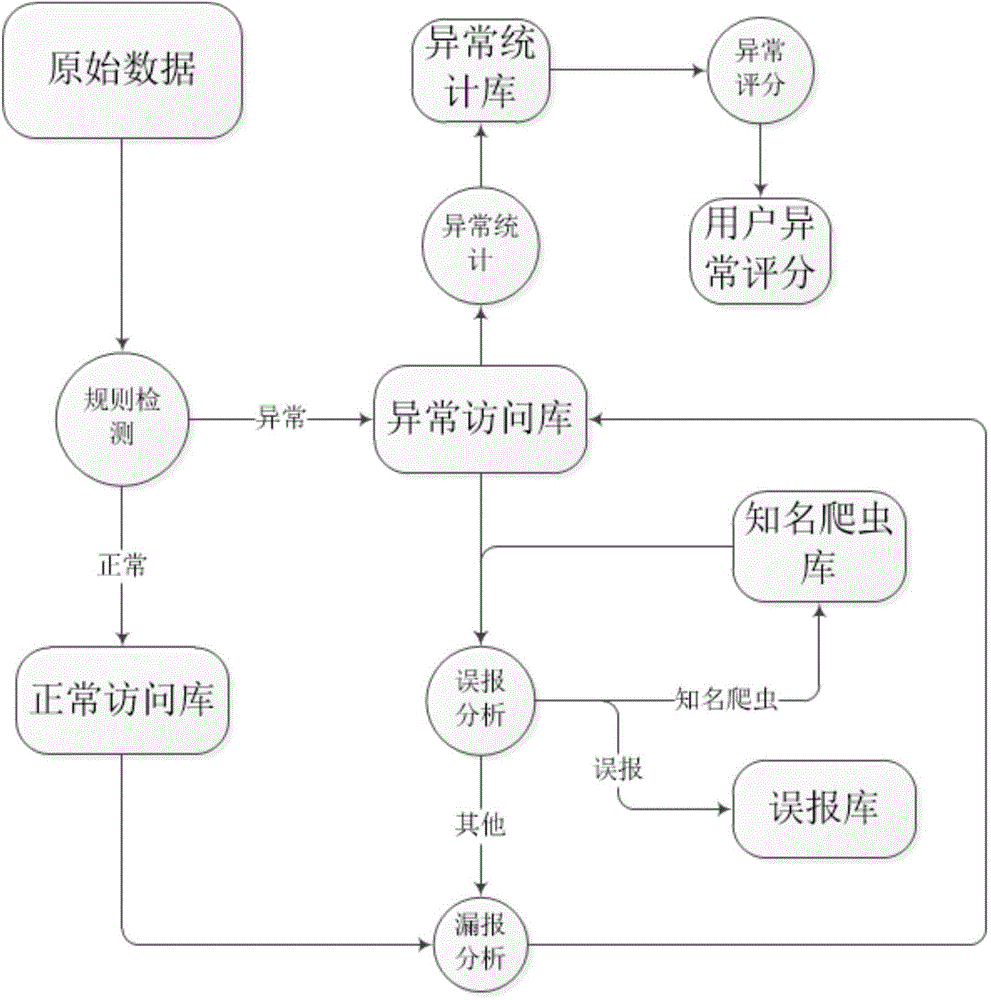
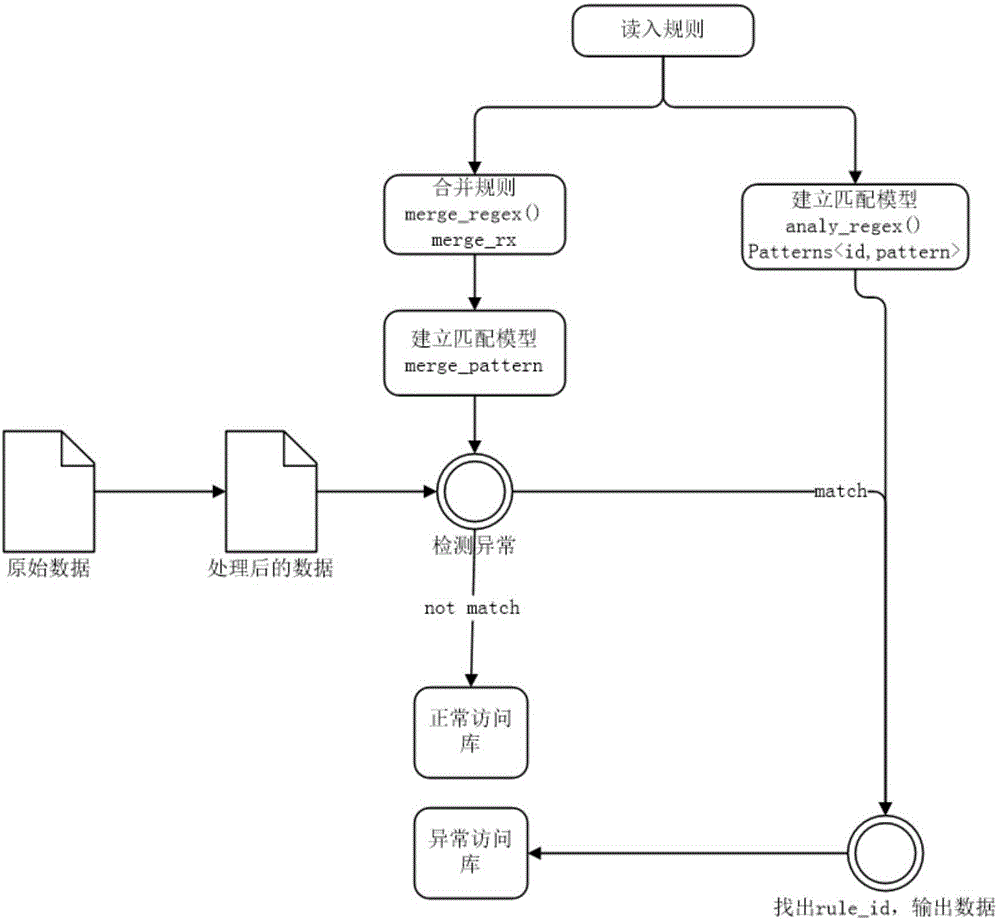
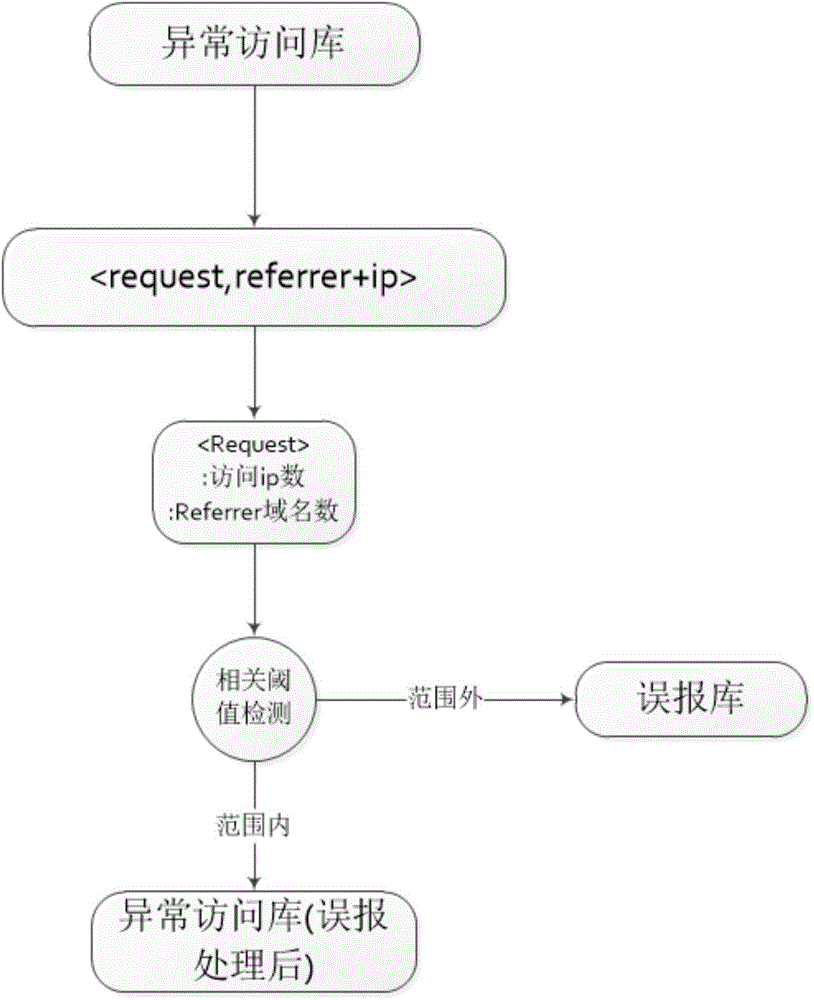
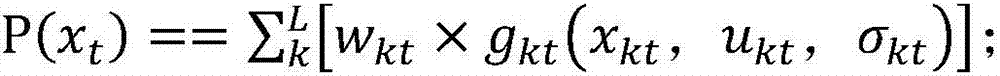Patents
Literature
1018results about How to "Reduce false negative rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
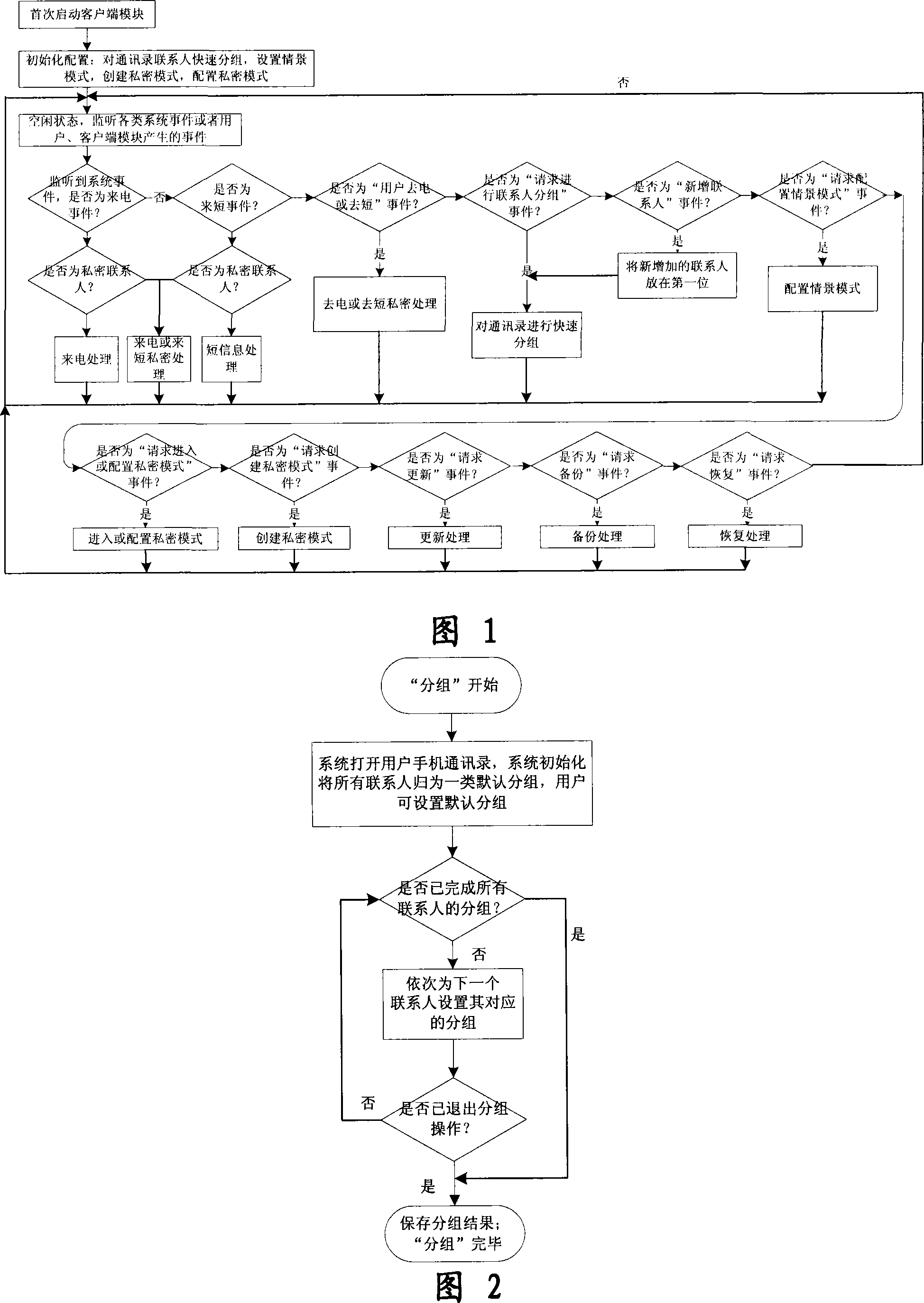
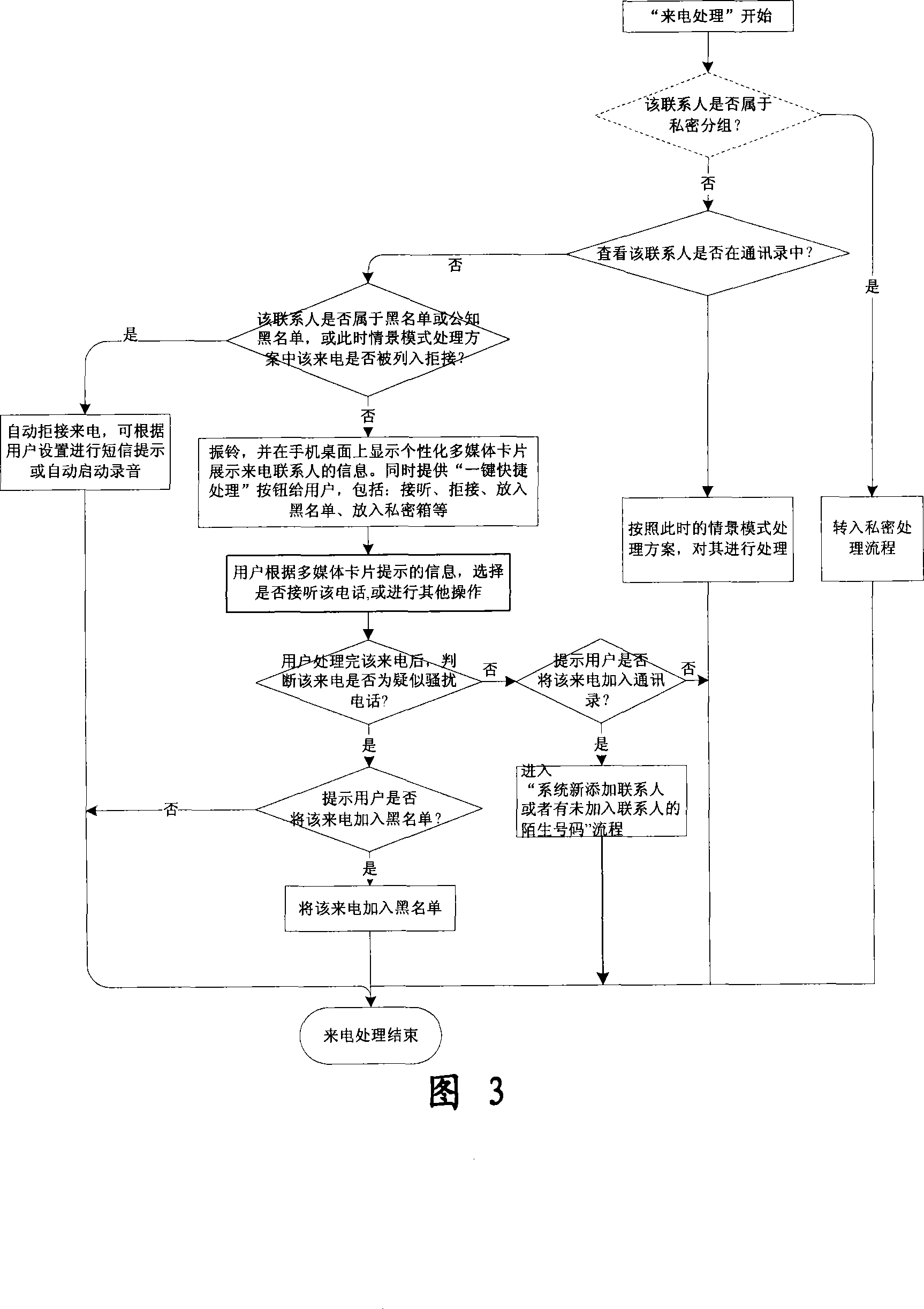
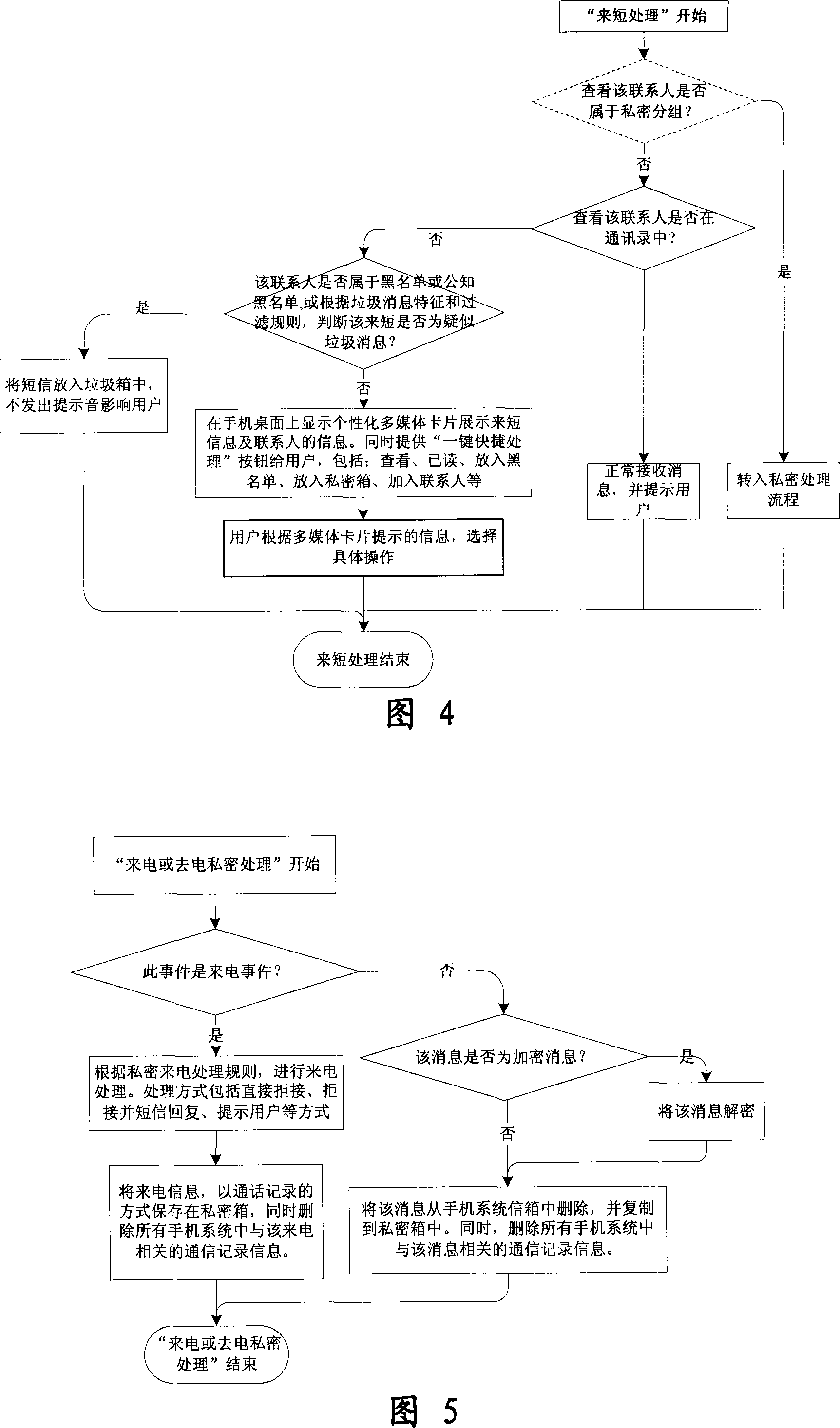
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
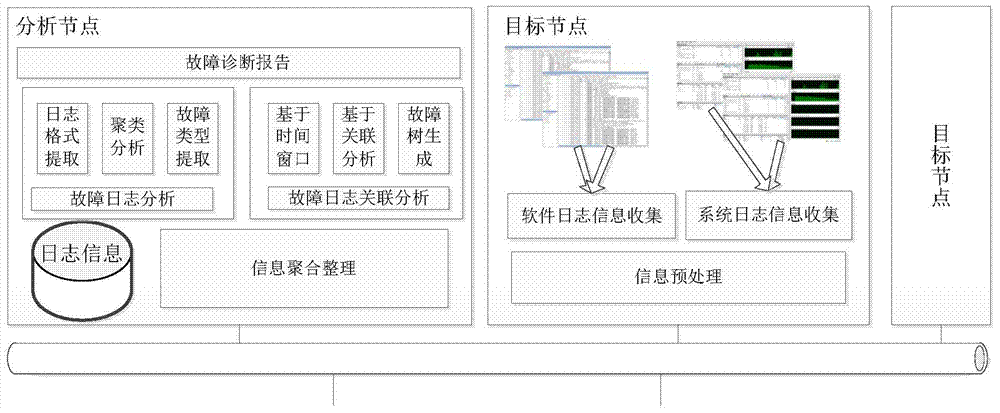
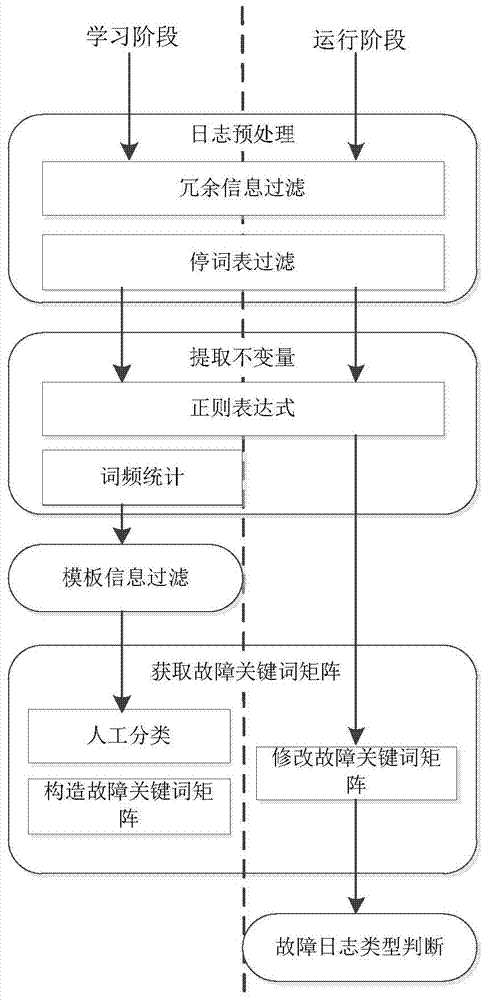
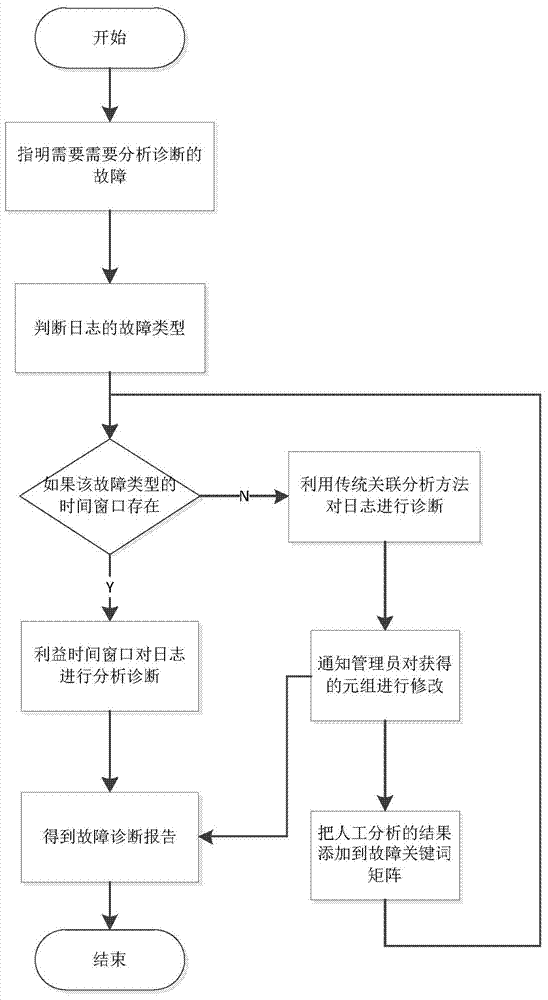
Log based computer system fault diagnosis method and device
InactiveCN103761173AConvenient and rapid fault classificationProcessing speedDetecting faulty computer hardwareHardware monitoringProcess systemsLog management
The invention discloses a log management and fault diagnosis method and device under multiple hosts. The method comprises fault log collection, fault log analysis and fault log correlation analysis. Fault log collection comprises collecting fault logs of all hardware and software in the cluster and storing the logs in a log server uniformly. Fault log analysis comprises filtering the fault logs, extracting log template information and classifying the logs according to log types. Fault log correlation analysis comprises performing fault reason analysis by using log analysis results and combining time windows, clustering the related faults caused by the same fault into a category and trying to find the root of the type of the faults. The method and the device are capable of analyzing the system operation condition effectively, assisting administrators to process system faults and improving the fault type determination accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
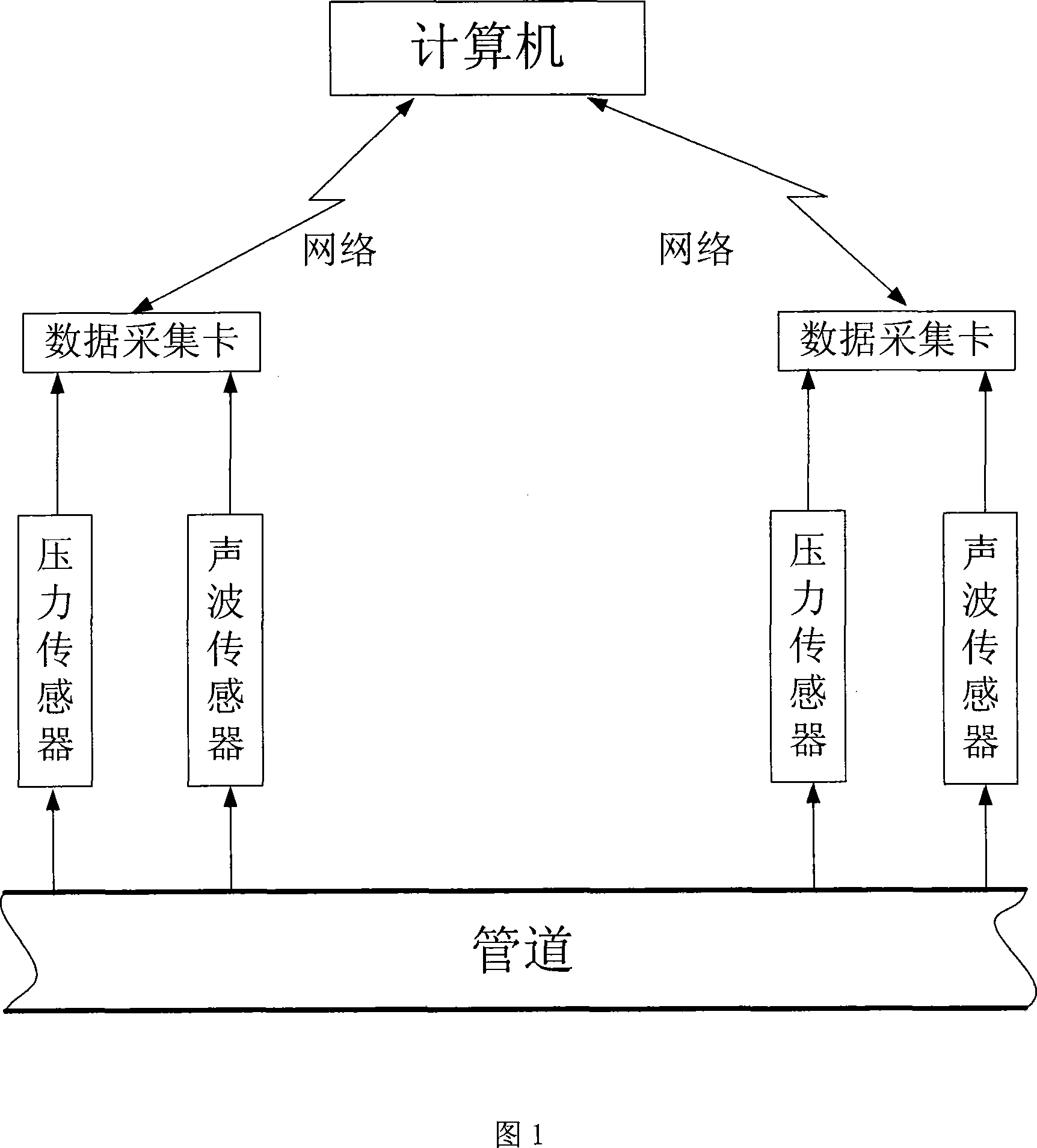
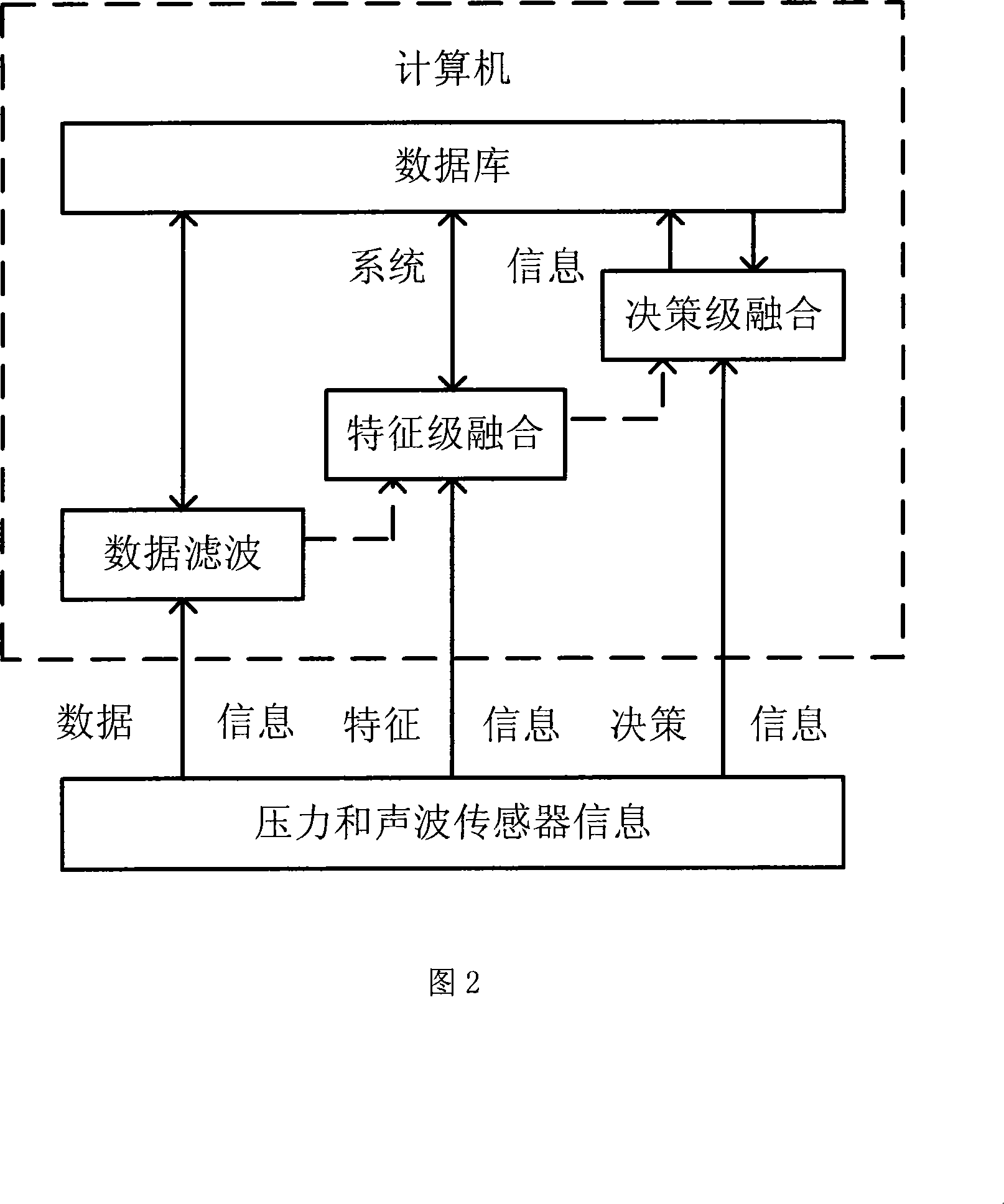
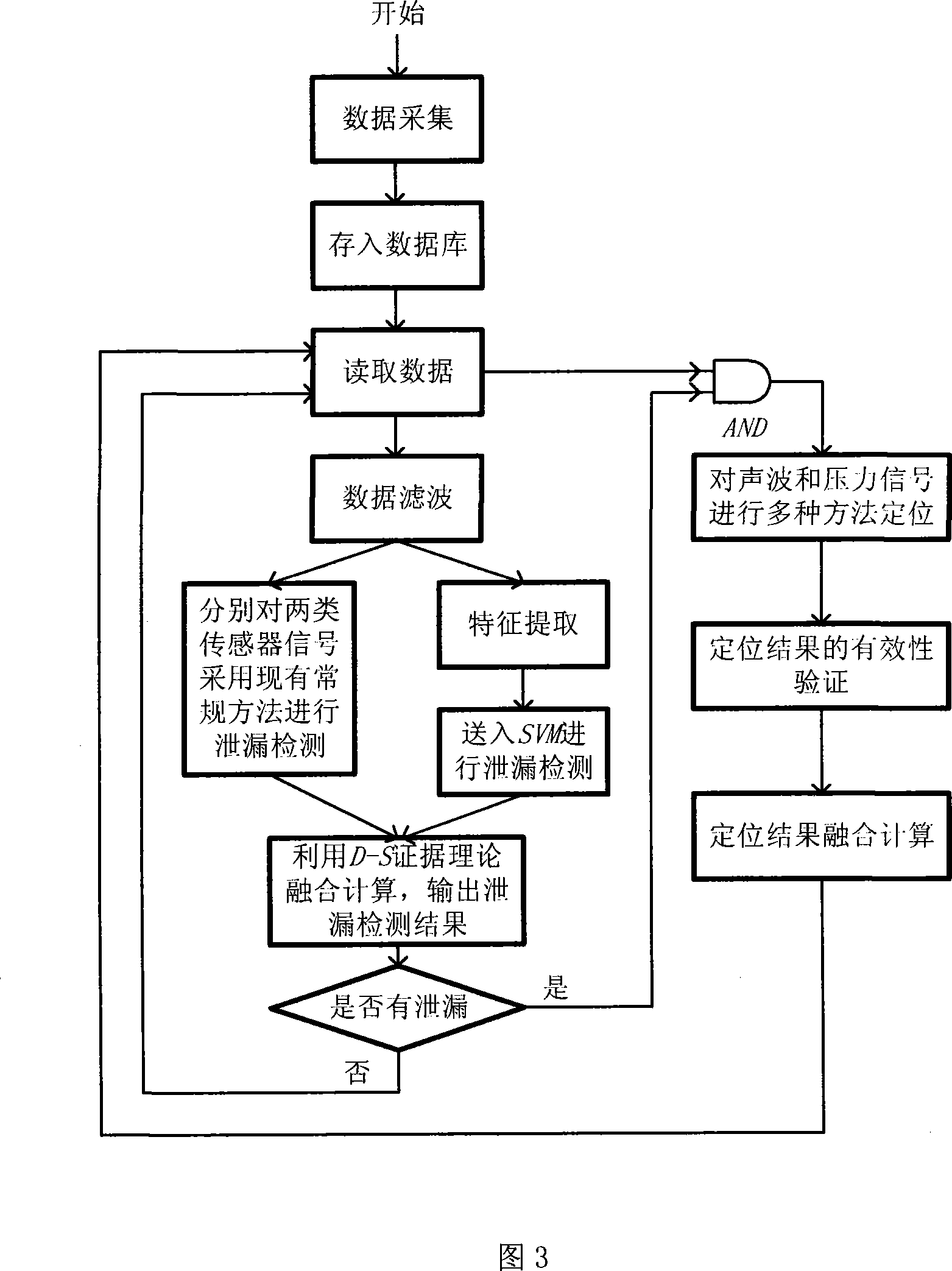
Leakage detecting and locating method based on pressure and sound wave information amalgamation
ActiveCN101196872AHigh precisionReduce false alarm ratePipeline systemsSpecial data processing applicationsThree levelAcoustic wave
A leakage detection location method based on pressure and sound information integration is provided, which belongs to the technology field of an oil (gas) pipeline fault diagnosis, and is characterized by leakage detection and leakage location based on information integration. The former comprises: separately acquiring the measurement data of the pressure on the upperstream end and downstream end of the pipeline and a sound wave sensor, sending the data to a computer and gaining final detection results through three levels processing including data filtering, characteristic level integration and decision level integration. If the detection result shows leakage, starting leakage location process based on information integration. The process first carries out leakage location by separately adopting the signals of two kinds of sensors and a plurality of different leakage location algorithms and finally gains the location results via integration of the location results based on the same sensor and different location methods and two levels processing based on the integration of the location results of two kinds of different sensors. The method can effectively reduce the false positive rate and false negative rate and improve the location precision.
