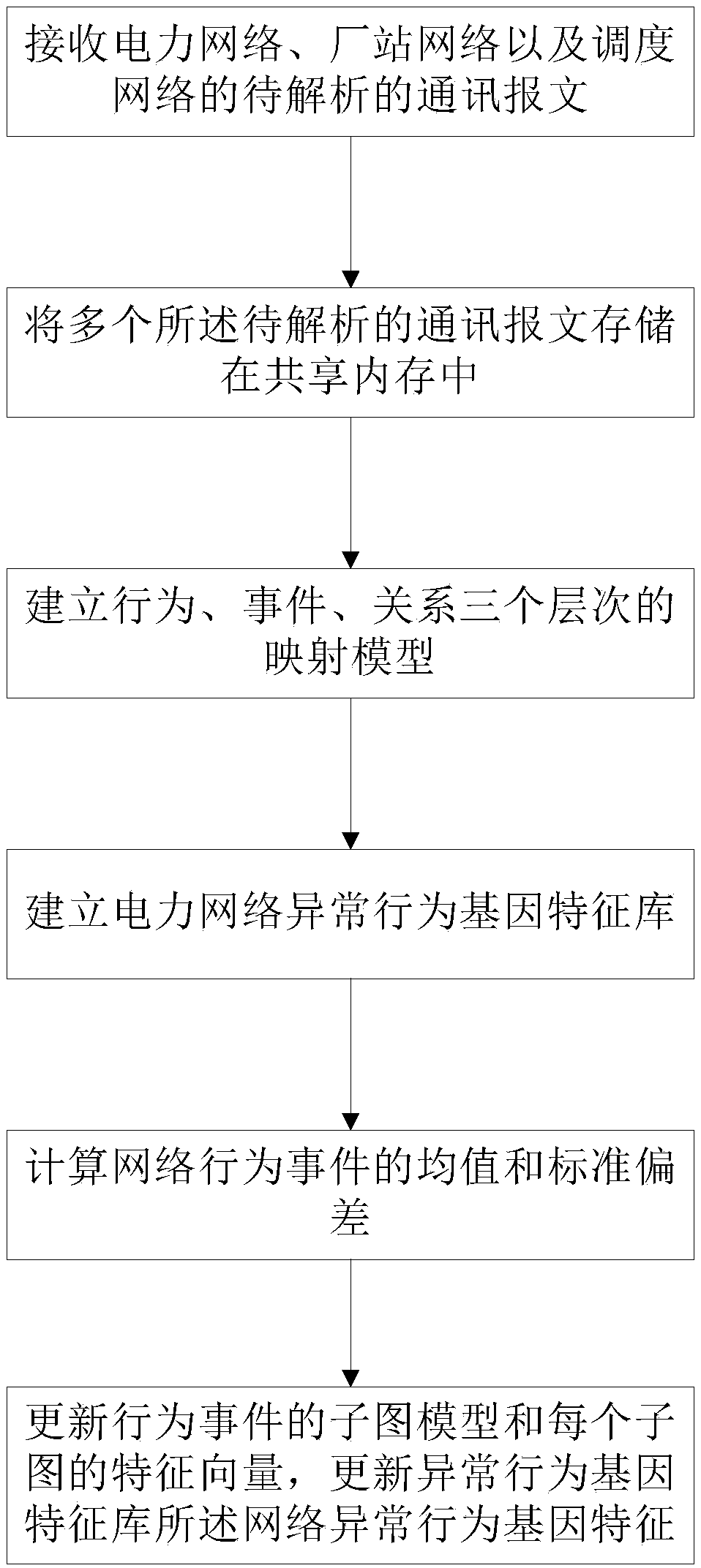
InactiveCN109600365AAvoid paralysisRealize active defenseCharacter and pattern recognitionData switching networksThree levelNODAL
The invention provides a gene similarity intrusion detection method based on an electric power network IEC protocol. The method comprises the following steps of carrying out information collection onkey nodes of an electric power monitoring system, performing protocol analysis on the acquired IEC message; establishing three levels of mapping models of behavior, events and relations; solving the relationship aggregation between events through automatic discovery of reasoning rules and depth relationship mining; merging of events, carrying out multi-dimensional relationship association, establishing a power network abnormal behavior gene feature library, discovery hidden attacks through gene similarity comparison based on a mean value and deviation model, achieving active defense of security events through multi-mode combination alarm, and blocking network attacks in real time. Local monitoring system paralysis and out-of-control are prevented, hazard spreading is prevented, and situation development is avoided.
