Network malicious data detection method, device and system
A technology for malicious data and network data, applied in transmission systems, electrical components, etc., can solve problems such as false positives and false negatives, and cannot detect unknown intrusions, and achieve the effect of reducing false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
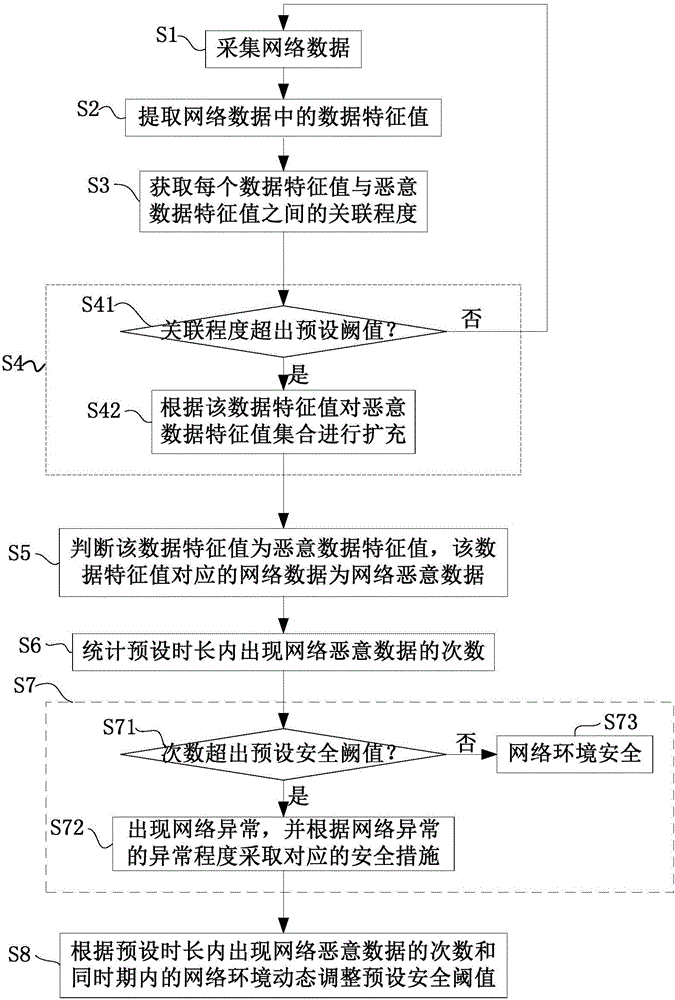
[0055] This embodiment provides a method for detecting network malicious data, such as figure 1 shown, including:
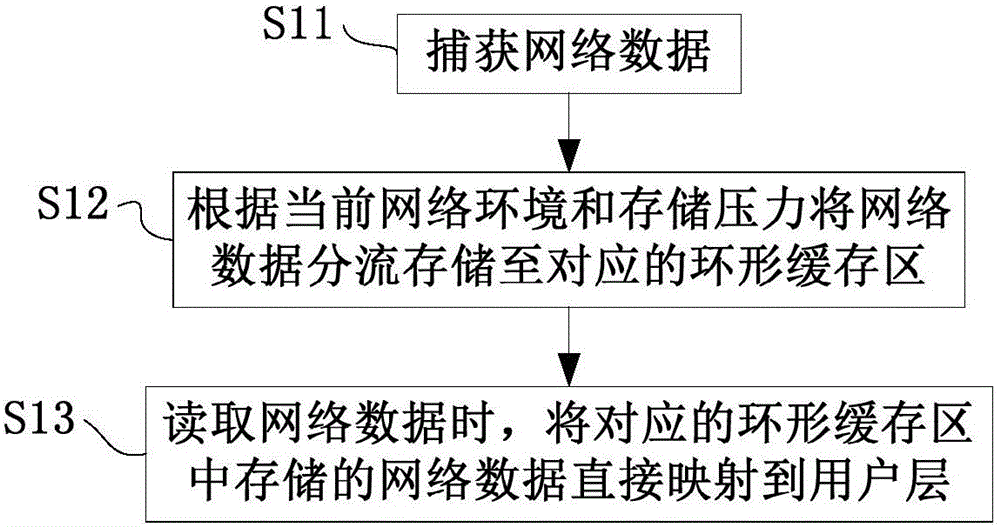
[0056] S1. Collect network data. Specifically, the network data of the local area network or the Internet that needs to be monitored can be collected continuously; the network data of the local area network or the Internet that needs to be monitored can also be collected every preset time, such as 5s. Specifically, the applicable collection method can be selected according to the network environment or security level requirements of the local area network or the Internet to be monitored.