Owner:TSINGHUA UNIV
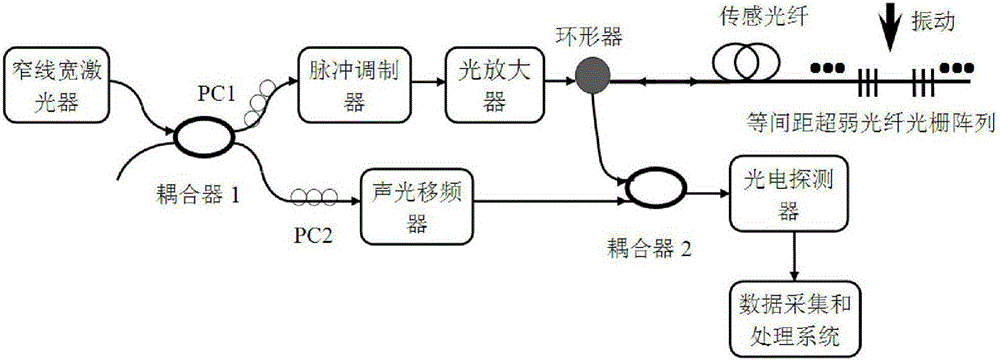
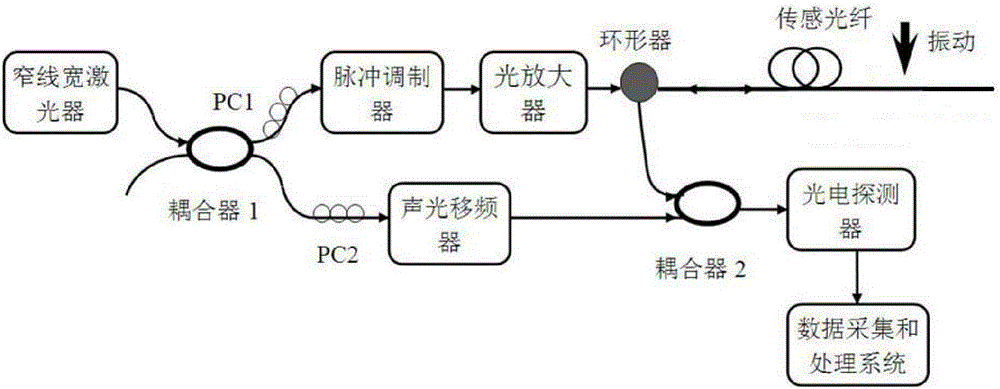
Full-distributed optical fiber strain and vibration sensor based on coherent heterodyne detection
InactiveCN102168953AImprove signal-to-noise ratioReduce false negative rateSubsonic/sonic/ultrasonic wave measurementUsing optical meansContinuous lightPolarization-maintaining optical fiber
The invention relates to a full-distributed optical fiber strain and vibration sensor based on coherent heterodyne detection, which comprises a laser (1), a coupler, a pulse modulation module, a programming gain amplifier (4), an optical amplifier, a circulator (6), a sensing fiber (7), a polarization-preserving fiber (8), the coupler, a balancing photoelectric detector (10), a reversal switch, a mixer, a microwave source, a band-pass filter, and a signal processing unit, wherein the continuous light output by the laser (1) is divided into two paths after passing through the coupler (2); an output end of the balancing photoelectric detector is connected to the reversal switch; the reversal switch is switched to a channel 1 and a channel 2; when the channel 1 is switched on, the system utilizes the Brillouin optical fiber time domain reflection to measure; and when the programming gain amplifier (4) is closed and the channel 2 is switched on, the system utilizes the polarization optical time-domain reflection to measure. By using the full-distributed optical fiber strain and vibration sensor provided by the invention, the full-distributed measurement for strain as well as the weak vibration and the full-distributed measurement for vibration can be performed on a single optical fiber.
Owner:NANJING UNIV
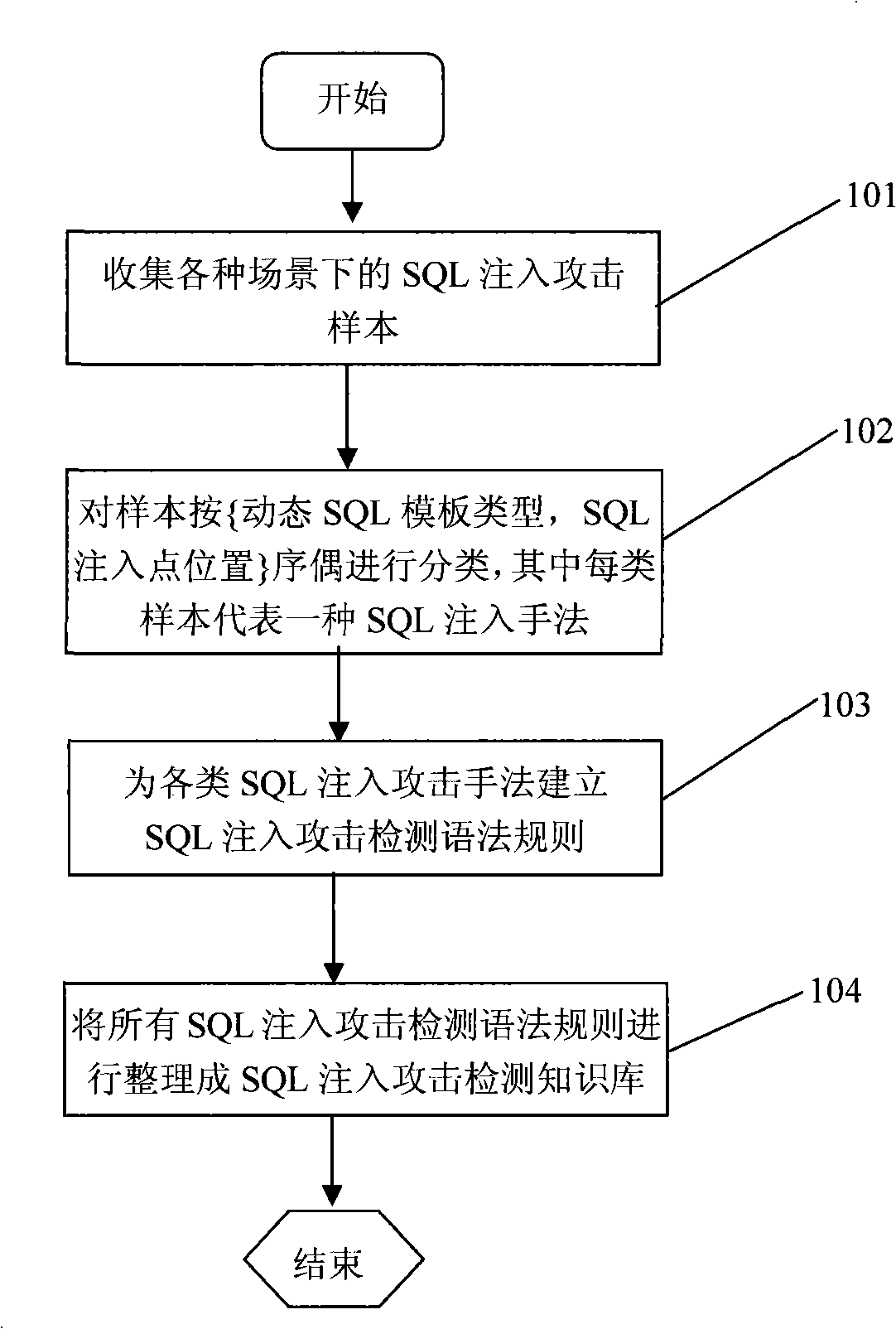
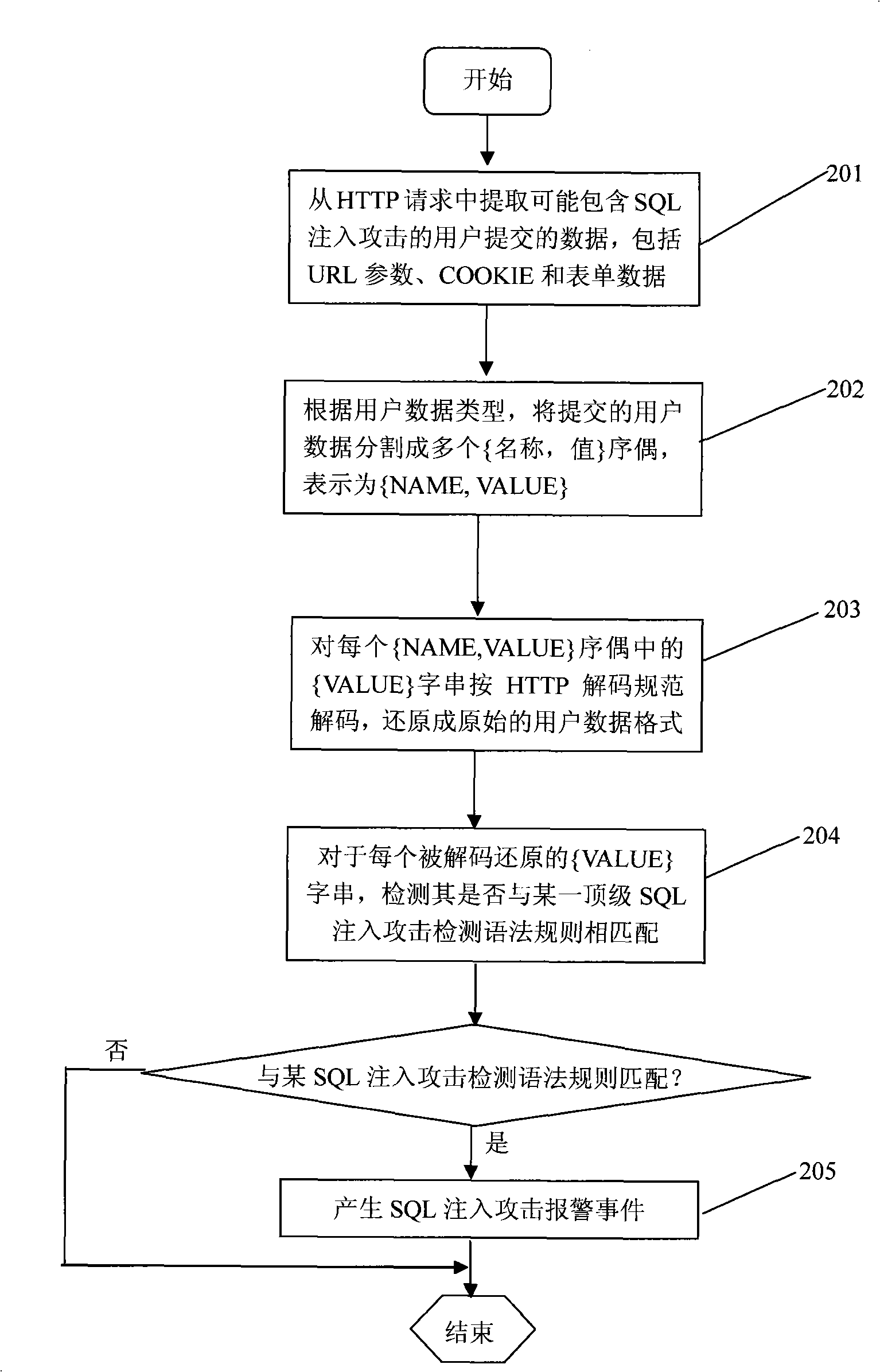
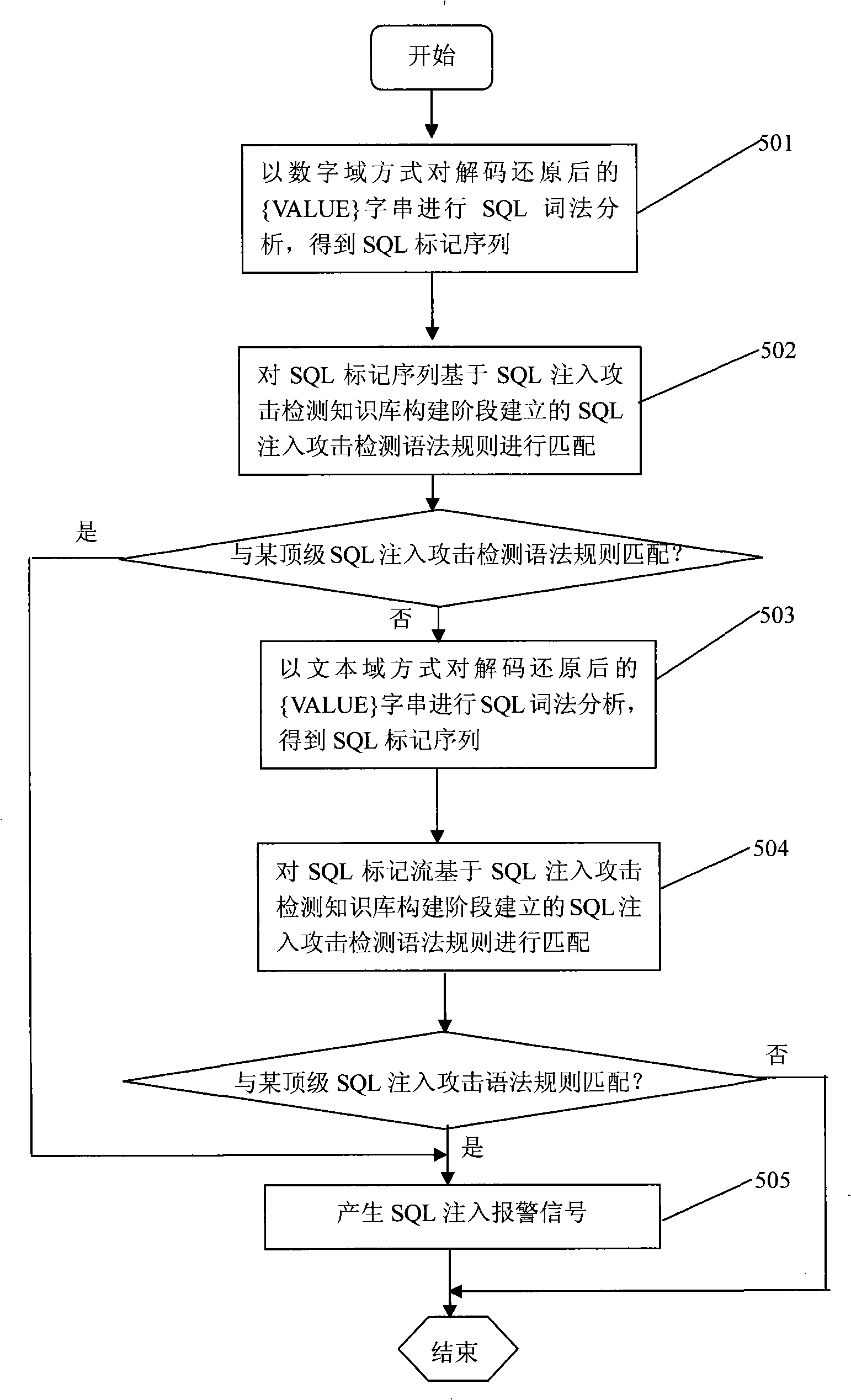
A SQL injection attack detection method and system
InactiveCN101267357AOvercoming difficult extractionOvercome shortcomings such as being easily deceivedUser identity/authority verificationData switching networksSQL injectionUser input
An SQL injection attack detecting method and system are provided, comprising building phase of SQL injection attack detecting knowledge base and detecting phase for real-time SQL injection attack. The build of SQL injection attack detecting knowledge base comprises collection of SQL injection attack sample for sorts of scenes, classification of SQL injection ways, and build of SQL injection attack detecting grammar rules aiming at sorts of SQL injection ways; the detecting phase for real-time SQL injection attack comprises extraction and decoding of user inputting data in HTTP request message and matching of the SQL injection attack detecting grammar rules and so on. This invention defines the SQL injection attack detecting grammar rules by using SQL grammar instead of defining the SQL injection attack detecting grammar rules based on the traditional attack characteristic. The invention overcomes shortcomings of uneasy extraction and inclined fraud of the attach characteristic sign of the SQL injection attack incident, which significantly reduces rate of wrong report and rate of missing report while invading the detecting system for detecting SQL injection attack.