Owner:沈阳安信合科技有限公司
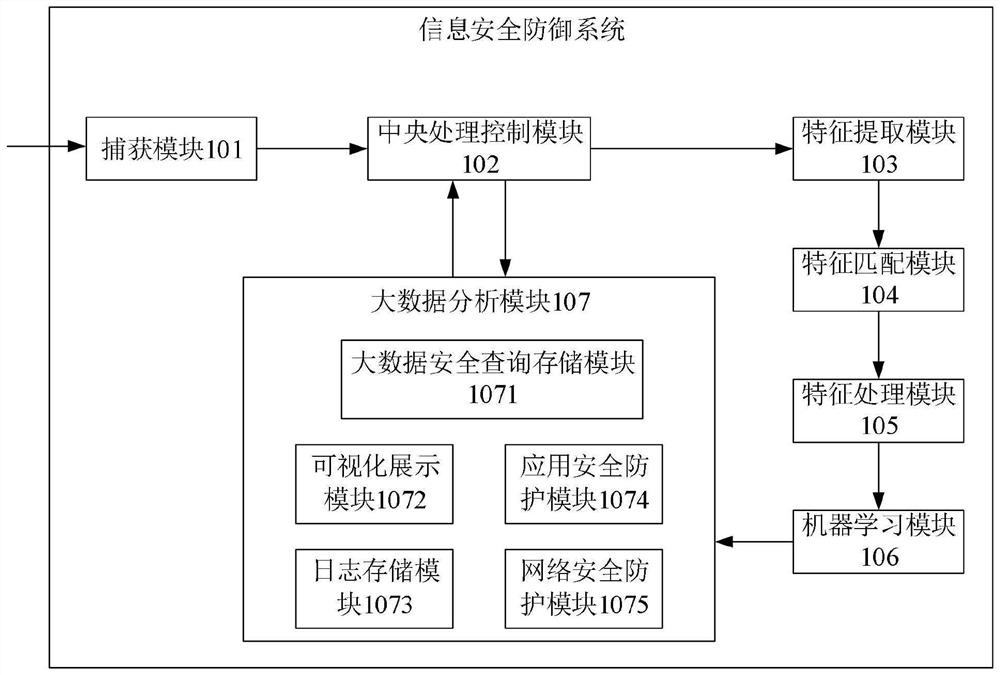
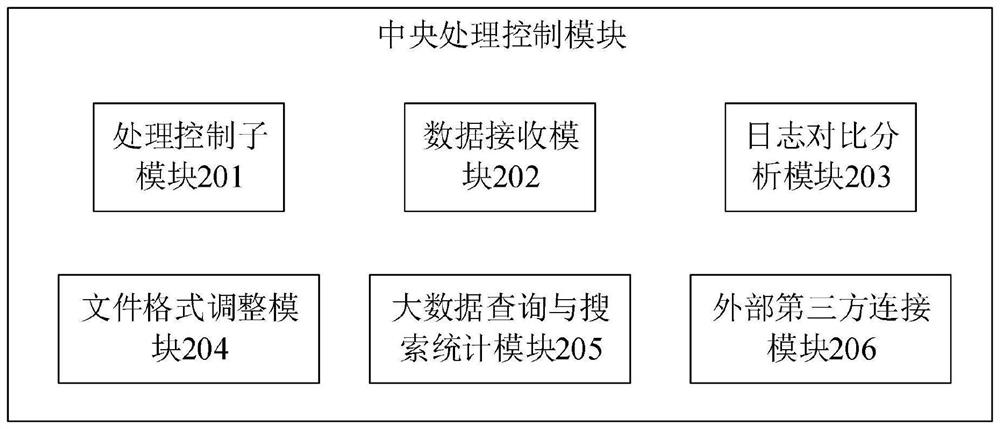
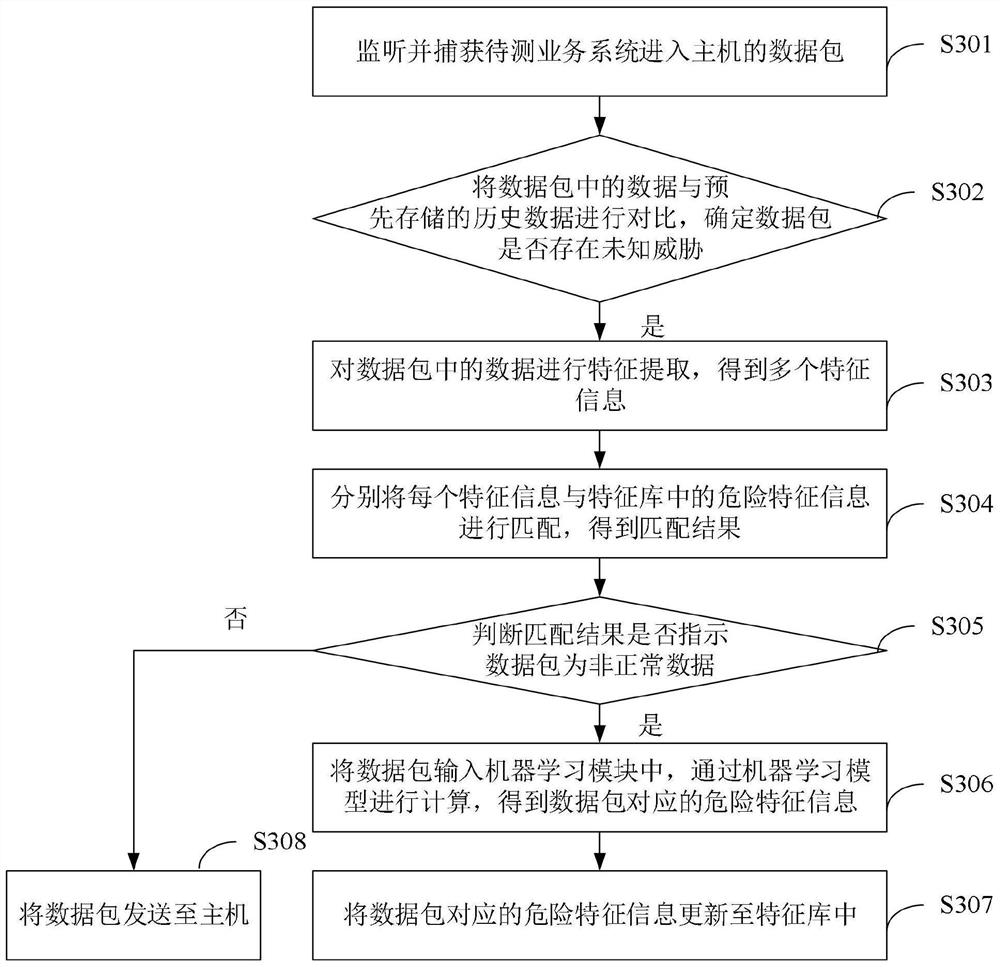
Information security defense method and system, electronic equipment and storage medium
ActiveCN113381980ARealize active defenseEnsure safetyMachine learningTransmissionData packInformation networks
The invention discloses an information security defense method and system, electronic equipment and a storage medium. The method mainly comprises the following steps: monitoring and capturing a data packet of a to-be-tested service system entering a host; comparing data in the data packet with pre-stored historical data, and determining whether the data packet has unknown threats; if it is determined that the unknown threat exists in the data packet, feature extraction is carried out on data in the data packet to obtain multiple pieces of feature information; respectively matching each piece of feature information with dangerous feature information in a feature library to obtain a matching result; if the matching result indicates that the data packet is abnormal request data, inputting the data packet into a machine learning module, performing calculation through a machine learning model to obtain dangerous feature information corresponding to the data packet, and updating the dangerous feature information into a feature library; if the matching result indicates that the data packet is normal request data, sending the data packet to the host. Therefore, a timely and effective defense method for information network security is realized based on machine learning.