[0057] S2. Extracting data feature values in the network data. Specifically, any data analysis method in the prior art may be selected to extract data characteristic values in the network data to obtain the network environment situation of the currently monitored local area network or the Internet.
[0058] S3. Obtain the degree of association between each data character...
Embodiment 2
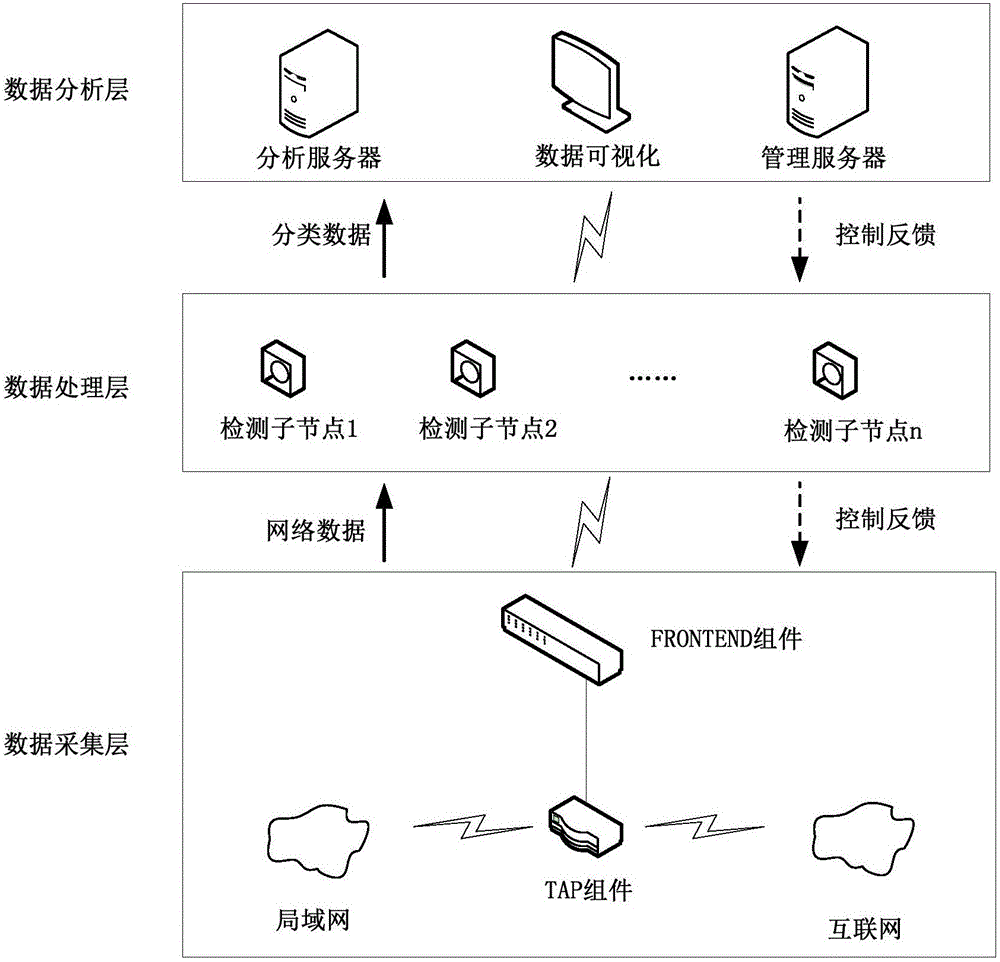
[0105] This embodiment provides a network malicious data detection device, such as figure 2 shown, including:
[0106] The data collection unit 1 is used for collecting network data.
[0107] The data processing unit 2 is configured to extract data feature values in the network data.
[0108] The data analysis unit 3 is used to obtain the degree of association between each data characteristic value and the malicious data characteristic value in the pre-stored malicious characteristic value set; if the degree of association between a certain data characteristic value and the malicious data characteristic value exceeds The threshold of the degree of association is preset, and the malicious data feature value set is expanded according to the data feature value. Specifically, if the degree of correlation between a certain data feature value and malicious data feature value in the collected network data exceeds the preset correlation degree threshold, it means that even if the...
Embodiment 3
[0127] This embodiment provides a network malicious data detection system, including the network malicious data detection device and the display device in Embodiment 2.
[0128] The display device is used to receive and display the data transmitted by the network malicious data detection device. Specifically, the display device may be a display screen.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com