Owner:BEIJING VENUS INFORMATION TECH
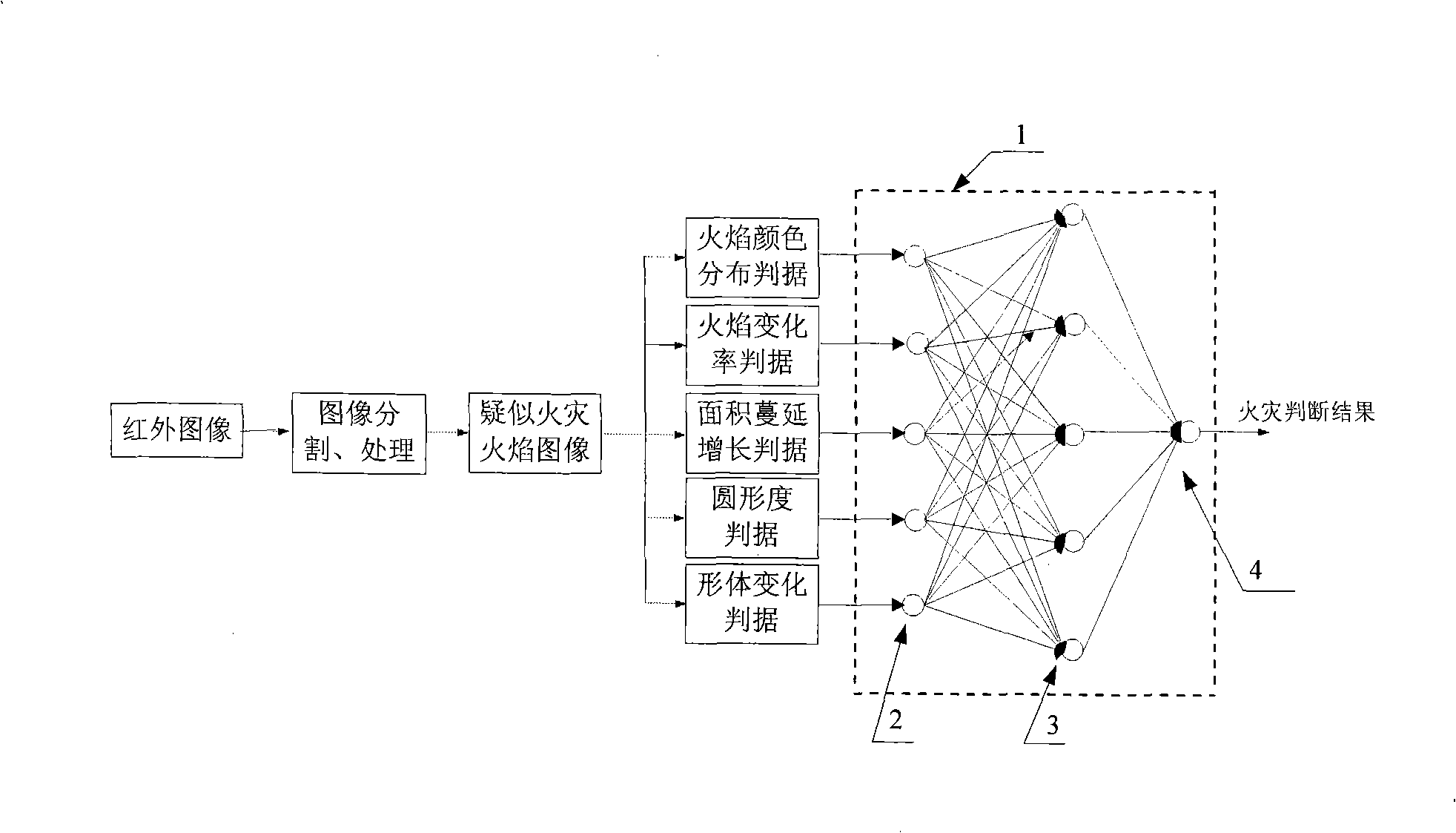
Multi-characteristic synthetic recognition method for outdoor early fire disaster
InactiveCN101315667AAvoid interferenceReduce false negative rateCharacter and pattern recognitionFire alarm radiation actuationImaging processingShape change
The invention relates to a method for the comprehensive recognition of various features of outdoor incipient fire, pertaining to the technical field of fire monitoring and image processing. The method comprises the steps that: 1. an infrared image is obtained by a thermal imaging instrument; 2. grey scale processing, threshold segmentation and filtration processing are carried out to the fire infrared image; 3.further analysis is carried out to a suspected fire flame image to obtain the following five criterions: (1) the flame image color distribution criterion; (2) the flame image change rate criterion; (3) the flame image area extending and increasing criterion; (4) the flame image circularity criterion; (5) the flame image shape changing criterion; 4. judgment is comprehensively carried out by utilizing a neural network and taking the criterions of 1 to 5 as input so as to obtain the final result that whether the fire occurs. The method overcomes interference to aspects such as natural lights, etc. in the fire recognition process, and reduces the rate of missing report and the rate of false report of the fire.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
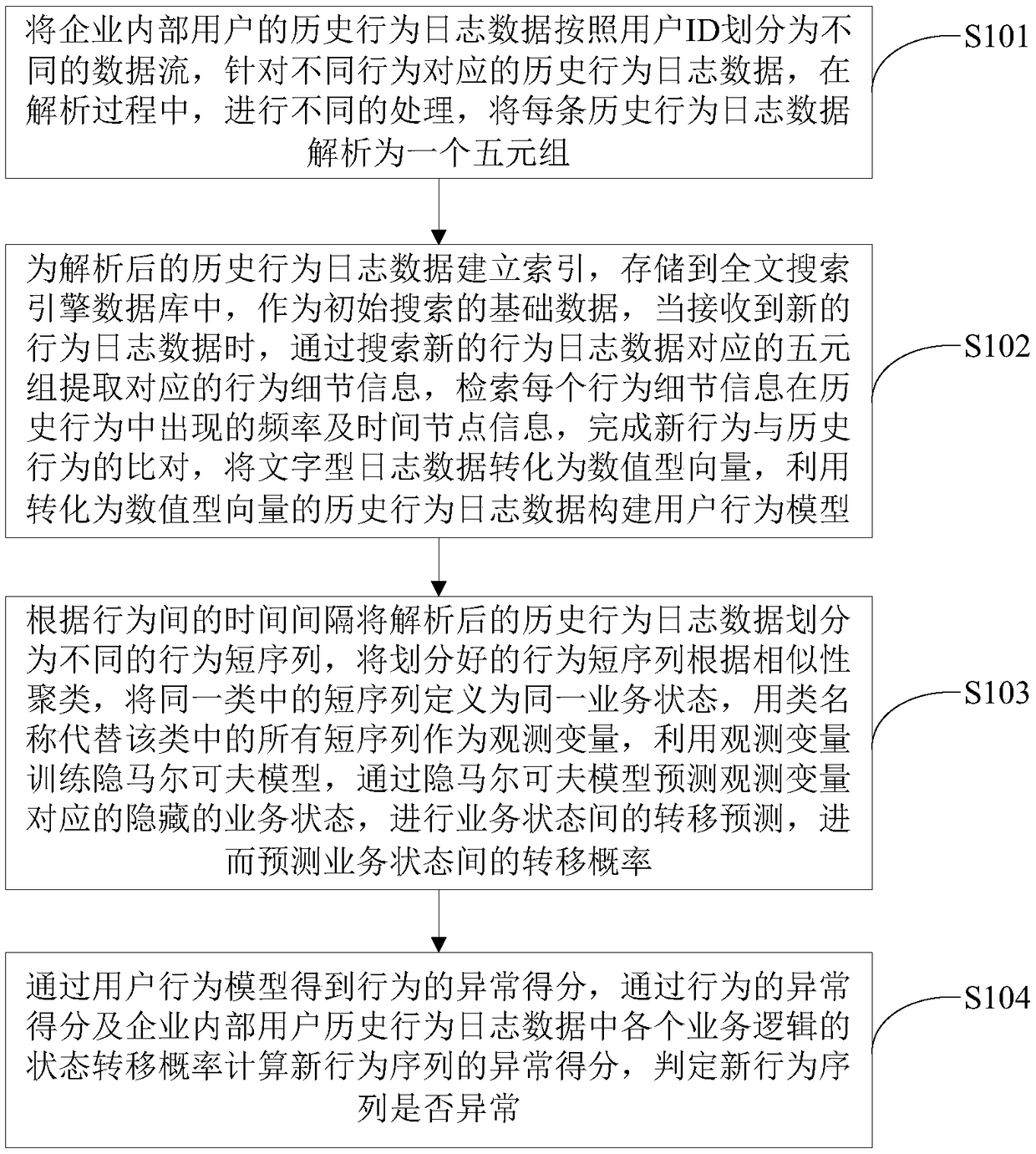
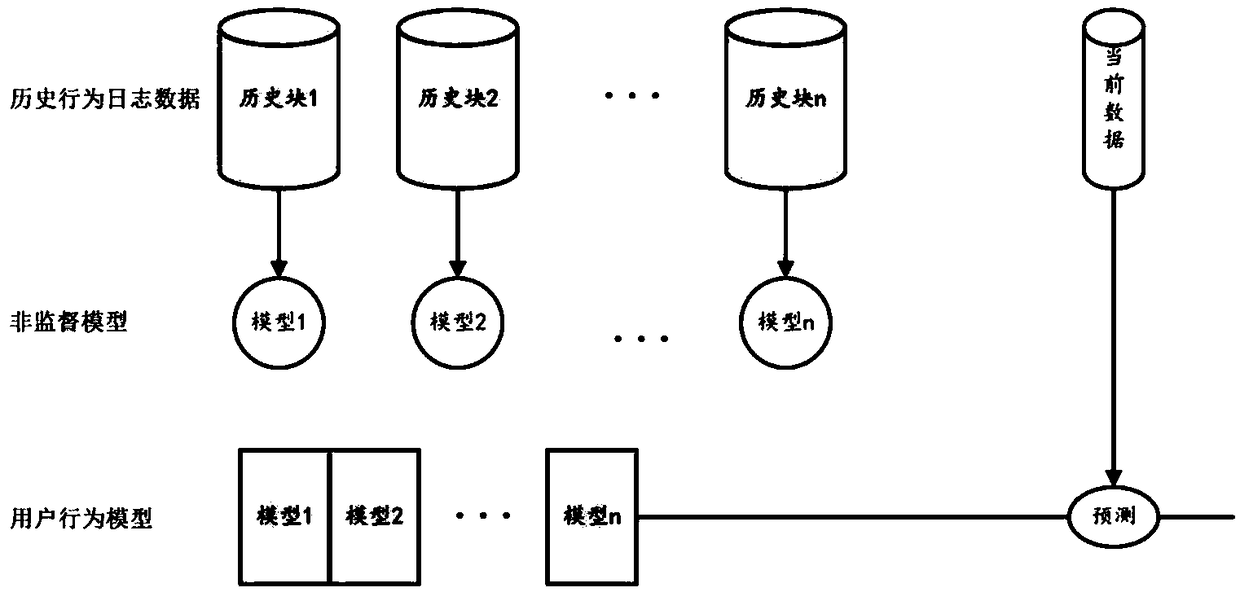
Enterprise internal user abnormal behavior detection method and device
ActiveCN108881194ATake advantage ofSolve the problem of missing detailsCharacter and pattern recognitionTransmissionInternet privacyAnomalous behavior
The invention relates to the technical field of network security, in particular to an enterprise internal user abnormal behavior detection method and device, discloses an enterprise internal user abnormal behavior detection method, and further discloses an enterprise internal user abnormal behavior detection device. The enterprise internal user abnormal behavior detection device comprises a behavior log acquiring and preprocessing module, a behavior detail modeling module, a service state transfer prediction module and a malicious behavior score discrimination module. According to the enterprise internal user abnormal behavior detection method and device, an unsupervised machine learning method is used, a user behavior model is built by fully utilizing unmarked unhistorical behavior log data in an enterprise, the accurate rate of abnormal behavior detection is increased, the false reporting rate and the missing reporting rate are decreased, and an effective means is provided for detecting enterprise internal threats.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +2
Indoor fire and flame detection method based on high-definition video images
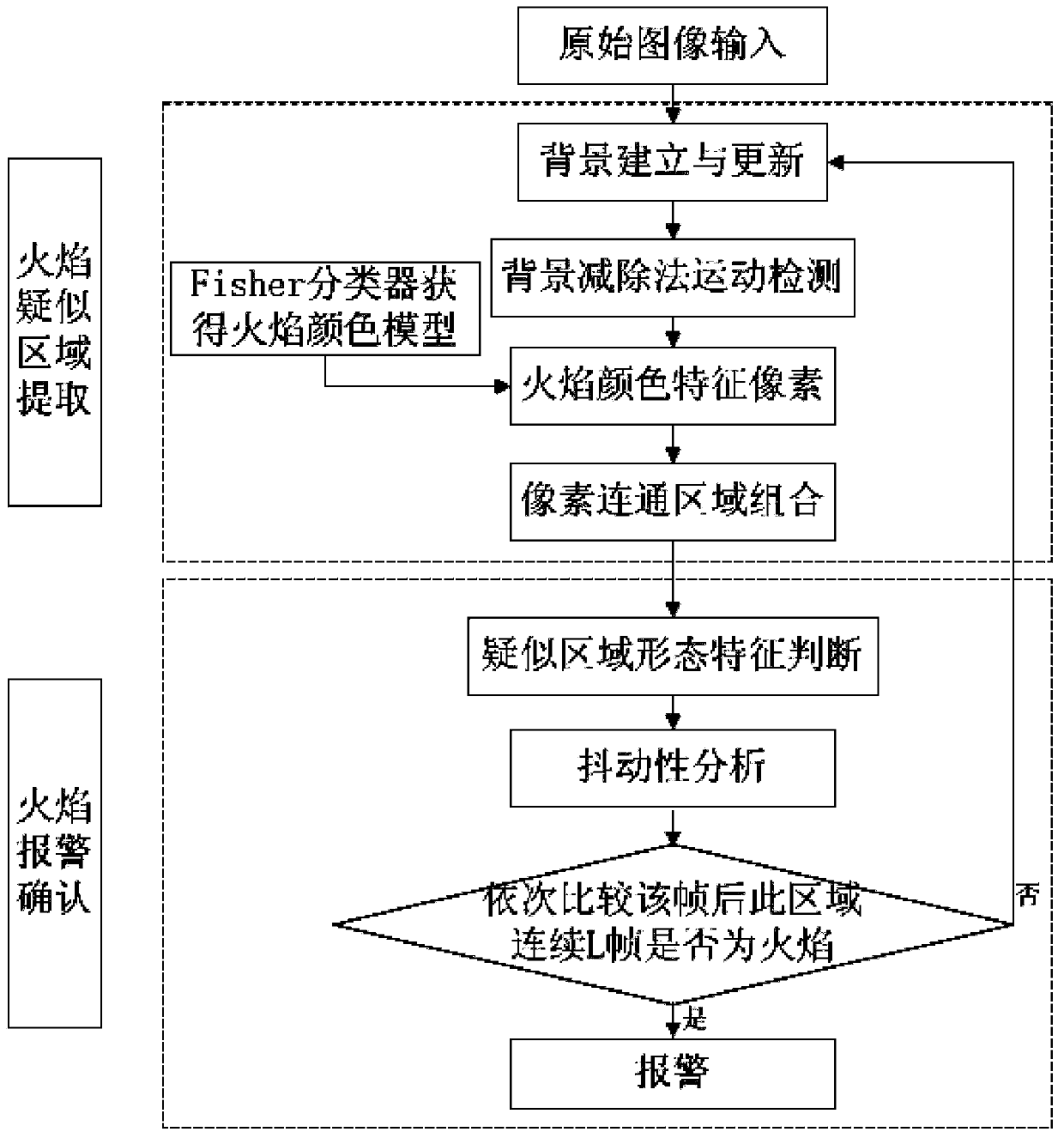
ActiveCN103473788AMeet the requirements of real-time fire detectionEffectively removes distractionsImage analysisVideo monitoringFlame detection
The invention proposes an indoor fire and flame detection method based on high-definition video images. Firstly, a background image is established and updated in video monitoring images; sample picture elements are trained by a Fisher classifier so that a color model of flames is acquired; a foreground moving image is acquired through a background differencing method; flame suspected pixels are detected through color features of the fire flames, that is, pixel points (that is, suspected flame pixel points) with the color features of the flames are found in the foreground moving image and all of the suspected flame pixel points form a flame area; pixel connection areas are combined so that an external rectangle of the suspected flame area is acquired; circularity of the connection areas in the external rectangle is calculated according to morphological characteristics of the flames and a suspected flame area is judged according to the circularity, jitter analysis and flame continuity analysis and the like in the external rectangle; and if preset requirements are met, the suspected flame area is a real flame area and an alarm signal is sent out.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
Method for judging refrigerant leakage of air-conditioner
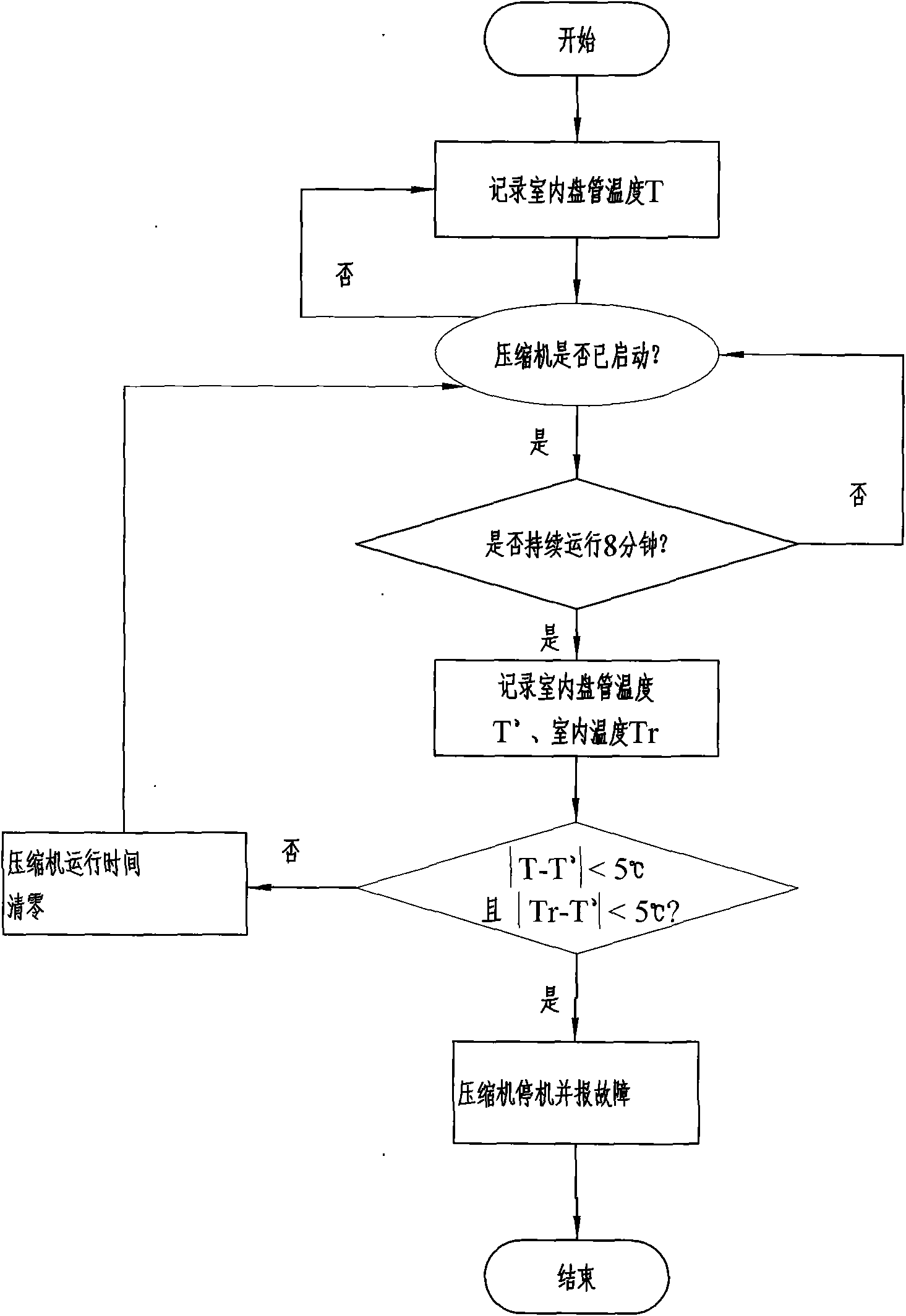
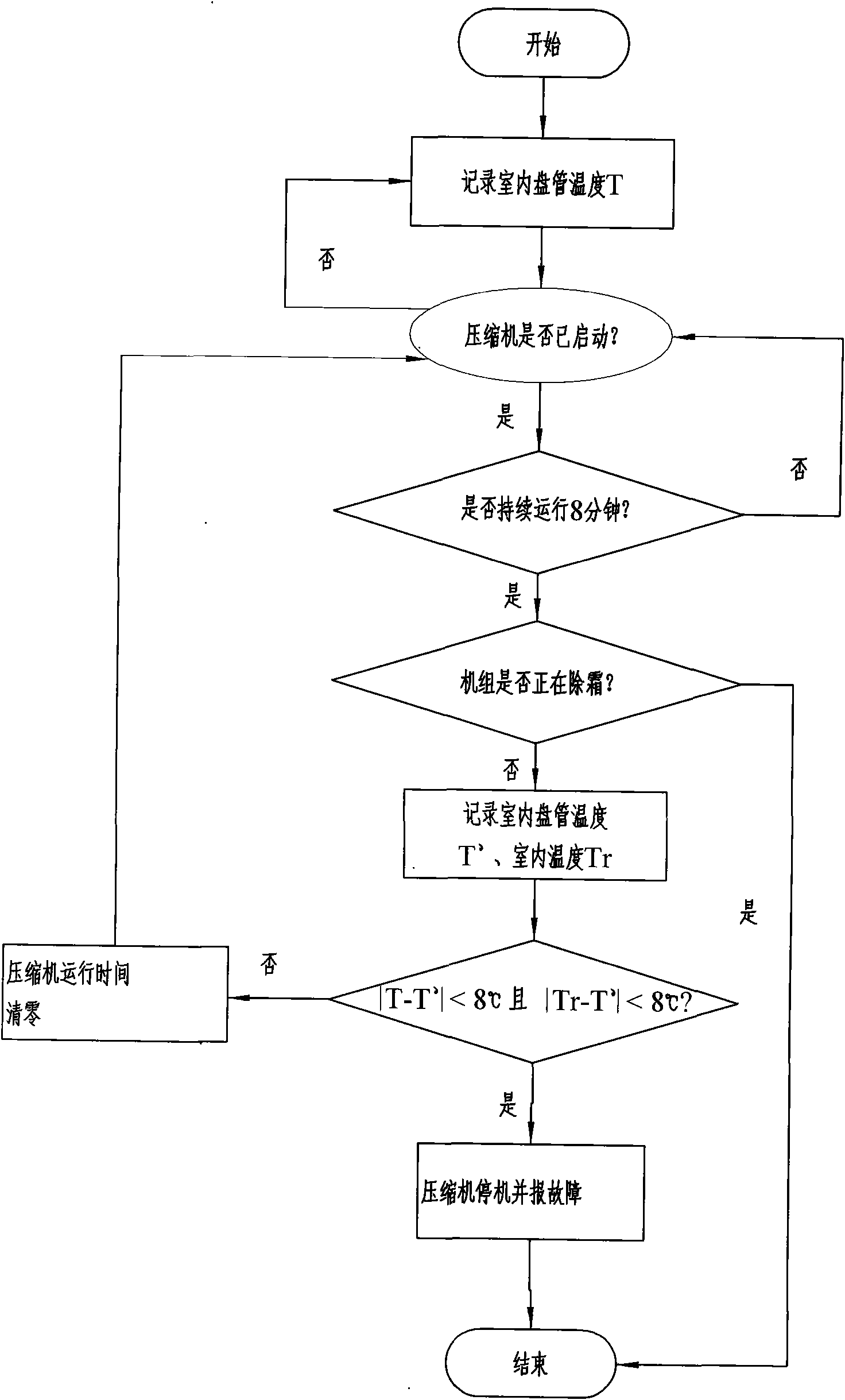
ActiveCN101566517AAchieve real-time protectionHigh sensitivityProgramme controlComputer controlTwo temperatureTemperature difference
The invention discloses a method for judging the refrigerant leakage of an air-conditioner, comprising following steps of: a. recording the temperature T of an indoor pipe coil before starting a compressor; b. judging whether the compressor is started or not, if so, conducting the next step, if not, returning to the step a; c. judging whether the compressor keeps running for x minutes, if so, conducting the next step, if not, returning to the step b; d. recording the temperature T' of the indoor pipe coil when the compressor keeps running for x minutes and recording indoor temperature Tr simultaneously; e. calculating temperature difference between the temperature T' of the indoor pipe coil when the compressor keeps running for x minutes and the temperature T of the indoor pipe coil before starting the compressor, calculating the temperature difference between the temperature T' of the indoor pipe coil when the compressor keeps running for x minutes and the indoor temperature Tr recorded simultaneously, to see whether the two temperature differences are less than y, if so, conducting step f, if not, then clearing the running time of the compressor and returning to the step b; and f. shutting down to report faults. The method for judging refrigerant leakage in the air-conditioner has high accuracy.