Owner:优刻得(上海)数据科技有限公司
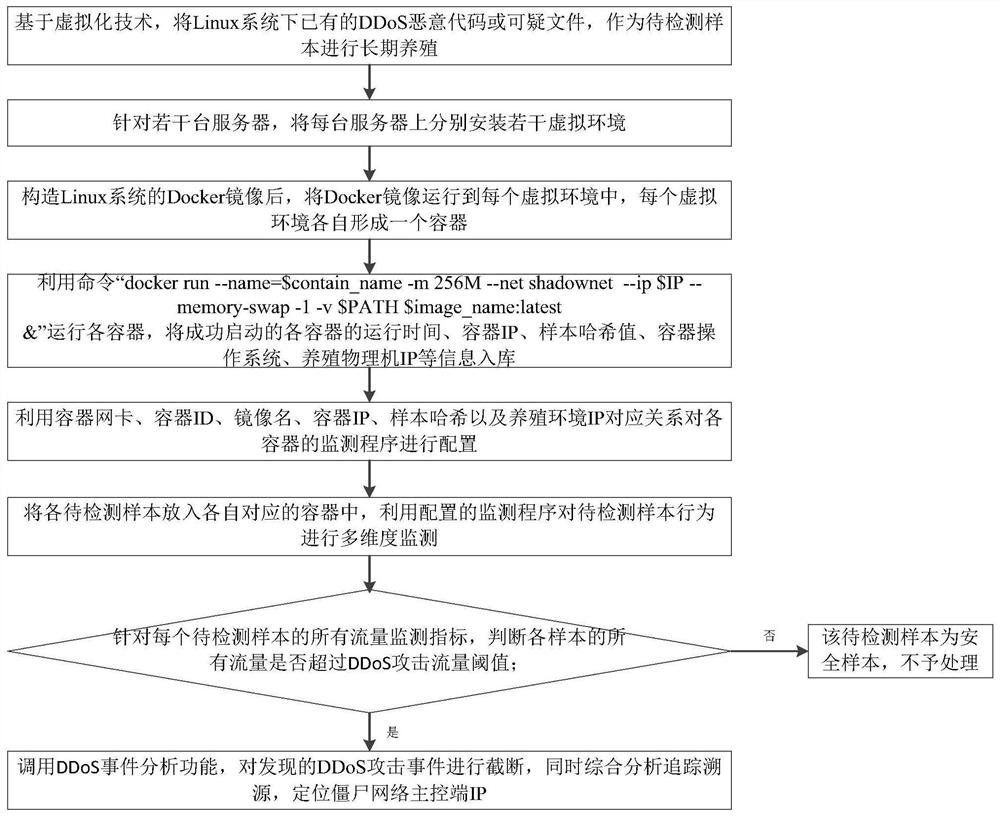
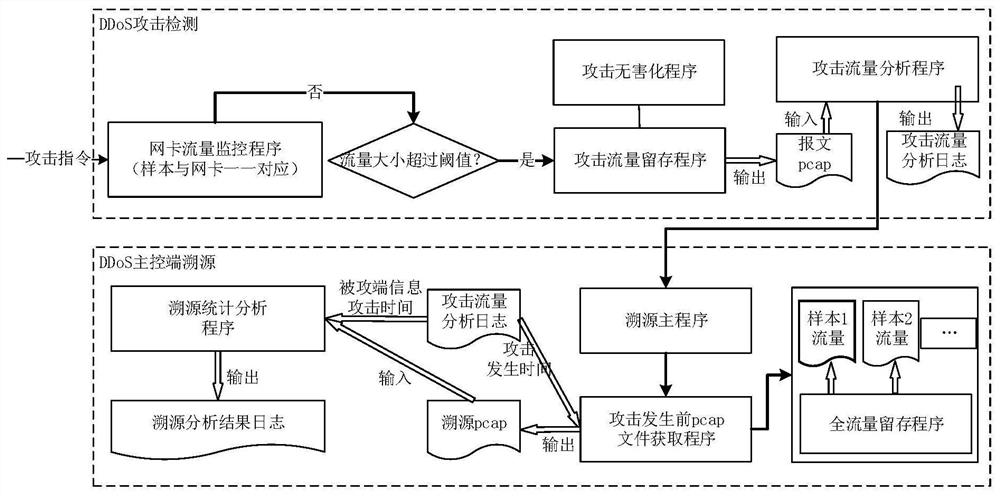
DDoS malicious code detection and traceability method based on breeding
ActiveCN112261029AAccurate analysisImprove farming efficiencyPlatform integrity maintainanceTransmissionAttackEngineering
The invention discloses a breeding-based DDoS malicious code detection and tracing method, and relates to the technical field of network security. The method specifically comprises the steps that firstly, existing DDoS malicious codes or suspicious files under a Linux system serve as samples to be detected to be bred for a long time; constructing a Docker mirror image of the Linux system, runningthe Docker mirror image into each virtual environment of each server to form a container, successfully starting each container, storing running information into a database, and configuring a monitoring program of each container; then, putting each to-be-detected sample into a respective corresponding container, and carrying out multi-dimensional monitoring on the behavior of the to-be-detected sample by utilizing a monitoring program; and judging whether all traffic of each sample exceeds a DDoS attack traffic threshold, and if so, calling a DDoS event analysis function to cut off a discoveredDDoS attack event, comprehensively analyzing, tracking and tracing, and positioning an IP of a botnet main control end. Otherwise, the to-be-detected sample is a safe sample and is not processed. Themaster control end of the puppet machine can be effectively tracked.