Owner:NINGBO AUX ELECTRIC
WebShell detection method and system
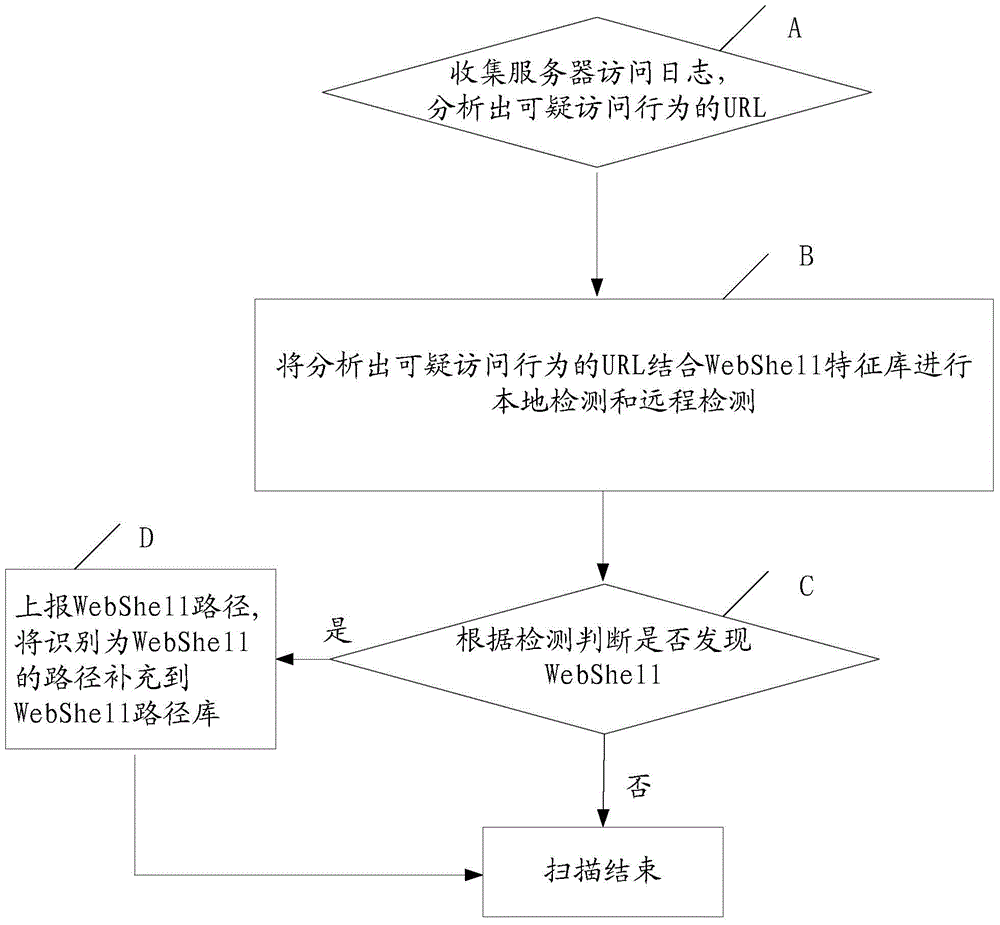
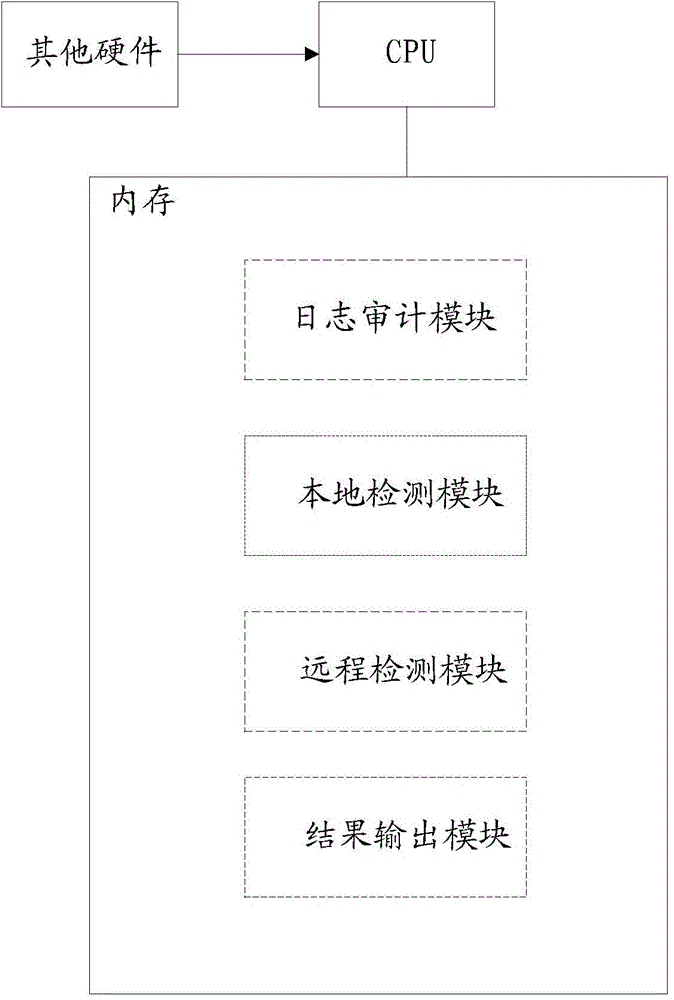
ActiveCN104468477AImprove accuracyImprove the detection rateTransmissionWeb applicationUniform resource locator
The invention provides a WebShell detection method and system. The system comprises a log auditing module, a local detection module, a remote detection module and a result output module. The system executes the following processing flow: A, collecting a server access log, and analyzing a URL (Uniform Resource Locator) with suspicious access behaviors; B, performing local detection and remote detection on the analyzed URL with suspicious access behaviors in combination with a WebShell feature library; C, and performing judgment according to the detection, reporting a WebShell path if WebShell is found, and meanwhile adding the path identified as WebShell into a WebShell path library. Through adoption of the method and the system, the detection rate and detection efficiency of WebShell detection in network Web application are increased, and the missing report rate and false report rate are lowered.
Owner:杭州迪普信息技术有限公司
Database SQL infusion protecting method based on self-learning
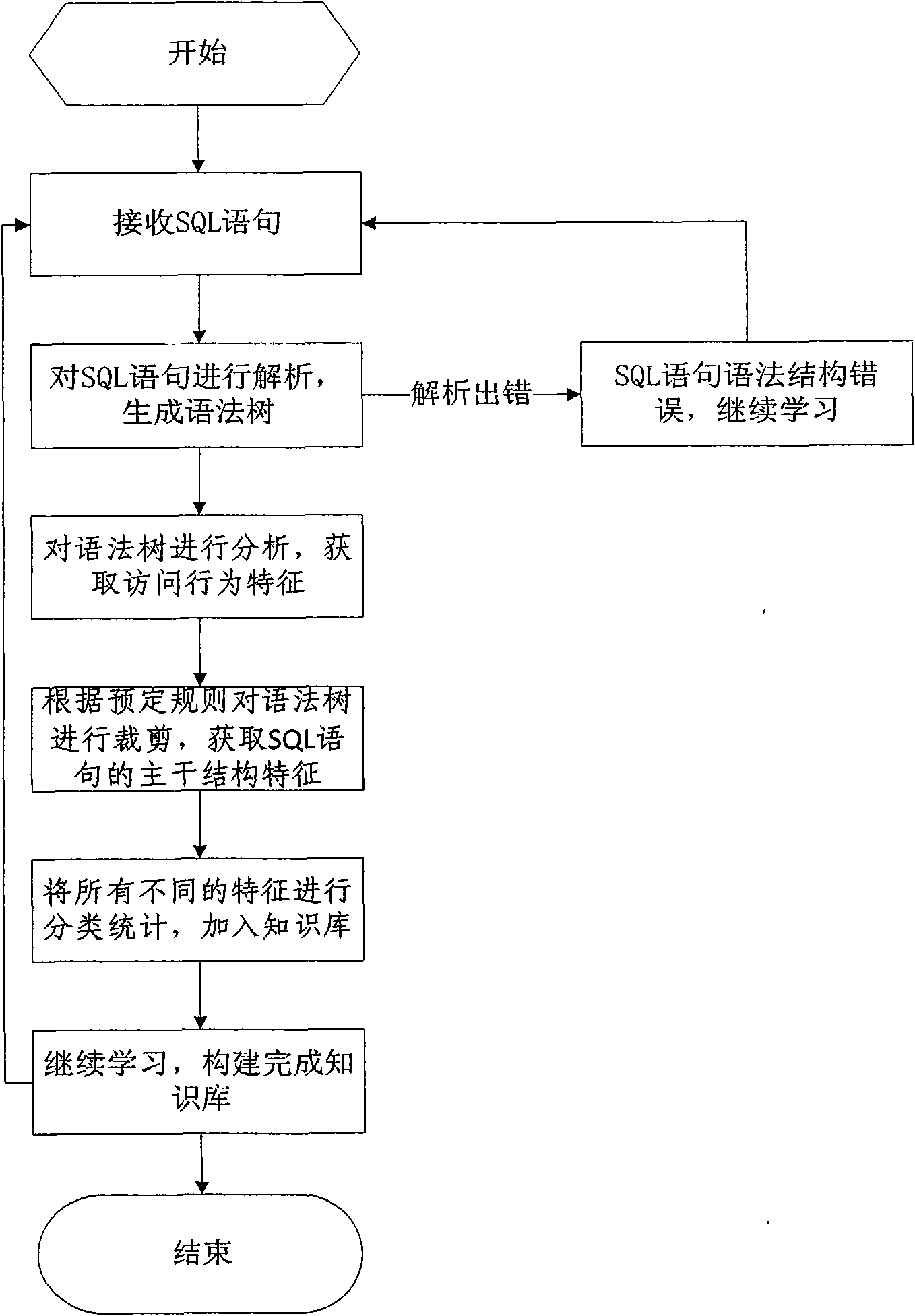
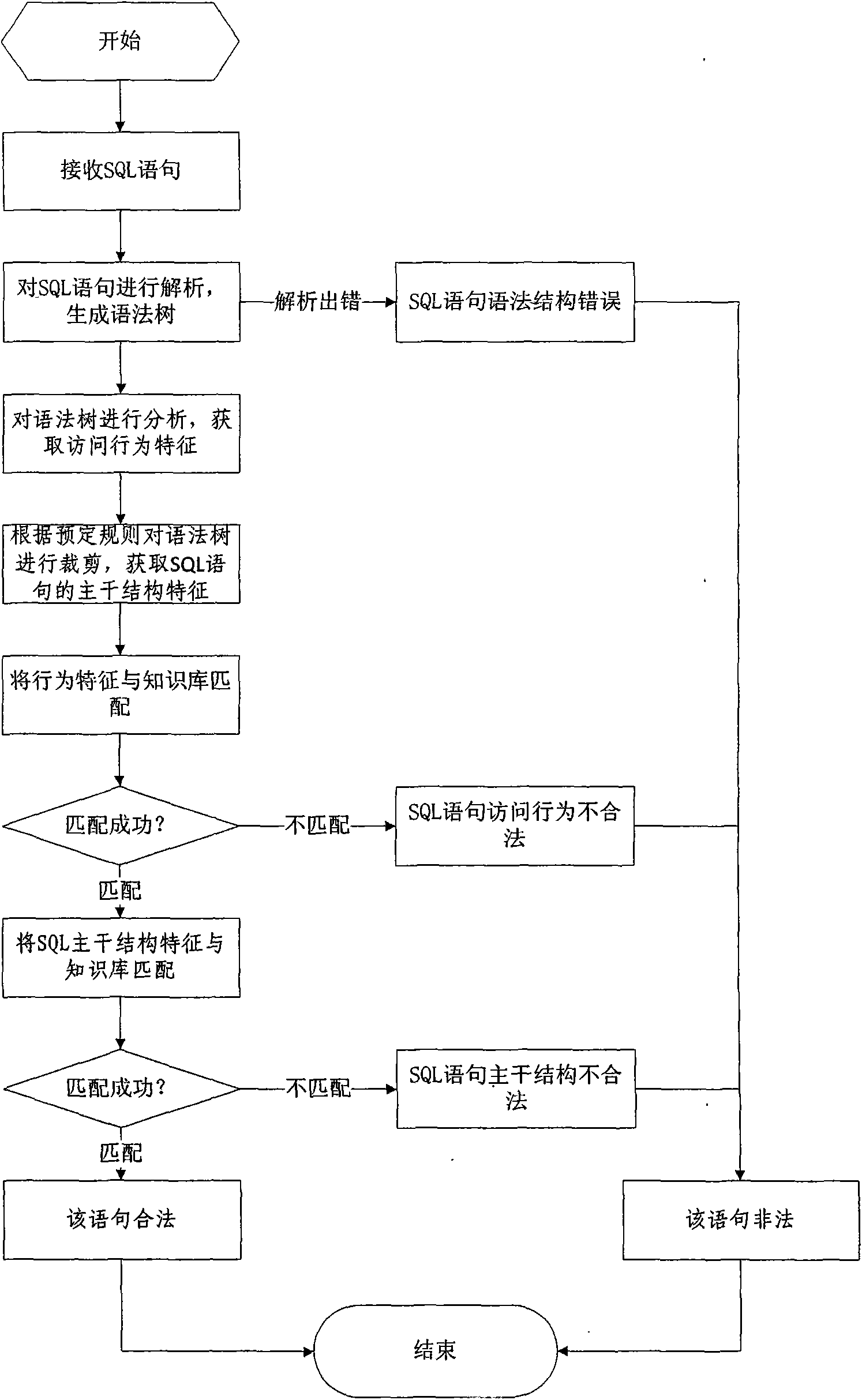
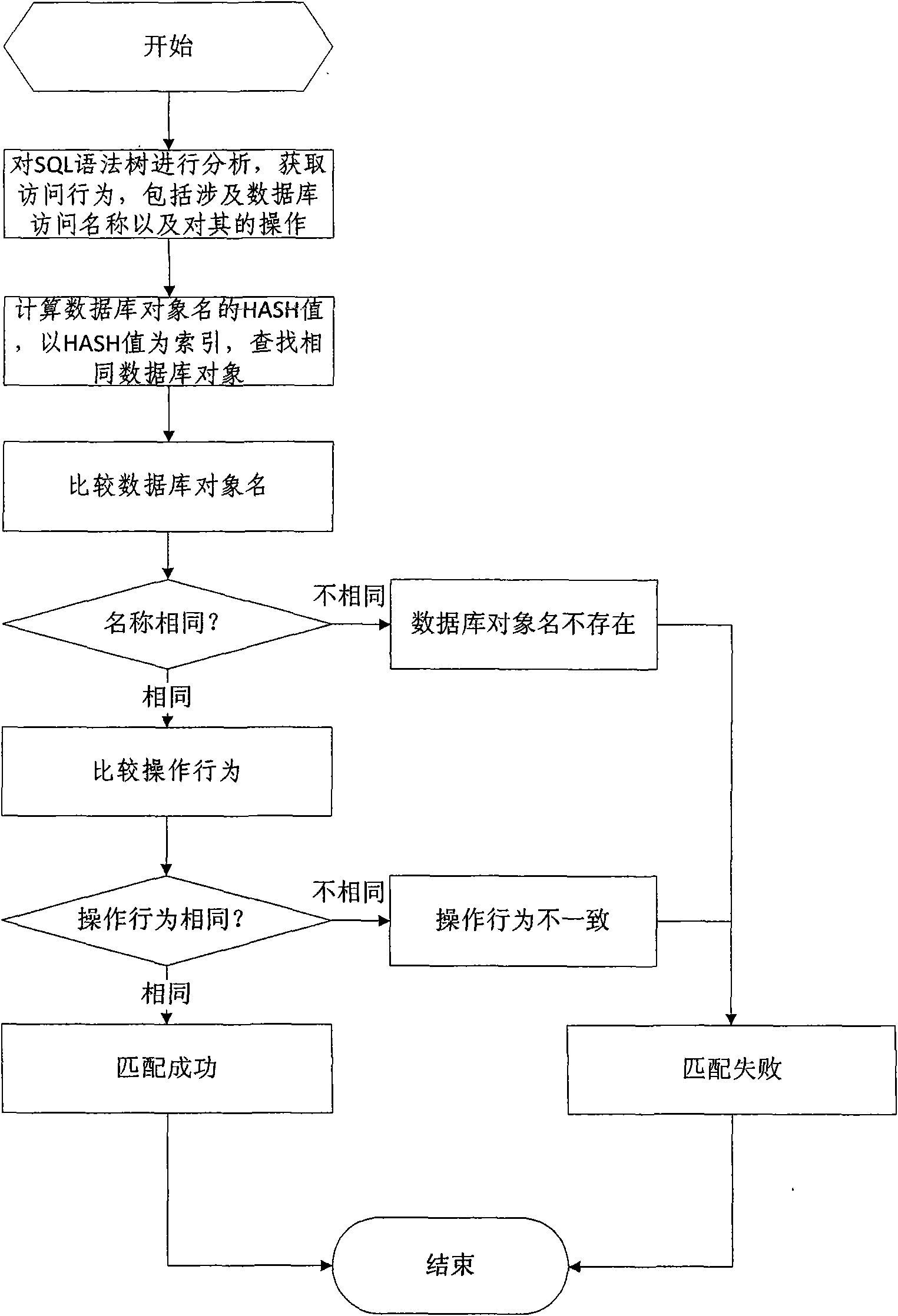
InactiveCN101609493AOvercome false negativesOvercome the False Positive FlawComputing modelsDigital data protectionLearning basedSQL injection
The invention discloses a database SQL infusion protecting method based on self-learning, comprising a learning phase and a filtering phase. The learning phase works in safe environment. At the moment, all SQL sentences are legitimate SQL sentences generated by an application system. A knowledge model (knowledge base) of the legitimate SQL sentences can be constituted by analyzing the sentences as well as analyzing and summarizing the characteristics of the sentences on the basis of sentence analysis results. The filtering phase works in real environment. At the moment, all SQL sentences are assumed to be possibly illegitimate SQL sentences. The sentences undergo pattern matching with the knowledge base established in the safe environment. If the matching is successful, the sentences are legitimate SQL sentences, otherwise, the sentences are illegitimate SQL sentences. The database SQL infusion protecting method has the advantage that an SQL infusion protecting system based on learning the legitimate SQL sentences can greatly reduce the false report rate and missing report rate which are caused by traditional SQL infusion protection, and the defending capability of the whole system can be improved.
Owner:STATE GRID ELECTRIC POWER RES INST +1
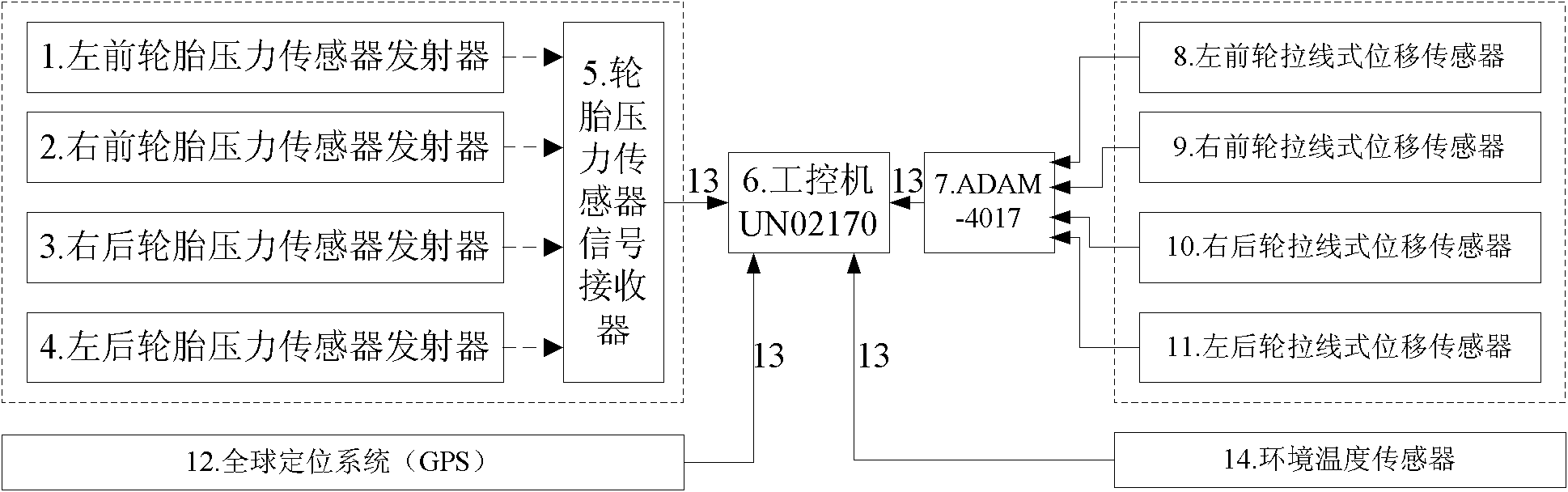
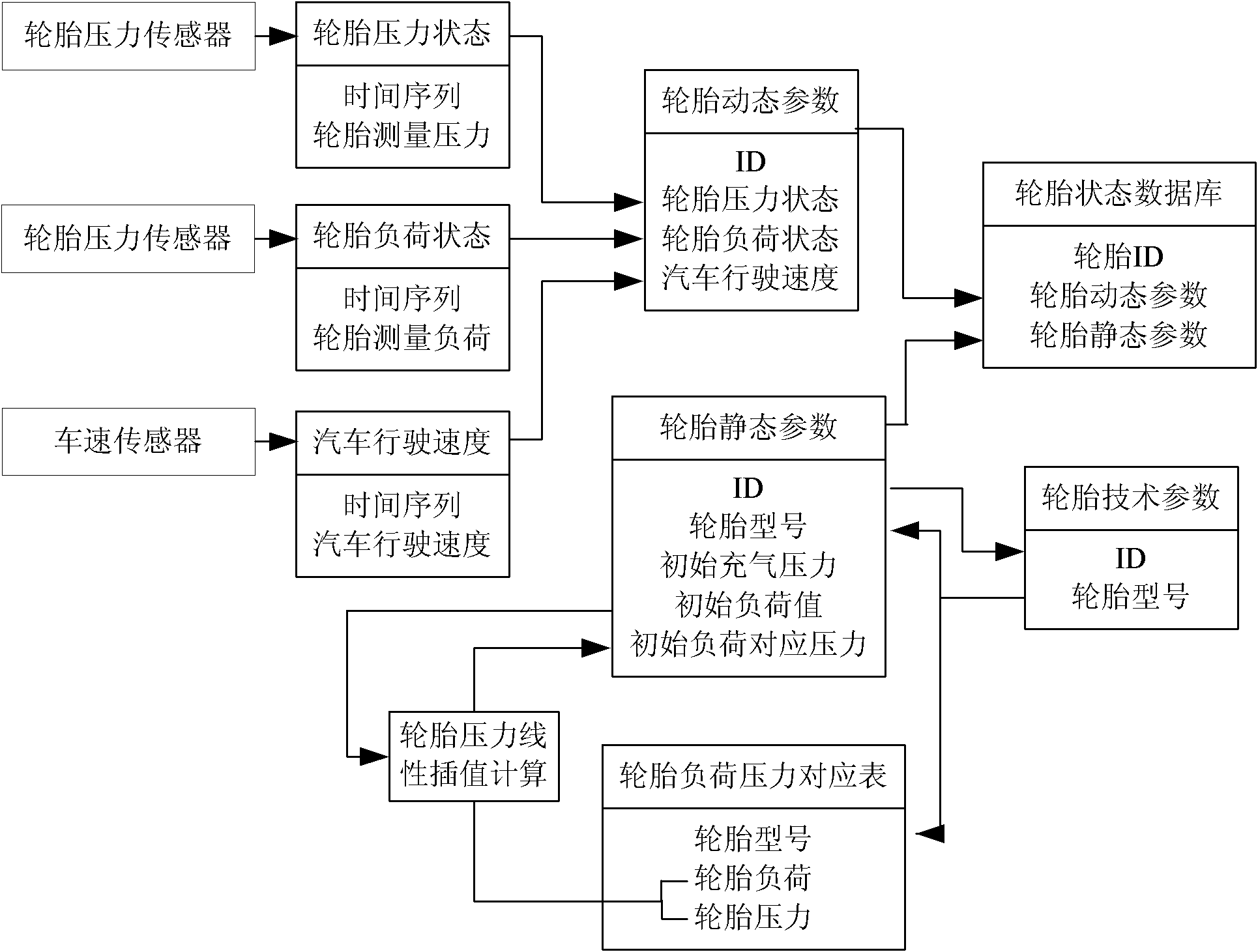
Abnormal condition identification method for tire pressure of goods wagon
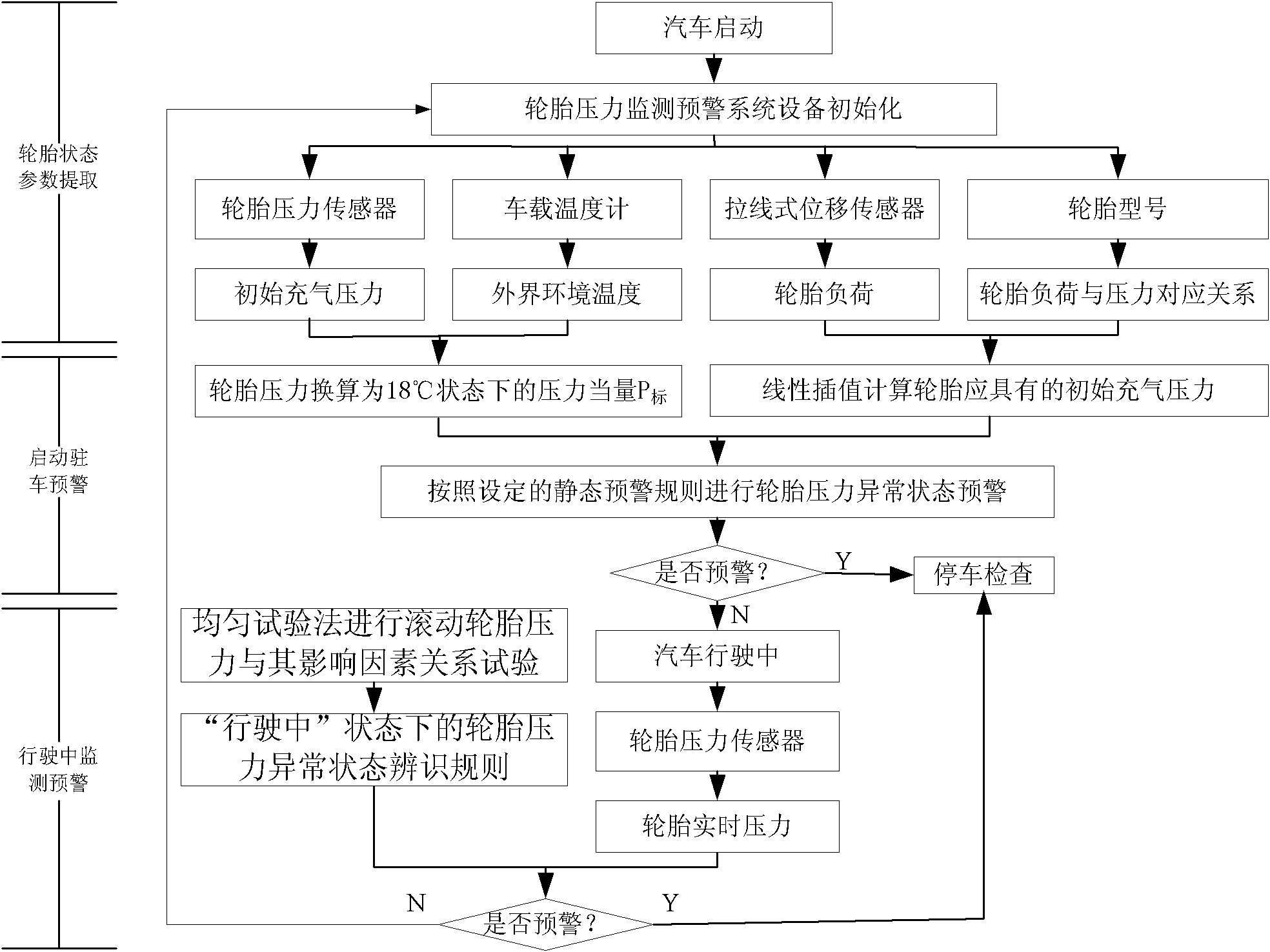
InactiveCN102107591AReduce the probability of false positives and false negativesImprove accuracyTyre measurementsEngineeringData processing
An abnormal condition identification method for the tire pressure of a goods wagon belongs to the technical field of secure state detection of an automobile. The abnormal condition identification method comprises the steps as follows: a tire state data base comprising tire models, the relation between load and initial inflation pressure, real-time tire pressure, load, vehicle speed and external environmental temperature is created; frequency is acquired on the basis of set data so as to measure tire state parameters which are then input to the tire state data base in an industrial computer; the prewarning threshold value of the abnormal condition identification of the tire pressure is confirmed on the basis of a test on the relation between the rolling tire pressure and influence factors thereof; in addition, data processing programs of the abnormal condition identification of the tire pressure are written, and the tire pressure states of start-up, parking and driving of the automobile can be monitored and prewarned respectively. The abnormal condition identification method effectively solves the difficult problem that the prewarning threshold value of the rolling tire pressure varies with the changes of working conditions, can greatly reduce the probability of misinformation and omission, improves the prewarning accuracy of the abnormal condition of the tire pressure, and canprovide the theory basis for the setting of prewarning regulations of a tire pressure monitoring prewarning system at the same time.
Owner:JILIN UNIV
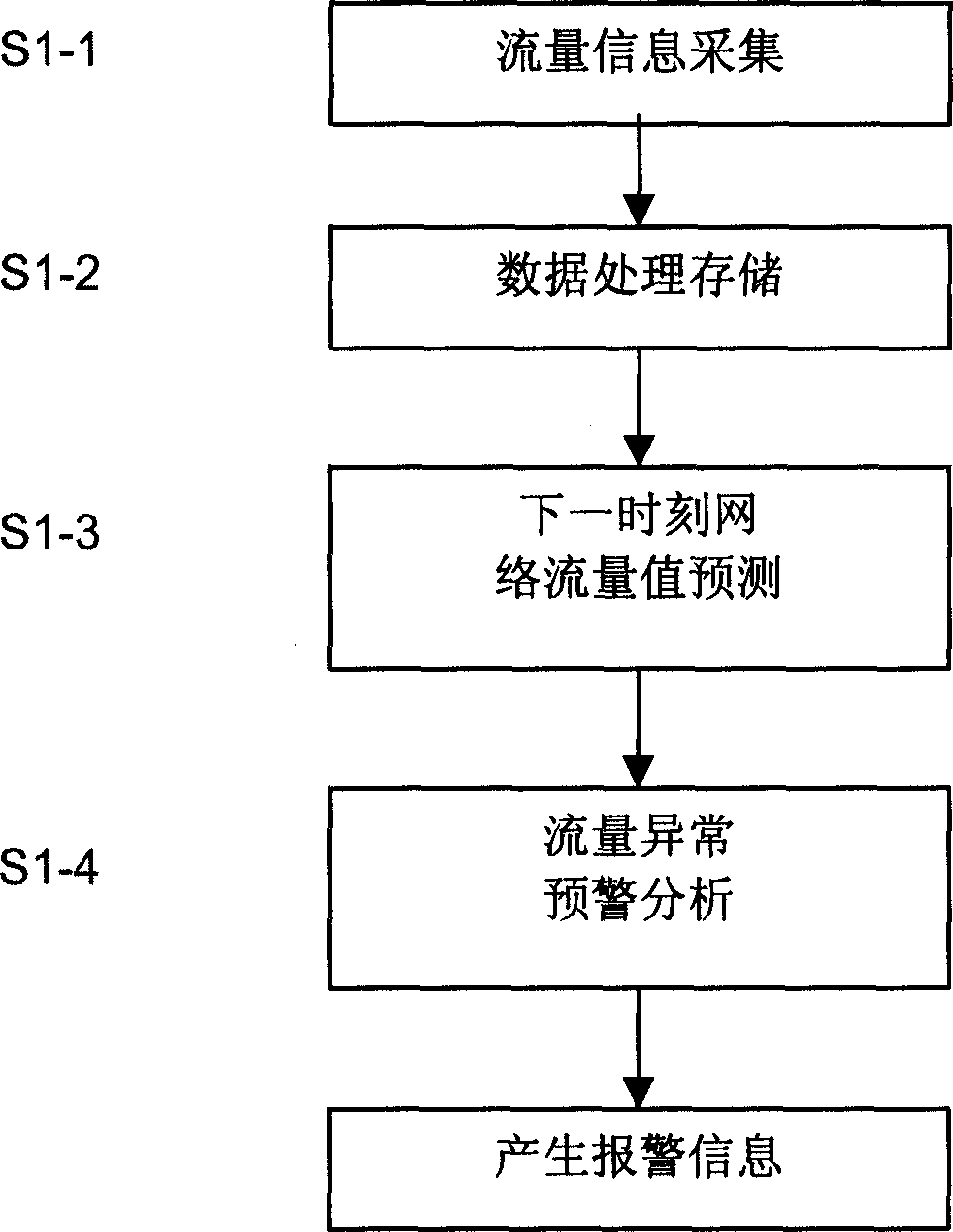
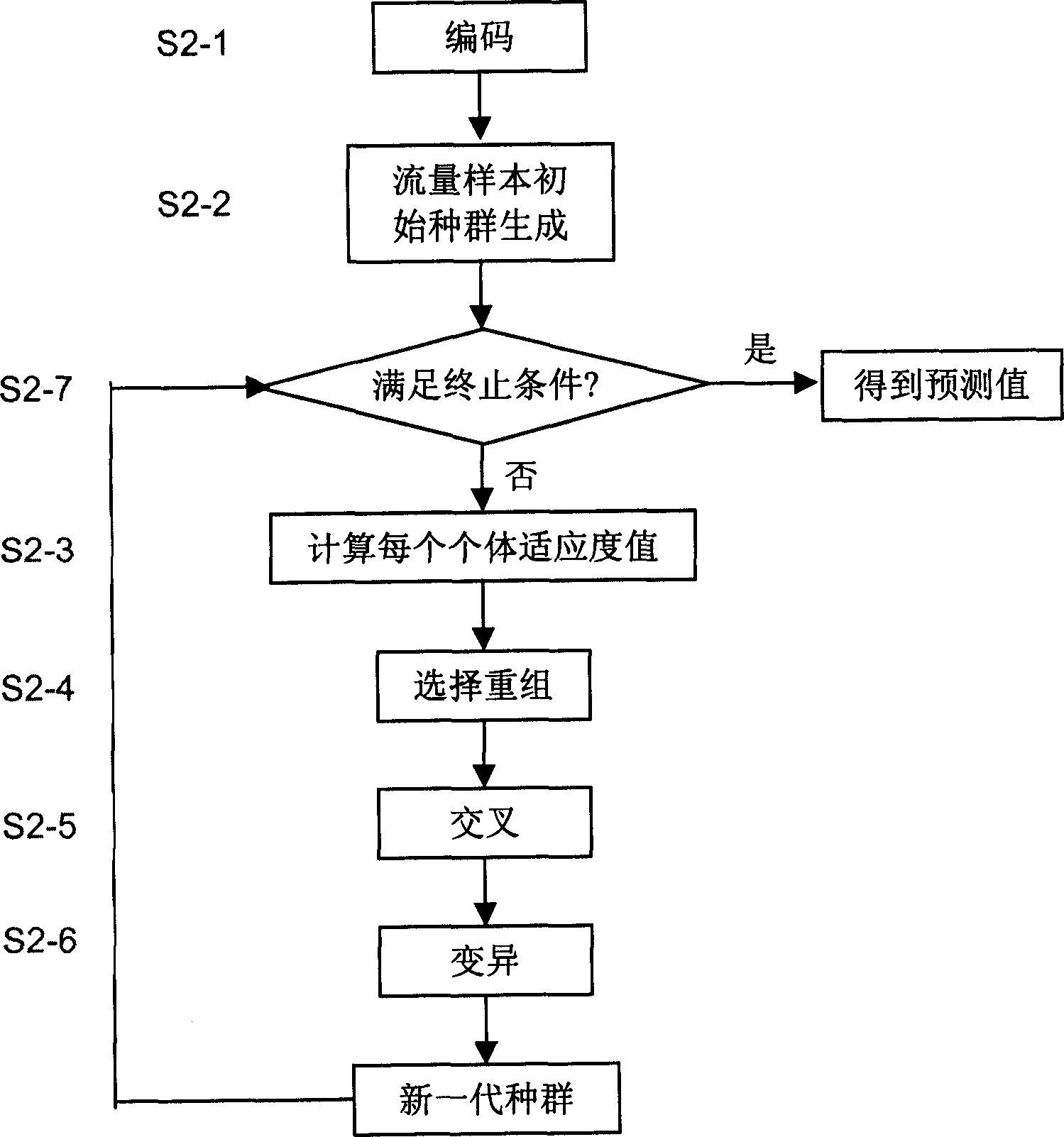
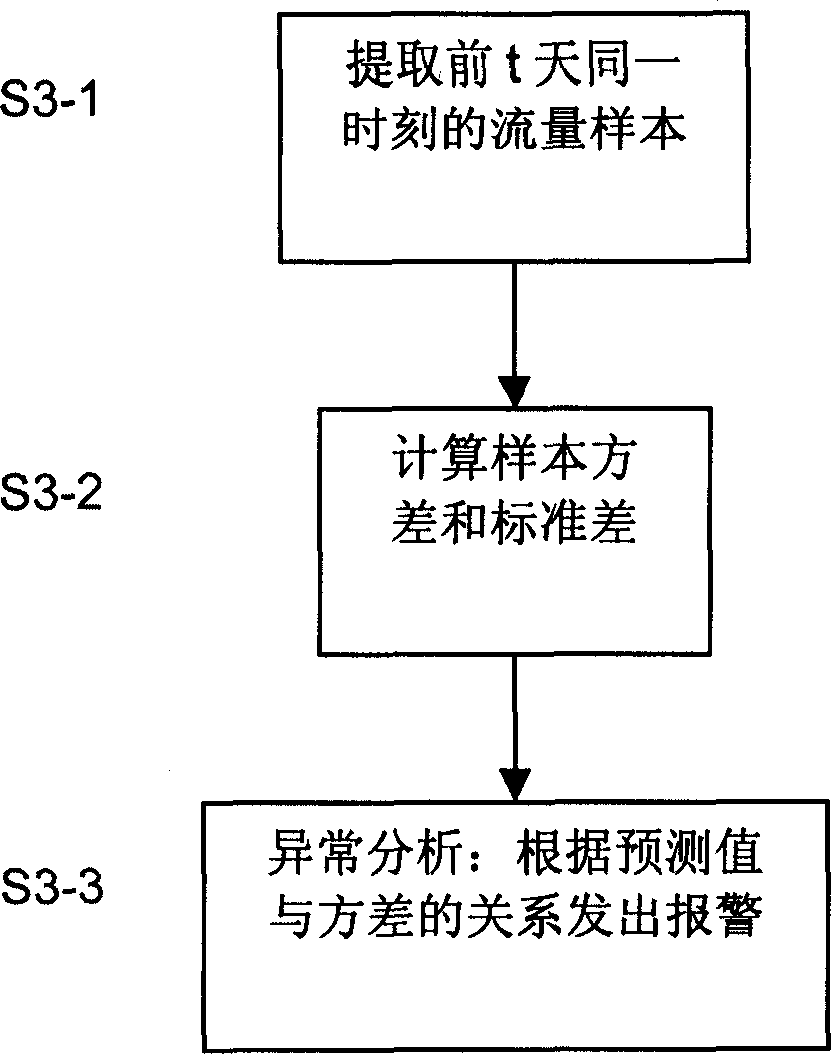
Adaptive network flow forecasting and abnormal alarming method
InactiveCN1617512AExact expected valueAdaptableData switching networksTraffic predictionGenetic algorithm
This invention provide a network flow performance prediction and abnormal alarming technology and a method based on the genetic algorithms, which utilizes genetic algorithms to predict the flow state of the next time from the horizontal time degree then to utilize the statistics method to judge the abnormal situation of said flow based on the flow sample in a related time period of each day in the historical flow information from the longitudinal time degree. The method is realized by four steps of network flow data collection, process and storage, prediction and abnormal alarming.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
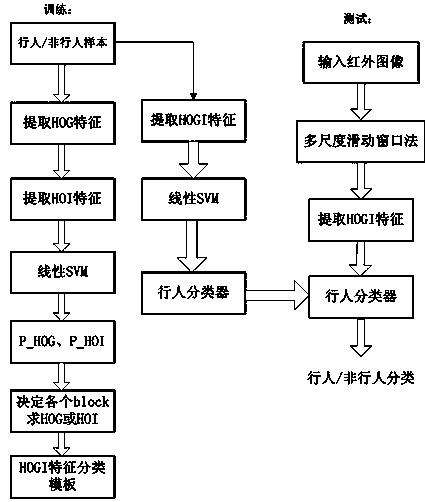
Pedestrian detection method based on infrared image
InactiveCN103902976AImprove detection rateReduce computational complexityCharacter and pattern recognitionSample imageGradient direction
The invention discloses a pedestrian detection method based on an infrared image. The method comprises the steps that a pedestrian standard data set and a non-pedestrian standard data set of the infrared image are established; sample image characteristics of an HOG are extracted; sample image characteristics of an HOI are extracted; the pedestrian classification features and the characteristics of an HOGI are designed; the sample image HOGI characteristics are extracted, and a pedestrian classifier is trained; the searching detection is carried out on the infrared image based on the multi-scale sliding window method; multi-window classification results can be combined to determine the pedestrian position. The pedestrian detecting characteristics special for the infrared image are provided on the basis of studying the present pedestrian detecting characteristics. The advantages of the HOG characteristics and the advantages of the HOI characteristics are combined, and the HOGI characteristics suitable for infrared image pedestrian detection are obtained through an SVM. According to the pedestrian detection method, pedestrians walking at night are detected, and the pedestrian detection method has the advantages of being high in detection ratio, low in false drop rate, good in environmental adaptability and the like.