Owner:BEIJING RUICHI XINAN TECH
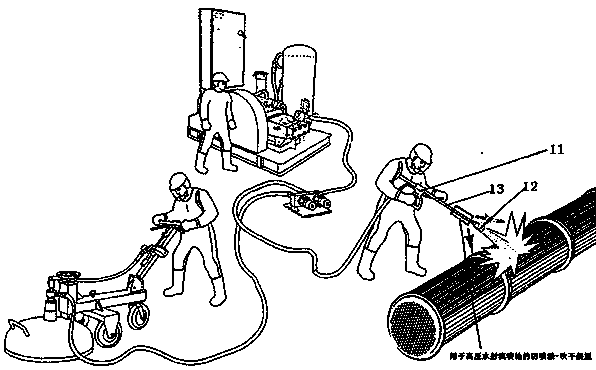
Splashing prevention-drying device for high-pressure water jet spray gun
InactiveCN107855233AEffectively intercept and drive awayJob Impact and RestrictionsSpray nozzlesLiquid spraying apparatusThroatInjection port
The invention belongs to the technical field of physical cleaning, and in particular relates to an anti-splash-drying device for a high-pressure water jet spray gun. Aiming at the problems of dirt particles splashing, sewage and mist continuously rushing towards the operator and the problem of target rust returning in high-pressure water jet cleaning, we disclose a splash-proof-drying device for high-pressure water jet spray guns. The above-mentioned anti-splash-drying device is combined with the barrel to form a hollow structure with an air inlet, an air outlet, and airflow directional guides and increments. The device combines with the gun barrel, uses pressurized air as the power source, and controls the flow path of the air flow through a specific structure to form a conical air jet curtain at the nozzle, thereby changing the trajectory of the splash and realizing interception and drive. The purpose of blowing away the splash and blowing off the moisture of the target at the same time.