Owner:ZHEJIANG UNIV
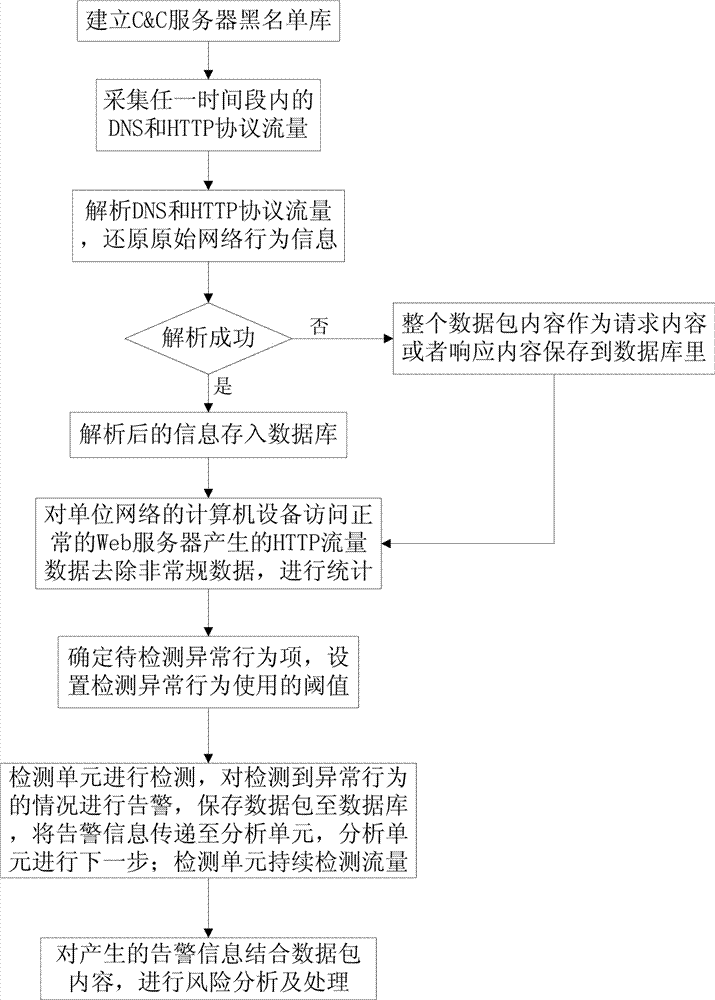
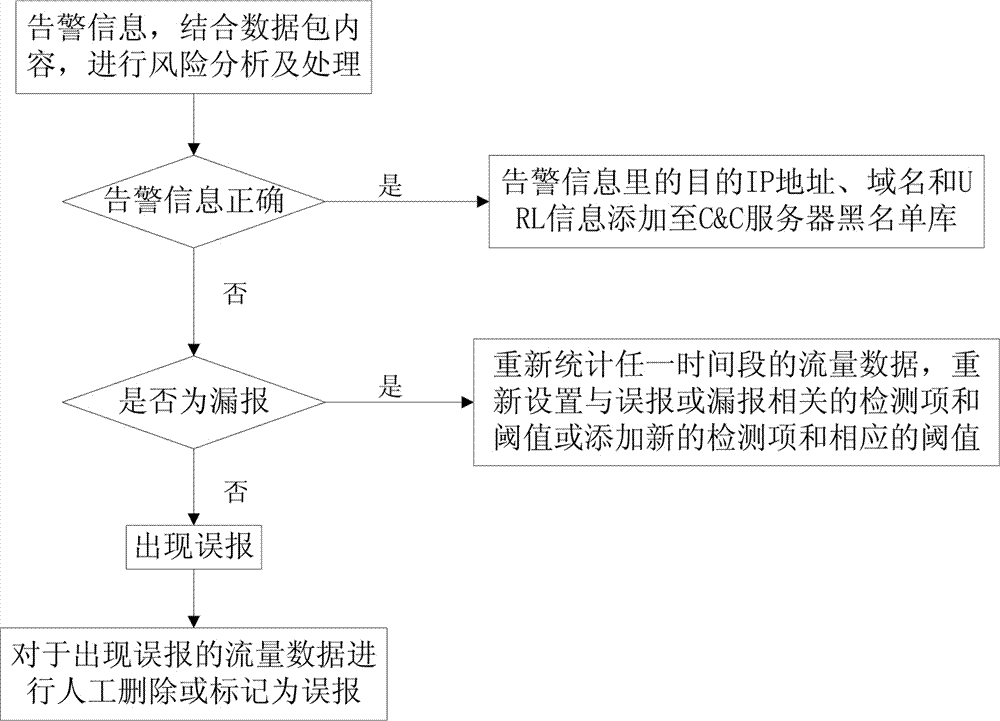
Network theft behavior detecting method based on HTTP flow analysis
ActiveCN107454109AReduce false alarm rateReduce false negative rateTransmissionRisk profilingTime segment
The invention relates to a network theft behavior detecting method based on HTTP flow analysis. The method comprises the steps of establishing a C&C server blacklist database, acquiring DNS and HTTP protocol flow in a random time segment and performing analysis restoring, performing abnormal data elimination on HTTP traffic data generated in accessing a normal server, performing statistics, determining a to-be-determined abnormal behavior item and a detecting use threshold, detecting whether an abnormal behavior of a computer device in a network of an organization, if yes, performing alarming, storing a data packet in a database, and performing risk analysis and processing on alarming. According to the network theft behavior detecting method, network behavior characteristic analysis is performed on a tool and malicious software which transmit sensitive data based on an HTTP protocol, thereby determining an abnormal behavior characteristic. A threshold value is determined through performing statistics on the HTTP traffic at the network entrance of the organization, thereby identifying a sensitive data transmission behavior by a trojan horse on the attacked computer device. The network theft behavior detecting method has advantages of low alarm error rate, low alarm omission rate, high accuracy and high feasibility. The network theft behavior detecting method is suitable for organizations, individuals and large-scale high-speed network.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
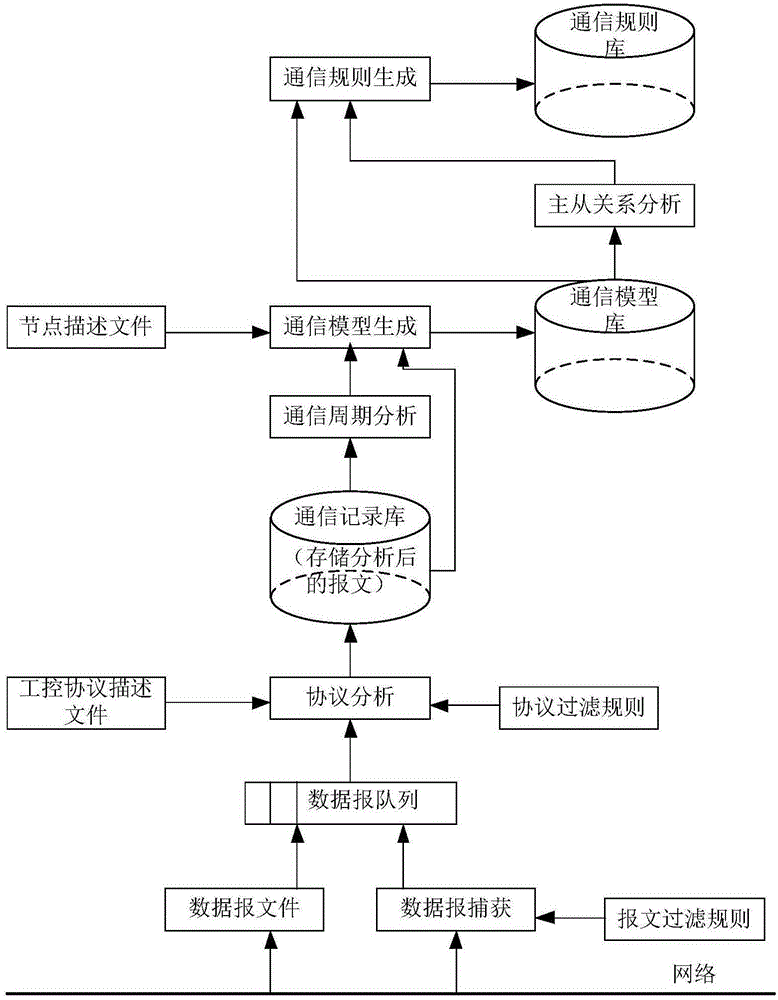
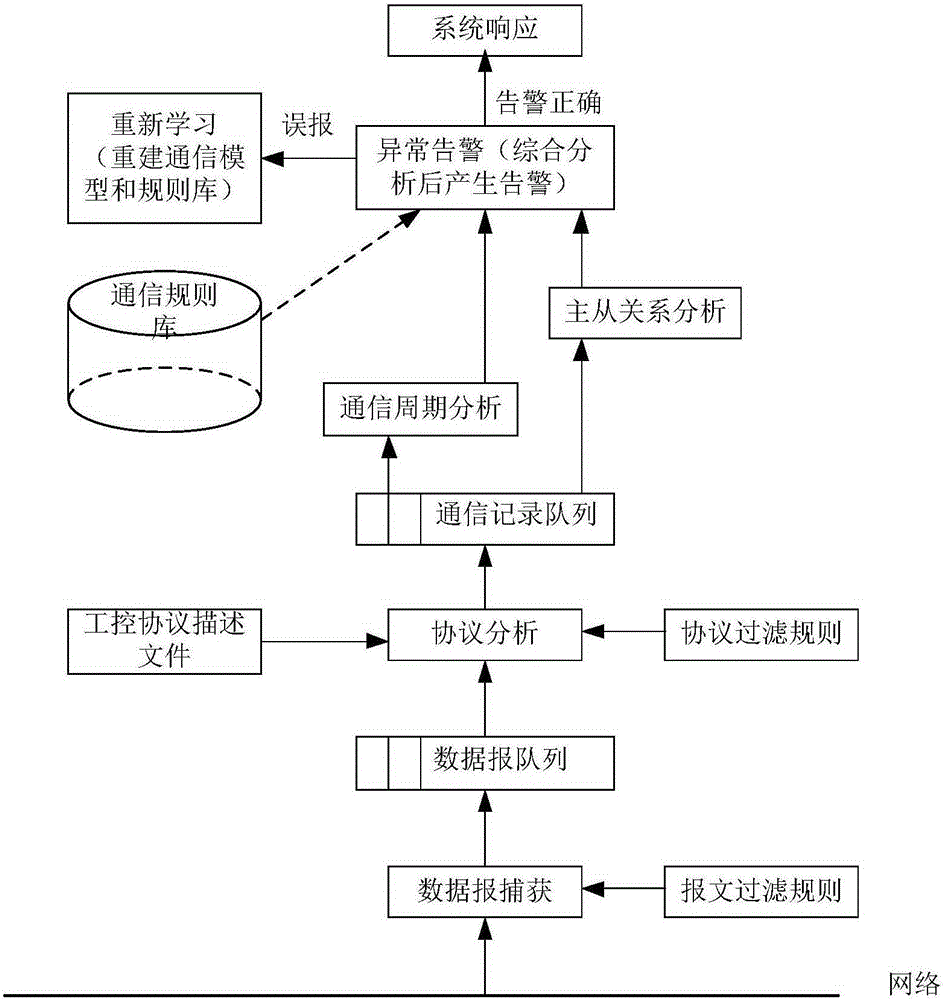
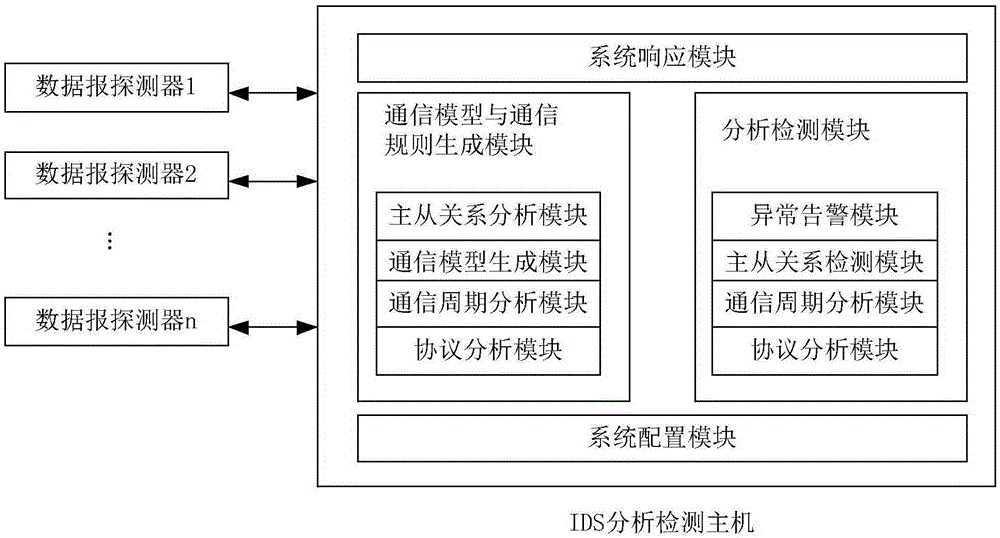
Intrusion detection method and intrusion detection system for industrial control system based on communication model
InactiveCN105204487AImprove accuracyGuaranteed practicalityElectric testing/monitoringComputer moduleResponse strategy
The invention provides an intrusion detection method and an intrusion detection system for an industrial control system based on a communication model. The accuracy of intrusion detection is improved to the maximum degree while the practicability is guaranteed. The intrusion detection method comprises the steps of firstly establishing a communication model and communication rules of the industrial control system, wherein the communication model comprises node information and communication connection information; generating a legal communication rule set on the basis of the communication model after the communication model of the industrial control system is established, learning in an installation and debugging stage and a stage before an attack happens of the industrial control system, and establishing a communication model and a communication rule set; then deploying detectors in an industrial control network, capturing a datagram, analyzing and extracting the communication connection information through the datagram, comparing the communication connection information with the generated legal communication rule set, and giving out an alarm when communication connection which violates the legal communication rule set exists; and calling a system response module to adopt corresponding response strategies if intrusion is discovered, and carrying out analysis and learning again if actual detection is wrong.
Owner:BEIJING UNIV OF POSTS & TELECOMM
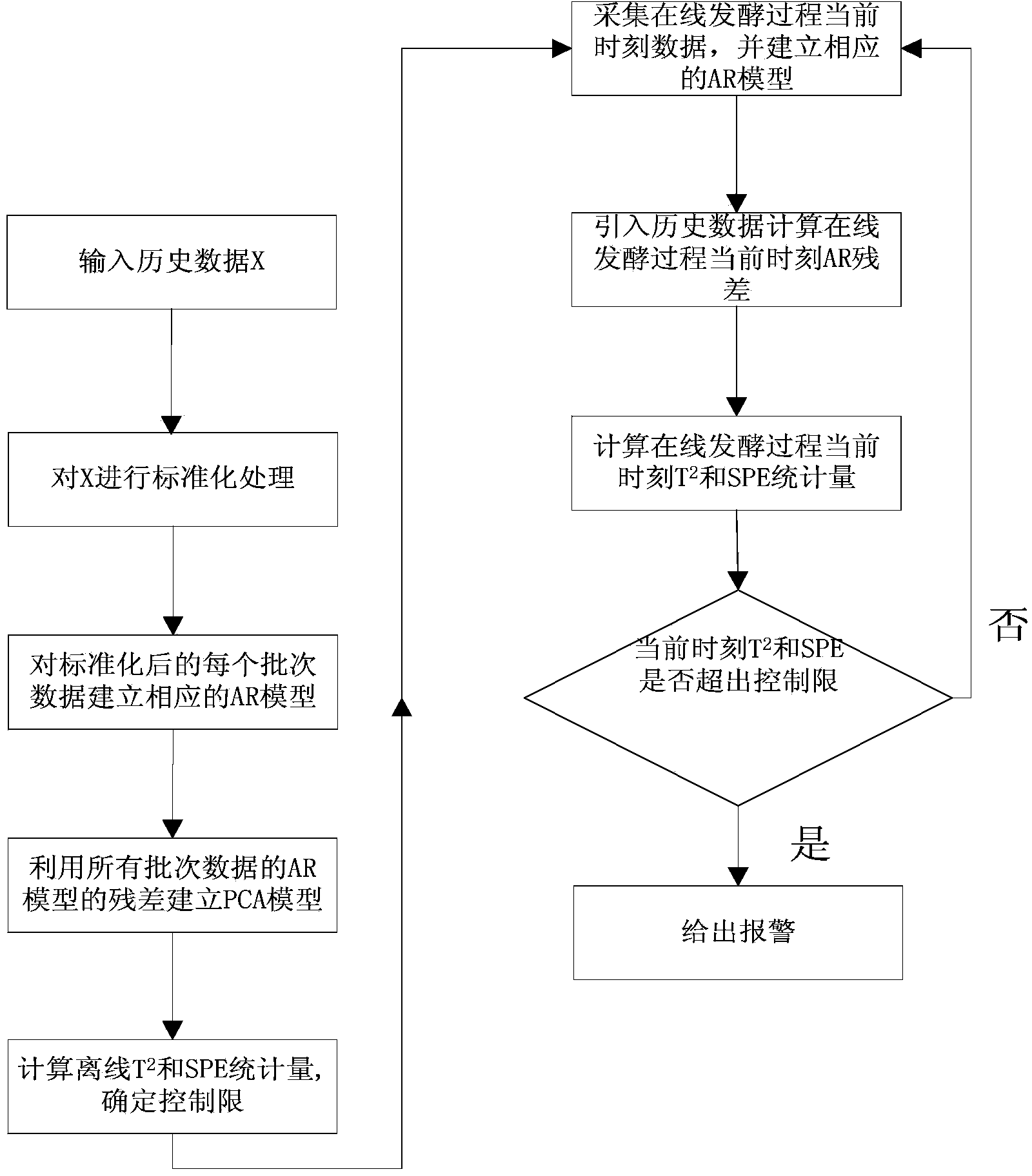
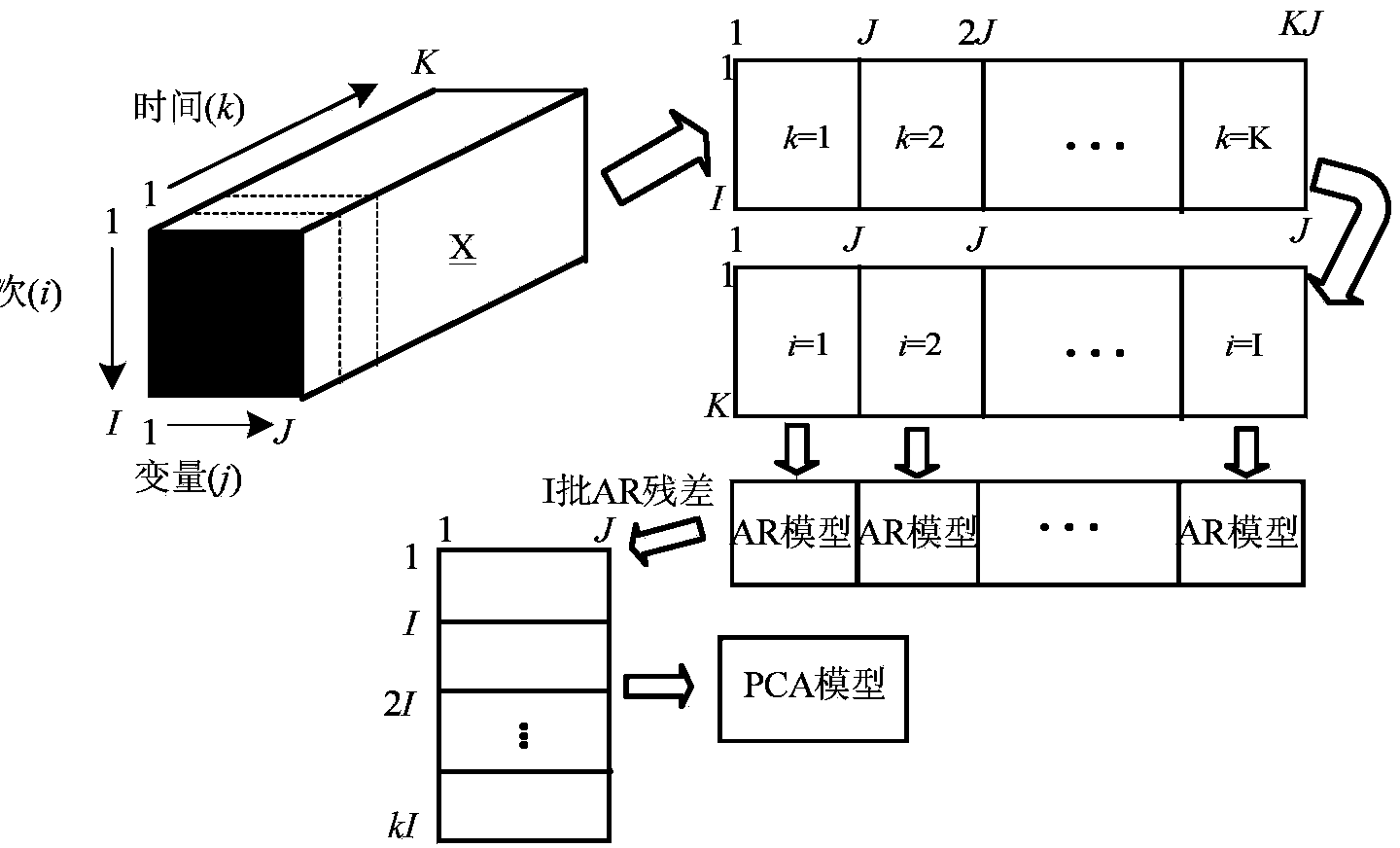
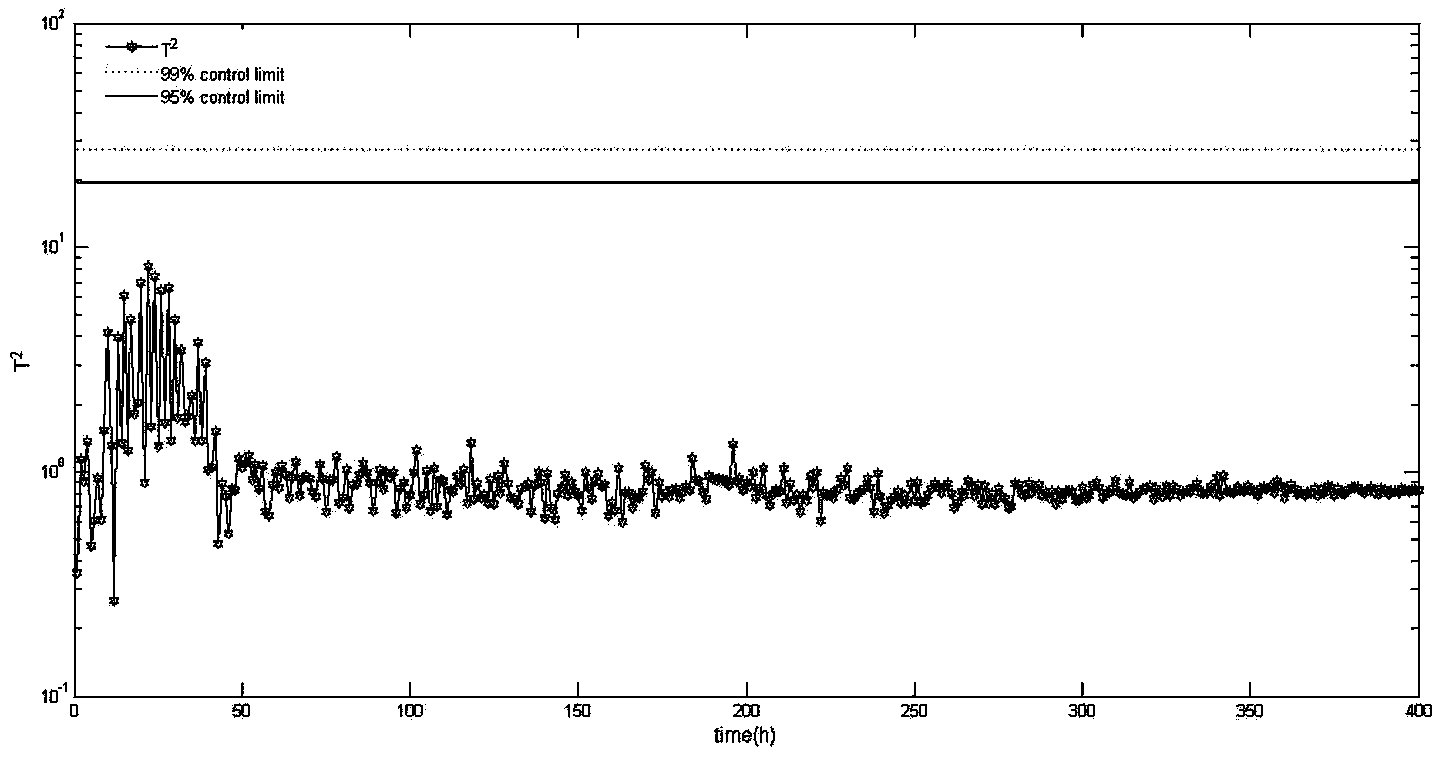
Batch process failure monitoring method based on AR-PCA (Autoregressive Principal Component Analysis)
ActiveCN103853152AReduce false alarm rateReduce false negative rateElectric testing/monitoringLeast squaresMulti variable
The invention discloses a batch process failure monitoring method based on AR-PCA (Autoregressive Principal Component Analysis). Through the batch process failure monitoring method, the batch process with strong dynamics can be monitored online; when monitoring the bath process, a conventional MPCA (Multiway Principal Component Analysis) does not take corresponding self-correlation and mutual correlation of variables due to the existence of various random noises and interferences into account, so that a large quantity of false alarm is generated in the online monitoring process. The batch process failure monitoring method comprises the following steps: firstly, building a multi-variable autoregressive (AR) model according to measurement variables, recognizing a model coefficient matrix by using a PLS (Partial Least Squares) method and recognizing a model order by using an AIC (Akaike Information Criterion); and then building a PCA model for a residual error of the AR model. Meanwhile, training data is introduced when a new bath of data is monitored online through the algorithm, so that the monitoring effect of the algorithm is improved. Through the batch process failure monitoring method, the defect of a large quantity of false alarm of the conventional MPCA method during the process of monitoring the batch process with strong dynamics can be made up; and the batch process failure monitoring method is of great significance to monitoring of an actual bath production process.
Owner:BEIJING UNIV OF TECH
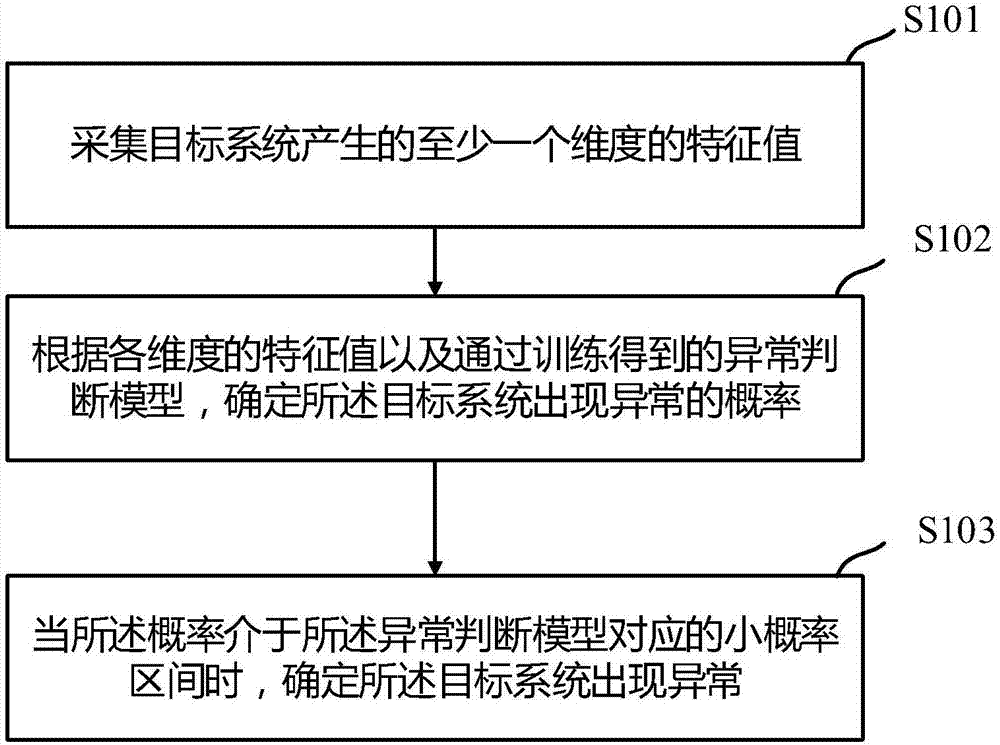
System exception monitoring method and apparatus
ActiveCN107066365AReduce false positivesReduce false negative rateHardware monitoringSmall probabilityGoal system
The invention discloses a system exception monitoring method and apparatus. The method comprises the steps of firstly, determining an eigenvalue of each dimension generated by a target system; then according to a pre-trained exception judgment model, determining a probability of generating an exception in the target system; and when the probability is in a small probability interval corresponding to the exception judgment model, determining that the exception is generated in the target system. Through the method provided by the invention, the running condition of the target system is determined according to the trained exception judgment model, and corresponding processing can be performed according to the actual running condition of the target system; and compared with the prior art, the false reporting and missing reporting probabilities of target system exception are reduced and the monitoring accuracy and efficiency are improved.
Owner:ADVANCED NEW TECH CO LTD
Detection method of abnormal event of multi-variable water quality parameter time sequence data
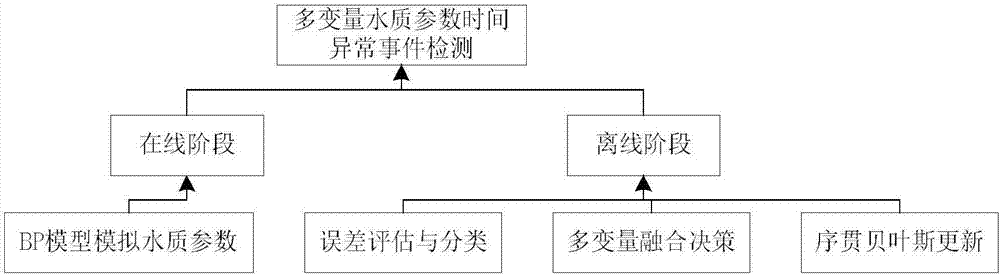
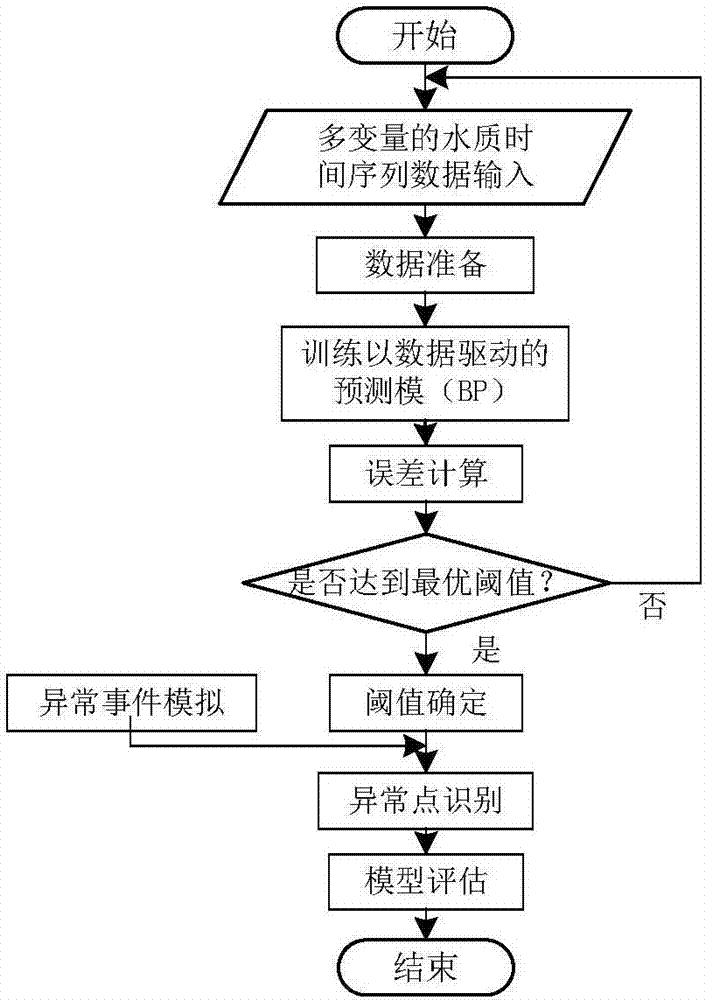
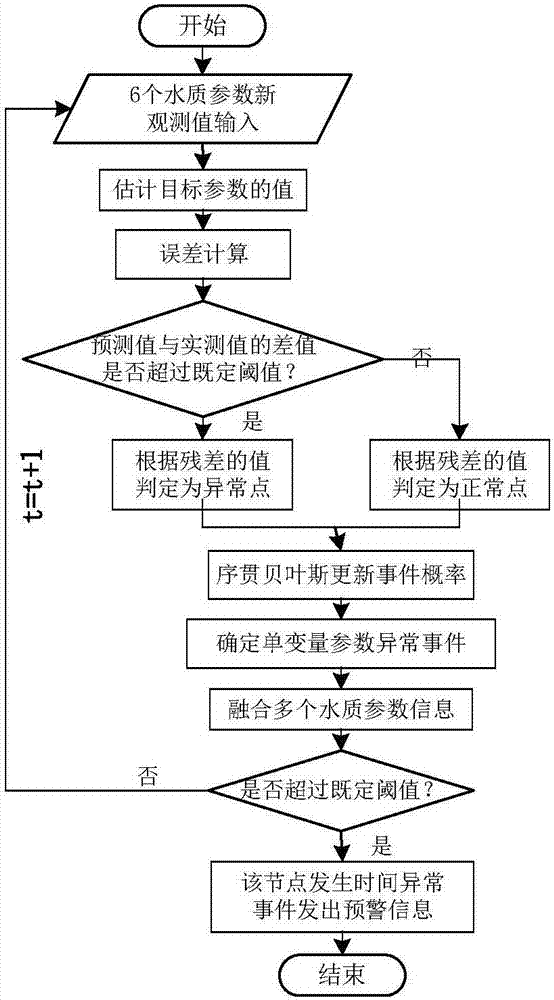
ActiveCN106872657AImprove monitoring accuracyReduce precisionTesting waterNeural learning methodsNODALWater quality
The invention discloses a detection method of an abnormal event of multi-variable water quality parameter time sequence data. The detection method comprises the following steps: firstly, inputting a plurality of water quality parameter models; training and constructing a data driven predication model (BP model); analyzing multi-variable water quality time sequence data in a water supply pipe net and estimating the model; secondly, predicating through the BP model to obtain a predicated value of water quality data; comparing an actually measured value of a current state and the predicated value obtained by the predication model and carrying out error estimation and classification analysis, so as to determine a single-variable parameter abnormal event; classifying based on an error counting result, and updating and determining the event probability of single-variable water quality parameters through sequential Bayesian updating; carrying out multi-variable fusion decision-making and fusing information from a plurality of water quality monitoring indexes; providing a unified decision-making result and determining whether the water supply pipe net has the abnormal event on a specific node or not.
Owner:HOHAI UNIV
Neural network and fuzzy control fused electrical fire intelligent alarm method
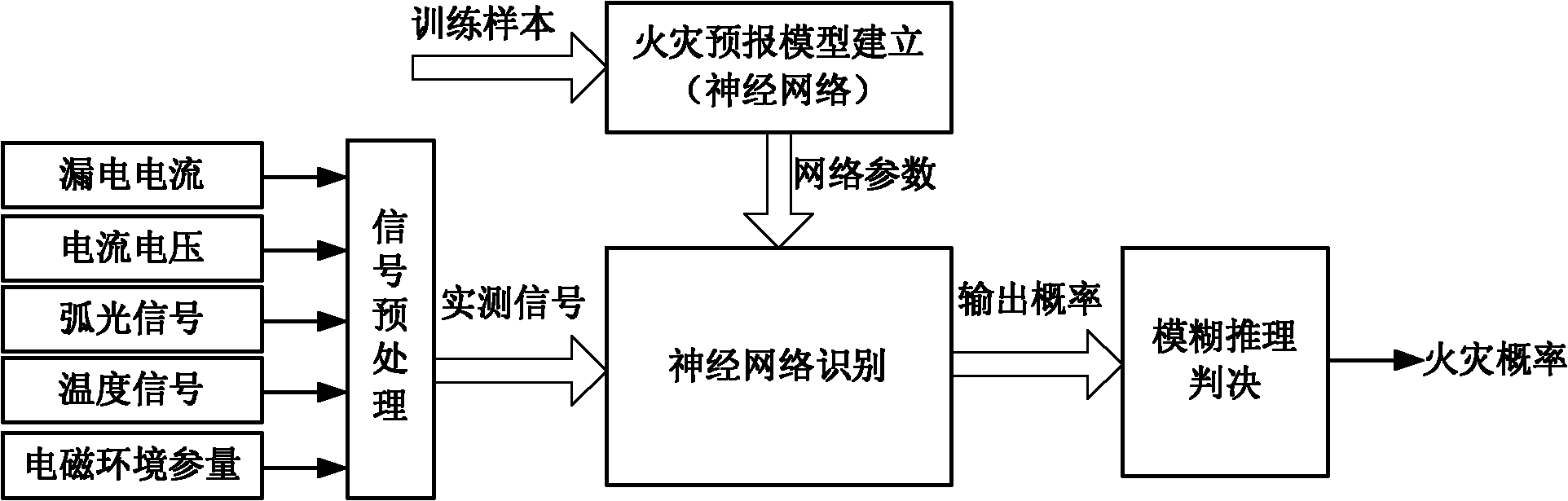
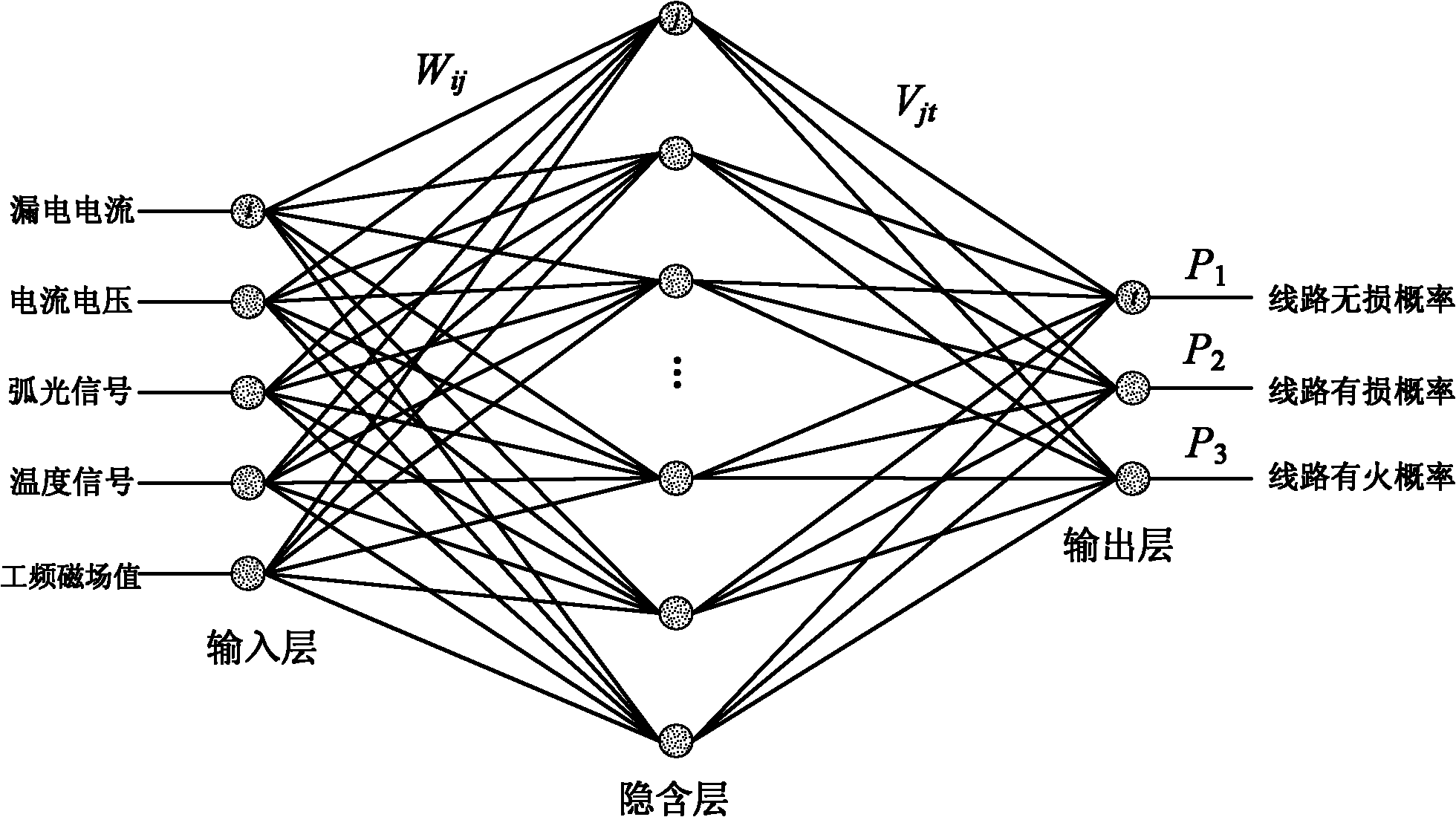
InactiveCN101986358AReduce false negative rateReduce false alarm rateFire alarmsDeep knowledgeFuzzy inference
The invention discloses a neural network and fuzzy control fused electrical fire intelligent alarm method. The method comprises the following steps of: 1, acquiring a leakage current signal, current and voltage signals, an arc light signal, a temperature signal and a field electromagnetic environment parameter signal by using a sensor on site, and pre-processing signals acquired by the sensor by using a velocity detection algorithm; 2, transmitting processed data to a three-layer feedforward error counterpropagation neural network and processing, wherein the neural network is subjected to supervised learning and establishes a weight matrix in advance; and 3, transmitting electrical circuit undamage probability, electrical circuit damage probability, and electrical circuit fire probability output by the neural network to a fuzzy inference module and performing fuzzy inference to acquire a forecast result of electrical fire. In the method, the probability of the electrical fire is accurately forecast by using the advantages of advanced theories, such as neural network, fuzzy control and the like, and without depending on deep knowledge of an object, the electrical fire forecasting accuracy is obviously improved and the damage of the electrical fire can be effectively prevented and reduced.
Owner:彭浩明
Continuous casting breakout prediction method based on neural network
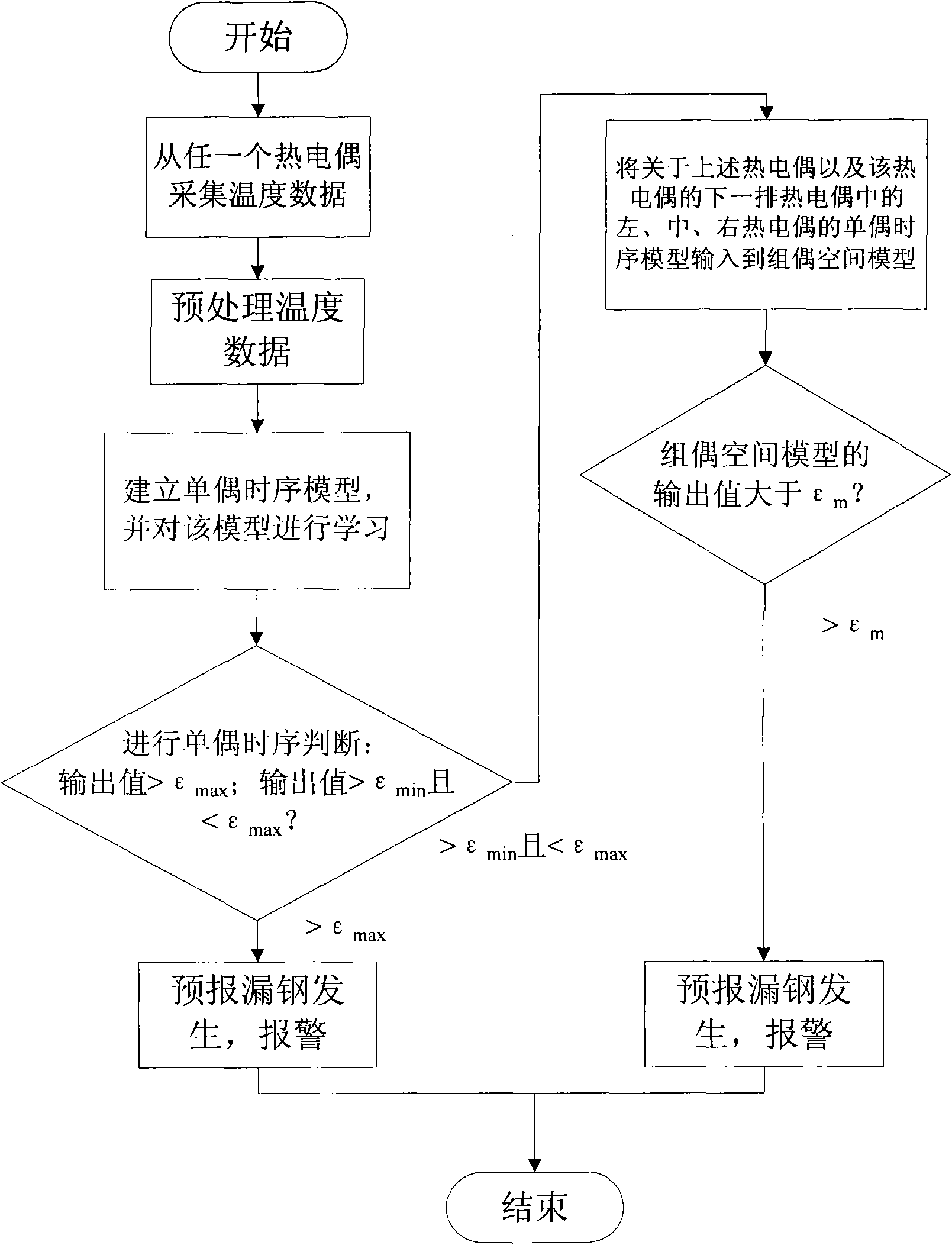
InactiveCN101850410AFast operationImprove recognition effect and forecast accuracyPre treatmentPrediction rate
The invention discloses a continuous casting breakout prediction method based on a neural network, which comprises the following steps that: step 1: the temperature data of a thermocouple on a continuous casting site is collected on line and saved; step 2: the temperature data is pre-processed; step 3: the temperature data which is collected from any one thermocouple and is pre-processed is input a single-couple time sequence network breakout prediction model, the output value of the single-couple time sequence network breakout prediction model is compared with the maximum determination threshold, and if the output value of the model is more than the maximum determination threshold, the breakout is predicted; and the method is characterized in that genetic algorithm is used for initializing the connection weights and thresholds of the single-couple time sequence network breakout prediction model. The method can improve the identification effect and the prediction precision of a continuous casting bonding breakout process so as to greatly reduce the false prediction rate and missing prediction rate.