Owner:南京洁德美环境技术有限公司
Network security equipment knowledge reasoning method, device and system and storage medium
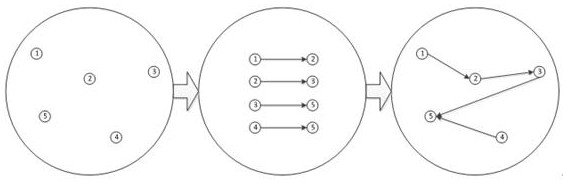
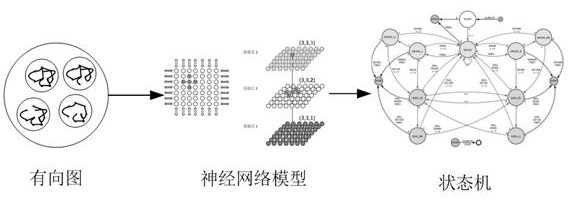
ActiveCN113254674ATimely detection of security risksRealize active defenseNeural architecturesInference methodsState predictionKnowledge state
The invention discloses a network security equipment knowledge reasoning method, device and system and a storage medium, and the method comprises the steps: obtaining data collected by distributed deployment network security equipment in real time, and carrying out the multiple fusion to obtain a knowledge state directed graph containing the directed relationship between the network security equipment; making the directed relationship of the knowledge state directed graph into a multivariate matrix, and sending the multivariate matrix into a risk reasoning state machine constructed by a pre-trained multi-layer deep neural network to obtain a state prediction result containing the directed relationship between the network security devices; and comparing the obtained state prediction result with a knowledge state directed graph obtained based on data collected by the network security equipment at the next moment, and if the state prediction result is inconsistent with the knowledge state directed graph, judging that a security risk situation occurs. According to the method, device and system, safety risks are found in time, active defense is achieved, the whole process of the system and the mutual relation are considered in the whole reasoning process, the whole process is highly integrated, and the reasoning result is more accurate.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Device and method for implementing endogenous security of forwarding flow table
ActiveCN113079096BAchieving endogenous securityRealize active defenseSecuring communicationData packService flow
The invention discloses a device and method for implementing endogenous security of forwarding flow tables. The control unit calculates the forwarding flow tables of the current network equipment based on different algorithms through different executive bodies, and allocates a unified forwarding flow table for each forwarding flow table according to the attributes of business flows. After the distribution is completed, each forwarding flow table is sent to the security processing unit; the security processing unit detects the security of each executive by comparing different forwarding flow tables, and according to the detection result, forwards the forwarding flow table generated by the security executive Send to the data plane; after receiving the data packet, the data plane calculates the flow ID according to the key field, and based on the flow ID, finds the corresponding entry from the received secure forwarding flow table to forward the data packet. The present invention generates dynamic heterogeneous redundancy of forwarding flow tables based on different algorithms, avoids the problem that a single algorithm is vulnerable to attack and cannot be trusted, and realizes endogenous security of network equipment in a more optimal heterogeneous manner.
Owner:FENGHUO COMM SCI & TECH CO LTD
Active defense method and device
ActiveCN104239797BRealize active defenseRealize dynamic active defensePlatform integrity maintainanceComputer compatibilityComputer science
The invention provides an active defense method and device. The method includes the following steps of responding to an instruction used for running a target application and running a corresponding shell application; sequentially loading a monitoring unit and the target application by means of the shell application, monitoring and capturing event behaviors of the target application through the monitoring unit; obtaining an event behavior processing strategy after specific event behaviors are captured, and processing the specific event behaviors according to the processing strategy. According to the active defense scheme, an existing system is modified a little, compatibility of the system is not influenced, and the method is easy and efficient to implement.
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com