Owner:PANGANG GROUP VANADIUM TITANIUM & RESOURCES +3
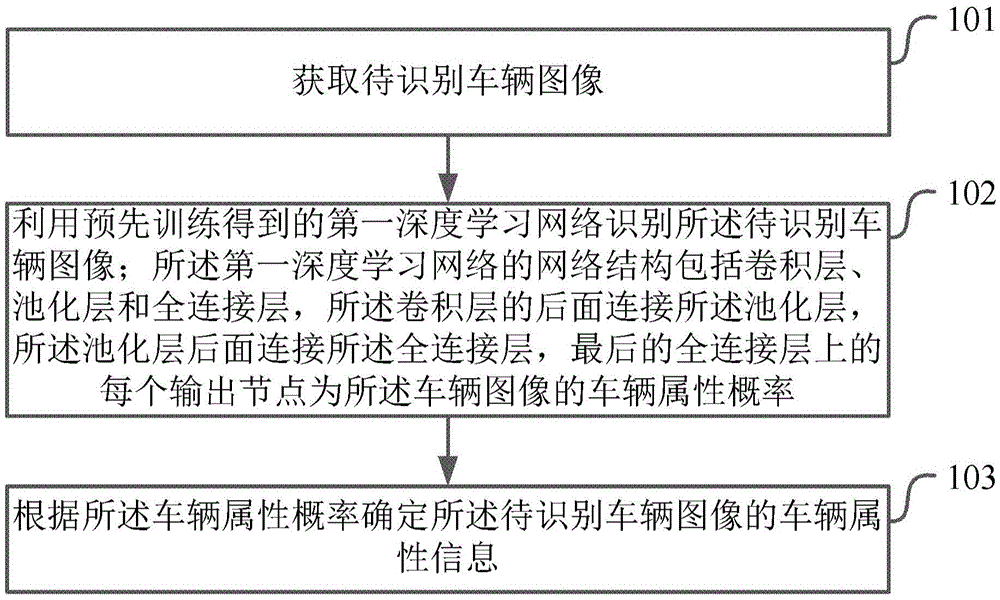
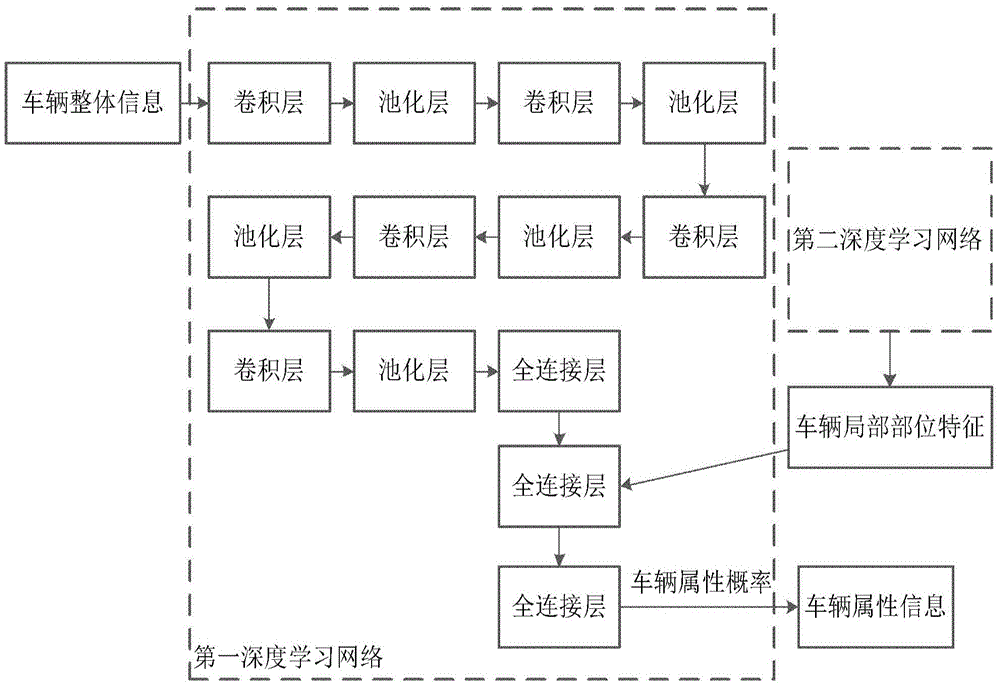
Vehicle identification method and device
ActiveCN105574550AImprove accuracyReduce false alarm rateBiological neural network modelsCharacter and pattern recognitionPattern recognitionNetwork structure
This application provides a vehicle identification method and device. The method includes the following steps that: a vehicle image to be identified is obtained; a first deep learning network which is obtained through pre-training is utilized to identify the vehicle image to be identified; the network structure of the first deep learning network includes convolutional layers, pooling layers and all-connection layers, the pooling layers are connected behind the convolutional layers, the all-connection layers are connected behind the pooling layers, and each output node on the all-connection layers is the vehicle attribute probability of the vehicle image; and the vehicle attribute information of the vehicle image to be identified is determined according to the vehicle attribute probability. According to the method provided by the technical schemes of the invention, since the deep learning network is utilized to identify a vehicle, the deep learning network is competent enough to describe and distinguish objects, and therefore, compared with a method according to which features are defined manually to carry out classification, the method of the invention has higher accuracy as well as lower false positive rate and false negative rate.
Owner:BEIJING DEEPGLINT INFORMATION TECH
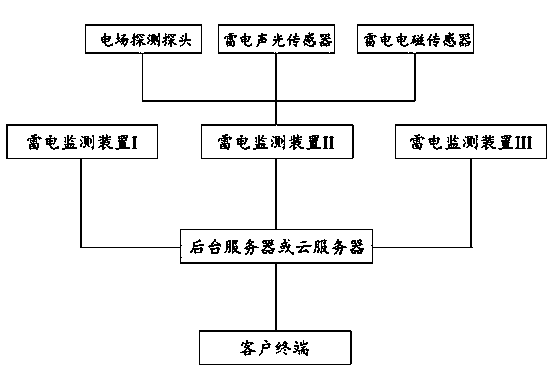
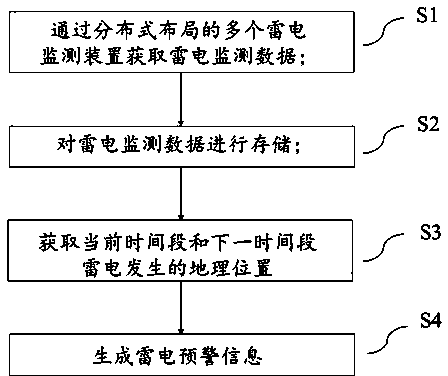
Lightning early warning method and system based on lightning monitoring devices arranged in distributed mode
InactiveCN104574833AReduce false positive and false negative ratesImprove accuracyElectromagentic field characteristicsAlarmsData transmissionMonitoring data
The invention discloses a lightning early warning system based on lightning monitoring devices arranged in a distributed mode. The lightning early warning system comprises a background server or a cloud server, the lightening monitoring devices and a communication module, wherein the lightning monitoring devices are arranged in a region in the distributed mode, and each lightning monitoring device transmits lightning monitoring data to the background server or the cloud server through the communication module. The background server or the cloud server stores and analyzes the lightning monitoring data and generates lightning early warning information. The invention further discloses a lightning early warning method based on the lightning monitoring devices arranged in the distributed mode. By means of the lightning early warning method and system, accurate forecasting can be achieved for the local thunder cloud expected direction and the possible thunderstorm occurrence time, the rate of false forecast and the rate of missing forecast are effectively decreased, the background server or the cloud server of the early warning system can be further checked and modified, and furthermore, the lightning early warning and forecasting accuracy is unceasingly perfected and improved.
Owner:CHINA PETROLEUM & CHEM CORP QINGDAO RES INST OF SAFETY ENG +1
Network security verifying device based on improved K-means algorithm
The invention provides a network security verifying device based on an improved K-means algorithm. A data mining method is used for the extraction of network attack characteristics. Firstly, traffics entering and exiting a system are monitored through creating a height-controllable target range verifying environment, then abnormal traffics and abnormal behaviors which enter and exit the system are captured by layers by using a layering mechanism, and finally, collected information data are subjected to characteristic analysis by using an improved K-means algorithm, and therefore, the attack behaviors can be efficiently detected and a potential unknown attack in a network is accurately found.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Pedestrian detecting method based on improved HOG feature and PCA (Principal Component Analysis)
ActiveCN102609716AImprove detection rateReduce training speedCharacter and pattern recognitionFeature vectorPrincipal component analysis
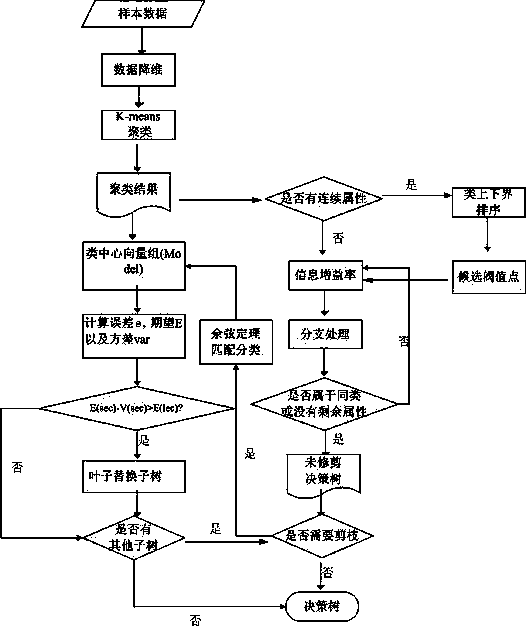
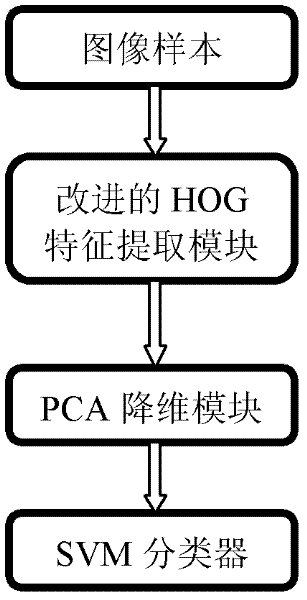
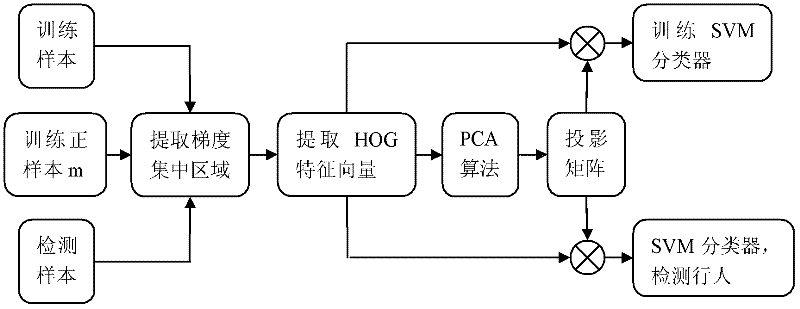
The invention relates to a pedestrian detecting method based on improved HOG feature and PCA (Principal Component Analysis). The method comprises the following steps: extracting a sample feature by using a feature extracting algorithm for HOG feature cascaded PCA in a concentrated area of gradient information of a pedestrian in a sample image; training a SVM classifier by utilizing the feature extracted from the sample; and utilizing a feature extracting method to extract a feature vector for a detected sample and utilizing the trained and obtained SVM classifier to detect the pedestrian. The invention provides a pedestrian detecting method based on improved HOG feature and PCA, with the capabilities of efficiently reducing the training speed and reducing the false detecting rate and missing report rate.
Owner:ENJOYOR COMPANY LIMITED +1
Attack detection method and system for WEB
The invention discloses an attack detection method and system for WEB; the method comprises the following steps: firstly implementing attack characteristic detection to the url accessed by a user; then implementing misinformation analysis and fail-to-declare analysis treatment to the detection result, wherein the misinformation analysis mainly solves the misinformation caused by normal embedded resources of the website and the web crawlers, the fail-to-declare analysis is to treat the undetected abnormal behaviors conducted by the detected abnormal users. Based on the results of the treatment above, calculating the total normal access time of each abnormal user under each domain name; when the access time is less than the average value of all users, taking the ratio between the access time and the average value as an abnormality scoring index of the abnormal user; otherwise, the abnormality score is a weighted value w of the ratio between the access time and the maximum access time of all users. By the misinformation analysis and fail-to-declare analysis treatment, the efficiency of the attack detection method and system for WEB is significantly increased.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
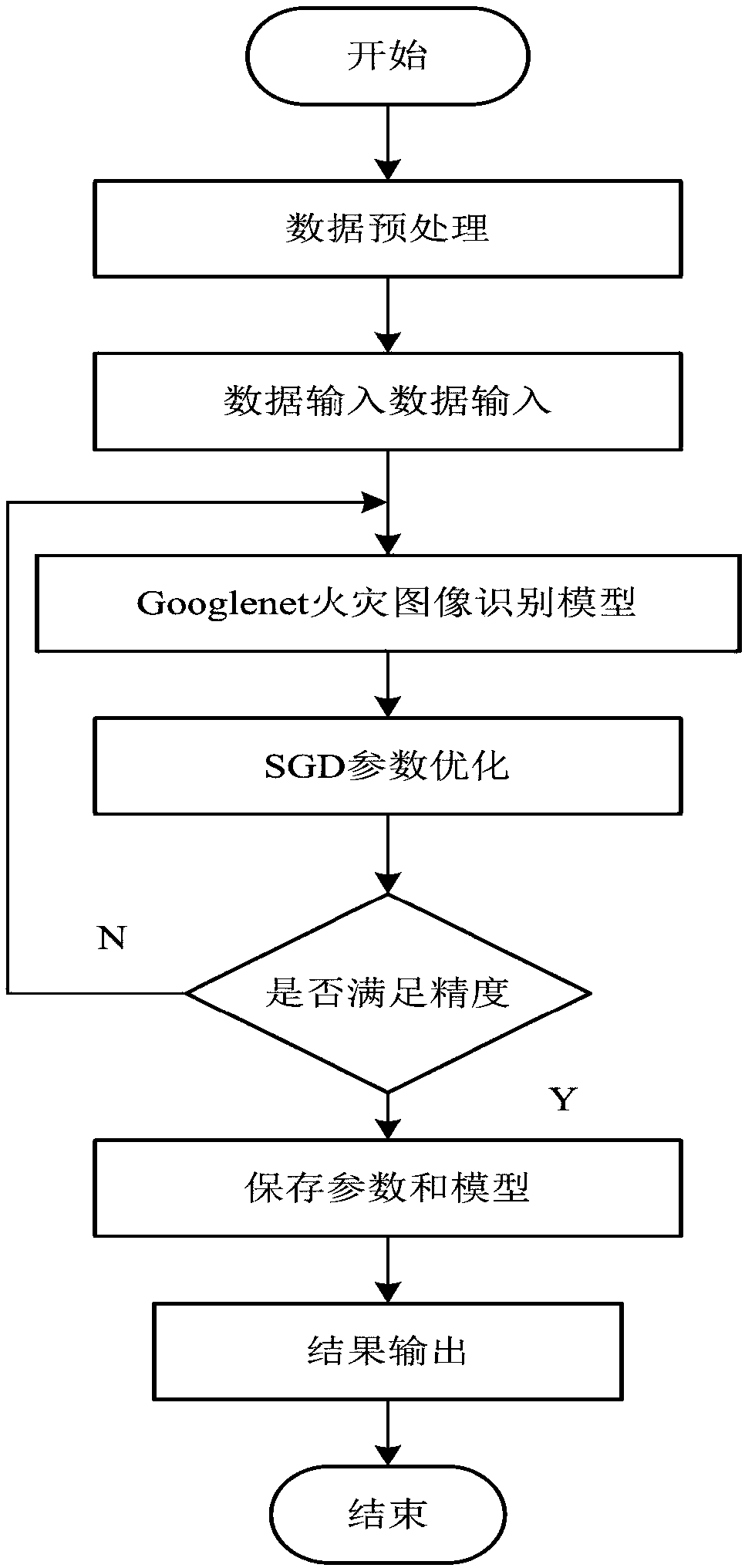
Method for depth learn pattern recognition of fire image
InactiveCN109063728AImprove accuracyHigh speedCharacter and pattern recognitionTest sampleNetwork structure
The invention discloses a fire image depth learning pattern recognition method, comprising the following steps: preprocessing a test sample and a training sample of the fire image; designing an improved GoogleNet-based deep learning network, which extracts features automatically through training to eliminate artificial traces; deep features are used to train the classifier and identify the fire test samples. The invention applies the image multi-scale convolution fusion network to the fire image pattern recognition technology, remarkably improves the training efficiency of the network, effectively solves the problems encountered in the fire recognition method, such as the accuracy and real-time property are not ideal, the network structure is complex, and the training time is long, the stability and the robustness are poor, and the like. The recognition accuracy of the trained network is 99.2% in three types of fire images.
Owner:YANSHAN UNIV
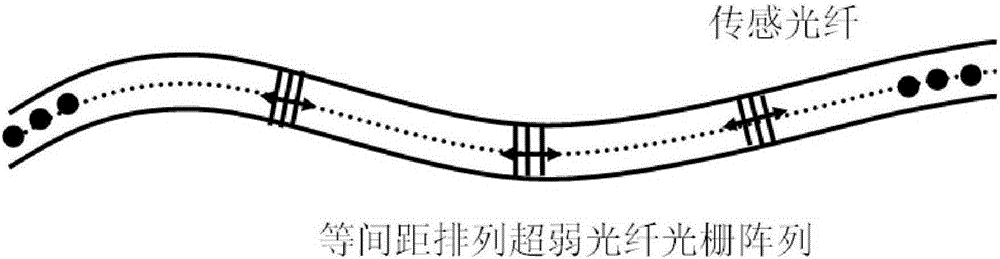
Ultraweak fiber bragg grating array and Phi-OTDR combined optical fiber vibration sensing system
InactiveCN105181111AImprove sensitivity and signal-to-noise ratioImprove dynamic rangeSubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansOptical powerSignal-to-noise ratio (imaging)
The present invention discloses an ultraweak fiber bragg grating array and Phi-OTDR combined optical fiber vibration sensing system. According to the system, the ultraweak fiber bragg grating arrays are accessed in a sensing optical fiber with the same spacing, and the spacing selection must be same with the spatial resolution of a Phi-OTDR optical fiber sensing system or must be integer multiples of the spatial resolution. By utilizing the reflection characteristics of the ultraweak fiber bragg gratings, the optical power of the detected backward rayleigh scattered light is improved, thereby improving the signal to noise ratio and the sensitivity of the Phi-OTDR optical fiber vibration sensing system.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Machine-learning-based flow identification technology
ActiveCN108833360AReduce the impact of targetingReduce false alarm rateCharacter and pattern recognitionTransmissionLearning basedNetwork attack
The invention relates to a machine-learning-based flow identification technology. An identified object is an encrypted malicious flow. The provided machine-learning-based flow identification technology is not only mainly applied to the flow identification filed but also applied to the field of network attack detection in an assisted manner. The machine-learning-based flow identification technologyis characterized by establishing malicious encrypted flow identification model by using a machine learning algorithm and identifying a new flow by the model. The working flow of the novel technologyis as follows: lots of known attribute flow data are read; statistical characteristics of the flow are extracted and the extracted characteristics are used as attributes; a model is established by using a random forest algorithm; and then a newly inputted flow is identified by using the model. The identification process of the newly inputted flow is as follows: extracting statistical characteristics of the flow, inputting the statistical characteristics into the model for identification, and acquiring an identification result. According to the invention, the technology is oriented at the encrypted and coded flows and data participating in modeling are formed by normal encrypted flow and the malicious encrypted flow. At present, the existing non-encrypted flow identification technology is mature but the encrypted or coded flow identification can not be carried out easily; however, the invention provides a novel solution method for identification of the encrypted flow.
Owner:SICHUAN UNIV
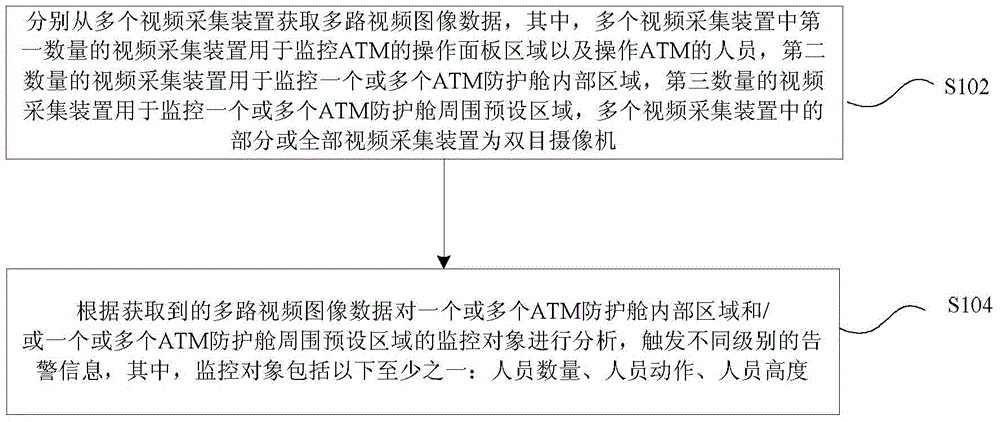
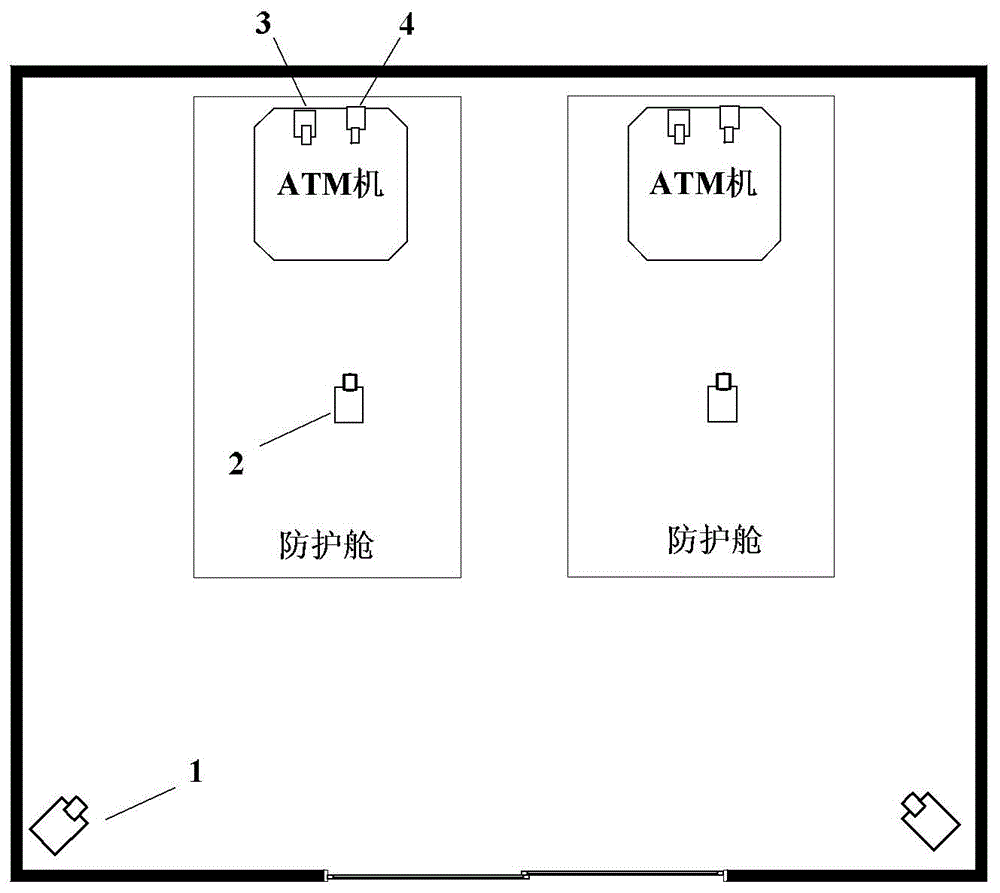
Automatic teller machine (ATM) video surveillance method and apparatus
ActiveCN105100689ASolve the problem of low analysis accuracyStable and reliable outputComplete banking machinesClosed circuit television systemsVideo imageFalse positives and false negatives
The invention discloses an automatic teller machine (ATM) video surveillance method. The method comprises the steps of acquiring multi-channel video image data from a plurality of video acquisition unit; and conducting analysis of surveillance objects in internal regions of one or more ATM protective cabins and / or preset regions surrounding the one or more ATM protective cabin according to the acquired multi-channel video image data, and triggering alarm information at different levels. The surveillance objects include at least one of the following: the number of persons, actions of a person and the height of a person. The technical scheme provided by the invention can be used for improving the accuracy of the video analysis, reducing false positives and false negatives and outputting reliable alarm information.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com